Patents
Literature
354 results about "Authorization certificate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
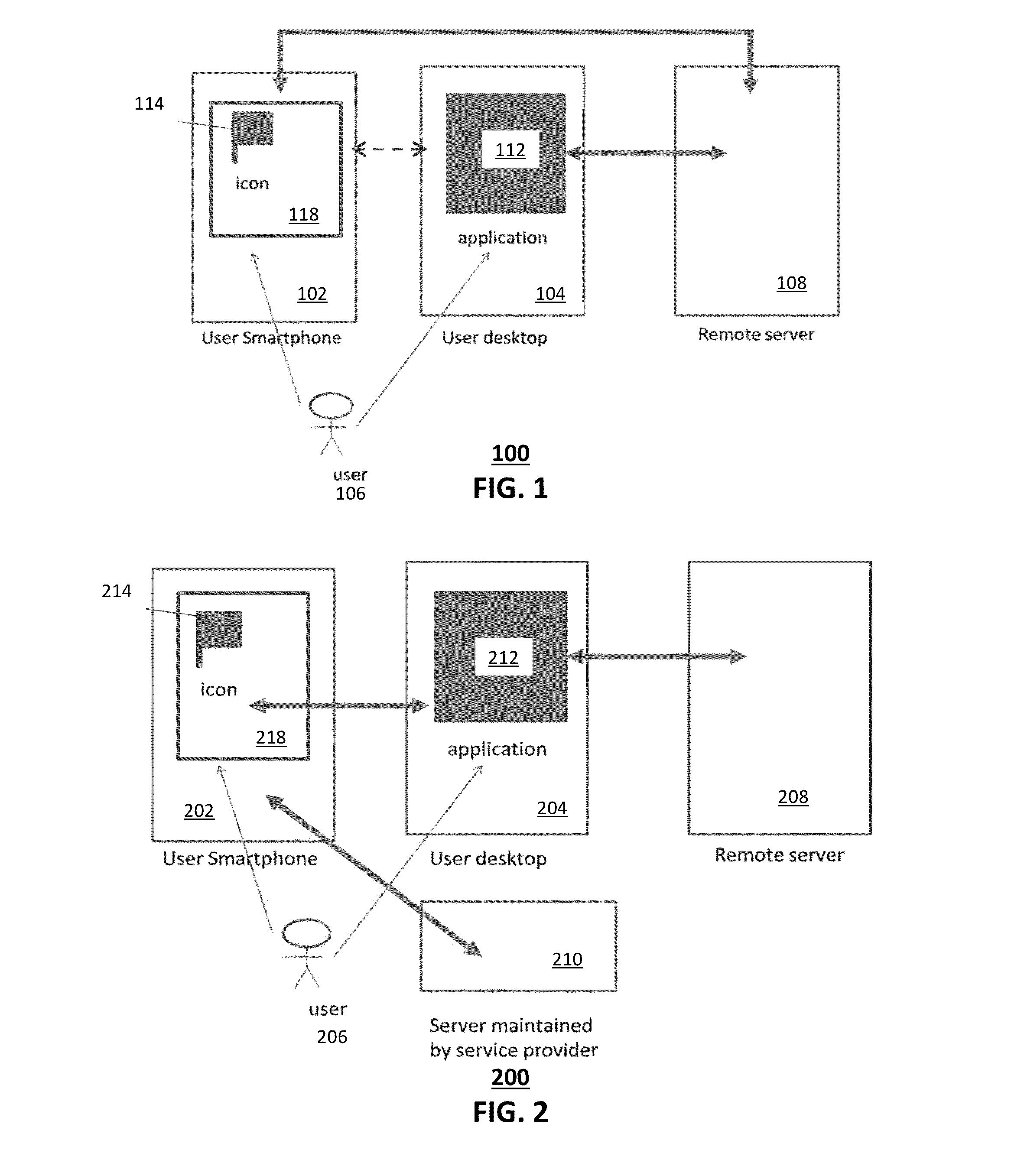
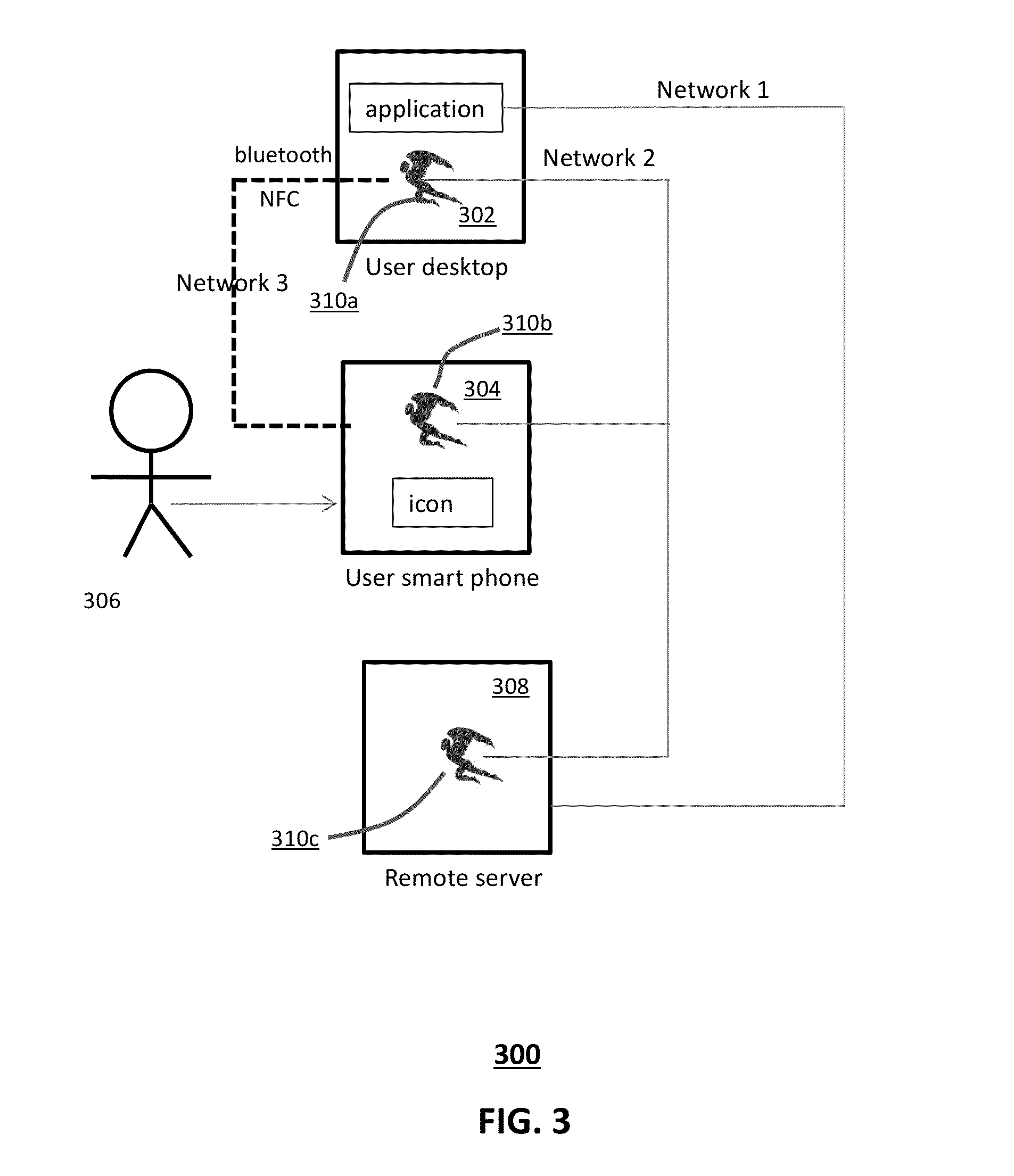
In computer security, an attribute certificate, or authorization certificate (AC) is a digital document containing attributes associated to the holder by the issuer. When the associated attributes are mainly used for the purpose of authorization, AC is called authorization certificate. AC is standardized in X.509. RFC 5755 further specifies the usage for authorization purpose in the Internet.
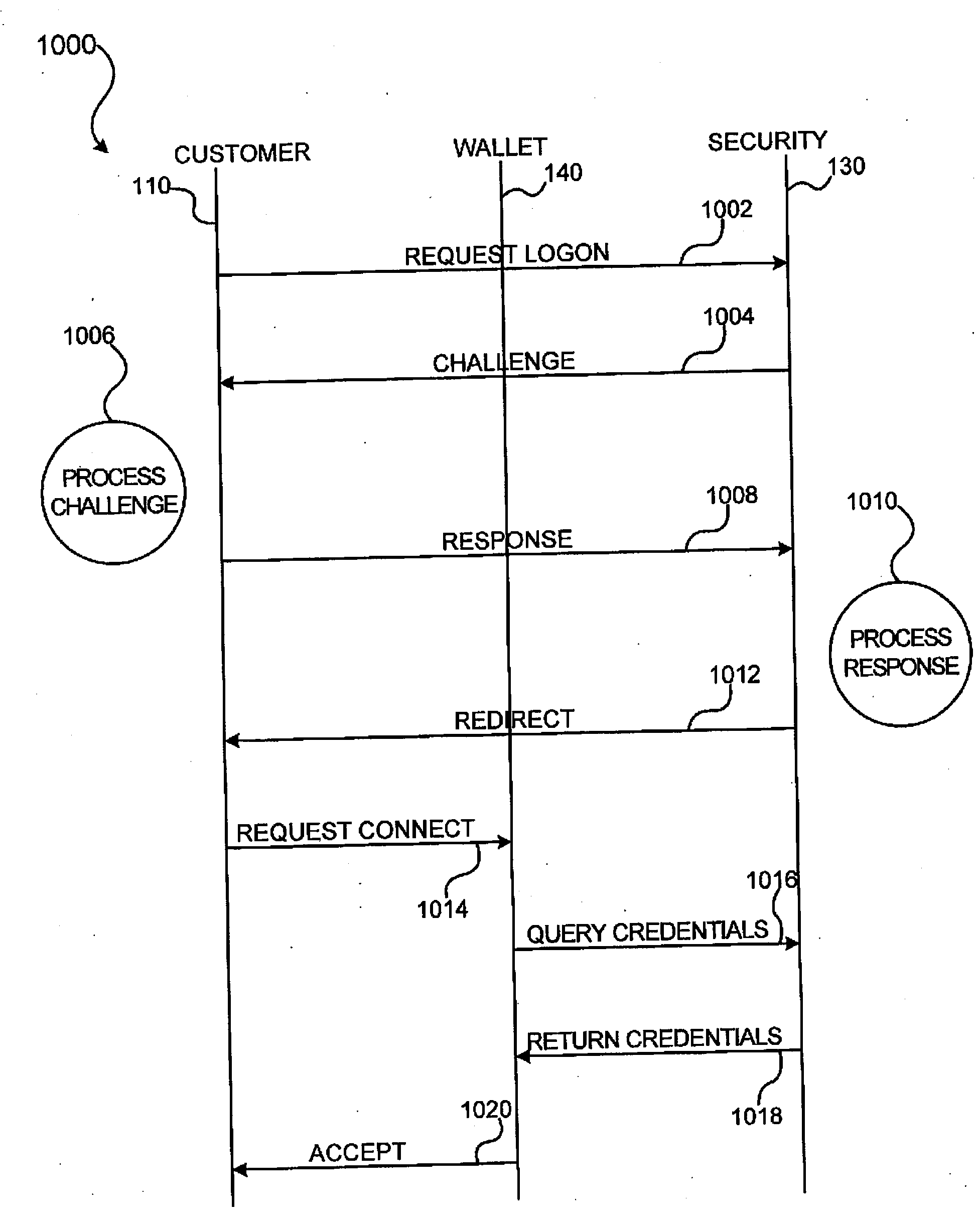
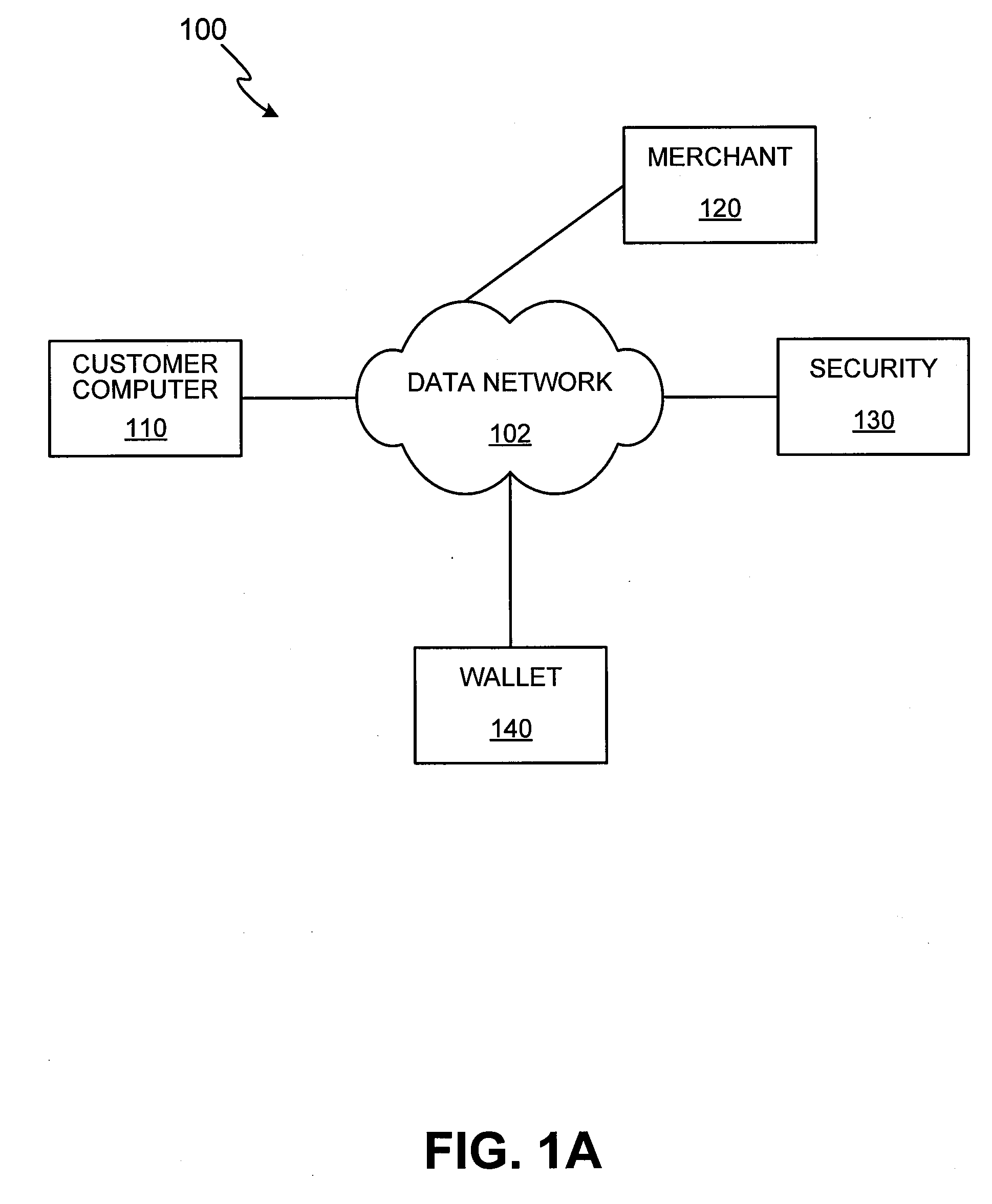
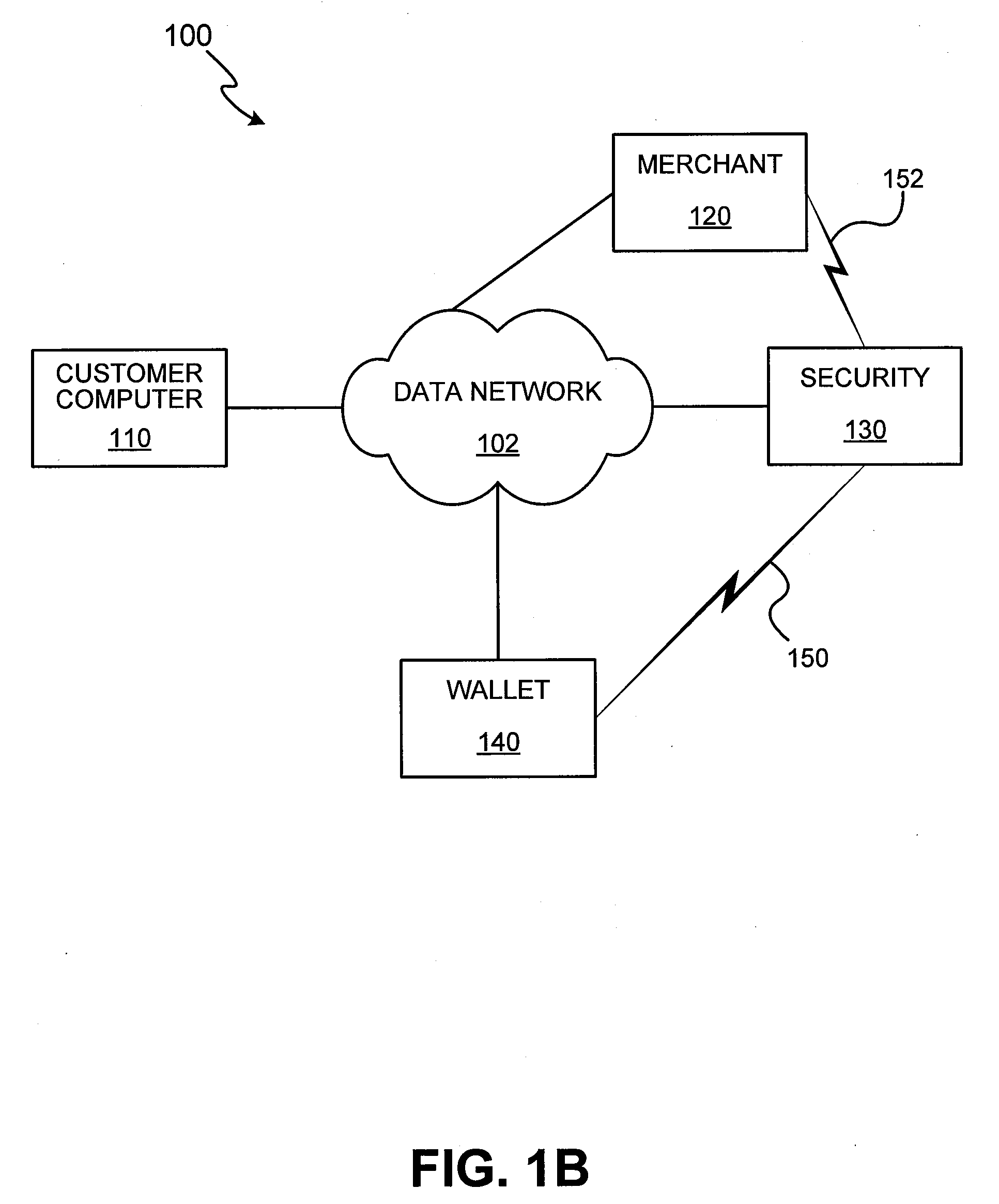
Methods and apparatus for conducting electronic transactions
InactiveUS20090076966A1Enhanced reliability and confidenceReduce security risksComplete banking machinesAcutation objectsAuthorization certificateChallenge response
A system and method for facilitating electronic transactions using an intelligent instrument is disclosed. An authorization server enables users to obtain authorization credentials through the use of the intelligent instrument by issuing a challenge to an intelligent token of the intelligent instrument. The intelligent token generates a challenge response and transmits the challenge response to the authorization server, which assembles credentials including a key for the electronic transaction upon validating the response. The authorization server sends the assembled credentials to the intelligent instrument and the intelligent instrument transmits the assembled credentials to the authorization server during a subsequent transaction. The authorization server validates the assembled credentials and provides authorization for the transaction in response to the validating the assembled credentials.
Owner:LIBERTY PEAK VENTURES LLC
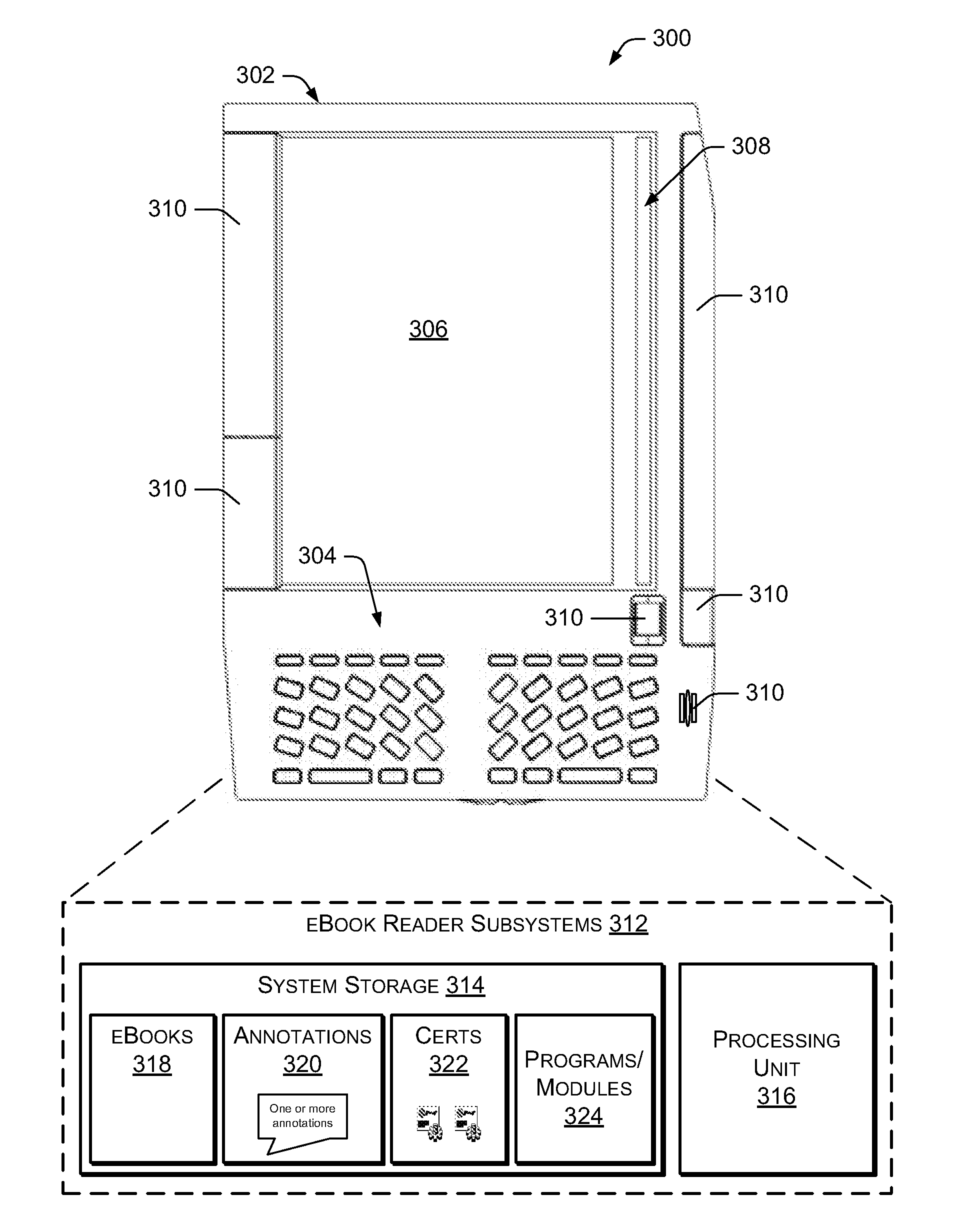
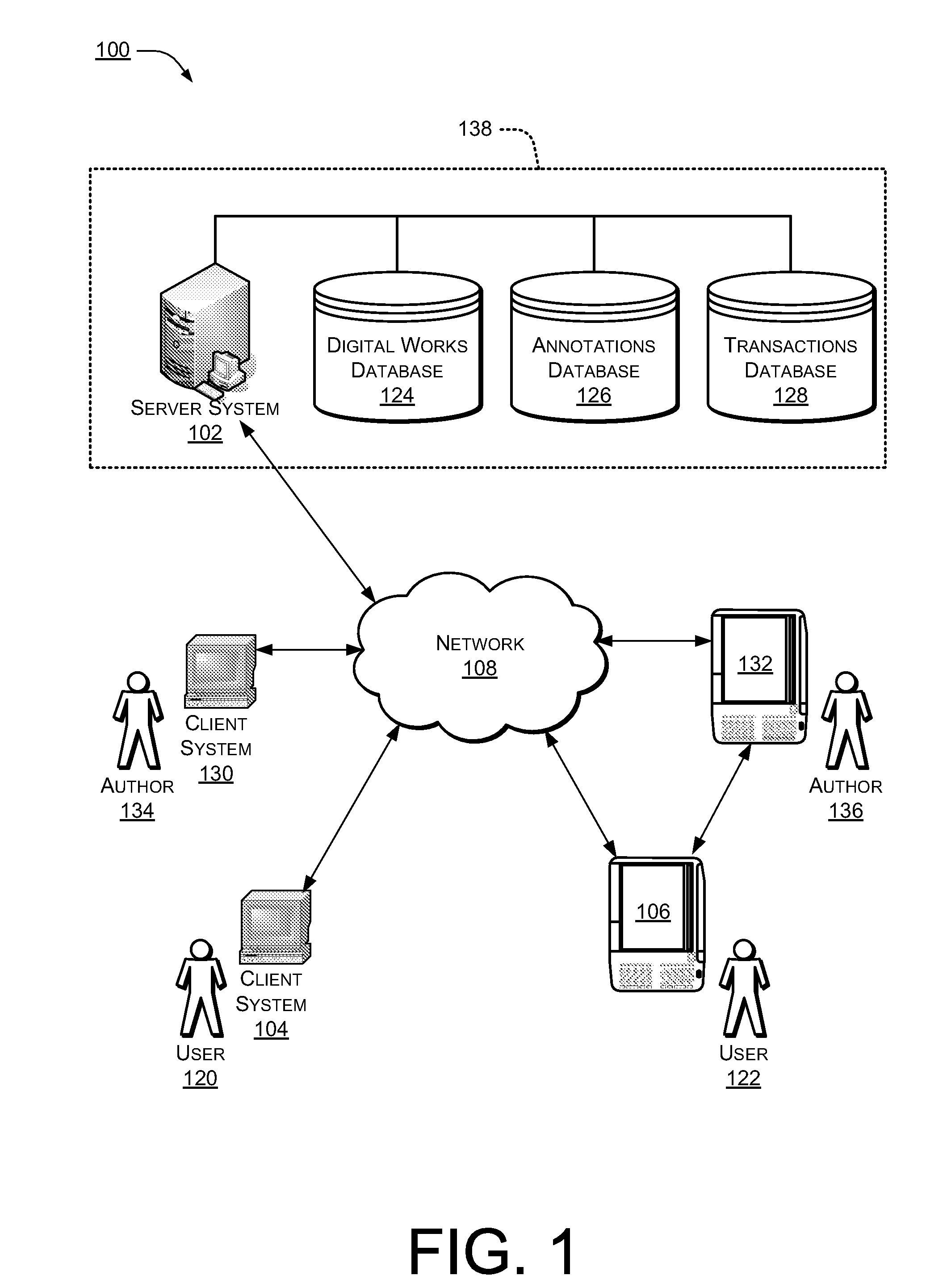
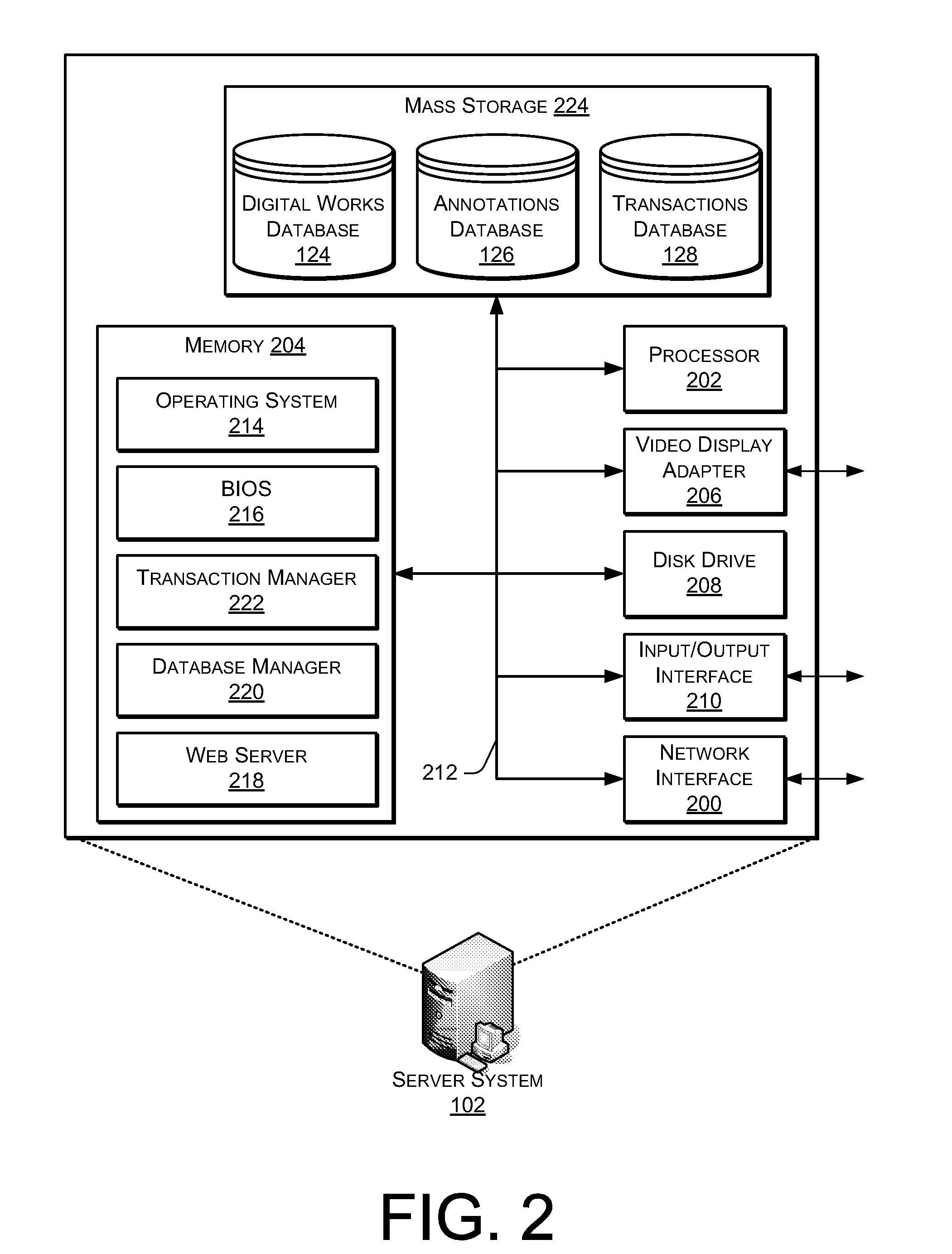
Providing Annotations of a Digital Work
ActiveUS20080168073A1Wide applicabilityReduce fatMultimedia data indexingNatural language data processingAuthorization certificateAuthorization
A digital work may be annotated using an eBook reader device. Upon receiving an annotation relating to a specific portion of the digital work, an invariant location reference identifier corresponding to the specified portion of the digital work may be appended to the annotation. The annotation may then be stored in association with the digital work for later reference. In some instances, an annotation may be presented on an eBook reader device upon receipt of a valid authorization credential granting access to the annotation.
