Patents
Literature
258results about How to "Avoid recovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
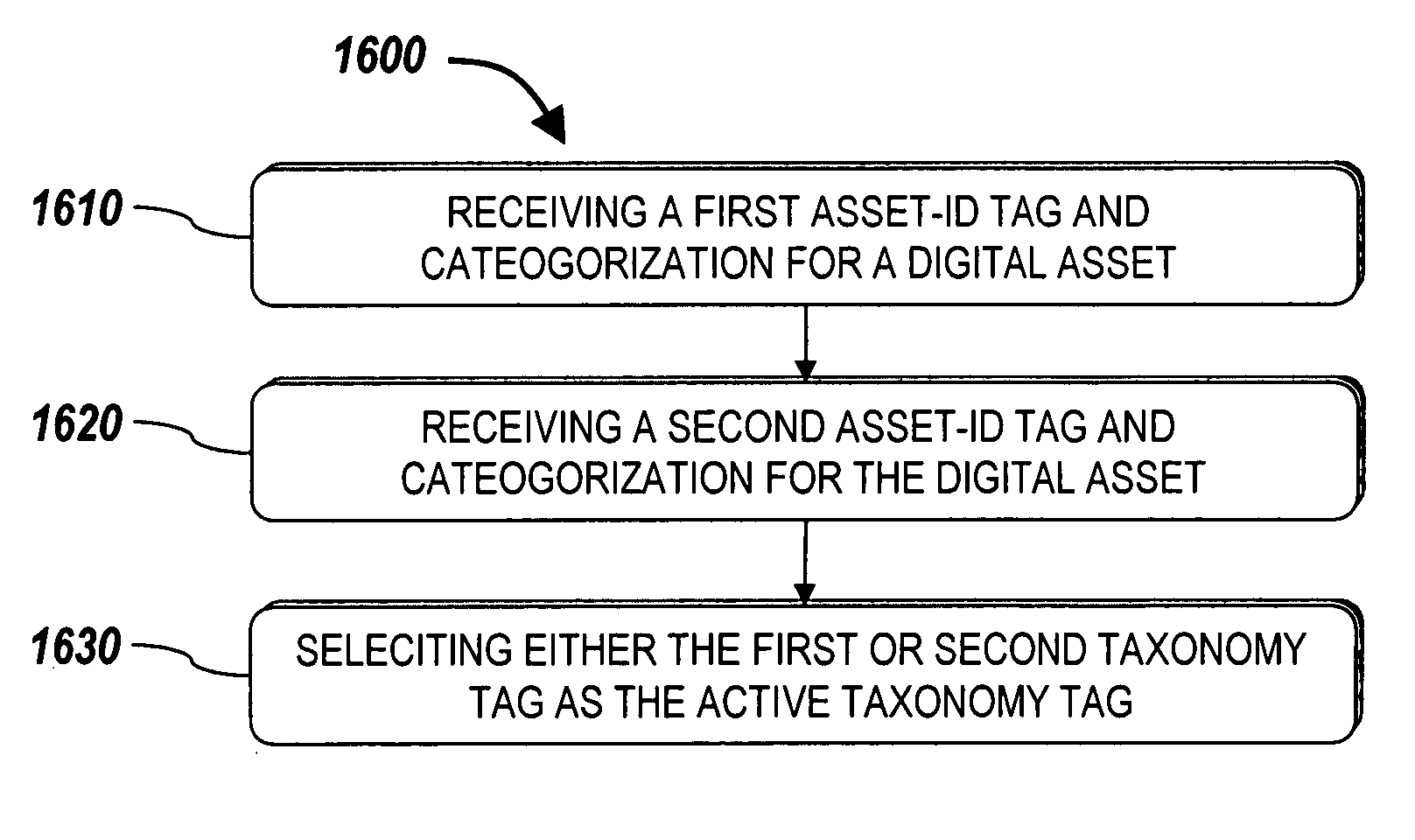
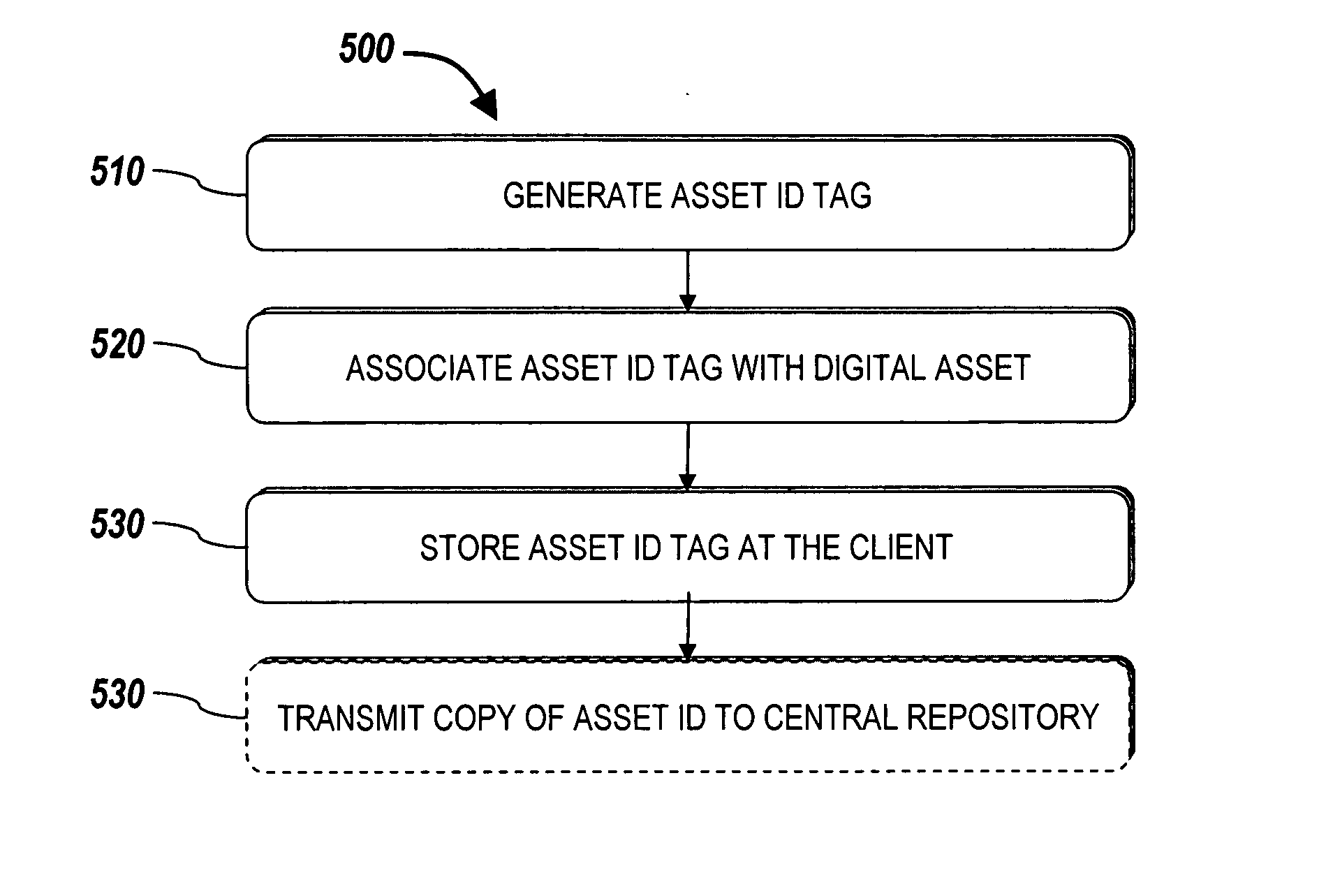
Systems and methods for unioning different taxonomy tags for a digital asset
InactiveUS20060106814A1Easy retrievalImprove productivityDigital data protectionOffice automationDistributed Computing EnvironmentComputer science
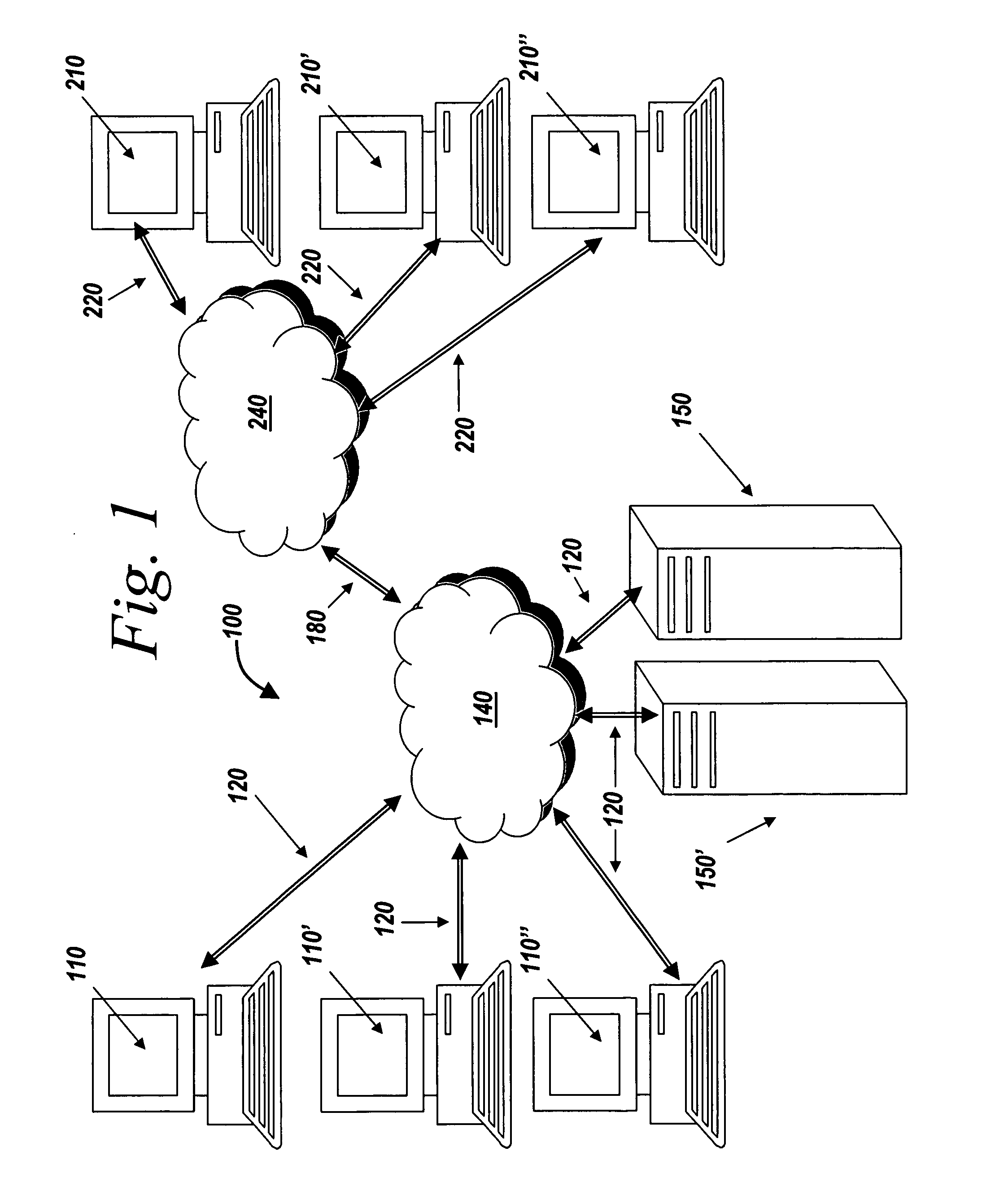
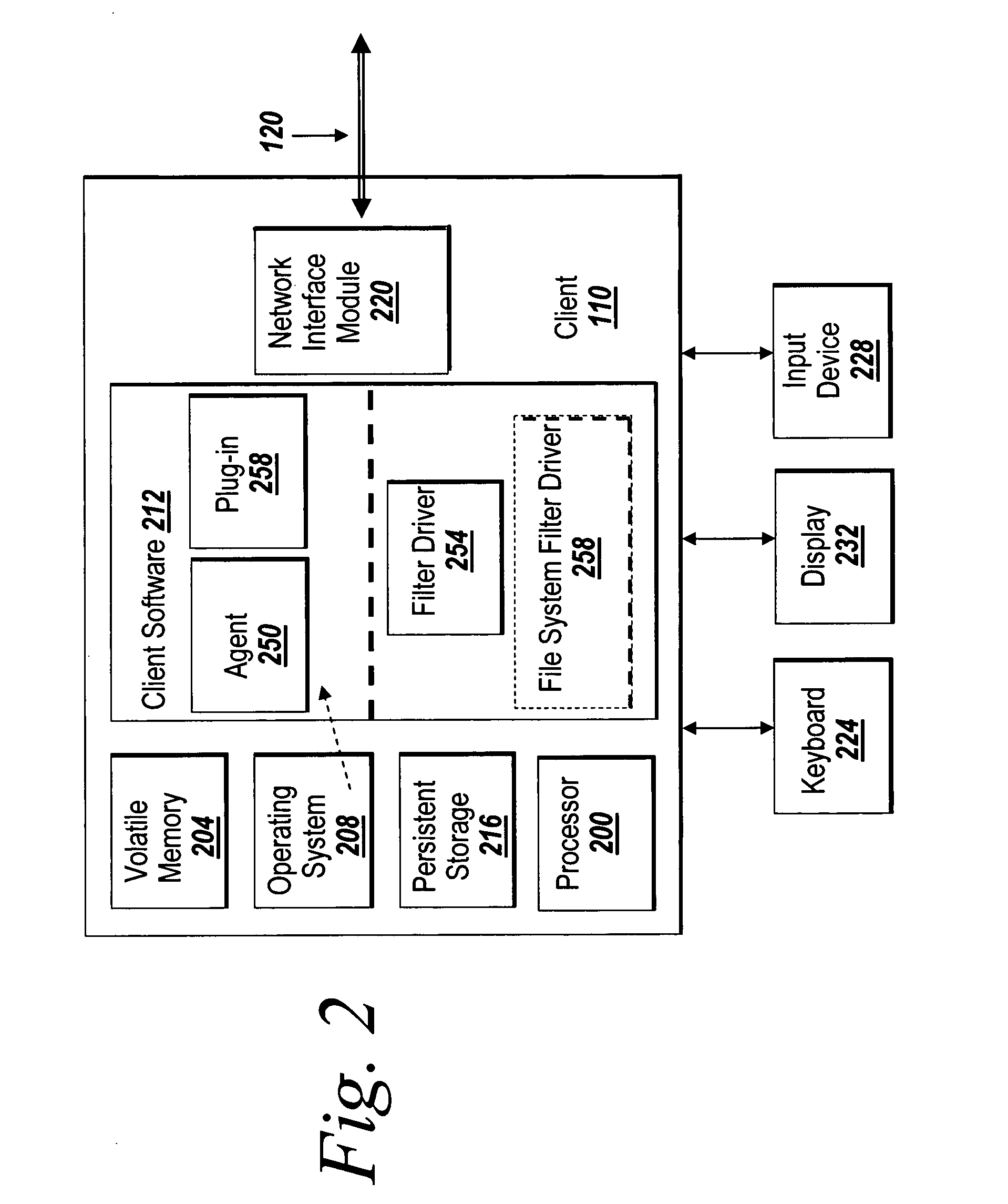
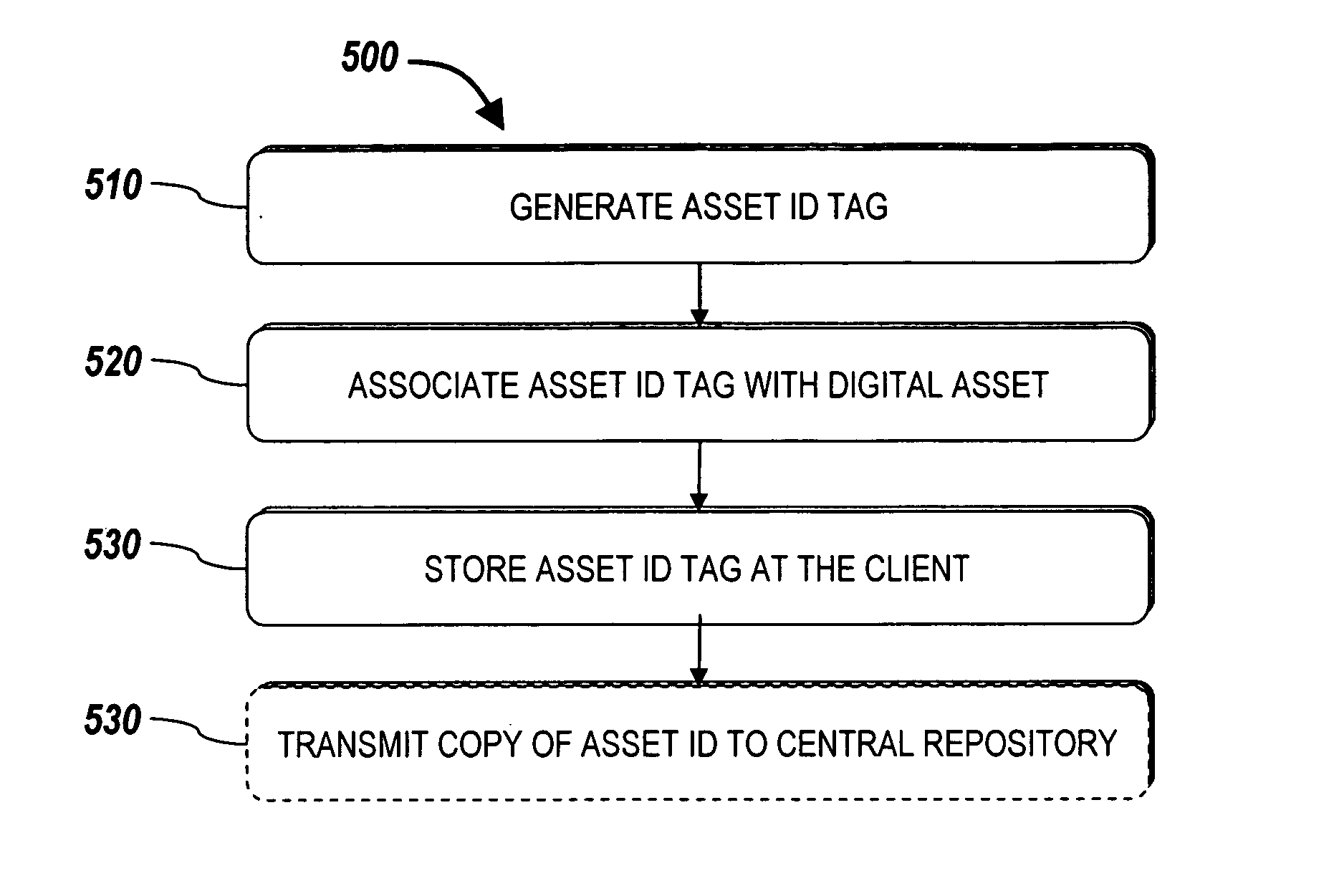
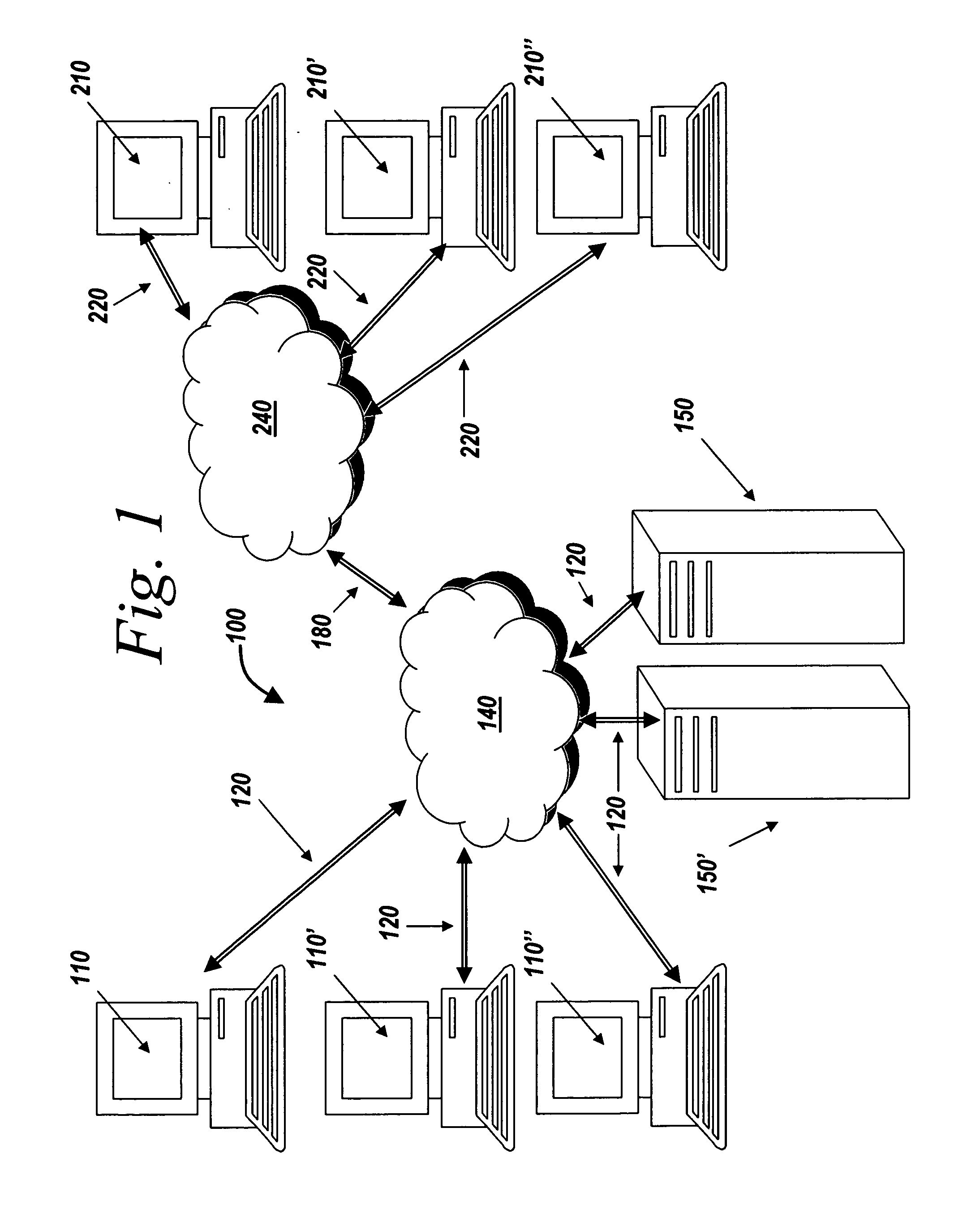
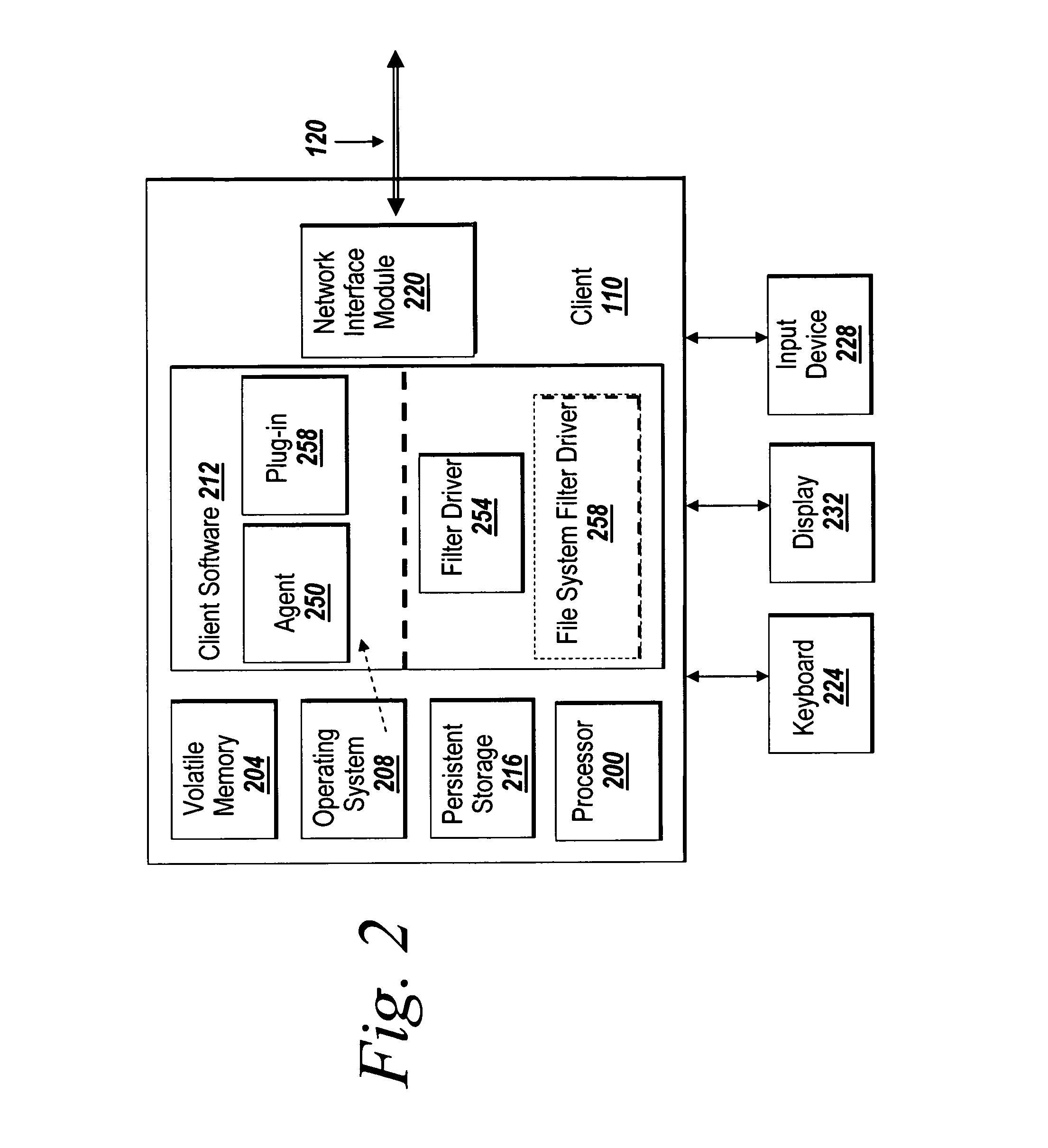
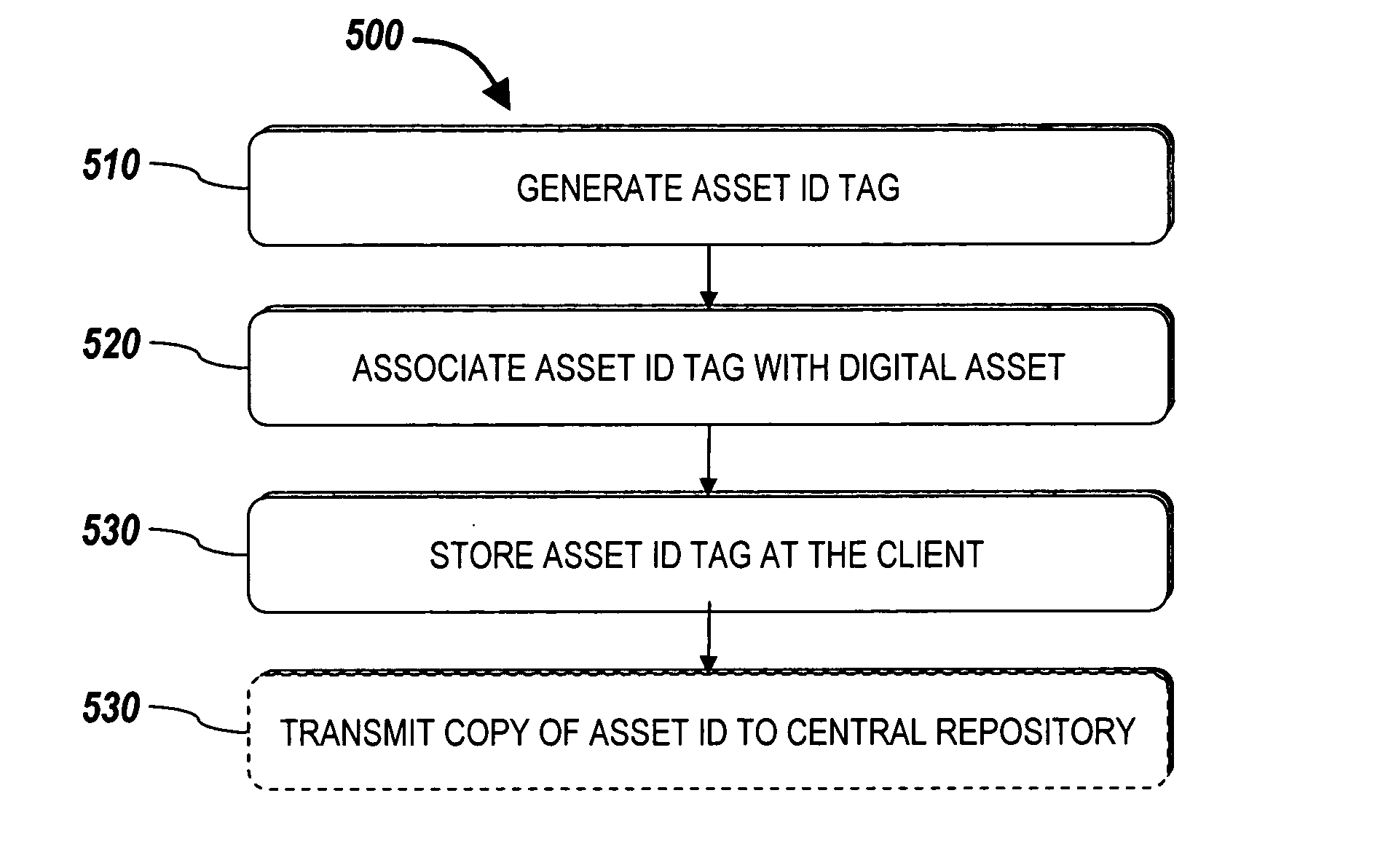
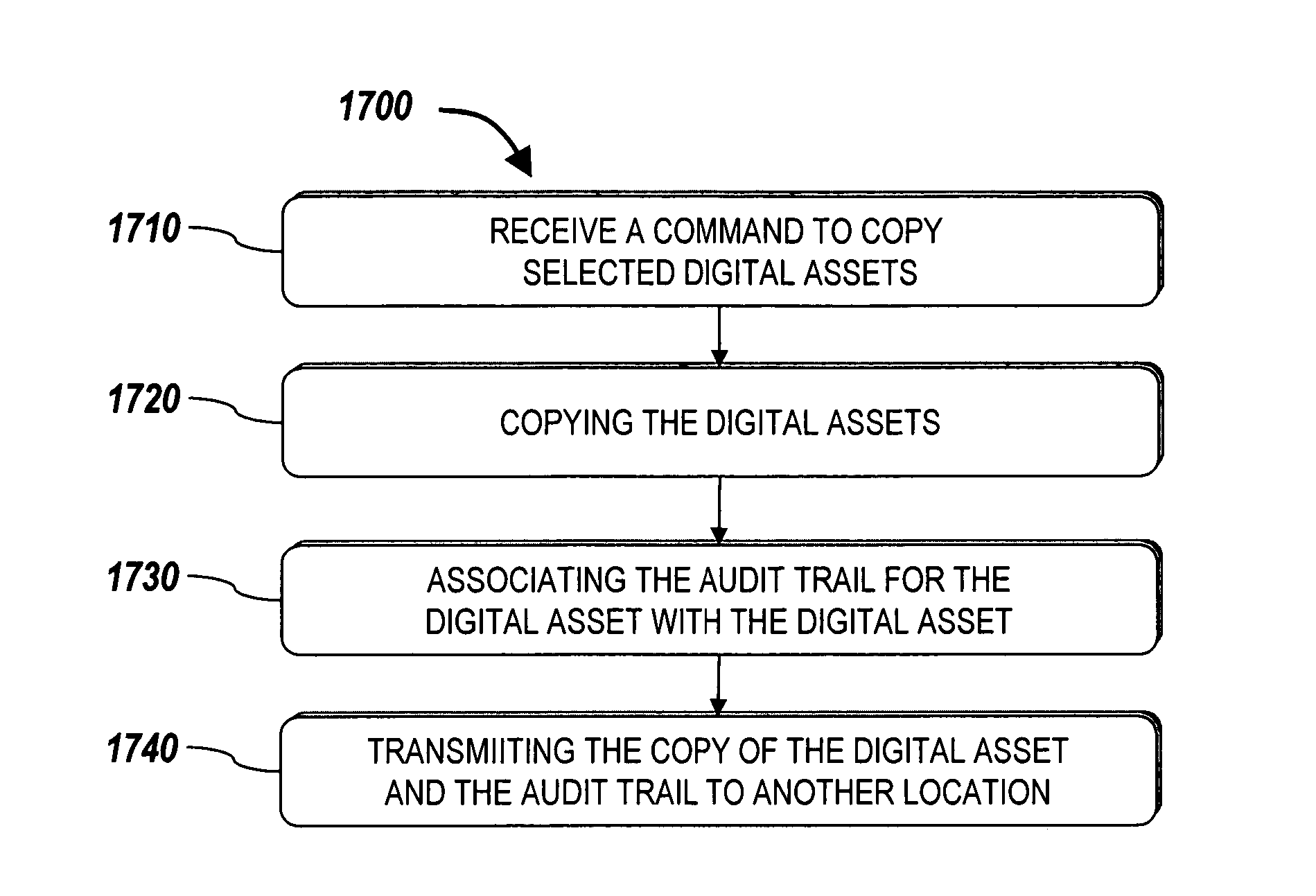
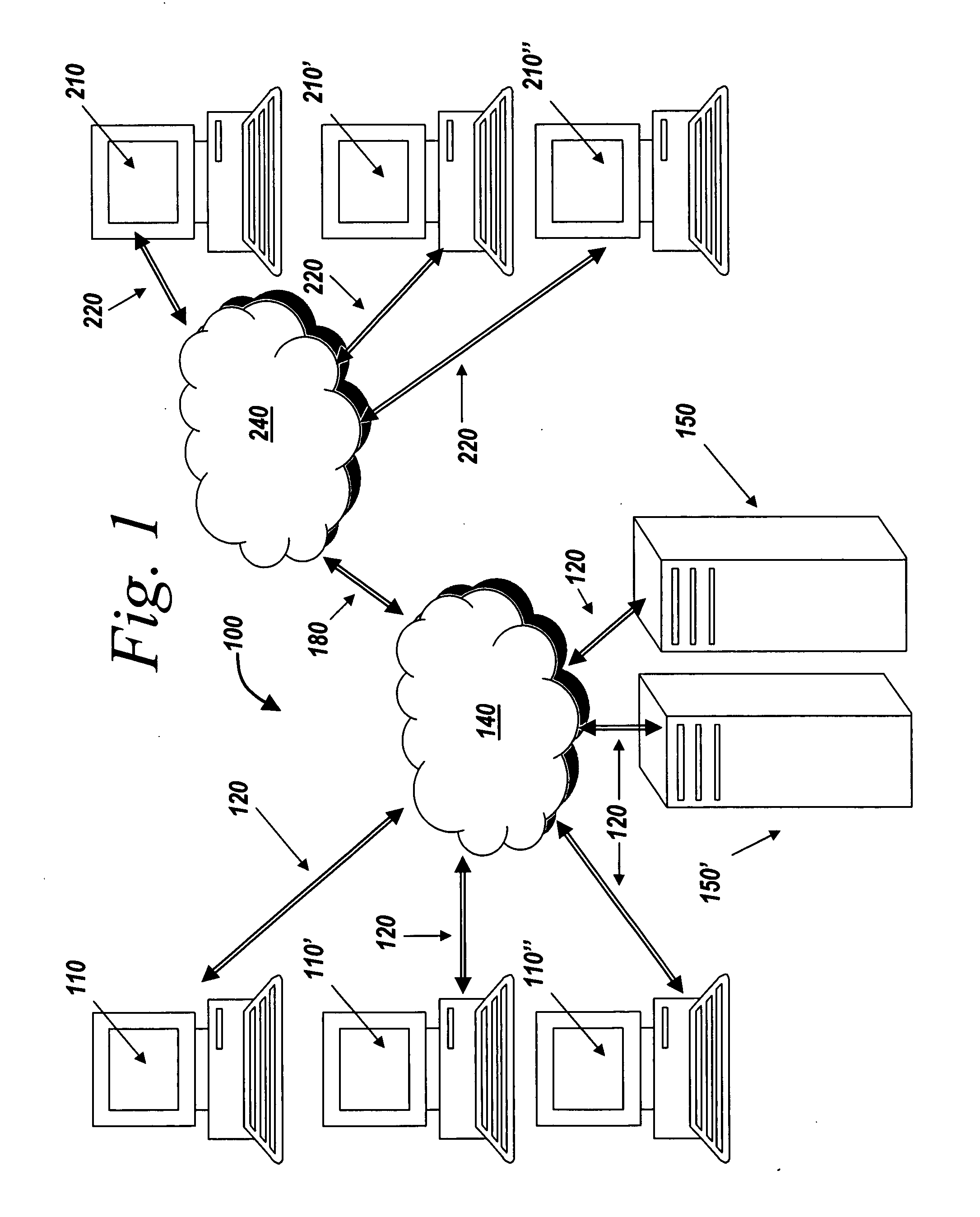
