Patents
Literature
308 results about "Sequence processing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Sequence processing. This subsection of the Sequence section indicates if the canonical sequence displayed by default in the entry is in its mature form or if it represents the precursor.
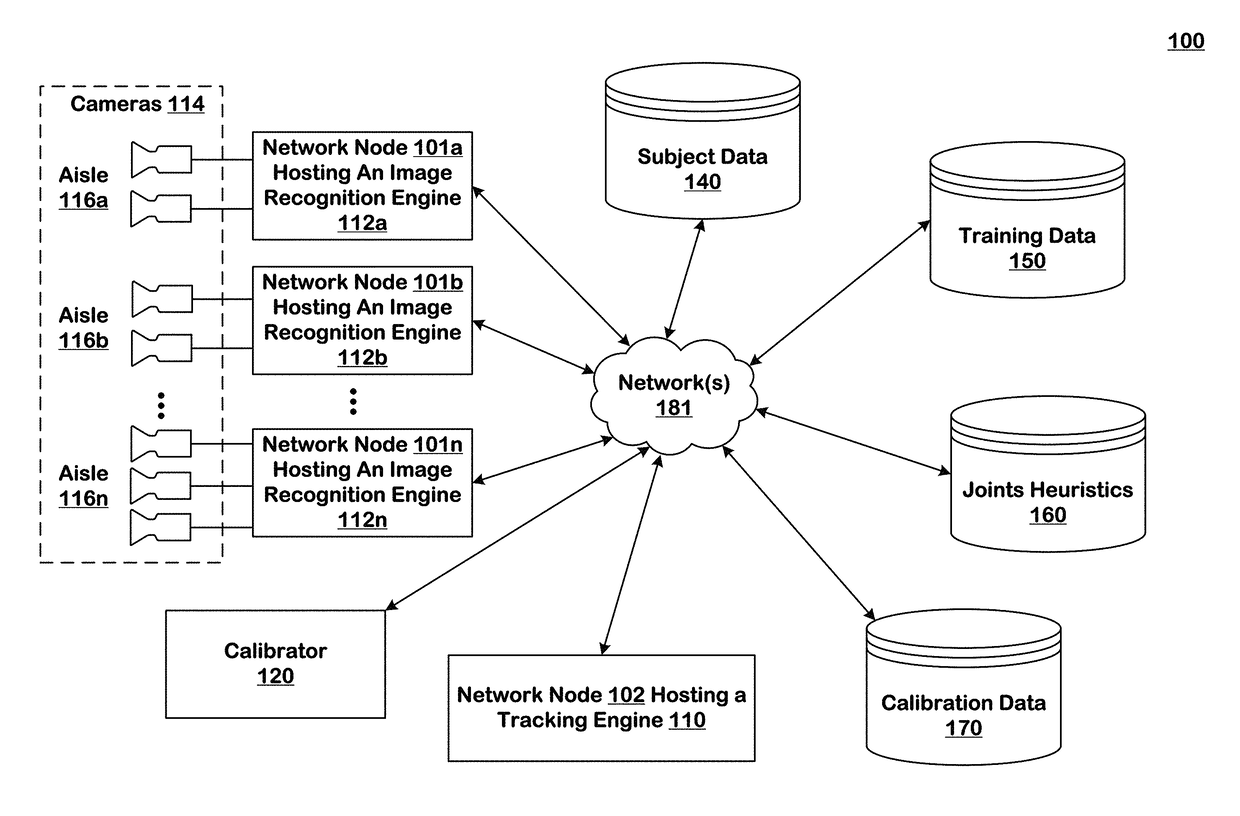
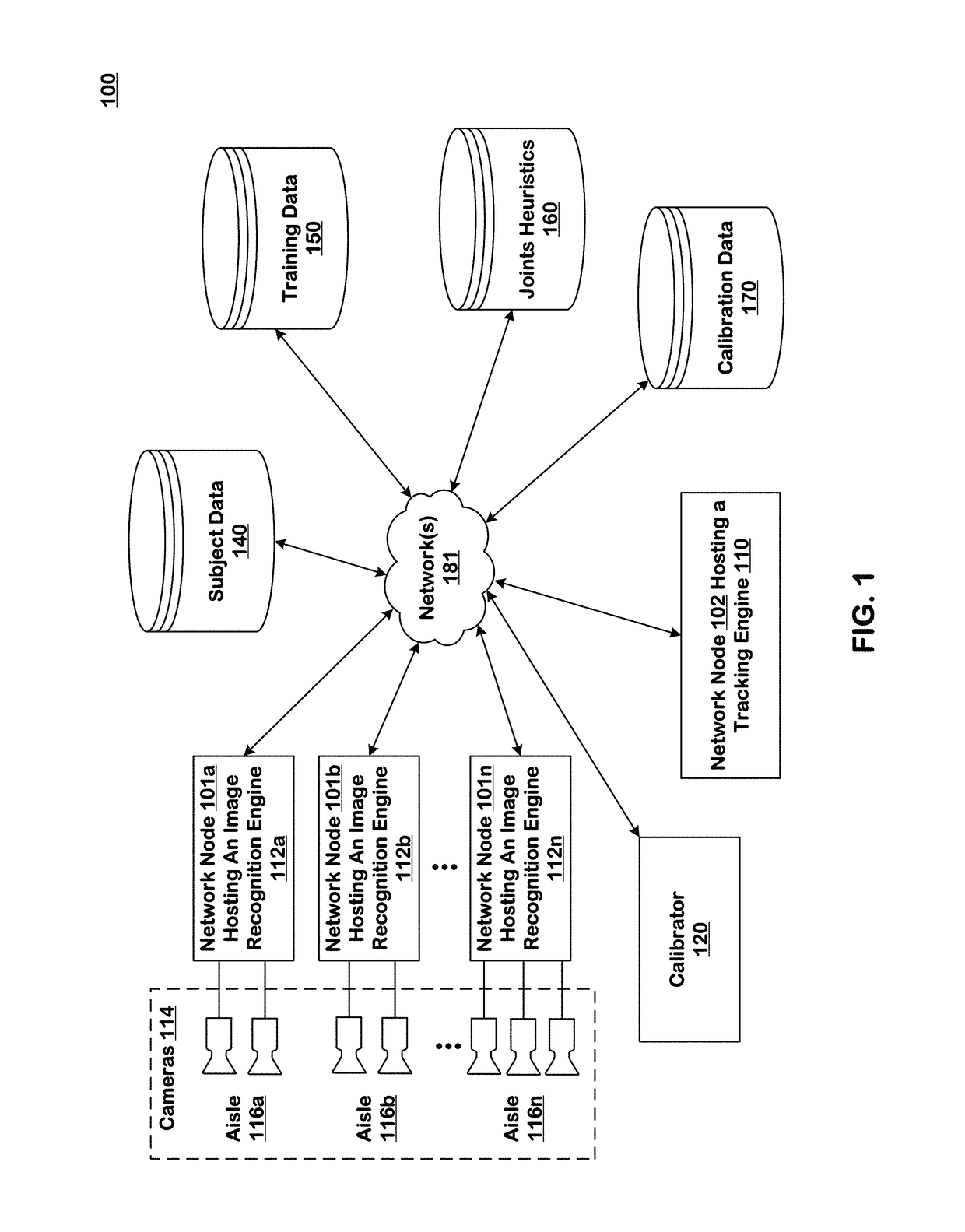
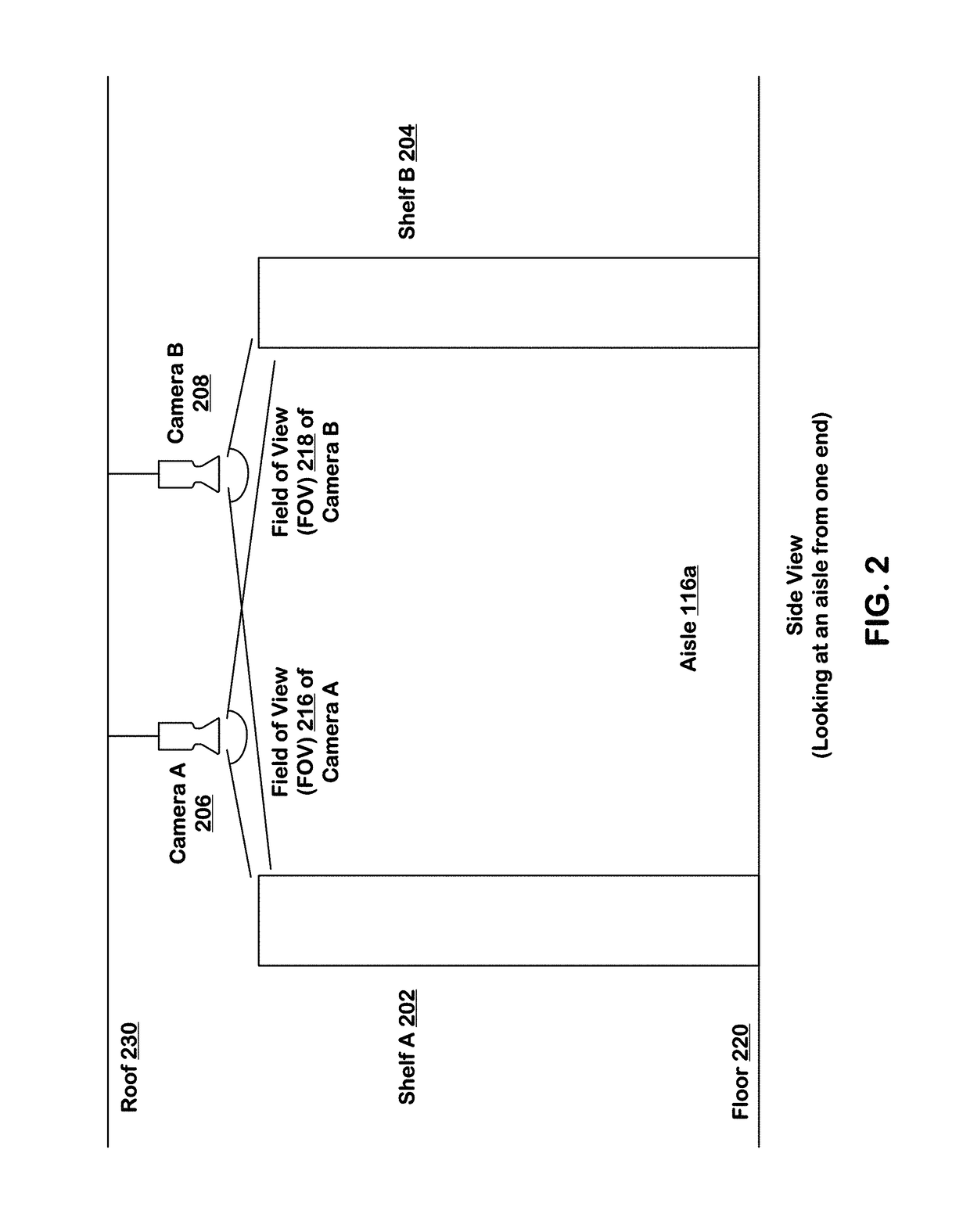
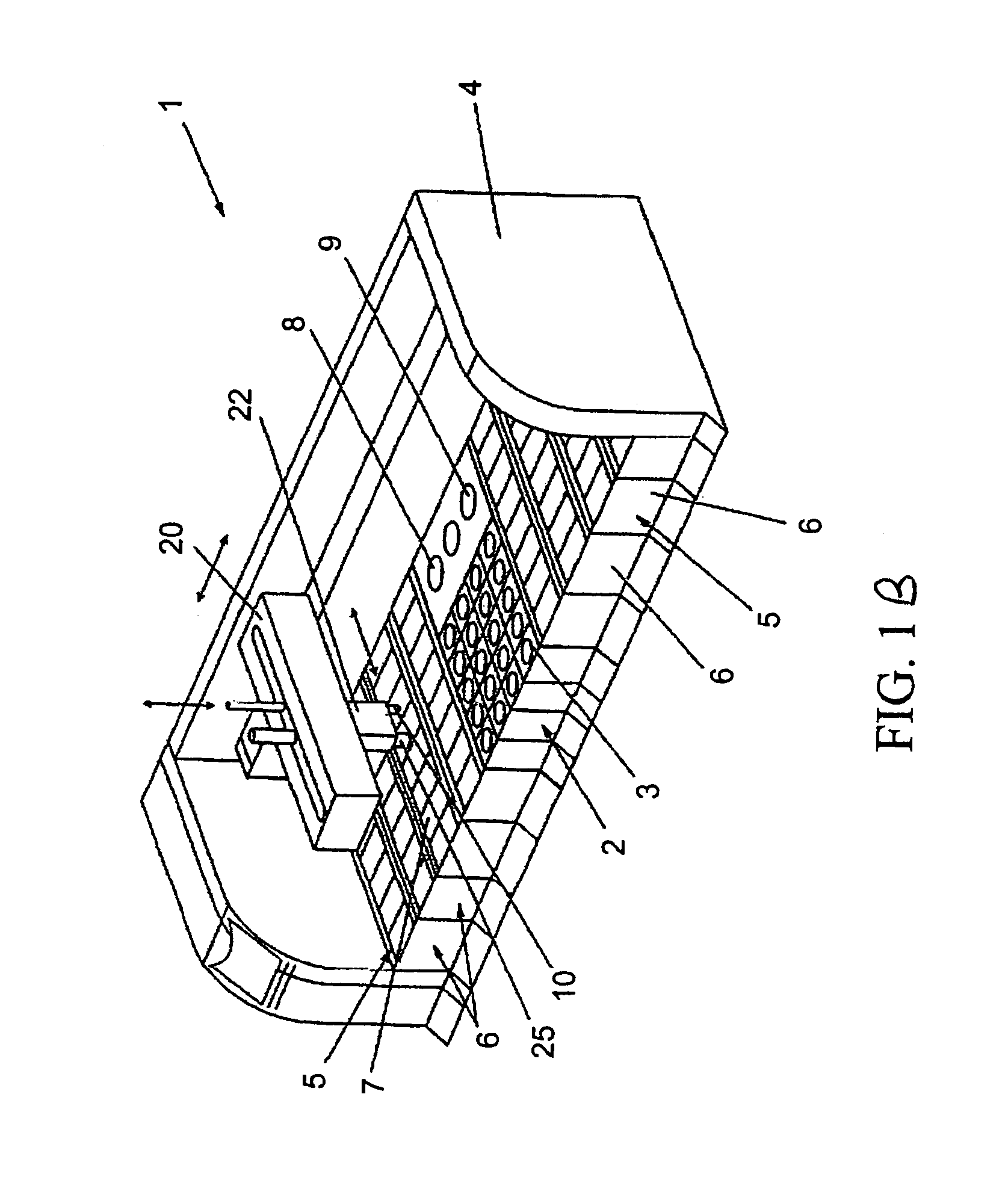
Item put and take detection using image recognition
ActiveUS10133933B1Improve reliabilityImage enhancementImage analysisSequence processingHandling system
Systems and techniques are provided for tracking puts and takes of inventory items by subjects in an area of real space. A plurality of cameras with overlapping fields of view produce respective sequences of images of corresponding fields of view in the real space. A processing system is coupled to the system. In one embodiment, the processing system comprises image recognition engines receiving corresponding sequences of images from the plurality of cameras. The image recognition engines process the images in the corresponding sequences to identify subjects represented in the images and generate classifications of the identified subjects. The system processes the classifications of identified subjects for sets of images in the sequences of images to detect takes and puts of inventory items on shelves by identified subjects.
Owner:STANDARD COGNITION CORP
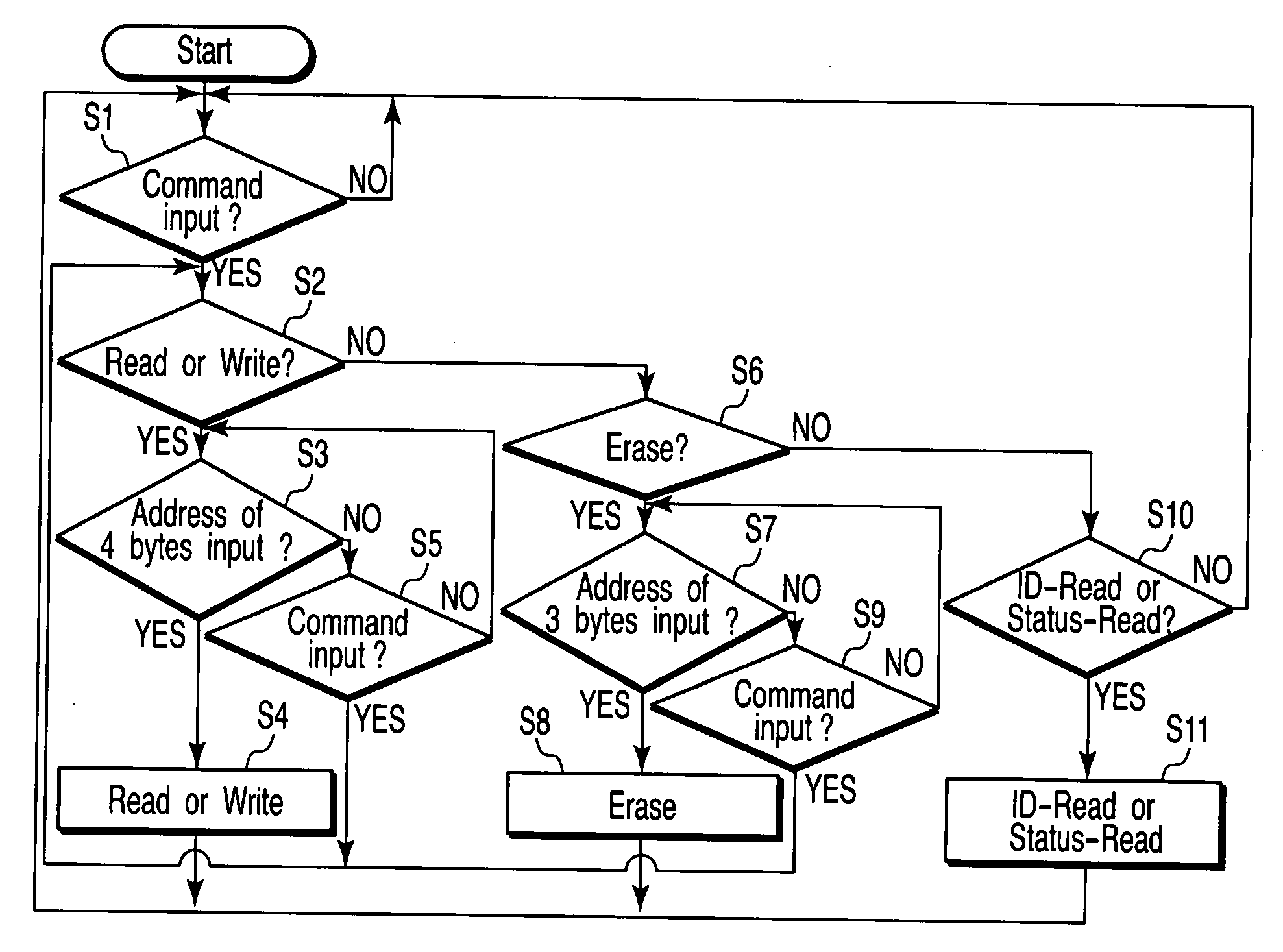
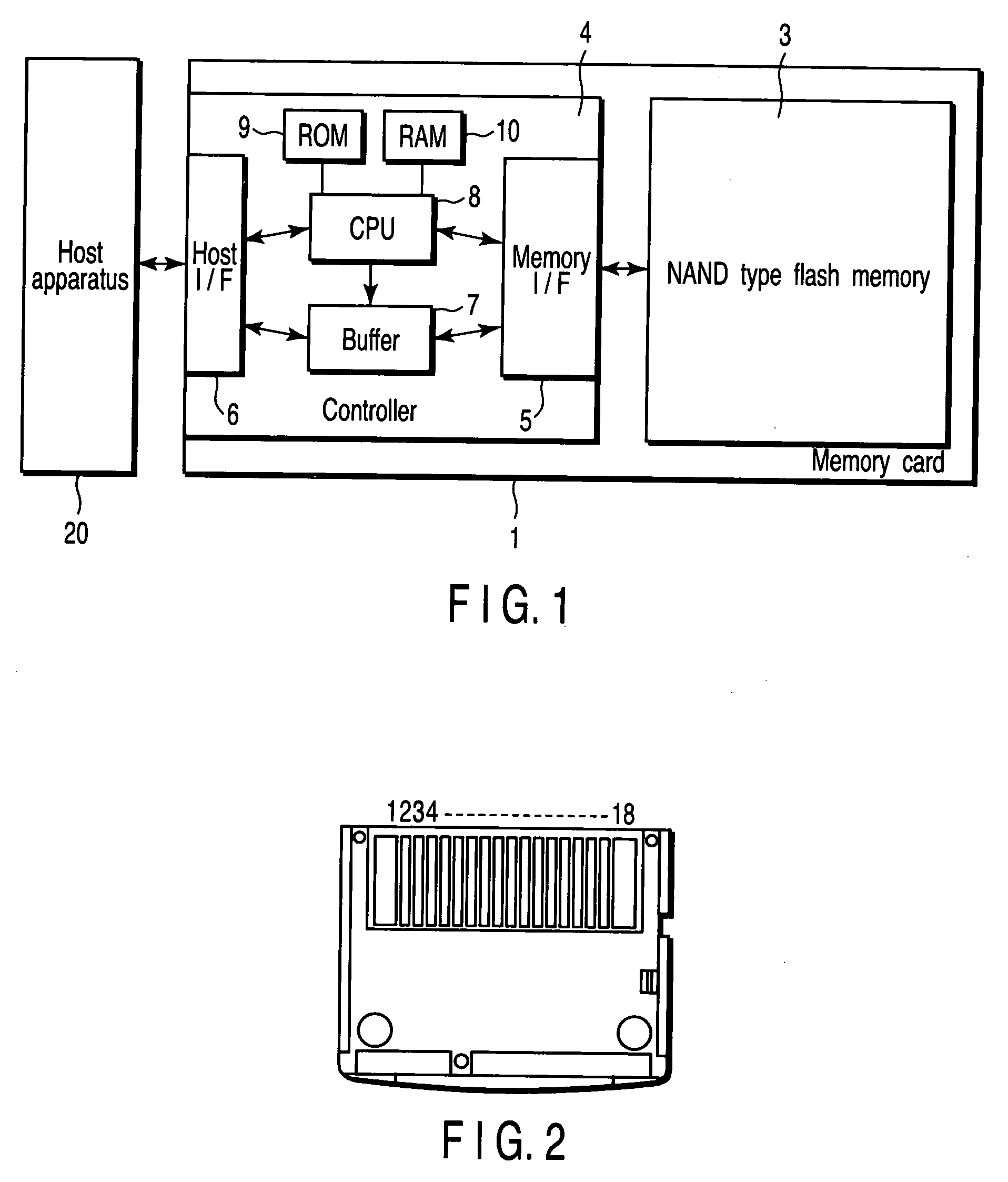
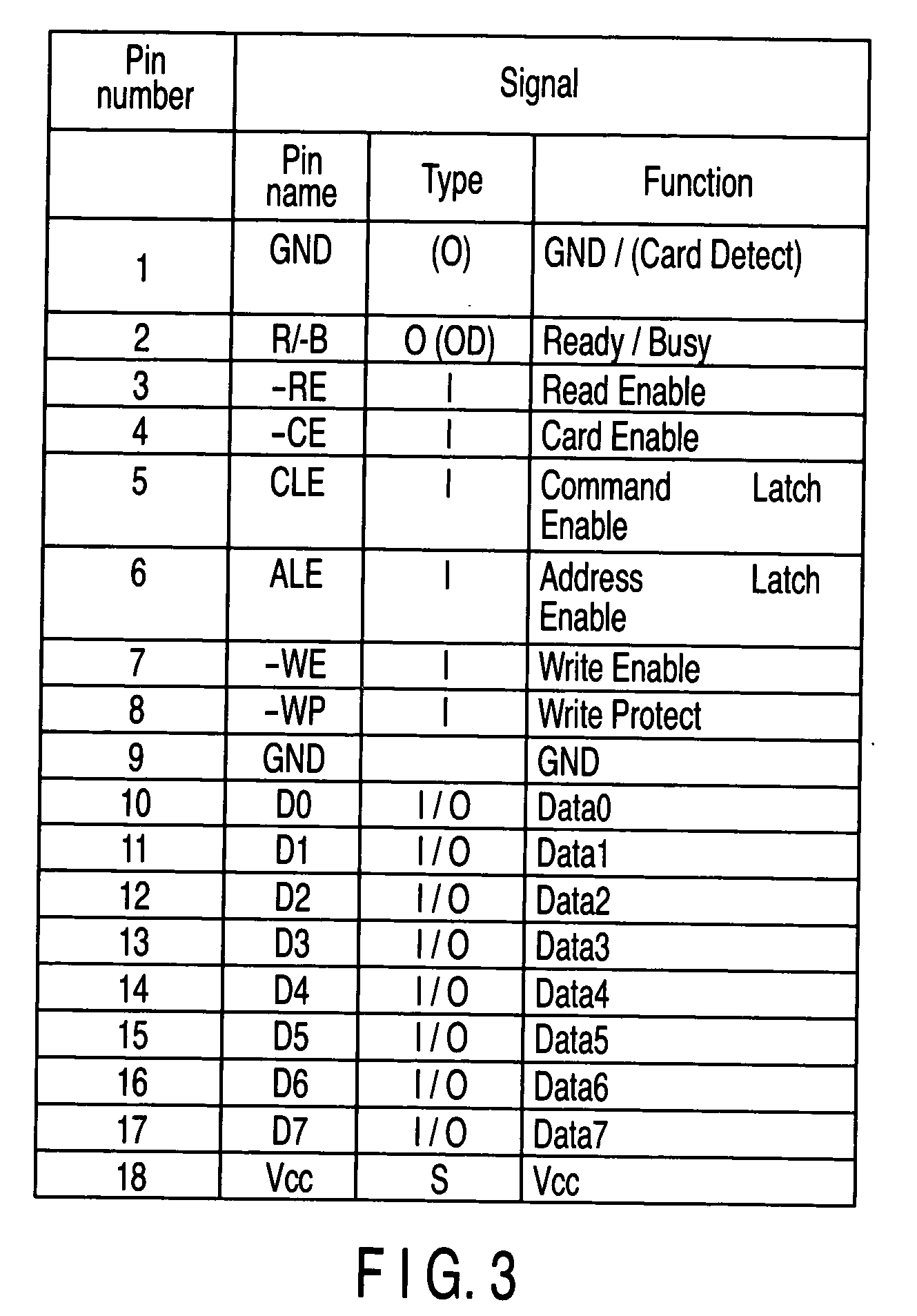
Memory card having a storage cell and method of controlling the same
A controller comprises a host interface section and a processing circuit. The host interface section receives a command sequence outputted from a host apparatus to a first nonvolatile semiconductor memory. The processing circuit processes the command sequence outputted from the host apparatus to the first nonvolatile semiconductor memory, and controls writing, reading and erase of data to a second nonvolatile semiconductor memory, according to the command sequence.
Owner:KIOXIA CORP
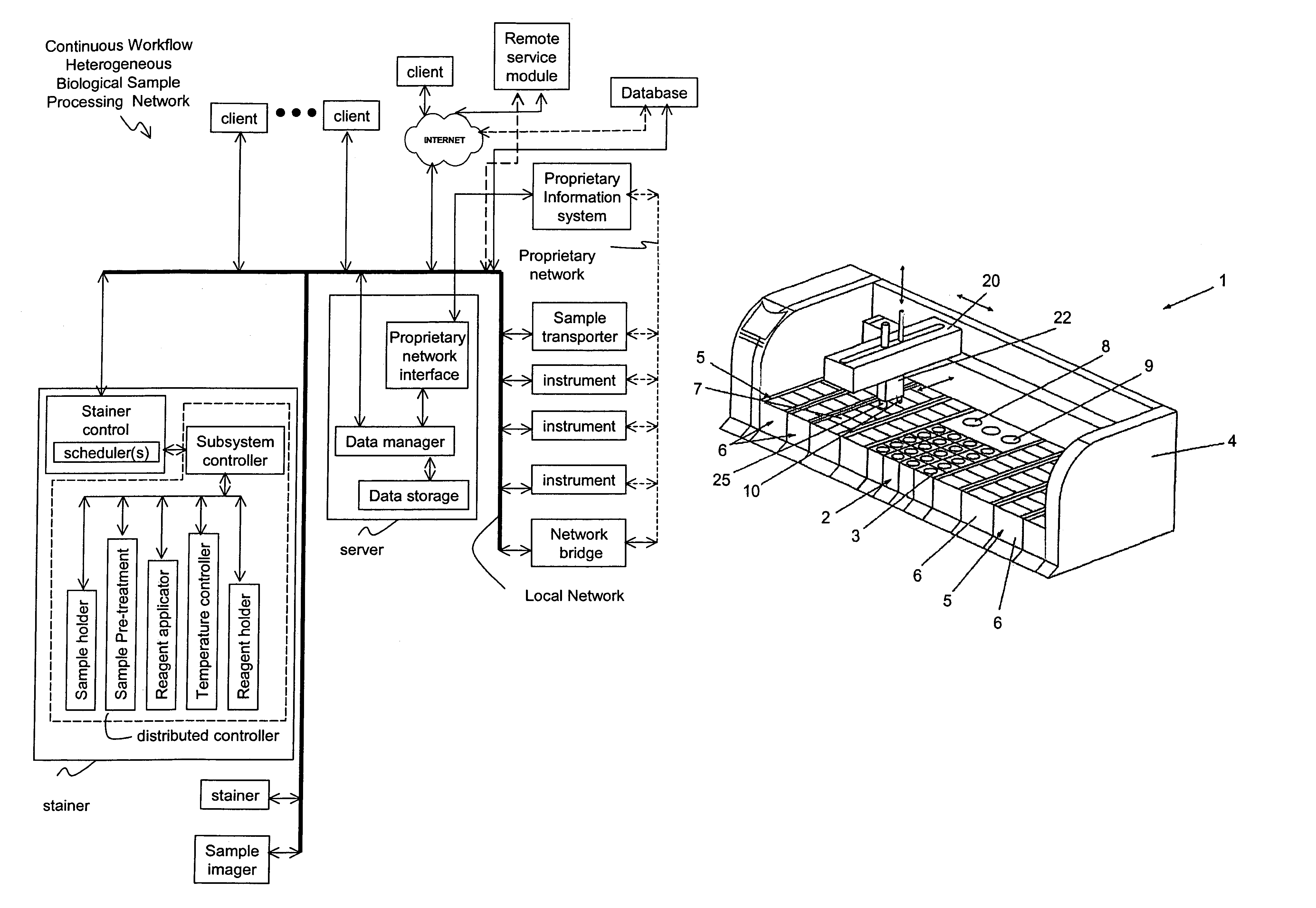
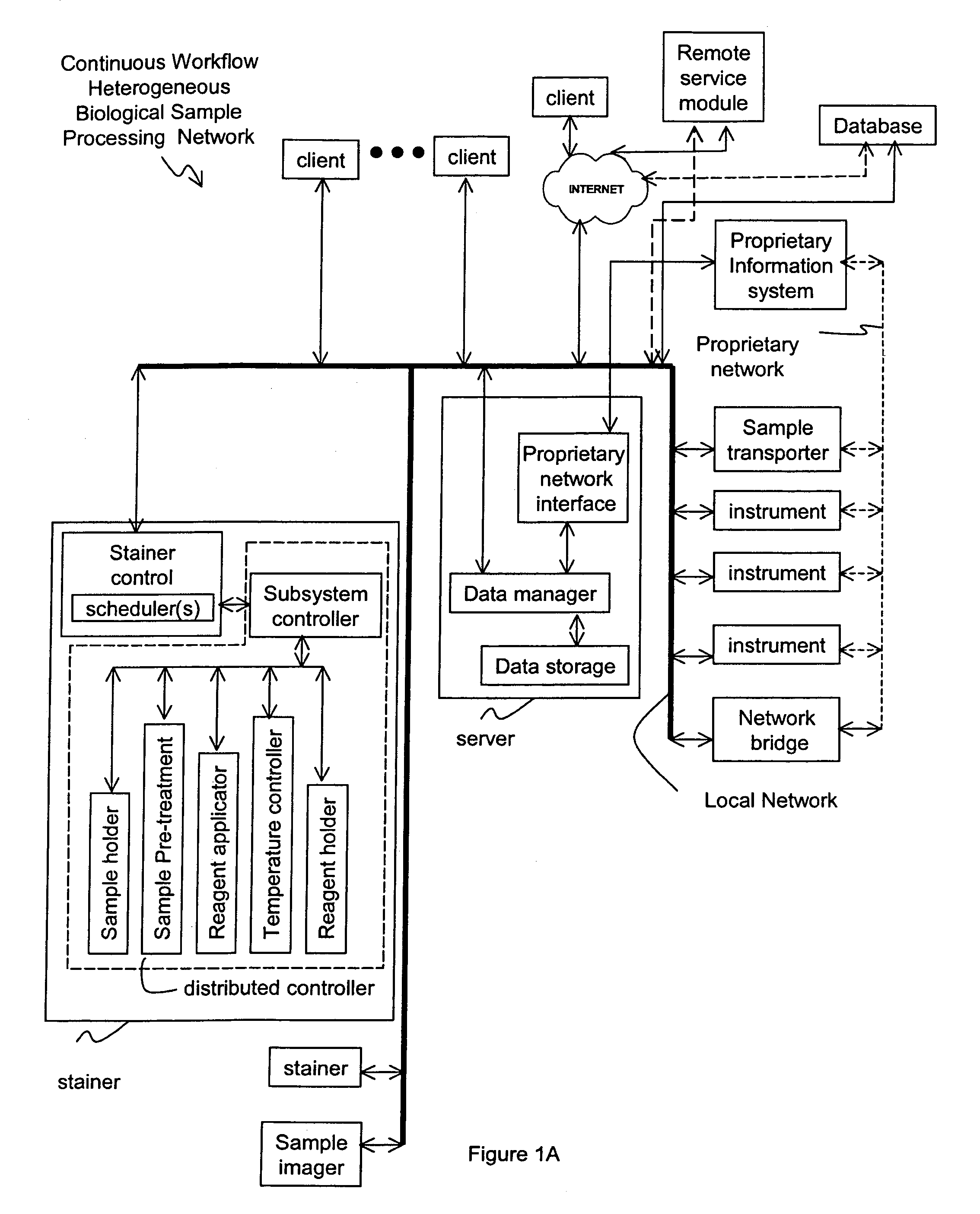
Method and apparatus for automated pre-treatment and processing of biological samples
ActiveUS7850912B2Unstable over timeShort timeBioreactor/fermenter combinationsBiological substance pretreatmentsSequence processingWork flow
A method and apparatus for continuous workflow processing of biological samples. In one embodiment, the apparatus includes a probe for dispensing one or more reagents from one or more reagent containers onto one or more biological sample carriers. The method and apparatus includes processing each biological sample according to a respective sequence of protocol steps which may be ordered by a scheduler protocol. The method and apparatus also includes network capability for connectivity with additional equipment for receiving or transmitting pertinent data via the network.
