System and method for using a separate device to facilitate authentication
a technology of a separate device and an authentication method, applied in the field of system and method for using a separate device to facilitate authentication, can solve the problems of rogue employees, stolen id and passwords, and subject to detection by adversaries,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
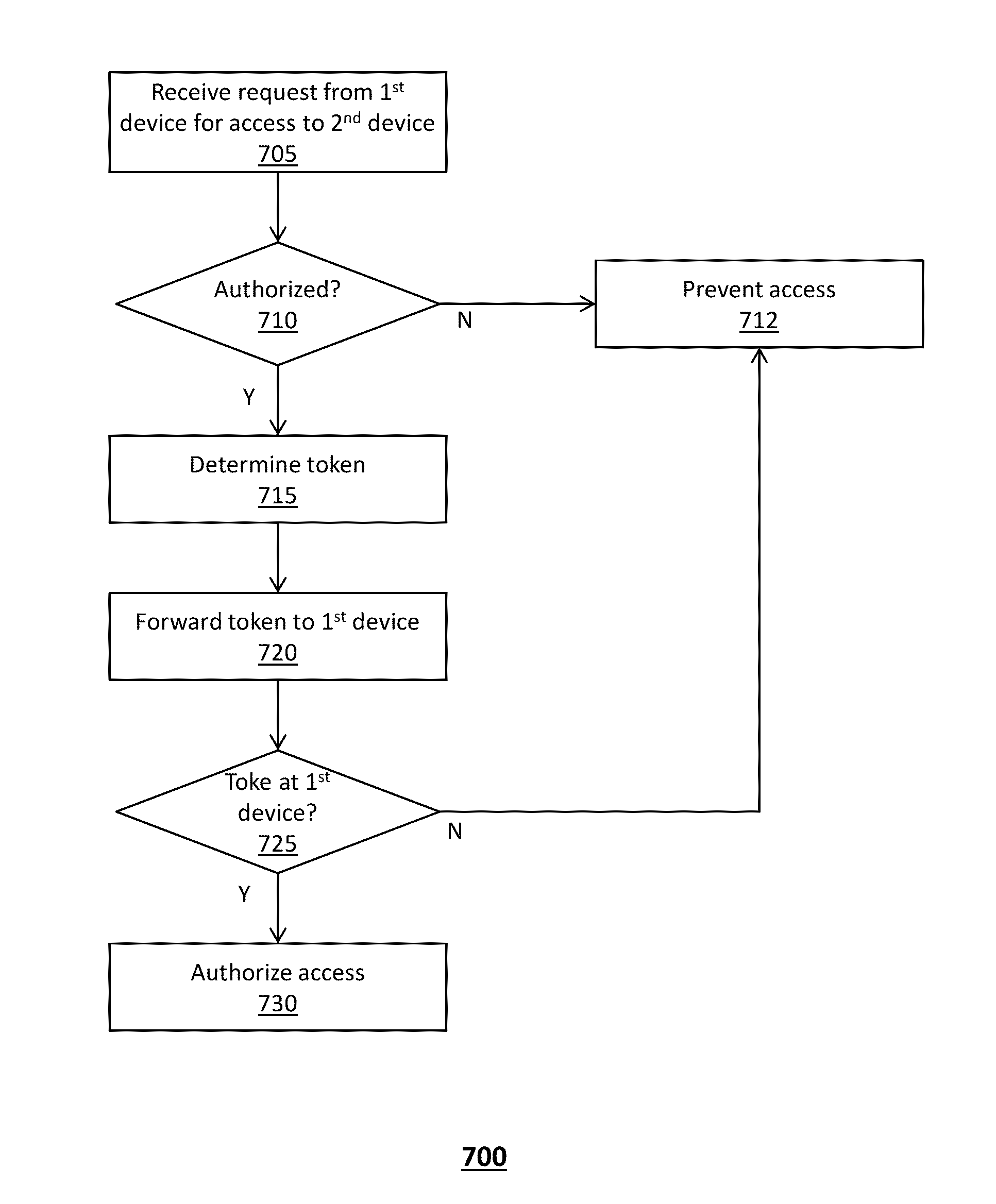
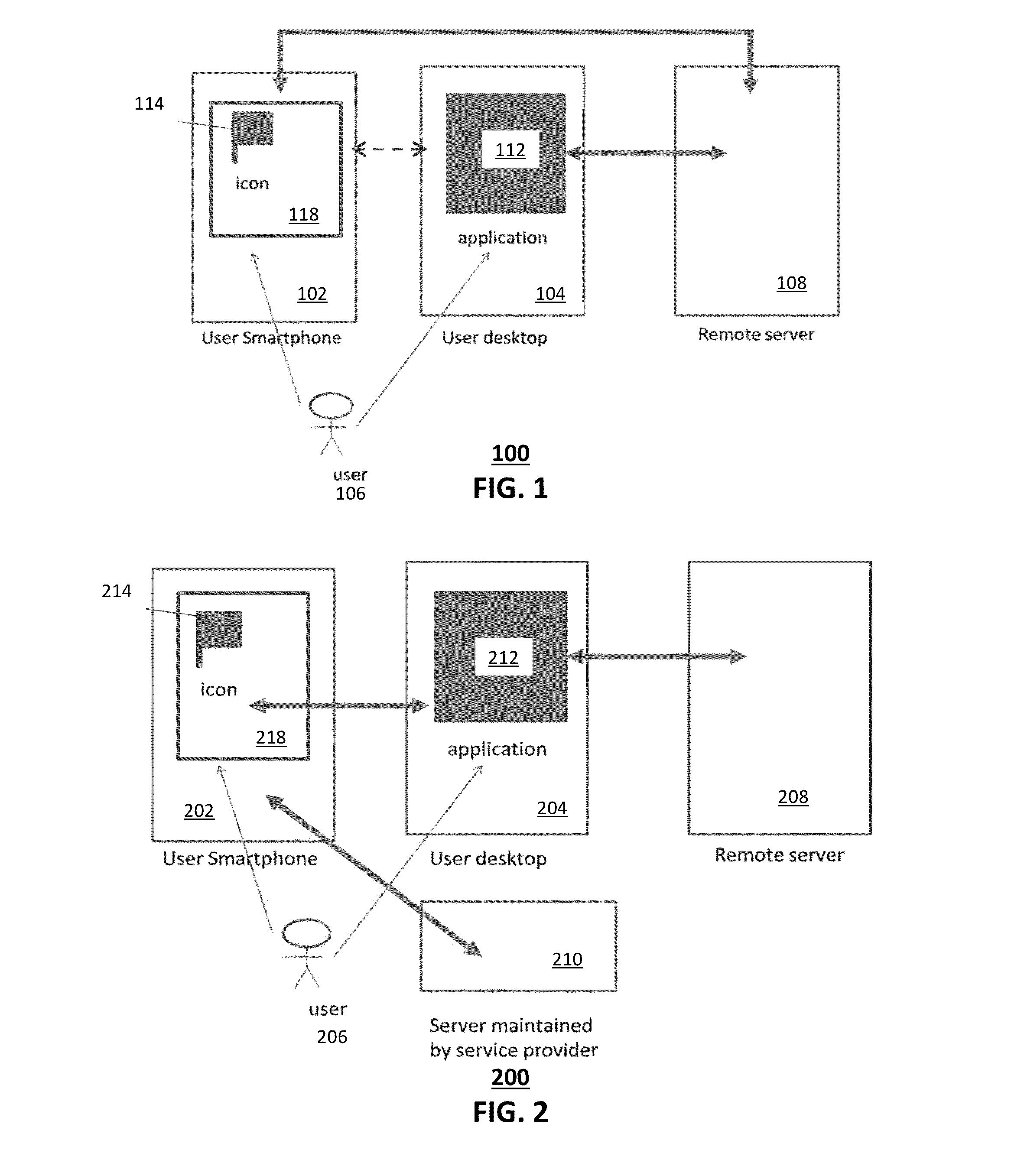
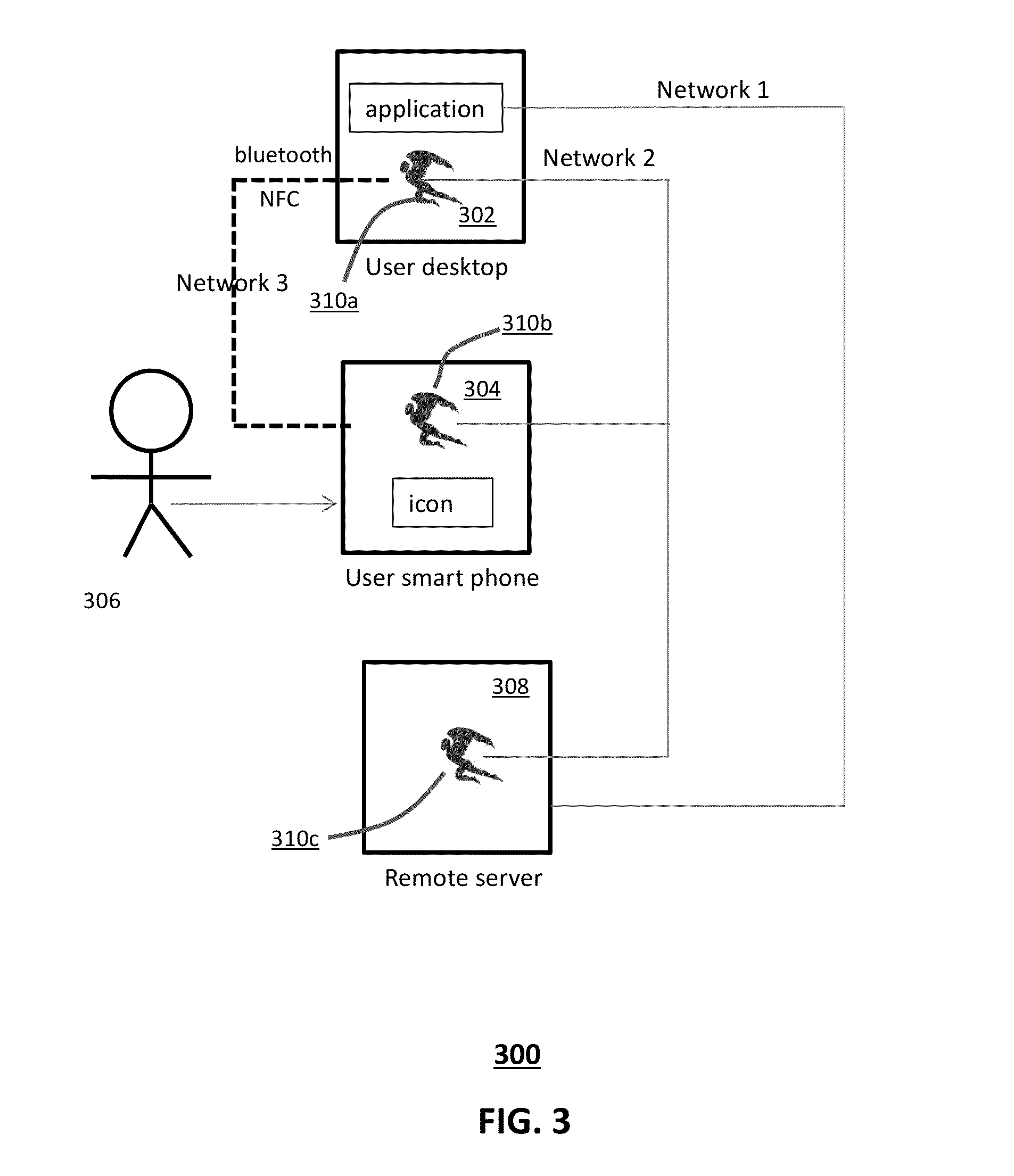
[0015]A server can use an encryption key to decrypt authentication information thereby facilitating communication with network-accessible applications that may be remotely located from the server. Servers can also use encryption keys to decrypt files containing sensitive data.
[0016]Encryption keys required by the server to obtain such authentication information and / or to access such files containing sensitive data can be stored in files on an encrypted file system. A chain of software agents, e.g., a chain software agent network, includes several software agents collaborating to conduct a common function. For example, a chain of software agents, such as the software agents (ANGELs) described in the references below, can provide an encryption key to decrypt an encrypted file system.
[0017]For example, when the server requires access to a particular encrypted file system, a chain of software agents is invoked to collectively provide the key allowing decryption of the file system so tha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com