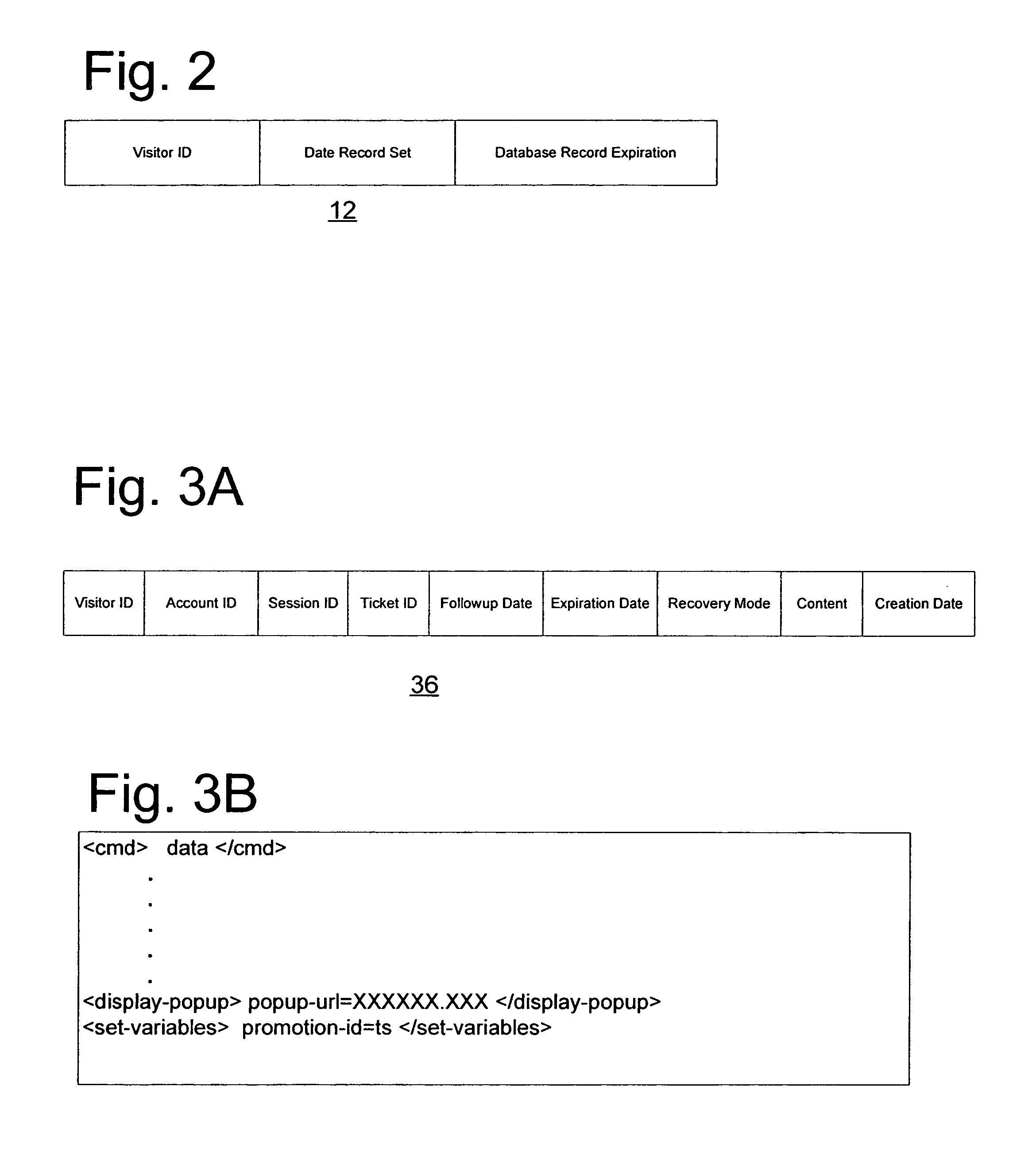
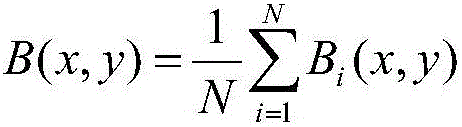Patents
Literature
1102results about How to "Effective judgment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
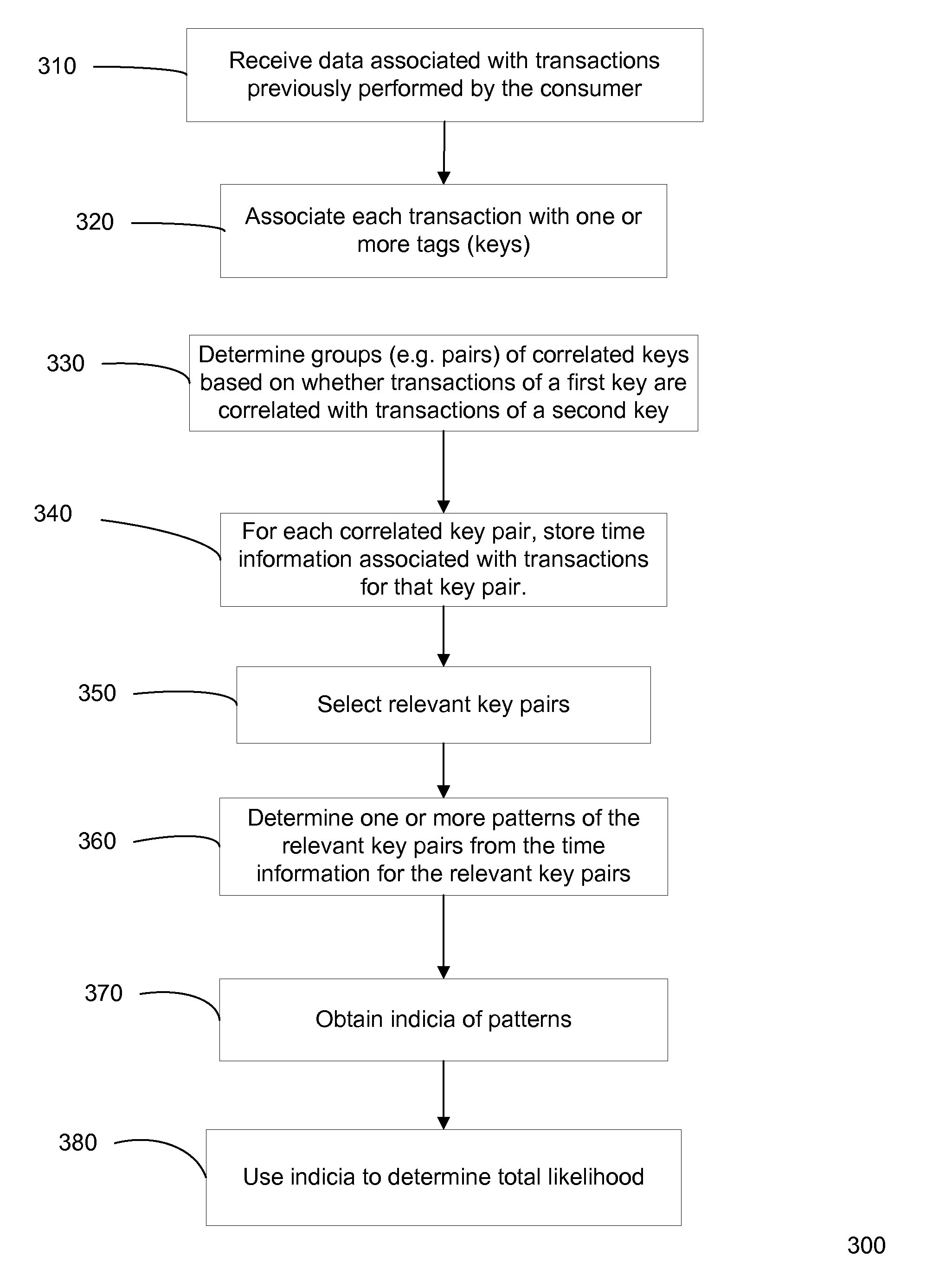
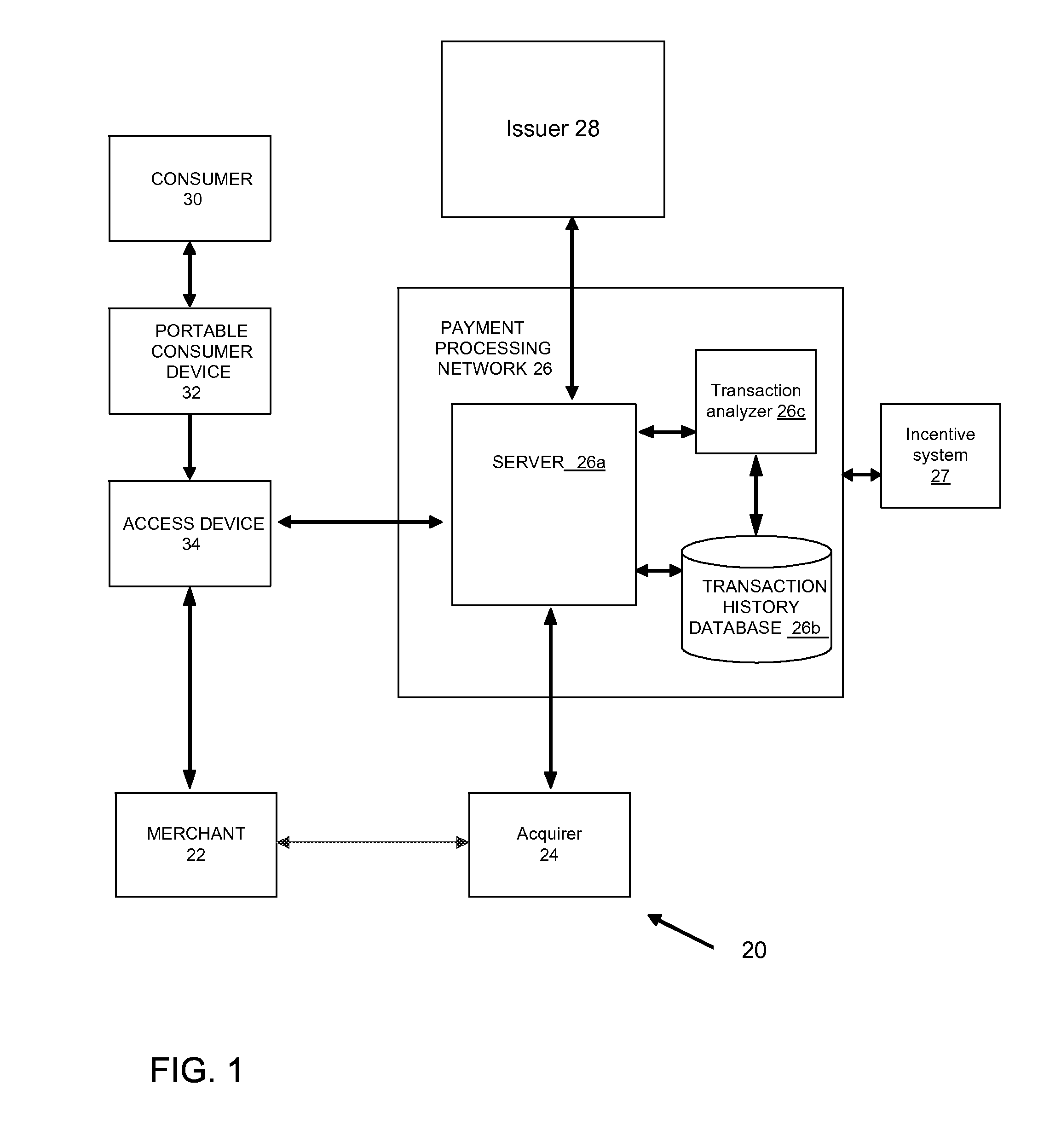
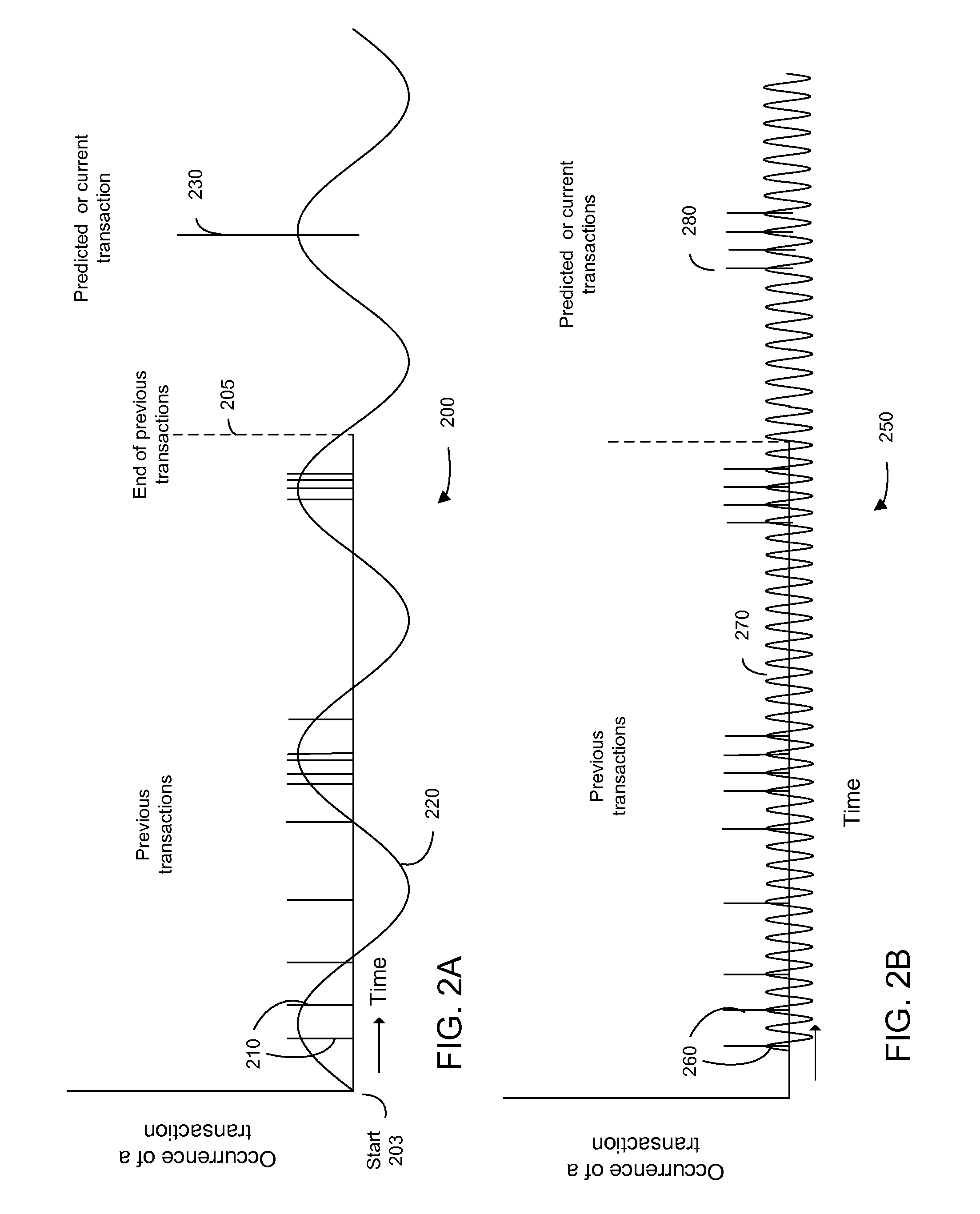
Frequency-based transaction prediction and processing
ActiveUS20100280882A1Efficient access to dataBetter customer serviceMarket predictionsFinanceSpecific timeHard disc drive
Methods, apparatus, and systems are provided for tracking and analyzing data of consumer activity. The tracked data can be organized (e.g. as stored in cache, RAM, hard drives) in certain types of tables, where the tables can be associated with certain tags (keys) for efficiently accessing the data. The organization and associations of the data can also provide simple mechanisms for manipulating the data to obtain results specifically relevant for a task, such as detection of fraud or prediction of consumer behavior to provide better customer service or new services. For example, the tables may contain counters that store the number of times that two correlated consumer events occur within specific time intervals of each other. Such time data can provide efficient determination of patterns of consumer activity.
Owner:VISA INT SERVICE ASSOC
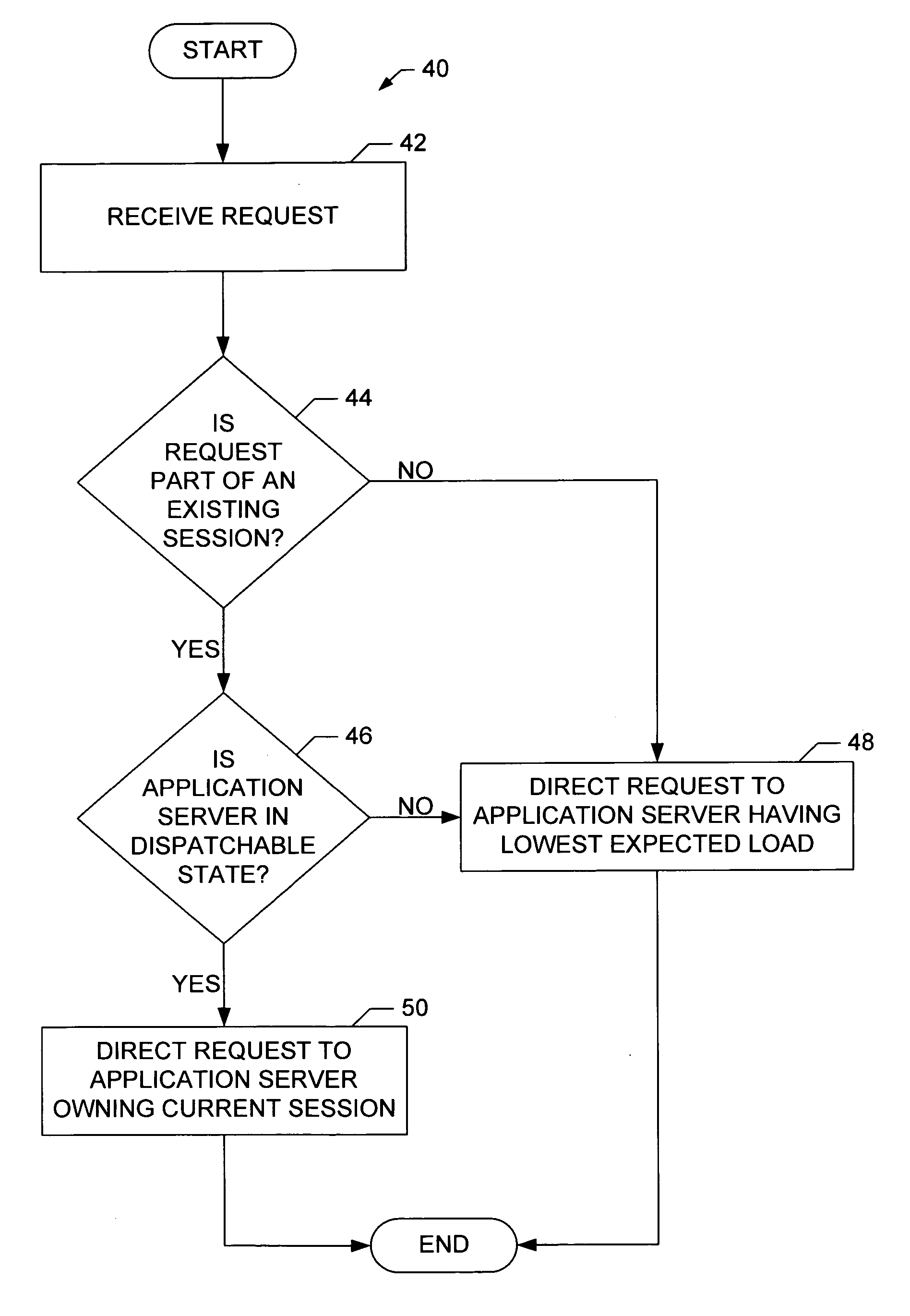
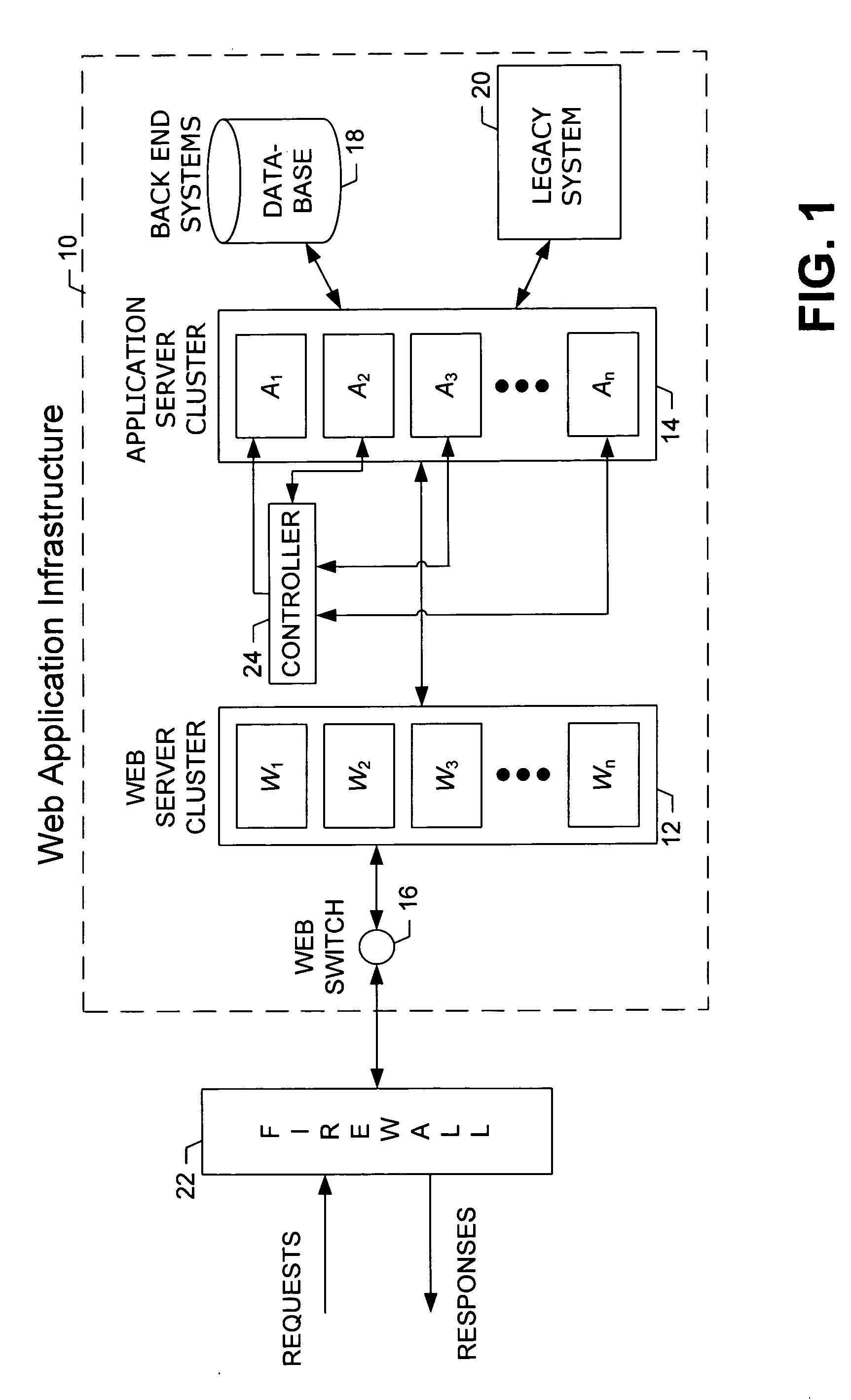
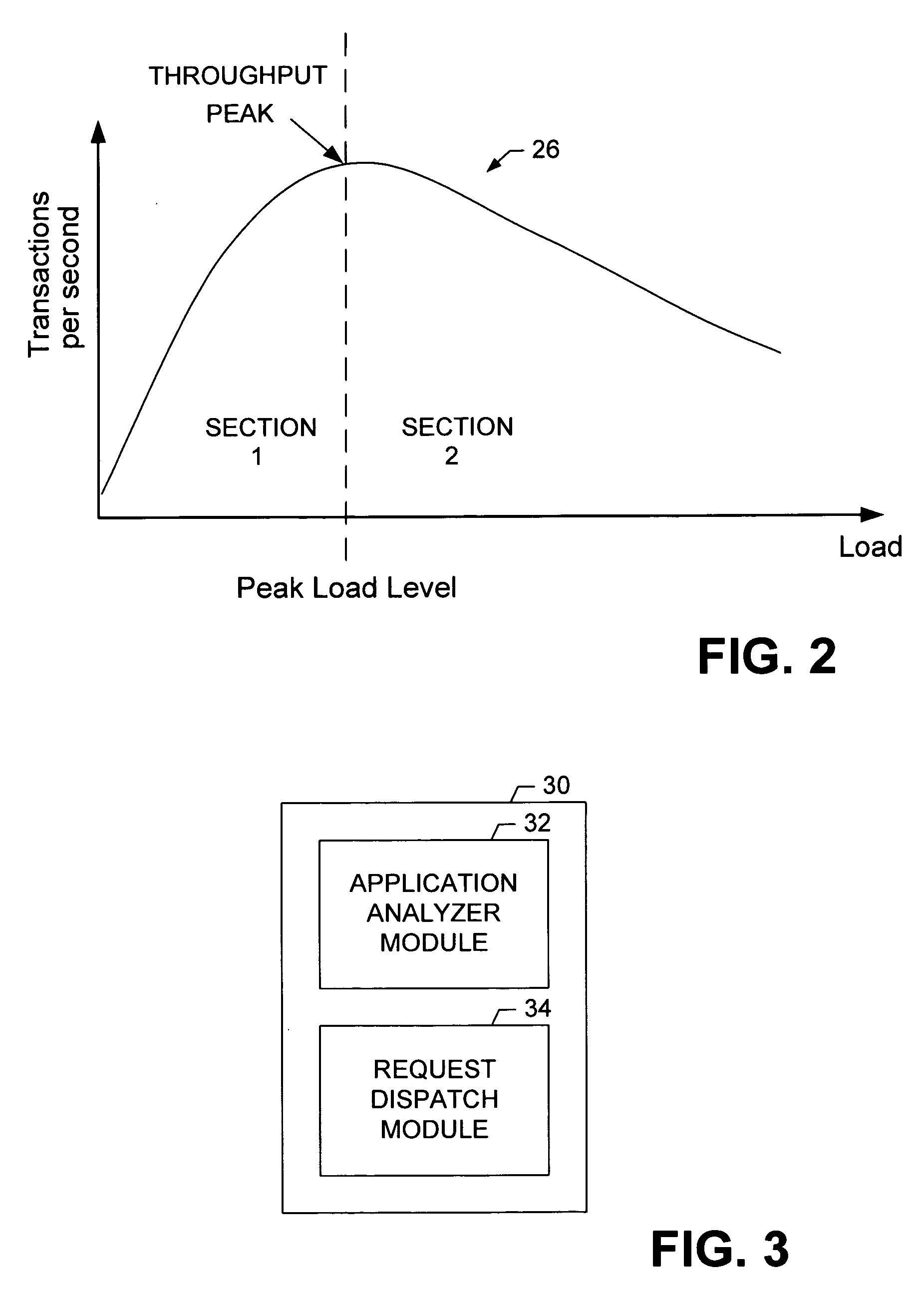
Apparatus and method for distributing requests across a cluster of application servers
InactiveUS20060129684A1Efficient preparationEffective judgmentMultiple digital computer combinationsTransmissionApplication serverDistributed computing
A method and apparatus for distributing a plurality of session requests across a plurality of servers. The method includes receiving a session request and determining whether the received request is part of an existing session. If the received request is determined not to be part of an existing session, then the request is directed to a server having the lowest expected load. If, however, the request is determined to be part of an existing session, then a second determination is made as to whether the server owning the existing session is in a dispatchable state. If the server is determined to be in a dispatchable state, then the request is directed to that server. However, if the server is determined not to be in a dispatchable state, then the request is directed to a server other than the one owning the existing session that has the lowest expected load.
