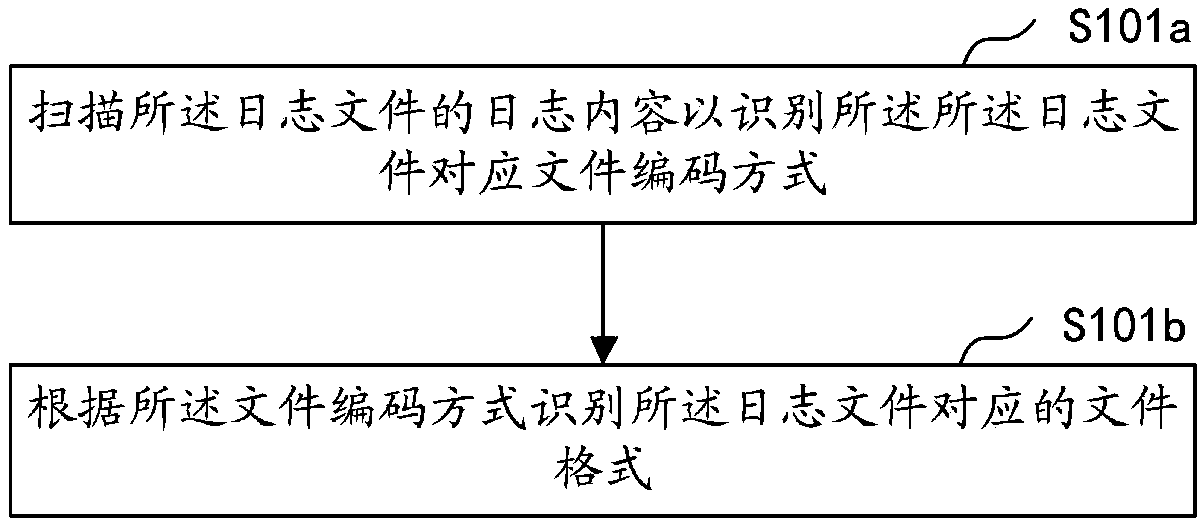
Patents
Literature
2980results about "File system types" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Shared Internet storage resource, user interface system, and method
InactiveUS20100185614A1Promote activeDigital data processing detailsMultiple digital computer combinationsData streamWeb service
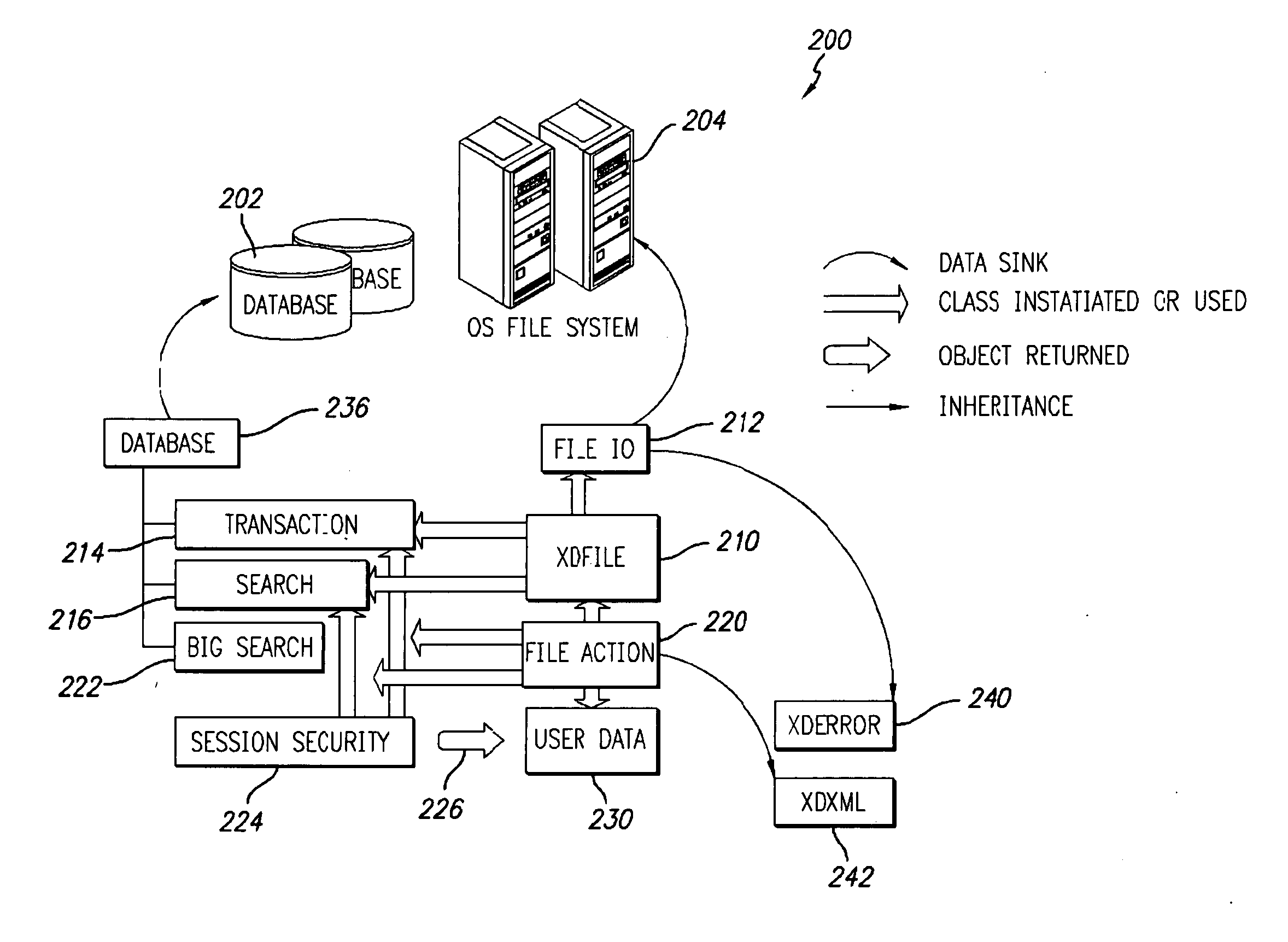
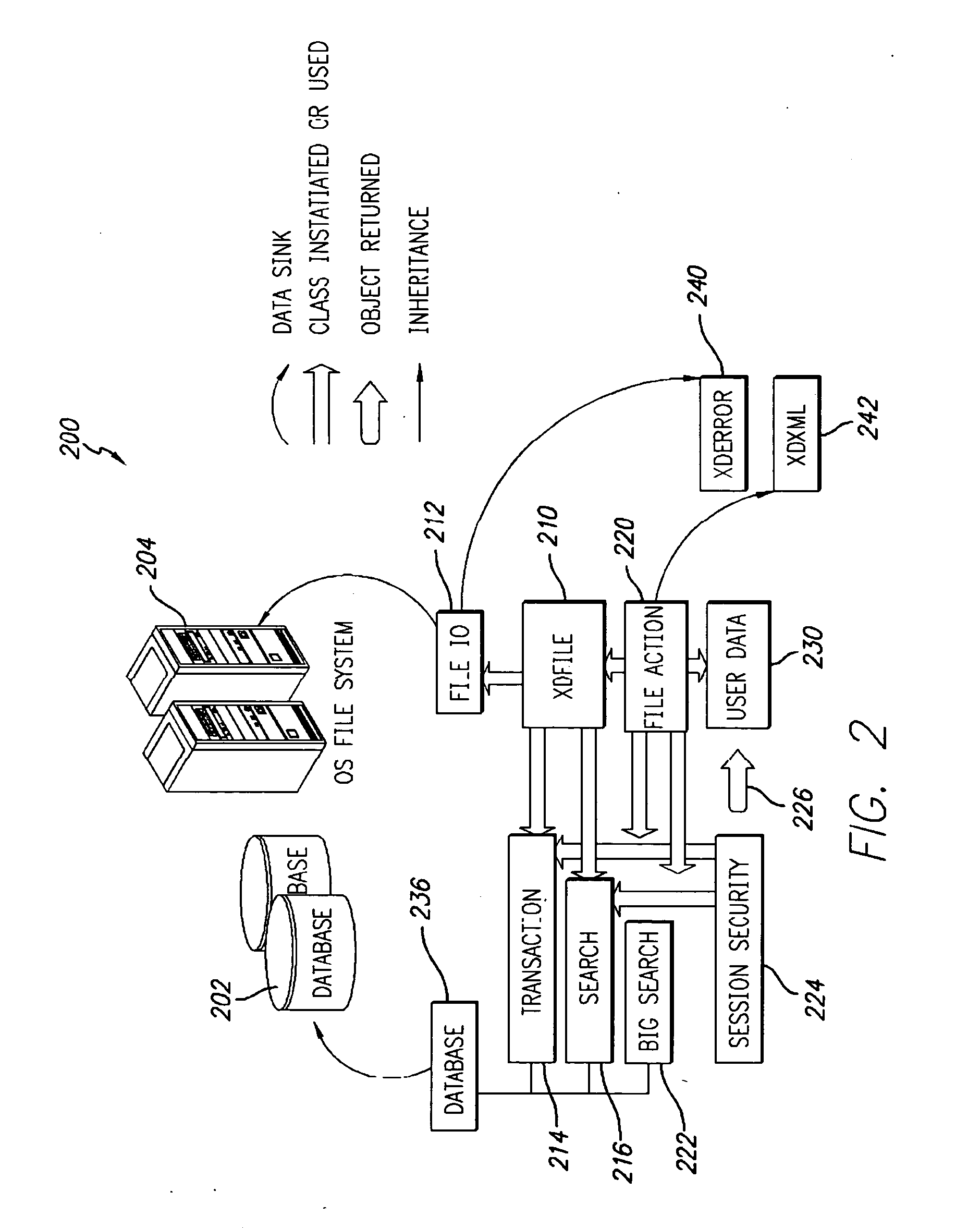
The Shared Internet Storage Resource provides Internet-based file storage, retrieval, access, control, and manipulation for a user. Additionally, an easy-to-use user interface is provided both for a browser or stand-alone application. The entire method provides means by which users can establish, use, and maintain files on the Internet in a manner remote from their local computers yet in a manner that is similar to the file manipulation used on their local computers. A high capacity or other storage system is attached to the Internet via an optional internal network that also serves to generate and direct metadata regarding the stored files. A web server using a CGI, Java®-based, or other interface transmits and retrieves TCP / IP packets or other Internet information through a load balancer / firewall by using XML to wrap the data packets. File instructions may be transmitted over the Internet to the Shared Resource System. The user's account may be password protected so that only the user may access his or her files. On the user's side, a stand-alone client application or JavaScript object interpreted through a browser provide two means by which the XML or other markup language data stream may be received and put to use by the user. Internet-to-Internet file transfers may be effected by directly downloading to the user's account space.
Owner:OBRIEN BRETT +3
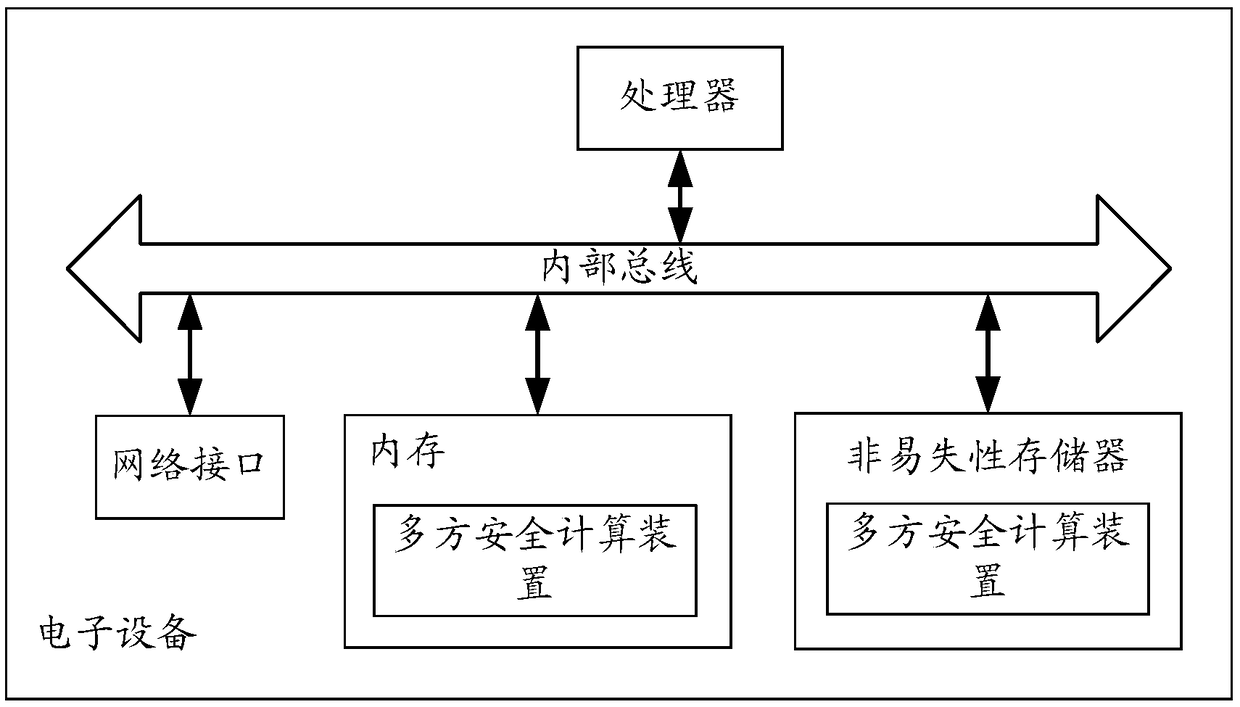
Multi-party safety calculation method and device, and electronic equipment
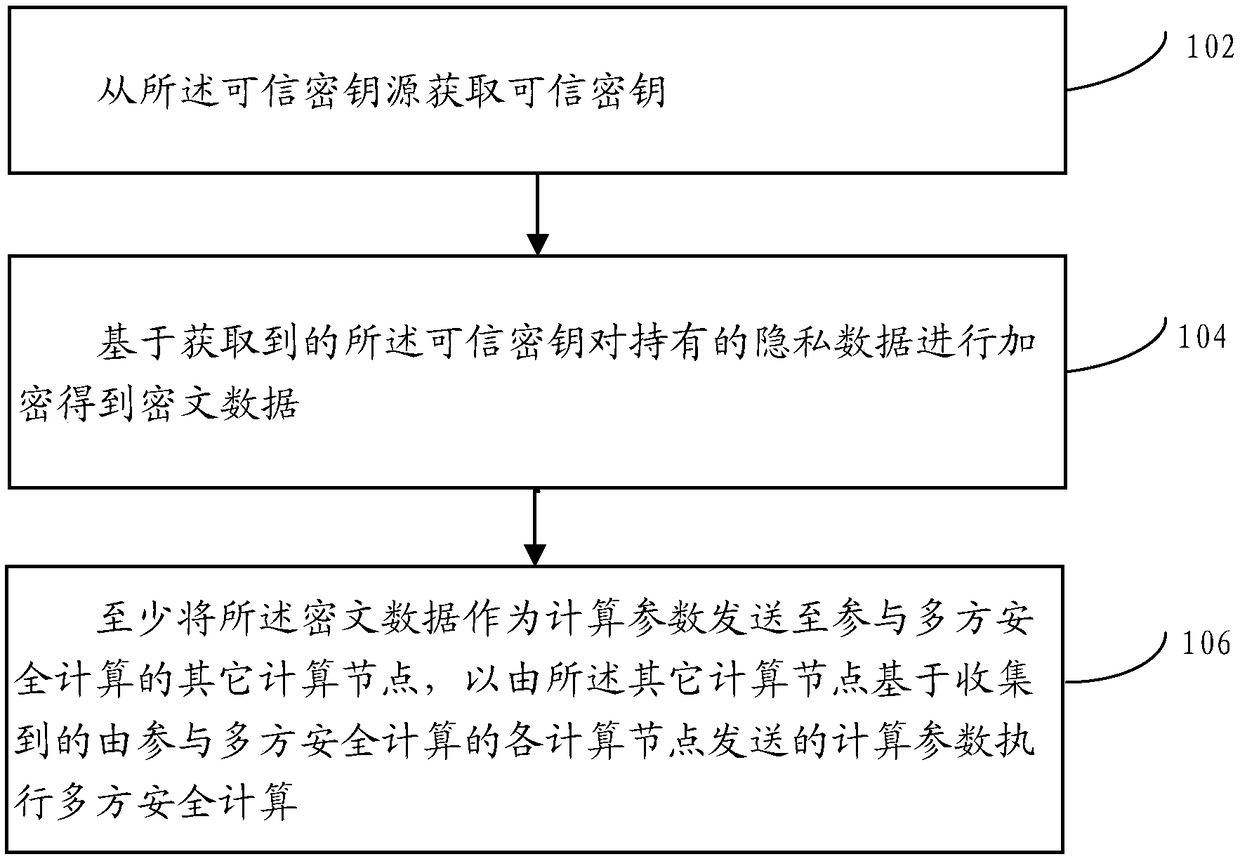
ActiveCN109241016AAvoid the Risk of Privacy LeakageKey distribution for secure communicationData stream serial/continuous modificationCiphertextCalculation methods
A multi-party secure computing method is applied to any computing node deployed in a distributed network. A plurality of computing nodes are deployed in the distributed network, and the plurality of computing nodes participate in the multi-party secure computing together based on the privacy data held by the plurality of computing nodes respectively; Wherein the computing node is corresponding toa trusted key source; The method includes obtaining a trusted key from the trusted key source; Encrypting the held privacy data based on the obtained trusted key to obtain ciphertext data; sending atleast the ciphertext data as computational parameters to other computational nodes participating in the multi-party security computation to perform the multi-party security computation by the other computational nodes based on the collected computational parameters sent by each computational node participating in the multi-party security computation.
Owner:ADVANCED NEW TECH CO LTD
Media aware distributed data layout
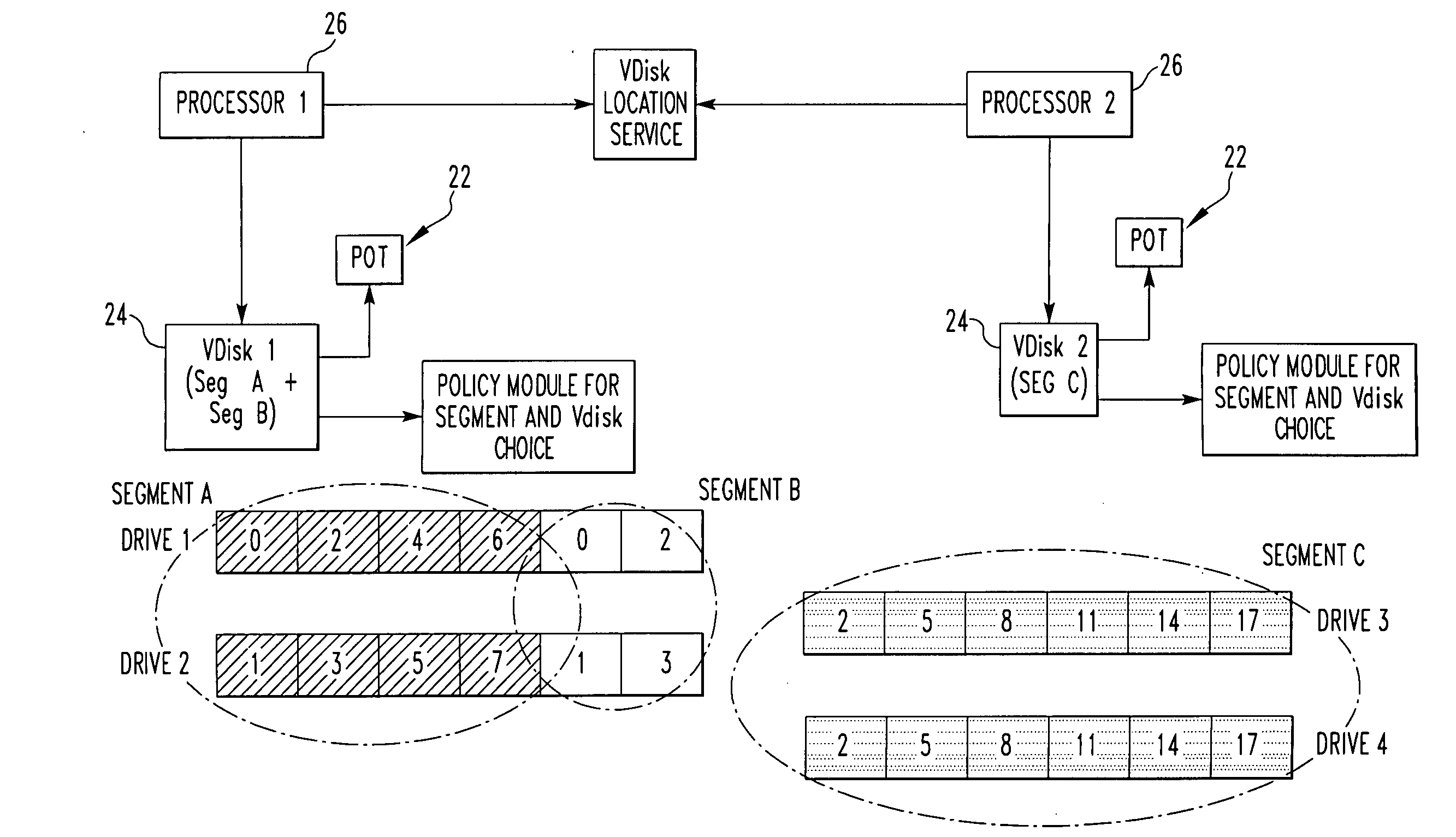
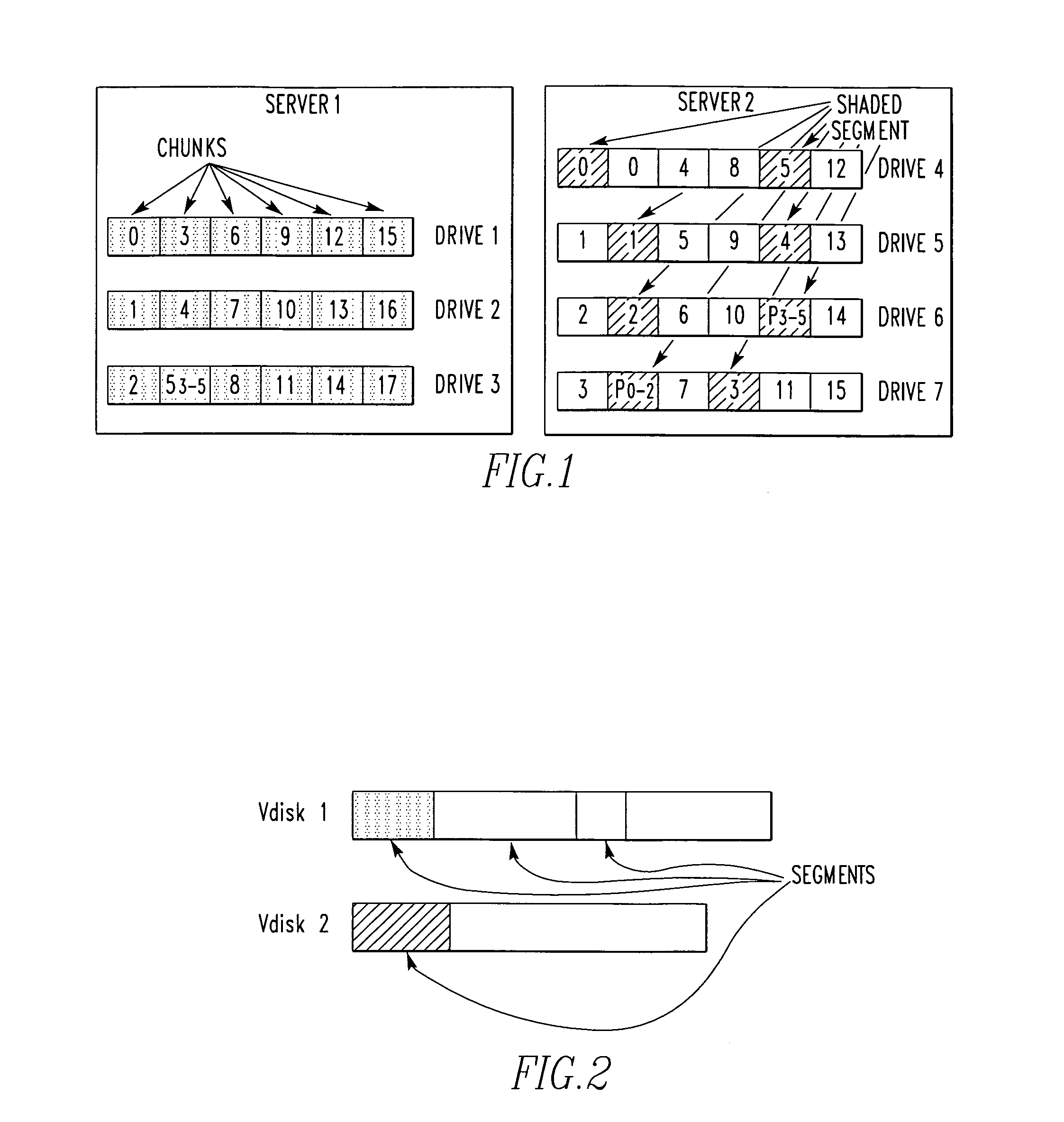
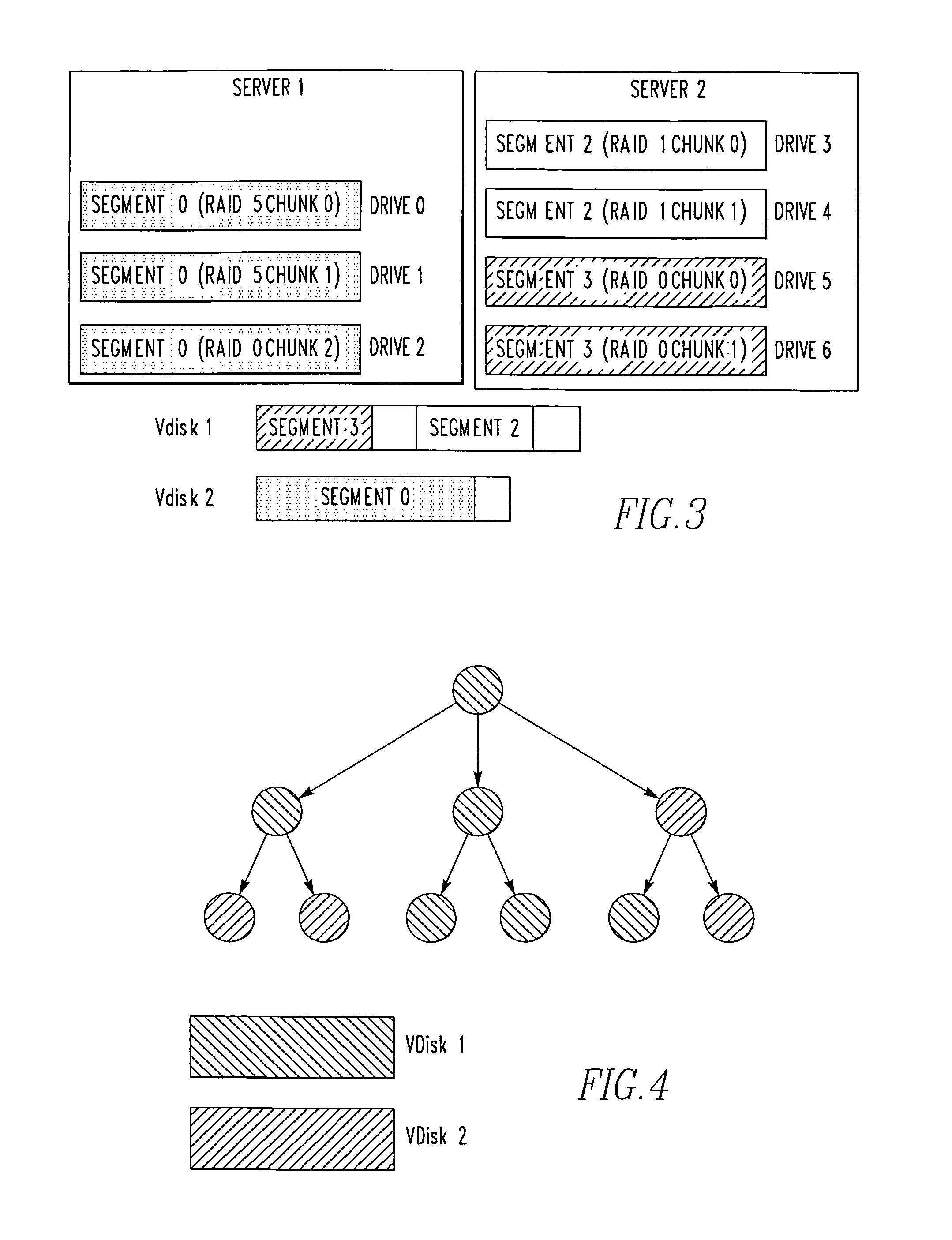
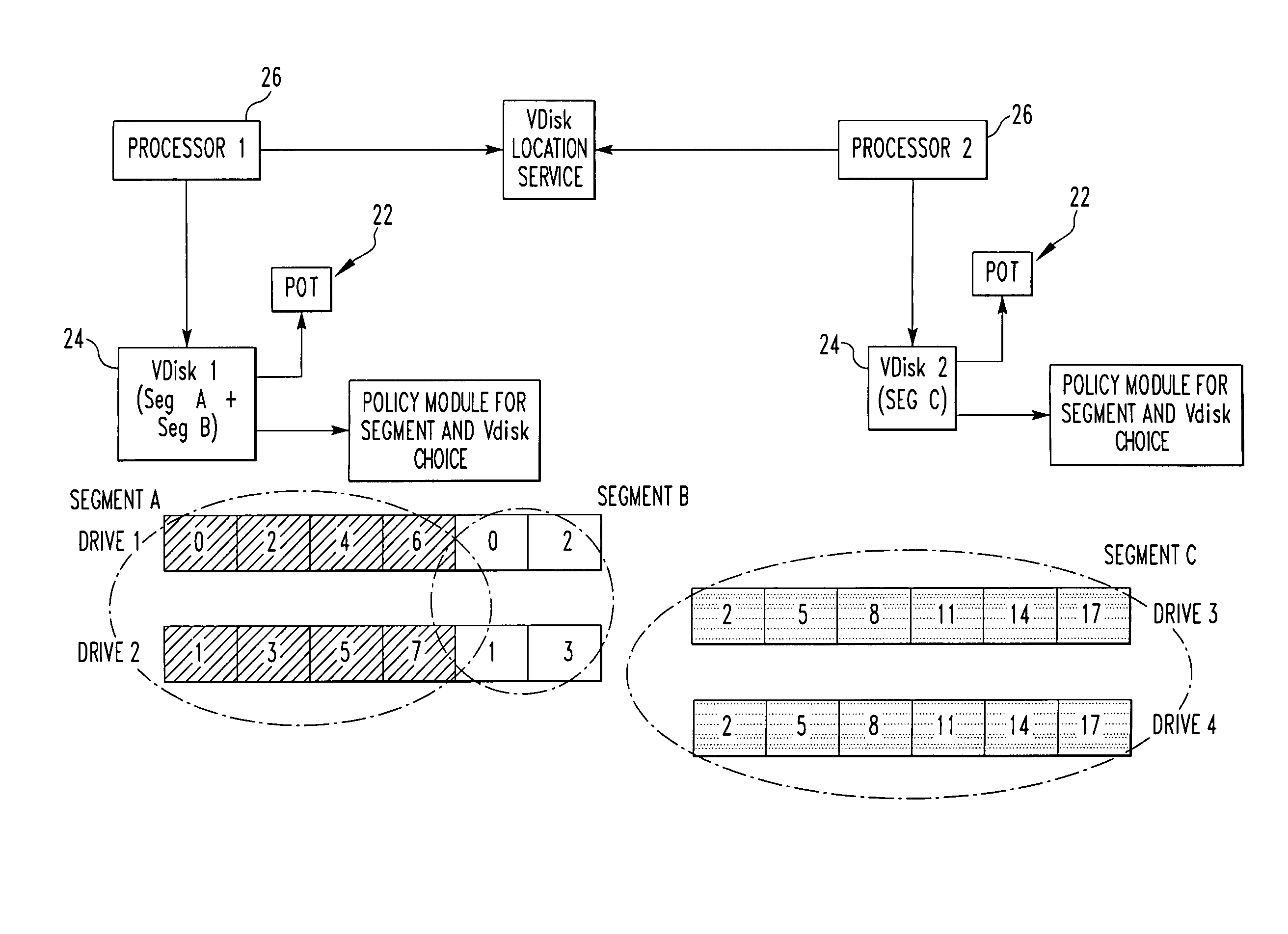
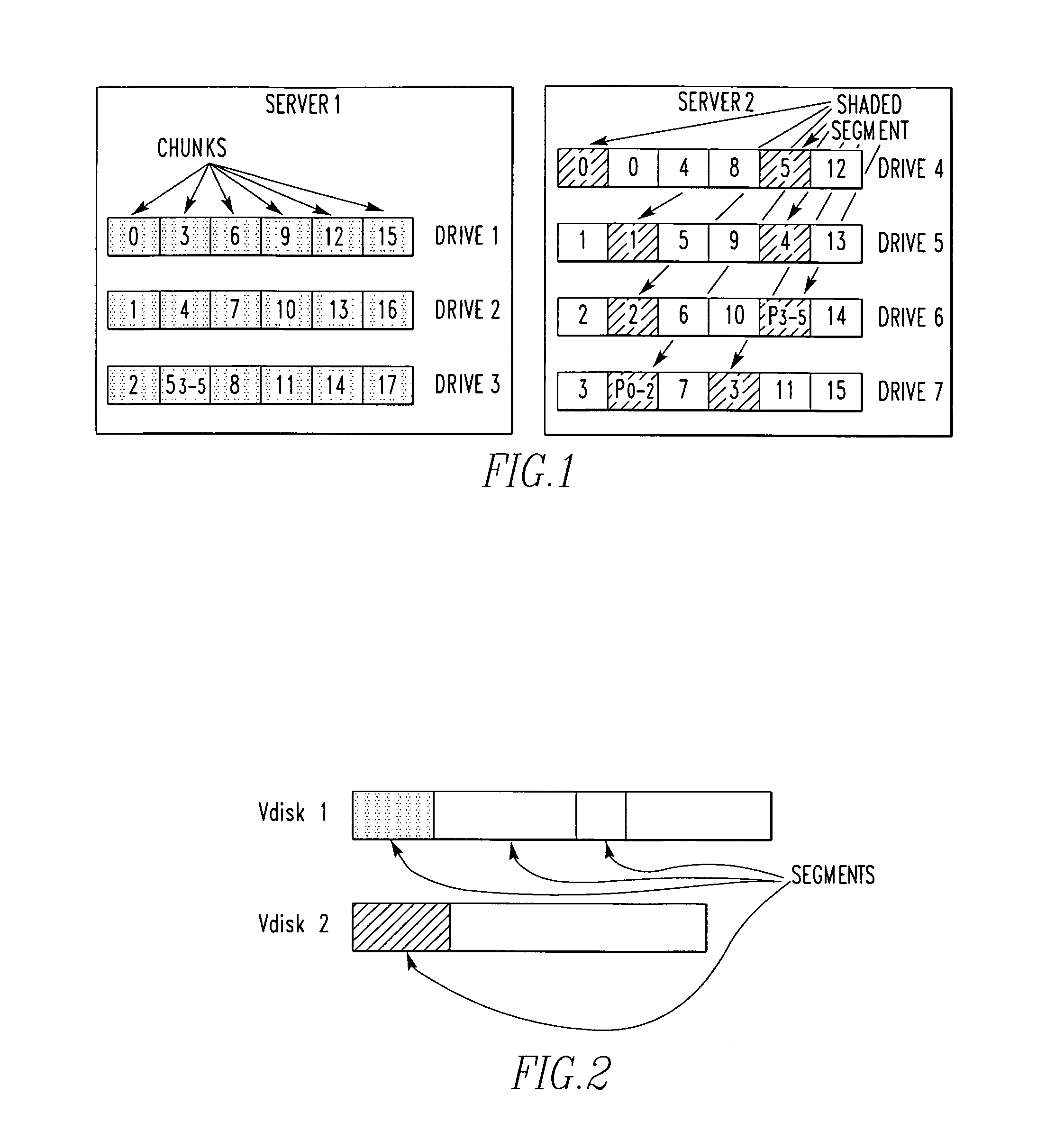
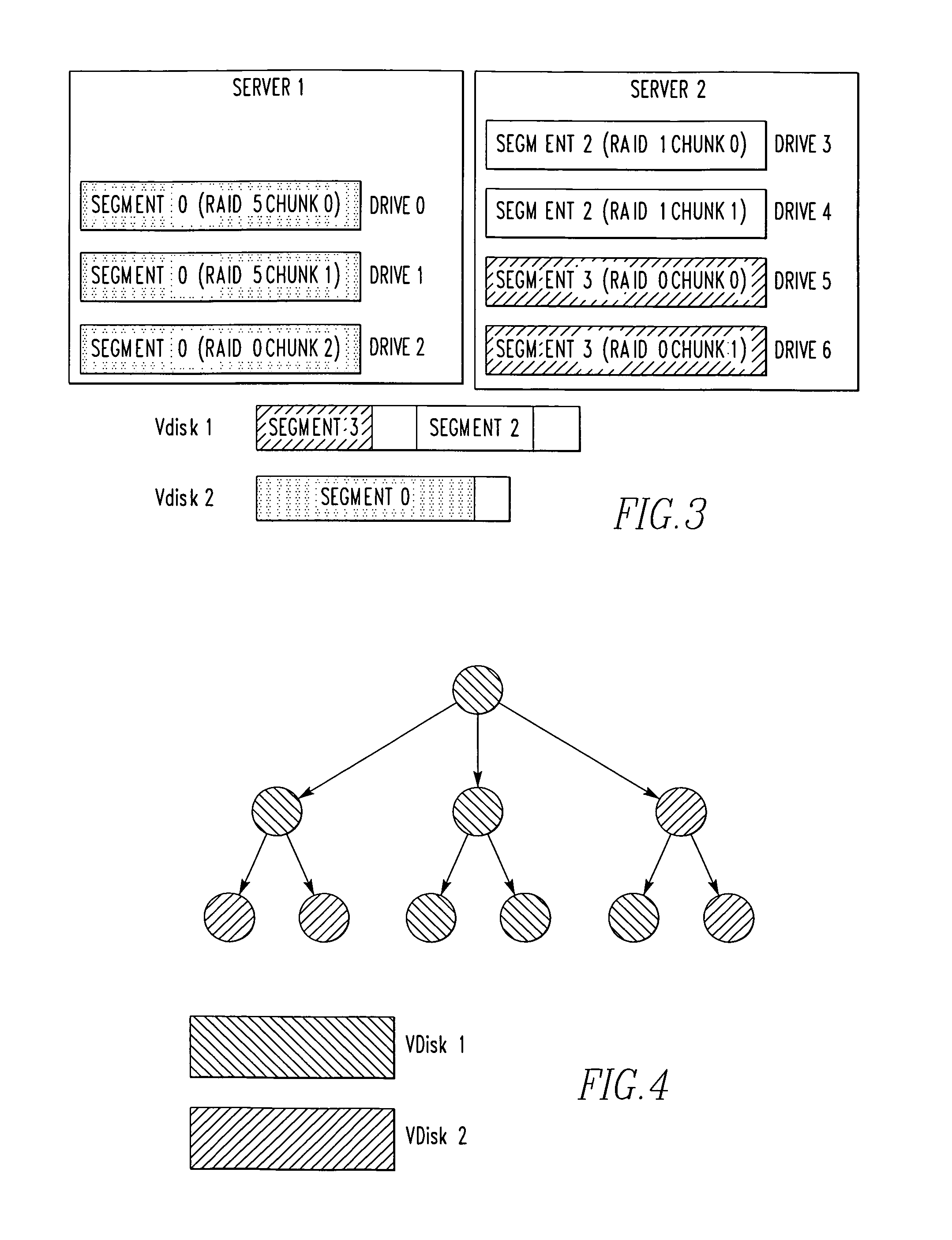
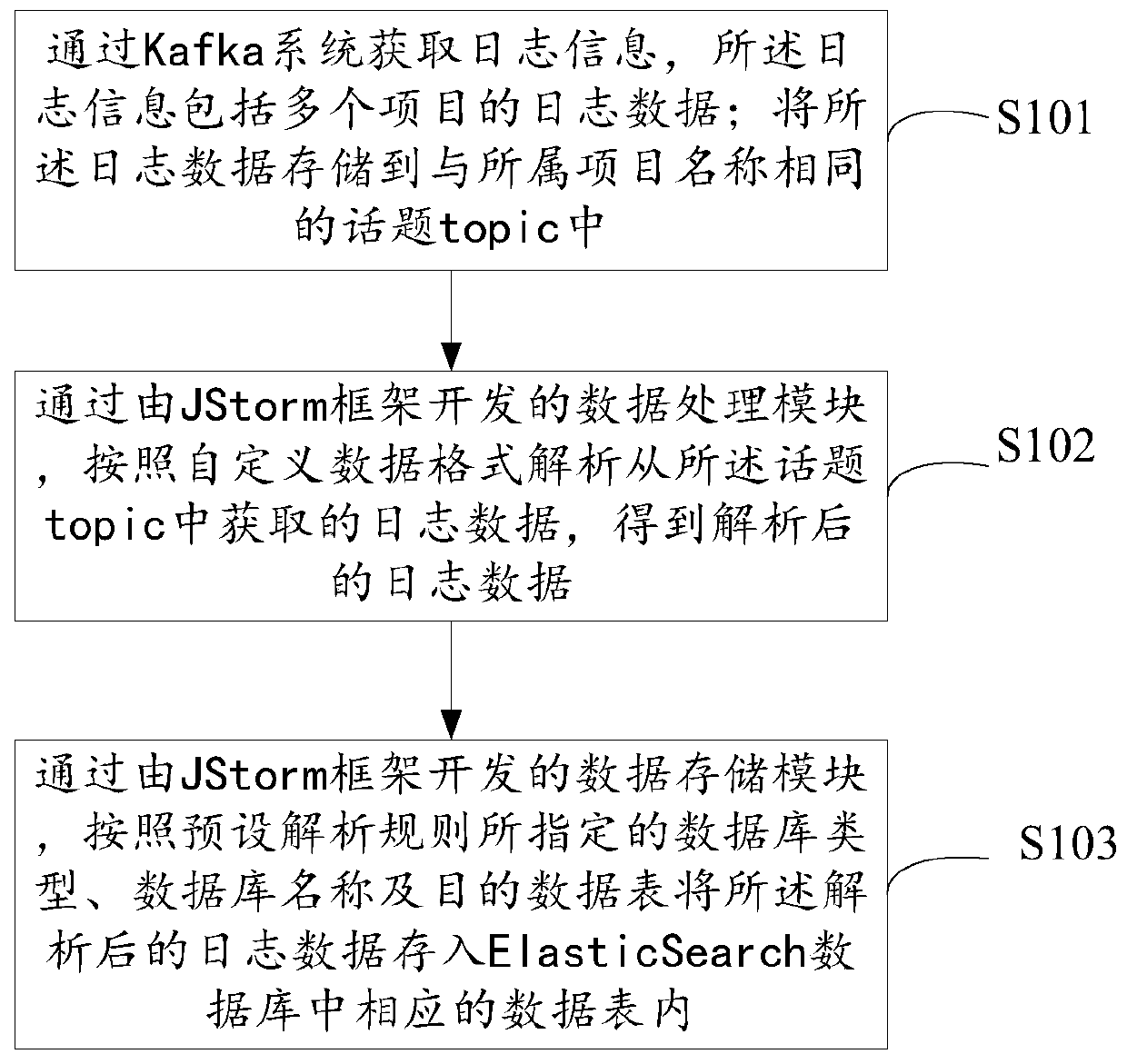
InactiveUS20100011037A1Reduce amountLimited amountData processing applicationsDigital data processing detailsClass of serviceInode
A storage system comprises a plurality of vdisks, with each vdisk containing a plurality of storage segments, and each segment providing a specific class of service (CoS). Each vdisk stores files with data and meta data distributed among its storage segments. A storage system comprises a memory having multiple classes of service. The system comprises an interface for storing a file as blocks of data associated with a class of service in the memory. The interface chooses the class of service for a block on a block by block basis. A file system for storing a file comprises a plurality of vdisks, with each vdisk having a plurality of inodes. Each inode of each vdisk stores data on one or more segments, with each segment having a different class of service. The system comprises a controller which stores data of a file in an inode of a vdisk, in one or more segments of that vdisk. A file system for storing a file comprises a plurality of vdisks, and each vdisk having a plurality of inodes. The system comprises a controller including a plurality of processors, with each processor serving one or more of the vdisks. A file system for storing comprises a plurality of vdisks, with each vdisk having a plurality of inodes, a plurality of inodes of at least one vdisk storing data on a plurality of segments, each segment having a different class of service. The system comprises a controller which stores data of the file in one or more segments of one vdisk. A method for storing a file.
