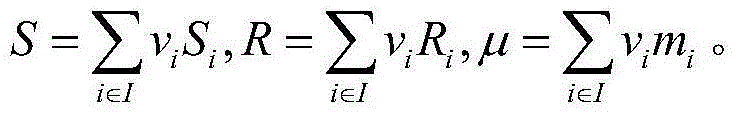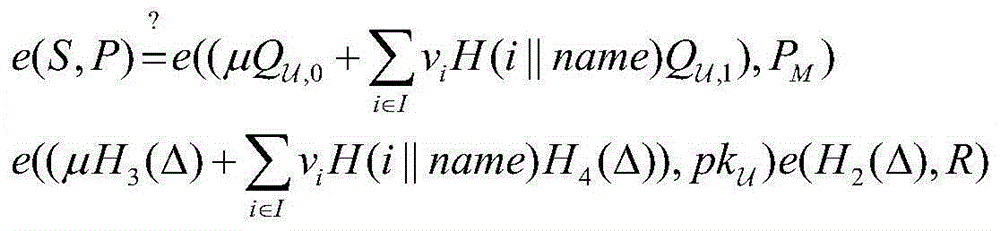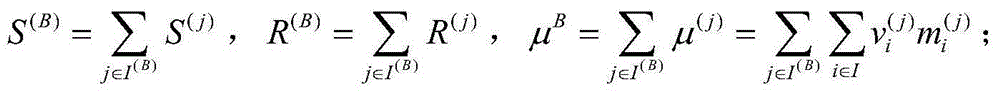Method for testing integrity of cloud storage data
A technology of data integrity and verification methods, applied in the field of cloud storage data integrity verification, can solve problems such as lack of computing capability for periodic verification of cloud data integrity, program security threats, and inability to guarantee fairness.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] Describe technical scheme of the present invention in detail below:
[0067] The present invention mainly comprises the following steps:
[0068] System initialization phase: the system generates the necessary public parameters, and generates the user's signature key and corresponding authentication key.
[0069] User data processing stage: the user names the file to be outsourced for storage, calculates a file label, divides the file into n data blocks, and then signs each data block using a certificate-free aggregate signature algorithm. Finally, upload the file, file label, and all corresponding signatures to the cloud server. After receiving the data, the cloud server verifies whether the data is uploaded correctly.
[0070] TPA audit cloud server stage: In order to verify the integrity of outsourced data stored on the cloud server, TPA first generates a challenge message and sends the challenge message to the cloud server. After receiving the challenge informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com