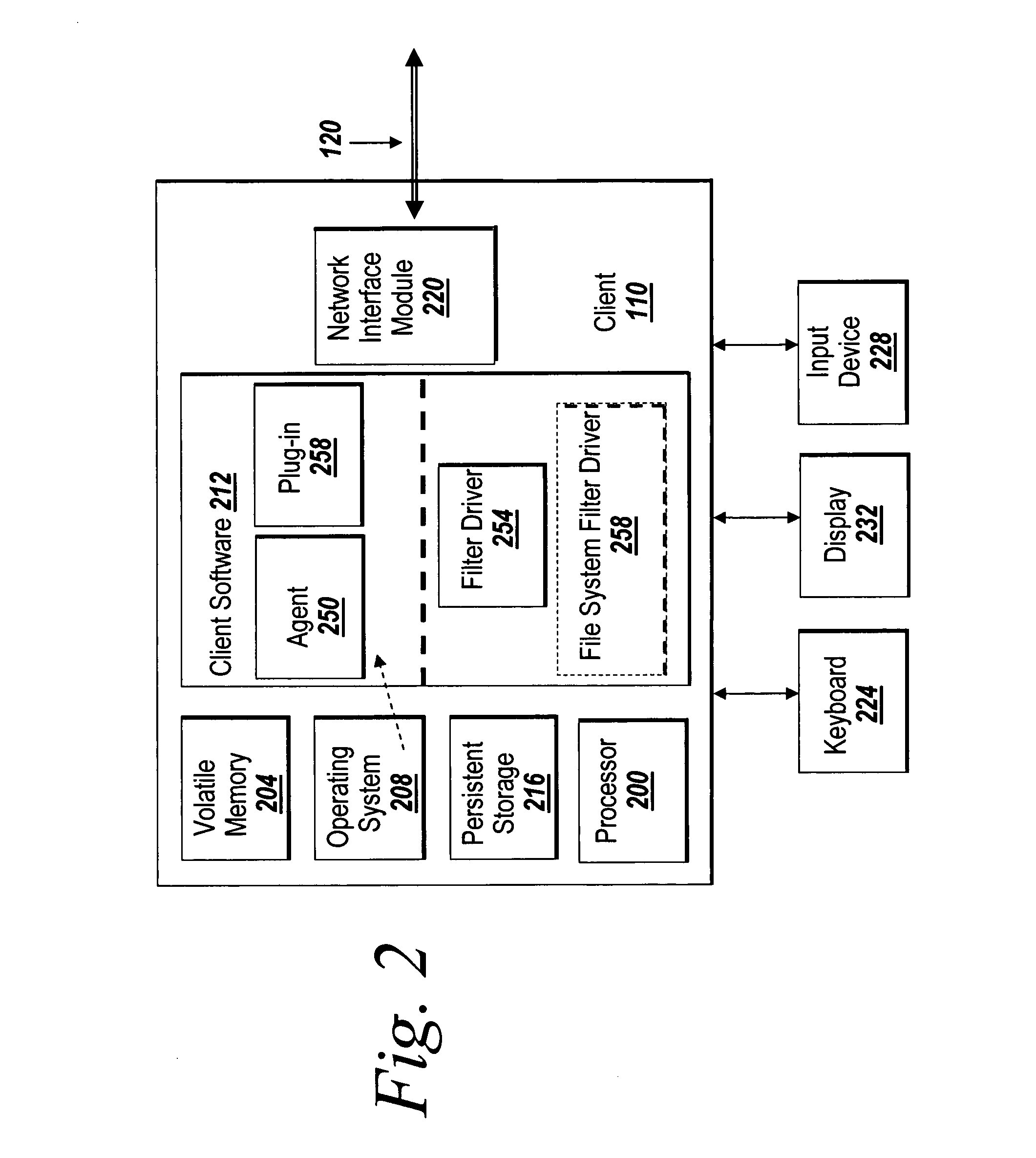
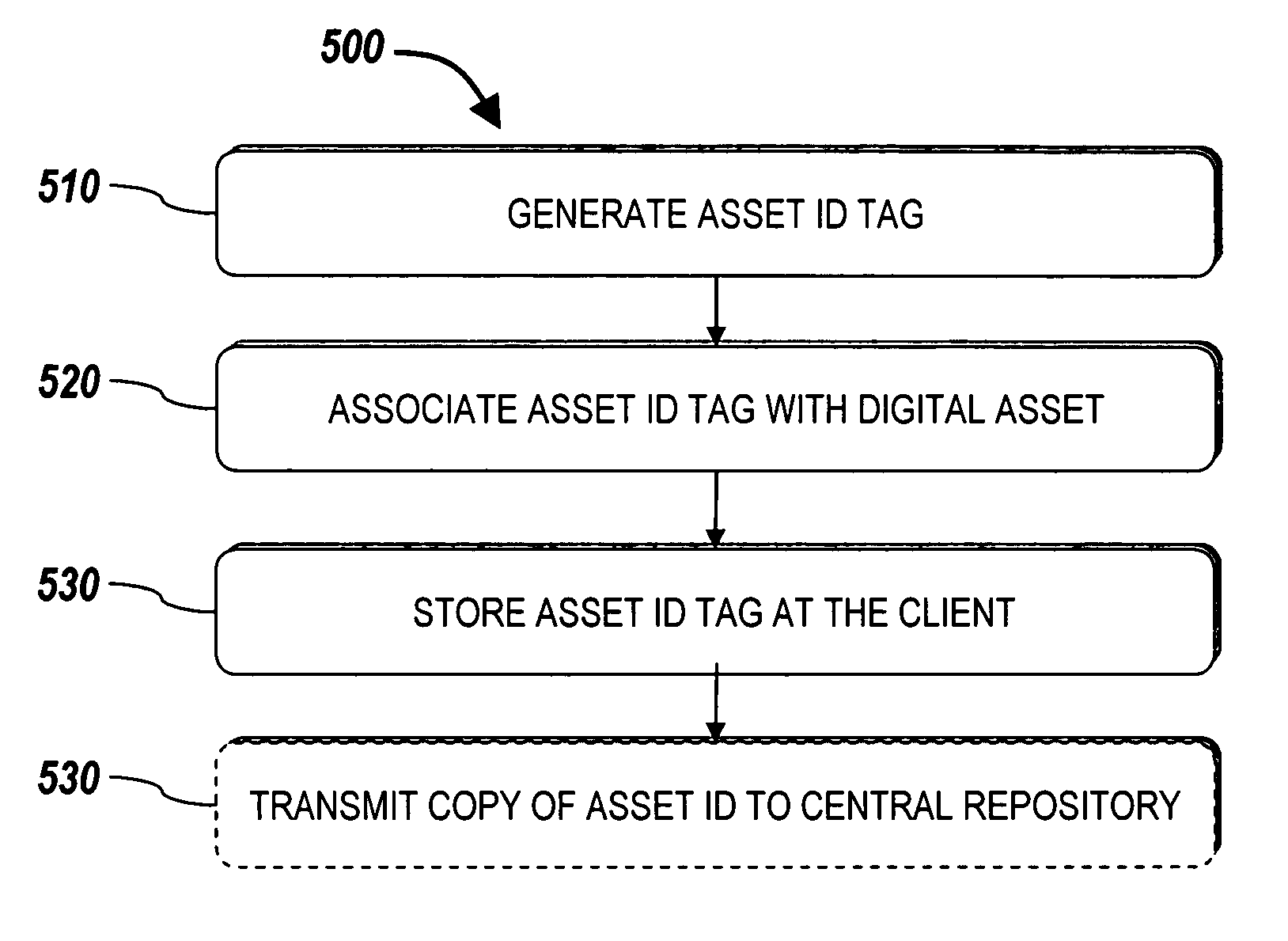
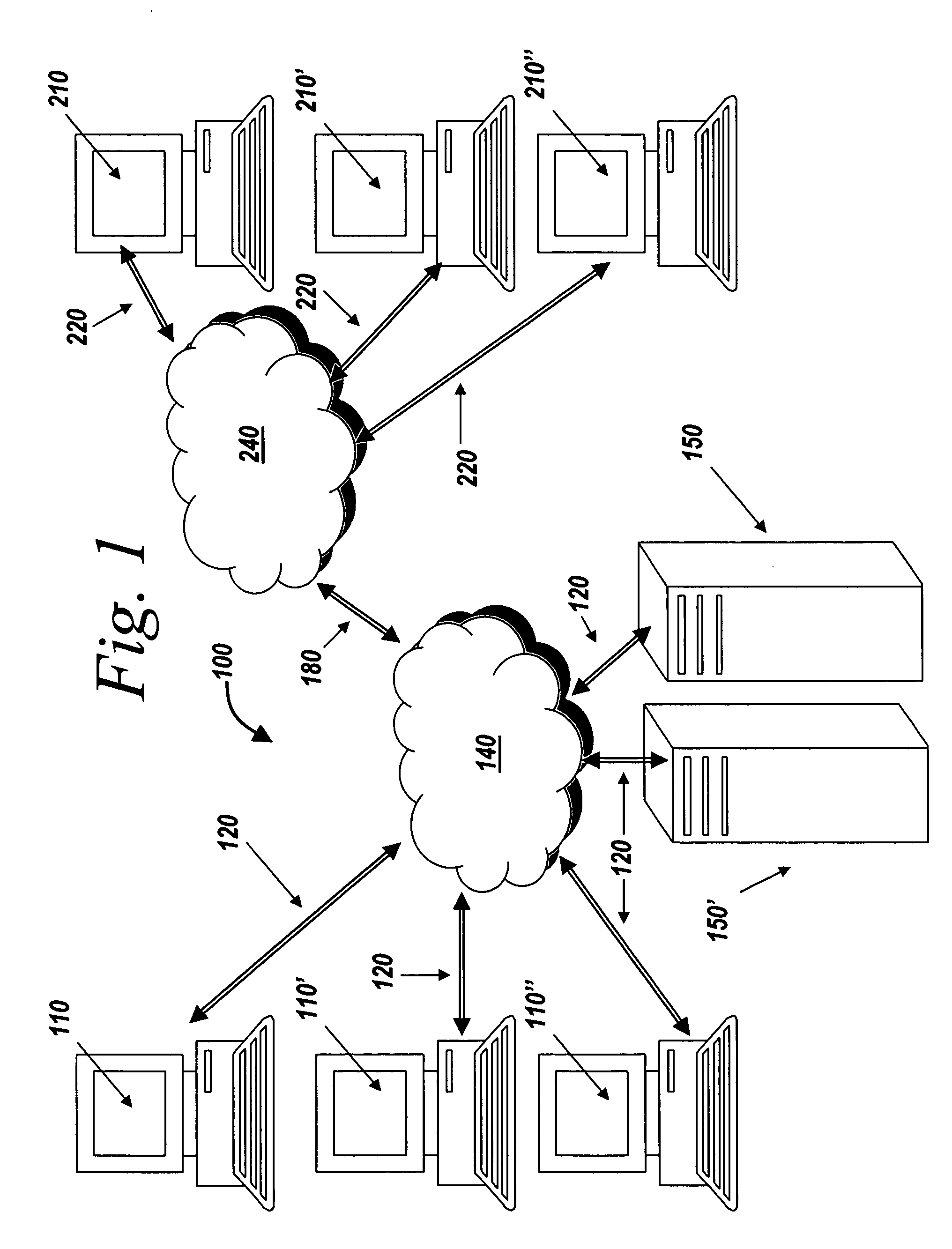
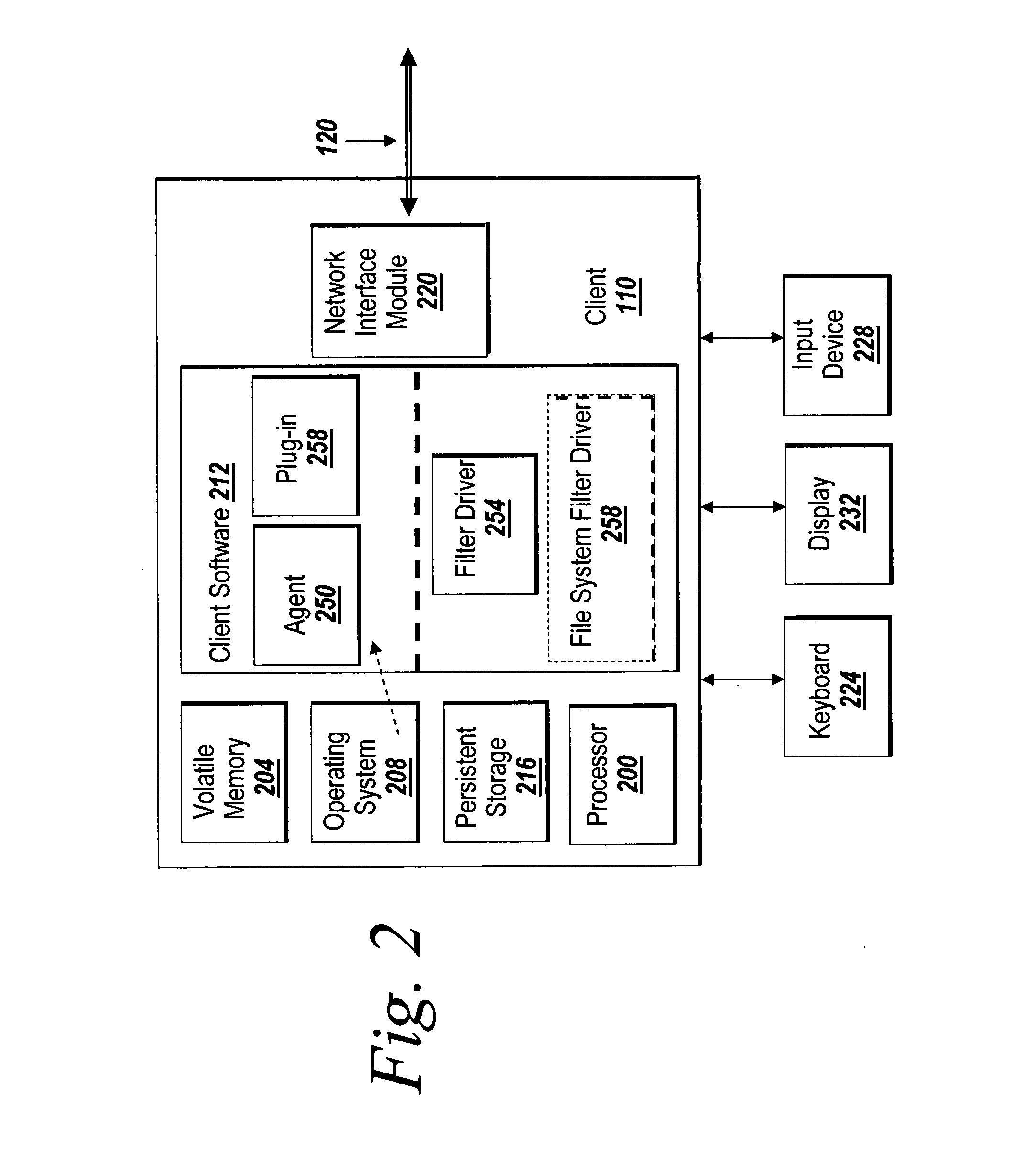
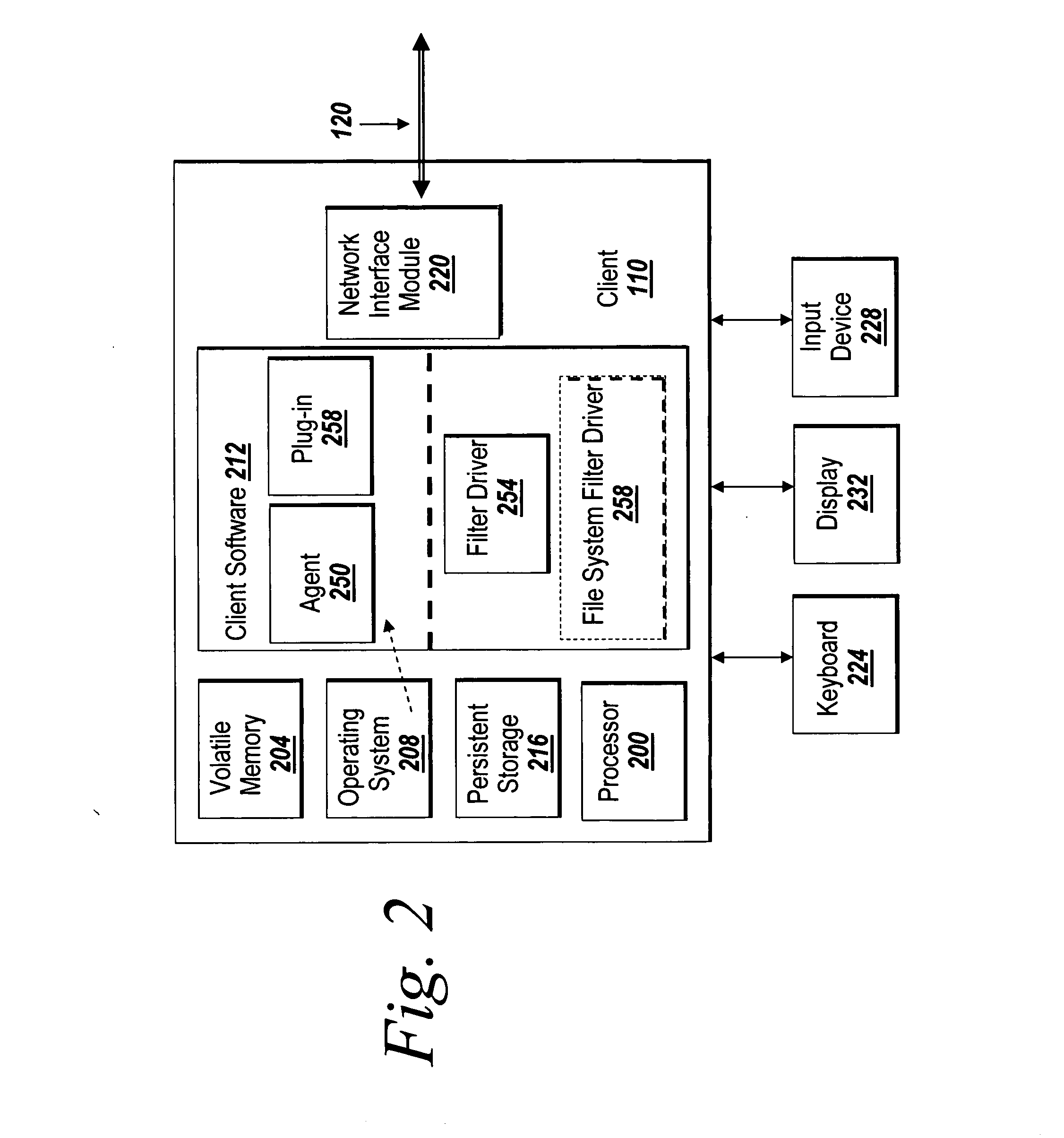
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:MICRO FOCUS LLC
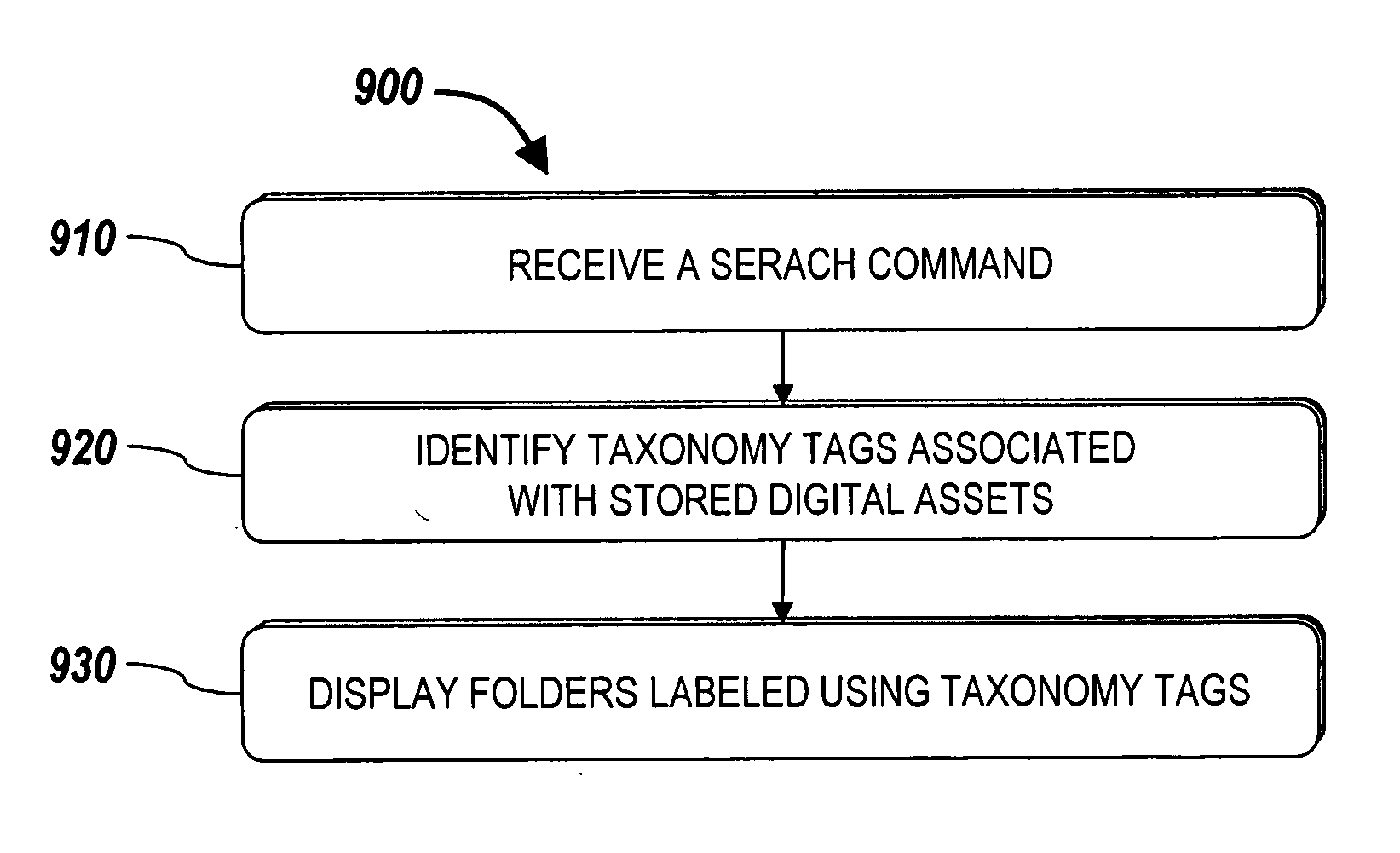
Systems and methods for searching digital assets using virtual folders having labels based on taxonomy tags
InactiveUS20060106782A1Easy retrievalImprove productivityDigital data protectionOffice automationDistributed Computing EnvironmentMetadata
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:IRON MOUNTAIN INCORPORATED
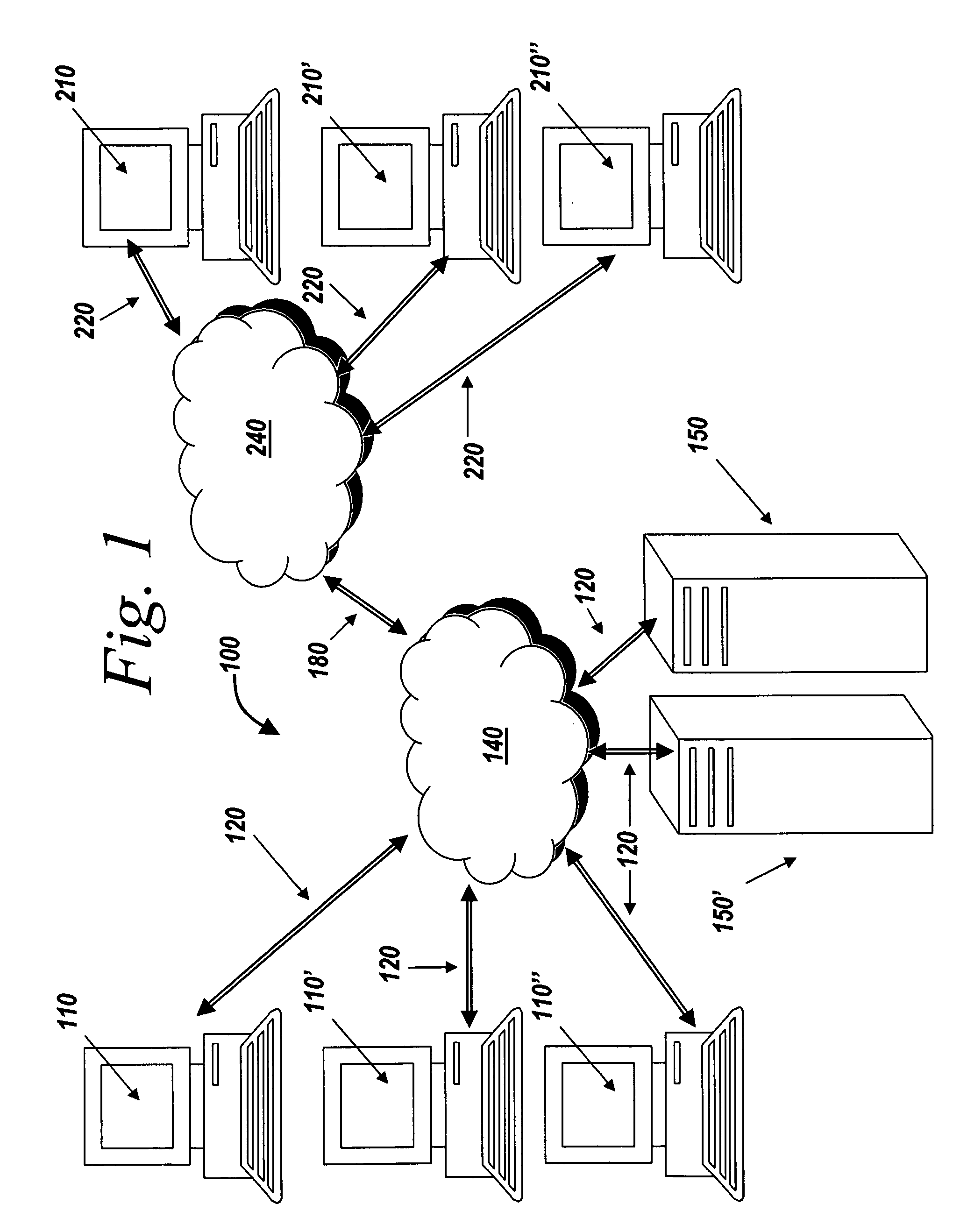
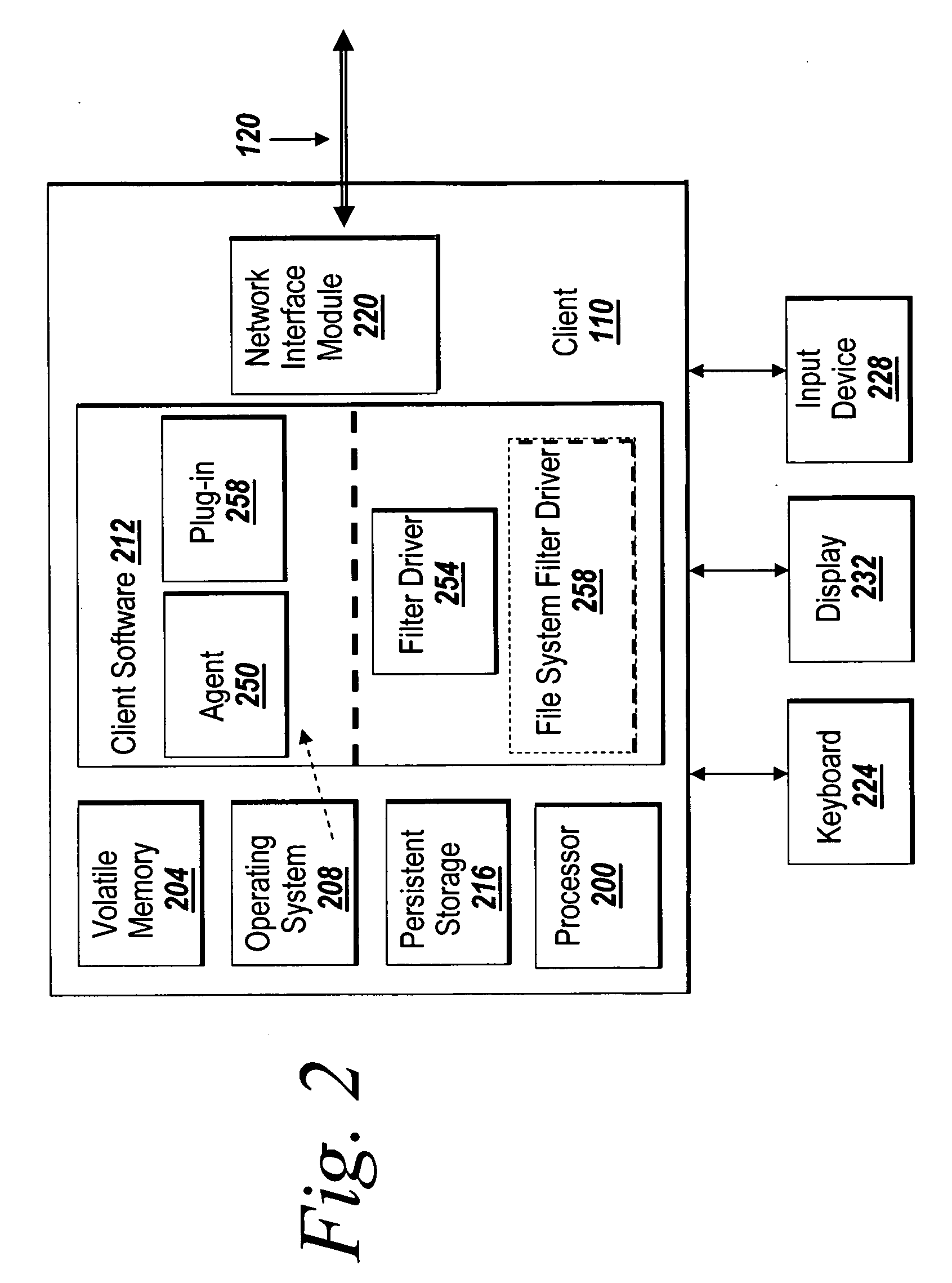
