Patents
Literature
168 results about "Login session" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
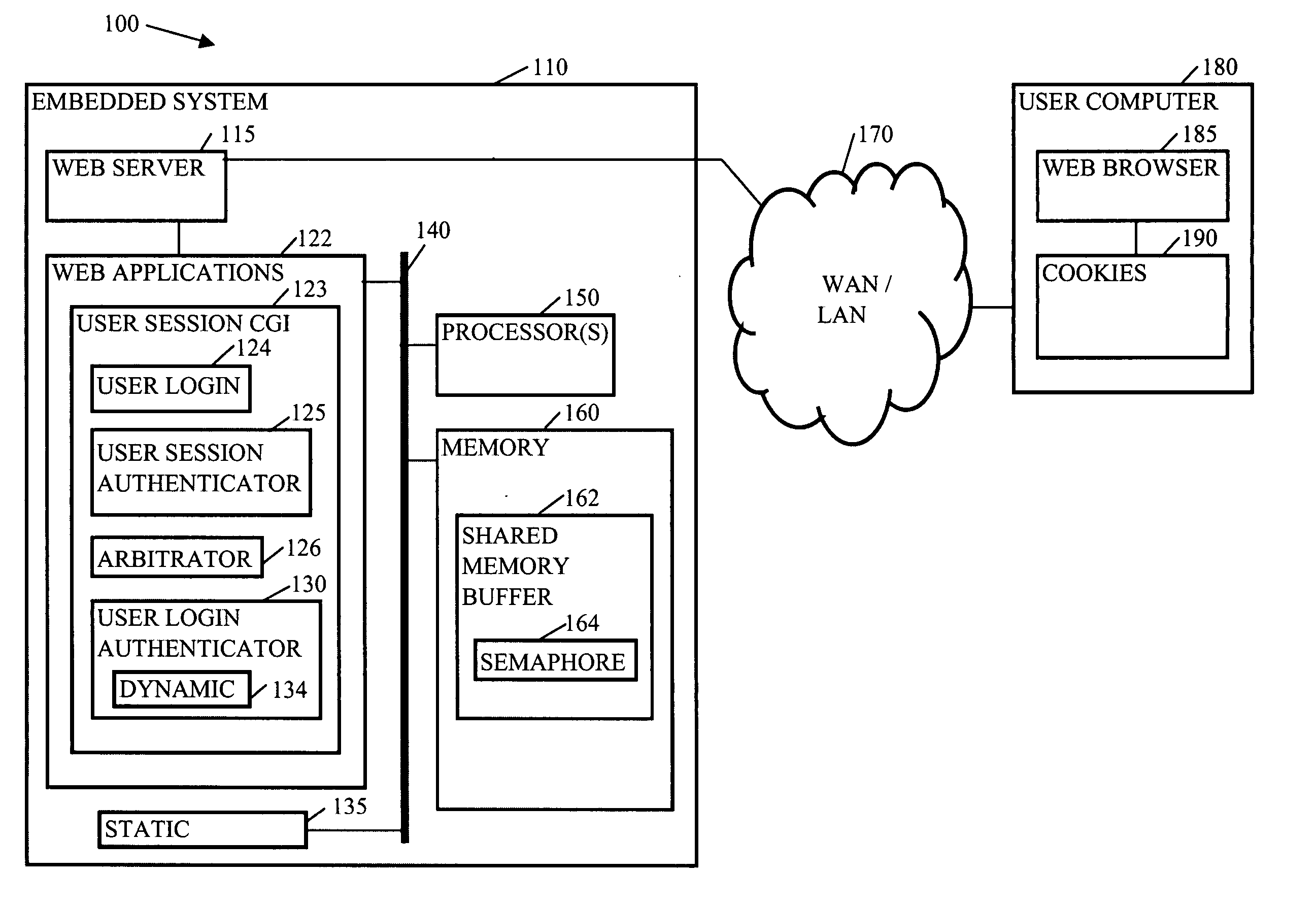
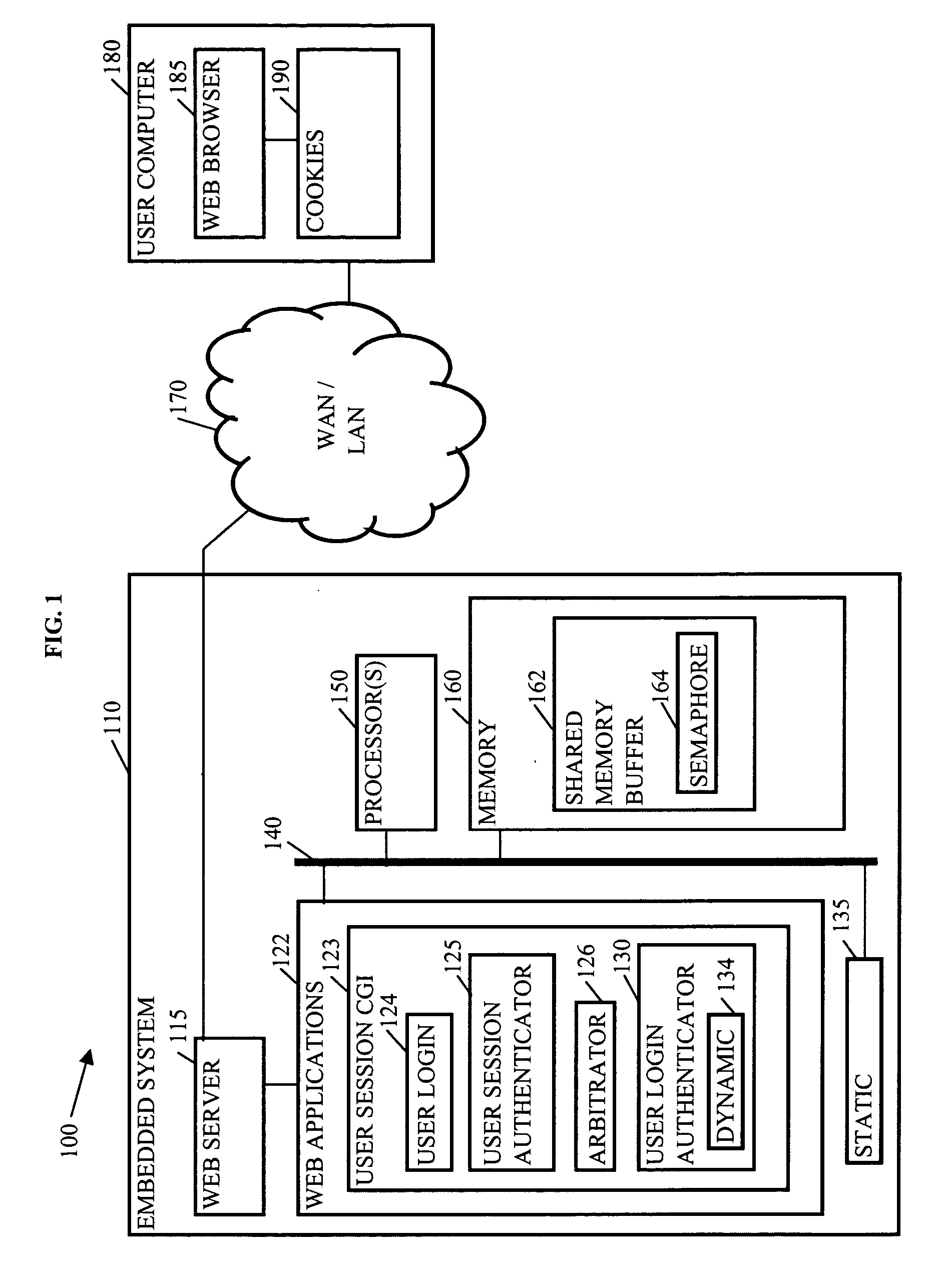
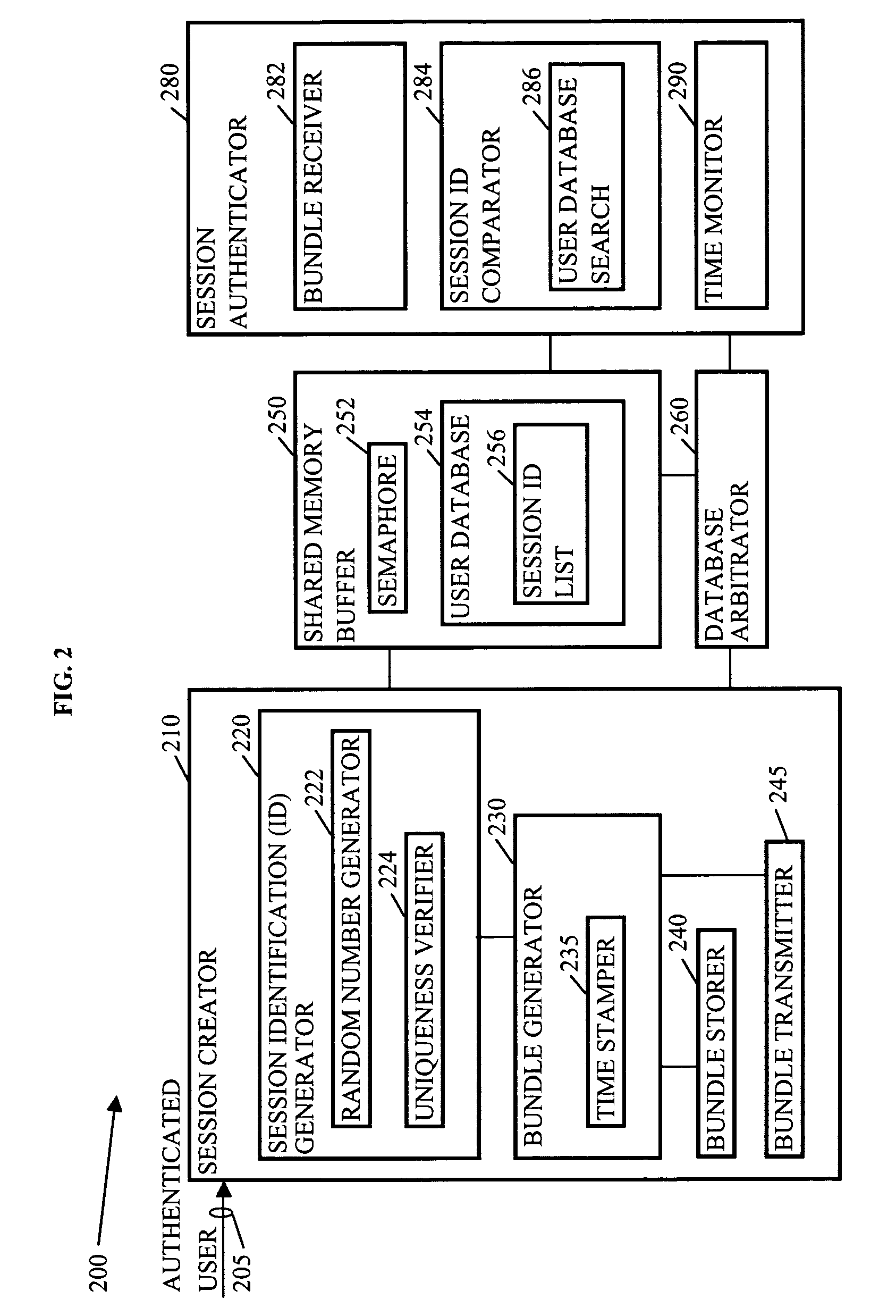
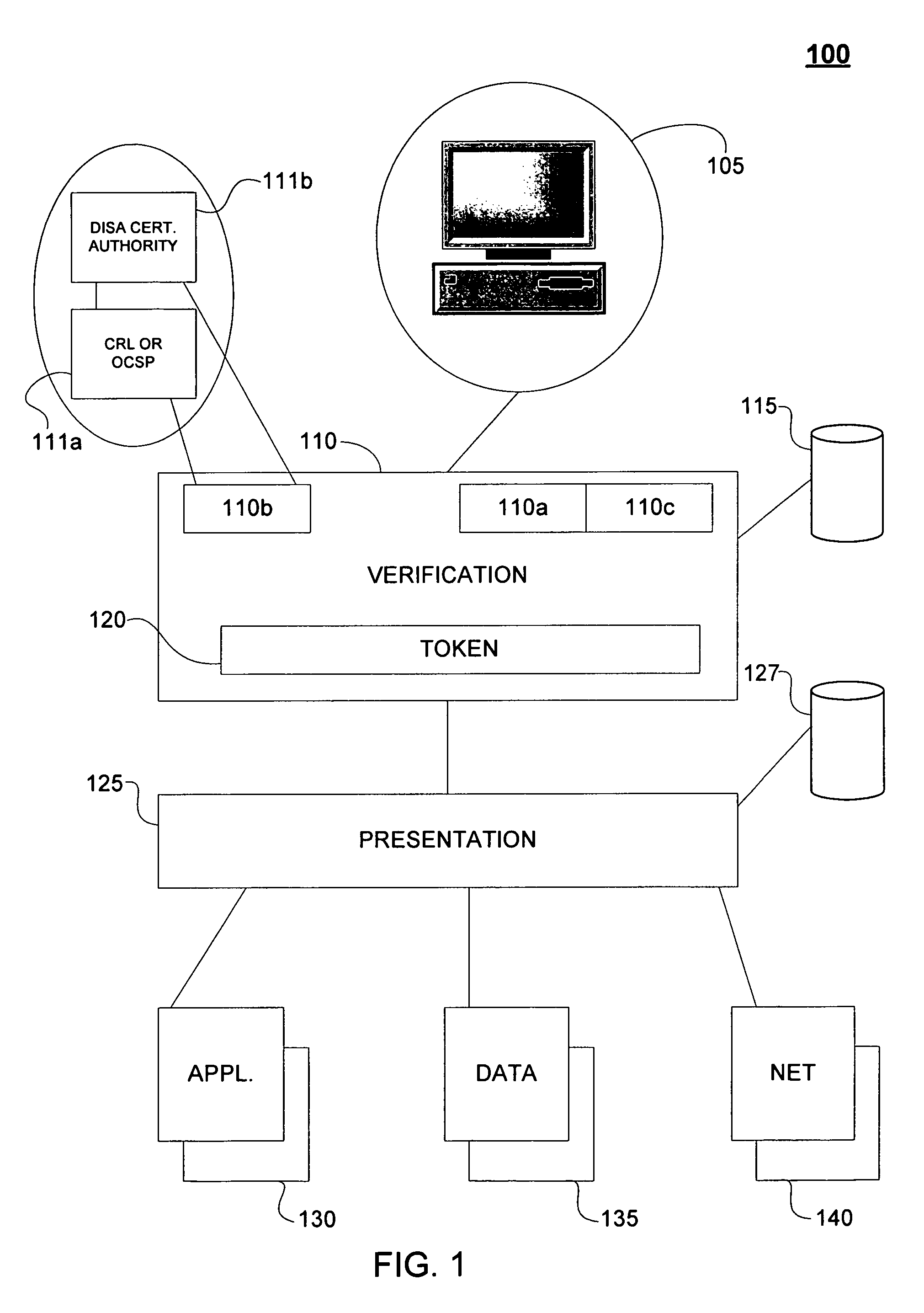
In computing, a login session is the period of activity between a user logging in and logging out of a (multi-user) system.
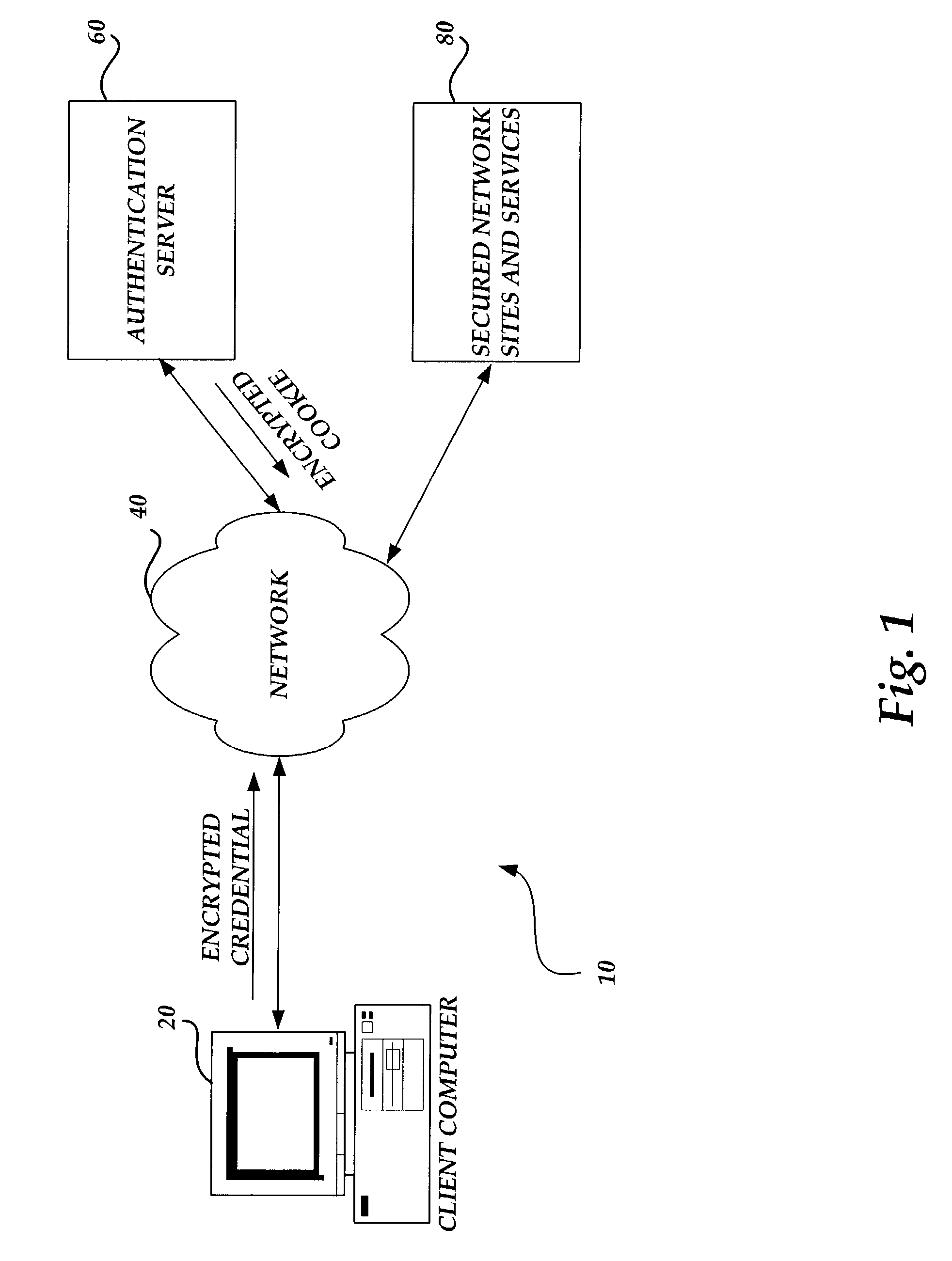
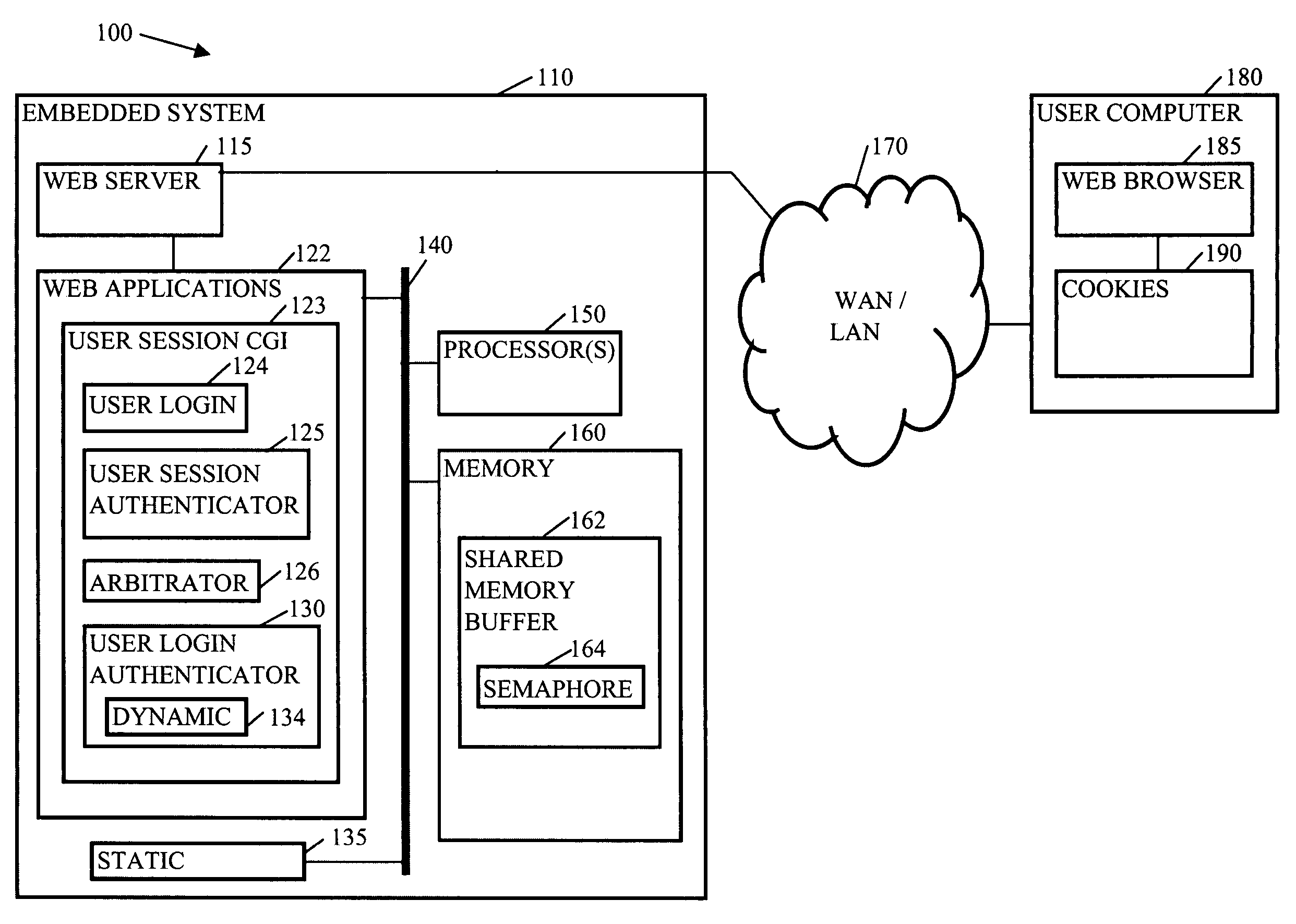
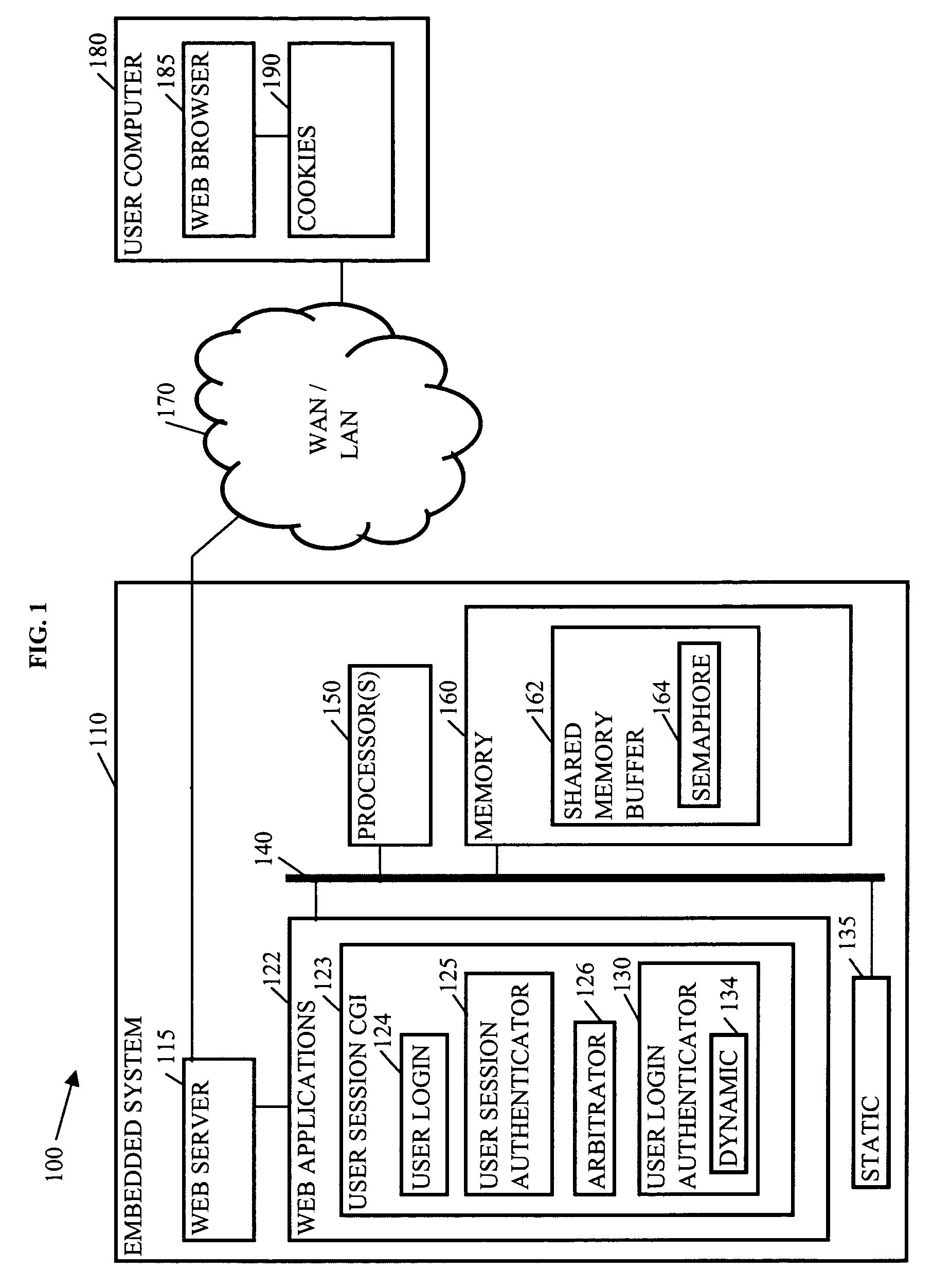
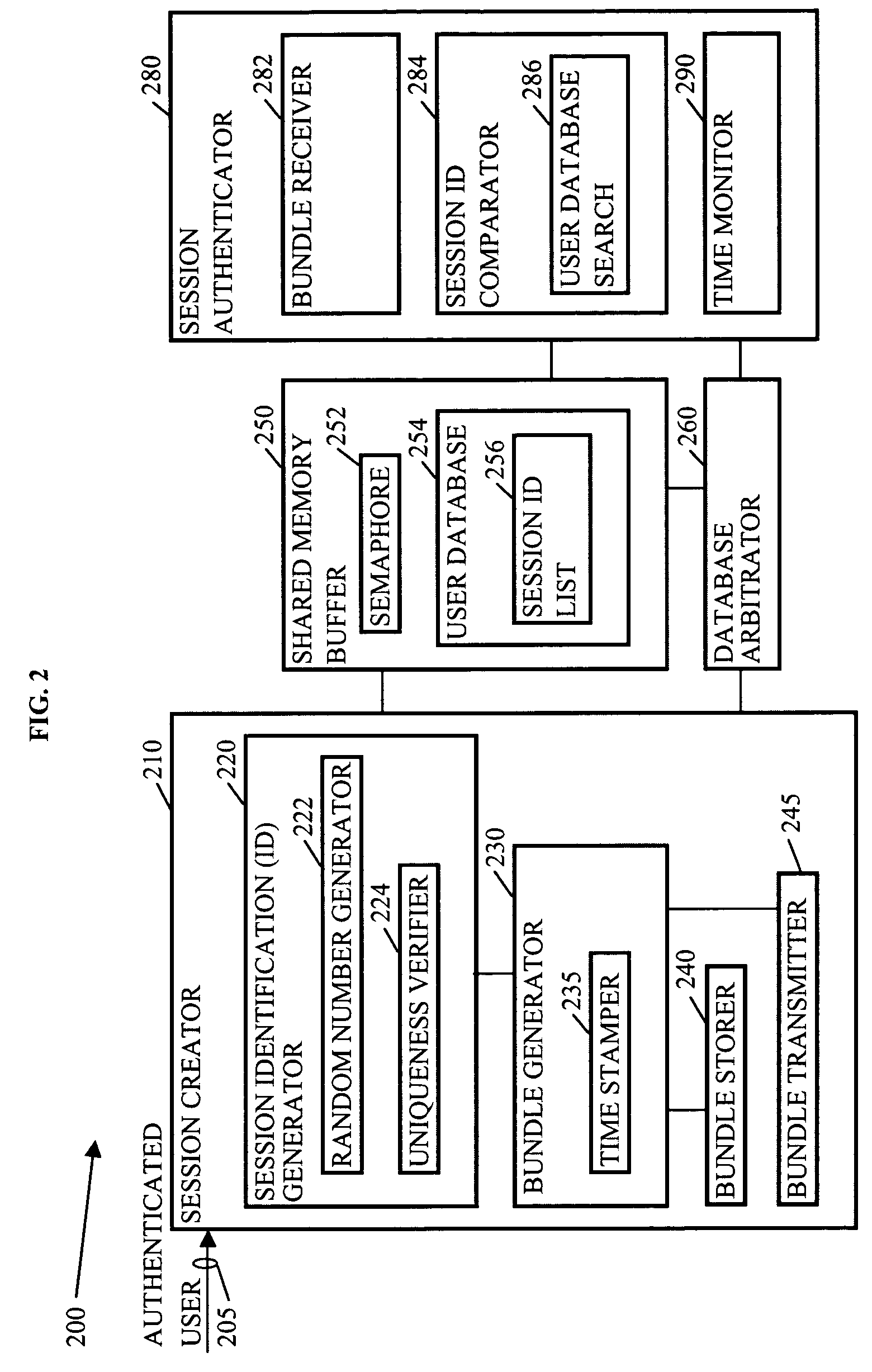
Methods, systems, and media to authenticate a user
InactiveUS20050015601A1Digital data processing detailsComputer security arrangementsWeb browserLogin session
Methods, systems, and media to authenticate a user for interaction with applications on a server are disclosed. Embodiments include hardware in and / or software on a server adapted to generate a unique, session identification like a random number to identify a user's login session. The identification is stored in memory that will not be de-allocated upon termination of applications on the server and is transmitted via, e.g., a cookie to the user's browser, or the like. Subsequent user accesses can be verified by comparing the session identification from the web browser with the corresponding entry in the memory. Once the user's identification is verified, the user is authorized to access to applications associated with the user's login session, providing independence from the architecture of the applications executed by the server. Further embodiments include additional session information with the identification in the memory. Some embodiments monitor login sessions for expiration.
