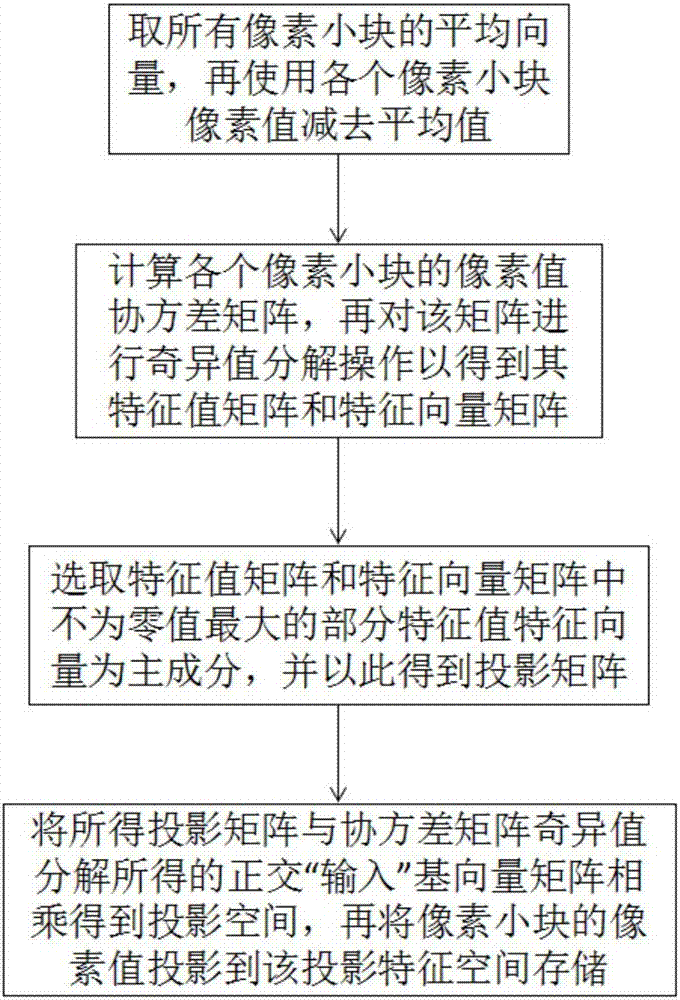
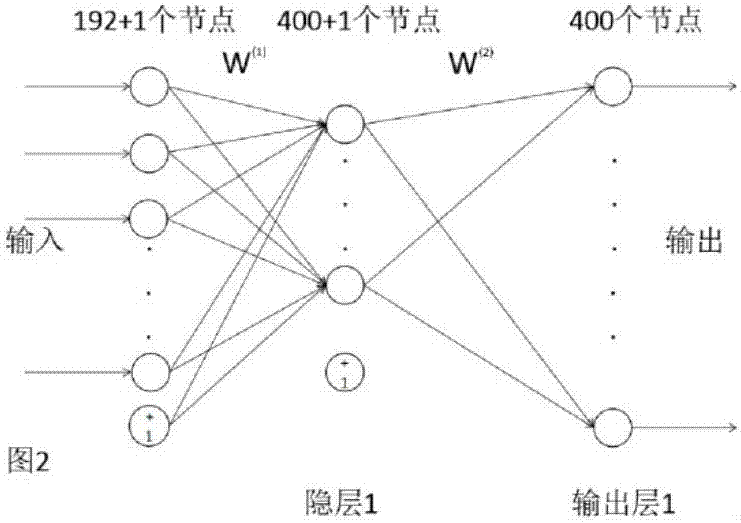
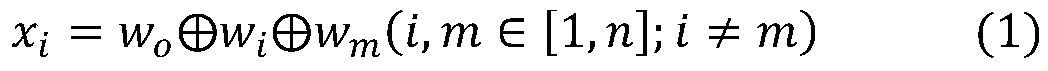Patents
Literature
52 results about "Type signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
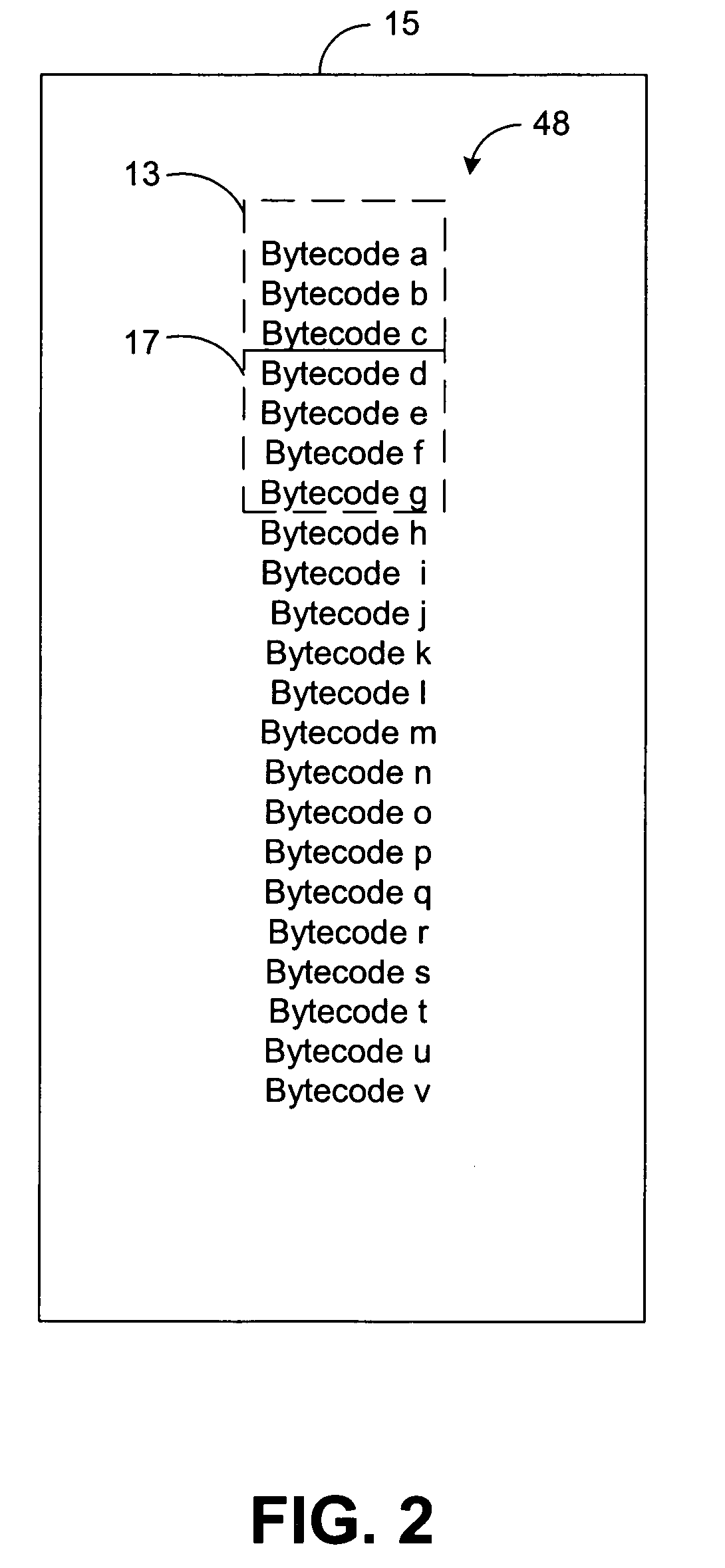
In computer science, a type signature or type annotation defines the inputs and outputs for a function, subroutine or method. A type signature includes the number, types and order of the arguments contained by a function. A type signature is typically used during overload resolution for choosing the correct definition of a function to be called among many overloaded forms.
Band-width spreading method and system for voice or audio signal
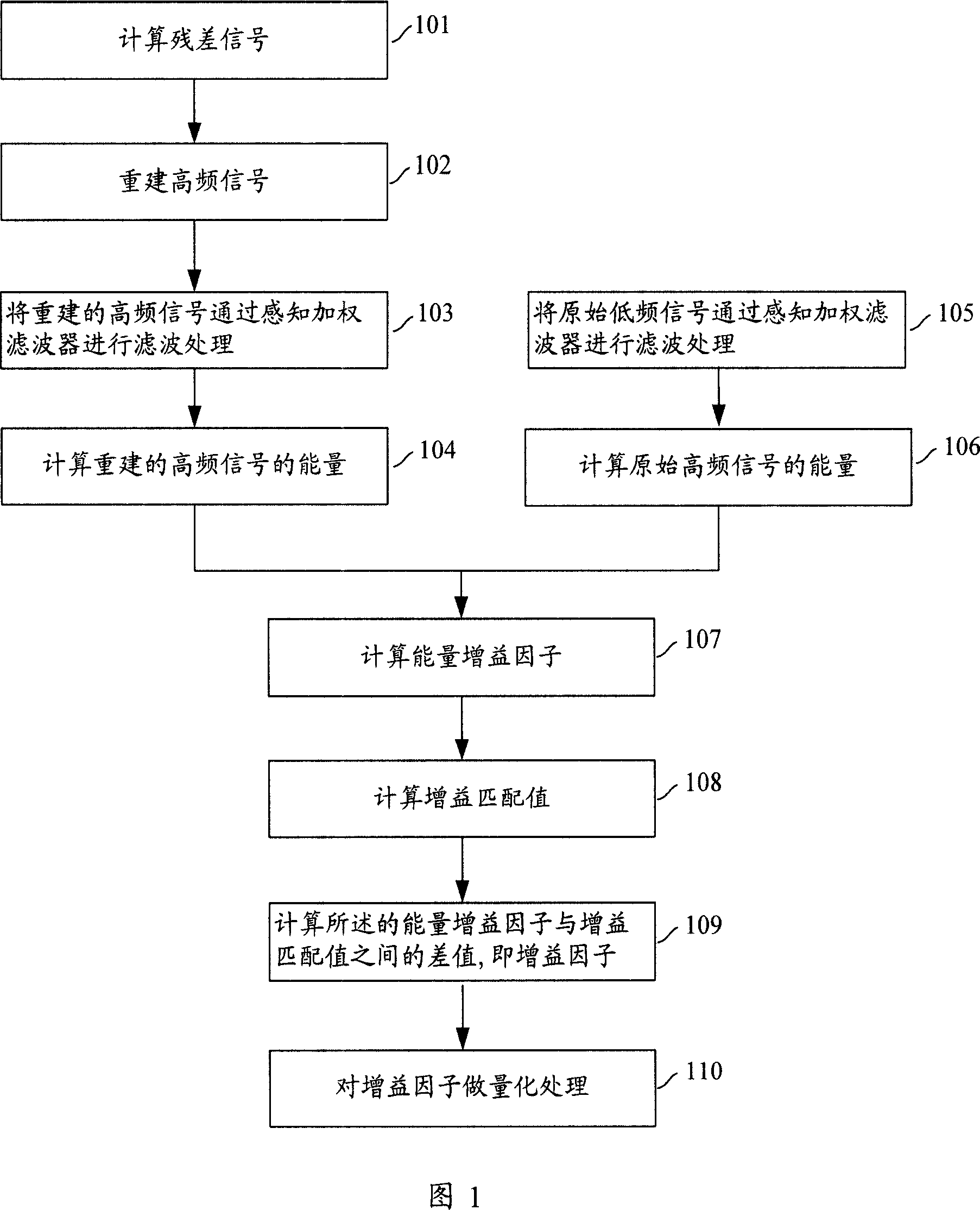
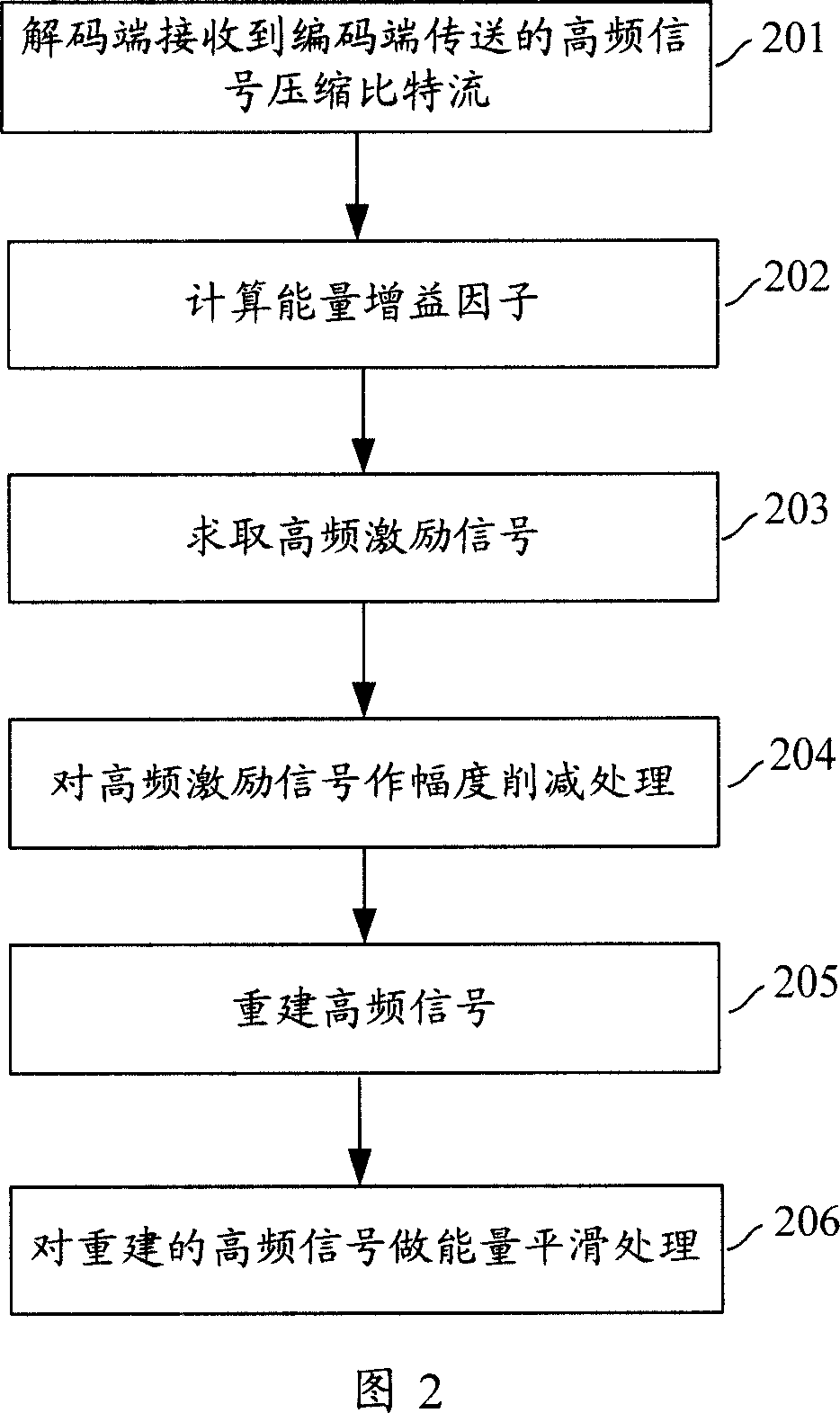
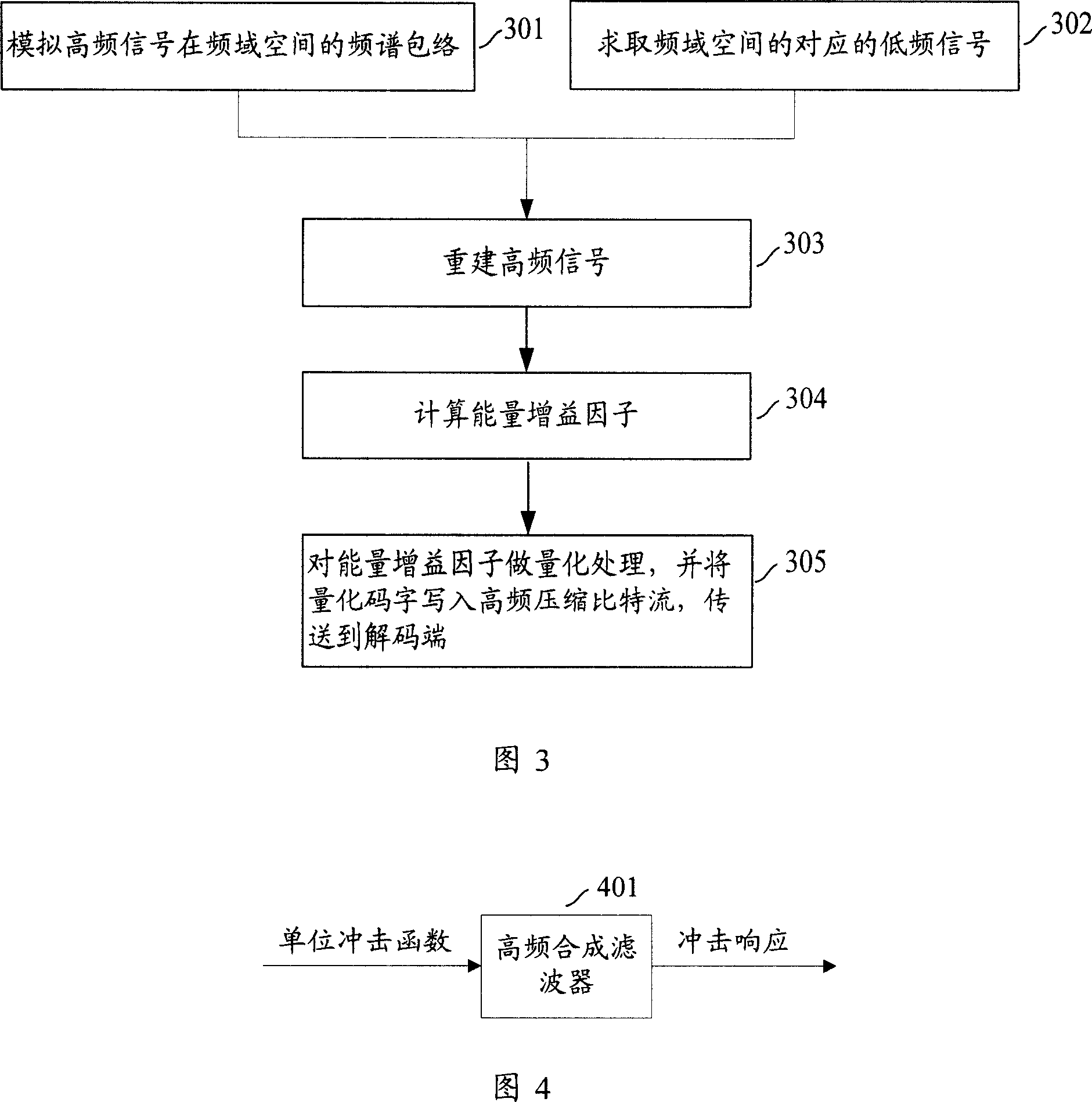
The invention discloses a method and system for speech or audio signal bandwidth expansion, which comprises: A. to simulate spectral envelope of the high-frequency signal components in the speech or audio signal. B. to make a synthesis of the said spectrum envelope and the low-frequency signal components corresponding to the high-frequency signal components in the frequency and spatial domain to obtain the reset high-frequency signal components. The invention also discloses the method and system to realize the said bandwidth expansion, the technical scheme offered by which has the advantage of less bit number of coding that can be adaptively adjusted based on the type features of the signals. Besides, by extracting spectrum envelope of the high-frequency signal components, the invention makes the fine structure acted on the low-frequency signal components corresponding frequency and spatial domain to guarantee the correlation between the reset high-frequency signal spectrum and the harmonization of the high-frequency signal spectrum lopped during coding.
Owner:HUAWEI TECH CO LTD +1
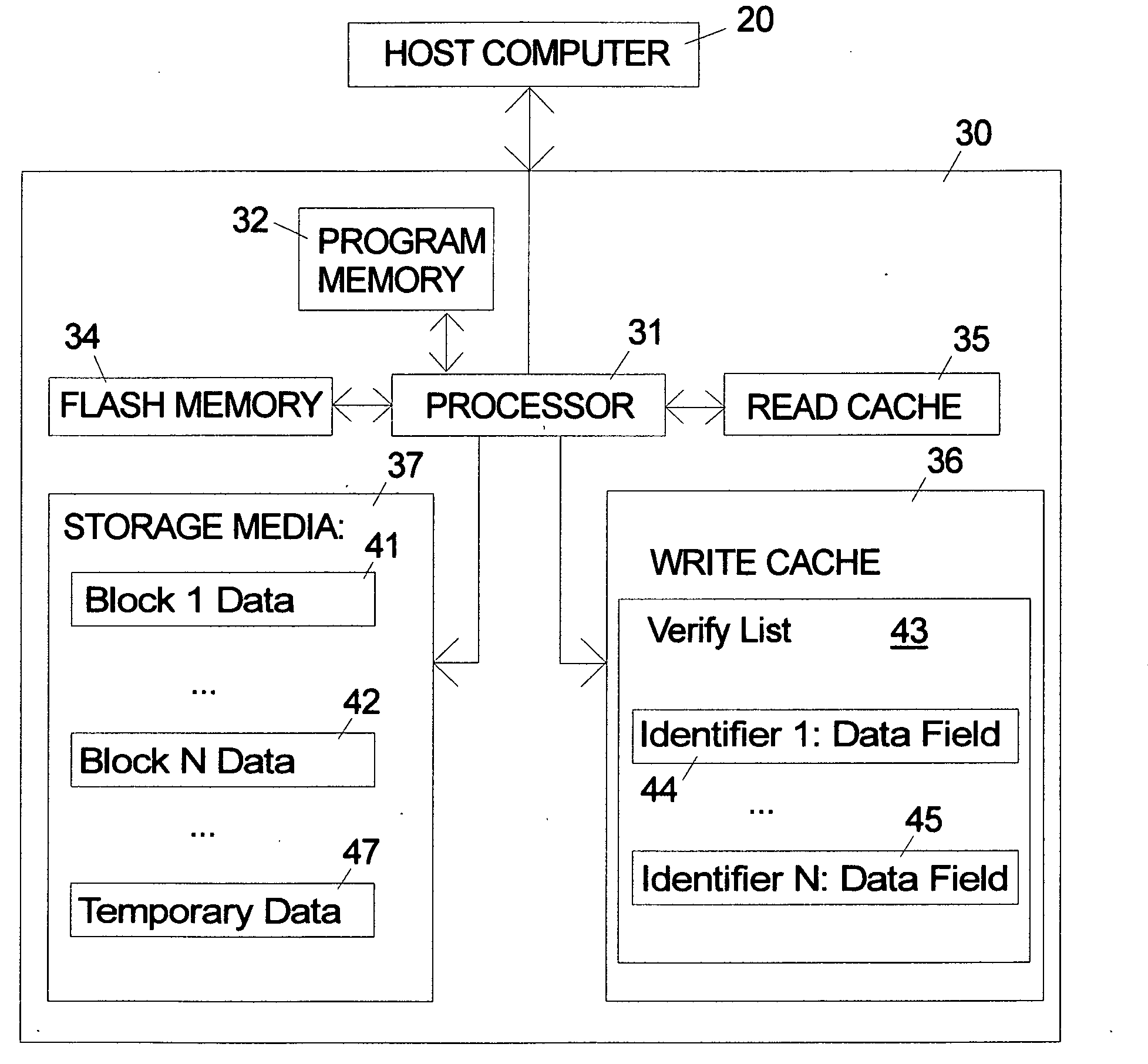
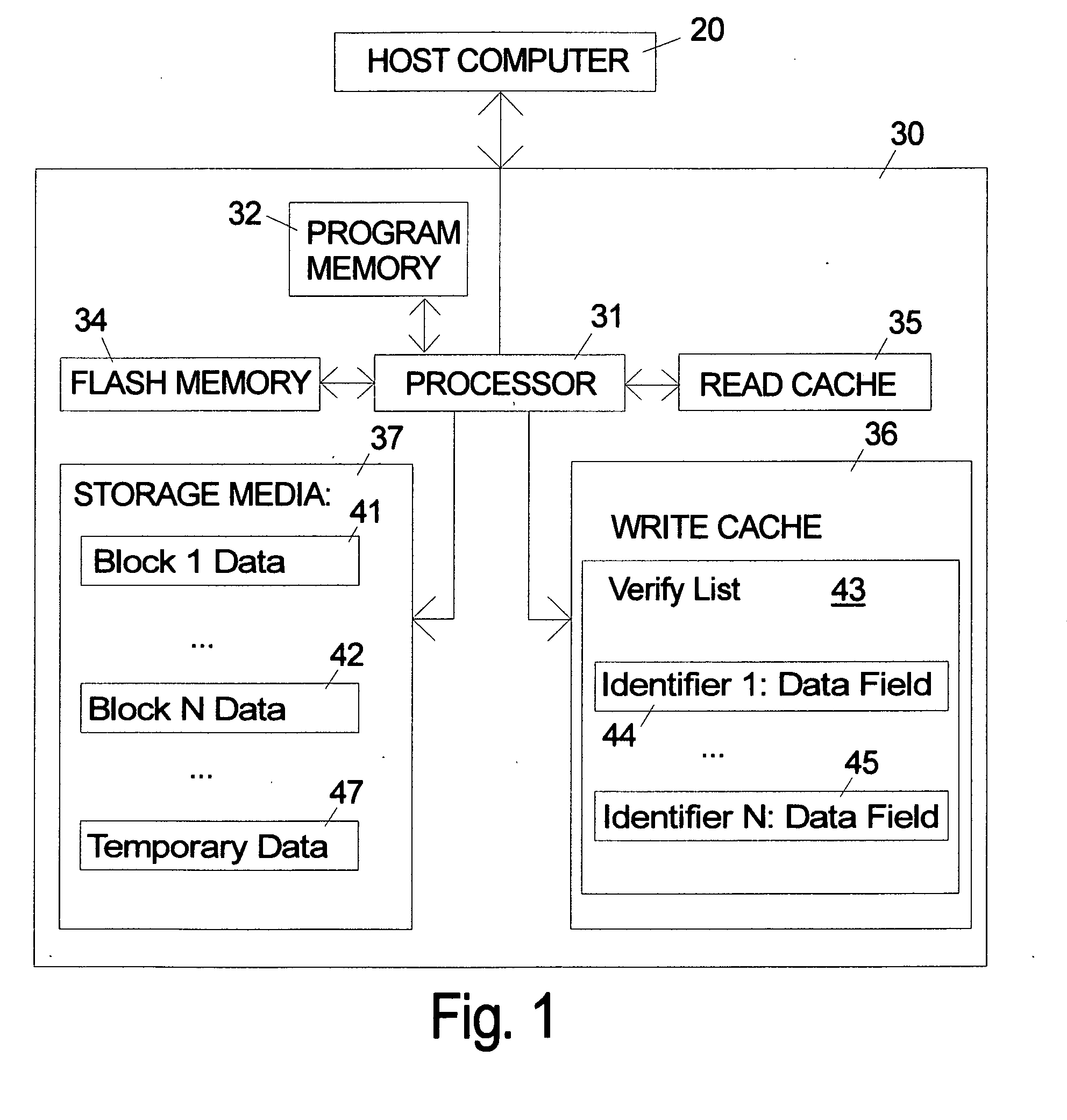
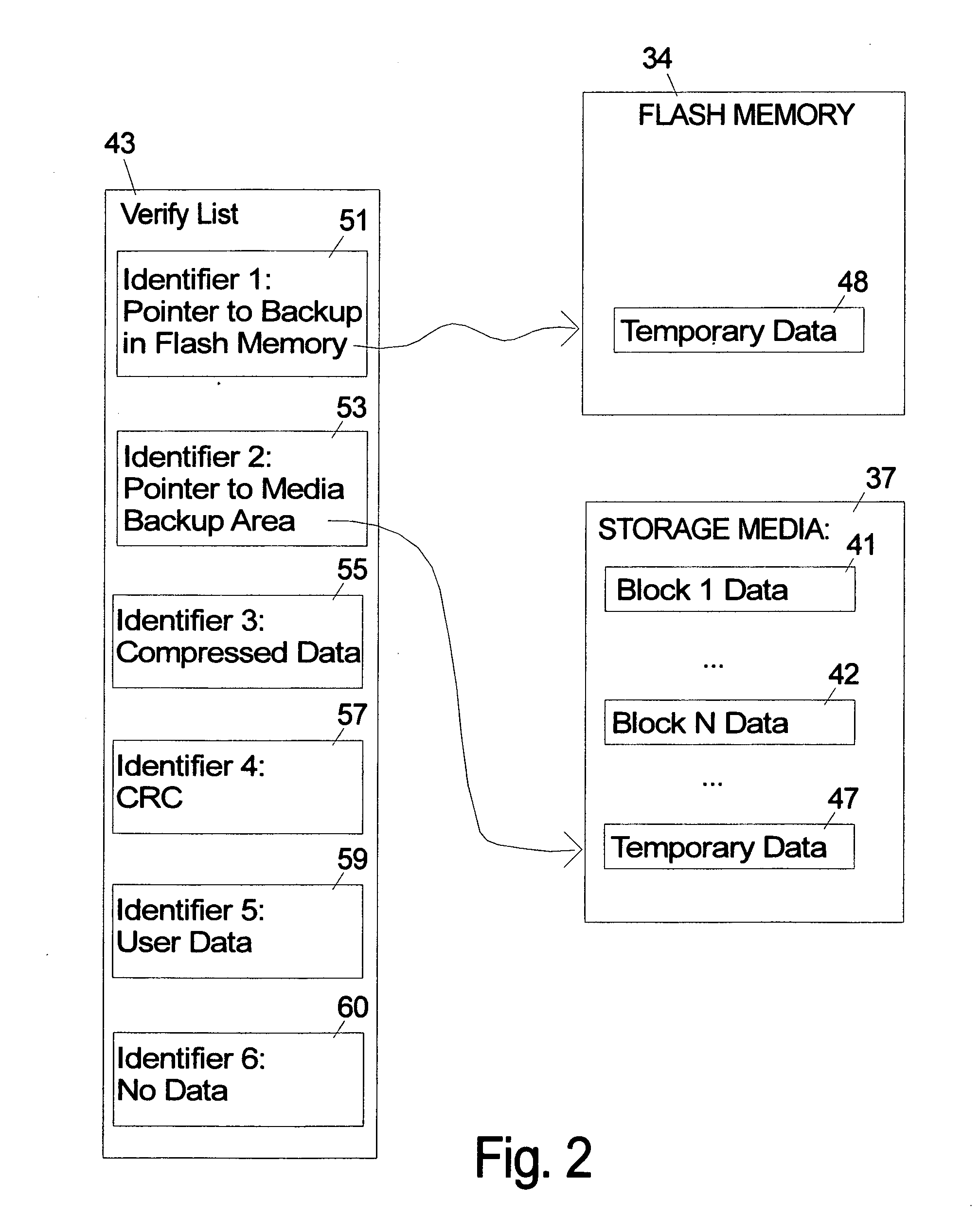
Storage system and method for opportunistic write-verify
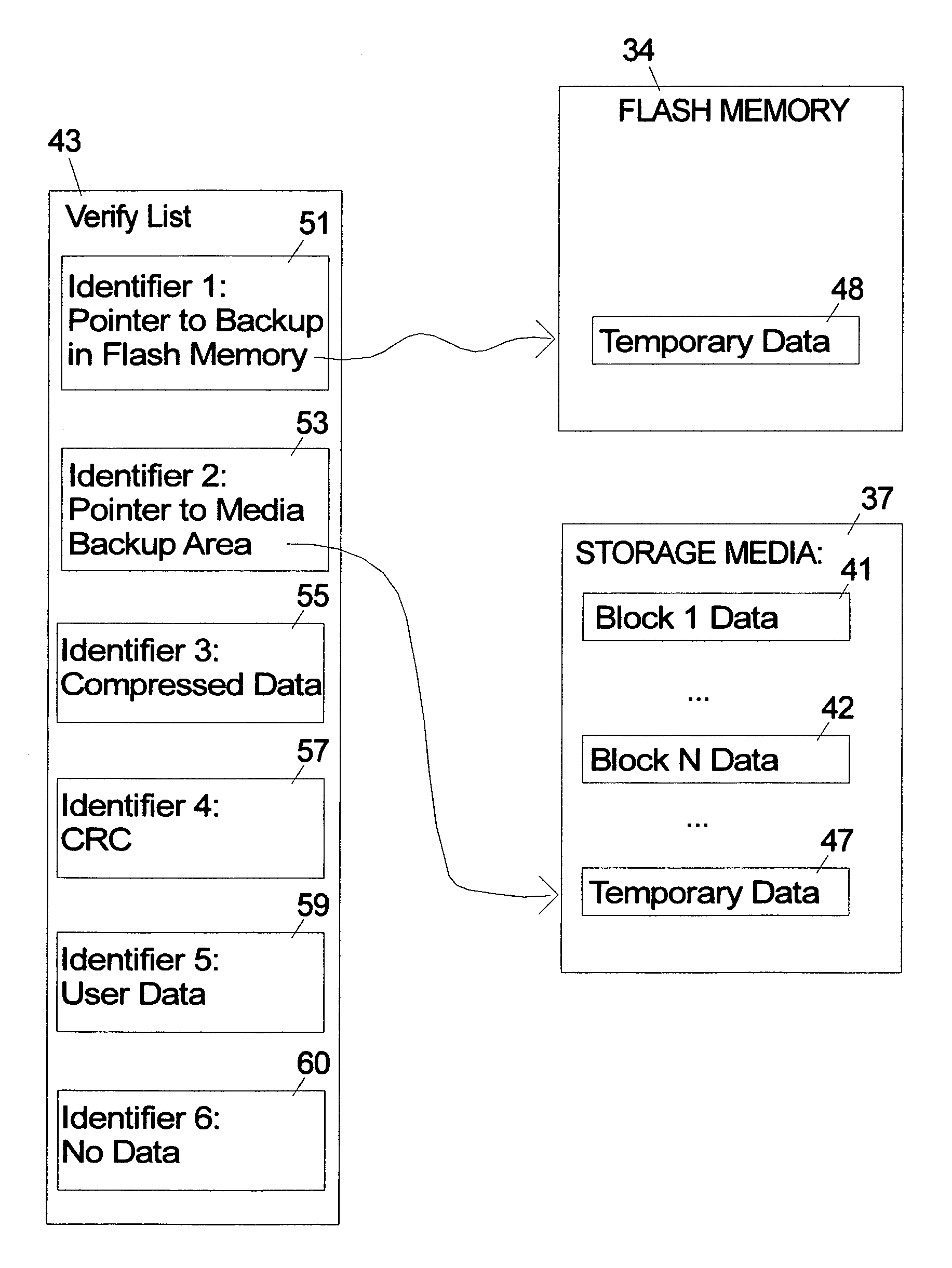
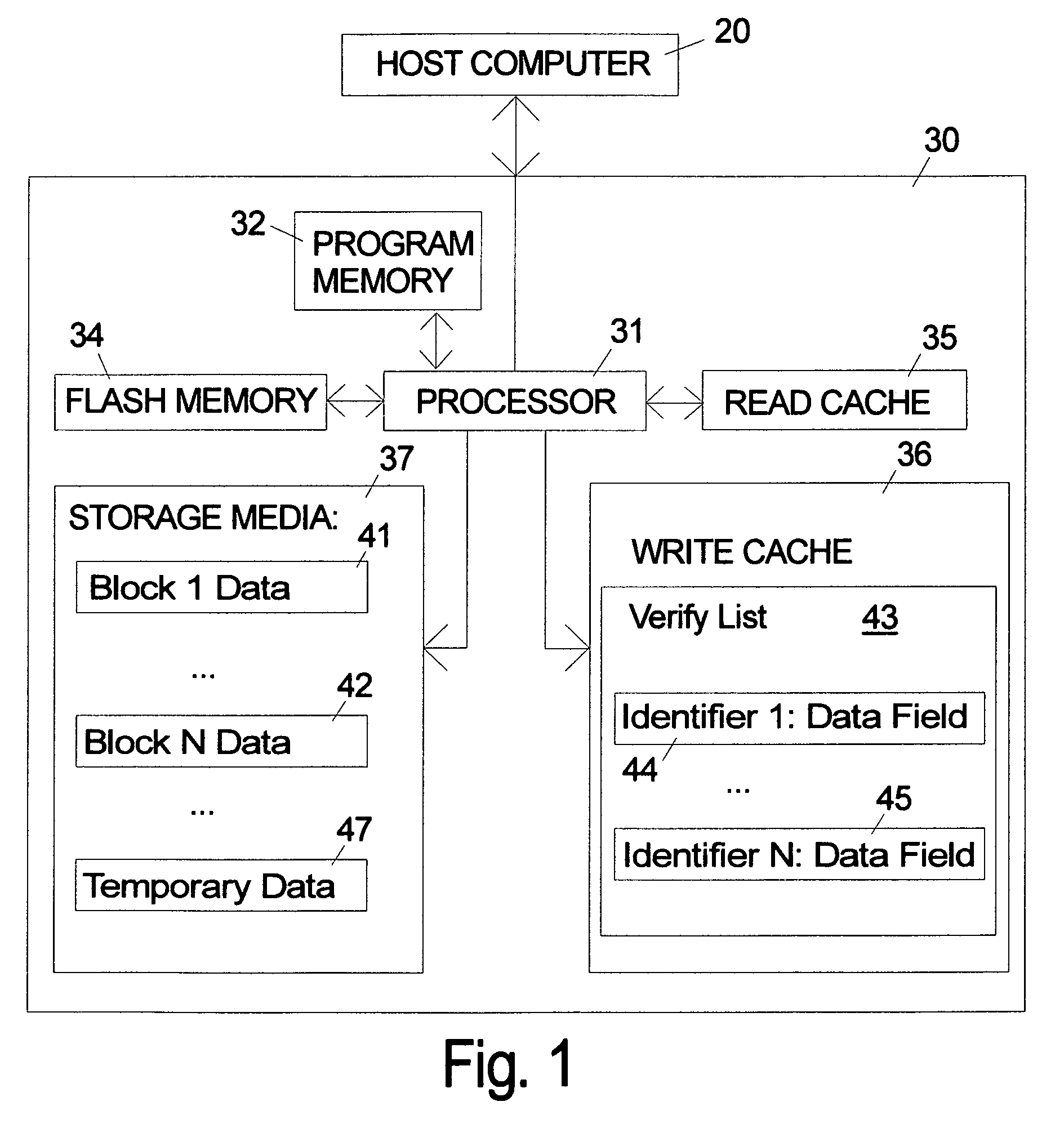
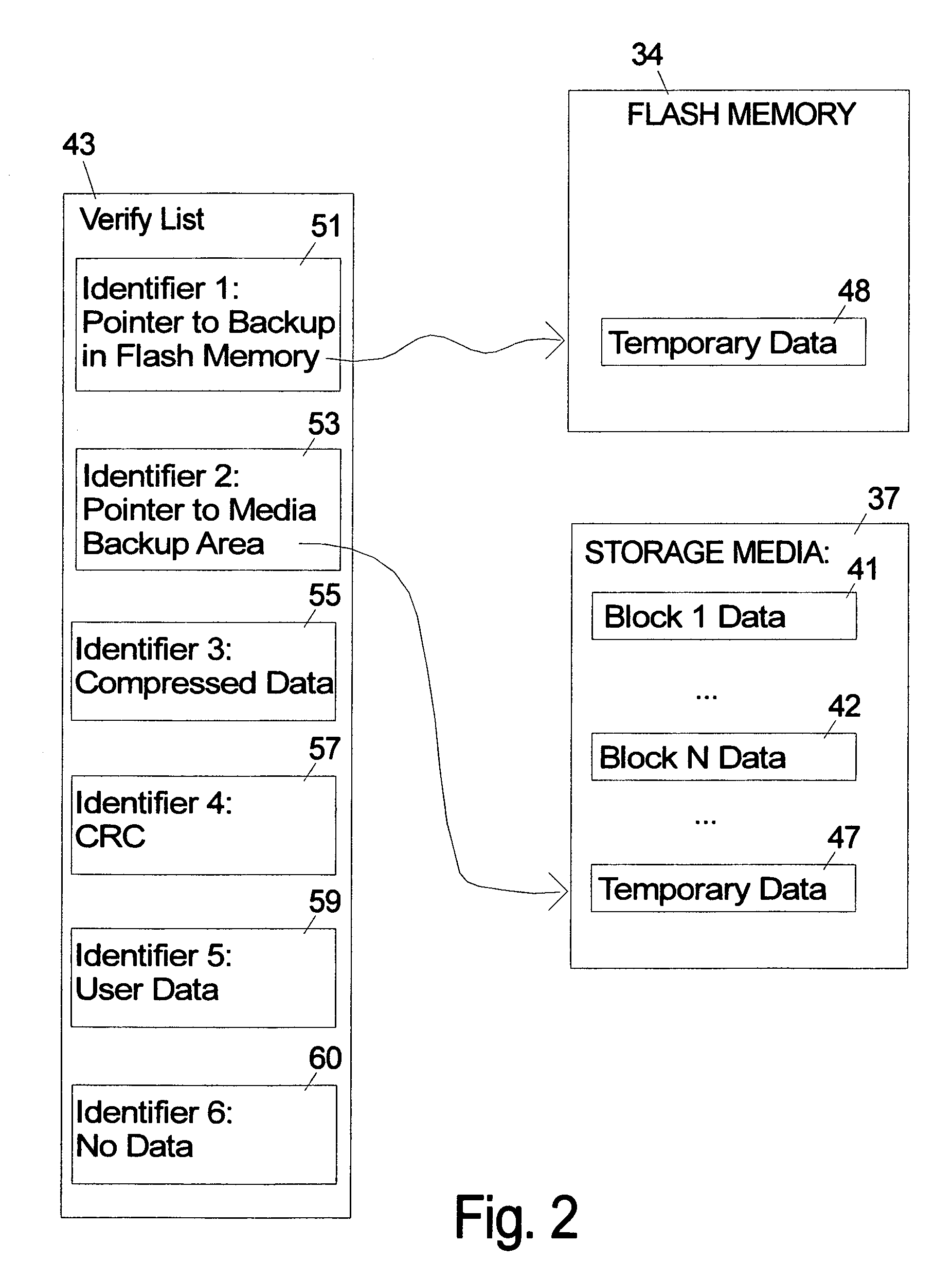
A storage system that stores verify commands for all the write commands requiring verification in a verify-list that will be processed as a background task is described. The verify-list can include coded data fields that flexibly designate selected alternative states or possibilities for how and where the user data is actually stored. Alternatives for the verify-list include storing the actual raw data, no data, the data in compressed form, a CRC type signature of the data and / or a pointer to a backup copy of the data that is stored either in non-volatile memory such as flash memory or on the disk media in a temporary area. In case of a verification error in various alternative embodiments the user data can be recovered using the backup copy in the verify-list in the write cache, the backup copy in flash memory or on the disk, or from the host.
Owner:WESTERN DIGITAL TECH INC
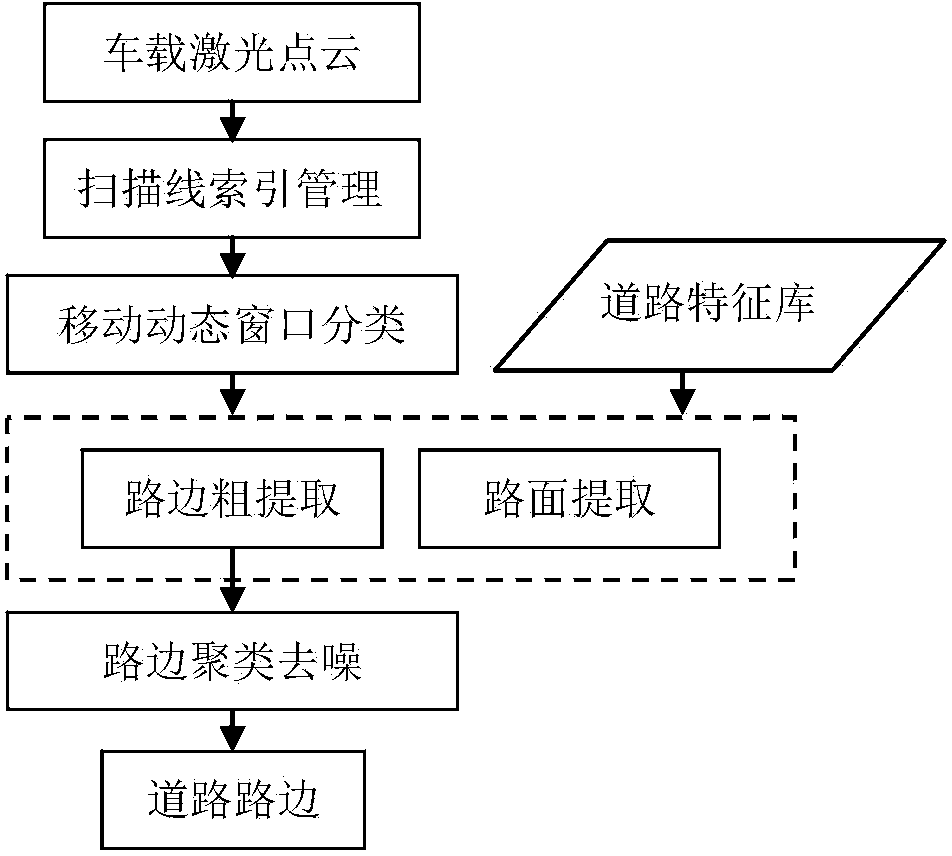
