Automated network attack characteristic generation method
A network attack and tainted data technology, applied in the field of network security, can solve the problems of manual analysis, application situation limitation, and a large amount of manual analysis time, etc., and achieve the effect of accurate attack features, conducive to extraction, and automatic and fast attack feature generation process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
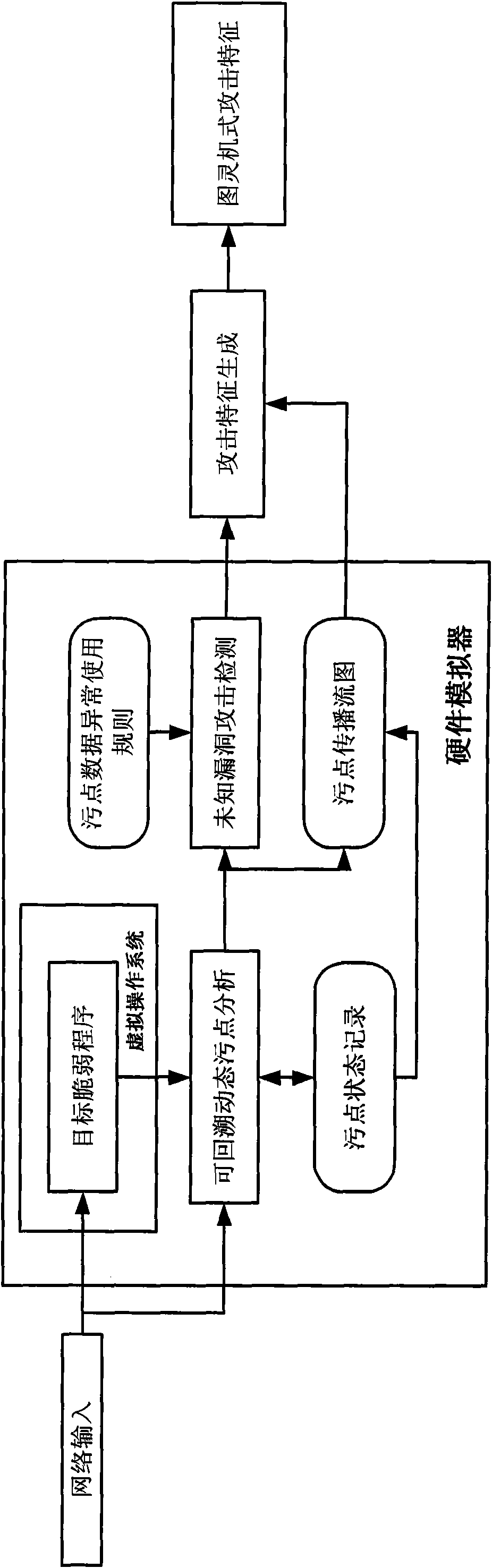
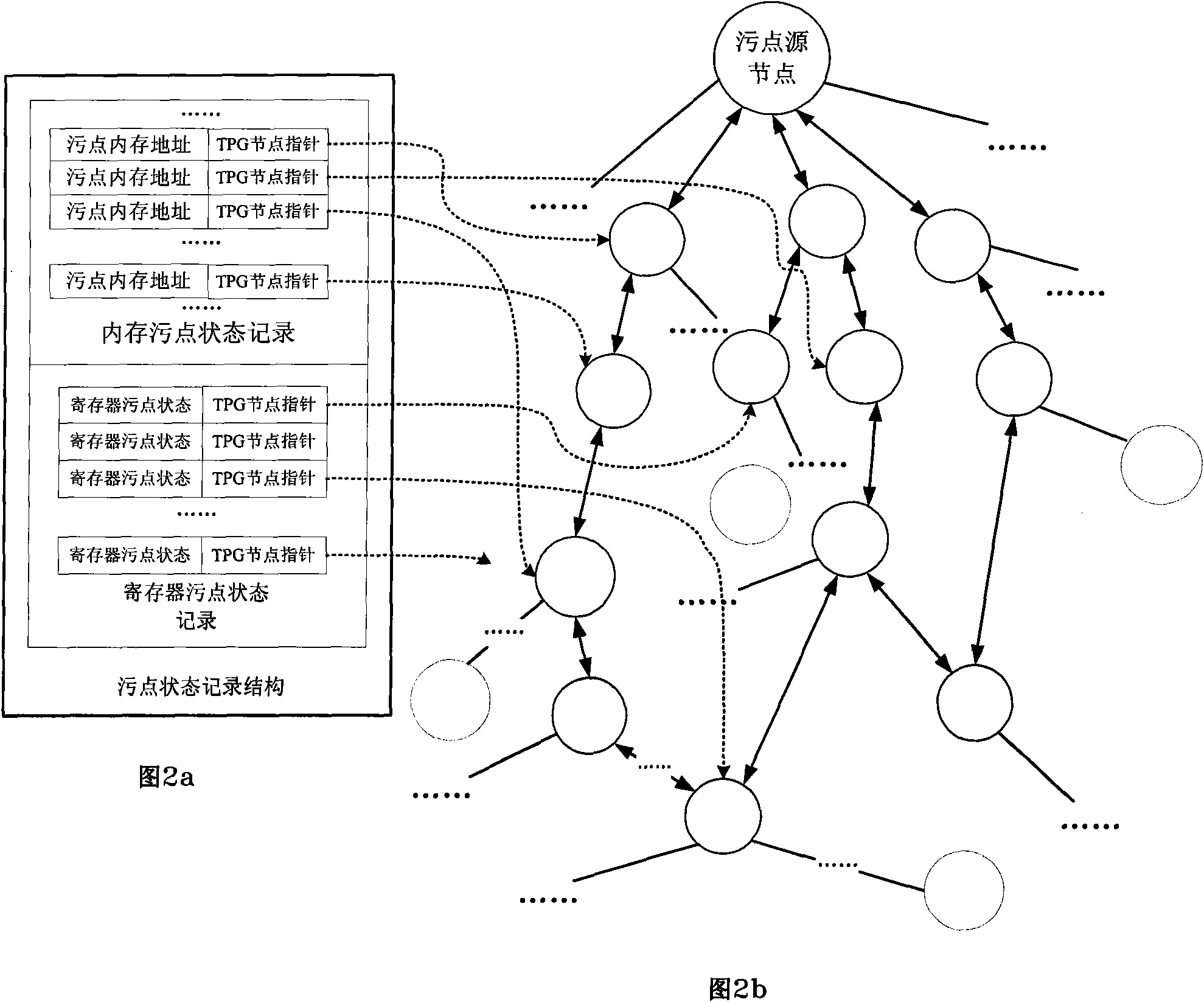
[0032] The present invention utilizes dynamic taint analysis technology to taint the input of untrusted sources of the analysis target program, and then record the use of taint data in the entire code execution process, and according to the data between parameters in the operation containing taint data The dependency propagates the tainted state to the related data, and monitors whether the tainted data is used unsafely according to the pre-set rules, so as to detect the attack behavior.
[0033] The specific embodiment of the present invention is described in detail below in conjunction with accompanying drawing: as figure 1 As shown, the implementation process of the automatic network attack feature generation method of the present invention is as follows:
[0034] 1. Construct a retroactive dynamic stain analysis system based on hardware simulator
[0035] The invention realizes the dynamic stain analysis at the instruction level by intercepting the single-step running int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com