Owner:IBM CORP
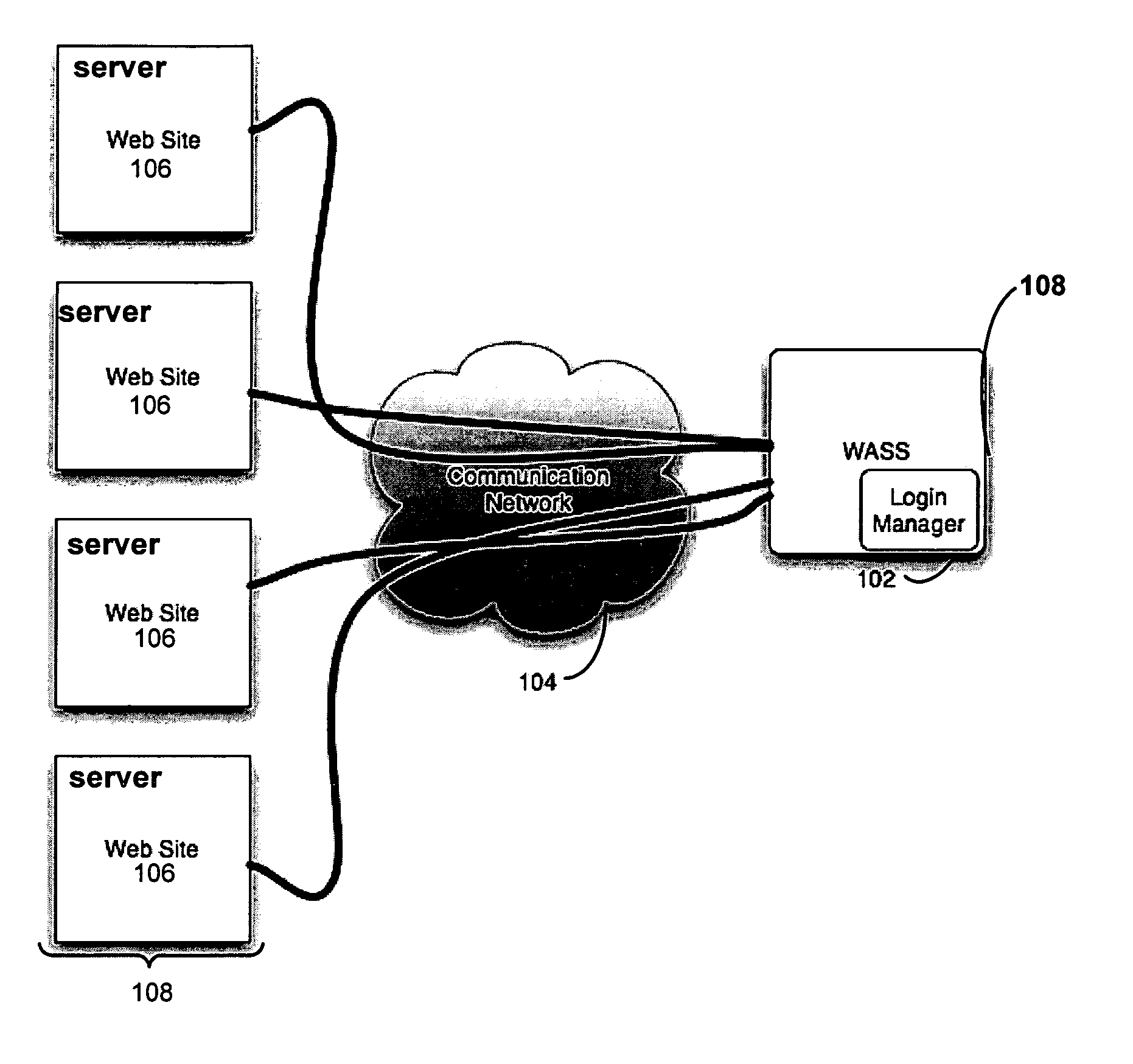
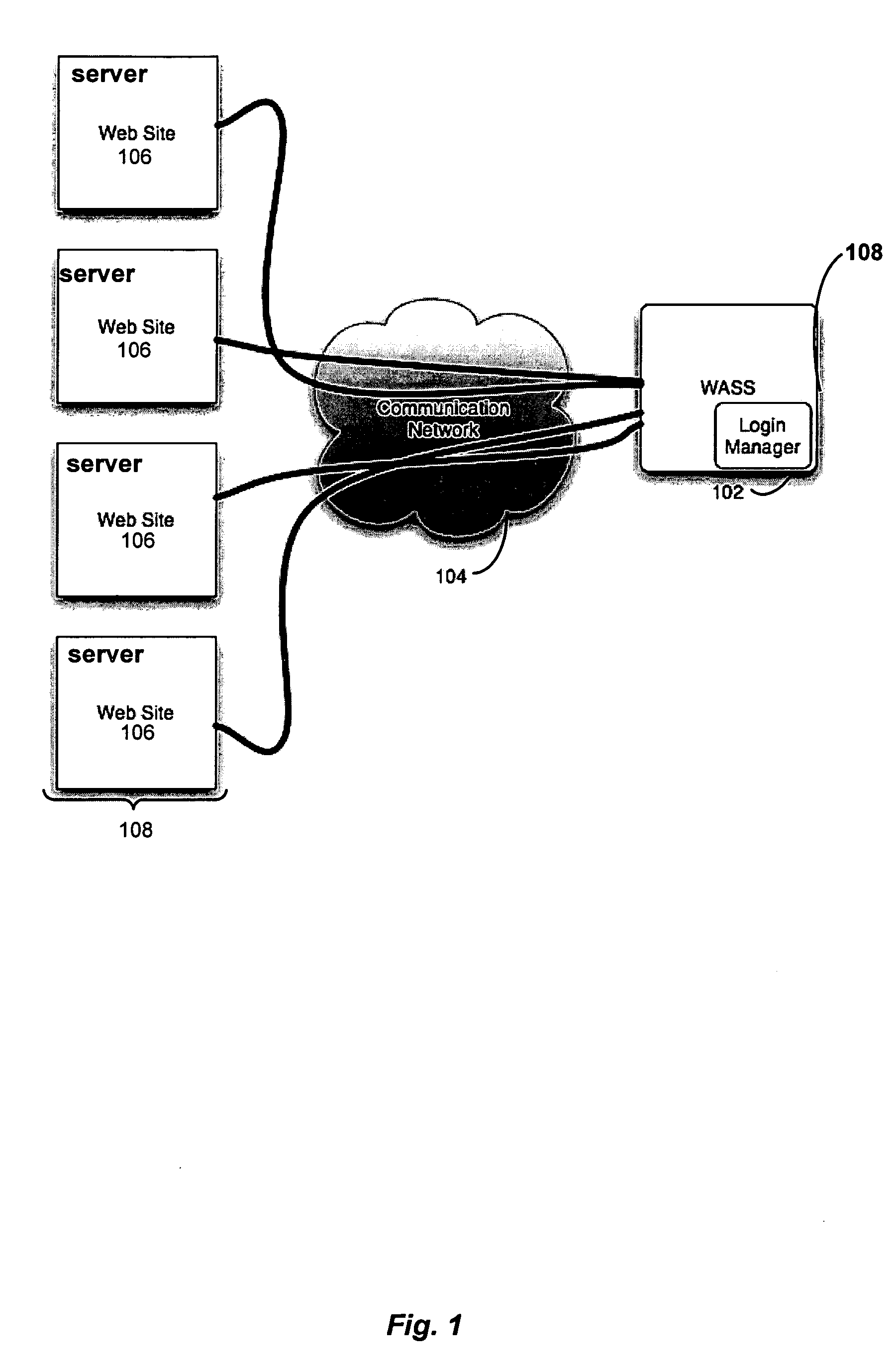
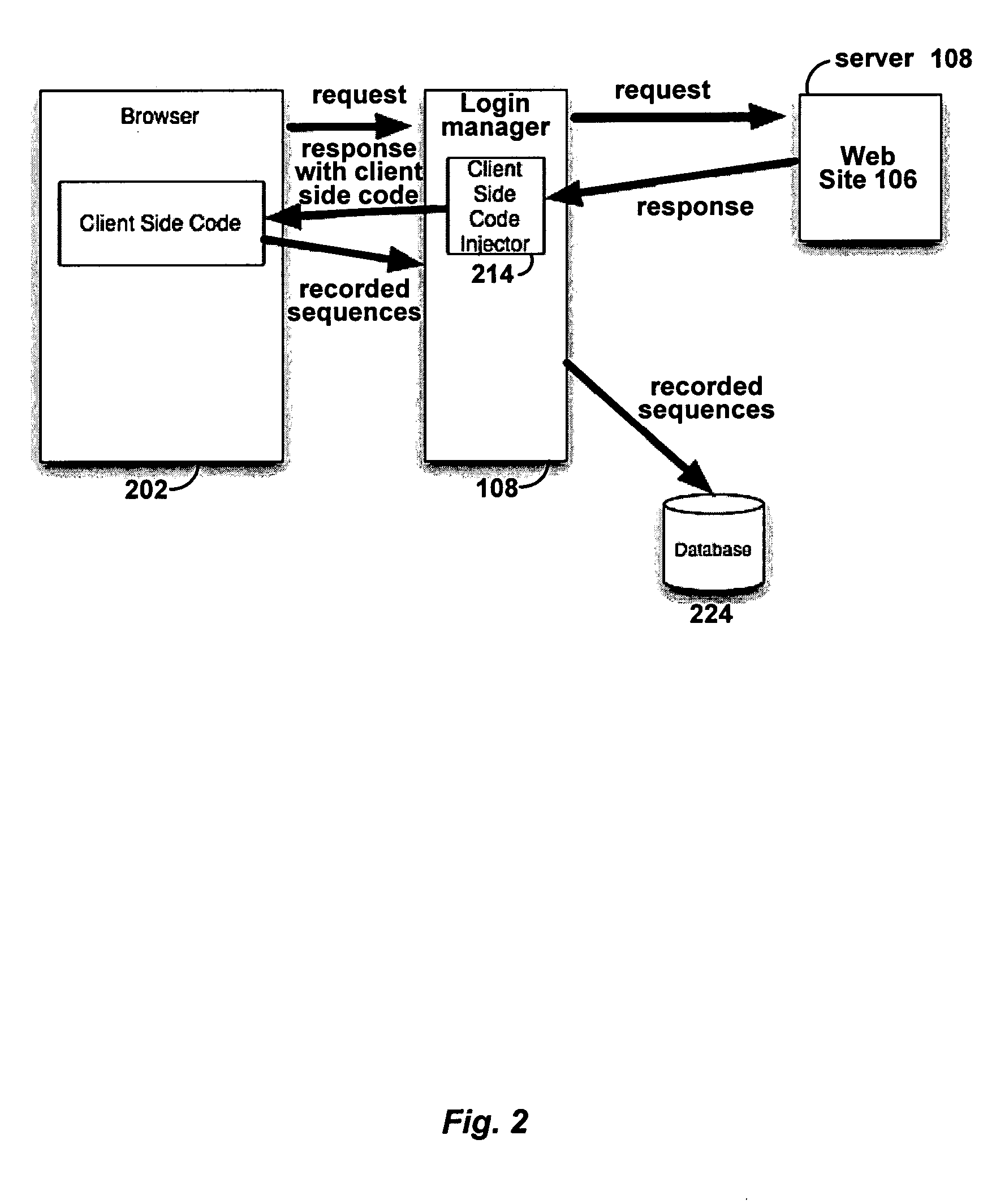
Automated login session extender for use in security analysis systems
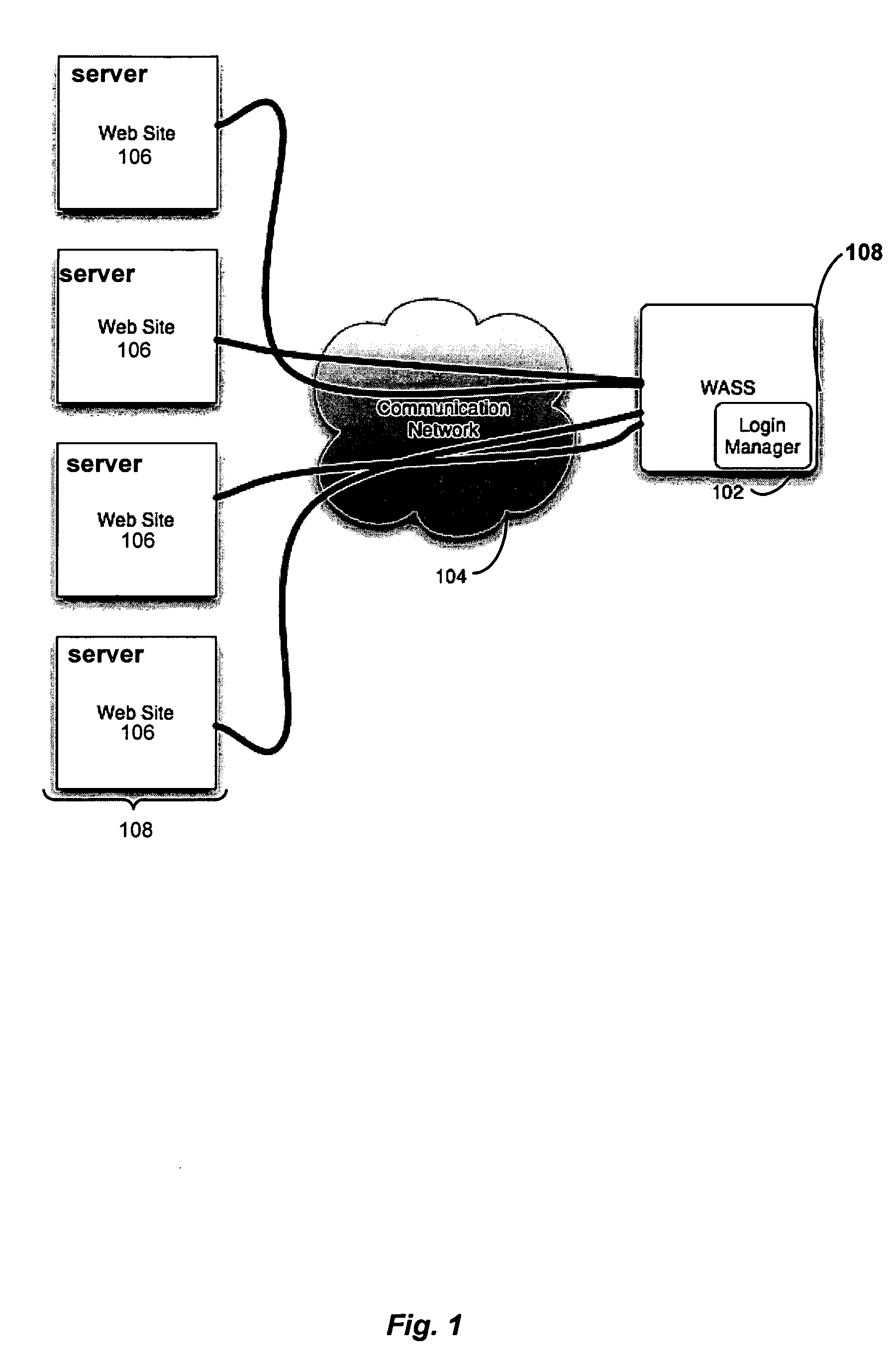
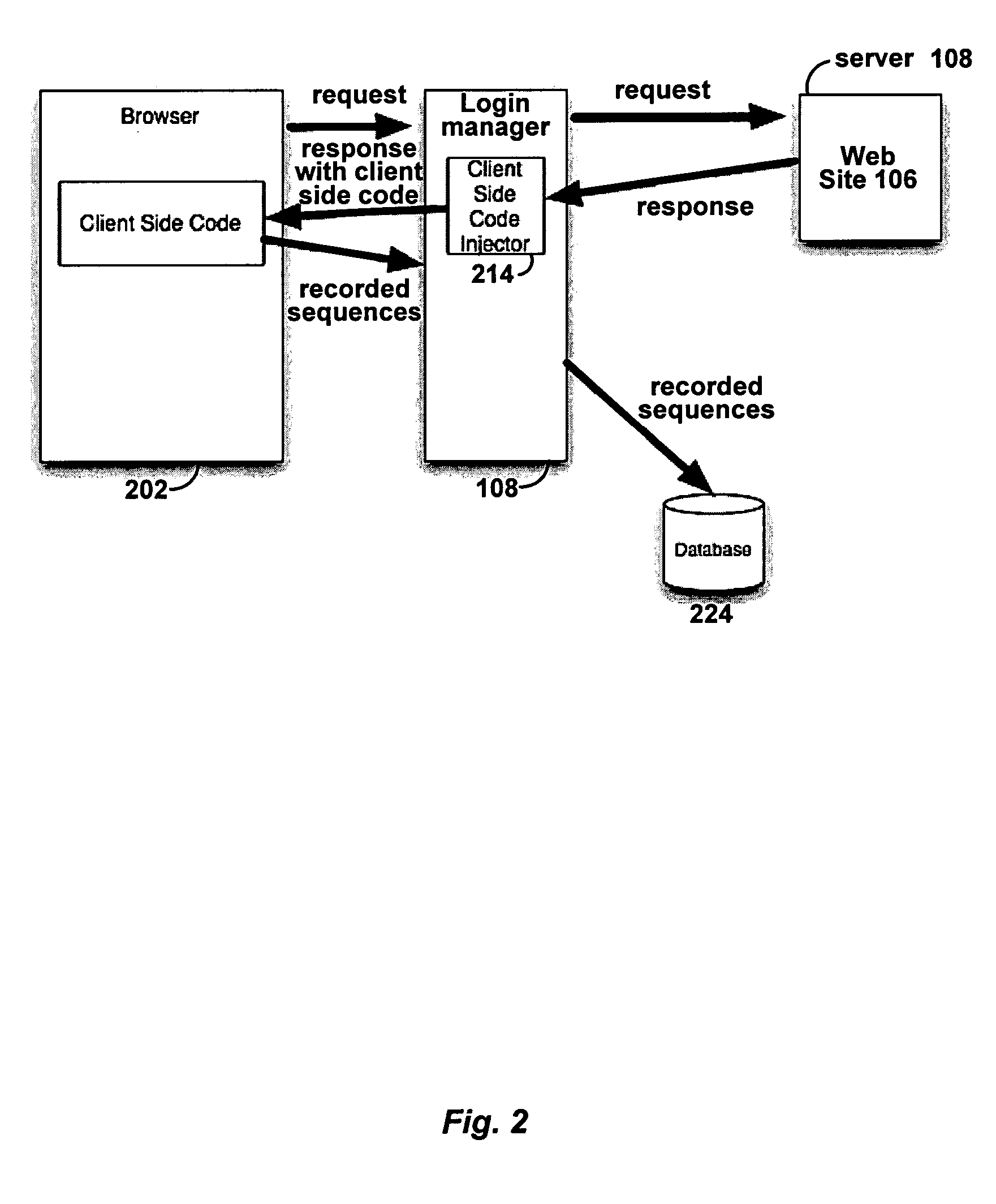
ActiveUS20060048214A1Digital data processing detailsUser identity/authority verificationWeb siteProgram security
A web application security scanner (WASS) includes a login manager configured to perform an automated login to a web site. The automated login may be performed when the login manager detects that a login session has ended. The login manager is configured to determine credentials for the web site to allow the WASS to access the web site. The WASS may then use the credentials to continue scanning the web site. Thus, previously unscannable web pages may be accessed in the web site because of the automated login process.
Owner:SYNOPSYS INC
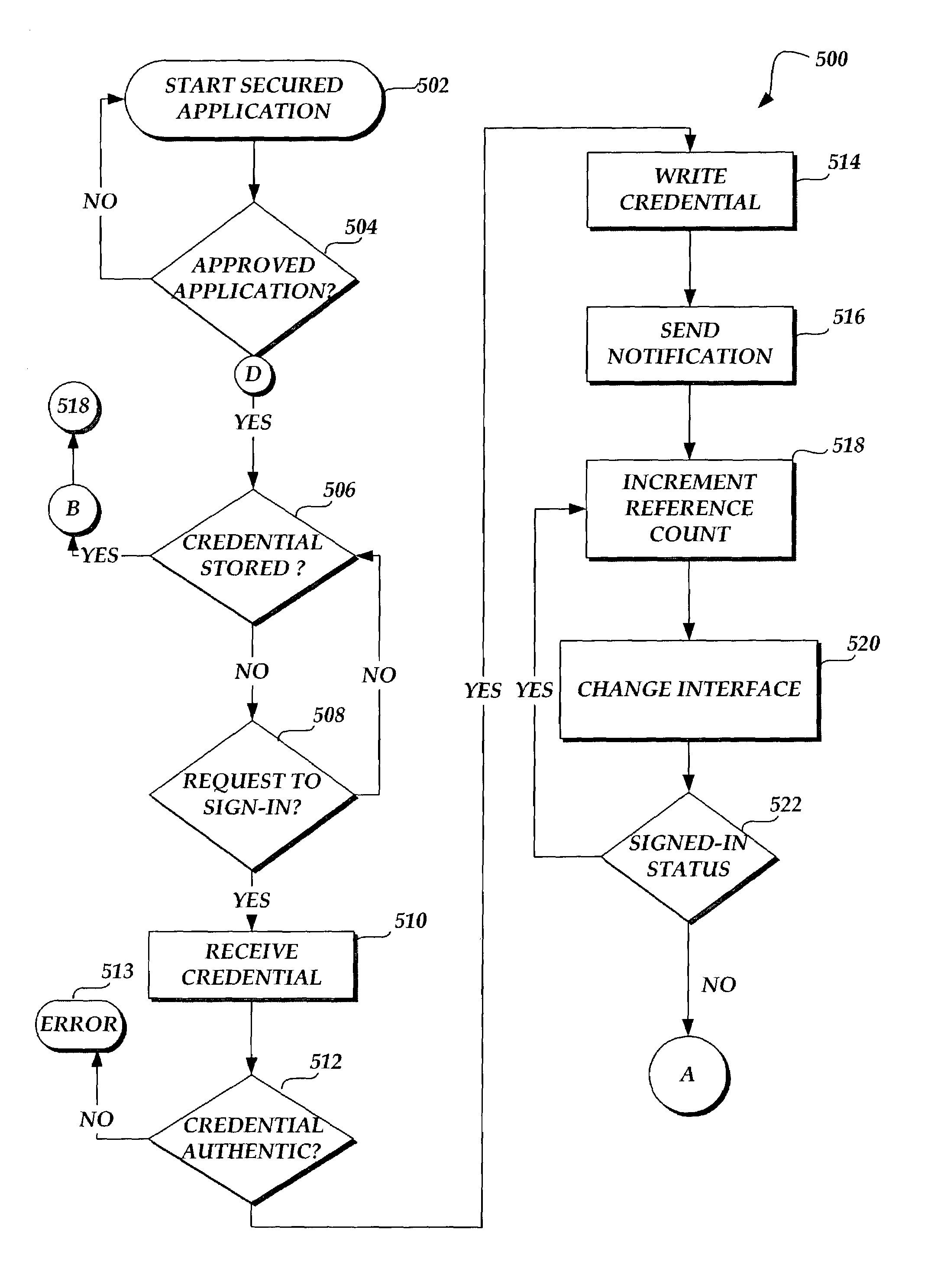
Sharing a sign-in among software applications having secured features
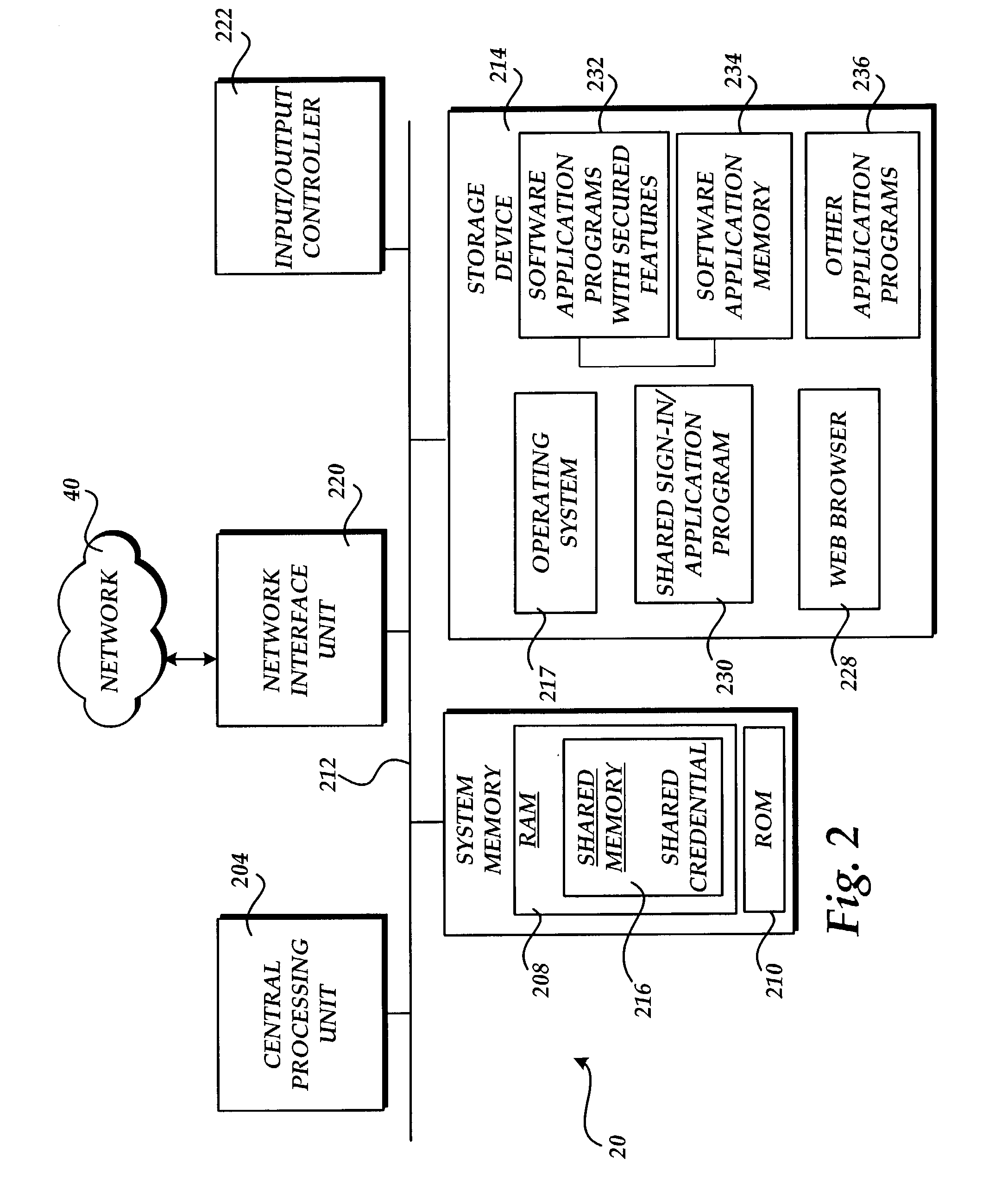
ActiveUS7254831B2Improve network efficiencyReduce network trafficDigital data processing detailsMultiple digital computer combinationsPasswordApplication software
In the present invention, when one open or running software application having secured features enters an access signed-in or logged-in state, other open or running software applications having secured features enter a ready signed-in state automatically, without prompting user intervention. The same operation that signed-in or logged-in the initial software application will transition other software applications that are presently open, active to run, or that start in run mode to a ready signed-in state. The access signed-in state fully authenticates the user's identity and grants access to secured features. The ready signed-in state places the software application in a state of readiness to authenticate and access secured features without prompting user intervention. One feature of the present invention is the sharing of a sign-in or login credential (e.g. username and password) and the processing of the shared credential in order to provide a universal, shared sign-in session between open software applications having secured features. This feature helps provide a user experience that in effect, has only one sign-in or login session for software applications with secured features.
Owner:MICROSOFT TECH LICENSING LLC
Single sign on with multiple authentication factors
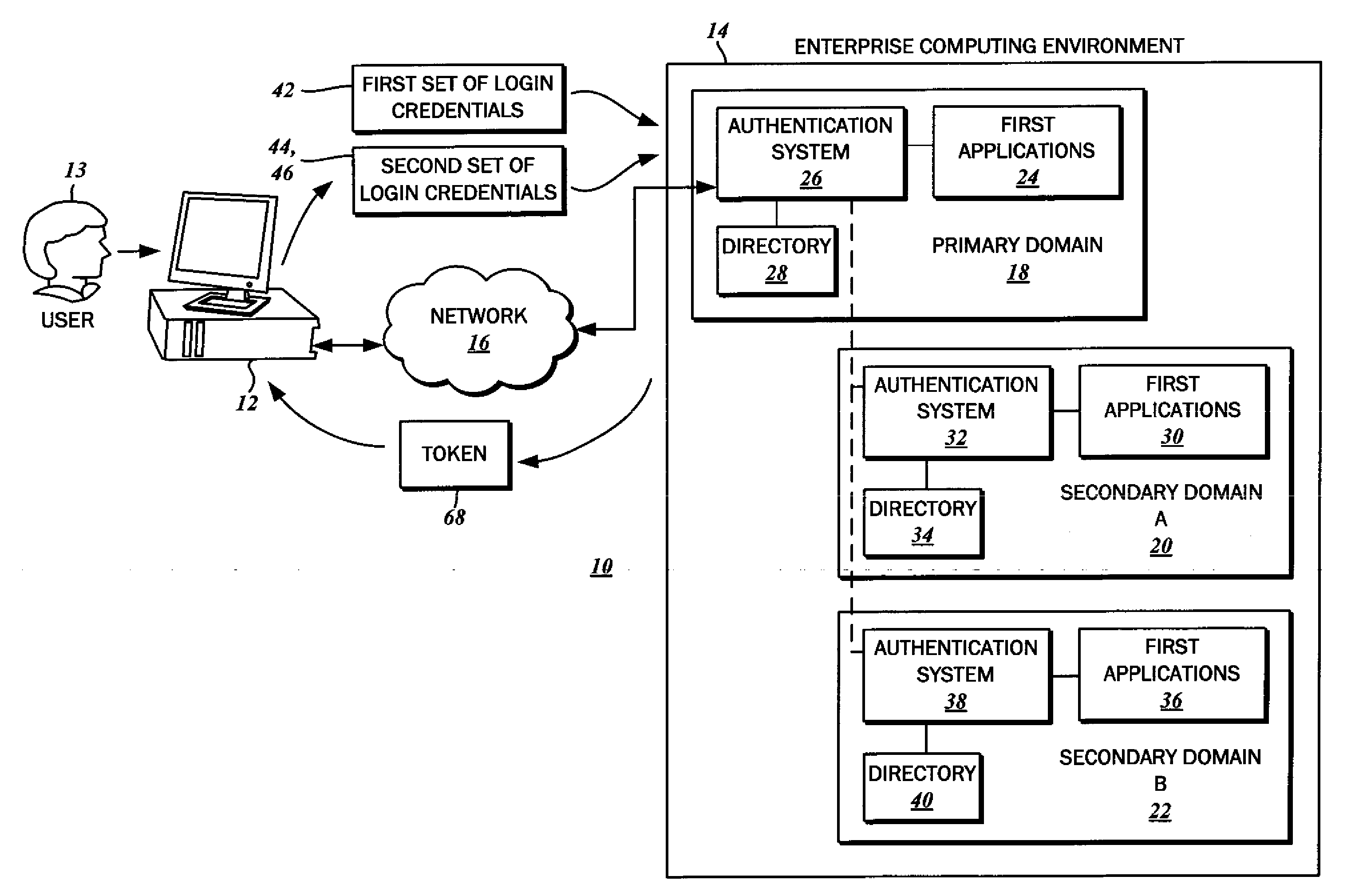
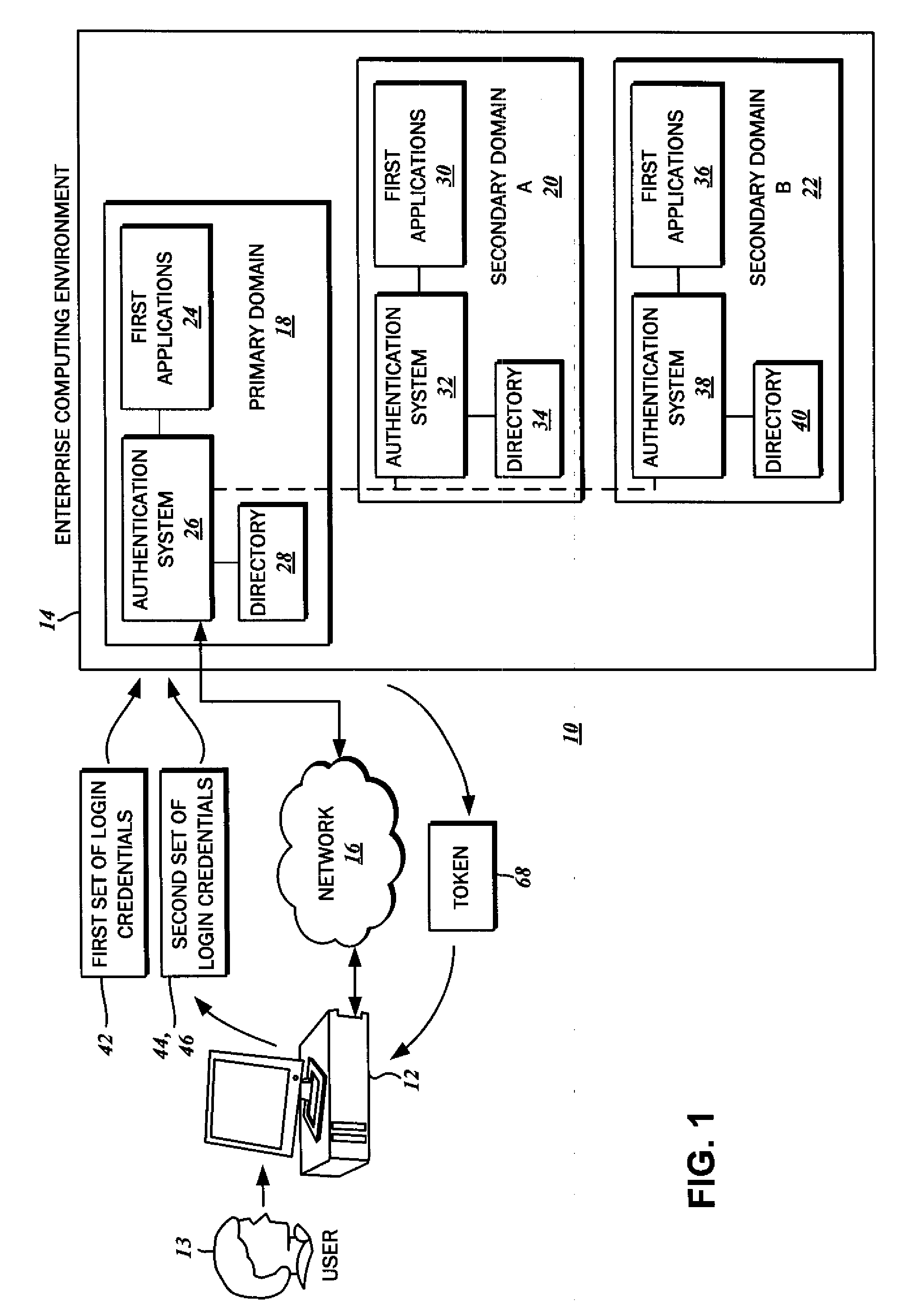
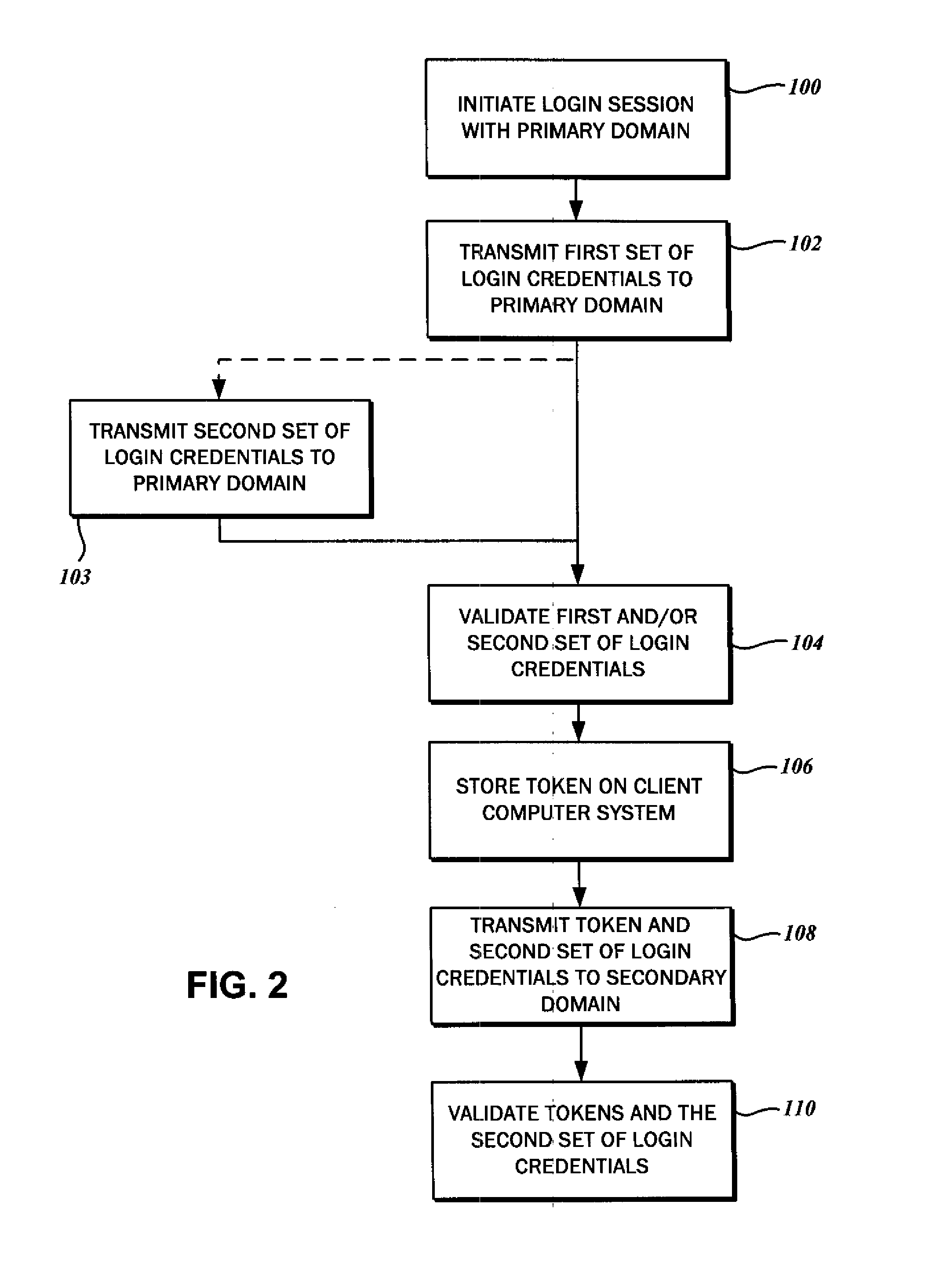
ActiveUS20110119747A1Reduce decreaseMinimize the numberDigital data processing detailsUser identity/authority verificationClient-sideAuthentication system
The authentication of a client to multiple server resources with a single sign-on procedure using multiple factors is disclosed. One contemplated embodiment is a method in which a login session is initiated with the authentication system of a primary one of the multiple server resources. A first set of login credentials is transmitted thereto, and validated. A token is stored on the client indicating that the initial authentication was successful, which is then used to transition to a secondary one of the multiple resources. A second set of login credentials is also transmitted, and access to the secondary one of the multiple resources is granted on the basis of a validated token and second set of login credentials.