Owner:AMAZON TECH INC
Methods and systems for administering imaging device notification access control
InactiveUS8015234B2Multiple digital computer combinationsInternal/peripheral component protectionAuthorization certificateImaging equipment
Owner:SHARP KK
Method and system for authorizing a client computer to access a server computer
InactiveUS7089585B1Key distribution for secure communicationDigital data processing detailsAuthorization certificateHash function
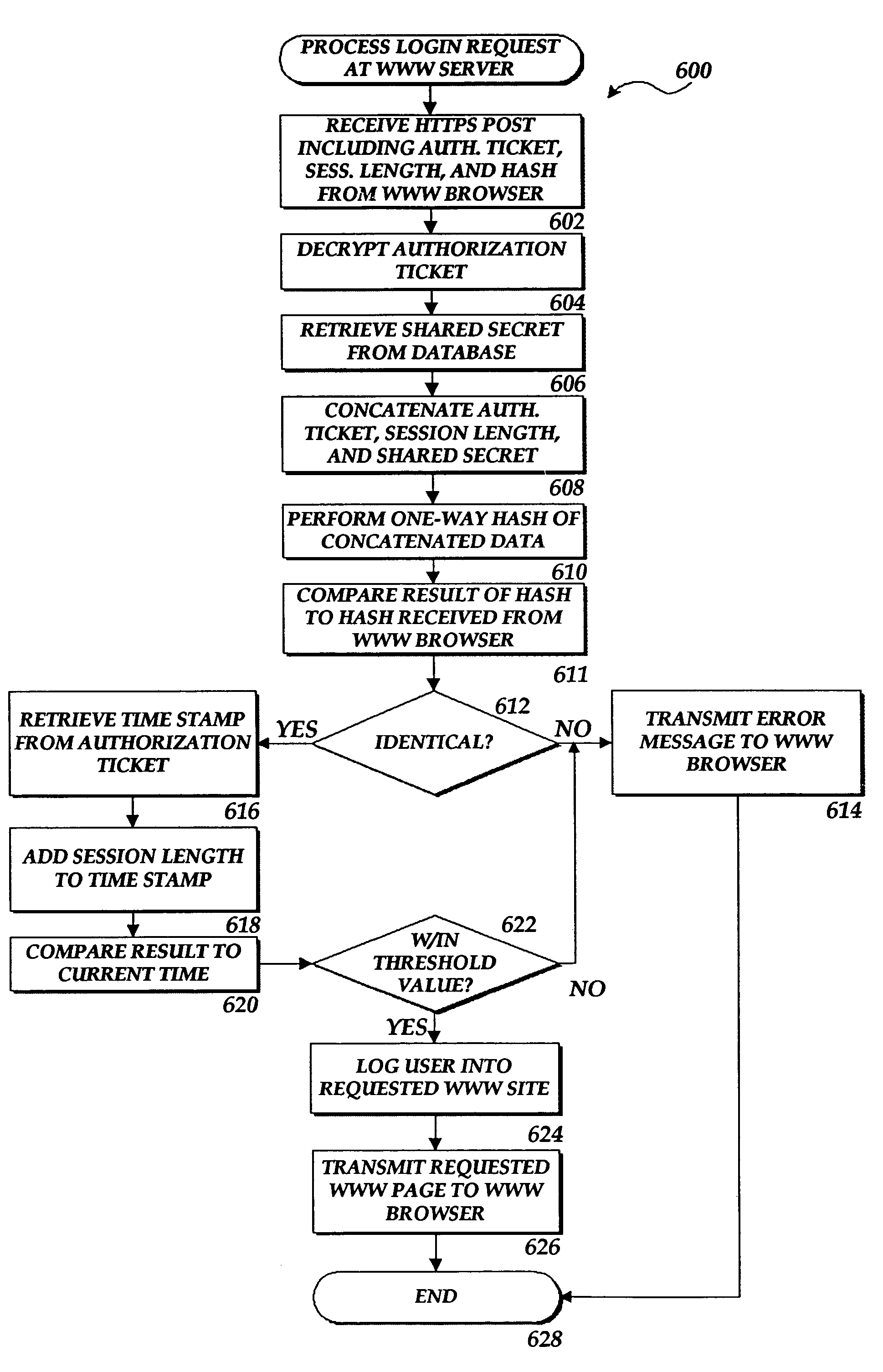
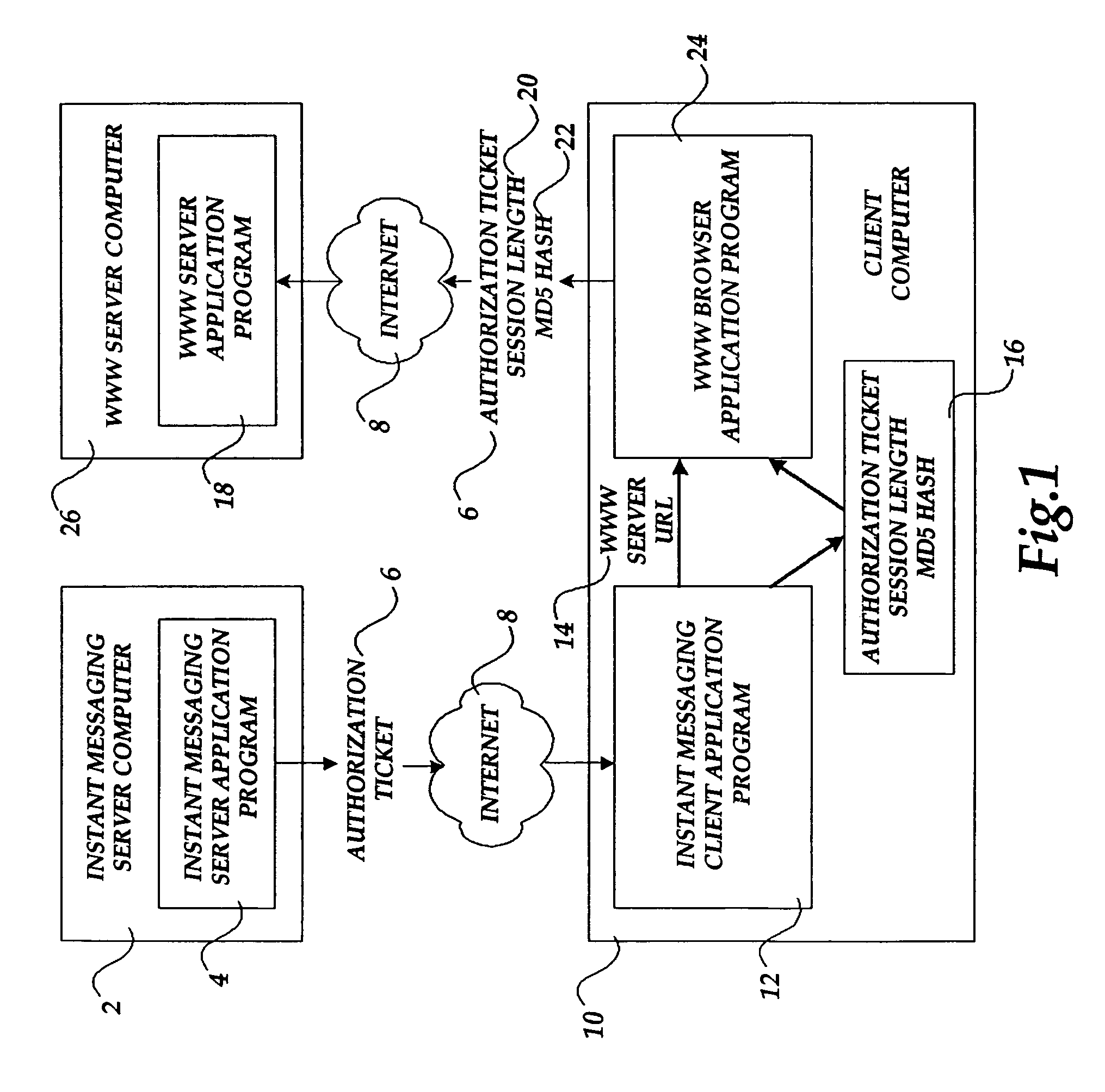
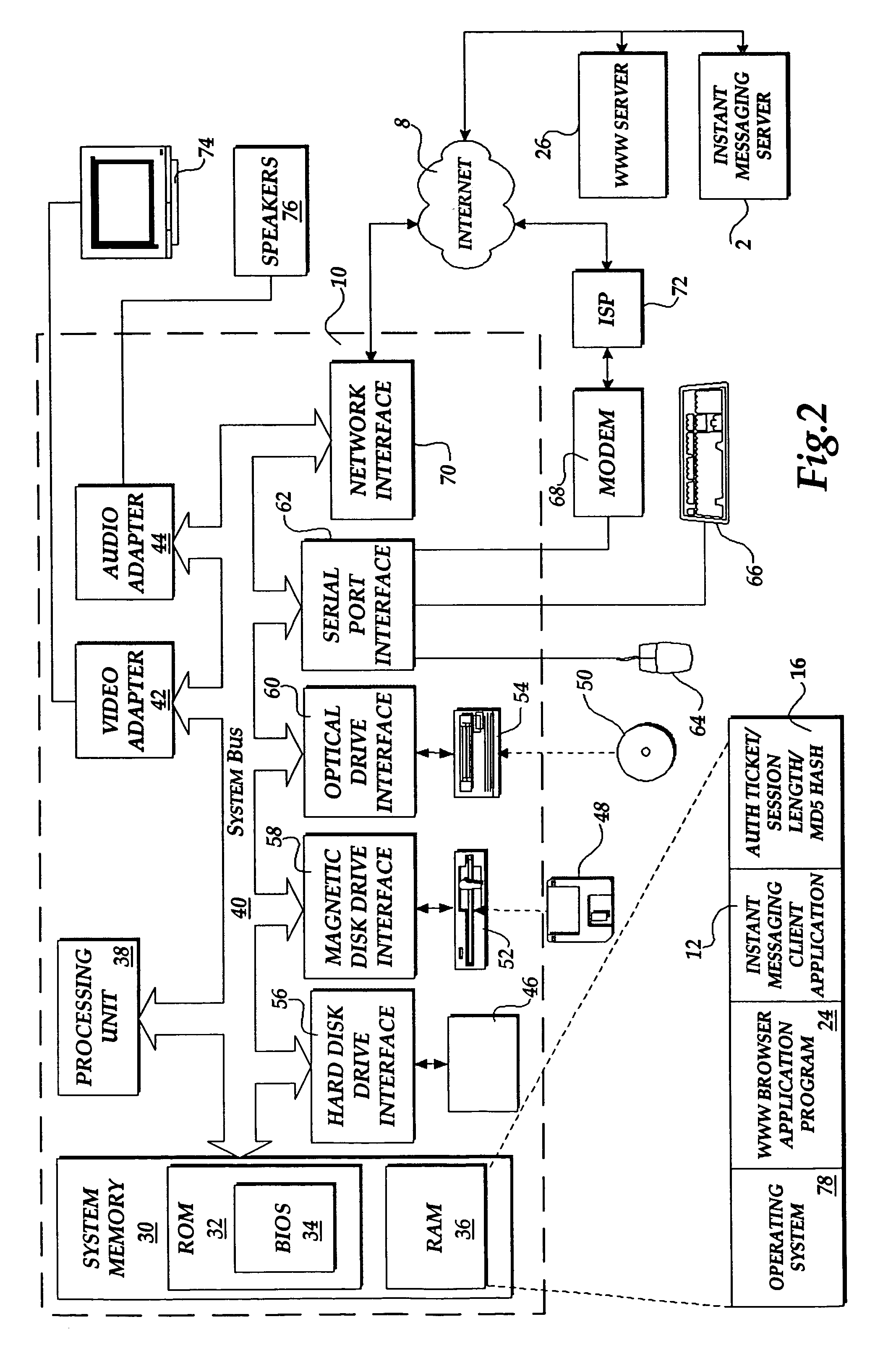
The present invention includes a client computer, a first server computer, and a second server computer. The first server provides an authorization ticket containing a time stamp to the client computer when the client computer is authorized to access the first server. An elapsed time counter is started at the client computer when access is provided to the first server. When a request is received at the client computer to access the second server, the client computer determines the session length based upon the elapsed time counter. The client computer calculates a hash value for the authorization ticket, the session length, and a secret shared with the second server computer. The client computer transmits a login request to the second server including the authorization ticket, the session length, and the hash. The second server decrypts the authorization ticket and retrieves a copy of the shared secret. The second server executes a hash function on the authorization ticket, the session length, and the shared secret. The second server then compares the computed hash to the hash value received from the second client application. If the two hash values are identical, the second server retrieves the time stamp from the authorization ticket and adds the session length to the time stamp. The second server then compares the resulting value to the current time. If the resulting value and the current time are within a preset threshold value, the client computer is provided.
Owner:MICROSOFT TECH LICENSING LLC
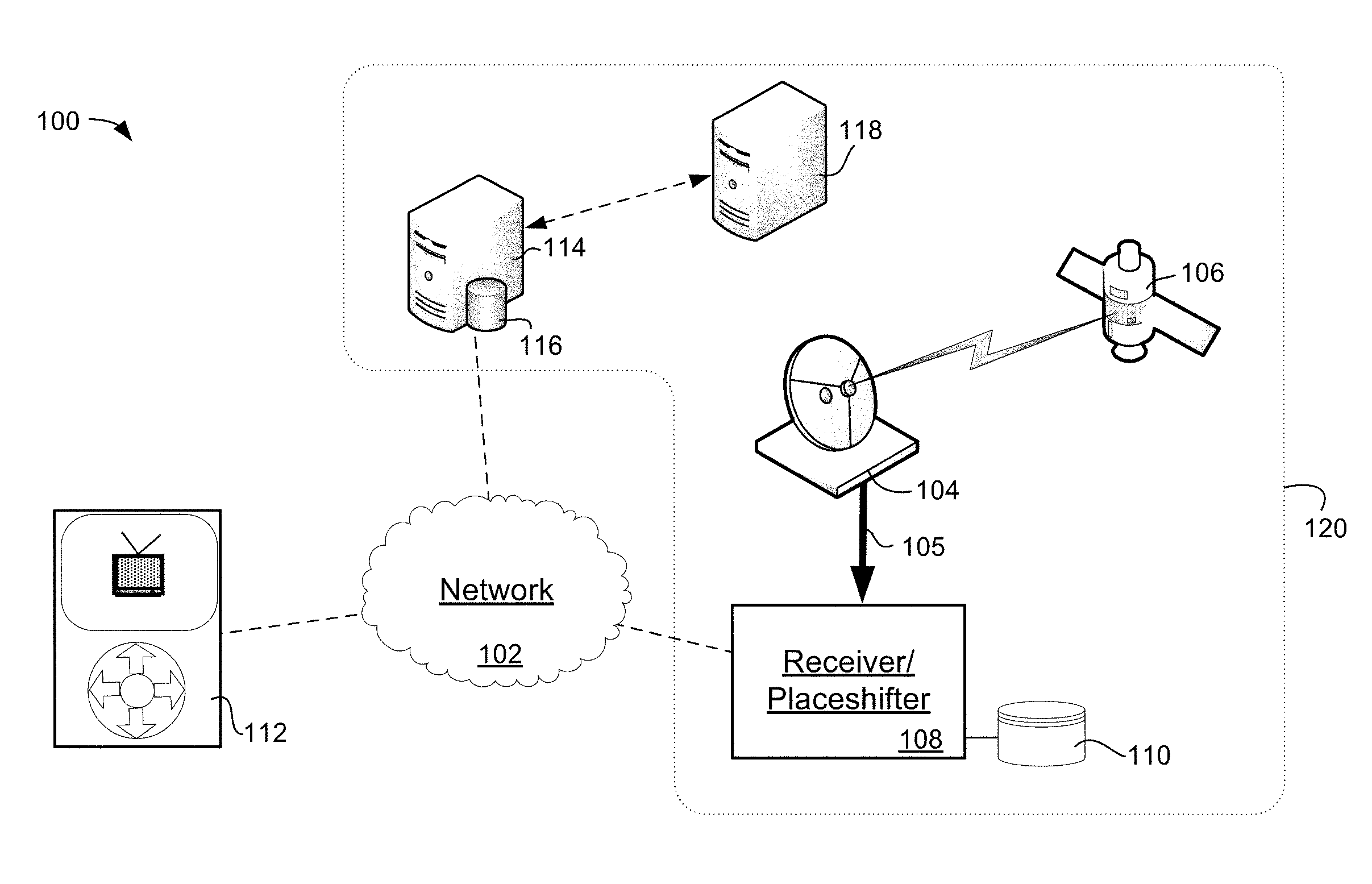
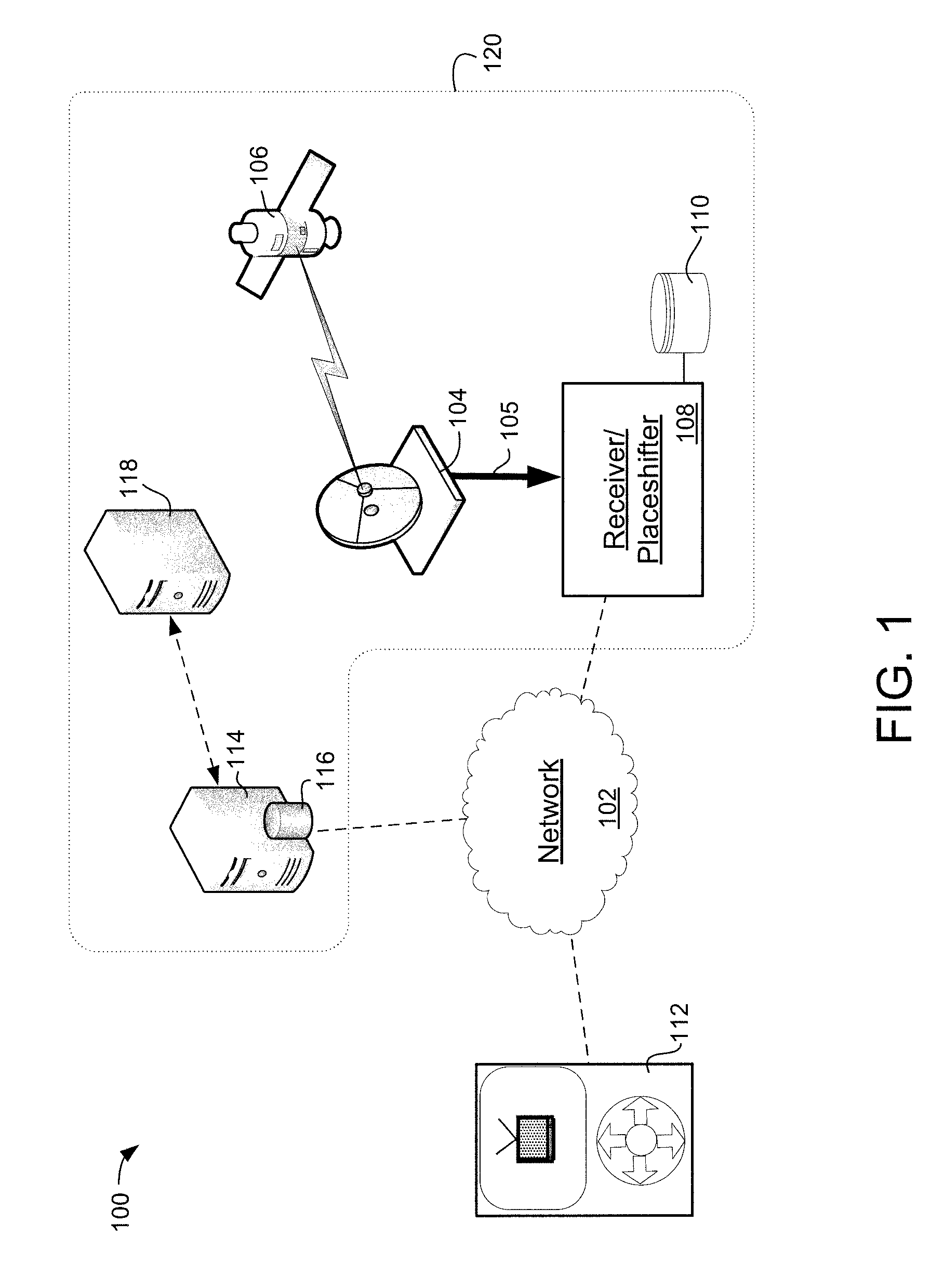
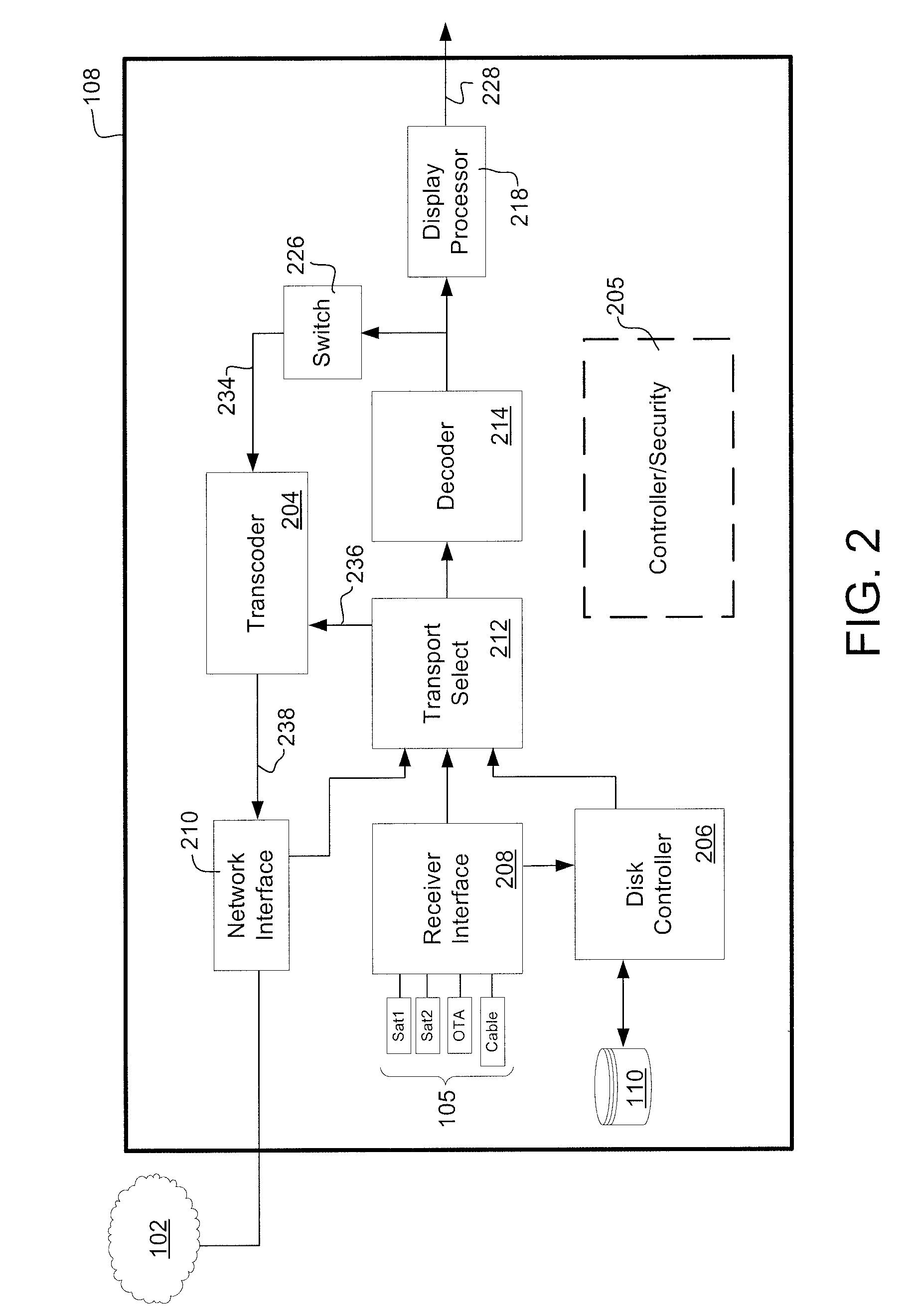
Systems and methods for securely place shifting media content
ActiveUS20100005483A1Analogue secracy/subscription systemsTwo-way working systemsAuthorization certificateAuthorization
Systems and methods are provided for securely providing a place-shifted media stream from a place shifting device to a remote player via a communications network. A request for a connection is received from the remote player at the place shifting device via the communications network. In response to the request for the connection, an authorization credential is requested from a central server via the communications network. Further, in response to the authorization credential received from the central server, the place-shifted media stream between the place shifting device and the remote player can be established over the communications network. At least a portion of the place-shifted media stream may be encrypted based upon the authorization credential.
Owner:SLING MEDIA LLC
Cloud database sharing
InactiveUS20130031136A1Digital data processing detailsDigital computer detailsAuthorization certificateResource pool
A method, system and computer program product is provided achieving database sharing by providing an interface to contribute a database and a set of resources to a resource pool in a first cloud environment. The interface further allowing a user to input parameters identifying a database, a set of resources, a set of authorization credentials, and a sharing policy. The interface further comprising responsive to the user using the interface and providing the interface parameters which identify the database, the set of resources, the set of authorization credentials, and the sharing policy, adding the database, the set of resources, the set of authorization credentials, and the sharing policy to the database resource pool in the cloud environment, sharing the database, the set of resources, according to the sharing policy, and utilizing the set of authorization credentials.
Owner:IBM CORP +1
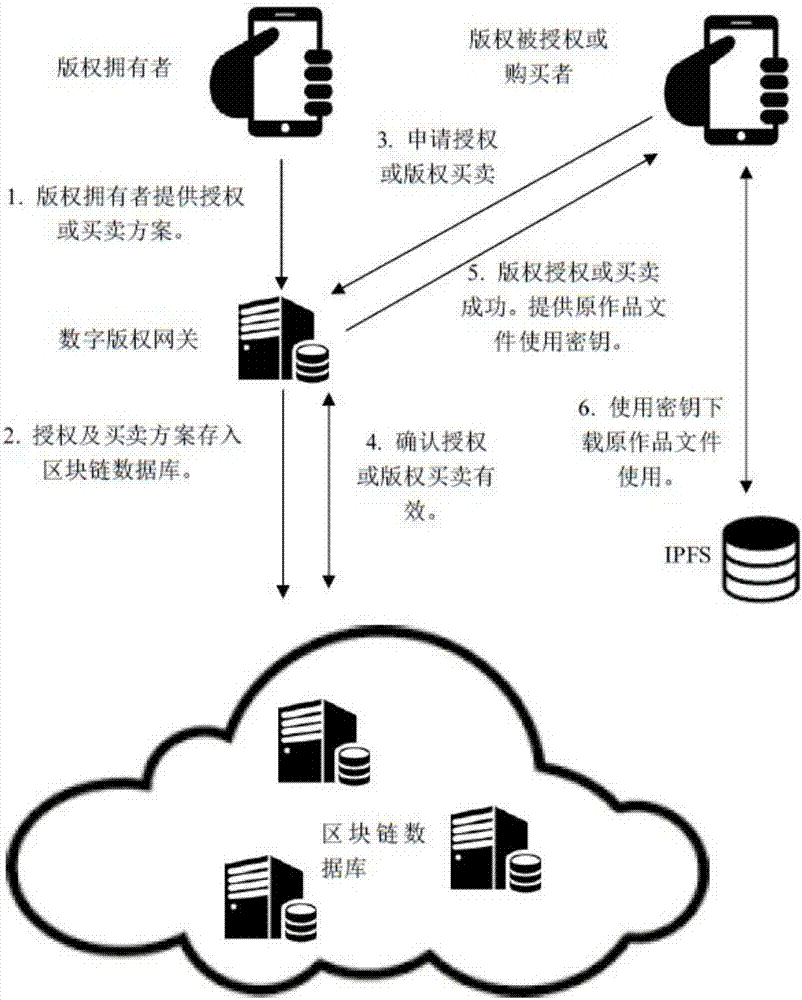
Copyright authorization method based on block chain
InactiveCN107086920AGuaranteed confidentialityShorten the overall cycleUser identity/authority verificationAuthorization certificateFinancial transaction
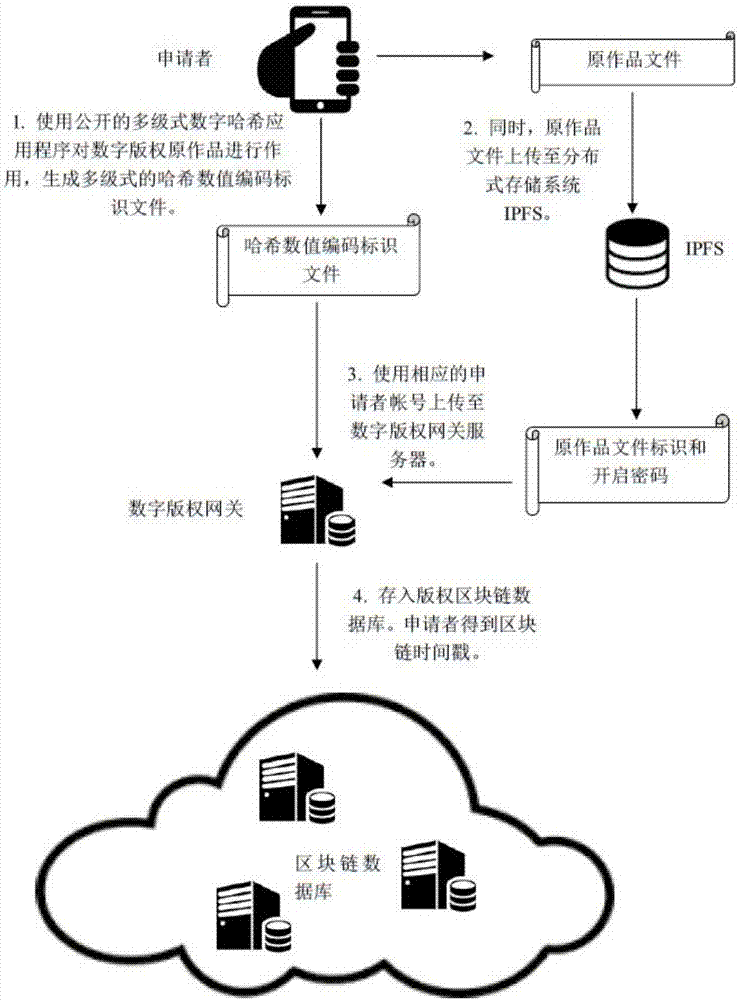
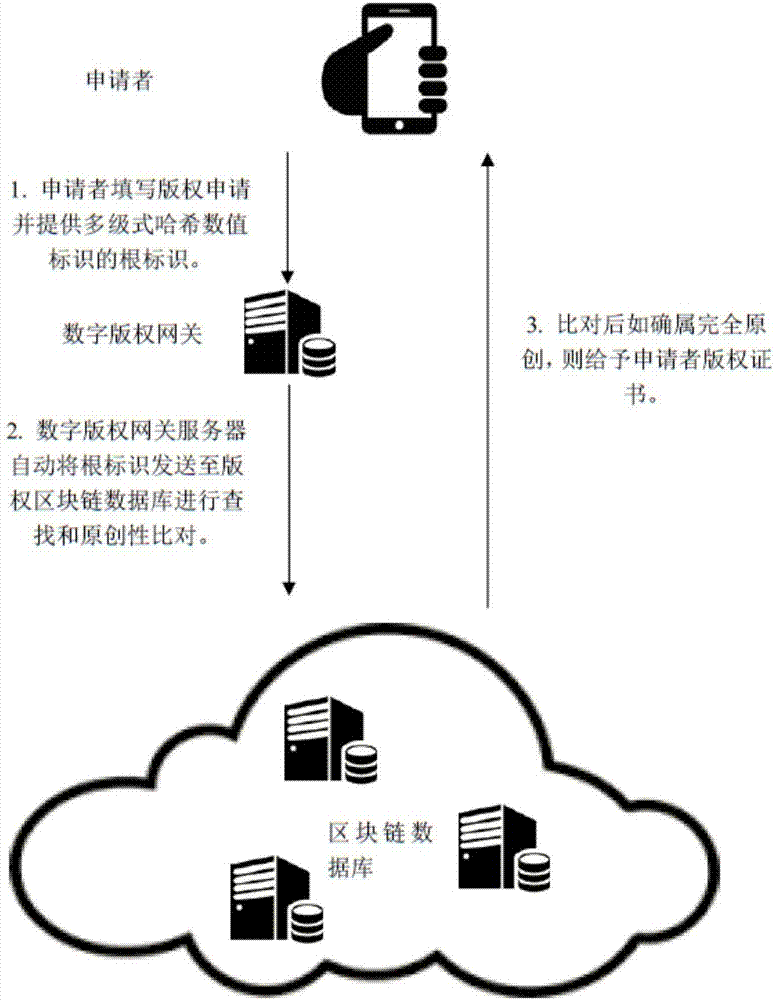
The invention discloses a copyright authorization method based on a block chain. The method comprises steps of: 1, uploading a work to a client so as to enable the work to become a multi-level hash value code identification document; 2, generating a self identity identifier in a copyright block chain database; 3, enabling a digital copyright gateway server to store the generated multi-level hash value code identification document uploaded by an applicant in self identity into a copyright block chain database; 4, enabling the applicant to fill in a copyright application agreement in detail through a digital copyright application website; 5, enabling the digital copyright application website system to search the duplicate records of various levels of digital identification codes in the block chain database, and to give a copyright authorization conclusion; 6, determining the ownership of copyright according to the copyright authorization conclusion, and sending to the applicant a copyright authorization certificate or an electronic copyright authorization certificate; and 7, enabling two copyright traders to apply for authorization and an authorization transaction at the digital copyright application website system. The method solves the shortcomings of conventional copyright authorization and ensures the high security and reliability of the copyright.
