Patents
Literature
158results about How to "Quick Login" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
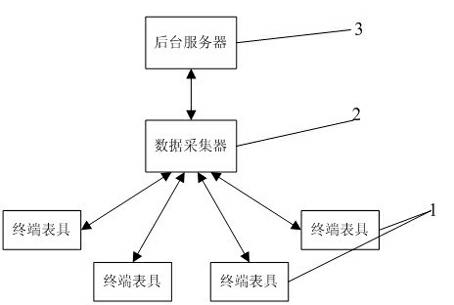
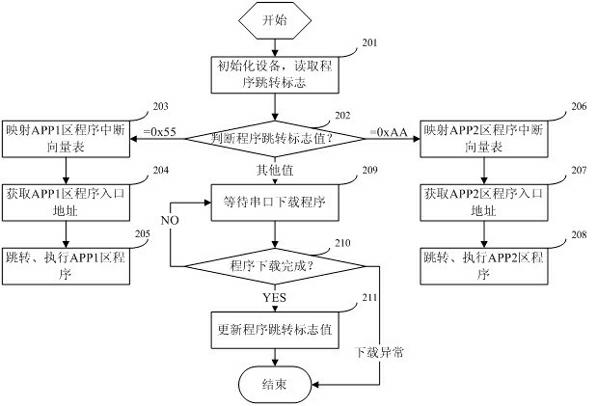
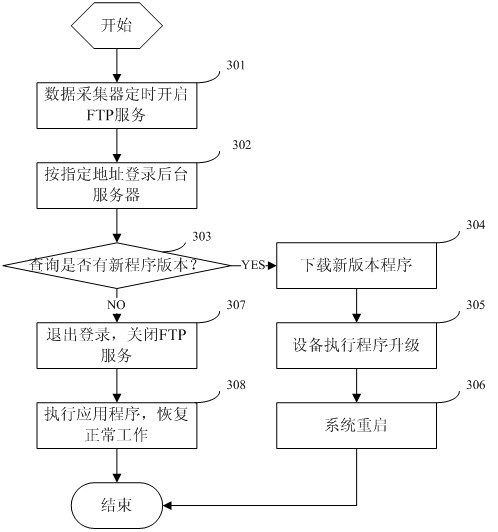
Self-upgrade method for equipment in remote online monitoring system
ActiveCN102314369AResolve escalationSolve problemsProgram loading/initiatingTransmissionGeneral Packet Radio ServiceSelf maintenance
The invention belongs to the field of wireless communication, and particularly relates to a self-upgrade method for equipment in a remote online monitoring system. The method is characterized in that: each piece of terminal equipment performs self-upgrade and self-maintenance through the remote online monitoring system consisting of a terminal table tool, a data acquisition unit and a background server based on a GPRS (General Packet Radio Service). The method mainly comprises the following steps that: the background server manages an application program and version information; the data acquisition unit periodically inquires a version log and downloads a new version program; the data acquisition unit realizes self-upgrade and upgrades the terminal table tool; and after the new version program is updated successfully, skipping is performed and an old version program is still kept for later use. In the method, the GPRS, storage space management, a file sub-package mechanism, a transmission response mechanism, a mode for continuous transmission at break-points and an IAP (Internet Access Provider) program programming mode are combined, and the accuracy and reliability of data transmission are ensured; and under the condition of not influencing normal use of a user, the equipment upgrading and maintaining problems of large quantity and wide distribution are solved quickly and efficiently.
Owner:杭州先锋电子技术股份有限公司
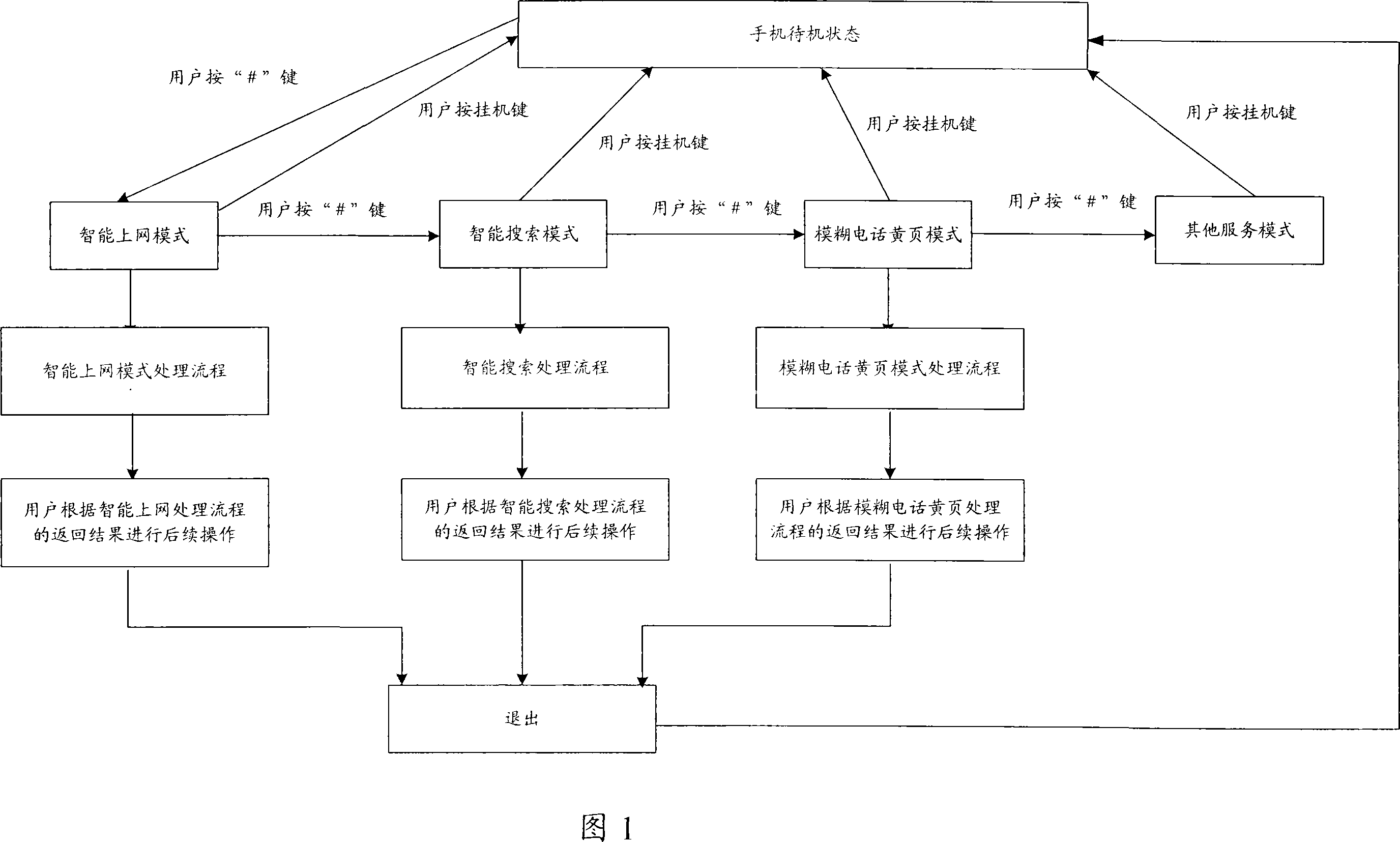
Method and system for quickly obtaining network information service at mobile terminal
InactiveCN101127784AQuick to useFix fast internetRadio/inductive link selection arrangementsTransmissionThe InternetNetwork service
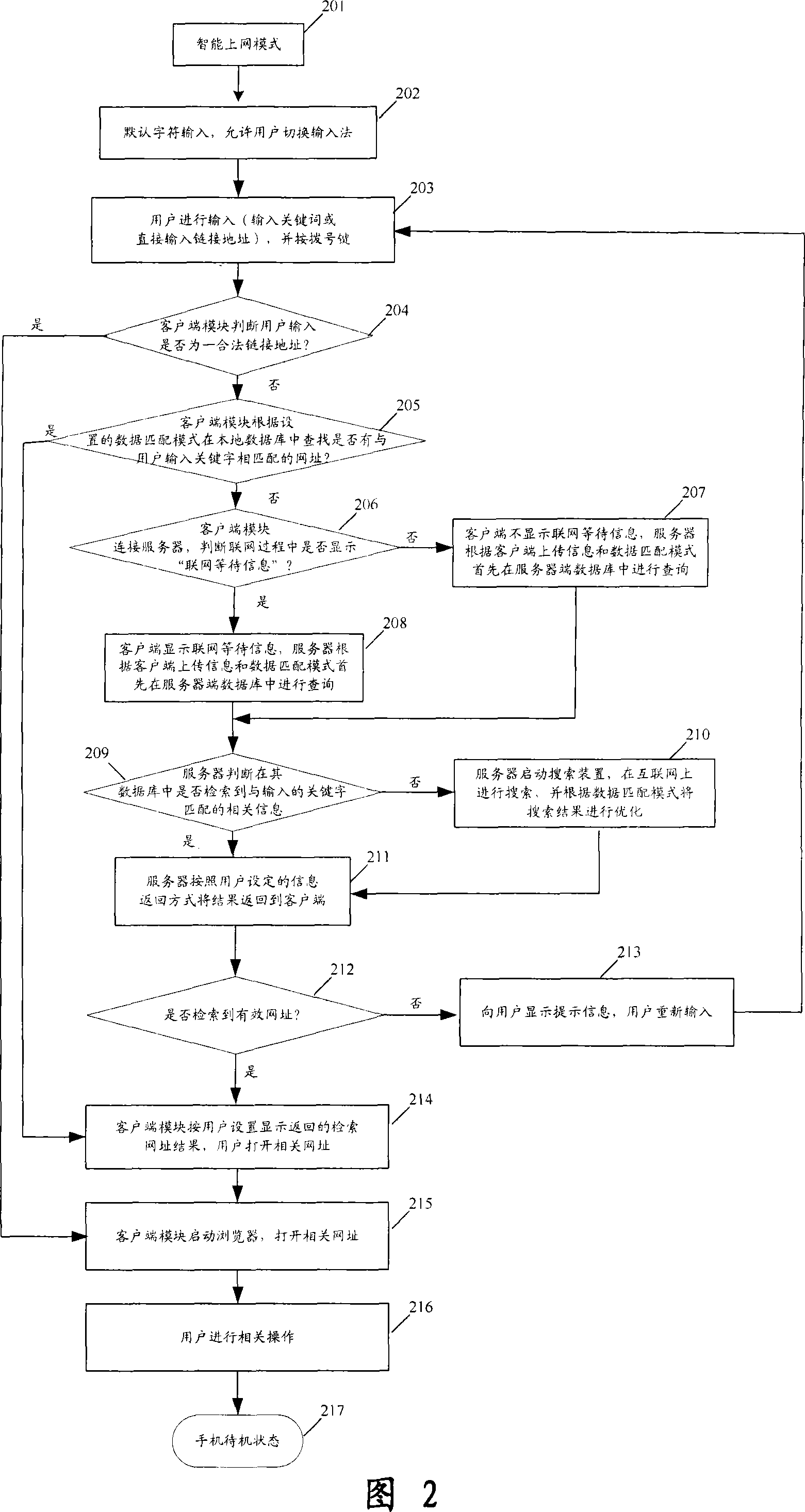
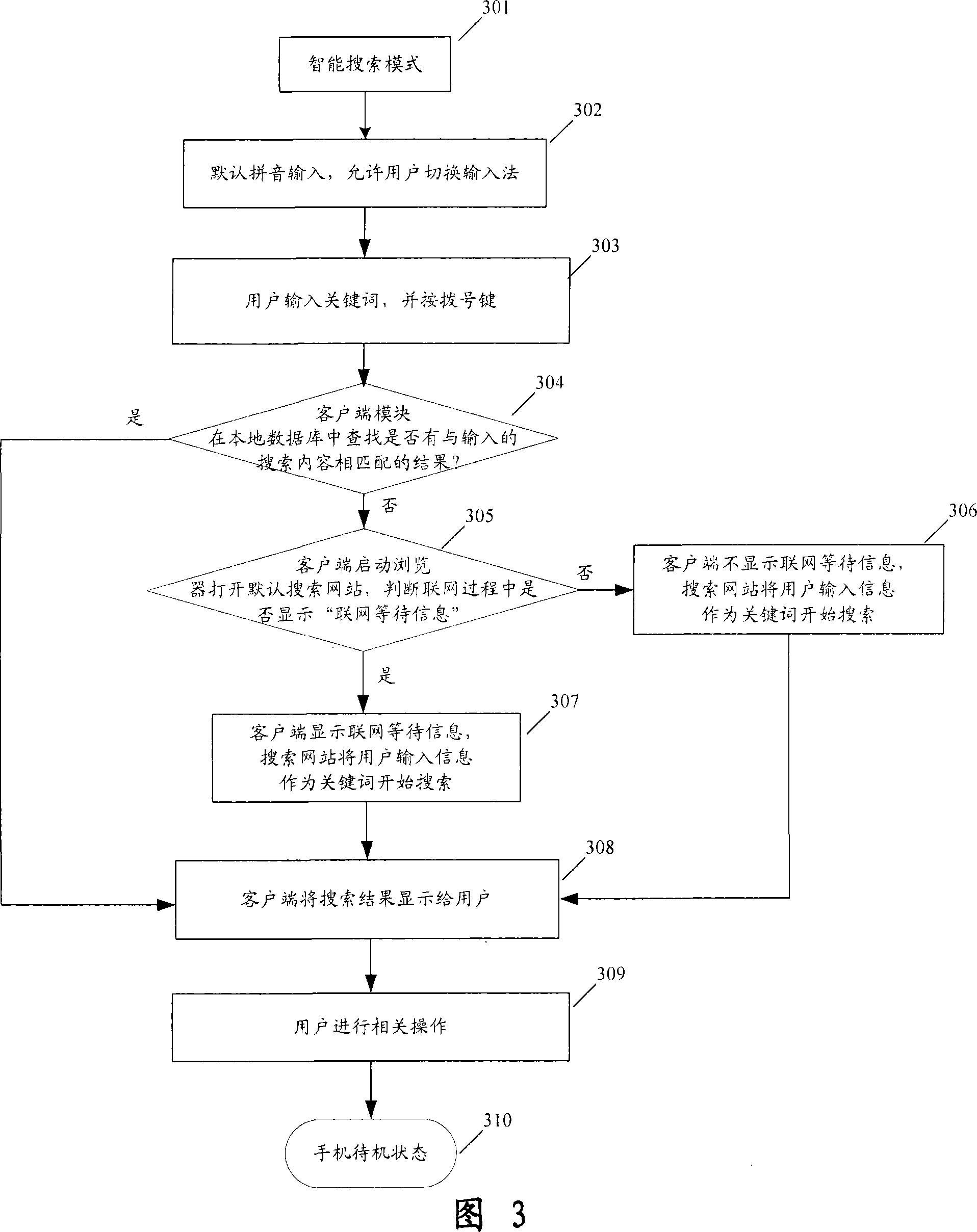
The utility model relates to a method of easily getting network information services from a mobile terminal, which adopts a structure of client / server. A user is directly interactive with a server and gets network information services via the client module binding at the terminal: when the terminal is in a standby state, the user clicks a mode switching key to switch the terminal to the given different service modes or switch the terminal among different service modes; and in a certain service mode, the user directly inputs a keyword on the terminal desktop, the client module separately inquires a client database, a server database or a server search equipment according to the current service mode and the information which is input by the user, and gets the corresponding network services and content resources, and separately chooses a related network as a service carrier according to the service mode, directly leads the user into the network services for information services. The utility model has advantages that the operation is simple, and the user can fast and easily land Internet and other networks from the terminal desktop, easily finishes the switchovers of service modes and gets corresponding services.
Owner:网秦无限(北京)科技有限公司
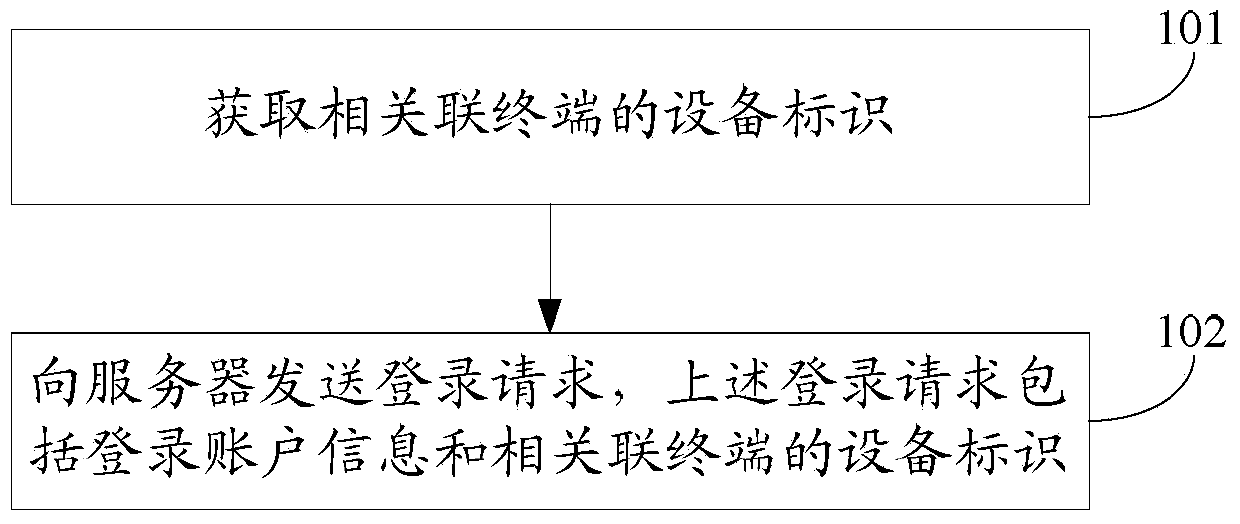
Method and device for allowing multiple terminals to login to server
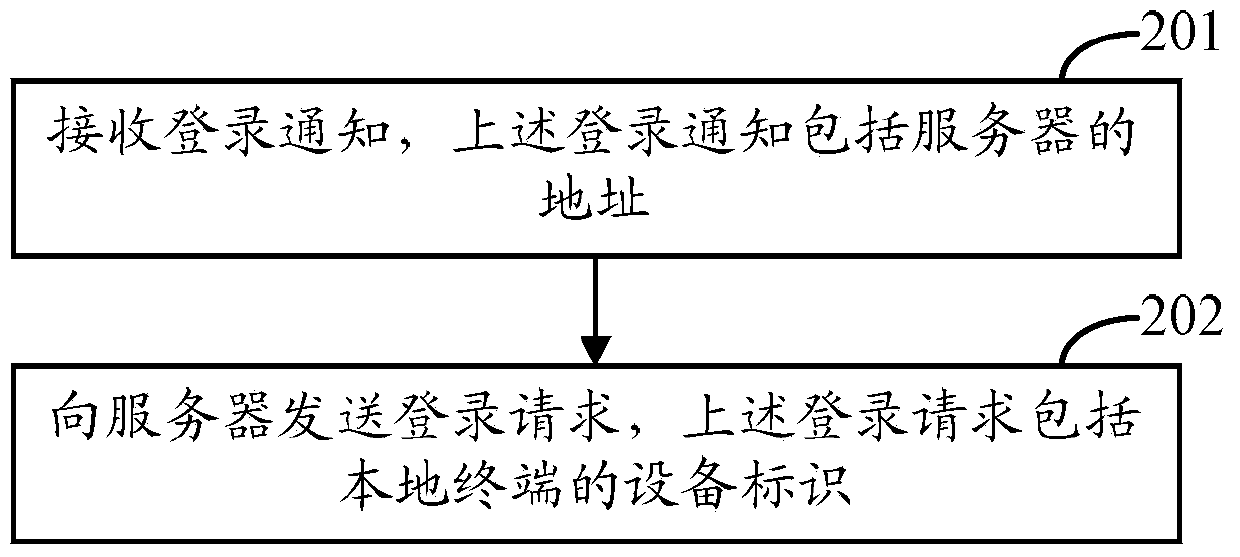
ActiveCN103457951AQuick LoginEasy loginDigital data authenticationTransmissionComputer terminalComputer security
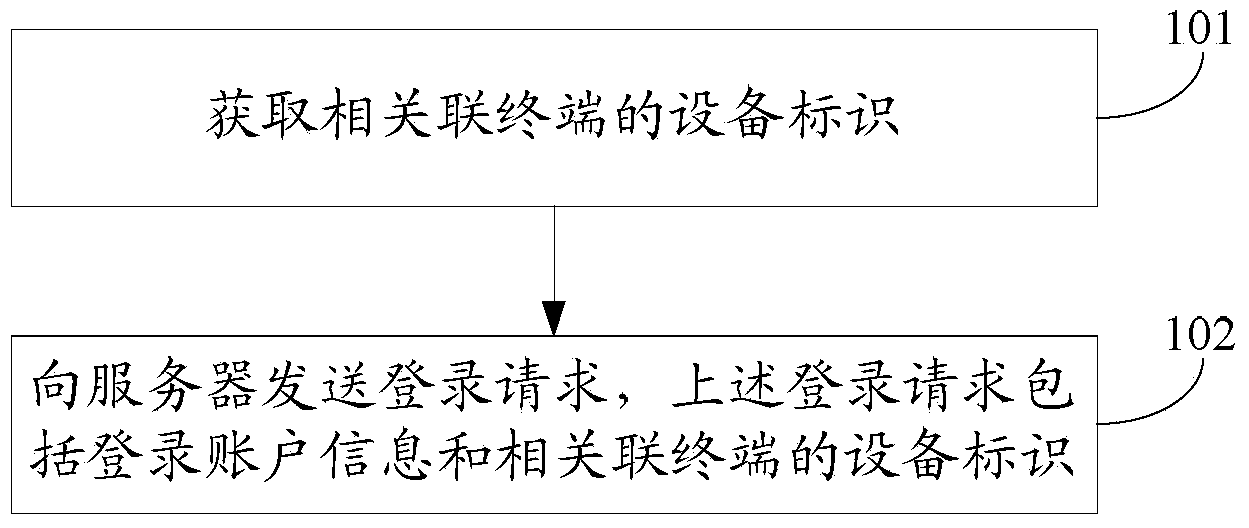
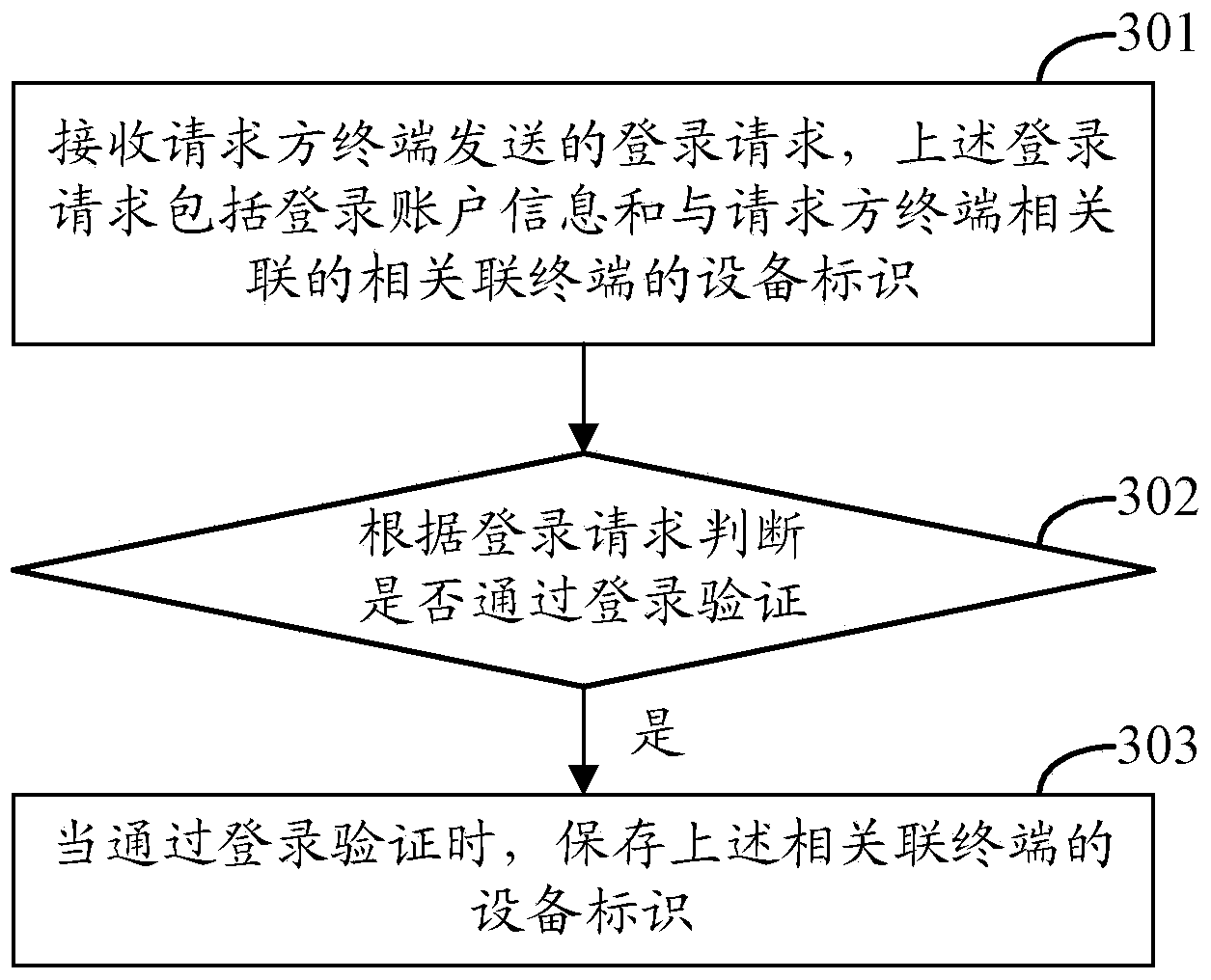
The invention discloses a method and device for allowing multiple terminals to login to a server. The method and device are used for allowing the multiple terminals to rapidly login to the server. The method includes the following steps that equipment identification of the associated terminals is acquired and login requests are sent to the server, wherein the login requests comprise login account information and the equipment identification of the associated terminals. By the adoption of the method for allowing the multiple terminals to login to the server, the multiple terminals can login to the server only through one-time verification of login account information, the login account information is prevented from being repeatedly input, and operation is rapidly and conveniently conducted.