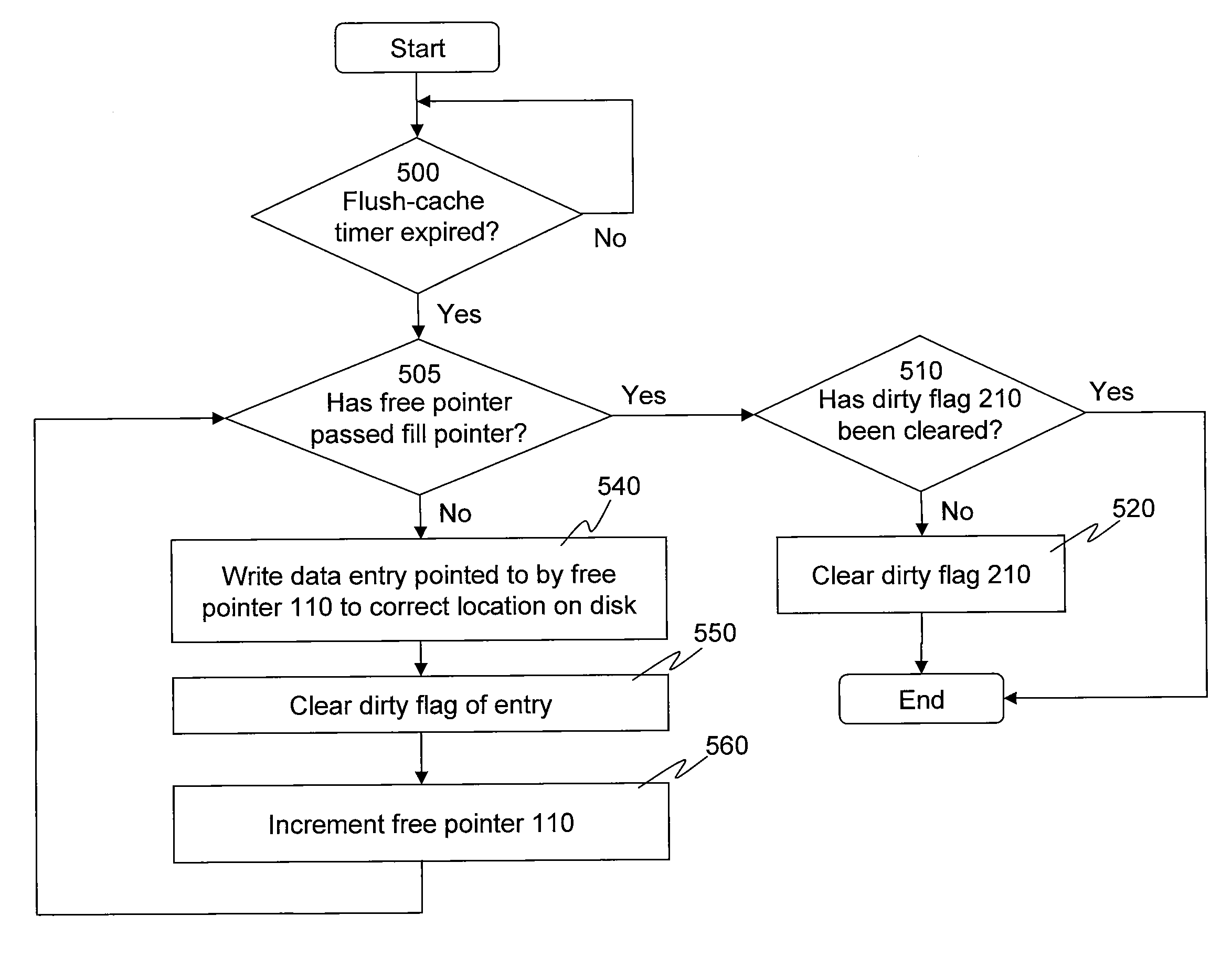
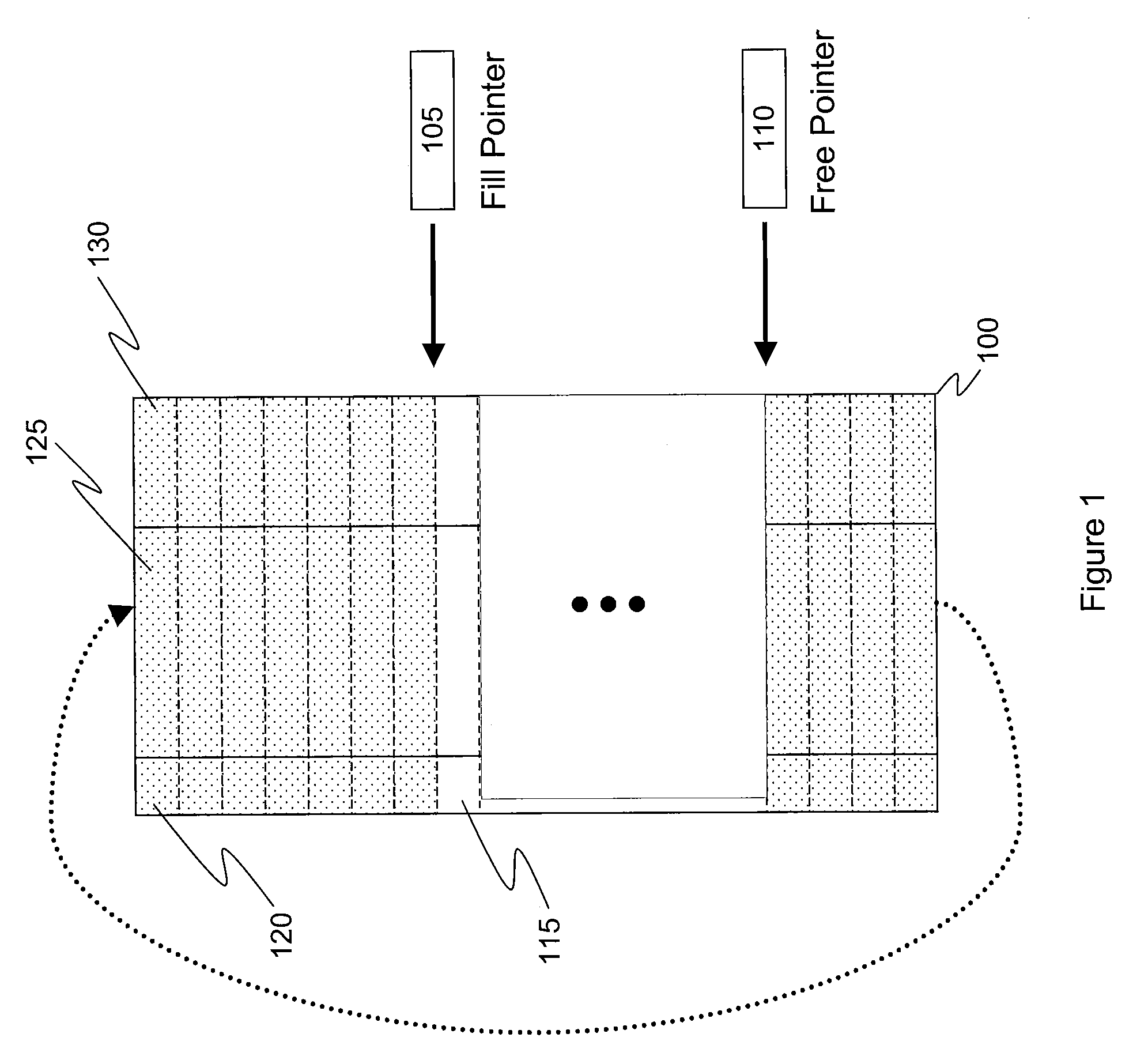
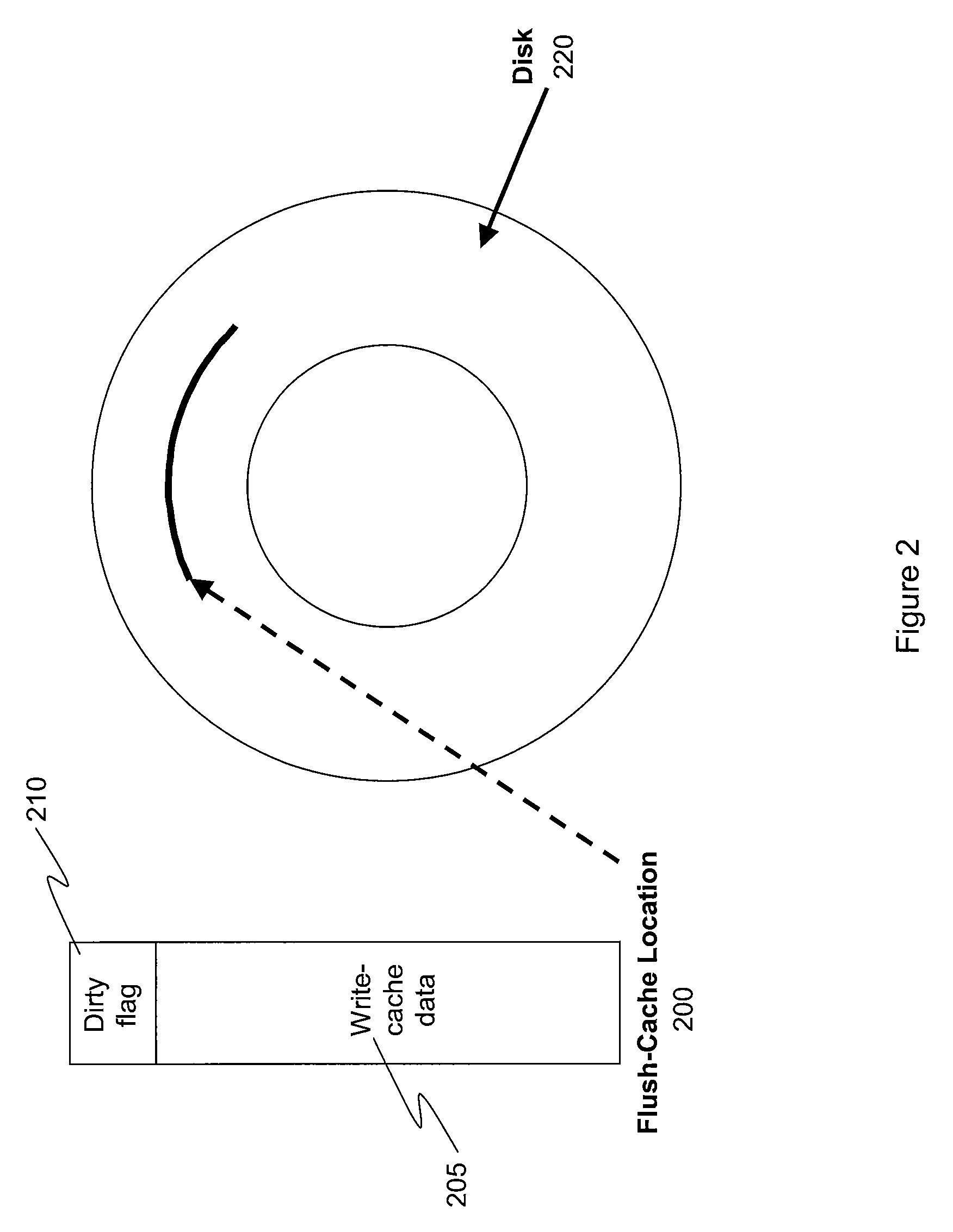
Method And System For Maintaining Cache Data Integrity With Flush-Cache Commands
InactiveUS20100205367A1Avoid recoveryMemory adressing/allocation/relocationOperating systemNon-volatile memory
A non-volatile memory location in a disk drive is utilized to store data residing in a write-cache upon receiving a flush-cache command from a host computer. If a subsequent flush-cache command is not issued within a predetermined time period, any data residing in the write-cache and stored in the non-volatile memory location that has not yet been written to its correct location on disk will be written to its correct location on disk.
