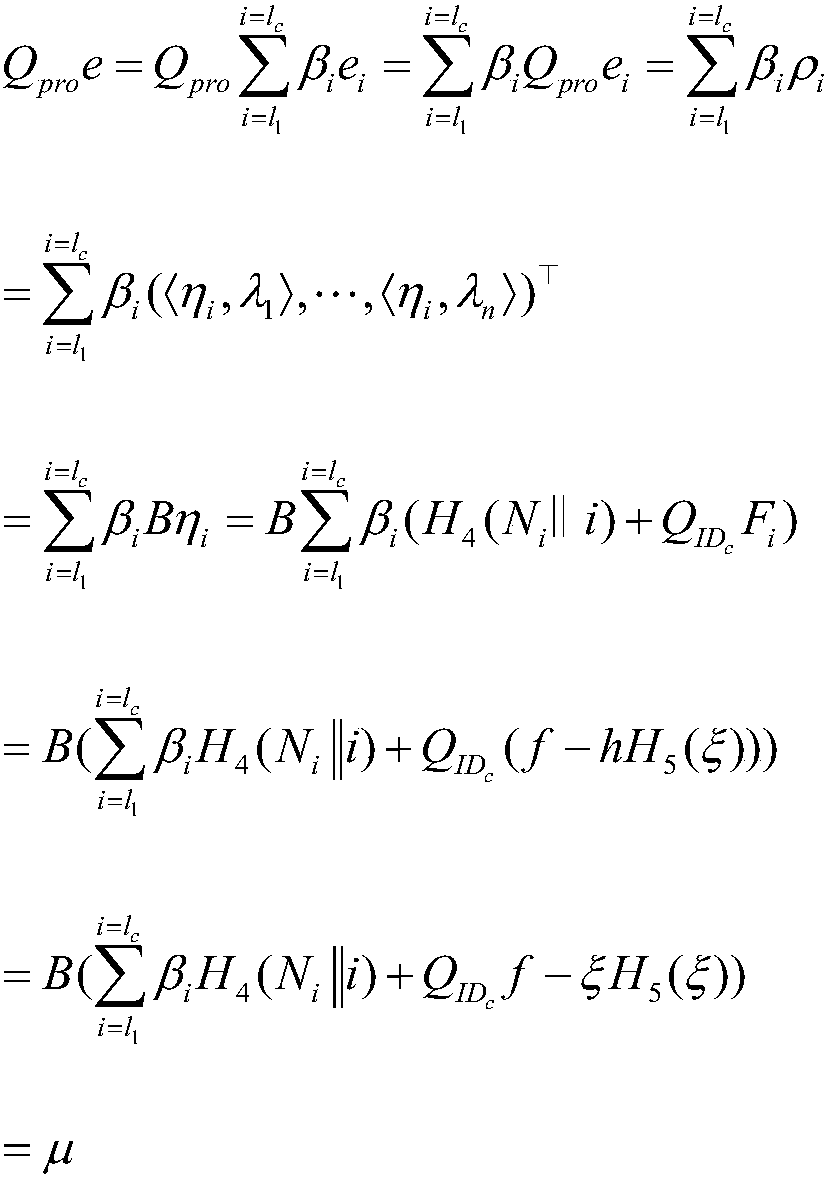Lattice-based cloud storage data safety auditing method supporting data proxy uploading
A data agent and data storage technology, applied in the field of information security, can solve problems such as the ability to resist quantum computer attacks, security cryptography difficulties, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The technical solution of the present invention has been described in detail in the part of the summary of the invention, and will not be repeated here.
[0059] What needs to be added is:
[0060] The last trusted auditor TPA verifies the equation Q pro e = μmodq and the inequality Whether it is established or not, the derivation process of verifying the correctness of the equation is as follows:
[0061]
[0062] Thus, verifying the equation Q pro e=μ mod q is established. Furthermore, since the vector (an m-dimensional vector modulo q) is the data block F i signature, such that for any therefore, established.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com