Owner:无锡井通网络科技有限公司
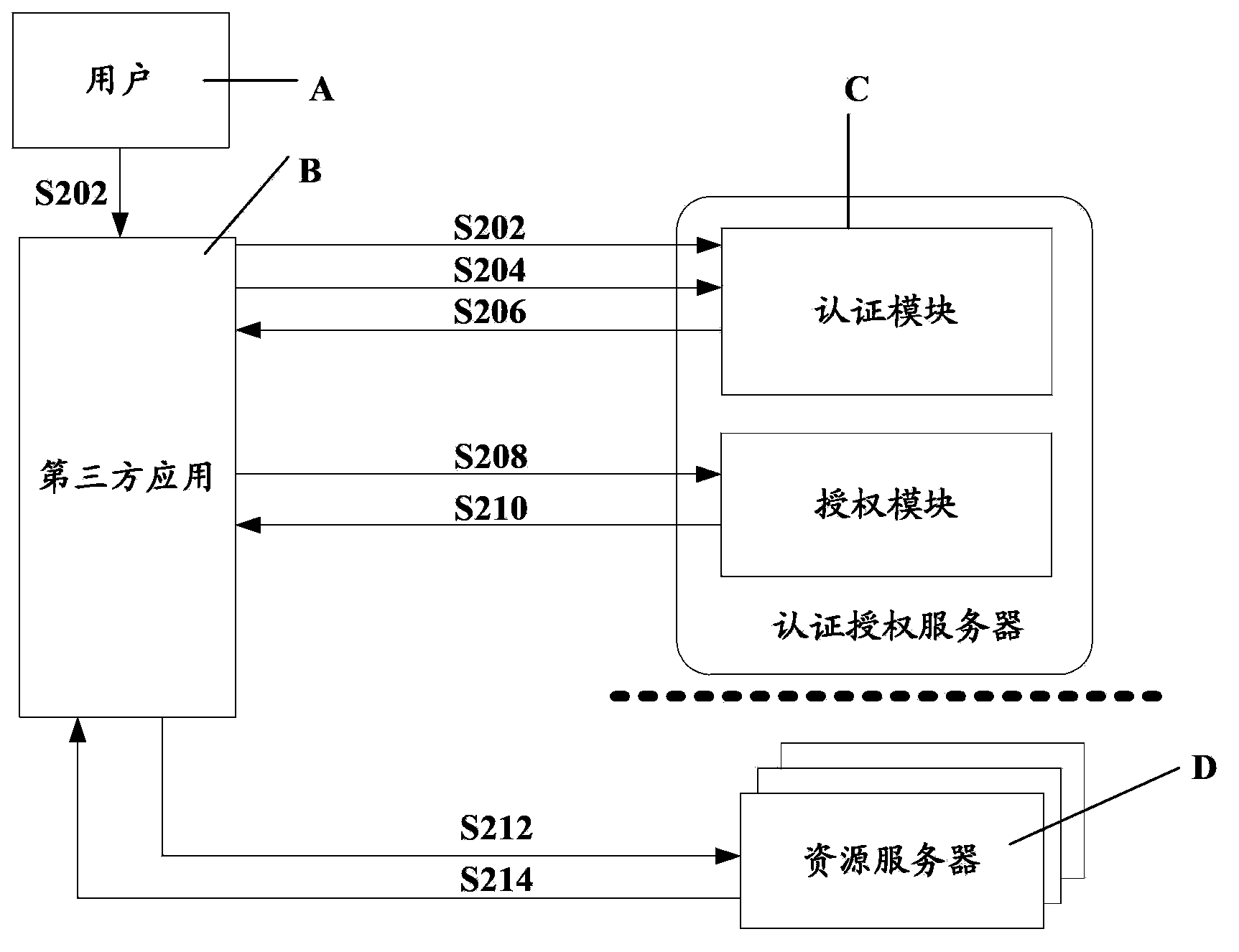
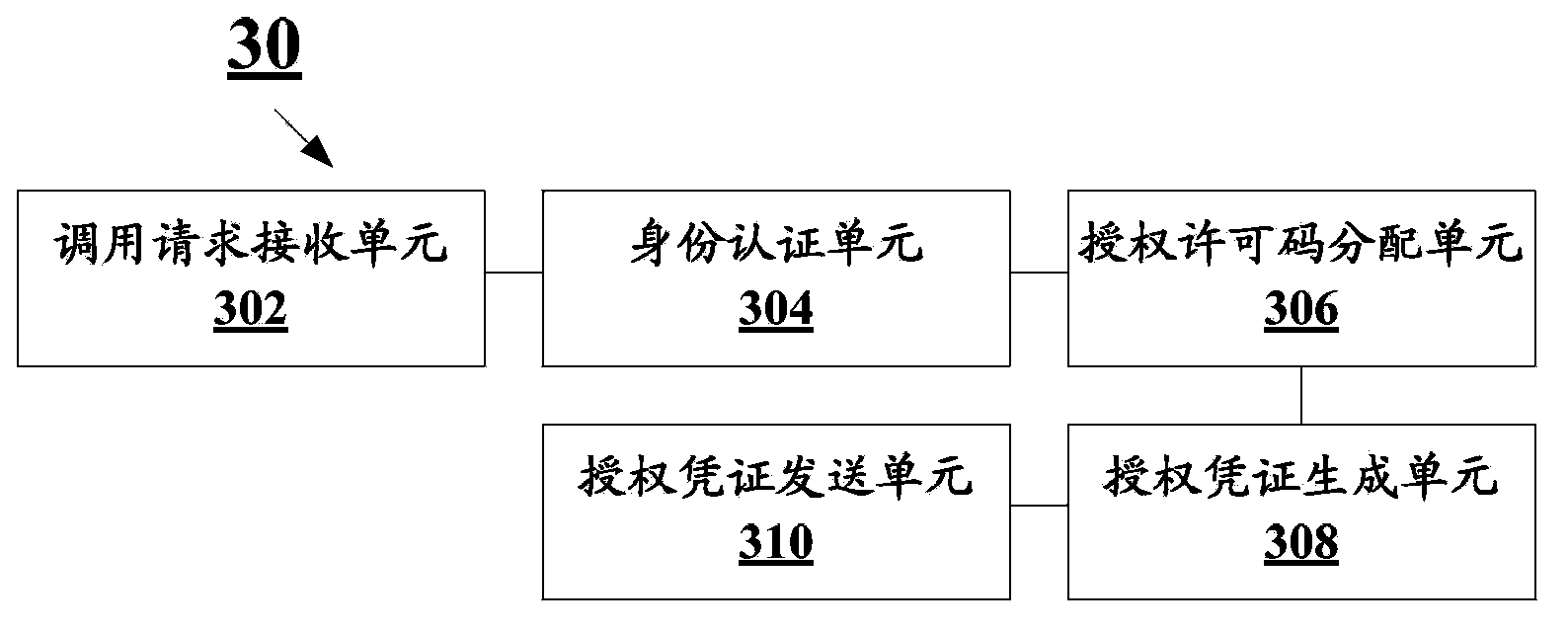
Open authorization method, open authorization system and authentication and authorization server
ActiveCN103795692AAvoid synchronizationGuaranteed success rateUser identity/authority verificationThird partyAuthorization certificate
The embodiment of the invention discloses an open authorization method, an open authorization system and an authentication and authorization server. The method comprises the following steps: receiving a call request initiated by a third party application for resource contained in a resource server; authenticating the identity of a user using the third party application; allocating an authorization license code to the third party application in response to the success of identity authentication and calling of the third party application on the resource contained in the resource server under authorization of a resource user; receiving a request of the third party application for an authorization certificate, and generating an authorization certificate in a private key encryption method based on an authorized resource identifier, the identity information of the user using the third party application, and the authorization license code and a timestamp which are contained in the authorization certificate request; and sending the authorization certificate to the third party application to enable the third party application to carry the authorization certificate and directly access the resource authorized by the resource server. According to the embodiment of the invention, the success rate of user authorization of a distributed system architecture is improved.
Owner:CHINA TELECOM CORP LTD
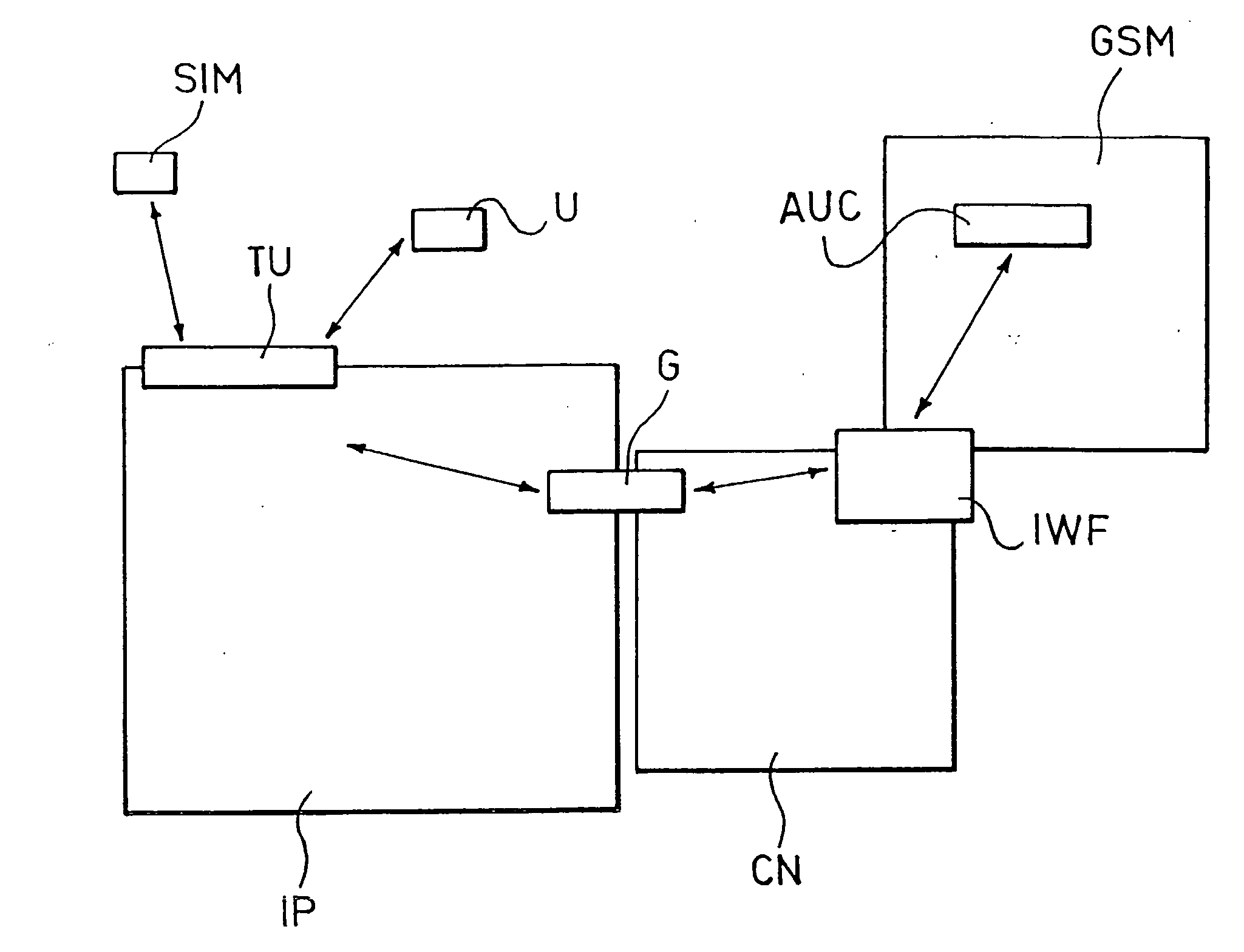
Method And System For A Secure Connection In Communication Networks
ActiveUS20080052769A1High operating costsEasy to adaptDigital data processing detailsUser identity/authority verificationComputer hardwareAuthorization certificate
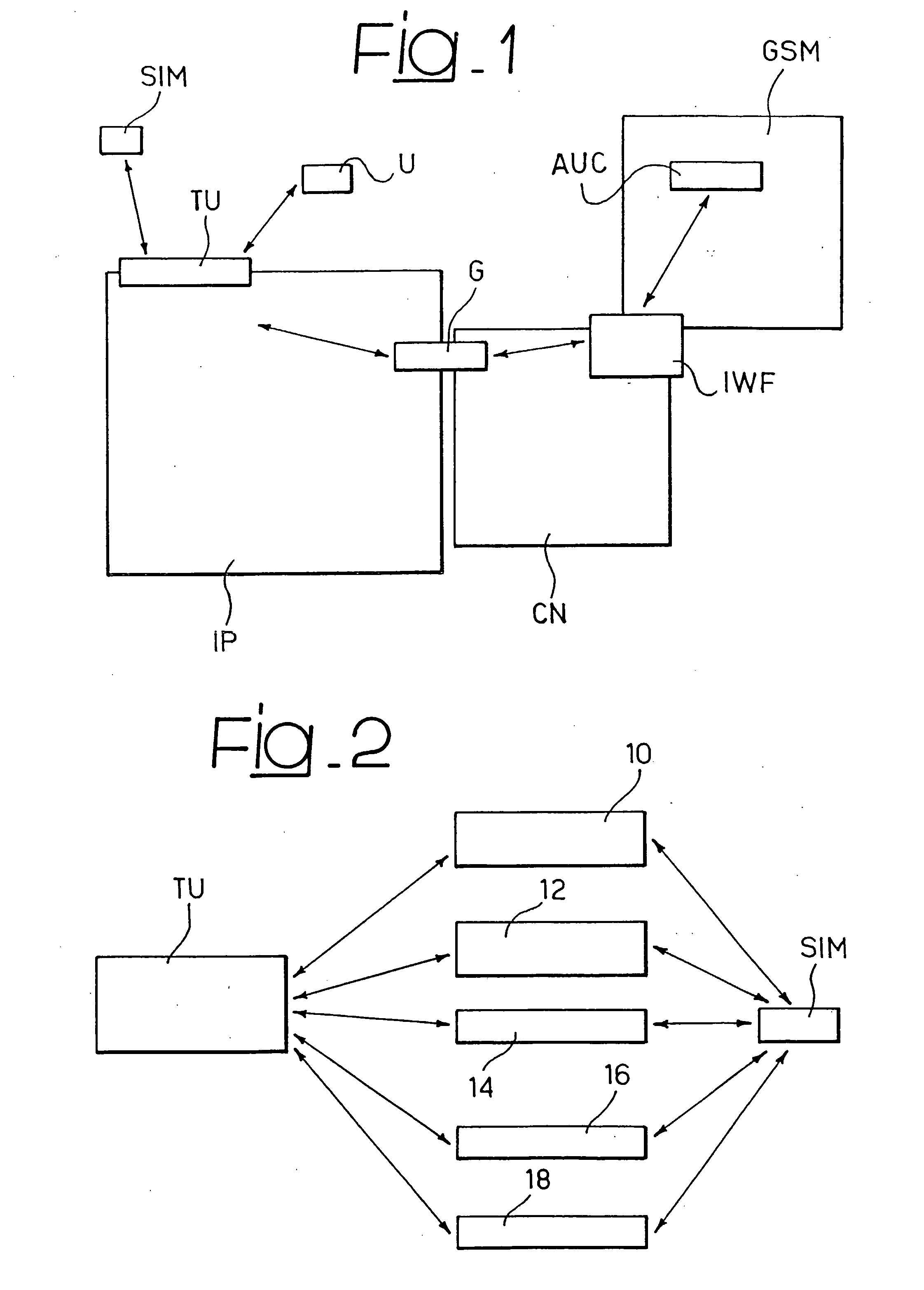
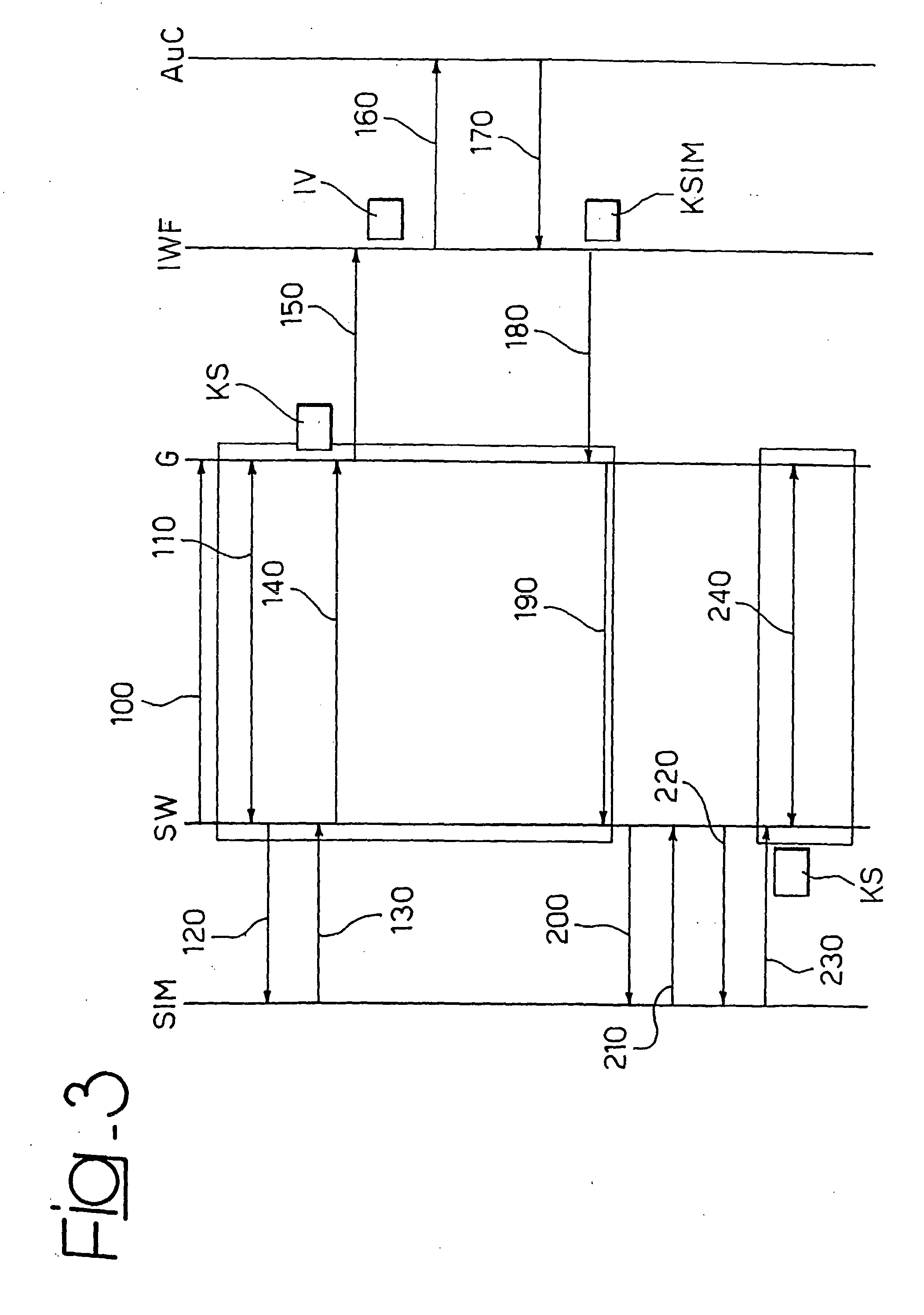
A system for enabling a user to communicate on a virtual private network through a public communication network, the possibility of communicating on the private network depending on the availability to the user of at least one enabling credential sent to the user in encrypted form. The system includes at least one SIM type module available to the user and bearing an encryption mechanism and it is configured to decrypt the enabling credential at the user exploiting the encryption mechanism home by the SIM type module, the SIM type module being able to interact with at least one additional communication network to activate the encryption mechanism.
Owner:TELECOM ITALIA SPA
Systems and methods for geolocation-based authentication and authorization
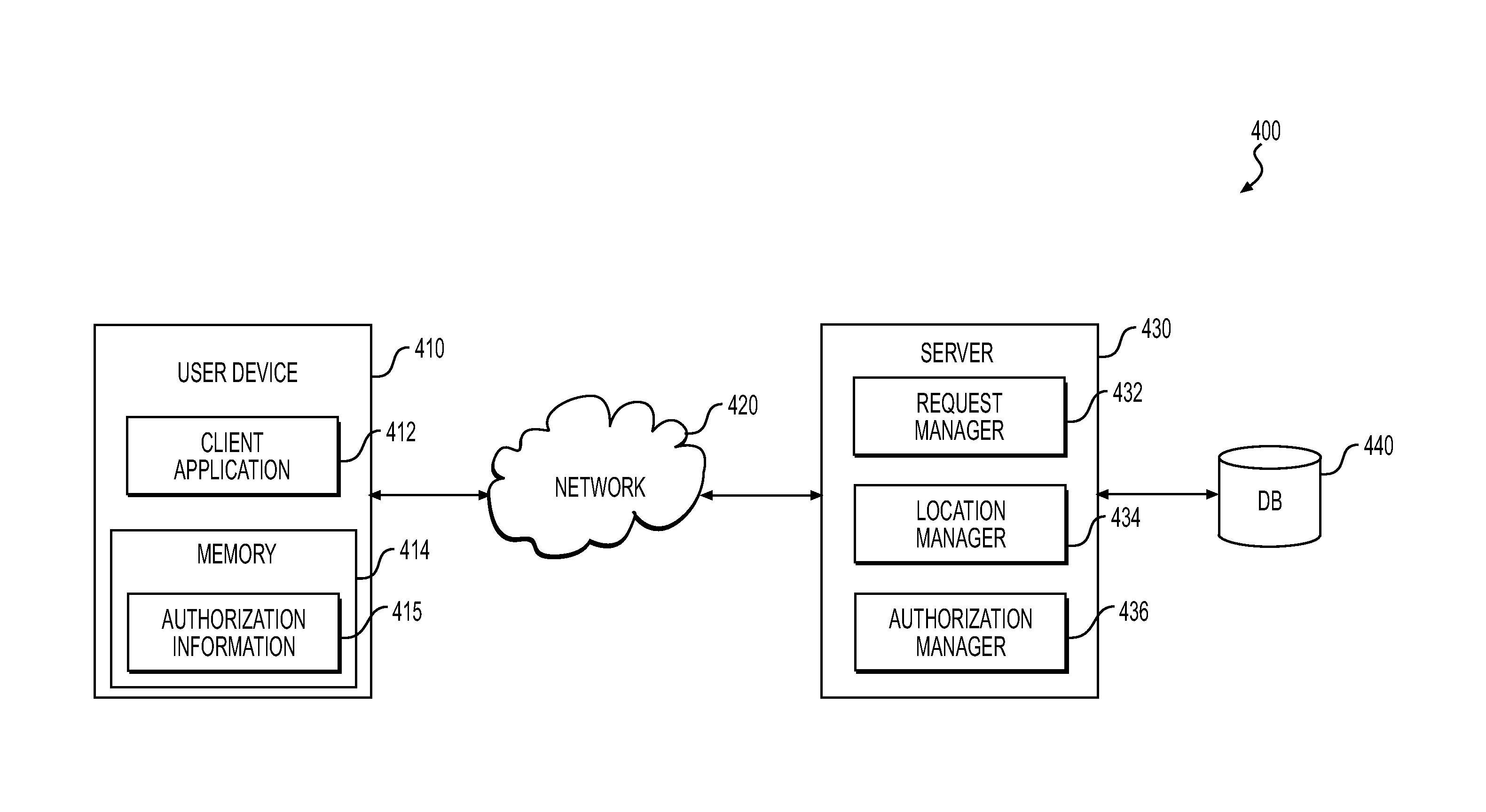
ActiveUS20150121464A1Digital data processing detailsMultiple digital computer combinationsAuthorization certificateGeolocation
Systems and methods are provided for controlling the authentication or authorization of a mobile device user for enabling access to the resources or functionality associated with an application or service executable at the user's mobile device. The user or user's mobile device may be automatically authenticated or authorized to access application or system resources at the device when the current geographic location of the user's mobile device is determined to be within a preauthorized zone, e.g., based on a predetermined geo-fence corresponding to the preauthorized zone. A security level or amount of authorization credentials required to authorize a user for data access may be varied according any of a plurality of security levels, when the current or last known geographic location of the user's mobile device is determined to be outside the preauthorized zone.
Owner:VERIZON PATENT & LICENSING INC
Method and system for logging on third party server through instant communication software
ActiveCN101350717AEasy to operateImprove user experienceData switching networksSecuring communicationAuthorization certificateThird party
The present invention discloses a method of logging on a third party server through instant communication software. In the method, when the user logs on the instant communication IM server through a single-point logging-on SSI server, the client acquires the authority certificate information of the user to log on the third party server from the SSI server, according to the operating command of the user, and then transmits the login request information with the authority certificate information to the third party server; the authority certificate information is encrypted by a first secret key corresponding to the third party server; the third party server deciphers the authority certificate information in the login request information according to the first secret key; the user logs on after the identity of the user is confirmed at the client. The user can log on the IM server through the client, and can visit all the mutually trusting application systems only by inputting the name and the password of the user once. Therefore, the method simplifies the operating processes of the user, and improves the experience of the user to certain extent.