Owner:MICROSOFT TECH LICENSING LLC
System and method for performance testing of scalable distributed network transactional databases
ActiveUS20190140935A1Shorten the timeEasy loadingEncryption apparatus with shift registers/memoriesDesign optimisation/simulationComputer hardwareScalable distributed
A system for performance testing of scalability implementations and testing of stability in blockchain database implementations. The testing system comprises a cluster of private blockchain nodes instantiated on a network and a control console that allows the user to set the number of nodes in the network and the number of clients for testing of a particular blockchain implementation. Performance metrics are established and tested. The test system allows for staged testing using generated databases, wallets, and accounts starting with simple 5-node networks, expanding to larger networks, then testing with decreased block validation times, continuing to testing using alternative, faster trust schemes, then testing implementation on divided blockchains, and finally testing on shared blockchains.
Owner:LIQUINEQ AG
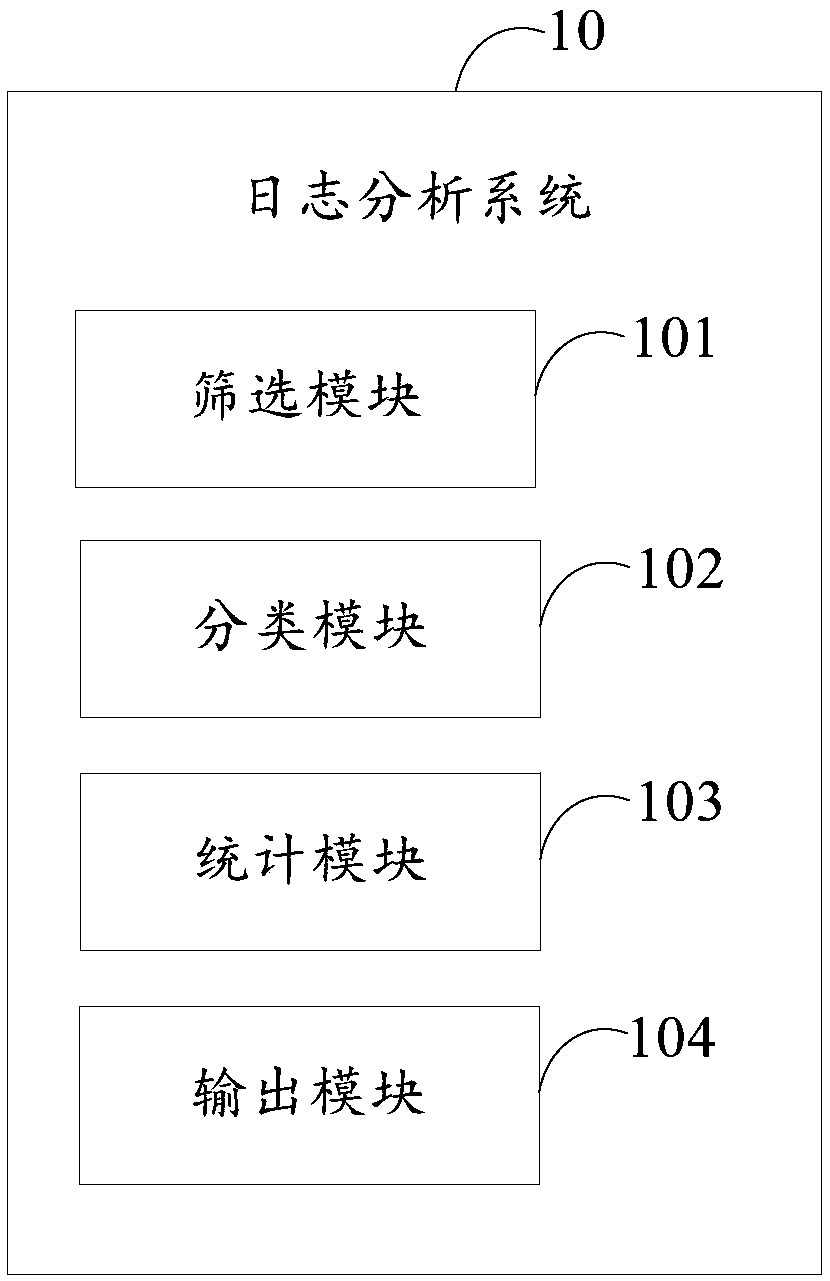
Log analysis method and system, terminal and computer-readable storage medium
PendingCN109634818AIncrease richnessEasy to locate and handleHardware monitoringFile system typesStatistical analysisAnalysis method
The invention provides a log analysis method and system, a terminal and a computer-readable storage medium. The log analysis method comprises the following steps of: screening target log data from a log system according to a screening rule; Classifying and processing the target log data to obtain log data of each category; Carrying out statistical analysis on each category log data according to apreset statistical rule to obtain a statistical result corresponding to each category log data; And comparing each of the statistical results with a corresponding preset threshold value, and outputting alarm information corresponding to the first class log data when a first statistical result exceeds the first preset threshold value, wherein the first statistical result corresponds to the first class log data. The invention can realize that the state data of the monitoring object can be screened out from the log system, and whether the alarm needs to be output is judged by comparing with the threshold value, and the abnormality can be found and handled in time.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
Method and system for staging content
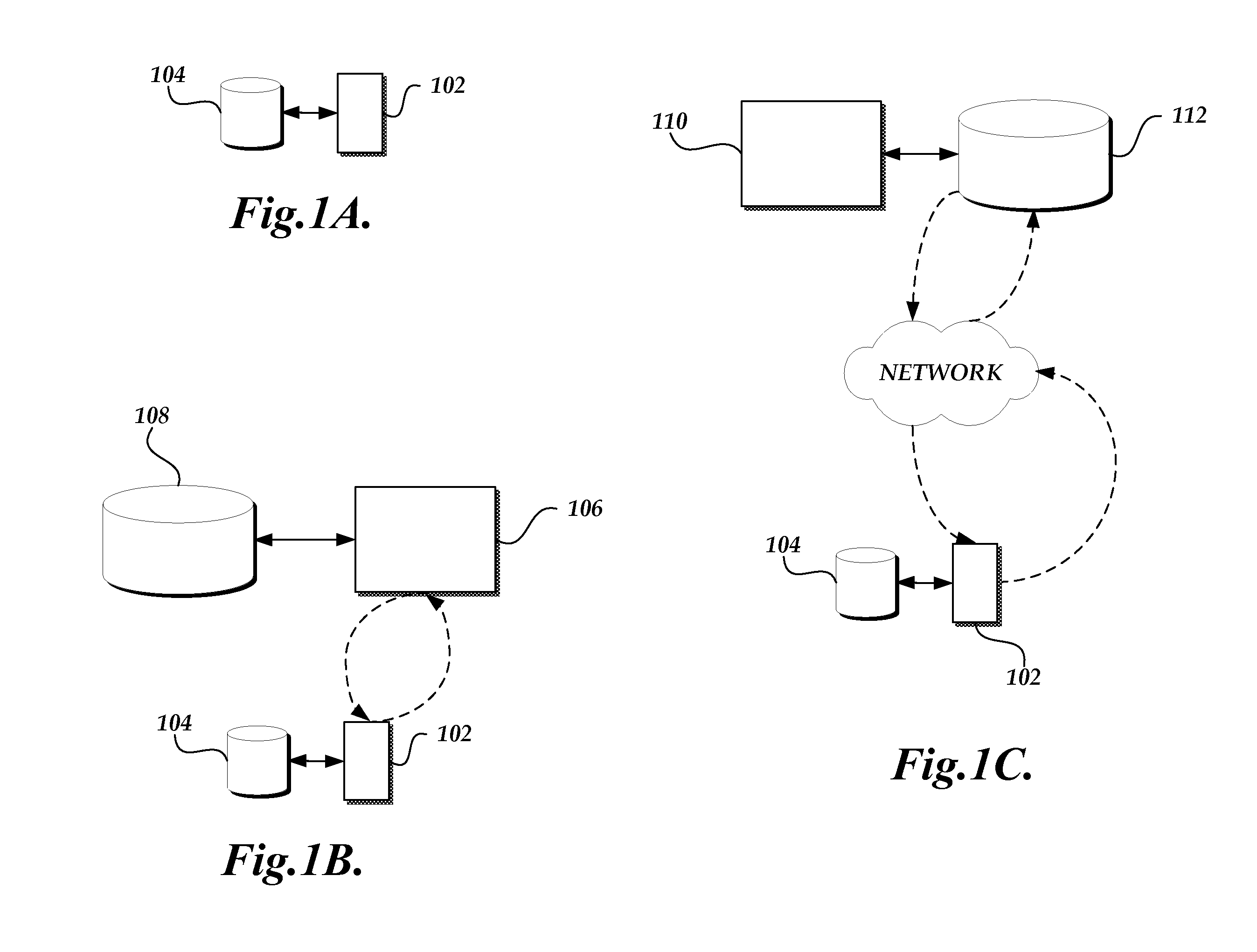
InactiveUS20030149742A1Multiple digital computer combinationsSpecial data processing applicationsThe InternetClient-side
A host server is disclosed that includes a content staging system. The content staging system enables the content providers to localize and verify the accuracy and error-free status of their content so that it may be made available to clients desiring the content while minimizing or preventing any errors before posting on the Internet. In order for these content providers to be able to publish their data to the website, they must first copy their data and attributes to the staging system. This staging system processes the data in a timely manner and makes it available to the content provider who submitted it in a first-in, first-out queue.
Owner:HEWLETT PACKARD DEV CO LP
A system and method for processing big data using electronic document and electronic file-based system that operates on RDBMS
InactiveUS20190332606A1Reduced RDBMS vertical stack sizeImprove data retrieval speedDatabase updatingDatabase management systemsData setData field
Owner:KEE KIM SENG
Log file processing method and device, computer device and storage medium
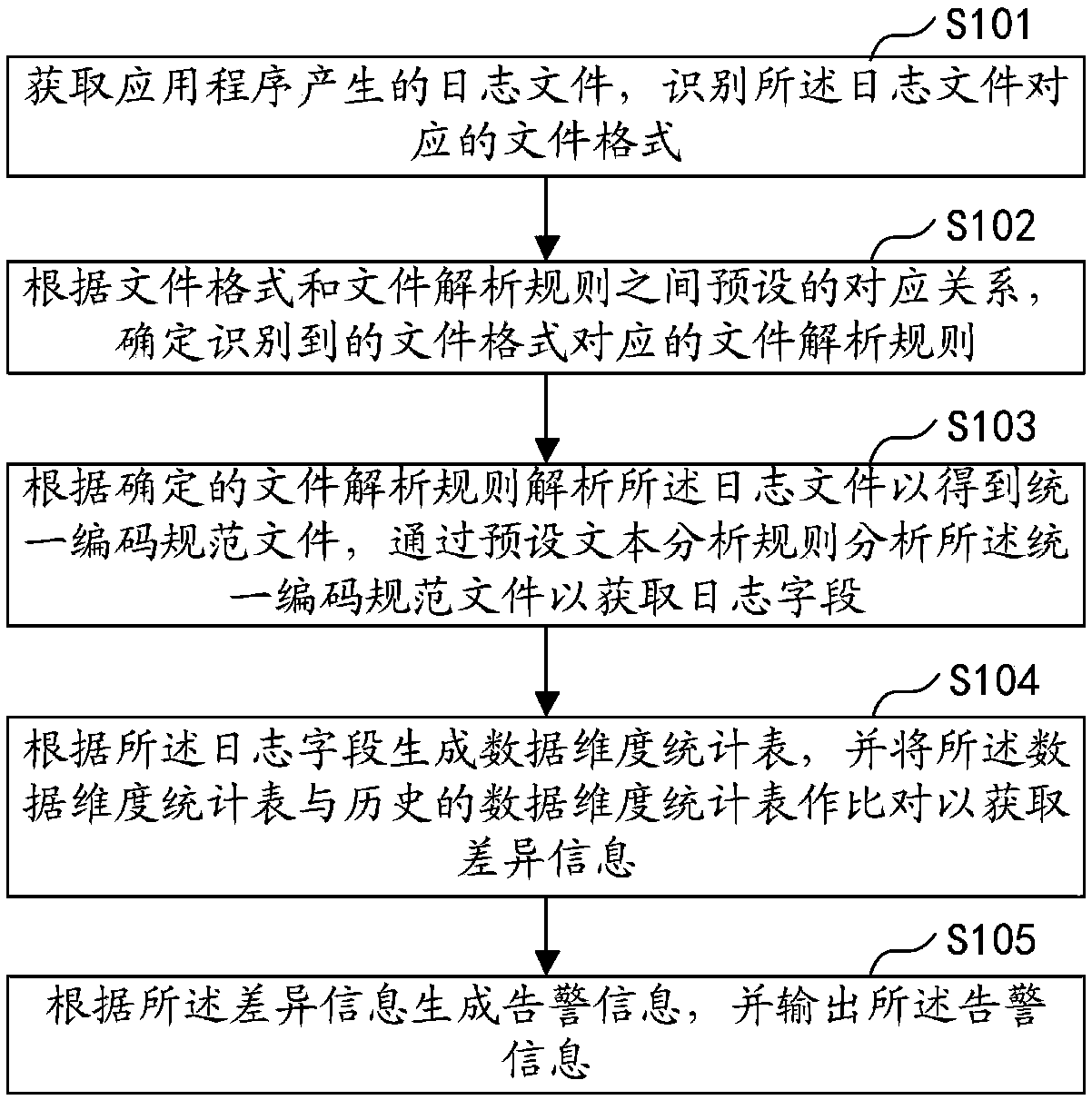
ActiveCN109324996ARealize managementRealize dynamic monitoringFile system administrationFile system typesSpeed of processingApplication software
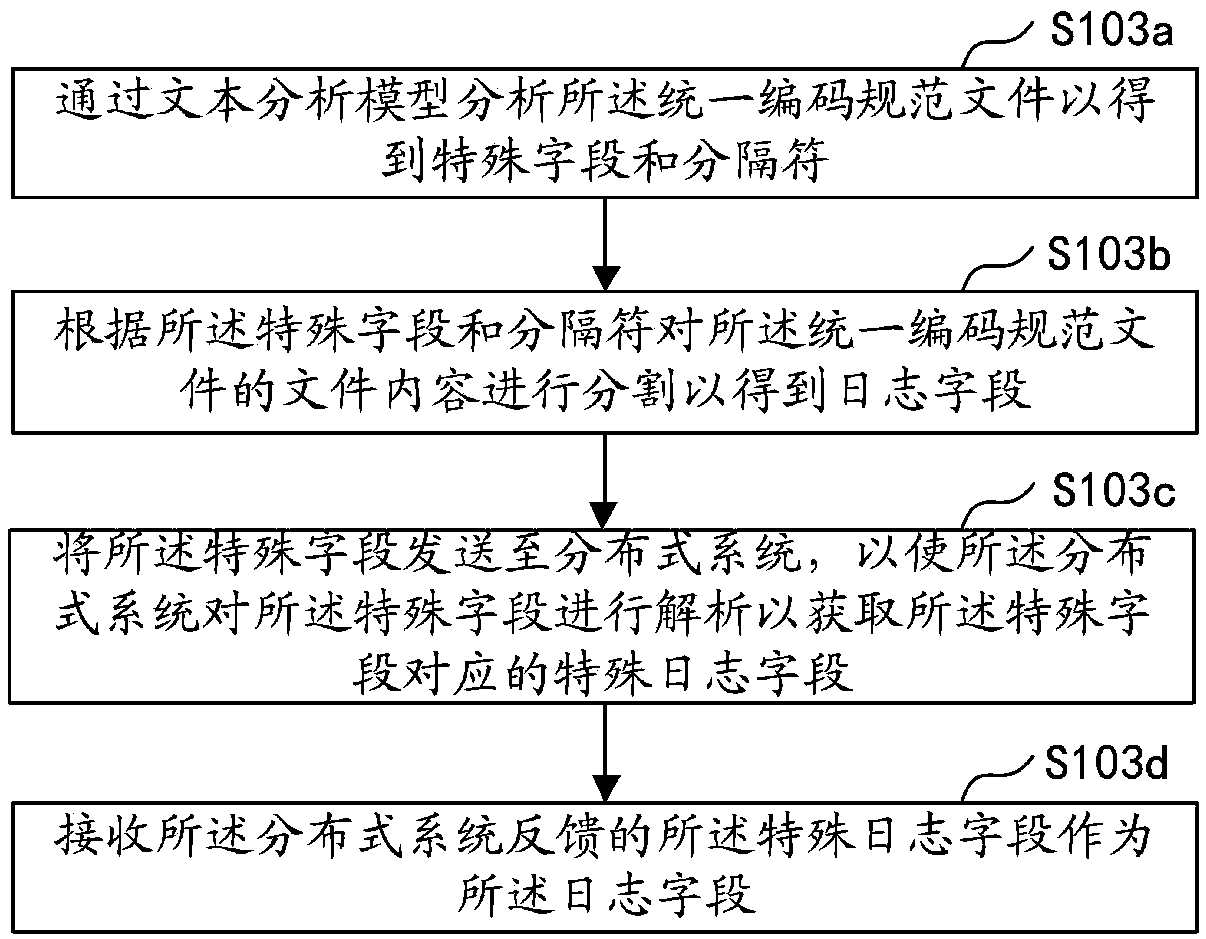
The invention belongs to the abnormal monitoring field of cloud monitoring, in particular to log monitoring, and discloses a log file processing method and device, a computer device and a storage medium. The method comprises the following steps of obtaining log files generated by an application program and identifying a file format corresponding to the log files; determining a file parsing rule corresponding to the recognized file format; parsing the log file according to the determined file parsing rules to obtain a unified coding specification file, and analyzing the unified coding specification file through preset text parsing rules to obtain log fields; generating a data dimension statistical table according to the log field, and comparing the data dimension statistical table with a historical data dimension statistical table to obtain difference information; generating alarm information according to the difference information, and outputting the alarm information. The method improves the processing speed of log files in different formats and reduces the workload of developers.