Owner:KK TOSHIBA
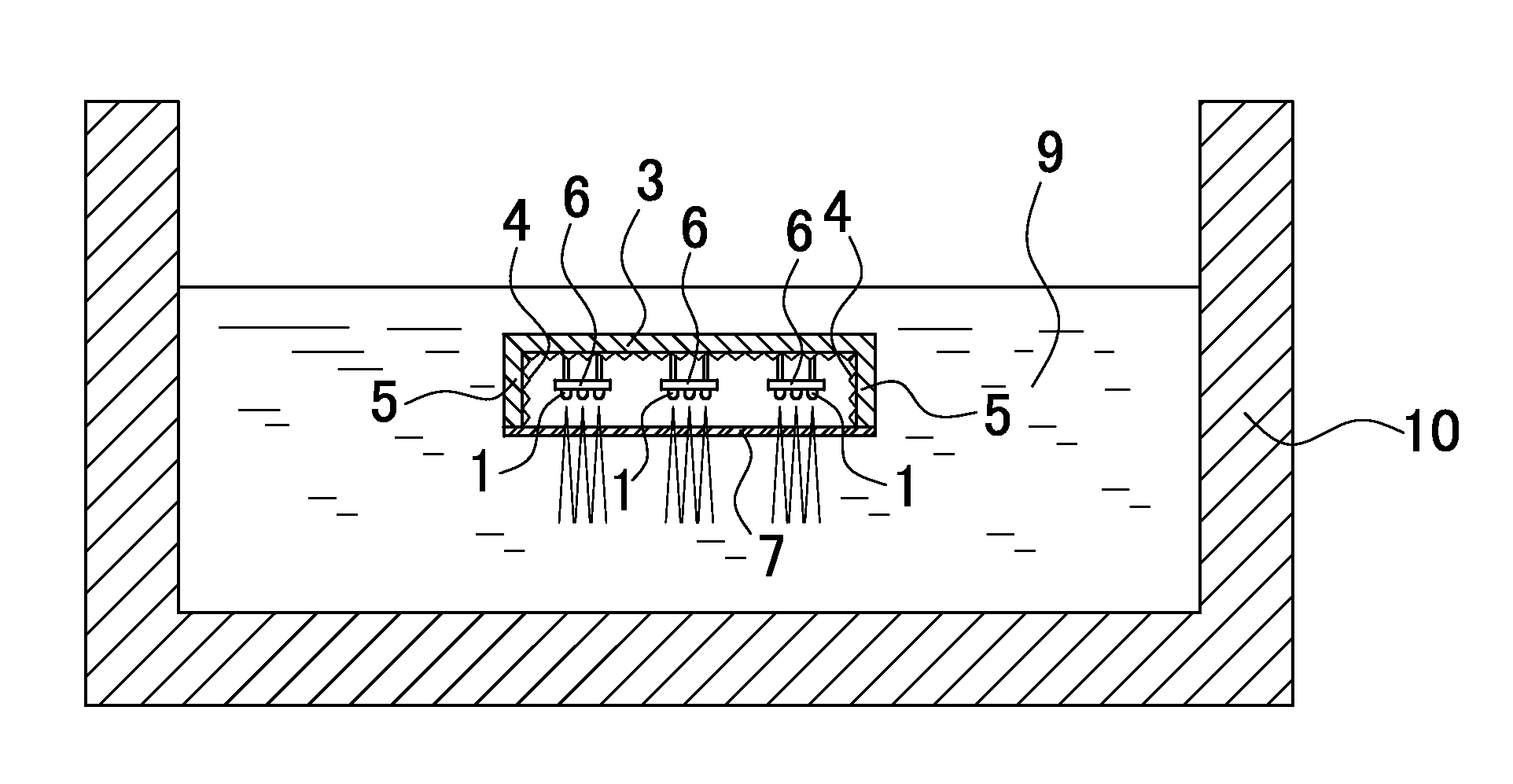
Outdoor water treatment apparatus to kill bacteria with ultraviolet light
ActiveUS20110226966A1Suppress bacteria increaseEfficient killingScattering properties measurementsDead animal preservationUva lightUltraviolet lights
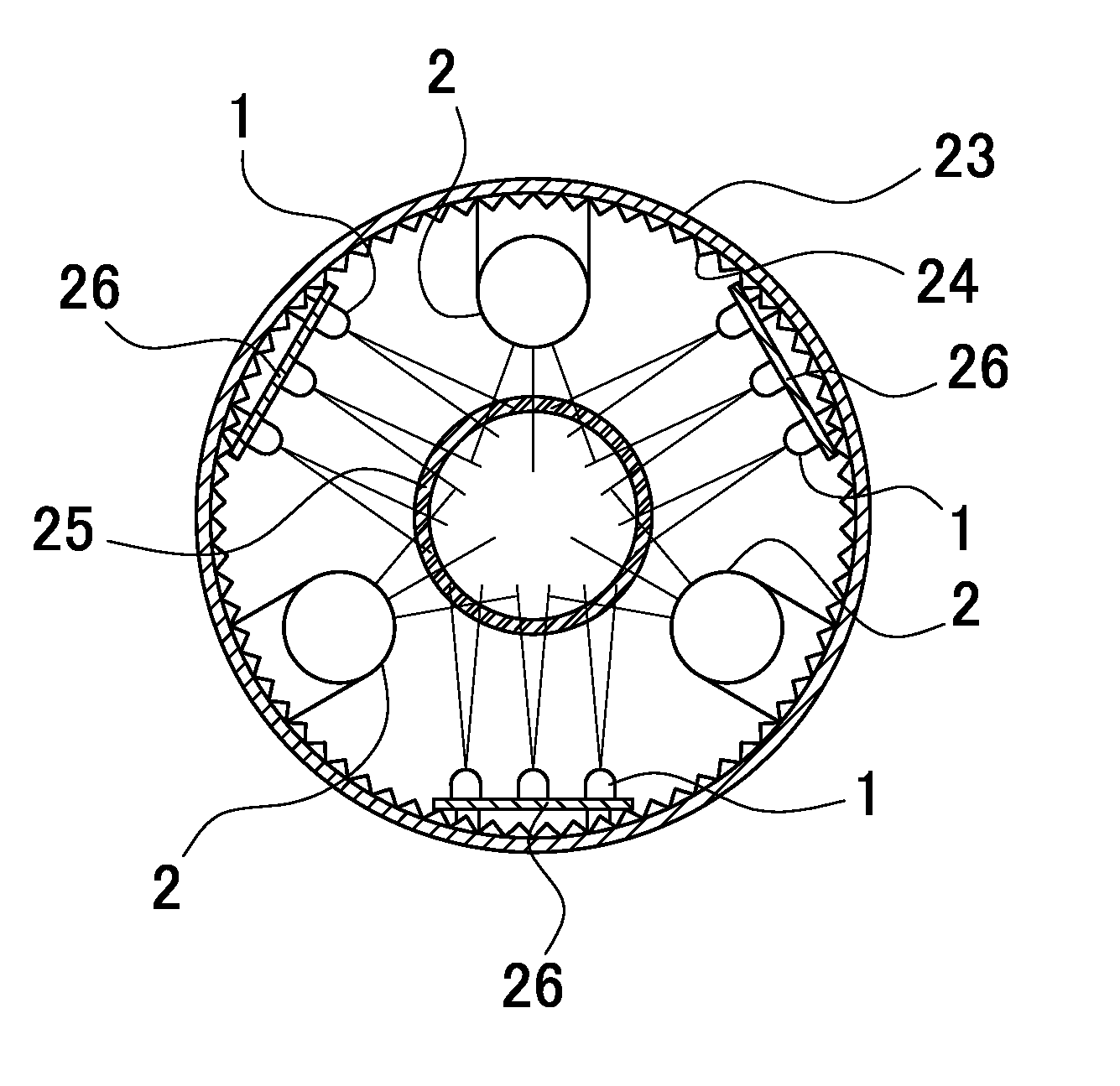
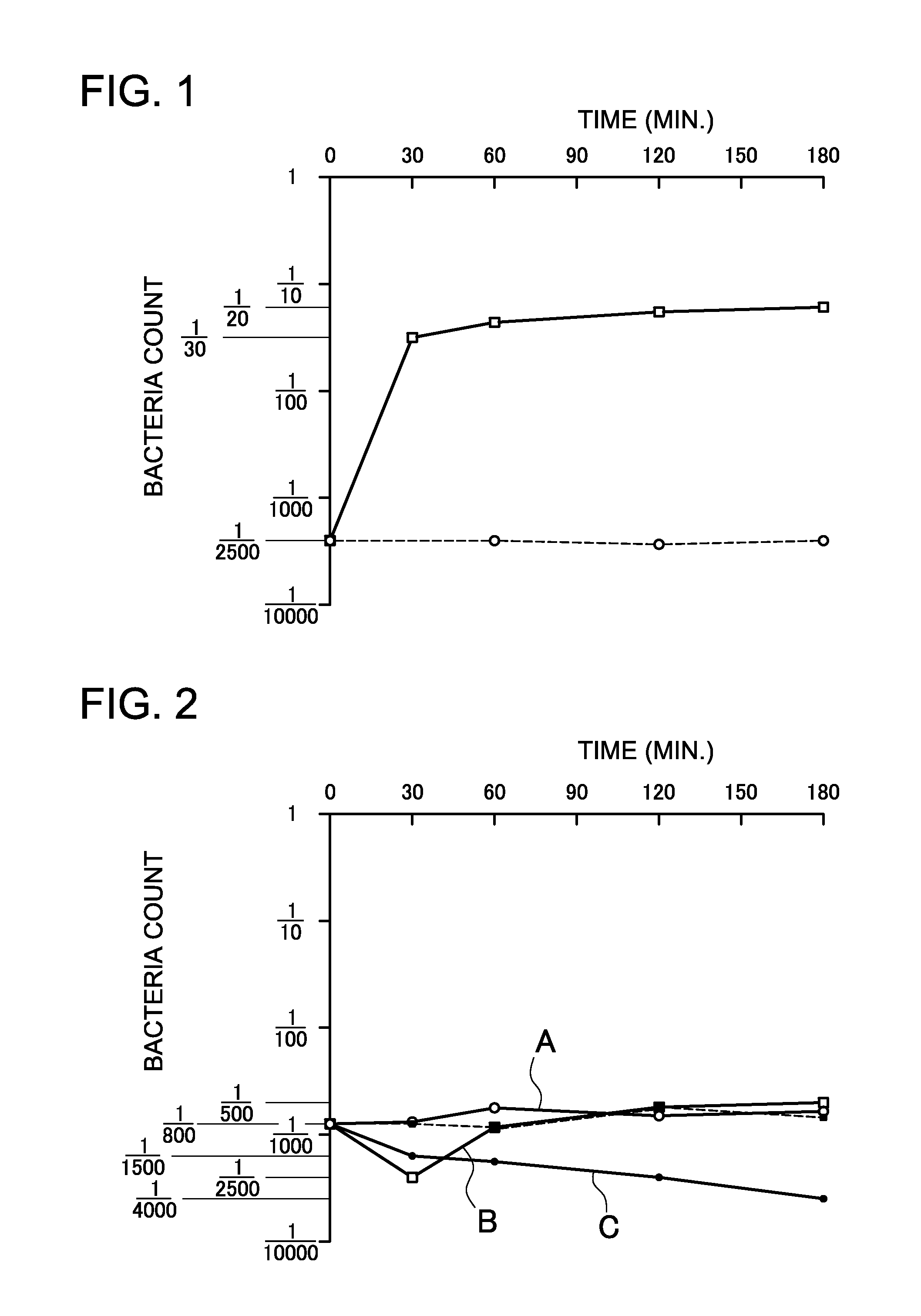
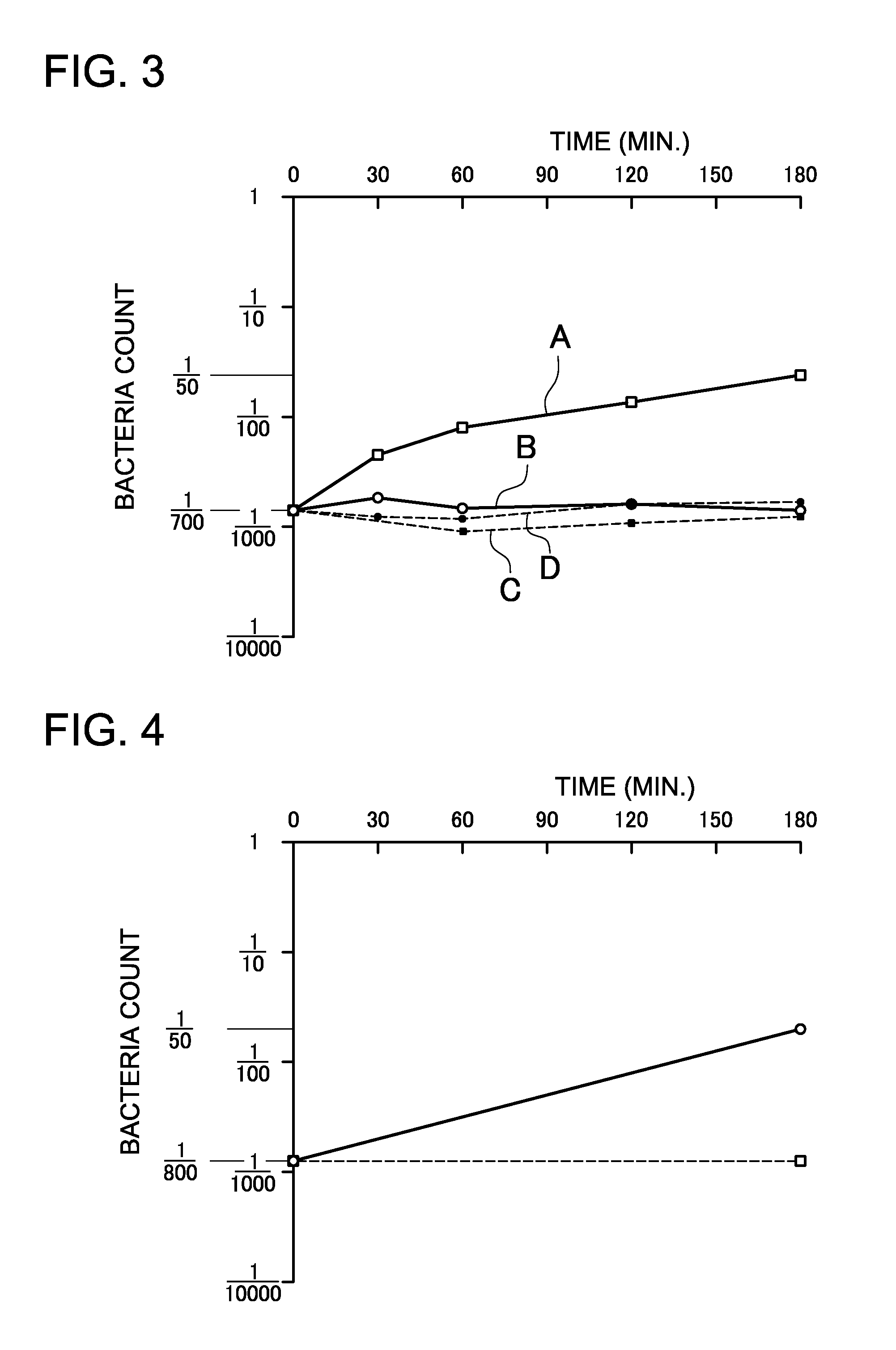
Bacteria in water 9 exposed outdoors are effectively killed with ultraviolet (UV) light by suppressing post-treatment increase in the bacteria population due to photoreactivation. The apparatus shines UV light on the water 9 to kill bacteria and has UV light emitting diodes (LEDs) 1 that emit UVA light with a primary emission peak of 320 nm-400 nm. The antibacterial action of the UVA light emitted by the UV LEDs 1 prevents proliferation of bacteria in the disinfected water 9 due to photoreactivation.
Owner:UNIVERSITY OF TOKUSHIMA
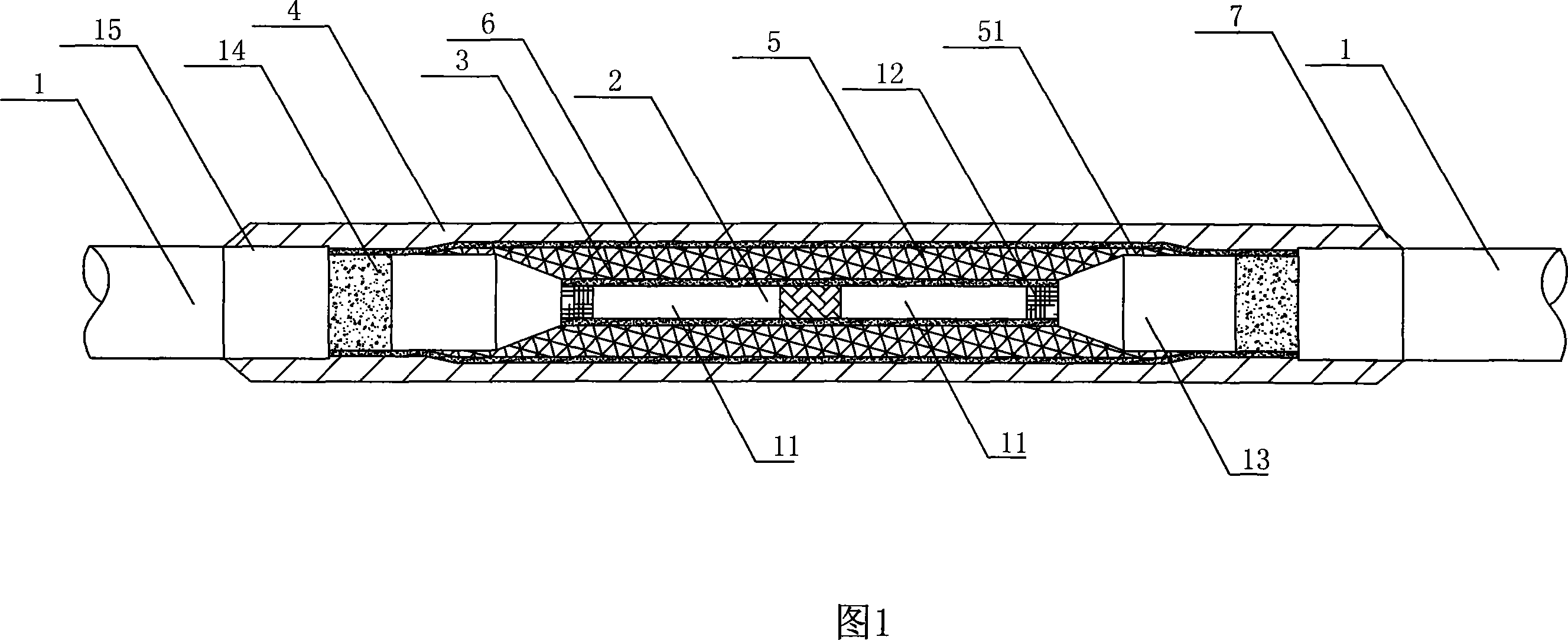
Soft joint for cross-linked polyethylene cable and producing method thereof
ActiveCN101068075AElectrical performance improvements and enhancementsEliminate void defectsCable junctionsApparatus for joining/termination cablesInsulation layerEngineering
This invention discloses a soft joint of a cross-linked polythene cable including an inner semiconductive layer and metal jacket sleeves, in which, two core leads between two cables are welded to form a core connection part, the inner semiconductive layer is combined with a preserved section of the inner screen layer of the cable characterizing in setting a polythene filled vulcanized insulation layer out of the inner semiconductive layer to be fused with the polythene insulation layer of the cable, and wrapping the polythene insulation of the cable with a transition connection section and an outer semiconductive layer combining with the preserved section of the outer screen of the cable is set out of the polythene filled vulcanized insulation layer, two ends of the metal jacket sleeve are welded with the out surfaces of lead protection pipe of the cable and set with slope connection sections.
Owner:宁波东方电缆股份有限公司
Systems and methods for tracking replication of digital assets
InactiveUS20060106885A1Easy retrievalImprove productivityDigital data protectionOffice automationDistributed Computing EnvironmentMetadata
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:MICRO FOCUS LLC
Cloud storage data common auditing method possessing secret key leakage resistance characteristic
The invention belongs to the communication technology field and especially relates to a cloud storage data common auditing method possessing a secret key leakage resistance characteristic. The method mainly comprises the following steps of system initialization: blocking processing is performed on a data file so as to generate public and private key pairs of a cloud user and a cloud server; auditing identification generation: the cloud user sends the data file and a label, and a signature set of a data block to the cloud server; auditing challenge response: a third party auditor generates auditing challenge information and sends to the cloud server; the cloud server calculates combination information according to the auditing challenge information, gets signatures together and sends an auditing identification response information to the third party auditor; and the third party auditor verifies validity of the auditing identification response information. The method has advantages that a condition that digital signature forgery and auditing identification response information forgery caused by leakage of a user signature private key can be prevented; and a malicious cloud server is ensured not to generate the forged auditing identification response information to cheat a TPA and to pass through an auditing verification process.
Owner:SOUTHWEST PETROLEUM UNIV
Systems and methods for storing meta-data separate from a digital asset
ActiveUS20060106884A1Easy retrievalImprove productivityDigital data protectionOffice automationDistributed Computing EnvironmentMetadata
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:MICRO FOCUS LLC
Distributed storage method and device, computer equipment and storage medium
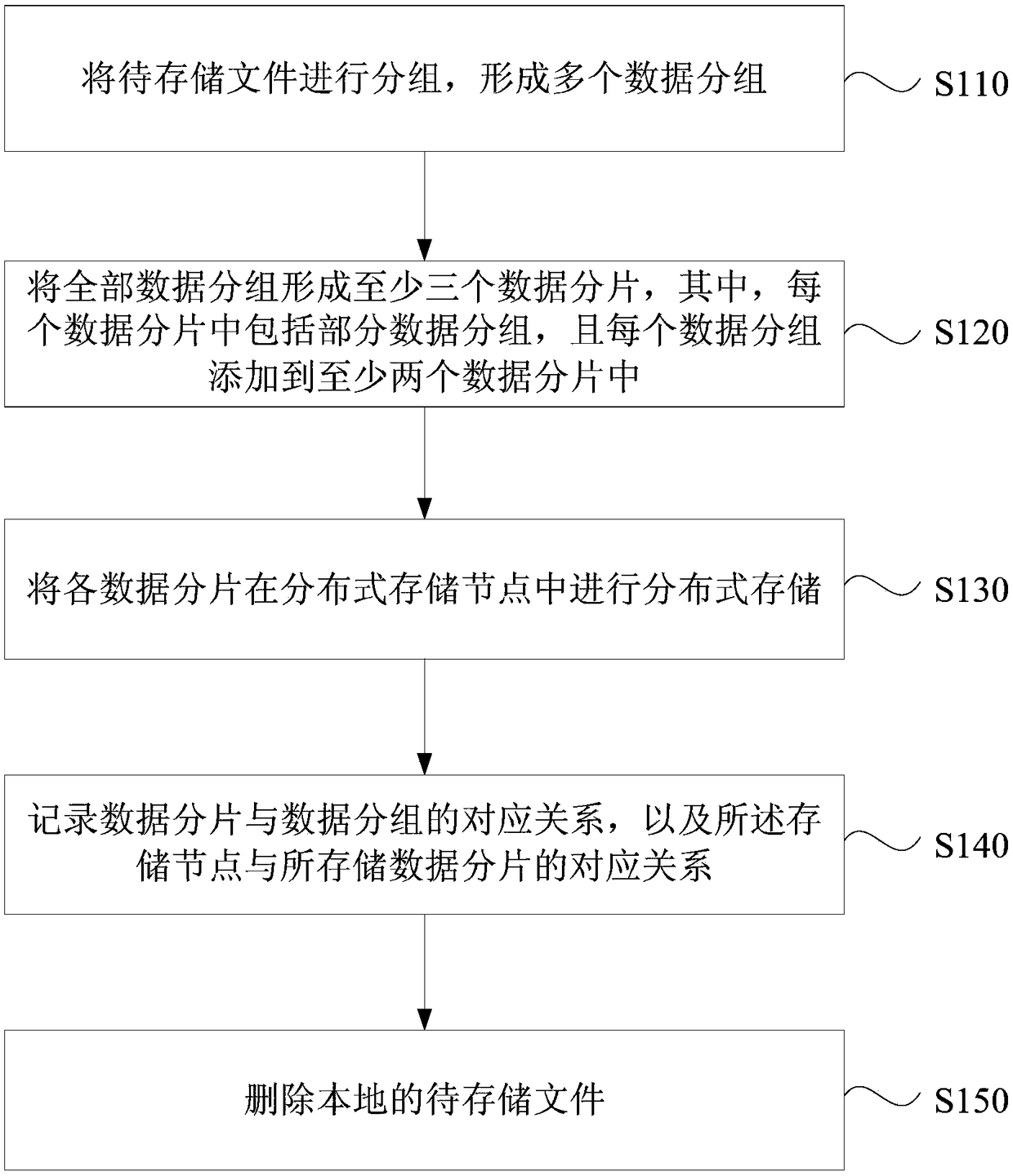
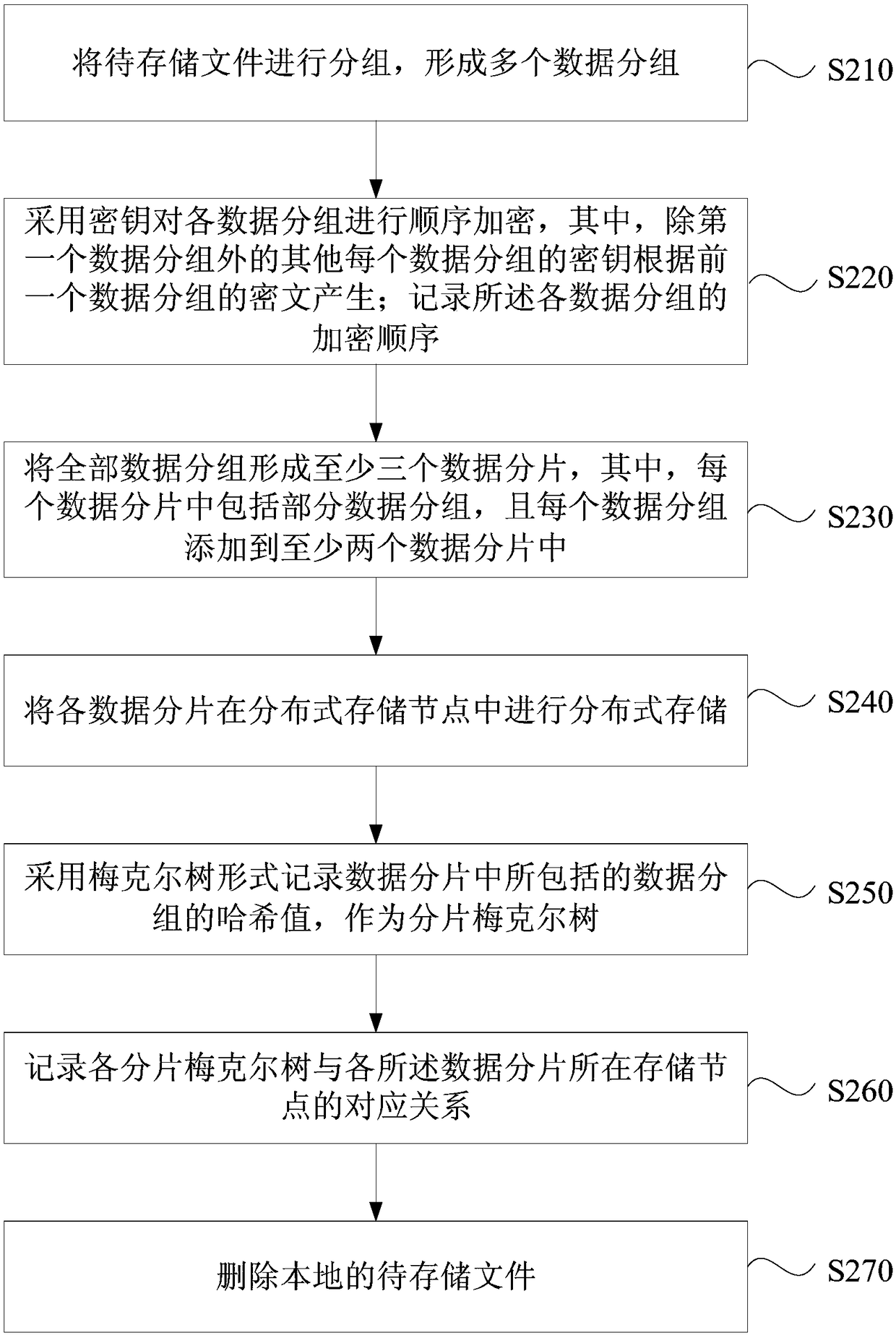
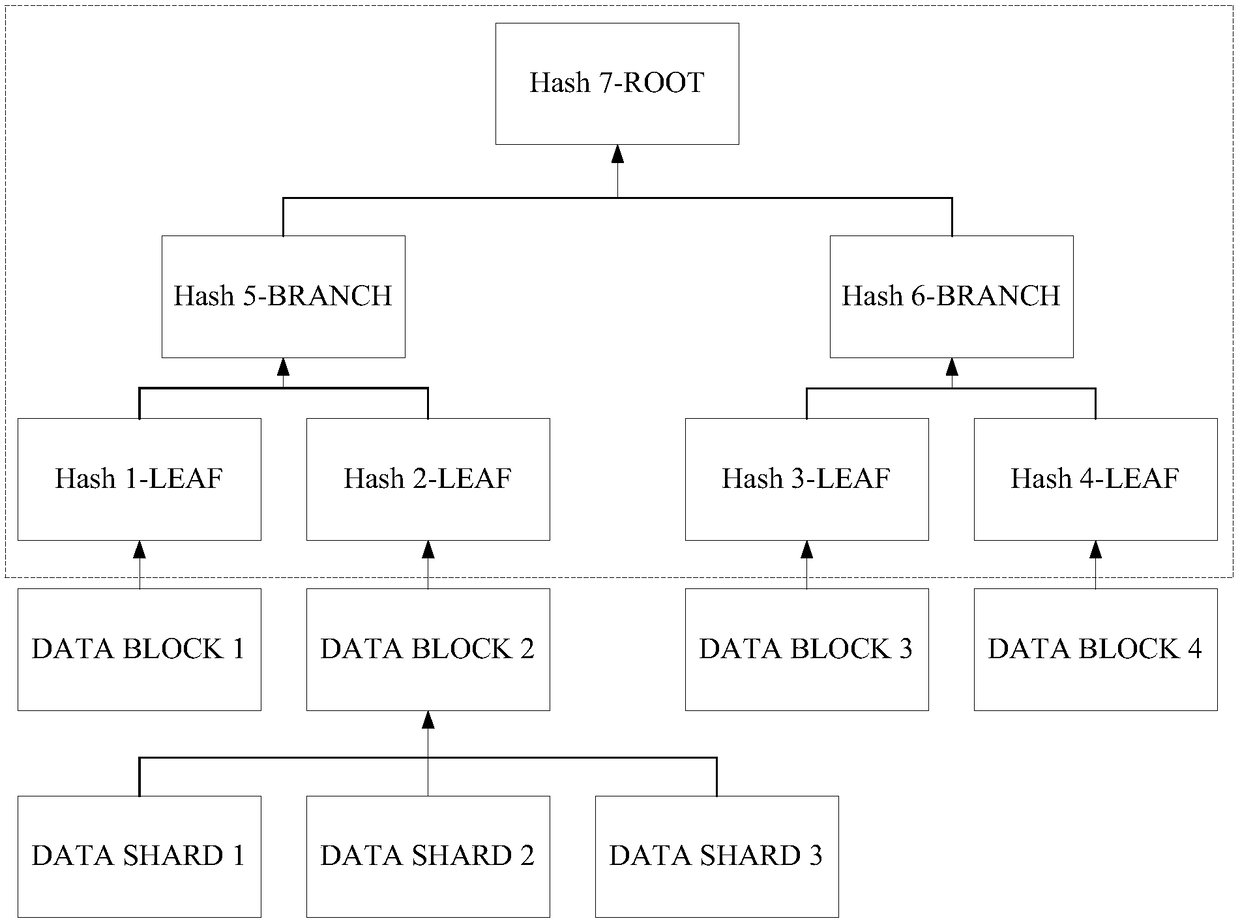
ActiveCN108664223AImprove privacyImprove securityInput/output to record carriersComputer security arrangementsComputer equipmentFile storage