Owner:CHUTNEY TECH
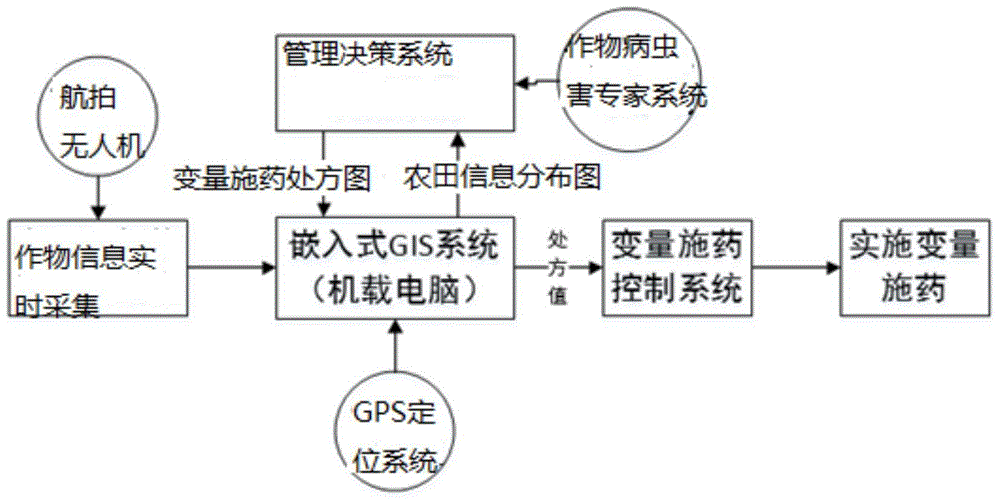
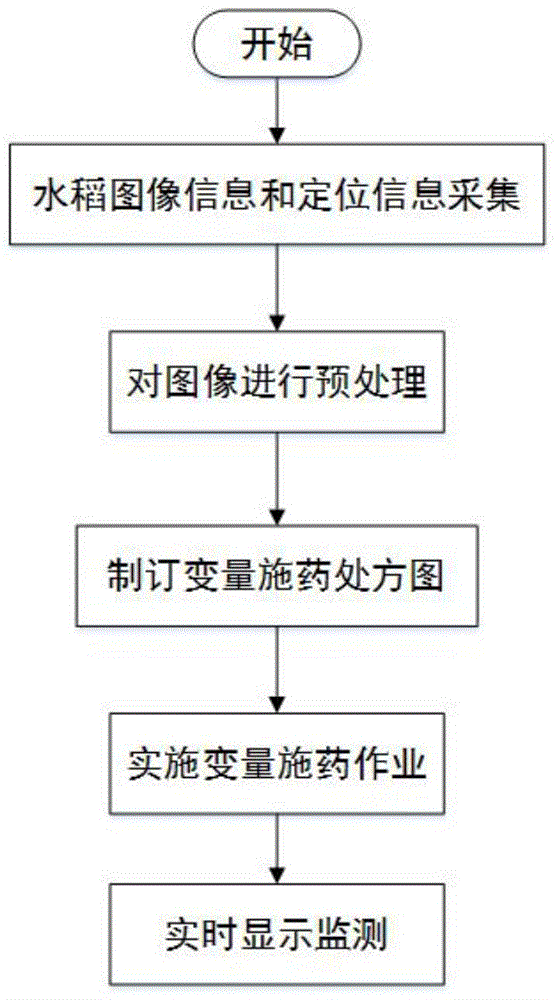
Automatic control system and method for variable pesticide spraying of unmanned aerial vehicle
InactiveCN105173085AReduce usageReduce pollutionAircraft componentsLaunching weaponsInformation processingAutomatic control
The invention provides an automatic control system for variable pesticide spraying of a rice unmanned aerial vehicle based on image processing. The automatic control system comprises a field information acquiring module, an information processing module, an information management decision-making module and an unmanned aerial vehicle variable spraying control module. The automatic control system and the automatic control method for variable pesticide spraying of the rice unmanned aerial vehicle based on image processing can set different dose prescription values according to disaster severity degrees of different plots so as to achieve better pest control effect, reduces agricultural cost and reduces dose. By combining the unmanned aerial vehicle pesticide spraying with a variable pesticide spraying technology, the pesticides are sprayed according to the practical damage condition changes of crops, so that the operation efficiency is improved, the dose of pesticides is reduced, the environmental pollution is relieved, the crop growth is facilitated, and the visual operation is realized by virtue of a real-time monitoring and display system.
Owner:SHANDONG AGRICULTURAL UNIVERSITY
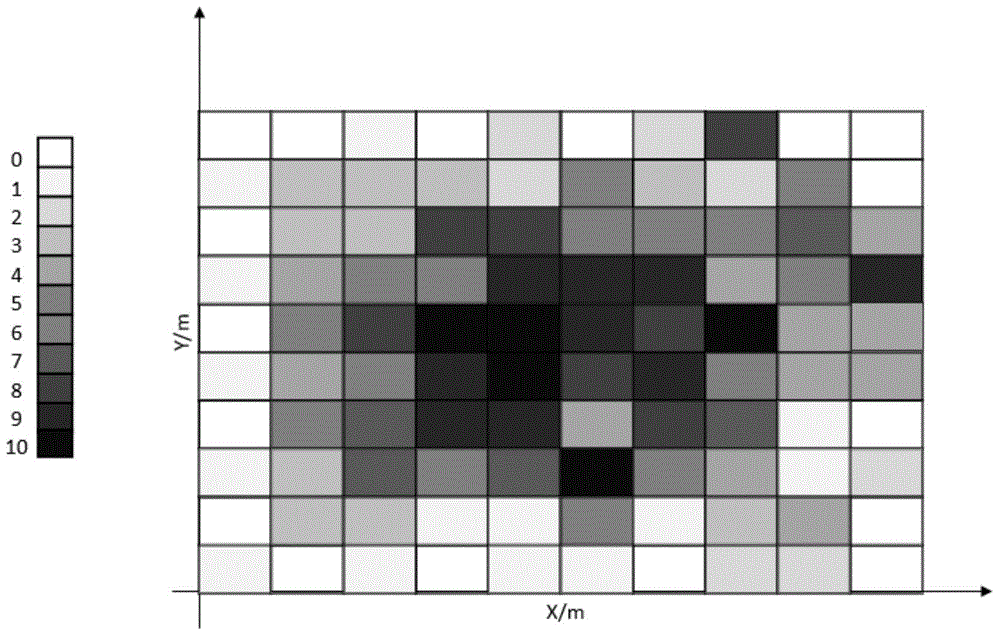
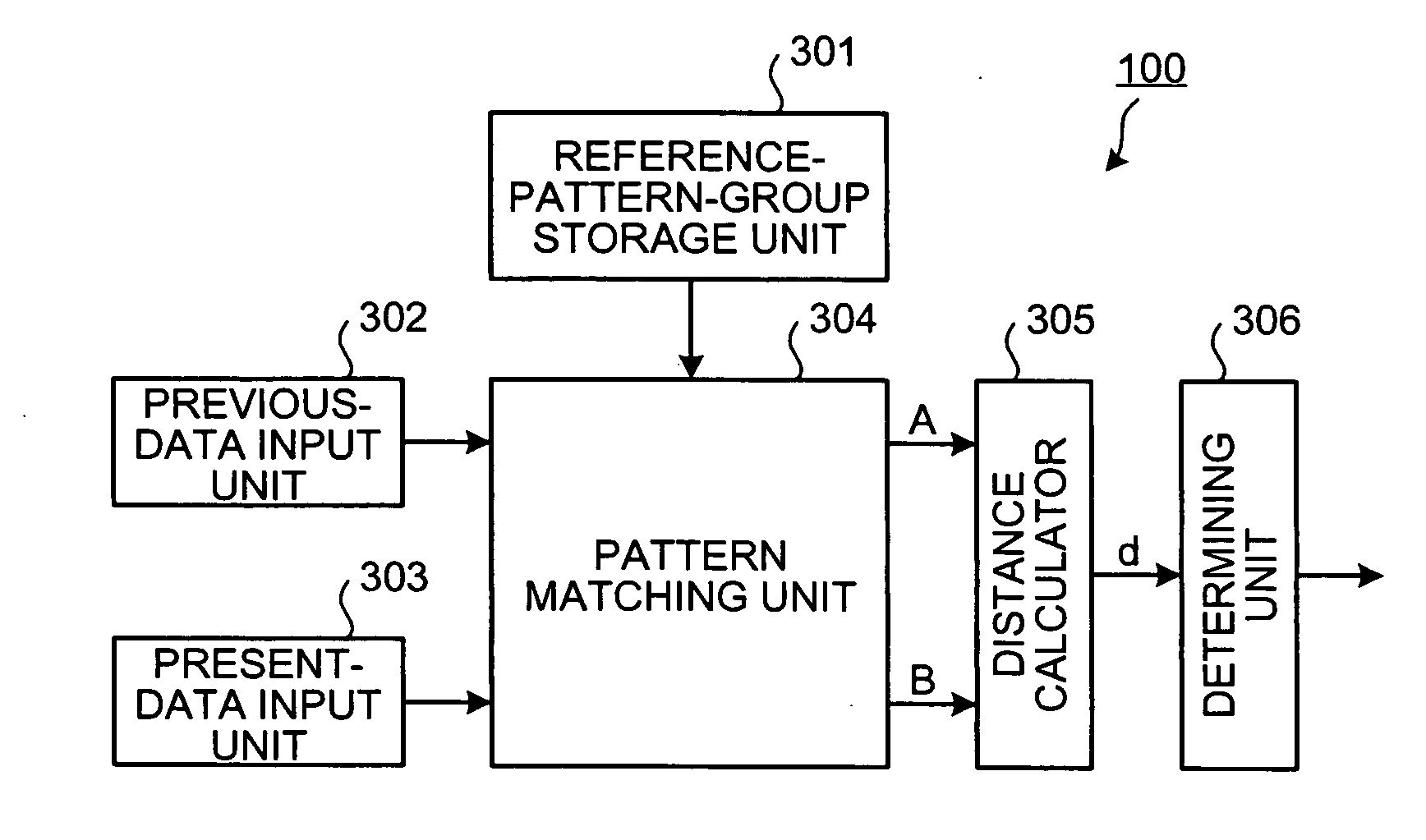
Clinical examination analyzing device, clinical examination analyzing method, and program for allowing computer to execute the method
InactiveUS20060190195A1Improve reliabilityEfficient determinationCharacter and pattern recognitionBiological testingReference patternsCalculator
A pattern matching unit performs pattern matching on present data obtained this time in clinical examination of a part of a subject and previous data obtained last time in the clinical examination of the part with reference patterns. Reference patterns that are most closely approximate to the present data and the previous data are selected. A distance calculator calculates a distance between selected reference patterns. A determining unit determines whether a re-examination is necessary based on the distance.
Owner:A&T +1
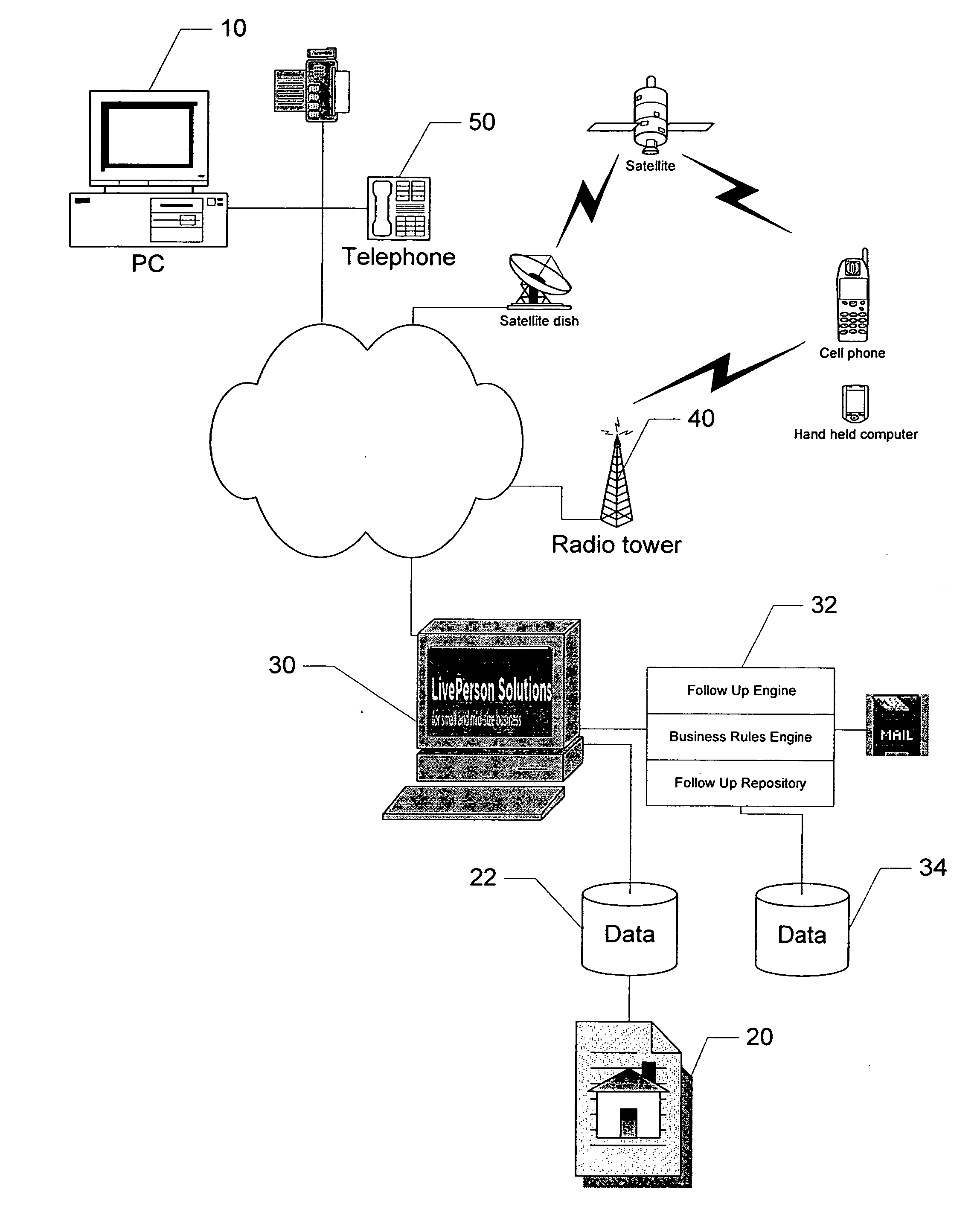
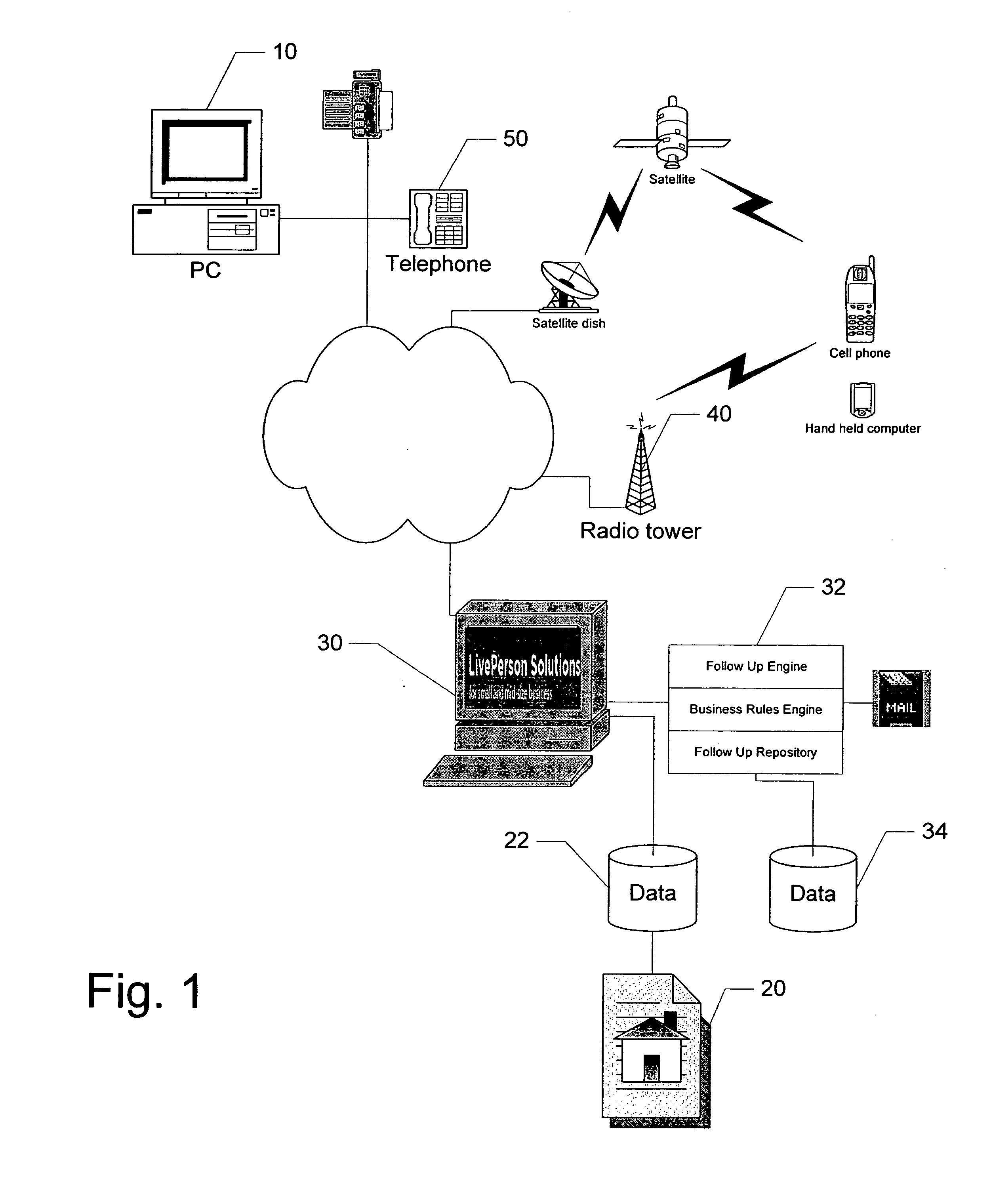
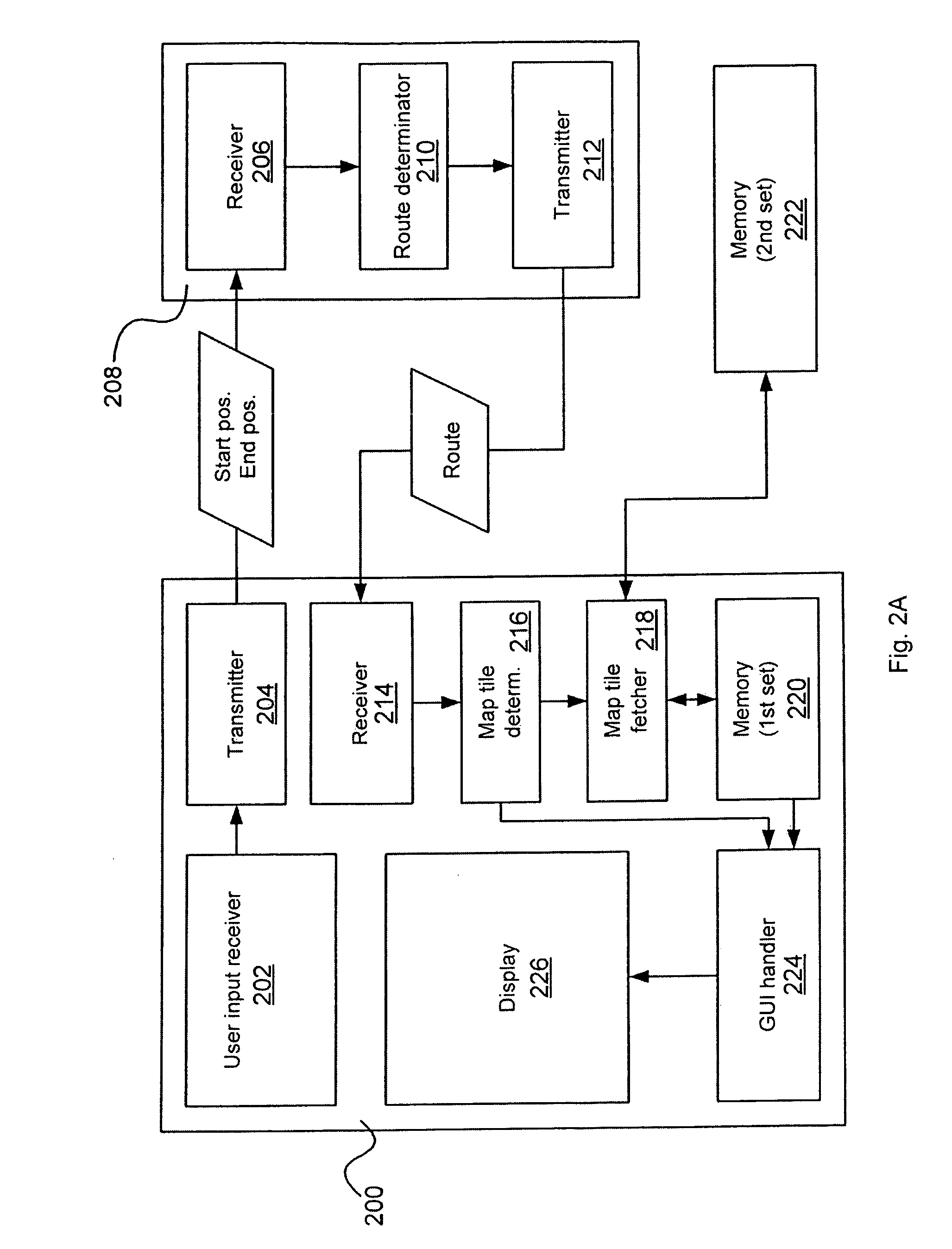
System and method for performing follow up based on user interactions
ActiveUS20070061421A1Reduce needEffective judgmentComputer security arrangementsMultiple digital computer combinationsDatabaseBusiness rule
A system and method for follow up management comprising determining if a user has an unexpired repository record, extracting information from the repository record associated with the user; and acting on instructions stored in the repository record. The method is practiced on a system for managing online interaction comprising a business rules engine a follow up repository, and a follow up engine.
Owner:LIVEPERSON
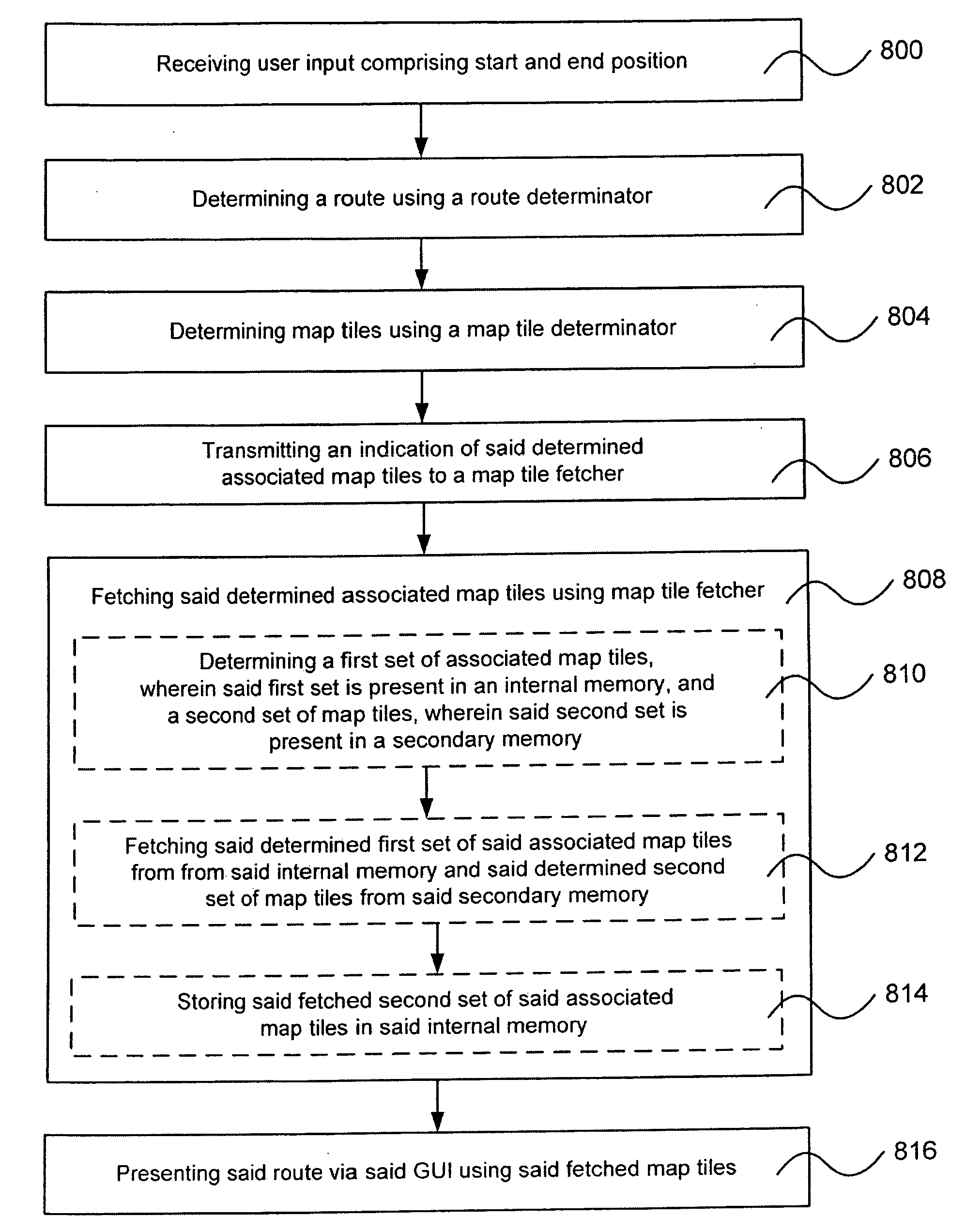
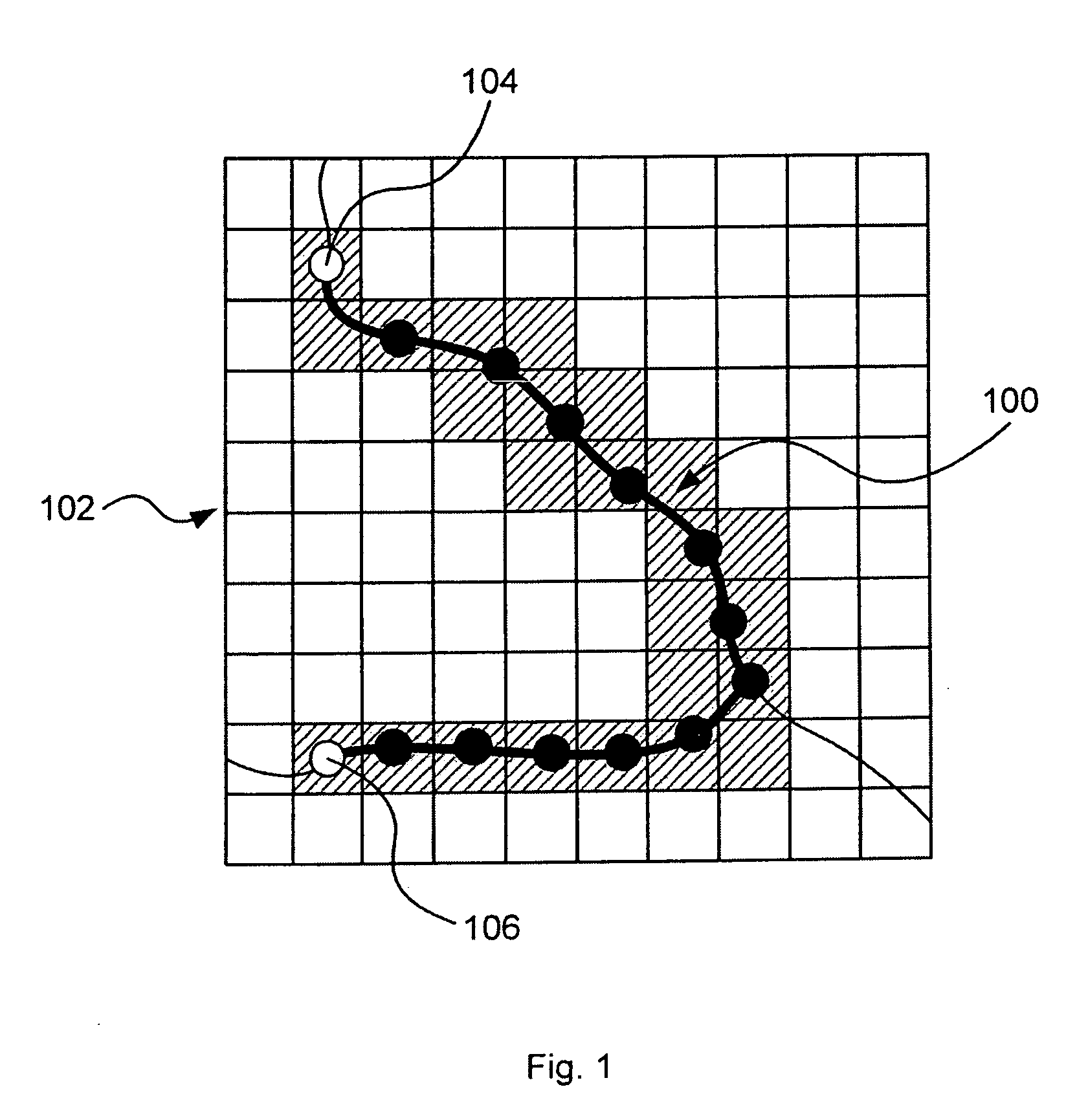
Pre-fetching navigation maps
InactiveUS20090063042A1Efficient memory handlingAvoid excessive trafficInstruments for road network navigationRoad vehicles traffic controlComputer scienceMarine navigation
A method for providing map tiles associated to a route is described. Generally, a route comprising a number of route segments is received. Then, a respective route segment attribute for each of the route segments is determined. Next, associated map tiles for each of the route segments are determined, using said route segment attributes, and finally an indication of the determined map tiles are transmitted to a map tile fetcher.
