Patents
Literature
55 results about "Communication Analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The examination of the different ways that information is exchanged between parties.
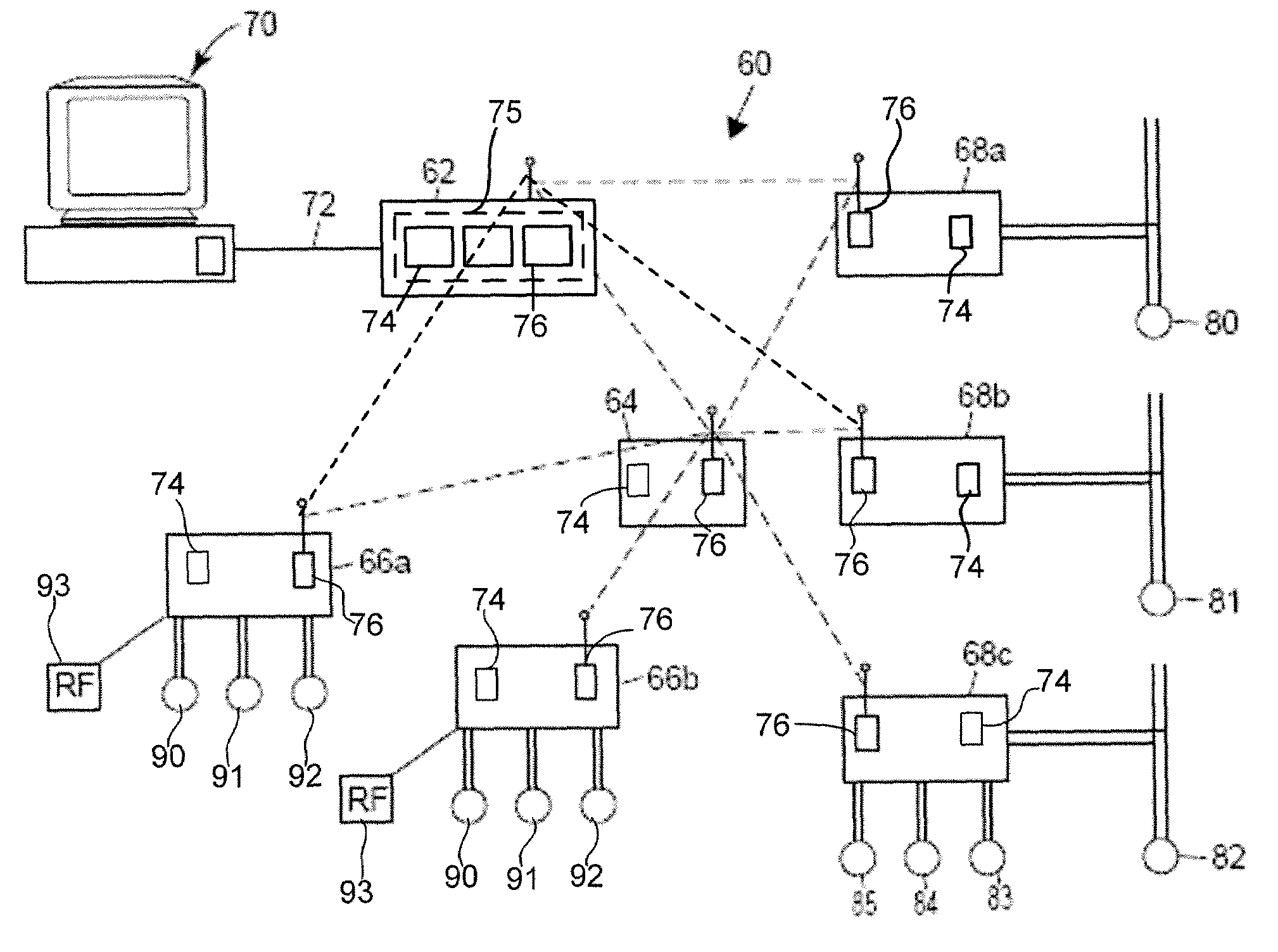
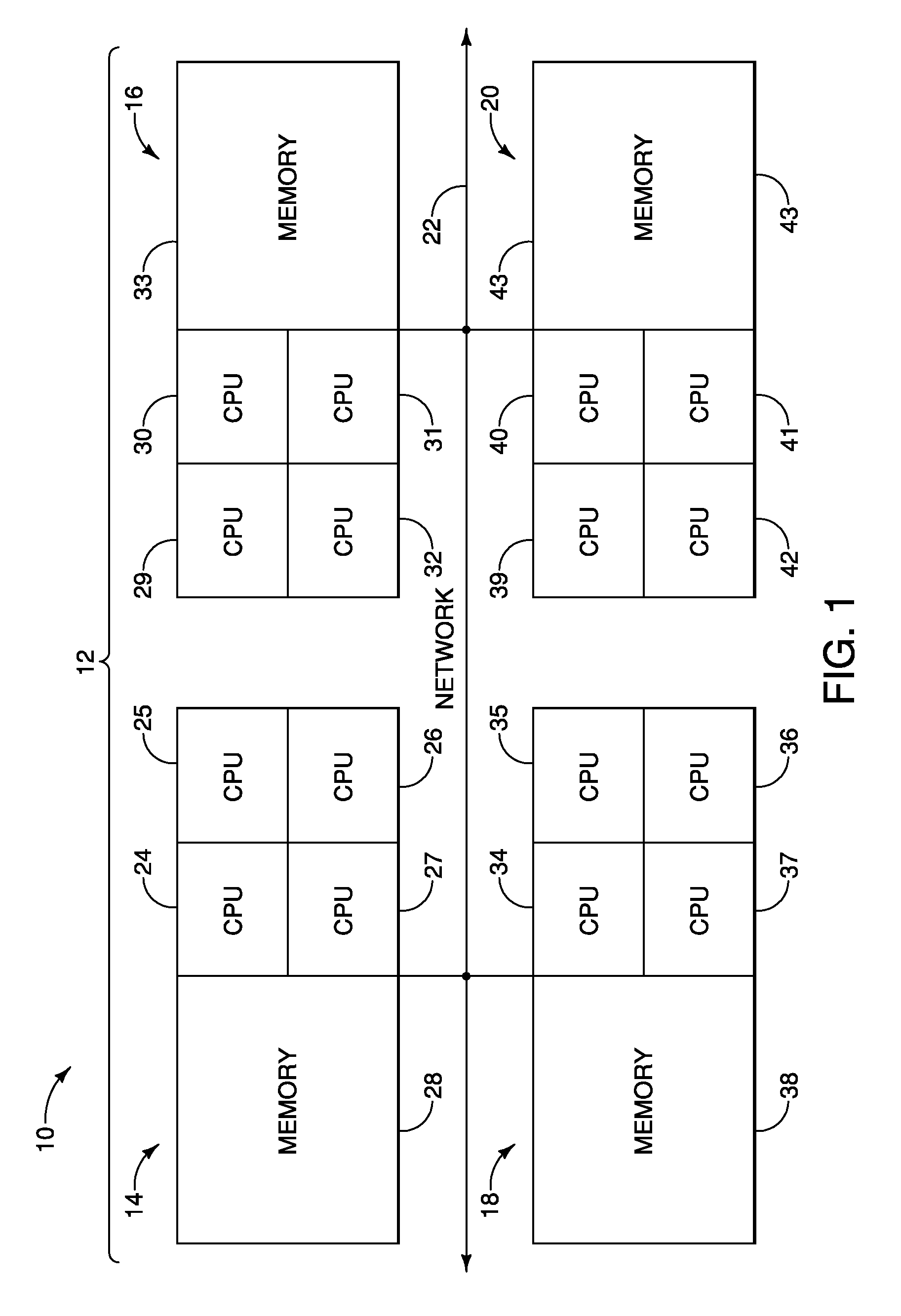
Wireless architecture and support for process control systems
InactiveUS20050276233A1Easy to changeEasy to configureNetwork topologiesElectric testing/monitoringCommunication AnalysisTelecommunications
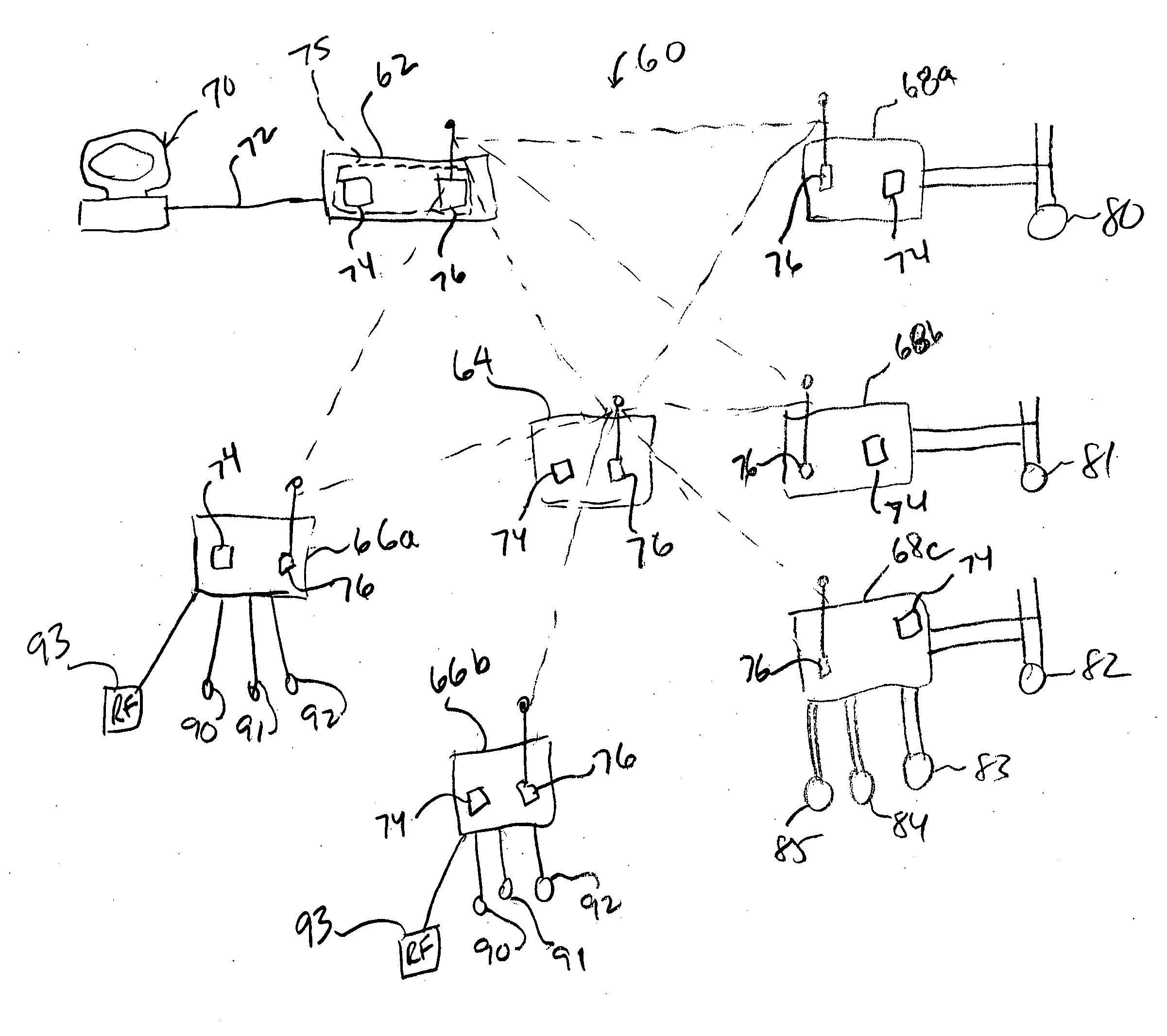
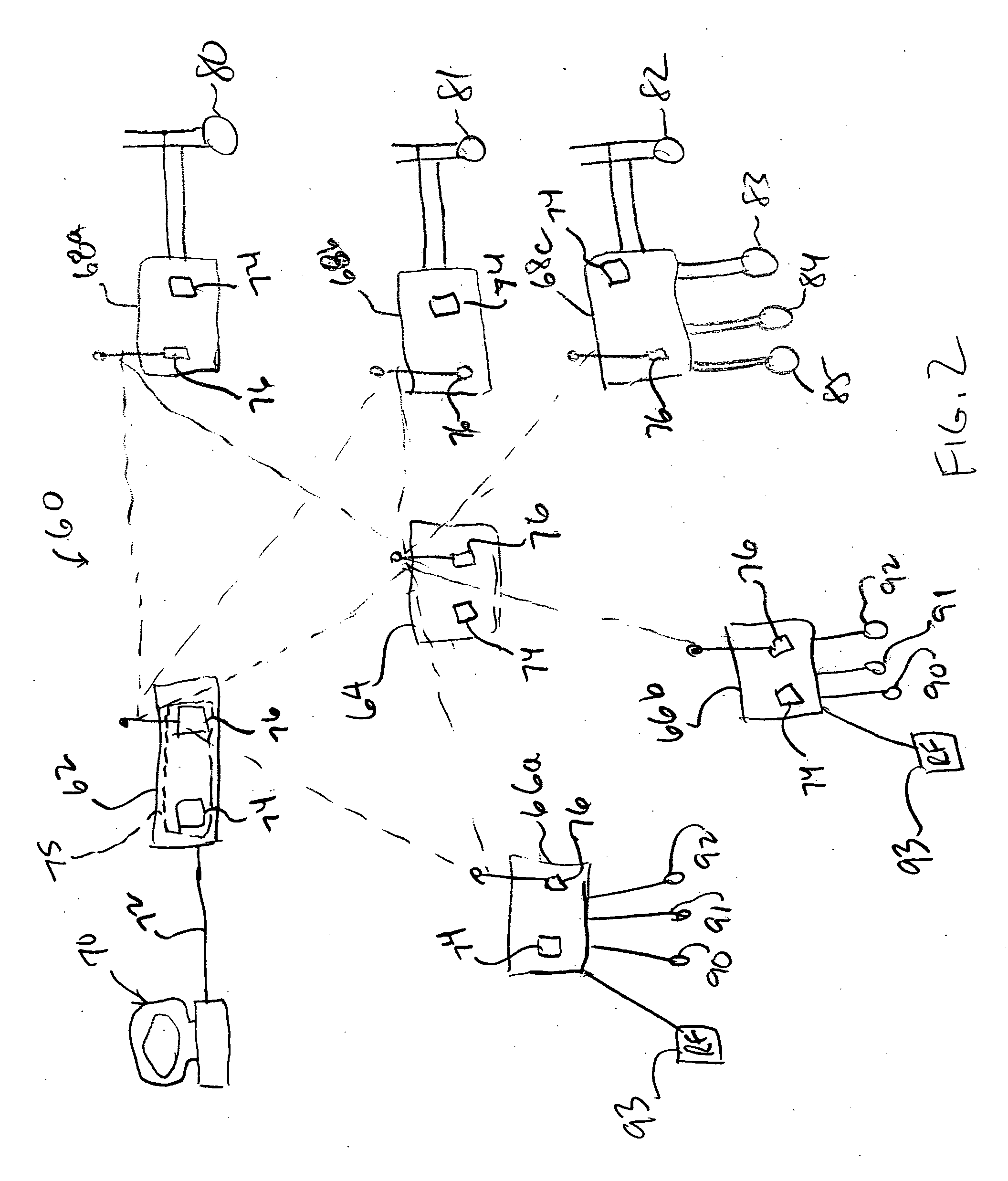
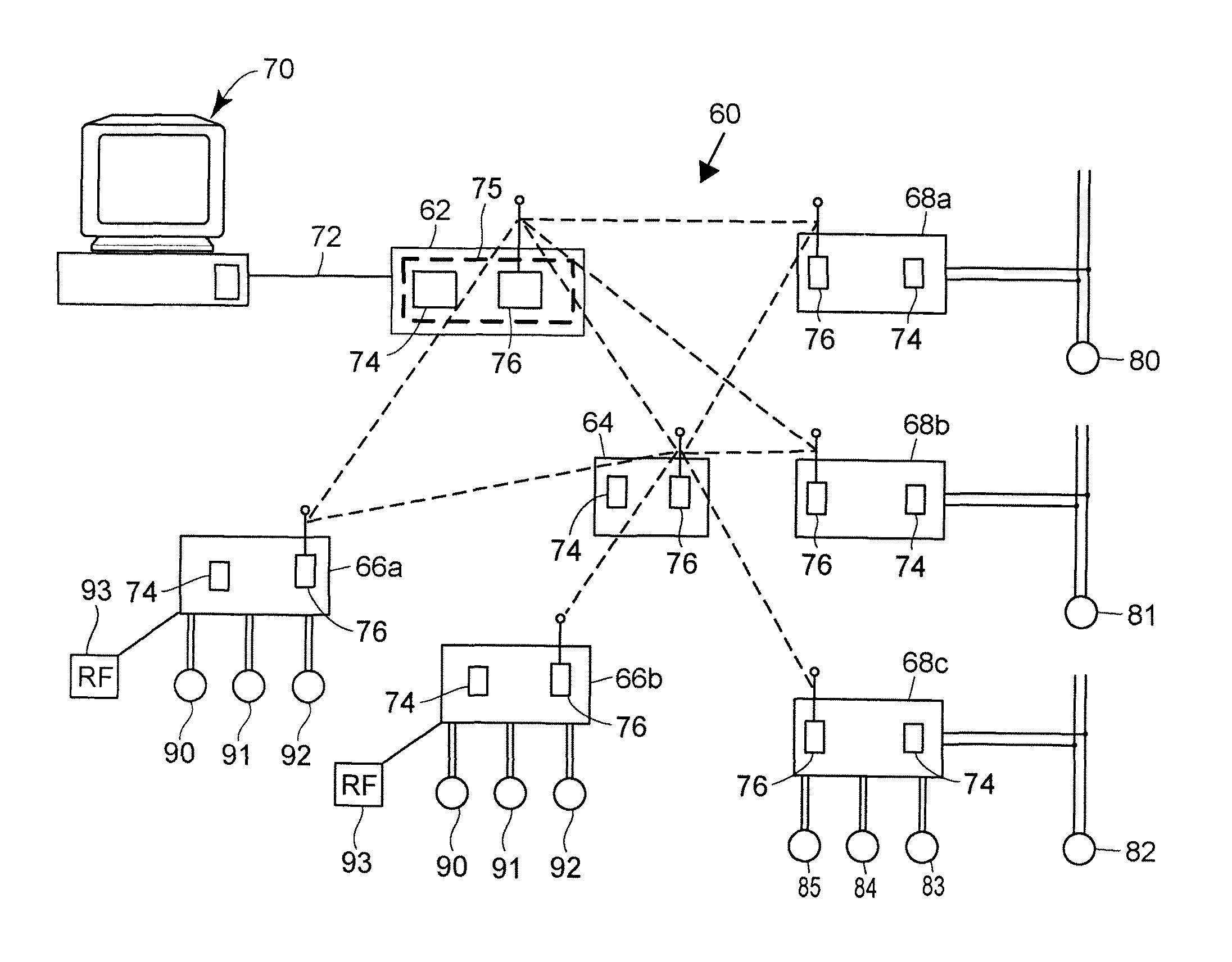
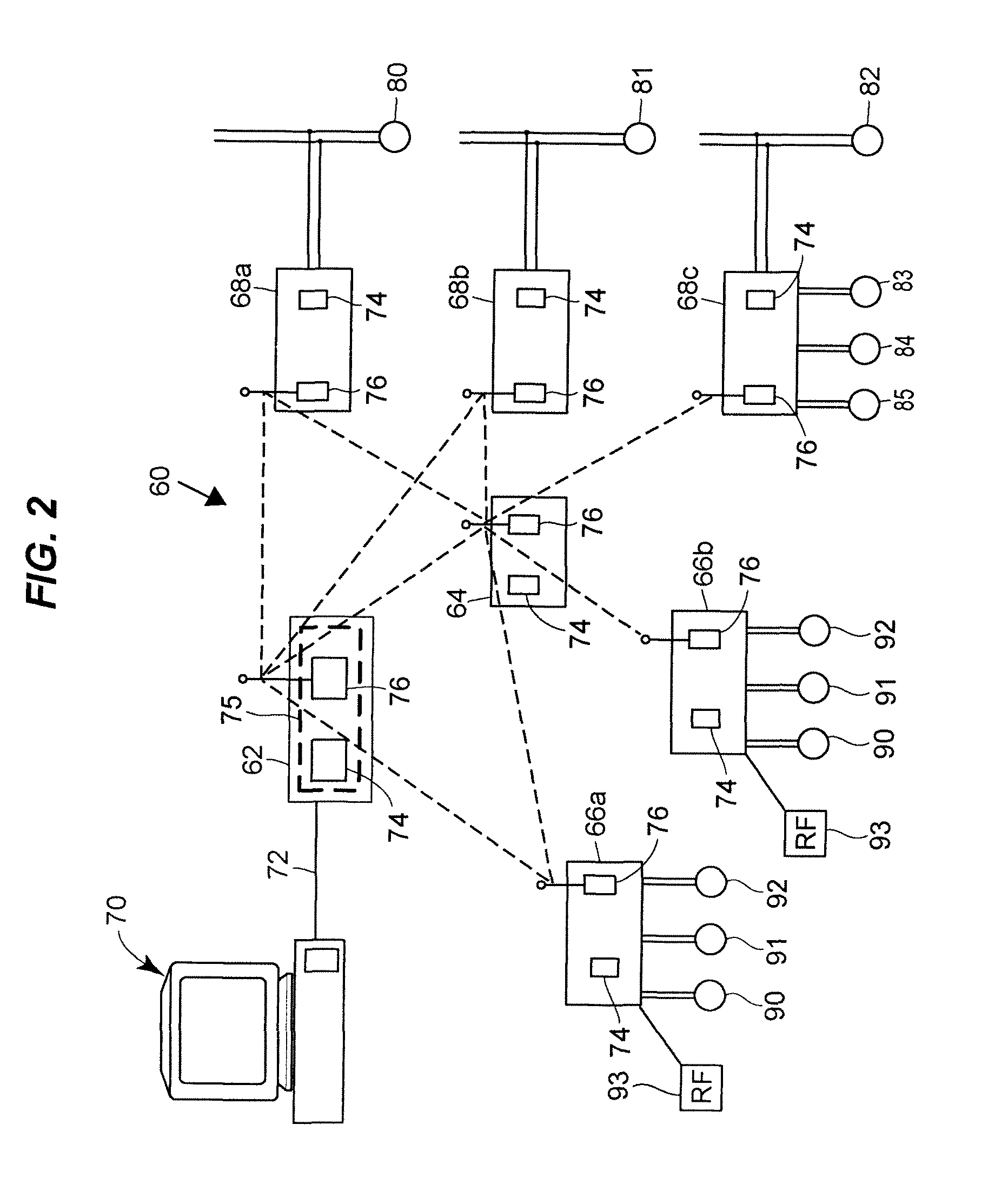
A wireless communication system for use in a process environment uses mesh and possibly a combination of mesh and point-to-point communications to produce a wireless communication network that can be easily set up, configured, changed and monitored, thereby making a wireless communication network that is less expensive, and more robust and reliable. The wireless communication system allows virtual communication paths to be established and used within the process control system in a manner that is independent of the manner in which the wireless signals are sent between different wireless transmitting and receiving devices within the process plant, to thereby operate in a manner that is independent of the specific messages or virtual communication paths within the process plant. Still further, communication analysis tools are provided to enable a user or operator to view the operation of the wireless communication network to thereby analyze the ongoing operation of the wireless communications within the wireless communication network.
