Patents
Literature
79 results about "Fully qualified domain name" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A fully qualified domain name (FQDN), sometimes also referred to as an absolute domain name, is a domain name that specifies its exact location in the tree hierarchy of the Domain Name System (DNS). It specifies all domain levels, including the top-level domain and the root zone. A fully qualified domain name is distinguished by its lack of ambiguity: it can be interpreted only in one way.
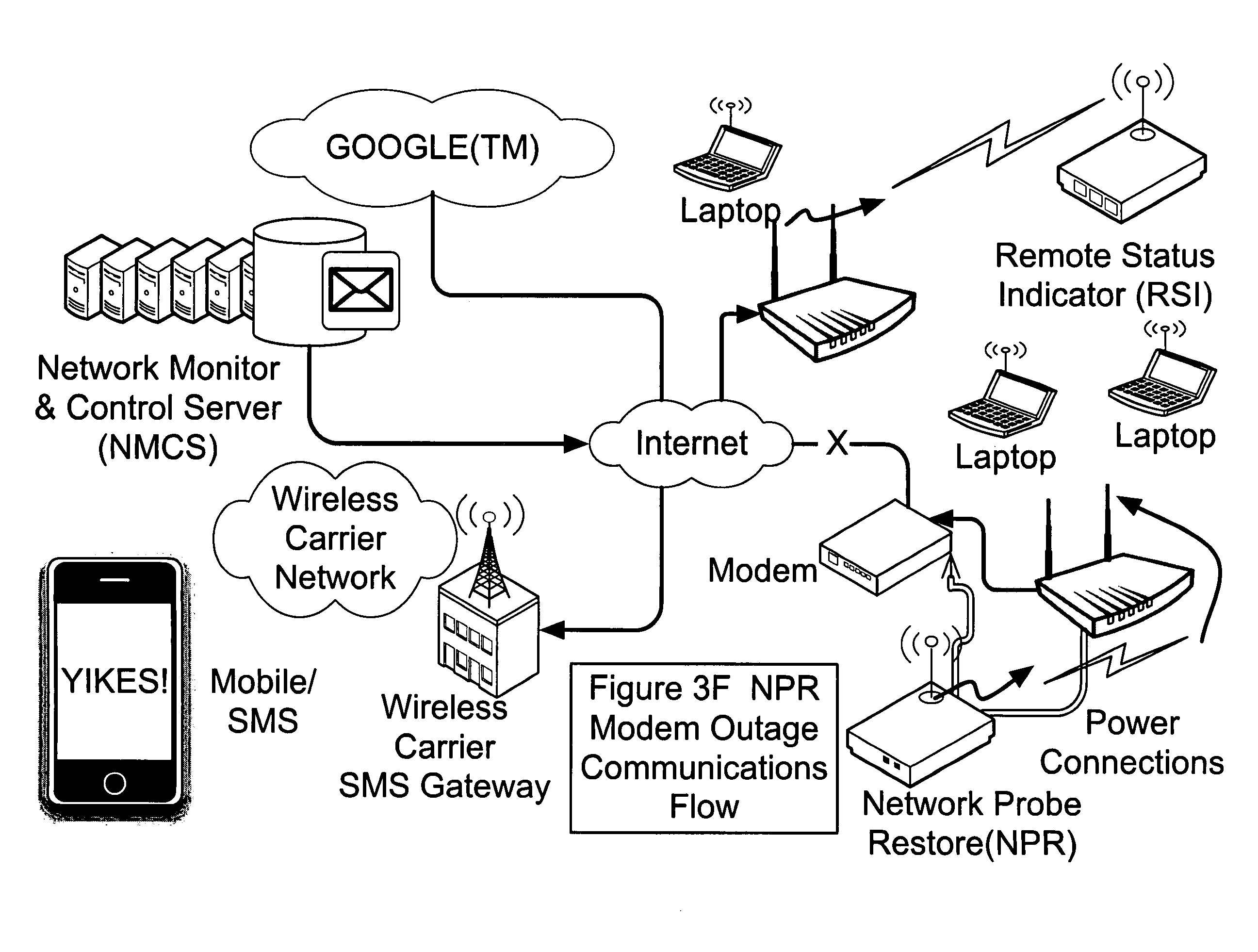
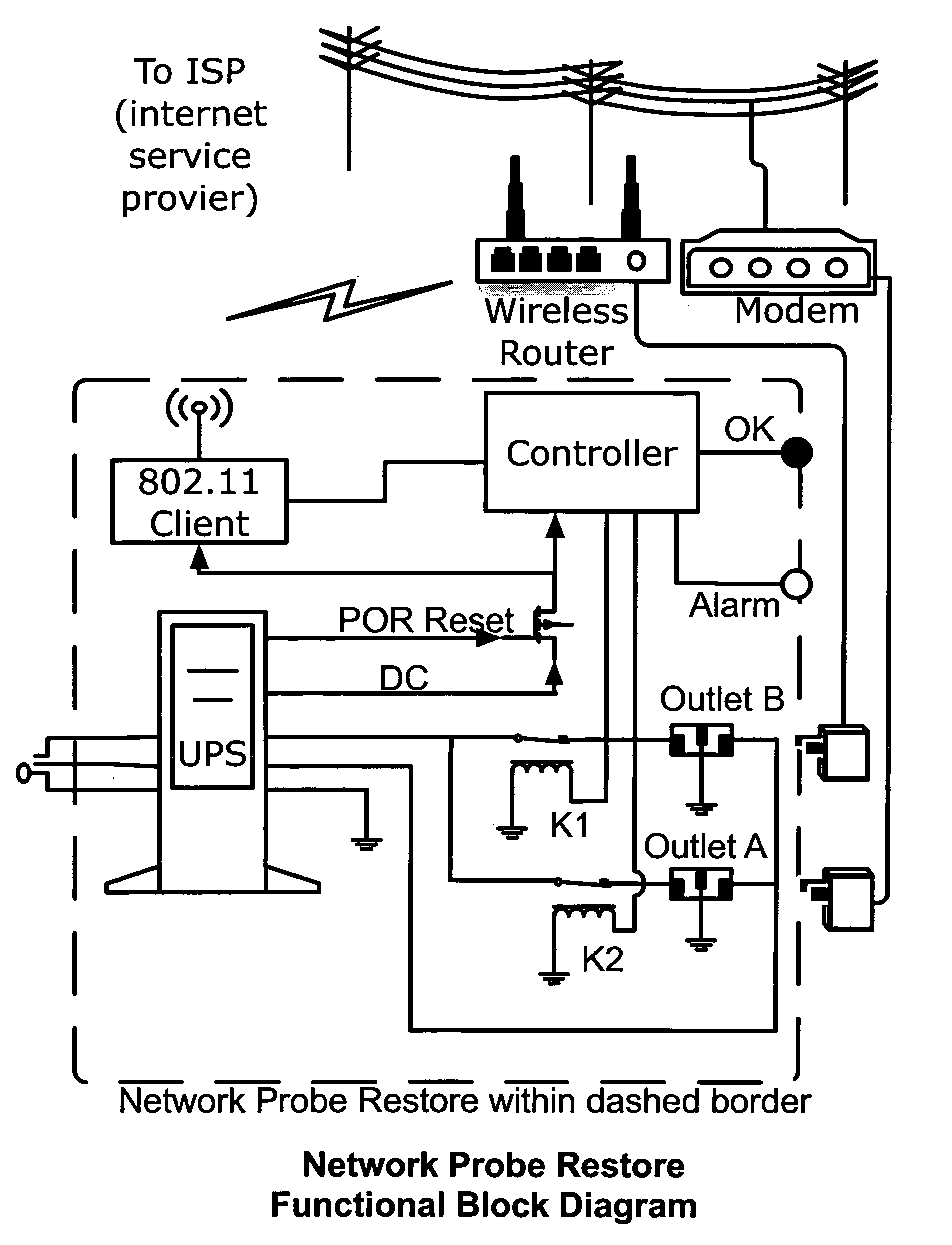
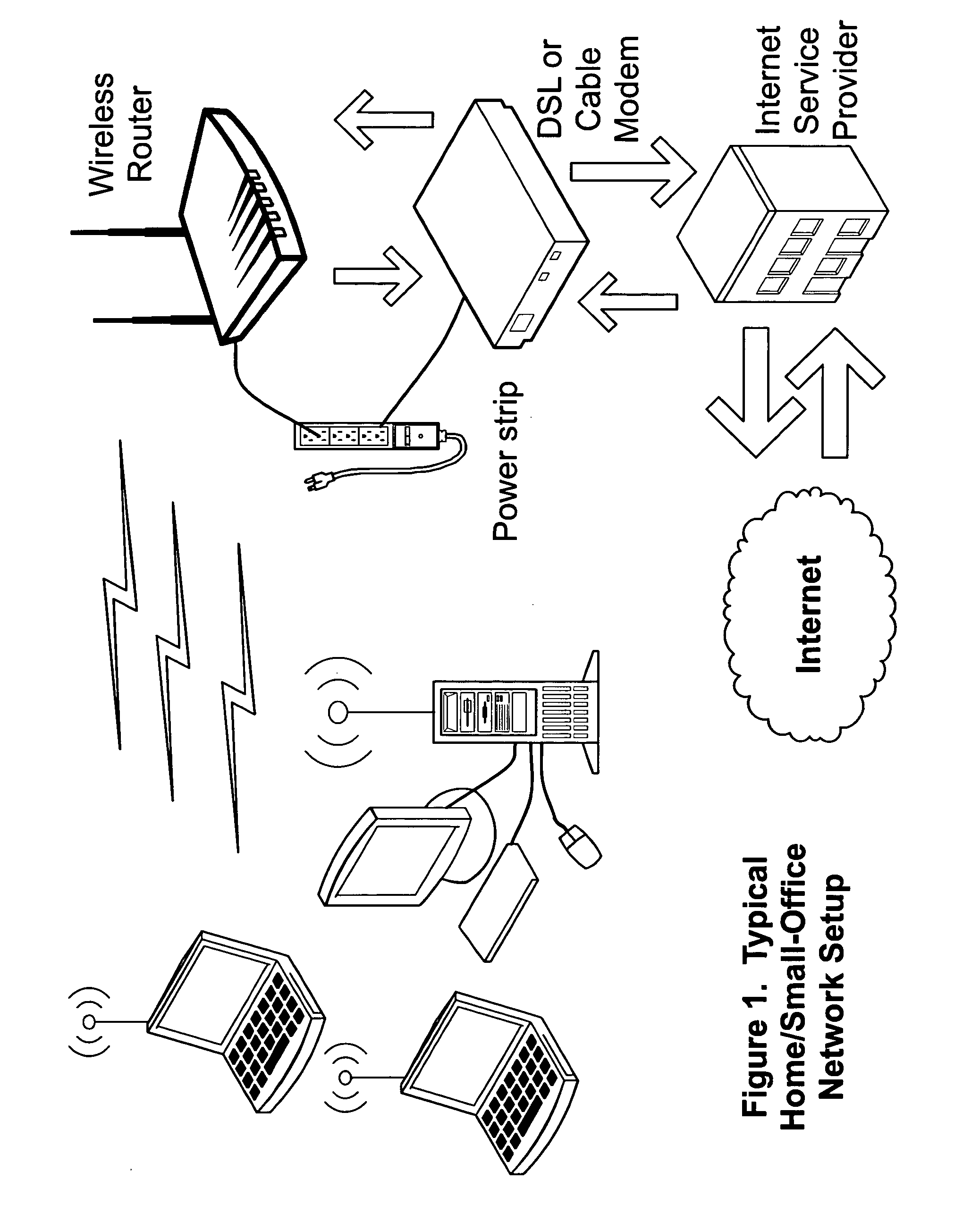
Systems, devices, agents and methods for monitoring and automatic reboot and restoration of computers, local area networks, wireless access points, modems and other hardware
ActiveUS20090013210A1Data switching networksRedundant operation error correctionDomain nameFully qualified domain name
An embodiment of the invention is a client on a local area network that periodically and automatically evaluates its physical connectivity with the local area network, exercises local-network services such as DHCP, and verifies Internet connectivity and function by pinging one or more numerically specified IP addresses and by pinging one or more IP addresses specified by an FQDN (Fully Qualified Domain Name) known to the assigned DNS servers. An embodiment of the invention may include a plurality of client elements monitoring one or more networks. Functionality according to embodiments of the invention can send notices, automatically initiate action, and otherwise assist in, among other things, remote monitoring and administration of networks, and particularly wireless networks.
Owner:SAND HLDG LLC
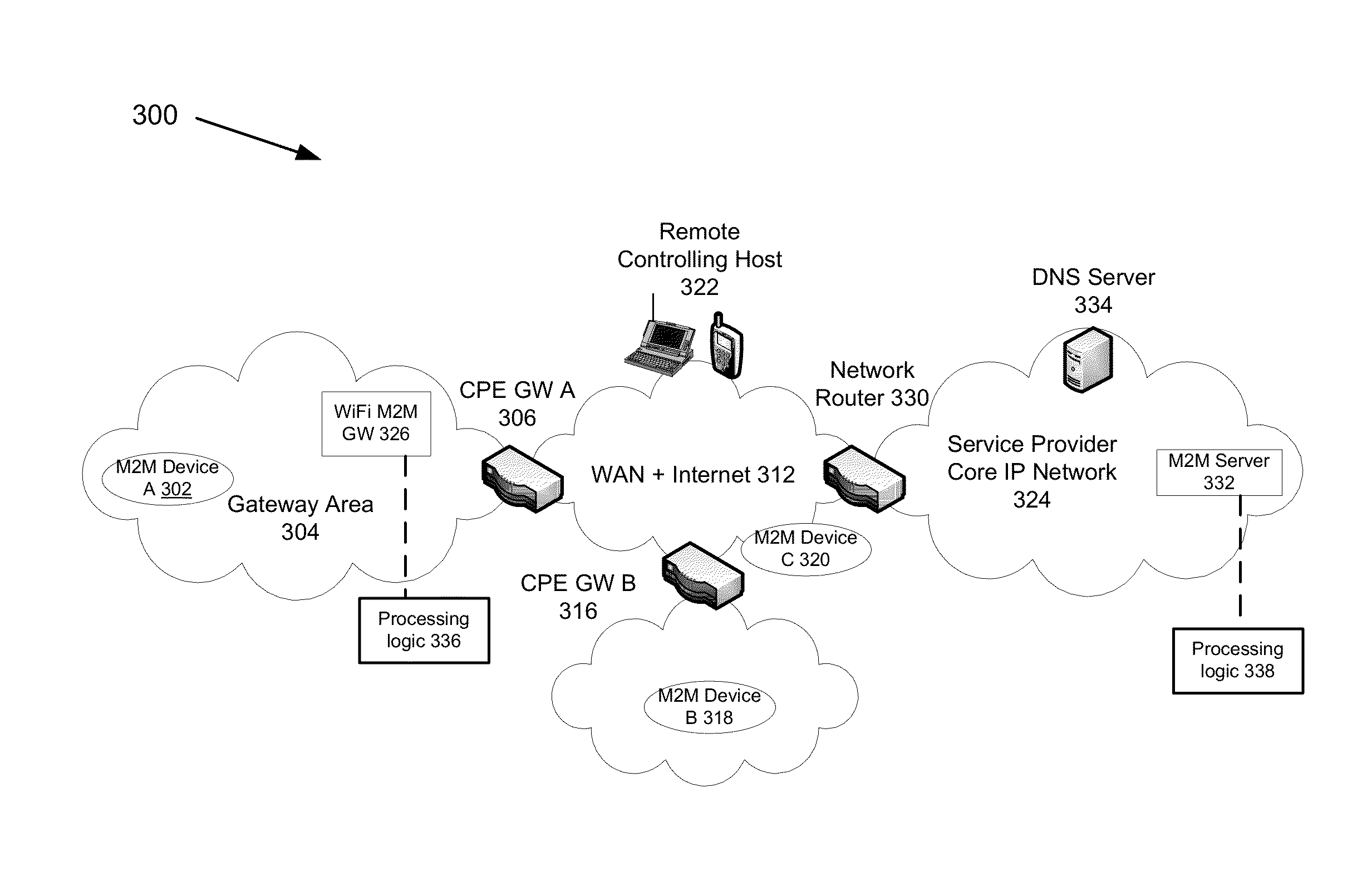
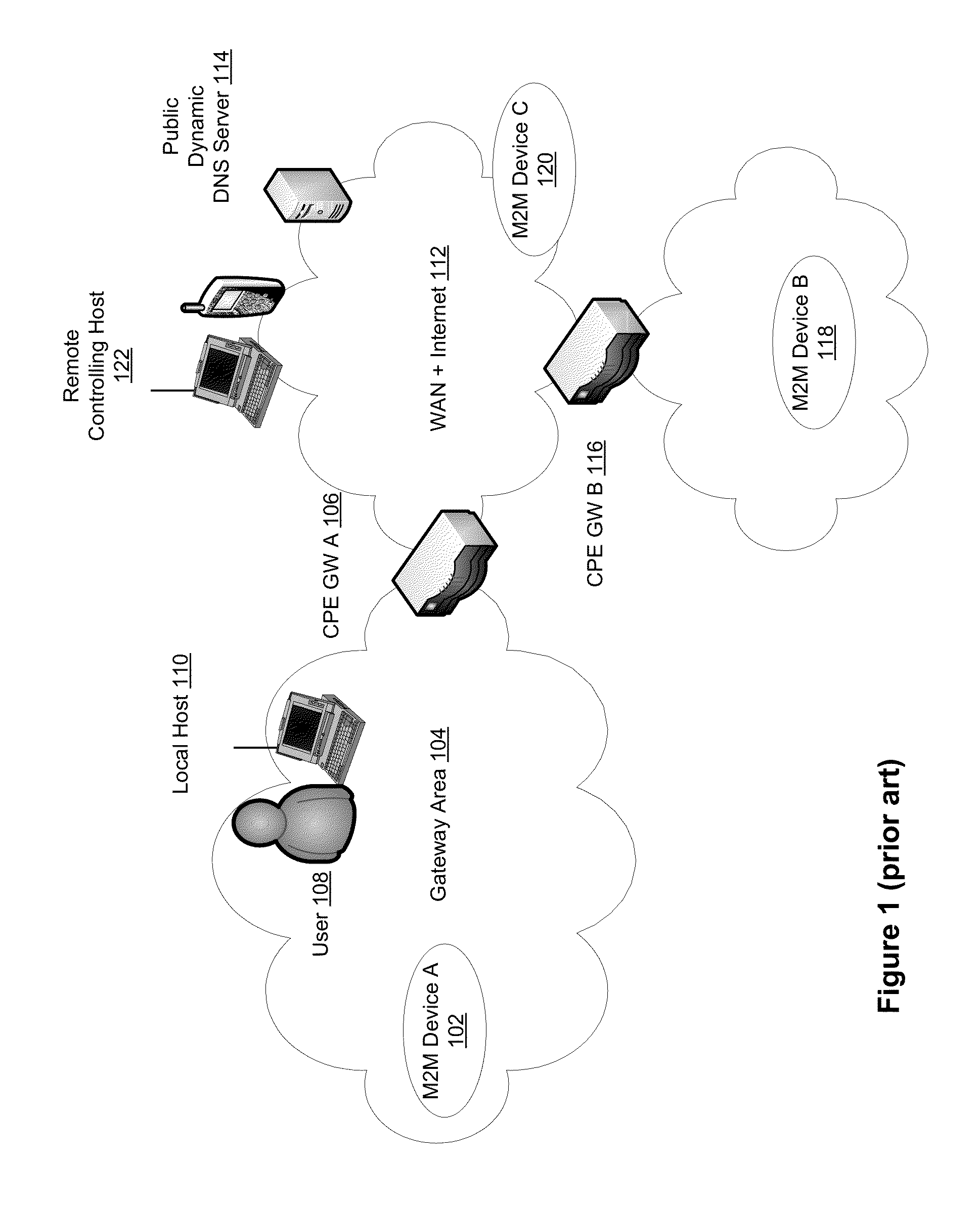
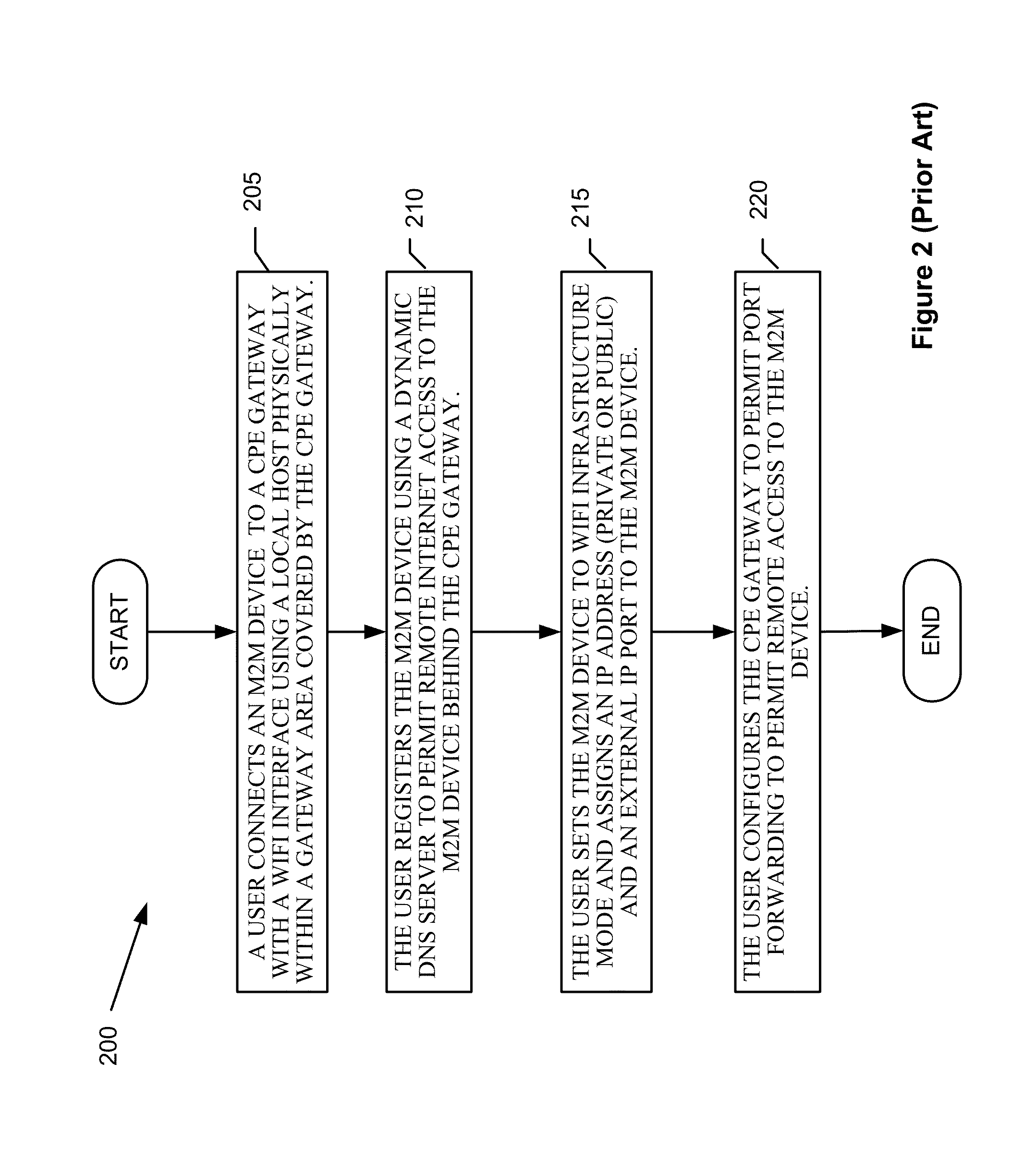
Automatic provisioning of an m2m device having a WIFI interface
InactiveUS20130094444A1Facilitate fast responseService provisioningNetwork topologiesDomain nameFully qualified domain name
A method for automatically provisioning a WiFi-equipped machine-to-machine (M2M) device is disclosed. A WiFi M2M gateway identifies a WiFi network identifier broadcast by a powered-on M2M device in WiFi ad hoc mode through a scanning procedure and joins the ad hoc network defined by the M2M device. The WiFi M2M gateway obtains device information (e.g., MAC address) of the M2M device. The WiFi M2M gateway transmits a command to the M2M device to switch from ad hoc mode to infrastructure mode. The WiFi M2M gateway registers the M2M device with an M2M server associated with a service provider based on the device information of the M2M device. The WiFi M2M gateway receives a fully qualified domain name (FQDN) associated with the M2M device from the M2M server.