Owner:CHINA MOBILE COMM GRP CO LTD +1
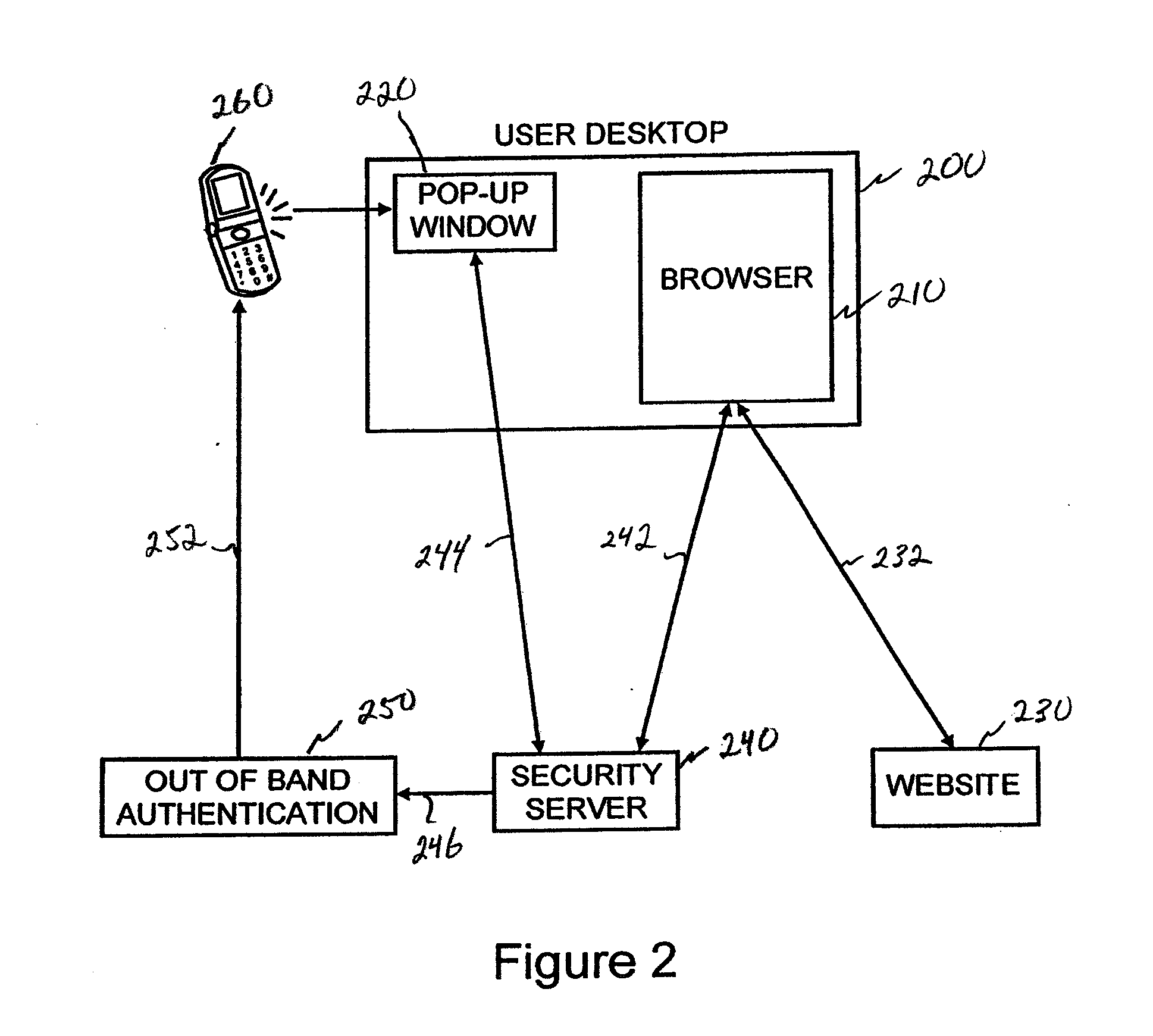
Method and system for securely streaming content
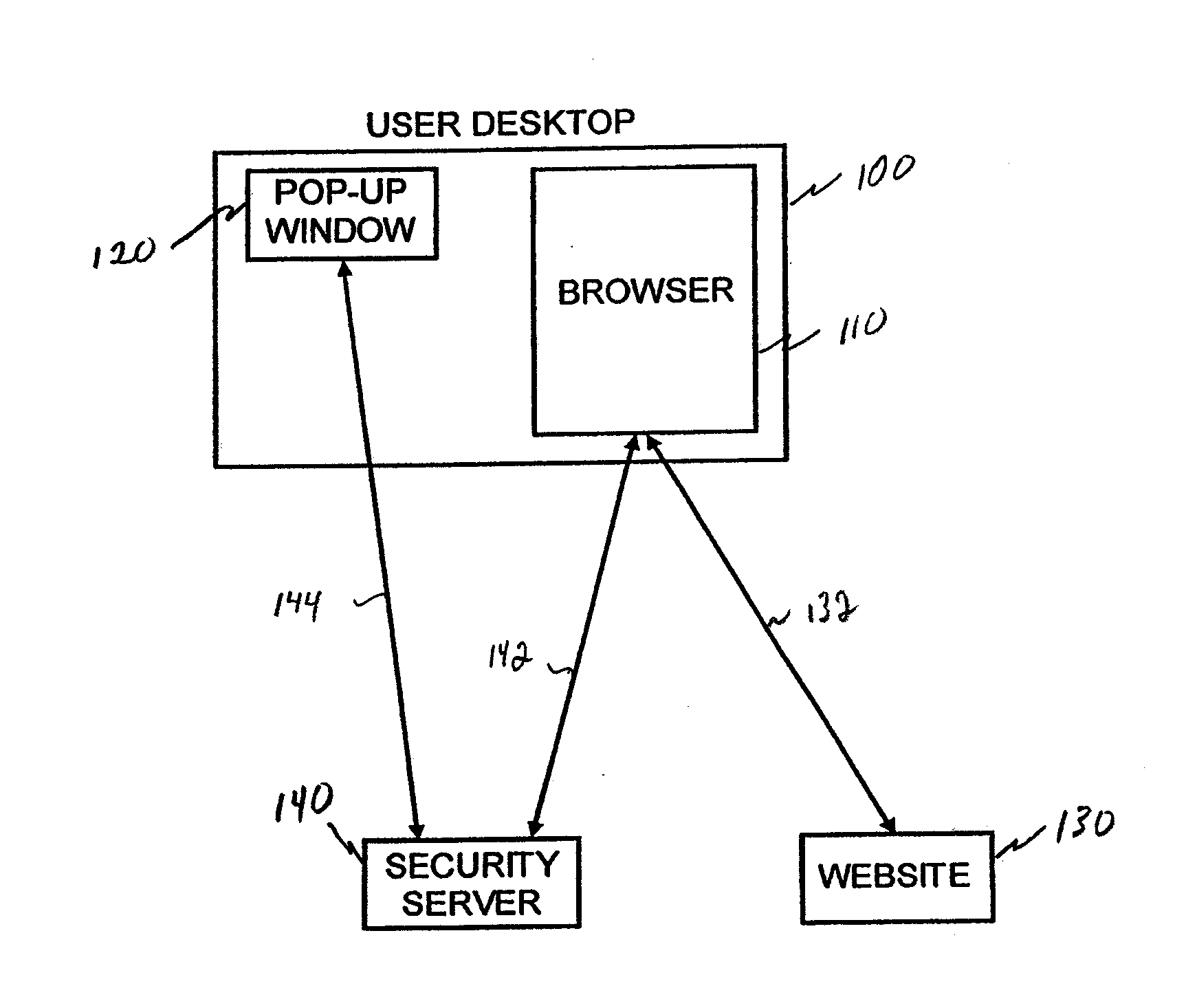
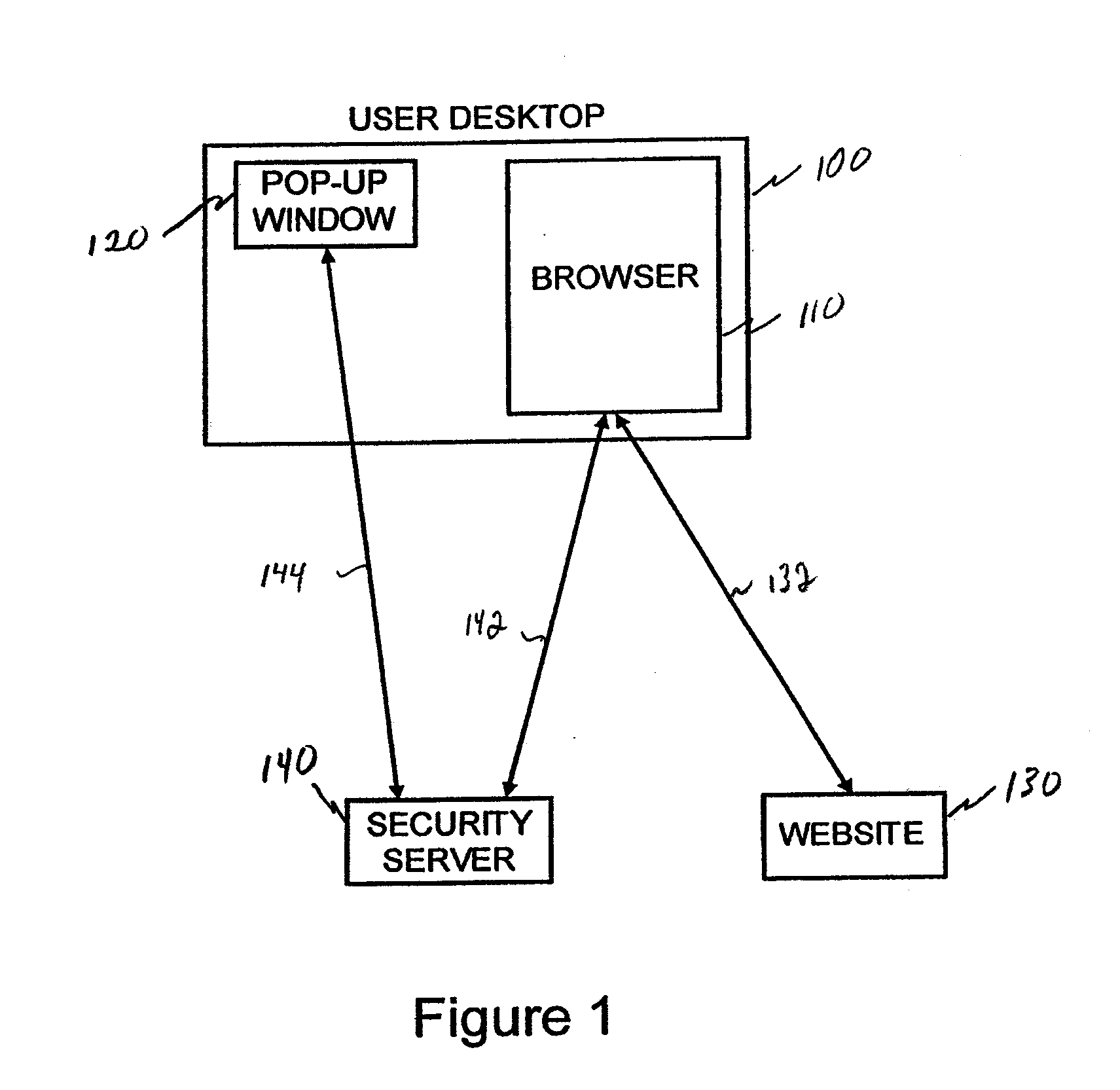
ActiveUS20090235347A1Digital data processing detailsUser identity/authority verificationAuthorization certificateWhitelist
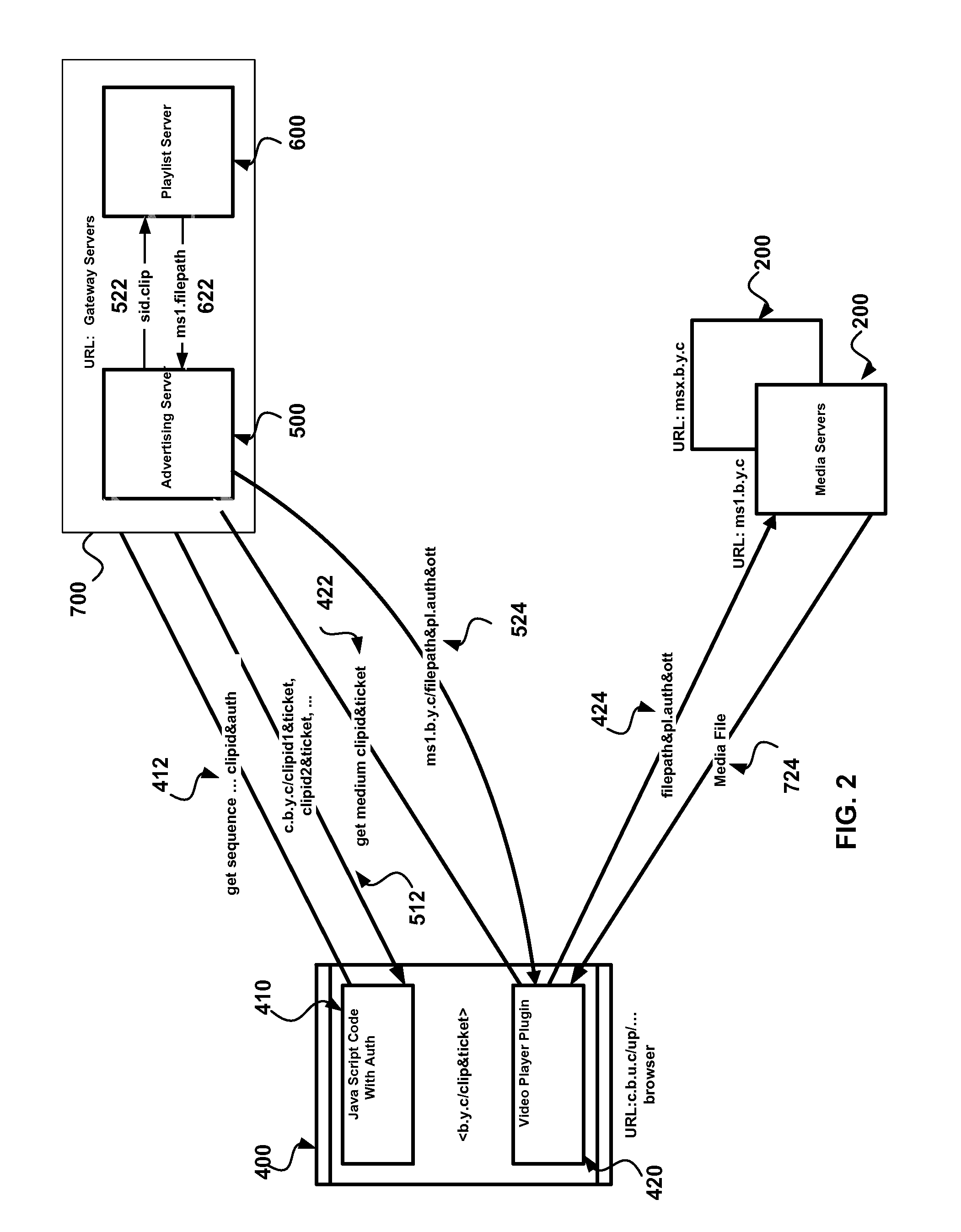
A system and method for securely streaming media. The system includes a gateway server that receives requests for access to a secured data resource from an end users. The request include an authorization ticket and a referring website. The gateway server validates the authorization ticket using a secret key shared with the referring website, and validates the referring website by verifying that referring website is on a white-list for the secured data resource. The gateway server selects a data server to service the request, and formats a data server access request containing the data server location and data server request parameter data and transmits the data server access request to the end users. When end users transmit the data server access requests to a data server, the data server validates the request and transmits it to the end user.
Owner:VERIZON PATENT & LICENSING INC
System and method for using a separate device to facilitate authentication
ActiveUS20140157392A1Digital data processing detailsNetwork topologiesAuthorization certificateAuthorization
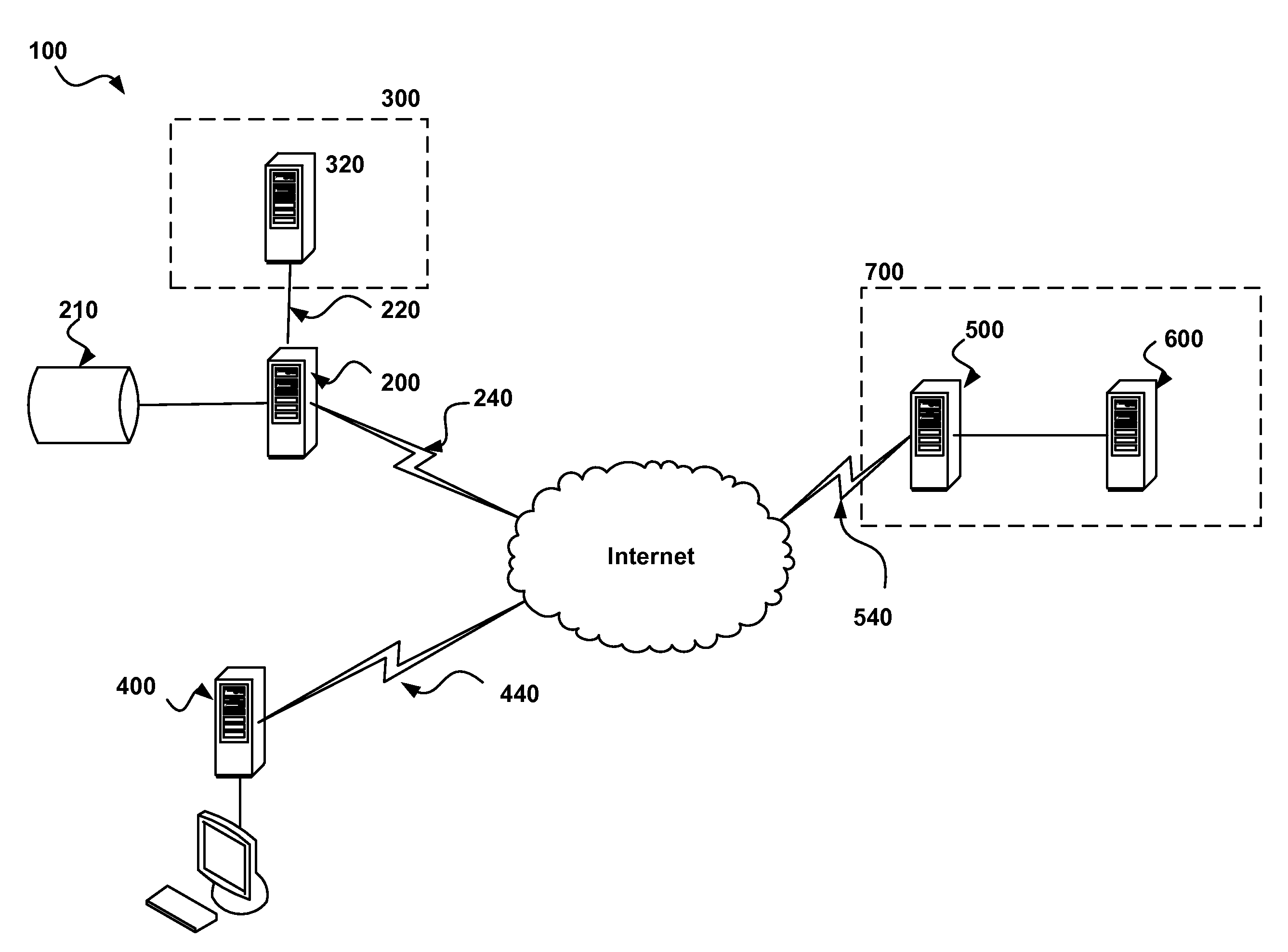
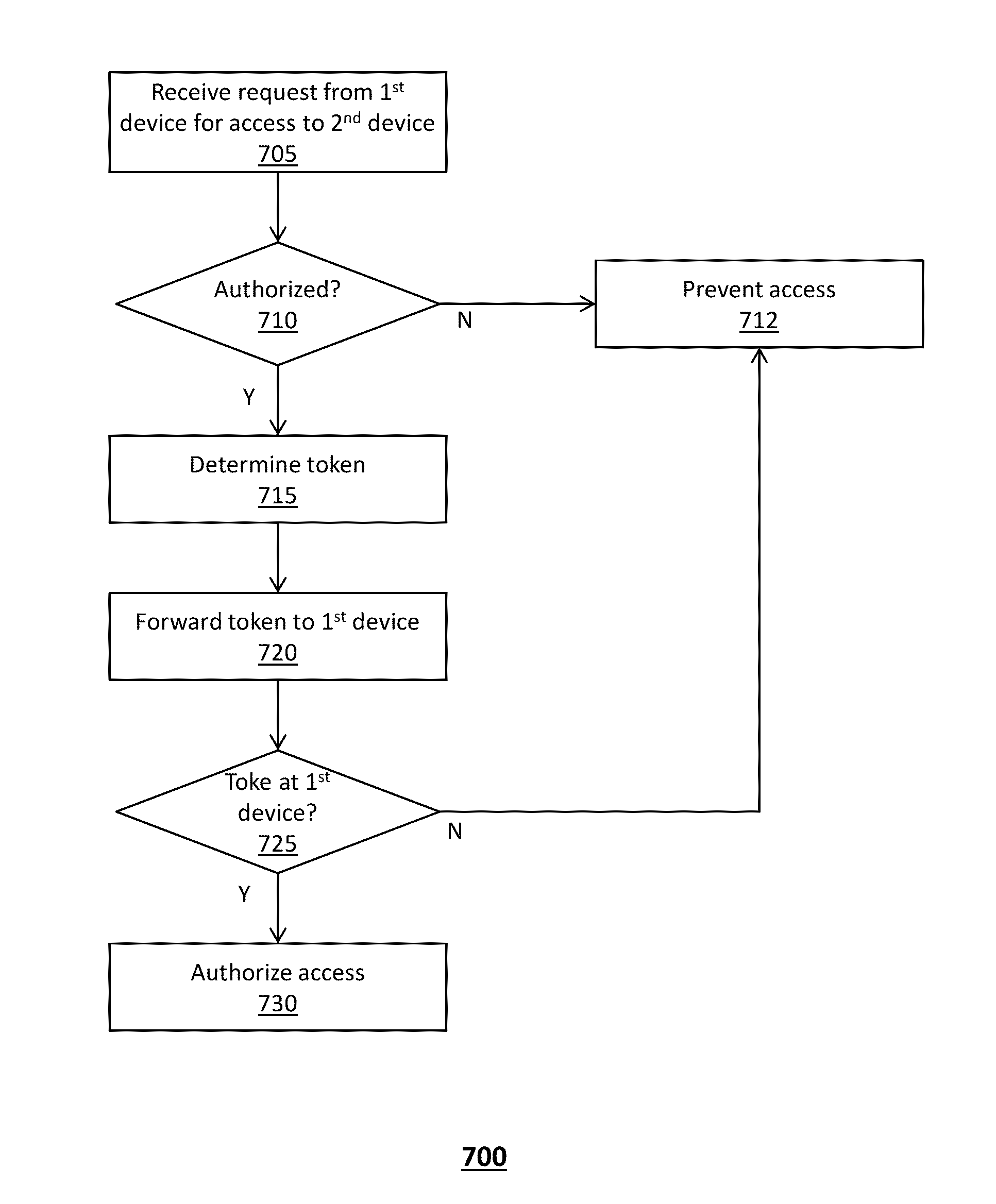
A system that incorporates the subject disclosure may perform, for example, operations including receiving a request from a first device to access information content of a second device. The process further includes determining that the first device is authorized to access the information content according to authorization credentials, and determining a token associated with the request in response to determining that the first device is authorized to access the information content. The token is forwarded to the first device, and it is confirmed that the token was received at the first device. Access to the information content of the second device is authorized in response to confirming that the token was received at the first device. Other embodiments are disclosed.
Owner:SMITH FRED H
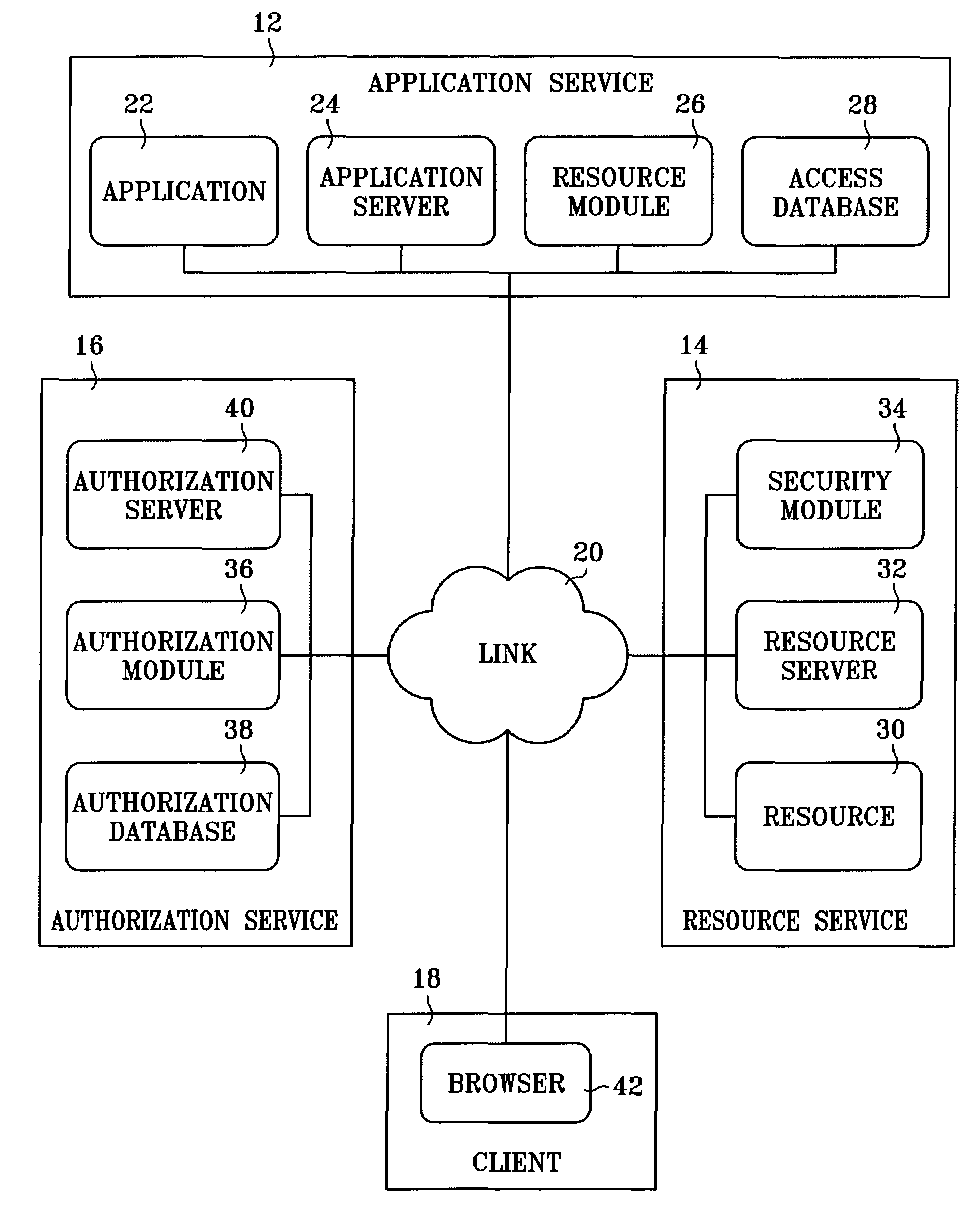
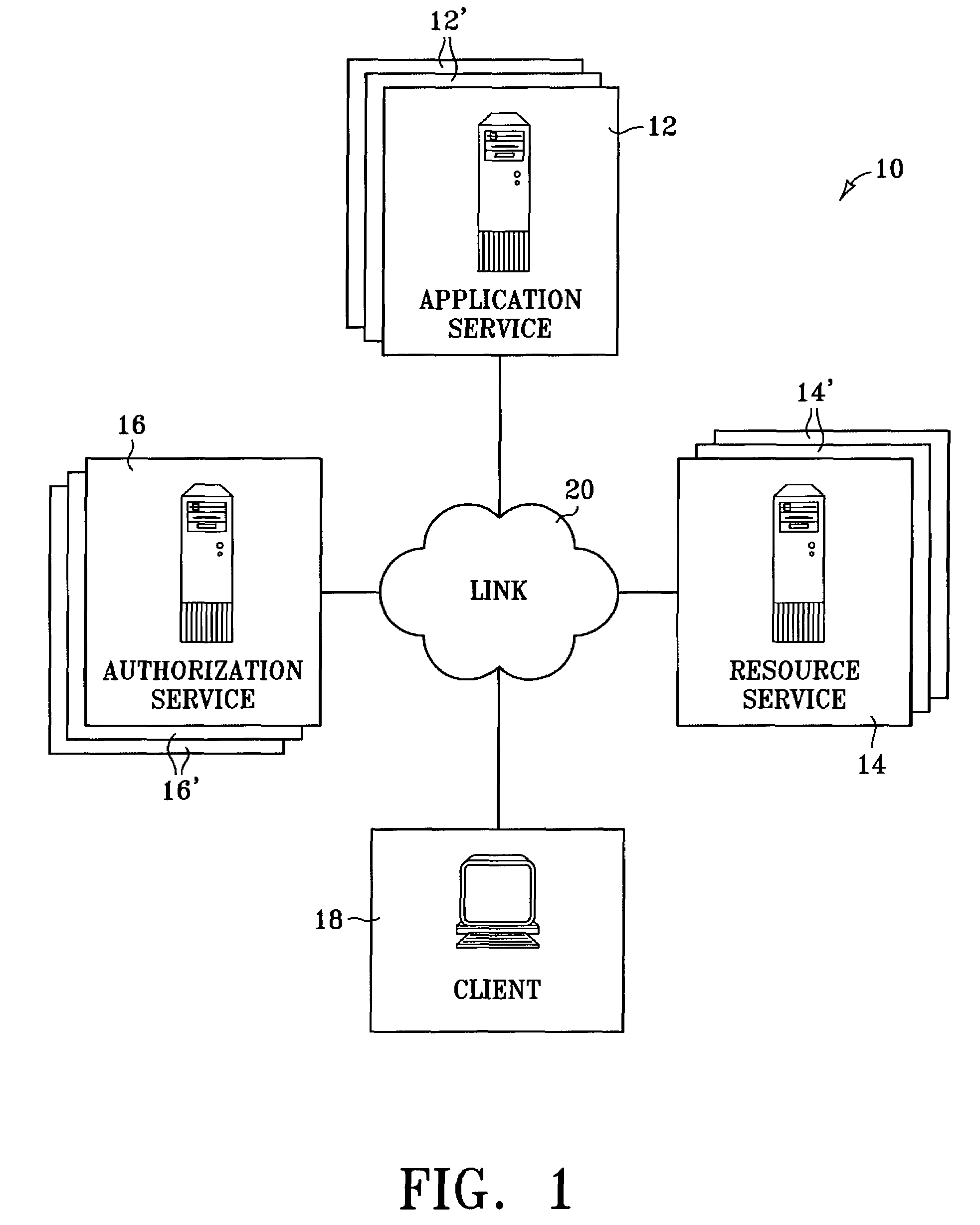
Secure resource access in a distributed environment
InactiveUS7444414B2Digital data processing detailsComputer security arrangementsAuthorization certificateLimited access
A method and system for providing a first network resource with secure but limited access to a second network resource. A method embodying the invention includes receiving, from a client, a request to access the first resource. The client is then directed to an authorization service. The authorization service generates an authorization ticket and provides the authorization ticket to the first resource. On behalf of the first resource, the authorization ticket is presented to the second resource with a request to access the second resource. The request is granted only if it can be verified that the authorization ticket was generated by a source trusted by the second resource.
Owner:HEWLETT PACKARD DEV CO LP
System for using an authorization token to separate authentication and authorization services
ActiveUS20080127317A1Reduce chanceReduce theftDigital data processing detailsUser identity/authority verificationAuthorization certificateAuthentication server
A novel system for utilizing an authorization token to separate authentication and authorization services. The system authenticates a client to an authenticating server; generates an authorization token with the authenticating server and the client; and authorizes services for the client using the generated authorization token.