Owner:FISHER-ROSEMOUNT SYST INC
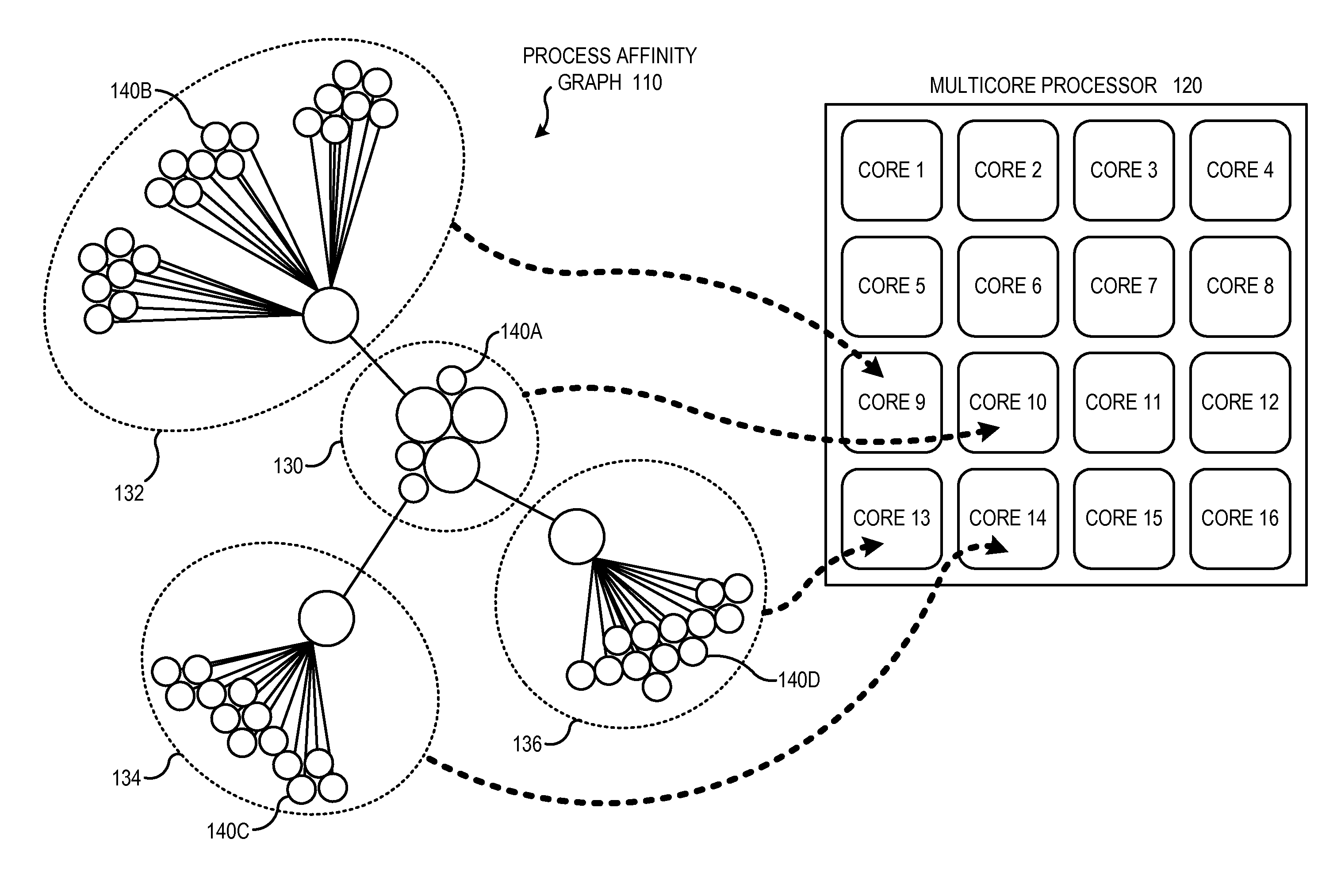
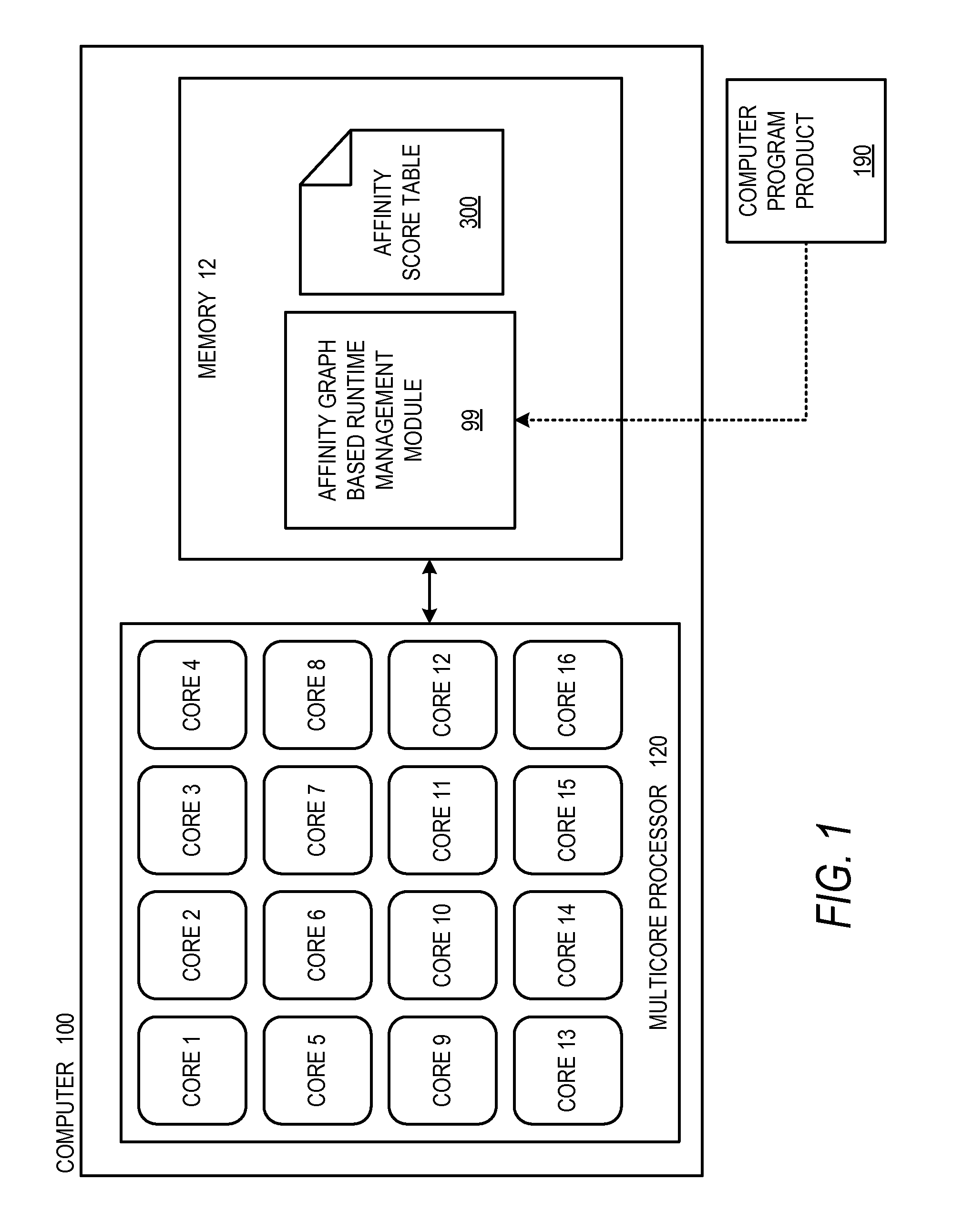
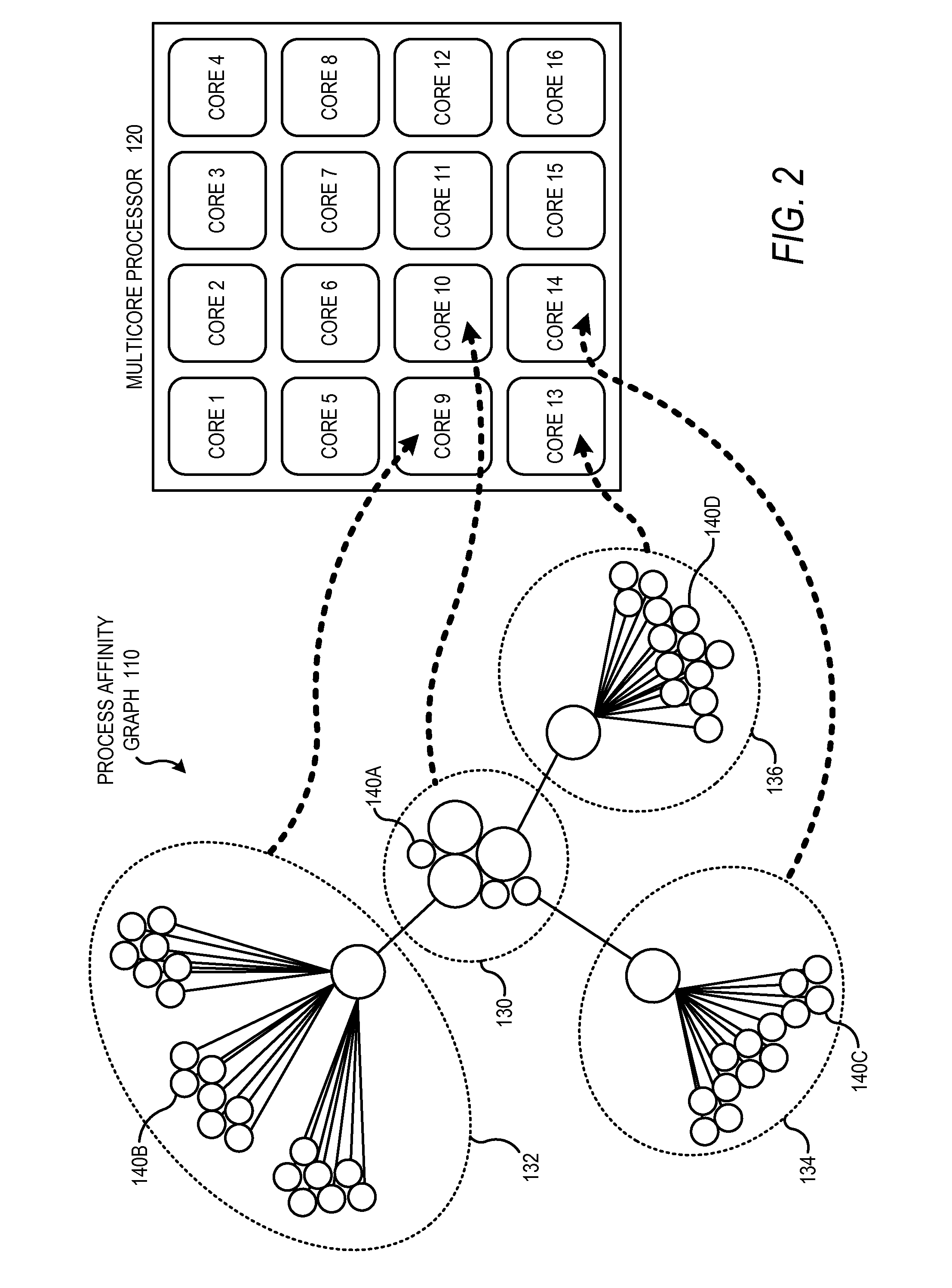
Multicore Runtime Management Using Process Affinity Graphs
InactiveUS20110088038A1Interprogram communicationMemory systemsProcess systemsCommunication Analysis
Technologies are generally described for runtime management of processes on multicore processing systems using process affinity graphs. Two or more processes may be determined to be related when the processes share interprocess messaging traffic. These related processes may be allocated to neighboring or nearby processor cores within a multicore processor using graph theory techniques as well as communication analysis techniques to evaluate interprocess communication needs. Process affinity graphs may be established to aid in determining grouping of processors and evaluating interprocess message traffic between groups of processes. The process affinity graphs may be based upon process affinity scores determined by monitoring and analyzing interprocess messaging traffic. Process affinity graphs may further inform splitting process affinity groups from one core onto two or more cores.
Owner:EMPIRE TECH DEV LLC +1
Wireless architecture and support for process control systems
InactiveUS7436797B2Easy to changeEasy to configureNetwork topologiesElectric testing/monitoringCommunications systemTelecommunications
A wireless communication system for use in a process environment uses mesh and possibly a combination of mesh and point-to-point communications to produce a wireless communication network that can be easily set up, configured, changed and monitored, thereby making a wireless communication network that is less expensive, and more robust and reliable. The wireless communication system allows virtual communication paths to be established and used within the process control system in a manner that is independent of the manner in which the wireless signals are sent between different wireless transmitting and receiving devices within the process plant, to thereby operate in a manner that is independent of the specific messages or virtual communication paths within the process plant. Still further, communication analysis tools are provided to enable a user or operator to view the operation of the wireless communication network to thereby analyze the ongoing operation of the wireless communications within the wireless communication network.
Owner:FISHER-ROSEMOUNT SYST INC
Active social network
A communication analysis system for an online game is described. A communication history among players of the online game is retrieved. Communication tracking metrics are generated based on the communication history of the players of the online game. A retention analysis is performed with the communication tracking metrics to determine retention of players of the online game. A retention recommendation is generated based on the retention analysis.
Owner:ZYNGA
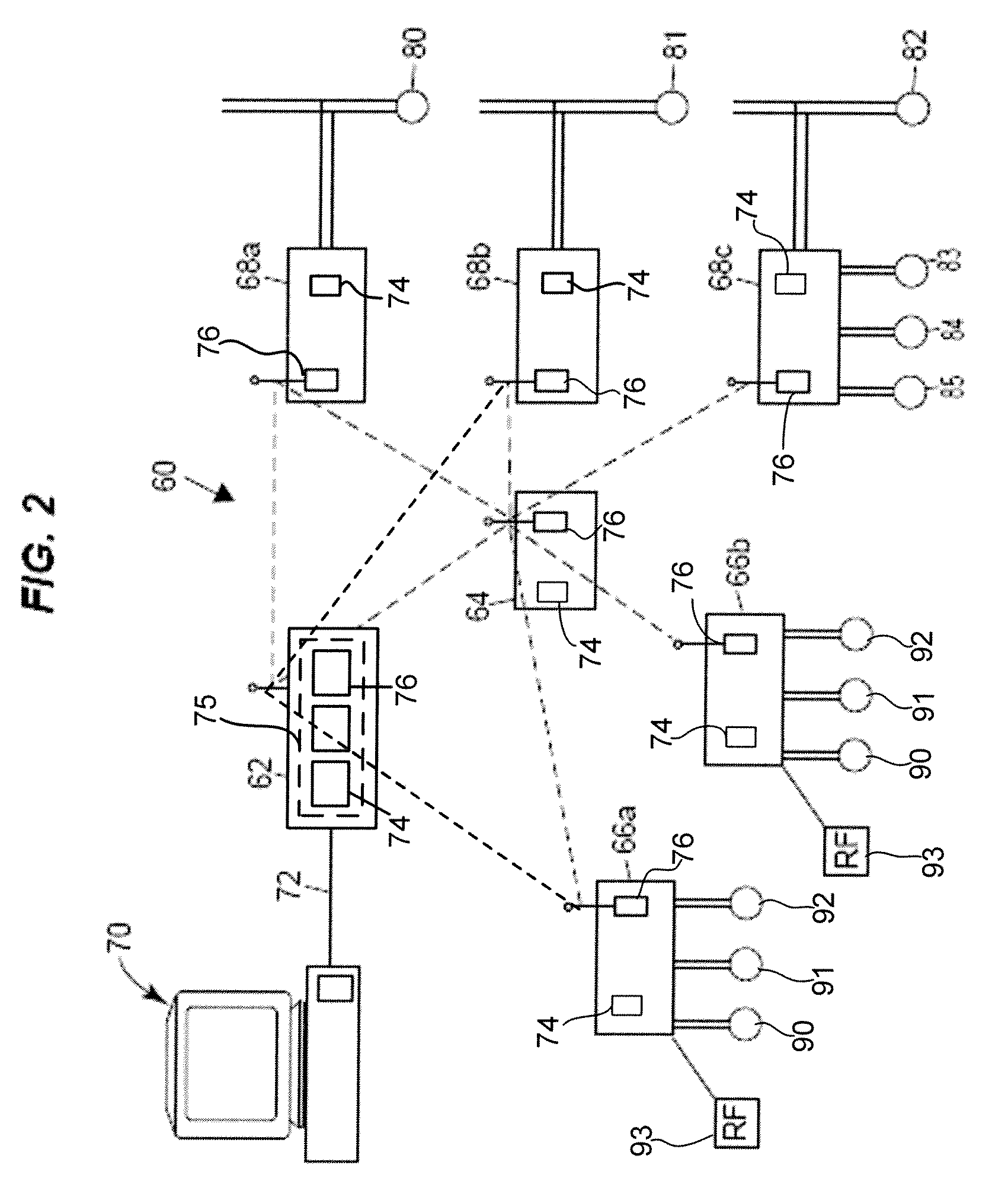
Communication analysis apparatus
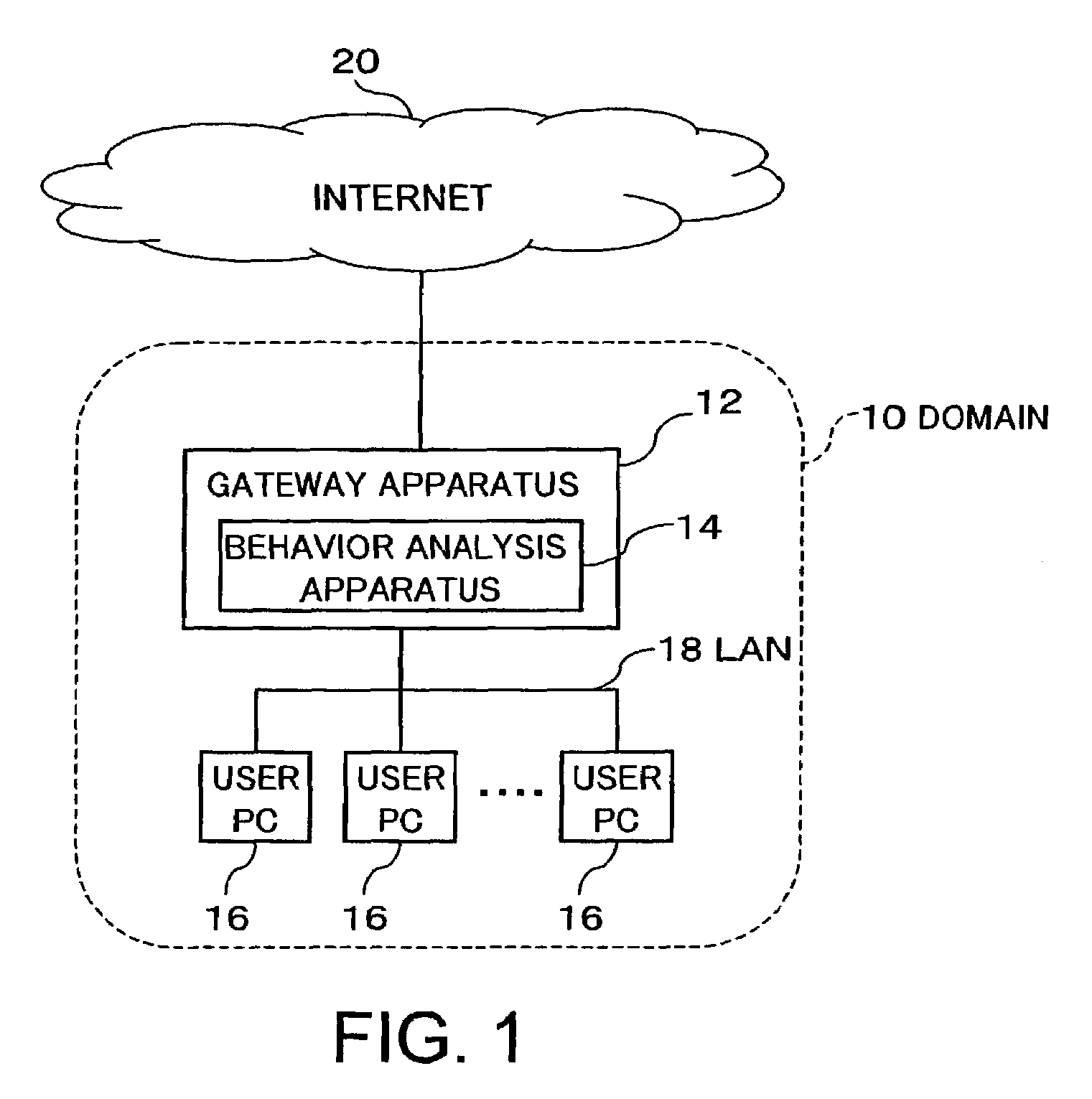
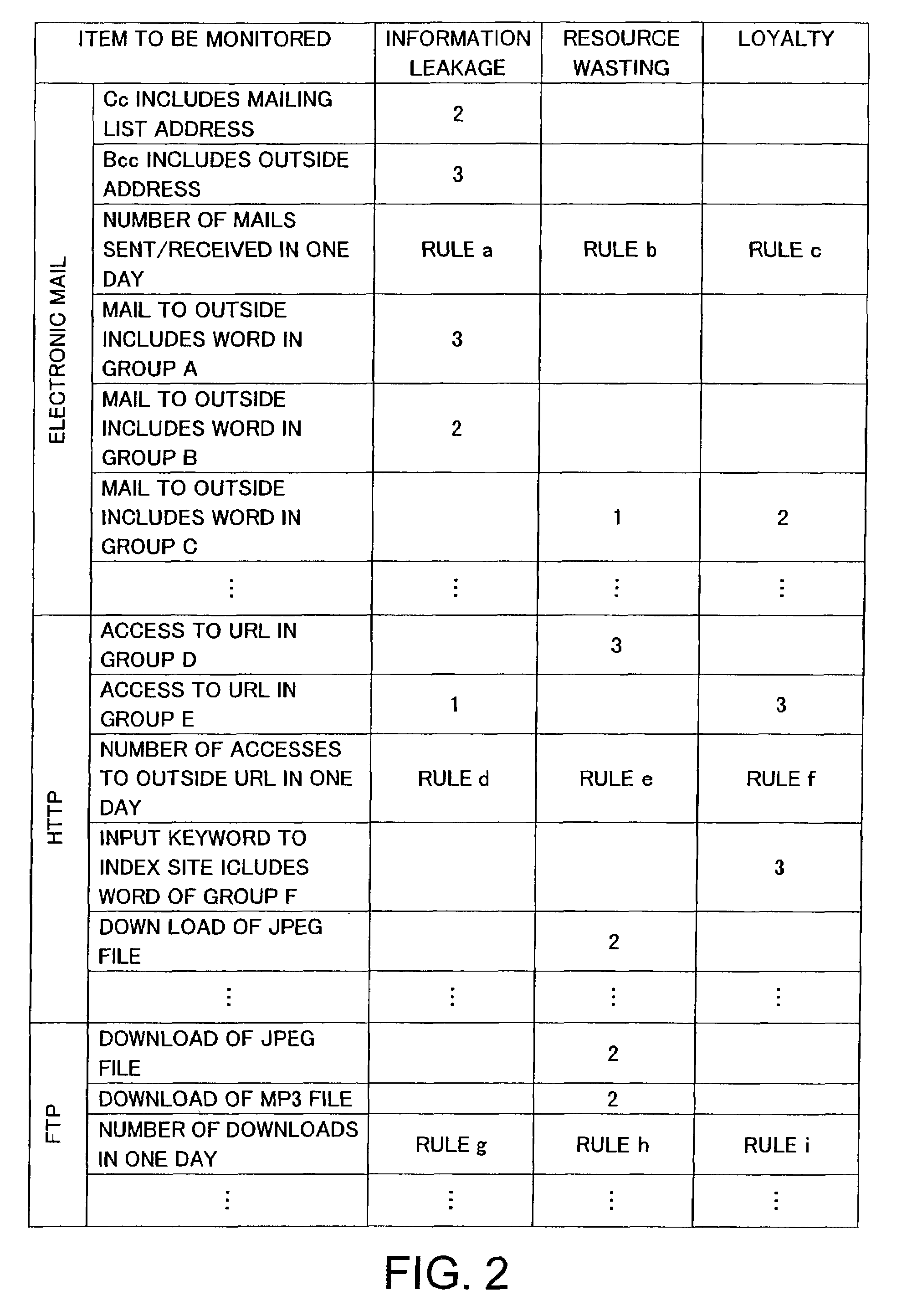
To deal with user network communication activity which cannot easily and clearly be determined as problematic behavior, a behavior analysis apparatus 14 monitors communication between each user PC 16 in a domain 10 and Internet 20 via a gateway apparatus 12. For example, when there is a monitored item related to information leakage of the user in the detected communication, a weight value corresponding to the monitored item is added to a score concerning a possibility of the user leaking information. Subsequently, the scores are totaled and recorded for each unit of time. The behavior analysis apparatus 14 inputs data of time-series transition of the total value to a neural network which has performed learning for prediction processing, and predicts the possibility of the user's information leak at a time in the near future. When an increasing risk of leakage is predicted, the behavior analysis apparatus 14 communicates an alarm to a security manager.
