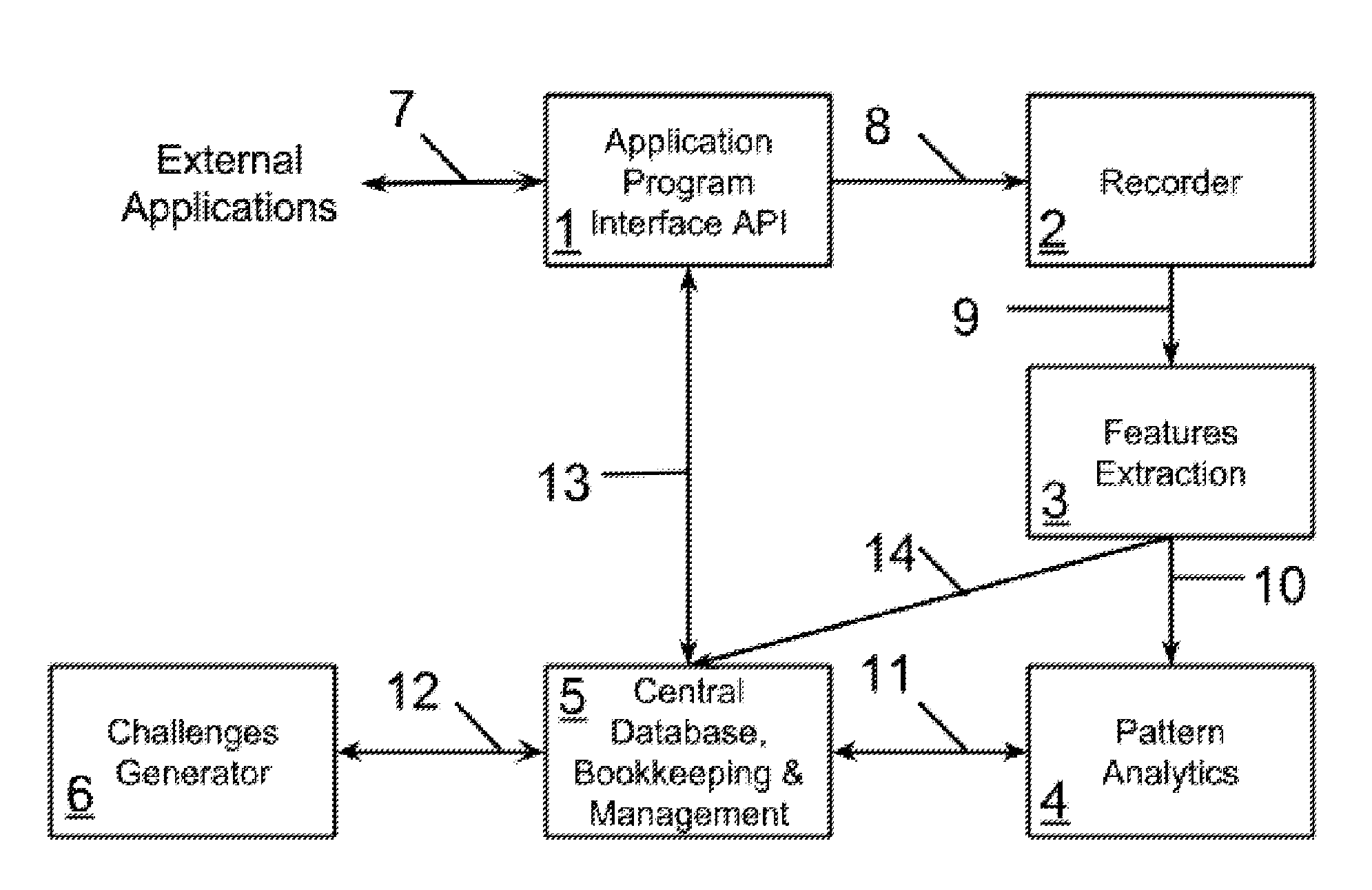
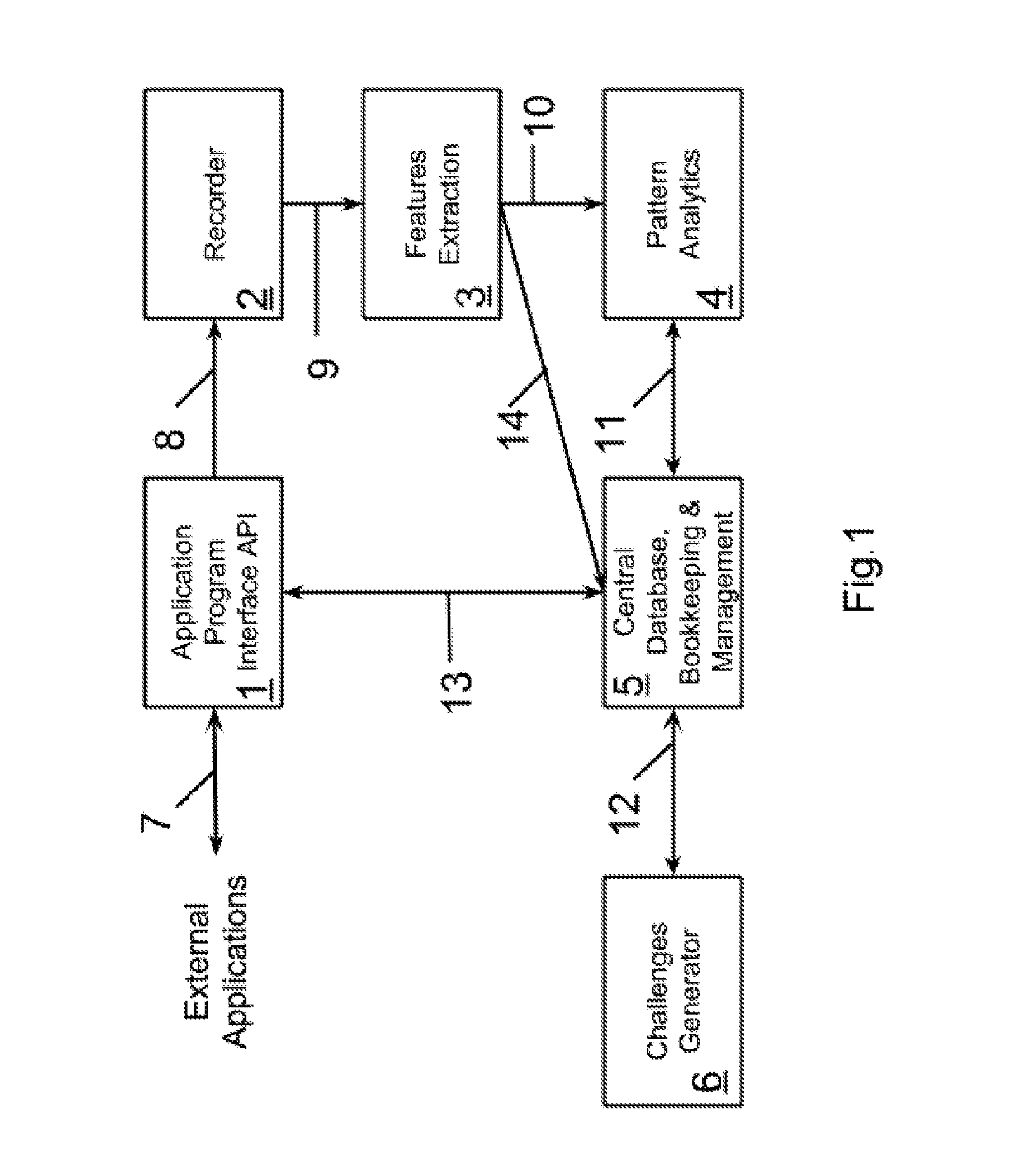
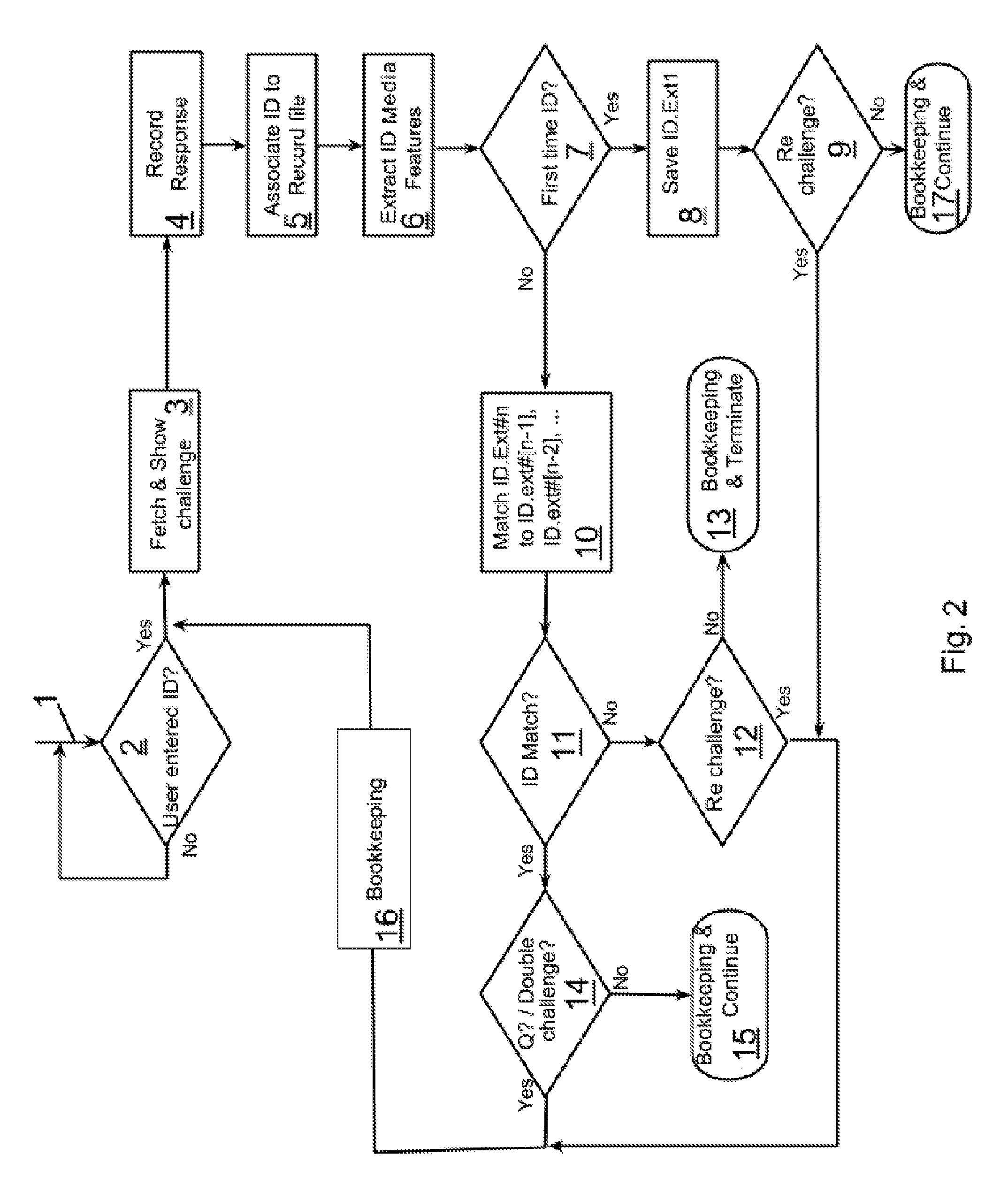
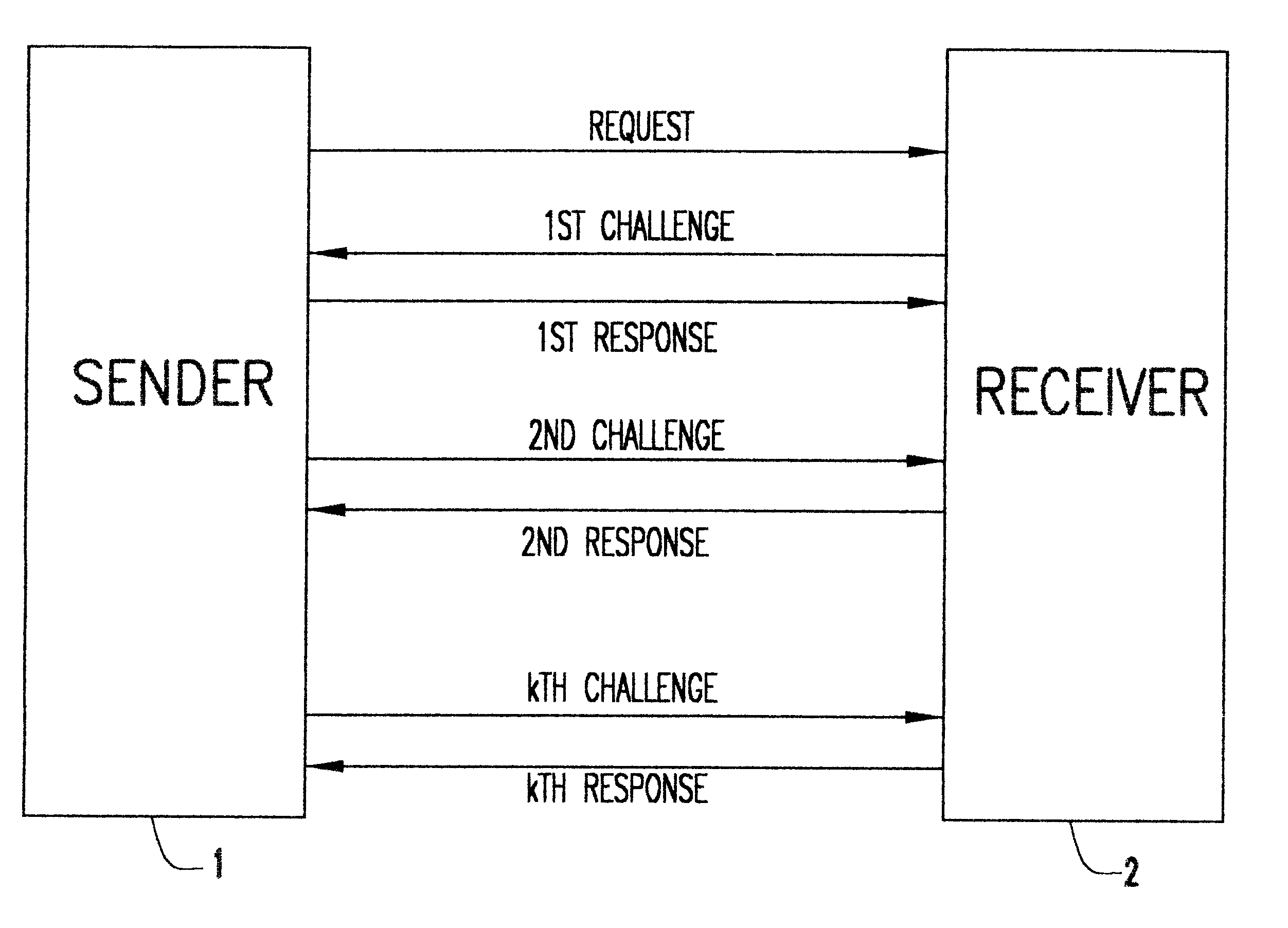
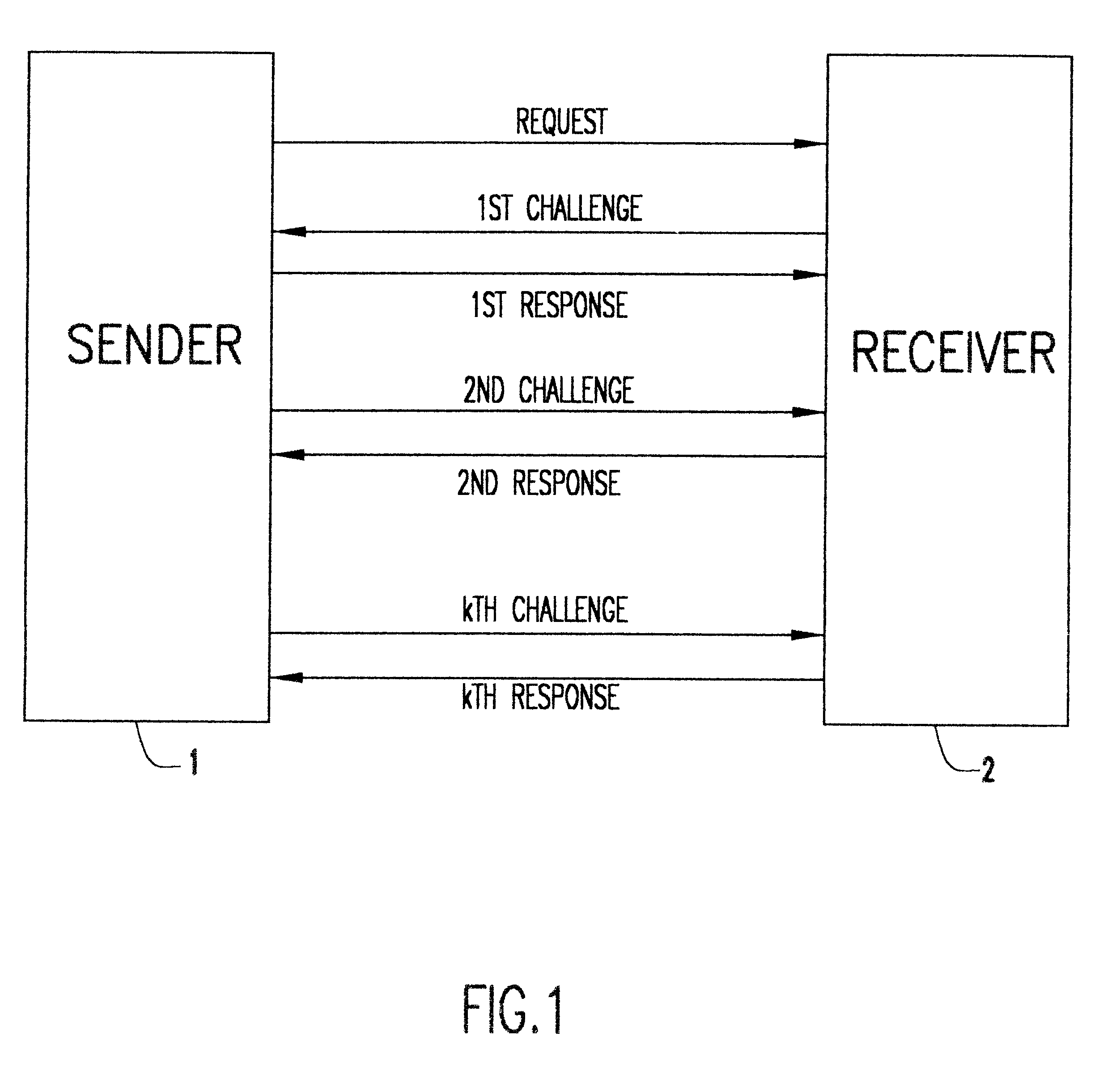
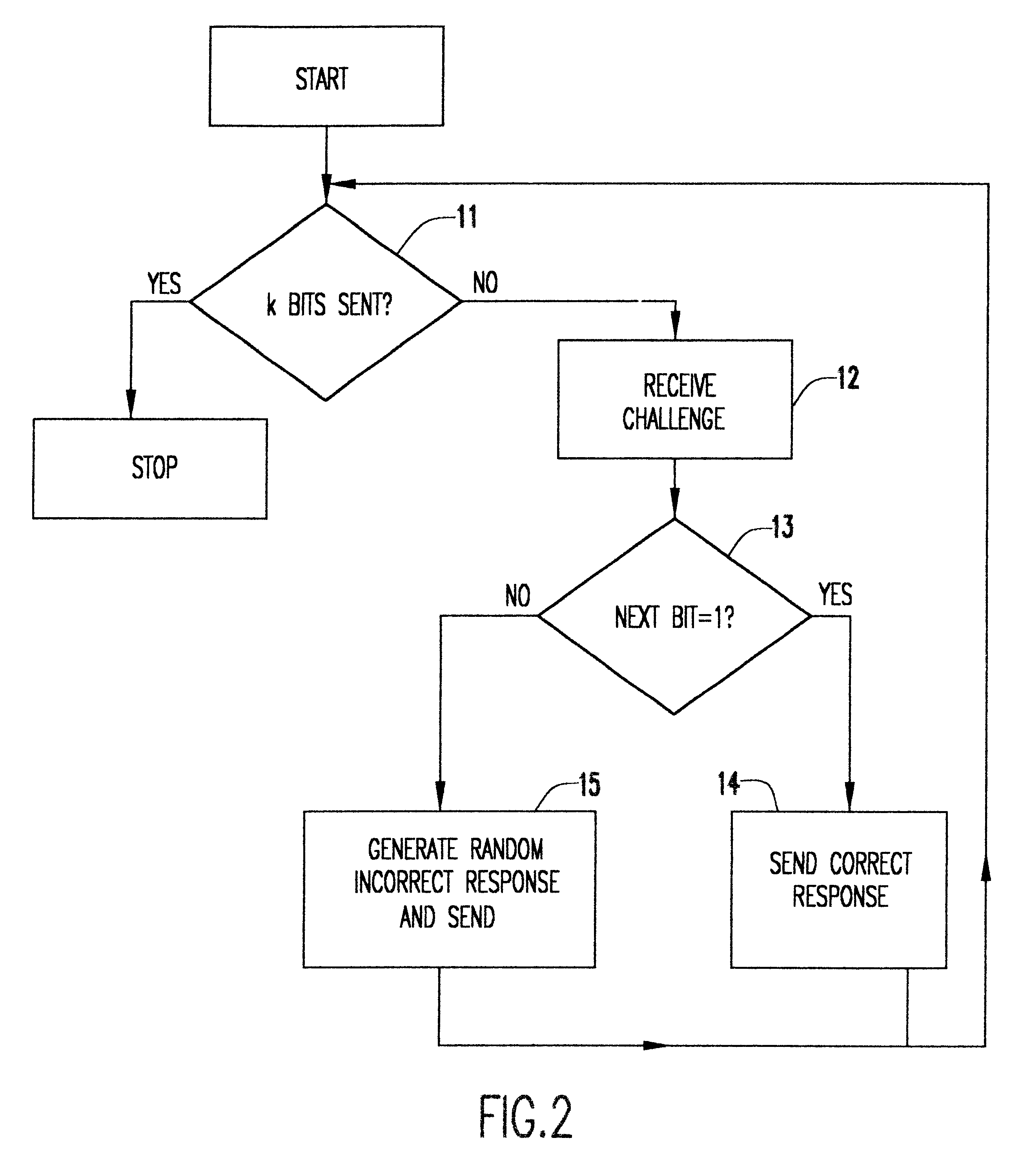
Patents
Literature
338 results about "Challenge response" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
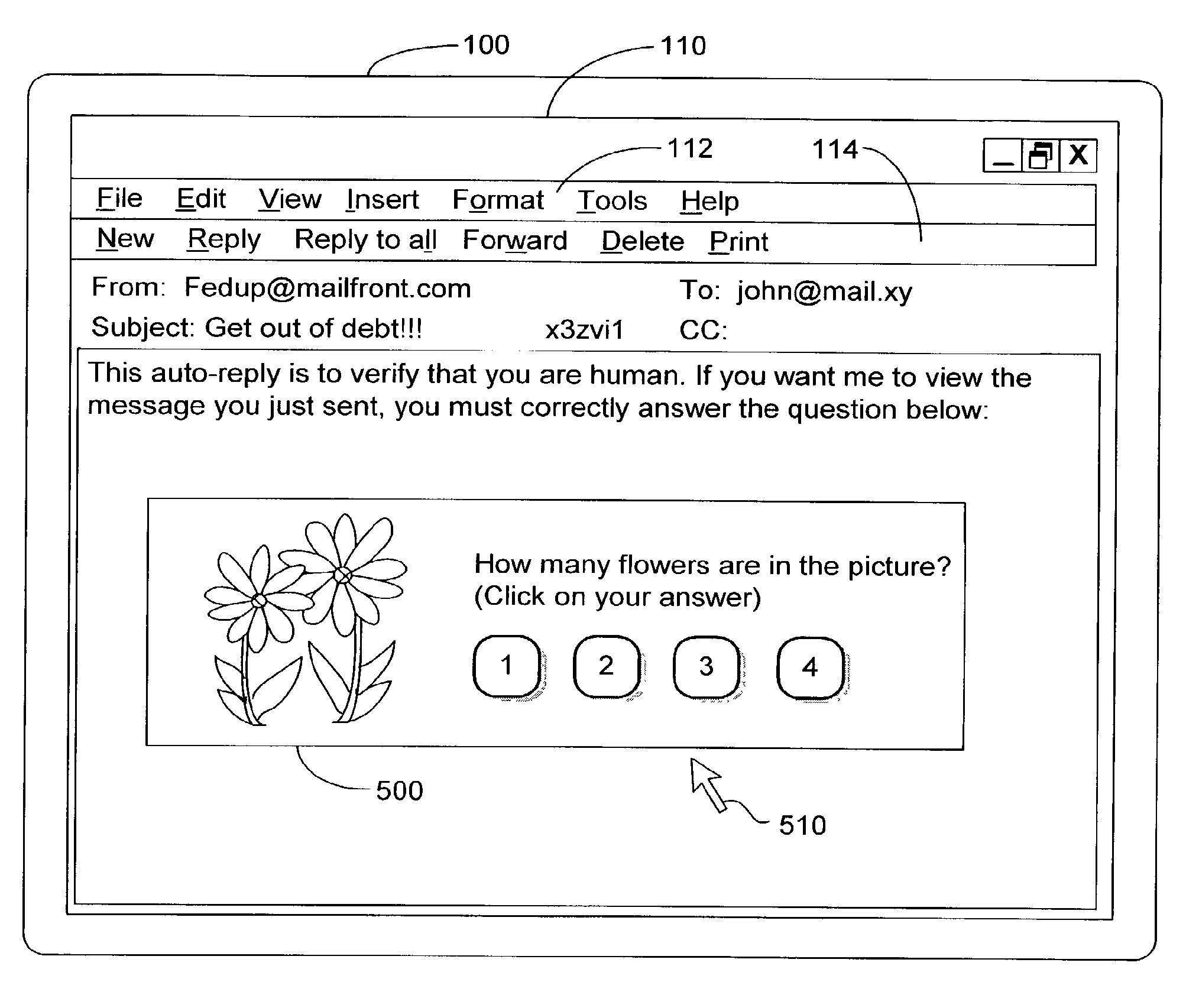
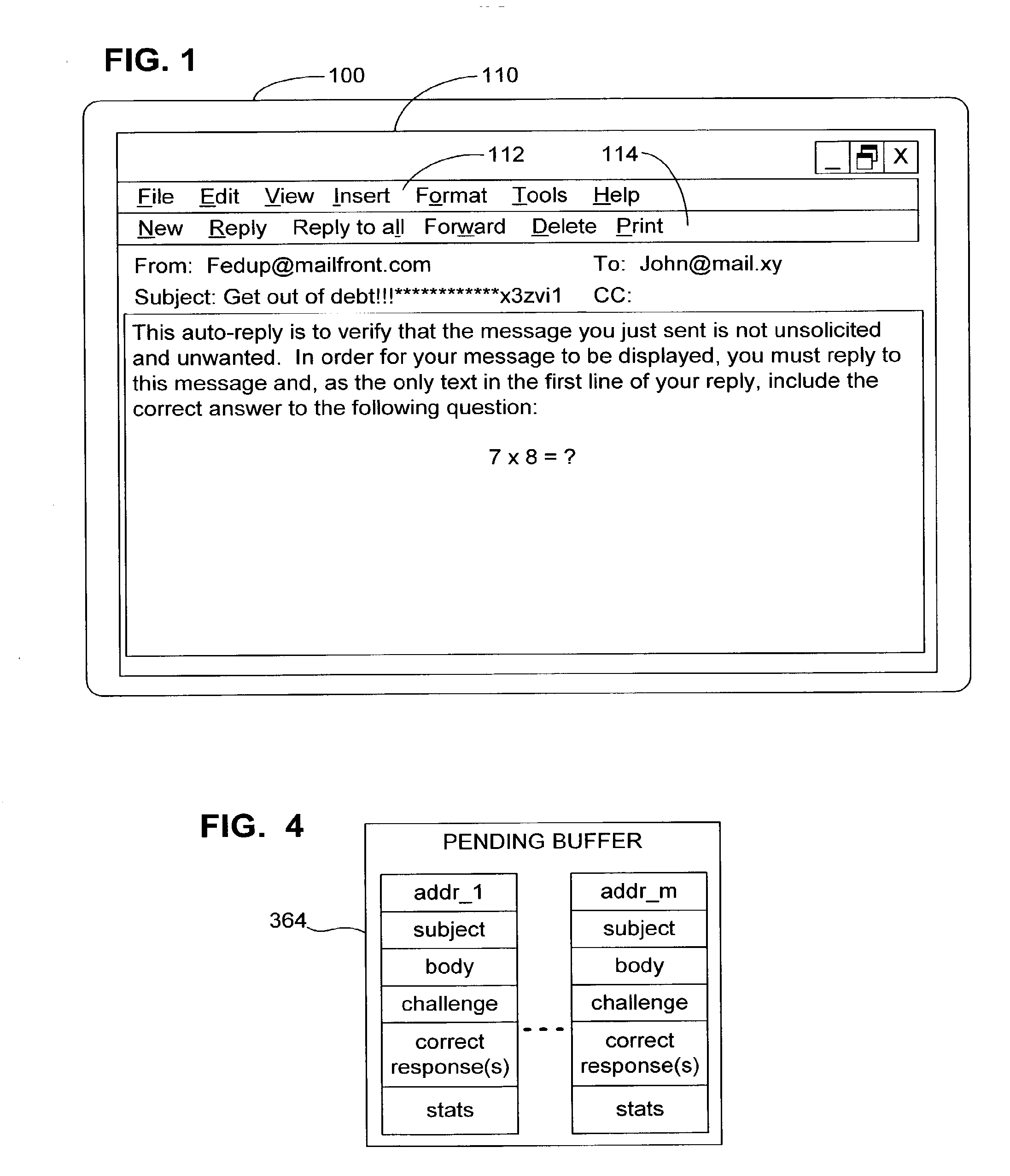
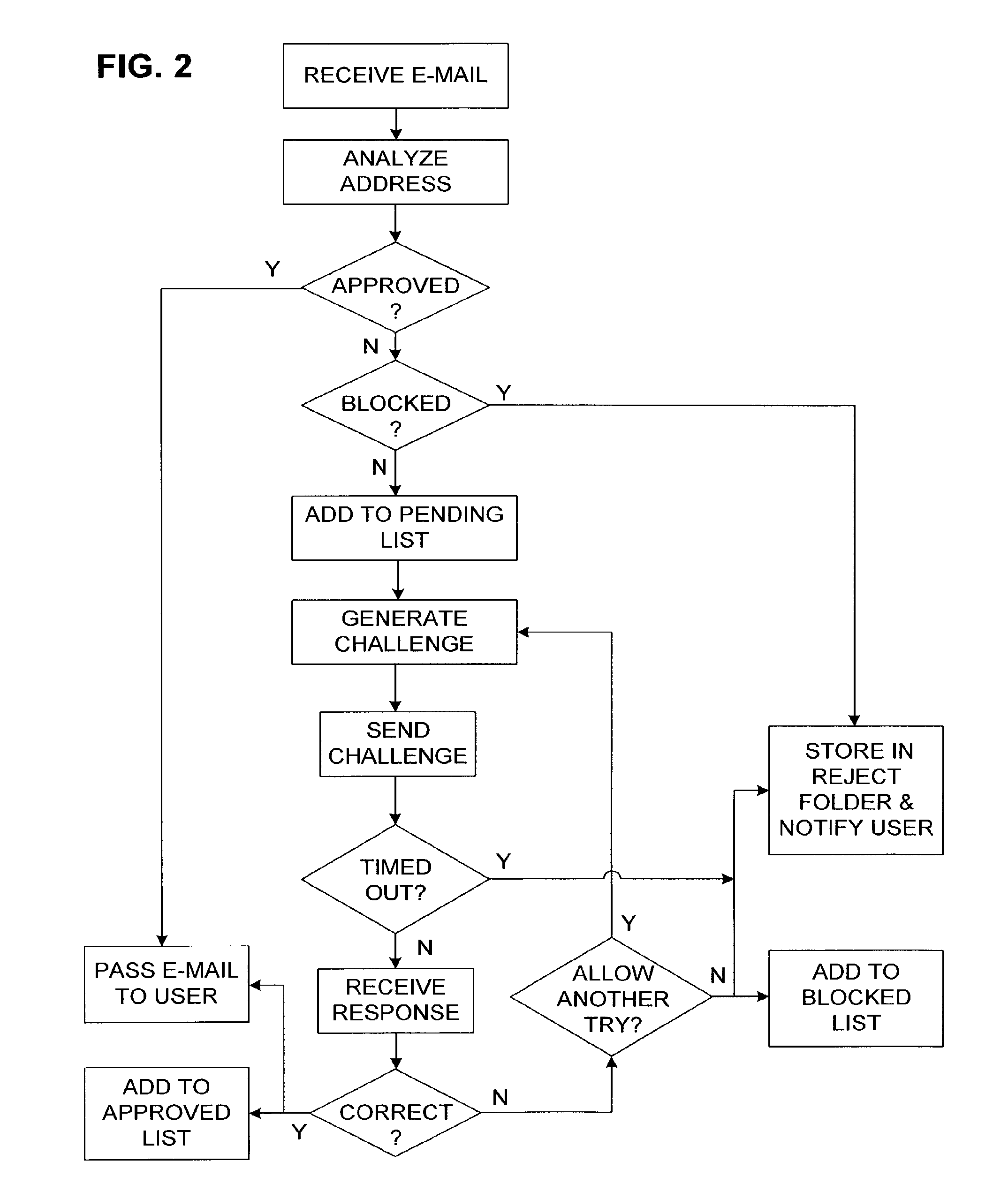
A challenge–response (or C/R) system is a type of spam filter that automatically sends a reply with a challenge to the (alleged) sender of an incoming e-mail. It was originally designed in 1997 by Stan Weatherby, and was called Email Verification. In this reply, the sender is asked to perform some action to assure delivery of the original message, which would otherwise not be delivered. The action to perform typically takes relatively little effort to do once, but great effort to perform in large numbers. This effectively filters out spammers. Challenge–response systems only need to send challenges to unknown senders. Senders that have previously performed the challenging action, or who have previously been sent e-mail(s) to, would be automatically whitelisted.