Owner:SECUREAUTH CORP
System and method for permission-based access using a shared account
ActiveUS20060161783A1Quick switchFast authenticationRandom number generatorsUser identity/authority verificationUser verificationOperational system
Owner:CITRIX SYST INC
Method and system for multiple instant messaging login sessions
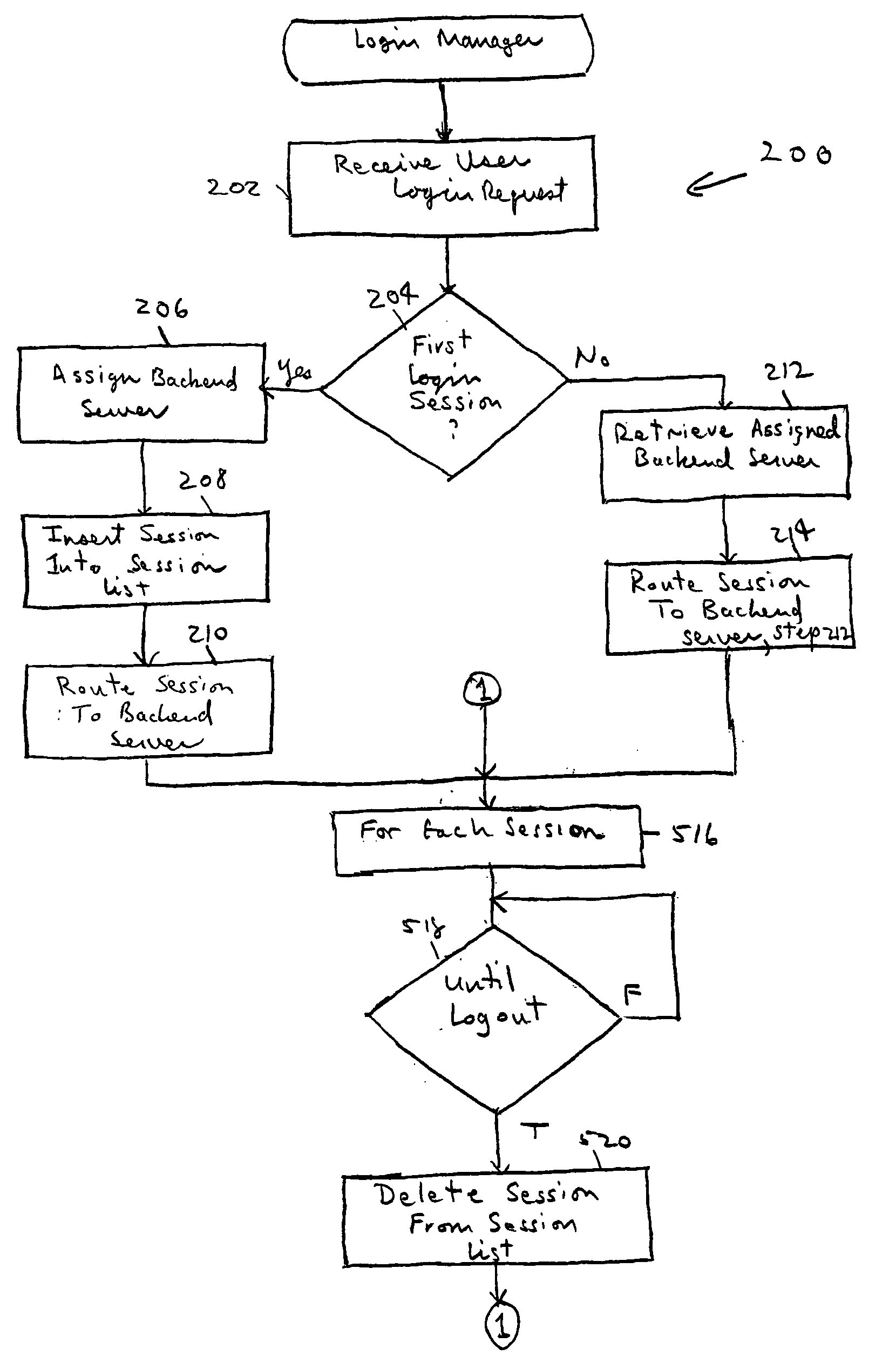
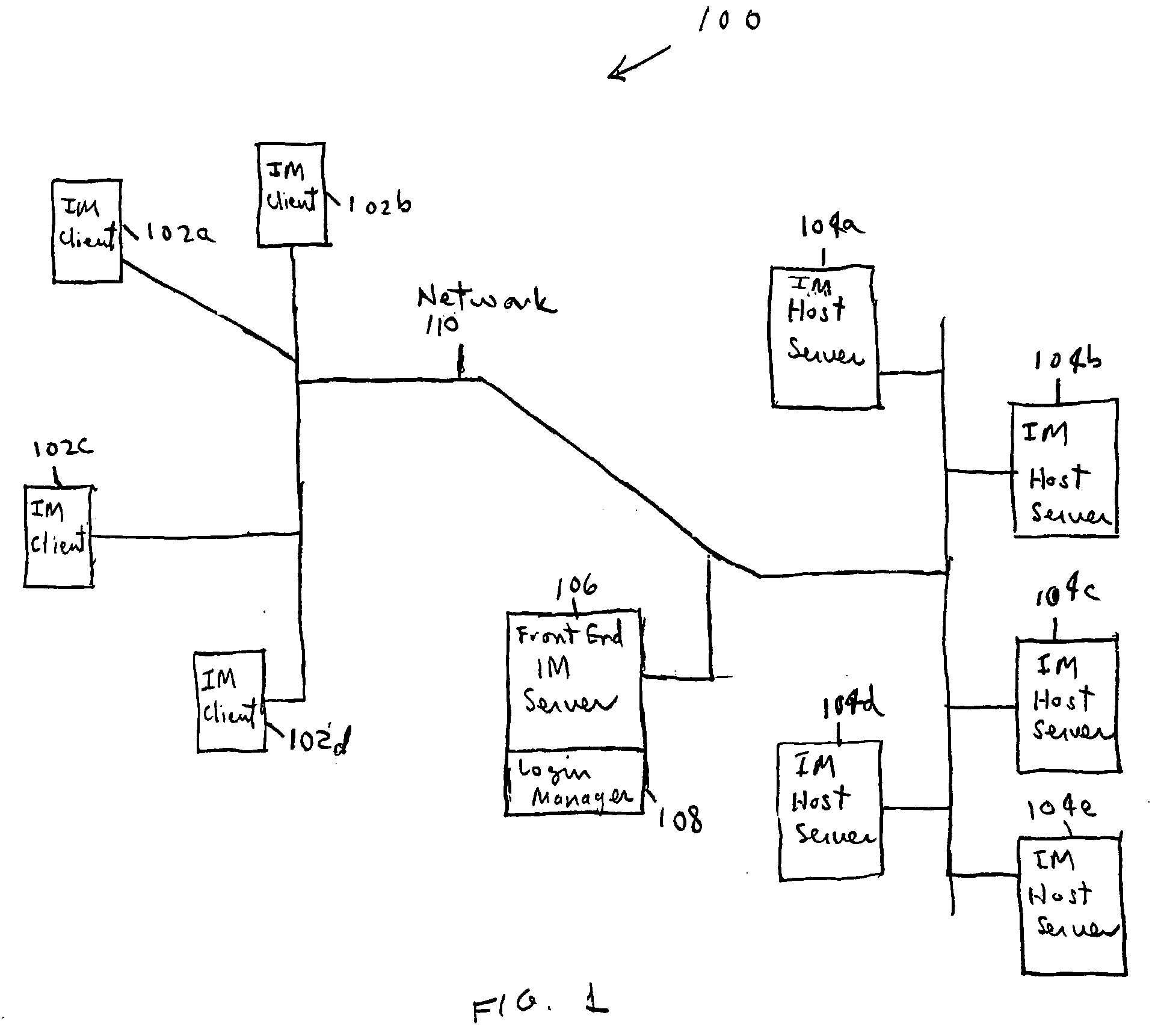
ActiveUS20050102365A1Special service provision for substationMultiple digital computer combinationsBack end serverLogin session
A mechanism for multiple instant messaging (IM) sessions associated with a single user name is provided. A frontend server receives user login requests and routes the instant messaging system to a back-end server. Each login associated with a particular user name is routed to the same backend server (or IM host). Messages targeted to a recipient having a plurality of active IM sessions are broadcast to all the active sessions. Messages targeted to recipients having a single IM session are unicast.
Owner:SINOEAST CONCEPT
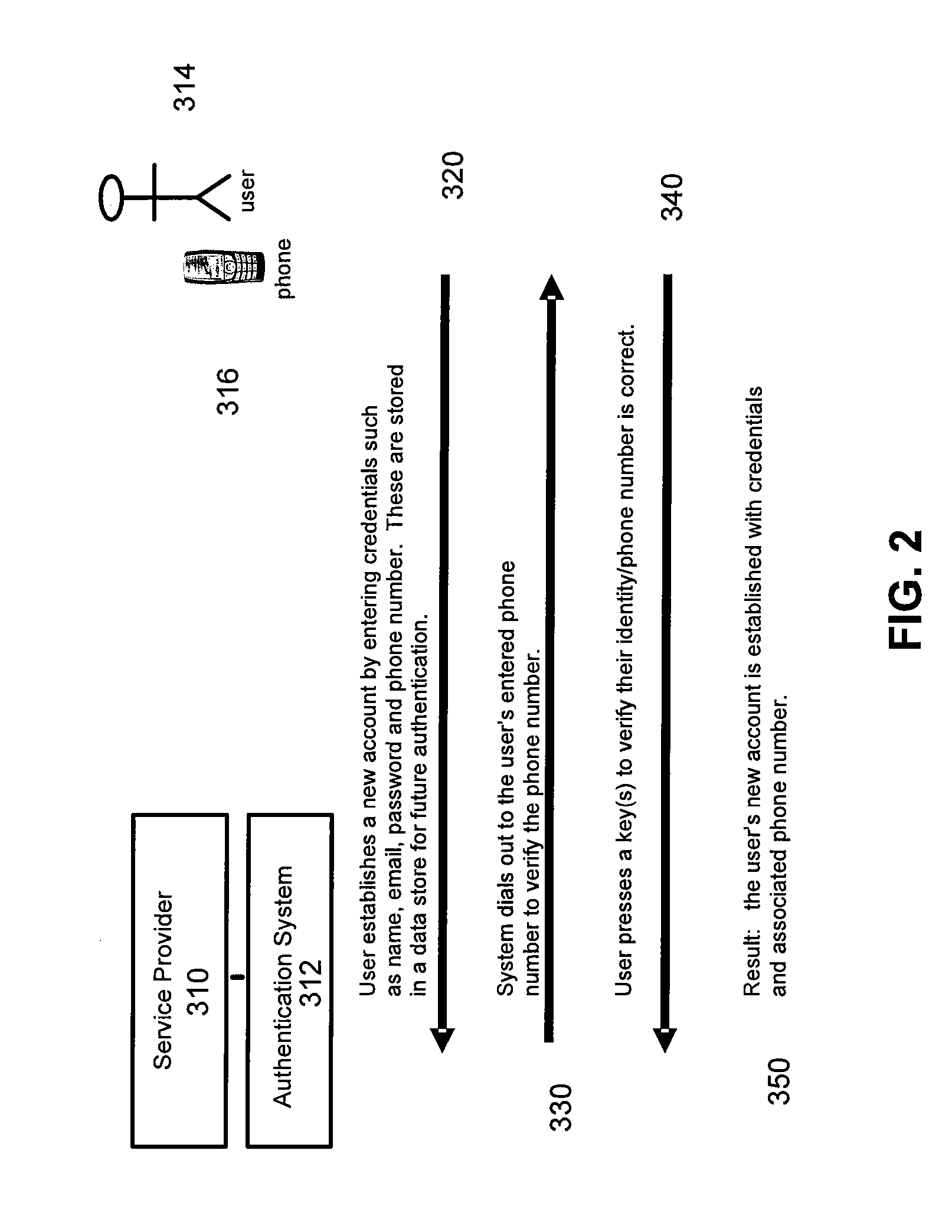
WEB AUTHORIZATION BY AUTOMATED INTERACTIVE PHONE OR VoIP SESSION
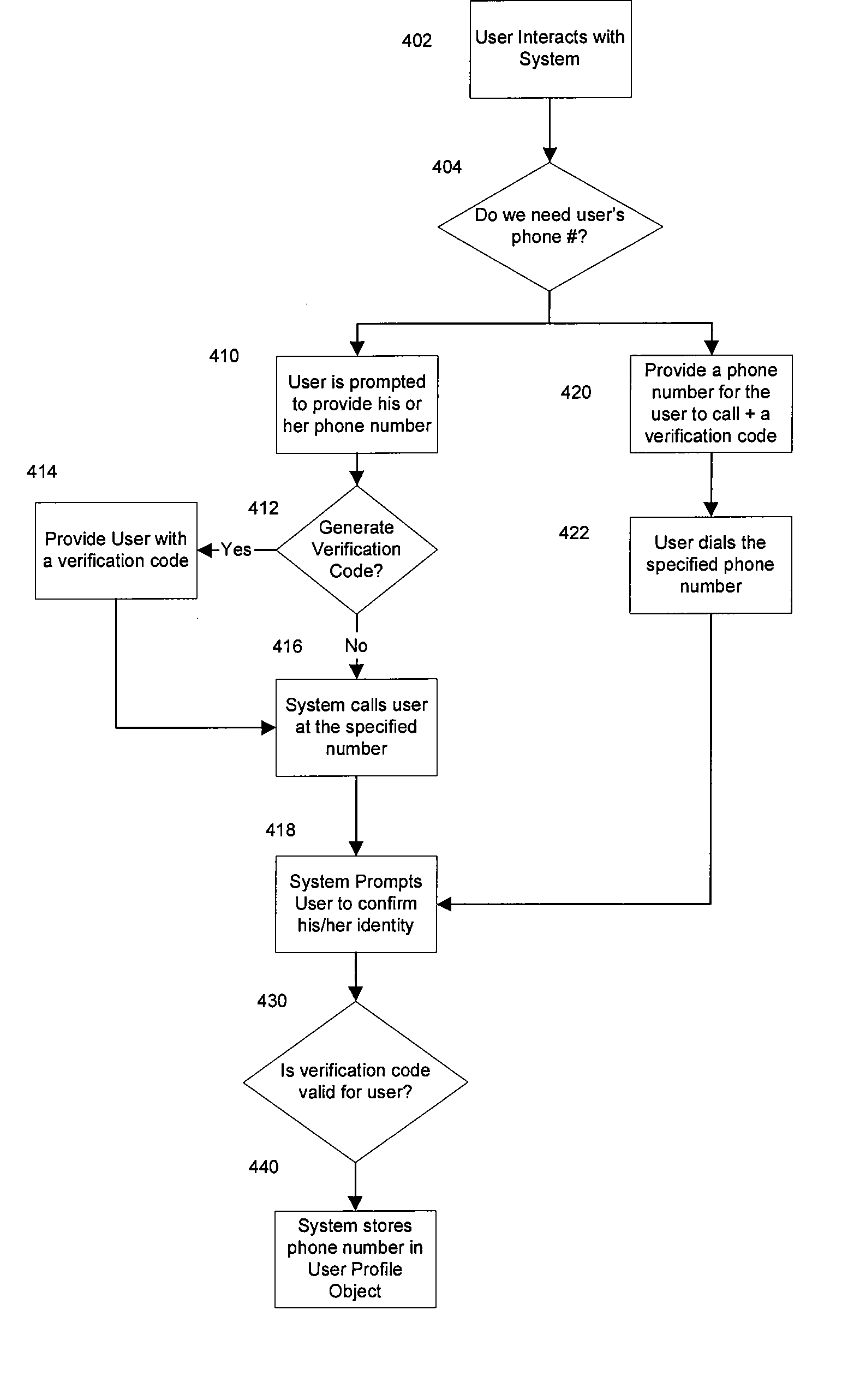
InactiveUS20070220275A1Improve securitySafe handlingComputer security arrangementsSecret communicationPasswordThe Internet
A system and associated apparatus and methods for providing enhanced security for transactions conducted over a network, such as eCommerce or a financial transaction conducted over the Internet. The system strengthens the security processes (e.g., user registration, authentication, and transaction acceptance or authorization) that are part of such a transaction to provide additional security for transactions conducted over a network (e.g., the Internet). The invention includes the use of a first communication channel or mode (e.g, the Internet) for entering user data and a second communication channel or mode (e.g., a response entered on a personal phone or VoIP connection) as a supplementary method of verifying the user's identity. The supplementary method may involve placing a call to a fixed line or mobile phone and requesting the user to confirm their identity by entering a alphanumeric string, speaking a password, executing a function on the device, or another similar action.
Owner:WHITEPA COM
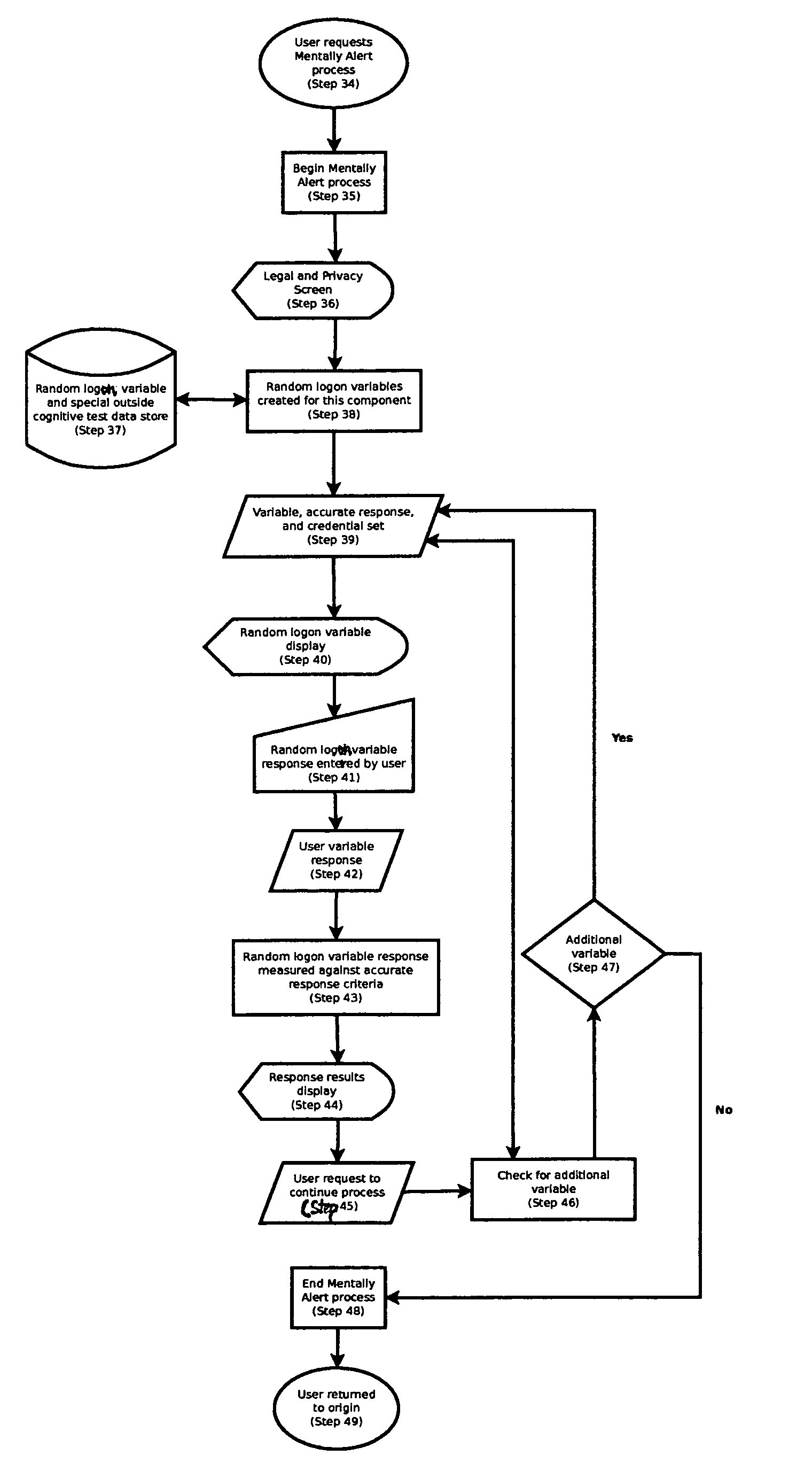
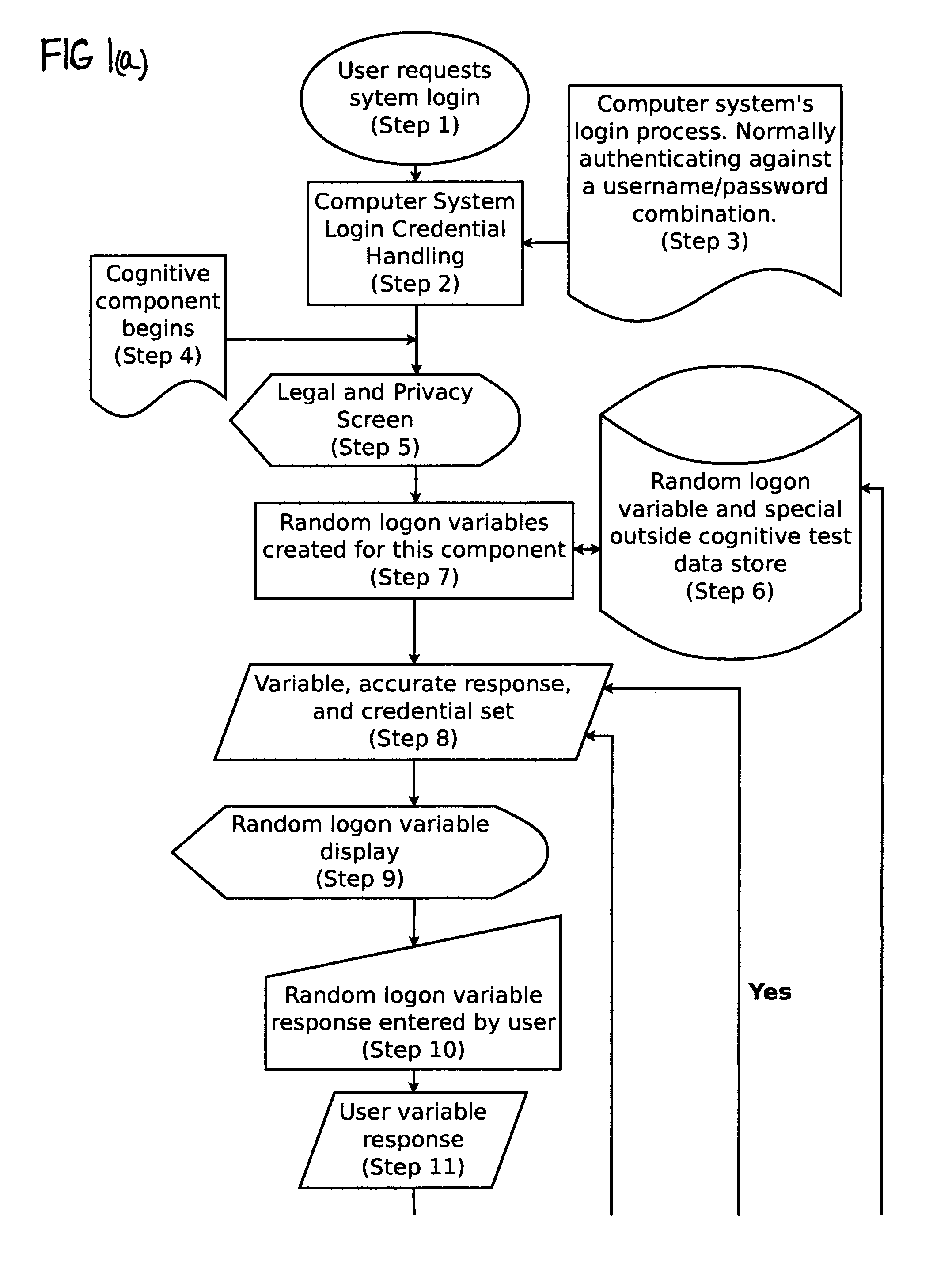
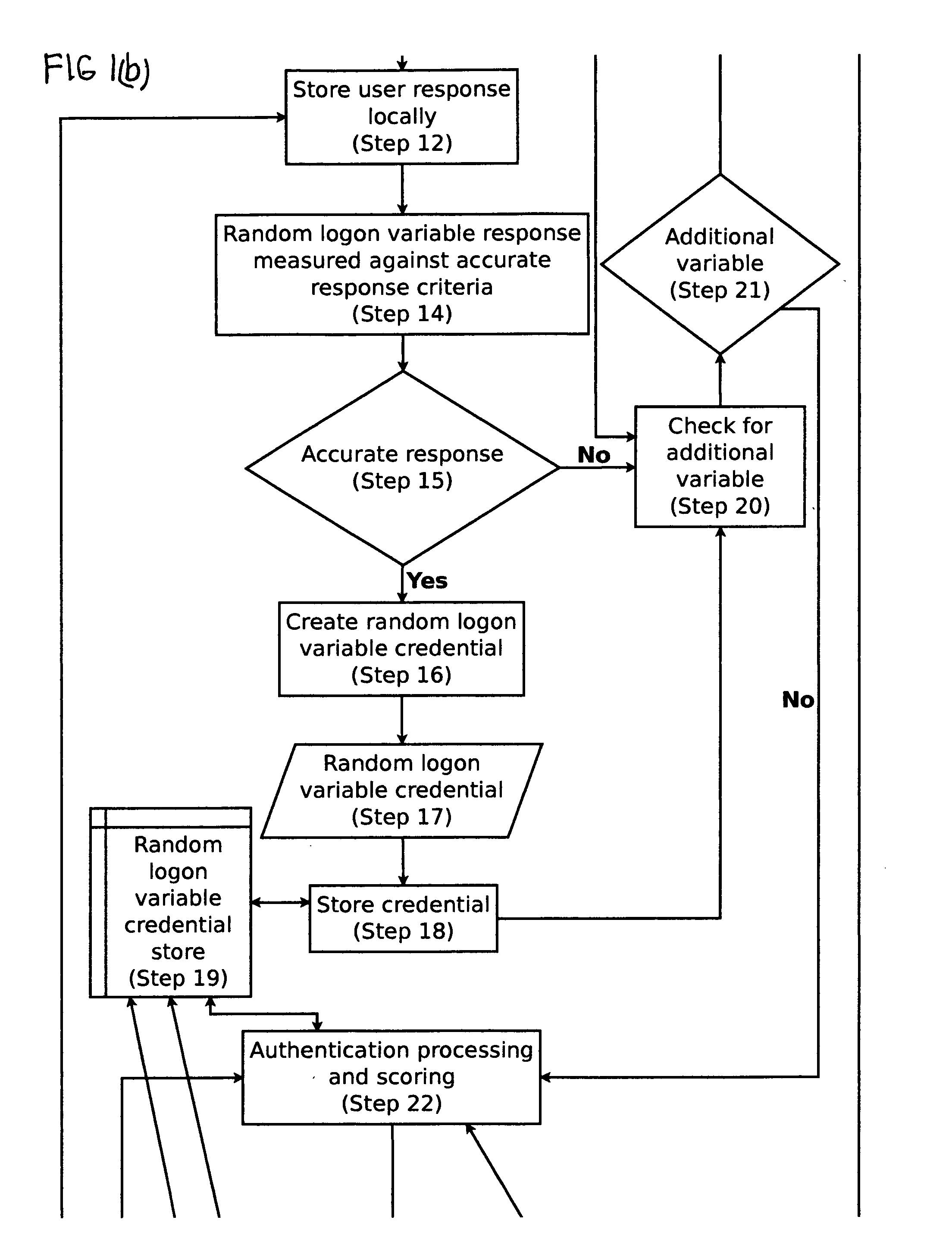
Cognitive-based loon process for computing device
ActiveUS20110162067A1Accurately respondDigital data processing detailsUnauthorized memory use protectionPasswordEngineering
A method of user logon to a computing device or computer system that, distinct from requiring entry of a set of known logon credentials such as a username and password, introduces an additional thought-directed user interface whereby the user must respond to one or more prompts that measure the user's cognitive function at the time of logon or during an active logon session. The user's responses to these prompts are evaluated for several purposes, including determining whether the user demonstrates the required level of cognitive function to gain access to the computer system or continue an active logon session. The user's responses and associated data may also be stored and retrieved at a later time for various purposes, including determining whether and to what extent the user's level of cognitive function is improving, diminishing, or remaining static over time.
Owner:SHUART LAIRD H +4
System and method for user authentication with exposed and hidden keys
InactiveUS20080240447A1Key distribution for secure communicationMultiple keys/algorithms usageDigital contentOnline and offline
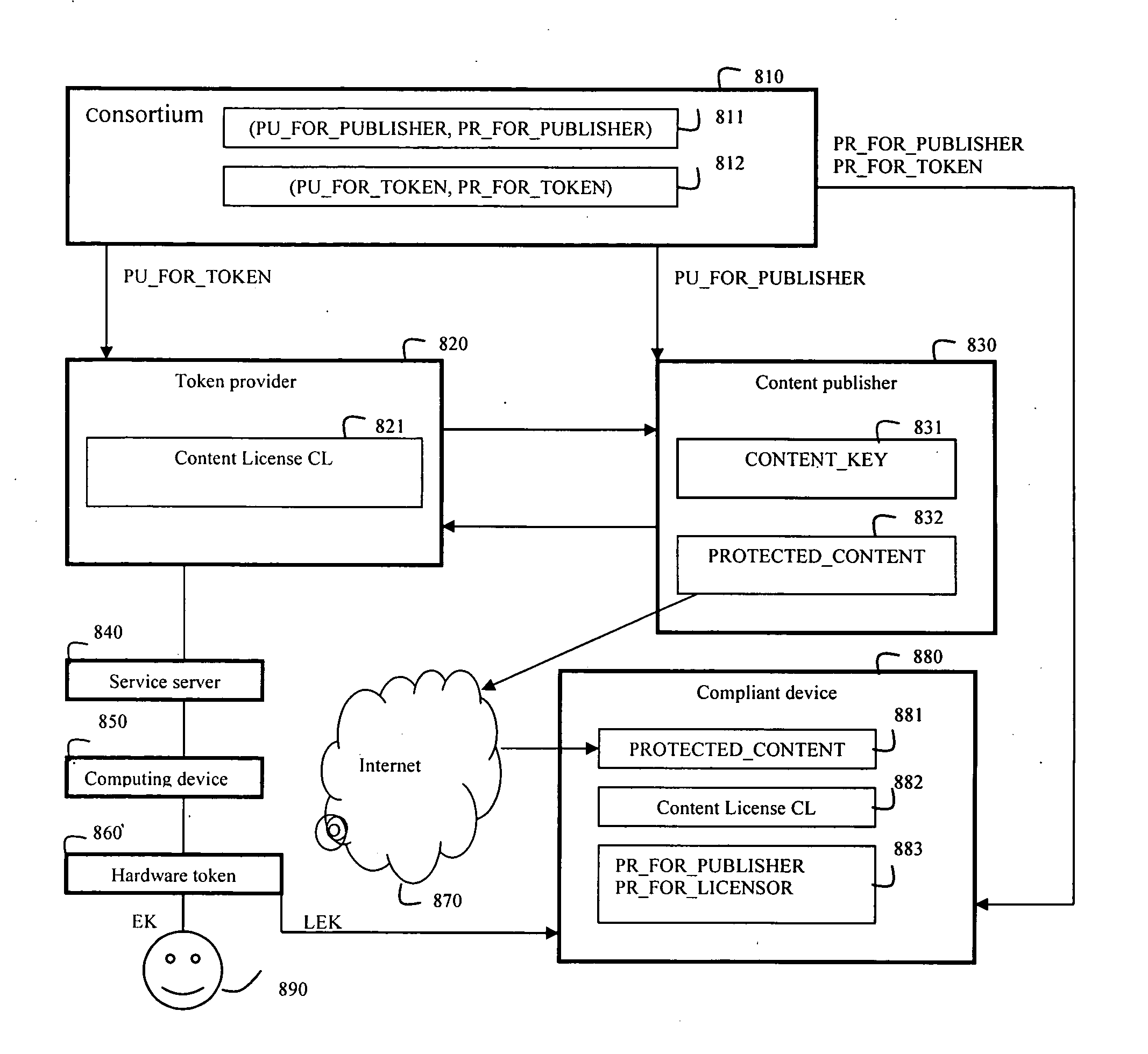
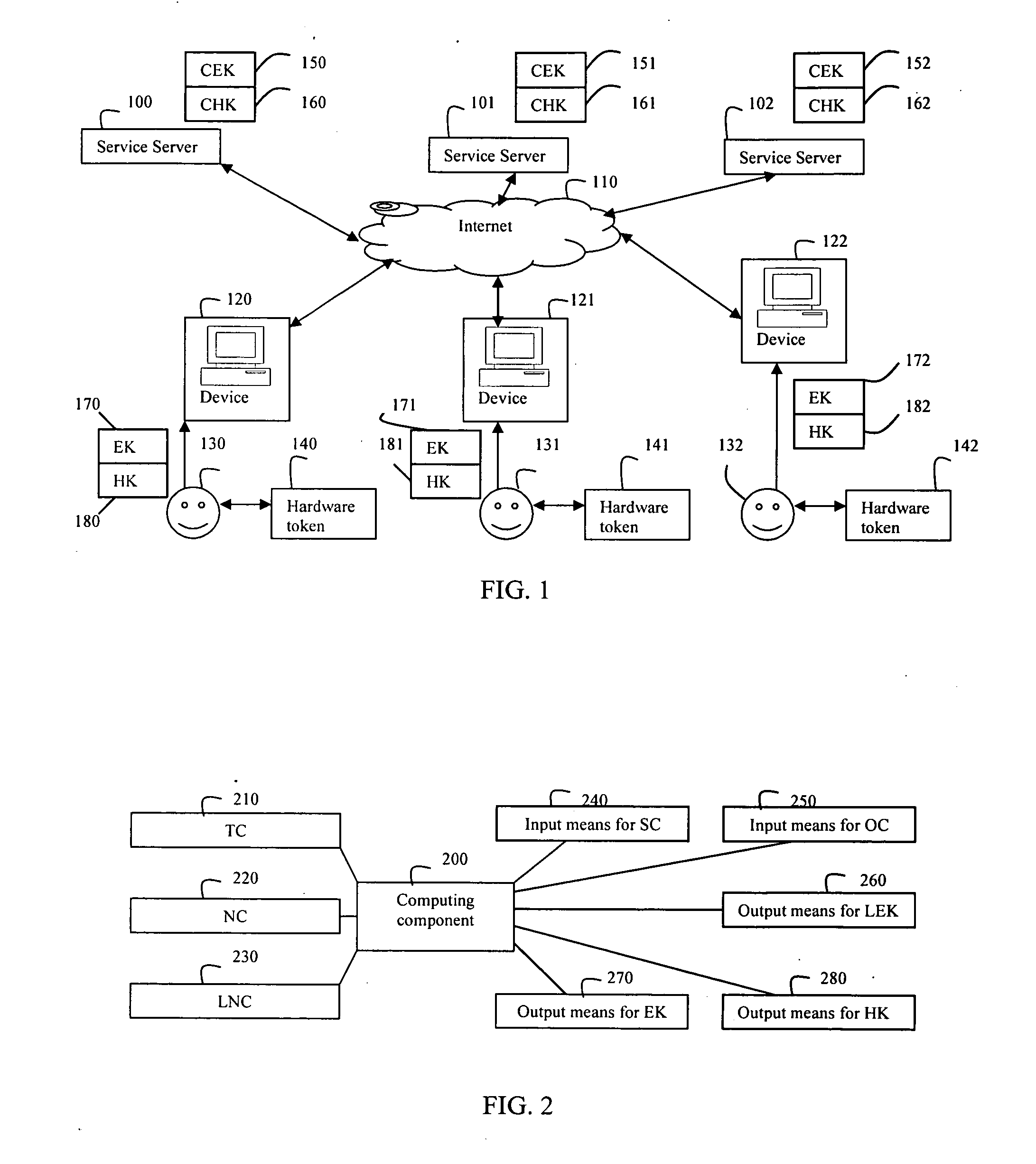
The present invention relates to a system and method for digitally authenticating users both online and offline. In one embodiment, a hardware token assigned by a trusted token provider to the user is employed to ensure the identity of the user. In the online authentication, the token is adapted for generating an exposed key EK and a hidden key HK based on a noise code NC and a time code TC of the token, a space code SC of a service server, and an owner code OC of the user. A login session is initialized by entering a user identifier at the service server and the generated EK from a computing device. The service server computes an expose key CEK and a hidden key CHK based one an authentication license generated by the token provider. The service server authenticates the user if the CEK is same as the EK, and sends a response message encrypted the CHK to the computing device. Then, the user provides the HK to the computing device to decrypt the encrypted response message so as to access his / her account. In the offline authentication, the token is adapted for generating a license exposed key LEK used to render the encrypted digital content on an offline compliant device. The compliant device authenticates the user if a license exposed key computed by the compliant device based on a content license of which the user bought is same as LEK, so as to render the protected digital content after authentication.
