Cipher protection system and method
A password protection and password technology, applied in the computer field, can solve problems such as cumbersome operation steps and inconvenient use, and achieve the effects of ensuring information security, simplifying operations, and increasing the difficulty of decryption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
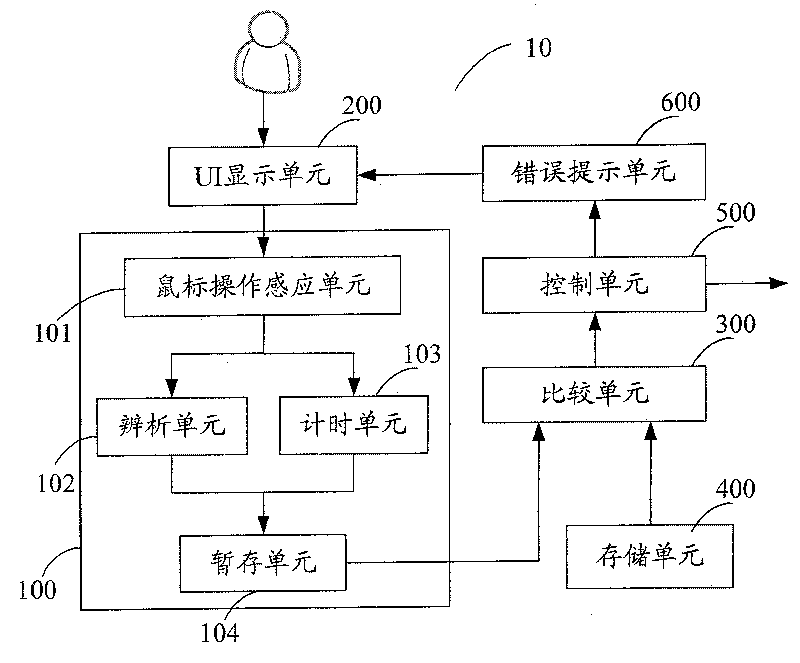
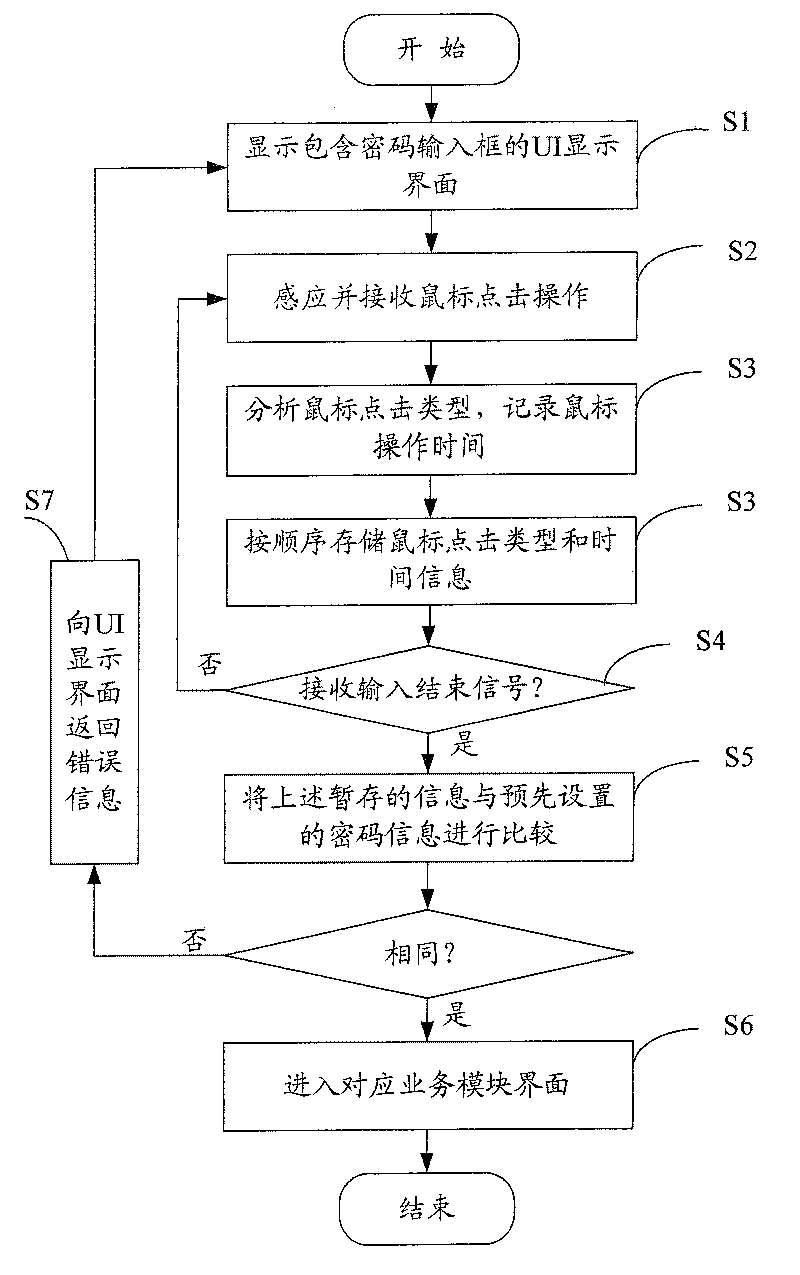
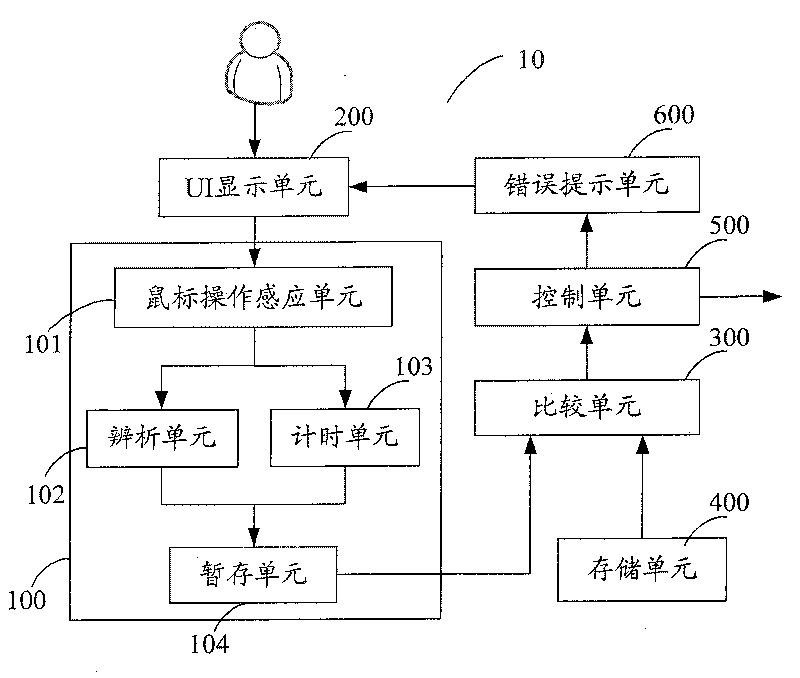
Image
Examples
Embodiment Construction
[0016] In order to understand the present invention better, at first briefly introduce existing serial mouse:
[0017] 1. The serial mouse uses four wires in the DB9 connector:
[0018] 2 (RXD: for the positive power supply of the mouse);
[0019] 3 (TXD: used to send data);
[0020] 4 (DTR: for positive power supply, reset and mouse detection);
[0021] 7 (RTS: optional, for positive power supply)
[0022] 2. Simple communication protocol of serial mouse
[0023] (1) The serial data format of the mouse
[0024] The commonly used Microsoft mouse has two buttons, which are supported by most operating systems. The data format it sends is: baud rate 1200bps, stop bit 1.0, valid data per byte 7 bits, each byte Frame 3 bytes. There are also mice from other companies, such as Logitech, that use mice with 3 buttons (some with a scroll wheel). Logitech has extended the protocol of the Microsoft mouse, using a baud rate of 1200bps, a stop bit of 1.0 bits, 8 bits of valid data pe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com