A cloud user behavior audit system and method based on cloud log analysis
A log and behavior technology, which is applied in the field of cloud user behavior audit system based on cloud log analysis, can solve the problems of large data volume, unpredictable log format, and inability to run analysis algorithms, etc., to achieve the effect of improving overall security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] In order to better understand the present invention, the present invention will be described in detail below in conjunction with the accompanying drawings.
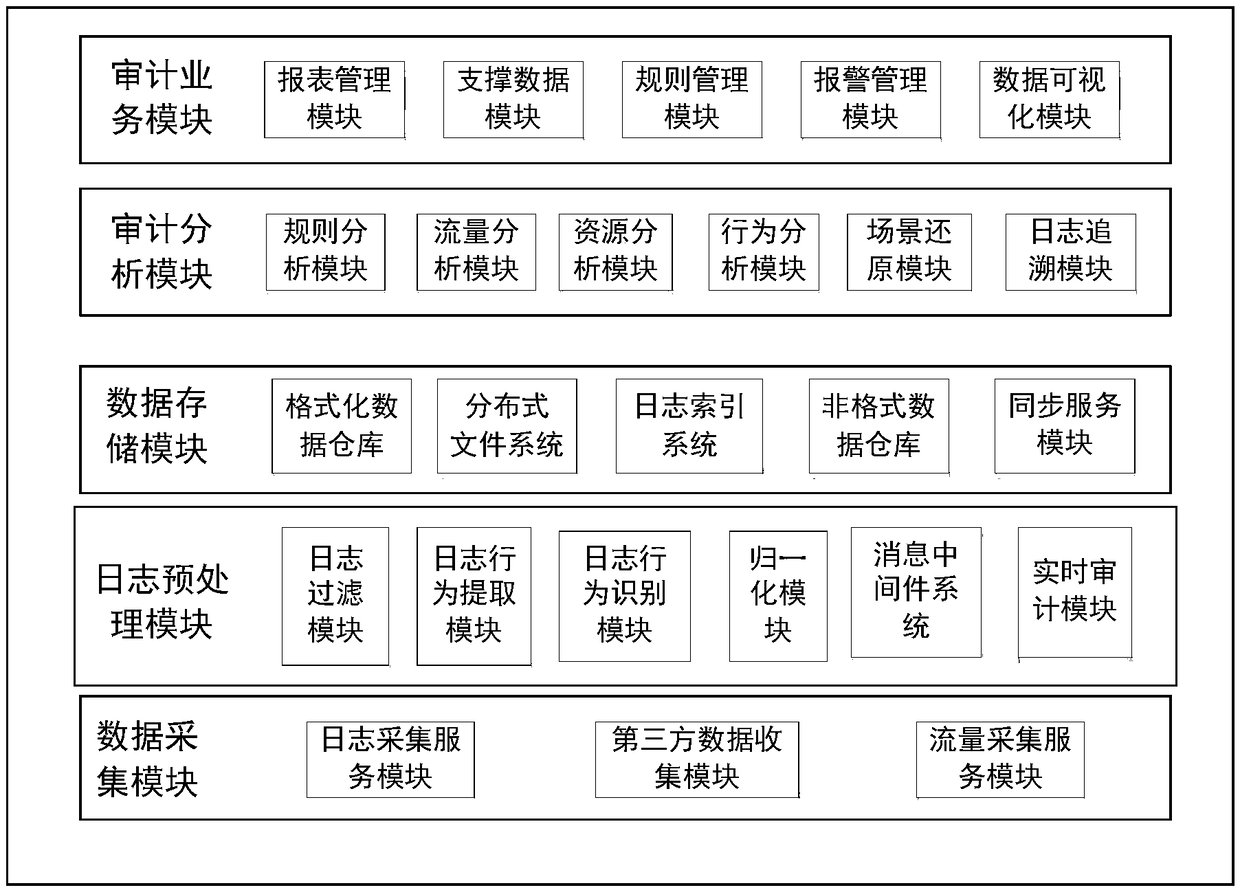
[0014] The present invention mainly extracts user operation behavior information by analyzing the operation log of the cloud, thereby recording the user operation behavior, understanding the operation status of the cloud, and discovering risks and illegal operations on the cloud in time. The invention extracts user operation behavior information from the operation log of the cloud system, and audits the user's operation behavior; the system automatically collects the full amount of logs of all sub-modules in the cloud system, uses a combined filtering algorithm to effectively filter out invalid logs, and retains Effective logs of information are required to improve system processing capabilities; the system can process logs in any format, and use the log type extraction algorithm to automatically identify all log fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com