Owner:FUJIFILM BUSINESS INNOVATION CORP
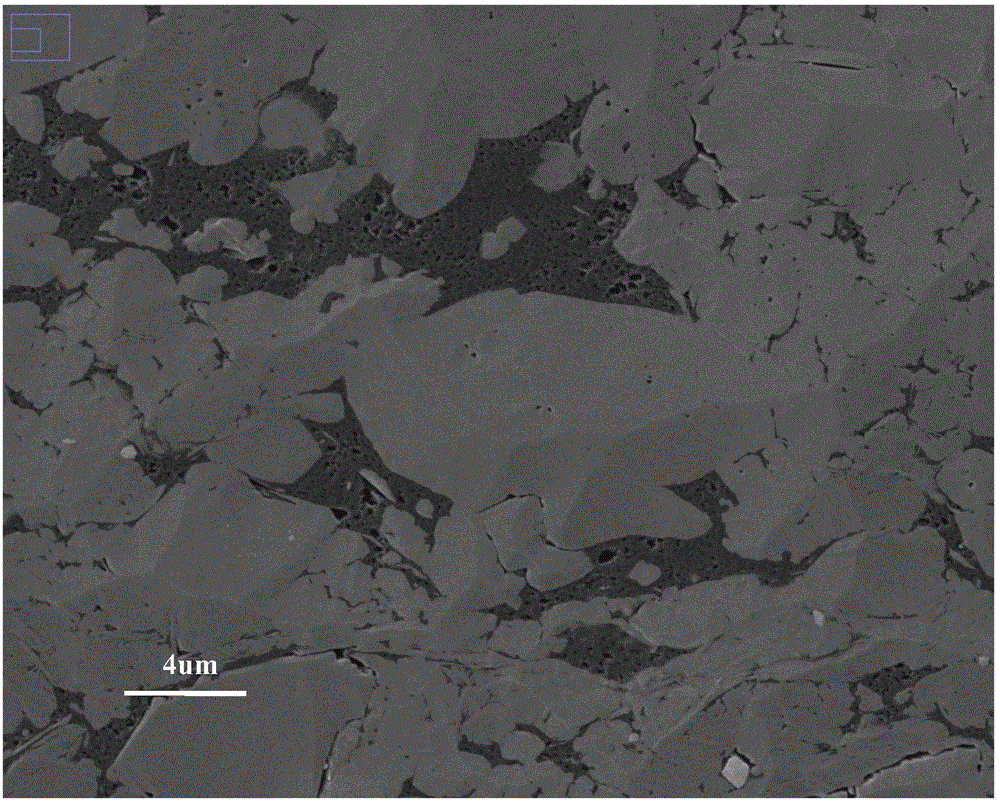
Automatic identifying and quantitative analyzing method for organic and inorganic holes in shale electron microscope images
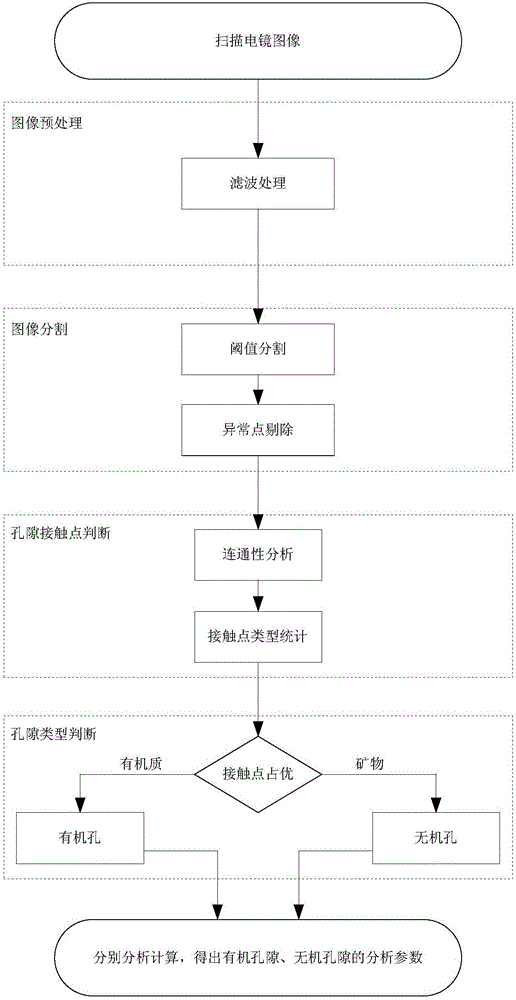
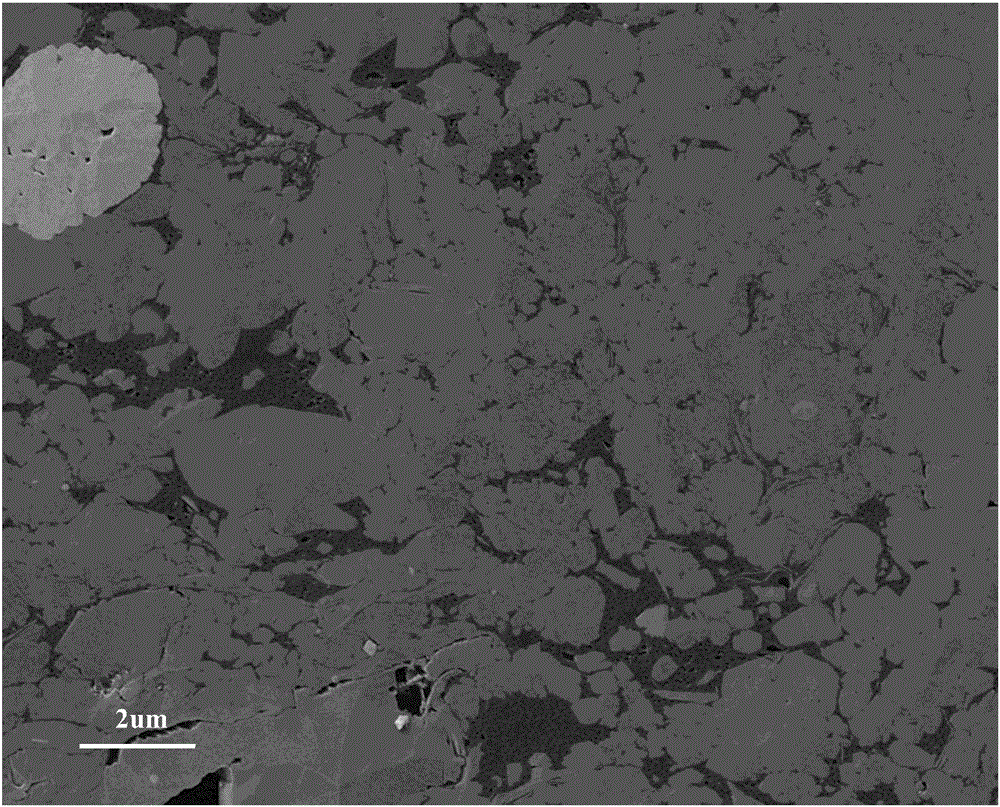
InactiveCN106651839AAddress effectivenessUniversalImage enhancementImage analysisGray levelScanning electron microscope
The invention mainly belongs to the technical field of petroleum geological exploration and specifically relates to an automatic identifying and quantitative analyzing method for organic and inorganic holes in a shale electron microscope image. According to the invention, a scanning electron microscope is utilized for scanning a shale sample and the shale electron microscope image containing organic matter, inorganic matter and holes is obtained. The shale electron microscope image is divided into a organic matter zone, an inorganic matter zone and a hole zone according to gray level. The number of the holes is obtained through communication analysis of the holes in the hole zone and the holes are marked. Then the holes are judged and divided into organic holes and inorganic holes. A problem that the effective classification and quantitative analysis of the holes cannot he realized in the prior art is solved and a foundation is provided for follow-up evaluation of shale oil and gas storage capability, existing states of oil and gas in the holes and migration mechanism and capability.
Owner:INST OF GEOLOGY & GEOPHYSICS CHINESE ACAD OF SCI
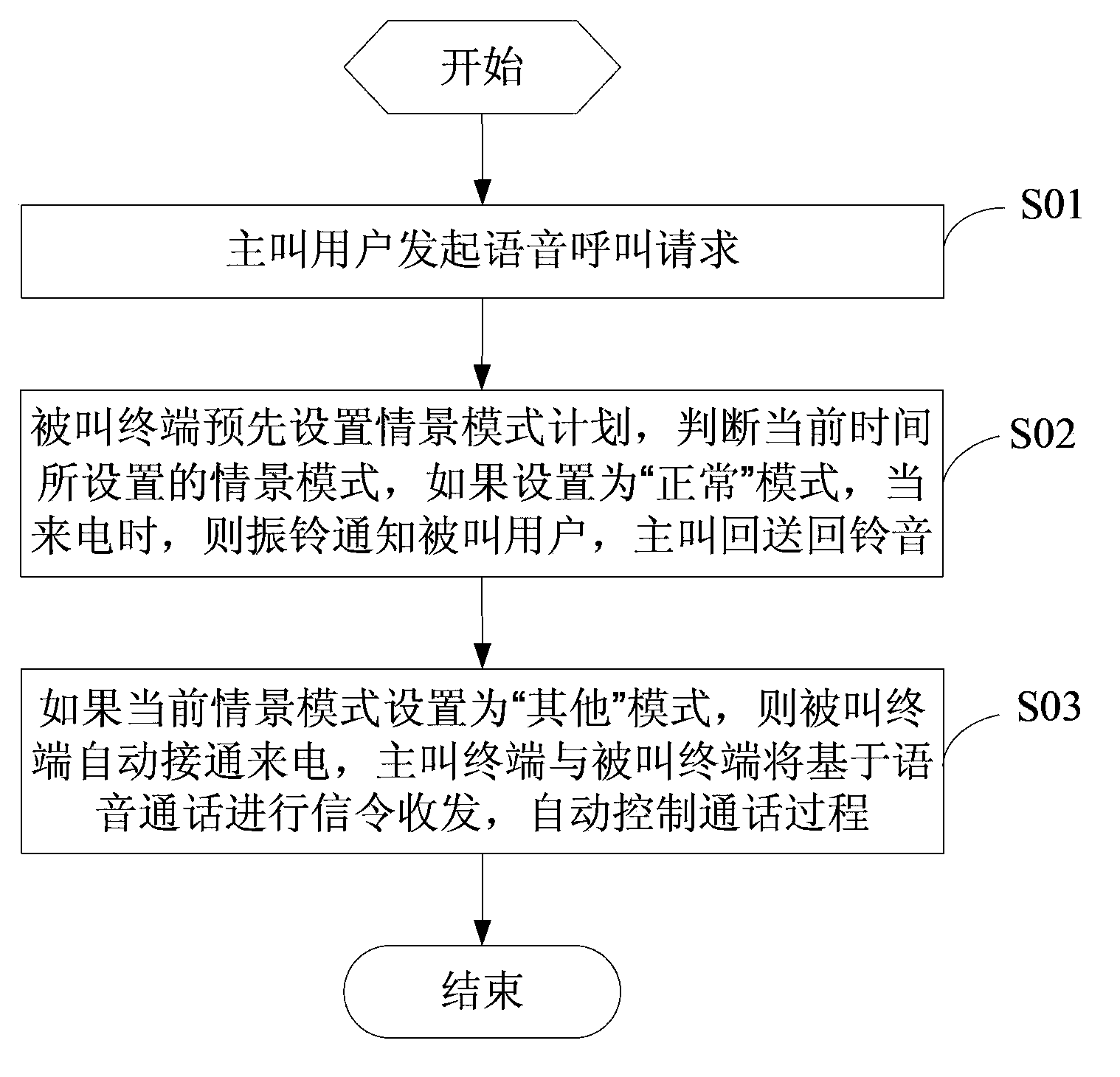
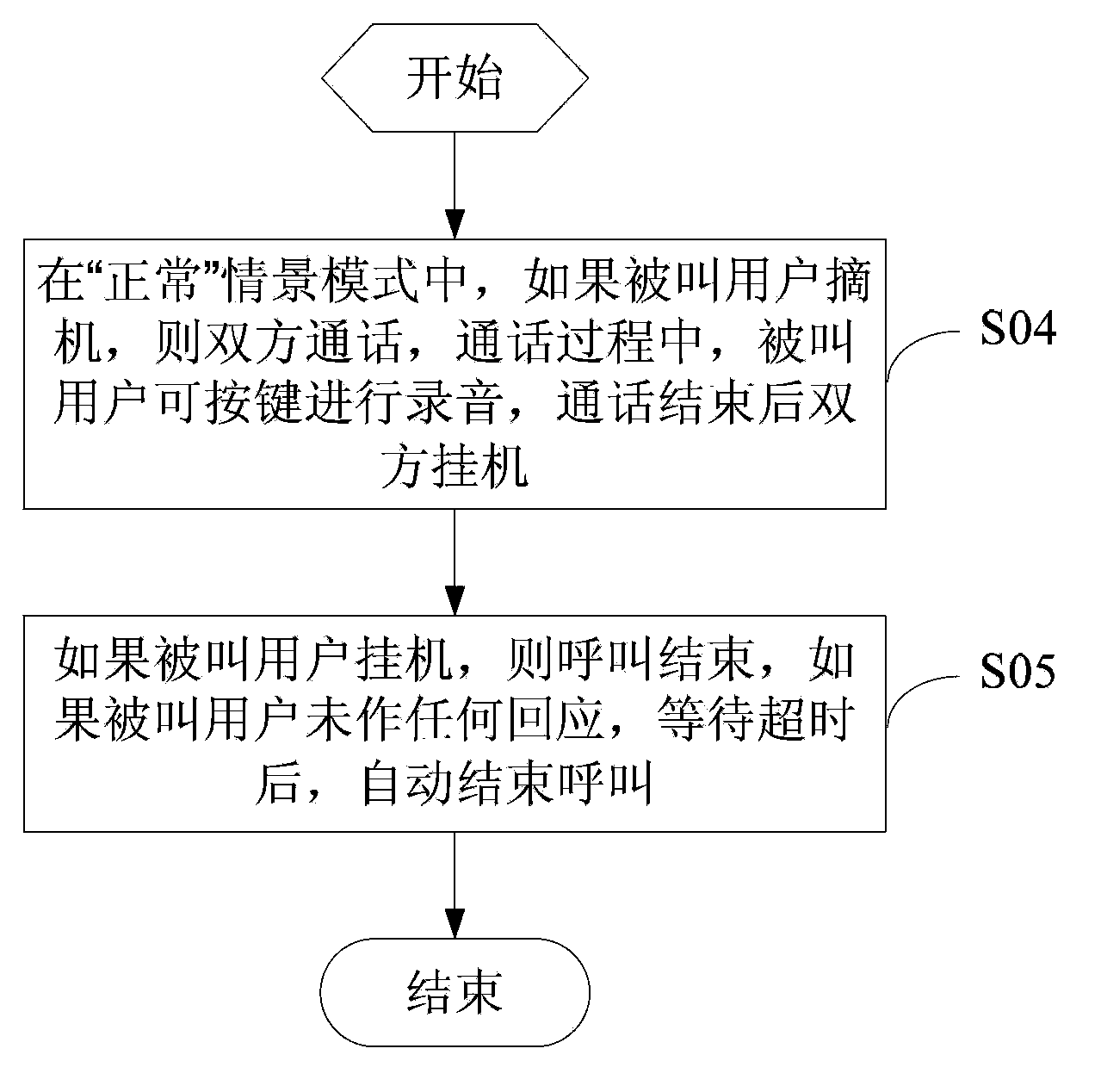
Call control and processing method based on automatic connection of mobile phone
InactiveCN103685711AImprove communication efficiencySubstation equipmentAutomatic controlCommunications system
This invention discloses a call control and a processing method based on automatic connection of a mobile phone. The call control and the processing method comprises steps: a calling party initiates a voice calling; a called terminal preset the scene mode and determines the current scene mode, and if the current scene mode is set in a normal mode, the mobile phone can prompt the called party by vibration when a call is coming in, and a ring-back tone is sent to the calling part ; the scene mode is set into different modes according to different time frames, and the scene mode is automatically switched according to the time frame on the called terminal; if the current scene mode is set into an "other" mode, the called terminal automatically connects the incoming call, and the calling party and the called party perform signaling receiving and transmitting based on voice communication, and the communication process is automatically controlled. By call communication analysis and interactive processing after automatically connecting the voice call of the mobile phone, the communication efficiency is improved without support of an operator and communication system alternation.
Owner:崔玉珩
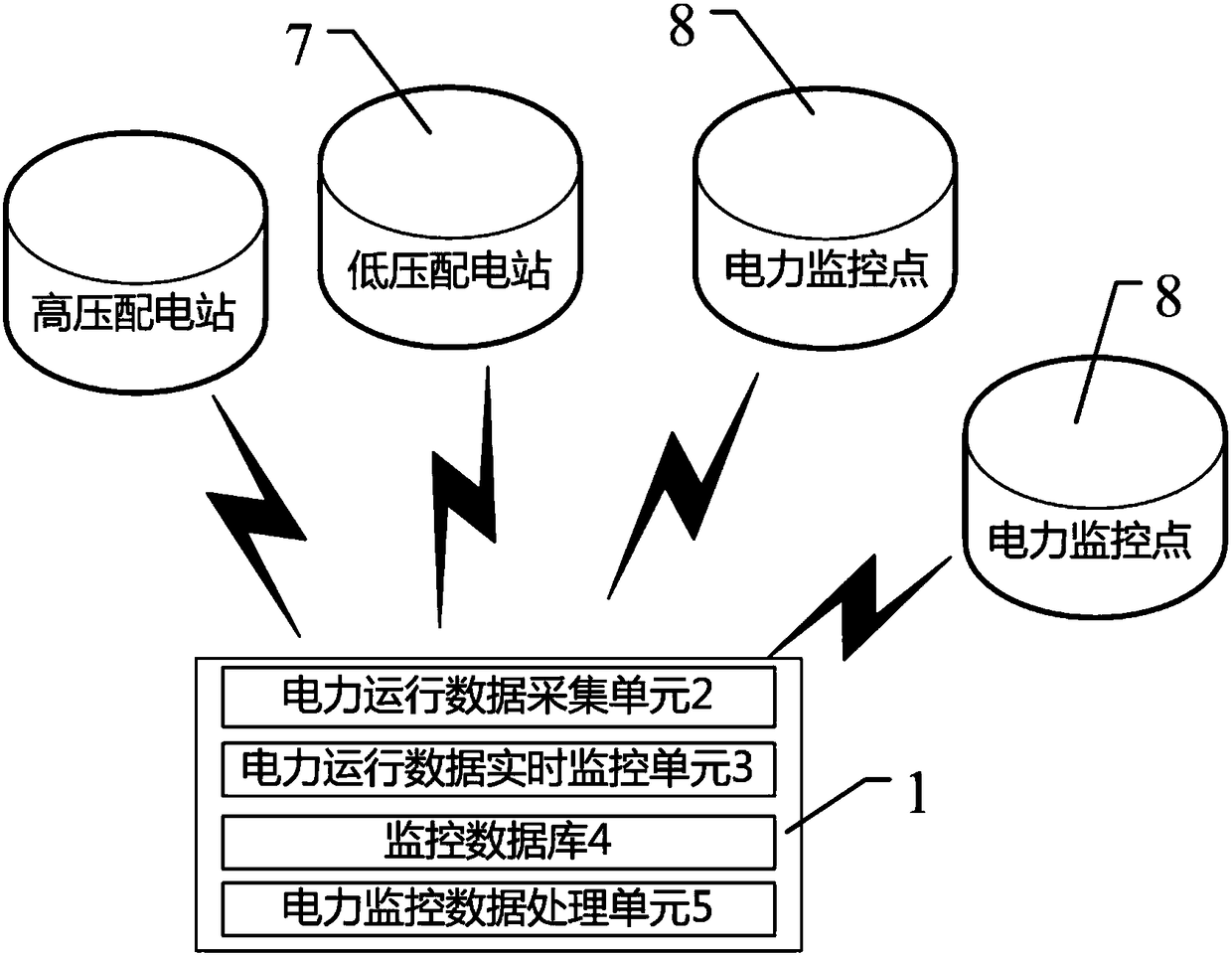
Power operation data monitoring and communication analysis system
The invention provides a power operation data monitoring and communication analysis system. The system is characterized by using data acquisition terminals arranged on a high voltage distribution station, a low voltage distribution station and each power monitoring point to collect power operation data and carry out real-time tracking on the data; based on the data which is collected and tracked in real time by a power operation data acquisition unit, carrying out monitoring, and when the collected and tracked data exceeds a threshold value, emitting an alarm prompt; and classifying and storing the data collected and tracked by the power operation data acquisition unit and the data monitored by a power operation data real-time monitoring unit and forming a power operation database so as to provide a basis for the later-period analysis management deployment of the power operation data. The power monitoring data can be sent to a power management person in real time, and the data can beused to form analysis data so as to guide the power management person to well deploy a power plan and form a power management decision.
Owner:SHANDONG JINREN ELECTRIC
Security system for machine to machine cyber attack detection and prevention
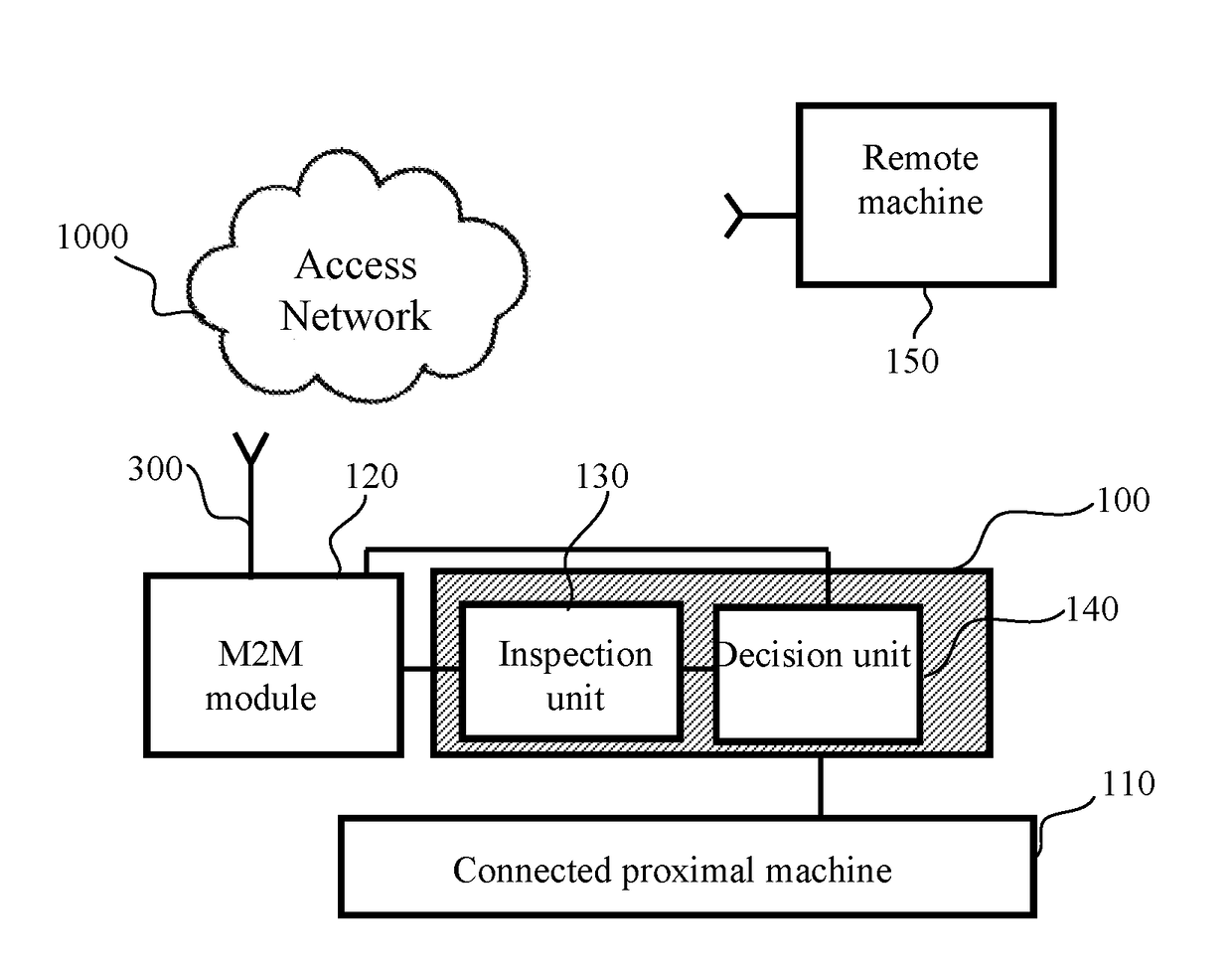
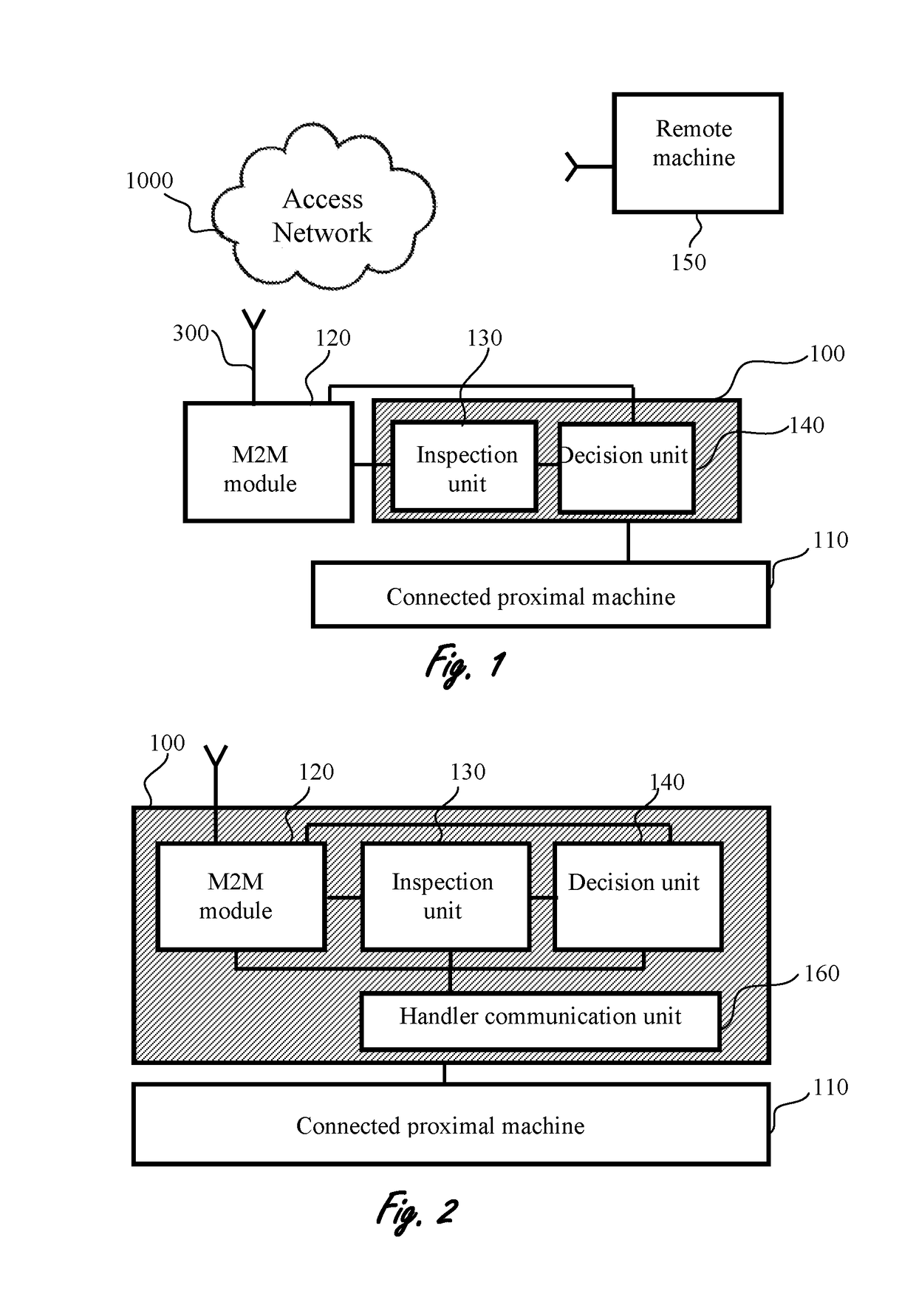
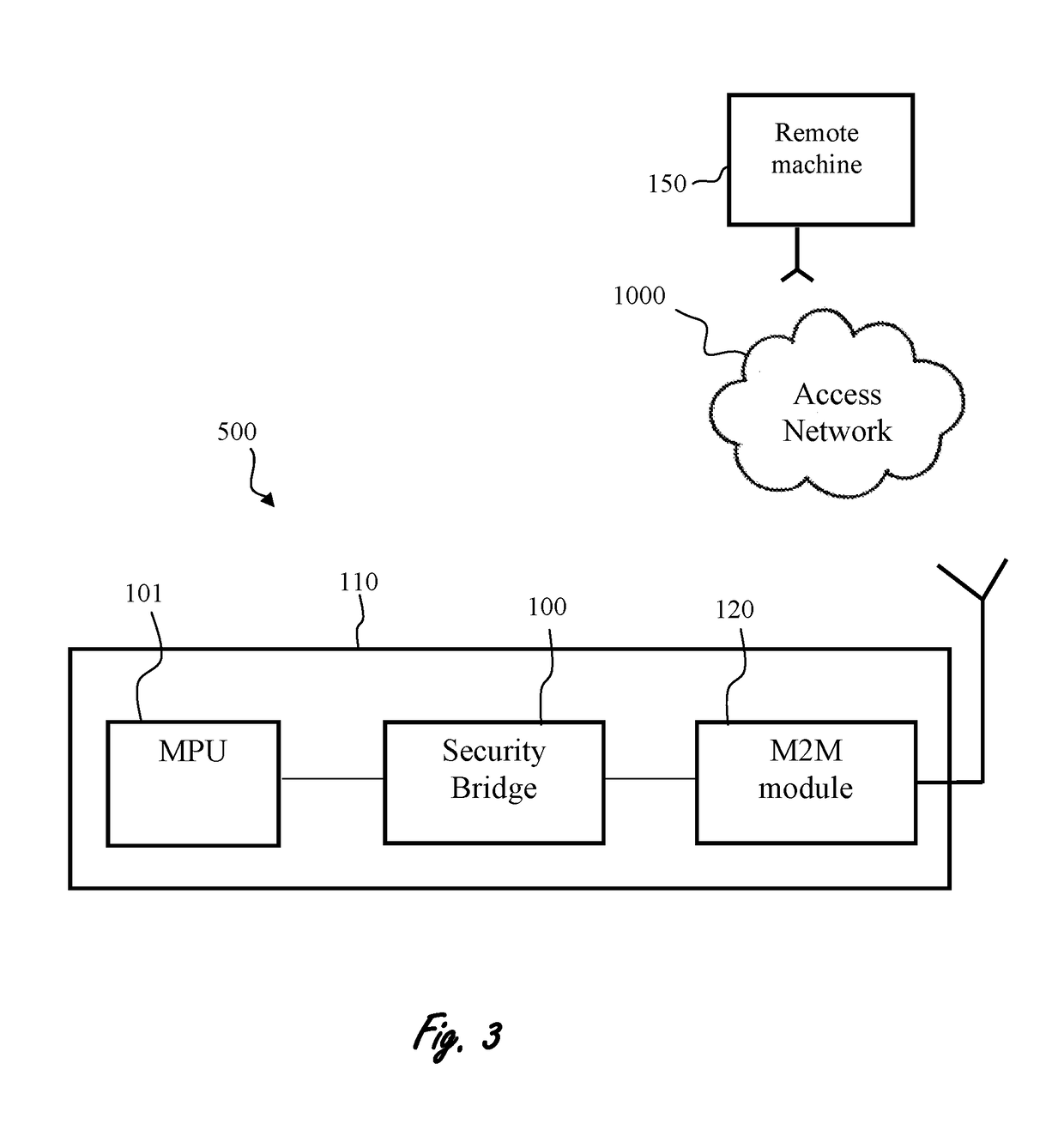
Apparatus, system and method useful for machine to machine (M2M) communication cyber-attack detection and prevention, are provided. An embedded security bridge (ESB), operatively connected to at least one proximal machine and at least one M2M module. The M2M module is in communication with at least one remote machine, and configured to enable communication between at least one remote machine and at least one proximal machine through the ESB. The ESB includes: one or more inspection units, configured for communication analysis for identifying communication and / or content suspicious as malicious, and, one or more decision units operatively connected to the inspection unit. The decision unit is configured to perform at least one action based on analysis of at least one inspection unit. The ESB is configured to detect by means of the inspection unit and prevent by means of the decision unit cyber-attacks on the proximal machine, the remote machine, or both.
