Patents
Literature
41results about How to "Simplify login operations" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
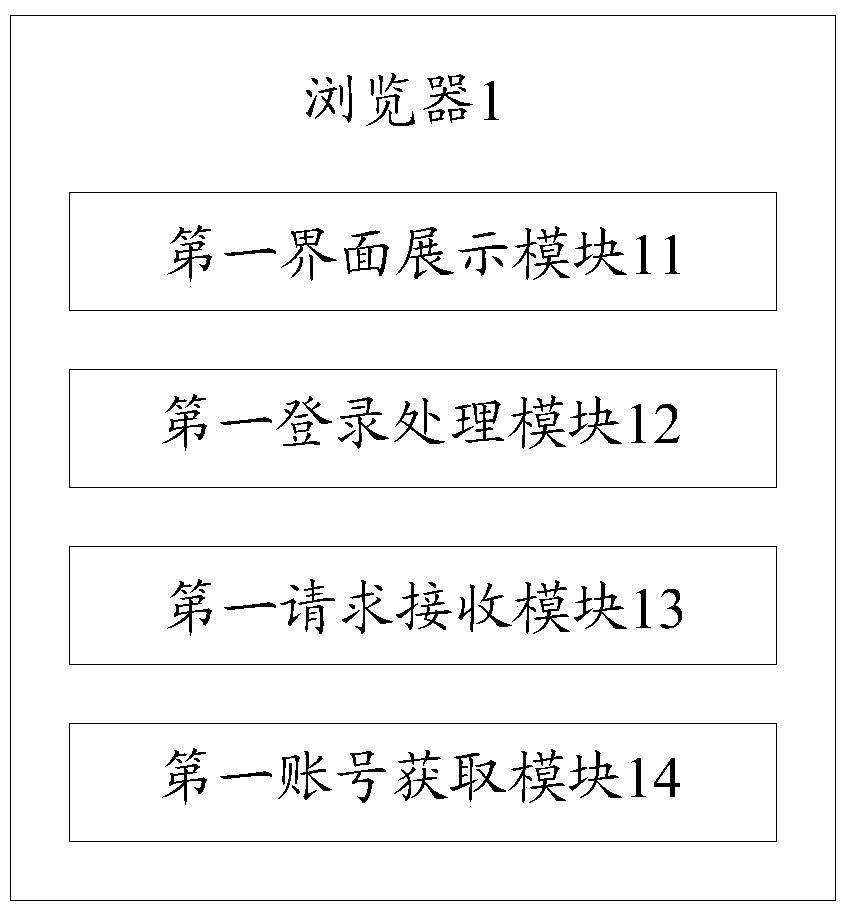
Method, system and cloud server for multi-device safe logging
ActiveCN103281327ASimplify login operationsImprove experienceTransmissionLogin sessionOperating system
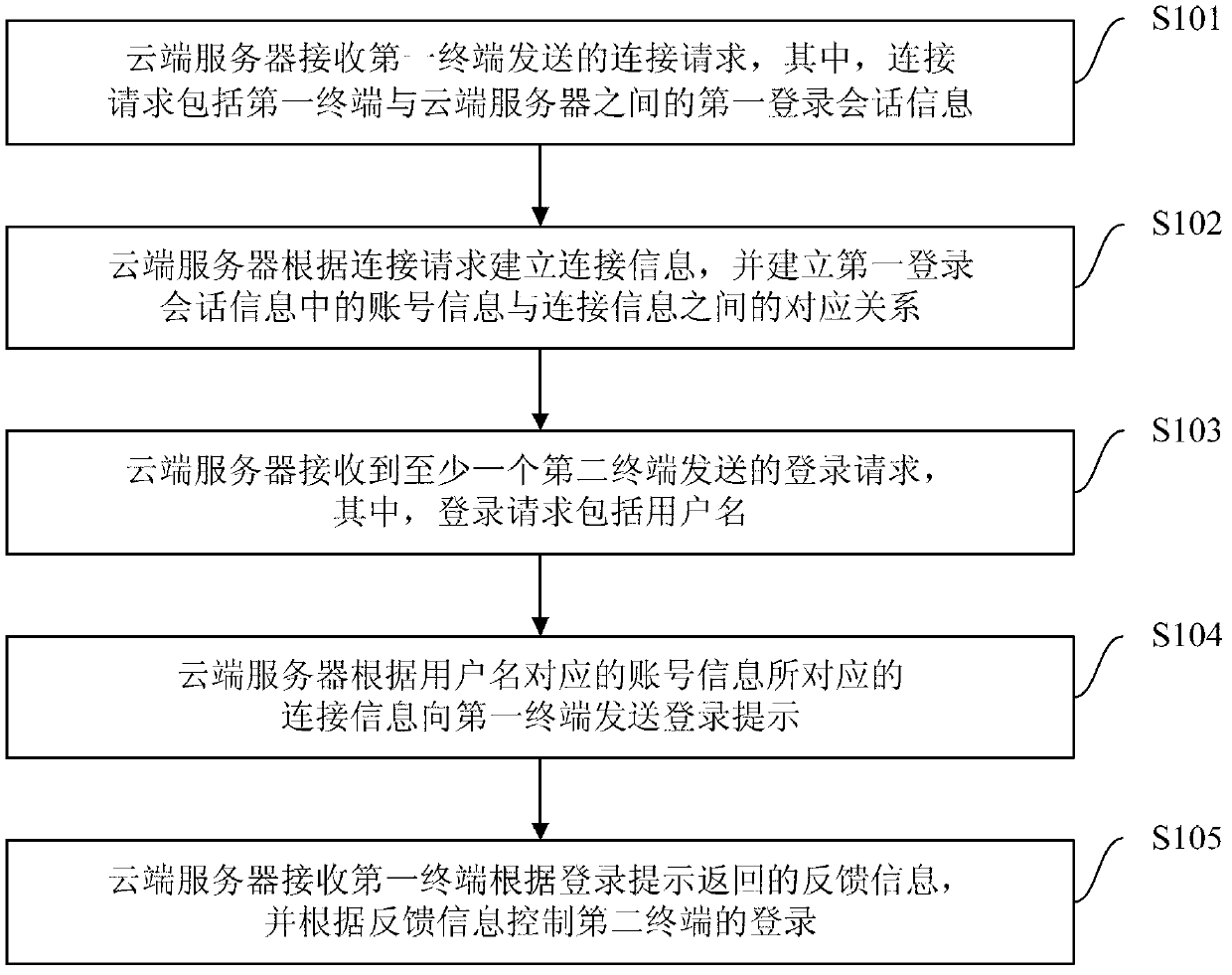
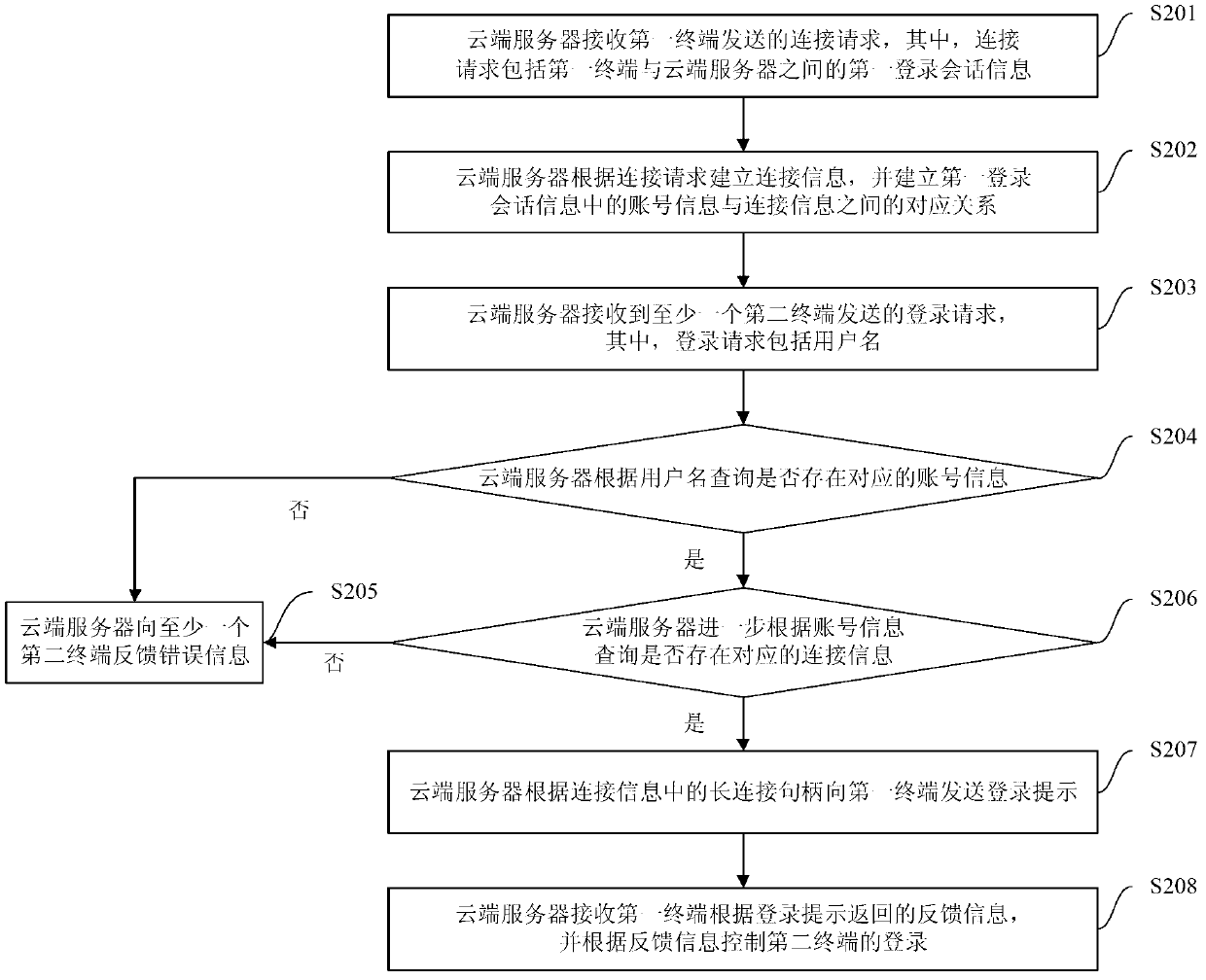
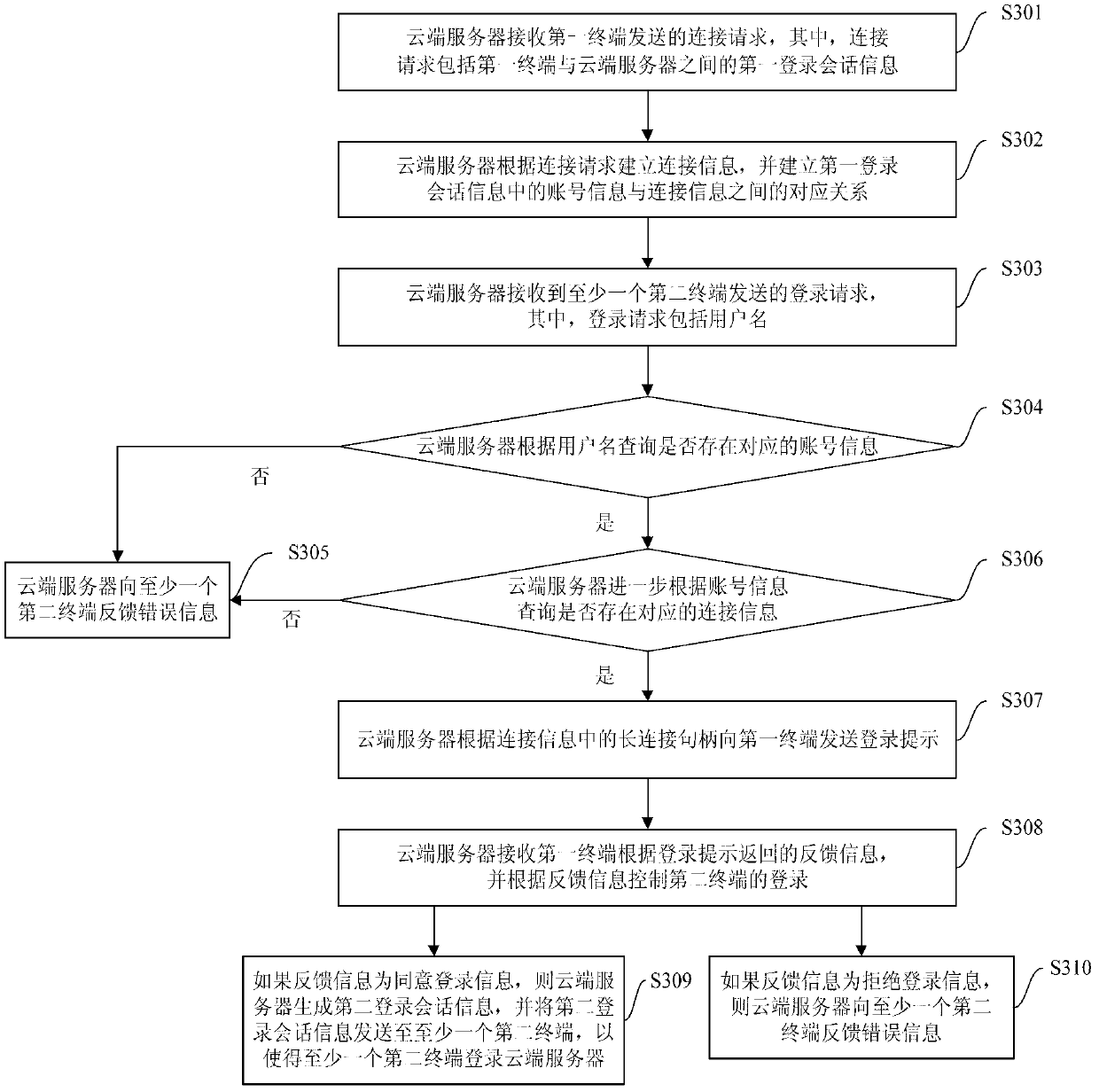
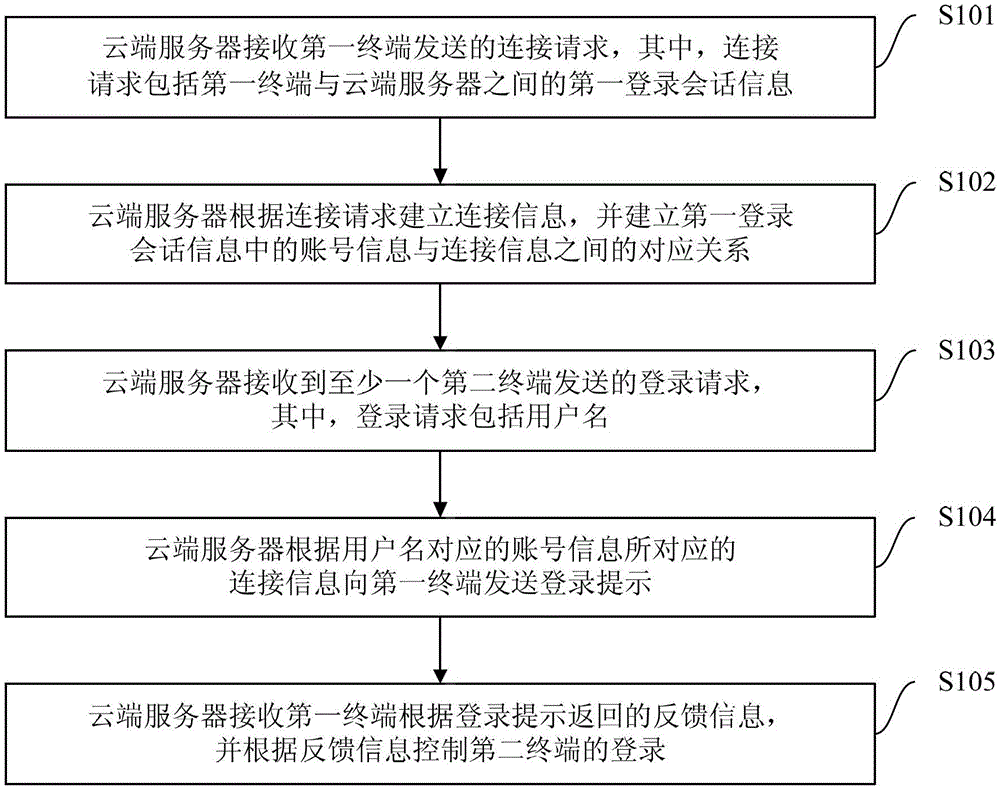
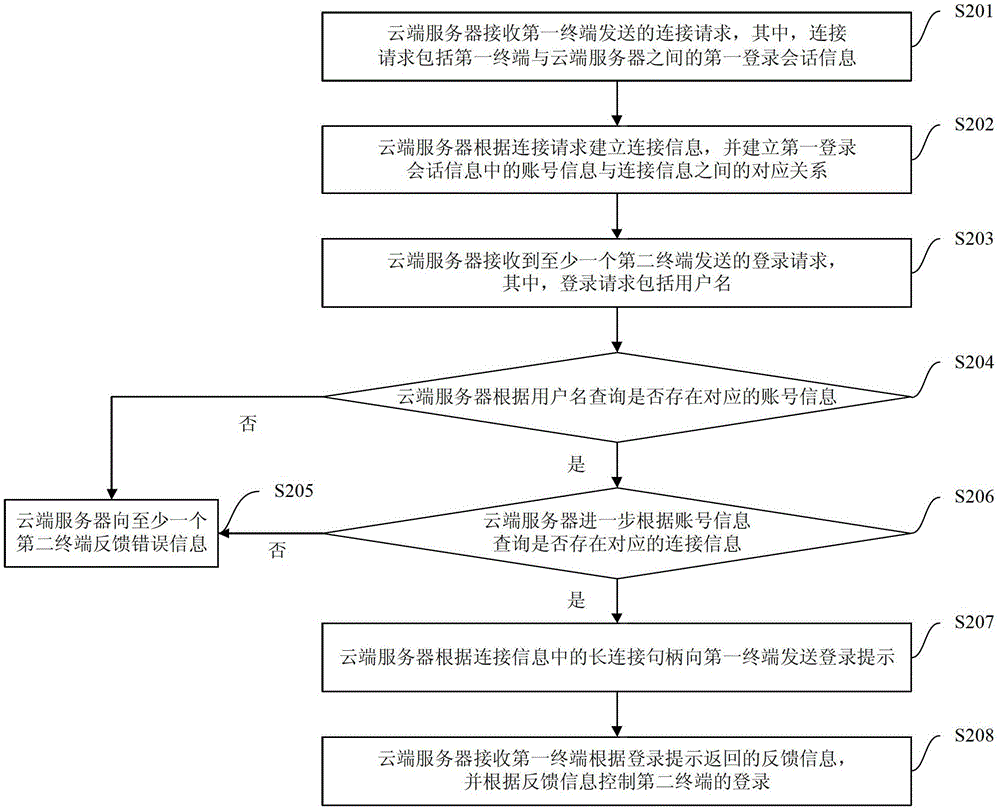
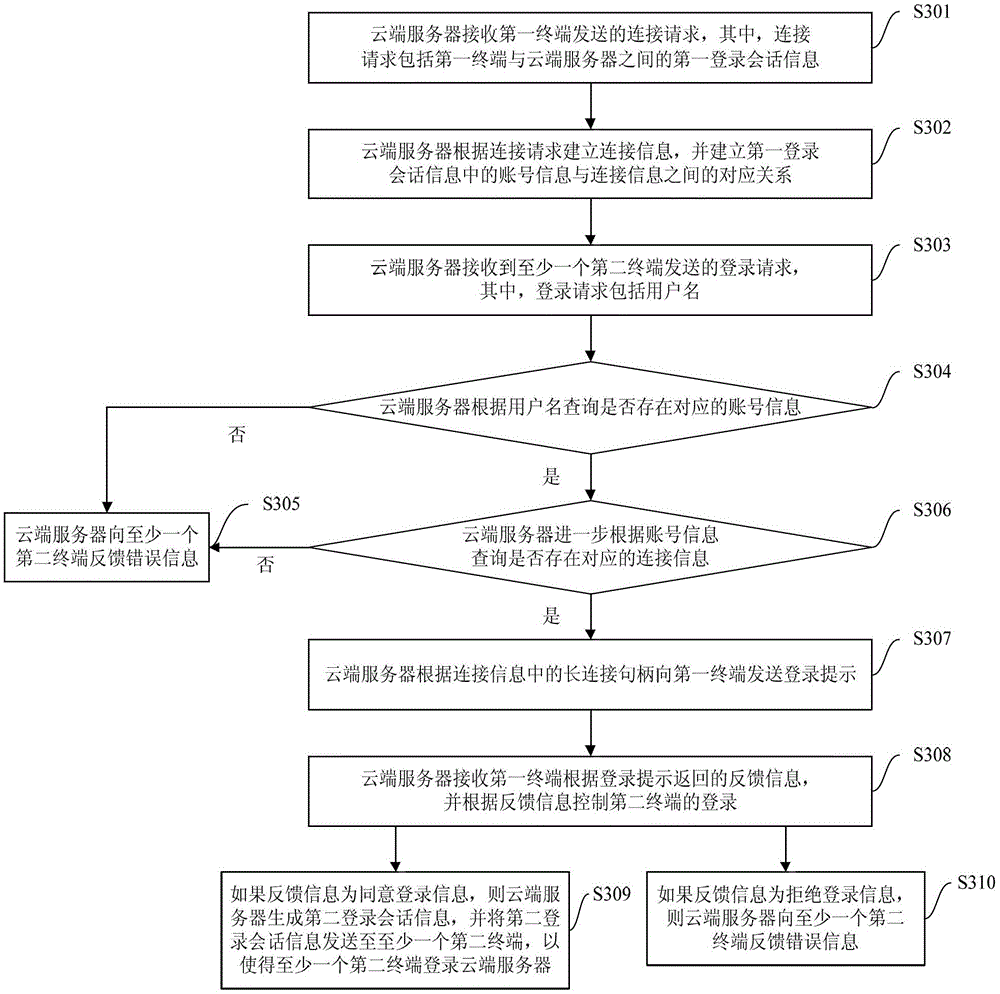
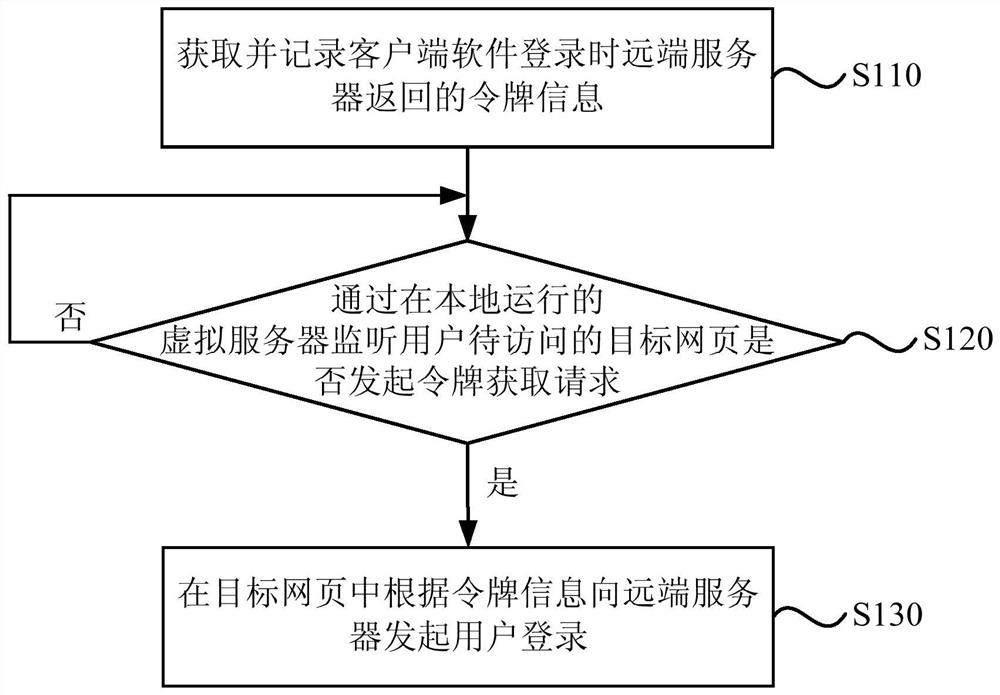
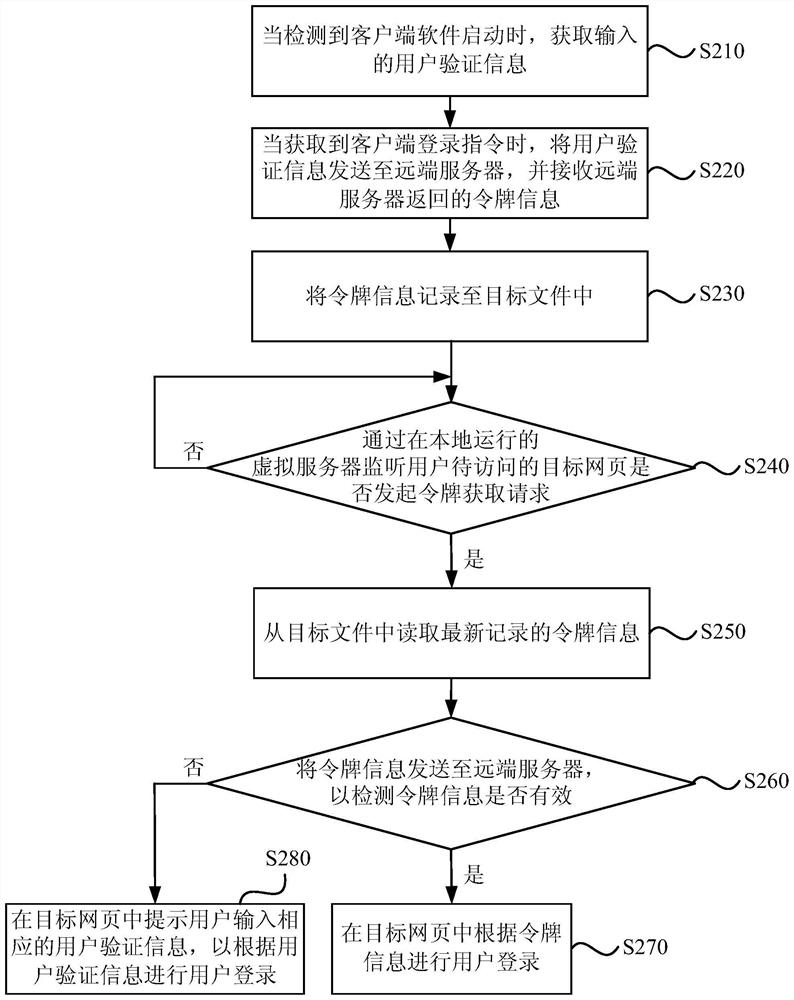
The invention provides a method, system and cloud server for multi-device safe logging, wherein the method comprises the steps that the cloud server creates connection information according to a connection request sent by a first terminal and creates a corresponding relation between account information in first logging session information and the connection information; the cloud server can send a login prompt to the first terminal according to the connection information corresponding to the account information corresponding to a user name sent by a second terminal, receives feedback information returned according to the login prompt, and controls logging of the second terminal according to the feedback information. According to the method, after a user normally logs in a device (such as the first terminal), a logging process can be completed only through inputting of the user name on other devices (such as the second terminal), logging operation of a user on multiple devices is simplified, user experience is promoted, the cloud server controls the logging of other equipment (such as the second terminal) according to the feedback information, and safety is guaranteed.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
A network logging on system and the corresponding configuration method and methods for logging on the application system
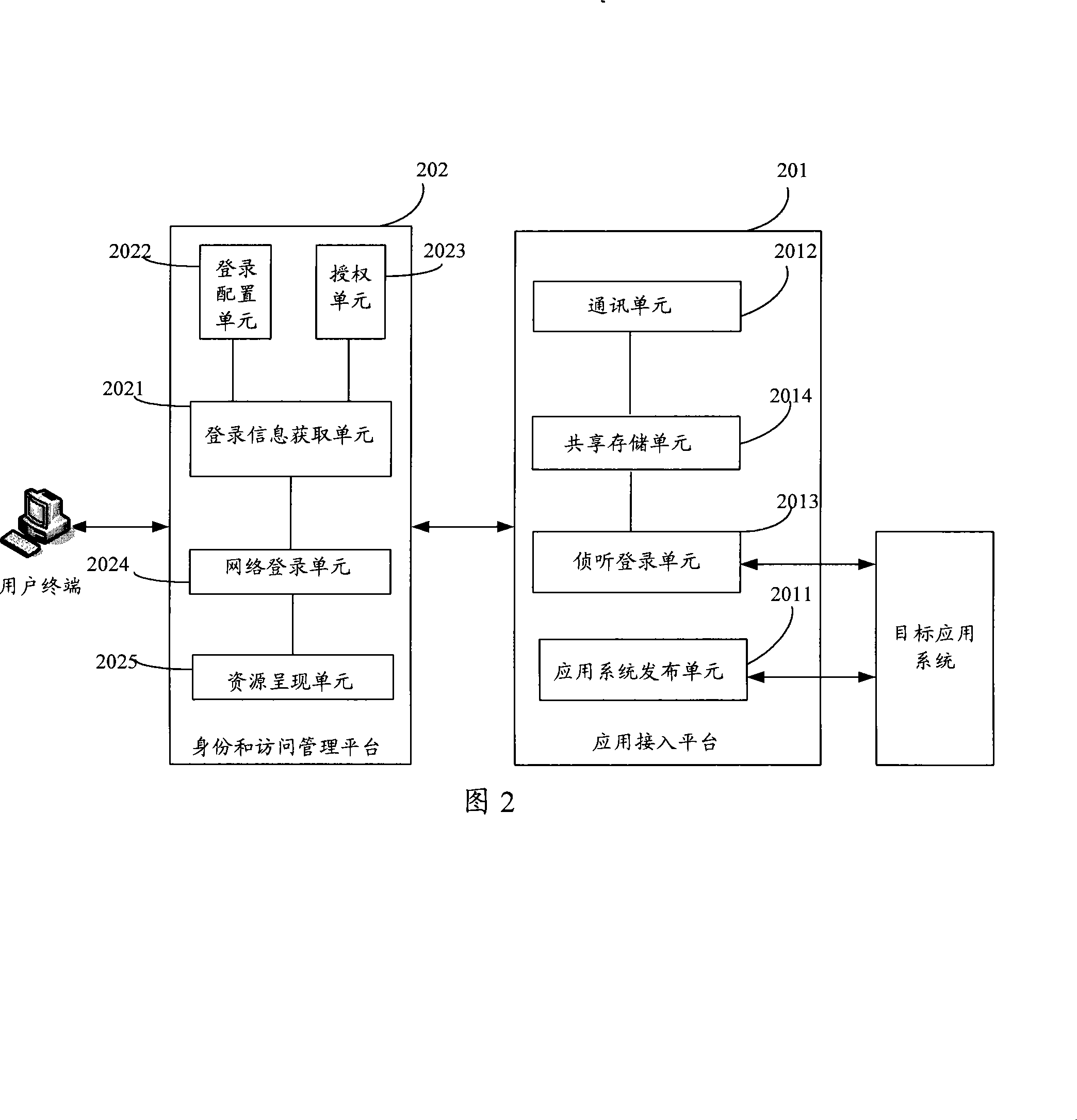
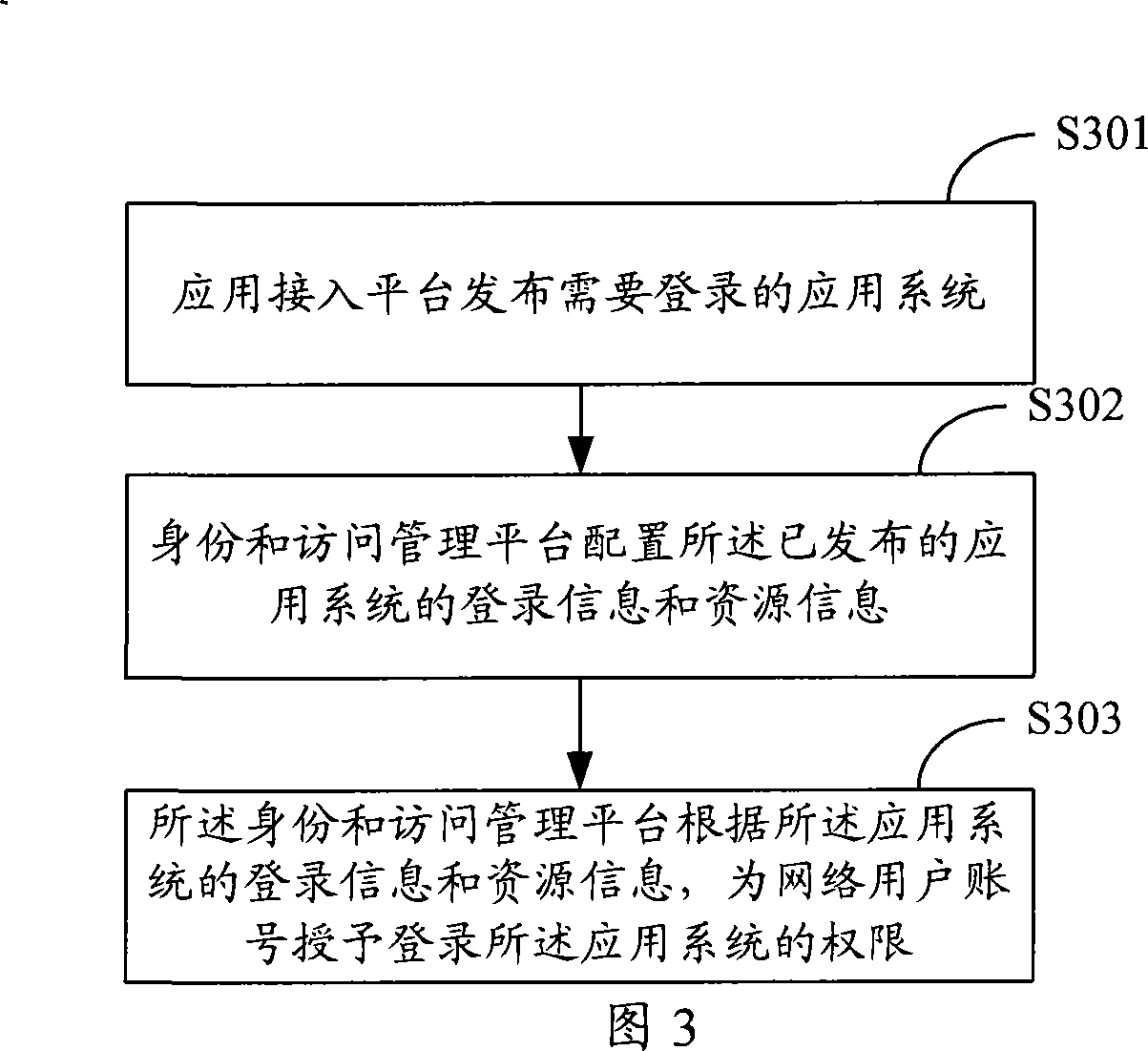
InactiveCN101217368AImplement security managementSimplify login operationsUser identity/authority verificationDigital data authenticationRelevant informationResource information
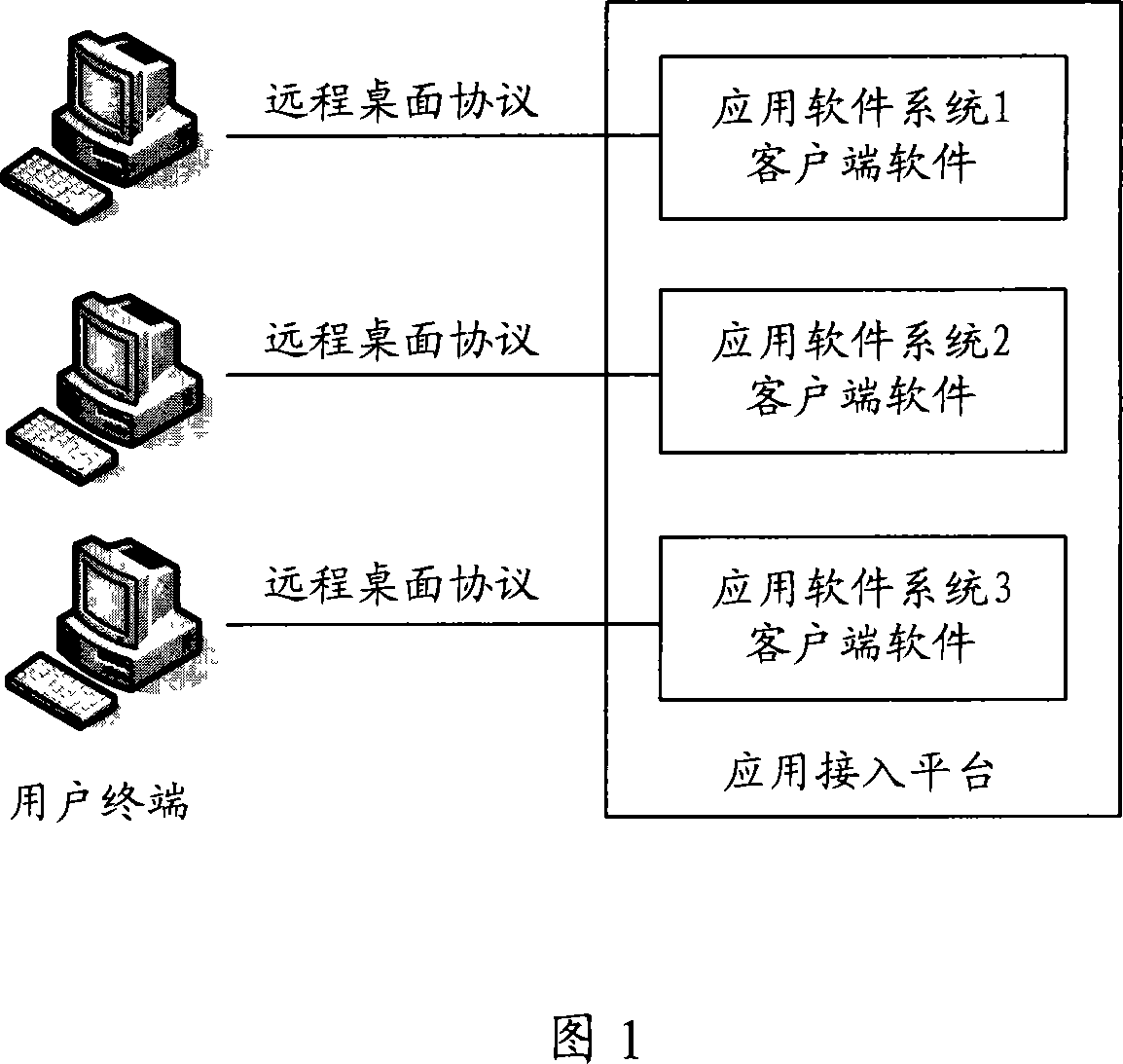
The invention relates to the technical field of network security and discloses a login system which comprises an application access platform and an identity and access management platform; wherein, the application access platform is used for installing and issuing an application system so as to lead users to login the application access platform and realize the logging in the application system which can pre-arrange and store related information of the application system; the identity and access management platform is used for obtaining the logging information and resource information of the