Owner:XIAOMI INC
Login method and system, computer device and storage medium
InactiveCN108769041AQuick LoginUser identity/authority verificationInformation accessUser identifier
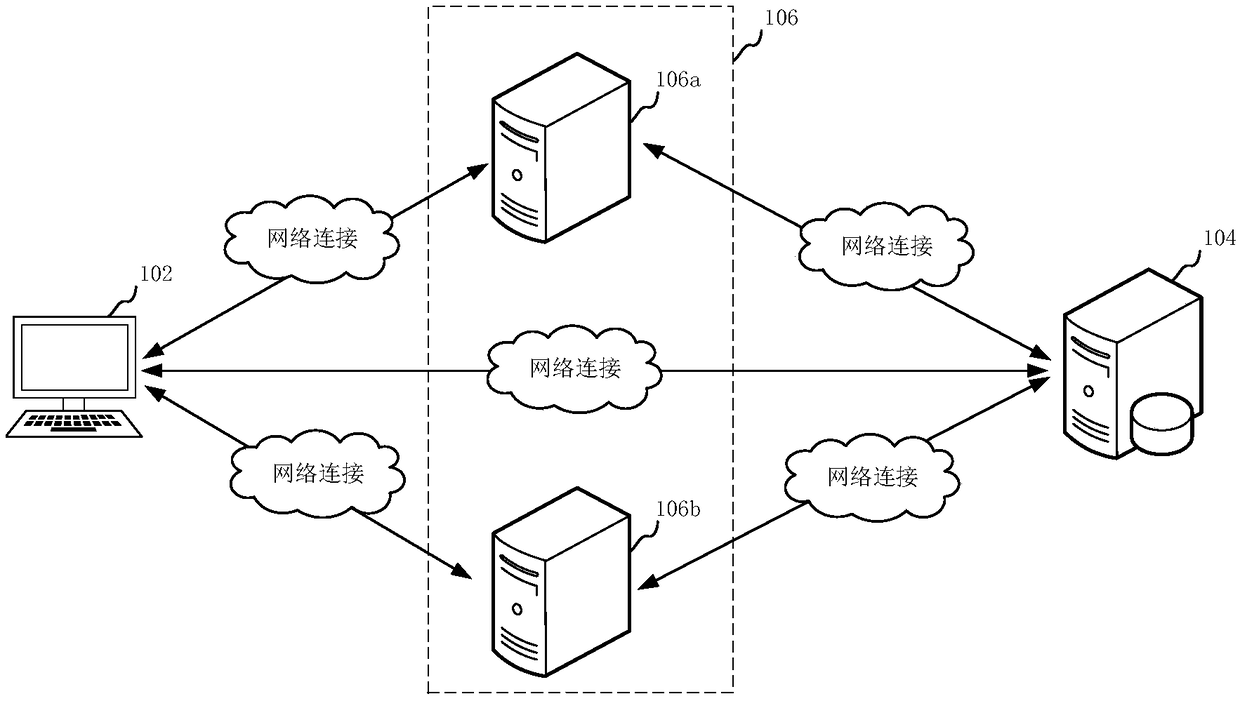
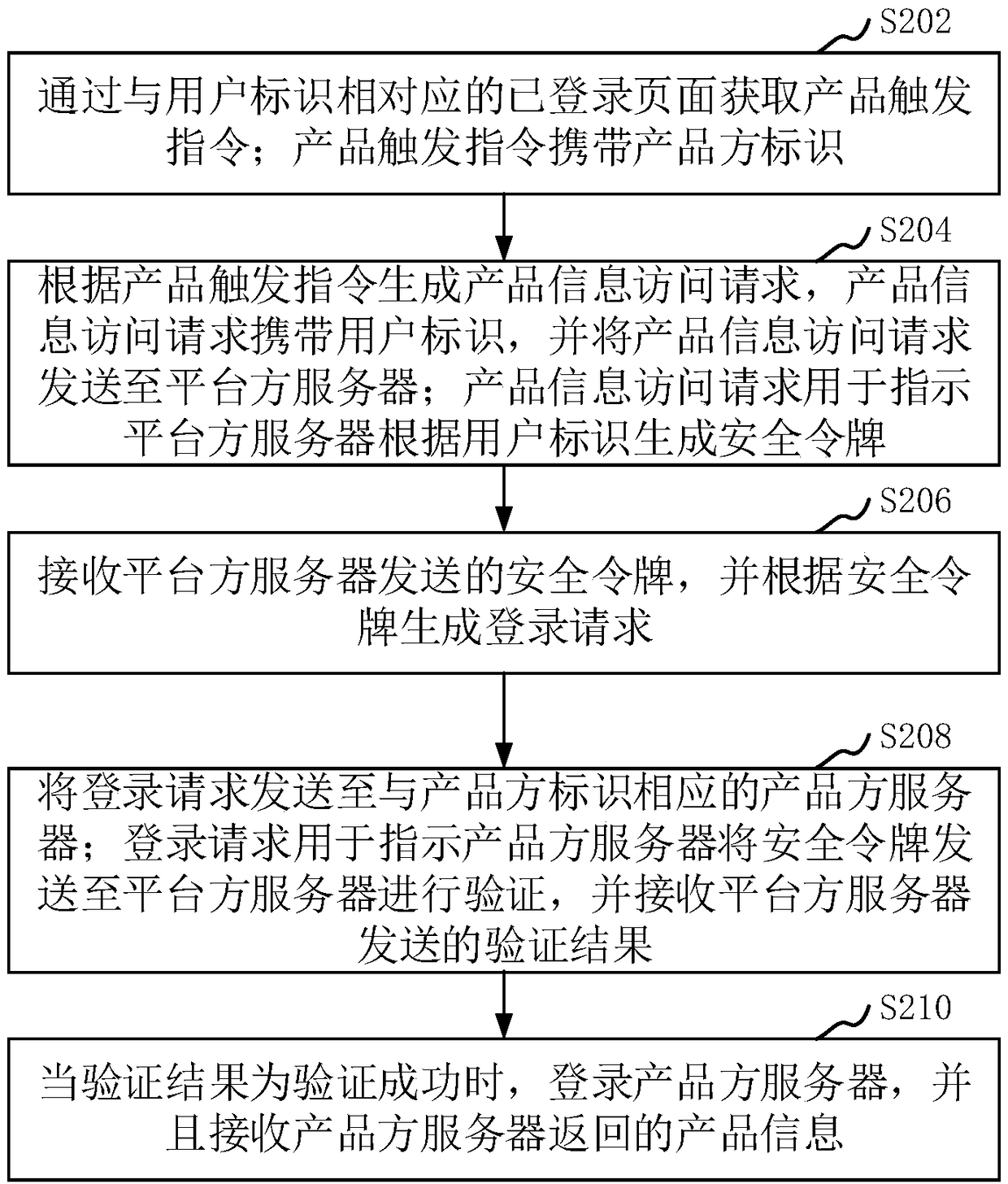
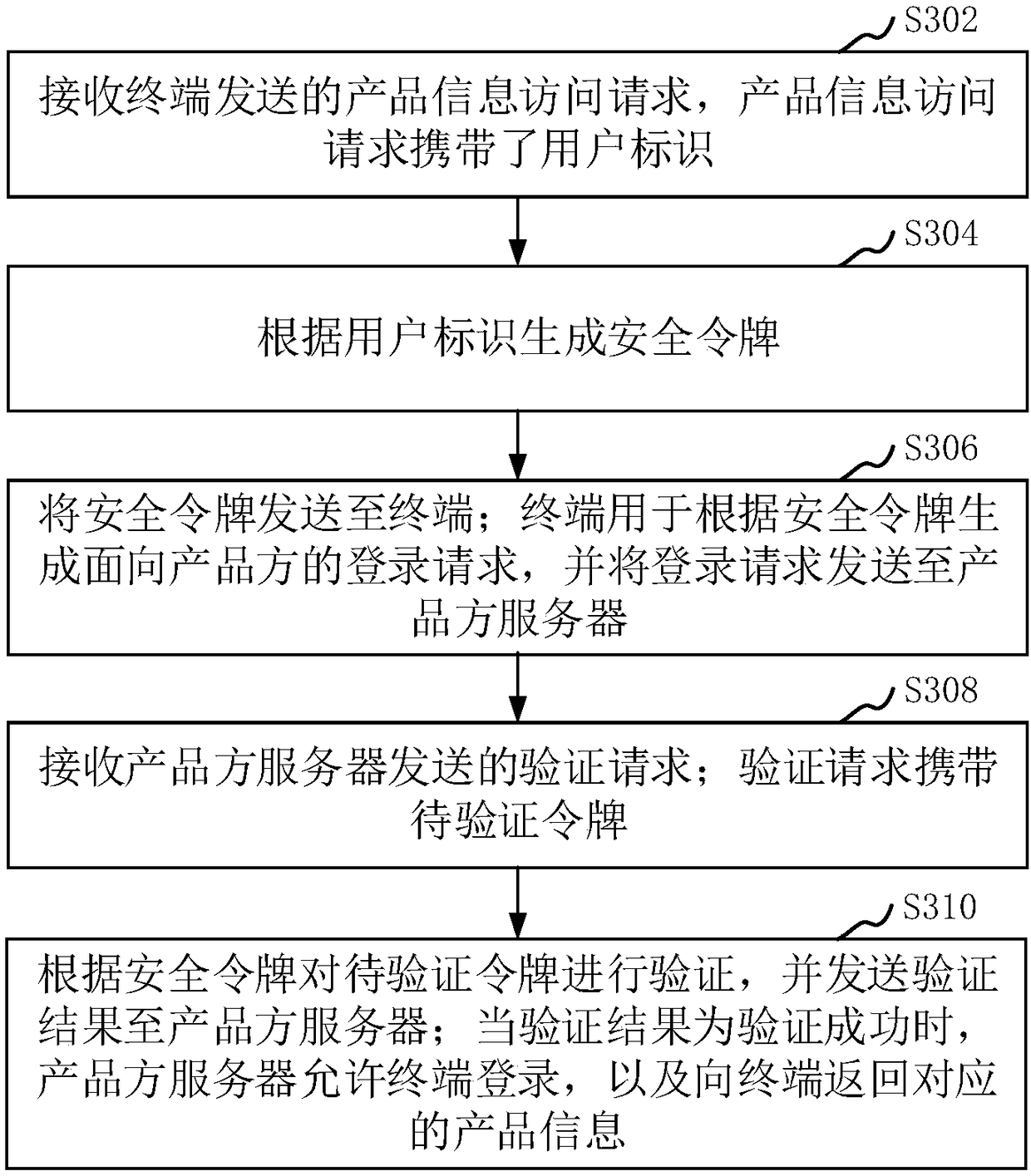
The invention relates to a login method and system, a computer device and a storage medium. The method comprises the steps of acquiring a product trigger instruction via a logged-in page correspondingto a user identifier, wherein the product trigger instruction carries a product-party identifier; generating a product information access request according to the product trigger instruction, and sending the product information access request to a platform-party server, wherein the product information access request carries the user identifier, and the product information access request is used for indicating the platform-party server to generate a security token according to the user identifier; receiving the security token sent by the platform-party server, and generating a login request according to the security token; sending the login request to a product-party server corresponding to the product-party identifier, and receiving a verification result sent by the platform-party server,wherein the login request is used for indicating the product-party server to send the security token to the platform-party server for verification; and when the verification result is that the verification is successful, logging in the product-party server, and receiving product information returned by the product-party server. By adopting the method, a product-party system can be logged in quickly.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
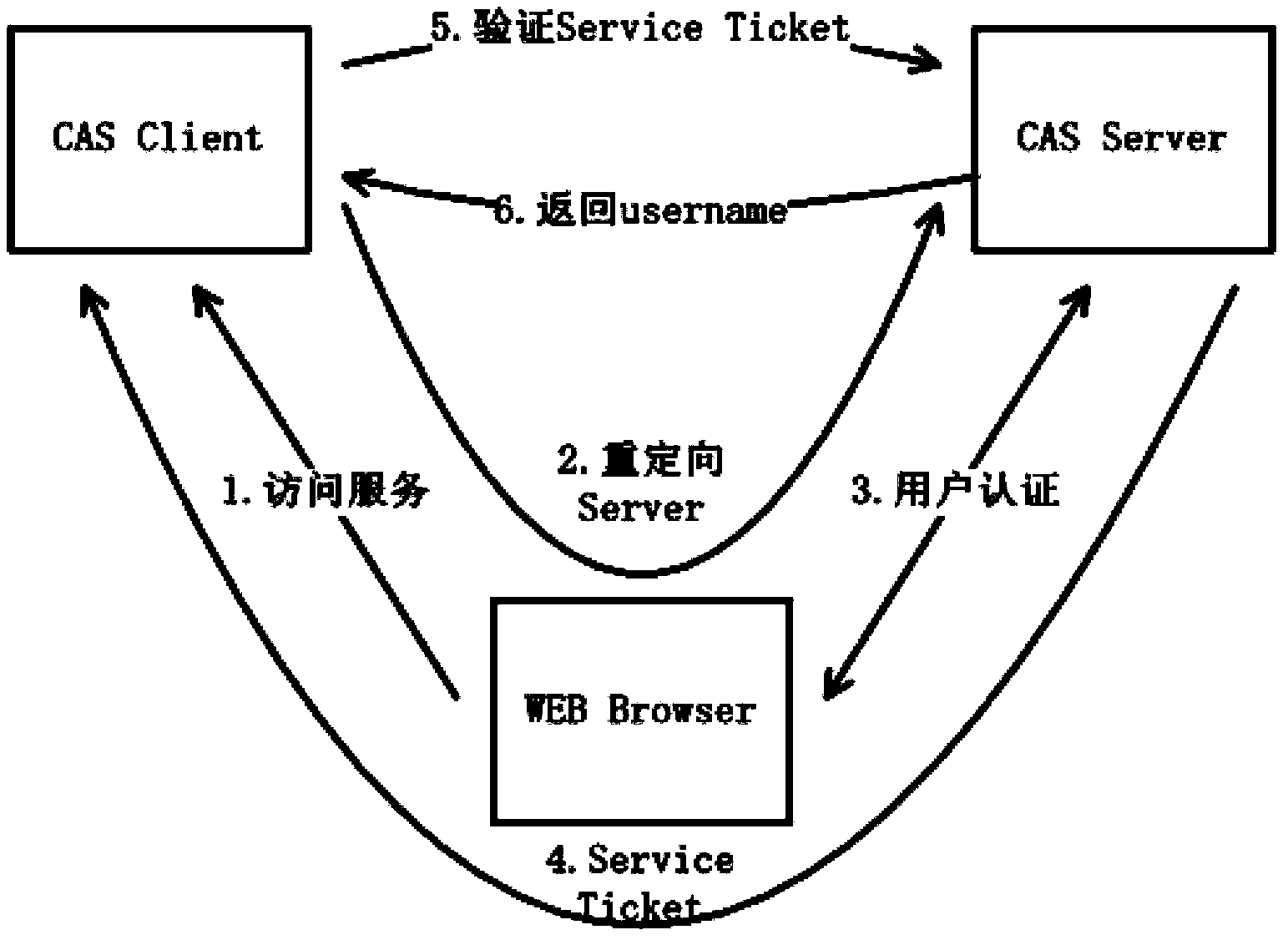
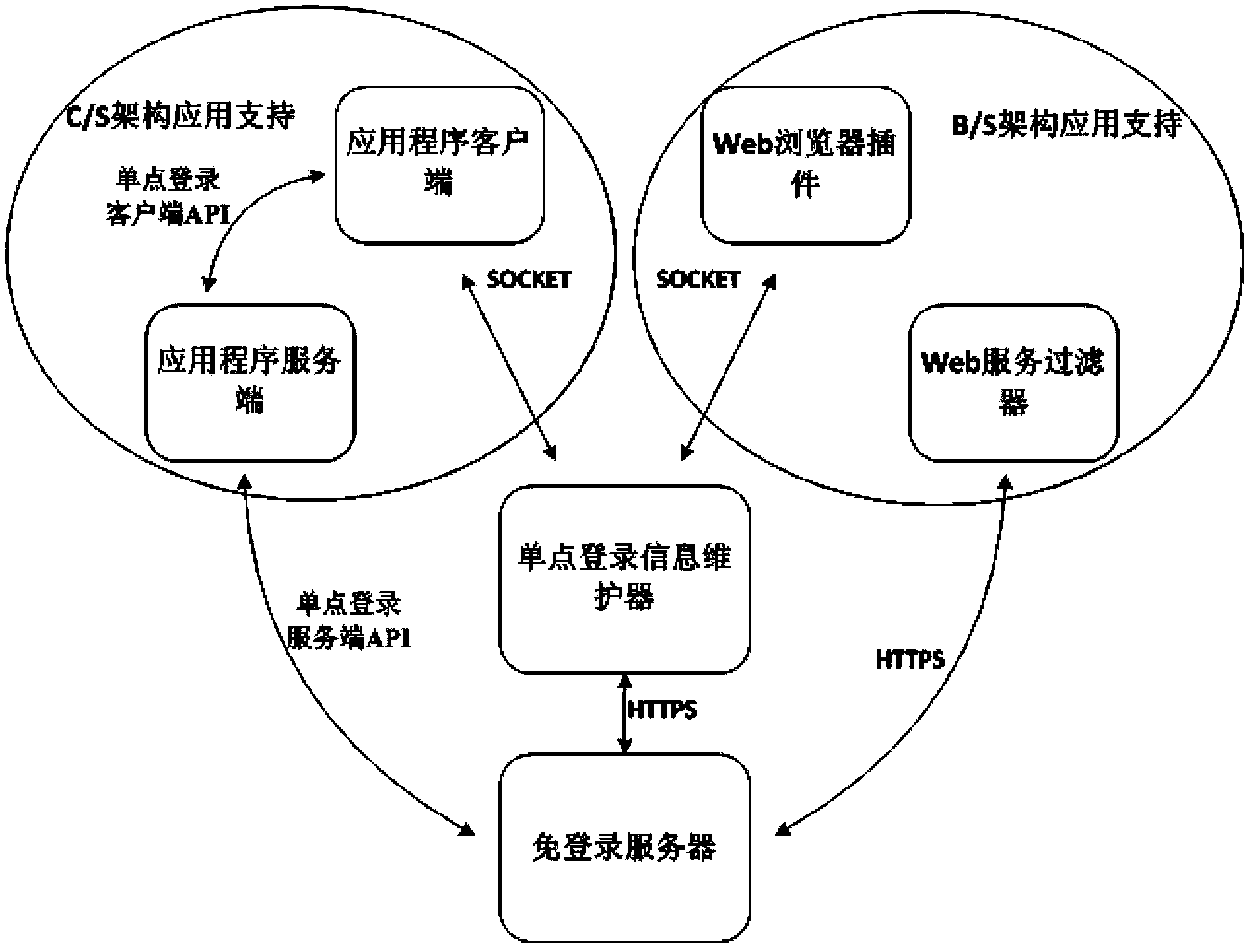
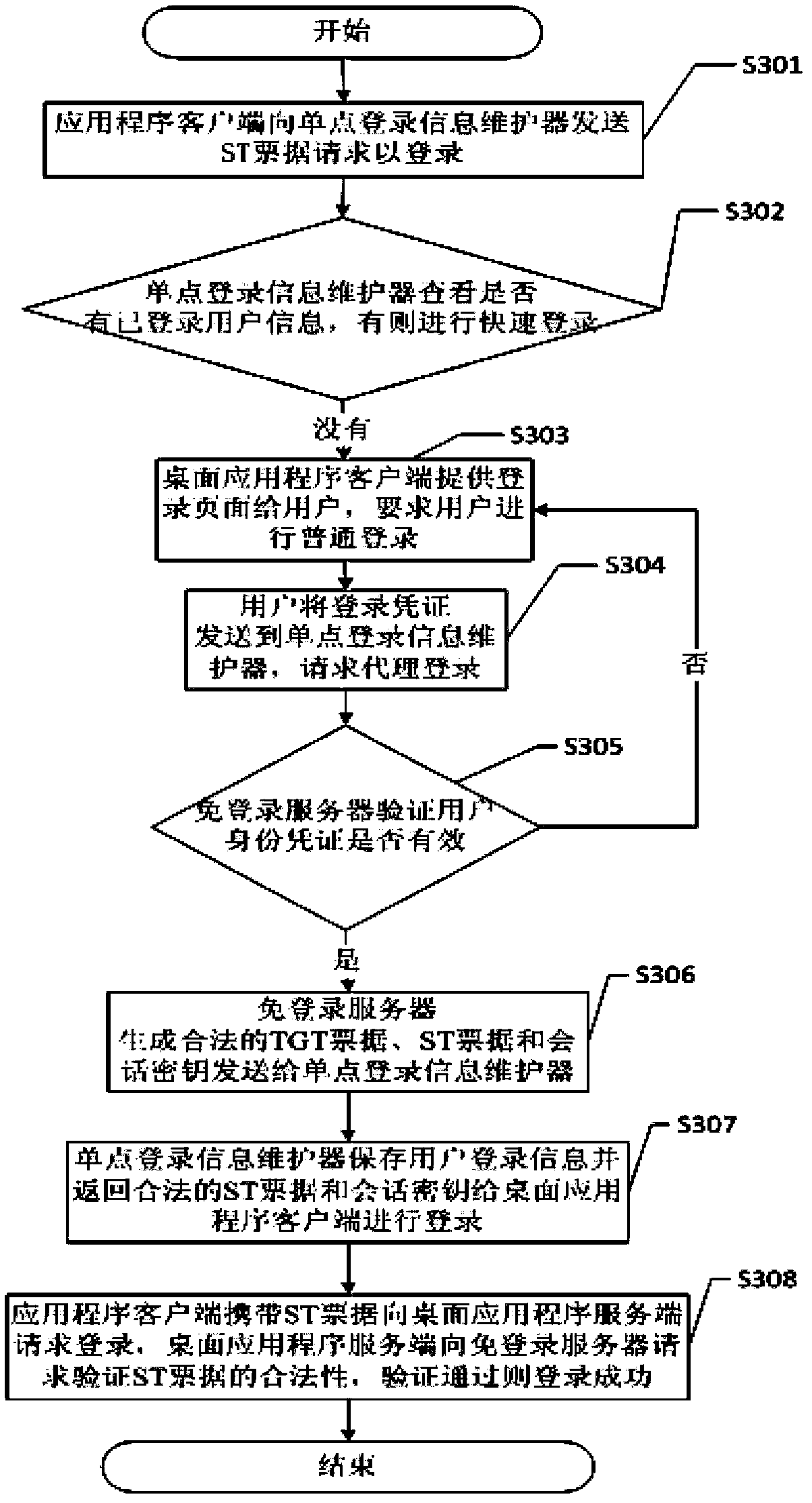
Single sign-on method and system
The invention discloses a single sign-on method and a single sign-on system. The single sign-on method comprising the steps of: requesting ST tickets from a single sign-on information maintainer through a browser plug-in when a B / S application client side needs to log in, then requesting fast login from an application server side, or carrying out normal login if the ST ticket information does not exist, and then synchronizing the login information to the single sign-on information maintainer through the browser plug-in; and requesting ST tickets from the single sign-on information maintainer when a C / S application client side logs in, then requesting fast login from the application server side, or carrying out normal login if the ST ticket information does not exist, and then responding to the single sign-on information maintainer. When the client sides requests ST tickets of target service from the single sign-on information maintainer, if the weight of TGT tickets of current logged-in user is not lower than login weight of the target service, then the ST tickets of target service are generated for the client sides, otherwise the \permission is insufficient, and the fast login fails.