Online challenge-response
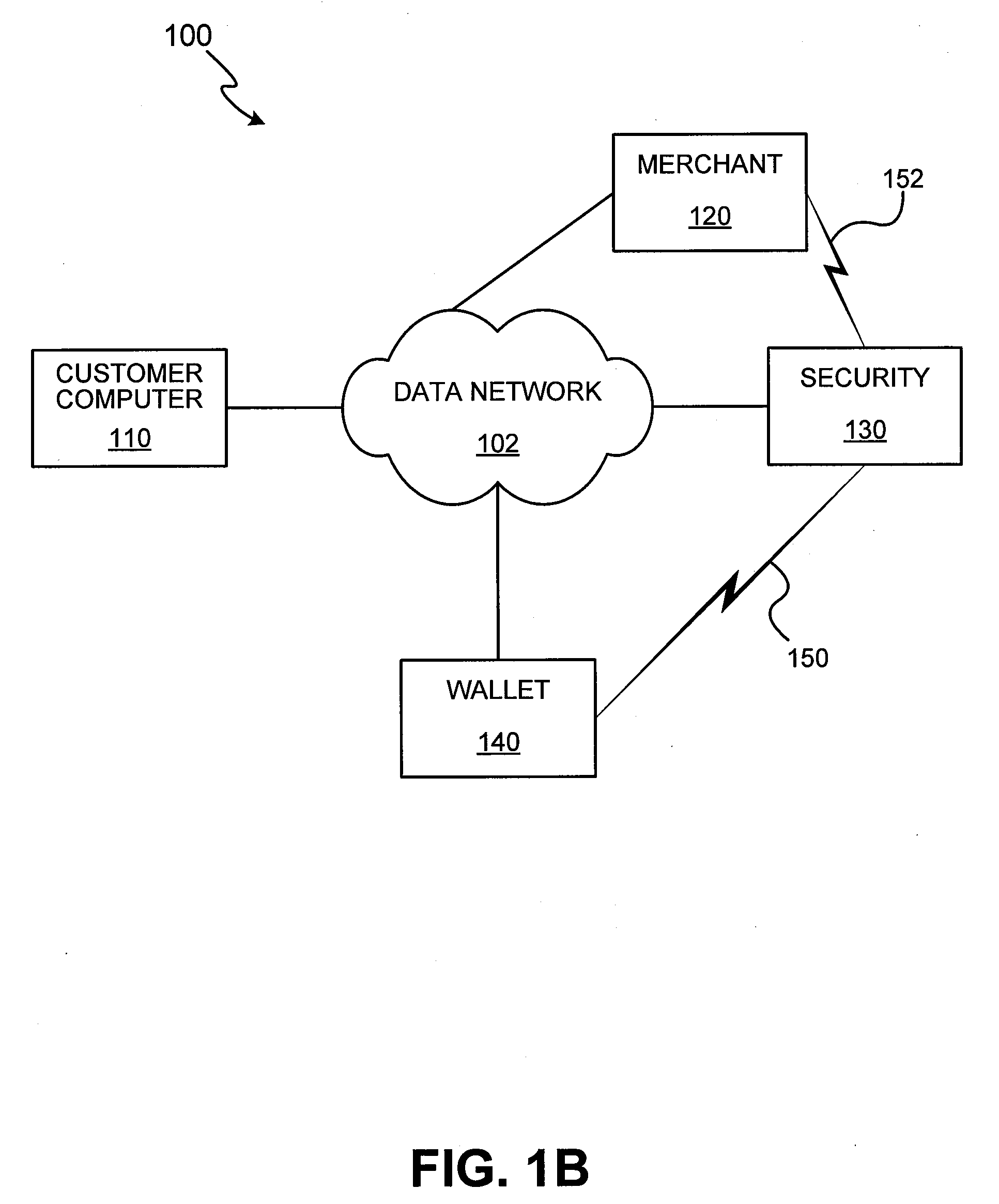
ActiveUS20100114776A1Reduce theftStreamlined and enhanced referral processFinanceDigital data processing detailsThird partyApplication software
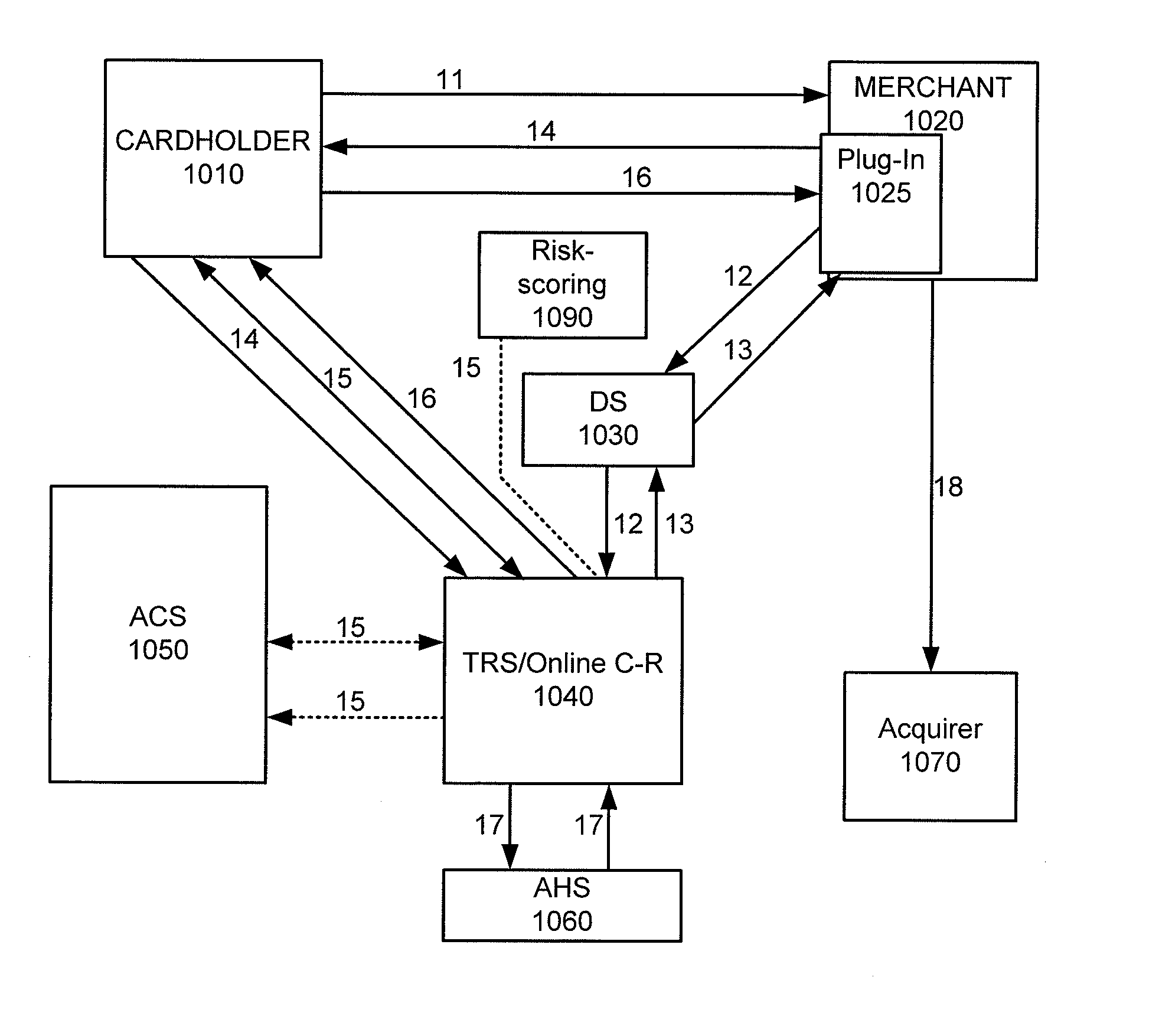
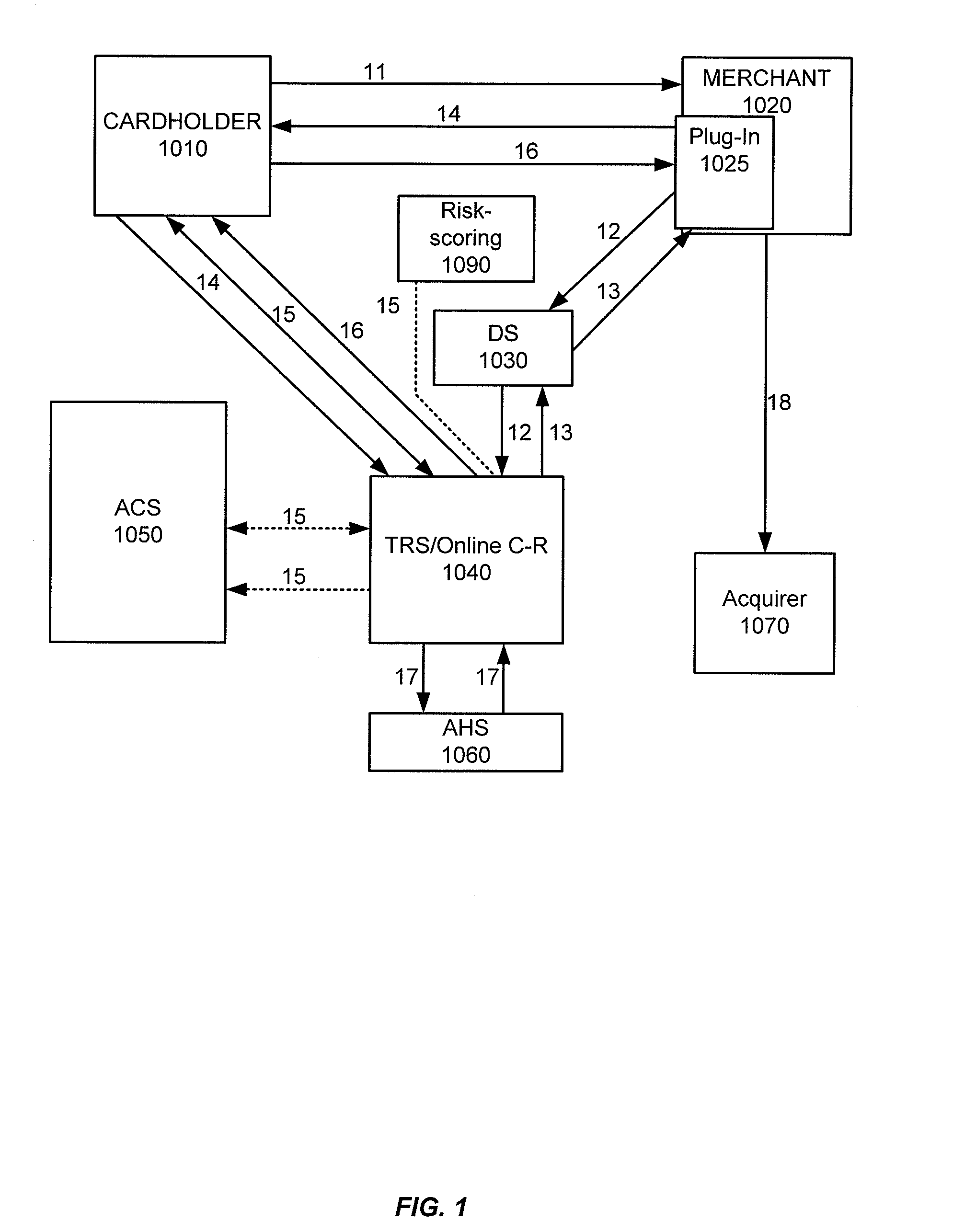
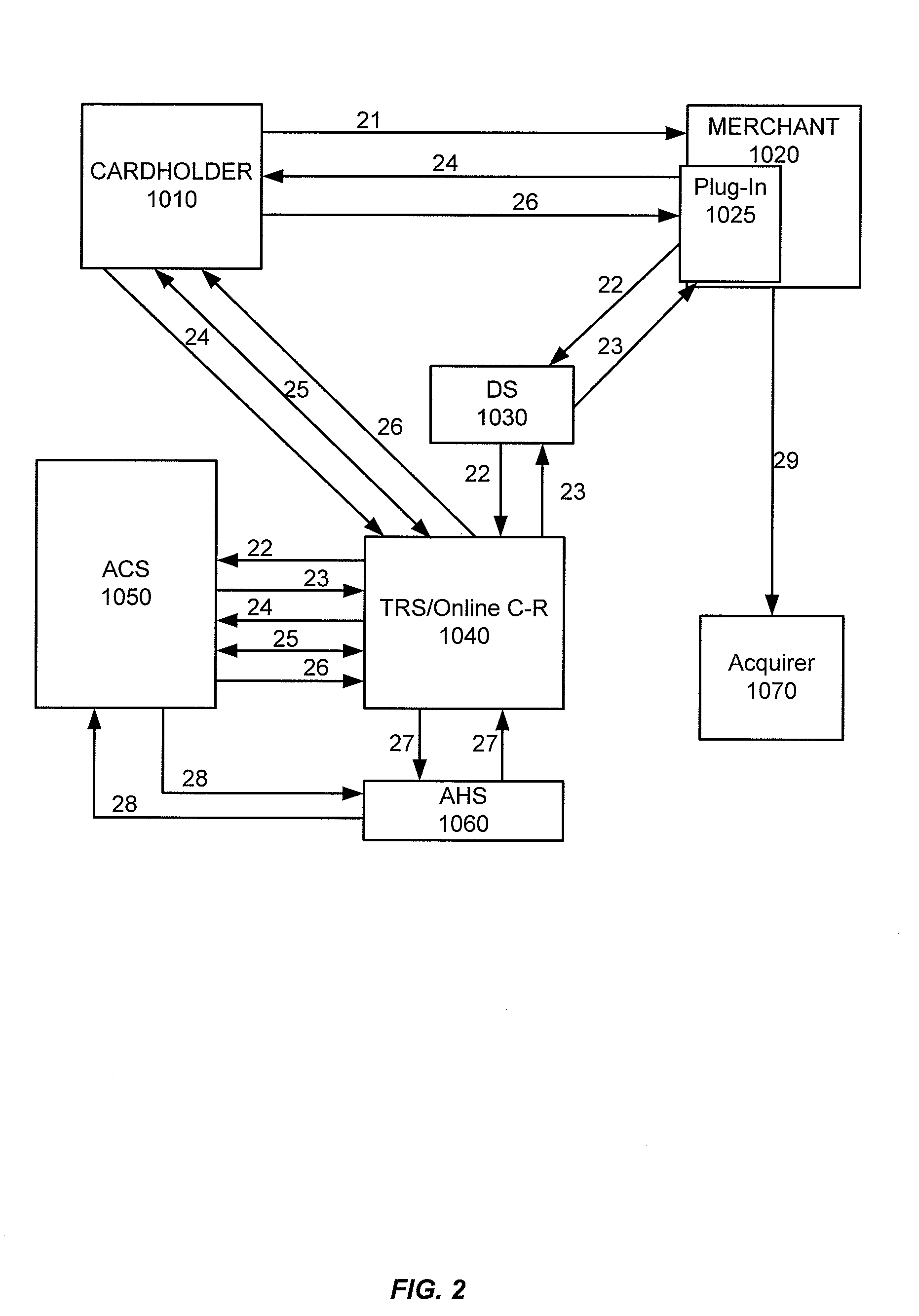
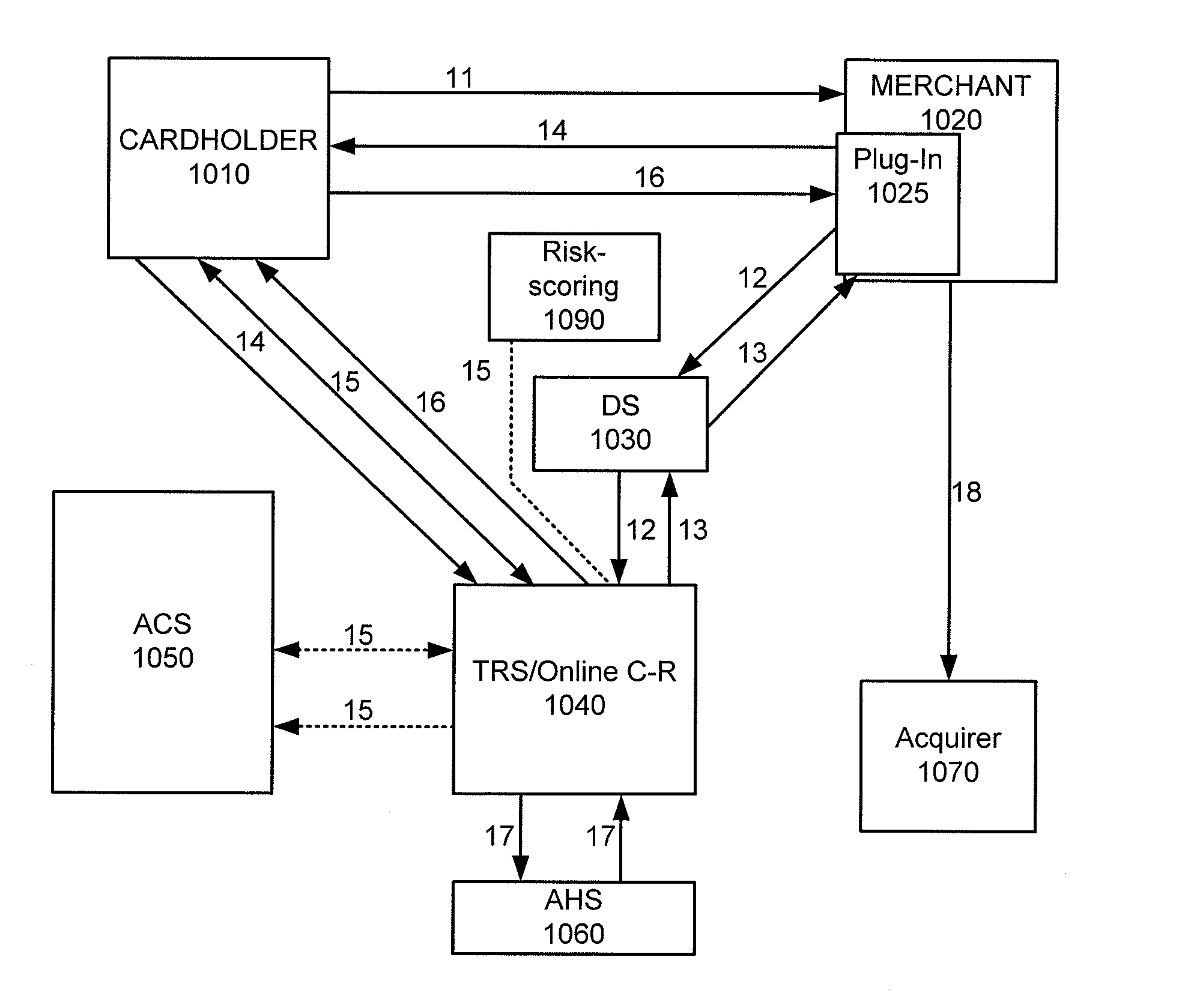
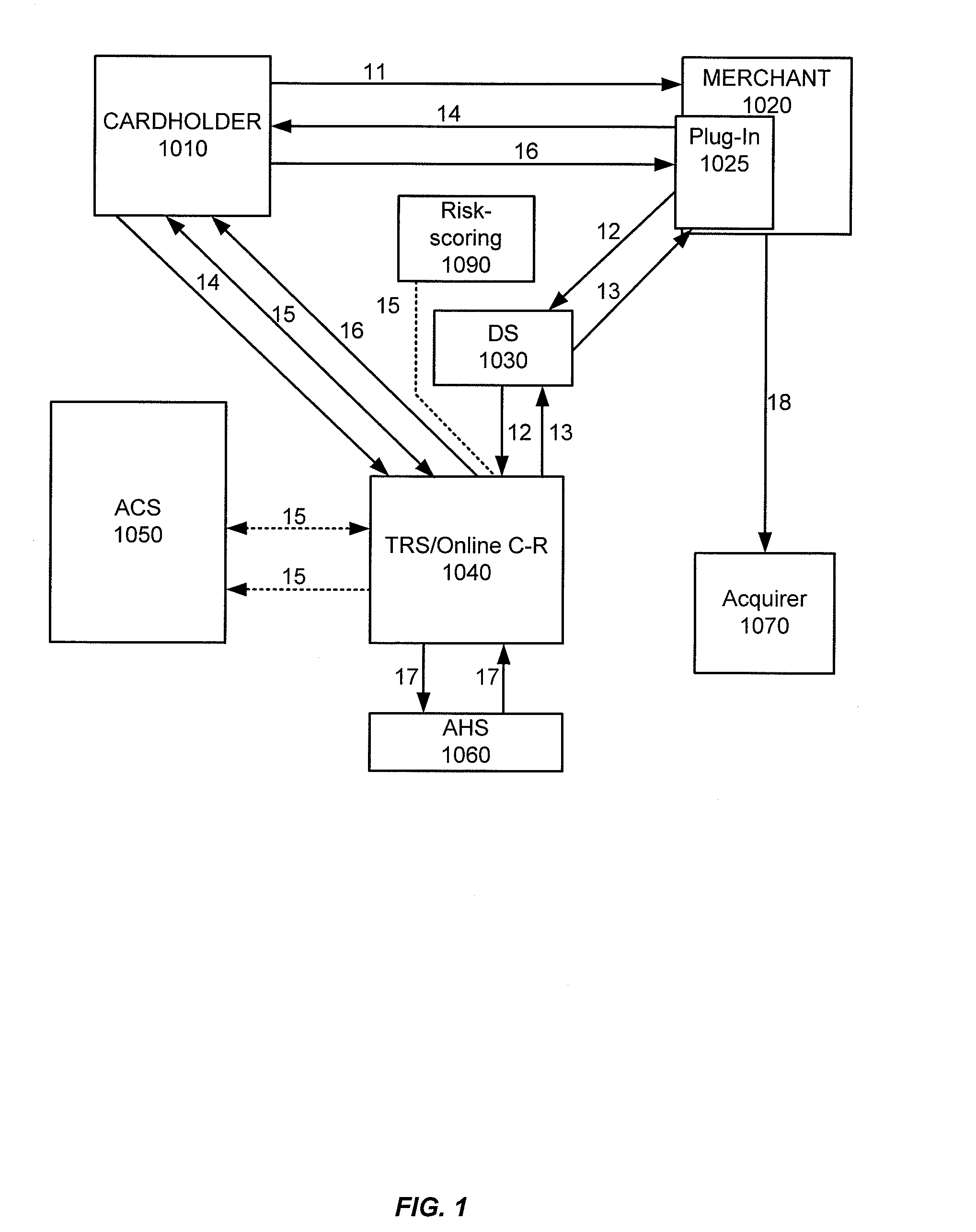
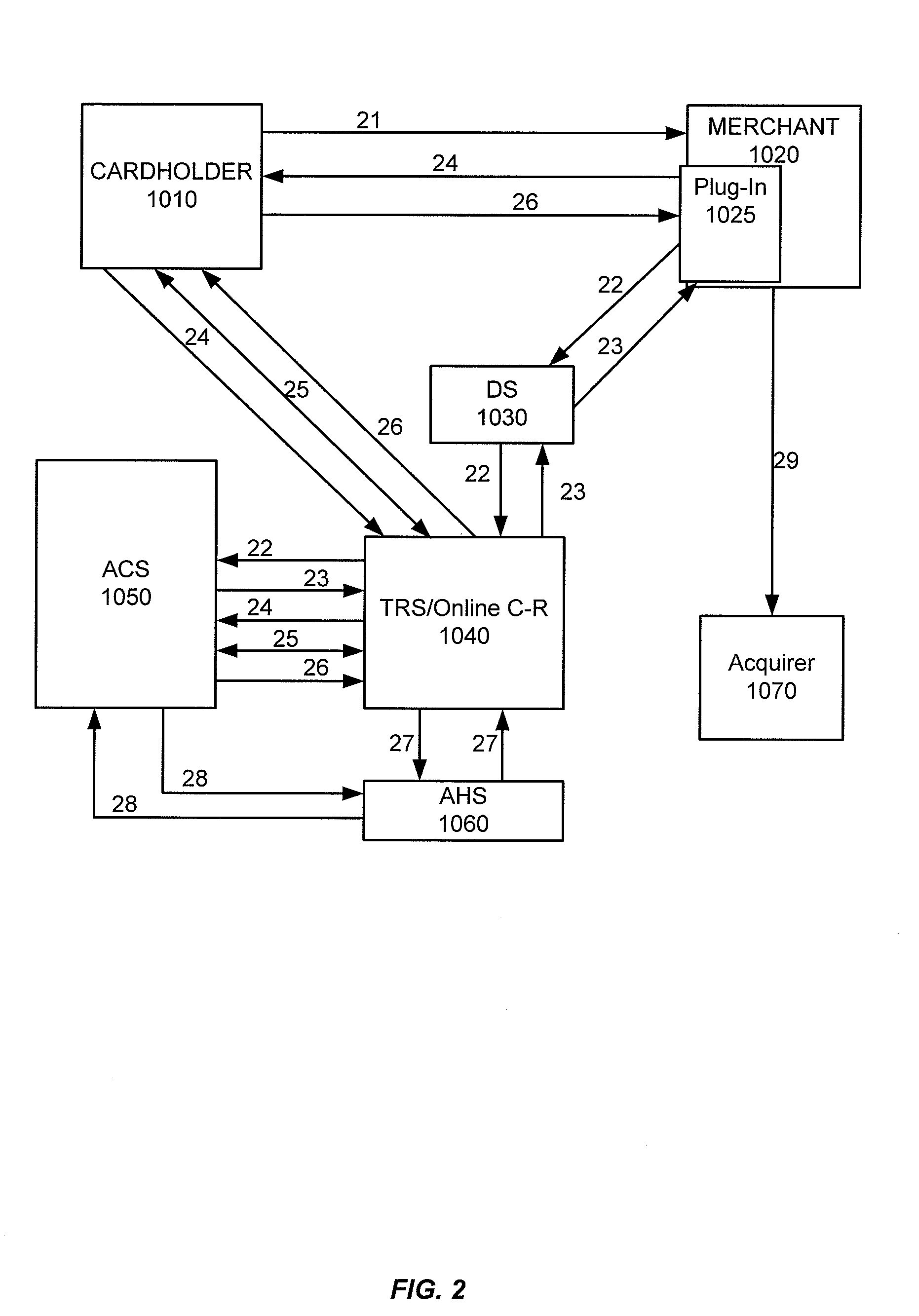
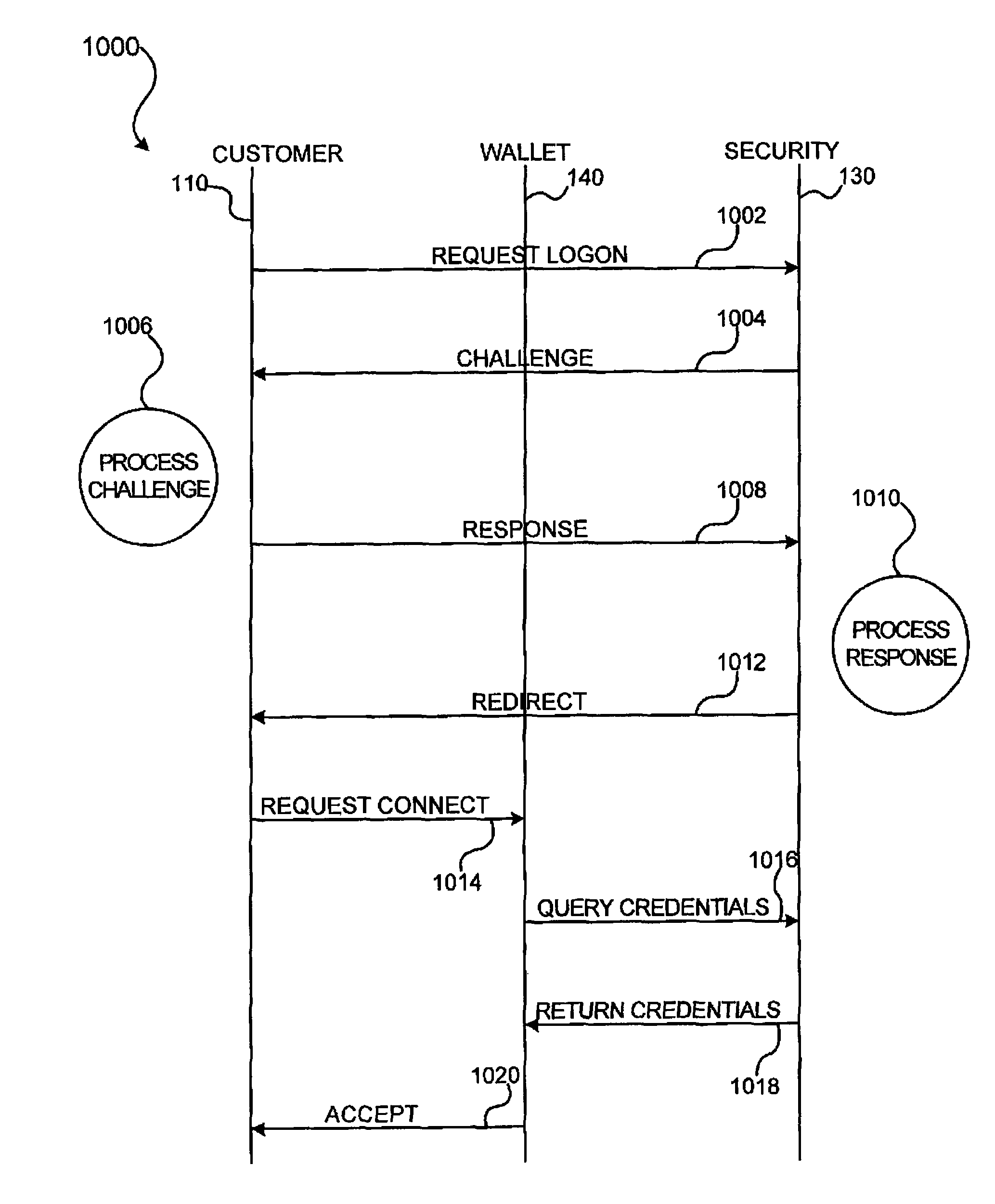
Embodiments of the invention enable cardholders conducting an online transaction to be authenticated in real-time using a challenge-response application. The challenge-response application can be administered by an issuer or by a third party on-behalf-of an issuer. A challenge question can be presented to the cardholder, and the cardholder's response can be verified. The challenge question presented can be selected based on an analysis of the risk of the transaction and potentially other factors. A variety of dynamic challenge questions can be used without the need for the cardholder to enroll into the program. Additionally, there are many flexible implementation options of the challenge-response application that can be adjusted based on factors such as the location of the merchant or the location of the consumer.
Owner:VISA INT SERVICE ASSOC
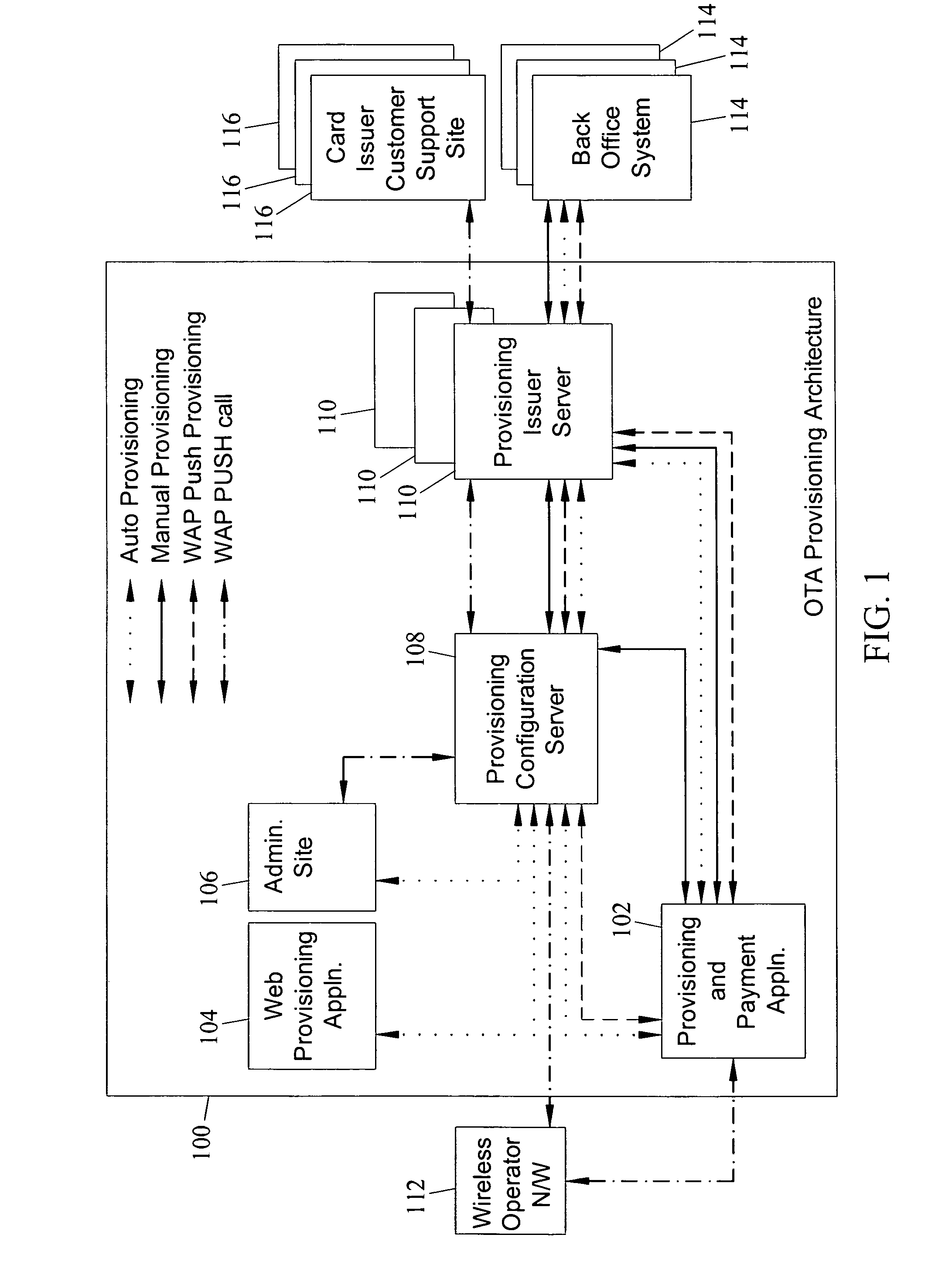
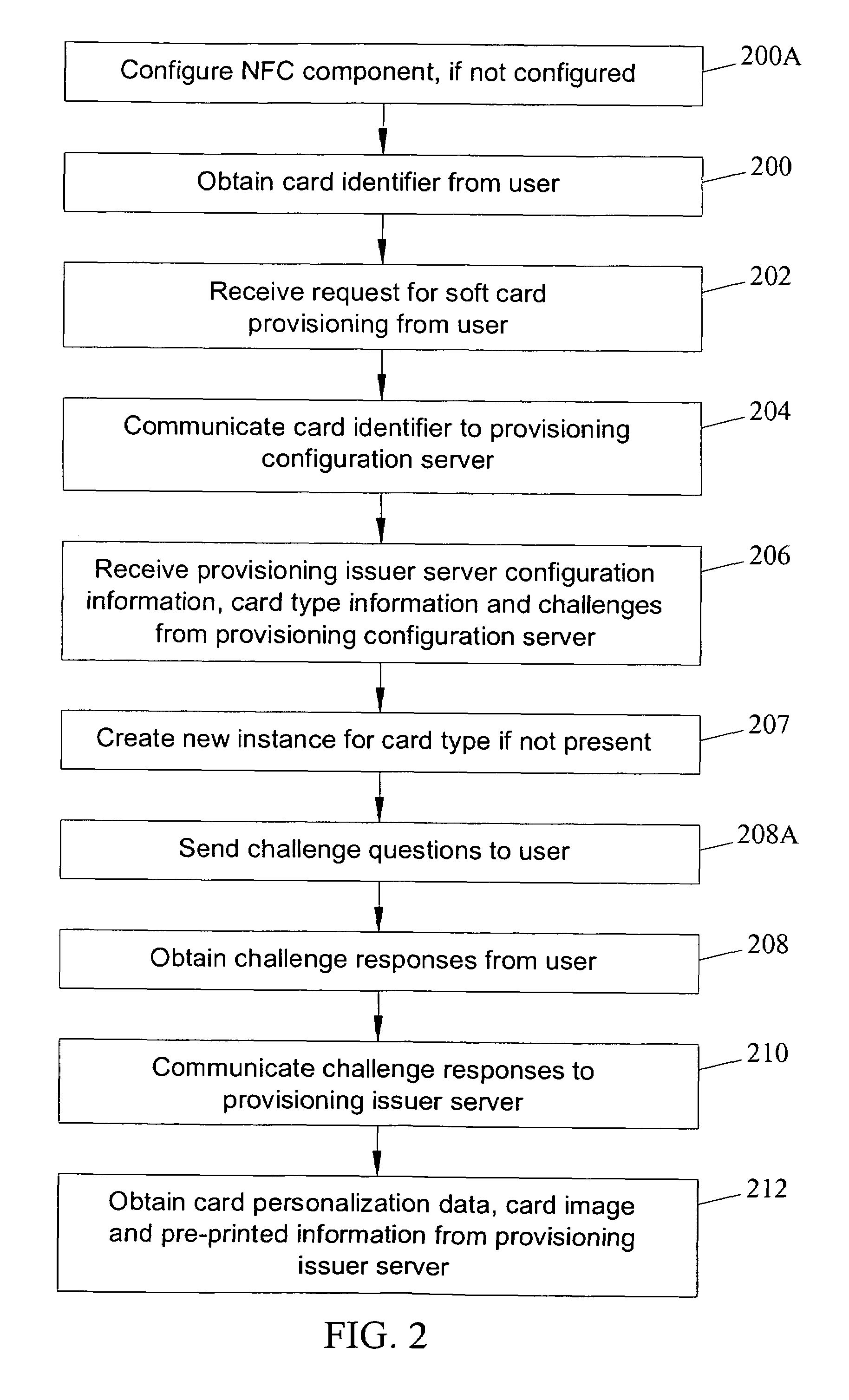
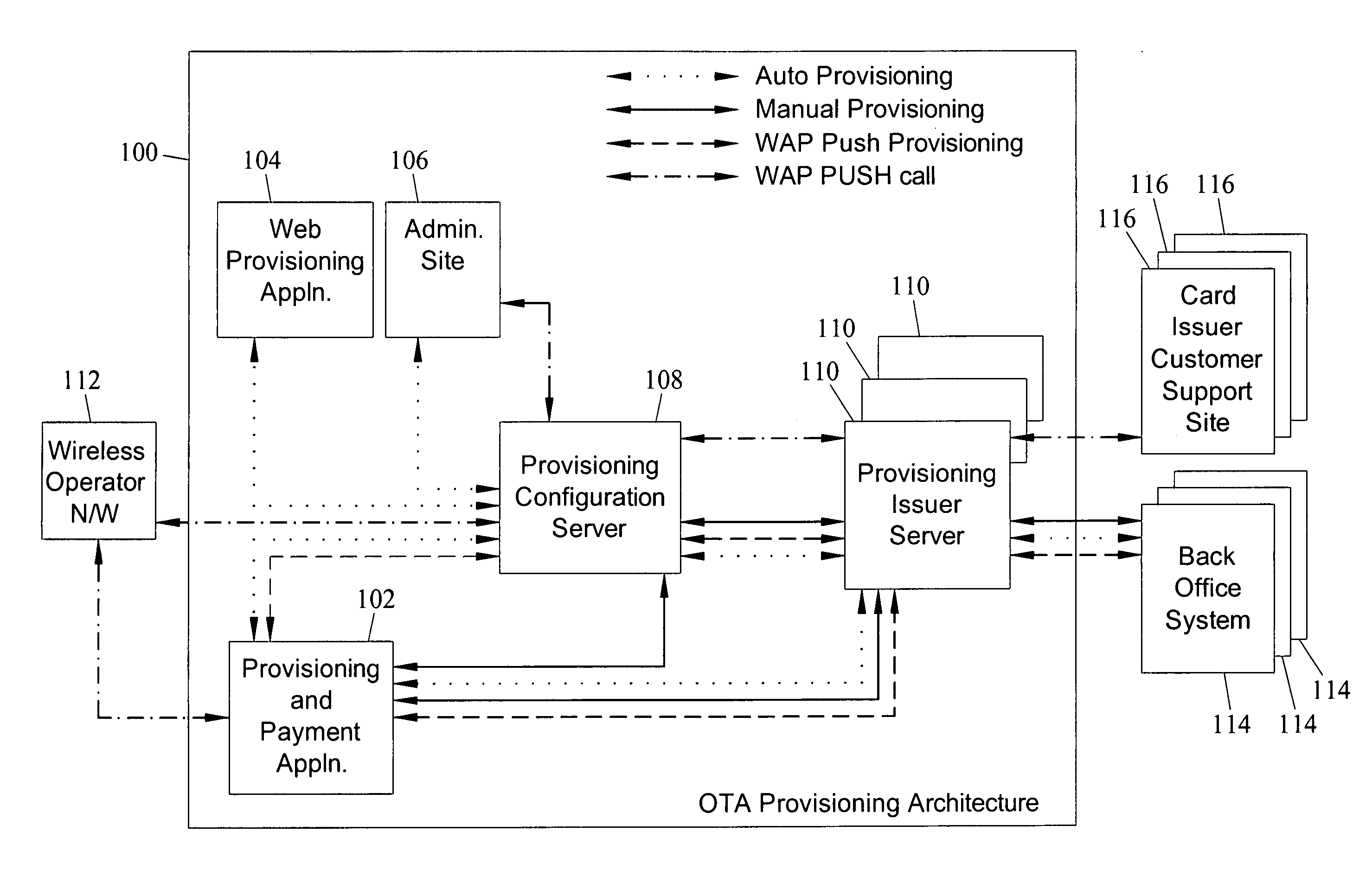
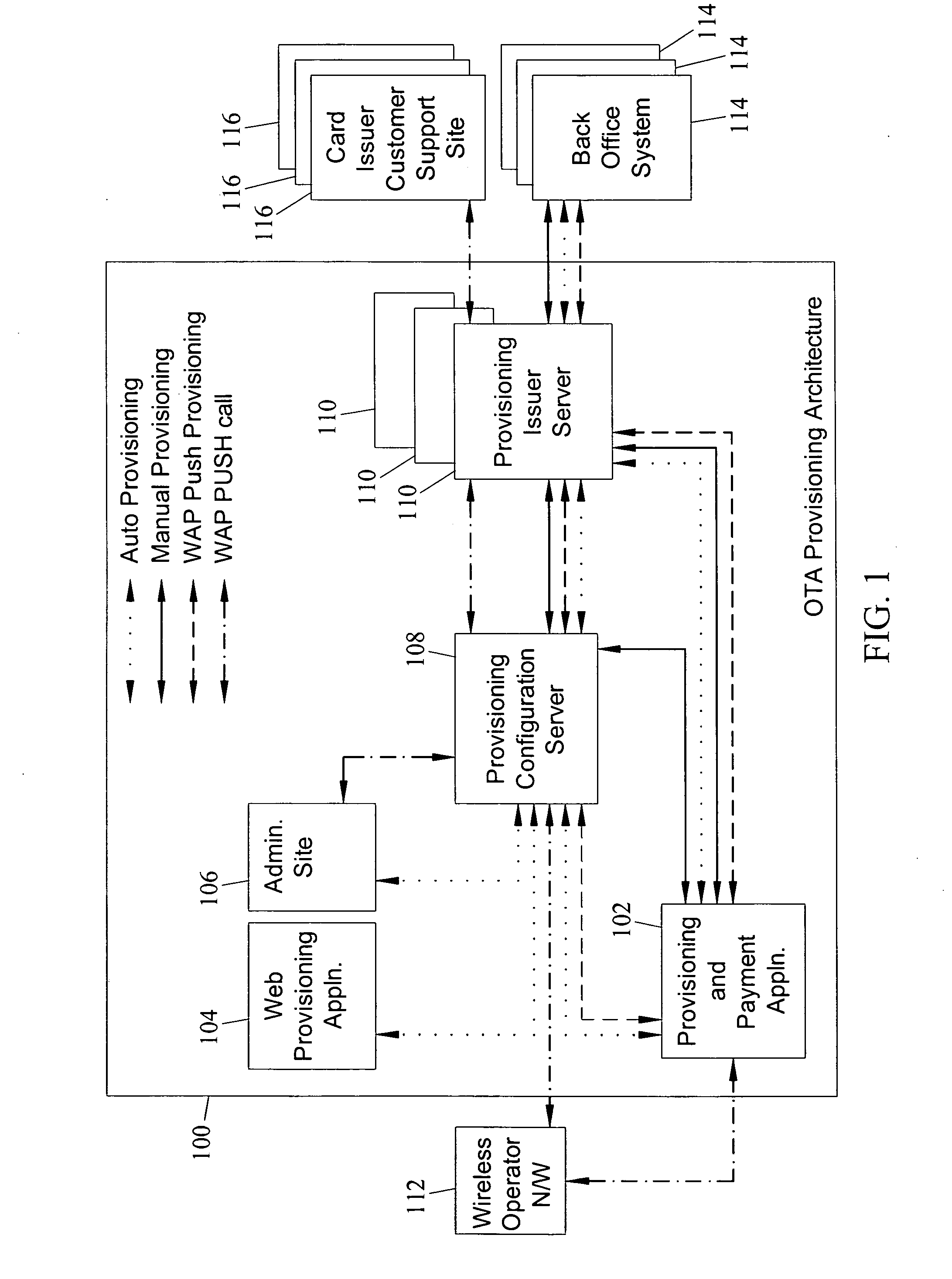
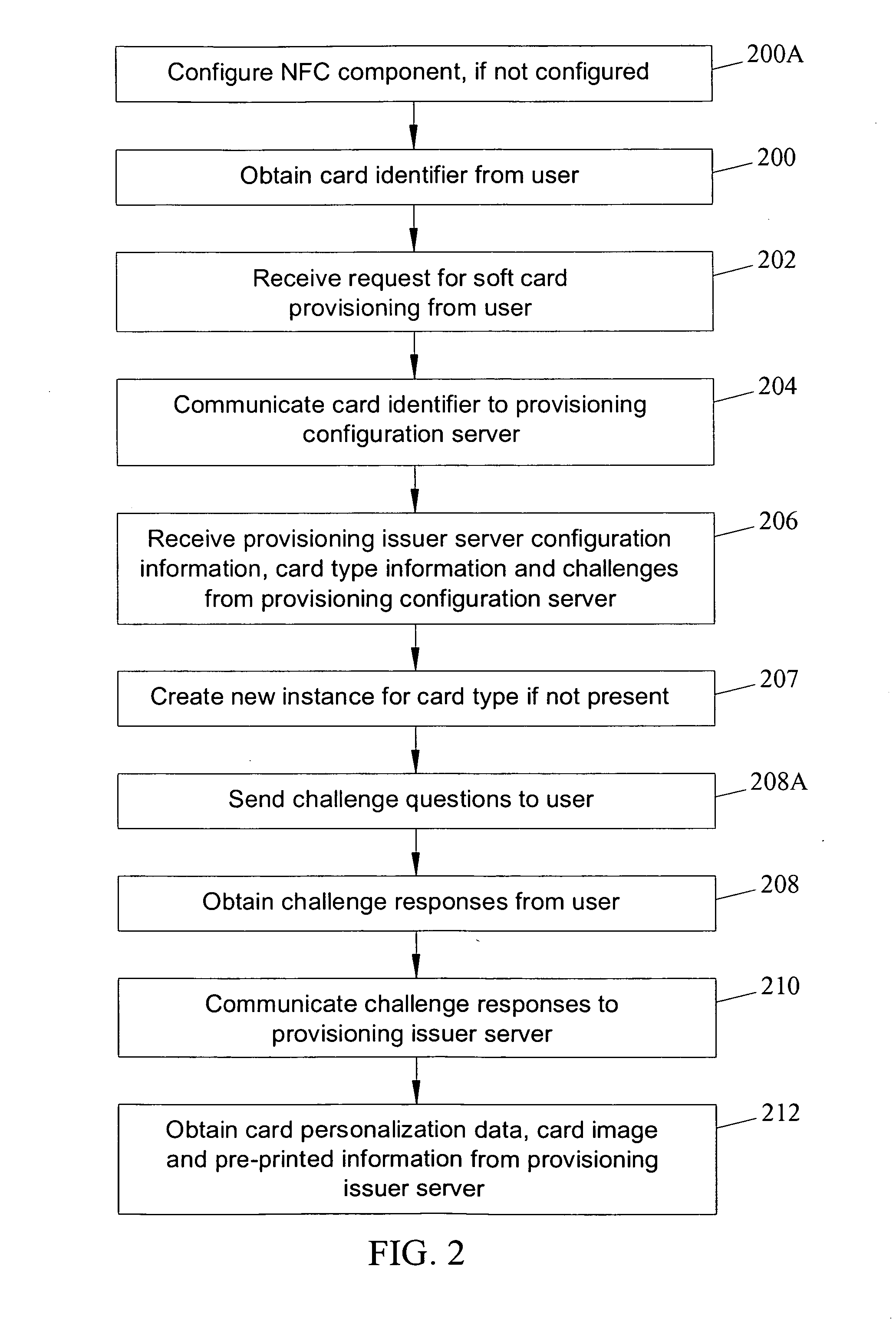
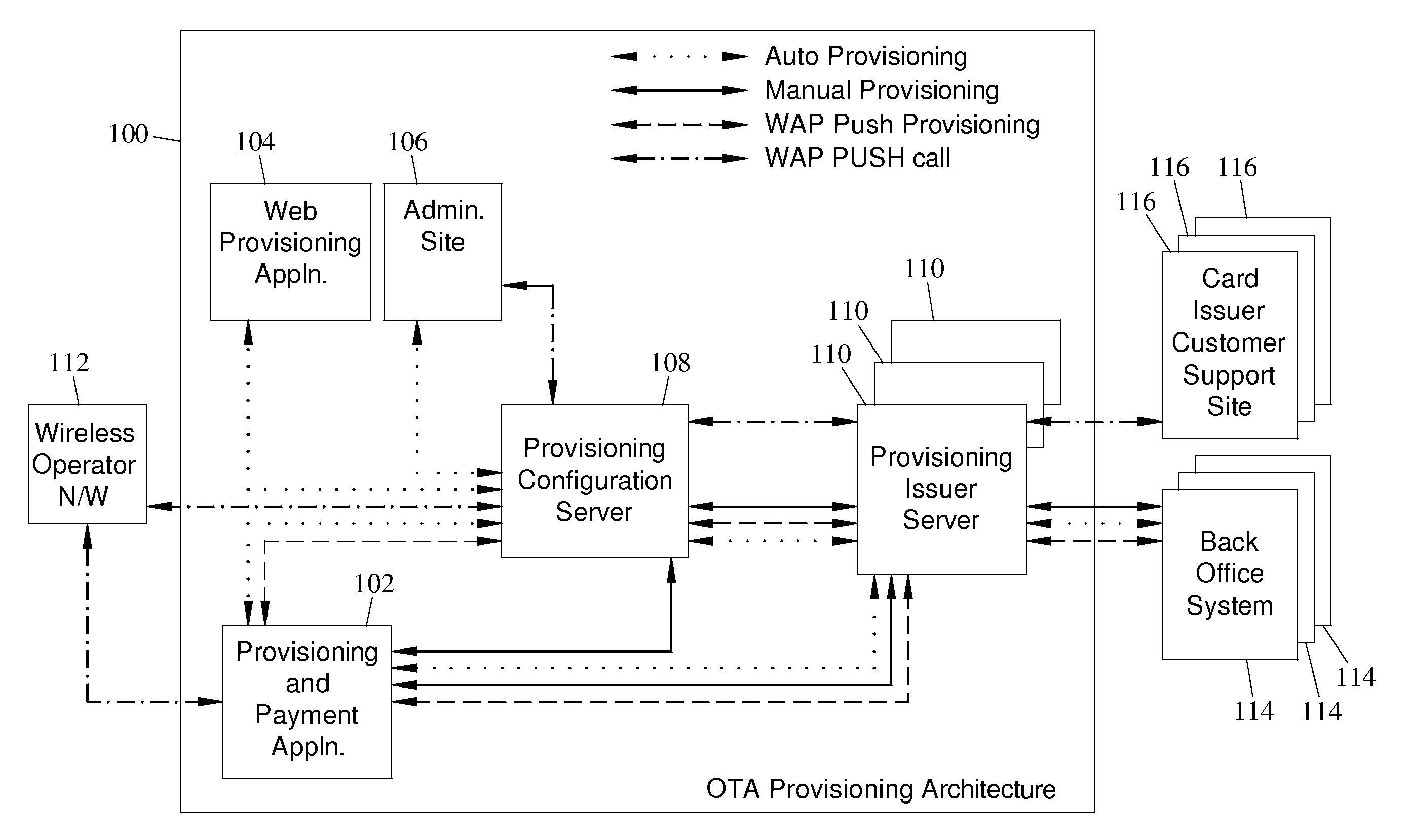
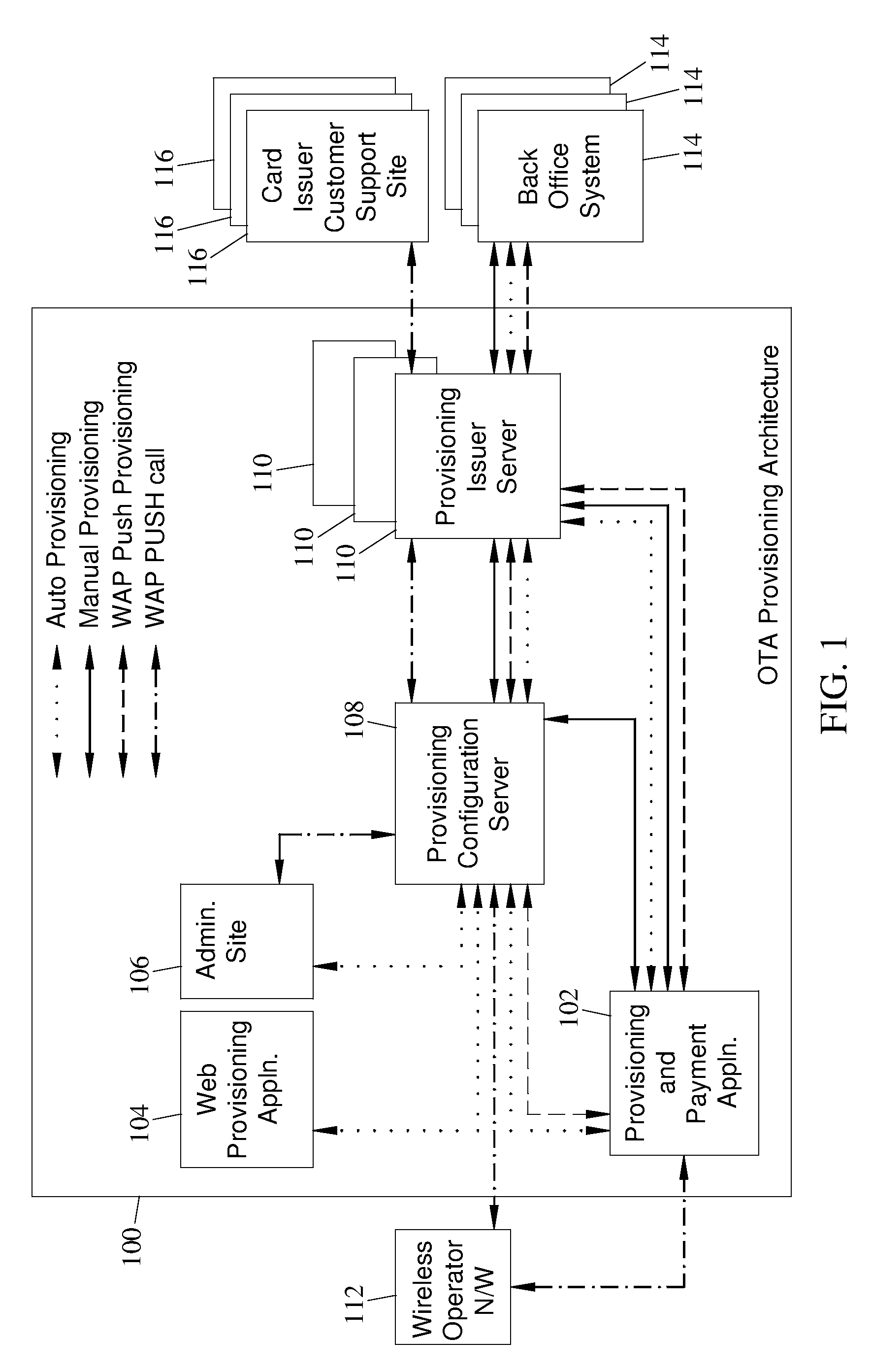
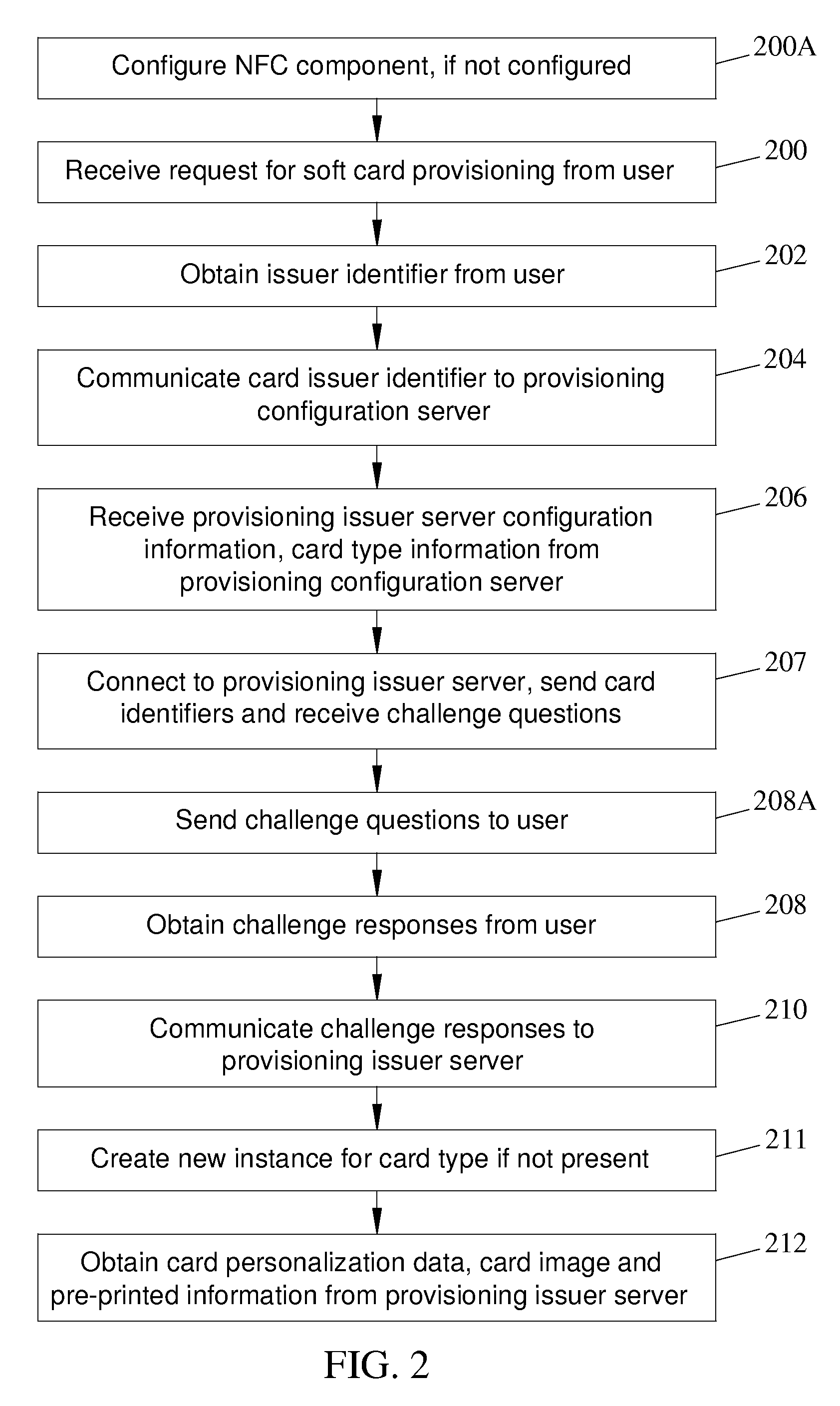
Methods, systems and computer program products for over the air (OTA) provisioning of soft cards on devices with wireless communications capabilities
ActiveUS7469151B2Shorten the timeEliminate needAcutation objectsSpecial service for subscribersComputer hardwarePersonalization
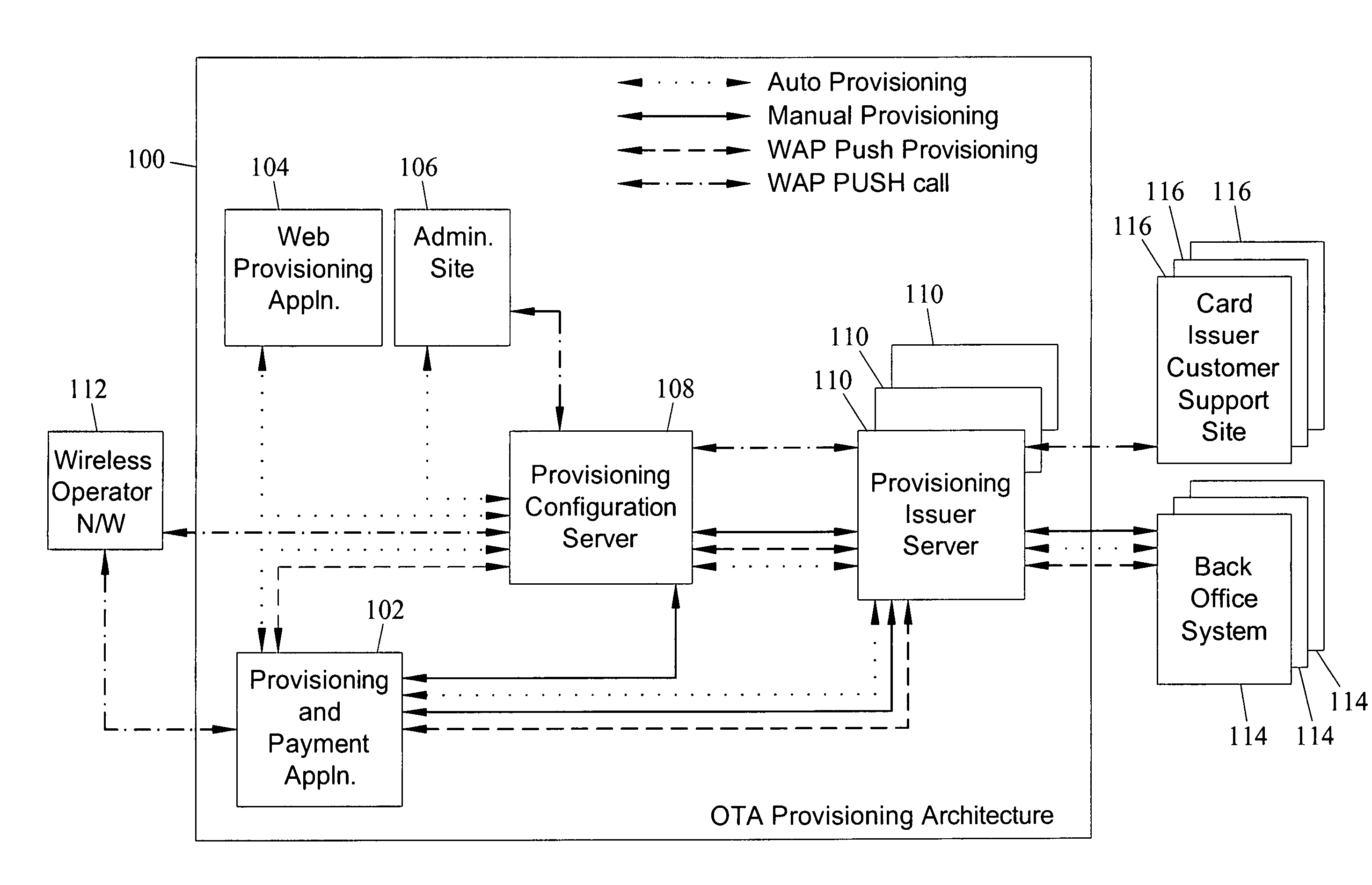
Methods, systems, and computer program products for over the air provisioning of soft cards on devices with wireless communications capabilities are disclosed. According to one method, a soft card provisioning application is instantiated on a device with wireless communications capabilities. A card number for a soft card desired to be provisioned on the device is obtained from a user of the device. The card number is communicated to a provisioning configuration server over an air interface. Card-issuer-specific challenges corresponding to the card number and a provisioning issuer server network address are obtained from the provisioning configuration server. The challenges are presented to the user, and the user's responses to the challenges are received. A connection is made to the provisioning issuer server corresponding to the network address. The challenge responses are communicated to the provisioning issuer server. Soft card personalization data for activating the soft card is received from the provisioning issuer server. The soft card is provisioned for use on the device based on the personalization data.