Owner:FUTUREWEI TECH INC
Application program as key for authorizing access to resources
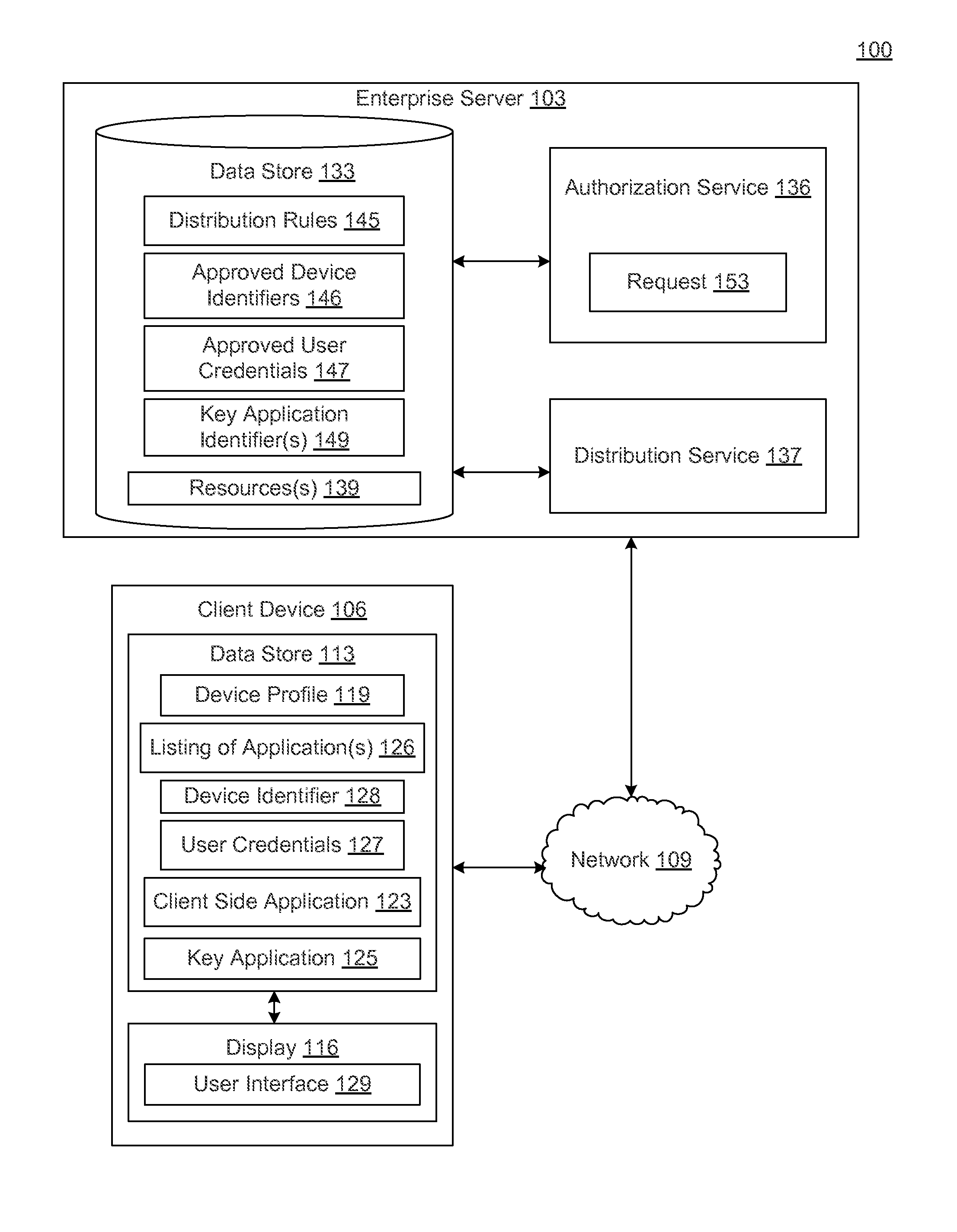
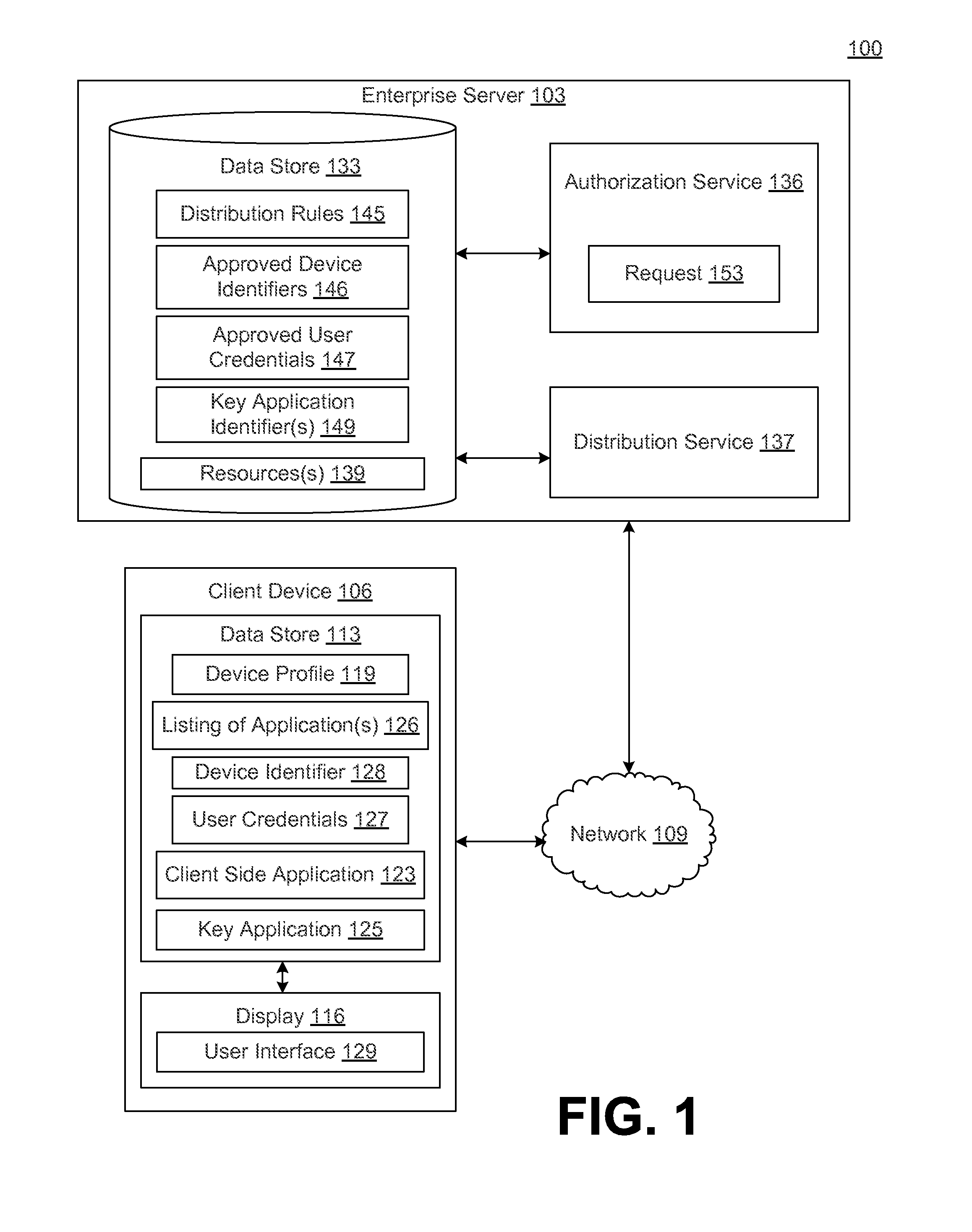
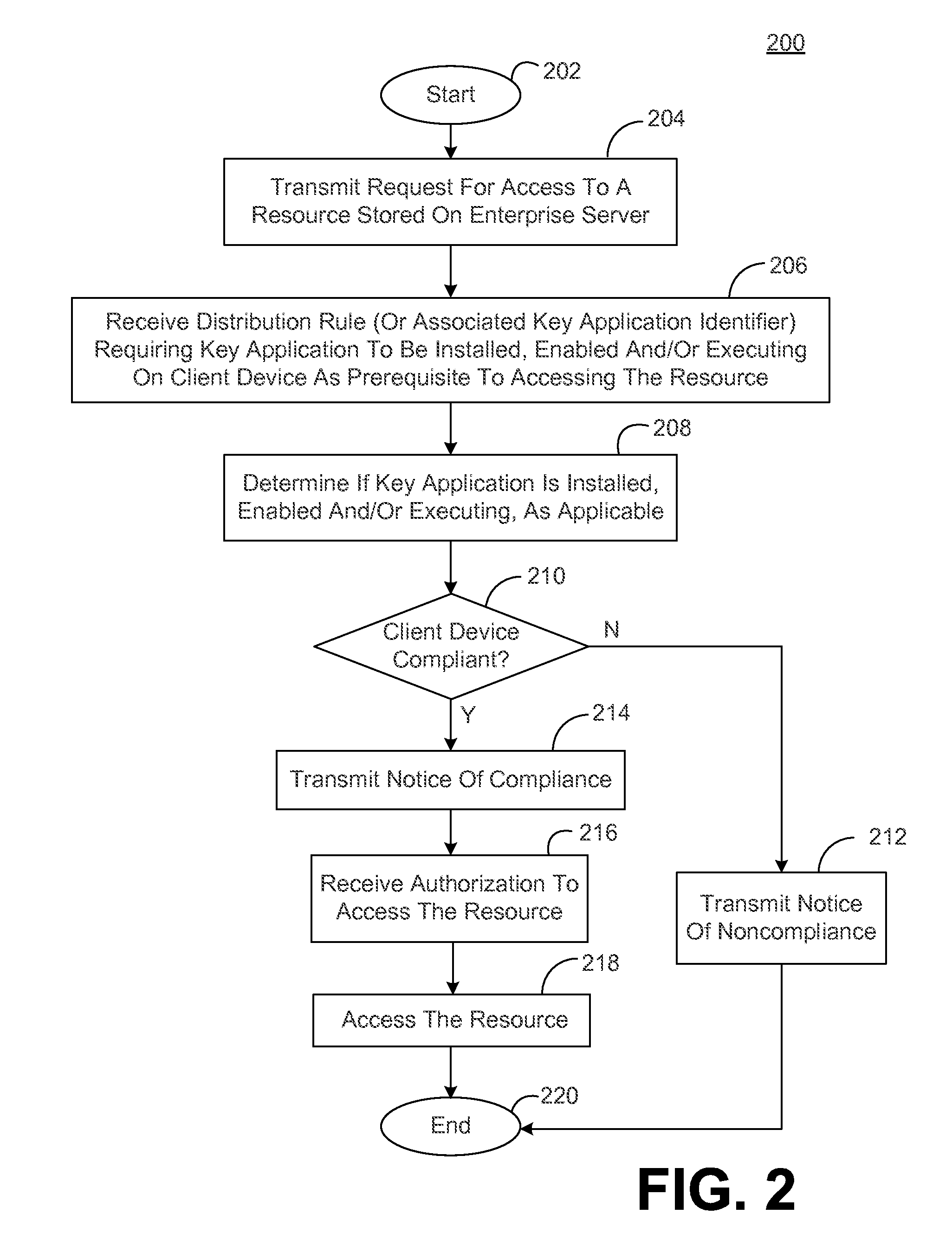
ActiveUS20140282897A1Digital data processing detailsMultiple digital computer combinationsAuthorization certificateClient-side
In a networked environment, a client side application executed on a client device may transmit a request to an authorization service for access to a resource. The authorization service may authenticate the user of client device and / or the client device based on user credentials and / or a device identifier. In response to authenticating the user and / or the client device, the authorization service may send to the client side application a request for confirmation that the client device complies with a distribution rule associated with the resource, where the distribution rule requires a specific application or specific type of application to be installed, enabled and / or executing on the client device as a prerequisite to accessing the resource. If the client device complies with the distribution rule, the client side application accesses the resource. Accessing the resource may include receiving an authorization credential required for access to the resource.
Owner:AIRWATCH
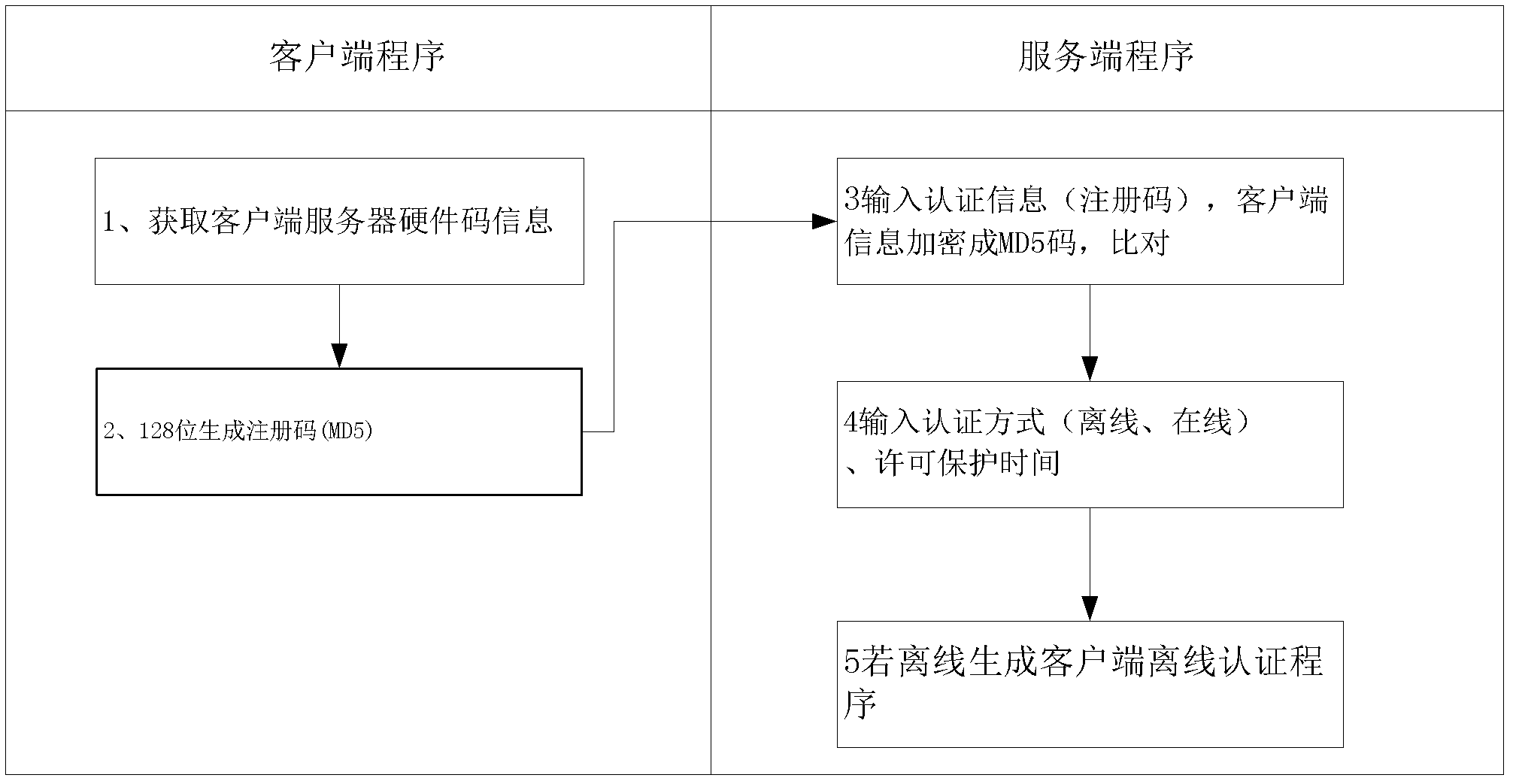
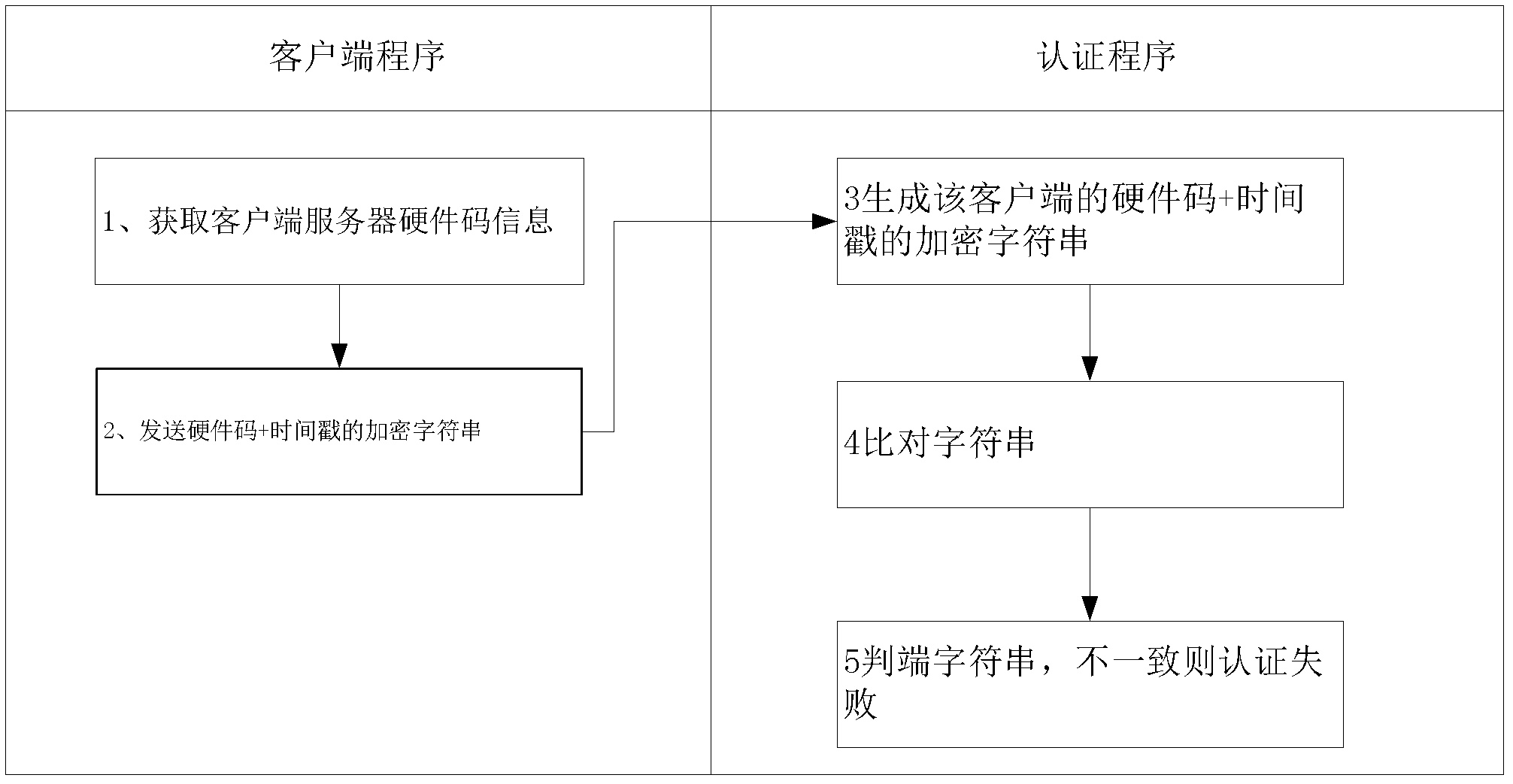
Software authorization system based on public key cryptosystem
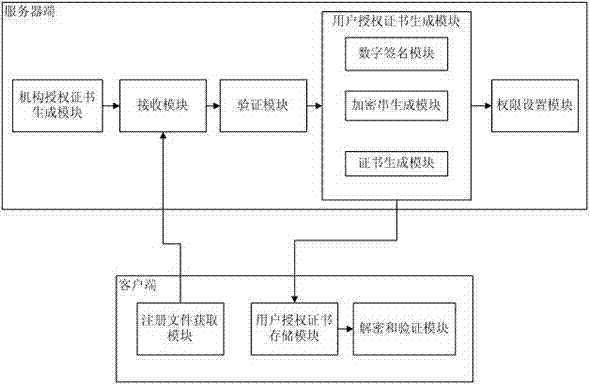
ActiveCN103491097APrevent illegal copyingEasy to upgradeVersion controlUser identity/authority verificationAuthorization certificateAuthorization Mode
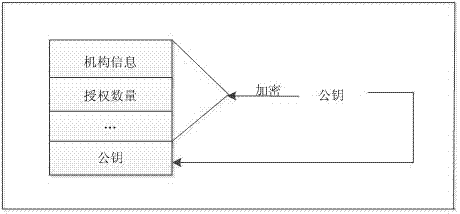
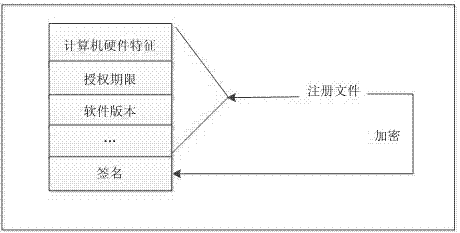
The invention discloses a software authorization system based on public key cryptosystem. The software authorization system comprises a server end and a client end, wherein the server end comprises an institution authorization certification generation module, a receiving module, a verification module and a user authorization certificate generation module. The user authorization certificate generation module comprises a digital signing module used for carrying out digital signing on computer hardware characteristics h0 in a user registration file with an RSA private key to generate S0, an encryption string generation module used for carrying out preset hybrid operations on obtained software version information v, user information u, an authorization term ex, current time cur and s0 to generate an encryption string signB64 and a certificate generation module used for generating a user authorization certificate with the encryption string signB64 and the RSA public key. The method can prevent software from being illegally copied, meanwhile, the software can be managed by a software issuer in a concentrated mode, and upgrading and tracking of the software, pushing personalized services for users and other after-sale management are facilitated.
Owner:HUAZHONG NORMAL UNIV
Secure and efficient authentication using plug-in hardware compatible with desktops, laptops and/or smart mobile communication devices such as iPhones
ActiveUS8769784B2Enhanced authenticationImproved transactionPattern makingDigital data processing detailsAuthorization certificateTelecommunications link
A portable apparatus is removably and communicatively connectable to a network device to communicate authentication or authorization credentials of a user in connection with the user logging into or entering into a transaction with a network site. The apparatus includes a communications port to connect and disconnect the apparatus to and from the network device and to establish a communication link with the network device when connected thereto. A processor receives a secure message from the network security server via the port. The message has a PIN for authenticating the user to the network site, and is readable only by the apparatus. The processor either transfers, via the port, the received PIN to an application associated with the network site that is executing on the network device or causes the apparatus to display the received PIN for manual transfer to the application associated with the network site.
Owner:PAYFONE
Authorization method and authorization system of intelligent key in wireless terminal as well as terminal and server
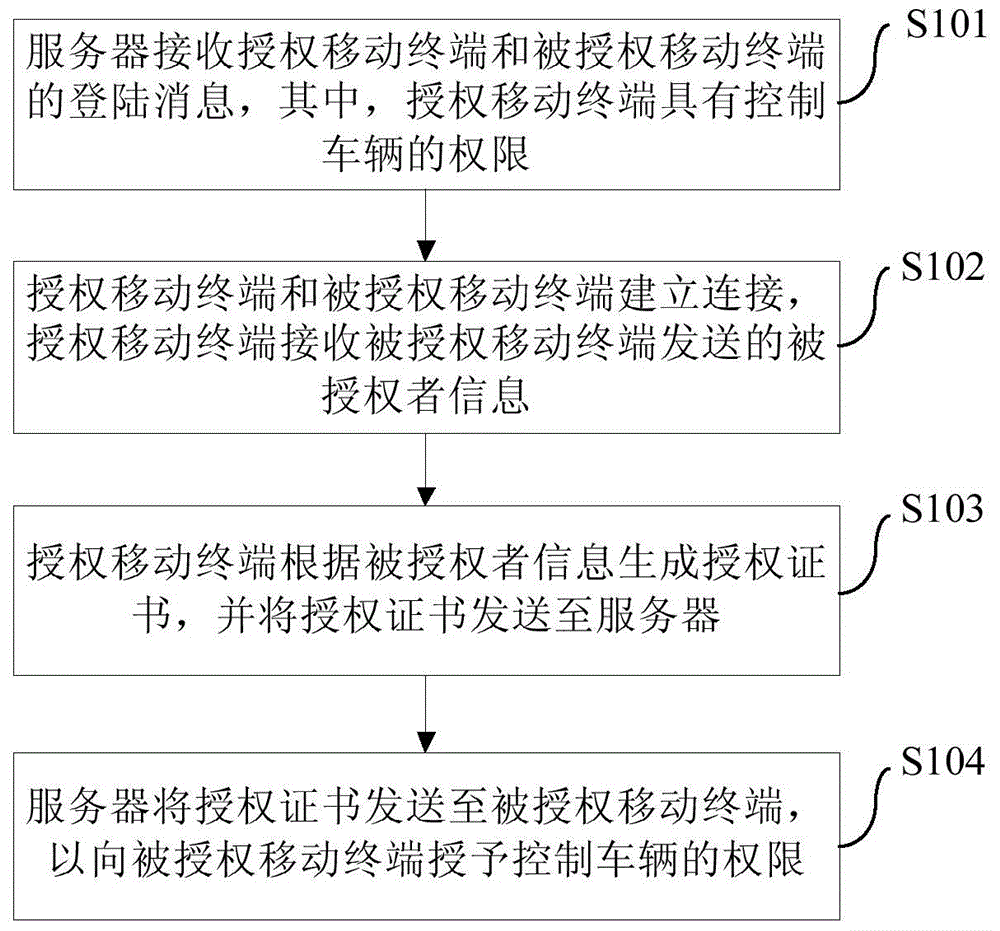
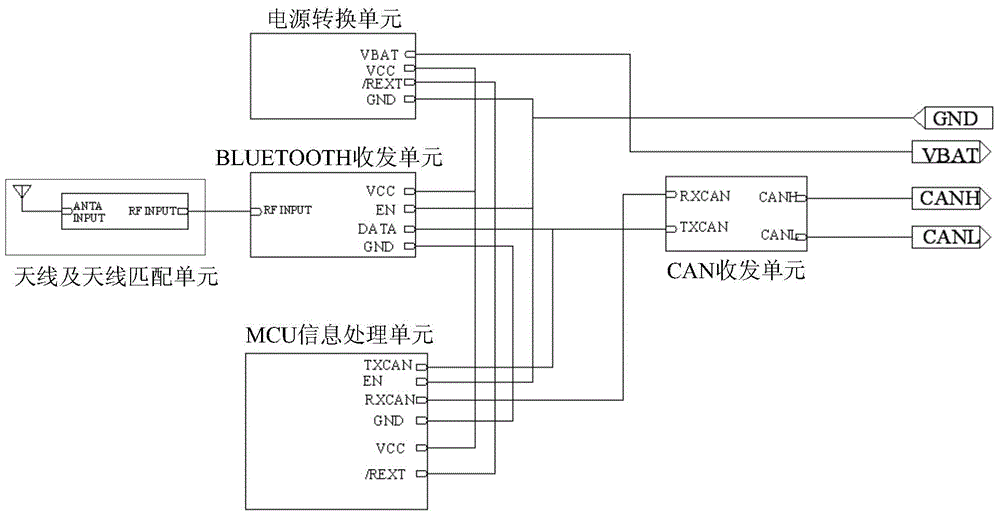
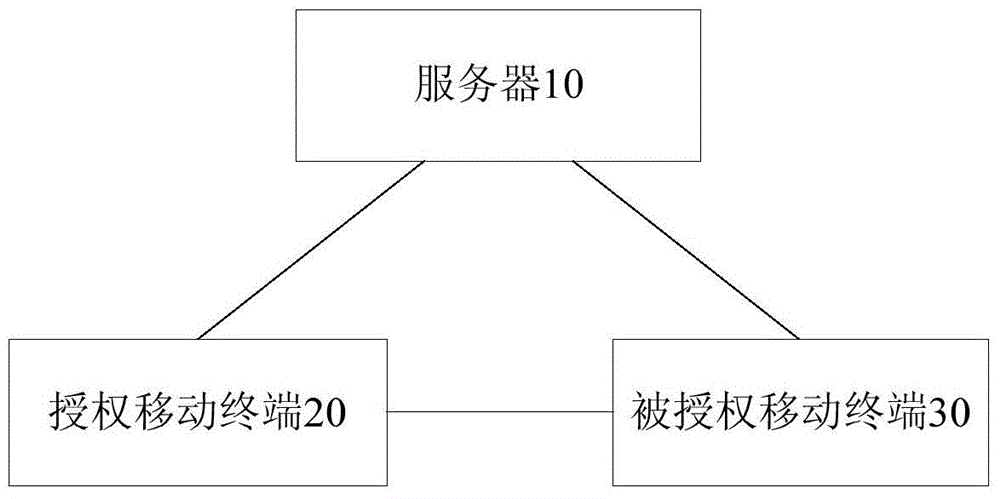
ActiveCN104424679AEasy to useUse humanizationIndividual entry/exit registersAuthorization certificateComputer terminal
The embodiment of the invention provides an authorization method and an authorization system of an intelligent key in a wireless terminal as well as the terminal and a server. The method comprises the following steps: receiving a log-in message of an authorization mobile terminal and the authorized mobile terminal by the server, wherein the authorization mobile terminal has a permission for controlling a vehicle; establishing connection between the authorization mobile terminal and the authorized mobile terminal, and receiving authorized information transmitted from the authorized mobile terminal by the authorization mobile terminal; generating an authorization certificate according to the authorized information by the authorization mobile terminal, and transmitting the authorization certificate to the server; and transmitting the authorization certificate to the authorized mobile terminal by the server, so that the permission for controlling the vehicle is authorized to the authorized mobile terminal. According to the method, the authorization for giving the permission for other people to utilize the vehicle can be realized in a wireless communication way, inconvenience caused by private information or no other key of a user at the moment when the vehicle is lent to other people can be avoided, and the user experience can be enhanced.