The embodiment of the invention discloses a distributed storage method and device, computer equipment and a storage medium. The method comprises the steps of grouping a to-be-stored file to form multiple data groups; forming at least three data fragments from all the data groups, wherein each data fragment comprises part of data groups, and each data group is added to at least two data fragments;distributedly storing all the data fragments in distributed storage nodes; recording a corresponding relationship between the data fragments and the data groups, and a corresponding relationship between the storage nodes and the stored data fragments; deleting the local to-be-stored file. According to the technical scheme, a user conveniently stores files in a distributed network to lower the storage cost, the privacy and safety of the stored files can be effectively improved, and thus an attacker is prevented from restoring original files.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
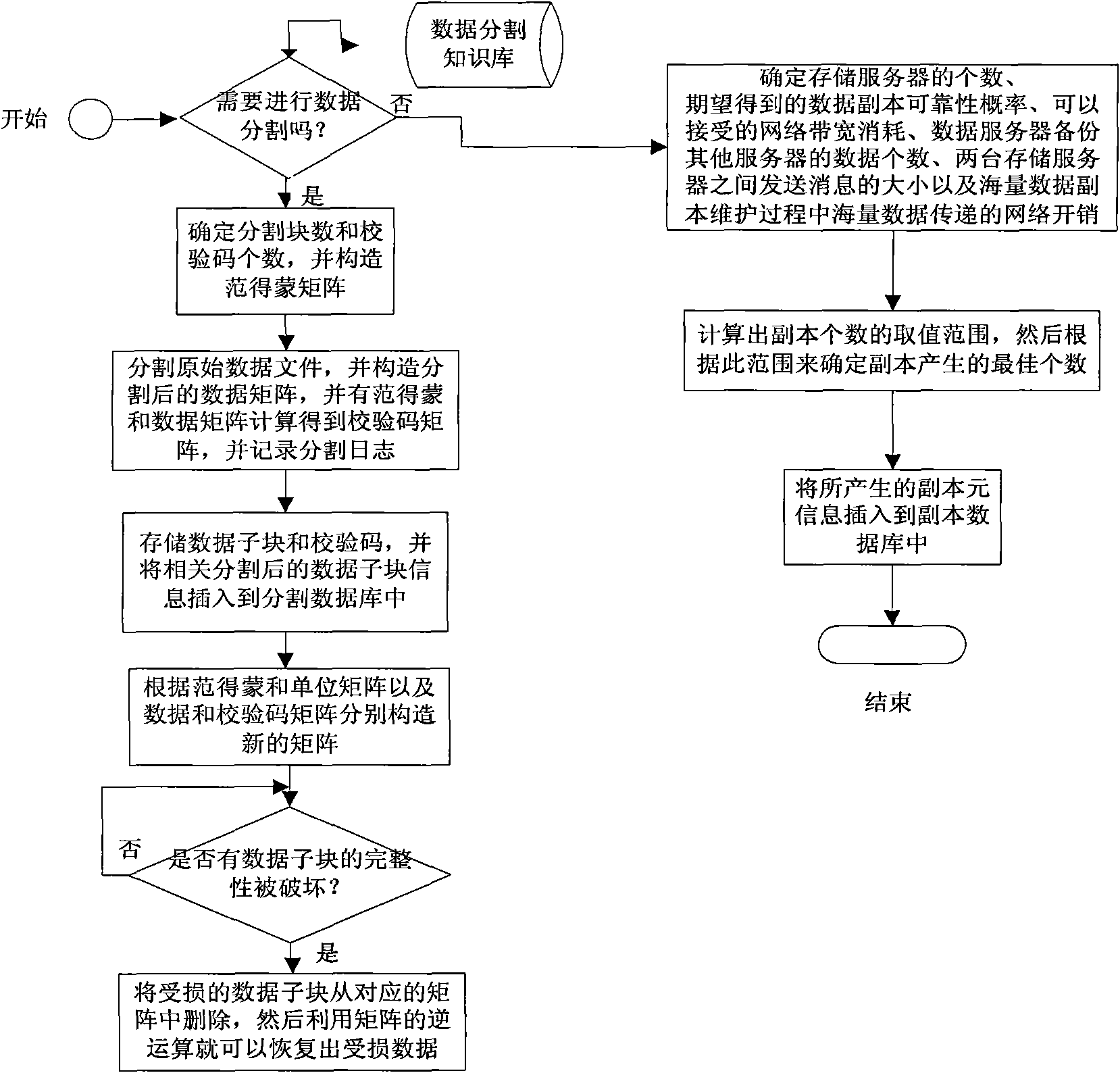
Data backup method based on Erasure coding and copying technology
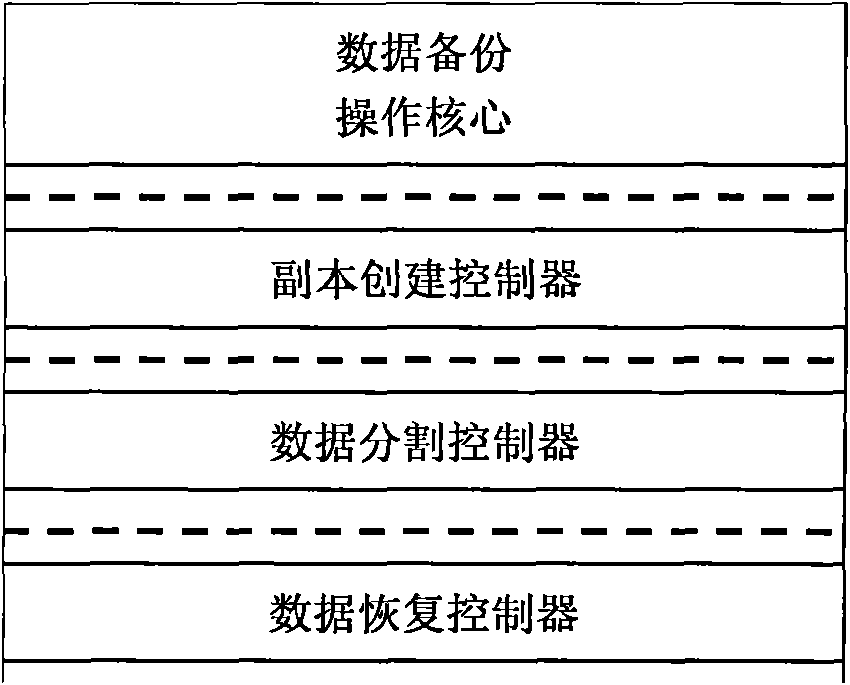
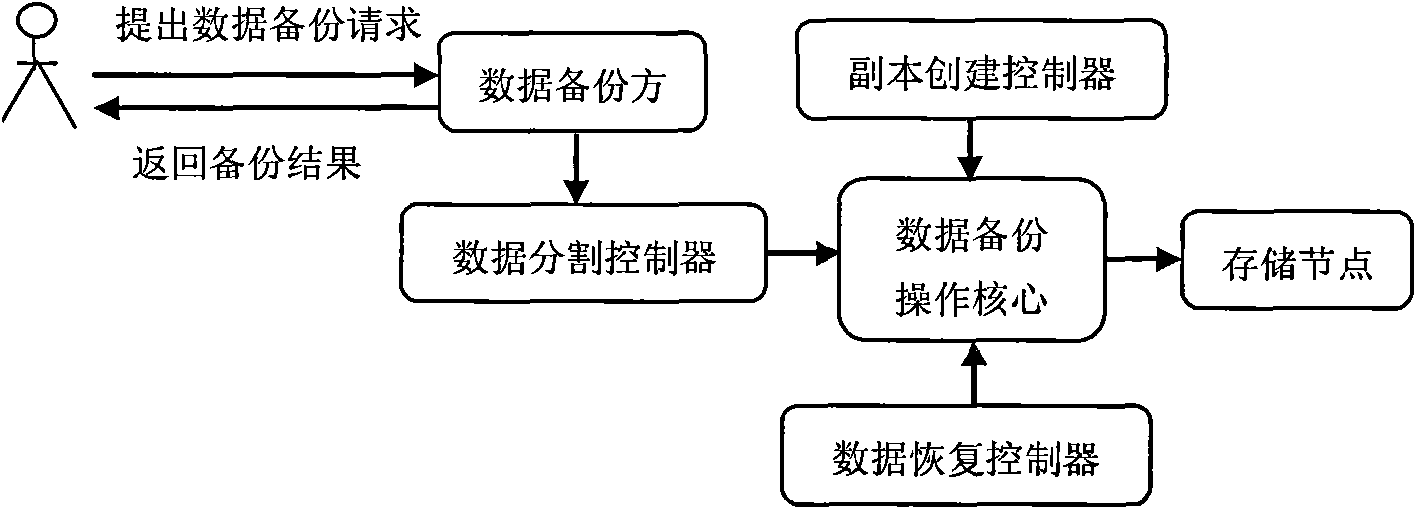
ActiveCN101630282AAvoid recoveryGuaranteed continuityRedundant operation error correctionSpecial data processing applicationsData capacityOriginal data
The invention discloses a data backup method based on an Erasure coding and copying technology. When data to be stored exceed the maximum capacity of a storage source, the data are stored in a distributed way after being divided so as to improve the storage efficiency. Meanwhile, check codes of divided data subblocks are calculated and stored, and the damaged data subblocks are restored by utilizing an Erasure code under the condition that partial data subblocks are damaged, thereby ensuring the integrality of original data. The original data are backed up by a copying method, and meanwhile, the amount of generated data copies is confirmed according to parameters such as the amount of storage servers, and the like. Finally, the metadata information of the generated data copies is stored in a copy database so that a user can restore the original data through inquiring the copy database and utilizing the data copies when a data disaster happens. a data dividing and copy creating technology is used for better solving the problem of data backup in a data capacity disaster, thereby not only improving the storage efficiency of the data, but also ensuring the integrality of the data.
Owner:STATE GRID ELECTRIC POWER RES INST +1
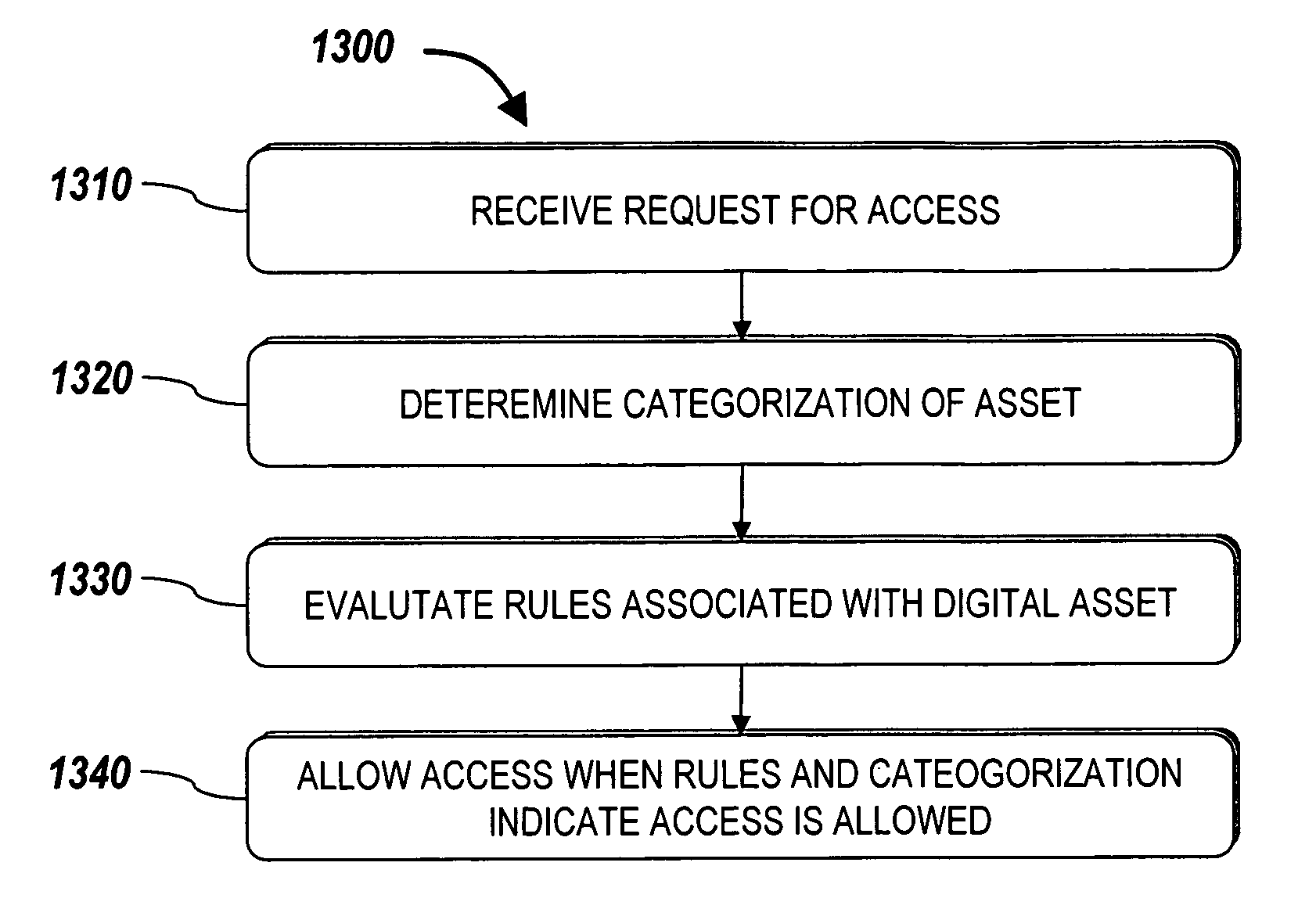
Systems and methods for providing categorization based authorization of digital assets
InactiveUS20060106811A1Easy retrievalImprove productivityDigital data protectionOffice automationDistributed Computing EnvironmentAuthorization
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:AUTONOMY CORPORATION
Systems and methods for expiring digital assets using encryption key
InactiveUS20060106812A1Easy retrievalImprove productivityDigital data protectionOffice automationDistributed Computing EnvironmentEncryption
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:IRON MOUNTAIN INCORPORATED
Systems and methods for freezing the state of digital assets for litigation purposes
InactiveUS20060106834A1Simple retrievalIncrease productivityDigital data processing detailsOffice automationDigital assetMetadata
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:MICRO FOCUS LLC
Systems and methods for propagating categorization information with a digital asset
InactiveUS20060106813A1Easy retrievalImprove productivityDigital data protectionOffice automationDistributed Computing EnvironmentMetadata
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:IRON MOUNTAIN INCORPORATED
Systems and methods for dynamically adjusting a taxonomy used to categorize digital assets
InactiveUS20060106862A1Easy retrievalImprove productivityDigital data processing detailsDigital data protectionDistributed Computing EnvironmentMetadata
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:IRON MOUNTAIN INCORPORATED
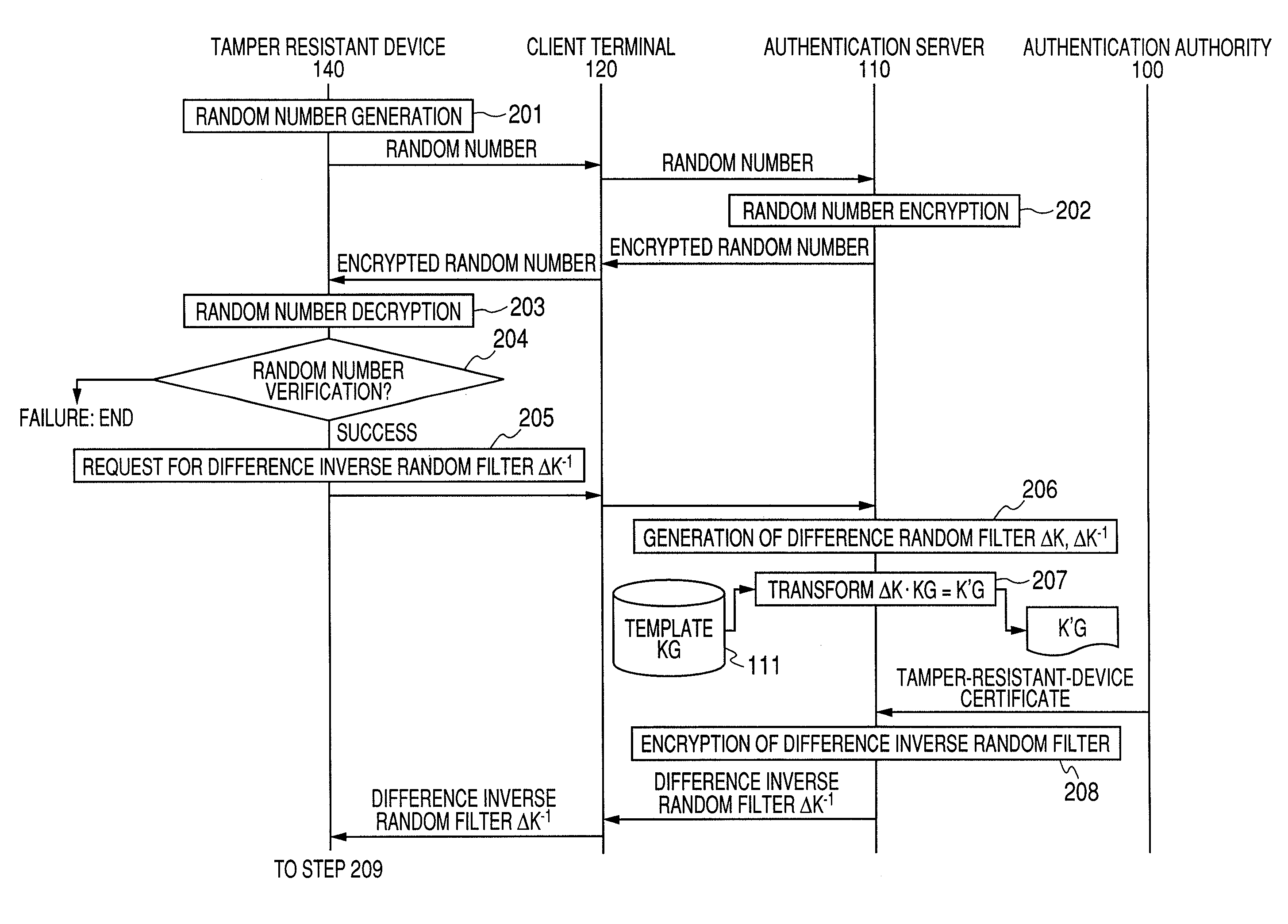
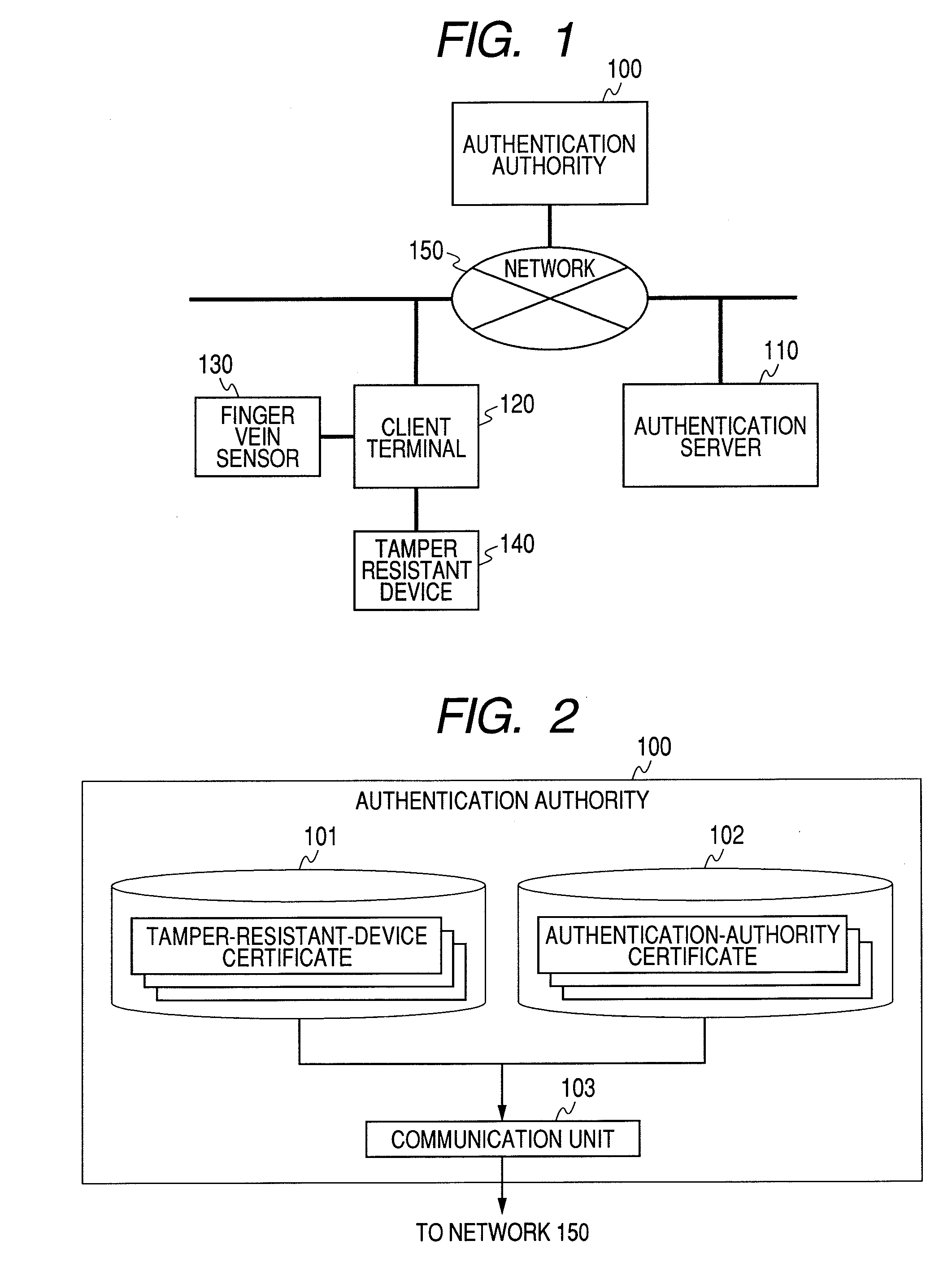
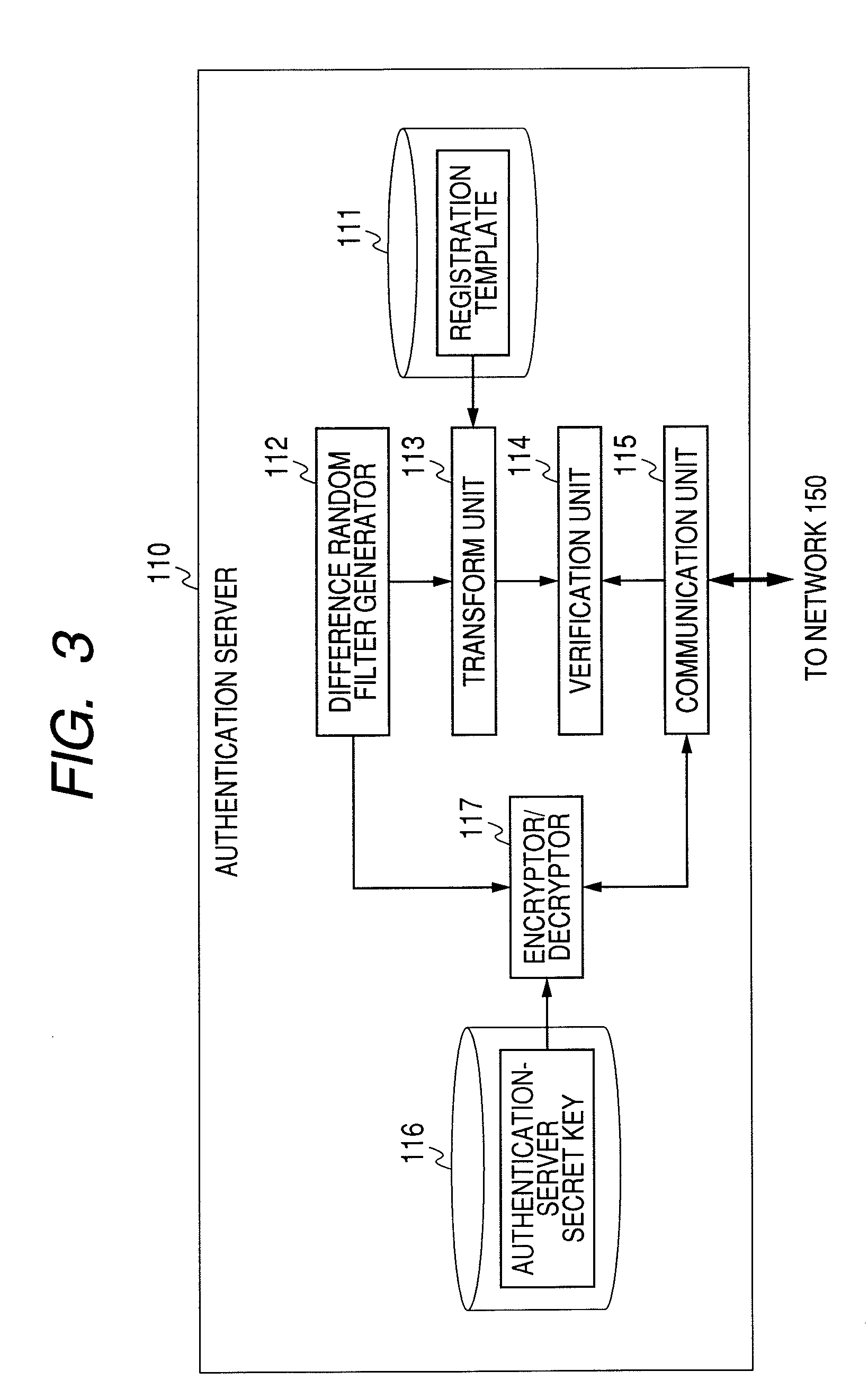
System, Server, Terminal and Tamper Resistant Device for Authenticating a User
InactiveUS20080178002A1Improve securityImprove protectionDigital data processing detailsUser identity/authority verificationTransformation parameterAuthentication server
The authentication server authenticated by a public key certificate at the time of authentication generates a difference parameter, transforms a template by the difference parameter to create a temporary registration template, and transmits the difference parameter to a tamper resistant device. The tamper resistant device generates a temporary parameter from the held transformation parameter and the difference parameter. A client terminal transforms feature using the temporary parameter, and generates temporarily-transformed feature. An authentication server receives the temporarily-transformed feature, and verifies whether the temporary registration template is in agreement with the temporarily-transformed feature.
