Malicious code type detection method based on cloud mode
A malicious code and detection method technology, which is applied in the field of malicious code category detection based on cloud mode, can solve the problems of high dependence on network speed, decreased detection and killing efficiency, and inability to deal with it, so as to achieve high efficiency, avoid repeated detection, slow down the effect of expansion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described in detail below in conjunction with the accompanying drawings.
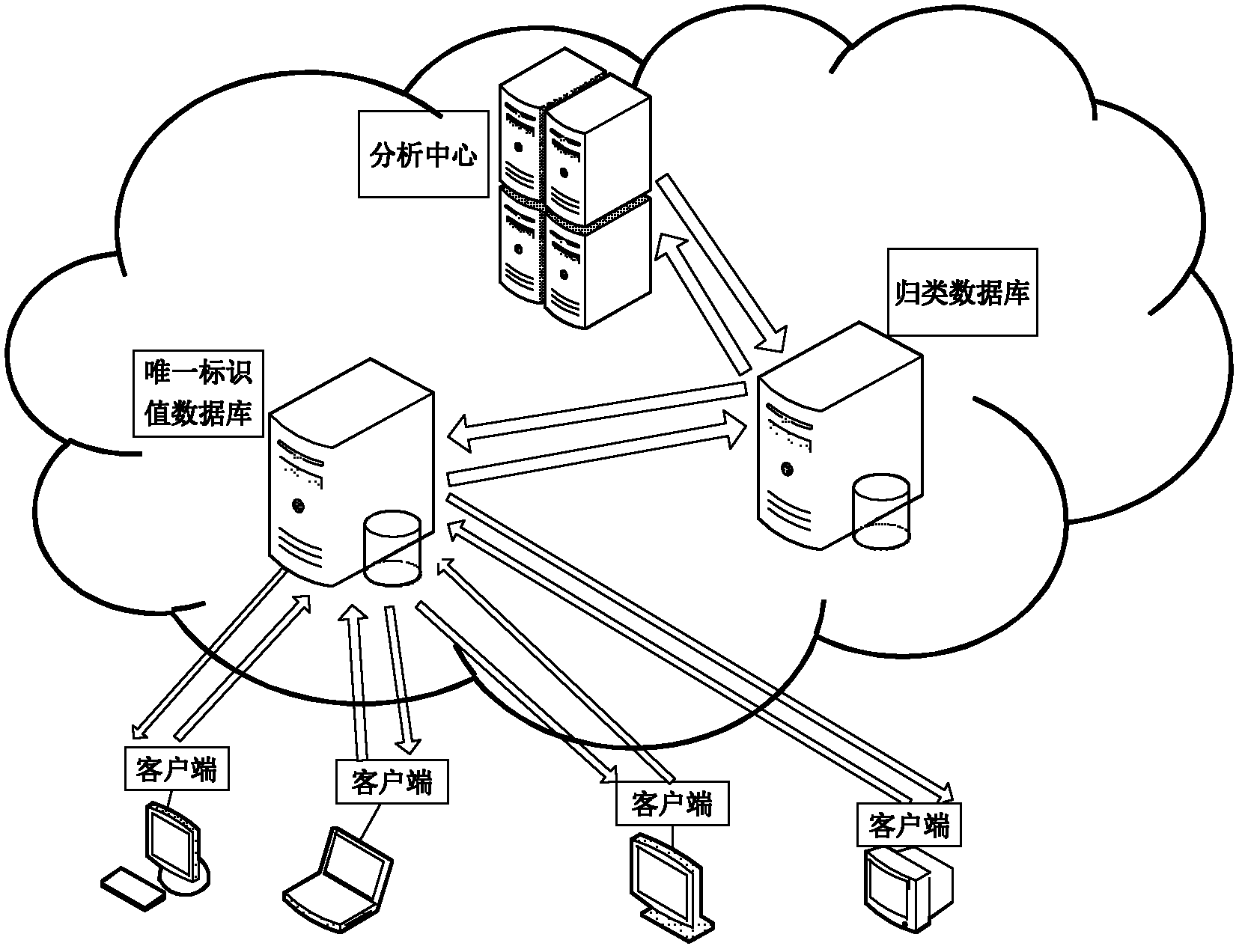
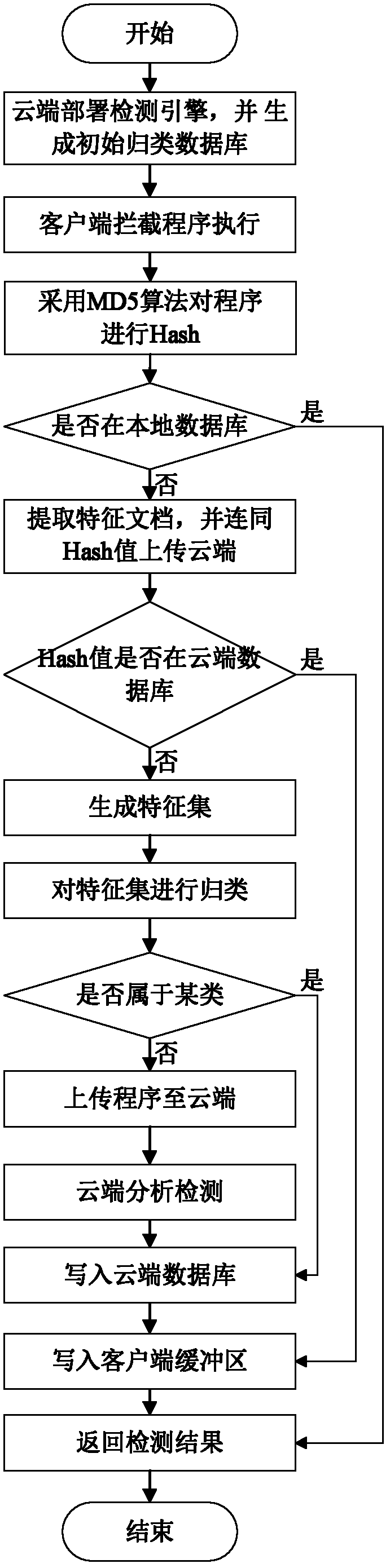
[0038] like figure 1 As shown, the client intercepts the running of the program; the unique identification code database judges the uploaded unique identification