Recognition method of privacy leakage behavior between Android components based on context information
A privacy leakage and context technology, applied in the field of privacy leakage behavior identification, can solve the problems of not distinguishing privacy transmission behavior privacy leakage behavior, privacy leakage between components, no data flow analysis, and incomplete consideration of components.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below through specific examples and accompanying drawings.
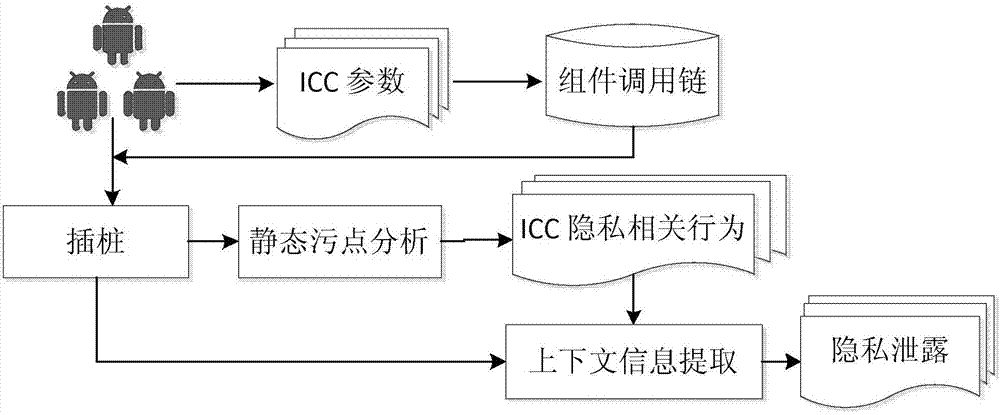
[0029] Such as figure 1 As shown, a method for identifying privacy leakage behavior between Android components based on context information, the steps include:
[0030] 1. Application decompilation module
[0031] The invention is based on the jimple file, performs static analysis, and obtains parameter information related to communication between Android application program components. Specifically, in this embodiment, the soot tool is used to decompile the Android application program.
[0032] 2. Component call chain construction module
[0033] An inter-component communication link is a connection between a source component and a destination component. The source component code contains the ICC function and sends an Intent message to the destination component. The Intent message describes various information of the target component. In order to match the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com