Owner:HITACHI LTD
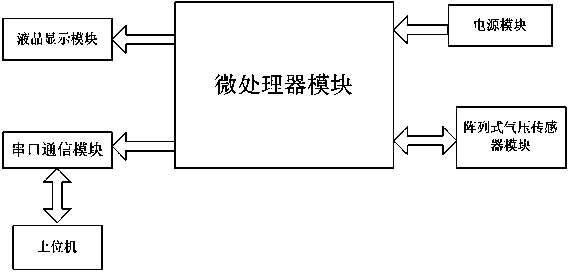
Relative height measuring device and method
ActiveCN103712599AEliminate measurement errorsReduce random errorHeight/levelling measurementNeural learning methodsMeasurement deviceLiquid-crystal display
The invention discloses a relative height measuring device which comprises a host computer, a microprocessor module, as well as an array type gas pressure sensor module, a power supply module, a liquid crystal display module and a serial port communication module which are respectively connected with the microprocessor module. A measuring method employing the relative height measuring device comprises the following steps: accomplishing a genetic algorithm optimized BP (Back Propagation) neural network in a host computer, transmitting obtained weights, thresholds and relative height calculation equations to the microprocessor module, acquiring gas pressure and temperature through the array type gas pressure sensor module and transmitting the gas pressure and temperature to the microprocessor module, processing the received air pressure and temperature through the microprocessor module so as to obtain the relative height, and transmitting the result to the liquid crystal display module to be displayed and stored in the host computer. With the combination of software and hardware, noise can be suppressed, useful signals can be recovered, enhanced and extracted, and the great precision and stability are achieved.
Owner:广东华工工程建设监理有限公司
Systems and methods for preventing digital asset restoration
InactiveUS20060106754A1Easy retrievalImprove productivityDigital data protectionOffice automationDistributed Computing EnvironmentMetadata
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:MICRO FOCUS LLC
Systems and methods for expiring digital assets based on an assigned expiration date
InactiveUS20060106883A1Easy retrievalImprove productivityDigital data protectionOffice automationExpiration dateDigital asset
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system.
Owner:MICRO FOCUS LLC
Outdoor water treatment apparatus to kill bacteria with ultraviolet light
ActiveUS8324595B2Suppress bacteria increaseEfficient killingScattering properties measurementsDead animal preservationUva lightUltraviolet lights
Bacteria in water 9 exposed outdoors are effectively killed with ultraviolet (UV) light by suppressing post-treatment increase in the bacteria population due to photoreactivation. The apparatus shines UV light on the water 9 to kill bacteria and has UV light emitting diodes (LEDs) 1 that emit UVA light with a primary emission peak of 320 nm-400 nm. The antibacterial action of the UVA light emitted by the UV LEDs 1 prevents proliferation of bacteria in the disinfected water 9 due to photoreactivation.
Owner:UNIVERSITY OF TOKUSHIMA
Virtual machine image management optimization method based on data de-duplication
InactiveCN103139300AAvoid duplicate transmissionImprove transmission efficiencyTransmissionSoftware simulation/interpretation/emulationFile systemThe Internet
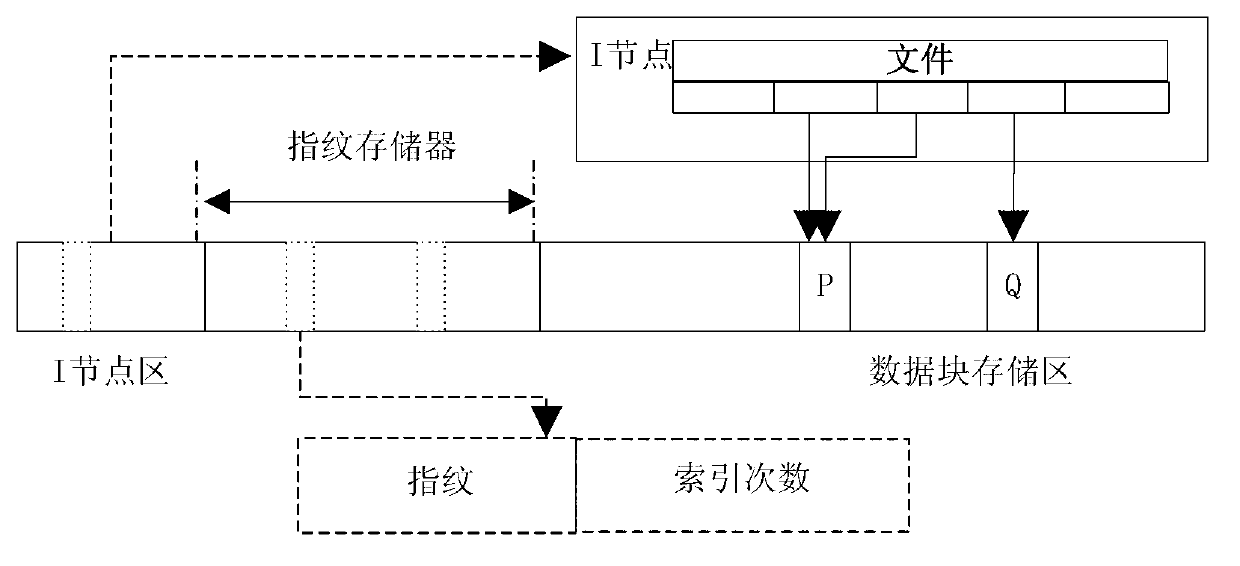
The invention discloses a virtual machine image management optimization method based on data de-duplication. The specific steps of the virtual machine image management optimization method based on the data de-duplication include that when a virtual machine image is uploaded, a fixed size partitioning method is adopted by a user end to divide an image file into a plurality of data blocks, the size of each data block is the same as the size of a cluster of a local file system, a mini disk (MD) 5 value of each data block is calculated, Socket programming technology is used, a finger print is sent to a server end, the server end searches the finger print and returns the result to the user end, whether the data blocks are sent is judged by the user end according to the result, and the network sources are saved; when the server end searches the finger print, by using a finger print filter and a finger print storage device, the memory usage amount and disk access amount are reduced; when the data are saved, the data blocks are directly stored in a complete cluster, the repetitive job of image renewing and segmentation is eliminated. The virtual machine image management optimization method based on the data de-duplication achieves a kernel mode file system of the online data de-duplication, reduces the disk storage amount and reduces internet consumption.
Owner:HANGZHOU DIANZI UNIV
Lattice-based cloud storage data safety auditing method supporting data proxy uploading
InactiveCN107124272AAvoid complex managementResist attackKey distribution for secure communicationUser identity/authority verificationCommunications securityOriginal data
The invention belongs to the technical field of information safety, and in particular relates to a lattice-based cloud storage data safety auditing method supporting data proxy uploading. The auditing method provided by the invention helps a data owner authorize a proxy signature generating data to a proxy signer and upload the proxy signature to a cloud server, and also helps a credible auditor to audit completeness of the cloud storage data. The auditing method provided by the invention achieves construction of a random mask code based on an original image sampling algorithm on the lattice, so that the credible auditor can be effectively prevented from recovering original data block information of an original signer from a data file. The credible auditor only needs to compute a linear combination with limited a computation amount instead of computing bilinear pairings with higher cost and modular exponentiation during a cloud storage data completeness verification process, so that the auditing method is very beneficial to the credible auditor in the aspect of computing efficiency. Meanwhile the method provided by the invention can effectively resist attacks of a quantum computer, and thus have very important application value in cloud computing environment of post-quantum communication security.
Owner:SOUTHWEST PETROLEUM UNIV
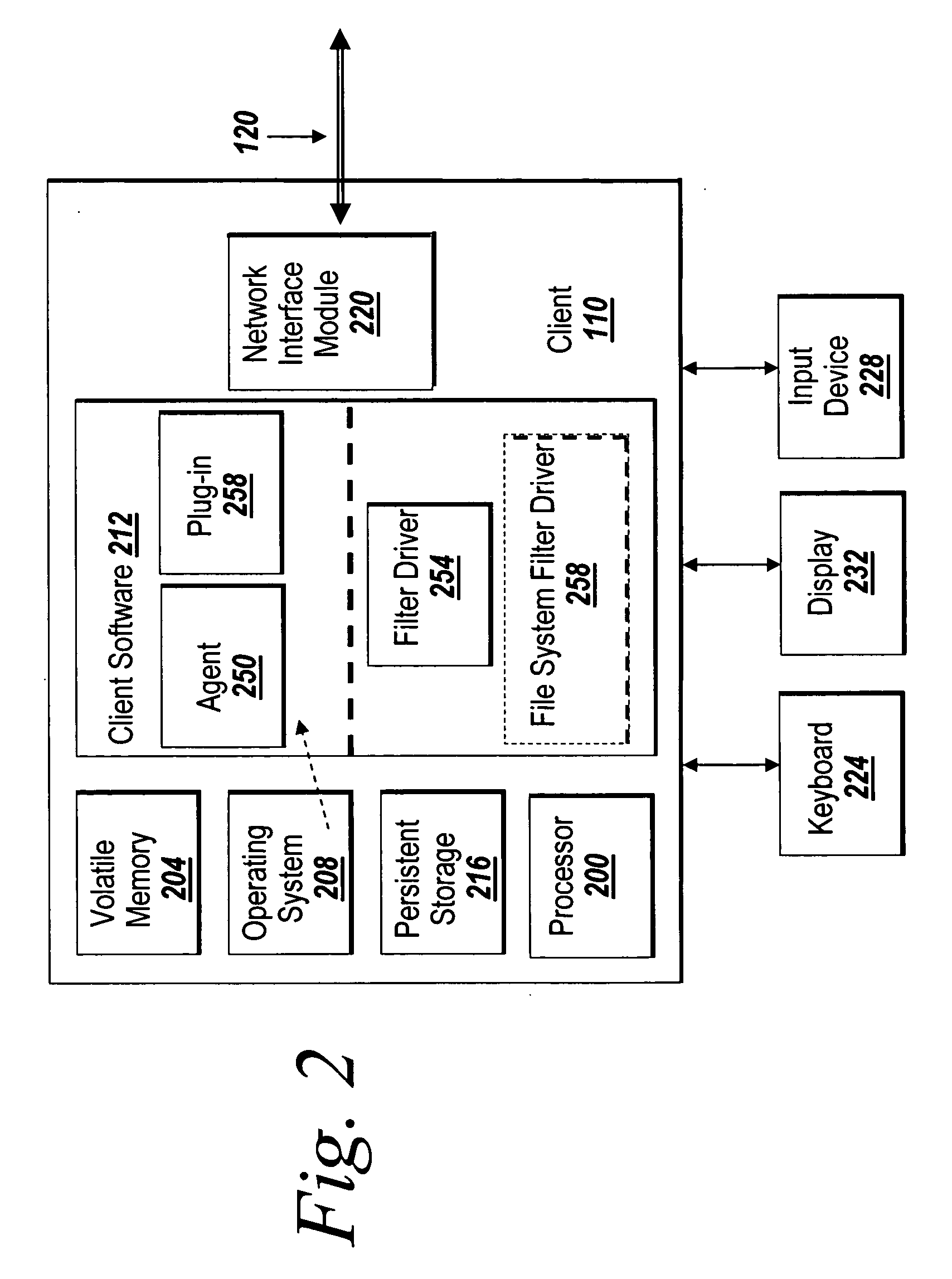
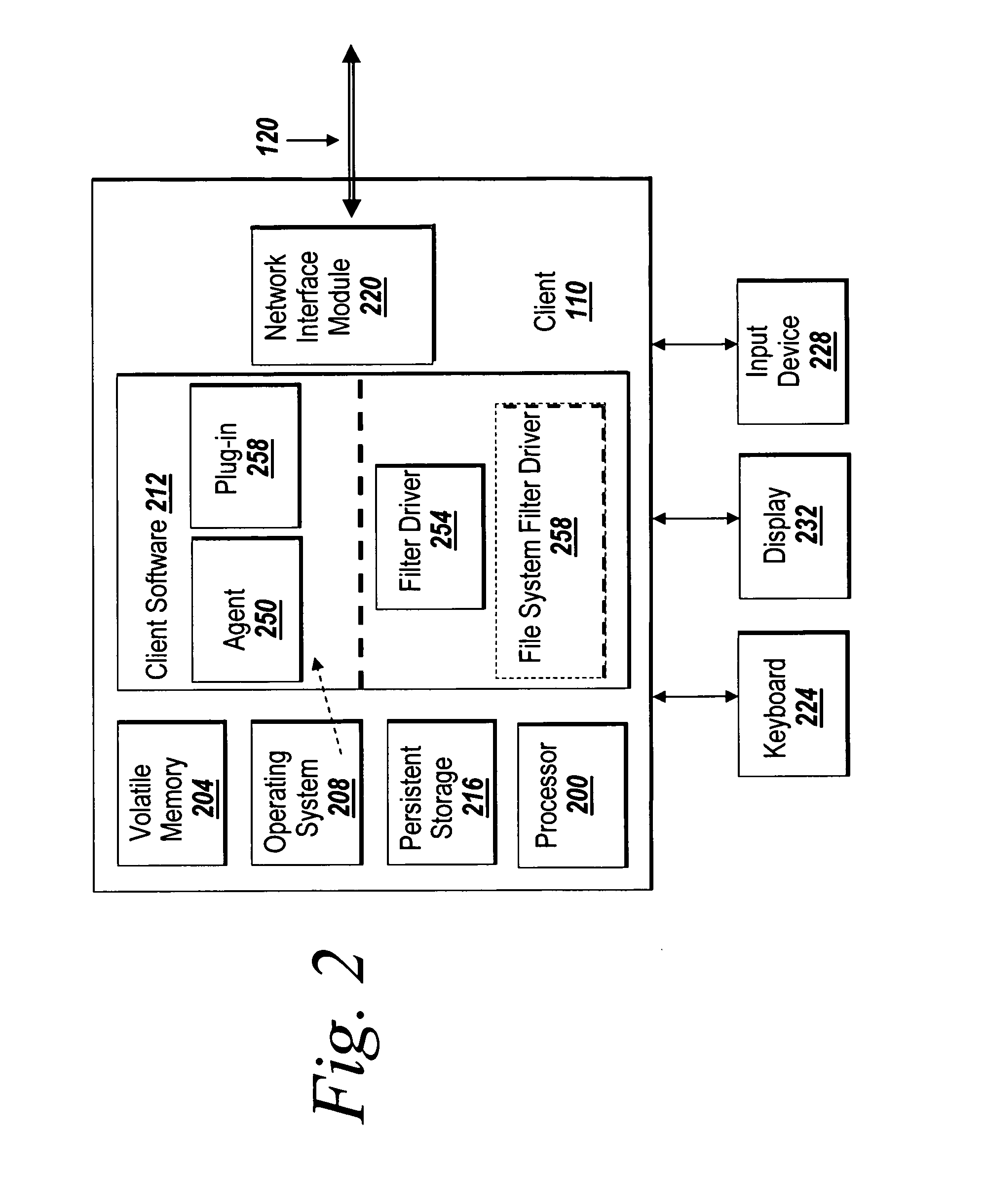
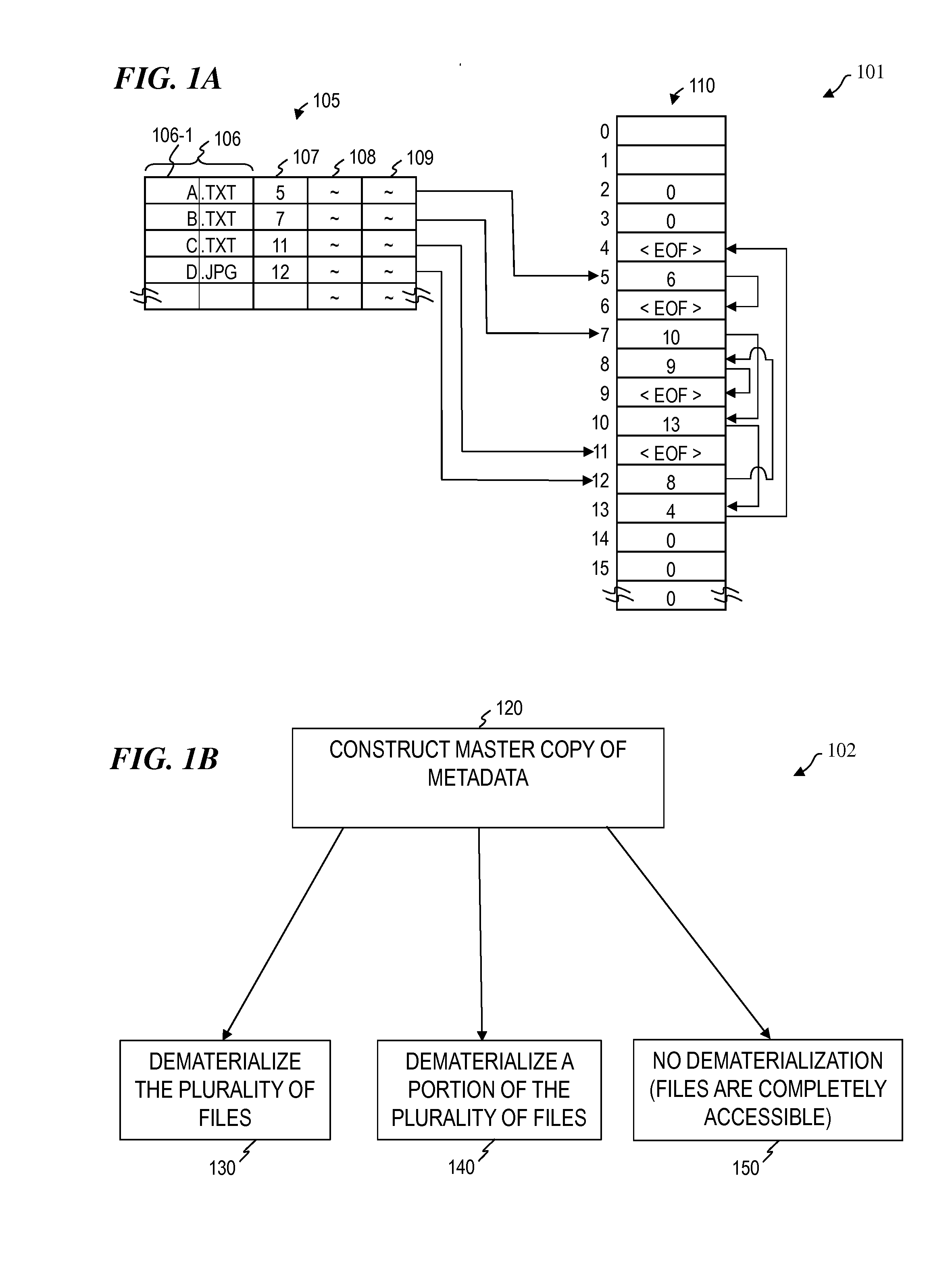
System and method for metadata modification
ActiveUS20140279950A1Easy to removeAvoid recoveryDigital data processing detailsFile/folder operationsOperational systemMetadata
The present invention provides a method for modifying a first storage medium having a plurality of files, the method including providing a first modification tool; operatively coupling the first storage medium to the modification tool, wherein the operatively coupling includes bypassing a first operating system used to access the plurality of files; and dematerializing, using the first modification tool, at least a first file to form one or more dematerialized files. In some embodiments, the present invention provides a modification system for modifying a first storage medium having a plurality of files, the system including a first modification tool that includes an attachment module configured to operatively couple the modification tool to the first storage medium such that a first operating system used to access the plurality of files is bypassed; and a dematerialization module configured to dematerialize at least a first file to form one or more dematerialized files.
Owner:SHAPIRO ALAN JOSHUA
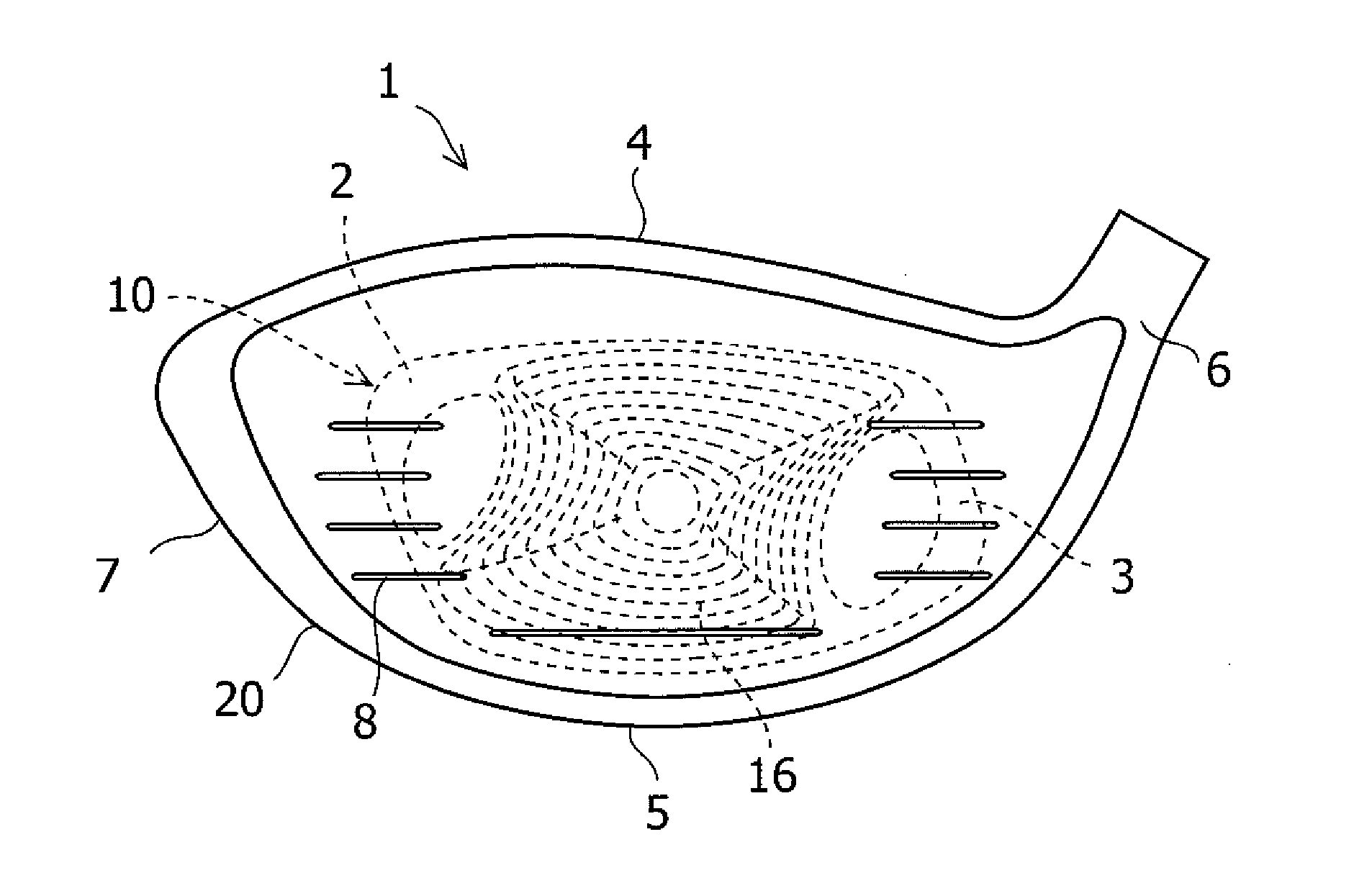
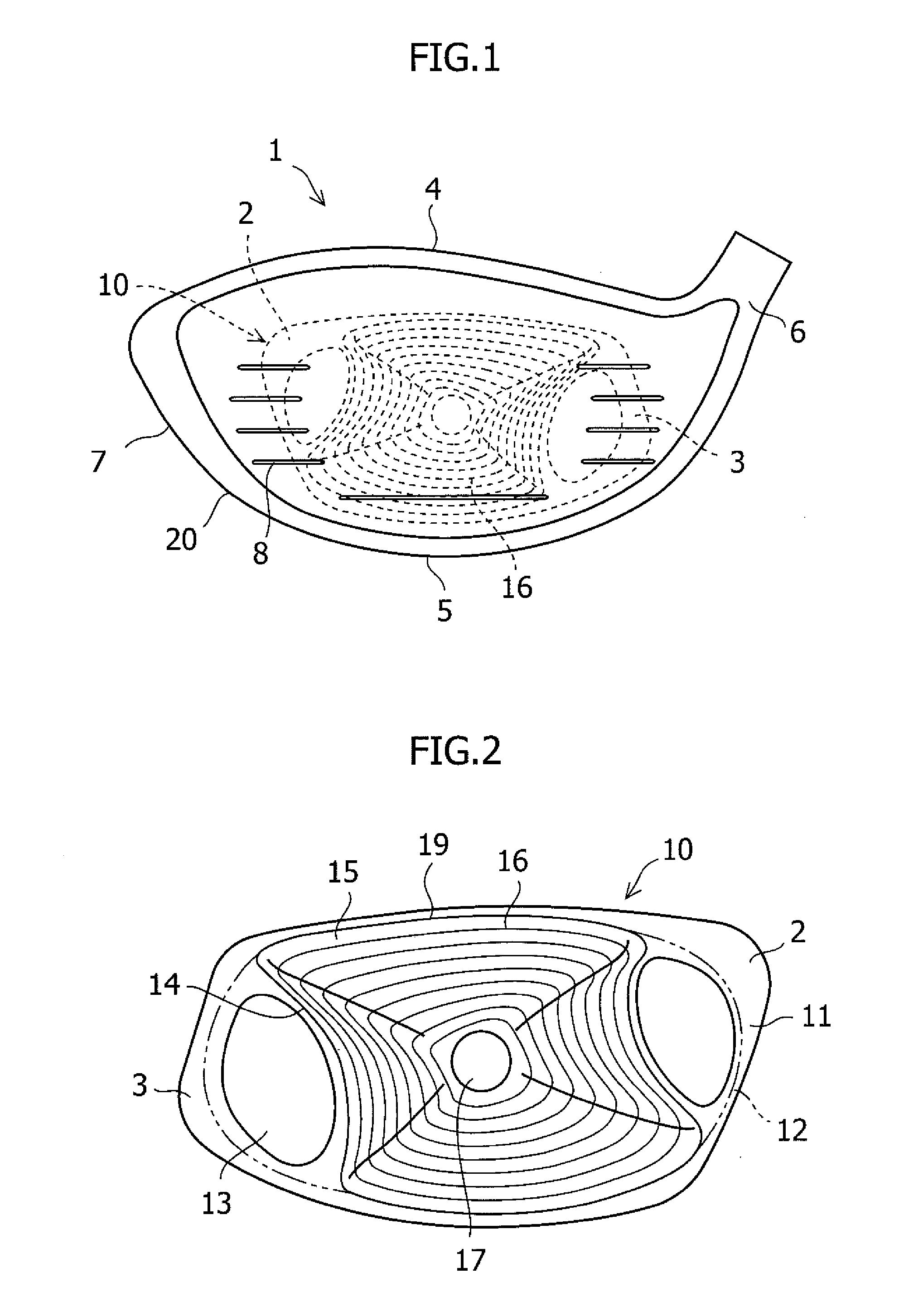
Golf club head
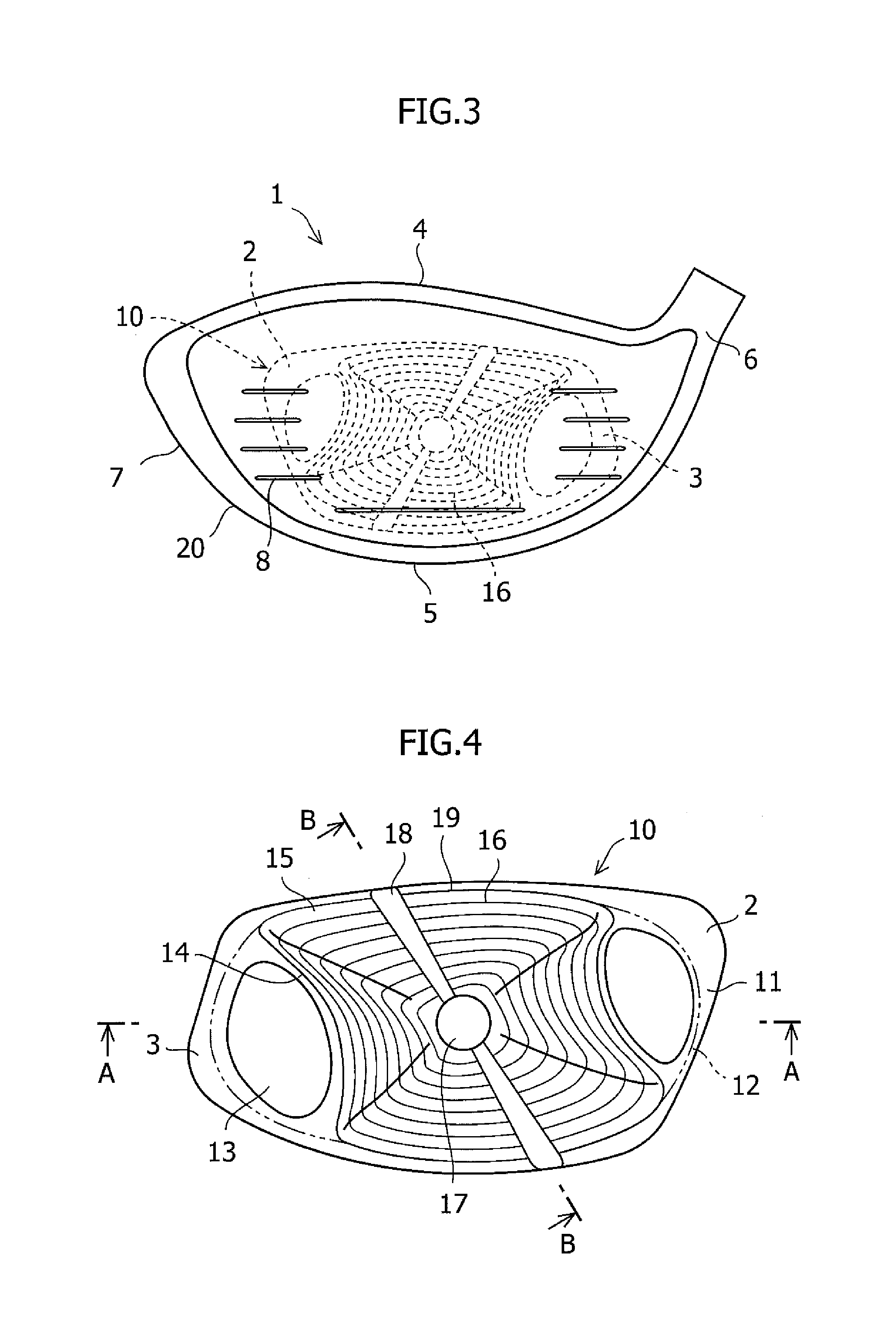
InactiveUS20110159987A1Maintaining light weightAvoid recoveryGolf clubsRacket sportsEllipseArcuate shape
A hollow golf club head has a head body having a face aperture part and a face member held to the face aperture part by welding, the face member formed by forging a rolled material of a titanium alloy having an α phase, and the face member comprising a thick-material part positioned in the center of the face member, an outer peripheral part positioned at the periphery of the thick-material part, and a thin-material part partially positioned between the thick-material part and the outer peripheral part. The thick-material part is formed in an area having a shape obtained by depressing a substantially elliptical or substantially circular shape in a substantially arcuate shape toward the center of the ellipse at two opposite sides thereof. The thick-material part, the thin-material part, and the peripheral part are formed by the forging so as to destroy an orientation of the α-phase.