Owner:AGILENT TECH INC
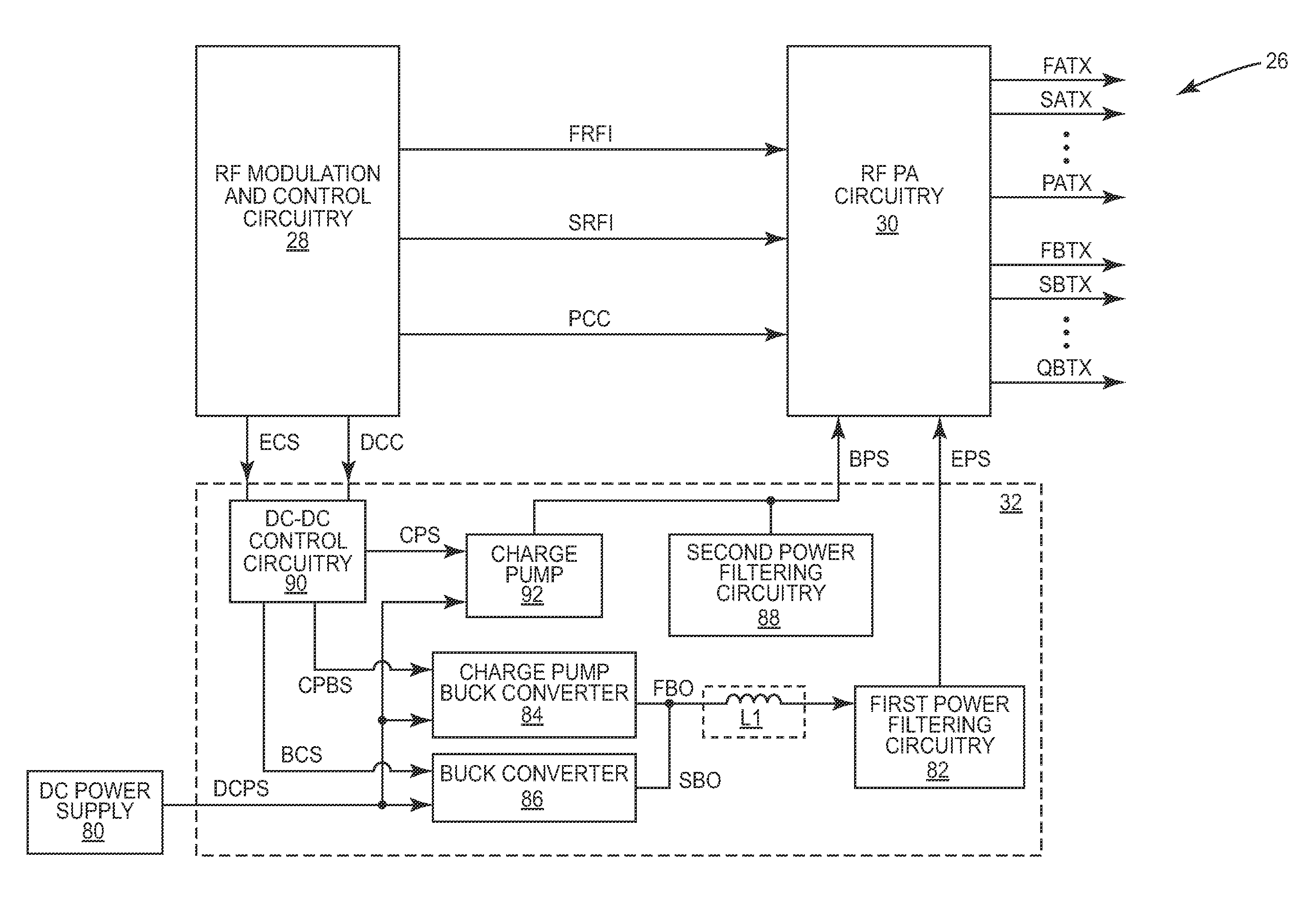
Auto configurable 2/3 wire serial interface
InactiveUS20120170690A1Gated amplifiersAmplitude-modulated carrier systemsAuto-configurationSequence processing
An automatically configurable 2-wire / 3-wire serial communications interface (AC23SCI), which includes start-of-sequence (SOS) detection circuitry and sequence processing circuitry, is disclosed. When the SOS detection circuitry is coupled to a 2-wire serial communications bus, the SOS detection circuitry detects an SOS of a received sequence based on a serial data signal and a serial clock signal. When the SOS detection circuitry is coupled to a 3-wire serial communications bus, the SOS detection circuitry detects the SOS of the received sequence based on a chip select (CS) signal. The SOS detection circuitry provides an indication of detection of the SOS to the sequence processing circuitry, which initiates processing of the received sequence using the serial data signal and the serial clock signal upon the detection of the SOS. As such, the AC23SCI automatically configures itself for operation with some 2-wire and some 3-wire serial communications buses without external intervention.
Owner:QORVO US INC
Temporal memory using sparse distributed representation
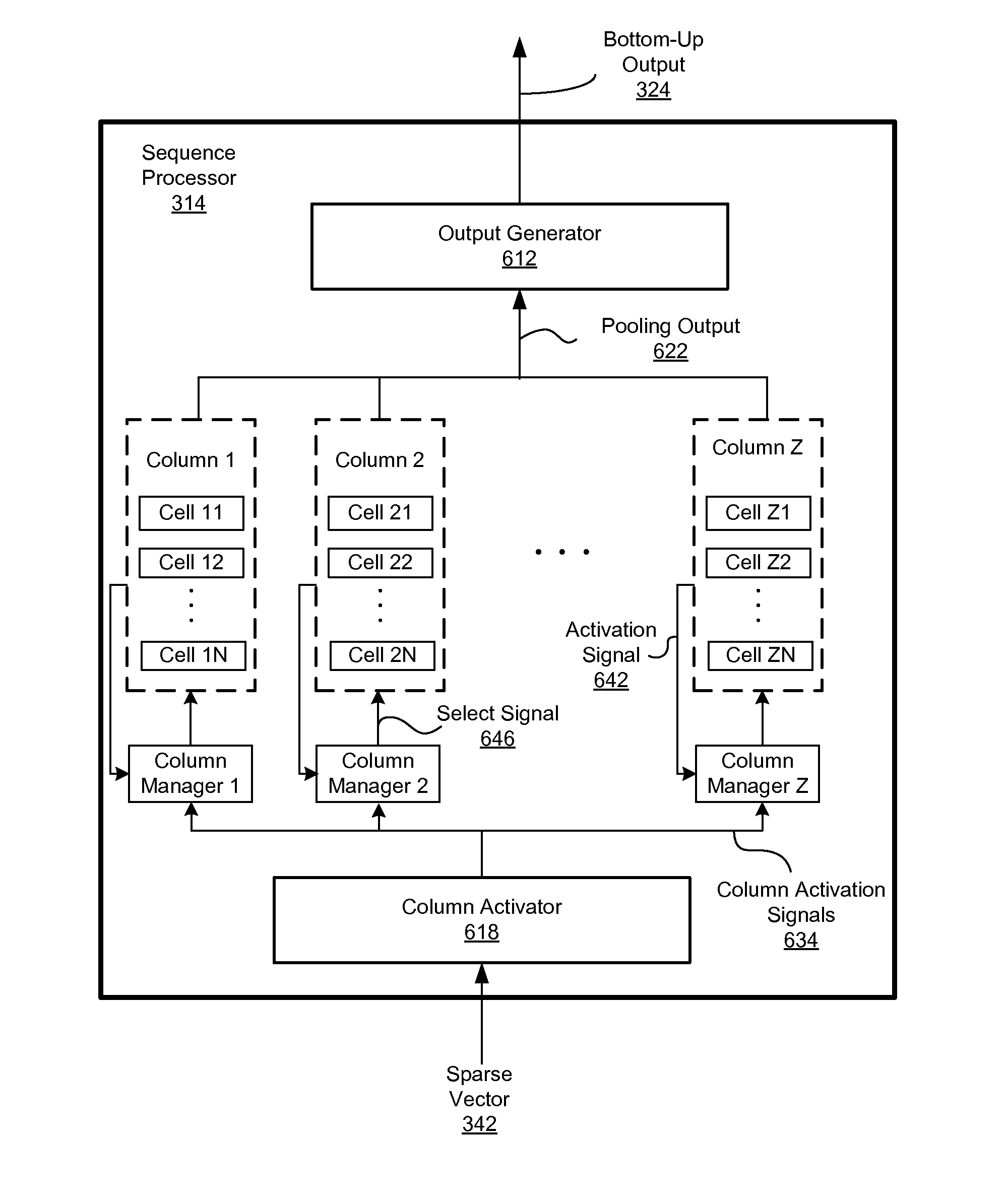
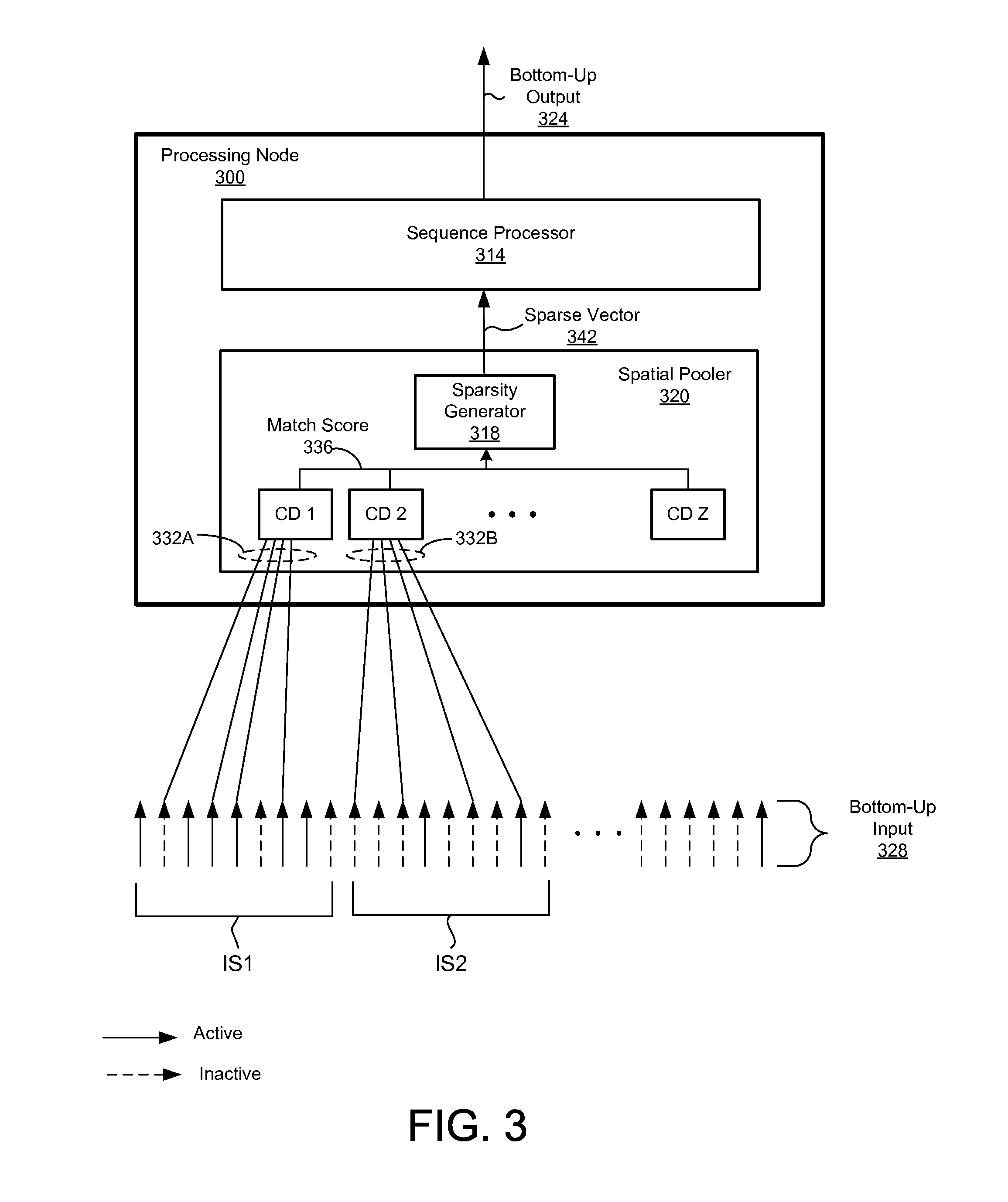
ActiveUS20110225108A1Robust to noise in inputNoise robustDigital computer detailsProbabilistic networksSequence processingCo-occurrence
A processing node in a temporal memory system includes a spatial pooler and a sequence processor. The spatial pooler generates a spatial pooler signal representing similarity between received spatial patterns in an input signal and stored co-occurrence patterns. The spatial pooler signal is represented by a combination of elements that are active or inactive. Each co-occurrence pattern is mapped to different subsets of elements of an input signal. The spatial pooler signal is fed to a sequence processor receiving and processed to learn, recognize and predict temporal sequences in the input signal. The sequence processor includes one or more columns, each column including one or more cells. A subset of columns may be selected by the spatial pooler signal, causing one or more cells in these columns to activate.
Owner:NUMENTA INC
System and method for securely utilizing basic input and output system (BIOS) services
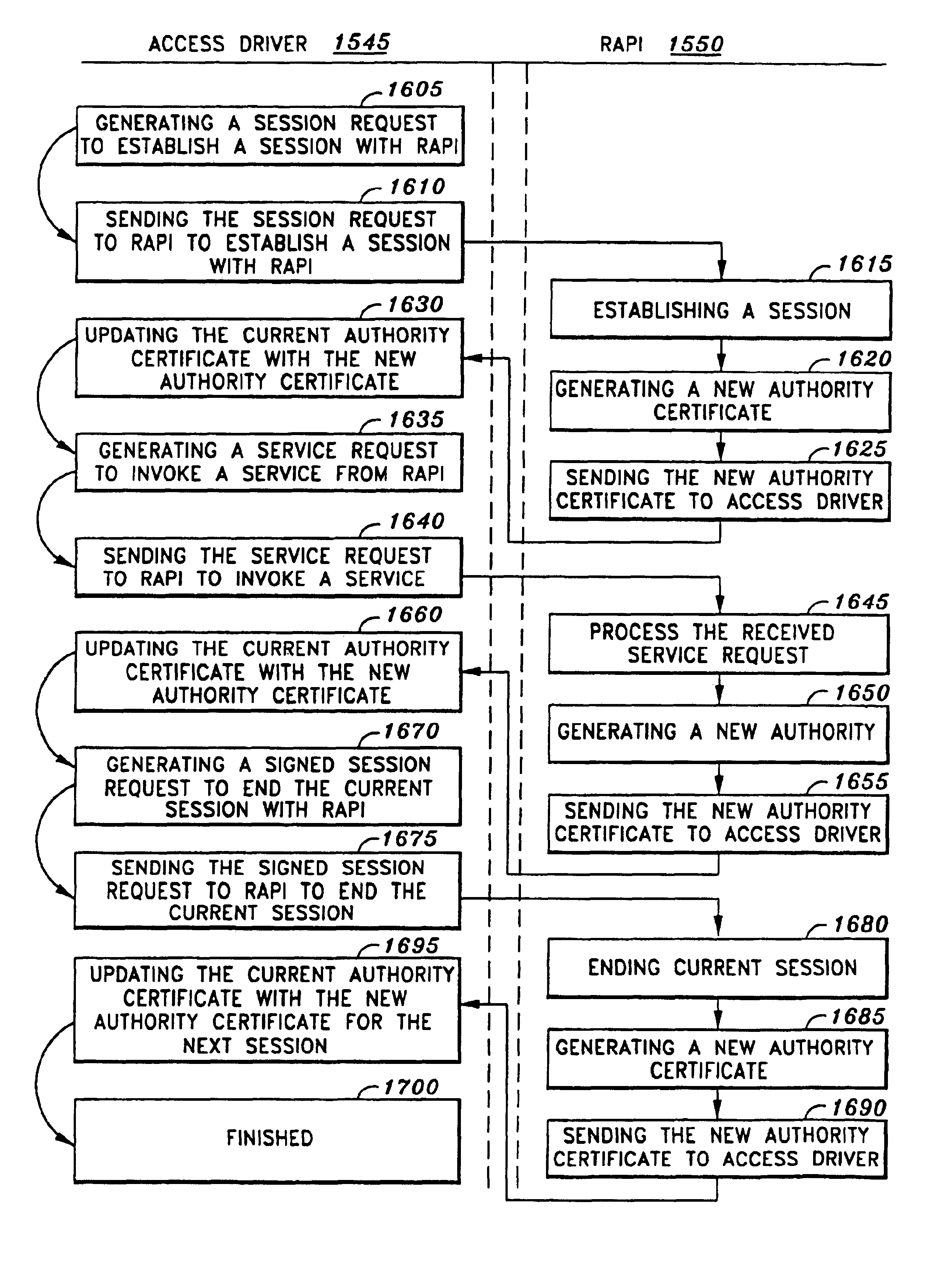
InactiveUS6892304B1Resource allocationDigital data processing detailsVirtual memorySequence processing
In accordance with one aspect of the current invention, the system comprises a memory for storing instruction sequences by which the processor-based system is processed, where the memory includes a physical memory and a virtual memory. The system also comprises a processor for executing the stored instruction sequences. The stored instruction sequences include process acts to cause the processor to: map a plurality of predetermined instruction sequences from the physical memory to the virtual memory, determine an offset to one of the plurality of predetermined instruction sequences in the virtual memory, receive an instruction to execute the one of the plurality of predetermined instruction sequences, transfer control to the one of the plurality of predetermined instruction sequences, and process the one of the plurality of predetermined instruction sequences from the virtual memory. In accordance with another aspect of the present invention, the system includes an access driver to generate a service request to utilize BIOS services such that the service request contains a service request signature created using a private key in a cryptographic key pair. The system also includes an interface to verify the service request signature using a public key in the cryptographic key pair to ensure integrity of the service request.
Owner:KINGLITE HLDG INC
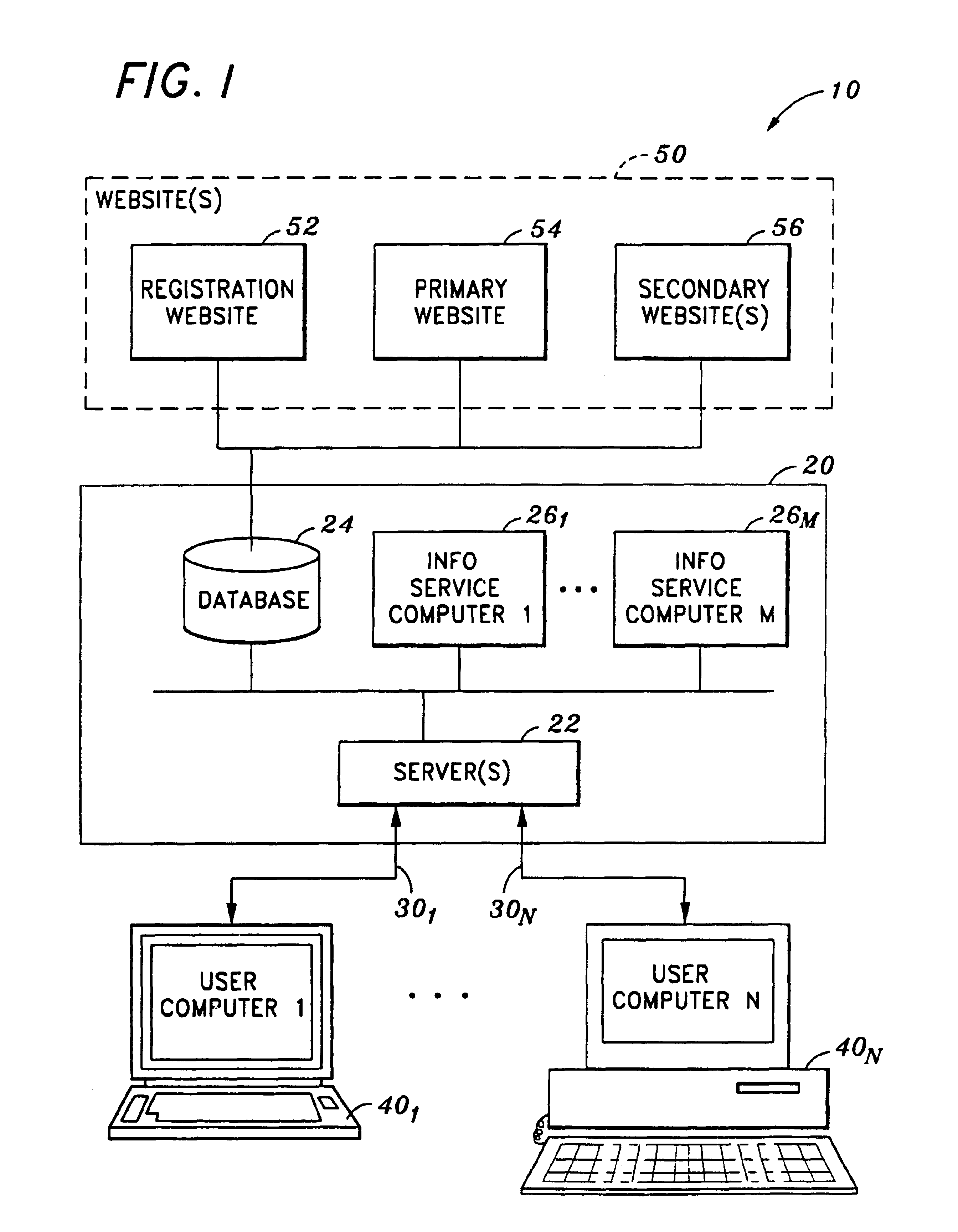
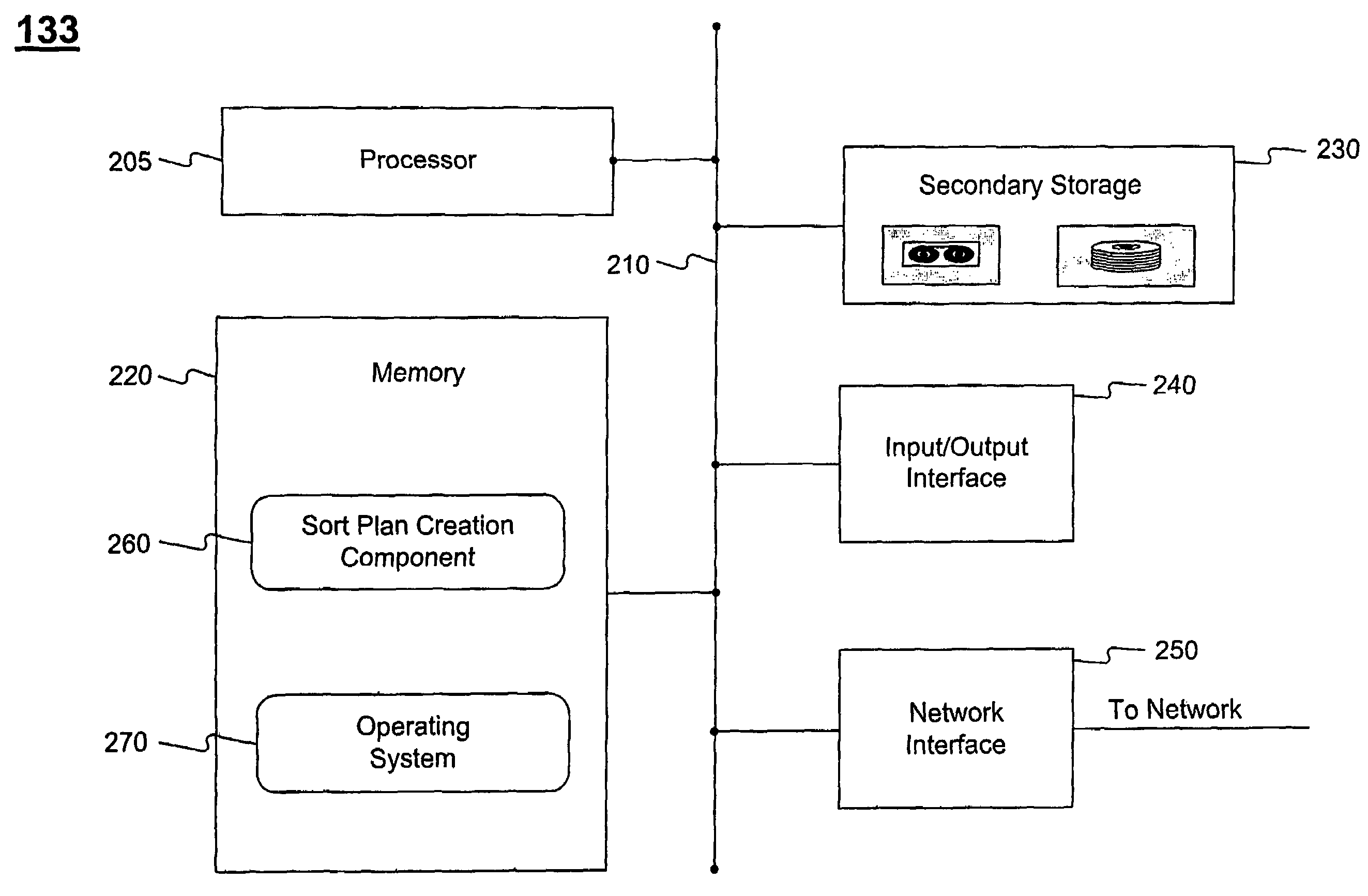
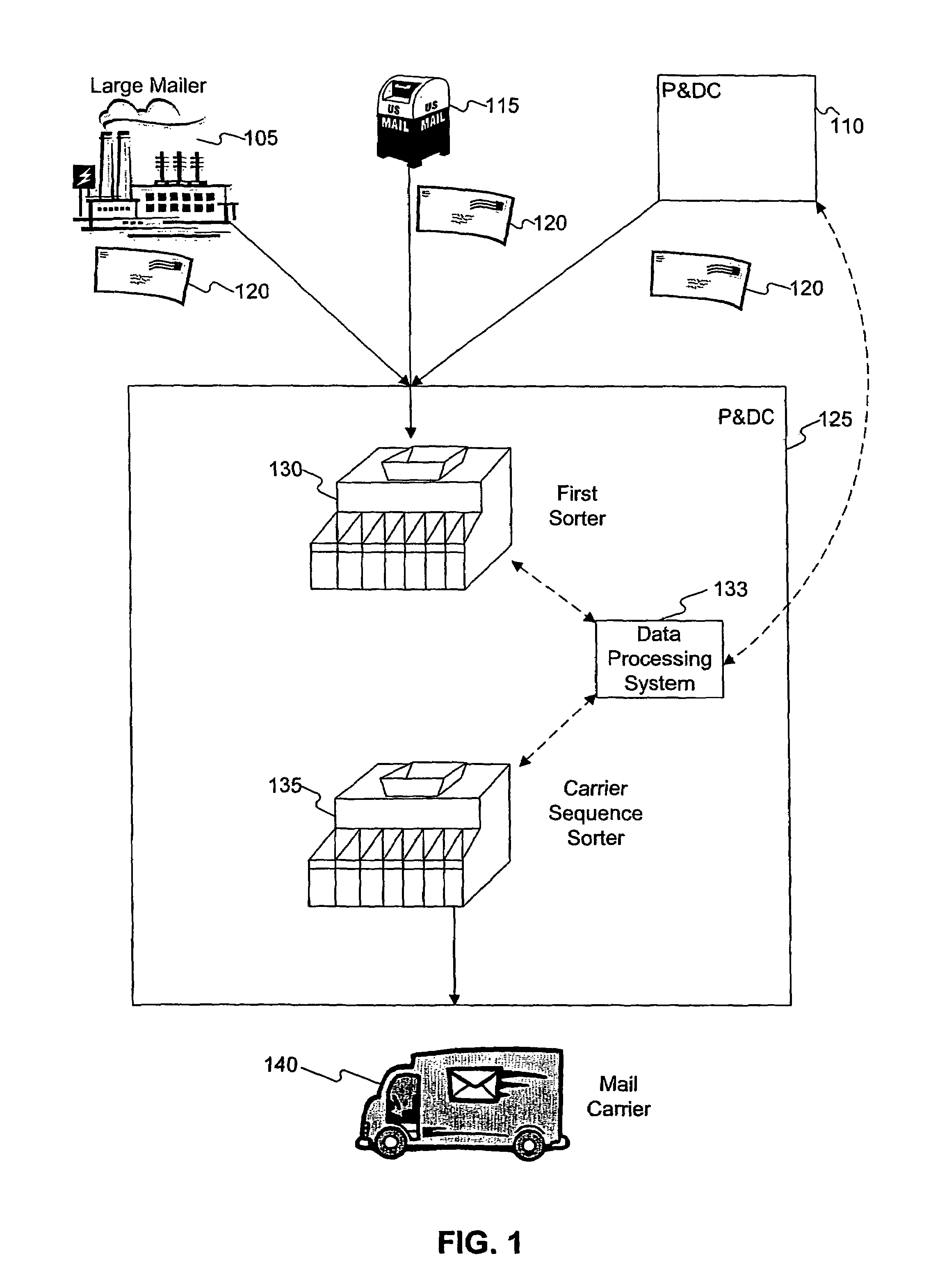
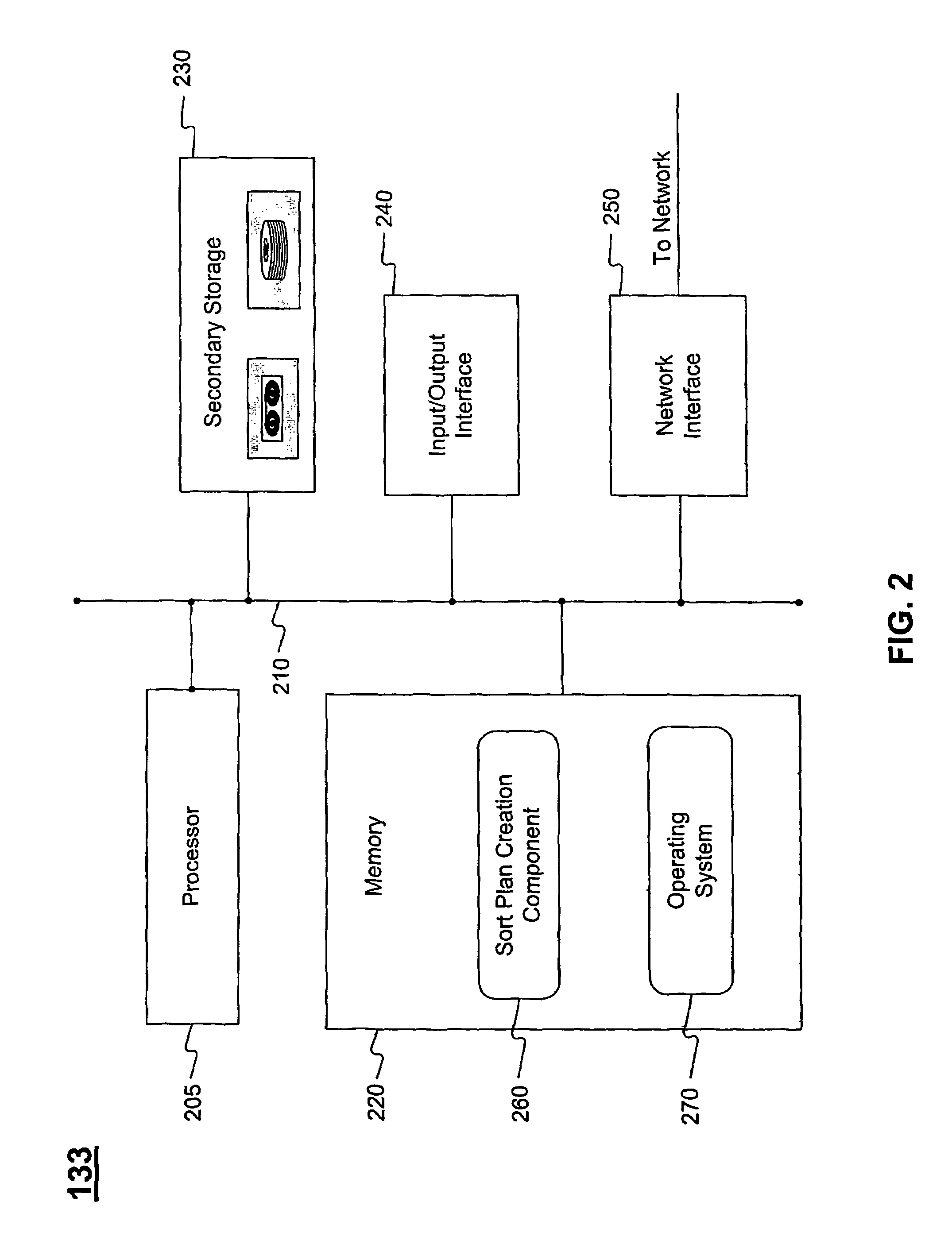
Just-in-time sort plan creation
InactiveUS7518080B2Separation devicesCharacter and pattern recognitionSequence processingProgram planning
Systems and methods are disclosed for creating a delivery sequence sort plan for automated sorting of mailpieces to a carrier sequence sorter. The delivery sequence sort plan is generated based on information about an incoming mail batch, such that the sort plan is created just prior to the delivery sequence processing of the incoming mail batch.