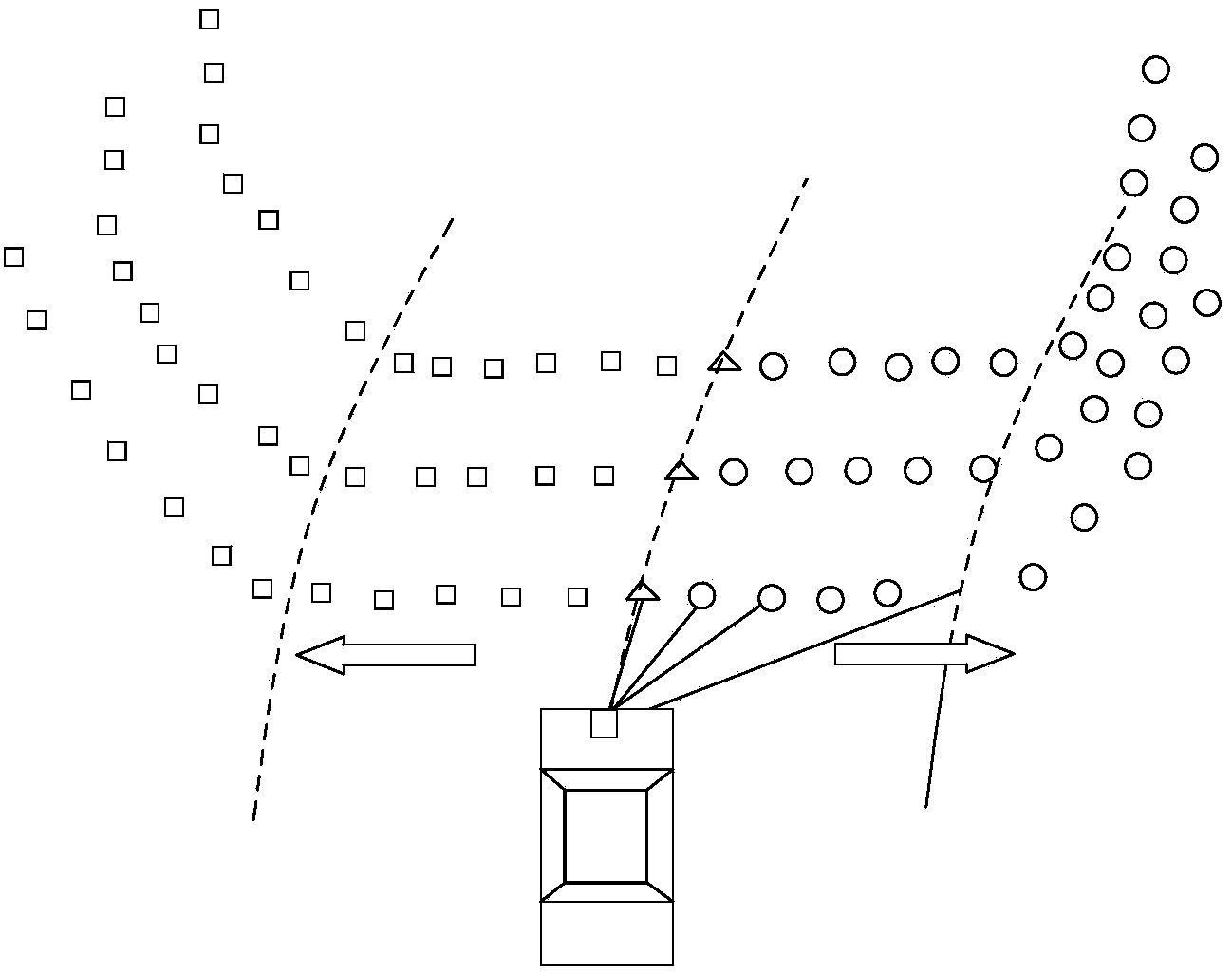
Method for automatically extracting road information in vehicle-mounted laser scanning point cloud
The invention discloses a method for automatically extracting road information in a vehicle-mounted laser scanning point cloud. The method for automatically extracting the road information in the vehicle-mounted laser scanning point cloud comprises the steps that all scanning lines are extracted from the discrete point cloud according to the information, such as the traveling track, the laser point scanning angle and the scanning time, which is recorded by a vehicle-mounted system, and a half scanning line index suitable for data processing is established; the spatial relation between two adjacent points is analyzed, laser point generation clustering is conducted, and dynamic window point sets which can describe the type characteristics of certain types of ground objects are generated; the main geometrical characteristic factors, comprising elevation difference factors and horizontal projection distance factors, of the different ground object window point sets are analyzed; window starting point types are judged according to the main geometrical characteristic factors of the window point sets, movement type dynamic window classification is conducted from a central angle point to the two sides according to the half scanning line index until a non-road-surface point is found; clustering and denoising are conducted on roadside points according to the distribution relation of bottom points of roadside stones and by the adoption of the principle of consistency between the scanning angle and the distance.
Owner:QINGDAO XIUSHAN MOBILE SURVEYING CO LTD
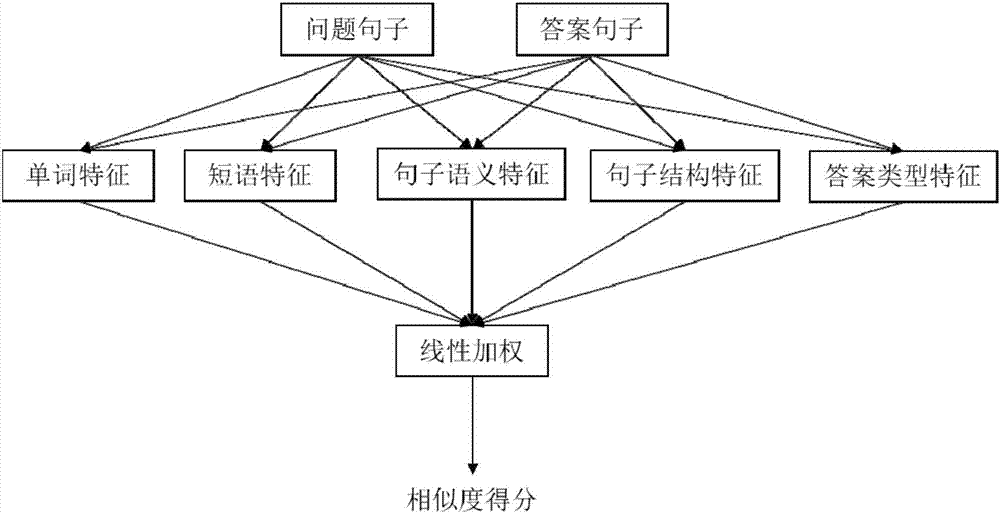
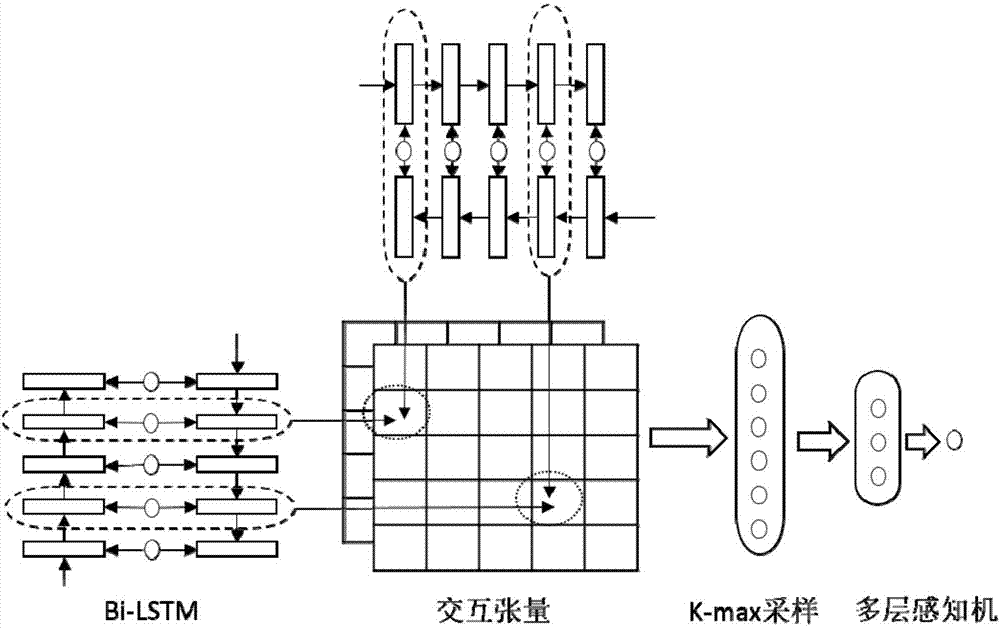
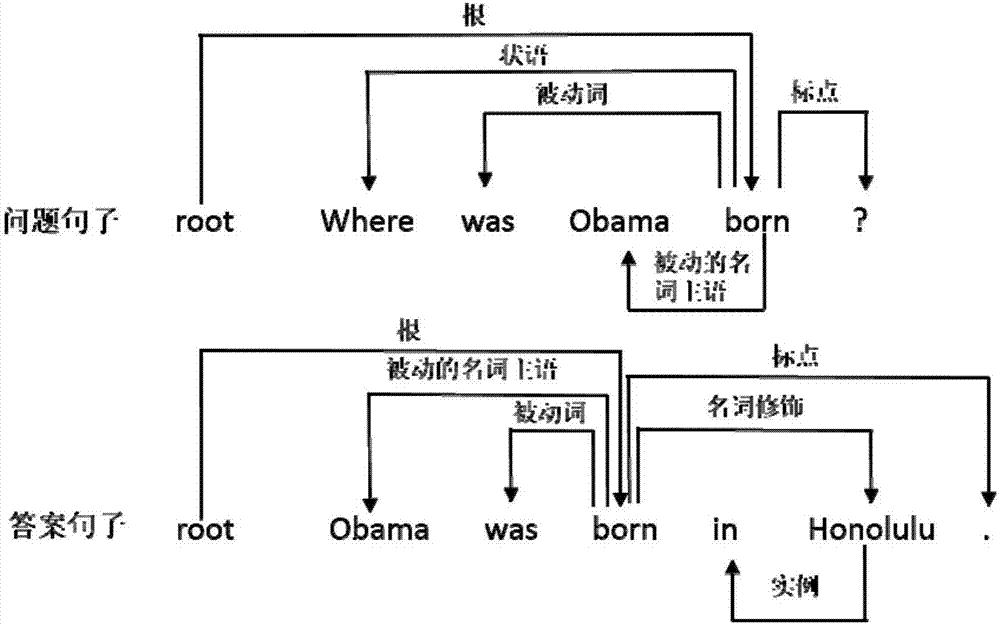
Question and answer sentence similarity calculation method based on multilevel characteristics
The invention discloses a question and answer sentence similarity calculation method based on multilevel characteristics, and is mainly applied to an automatic question-answering system. The method totally comprises five characteristic functions, wherein each characteristic function is independently used for measuring a similarity among different angles between two sentences; a word-level characteristic measures the similarity of two sentences on an aspect of words; a phrase-level characteristic can measure a similarity between an idiom and a phrase in common use; a sentence semantic characteristic can measure the similarity of the two sentences on an aspect of meanings; a sentence structure characteristic can measure the similarity of the two sentences on an aspect of grammar and syntax; an answer type characteristic can measure whether a required answer type is contained in an answer sentence; and finally, through a linear function, the five characteristic functions are subjected to weighted summation to form a question and answer sentence similarity algorithm based on multilevel characteristics. By use of the method, the similarity between a question sentence and an answer sentence can be comprehensively measured.