Owner:MASTERCARD INT INC
Methods and apparatus for conducting electronic transactions
InactiveUS20090076966A1Enhanced reliability and confidenceReduce security risksComplete banking machinesAcutation objectsAuthorization certificateChallenge response
A system and method for facilitating electronic transactions using an intelligent instrument is disclosed. An authorization server enables users to obtain authorization credentials through the use of the intelligent instrument by issuing a challenge to an intelligent token of the intelligent instrument. The intelligent token generates a challenge response and transmits the challenge response to the authorization server, which assembles credentials including a key for the electronic transaction upon validating the response. The authorization server sends the assembled credentials to the intelligent instrument and the intelligent instrument transmits the assembled credentials to the authorization server during a subsequent transaction. The authorization server validates the assembled credentials and provides authorization for the transaction in response to the validating the assembled credentials.
Owner:LIBERTY PEAK VENTURES LLC
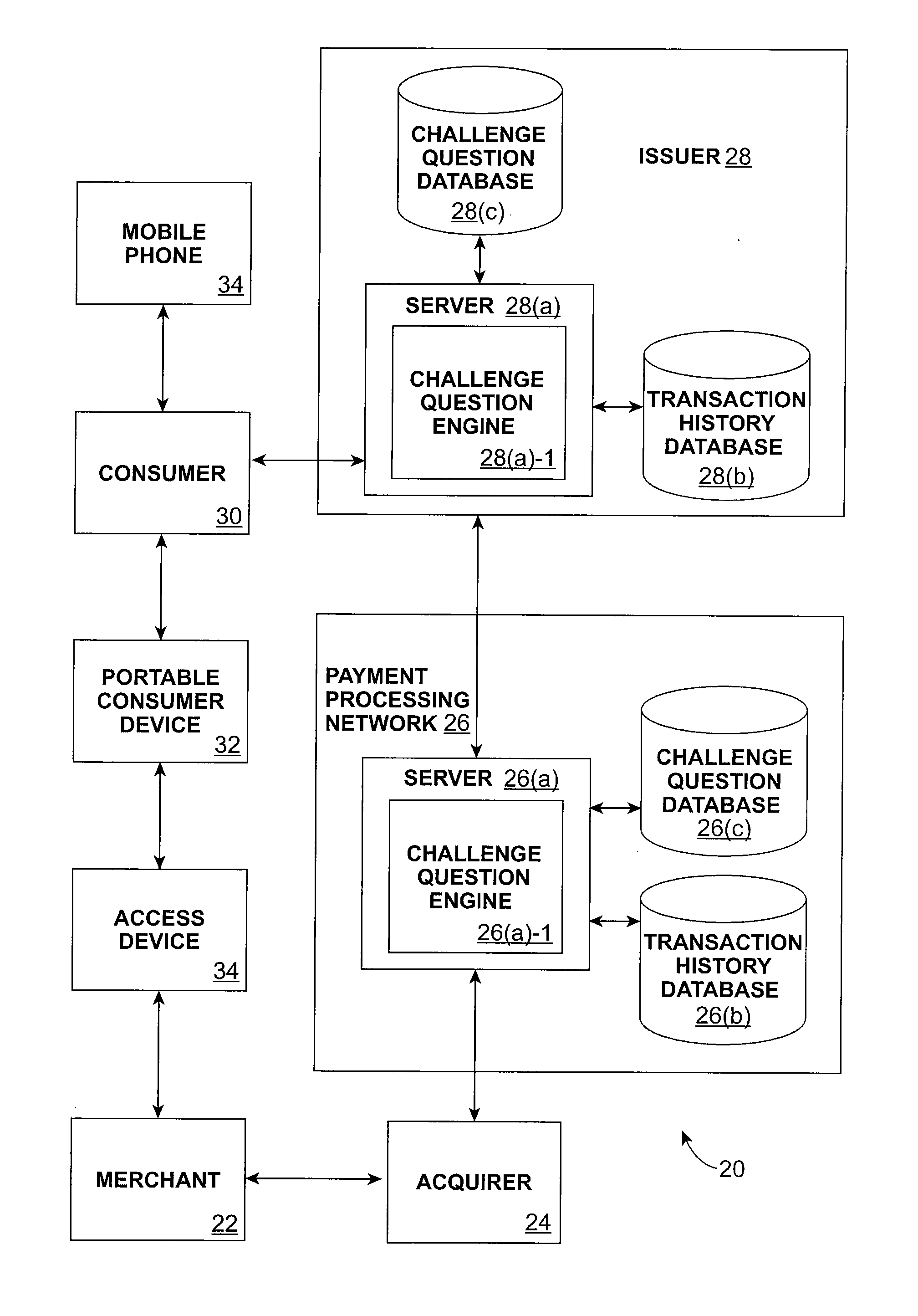
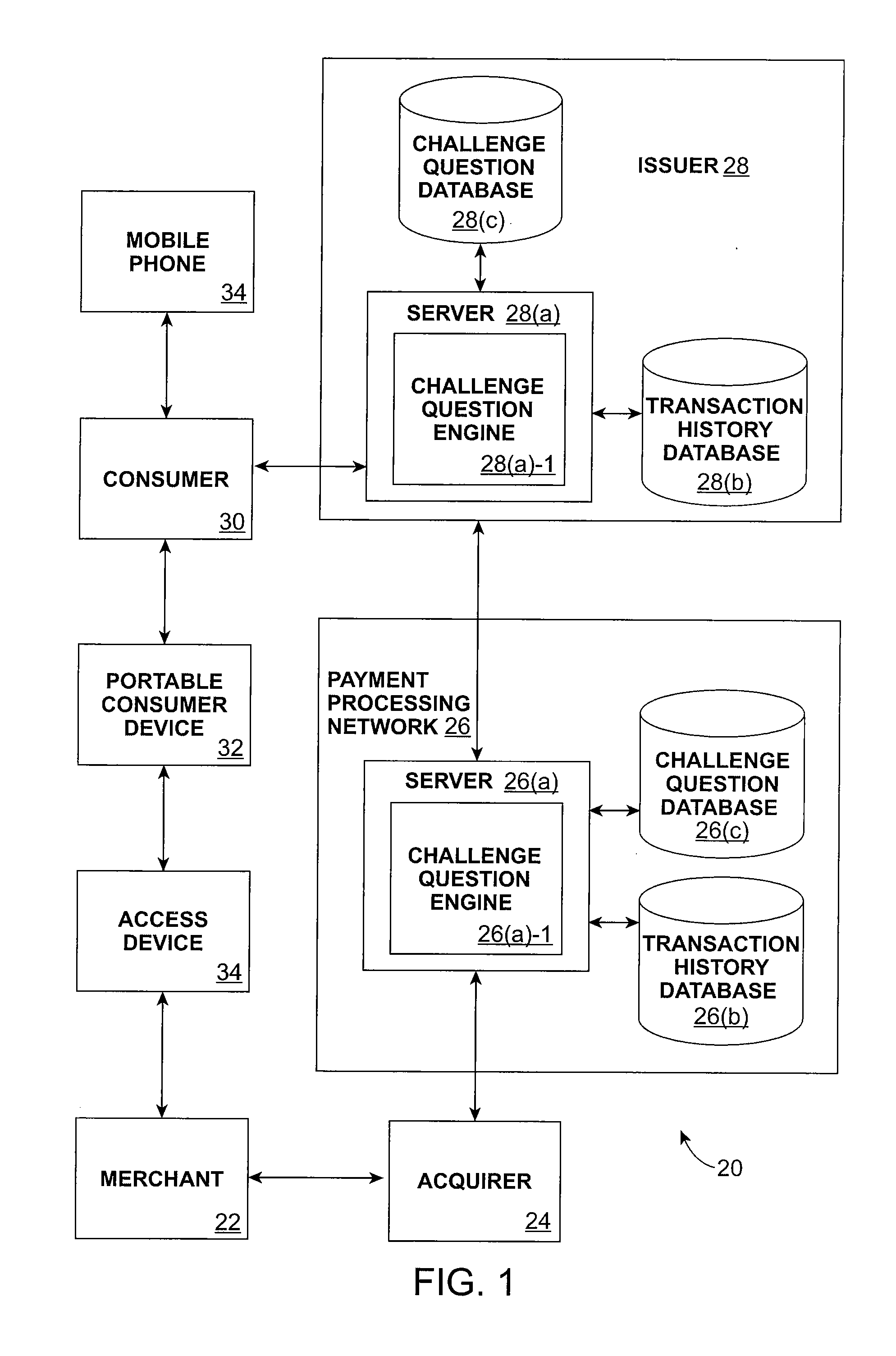
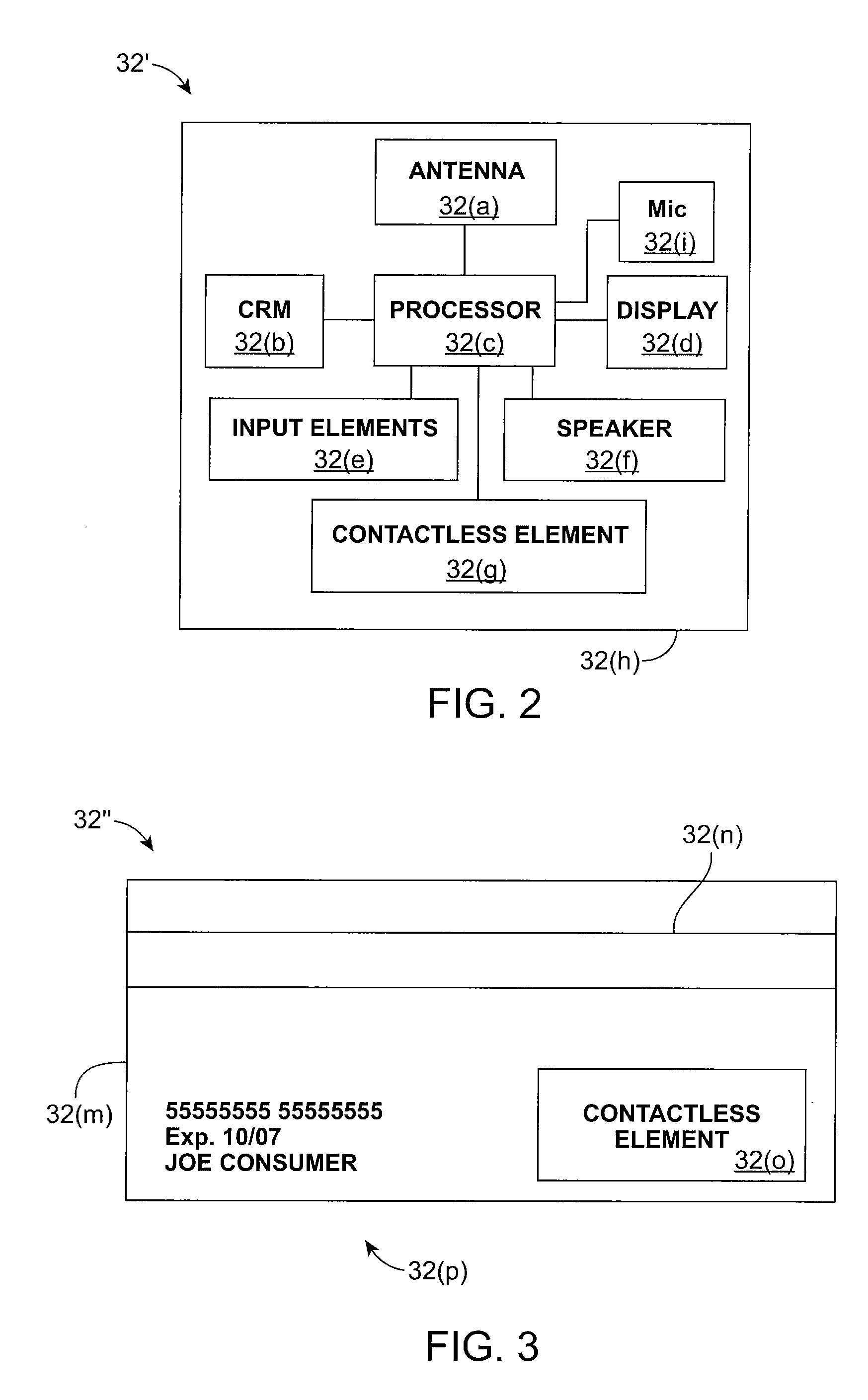
Consumer authentication system and method
A method for authenticating a consumer. The method includes receiving an authorization request message associated with a consumer conducting a transaction with a portable consumer device. A challenge message is sent to the consumer, where the challenge message is dynamic or semi-dynamic. A challenge response message is received from the consumer, and an authorization response message is sent to the consumer. The authorization response message indicates whether or not the transaction is authorized.
Owner:VISA USA INC (US)
Active E-mail Filter with Challenge-Response
InactiveUS20080168145A1Accurate answerMultiple digital computer combinationsOffice automationCorrect responseChallenge response
Owner:QUEST SOFTWARE INC
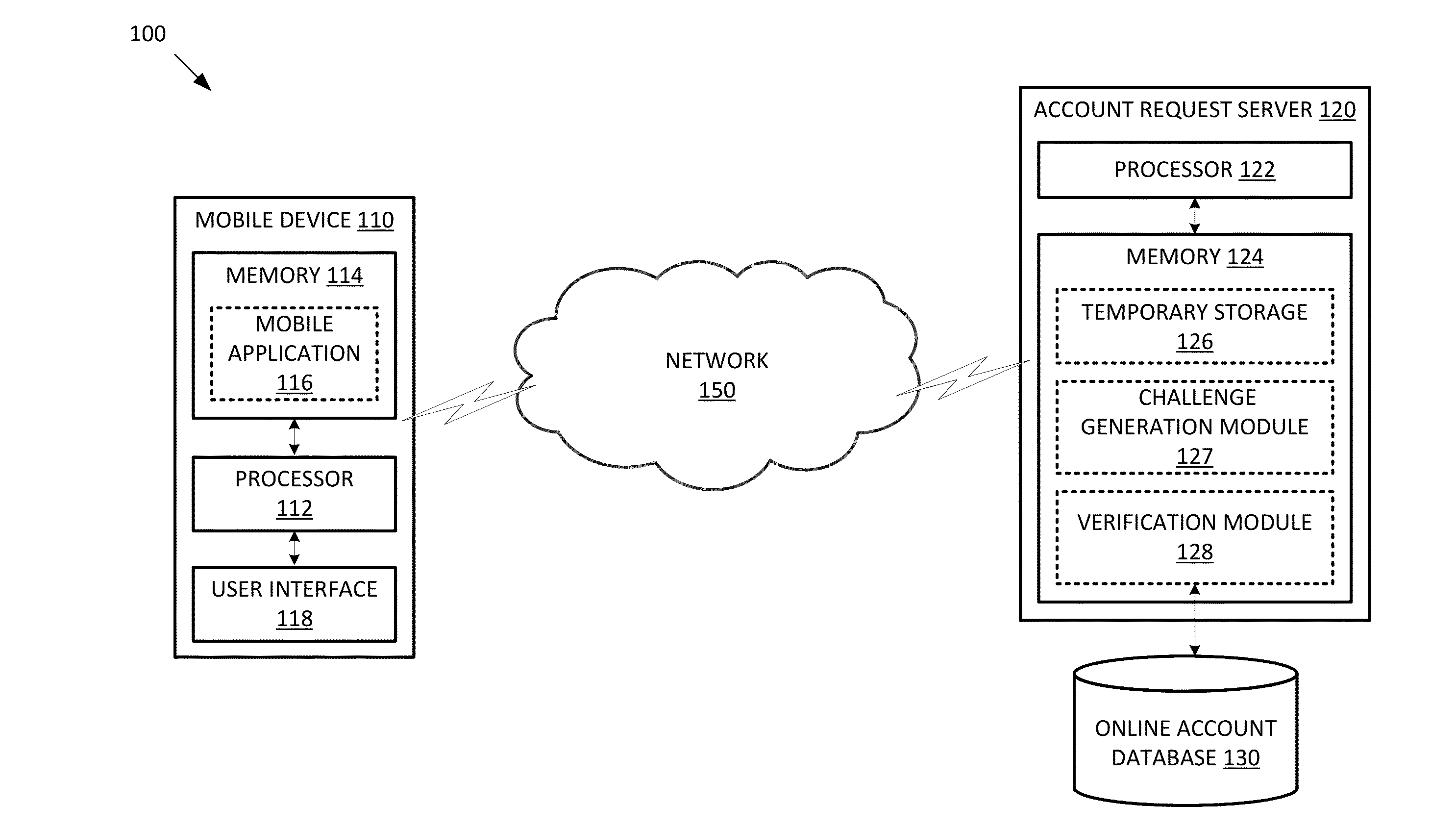
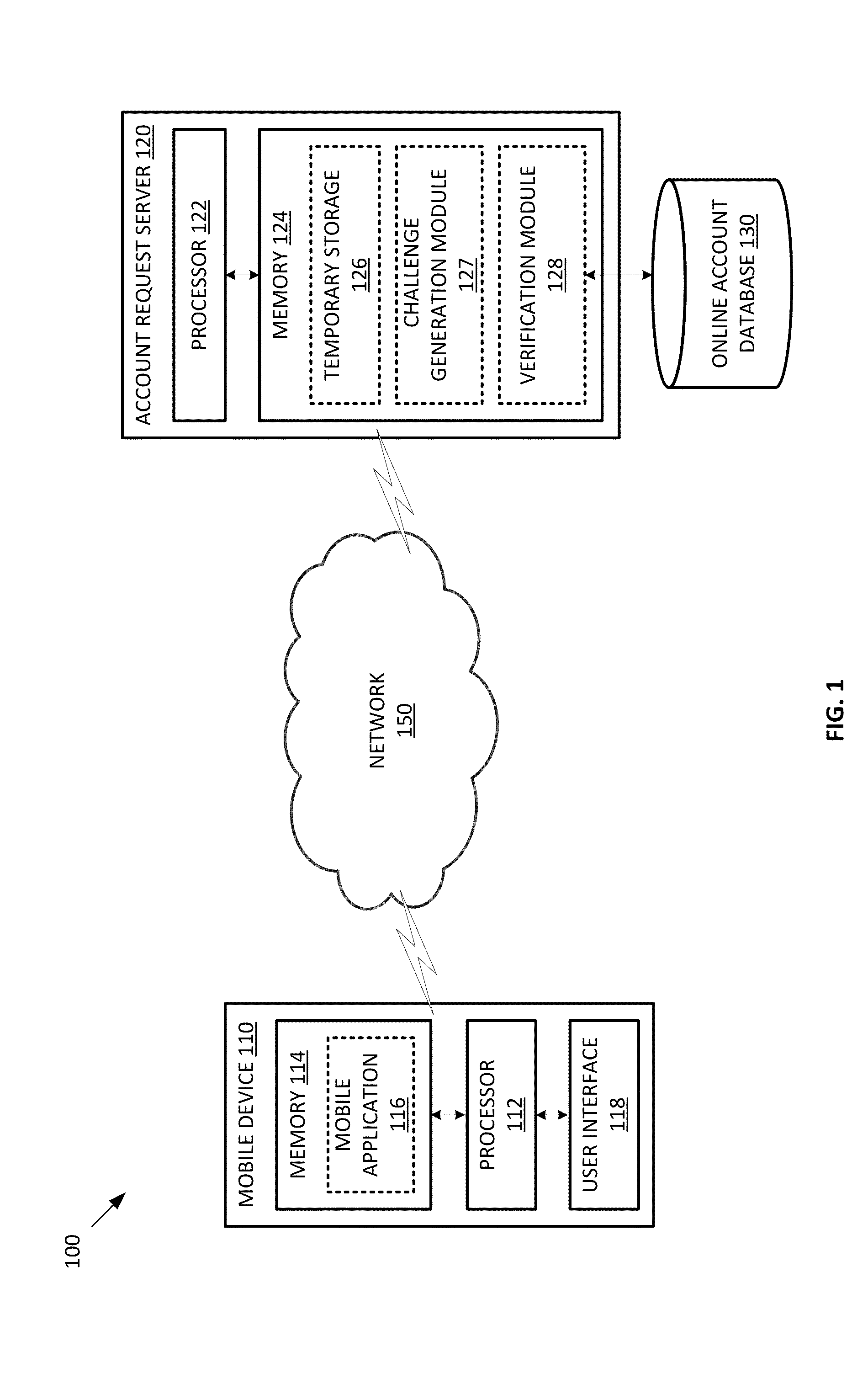
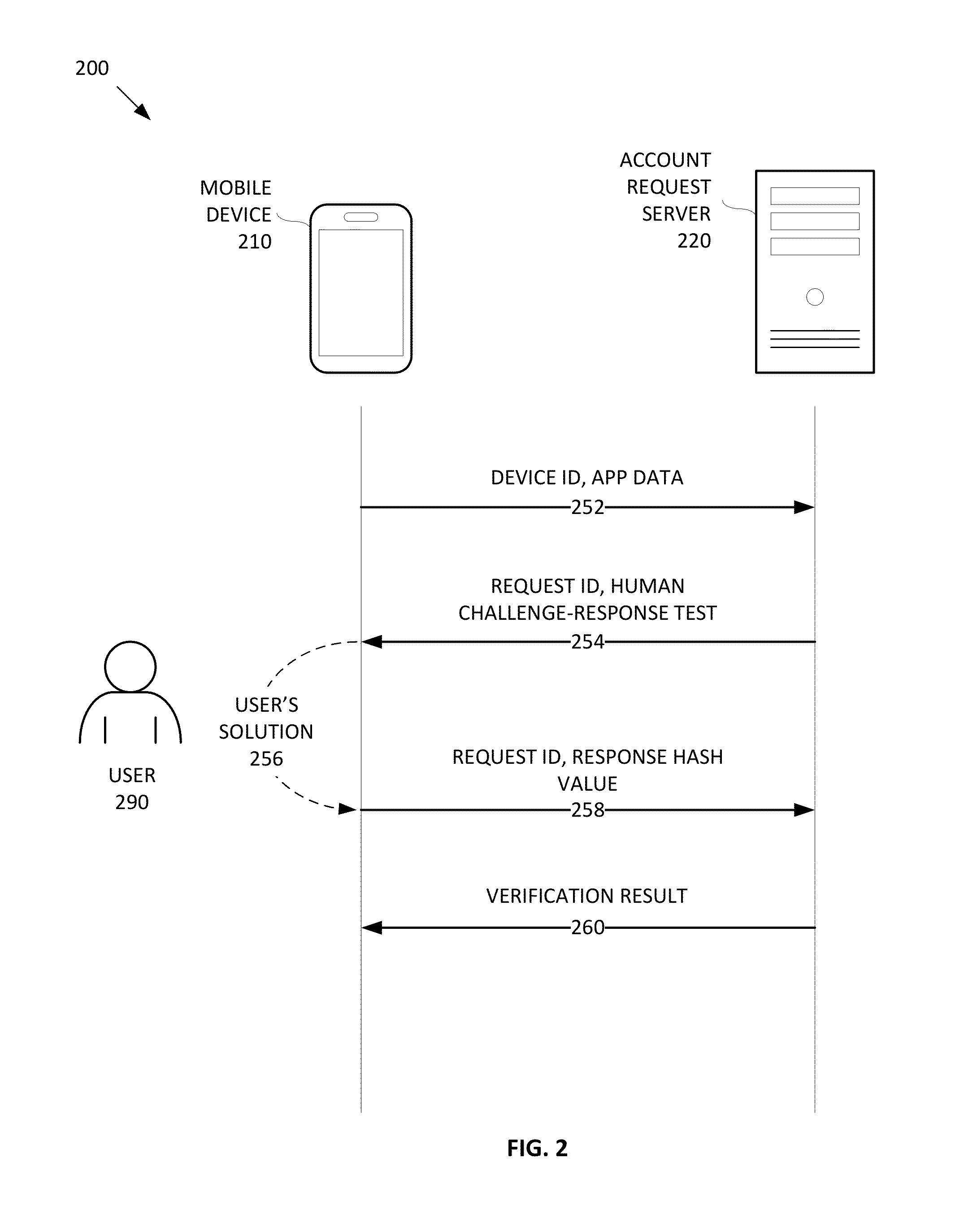
Mobile human challenge-response test
ActiveUS20130205370A1Digital data processing detailsMultiple digital computer combinationsHuman–computer interactionMobile device
Methods and systems for verifying whether a user requesting an online account is likely a human or an automated program are described. A request for an online account may be received from a mobile device. A human challenge-response test adapted for displaying on a mobile device is displayed on the mobile device. Upon viewing the human challenge-response test, the user enters the user's solution to the human challenge-response test on the mobile device. A response hash value is created based on the user's solution. The response hash value is sent to an account request server for verification.