Owner:PING AN TECH (SHENZHEN) CO LTD
Multi-source heterogeneous data real-time processing system and method based on Flink stream computing technology
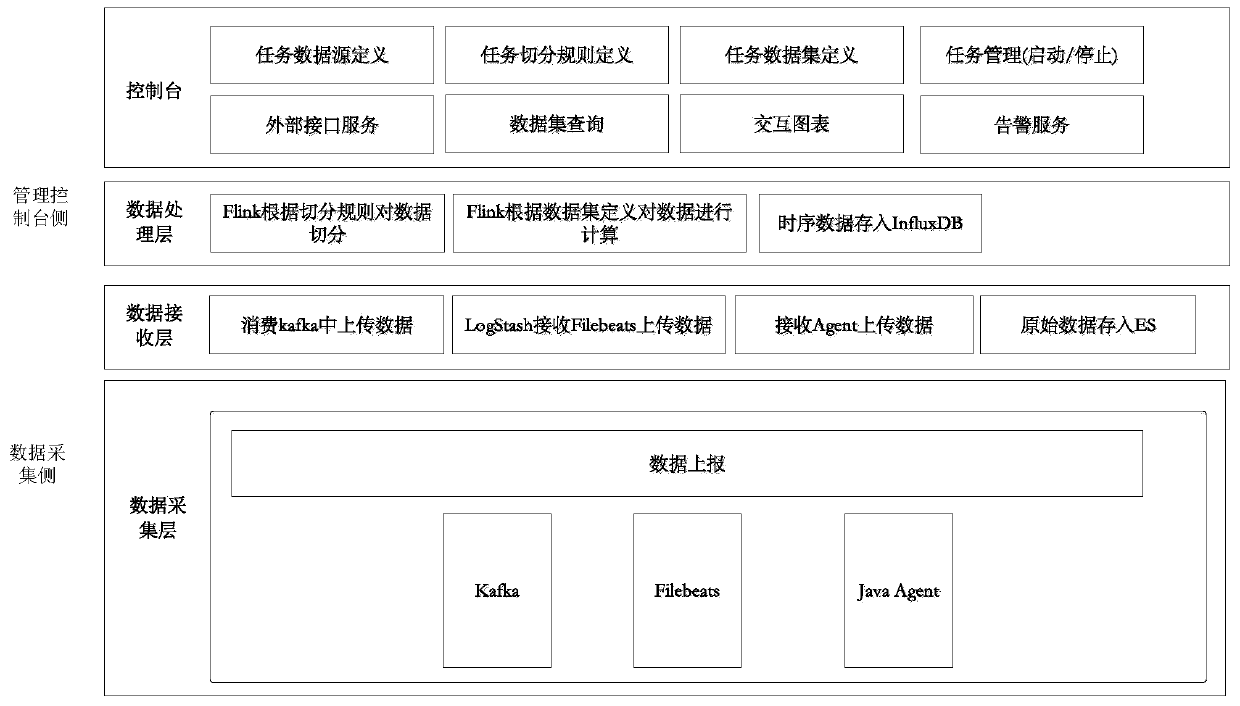
PendingCN110245158AImprove efficiencySpecial data processing applicationsFile system typesData setData acquisition
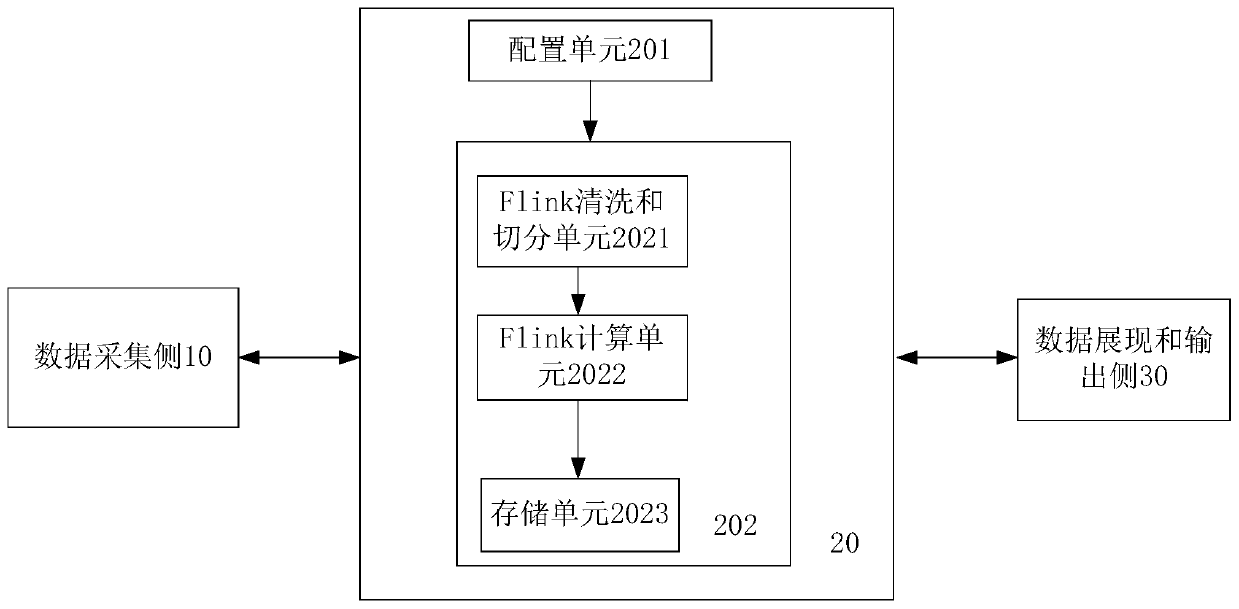
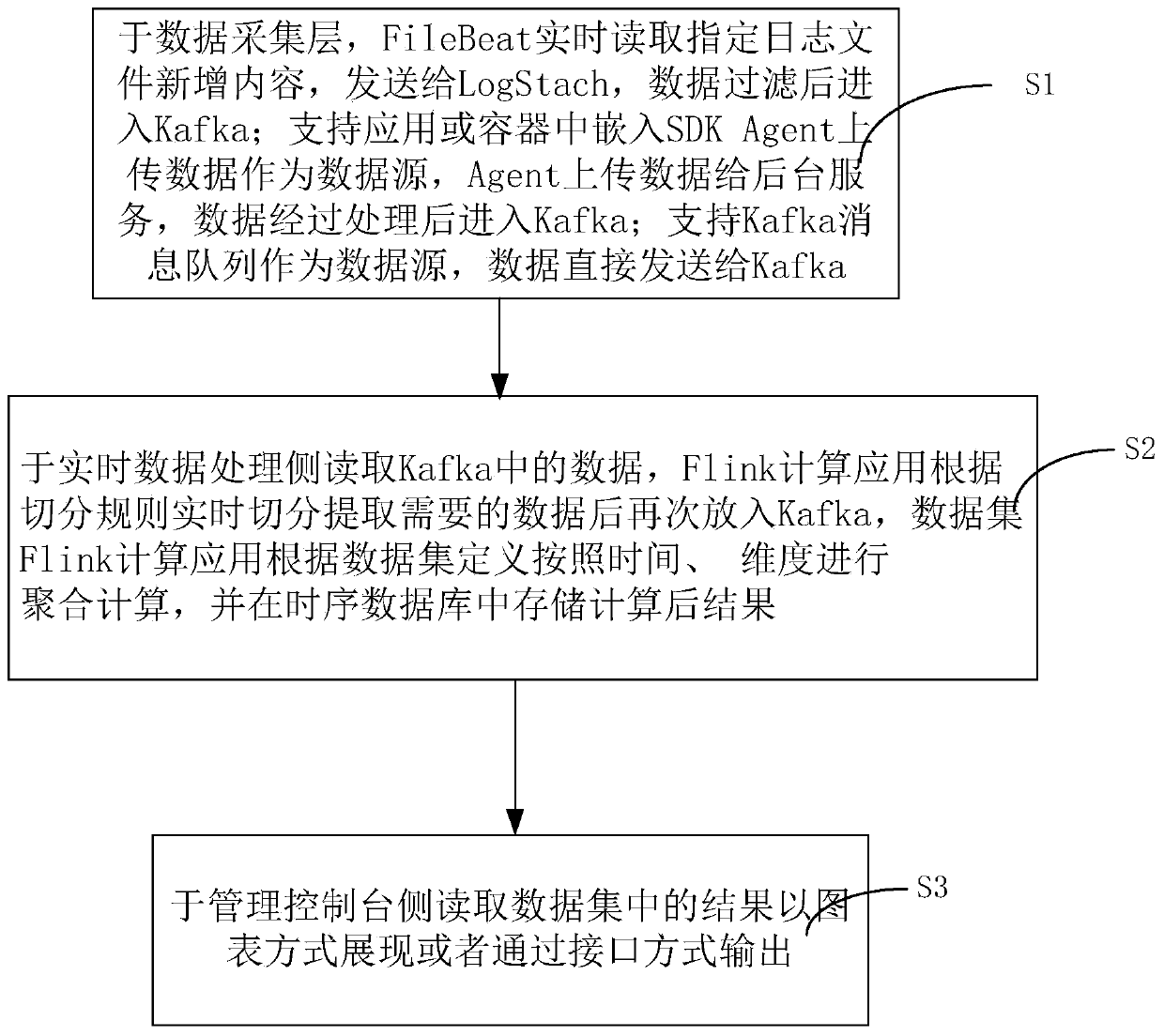
The invention discloses a multi-source heterogeneous data real-time processing system and method based on a Flink stream computing technology. The system comprises a data acquisition side which acquires heterogeneous data dispersed in a plurality of system components in a log mode and / or an SDK mode and / or an MQ mode, and sends the data to Kafka in a continuous flow mode after preliminary processing; a task management platform side which configures a data source type, configures cleaning and segmentation rules of heterogeneous data and dimensions and indexes of a configuration data set, starts a data real-time processing task based on an Flink stream computing technology after all configurations are completed, and defines and stores the data according to the data set after real-time computing of the data; and a data presentation and output side which obtains the result output of the data set. The system can analyze the data with multiple sources and different structures output in the existing service system to find the correlation between the log event and the service so as to help the operation and maintenance personnel improve the efficiency and provide supplementation for the existing service analysis system.
Owner:CHINA TELECOM SHANGHAI IDEAL INFORMATION IND GRP
Link tracking method and device
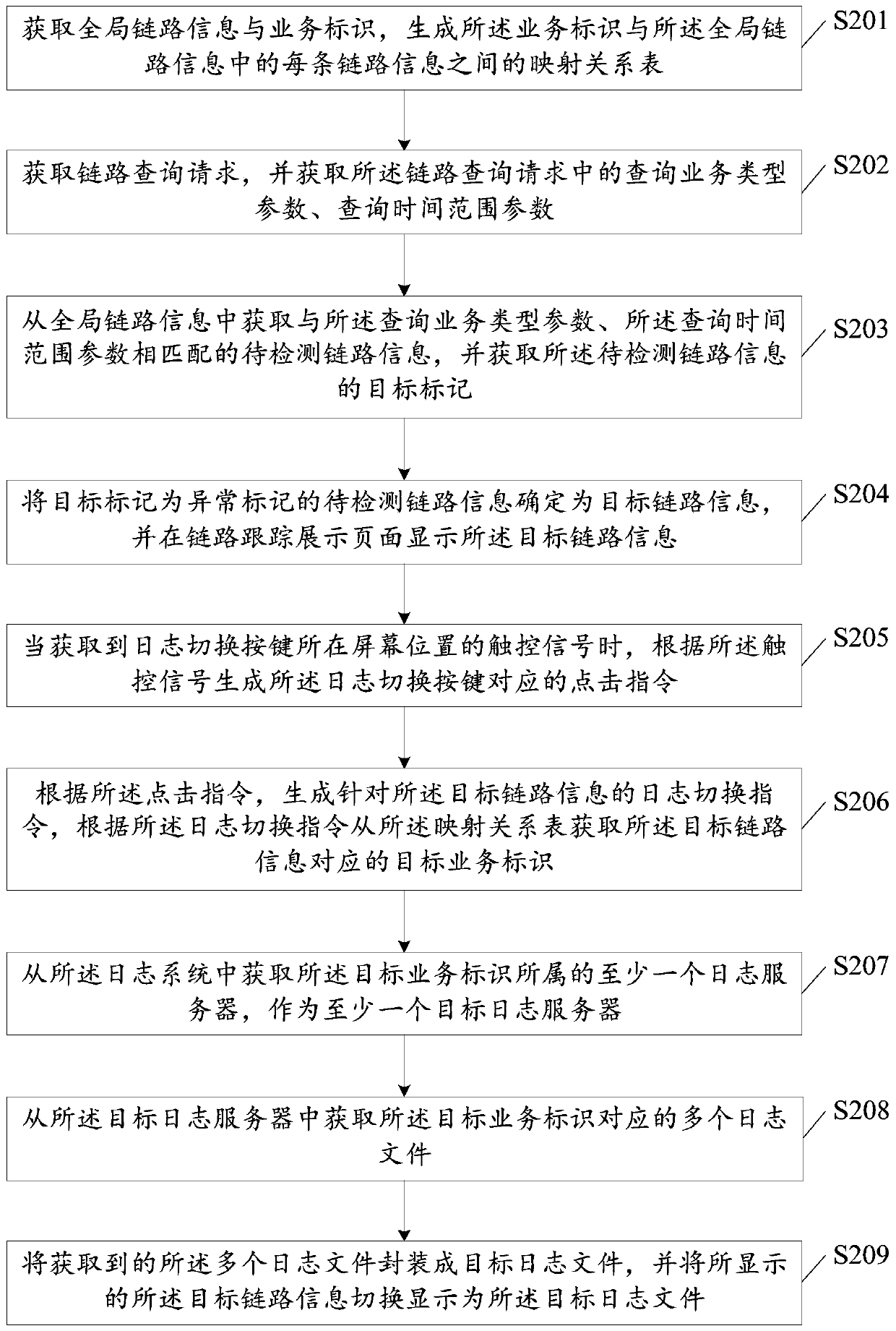
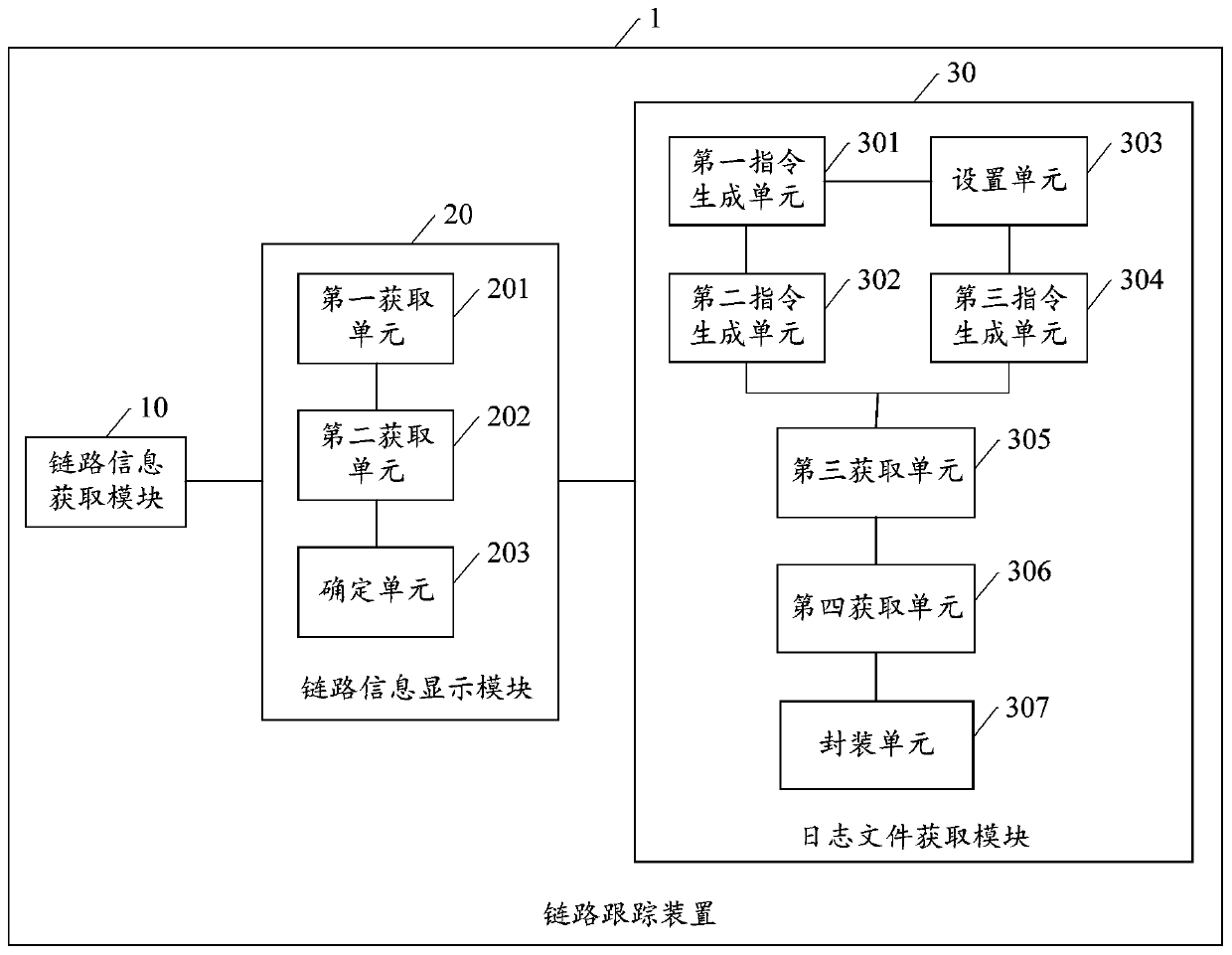
PendingCN110245035AImprove exception handling efficiencyRapid positioningFault responseSpecial data processing applicationsWorld Wide WebException handling
The embodiment of the invention discloses a link tracking method and device, and the method is suitable for the application of a micro-service architecture, and can optimize the link exception processing efficiency. The method comprises the following steps of obtaining the global link information and a service identifier, and generating a mapping relation table between the service identifier and each piece of link information in the global link information; obtaining a link query request, obtaining the target link information according to the link query request, and displaying the target link information on a link tracking display page; and obtaining a log switching instruction for the target link information, obtaining a target service identifier corresponding to the target link information from the mapping relation table according to the log switching instruction, obtaining a target log file corresponding to the target service identifier, and switching and displaying the displayed target link information as a target log file. By adopting the embodiment of the invention, the error root of the link exception can be quickly positioned, so that the link exception processing efficiency is improved.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
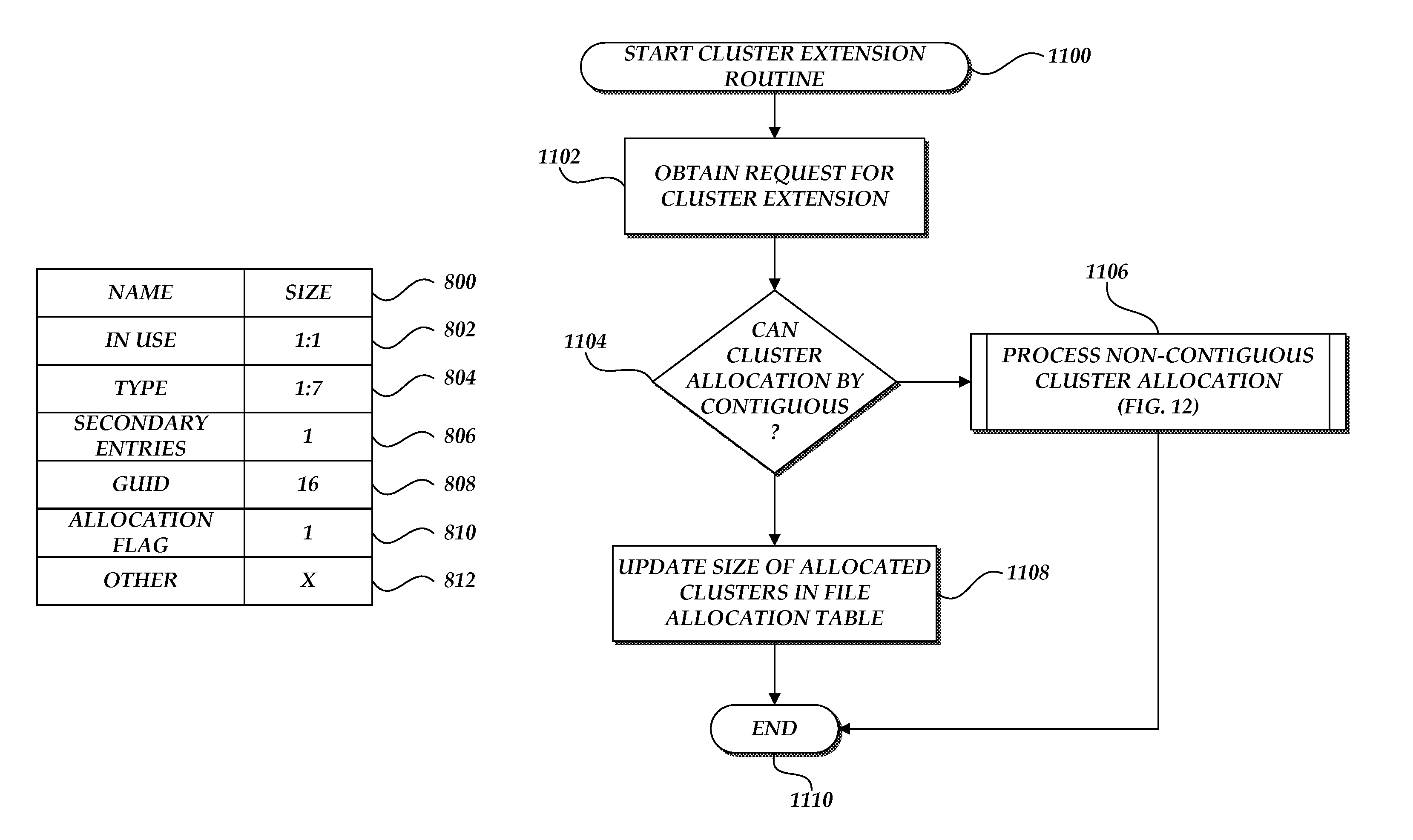
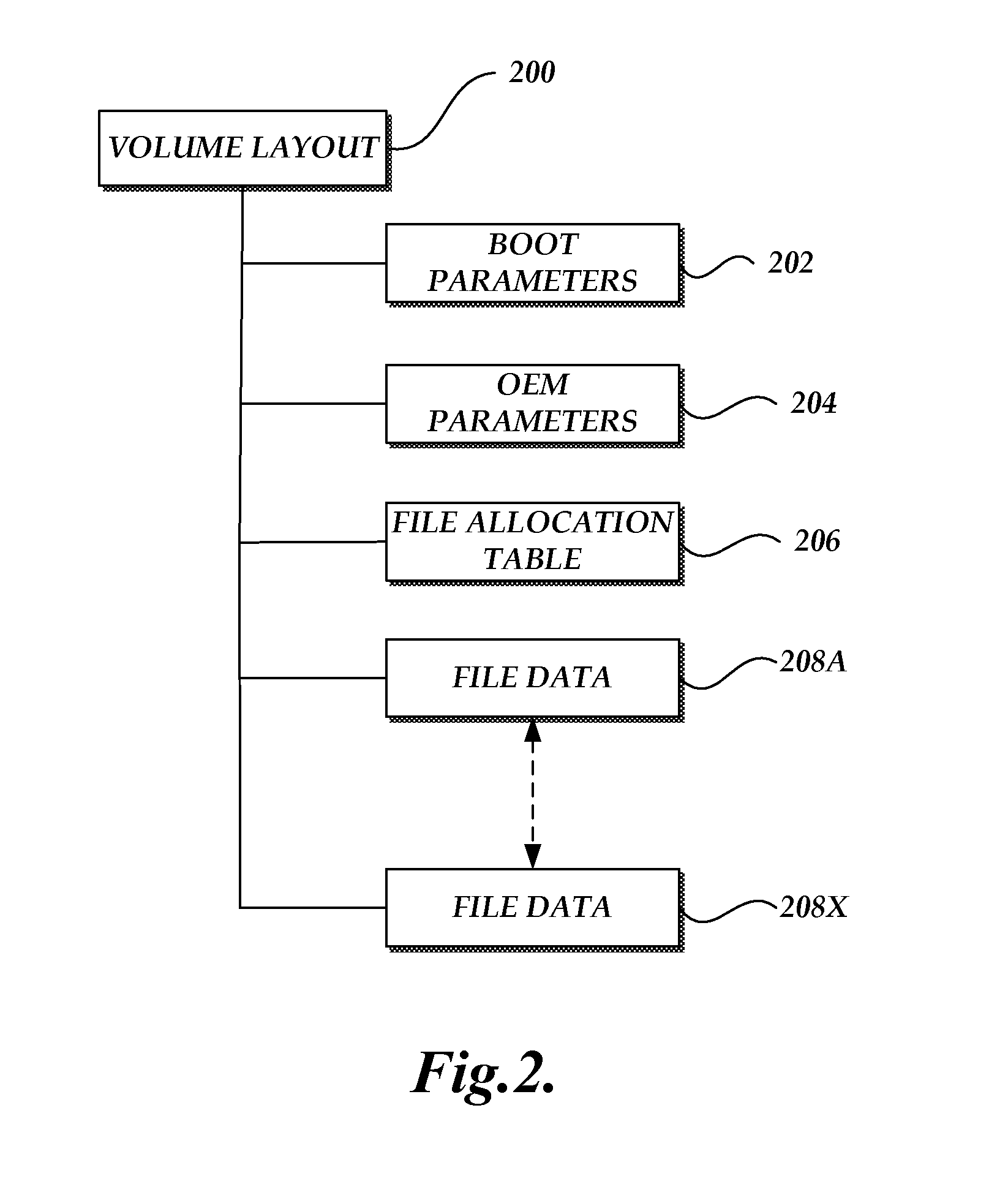
Extending cluster allocations in an extensible file system
An extensible file system format for portable storage media is provided. The extensible file system format includes the specification of primary and secondary directory entry types that may be custom defined. The primary and secondary directory entry types can be further classified as critical and benign directory entries. The directory entry types can define whether a cluster chain corresponding to a file can be contiguously allocated.
