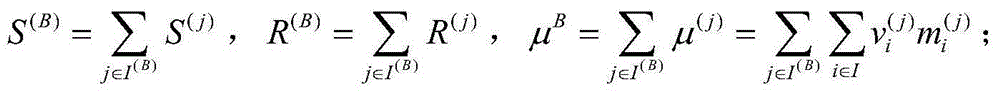Patents
Literature
218 results about "Cloud user" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Education cloud platform and implementation method thereof
InactiveCN104537589ARealize informatizationData processing applicationsSpecial data processing applicationsResource poolCloud user
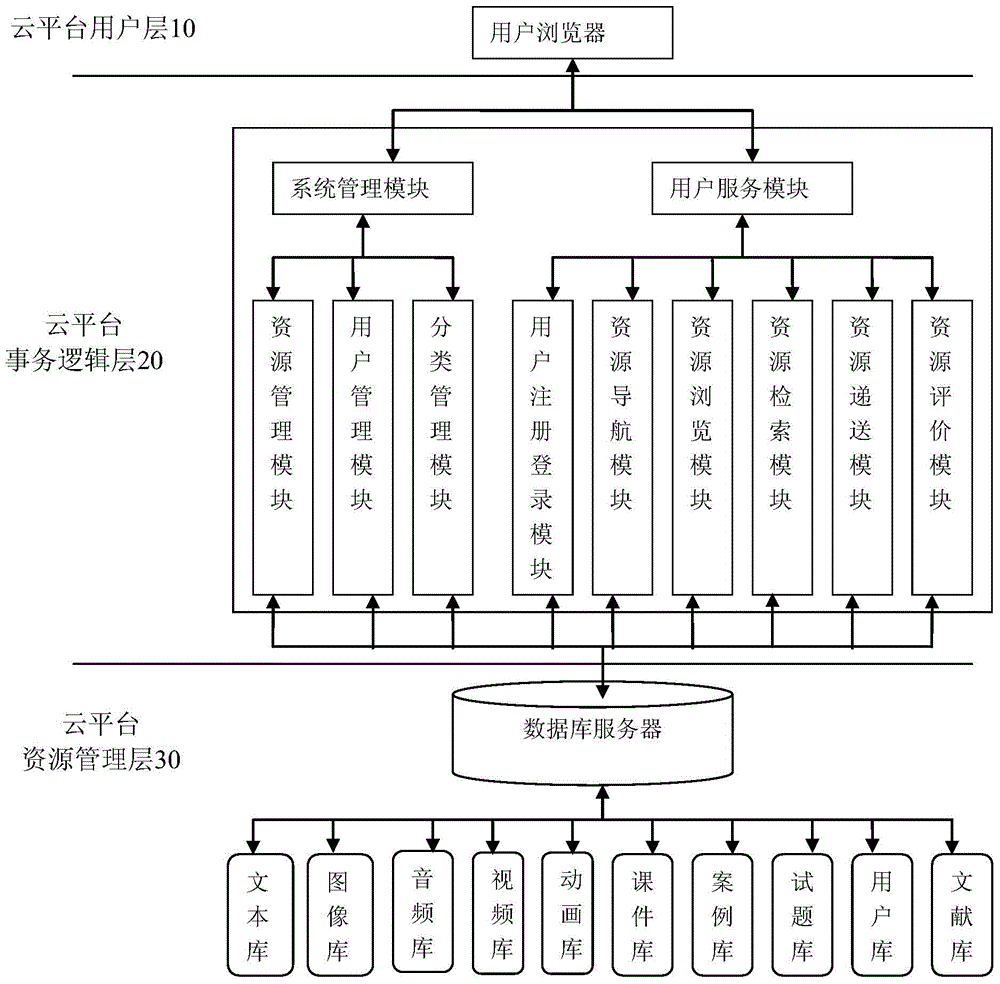
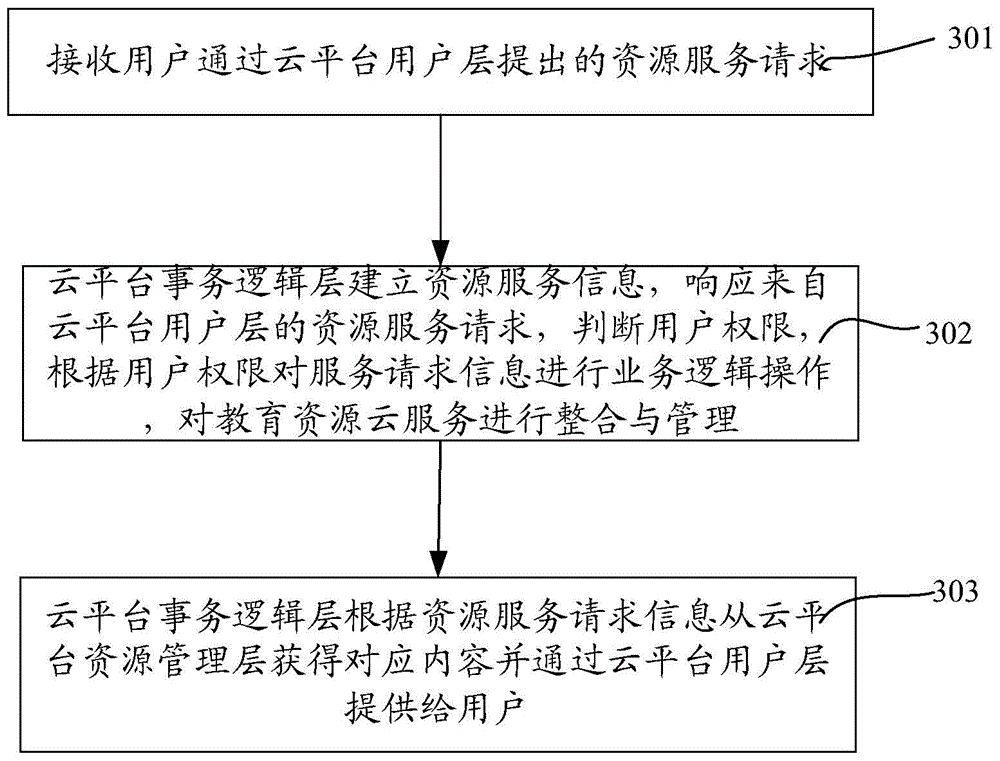
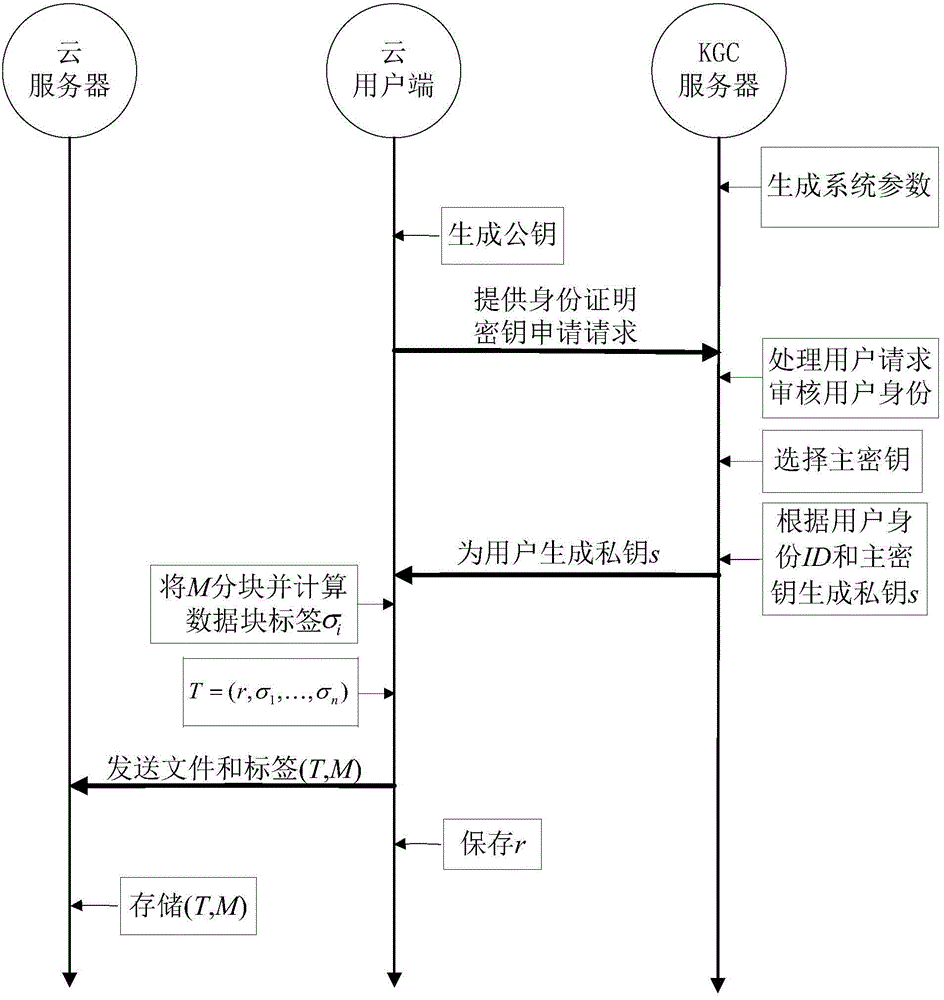
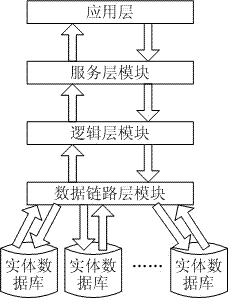
The invention discloses an education cloud platform and an implementation method thereof. The education cloud platform comprises a cloud platform user layer, a cloud platform service logic layer and a cloud platform resource management layer. The cloud platform user layer orientates to a terminal user, is cloud equipment physically, provides a graphic user interface based on a browser for the user, responds to a user resource request of the client end, and displays the process interface and the result information of services to the user. The cloud platform service logic layer is used for establishing source service information, responding to the resource service request from the cloud platform user layer, conducting service logic operation on service request information, and integrating and managing the cloud platform resource management layer. The cloud platform resource management layer is used for conducting open description capable of being recognized by a computer on education resource information, conducting storing in a database table mode, completing the daily service management of an underlying resource pool and classifying and checking upload resources. According to the education cloud platform and the implementation method thereof, cloud service modules can be quickly selected according to the learning activity demand of the cloud user, a service process integration scheme is generated, and therefore the scheme is delivered to the cloud user in a cloud service mode.
Owner:SHANGHAI DIANJI UNIV
Data storage method based on identity in cloud computing and integrity verification method based on identity in cloud computing
InactiveCN104811450ALow costReduce complexityUser identity/authority verificationCloud userCloud storage
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
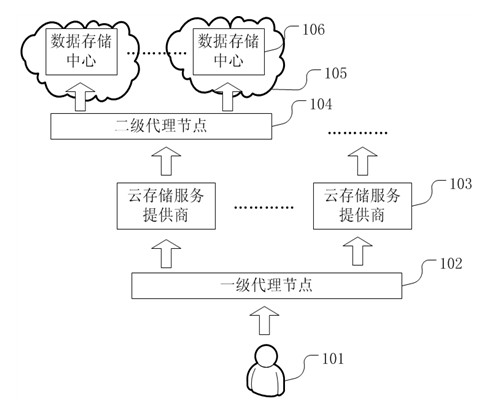
Cloud storage system and data deployment method thereof
InactiveCN102035884ABroaden your optionsFlexible adjustmentTransmissionService provisionCloud storage system
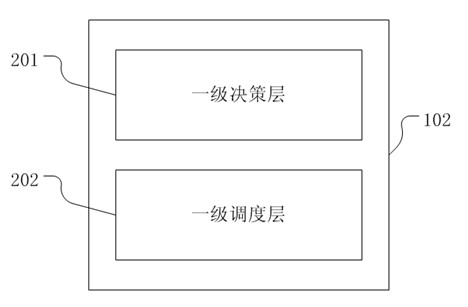
The invention discloses a cloud storage system for providing cloud storage service for users. The cloud storage system is characterized by comprising a cloud storage service provider (103), a primary agent node (102), a secondary agent node and a storage cloud (105), wherein a user sends a service request, the primary agent node selects the service scheme provided by the configuration of the optimal cloud storage service provider according to the request, and the secondary agent node selects the storage center in the data storage cloud to realize the cloud storage service. The invention also provides a data deployment method of the cloud storage system, which is used for deleting, modifying or adding user data. The invention can support services provided by multiple cloud storage service providers to accelerate the response speed of service used by the users, and can dynamically configure a bottom storage architecture according to the characteristics of the users, thereby simultaneously having the advantages of a master-slave mode architecture and a peer to peer storage architecture.
Owner:HUAZHONG UNIV OF SCI & TECH
Effective and verifiable public key searching encryption method based on KP-ABE
ActiveCN104038349APrevent Offline Guessing AttacksReduce computationPublic key for secure communicationUser identity/authority verificationCloud userPassword
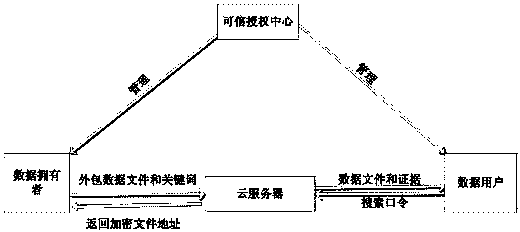
The invention discloses an effective and verifiable public key searching encryption method based on the KP-ABE. According to the method, a creditable authority center, a data owner, a cloud server and a data user are included. The creditable authority center generates a certificate for all cloud users; the data owner outsources a data file and a keyword to the cloud server; the cloud server executes searching operation after providing a storage service and receiving a searching request sent by a user; the data user generates a searching password and sends the password to the cloud sever to search for a target file. According to an effective and verifiable public key searching encryption method based on the KP-ABE, a public and private key pair is generated for the data owner and the cloud server, when the ciphertext keyword and the searching command are sent, the public key pair of the cloud sever is used for encrypting the ciphertext keyword and the searching command firstly, the off-line conjecture aggressive behavior of an external attacker is effectively prevented, and the safety of information and data is improved. In addition, complexity is lowered, the calculation amount of the user is largely reduced, and the efficiency is largely improved.
Owner:XIDIAN UNIV
Self-adaptive cloud access control method based on dynamic authorization mechanism
ActiveCN105871854AGuaranteed reliabilityThe mapping relationship is simpleTransmissionCloud userSelf adaptive
The invention relates to a self-adaptive cloud service access control method based on a dynamic authorization mechanism. Credibility modelling of user behaviours is carried out at first; the access permissions of cloud users are hierarchically described by using inheritance idea; a cloud authentication centre constructs the mapping relationship of a model according to the historical creditworthiness and role trees of the users, gives different cloud user identity tokens, and recommends cloud services allowed to access to the users; the cloud authentication centre dynamically adjusts the comprehensive creditworthiness of the users by monitoring change of the user behaviours in real time, such that the credibility of the users is judged; if the users are credible, the cloud authentication centre gives the cloud service access tokens to the users; the cloud users obtain services by the cloud service access tokens; and otherwise, access is refused. The self-adaptive cloud service access control method based on the dynamic authorization mechanism provided by the invention has relatively high security and reliability.