Owner:VISA INT SERVICE ASSOC
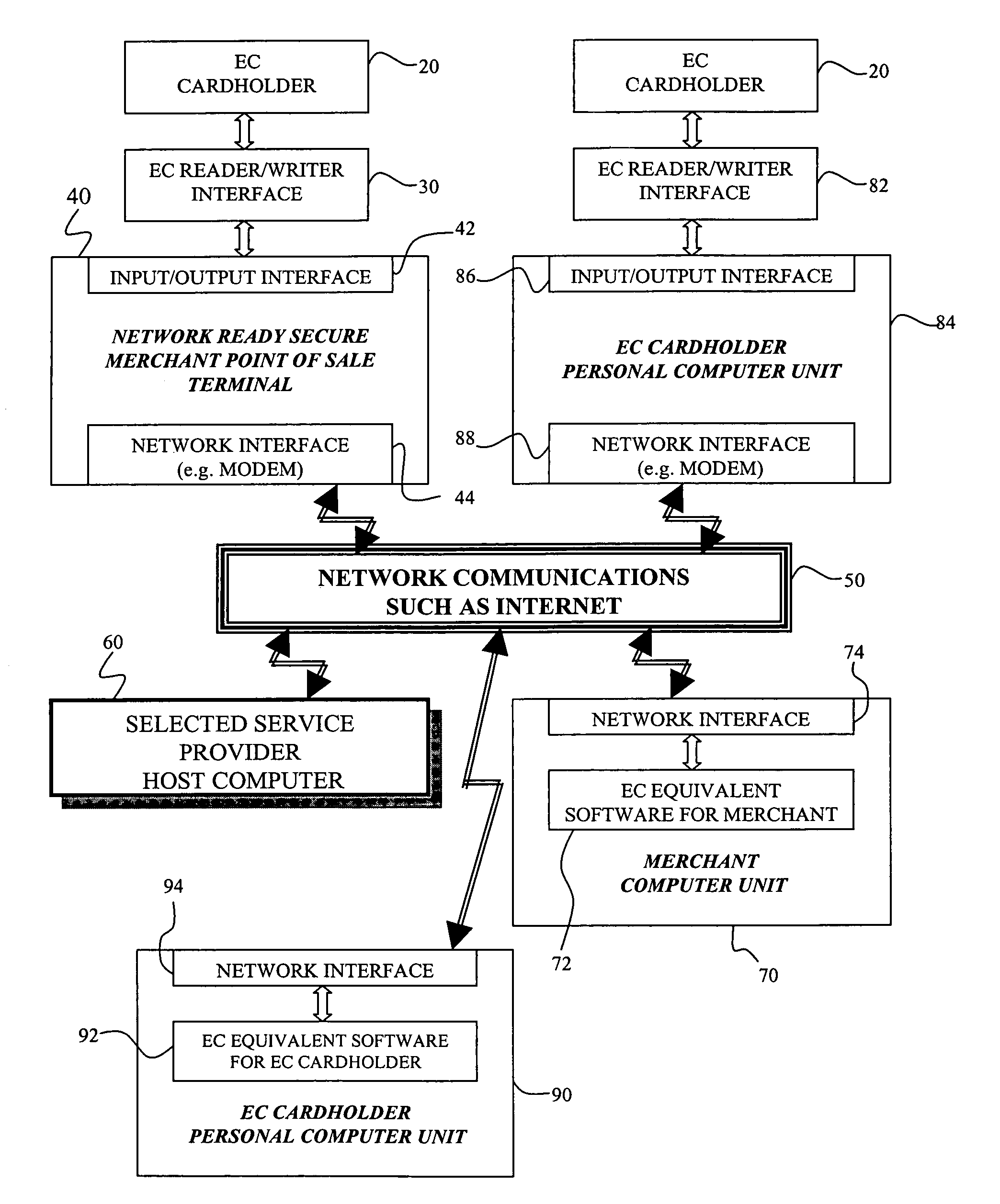
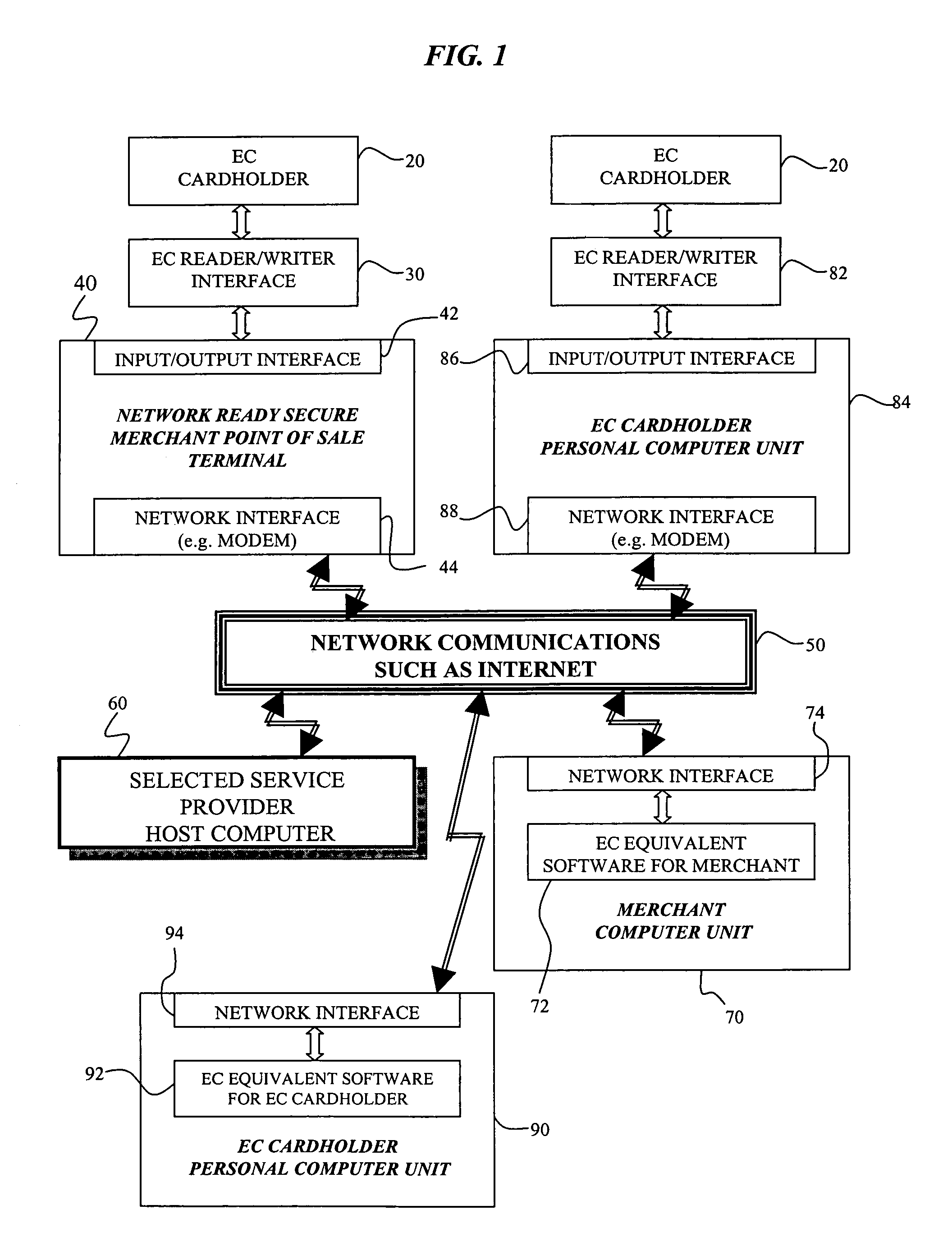
Cryptographic system and method for electronic transactions
InactiveUS7096494B1Key distribution for secure communicationFinanceCredit cardSecure Electronic Transaction
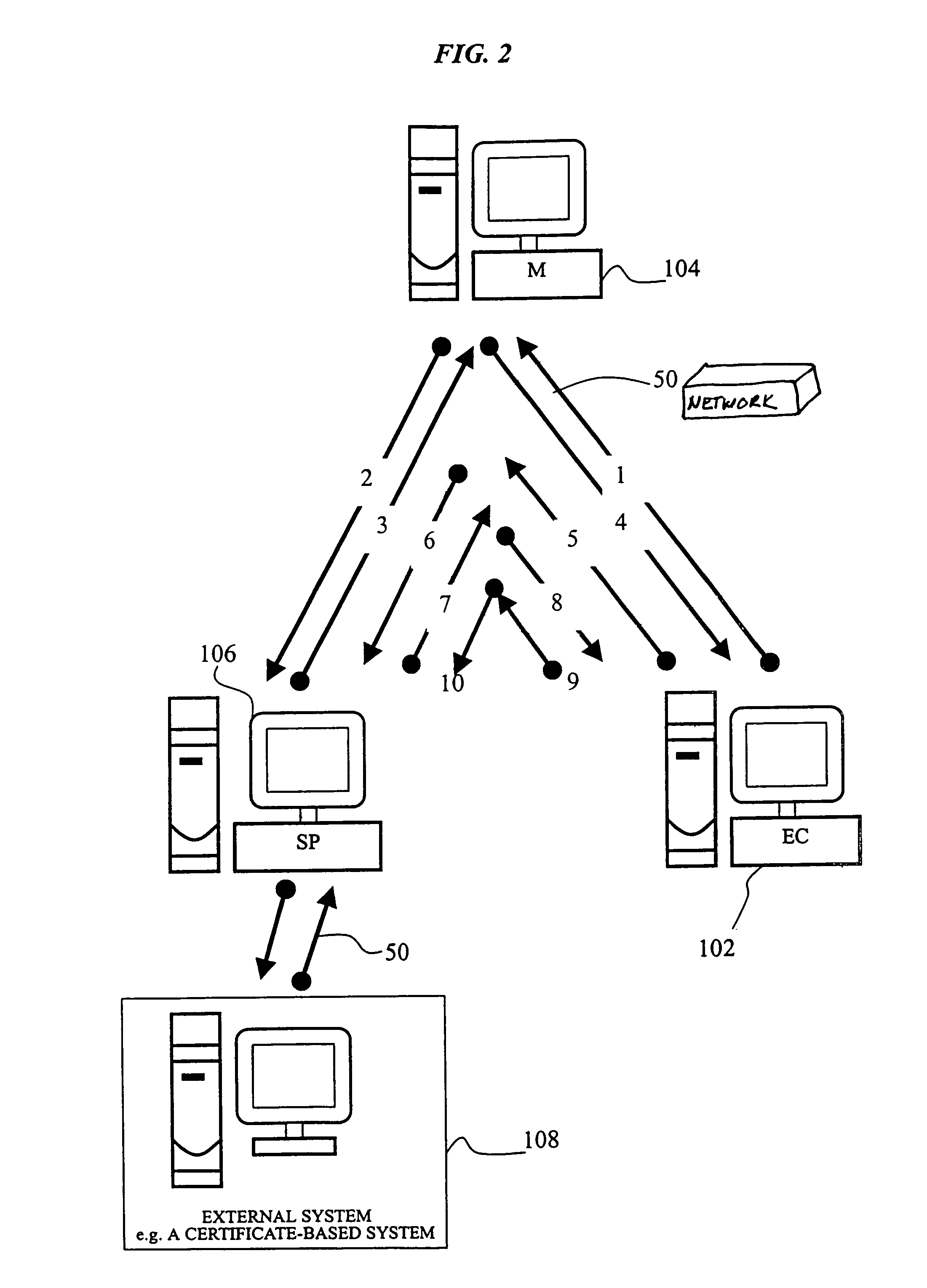
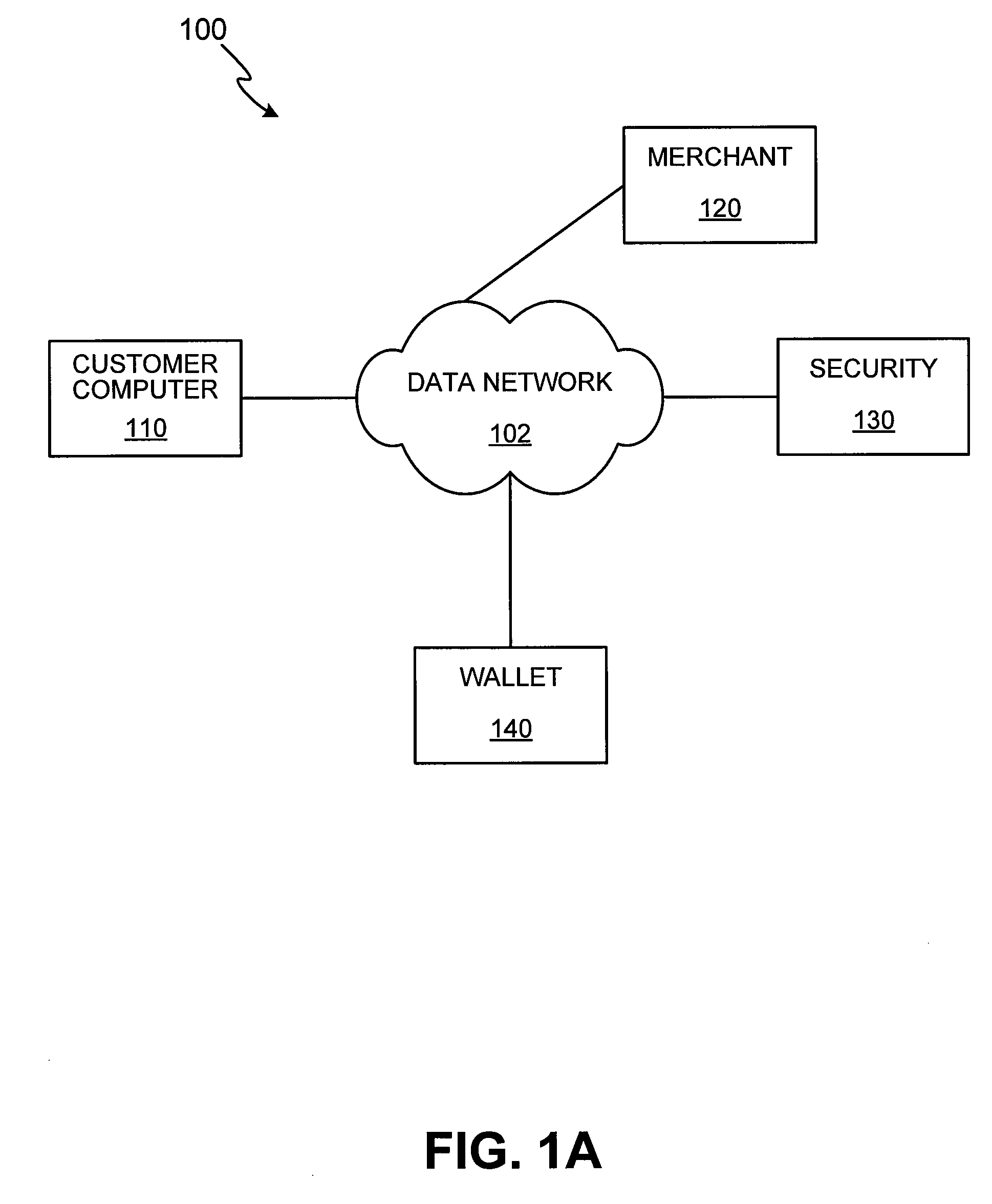
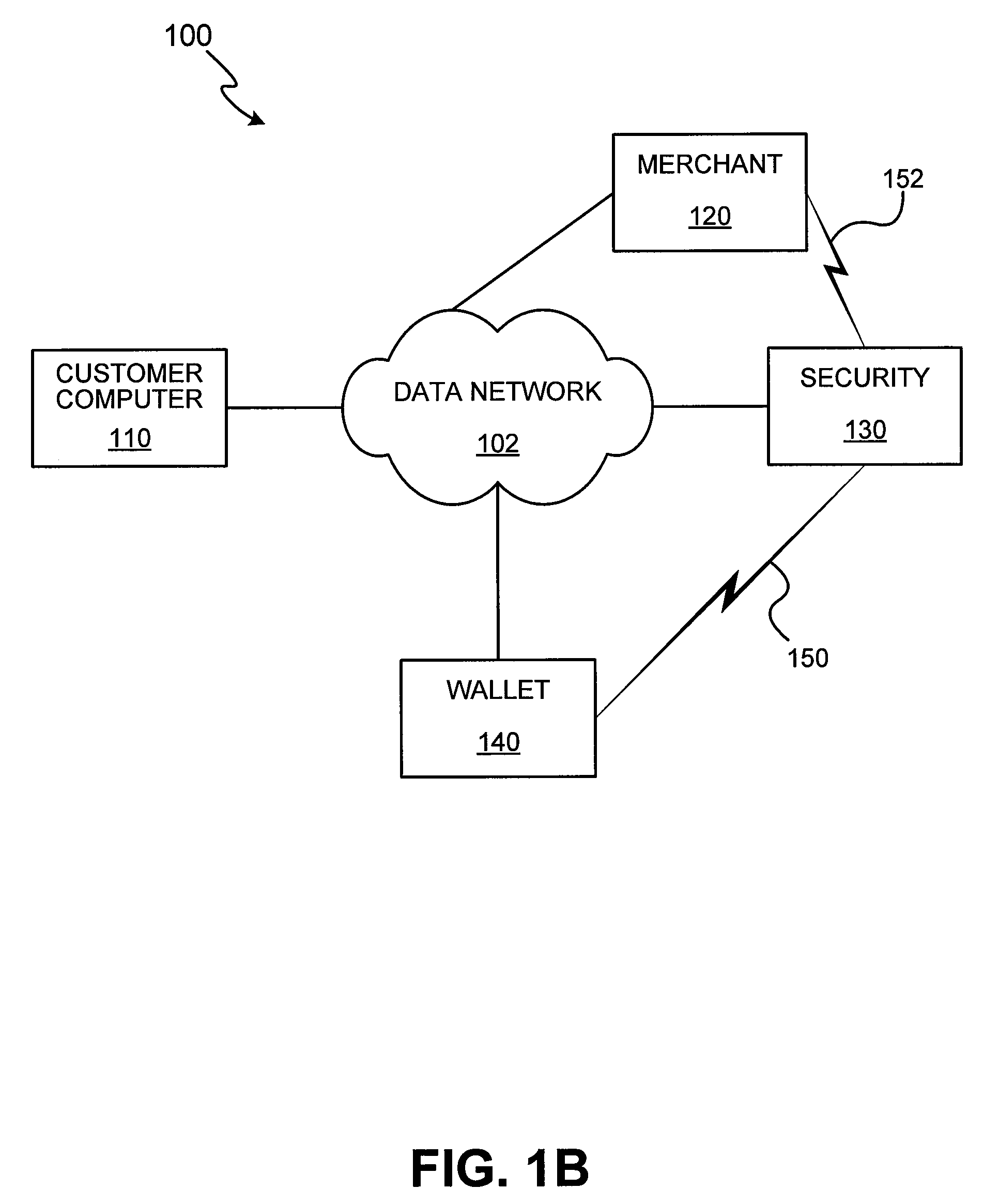
An electronic transaction system, which facilitates secure electronic transactions among multiple parties including cardholders, merchants, and service providers (SP). The system involves electronic cards, commonly known as smart cards, and their equivalent computer software package. The card mimics a real wallet and contains commonly seen financial or non-financial instruments such as a credit card, checkbook, or driver license. A transaction is protected by a hybrid key cryptographic system and is normally carried out on a public network such as the Internet. Digital signatures and challenges-responses are used to ensure integrity and authenticity. The card utilizes secret keys such as session keys assigned by service providers (SPs) to ensure privacy for each transaction. The SP is solely responsible for validating each participant's sensitive information and assigning session keys. The system does not seek to establish a trust relationship between two participants of a transaction. The only trust relationship needed in a transaction is the one that exists between individual participants and the SP. The trust relationship with a participant is established when the SP has received and validated certain established account information from that particular participant. To start a transaction with a selected SP, a participant must have the public key of the intended SP. Since the public key is openly available, its availability can be easily established by the cardholder. The SP also acts as a gateway for the participants when a transaction involves interaction with external systems.
Owner:CINGULAR WIRELESS II LLC
Online challenge-response
ActiveUS8533118B2Reduce theftSpeed up the processFinanceDigital data processing detailsThird partyChallenge response
Embodiments of the invention enable cardholders conducting an online transaction to be authenticated in real-time using a challenge-response application. The challenge-response application can be administered by an issuer or by a third party on-behalf-of an issuer. A challenge question can be presented to the cardholder, and the cardholder's response can be verified. The challenge question presented can be selected based on an analysis of the risk of the transaction and potentially other factors. A variety of dynamic challenge questions can be used without the need for the cardholder to enroll into the program. Additionally, there are many flexible implementation options of the challenge-response application that can be adjusted based on factors such as the location of the merchant or the location of the consumer.
Owner:VISA INT SERVICE ASSOC
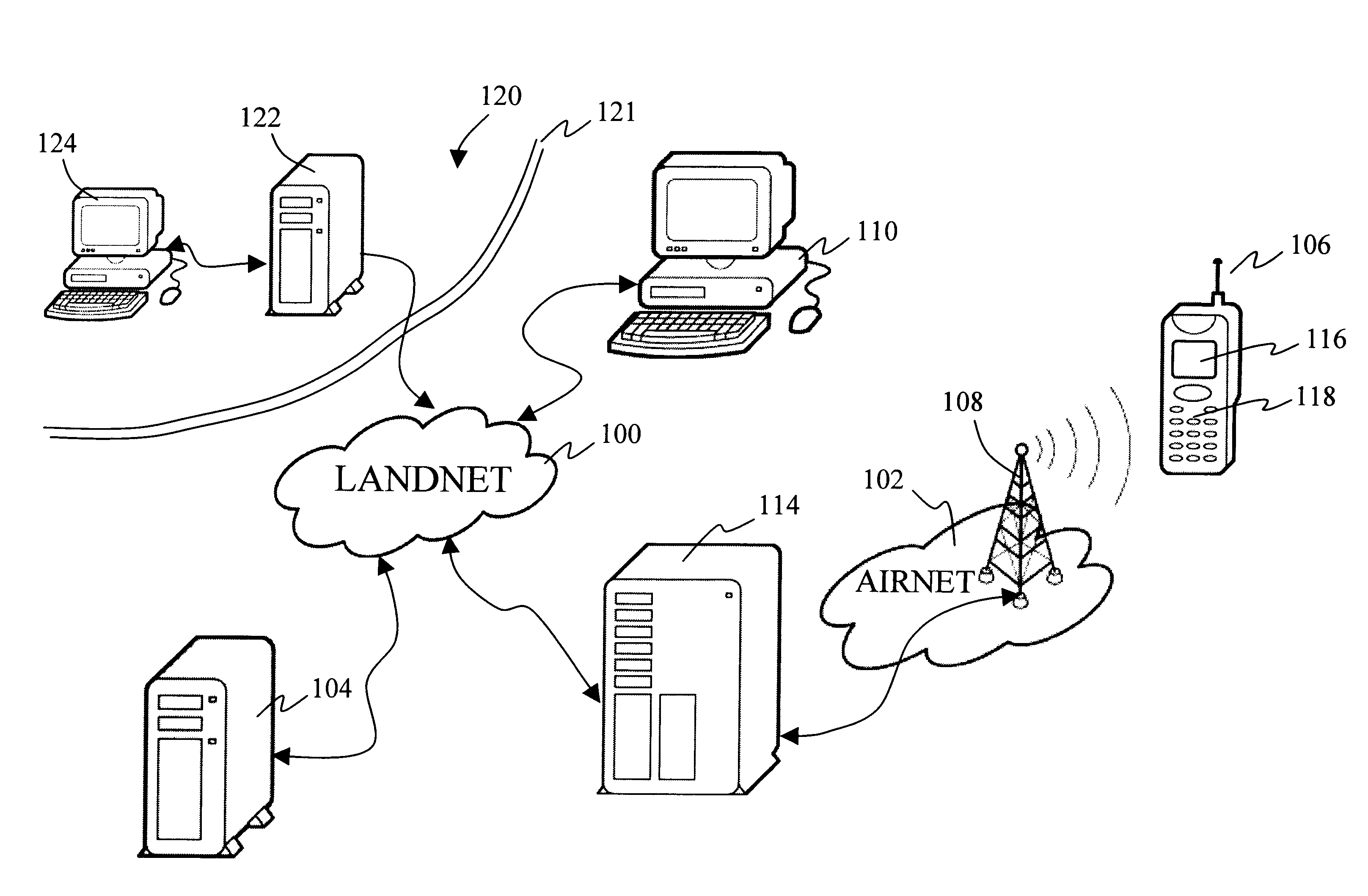
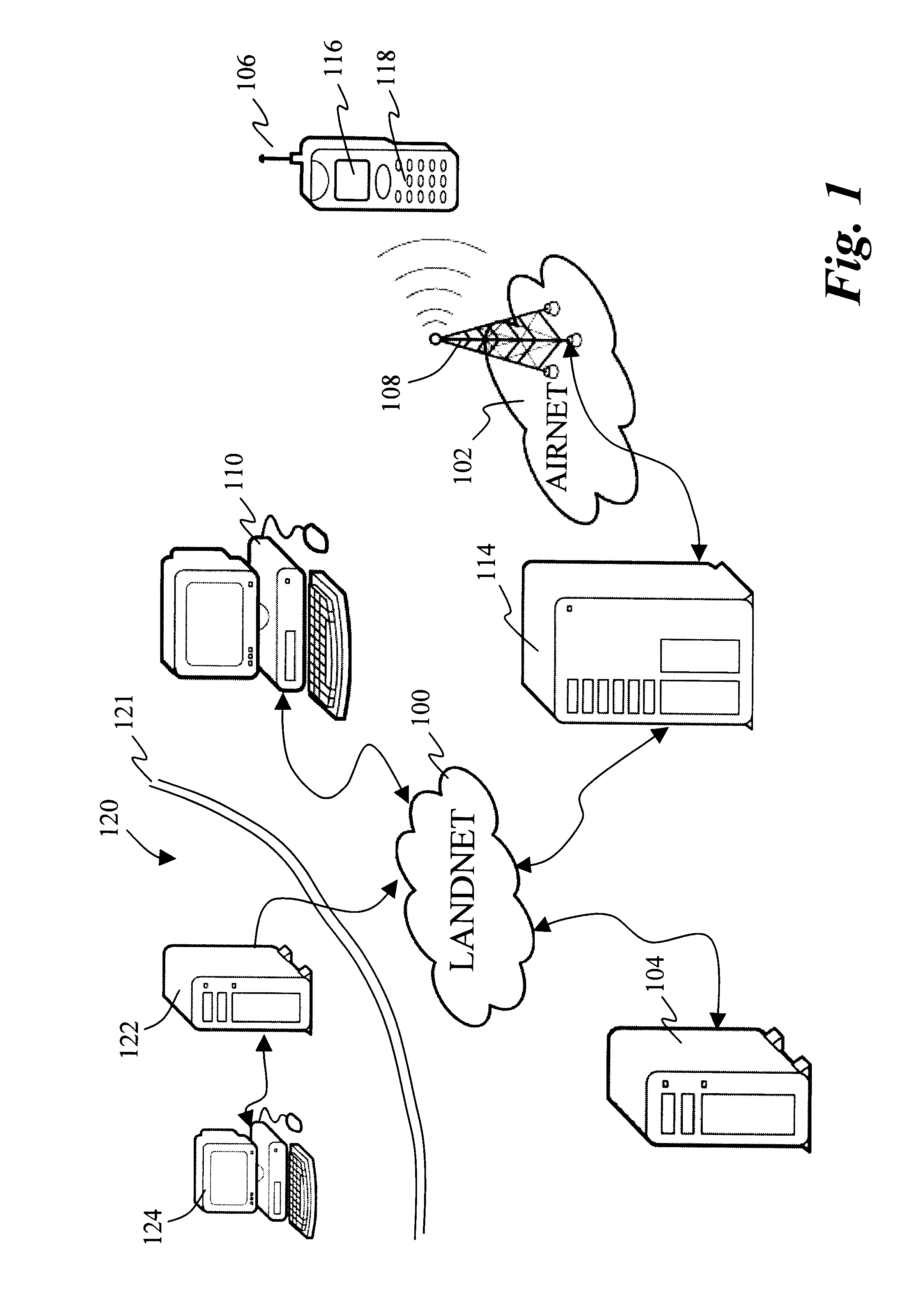
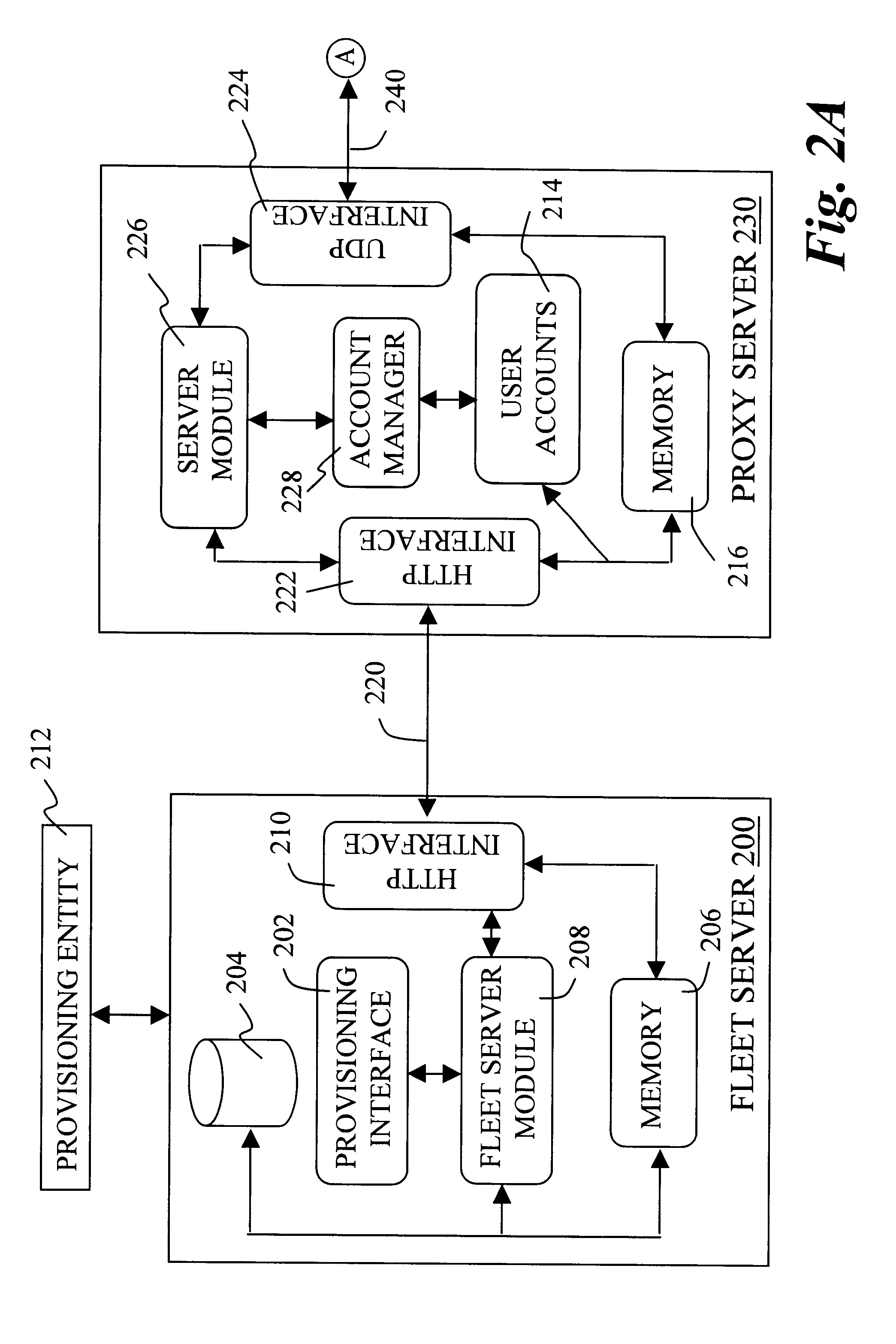
Method and architecture for managing a fleet of mobile stations over wireless data networks
InactiveUS6292657B1Frequency-division multiplex detailsUnauthorised/fraudulent call preventionFleet managementWireless data
The present invention discloses a fleet managing system in which fleet data can be securely managed and disseminated to a selective group of mobile stations serviced by a carrier infrastructure. The fleet managing system relies on a series of consecutive transitive trusts between pairs of components in the system so that all communications from a provisioning entity to the mobile stations are secure. The access to the fleet managing system is guarded with a challenge response every time there is a request arriving at the system while the mobile stations are verified by an account manager in the system to ensure that the fleet data is eventually pushed to the correct group of mobile stations. Apart distinctly from existing fleet managing systems for mobile stations, the present invention provides secure means for an authorized entity, from anywhere at any time, to control the dissemination of mobile data to a specified group of mobile stations without incurring additional costs to or direct involvement of a service carrier.