Owner:APPLIED COMMUNICATION SCIENCES
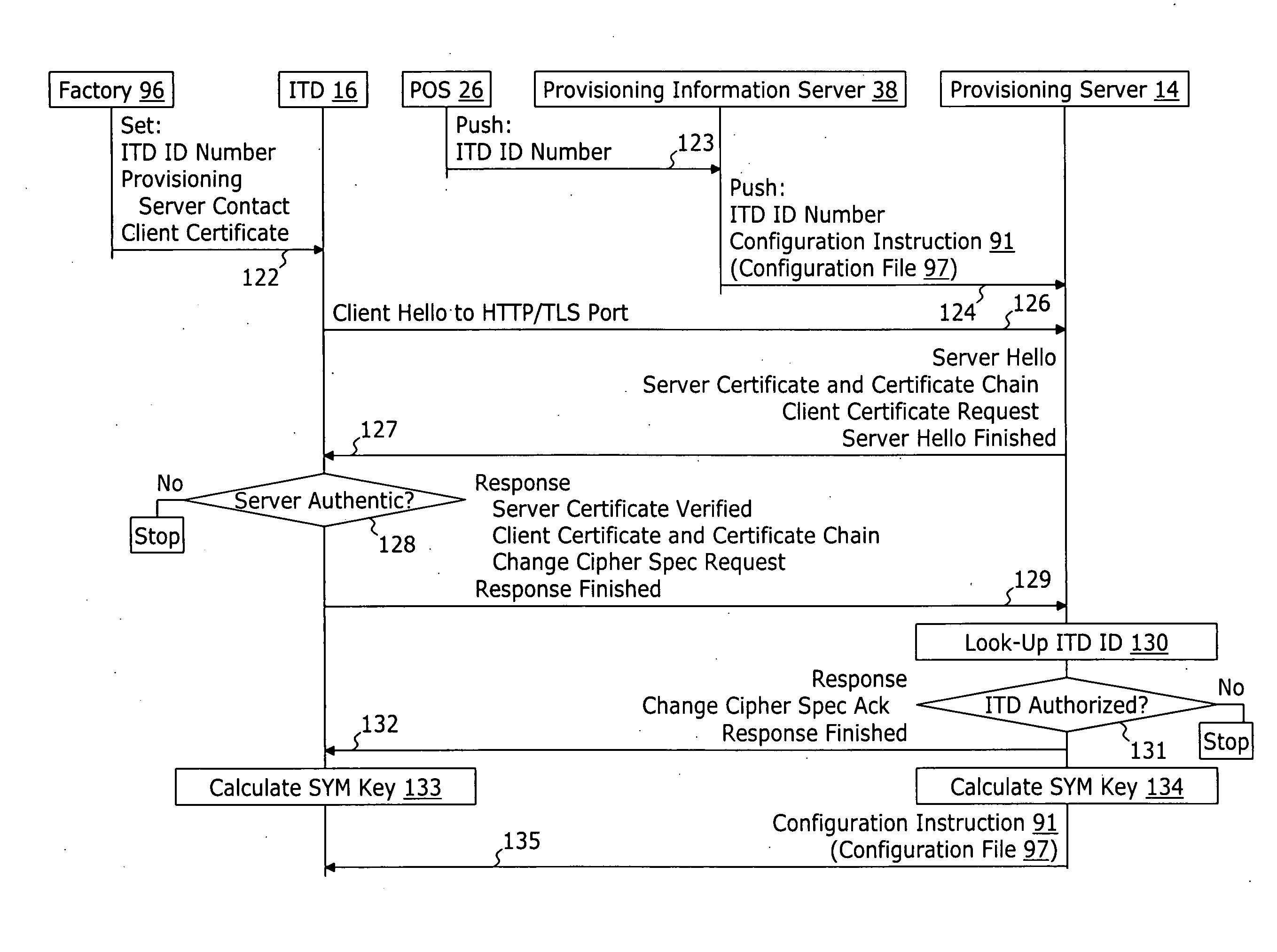
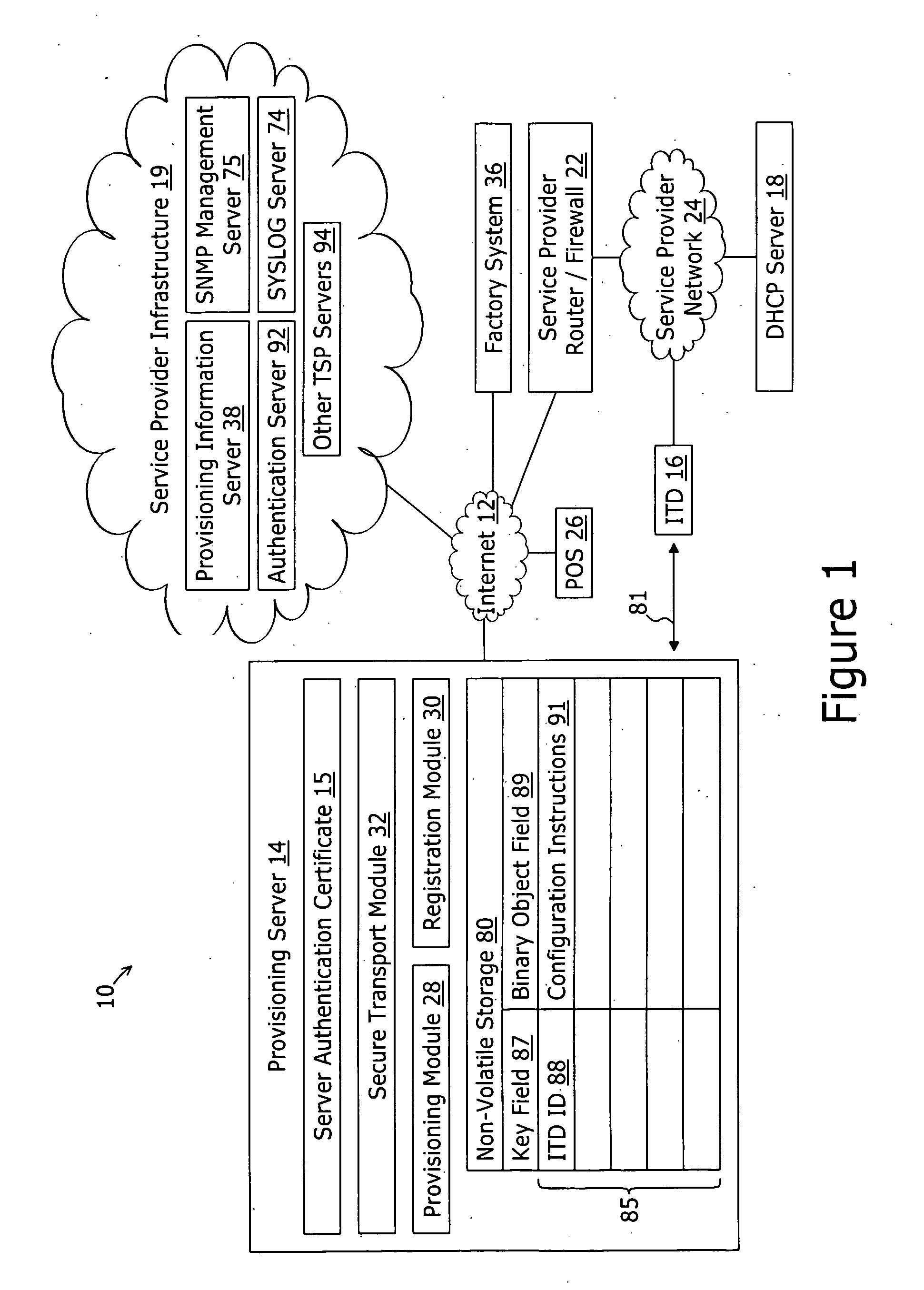
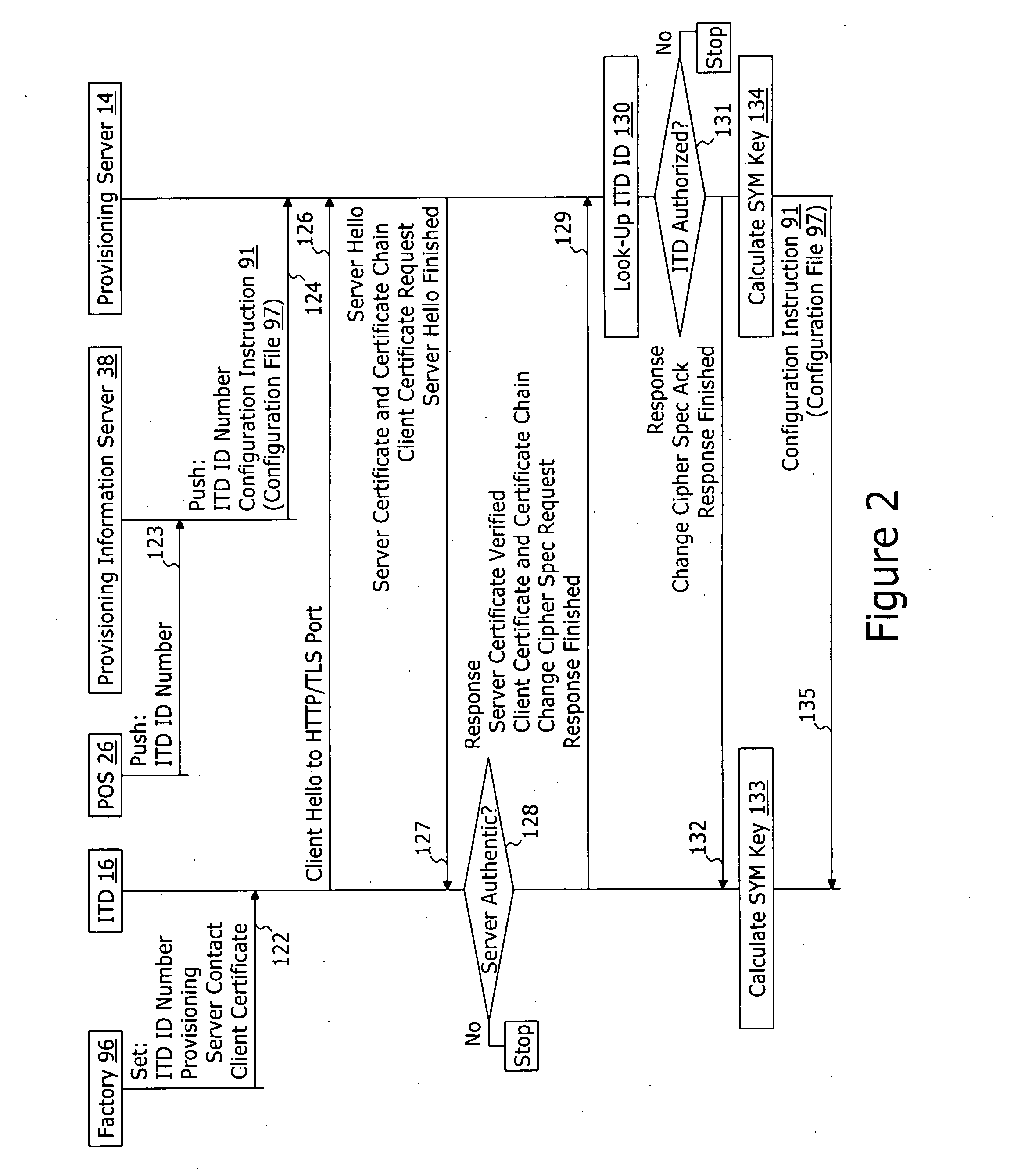
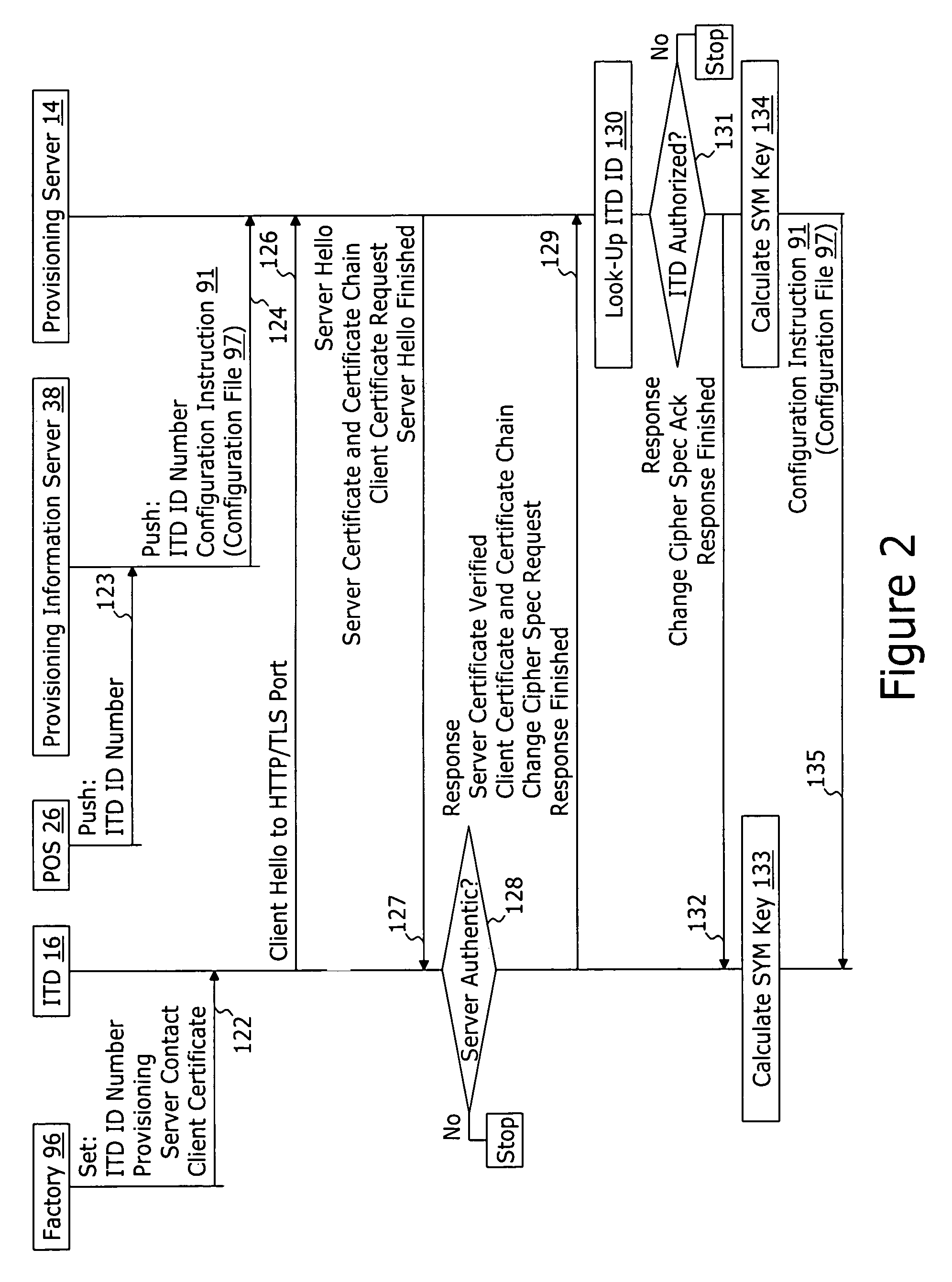
System and method for securely providing a configuration file over and open network
ActiveUS20060174018A1User identity/authority verificationUnauthorized memory use protectionDomain nameNetwork connection
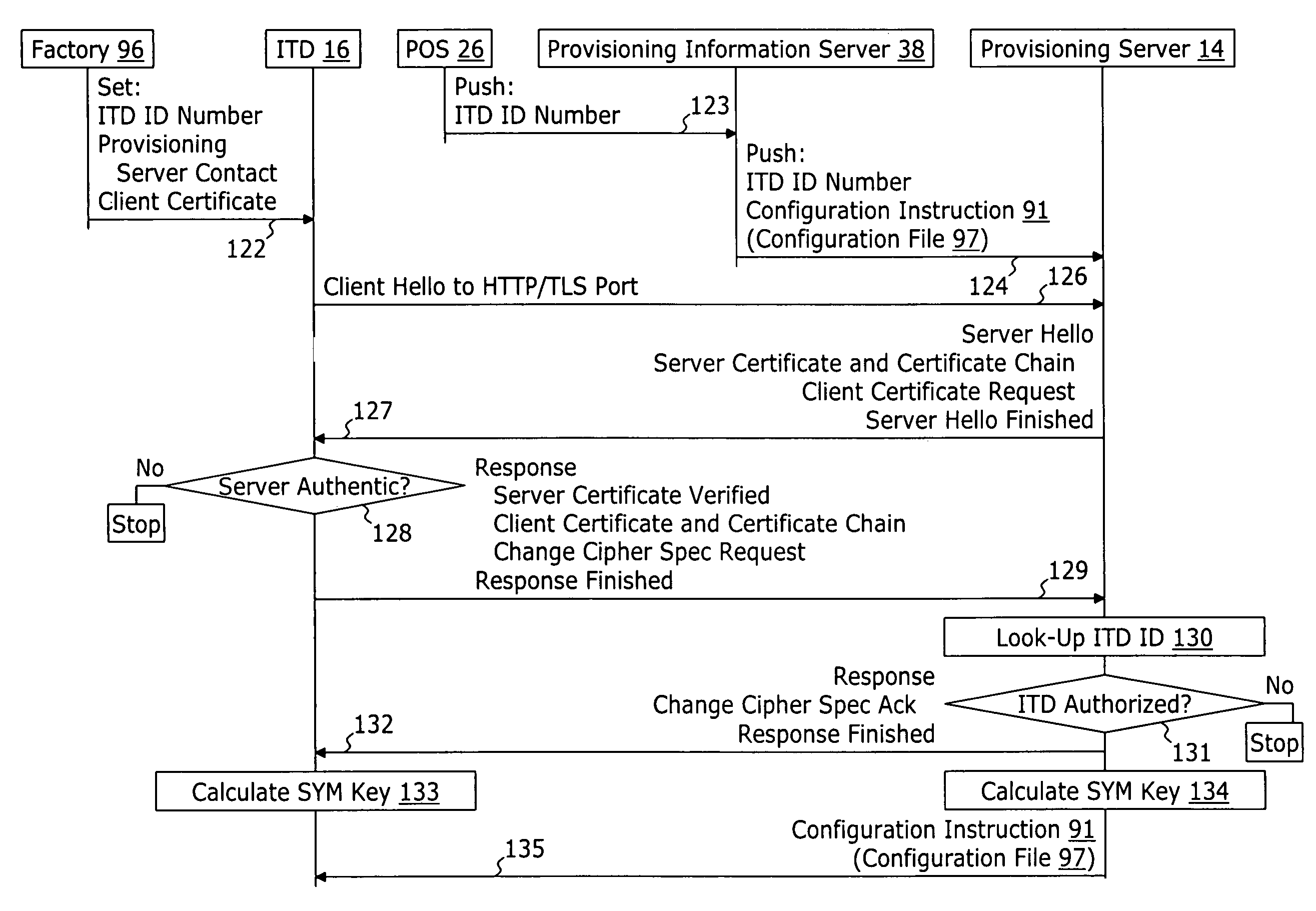
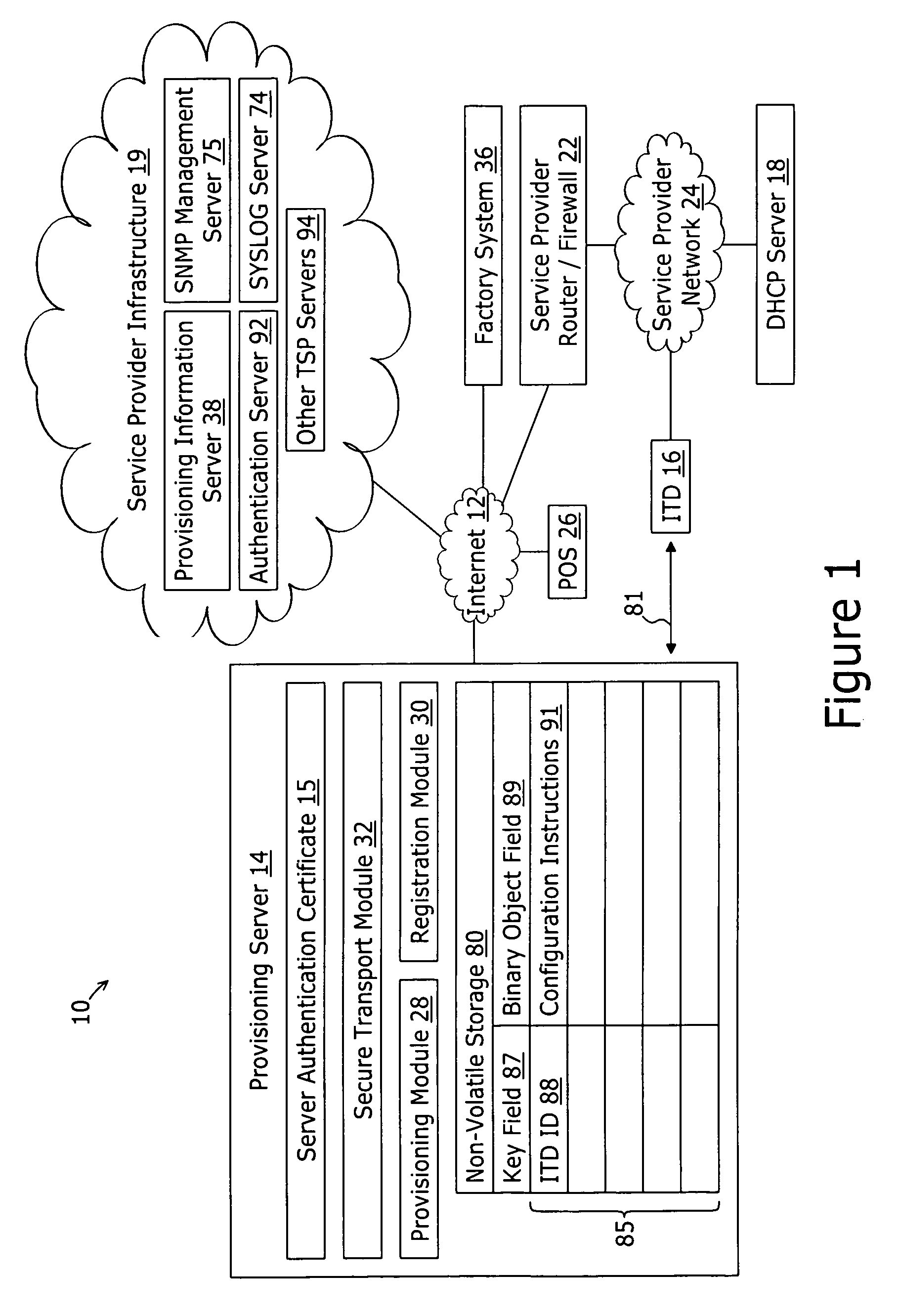
A method for securely provisioning a device for operation within a service provider infrastructure over an open network comprises the device establishing physical and data link layer network connections for communication on at least a subnet of the open network and obtaining a network configuration data such as an IP address and a subnet mask from a provisioning server that responds to a network configuration broadcast request. A device establishes a secure hypertext transport protocol connection to a first provisioning server that corresponds to one of: i) and IP address and port number; and ii) a fully qualified domain name stored in a non-volatile memory of the device. After mutual authentication, the first provisioning server provides at least one of: i) a configuration file; and ii) identification of a second provisioning server and a cipher key through the secure connection. If the first provisioning server provided identification of a second provisioning server, the device establishes a transport connection to the identified second provisioning server. The second provisioning server provides an encrypted file which, when decrypted using the cipher key yields the configuration information needed by the device for operation with the service provider infrastructure.