Owner:RED BEND LTD
Method and apparatus for scanning connected region in combined image
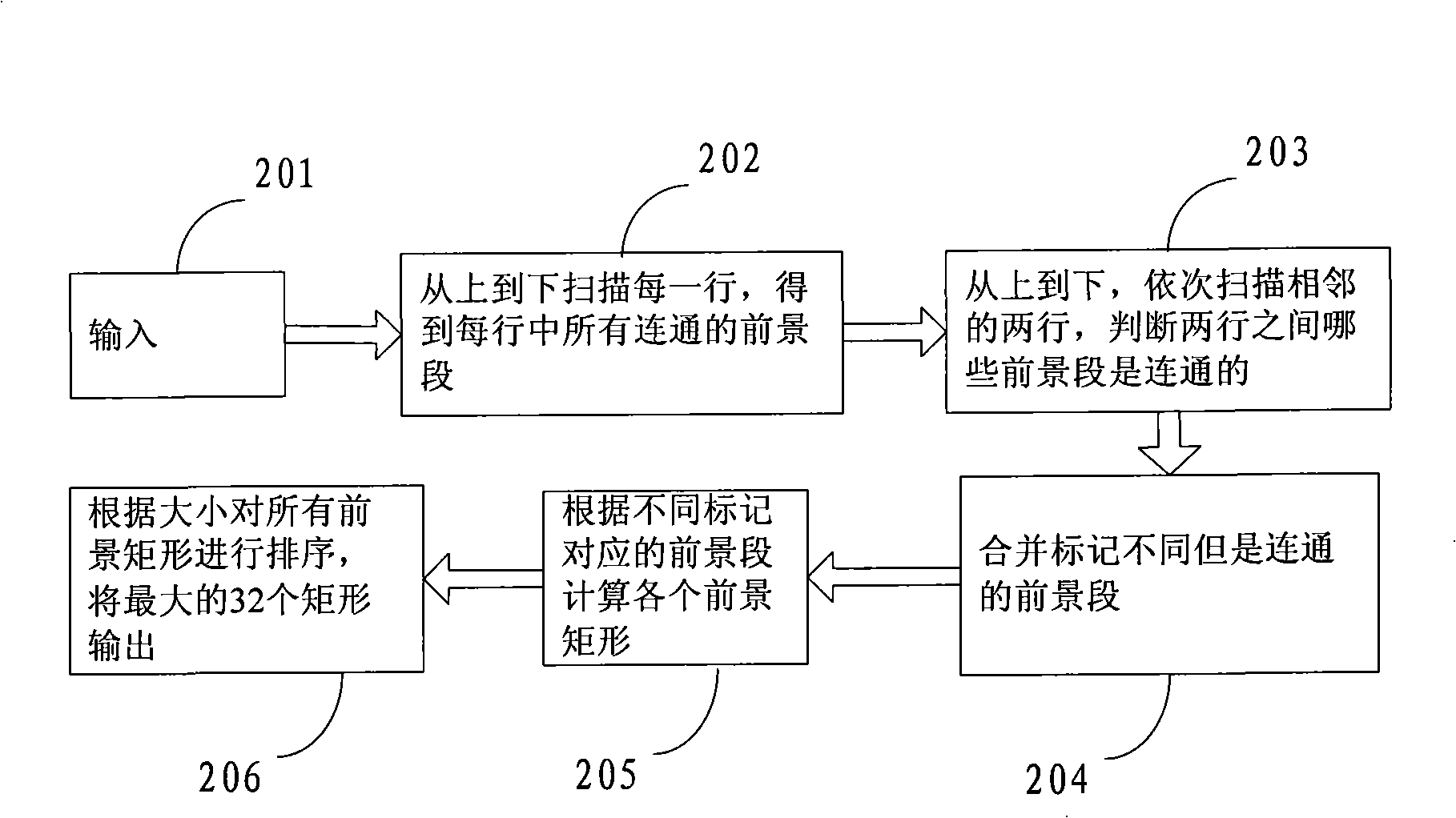
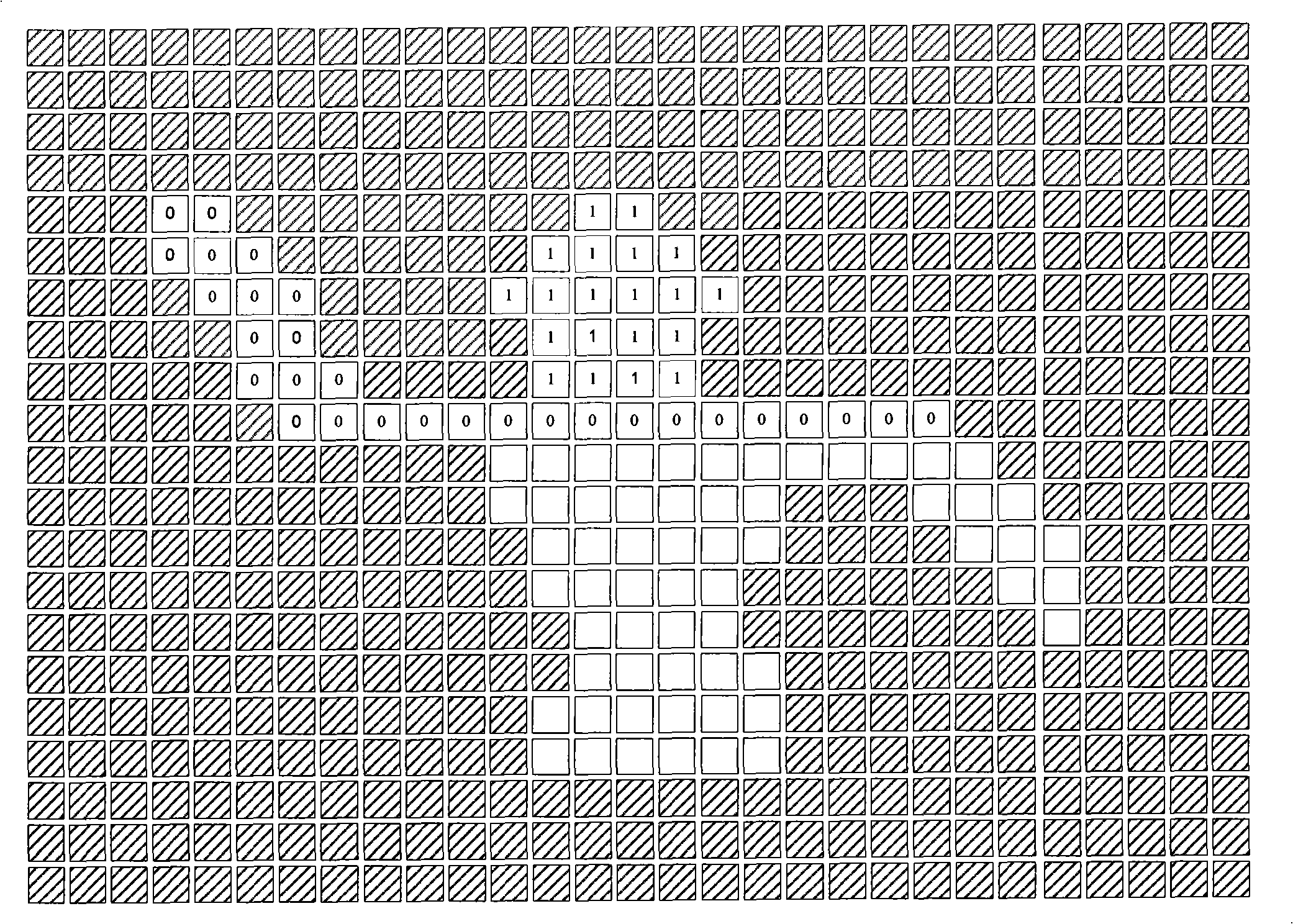
InactiveCN101499169ASecondary scan method improvementsImage analysisCommunication AnalysisProcess communication
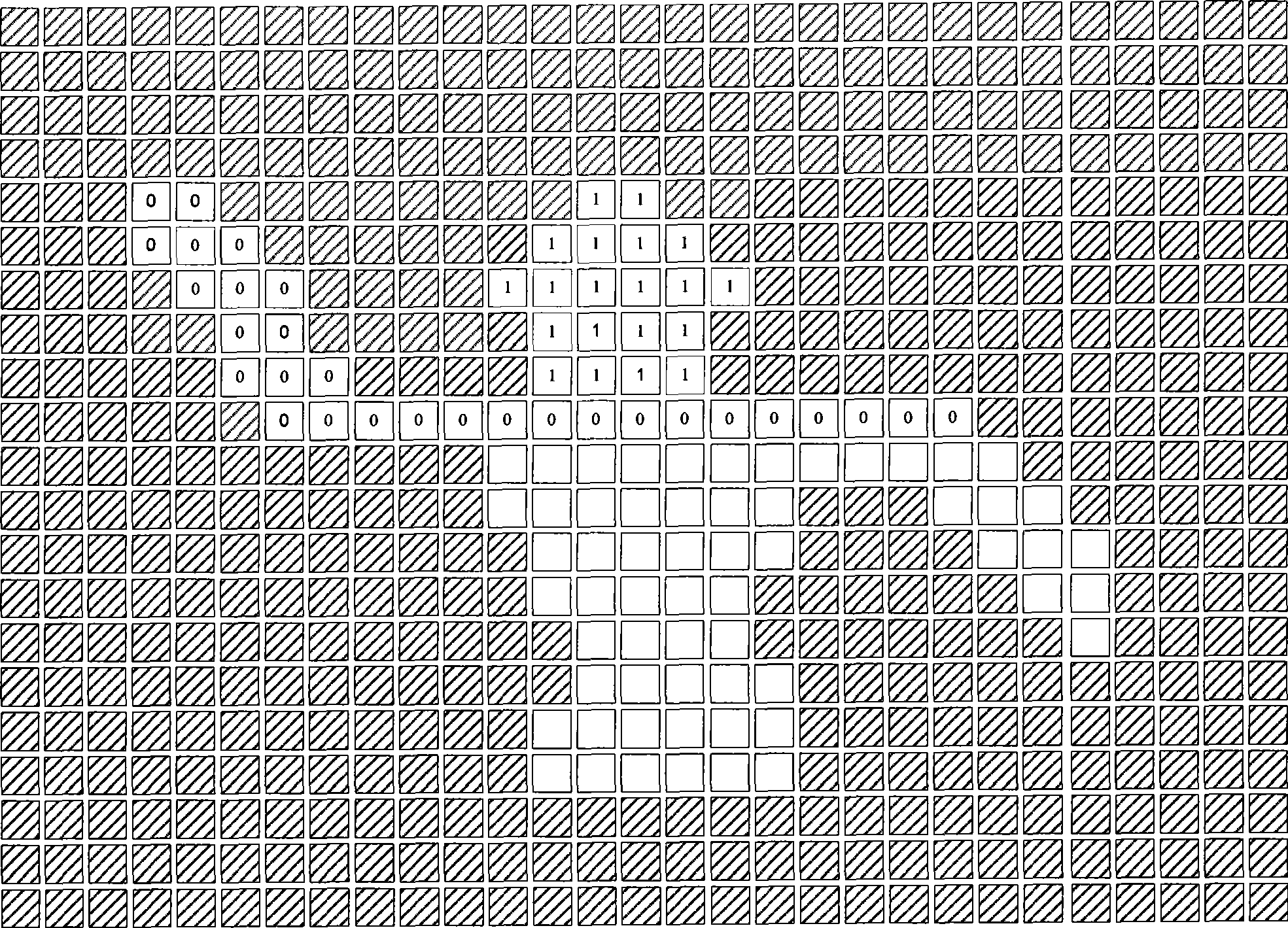
The invention provides a method for communicating region in a scan unite image and a device thereof. The method includes steps as follows: firstly, scanning present line of the image for obtaining a communication segment of the present line; secondly, taking out a communication segment as the present segment for processing communication analysis; thirdly, judging upper line whether having a communication segment communicated with the present segment, if yes, executing fifth step, if no, executing fourth step; fourthly, distributing target sequence number for the present segment, and storing the position information of the present segment to a structure body corresponding to the target sequence number; fifthly, confirming a first communication segment, uniting the present segment and each non-first communication segment into the first communication segment, and releasing the structure body stored the non-first communication segment. The method can complete unite only needing once scanning, needs not be distributed overfull temporary data cache which can solve technique problem that the prior technique is not suitable for operating in a hardware environment.
Owner:VIMICRO CORP
Machine vision establishment method applied to elevator safety monitoring
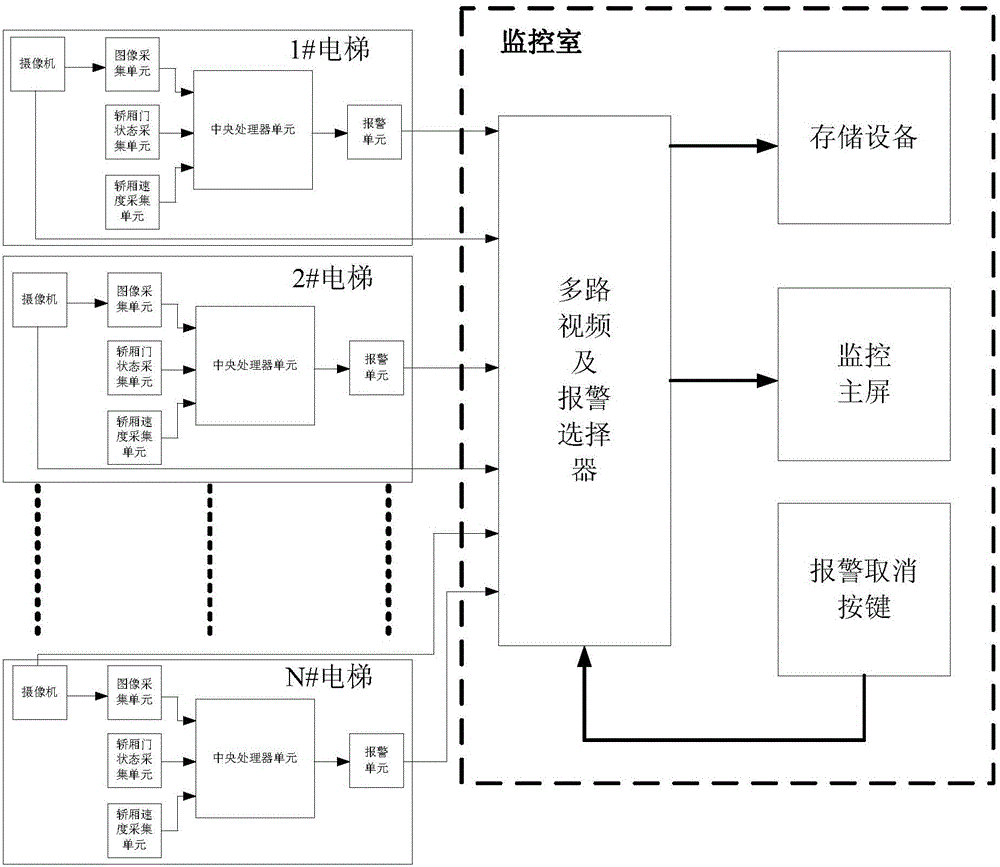
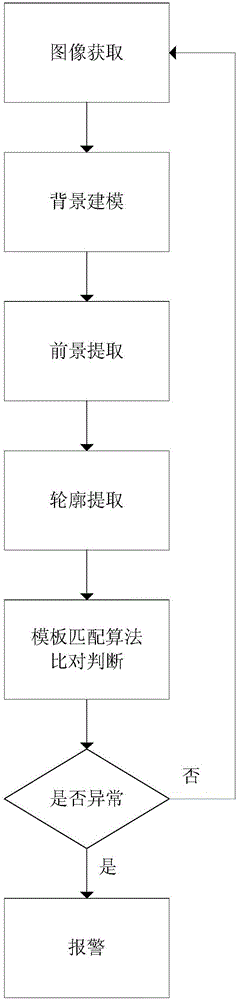
ActiveCN106006266ALittle change in strengthReduce collectionElevatorsTemplate matchingMachine vision
The invention provides an image information acquiring method applied to elevator safety monitoring, which can be convenient for later video analysis to quickly and effectively realize automatic warning of an abnormal elevator operation state and / or an abnormal activity in an elevator. The method comprises the following steps: images shot by cameras with fixed positions serve as background models; differential images are obtained through differences between present video frames and the background models by a background subtracting method, the binarization processing is performed for the differential images according to binarization formulas, the noise is removed through a morphological filter algorithm, and finally, the area communication analysis is performed for denoised results; edge profiles of the binarized images are extracted by Canny calculators; and human body standing images are modeled in an edge profile form, and are stored to compare with foreground profiles extracted in real time through a template matching algorithm so as to build basic machine vision.
Owner:XIAN SPECIAL EQUIP INSPECTION INST
Wireless architecture and support for process control systems
InactiveUS8144622B2Easy to changeEasy to configureProgramme controlDigital computer detailsCommunications systemControl system
A wireless communication system for use in a process environment uses mesh and possibly a combination of mesh and point-to-point communications to produce a wireless communication network that can be easily set up, configured, changed and monitored, thereby making a wireless communication network that is less expensive, and more robust and reliable. The wireless communication system allows virtual communication paths to be established and used within the process control system in a manner that is independent of the manner in which the wireless signals are sent between different wireless transmitting and receiving devices within the process plant, to thereby operate in a manner that is independent of the specific messages or virtual communication paths within the process plant. Still further, communication analysis tools are provided to enable a user or operator to view the operation of the wireless communication network to thereby analyze the ongoing operation of the wireless communications within the wireless communication network.
Owner:FISHER-ROSEMOUNT SYST INC
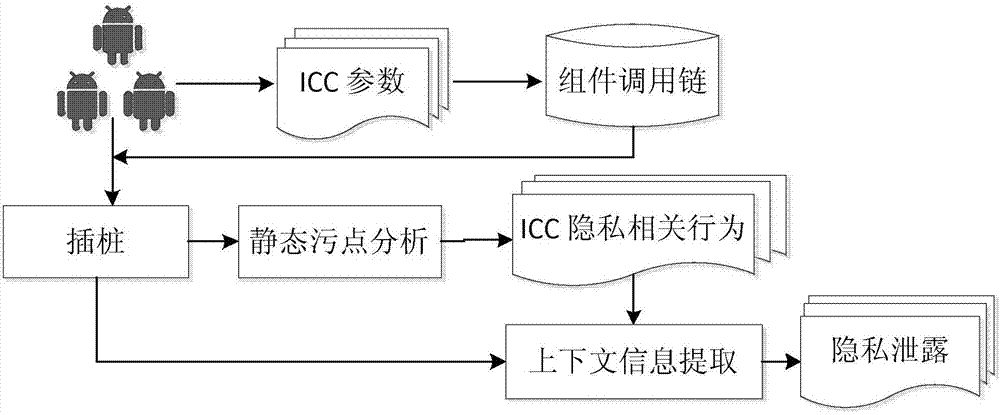
Recognition method of privacy leakage behavior between Android components based on context information
InactiveCN107103240ADigital data protectionPlatform integrity maintainanceInformation transmissionInternet privacy
The invention discloses a recognition method of a privacy leakage behavior between Android components based on the context information. The method comprises the steps that firstly, communication parameter information between the components in an Android application program is extracted; secondly, according to the extracted communication parameter information between the components, two mutually communicated components in the Android application program are matched, and a component call chain is formed; thirdly, according to the component call chain information, static instrumentation is conducted on the Android application program, the two mutually communicated components are connected; fourthly, the application program codes obtained after instrumentation are subjected to static taint analysis, the behavior path associated with the privacy information transmission between the components is obtained, and the context information of the behavior path is extracted; fifthly, according to the obtained context information of the behavior path, whether the privacy information transmission behavior between the components is the privacy leakage behavior or not is judged. By means of the method and system, the accuracy of the communication analysis between the components is greatly improved.