Owner:US POSTAL SERVICE
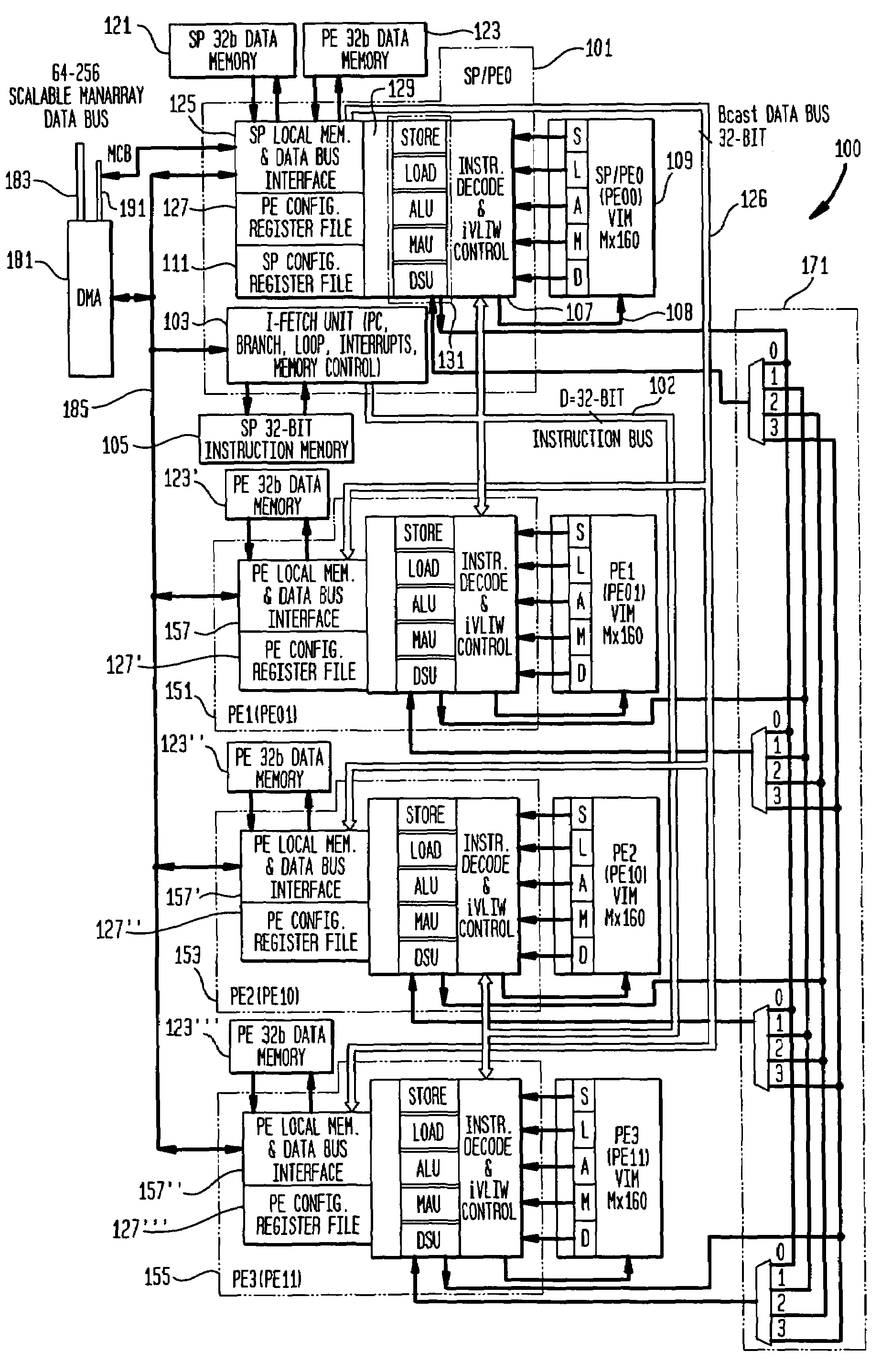
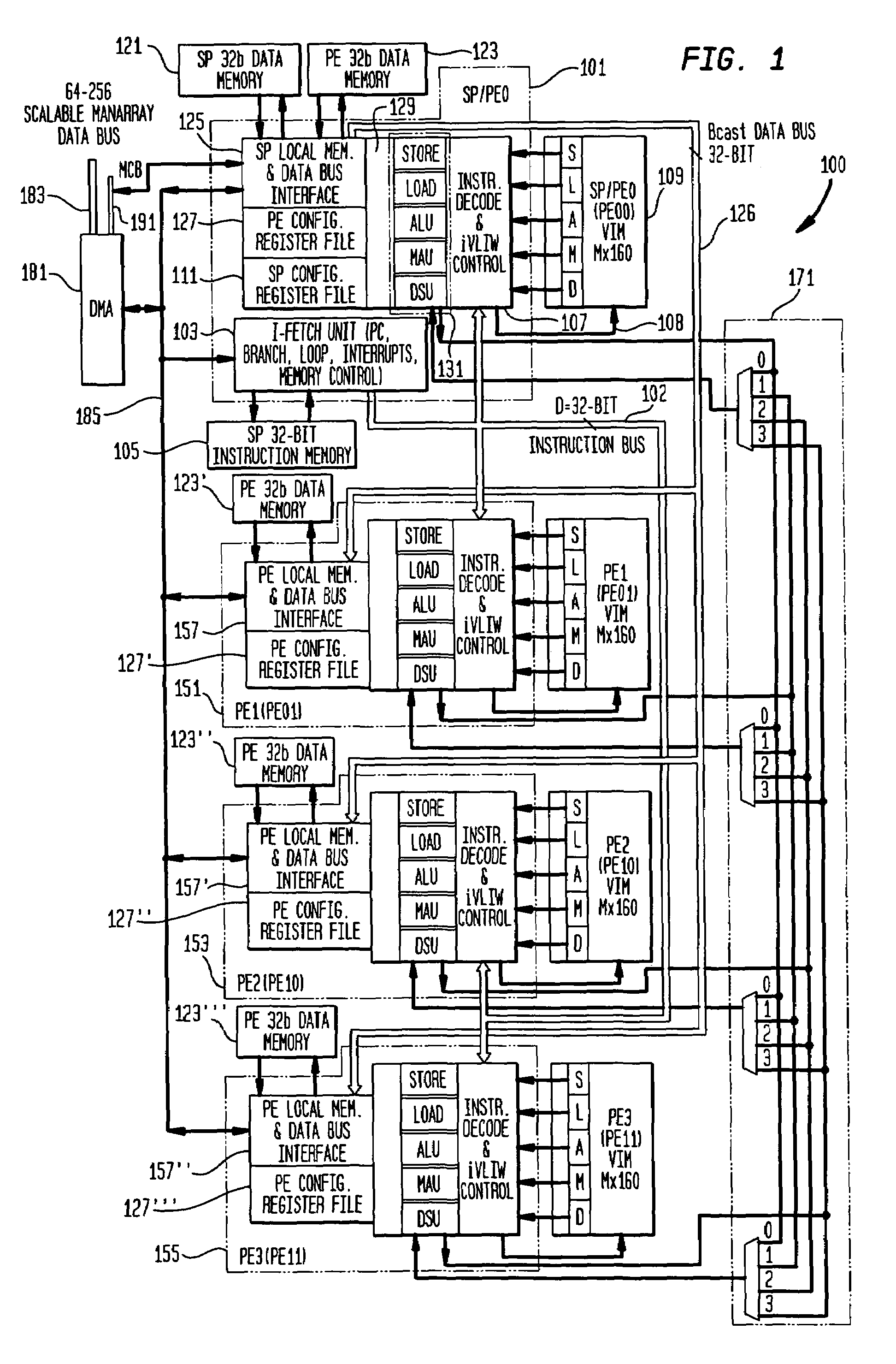
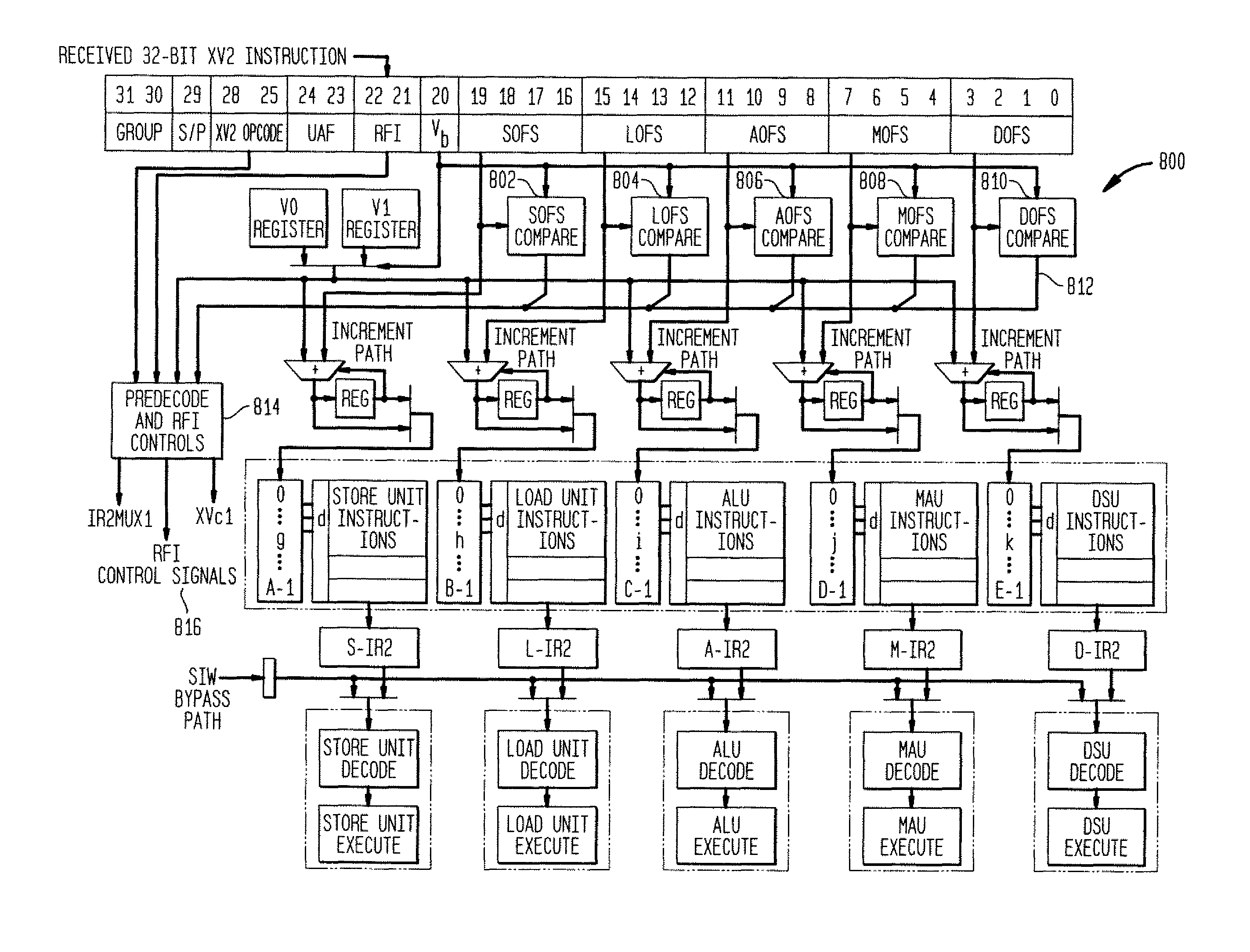
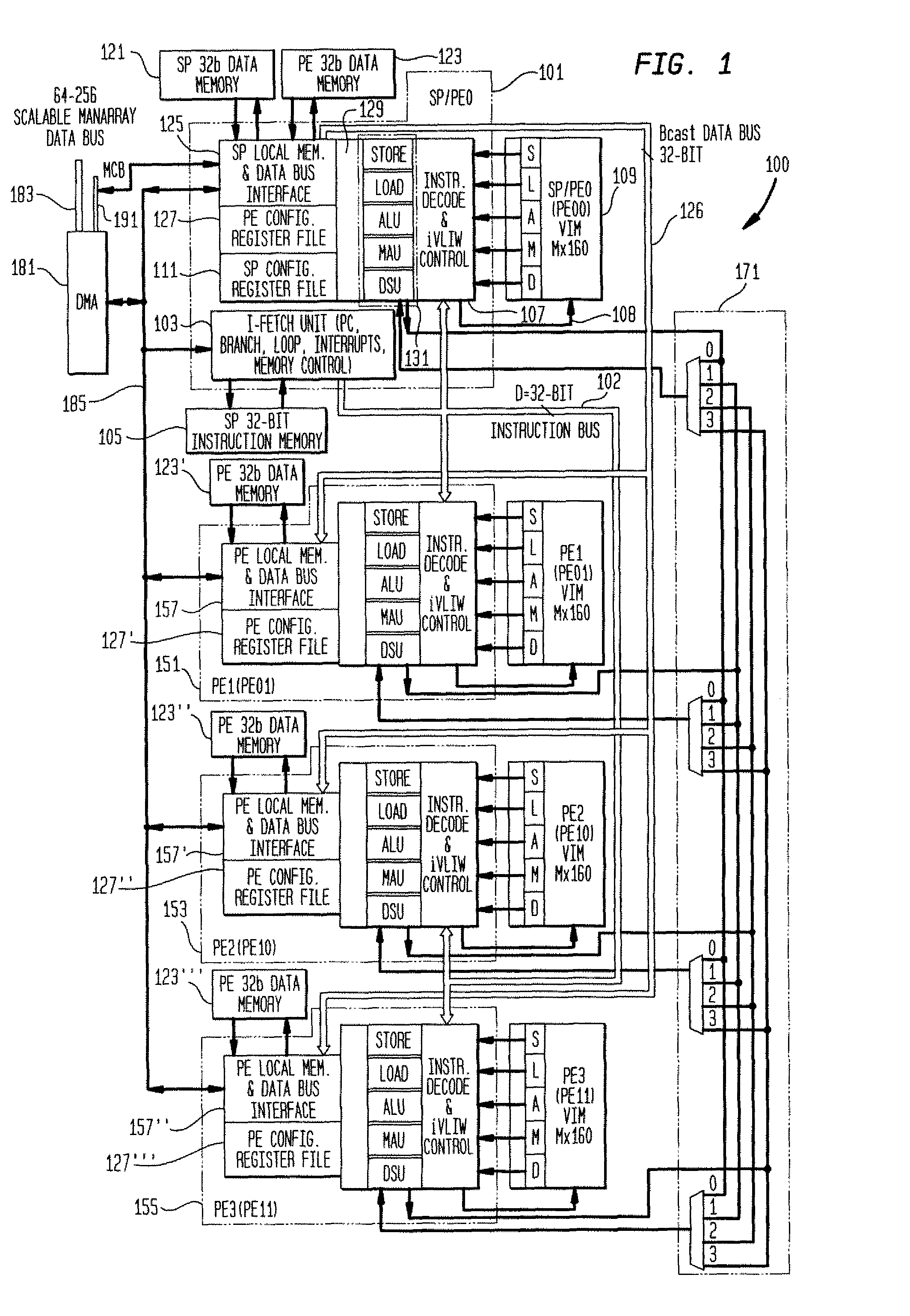
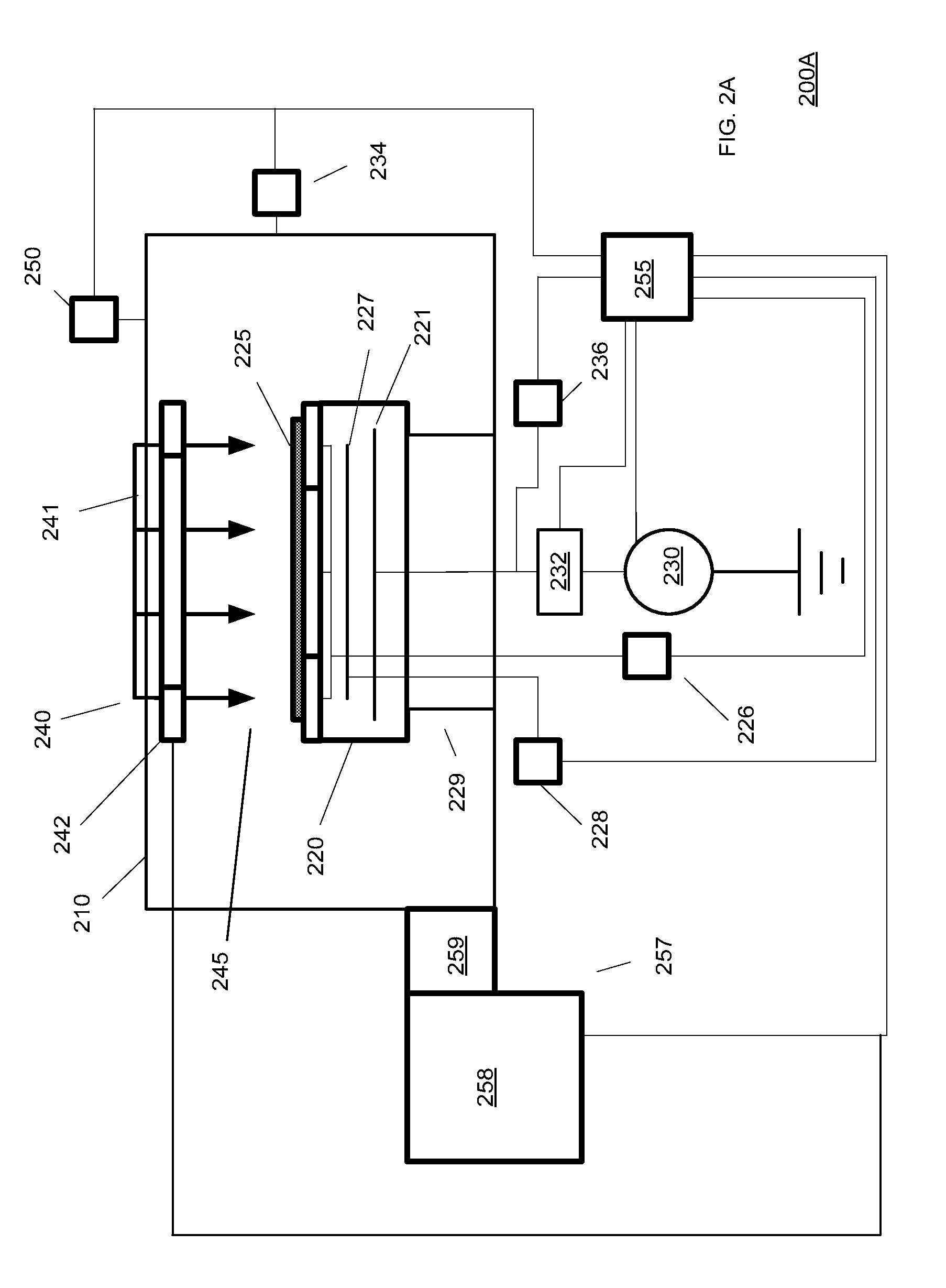
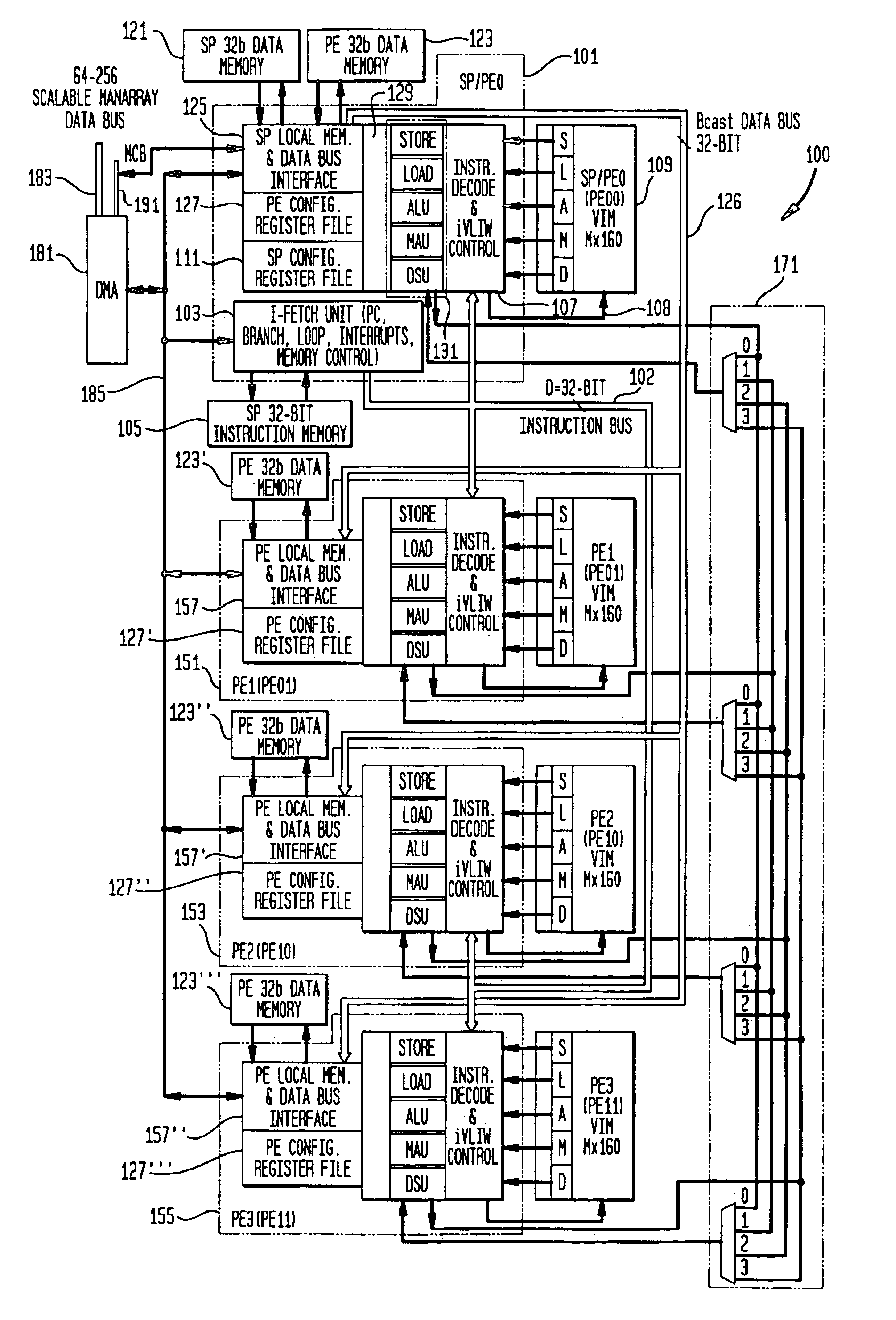
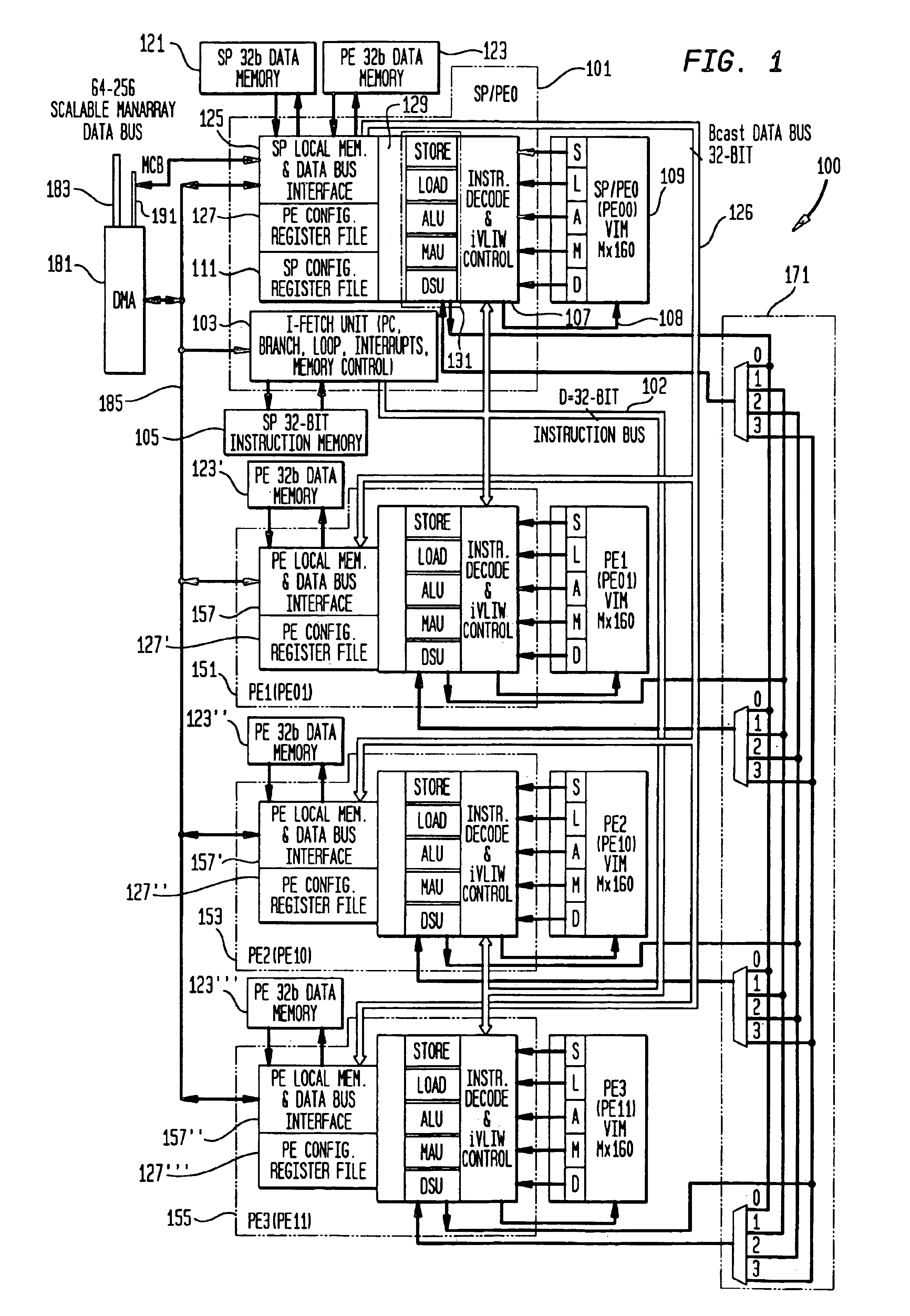
Methods and apparatus for power control in a scalable array of processor elements
InactiveUS7263624B2Reduce the required powerEnergy efficient ICTVolume/mass flow measurementSequence processingProcessor element
Low power architecture features and techniques are provided in a scalable array indirect VLIW processor. These features and techniques include power control of a reconfigurable register file, conditional power control of multi-cycle operations and indirect VLIW utilization, and power control of VLIW-based vector processing using the ManArray register file indexing mechanism. These techniques are applicable to all processing elements (PEs) and the array controller sequence processor (SP) to provide substantial power savings.