Owner:ZHU YUNZHOU +1
Single sign-on with common access card
ActiveUS20060031683A1Reduce the number of timesImprove efficiencyDigital data processing detailsUser identity/authority verificationUser needsOff the shelf
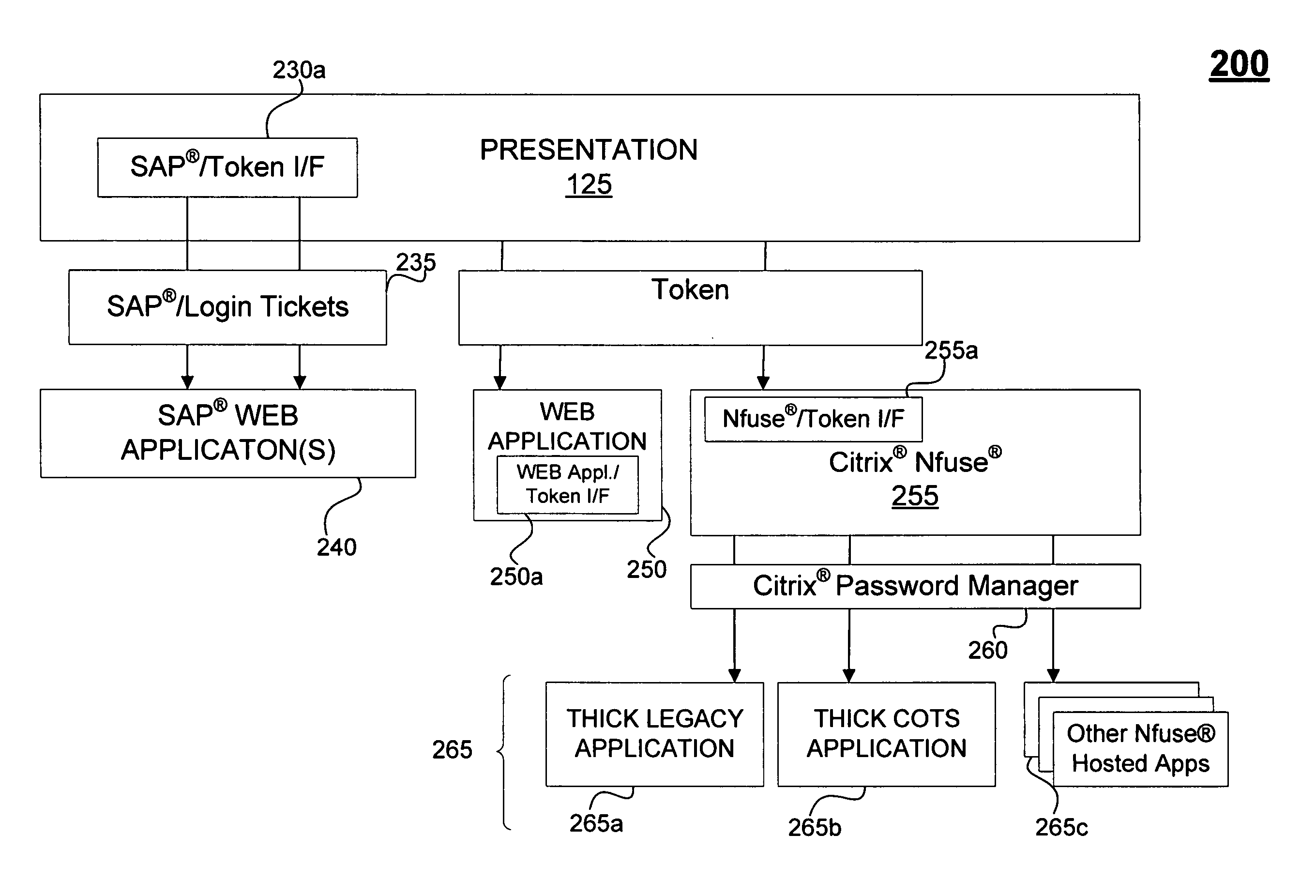
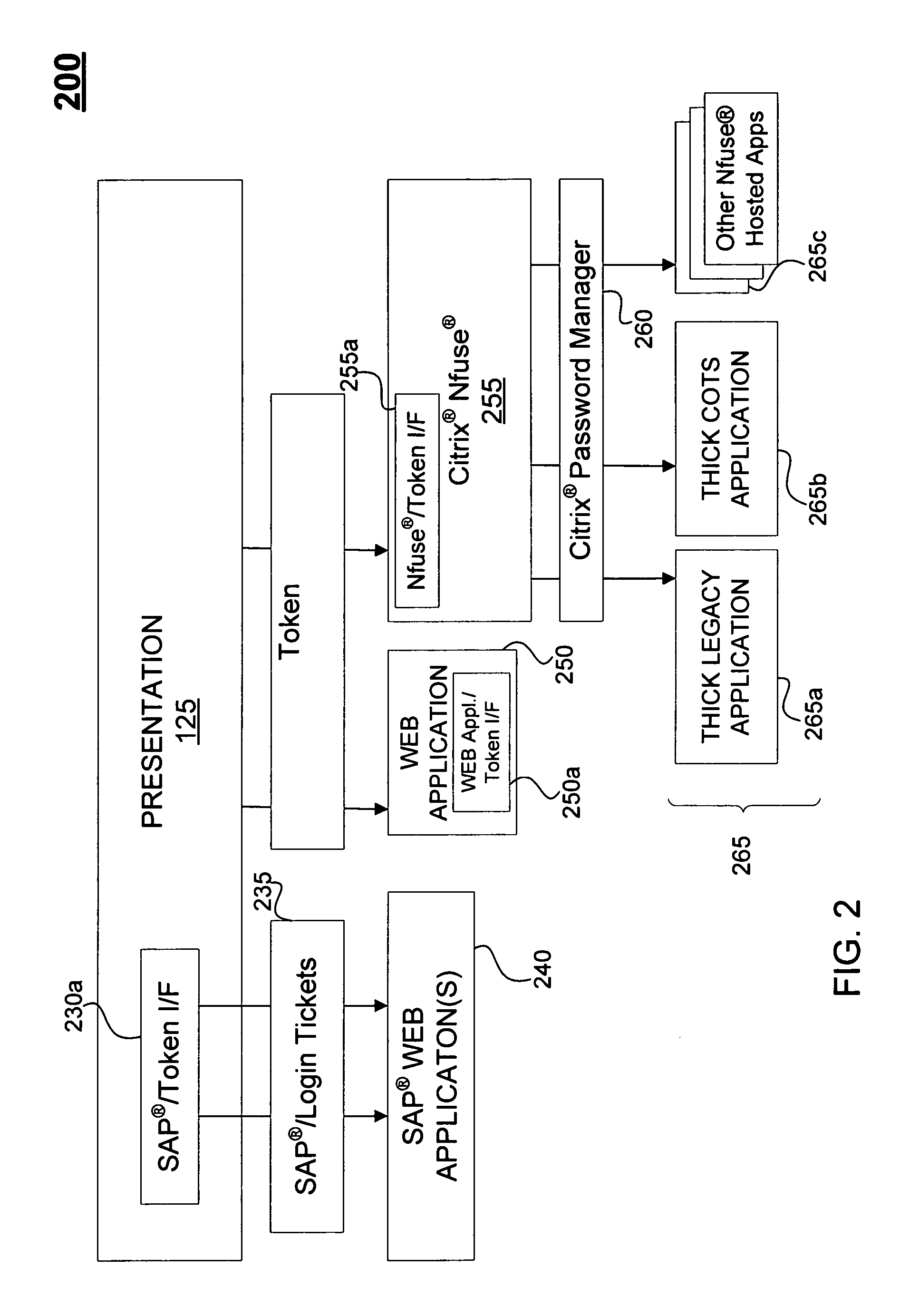
A mechanism eliminates the number of times a user must login to individual services after initially logging into a computer system. A user only logs once into a computer system, and subsequent login requests by multiple services are handled automatically and transparently by the system. In one implementation, a user need only present a card to a card reader and enter a PIN, and the user is logged-in after presenting the card and a valid PIN. The system generates a token that is valid for this particular login session of the user, and when the user accesses a permissioned service, the system automatically logs-in the user to the application using the token. The system can perform the automatic login the user to a variety of applications including legacy applications, web-enabled applications, and commercial, off-the-shelf applications.
Owner:ACCENTURE GLOBAL SERVICES LTD
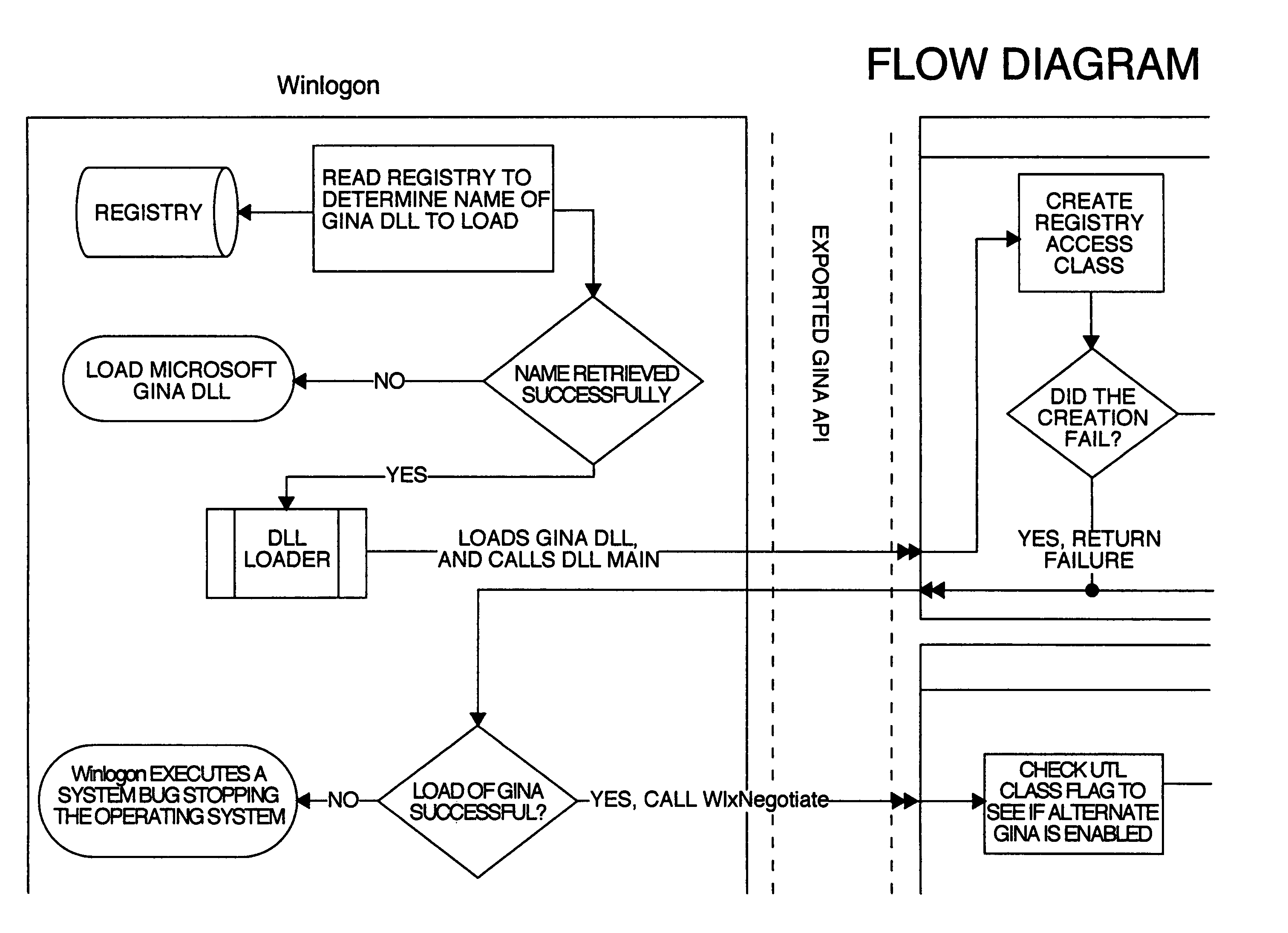
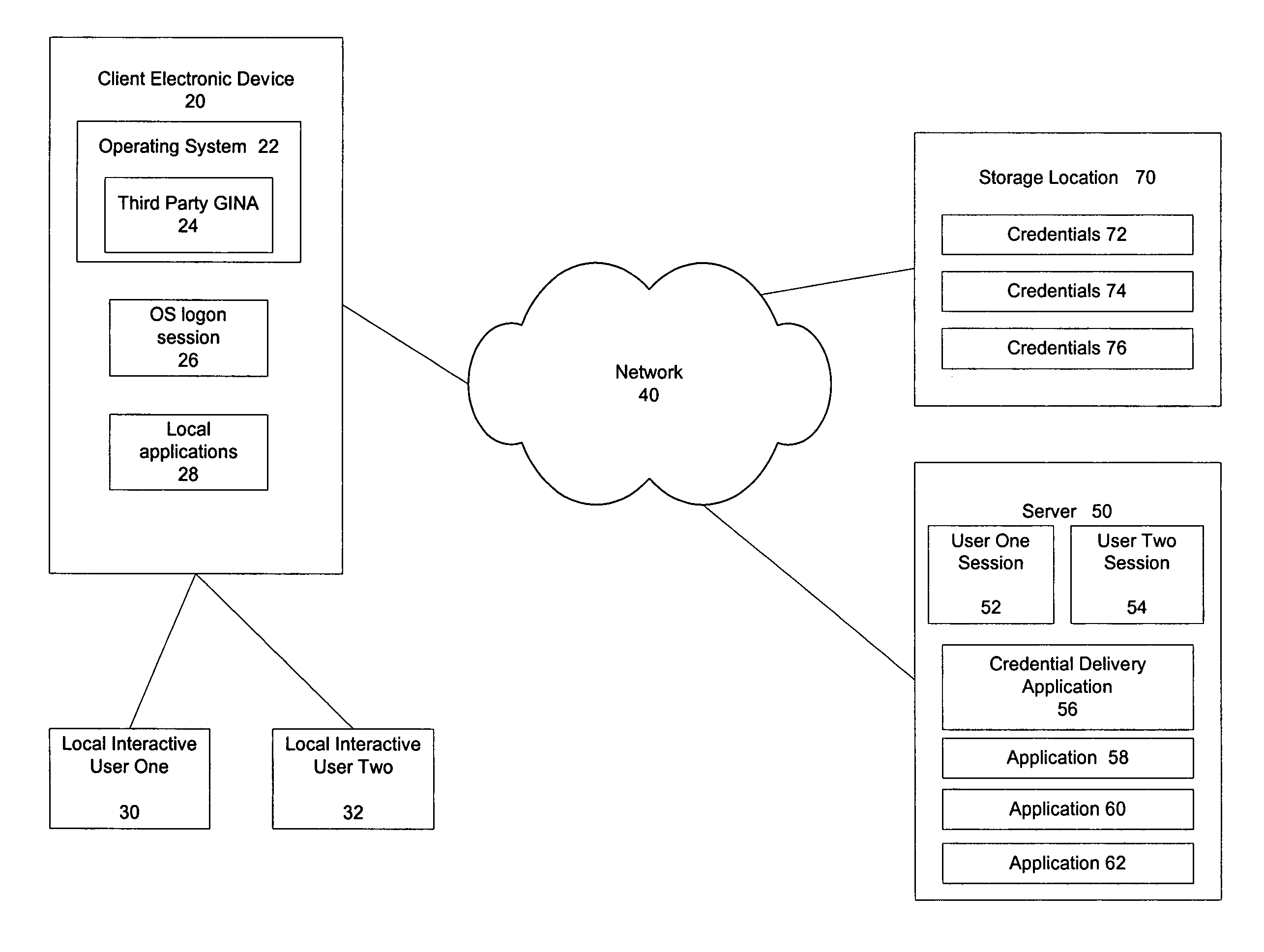
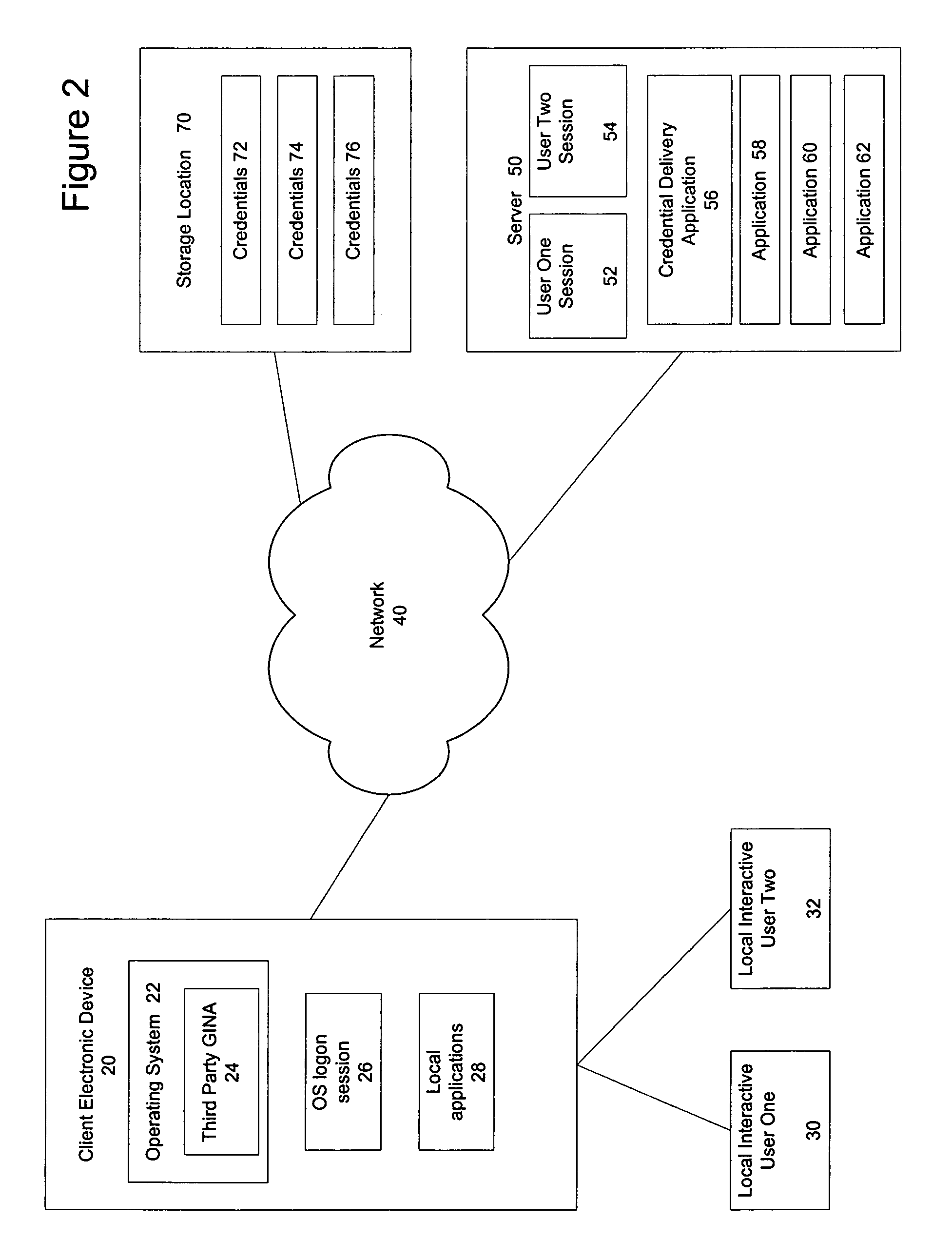
Multiple user desktop graphical identification and authentication
InactiveUS8438400B2Process safetyImprove securityUnauthorized memory use protectionHardware monitoringGraphicsA domain
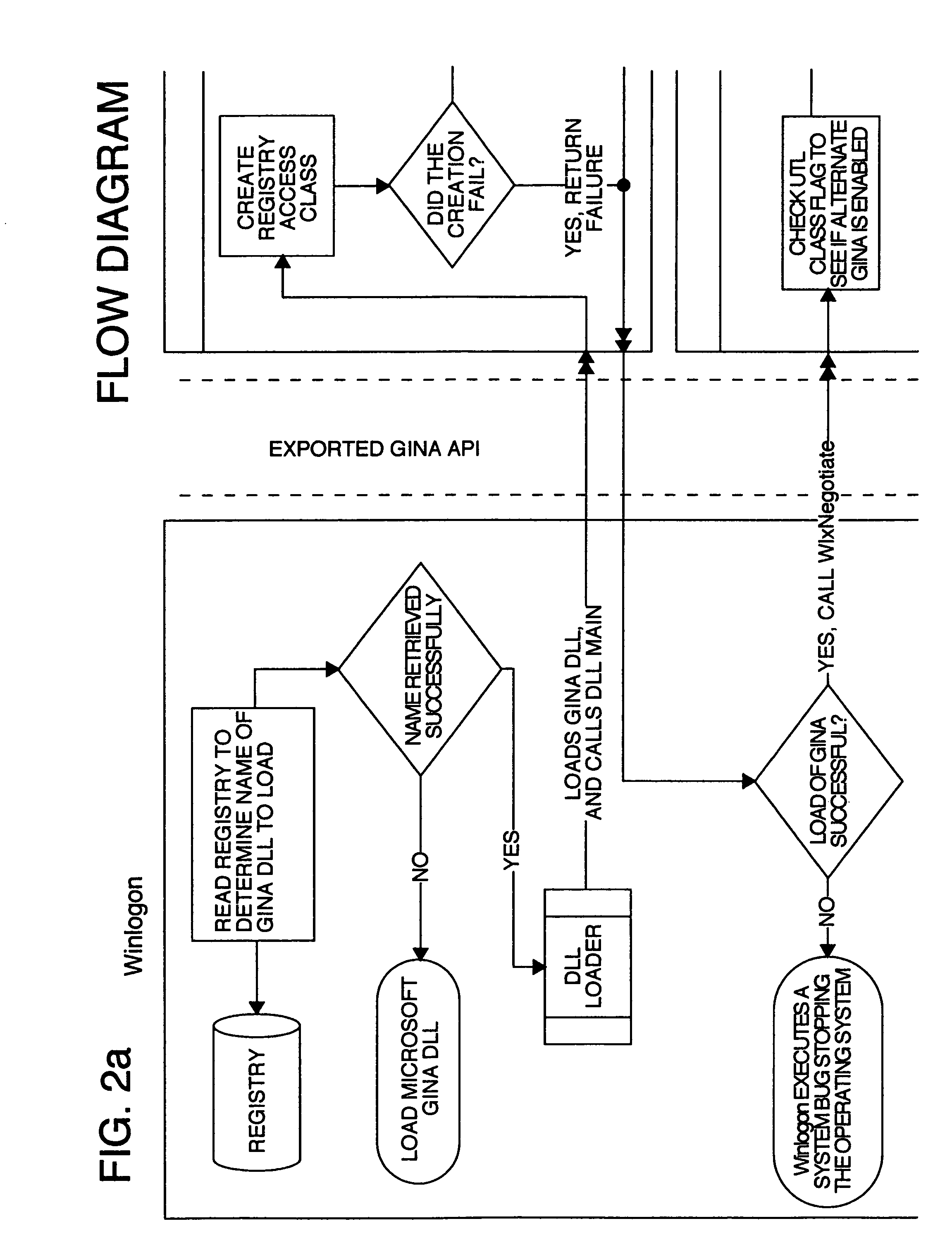
A multiple user desktop graphical identification and authentication configured as a loadable dynamic link library (DLL) intended to replace the default Microsoft graphical identification and authentication. It has the ability to create secure, private logon sessions for each user that logs on to the system. There can be up to at least thirteen users logged in at the same time and each user will have their own desktop environment. Auto log off functions may be set based on time of inactivity and / or number of individual users. The multiple user desktop graphical identification and authentication functions in a domain and non-networked environments and needs no added hardware.