Owner:UNWIRED PLANET
Method and system for encrypting and decrypting data using an external agent
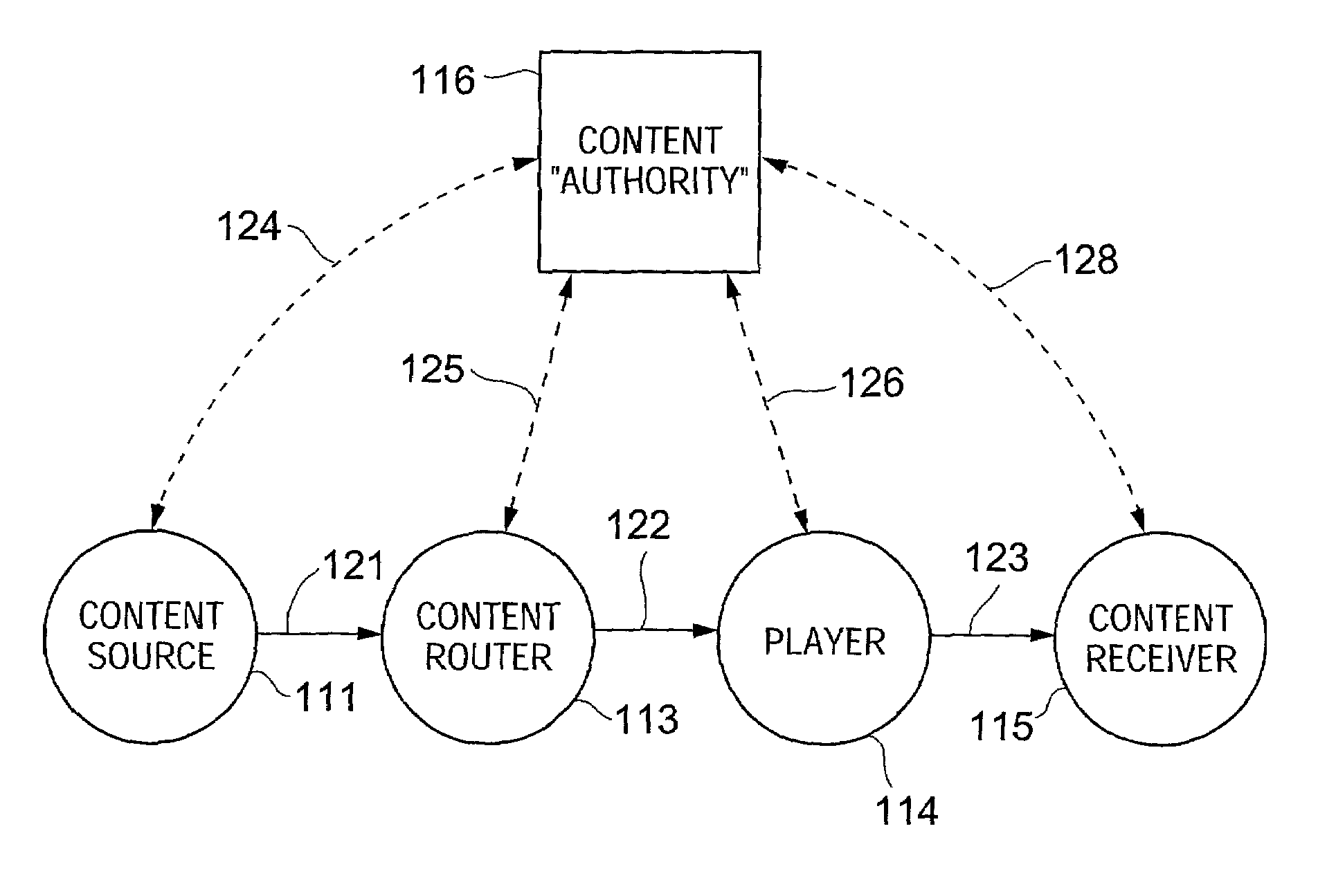
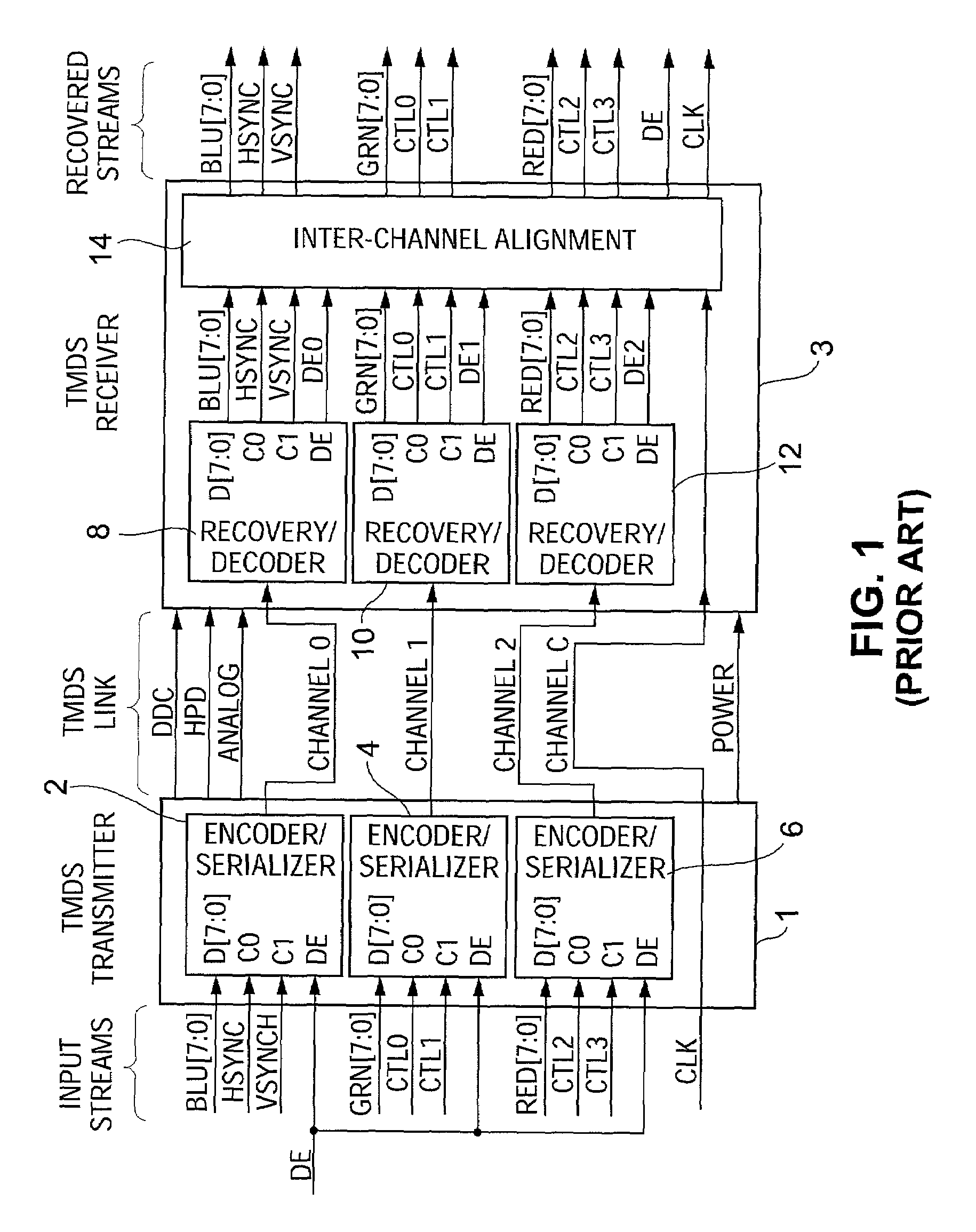
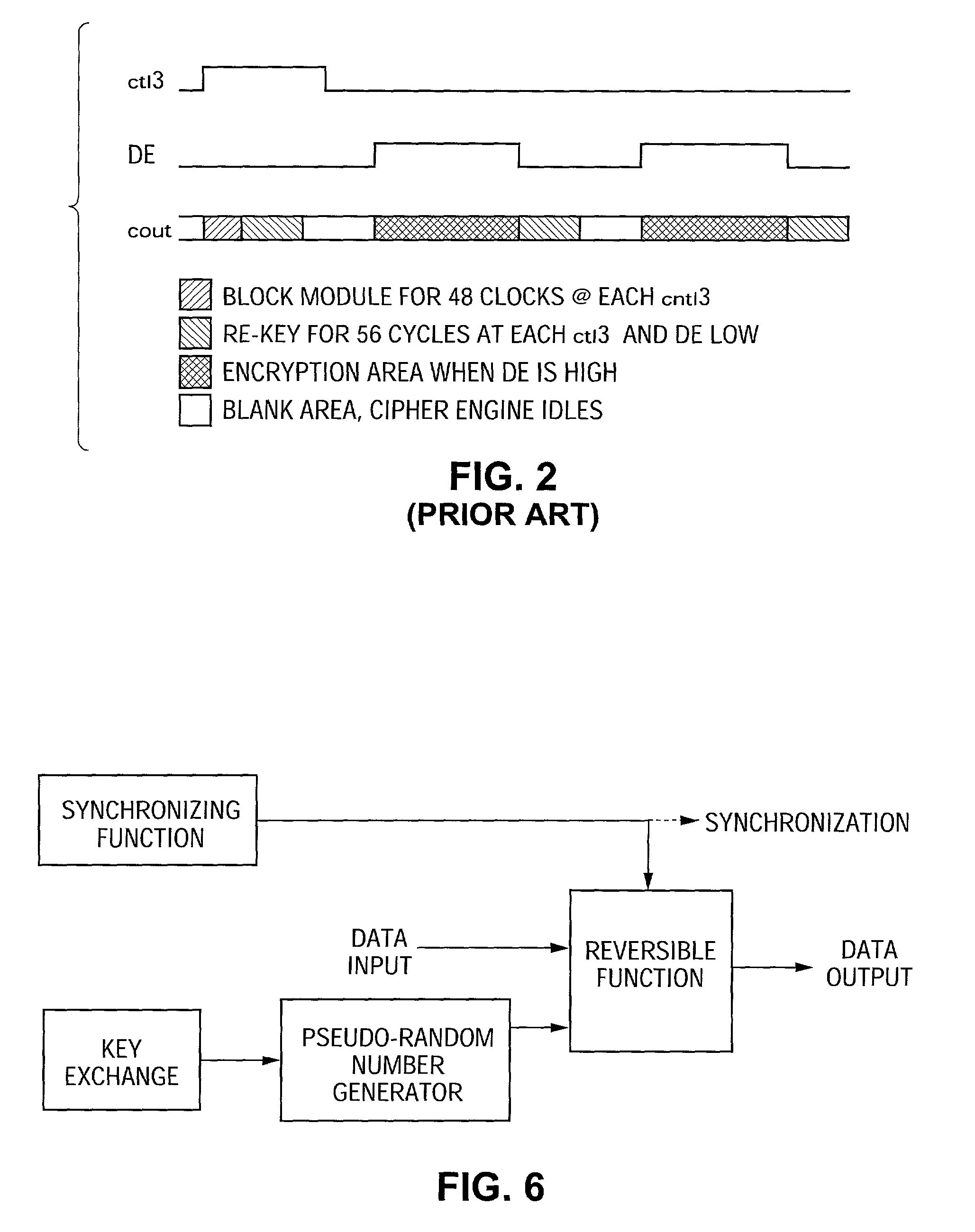
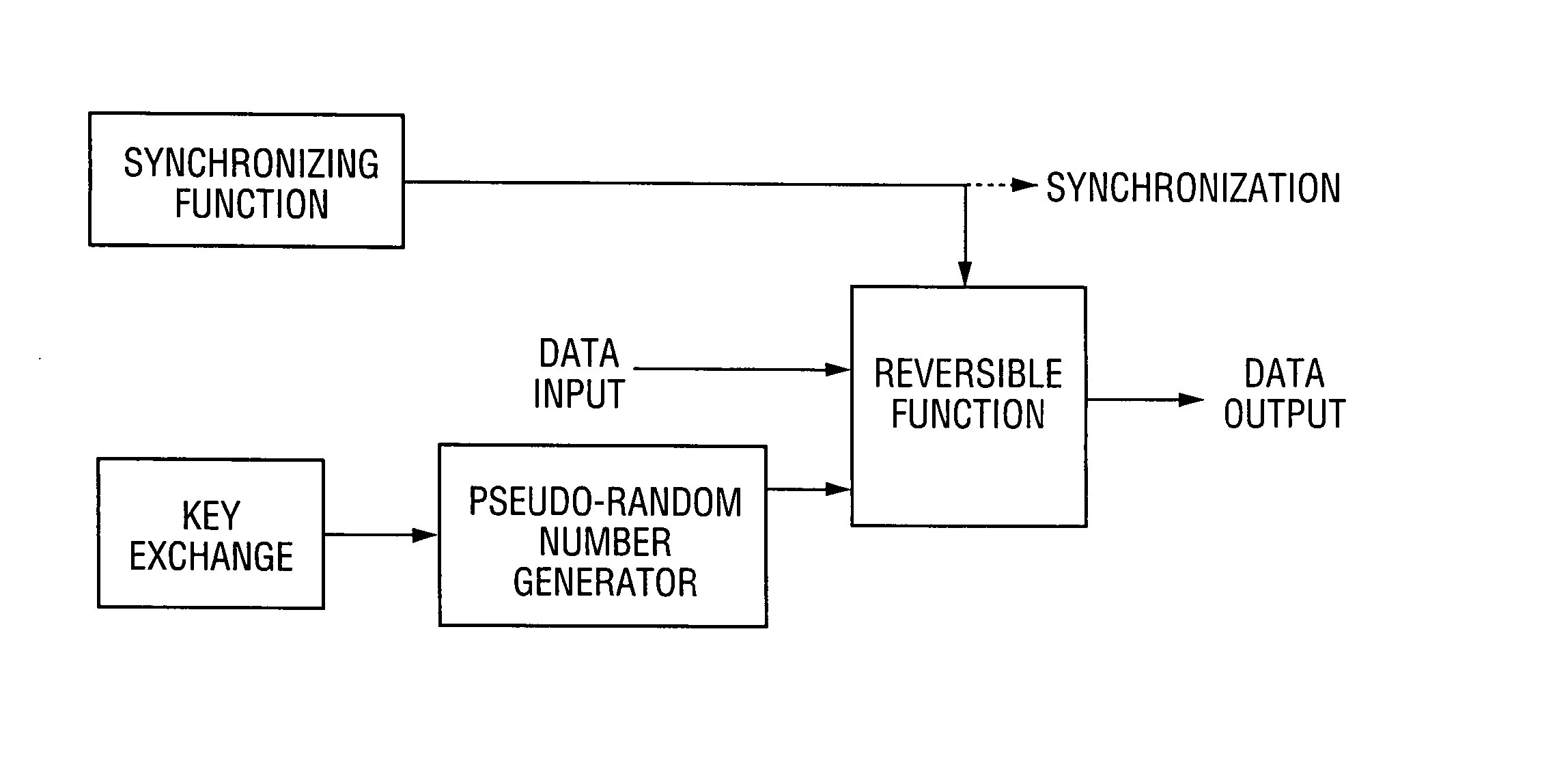
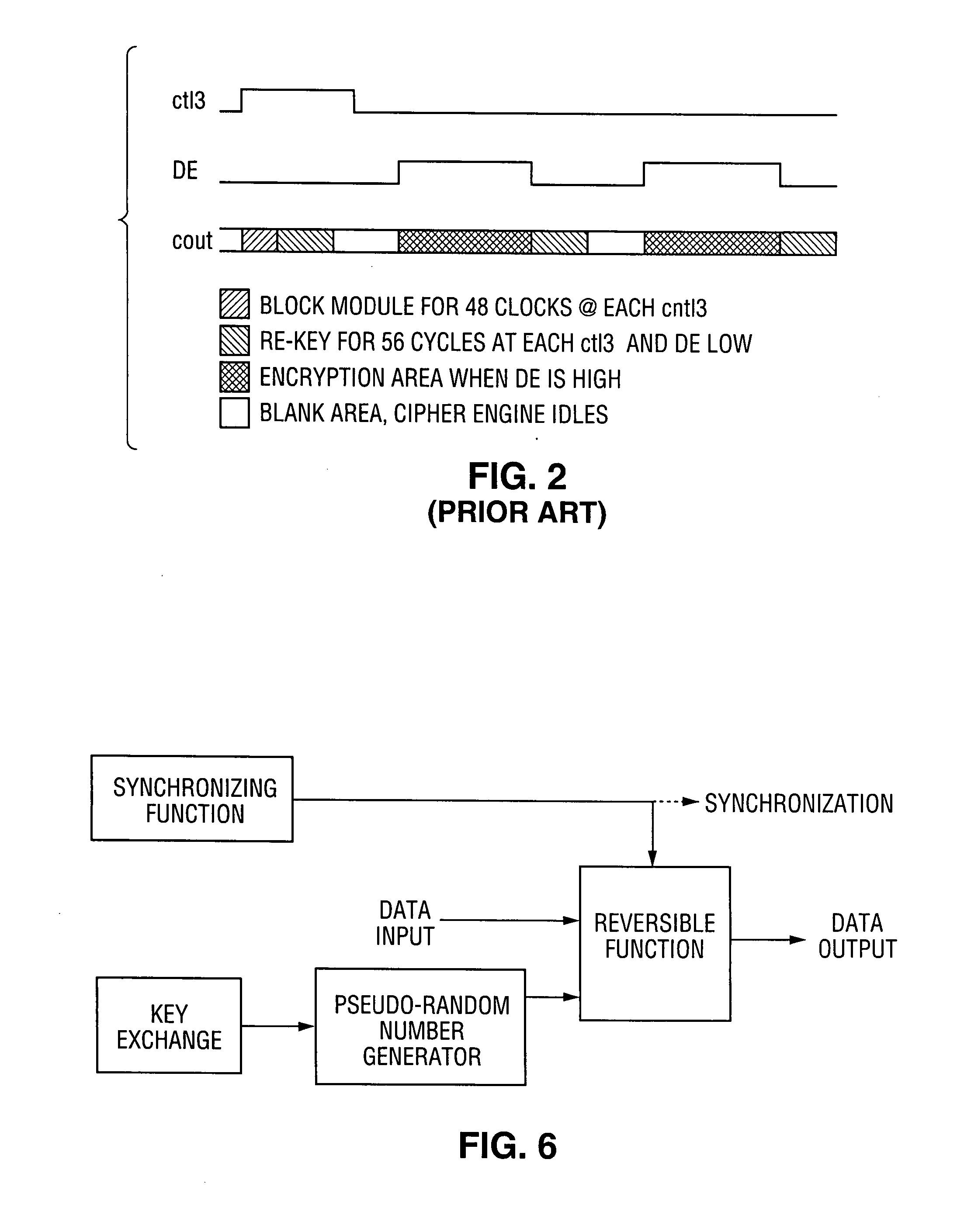
ActiveUS7242766B1Improve securitySynchronising transmission/receiving encryption devicesSecret communicationResponse processTelecommunications link
A communication system including a transmitter, a receiver, a communication link (for example, a TMDS-like link), and preferably also an external agent with which the transmitter and receiver can communicate, in which video data (or other data) are encrypted, the encrypted data are transmitted from the transmitter to the receiver, and the transmitted data are decrypted in the receiver, a transmitter and a receiver for use in such a system, a cipher engine for use in such a transmitter or receiver, a method for operating such a transmitter or receiver to encrypt or decrypt data, and a method for distributing keys to the transmitter and receiver. The receiver can be a player coupled to a downstream receiver by a TMDS-like link, and configured to re-encrypt the decrypted data (for example, using an AES or HDCP protocol) and send re-encrypted data over the link to the receiver. Optionally, the player is a repeater which translates the decrypted data from the transmitter, and then re-encrypts the translated data for transmission to the downstream receiver. The transmitter can itself be a player that receives and decrypts encrypted data from an upstream source. In preferred embodiments, the system implements a content protection protocol including a challenge-response procedure. After a new key is supplied to the receiver (and the same new key should have been supplied to the transmitter) and before the receiver can use the new key, the challenge-response procedure requires that the receiver validate the transmitter by verifying that the transmitter has proper knowledge of the new key.
Owner:LATTICE SEMICON CORP
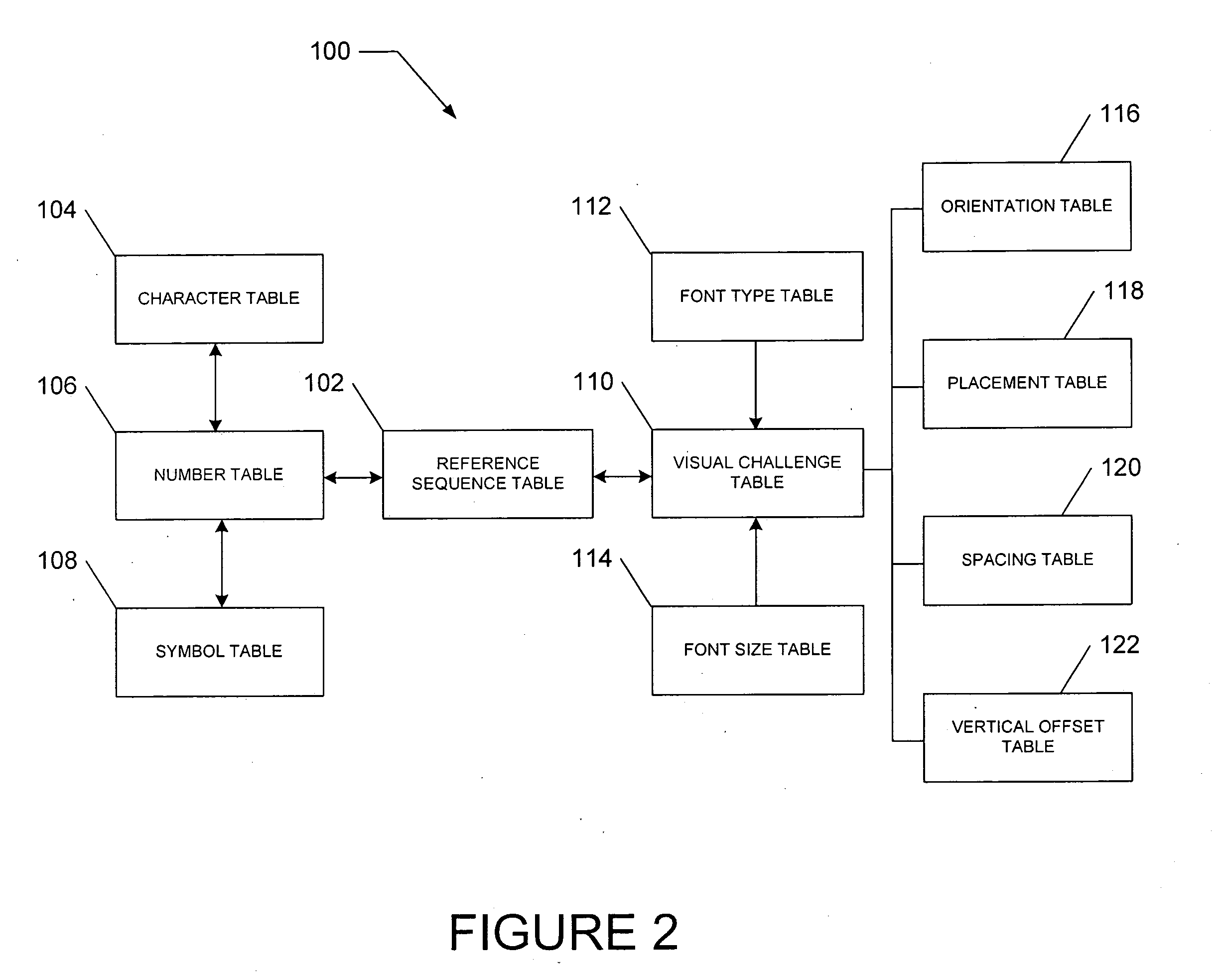
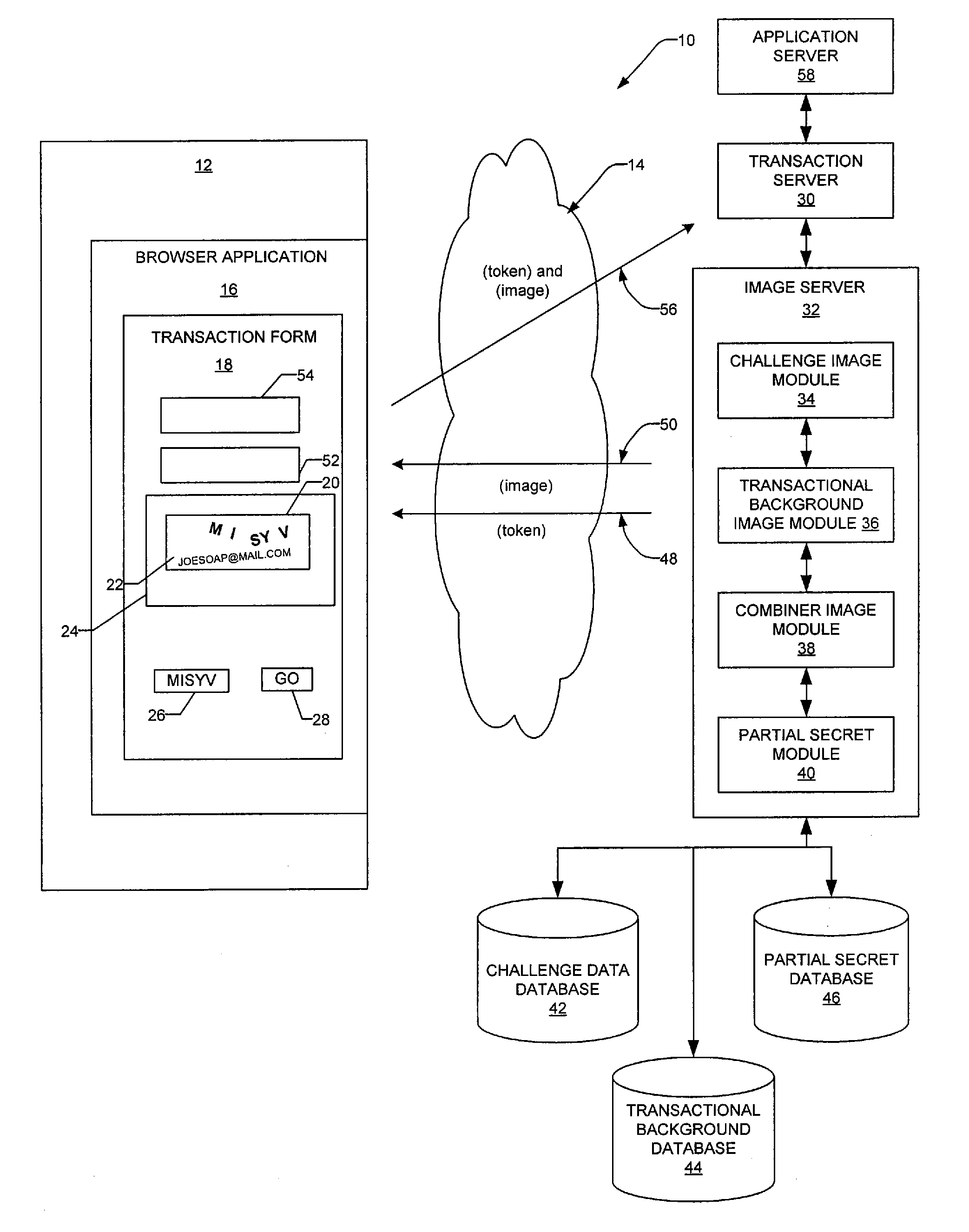
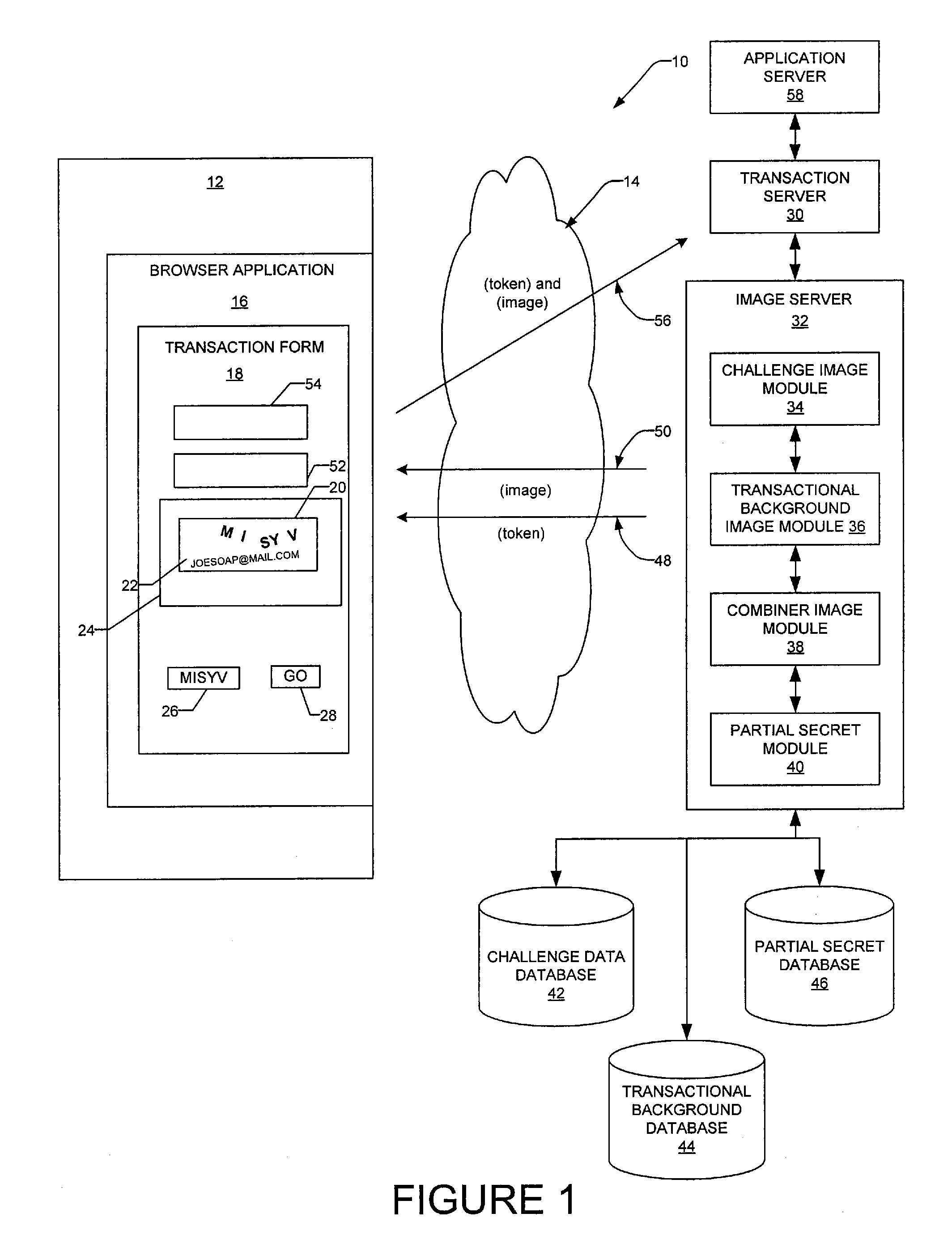
Contextual visual challenge image for user verification
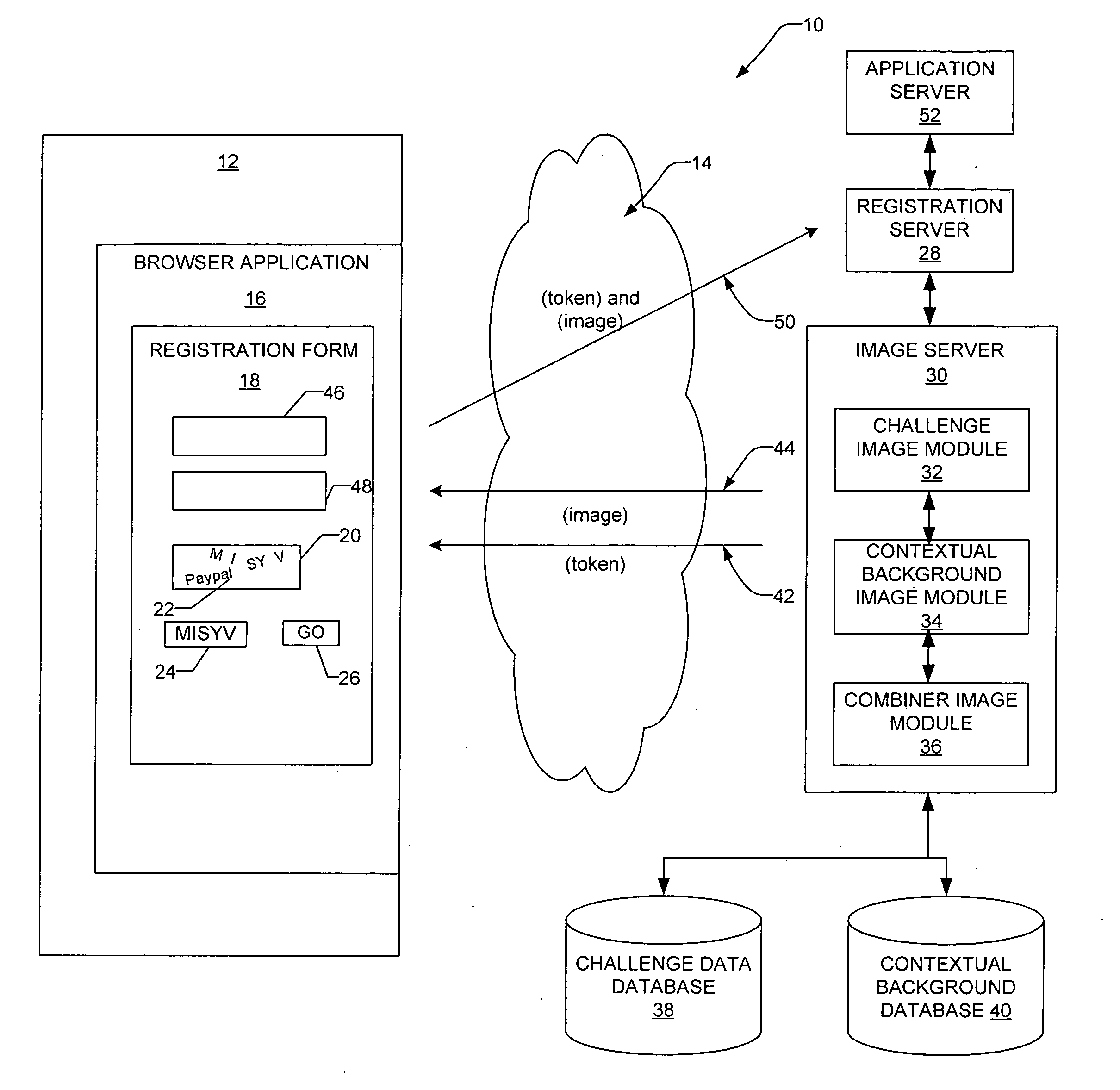
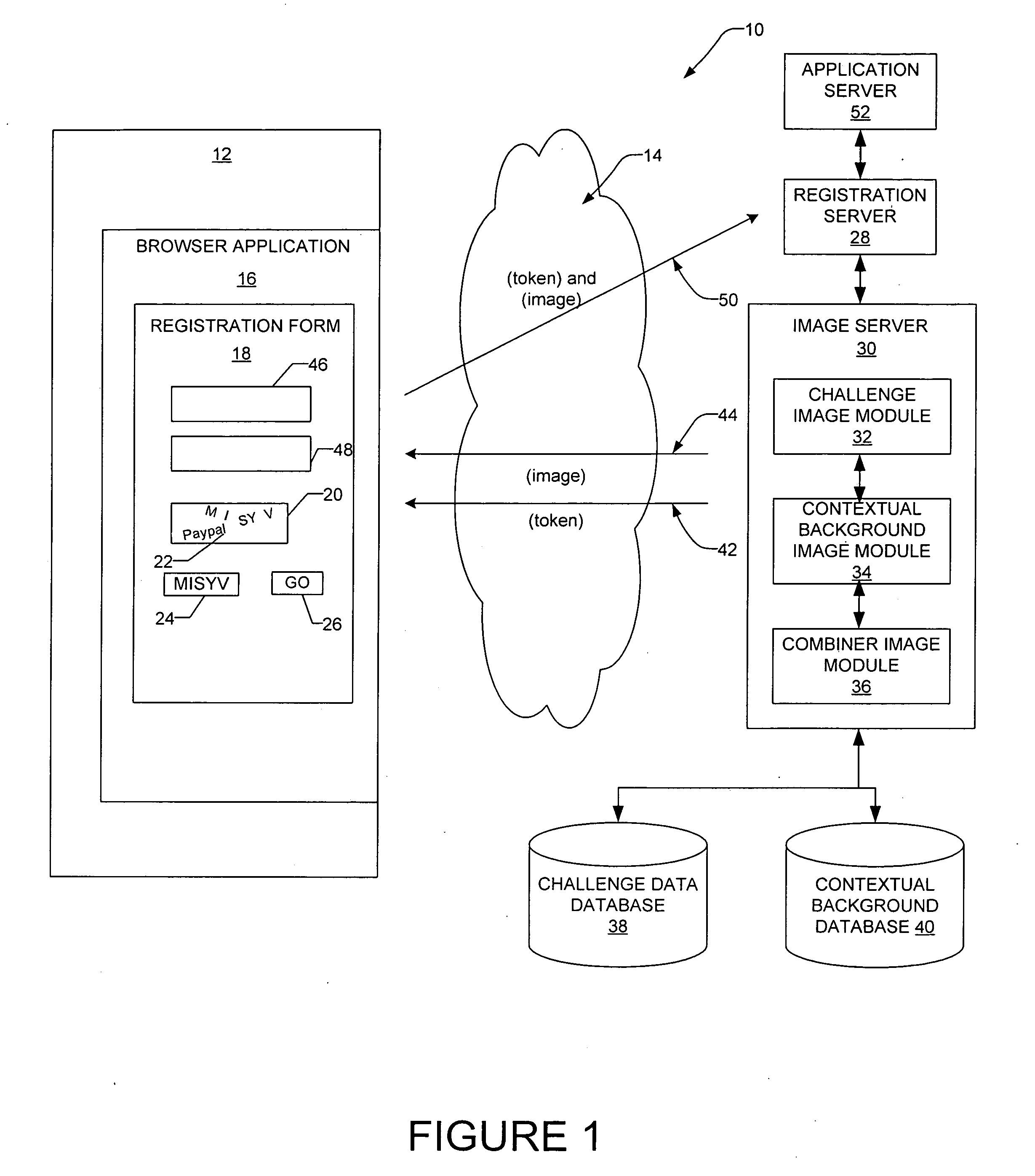
InactiveUS20080072293A1Digital data processing detailsUser identity/authority verificationUser verificationHuman–computer interaction
A method and a system generate a contextual visual challenge image to be presented to a user thereby to verify that the user is human. For example, an image module generates a visual challenge to be presented to a user as part of a challenge-response to verify that the user is human. A contextual background module identifies a contextual background that is contextual to a specific environment and a combiner image module combines the visual challenge and the contextual background into an image which is to be presented to the user in the specific environment, the contextual background associating the visual challenge with the specific environment.