Owner:ALTERA CORP
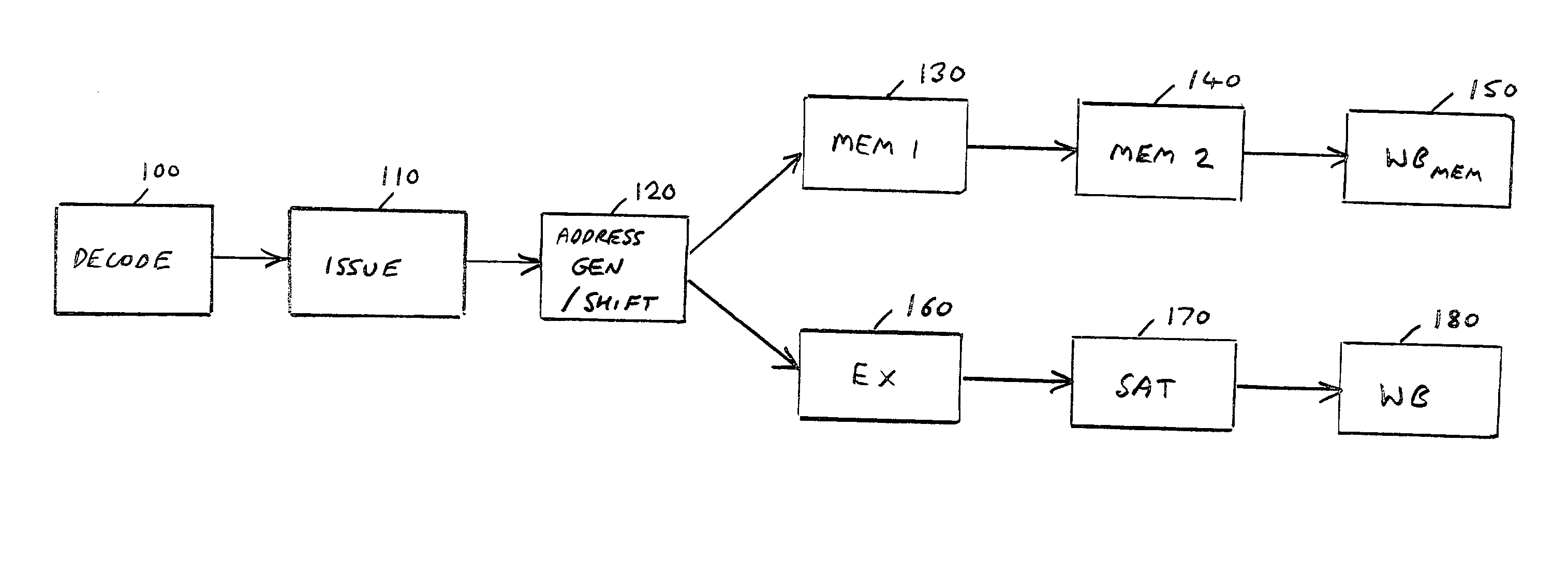
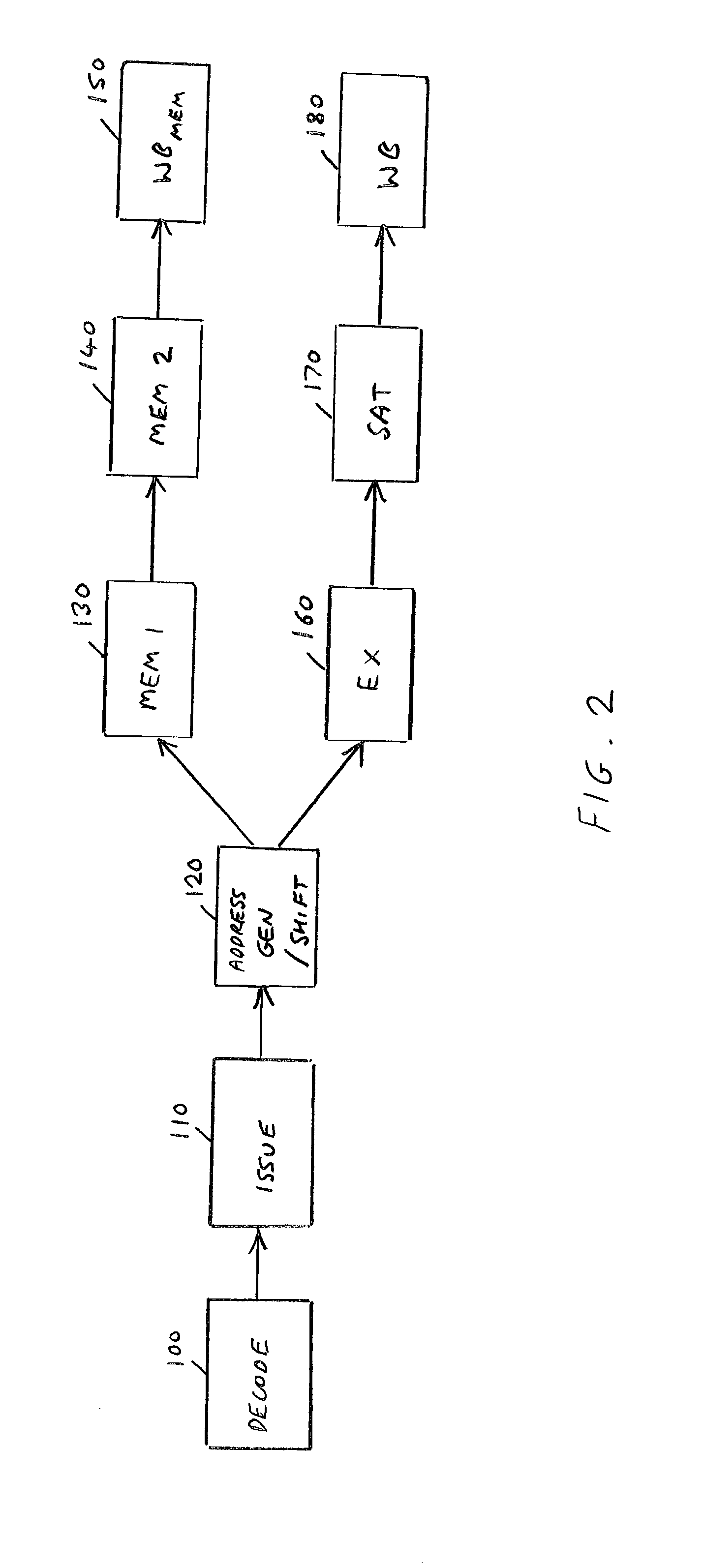
Synchronising pipelines in a data processing apparatus
ActiveUS20040054876A1Simple and efficient techniqueSmall sizeDigital computer detailsConcurrent instruction executionComputer hardwareSequence processing
The present invention provides an apparatus and method for synchronizing a first pipeline and a second pipeline of a processor arranged to execute a sequence of instructions. The processor is arranged to route an instruction in the sequence through either the first or the second pipeline dependent on predetermined criteria, each pipeline having a plurality of pipeline stages including a retirement stage. Counter logic is provided for maintaining a first counter relating to the first pipeline and a second counter relating to the second pipeline. For each instruction in the first pipeline a determination is made as to when that instruction reaches a point within the first pipeline where an exception status of that instruction is resolved, and the counter logic is arranged to increment the first counter responsive to such determination. The processor is arranged to generate an indication within the second pipeline each time an instruction is routed to the first pipeline, and the counter logic is further arranged to increment the second counter responsive to that indication. Synchronisation logic is then provided which is arranged, when an instruction is in the retirement stage of the second pipeline, to determine with reference to the values of the first and second counters whether that instruction can be retired. If so, the retirement stage is arranged to cause an update of a state of the data processing apparatus dependent on the result of execution of that instruction.
Owner:ARM LTD
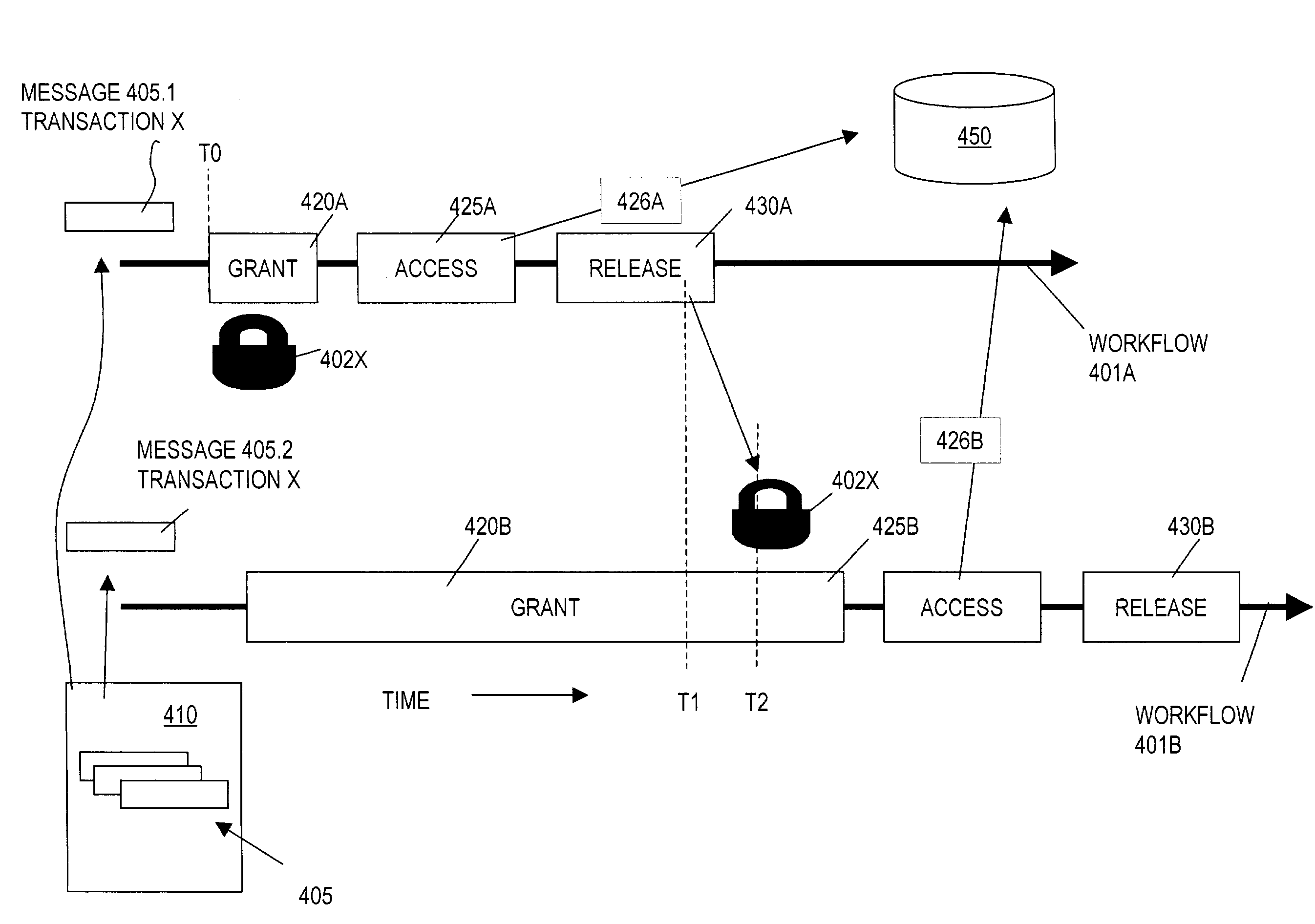
Method, apparatus and computer program product for managing message flow in a multithreaded, message flow environment
ActiveUS7401334B2Instruments for road network navigationError preventionMessage flowSequence processing
In one form, a method for managing message flow includes processing messages concurrently by processing nodes in a computer software application. The processing nodes include at least one set of lock acquisition, system resource access and lock release nodes interconnected in a flow path. In such a set, the nodes are interconnected in a flow path and process a respective one of the messages in a sequence defined by the flow path. The processing includes granting access to a system resource exclusively for the set's respective message responsive to the lock acquisition node processing its respective message. The system resource is accessed for the message responsive to the set's system resource node processing the message. The accessing of the resource for the message includes changing a certain system state. The exclusive accessing of the system resource is released responsive to the set's lock release node processing the message.
Owner:META PLATFORMS INC
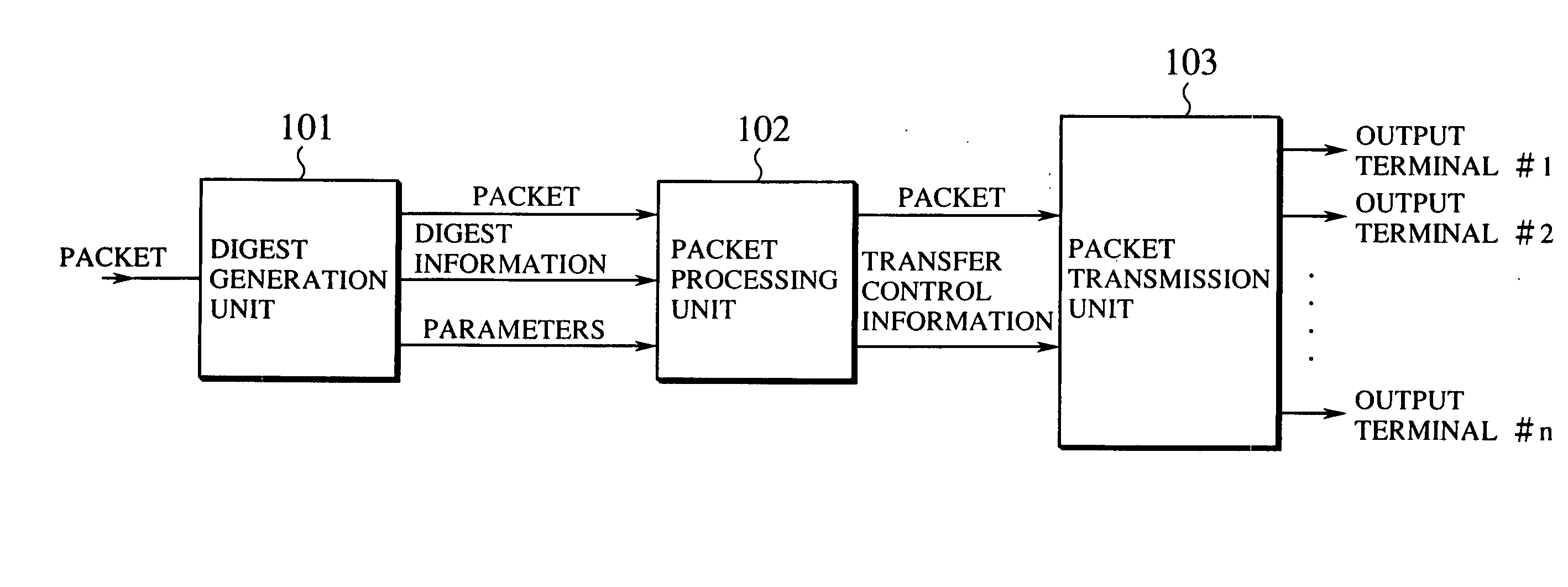
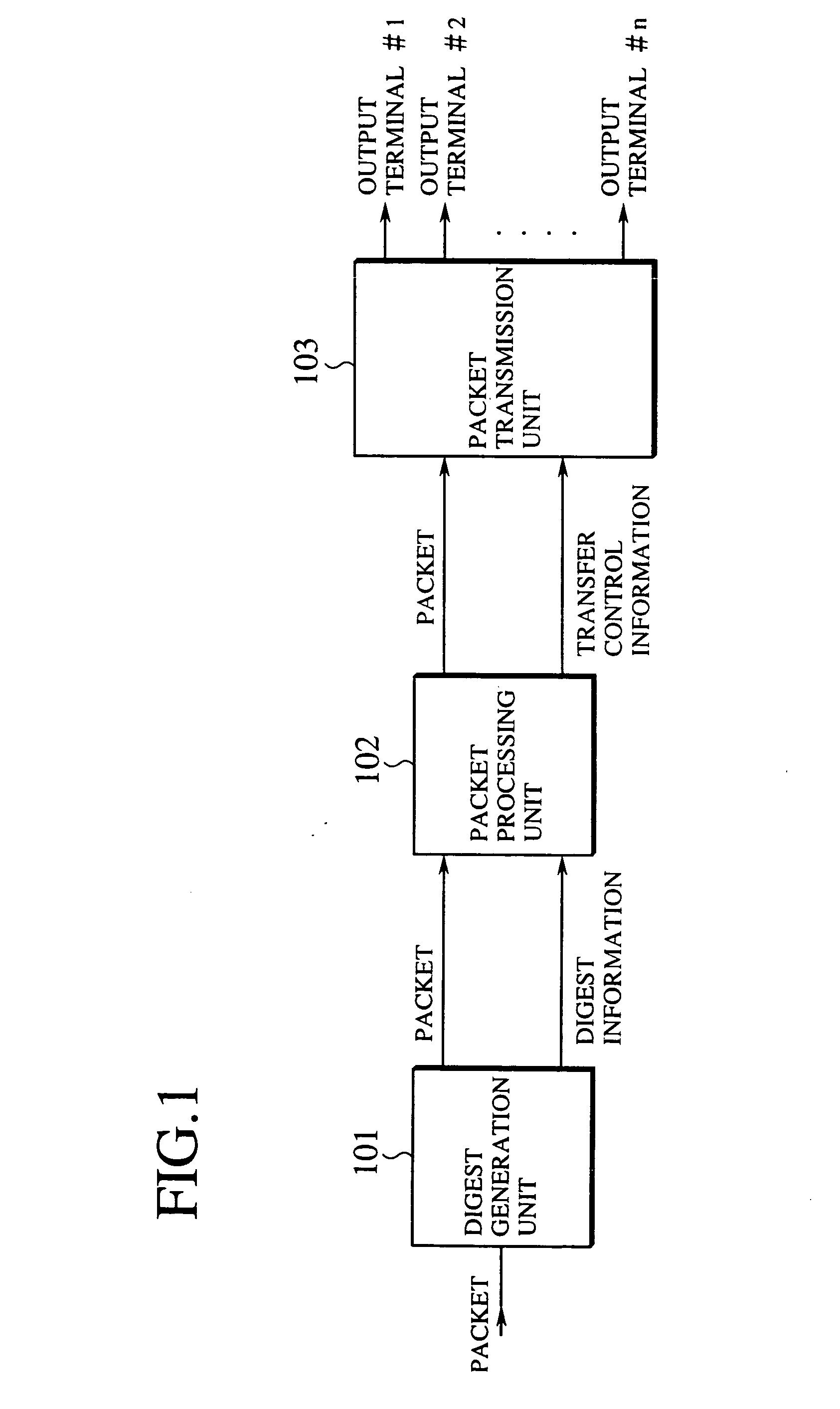
Fast and adaptive packet processing device and method using digest information of input packet
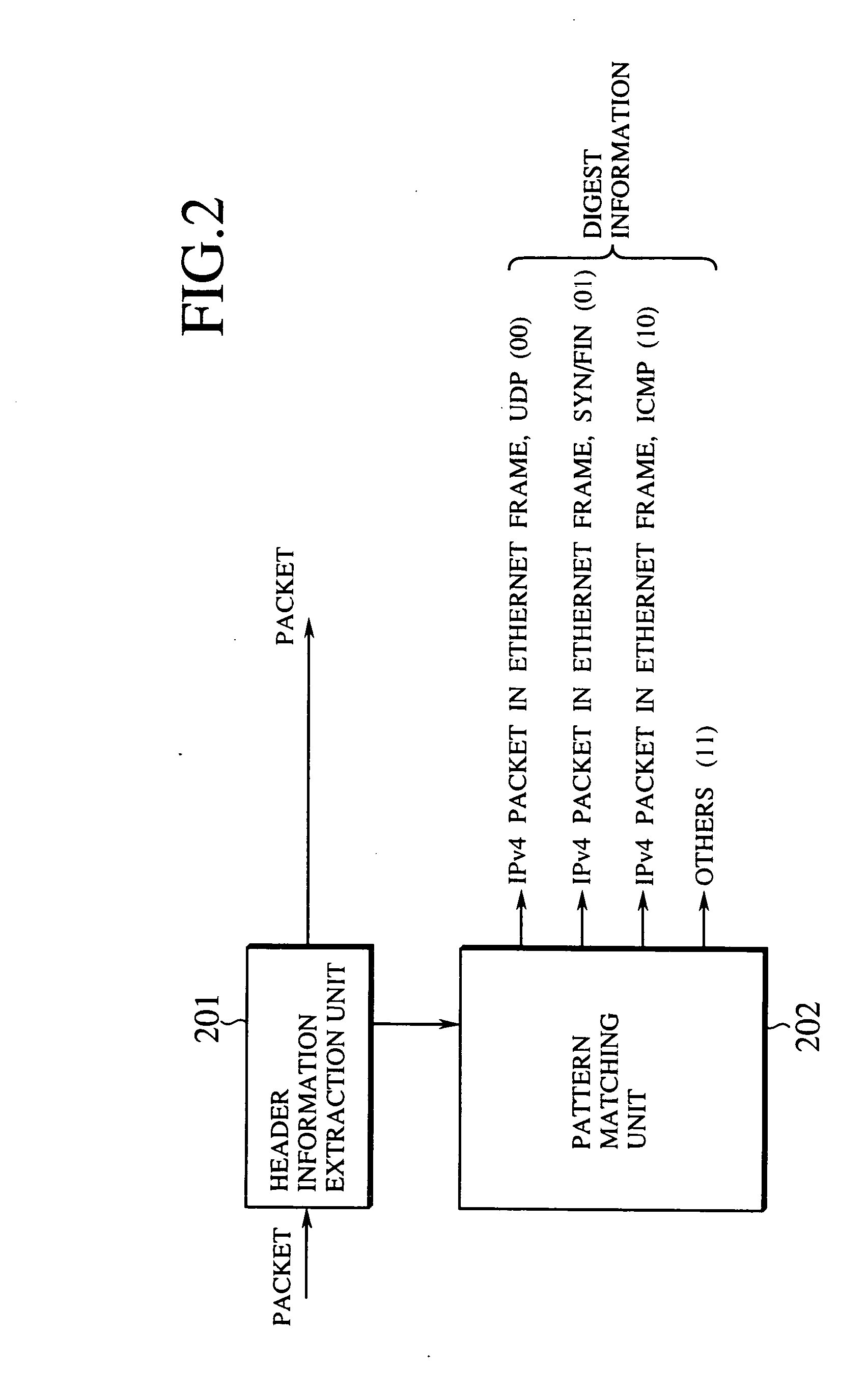
InactiveUS20050086353A1Improve adaptabilityEasy to handleOperational speed enhancementMultiple digital computer combinationsSequence processingInstruction sequence
A packet processing device is formed by a digest information generation unit configured to extract a plurality of prescribed bit sequences from an input packet, and generate a digest information capable of specifying at least a part of a processing to be applied to the input packet, according to values of the plurality of prescribed bit sequences; and a packet processing unit configured to process the input packet using an instruction sequence to be applied to the input packet that is obtained according to the digest information generated by the digest information generation unit, where the digest information generation unit generates the digest information with respect to a next input packet while the packet processing unit carries out a processing for one packet.
Owner:KK TOSHIBA
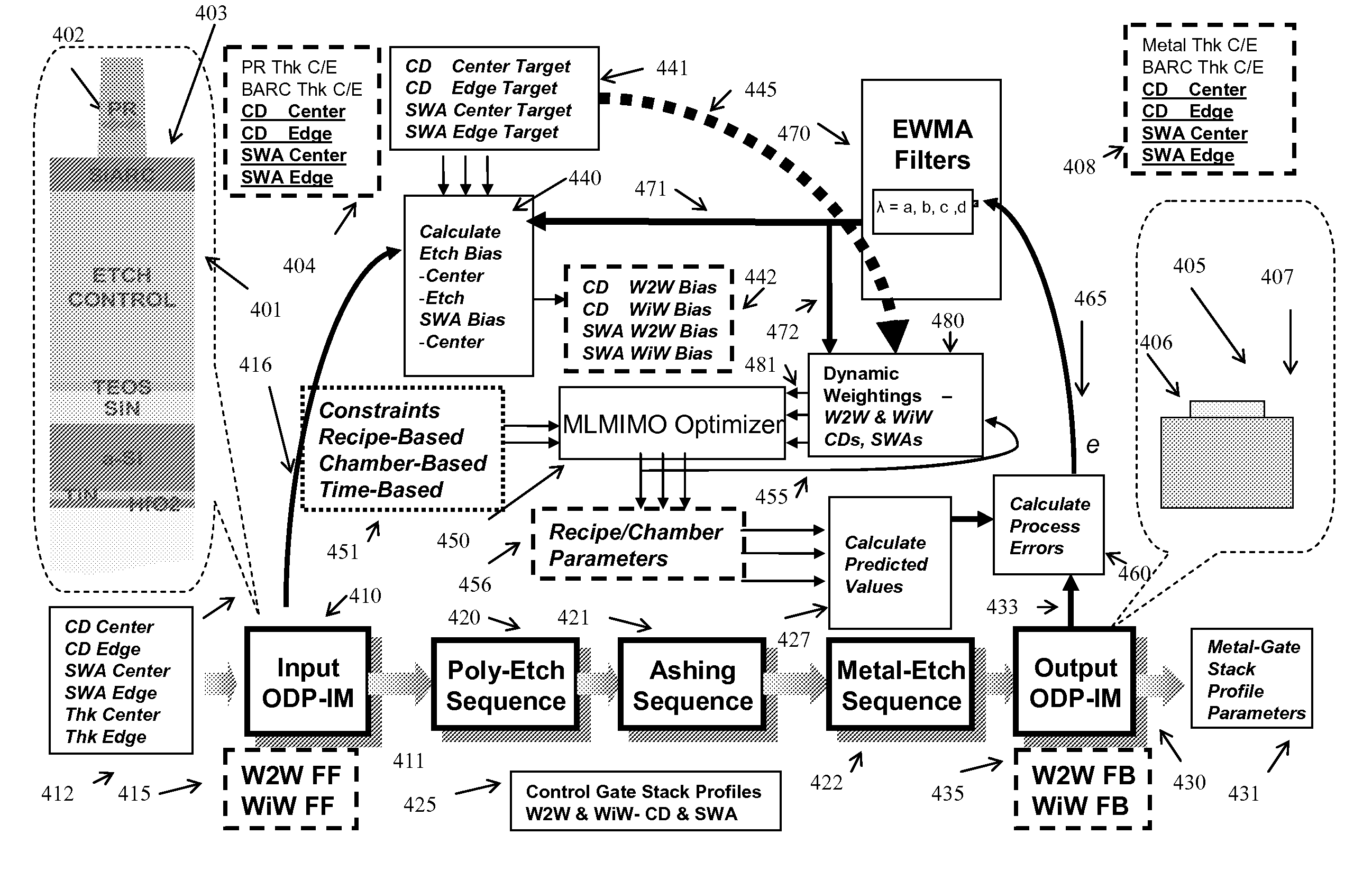
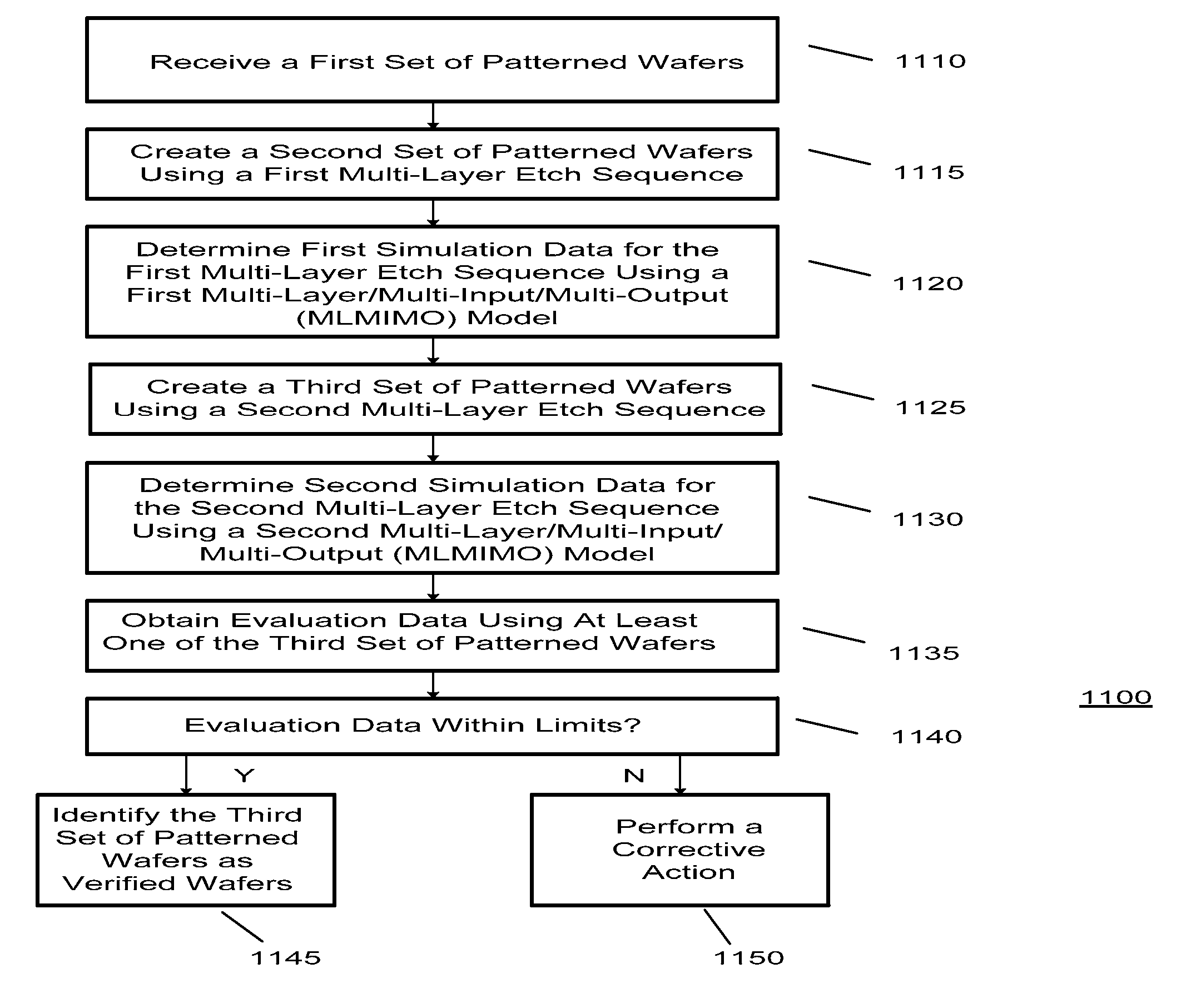
Using Multi-Layer/Multi-Input/Multi-Output (MLMIMO) Models for Metal-Gate Structures
InactiveUS20100036518A1Semiconductor/solid-state device testing/measurementSolid-state devicesMulti inputSequence processing
The invention provides a method of processing a wafer using multilayer processing sequences and Multi-Layer / Multi-Input / Multi-Output (MLMIMO) models and libraries that can include one or more measurement procedures, one or more Poly-Etch (P-E) sequences, and one or more metal-gate etch sequences. The MLMIMO process control uses dynamically interacting behavioral modeling between multiple layers and / or multiple process steps. The multiple layers and / or the multiple process steps can be associated with the creation of lines, trenches, vias, spacers, contacts, and gate structures that can be created using isotropic and / or anisotropic etch processes.
Owner:TOKYO ELECTRON LTD
Methods and apparatus for power control in a scalable array of processor elements
InactiveUS7836317B2Reduce the required powerEnergy efficient ICTRegister arrangementsSequence processingProcessor element
Low power architecture features and techniques are provided in a scalable array indirect VLIW processor. These features and techniques include power control of a reconfigurable register file, conditional power control of multi-cycle operations and indirect VLIW utilization, and power control of VLIW-based vector processing using the ManArray register file indexing mechanism. These techniques are applicable to all processing elements (PEs) and the array controller sequence processor (SP) to provide substantial power savings.