application system from the application access platform, arranging the relatively accessible resource content and corresponding relations of network users and the users logging the application system, receiving the logging and making authentication of the network users. After the network users login the identity and access management platform with the application of the system disclosed by the invention, the identity and access management platform accesses the resource of the application system as legal users of the application system without leading the users directly to access the application system and the invention is high in access security and simple in the login operation of users.
Owner:亿阳安全技术有限公司
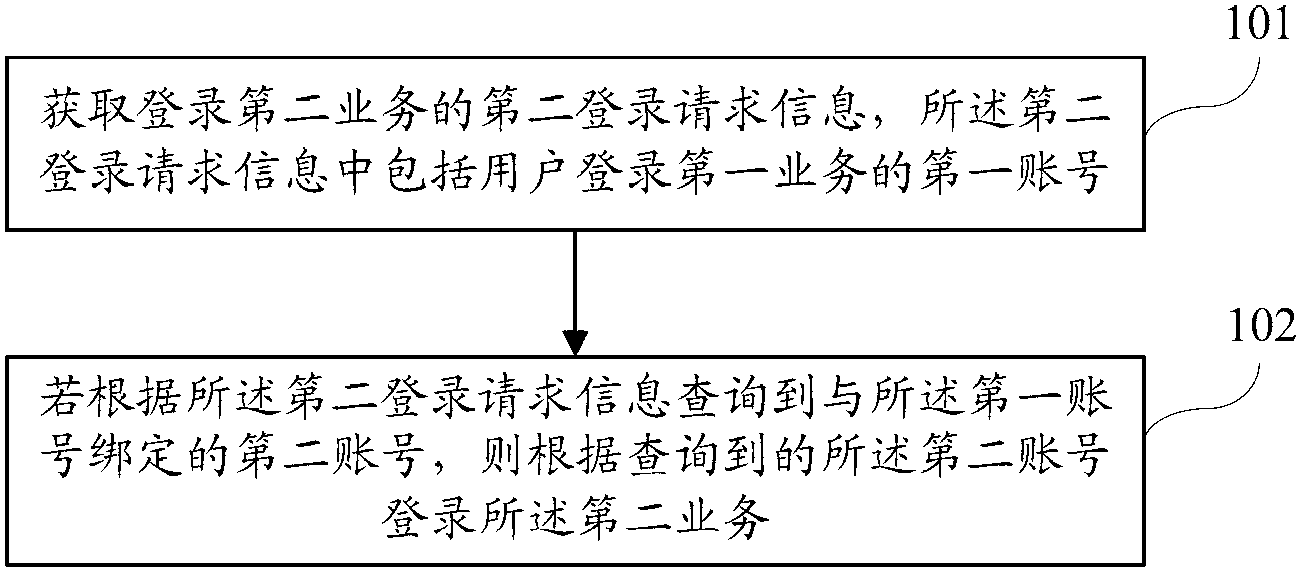
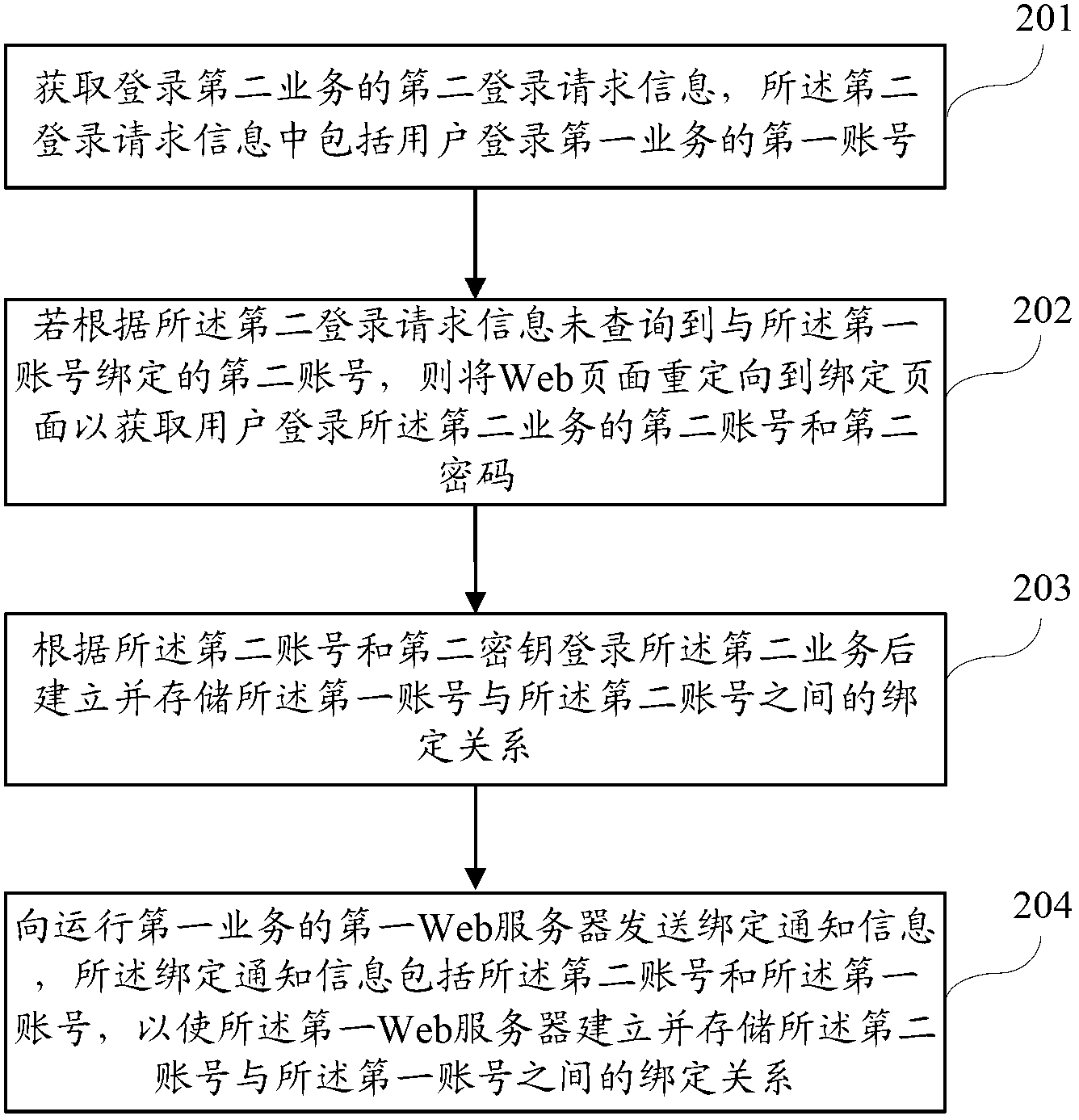
Web server, business logging method and system
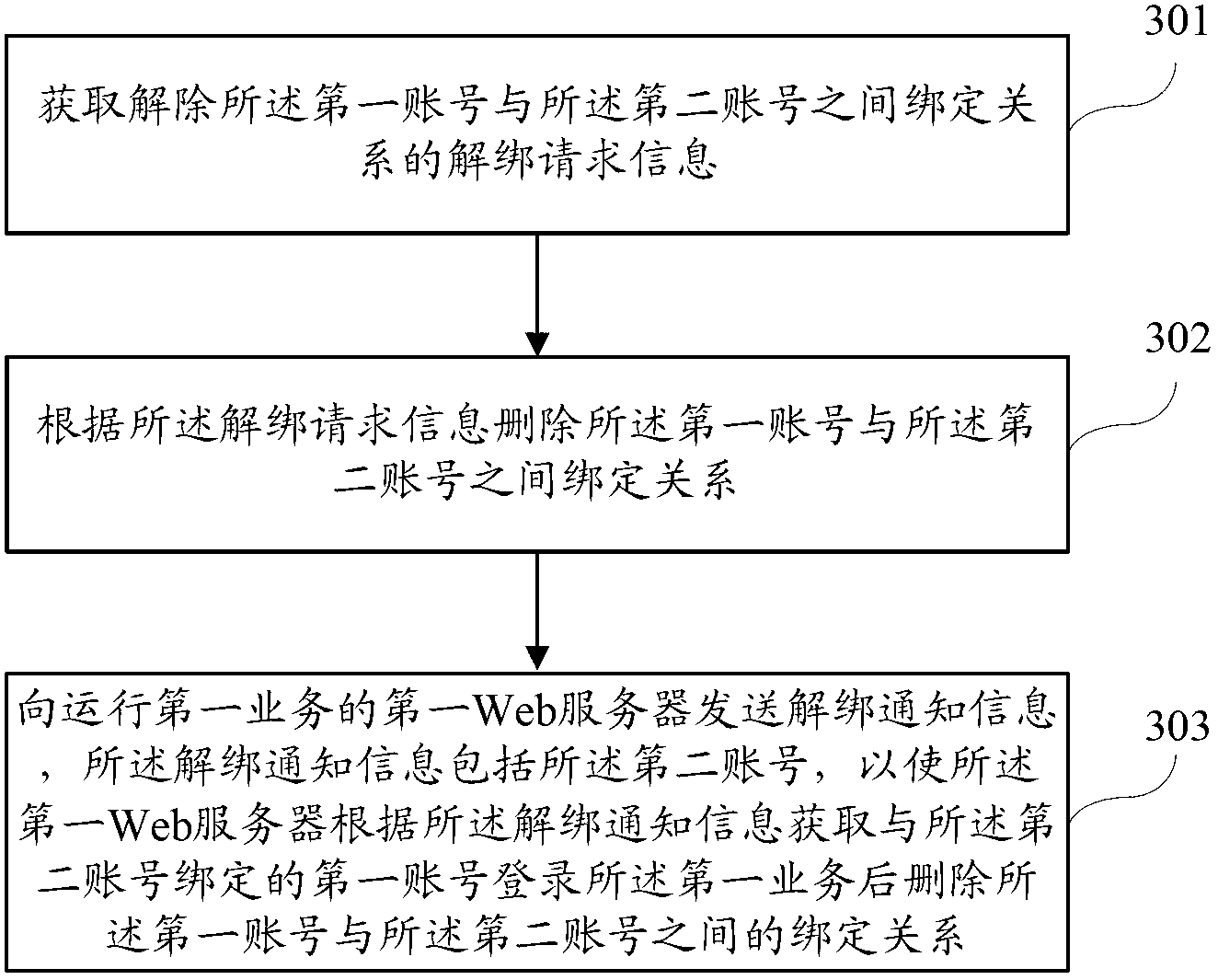
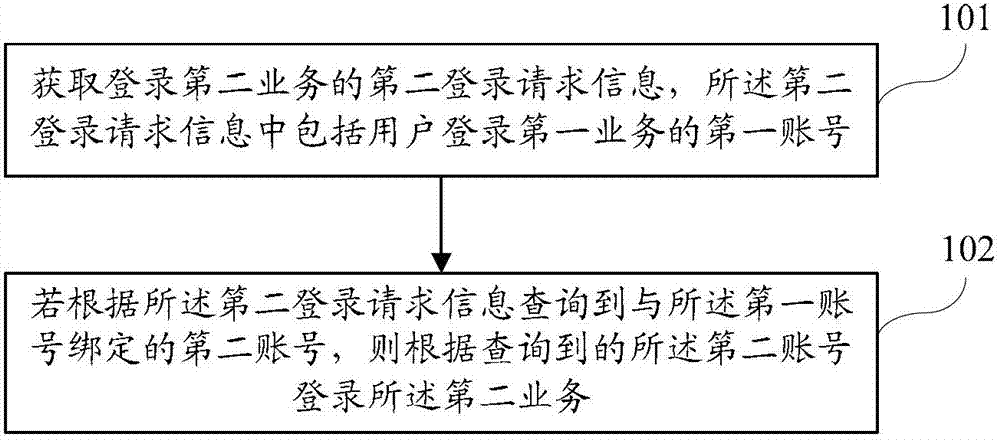
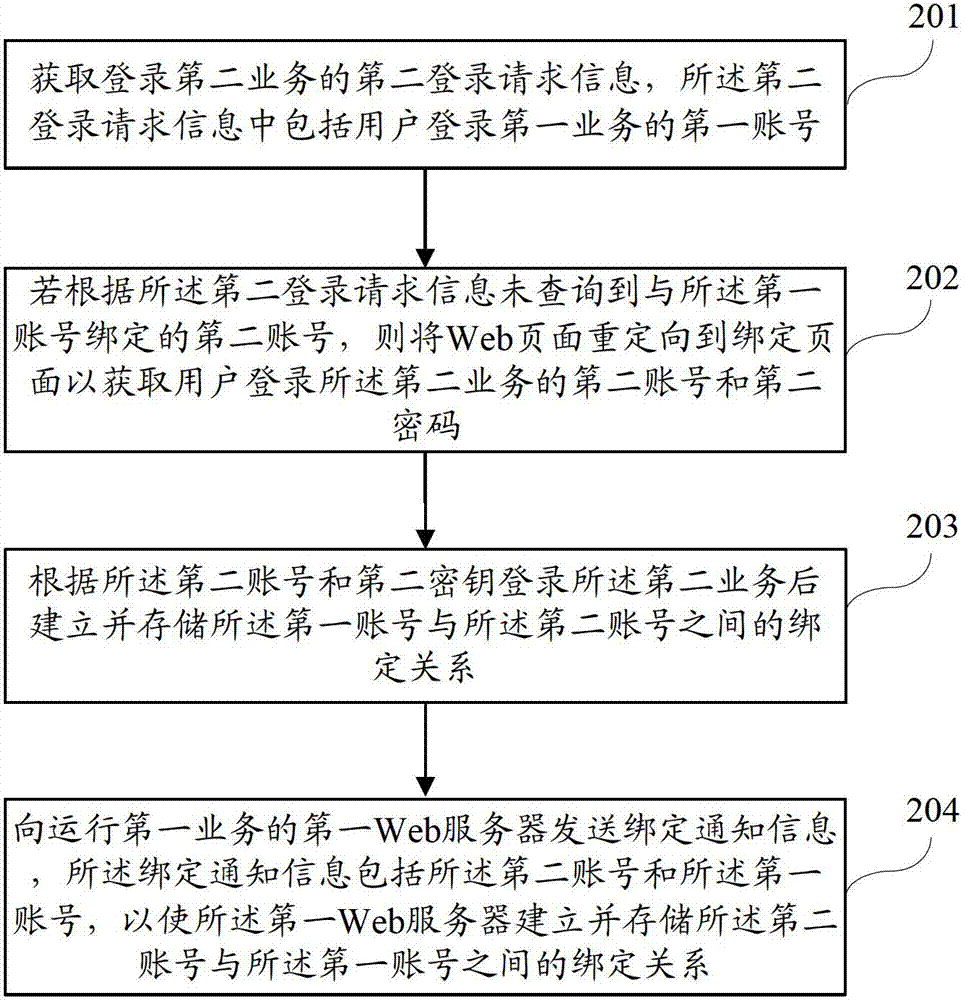
The invention discloses a Web server, a business logging method and a business logging system, wherein the business logging method comprises the steps of: obtaining a second logging request information for logging on a second business, wherein the second logging request information comprises a first account number for logging on a first business by a user; and if the second account number bound to the first account number is inquired according to the second logging request information, logging on the second business according to the inquired second account number. According to the logging method disclosed by the invention, the user can achieve one-key logging when the user skips to another business with an account number binding relationship from one business, so the user operation is simplified.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
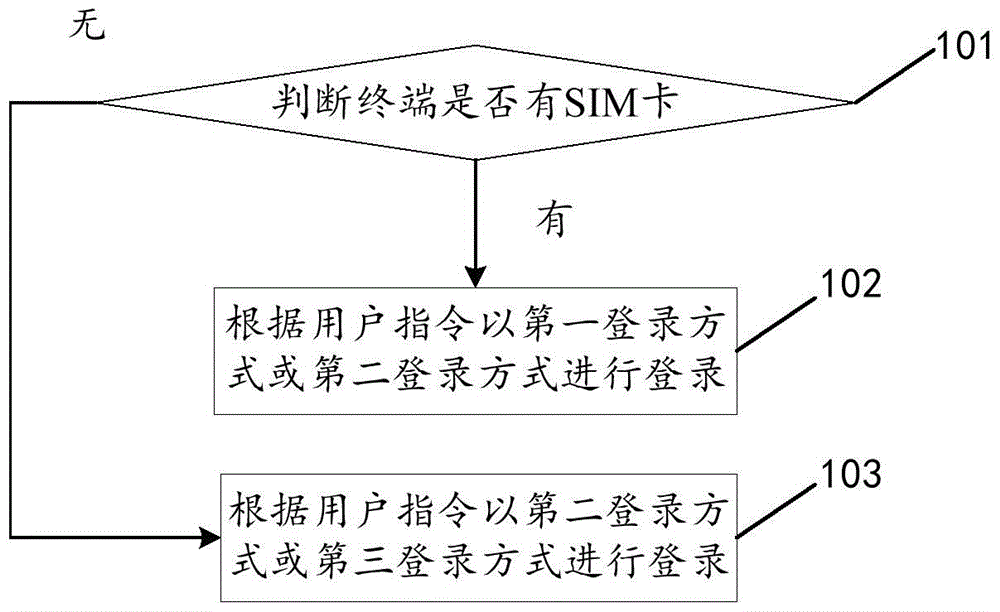
Terminal application log-in method, device, client and electronic device
ActiveCN104093141ASimplify login operationsMeet needsNetwork data managementComputer hardwareClient-side
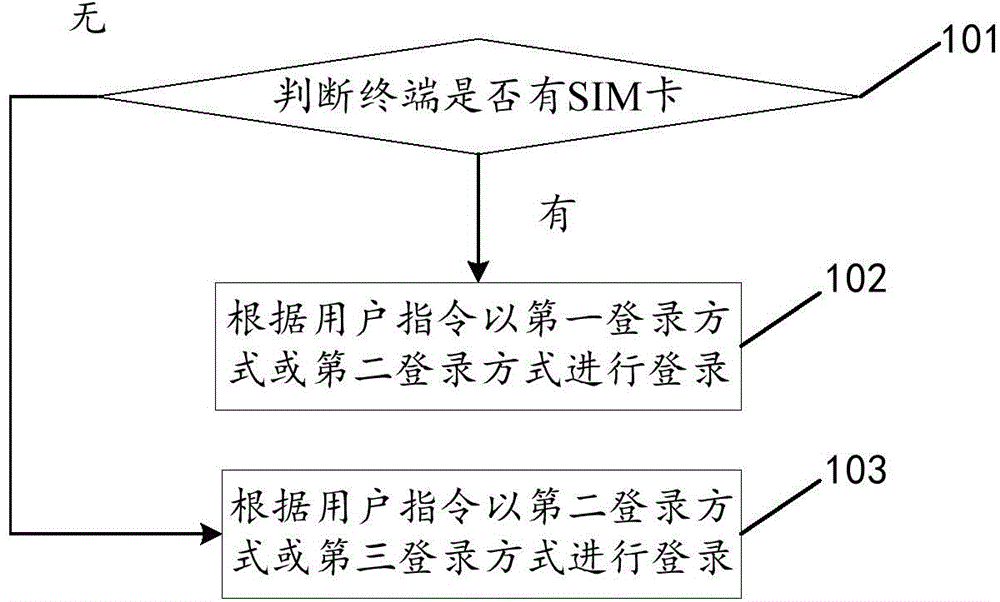
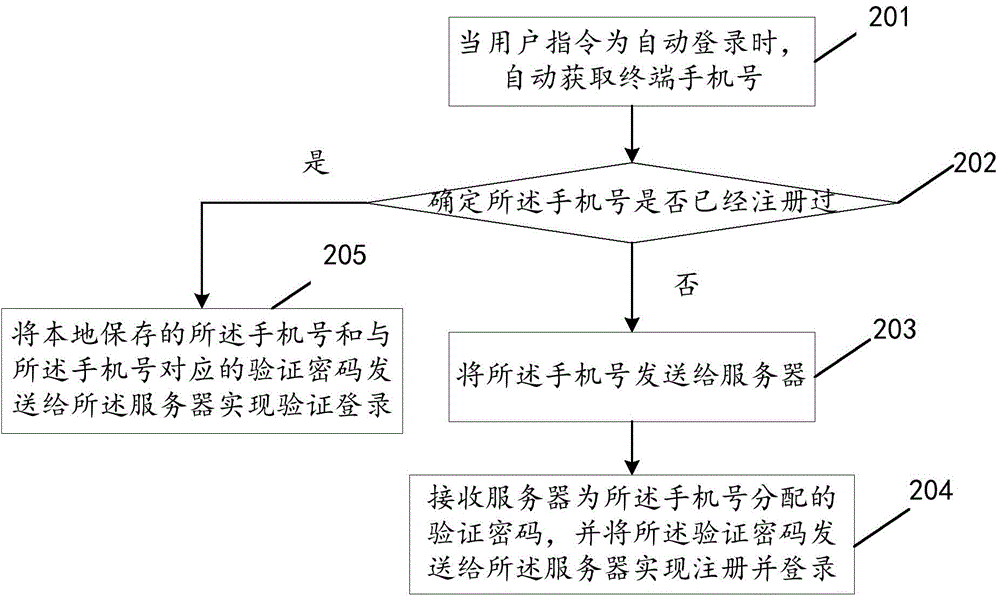
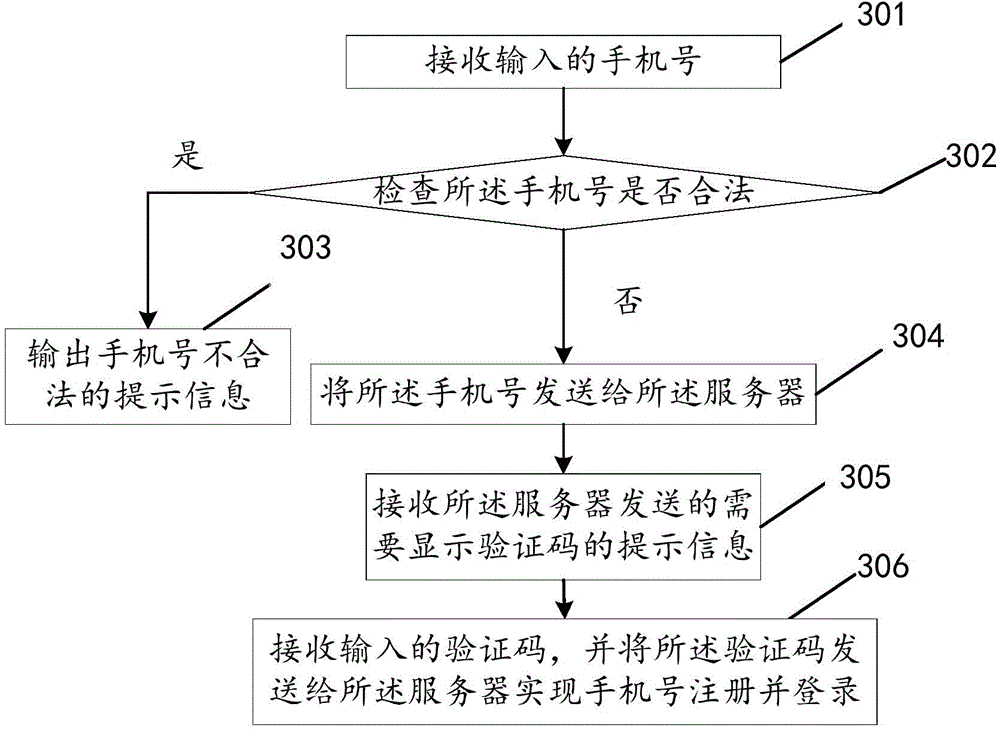
The invention discloses a terminal application log-in method and device, a client and an electronic device, and relates to the technical field of terminal application. According to the technical scheme, when an operation needing to be logged in is trigged in an application is received, whether an SIM card is available to a terminal is judged; if the SIM card is available to the terminal, a log-in operation is carried out in a first log-in mode or a second log-in mode according to user instructions, wherein the first log-in mode is automatic registering and / or logging-in and the second log-in mode is achieved through a registered account; if the SIM card is unavailable to the terminal, the log-in operation is carried out in the second log-in mode or a third log-in mode according to a user instruction, wherein the third log-in mode means to log in after registering is carried out through a mobile phone number or a mail box. The terminal application log-in method and device are mainly used in the log-in process of the terminal application.