Owner:SOUTH CHINA UNIV OF TECH
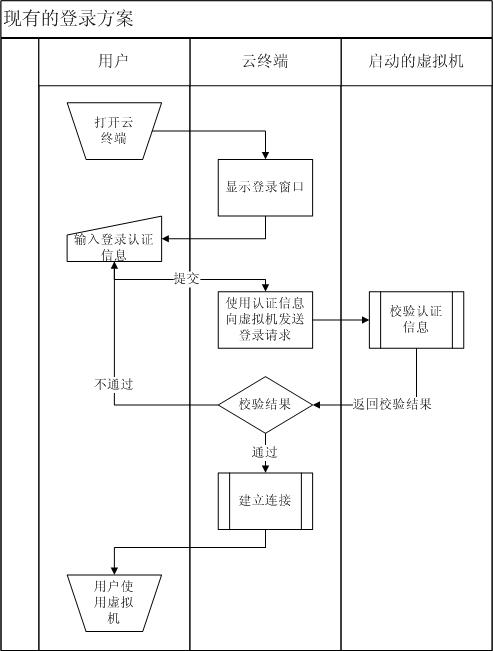
Method for mini-station to authenticate and log in virtual machine in cloud system and login system
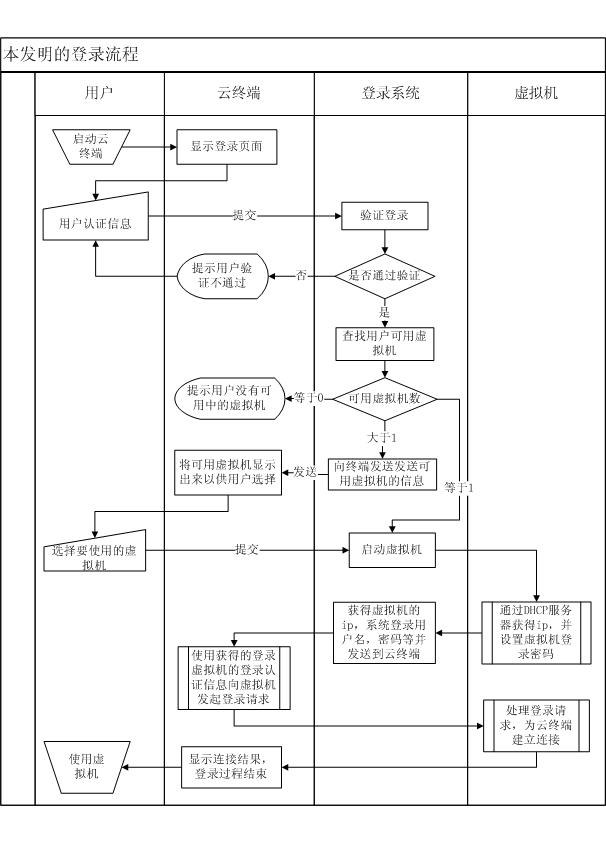
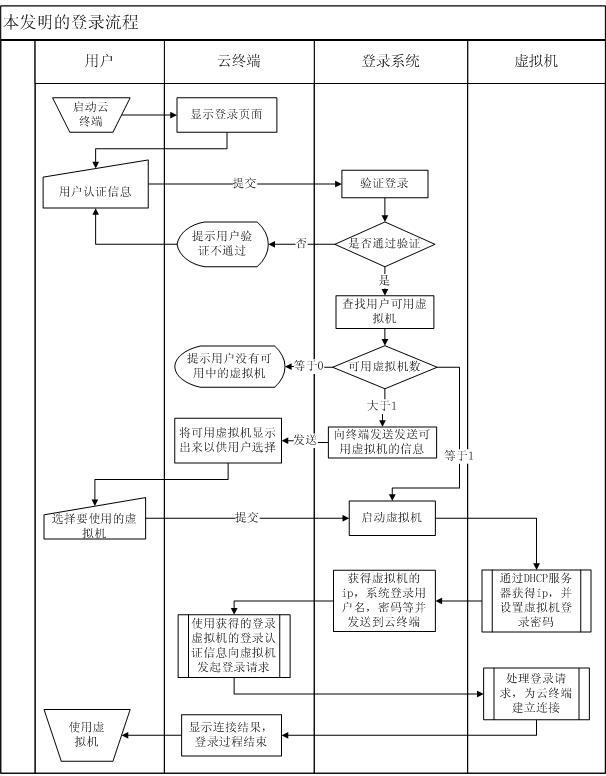
The invention discloses a method for a mini-station to authenticate and log in a virtual machine in a cloud computing system and a login system. The method comprises the following steps that: (1) the mini-station logs in the cloud computing system by the login system; (2) the login system searches for the number of available virtual machines in the cloud computing system; (3) the login system starts the virtual machine in the cloud computing system according to virtual machine selection rules and executes steps (4) to (6) if the number of the available virtual machines is more than or equal to 1, otherwise returns information indicating that the cloud computing system does not have available resources to the mini-station, and the mini-station quits; (4) the virtual machine generates virtual machine login information, and transmits the virtual machine login information to the login system; (5) the login system transmits the virtual machine login information to the mini-station; and (6) the mini-station logs in the virtual machine. By the method and the login system, the mini-station can rapidly authenticate and log in the virtual machine, and the virtual machine is not required to be kept in a starting state so as to make safer the system and effectively save resources.
Owner:GCI SCI & TECH
Method and device for terminal authentication
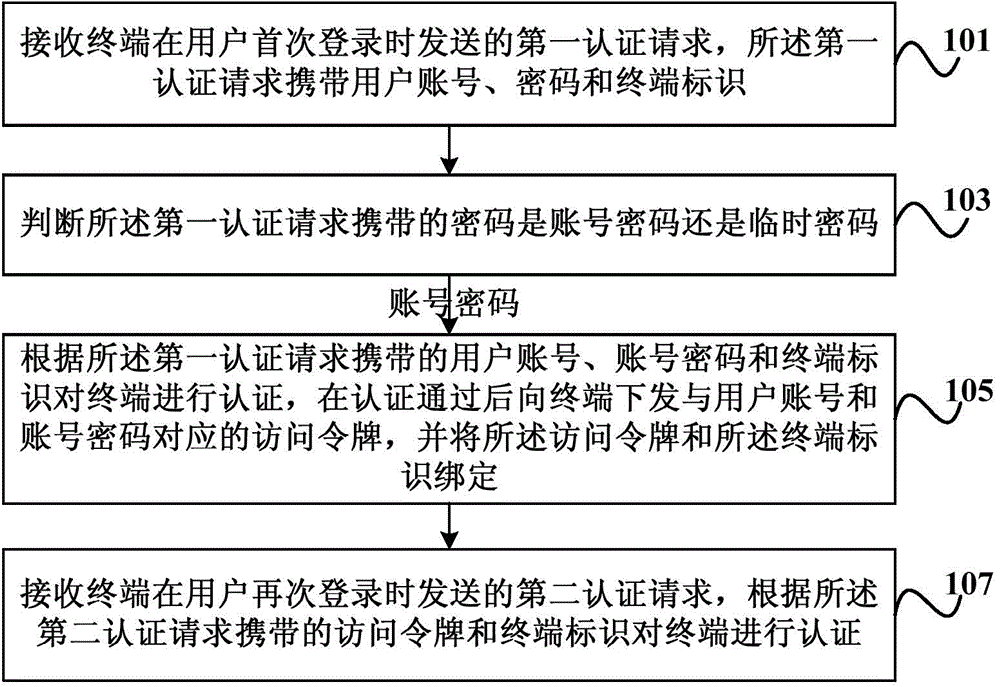
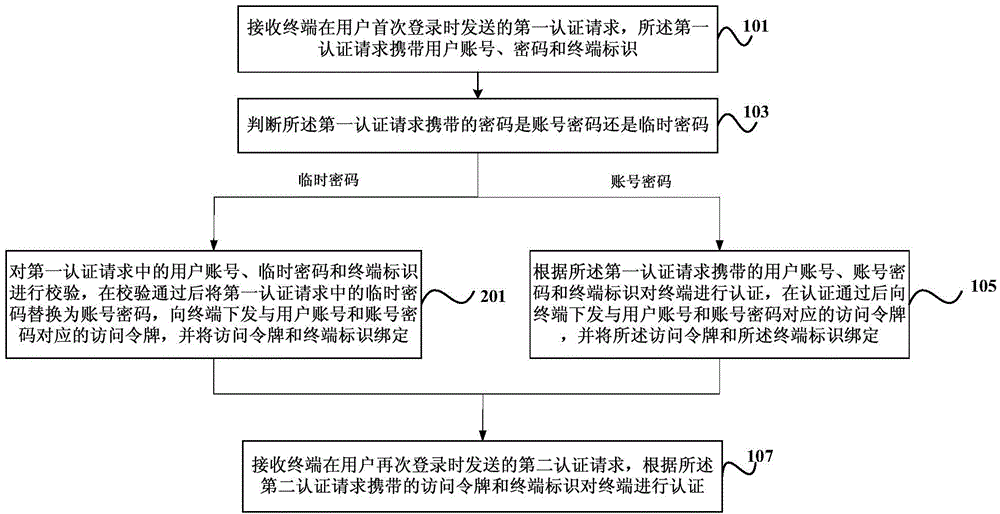
ActiveCN105530224AImplement an independent certification processIndependently certified process safetyTransmissionSecurity arrangementAccess tokenMobile internet
The invention discloses a method and a device for terminal authentication and belongs to the mobile Internet technology field. The method comprises steps that a first authentication request sent by a terminal during first registration of a user is received, and the first authentication request contains a user account, a cipher and a terminal identification; whether the cipher is an account cipher or a temporary cipher is determined; if the cipher is the account cipher, the terminal is authenticated according to the user account, the cipher and the terminal identification contained in the first authentication request, an access token corresponding to the user account and the account cipher is sent to the terminal after authentication, and the access token and the terminal identification are bound; a second authentication request sent by the terminal during second registration of the user is received, and the terminal is authenticated according to the access token and the terminal identification contained in the second identification request. Through the method, safe and independent authentication of the terminal can be realized.
Owner:CHINA TELECOM CORP LTD
Application program login method, application program login device and terminal
InactiveCN105760045AEasy loginQuick LoginInput/output processes for data processingApplication softwareComputer engineering
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
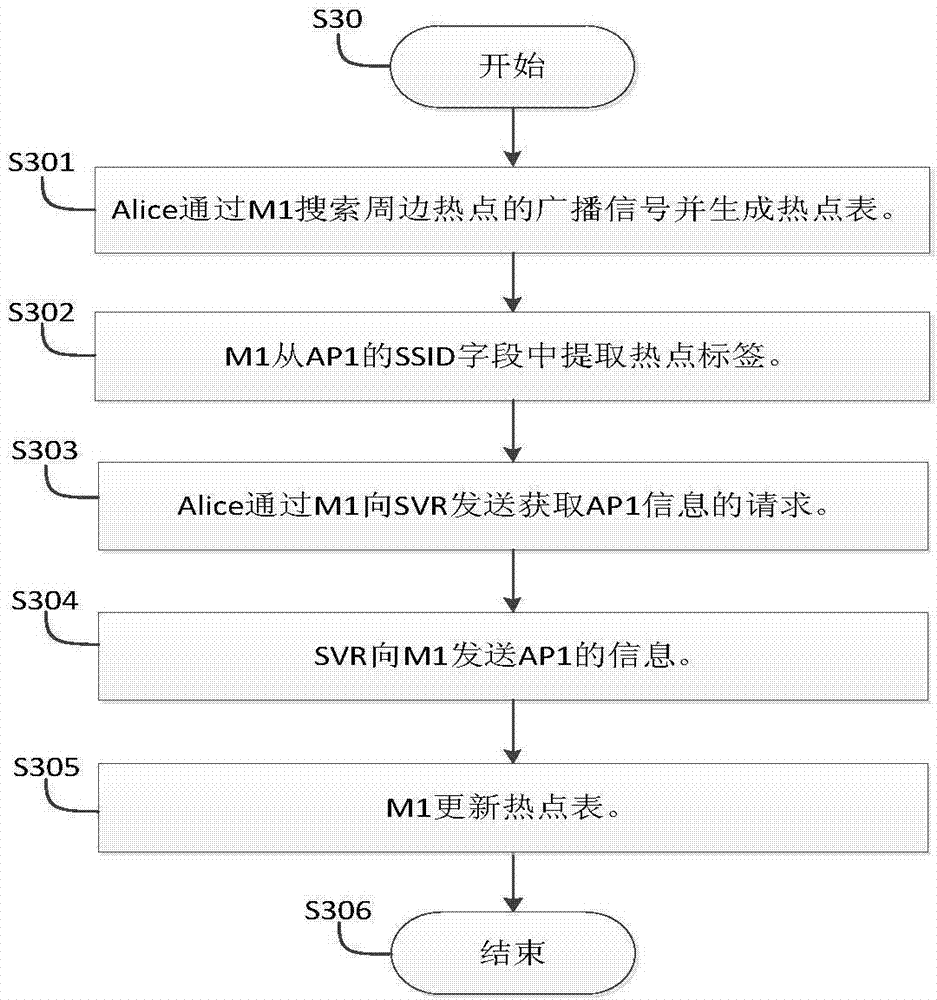
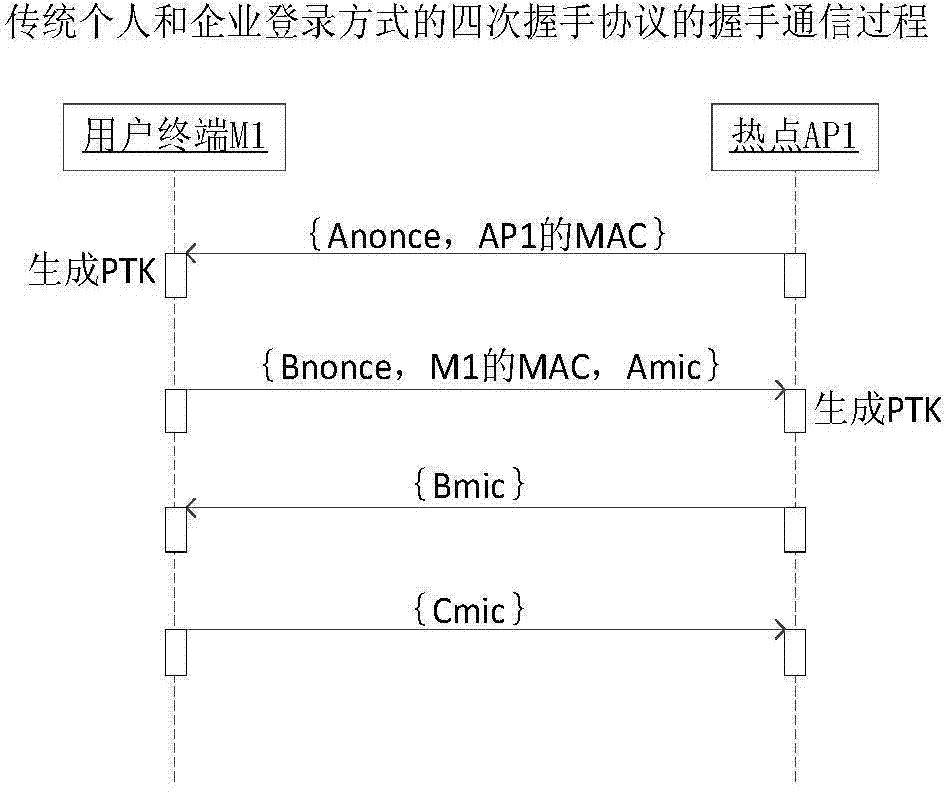
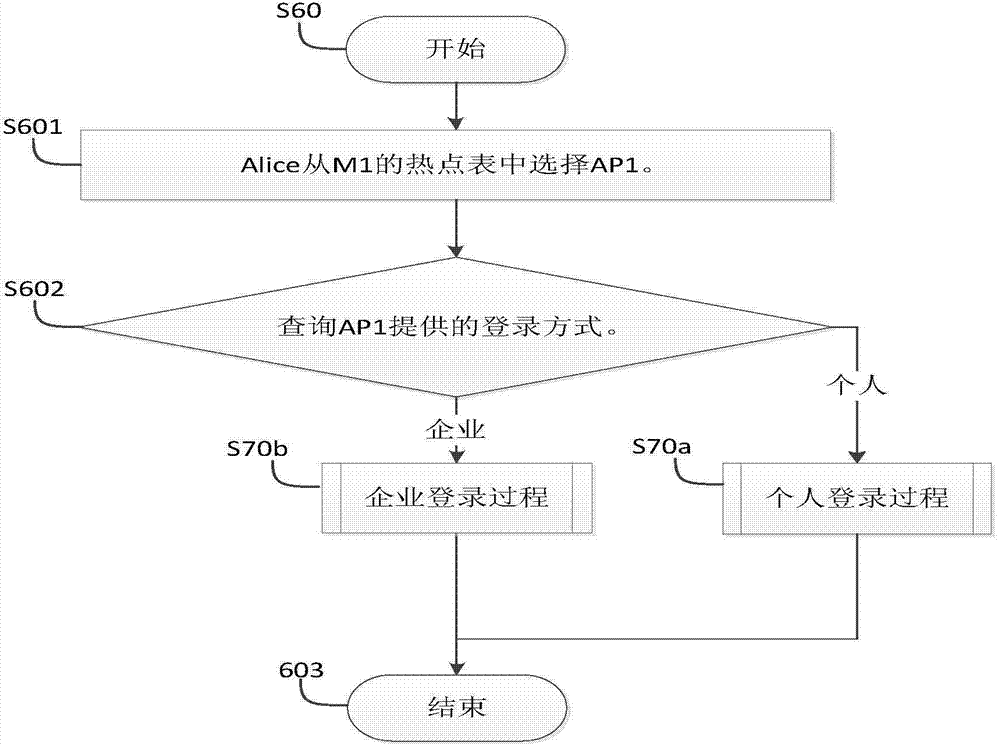
WiFi hot spot safe login method and system
ActiveCN104735052AReduce leakageReduce the difficulty of implementationKey distribution for secure communicationUser identity/authority verificationPasswordThe Internet
The invention provides a WiFi hot spot safe login method and system. A label which is unique globally is embedded in an SSID of a hot spot, a server inquires description information of the hot spot with the label as a key clue, and a user identifies peripheral hot spots through the hot spot description information sent from the server; a contact relation is established between the user with the hot spot login request and owners of the hot spots so that the user can log into all the hot spots with the owners being the user or contacts of the user; the server located in the internet is maintained, a temporary key needed by the user in a personal login mode is generated through a pre-shared key, a terminal used by the user is in handshake communication with the hot spots through the temporary key distributed from the server, and the possibility of pre-shared key leakage or cracking is lowered. The user logs into the hot spots working in any login mode through an account number registered in the server and a password, the different login modes of the hot spots can be switched at will, and the whole switching process is transparent to the user.
Owner:SUN YAT SEN UNIV
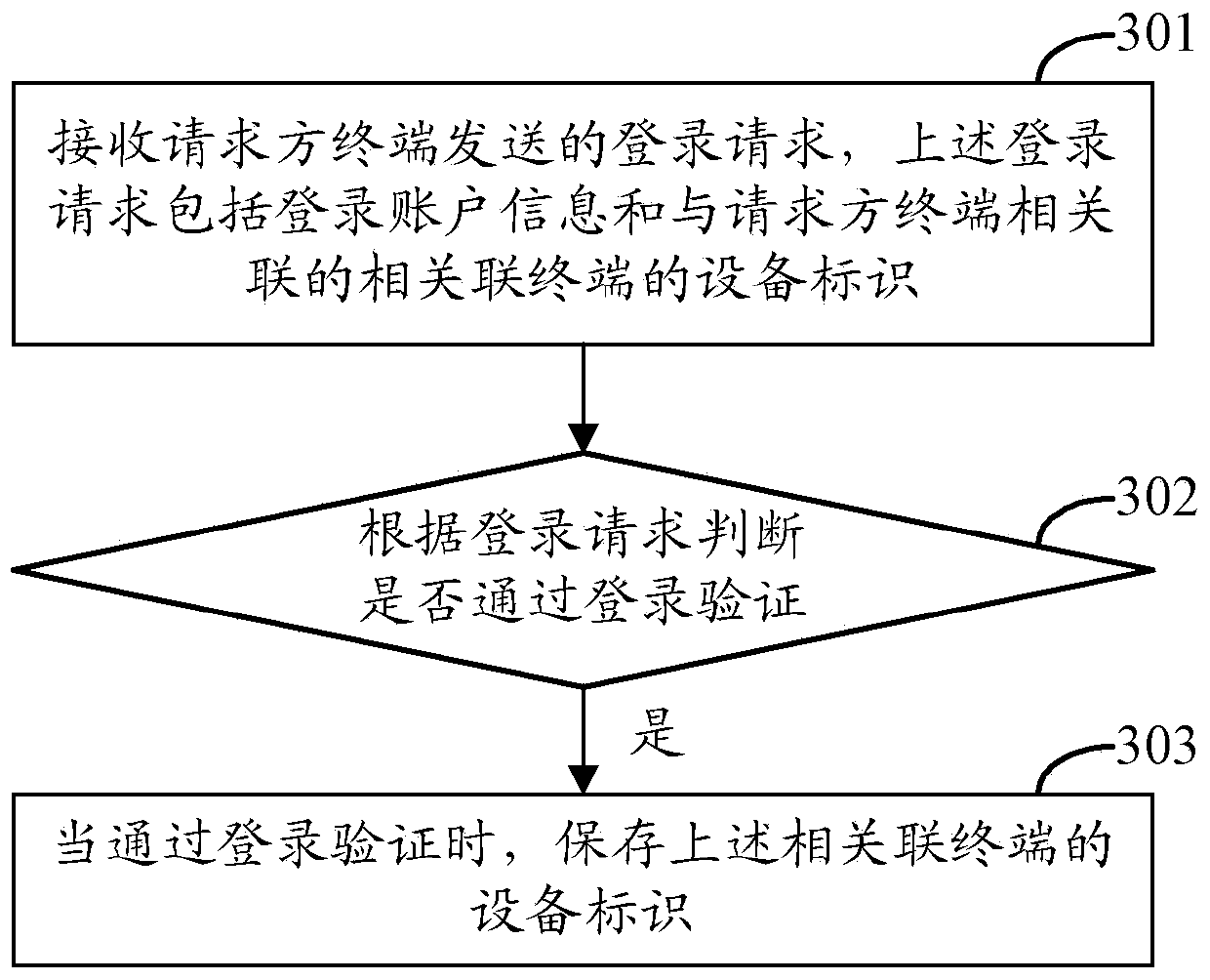
Method and device for logging in server by multiple terminals
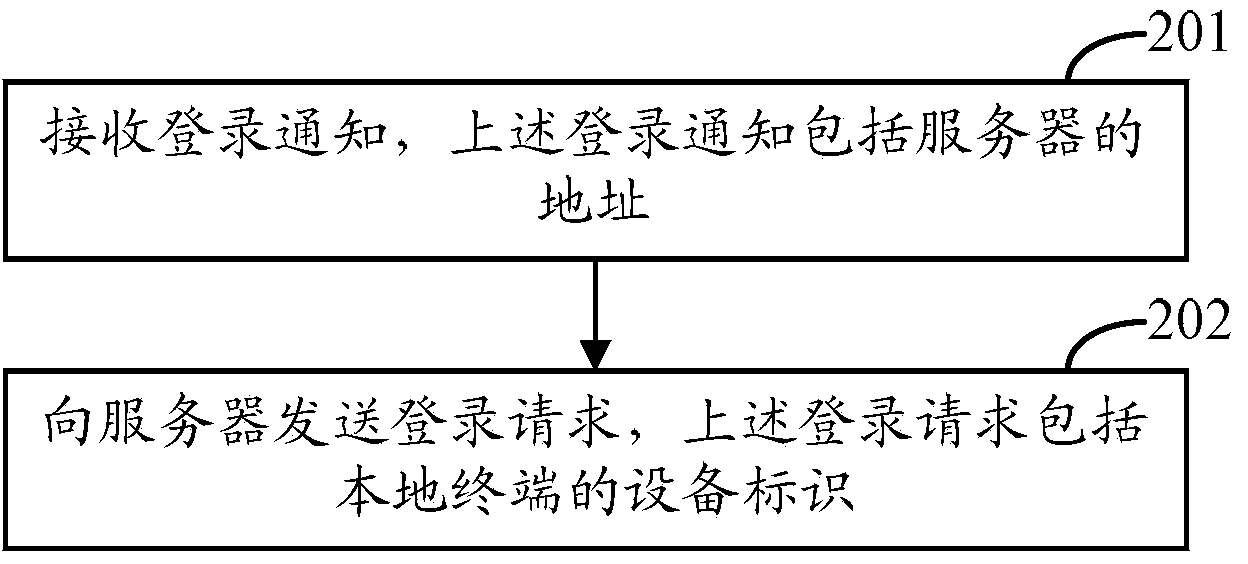
ActiveCN103475476AQuick LoginEasy loginUser identity/authority verificationComputer scienceDevice Identifiers
The invention discloses a method and a device for logging in a server by multiple terminals, and the method and the device are used for achieving the purpose that the multiple terminals rapidly log in the server. The method comprises the following steps: obtaining device identifiers of the related terminals; transmitting logging requests to the server, wherein the logging requests comprise logging account information and the device identifiers of the related terminals. The method for logging in the server by the multiple terminals has the advantages that the multiple terminals can log in the server only through one-time verification of logging account information, and the repeated inputting of the logging account information is avoided, so that the operation is relatively rapid, convenient and efficient.