Owner:INDIGO IDENTITYWARE INC
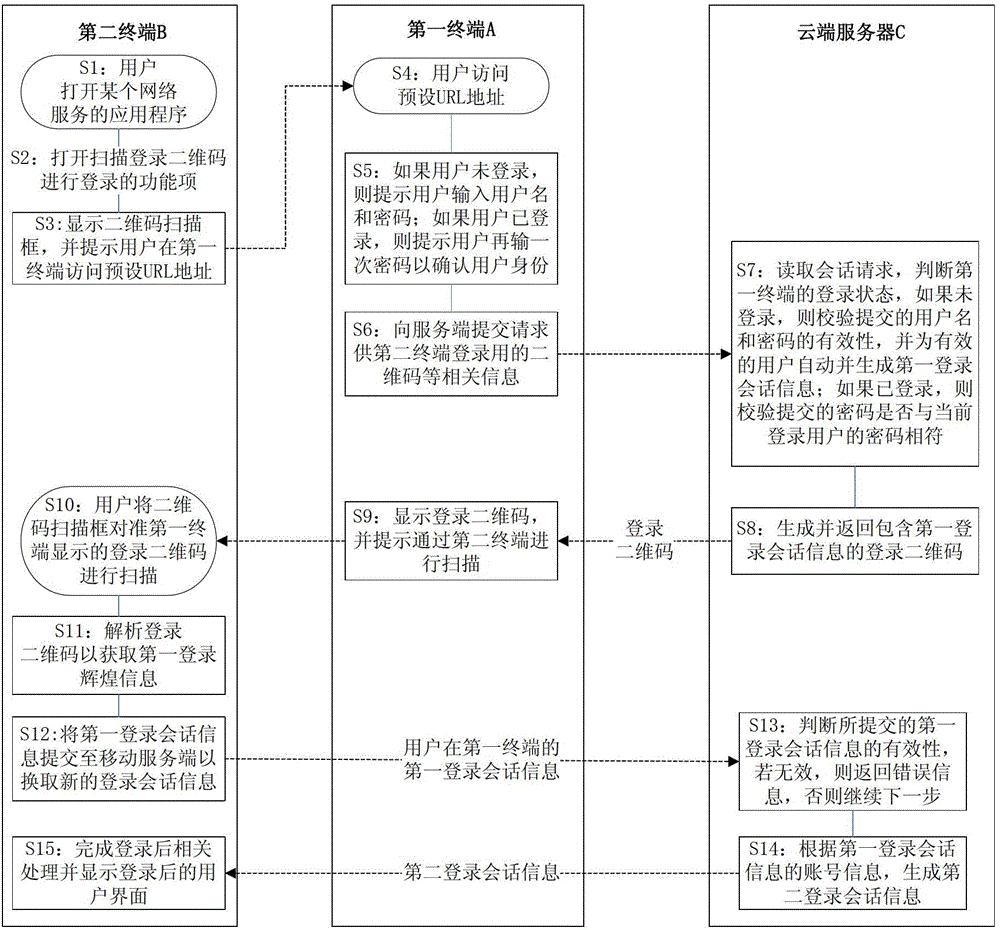
Log-in control method and system based on two-dimension code
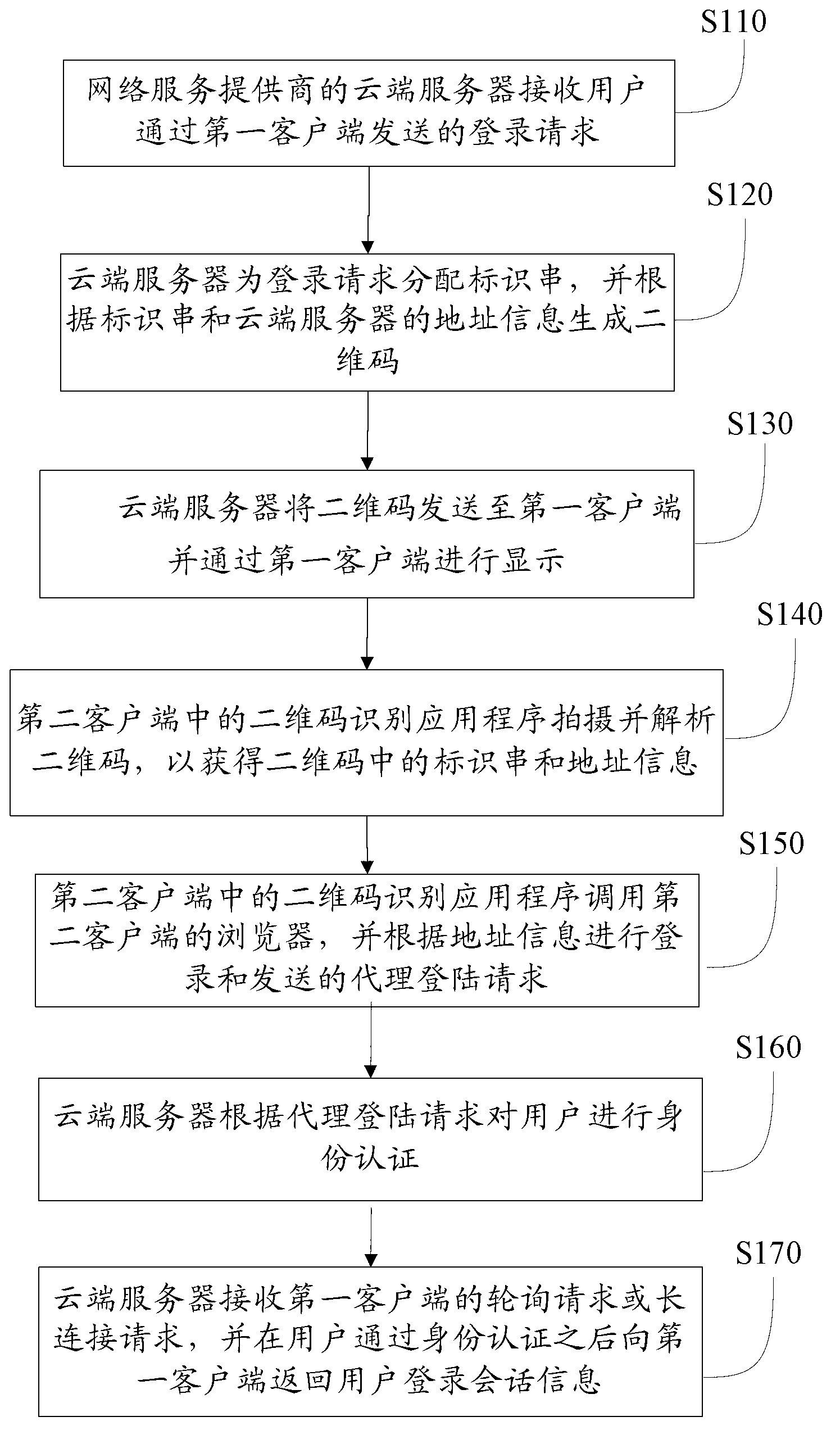
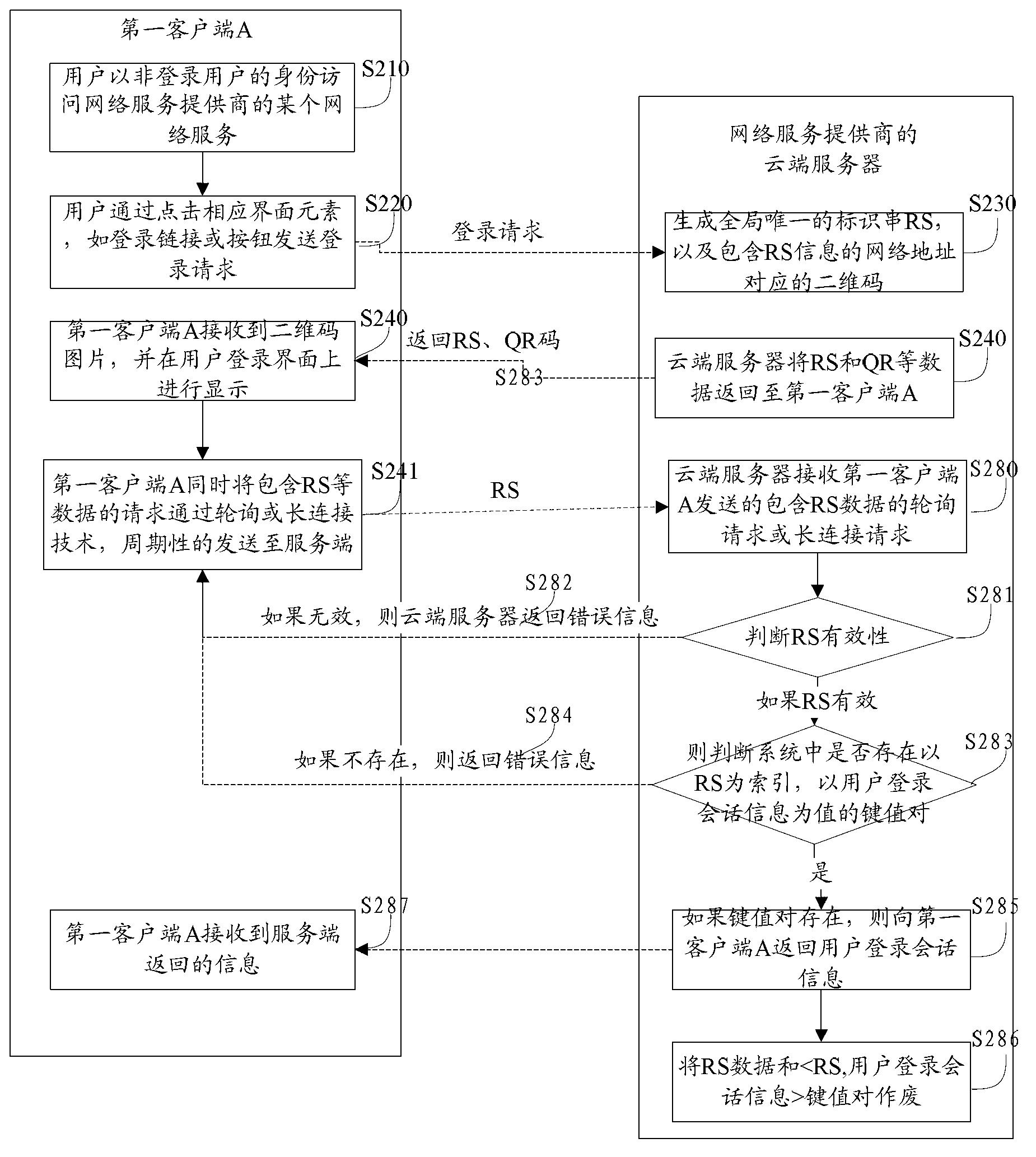
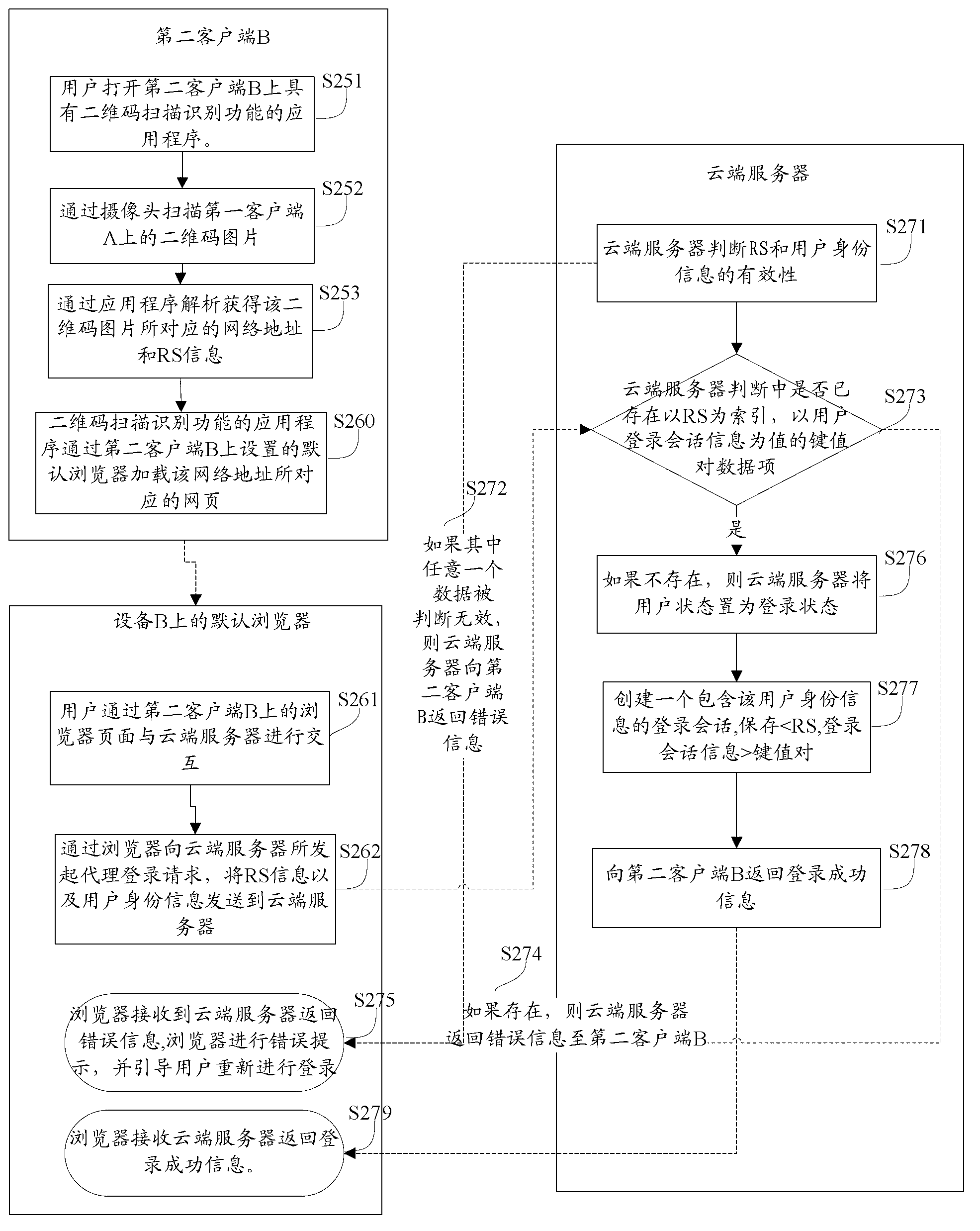
The invention provides a log-in control method based on a two-dimension code. The log-in control method based on the two-dimension code comprises the steps that a network service provider cloud server receives a log-in request sent through a first client-end by a user, the cloud server generates a two-dimension code, sends the two-dimension code to the first client-end and displays the two-dimension code through the first client-end, a second client-end obtains an identification string and an address message in the two-dimension code, the second client-end logs in and sends an agency log-in request according to the address message, the cloud server carries out identity authentication of the user according to the agency log-in request, and the cloud server receives a polling request or a long connection request of the first client-end and returns a user log-in conversation message to the first client-end after the identity authentication of the user is carried out. According to the log-in control method based on the two-dimension code, inconvenience brought by a large amount of input during a user log-in process is avoided, safety of a user account is improved, operating cost is low, and user experience is good. Further disclosed is a log-in control system based on the two-dimension code.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Remote access authorization of local content
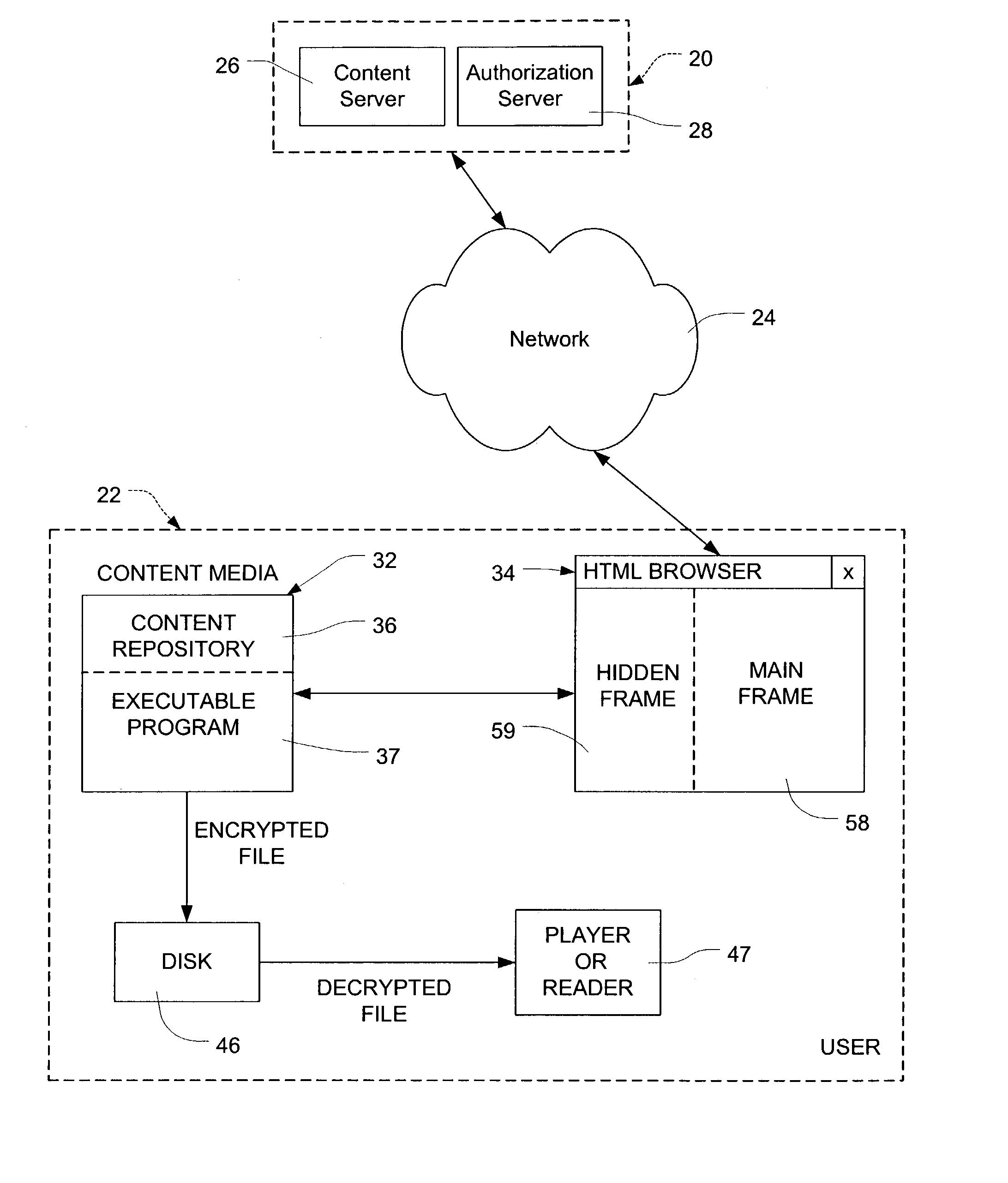
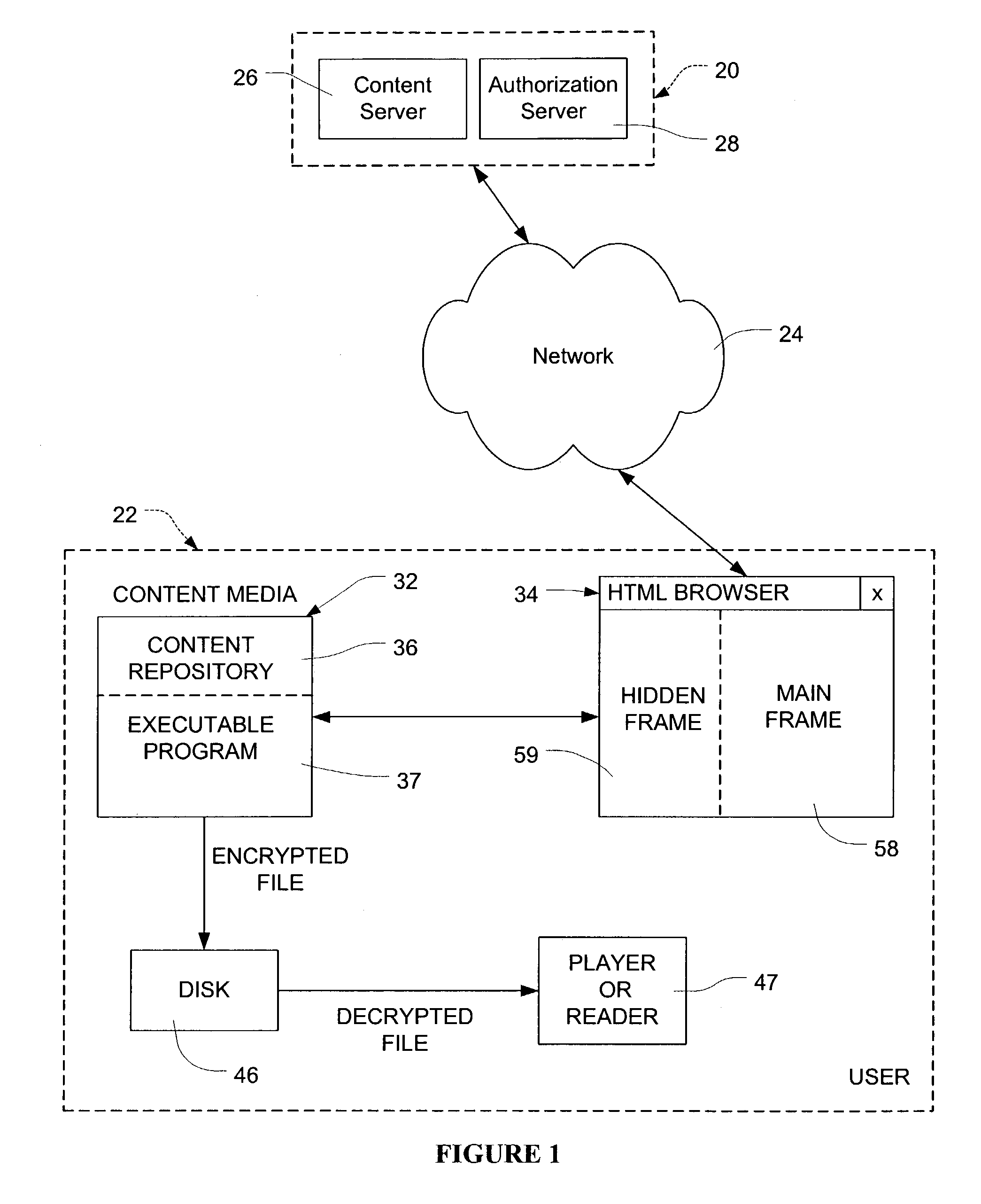
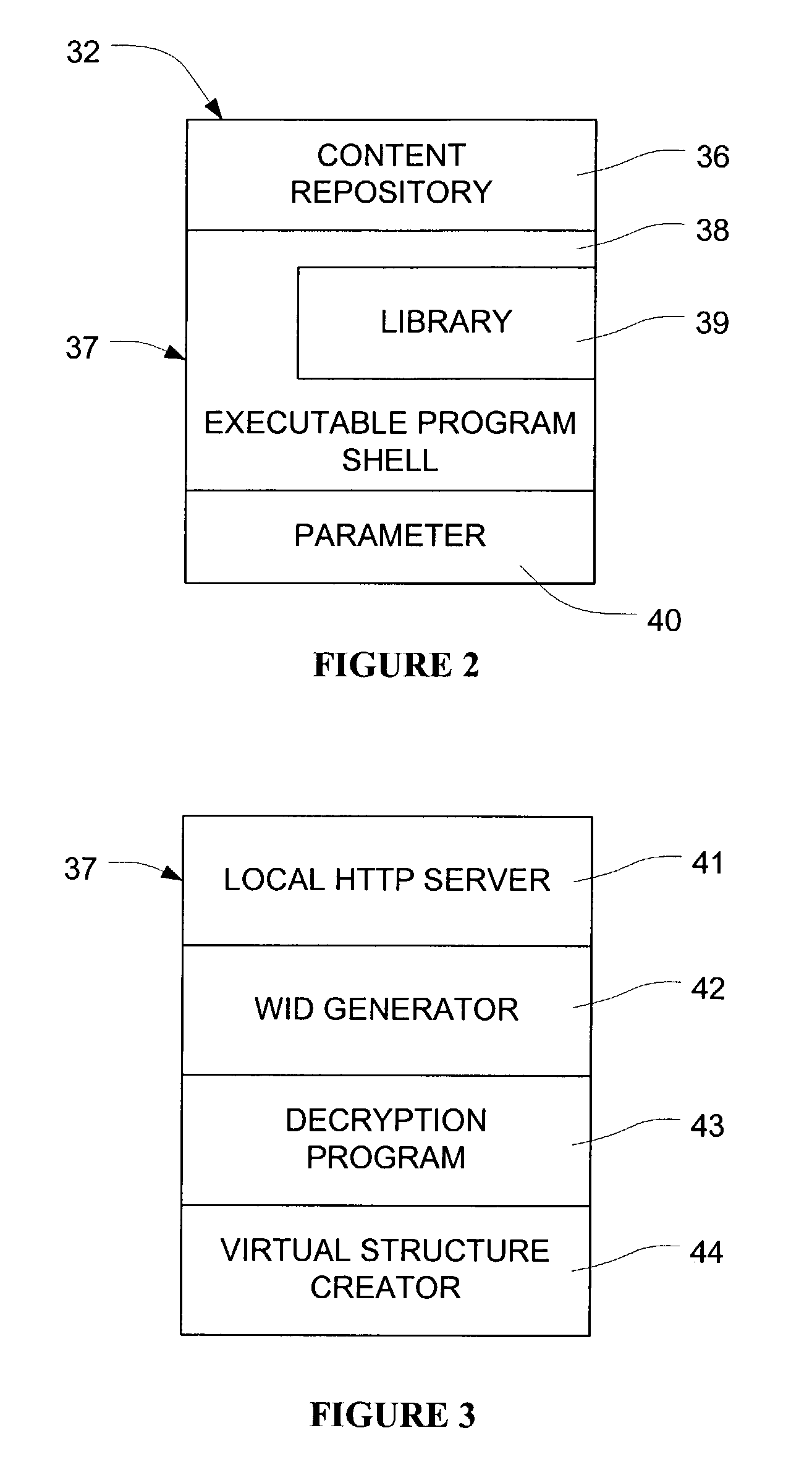
InactiveUS7089425B2Digital data processing detailsUser identity/authority verificationPersonalizationLogin session
Network users are authorized individual access during a log-on session to encrypted content on content media at the user without the necessity of individualizing the content media for the particular user. The content may comprise multimedia data. The content media, which may be mass produced and distributed, includes a computer program which generates a unique configuration identifier upon instantiation of the program to begin a user access session. The program creates a virtual directory structure for the content that is uniquely determined for that session by the configuration identifier. The configuration identifier is uploaded to a remote server which uses the configuration identifier with other information identifying the content media and the user authorize user access. The remote server creates and downloads to a browser of the user an encrypted message containing URLs for accessing the content in the virtual directory structure and containing transformations of a decryption algorithm and decryption keys for the encrypted content. Encrypted multimedia content selected by the user is stored in a temporary file, decrypted in a moving time window, and rendered After rendering, the decrypted portion of the temporary file is scrambled to preclude further access.
Owner:C14 TECH
Reporting function in gaming system environment
ActiveUS20080153599A1Apparatus for meter-controlled dispensingVideo gamesUser identifierLibrary science
A gaming related system employs a front end application that allows access to various reports from various, disparate databases. Such may avoid reviewing reports in SQL Reporting services. Identification of reports and / or categories of reports, as well as access to reports and categories of reports may be limited based on a user role associated with a user identifier and / or pass phrase. Users may only need to provide log in information once per log in session.
Owner:LNW GAMING INC
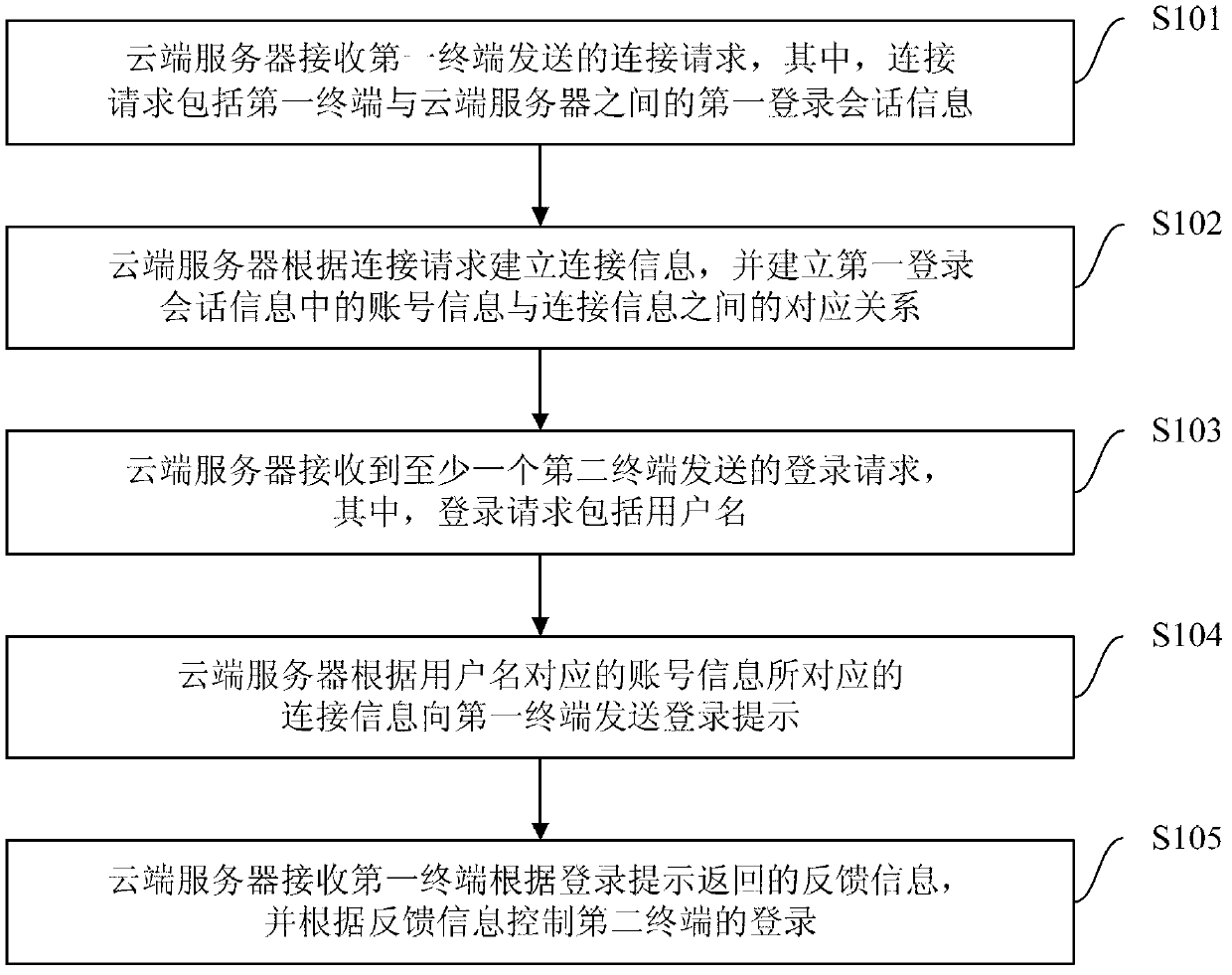
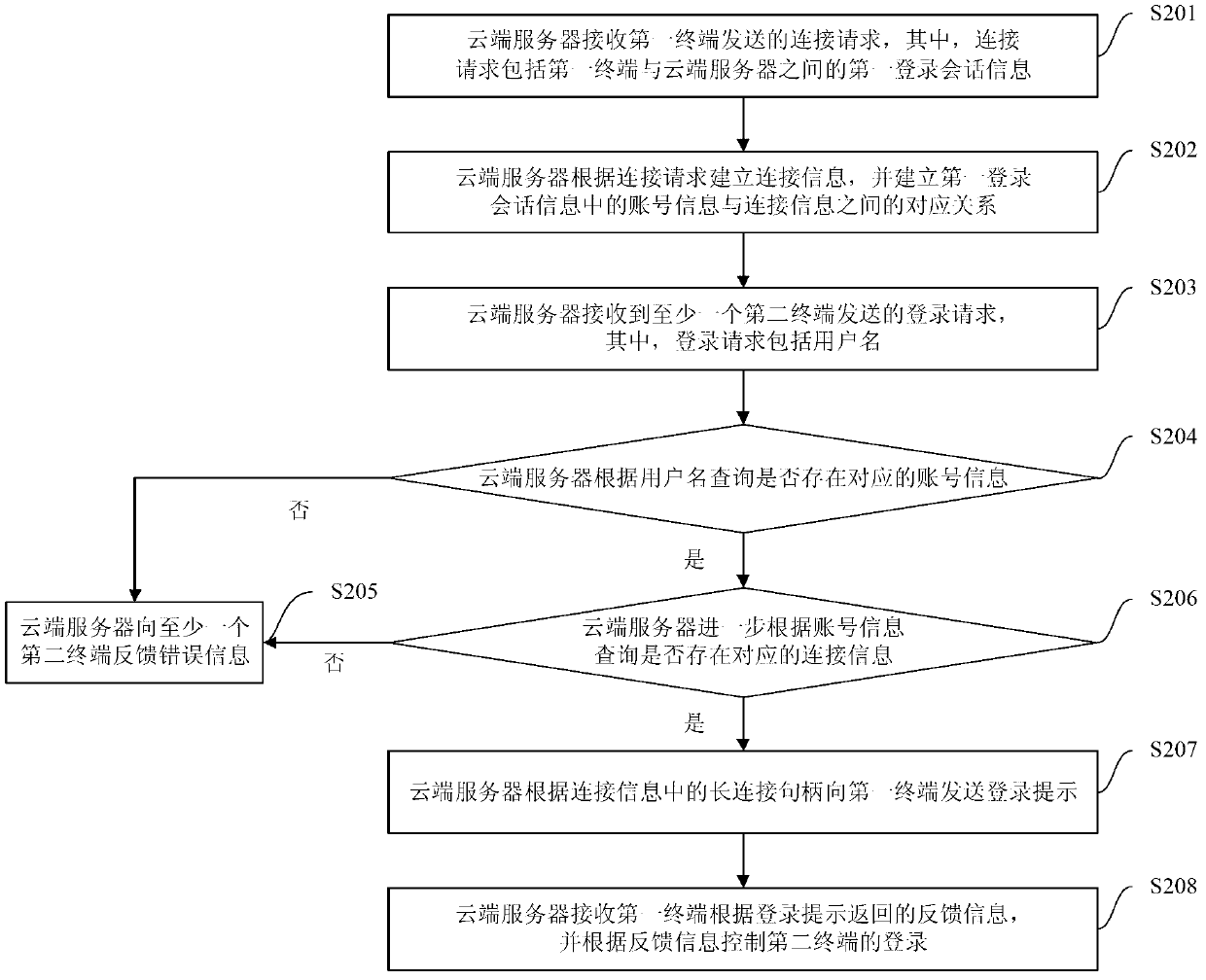
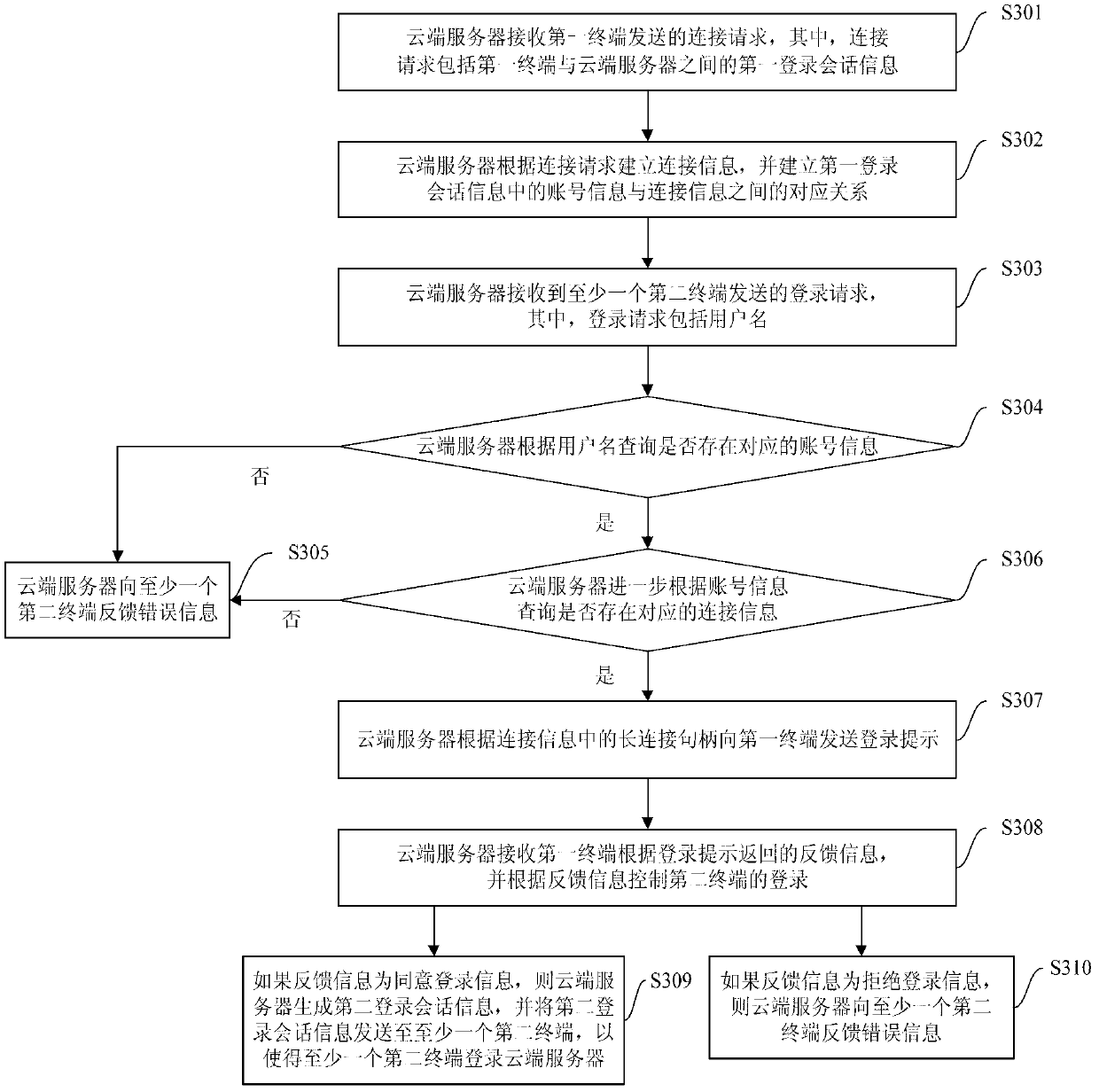
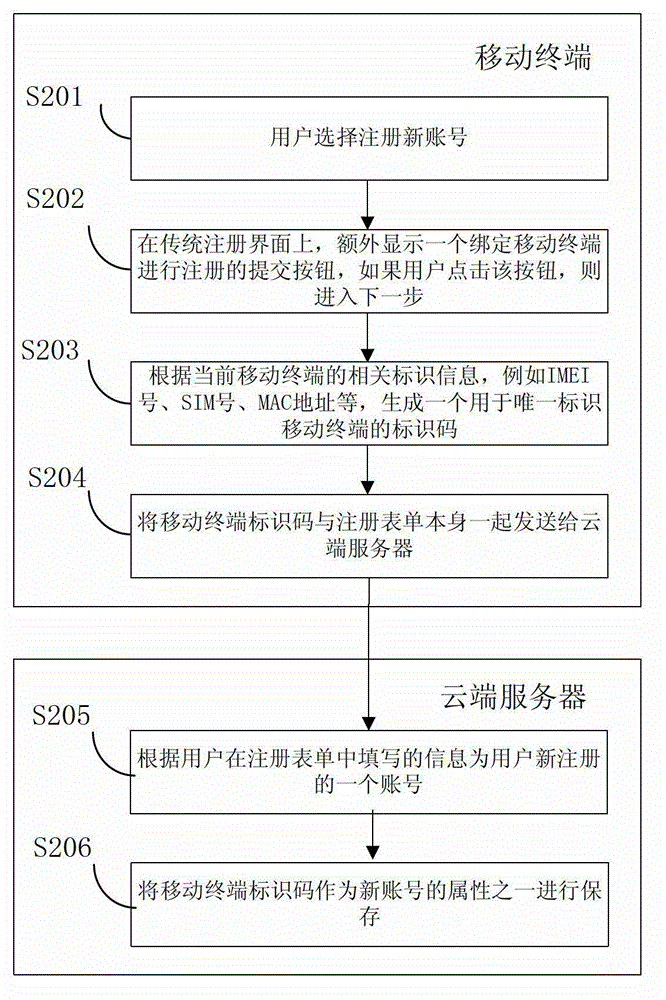
Method, system and cloud server for multi-device safe logging
ActiveCN103281327ASimplify login operationsImprove experienceTransmissionLogin sessionOperating system
The invention provides a method, system and cloud server for multi-device safe logging, wherein the method comprises the steps that the cloud server creates connection information according to a connection request sent by a first terminal and creates a corresponding relation between account information in first logging session information and the connection information; the cloud server can send a login prompt to the first terminal according to the connection information corresponding to the account information corresponding to a user name sent by a second terminal, receives feedback information returned according to the login prompt, and controls logging of the second terminal according to the feedback information. According to the method, after a user normally logs in a device (such as the first terminal), a logging process can be completed only through inputting of the user name on other devices (such as the second terminal), logging operation of a user on multiple devices is simplified, user experience is promoted, the cloud server controls the logging of other equipment (such as the second terminal) according to the feedback information, and safety is guaranteed.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Methods, systems, and media to authenticate a user
InactiveUS7546630B2Digital data processing detailsUser identity/authority verificationWeb browserApplication software
Methods, systems, and media to authenticate a user for interaction with applications on a server are disclosed. Embodiments include hardware in and / or software on a server adapted to generate a unique, session identification like a random number to identify a user's login session. The identification is stored in memory that will not be de-allocated upon termination of applications on the server and is transmitted via, e.g., a cookie to the user's browser, or the like. Subsequent user accesses can be verified by comparing the session identification from the web browser with the corresponding entry in the memory. Once the user's identification is verified, the user is authorized to access to applications associated with the user's login session, providing independence from the architecture of the applications executed by the server. Further embodiments include additional session information with the identification in the memory. Some embodiments monitor login sessions for expiration.