Owner:BYD CO LTD
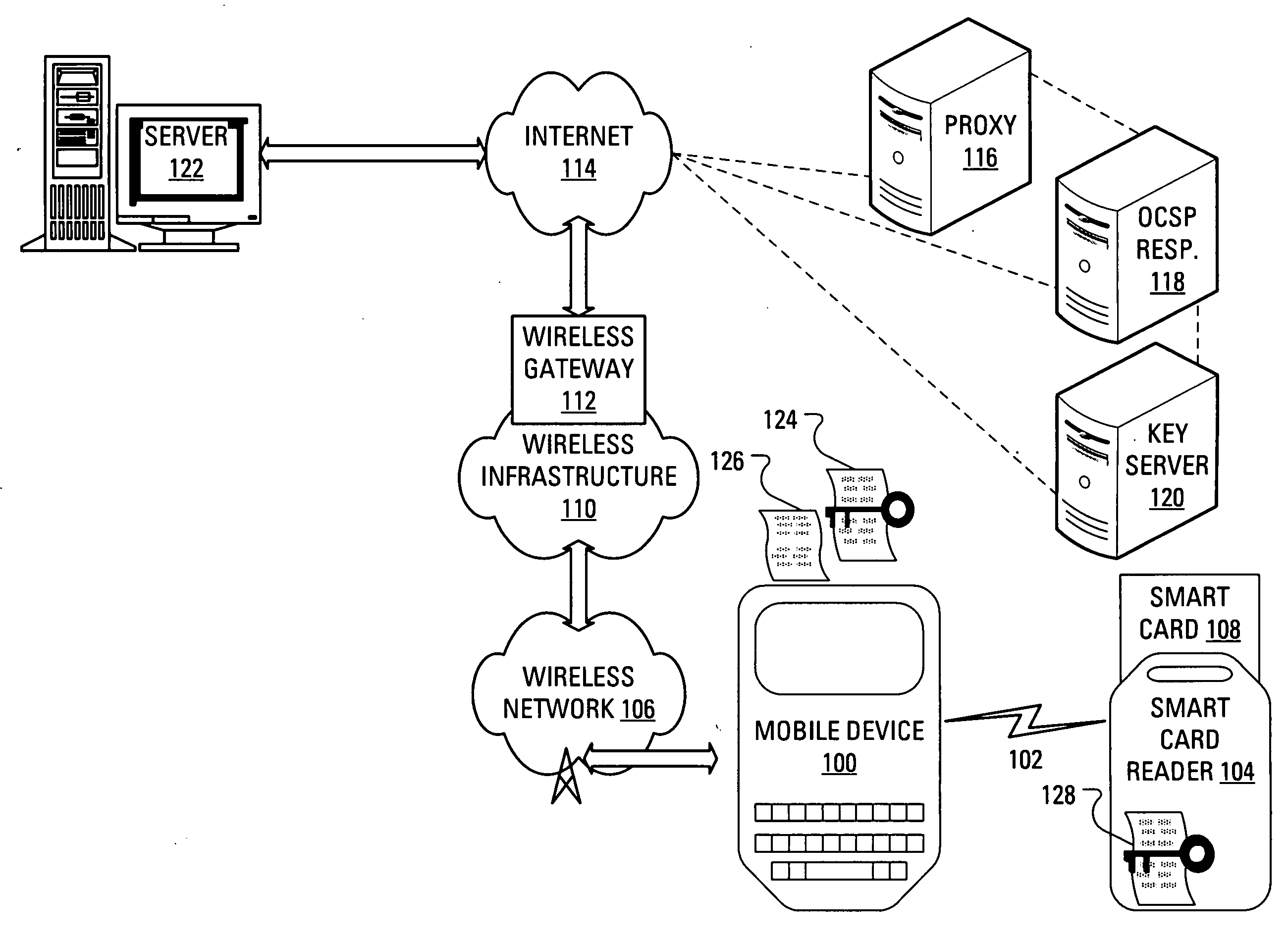
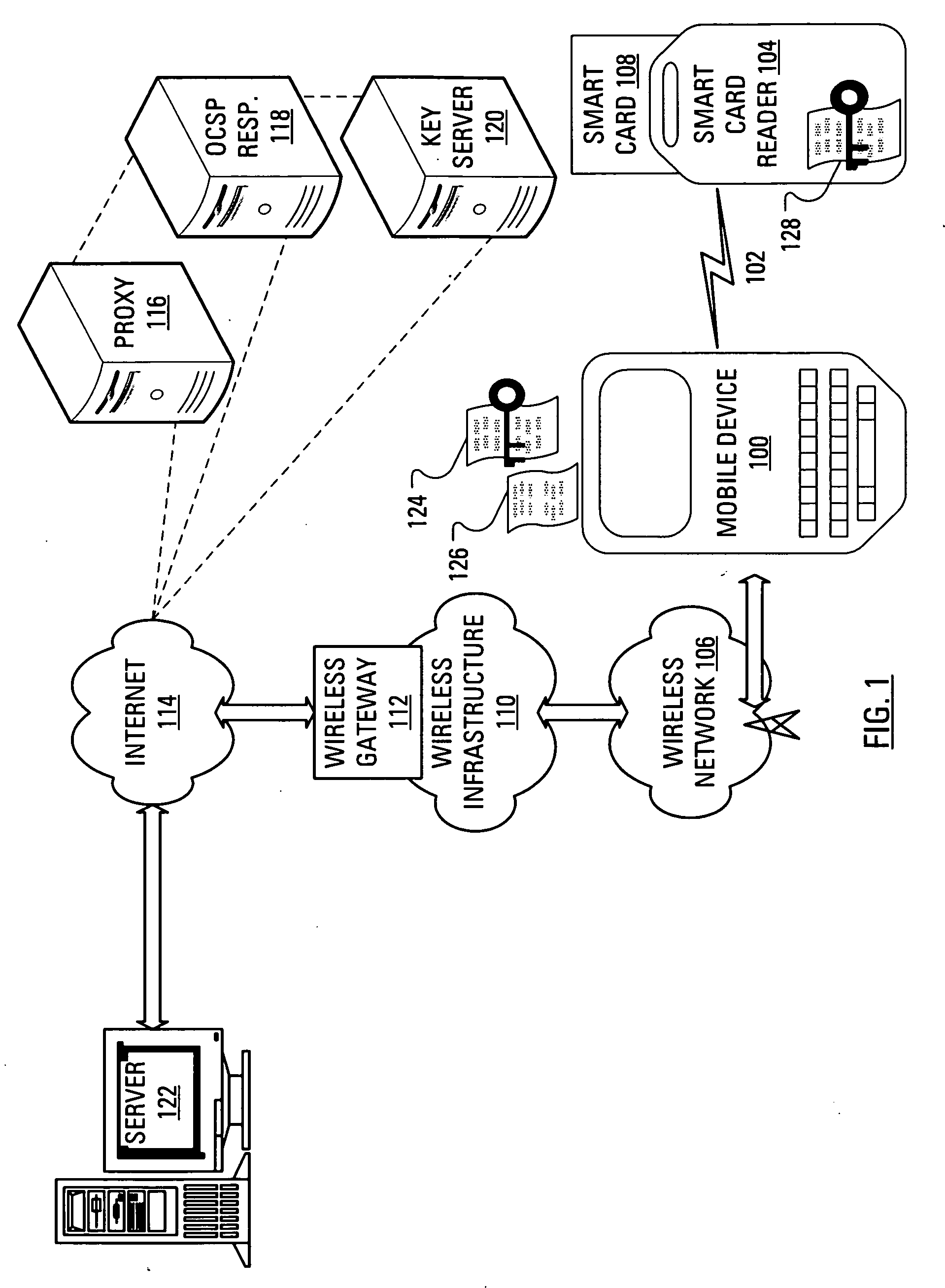
Method and apparatus for authenticating a digital certificate status and authorization credentials
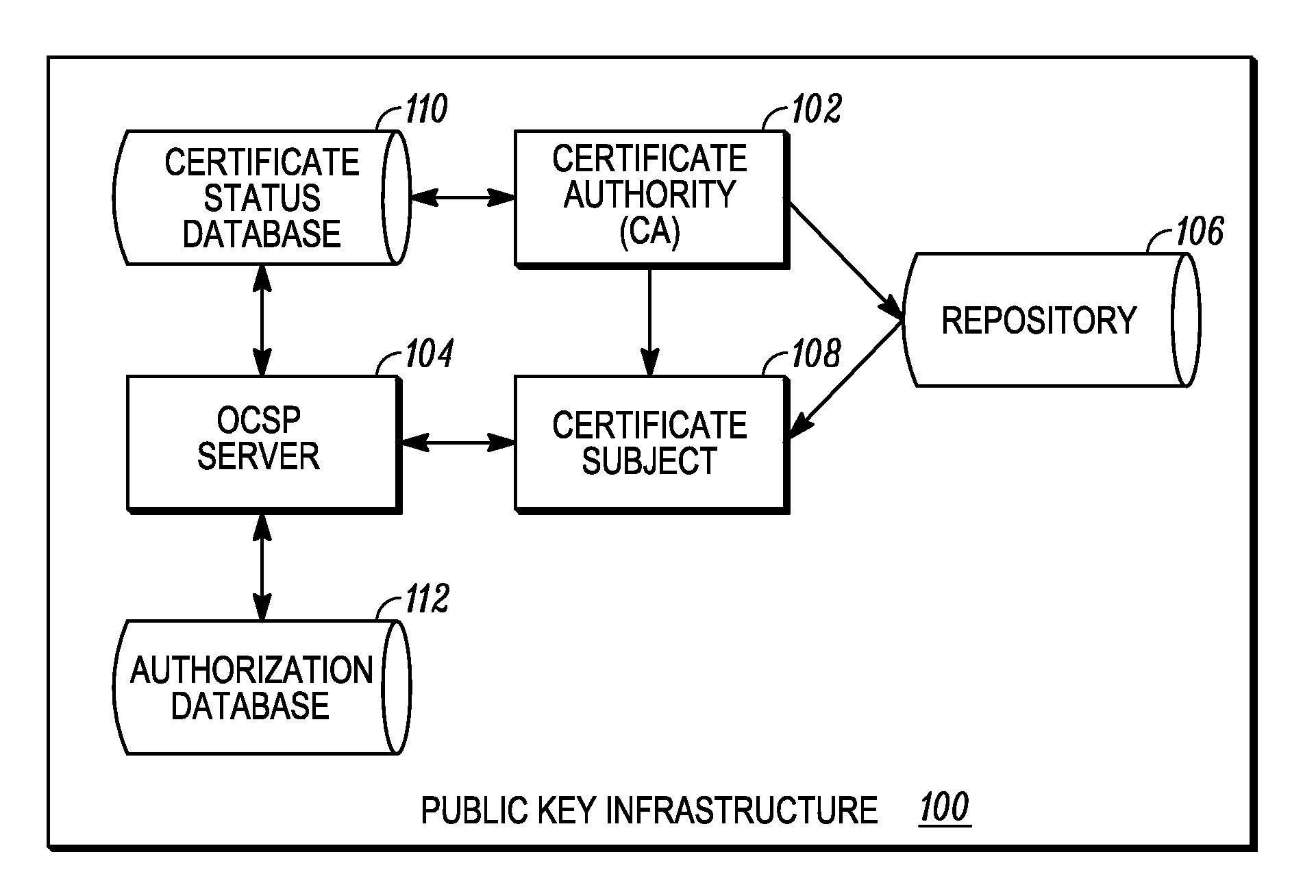
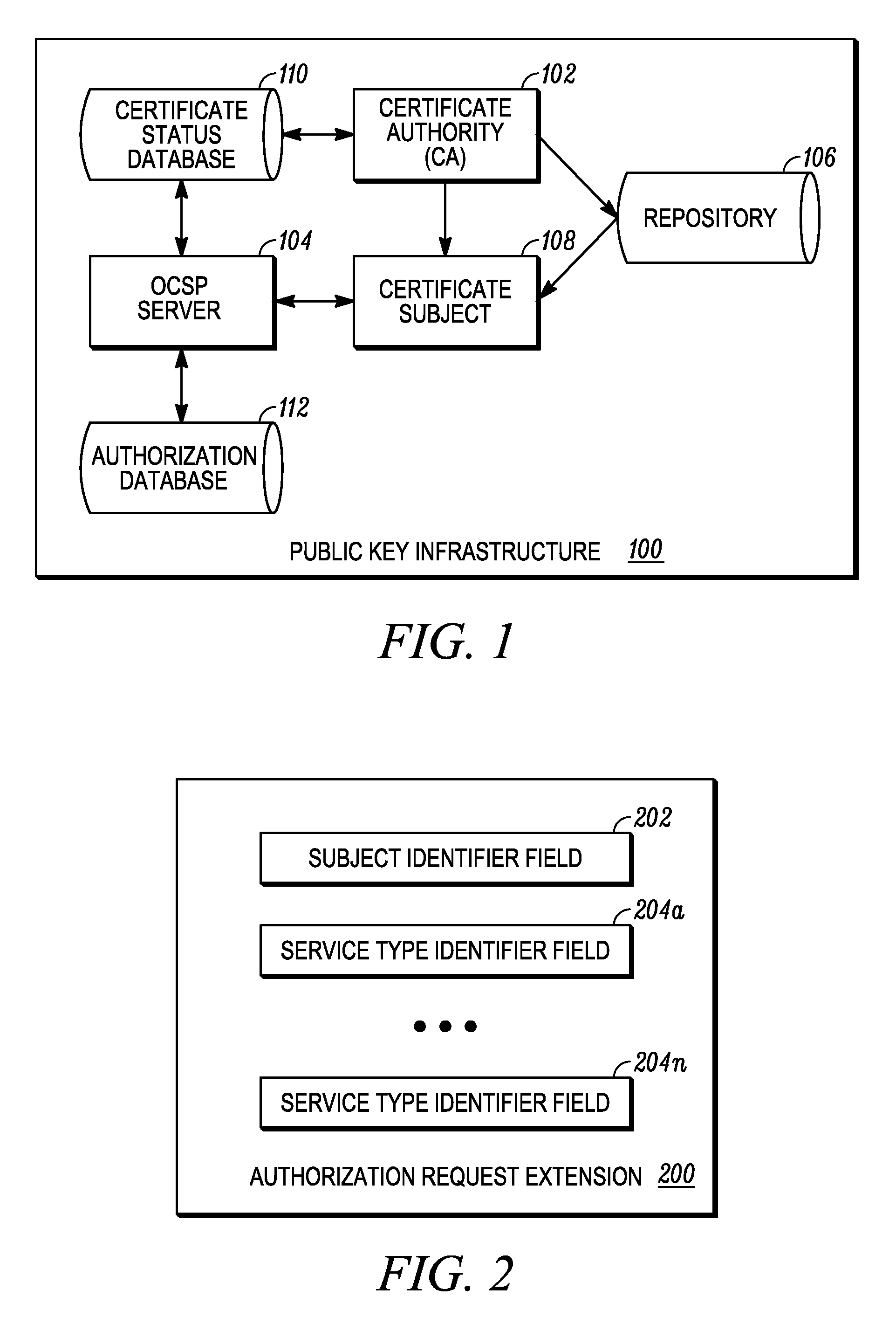
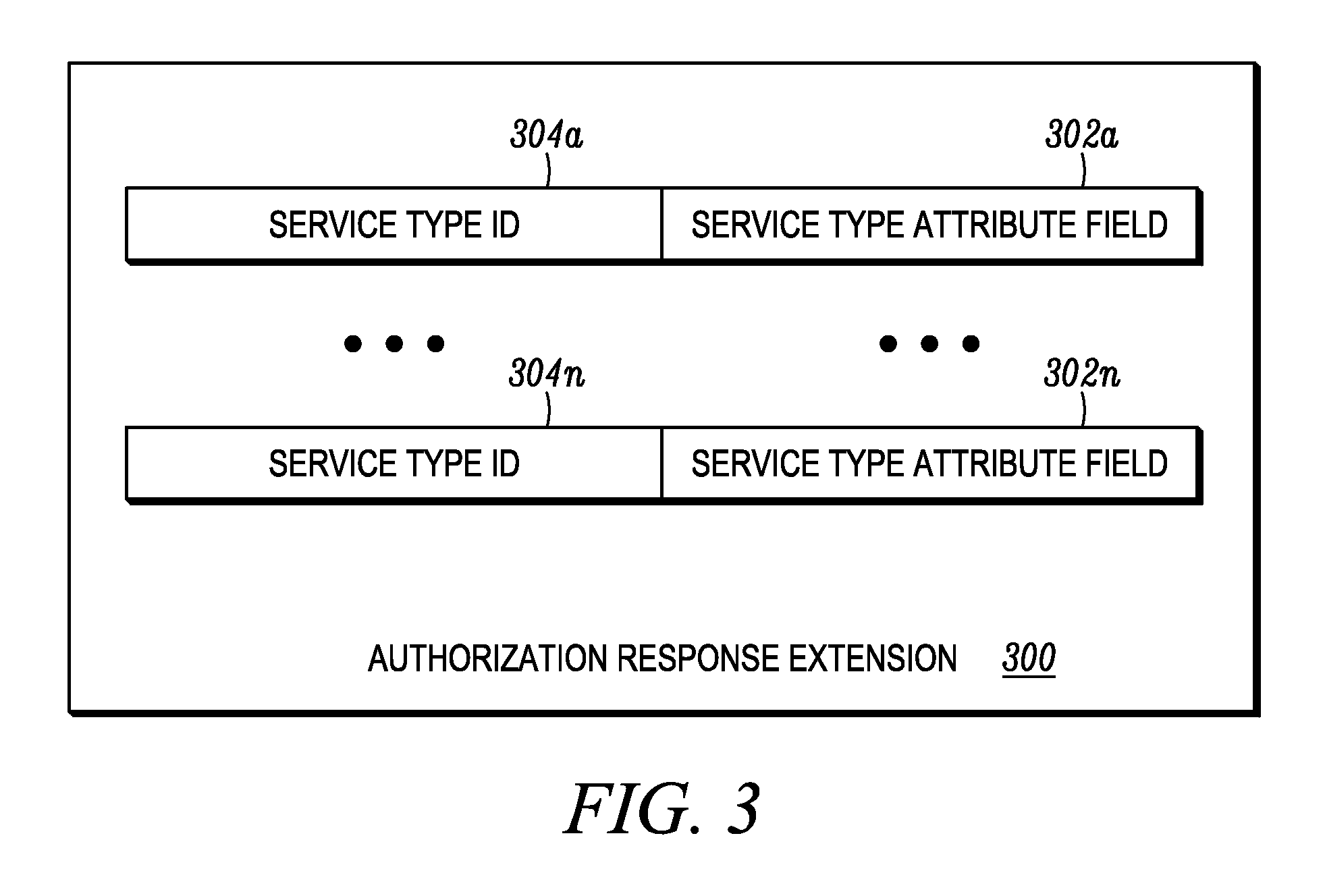
ActiveUS20130117558A1User identity/authority verificationDigital data authenticationAuthorization certificateInformation object
A relying party obtains a certificate of a certificate subject and acquires a status information object for the certificate. The relying party validates the certificate using information in the status information object and compares authorization attributes present in the status information object with policy attributes associated with the requested service. A policy attribute is a set of constraints used by the relying party to determine if the authorization attributes associated with the certificate subject are sufficient to allow the certificate subject to access the requested service. If the authorization attributes present in the status information object match the policy attributes associated with the requested service, the relying party may grant the certificate subject access to the requested service.
Owner:MOTOROLA SOLUTIONS INC
Off-line available software license centralized security authentication system based on cloud computation, and method of the same
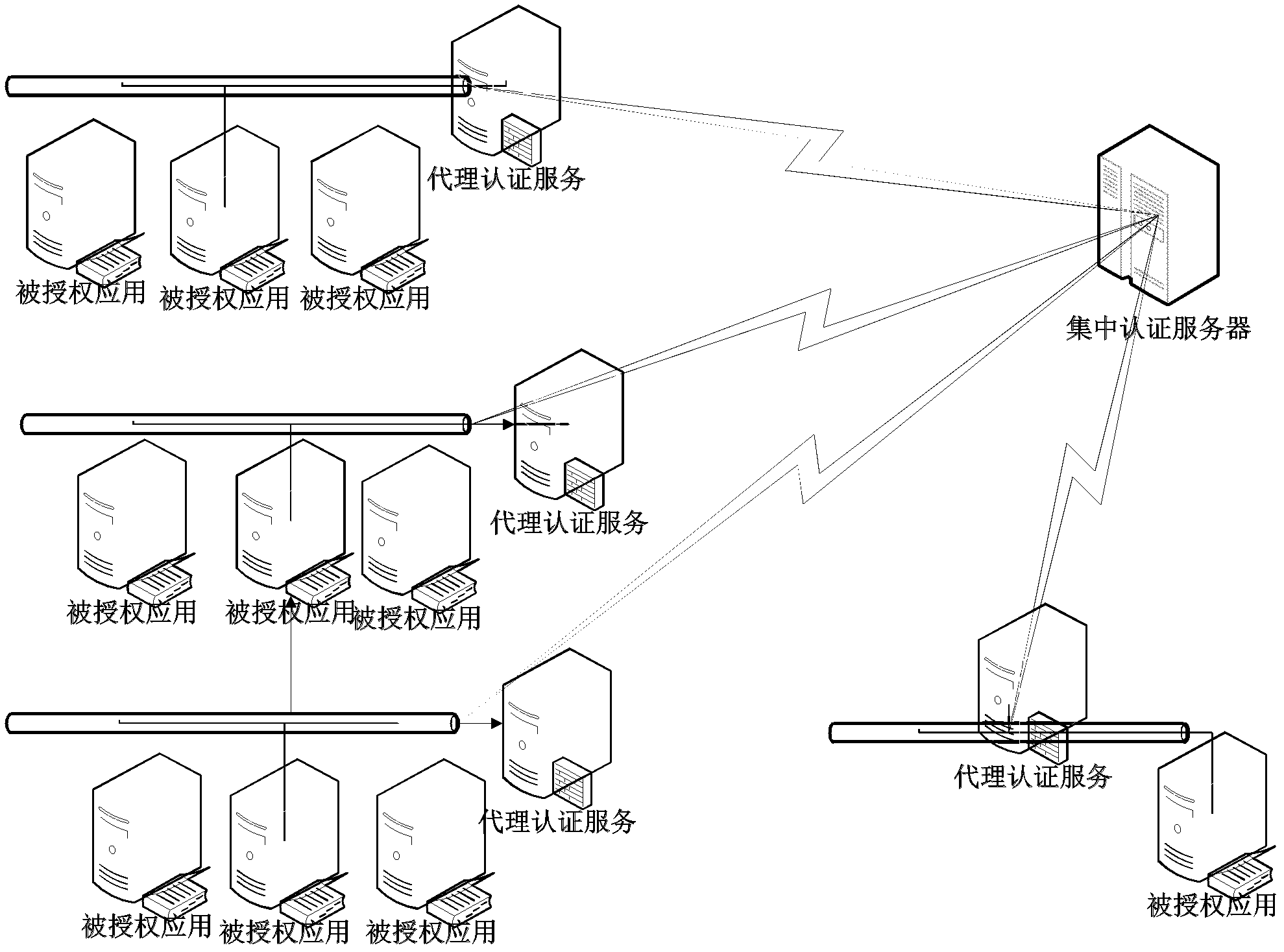
InactiveCN102497374ALower requirementAvoid breakingData switching networksAuthorization certificateSoftware license
The invention discloses an off-line available software license centralized security authentication system based on cloud computation, comprising an internetwork composed of a centralized authentication server, a proxy authentication server and a client. The system is characterized in that the centralized authentication server is responsible for producing an authorization certificate, and granting the authorization certificate to the proxy authentication server or the client; the proxy authentication server is responsible for accepting the proxy authentication authorization of the centralized authentication server, and acts on behalf of the centralized authentication server to execute an off-line authorization service for the client; in off-line condition, the client sends heartbeat detection information to a proxy authorization service program of the proxy authentication server to perform proxy authentication; or, in on-line condition, the client and the centralized authentication server performs heartbeat detection to check the validity of the authorization certificate. The system simultaneously supports off-line authentication, proxy authentication and on-line authentication.
Owner:FOUNDER INTERNATIONAL CO LTD
Certificate management with consequence indication
ActiveUS20090144540A1Digital data authenticationSecurity arrangementAuthorization certificateUser interface
A certificate management operation request is managed on a device, access to which is governed by an authentication certificate. Upon receiving a request to perform a certificate management operation on a certificate, a consequence of performing the certificate management operation is determined and the consequence is indicated via a user interface of the device. For example, anytime a user attempts to use a certificate management application to delete, distrust or revoke a certificate, it is determined whether the certificate meets certain criteria, such as the certificate being the authentication certificate or being in the certificate chain of the authentication certificate. If the certificate meets the criteria, the user may be notified of a lack of permission to perform the requested operation and the operation may be prevented from completing. Alternatively, the user may be permitted to confirm the instruction to perform the requested operation, and the operation may be completed.
Owner:MALIKIE INNOVATIONS LTD
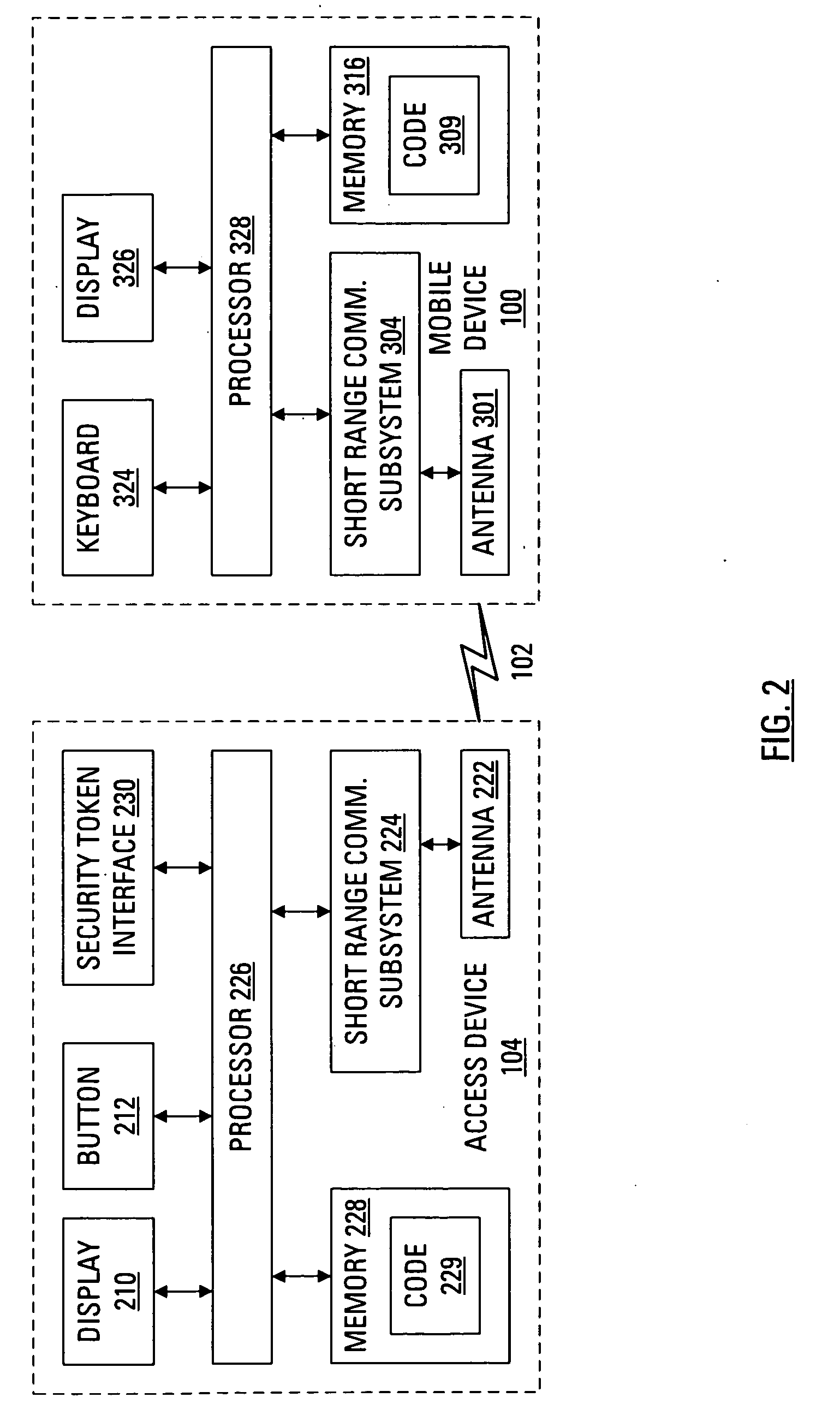
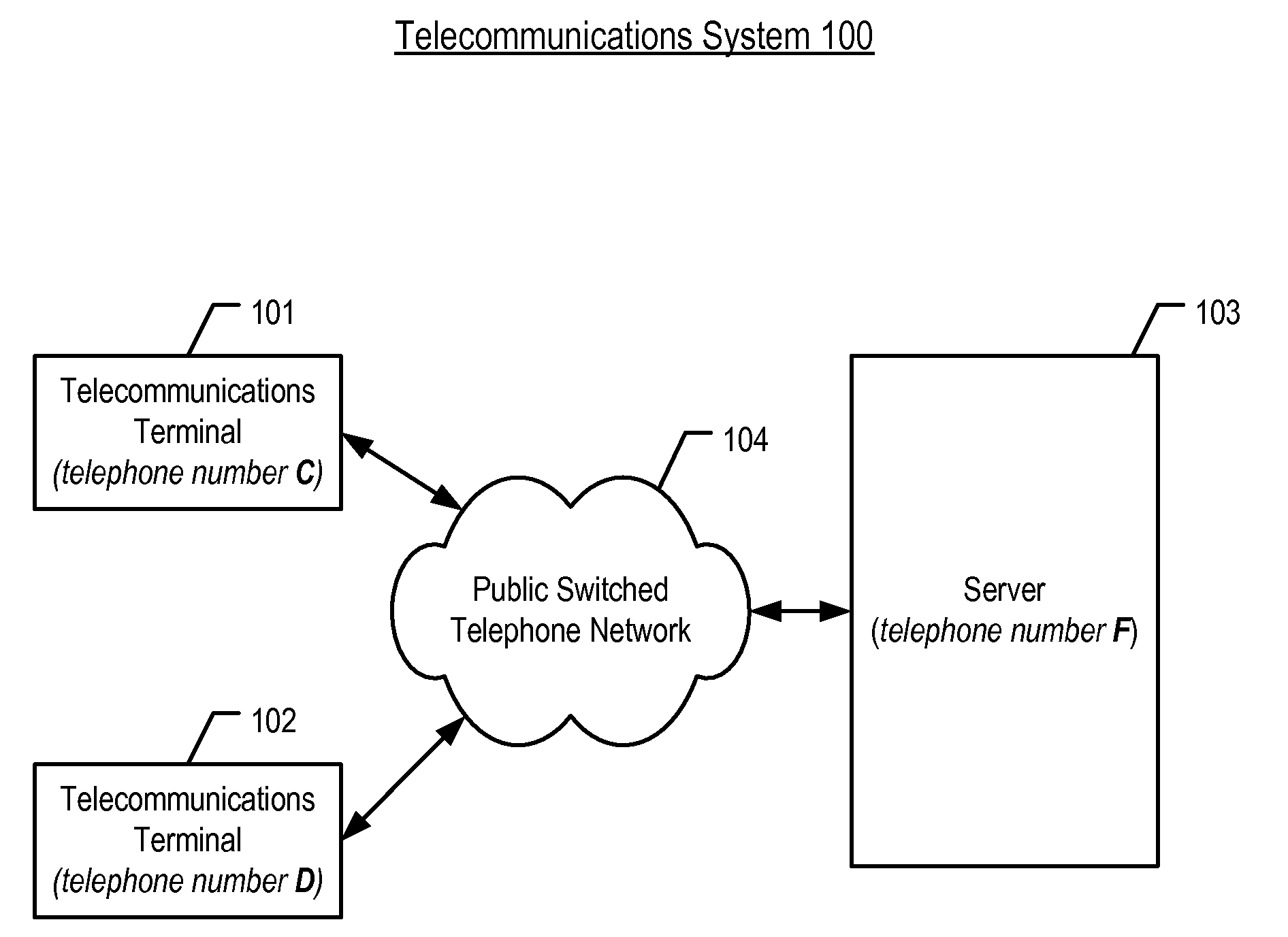
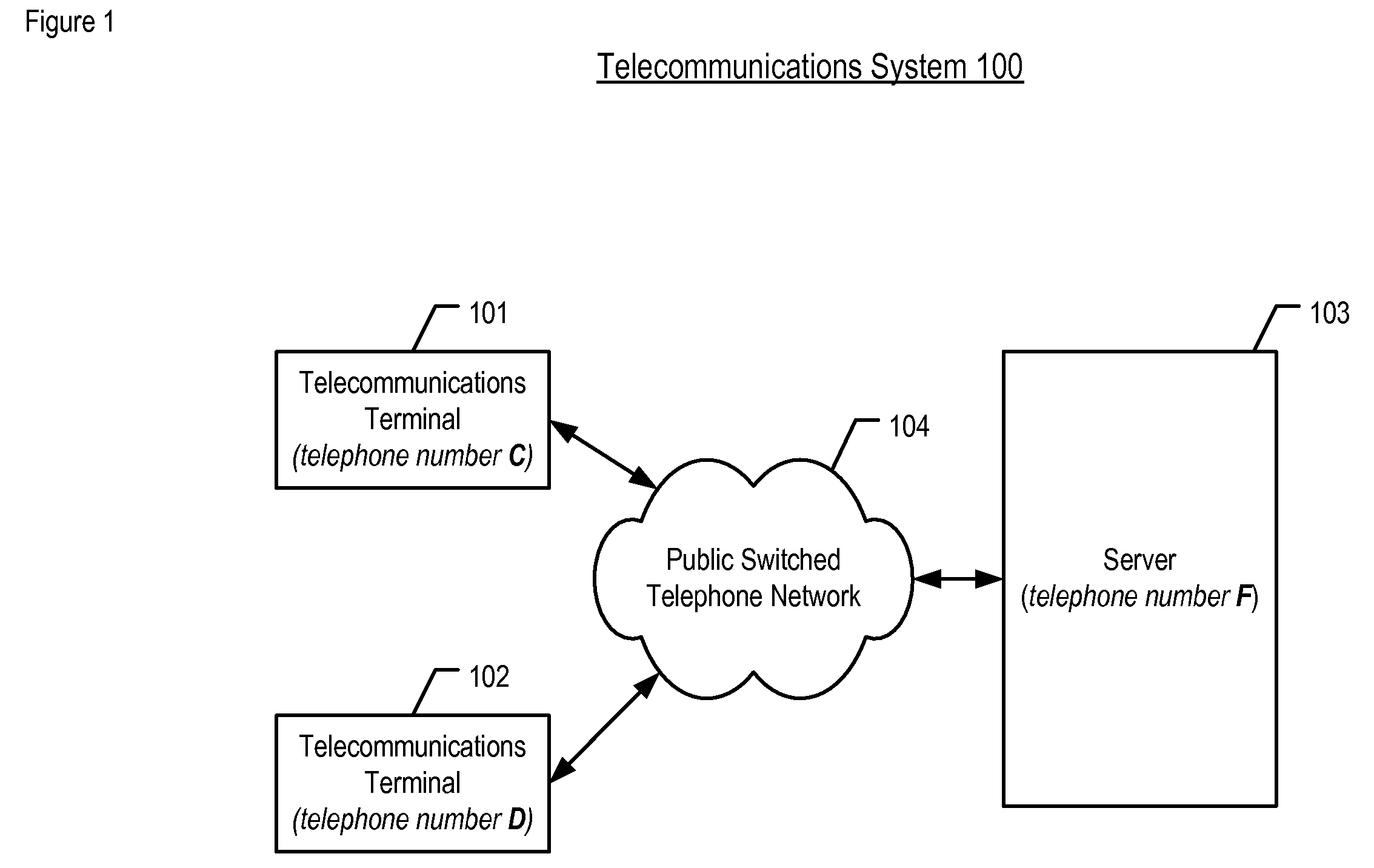
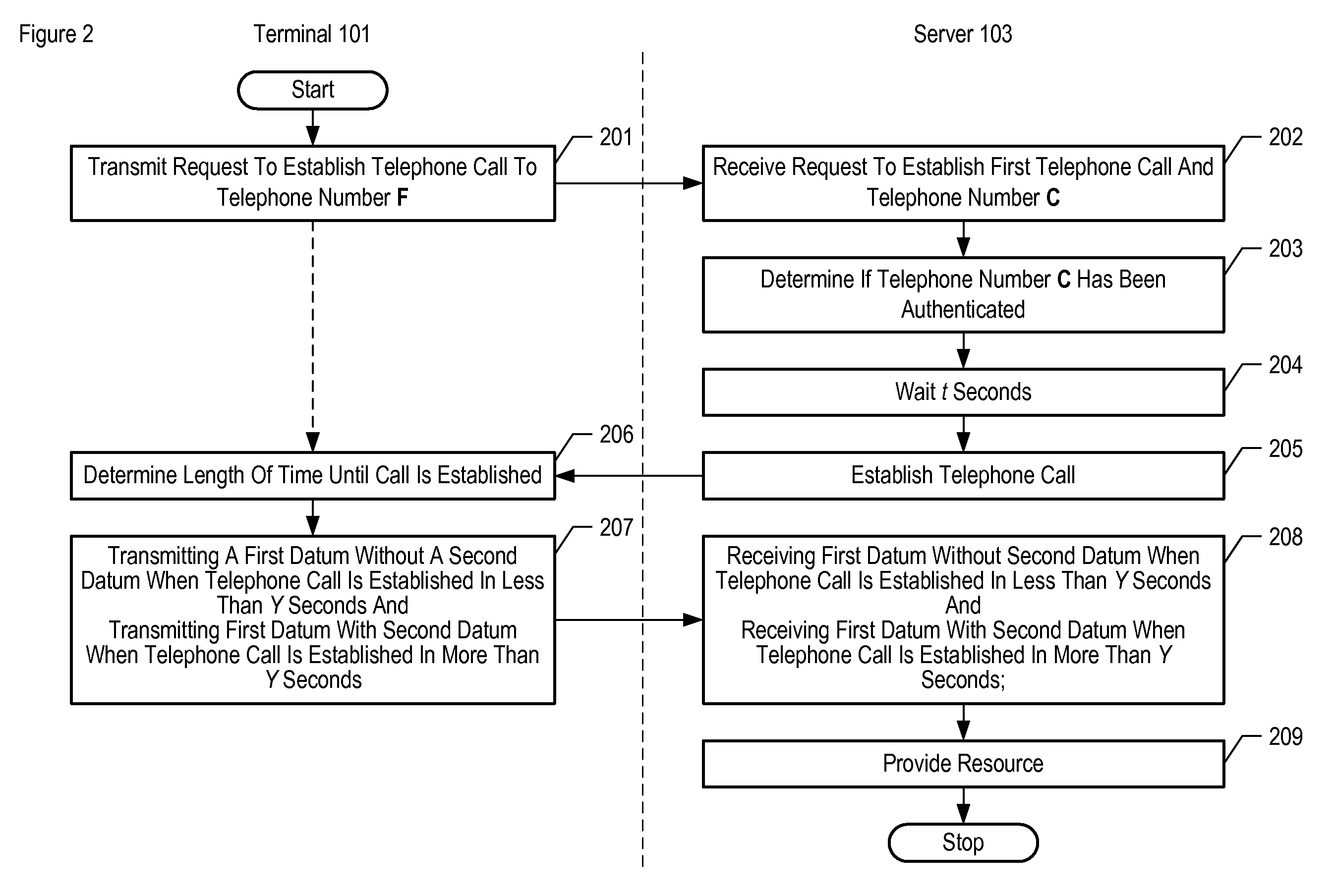
Determining Whether to Provide Authentication Credentials Based on Call-Establishment Delay
ActiveUS20080123825A1Special service for subscribersGraded-service arrangementsAuthorization certificateTelecommunications link
A method of authenticating an authorized entity via the telephone network is disclosed. A telephone call is placed from a telecommunications terminal to a server that comprises a valuable resource and that only provides the resource to authorized entities. When the terminal has already demonstrated its authorization to the server, the server indicates to the terminal that the terminal need not provide its authorization credentials. In contrast, when the terminal has not yet demonstrated its authorization to the server, the server indicates to the terminal that the terminal does need to provide its authorization credentials. The server indicates to the terminal whether or not it needs to provide its authorization credentials by deliberating waiting to establish the call with the terminal, wherein in the length of the wait is indicative of whether or not the terminal needs to provide its authorization credentials.