Owner:INST OF INFORMATION ENG CAS
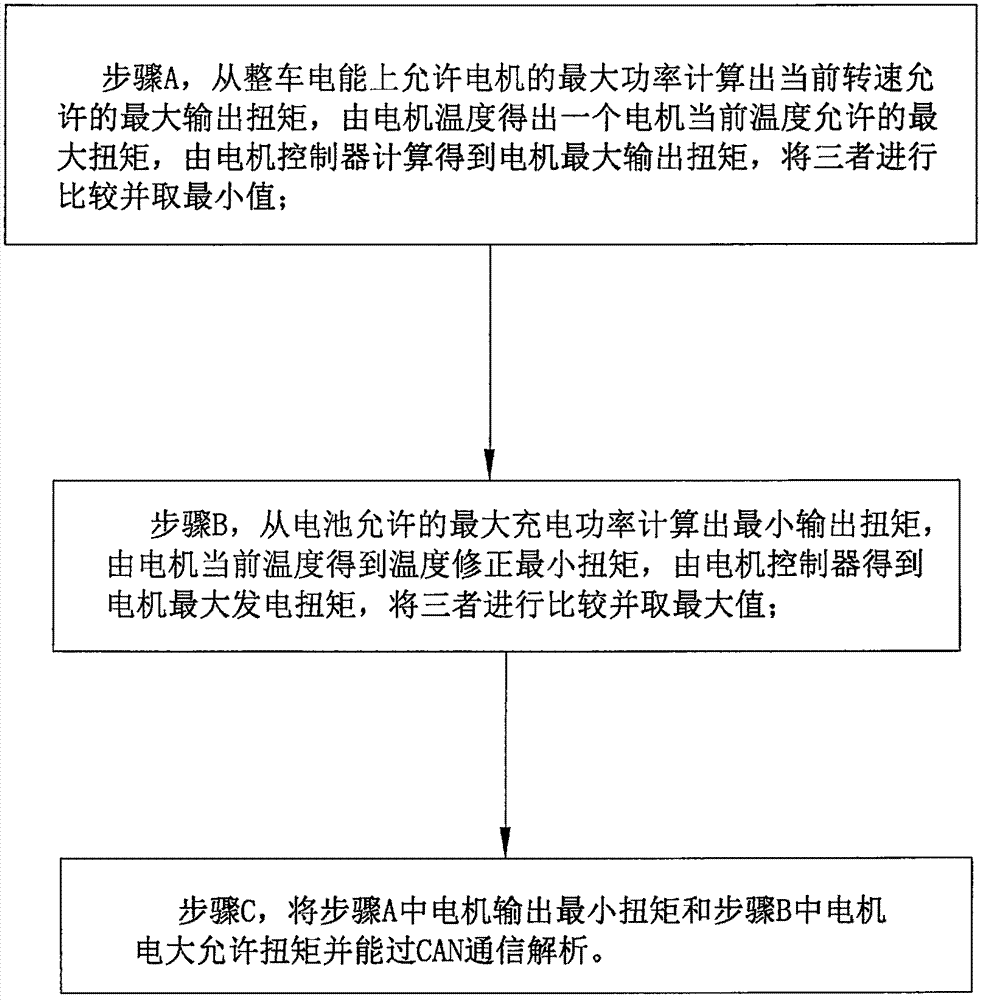
Motor output capability calculating method
PendingCN107323306AEasy to adjust controlImprove the stability of useSpeed controllerElectric vehicle charging technologyMaximum torqueIn vehicle
Owner:中汽院智能网联科技有限公司
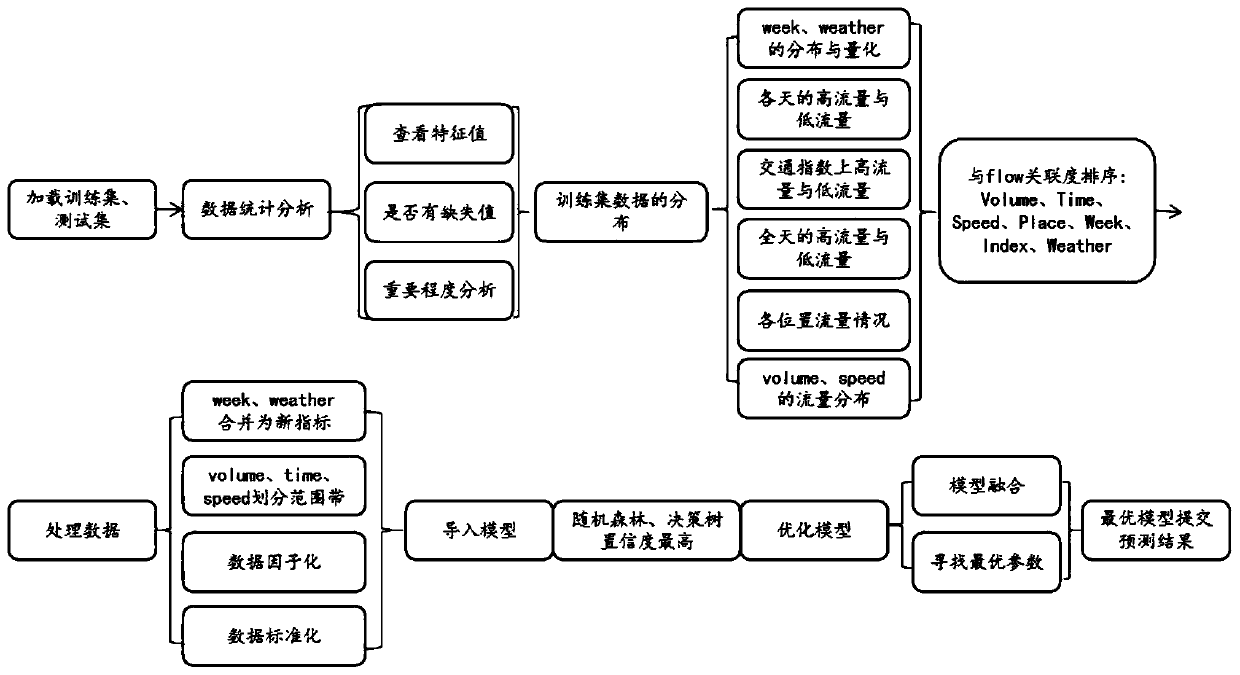
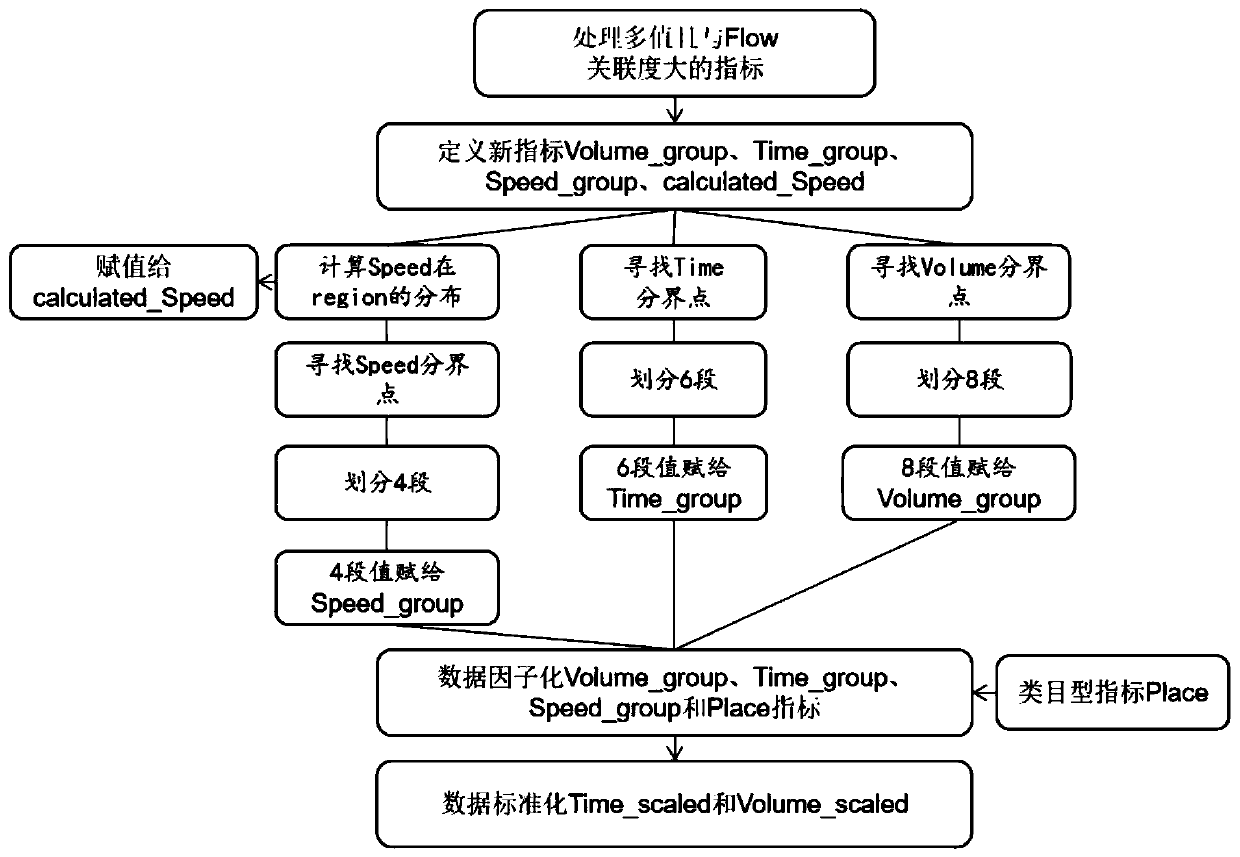
Traffic prediction method for Internet of Vehicles communication based on machine learning
ActiveCN110266528AEasy to buildImprove generalizationData switching networksTraffic predictionData platform
The invention discloses a traffic prediction method for Internet of Vehicles communication based on machine learning, and the method comprises the steps: selecting eight types of data indexes by utilizing a traffic speed database issued by a traffic data platform, and completing the all-weather traffic flow prediction through a random forest algorithm after parameter optimization; exporting an urban road vehicle traffic scene in a certain place by utilizing the openstreetmap, obtaining traffic data, configuring a communication simulation file, obtaining communication data, mixing the two kinds of data, and analyzing the relationship between the traffic flow and the communication flow; exporting a road section selected by a traffic data platform by utilizing openstreetmap, configuring a communication simulation file, acquiring communication data, selecting nine types of related indexes from flow speed data and communication data released by the traffic data platform, and performing communication flow prediction through a Bagging model. The method is good in generalization performance and high in accuracy, a reliable vehicle-mounted communication analysis method can be provided for later-stage utilization of economic and efficient data distribution, and the driving safety of vehicle users is enhanced.
Owner:NANJING UNIV OF SCI & TECH
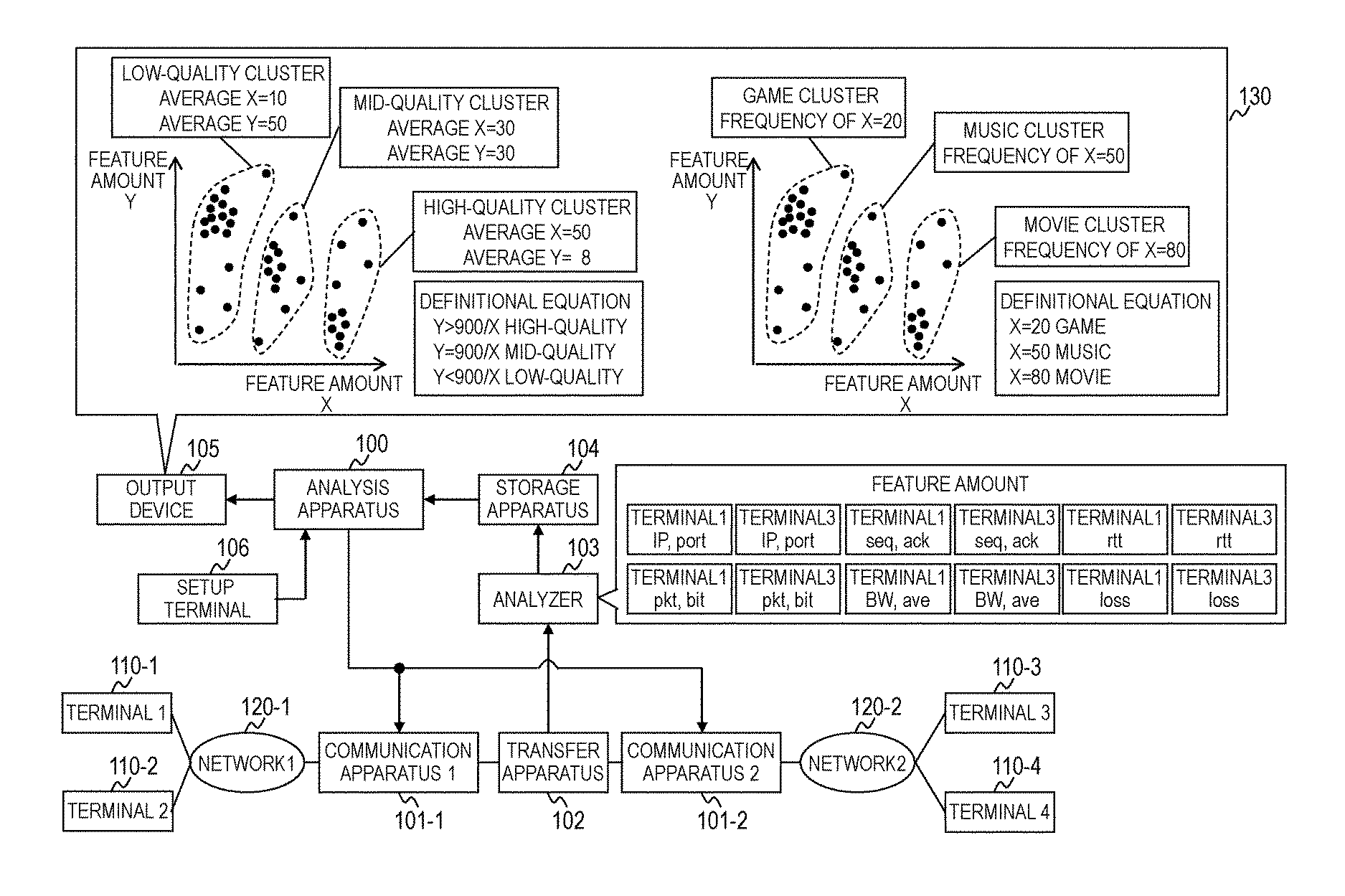
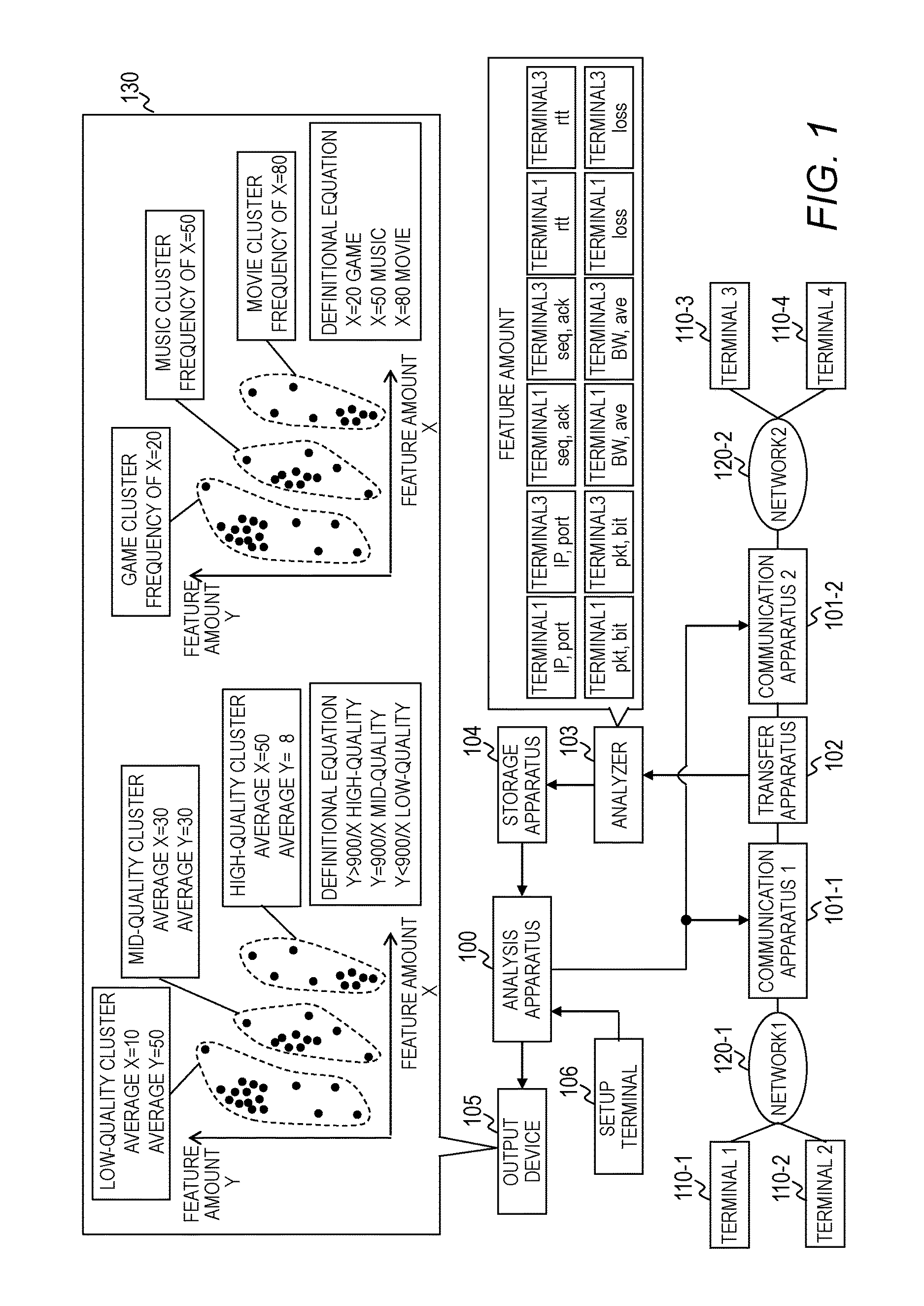
Network system, communication analysis method and analysis apparatus
A network system comprising a plurality of communication apparatuses, wherein the network system includes an analysis part for analyzing a communication flow to classify a plurality of communication flows by communication types. The analysis part includes: a feature amount obtaining part for obtaining, for each of the plurality of communication flows, management information on the communication flow including a plurality of feature amounts; a cluster analysis part for analyzing the management information on the communication flow to generate a plurality of clusters each made up of the plurality of communication flows; and a cluster classification part for classifying the plurality of clusters by communication types based on an analysis result obtained using at least one of the plurality of feature amounts of the plurality of communication flows included in each of the plurality of clusters.
Owner:HITACHI LTD
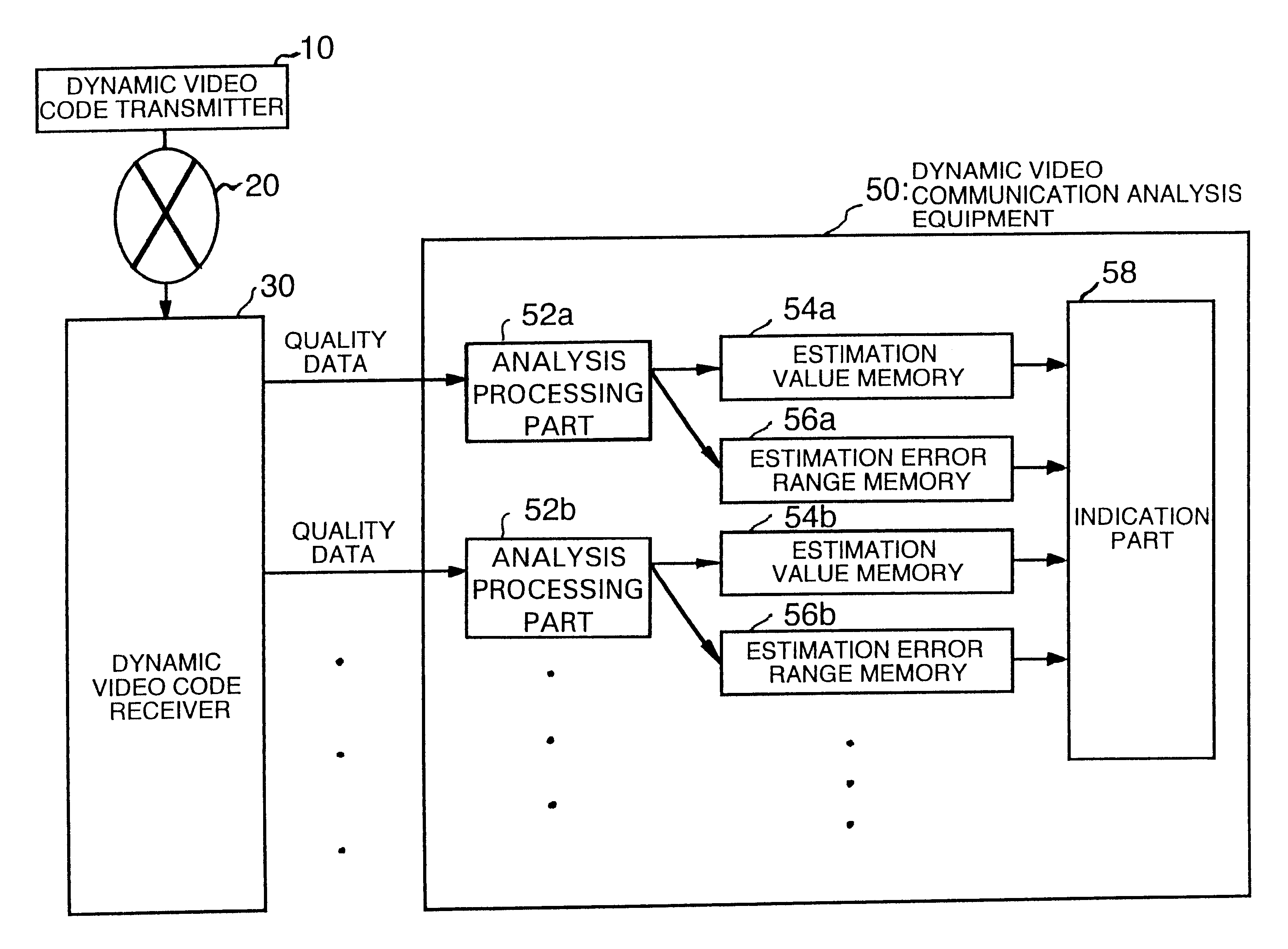
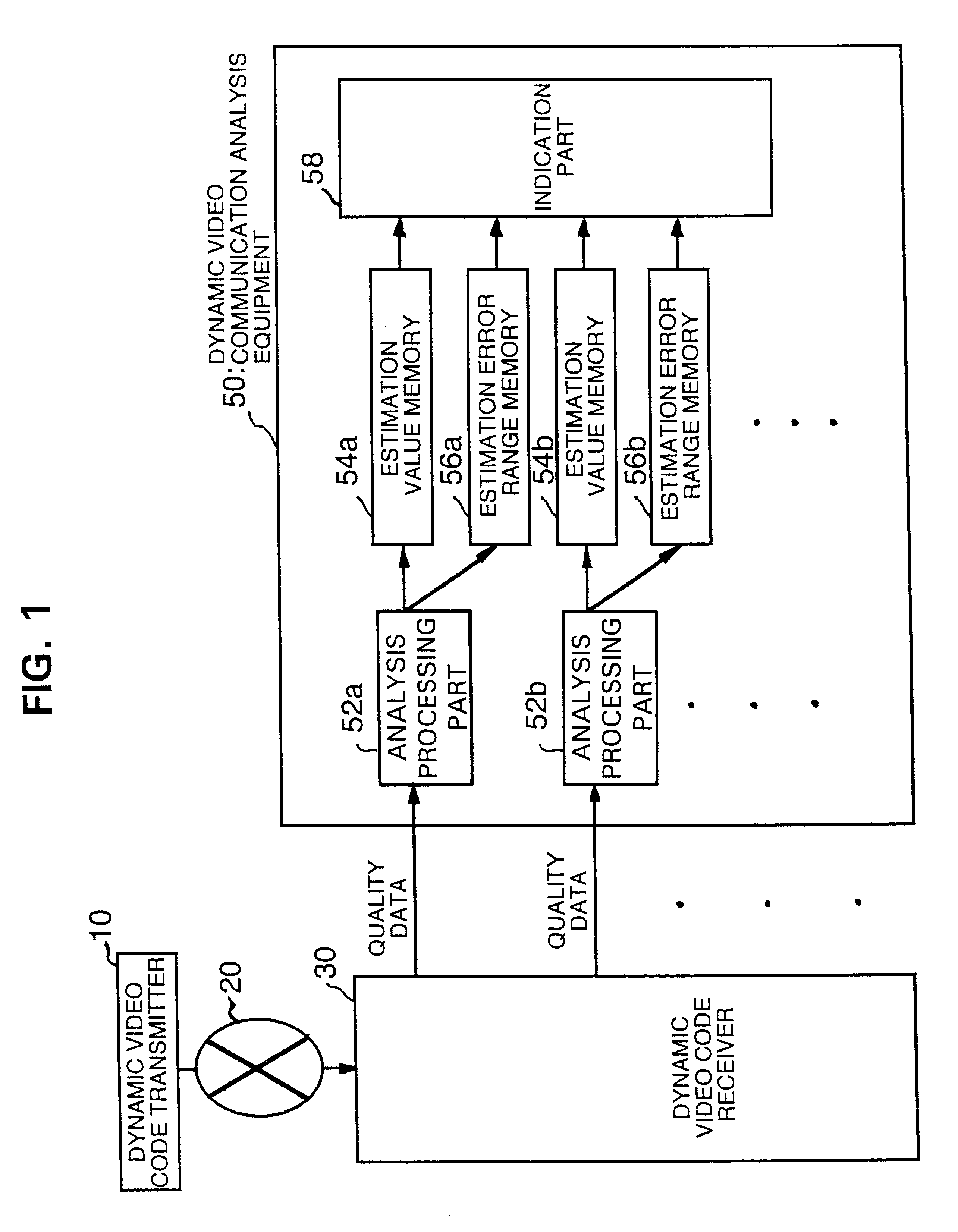
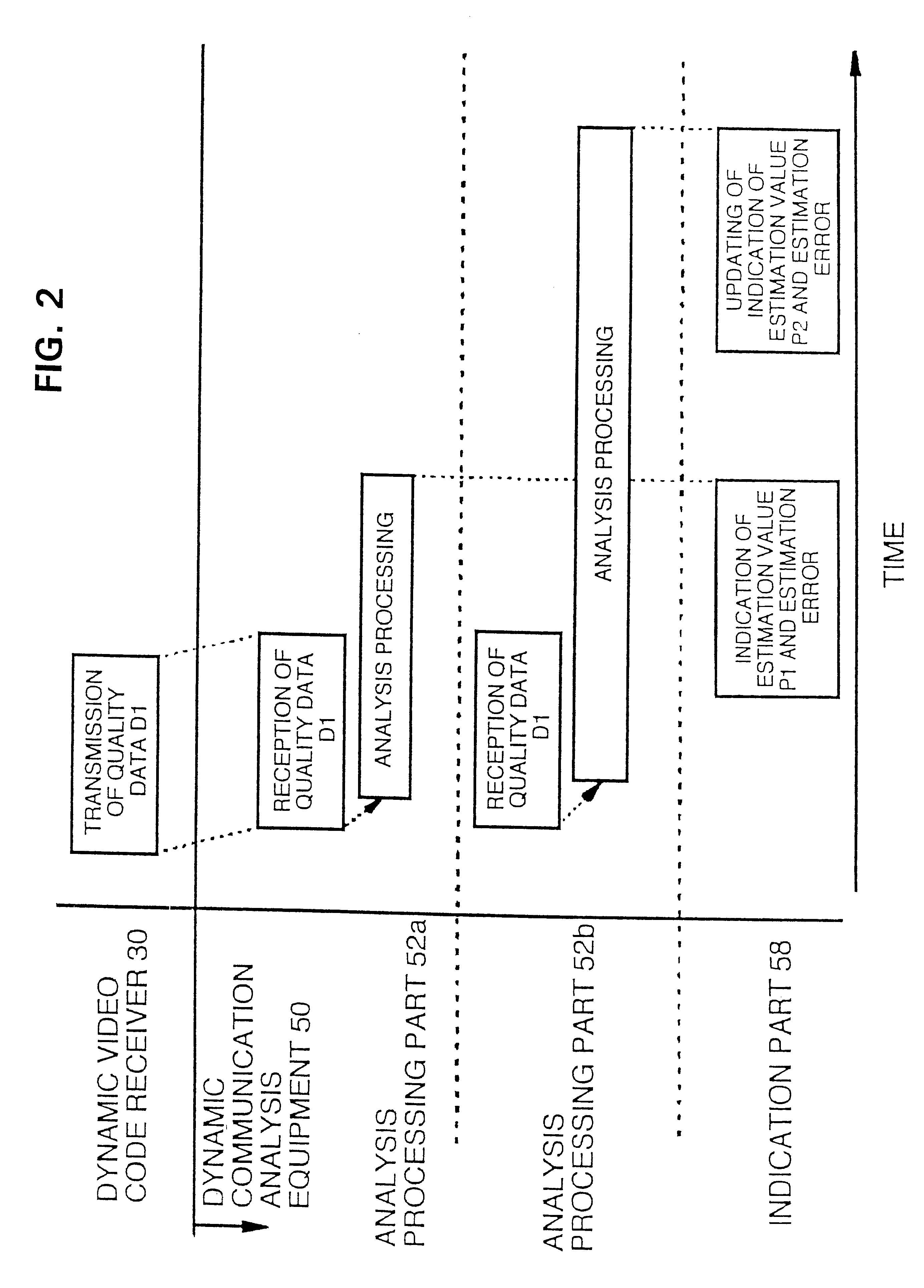
Dynamic video communication evaluation equipment
InactiveUS6513162B1Television system detailsPicture reproducers using cathode ray tubesComputer hardwareVideo encoding
In a dynamic video communication evaluation equipment for analyzing codes by multiple methods for evaluating a dynamic video image, an analysis including estimation is performed to fix a reliability of the analysis result, enabling a processing termination in response to the analysis result in view of effective utilization of time or cost. The dynamic video communication evaluation equipment comprises a dynamic video code transmitter which transmits a dynamic video as a digital dynamic video code via a network by selecting it from multiple dynamic video coding methods and multiple communication protocols, a dynamic video code receiver for receiving and decoding the digital dynamic video code which are transmitted via the network conforming to the video coding method and communication protocol used for the digital dynamic video code, and a dynamic video communication analysis equipment composed of analysis means which calculates both of estimation value of dynamic video image quality evaluation value and an error range of said estimation value according to said dynamic video coding method and said communication protocol, and indication means to indicate said estimation value and said error range.