Owner:INOMEDIA
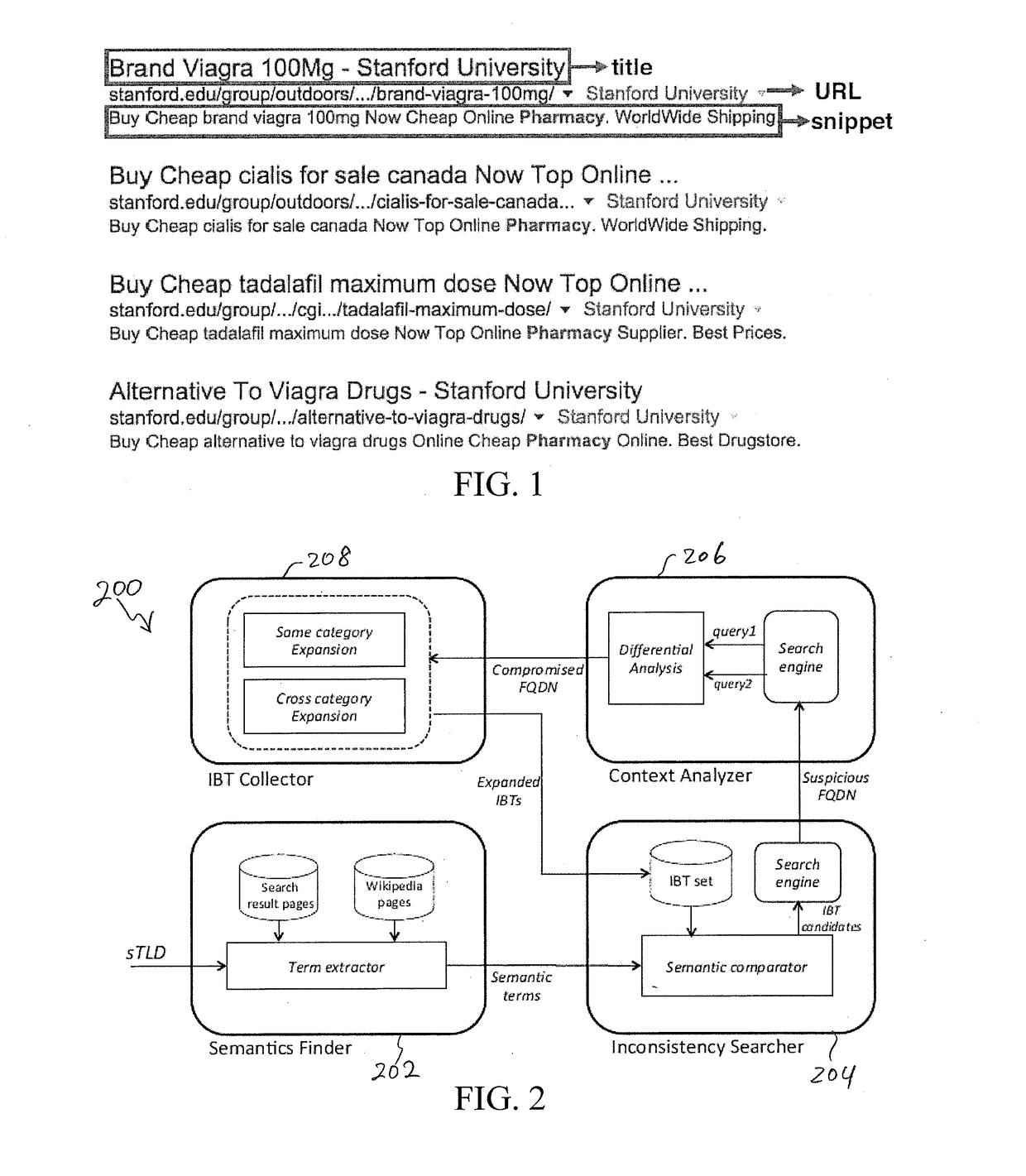
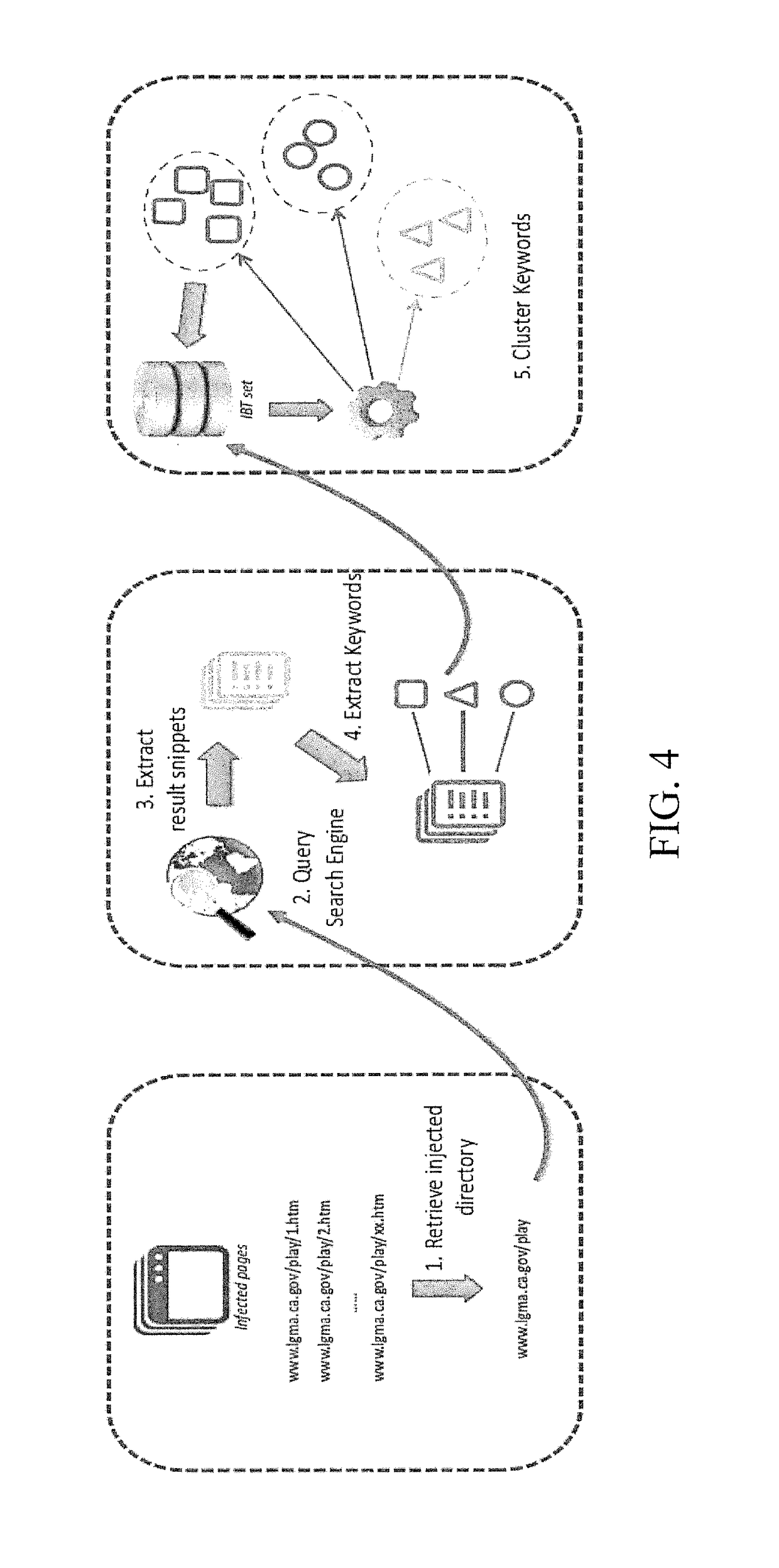
Systems and methods for detection of infected websites
ActiveUS20180375896A1Efficient detectionRaise the barSemantic analysisComputer security arrangementsFully qualified domain nameSemantics
System and method for detecting an infected website are disclosed. A semantic finder receives top-level domains and identifies keywords of the top-level domains representing a predetermined semantics. The keywords are compared with irrelevant bad terms to find at least one irrelevant term. An inconsistency searcher searches the top-level domains and detects at least one fully-qualified domain name carrying the at least one irrelevant term. A context analyzer evaluates context information associated with the irrelevant term, identifies at least one frequently-used term identified in the context information, and determines whether the at least one frequently-used term is unrelated to a generic content of the at least one fully-qualified domain name An irrelevant bad term collector extracts the at least one frequently-used term unrelated to the generic content and adds the extracted frequently-used term to an irrelevant bad term list for detecting the infected website.
Owner:INDIANA UNIV RES & TECH CORP +1
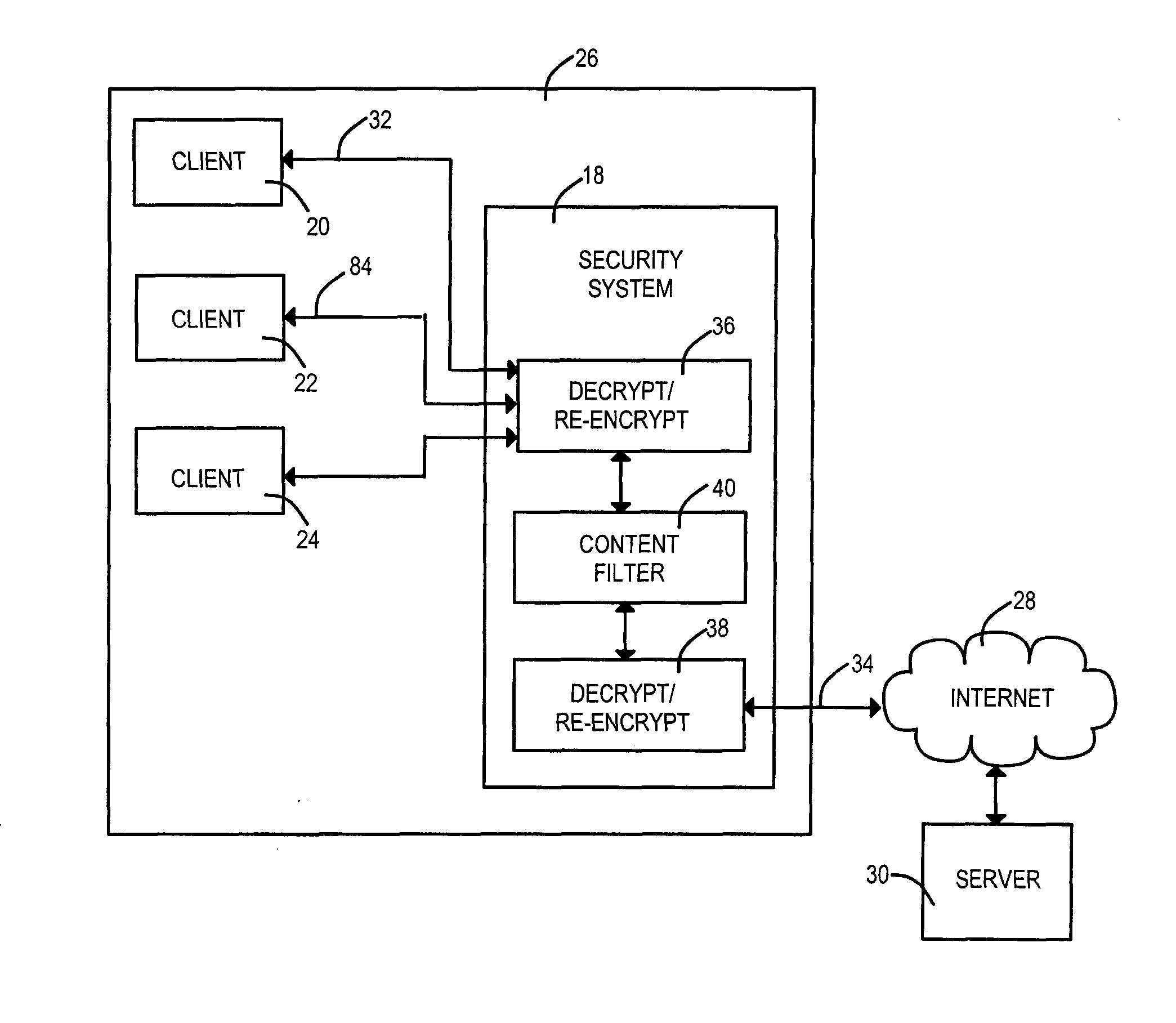
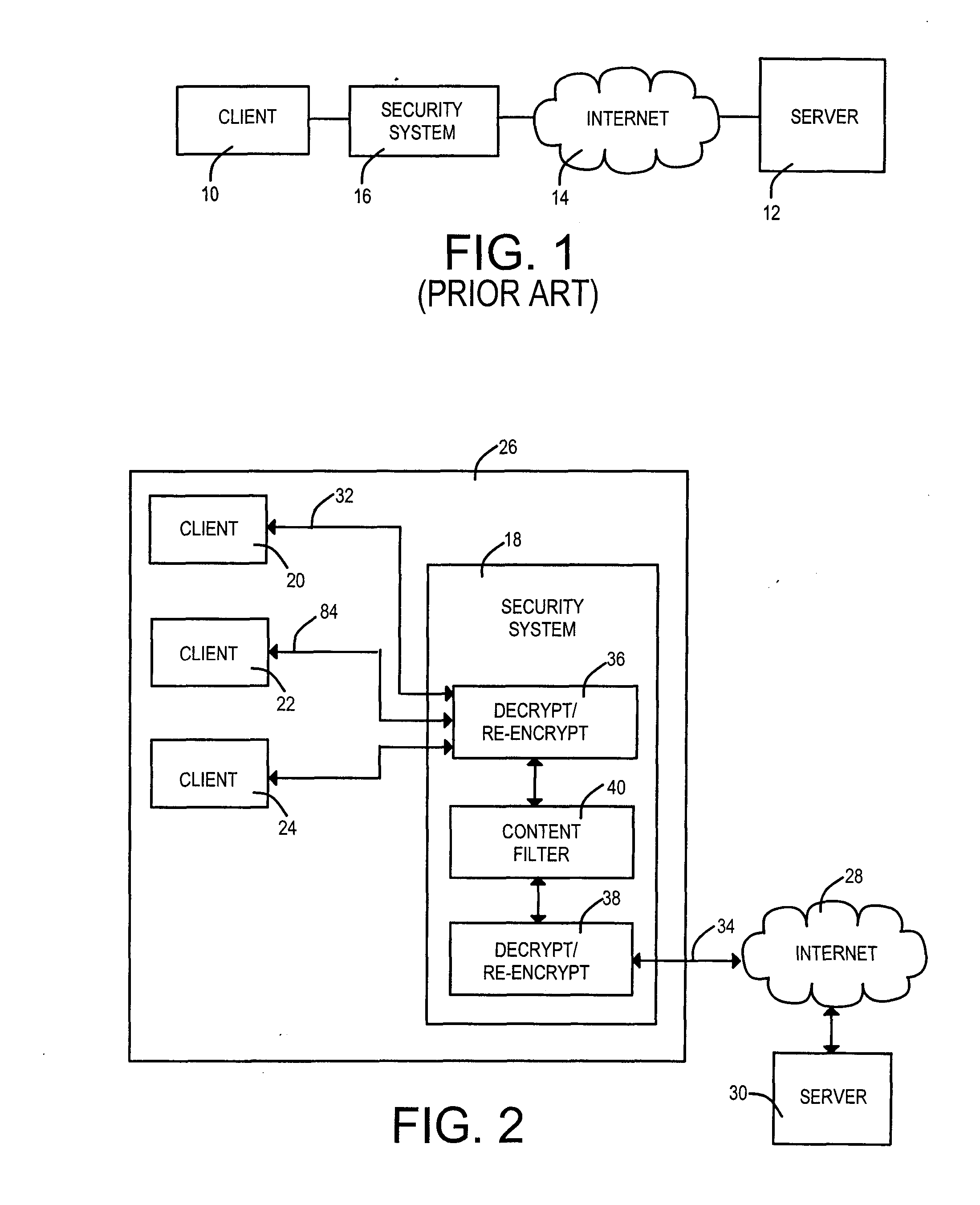
Tandem encryption connections to provide network traffic security method and apparatus
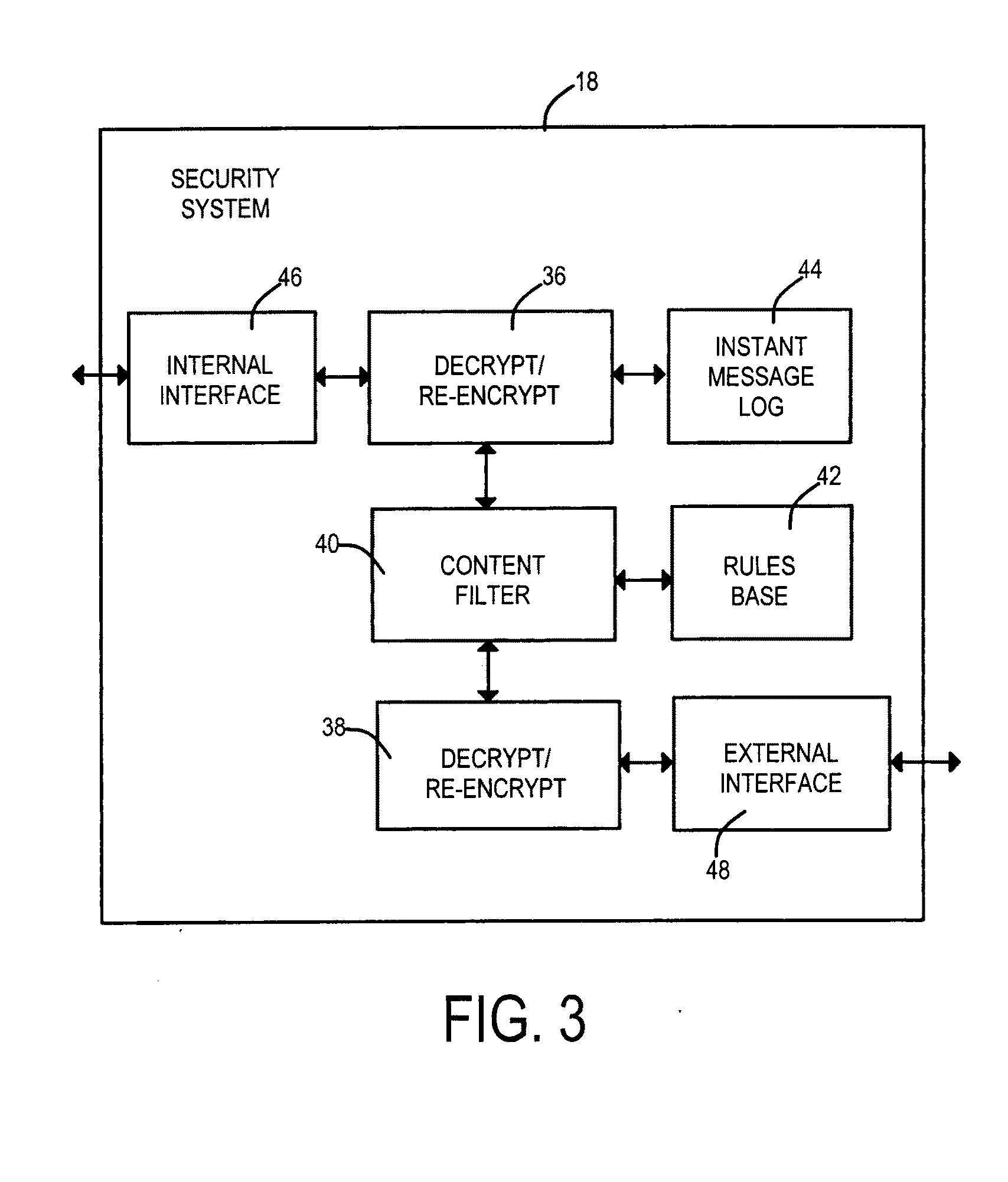
Security measures are applied to encrypted data exchanges by enabling content decryption, rule application, and content re-encryption at a network location. A certificate, self-signed or authenticated by an official Certificate Authority is obtained for and installed within the secure proxy apparatus. A link to a secure page is replaced with a link to a page having a fully qualified domain name of the proxy apparatus as the suffix. An encrypted session between the client is established between the client and the proxy apparatus without deceit in the later case. A first encryption-enabled connection is established from the first node to a content filter, while a second encryption-enabled connection is established from the content filter to the second node. Following decryption, a determination is made as to whether the content includes Undesired Data. Restricted material is blocked, while unrestricted material is re-encrypted and delivered to the destination node. For a self-signed certificate, the destination node comprises a private security system-signed root certificate installed in the destination node's Trusted Root Certification Authorities certificate store. In another aspect of the invention, at least one of encrypted Instant Messages, e-mail messages and web pages are decrypted and recorded at a location between sources and destinations of the transmissions. The look and feel is maintained of a single encrypted link between the requestor and the external source by the inventive use of a wildcard certificate within the network local to the requestor.