Owner:XIAOMI INC
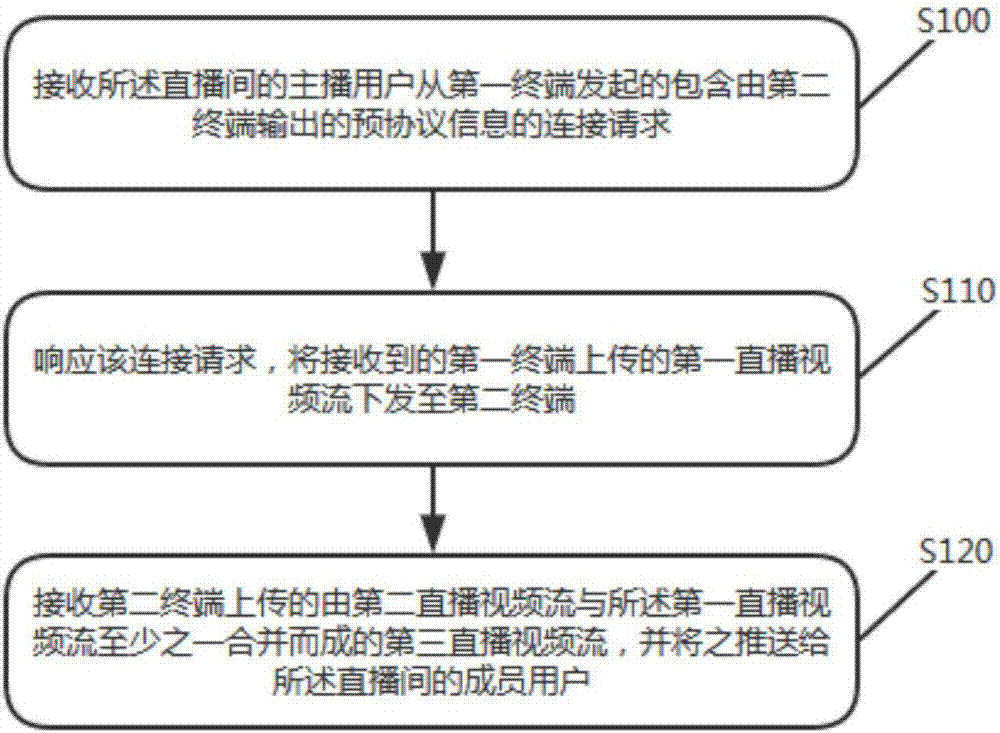
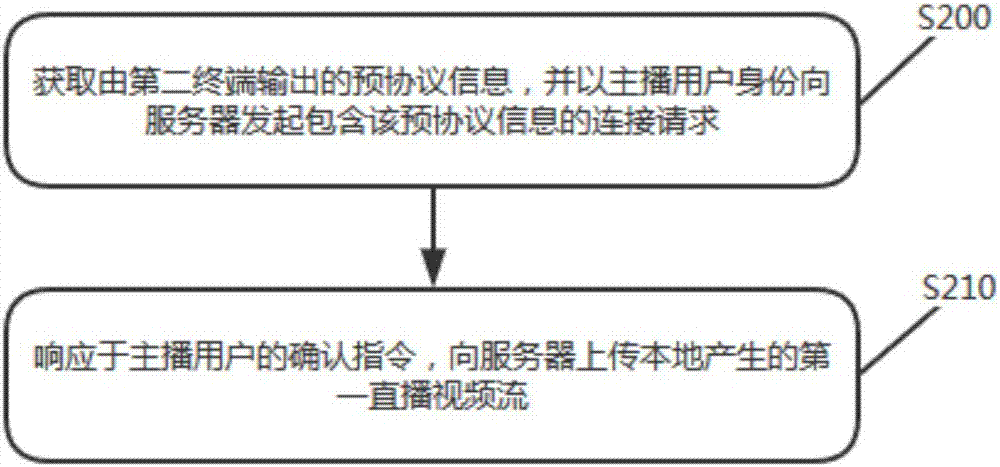
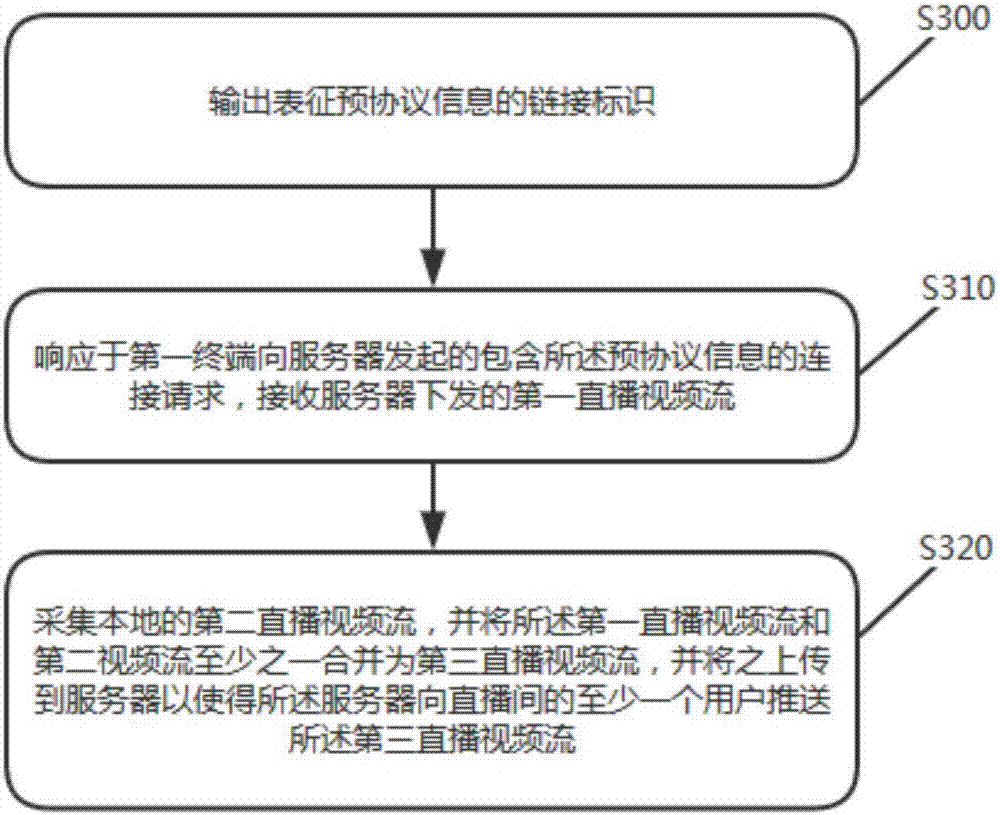
Direct broadcasting room video stream pushing control method and corresponding server and mobile terminal
ActiveCN107005721ASave resourcesLower the threshold for broadcastingTransmissionSelective content distributionMulti platformBroadcasting technology
The invention relates to a network direct broadcasting technology, in particularly to a direct broadcasting room video stream pushing control method and a corresponding server and a mobile terminal. The method includes the following steps: receiving a connection request including pre-protocol information output by a second terminal, issued by a host user in a direct broadcasting room from a first terminal; responding to the connection request, sending a received first direct broadcasting video stream uploaded by the first terminal to the second terminal; and receiving a third direct broadcasting video stream combined by at least one of a second direct broadcasting video stream uploaded by the second terminal and the first direct broadcasting video stream, and pushing the third direct broadcasting video stream to a member user in the direct broadcasting room. The method can achieve multi-platform synchronous direct broadcasting on the basis of separation and combination of video streams, can achieve sharing and flexible combination of the video streams, makes multi-platform direct broadcasting more convenient and fast, can improve the direct broadcasting efficiency, the direct broadcasting content, and can improve the user experience.
Owner:BIGO TECH PTE LTD
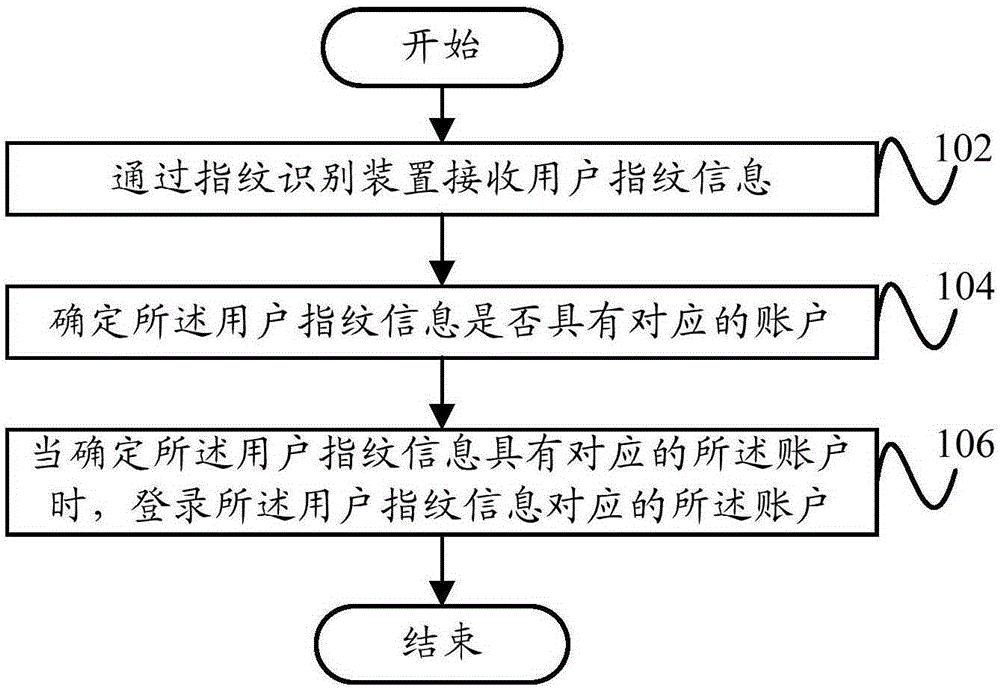
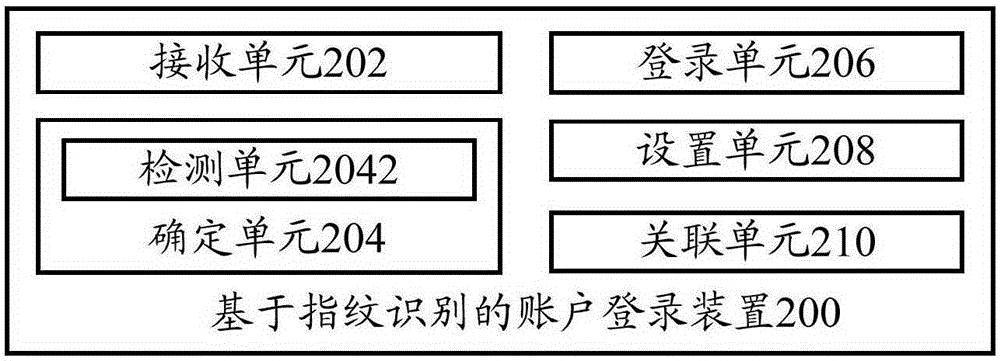
Fingerprint-identification-based account logging-in method and apparatus, and terminal
InactiveCN105208008AEasy loginQuick LoginUser identity/authority verificationIdentification deviceComputer terminal
The invention provides a fingerprint-identification-based account logging-in method and apparatus, and a terminal. The method comprises: user fingerprint information is received by a fingerprint identification device; whether the user fingerprint information has a corresponding account is determined; and if so, the account corresponding to the user fingerprint information is logged in. On the basis of the technical scheme, a problem that account switching can not be carried out conveniently when a user logs in a terminal having multiple accounts can be solved; and thus the user can log in the account conveniently and rapidly. Meanwhile, safety and privacy of account logging in by the user are improved and thus the user experience is enhanced.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method and system for user information sharing
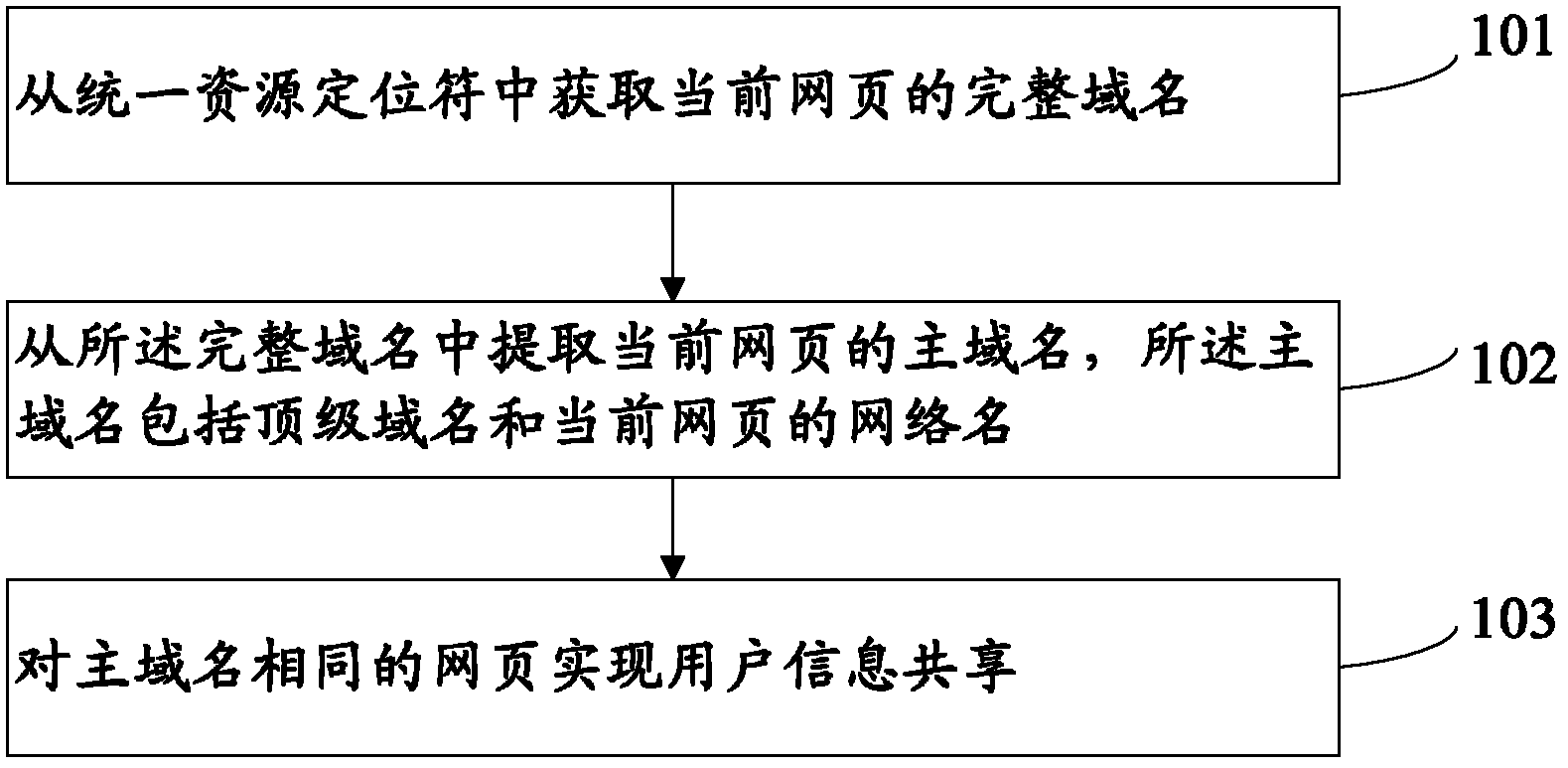
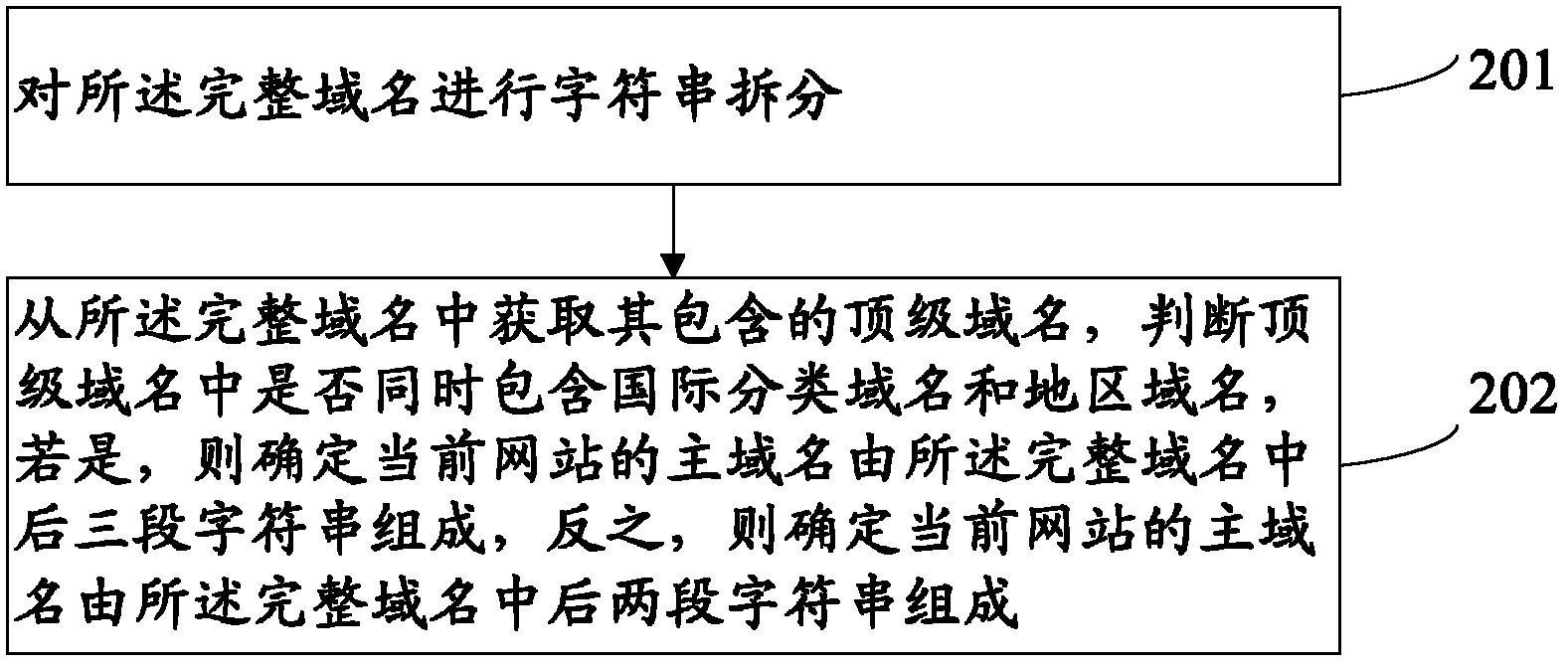
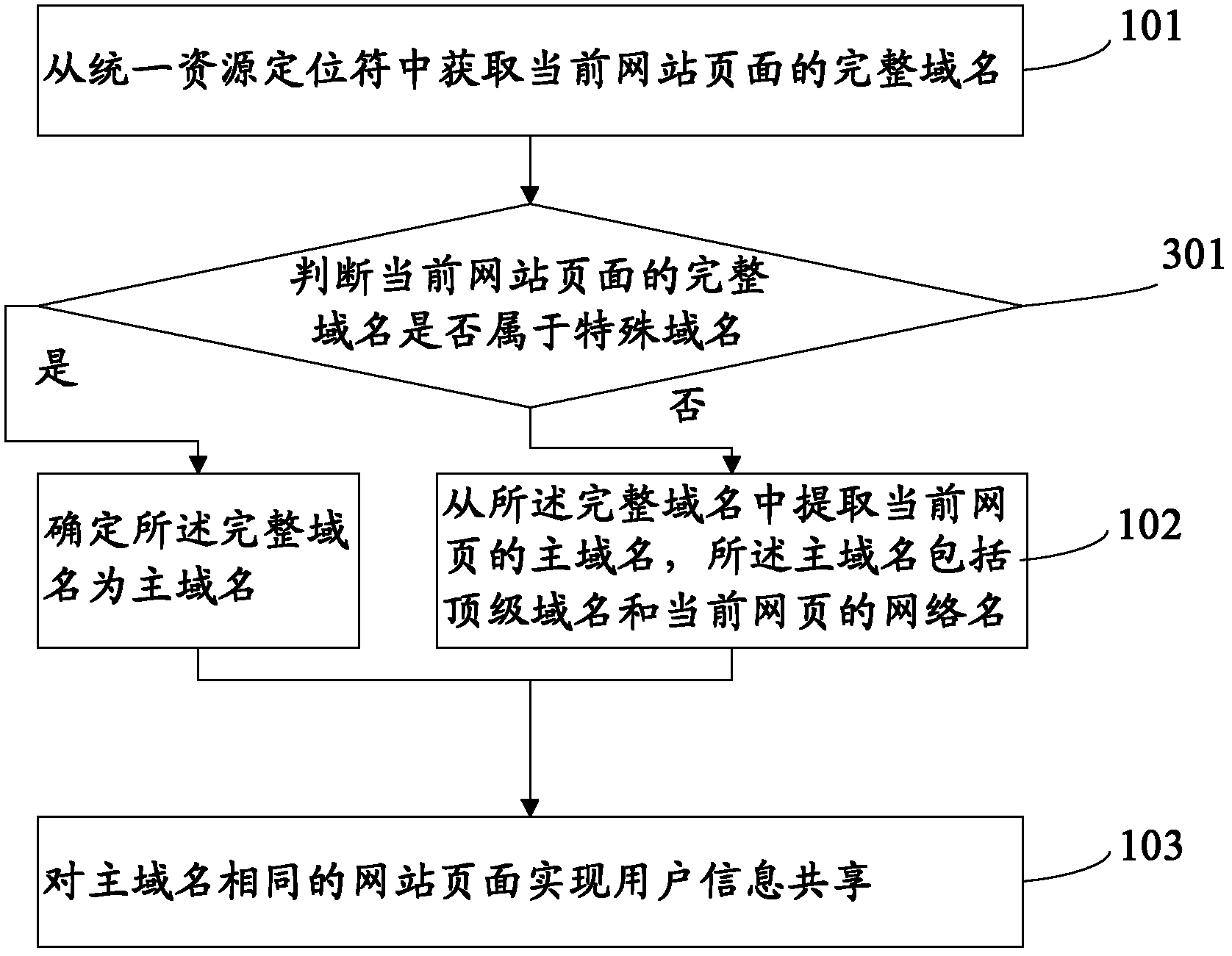
ActiveCN102664926AAchieve sharingReduce storageTransmissionInformation sharingFully qualified domain name
The application provides a user information sharing method, comprising the following steps: obtaining a complete domain name of a current webpage from a uniform resource locator; extracting a main domain name of the current webpage from the complete domain name, wherein the main domain name includes a top level domain name and a network name of the current webpage; and realizing user information sharing for webpages with same main domain names. In addition, the application also discloses a user information sharing system for realizing the method. According to the method and the system for user information sharing, occupation of system resources by user information records can be reduced; and sharing of user information can be realized.