Owner:IBM CORP
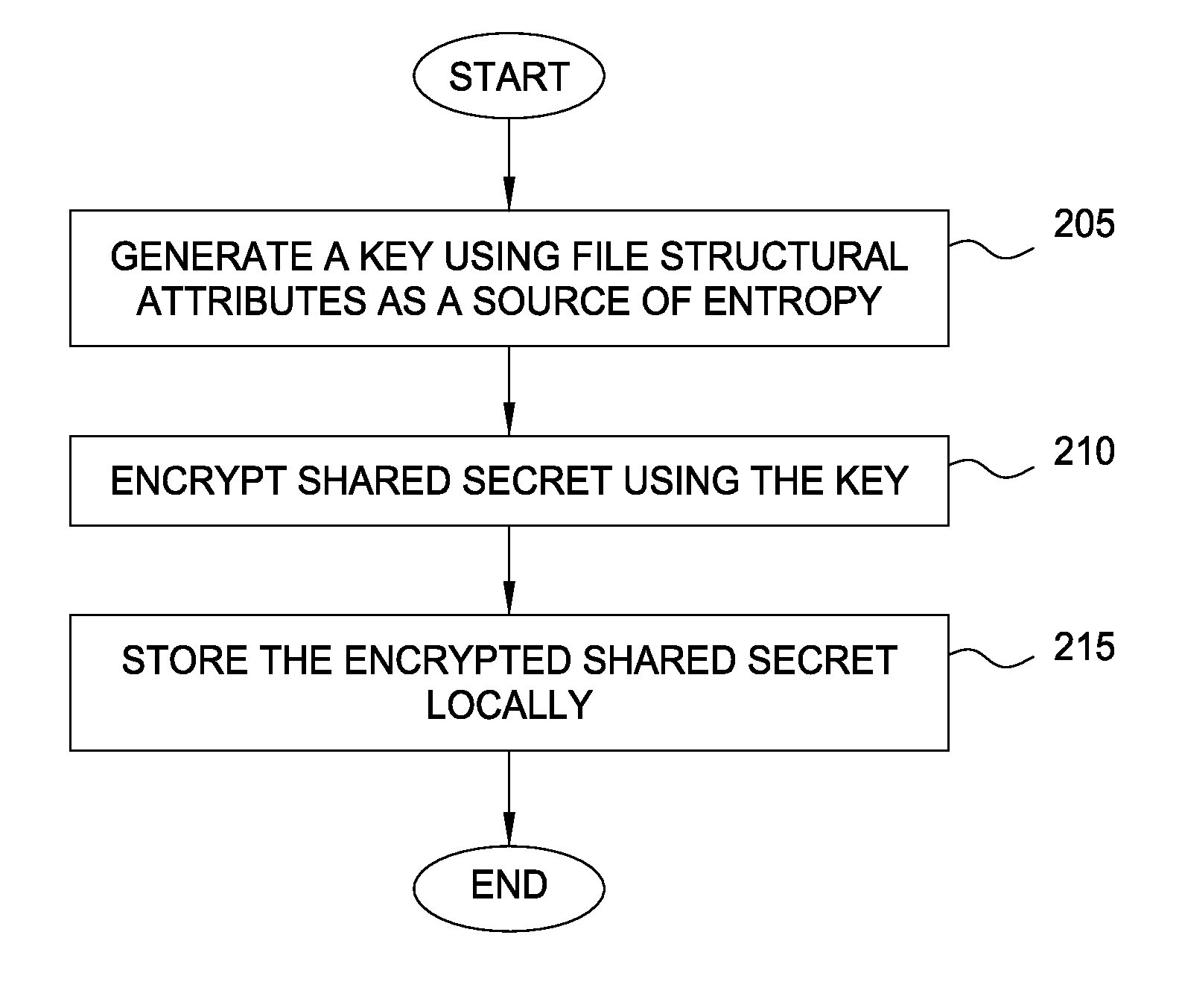
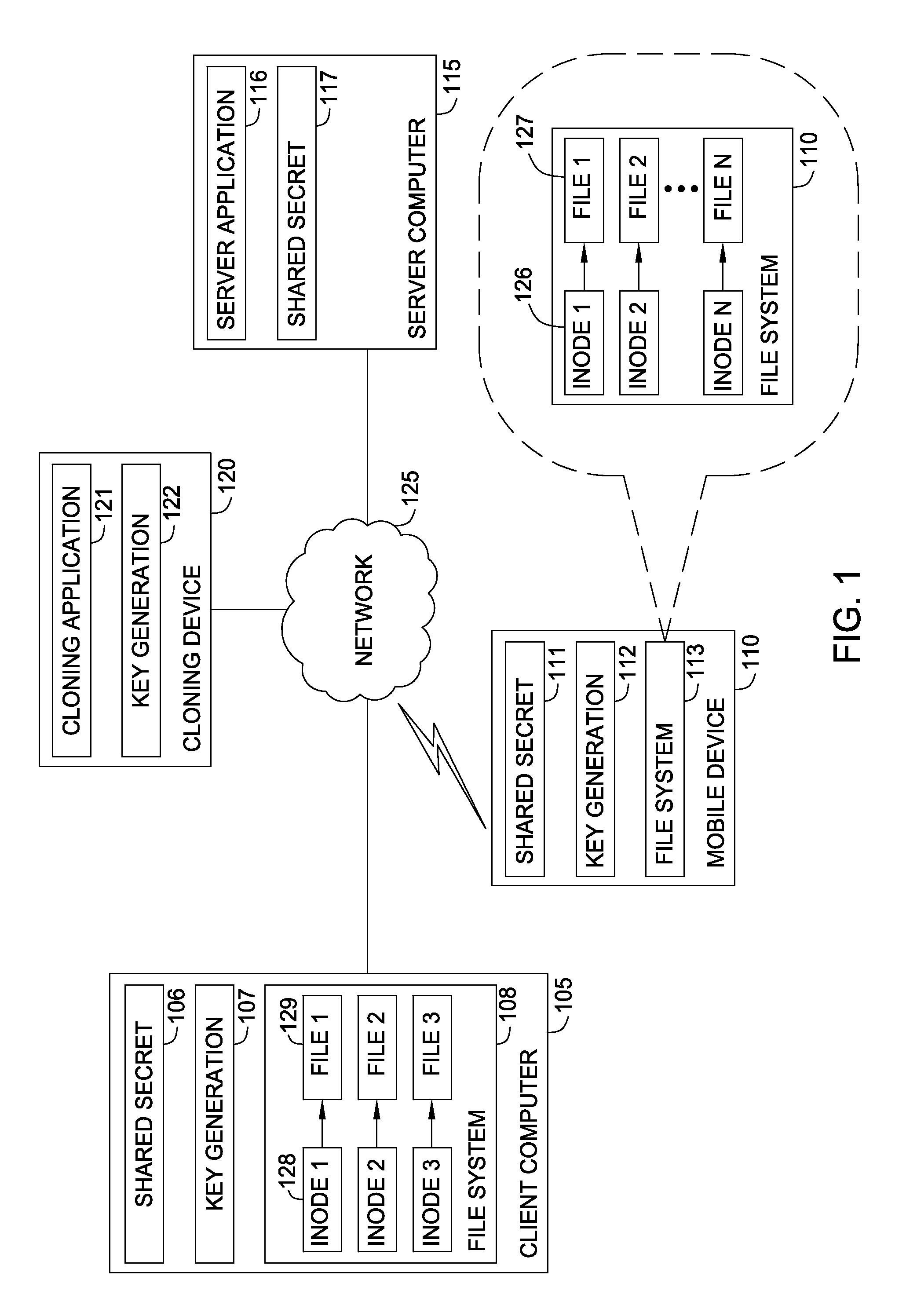
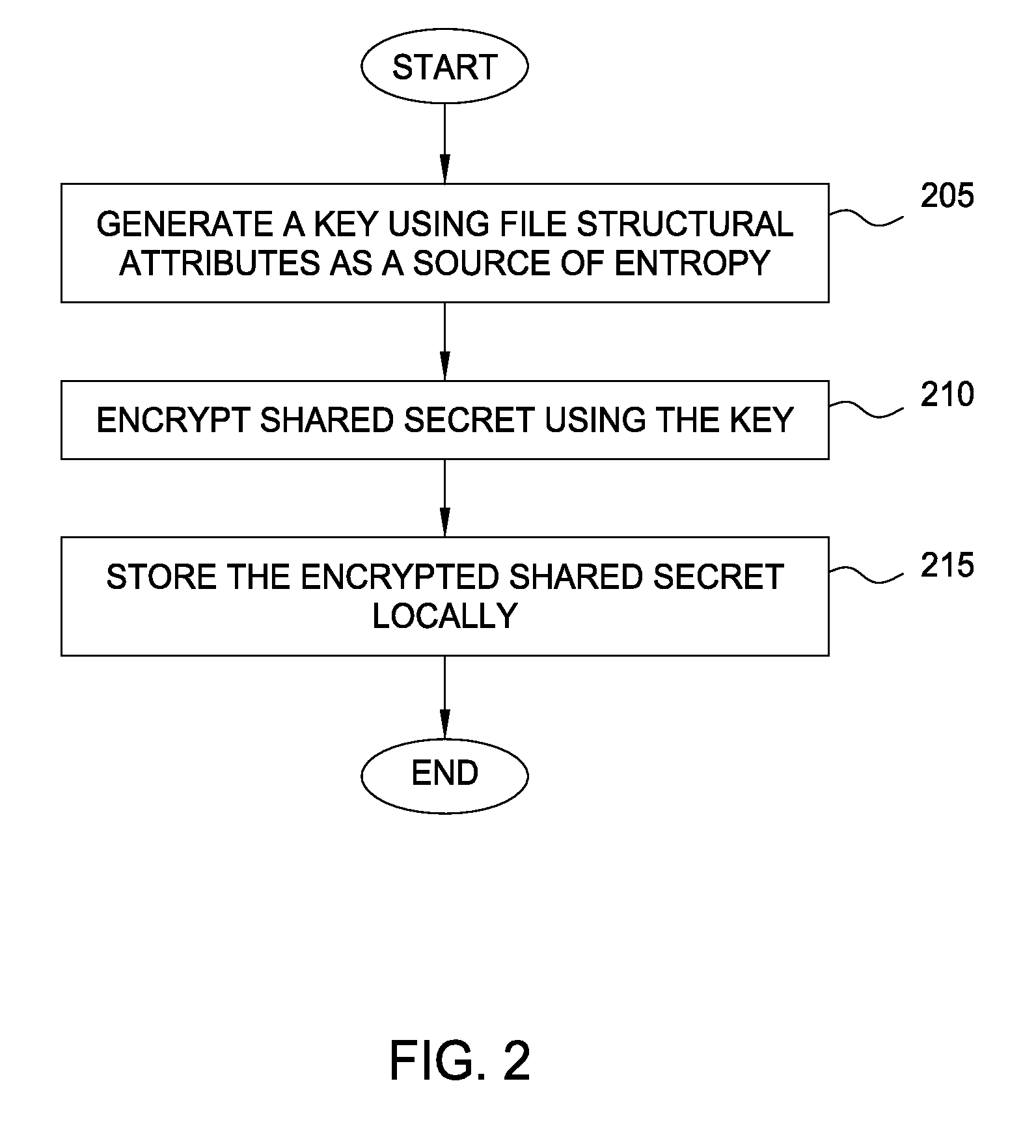
Protecting cryptographic secrets using file system attributes
Techniques are disclosed for protecting cryptographic secrets stored locally in a device, such as a mobile phone. A client device creates or downloads a shared secret to be used in a server transaction. To protect this shared secret locally, the client device encrypts the shared secret using a key generated a file system attributes value, along with other sources of entropy. The file system attributes value may correspond to the inode of a file in a UNIX-based file system. Thereafter, when the shared secret is required for logical computation, the client device reconstructs the key using the file system attributes value and the other previous sources of entropy. The client device may use the key to decrypt the information and use the shared secret for its required purpose, e.g., in generating a one-time password for a login session.
Owner:CA TECH INC
Automated login session extender for use in security analysis systems
ActiveUS7467402B2Random number generatorsUser identity/authority verificationWeb siteProgram security
A web application security scanner (WASS) includes a login manager configured to perform an automated login to a web site. The automated login may be performed when the login manager detects that a login session has ended. The login manager is configured to determine credentials for the web site to allow the WASS to access the web site. The WASS may then use the credentials to continue scanning the web site. Thus, previously unscannable web pages may be accessed in the web site because of the automated login process.
Owner:SYNOPSYS INC
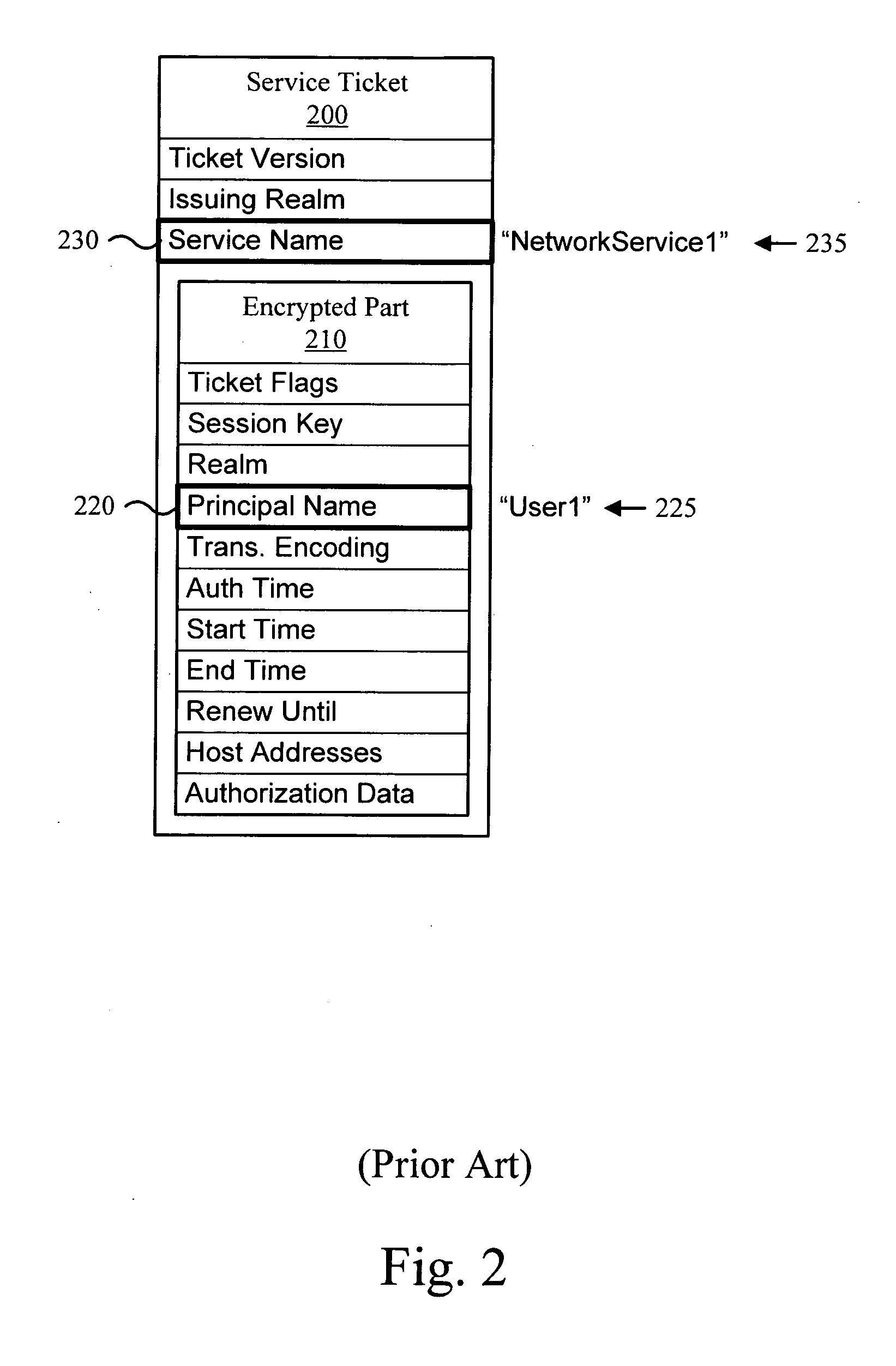
Disconnected credential validation using pre-fetched service tickets
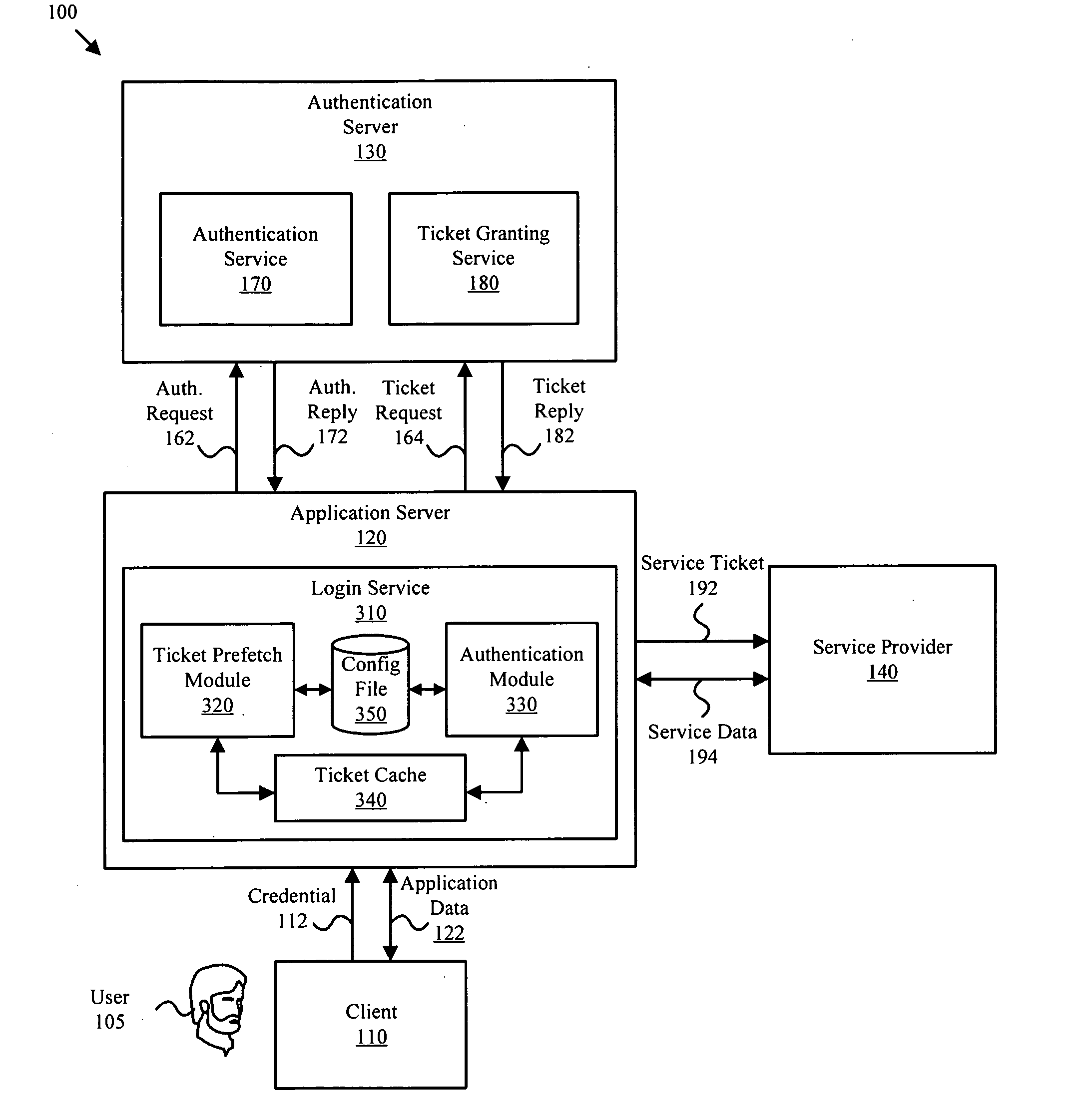
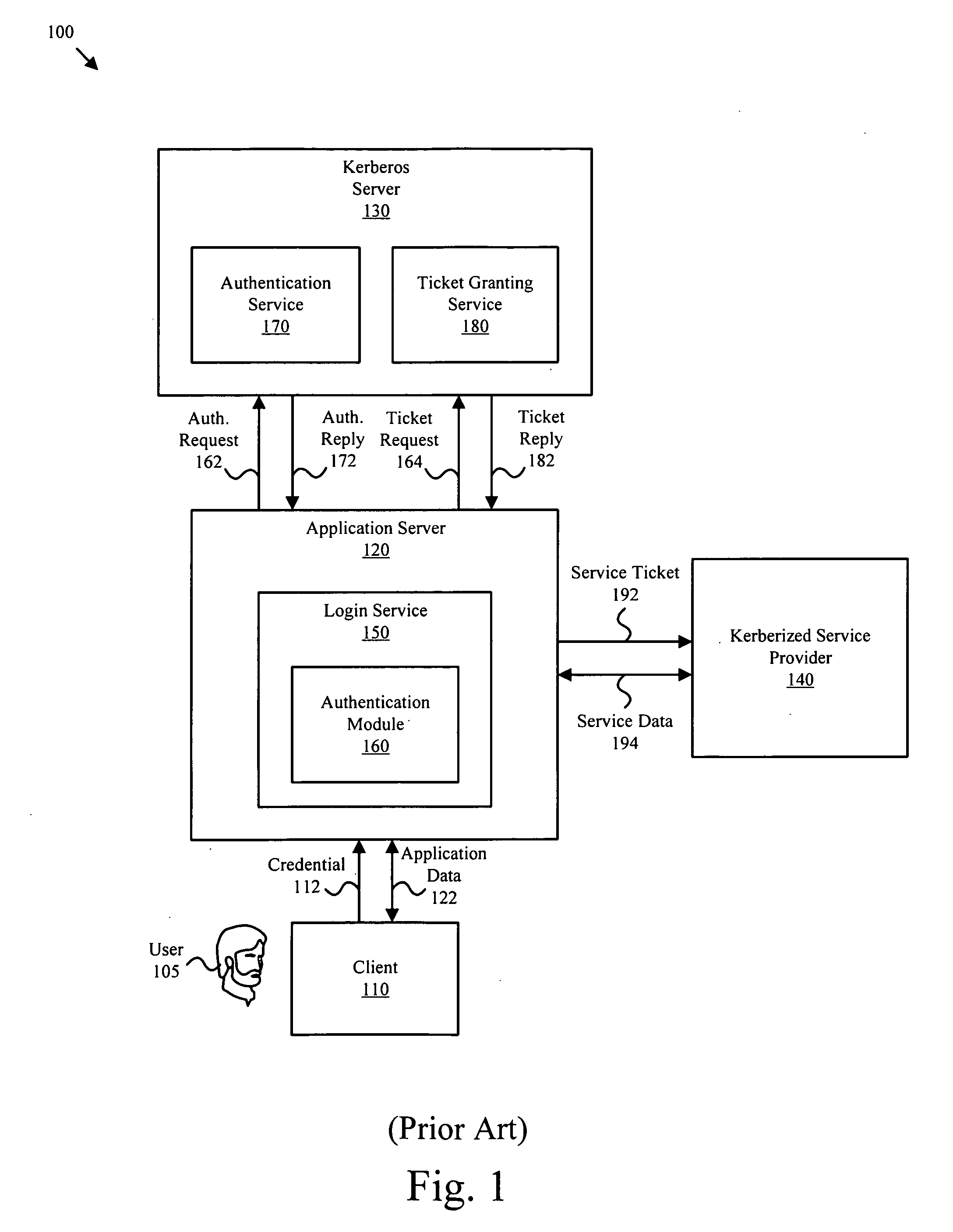
ActiveUS20070192843A1Digital data processing detailsUser identity/authority verificationAuthentication serverLogin session
One or more user service tickets are obtained (i.e. pre-fetched) from an authentication server and stored in a ticket cache. The user service tickets facilitate a login device communicating with one or more users or group members associated with the login device. Login credentials for the users or group members may be subsequently authenticated against the user service tickets within the ticket cache thereby eliminating the need for immediate access to the authentication server or a previous login session by the users or group members. The user service tickets within the ticket cache may be refreshed as needed. In one embodiment, the user service tickets are refreshed daily and also in response to login attempts if the authentication service is readily accessible.
Owner:QUEST SOFTWARE INC
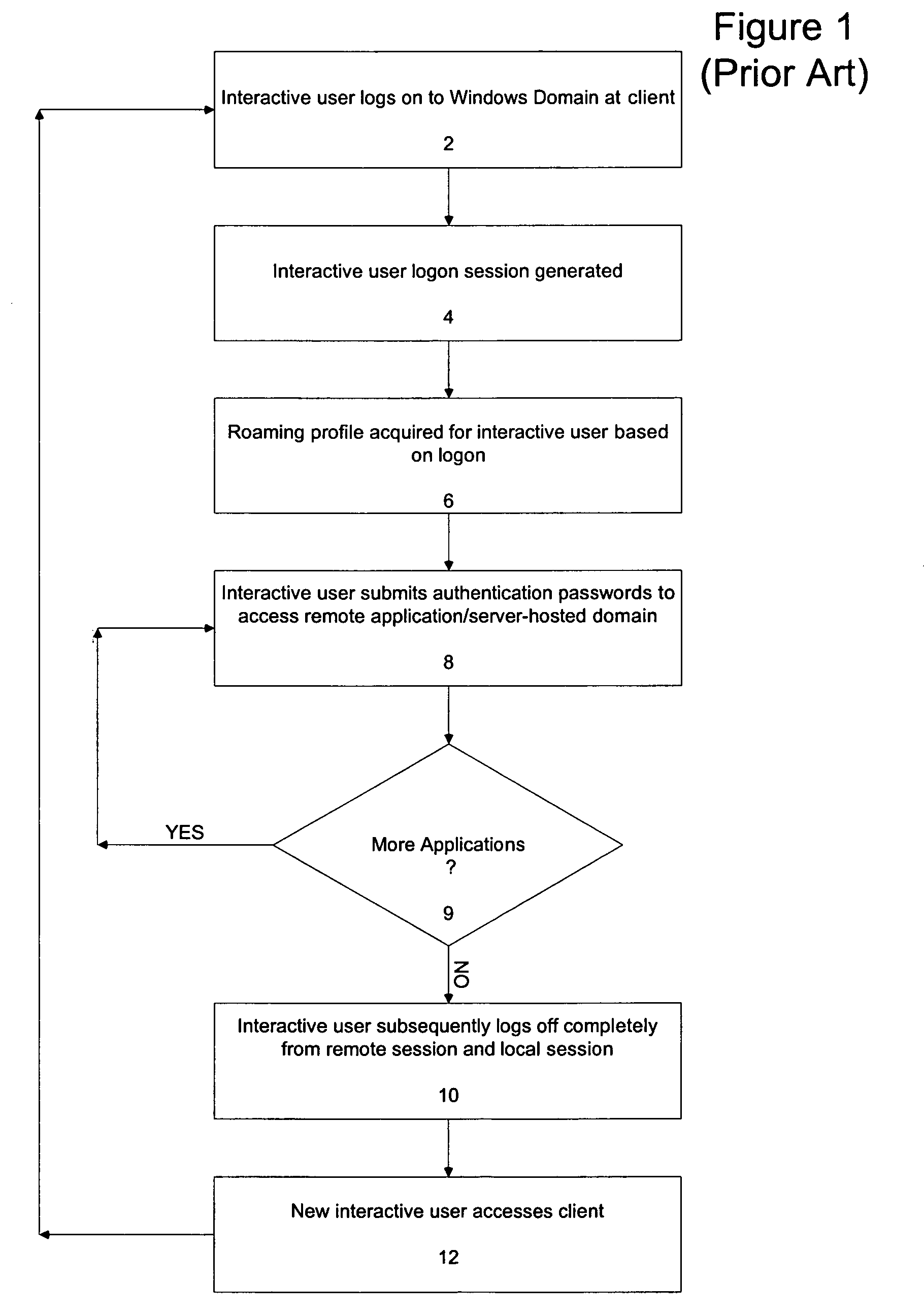
System and method for permission-based access using a shared account
ActiveUS7562226B2Quick switchFast authenticationDigital data processing detailsComputer security arrangementsOperational systemLocking mechanism
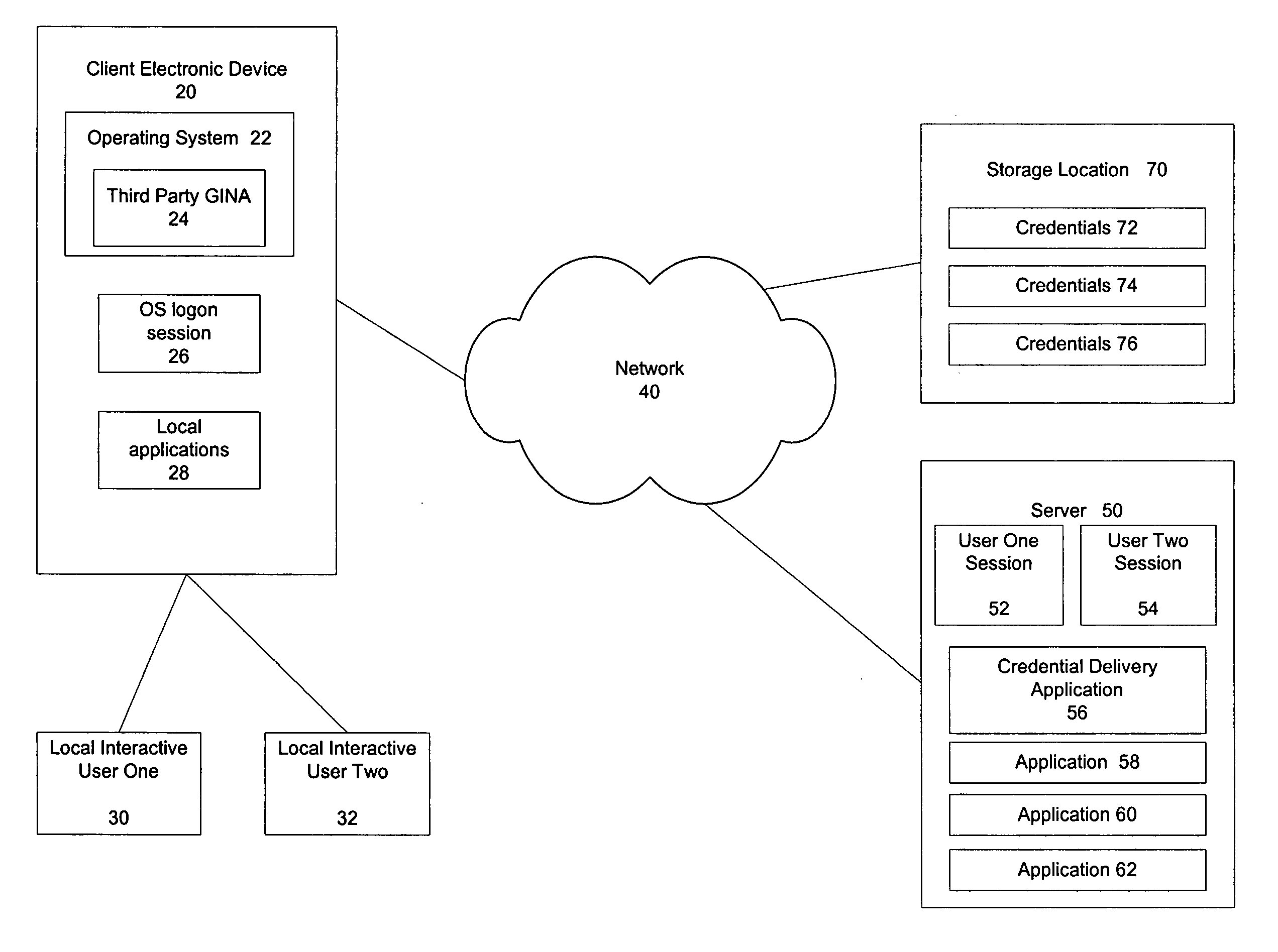
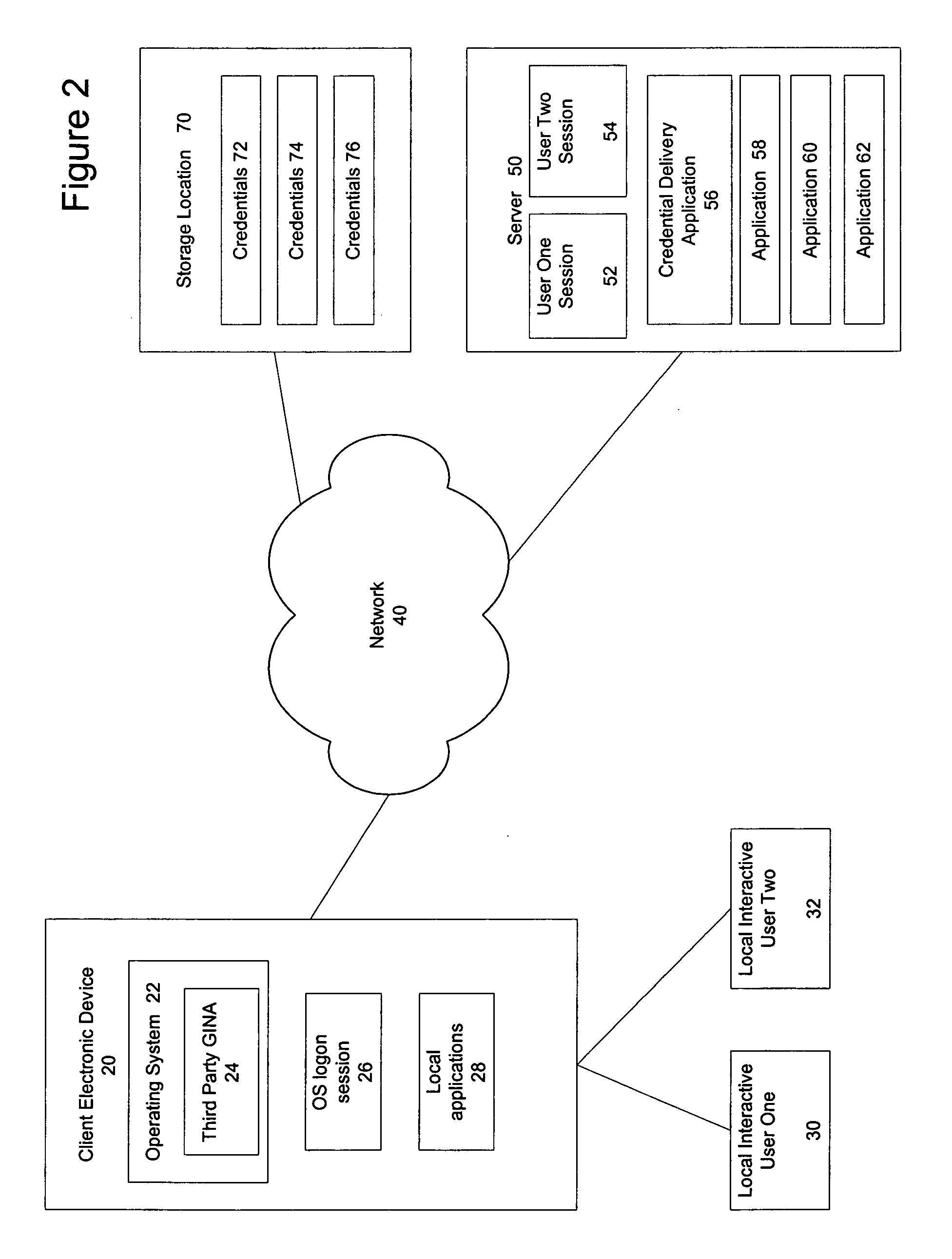
A mechanism for rapidly authenticating an interactive user in an operating system logon session based on a shared account by using a credential delivery application to enable permission-based access to a user's remote session from the shared account is disclosed. The present invention provides the ability to switch local interactive users, authenticate the new interactive user, and switch the remote session without requiring the client to first establish a new logon session tied to the new local interactive user. The present invention also alters the normal locking mechanism found in operating system logon sessions so as to restrict access to an interactive local user's applications (both local and remote) while still allowing the rapid switching of interactive users at the client device.