Owner:YOKOGAWA ELECTRIC CORP
A data analysis system based on electronic physical evidence rapid extraction
InactiveCN109787971AEasy accessEasy to analyzeDigital data information retrievalTransmissionAddress bookStatistical analysis
The invention provides a data analysis system based on electronic physical evidence rapid extraction. The data analysis system comprises a mobile phone communication analysis module; The mobile phonecommunication analysis module comprises a statistical analysis graph unit which is used for formulating a communication activity rule, a time-sharing activity rule and an average daily call time rulestatistical graph and classifying communication opposite ends according to social relations between regions and owners of the mobile phone; The address book collision unit is used for collision of atleast two address books; The call record unit is used for screening and querying all call records, and screening different query conditions according to different case analysis dimensions to obtain corresponding key call information; And the short message unit is used for extracting the consumption information in the mobile banking short message. The data analysis system based on rapid extractionof the electronic physical evidence solves the problem that the working efficiency of police officers is low due to the fact that the police officers manually find the electronic physical evidence inthe prior art.
Owner:重庆市千将软件有限公司
Process mapping in parallel computing
InactiveUS20100218190A1Easy to learnReduce communication overheadDigital data information retrievalInterprogram communicationMessage Passing InterfaceCommunication Analysis
A method of mapping processes to processors in a parallel computing environment where a parallel application is to be run on a cluster of nodes wherein at least one of the nodes has multiple processors sharing a common memory, the method comprising using compiler based communication analysis to map Message Passing Interface processes to processors on the nodes, whereby at least some more heavily communicating processes are mapped to processors within nodes. Other methods, apparatus, and computer readable media are also provided.
Owner:IBM CORP
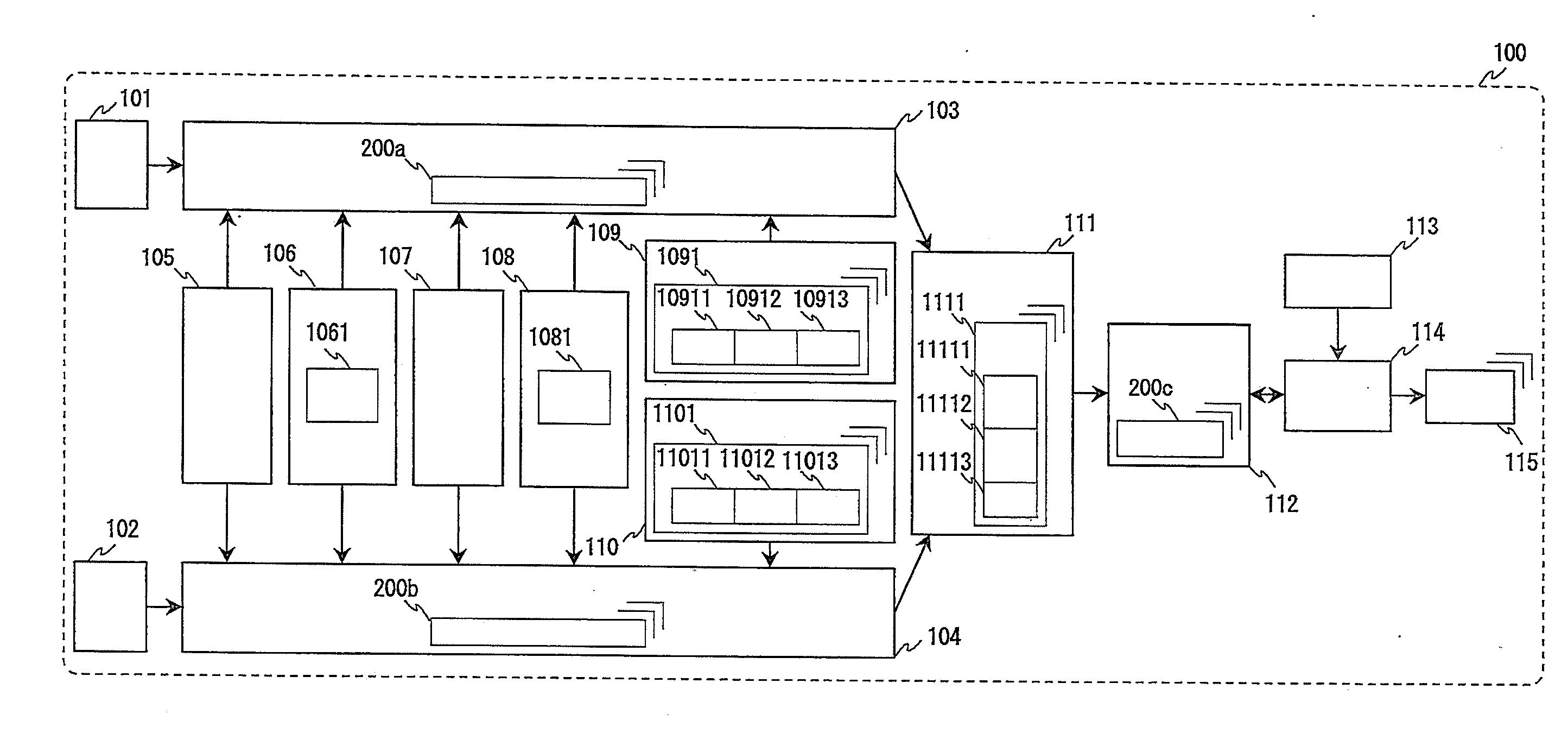
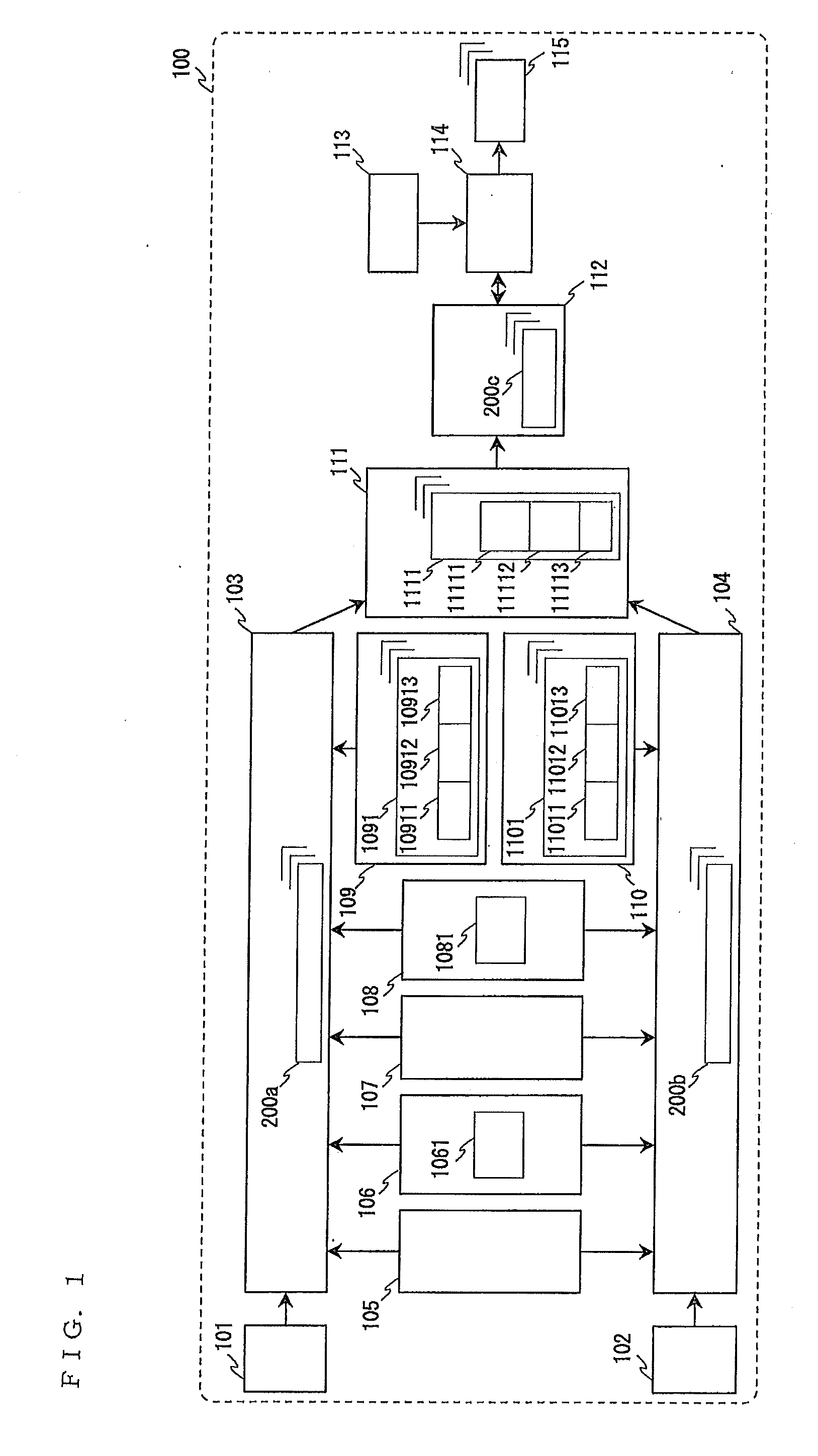
Communication analysis apparatus and communication analysis method
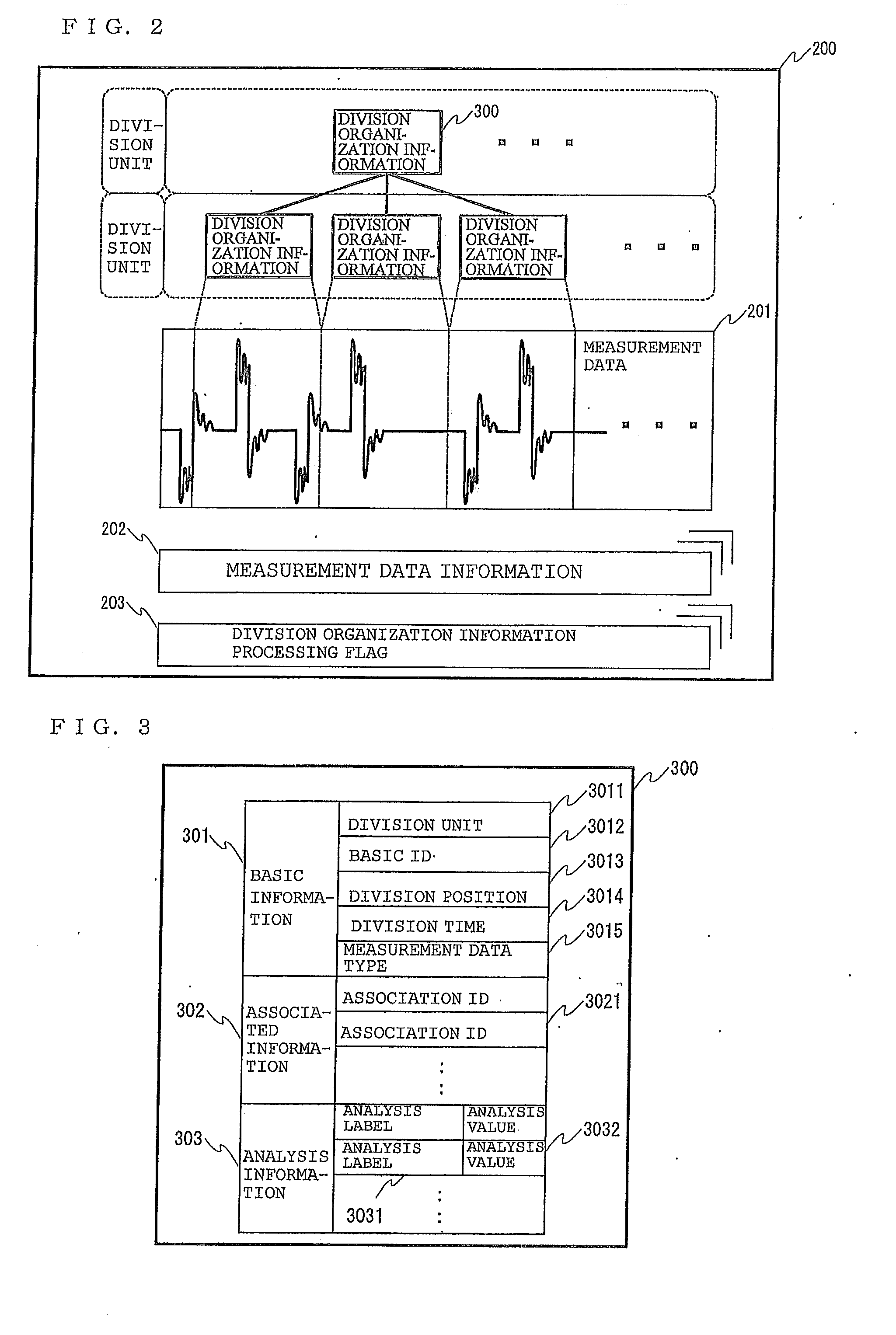
ActiveUS20110051789A1Spectral/fourier analysisCorrect operation testingCommunication AnalysisReal-time computing
To obtain a communication analysis apparatus and a communication analysis method that are allowed to analyze a communication message and a waveform signal in such a manner that the communication message and waveform signal are associated with each other.A communication analysis apparatus includes division organization information addition means for adding, to a plurality of division data obtained by dividing data into predetermined lengths, division organization information 300 including a division unit 3011 for defining the predetermined lengths and a division position 3013 that is information about the start position and end position of division data in the data.
Owner:MITSUBISHI ELECTRIC CORP
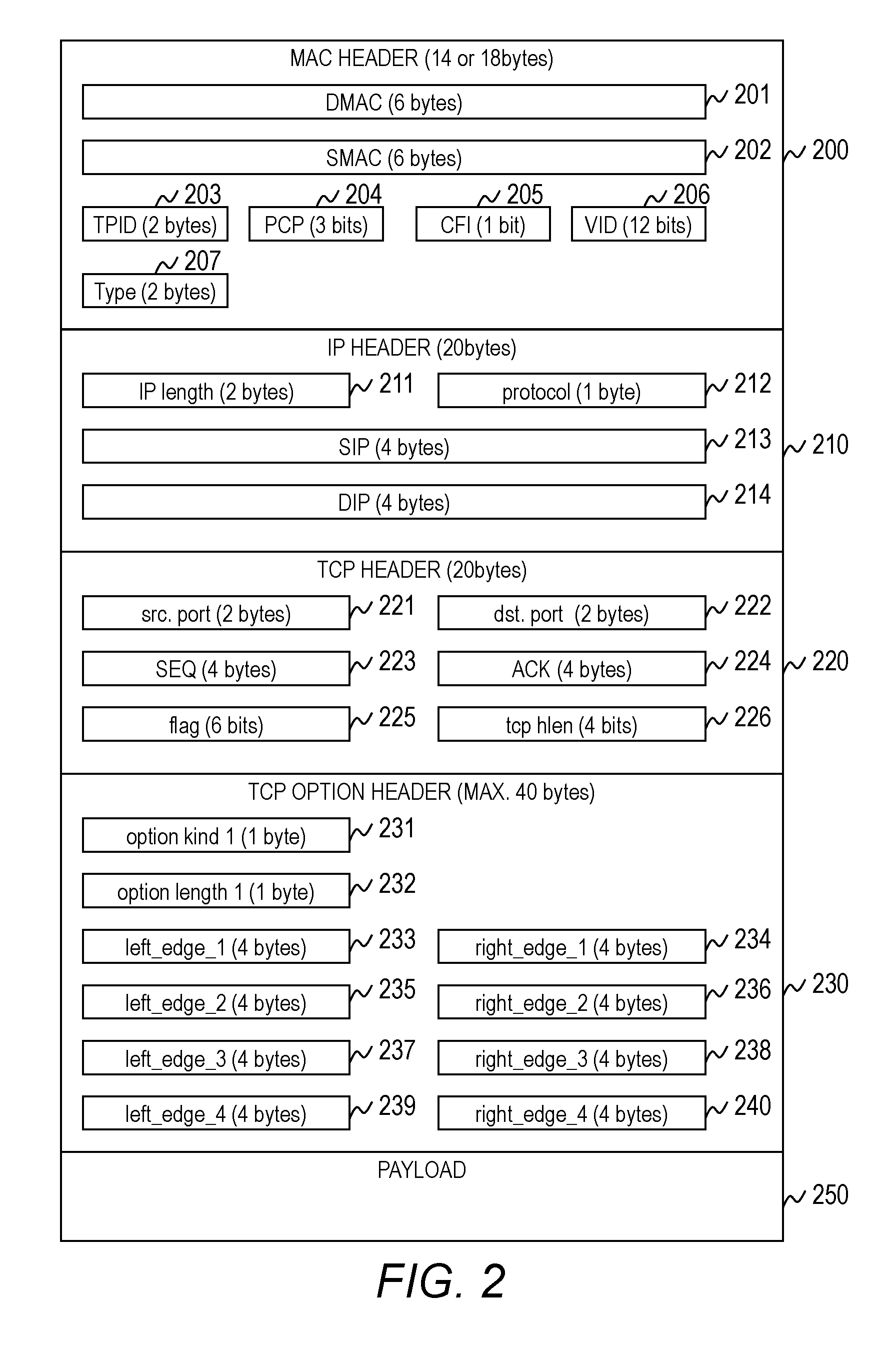
A TCP stream length connection data analysis method
The invention discloses a TCP stream long connection data analysis method. For the established TCP connection data stream, sending the TCP connection data stream to the server; establishing a sessionaccording to the quaternion information; caching few TCP data, the content is detected by data packet boundary and port number information; the characteristics of a known protocol are matched; analyzing a protocol message, distinguishing a connection direction according to content, an IP address and port information analyzed by the protocol, completely analyzing the protocol message, distinguishing a boundary of a message body, adding simulated handshake connection information in an existing communication analysis process, keeping a TCP standard communication protocol in a compatible manner, and continuously analyzing subsequent effective data. According to the invention, protocol identification, analysis and effective data reduction are carried out on data with established connection in traffic, and complete session behaviors of an application layer protocol are restored in network traffic data for an information source for behavior audit and risk discovery; information sources associated with a data flow are discovered through the data flow on an unknown system service.
Owner:全知科技(杭州)有限责任公司
Risk exchange management method and system and computer readable storage medium
ActiveCN110619450AImprove arrangement efficiencyImprove targetingResourcesConference managementContact method
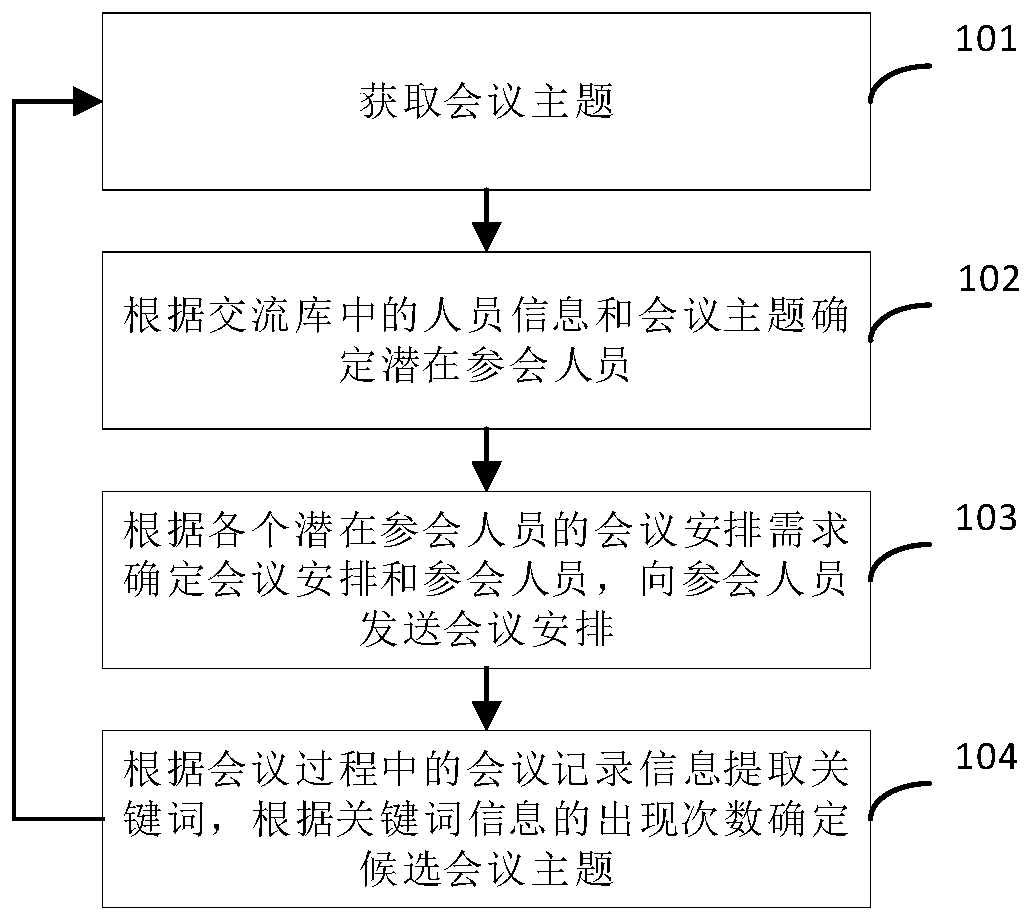
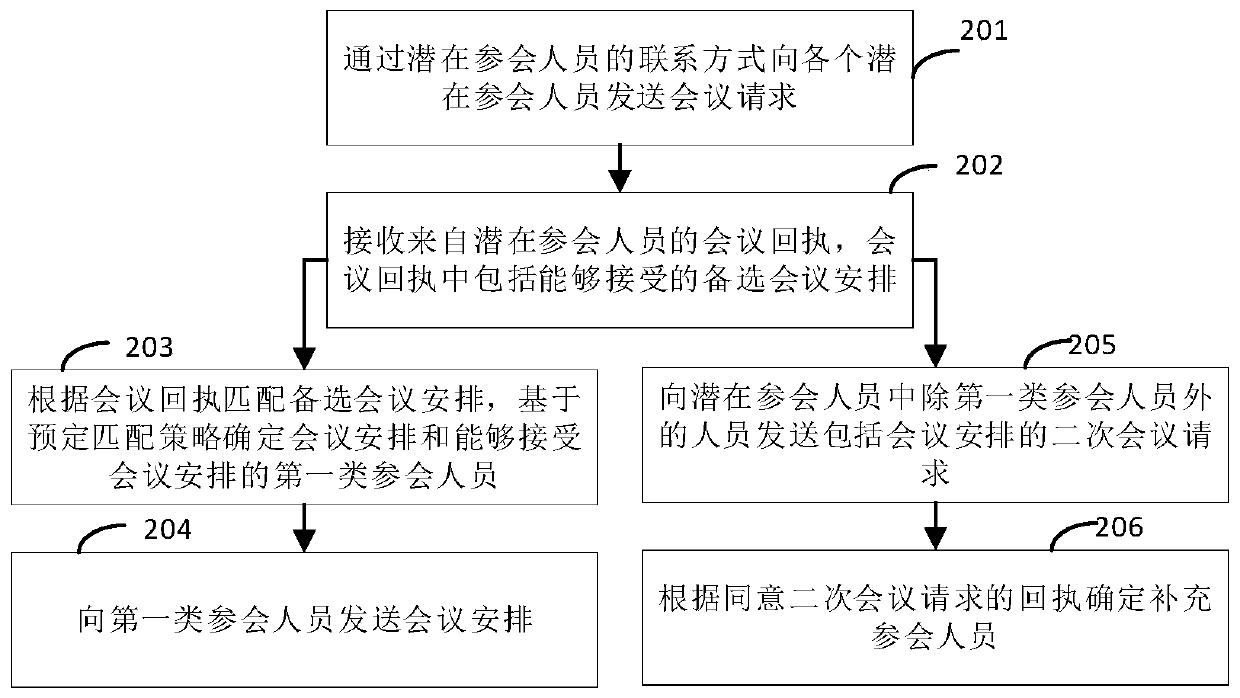
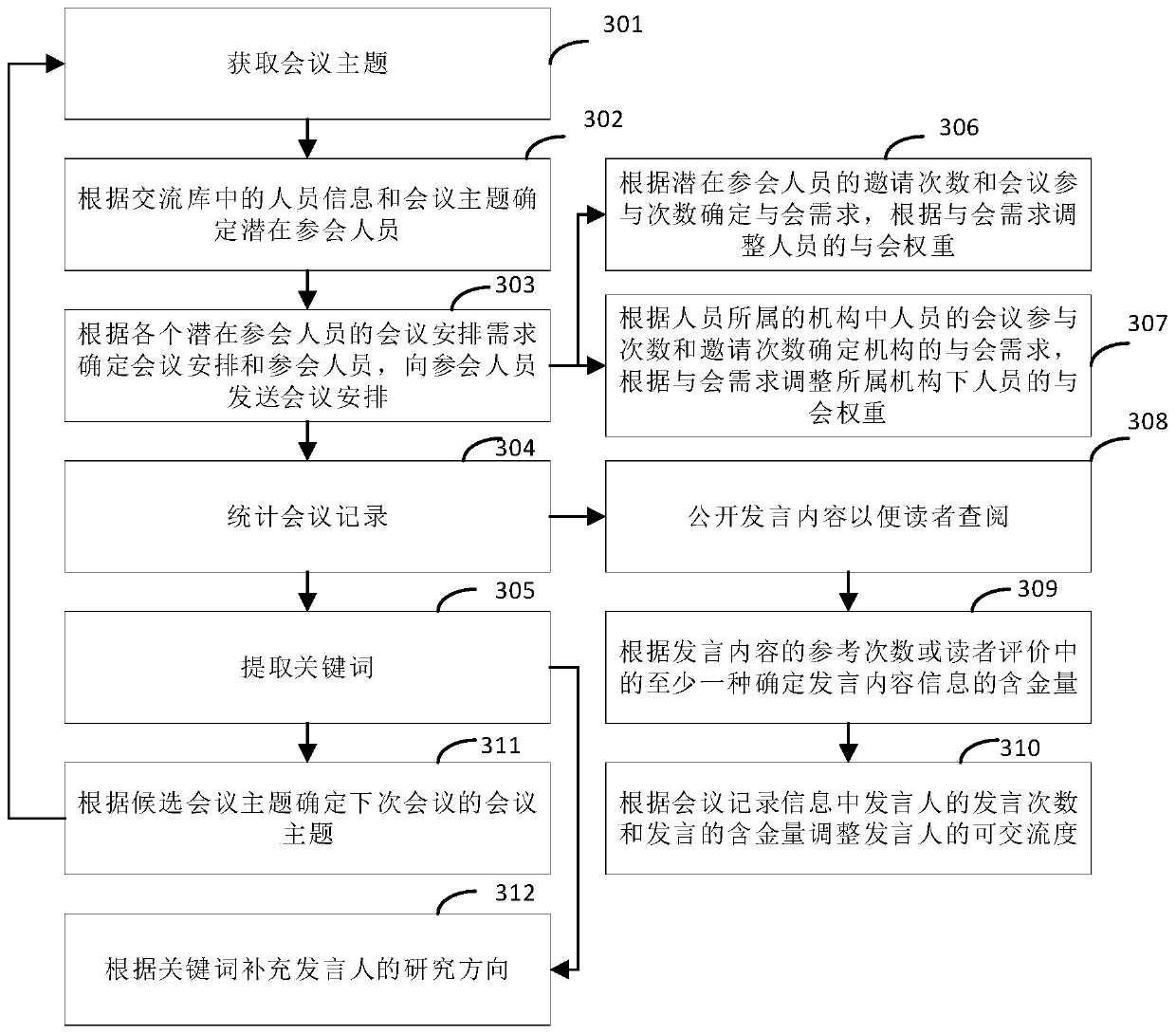
The invention provides a risk exchange management method and system and a computer readable storage medium, and relates to the technical field of data analysis. The conference management method disclosed by the invention comprises the following steps: acquiring a conference theme; determining potential conference participants according to personnel information and conference themes in the communication library, and the personnel information comprising personnel names and contact information and further comprising at least one of research directions and affiliated institutions; determining conference arrangements and conference participants according to the conference arrangement requirements of the potential conference participants, and sending the conference arrangements to the conferenceparticipants; and extracting keywords according to the conference record information in the conference process, and determining candidate conference themes according to the occurrence frequency of the keyword information so as to determine the conference themes of the next conference according to the candidate conference themes. Through the method, on one hand, the conference arrangement efficiency is improved, and on the other hand, the issue can accord with the current hotspot, the pertinence of communication to problem solving is improved, and the communication analysis efficiency is further improved.