Owner:北京鸿享技术服务有限公司
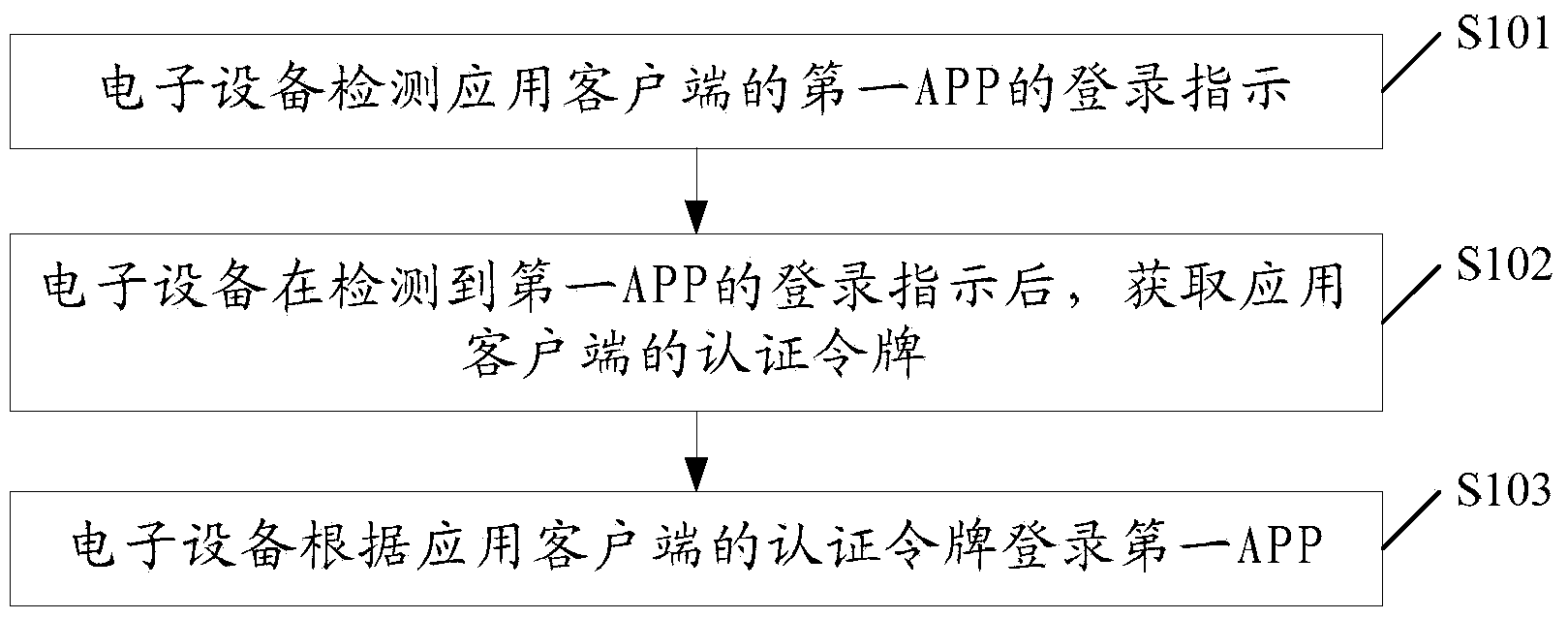
Account login method and electronic equipment
InactiveCN103634316ASimplify login operationsImprove login efficiencyUser identity/authority verificationClient-sideInformation technology
The embodiment of the invention discloses an account login method and electronic equipment, and relates to the field of electronic information technology. The account login operation can be simplified, automatic account login is realized, and account login efficiency is improved. The invention adopts the concrete scheme that the account login method comprises the steps: detecting login notification of a first APP (Application) of an application client by the electronic equipment; obtaining an authentication token of the application client after the login notification of the first APP is detected, wherein the authentication token of the application client is generated after any APP of the application client is logged in by the electronic equipment; logging the first APP according to the authentication token of the application client. The account login method and the electronic equipment disclosed by the invention are used in the account login process of the application client.
Owner:LETV INFORMATION TECH BEIJING
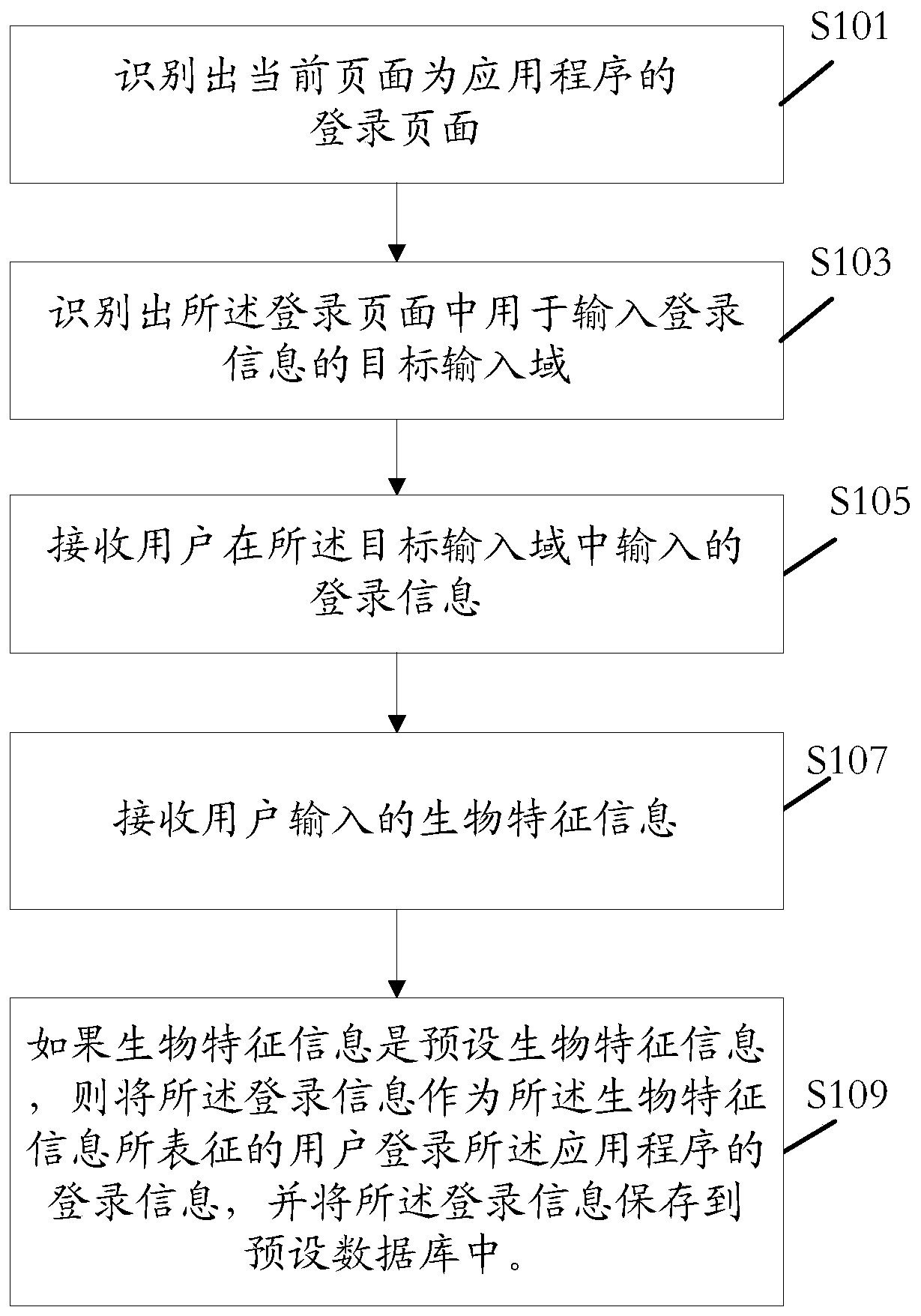
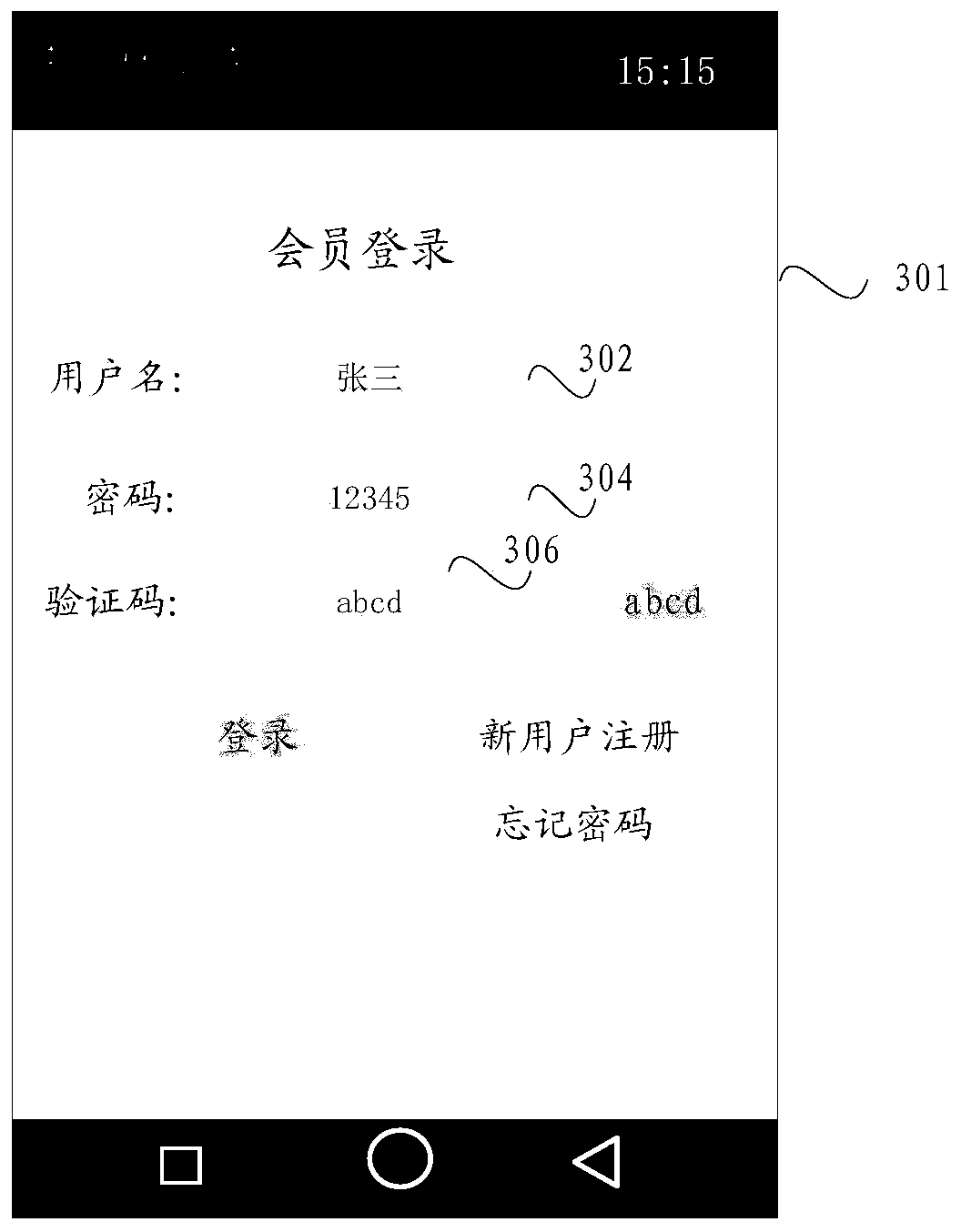
Login information inputting method, login information storing method and related device
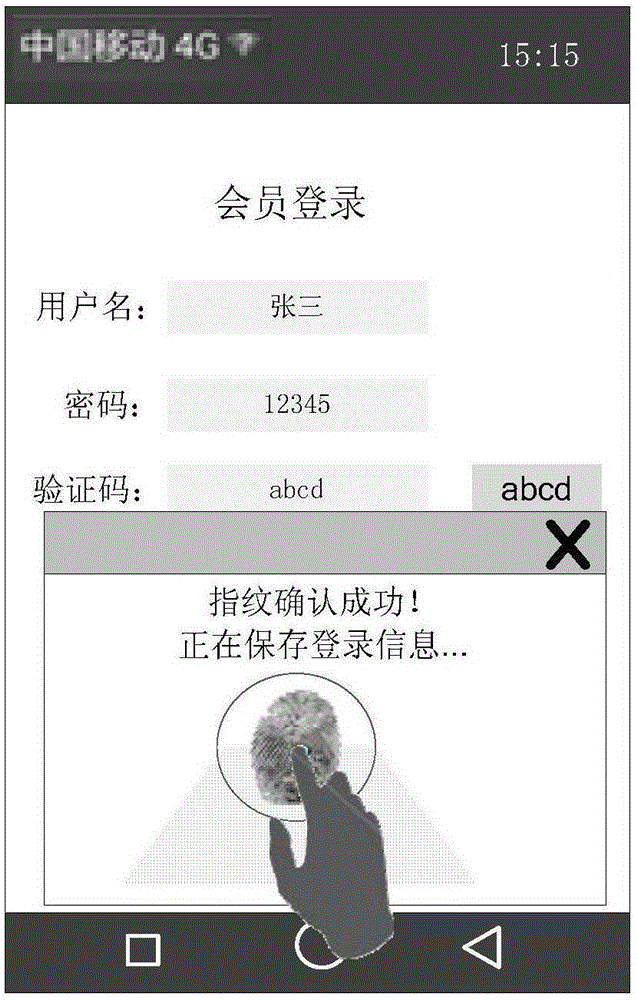
The embodiment of the invention discloses a login information inputting method, a login information storing method and related devices. The login information inputting method comprises the steps of identifying that a current page is a login page of an application program; identifying a target input domain which is used for inputting login information in the login page; receiving biological characteristic information input by a user; if the biological characteristic information is preset biological characteristic information, obtaining the login information which is characterized by the biological characteristic information and that the user logs in the application program from a preset database; and filling the target input domain with the login information. By adopting above scheme, the target input domain in the login page can be filled automatically, so a login operation of the user is simplified; and furthermore, the application scope is wide, and the login information inputting method, the login information storing method and the related devices are not limited by an application program development platform.