Owner:ALTERA CORP
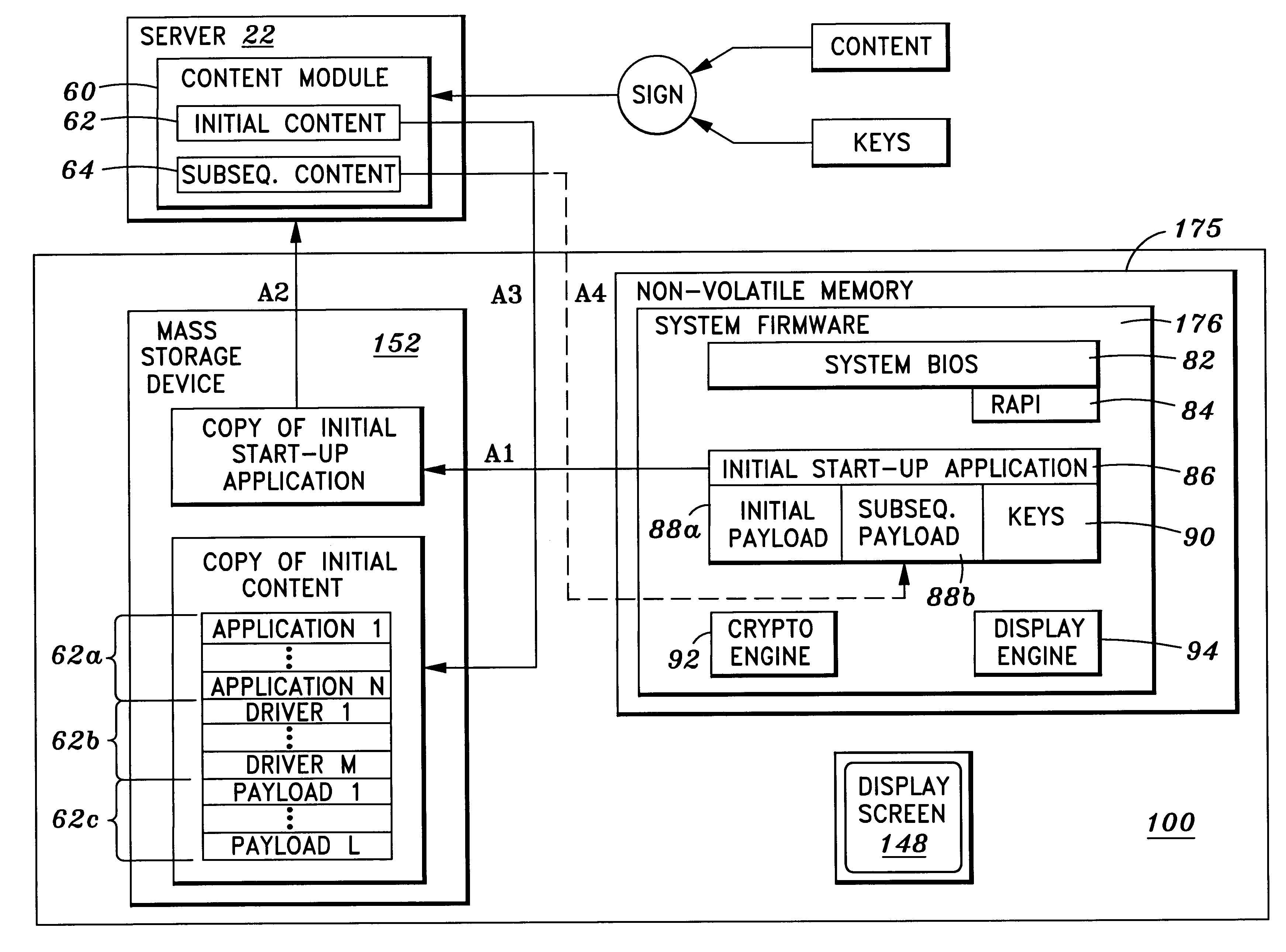
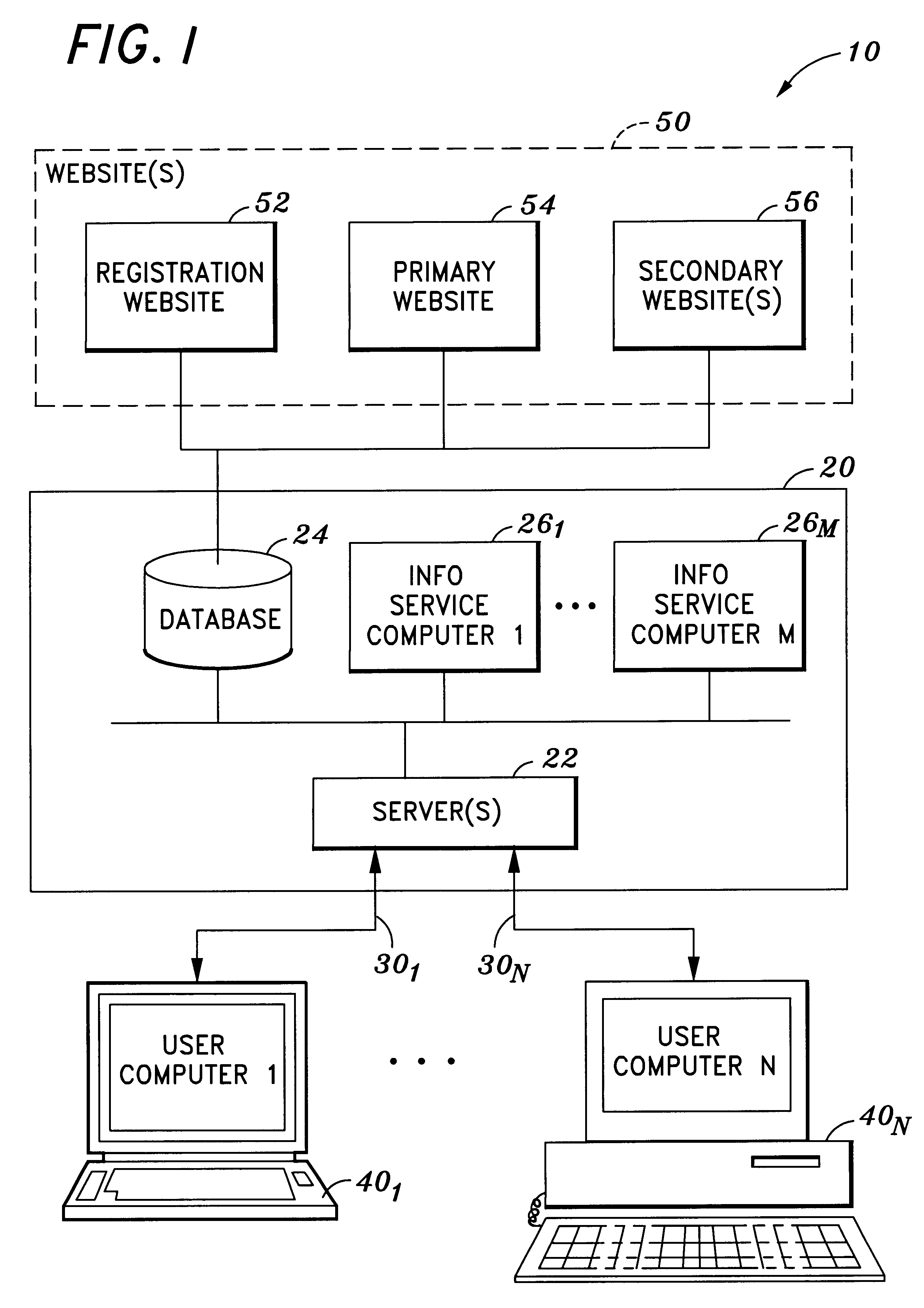
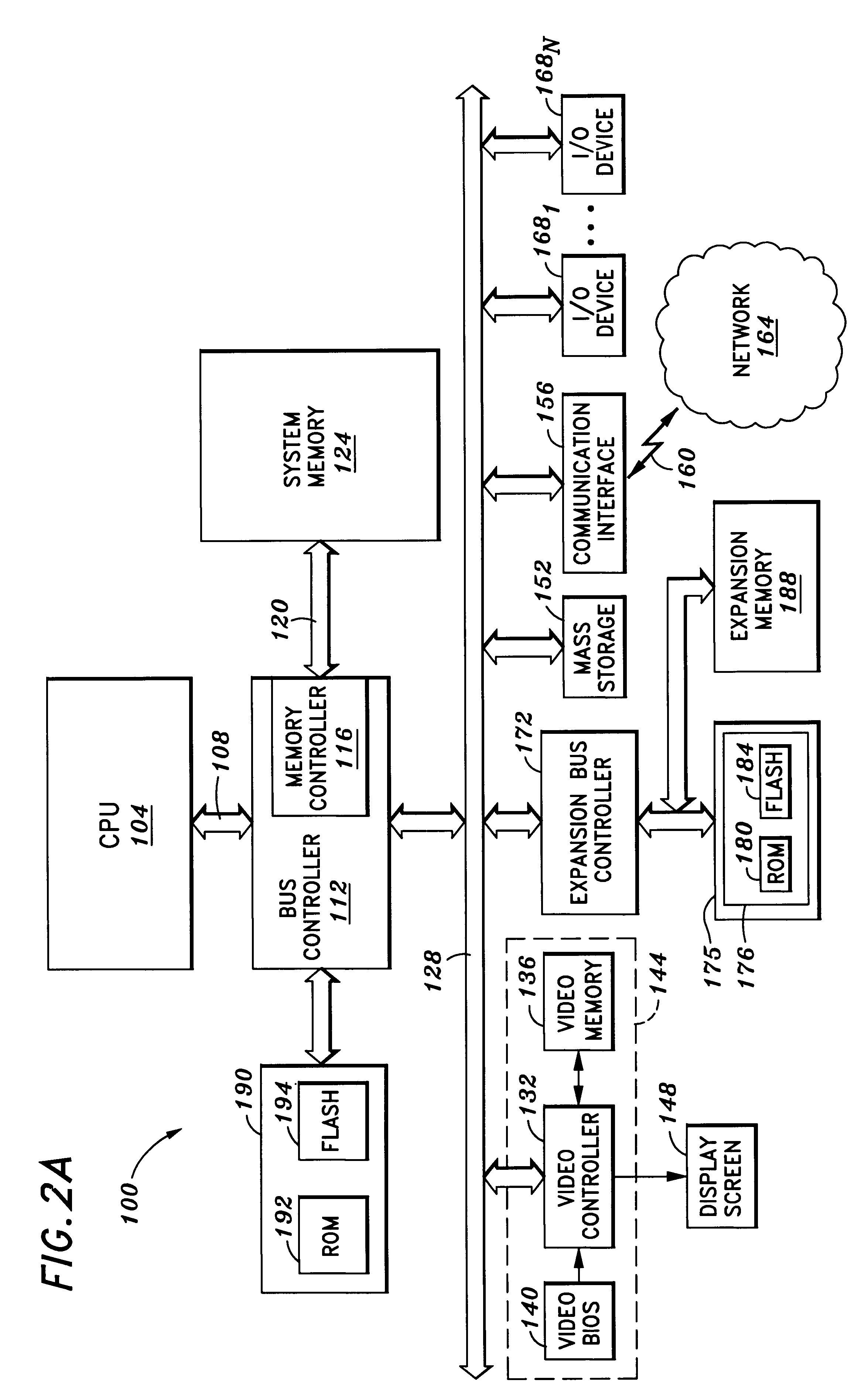
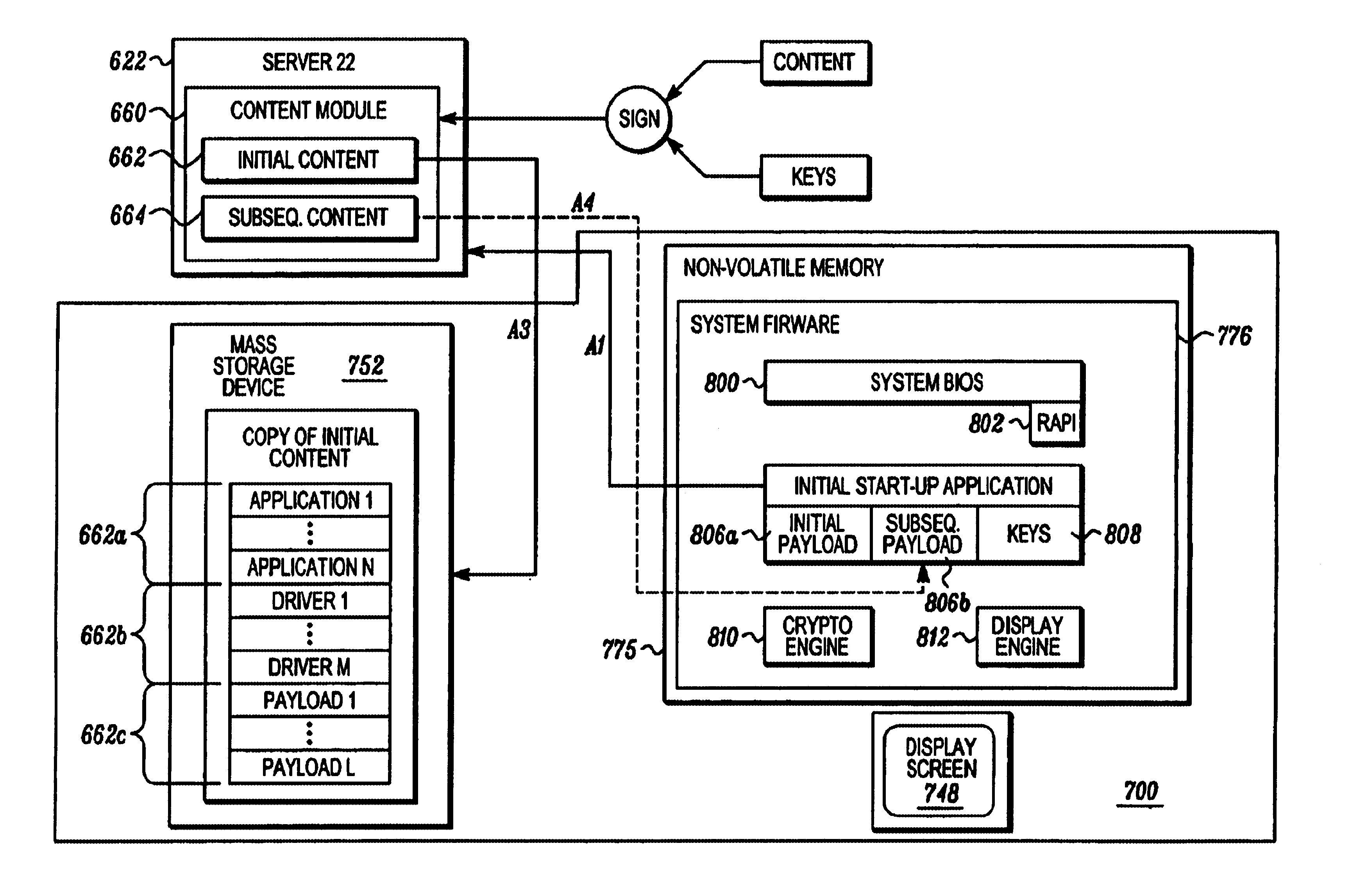
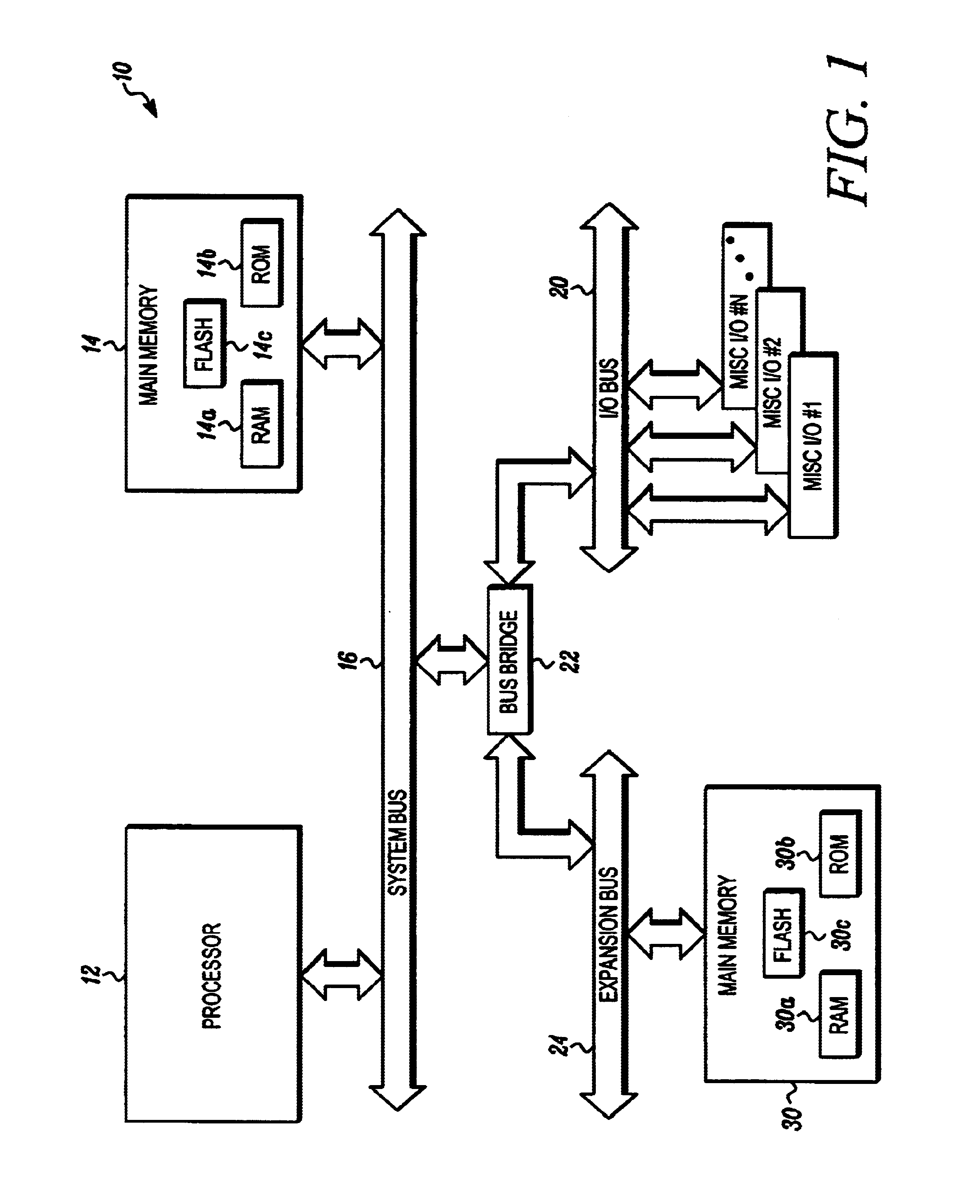
Method and system for transferring an application program from system firmware to a storage device
InactiveUS6519659B1Program control using stored programsDigital computer detailsSequence processingOperational system
One aspect of the invention is a method and system for accessing at least one storage element in a processor-based system. The system comprises a memory for storing instruction sequences by which the processor-based system is processed. The memory has at least one storage element. A processor is coupled to the memory, and a storage device is coupled to the processor. Prior to booting an operating system on the processor-based system, the stored instruction sequences cause the processor to write the contents of the at least one storage element to the storage device. Another aspect of the invention relates to a computer system having a user computer in communication with a remote service computer. The remote service computer has access to a database identifying information available to the service computer. A computer implemented method for transferring information to the user computer, comprises: writing the contents of at least one storage element to a storage device on the user computer prior to booting an operating system on the user computer, establishing a communications link between the user computer and the service computer, and presenting at the user computer, information available to the user computer.
Owner:KINGLITE HLDG INC
Method and system for providing memory-based device emulation
InactiveUS6715043B1Input/output to record carriersMemory adressing/allocation/relocationSequence processingInstruction sequence
The present invention is a method and system for accessing at least one emulated readable storage in a processor-based system. The system comprises a memory for storing instruction sequences by which the processor-based system is processed. The memory has at least one readable emulated storage location. A processor is coupled to the memory, and the stored instruction sequences cause the processor to (a) detect an access to at least one readable storage element; (b) transfer the access to the at least one readable storage element to an access to at least one readable emulated storage location; and (c) process an instruction sequence corresponding to the access to the at least one readable storage element.
Owner:PEGATRON
Implicit signalling in OFDM preamble with embedded signature sequence, and cyclic prefix and postfix aided signature detection
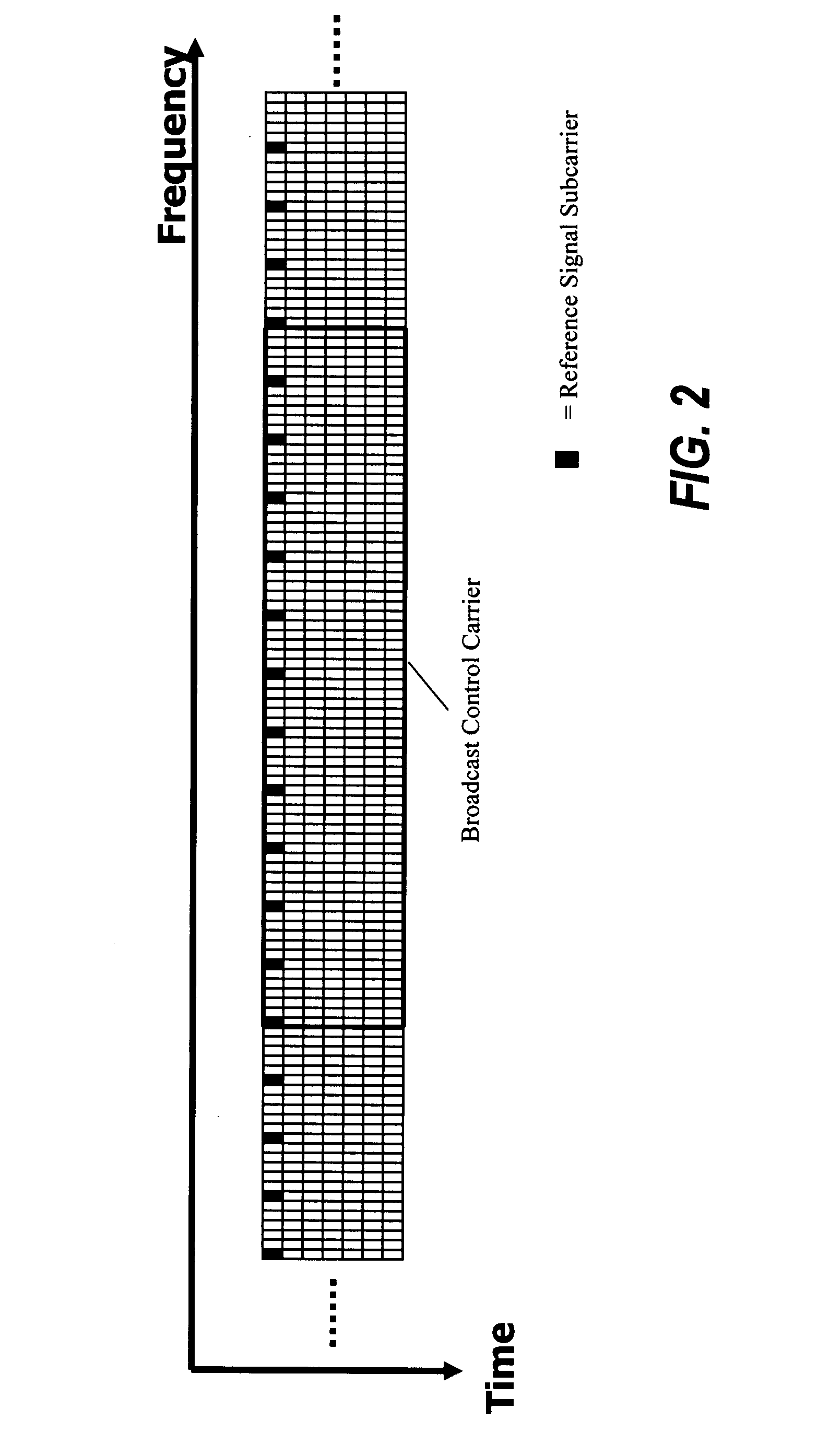
ActiveUS20160142237A1Reduce processReduce processing timeSecret communicationMulti-frequency code systemsTime domainCyclic prefix
A transmitter transmitting payload data using Orthogonal Frequency Division Multiplexed (OFDM) symbols, including: a frame builder configured to receive the payload data and to receive signalling data to use in detecting and recovering the payload data at a receiver, and to form the payload data with the signalling data into frames for transmission; a modulator configured to modulate a first OFDM symbol with the signalling data and to modulate one or more second OFDM symbols with the payload data; a signature sequence processor circuit providing a signature sequence; a combiner circuit combining the signature sequence with the first OFDM symbol; a prefixing circuit prefixing a guard interval to the first OFDM symbol to form a preamble; and a transmission circuit transmitting the preamble and the one or more second OFDM symbols. The guard interval is formed from time domain samples of a part of the signature sequence.
Owner:SATURN LICENSING LLC
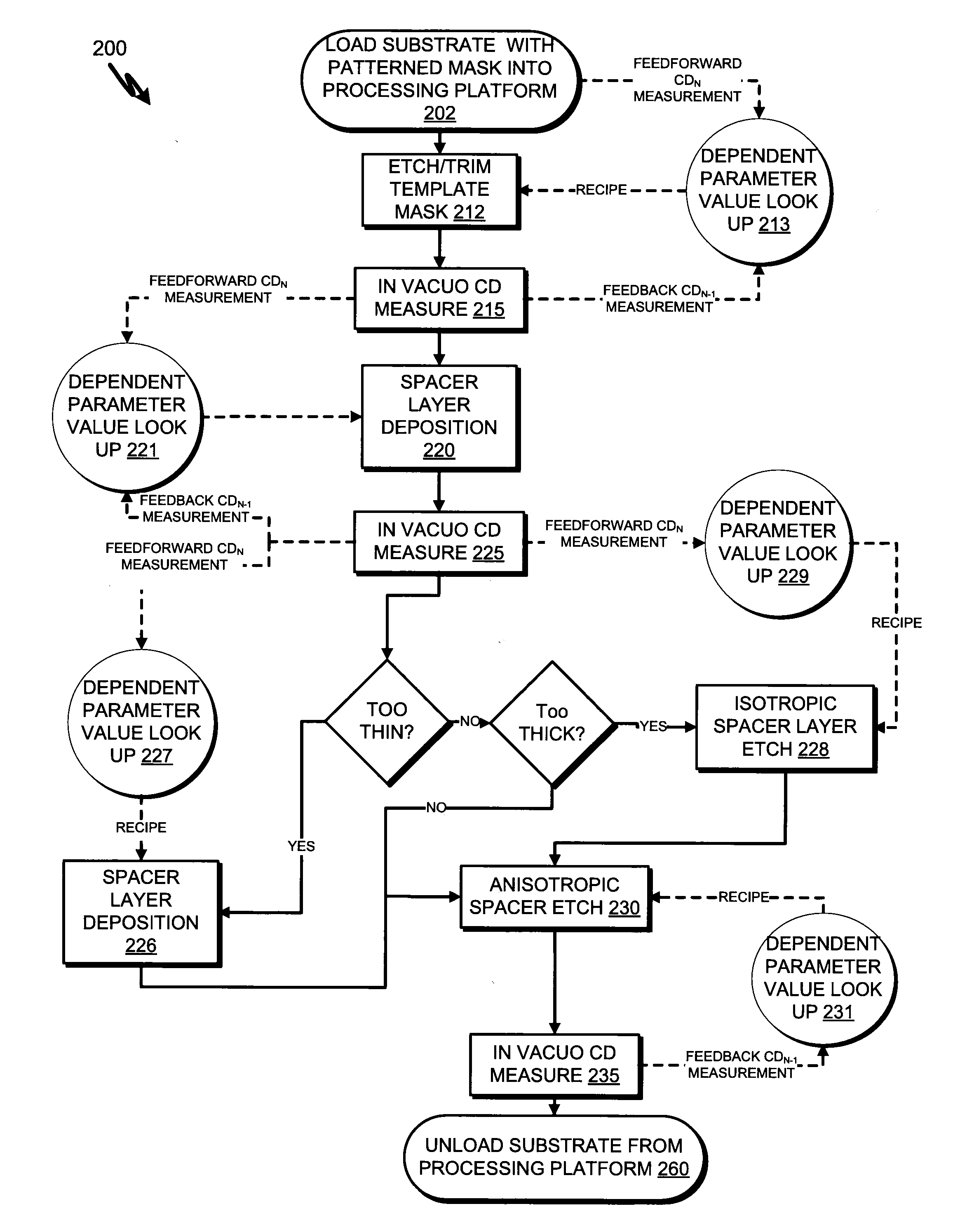
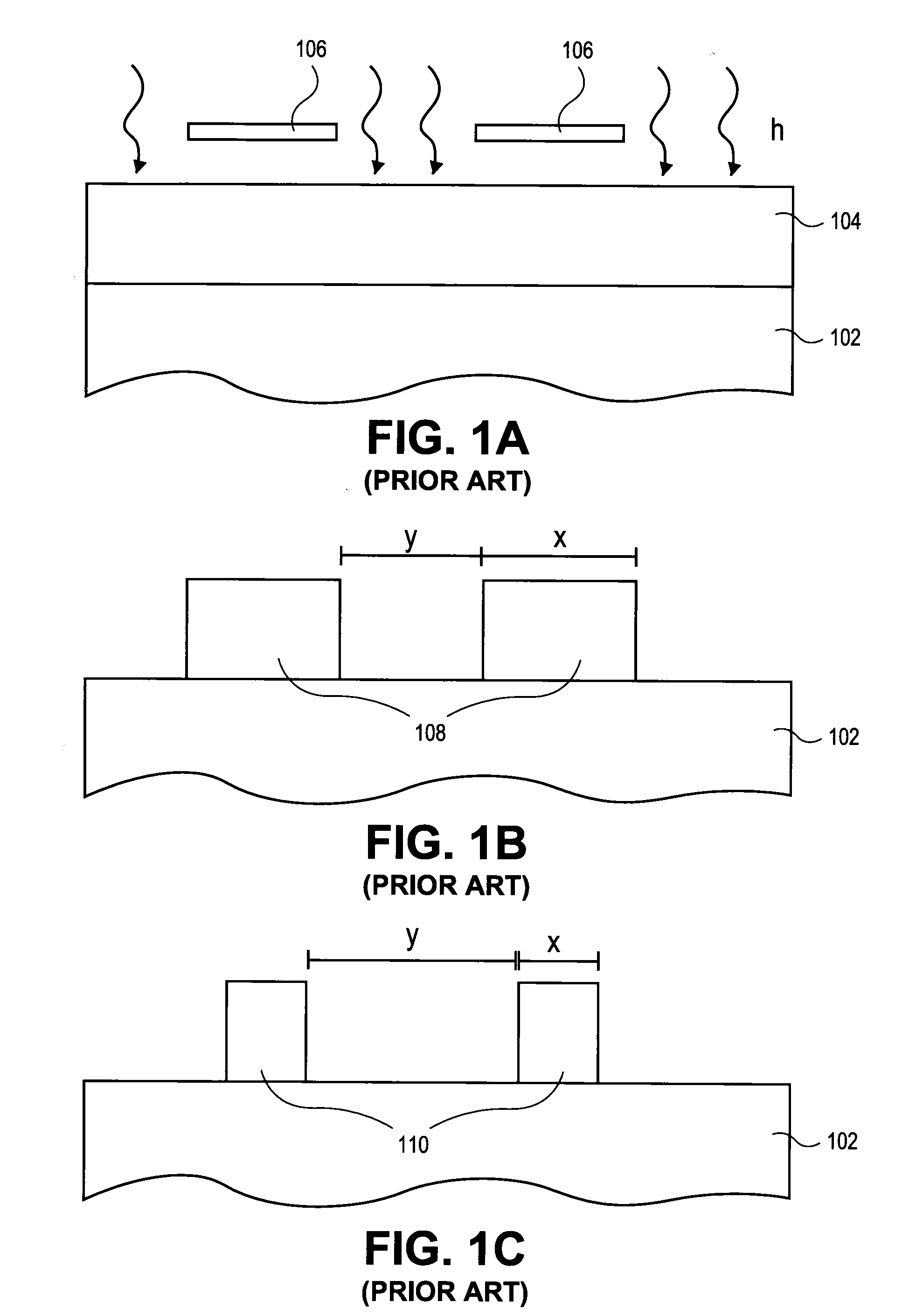
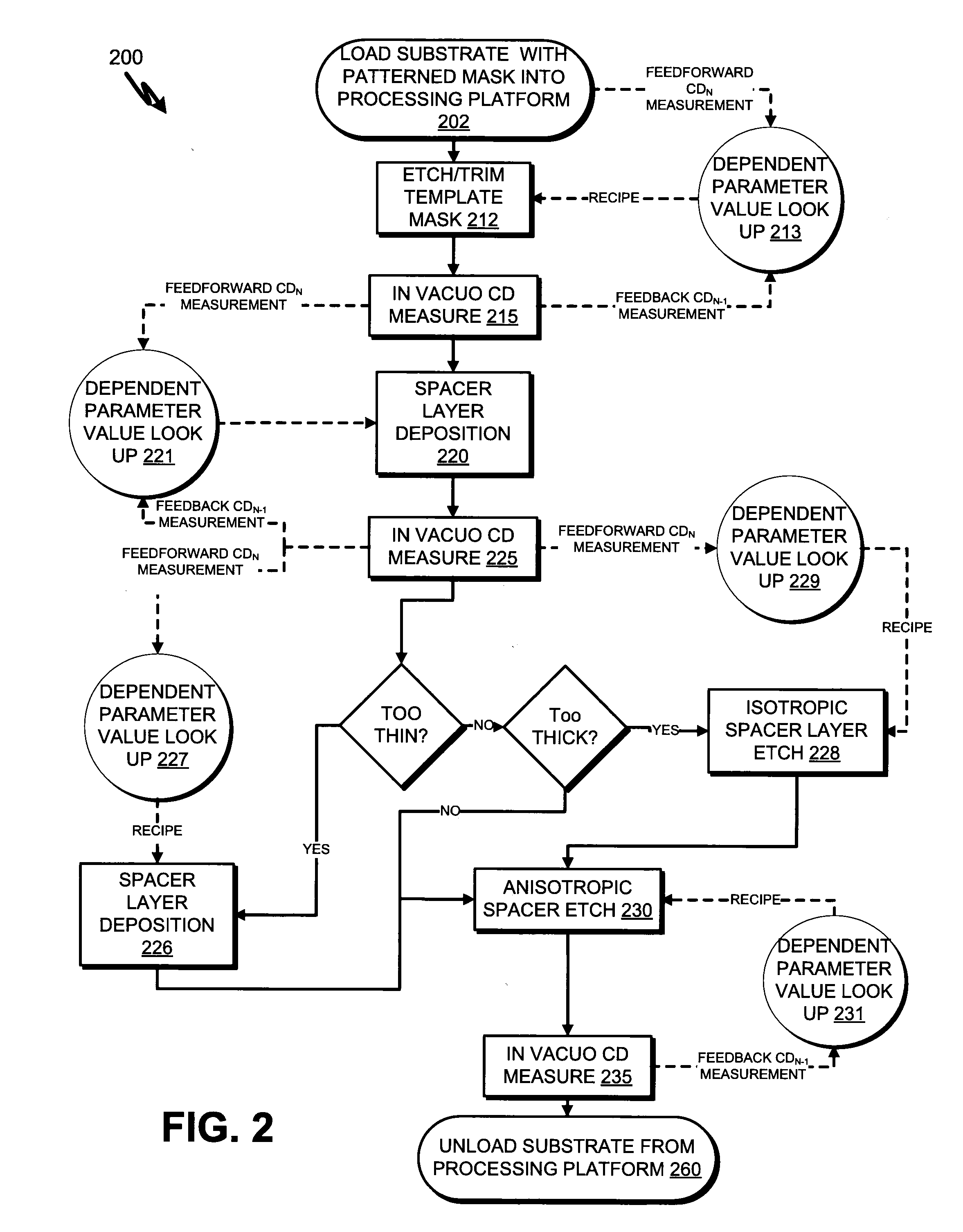
Within-sequence metrology based process tuning for adaptive self-aligned double patterning
InactiveUS20100009470A1Semiconductor/solid-state device testing/measurementVacuum gauge using ionisation effectsSequence processingMetrology
An apparatus for adaptive self-aligned dual patterning and method thereof. The method includes providing a substrate to a processing platform configured to perform an etch process and a deposition process and a metrology unit configured for in-vacuo critical dimension (CD) measurement. The in-vacuo CD measurement is utilized for feedforward adaptive control of the process sequence processing platform or for feedback and feedforward adaptive control of chamber process parameters. In one aspect, a first layer of a multi-layered masking stack is etched to form a template mask, an in-vacuo CD measurement of the template mask is made, and a spacer is formed, adjacent to the template mask, to a width that is dependent on the CD measurement of the template mask.