Owner:MICROSOFT TECH LICENSING LLC
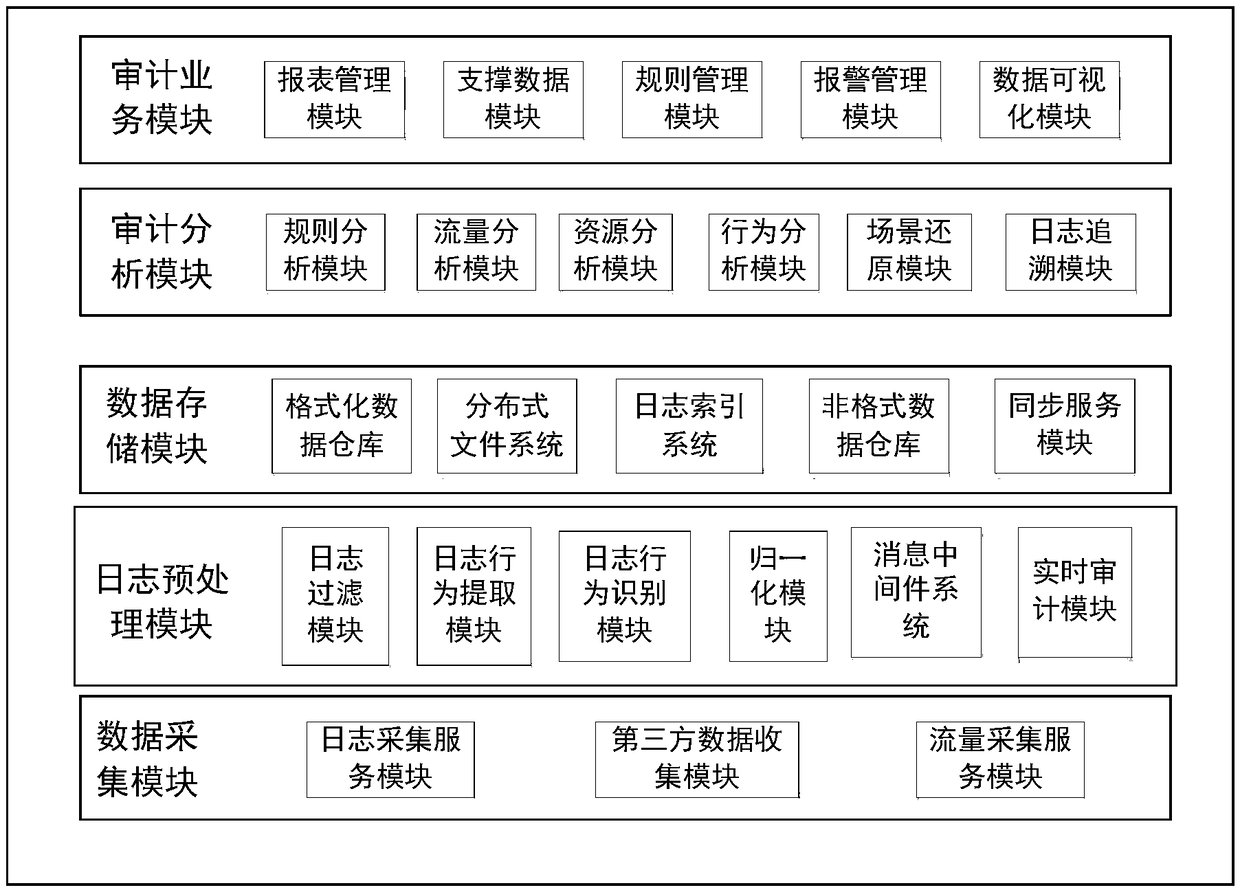
A cloud user behavior audit system and method based on cloud log analysis
InactiveCN109471846AEfficient extractionAccurate extractionSpecial data processing applicationsFile system typesCloud userInto-structure
The cloud user behavior auditing system and the cloud user behavior auditing method based on cloud log analysis provide a unique cloud log processing algorithm, which can efficiently and accurately extract effective information from a mass of original logs with uncertain format, and convert the effective information into structured user operation behavior data which can be used for large data analysis. Based on the operation behavior data, the invention provides the functions of user operation behavior audit, record, multi-dimensional display, violation alarm, compliance analysis, complex process audit, automatic generation of audit strategy and the like, which greatly improves the overall security of the cloud system.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
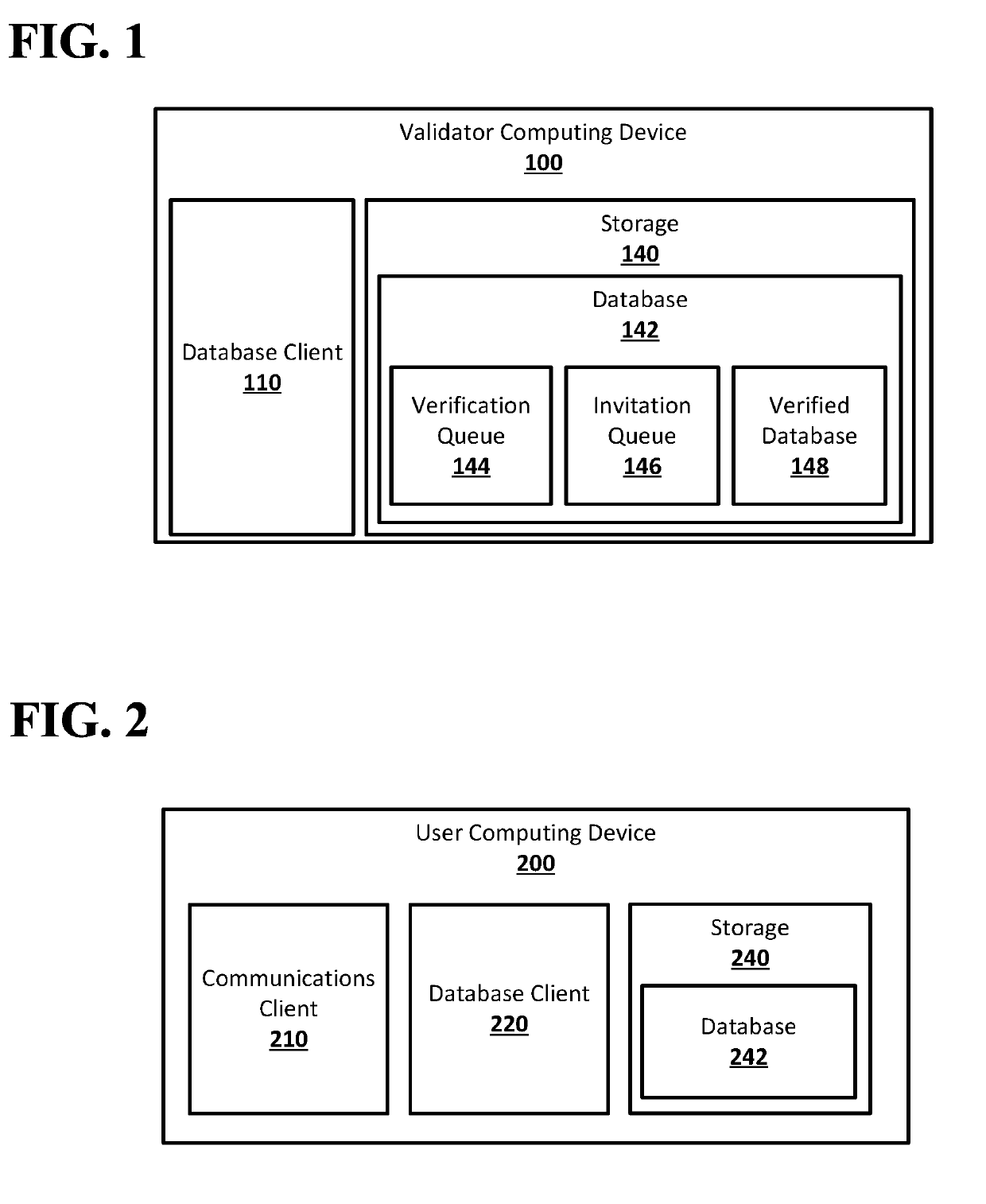
Decentralized database associating public keys and communications addresses
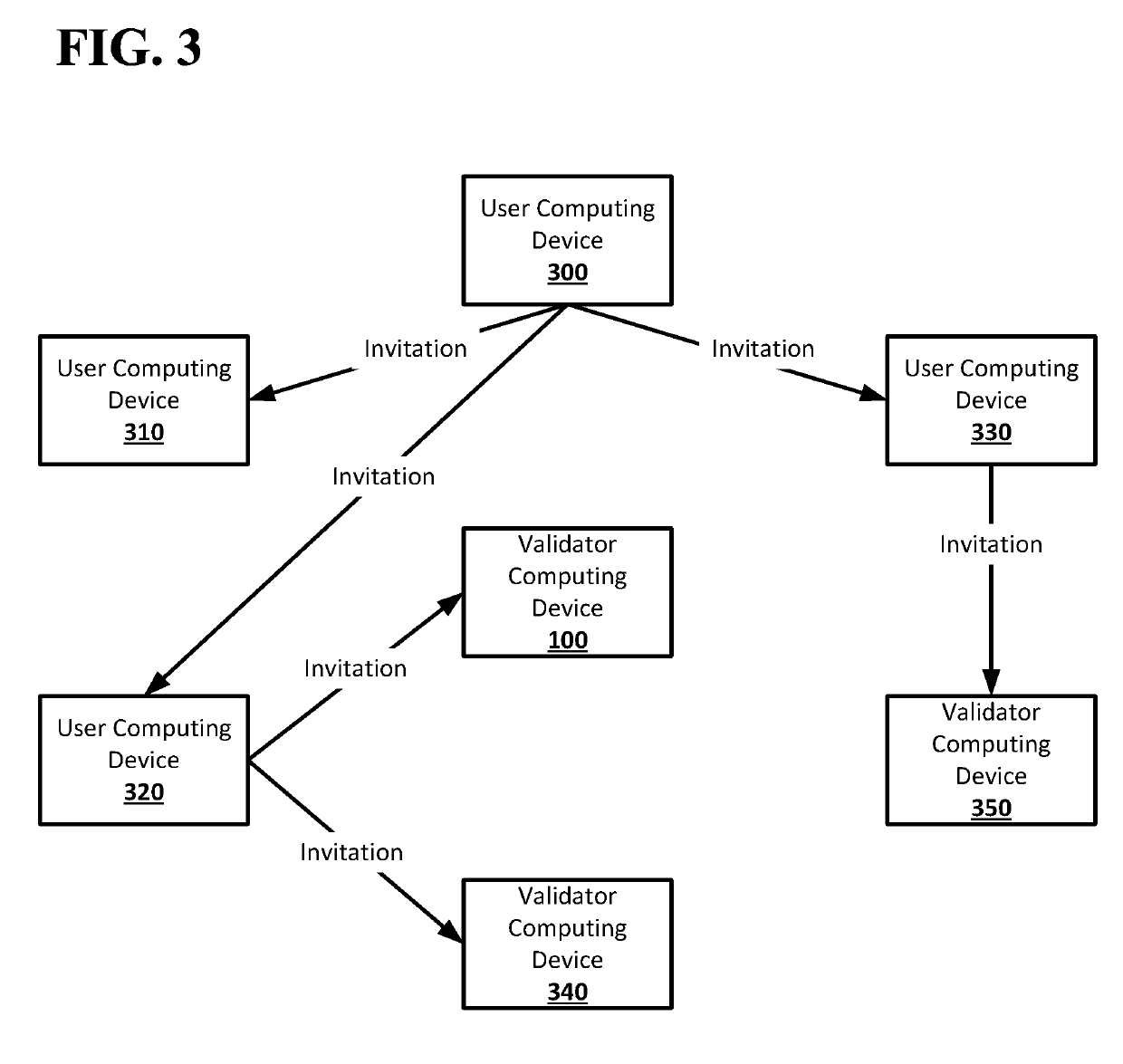
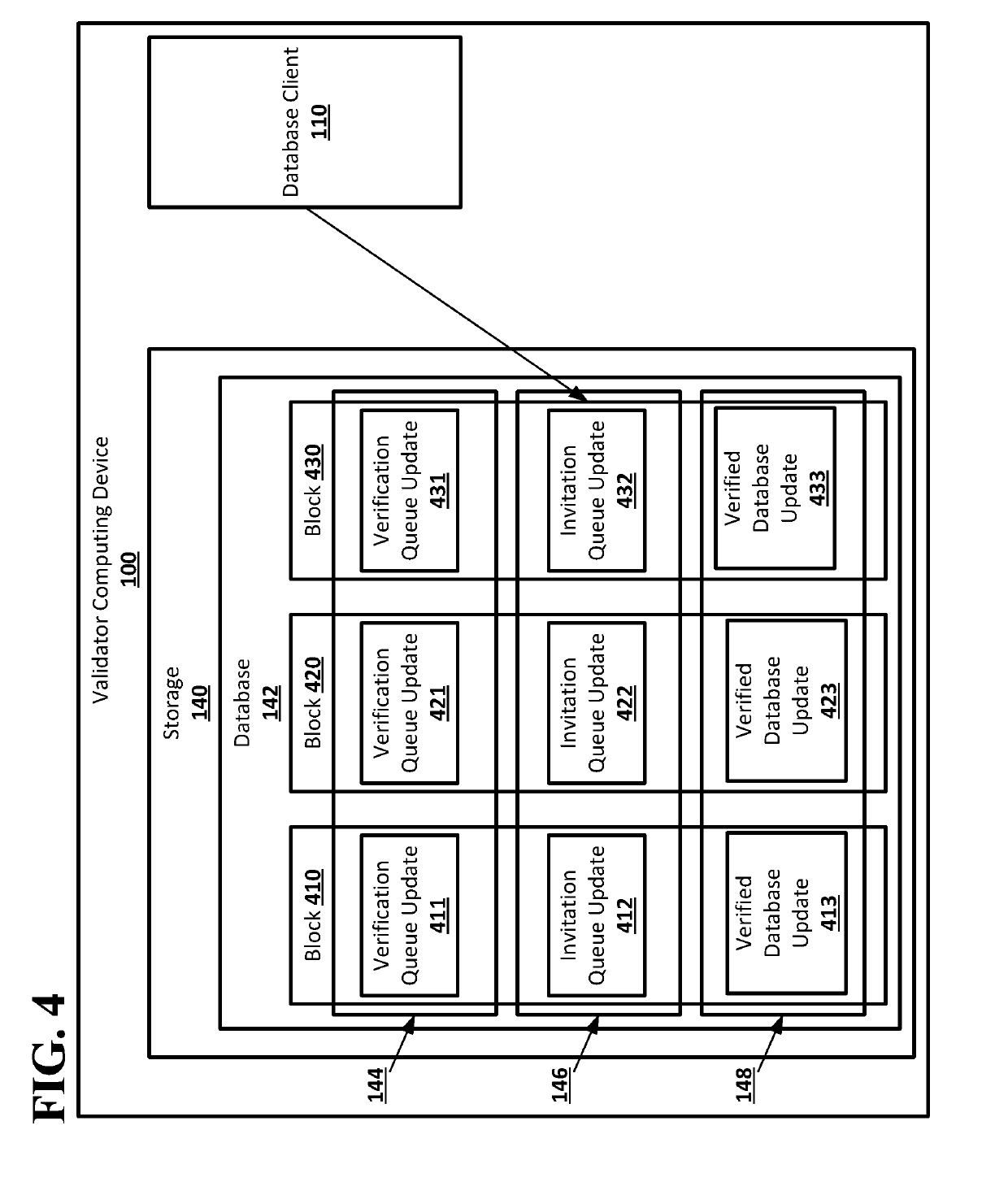
ActiveUS20190179806A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesValidatorComputer science
Systems and techniques are provided for a decentralized database associating public keys and communications addresses. A signed secret message may be sent by a validator computing device of a peer-to-peer network for a decentralized database to a communications address from a request for verification entry in a verification queue of the decentralized database. A second request for verification including the communications address and a user-signed secret message may be received. The user-signed secret message may be verified using a public key from the request for verification entry in the verification queue. The communications address and public key may be written to a verified database of the decentralized database when verifying the user-signed secret message causes a number of user-signed secret messages received in requests for verification with the communications address and successfully verified to meet a threshold number.
Owner:CELO LABS INC
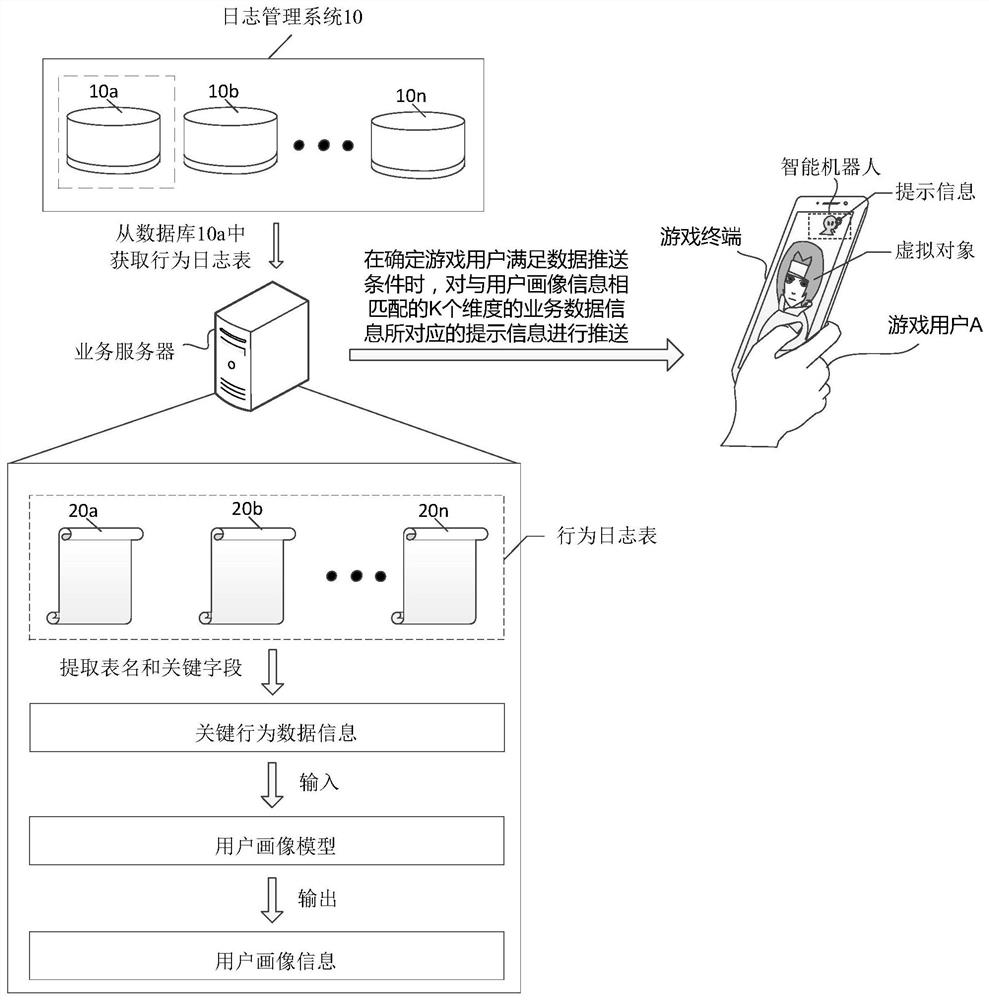
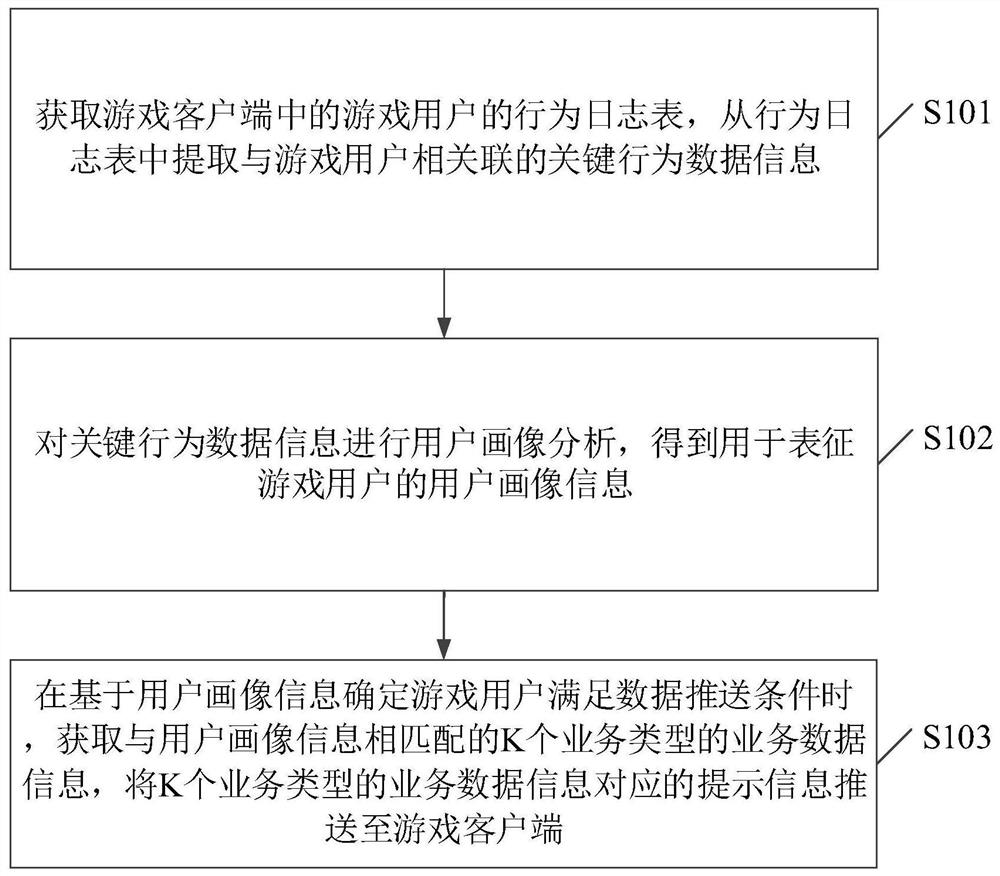
Business data pushing method and device and storage medium
ActiveCN111953763AImprove fitRealize proactive touchTransmissionSpecial data processing applicationsEngineeringBusiness data
The embodiment of the invention discloses a business data pushing method and device and a storage medium, and the method comprises the steps: obtaining a behavior log table of a game user in a game client, and extracting key behavior data information associated with the game user from the behavior log table; carrying out user portrait analysis on the key behavior data information to obtain user portrait information used for representing the game user; and when it is determined that the game user satisfies a data pushing condition based on the user portrait information, obtaining service data information of K service types matched with the user portrait information, and pushing prompt information corresponding to the service data information of the K service types to a game terminal corresponding to the game user, and enabling the game terminal to display the prompt information in a game display interface corresponding to the game client, wherein k is a positive integer. By adopting themethod and the device, active touch of the prompt information can be realized, and the accuracy of data recommendation can be improved based on the user portrait information.
Owner:TENCENT TECH (SHENZHEN) CO LTD
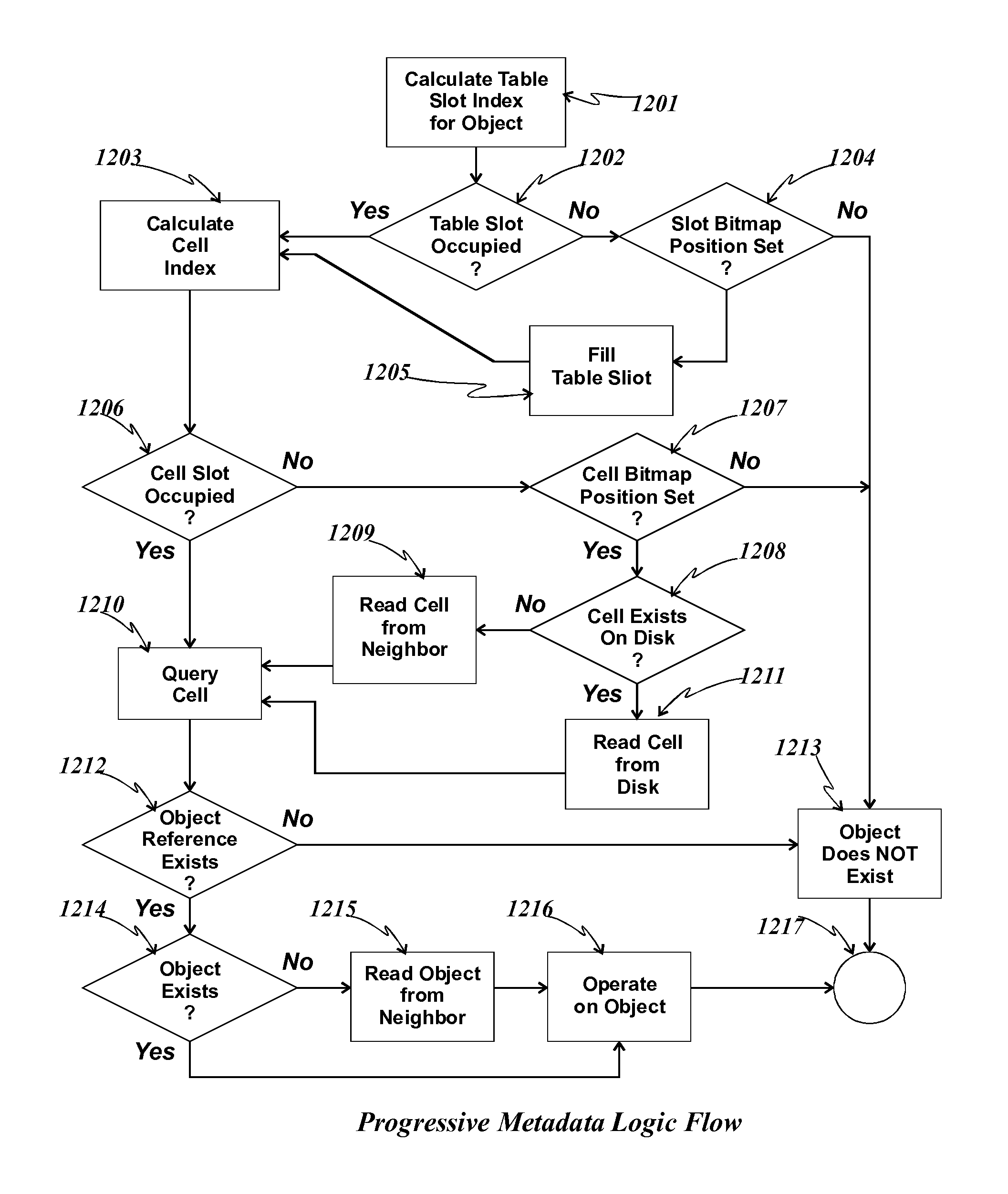
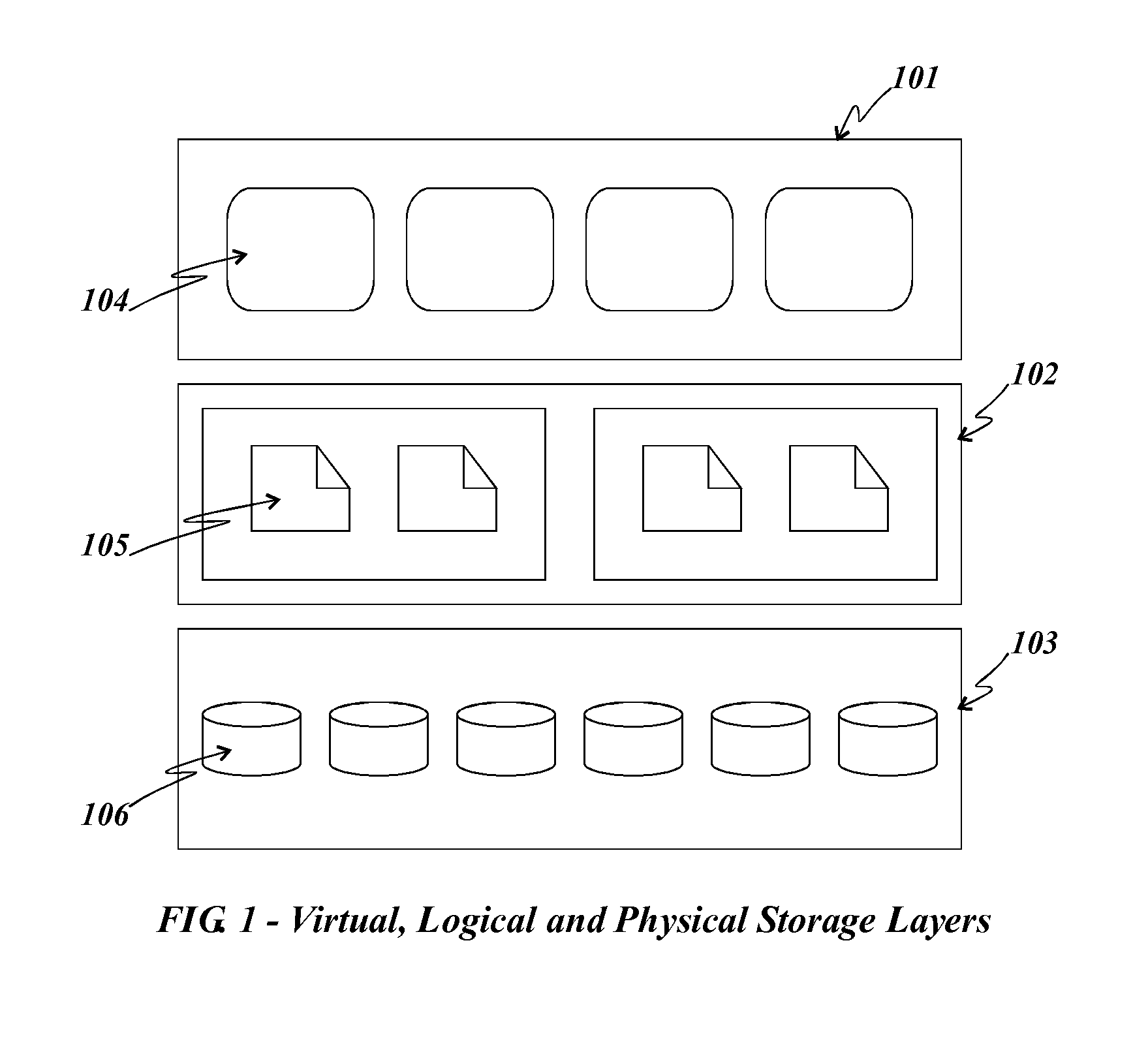
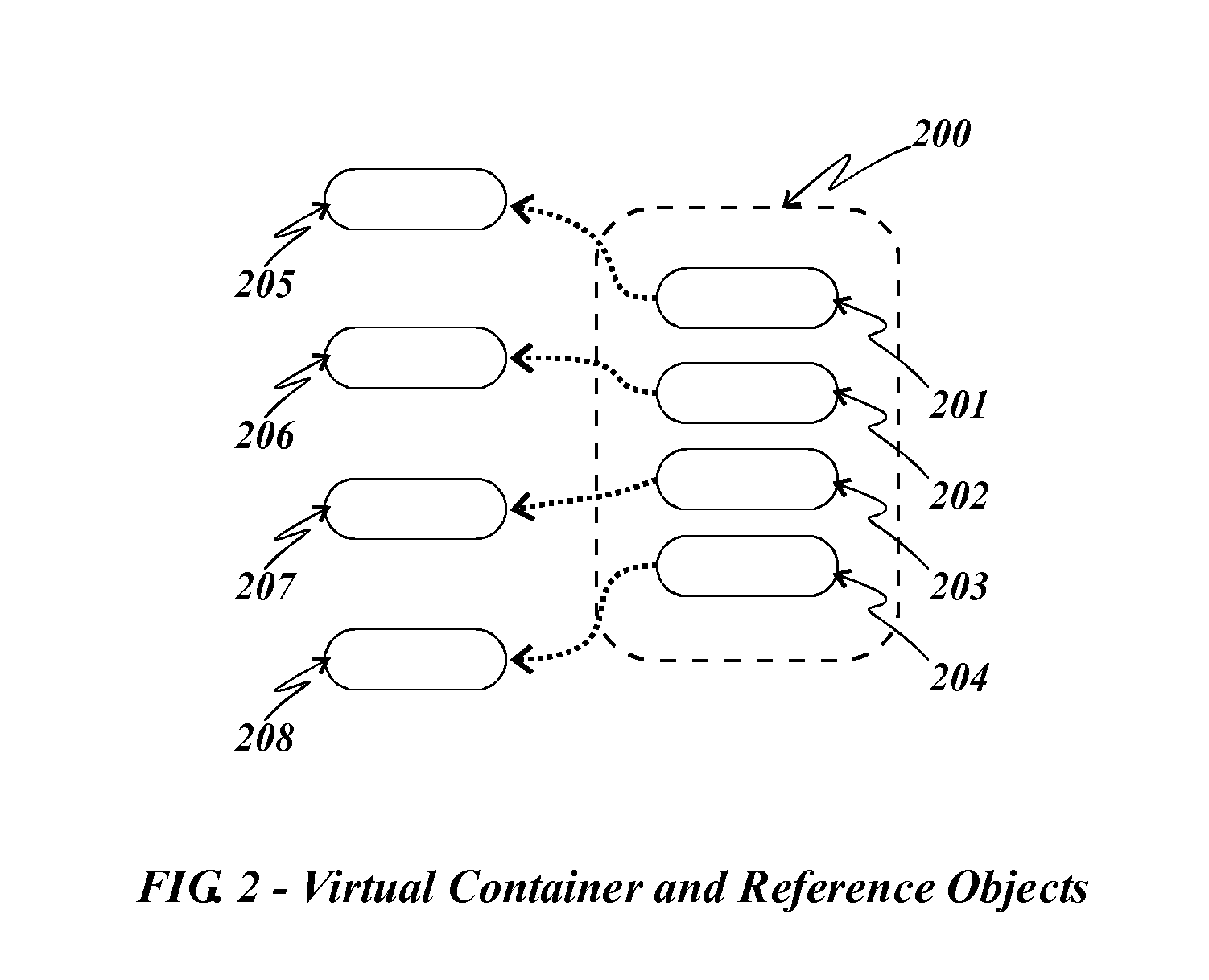
Method and apparatus for large scale data storage
A logical apparatus and associated methods provide highly scalable and flexible data storage in a network of computers. The apparatus provides flexible organizational and access control mechanisms and a practical and efficient way to work with smaller portions of a data storage system at a given time to enable sparse population, caching, paging and related functions. A data structure, called a virtual container, comprises references to objects stored in a data storage system such that the same object can be visible from different virtual containers, if such virtual containers hold references to said object. Access controls further enhance the effectiveness of the methods and structures to enable multiple simultaneous organizational schemes and selective sharing of objects. Participating nodes provide access to objects stored on said nodes and their participating peer nodes, employing the data storage apparatus, such that balance in the network is achieved by data placement decisions that may combine common constraints and a node's individual self interest.