Owner:CITRIX SYST INC
Method and system for logging in through mobile terminal and cloud server
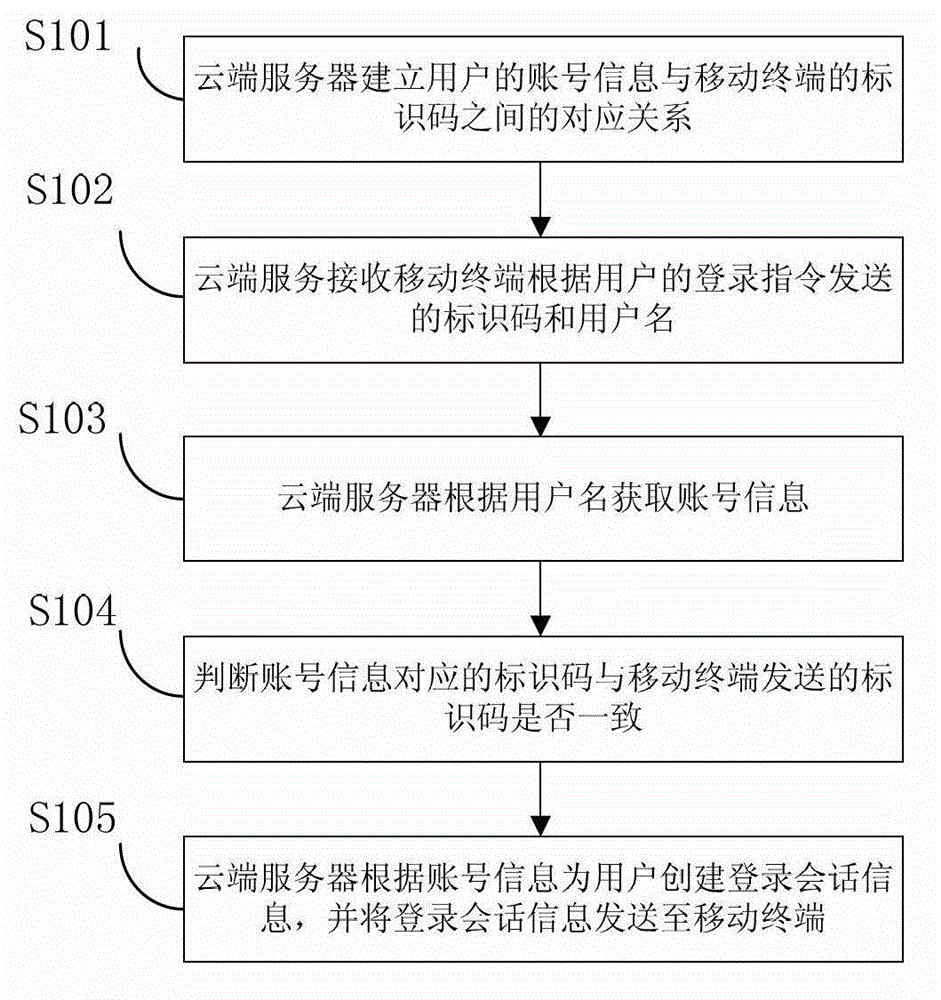
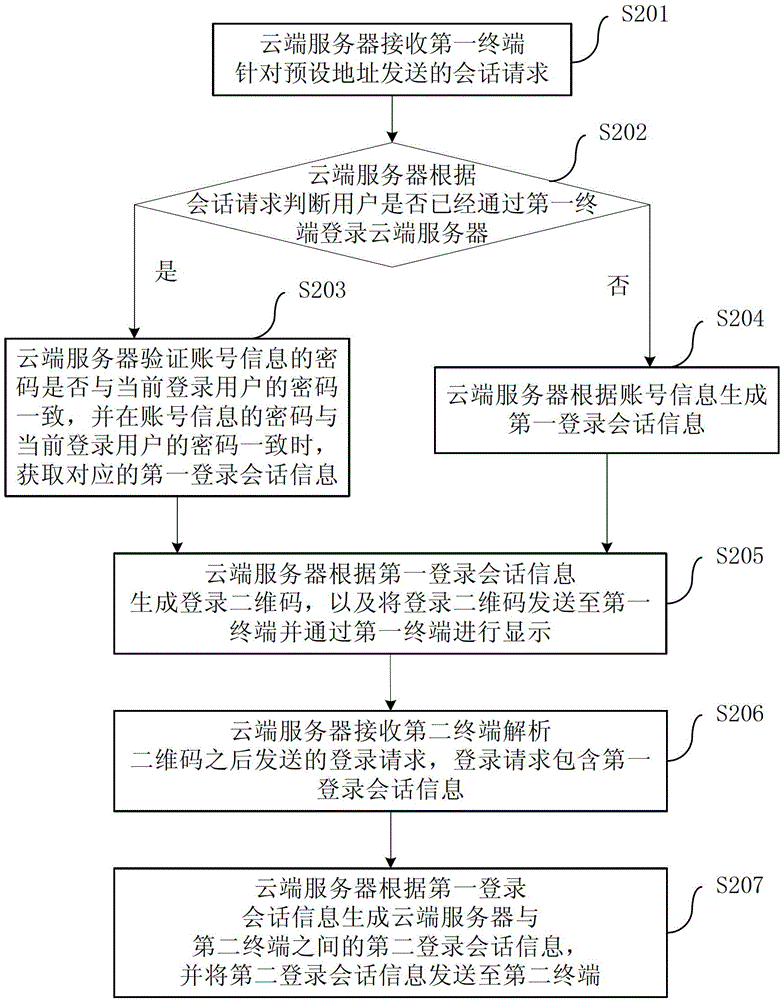
InactiveCN103152402AEliminate input costsImprove experienceSubstation equipmentTransmissionComputer terminalLogin session
The invention provides a method for logging in through a mobile terminal. The method comprises the following steps that a cloud server establishes a corresponding relation between the account information of a user and the identification code of a mobile terminal; the cloud server receives an identification code and a user name transmitted by the mobile terminal according to the login command of the user; the server acquires the account information according to the user name and judges whether the identification code which corresponds to the information is consistent with the identification code transmitted by the mobile terminal or not; and if the identification code which corresponds to the information is consistent with the identification code transmitted by the mobile terminal, the cloud server establishes login session information for the user according to the account information and transmits the session information to the mobile terminal. Due to the adoption of the method, the input cost of a user login process can be reduced and even eliminated, and the user experience is improved; and the method has the advantages of rapidness, safety and applicability. The invention further discloses a system for logging in through the mobile terminal, and a cloud server.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
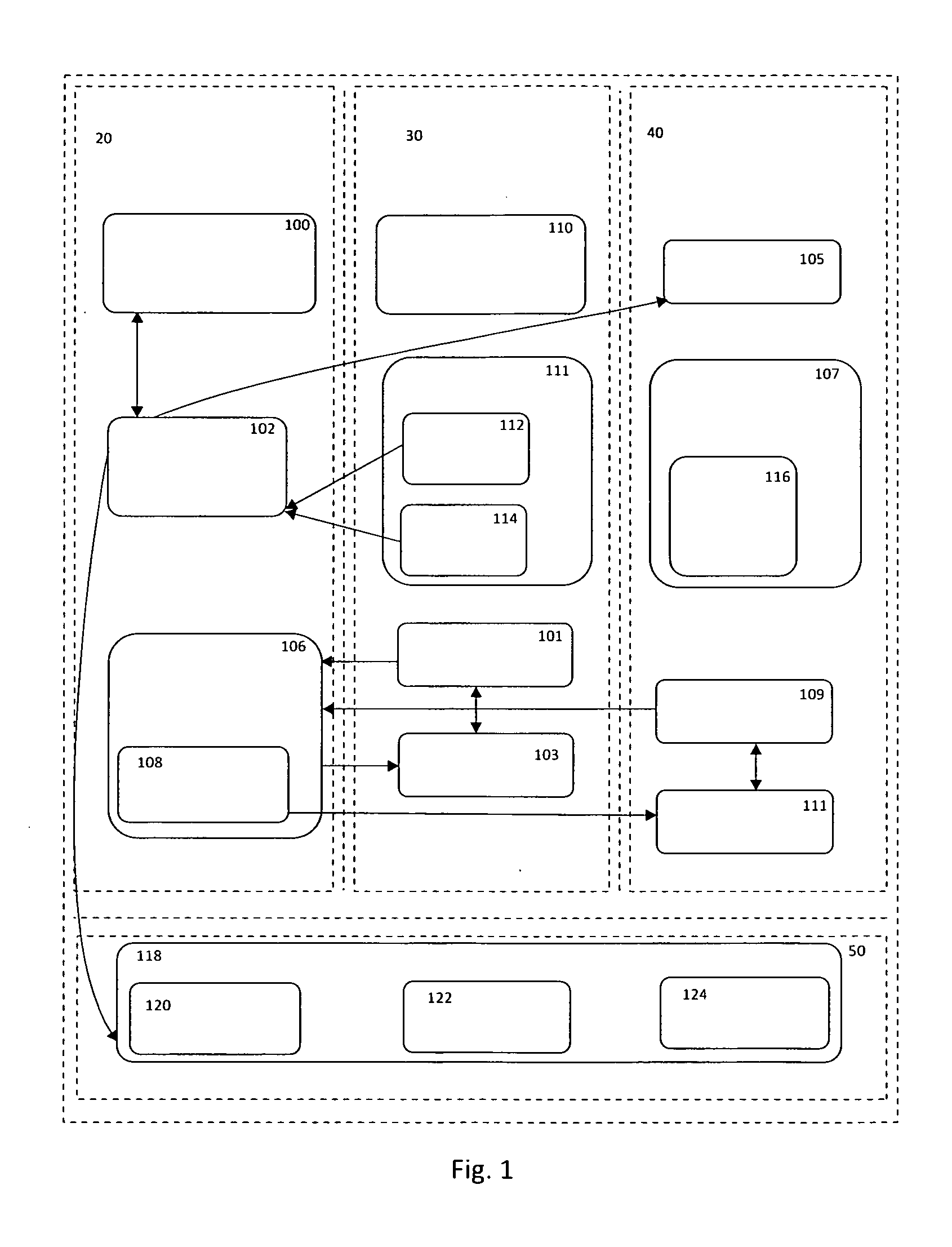
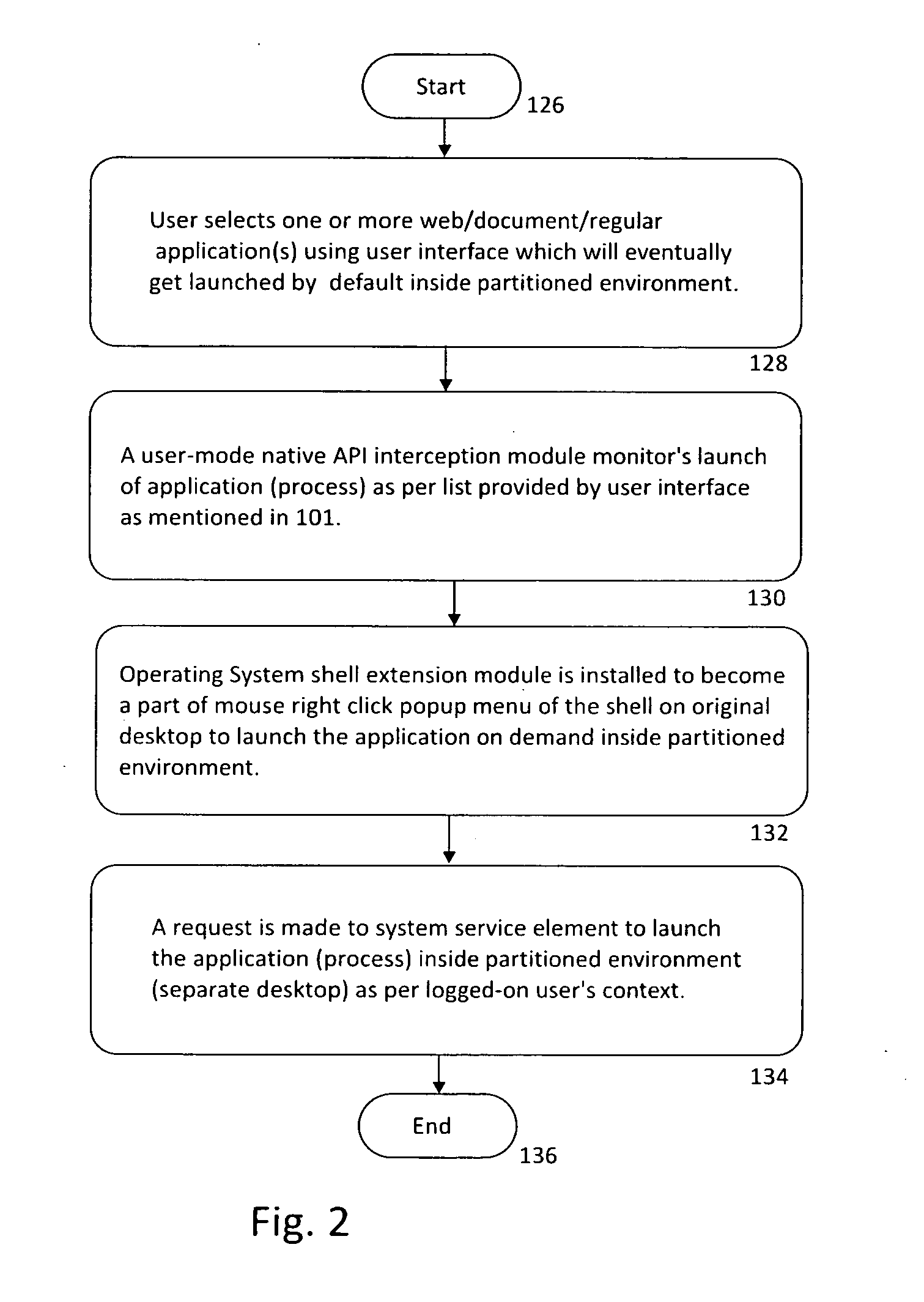
System and method for protecting computer systems from malware attacks
ActiveUS20140075555A1Limited accessMemory loss protectionError detection/correctionOperational systemLimited access
The malware protection system provides a virtual logon session which runs in the background invisible to the user. The virtual logon session is created on a computer system with the help of the operating system using a separate / partitioned kernel resources such as a desktop, that provides a limited access environment under the context of a logged-on user. The system is configured to run applications inside virtual logon sessions under the logged-on user's credentials with limited access. The system also includes an interceptor module that launches the web browser or web application inside the virtual logon session. The interceptor module intercepts every URL passing through the web browser or web application being run in the virtual logon session. The module checks if the primary web URL is infected by malware and adds the malicious URL to a malicious URL database and a non-malicious URL to a non-malicious URL database.
Owner:QUICK HEAL TECH PRIVATE +1
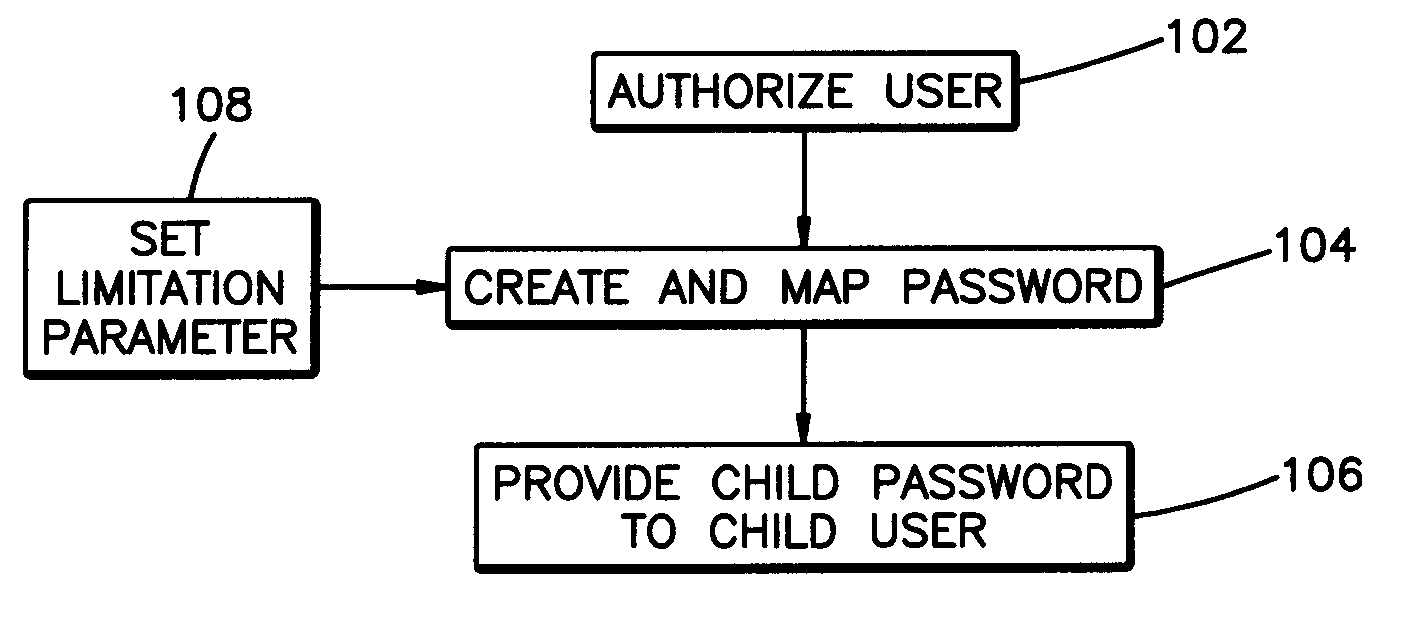
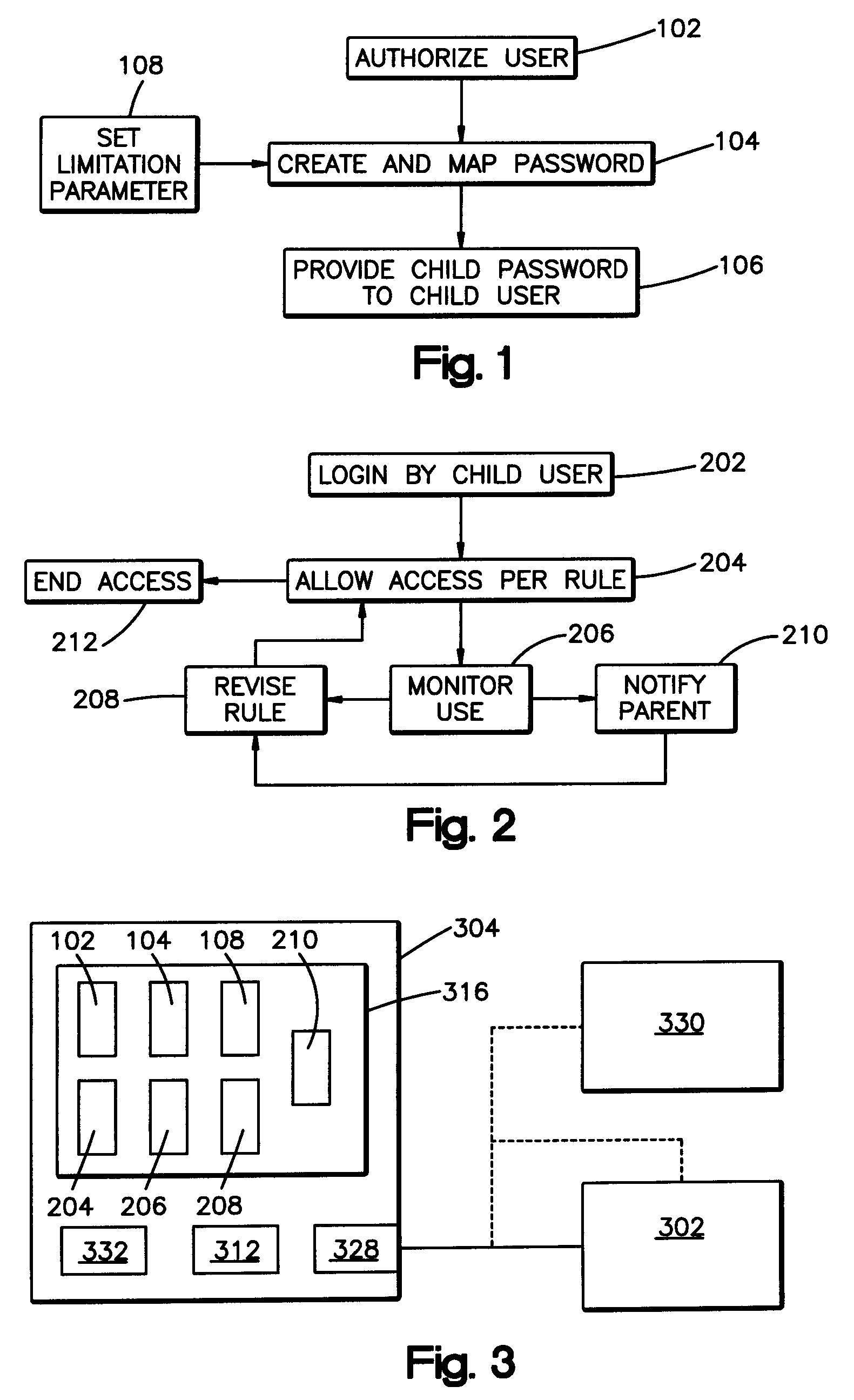
Method and system for password application
ActiveUS20080263643A1Digital data processing detailsUser identity/authority verificationPasswordApplication software
Methods, systems, and program products for a client application provide child passwords mapped to a parent password authorized for login to a secure network resource server. A child user logs in to the client application by entering the child password. When a child user properly requests a secure resource from the secure network resource server, the client application uses the authorized parent password to login to the secure server and retrieve a secure resource without communicating the child password to the secure server. The child user login session is administered by the local application pursuant to access rules or limitation parameters associated with the child password. Child passwords may be set to expire. The client application may also monitor secure server access by a child user; monitored use may also be reported, and an access rule or password limitation parameter may be revised in response to monitoring and use reporting.
Owner:KYNDRYL INC
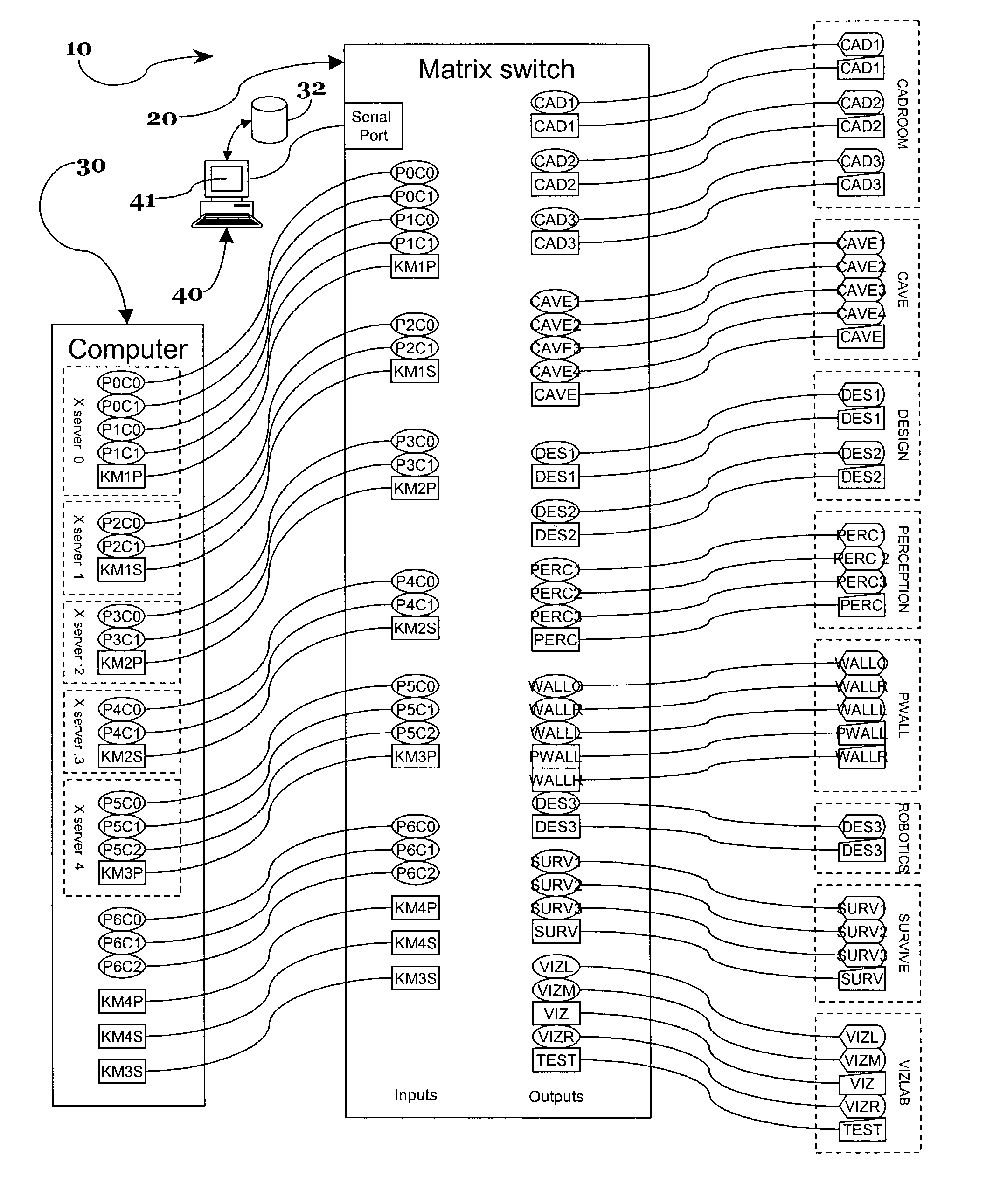
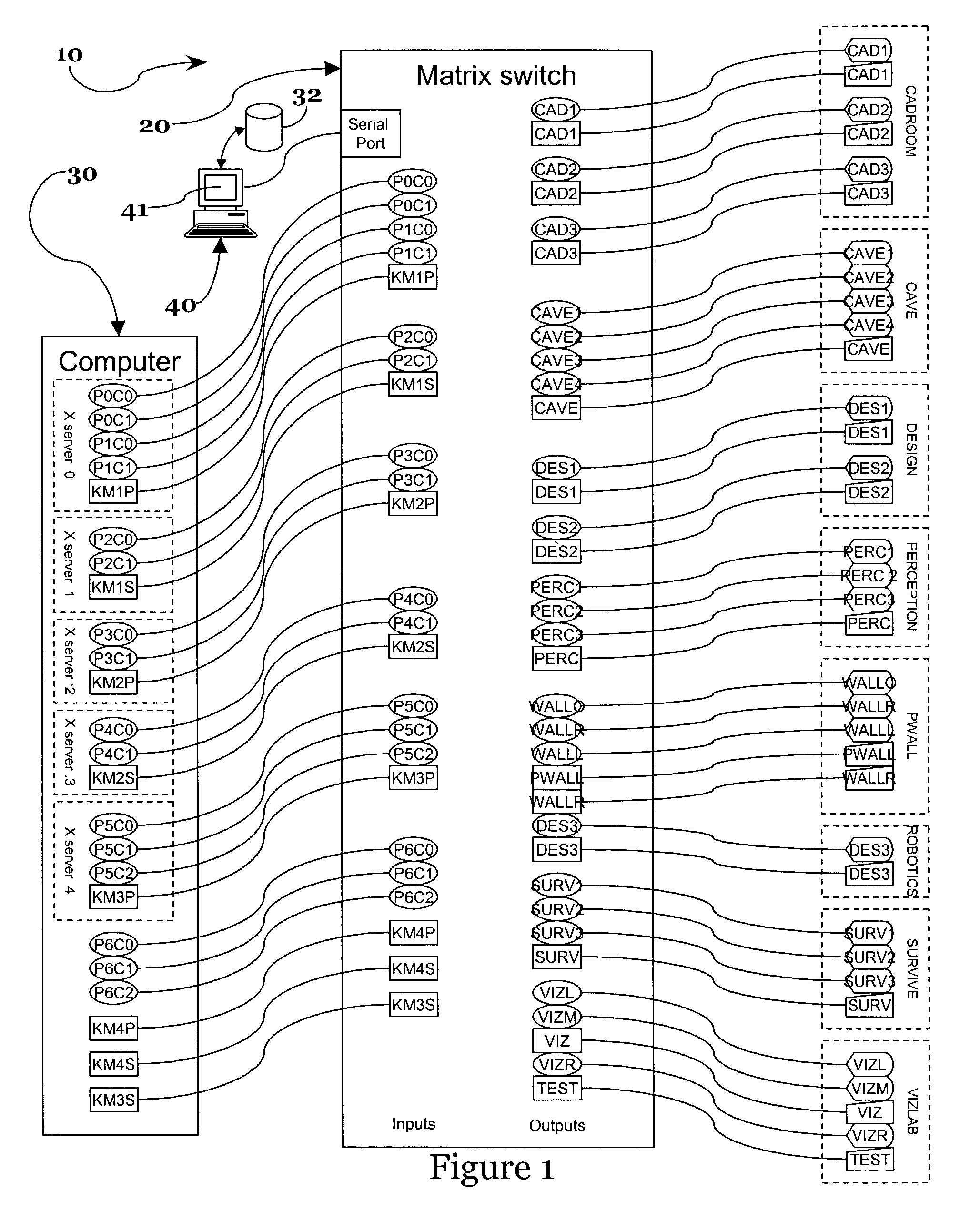
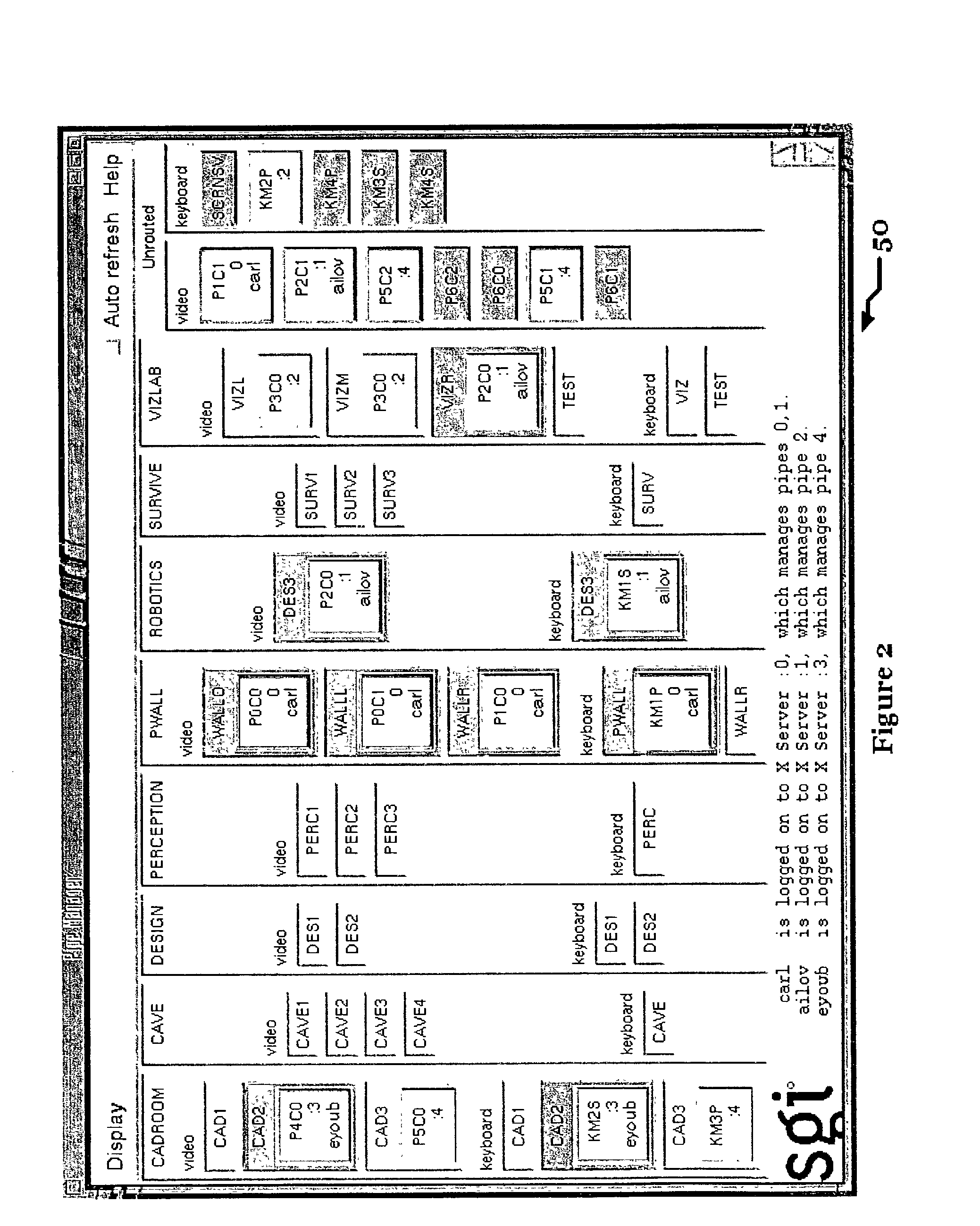
System and method for allocating computing resources
A system and method for allocating computing resources. The system obtains a current set of connections from the matrix switch and then renders a display which reflects the current state of the connections. Source and destination ports are displayed as icons with each icon bearing a label that describes the corresponding source or destination. In some embodiments, a user clicks on a source icon and drags it onto a destination icon to route a particular source to a destination. Dragging a source icon off of a destination icon breaks the connection between the source and destination. The display uses a variety of icons, colors, and grouping schemes to indicate other attributes of the ports, such information regarding X Server configuration, physical location of destination devices, and user login sessions.