Owner:VODAFONE IP LICENSING
System and method for performing follow up based on user interactions
ActiveUS8738732B2Reduce needEffective judgmentComputer security arrangementsMultiple digital computer combinationsDatabaseBusiness rule
A system and method for follow up management comprising determining if a user has an unexpired repository record, extracting information from the repository record associated with the user; and acting on instructions stored in the repository record. The method is practiced on a system for managing online interaction comprising a business rules engine a follow up repository, and a follow up engine.
Owner:LIVEPERSON
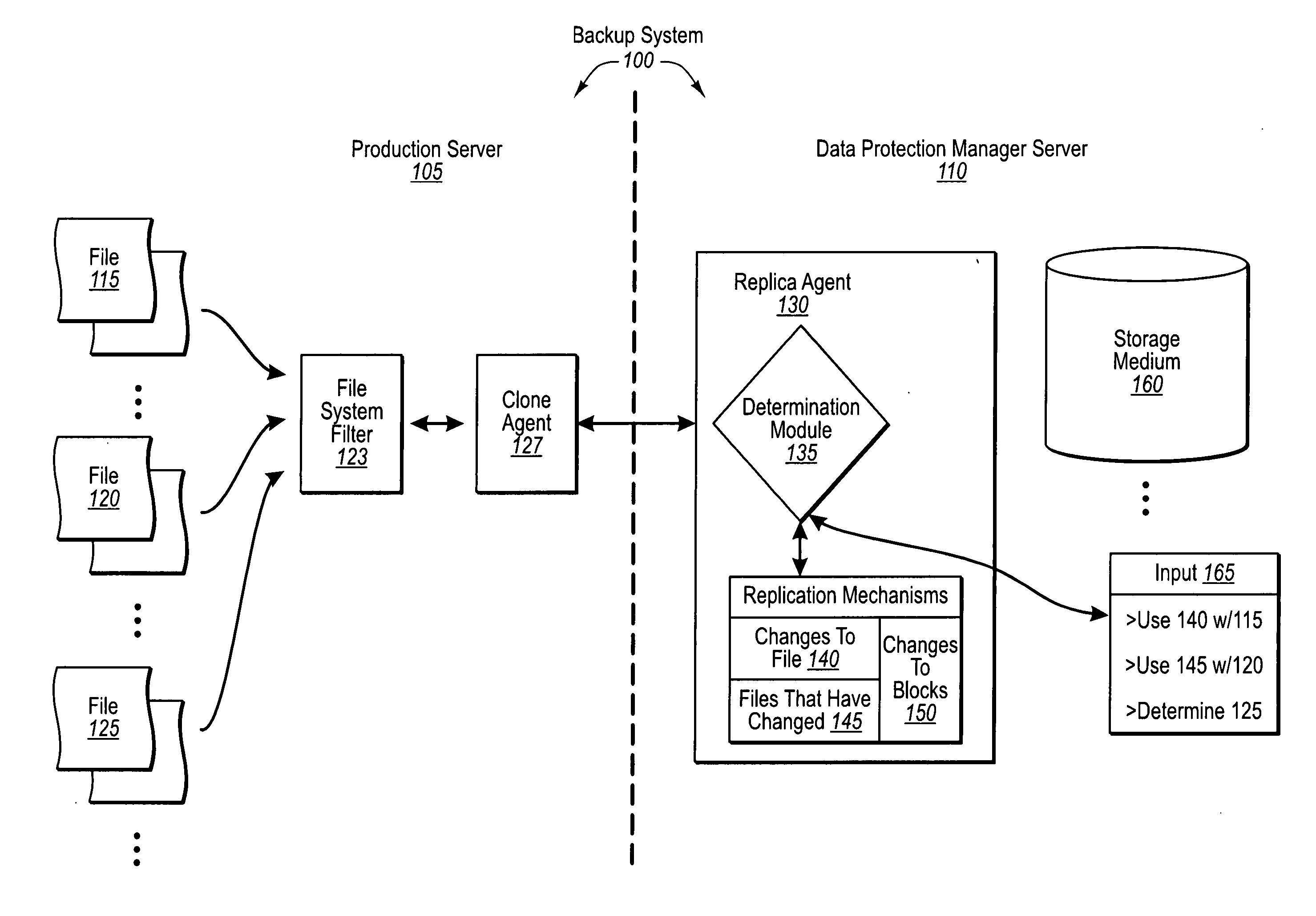
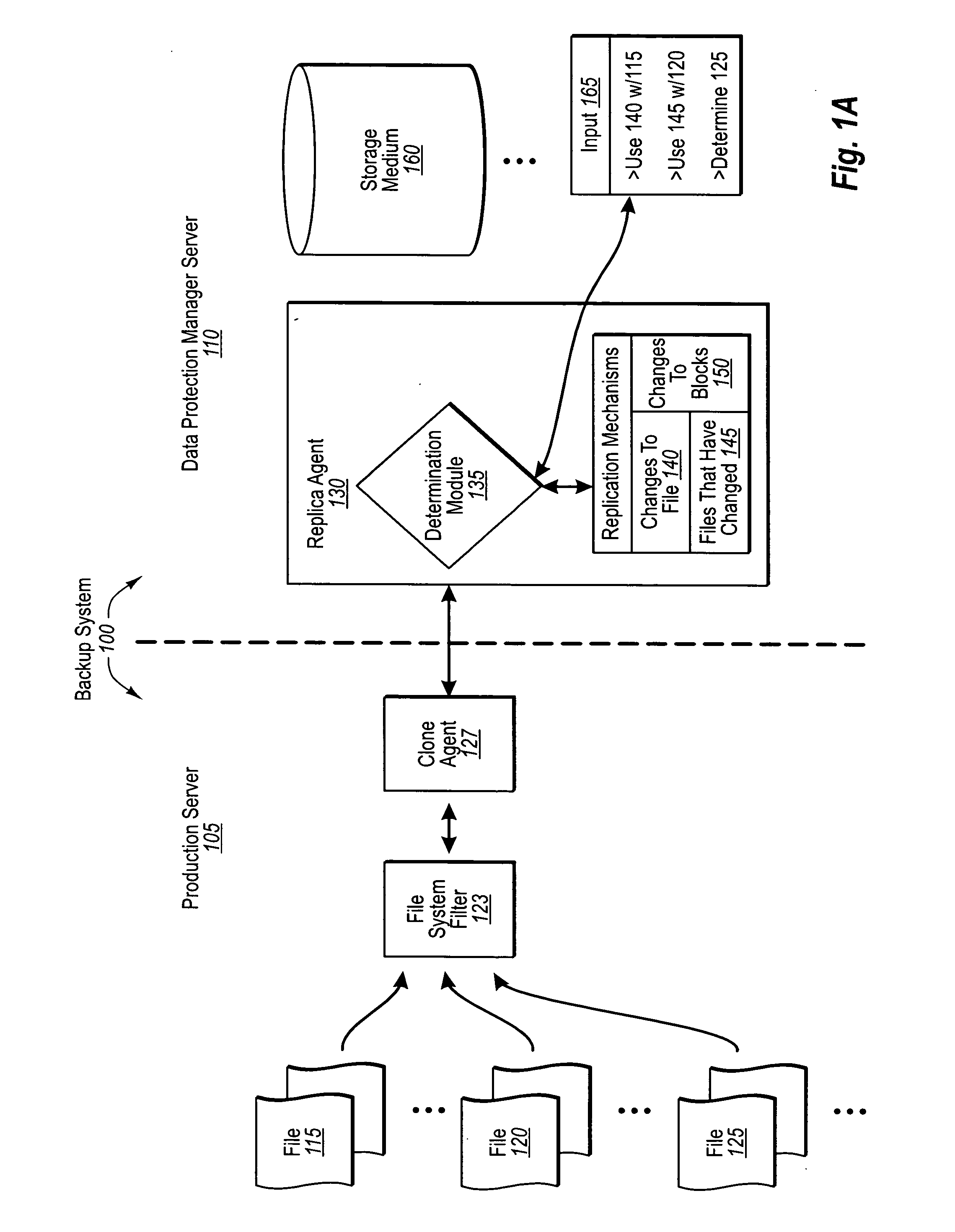
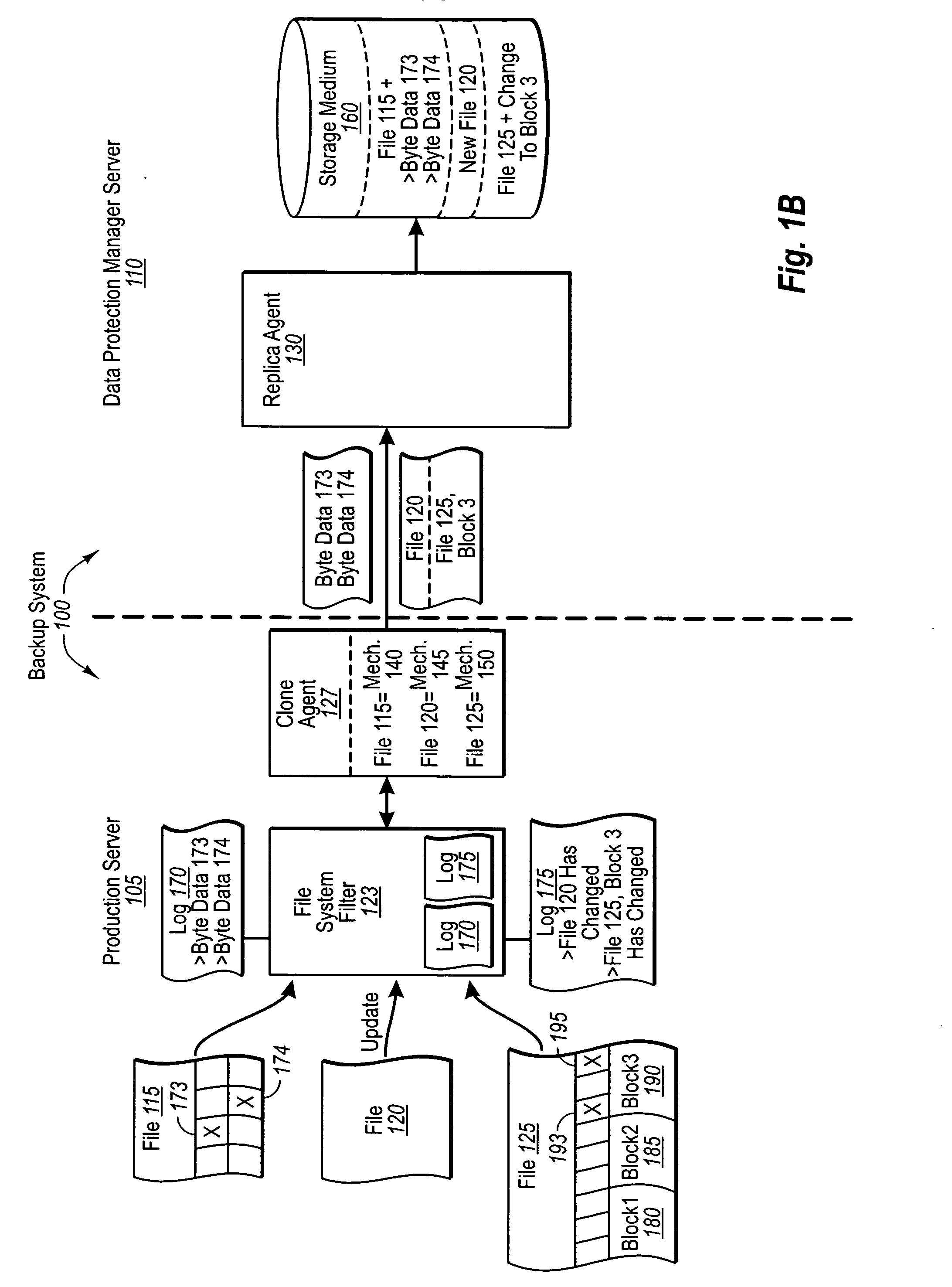
Automatically determining file replication mechanisms
InactiveUS20070192386A1Effective judgmentProgram control using stored programsMemory loss protectionFile replicationByte
A backup administrator can backup files from a production server on any of a plurality of different bases. In particular, some files can be replicated on a changed-byte basis. In other cases, files can be backed up by replicating updated copies of the entire file, or even byte blocks of the file. Determinations as to how a replication agent will back up a certain file or set of files can be made by a backup administrator, automatically through a predefined logic, or dynamically based on defined criteria. Corresponding agents at the production server can then flag these files as indicated. Thus, at a later point, when the DPM server requests the updates of each file, the production server can either send over copies of the changed file bytes, entire copies of the changed file itself, or even changed blocks of a file, as appropriate.
Owner:MICROSOFT TECH LICENSING LLC
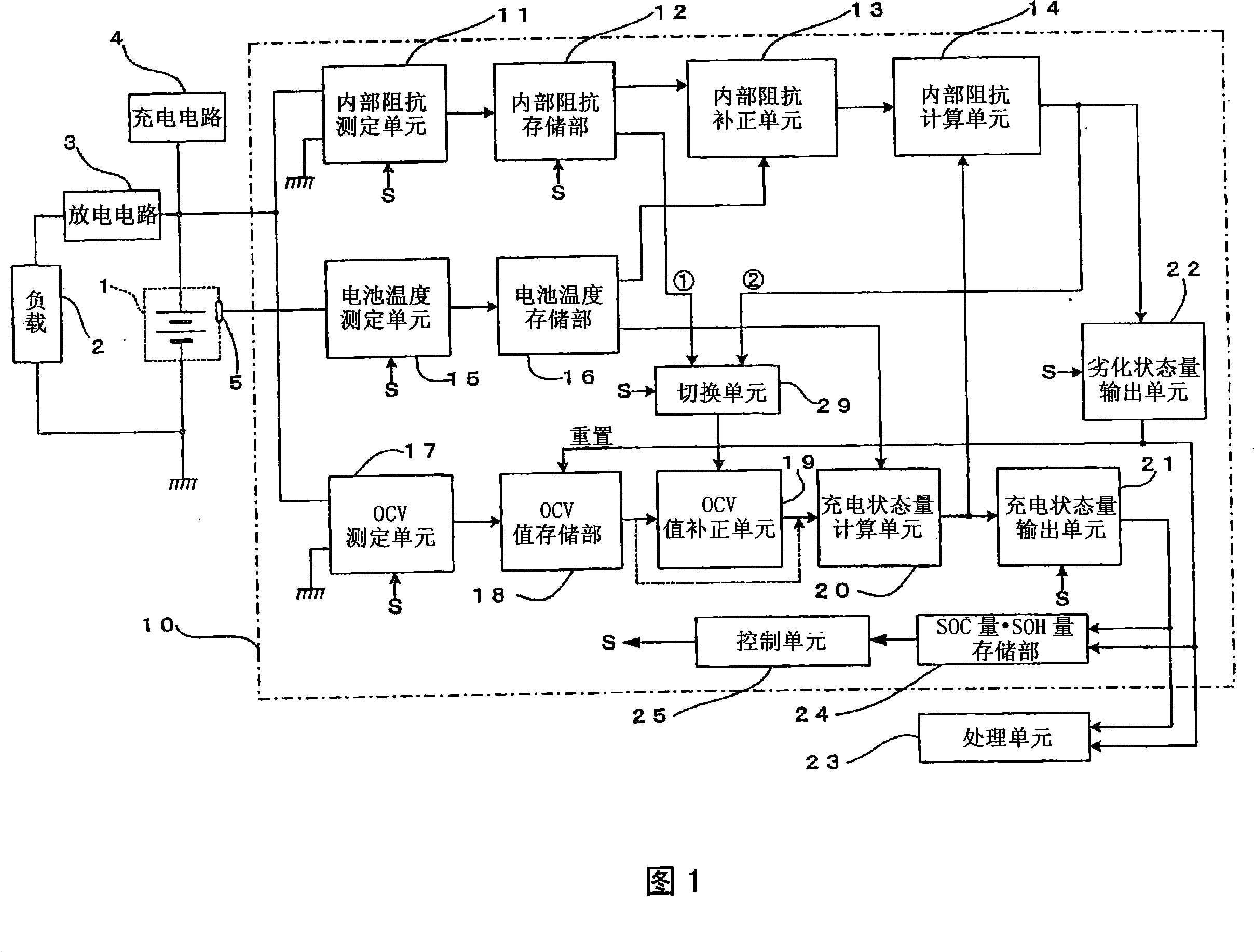
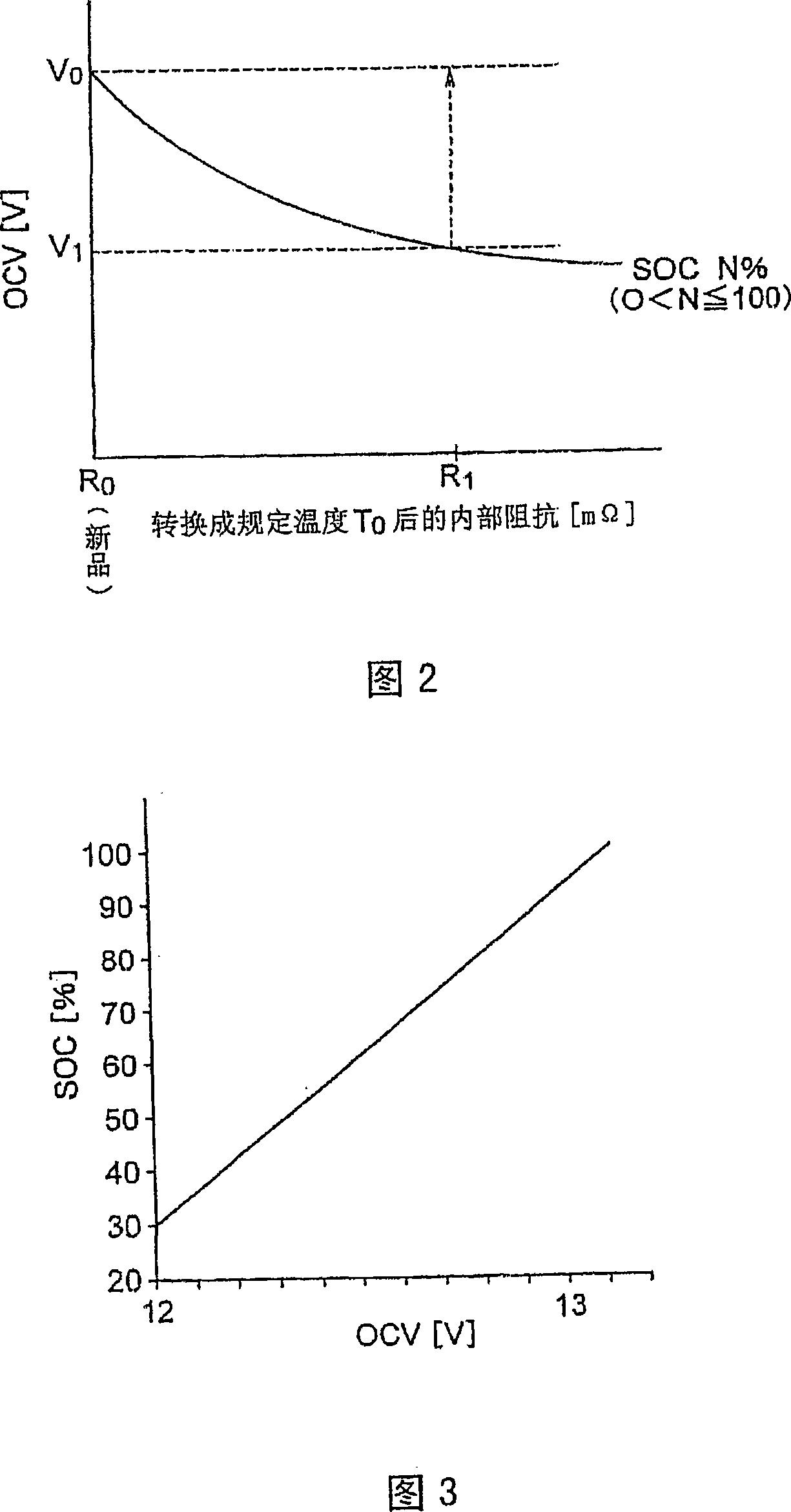
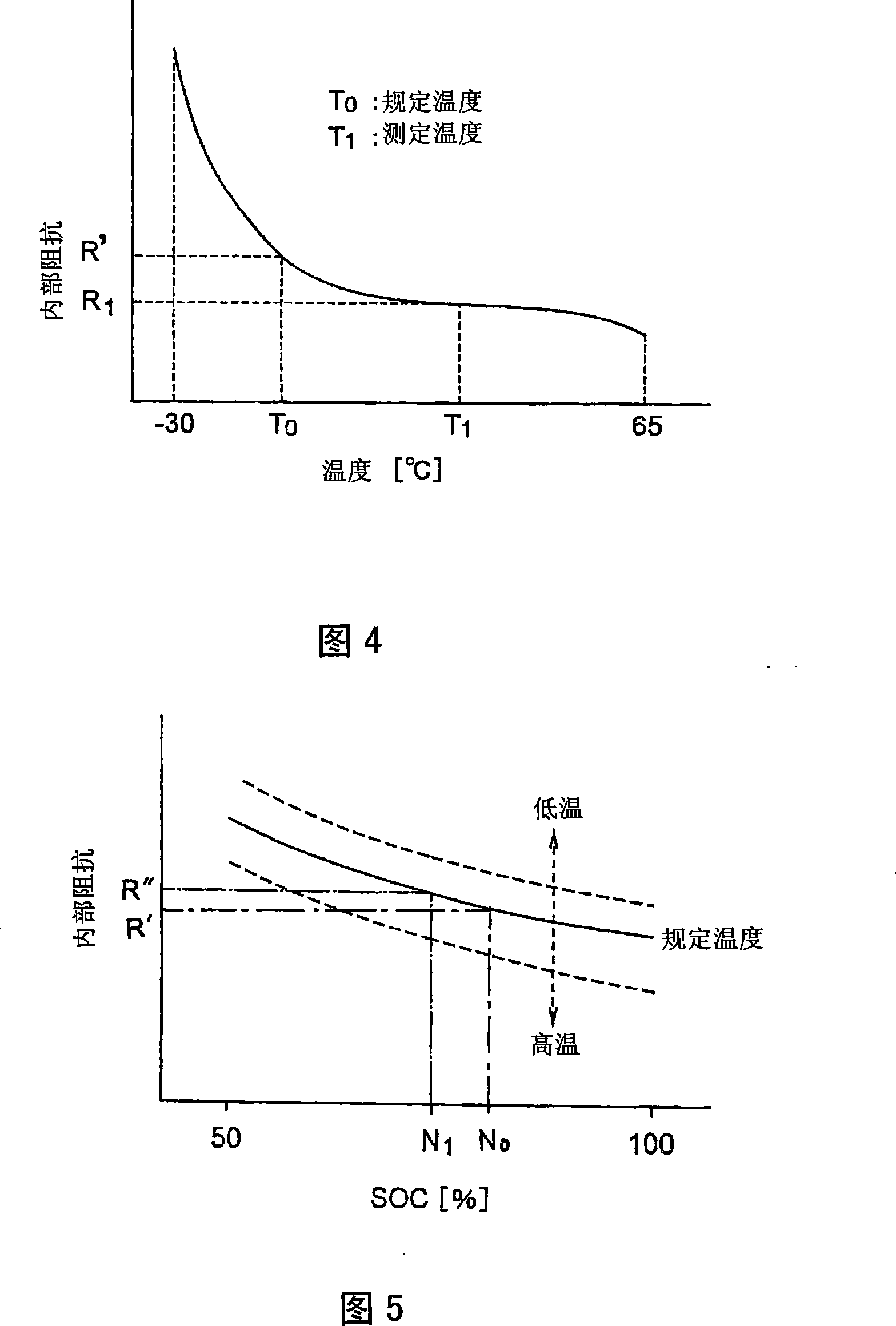
Method and apparatus for determining deterioration of secondary battery, and power supply system therewith
ActiveCN101243325AHigh-precision detectionPrecise managementElectrical testingElectrical batteryEngineering
Owner:FURUKAWA ELECTRIC CO LTD
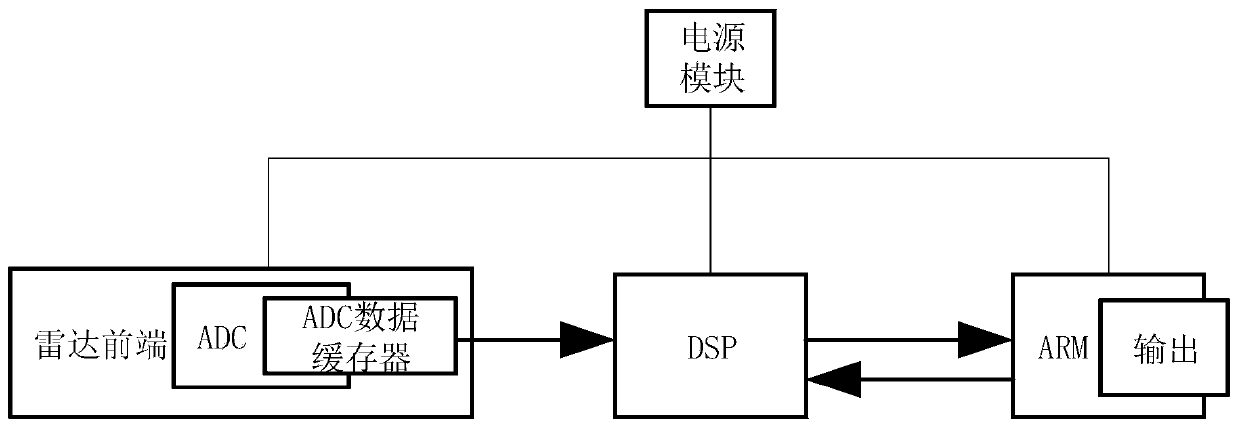
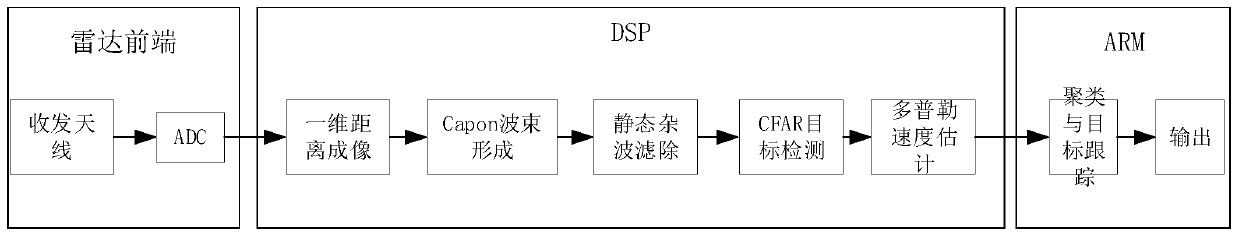
Personnel detection and counting system based on millimeter wave radar
ActiveCN110118966AEasy to detectAchieve countRadio wave reradiation/reflectionDigital signal processingData set
The invention provides a personnel detection and counting system based on a millimeter wave radar, wherein the millimeter wave radar is installed at a set position of a monitoring area, the millimeterwave radar transmits millimeter wave band radio frequency signals to the monitoring area through a multi-transmitting and multi-receiving antenna of the millimeter wave radar and receives echo signals at the same time, the echo signals are subjected to frequency mixing with the transmitted signals and then subjected to down-conversion to obtain beat intermediate frequency signals, and the beat intermediate frequency signals are sampled to obtain an echo sampling sequence. A digital signal processor reads the echo sampling sequence and performs signal processing to obtain a detected point cloud data set. An ARM processor reads the point cloud data set, meanwhile, Kalman filtering tracking is carried out on the point cloud data, continuous observation of states and the number of a pluralityof human body moving targets is achieved, the positions and the number of people in the monitoring area are obtained, and the number of people in the monitoring area is counted. The personnel detection and counting system based on the millimeter wave radar can track at least 20 targets simultaneously, provide the position and speed information of the targets, effectively judge the state of the targets and give early warning in time.