Owner:EBAY INC
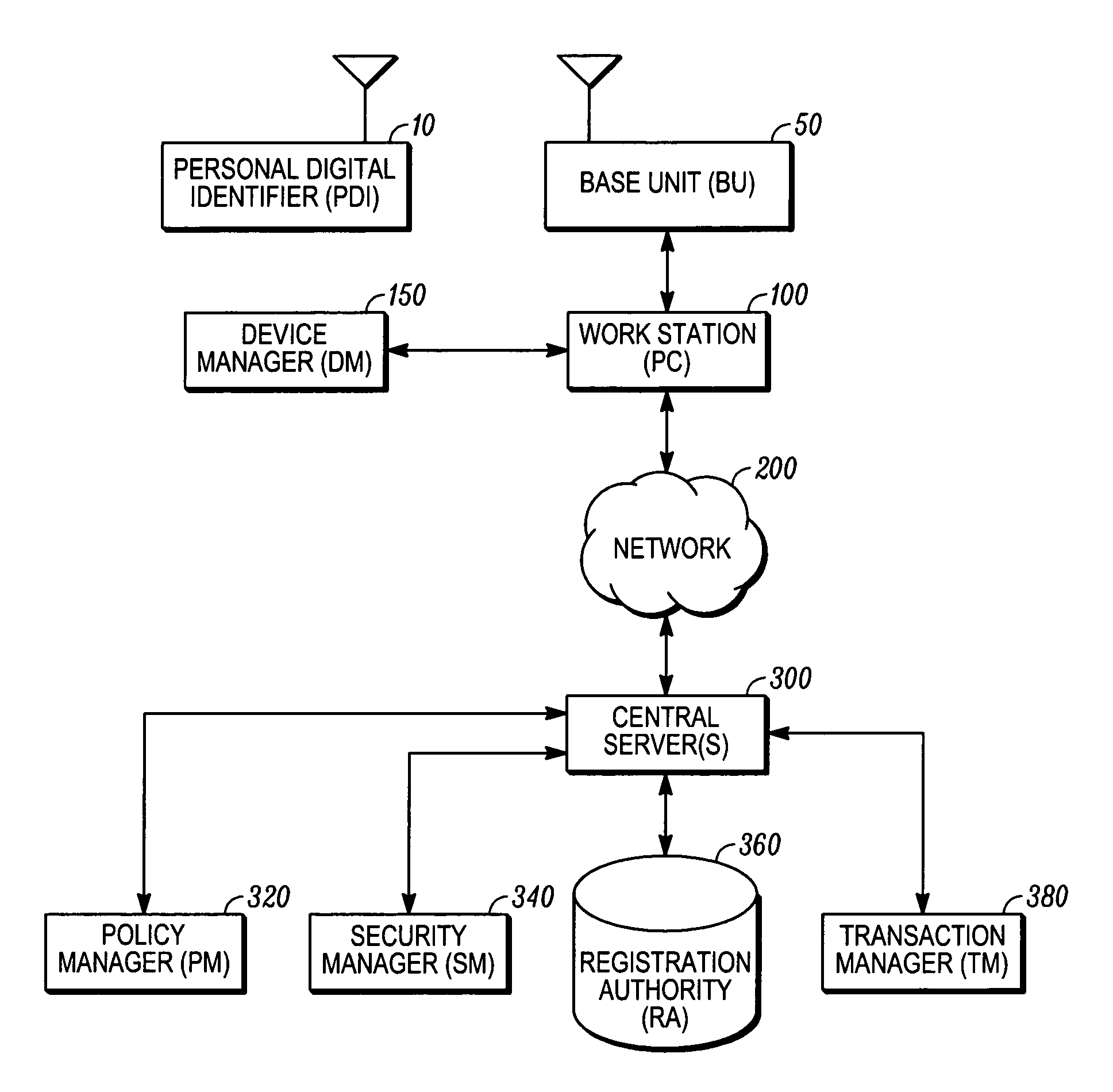
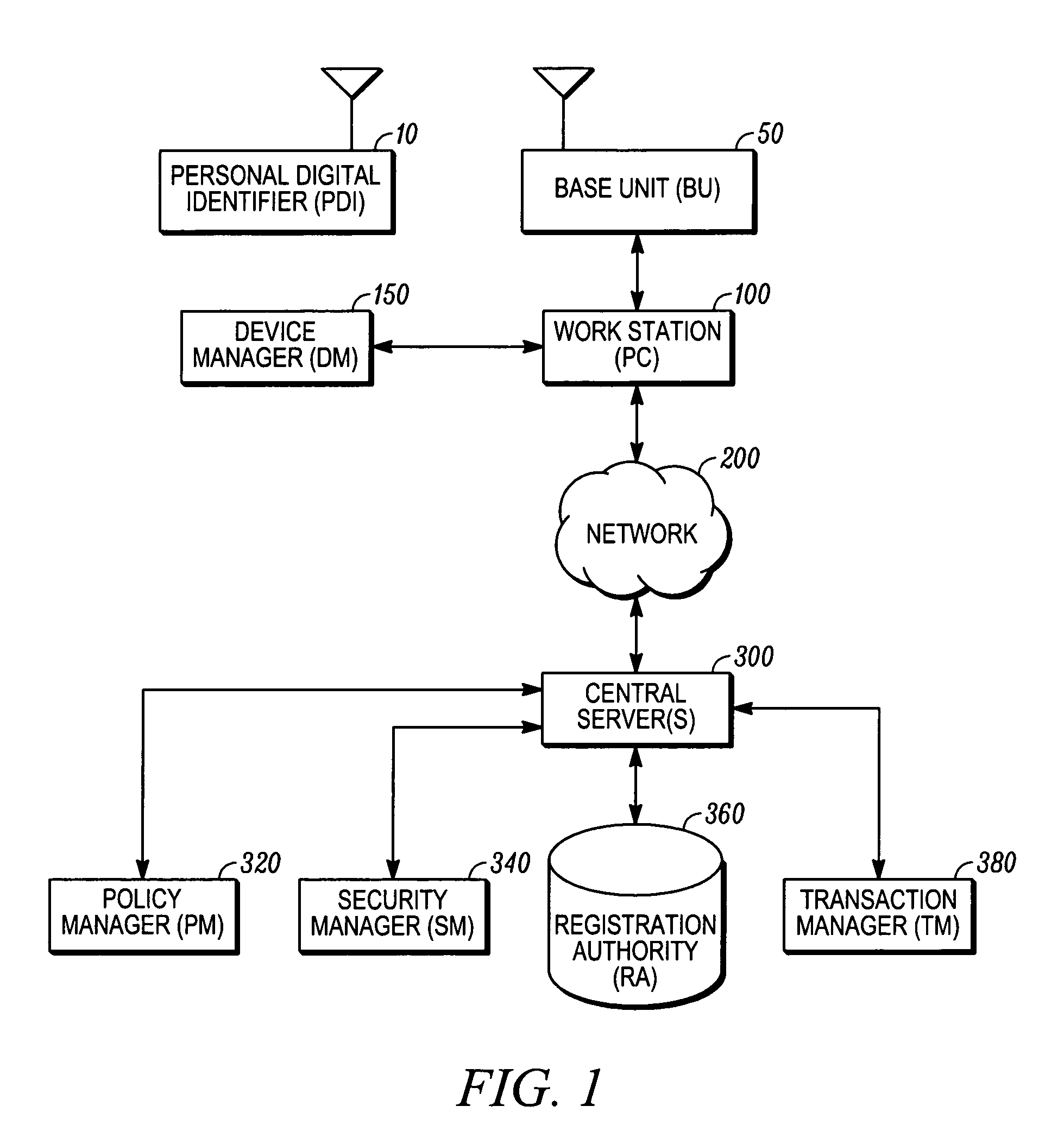
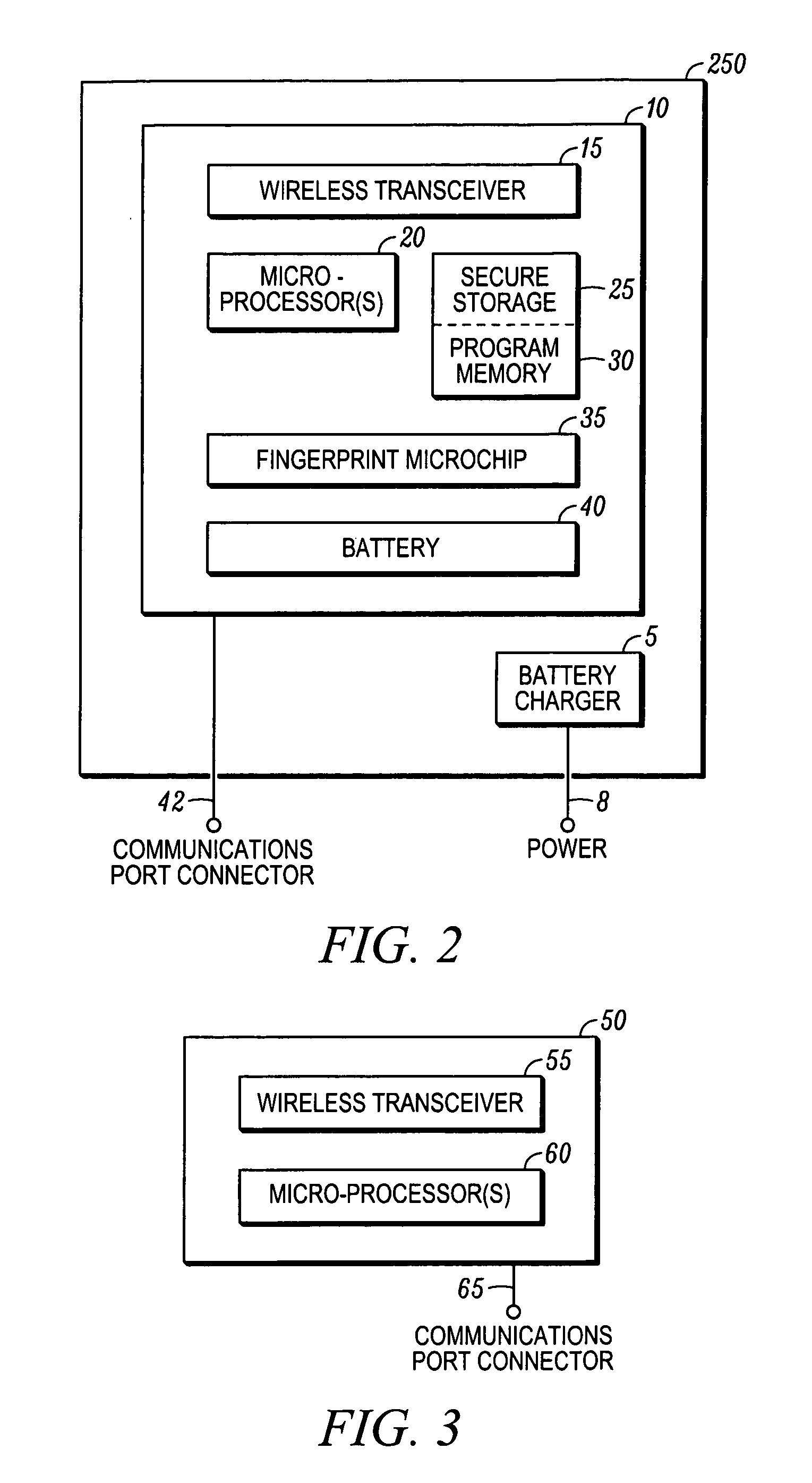
Method and system for securing a computer network and personal identification device used therein for controlling access to network components
InactiveUS7310734B2Real-time authenticationDigital data processing detailsUser identity/authority verificationDigital signatureIdentification device
An improved computer network security system and a personal identifier device used for controlling network with real time authentication of both a person's identity and presence at a computer workstation is provided. A new user is registered to a portable personal digital identifier device and, within the portable personal digital identifier device, an input biometric of the user is received and a master template is derived therefrom and securely maintained in storage. A private key and public key encryption system is utilized to authenticate a user registered to the portable personal digital identifier device. The personal digital identifier device verifies the origin of a digitally signed challenge message from the network security manager component. A digitally and biometrically signed challenge response message is produced and transmitted by the personal digital identifier device in response to the verified challenge message.
Owner:3M INNOVATIVE PROPERTIES CO
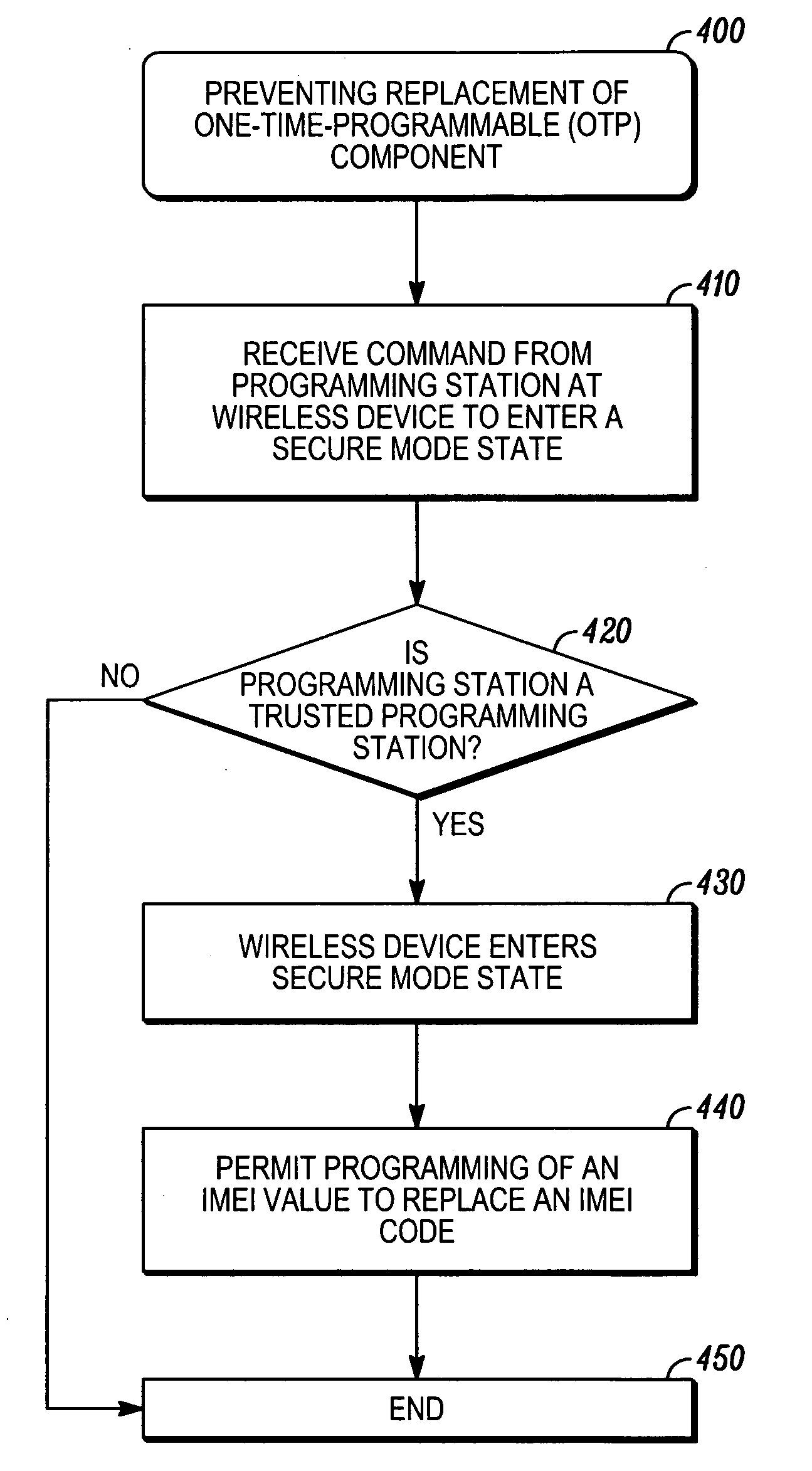
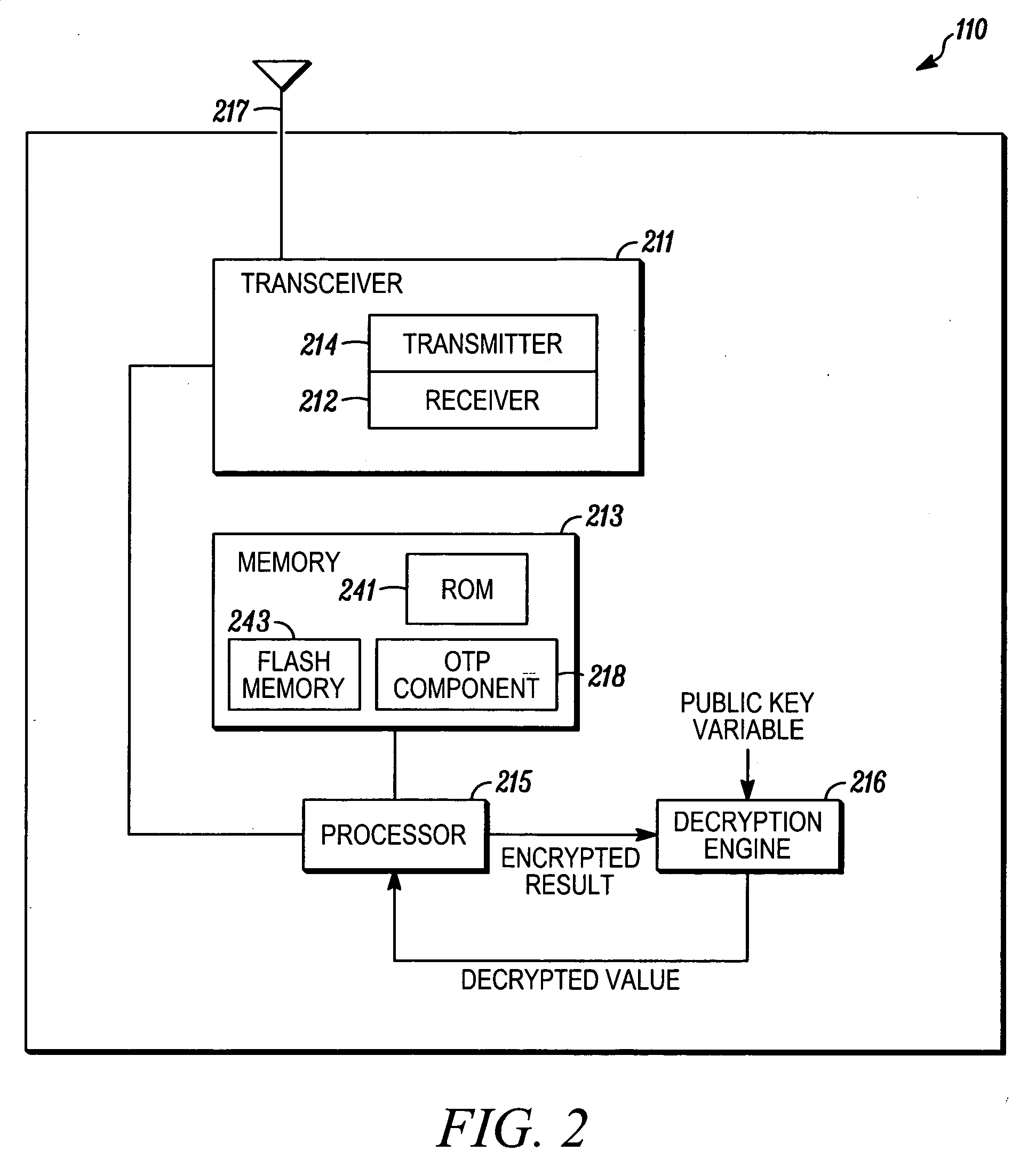
Method, system and apparatus for prevention of flash IC replacement hacking attack
InactiveUS20070050622A1User identity/authority verificationComputer security arrangementsChallenge responseOne time programmable
Techniques are provided for preventing replacement of a one-time-programmable (OTP) component. The OTP component can be part of a wireless device. The wireless device is configured such that programming of a new IMEI code into the OTP component is permitted only when the wireless device is in a secure-mode state. A challenge-response protocol is used to place the wireless device in this secure-mode state.
Owner:MOTOROLA INC
Transactional visual challenge image for user verification
InactiveUS20080209223A1User identity/authority verificationDigital data authenticationUser verificationInternet privacy
A method and a system generate a transactional visual challenge image to be presented to a user thereby to verify that the user is human. For example, an image module generates a visual challenge to be presented to a user as part of a challenge-response to verify that the user is human. A transactional background image module identifies a transactional background that is associated with a specific transaction and a combiner image module combines the visual challenge and the transactional background into an image which is to be presented to the user during transaction authorization, the transactional background associating the visual challenge with the particular transaction.
Owner:EBAY INC
Methods, systems and computer program products for over the air (OTA) provisioning of soft cards on devices with wireless communications capabilities
ActiveUS20080058014A1Shorten the timeEliminate needAcutation objectsSpecial service for subscribersComputer hardwarePersonalization
Methods, systems, and computer program products for over the air provisioning of soft cards on devices with wireless communications capabilities are disclosed. According to one method, a soft card provisioning application is instantiated on a device with wireless communications capabilities. A card number for a soft card desired to be provisioned on the device is obtained from a user of the device. The card number is communicated to a provisioning configuration server over an air interface. Card-issuer-specific challenges corresponding to the card number and a provisioning issuer server network address are obtained from the provisioning configuration server. The challenges are presented to the user, and the user's responses to the challenges are received. A connection is made to the provisioning issuer server corresponding to the network address. The challenge responses are communicated to the provisioning issuer server. Soft card personalization data for activating the soft card is received from the provisioning issuer server. The soft card is provisioned for use on the device based on the personalization data.
Owner:MASTERCARD INT INC
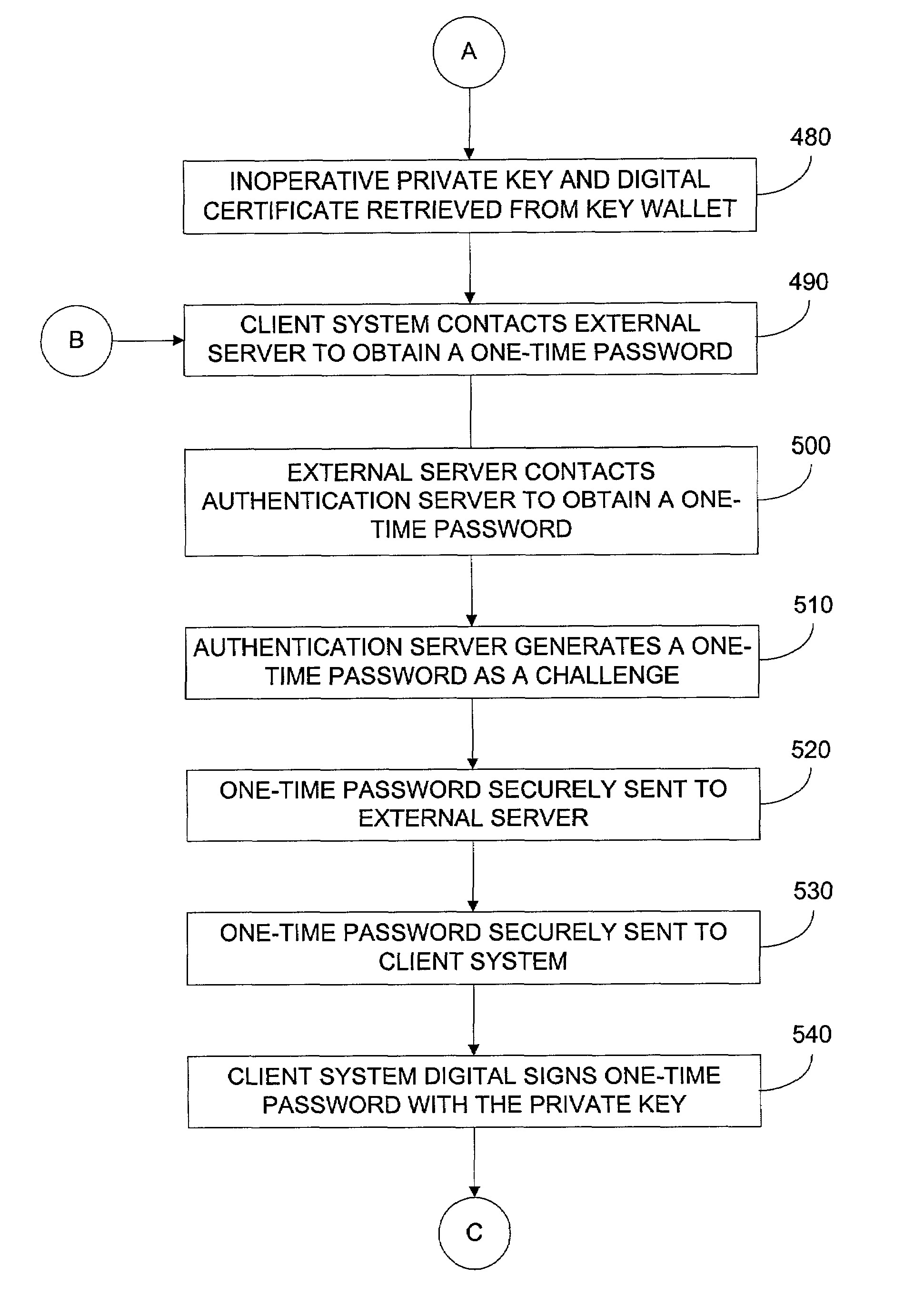
Methods for pre-authentication of users using one-time passwords
InactiveUS6983381B2User identity/authority verificationData resettingDigital signatureAuthentication server
A method for communicating passwords includes receiving at a server a challenge from a authentication server via a first secure communications channel, the challenge comprising a random password that is inactive, communicating the challenge from the server to a client computer via a second secure communications channel, receiving at the server a challenge response from the client computer via the second secure communications channel, the challenge response comprising a digital certificate and a digital signature, the digital certificate including a public key in an encrypted form, the digital signature being determined in response to the random password and the private key, and communicating the challenge response from the server to the authentication server via the first secure communications channel, wherein the random password is activated when the authentication server verifies the challenge response.
Owner:CA TECH INC
Methods and apparatus for conducting electronic transactions
InactiveUS7953671B2Enhanced reliability and confidenceReduce security risksComplete banking machinesAcutation objectsChallenge responseAuthorization
A system and method for facilitating electronic transactions using an intelligent instrument is disclosed. An authorization server enables users to obtain authorization credentials through the use of the intelligent instrument by issuing a challenge to an intelligent token of the intelligent instrument. The intelligent token generates a challenge response and transmits the challenge response to the authorization server, which assembles credentials including a key for the electronic transaction upon validating the response. The authorization server sends the assembled credentials to the intelligent instrument and the intelligent instrument transmits the assembled credentials to the authorization server during a subsequent transaction. The authorization server validates the assembled credentials and provides authorization for the transaction in response to the validating the assembled credentials.
Owner:LIBERTY PEAK VENTURES LLC
Challenge-response user authentication
ActiveUS20030233546A1Easy to migrateAvoid attackUser identity/authority verificationDigital data authenticationInternet privacyUser authentication
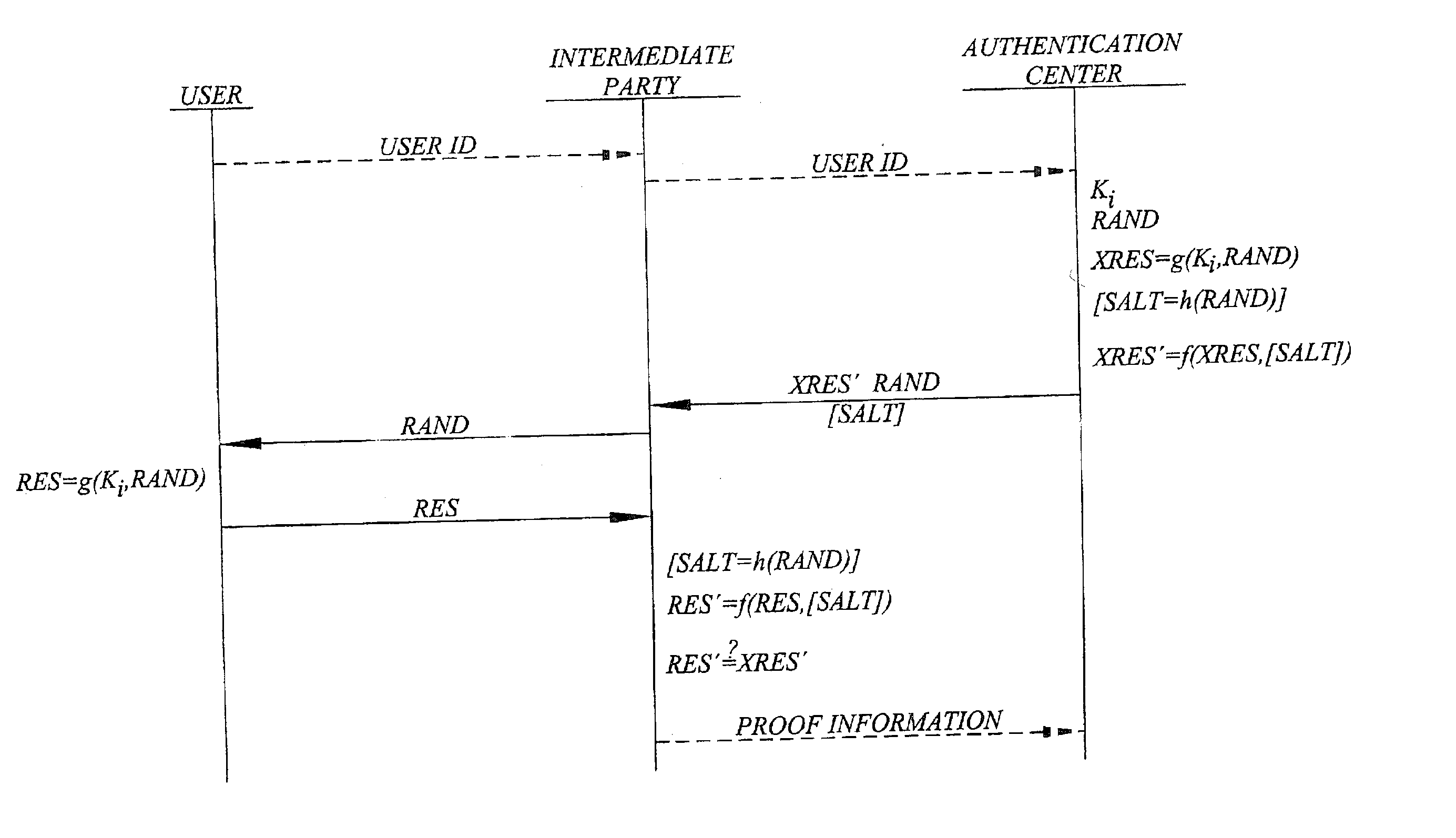
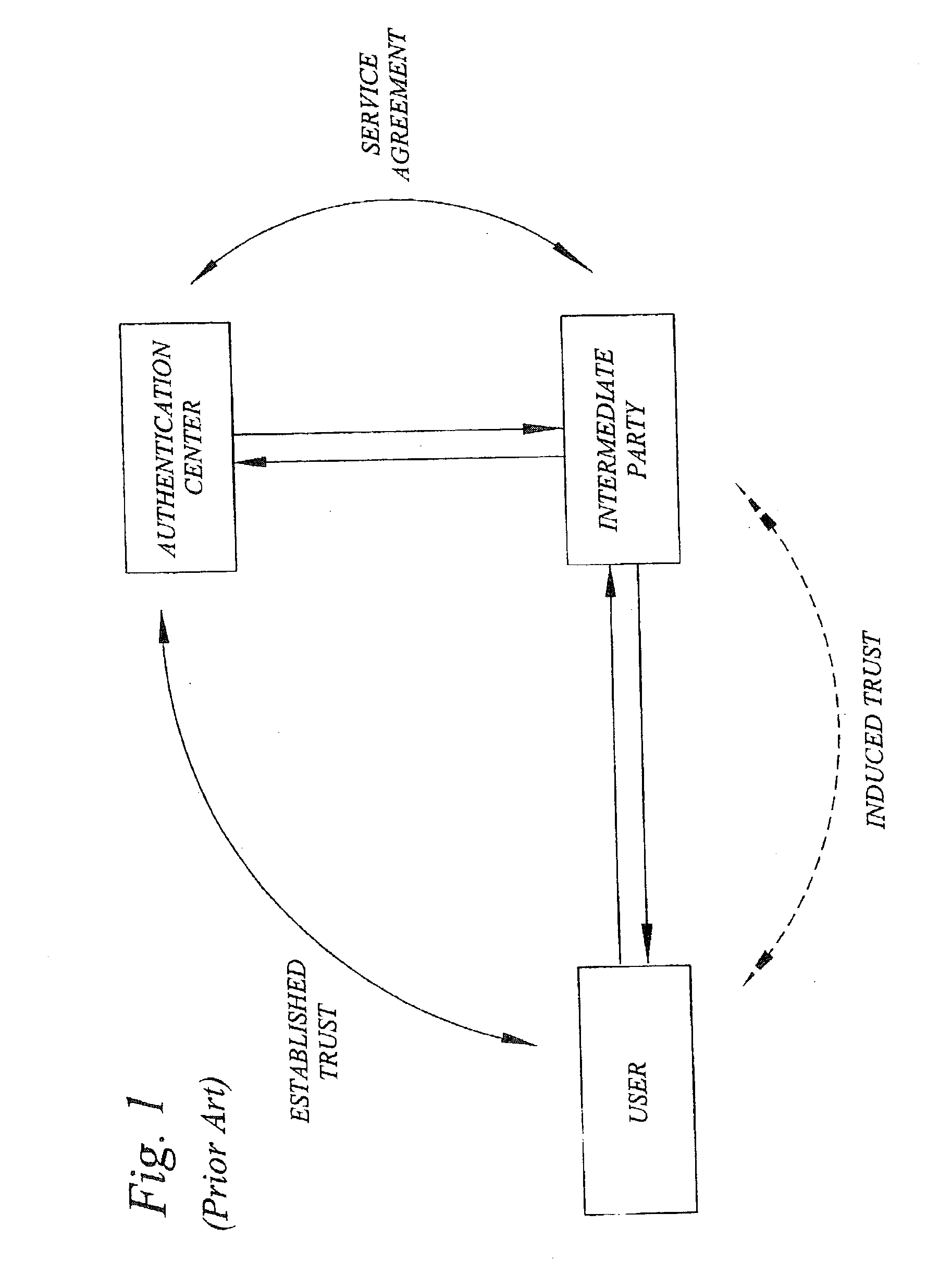
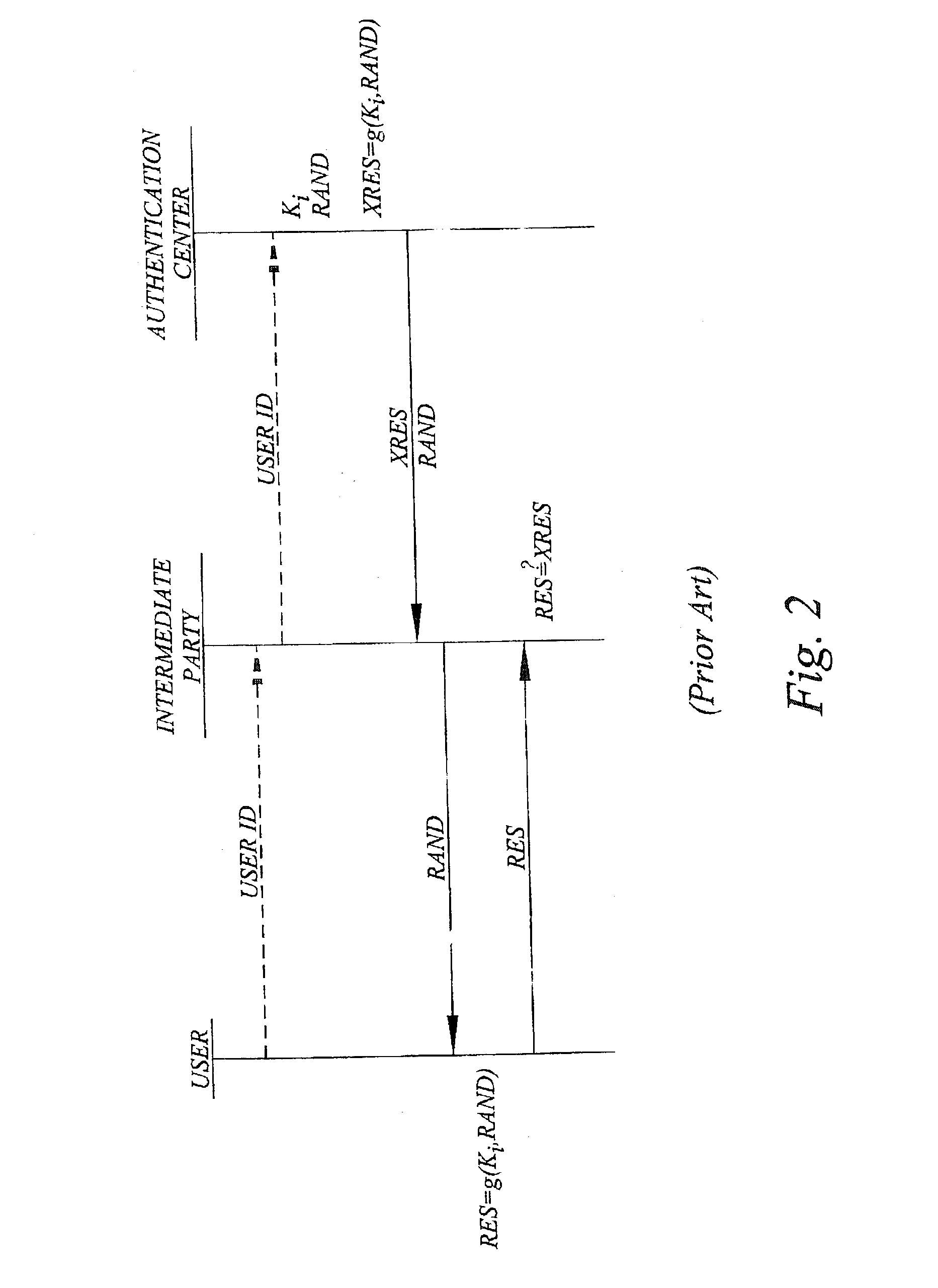
A challenge-response authentication procedure includes masking of the expected response (XRES) generated by an authentication center by means of a masking function (f), and transmission of the masked expected response (XRES'), instead of the expected response itself, to an intermediate party at which the actual user authentication takes place. The intermediate party also receives a user response (RES) from the user and generates a masked user response (RES') using the same masking function (f) as the authentication center did. In order to authenticate the user, the intermediate party then verifies that the masked user response (RES') corresponds to the masked expected response (XRES') received from the authentication center. The above procedure enables the intermediate party to prove that user authentication has taken place, keeping in mind that only the legitimate user knows the response beforehand.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and apparatus for secure remote system management
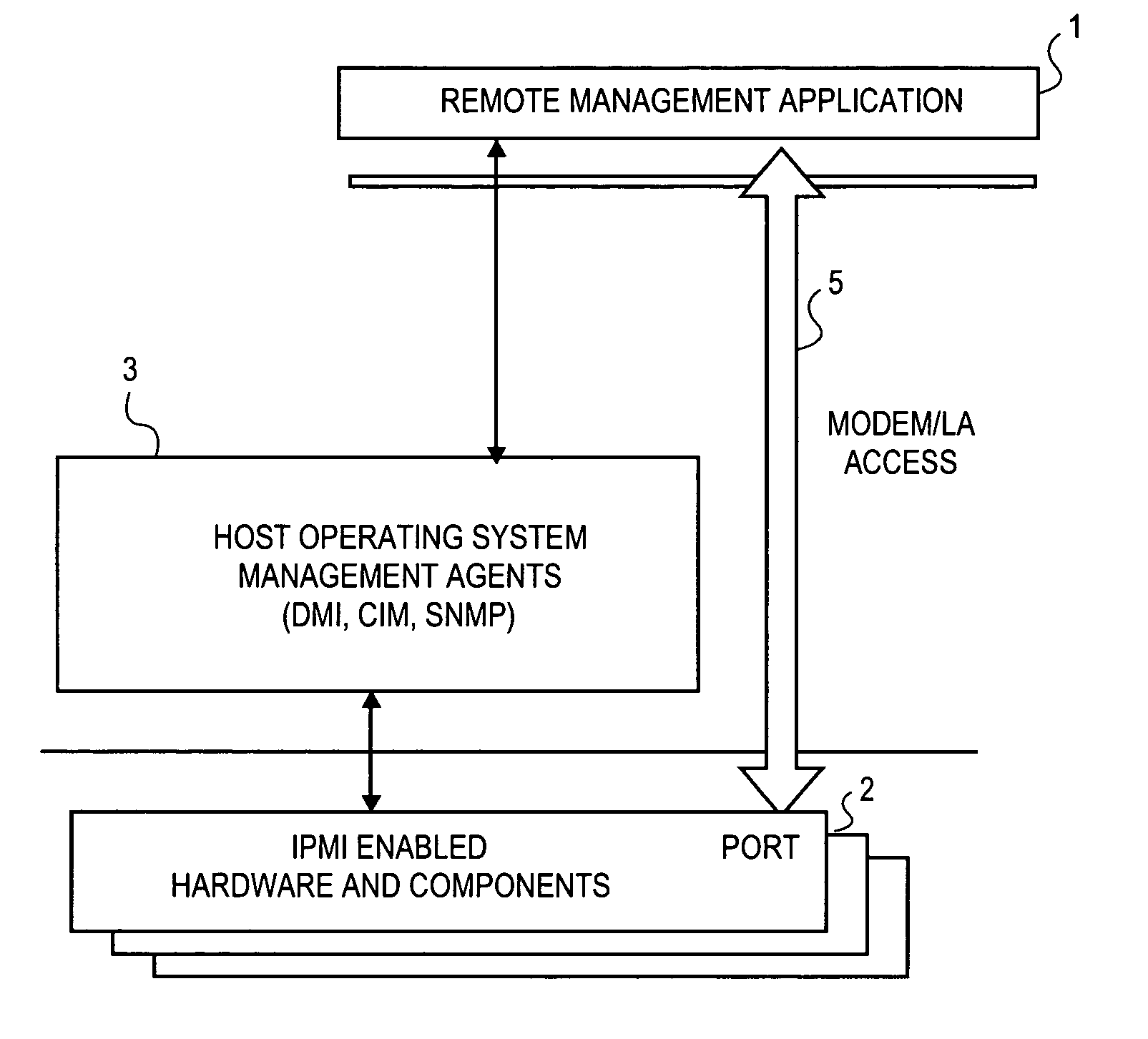
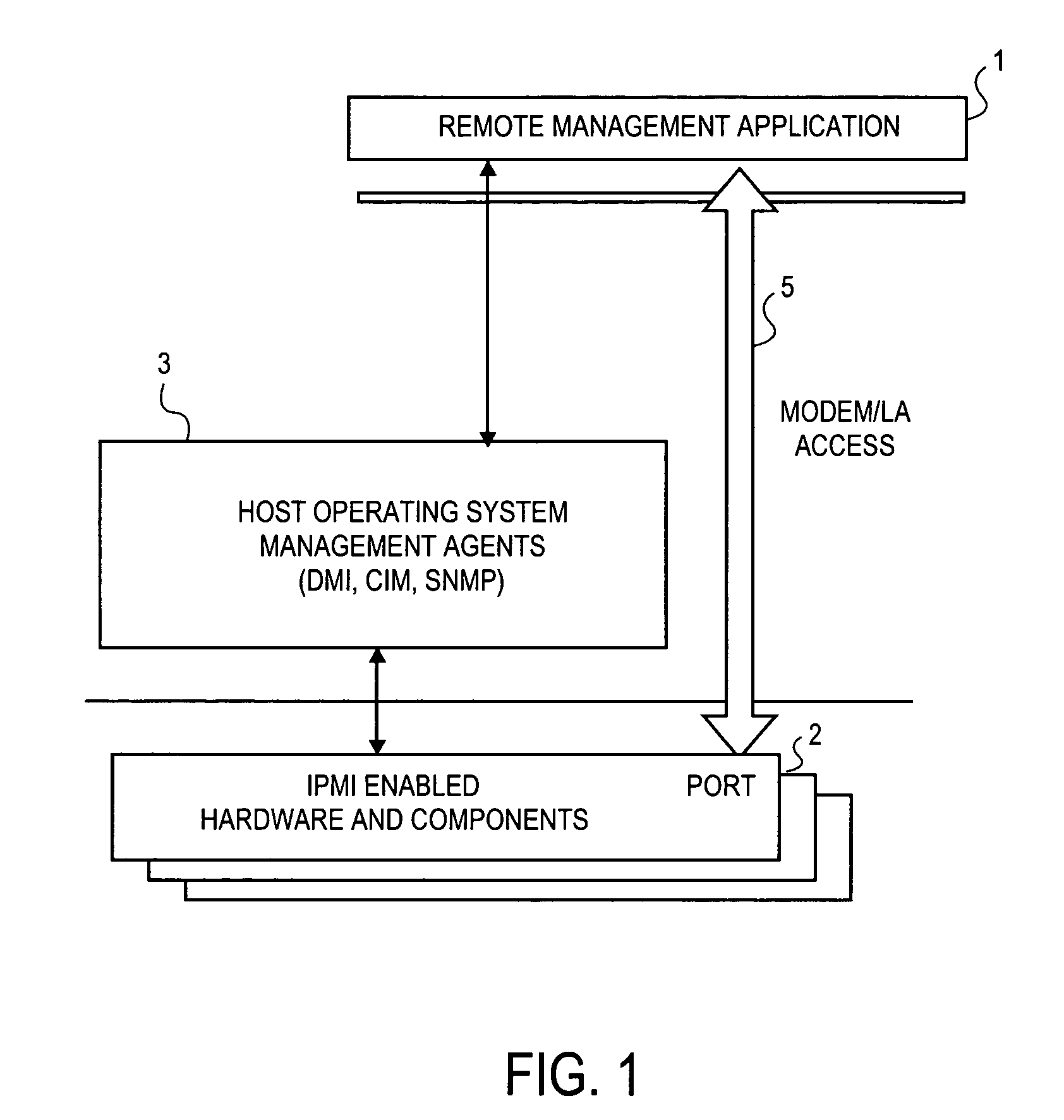
InactiveUS7024695B1Digital data processing detailsAnalogue secracy/subscription systemsComputer hardwareOperational system
To prevent unauthorized access to hardware management information in an out-of-band mode, i.e., when the operating system of the hardware is not executing, a method and apparatus employ an authentication protocol. Upon receiving a request for hardware component information in a service processor that is disposed in a hardware component, which request is received as an open session request and which request passes external to an operating system controlling the hardware component, the service processor transmits a challenge string to the requesting client application. In response to a challenge response received from the requesting client application, the service processor compares the challenge response to an expected response to the challenge. The expected challenge response is calculated by the service processor. Based on the result of the comparison, the service processor transmits an authentication response to the requesting client application indicating success or failure of the authentication process. On the client side, in response to a challenge string from the service processor, the requesting client application transmits to the service processor a challenge response, which includes an sequence number that increments with every new message from the requesting client application. The challenge response also includes a hash number calculated by the requesting client application, which hash number is a function of the challenge string, session identification number, sequence number and / or a password. Each new packet including data and / or commands from the client application includes a similarly calculated hash number.