Owner:BRIDGESTONE SPORTS
Dry-cleaning machine
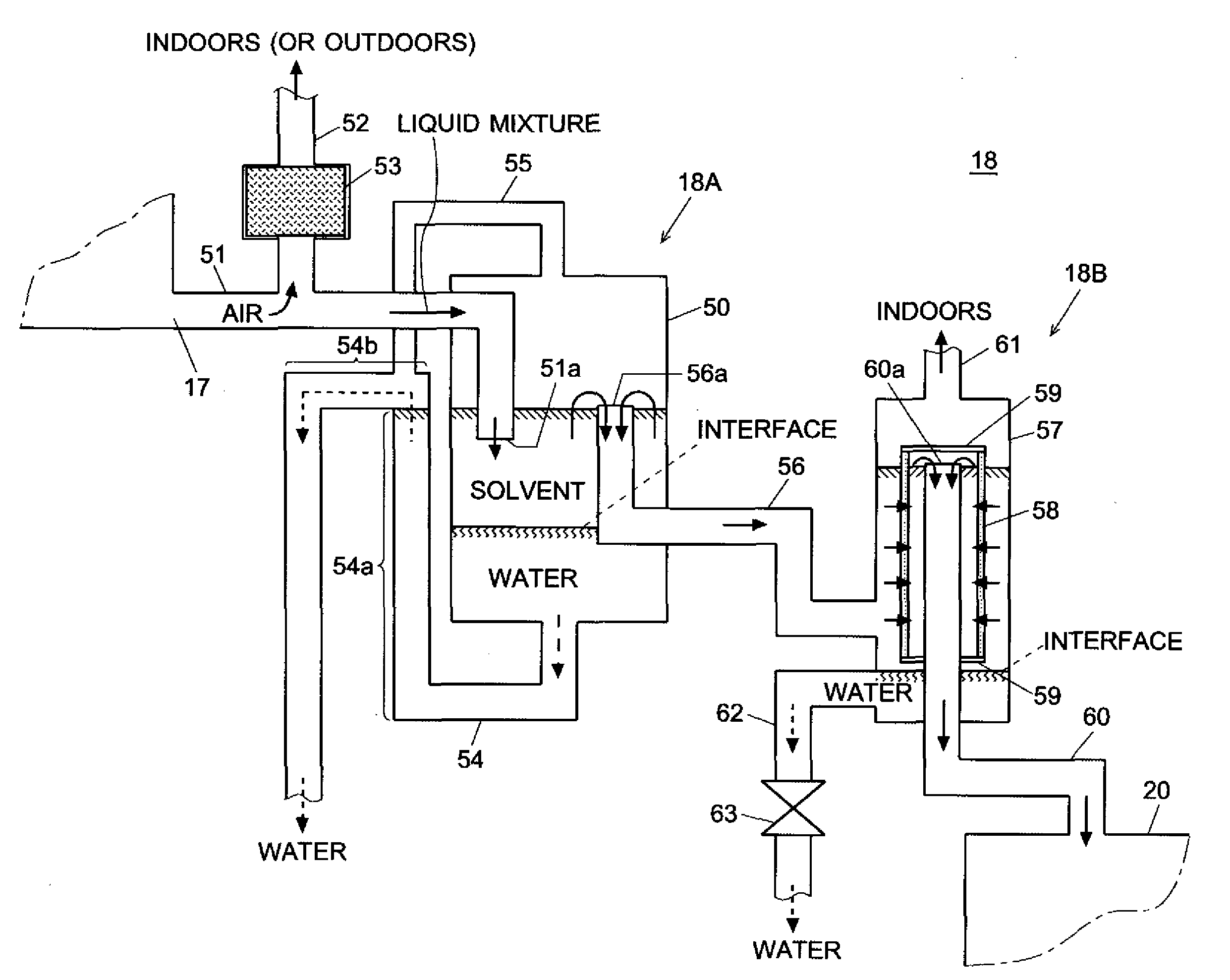
ActiveUS20090049872A1Efficiently recoverEasily separateDry-cleaning apparatusTextiles and paperVertical motionSolvent
A vaporized solvent emitted from the laundry in the drum during the drying process is condensed within an air passage. From this passage a liquid mixture (solvent and water) is guided to a first liquid storage tank 50 through a liquid mixture line 51. An air relief pipe 52 is connected to an intermediate point of this line so that air coming from the air passage is released through an activated carbon filter 53 to the outside. The outlet end 51a of the liquid mixture line 51 is immersed in the solvent in the upper layer within the first liquid storage tank 50. Due to the hydraulic pressure acting on the outlet end 51a, the air tends to flow toward the air relief pipe 5. This reduces the current pressure of the air coming from the air passage and alleviates its influence within the first liquid storage tank 50, so that a vertical motion of the interface between the solvent and water due to the current pressure is suppressed. Thus, unwanted matter gathering around the interface is prevented from sticking to a filter, and the solvent is prevented from being discharged.
Owner:QINGDAO HAIER WASHING MASCH CO LTD +1
Fuel cell system and water recovery method thereof
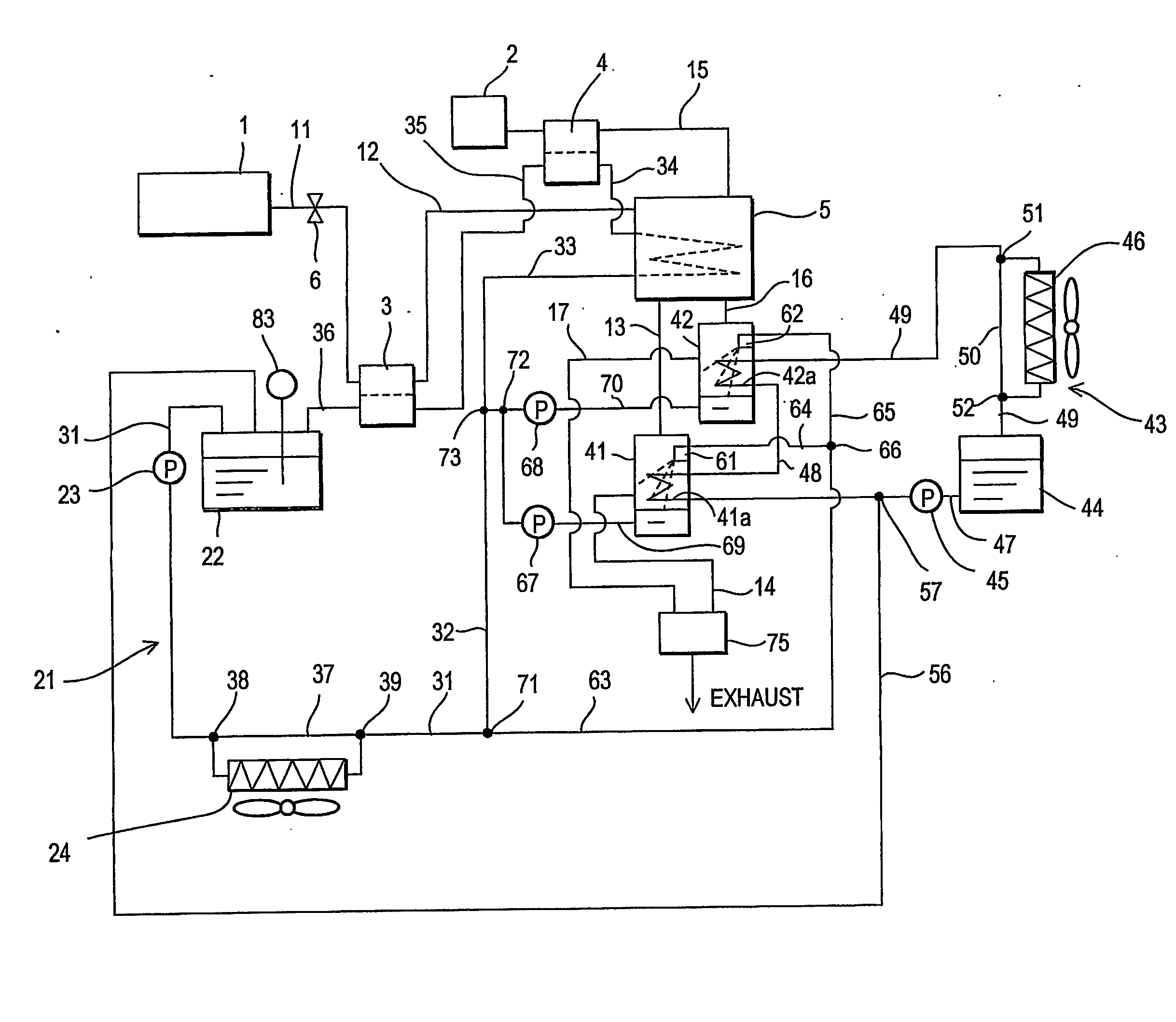
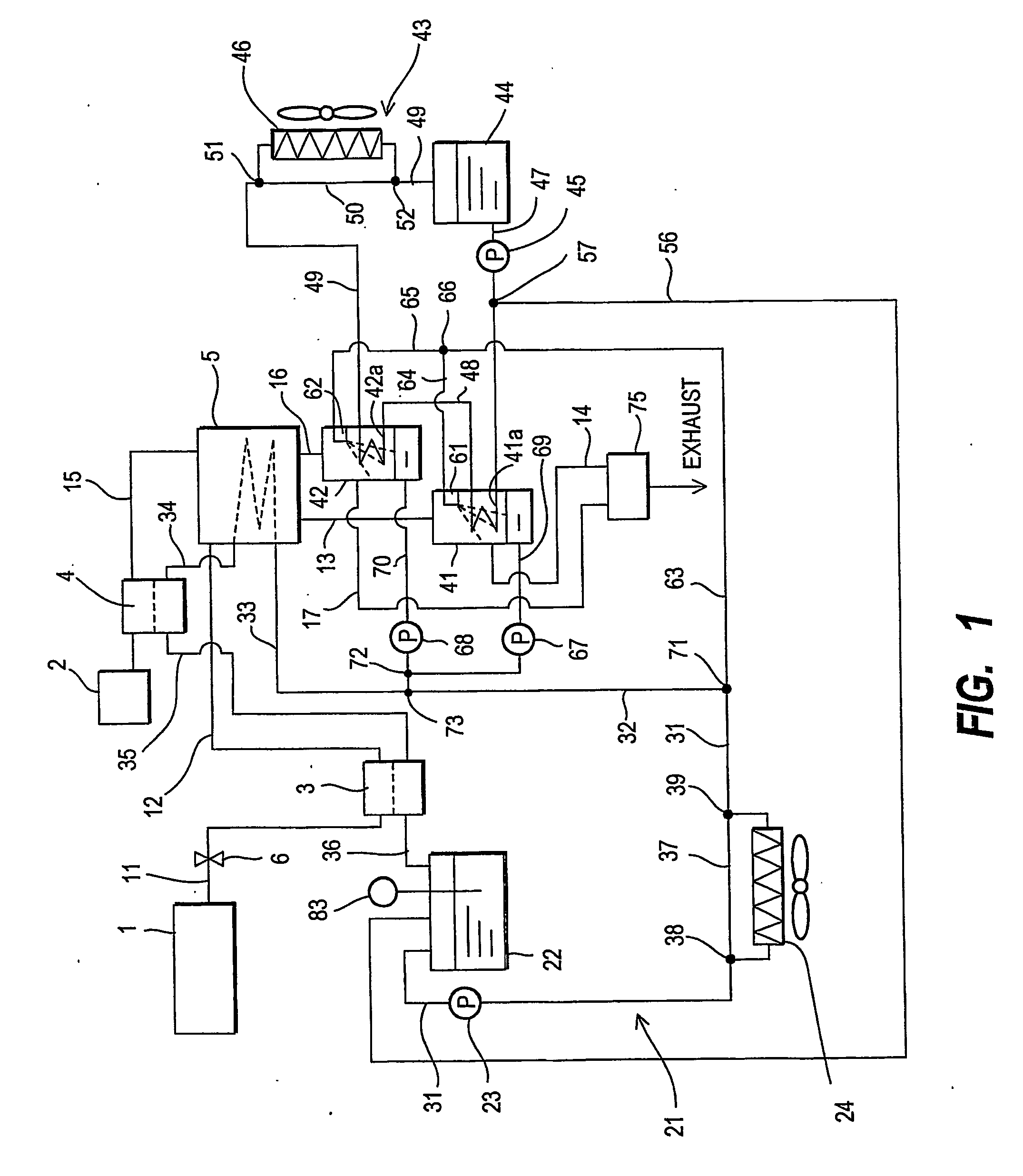
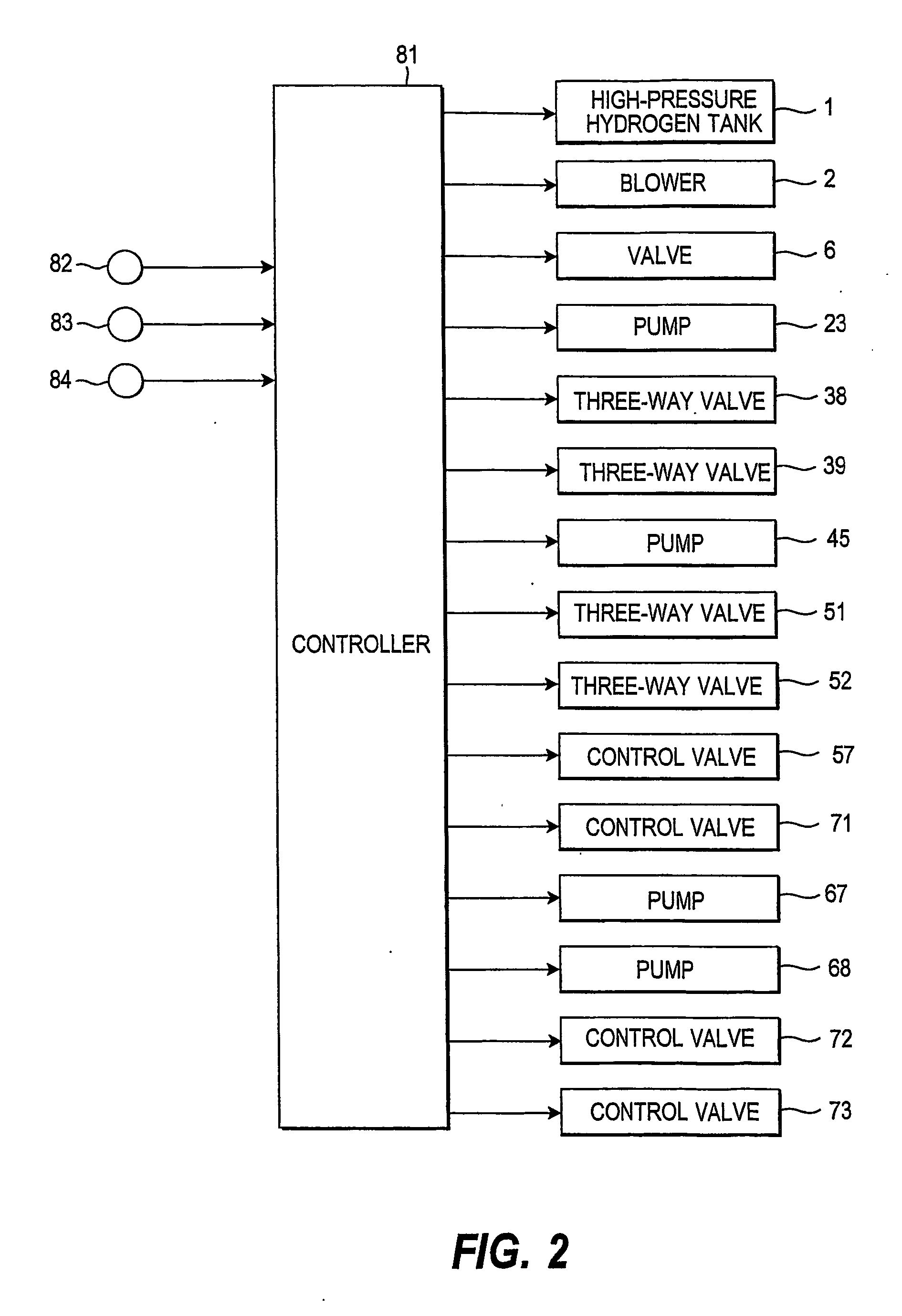
InactiveUS20070134526A1Avoid recoveryFuel cell heat exchangeSolid electrolyte fuel cellsExhaust gasAutomotive engineering
A fuel cell system comprises a fuel gas supply mechanism (1, 91-97) which supplies a fuel gas, an oxidizing gas supply mechanism (2) which supplies an oxidizing gas, a fuel cell (5) which generates power using the fuel gas supplied from the fuel gas supply mechanism (1, 91-97) and the oxidizing gas supplied from the oxidizing gas supply mechanism (2), and a water recovery device (41, 42) which separates and recovers water contained in exhaust gas from the fuel cell (5), and mixes the recovered water with a water-compatible liquid in the location where the water is separated and recovered.