Owner:长沙莫之比智能科技有限公司
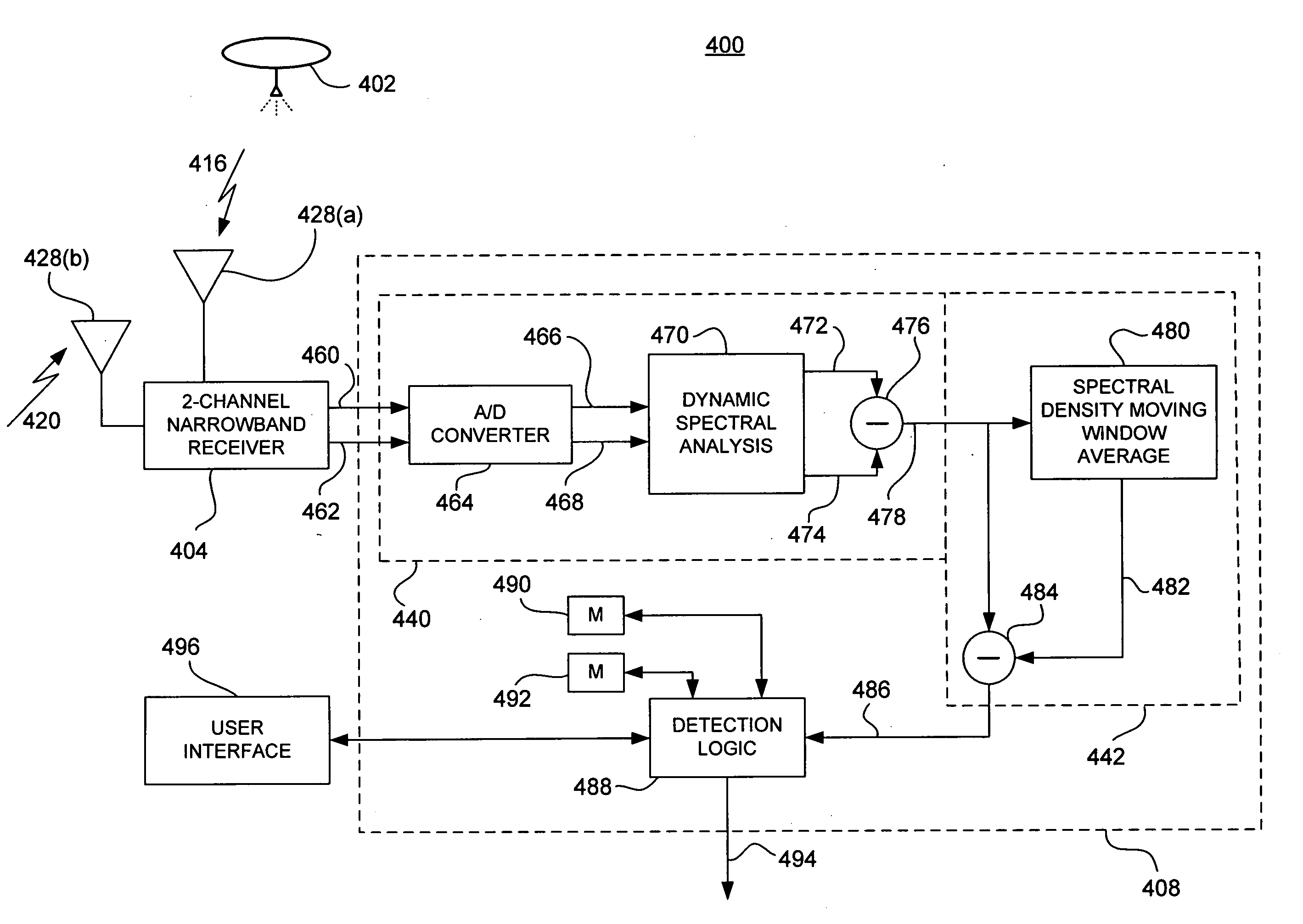
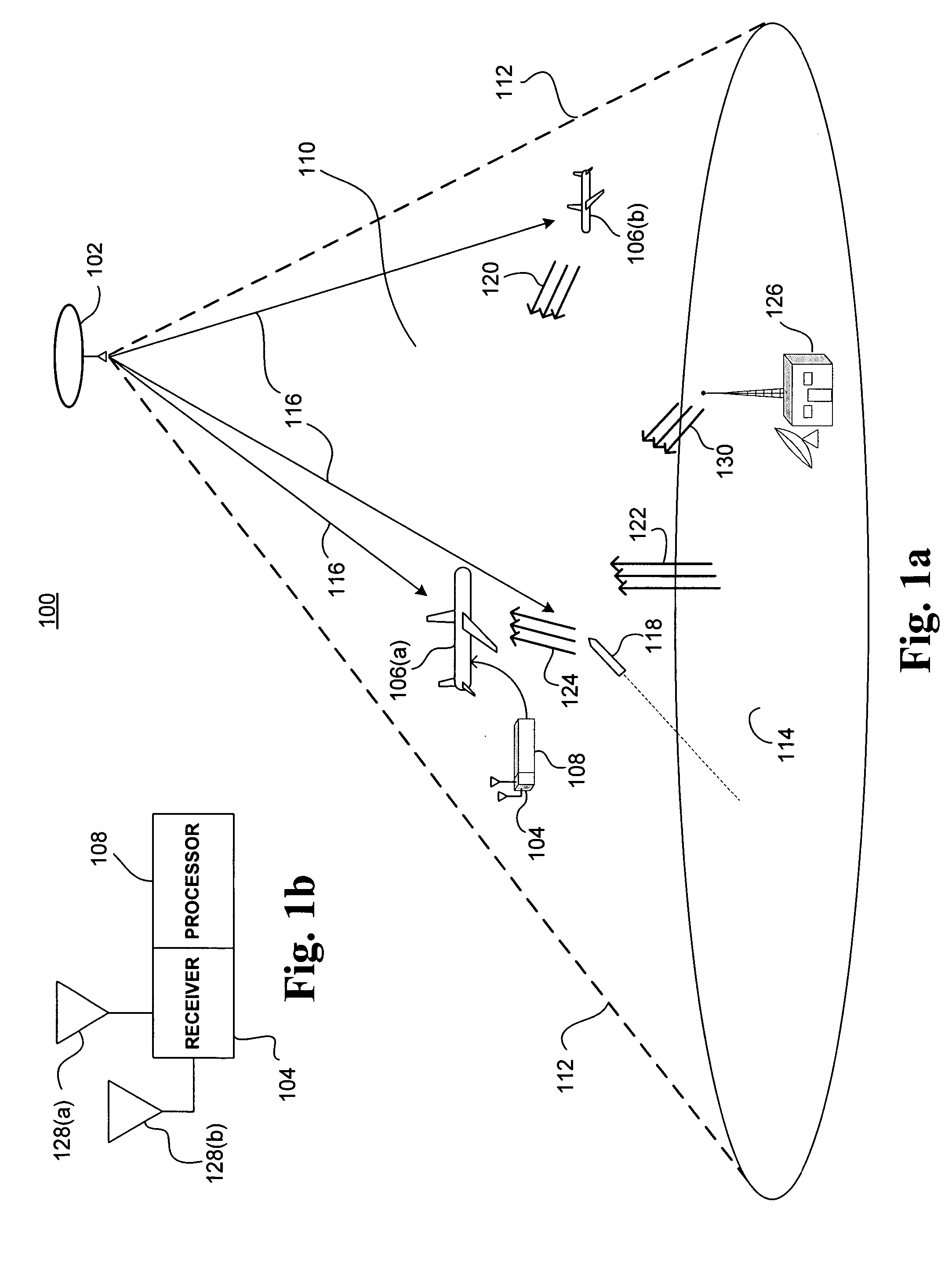
System and method for onboard detection of ballistic threats to aircraft
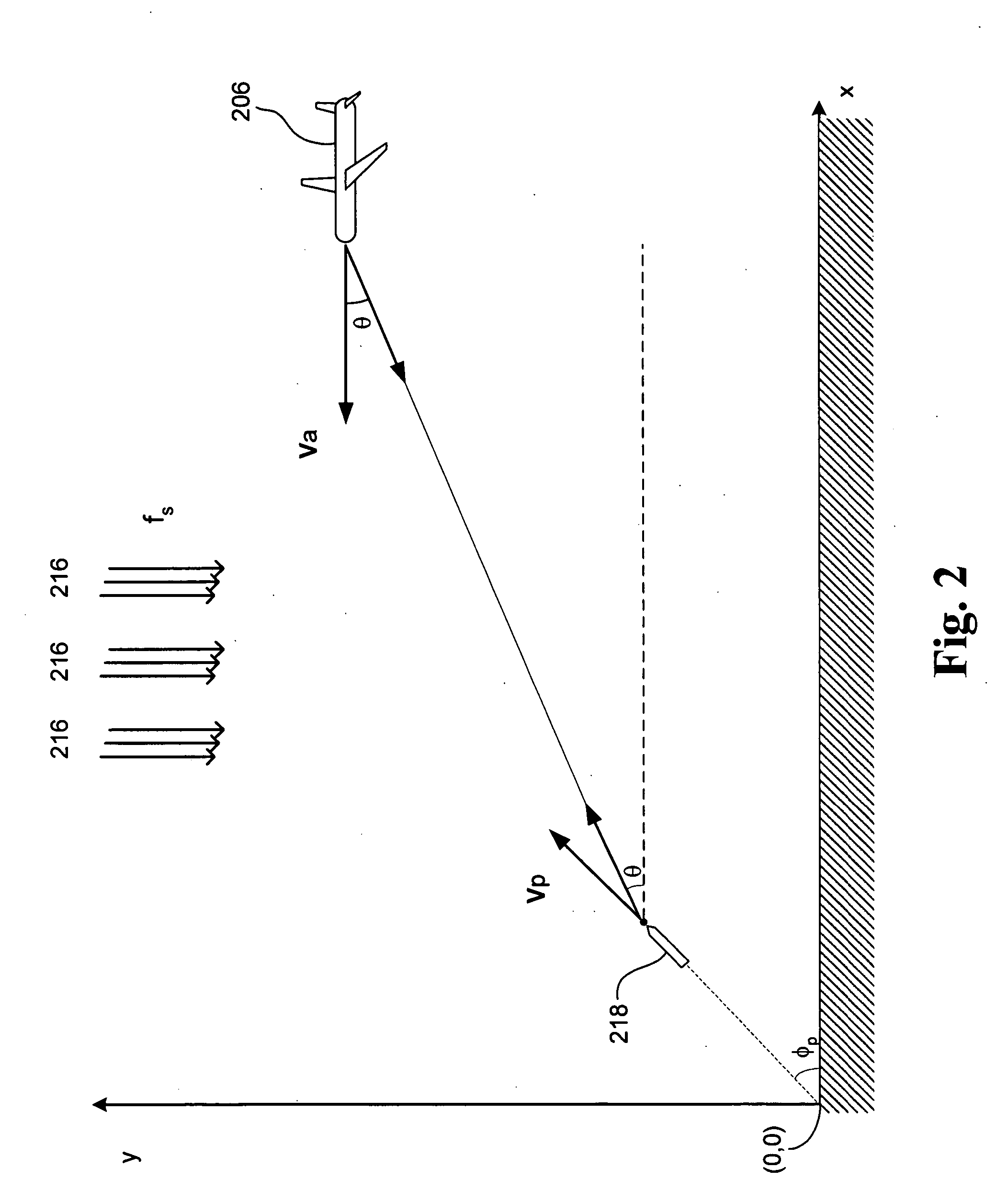
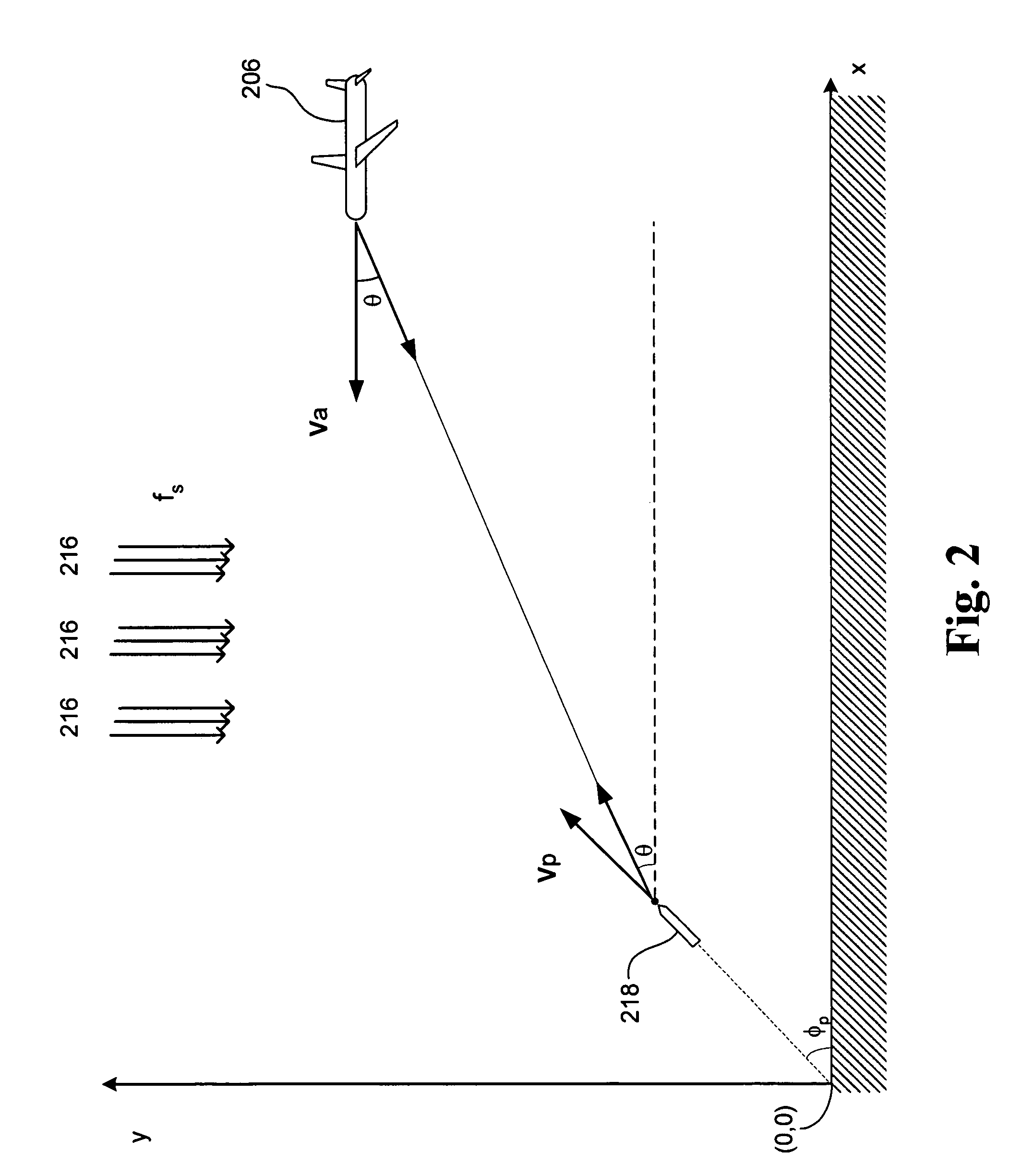
InactiveUS20050275582A1Low costMinimize per-aircraft costCommunication jammingAntennasCountermeasureAcquired characteristic
A bi-static continuous wave radar system and related methods for detecting incoming threats from ballistic projectiles includes a remote source of RF illumination, and a local receiver installed in one or more target aircraft. A first receiving channel acquires direct path illumination from the source and provides a reference signal, and a second receiving channel acquires a scatter signal reflected by a projectile. A processor coupled to each receiver corrects scatter signal Doppler offset induced by relative source motion, isolates narrowband Doppler signals to derive signatures characteristic of the projectile, and by executing appropriate algorithms, compares the derived signatures to modeled signatures stored in memory. If the comparison yields a substantial similarity, the processor outputs a warning signal sufficient to initiate defensive countermeasures.
Owner:MDA INFORMATION SYST
System and method for onboard detection of ballistic threats to aircraft
InactiveUS6980151B1Minimize per-aircraft costEffective judgmentCommunication jammingAntennasCountermeasureFlight vehicle
A bi-static continuous wave radar system and related methods for detecting incoming threats from ballistic projectiles includes a remote source of RF illumination, and a local receiver installed in one or more target aircraft. A first receiving channel acquires direct path illumination from the source and provides a reference signal, and a second receiving channel acquires a scatter signal reflected by a projectile. A processor coupled to each receiver corrects scatter signal Doppler offset induced by relative source motion, isolates narrowband Doppler signals to derive signatures characteristic of the projectile, and by executing appropriate algorithms, compares the derived signatures to modeled signatures stored in memory. If the comparison yields a substantial similarity, the processor outputs a warning signal sufficient to initiate defensive countermeasures.
Owner:MDA INFORMATION SYST
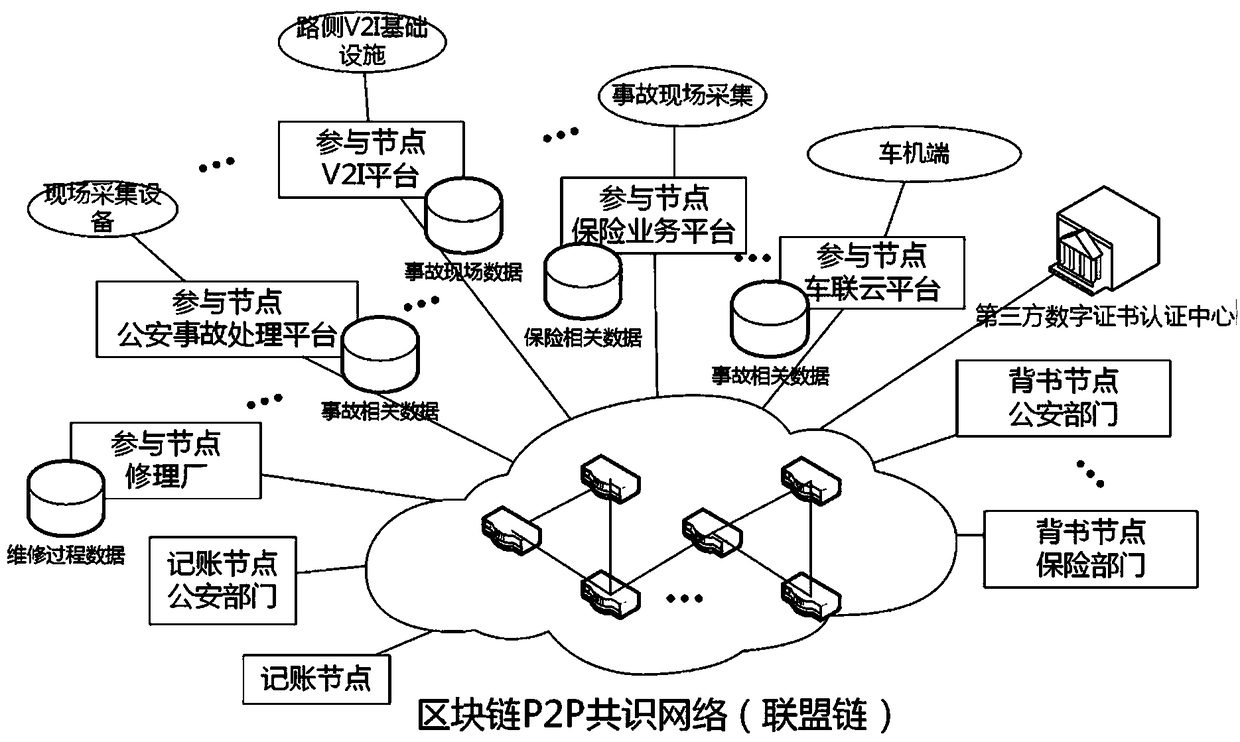
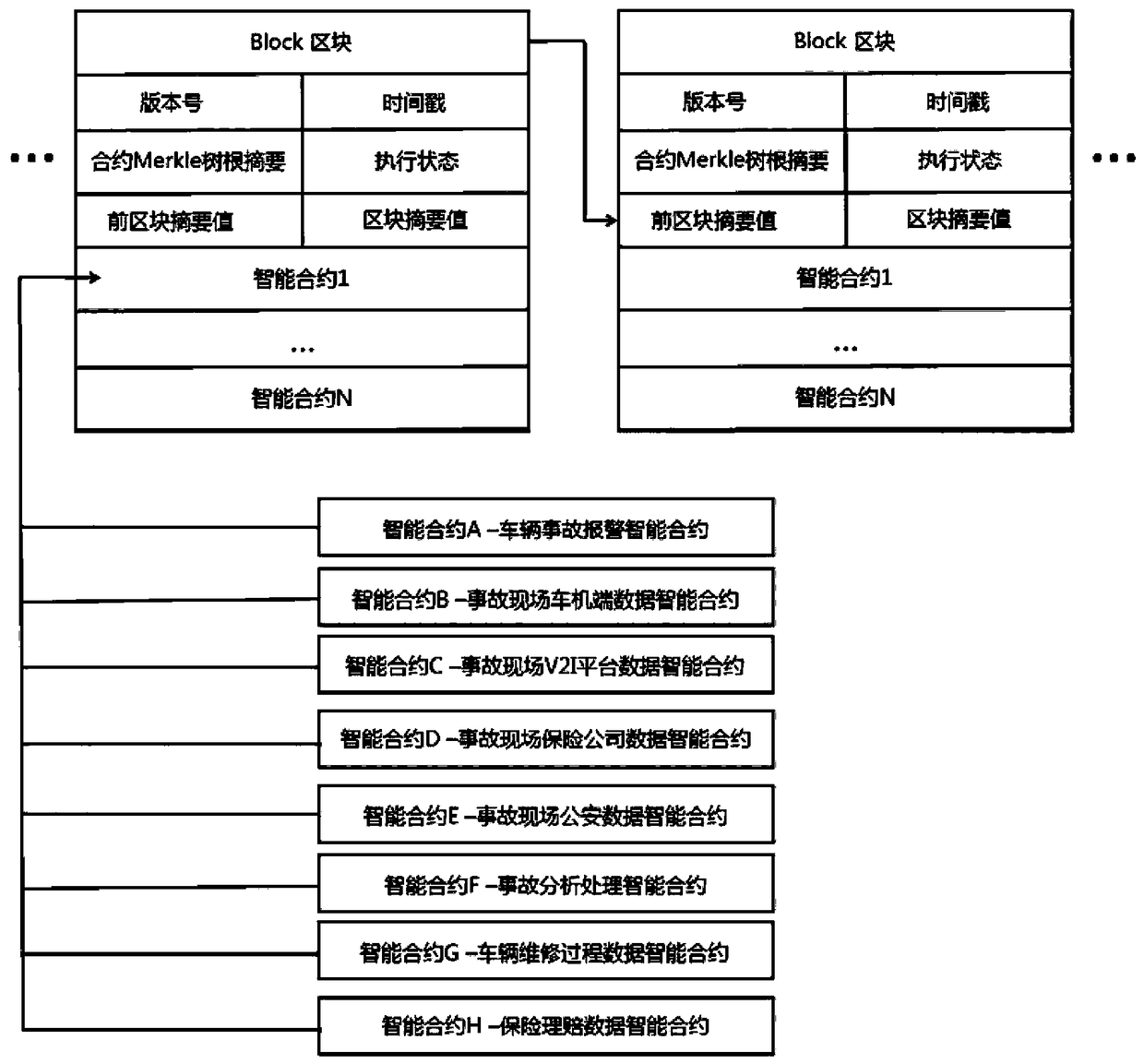
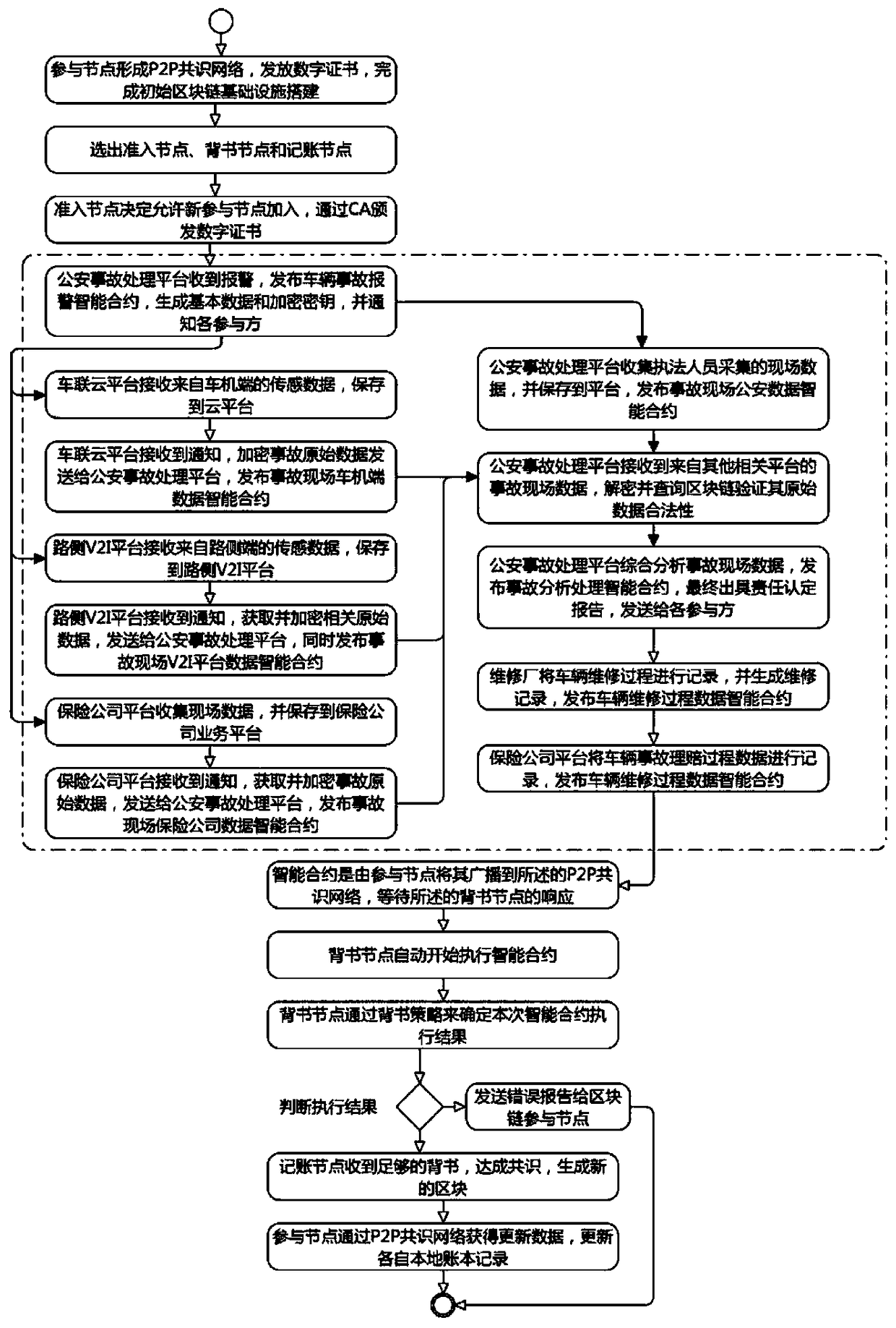
Network connected vehicle accurate accident handling method based on block chain
InactiveCN108446992AImprove accuracyImprove processing speedFinanceUser identity/authority verificationReal-time computingBlockchain
The invention discloses a network connected vehicle accurate accident handling method based on block chain. The implementation process of the method comprises: 1, firstly, through a block chain technology, connecting all participated joints which are associated with accident handling, based on a P2P consensus network, establishing an alliance chain, putting life cycle of accident handling in the block chain to record; through an intelligent terminal on a vehicle accident site, acquiring on-site data and uploading, the participated joints which are associated with accident handling completing accident handling. Compared with the prior art, the network connected vehicle accurate accident handling method based on block chain effectively solves a mutual trust problem of involve parties throughan unified and decentralized method, improves accident responsibility confirmation accuracy rate and handling speed, and provides an accident retroactive function, improves transparency of accident handling process, shortens accident handling time, and saves vehicle accident handling cost.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
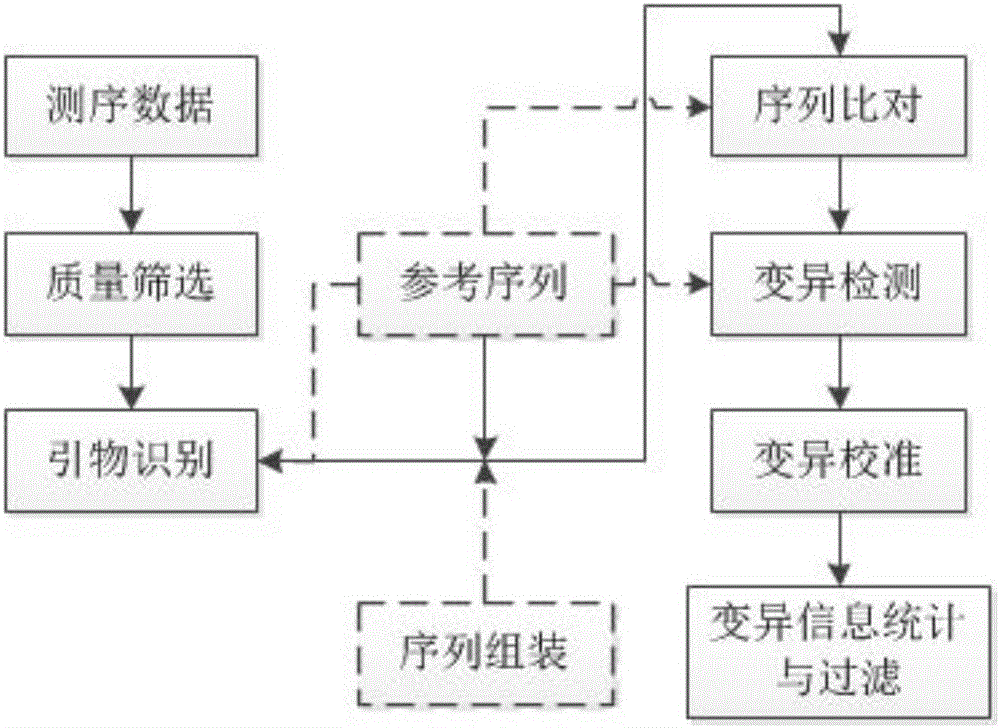
Method for detecting mutation information in multiplex amplification sequencing product of genome
ActiveCN106202991AEfficient identificationQuick identificationHybridisationSpecial data processing applicationsReference genesNatural abundance
The invention discloses a method for detecting mutation information in a multiplex amplification sequencing product of a genome. The method comprises steps as follows: sequencing data are subjected to quality assessment and preprocessing; a recognizable sequencing sequence is selected for sequence assembling; the recognizable sequencing sequence or a sequence obtained through assembling is compared with a reference gene sequence, and preliminary variation information is obtained; fine calibration of sequence variation is performed according to different types of conditions; a calibrated sequencing fragment is obtained; the homozygosis or heterozygosis state of a target fragment is obtained according to the type of the sequencing fragment with the highest abundance; finally, the mutation information in the multiplex amplification sequencing product of the genome is obtained. By means of the method, the amplification product can be rapidly, efficiently and accurately recognized, and the calculation resources are saved; the sequence assembling process is compatible, and the problem of reduction of the quality value of basic groups produced in the sequencing process can be effectively solved; the homozygosis / heterozygosis state of variation information can be more effectively and stably judged, and random errors introduced in the PCR (polymerase chain reaction) process and the sequencing process are eliminated.