Owner:HUAWEI DEVICE CO LTD
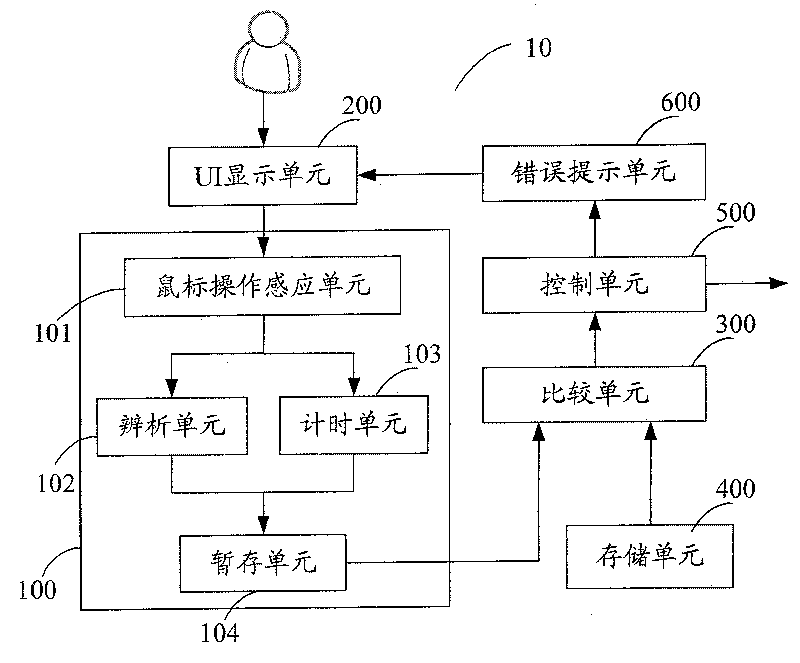
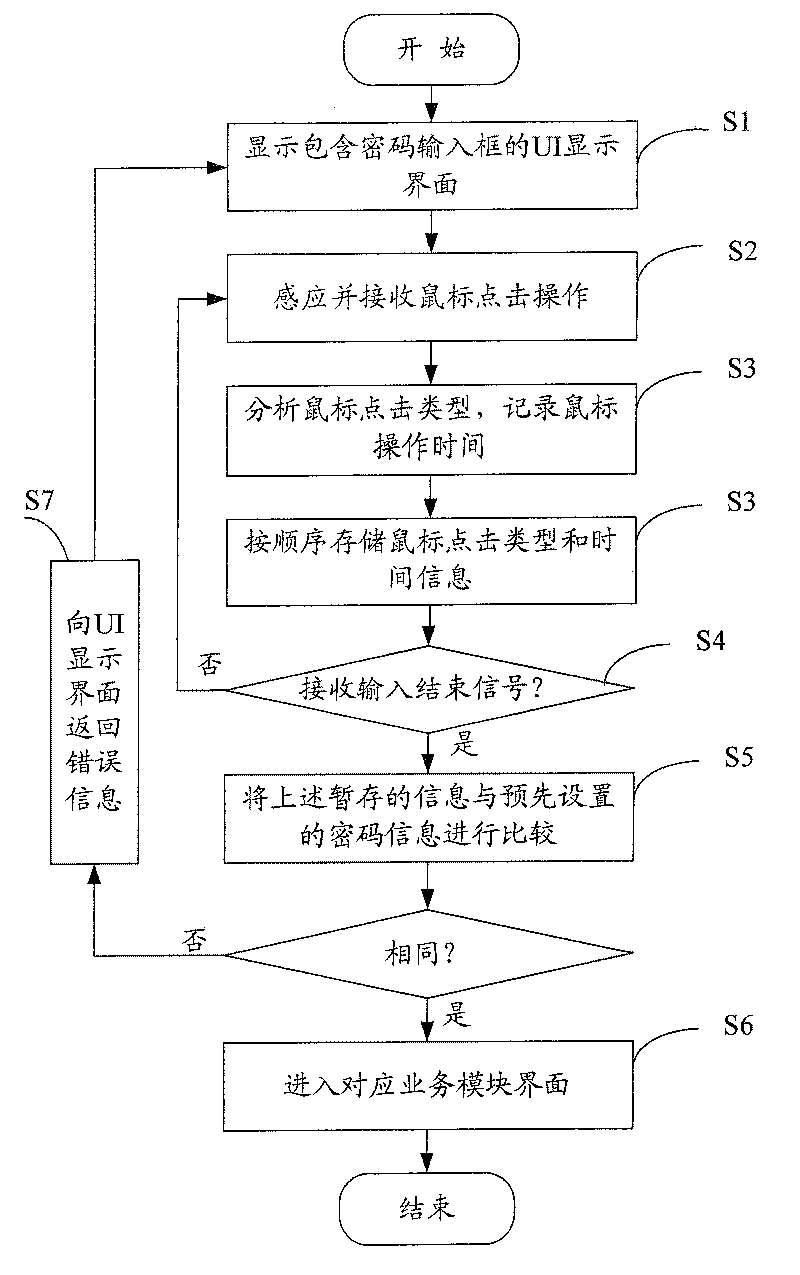
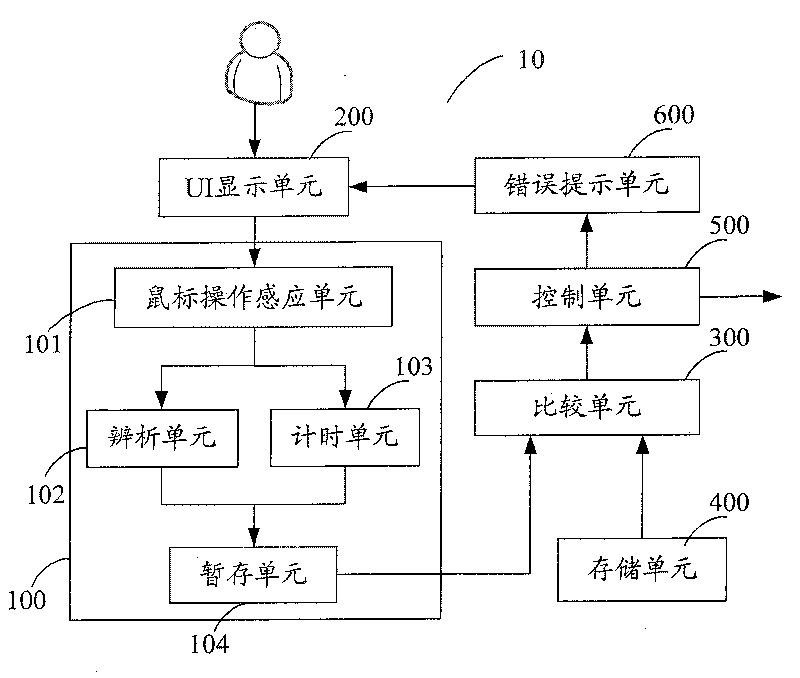
Cipher protection system and method
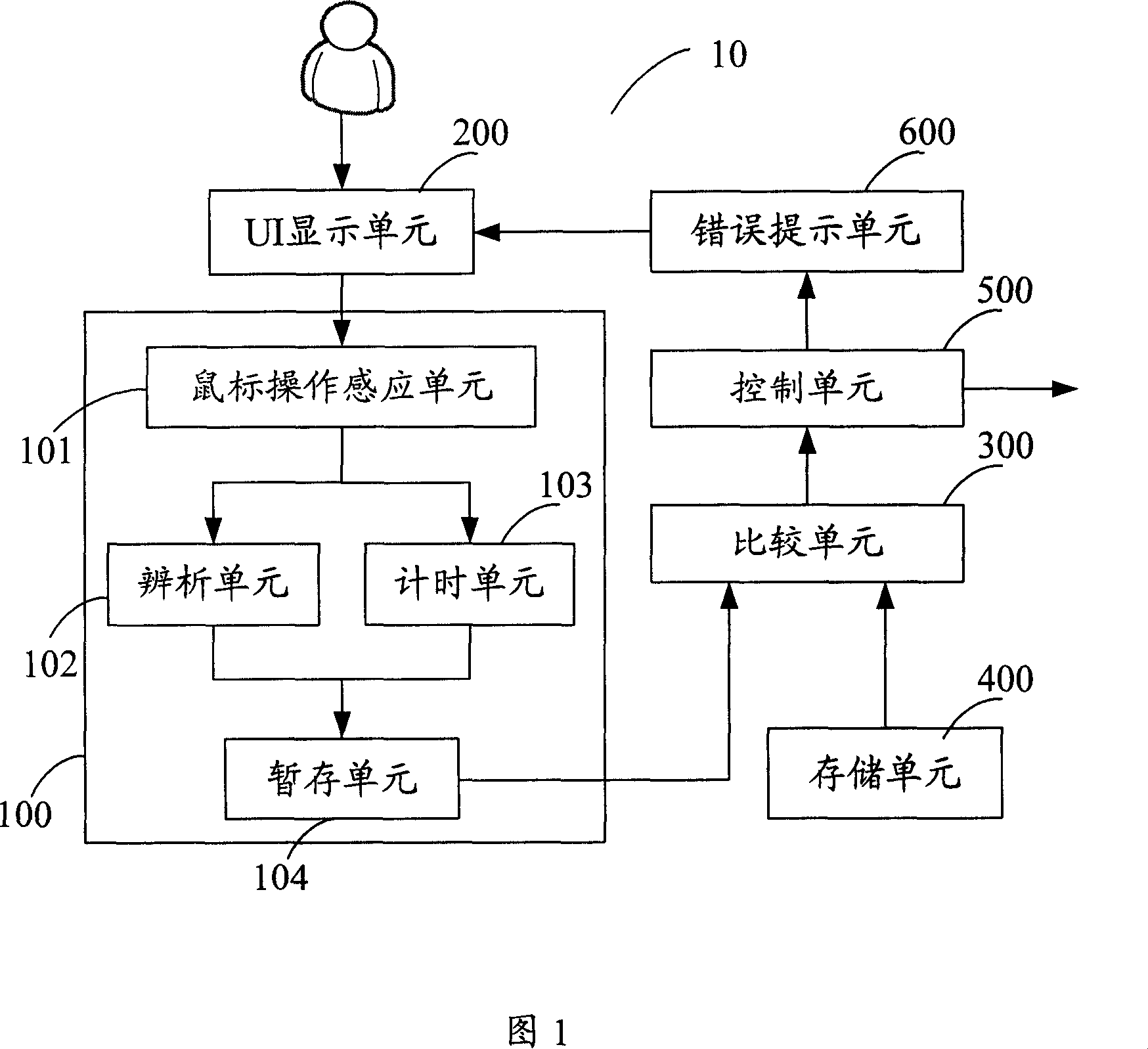
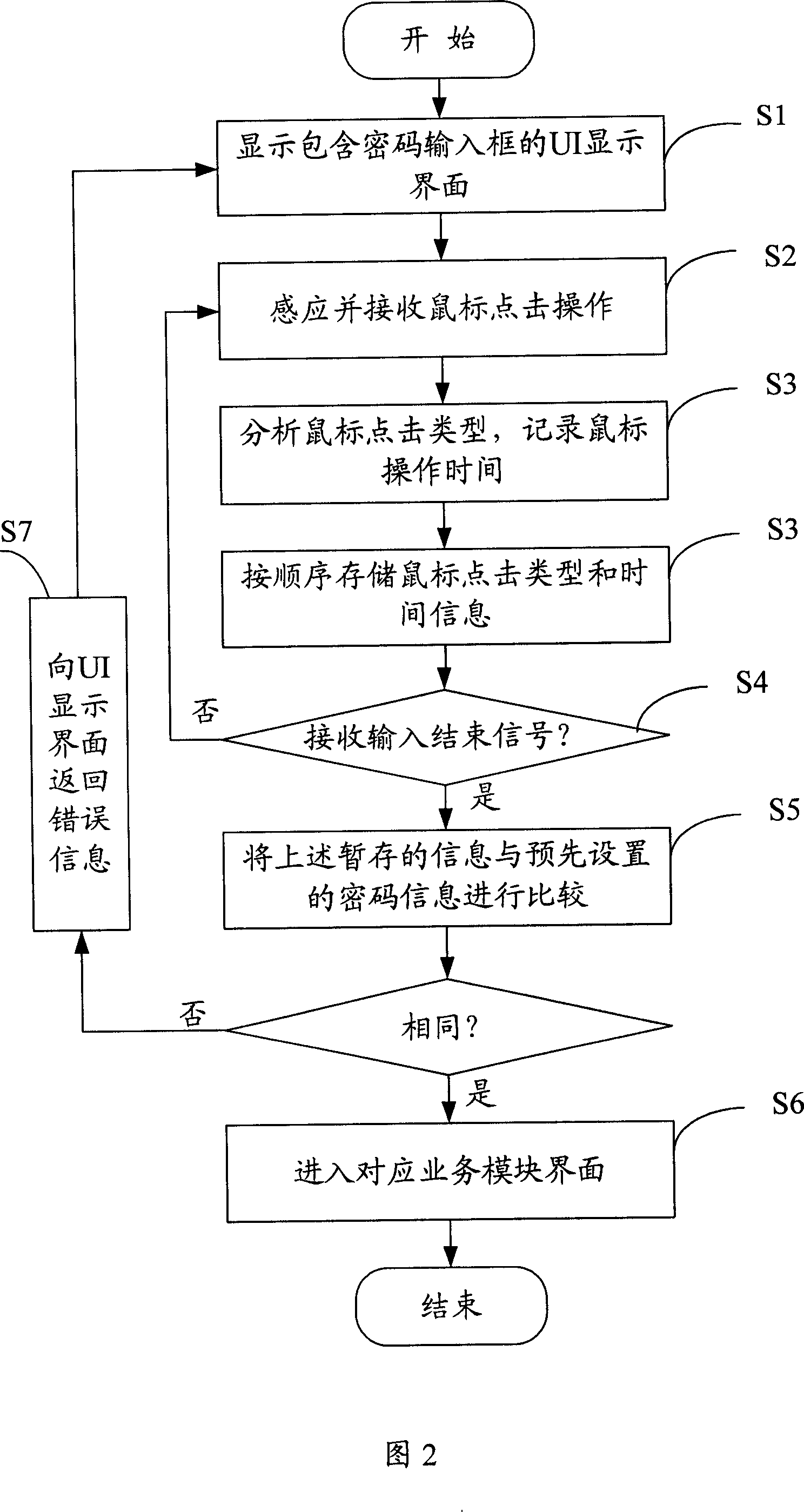
ActiveCN101079088AAdd login operationSimplify login operationsDigital data authenticationInput/output processes for data processingPassword protectionProtection system
The invention discloses a password protection system, which comprises the following parts: an user boundary UI display unit, a saving unit with the password information and a comparison unit, wherein the password protection system includes a mouse operation dealing modular for sensing the mouse operation information in the password input frame of the UI display unit, analyzing the operation information and getting and outputting the mouse press key type information, the comparison unit is used to compare the output information of the mouse operation dealing modular with the saving password information in the saving unit, if the same, the right password signal is outputted, or the wrong password signal is outputted. The invention discloses a password protection method. The invention simplifies the landing operation, which safeguards the safety of the user' s information.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and apparatus for logging in client
ActiveCN105827600ASimplify login operationsShorten login timeDigital data authenticationTransmissionLoggingDatabase
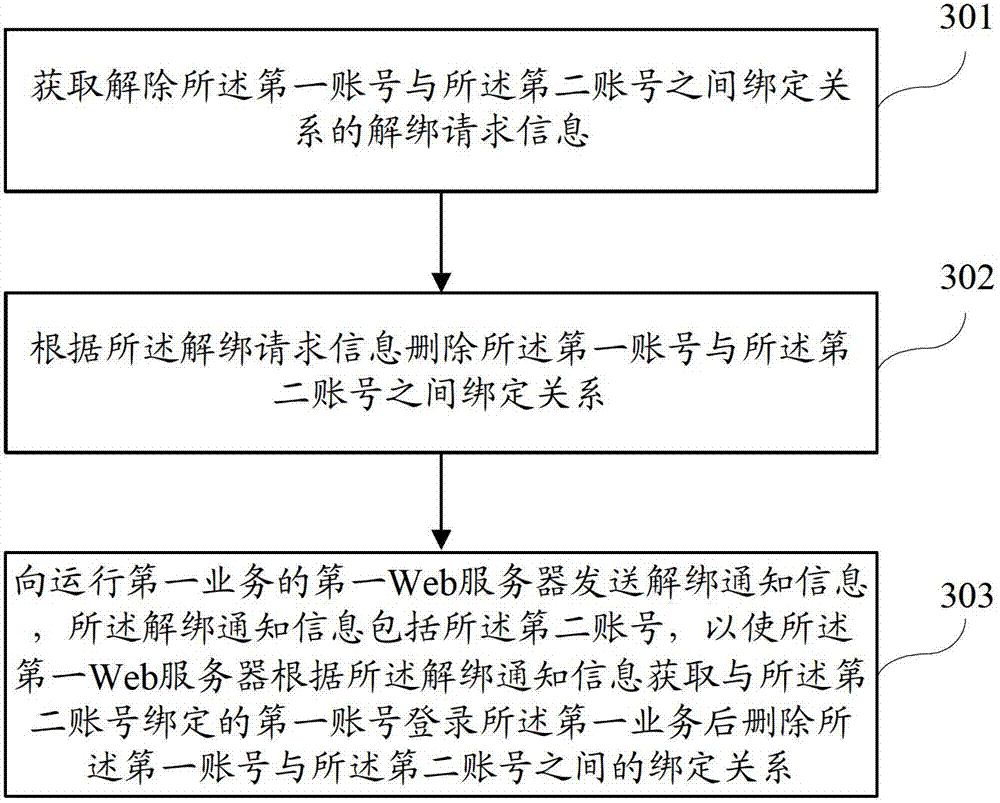
The invention discloses a method and apparatus for logging in a client. The method comprises: a logging-in account number that is logged in currently by a second client operated at a terminal is obtained at a logging-in interface of a first client operated at the terminal, wherein the second client and the first client have an association relationship; a logging-in request that is generated after operation execution on the logging-in account number is obtained at the logging-in interface of the first client, wherein the logging-in request is used for requesting to use the logging-in account number to log in the first client; and the first client is logged in by using the logging-in account number to respond to the logging-in request. According to the invention, a technical problem of low logging-in efficiency due to utilization of the existing logging-in method can be solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
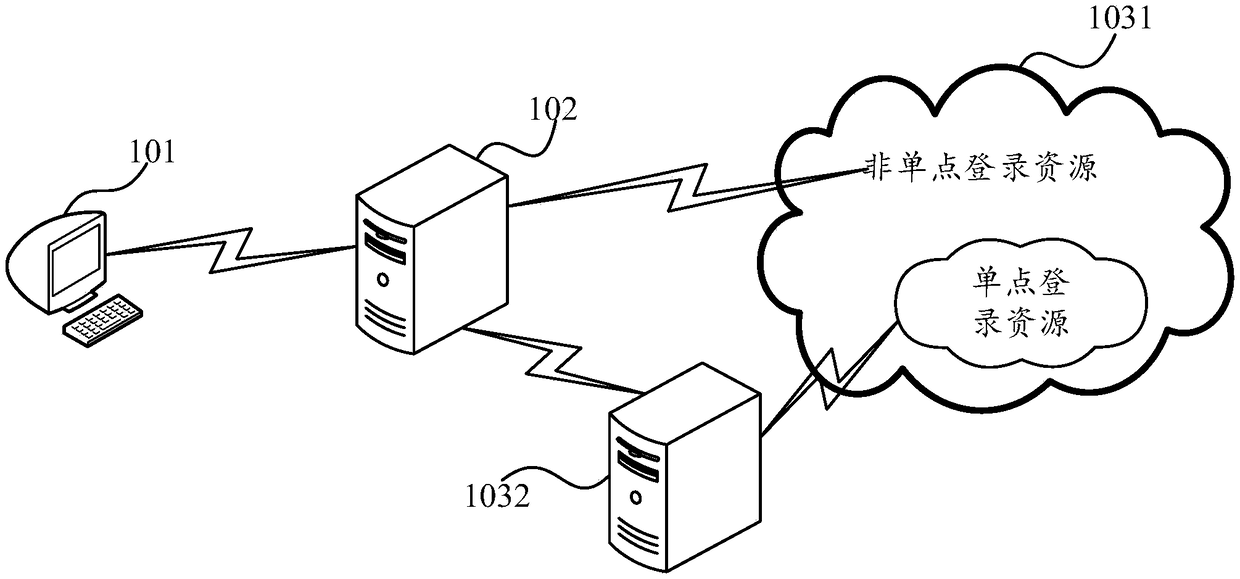
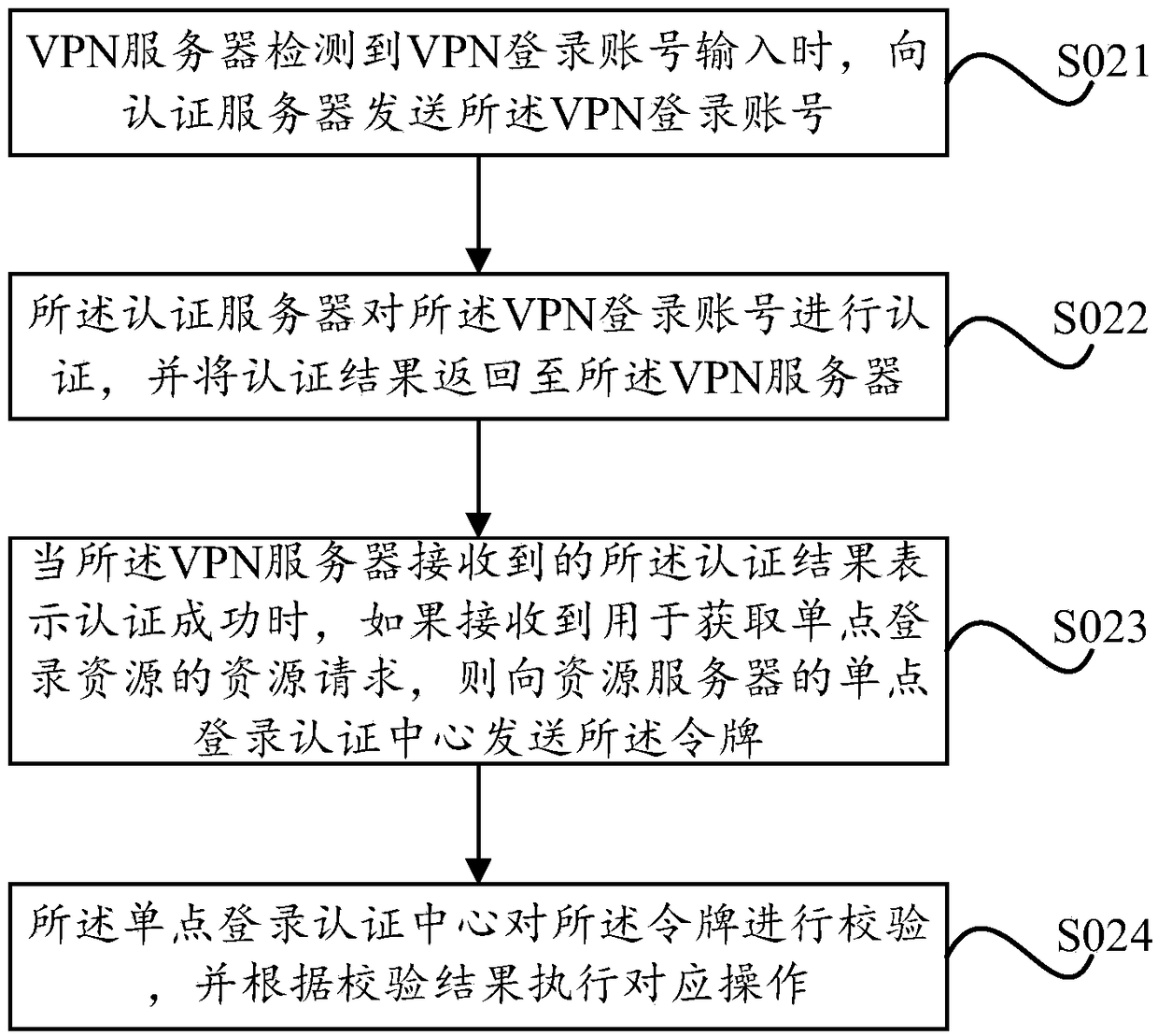
Single sign on methods and devices based on virtual private network (VPN)
ActiveCN109347864AFlexible configurationImprove resource acquisition efficiencyNetworks interconnectionMobile virtual private networkSingle sign-on
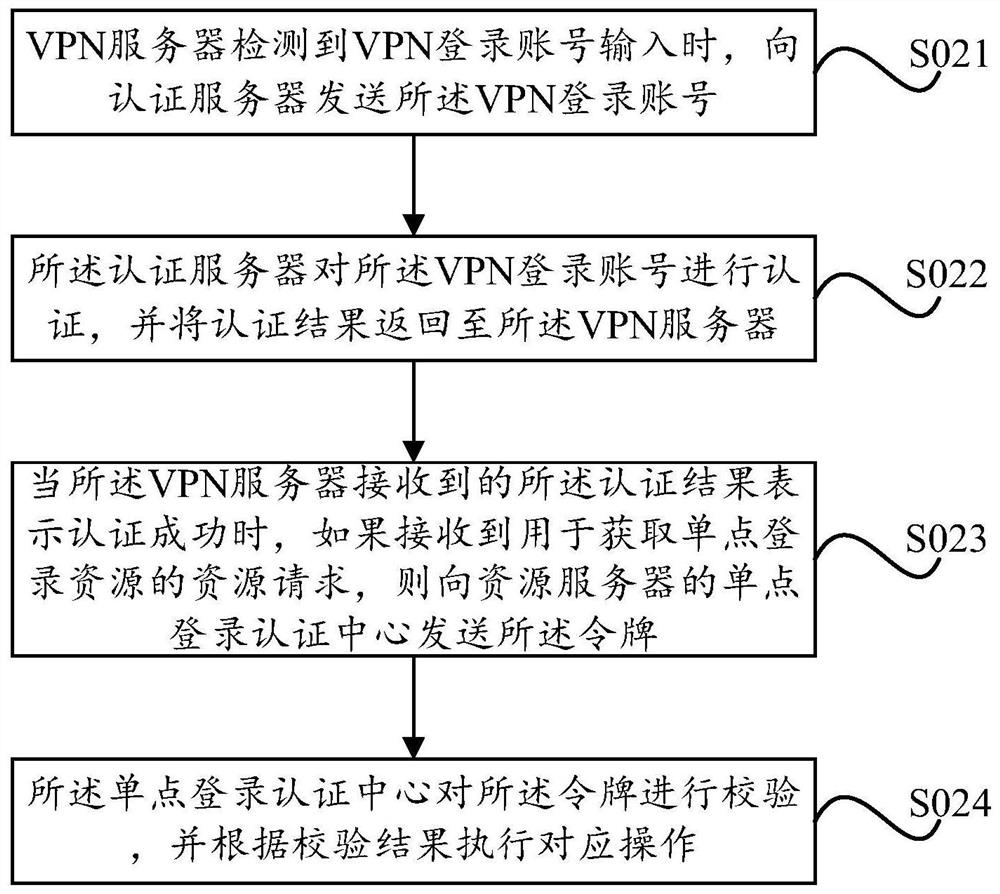
The invention provides single sign on methods and devices based on a virtual private network (VPN). A method comprises the steps that when a VPN server detects that a VPN sign on account is input, theVPN server sends the VPN sign on account to an authentication server; the authentication server authenticates the VPN sign on account and returns an authentication result to the VPN server, wherein when authentication is successful, the authentication result comprises a token as a single sign on authentication evidence; when the authentication result received by the VPN server indicates that theauthentication is successful, if a resource request for obtaining a single sign on resource is received, the VPN server sends the token to a single sign on authentication center of a resource server,wherein the resource server comprises the single sign on authentication center and a resource system; and the single sign on authentication center checks the token and carries out corresponding operation according to a check result. The embodiment of the invention has the advantages of simple configuration, high account security and rapid sign on.