Owner:RPX CORP +1
Single sign-on with common access card
ActiveUS7818582B2Reduce the number of timesImprove efficiencyDigital data processing detailsUser identity/authority verificationUser needsOff the shelf
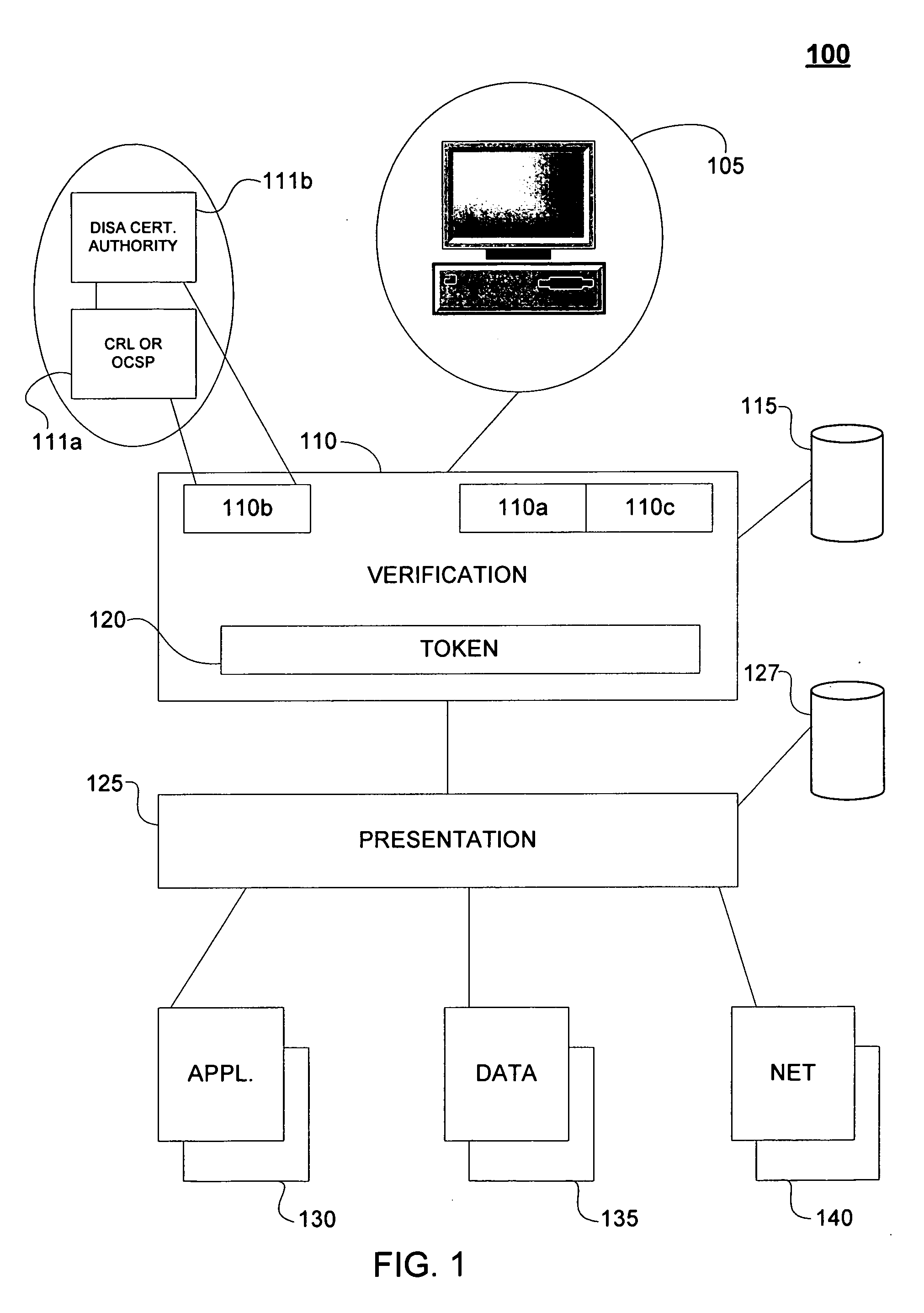
A mechanism eliminates the number of times a user must login to individual services after initially logging into a computer system. A user only logs once into a computer system, and subsequent login requests by multiple services are handled automatically and transparently by the system. In one implementation, a user need only present a card to a card reader and enter a PIN, and the user is logged-in after presenting the card and a valid PIN. The system generates a token that is valid for this particular login session of the user, and when the user accesses a permissioned service, the system automatically logs-in the user to the application using the token. The system can perform the automatic login the user to a variety of applications including legacy applications, web-enabled applications, and commercial, off-the-shelf applications.
Owner:ACCENTURE GLOBAL SERVICES LTD
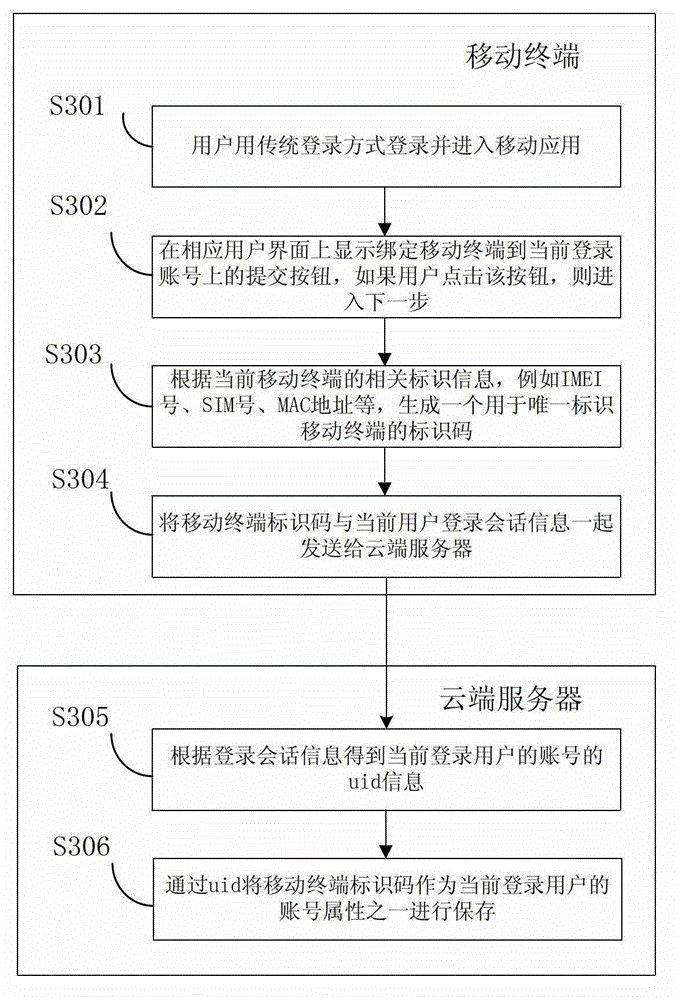
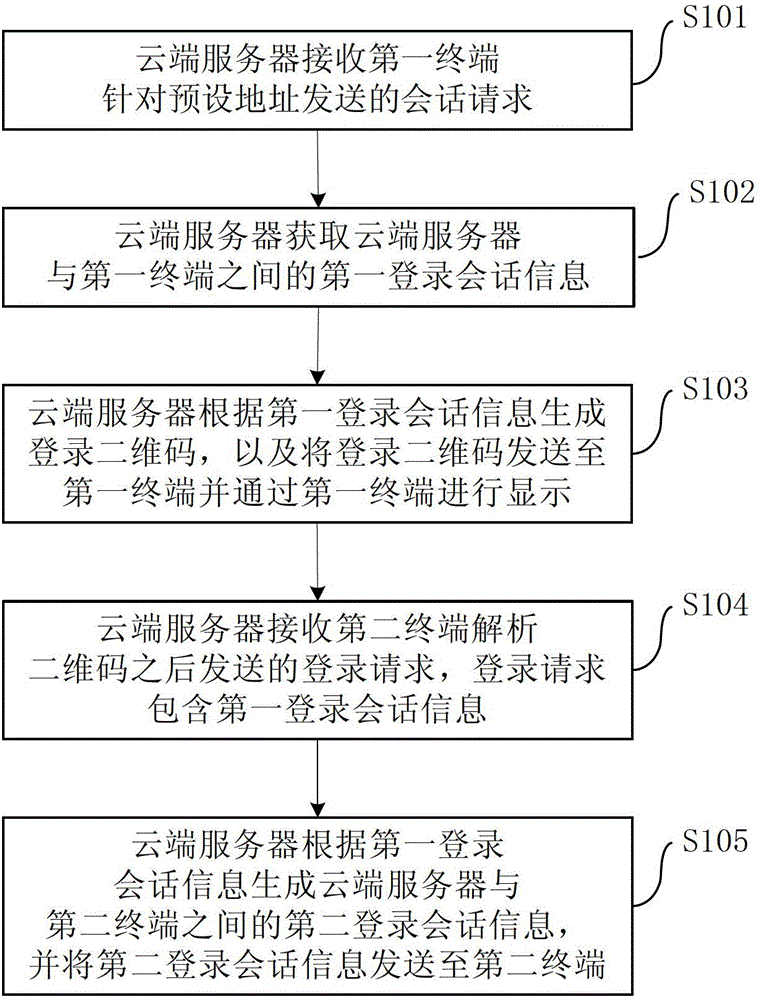
Login method, login system and cloud server
InactiveCN103152330AReduce or even completely eliminate input costsImprove experienceTransmissionComputer scienceLogin session
The invention provides a login method, a login system and a cloud server. The login method comprises the following steps that the cloud server receives a session request which is transmitted by a first terminal aiming at a preset address; the cloud server obtains first login session information between the cloud server and the first terminal; the cloud server generates a login two-dimensional code according to the first login session information and transmits the login two-dimensional code to the first terminal to display the two-dimensional code through the first terminal; the cloud server receives a login request which is transmitted by a second terminal after the second terminal resolves the login two-dimensional code, wherein the login request contains the first login session information; and the cloud server generates second login session information between the cloud server and the second terminal according to the first login session information, and transmits the second login session information to the second terminal. According to the method provided by the embodiment of the invention, the input cost in the user login process is reduced or even fully eliminated, the user experience is improved, and the rapidness, the security and the applicability are good.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
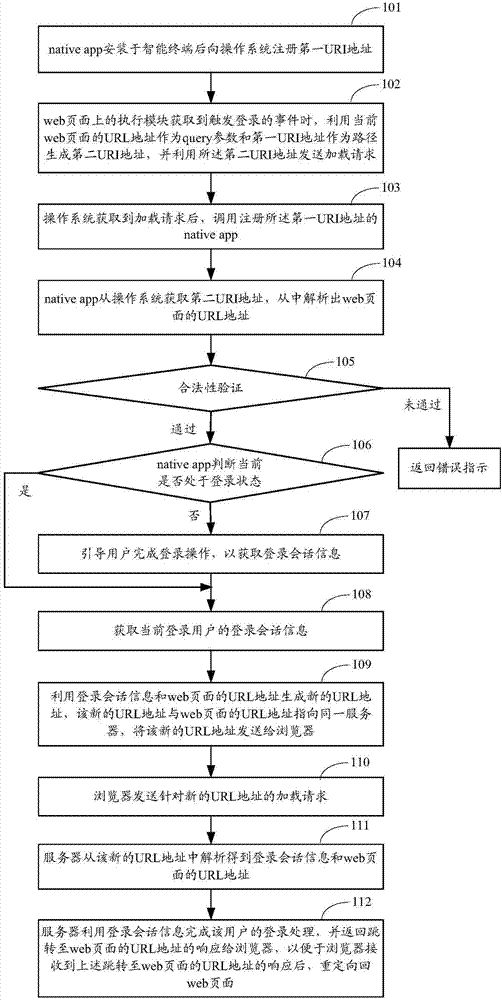
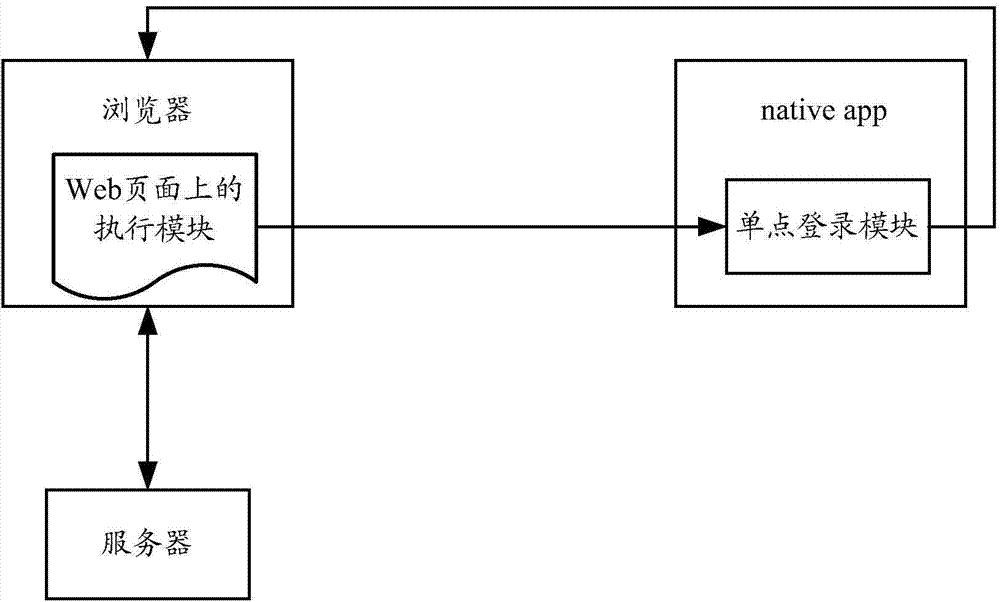
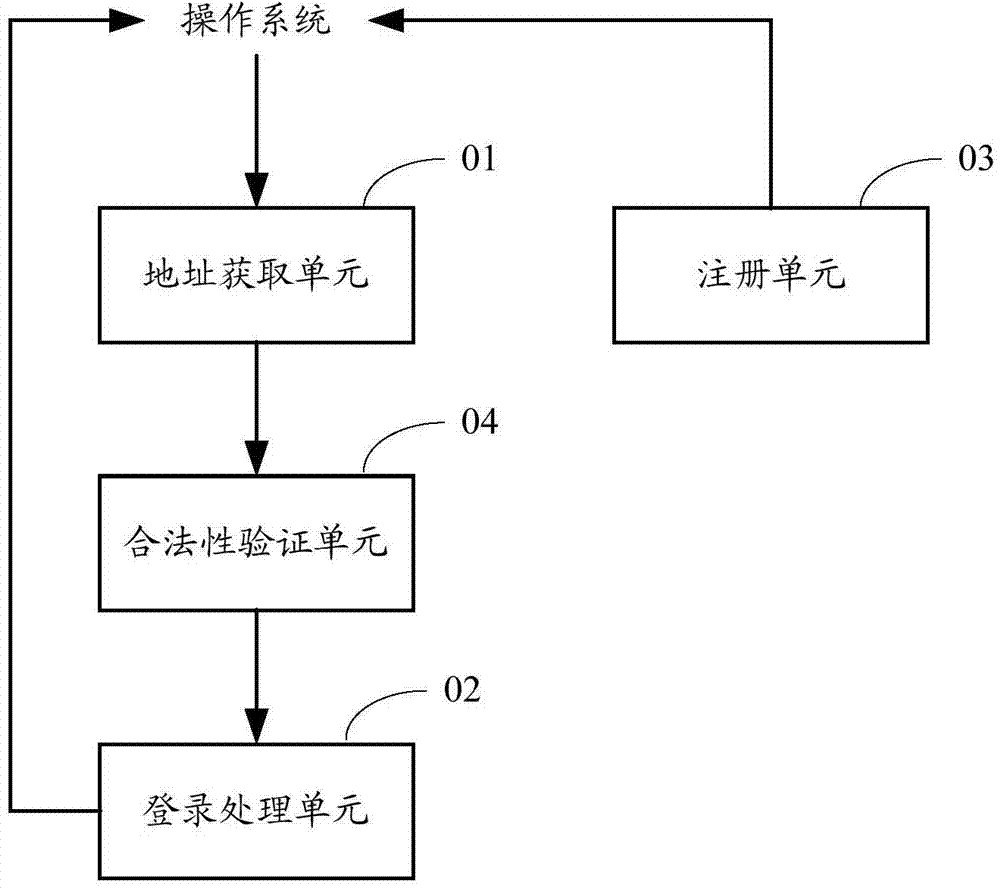
Single sign-on method, device and system oriented to web page applications
The invention provides a single sign-on method, device and system oriented to web page applications. The method includes the steps that when an executing module on a web page acquires an event triggering login, the URL address of the current web page is sent to local applications; the local applications send login session information of current login users and the URL address of the web page to a browser, and the browser utilizes the login session information and the URL address of the web page to perform automatic login. Through the single sign-on method, device and system oriented to the web page application, when the users have access to the web page through the browser to trigger the login event, if the local applications belonging to the same login system as the web page are in the login state, automatic login of the web page is achieved through the login session information of the current login users of the local applications, operation of the users is simplified, and system resources are saved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Dual authentication method, system and device for SSH safe login
InactiveCN105162764ARealize remote login authenticationWithout compromising securityTransmissionPasswordIdentity theft
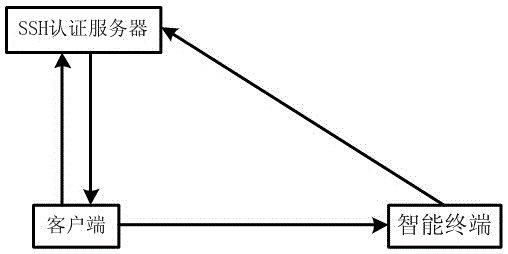
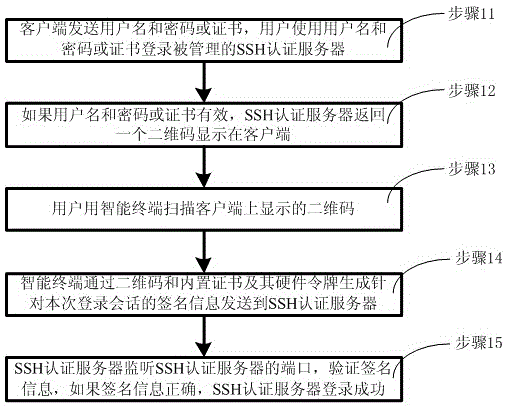
The invention discloses a dual authentication method for SSH safe login. The method includes the following steps: a client sends a user name and a password or certificate, and a user uses the user name and the password or certificate to log in a managed SSH authentication server; if the user name and the password or certificate are valid, the SSH authentication server returns a two-dimensional code to be displayed on the client; the user uses an intelligent terminal to scan the two-dimensional code displayed on the client; the intelligent terminal generates signature information for a login session of this time to a two-dimensional verification server or the SSH authentication server through the two-dimensional code, a built-in certificate and a hardware token thereof; and the SSH authentication server verifies whether the signature information is correct, and if the signature information is correct, the SSH authentication server logs in successfully. The dual authentication method for SSH safe login has the beneficial effects that a secondary authentication process based on a two-dimensional code is added, and two-dimensional code information is leaked, is unique and cannot be repetitive, thereby greatly improving security of login verification of the SSH authentication server, and preventing the problem of identity theft caused by user password loss.
Owner:BEIJING STONE SHIELD TECH
Multiple user desktop system
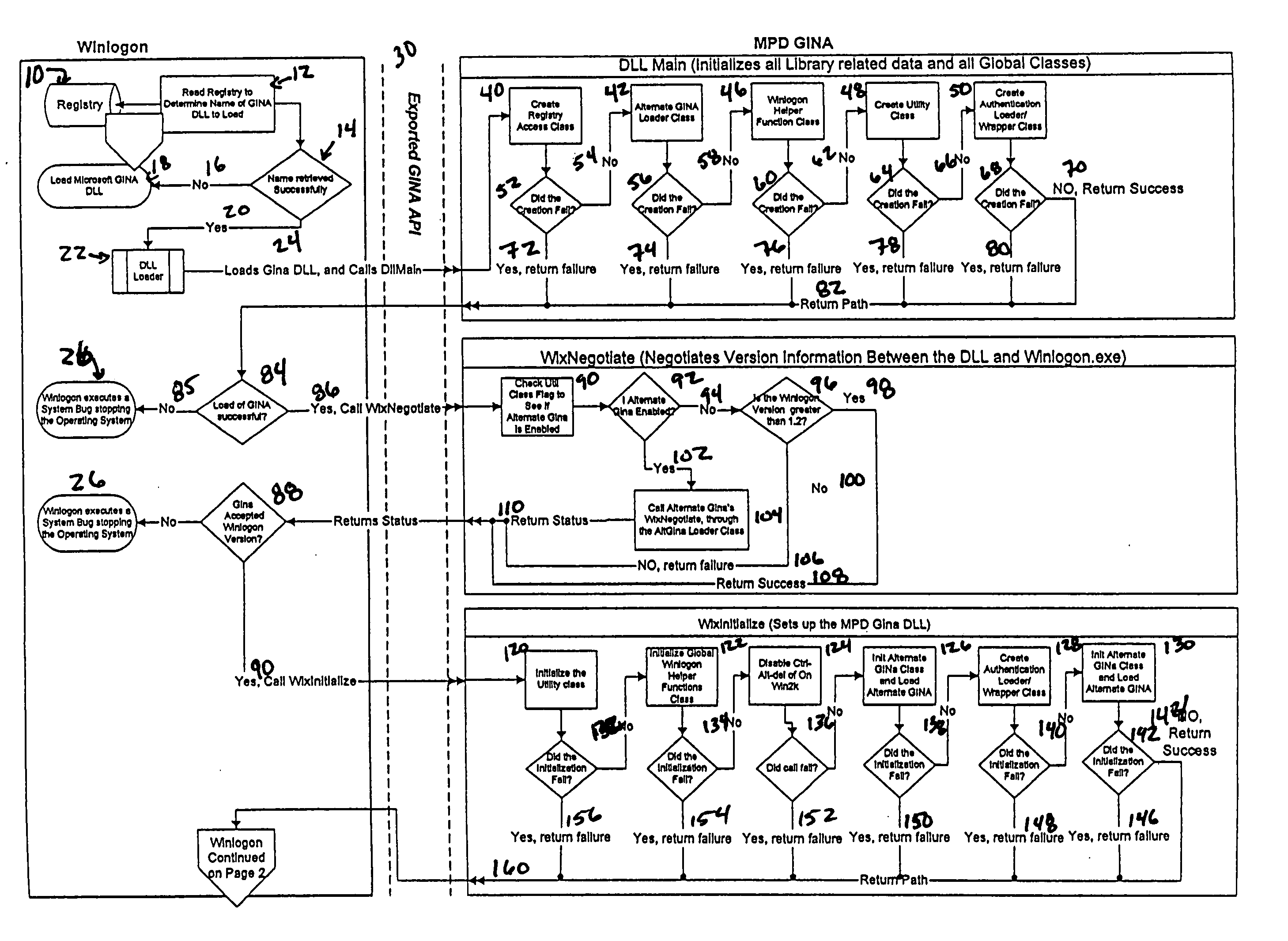
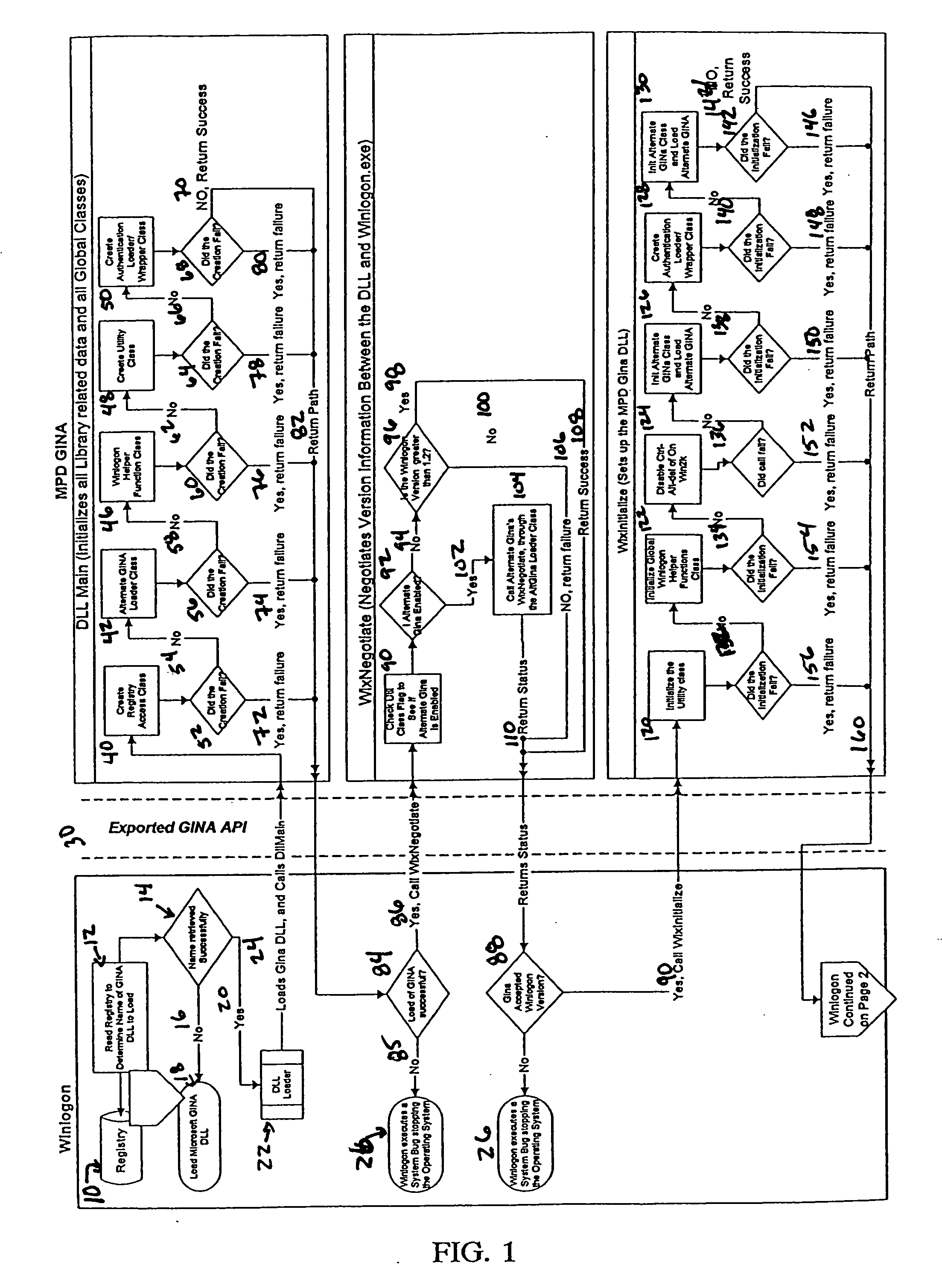
The multiple user desktop (MUD) GINA is a loadable dynamic link library (DLL) intended to replace the default Microsoft GINA. It has the ability to create secure, private logon sessions for each user that logs on to the system. There can be up to fourteen (14) users logged in at the same time and each user will have their own desktop environment. Auto log off functions may be set based on time of inactivity and / or number of individual users. The MUD Gina functions in a domain and non-networked environments and needs no added hardware.
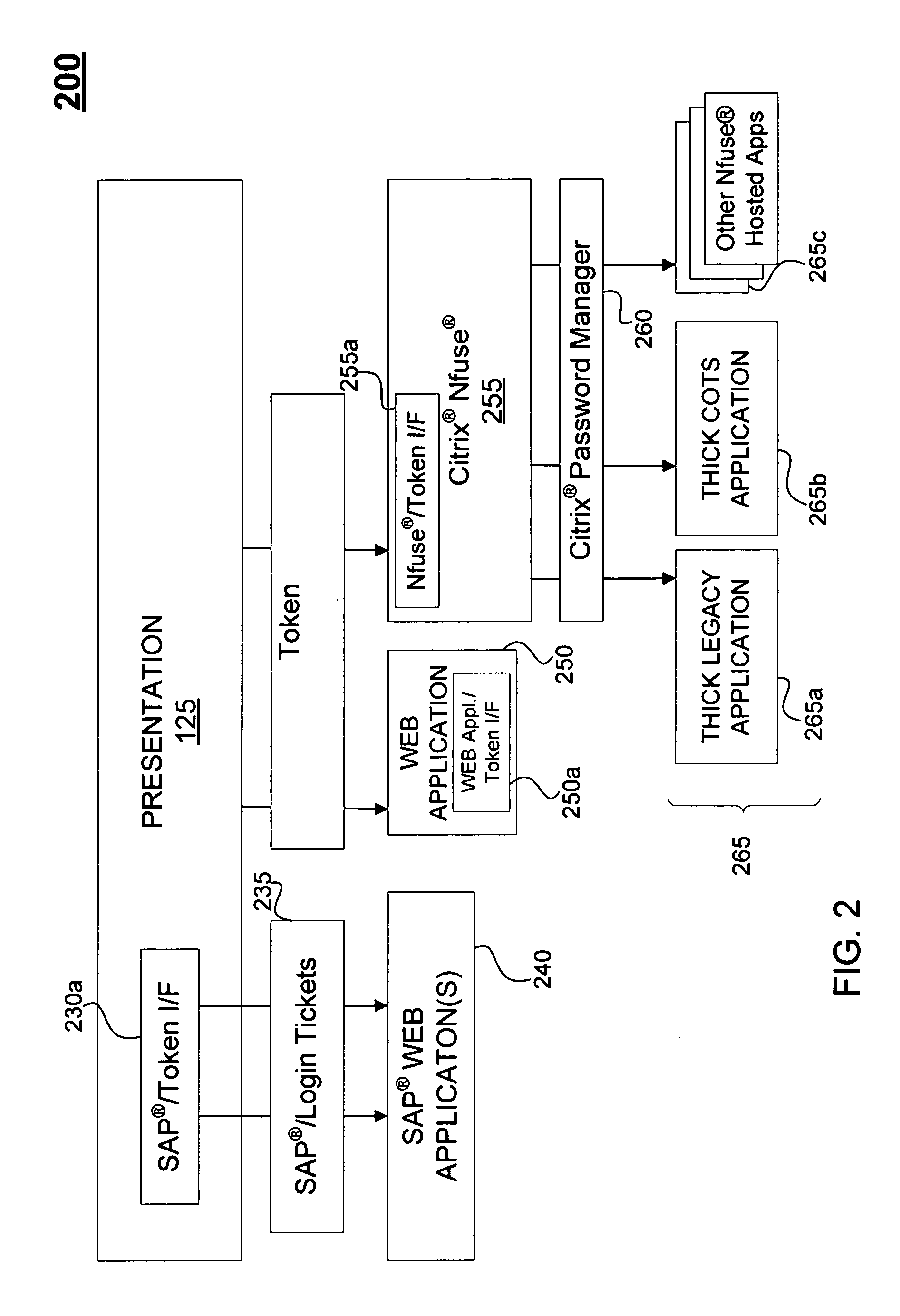
Owner:HOGHAUG ROBERT JOHN +1
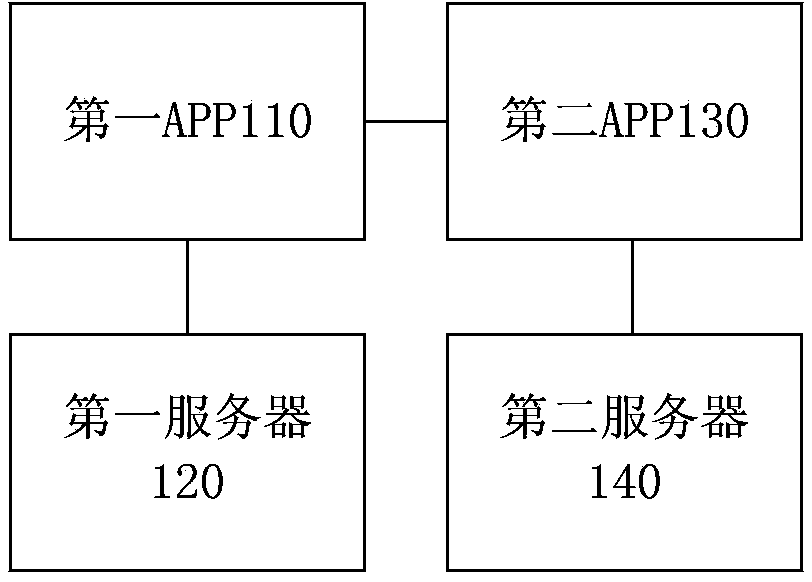
System and method for logging in applications (APPs)
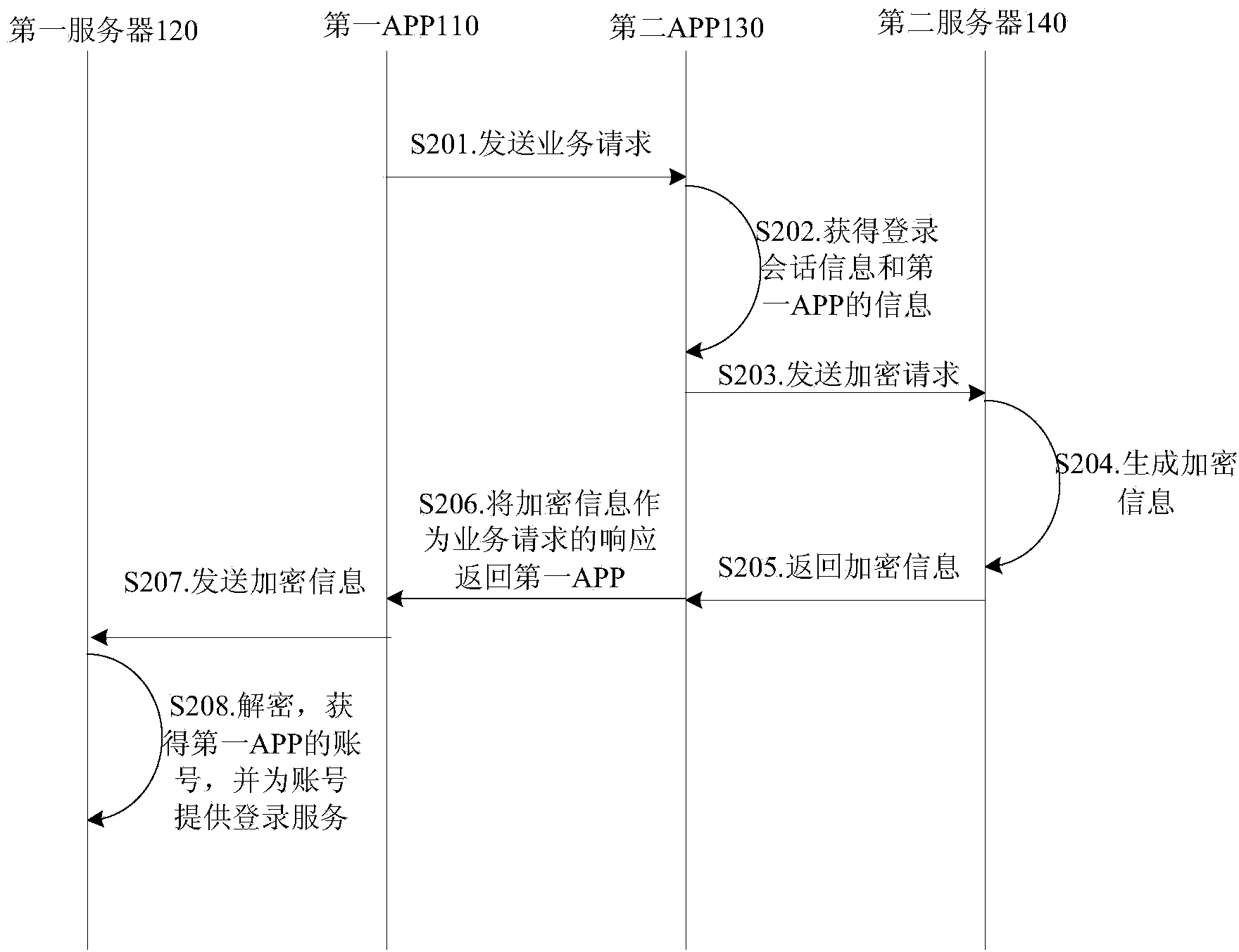
ActiveCN104113534AEliminate operating costsThe login process is smoothTransmissionLogin sessionEncryption
The invention provides a system and method for logging in applications (APPs). The system includes a first APP, a first server, a second APP and a second server, wherein the first APP is sued for sending a service request to the second APP, receiving encrypted information from the second APP, and sending the encrypted information to the first server; the second APP is sued for obtaining information of the first APP according to the service request, obtaining login session information, then sending an encryption request containing the information of the first APP, the service request and the login session information to the second server, and sending encrypted information from the second server to the first server; the second server is used for generating encrypted information according to the encryption request, and sending the encrypted information to the second APP; and the first server is used for receiving the encrypted information send by the first APP, decrypting the encrypted information, obtaining an account number of the first APP according to a decrypted result, and providing a login service for the account number. According to the abovementioned system and method, operating cost for initiative login of a user is omitted, and no page jump occurs in a login process.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com