Owner:AMOY DIAGNOSTICS CO LTD +1
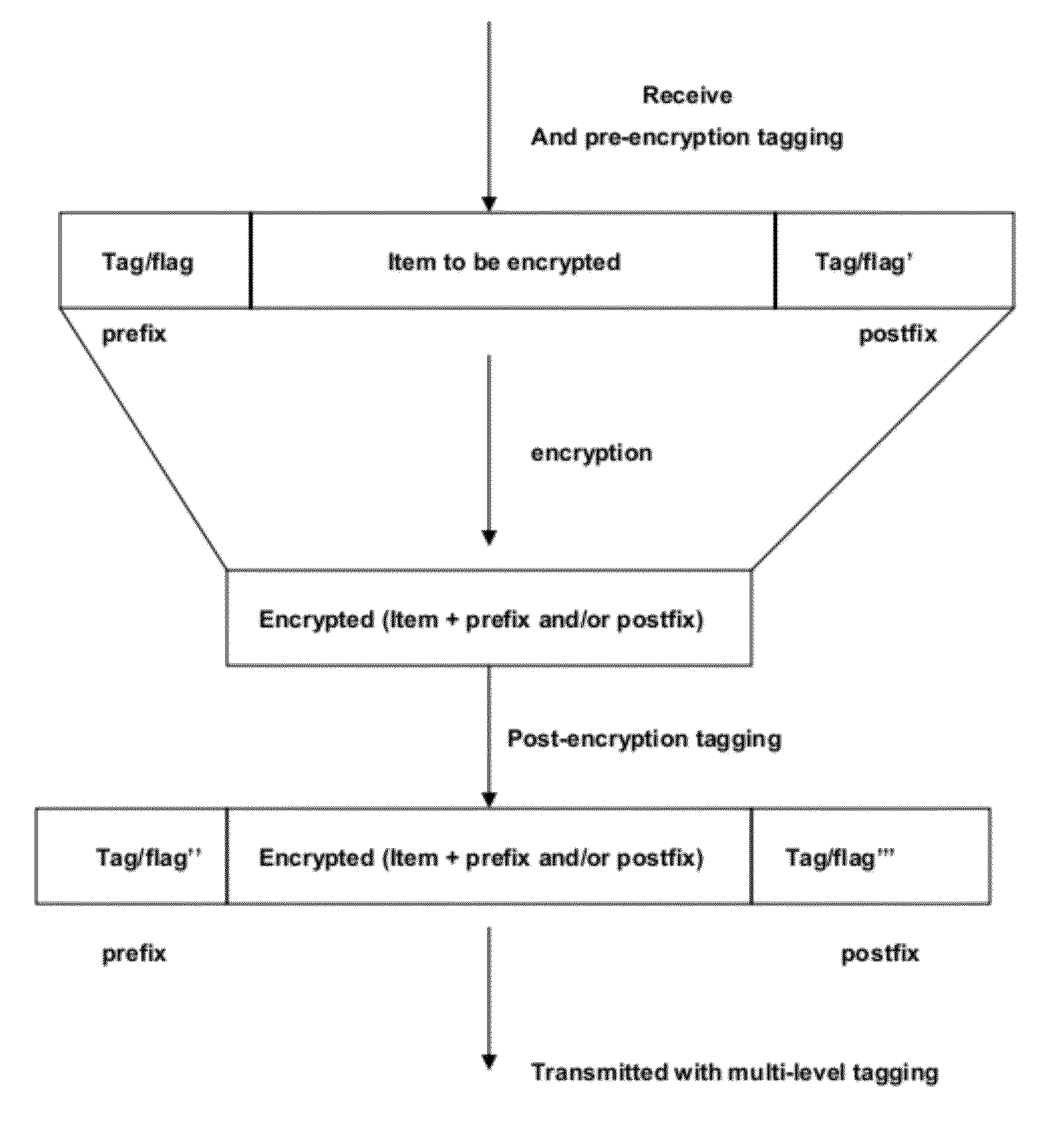
Systems and Methods for Multi-Level Tagging of Encrypted Items for Additional Security and Efficient Encrypted Item Determination
ActiveUS20120173870A1Efficient encrypted item determinationImprove securityComputer security arrangementsTransmissionClient-sideComputer security
The present disclosure is directed towards systems and methods for performing multi-level tagging of encrypted items for additional security and efficient encrypted item determination. A device intercepts a message from a server to a client, parses the message and identifies a cookie. The device processes and encrypts the cookie. The device adds a flag to the cookie indicating the device encrypted the cookie. The device re-inserts the modified cookie into the message and transmits the message. The device intercepts a message from a client and determines whether the cookie in the message was encrypted by the device. If the message was not encrypted by the device, the device transmits the message to its destination. If the message was encrypted by the device, the device removes the flag, decrypts the cookie, removes the tag from the cookie, re-inserts the cookie into the message and transmits the message to its final destination.
Owner:CITRIX SYST INC
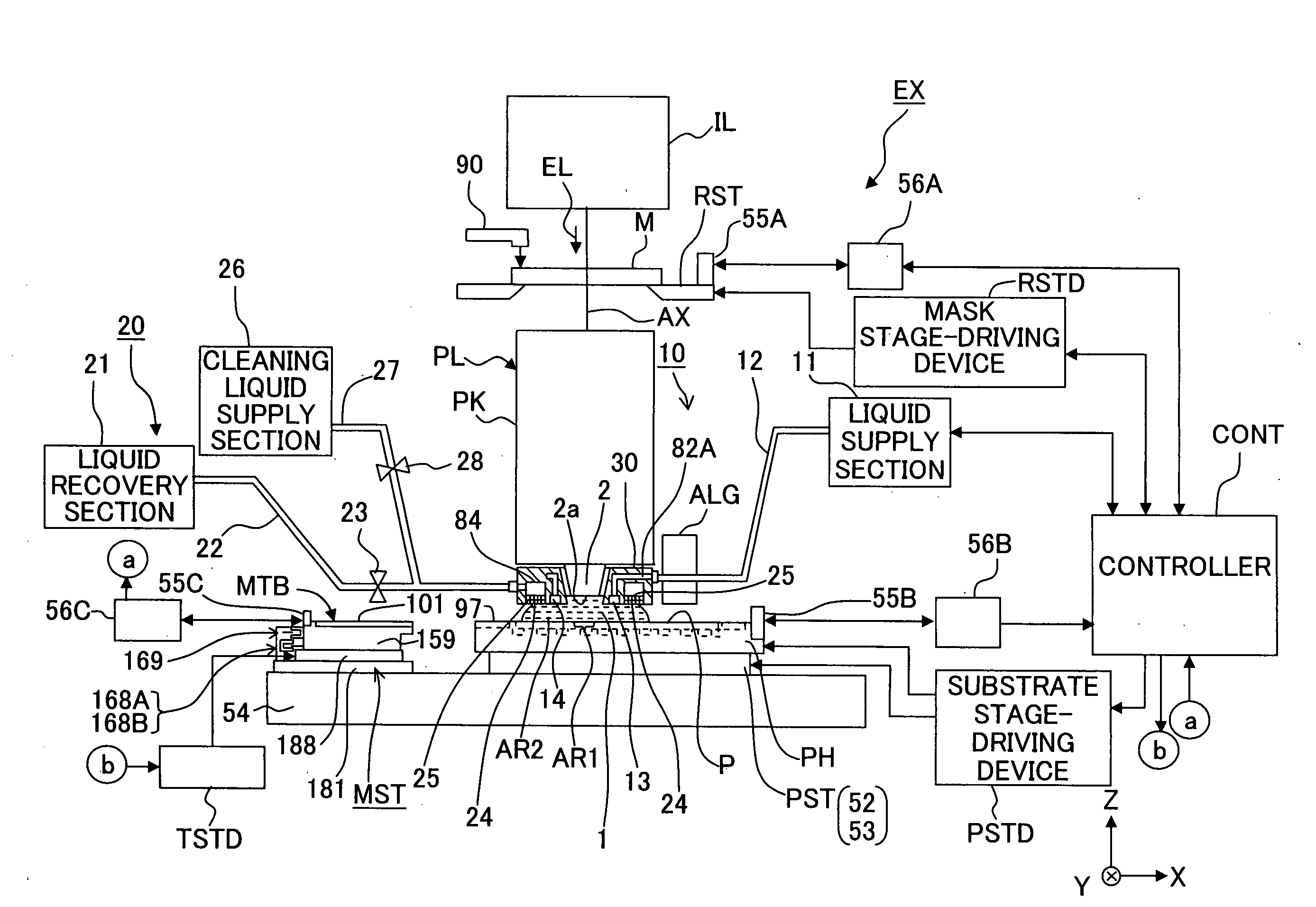
Exposure method and apparatus, maintenance method, and device manufacturing method
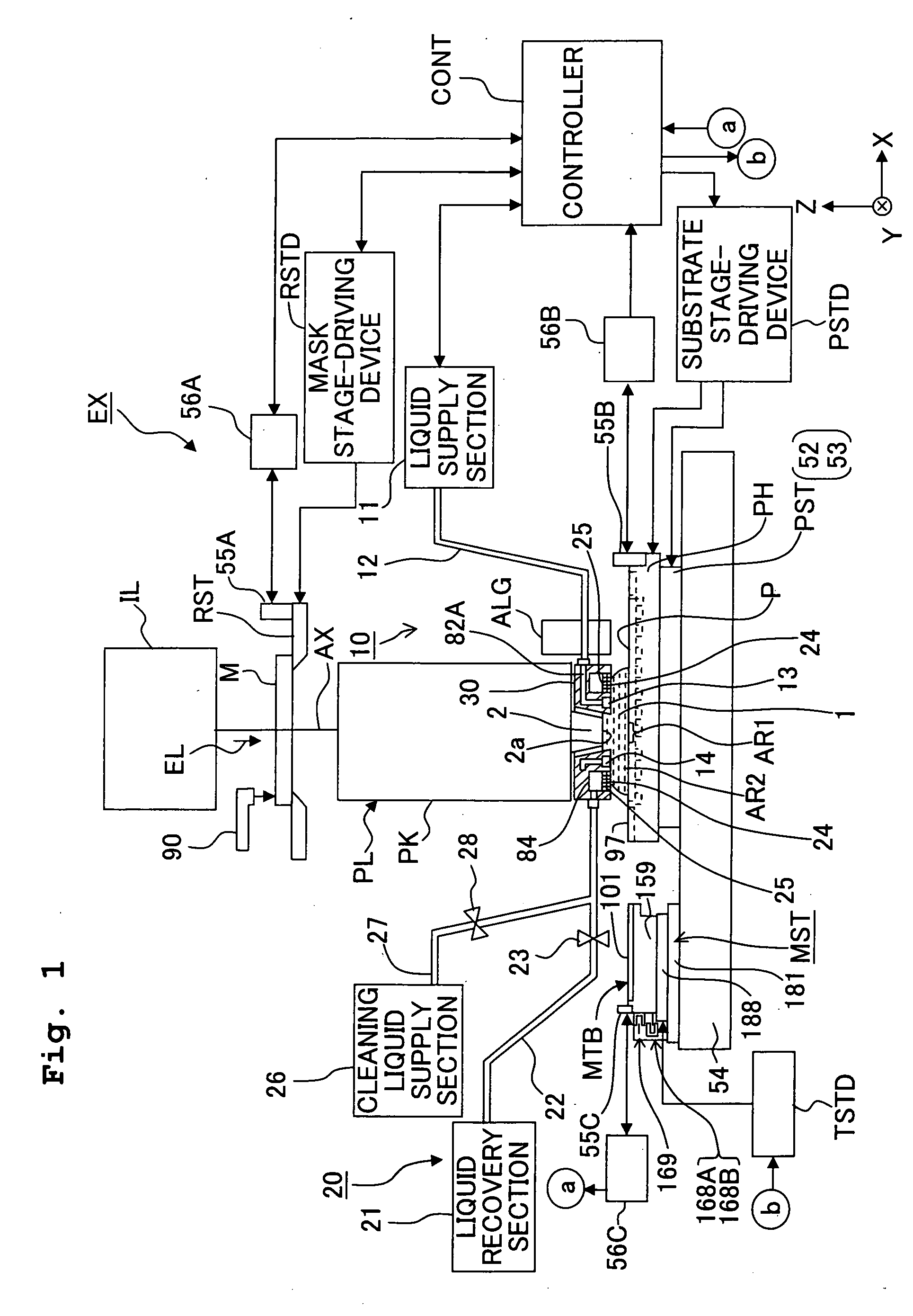
InactiveUS20090061331A1Effective judgmentReduce probabilityHandling using diaphragms/collimetersMaterial analysis by optical meansOptical observationImaging data
An exposure method for exposing a substrate with an exposure light via an projection optical system and a liquid includes: a first step of optically observing a liquid contact portion which comes into contact with the liquid and storing first image data obtained by the optical observation; a second step of optically observing the liquid contact portion after the liquid contact portion came into contact with the liquid, for example, after the liquid immersion exposure and obtaining second image data obtained by the optical observation; and a third step of comparing the first image data and the second image data to judge whether abnormality of observation objective portion is present or absent. It is possible to efficiently judge whether or not the abnormality of the liquid-contact portion, of the exposure apparatus which performs the exposure by the immersion method, is present or absent.
Owner:NIKON CORP
Support and closure assembly for discharge port of a syringe and tracking system therefore
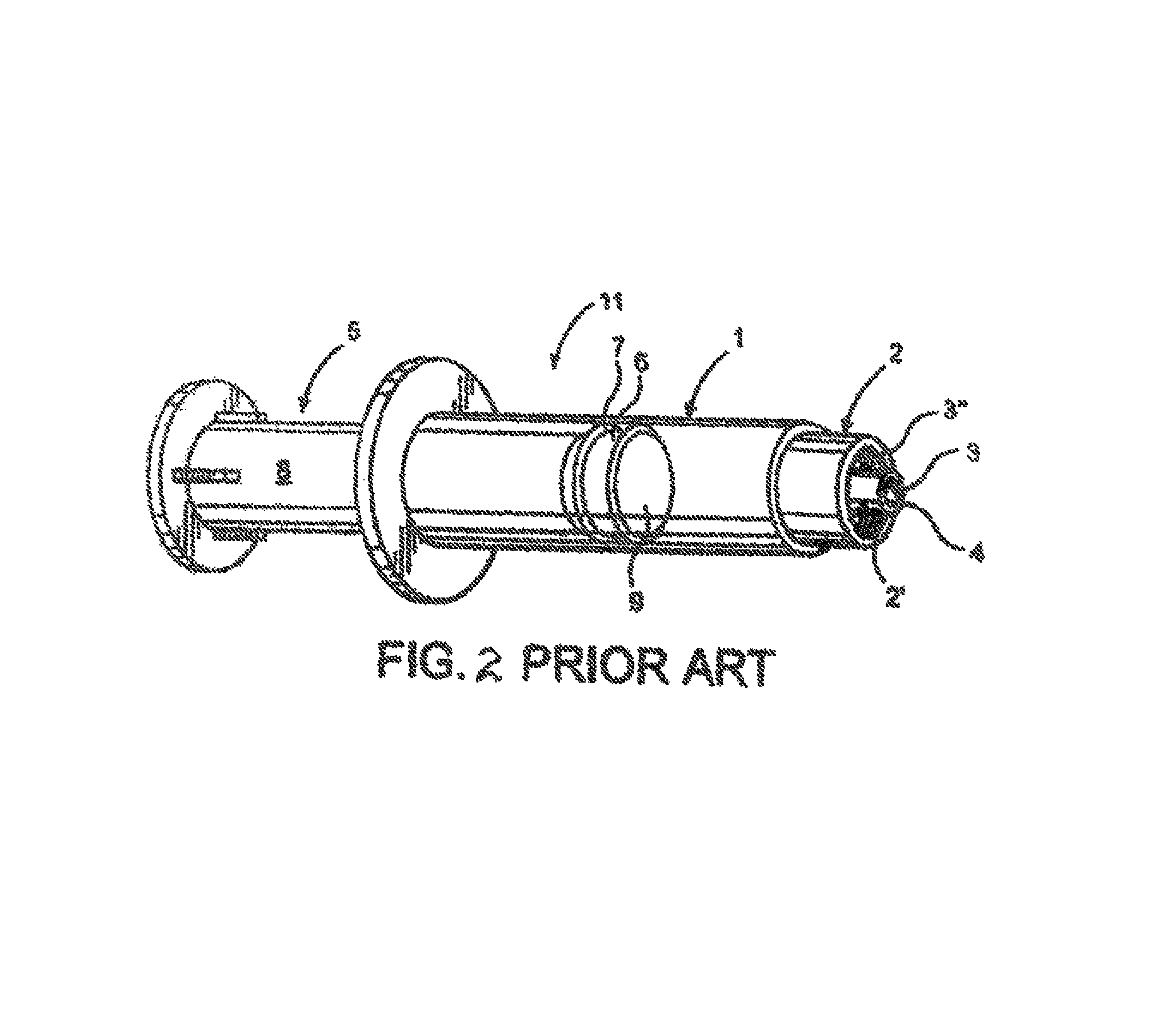
ActiveUS8864021B1Facilitate trackingFacilitate determinationMedical devicesIntravenous devicesPrefilled SyringeEngineering
A system for tracking a multi-component, tamper evident closure assembly for a pre-filled syringe along a distribution route, including a predetermined code applied to each of a plurality of components of the same closure assembly and comprising electronically readable coded indicia, is structured to identify and distinguish each of a plurality of closure assemblies from one another. A reading and recording of predetermined code for each closure assembly along the distribution route is accomplished. The location at which tampering of a closure assembly has occurred along the corresponding distribution route can be accomplished by reading the coded indicia segments on any of detached or assembled ones of the plurality of originally assembled components of the same closure assembly.
Owner:MEDICAL DEVICE ENG
Method, device and computer program product for determining an electromagnetic near-field of a field excitation source of an electrical system
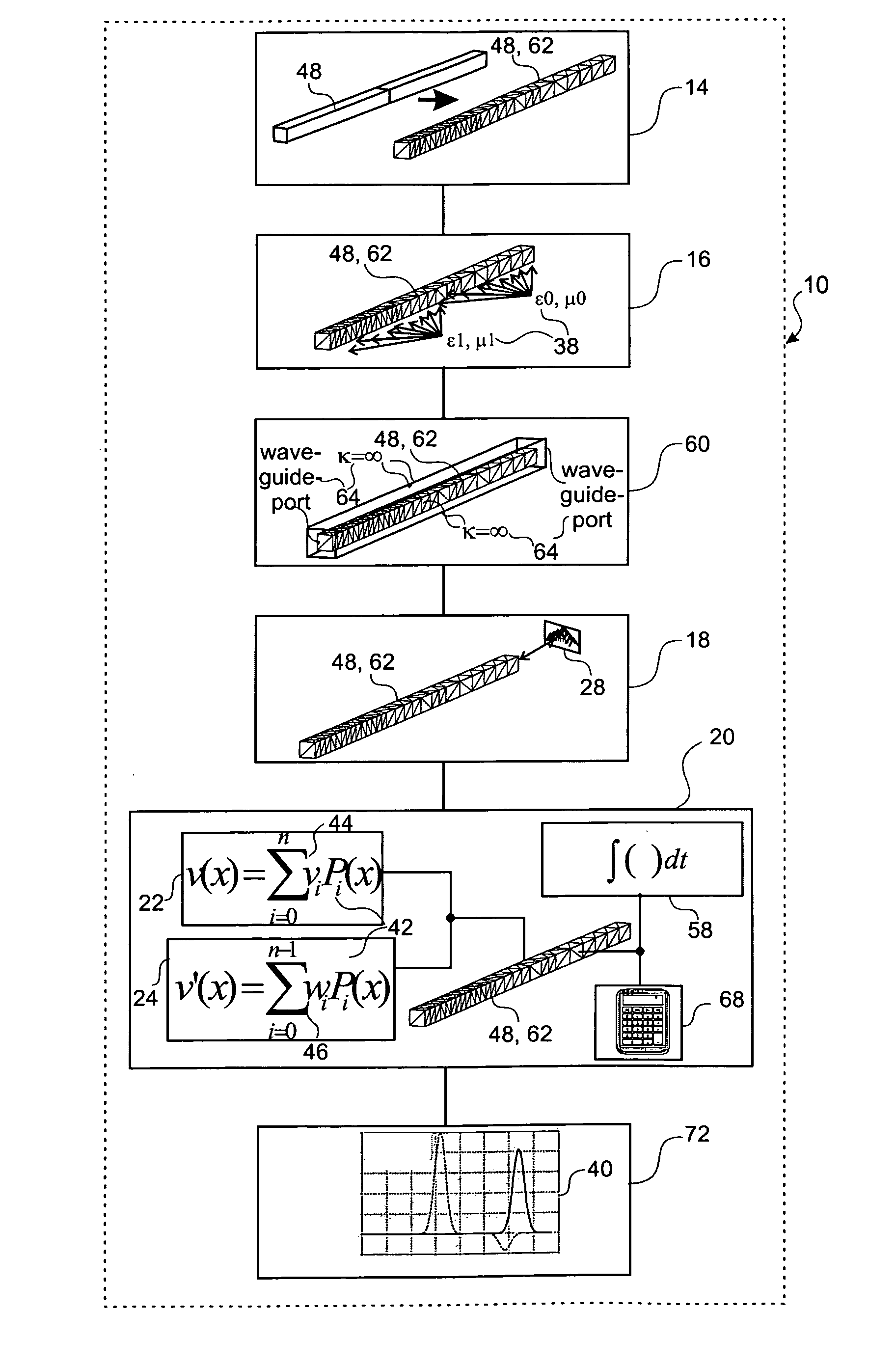
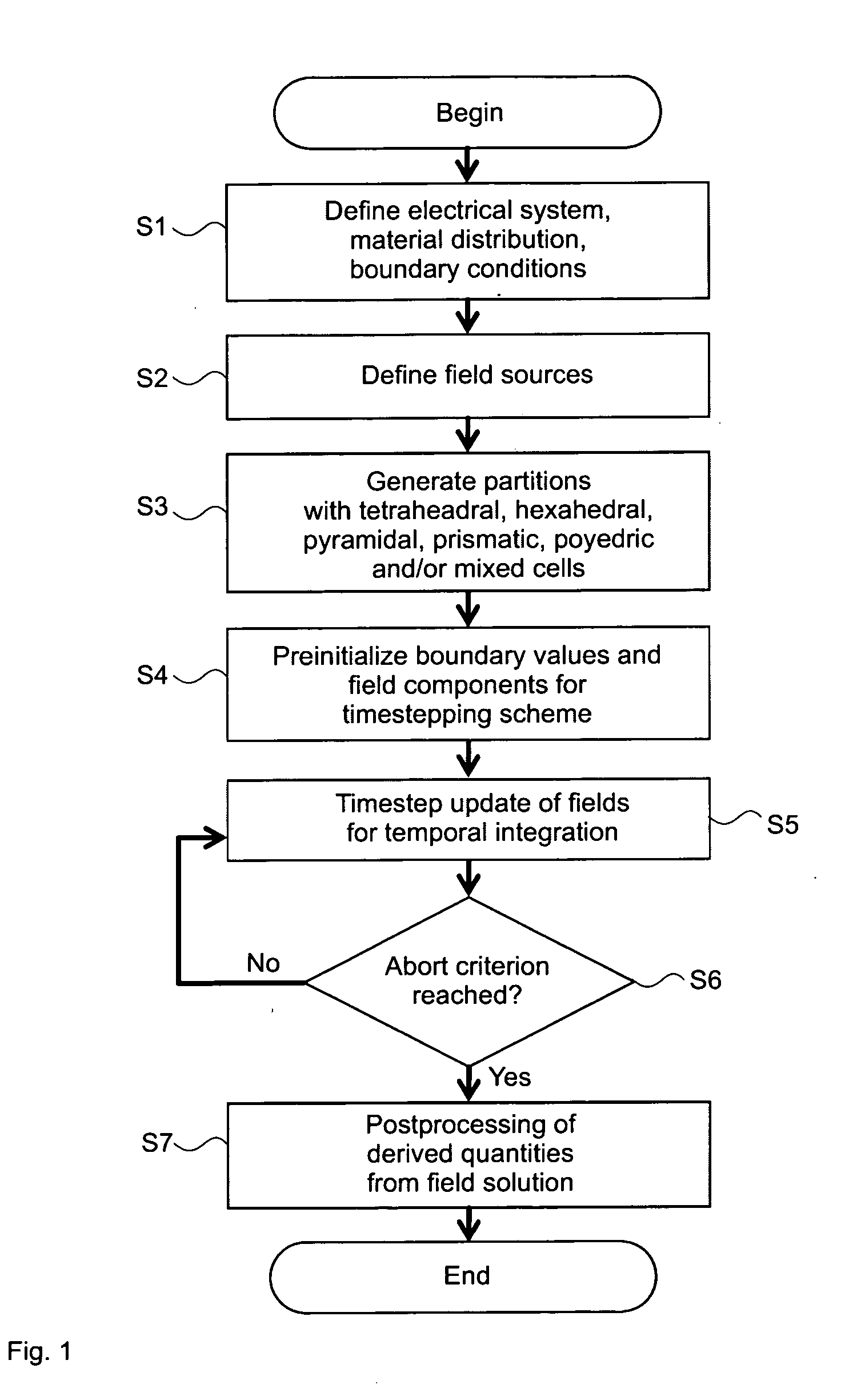
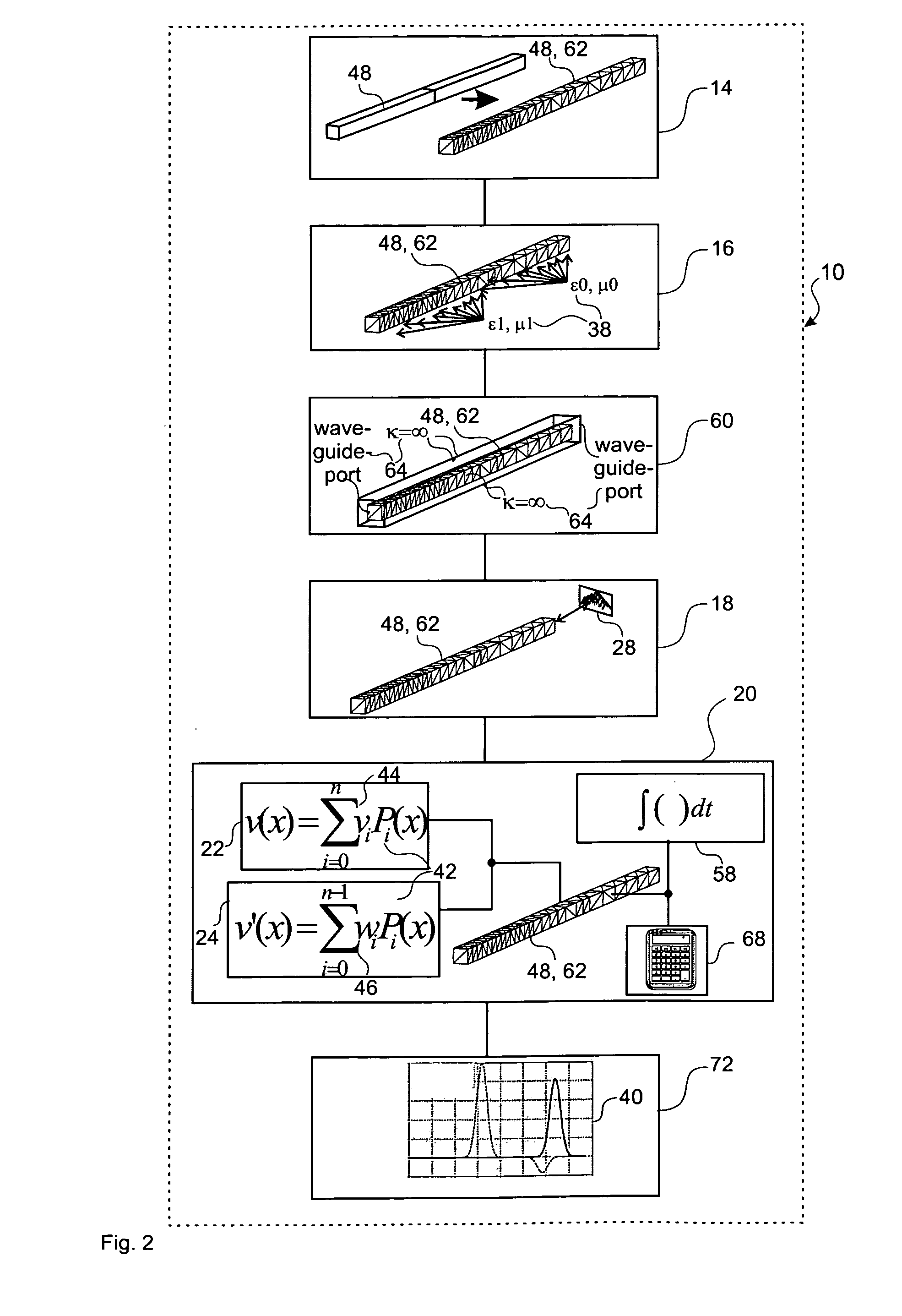
ActiveUS20110251832A1Efficient determinationSimple addressingComputation using non-denominational number representationDesign optimisation/simulationComputational physicsSignal reflection
A method, a device and a computer program product for determining an electromagnetic near-field of a field excitation source of an electrical system are provided, in particular for analysis and / or optimization of an antenna radiation, of a cross-talk problem, of a signal reflexion / transmission, of a stray field, of an irradiation problem or the like. The method includes defining electrical and magnetic properties of the material distribution of the system, defining at least one field excitation source, and determining the electromagnetic near-field components within at least one and in particular all partitions by solution of the Maxwell's equations of the near-field, where each near-field component of each partition can be represented by a linear position of M predetermined ansatz functions Pi orthogonal to one another with regard to a scalar product and weighted with field coefficients vi, and the spatial and / or time derivative of the near-field component can be determined as a linear position of these ansatz functions Pi weighted with derivative coefficients wi, and where each coefficient wi can be determined from a quantity of previously determined field coefficients vi and derivative coefficients wi, so that the determination effort of the near-field of the system rises in substantially linear manner to the number N of partitions in the domain under consideration and to the number M of ansatz functions Pi used in the linear position.