Owner:ZHEJIANG UNIV
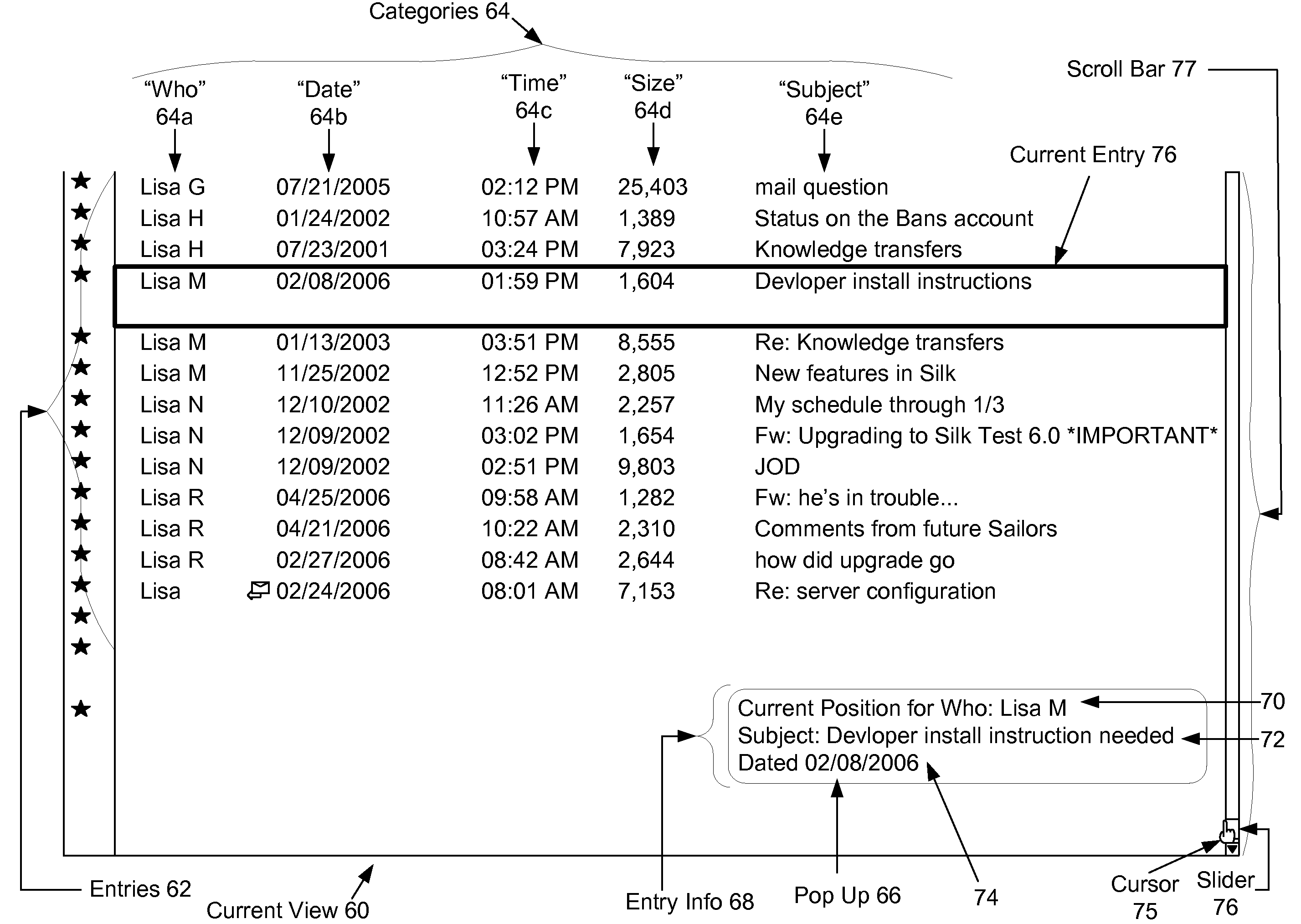
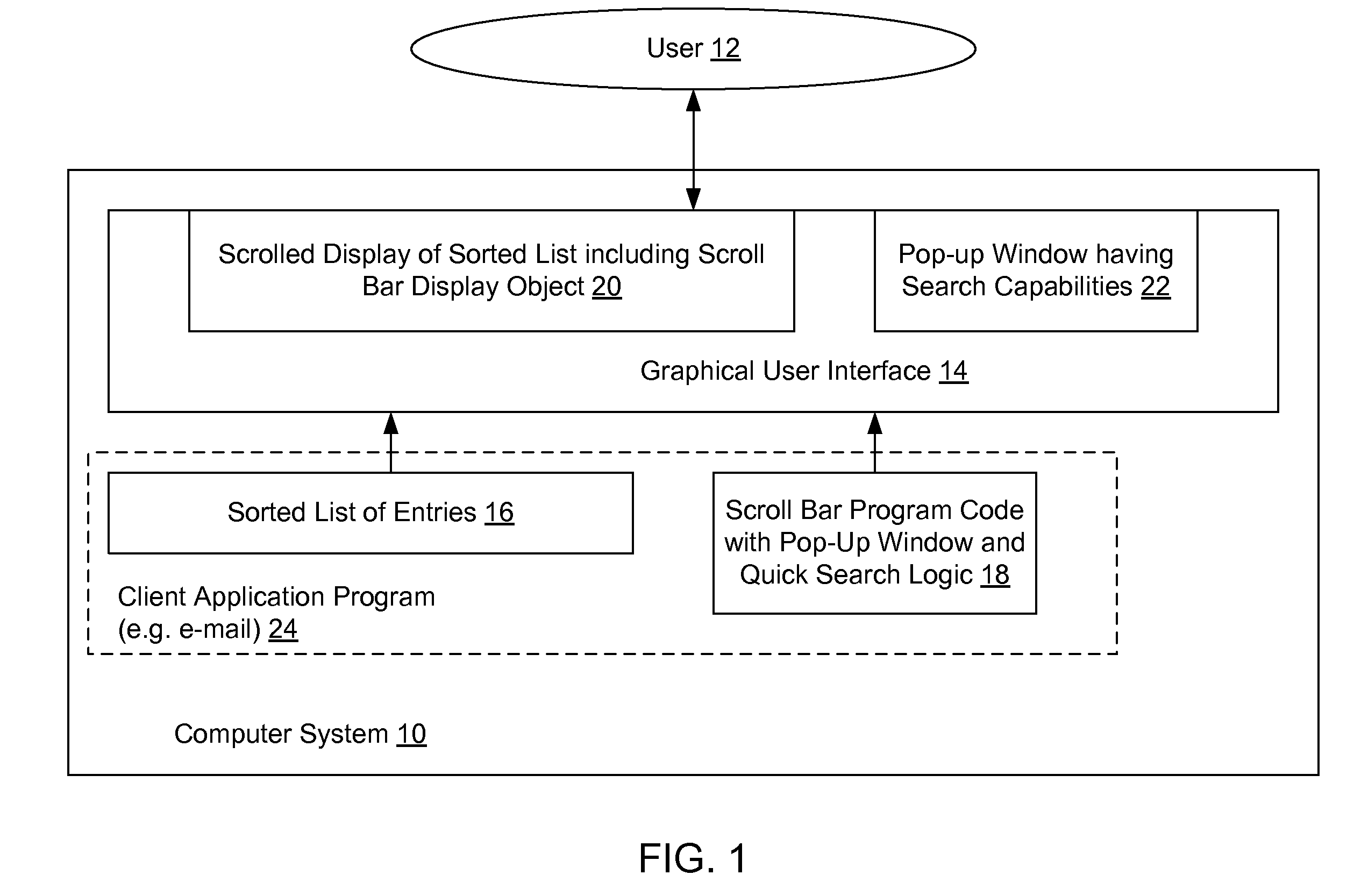
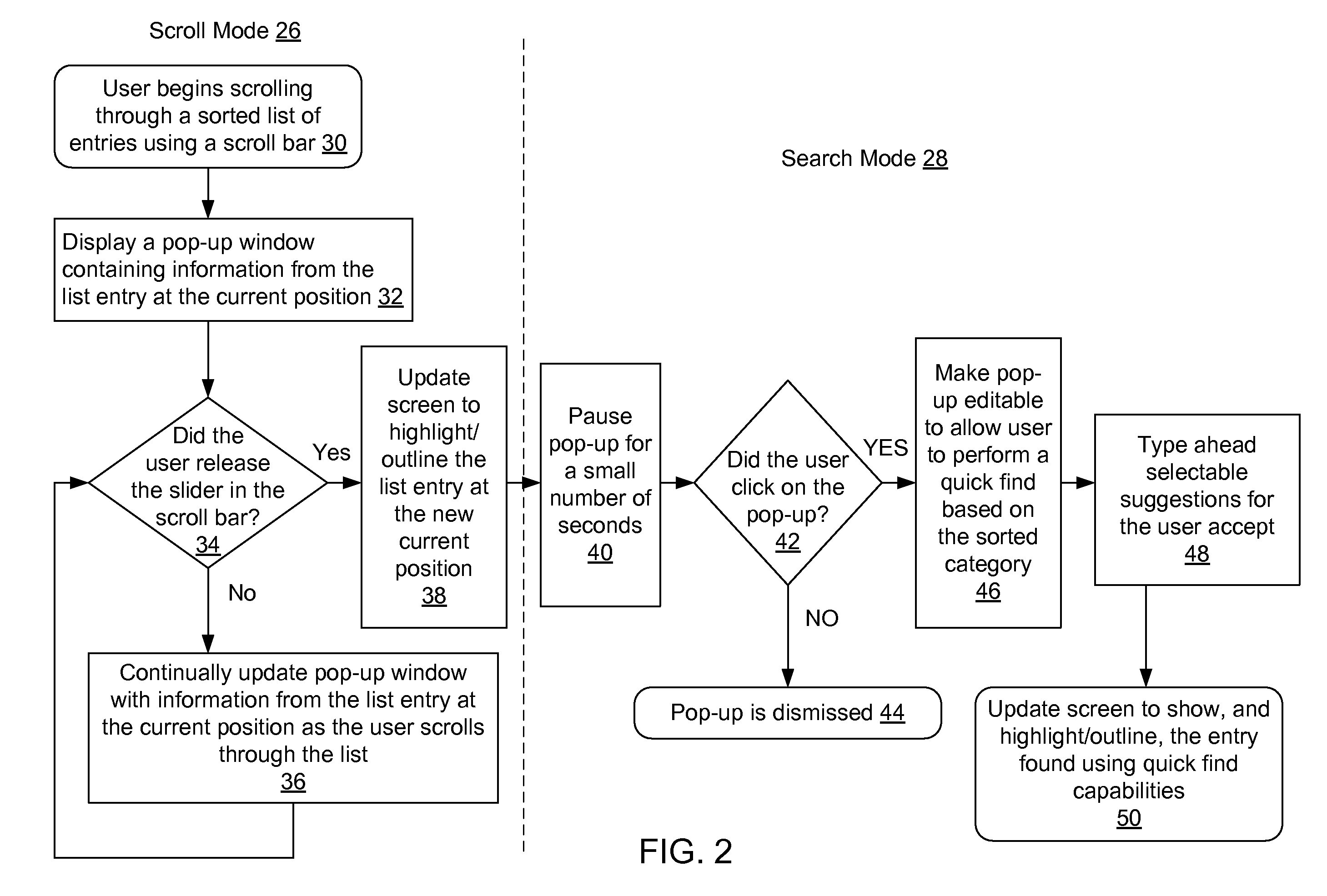
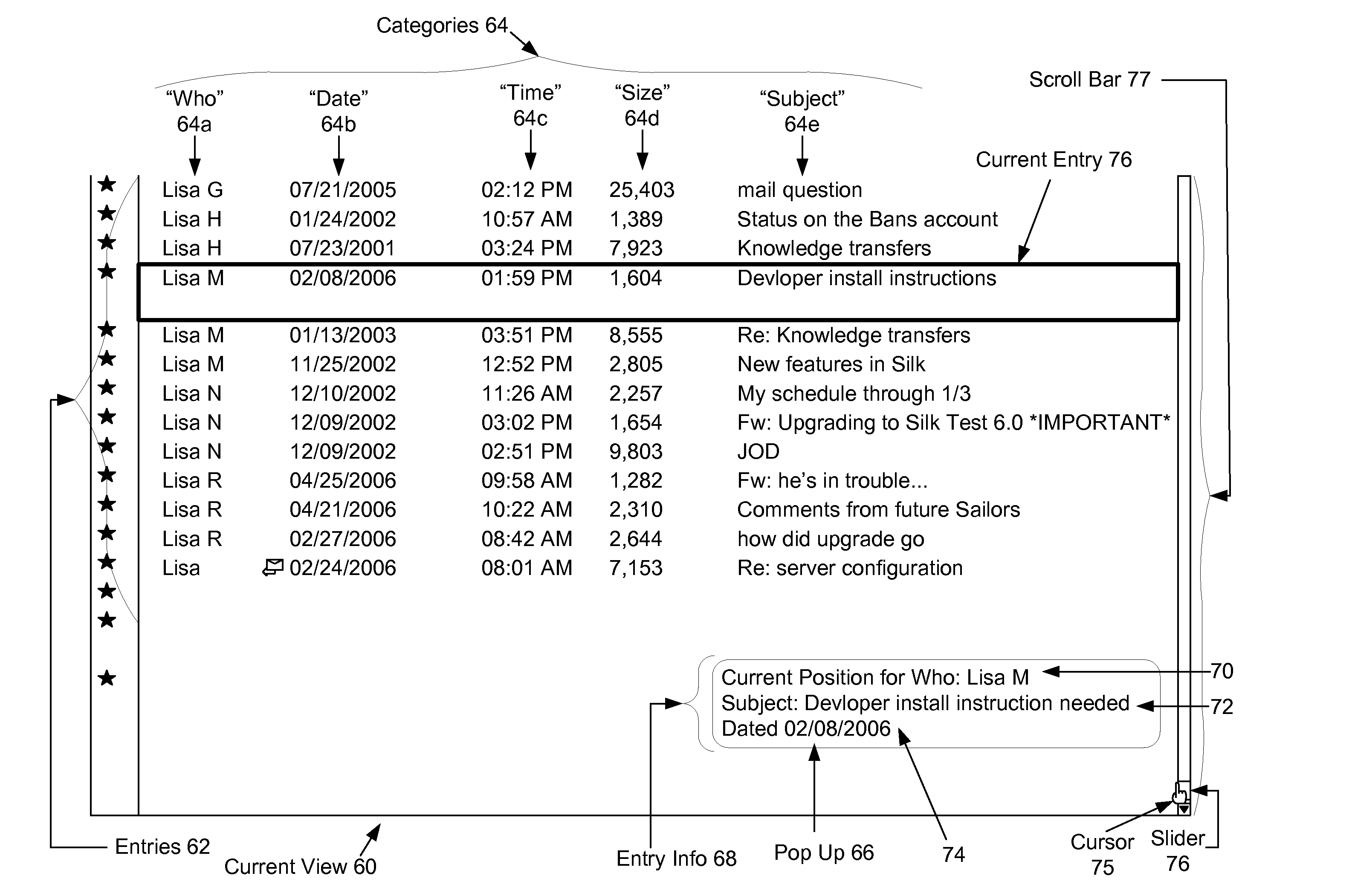
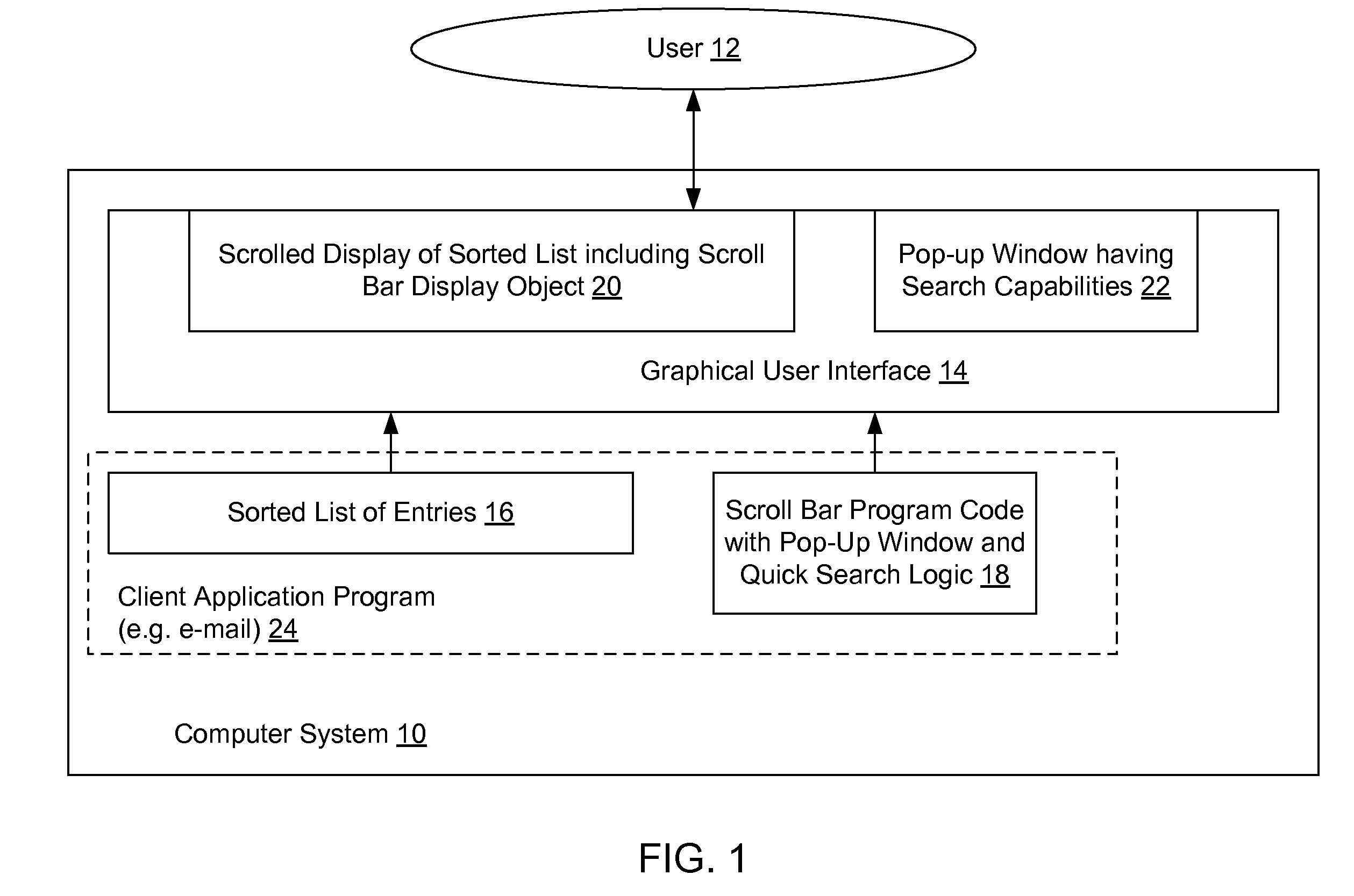
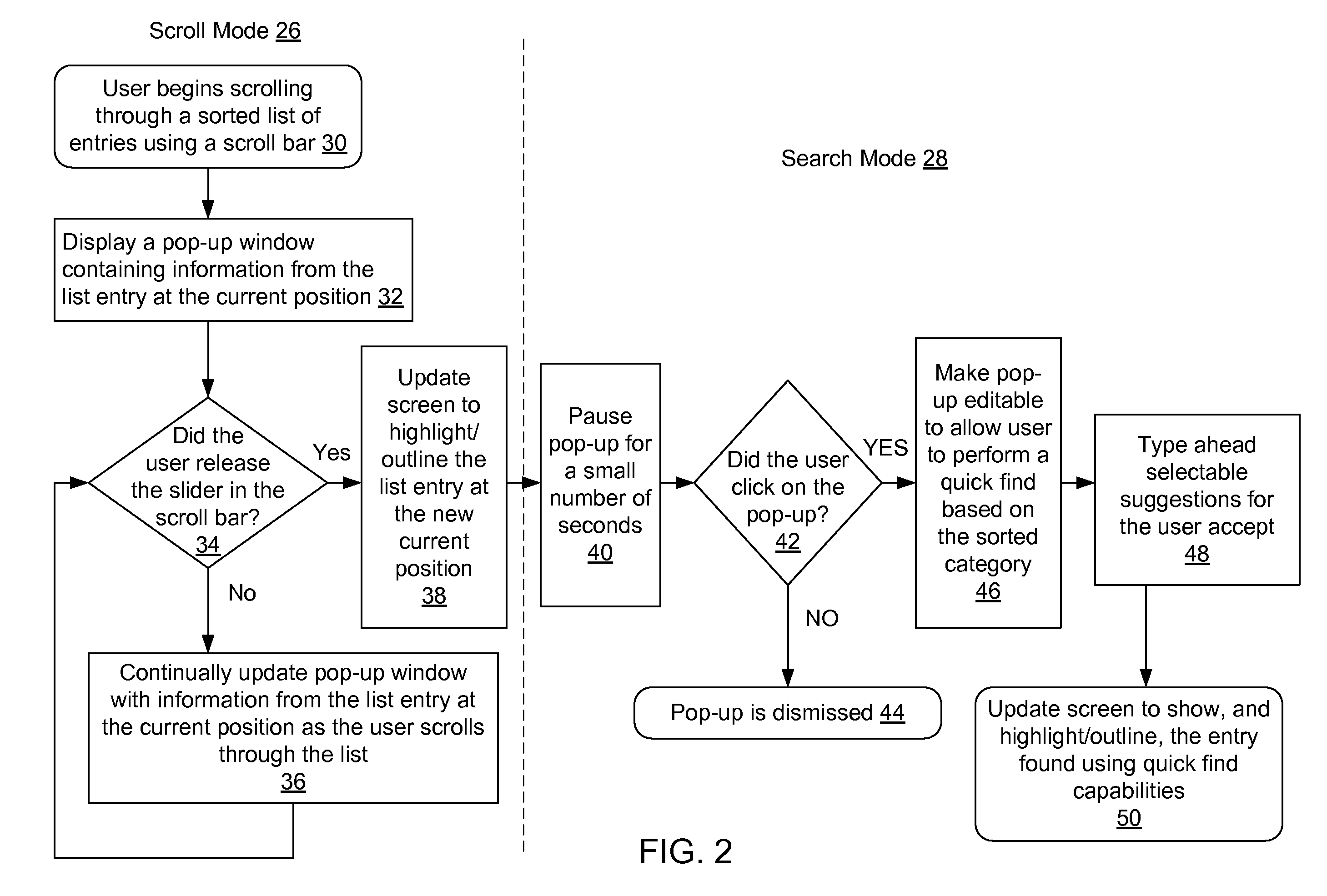
Method and system for providing a scroll-bar pop-up with quick find for rapid access of sorted list data
InactiveUS20080155464A1Easy to modifyAddressing slow performanceInput/output processes for data processingRapid accessMultiple category
A pop-up window is generated when the user clicks on the slider within the scroll bar display object. The pop-up window displays information from one or more categories in a currently selected list entry, including the category on which the list is currently sorted. As the user moves the slider, the information in the pop-window is updated to reflect the current location in the list, as determined by the current location of slider within the scroll bar. When the user stops scrolling, i.e. releases the scroll slider, the matching entry for the current location becomes highlighted, and the system enters a search mode. In the search mode, the disclosed system continues to display the pop-up window for a few seconds to allow the user the option of editing the text in the pop-up (as derived from the current position in the list) in order to go to another entry in the sorted list. Accordingly, the sorted category information loaded from the current list entry becomes editable within the pop-up window with a type ahead feature allowing the user to see and select from and search based on information from list entries in the sorted data that closely match the text that the user has typed into the pop-up window. When the user presses “Enter”, the current view and scroll bar position are relocated to reflect the position of the entry matching the selected search information.
Owner:GOOGLE LLC
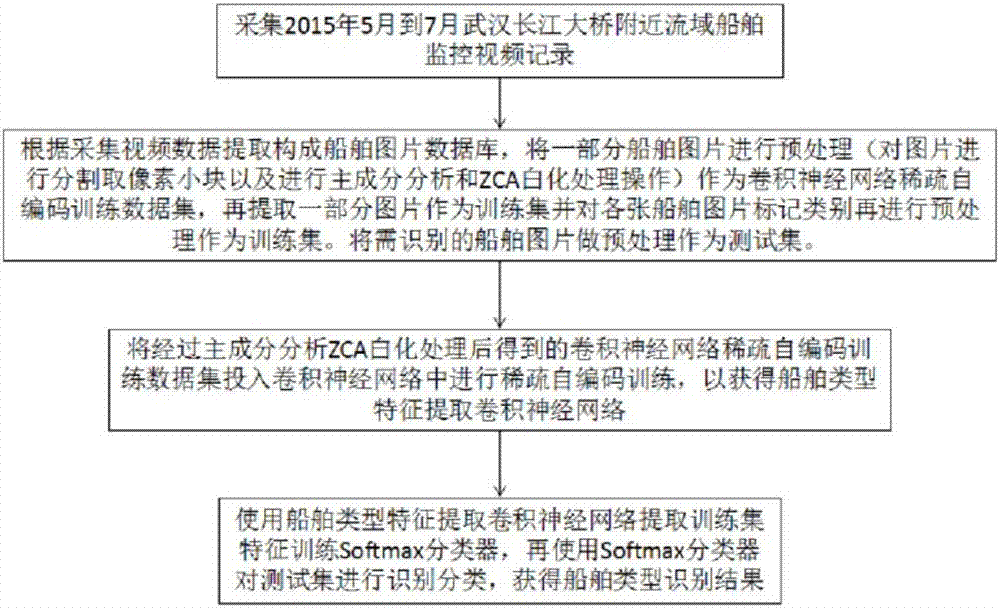
Convolutional neural network picture feature extraction-based ship type identification method
InactiveCN107145903AFunctionalCharacter and pattern recognitionNeural learning methodsData setFeature extraction
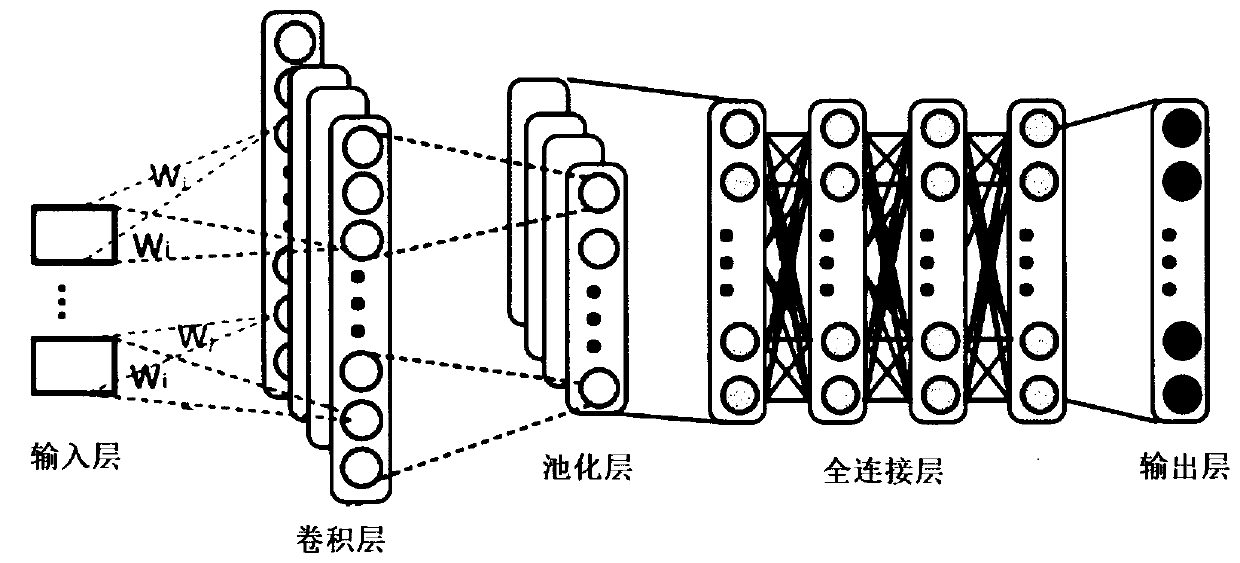
A convolutional neural network picture feature extraction-based ship type identification method disclosed by the present invention comprises the following steps of 1) acquiring a lot of unclassified water running ship pictures to carry out the image pre-processing, taking the processed pictures as a convolutional neural network sparse self-coding training data set to train to obtain a ship type feature extraction convolutional neural network; 2) extracting the training set from the water running pictures, marking the types of the ship pictures, and then inputting in the trained convolutional neural network to extract the picture features of the pictures as the training data set of a Softmax classifier to train; 3) inputting the ship pictures needing to be identified in the convolutional neural network to extract the ship features in the pictures, and inputting the ship features in the trained Softmax classifier to classify and outputting the ship types corresponding to the ships. The convolutional neural network picture feature extraction-based ship type identification method of the present invention can apply to the continuous changing environments and the undetermined inputted data, and can identify the ship types rapidly and accurately.