Owner:浙江刨子科技有限公司
Cloud data public auditing method with duplication eliminating function
ActiveCN106254374ASave bandwidthRealize deduplication storageKey distribution for secure communicationUser identity/authority verificationCloud userData integrity
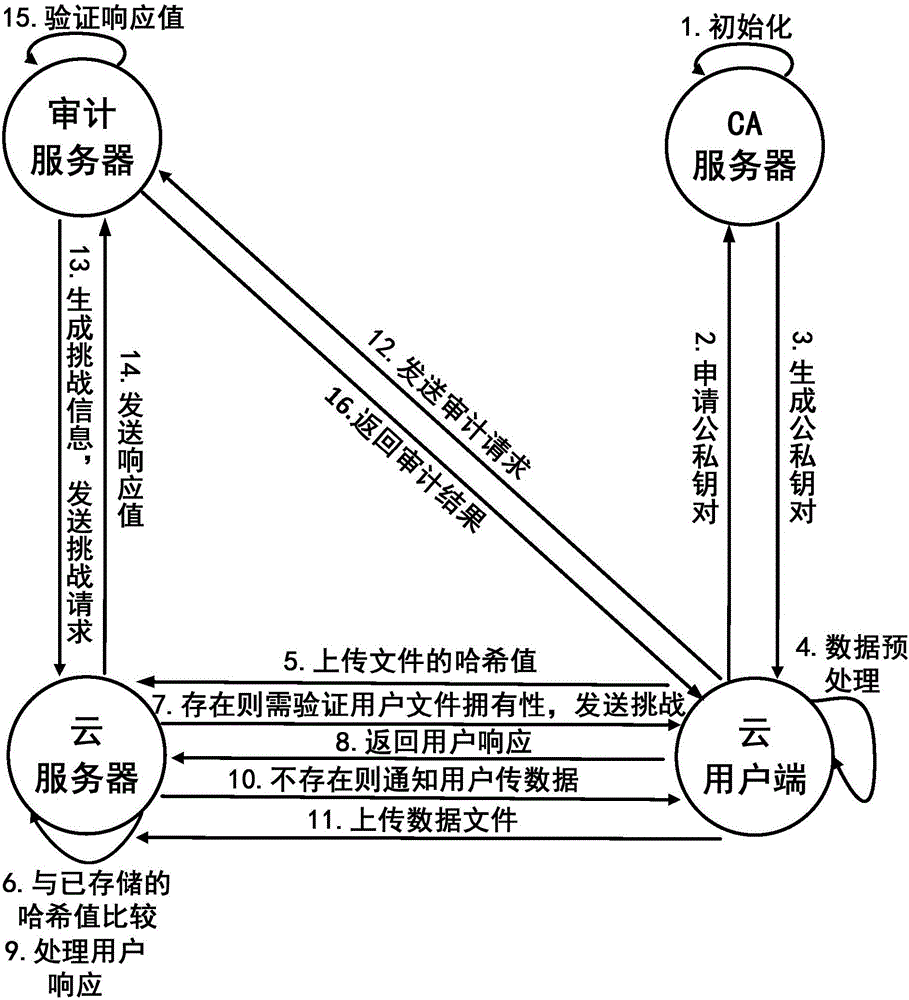
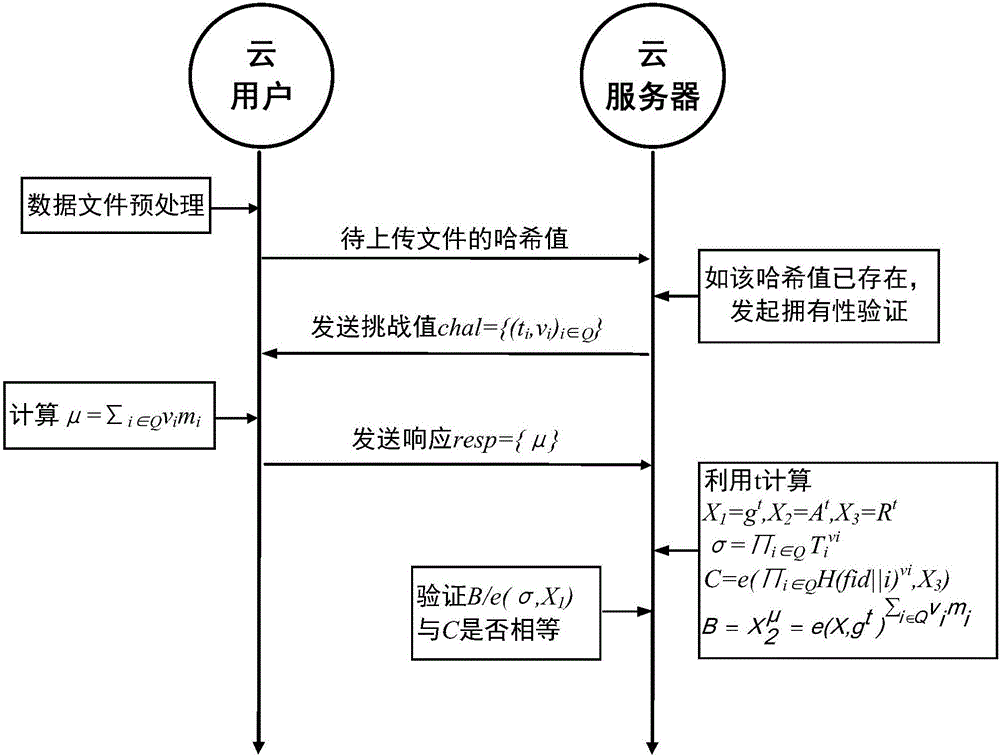
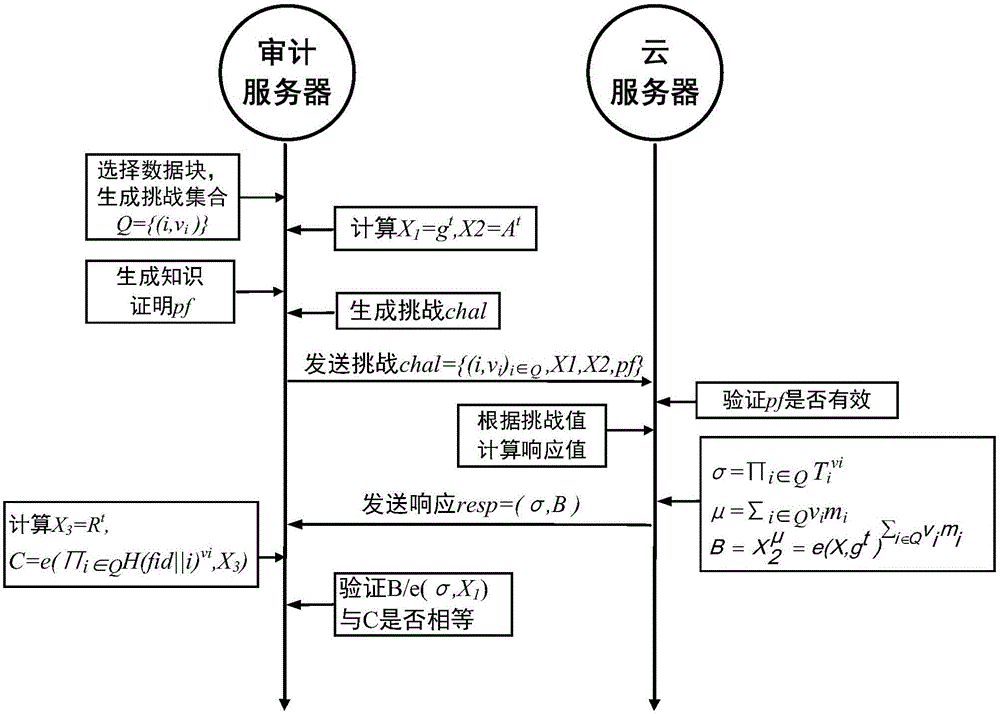
The invention discloses a cloud data public auditing method with a duplication eliminating function, and the cloud data public auditing method belongs to the technical field of network security. The cloud data public auditing method comprises the steps that: a CA server sets system parameters, and a user applies for a public-private key pair to the CA server after renting a storage space of a cloud server; a cloud user sends a hash value of a file to be stored to the cloud server at first when storing the file, the cloud server detects the hash value and sends challenge information to the cloud user for verifying ownership if the file is stored in the server, and the cloud server verifies whether the user really owns the data file according to responses; otherwise, the cloud user uploads the file and a label to the cloud server; in addition, an auditing server can verify integrity of data in the cloud server according to a user request. The cloud data public auditing method realizes data integrity verification by adopting a round of asymmetric key agreement algorithm, and realizes the zero knowledge privacy protection; moreover, the practical data duplication eliminating technology is introduced, thereby greatly improving the utilization rate of the cloud server.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Cloud storage data common auditing method possessing secret key leakage resistance characteristic
The invention belongs to the communication technology field and especially relates to a cloud storage data common auditing method possessing a secret key leakage resistance characteristic. The method mainly comprises the following steps of system initialization: blocking processing is performed on a data file so as to generate public and private key pairs of a cloud user and a cloud server; auditing identification generation: the cloud user sends the data file and a label, and a signature set of a data block to the cloud server; auditing challenge response: a third party auditor generates auditing challenge information and sends to the cloud server; the cloud server calculates combination information according to the auditing challenge information, gets signatures together and sends an auditing identification response information to the third party auditor; and the third party auditor verifies validity of the auditing identification response information. The method has advantages that a condition that digital signature forgery and auditing identification response information forgery caused by leakage of a user signature private key can be prevented; and a malicious cloud server is ensured not to generate the forged auditing identification response information to cheat a TPA and to pass through an auditing verification process.
Owner:SOUTHWEST PETROLEUM UNIV
Cloud computing resource scheduling method based on game theory
InactiveCN107193658ASolve resource problemsSolve UtilizationResource allocationCloud userResource utilization
The invention discloses a cloud computing resource scheduling method based on game theory. The method is characterized by including the specific steps of step 1, receiving a user request, analyzing and judging whether available resources meet a demand, rejecting the request if the available resources do not meet the demand, and otherwise, entering the next step; step 2, issuing a receiving request confirmation message; step 3, establishing a cloud user resource scheduling game model with users as game participants or a cloud provider resource scheduling game model with available physical machines of a cloud data center as game participants, and forming an optimal resource allocation scheme; and step 4, completing a virtual unit creation process, and executing the task request of the user. According to the method, a theory method of the game theory is introduced, different optimization targets are customized for different cloud computing environments, the corresponding resource scheduling game models are established, the cloud user resource scheduling game model with the cloud users and cloud providers as the game participants is established, and problems of unfair resource allocation and an insufficient resource utilization ratio are solved by corresponding resource scheduling algorithms.