Owner:DASSAULT SYST DEUT GMBH
N-Gram participle model-based reverse neural network junk mail filter device
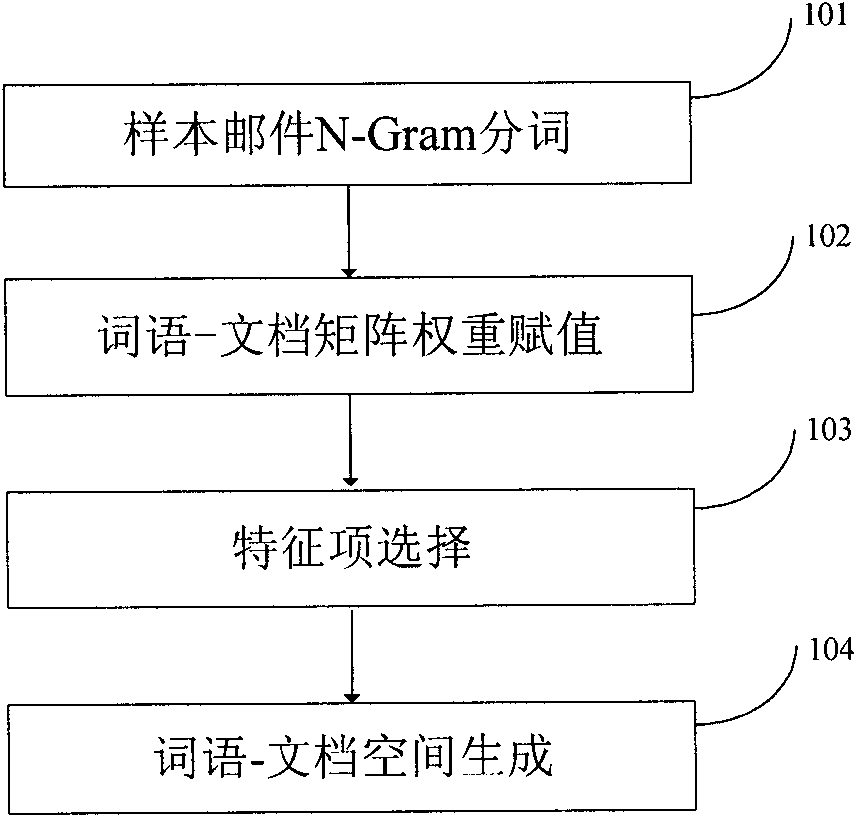
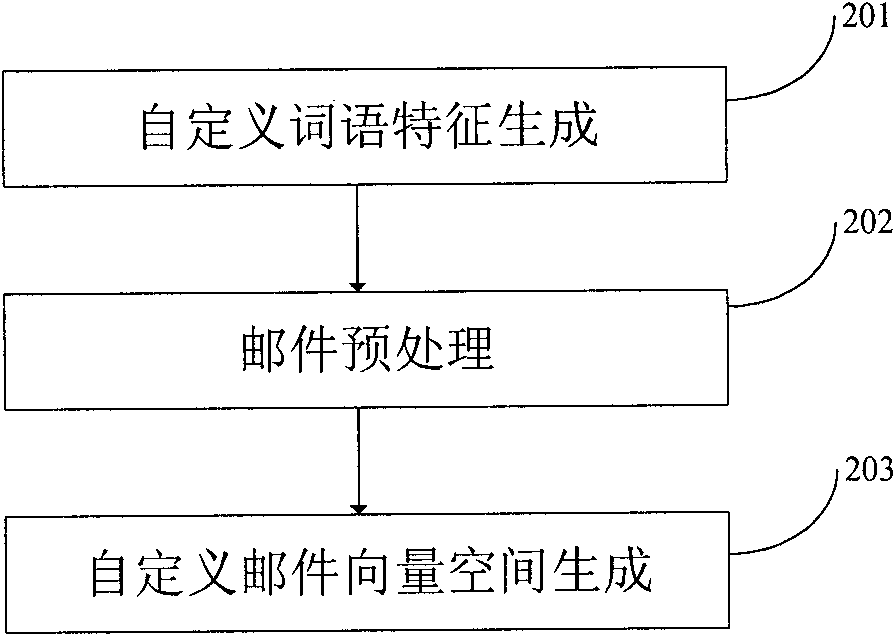
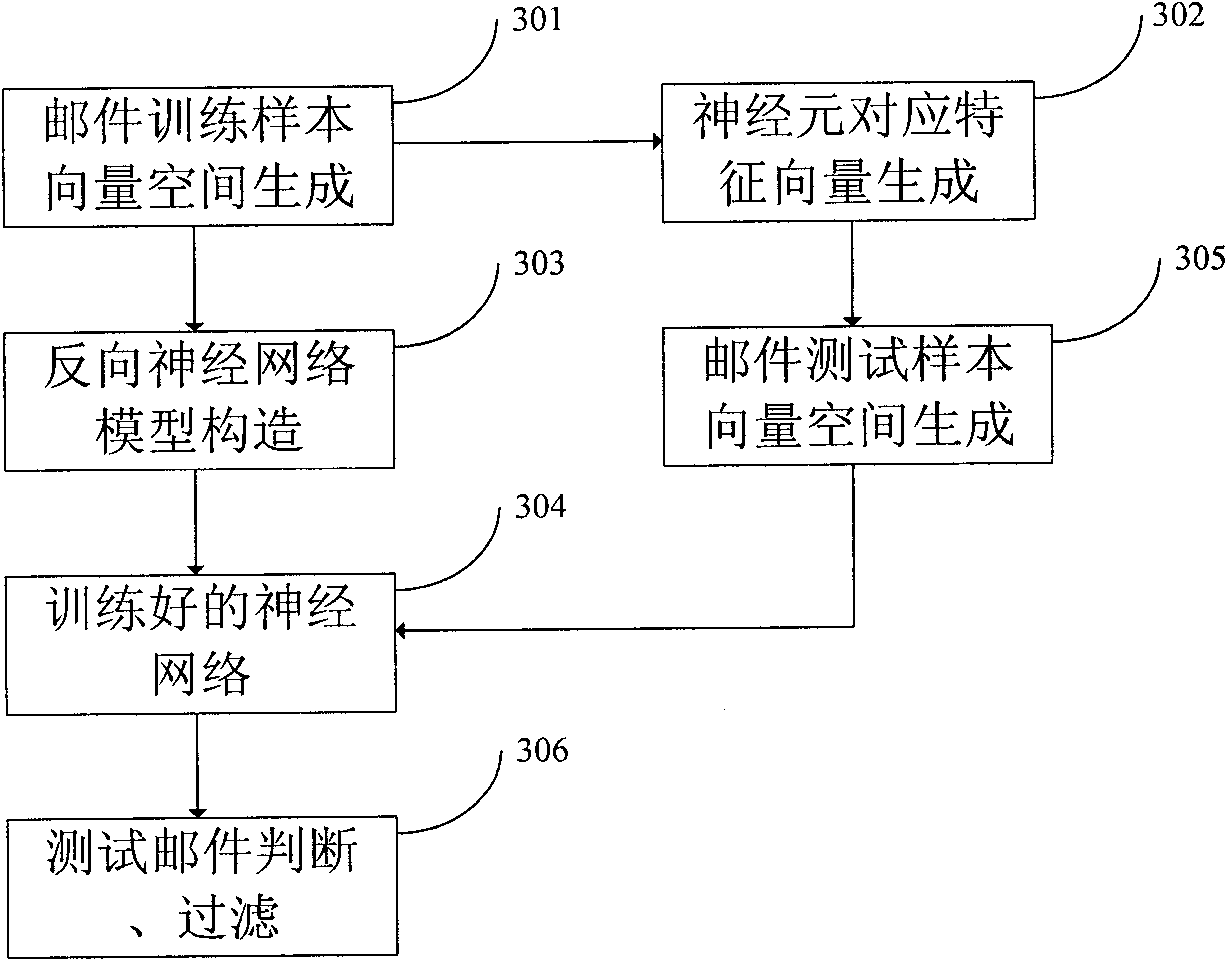
InactiveCN101930561AFully characterizedEffective judgmentBiological neural network modelsOffice automationTest sampleSpamming
The invention relates to the technical field of text processing, in particular to an N-Gram participle model-based reverse neural network junk mail filter device. Customized word characteristic items are added to mail particles by using N-Gram technology, and judgment and filter of junk mails are implemented by combining a reverse neural network. The device is implemented by the following steps of: firstly, processing the mails by using a Markov chain and an N-Gram technique, extracting mail sample characteristics, and obtaining a sample mail word-document space by weight calculation and characteristic selection; secondly, matching a mail sample by using the customized word characteristic items to generate a customized characteristic-document space, and combining the document characteristics generated by the two methods to generate a new mail vector space; thirdly, constructing a reverse neural network model, generating characteristic vectors corresponding to network neurons according to the characteristic items of a mail training sample space, and training the network model by using the mail training sample vector space to obtain a trained mail classifier; and finally, generating a test sample vector space by the mail test sample according to the generated characteristic vectors corresponding to the network neurons, and testing the mail type judgment accuracy of the trained mail classifier. The embodiment of the invention can judge the junk mails so as to filter the junk mails.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Malicious code type detection method based on cloud mode
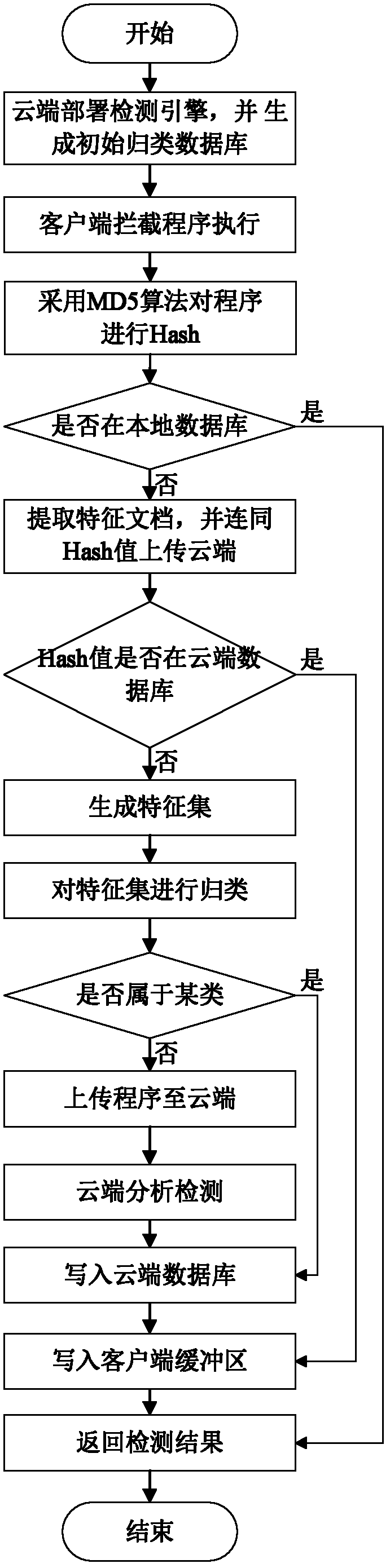
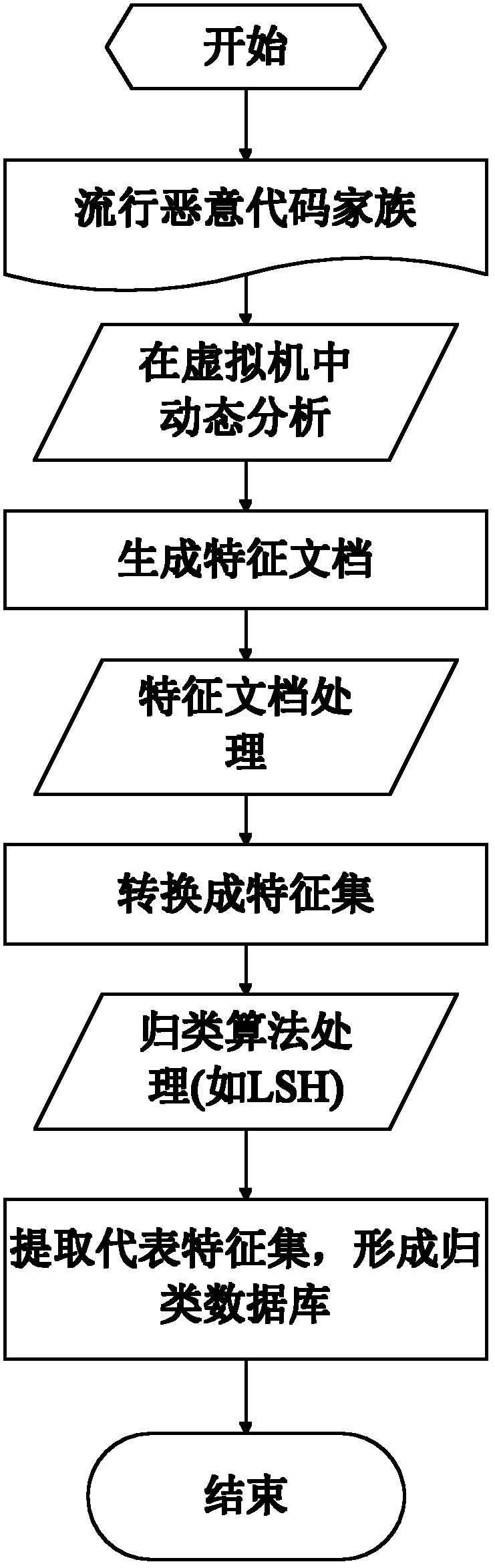
InactiveCN102664875AReduce bloatAvoid duplicate detectionPlatform integrity maintainanceTransmissionFeature setClient-side
The invention discloses a malicious code type detection method based on a cloud mode. The method comprises the following steps that: a cloud terminal carries out processing and analysis on a malicious code family to generate an initial classification database, generates a representative feature set for each category of malicious code family in the initial classification database, an access or execution operation of a program is intercepted at a client, an only identity value of the intercepted program is calculated, whether the only identity value exists in a local database or not is determined, if not, a specific feature document of the intercepted program is extracted, the only identity value and a specific feature document of the intercepted program is uploaded to the cloud terminal by the client, whether the only identity value exists in a cloud terminal database or whether the feature document belongs to a classification is determined, a final determination result is returned to the client, and the only identity value and the final determination result are written into the cloud terminal database and a client database respectively. According to the method, the rapid expansion of a feature library can be slowed down, the upload of suspicious programs is reduced, and the killing prevention efficiency of cloud security is raised.
Owner:HUAZHONG UNIV OF SCI & TECH
CAN bus authentication method and system based on broadcasting
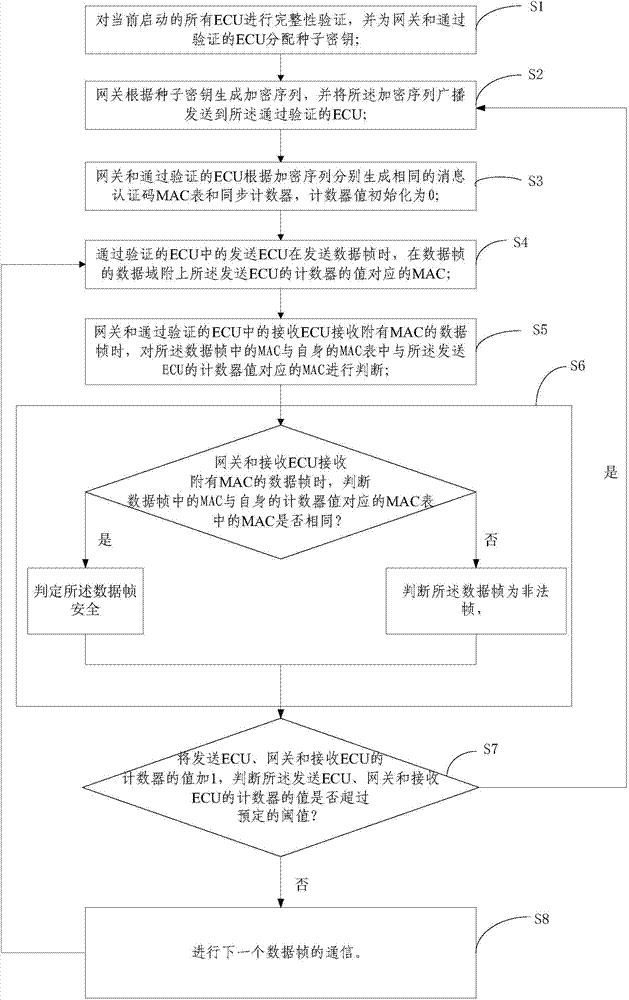
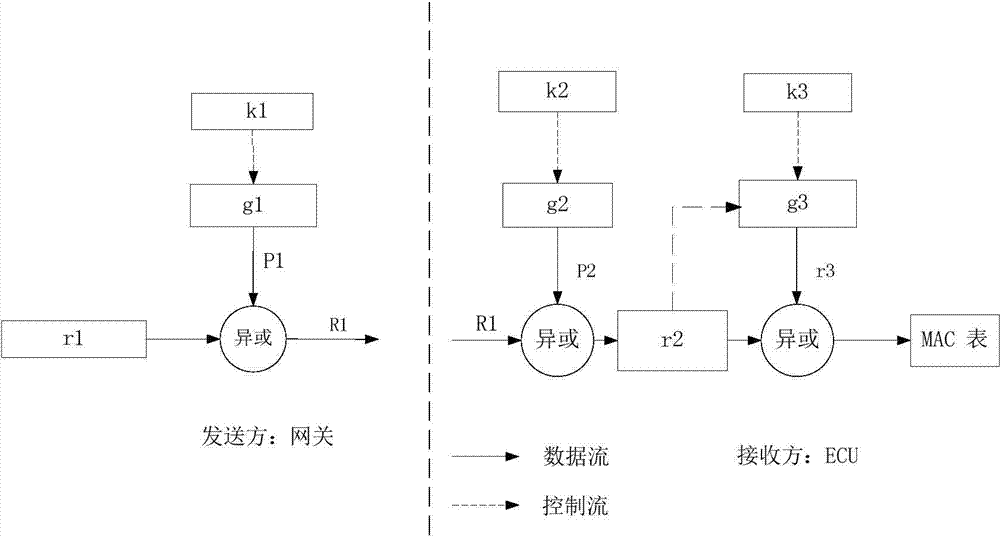
ActiveCN104767618AAvoid attackEffective judgmentUser identity/authority verificationBus networksComputer hardwareData field
The invention relates to a CAN bus authentication method and system based on broadcasting. The method includes the steps that completeness verification is conducted on all ECUs, seed secret keys are distributed for a gateway and the ECUs passing the verification; the gateway generates an encryption sequence, and the encryption sequence is sent to the ECUs passing the verification through broadcasting; the gateway and the ECUs passing the verification generate identical message authentication code (MAC) tables and identical synchronous counters, wherein the initial value of the counters is zero; the sending ECU attaches the MAC corresponding to the value of the counter of the sending ECU to the data field of a sending data frame; the gateway and the receiving ECU judge whether the MAC in the data field is identical with the MAC in the MAC tables corresponding to the counters of the gateway and the receiving ECU or not; if yes, the data frame is judged to be safe, and if not, the data frame is judged to be the illegal frame; the values of the counters of the sending ECU, the gateway and the receiving ECU are added by one, and whether the values of the counters of the sending ECU, the gateway and the receiving ECU exceed the preset threshold value or not is judged; if yes, an MAC table is generated again; if not, the next frame of communication is conducted, and communication of a next data frame is conducted. According to the CAN bus authentication method and system, due to the fact that a message authentication code is added to the data frames in communication, the attack on the CAN bus can be defended.
Owner:TSINGHUA UNIV
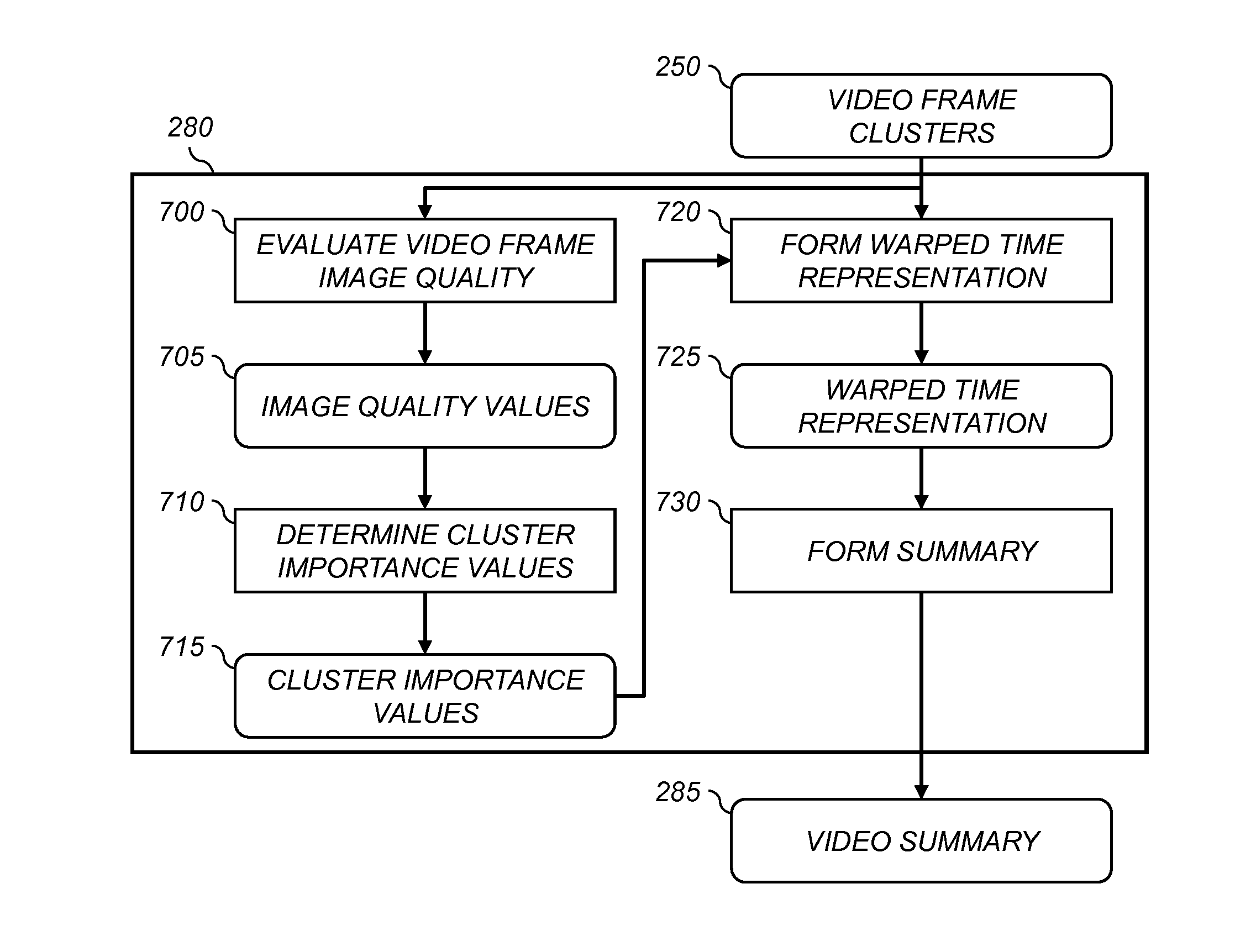
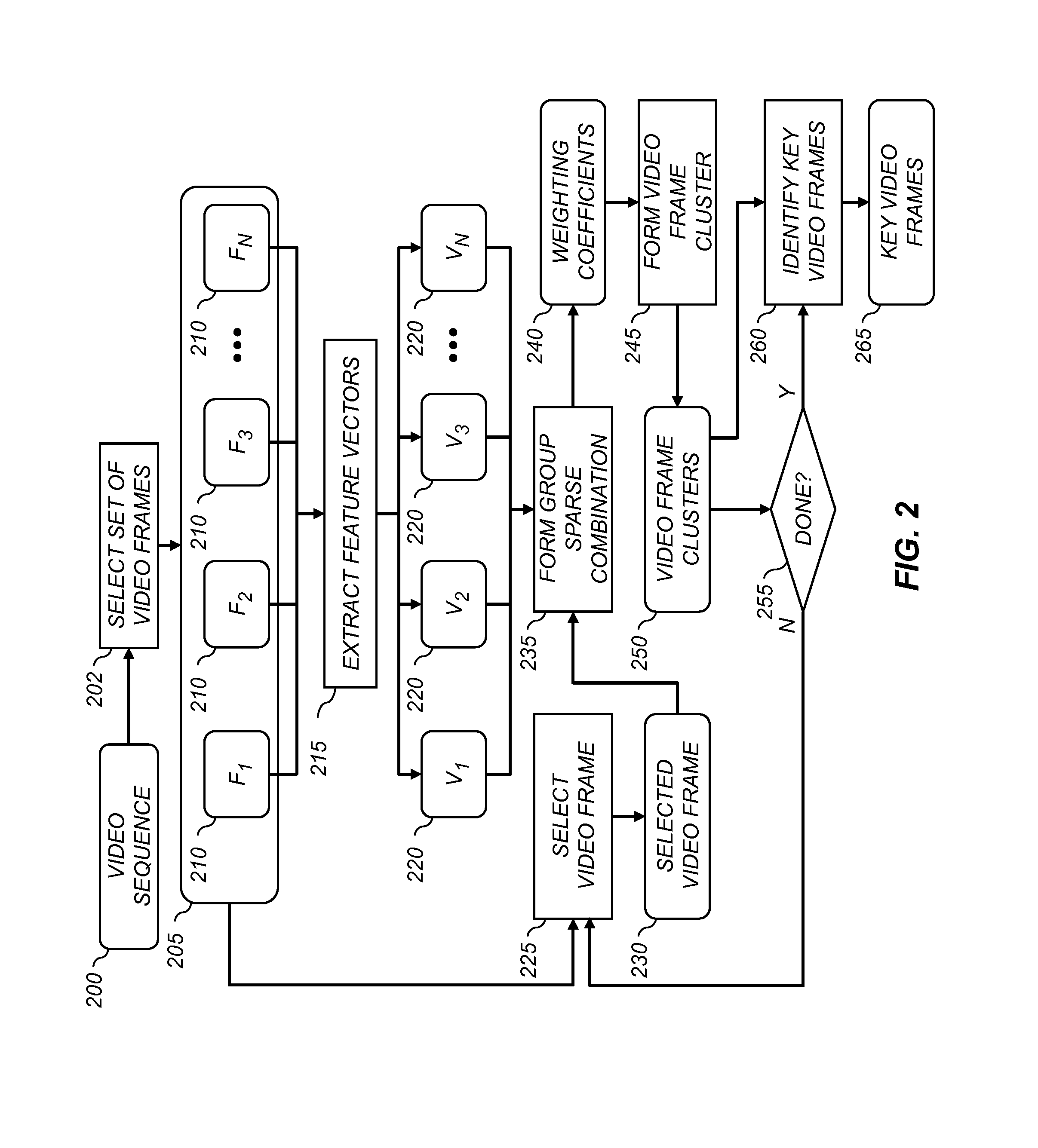
Video summarization using group sparsity analysis
ActiveUS20140037269A1Conveniently capturedReduce complexityTelevision system detailsElectronic editing digitised analogue information signalsFeature vectorWeight coefficient
A method for identifying a set of key video frames from a video sequence comprising extracting feature vectors for each video frame and applying a group sparsity algorithm to represent the feature vector for a particular video frame as a group sparse combination of the feature vectors for the other video frames. Weighting coefficients associated with the group sparse combination are analyzed to determine video frame clusters of temporally-contiguous, similar video frames. A summary is formed based on the determined video frame clusters.