Owner:WUHAN UNIV OF TECH
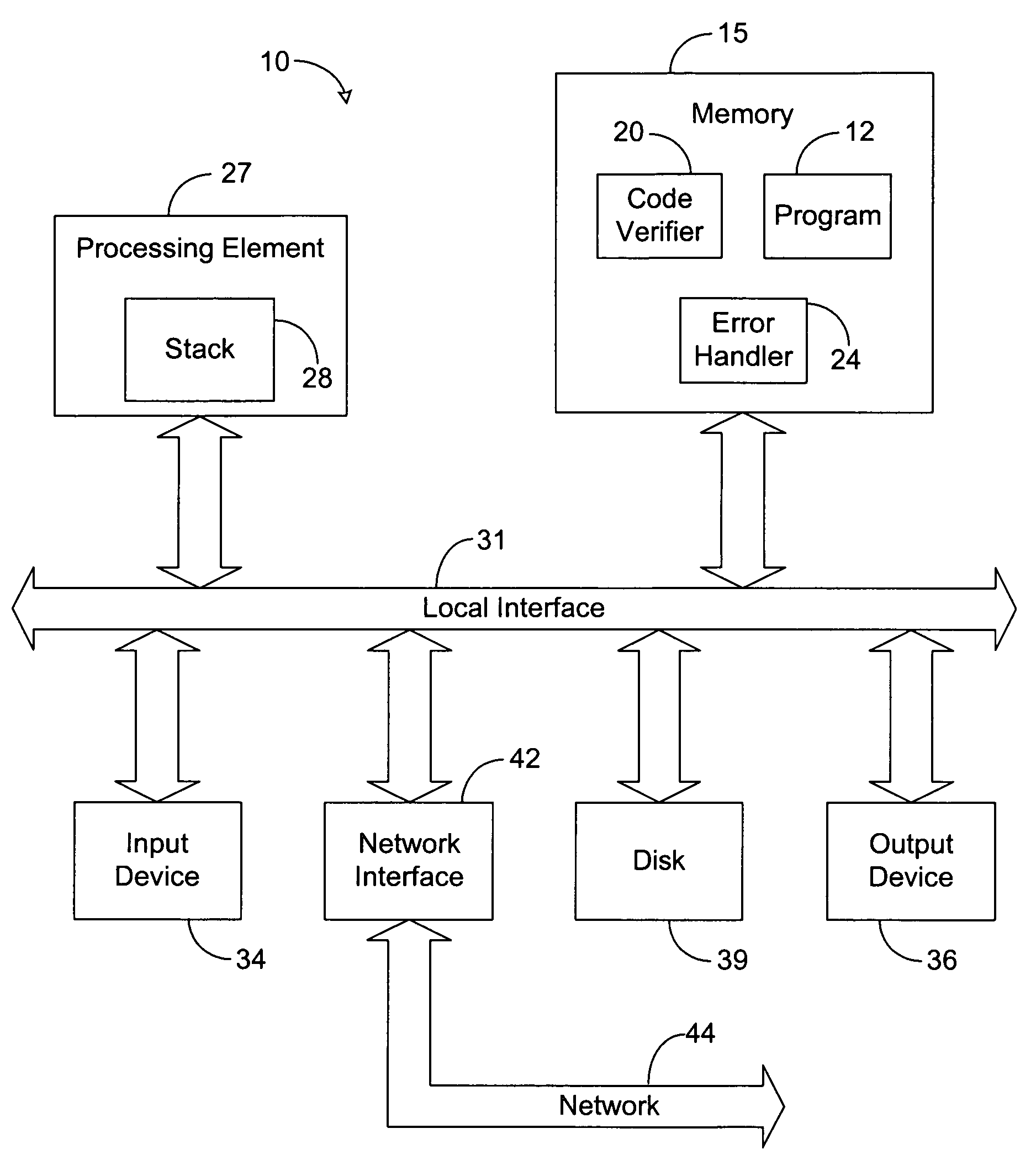
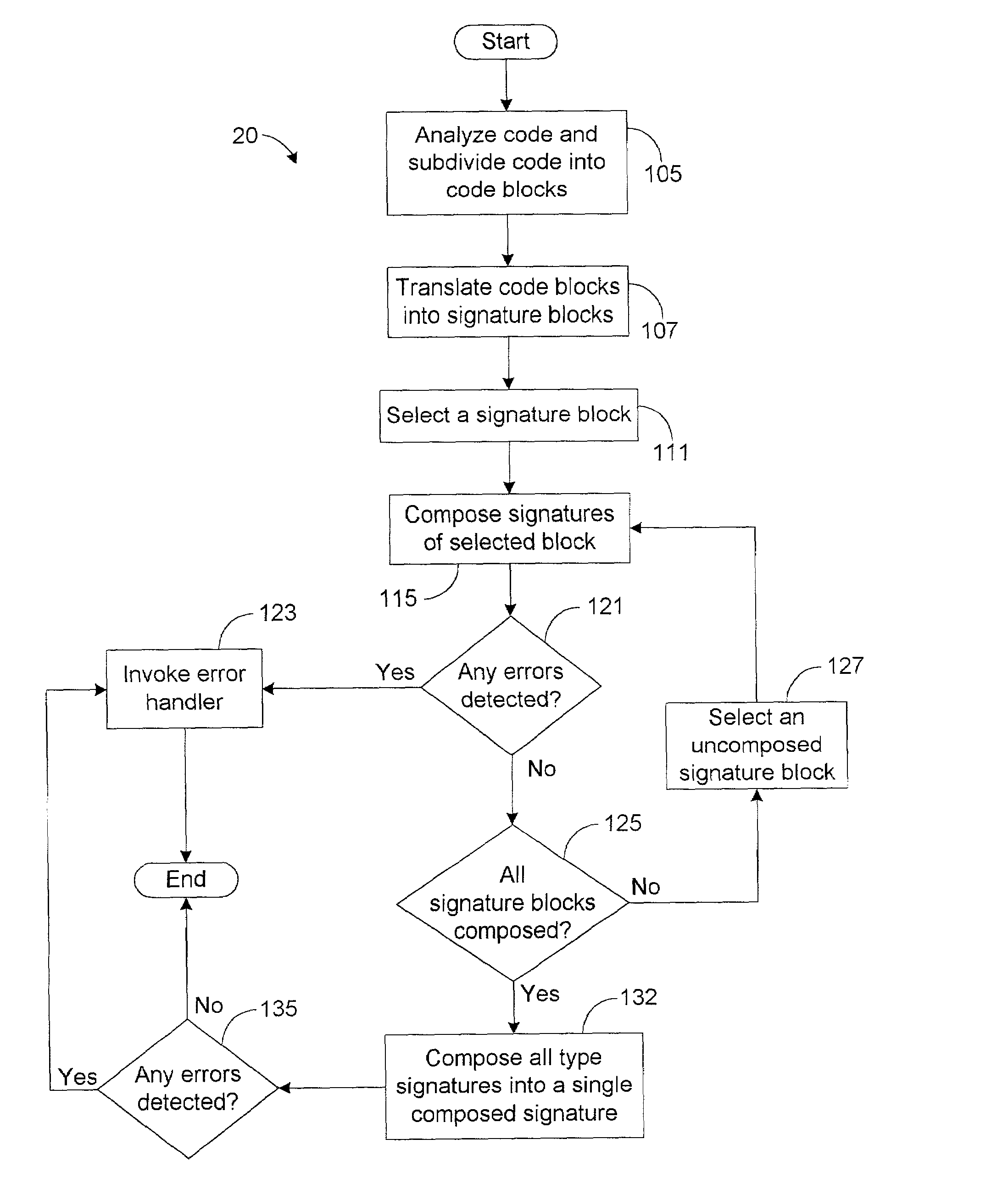
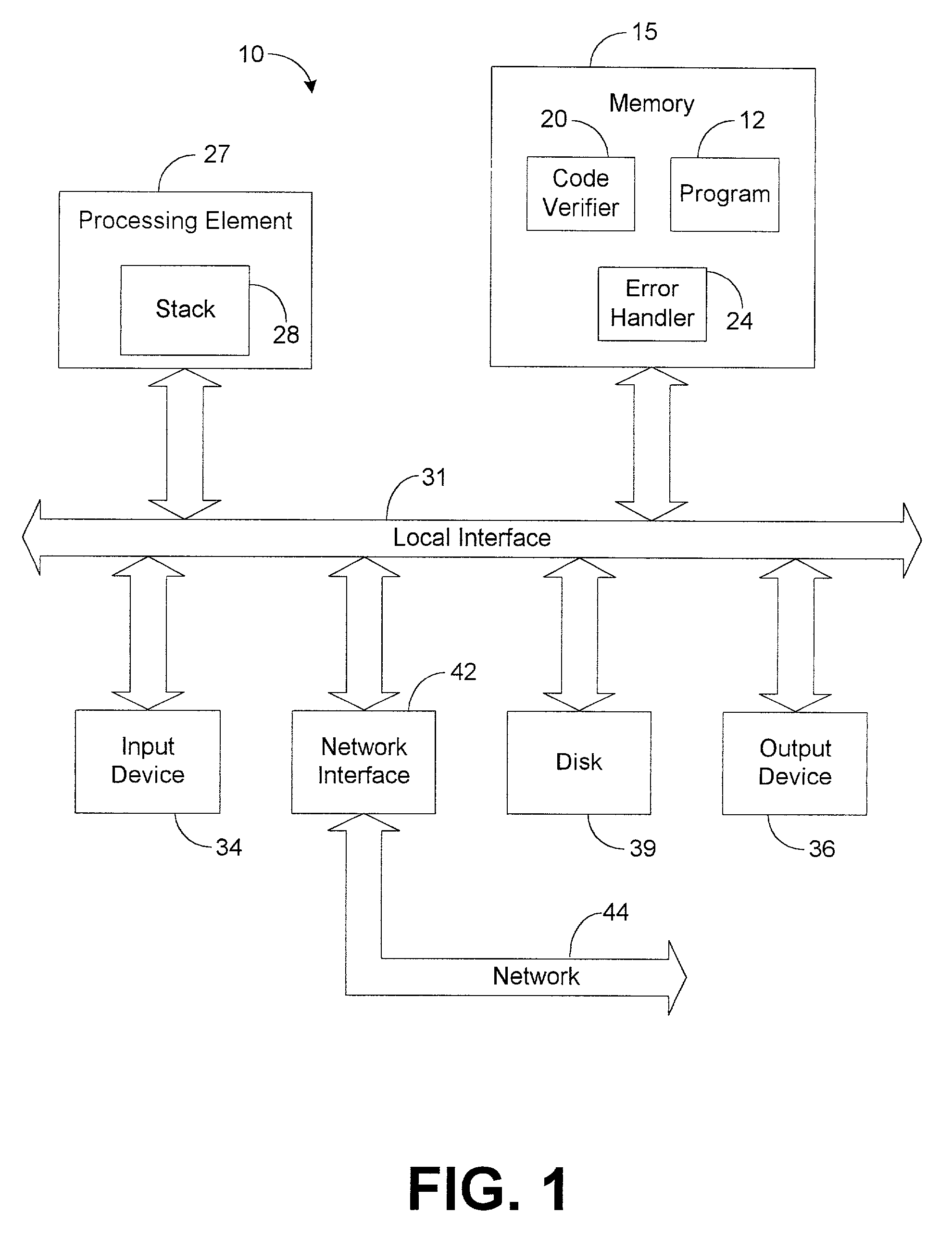
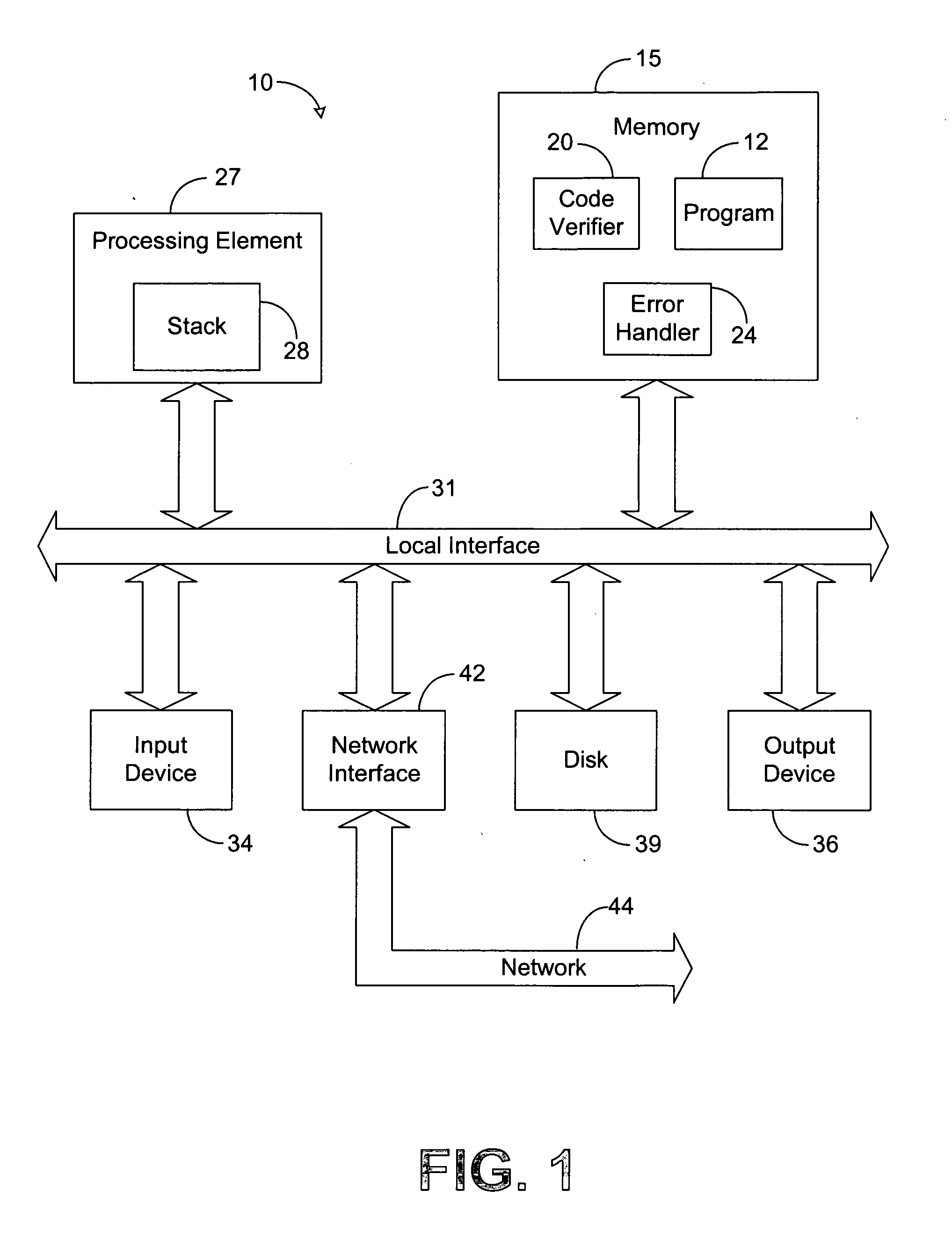
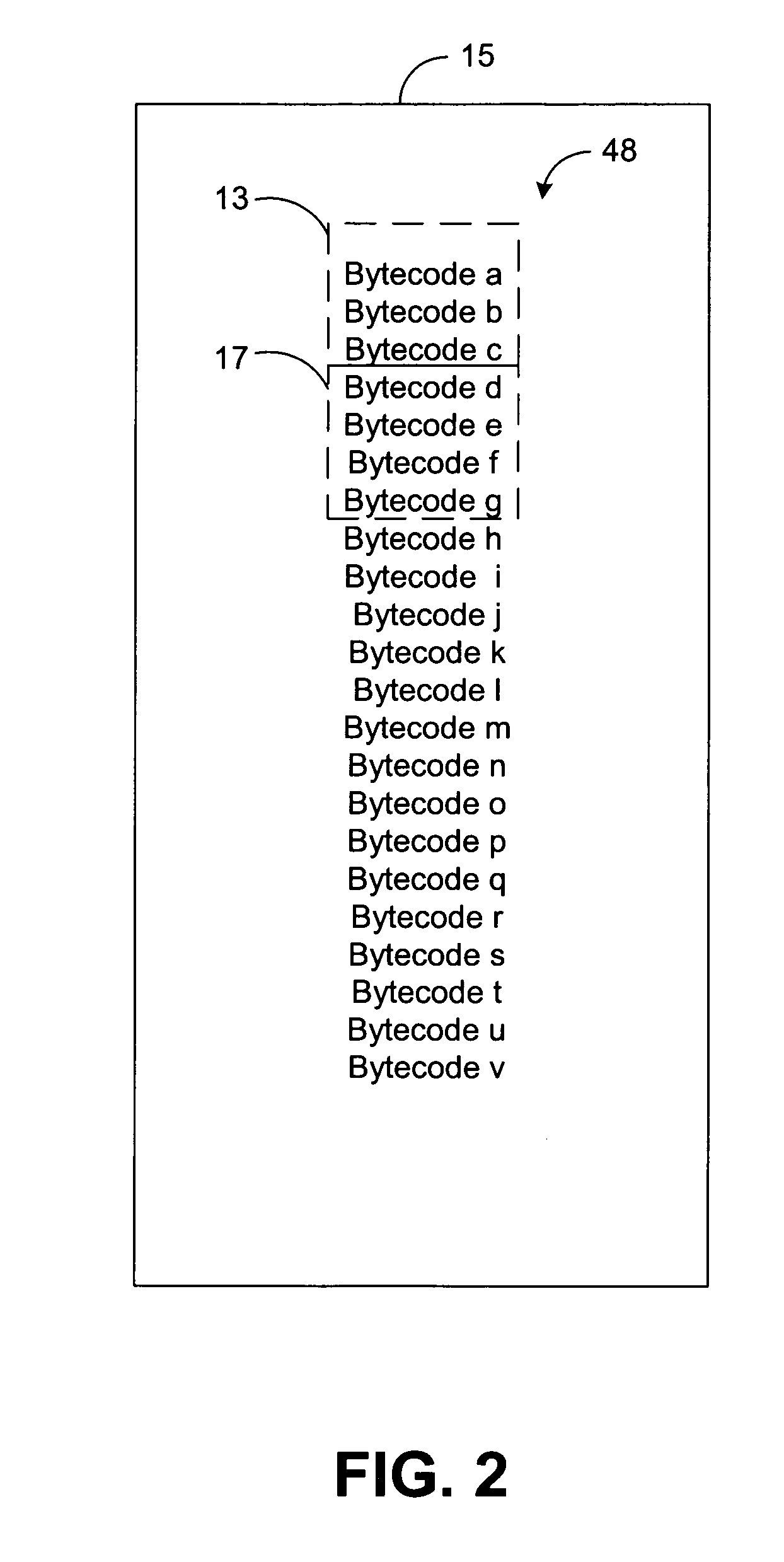
Code verification system and method
InactiveUS7287243B2Error detection/correctionSpecific program execution arrangementsType signatureVerification system
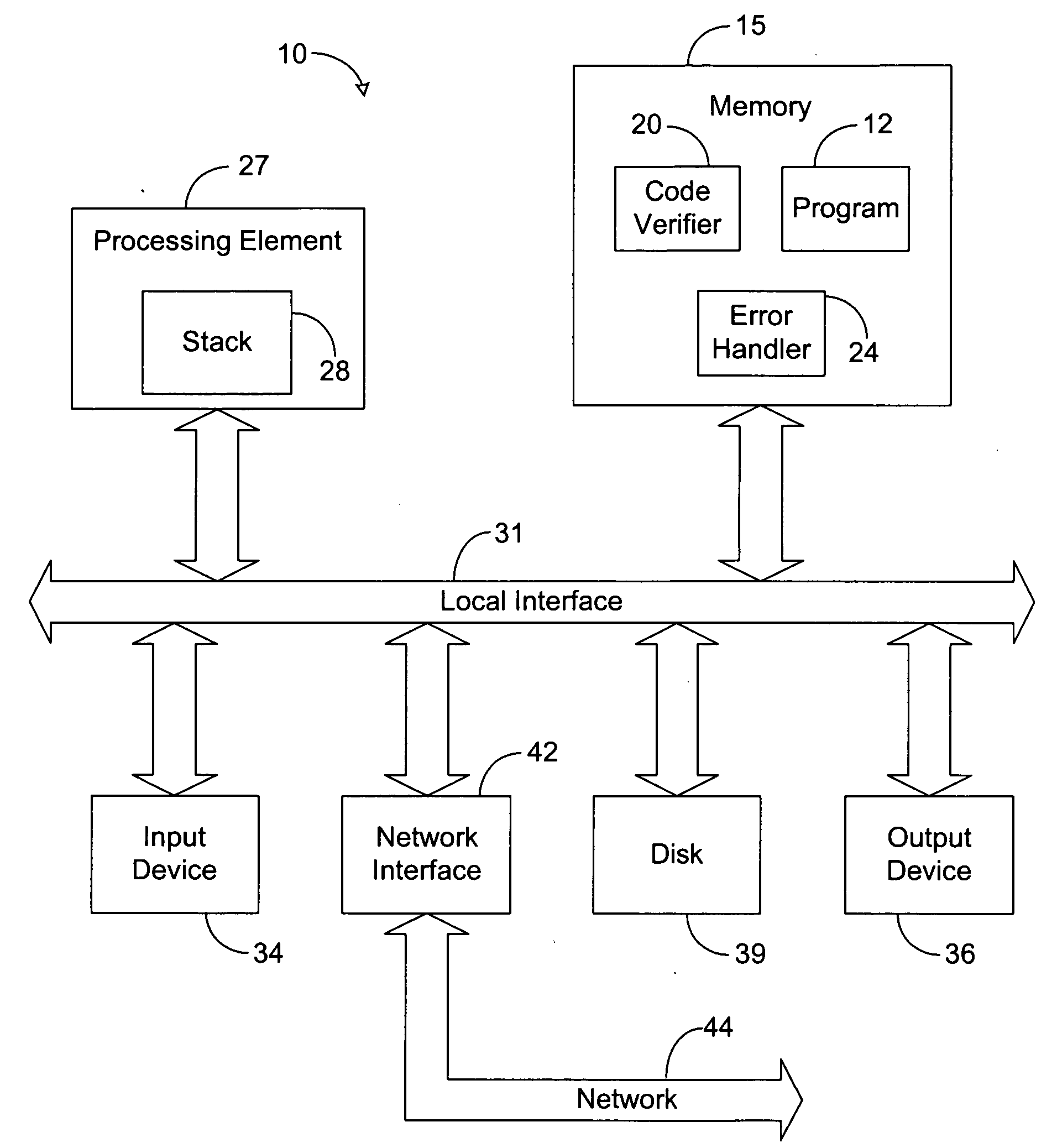
The system of the present disclosure comprises memory for storing a compiled program. The system further comprises logic configured to translate the compiled program into a set of human-readable instructions and construct a coarse tree representing the program flow of the set of human-readable instructions. The logic is further configured to compute a first type signature representative of a code construct comprising alternative code paths within the program flow and determine a second type signature representative of the coarse tree based upon the first type signature.
Owner:HEWLETT PACKARD DEV CO LP
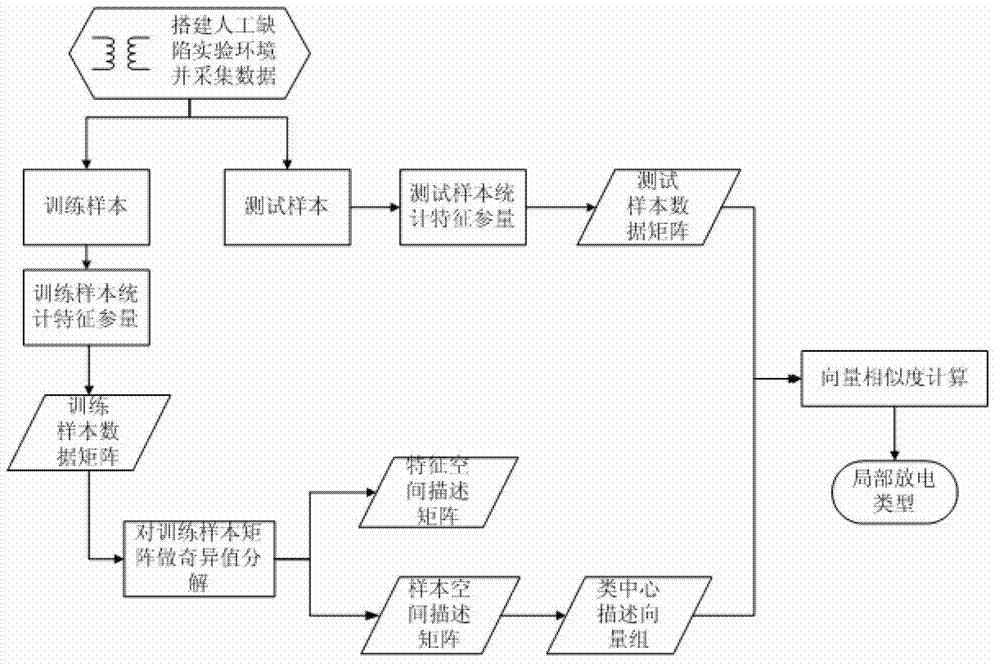
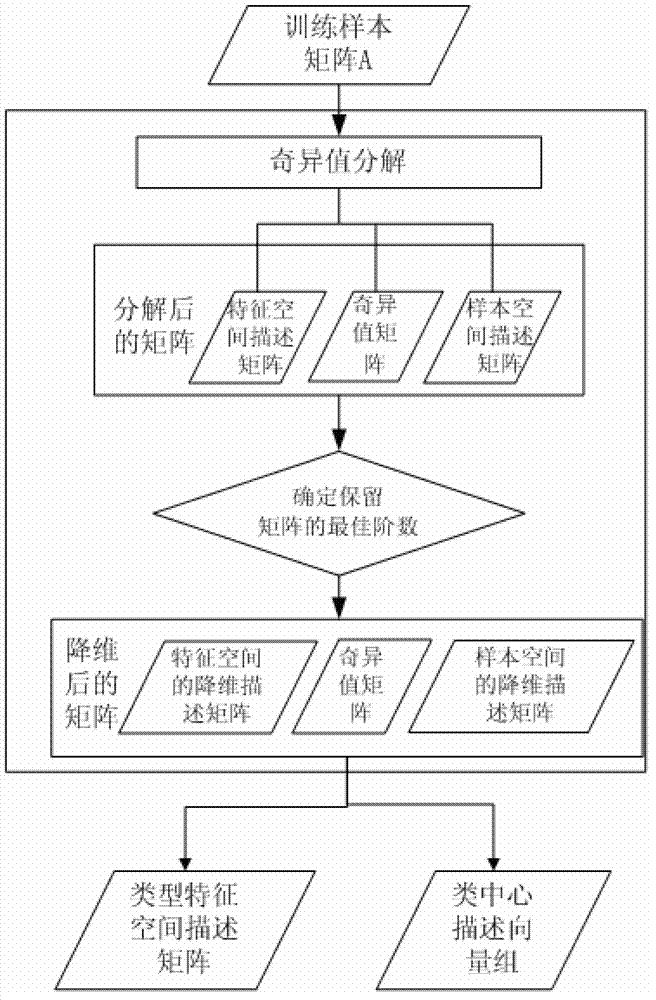
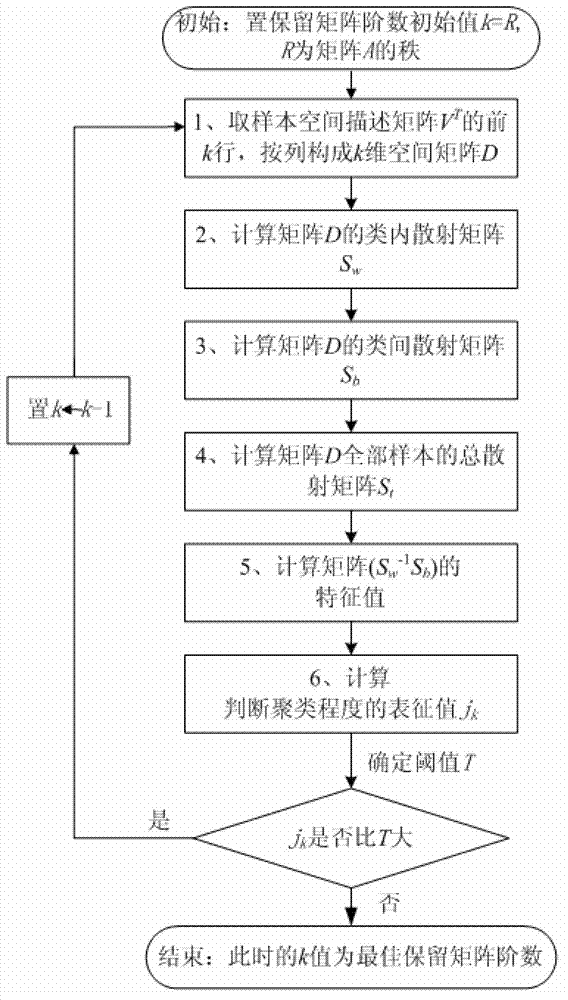
Transformer partial-discharging mode recognition method based on singular value decomposition algorithm
ActiveCN103077402AImprove efficiencyIncrease profitTesting dielectric strengthTransformers testingSingular value decompositionTransformer
The invention discloses a transformer partial-discharging mode recognition method based on a singular value decomposition algorithm, and the transformer partial-discharging mode recognition method comprises training model and classification recognition process, and the method comprises the steps of firstly establishing an artificial defect experimental environment, collecting data samples, calculating statistic characteristic parameter of each sample to form a data sample matrix; conducting singular value decomposition for the sample matrix, determining an order of an optimum reserved matrix by judging whether the characteristic of the reserved matrix is obvious or not, and obtaining a type characteristic space description matrix after the dimensionality reduction and a class center description vector group; preprocessing the sample to be recognized to obtain a sample vector, utilizing the type characteristic space description matrix to linearly convert the sample vector to obtain the sample description space vector after the dimensionality reduction, and then calculating the similarity of the vector with each vector in the type vector group to obtain a classification judgment result. The algorithm is simple and high efficient, reliability for distinguishing an interference signal and a discharging signal in the partial-discharging detection can be realized, and the accuracy for diagnosing the partial-discharging mode can be improved.