Owner:AVAYA INC
Method of adding a client device or service to a wireless network
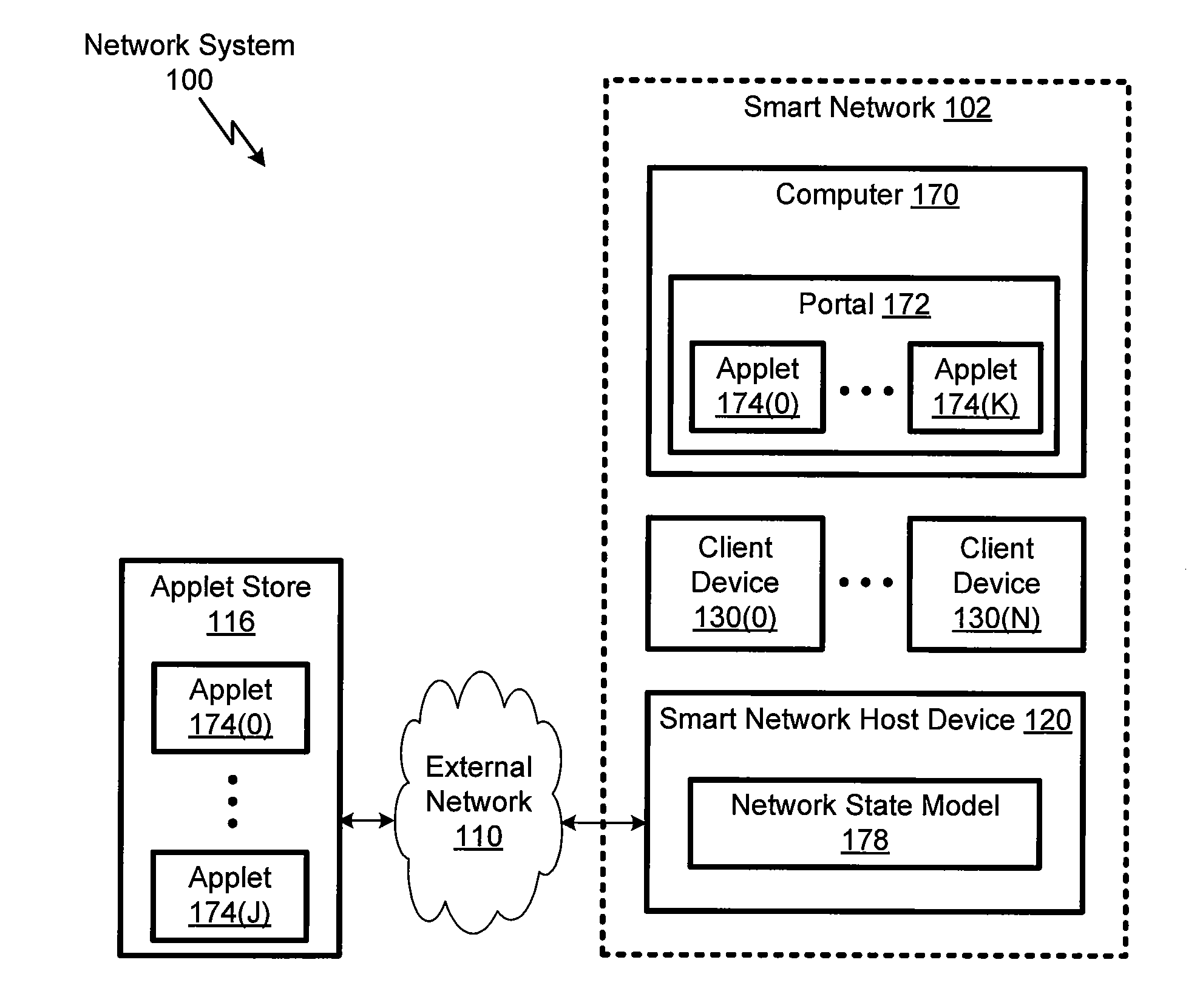
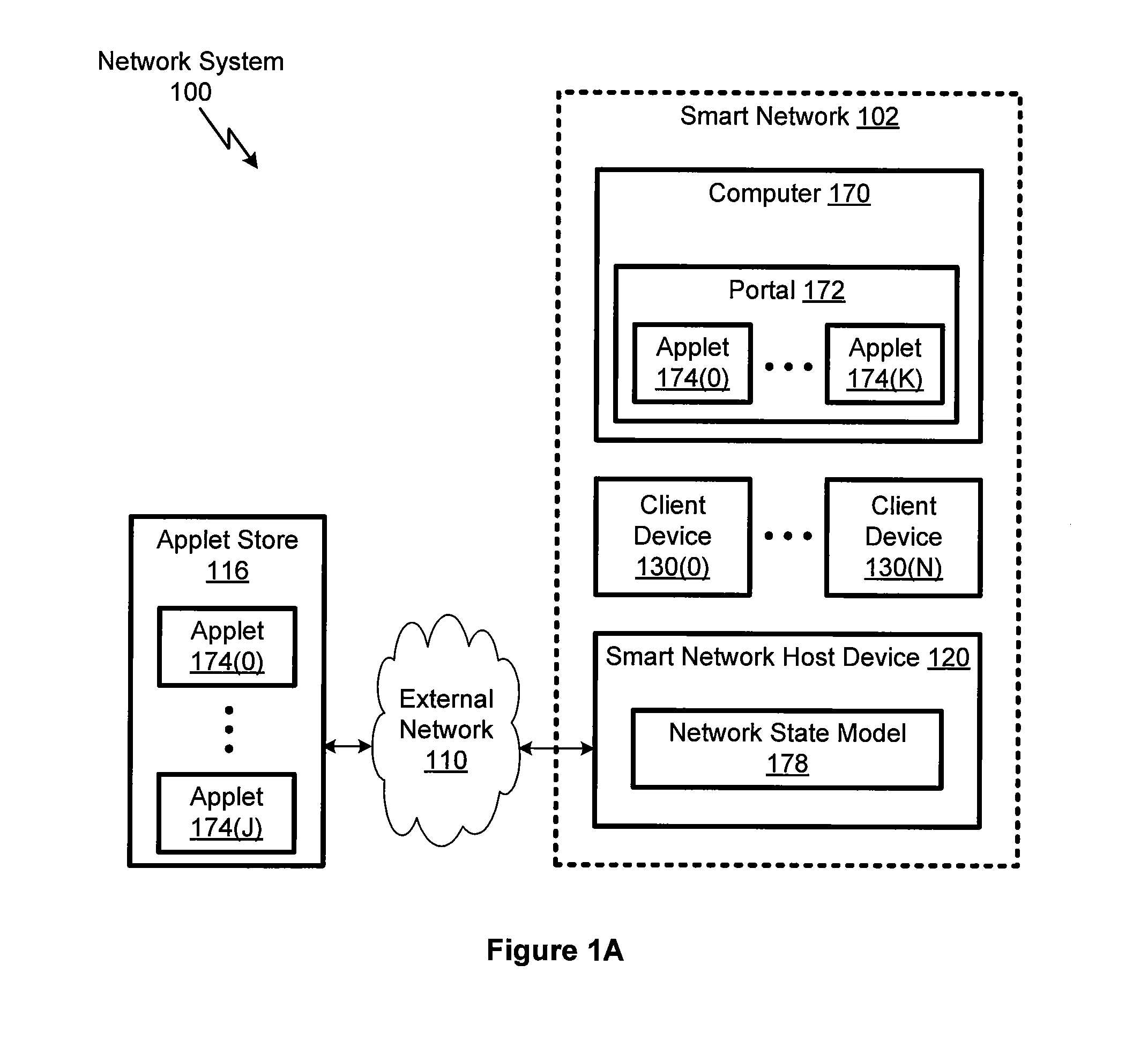
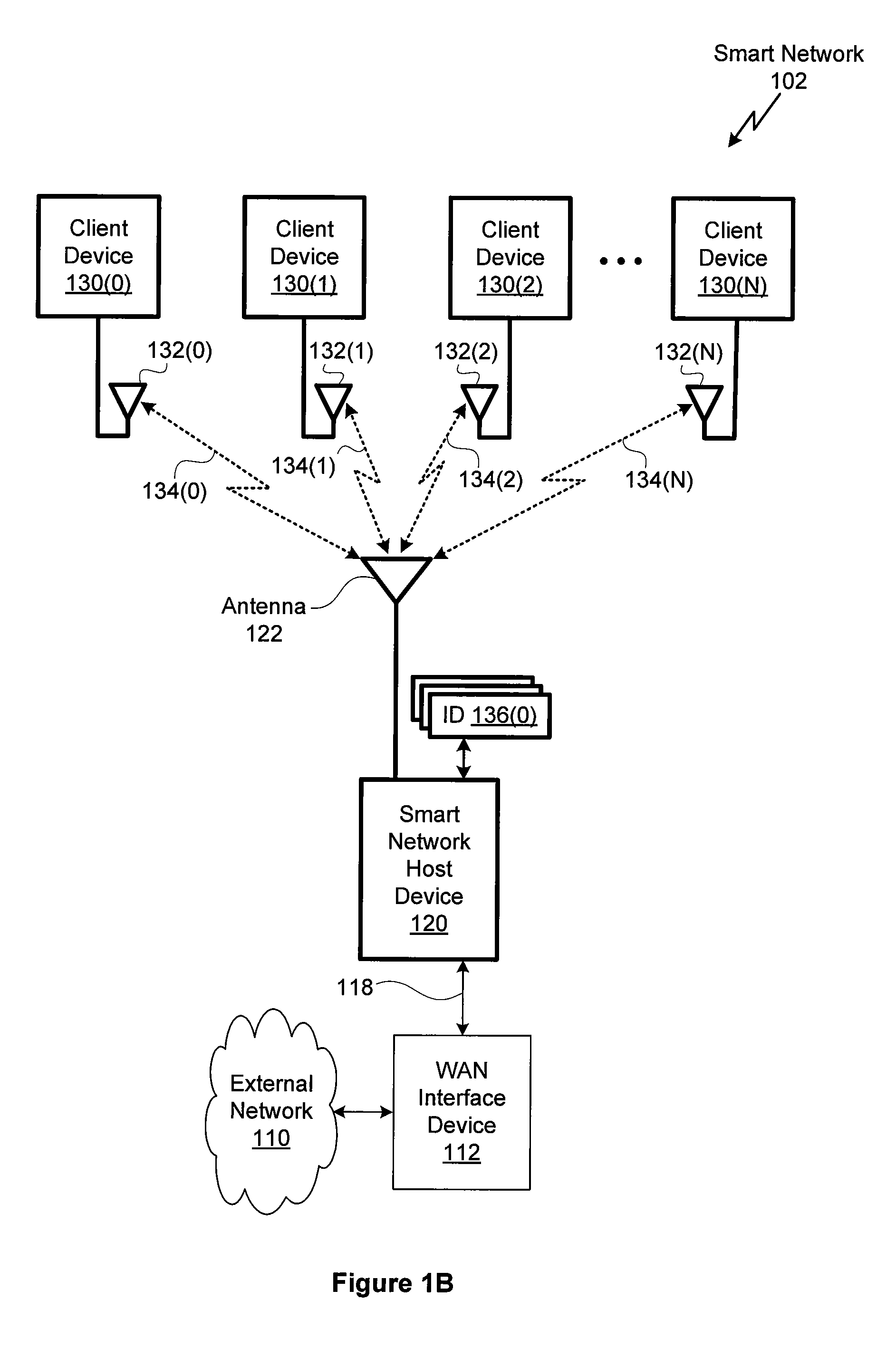
InactiveUS20110265151A1Assess restrictionDigital data processing detailsAuthorization certificateSmart network
A smart network host device automatically registers a device or service with a wireless network using identification information and an authorization credential associated with the device or service. The smart network host device obtains the requisite identification information and authorization credential from a network association apparatus associated with the specific device or service to be registered with the wireless network. The smart network host device performs the registration automatically once the smart network host device confirms that the device or service has been associated with the wireless network and a secure password authentication protocol is successfully performed by the smart network host device and the device or service. The network association apparatus may comprise an RFID tag.
Owner:BELKIN INT
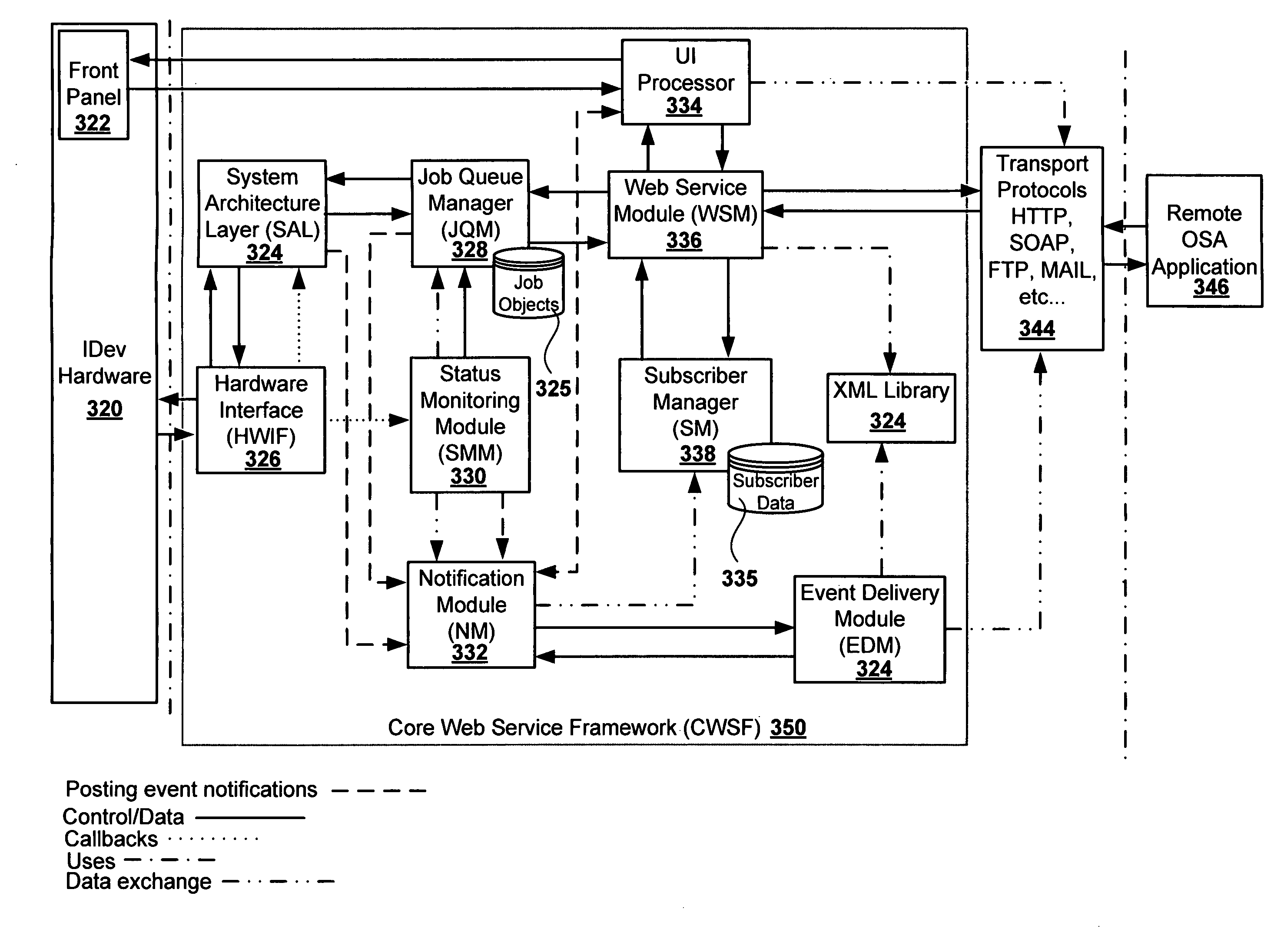
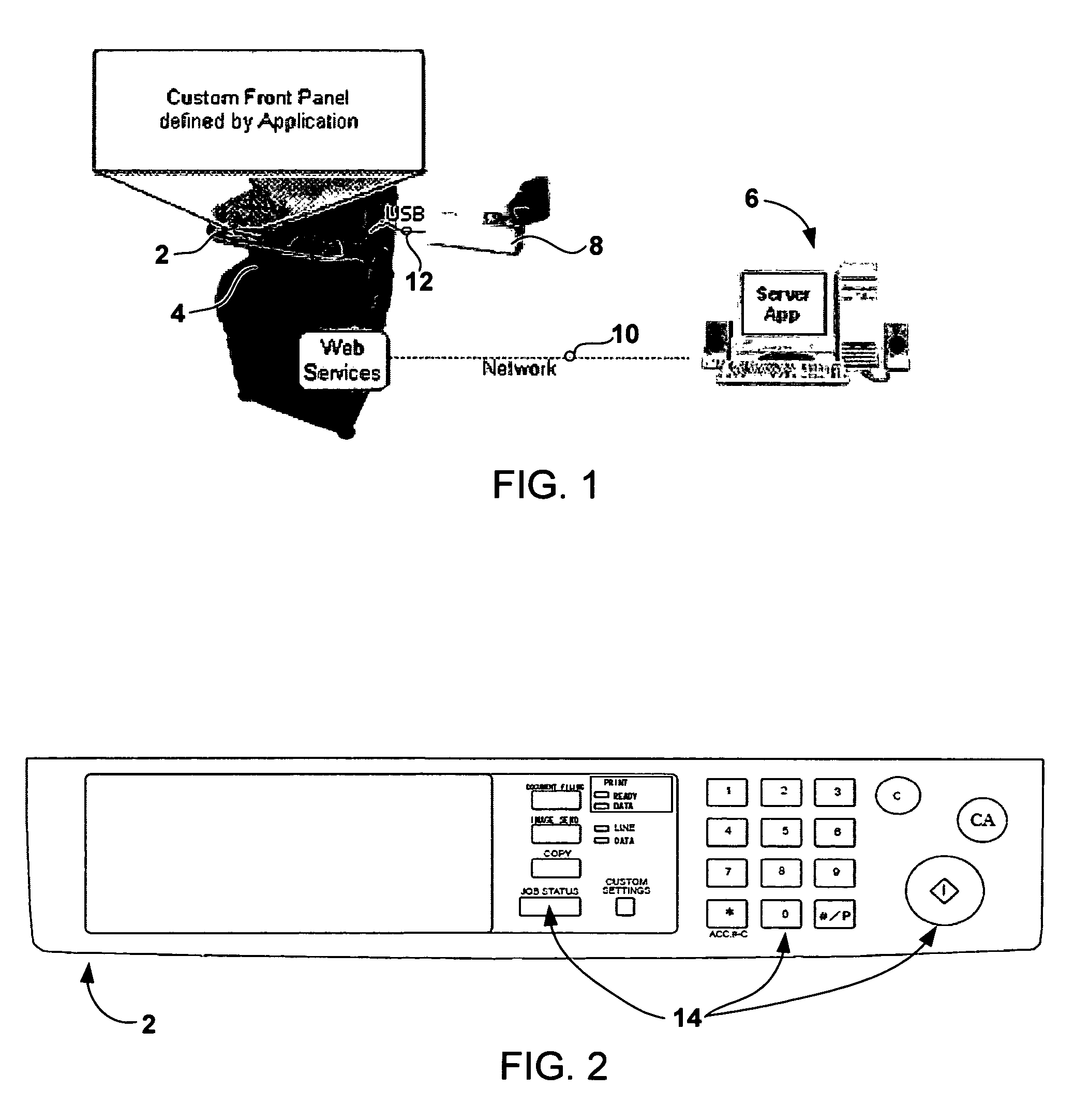
Methods and systems for imaging device event notification subscription
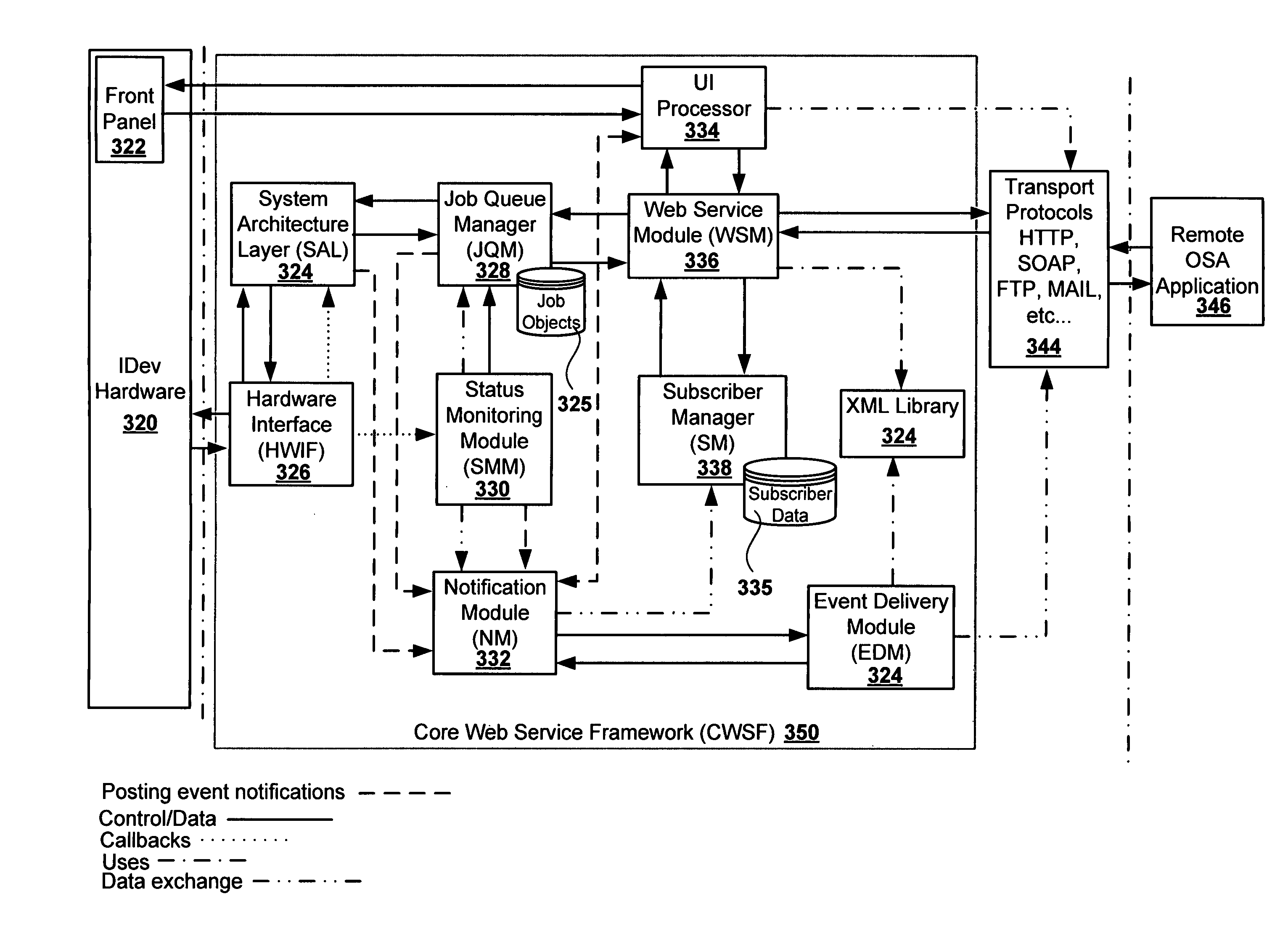
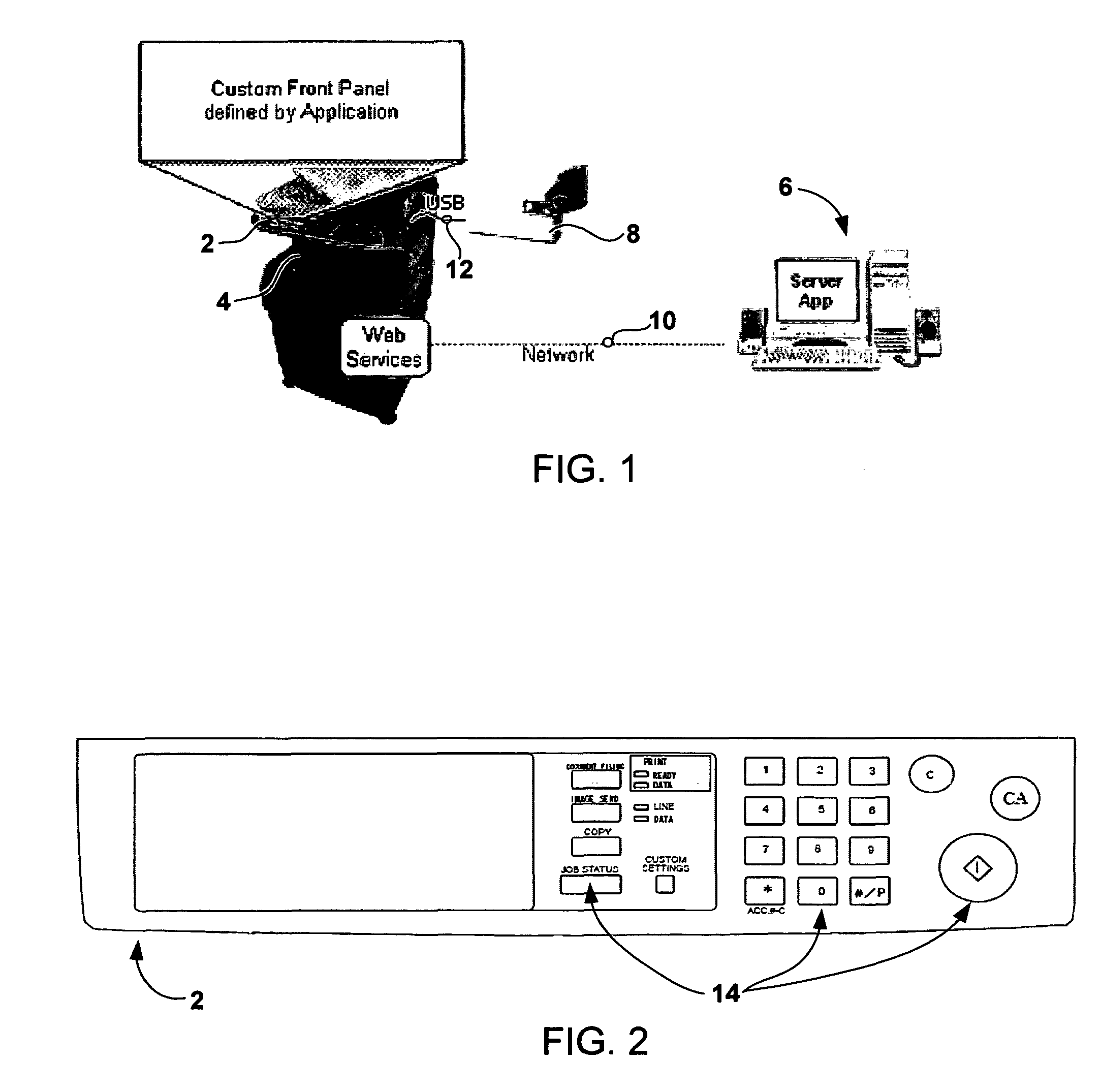
ActiveUS8065384B2Multiple digital computer combinationsInternal/peripheral component protectionAuthorization certificateApplication software
Aspects of the present invention relate to systems, methods and devices for imaging device event notification, administration and subscription. Some aspects relate to a subscription application executable on a remote computing device, wherein the subscription application may generate and send a subscription request. Some aspects may limit notification subscription to authorized credential holders. Some aspects relate to event notification message formats and destinations.
Owner:SHARP KK
Secure and efficient authentication using plug-in hardware compatible with desktops, laptops and/or smart mobile communication devices such as iphones.tm.
ActiveUS20140298011A1Enhanced authenticationImproved transactionUser identity/authority verificationDigital data authenticationAuthorization certificateTelecommunications link
A portable apparatus is removably and communicatively connectable to a network device to communicate authentication or authorization credentials of a user in connection with the user logging into or entering into a transaction with a network site. The apparatus includes a communications port to connect and disconnect the apparatus to and from the network device and to establish a communication link with the network device when connected thereto. A processor receives a secure message from the network security server via the port. The message has a PIN for authenticating the user to the network site, and is readable only by the apparatus. The processor either transfers, via the port, the received PIN to an application associated with the network site that is executing on the network device or causes the apparatus to display the received PIN for manual transfer to the application associated with the network site.