Owner:BARRACUDA NETWORKS
Computer network with unique identification
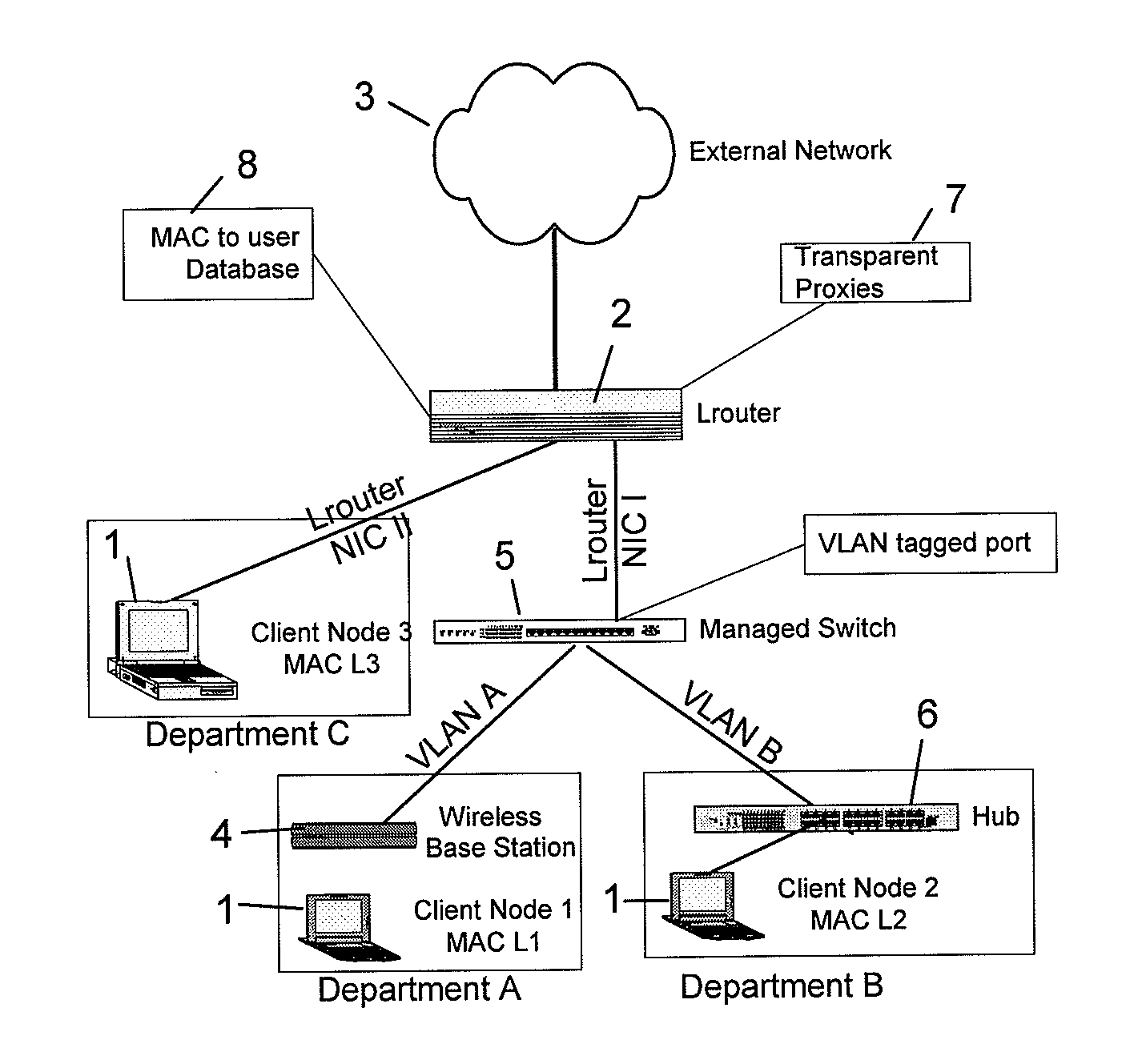
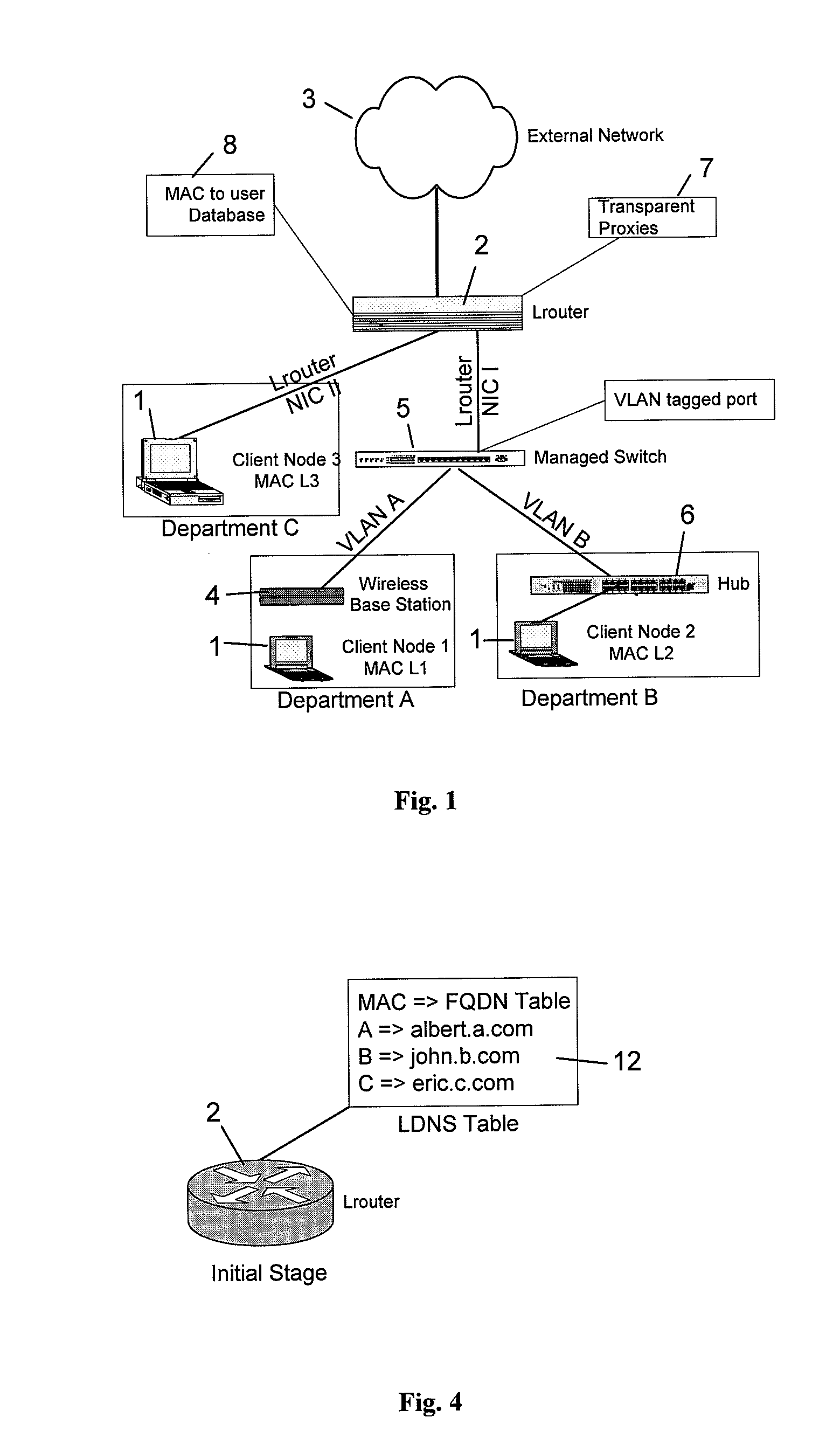
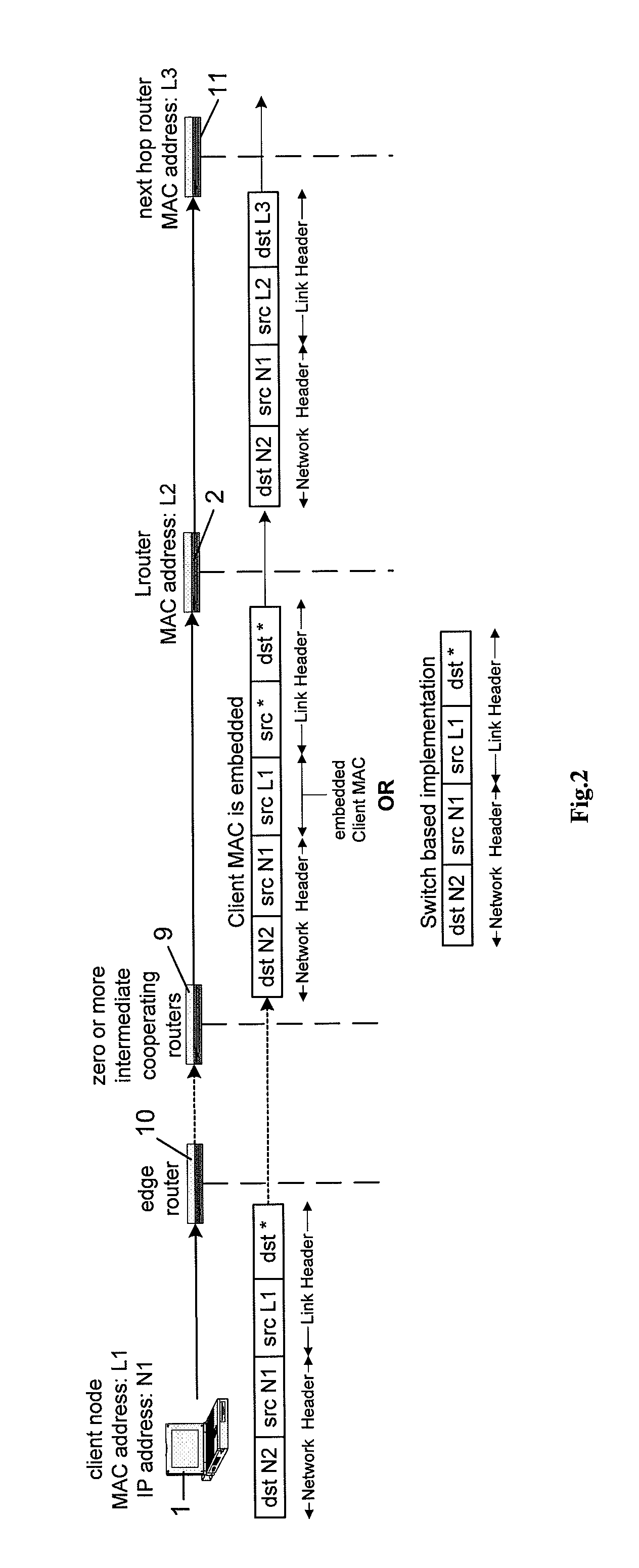
InactiveUS8005981B2Function increaseMultiple digital computer combinationsData switching networksDomain nameComputer network server
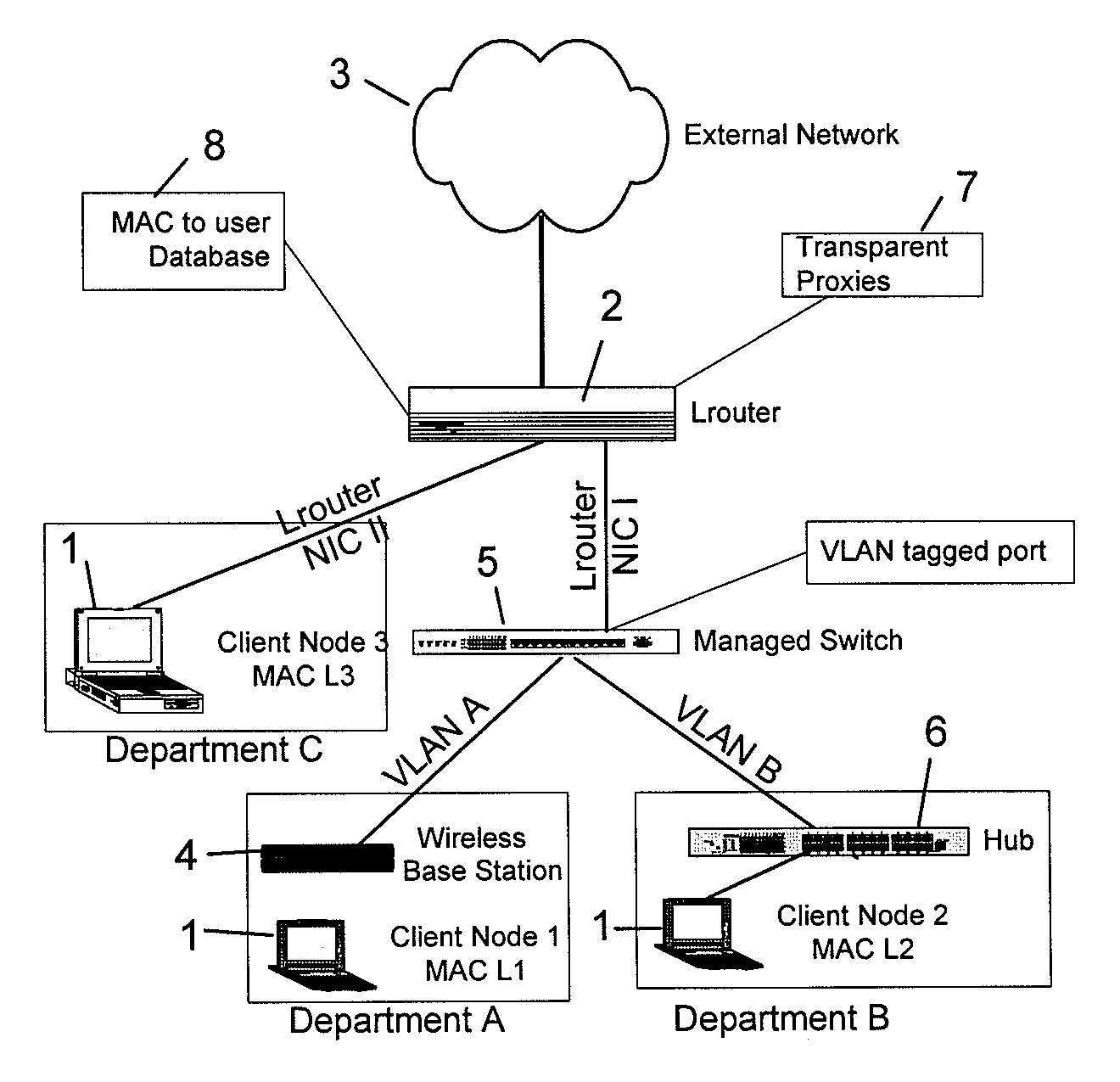
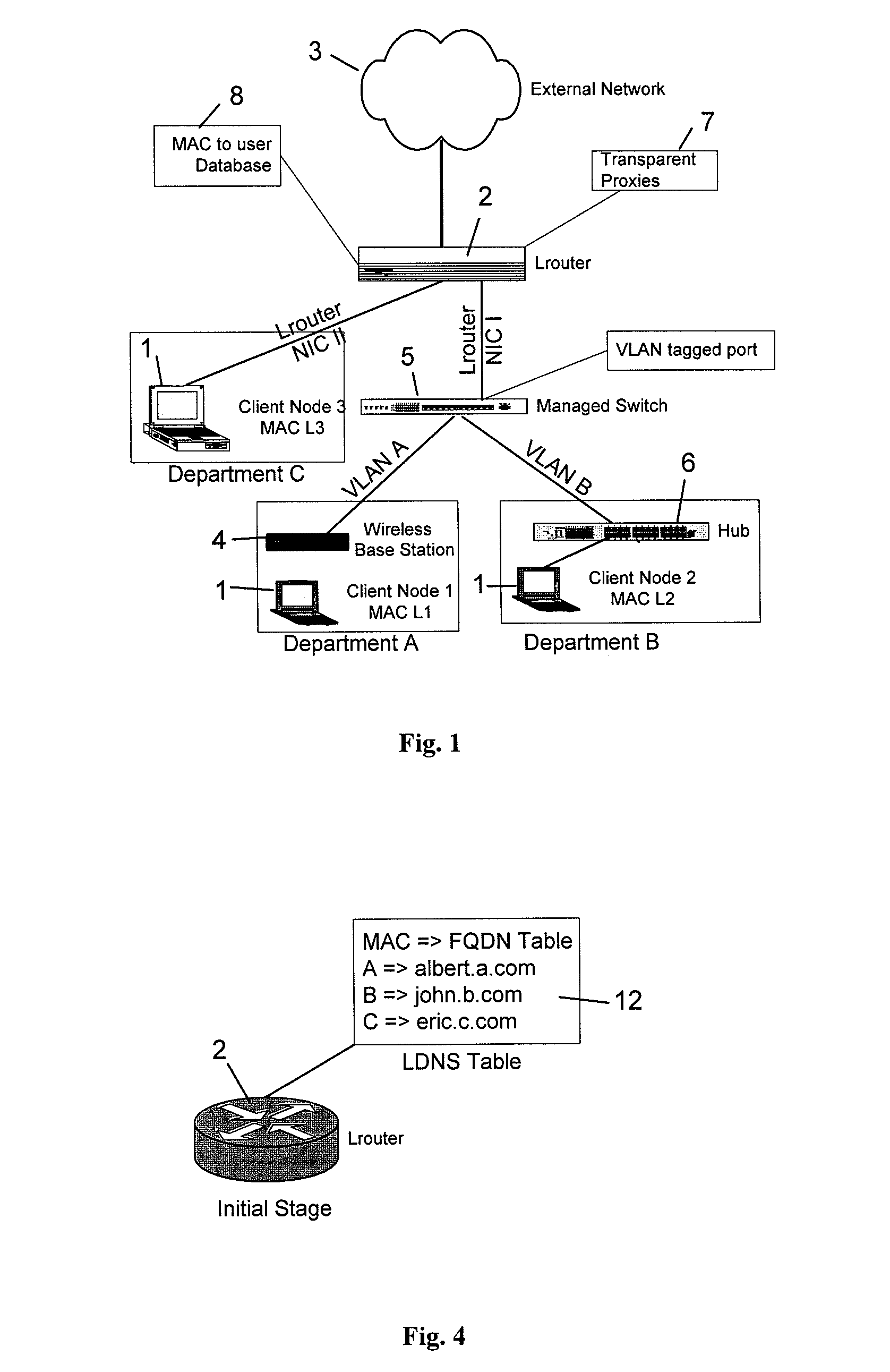
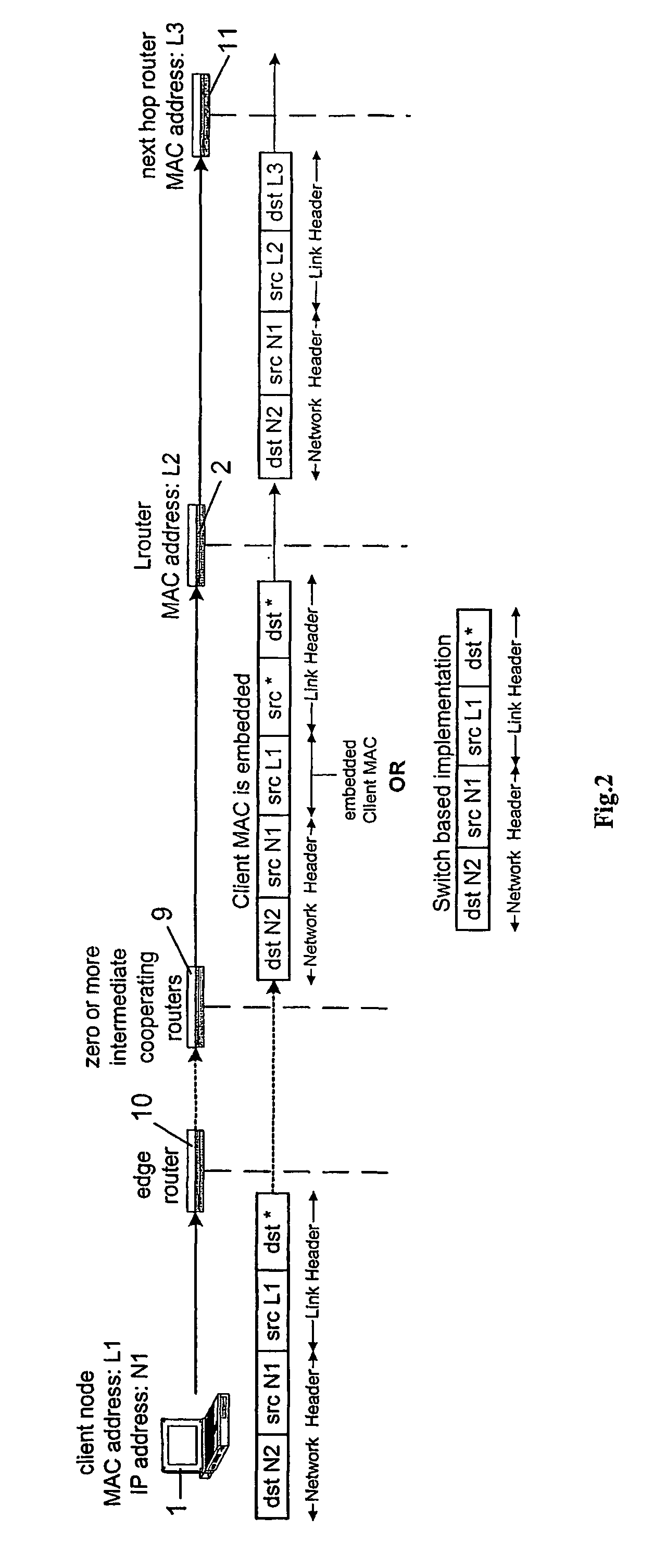
A computer network is described in which the data link layer address, e.g., MAC address, of the network cards of client nodes are used to uniquely identify the nodes in the provision of network to application layer services. A link layer aware router may determine the MAC address of a client node from a data packet transmitted by the client node, and determines the services to provide to the user, e.g., a proxy redirect of the packet, based on a database of client node MAC addresses to user attributes. By determining MAC addresses, the router can also identify unregistered MAC addresses, and can forward an HTTP request by an unregistered user to a remote configuration web page for registering the user, or to a security warning web page. The router may also support Network Address Translation and Domain Name System services using the MAC addresses, with a fully qualified domain name, hostname, or the like, being assigned to the MAC addresses.
Owner:ADVANCED NETWORK TECH LAB
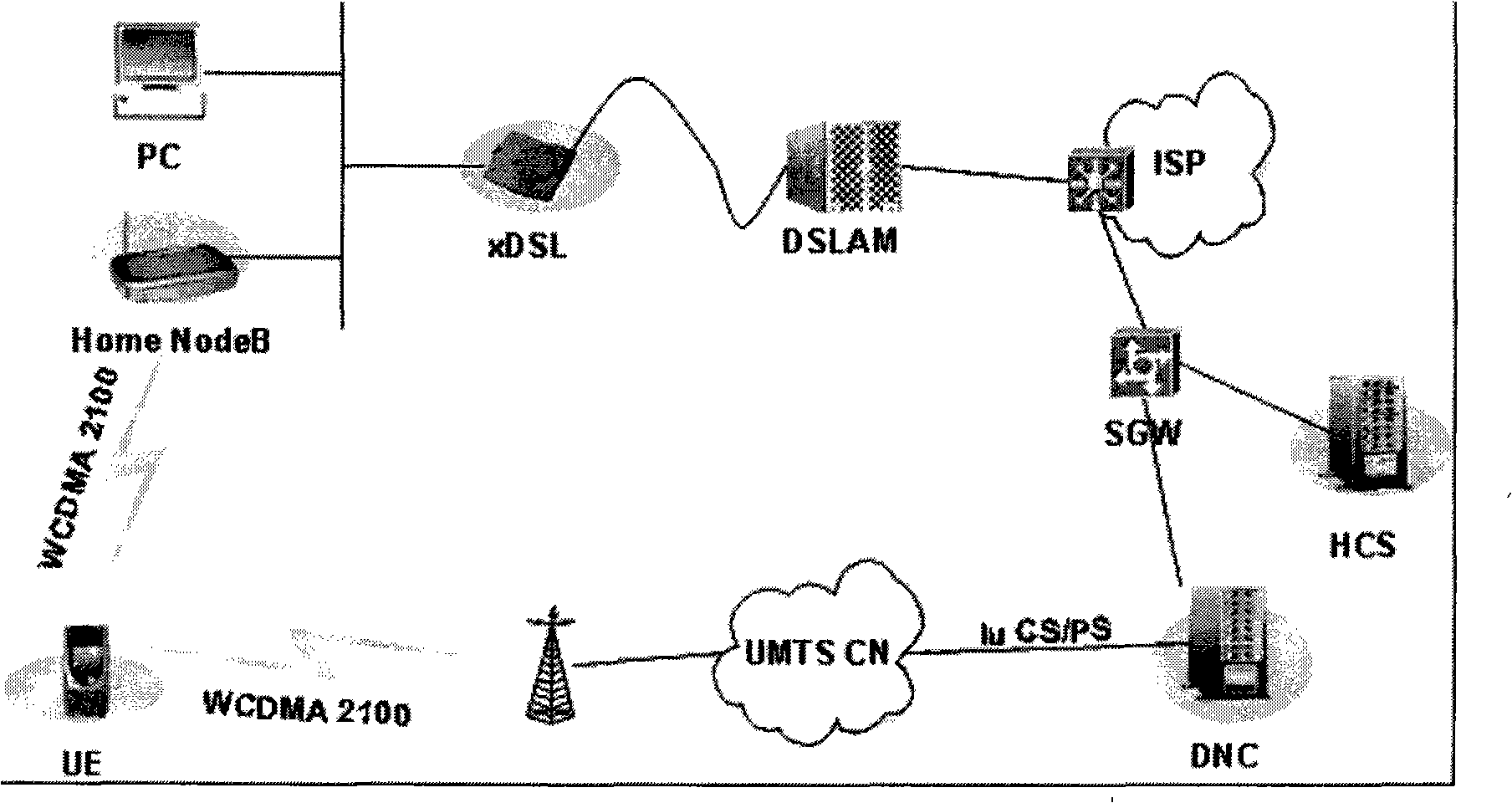
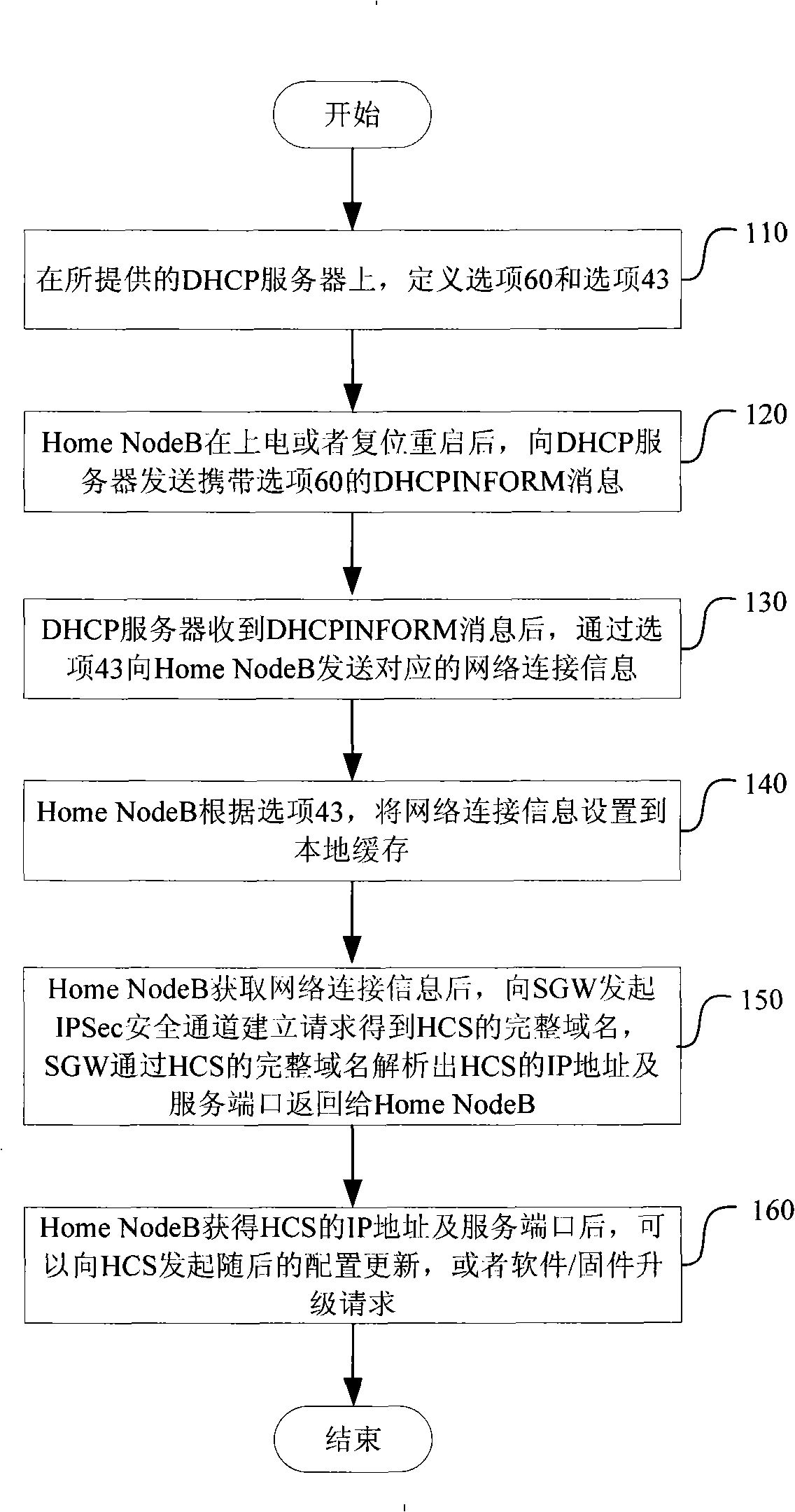
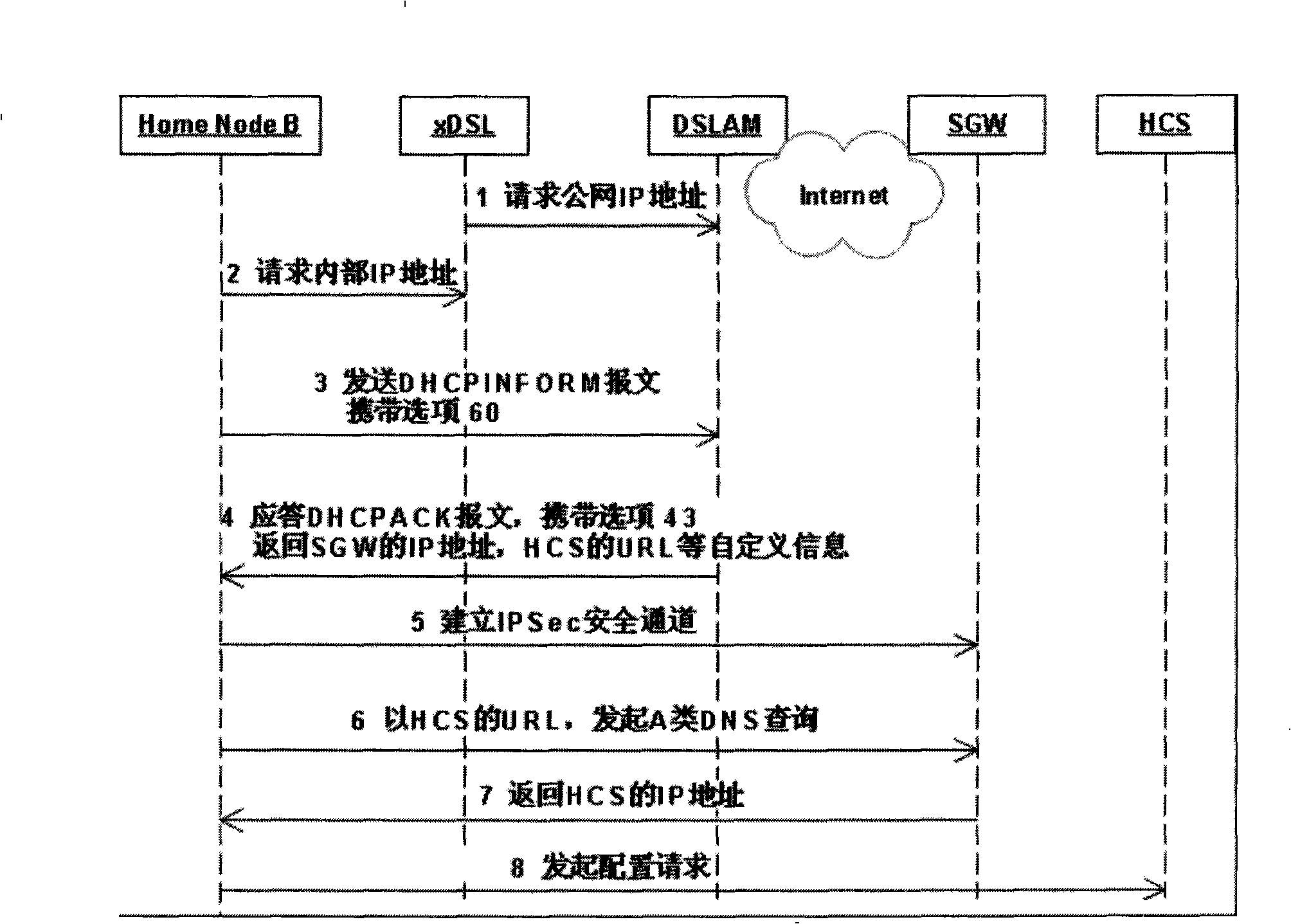
Method for server automatic discovery configuring by house base station
InactiveCN101360094AAvoid cost burdenFlexible adjustmentData switching by path configurationDomain nameFully qualified domain name
Disclosed is a method of automatically discovering the server disposed in the femtocell, comprising the following: firstly, an option 60 and an option 43 are defined in a dynamic host distribution protocol server; after the femtocell is powered up or reset to be restarted, the femtocell sends a DHCPINFORM message which carries the option 60 to the dynamic host distribution protocol server, and after the dynamic host distribution protocol server receives the DHCPINFORM message, the dynamic host distribution protocol server sends corresponding network connection information to the femtocell through the option 43; finally, the femtocell obtains the network connection information according to the option 43, and then initiates an IPSec secure channel to a security gateway for establishing the request, and the security gateway parses the IP address of the server disposed in the femtocell through the obtained complete domain name of the server disposed in the femtocell, and returns the IP address of the server disposed in the femtocell, thereby completing the automatic discovery of the server disposed in the femtocell. The invention solves the problems that the present equipment is of Home NodeB burn network information when manufactured, if the network structure is adjusted, all the swept Home NodeB have to be modified, the flexibility of the present equipment is low, and the cost of the present equipment is high.