Owner:STATE GRID CORP OF CHINA +1
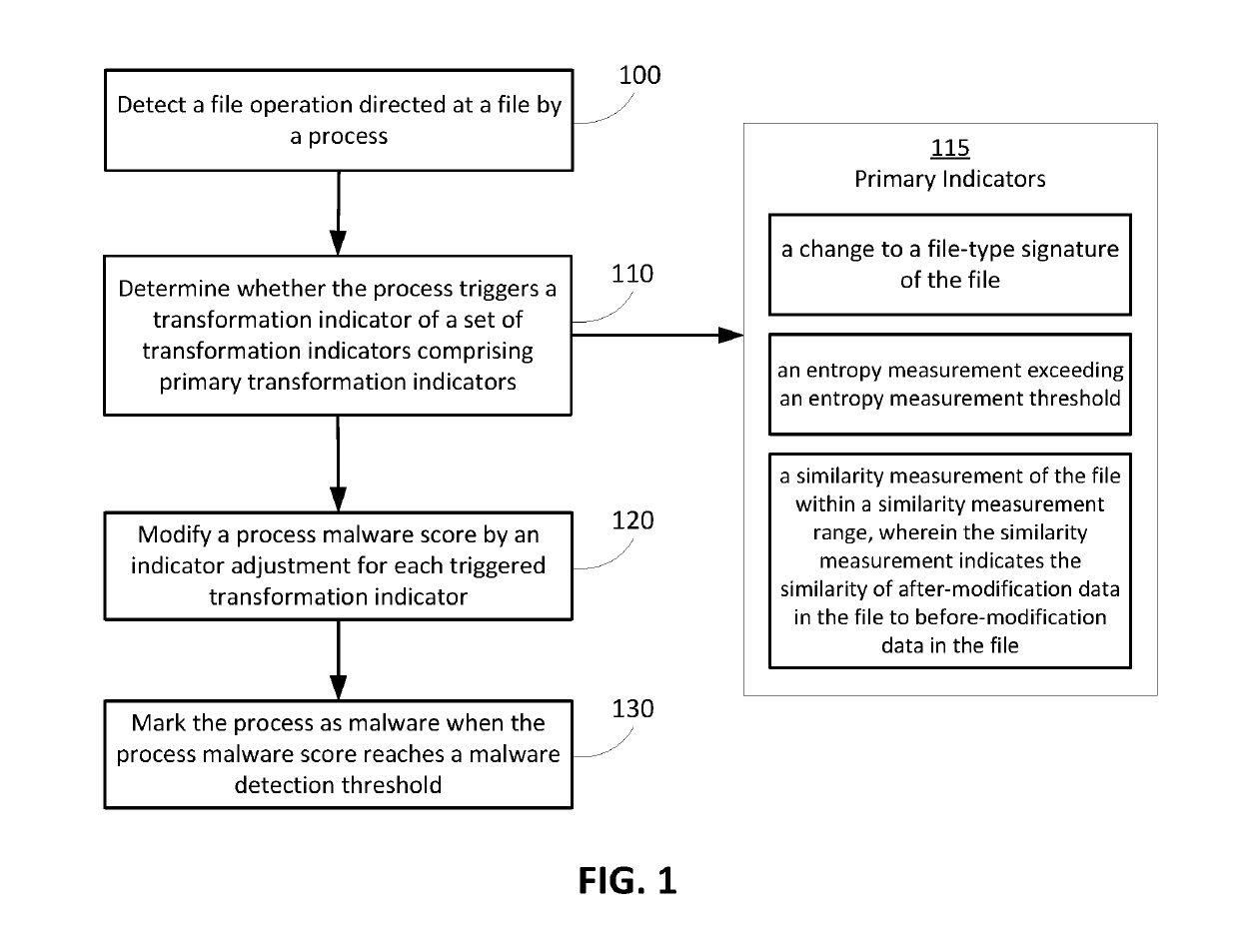
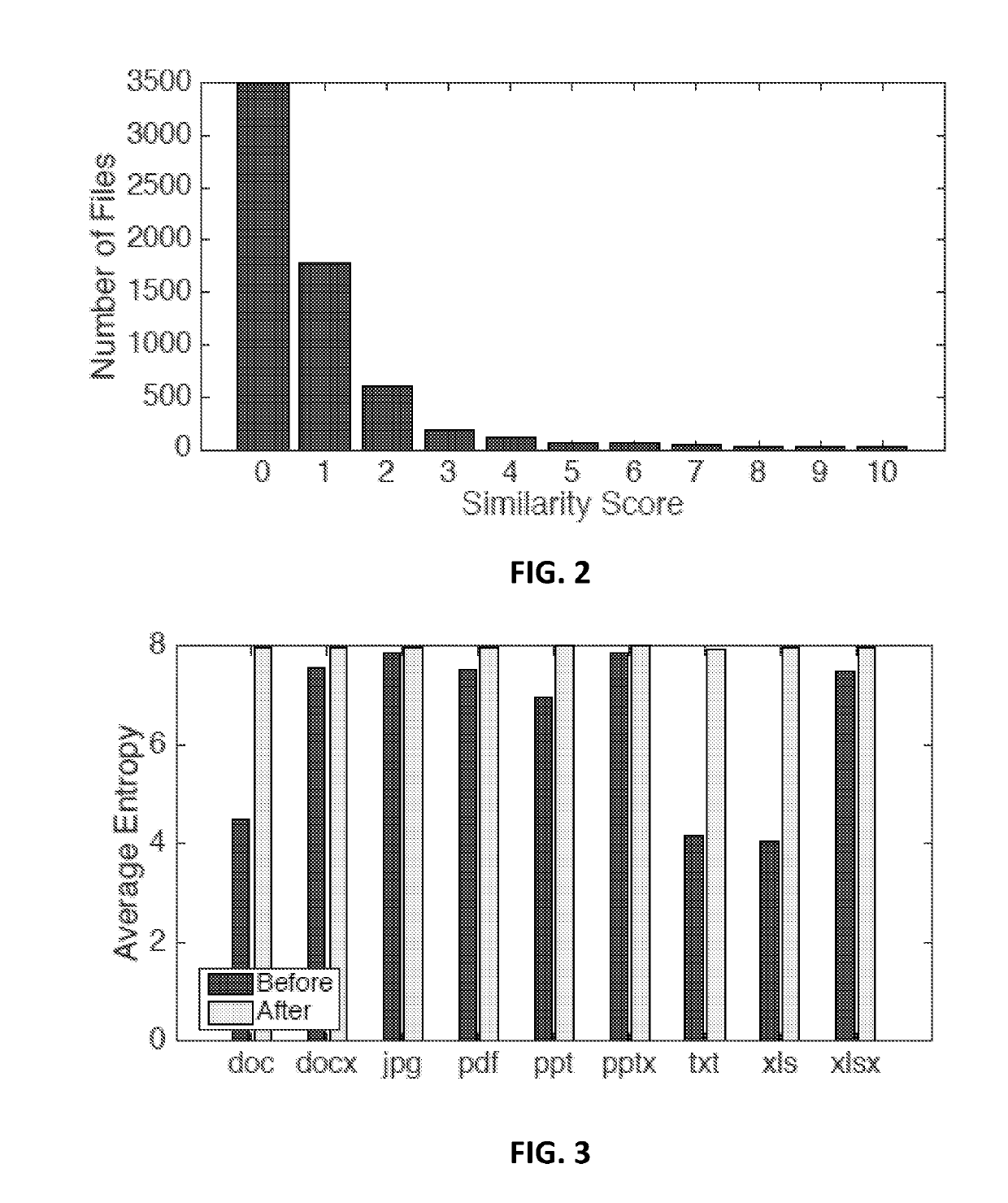
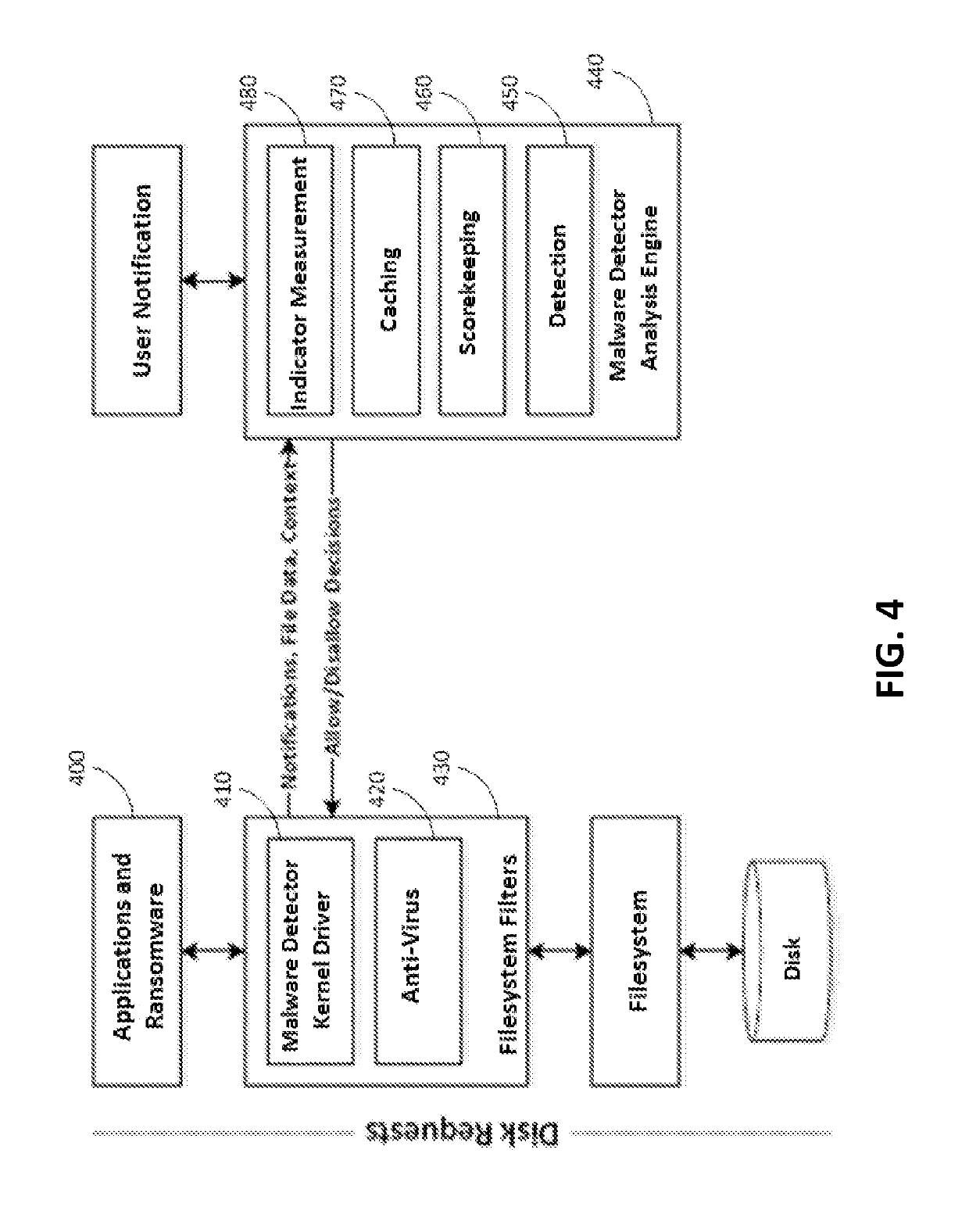
Malware detection via data transformation monitoring
ActiveUS20190228153A1Easy to detectImprove accuracyPlatform integrity maintainancePrimary IndicatorMalware
Techniques and systems are described for detecting malware's bulk transformation of a user's data before the malware is able to complete the data transformation. Included are methods and systems for enabling malware detection by monitoring the file operations of a computer application or process for particular kinds of suspicious data transformation indicators. Indicators include primary indicators, such as file-type signature changes, notable changes in file data entropy, and out-of-range similarity measurements between the read and write versions of file data, as well as secondary indicators, such as a large number of file deletions and a large reduction in the number of file-types written versus read by a process over time. When indicators are triggered by a process, an adjustment to the process' malware score is made; in the event that the process' malware score reaches a malware detection threshold, the process is marked as malware and appropriate actions are taken.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
Method and system for providing a scroll-bar pop-up with quick find for rapid access of sorted list data
InactiveUS7523412B2Easy to browseEasy to startInput/output processes for data processingRapid accessMultiple category
Owner:GOOGLE LLC
System and method for excavating abnormal features of time series data
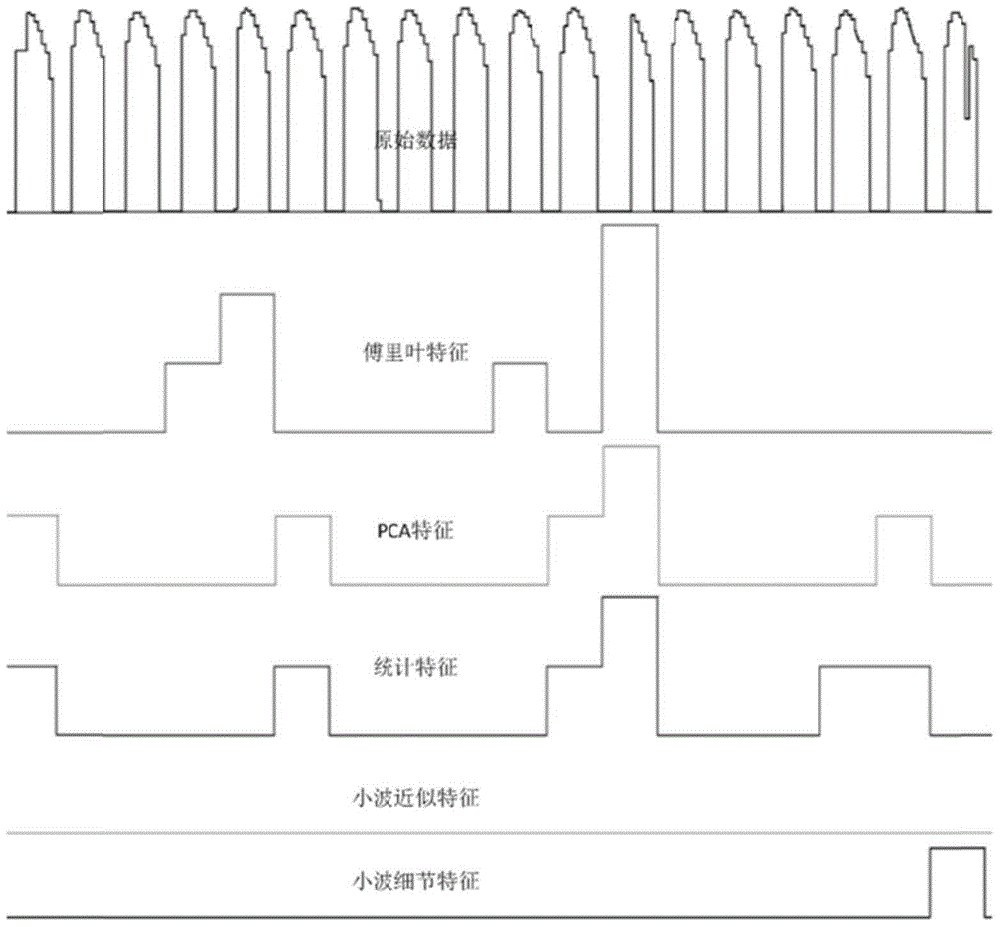
InactiveCN105205112AEfficient use ofDealing with uncertaintyCharacter and pattern recognitionOther databases queryingFeature vectorPrincipal component analysis
The invention discloses a system and a method for excavating abnormal features of time series data. A minimum complete period having obvious periodic data can be acquired in a self-adaptive manner, so that a feature observation window is determined; then the Fourier feature, the principal component analysis feature, the statistic feature and the wavelet feature are extracted from the observation window respectively; finally, clustering is performed on single feature vectors respectively with a KT-Means method, and various features are abstracted and expressed as feature characters. The problem of fuzzy matching of data can be better solved by expressing features of the time series data with the feature characters in a formalized manner, and establishment of a feature library is facilitated for rapid judgment and retrieval of an abnormal process. With the adoption of the method, various feature information is contained, the abnormal process of the time series data can be known more comprehensively and integrally, and the applicability and the generalization ability of a system for abnormity monitoring and fault diagnosis of the time series data can be improved.
Owner:XI AN JIAOTONG UNIV +1
Code verification system and method
A code verification system is utilized to type check compiled code. The code verification system includes memory and a code verifier. The memory is utilized to store a compiled program. The code verifier analyzes instructions of the program and generates a plurality of type signatures based on the instructions The type signatures indicate the input type constraints and the output type descriptions of the instructions, and the code verifier analyzes the type signatures to detect a type error.
Owner:HTC CORP
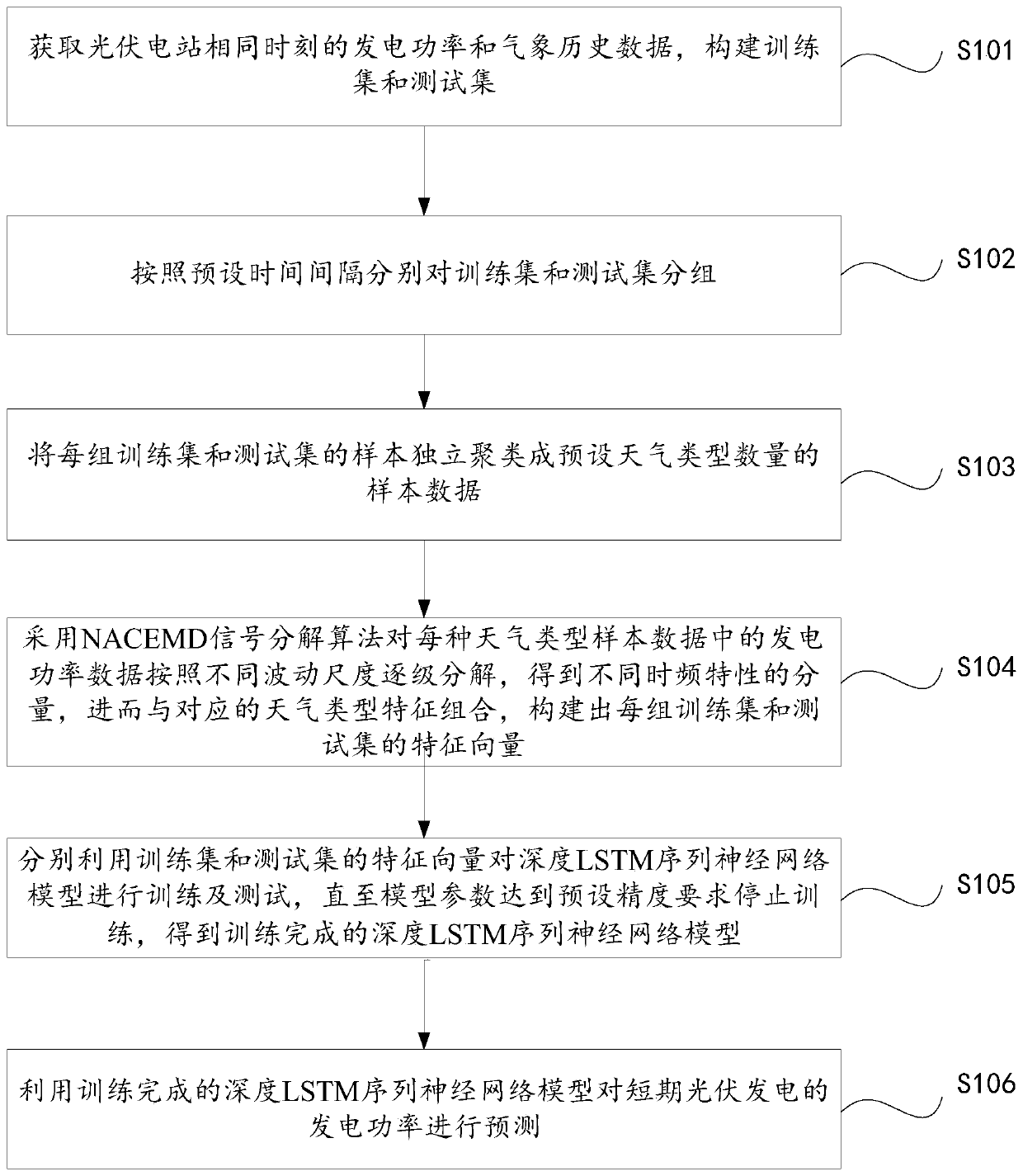
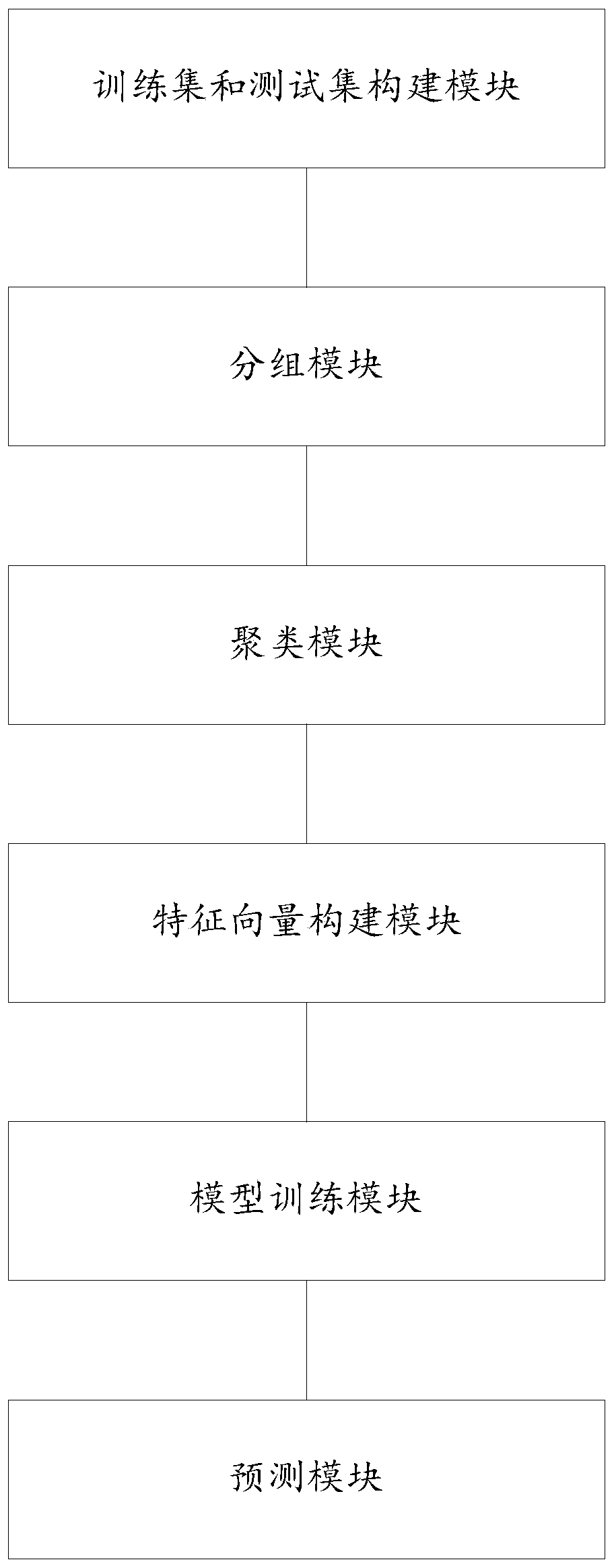
Short-term photovoltaic power generation prediction method and system
ActiveCN110322364AHigh precisionReduce modal aliasingForecastingNeural architecturesFeature vectorDecomposition
The invention provides a short-term photovoltaic power generation prediction method and system. The short-term photovoltaic power generation prediction method comprises the following steps: acquiringpower generation power and meteorological historical data of a photovoltaic power station at the same moment, and constructing a training set and a test set; grouping the training set and the test setaccording to a preset time interval; independently clustering the samples of each group of training set and test set into sample data of a preset number of weather types; generating power data in thesample data of each weather type is decomposed step by step according to different fluctuation scales by adopting an NACEMD signal decomposition algorithm to obtain components with different time-frequency characteristics, and then combining the components with corresponding weather type characteristics to construct characteristic vectors of each group of training set and test set; training and testing the deep LSTM sequence neural network model by using the feature vectors of the training set and the test set respectively; and predicting the generated power of short-term photovoltaic power generation by using the trained deep LSTM sequence neural network model.
Owner:SHANDONG UNIV
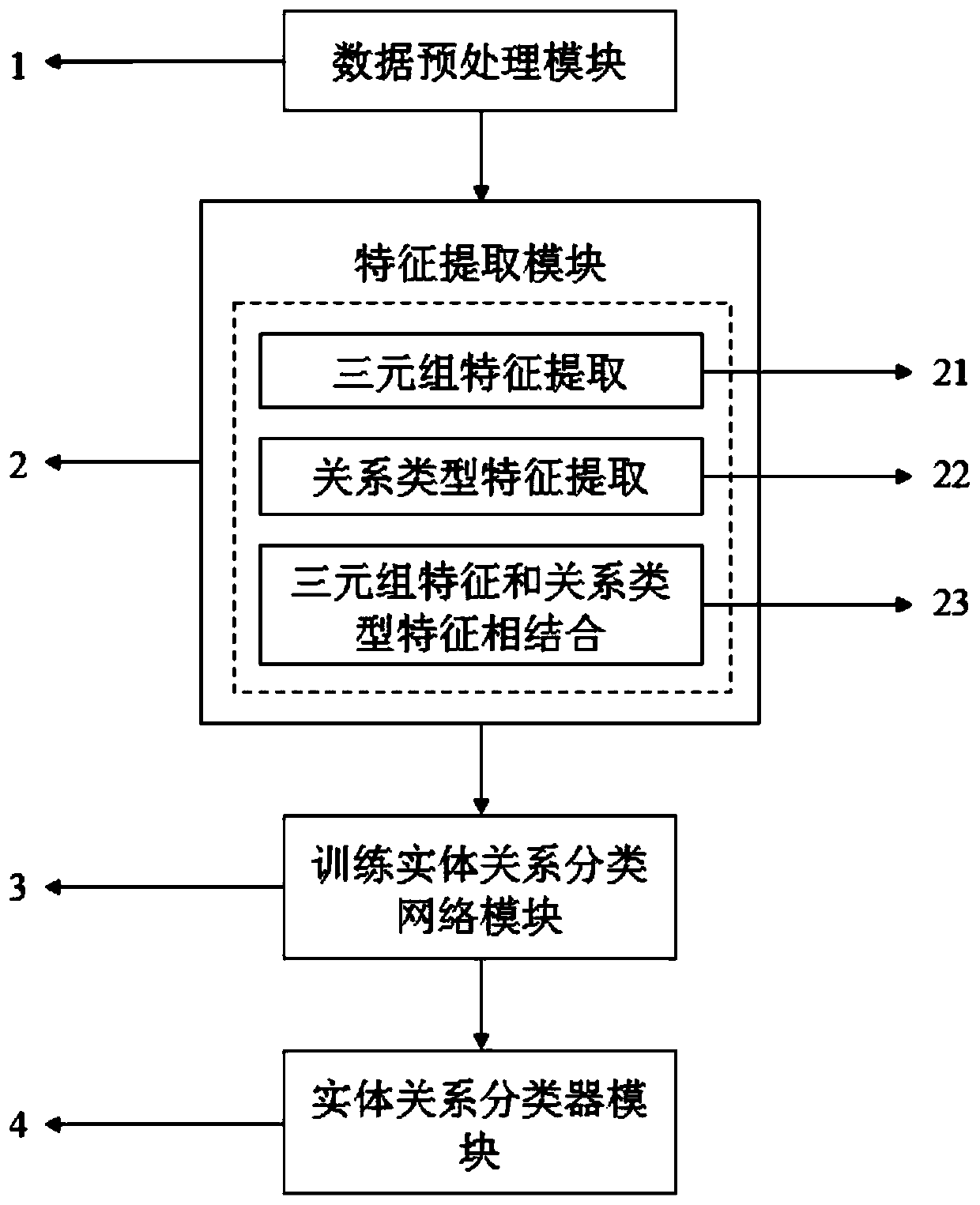
Unsupervised entity relationship extraction method based on zero-shot
ActiveCN110555083AImprove accuracyReduce the cost of manual labelingRelational databasesSpecial data processing applicationsManual annotationNetwork model
The invention discloses an unsupervised entity relationship extraction method based on zero-shot, and belongs to the field of computers. An entity relationship category is judged by extracting triplefeatures in text data and entity relationship type features in a domain knowledge graph and calculating the similarity between the triple features and the entity relationship type features, so that the dependence of a traditional entity relationship extraction method on manual annotation is reduced, and the accuracy of entity relationship extraction is improved. The method comprises the steps of data preprocessing, feature extraction, relation extraction network model training and entity relation classifier training. A convolutional neural network model which is good at capturing sentence information is adopted to respectively extract triple and relationship type features, and finally softmax is used to predict entity relationship type tags. In a model construction process, a sparse taggedcorpus can be used as a training set, and in a test process, the same parameters as those in the training process can also be used for predicting the type of an untagged triad.