Owner:BEIJING QIHOO TECH CO LTD
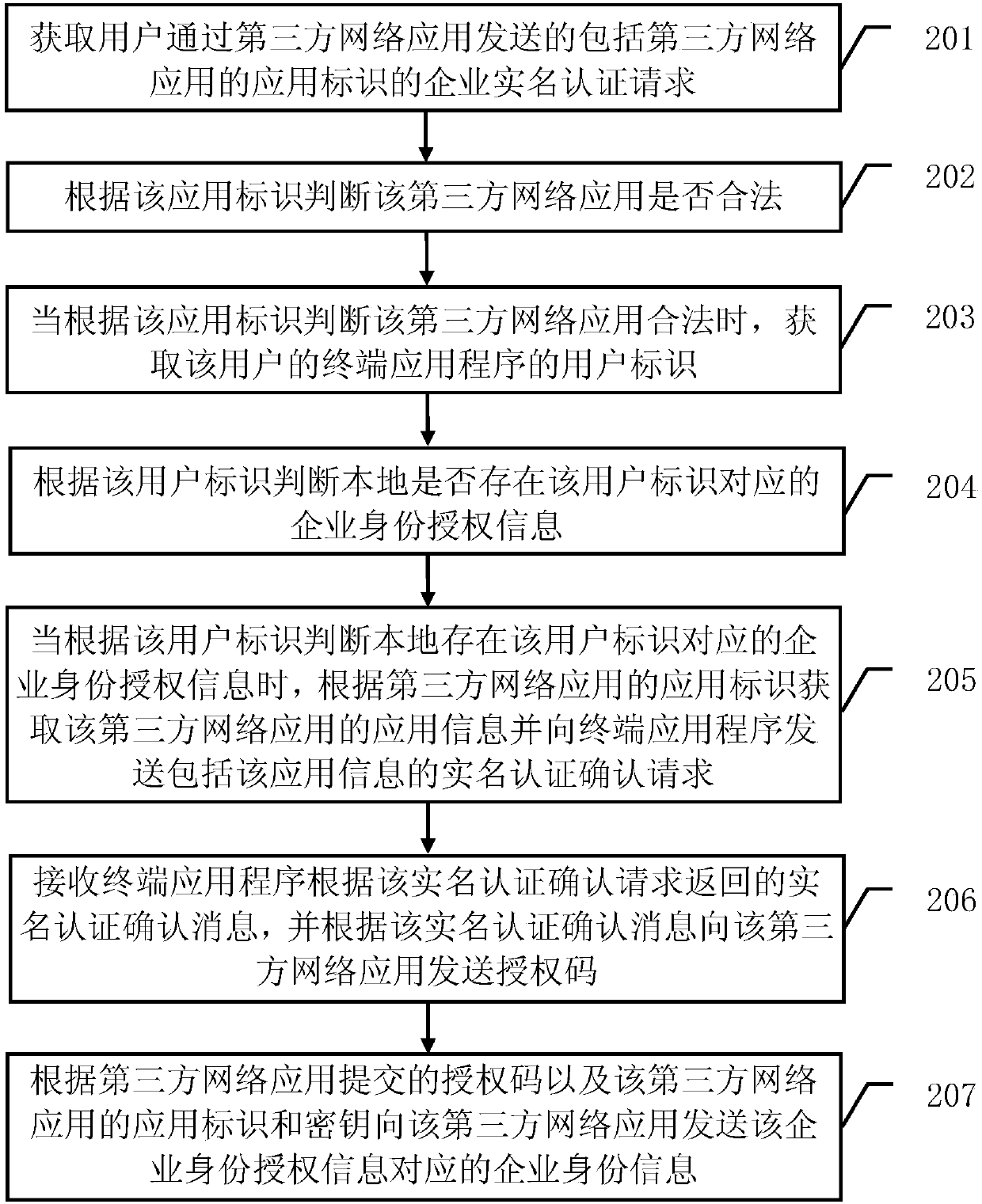
Enterprise real name authentication method and authentication server
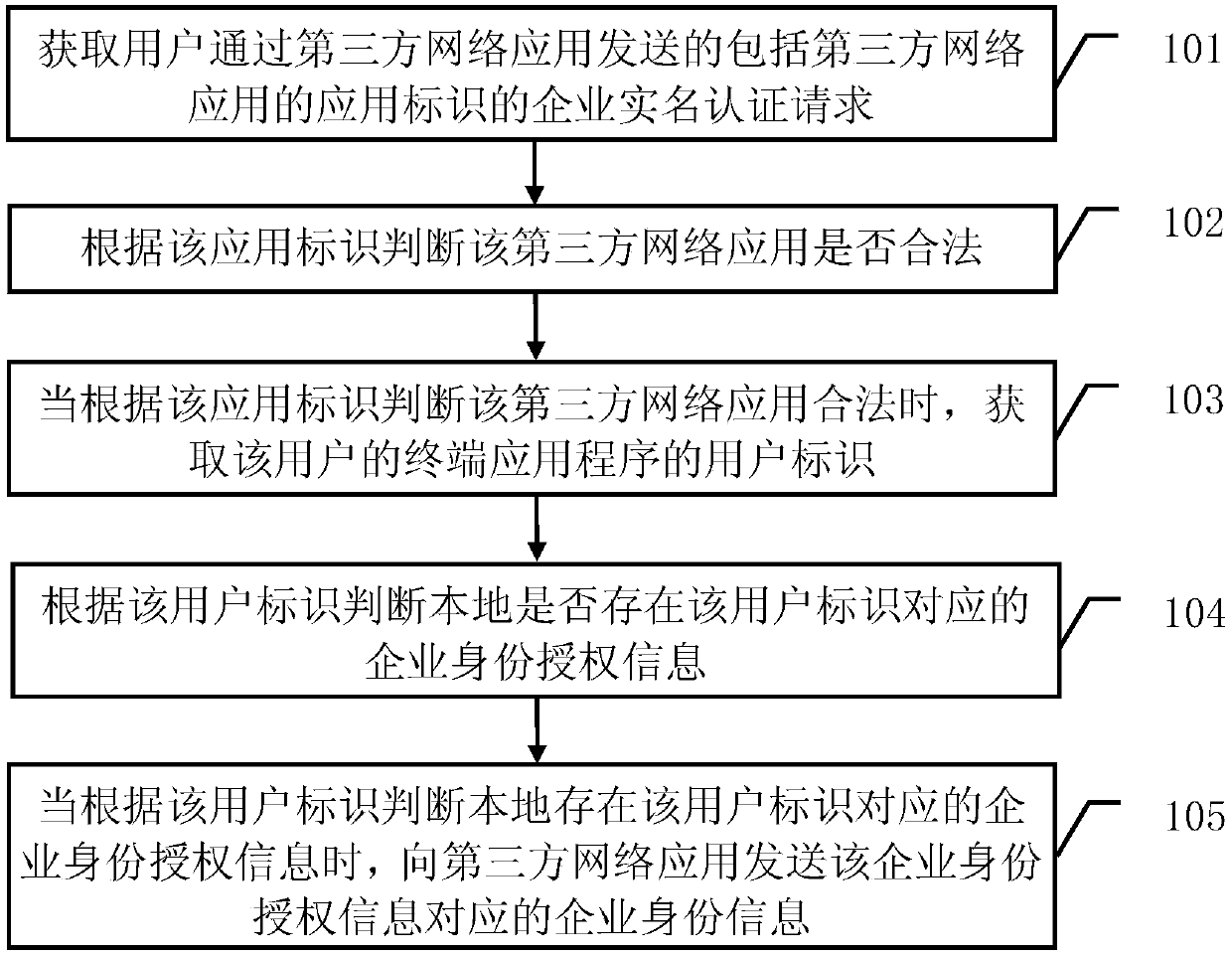
ActiveCN109660484AEfficient and convenient online real-name authentication serviceImproved user login experienceUser identity/authority verificationAuthentication systemUser identifier
The embodiment of the invention provides an enterprise real name authentication method and an authentication server, and belongs to the technical field of the information security. The method comprises the following steps: acquiring an enterprise real name authentication request sent by a user through a third-party network application, wherein the enterprise real name authentication request comprises an application identifier of the third-party network application; judging whether the third-party network application is legal according to the application identifier; if the third-party network application is legal, acquiring a user identifier of a terminal application program of the user, and judging whether enterprise identity authorization information corresponding to the user identifier is existent at local according to the user identifier; if the enterprise identity authorization information corresponding to the user identifier is existent at local, sending the enterprise identity information corresponding to the enterprise identity authorization information to the third-party network application. Through the enterprise real name authentication method provided by the embodiment of the invention, an efficient and convenient online real name authentication service can be provided for the enterprise, so that an enterprise user can directly and quickly login the third-party network application based on the identity authorization of the enterprise, and the user login experience is improved.
Owner:爱信诺征信有限公司
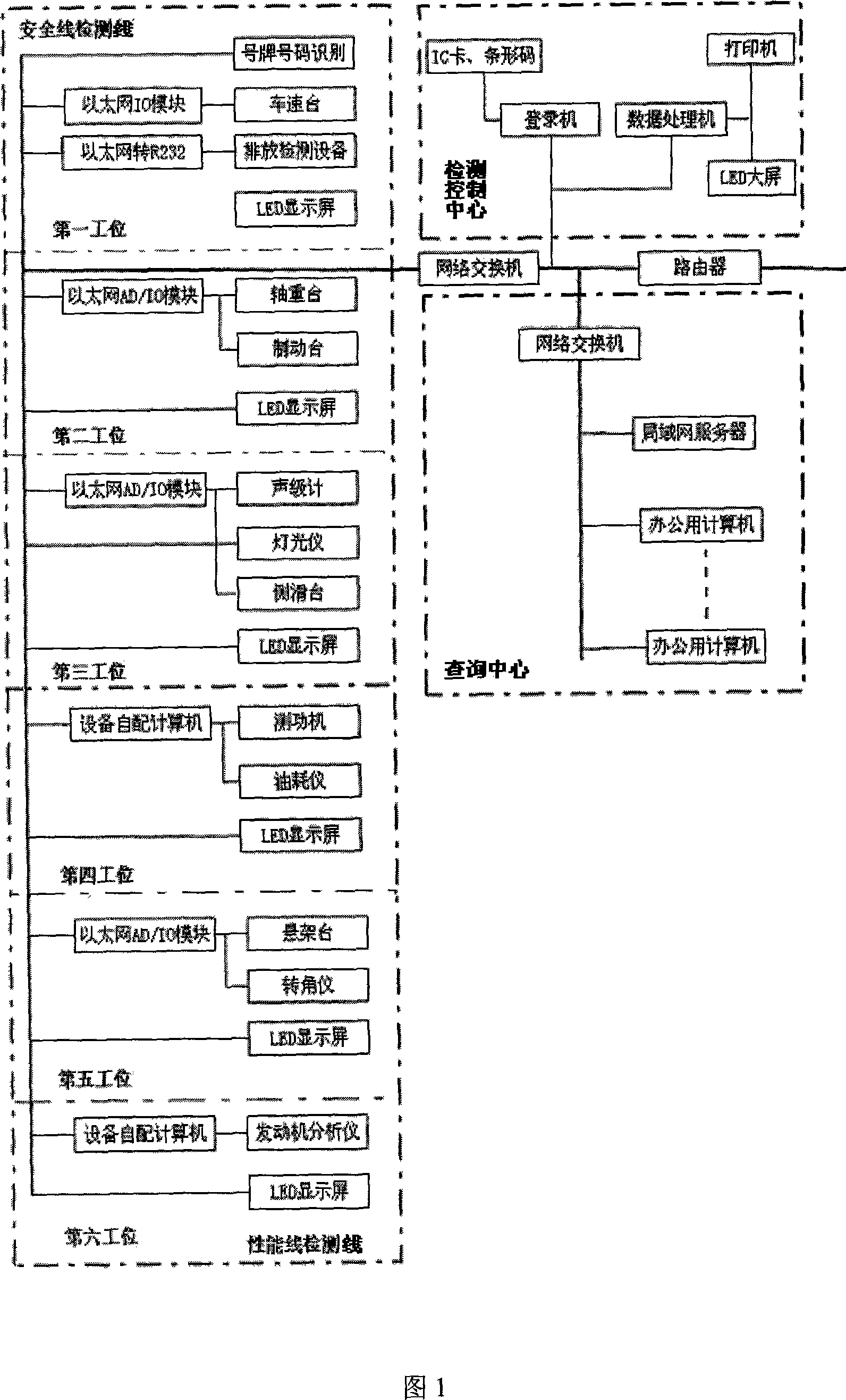
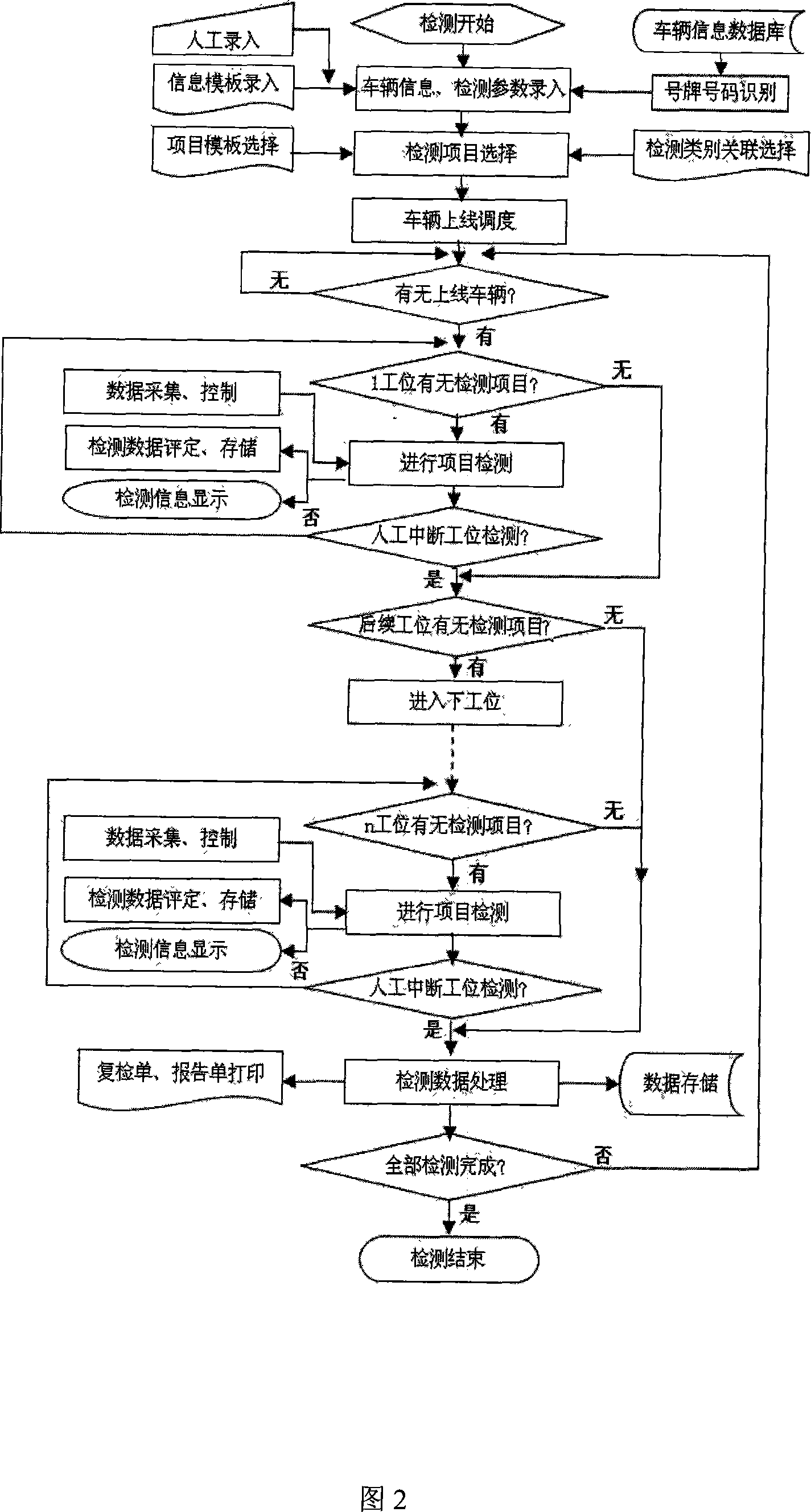
Automatic motor vehicle detecting system and its operation process
InactiveCN101046430ASolve the disorderly registration problemRun fastVehicle testingElectric signal transmission systemsComputer printingRemote control
The automatic motor vehicle detecting system and its operation process belongs to the field of motor vehicle detecting technology. The automatic motor vehicle detecting system consists of one detection control center and detection sites. The detection control center including a log-on computer, a site data acquiring, controlling and processing computer, a printer and auxiliary equipment is installed in a service hall, accessed to LAN and operated in networked 'distributive acquisition and centralized processing' mode. The automatic motor vehicle detecting system may constitute different safety detection line or performance detection line as required. It completes data acquisition data transmission, equipment control, etc through network and remote control. The automatic motor vehicle detecting system possesses detection site control function, increased plate number recognizing function and B / S programming.
Owner:张在新
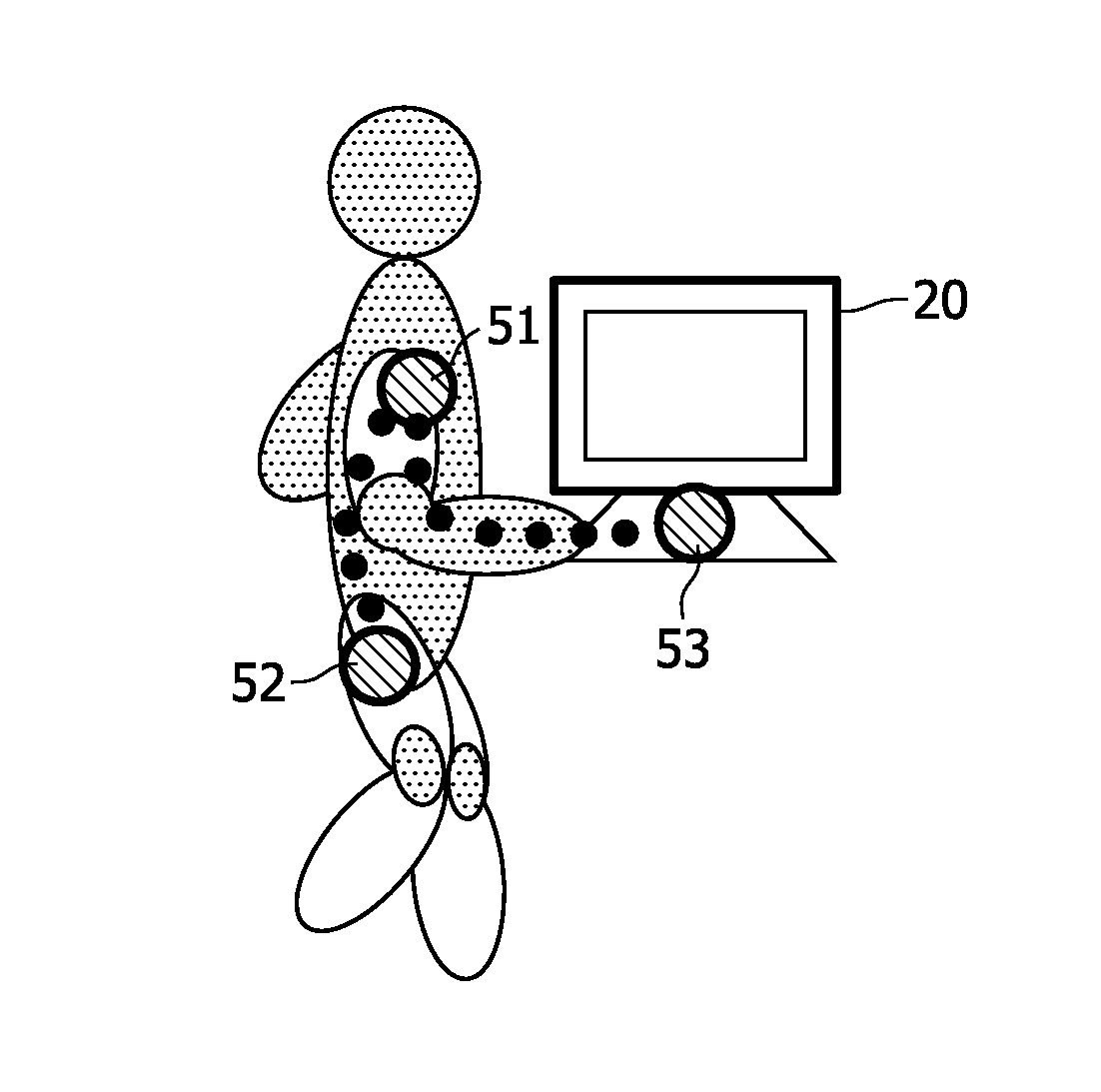
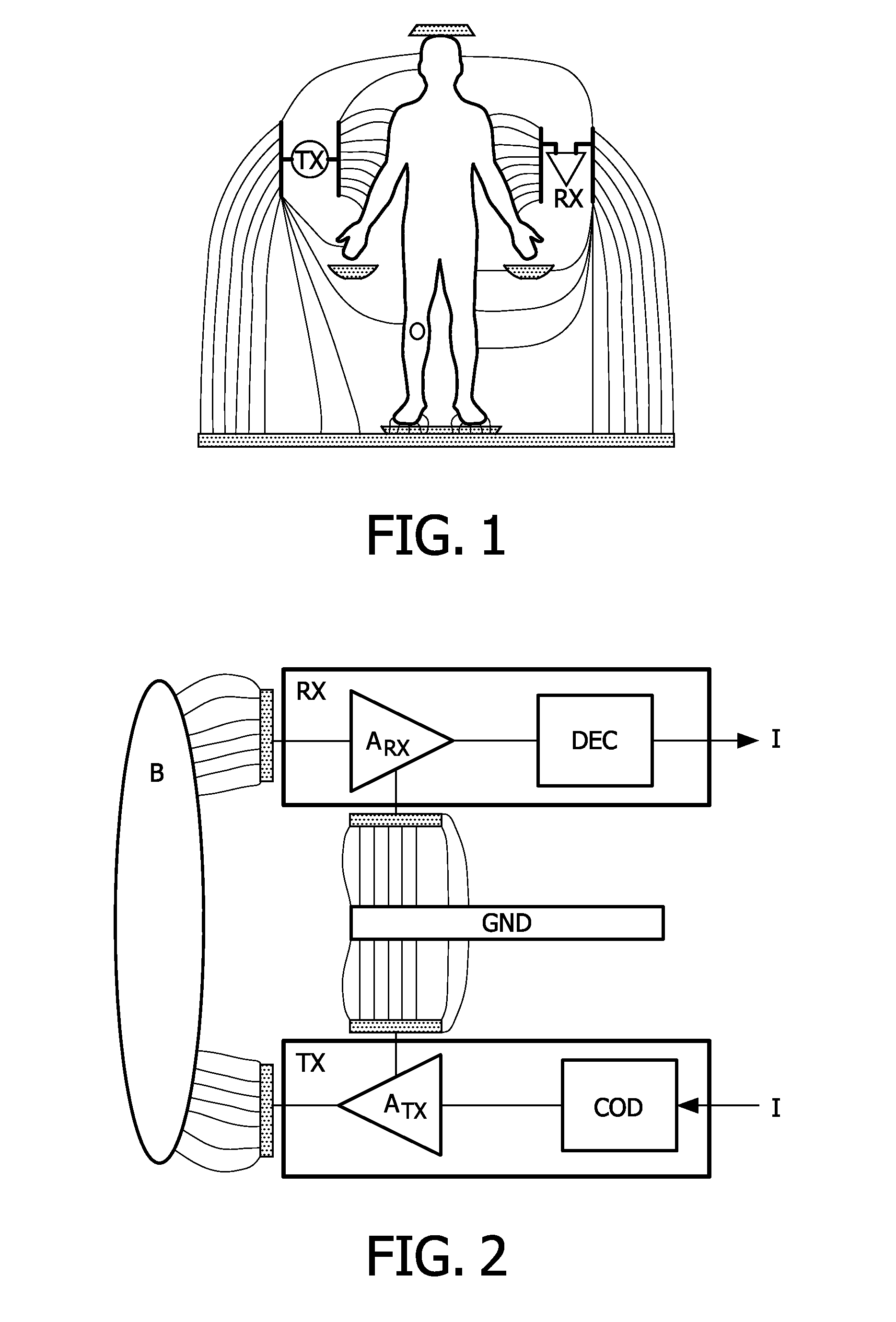
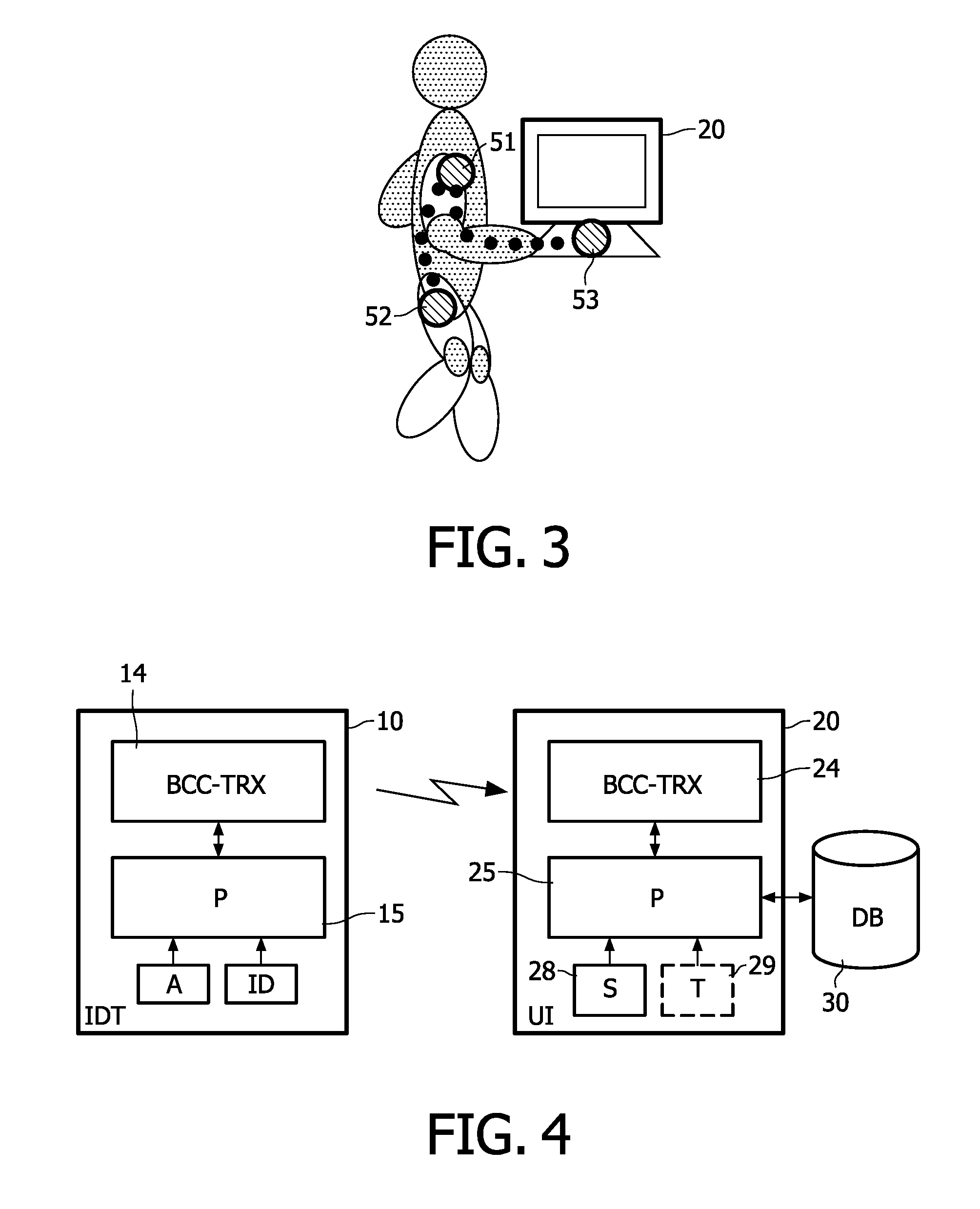
User identification based on body-coupled communication
InactiveUS8866760B2Reliable identificationEasy accessElectric signal transmission systemsDigital data processing detailsIdentification deviceUser interface
Owner:KONINK PHILIPS ELECTRONICS NV
Log-in method of application client and relevant device
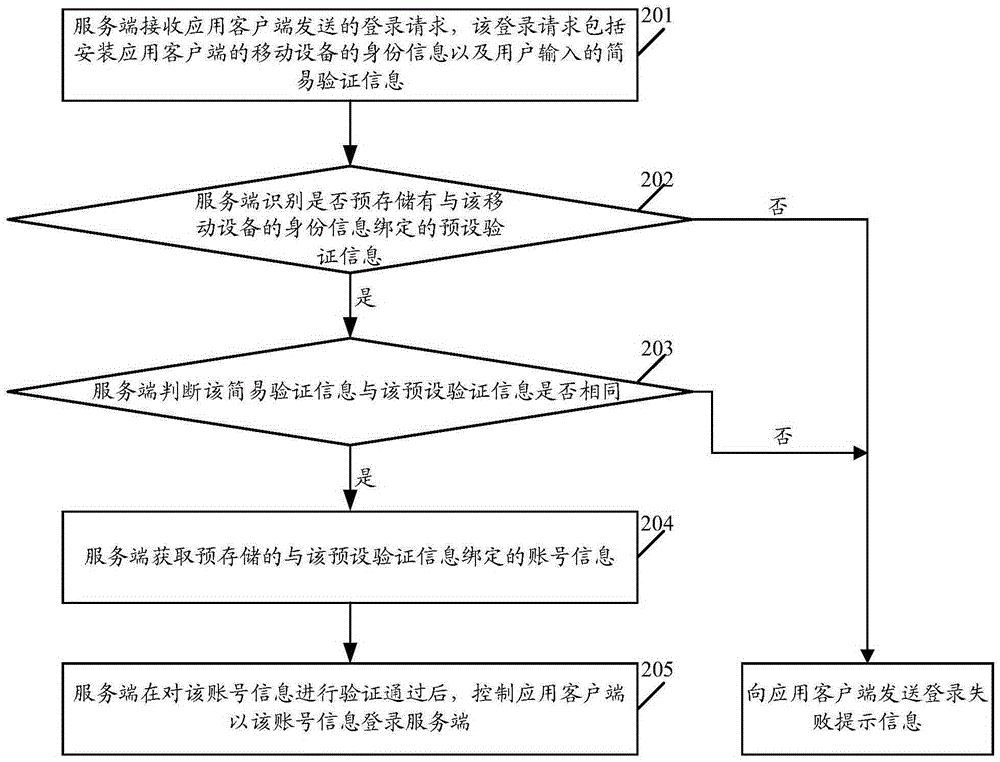
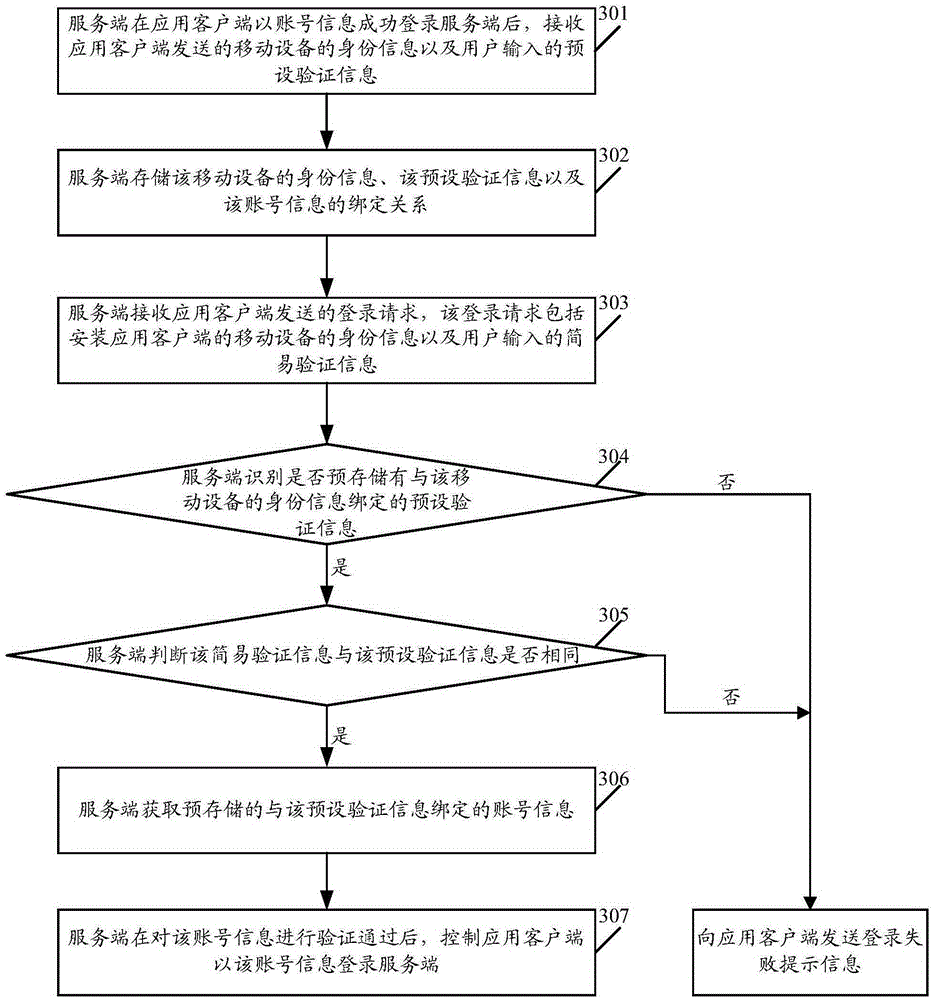
ActiveCN105337997AQuick LoginImprove experienceTransmissionSecurity arrangementClient-sideMobile device
The embodiment of the invention relates to the technical field of mobile Internet and discloses a log-in method of an application client and a relevant device. The method includes the steps that a log-in request sent by the client is received, and the log-in request comprises identity information of a mobile device provided with the application client, and simple verification information input by a user; whether preset verification information bound with the identity information of the mobile device is pre-stored or not is recognized, if the preset verification information bound with the identity information of the mobile device is pre-stored, whether the simple verification information is the same as the preset verification information or not is judged, and if the simple verification information is the same as the preset verification information, pre-stored account number information bound with the preset verification information is acquired; after verification of the account number information passes, the application client is controlled to log in a server through the account number information. By means of the log-in method of the application client and the relevant device, the application client can log in the server easily and fast, and the risk that the application client illegally logs in the server is reduced.