Owner:ZTE CORP
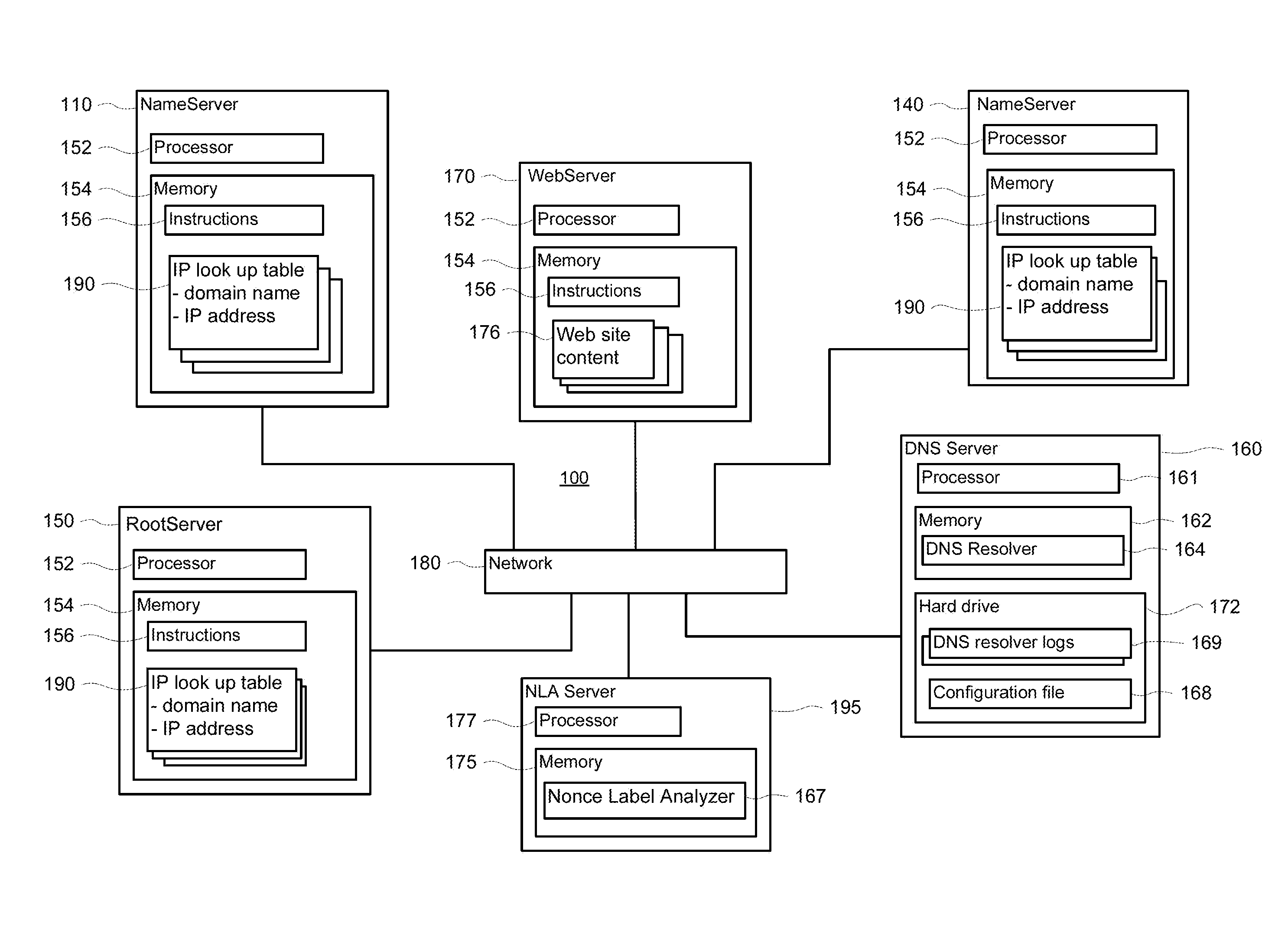
Systems and methods for prepending nonce labels to DNS queries to enhance security
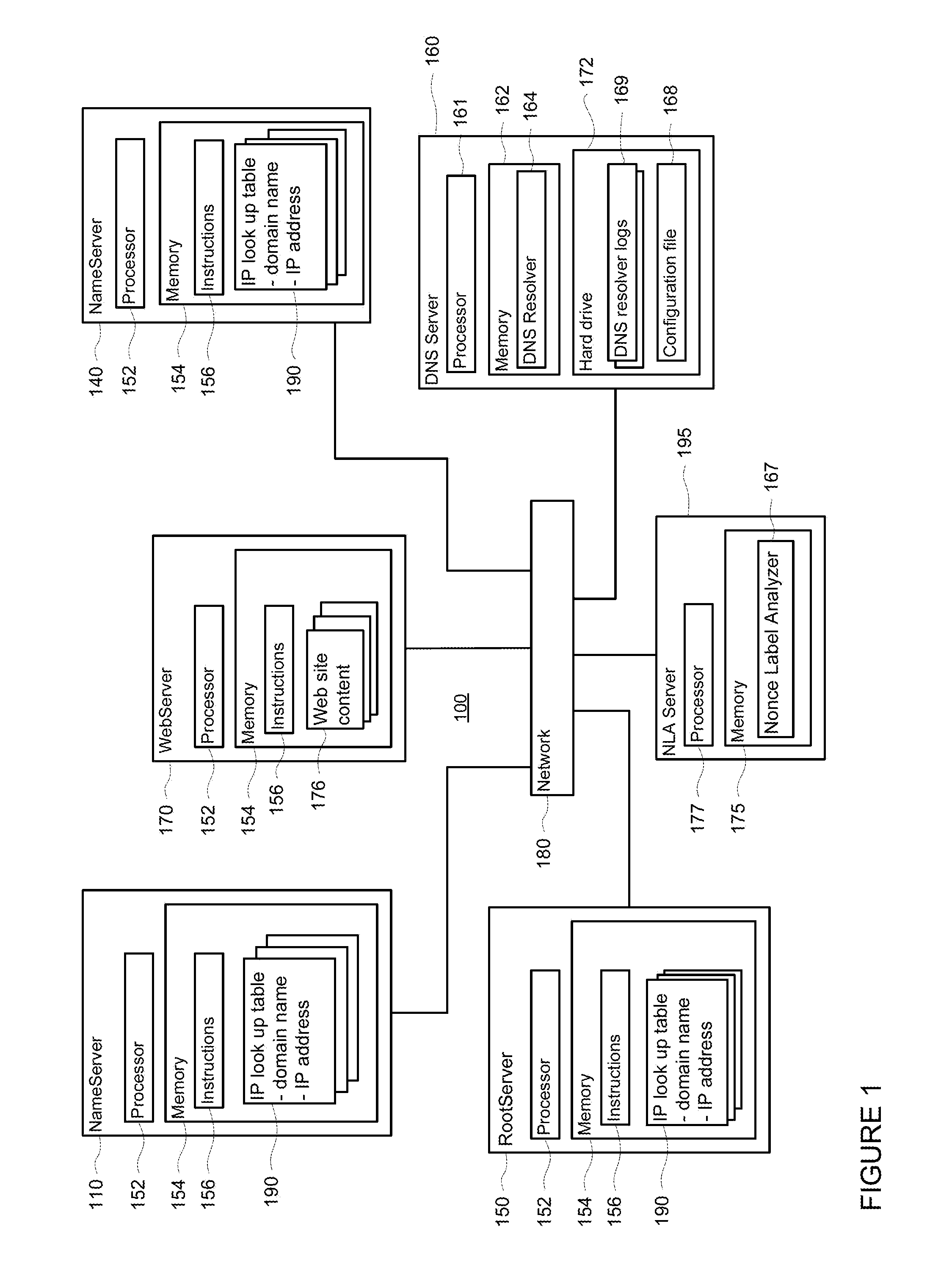
ActiveUS8484377B1Memory loss protectionError detection/correctionDomain nameFully qualified domain name
A method for prepending nonce labels to DNS queries includes determining whether a log contains a past entry of a domain name resolution query (“query”) to a name server for a full domain name that resulted in a positive reply indicating that the full domain name exists. It is determined whether the log contains a recent entry of the query that resulted in a negative reply indicating that the full domain name did not exist. The server is then queried with a nonce-less query for the full domain name. The server is queried again with a nonce label prepended query for the full domain name to determine if it currently results in the negative reply. The full domain name is flagged as inappropriate for nonce prepending upon determination that querying with a nonce prepended query results in a negative reply and a nonce-less query results in a positive reply.
Owner:GOOGLE LLC
Discerning web content and services based on real-time DNS tagging
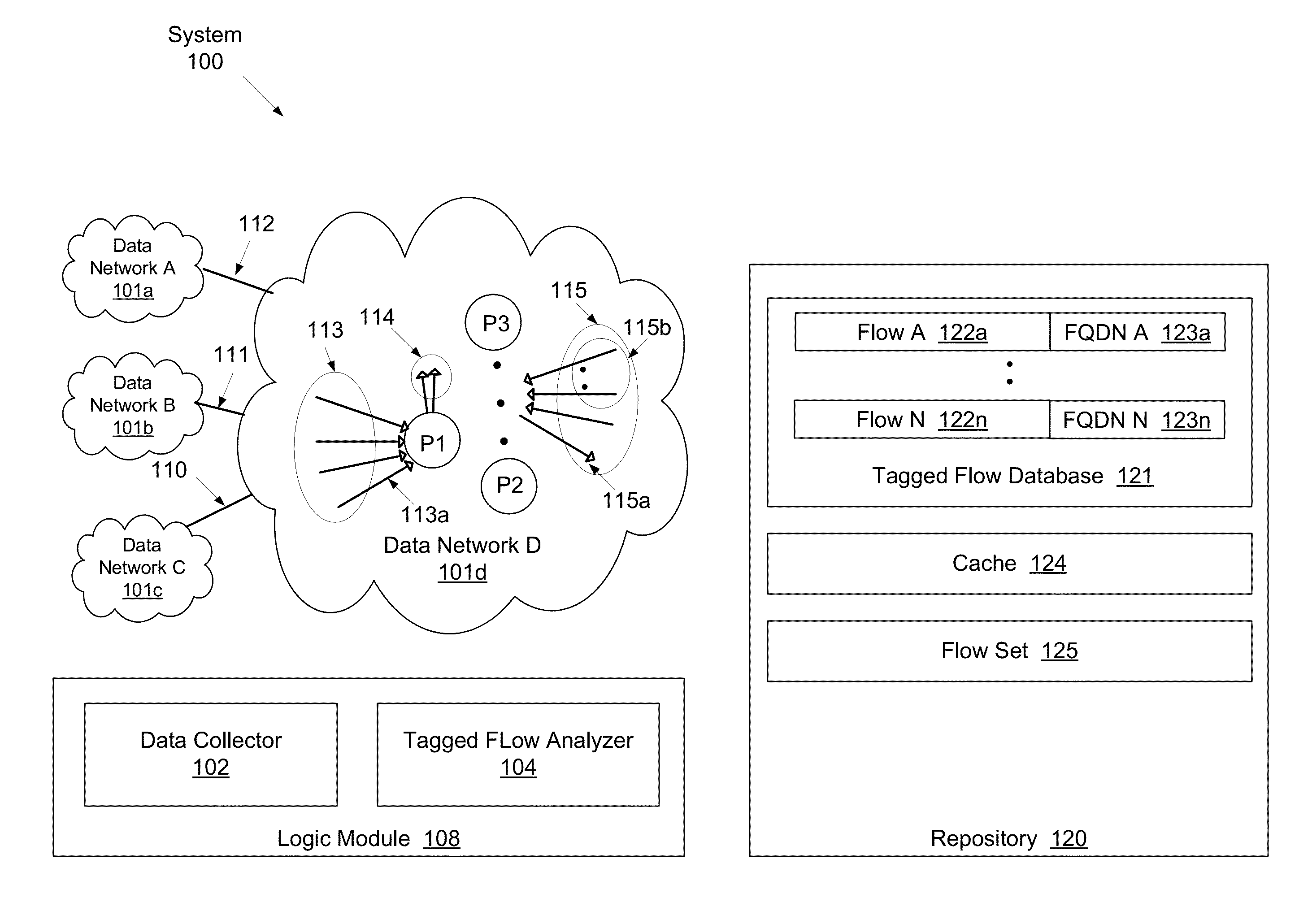
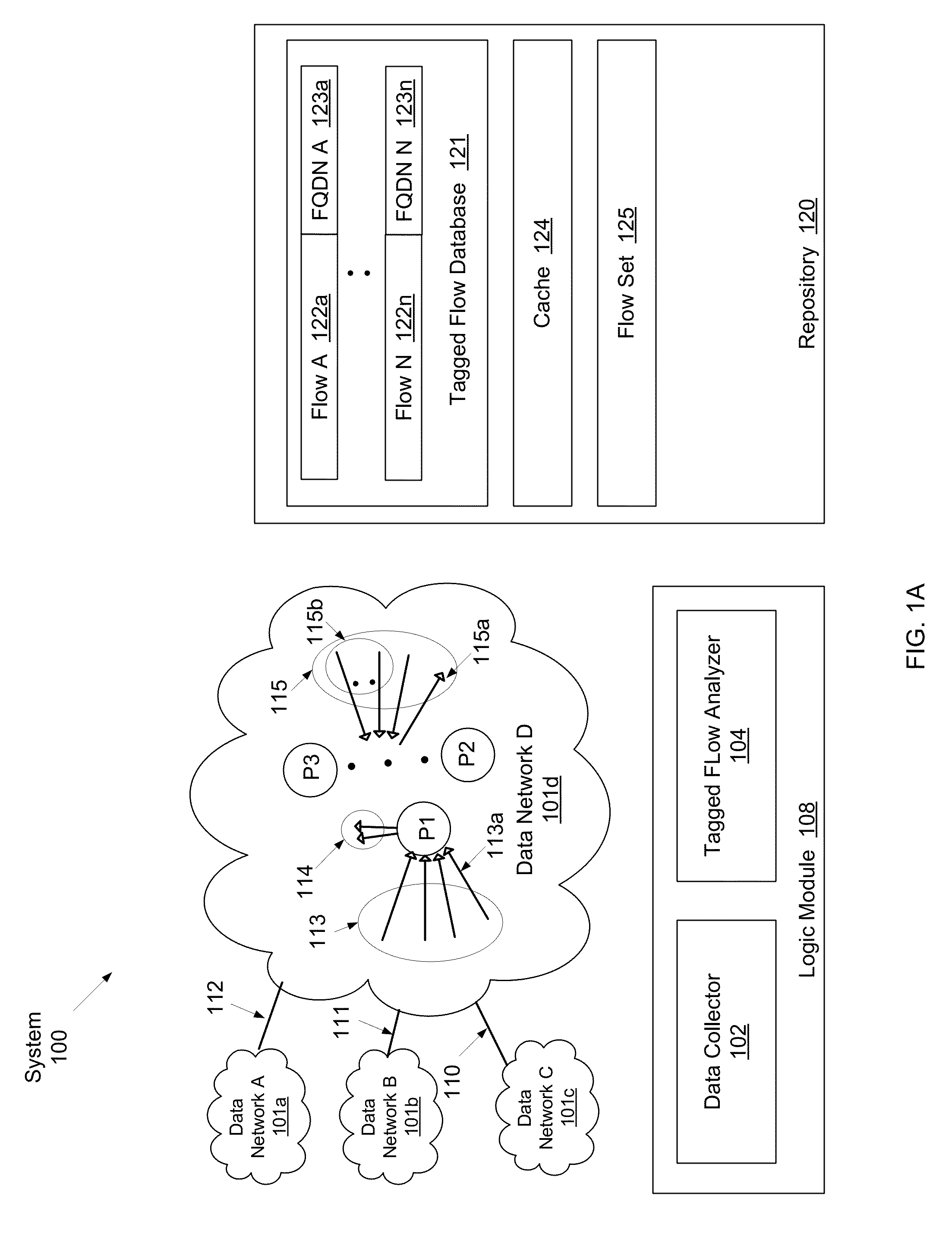
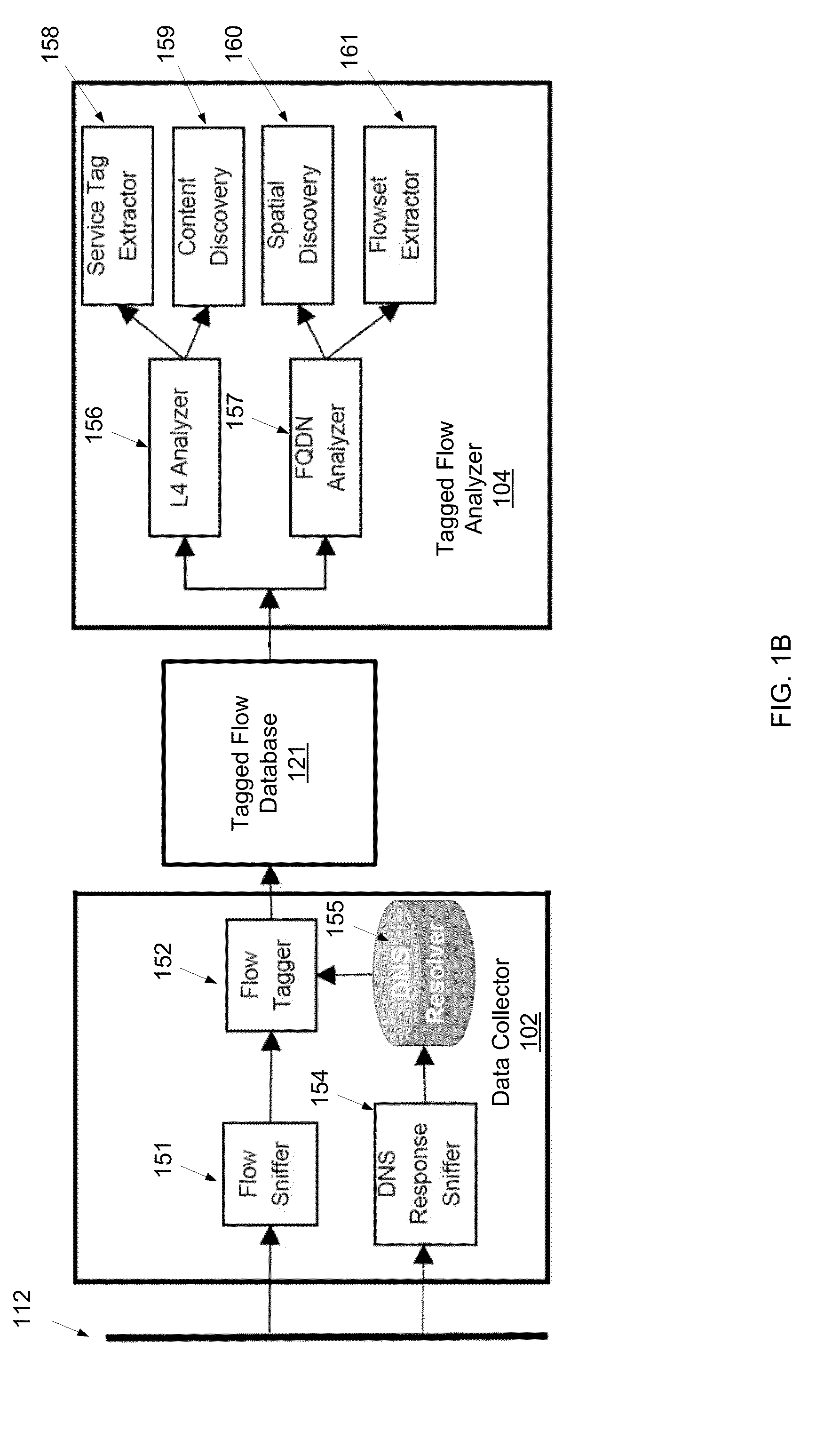
ActiveUS8819227B1Multiple digital computer combinationsTransmissionFully qualified domain nameIp address
A method for profiling network traffic of a network, including obtaining a plurality of flows comprising a plurality of client IP addresses, a plurality of server IP addresses, and a plurality of server ports, extracting a plurality of fully qualified domain names (FQDNs) from a plurality of DNS flows in the network traffic, analyzing correlation between the plurality of flows and the plurality of FQDNs to generate a result, and presenting the result to an administrator user of the network.