Owner:APPLIED MATERIALS INC
Interaction of transactional storage accesses with other atomic semantics
InactiveUS20140047205A1Unauthorized memory use protectionInput/output processes for data processingProgramming languageSequence processing
In a processor, an instruction sequence including, in order, a load-and-reserve instruction specifying a read access to a target memory block, an instruction delimiting transactional memory access instructions belonging to a memory transaction, and a store-conditional instruction specifying a conditional write access to the target memory block is detected. In response to detecting the instruction sequence, the processor causes the conditional write access to the target memory block to fail.
Owner:IBM CORP
Creating Multi-Layer/Multi-Input/Multi-Output (MLMIMO) Models for Metal-Gate Structures
ActiveUS20100036514A1Polycrystalline material growthSemiconductor/solid-state device testing/measurementMulti inputSequence processing
The invention provides a method of processing a wafer using multilayer processing sequences and Multi-Layer / Multi-Input / Multi-Output (MLMIMO) models and libraries that can include one or more measurement procedures, one or more Poly-Etch (P-E) sequences, and one or more metal-gate etch sequences. The MLMIMO process control uses dynamically interacting behavioral modeling between multiple layers and / or multiple process steps. The multiple layers and / or the multiple process steps can be associated with the creation of lines, trenches, vias, spacers, contacts, and gate structures that can be created using isotropic and / or anisotropic etch processes.
Owner:TOKYO ELECTRON LTD
Automated network attack characteristic generation method
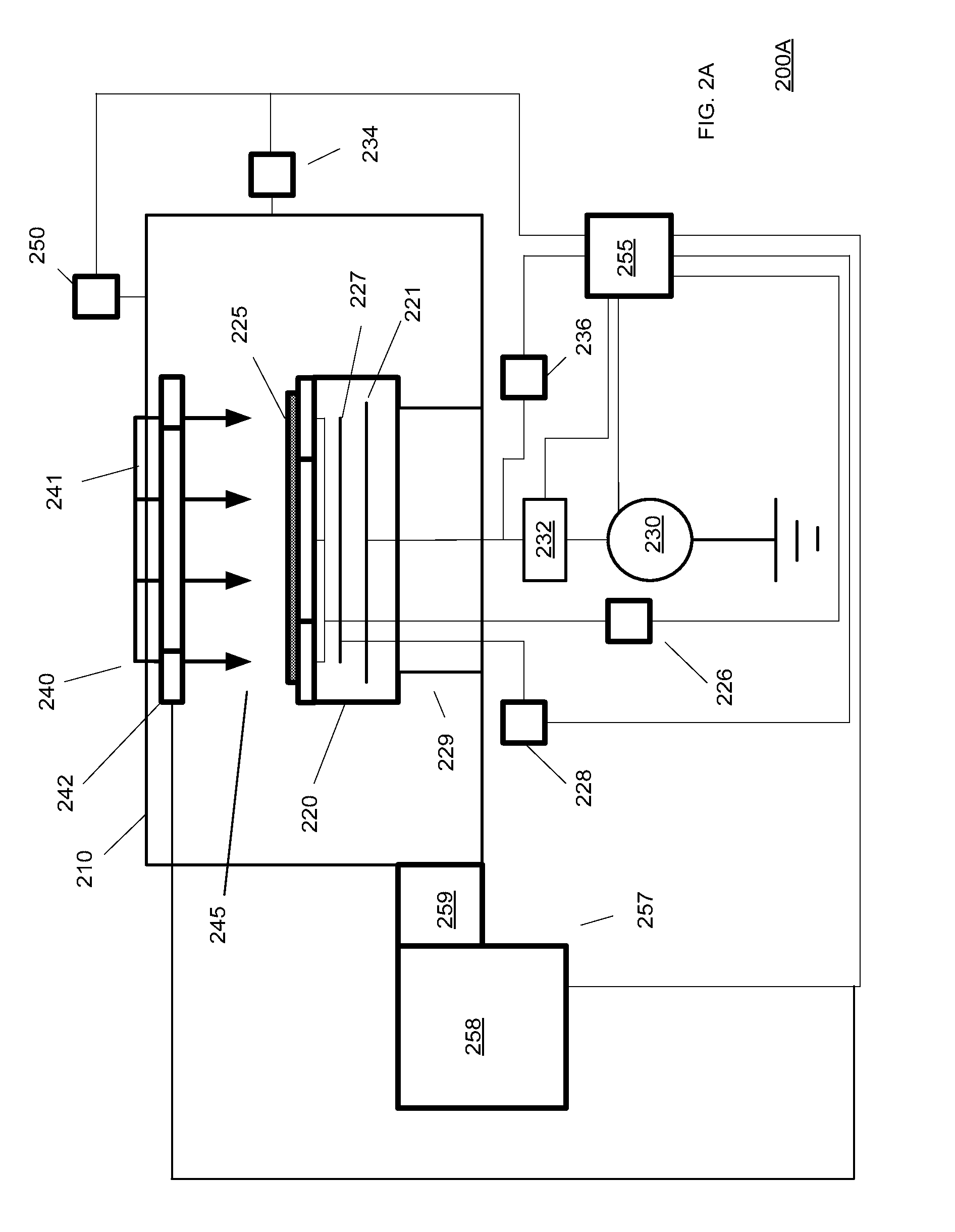
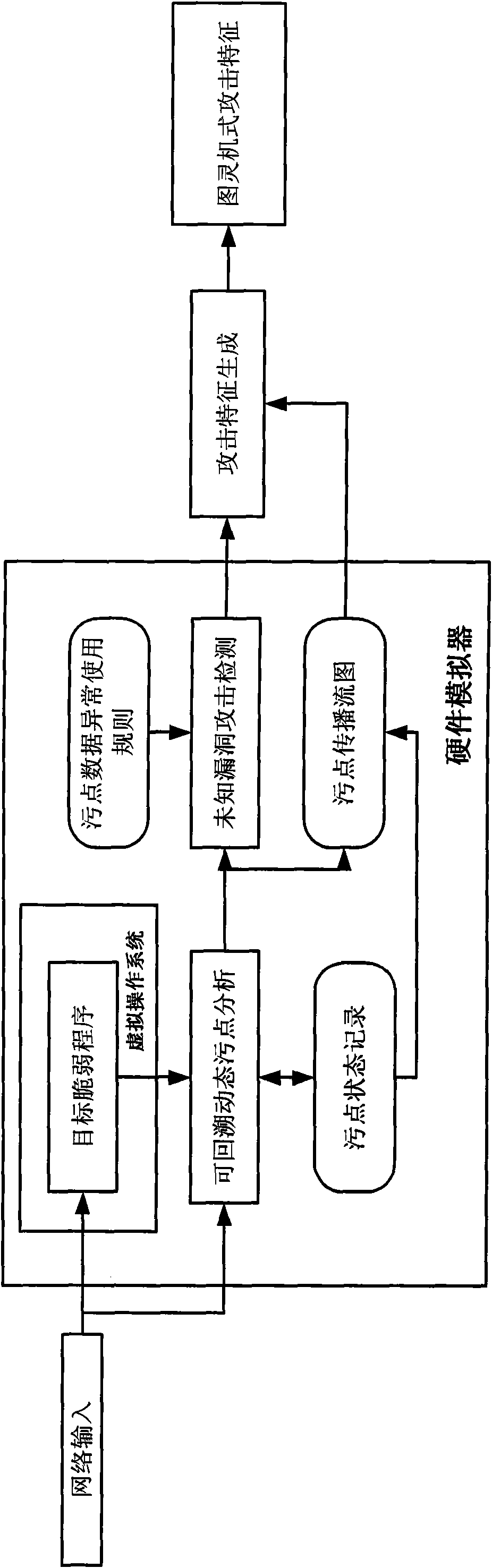
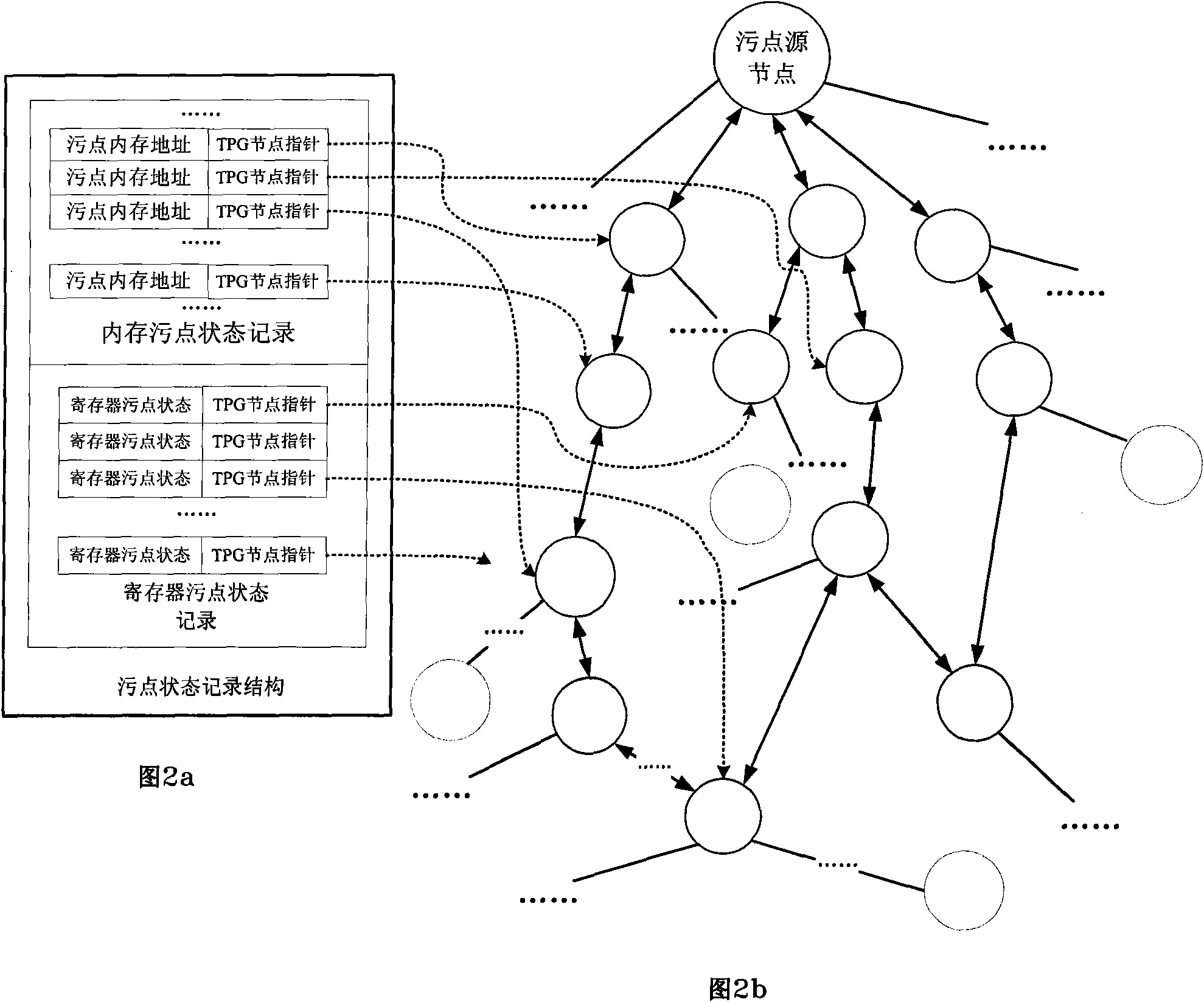
ActiveCN101616151AEasy to findEasy extractionData switching networksSpecific program execution arrangementsGeneration processSequence processing
The invention discloses an automated network attack characteristic generation method, comprising the following steps: 1) a virtual operating system is installed in a virtual host, an operation environment coincident with the real application of a brittle program is configured, and a taint data operation rule is configured; 2) the brittle program is started, all network input thereof is marked as the taint data to be monitored, the state of the taint data is recorded, and relative operation command of the taint data is recorded to form a taint transmission flow graph; 3) when the abnormal operation of the taint data is detected, a command sequence operated and handled by the brittle the taint data starting from the input data pack is obtained from the taint transmission flow graph; 4) the command sequence is processed to be a compiling performing command, and a judging output sentence is added to generate Turing-type attack characteristics. The method of the invention is favourable for finding unknown bug attack behaviour and extracting the attack flow and has no need of obtaining brittle program source code, the generated attack characteristics are more accurate, and the attack characteristic generation process is automatic and quick.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Cellular communication system and a method of operation therefor
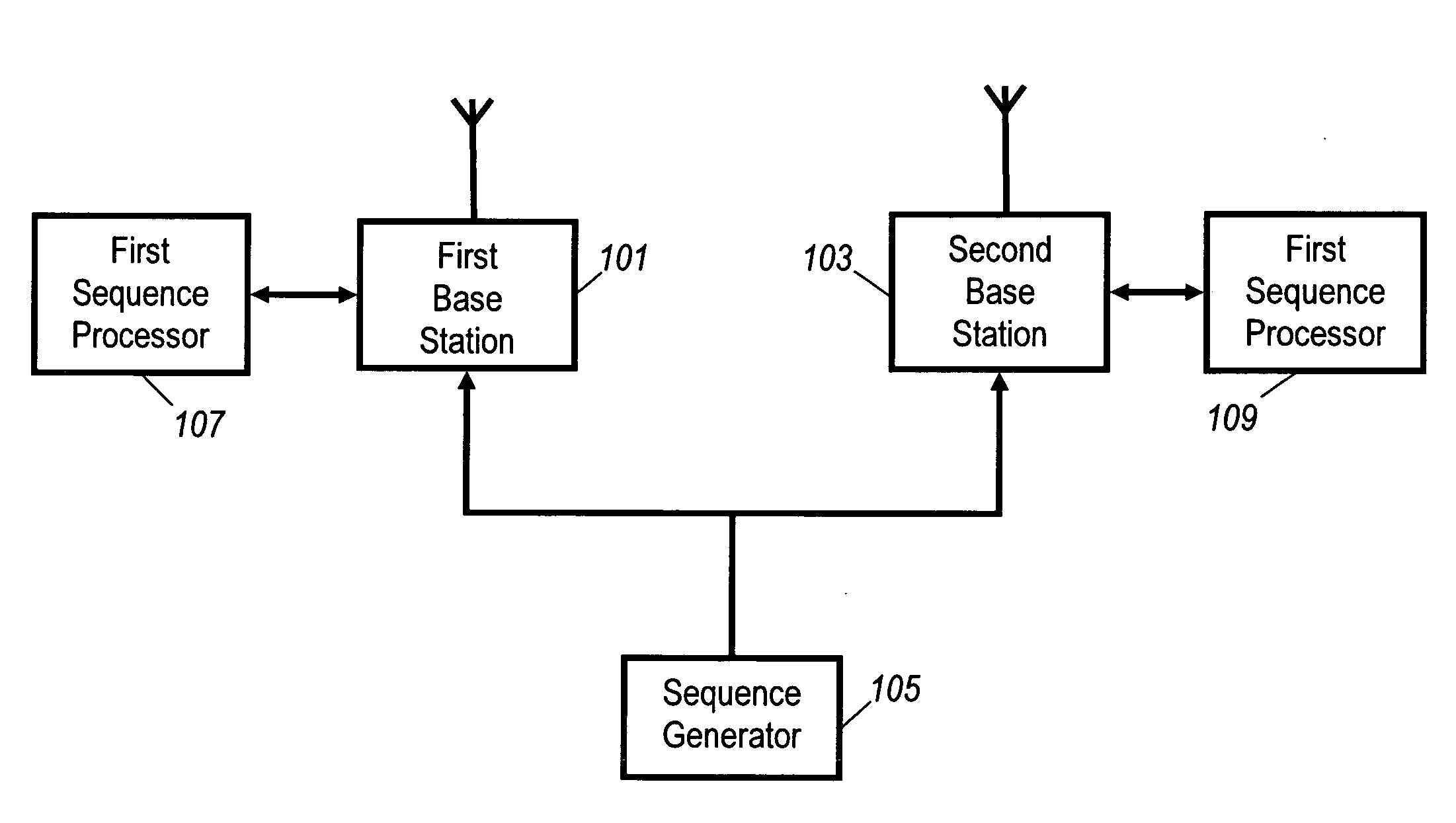
ActiveUS20090060003A1Easy to useSimplified and improved cell detection/search operationDiversity/multi-antenna systemsSecret communicationSequence processingCellular communication systems
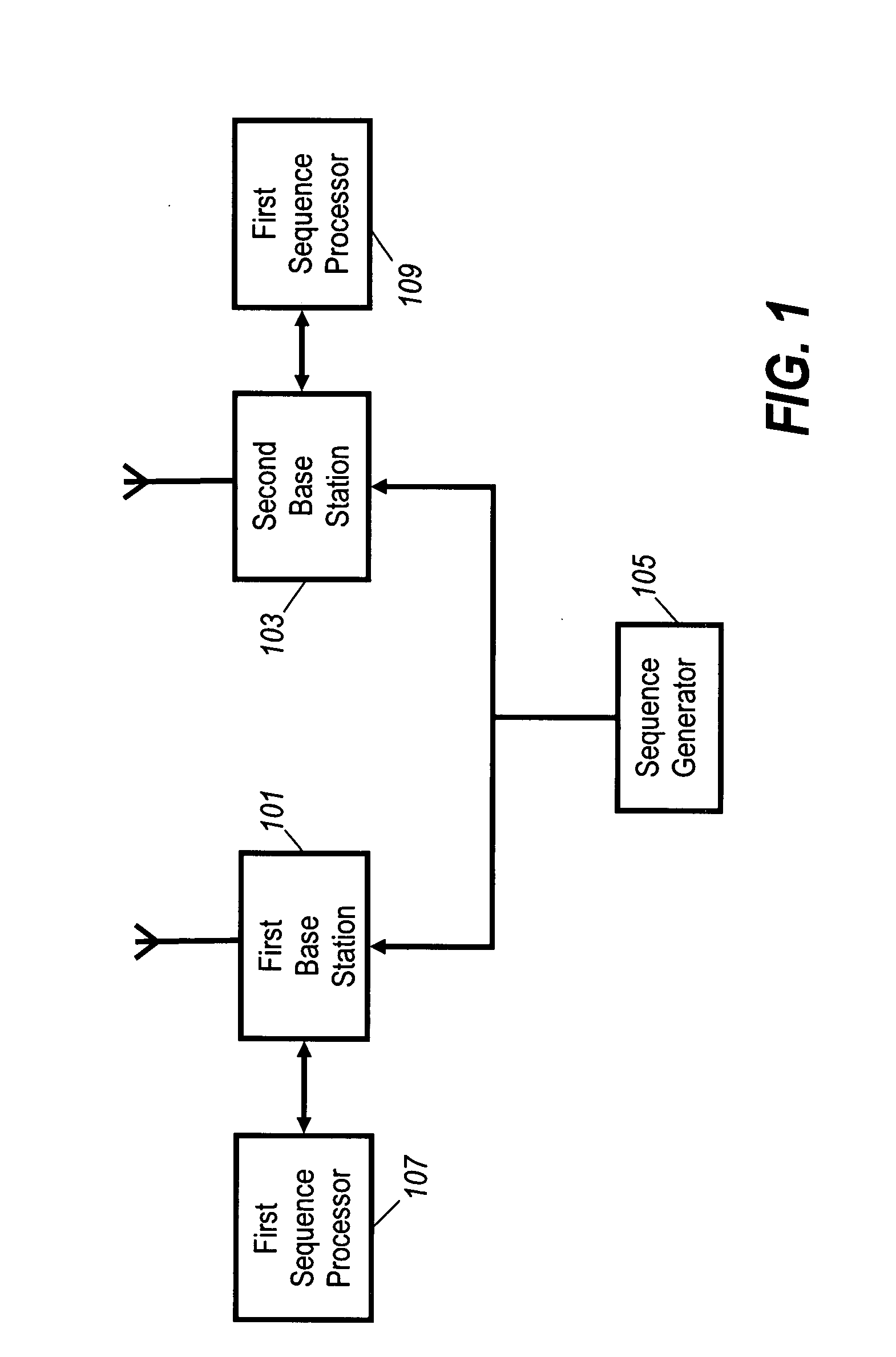
A cellular communication system employs a plurality of bandwidths. The cellular communication system comprises a plurality of base stations (101, 103) each of which transmits a reference signal comprising a Generalised Chirp-Like, GCL, sequence. The length of the GCL sequence is dependent on the bandwidth employed by the base station (101, 103). A sequence generator (105) provides a first subset of GCL sequences for a first bandwidth selected from a set of possible GCL sequences for the first bandwidth in response to properties of a sub-sequence of GCL sequences. The sub-sequence has a length corresponding to a different bandwidth. Sequence processors (107, 109) select GCL sequences for base stations (101, 103) employing the first bandwidth from the first subset of GCL sequences. The invention exploits characteristics of GCL sequences to enable, facilitate or improve multiple bandwidth operation.
Owner:GOOGLE TECH HLDG LLC
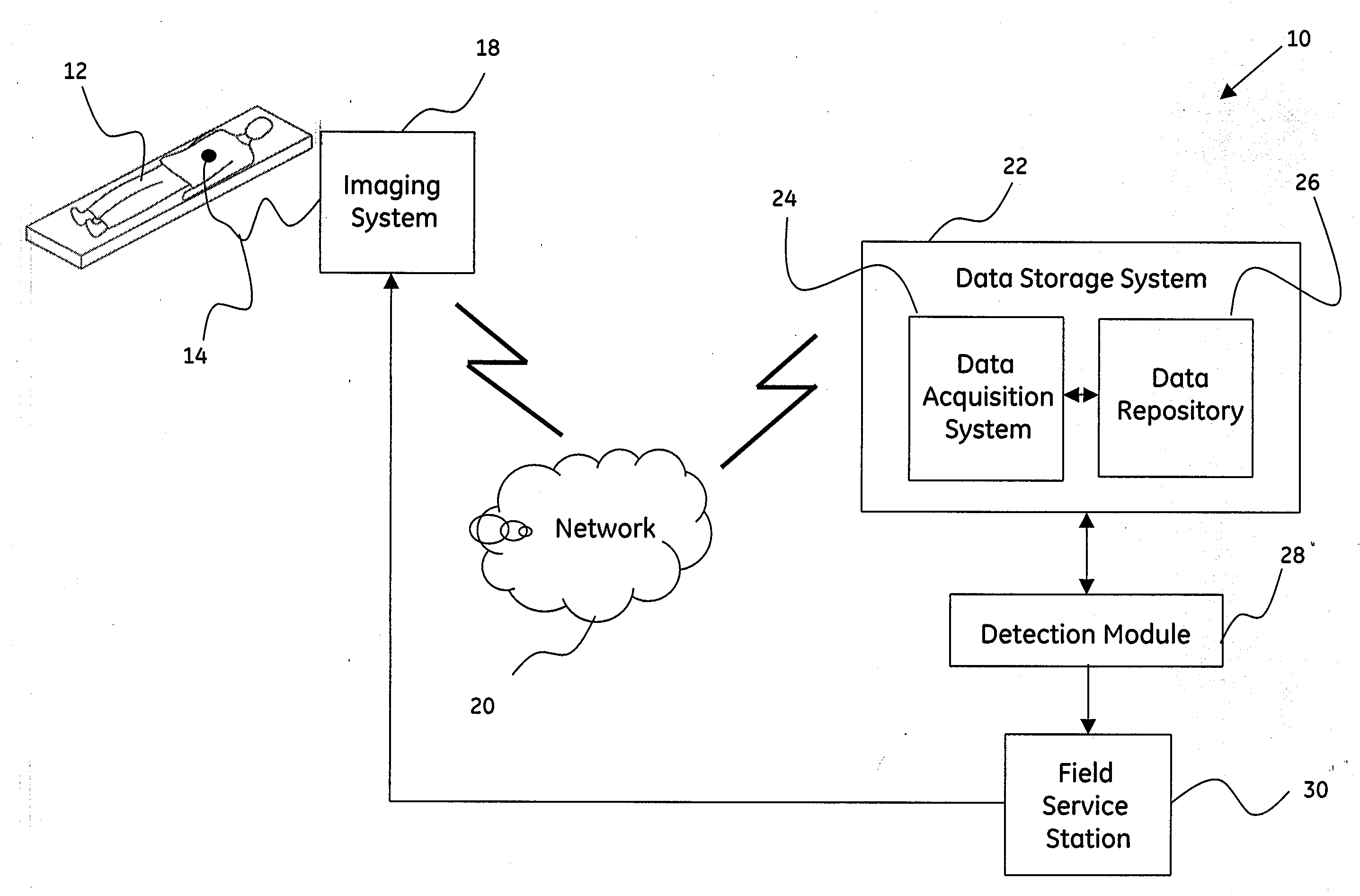
Method and system for enhanced fault detection workflow
InactiveUS20080221834A1Digital computer detailsNuclear monitoringSequence processingDynamical optimization
A method for fault detection workflow management is presented. The method includes determining a working environment, a rule application attribute, or both, where the working environment and the rule application attribute are associated with input data. Furthermore, the method includes dynamically optimizing a sequence of operations based on the determined working environment, the determined rule application attribute, or both. Additionally, the method includes processing the input data based on the optimized sequence of operations. Systems and computer-readable medium that afford functionality of the type defined by this method is also contemplated in conjunction with the present technique.