Owner:GUANGZHOU HUADUO NETWORK TECH
Login authorization method and device, login method and device
The invention relates to a login authorization method and device, a login method and device. The login authorization method comprises the following steps: receiving a login request sent by a terminal; extracting a login credential and a terminal identifier from the login request, wherein the extracted login credential is generated and issued to the terminal when the terminal finishes the previous login authorization; querying the login credential, which is generated and stored when finishing the previous login authorization, corresponding to the terminal identifier; when the extracted login credential is consistent with the queried login credential, performing the login authorization corresponding to the terminal identifier; updating the stored login credential corresponding to the terminal identifier; and issuing the updated login credential to the terminal. By use of the login authorization method and device, the login method and device provided by the invention, a user can rapidly and safely login.
Owner:TENCENT TECH (SHENZHEN) CO LTD
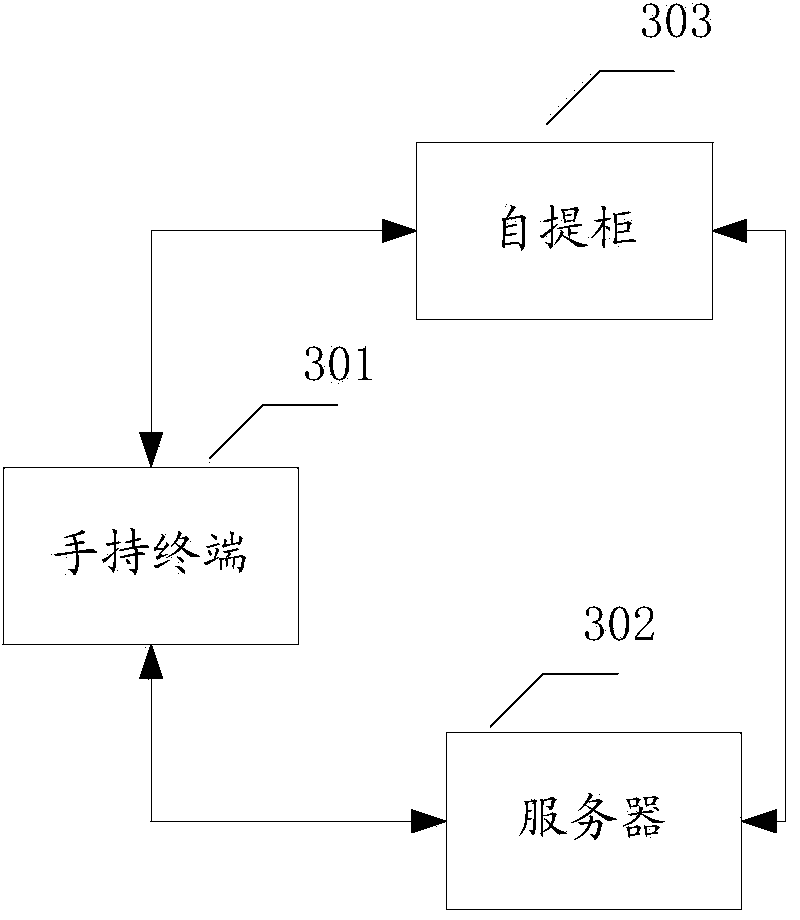
Method and system for logging in self-picking cabinet
InactiveCN103996111AQuick LoginEnsure safetyUser identity/authority verificationLogisticsComputer terminalManagement efficiency
The embodiment of the invention provides a method and system for logging in a self-picking cabinet. The method includes the steps that a user logs in a handheld terminal and sends an identity authentication request to a server side through the handheld terminal; the server side authenticates the identity of the user based on the identity authentication request, and when the user passes identity authentication, a two-dimensional code is generated and sent to the handheld terminal for display. The self-picking cabinet scans the two-dimensional code, generates a self-picking cabinet login request based on the two-dimensional code, and sends the self-picking cabinet login request to the server side; the server side determines whether the user is allowed to log in the self-picking cabinet or not based on the self-picking cabinet login request. Safety and management efficiency of the self-picking cabinet can be improved through the method and system.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Multiple-factor identity authentication method
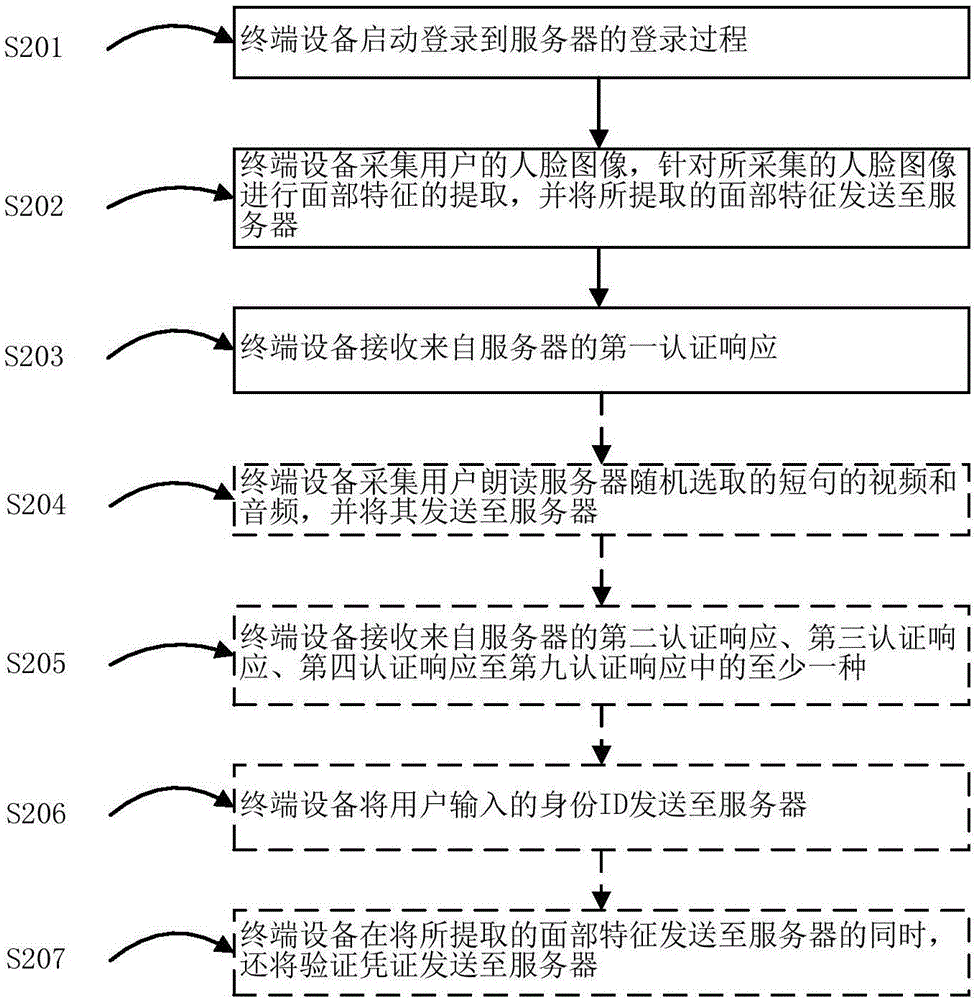
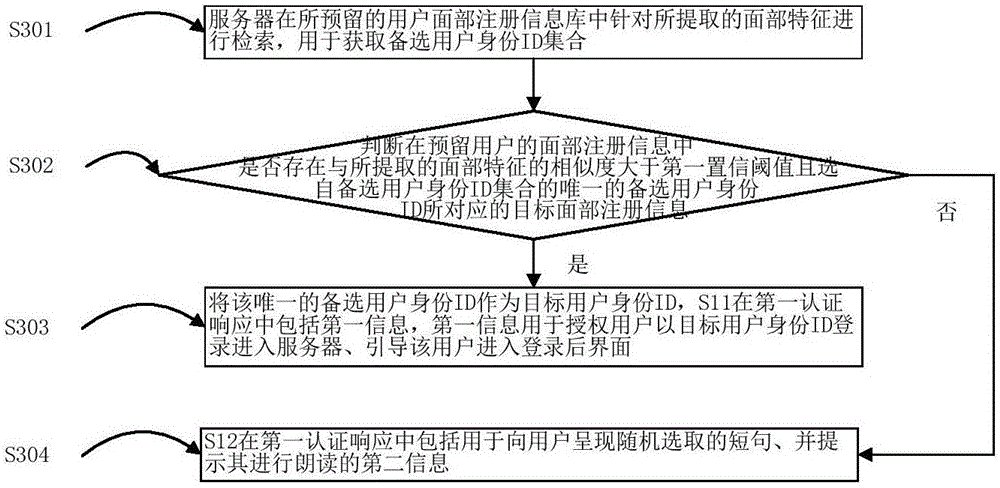
InactiveCN106790260AEliminate the probability of rejection and misrecognitionQuick loginCharacter and pattern recognitionTransmissionConfidence thresholdInternet privacy
The invention presents a multiple-factor identity authentication method, wherein the method includes steps of starting the process of logging in a server by a terminal device; collecting a human face image, extracting face features and sending to the server; receiving a first authentication response from the server, wherein the server indexes the face features reserved in a user face registration information base; acquiring an ID set of a standby user identity, and judging if the reserved face registration information of the user has the sole target face registration information of which similarity of the extracted face feature is more than the first confidence threshold value and which is selected from the ID set of the standby user identity and corresponding to the user identity ID; if it is, taking it as the target user identity ID, and transferring to S11;, wherein the first authentication response includes first information, and the first information is use for authorizing the user to enter the server by the target user identity ID, and guiding the user to enter the interface after logging in. the method is used for reducing and even eliminating the rejection probability and / or the mistake probability.
Owner:BEIJING GZT NETWORK TECH
Multi-user login method and apparatus
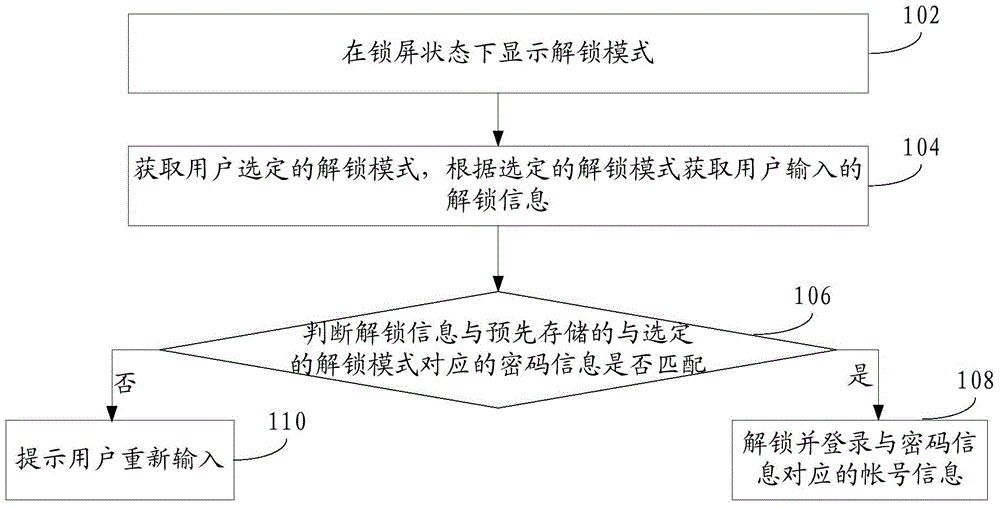
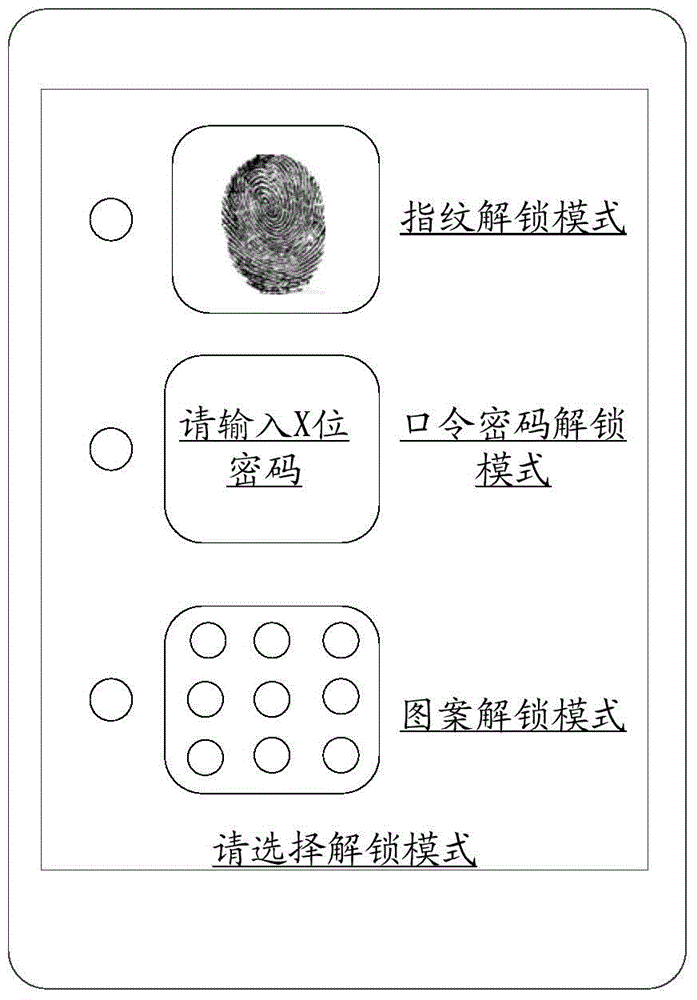
InactiveCN104966007AQuick loginEasy loginDigital data authenticationPlatform integrity maintainanceEmbedded systemPassword
The invention relates to a multi-user login method and apparatus. The method comprises: displaying unlocking modes in a screen locked state; acquiring an unlocking mode selected by a user, and acquiring unlocking information input by the user according to the selected unlocking mode; judging whether the unlocking information is matched with pre-stored password information that corresponds to the selected unlocking mode; and if matching is successful, then carrying out unlocking and logging in to an account that corresponds to the password information. According to the multi-user login method and apparatus which are provided by the invention, multi-user login can be conveniently and quickly realized.
Owner:ONEPLUS TECH SHENZHEN
Intelligent dustbin and operation method thereof
PendingCN108945885AEasy to operateEasy to useWaste collection and transferRefuse receptaclesSoftware engineeringMechanical engineering
The invention relates to the field of waste classification, in particular to an intelligent dustbin comprising a box body. Multiple containing cavities are formed in the box body. Each containing cavity of the box body is provided with a box door unit. The intelligent dustbin is characterized in that the box body is further provided with an external video identification unit and a central controlunit, the external video identification unit comprises a first camera used for shooting images containing a rubbish bag, and the central control unit identifies features of the rubbish bag in the images and opening one corresponding box door unit based on the identification information. Based on the structure, in the operation process of the dustbin, the first camera shoots the images containing the rubbish bag, the central control unit identifies the features of the rubbish bag from the images and opens one corresponding box door unit based on the identification information; by the adoption of the scheme, the intelligent dustbin can omit the step that a user selects the rubbish classification option which the rubbish needing to be thrown belongs to, and automatic judgment can be conductedthrough central control so as to open the corresponding box door; and therefore, the operation process is simplified for the user, and the intelligent dustbin is convenient to use for the user.