Owner:KODAK ALARIS INC
Multi-path monitor video management method and device
InactiveCN104915655AEfficiently judge abnormal situationsReduce investmentCharacter and pattern recognitionVideo monitoringTime efficient
The invention discloses a multi-path monitor video management method and device and relates to the management method for server side intelligent video detection and background multi-path videos. The method comprises the following steps: receiving pictures of multi-path monitoring cameras through a server, detecting targets of the picture images and carrying out target tracking according to the target detection results; and carrying out abnormity detection on the picture of each path of video according to the target detection and tracking result, carrying out classification on the abnormity and recording event attributes; and establishing a database and creating an index according to the abnormity classification and other abnormity attributes. The multi-path monitor video management method and device help people to search clues quickly in mass monitor videos, thereby saving time; not only manpower resource investment in conventional video monitoring can be reduced, but also abnormal conditions in videos can be judged quickly and efficiently; and the method and the device provide an unified plan for the videos globally, so that when people search the recordings, the trouble of multi-person multi-video searching is saved, and efficiency is improved.
Owner:XIDIAN UNIV
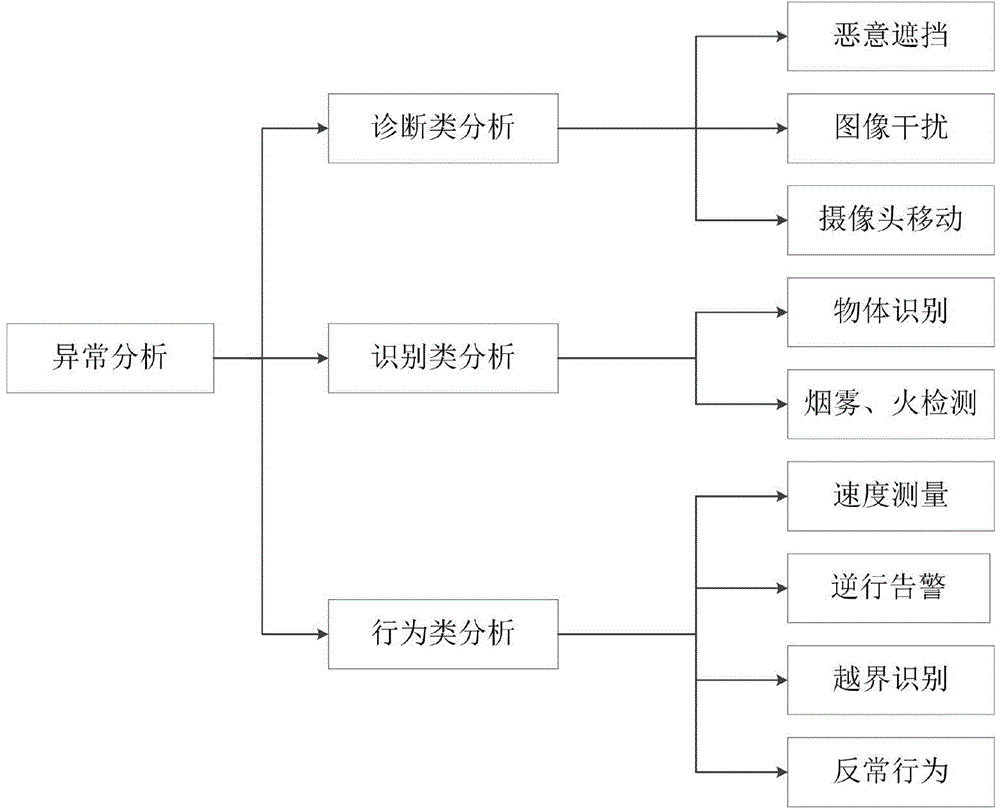
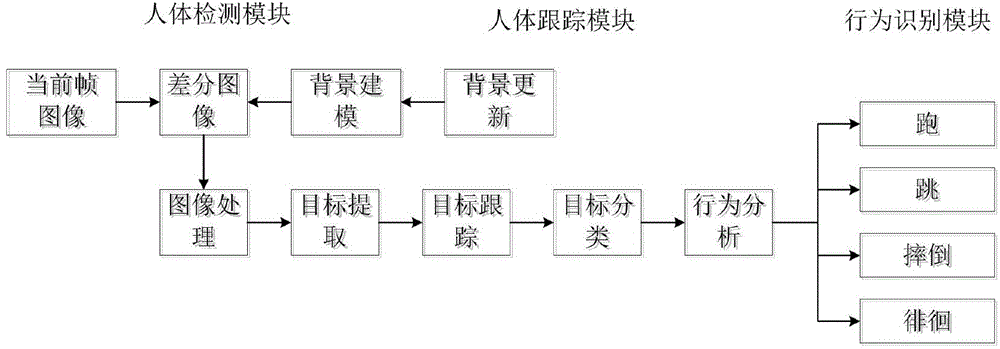
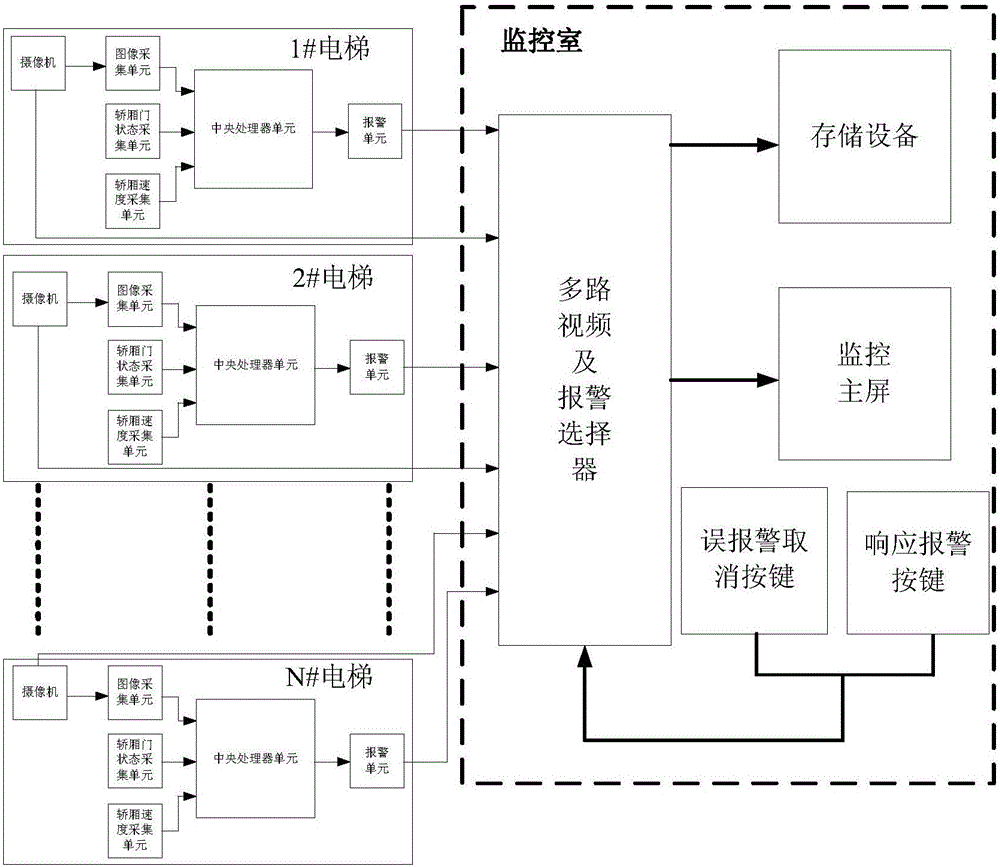
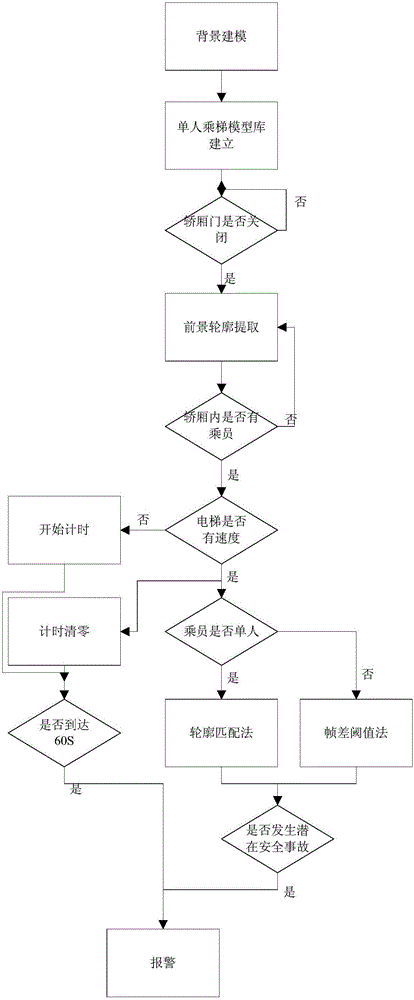
Elevator passenger comprehensive safety intelligent monitoring method based on machine vision
ActiveCN106241533ASimple environmentFast video analysisCharacter and pattern recognitionElevatorsCommunication AnalysisTemplate matching
The invention provides a comprehensive safety intelligent monitoring method capable of effectively and quickly judging if such abnormal activities as trapping, falling and violence are generated in a car to timely and accurately give an alarm so as to effectively relieve the burden of monitoring staff. The comprehensive safety intelligent monitoring method specifically comprises the following steps: an image shot by a camera with a fixed position is used as a background model; a differential image is obtained through a difference between a present video frame and the background model by a background subtracting method; the binarization processing is performed for the differential image according to a binarization formula; then, the noise is removed through a morphology filtering algorithm; finally, the area communication analysis is performed for the noise removing result; the edge profile of the binarized image is extracted by a Canny operator; and the extracted foreground profile is compared with a human body image template library by a template matching algorithm to judge if one or more persons are in the car and if the abnormal activities are generated to trigger warning.
Owner:XIAN SPECIAL EQUIP INSPECTION INST
Automatic trimming method, apparatus and program
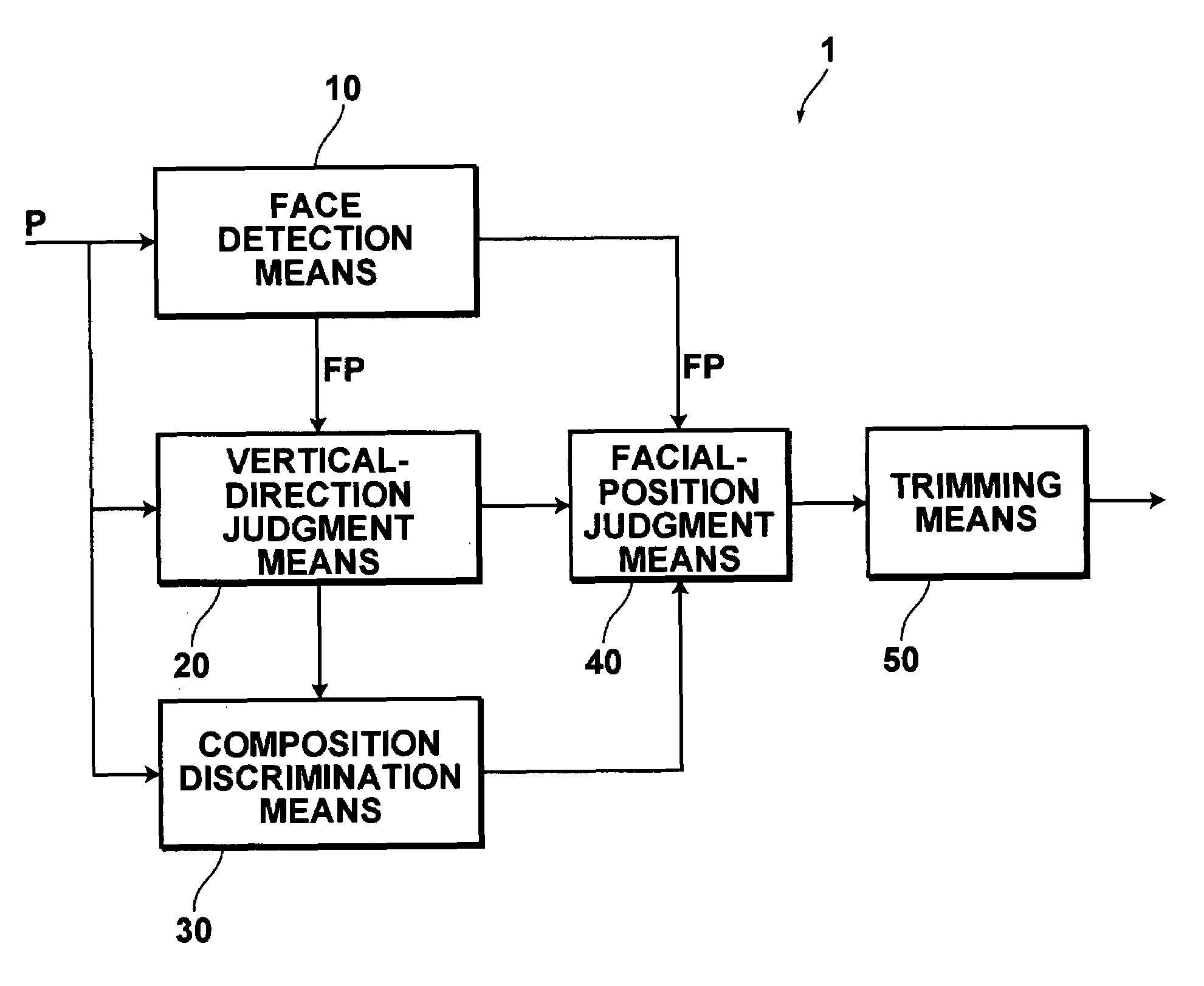
ActiveUS20070236762A1Effective judgmentCharacter and pattern recognitionPictoral communicationComputer vision
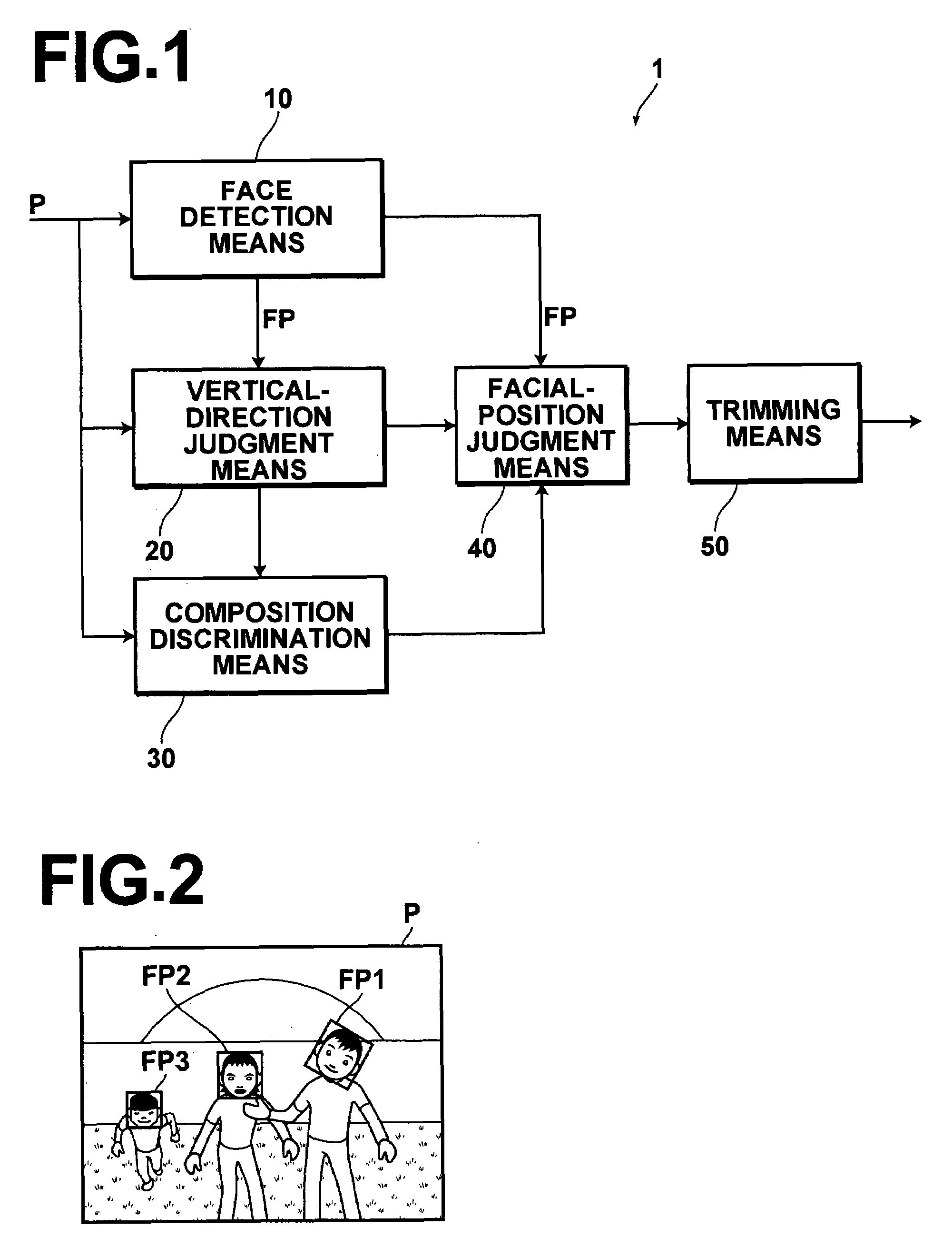
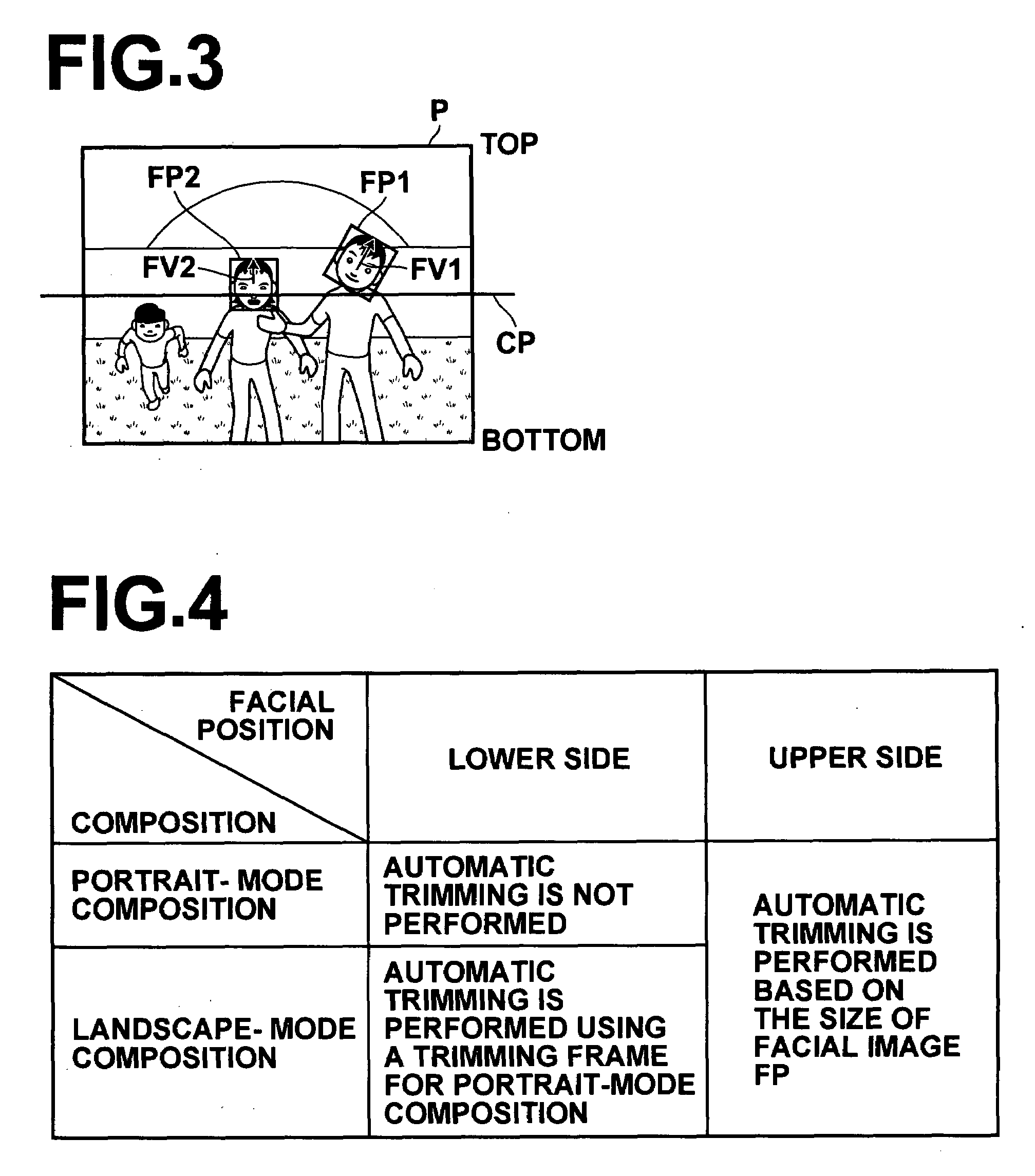
Trimming is automatically performed on an image by inferring a person and a background in which the photographer of the image has interest. Facial images FP1 and FP2 are detected in a whole image P, and the vertical direction of the whole image P is judged based the facial images FP1 and FP2. Further, processing is performed using the information about the vertical direction to discriminate whether the composition of the whole image P is portrait-mode composition or landscape-mode composition. If it is judged that the facial image FPl is positioned on the lower side of the whole image, and if a composition discrimination unit discriminates that the composition of the whole image P is landscape-mode composition, trimming is automatically performed using a trimming frame TG10 that has portrait-mode composition.
Owner:FUJIFILM CORP
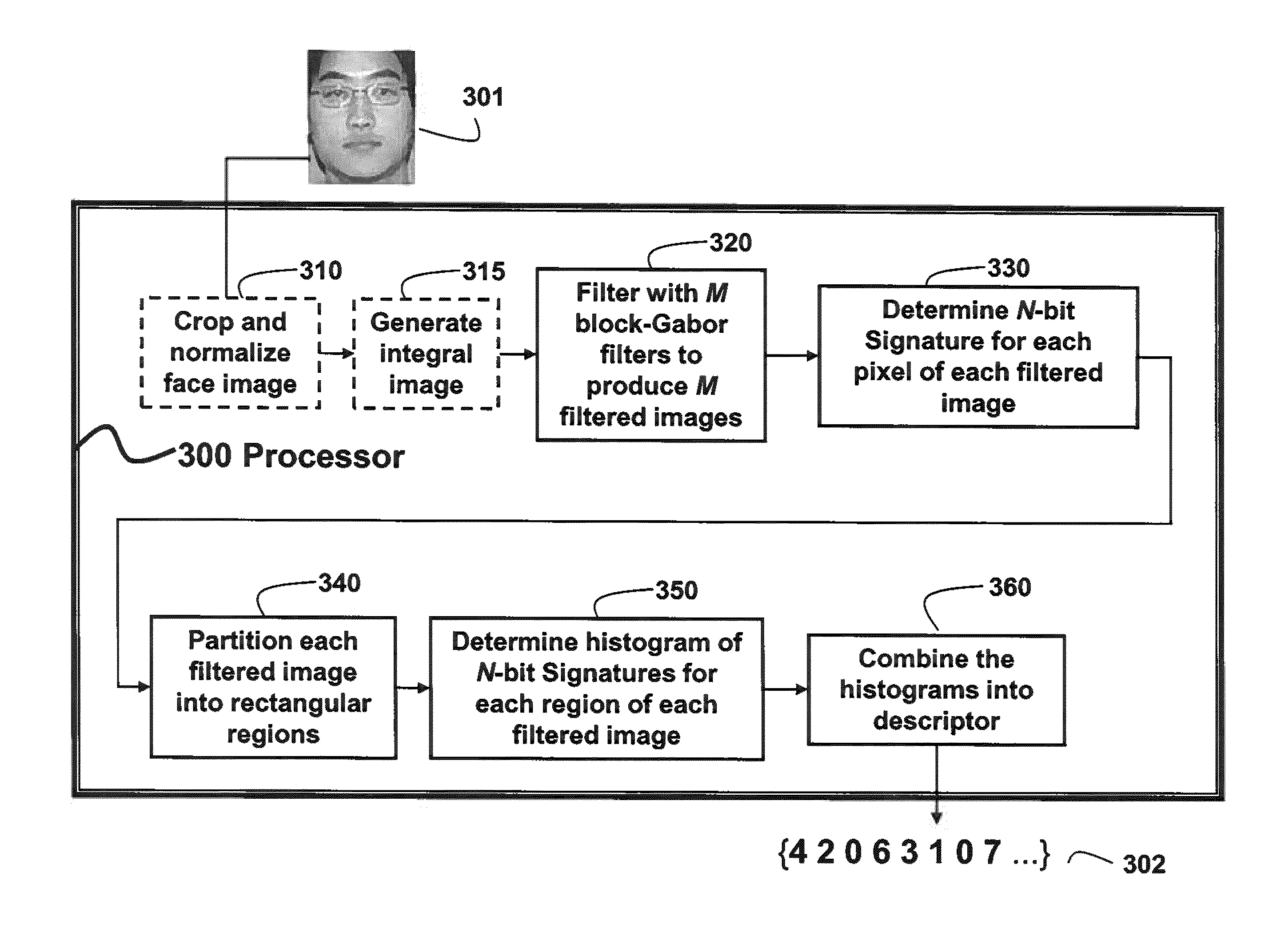
Method for Filtering Using Block-Gabor Filters for Determining Descriptors for Images
A Gabor filter is approximated as a block-Gabor filter. The Gabor filter is represented by a matrix of numbers in which each number is a sample derived from a continuous Gabor function. The block-Gabor filter is partitioned into a set of blocks. Identical filter values are assigned to all the pixels in any particular block based on the Gabor filter. Then, a feature can be extracted from an image by filtering the image with a set of the block-Gabor filters to obtain a corresponding set of filtered images. Each filtered image is partitioned into regions of pixels. For each pixel, an N-bit signature is determined. Histograms of the N-bit signatures of the pixels in each region are combined to form the feature. The features of multiple images can be used for face recognition.