Owner:CHONGQING INST OF ENG
Secret key updating method for cloud storage and implementation method of cloud data auditing system
InactiveCN104811300AReduce trafficNo need to consume bandwidthKey distribution for secure communicationCloud userCloud data
The invention discloses a secret key updating method for cloud storage and an implementation method of a cloud data auditing system, and belongs to the technical field of network security. The secret key updating method for cloud storage comprises the steps that when a cloud user needs to update a secret key, a CA server is requested to generate a new secret key, and a new file label and a new data block label are generated based on a file label and a data block label downloaded from a cloud server, the old secret key and the new secret key at present, are uploaded to the cloud server, and are used for replacing the corresponding old file label and the corresponding old data block label in the cloud server. Meanwhile, the invention further discloses the implementation method of the cloud data auditing system on the basis of zero-knowledge verification. When the cloud user needs to update the secret key, the corresponding file label and the corresponding data block label on the cloud server are updated based on the secret key updating method for cloud storage. The secret key updating method for cloud storage and the implementation method of the cloud data auditing system are used in a cloud network, the communication cost, caused by changing of the secret key, between the cloud server and the cloud user can be remarkably reduced, the calculation cost of the operation that the cloud user calculates the labels again is reduced, and the data privacy can be effectively protected in the auditing process.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Cloud platform trusted log auditing method for privacy protection based on trusted third party
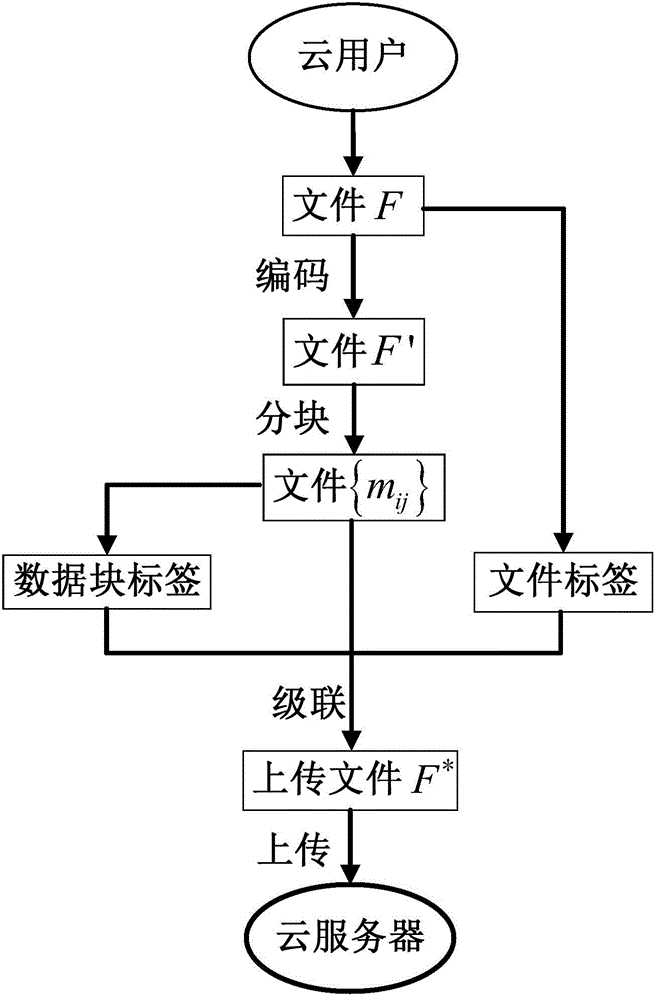
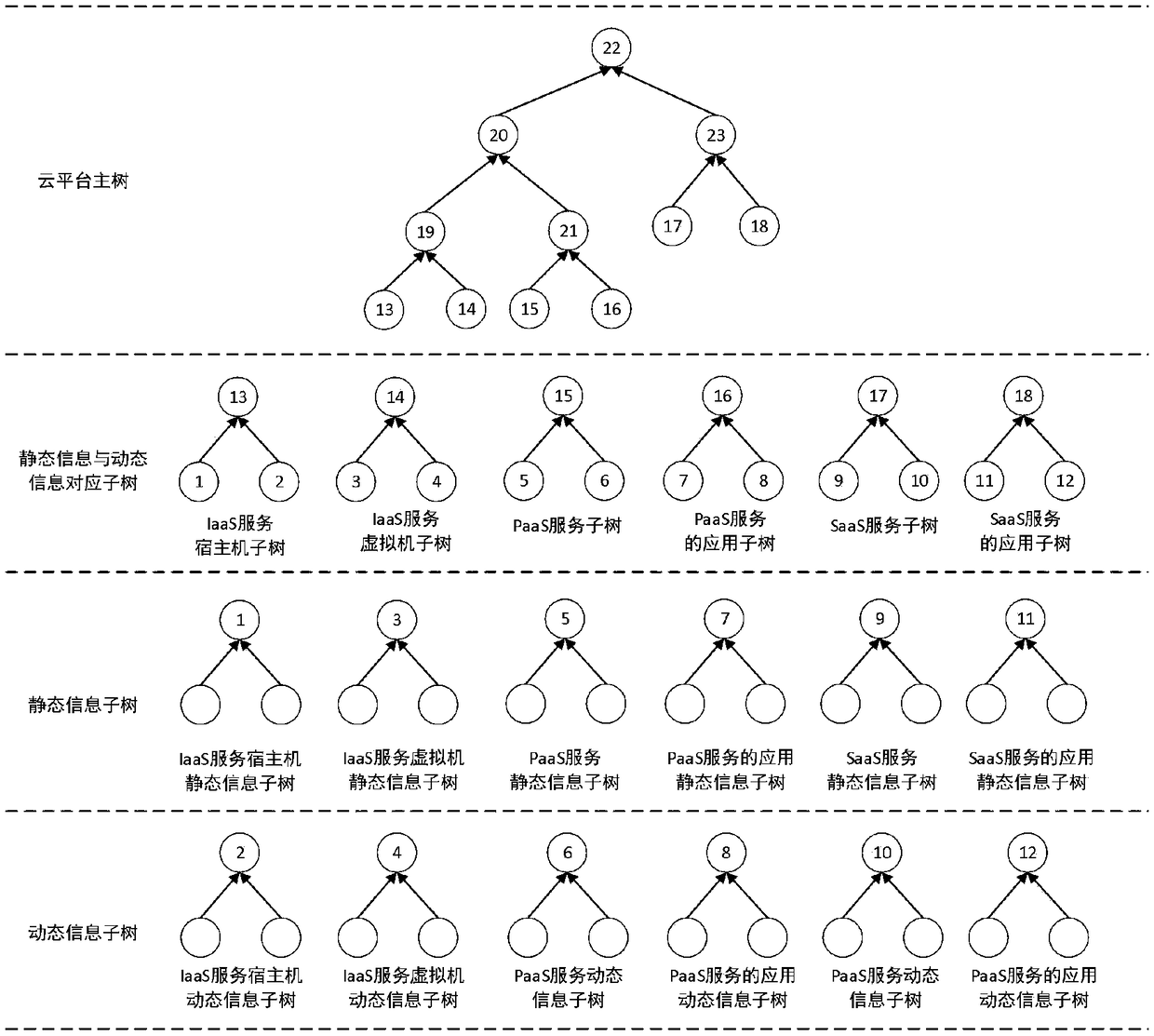
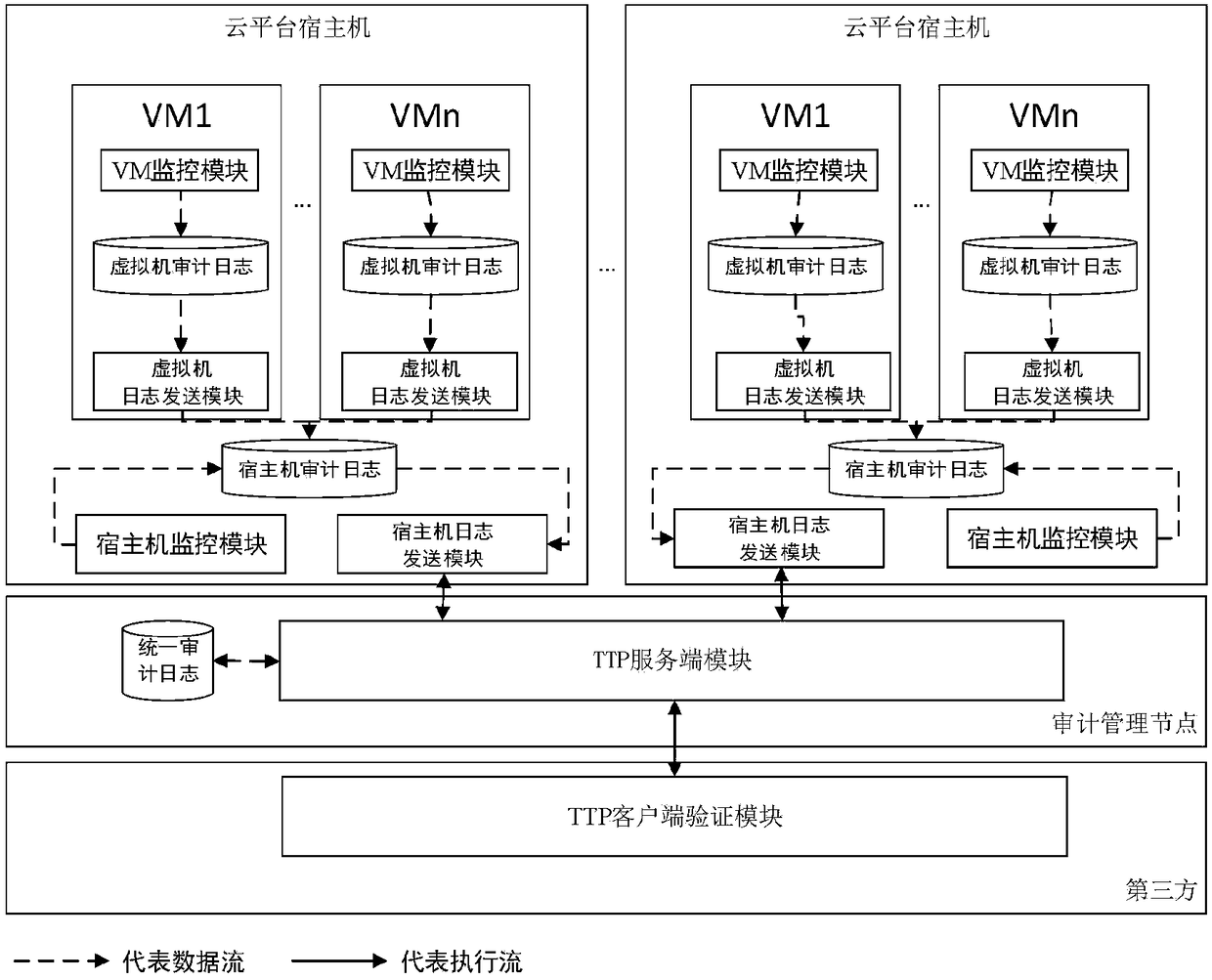
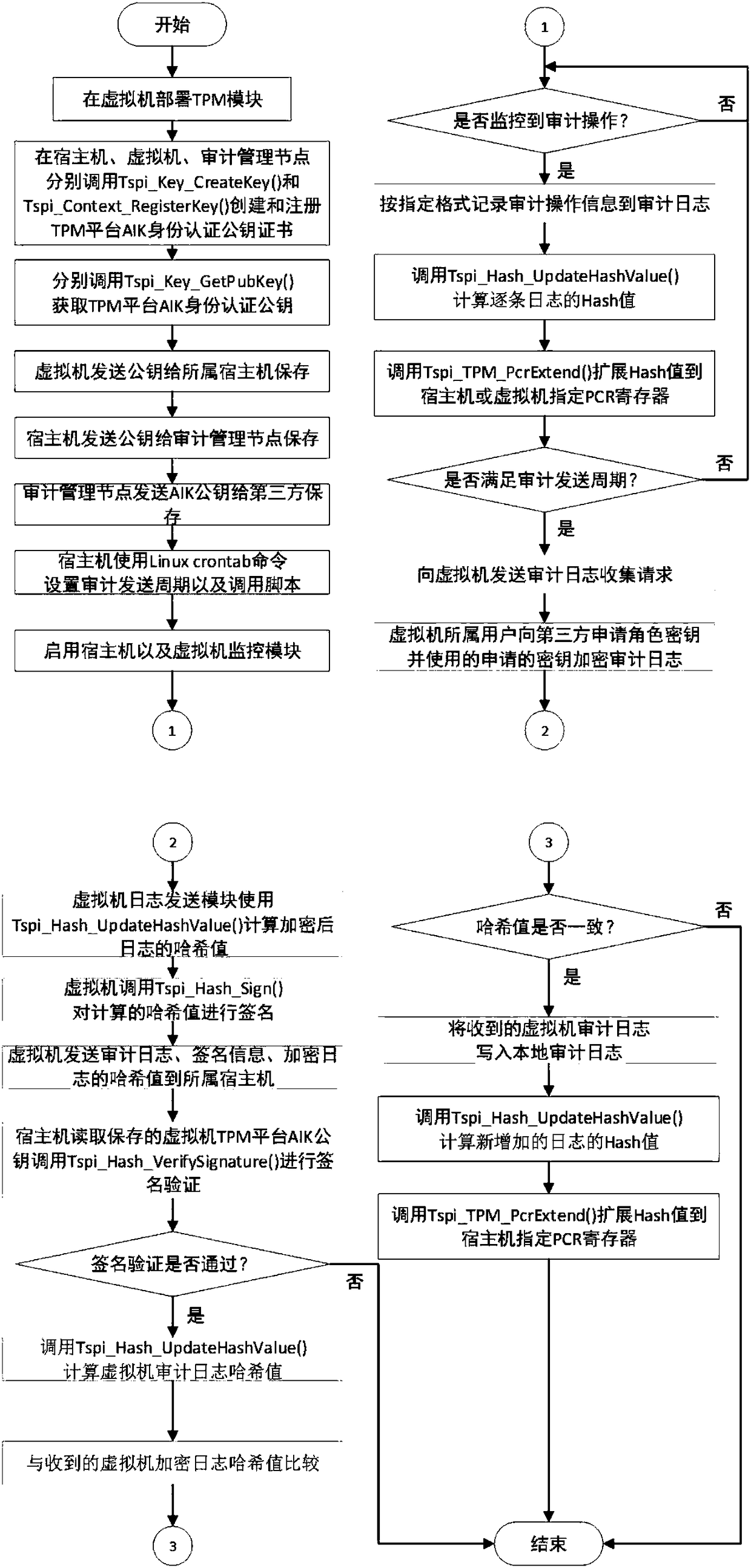
ActiveCN108322306ARealize the collectionGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationThird partyCloud user
The invention discloses a cloud platform trusted log auditing method for privacy protection based on a trusted third party, and belongs to the field of cloud computing. The method comprises the following steps: step 1: collecting a cloud platform auditing log; step 2: securely transmitting the auditing log; step 3: generating and publishing a verification data structure of a third party auditing log; and step 4 verifying the auditing logs of a cloud service provider and the cloud user. Auditing responsibility association objects are added in the auditing events of different cloud service modes(IaaS, PaaS, SaaS), reliable collection and transmission of the auditing logs are provided based on trusted hardware, auditing log verification supporting privacy protection is provided based on a hierarchical random Merkle hash tree, and the cloud auditing responsibility chasing of cloud service providers and cloud users is supported.
Owner:BEIJING UNIV OF TECH
Multi-virtualization computing platform method in cloud computing
InactiveCN102622264AMeet needsPromote standard settingTransmissionSoftware simulation/interpretation/emulationVirtualizationCloud user
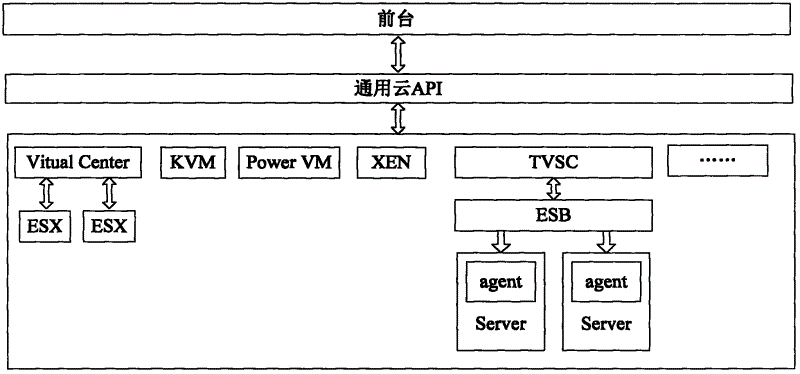
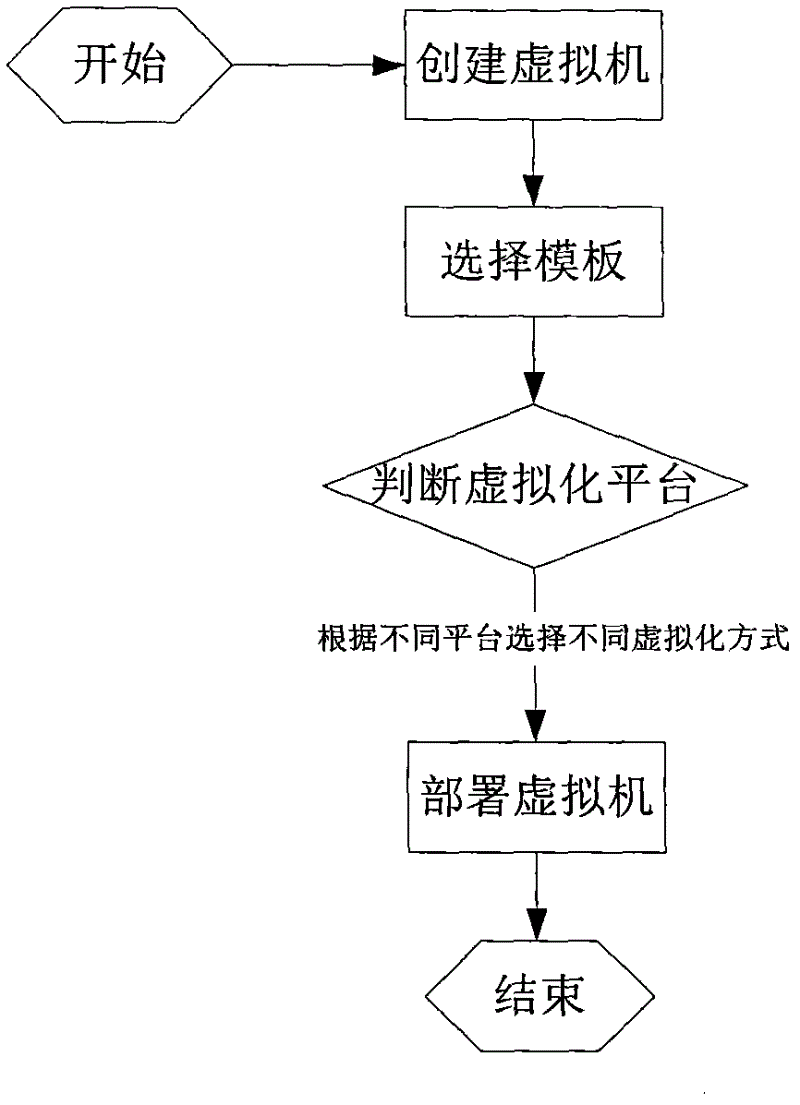
The invention relates to a multi-virtualization computing platform method in cloud computing, which is characterized by comprising the following steps of: I, selectively creating a virtual machine in an infrastructure as a service (IaaS) system by a cloud user; II, selecting a virtual machine template by the user according to the own requirement; III, automatically identifying an affiliated virtualization platform by a virtualization platform system according to the virtual machine template selected by the user; and IV, automatically calling a bottom layer application program interface (API) by the virtualization platform system to create the virtual machine in an automatically identified virtualization environment.