Owner:THE BOEING CO
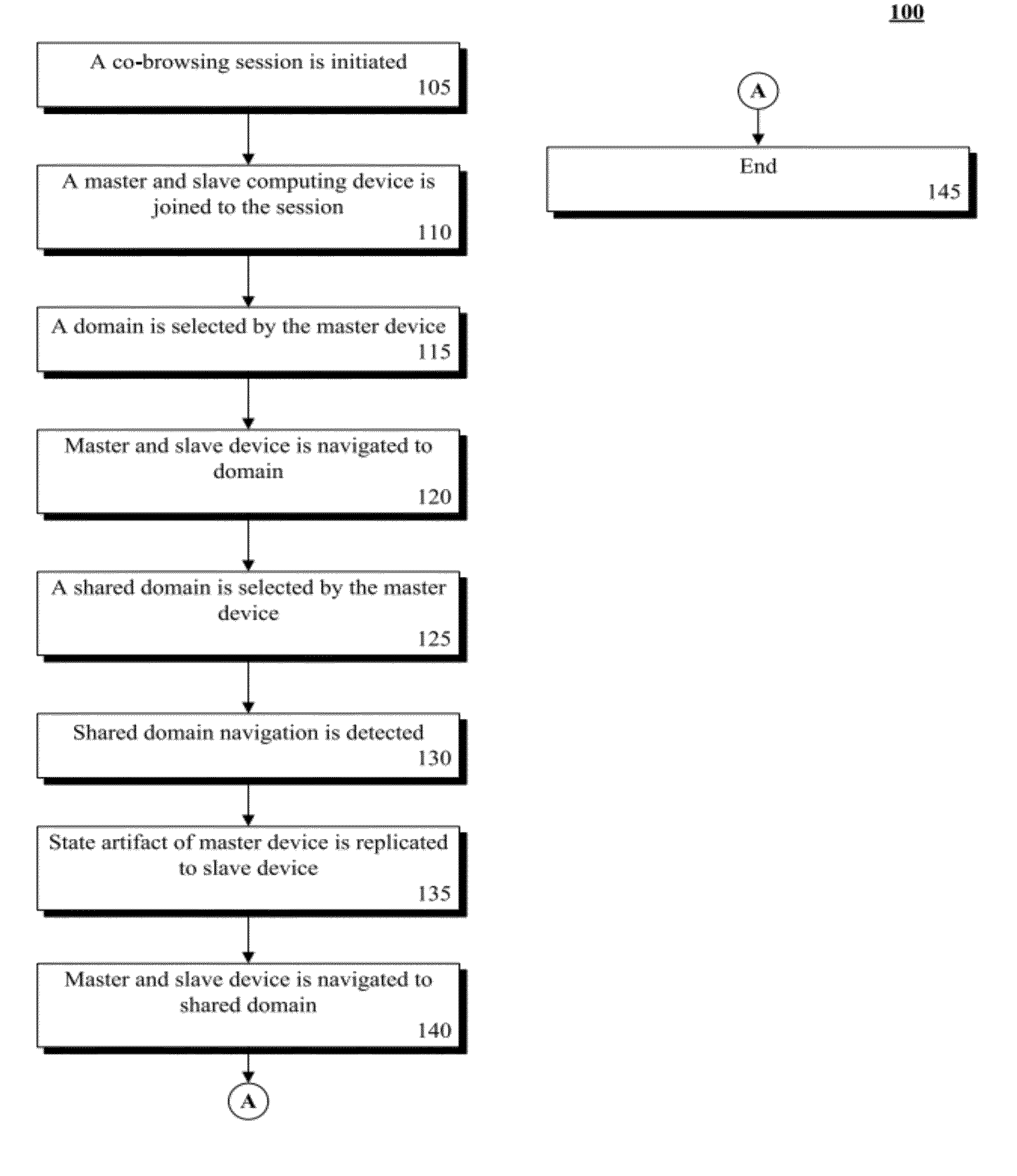
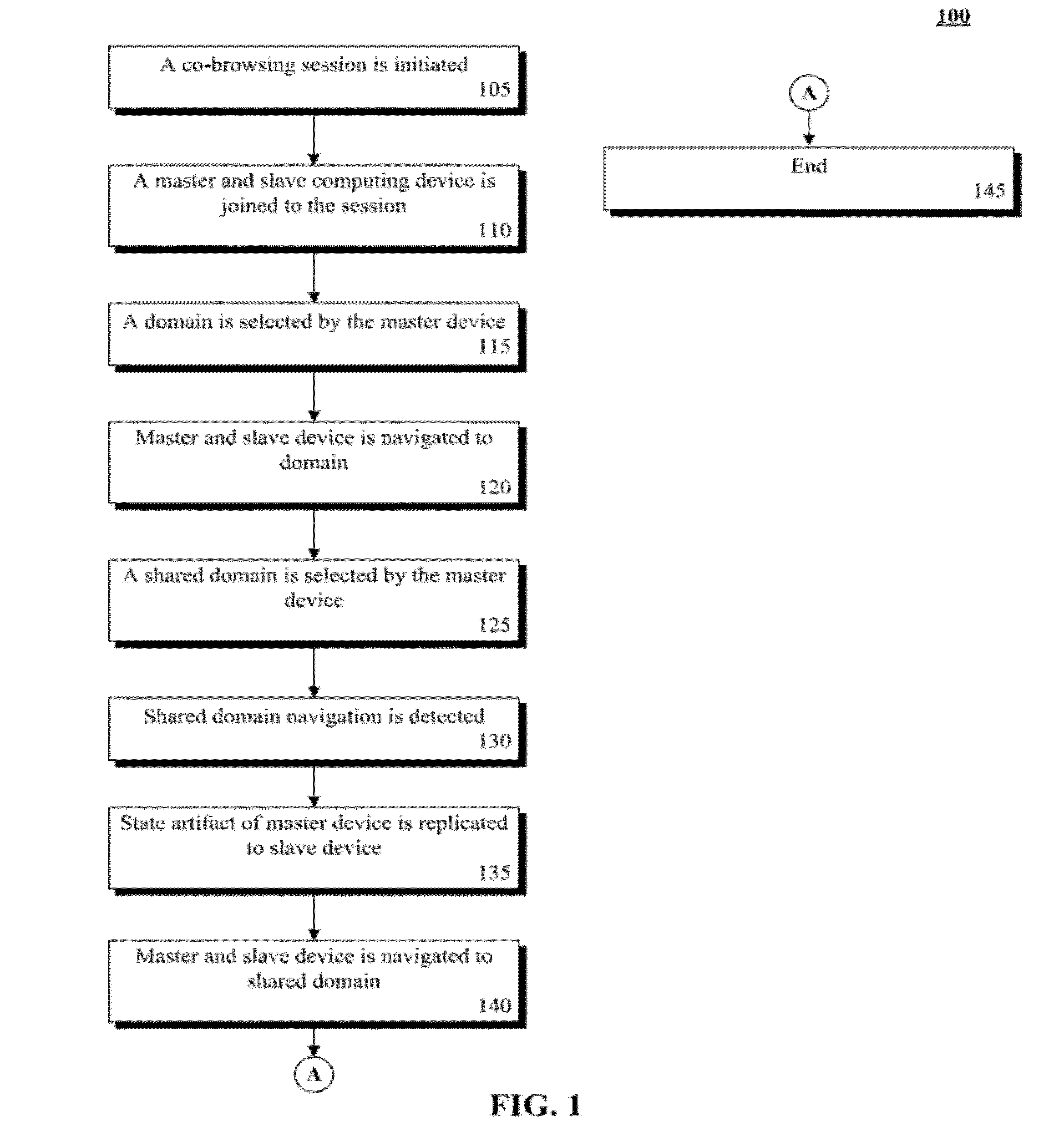
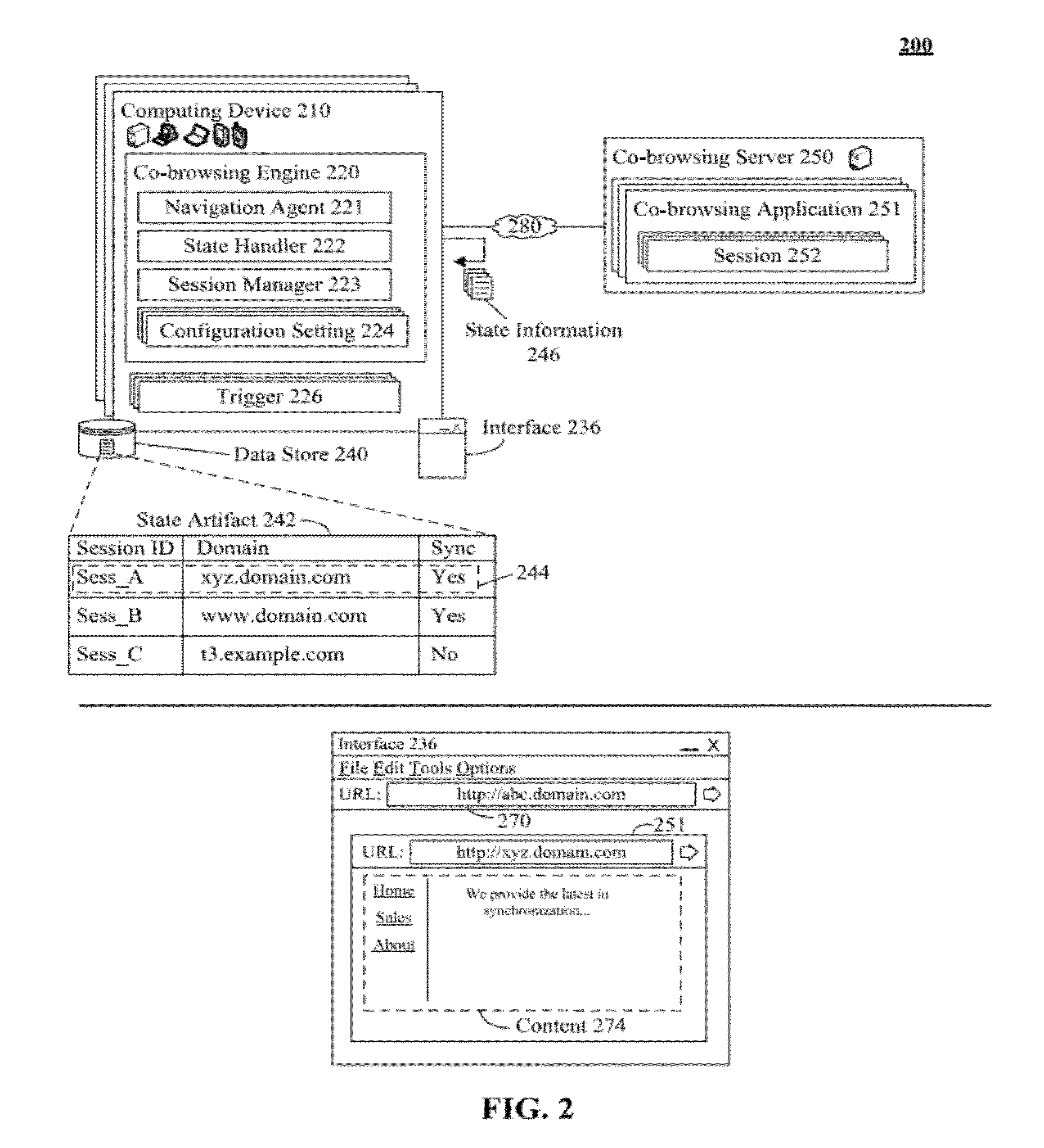
Multi-domain co-browsing utilizing localized state management
ActiveUS8856259B2Multiple digital computer combinationsTransmissionDomain nameFully qualified domain name
Owner:INT BUSINESS MASCH CORP
Method, system and position information server for acquiring IP geographic position information
ActiveCN101902442AMapping implementationGuaranteed accuracyTransmissionDomain nameFully qualified domain name
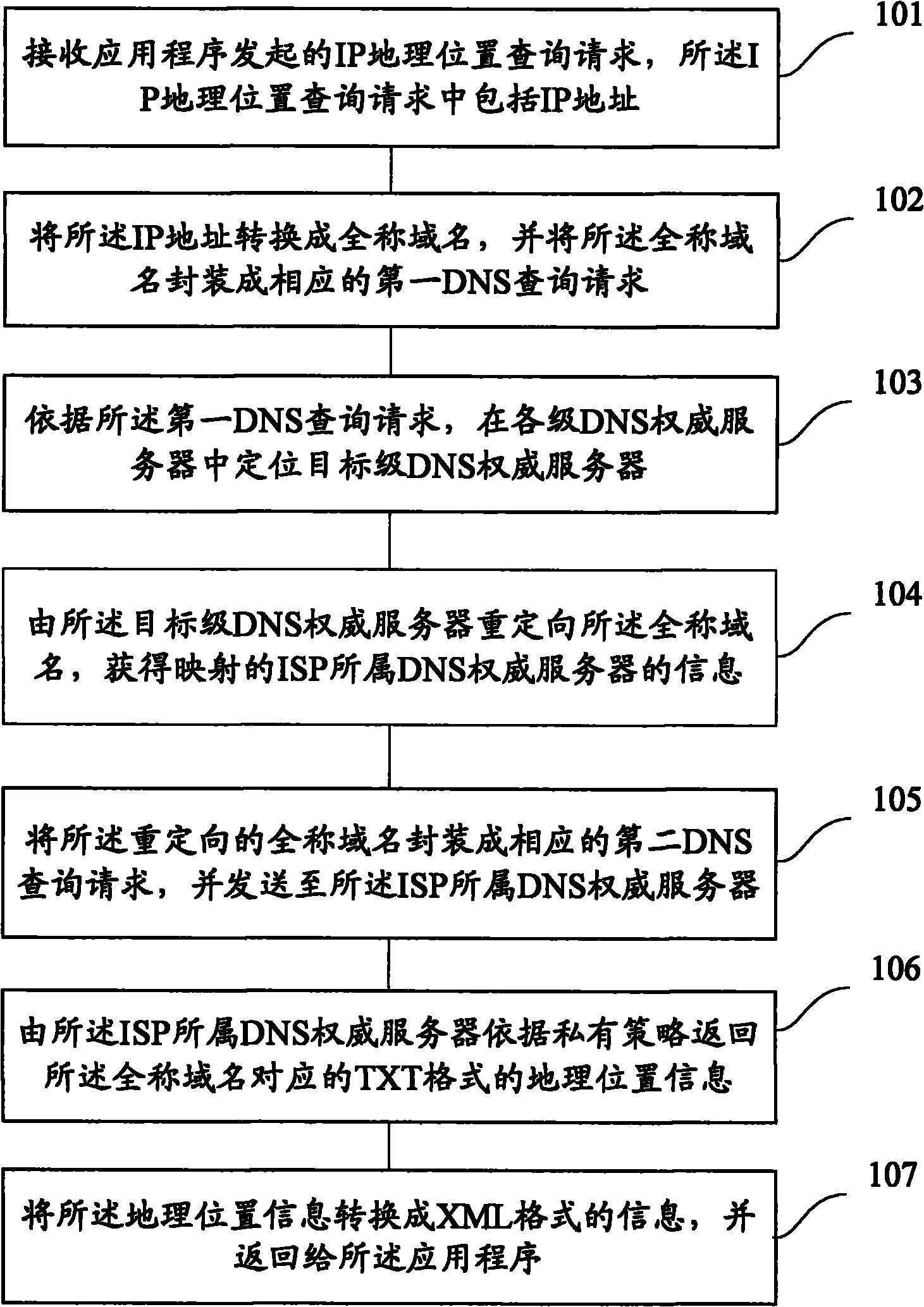
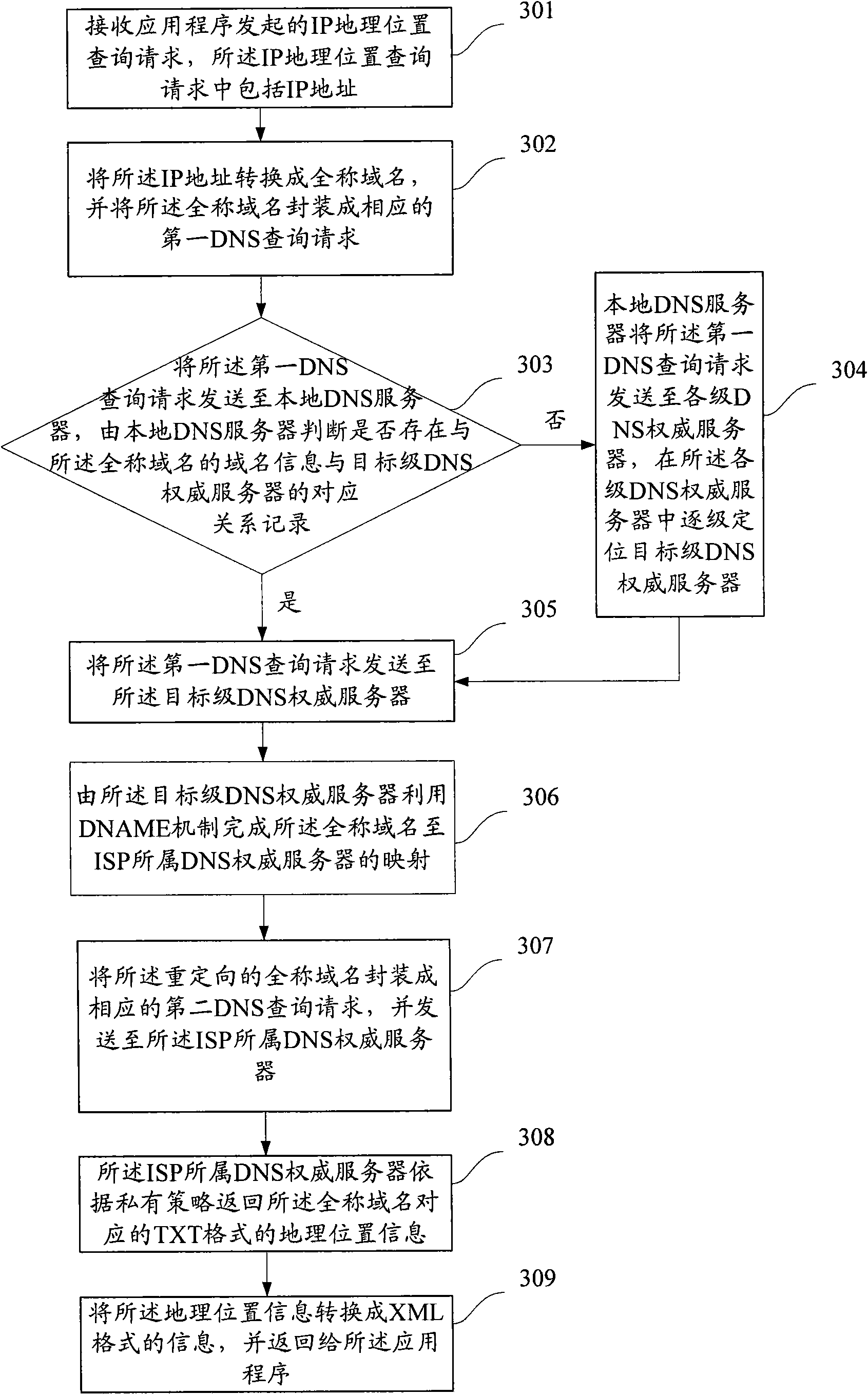
The invention provides a method for acquiring IP geographic position information, which comprises the following steps: receiving an IP geographic position inquiry request initiated by an application program, wherein the request comprises an IP address; converting the IP address into a fully qualified domain name, and packaging the fully qualified domain name into a corresponding first DNS inquiry request; positioning an object-level DNS authoritative server according to the first DNS inquiry request; redirecting the fully qualified domain name by the object-level DNS authoritative server to acquire the information of the DNS authoritative server to which the mapped ISP belongs; packaging the redirected fully qualified domain name into a corresponding second DNS inquiry request, sending the second DNS inquiry request to the DNS authoritative server to which the ISP belongs, and returning corresponding geographic position information in a TXT format by the DNS authoritative server to which the ISP belongs according to the private policy; and converting the geographic position information into the information in an XML format to be returned to the application program. The invention can ensure the accuracy of the acquired geographic position information.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Method and apparatus for updating DNS of host in ipv6 stateless address configuration
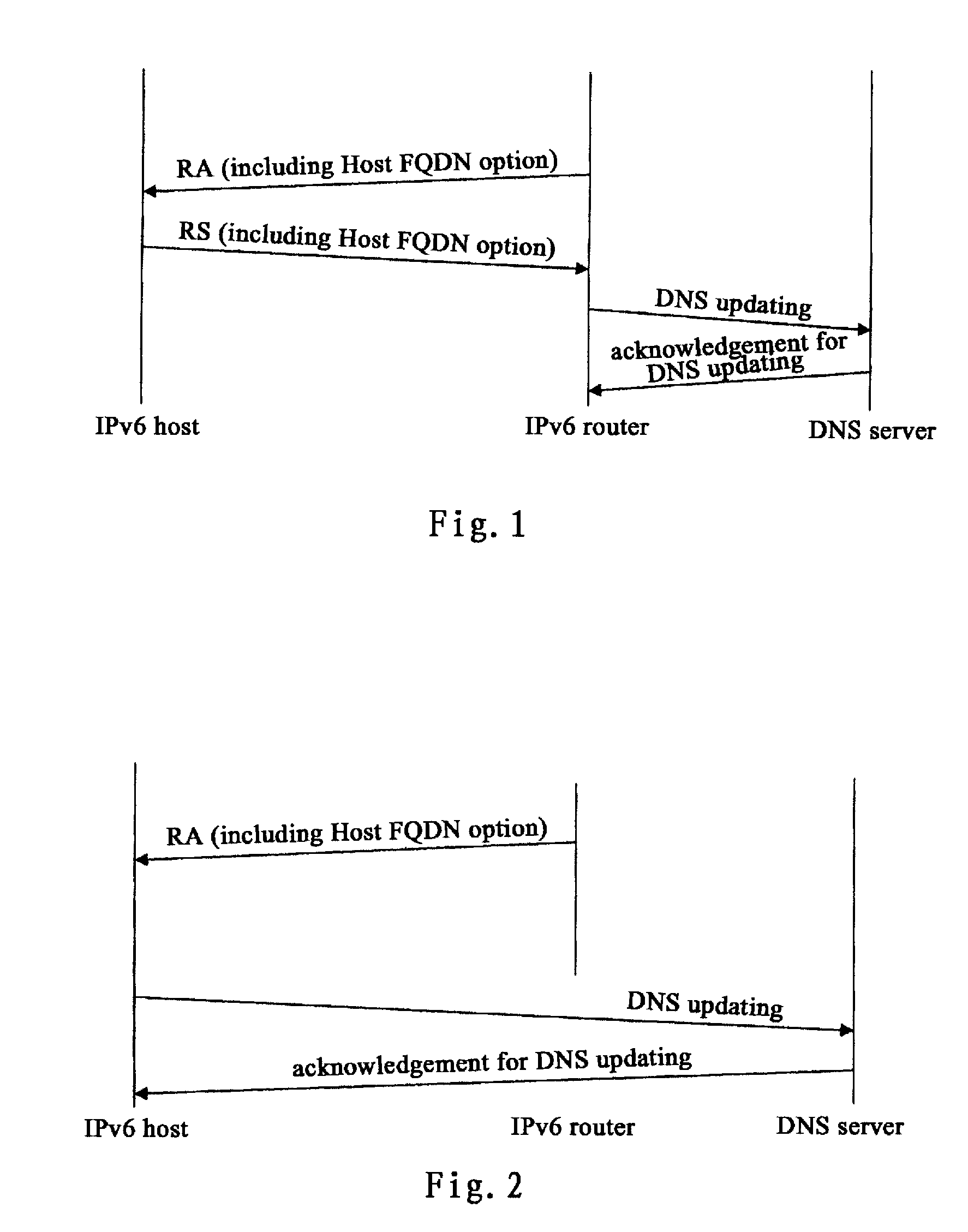
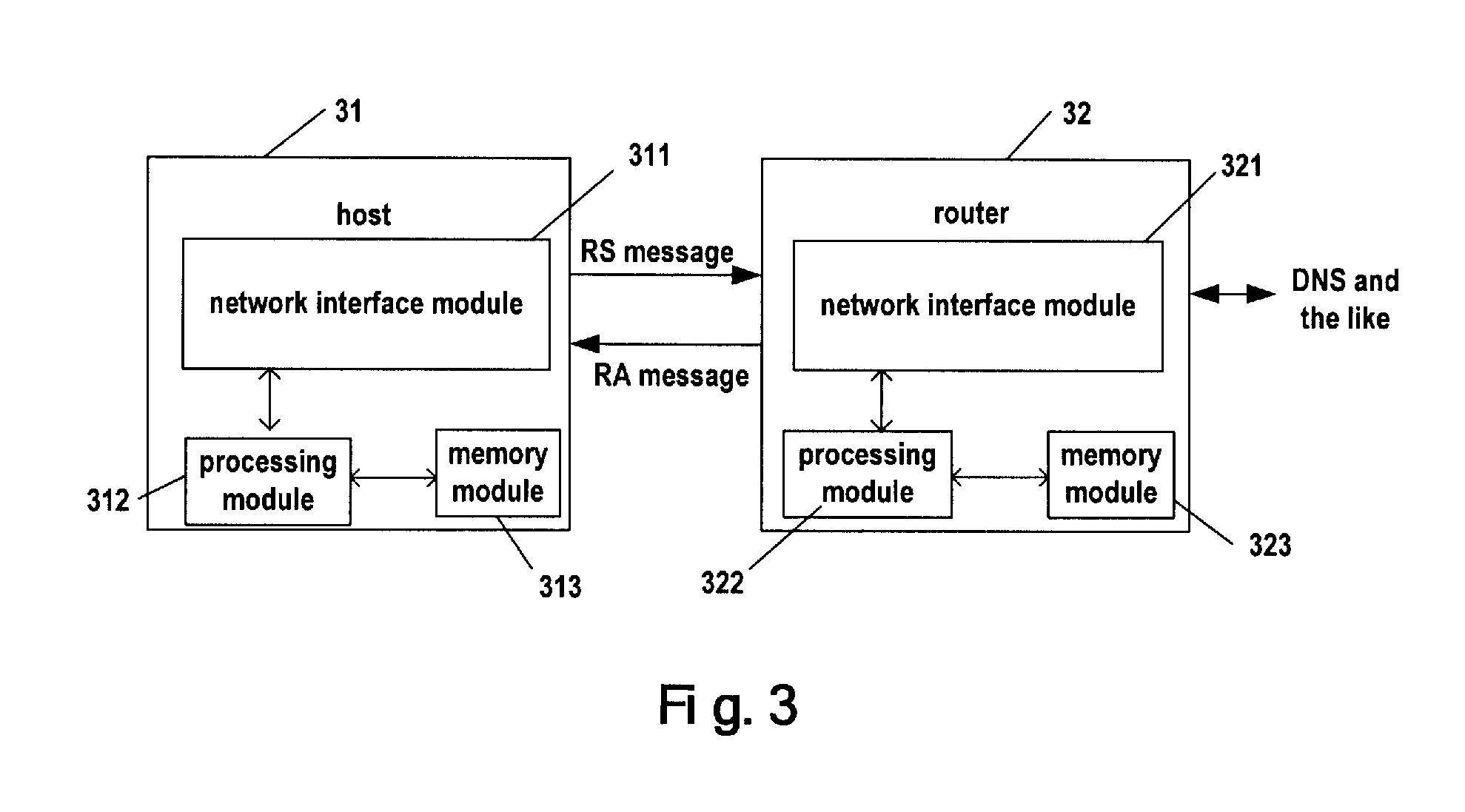
InactiveUS20090274062A1Effective and reliableAccurate identificationDigital computer detailsData switching by path configurationDomain nameFully qualified domain name
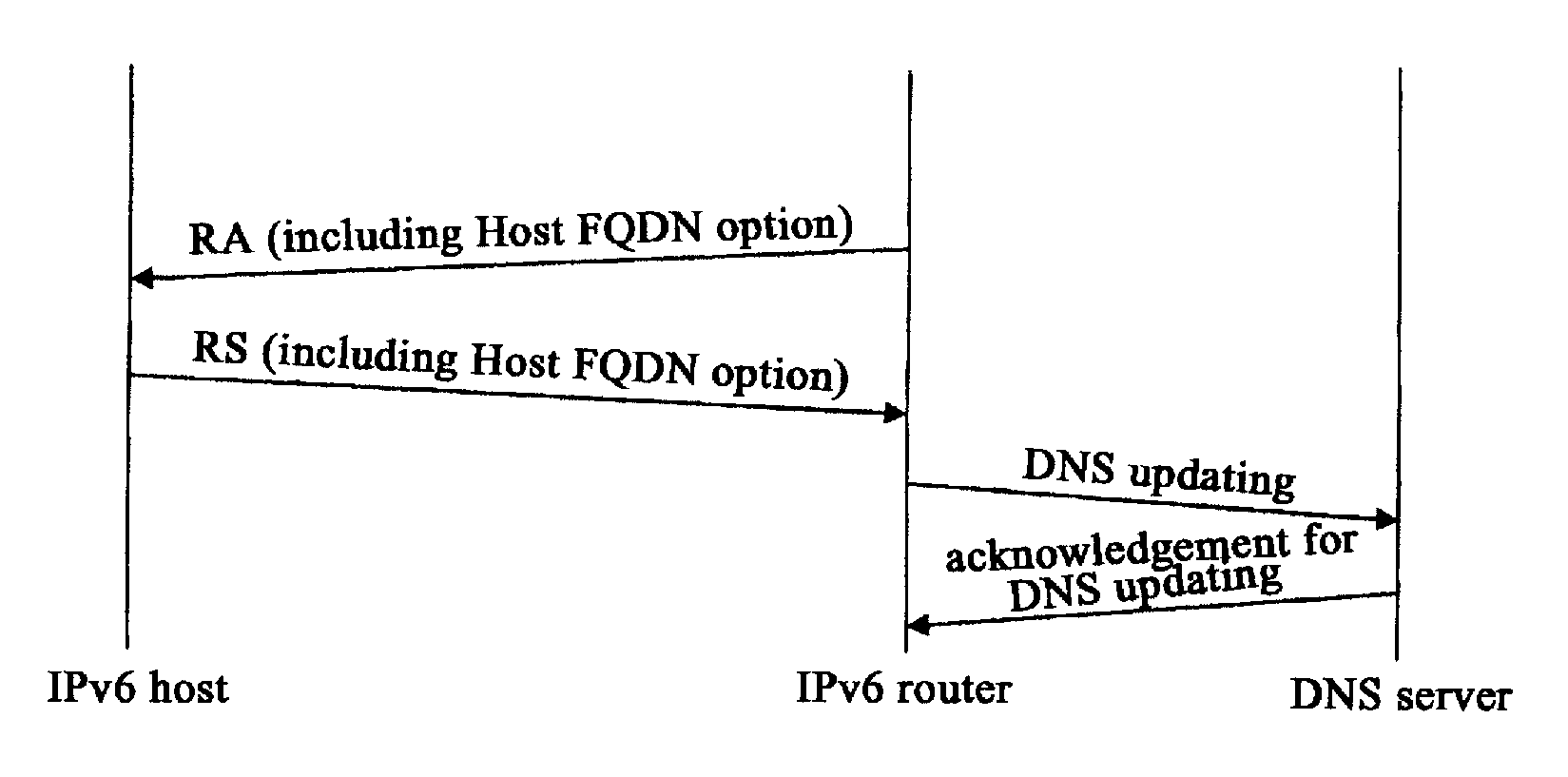
Disclosed is a method for updating DNS of host in IPv6 stateless address auto-configuration, wherein an option is added in the RS message sent by a host and / or RA message sent by a router, said option including information for negotiation of updating DNS of host. Based on said information, the host negotiates with the router to determine whether the host or the router register, the mapping between the global address of the host and the full domain name of the host, to a DNS server, to complete updating the DNS of the host. This invention enables the host to correctly identify the matching relation between domain name suffix information and address prefix, and achieves the negotiation of updating DNS domain name between the host and the router. Since DNS updating is performed by a router instead of the host, the DNS updating would become simple and safe.