Owner:MITSUBISHI ELECTRIC RES LAB INC
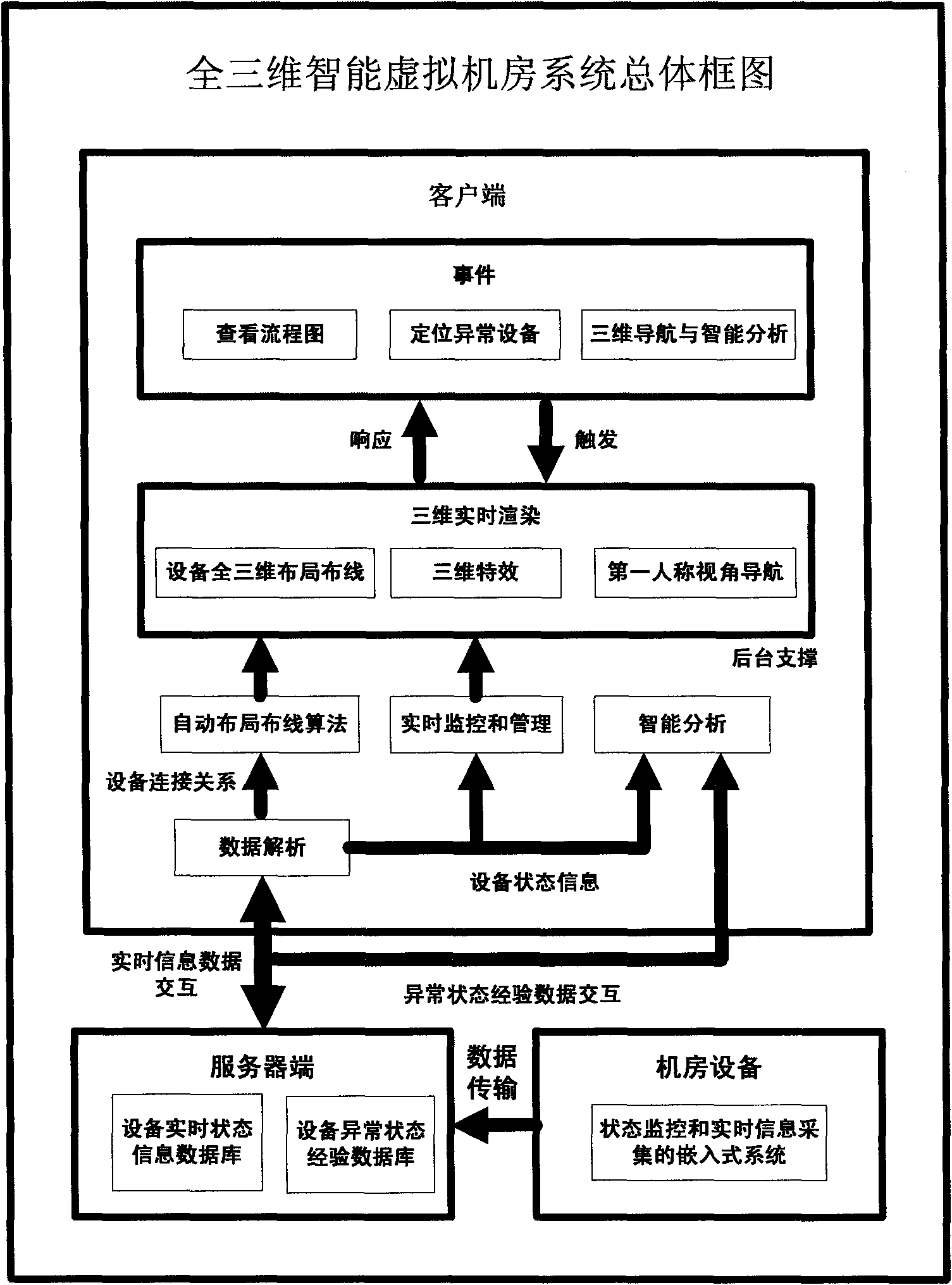
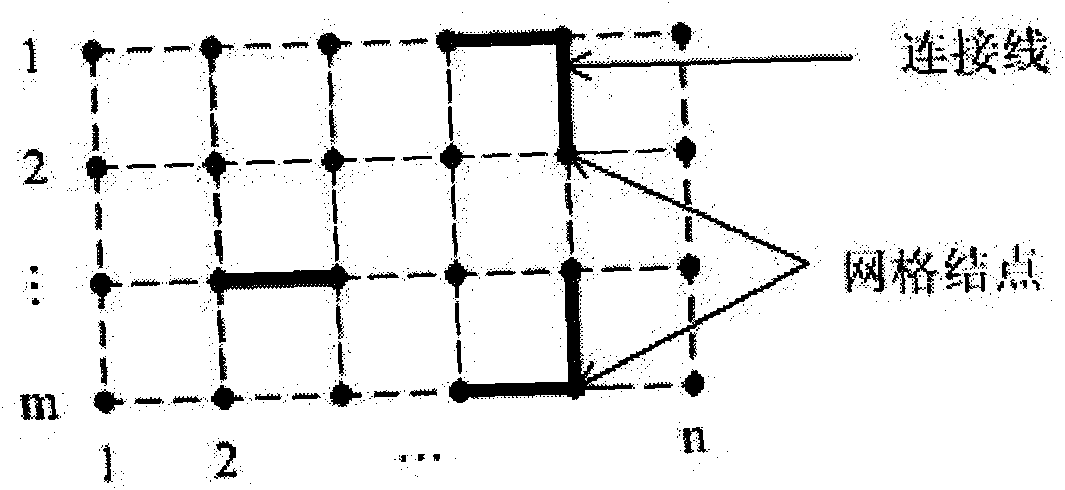
Method for realizing full three-dimensional intelligent virtual computer room
InactiveCN101820532ARapid positioningEffective judgmentClosed circuit television systemsSteroscopic systemsThree-dimensional spaceSimulation
The invention relates to a method for realizing a full three-dimensional intelligent virtual computer room, and belongs to the fields of computer graphics and virtual reality. The method comprises the following steps of: (1) simulating a full three-dimensional system structure and state; (2) monitoring and managing the running states of multiple kinds of large computer room equipment in real time; (3) performing monitoring, transmission and three-dimensional display on signals in real time based on a C / S architecture; (4) automatically laying out and wiring in a three-dimensional space system in real time; and (5) in a three-dimensional space, performing quick positioning, three-dimensional navigation and intelligent analysis on exceptional equipment. In the method, after a two-dimensional sketch map is changed into a full three-dimensional real-time intelligent layout map, according to equipment connection information updated by a server, all equipment is subjected to real-time layout and wiring at a client, the connection relationships of the multiple kinds of equipment are more clear and intuitively, the concept of layout is added, and a phenomenon that a flow chart only has a single function of the connection relationships is improved, so each equipment comprises definite real-time position information, the exceptional equipment is quickly positioned, and the navigation display and intelligent analysis in the three-dimensional space assist users to more effectively judge problems and solve problems.
Owner:SHANGHAI UNIV
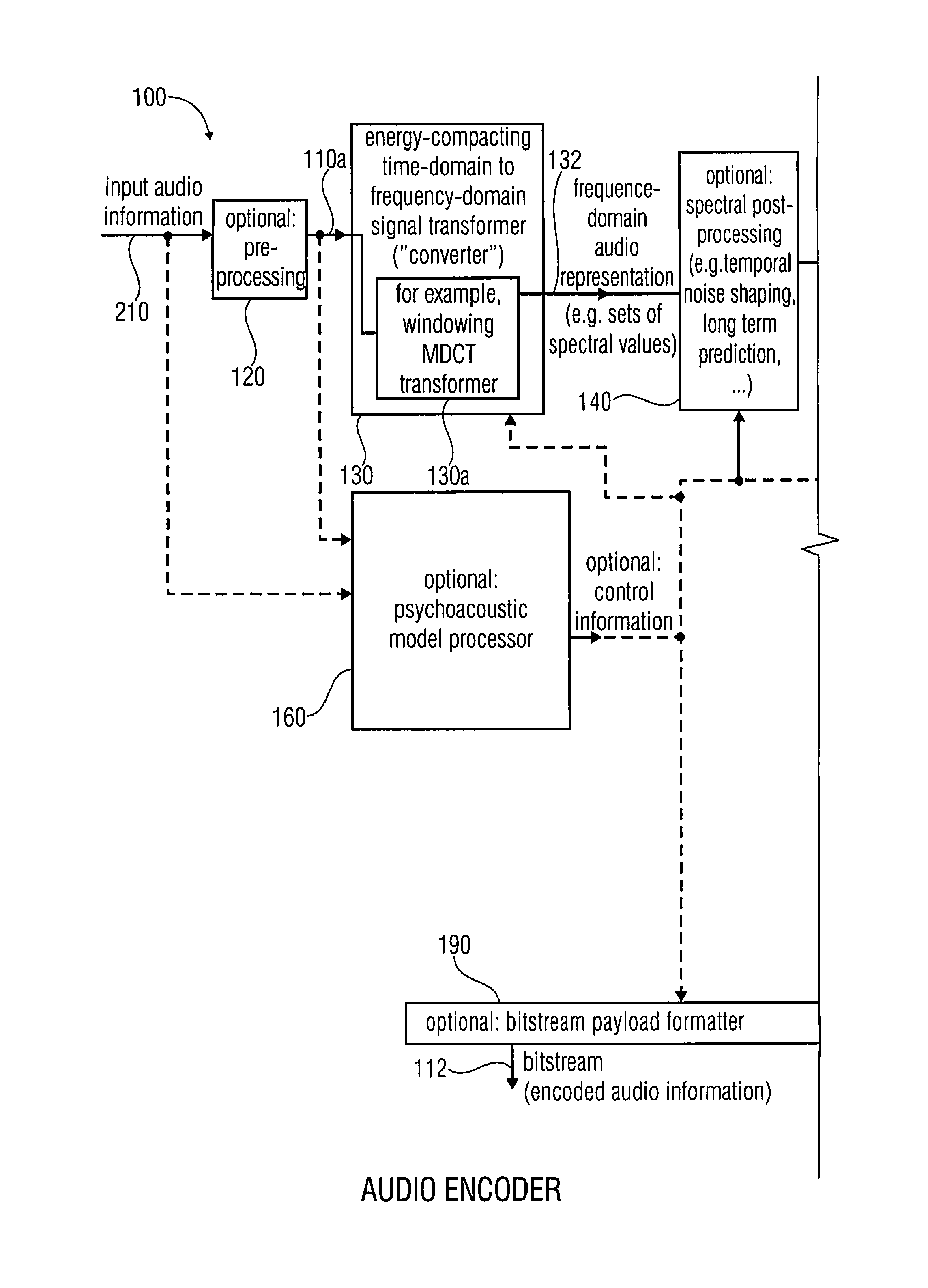
Audio encoder, audio decoder, method for encoding an audio information, method for decoding an audio information and computer program using a detection of a group of previously-decoded spectral values
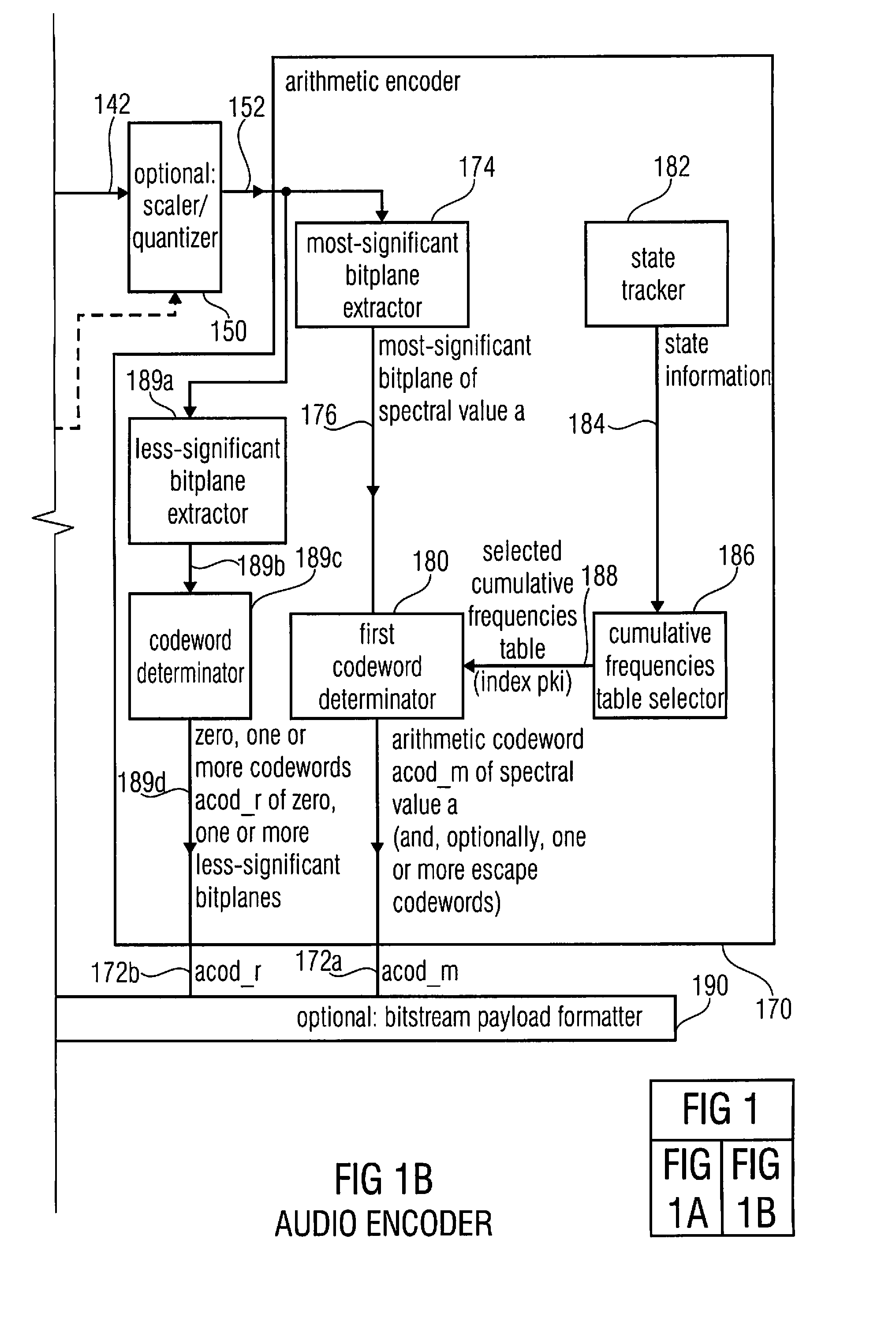
ActiveUS20120265540A1Easy to implementImprove coding efficiencySpeech analysisTime domainFrequency spectrum
An audio decoder for providing a decoded audio information includes a arithmetic decoder for providing a plurality of decoded spectral values on the basis of an arithmetically-encoded representation of the spectral values and a frequency-domain-to-time-domain converter for providing a time-domain audio representation using the decoded spectral values. The arithmetic decoder is configured to select a mapping rule describing a mapping of a code value onto a symbol code in dependence on a context state. The arithmetic decoder is configured to determine or modify the current context state in dependence on a plurality of previously-decoded spectral values. The arithmetic decoder is configured to detect a group of a plurality of previously-decoded spectral values, which fulfill, individually or taken together, a predetermined condition regarding their magnitudes, and to determine the current context state in dependence on a result of the detection.An audio encoder uses similar principles.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Mobile station apparatus, base station apparatus, and radio link synchronization determining method
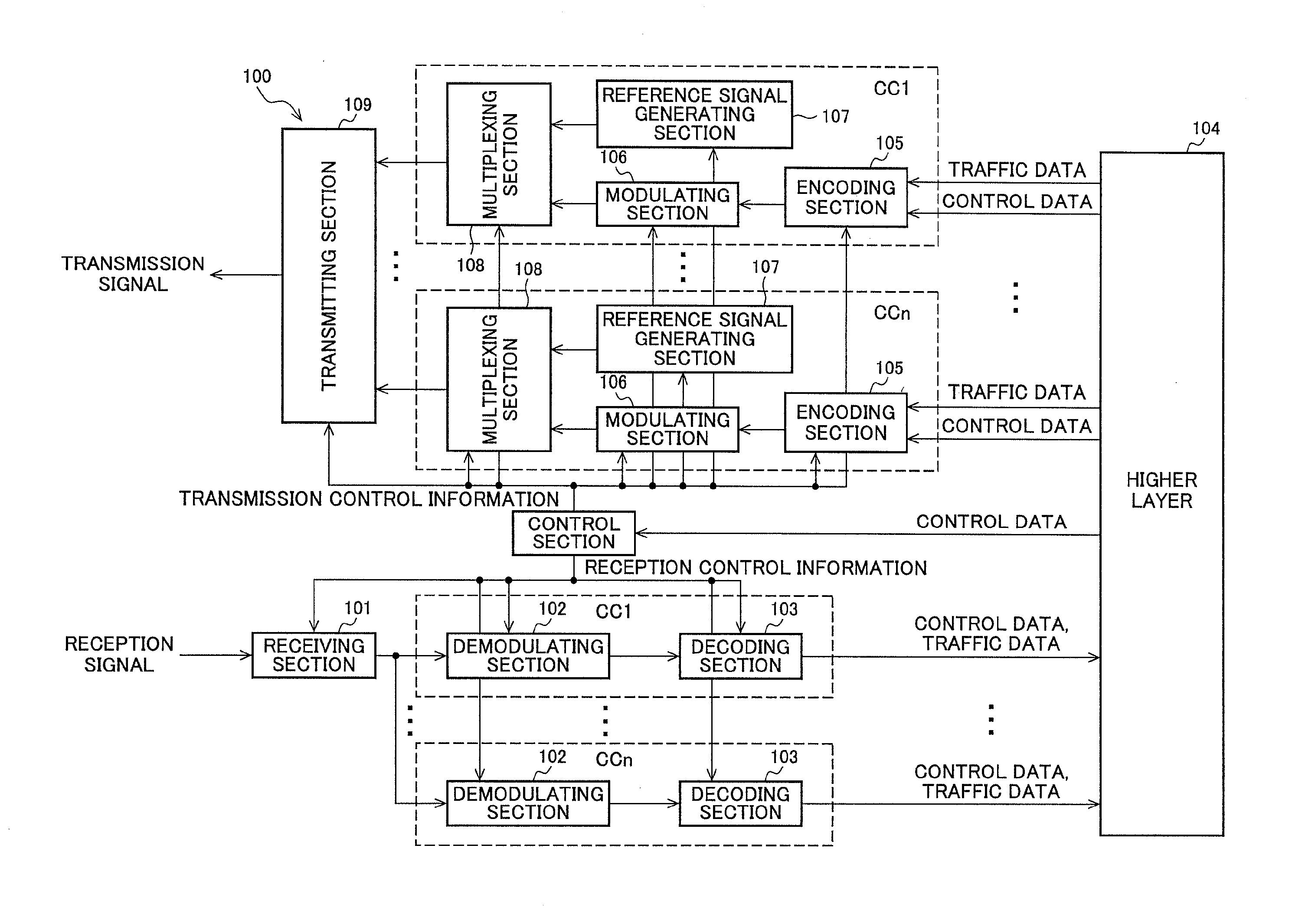
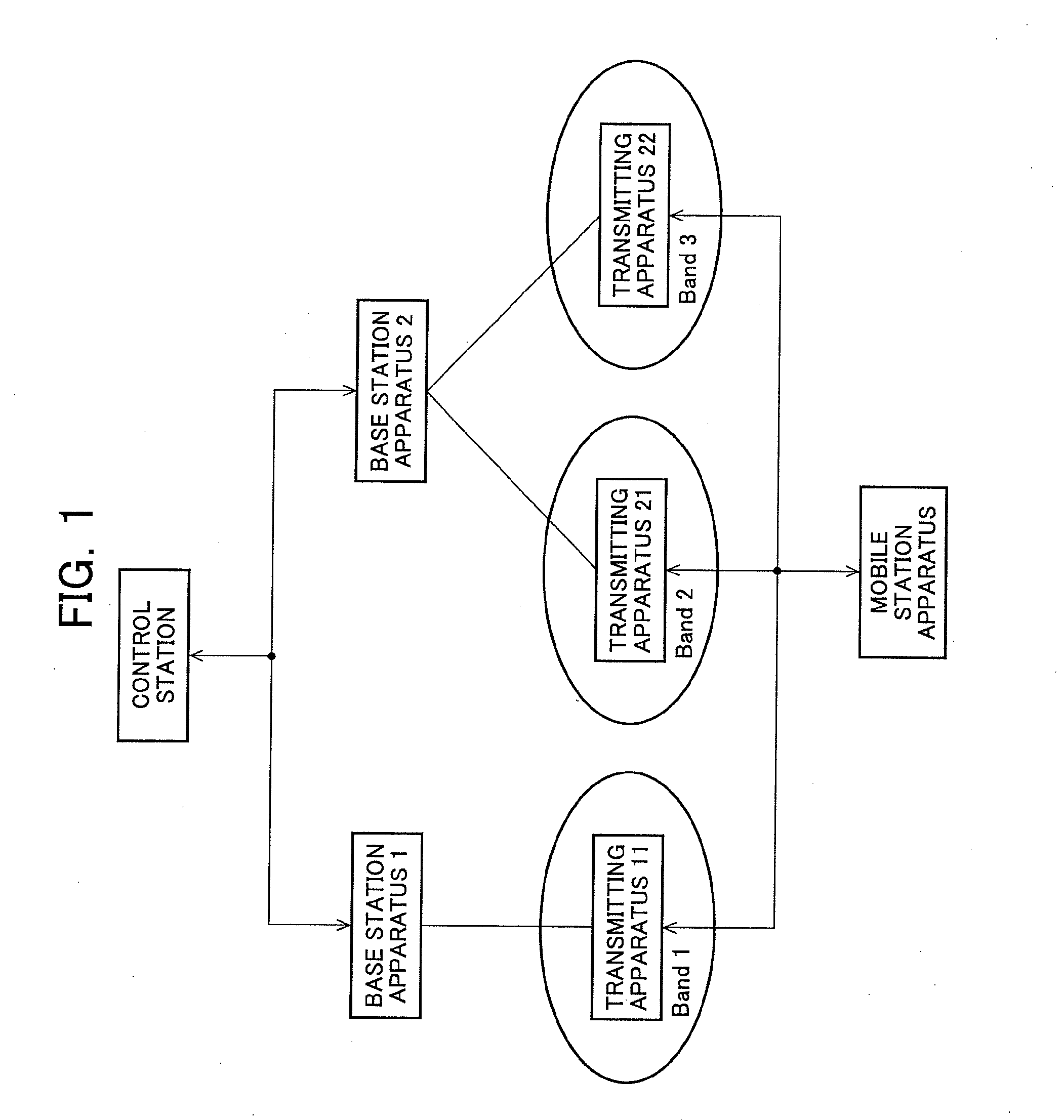
InactiveUS20110292824A1Efficient radio link synchronization determinationEffective judgmentSynchronisation arrangementError preventionEngineeringMobile station
While a mobile station apparatus is receiving a plurality of frequency bands, effective determinations of wireless link synchronization can be achieved. The mobile station apparatus measures the reception qualities of a plurality of different downlink frequency band signals (DL_CC1, DL_CC2) transmitted by one or more base station apparatuses and by the foregoing base station apparatuses. If all of the measured reception qualities are below a threshold value (Qout) (threshold value for determining downlink synchronizations), the mobile station apparatus determines that a downlink synchronization error has occurred, and then causes the downlink synchronization state to transition to an error detection part. If the mobile station apparatus successively detects the downlink synchronization error a predetermined number of times, then the mobile station apparatus causes the downlink synchronization state to transition to a synchronization protection part and simultaneously starts a downlink synchronization protection timer. If no downlink synchronization has been recovered by the expiration of the downlink synchronization protection timer, the mobile station apparatus determines that an out-of-downlink-synchronization has occurred, and then releases individually designated radio resources and thereafter starts a cell reselection.
Owner:SHARP KK
Power distribution network fault location method based on fault indicators
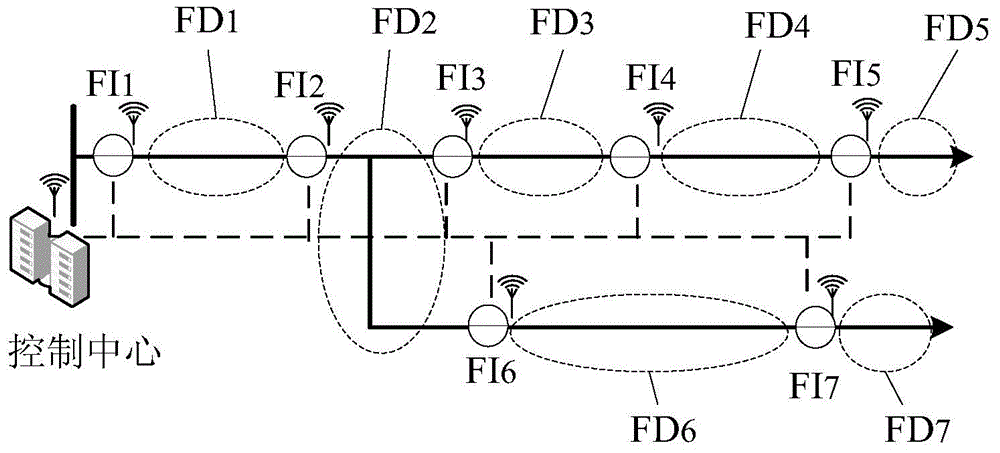
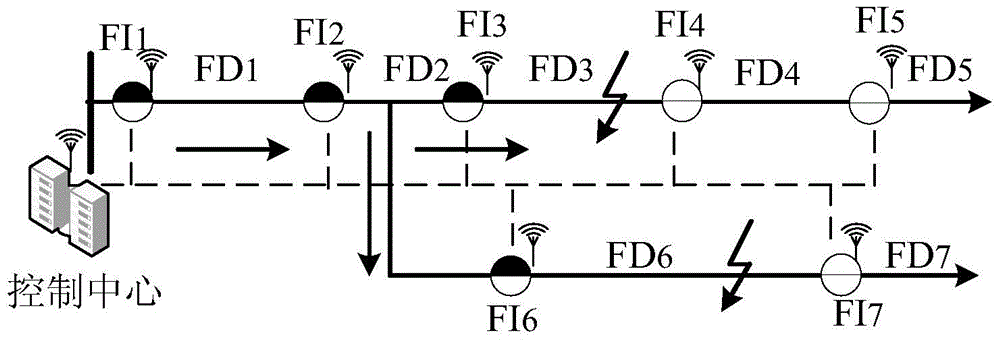
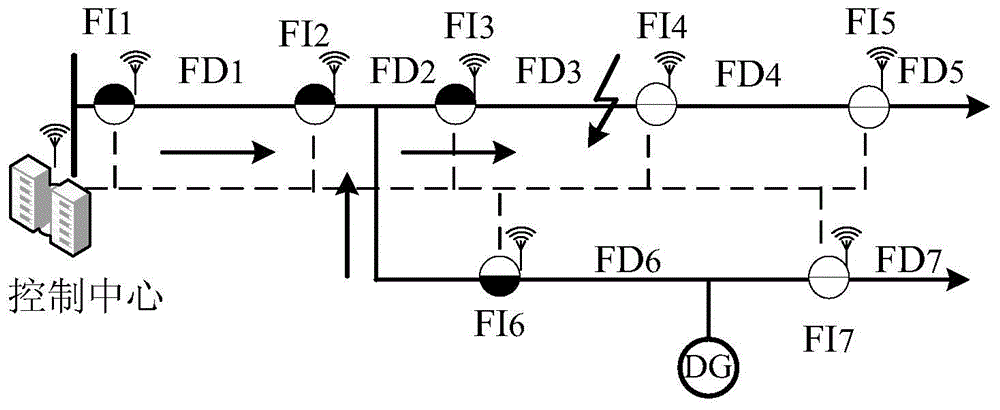
InactiveCN104483601ALow priceWide range of applicationsFault locationDistribution gridIncidence matrix
The invention discloses a power distribution network fault location method based on fault indicators. The method comprises several steps as follows: construction of an incidence matrix, sending of state information to a master station control center by the fault indicators, generation of a trigger vector and location of a fault section. An incidence matrix construction unit generates the incidence matrix, the fault indicators send the state information to a master station through a Zigbee wireless network, and a fault location unit generates a trigger vector, performs matrix operation on the trigger vector and the incidence matrix to acquire a fault section vector, analyzes and locates the fault section and diagnoses the fault information. Effective fault location of a power distribution network which has multiple faults and contains distributed power supplies can be realized. When the method is used for locating the faults of the power distribution network, a normalized incidence matrix is not required, and fault location of the complex power distribution network structure with multiple fault points and multiple power supply systems can be realized; the method has certain fault tolerance and is simple in judgment principle, small in calculation amount, stable, reliable, quick and accurate in fault location and low in cost.
Owner:GUANGXI UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com