code; the classification database judges the uploaded characteristic documents; the analysis center analyzes and judges the unknown program.
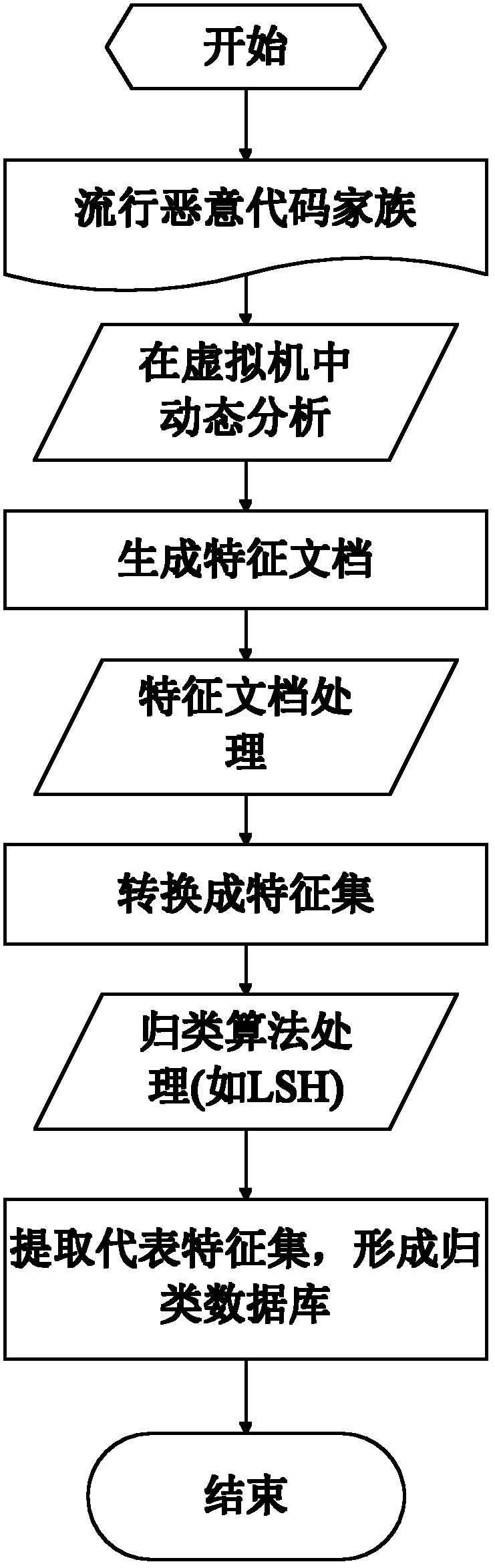
[0039] In the cloud mode, the client intercepts the running of the program. If it is a known program, it will directly judge whether the program is a malicious program; if it is an unknown program, it will extract the feature file of the unknown program through dynamic analysis, and upload it together with the unique identification code to On the cloud, if the identification code is hit on the cloud, the result will be returned directly. If it is still not hit, the feature document will be converted into a feature set for classification detection. If the clas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com