Owner:BEIJING UNIV OF TECH
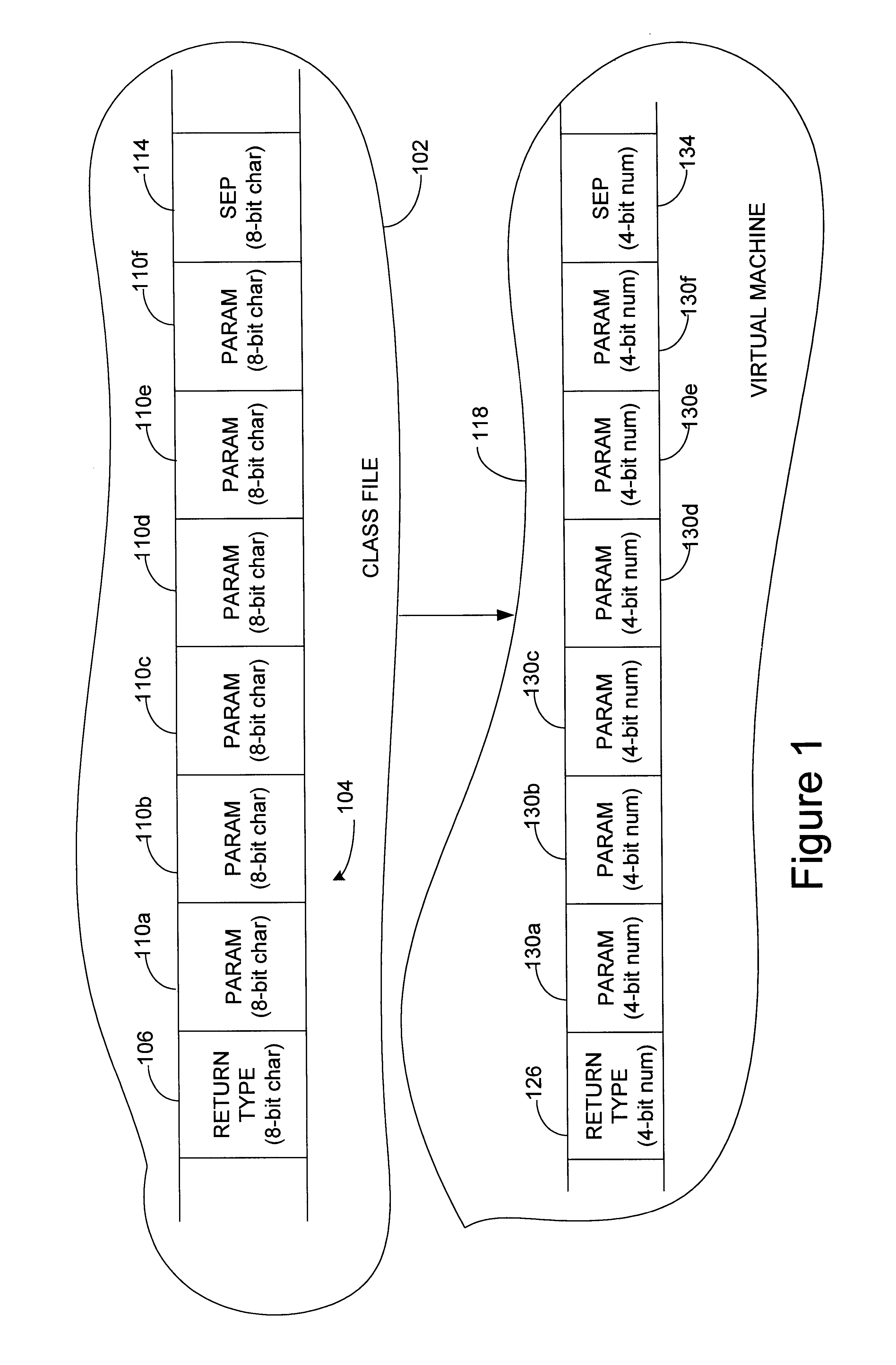
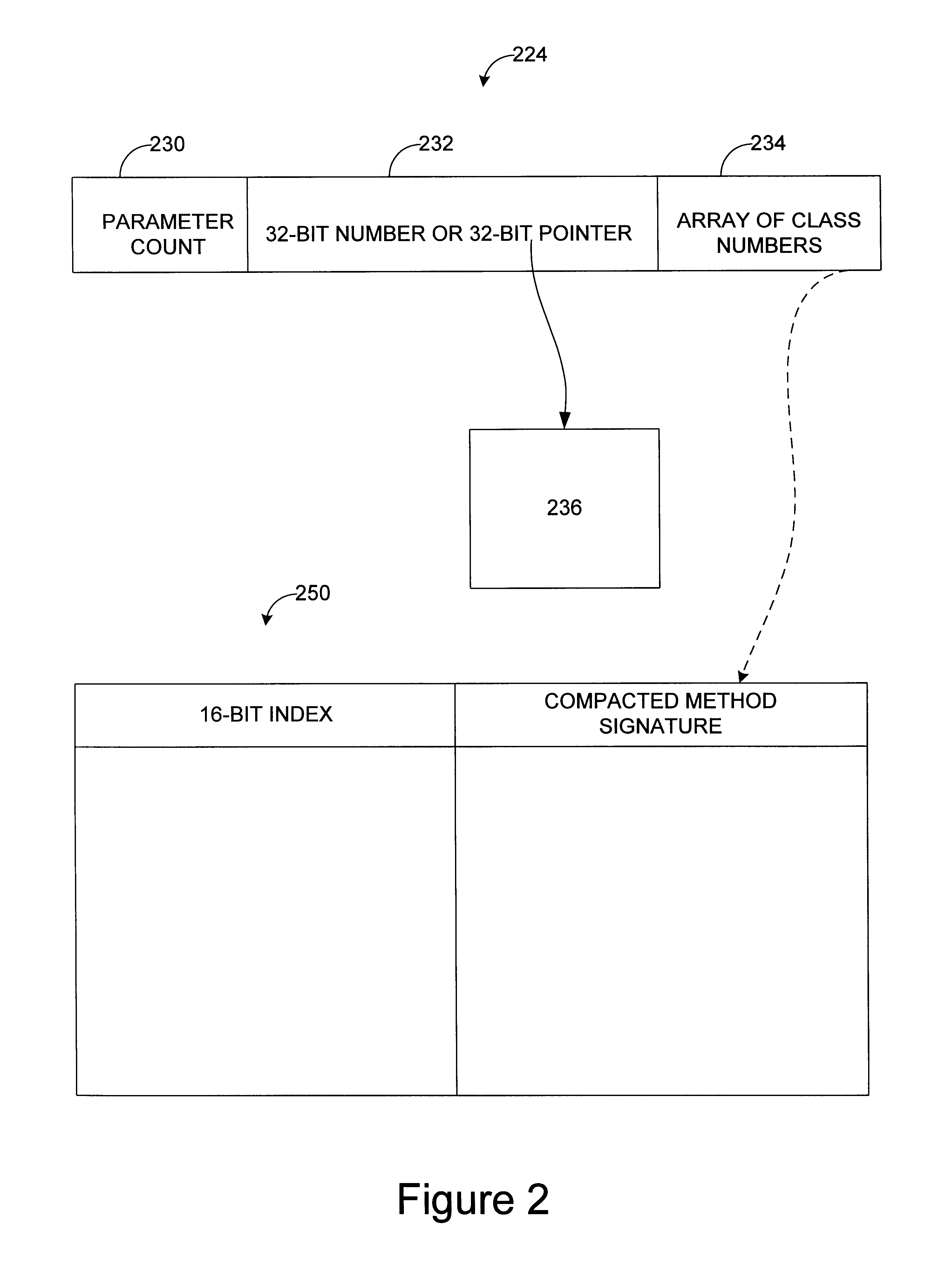
Method and apparatus for implementing compact type signatures in a virtual machine environment
Methods and apparatus for creating compacted method signatures from method signature representations in Java(TM) class files are disclosed. The use of compacted signatures reduces the amount of memory space occupied by the signatures and, further, improve the efficiency with which a virtual machine may operate. According to one aspect of the present invention, a method a method for creating a compact representation of a method signature using a virtual machine includes creating 4-bit representations for each of a first parameter, a separator, and a return type included in the method signature. Once the 4-bit representation are created, the representations are packed into a word. In one embodiment, the word is a 32-bit word. In such an embodiment, the 32-bit word may be a 32-bit integer.
Owner:SUN MICROSYSTEMS INC
Storage system and method for opportunistic write-verify
A storage system that stores verify commands for all the write commands requiring verification in a verify-list that will be processed as a background task is described. The verify-list can include coded data fields that flexibly designate selected alternative states or possibilities for how and where the user data is actually stored. Alternatives for the verify-list include storing the actual raw data, no data, the data in compressed form, a CRC type signature of the data and / or a pointer to a backup copy of the data that is stored either in non-volatile memory such as flash memory or on the disk media in a temporary area. In case of a verification error in various alternative embodiments the user data can be recovered using the backup copy in the verify-list in the write cache, the backup copy in flash memory or on the disk, or from the host.
Owner:WESTERN DIGITAL TECH INC
Code verification system and method
InactiveUS20050188270A1Error detection/correctionSpecific program execution arrangementsType signatureVerification system
The system of the present disclosure comprises memory for storing a compiled program. The system further comprises logic configured to translate the compiled program into a set of human-readable instructions and construct a coarse tree representing the program flow of the set of human-readable instructions. The logic is further configured to compute a first type signature representative of a code construct comprising alternative code paths within the program flow and determine a second type signature representative of the coarse tree based upon the first type signature.
Owner:HEWLETT PACKARD DEV CO LP
Summarization of audio and/or visual data
InactiveCN101137986APrecise positioningTypical voice featuresDigital data information retrievalSpeech analysisPattern recognitionObject based
Summarization of audio and / or visual data based on clustering of object type features is disclosed. Summaries of video, audio and / or audiovisual data may be provided without any need of knowledge about the true identity of the objects that are present in the data. In one embodiment of the invention are video summaries of movies provided. The summarization comprising the steps of inputting audio and / or visual data, locating an object in a frame of the data, such as locating a face of an actor, extracting type features of the located object in the frame. The extraction of type features is done for a plurality of frames and similar type features are grouped together in individual clusters, each cluster being linked to an identity of the object. After the processing of the video content, the largest clusters correspond to the most important persons in the video.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
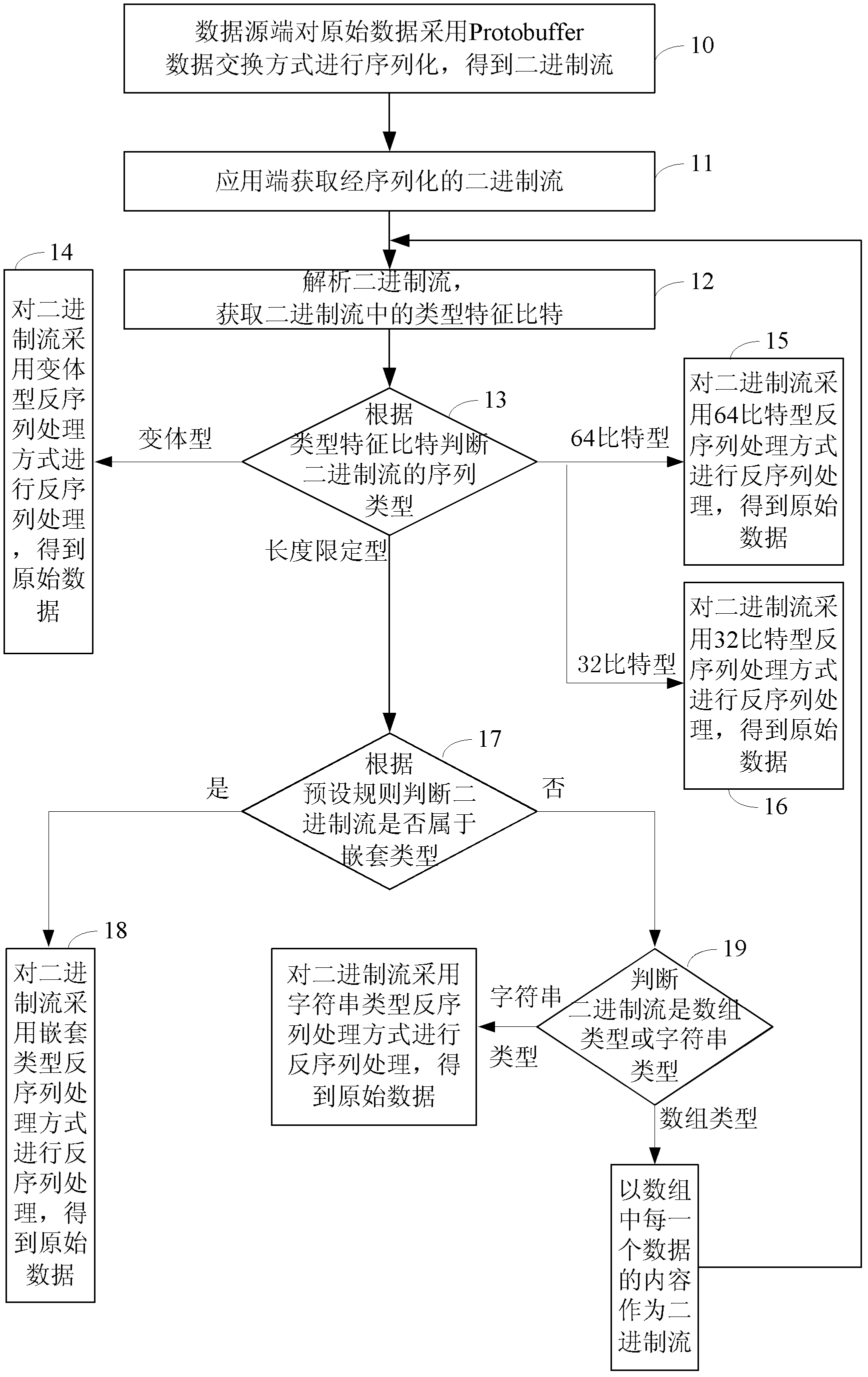
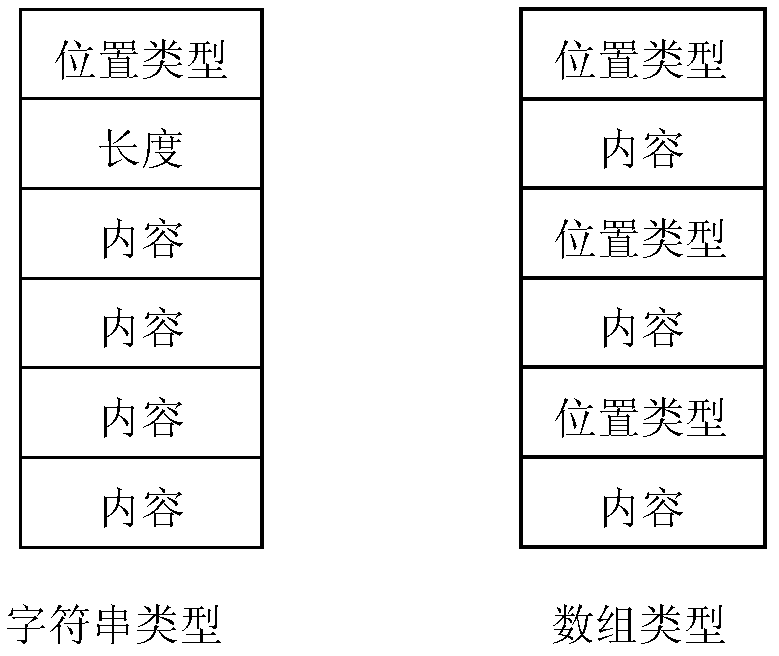
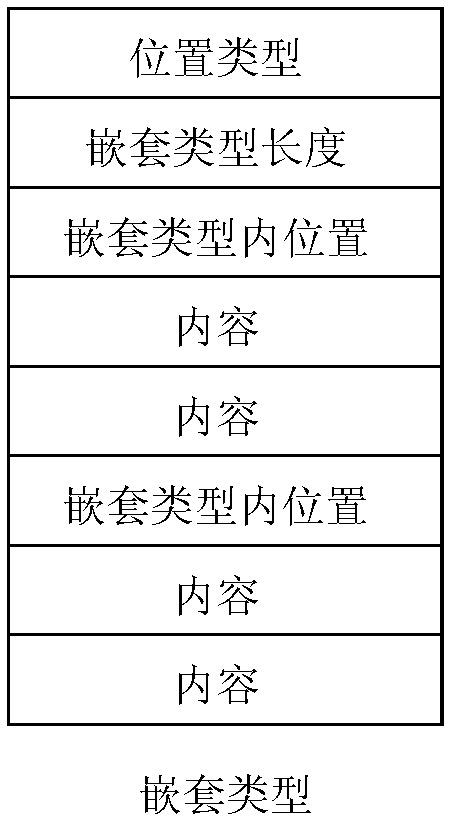
Method and system of data exchange and deserialization method
ActiveCN103036641AIncrease flexibilityError preventionProgram controlSequence processingOriginal data
The invention discloses a method of data exchange. The method of data exchange includes a data source terminal serializing an original data with a data exchange mode of Protobuffer to obtain a binary stream, an application terminal obtaining and parsing the serialized binary stream to obtain the type characteristic bits in the binary stream, determining the sequence type of the binary stream according to the type characteristic bits, and performing corresponding deserialization process to the binary stream according to the obtained sequence type to obtain the original data. The invention also discloses a data exchange system and a deserialization method. According to the methods and system of data exchange and deserialization method, the application flexibility of the deserialization can be improved and the application range of deserialization can be broadened.
Owner:BEIJING FEINNO COMM TECH
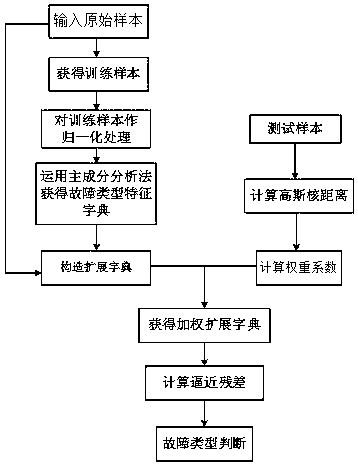
Fault diagnosis method for high voltage cable
InactiveCN108828402AImprove power supply reliabilityAccurate diagnosisFault location by conductor typesInformation technology support systemTest sampleDiagnosis methods
The invention relates to the field of fault diagnosis of high-voltage cables, in particular to a fault diagnosis method for a high-voltage cable. The method comprises the following steps: obtaining fault type characteristic information of a high-voltage cable sample by using a principal component analysis method, constructing a fault type characteristic dictionary, and jointly constructing an extended dictionary according to an original sample dictionary and the fault type characteristic dictionary of the high-voltage cable; calculating approximation residuals of all samples in the extended dictionary to the testing sample by utilizing a sparse representation method and judging fault types according to the approximation residuals. The invention provides the fault diagnosis method for analyzing cable fault information by using methods including dictionary expansion and sparse representation and the like, which can accurately judge the fault type of the high-voltage cable, greatly shorten the maintenance time and improve the power supply reliability of a power system.
Owner:GUANGDONG POWER GRID CO LTD +1
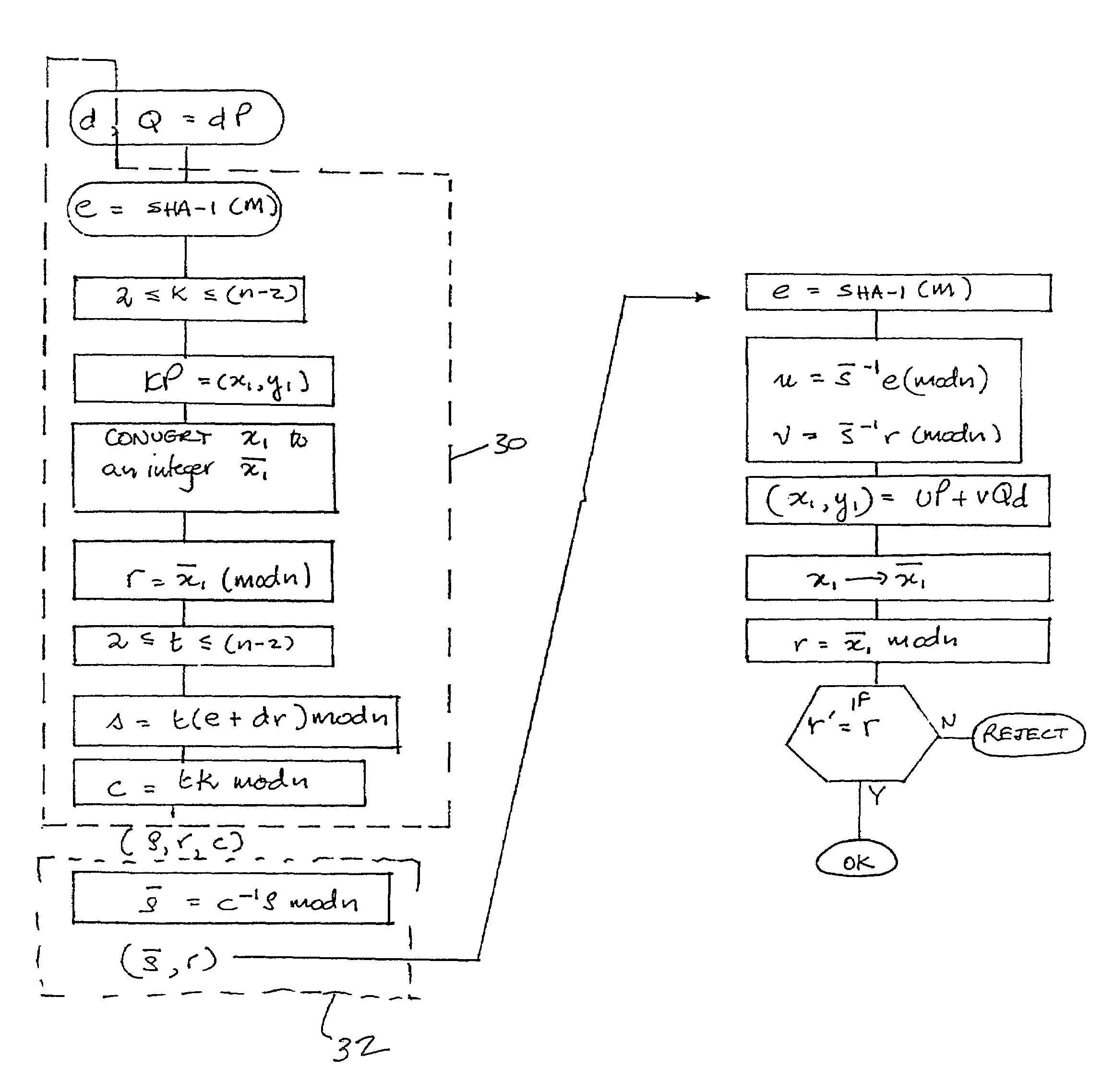
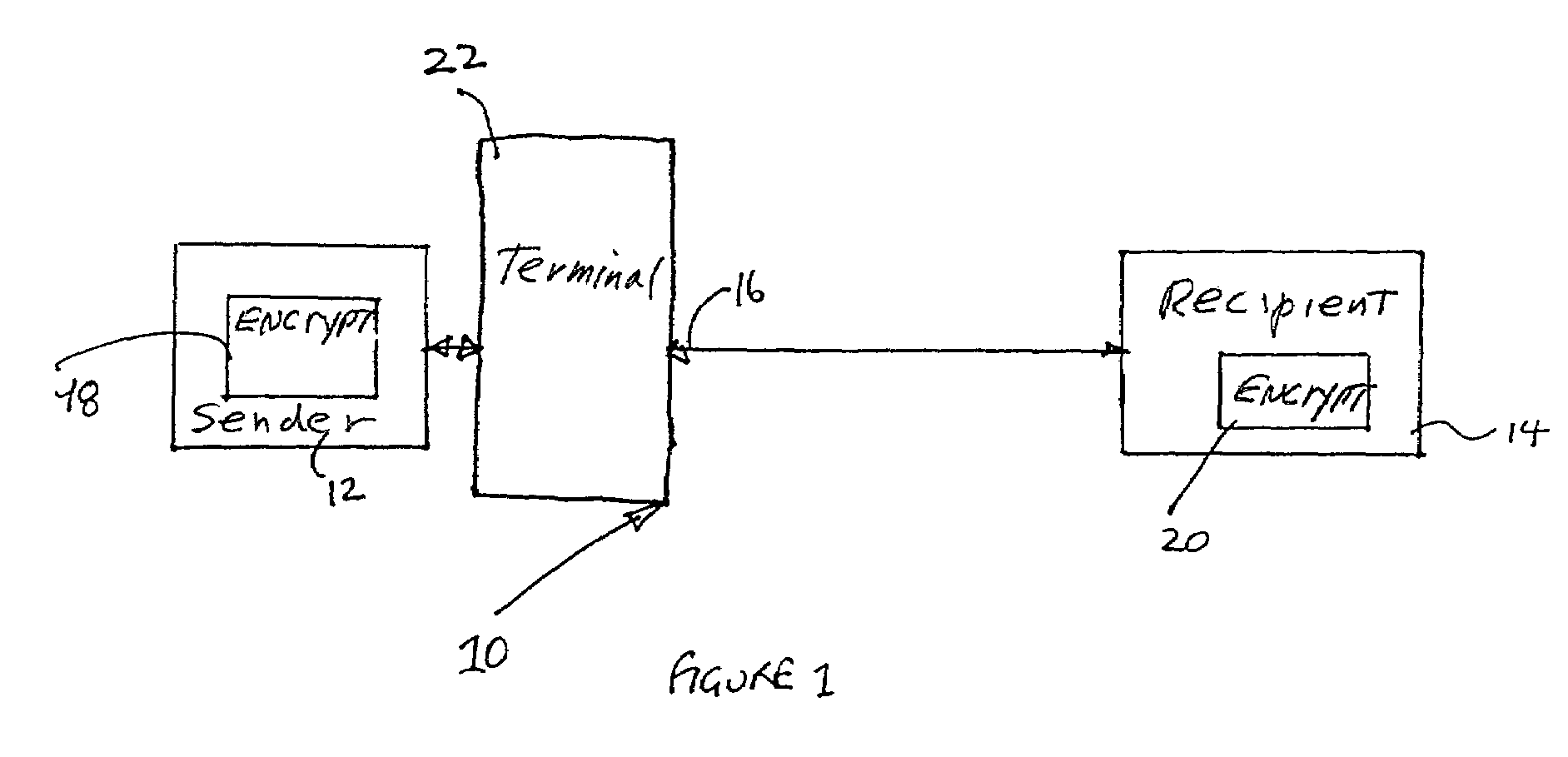
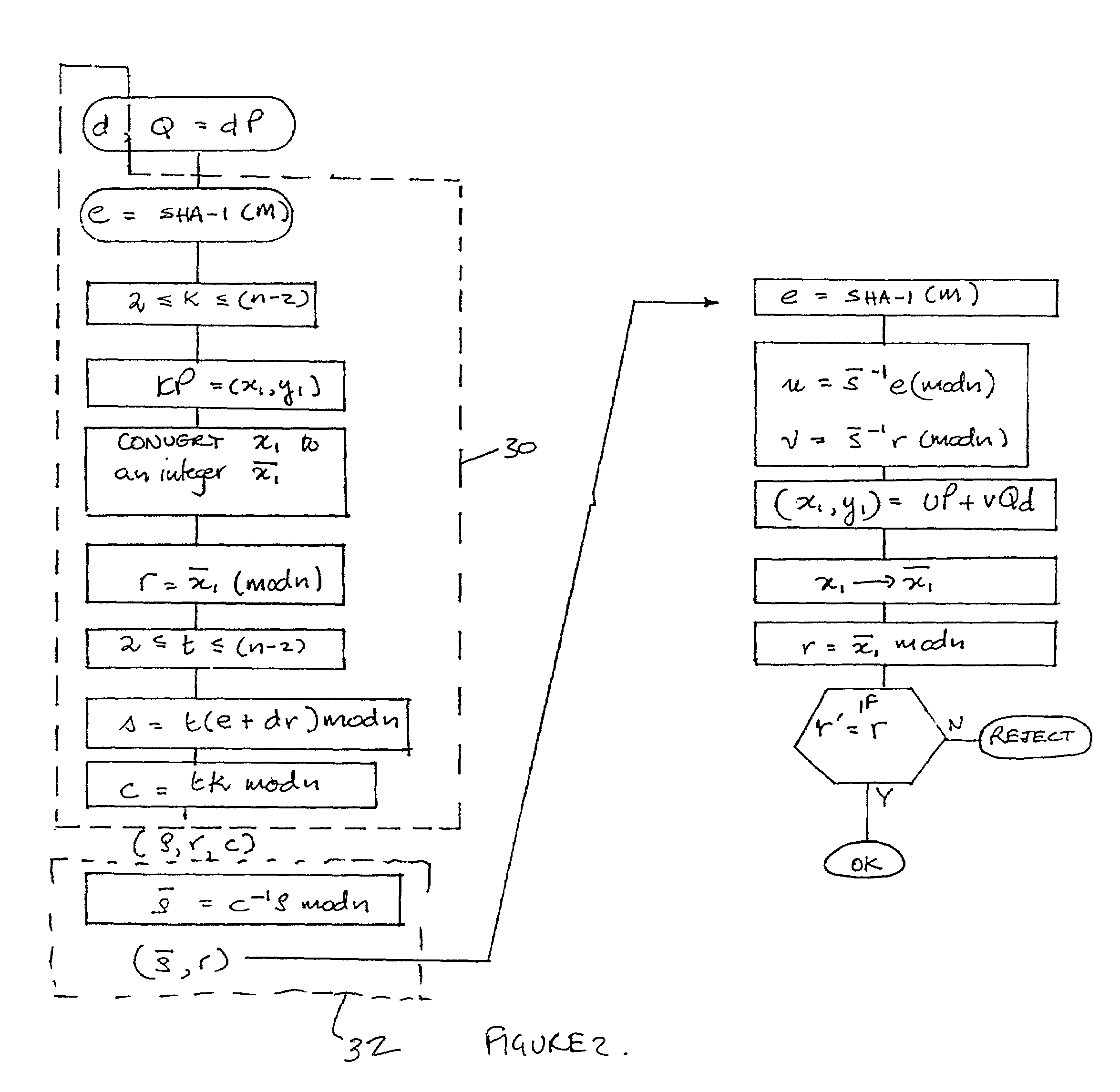
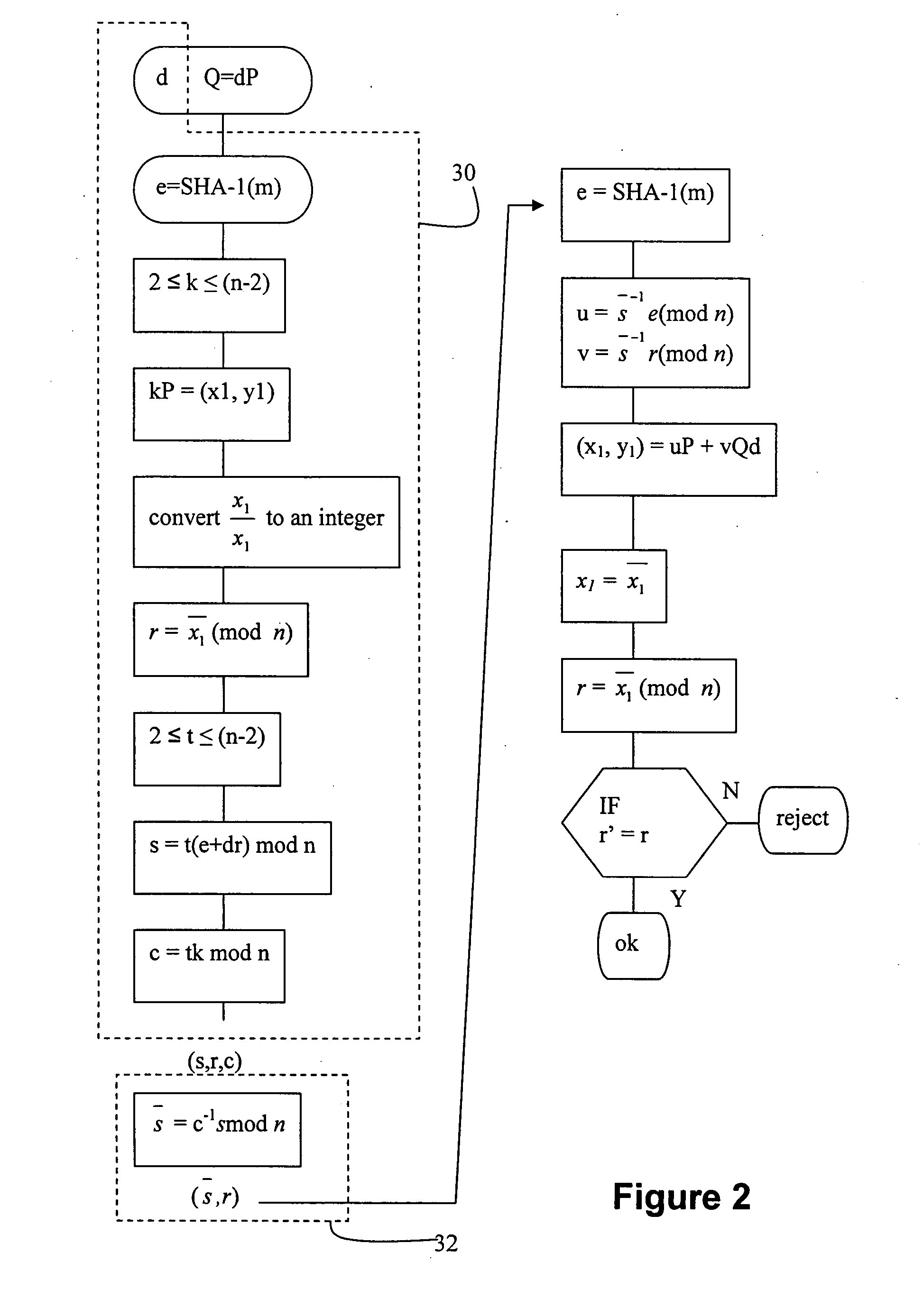
Masked digital signatures
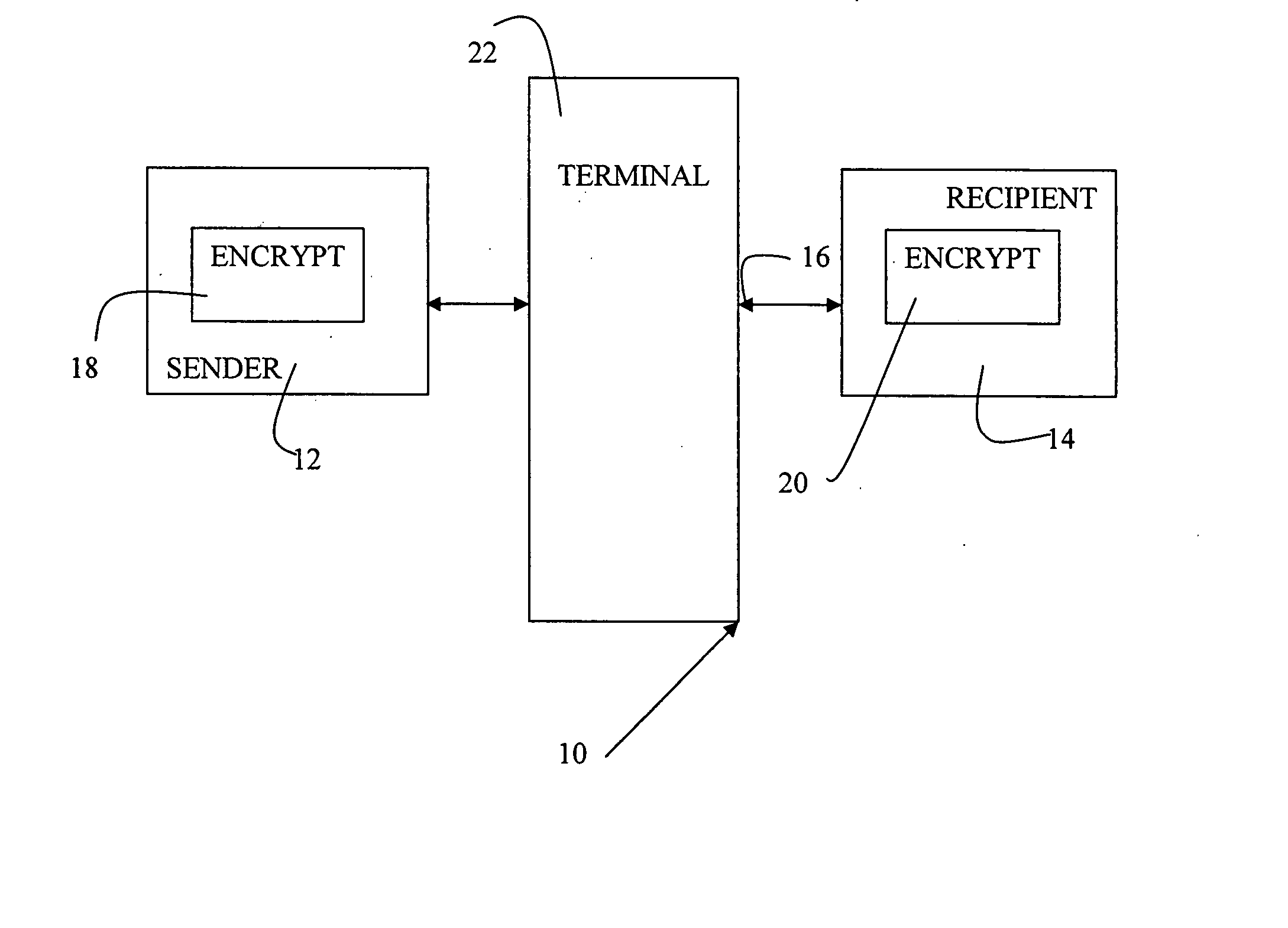
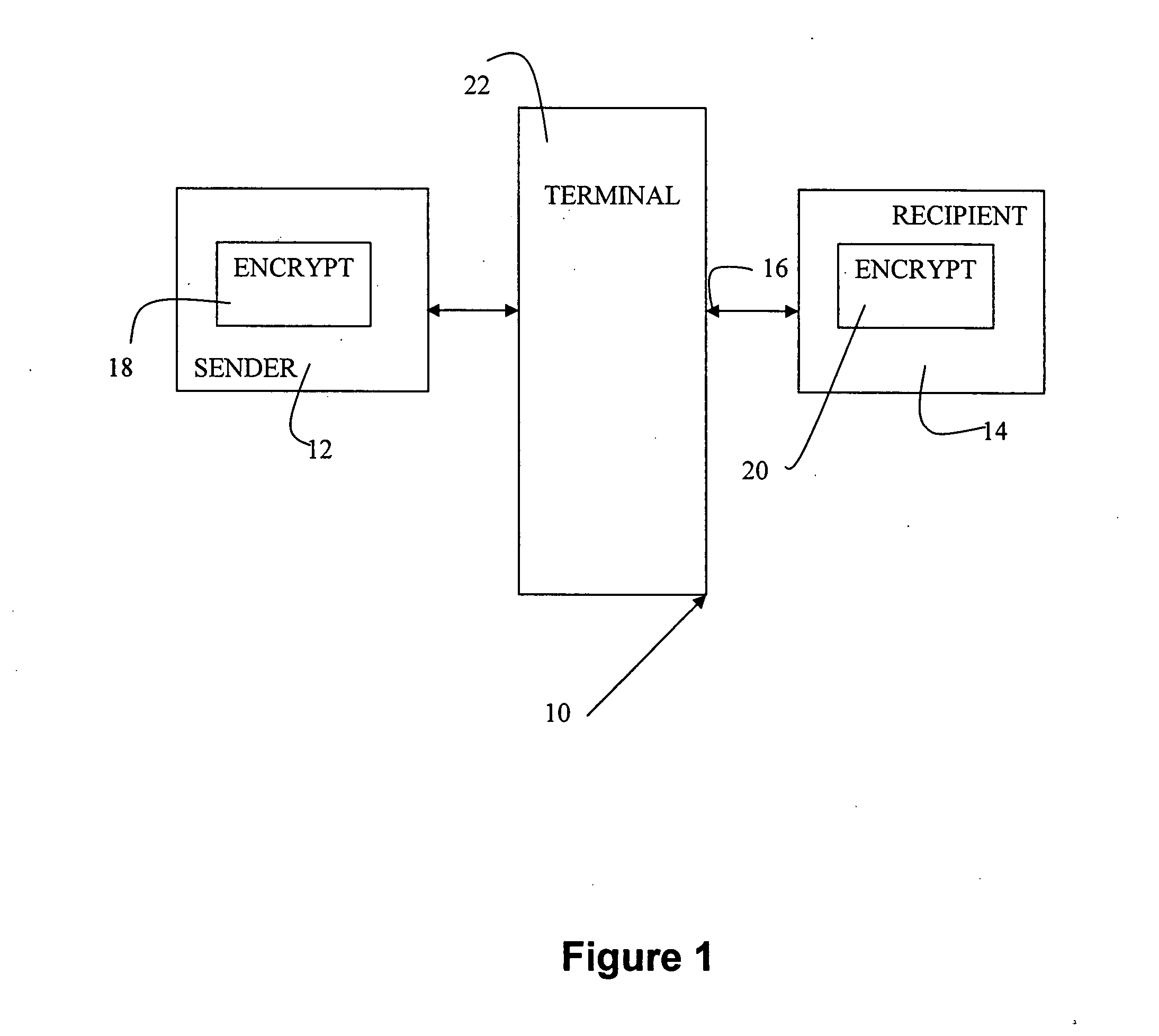
InactiveUS7260723B2Reduce disadvantagesEfficient implementationPublic key for secure communicationUser identity/authority verificationCommunications systemDigital signature