Owner:BEIJING TEAMSUN TECH
Resource distribution system based on service features under distributed cloud architecture and method thereof
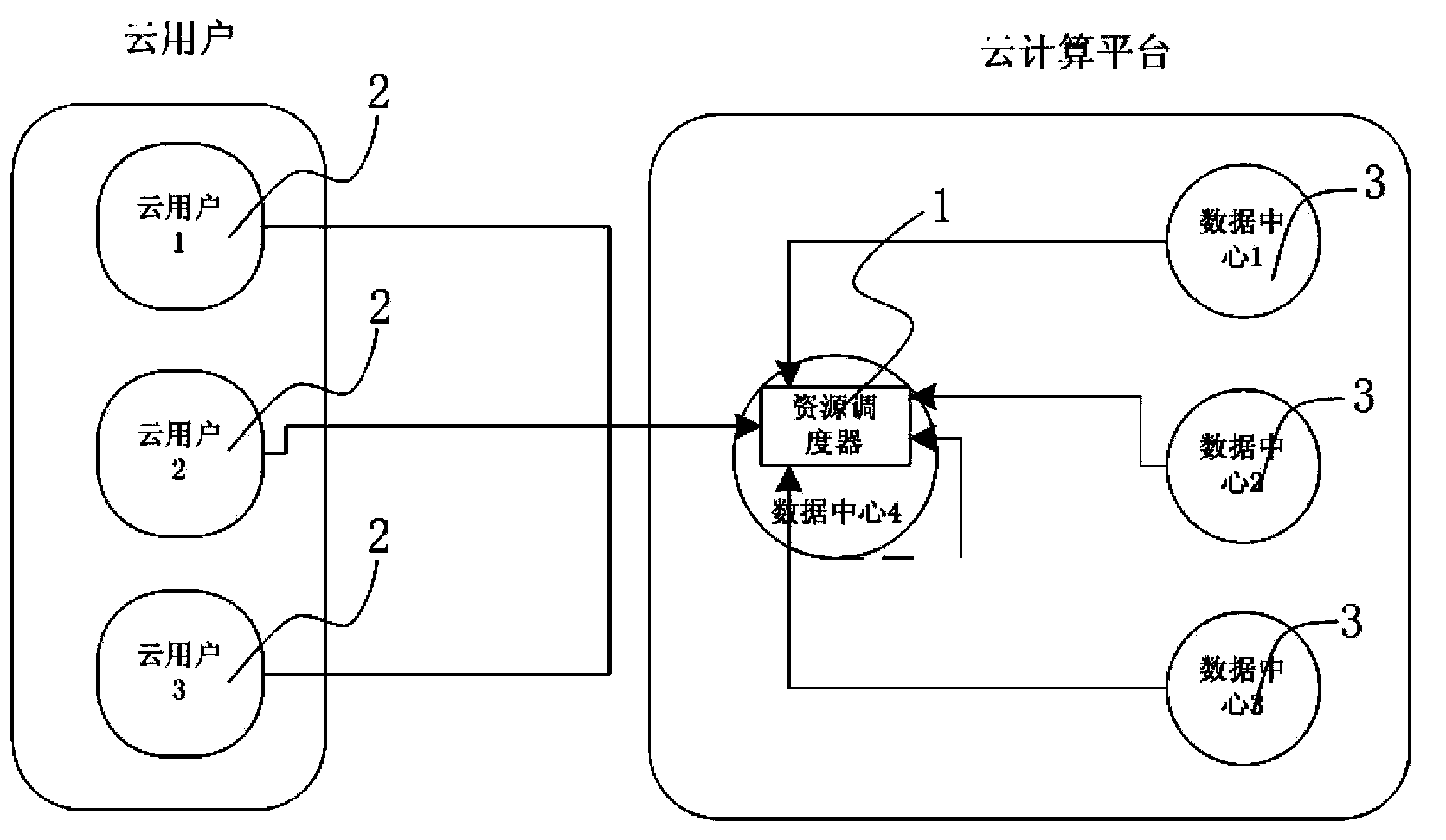
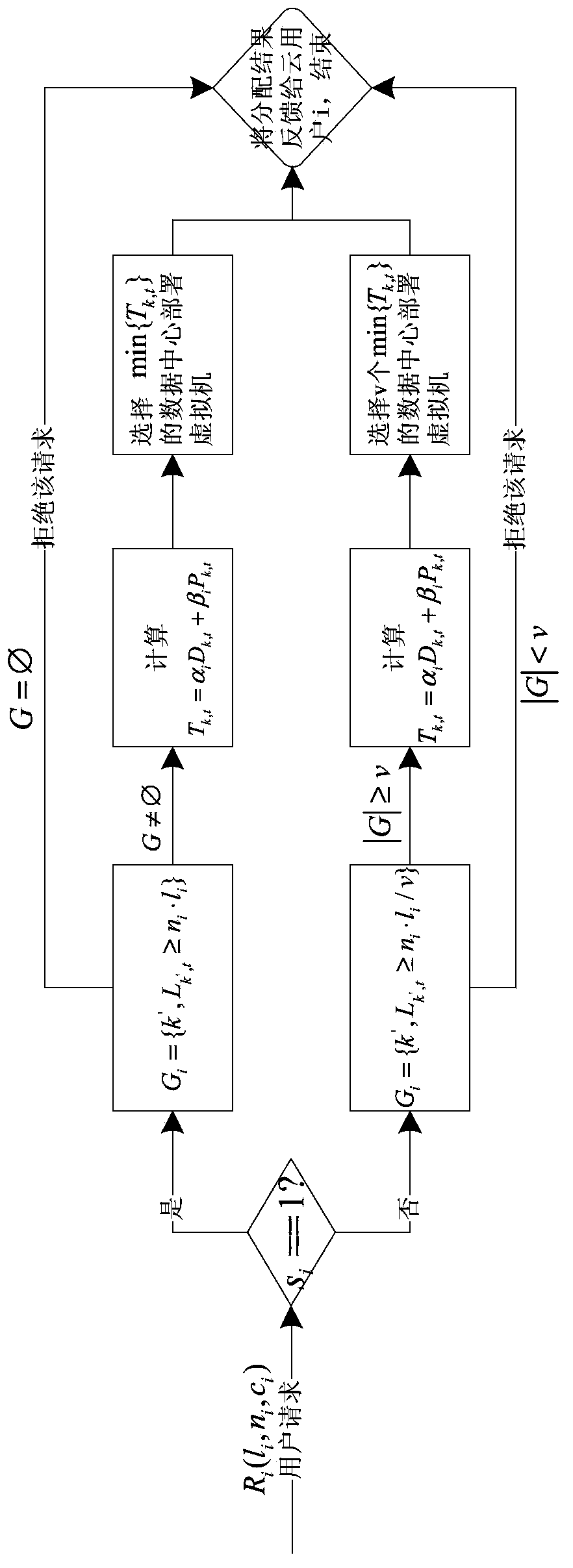
The invention discloses a resource distribution system based on service features under a distributed cloud architecture and a method thereof. The method comprises the following steps: (1) establishing a cloud resource distribution system based on service features; (2) establishing an updating mechanism of a data center state list; (3) making a cloud user submit a cloud resource request to a resource dispatcher; (4) selecting to carry out step (5) or step (6) according to the service feature of the cloud user; (5) deploying a virtual machine for the cloud user by adopting a centralized way; (6) deploying a virtual machine for the cloud user by adopting a distributed way; (7) finishing the distribution of the virtual machine, and feeding back a distribution result to the cloud user through a resource manager. The resource distribution system mainly aims to solve the problem of resource distribution of cloud user services with different service features in a distributed cloud computing environment.
Owner:广州市兰卡科技有限公司
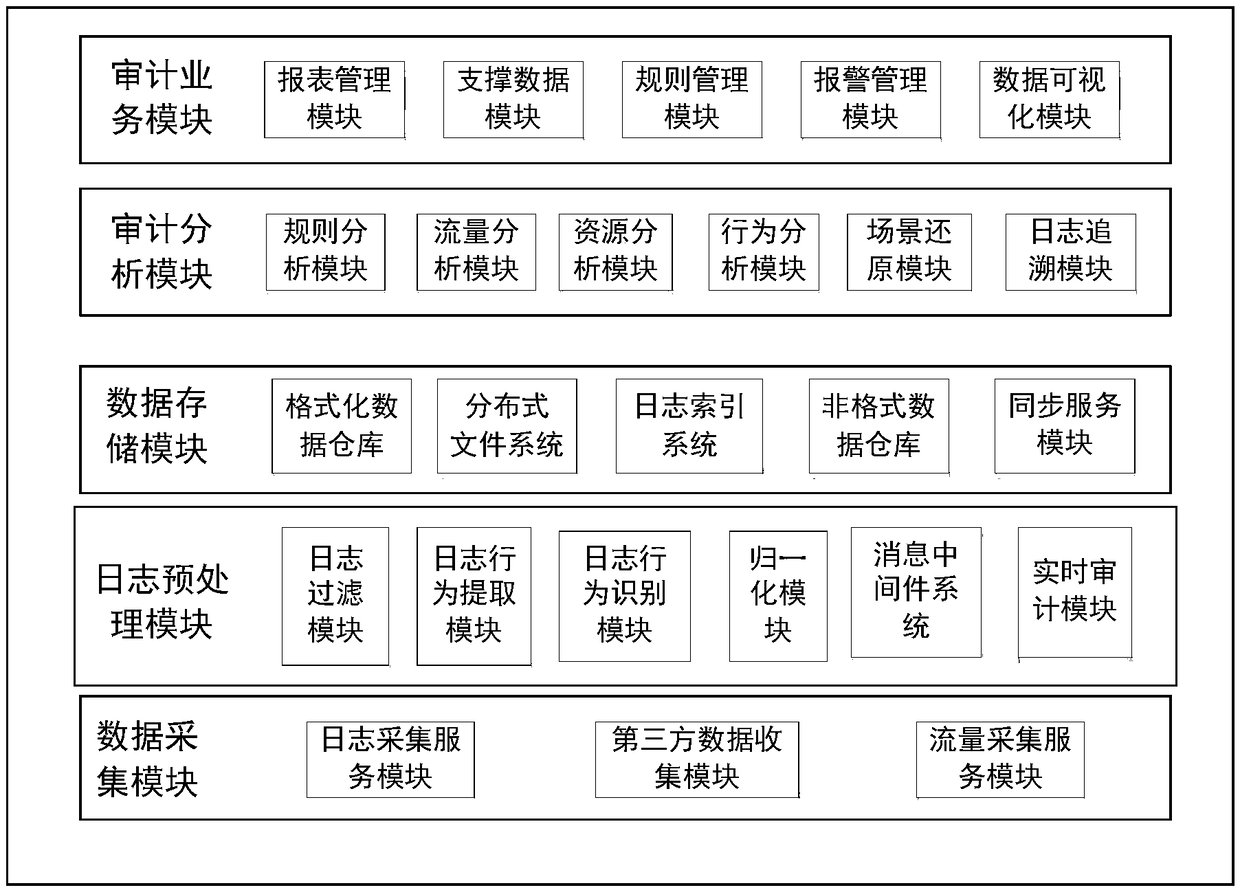
A cloud user behavior audit system and method based on cloud log analysis
InactiveCN109471846AEfficient extractionAccurate extractionSpecial data processing applicationsFile system typesCloud userInto-structure
The cloud user behavior auditing system and the cloud user behavior auditing method based on cloud log analysis provide a unique cloud log processing algorithm, which can efficiently and accurately extract effective information from a mass of original logs with uncertain format, and convert the effective information into structured user operation behavior data which can be used for large data analysis. Based on the operation behavior data, the invention provides the functions of user operation behavior audit, record, multi-dimensional display, violation alarm, compliance analysis, complex process audit, automatic generation of audit strategy and the like, which greatly improves the overall security of the cloud system.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
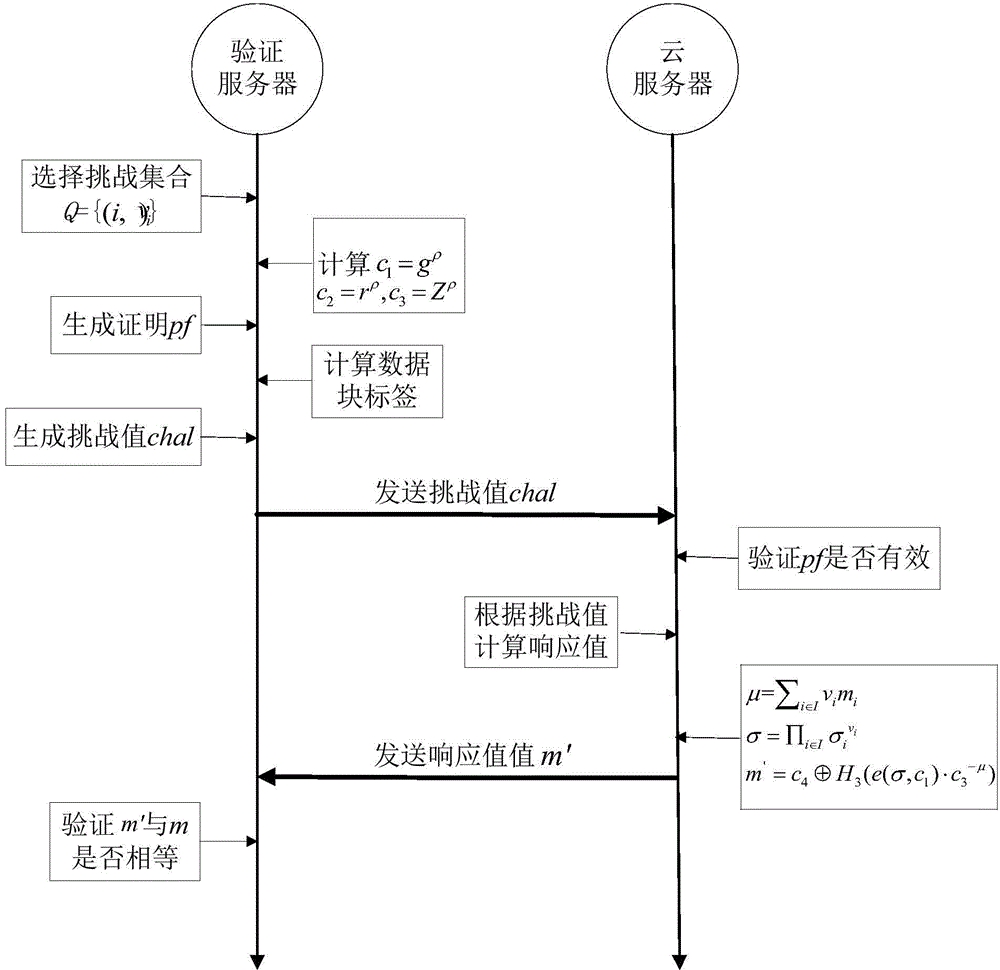
Method for assigning verifier for auditing cloud storage data
InactiveCN104994110AIntegrity guaranteedKey distribution for secure communicationCloud userData file
The invention belongs to the technical field of communication, and specifically relates to a method for assigning an verifier for auditing cloud storage data. The method provided by the invention mainly comprises the steps that: firstly, a system performs block processing on a data file to generate a public and private key pair for each of a cloud user and a cloud server, the cloud user generates a signature of each data block and a data file tag, and a signature set of the data blocks, the data file and the tag of the data file are sent to the cloud server; the cloud user calls a lattice-based agent algorithm to calculate a public and private key pair for an assigned verifier according to the identity of the assigned verifier, and sends the public and private key pair to the assigned verifier safely; and finally, the assigned verifier generates an audit challenge information for the cloud server, the cloud server acquires an audit response prove according to the audit challenge information and sends the audit response prove to the assigned verifier, and the assigned verifier verifies the audit response prove according to a lattice signature verification method.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method for testing integrity of cloud storage data
InactiveCN104993937AEffective defenseSecurity is not threatenedUser identity/authority verificationThird partyCloud user
The invention belongs to the field of communication technology, and specifically relates to a method for testing integrity of cloud storage data. The method provided by the invention mainly comprises: a system initializes and allocates a signature key and a corresponding authentication key to a user; the user uploads storage data to a cloud server; an independent third party auditor tests the integrity of the storage data stored on the cloud server; and the user judges the test correctness of the third party auditor. The process provided by the invention has the following advantages: the third party auditor needs no user management certificate, namely TPA faces no certificate management problem; moreover, the method in the scheme can be used for effectively resisting malicious third party auditors, and when the third party auditor deviates correct protocol contents, the security of the scheme will not be threatened, and the third party auditor cannot successfully cheat the cloud user and (or) the cloud server.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