Owner:PI CORAL
Log processing method and device, computer device and storage medium
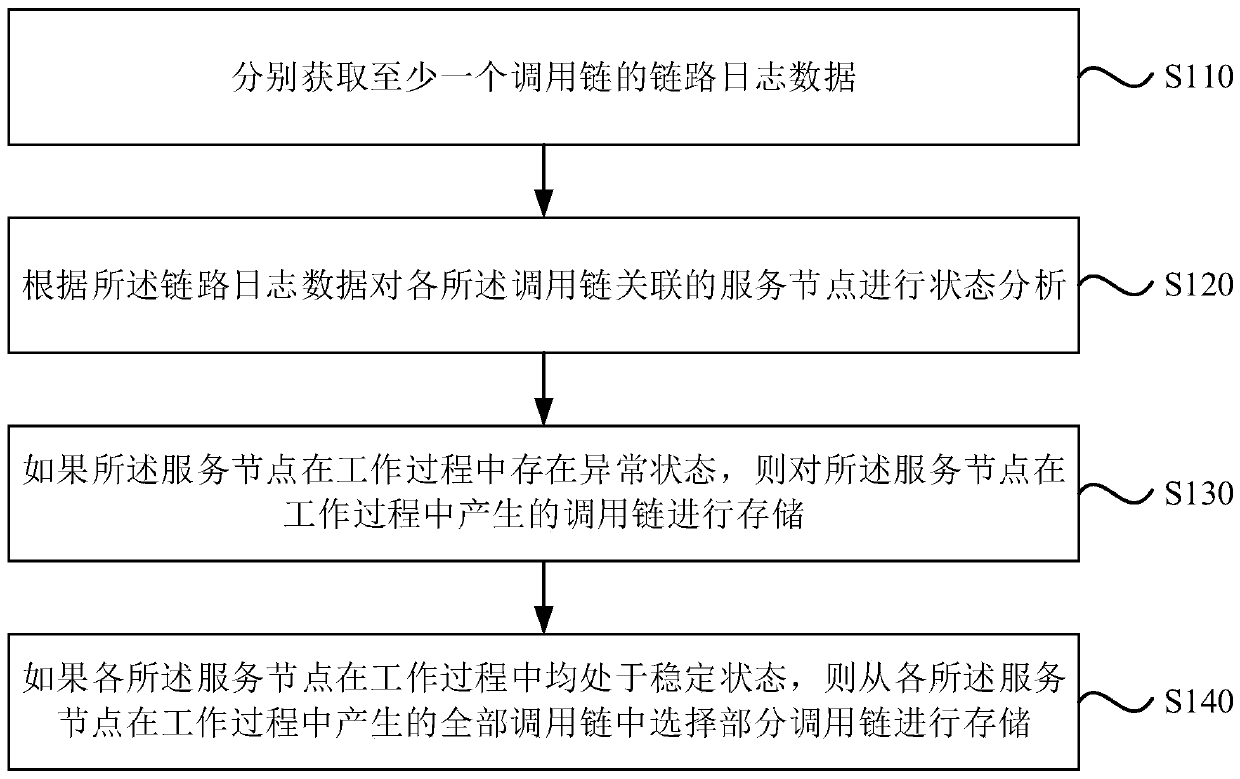
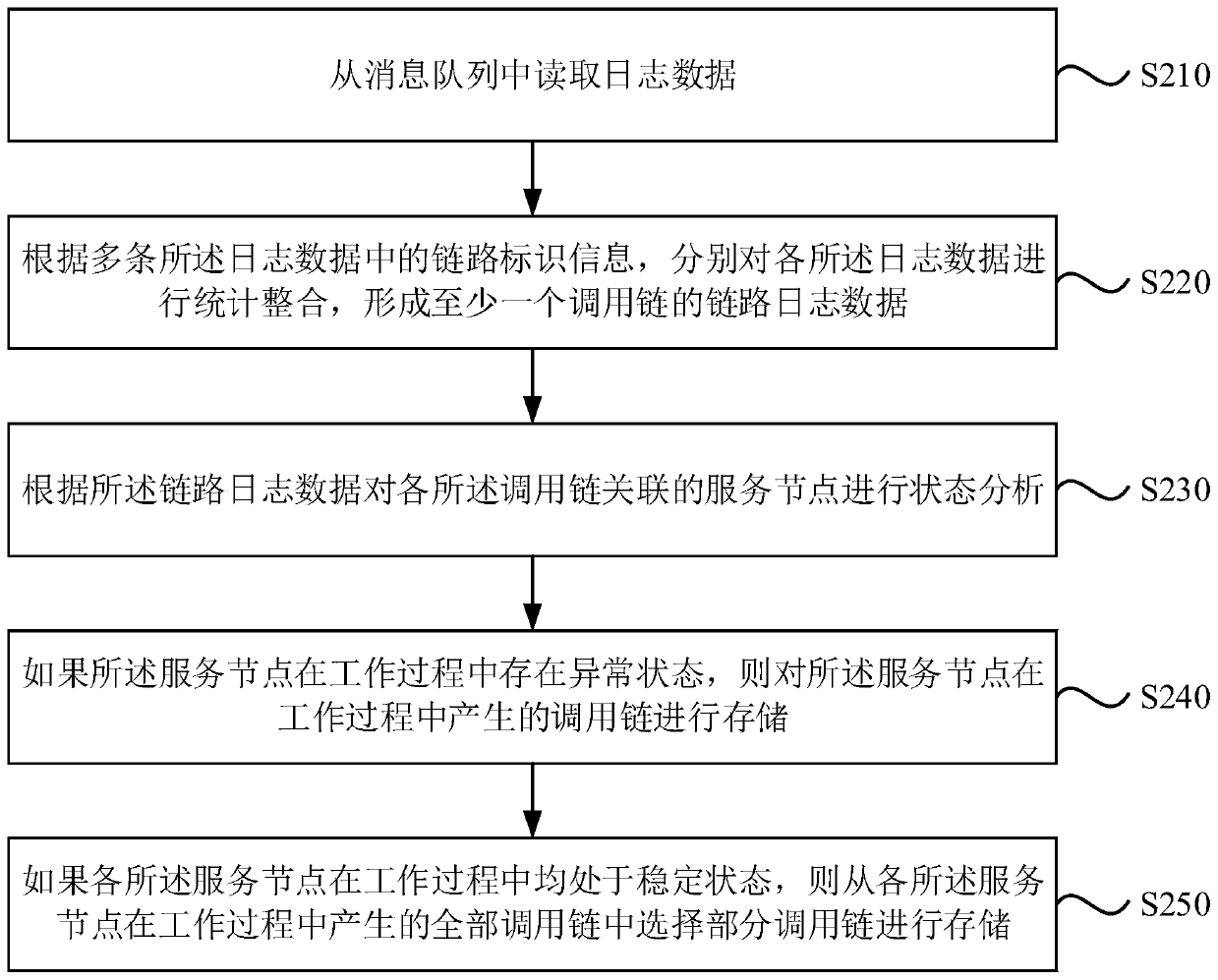
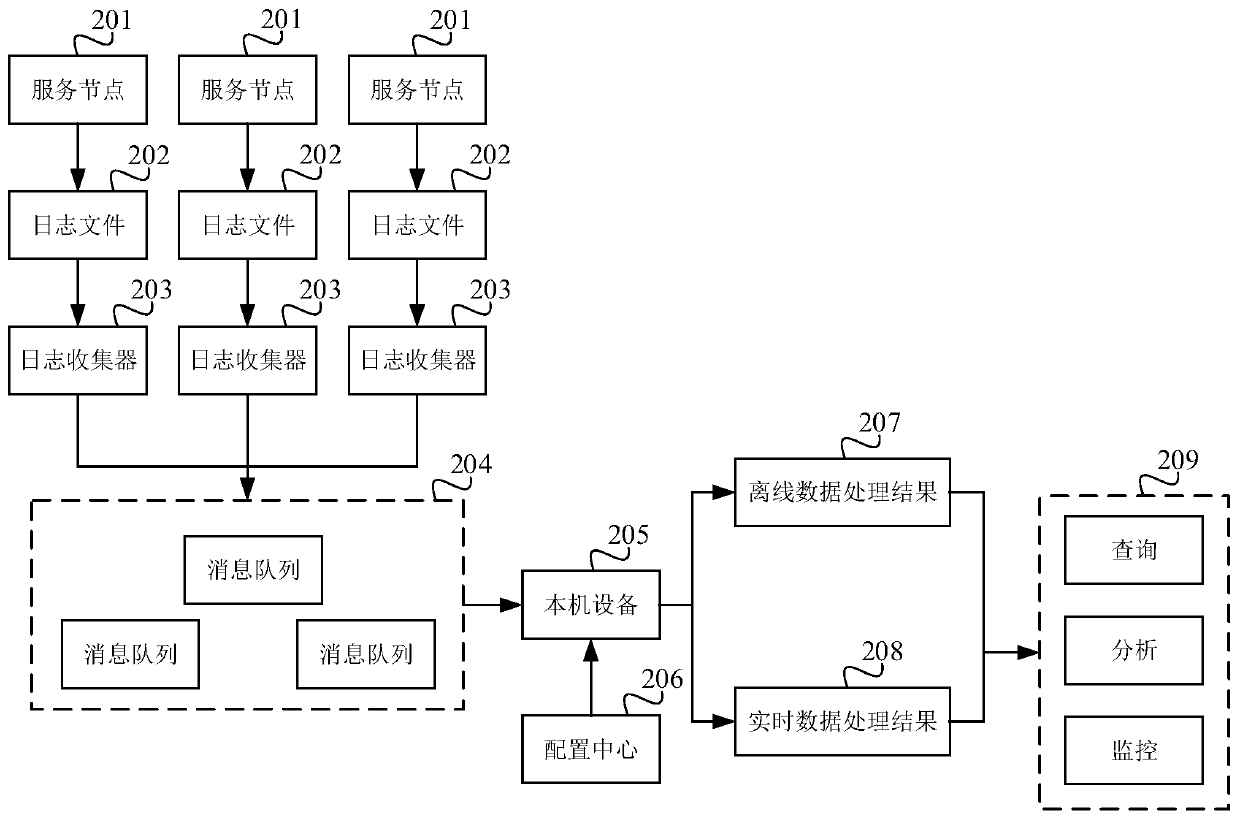
ActiveCN110502494AReduce distortionReduce storageSpecial data processing applicationsFile system typesStable stateDistortion
The embodiment of the invention discloses a log processing method and device, a computer device and a storage medium. The method comprises the following steps: respectively acquiring link log data ofat least one calling chain; wherein the link log data of the call chain is formed by counting and integrating log data collected in a full-amount collection mode; according to the link log data, carrying out state analysis on the service nodes associated with the call chains; if the service node has an abnormal state in the working process, storing a call chain generated by the service node in theworking process; and if each service node is in a stable state in the working process, selecting a part of call chains from all call chains generated by each service node in the working process for storage. According to the embodiment of the invention, the log storage amount can be reduced, and the distortion rate of acquired data is reduced.
Owner:北京思维造物信息科技股份有限公司
Log analysis method and device
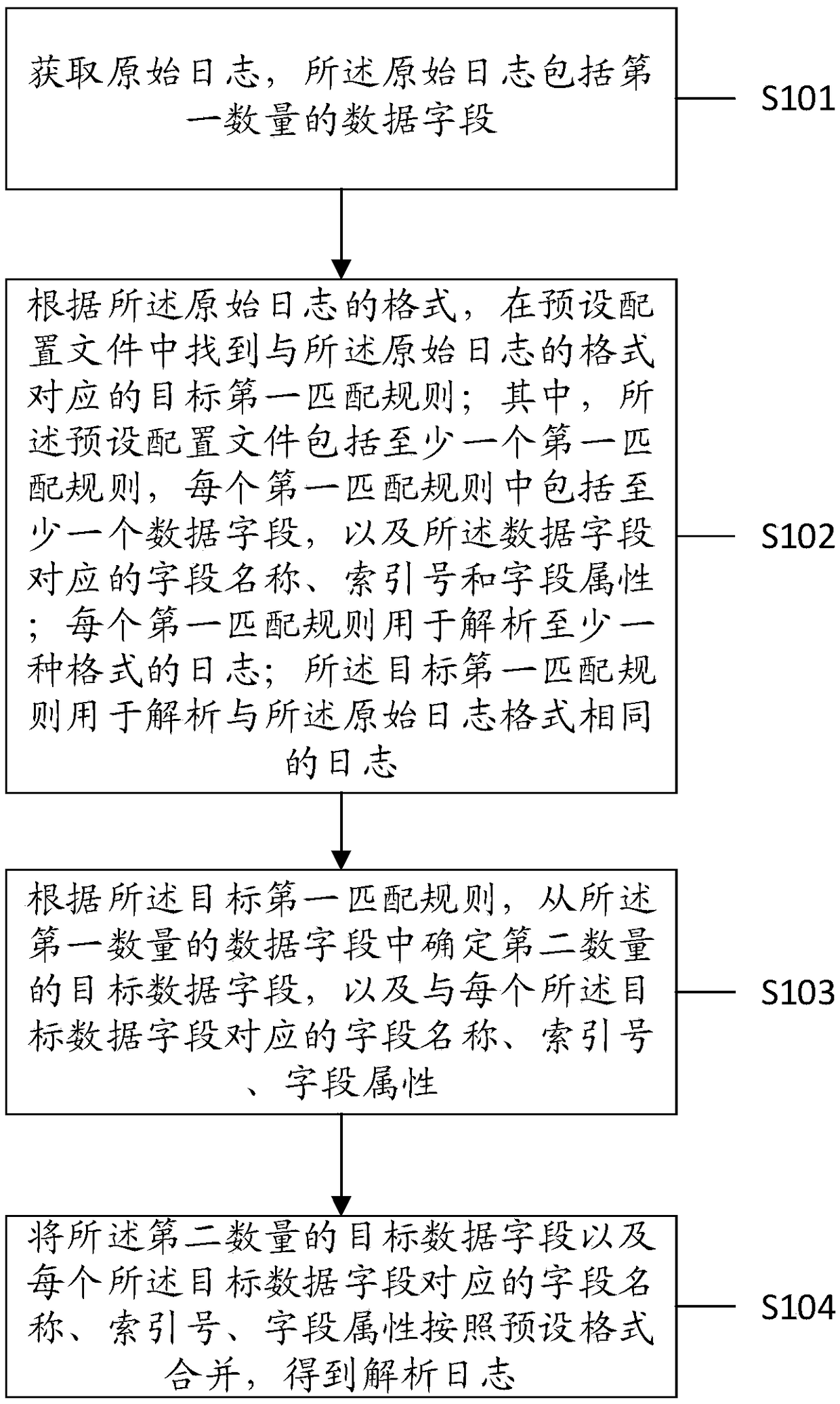
ActiveCN109325009AEasy for statistical analysisSave time and costSpecial data processing applicationsFile system typesStatistical analysisData field
The embodiment of the invention discloses a log analysis method and a log analysis device, which relate to the computer technical field and can perform data analysis on the unstructured data so as toconvert the unstructured data into structured data for the subsequent statistical analysis. The method comprises the following steps of obtaining an original log; according to the format of the original log, finding a target first matching rule corresponding to the format of the original log in the preset configuration file; determining a second number of target data fields from the first number of data fields, and a field name, an index number, and a field attribute corresponding to each of the target data fields according to a target first matching rule; combining the second number of targetdata fields and the corresponding field names, index numbers and field attributes of each target data field according to a preset format to obtain the analyzed log.
Owner:亚信科技(成都)有限公司
Log analysis method and device, computer equipment and storage medium
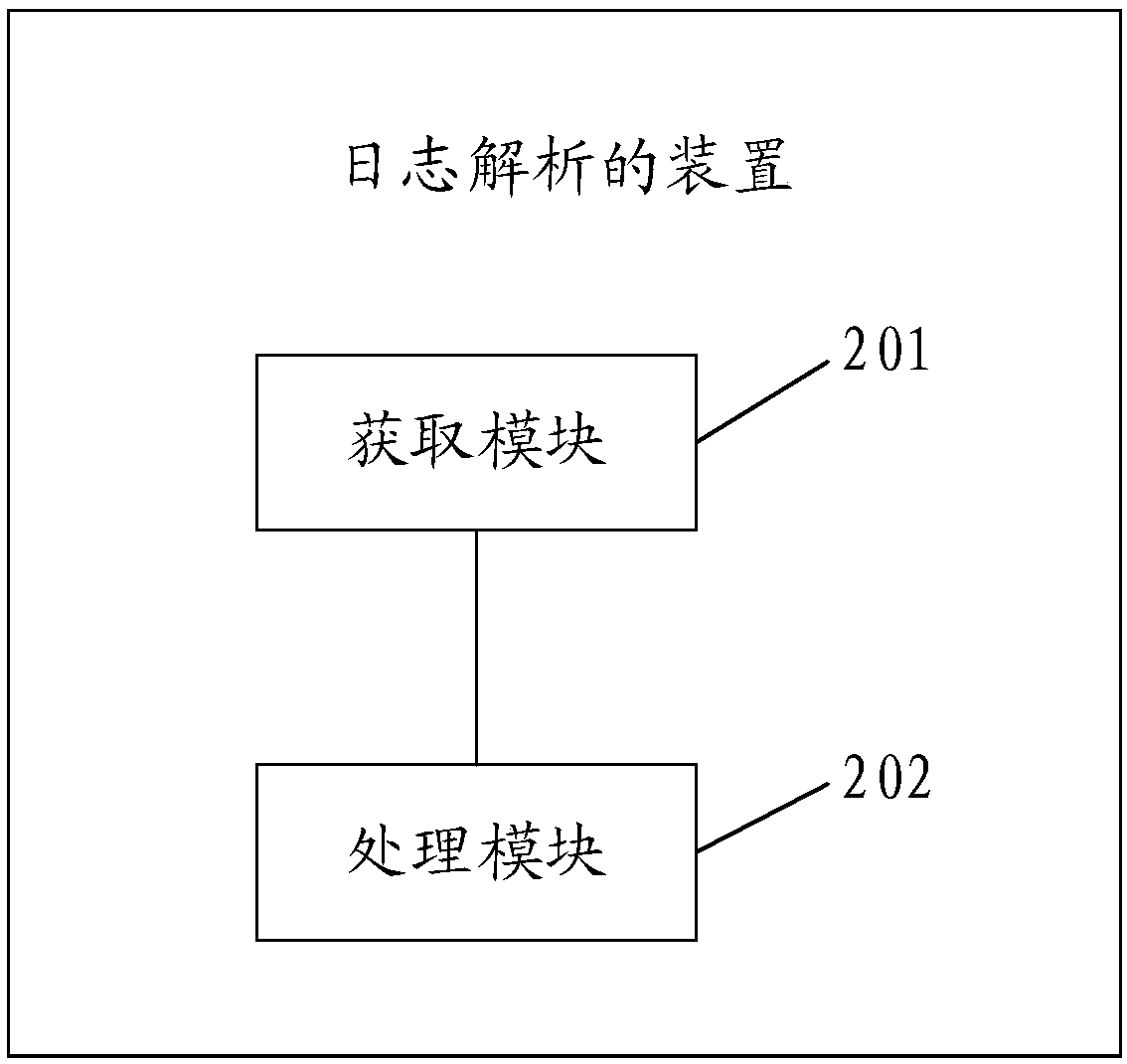
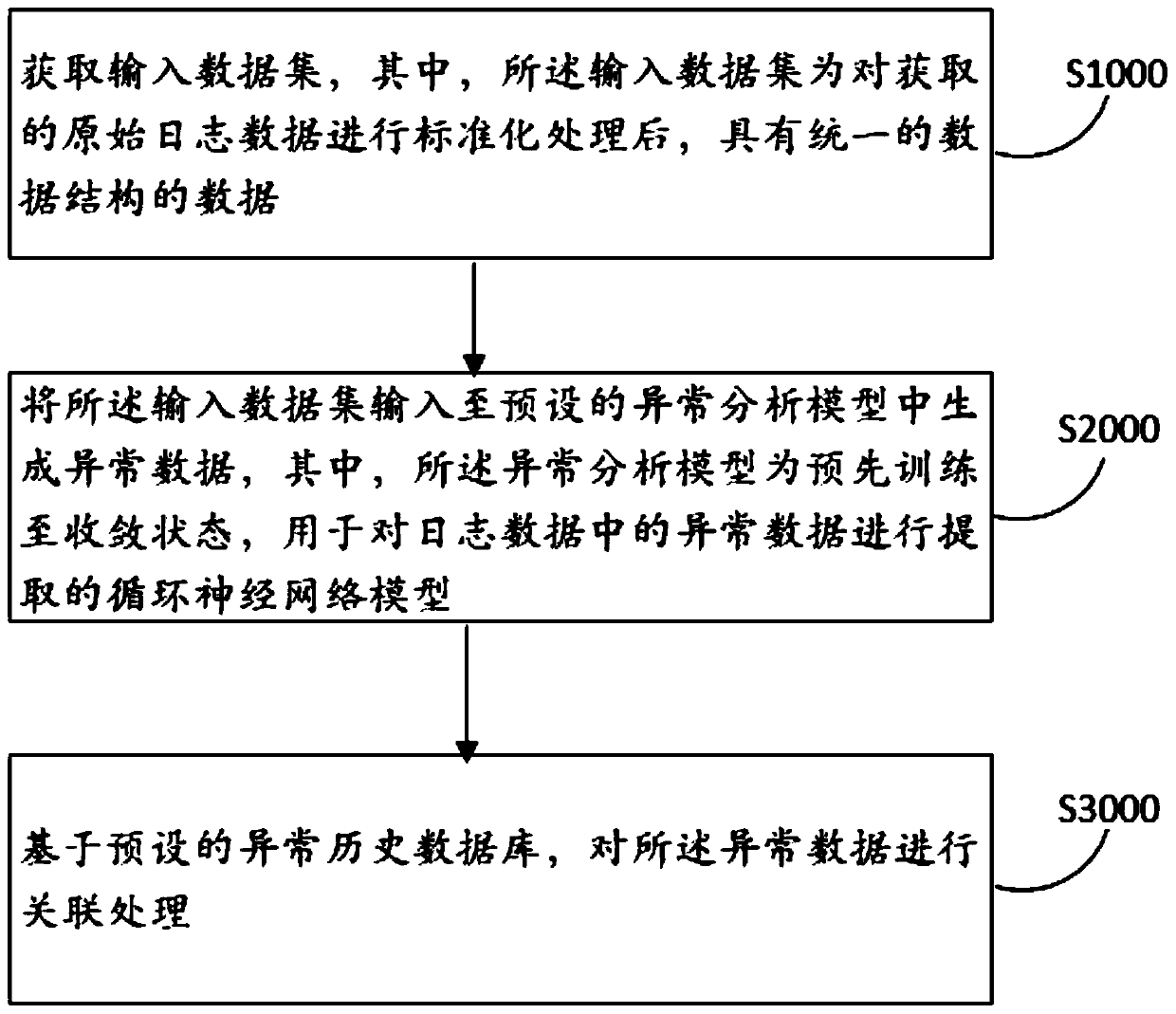
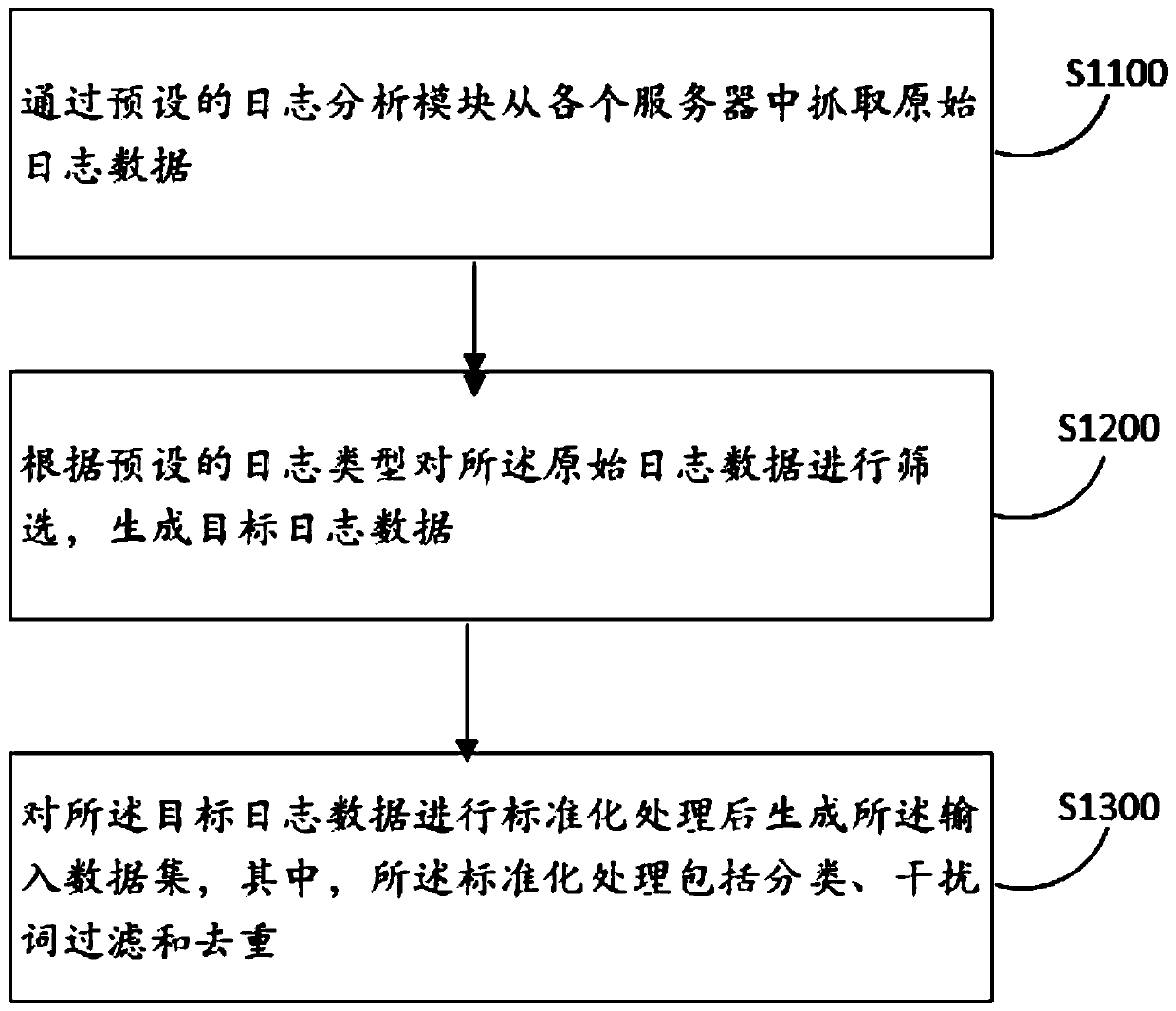
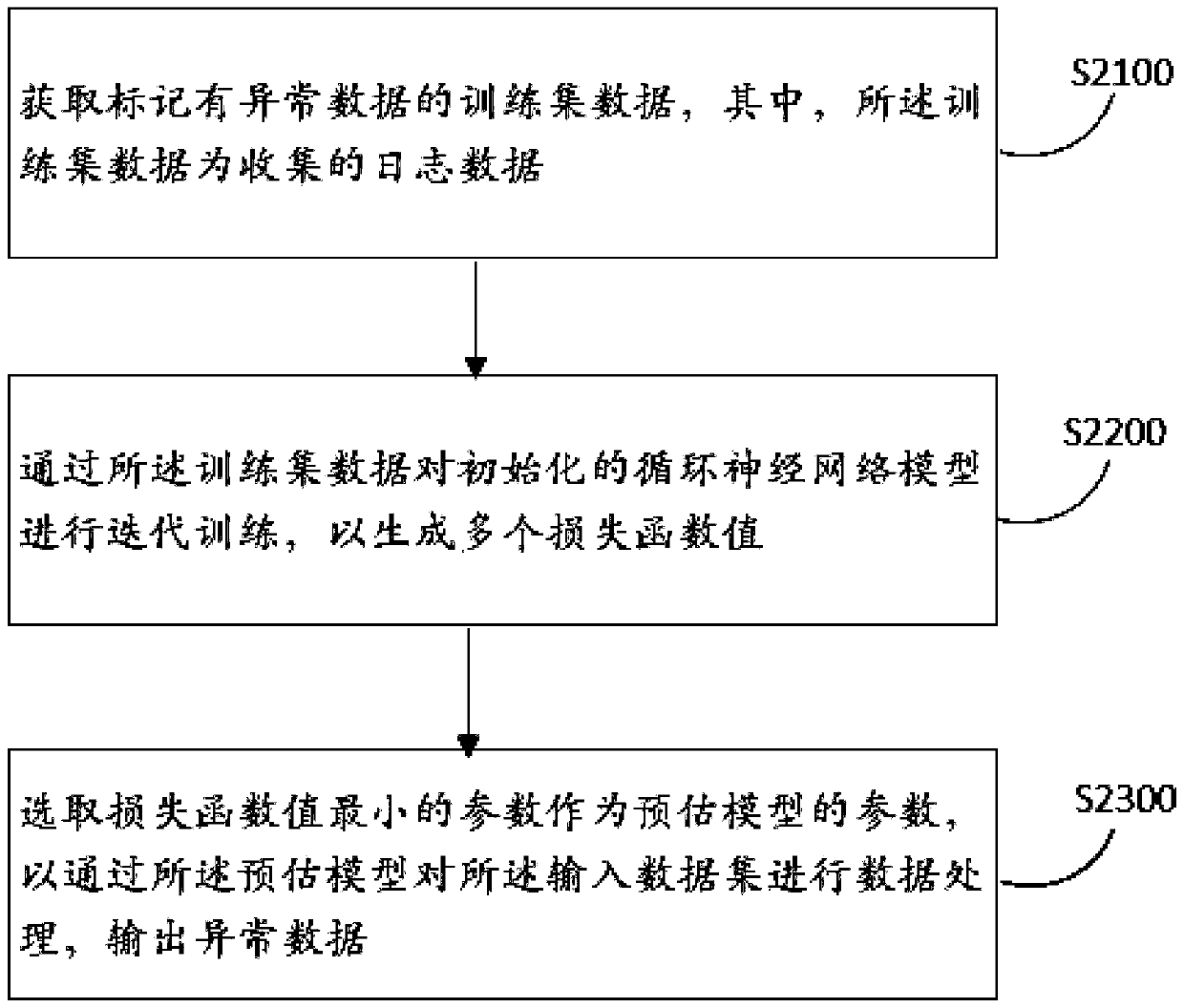
PendingCN111177095AImplement auto-scalingImprove adaptabilityHardware monitoringNeural learning methodsAnalytic modelData set
The invention discloses a log analysis method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining an input data set which is data with a unified data structure after the standardization of the obtained original log data; inputting the input data set into a preset exception analysis model to generate exception data, the exception analysis model being arecurrent neural network model which is trained to a convergence state in advance and is used for extracting the exception data in the log data; and performing association processing on the abnormaldata based on a preset abnormal historical database. According to the method, the original log data from different servers can be quickly acquired; the log data is subjected to standardization processing to have the same data structure, and then the log data is subjected to anomaly identification by adopting the recurrent neural network model, so that even if the data volume is huge, the log datacan be rapidly identified, and the abnormal data is subjected to correlation processing to accelerate the abnormal data processing speed and improve the abnormal data processing accuracy.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