Owner:HANGZHOU DPTECH TECH
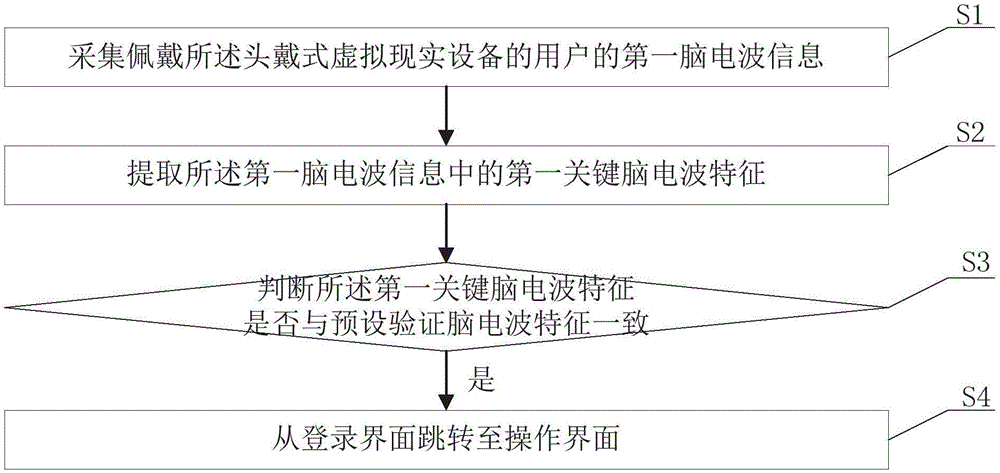
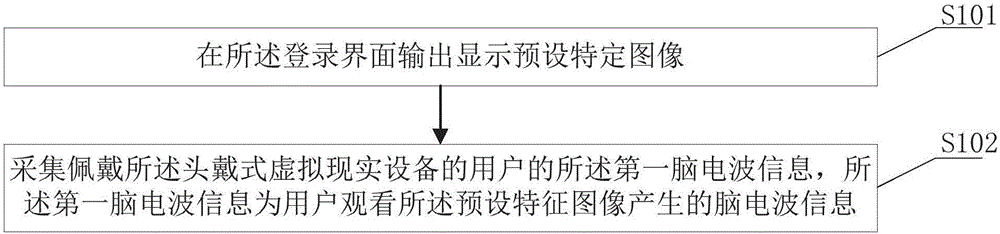
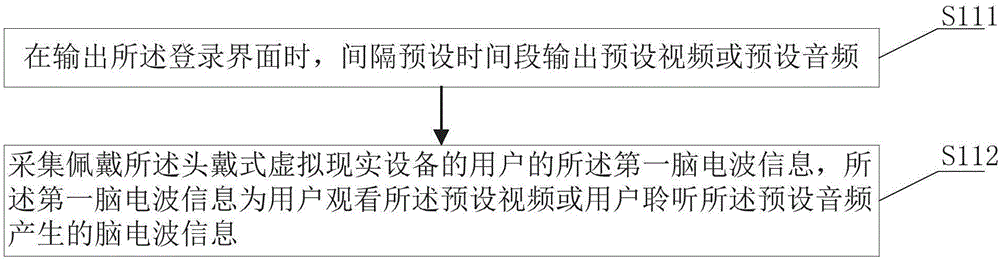
Access method on basis of brain waves and head-mounted virtual reality equipment
InactiveCN106843480ASimplify login operationsImprove login speed and user experienceInput/output for user-computer interactionDigital data authenticationAccess methodVirtual reality
The invention discloses an access method on the basis of brain waves and head-mounted virtual reality equipment. The access method is applied to the head-mounted virtual reality equipment. The access method particularly includes steps of acquiring first brain wave information of a user who wears the head-mounted virtual reality equipment; extracting first key brain wave features in the first brain wave information; judging whether the first key brain wave features are consistent with preset verification brain wave features or not; skipping login interfaces to operation interfaces if the first key brain wave features are consistent with the preset verification brain wave features. The access method and the head-mounted virtual reality equipment have the advantages that the login interfaces can be skipped to the operation interfaces when the key brain wave features are consistent with the preset verification brain wave features, accordingly, manual operation can be omitted, login operation can be simplified, the login speeds can be increased, and the use experience can be enhanced for the user; the head-mounted virtual reality equipment can have independent login functions without auxiliary equipment, and accordingly the application range of the head-mounted virtual reality equipment can be expanded.
Owner:SHENZHEN MAGIC EYE TECH CO LTD
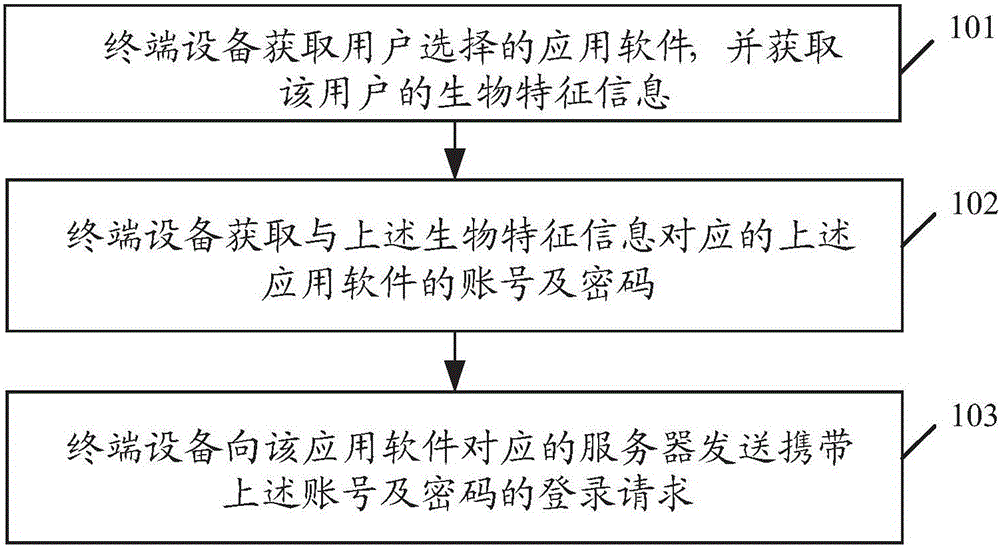
Account login method and terminal device
InactiveCN105721510AEasy loginQuick LoginDigital data authenticationTransmissionPasswordTerminal equipment
The embodiment of the invention relates to the technical field of communication, and discloses an account login method and a terminal device; wherein the method comprises that the terminal device obtains application software selected by a user and obtains biological characteristic information of the user; the terminal device obtains the account and password of the application software corresponding to the biological characteristic information; and the terminal device sends a login request carried with the account and the password to a server corresponding to the application software. Through application of the embodiment of the invention, the user does not need to input the account and the password each time when the user logs in; therefore, the login operation is simplified; and the account login process is convenient and rapid.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
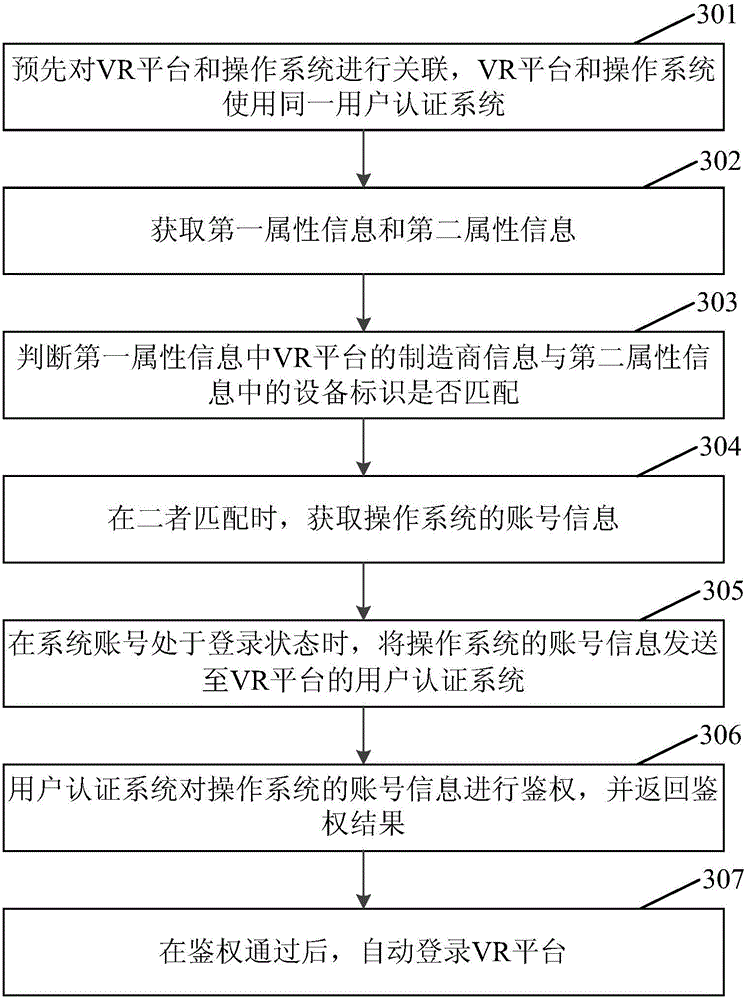
Method and apparatus for automatically logging in VR platform
InactiveCN105956430ASimplify login operationsImprove operational efficiencyDigital data authenticationOperational systemVirtual reality
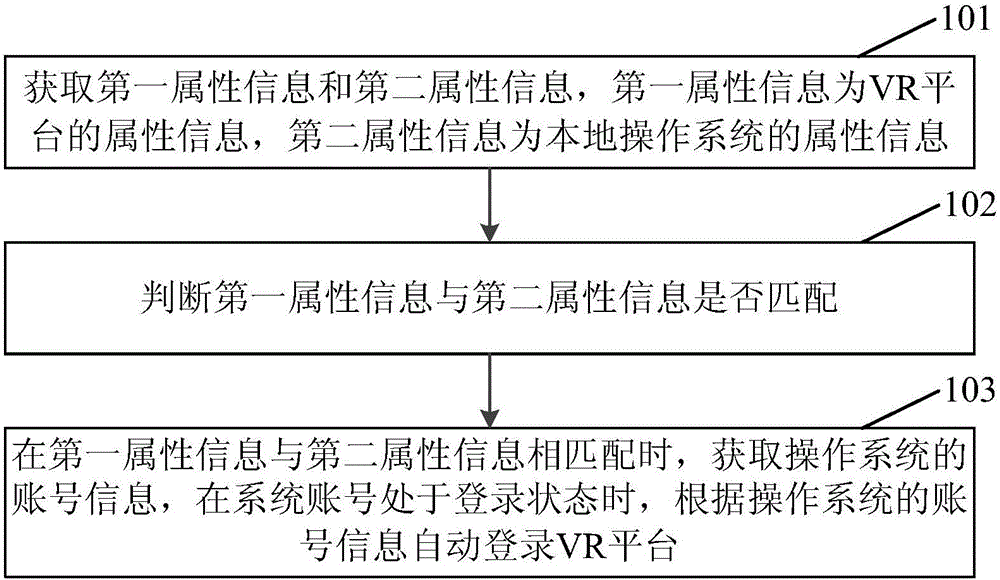
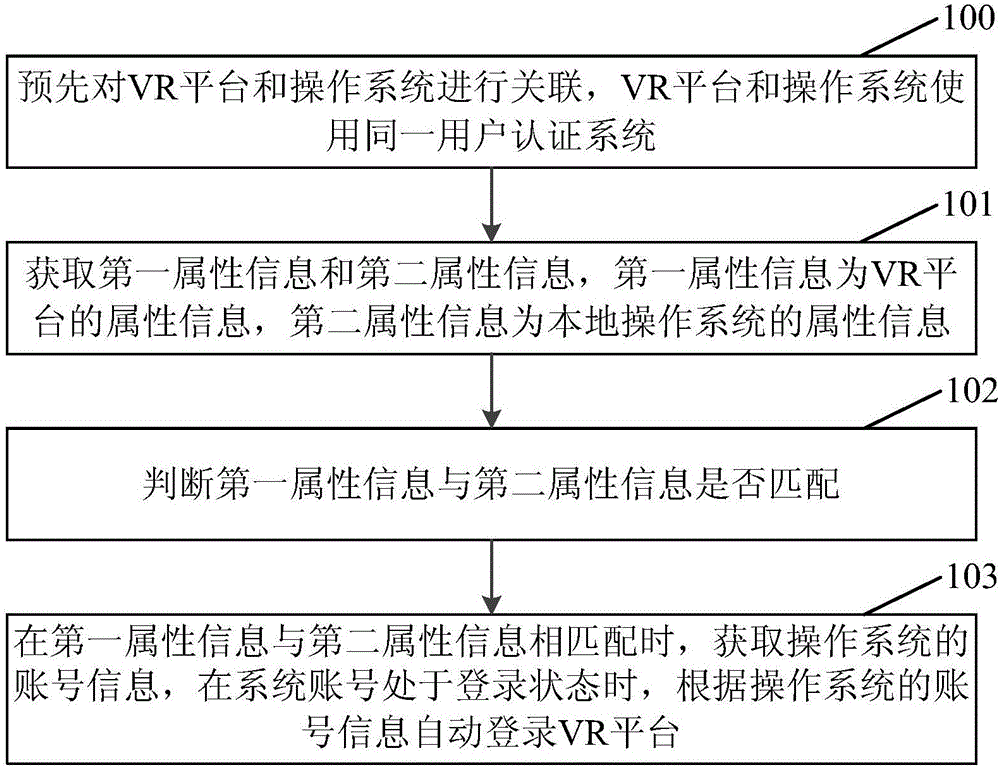
Embodiments of the invention disclose a method and an apparatus for automatically logging in a VR (Virtual Reality) platform. The method comprises the steps of obtaining first attribute information and second attribute information, wherein the first attribute information is attribute information of the VR platform, and the second attribute information is attribute information of a local operation system; judging whether the first attribute information is matched with the second attribute information or not; and when the first attribute information is matched with the second attribute information, obtaining account information of the operation system, and when a system account is in a login state, automatically logging in the VR platform according to the account information of the operation system. According to the method, a user can automatically log in the VR platform without actively inputting the account information of the VR platform, so that the login operation of the user is simplified, the user operation efficiency is improved, and the user experience can be enhanced.
Owner:LETV HLDG BEIJING CO LTD +1
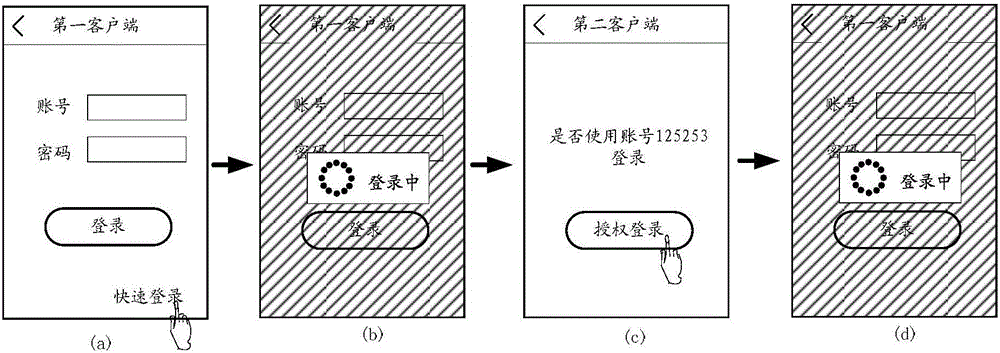
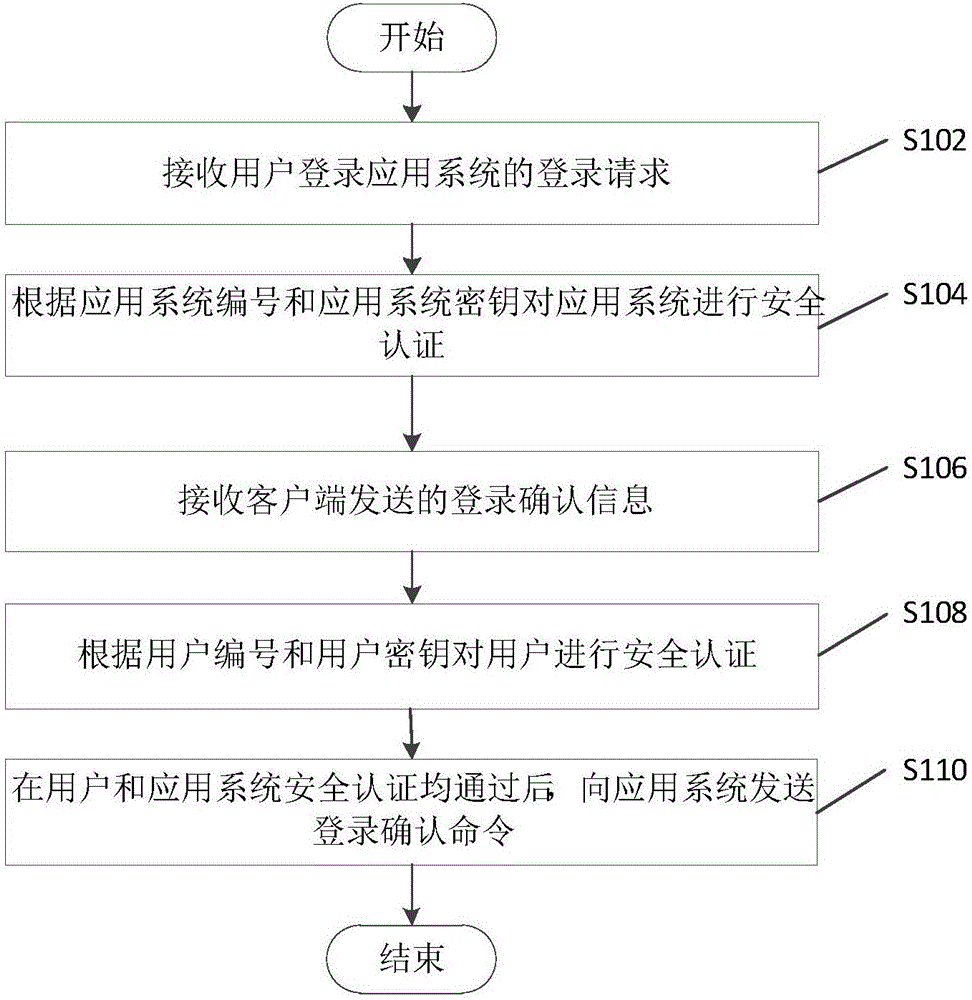
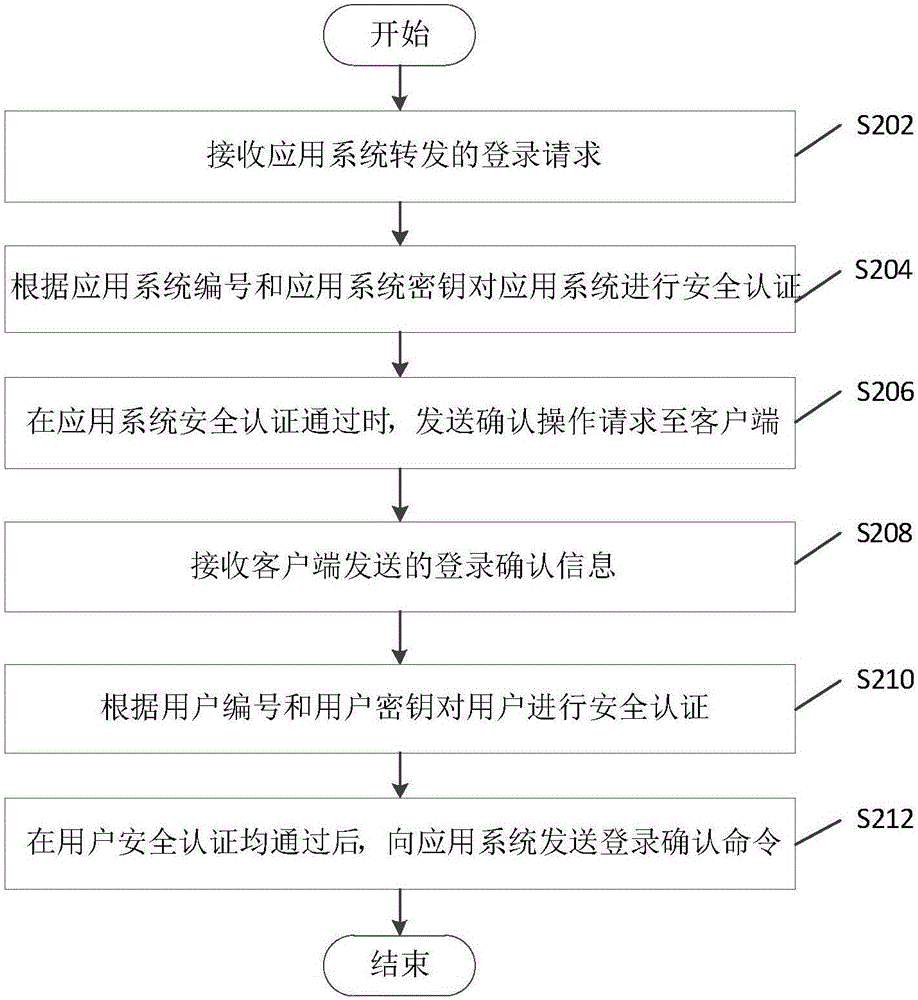
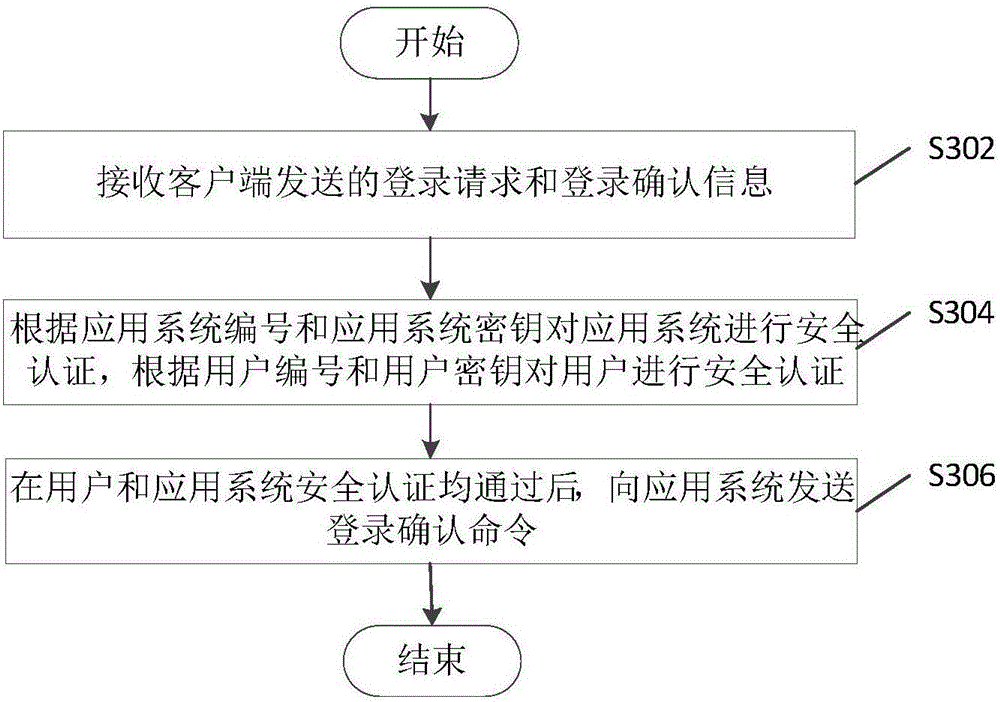
Login method without password based on third party authentication, device and system thereof
ActiveCN106790240AImprove experienceSimplify login operationsUser identity/authority verificationThird partyPassword
The invention discloses a login method without password based on third party authentication, a device and a system thereof. The system comprises a client, an application system, and a third-party authentication server. The client sends a login confirmation message to the third-party authentication server. The third-party authentication server, after receiving a login request of user login application system sent by the client or the application system and the login confirmation message, executes the security authentication for users according to the user number that the login request carries and the user key that the login confirmation message carries, and executes the security authentication for the application system according to the system number that the login request carries and the application system key. After the safety authentications for the user and application system are passed, the third-party authentication server sends a login confirmation order. The application system confirms the user corresponded to the user number and calls the login process to complete the user login after receiving the login confirmation order. By the login method without password based on third party authentication, the device and the system thereof, users login to any system without entering password and verification code.
