Encryption machine key injection system based on cloud environment, method and device
An injection system and encryption machine technology, applied in computer security devices, transmission systems, digital transmission systems, etc., can solve the problems of cloud management security risks, complicated key injection operation steps, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
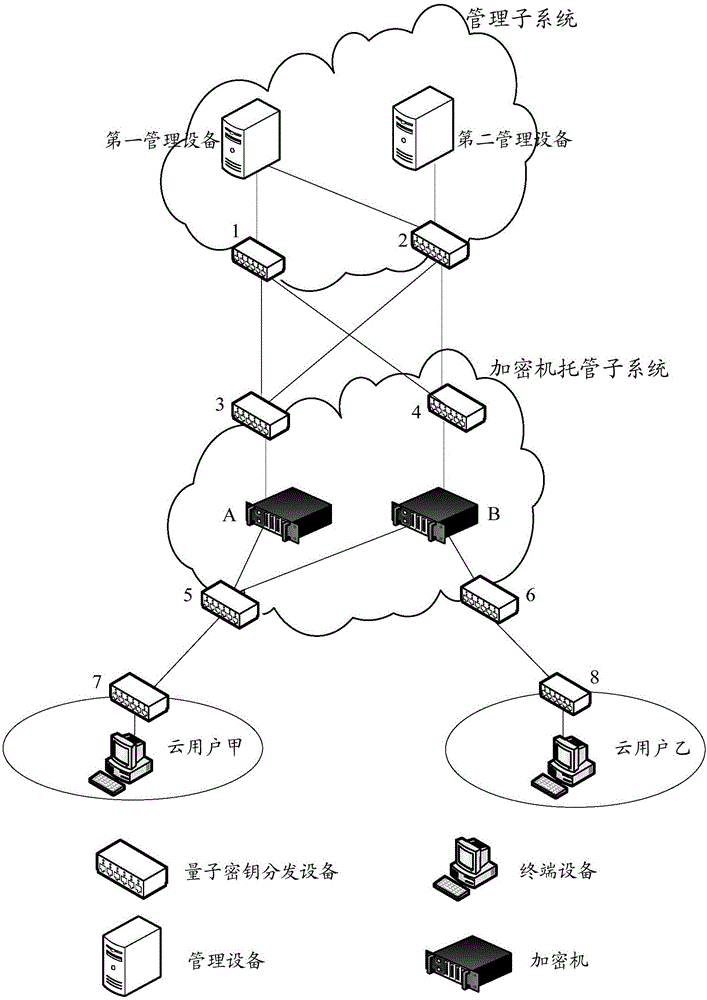
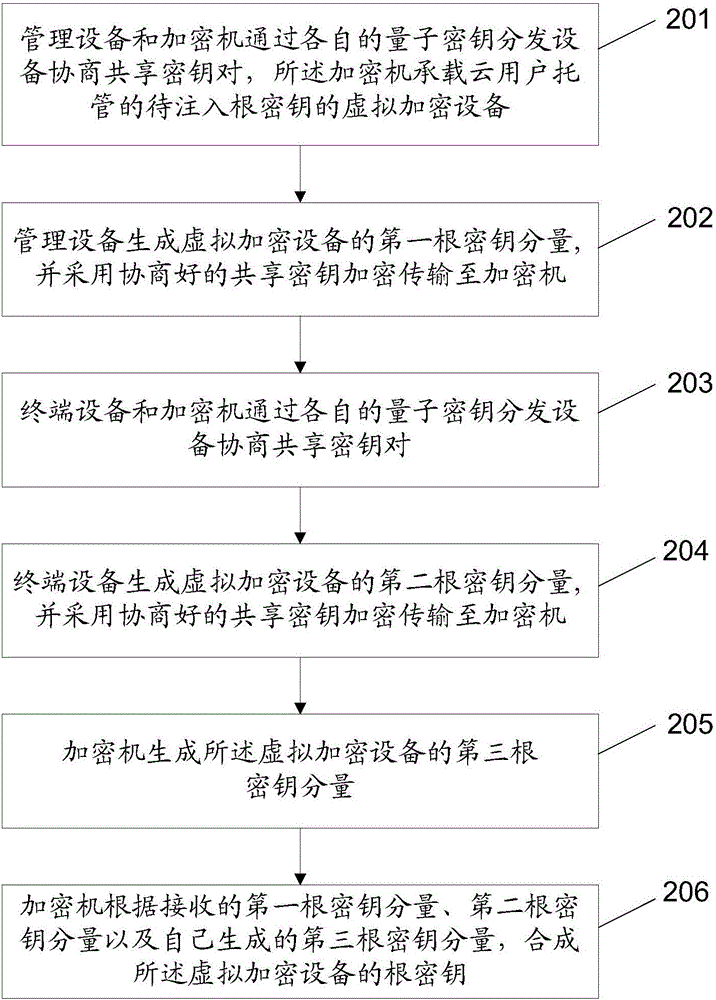
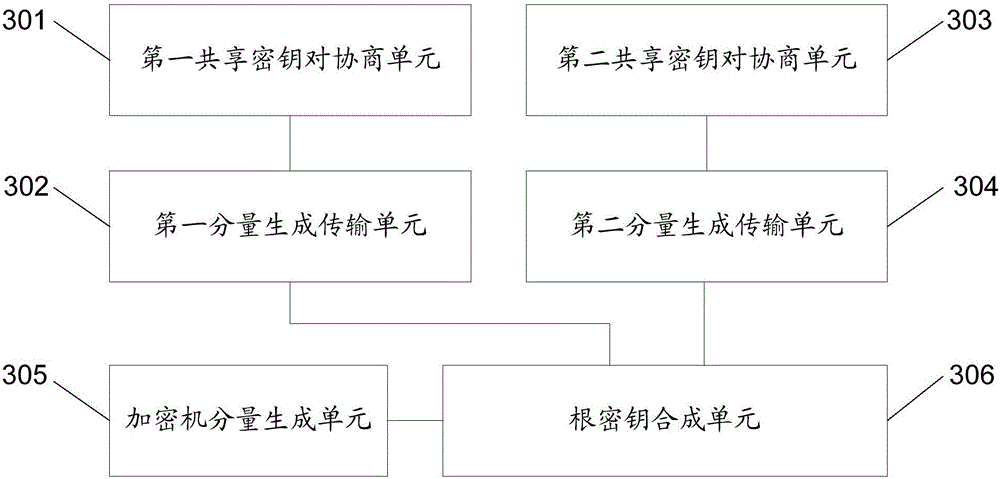
[0121] On the basis of the above implementation, in order to further ensure the security of the root key of the virtual encryption device, and also take into account the cloud user's trust in the cloud provider, this embodiment also provides a preferred implementation: the key The number of injection subsystems is the largest integer less than the preset number of root key components; the key generation device in each key injection subsystem is specifically used to generate a root key component of the virtual encryption device; The encryption machine is responsible for generating a root key component of the virtual encryption device, and synthesizes the root key component of the virtual encryption device according to the root key component received from each key injection subsystem and the generated root key component root key.
[0122] The above-mentioned preferred implementation of the system will be described in detail below in combination with the widely used traditional e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com