Owner:GENERAL ELECTRIC CO
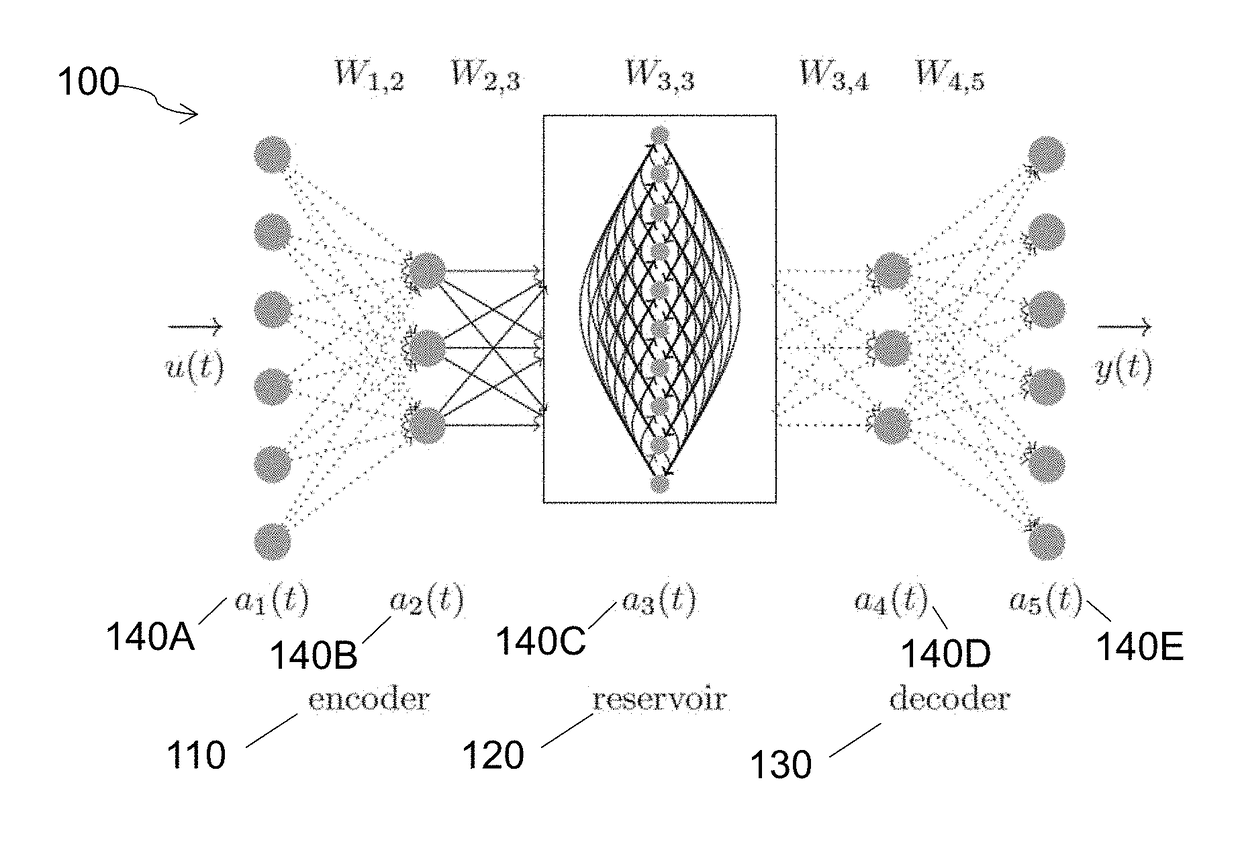
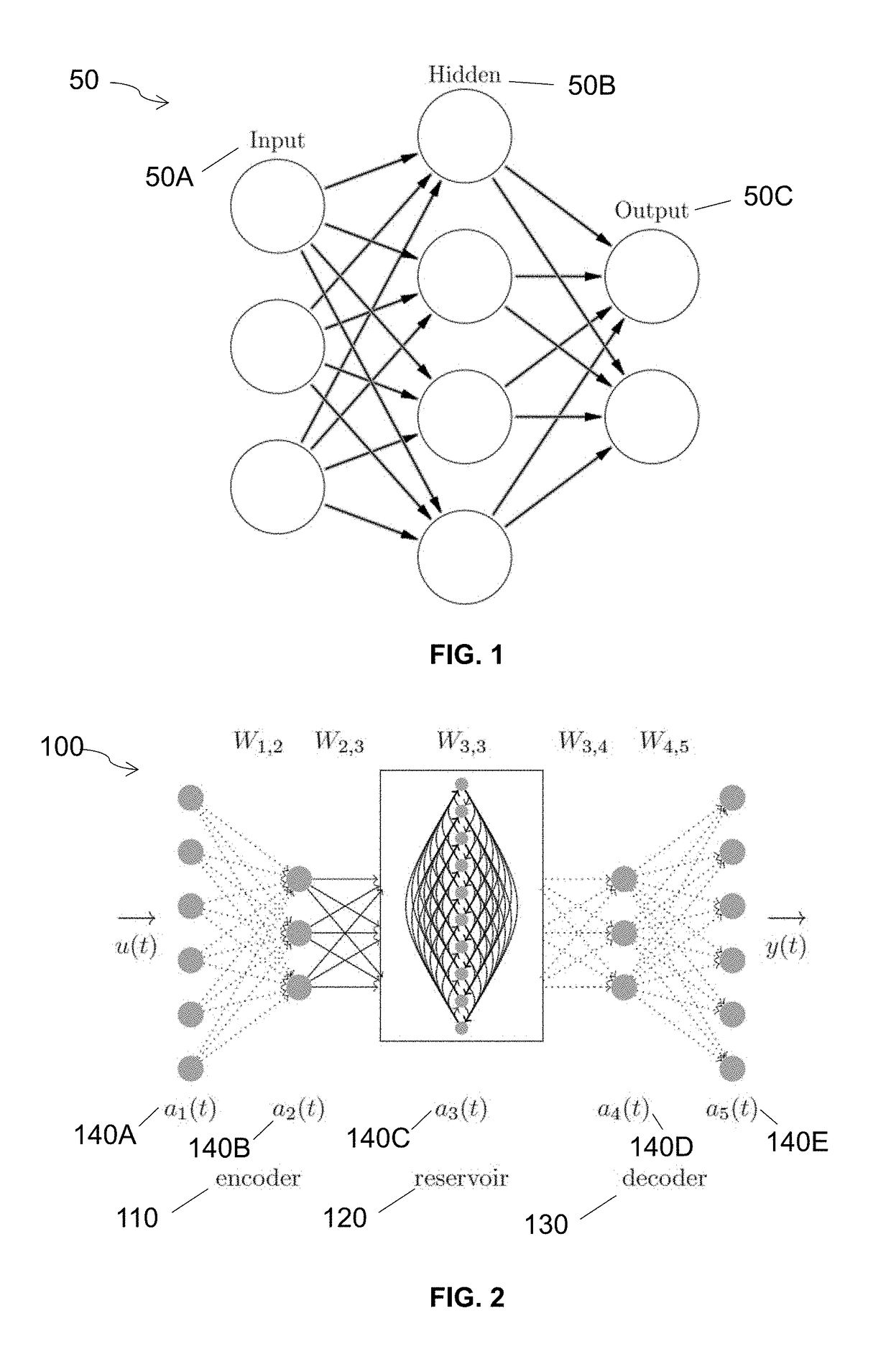
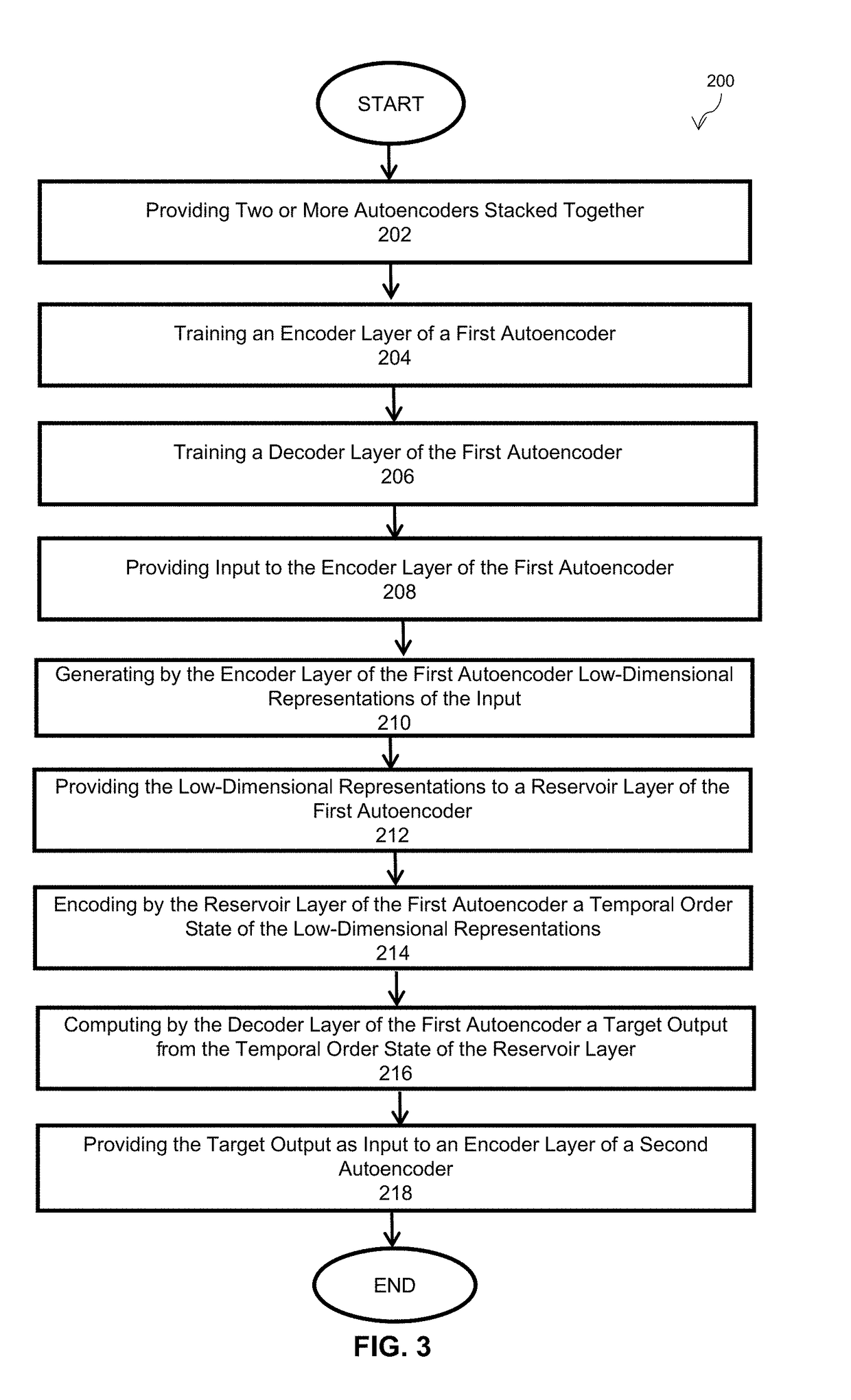
Hybrid architecture system and method for high-dimensional sequence processing
ActiveUS20180253640A1Preserve localityMedical automated diagnosisNeural architecturesSequence processingShort-term memory
The invention is directed to a hybrid architecture that comprises a stacked autoencoder and a deep echo state layer for temporal pattern discovery in high-dimensional sequence data. The stacked autoencoder plays a preprocessing role that exploits spatial structure in data and creates a compact representation. The compact representation is then fed to the echo state layer in order to generate a short-term memory of the inputs. The output of the network may be trained to generate any target output.
Owner:STC UNM
Configurable 2-wire/3-wire serial communications interface
ActiveUS20120117284A1Energy efficient computingElectric digital data processingSequence processingChip select
A configurable 2-wire / 3-wire serial communications interface (C23SCI), which includes start-of-sequence (SOS) detection circuitry and sequence processing circuitry, is disclosed. When the SOS detection circuitry is coupled to a 2-wire serial communications bus, the SOS detection circuitry detects an SOS of a received sequence based on a serial data signal and a serial clock signal. When the SOS detection circuitry is coupled to a 3-wire serial communications bus, the SOS detection circuitry detects the SOS of the received sequence based on a chip select (CS) signal. In response to detecting the SOS, the SOS detection circuitry provides an SOS detection signal to the sequence processing circuitry, which initiates processing of the received sequence using the serial data signal and the serial clock signal. The received sequence is associated with one of multiple serial communications protocols.
Owner:QORVO US INC
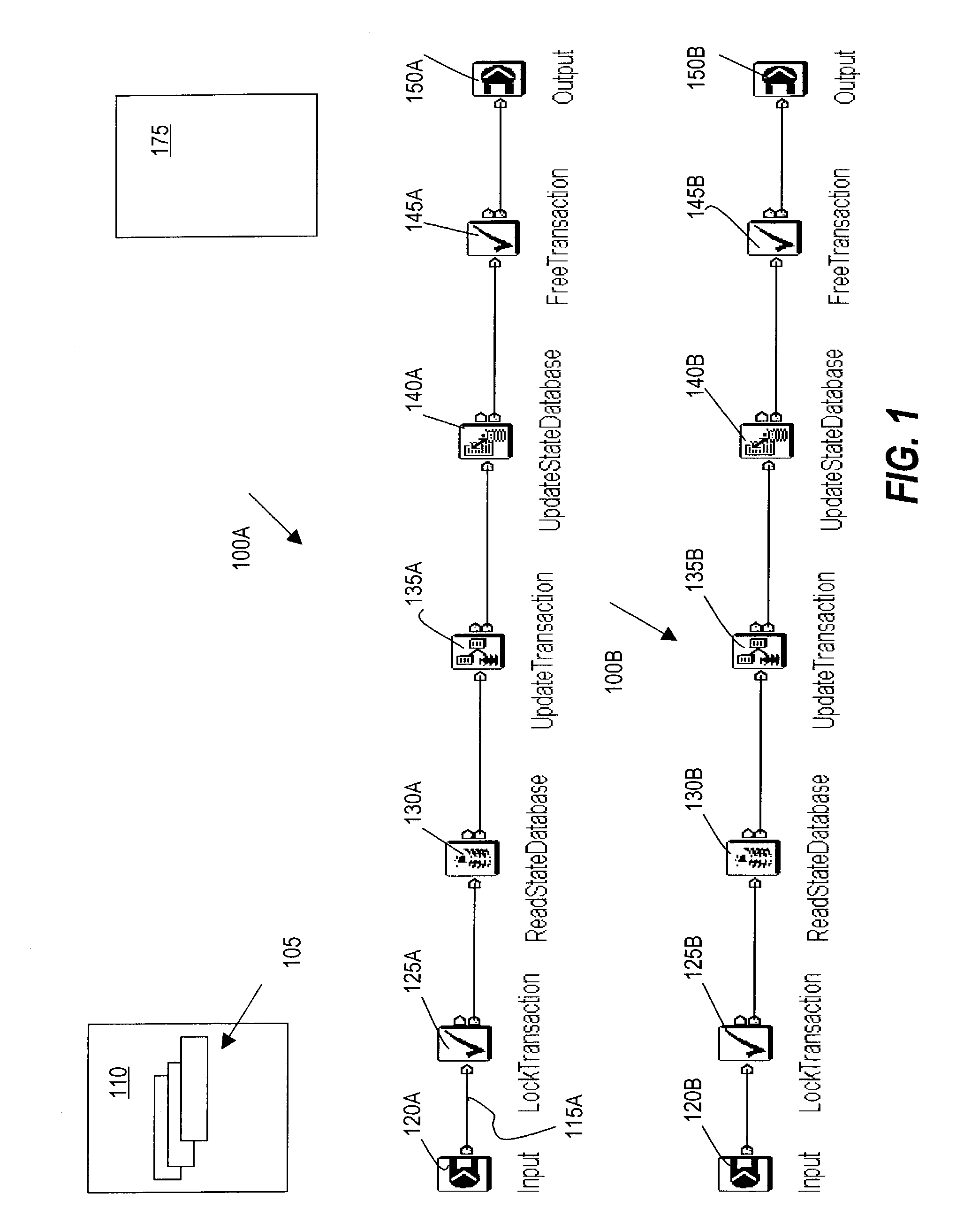
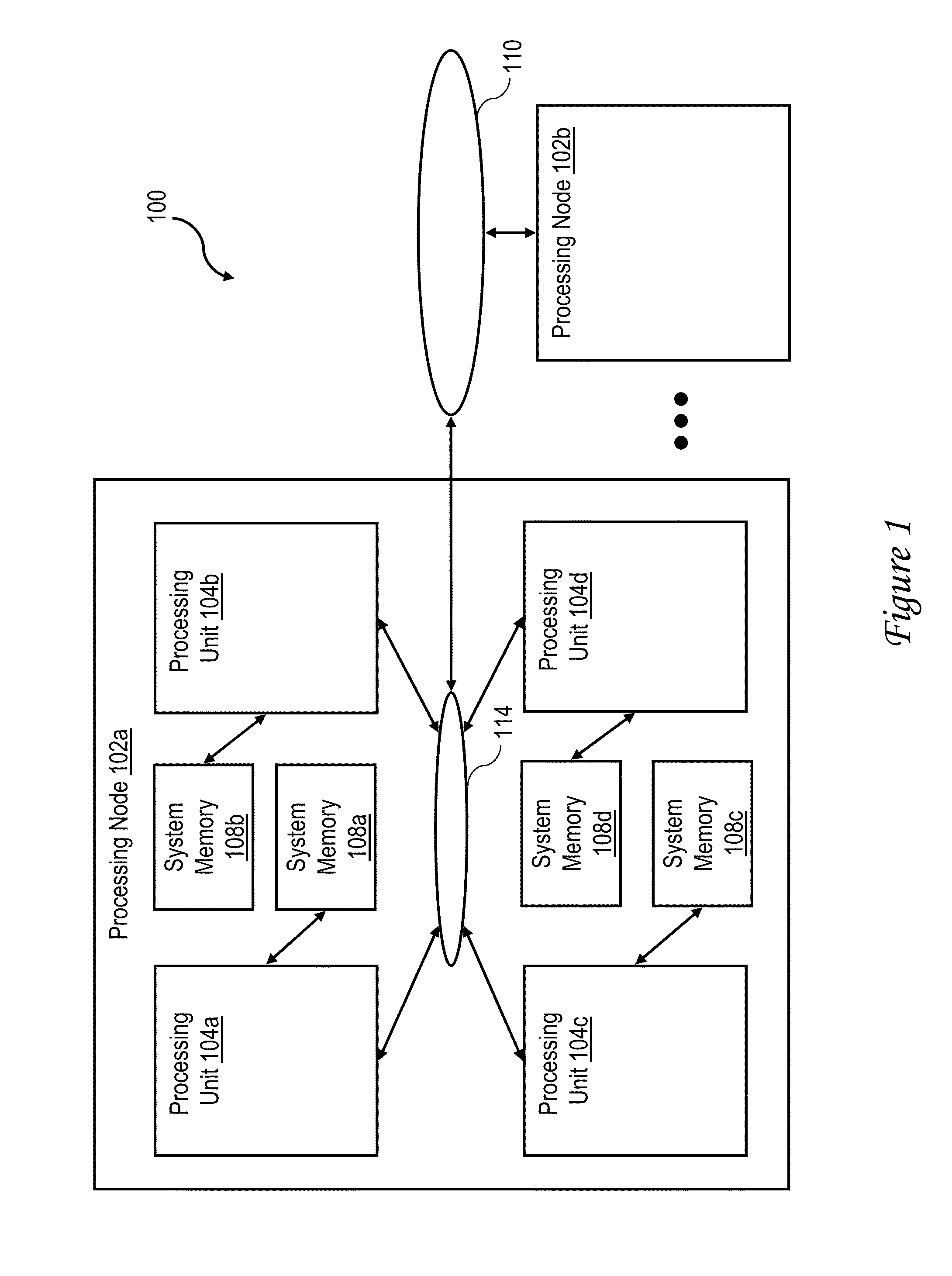
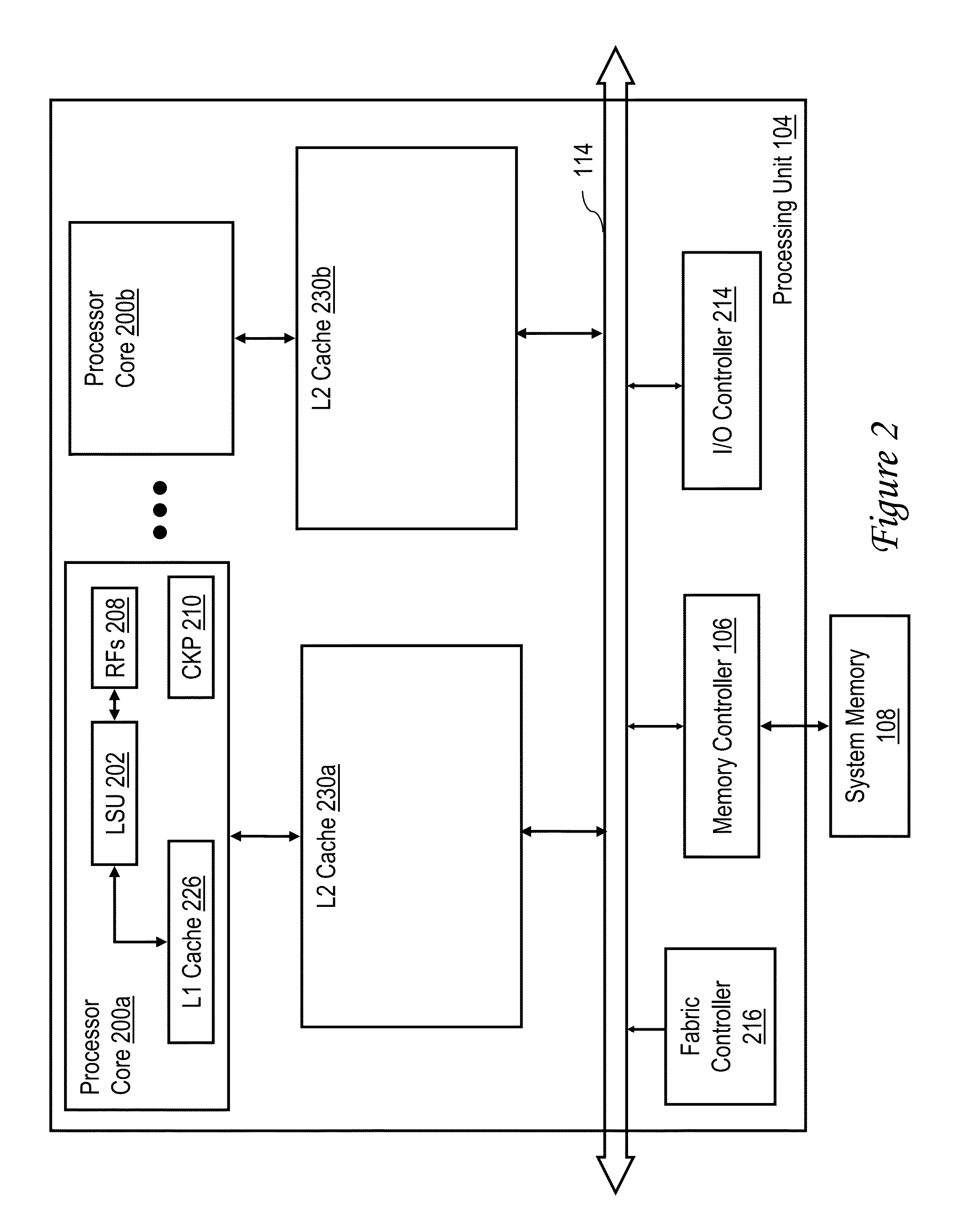
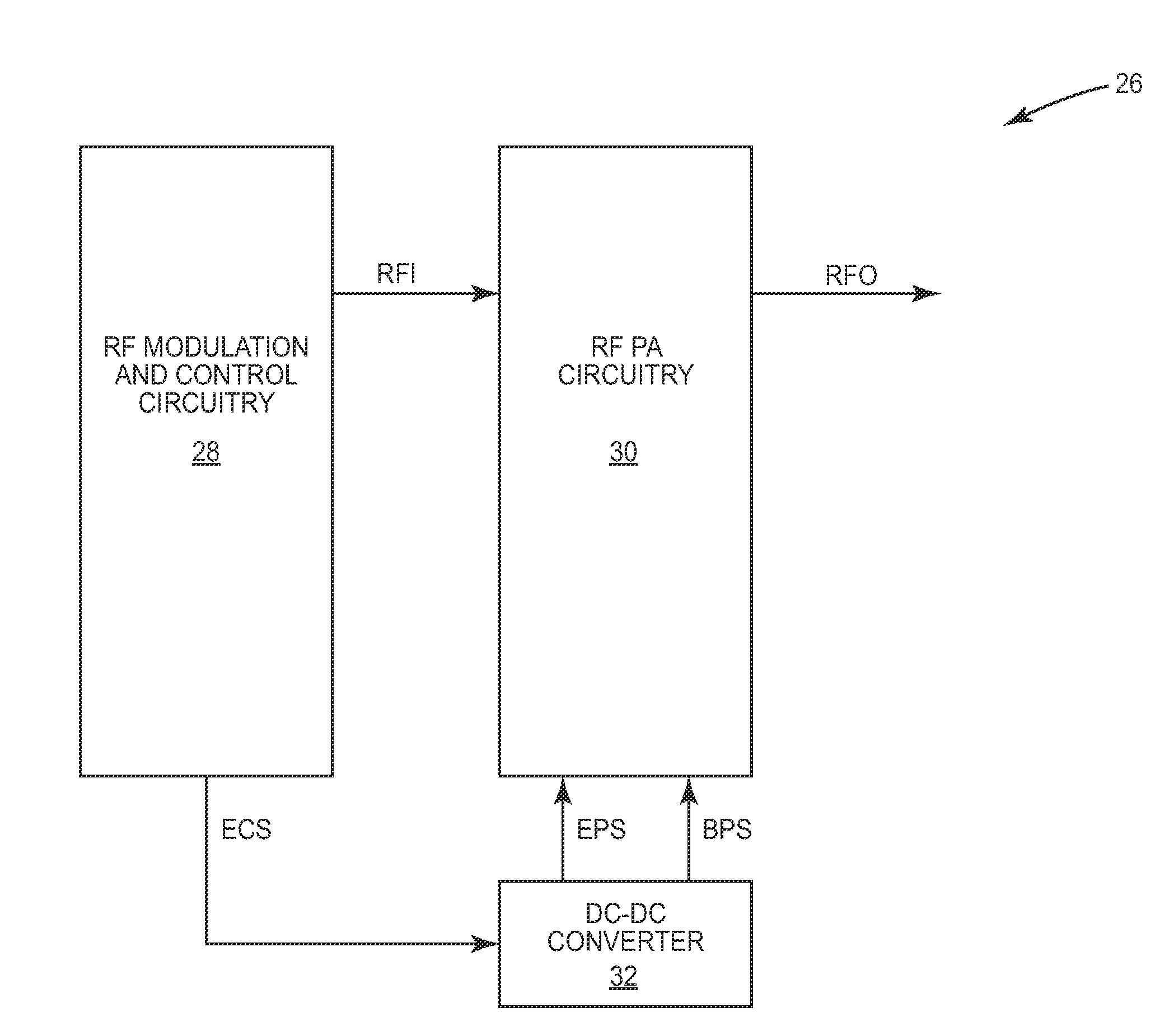
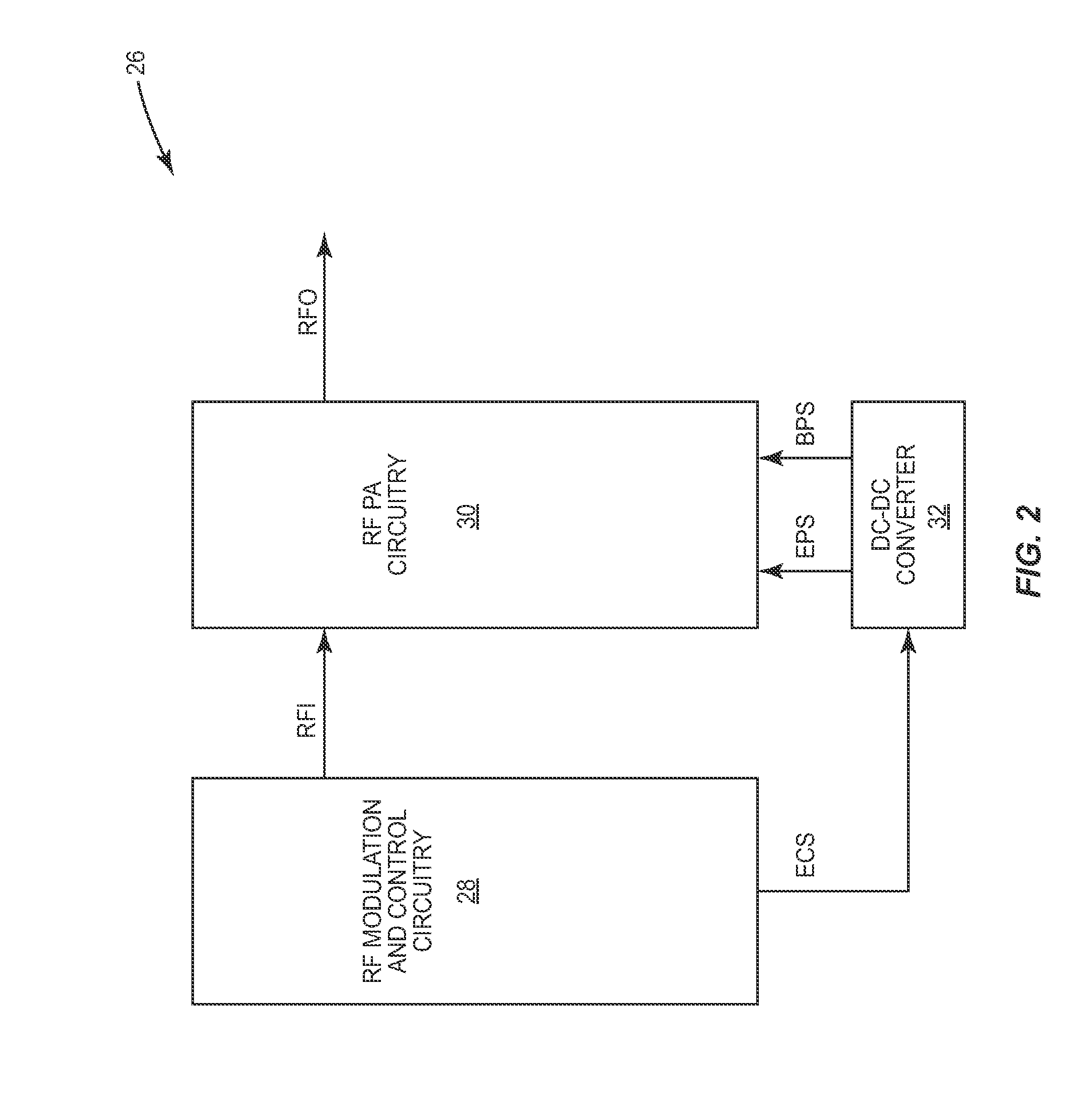
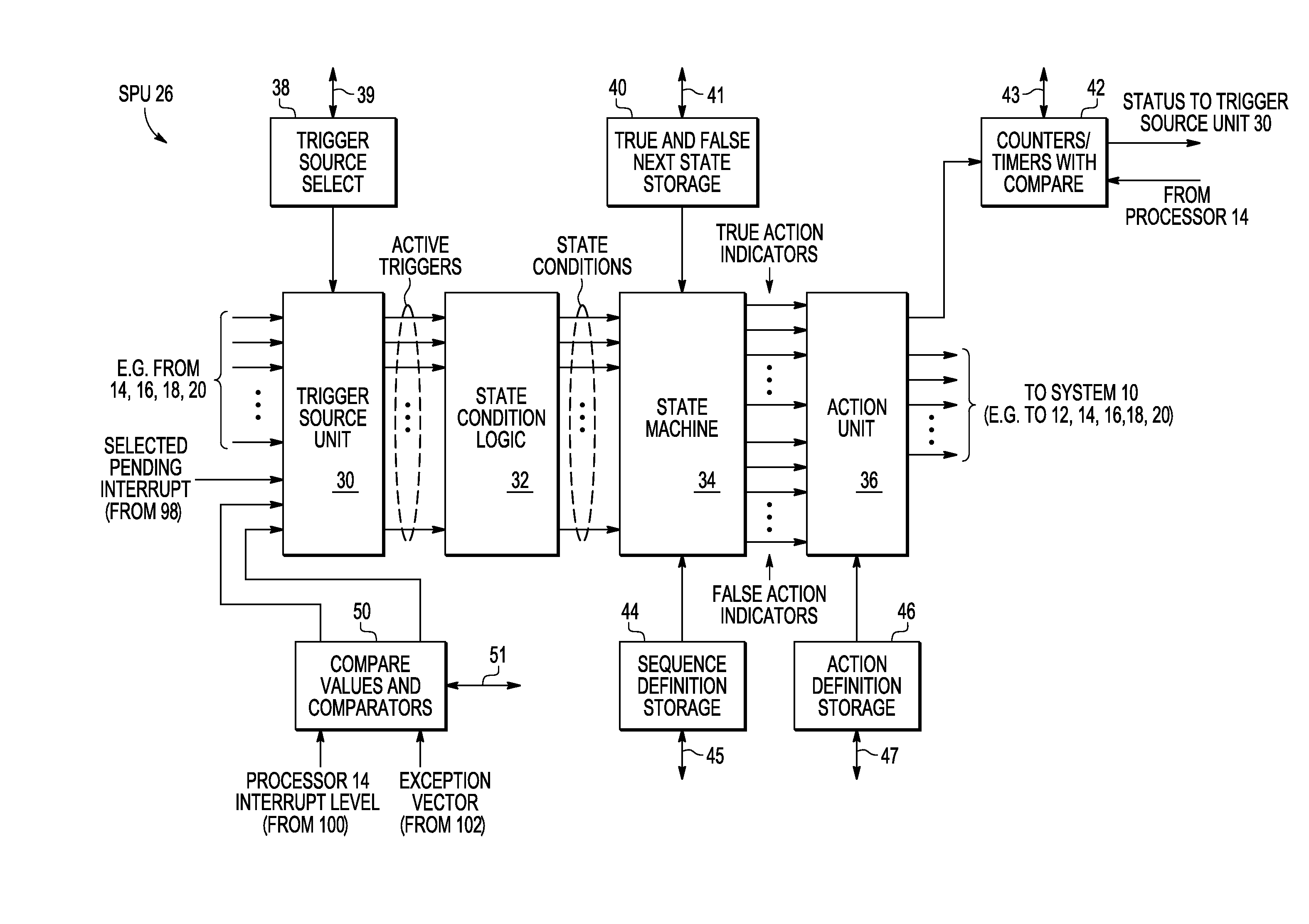
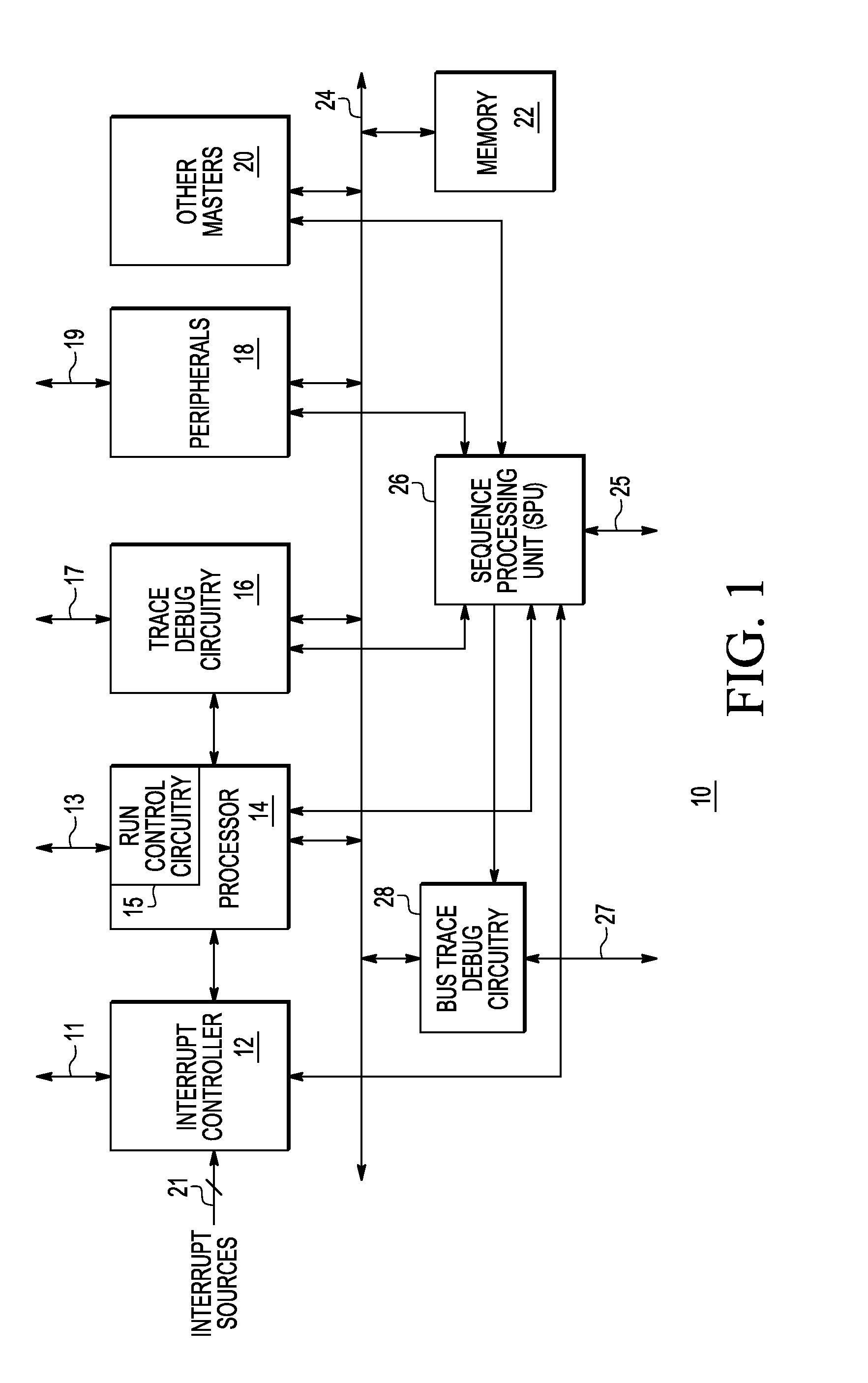
Data processing system having a sequence processing unit and method of operation
A system includes one or more processors; one or more trace debug circuits configured to monitor one or more of instruction, data, and watchpoint buses of the one or more processors, and record information determined from said monitoring; and a sequence processing unit configured to provide a control signal to a trace debug circuit of the one or more trace debug circuits, wherein in response to the control signal, the trace debug circuit controls one or more of said monitoring and recording, and a system on a chip comprises the one or more processors, the one or more trace debug circuits, and the sequence processing unit.