Log data processing method and device, computer device and storage medium
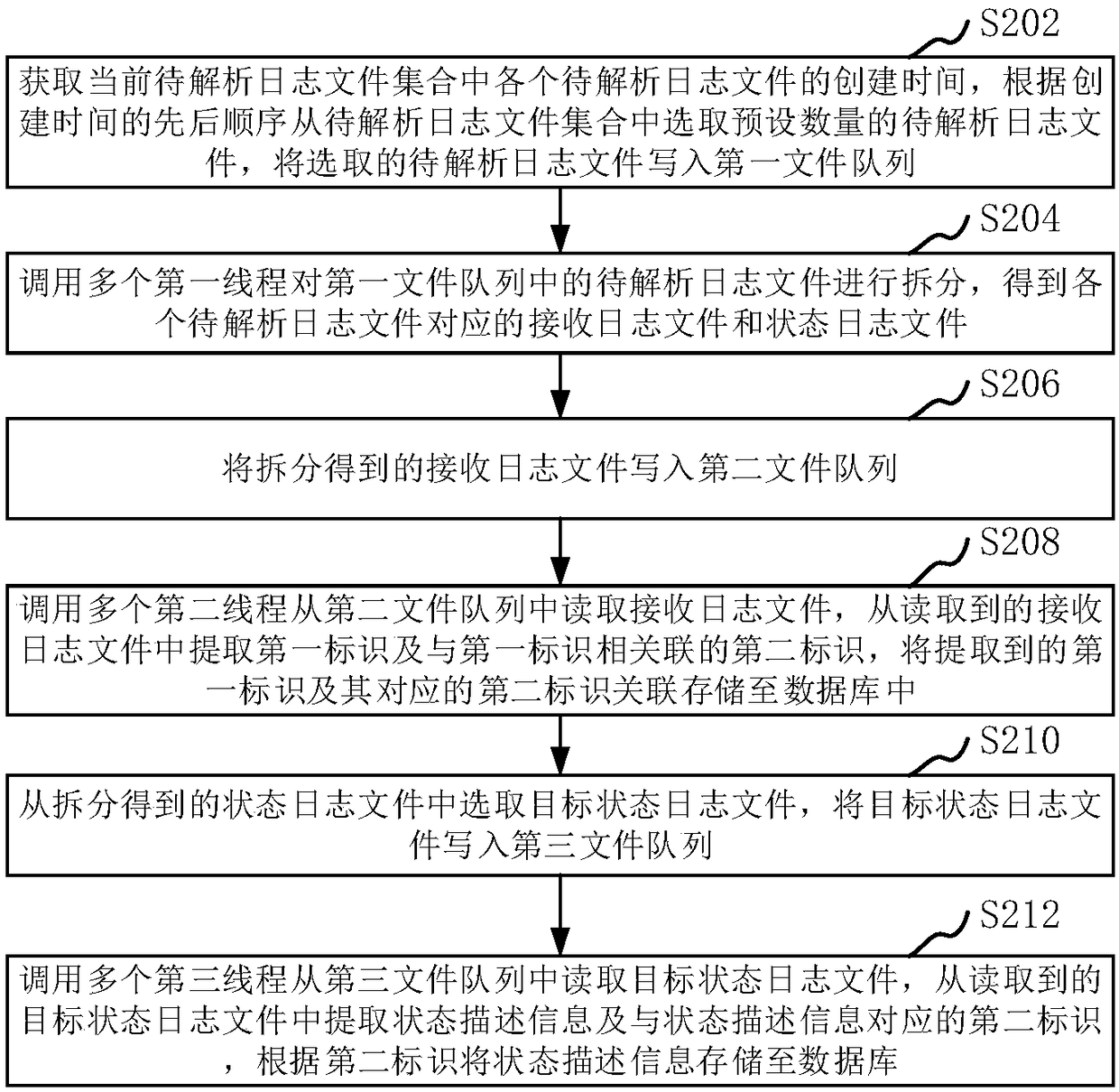
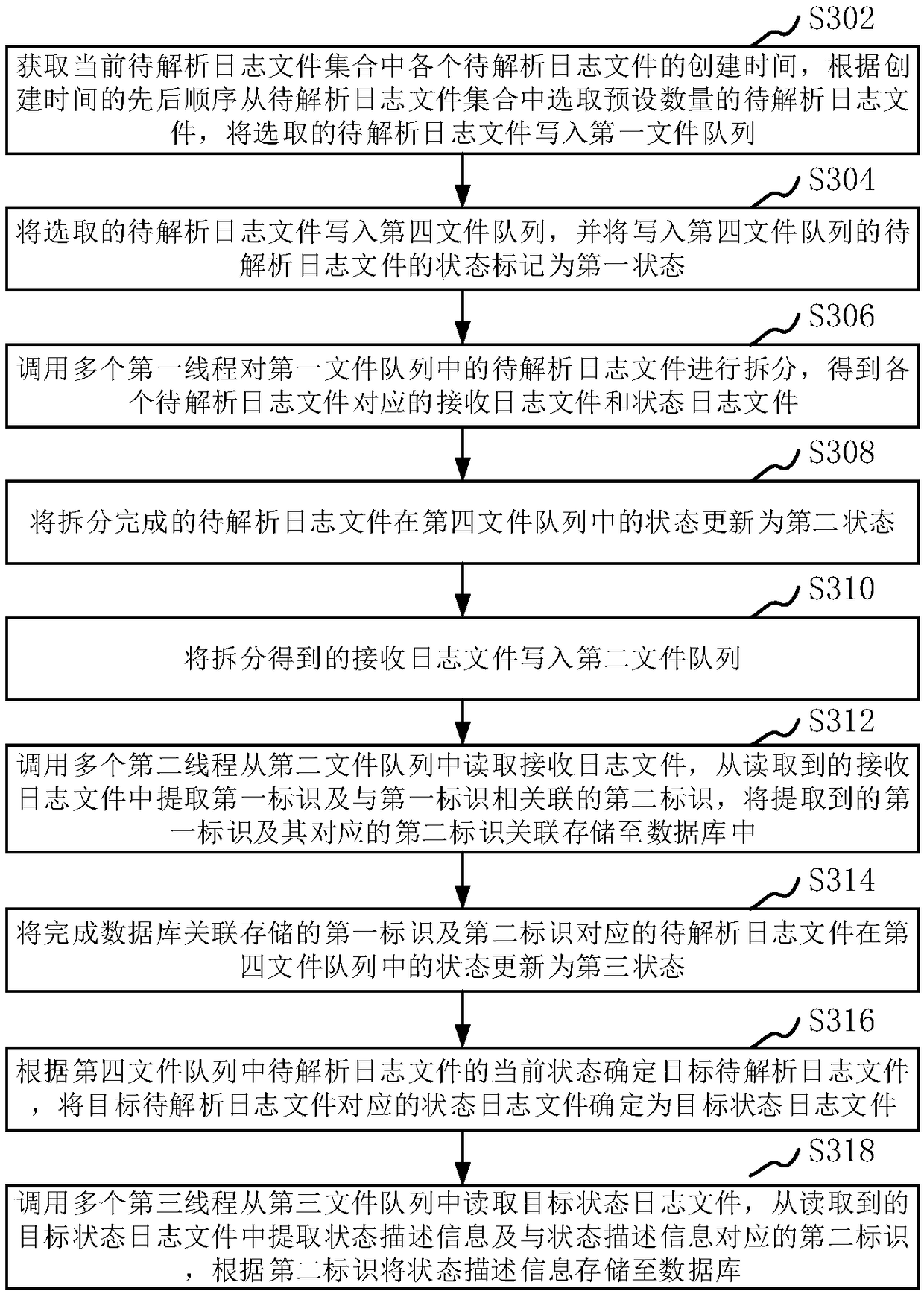
ActiveCN109446173AImprove acquisition efficiencyEnergy efficient computingFile system typesData libraryLogfile
The application relates to the basic operation technology, and discloses a log data processing method and device, a computer device and a storage medium. The method comprises the following steps of obtaining the creation time of each log file to be analyzed in the current log file collection to be analyzed, and selecting a preset number of log files to be analyzed to write into the first file queue according to the order of the creation time; calling a plurality of first threads to split the log files to be parsed to obtain the receiving log files and the state log files corresponding to eachlog file to be parsed; writing the received log file to the second file queue; calling a plurality of second threads to read the received log file to extract a first identification and a second identification associated with each other and store the associated identification in a database; selecting a target state log file from the split state log file, and writing the target state log file into athird file queue; calling the third thread to read the target status log file to extract the status description information and store it in the database.
Owner:PING AN TECH (SHENZHEN) CO LTD
Automatically retrying transactions with split procedure execution
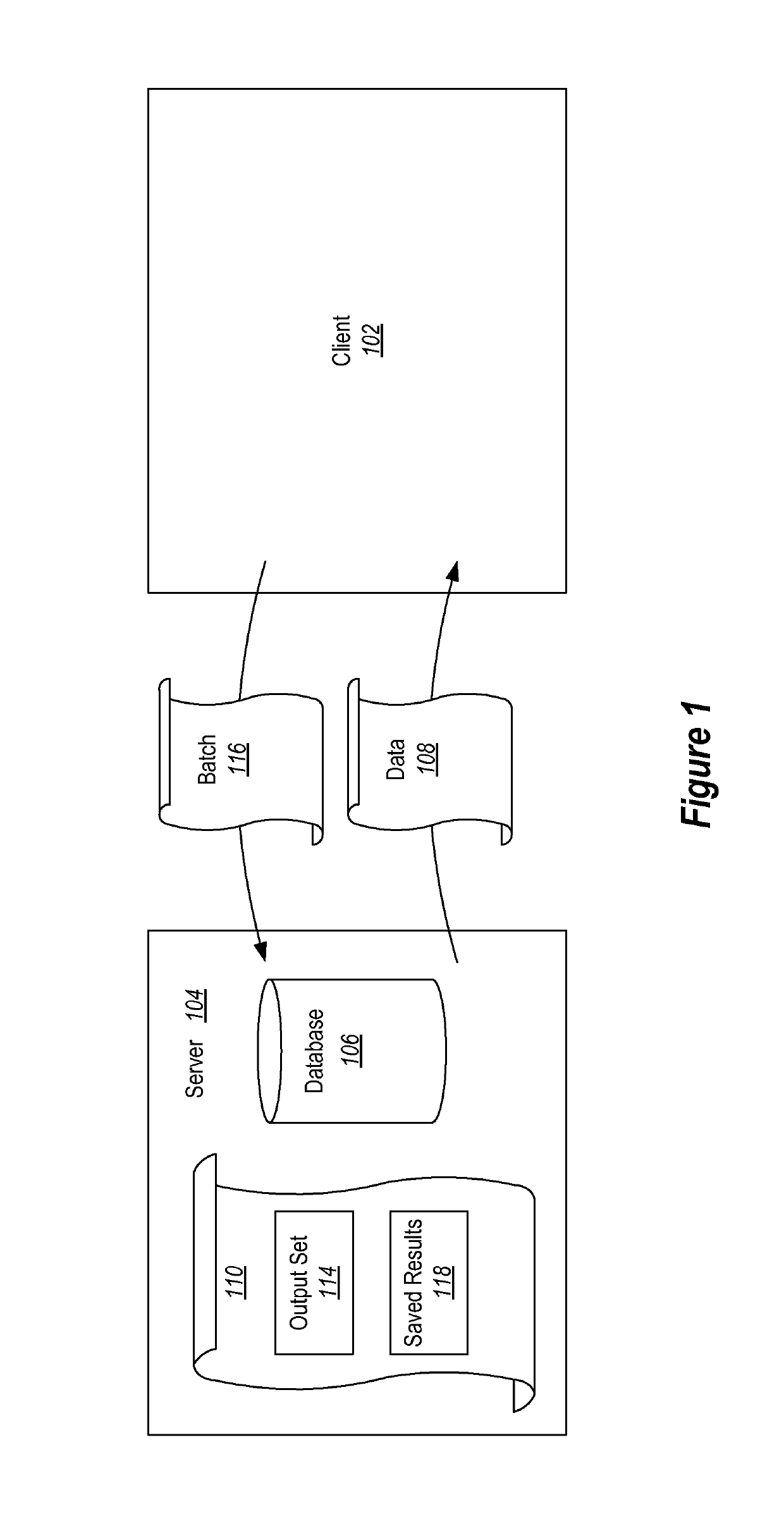
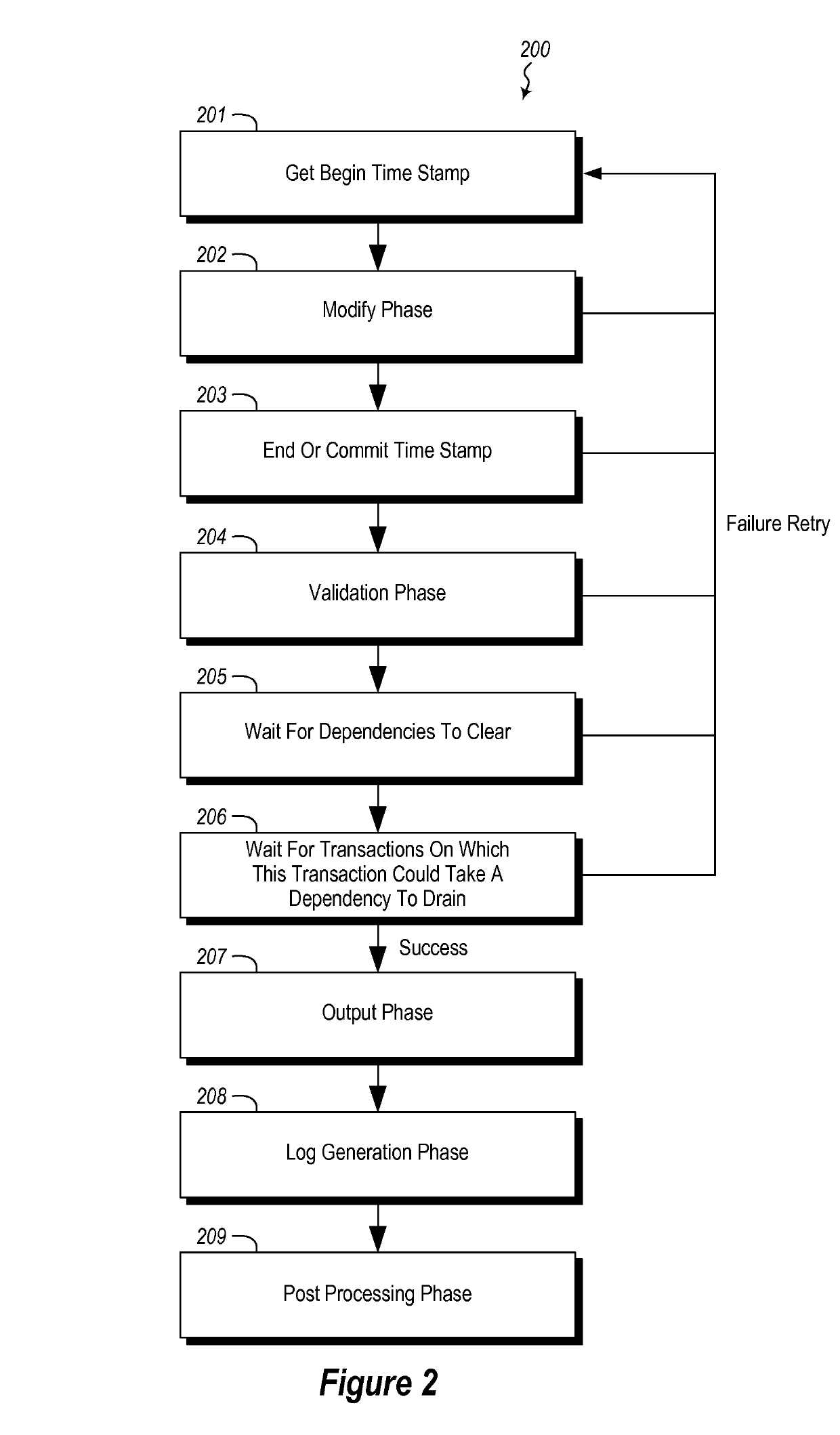
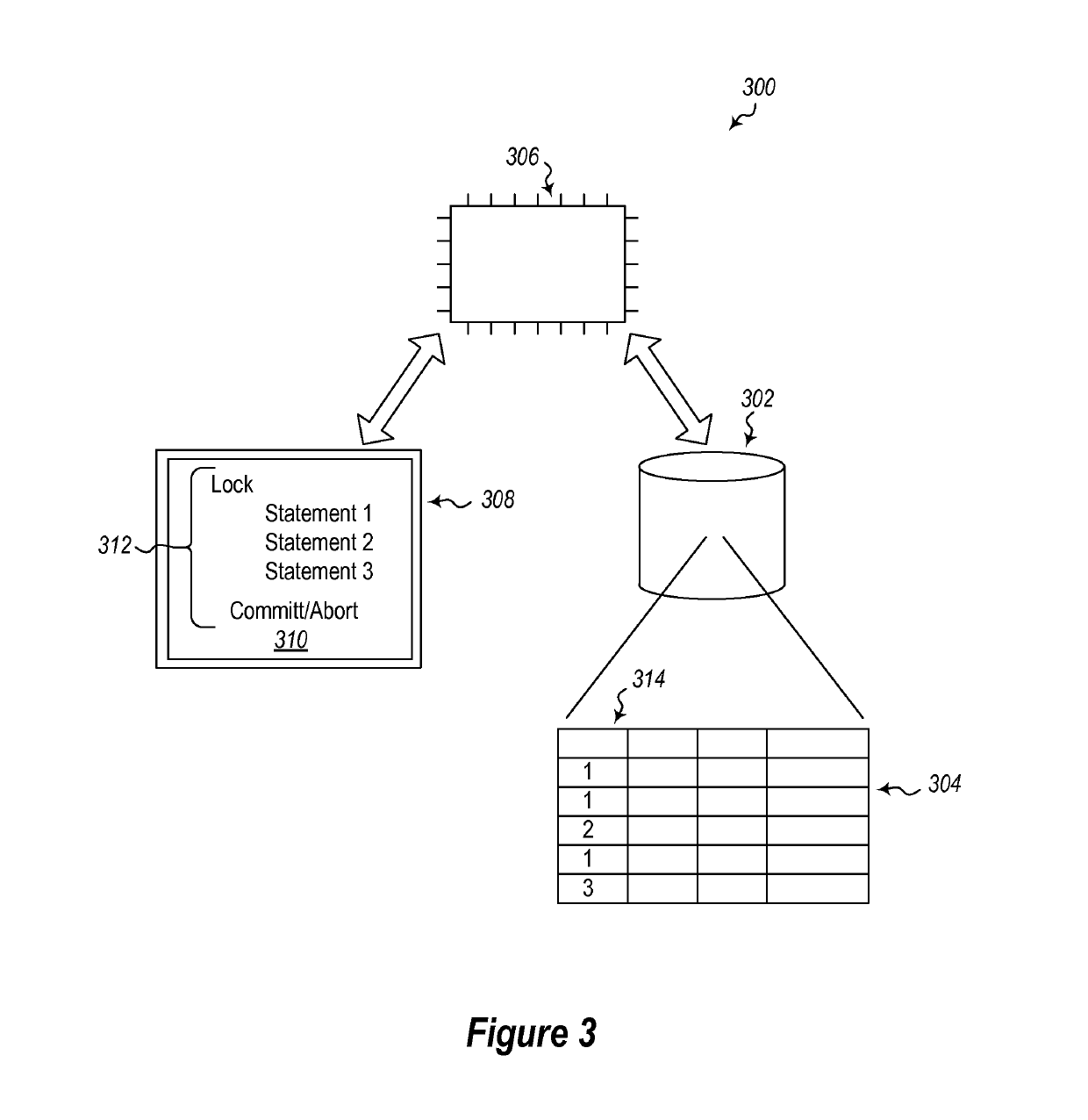
Running a transaction against a database that allows the transaction to be automatically retried when the transaction fails such that certain transaction failures that cause the transaction to be automatically retried are not visible to an entity that receives data as a result of the execution of the transaction. A first set of statements of a transaction is identified by identifying statements that will cause a change in the database state. A second set of statements is identified, that result in data being generated to be sent to the entity. The method further includes executing the first set of statements to change the database. The method further includes running the second set of statements separately from the first set of statements to generate data to be sent to the entity.
Owner:MICROSOFT TECH LICENSING LLC
Log processing system
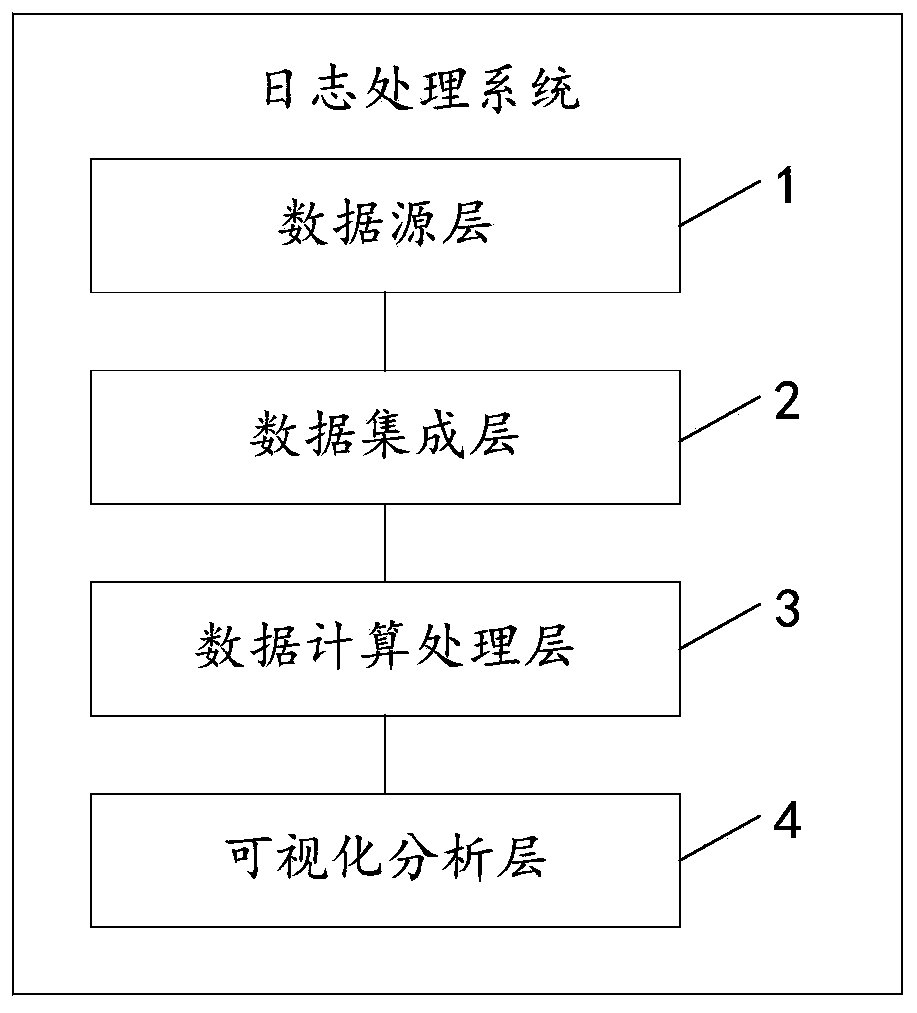
InactiveCN109902072AAssociation is easy to findData switching networksFile system typesOperational systemData source
The invention discloses a log processing system. The log processing system comprises a data source layer, a data integration layer and a data calculation processing layer, Wherein the data source layer is used for providing a data source object; Wherein the data source object comprises but is not limited to an operating system, a database, an application system and network equipment; The data integration layer is used for obtaining a log from the data source object in a distributed collection mode and carrying out preprocessing operation on the log; Wherein the preprocessing operation comprises at least one of normalization processing, classification processing, filtering processing and merging processing on the logs; And the data calculation processing layer is used for analyzing the logsthrough an association analysis engine and carrying out distributed storage on the logs. By adopting the embodiment of the invention, the operation and maintenance problem event can be effectively and intelligently pre-warned, and rich visual charts and instrument panels are integrated, so that the data is more vivid, and the association of log data is easy to find.