Owner:北京花晗科技有限公司
Network management system and internetworking unit
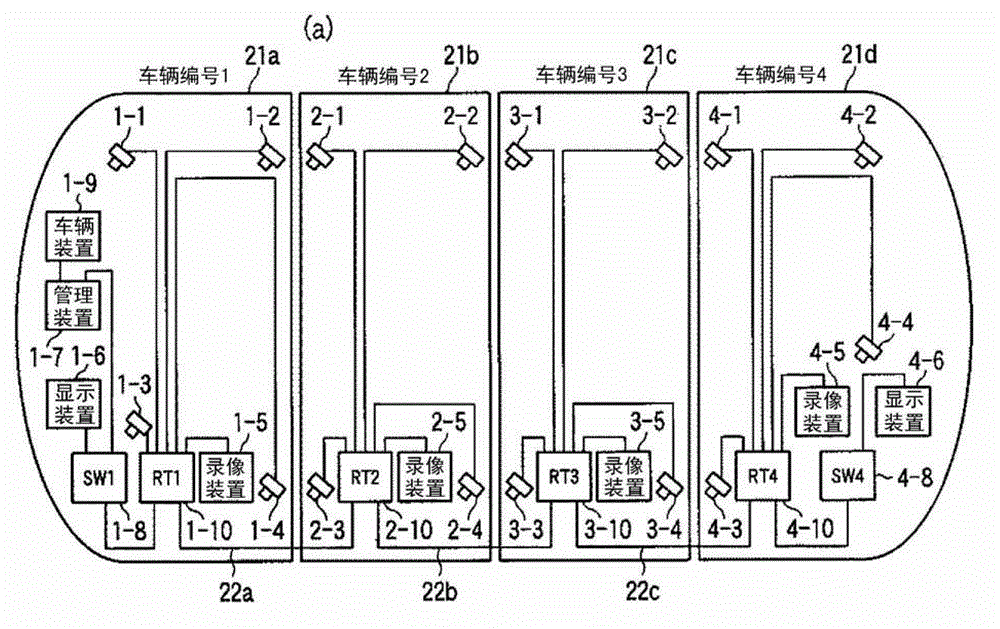
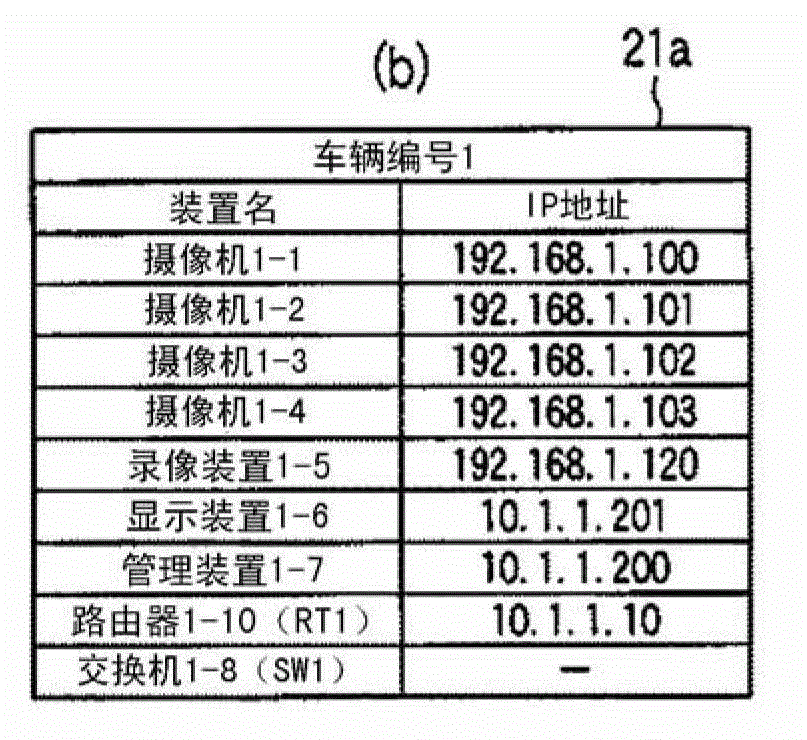
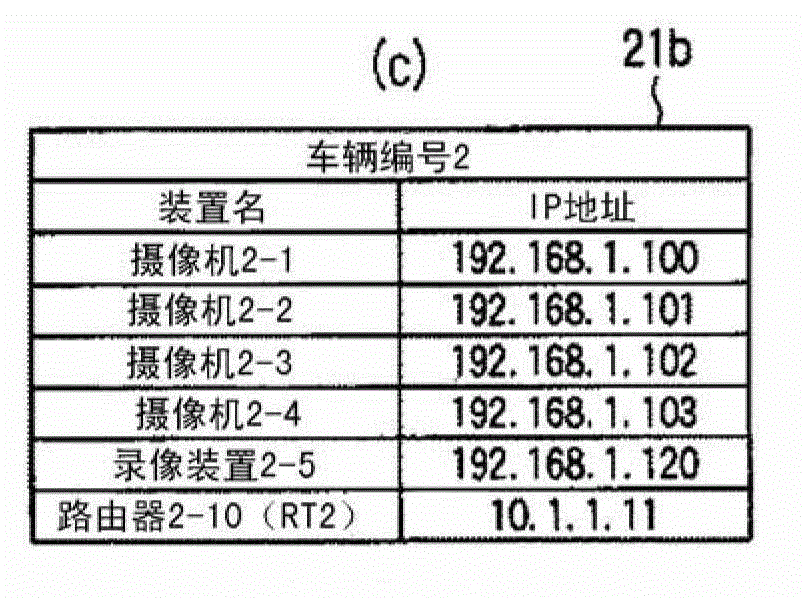
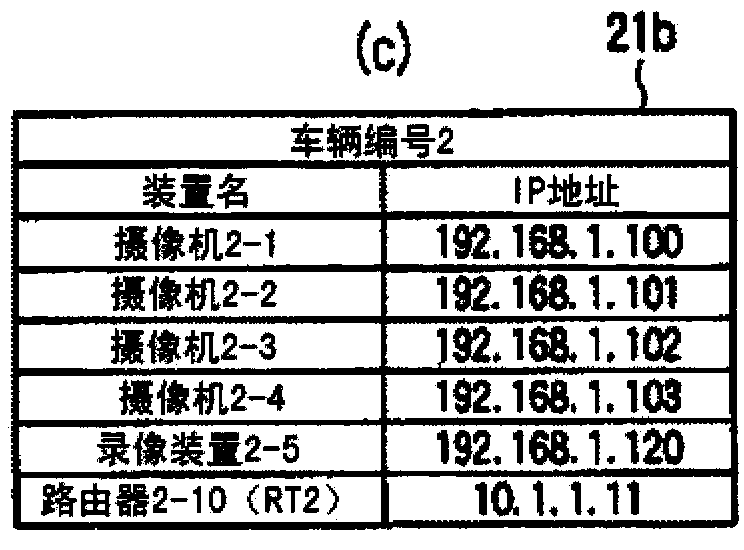
ActiveCN102804704ASimplify login operationsInhibition Use Stop CrisisEnergy efficient ICTStore-and-forward switching systemsSurveillance cameraImage recording
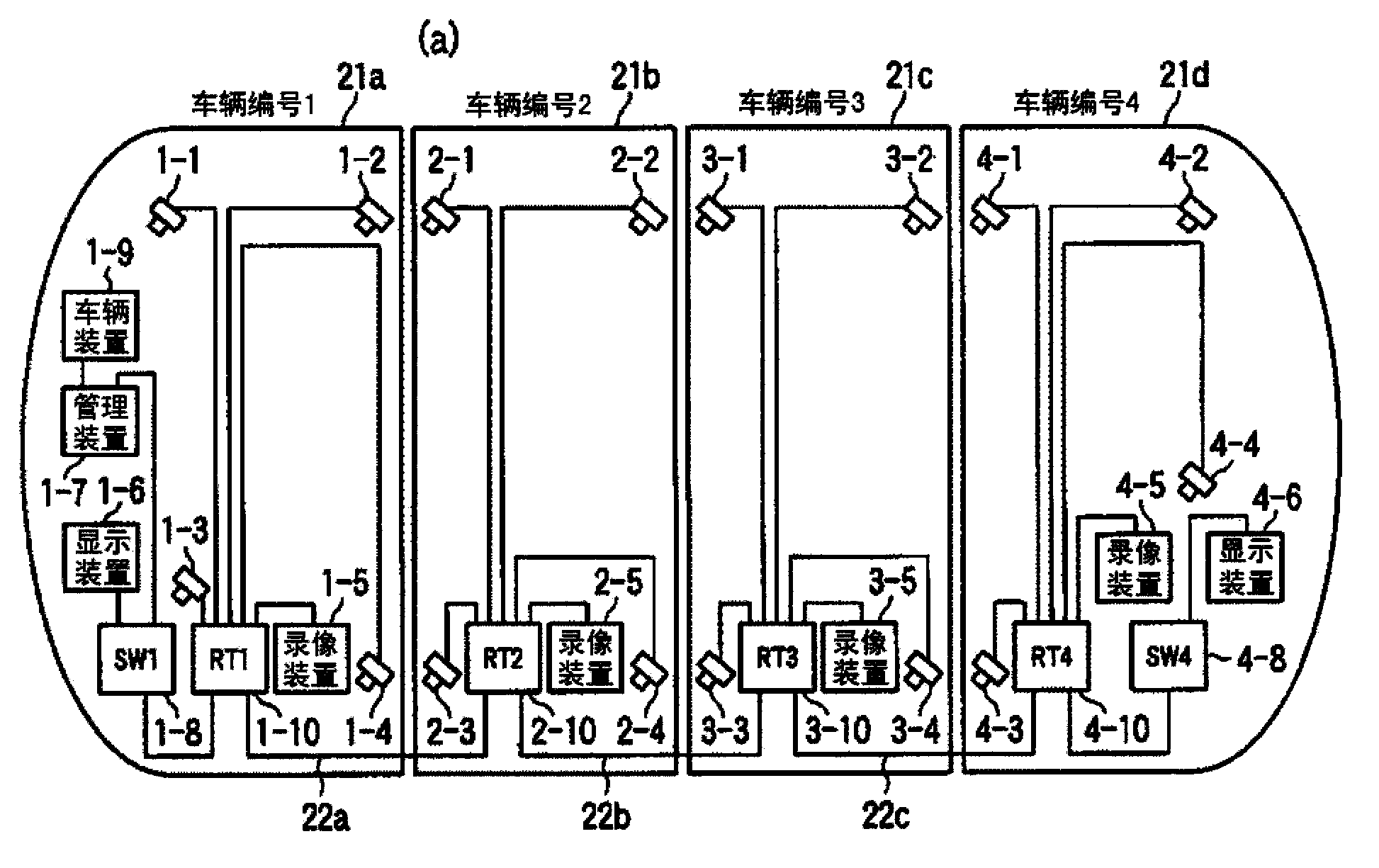
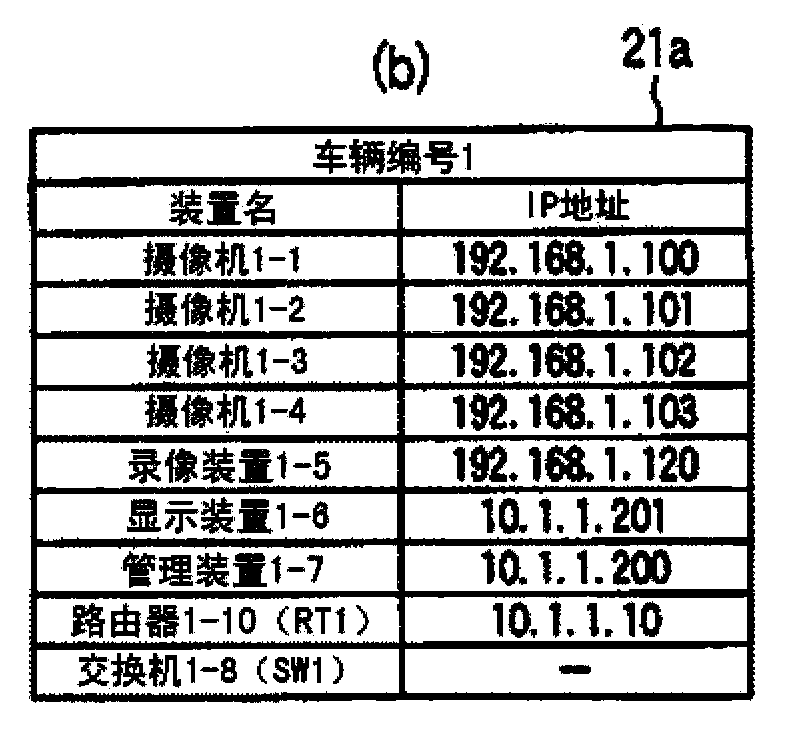
Disclosed is a network management system that allows a system to be easily rebuilt, even when there is a switch in the configuration of cars, etc. Surveillance equipment, which includes surveillance cameras (1-1 to 1-4, ...) and image recording devices (1-5, ...), is networked in each car (21a, 21b, ...). Each of said car networks is configured as a LAN, and an inter-car network is configured as a WAN by connecting a router (1-10 (RT1), ...) to the LAN of each car. For the surveillance equipment in each car, identical equipment and equipment installed in identical locations in each car is connected to ports with identical port numbers, and allocated identical LAN addresses. Also, for access from the WAN side, which equipment is accessed is defined solely by the difference in port number, and it is possible to configure the network information of a switched car merely by changing the WAN address setting of the router, ...
Owner:KOKUSA ELECTRIC CO LTD
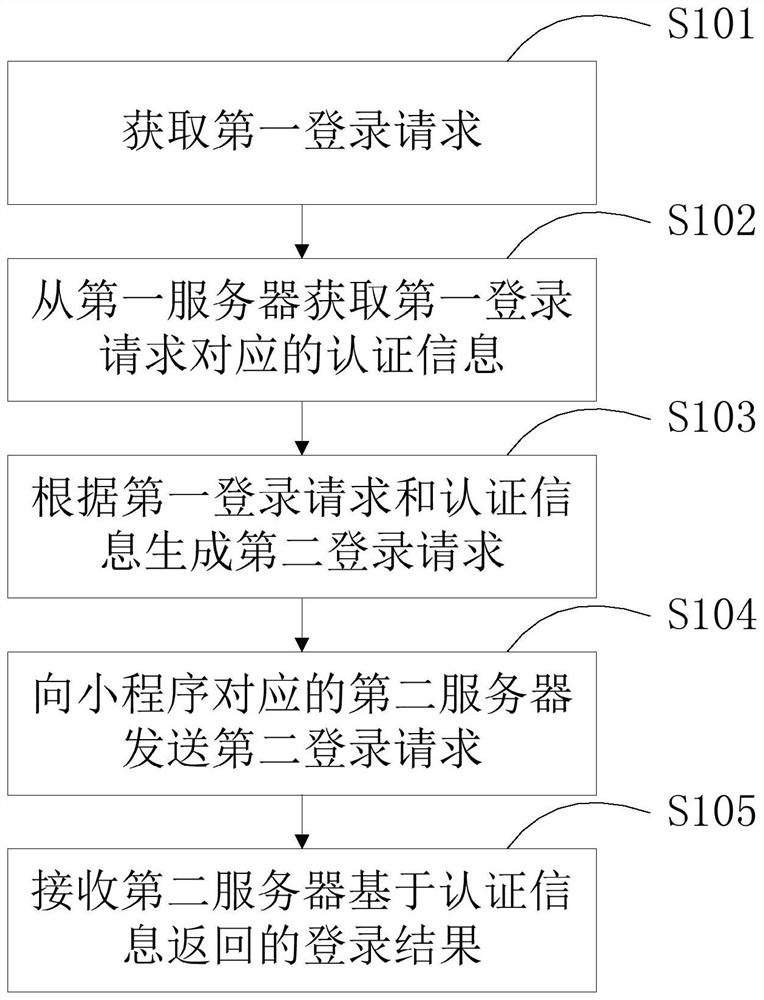
Login method and device based on applet, electronic equipment and storage medium
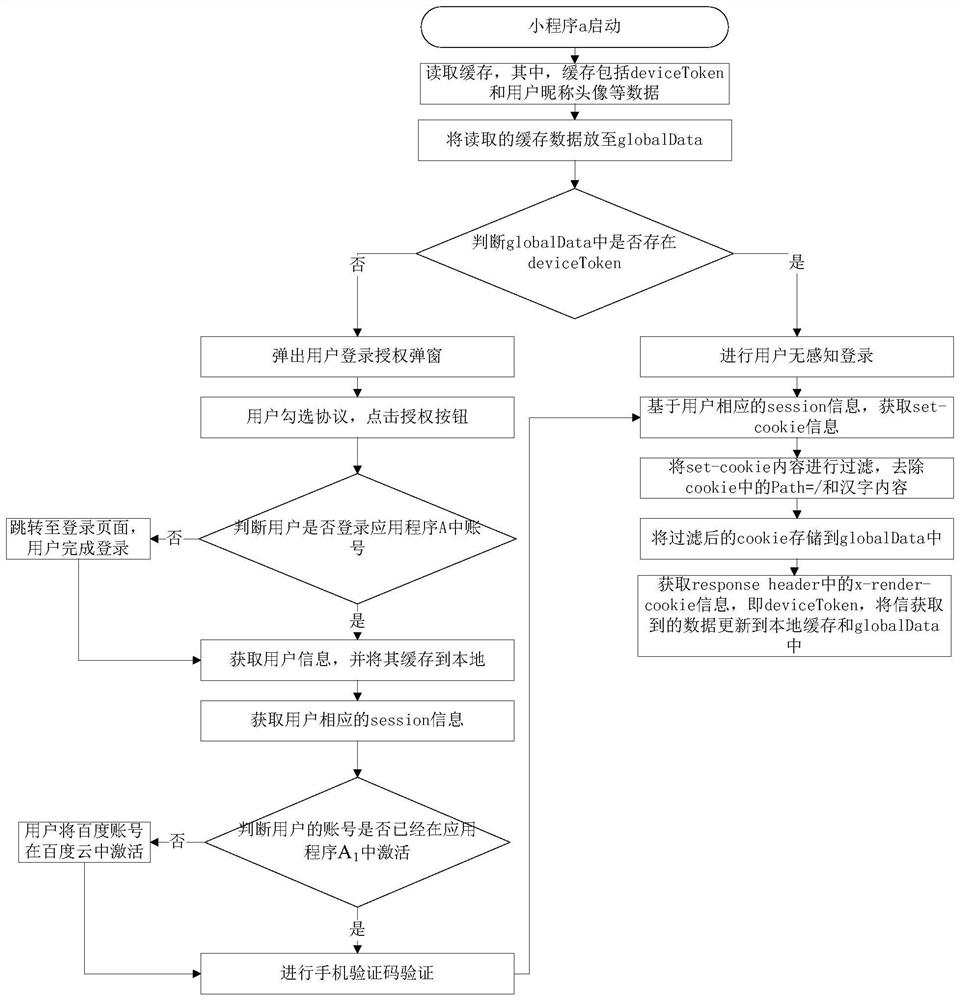
PendingCN114186206ASimplify login operationsSolve complex technical problems in login operationsDigital data authenticationEngineeringAuthorization
The invention provides a login method and device based on an applet, electronic equipment and a storage medium, and relates to the technical field of computers, in particular to the technical field of cloud services. The specific implementation scheme is as follows: acquiring a first login request; acquiring authentication information corresponding to the first login request from a first server; generating a second login request according to the first login request and the authentication information; sending a second login request to a second server corresponding to the applet; and receiving a login result returned by the second server based on the authentication information. It is easy to notice that the authentication information corresponding to the first login request can be obtained from the first server, the second login request capable of conducting user non-inductive login is obtained in combination with the authentication information, the user does not need to conduct authorization and login verification again, the technical effect of simplifying login operation is achieved, and the user experience is improved. The technical problem of complex login operation caused by tedious login steps in the prior art is solved.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Login information input method, login information storage method and related devices
The embodiment of the invention discloses a login information input method, a login information storage method and related devices. The login information input method comprises the following steps: identifying a current page as a login page of an application program; identifying a target input domain used for inputting login information in the login page; receiving biological characteristic information input by a user; if the biological characteristic information is preset biological characteristic information, obtaining login information, represented by the biological characteristic information, of logging in the application program by a user from a preset database; and filling the target input domain with the login information. According to the scheme, the target input domain in the login page can be automatically filled, the login operation of a user is simplified, the application range is wide, and the limitation of an application program development platform is avoided.