The present invention relates to digital signature operations using public key schemes in a secure communications system and in particular for use with processors having limited computing power such as ‘smart cards’. This invention describes a method for creating and authenticating a digital signature comprising the steps of selecting a first session parameter k and generating a first short term public key derived from the session parameter k, computing a first signature component r derived from a first mathematical function using the short term public key, selecting a second session parameter t and computing a second signature component s derived from a second mathematical function using the second session parameter t and without using an inverse operation, computing a third signature component using the first and second session parameters and sending the signature components (s, r, c) as a masked digital signature to a receiver computer system. In the receiver computer system computing a recovered second signature component s′ by combining a third signature component with the second signature component to derive signature components (s′, r) as an unmasked digital signature. Verifying these signature components as in a usual ElGamal or ECDSA type signature verification.
Owner:CERTICOM
Identity authentication method integrating multiple type features for palm print image recognition through hierarchical topic model
ActiveCN107944356AAchieve authenticationMeet real-time requirementsMatching and classificationPattern recognitionPalm print
The invention discloses an identity authentication method integrating multiple type features for palm print image recognition through a hierarchical topic model. According to the method, palm print images are converted into documents through analogy, palm print feature components are converted into words through analogy, and palms are converted into topics through analogy; first, topic model parameters and the number of the topics are calculated according to the palm print images for training; second, the hierarchical topic model is utilized to perform layering and grouping on the palm print images for training, and a topological structure of the hierarchical topic model is optimized according to recognition of palm print images for testing; and third, the trained topic model is used to classify to-be-detected palm print images into corresponding groups, features of the to-be-detected palm print images are matched with features of the palm print images in the corresponding groups one by one, and therefore identity authentication is realized. Through the method, acquired recognition accuracy is high, recognition speed is high, and the instantaneity requirement of a large-scale application place for identity authentication through palm print recognition can be met.
Owner:湖南工商大学
Intelligent signature seal with electronic label and two-dimensional bar code
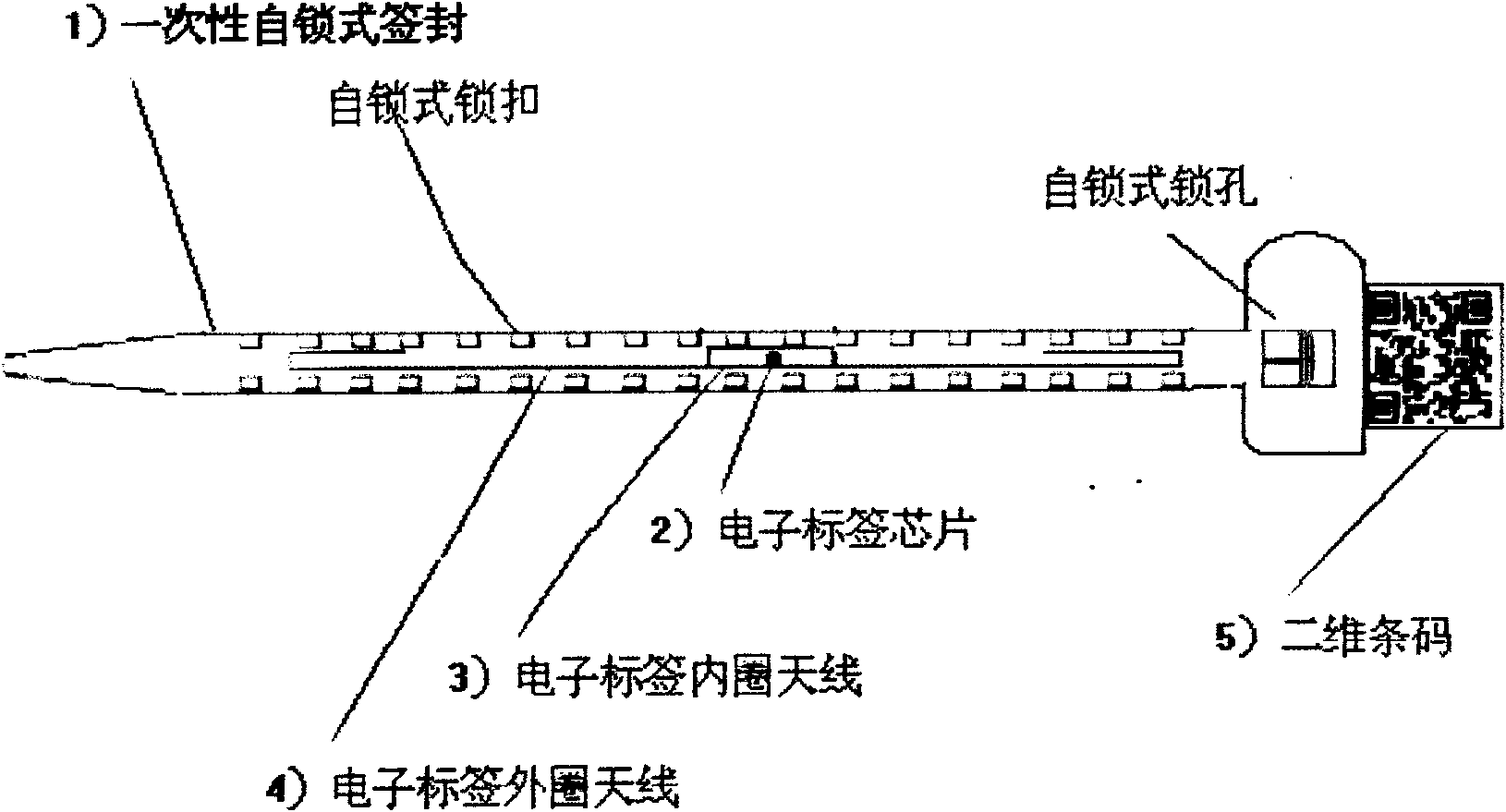
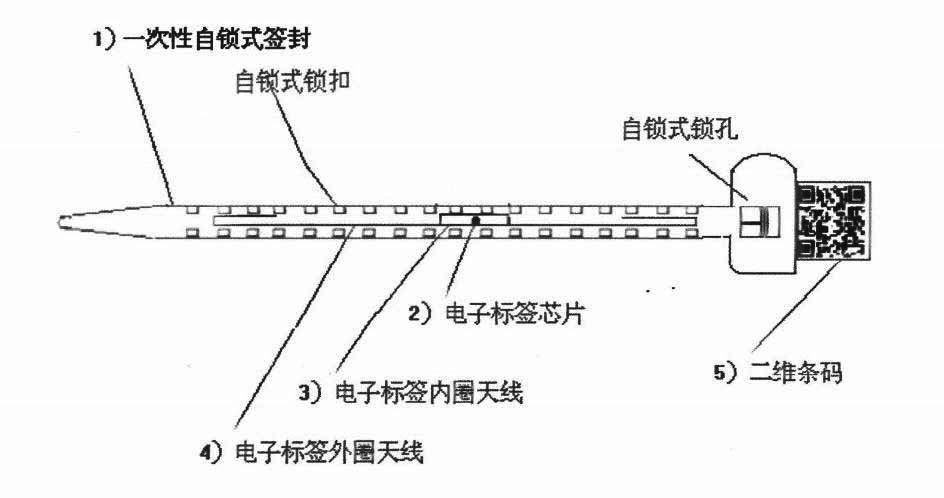
InactiveCN101872578ARealize simultaneous identificationRealize mobile reading and writingStampsRecord carriers used with machinesElectricitySelf locking
The invention discloses an intelligent signature seal with an electronic label and a two-dimensional bar code, which is characterized in that a disposable self-locking type signature seal (1) is internally embedded with an electronic label chip (2), an electronic label inner ring antenna (3), an electronic label outer ring antenna (4) and a two-dimensional bar code (5) with a injection molding method in one step; the electronic label in the signature has the structure with the inner ring antenna and the outer ring antenna; the outer ring antenna supports the identification range of 5m, so that the identification, the mobile reading and writing, the location and the long-term tracing management of a plurality of signatures can be realized at the same time. When the signature seal is cut off normally, only the outer ring antenna is damaged; the inner ring antenna can still support the identification distance of about 10cm and is kept for the secondary verification and the file archive. The invention provides a signature seal product having functions of the storage, identification, verification and anti-counterfeit of the electronic data. Particularly, the invention is suitable for various containers, container trucks, electricity meters, postal parcels, bank cash boxes and tail boxes, and the other sealed containers or packages required to supervise and trace the information.
Owner:上海希硕信息科技有限公司
Masked digital signatures
InactiveUS20080005570A1Efficient implementationUser identity/authority verificationPayment architectureCommunications systemDigital signature
The present invention relates to digital signature operations using public key schemes in a secure communications system and in particular for use with processors having limited computing power such as ‘smart cards’. This invention describes a method for creating and authenticating a digital signature comprising the steps of selecting a first session parameter k and generating a first short term public key derived from the session parameter k, computing a first signature component r derived from a mathematical function using the short term public key, selecting a second session parameter t and computing a second signature component s derived from a second mathematical function using the second session parameter t and without using an inverse operation, computing a third signature component using the first and second session parameters and sending the signature components (s, r, c) as a masked digital signature to a receiver computer system. In the receiver computer system computing a recovered second signature component s′ by combining a third signature component with the second signature component to derive signature components (s′, r) as an unmasked digital signature. Verifying these signature components as in a usual ElGamal or ECDSA type signature verification.
Owner:CERTICOM
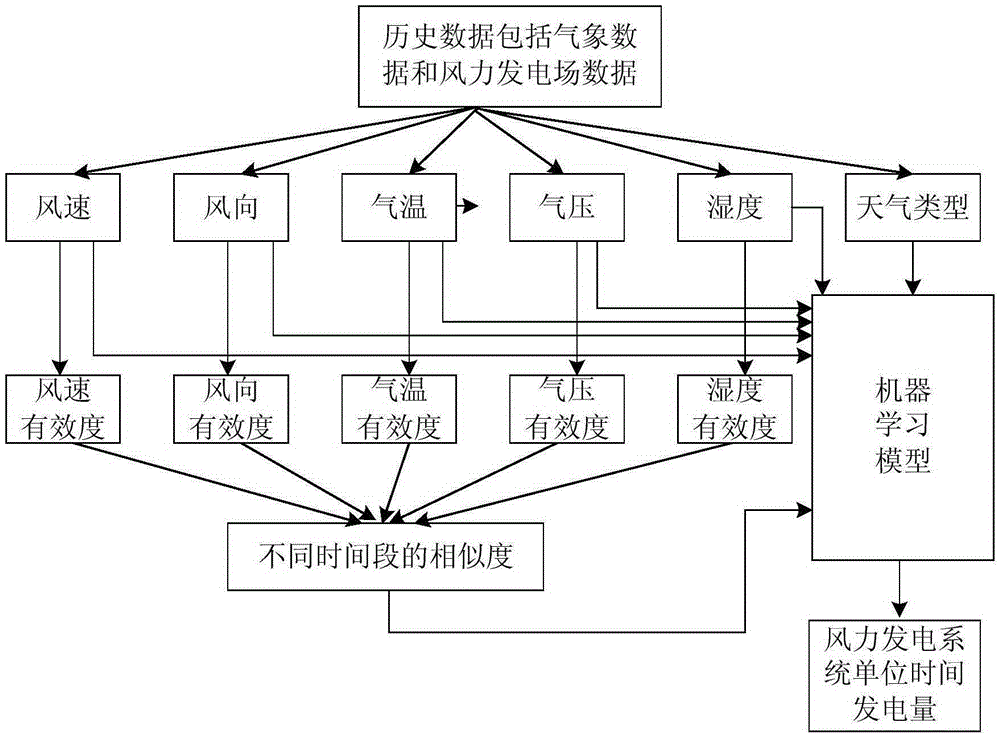
Wind power generation output power prediction method based on similarity theory
InactiveCN105303268AImprove forecast accuracyGood number of identificationForecastingInformation technology support systemFeature vectorSimilarity theory
The invention discloses a wind power generation output power prediction method based on the similarity theory. The method comprises steps of: using an appointed climate type and an appointed weather type as the characteristic vectors of similar time segments, normalizing the climate type, and mapping the characteristic vectors of the weather type into numerical value; performing mode identification analysis; acquiring the validities of all data classifications of the characteristic vectors of the climate type, using the data classification with the lowest validity as a classification result to form a sample set of the similar time segments; constructing a factor vector sample set influencing the wind power generation system output power and acquiring the similarity of different time segments; establishing a machine learning model and training the machine learning model by using the output power of the similar time segments and the sample set of the similar time segments; and predicting the output power of the time segment by using the machine learning model. The wind power generation output power prediction method is simple and feasible, and accurate in prediction.