Owner:HONGHE POWER SUPPLY BUREAU OF YUNNAN POWER GRID
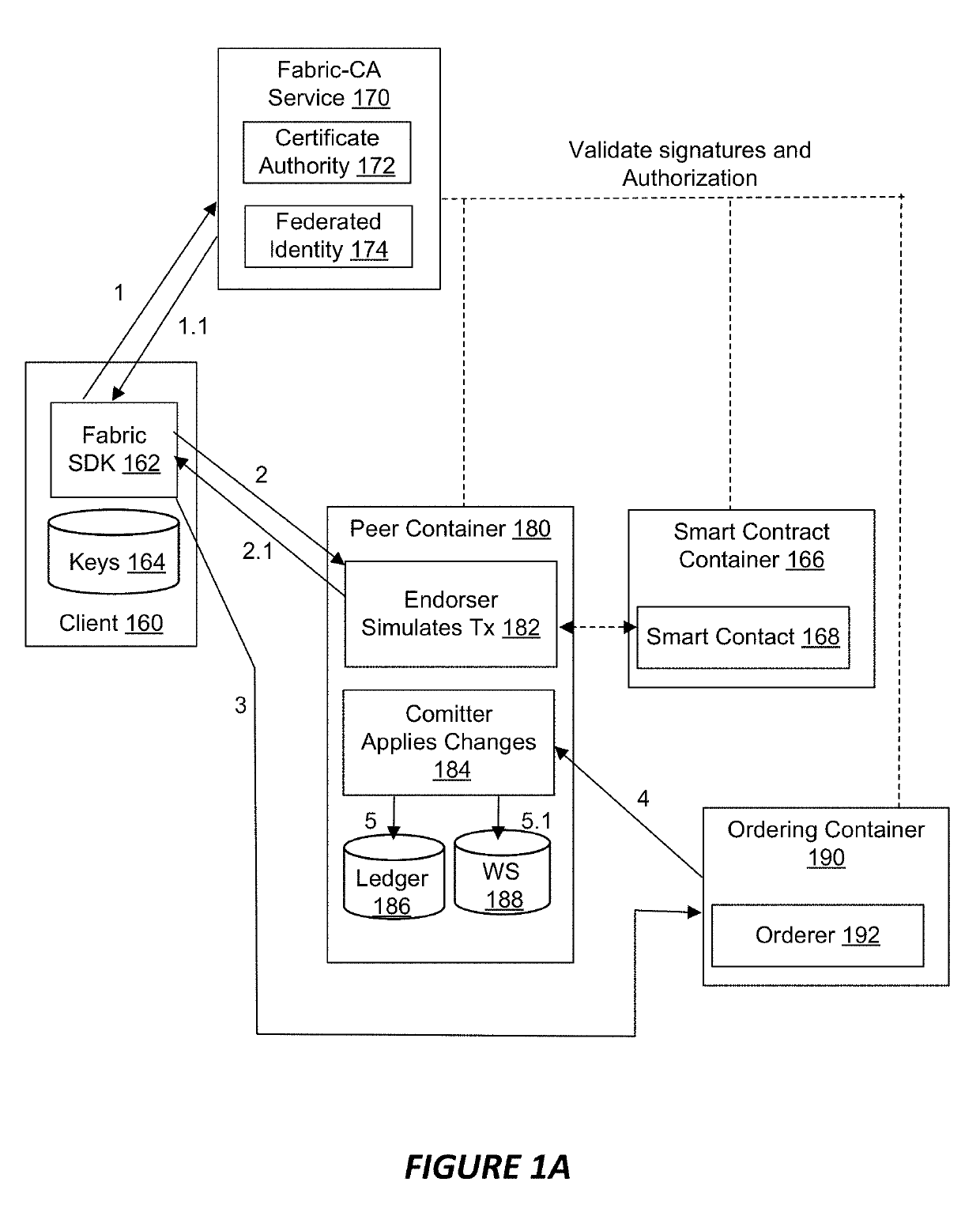
Systems and methods for secure smart contract execution via read-only distributed ledger
InactiveUS10333694B1Added security and privacyPreventing malicious smart contractsEncryption apparatus with shift registers/memoriesInternal/peripheral component protectionHardware architectureSmart contract
Systems and methods related to processing transaction verification operations in decentralized applications via a fixed pipeline hardware architecture are described herein. The fixed pipeline architecture may be included within a decoupled system architecture comprising a computer system configured to execute smart contracts and a physically separate hardware device configured to perform transaction verification operations. The computer system may be configured to maintain a read-only copy of a ledger shared by a plurality of nodes on a peer-to-peer network, and the hardware device may be configured to perform transaction verification operations. As such, the decoupled system architecture provides added security and privacy for the system and the ledger by preventing malicious smart contracts from accessing and / or updating the modifiable copy of the verified ledger.
Owner:ACCELOR LTD
Method and device for writing data based on common Internet file system
InactiveCN109309631AIncrease the amount of dataAvoid wastingData switching networksFile system typesFile systemServer Message Block
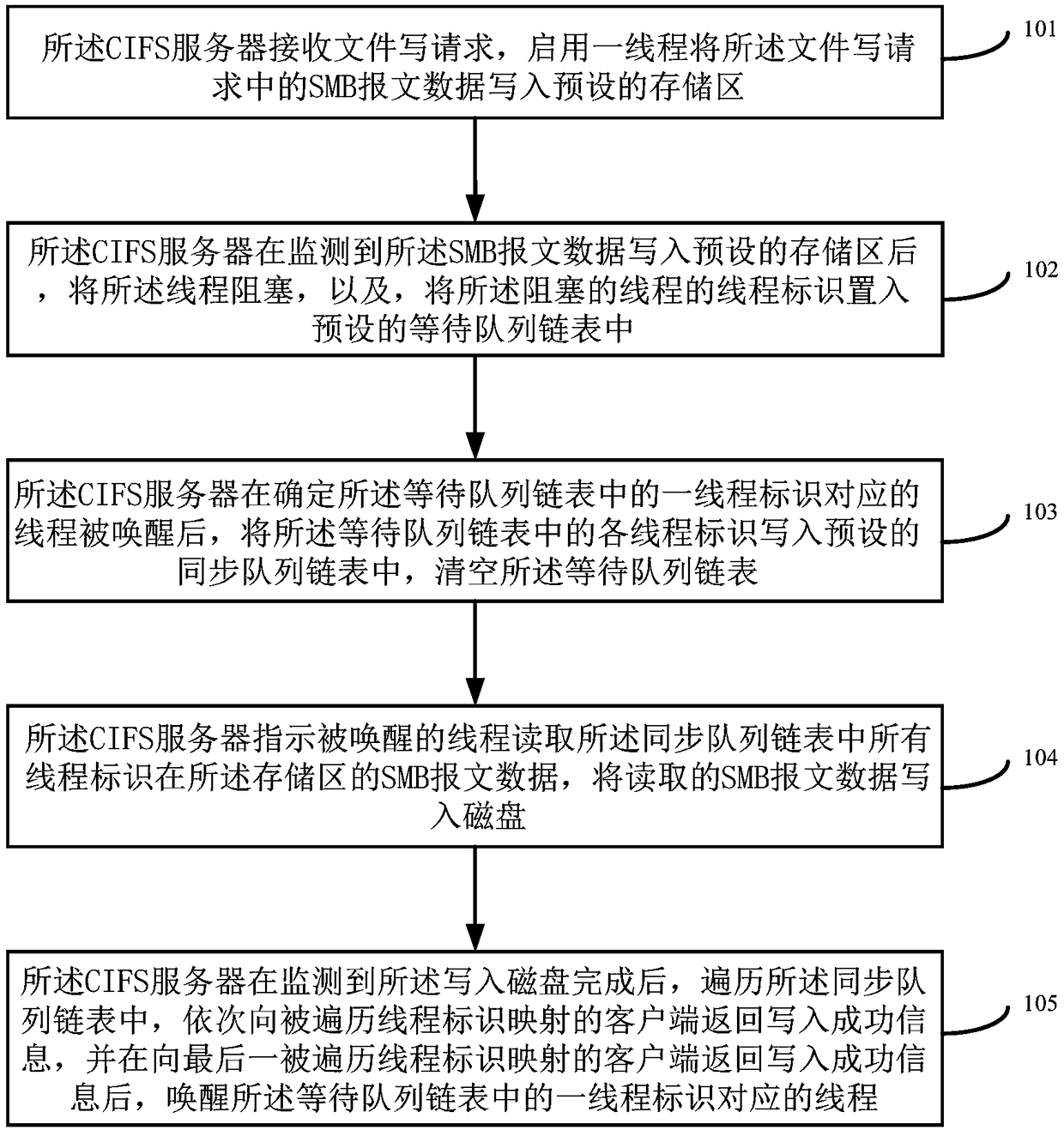
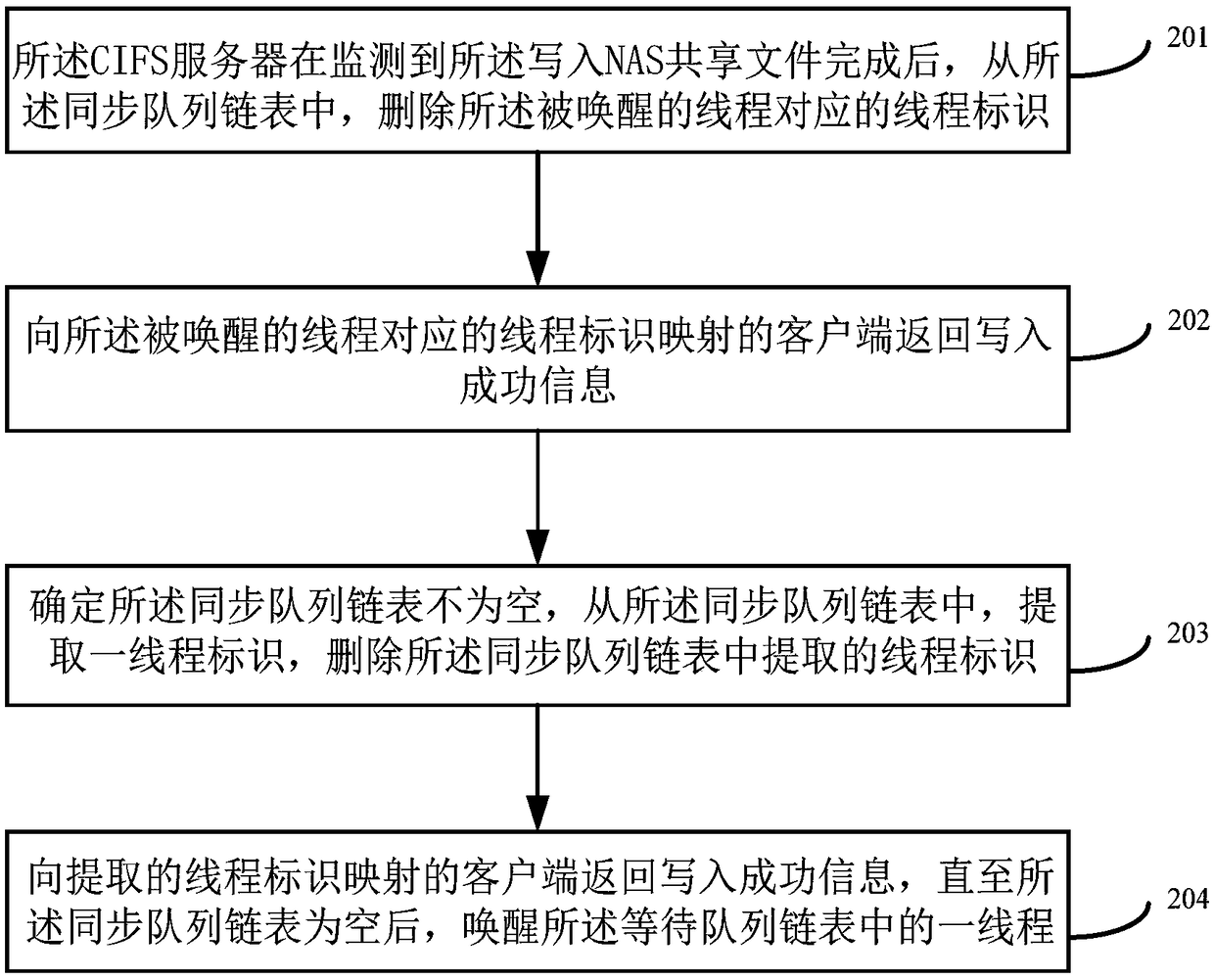
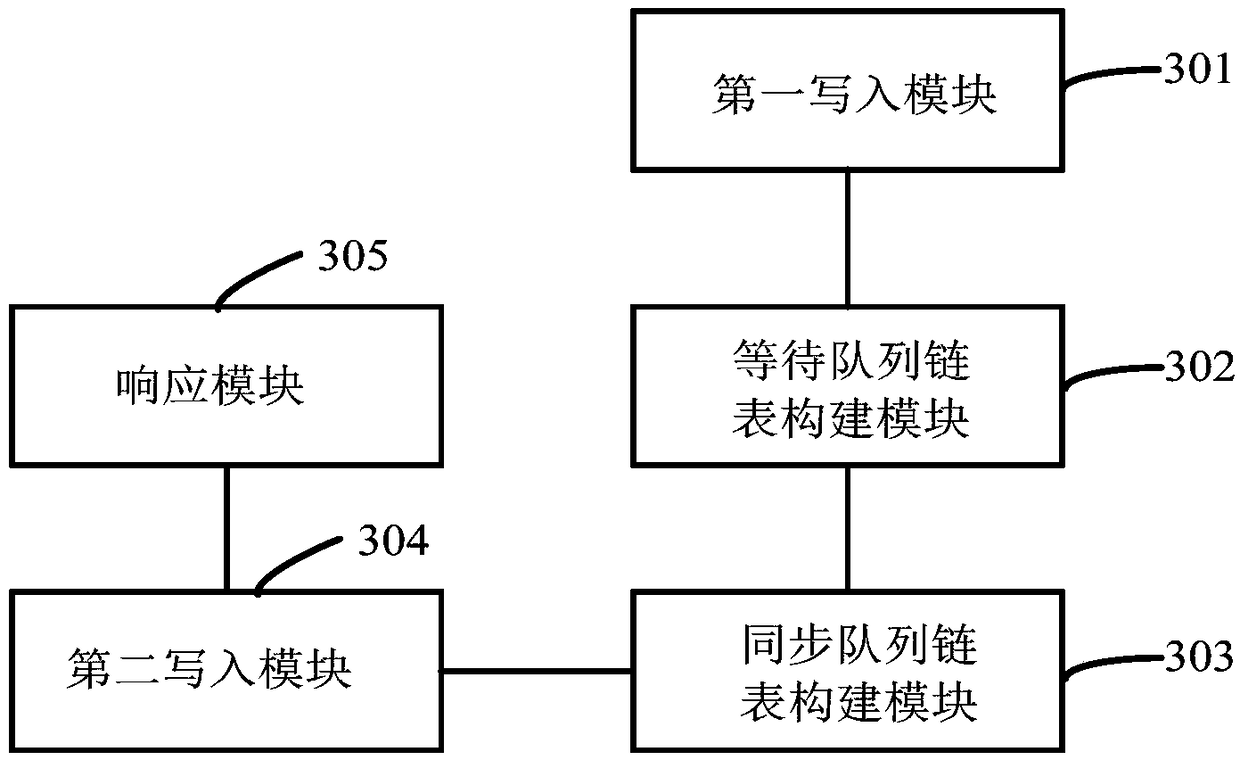
The invention provides a method and device for writing data based on a common Internet file system. The method comprises the steps of starting a thread to write SMB (Server Message Block) message datain a received file write request into a preset memory area; blocking the thread after it is monitored that the data is written into the preset memory area, and embedding a thread identity of the blocked thread into a preset waiting queue linked list; shearing each thread identity to a preset synchronization queue linked list after it is determined that the thread corresponding to the thread identity in the waiting queue linked list is woken up; indicating the woken thread to read the SMB message data of the synchronization queue linked list in the memory area, and writing the data into a disk; and traversing the synchronization queue linked list after the data is written into the disk, returning write success information to clients mapped by the traversed thread identities in sequence, and waking up the thread corresponding to the thread identity in the waiting queue linked list after the write success information is returned to the client mapped by the lastly traversed thread. A utilization rate of bandwidth resources can be effectively improved.
Owner:NEW H3C TECH CO LTD
A log storage method and system based on a data center
ActiveCN109902074AVerify validityProtection securityTransmissionFile system typesData centerOperability
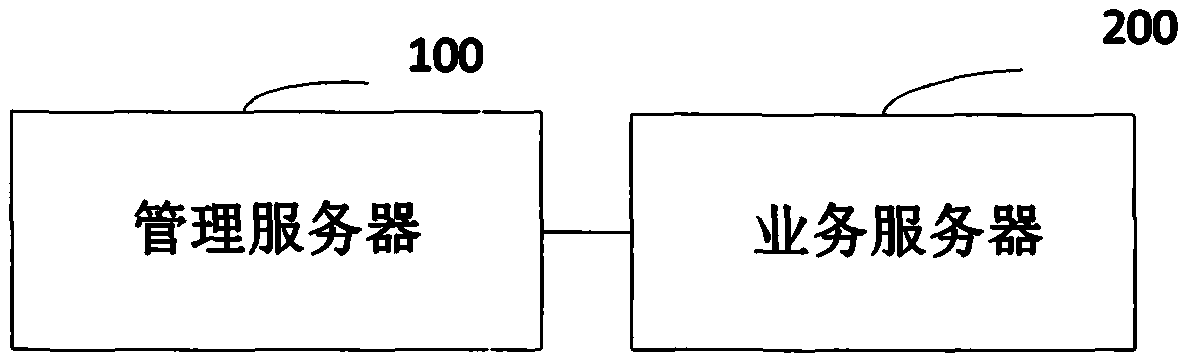
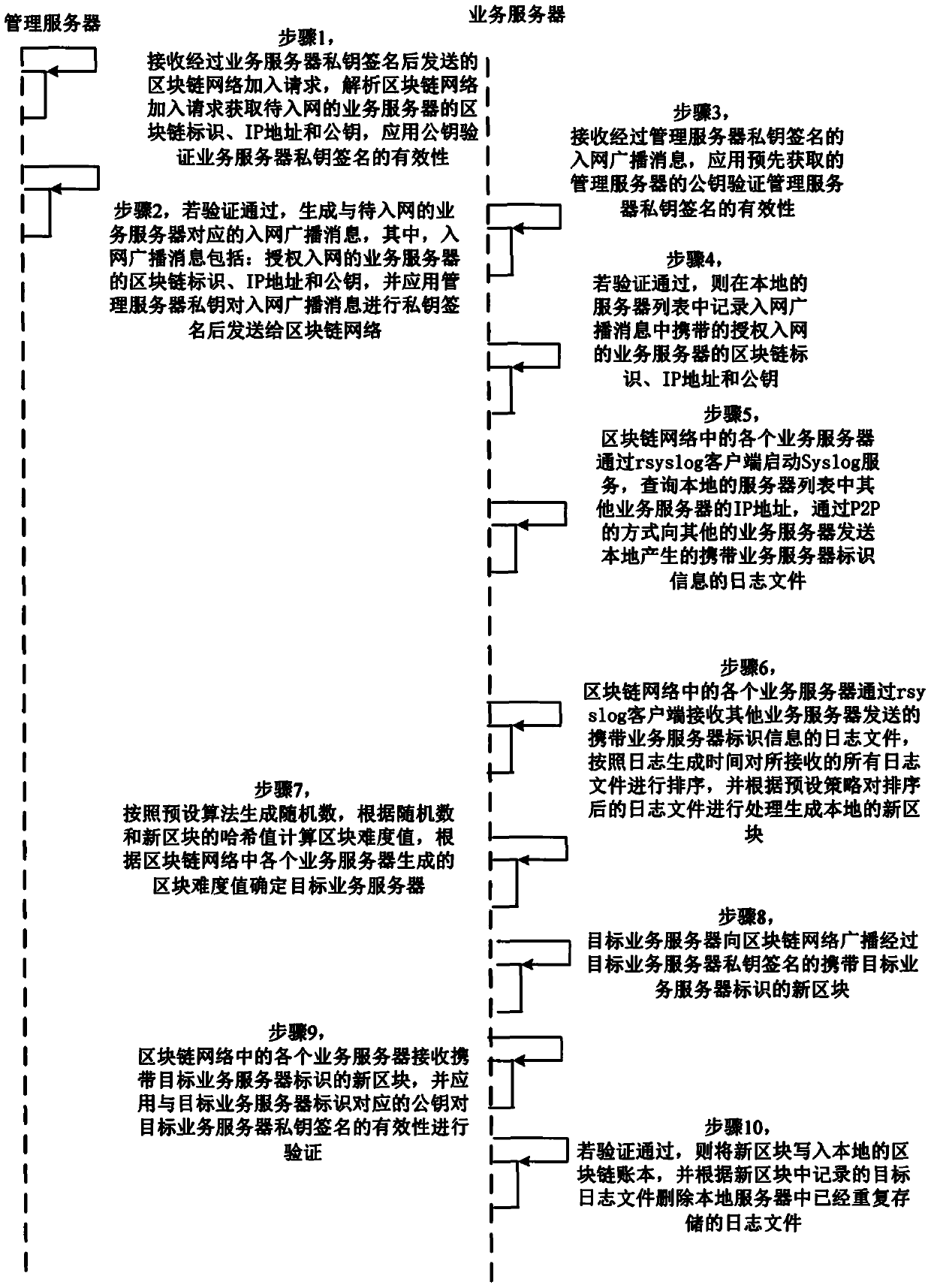
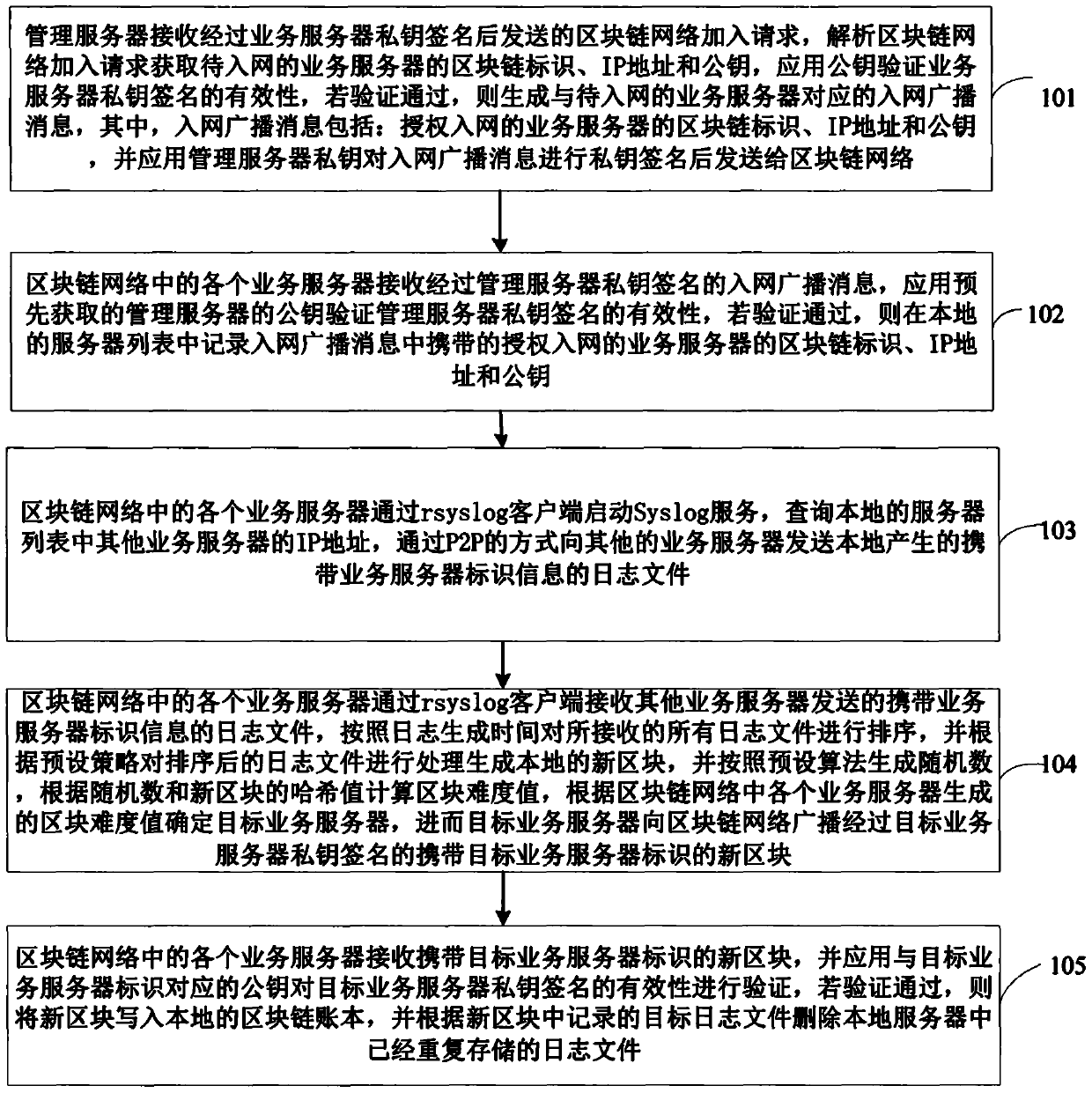
The invention discloses a log storage method and system based on a data center. The method comprises the following steps that the management server receives a network access request of the service server; after the verification is legal, the service server is allowed to join the block chain network, receive a log file sent by a service server of the block chain network, sort all the received log files according to the log generation time, process the log files to generate a local new block, and broadcast a new block which is signed by a target service server private key and carries a target service server identifier to the block chain network by the related target service server; And each service server deletes log files repeatedly stored in the local server according to the target log files recorded in the new block. Therefore, the block chain network is formed by the servers in the data center, the log files are stored in a distributed mode, the safety of the log files is protected,a firewall mechanism of the data center is spanned, and operability is high.