Owner:HUAWEI DEVICE CO LTD
Vehicle time sharing rental intelligent application system and method
InactiveCN109087652ASimplify login operationsEasy to operateApparatus for meter-controlled dispensingBuying/selling/leasing transactionsTime-sharingSpeech input
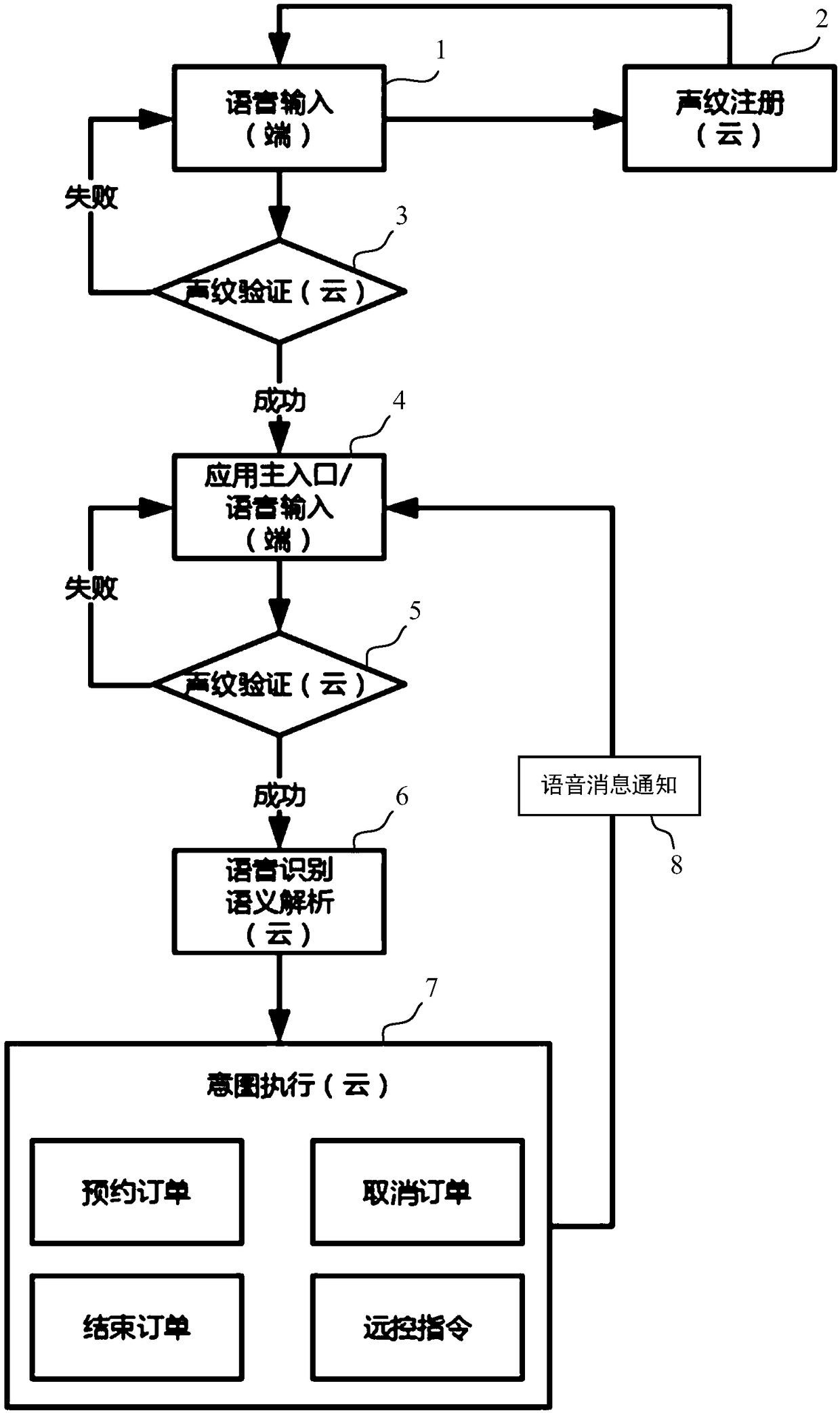
The invention provides a vehicle time sharing rental intelligent application system and method. The system includes a cloud and a terminal; the terminal is configured to receive a voice input and sendthe voice input to the cloud. The cloud includes: a voiceprint registration module configured to perform voiceprint registration on the voice according to the voice input sent by the terminal; a voiceprint verification module configured to perform voiceprint verification on the voice input; and a voice recognition and semantic analysis module configured to perform voice recognition and semantic analyzing after the voiceprint verification is passed; and a user behavior intention processing module configured to process the user behavior intention according to the voice recognition and semanticanalysis results, and feed the processing result back to the terminal in a voice message notification form.
Owner:WM SMART MOBILITY (SHANGHAI) CO LTD
Control method of intelligent TV set
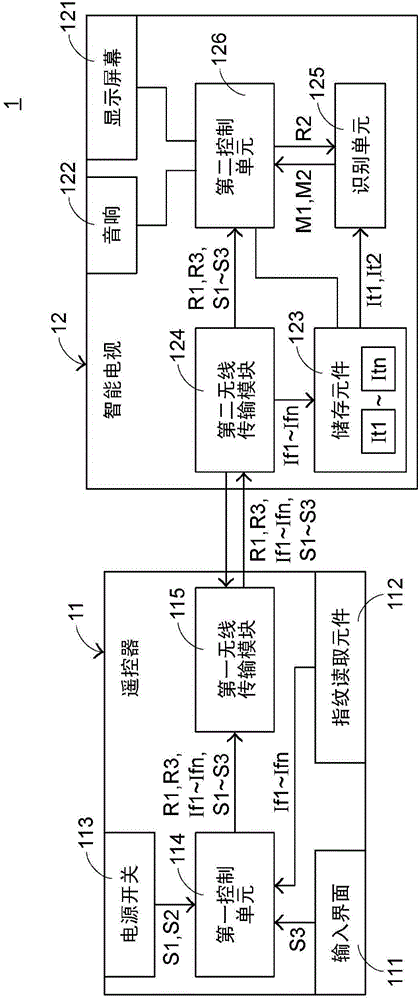
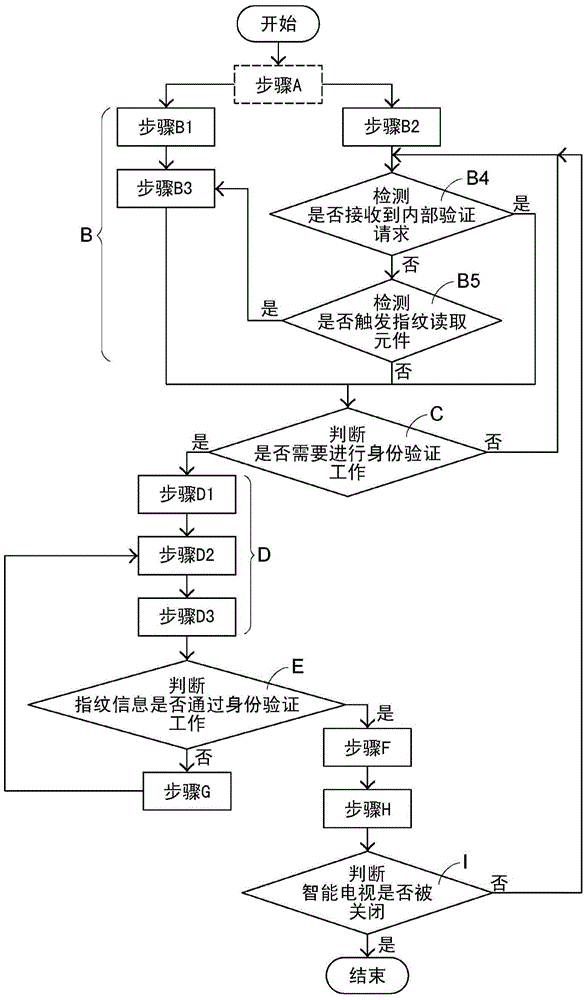
InactiveCN106303698ASimplify login operationsReduce lossSelective content distributionEmbedded systemElectric power
The invention relates to a control method of an intelligent TV set. A remote controller starts multiple buttons of the intelligent TV set, and the intelligent TV set determines whether identity verification is needed. When the intelligent TV set needs identity verification, fingerprint information provided by a fingerprint reading component of the remote controller is received, and identity verification is carried out. When the intelligent TV set determines that the fingerprint information passes identity verification, the intelligent TV set is in a user mode corresponding to the fingerprint information and controls the fingerprint reading component to be in a dormant mode, and power is saved.
Owner:PRIMAX ELECTRONICS LTD
Method, system and cloud server for multi-device secure login
ActiveCN103281327BSimplify login operationsImprove experienceTransmissionComputer terminalLogin session
The invention provides a method, system and cloud server for multi-device safe logging, wherein the method comprises the steps that the cloud server creates connection information according to a connection request sent by a first terminal and creates a corresponding relation between account information in first logging session information and the connection information; the cloud server can send a login prompt to the first terminal according to the connection information corresponding to the account information corresponding to a user name sent by a second terminal, receives feedback information returned according to the login prompt, and controls logging of the second terminal according to the feedback information. According to the method, after a user normally logs in a device (such as the first terminal), a logging process can be completed only through inputting of the user name on other devices (such as the second terminal), logging operation of a user on multiple devices is simplified, user experience is promoted, the cloud server controls the logging of other equipment (such as the second terminal) according to the feedback information, and safety is guaranteed.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Login method and device of application program, readable medium and electronic equipment
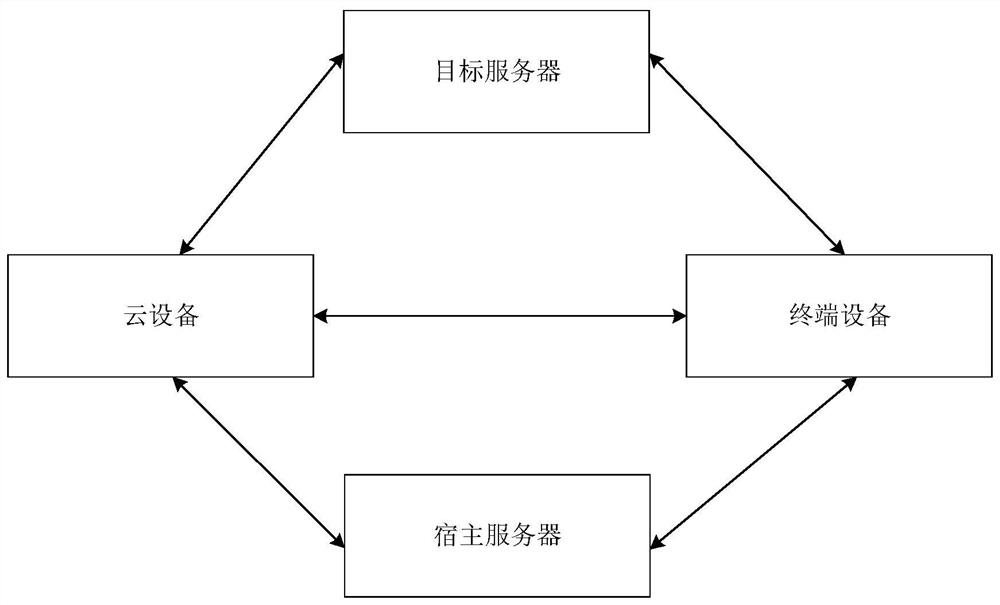
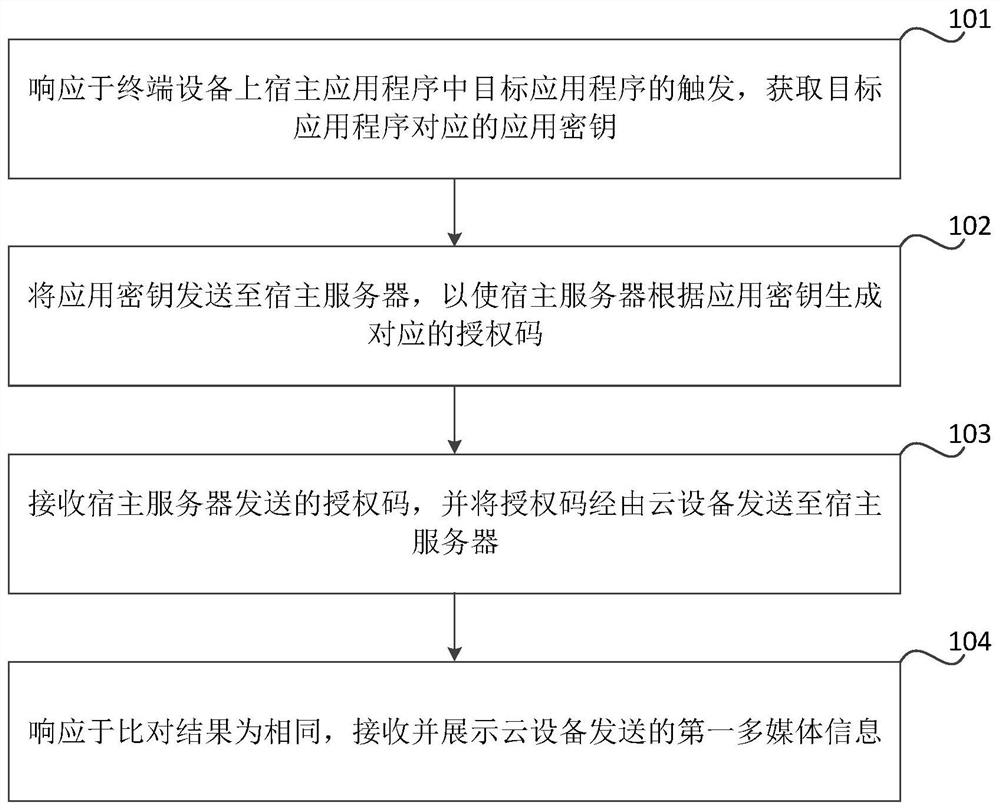
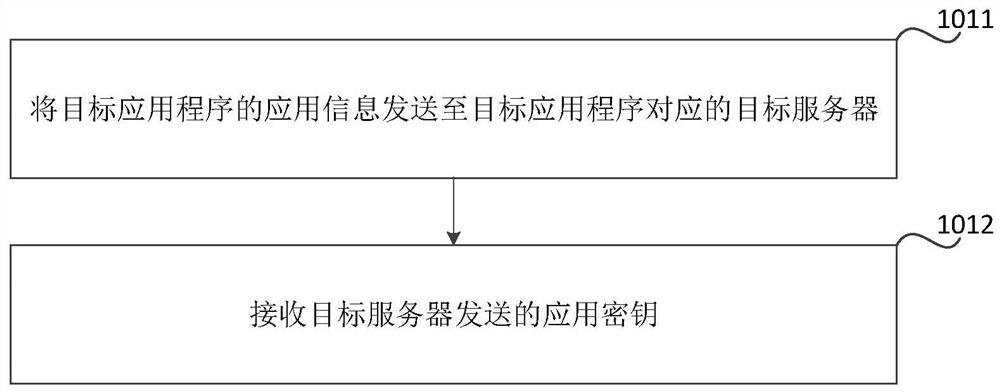
ActiveCN112968871AImprove interoperabilitySimplify login operationsDigital data authenticationTransmissionInformation processingSoftware engineering
The invention relates to a login method and device of an application program, a readable medium and electronic equipment, and relates to the technical field of electronic information processing. The method is applied to terminal equipment, and the method comprises the following steps: responding to triggering of a target application program in host application programs on the terminal equipment, and obtaining an application key corresponding to the target application program; sending the application key to a host server, so that the host server generates a corresponding authorization code according to the application key; receiving an authorization code sent by the host server, and sending the authorization code to the host server through the cloud device, so that the host server compares whether the authorization code received from the cloud device is the same as the authorization code generated according to the application key, and sends a comparison result to the cloud device; in response to the fact that the comparison result is the same, receiving and displaying first multimedia information sent by the cloud equipment, wherein the first multimedia information is information generated by the target application program after the cloud equipment logs in the target application program. According to the invention, the login efficiency can be improved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Web server, business logging method and system
The invention discloses a Web server, a business logging method and a business logging system, wherein the business logging method comprises the steps of: obtaining a second logging request information for logging on a second business, wherein the second logging request information comprises a first account number for logging on a first business by a user; and if the second account number bound to the first account number is inquired according to the second logging request information, logging on the second business according to the inquired second account number. According to the logging method disclosed by the invention, the user can achieve one-key logging when the user skips to another business with an account number binding relationship from one business, so the user operation is simplified.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
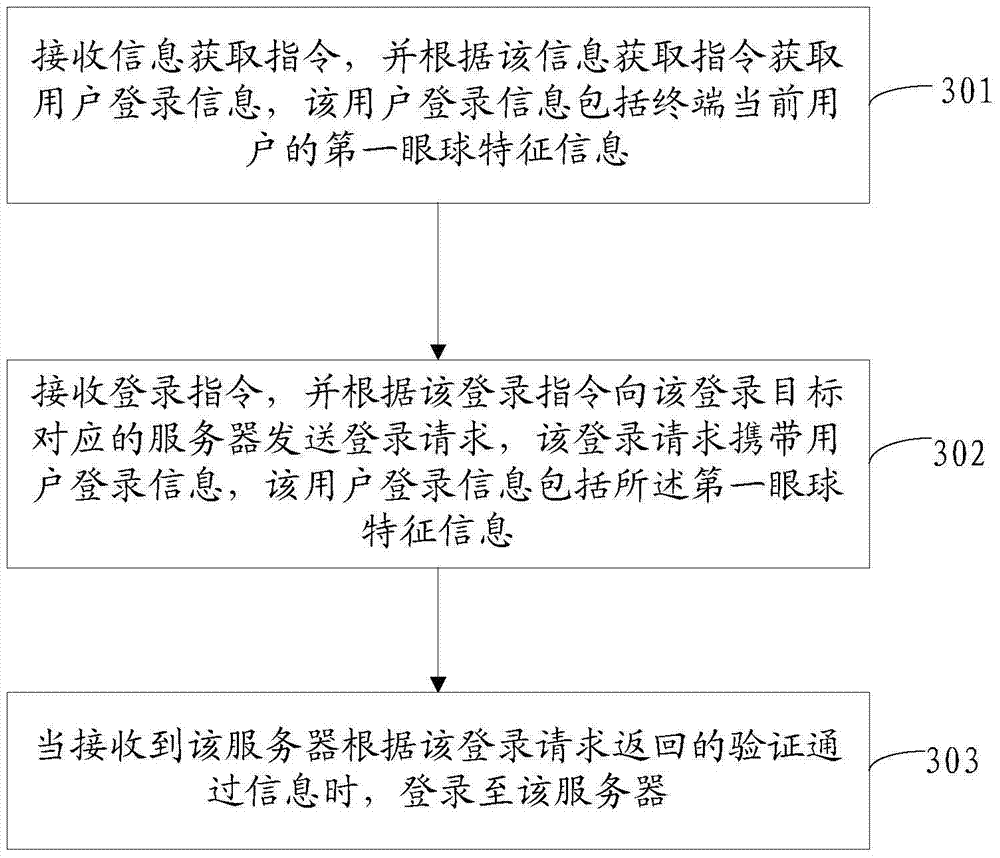
Eyeball registration method and device
ActiveCN105429954BImprove login efficiencyImprove securityTransmissionComputer graphics (images)Engineering
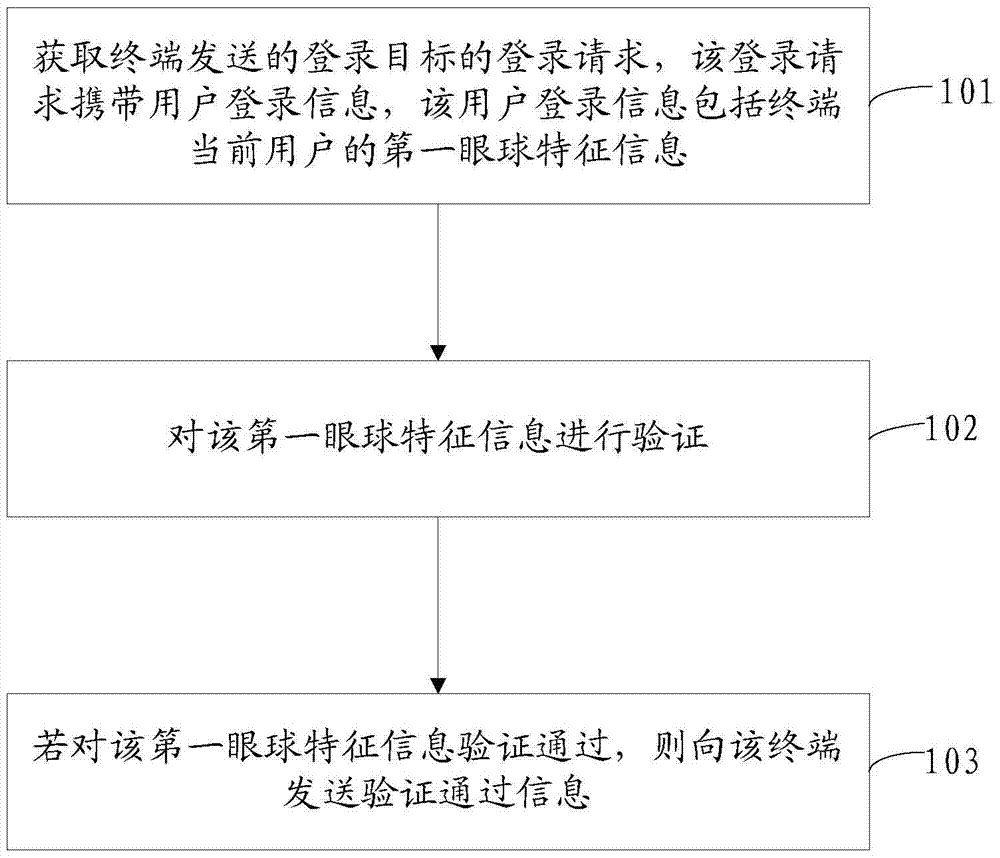
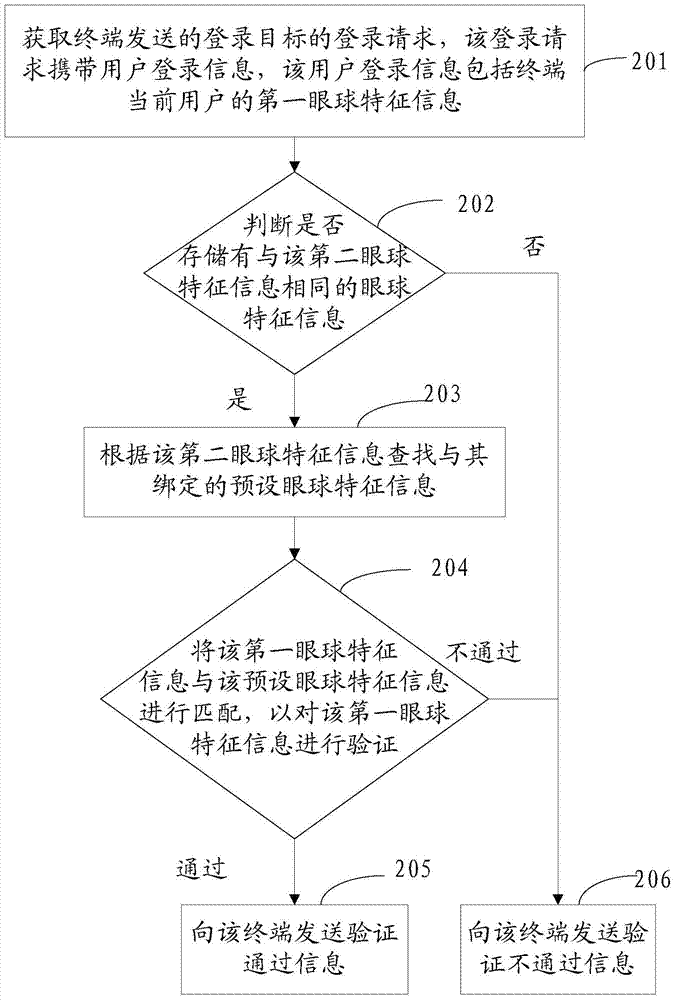
The embodiment of the invention discloses an eyeball registration method and device. The method comprises: employing a registration request of registering an object transmitted by a terminal, wherein the registration request carries user registration information, and the user registration information comprises the first eyeball characteristic information of a current user of the terminal; verifying the first eyeball characteristic information; and if the verification of the first eyeball characteristic information passes, sending verification pass information to the terminal. The scheme can simplify user registration operation, and improve terminal application program registration efficiency and registration information security.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Terminal application login method, device, client and electronic equipment
ActiveCN104093141BSimplify login operationsMeet needsNetwork data managementClient-sideComputer science
The invention discloses a terminal application login method, device, client and electronic equipment, and relates to the technical field of terminal applications. The main technical solution of the present invention is: when receiving an operation that triggers login in the application, judge whether the terminal has a SIM card; if the terminal has a SIM card, log in with the first login method or the second login method according to the user instruction , the first login method is automatic registration and / or login; the second login method is to log in using an existing account; if the terminal does not have a SIM card, log in with the second login method or the third login method according to user instructions, the The third login method includes registering and logging in through a mobile phone number or an email address. The present invention is mainly applied in the process of terminal application login.