Owner:王远喆
Method for accessing server by customer end
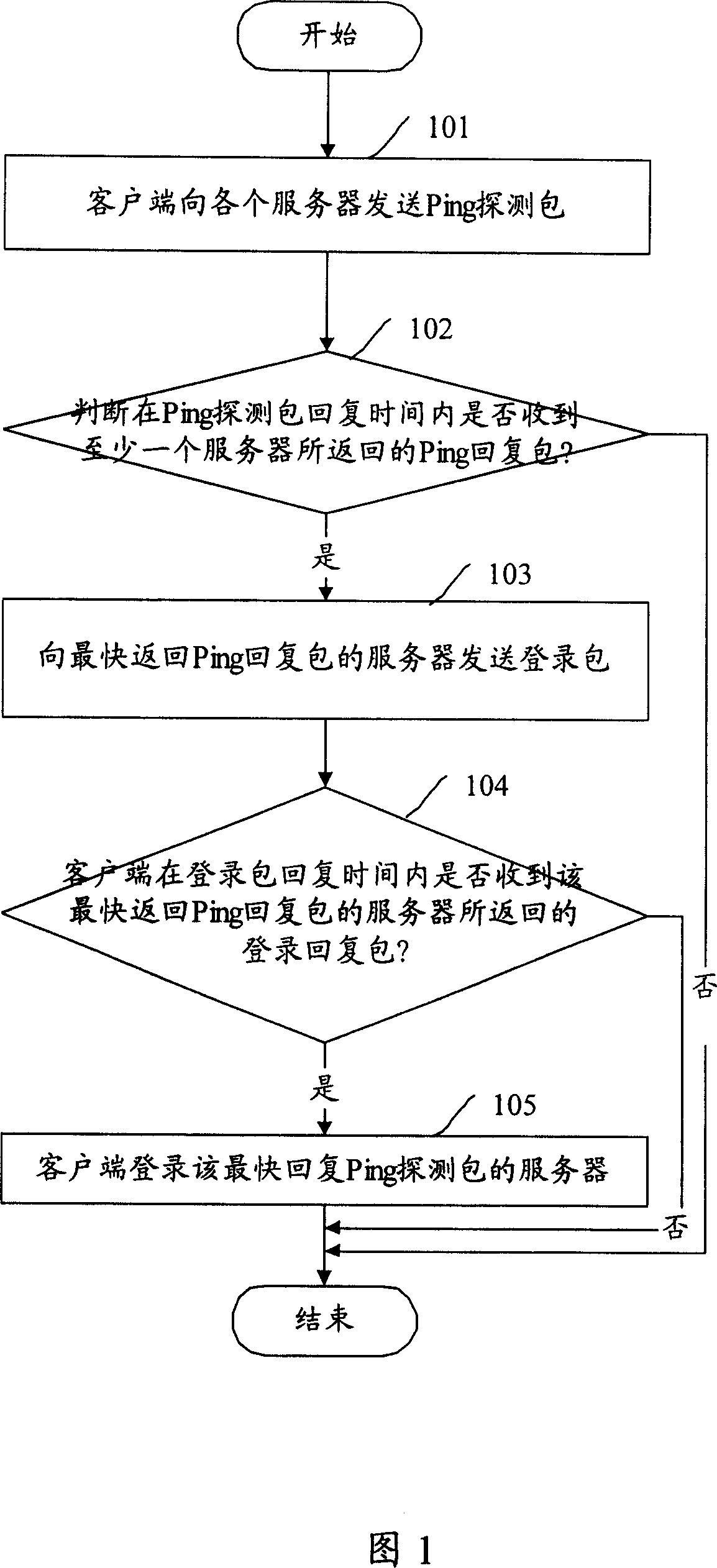
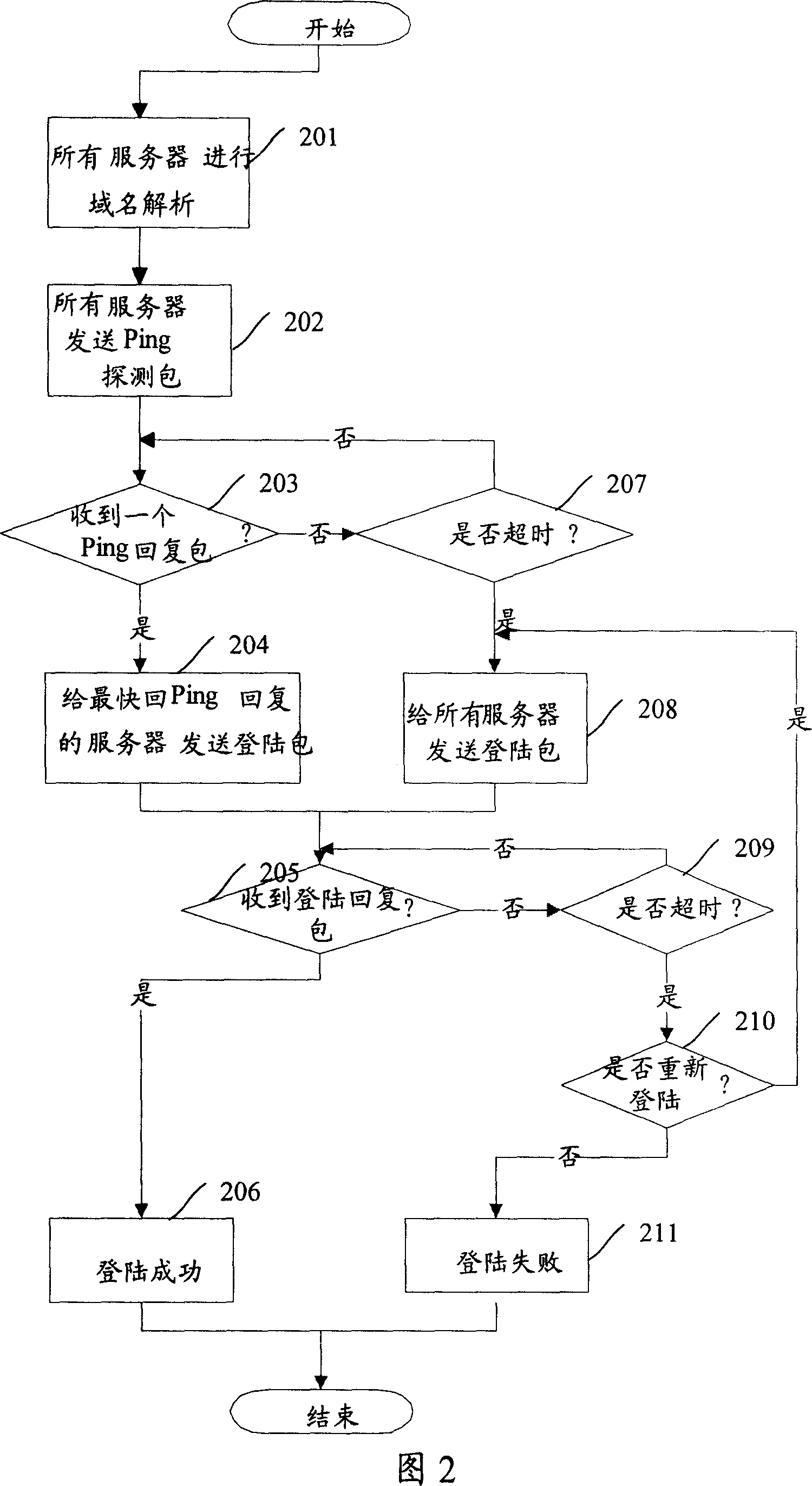
ActiveCN101075924AQuick LoginOvercome the disadvantage of being restricted by routingData switching by path configurationClient-sideReturn time
The method comprises: presetting the return time of Ping detection packet and the return time of the log-in packet; the client side sends Ping detection packet to each server, and decides if receiving the Ping return packet from at least one server in the time of returning the Ping detection packet; if yes, then sending the log-on packet to the server returning the Ping return packet in shortest time; if not, then quitting the process; b) deciding if the client side receives the log-on return packet from the server returning the Ping return packet in shortest time; if yes, the client side logs on the server; if not, quitting the process.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Heat exchanging units long-range control system
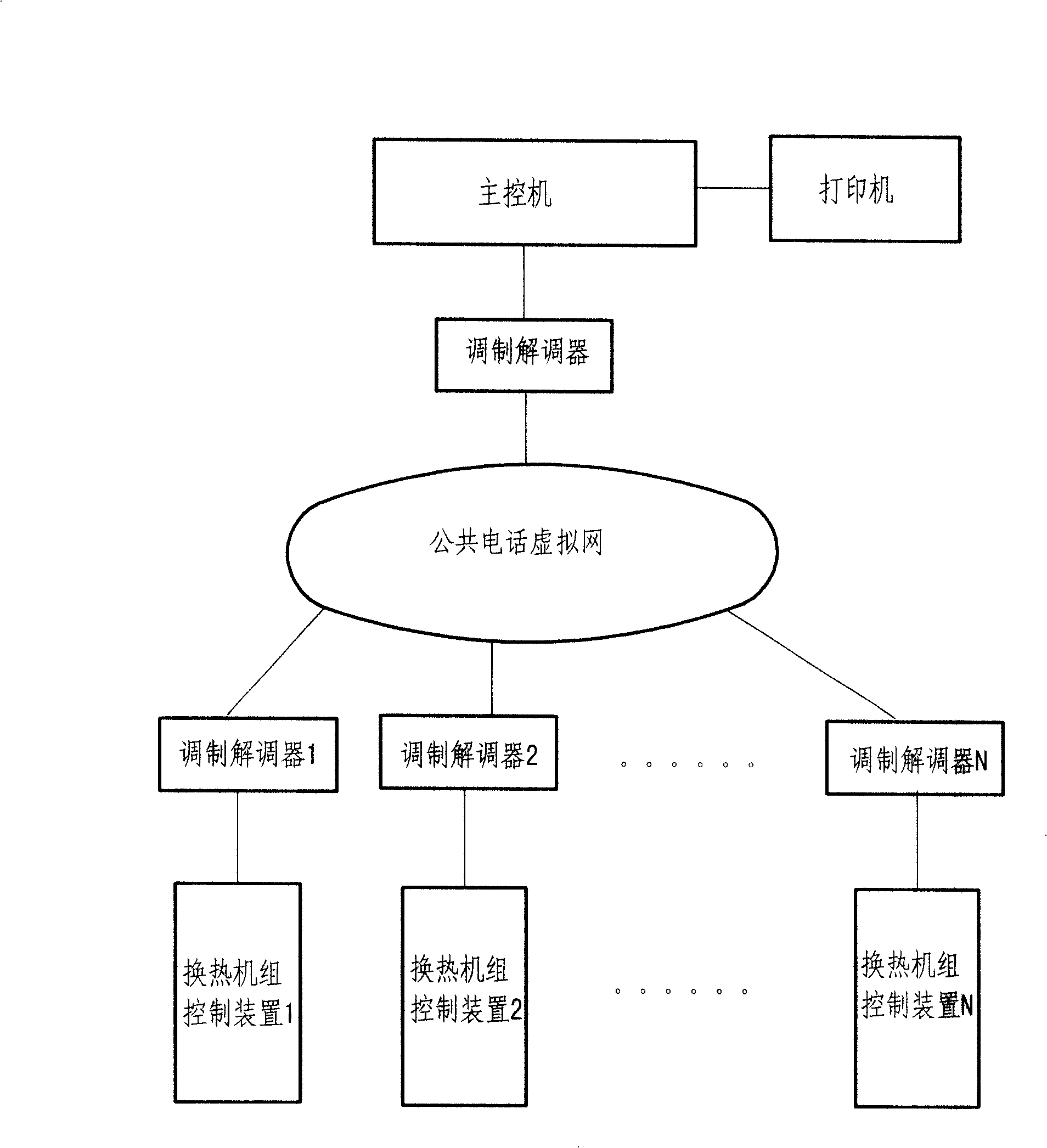
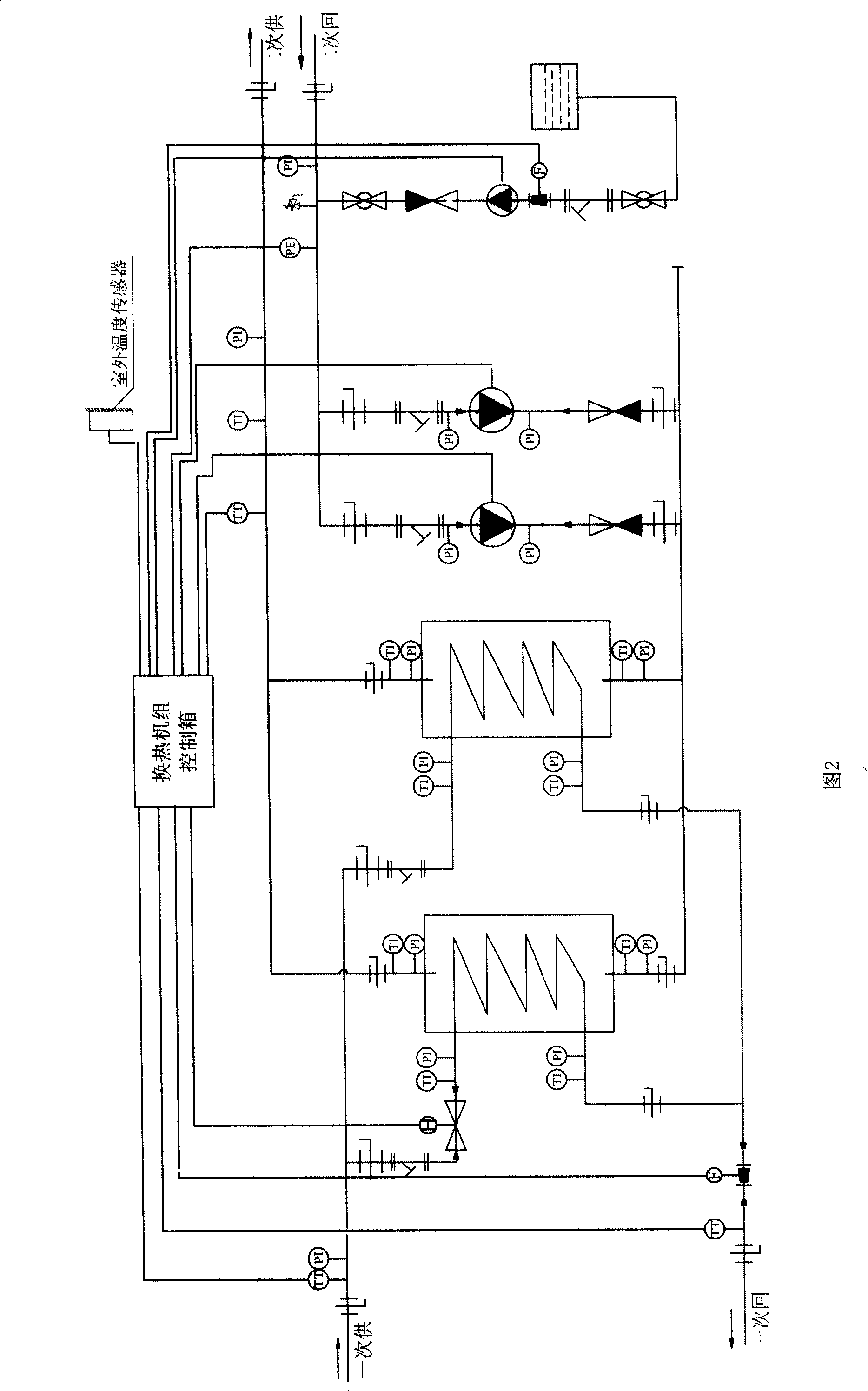
InactiveCN101261513AReal-time monitoring and control of working conditionsGuaranteed normal operationHeat exchange apparatusTotal factory controlCommunication interfaceModem device
The invention relates to a heat-exchanger unit remote control system in the heat exchange control field, the technology is mainly characterized in that: the system is composed of a main control machine which is positioned at a control center, a modulation demodulator which is connected with a communication interface thereof, control boxes of heat-exchanger units which are distributed in each heat supply station and modulation demodulators which are connected with the communication interfaces thereof by connection via a public telephone virtual network, and the heat exchanger unit control boxes are connected with a temperature sensor in a heat supply pipeline, a pressure sensor, a regulating valve, a circulating pump, a water supplementing pump and an outdoor temperature sensor. The heat-exchanger unit remote control system can carry out the real-time monitoring and the control of the operation situations of all the heat-exchanger units, once the devices of the heat supply stations are detected to have the faults, the processing can be carried out immediately, thus ensuring the normal operation of a heat supply system, automatically adjusting the opening degree of the regulating valve of a primary network, avoiding the waste of the resources due to the excessive heat supply or the inconvenience of a user due to the insufficient heat supply and stably supplying the heat to the user of a secondary network.
Owner:TIANJIN HONGYUAN HEATING EQUIP SCI & TECH
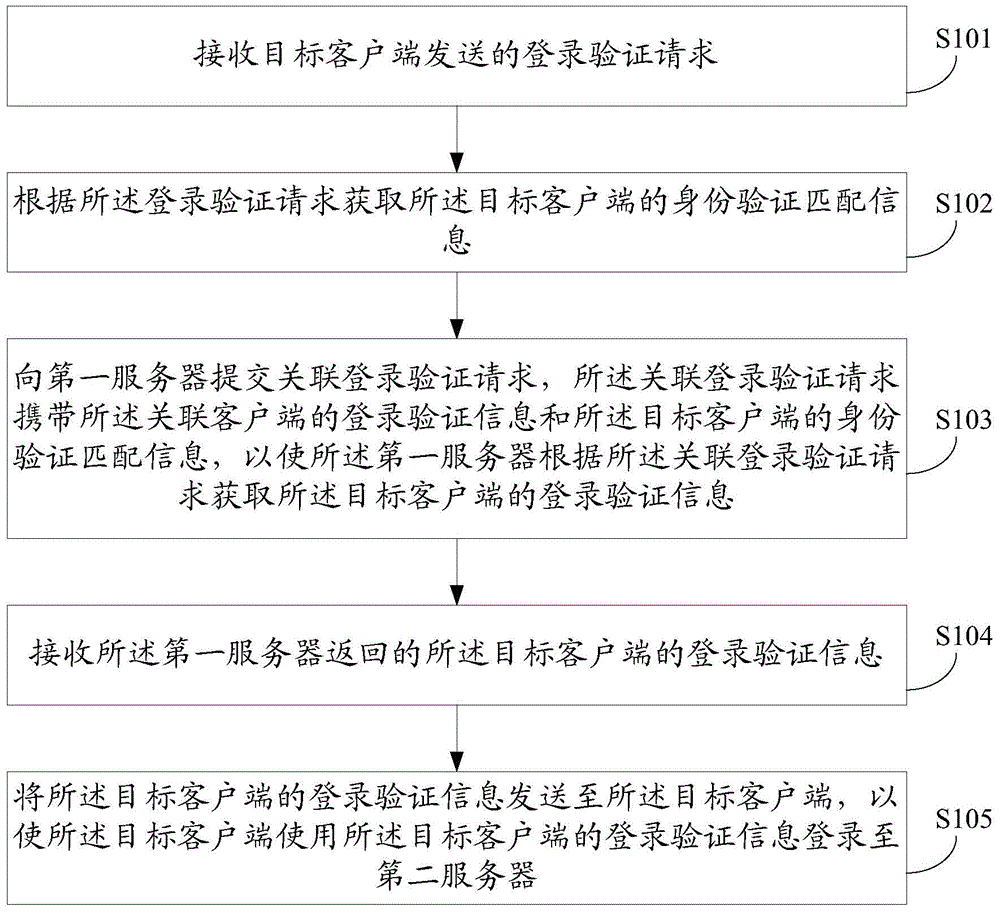
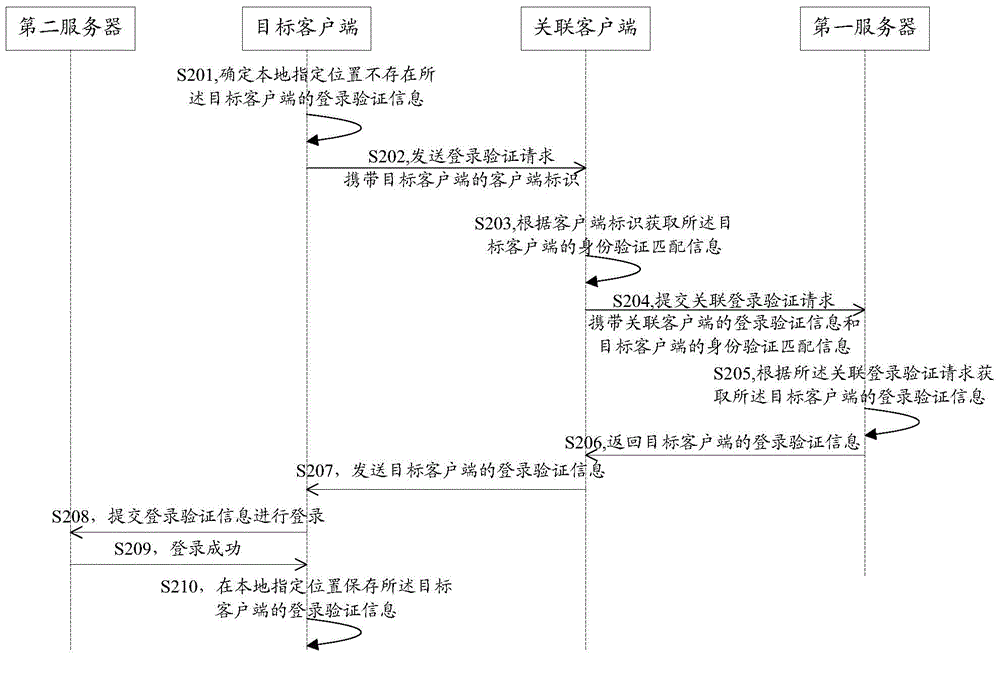
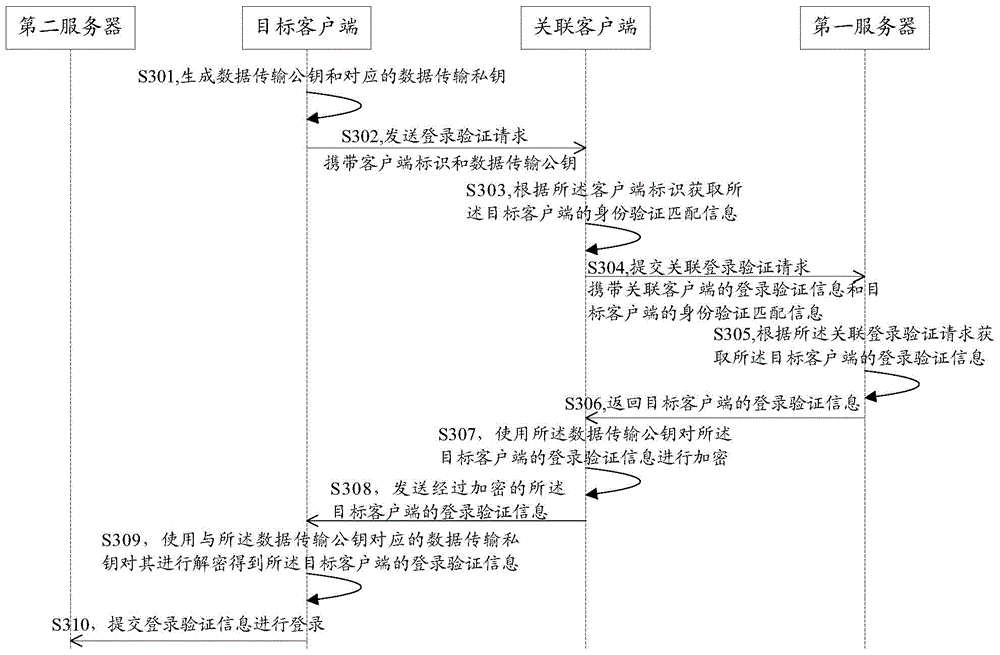
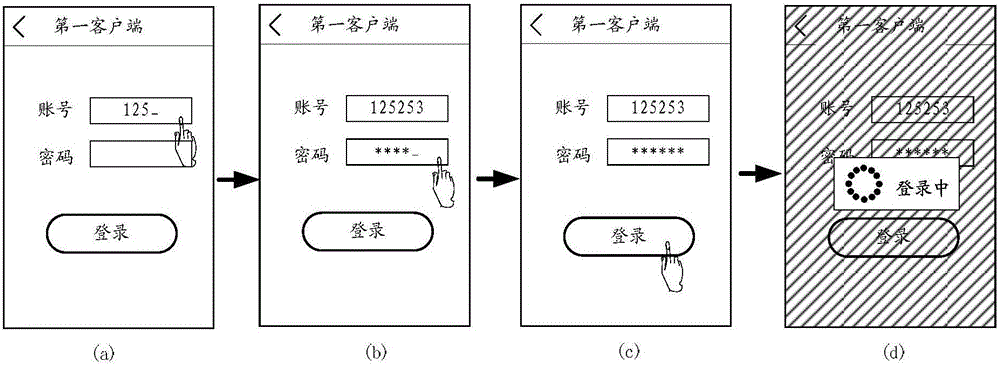
Method and system for logging in client and client
The embodiment of the invention discloses a method and system for logging in a client and a client. The method for logging in a client comprises: a logging-in verification request sent by a target client is received; according to the logging-in verification request, identity verification matching information of the target client is obtained; an associated logging-in verification request is submitted to a first server, so that the first server obtains logging-in verification information of the target client according to the associated logging-in verification request; the logging-in verification information, returned by the first server, of the target client is received; and the logging-in verification information of the target client is sent to the target client, so that the target client can log in a second server by using the logging-in verification information of the target client. According to the invention, rapid logging in of an application client can be realized and a risk of stealing logging-in verification information can be effectively eliminated, so that the logging-in security of the client can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and apparatus for logging in client
ActiveCN105827600ASimplify login operationsShorten login timeDigital data authenticationTransmissionLoggingDatabase
The invention discloses a method and apparatus for logging in a client. The method comprises: a logging-in account number that is logged in currently by a second client operated at a terminal is obtained at a logging-in interface of a first client operated at the terminal, wherein the second client and the first client have an association relationship; a logging-in request that is generated after operation execution on the logging-in account number is obtained at the logging-in interface of the first client, wherein the logging-in request is used for requesting to use the logging-in account number to log in the first client; and the first client is logged in by using the logging-in account number to respond to the logging-in request. According to the invention, a technical problem of low logging-in efficiency due to utilization of the existing logging-in method can be solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for executing security operation by using security device
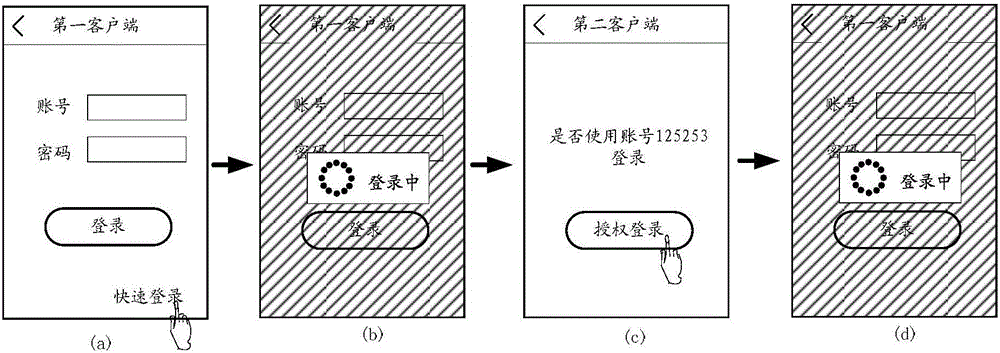
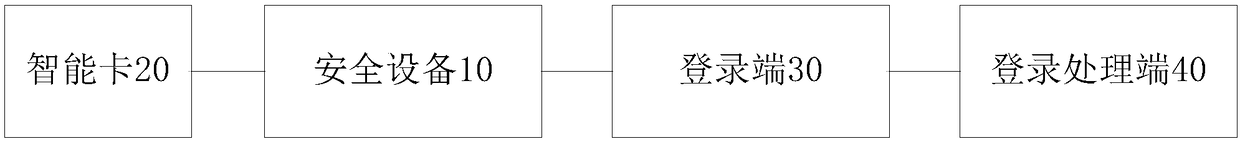
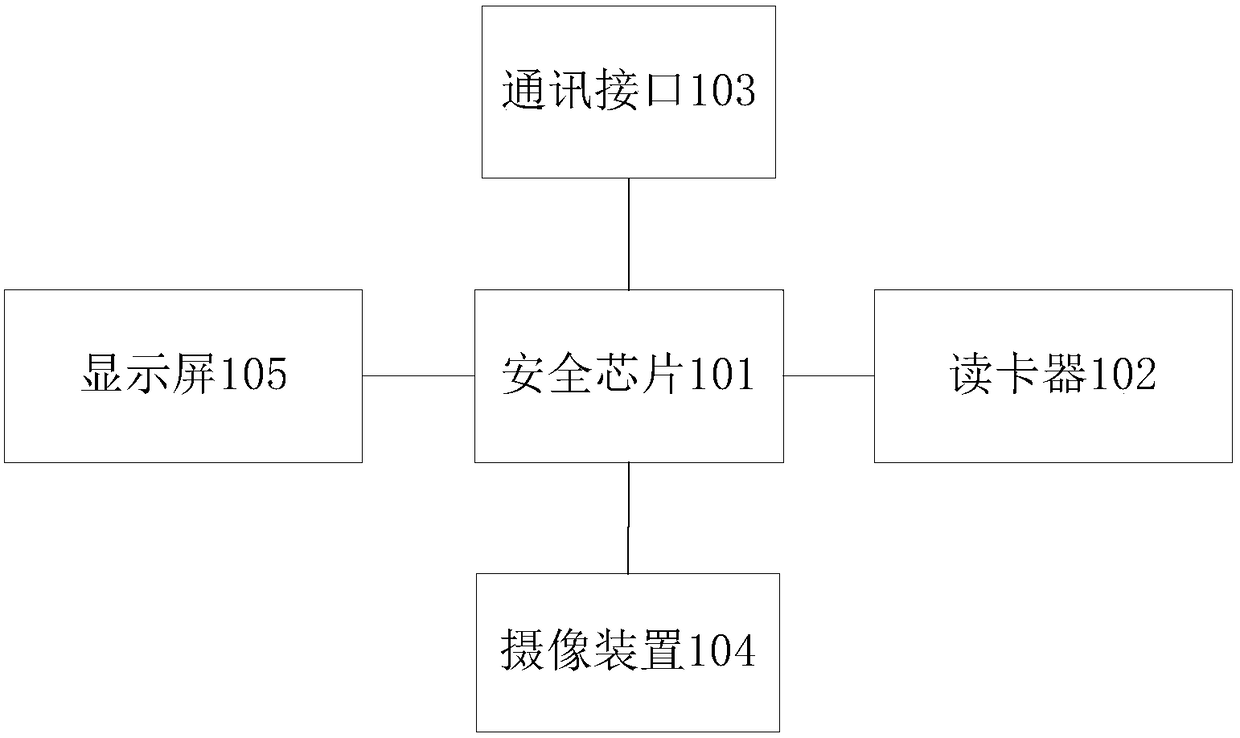