Owner:STATE GRID CORP OF CHINA +2
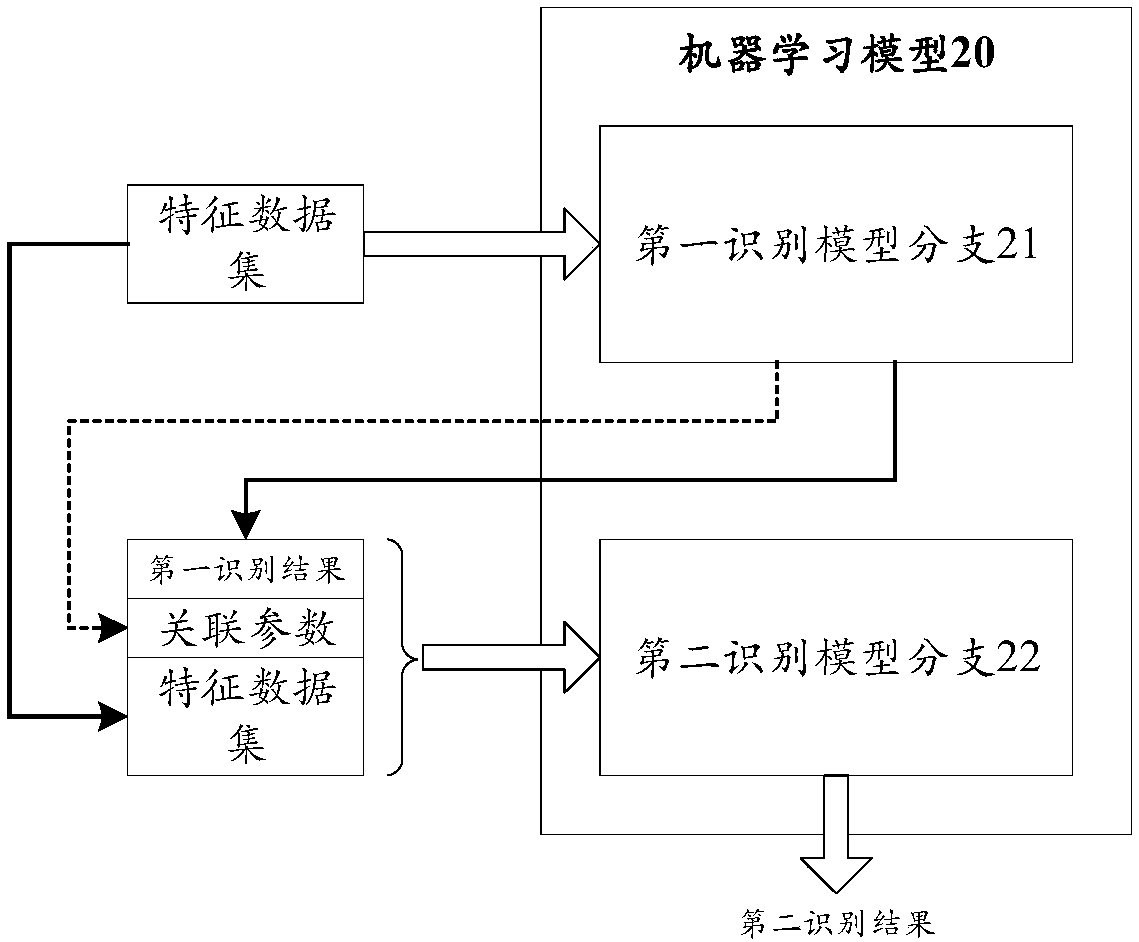
Terminal identification method and device
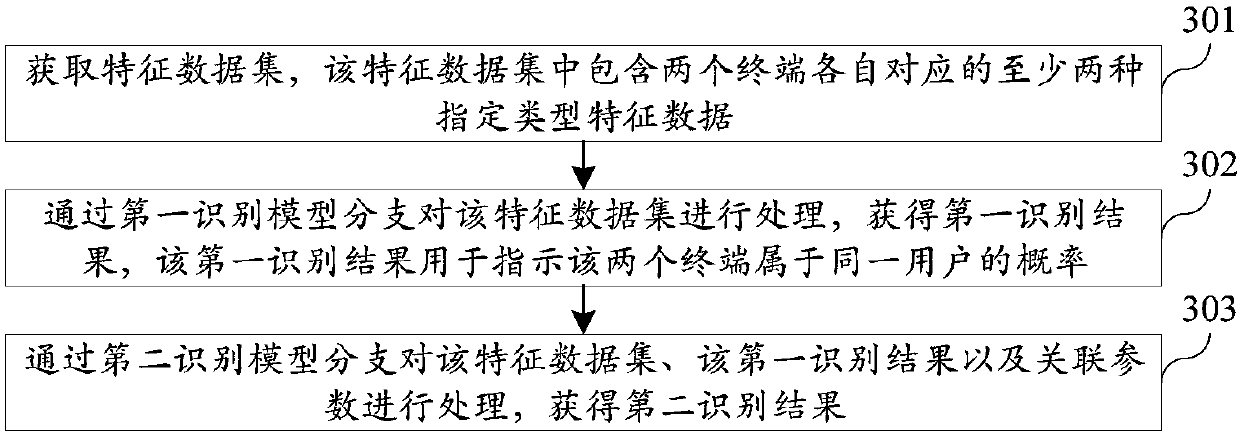
ActiveCN109961080AAchieve integrationImprove accuracyCharacter and pattern recognitionData switching networksData setThe Internet
The invention relates to a terminal identification method and device, and relates to the technical field of Internet application. The method comprises the following steps: acquiring a feature data setcomprising at least two specified types of feature data corresponding to two terminals respectively; processing the feature data set through a first identification model branch to obtain a first identification result, processing the feature data set, the first identification result and the associated parameters of the first identification model branch through the second identification model branch; according to the invention, the advantages of a plurality of machine learning models are fused while the relevance between the features is considered, so that the accuracy of identifying whether the two terminals belong to the same user is improved, and the identification effect is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Multi-period steel rail damage trend prediction method based on data mining
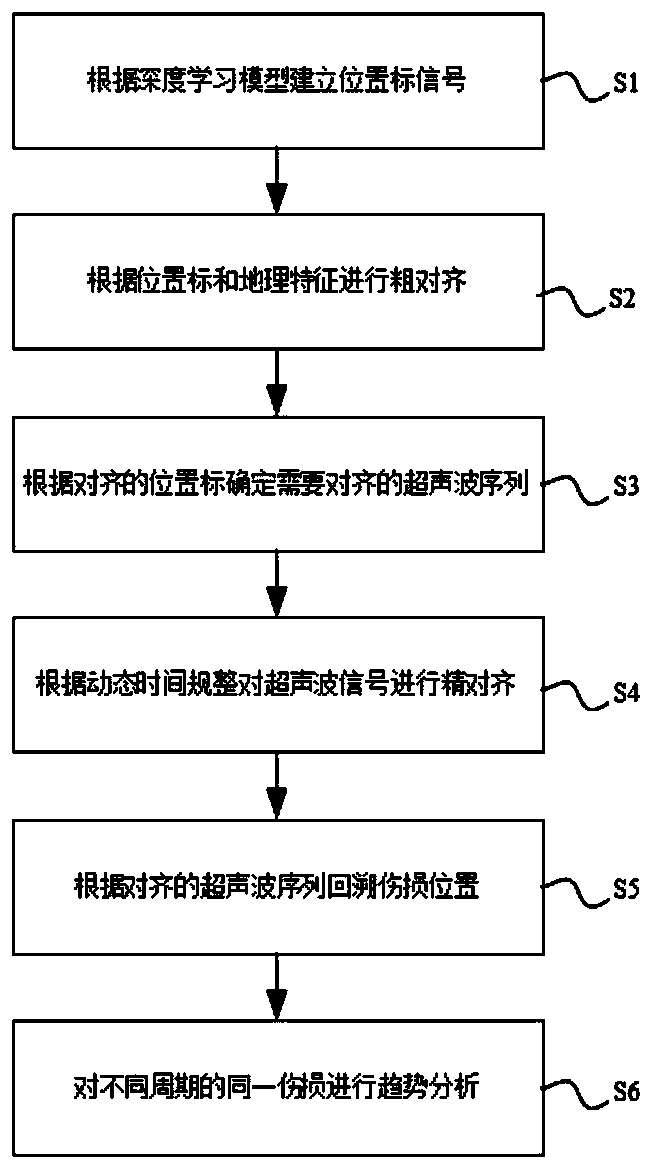
PendingCN110175422AEffective forecastEffective judgmentDesign optimisation/simulationData miningTrend predictionPredictive maintenance
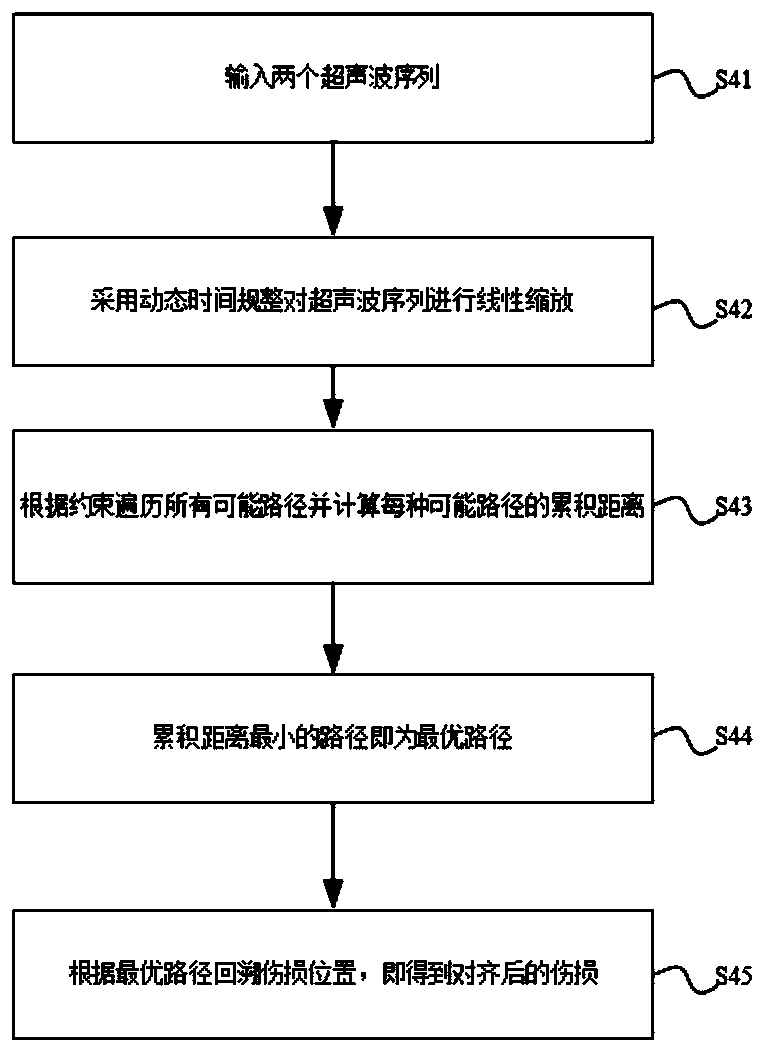
The invention relates to the field of rail transit and steel rail flaw detection, in particular to a multi-period steel rail damage trend prediction method based on data mining, which comprises the following steps: S1, training and judging a position mark A display waveform based on a deep learning model, and establishing a corresponding position mark signal; s2, combining position mark signals with geographic information such as mileage, rice blocks and GPS, and carrying out coarse alignment on all the position marks; s3, determining ultrasonic signal sequences C and Q which need to be aligned through the aligned position marks; s4, performing fine alignment on the ultrasonic signal sequences C and Q through a dynamic time warping method; s5, tracing the damaged position back according tothe aligned ultrasonic wave sequence; and S6, quantifying the development trend of the same damage in different periods, and analyzing the development trend of the damage. According to the method, based on a big data mining algorithm, the periodic change of various damage type characteristic data can be captured, a reliable damage growth data model is formed, and the damage condition of the railis effectively estimated and judged. Based on the prediction model, effective predictive maintenance work can be performed on the damage growth point appearing in the specific station section rail ina targeted manner, so that gradual change is prevented, and unnecessary periodic maintenance cost is saved to a great extent.
Owner:梁帆 +1
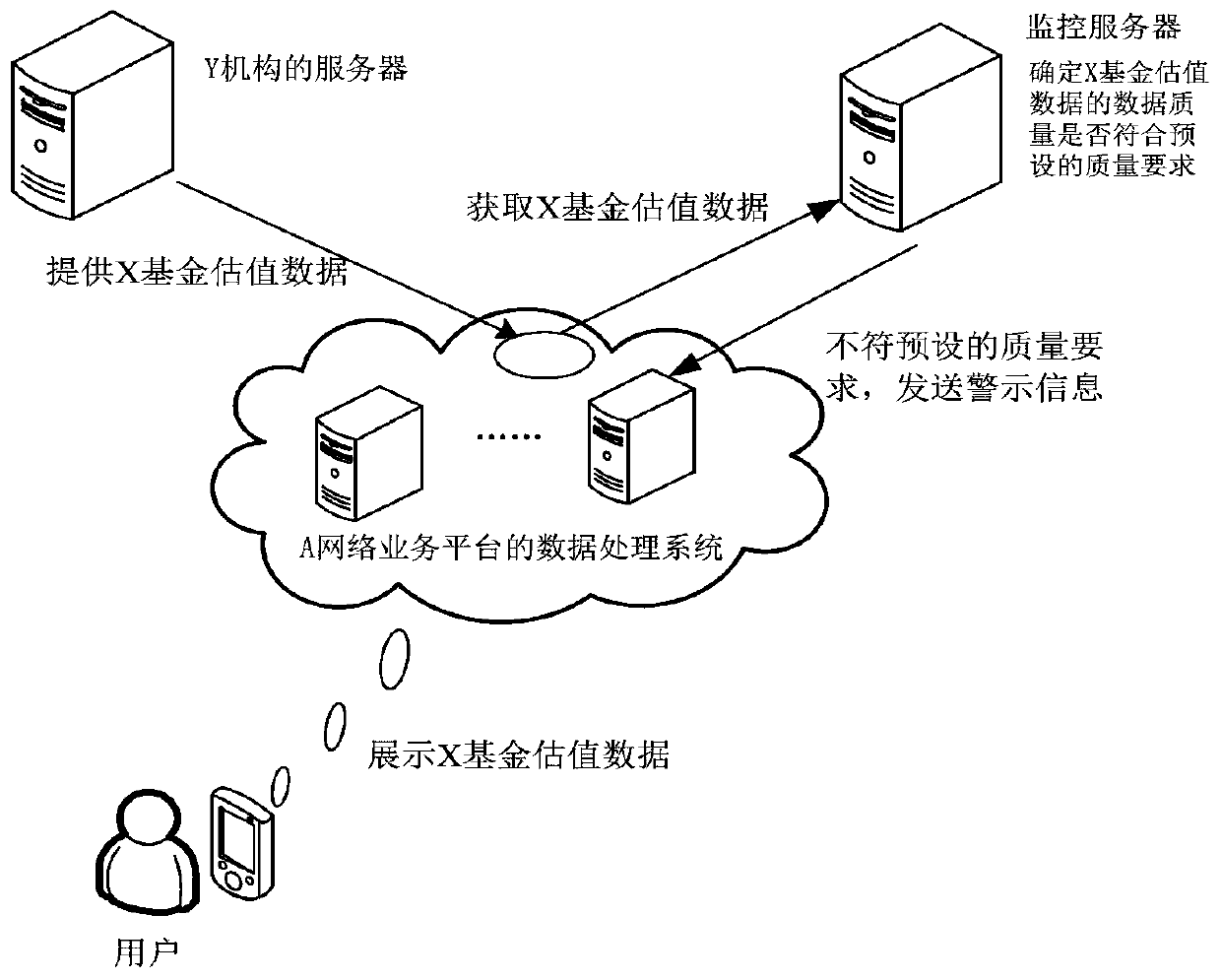
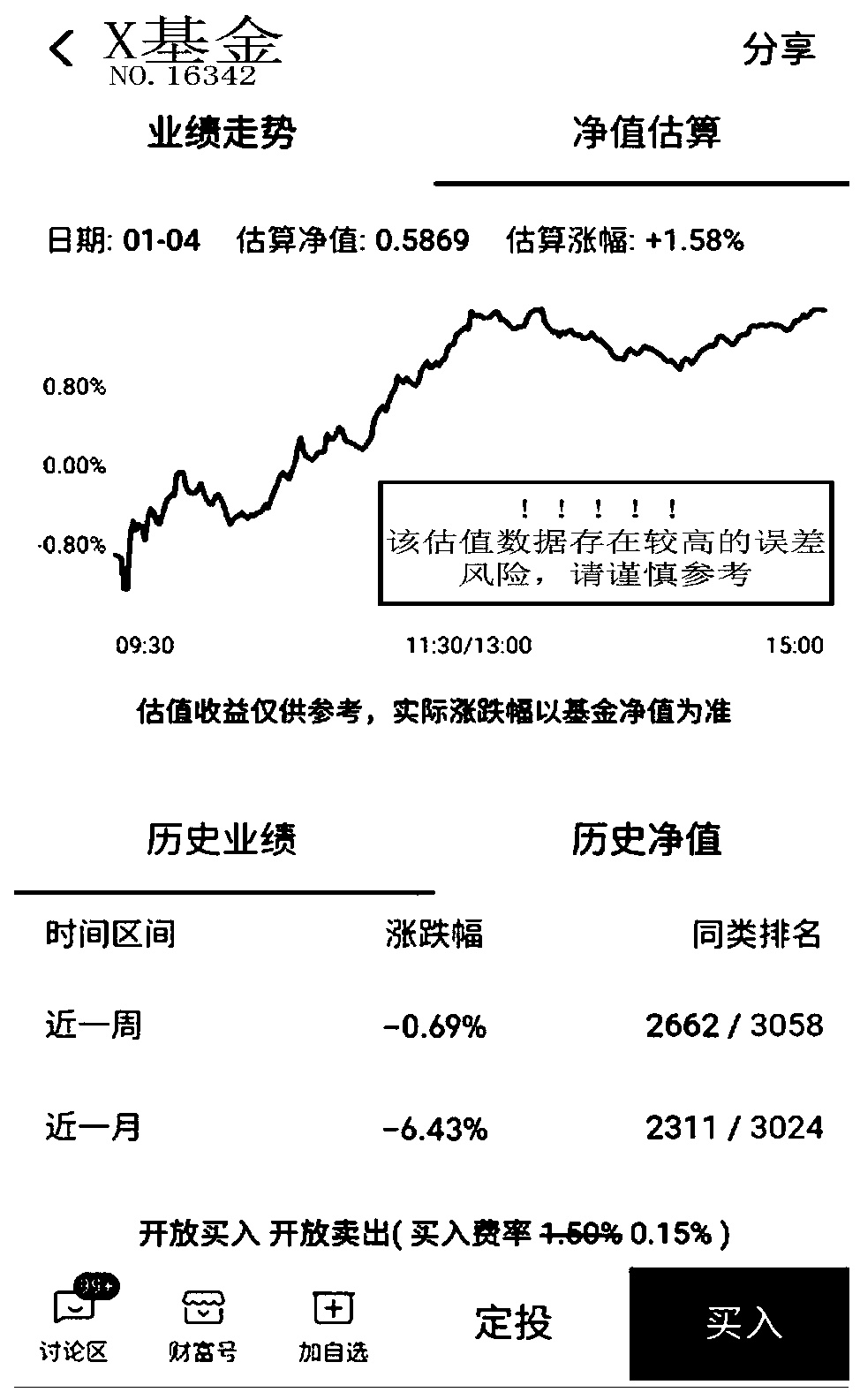
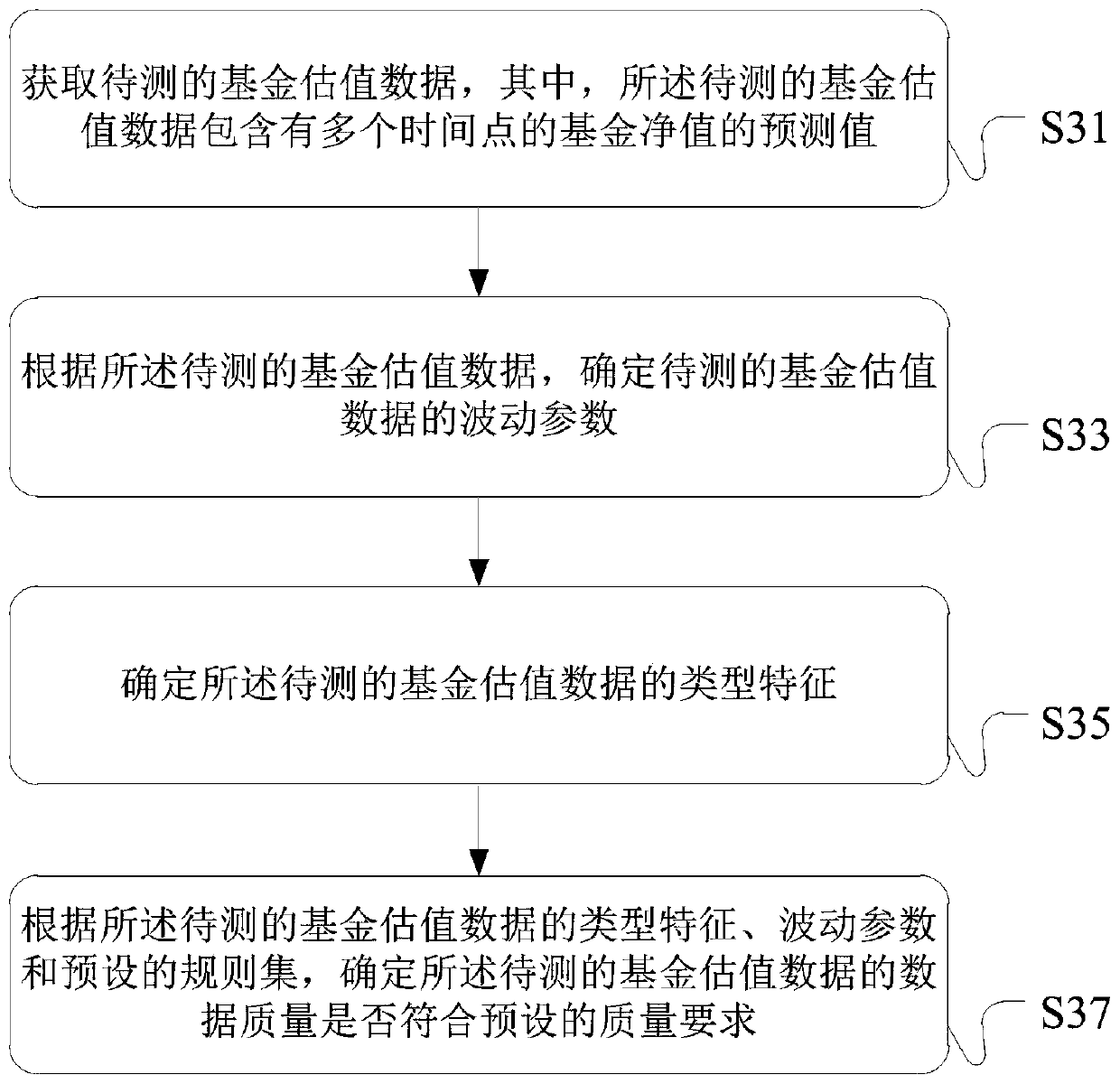
Method and device for determining data quality of fund valuation data and server
ActiveCN110059293AData quality is accurateAccurately determineDatabase queryingFinanceType signatureData quality
The invention provides a method and device for determining the data quality of fund valuation data and a server. The method comprises the following steps: obtaining fund estimation data to be tested;determining a fluctuation parameter of the fund estimation data to be tested according to the fund estimation data to be tested; determining type characteristics of the fund valuation data to be tested; and determining whether the data quality of the to-be-tested fund valuation data meets a preset quality requirement according to the type characteristics of the to-be-tested fund valuation data, the fluctuation parameter and a preset rule set. In the embodiment of the specification, the method comprises the steps of firstly determining type characteristics of fund valuation data to be tested; then, a preset rule set is utilized; according to the type characteristics, the fluctuation parameter of the fund valuation data to be detected is judged in a targeted mode so as to determine whether the data quality of the fund valuation data to be detected meets the preset quality requirement or not, and therefore the data quality of the fund valuation data can be efficiently determined, and inaccurate fund valuation data can be found in time.
Owner:ADVANCED NEW TECH CO LTD
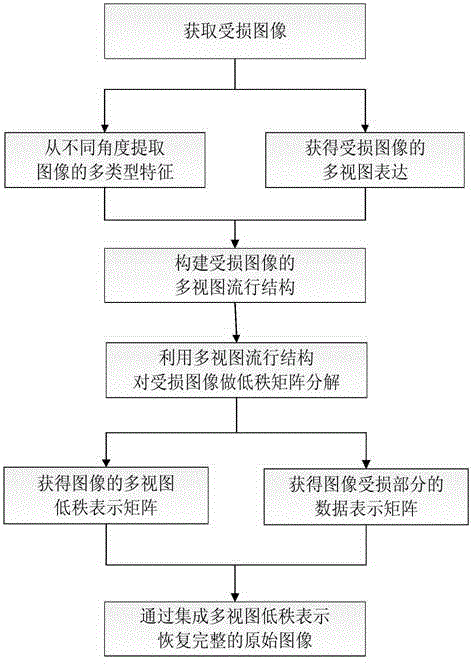
Damaged image repair method based on multi-view popular low-rank representation
ActiveCN103559683APromote recoveryImprove visual experienceImage enhancementComputer visionImage restoration
The invention provides a damaged image repair method based on multi-view popular low-rank representation. The following operations are carried out on a damaged image: firstly, the multi- type characteristic of the damaged image is extracted, and the multi-view representation of the damaged image is obtained; then the multi-view popular structure is constructed and used, the different local geometric structures of the damaged image are maintained, the damaged image is subjected to low-rank matrix decomposition, and the multi-view popular low-rank representation and damaged matrix representation of the image are obtained; finally the damaged image is repaired based on the integration of multi-view low-rank representations, and a complete original image is obtained. The method has the advantages that the multi-view compensation information and local popular structure characteristic of the damaged are fully considered, the clear and complete original image can be recovered well, the visual experience of a user is improved, and the method can be applied to the image restoration in the fields of biology, medicine, remote sensing and the like.
Owner:ZHEJIANG UNIV
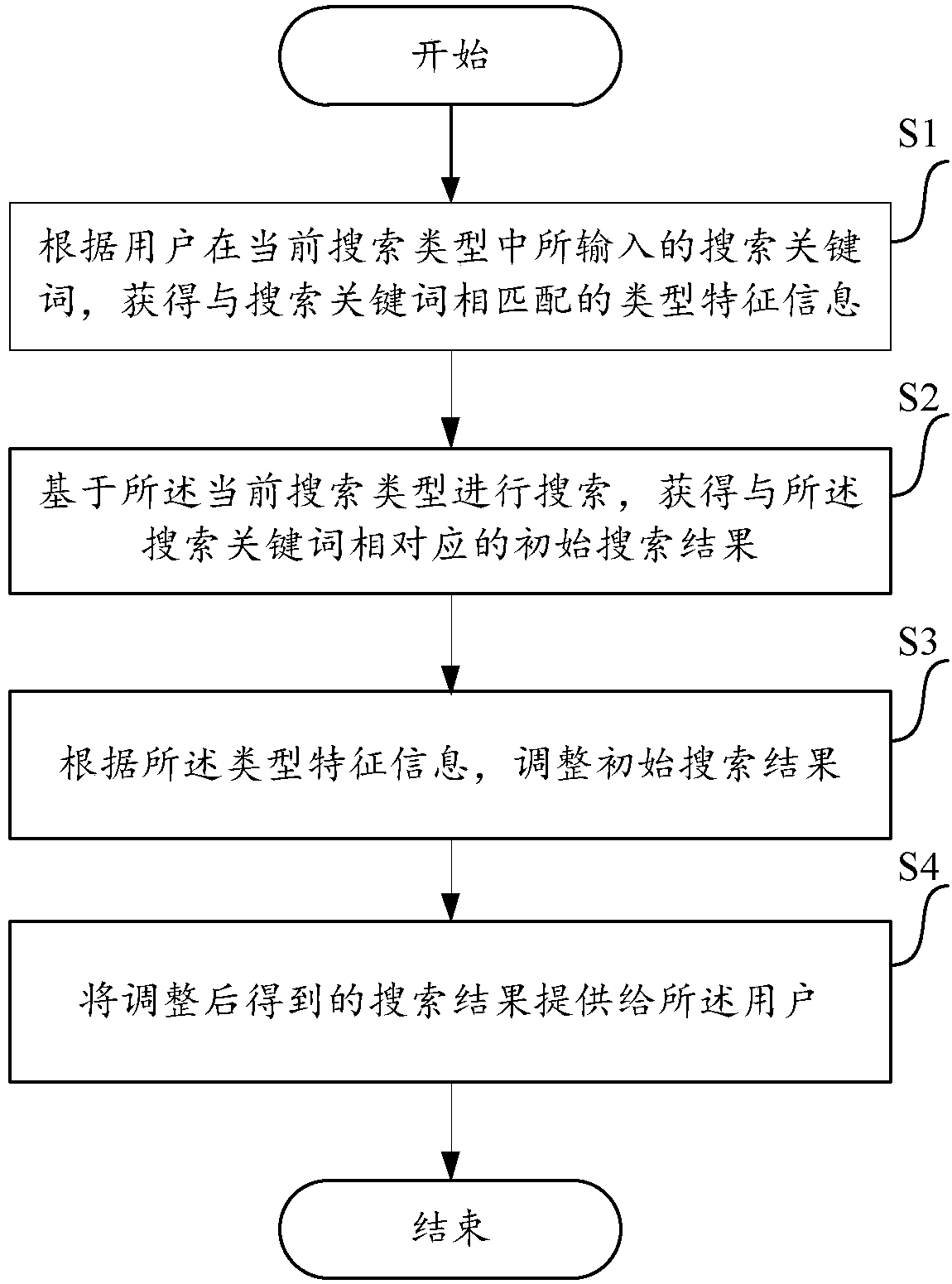
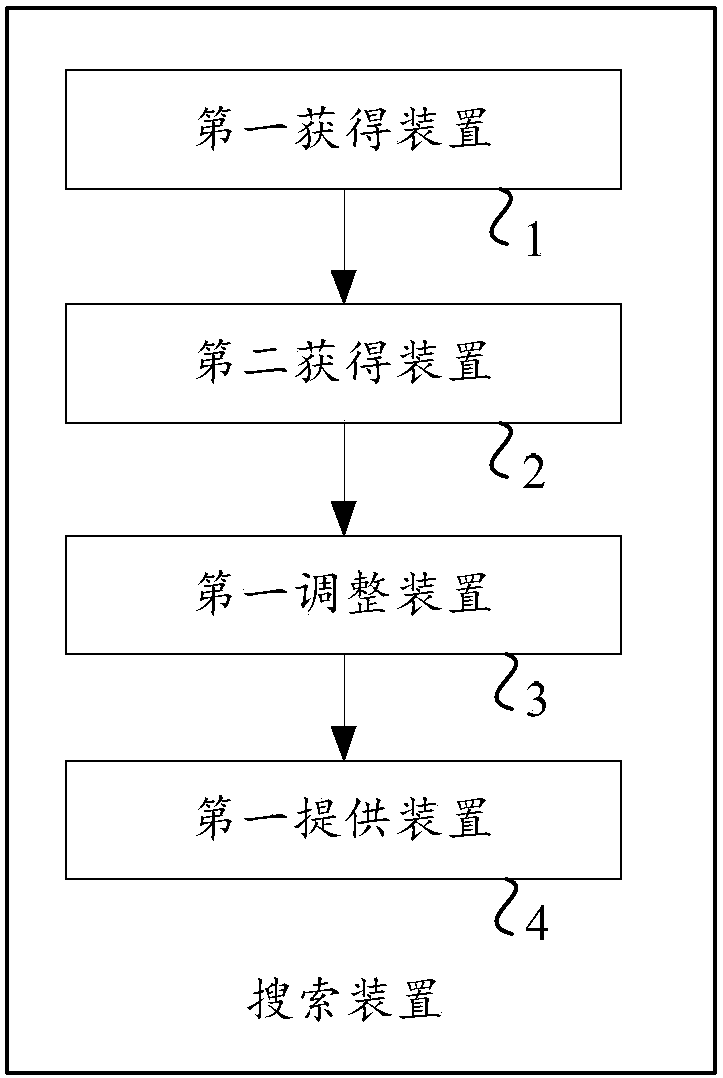
Method and device for providing search result
InactiveCN107562750APotential search needs matchSearch requirements matchSpecial data processing applicationsType signatureInformation retrieval
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com