Owner:INTEL CORP
System and Method for Encoding and Controlled Authentication
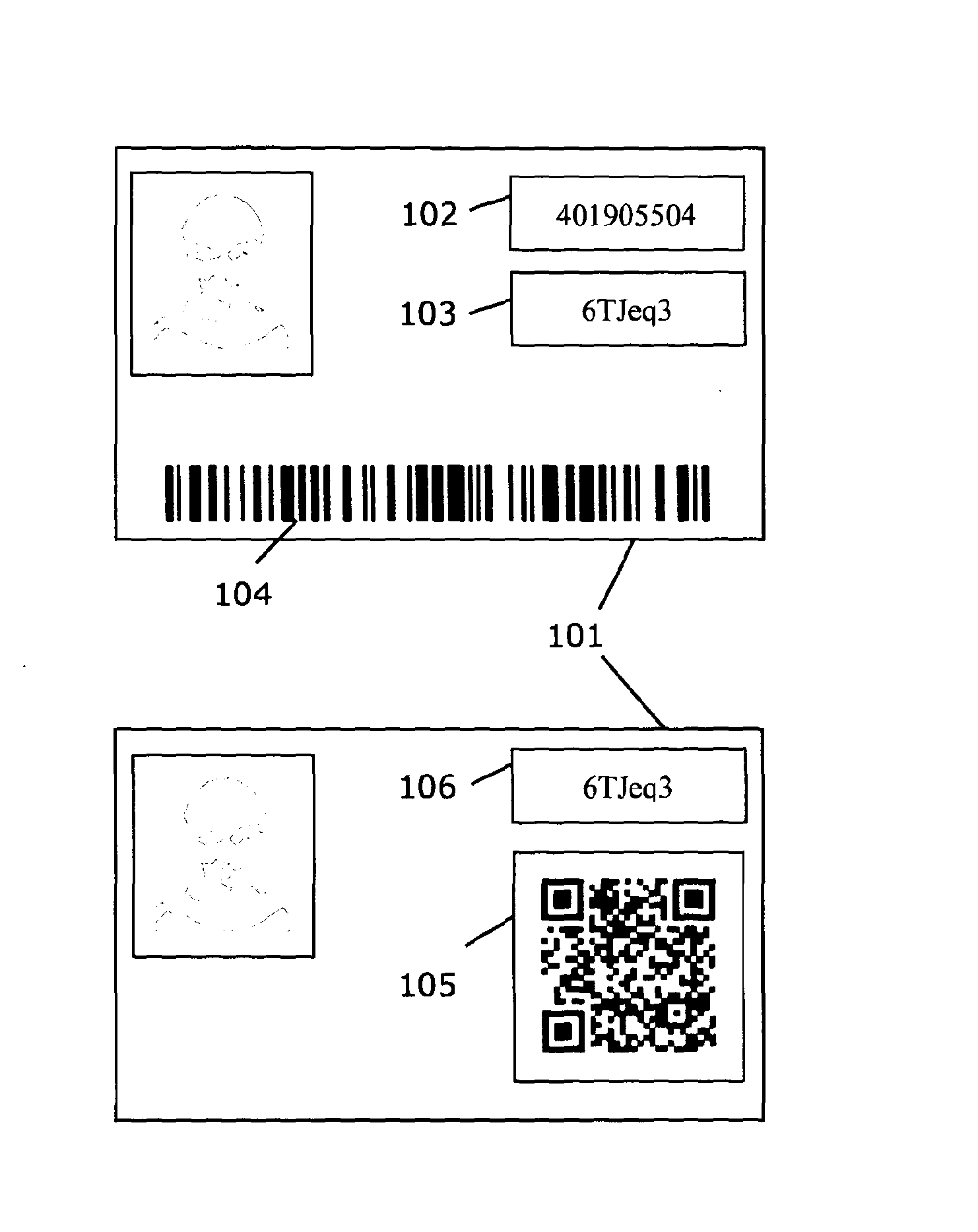
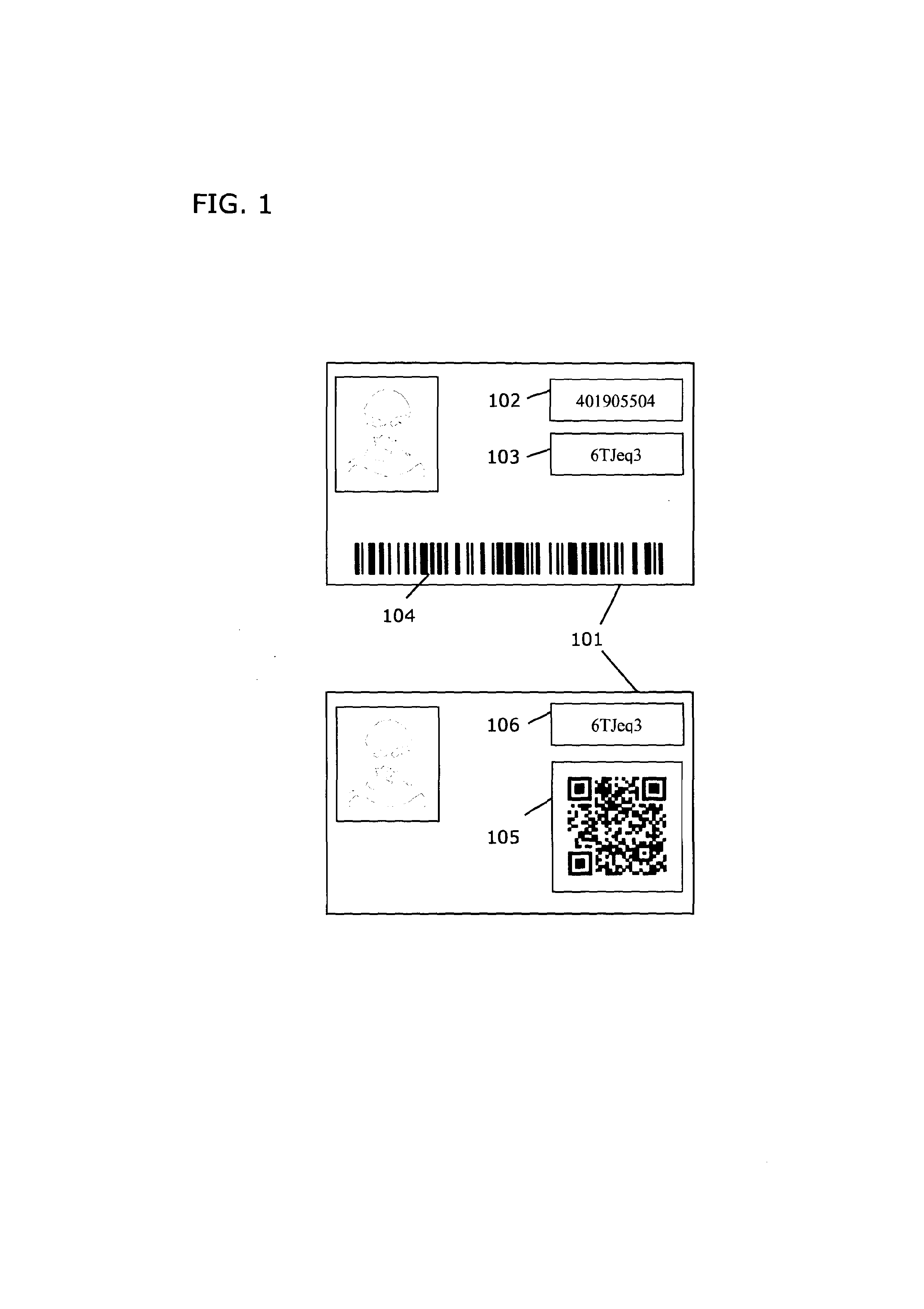
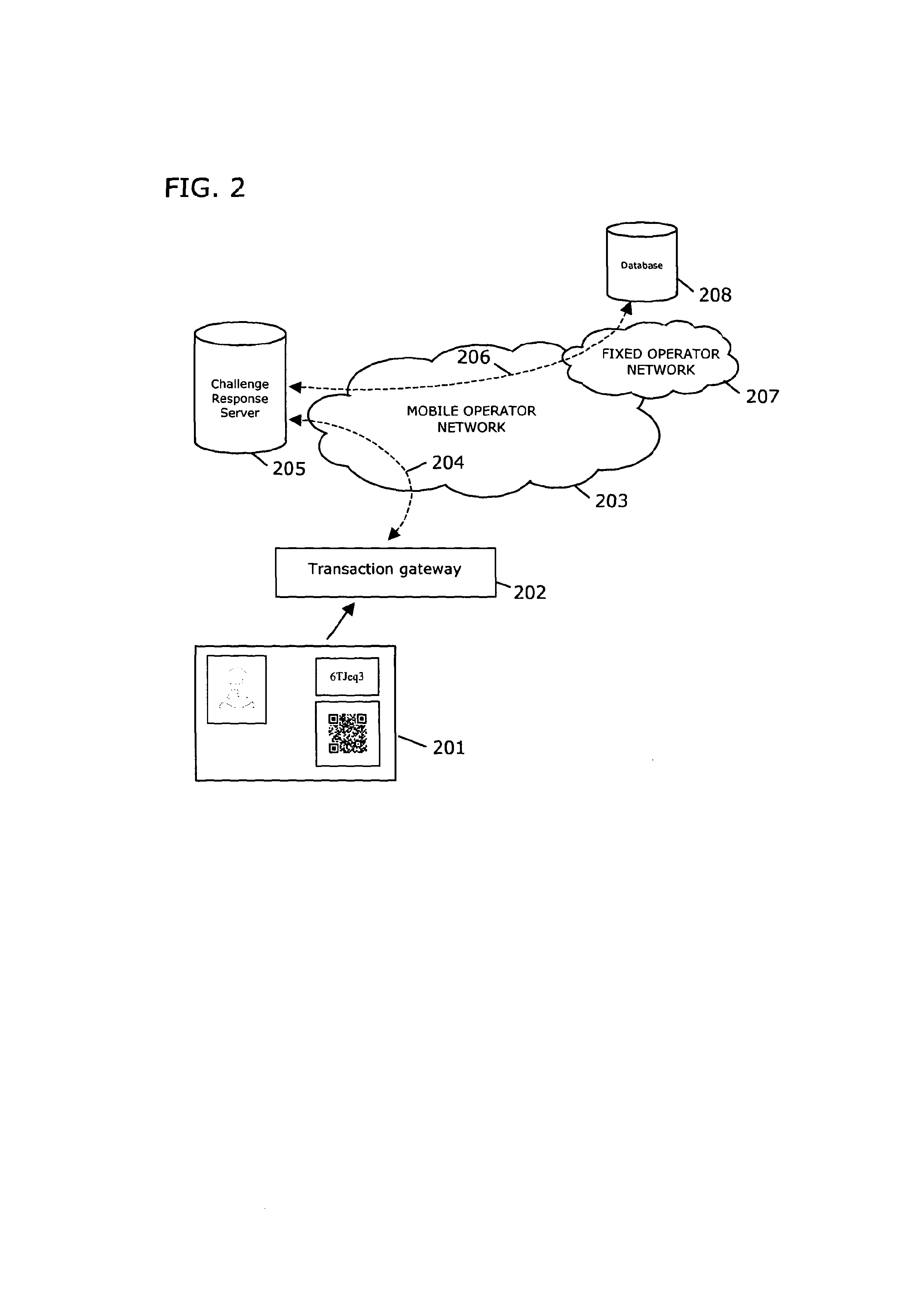
InactiveUS20130173484A1Improve securityPaper-money testing devicesSensing record carriersPasswordBarcode
A system and method for encoding and controlled authentication of security documents, ID cards, tickets and products and the like is described which can provide a secure means to determine them to be authentic. The method involves encoding the surface of the said security documents or ID cards or tickets and the like with of a pair of identity components comprising a pair of unique numbers, or a combination of a uniquely encoded image and a unique number, or a combination of a unique barcode and a unique number, or a combination of encoded images. The pair of identity components together comprise a challenge response pair and are related such that one component of the pair, the response, is a mathematical derivative of the other component, the challenge. A processing module determines the response by processing the challenge using complex mathematical functions such as one-way mathematical functions. If the processed response matches the encoded response, the challenge response pair is determined to be authentic. The use of one-way mathematical functions renders any attempt to compute the challenge response relation between the identity components outside polynomial time. The invention provides the means to modify the challenge response computation with a password or PIN number such that any document or ticket or product can be locked or unlocked accordingly. When locked, the password or PIN number corrupts the challenge response computation such that the challenge response pair is deemed non-authentic. The invention has direct application to Internet sales transactions.
Owner:WESBY PHILIP
Automatic Learning Multi-Modal Fraud Prevention (LMFP) System
ActiveUS20140289867A1Increase probabilityHigh quality factorDigital data processing detailsAnalogue secracy/subscription systemsRe challengeChallenge response
A computerized learning multi-modal fraud prevention system and method for generating a data signature of a user, such as one engaged in electronic commerce, to prevent fraudulent activities by machines and persons imitating the user. Steps comprise: fetching a signal of a user's signature stored in memory; generating at least one challenge sequence based on the signal to create a second signature; presenting the generated challenge sequence to the user; collecting the user's challenge response to the generated challenge sequence; computing a quality factor between the user's challenge response and the generated challenge sequence; computing a transaction quality factor and content quality factor and reporting an impostor or re-challenging if the quality factor is below a threshold. Lastly, generating a new signature based on any portion of a user's challenge response and / or any portion of the previously generated signature and / or any portion of collectable information from the user's device memory.
Owner:BUKAI DROR
Keyless encryption of messages using challenge response
InactiveUS6535980B1Key distribution for secure communicationUser identity/authority verificationComputer hardwareSecure transmission
A method of keyless encryption of messages allows secure transmission of data where data security is not available for some technical or legal reason. The method of data transfer uses a challenge response in which a correct response to a challenge is used to transmit the value "1", while a deliberately false response is made to transmit the value "0". Any message can be transmitted as a binary string using successive applications of this method.
Owner:IBM CORP
Methods, systems, and computer readable media for over the air (OTA) provisioning of soft cards on devices with wireless communications capabilities
ActiveUS20090164322A1Shorten the timeEliminate needDiscounts/incentivesFinanceComputer hardwarePersonalization
Methods, systems, and computer readable media for over the air provisioning of soft cards on devices with wireless communications capabilities are disclosed. According to one method, a soft card provisioning application is instantiated on a device with wireless communications capabilities. A card number for a soft card desired to be provisioned on the device is obtained from a user of the device. An issuer identification number retrieved from the card number is communicated to a provisioning configuration server over an air interface. A provisioning issuer server network address is obtained from the provisioning configuration server based on the issuer identification number. The provisioning information server is connected to, and card-issuer-specific challenge information is obtained therefrom. The challenges are presented to the user, and the user's responses to the challenges are received. A connection is made to the provisioning issuer server corresponding to the network address. The challenge responses are communicated to the provisioning issuer server. Soft card image data and personalization data, where the personalization data includes personalized embossed and pre-printed data, are received from the provisioning issuer server over the air interface. The soft card is provisioned for use on the device based on the data received over the air interface.
Owner:MASTERCARD INT INC
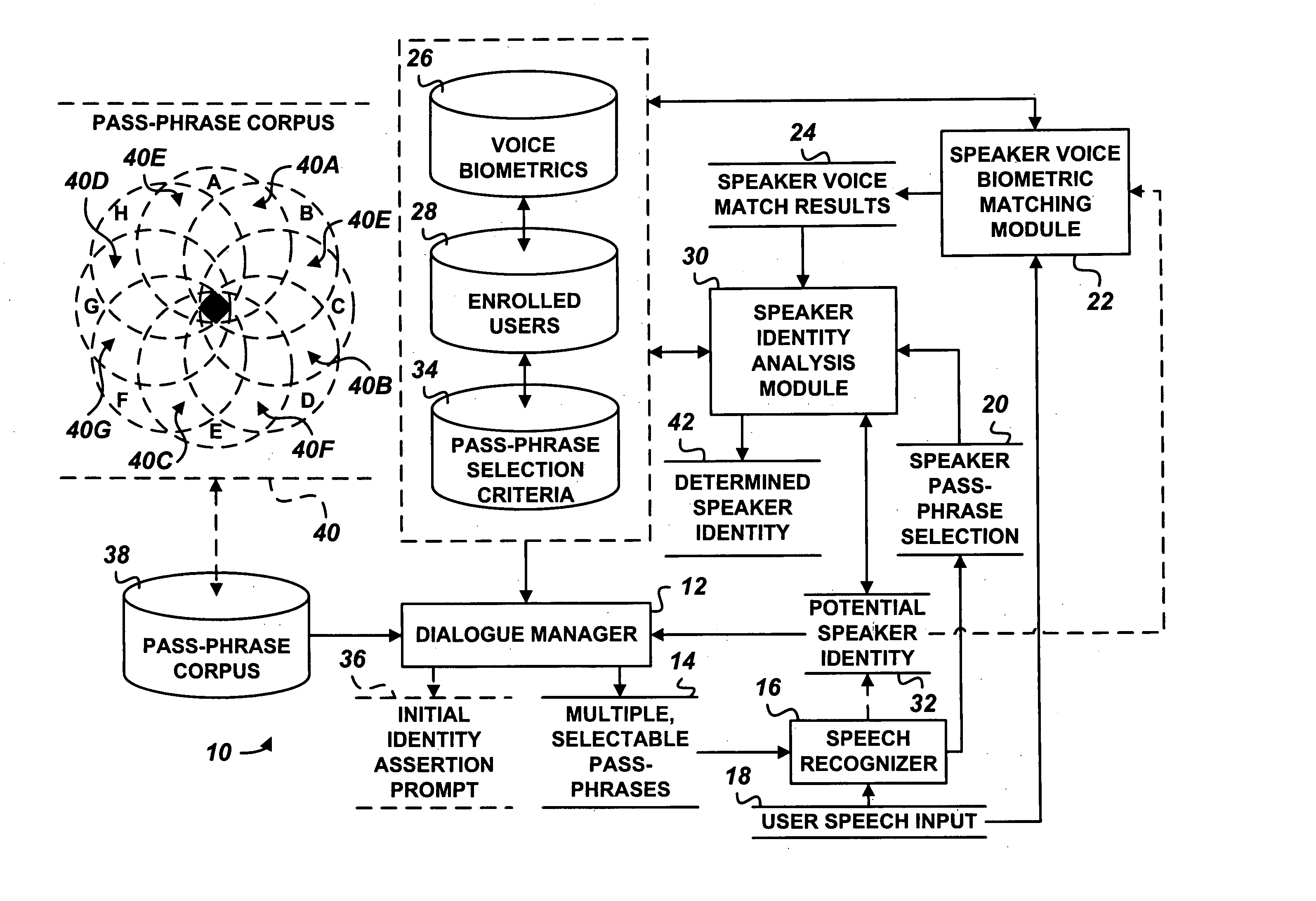
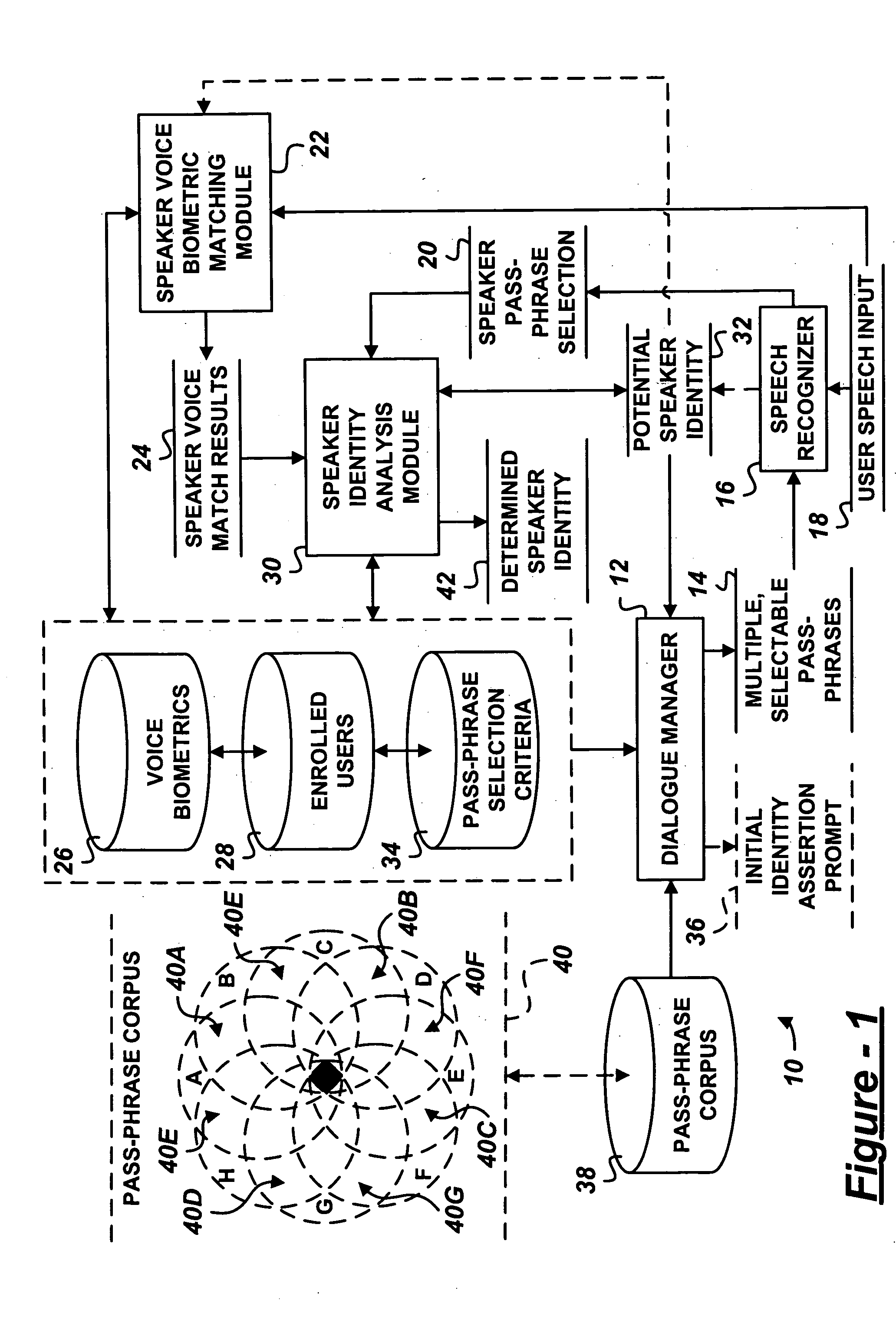
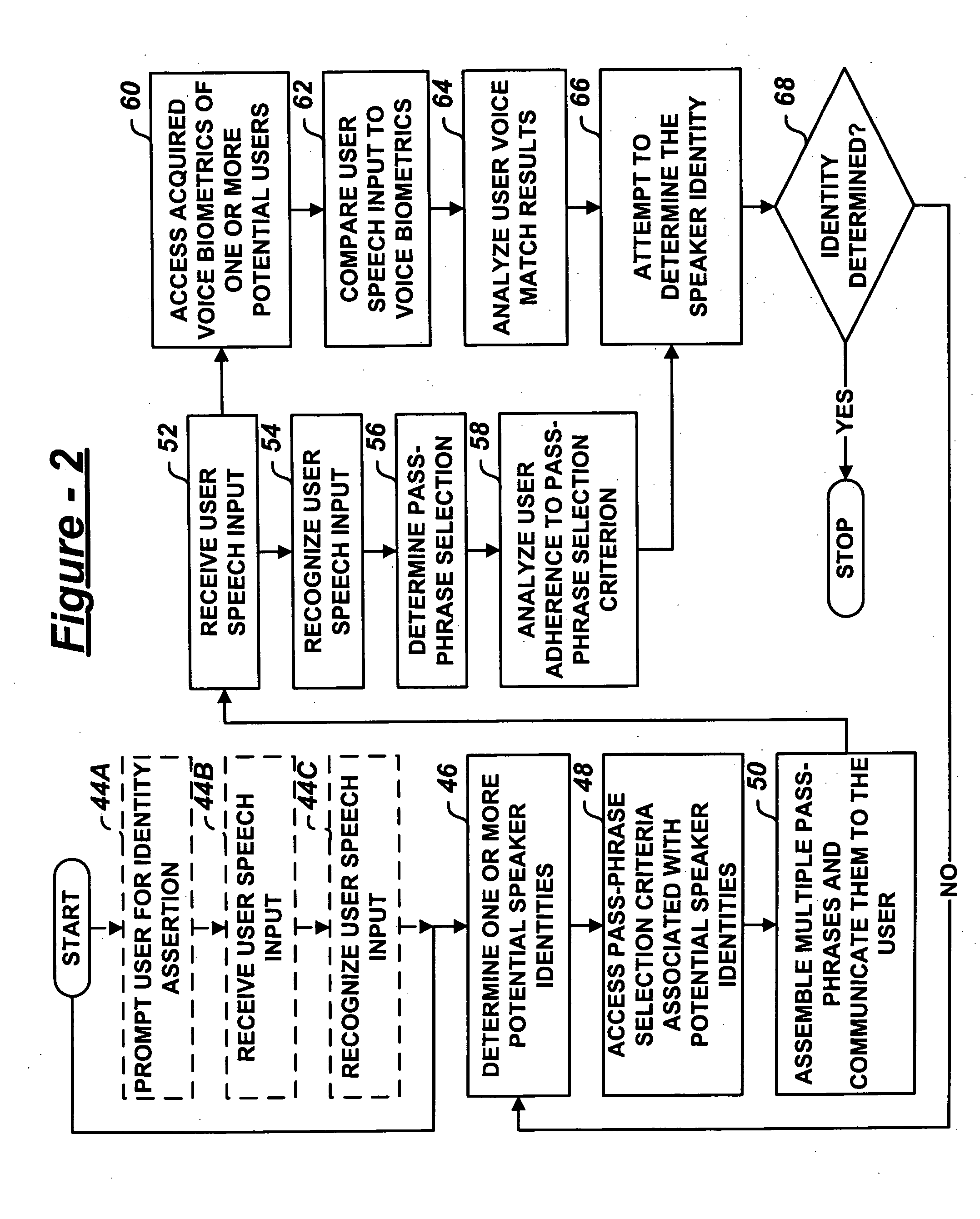
Multiple choice challenge-response user authorization system and method
ActiveUS20050171851A1Digital data processing detailsUnauthorized memory use protectionPassphraseSelection criterion
A user authentication system includes a dialogue manager adapted to prompt the user with multiple, selectable pass-phrases. A selection recognizer recognizes user selection of at least one of the multiple, selectable pass-phrases. A user identity analysis module analyzes one or more potential user identities based on adherence of user selection of the pass-phrase to predetermined pass-phrase selection criteria assigned one or more enrolled users.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Two-phase SIM authentication
InactiveUS20070178885A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsAccess networkPassword
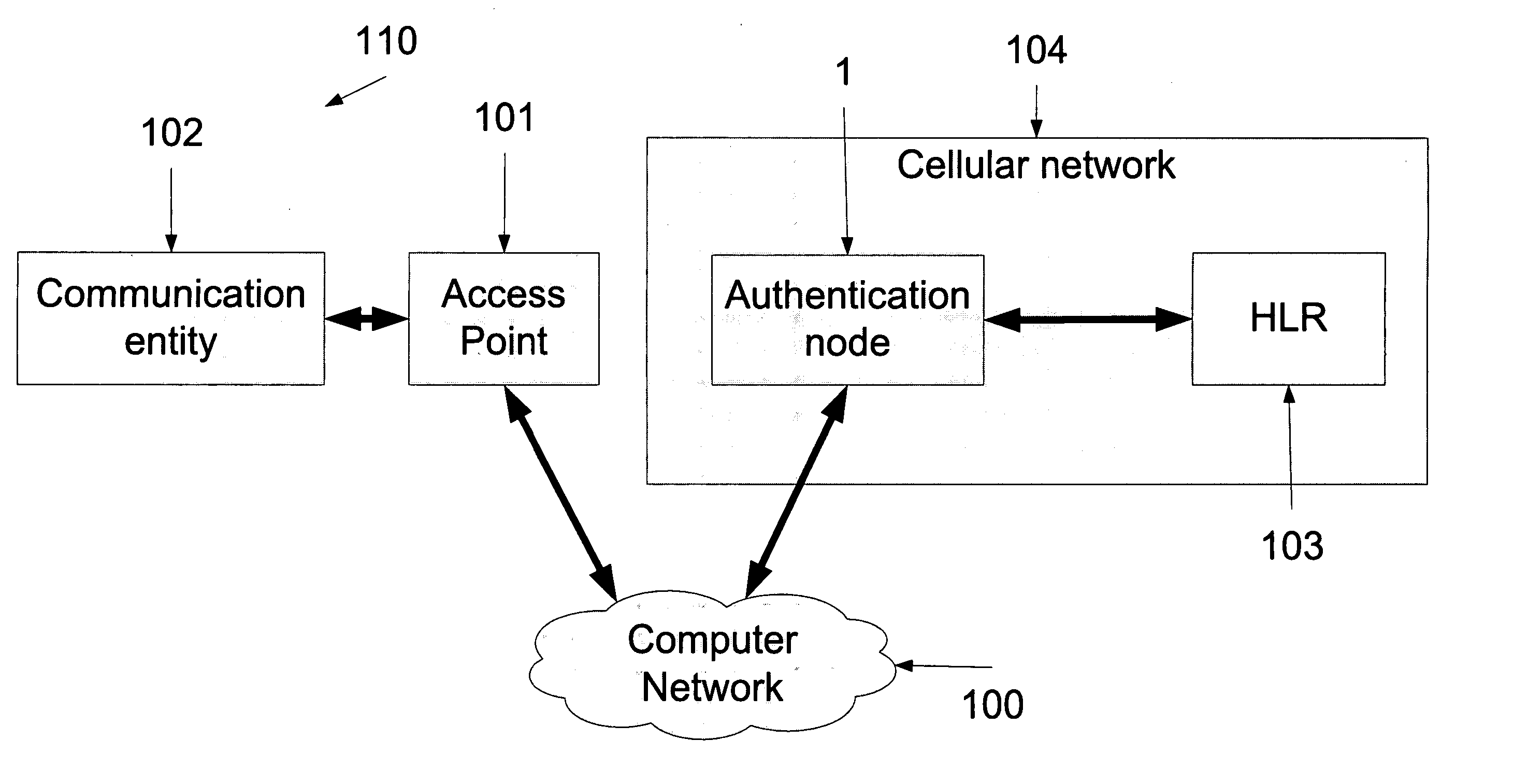
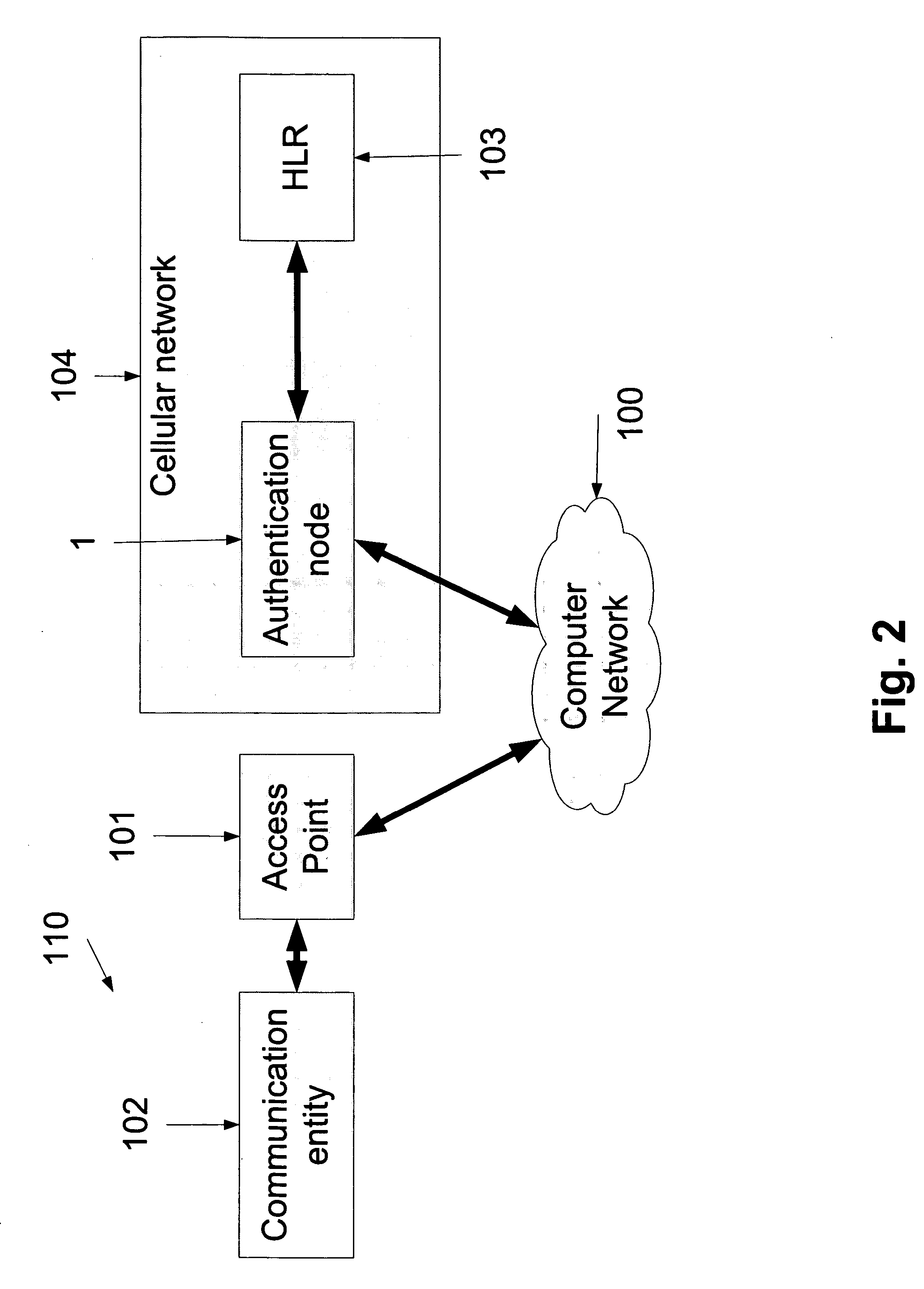
A method for challenge-based authentication of a communication entity to an access network. The access network uses a password-based communication protocol. The method comprises a) pre-supplying to the communication entity a challenge, thereby allowing the communication entity to provide a challenge response, b) supplying to the communication entity a password request, c) receiving the challenge response via the password request, and d) authenticating the communication entity if the challenge response is correct. Presupplying may be during a previous IP session, wherein communication entities are simply given challenges for next time they connect to the hotspot. Alternatively presupplying could be during a brief probationary connection that the access network gives to its users.