Owner:NXP USA INC
Audio comparison system and audio energy comparison method thereof
ActiveCN101593517ALittle impact on the external environmentReduce the impactSpeech recognitionSequence processingBroadcasting
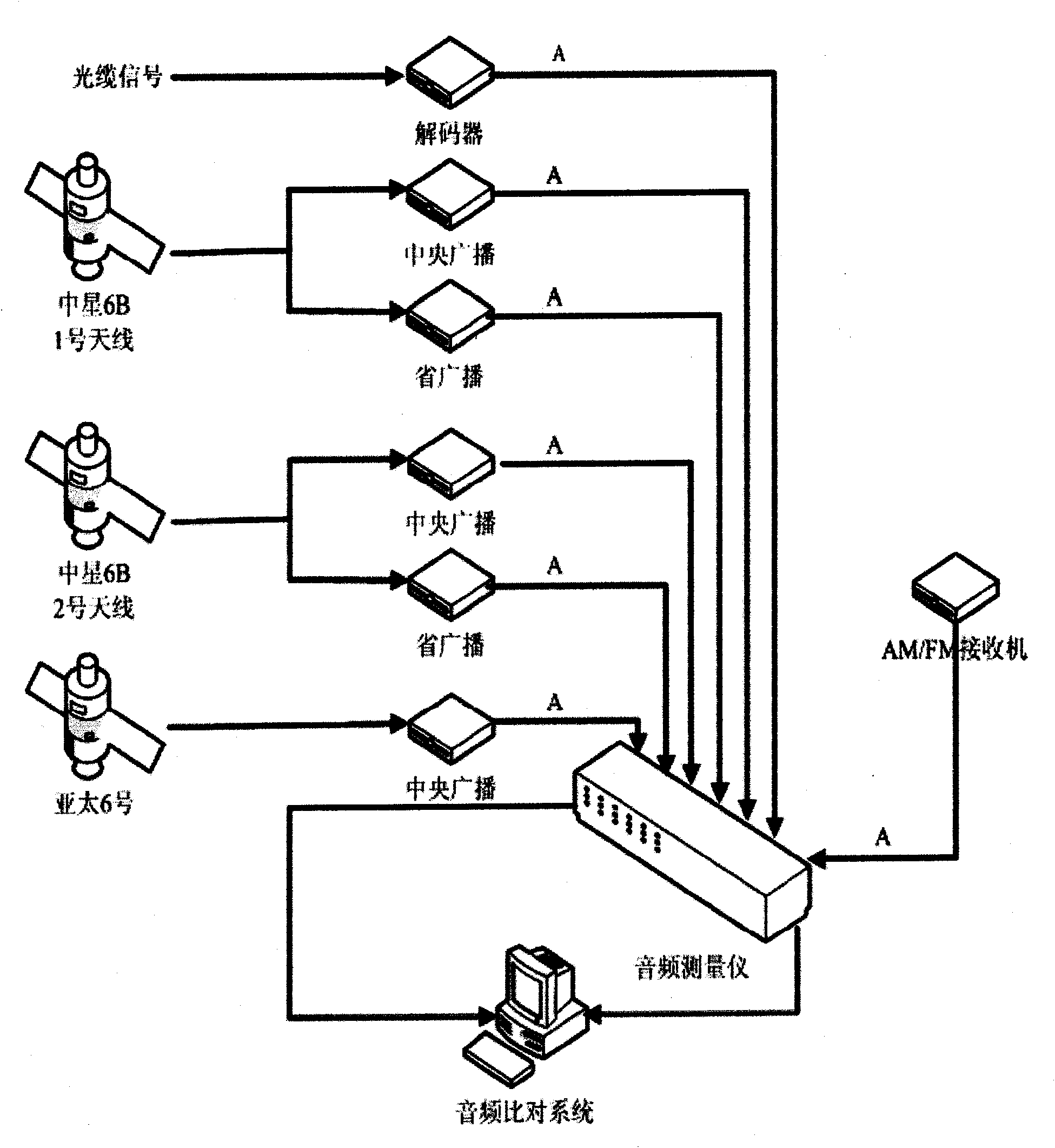
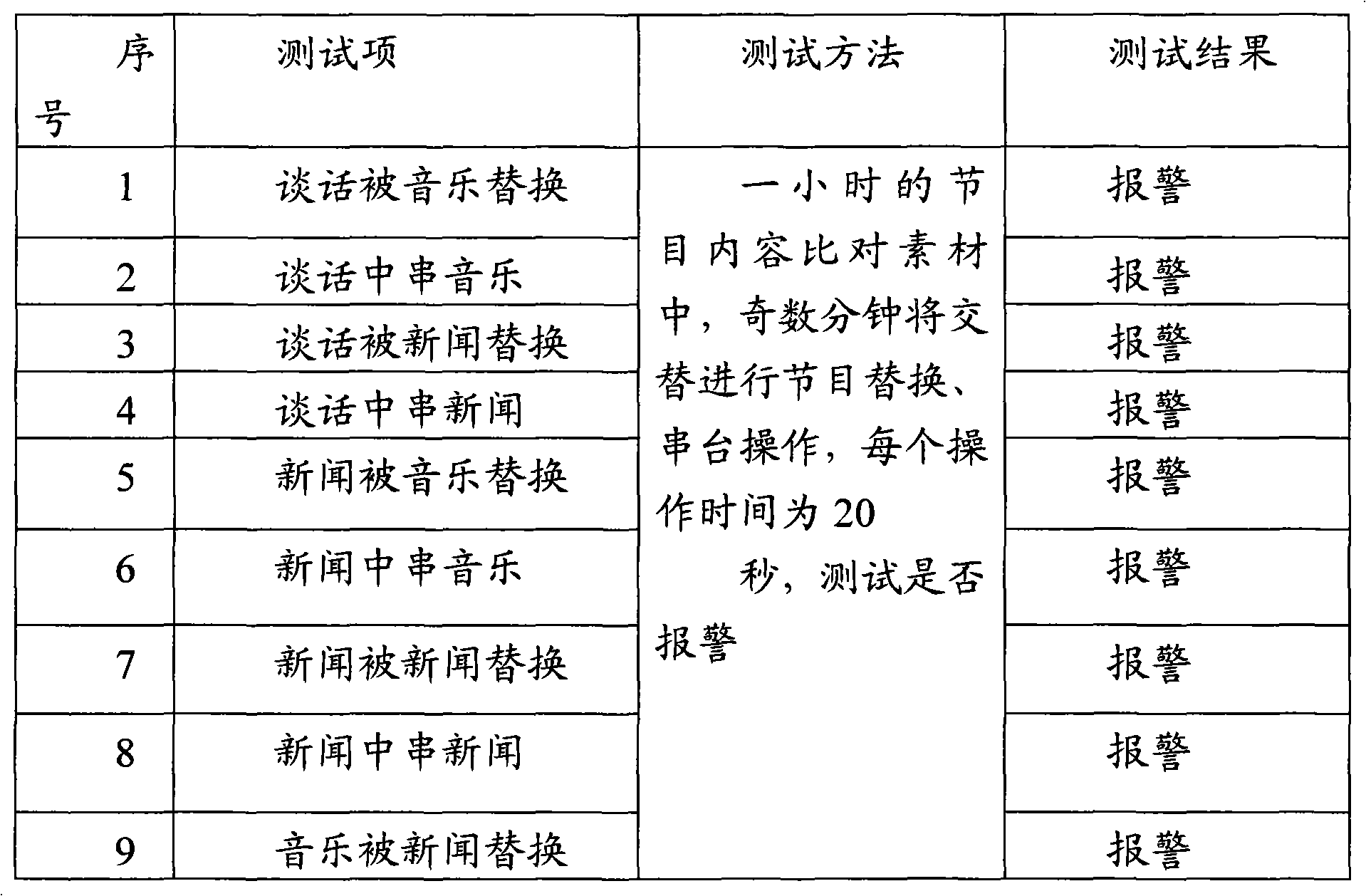
The invention discloses an audio comparison system and an audio energy comparison method thereof. The audio comparison system comprises an audio sequence determining unit, an audio sequence processing unit and an audio similarity judging unit. The audio energy comparison method comprises the steps of removing an abnormal frame to acquire an energy mean ratio (K value) and then counting points which are more than the K value in a normal interval to judge the similarity of two paths of audio frequencies. The audio comparison system of the invention integrally partitions the audio frequencies to be compared into a plurality of audio frames and uses the energy comparison among the audio frames to acquire the similarity of the compared audio frequencies, so the comparison mode is little influenced by the outside environment, does not cause error report phenomenon even under the environment with large noise and large disturbance, and has significance for audio transmission on broadcast.
Owner:北京市博汇科技股份有限公司
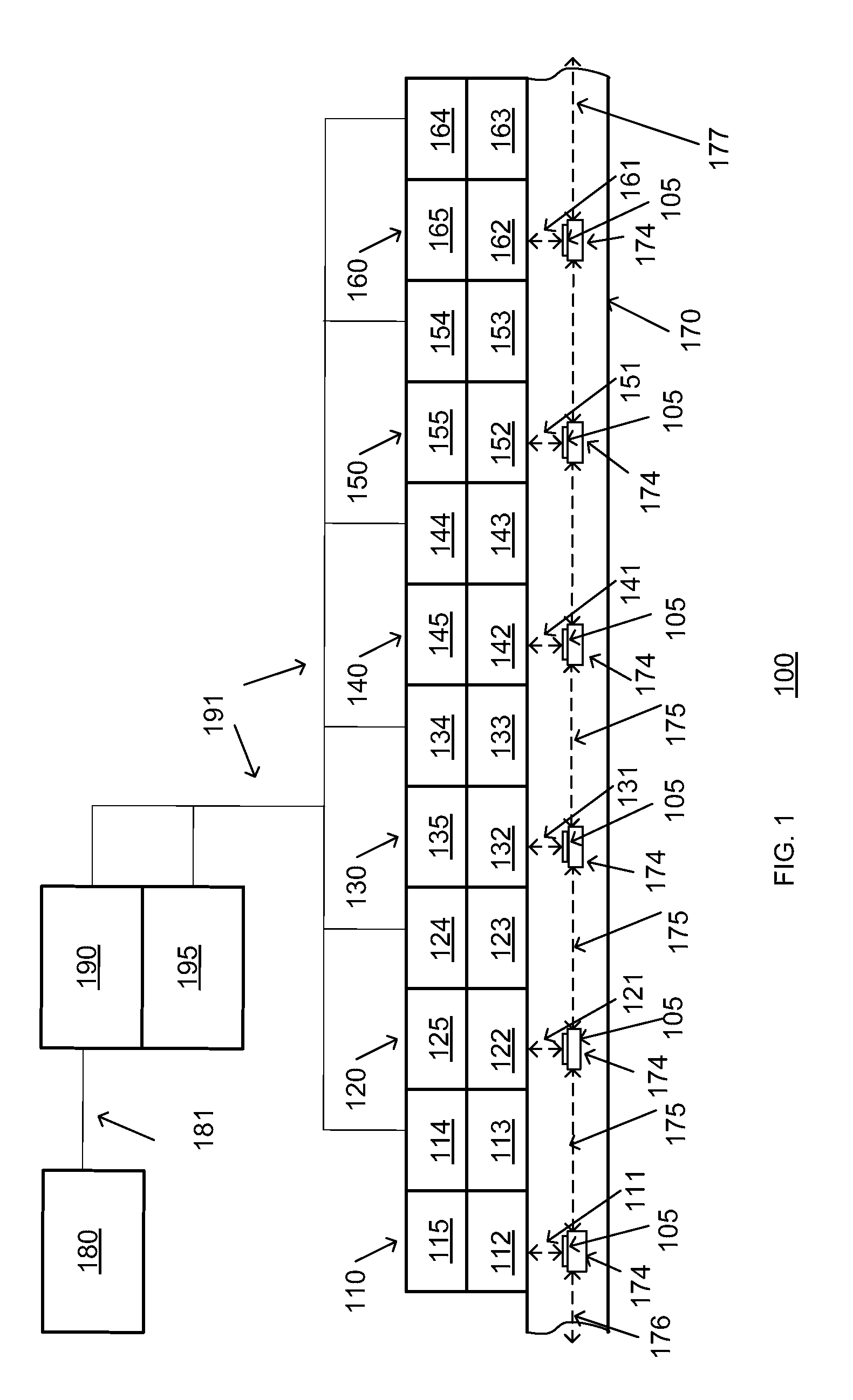
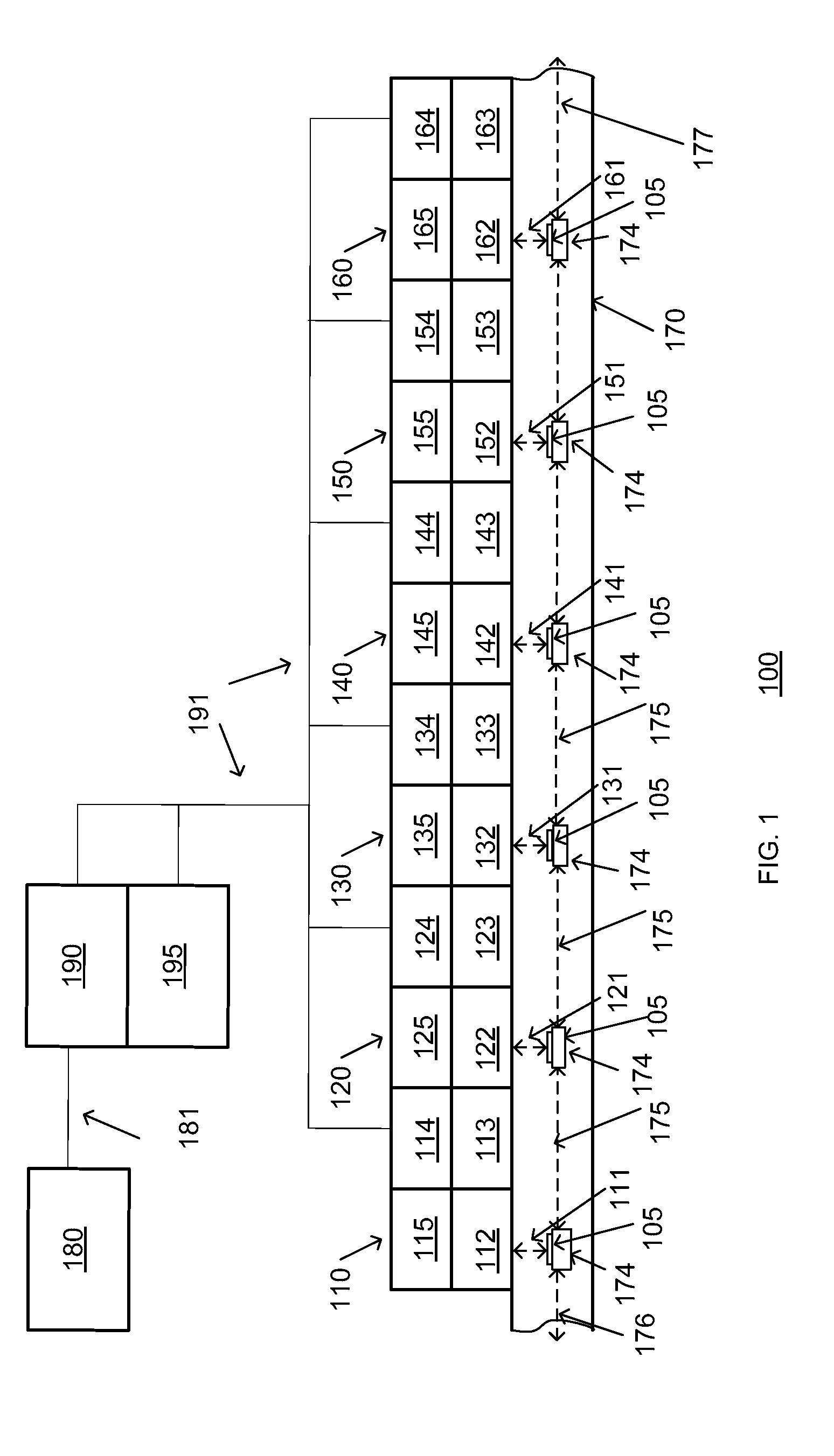
Auto-sequencing inline processing apparatus
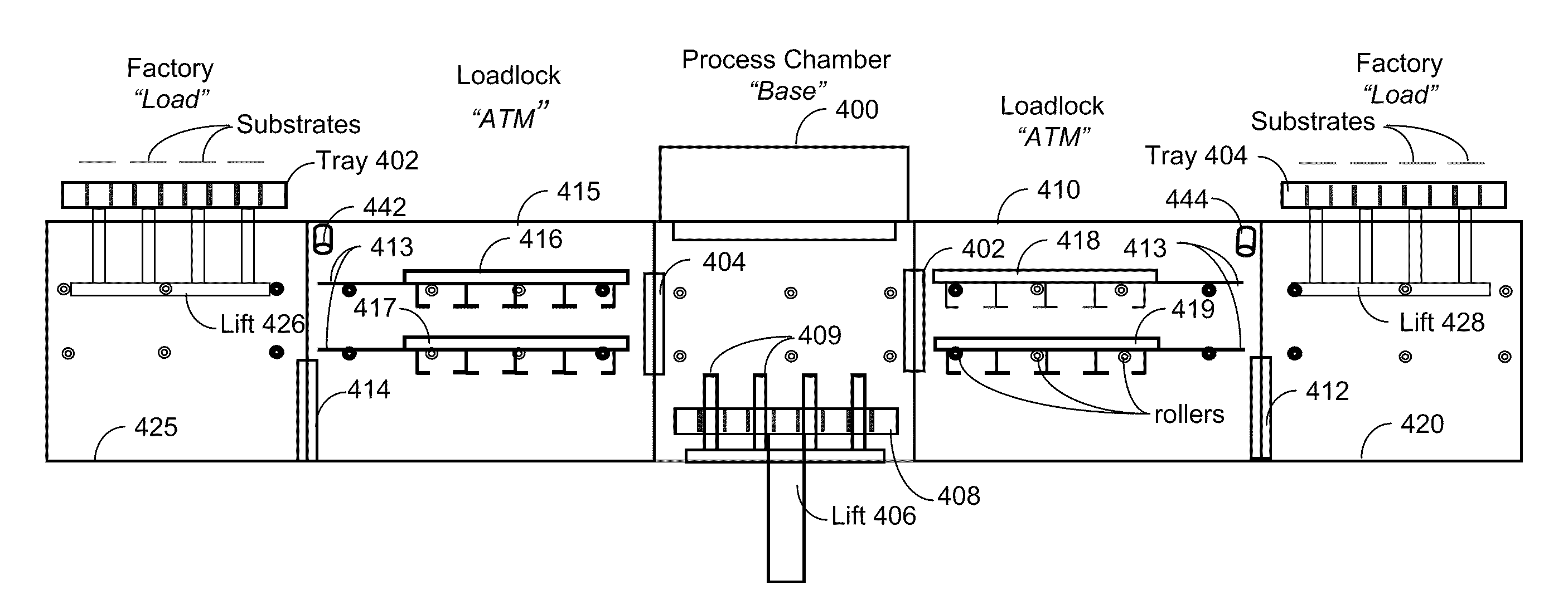
ActiveUS20110142572A1Improve throughputDetection of brokenImage analysisElectric discharge tubesSequence processingEngineering
An apparatus and method for concurrent processing of several substrates. The system employs a novel architecture which, while being linear, may autonomously sequence processing and move substrates in different directions as necessary. The system moves several substrates concurrently; however, unlike the prior art it does not utilize trays.
Owner:KLA TENCOR TECH CORP
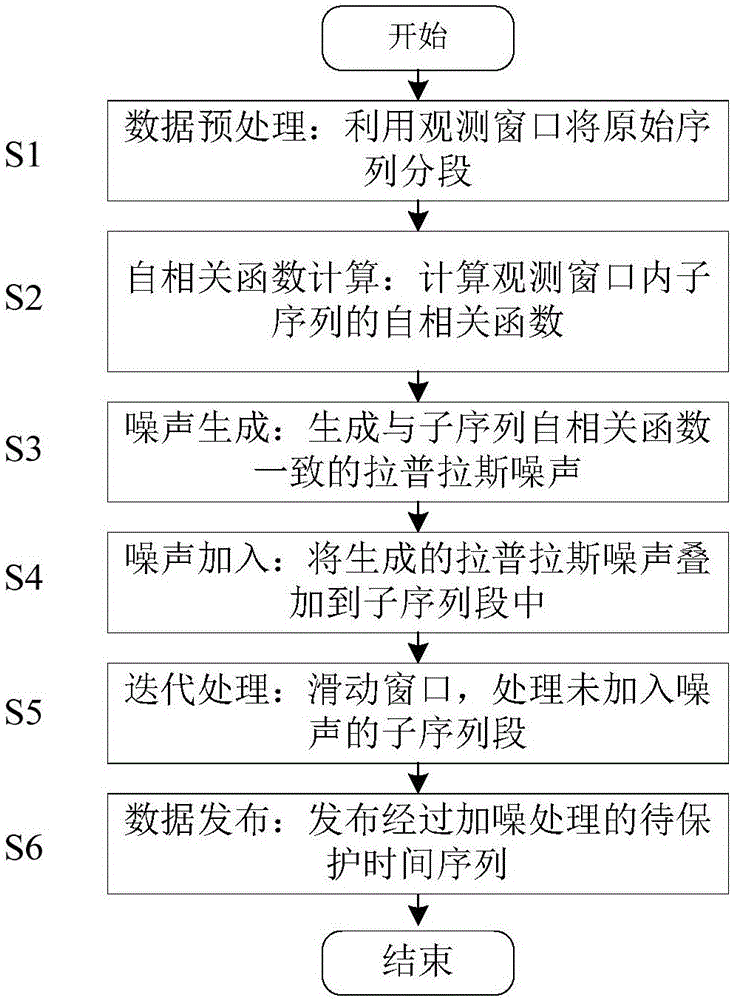
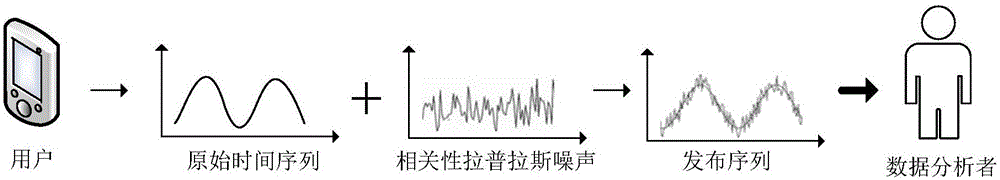
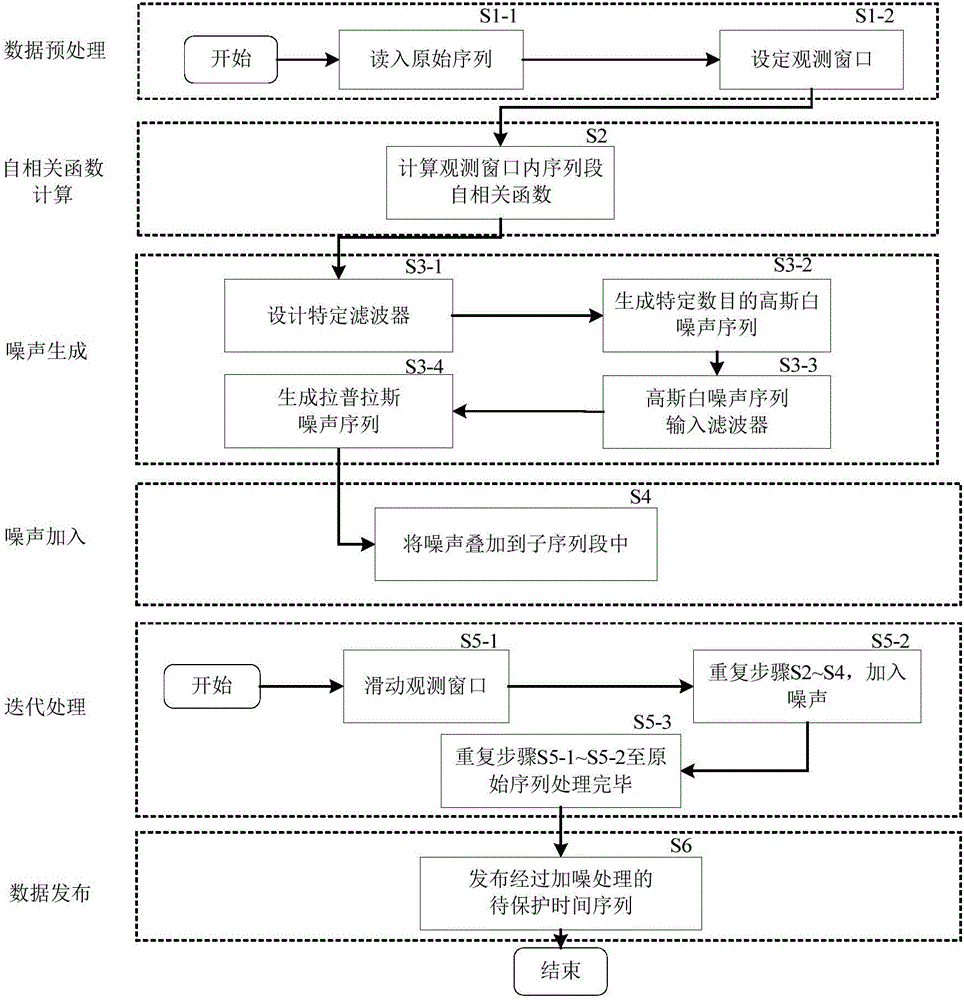
Correlation time series issuing method and system based on differential privacy
ActiveCN106407841APrevent Filtering AttacksEffective privacy protectionDigital data protectionSequence processingSlide window
Owner:WUHAN UNIV
Using Multi-Layer/Multi-Input/Multi-Output (MLMIMO) models for metal-gate structures
InactiveUS7894927B2Semiconductor/solid-state device testing/measurementSolid-state devicesMulti inputSequence processing
Owner:TOKYO ELECTRON LTD
Methods and apparatus for power control in a scalable array of processor elements
InactiveUS6845445B2Reduce the required powerVolume/mass flow measurementData resettingProcessor elementSequence processing
Low power architecture features and techniques are provided in a scalable array indirect VLIW processor. These features and techniques include power control of a reconfigurable register file, conditional power control of multi-cycle operations and indirect VLIW utilization, and power control of VLIW-based vector processing using the ManArray register file indexing mechanism. These techniques are applicable to all processing elements (PEs) and the array controller sequence processor (SP) to provide substantial power savings.
Owner:ALTERA CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com