Owner:江苏全链通信息科技有限公司
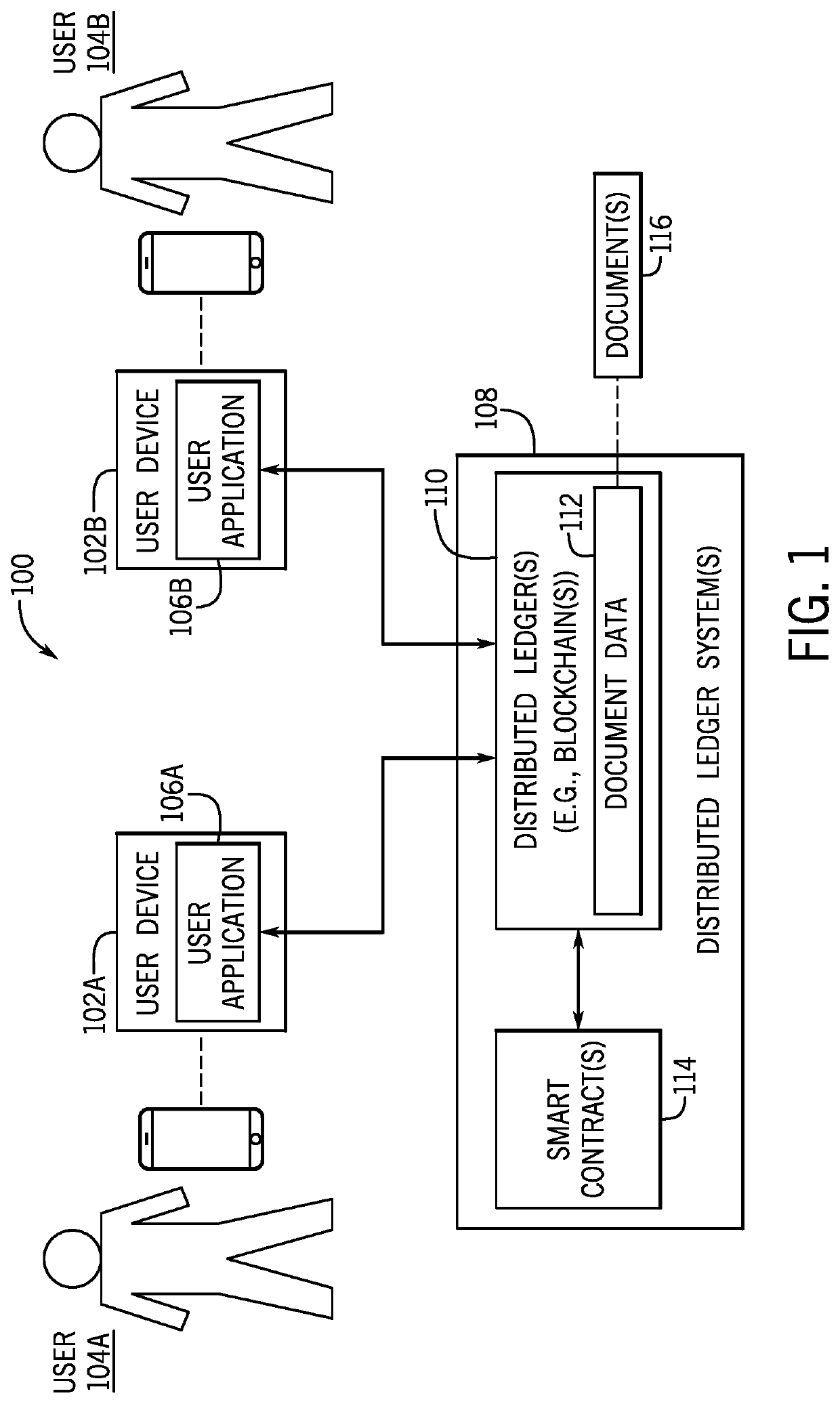
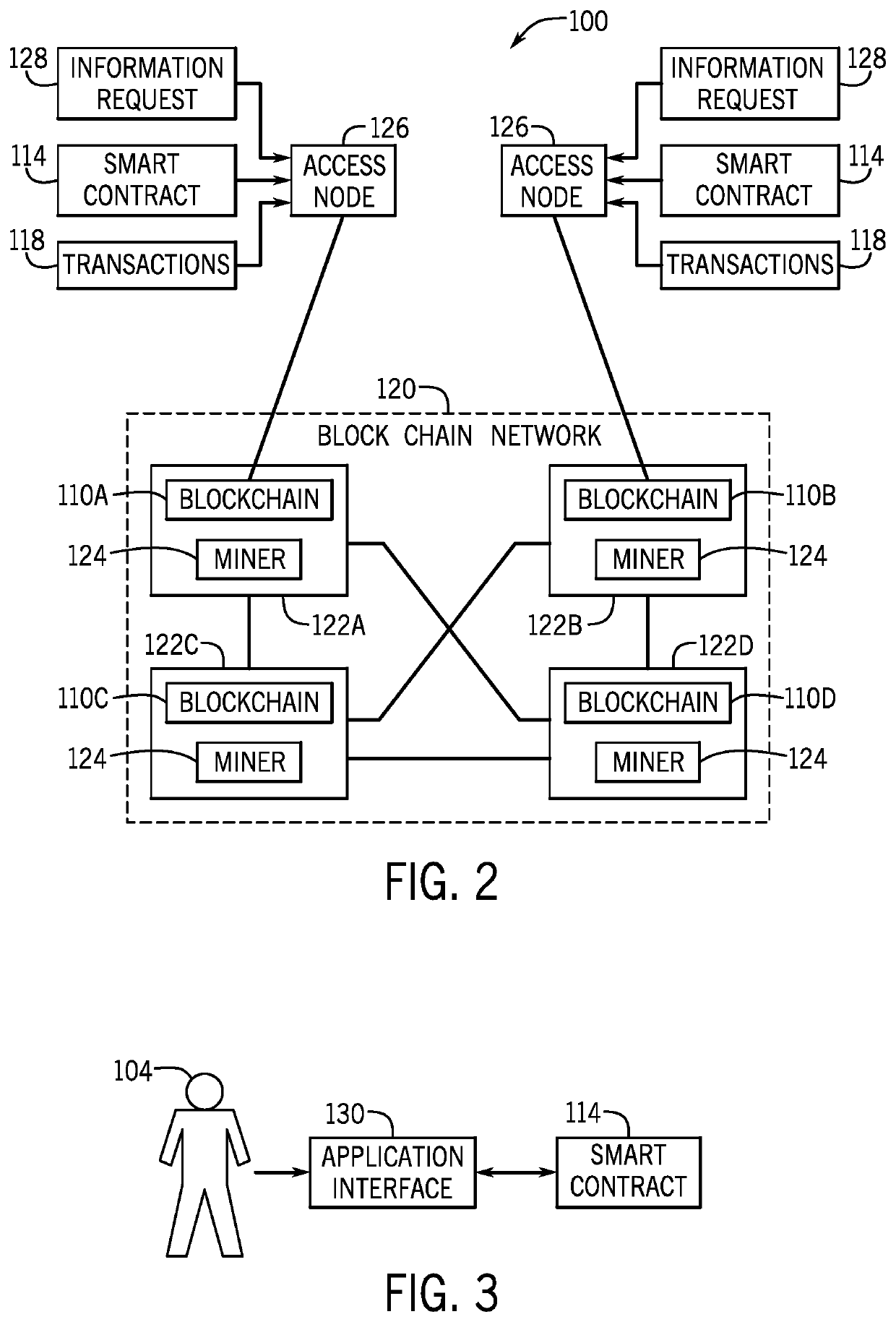
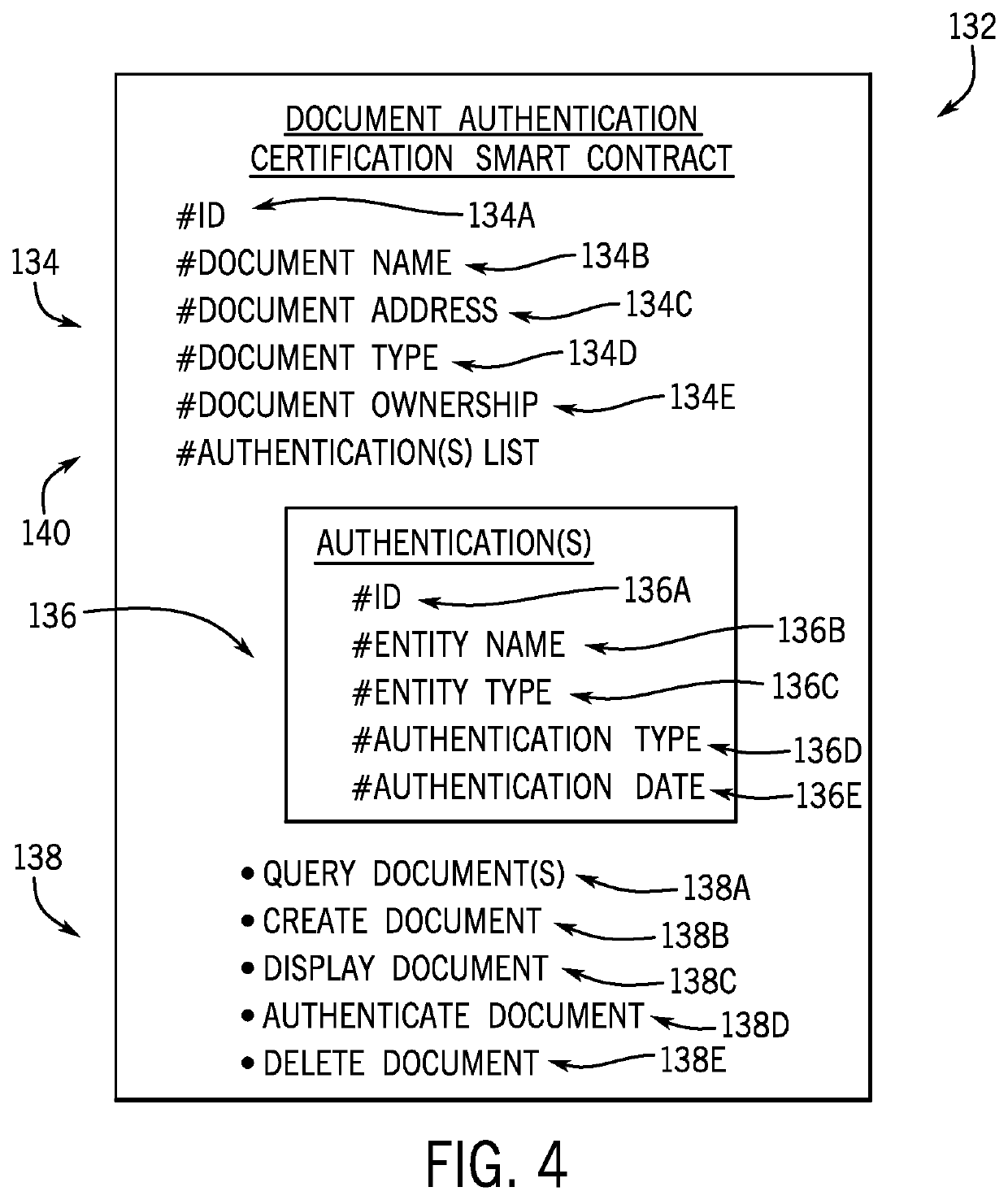
Document authentication certification with blockchain and distributed ledger techniques
ActiveUS11170092B1Guaranteed automatic operationEncryption apparatus with shift registers/memoriesUser identity/authority verificationNetwork onUnique identifier
Embodiments are described herein for document authentication certification using information stored on a distributed ledger such as a blockchain. A distributed ledger may securely store document data describing the document. Use of a distributed ledger may provide an immutable, readily auditable record of the history of the document. Each user participating in the system may be assigned a unique identifier to be used for conducting transactions on the distributed ledger network. A user may also be provided with a digital security token such as a cryptographic key that is useable to authenticate the user and enable access to the document data stored on the distributed ledger(s).
Owner:USAA
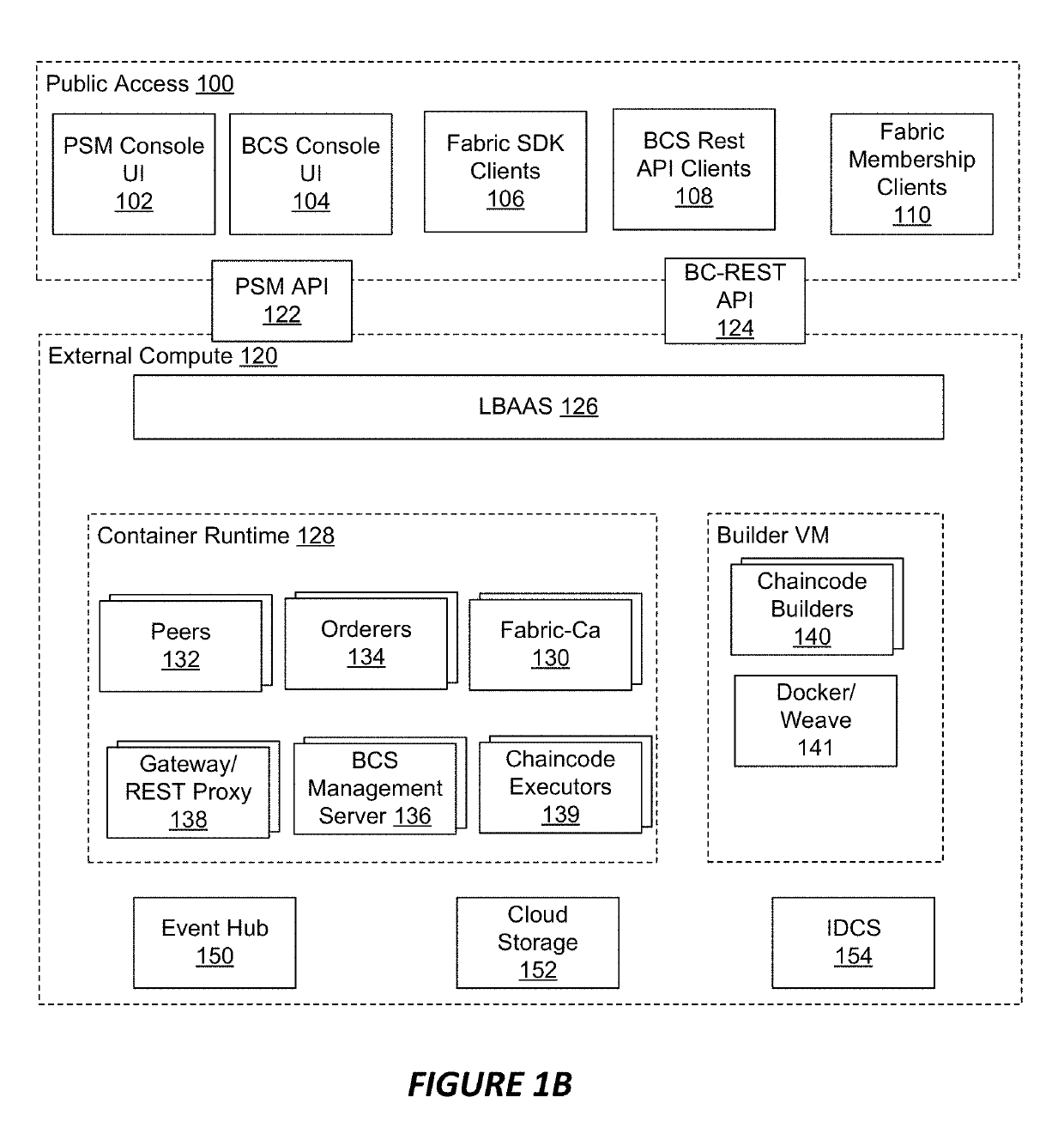
System and method for providing a representational state transfer proxy service for a blockchain cloud service
ActiveUS10528551B2Key distribution for secure communicationResource allocationRepresentational state transferService development
Systems and methods for implementing a distributed ledger as a blockchain cloud service are provided. The blockchain cloud service can include nodes of the distributed ledger and a REST proxy service component. The REST proxy service uses a service development kit for the distributed ledger to communicate with the distributed ledger, and can provide REST APIs for use by client applications to query through chaincodes, synchronously or asynchronously invoke transactions through the chaincodes, get transaction statuses, and get BCS proxy versions. The REST proxy service component can authenticate REST calls, and translate the REST calls into remote procedural calls, for use in interfacing with the distributed ledger. The REST proxy service component can further provide REST APIs that support the same functions which are provided by the BCS management console component, and provide a user interface for client applications to consume the BCS instance.
Owner:ORACLE INT CORP
Log management system and operation method thereof
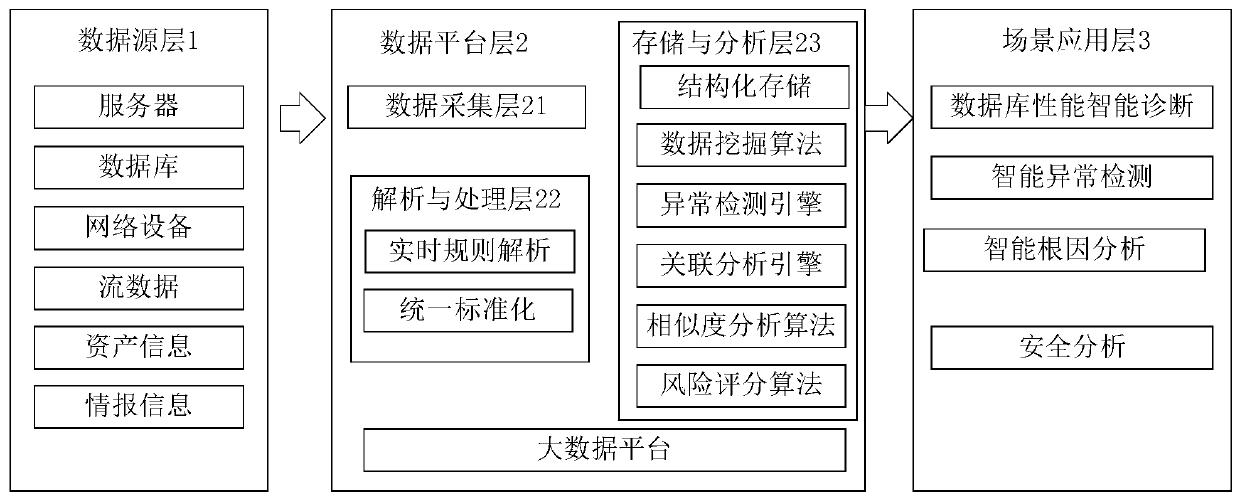
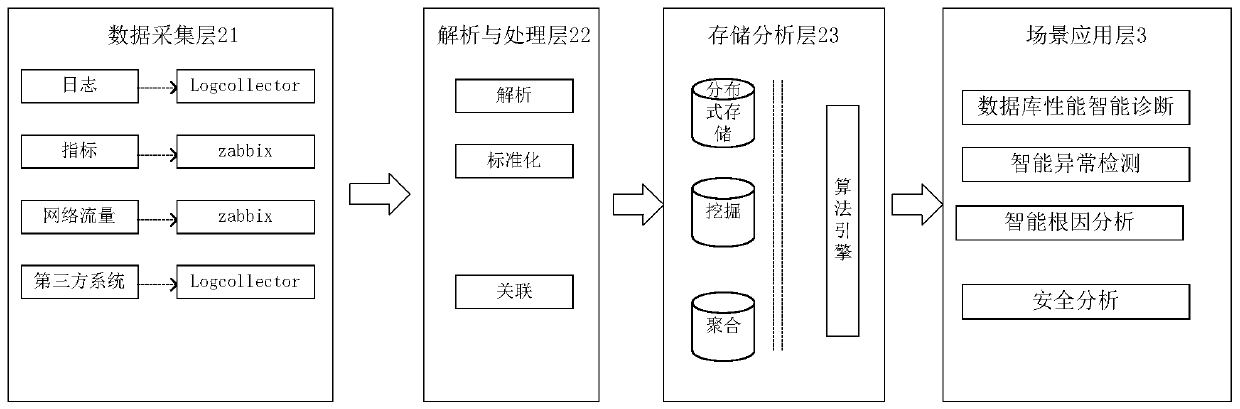
PendingCN111190876AImmediate responseRapid positioningTransmissionSpecial data processing applicationsAnalysis dataData platform
The invention provides a log management system and an operation method thereof. The log management system comprises a data source layer, a data platform layer and a scene application layer. The data acquisition layer is used for acquiring data of the data source layer; the analysis and processing layer is used for processing the data acquired by the data acquisition layer through a queue, enablingthe processed data to enter the data platform layer in real time to be filtered and cleaned, performing real-time rule analysis processing on heterogeneous data sources of different formats through an analysis engine, and then loading the processed data into the storage and analysis layer to be stored and analyzed; after being analyzed by the algorithm engine, the data is called by the scene application layer in real time; the scene application layer is used for carrying out real-time detection on suspicious indexes in combination with in-line requirements, quickly responding to abnormal events and problems, tracing the source and establishing an operation and maintenance knowledge base; a security situation awareness scene is established in combination with various network security equipment events and rules in rows, various security events and potential threats are perceived in real time, and timely response and processing, advanced prediction and risk avoidance capability are achieved.
Owner:天津浪淘科技股份有限公司
Database processing method, device and system
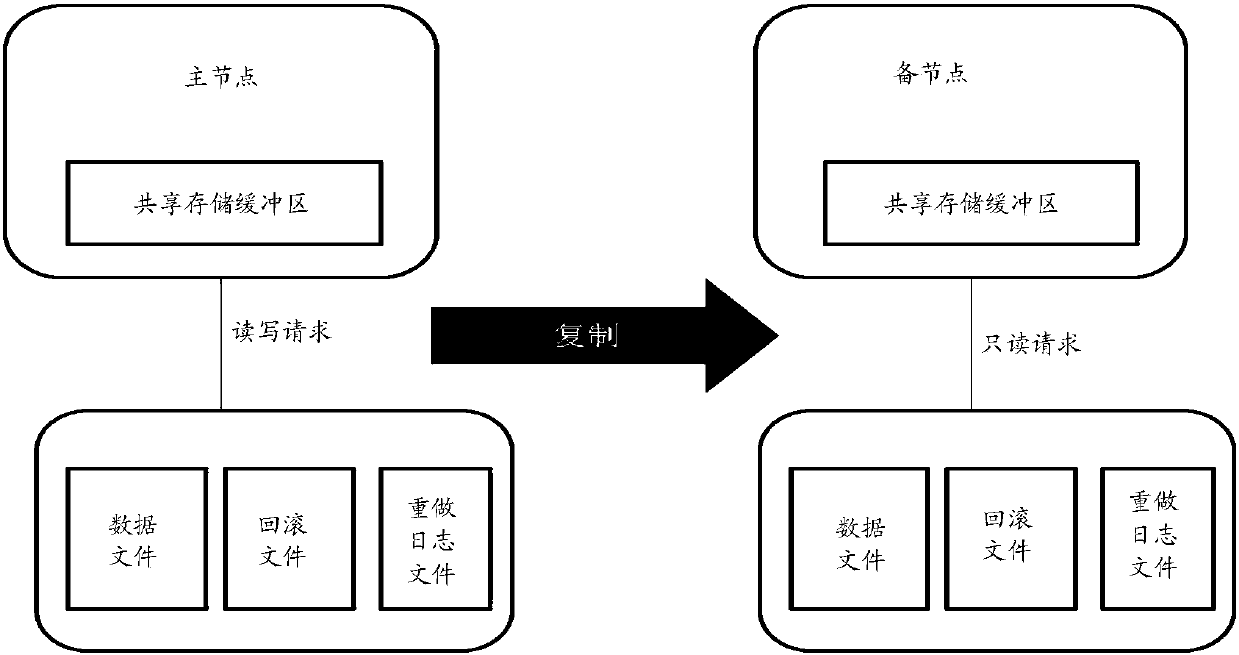
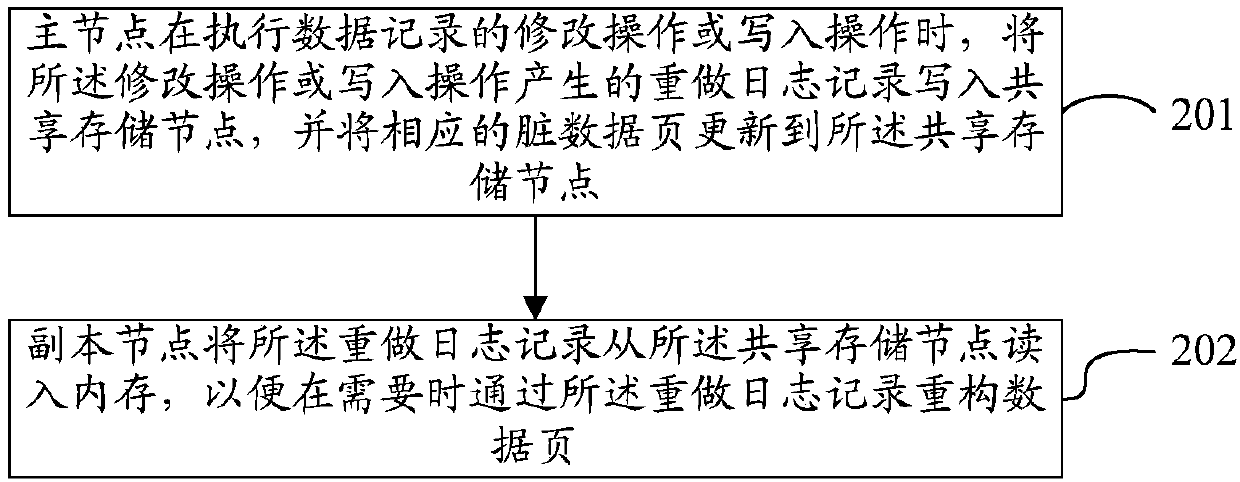
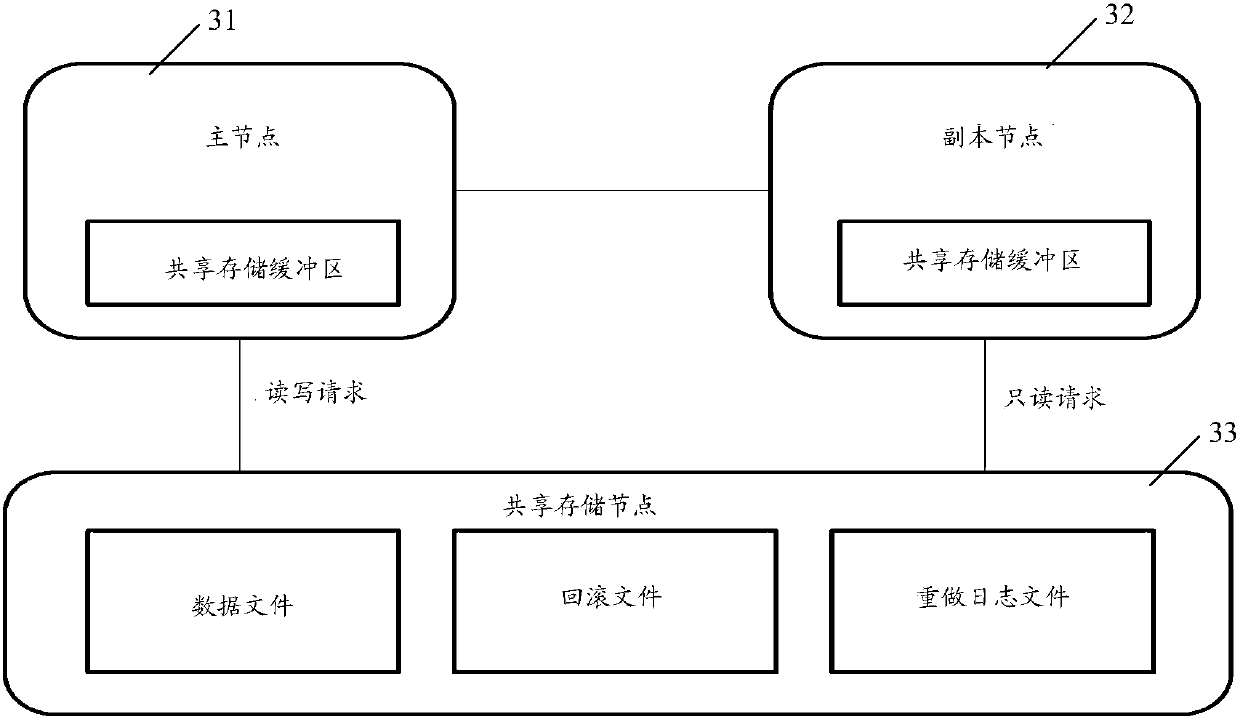
PendingCN110019066ALower deployment costsEasy to expand reading abilityFile system administrationFile access structuresDirty dataData records
The invention discloses a database processing method, device and system, and the method comprises the steps: enabling a main node to write a redo log record generated by a modification operation or awrite-in operation into a shared storage node when the main node executes the modification operation or the write-in operation of a data record, and updating a corresponding dirty data page to the shared storage node; and enabling the replica node to read the redo log record from the shared storage node into a memory, so that a data page can be reconstructed through the redo log record when needed. The deployment cost and the master-slave delay of the database for realizing read-write separation can be reduced.
Owner:ALIBABA CLOUD COMPUTING LTD
Media aware distributed data layout
InactiveUS8214404B2Reduce amountLimited amountData processing applicationsDigital data processing detailsClass of serviceInode
A storage system comprises a plurality of vdisks, with each vdisk containing a plurality of storage segments, and each segment providing a specific class of service (CoS). Each vdisk stores files with data and meta data distributed among its storage segments. A storage system comprises a memory having multiple classes of service. The system comprises an interface for storing a file as blocks of data associated with a class of service in the memory. The interface chooses the class of service for a block on a block by block basis. A file system for storing a file comprises a plurality of vdisks, with each vdisk having a plurality of inodes. Each inode of each vdisk stores data on one or more segments, with each segment having a different class of service. The system comprises a controller which stores data of a file in an inode of a vdisk, in one or more segments of that vdisk. A file system for storing a file comprises a plurality of vdisks, and each vdisk having a plurality of inodes. The system comprises a controller including a plurality of processors, with each processor serving one or more of the vdisks. A file system for storing comprises a plurality of vdisks, with each vdisk having a plurality of inodes, a plurality of inodes of at least one vdisk storing data on a plurality of segments, each segment having a different class of service. The system comprises a controller which stores data of the file in one or more segments of one vdisk. A method for storing a file.
Owner:MICROSOFT TECH LICENSING LLC
Log processing method, equipment, computer device and computer readable storage medium
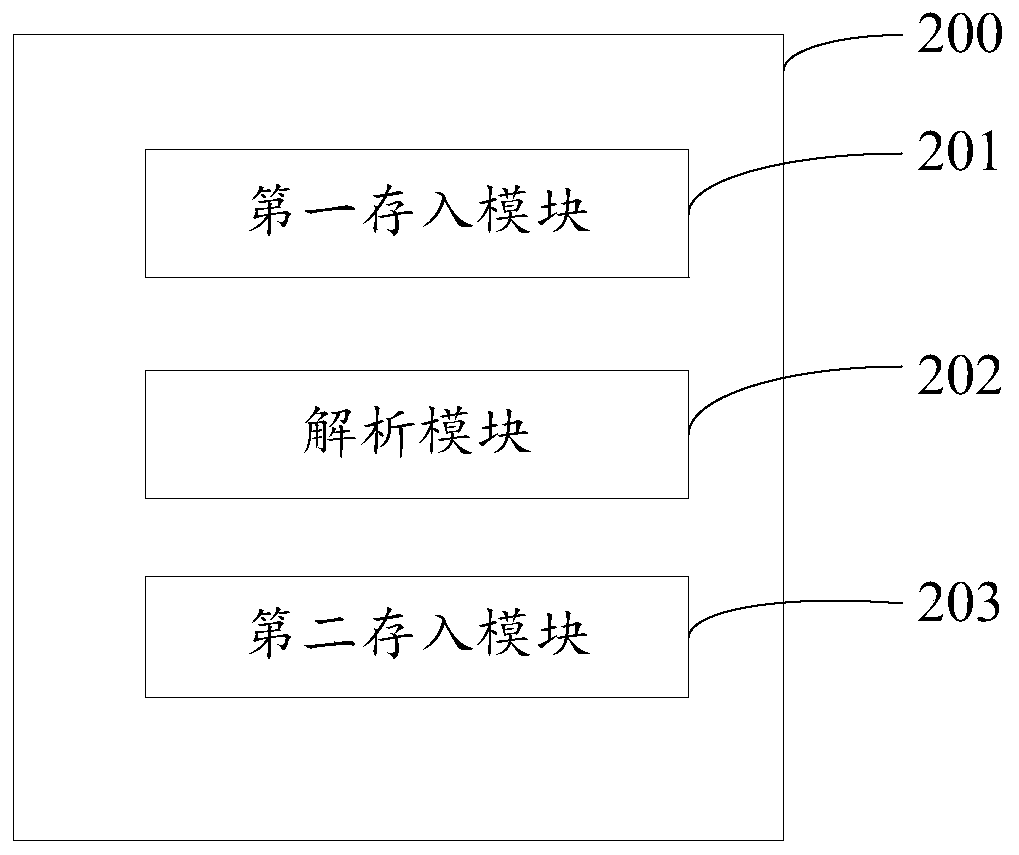
InactiveCN110515912AHigh clarityEasy to handleHardware monitoringSpecial data processing applicationsThe InternetData format
The invention is applicable to the technical field of the Internet, and provides a log processing method, equipment, a computer device and a computer readable storage medium. The method comprises thefollowing steps: acquiring log information through a Kafka system, the log information comprising log data of a plurality of items; storing the log data into topic topics with the same project names as the log data; analyzing log data obtained from topic topics according to a custom data format through a data processing module developed by a JStorm framework to obtain analyzed log data; and storing the analyzed log data into a corresponding data table in an ElasticSearch database through a data storage module developed by a JStorm framework according to a database type, a database name and a target data table specified by a preset analysis rule. According to the log processing method provided by the invention, the log data acquired from the Kafka system can be analyzed according to the self-defined data format, and the analyzed log data is stored into the corresponding table in the ElasticSearch database, so that the log data processing effect is improved.
Owner:湖南星汉数智科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com