Owner:INNER MONGOLIA YILI INDUSTRIAL GROUP CO LTD
Access gateway of internet of things
InactiveCN103139943ARealize logic multiplexingReduce design difficultyWireless communicationMultiplexingMulti operator
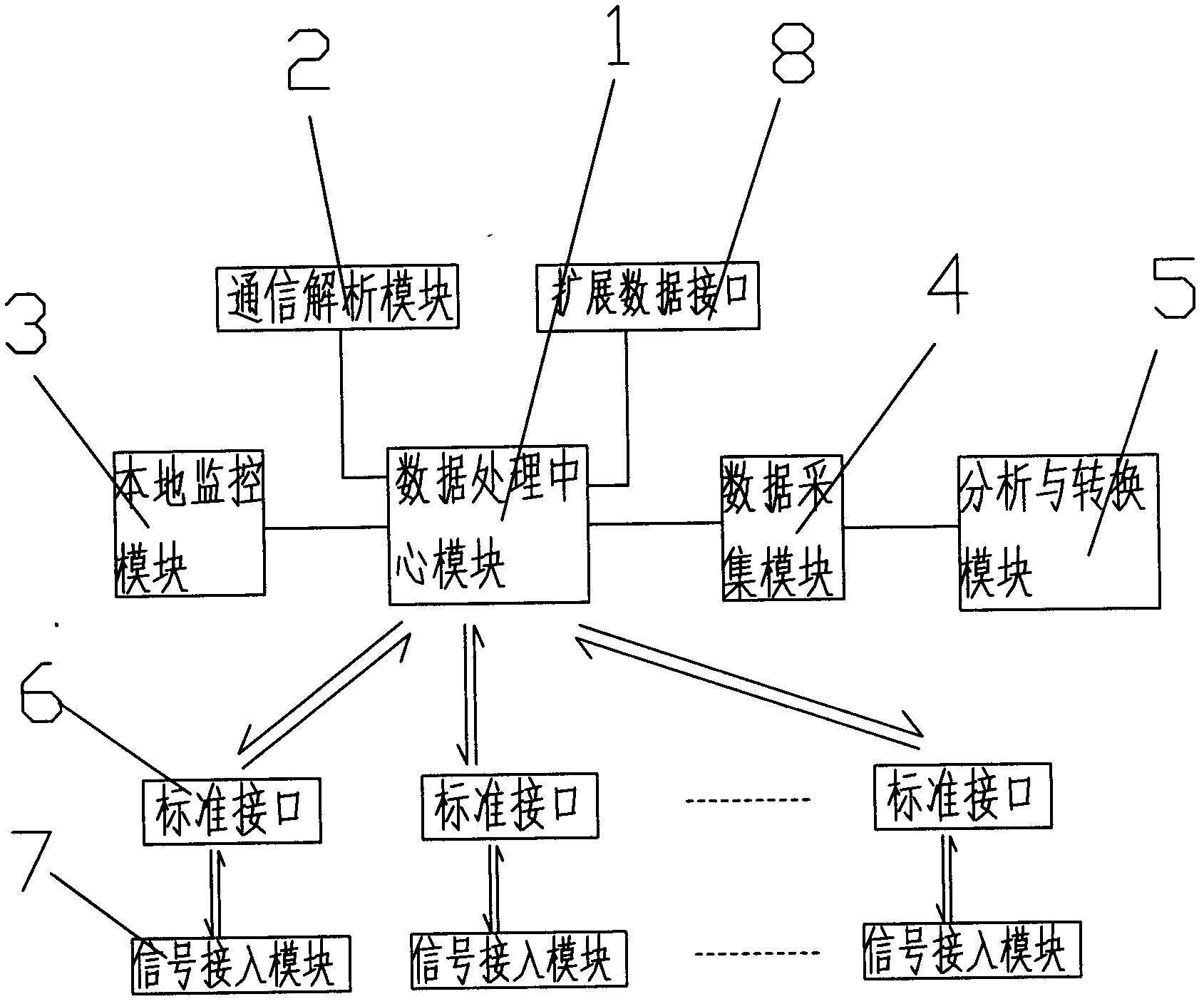
The invention discloses an access gateway of an internet of things. The access gateway comprises a data processing center module, a plurality of standard interfaces and a plurality of signal access modules. The plurality of standard interfaces are communicated with the data processing center module, the plurality of signal access modules are connected with the plurality of standard interfaces respectively, the data processing center module is connected with a communication analysis module, a data collection module and a local monitoring module, and the data collection module is connected with an analysis and conversion module. By means of the access gateway, the plurality of standard interfaces are arranged in the gateway, users can appoint the interfaces as upstream interfaces, downstream interfaces or any one type in configuration interfaces, various types of signal access modules can be inserted into the interfaces optionally, logic multiplexing, access mode multiplexing and multi-operator compatibility of the same physical interface are achieved, design difficulty and popularization and application difficulty of a hardware system under different operation networks are greatly reduced, and use cost is reduced.
Owner:CHANGZHOU PUSHI INFORMATION TECH
Remote entrance guard terminal
InactiveCN101833801ALow costIndividual entry/exit registersComputerized systemCommunication Analysis
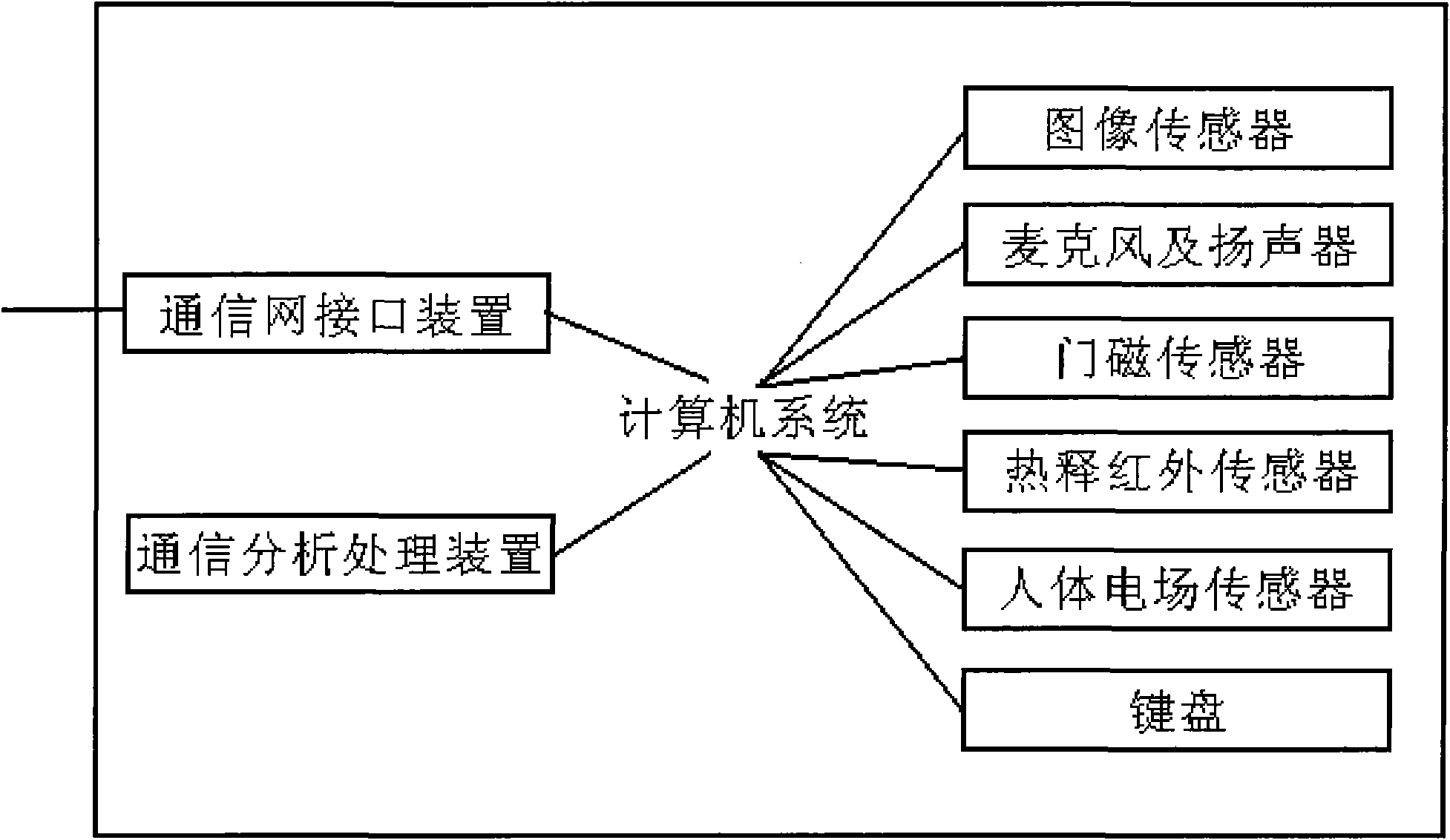
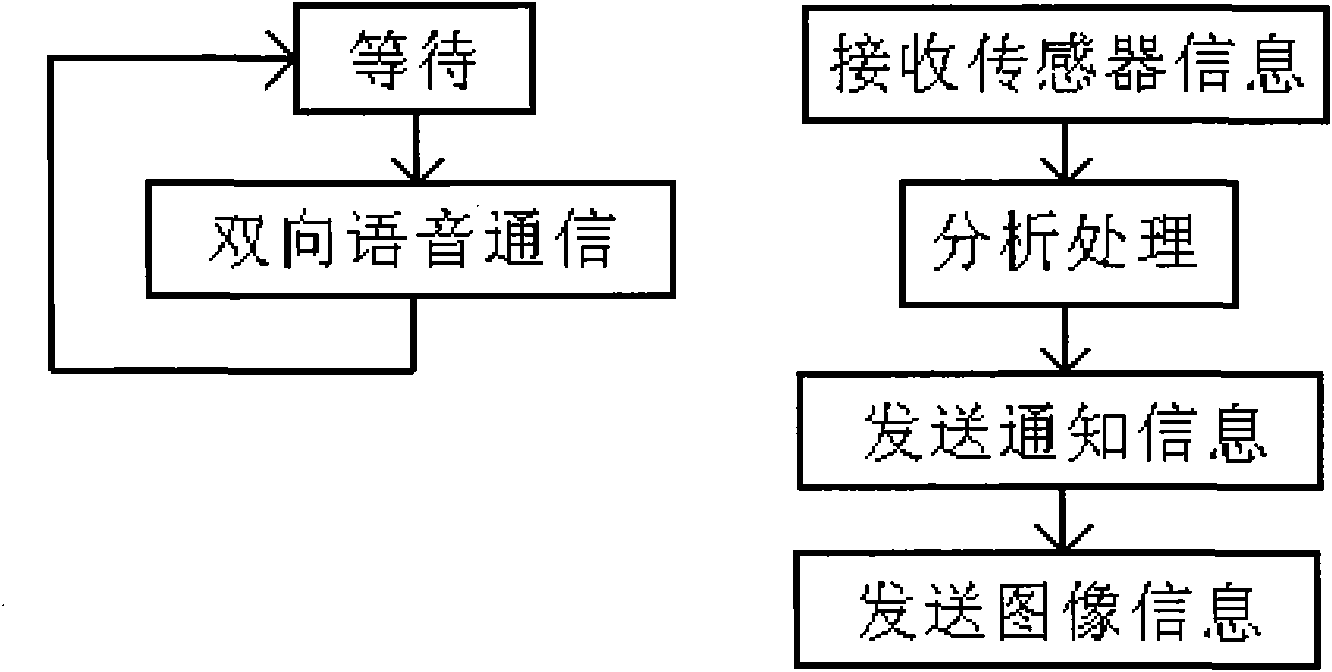
The invention relates to a remote entrance guard terminal which comprises a computer system, a communication network interface unit connected with the computer system, a (visitor or image) sensor, a microphone and a loudspeaker which are connected with the computer system; in addition, the computer system also comprises a communication analysis and processing unit.
Owner:韩燕
Integrated protection system communication protocol analysis test apparatus
InactiveCN105429827ASolve duplication of workSolve the problem that programs are becoming more and more difficult to maintainData switching networksComputer moduleData management
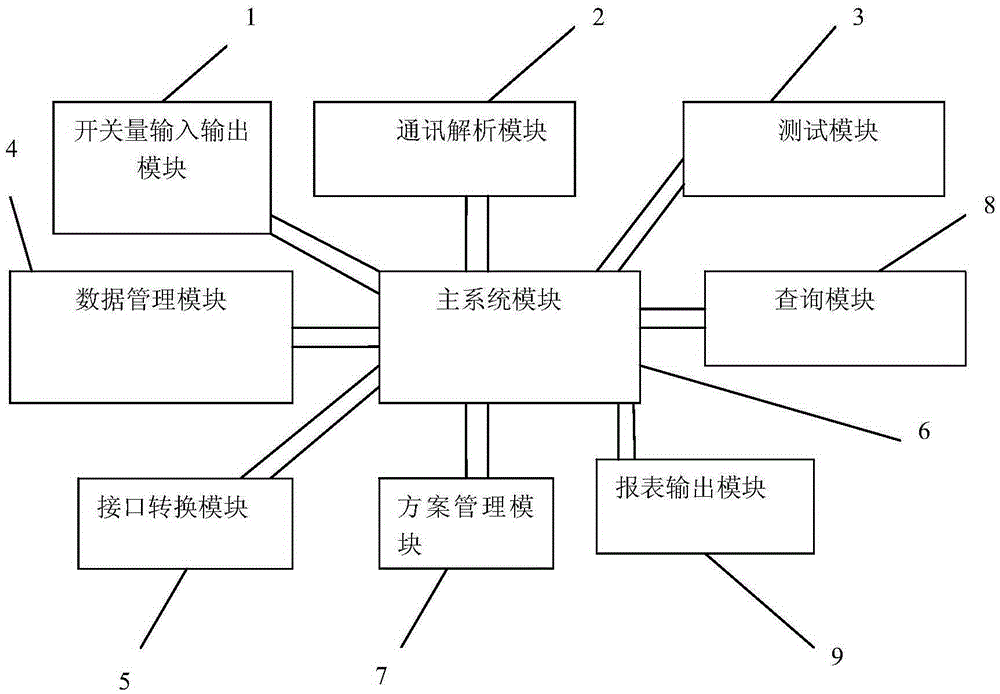
The invention discloses an integrated protection system communication protocol analysis test apparatus. The apparatus comprises a switching quantity input and output module, a communication analysis module, a test module, a main system module, a data management module, a query module, an interface conversion module, a scheme management module and a form output module, wherein the switching quantity input and output module, the communication analysis module, the test module, the data management module, the query module, the interface conversion module, the scheme management module and the form output module are connected with the main system module. The integrated protection system communication protocol analysis test apparatus can meet the communication verification demand of an integrated protection apparatus.
Owner:秦嘉喜
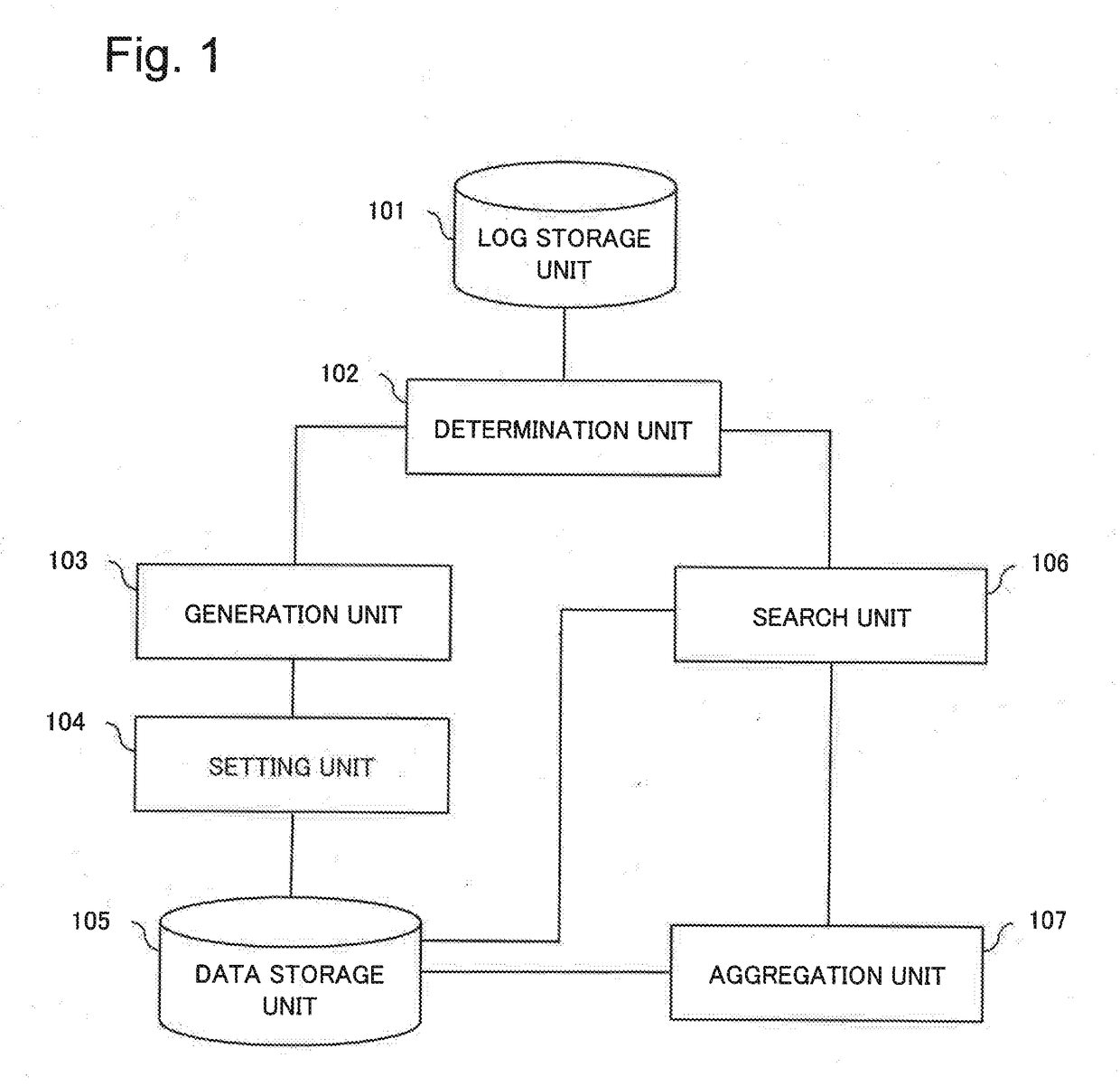
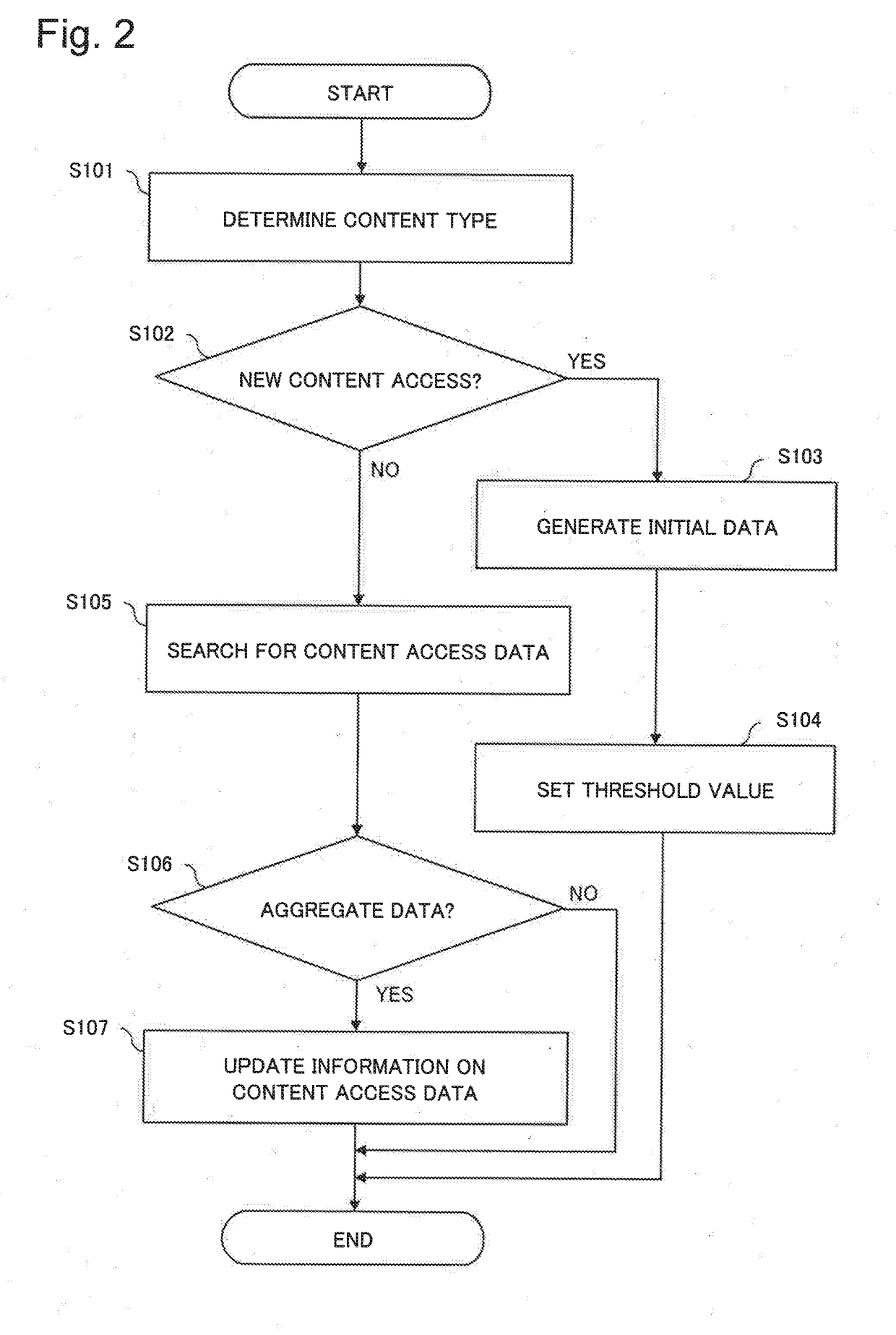
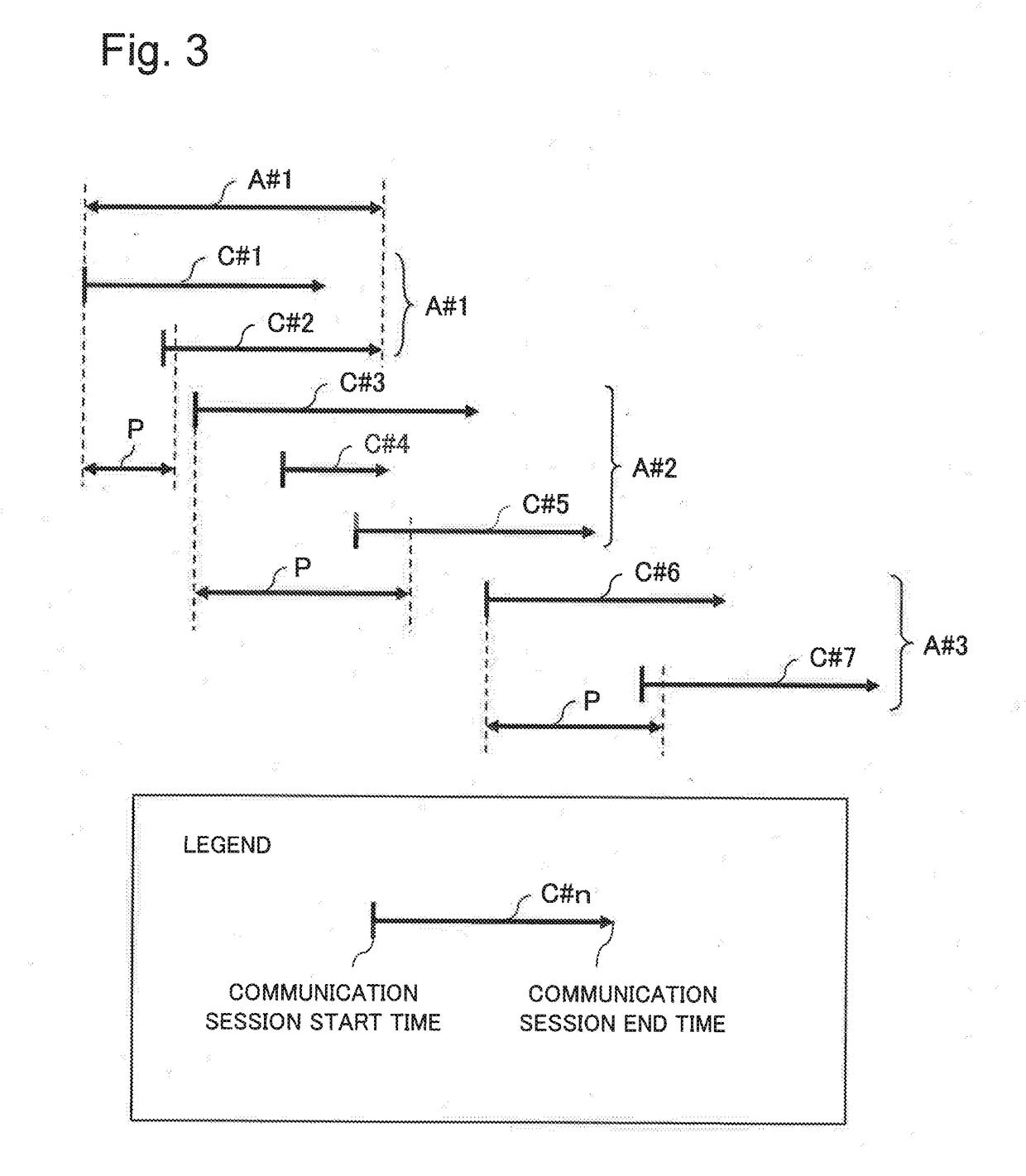
Communication analysis device, communication analysis method, and program recording medium
ActiveUS20190089795A1Accurate assessmentDigital data information retrievalTransmissionStart timeLapse time
A communication analysis device updates statistical information on a content access based on the communication session log of a user. The content access is an aggregation of a plurality of communication sessions needed for browsing one website. The communication analysis device acquires session information pertaining to one communication session, and determines whether a lapsed time from the start time or end time of a base communication session to the start time or end time of the one communication session is equal to or less than a threshold value. When the lapsed time is equal to or less than the threshold value, the communication analysis device determines that the one communication session is included in the same content access as the base communication session, and updates the statistical information of the content access. The communication analysis device stochastically sets the threshold value based on a prescribed probability distribution.