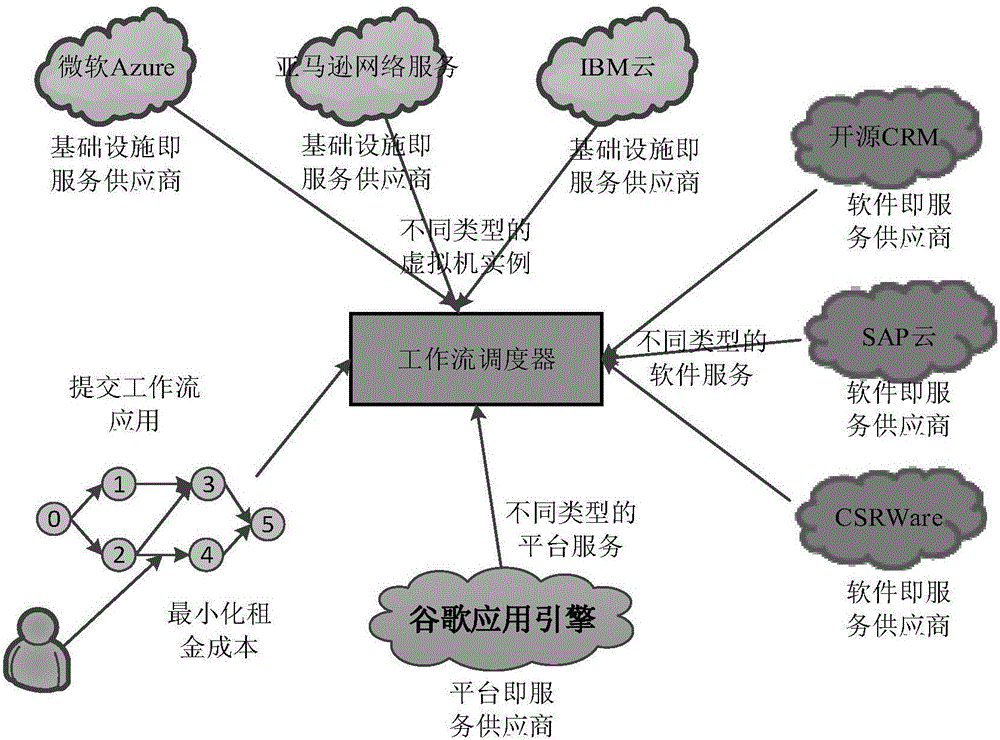
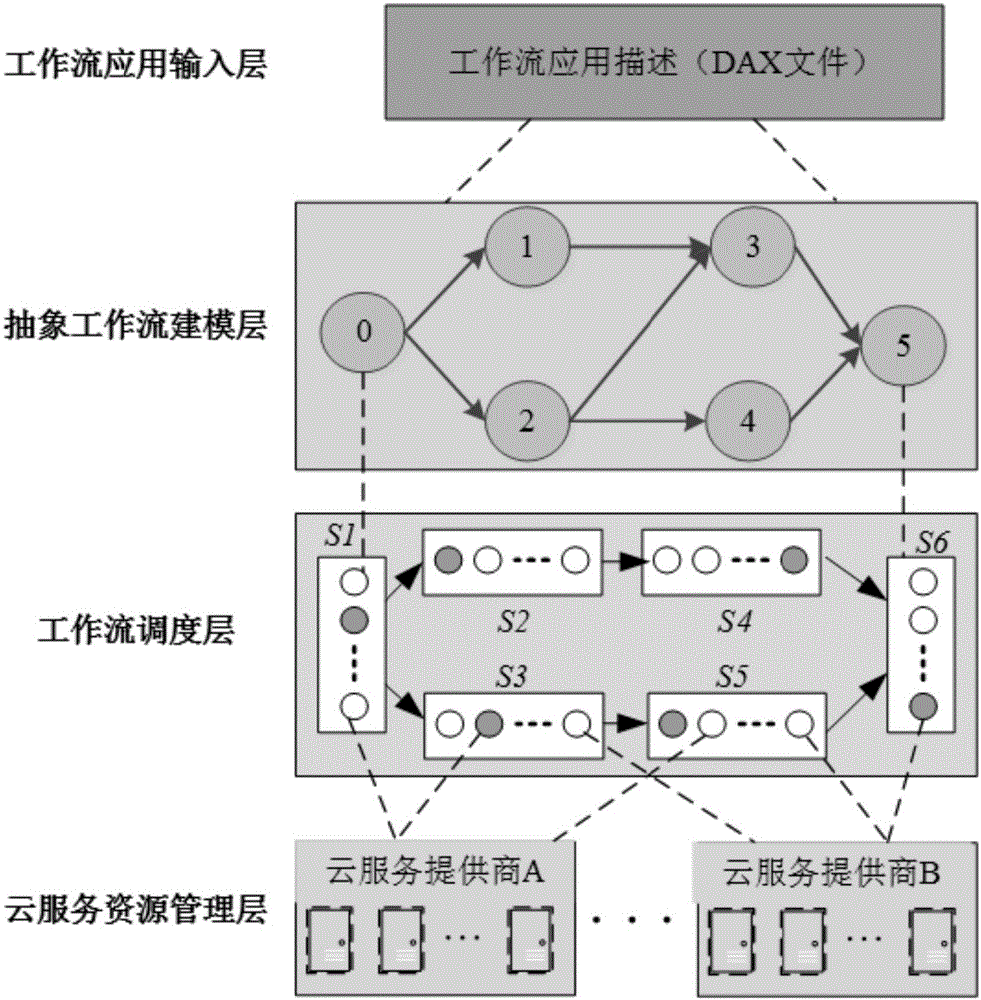
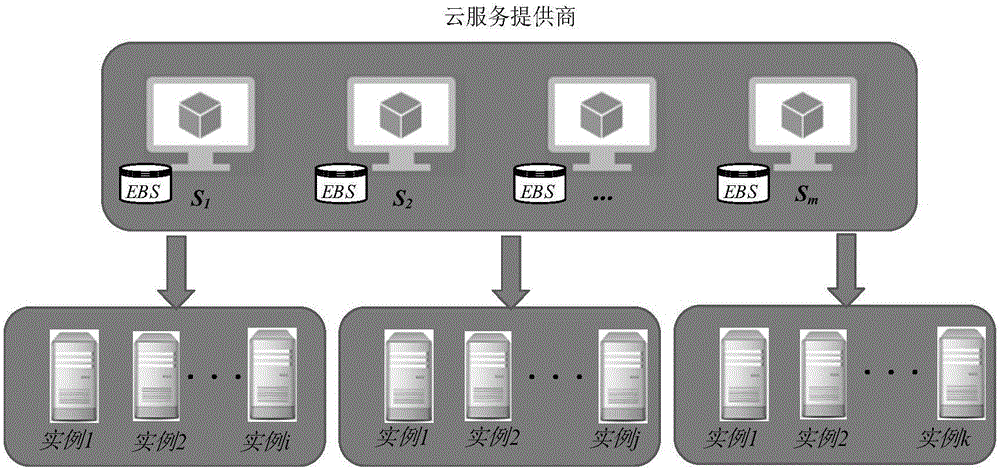
Method for constraining workflow scheduling in cloud environment based on ant colony optimization algorithm through deadline
InactiveCN106055395AGuaranteed feasibilityQuality assuranceProgram initiation/switchingCloud userWorkflow scheduling
The invention discloses a method for constraining workflow scheduling in a cloud environment based on the ant colony optimization algorithm through deadline. The method comprises the steps: employing an ant colony system with a candidate list; respectively searching a workflow scheduling scheme in the cloud environment through a plurality of ants; carrying out the communication of a workflow scheduling result among the ants in a pheromone mode, thereby guiding the deciding of the subsequent search direction of ants and the workflow scheduling scheme. Compared with a conventional workflow scheduling method, the method can reduce the cost of the workflow scheduling in the cloud environment and improves the service quality for cloud users under the condition of meeting the deadline time QoS requirements of users.
Owner:CENT SOUTH UNIV
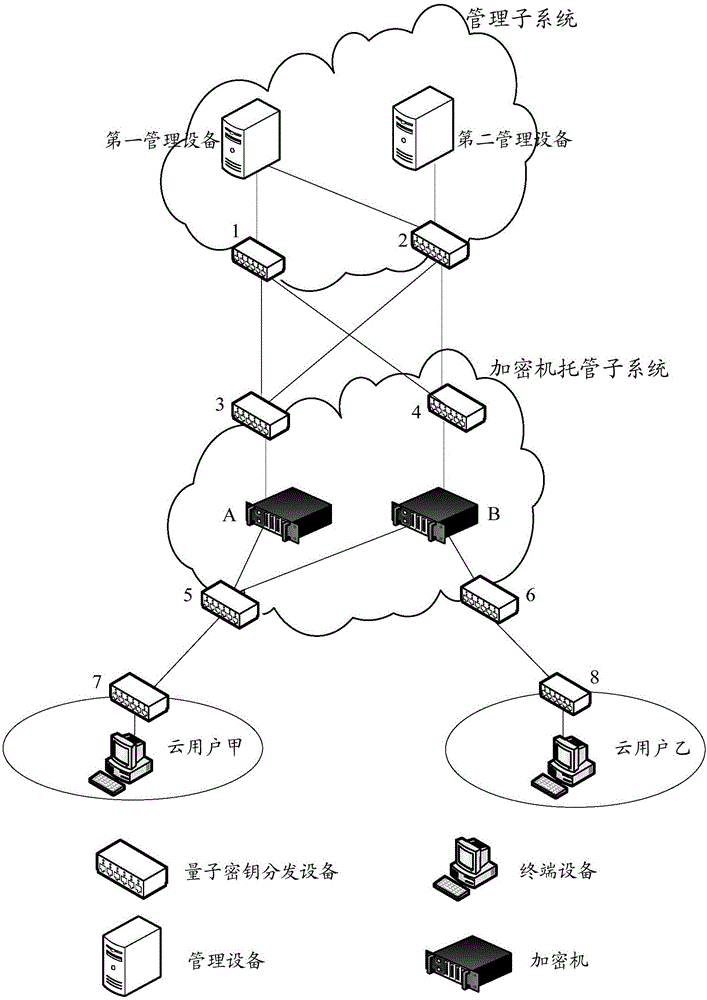
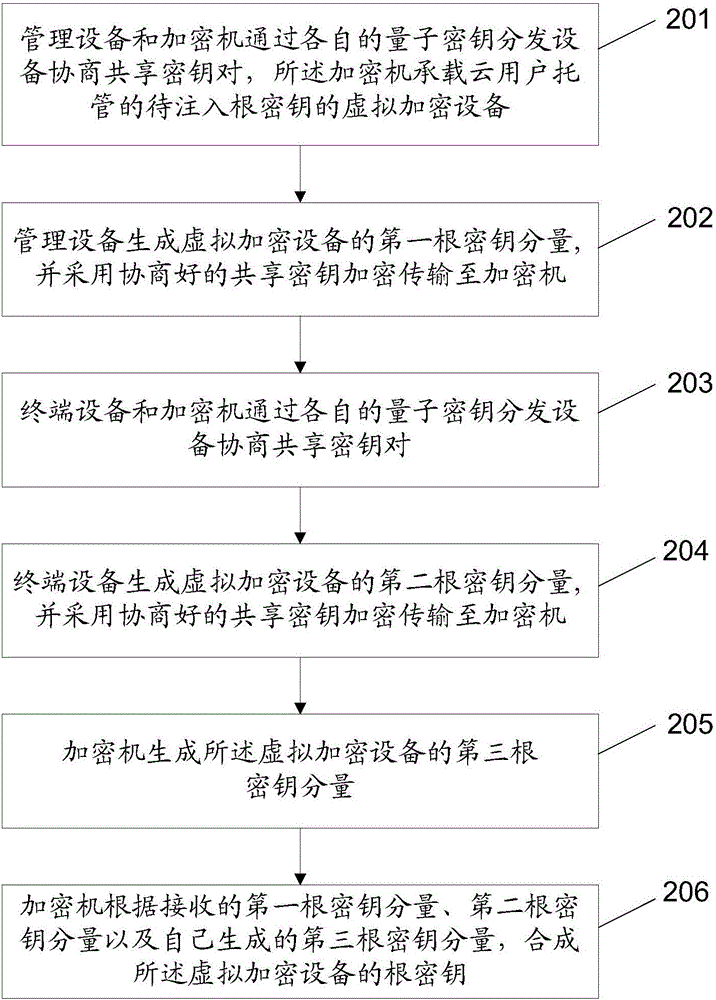
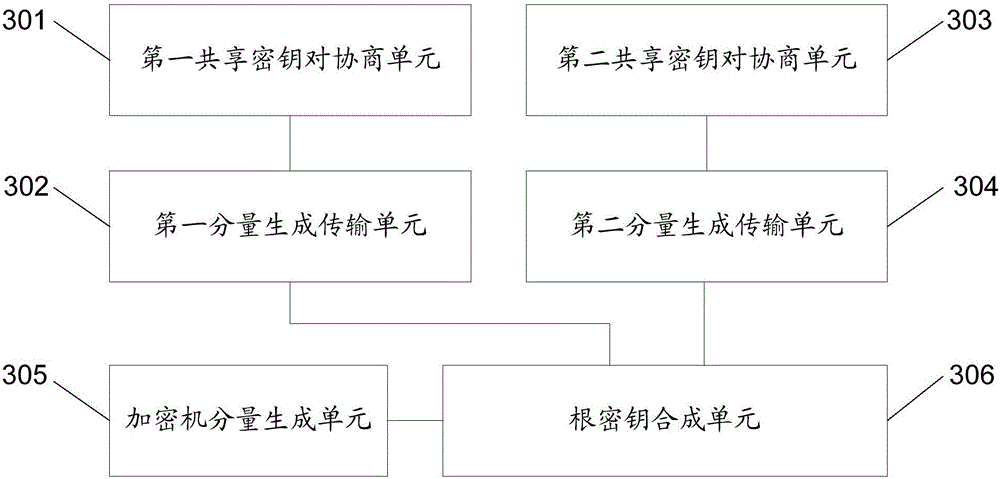
Encryption machine key injection system based on cloud environment, method and device
ActiveCN106161402AEasy to operateImplement remote injectionComputer security arrangementsSecuring communicationComputer hardwareCloud user
The invention discloses an encryption machine key injection system based on the cloud environment, a key injection method for an encryption machine and a device, and a method and a device for realizing cloud-end trusteeship of the encryption machine. The system comprises at least one key injection subsystem and an encryption machine trusteeship subsystem arranged at a cloud end, wherein the at least one key injection subsystem and the encryption machine trusteeship subsystem are connected through respective quantum key distribution equipment, the quantum key distribution equipment is used for negotiating a shared key pair between key generation equipment and the encryption machine which are connected with the quantum key distribution equipment, the key generation equipment is used for generating a root key component of virtual encryption equipment and employing the negotiated shared keys to carry out encryption transmission to the encryption machine on which the virtual encryption equipment is borne, the encryption machine is used for synthesizing a root key of the virtual encryption equipment according to received root key components, and the root key is further stored. Through the system, remote safe injection of the root key of the encryption machine is realized, a cloud user is not necessary to manually insert a card, and the key injection operation process is simplified.
Owner:ALIBABA GRP HLDG LTD
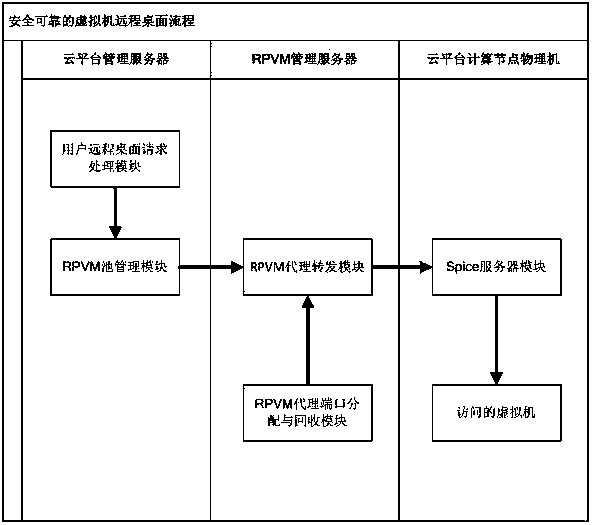
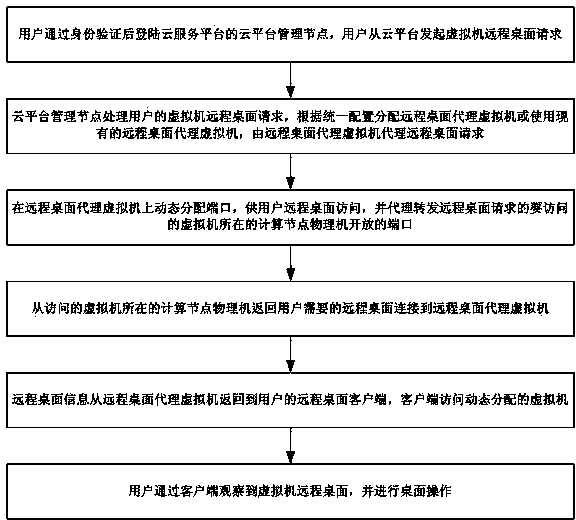
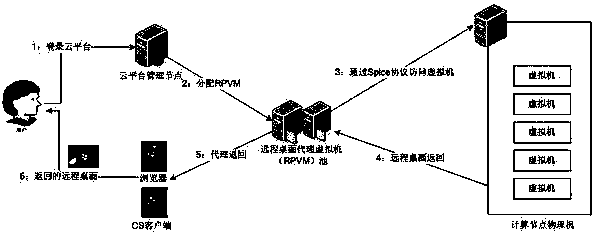
Virtual machine remote desktop safety access system and method
The invention discloses a virtual machine remote desktop safety access system and a virtual machine remote desktop safety access method. The system comprises a user remote desktop request processing module used for processing a request for user remote desktop connection, a remote desktop proxy virtual machine pool management module used for distributing and managing a remote desktop proxy virtual machine, a remote desktop proxy virtual machine proxy forwarding module user for forwarding a user remote desktop request and shielding an internet protocol (IP) and a port of an underlying real physical machine, a remote desktop proxy virtual machine proxy port distribution and recovery module used for distributing and recovering a remote desktop proxy virtual machine forwarding port, and a server module used for accessing a remote desktop of the virtual machine. A proxy server address and a random port are distributed for the user each time, access of the remote virtual machine desktop is realized by utilizing a proxy forwarding technology, the actual physical machine address and port information are hidden for the user, the address and port used by the user are randomly generated and changed, and thus the safety of the cloud platform and cloud user virtual machine is guaranteed.