Owner:NISSAN MOTOR CO LTD
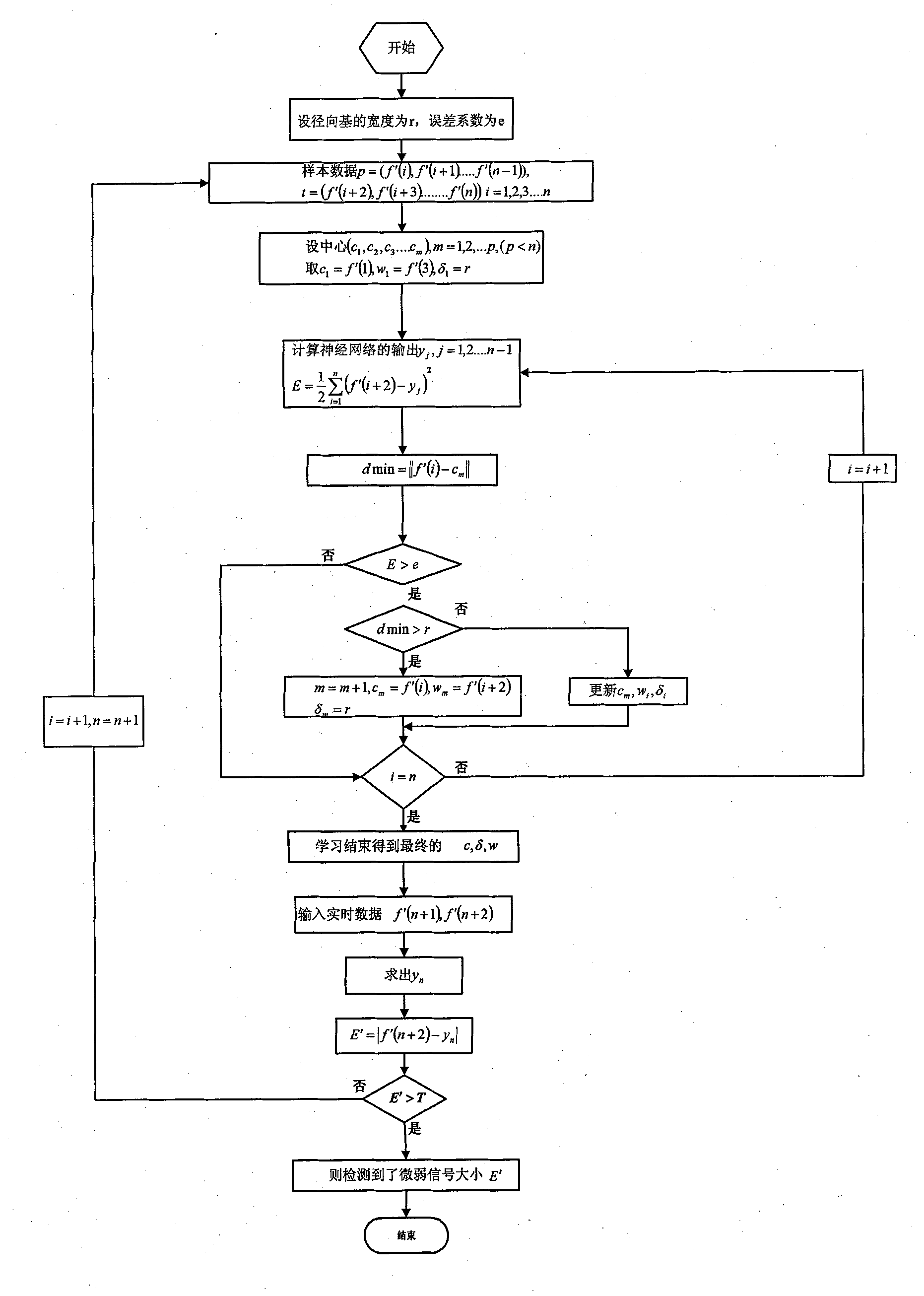
Weak signal detection device and method based on wavelets and RBF neural network
InactiveCN101943324ASuppress noiseAvoid recoveryPipeline systemsLow-pass filterSynchronous dynamic random-access memory
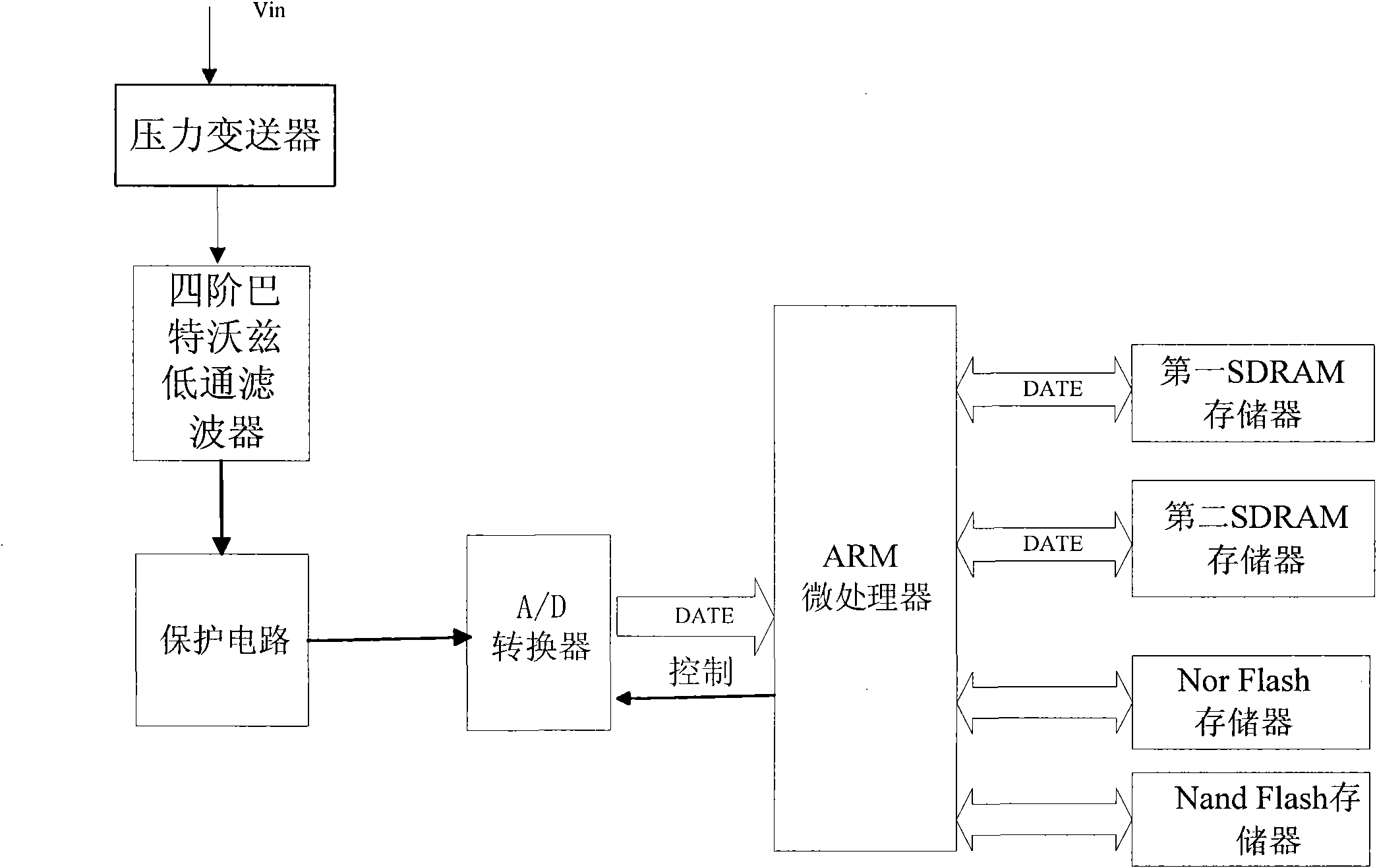
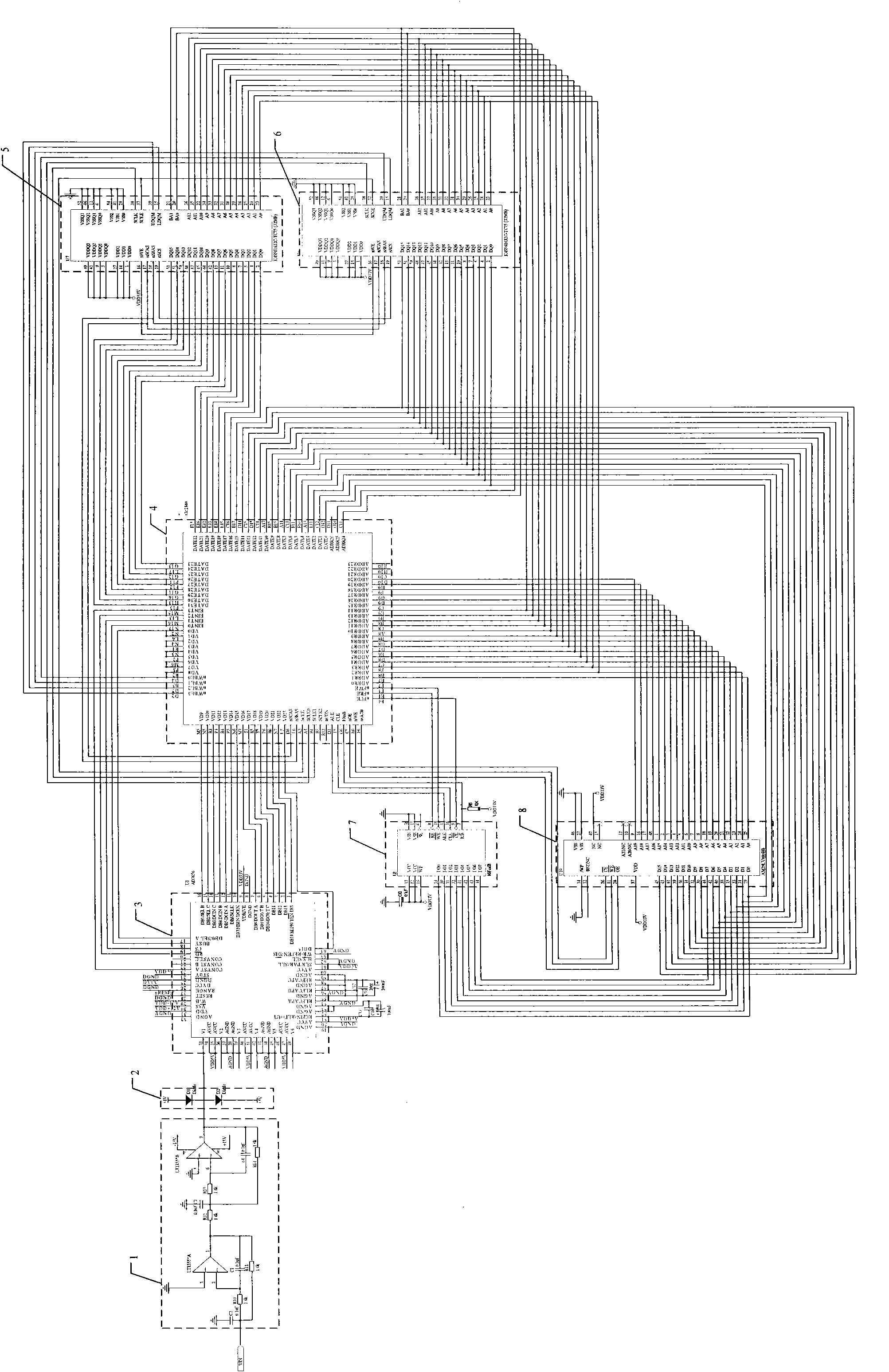
A weak signal detection device and method based on wavelets and a radial basis function (RBF) neural network belong to the technical field of signal detection. The device comprises a fourth-order Butterworth low pass filter, an A / D converter, an ARM microprocessor, a synchronous dynamic random access memory (SDRAM), a Nor Flash memory and a Nand Flash memory. The device is beneficial to inhibiting noises and restoring, enhancing and extracting useful signals. The method can realize detection of a few oil leakage accidents which can not be detected by the conventional leakage detection devices and detect fluctuation less than 3%.
Owner:NORTHEASTERN UNIV
Apparatus and method for processing partitioned data for securing content
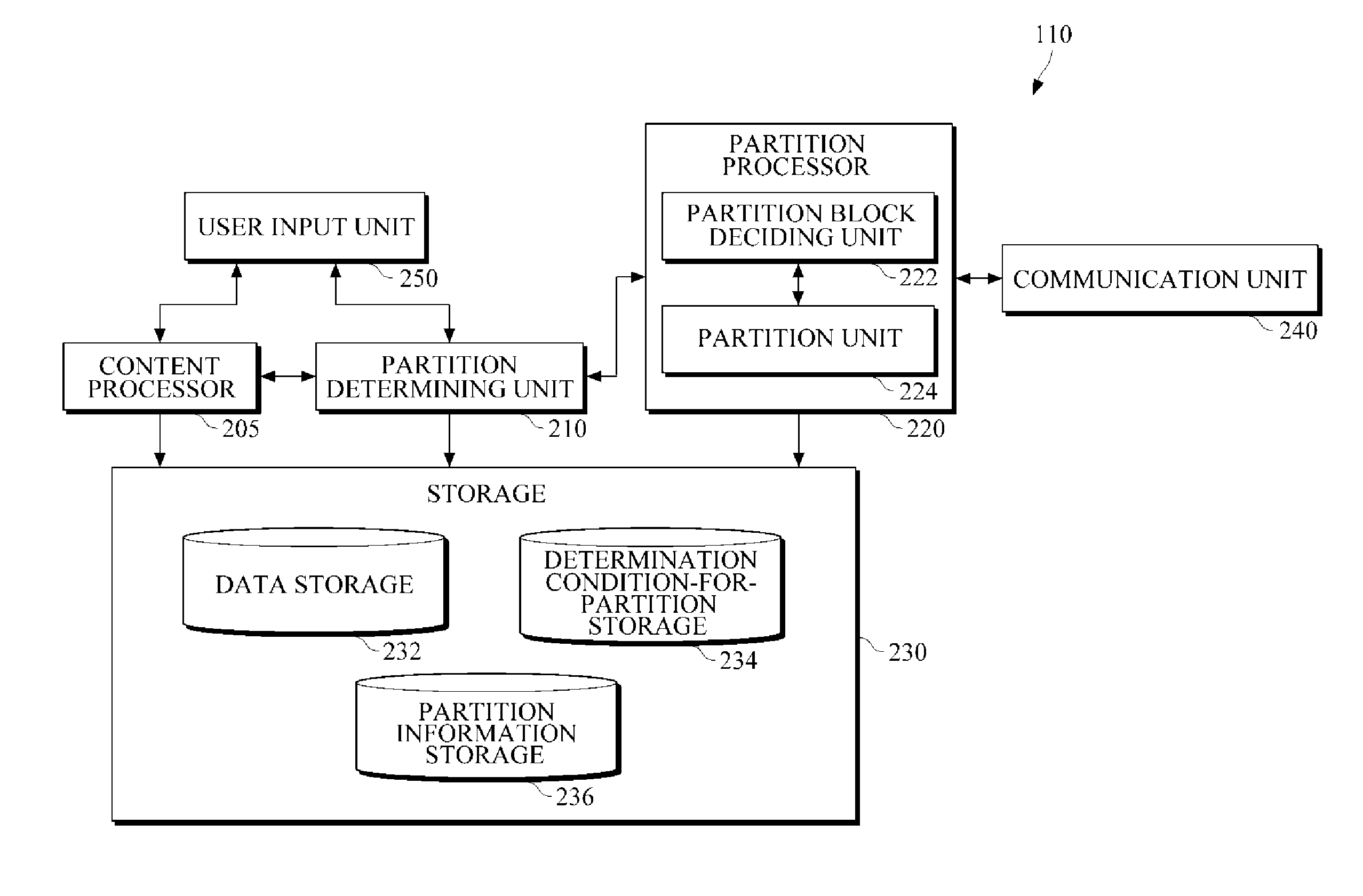
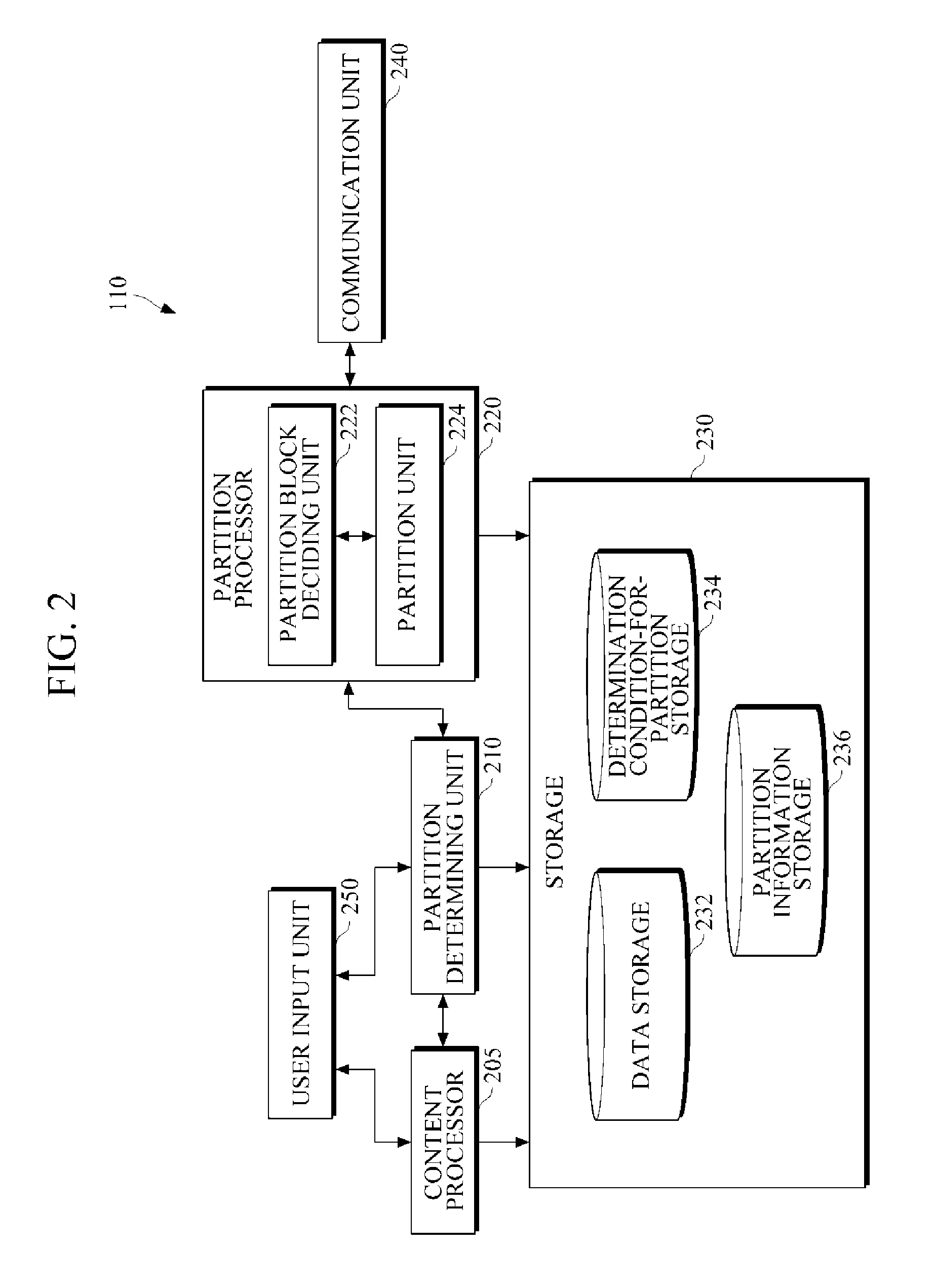
InactiveUS20130054611A1Avoid recoveryImprove network securityDigital data information retrievalDigital data processing detailsCommunication unitData file
An apparatus to process partitioned data includes a storage unit to store a first data portion of a data file; a communication unit to receive a second data portion of the data file from a device in response to an authentication between the apparatus and the device; and a recovery processing unit to obtain the data file, by merging the first data portion and the second data portion of the data file using partition information.
Owner:PANTECH CO LTD
Compositions and methods for the rapid growth and detection of microorganisms
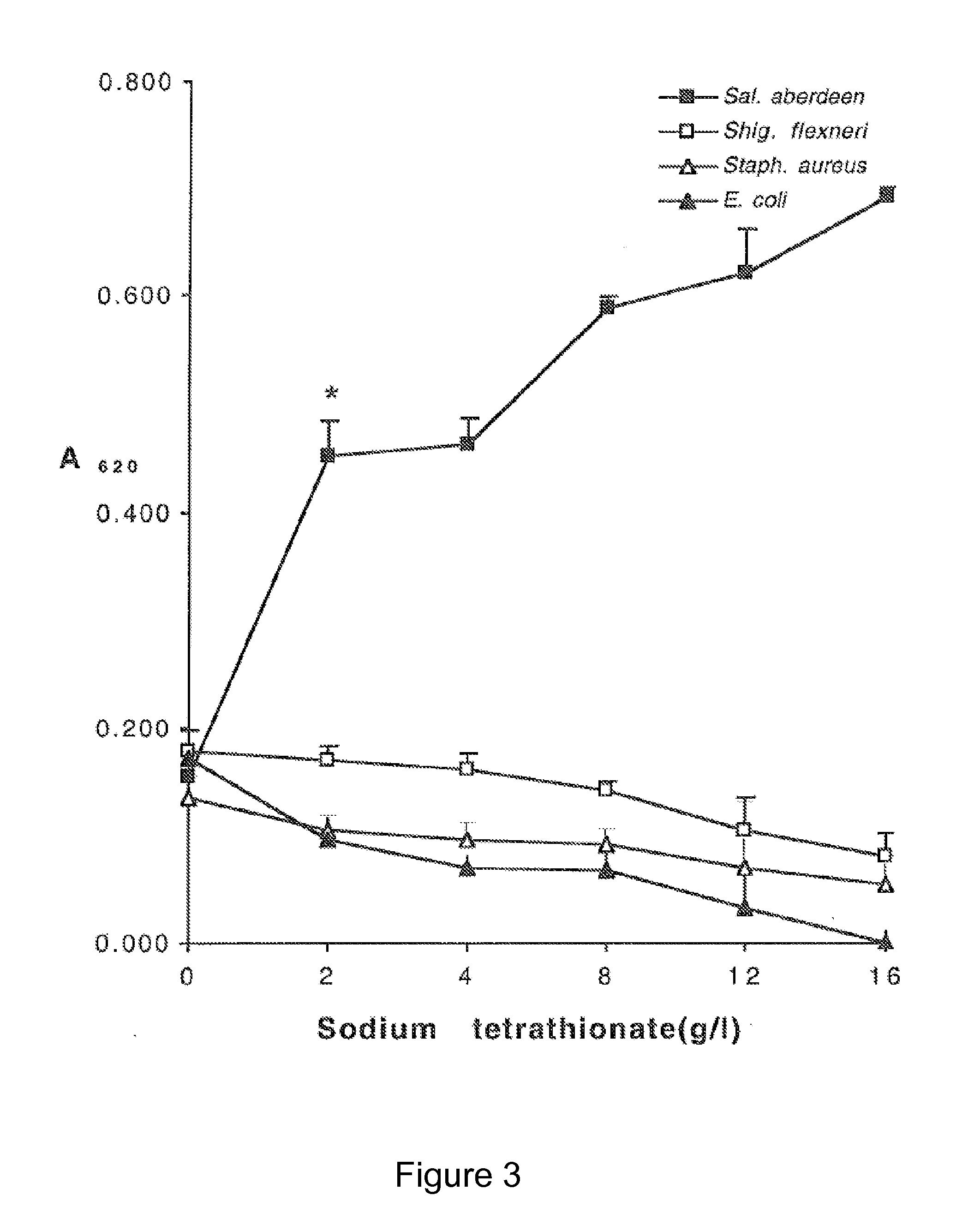
InactiveUS20110159515A1Efficient and rapid growthAvoid recoveryBacteriaMicrobiological testing/measurementPathogenic microorganismTest sample
The invention relates to assay methods for use in detecting specific materials such as core oligosaccharides derived from microorganisms, particularly pathogenic microorganisms, in a test sample. The invention further relates to compositions and methods for the rapid growth of such microorganisms enabling detection of same significantly earlier than is currently possible. In particular embodiments the invention is directed towards the rapid growth and / or detection of Salmonella, Shigella or Listeria.
Owner:SOLUS SCIENTIFIC SOLUTIONS LIMITED
A communication network connection method and an apparatus thereof
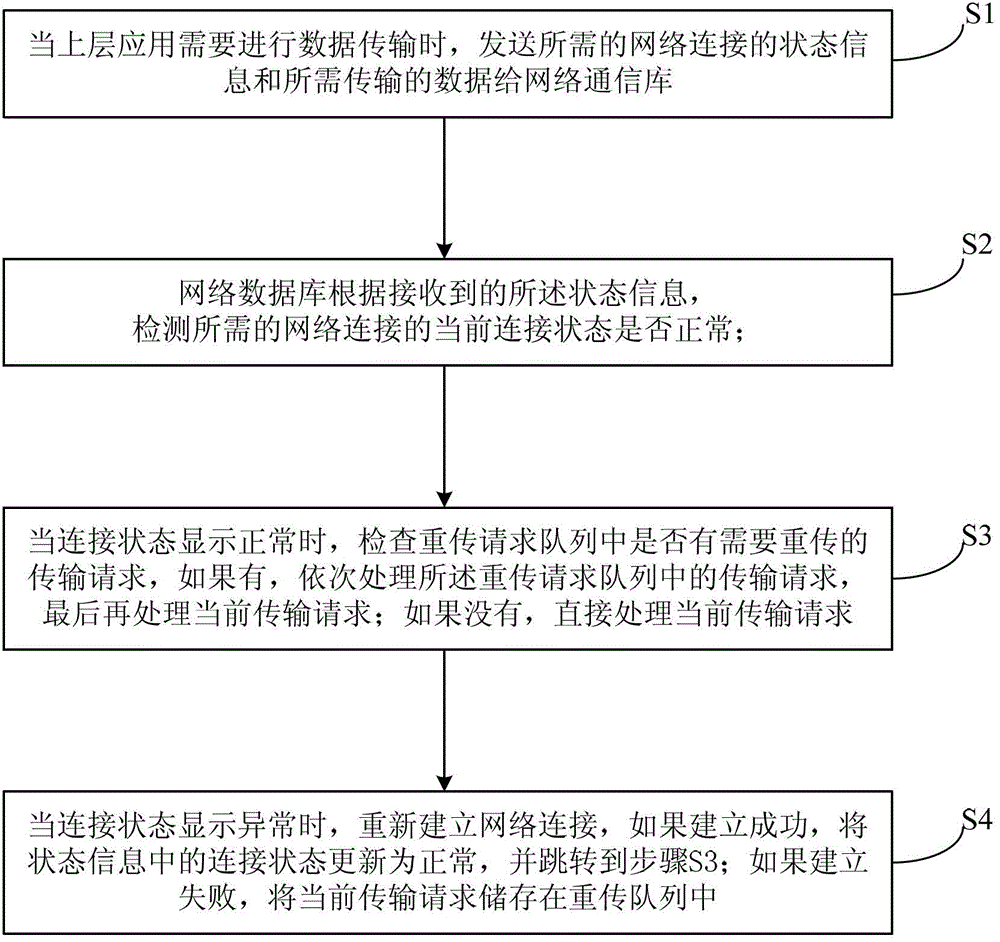
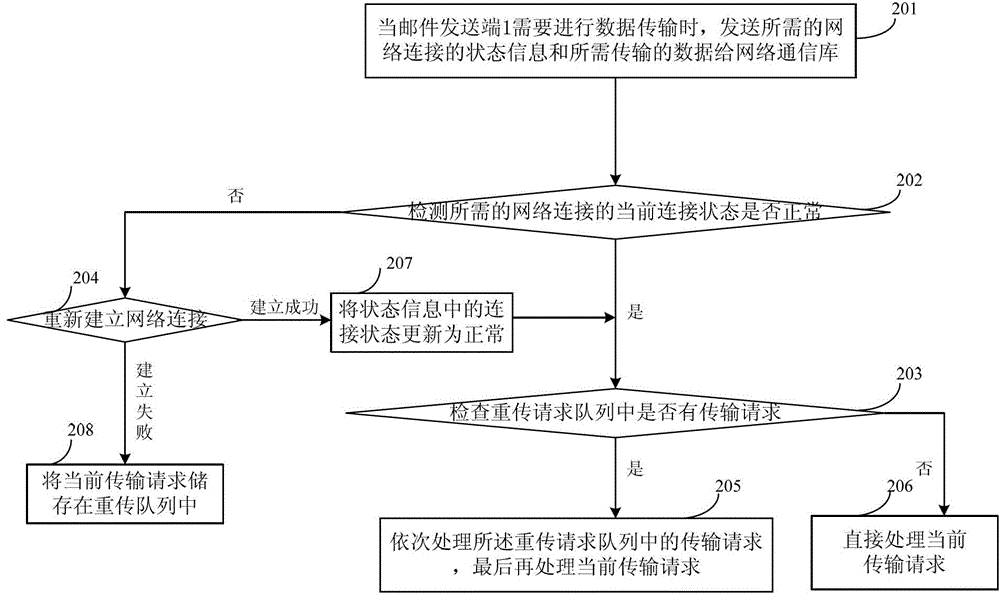
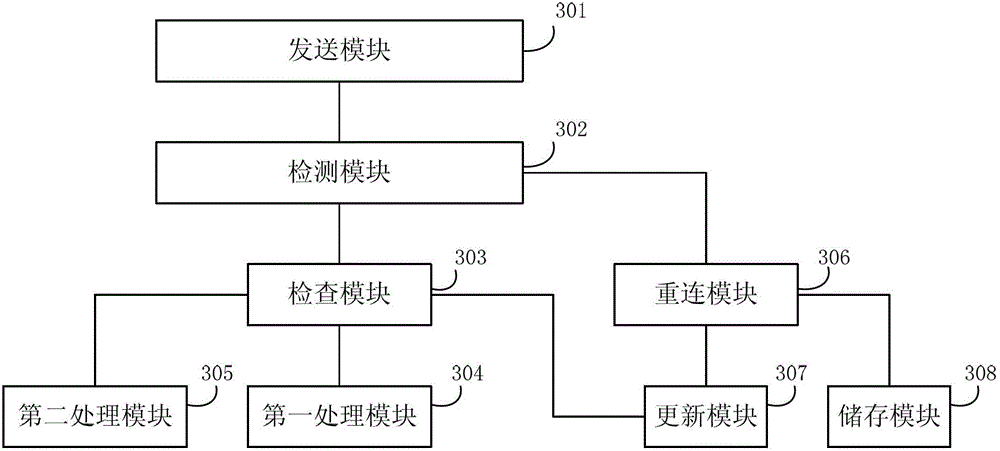
ActiveCN103338118AImprove real-time performanceAvoid recoveryError prevention/detection by using return channelData switching networksNetwork connectionNetwork communication
The embodiment of the invention discloses a communication network connection method and an apparatus thereof. Specifically, the method comprises the following steps: when an upper layer application needs to carry out data transmission, needed state information of network connection and data which needs to be transmitted are sent to a network communication database; connection state at present is detected to see whether the connection state is normal according to the state information; When the connection state is normal, a retransmission request queue is detected to see whether a transmission request which needs to be retransmitted exist; different treatments are carried out according to detected results; when the connection state is abnormal, a network connection is reestablished; if the reestablishment is successful, the connection state in state information is updated to be normal, and corresponding data transmission processing is carried out; if the reestablishment fails, the present transmission request is stored in the retransmission request queue. The connection method can reduce network reconnection operations, avoid unnecessary recovery operations. At the same time, the connection method can minimize the influence on the application by fault recovery, and improve real-time performance of the communication network.
Owner:BEIJING SOHU NEW MEDIA INFORMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com