Owner:NEC CORP
Method and apparatus for scanning connected region in combined image
InactiveCN101499169BSecondary scan method improvementsImage analysisCommunication AnalysisComputer science
The invention provides a method for communicating region in a scan unite image and a device thereof. The method includes steps as follows: firstly, scanning present line of the image for obtaining a communication segment of the present line; secondly, taking out a communication segment as the present segment for processing communication analysis; thirdly, judging upper line whether having a communication segment communicated with the present segment, if yes, executing fifth step, if no, executing fourth step; fourthly, distributing target sequence number for the present segment, and storing the position information of the present segment to a structure body corresponding to the target sequence number; fifthly, confirming a first communication segment, uniting the present segment and each non-first communication segment into the first communication segment, and releasing the structure body stored the non-first communication segment. The method can complete unite only needing once scanning, needs not be distributed overfull temporary data cache which can solve technique problem that the prior technique is not suitable for operating in a hardware environment.
Owner:VIMICRO CORP
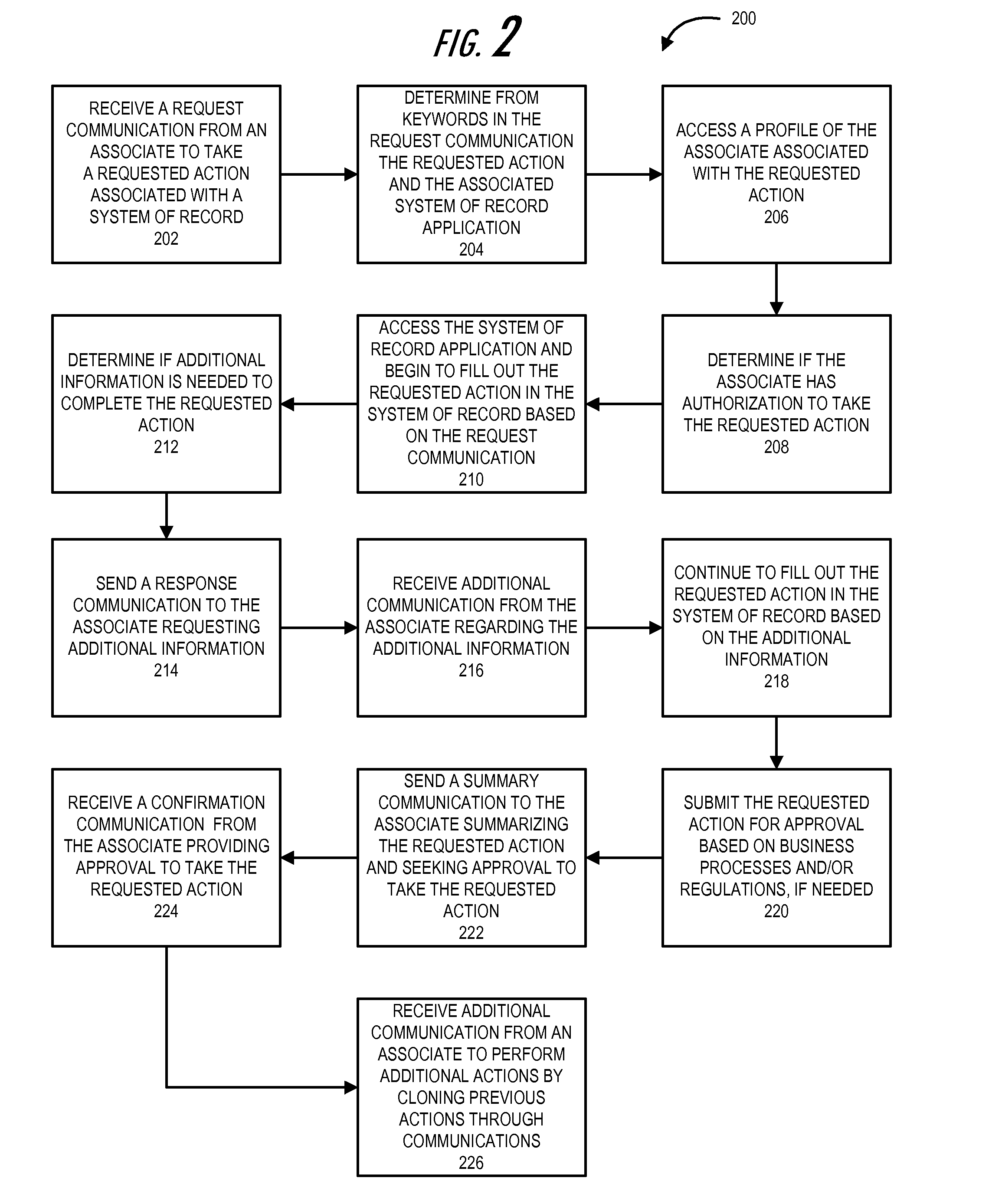
Associate communication analysis tool
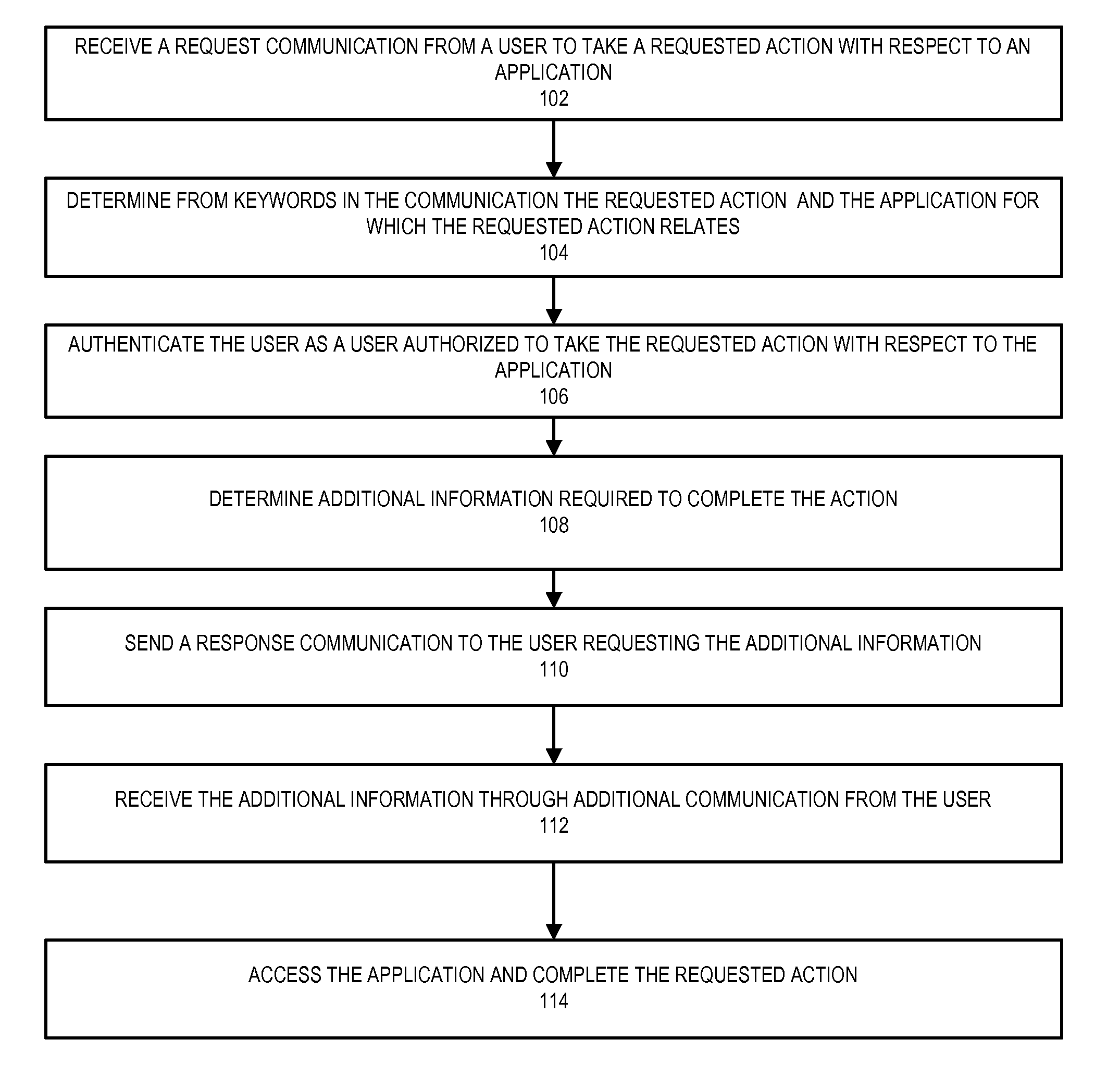
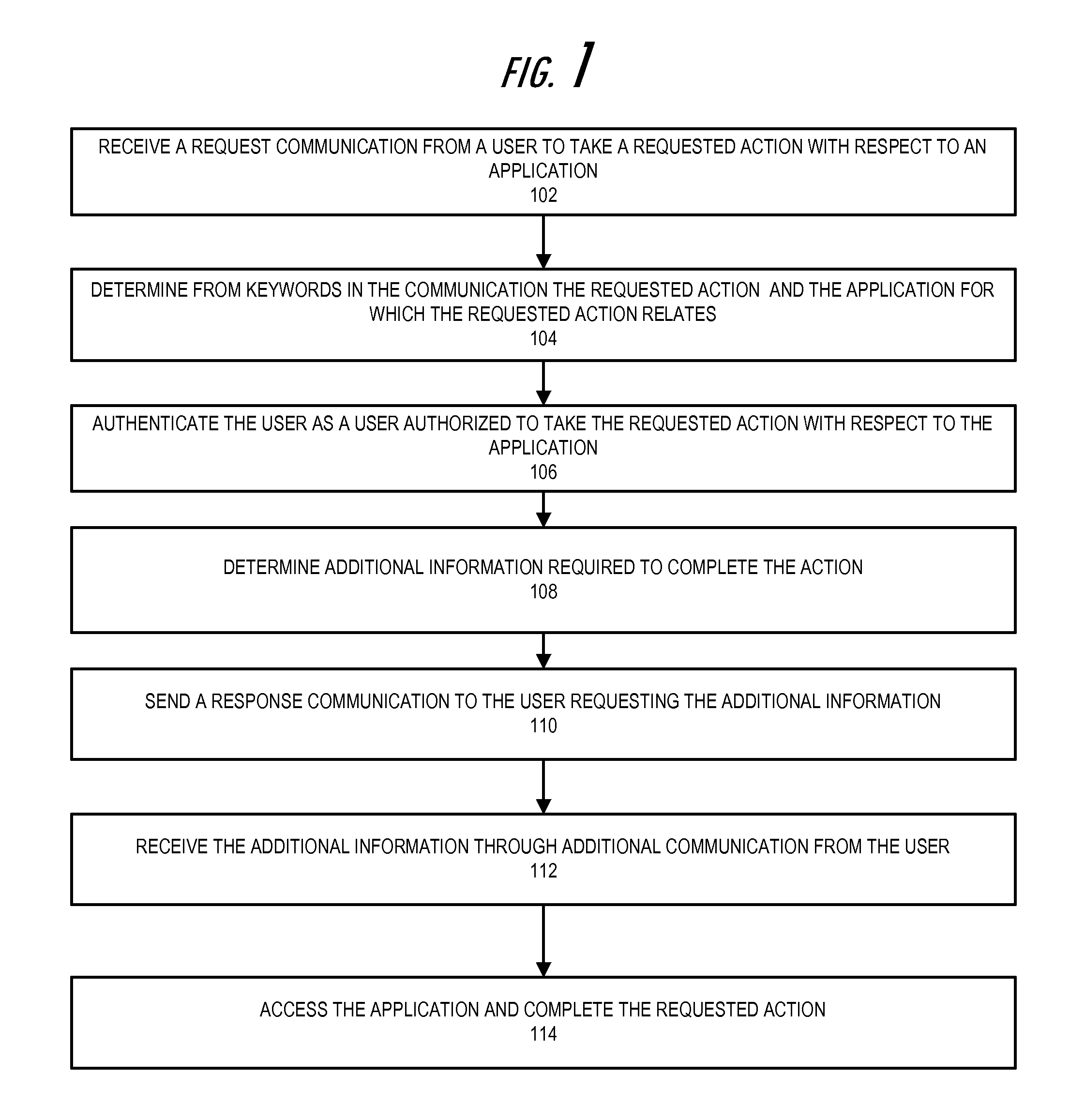
InactiveUS20150347518A1Web data indexingDigital data processing detailsVoice communicationThe Internet
Embodiments of the present invention help users (e.g., associates, customers, or the like) utilize communications to take actions with respect to systems or applications that do not directly allow for users to take actions using the communications. In some embodiments the communications are voice communications (e.g., phone calls, voice activation, voice services through the Internet, or the like) or written communications (e.g., e-mail communications, text communications, or the like) or other like voice communications or written communications. The present invention identifies keywords in the communications to determine the application for which the user wants to take an action, and the action that the user wants to take. The present invention takes the action within the application based on the keywords, or requests additional information from the user through the communication channel (or another communication channel).
Owner:BANK OF AMERICA CORP
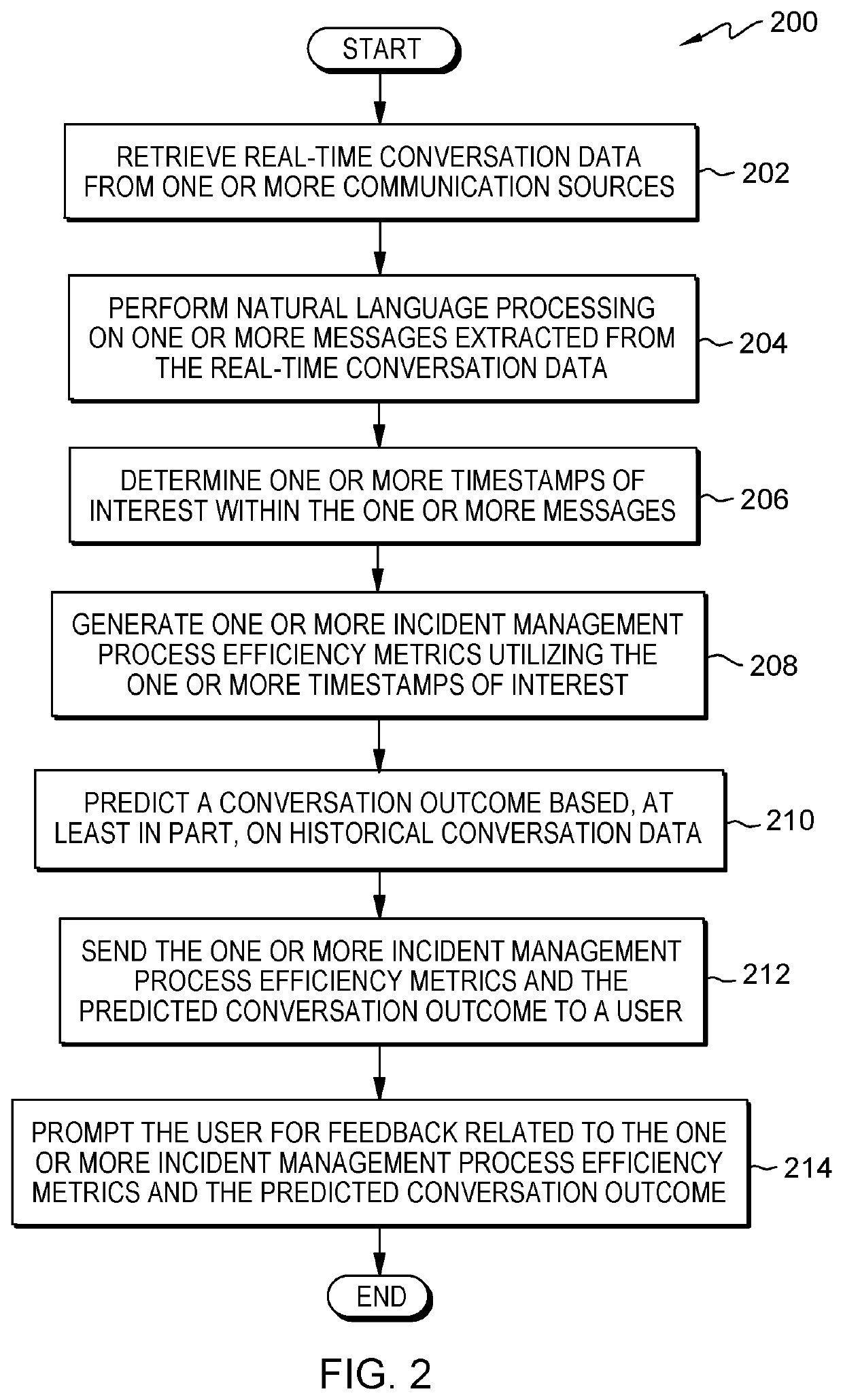
Measuring incident management process efficiency metrics utilizing real-time conversation analysis
A tool for automatically generating incident management process efficiency metrics utilizing real-time communication analysis. The tool retrieves real-time conversation data from one or more communication sources, wherein the real-time conversation data includes one or more messages having data related to an information technology (IT) incident. The tool performs conversation analysis on the one or more messages. The tool determines one or more timestamps of interest for the IT incident from the one or more messages. The tool generates one or more incident management process efficiency metrics for the IT incident utilizing the one or more timestamps of interest. The tool predicts based, at least in part, on historical conversation data, an outcome for the IT incident. The tool sends the one or more incident management process efficiency metrics and the outcome for the IT incident to a user in a notification.
Owner:IBM CORP
BAC monitoring system
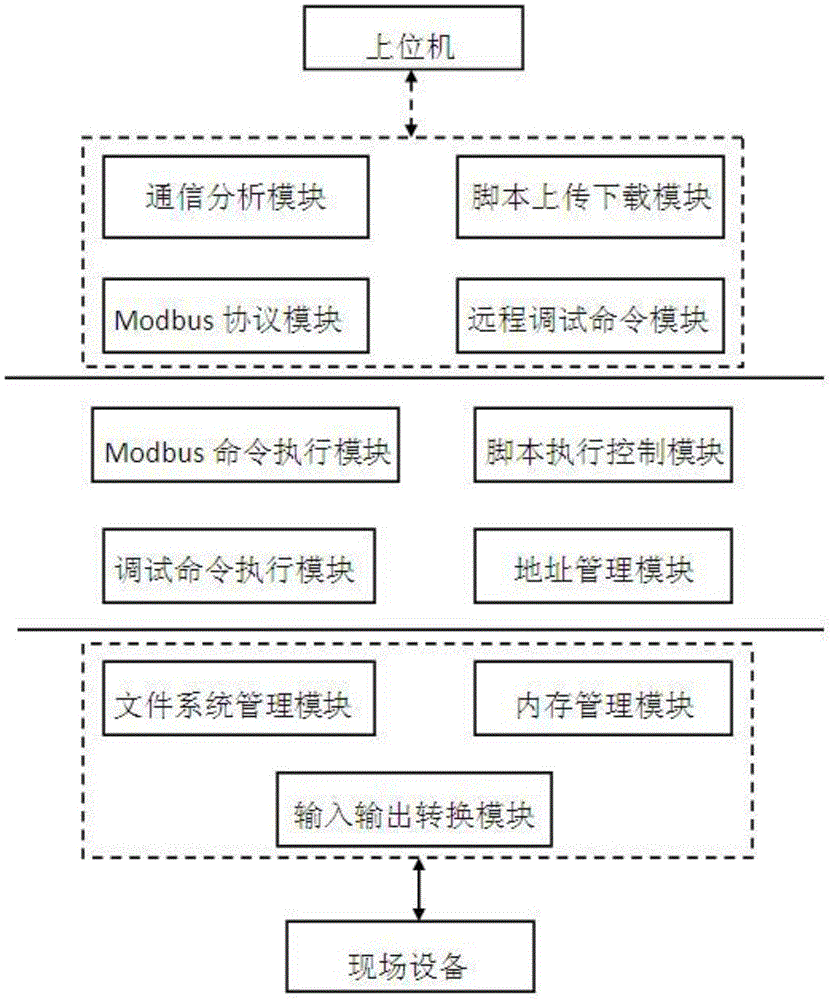
The invention discloses a BAC monitoring system The BAC monitoring system comprises a communication analysis module, a Modbus protocol module, a script uploading and downloading module, a remote debugging command module, a Modbus command execution module, a script execution control module, a debugging command execution module, an address management module, a file system management module, a memory management module and an input-output conversion module, wherein the communication analysis module, the Modbus protocol module, the script uploading and downloading module and the remote debugging command module are in communication connection with an upper computer, and the file system management module, the memory management module and the input-output conversion module are in line connection with field equipment. In the BAC monitoring system, the upper computer can monitor and control operation and state of the field equipment comprehensively, and improve stability and accuracy of field equipment control.
Owner:BEIJING DATANG XINGYE INT CONTROL TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com