Owner:CHINARS GEOINFORMATICS GUANG DONG
Method suitable for secure migration of data in storage cloud
The invention discloses a method suitable for secure migration of data in a storage cloud, belonging to the field of security of storage cloud environments. The method comprises the following steps of: (1) dividing storage cloud users into a plurality of departments, setting a tag for each department, establishing a tree structure tag of the users, and storing the tree structure tag into a central node in the storage cloud; (2) dividing data nodes in the storage cloud into a plurality of units, setting a tag for each unit, establishing a tree structure tag of a storage cloud system, and storing the tree structure tag into the central node of the storage cloud; (3) establishing a point-to-point incidence relation of the two tree structure tags to acquire a target unit security selection strategy in the data migration process of each department, and storing the target unit security selection strategy into the central node of the storage cloud; and (4) determining a target data node to be migrated in each data block to be migrated according to the target unit security selection strategy and then executing a migration command to perform migration by the central node. The method disclosed by the invention is easy in operation, and reduces the coupling degree between a customer and a provider.
Owner:PEKING UNIV
Method, equipment and system for controlling terminals during log file reporting
The invention discloses a method, equipment and a system for controlling terminals during log file reporting, and relates to the field of information transmission. The method, the equipment and the system are used for solving the problem of waste of network flow used by terminals during log reporting. The method includes enabling the cloud equipment to acquire historical log files in network elements of the cloud system; analyzing the acquired historical log files to obtain user behavior data; storing user behavior identities corresponding to the obtained user behavior data in a cloud user behavior identity list; determining a reporting state corresponding to a certain user behavior identity in a preset user behavior identity set list according to the cloud user behavior identity list when a terminal user behavior reporting state list request transmitted by a terminal is received; transmitting a terminal user behavior reporting state list to the terminal. The method, the equipment and the system have the advantage that the problem of the waste of the network flow generated when terminals report logs is solved.
Owner:JUHAOKAN TECH CO LTD
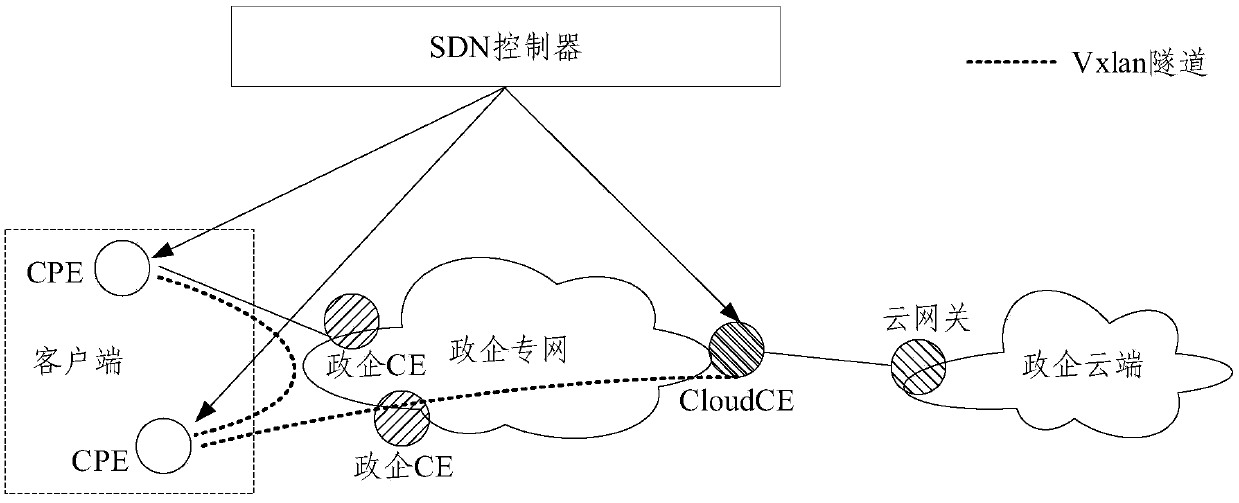
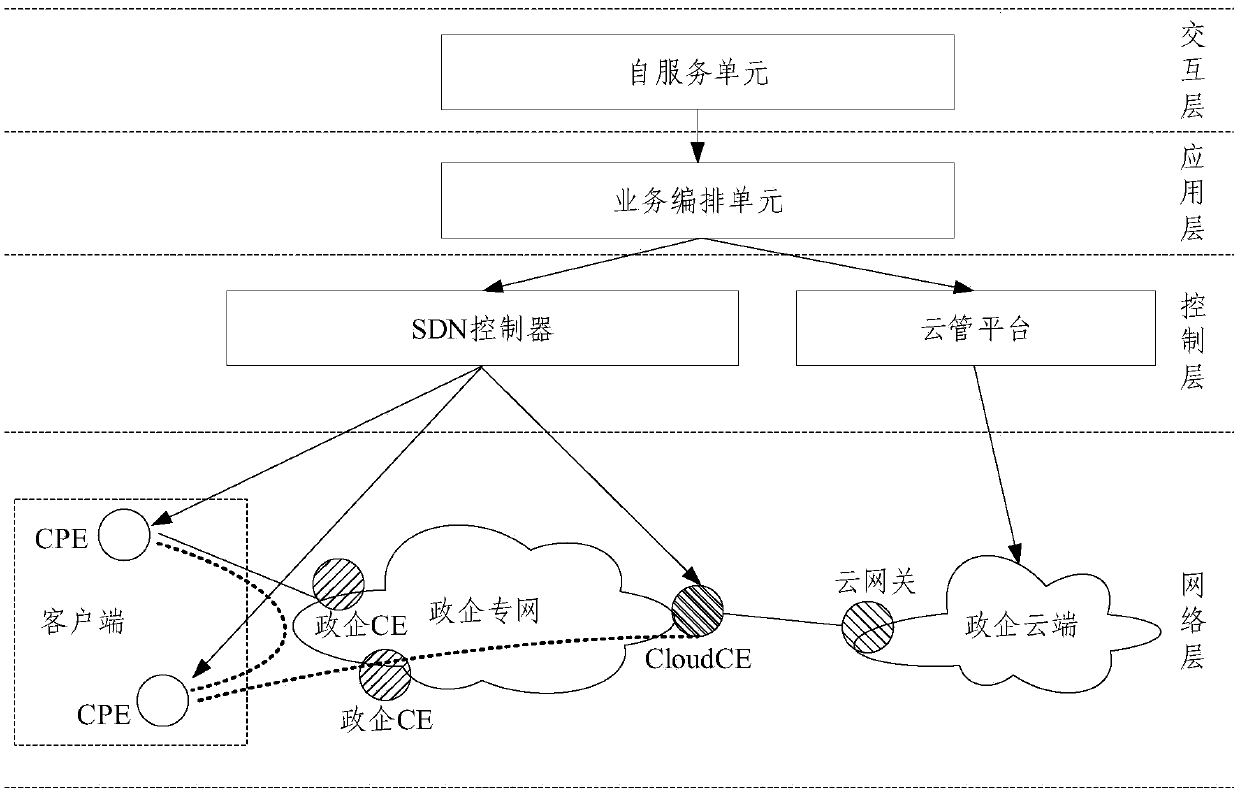
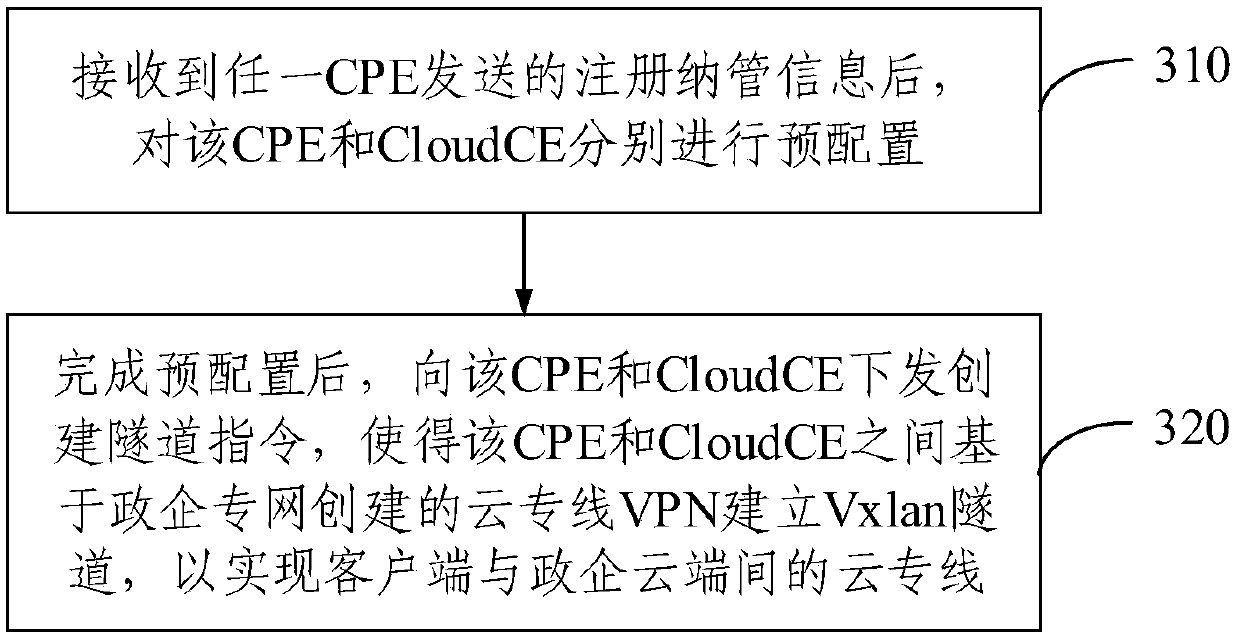
Cloud private line system and service issuing and opening method thereof
ActiveCN111106991AEnable secure accessSimplify the architecture processNetworks interconnectionCloud userTerminal equipment
The embodiment of the invention provides a cloud private line system and a service issuing and opening method thereof. The cloud private line system comprises a client, a government and enterprise private network, a government and enterprise cloud and an SDN controller. The client is deployed with a plurality of customer premise equipment CPE, the government enterprise private network is deployedwith a plurality of government enterprise CEs and a cloud user edge router Cloud CE, and the government enterprise cloud is deployed with a cloud gateway; the CPE is in butt joint with the governmentand enterprise CE, and the Cloud CE is in butt joint with the cloud gateway; and the SDN controller is used for controlling the client and the government and enterprise private network and establishing a Vxlan tunnel taking the CPE and the Cloud CE as end points so as to realize a cloud private line between the client and the government and enterprise cloud. According to the system and the methodprovided by the embodiment of the invention, safe access between the cloud on the local site and the sites is realized, the configuration process is simplified, the cost and equipment resources are saved, the problem of complex opening configuration is solved, and the opening process is simplified.
Owner:CHINA MOBILE GROUP ZHEJIANG
Batch self-auditing method for cloud storage data
InactiveCN105978695AGuaranteed confidentialityVerify integrityUser identity/authority verificationCloud userCiphertext
The invention belongs to the technical field of information security, and in particular relates to a batch self-auditing method for cloud storage data. The method of the present invention mainly includes: generating a public-private key pair based on an elliptic curve digital signature algorithm, a public-private key pair of a lightweight signature algorithm, and a lightweight symmetric encryption algorithm: calculating digital signatures of multiple data files, data files Tags and ciphertexts of data files are sent to the cloud server; cloud users generate audit challenge information and send it to the cloud server; the cloud server returns the aggregated audit proof response information to the cloud user; cloud users For the response information, use the digital signature algorithm based on the elliptic curve and the symmetric encryption algorithm to verify the legitimacy of the aggregated audit proof response. The beneficial effect of the present invention is that it solves the problem of batch integrity verification of cloud storage data, enabling users to effectively verify the integrity of multiple data files at the same time.