Owner:STARHOME GMBH
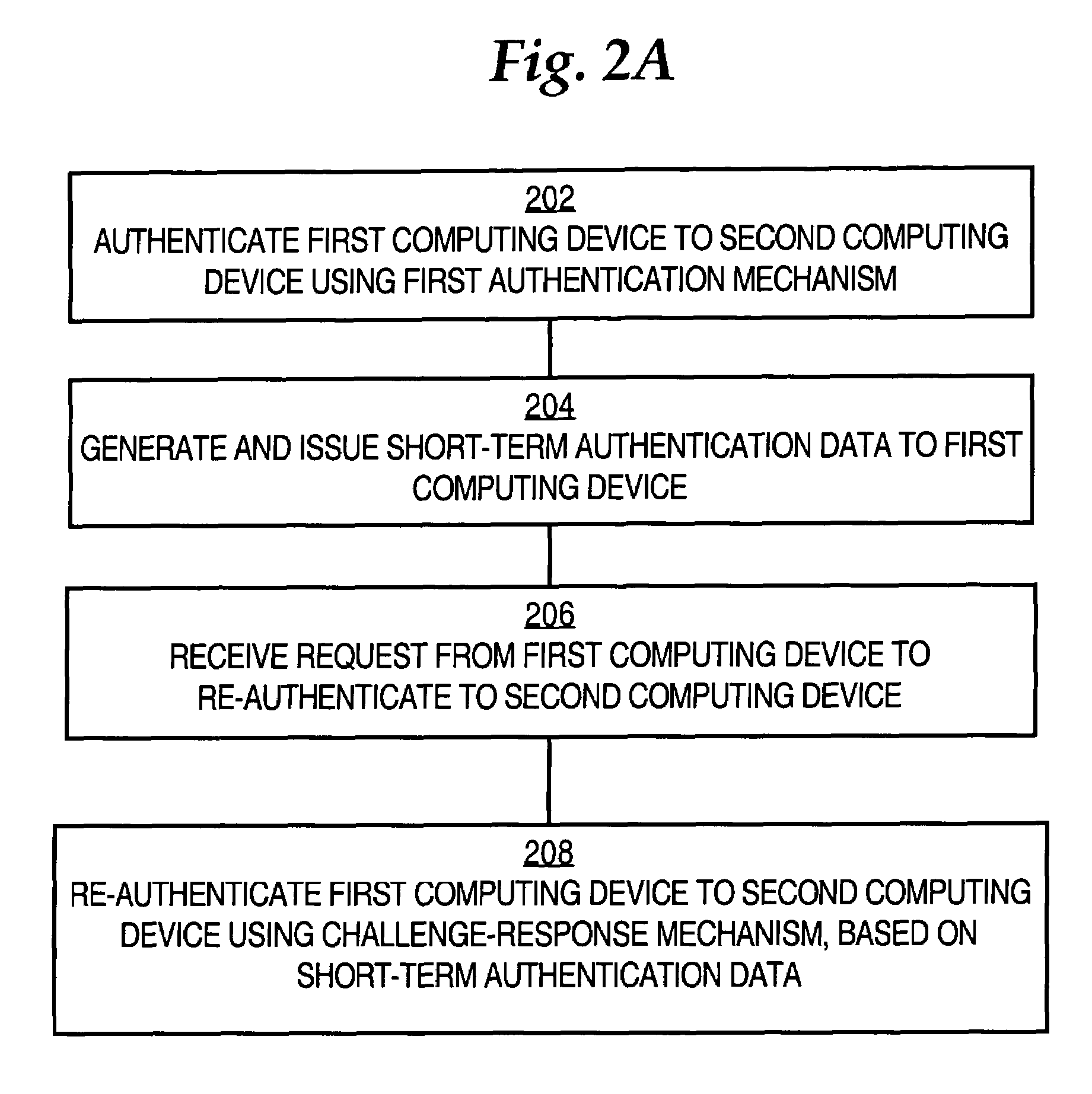
Method and apparatus for re-authenticating computing devices
ActiveUS7370350B1Few message exchangeDigital data processing detailsUser identity/authority verificationShort termsChallenge response
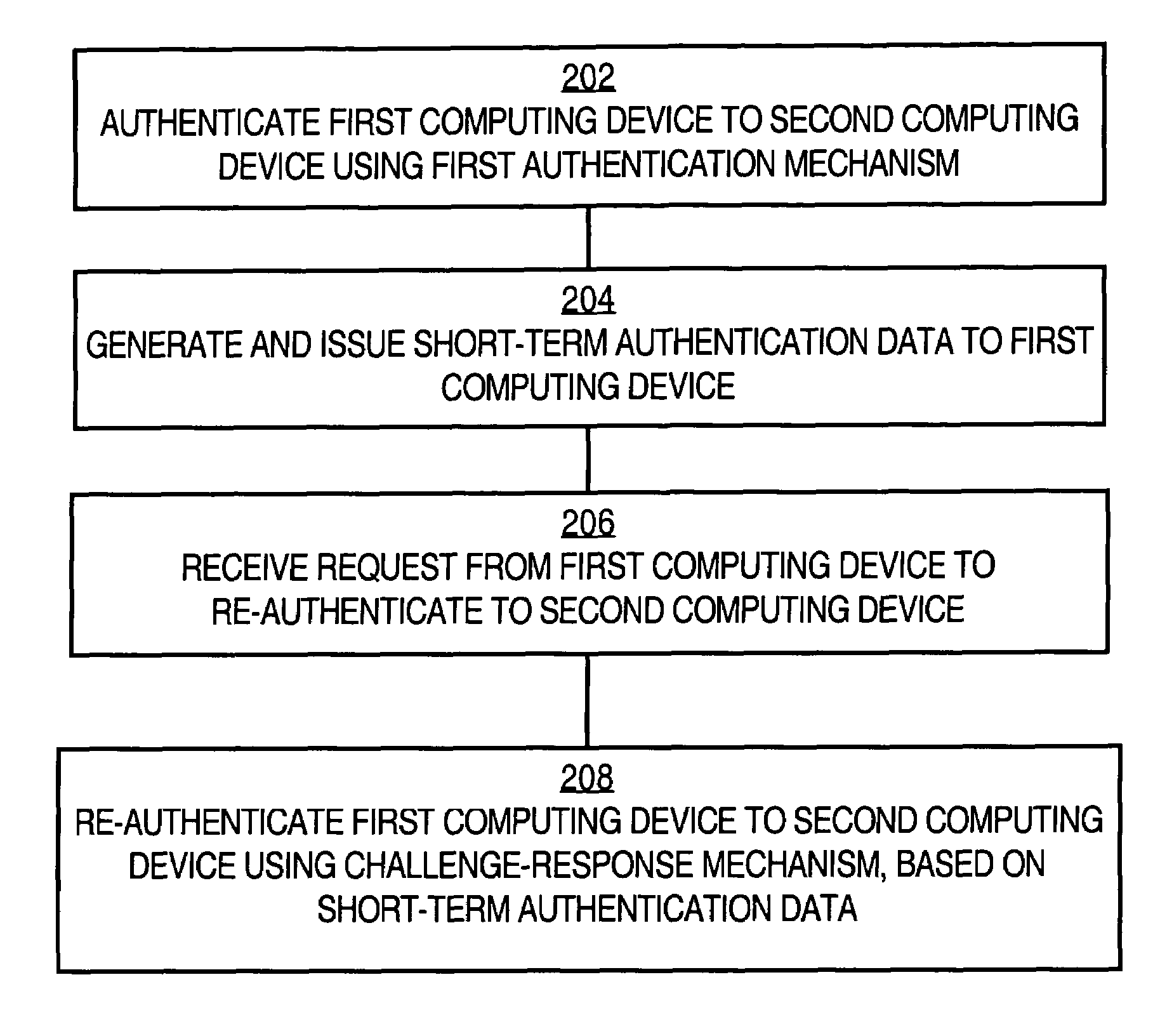
A method of authenticating a first computing device in communication over a network to a second computing device is disclosed. The first computing device is authenticated to the second computing device using a first authentication mechanism. The first authentication mechanism is based on Extensible Authentication Protocol (EAP) or IEEE 802.1x authentication. Short-term re-authentication data is generated and issued to the first computing device. Later, a request from the first computing device to re-authenticate to the second computing device is received. The first computing device is re-authenticated to the second computing device using a challenge-response mechanism in which the first computing device authenticates itself by presenting the short-term authentication credential to the second computing device. Accordingly, re-authentication proceeds more quickly and with fewer message exchanges.
Owner:CISCO TECH INC
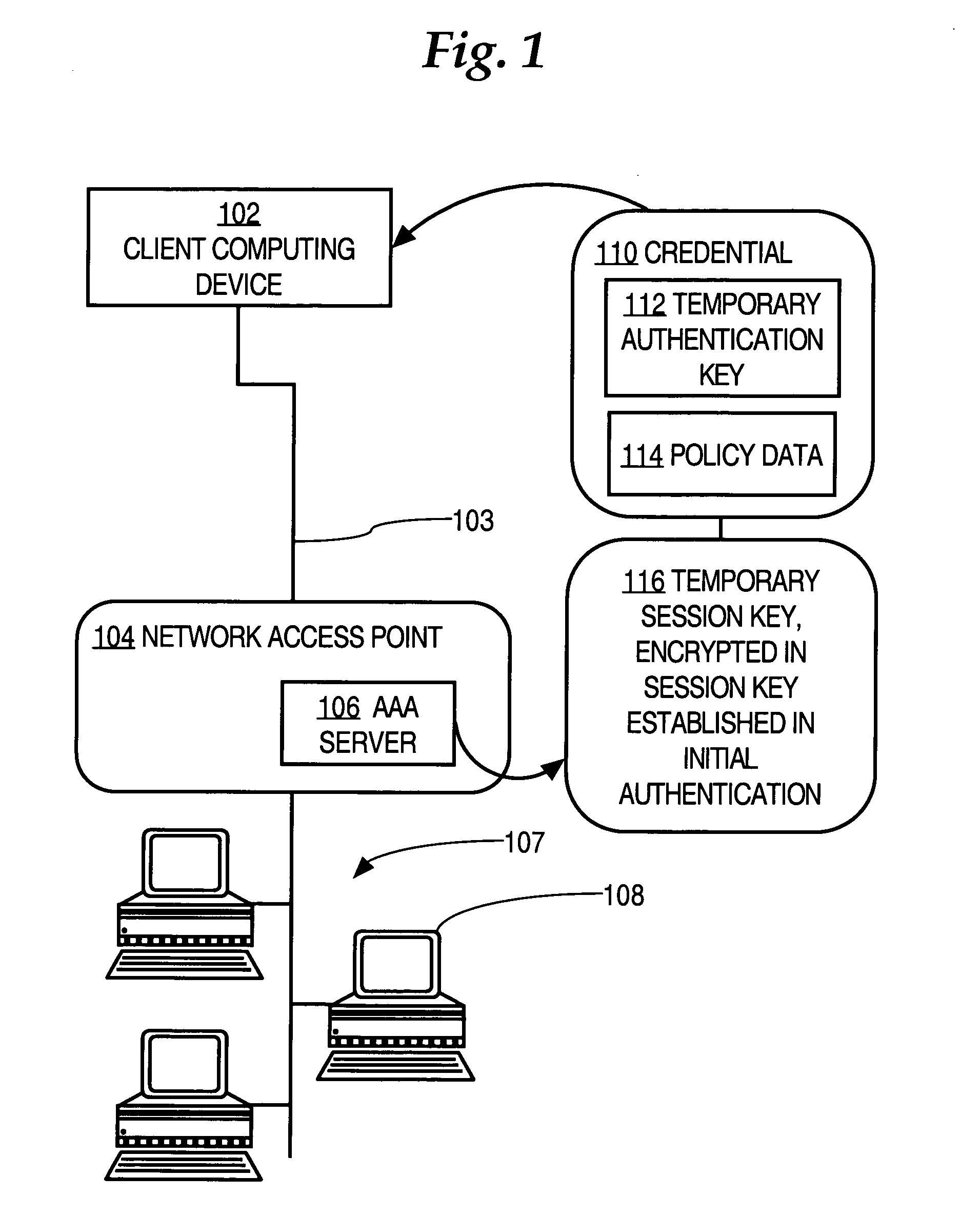
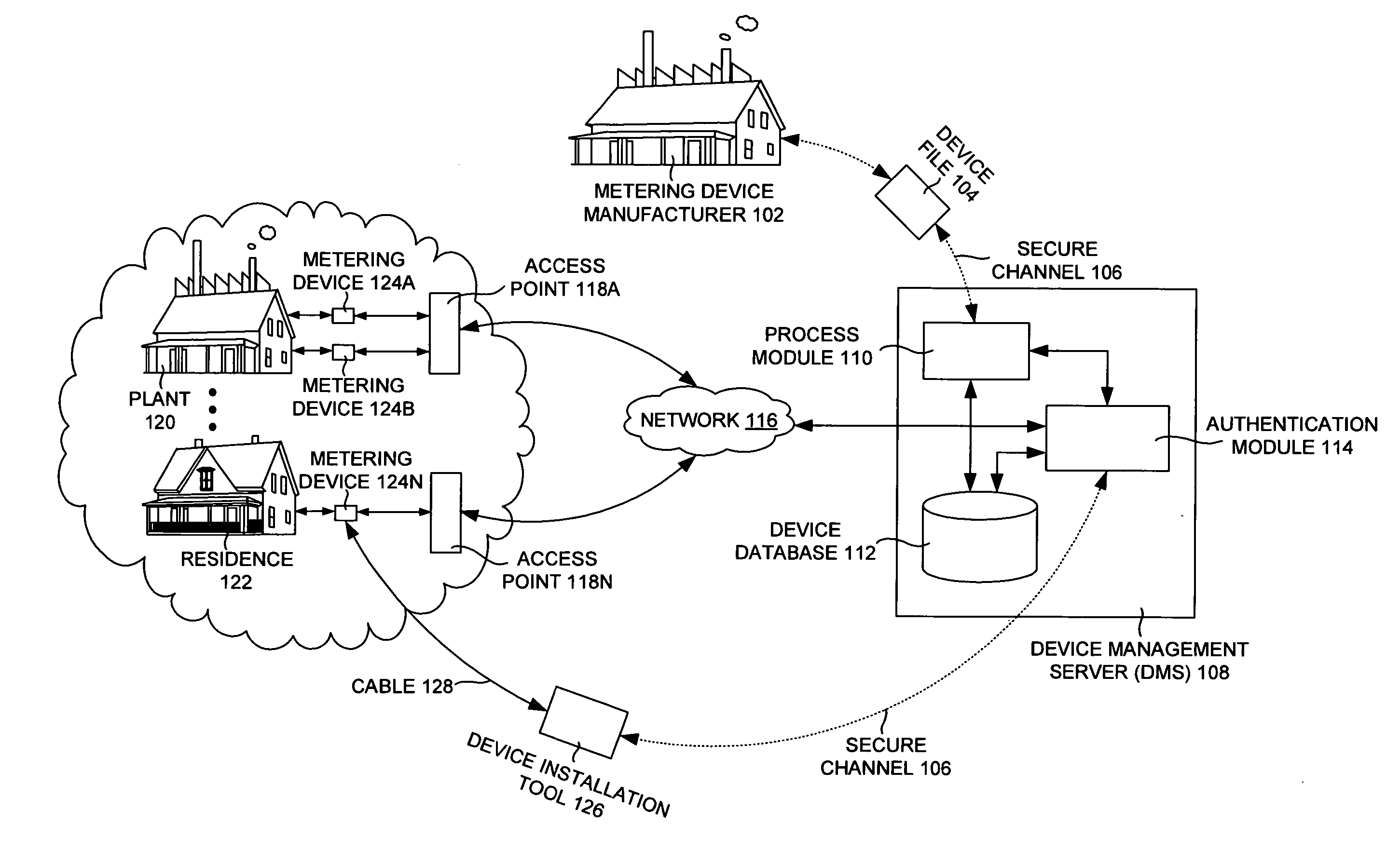
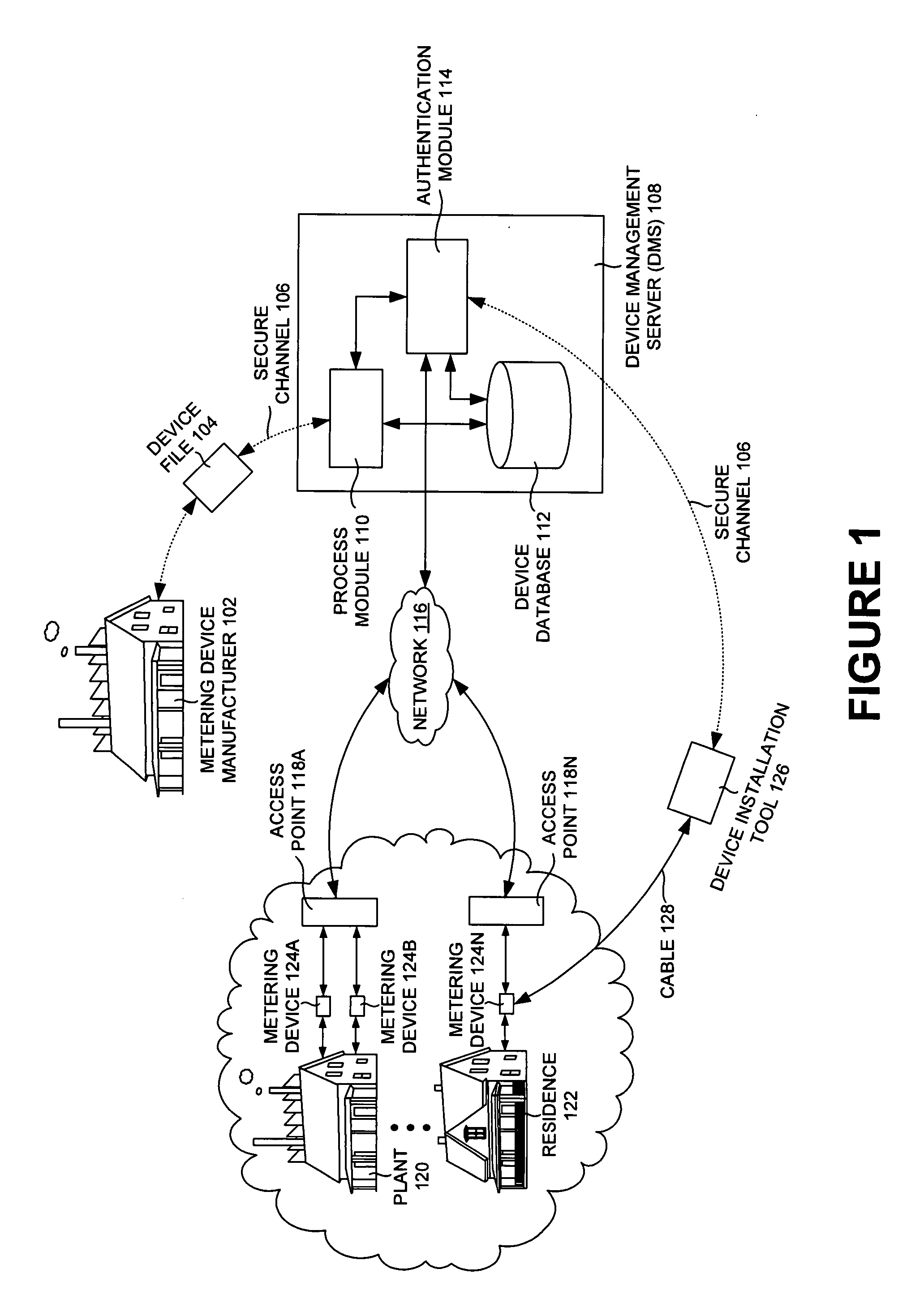
Secure network bootstrap of devices in an automatic meter reading network
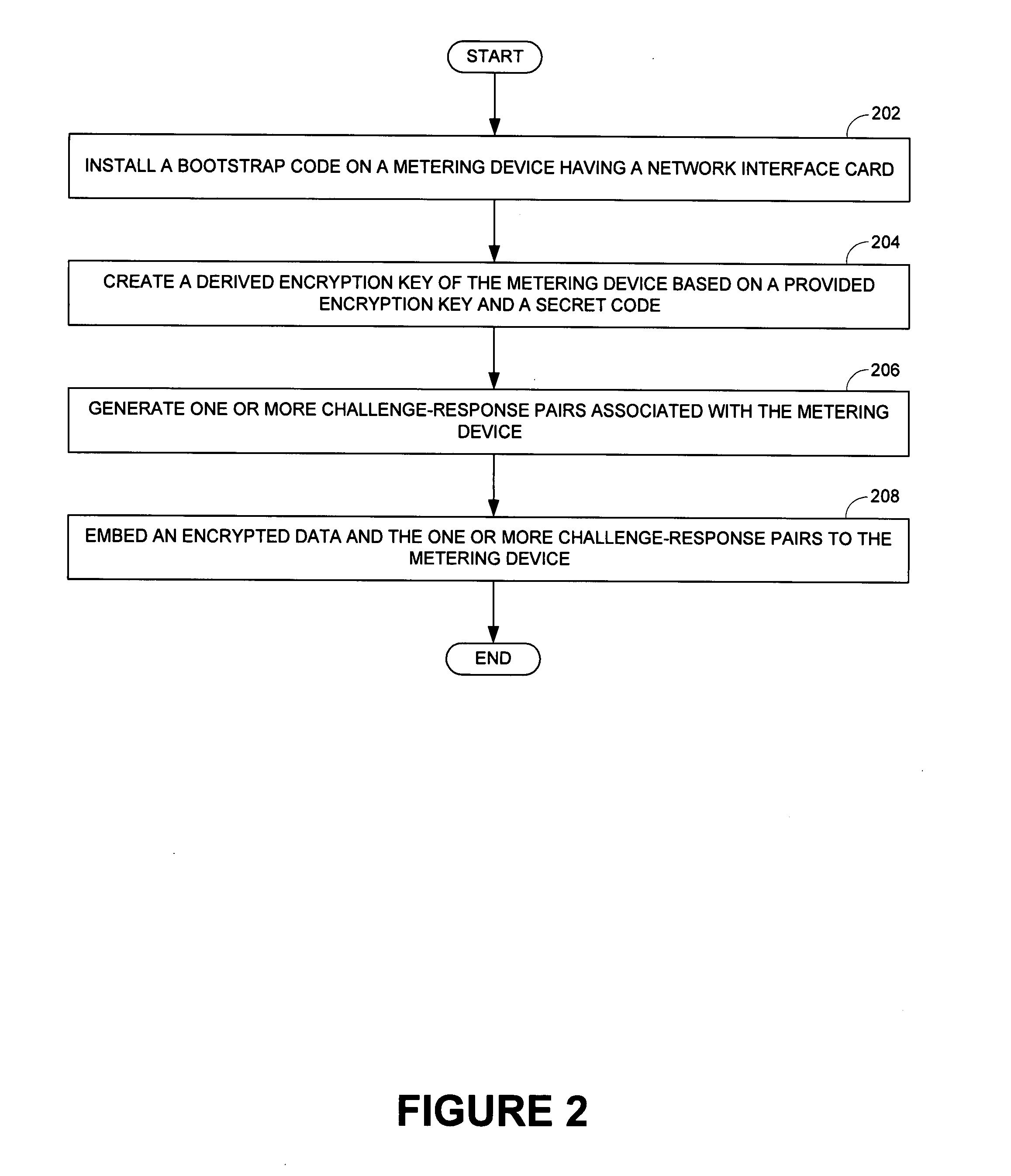
InactiveUS20070257813A1Prevent tamperingElectric signal transmission systemsTariff metering apparatusData shippingChallenge response
A method and / or a system of a secure network bootstrap of devices in an automatic meter reading network is disclosed. A method of a network interface card in an automatic meter reading network includes generating a derived security key based on a secret key embedded in a network interface card and a provided security key of a device management server of the automatic meter reading network. The method also includes communicating the derived security key and a challenge data of a challenge-response pair of the device management server to a metering device and generating a response data through processing a reply data of the metering device reacting to the challenge data. In addition, the method includes communicating the response data to the device management server to authenticate the network interface card and / or the metering device.
Owner:ITRON NETWORKED SOLUTIONS INC
Method and system for encrypting and decrypting data using an external agent
InactiveUS20070237332A1Improve securitySynchronising transmission/receiving encryption devicesTelecommunications linkCommunications system
A communication system including a transmitter, a receiver, a communication link (for example, a TMDS-like link), and preferably also an external agent with which the transmitter and receiver can communicate, in which video data (or other data) are encrypted, the encrypted data are transmitted from the transmitter to the receiver, and the transmitted data are decrypted in the receiver, a transmitter and a receiver for use in such a system, a cipher engine for use in such a transmitter or receiver, a method for operating such a transmitter or receiver to encrypt or decrypt data, and a method for distributing keys to the transmitter and receiver. The receiver can be a player coupled to a downstream receiver by a TMDS-like link, and configured to re-encrypt the decrypted data (for example, using an AES or HDCP protocol) and send re-encrypted data over the link to the receiver. Optionally, the player is a repeater which translates the decrypted data from the transmitter, and then re-encrypts the translated data for transmission to the downstream receiver. The transmitter can itself be a player that receives and decrypts encrypted data from an upstream source. In preferred embodiments, the system implements a content protection protocol including a challenge-response procedure. After a new key is supplied to the receiver (and the same new key should have been supplied to the transmitter) and before the receiver can use the new key, the challenge-response procedure requires that the receiver validate the transmitter by verifying that the transmitter has proper knowledge of the new key.
Owner:SILICON IMAGE INC
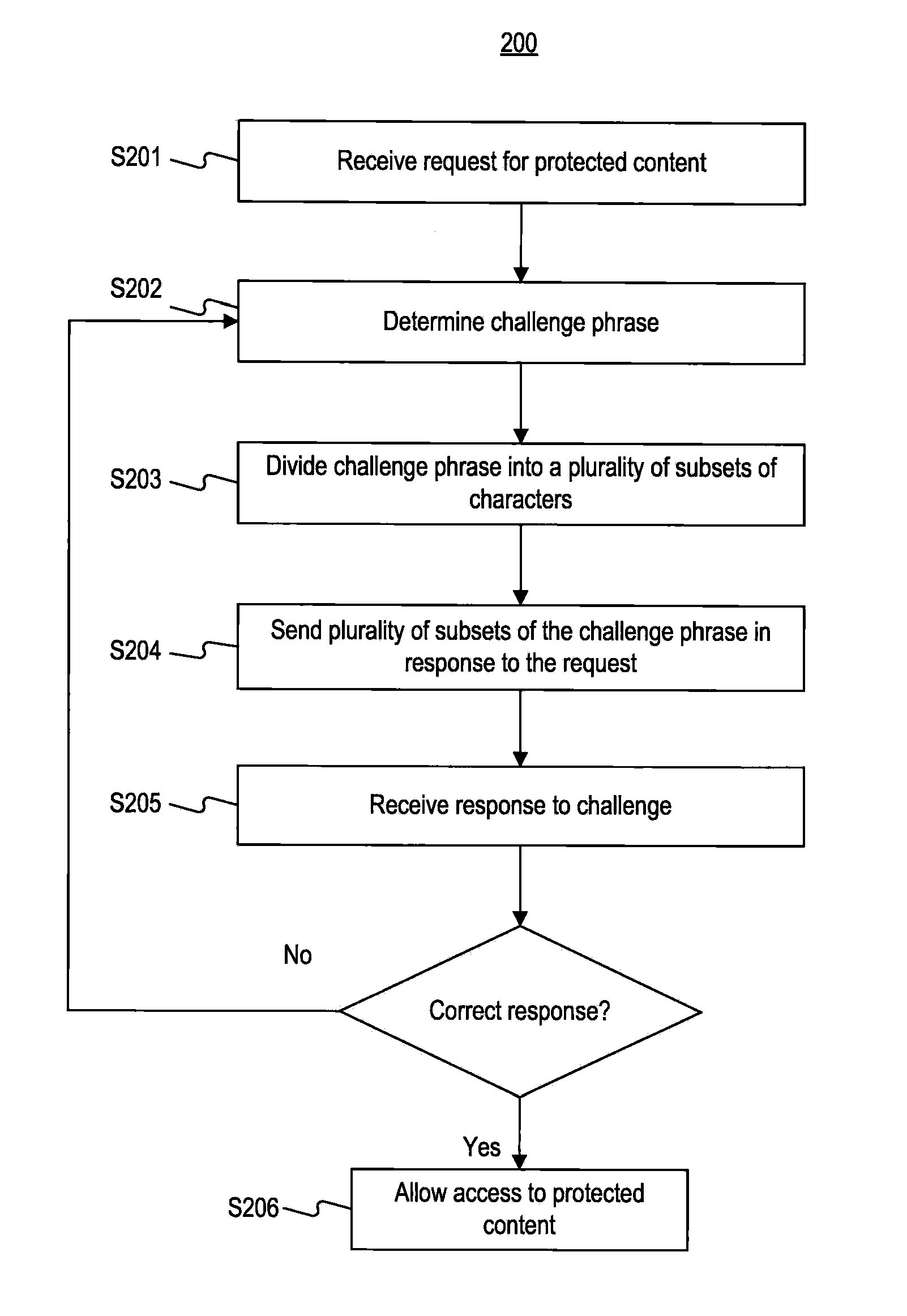
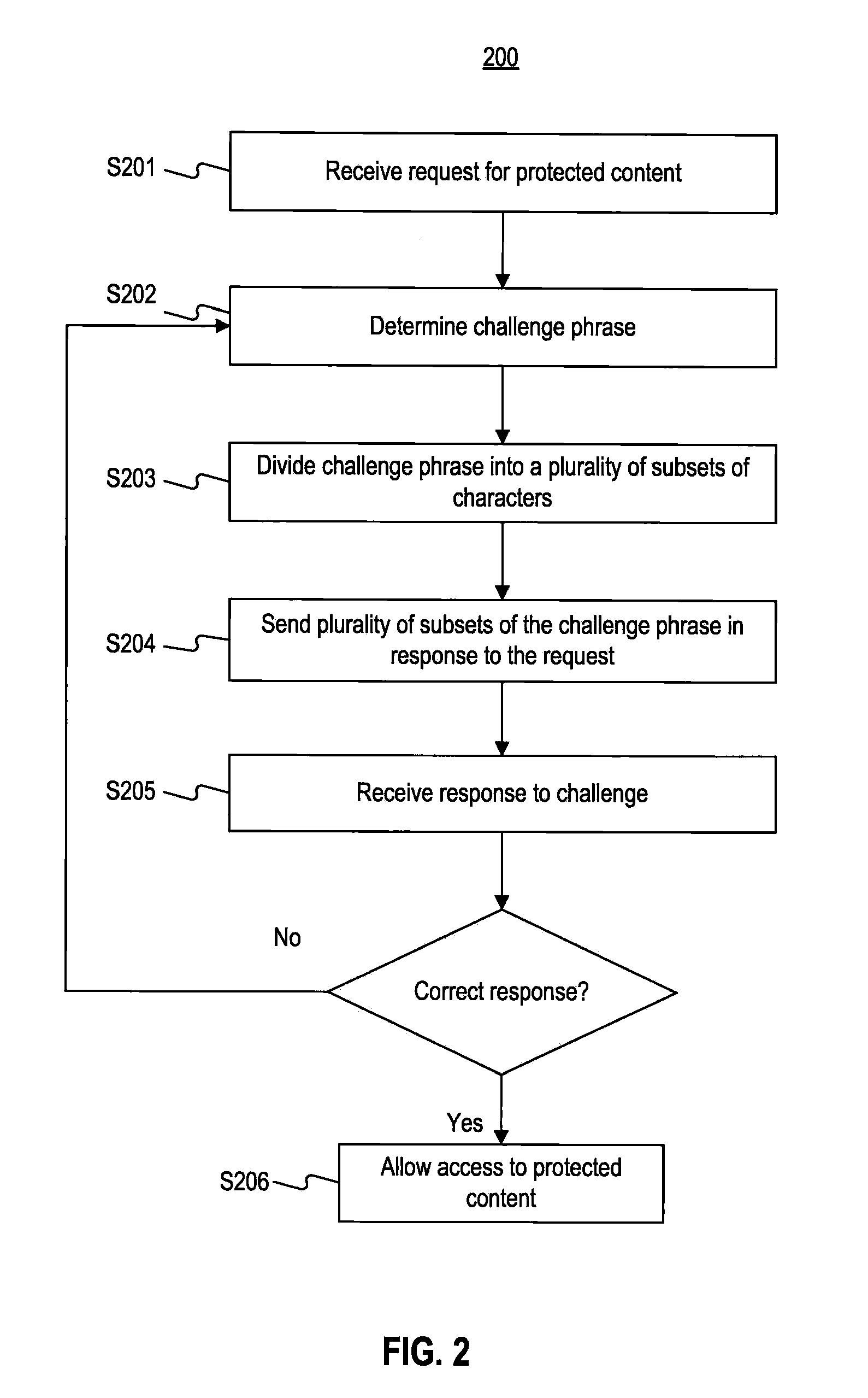
Systems and Methods for Challenge-Response Animation and Randomization Testing
ActiveUS20100251388A1Limited accessAccess to protected is limitedDigital data processing detailsUser identity/authority verificationAnimationInternet privacy
Systems and methods are provided for challenge / response animation. In one implementation, a request for protected content may be received from a client, and the protected content may comprise data. A challenge phrase comprising a plurality of characters may be determined, and a computer processor may divide the challenge phrase into at least two character subsets selected from the characters comprising the challenge phrase. Each of the at least two character subsets may include less than all of the characters comprising the challenge phrase. The at least two character subsets may be sent to the client in response to the request; and an answer to the challenge phrase may be received from the client in response to the at least two character subsets. Access to the protected content may be limited based on whether the answer correctly solves the challenge phrase.
Owner:VERIZON PATENT & LICENSING INC
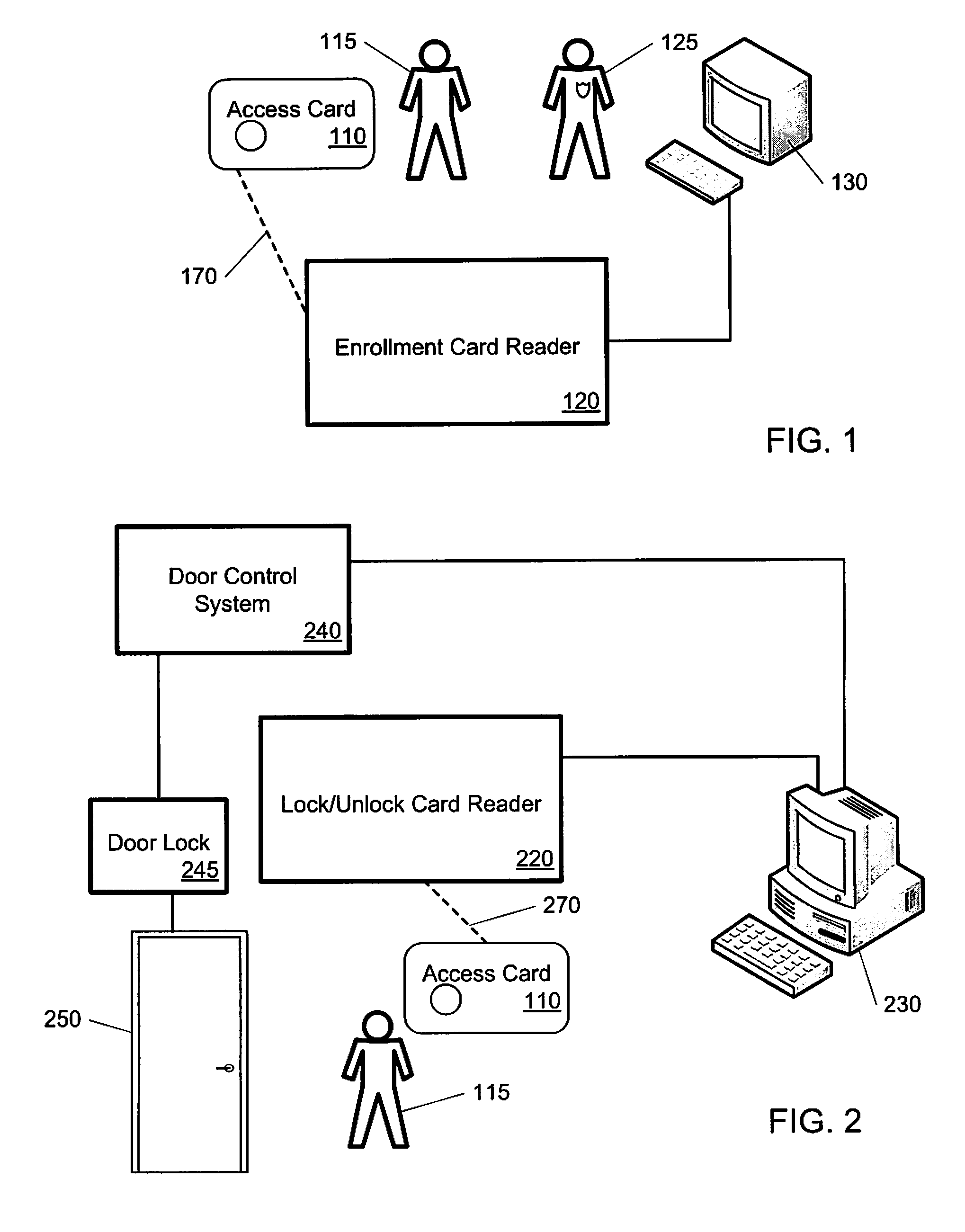
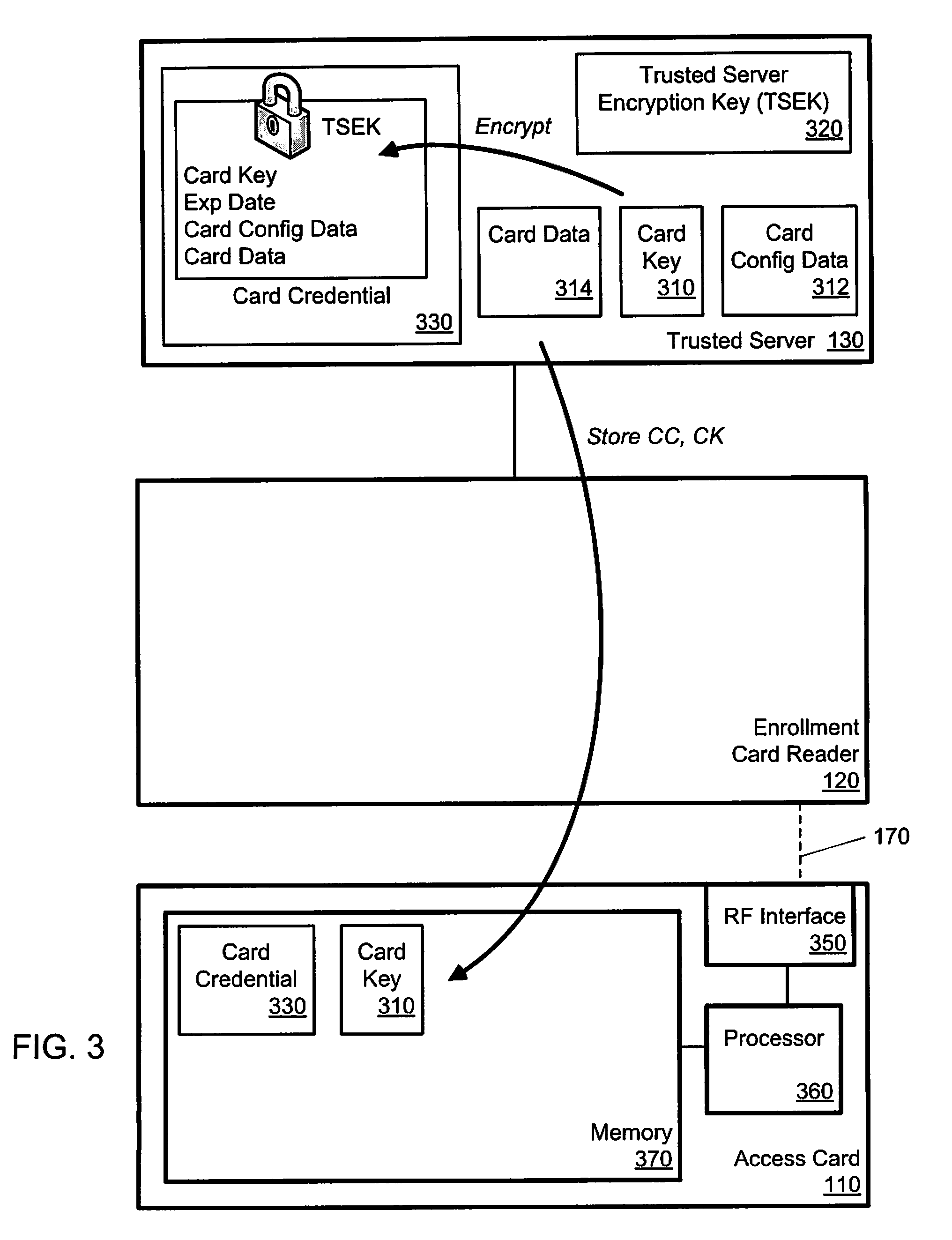
Card Credential Method and System
ActiveUS20100096452A1Unauthorized memory use protectionHardware monitoringComputer hardwareChallenge response
In one implementation, a method for providing access to a secure facility includes authenticating the user; generating a card credential, transmitting the card credential to an access card carried by of the user, and transmitting the card key to the access card in a form that is usable by the access card. The generating the card credential includes encrypting the card key using a server encryption key. The card key is usable for a challenge-response interaction during subsequent access requests by the user.
Owner:HABRAKEN G WOUTER
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com