Owner:PAYFONE
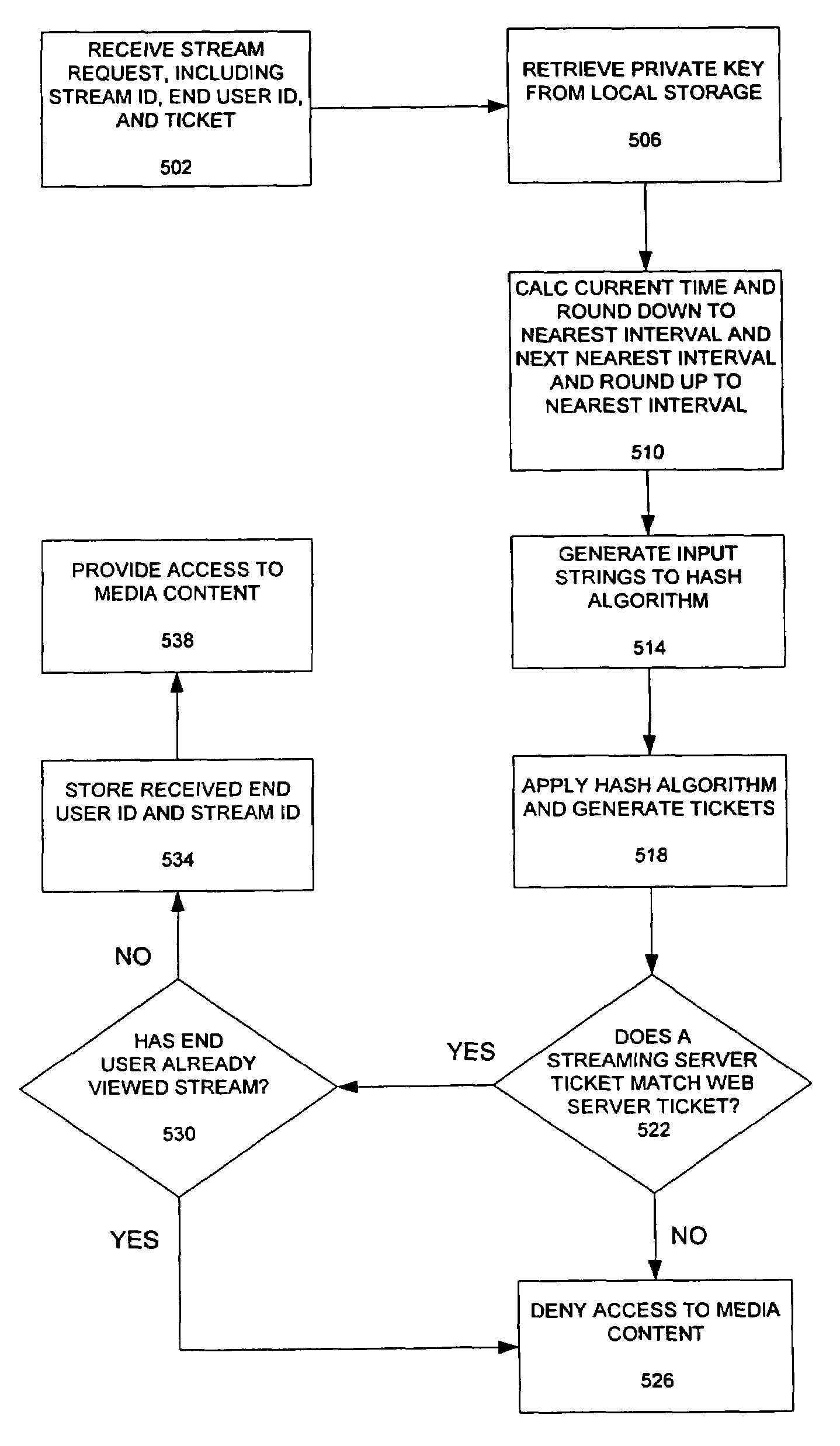
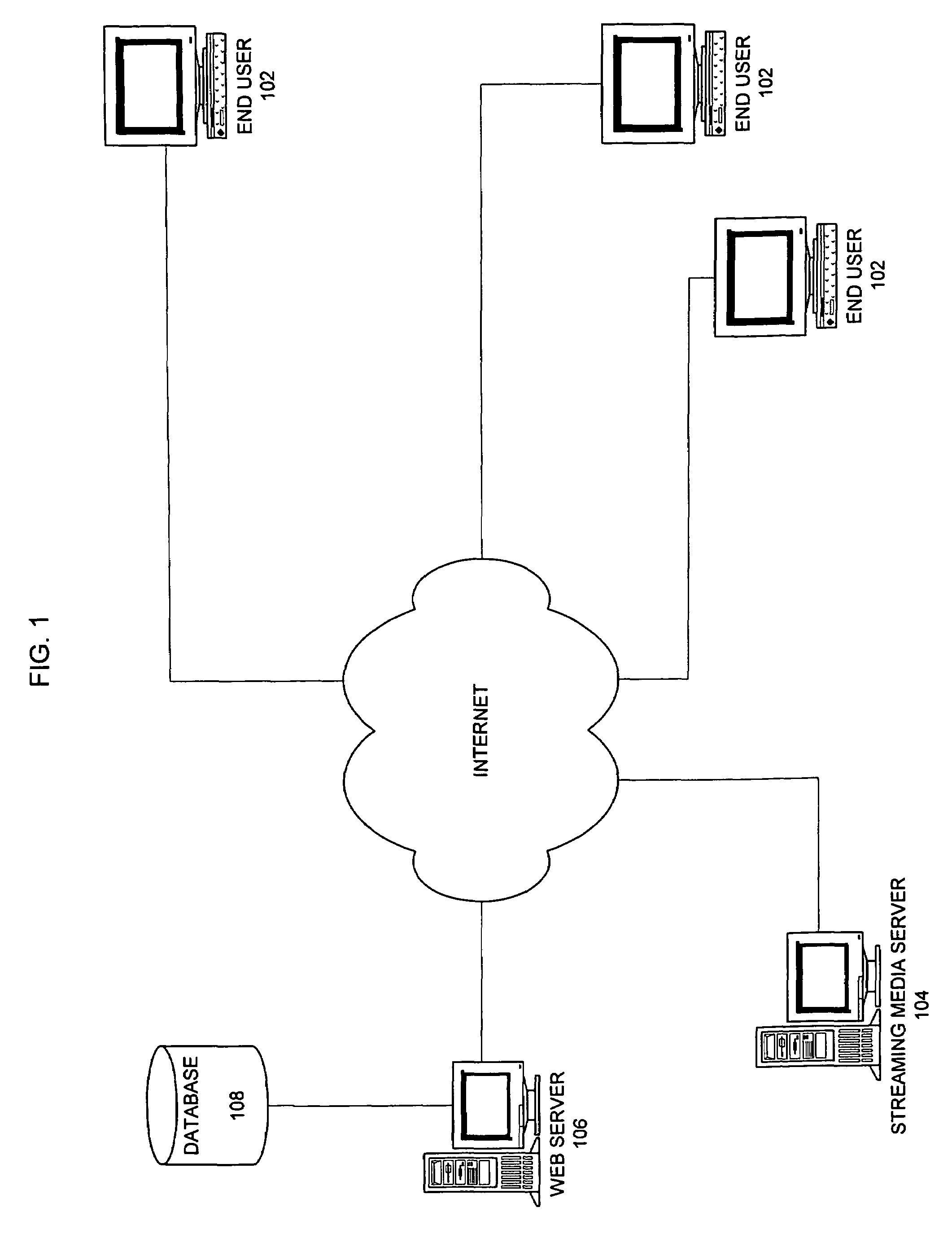
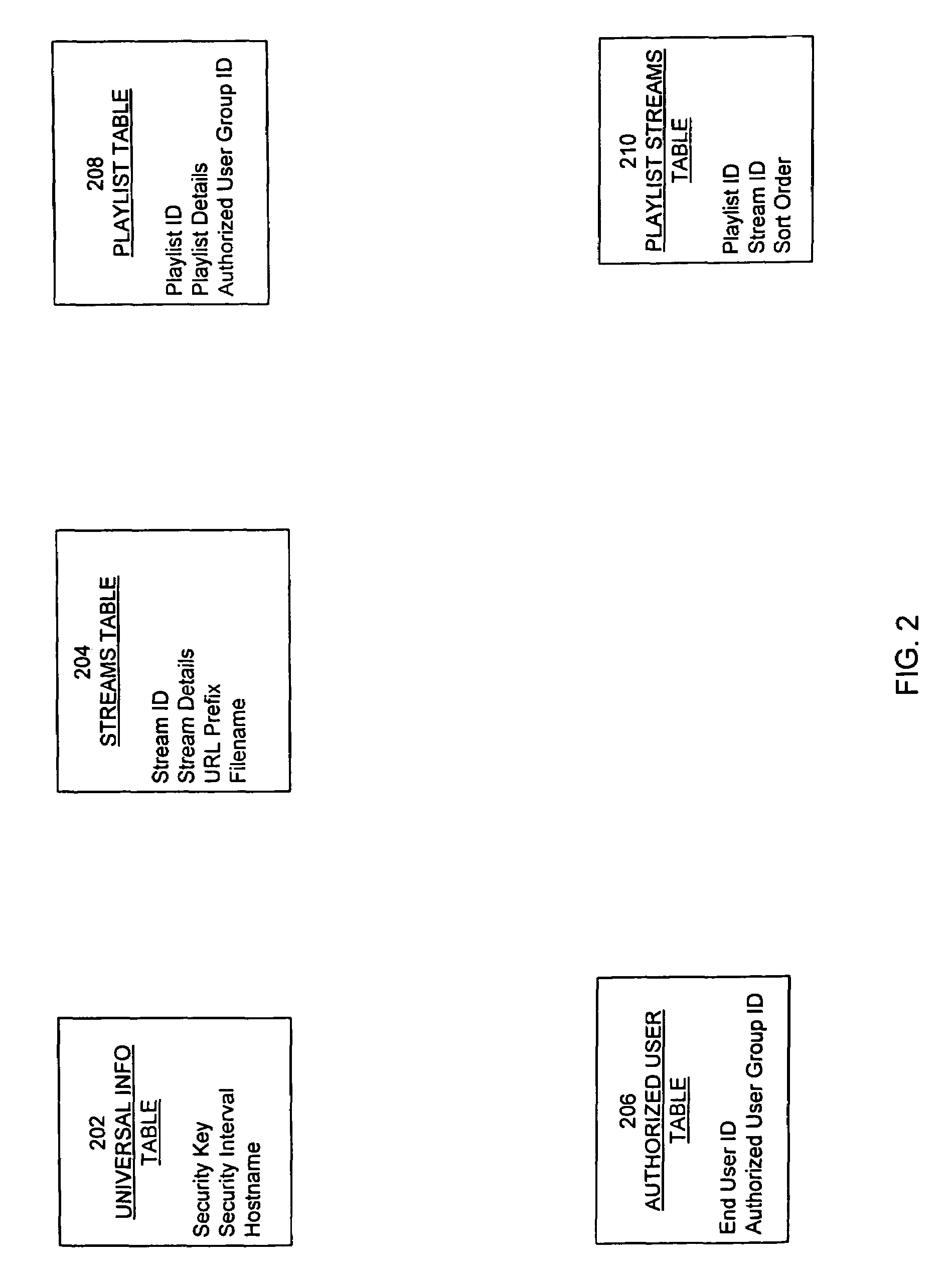
Method for controlling access to digital content and streaming media
ActiveUS7721339B2Digital data processing detailsUser identity/authority verificationAuthorization certificateDigital content
A system and method for controlling access to digital content, including streaming media. The system includes a web server, media server and end user processor, such as a personal computer, coupled to a network. The web server cryptographically generates a ticket in response to an end user's request for access to a file. The ticket is based, at least in part, on a time at or near when the ticket is generated. The media server generates an authorization ticket, preferably using the same cryptographic algorithm as the web server. The media server authorization ticket is based, at least in part, on a time at or near when the media server receives the request for access to the file. The media server determines whether to grant access to the file by comparing the ticket, as generated by the web server, to the ticket, as generated by the media server.
Owner:VERIZON PATENT & LICENSING INC
User data protection method for safety computer
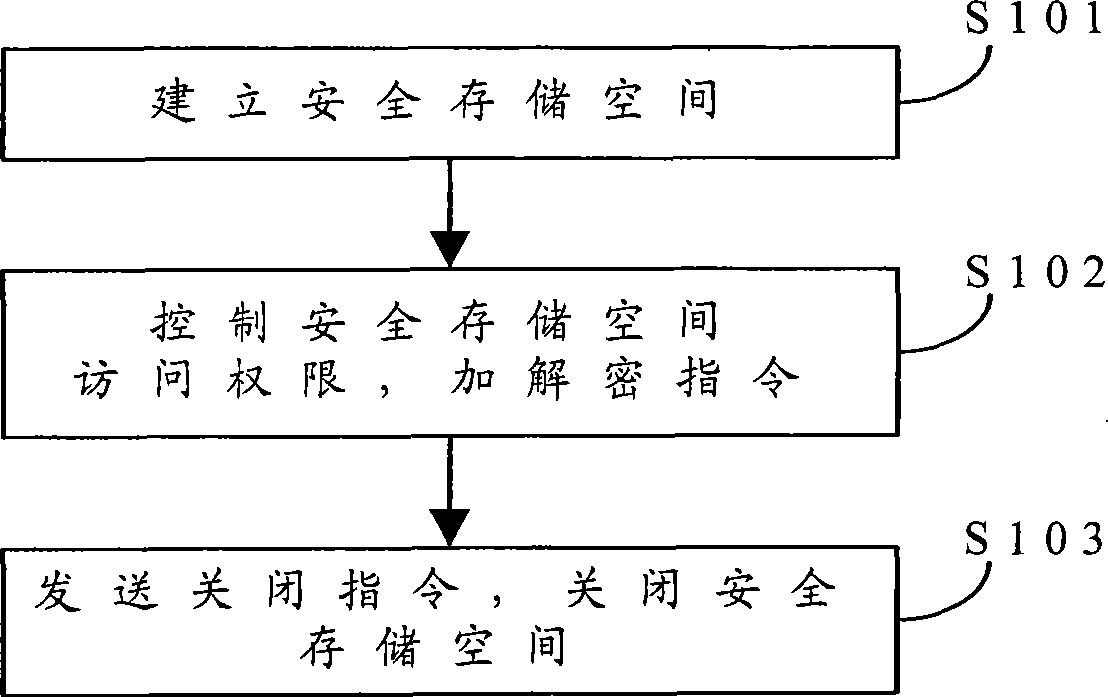
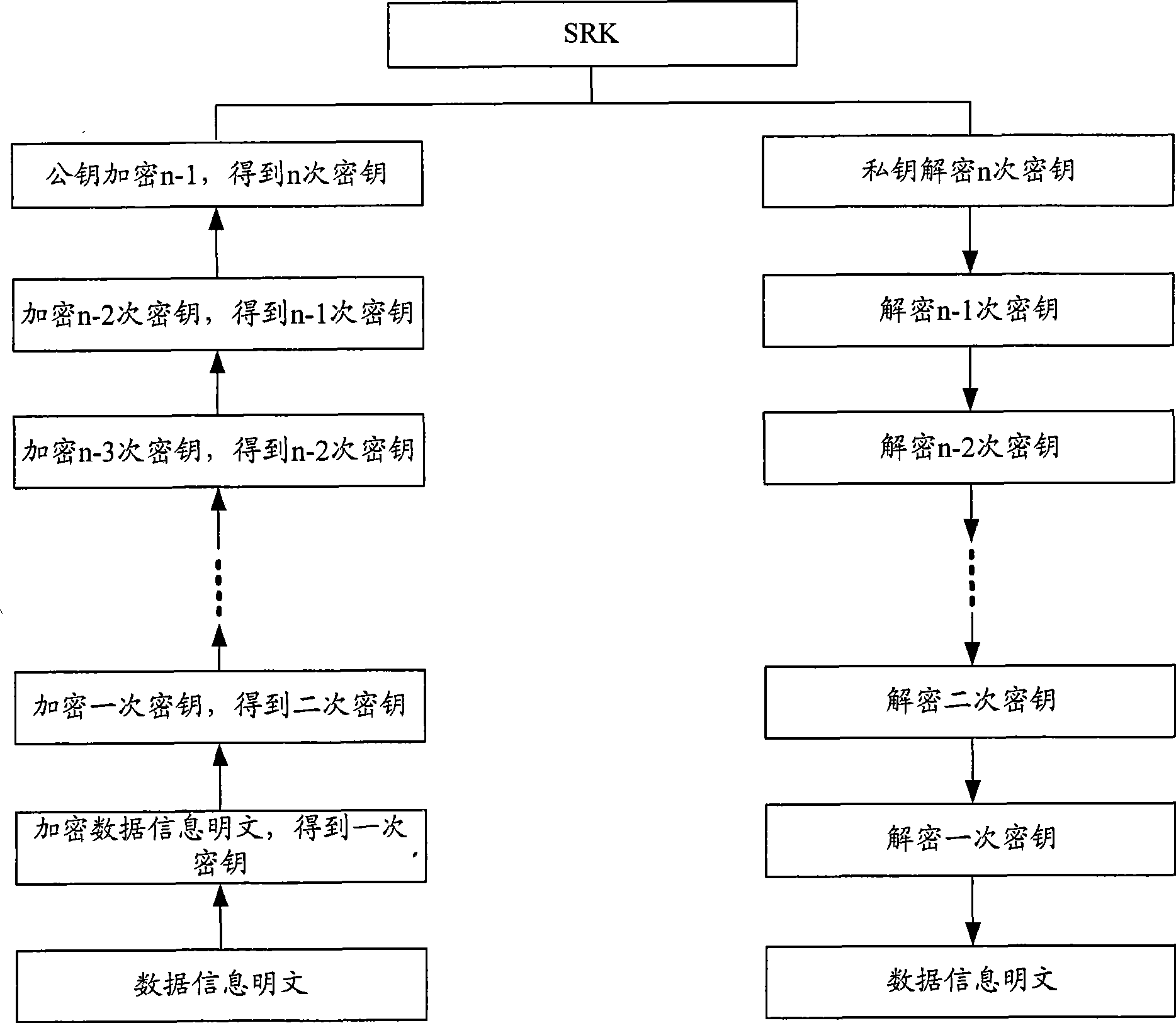
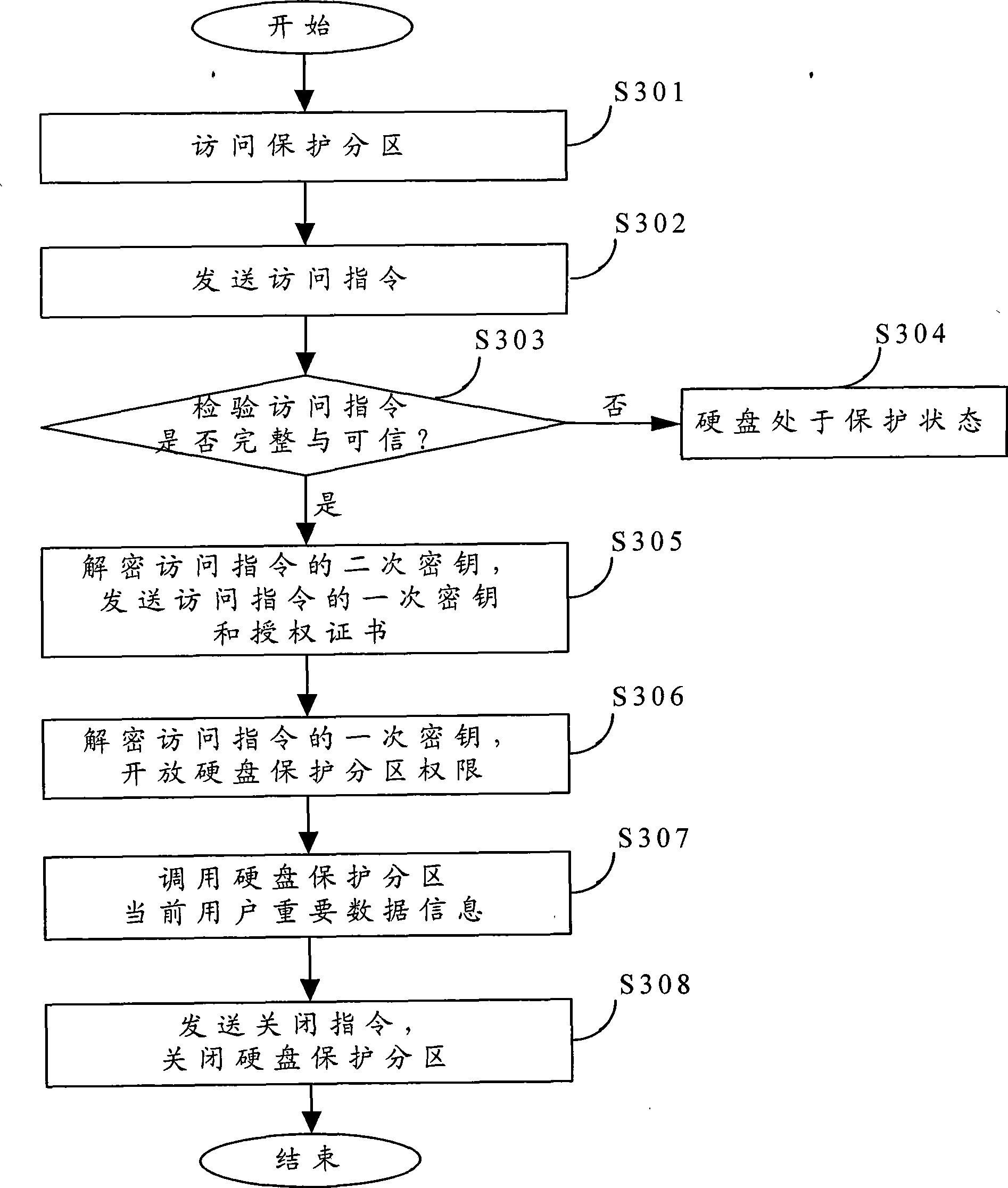
ActiveCN101452514AEnsure safetyInstructions to avoidUnauthorized memory use protectionDigital data protectionAuthorization certificateData information
The invention is suitable for the field of information security, and provides a user data protection method for a secure computer. The method comprises the following steps: establishing a secure storage space, and controlling the access right of the secure storage space; and enciphering instructions related to the secure storage space, and performing certification processing and decipherment on the instructions on the receiving end of the instruments. The method effectively prevents hacker interception software from intercepting transmitted instructions by enciphering and deciphering user data information of the secure storage space and the transmitted instructions for various times and performing validity certification by issuing credible authorization certificates between a transmitting part and a receiving part of the instructions, so as to guarantee the security of the user data information.
Owner:CHINA GREATWALL TECH GRP CO LTD
Method, apparatus and electronic device for acquiring and feeding back user resources
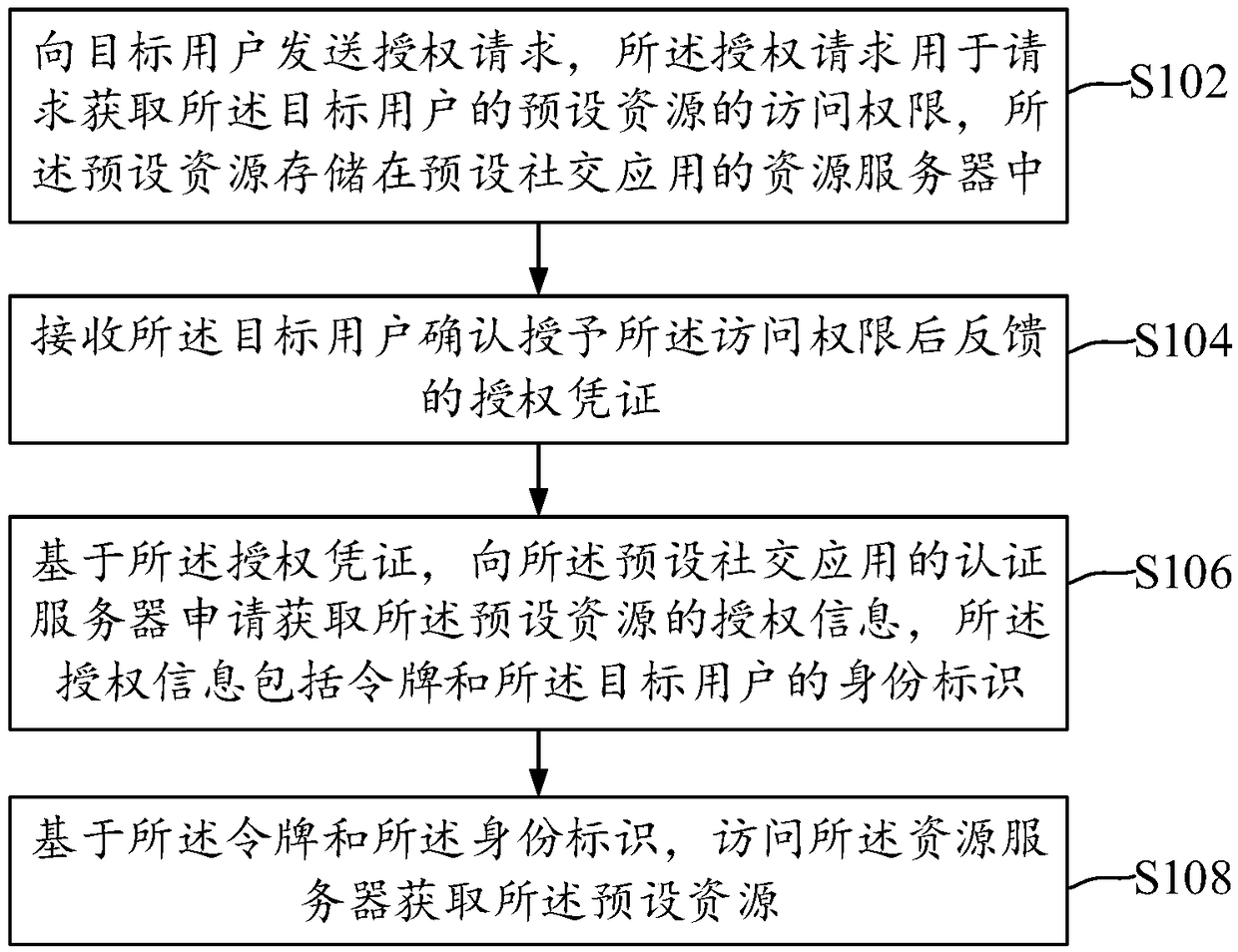
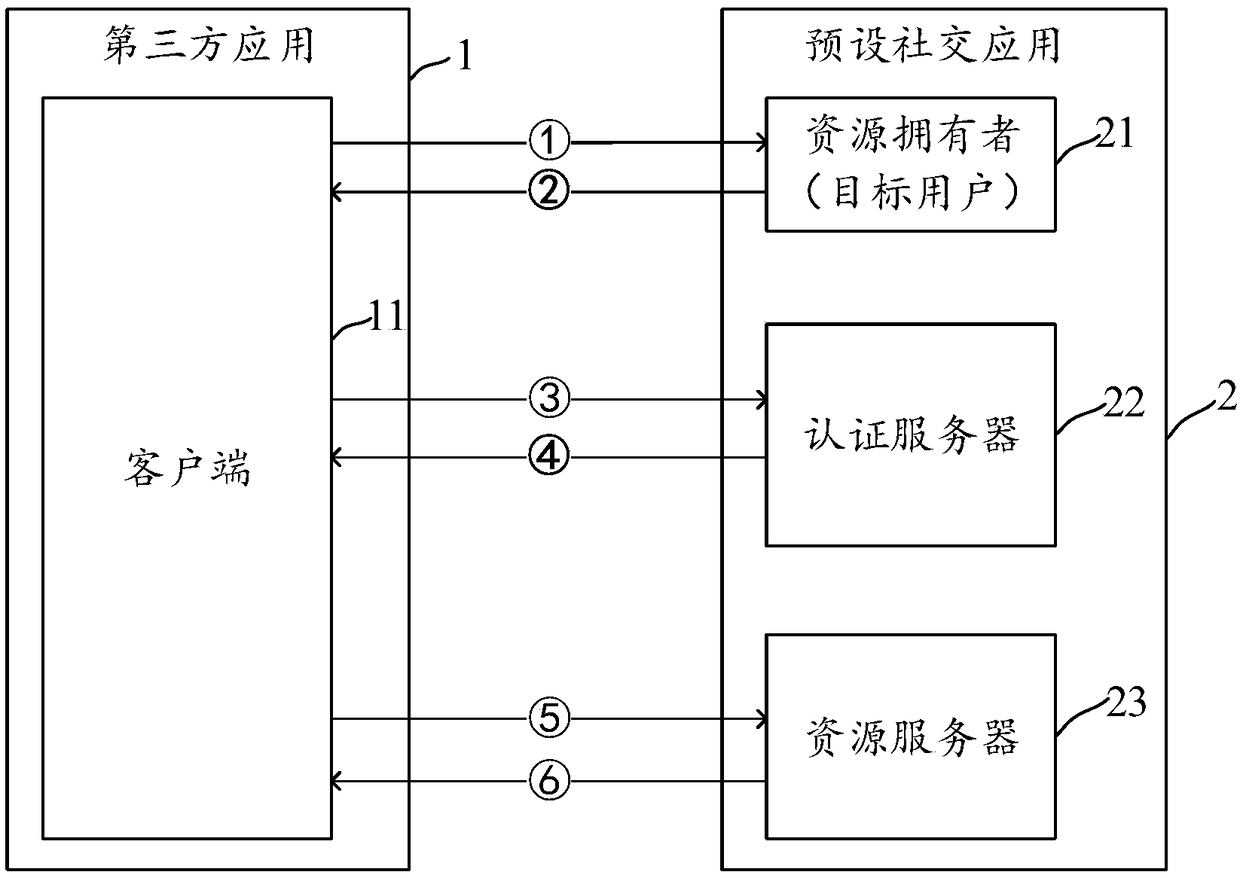
ActiveCN109033774AAvoid passing situationsProtect personal privacyDigital data authenticationAuthorization certificateResource based
The invention discloses a method, a device and an electronic device for obtaining and feeding back user resources. The method for obtaining user resources can send an authorization request for obtaining access rights of preset resources of the target user to a target user. The preset resources are stored in a resource server of a preset social application. Authorization credentials fed back by thetarget user are received after confirming the granting of the access right; it is applied for obtaining authorization information of the preset resources from an authentication server of the preset social application based on the authorization certificate, the authorization information comprises a token and an identity of the target user; the resource server is accessed to obtain the preset resource based on the token and the identity.
Owner:ADVANCED NEW TECH CO LTD
Method for realizing authorization management of vehicle networking device, device and systems
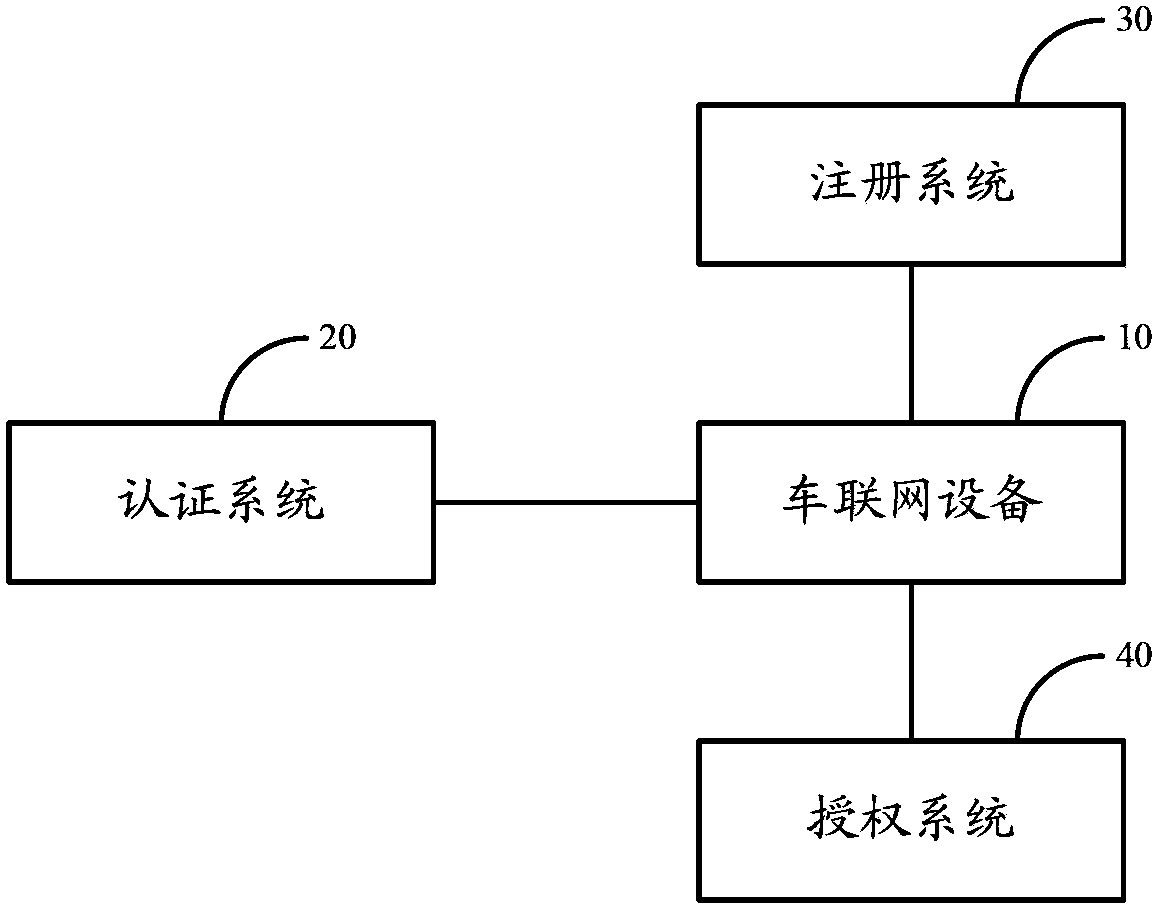
ActiveCN103986687AVerify validityImplement authorization managementTransmissionAuthorization certificateAuthentication system
The invention discloses a method for realizing authorization management of a vehicle networking device, a device and systems. The method includes the following steps: the vehicle networking device sends an authentication certificate application to an authentication system when determining that a device authentication certificate needs to be applied by the vehicle networking device, wherein the authentication certificate application carries identification information of the vehicle networking device; after the device authentication certificate issued by the authentication system for the vehicle networking device is received, according to the device authentication certificate, a registration certificate application is sent to a registration system, wherein the registration certificate application carries the device authentication certificate; and after a device registration certificate issued by the registration system for the vehicle networking device is received, according to the device registration certificate, an authorization certificate application is sent to an authorization system and a device authorization certificate issued by the authorization system for the vehicle networking device is received, wherein the authorization certificate application carries the device registration certificate.
Owner:DATANG GOHIGH INTELLIGENT & CONNECTED TECH (CHONGQING) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com