Owner:SOUTHWEST PETROLEUM UNIV
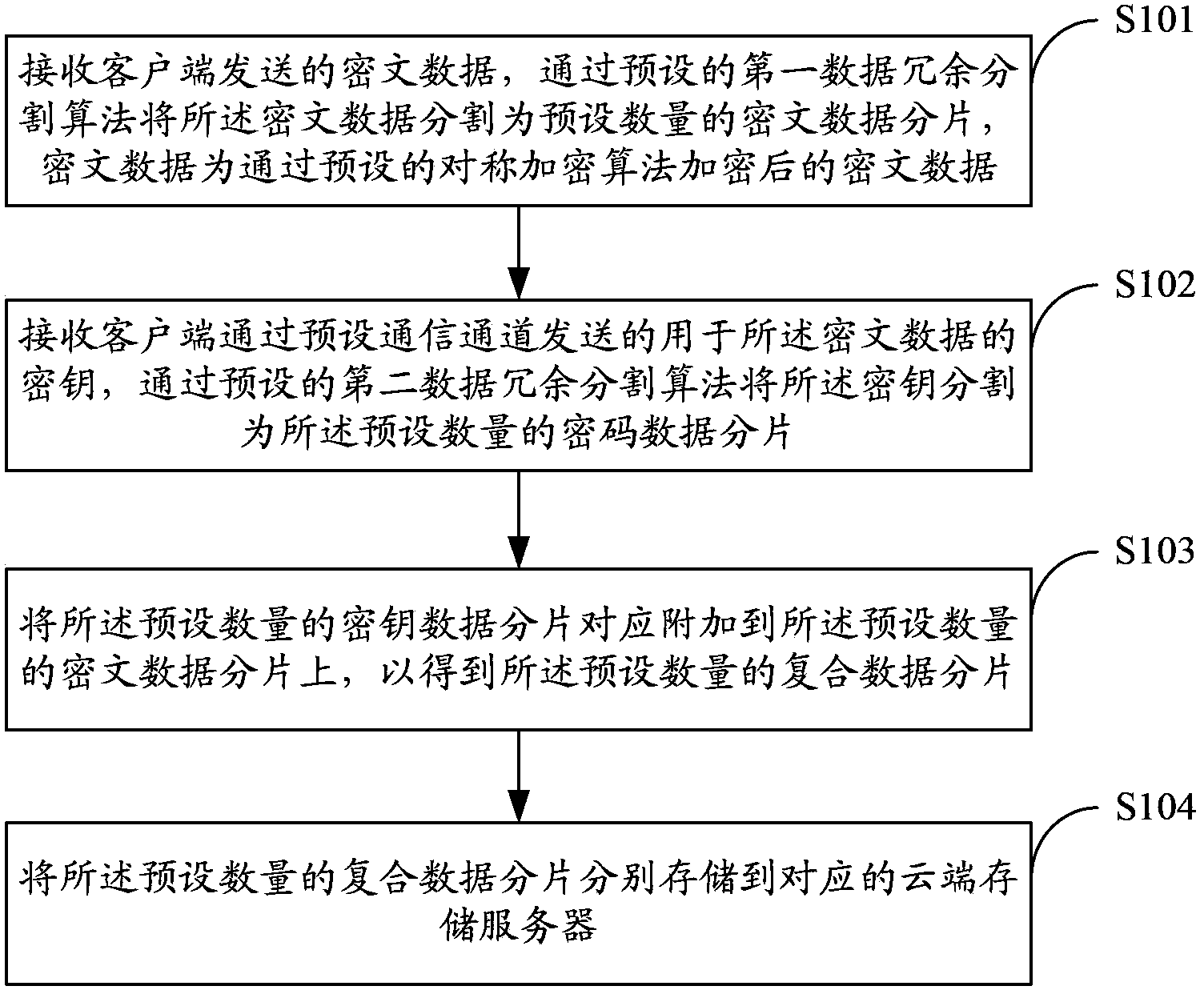
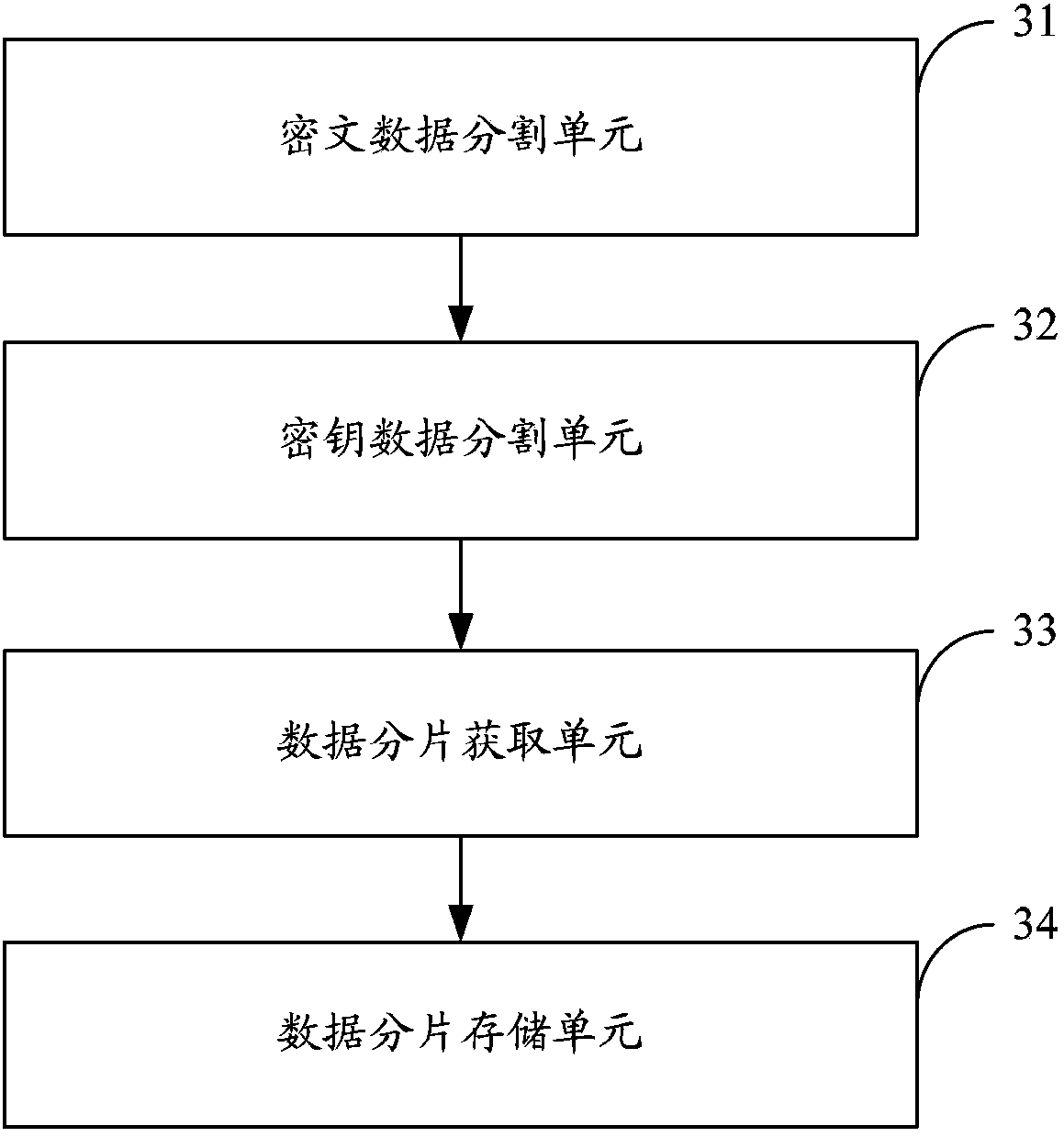
Method for cloud storage of data and system
The invention is applicable in the field of computer technology, and provides a method for cloud storage of data and a system. The method and the system comprise the steps of receiving ciphertext data sent by a client and segmenting the ciphertext data into a preset number of ciphertext data fragmentation through a preset first data redundancy segmentation algorithm; receiving a secret key for the ciphertext data which is sent by the client through a preset communication channel, and segmenting the secret key into a preset number of secret key data fragmentation through a preset second data redundancy segmentation algorithm; attaching the preset number of secret key data fragmentation correspondingly to the preset number of ciphertext data fragmentation; storing the preset number of composite data fragmentation respectively in the corresponding cloud storage servers. In an embodiment of the invention, the ciphertext data and the encrypted secret key are segmented into data fragmentation through the preset data redundancy segmentation algorithms, users do not need to save the secret keys and recovery of the secret key, and the ciphertext data is successful only with the preset number of data fragmentation, so that the security of the cloud user data and secret keys is improved.
Owner:SHENZHEN UNIV
Application cloud safety certification method based on third-party service
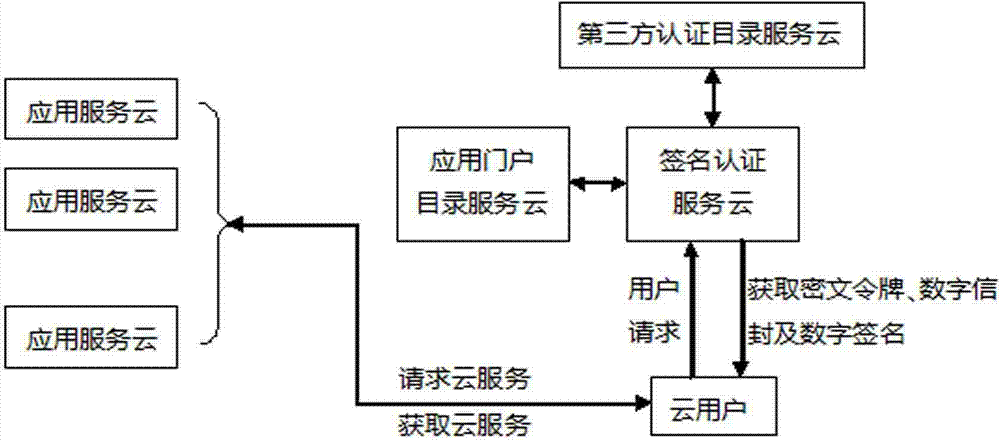
InactiveCN103490899AVerify authenticityVerify legitimacyUser identity/authority verificationThird partyInformation transmission
The invention provides an application cloud safety certification method based on a third-party service. The application cloud safety certification method based on the third-party service specifically comprises the steps that (1) a cloud user submits service demand information to a signature certification service cloud; (2) the signature certification service cloud receives the service demand information of the cloud user, and verifies validity of a certificate of the cloud user according to a third-party catalogue certification service cloud, carries out sign and issue on a ciphertext user login token and a digital envelope through an application portal catalogue service cloud, carries out certification service sign on the ciphertext user login token signed and issued through the application portal catalogue service cloud and the digital envelope signed and issued through the application portal catalogue service cloud, and sends the ciphertext user login token and the digital envelope back to the cloud user; (3) the cloud user carries out user sign on the obtained ciphertext user login token, the digital envelope and the certification service sign information, and submits the ciphertext user login token, the digital envelope and the certification service sign information to an application service to demand for the corresponding service; (4) the application service provides the corresponding service for the cloud user after being verified. Compared with the prior art, the application cloud safety certification method based on the third-party service ensures authenticity and non-repudiation of information sources, and improves safety of the process of information transmission.
Owner:INSPUR QILU SOFTWARE IND
Detecting behavior anomalies of cloud users for outlier actions
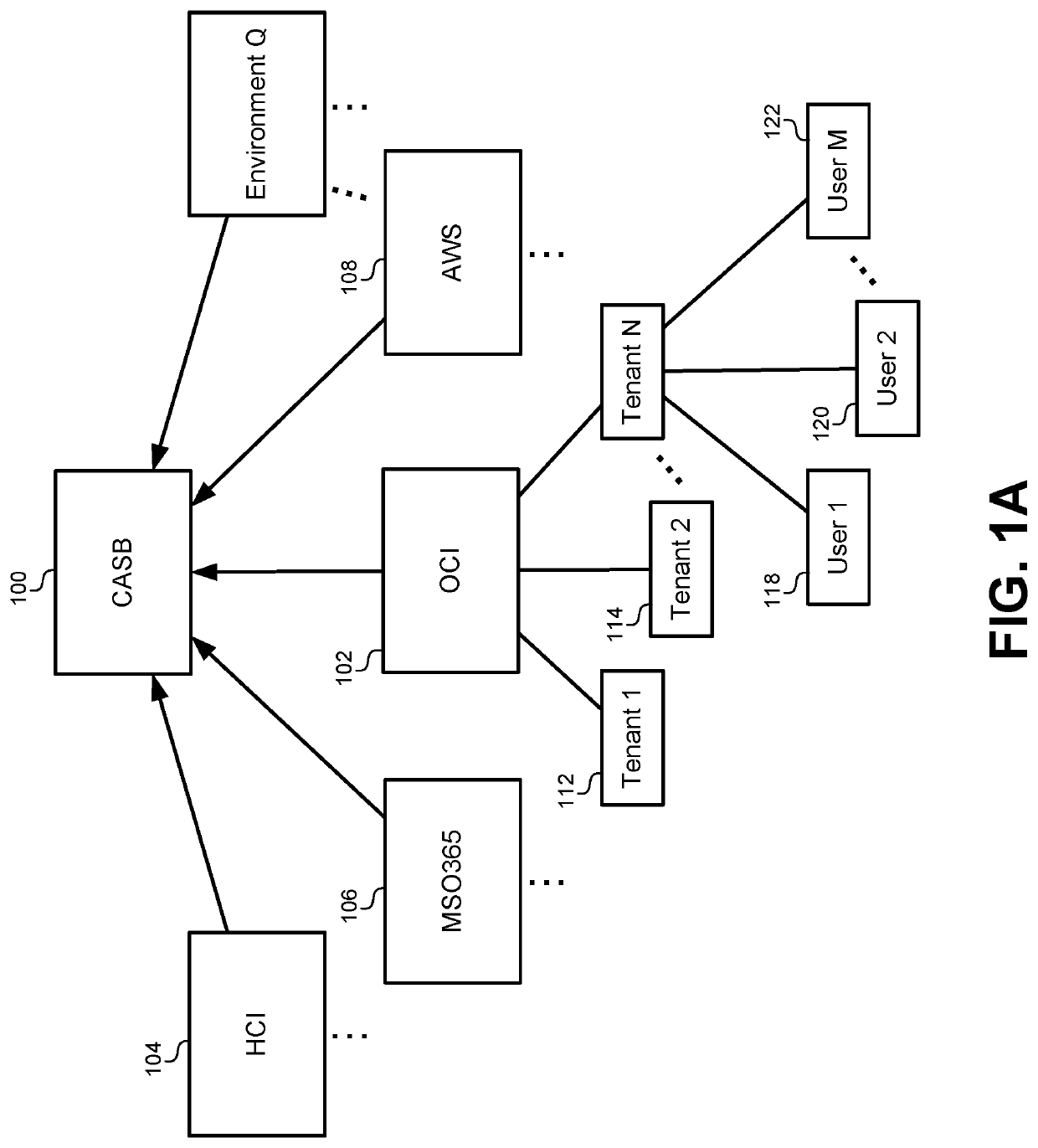
ActiveUS20200336503A1Hardware monitoringNatural language data processingCloud userAnomalous behavior
A method of detecting anomalous user behavior in a cloud environment includes receiving a vector that comprises counts of actions taken by the user during a current time interval; determining whether an action count in the vector is greater than a global mean; building a scale table by combining new action skills that are above a threshold and original action skills if below the threshold; and identifying outliers when the action count is greater than the global mean multiplied by a corresponding action scale from the scale table.
Owner:ORACLE INT CORP
Method for cloud workflow scheduling based on heuristic genetic algorithm
The invention discloses a method for optimizing cloud workflow scheduling based on a heuristic genetic algorithm. The algorithm aims at optimizing service quality parameter indexes appointed by users according to the demands of the cloud users under the condition of meeting performance constraint conditions appointed by the users, such as execution expense budget constraints, longest completion deadline constraints and minimum reliability constraints. In order to meet the requirement of optimizing multiple performance parameter indexes, a novel heuristic coding mode is adopted in the genetic algorithm. Eight kinds of heuristic information including reliability greed, time greed, expense greed, suggested budget, suggested deadline, time / expense, comprehensive performance and random is utilized in the mode. Each calculation mask is matched to a proper cloud calculation service to be executed according to the selected heuristic information, so that a cloud workflow scheduling scheme meeting the service quality demands appointed by the users can be efficiently found by the algorithm.