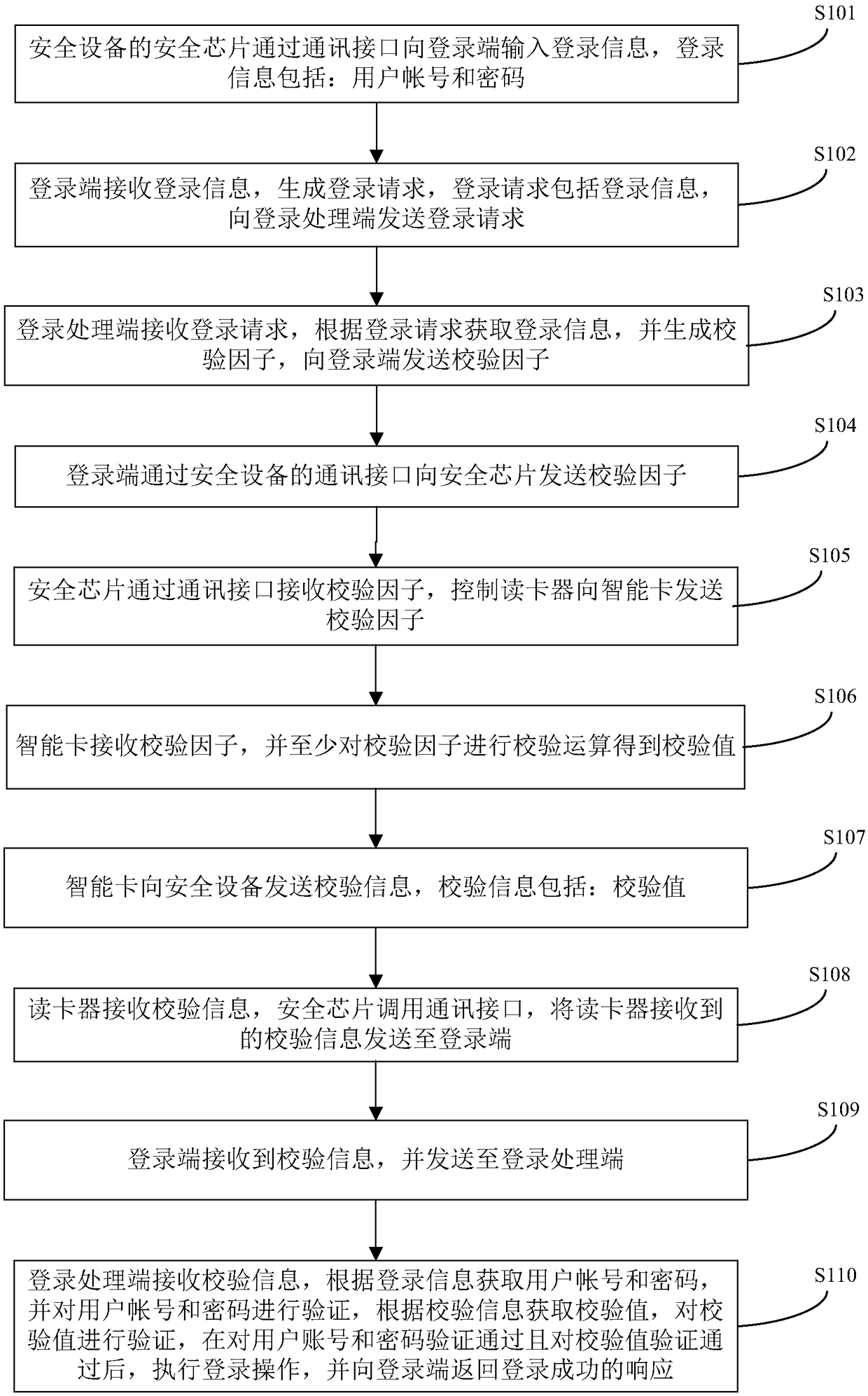
ActiveCN108200037AEnsure safetyProtect business secretsDigital data authenticationTransmissionSmart card
The invention provides a method and system for performing a security operation by using a security device. The method comprises the following steps: a security chip acquires login information and interacts with a smart card to obtain verification information, and sends the verification information to a login processing terminal through a login terminal, the login processing terminal verifies the login information and the verification information, and executes a login operation, after login success, the security chip sends an image collection instruction to a camera device, receives first collection information sent by the camera device, judges whether the collection information contains human face information, if so, judges whether the human face information is consistent with a user facepicture, if not, executes the security operation, if not, judges whether at least one of the disenabling conditions is satisfied, and if so, executes the security operation; or, the security chip sends the first collection information to the login terminal, the login terminal performs judgment, and executes the security operation according to the judgment result, therefore the business secret of the employee who logs in by using the security device is protected, and the unrelated personnel are prevented from using the security device.
Owner:TENDYRON CORP
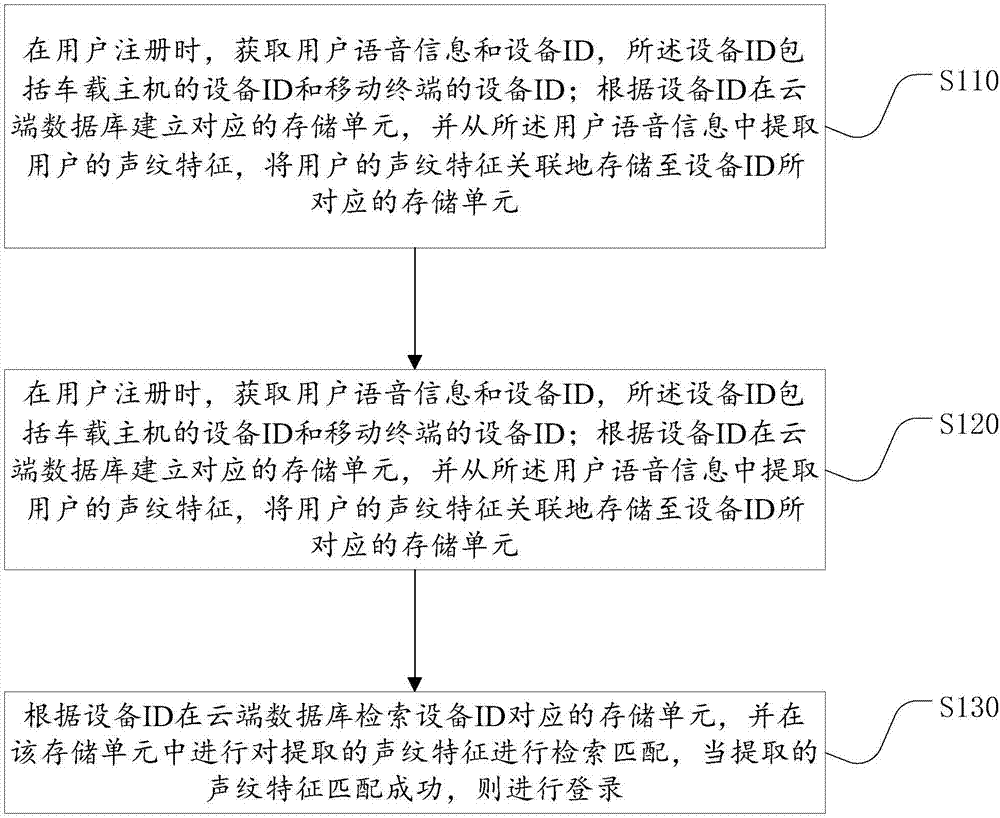
Method and device for quick voice login of intelligent vehicle
The invention relates to a method and a device for quick voice login of an intelligent vehicle. The method comprises the following steps of simultaneously obtaining vocal print features and a device ID of an on-board host computer or a device ID of a mobile terminal, which is provided by a user, when the user logs in; affirming a storage unit in a cloud database according to the device ID of the on-board host computer or the device ID of a mobile terminal, which is provided by the user; when the device ID is affirmed to be in the storage unit of the cloud database, carrying out matching and retrieval on the extracted vocal print features in the storage unit; and when the vocal print features are matched successfully, logging in successfully, otherwise failing to log in. The user information is classified and stored through the device ID, so that the time for matching and retrieval of the vocal print features is greatly reduced, and the login is realized through the vocal print features of the user while a username and a login password cannot be input, so that the login safety of vehicle-mounted terminals, such as an electronic control unit, is increased, the user login is greatly facilitated, and meanwhile, the user identity can be quickly identified to realize the quick login.
Owner:FJ MOTOR GRP YUDO NEW ENERGY AUTOMOBILE CO LTD
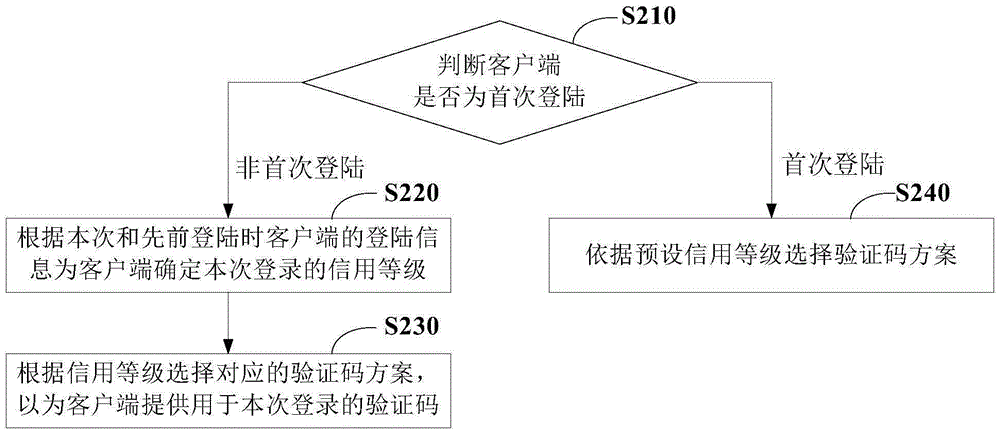
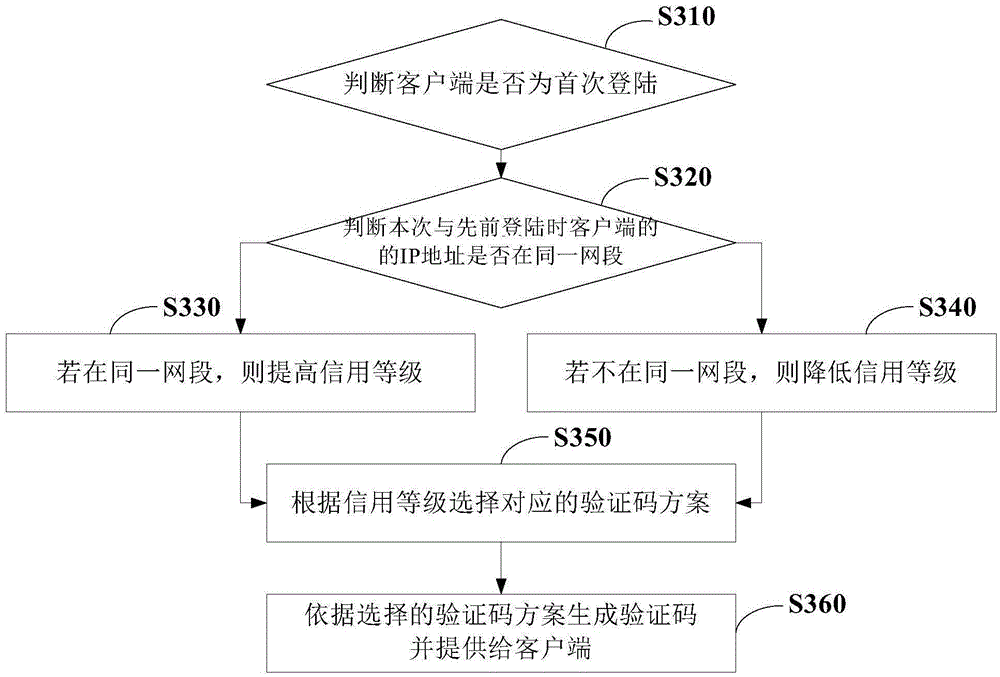
Method and device for generating verification code
The invention provides a method and a device for generating a verification code. The method comprises the steps of receiving a login request from a client, and judging whether the client logins for the first time; when the login of the client is not the first time, determining the credit grade of this time of login for the client according to the login information of the client in this time and the login information of the client in the previous time; selecting a corresponding verification code scheme according to the credit grade, thus providing the verification code for this time of login to the client. According to the method, the credit grade of the user can be determined according to the login history of the user, and the different grades of verification codes can be distributed for the users according to the credit grades of the users, thus the user security can be ensured while the user experience is enhanced.
Owner:BEIJING QIHOO TECH CO LTD +1
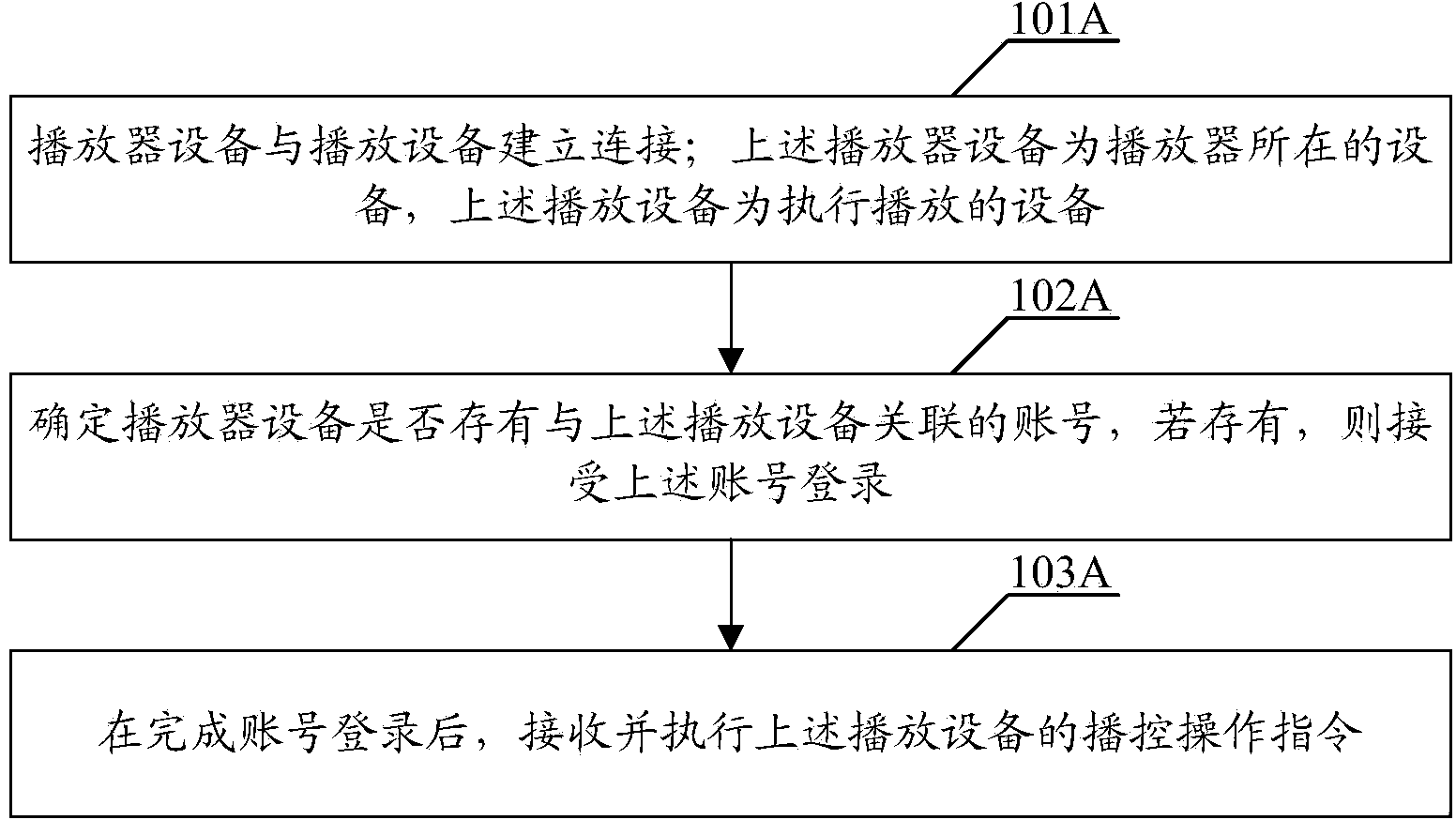
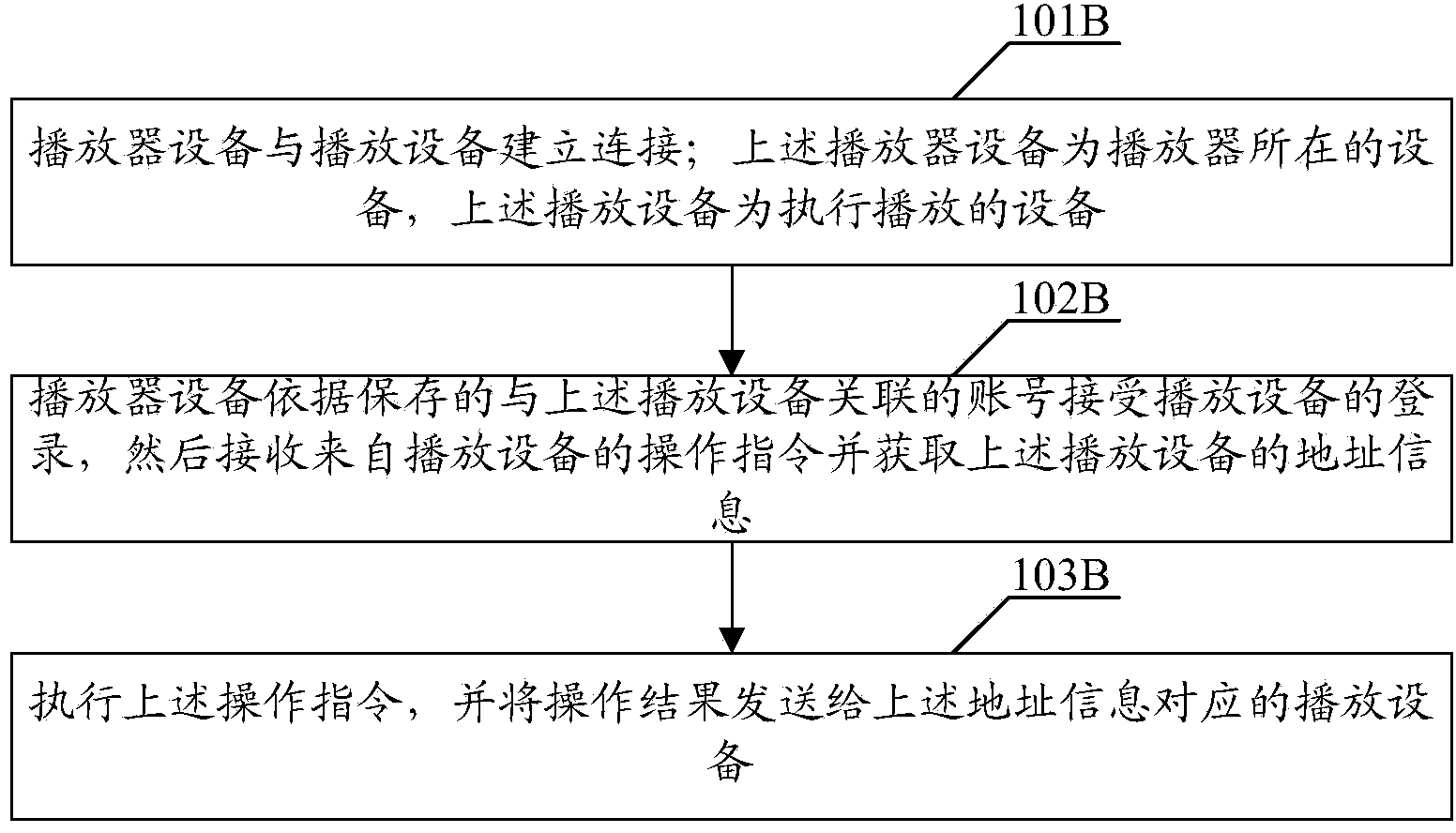
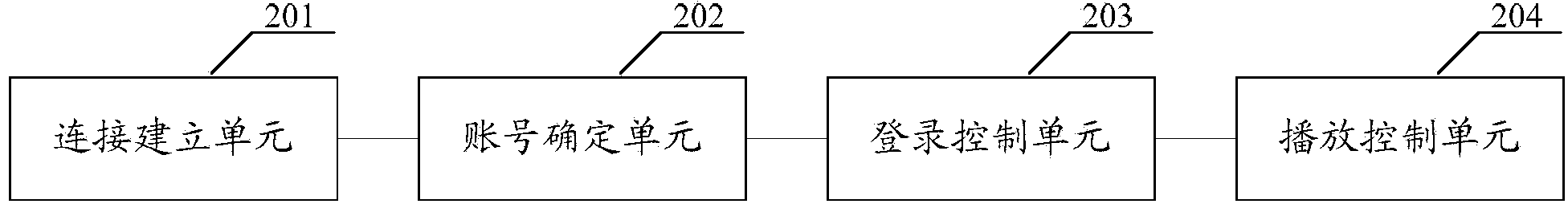
Playing control method and device
ActiveCN104091606AEasy loginQuick LoginNear-field transmissionRecord information storagePasswordComputer engineering
The embodiment of the invention discloses a playing control method and device. According to the method, a player device and a playing device are connected; the player device is the device of a player, and the playing device is a device which carries out playing; whether the player device has an account associated with the playing device is determined; if the player device has the account associated with the playing device, the login of the account is accepted; and after account login is completed, a broadcast control operation instruction of the playing device is received and executed. After the player device and the playing device are connected, whether the associated account is saved by the player device is determined. If the associated account is saved, the login of the account is directly accepted. A user does not need to input an account password. Convenient and rapid login is realized. The player device can save multiple associated accounts, which is convenient for the login of multiple users.
Owner:GUANGZHOU KUGOU TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com