Owner:北京鸿享技术服务有限公司
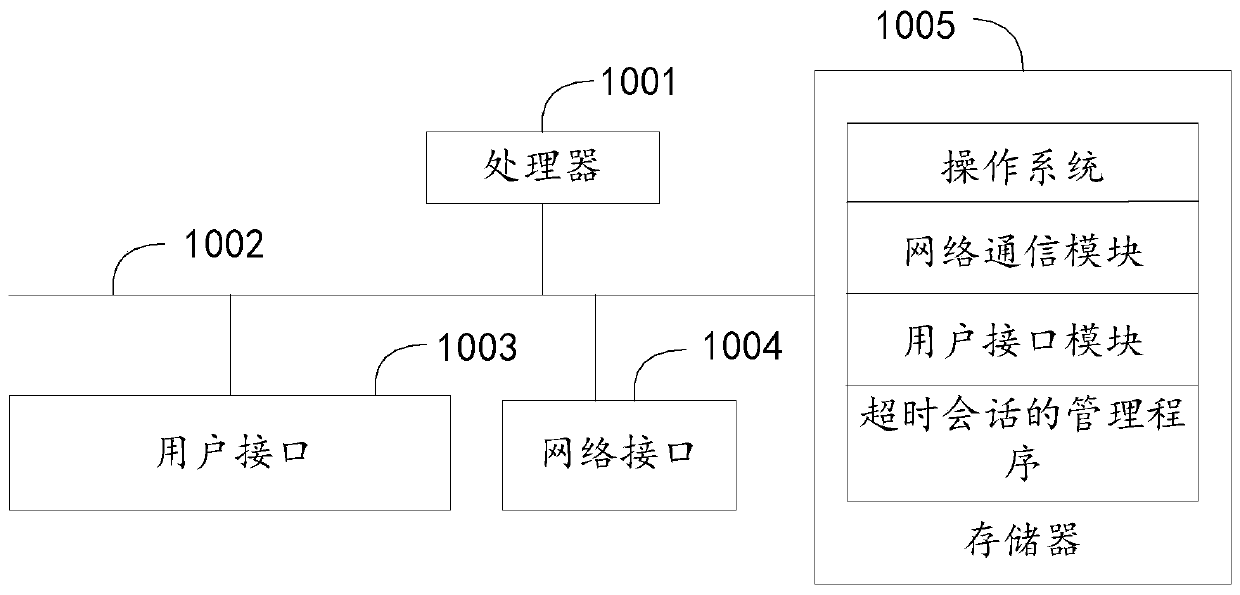
Timeout session management method and device, equipment and storage medium
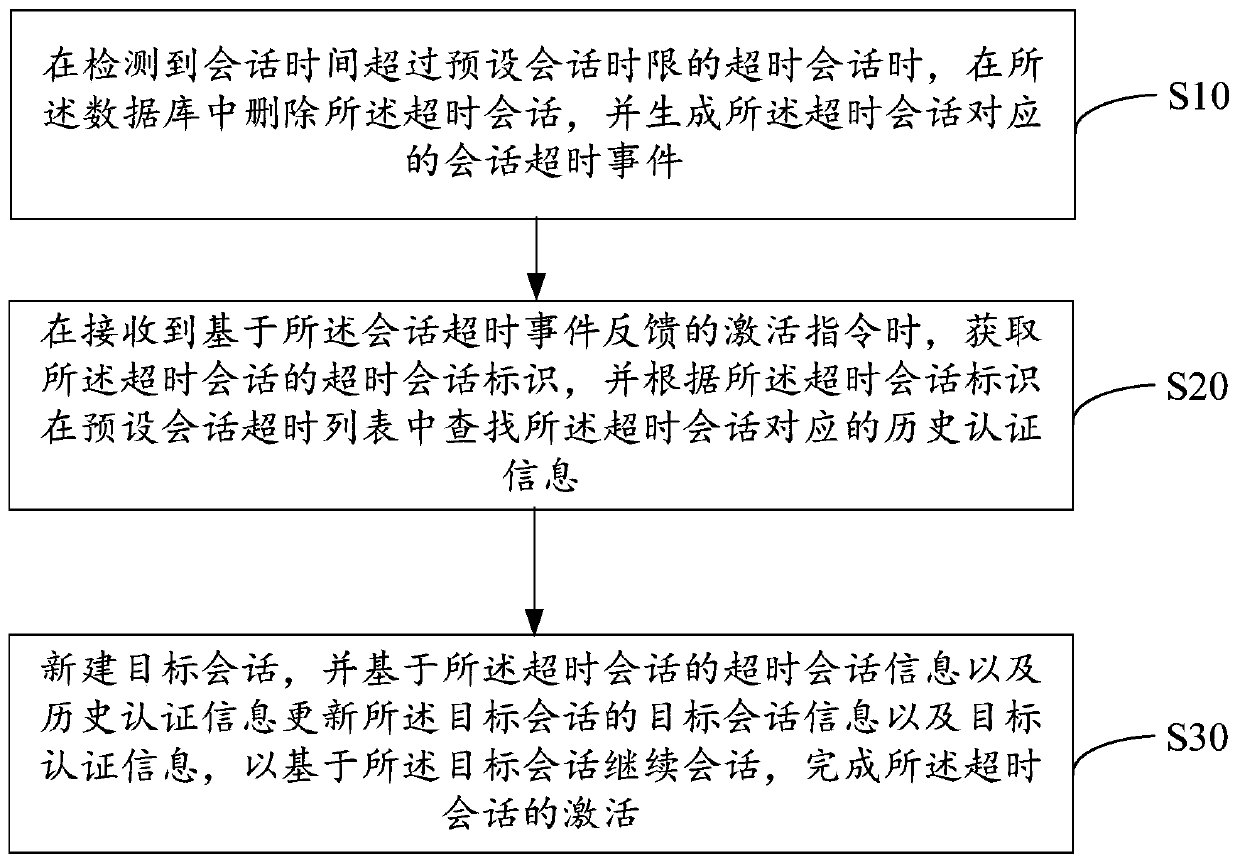
PendingCN111258804AImprove experienceSimplify login operationsFault responseHardware monitoringSession managementEngineering
The invention provides a timeout session management method and device, equipment and a storage medium. The method comprises the steps of: when a timeout session is detected, deleting the timeout session and generating a session timeout event; when an activation instruction is received, acquiring the timeout session identifier of the timeout session, and searching historical authentication information corresponding to the timeout session in a preset session timeout list according to the timeout session identifier; and creating a new target session, and updating the target session information and the target authentication information of the target session based on the timeout session information and the historical authentication information of the timeout session, so as to continue the session based on the target session and complete the activation of the timeout session. According to the invention, the session identifier and the authentication information of the timeout session are stored through the session timeout list, and the unauthenticated information of the newly built session is updated into the historical authentication information, so that the session with the user is continued through the newly built session, the user login operation is simplified, the session efficiency is improved, and the user experience is improved.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
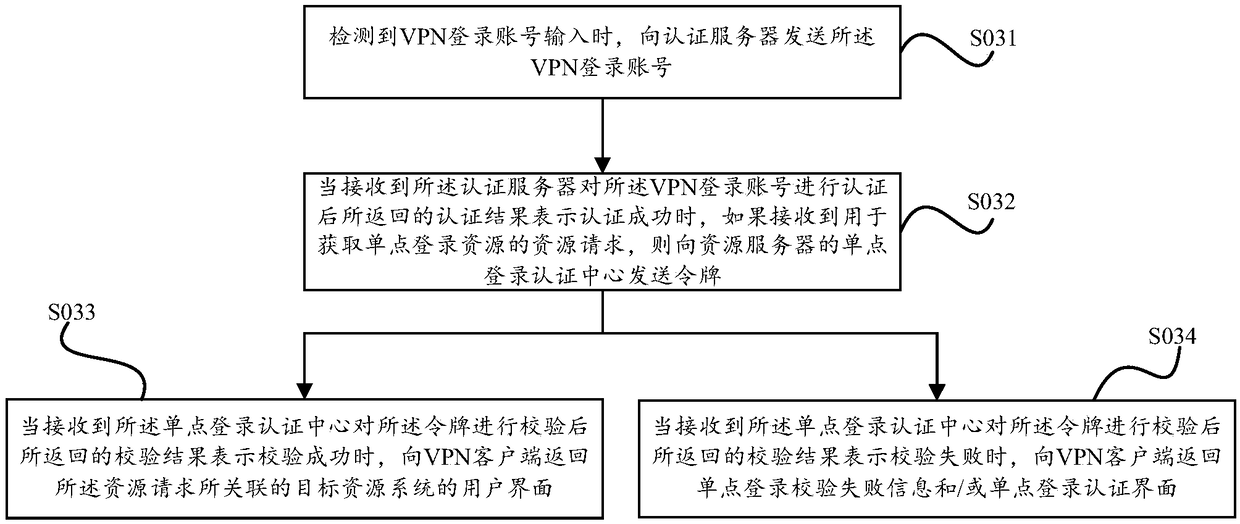
Single sign-on method and device based on virtual private network
ActiveCN109347864BSimplify login operationsImprove securityNetworks interconnectionInternet privacyPrivate network
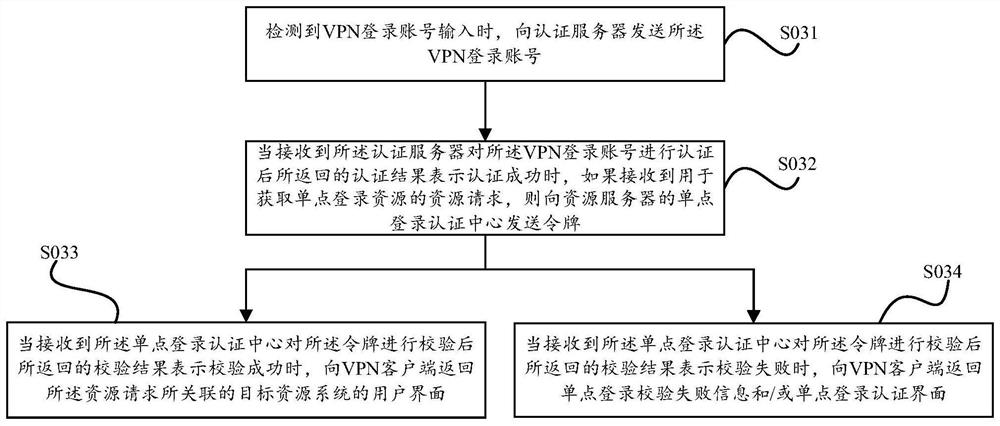
The present invention provides a single sign-on method and device based on a virtual private network, wherein the method includes: when a VPN server detects that a VPN login account is input, sending the VPN login account to an authentication server; Log in to the account for authentication, and return the authentication result to the VPN server; wherein, the authentication result when the authentication is successful includes a token used as a single sign-on authentication credential; when the authentication result received by the VPN server indicates that the authentication When successful, if a resource request for obtaining a single sign-on resource is received, the token is sent to the single sign-on authentication center of the resource server; wherein, the resource server includes a single sign-on authentication center and a resource system; The single sign-on authentication center verifies the token, and performs corresponding operations according to the verification result. Therefore, the embodiment of the present invention has the advantages of simple configuration, high account security and fast login.
Owner:HANGZHOU DPTECH TECH
Login method, browser, game server and terminal equipment of web game
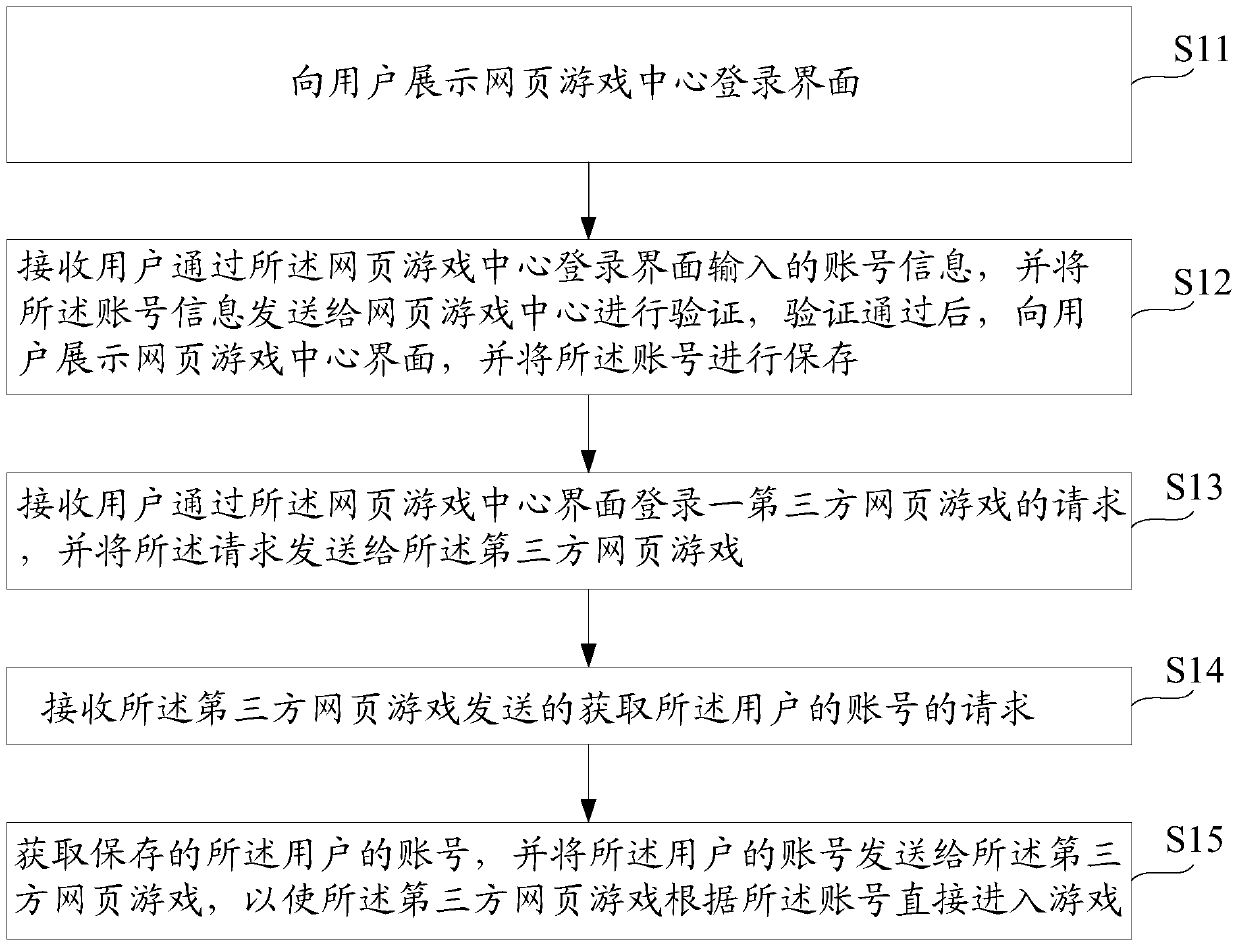
The embodiment of the invention discloses a web game login method, a browser, a game server and terminal equipment, which relates to the technical field of web game login and can realize simple and quick web game login. According to the web game login method, the browser, the game server and the terminal equipment, when a user logs in a third-party web game, the user can use an account for logging in a web game center or another third-party web game to enter the game directly. The web game login method, the browser, the game server and the terminal equipment can be applied to situations in which web game login is carried out in the web game center or the web game platform.
Owner:BEIJING KINGSOFT INTERNET SECURITY SOFTWARE CO LTD
Cipher protection system and method
ActiveCN101079088BAdd login operationSimplify login operationsDigital data authenticationInput/output processes for data processingPassword protectionProtection system
Owner:TENCENT TECH (SHENZHEN) CO LTD
Webpage-based login method, device, equipment and storage medium
ActiveCN107528858BSimplify login operationsImprove experienceUser identity/authority verificationSoftware simulation/interpretation/emulationEngineeringWeb page
Owner:GUANGZHOU SHIRUI ELECTRONICS +1
Application login method and device
ActiveCN104363205BSimplify login operationsImprove login efficiencyDigital data authenticationTransmissionSoftware engineeringThe Internet
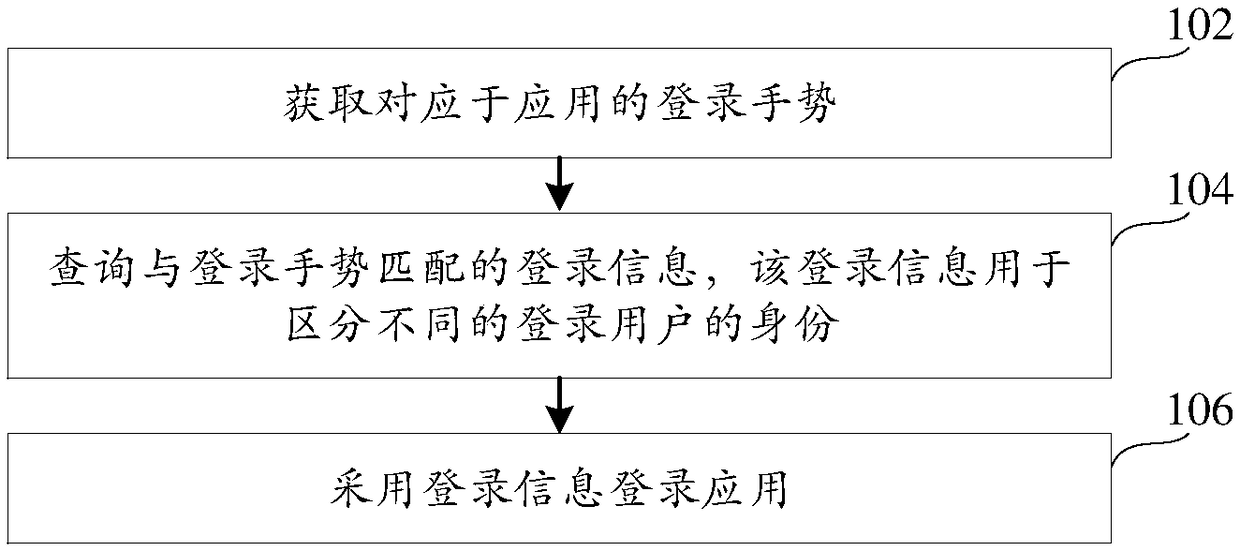
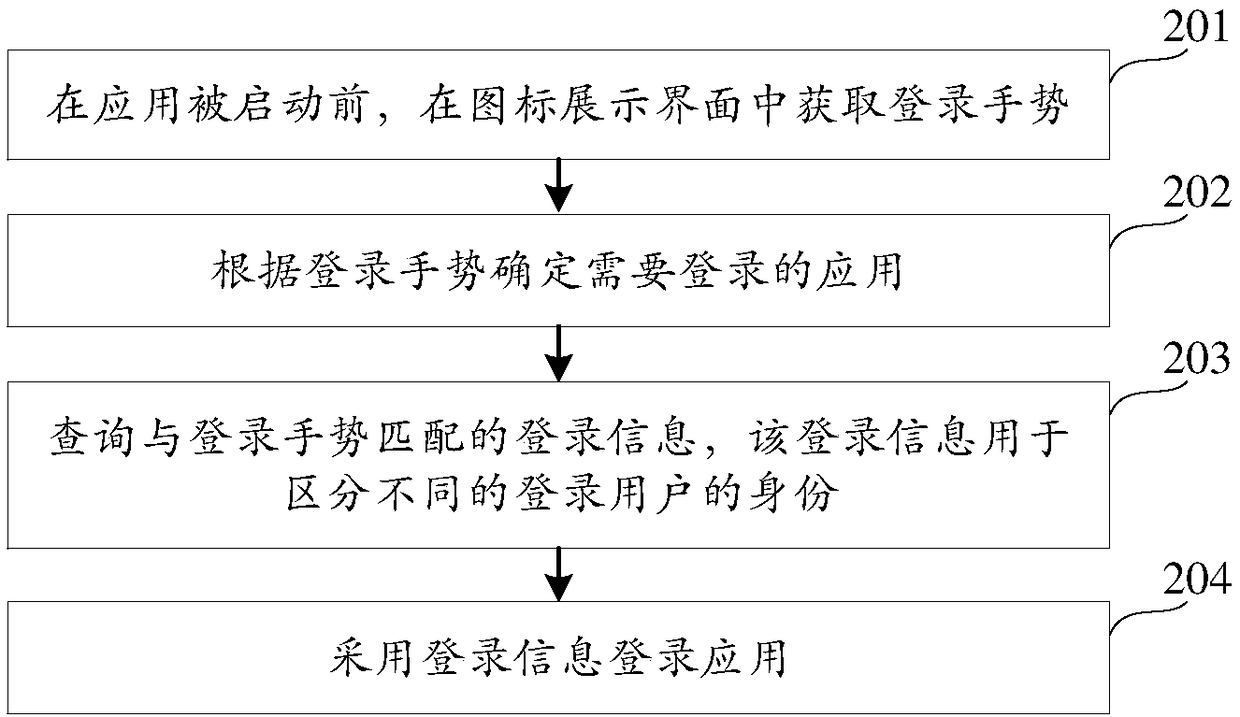
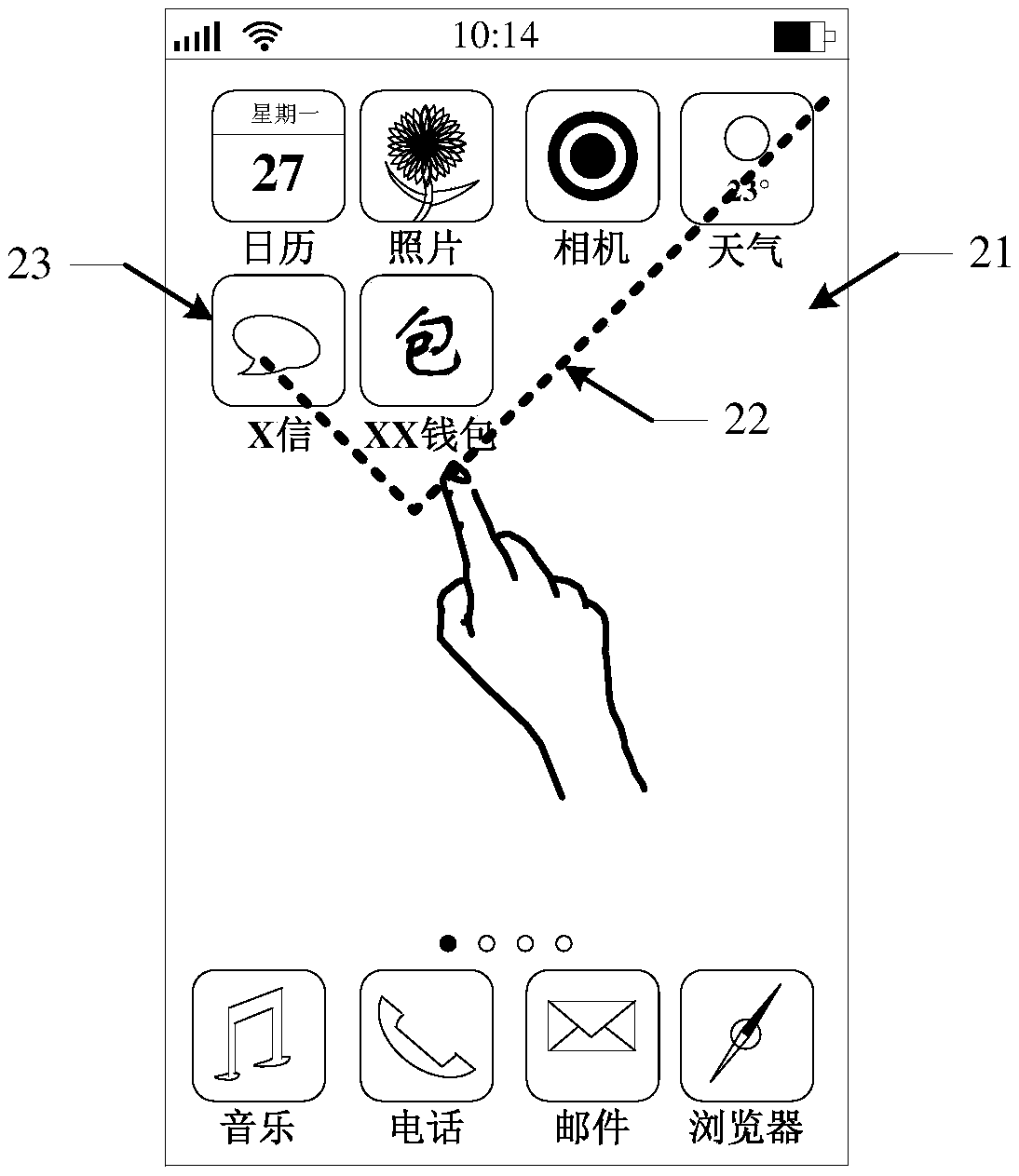
The invention relates to an application login method and device and belongs to the technical field of computers and Internet. The method includes: acquiring a login gesture corresponding to an application; querying login information matched with the login gesture, wherein the login information is used for distinguishing identities of different login users; and adopting the login information to log in the application. The problems of inconvenience in operation and time and energy waste in the login process due to the fact that a user has to input the login information when logging in the application every time in related technologies are solved; when logging in the application, the user only needs to input the login gesture to complete application login, login operation is simplified, and login efficiency is improved.
Owner:XIAOMI INC
Network management system
ActiveCN102804704BSimplify login operationsInhibition Use Stop CrisisEnergy efficient ICTStore-and-forward switching systemsNetwork managementComputer science
A network management system which can easily rebuild the system even when a switch in the configuration of cars occurs. A monitor apparatus including monitor cameras (1-1˜1-4, . . . ) and recording devices (1-5, . . . ) in each car (21a, 21b, . . . ) is networked. Each intra-car network is constructed as a LAN, a router (1-10 (RT1), . . . ) is connected to the LAN in each car, and an inter-car network is constructed as a WAN. The same apparatus in each car and apparatuses provided at the same positions are connected to a port of the same port number and the same LAN address is allocated to such an apparatus. As for an access from a WAN side, which apparatus is accessed is defined only by a difference in port number. Network information of the car switched car can be set merely by switching the setting of the WAN address of the router, . . . .
Owner:KOKUSA ELECTRIC CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com