Owner:SUN YAT SEN UNIV
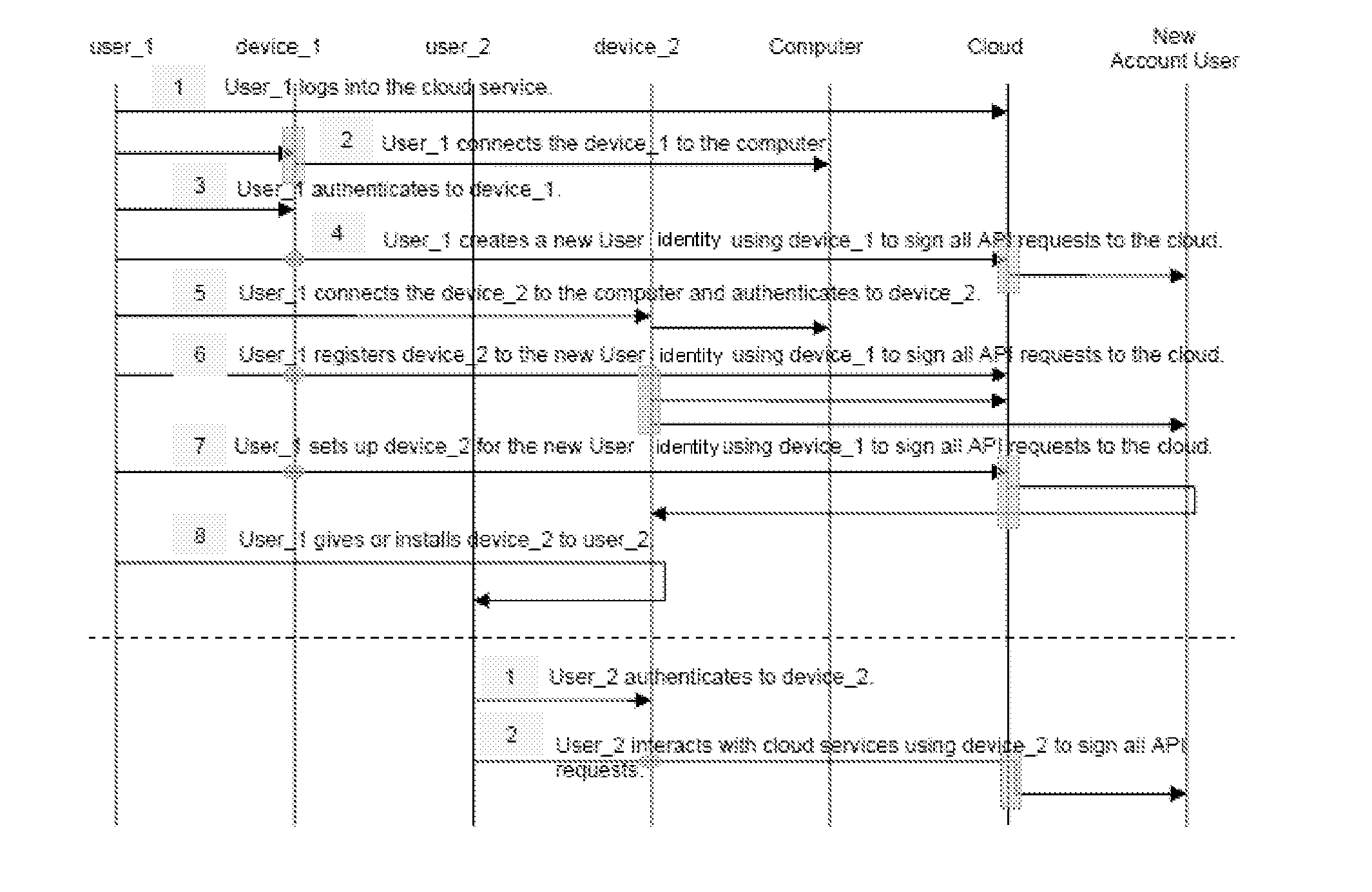
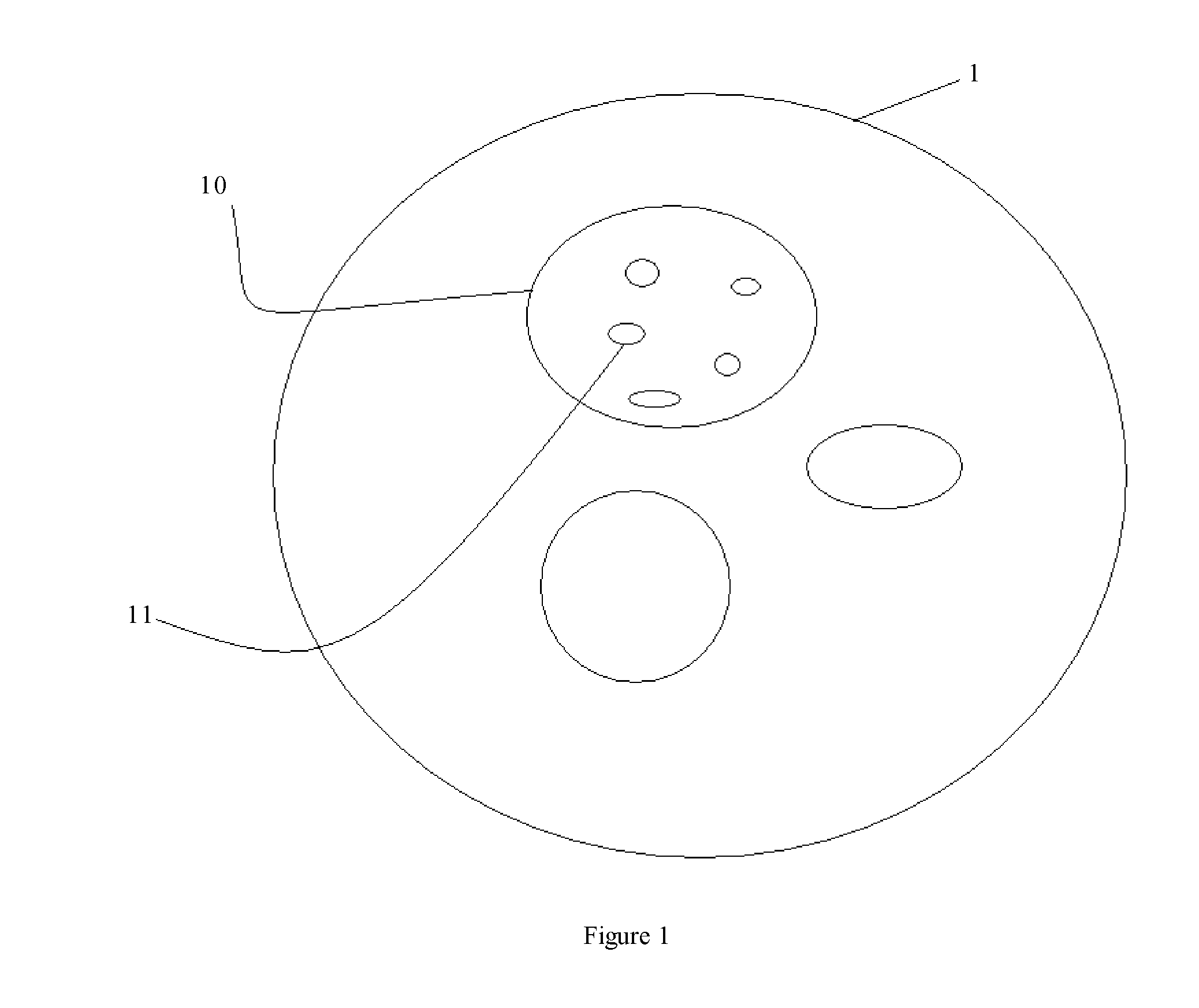
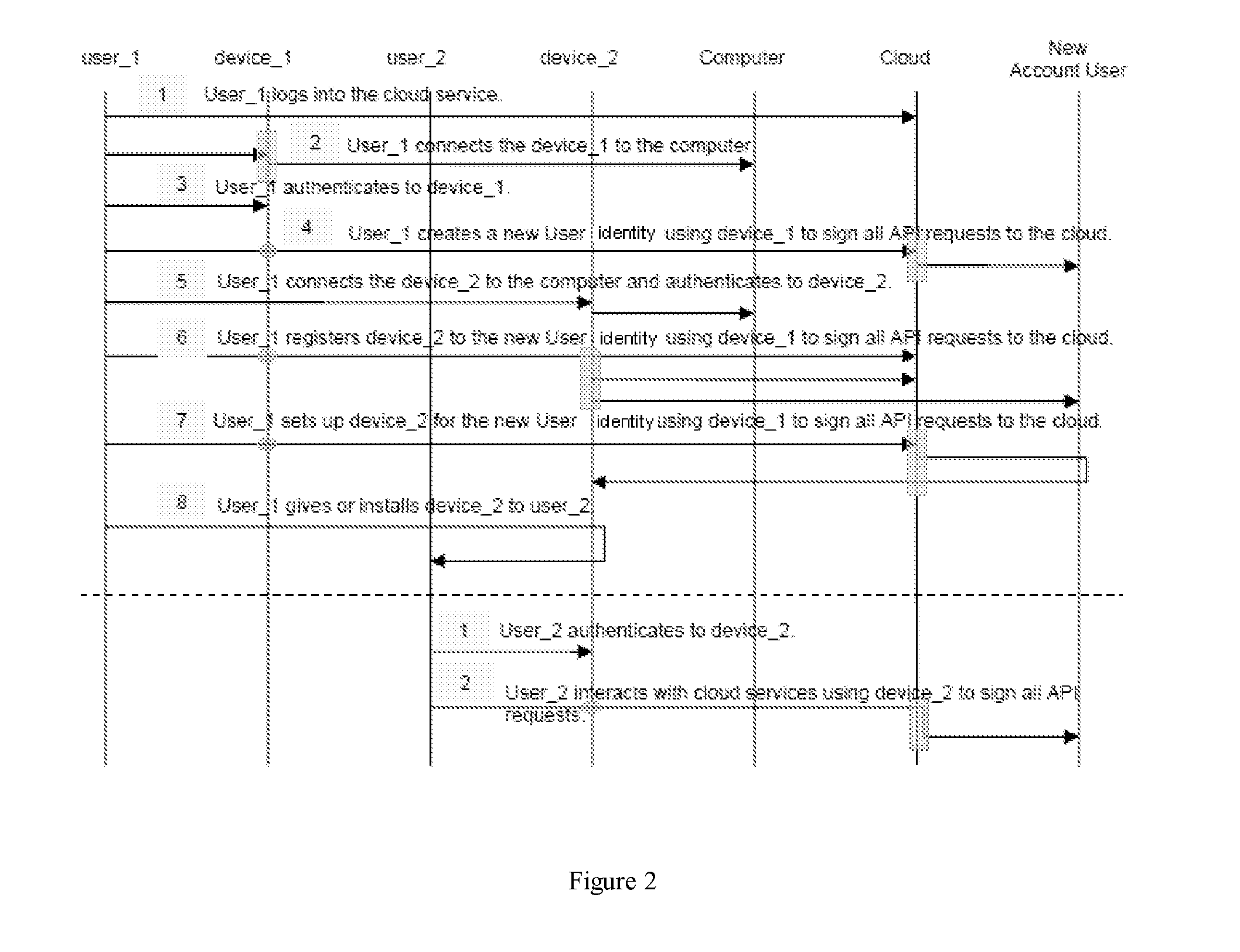
Method for securely creating a new user identity within an existing cloud account in a cloud computing system
ActiveUS20120278861A1Digital data processing detailsUser identity/authority verificationCloud userOperating system
The invention proposes a method for securely creating a new user identity within an existing cloud account in a cloud computing system, said cloud computing system providing cloud services and resources, said cloud account comprising cloud user identities, said method comprising enabling a first user to access the cloud services and resources using a first security device, wherein it comprises authenticating to the first security device, creating a new user identity within the cloud account for a second user using the first security device.
Owner:GEMPLU
Cloud storage medical data batch self-auditing method based on wireless body area network
InactiveCN106789082AUser identity/authority verificationCommunication with homomorphic encryptionCloud userBody area network
The invention belongs to the technical field of information security, and particularly relates to a cloud storage medical data batch self-auditing method based on a wireless body area network. The security of a cryptographic algorithm designed by the method is based on discrete logarithm problems, and thus it is guaranteed that a malicious cloud server cannot produce a piece of forged auditing proof response information which cheats a cloud user and makes the user pass an auditing verification process. In the cloud storage medical data batch self-auditing method based on the wireless body area network, the cloud user makes use of a linear homomorphic aggregation signature algorithm to construct a homomorphic linear identifier, and can conduct batch auditing on the completeness of multiple medical data files simultaneously, and in the auditing process, the bilinear pairing operation with large expenses does not need to be conducted, and the cloud storage medical data batch self-auditing method is particularly applicable to an application scenario in which the lightweight class calculated amount is needed, the memory space is limited and the wireless body area network needs to be efficiently achieved.
Owner:SOUTHWEST PETROLEUM UNIV
Data access method and database system based on cloud computing
InactiveCN102508898AAvoid direct connectionAchieve independenceSpecial data processing applicationsCloud userData access
The invention discloses a data access method and a database system based on cloud computing. The method comprises the following steps of: when receiving a database access instruction from a cloud user, matching the database metadata carried in the instruction with the metadata of each database in a cloud system, and determining the target database of the instruction; parsing the database access instruction to obtain a SQL (Structured Query Language) instruction; generating a database connection string, and locating in the determined database; then, executing the SQL instruction to obtain the execution result; converting the execution result into a data format used by the cloud user, and feeding back the converted result to the cloud user. With the method and the system, the tight coupling between the application and the database in the cloud computing environment can be broken, so that data access can be expanded on a wider platform.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
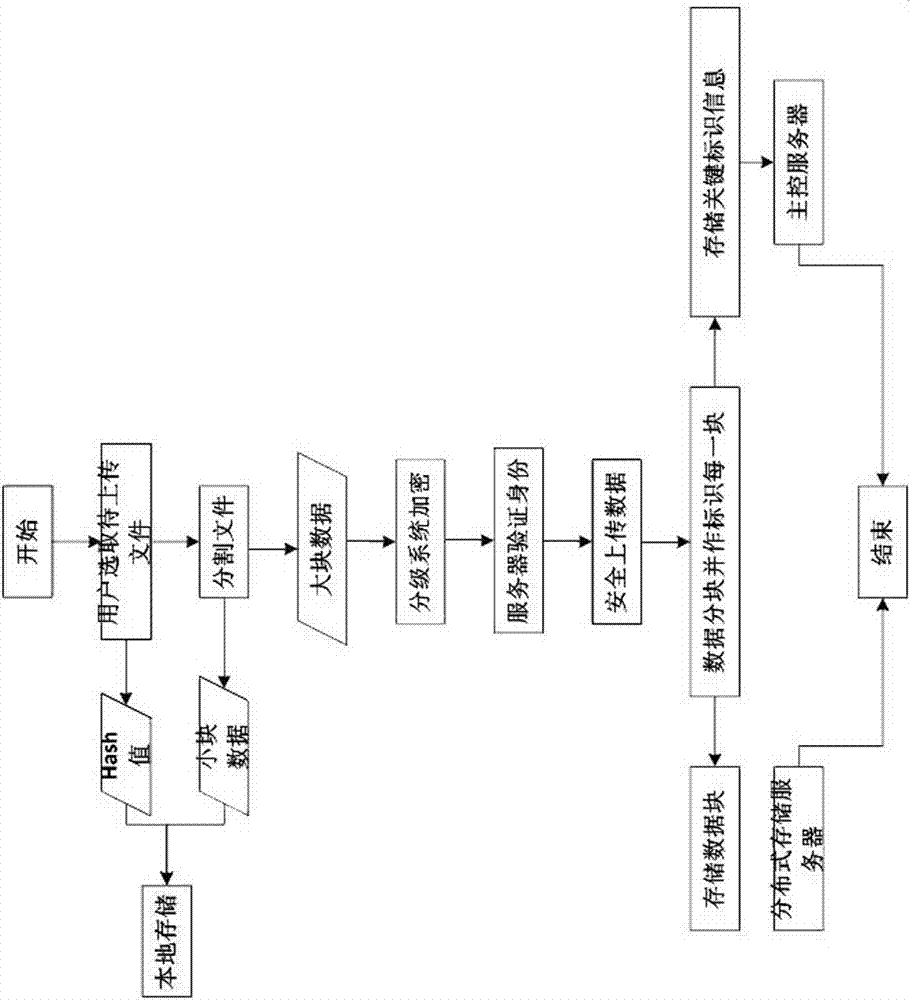
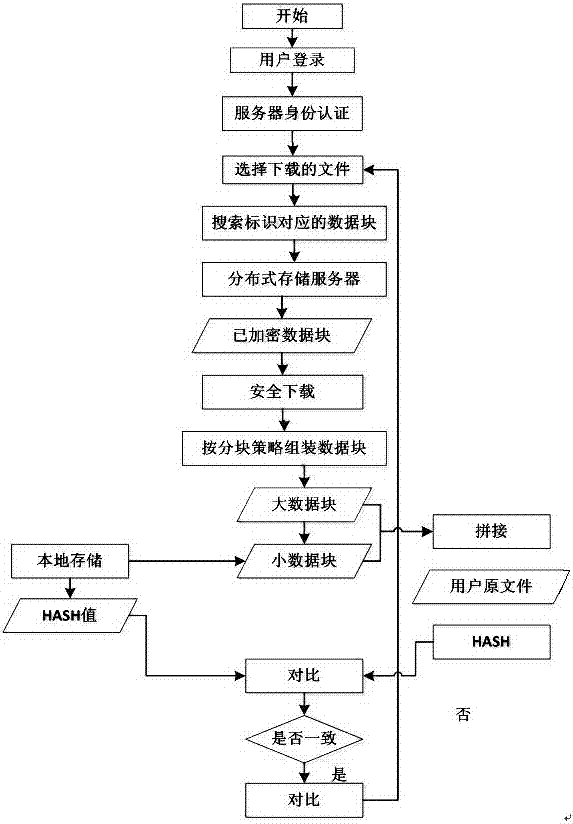
Cloud data protection method for data hierarchical encryption and segmentation
InactiveCN107425962AKey distribution for secure communicationMultiple keys/algorithms usageCloud userCloud data
The invention provides a cloud data protection method for data hierarchical encryption and segmentation, and belongs to the field of cloud data protection. The method of the invention includes the steps of firstly segmenting data into small and large data blocks rationally; then deploying the small block data and the large block data respectively in local and remote places; and then, according to different security level requirements of the data, performing data encryption using data encryption techniques of different strengths. In this way, the flexibility is increased and the system overhead is reduced while the cloud user data are protected.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com