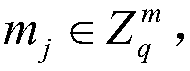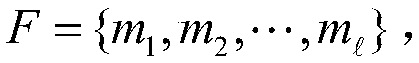Cloud storage data common auditing method possessing secret key leakage resistance characteristic
A cloud storage and key technology, applied in the field of communication, can solve problems such as slow computing efficiency and communication efficiency, complicated management of user public key certificates, and inability to resist quantum computer attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] Describe technical scheme of the present invention in detail below:
[0052] The steps of the present invention are divided into four parts:
[0053] The initial stage of the system: the system first divides the data file into blocks, and sets the security parameters of the lattice encryption algorithm and the secure hash function required in this stage. The key generation center PKG invokes the grid-based proxy algorithm to generate public and private keys of cloud users and cloud servers.
[0054] Key update phase: given the user identity, the key update period preset by the system, and the cloud user's signature private key at the current moment, the cloud user invokes the grid-based proxy algorithm to generate the cloud user's signature private key at the next moment.
[0055] Audit proof generation stage: the cloud user calls the identity-based forward secure homomorphic digital signature algorithm on the lattice to generate the signature of the data block, and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com