Owner:ALCATEL LUCENT SAS
System and method for securely providing a configuration file over and open network
ActiveUS7430664B2User identity/authority verificationUnauthorized memory use protectionDomain nameNetwork connection
A method for securely provisioning a device for operation within a service provider infrastructure over an open network comprises the device establishing physical and data link layer network connections for communication on at least a subnet of the open network and obtaining a network configuration data such as an IP address and a subnet mask from a provisioning server that responds to a network configuration broadcast request. A device establishes a secure hypertext transport protocol connection to a first provisioning server that corresponds to one of: i) and IP address and port number; and ii) a fully qualified domain name stored in a non-volatile memory of the device. After mutual authentication, the first provisioning server provides at least one of: i) a configuration file; and ii) identification of a second provisioning server and a cipher key through the secure connection. If the first provisioning server provided identification of a second provisioning server, the device establishes a transport connection to the identified second provisioning server. The second provisioning server provides an encrypted file which, when decrypted using the cipher key yields the configuration information needed by the device for operation with the service provider infrastructure.
Owner:INOMEDIA
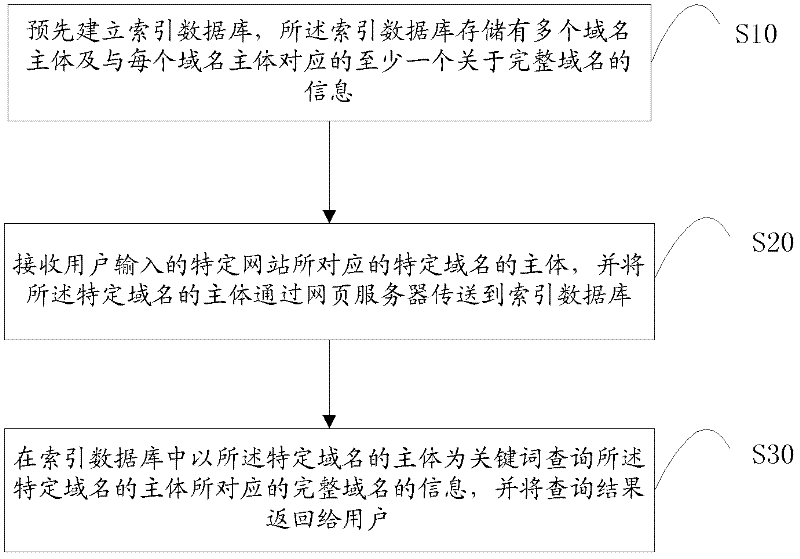
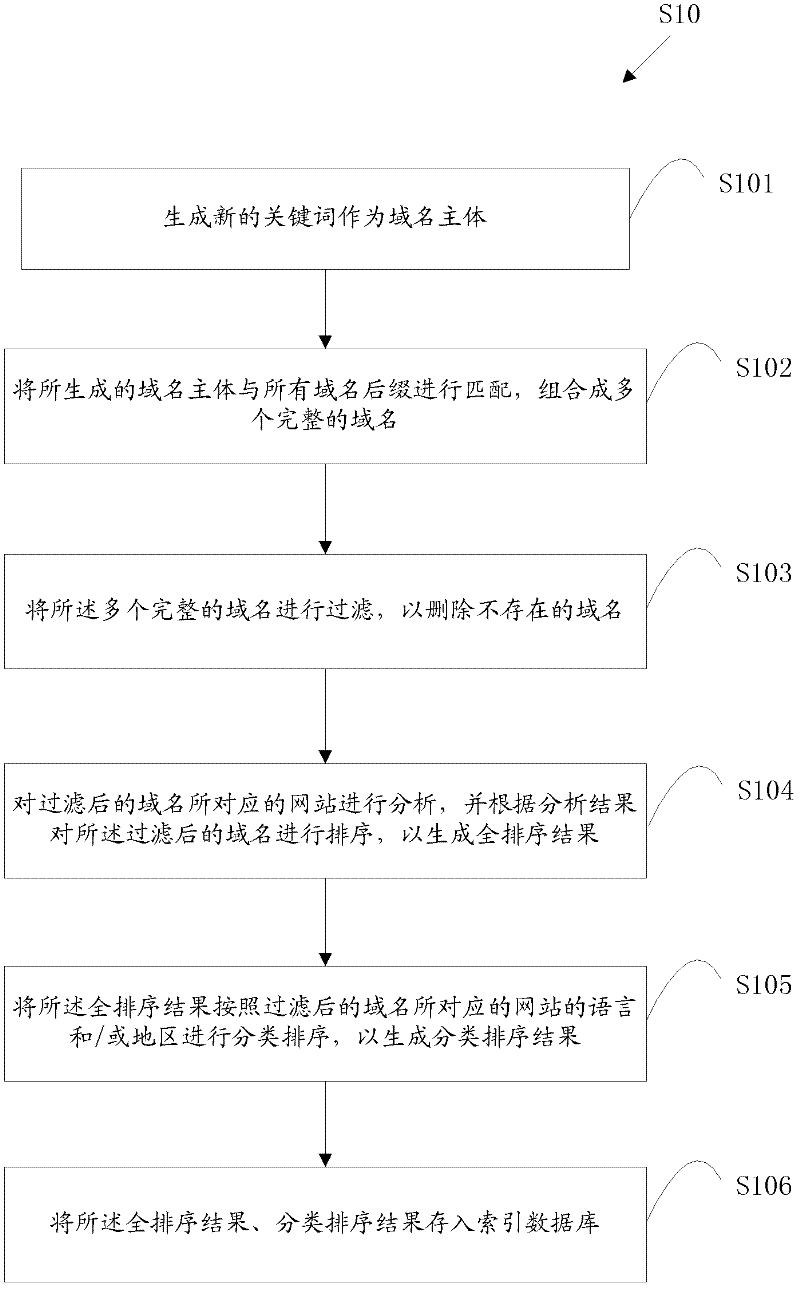
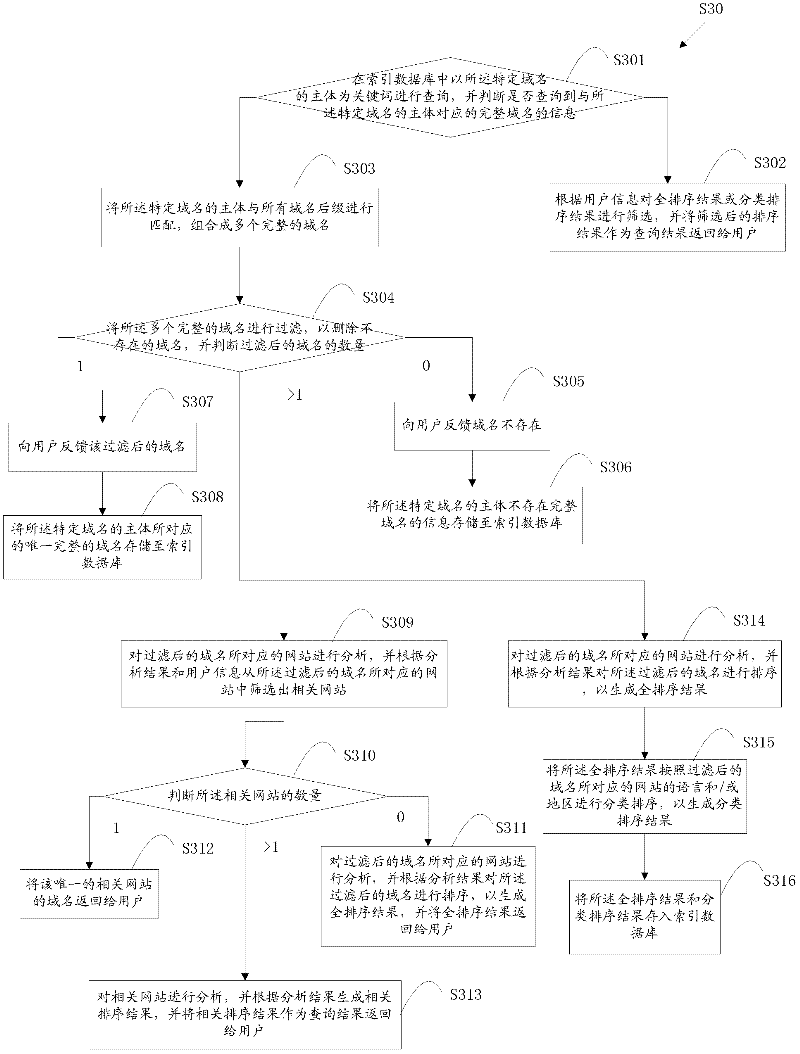
Method and system for website accessing
ActiveCN102609473AImprove experienceShorten the timeSpecial data processing applicationsDomain nameFully qualified domain name
The invention disclosed a method and a system for website accessing. The method includes steps of A, building an index database in advance, a plurality of domain name bodies and at least one piece of information about an integral domain name corresponding to each domain name body; B receiving the body of a specific domain name corresponding to a specific website input by a user and sending the body of the specific domain name to the index database through a webpage server; C, using the body of the specific domain name as a key word to search for the integral domain name information corresponding to the body of the specific domain name and returning the searching results to the user. The invention further constructs the website accessing system. By the method, the user can access the specific website without inputting a suffix of the domain name, website accessing time is saved, problems caused by misspelling of the suffix are avoided, and accordingly user experience is enhanced.
Owner:钟进发
Mobile management method and entity
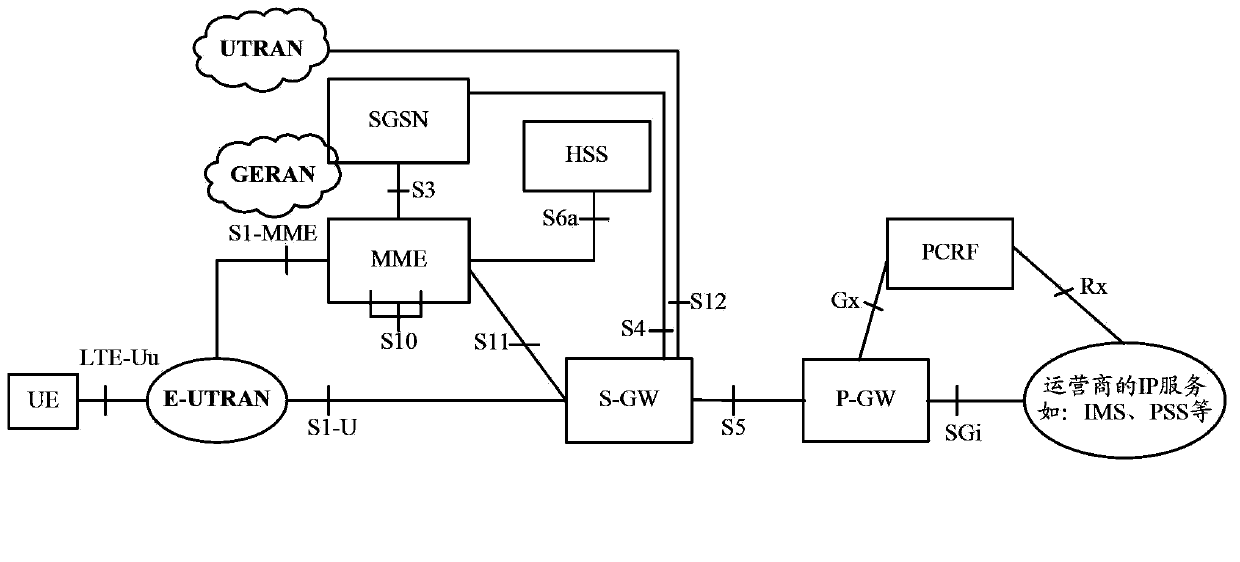
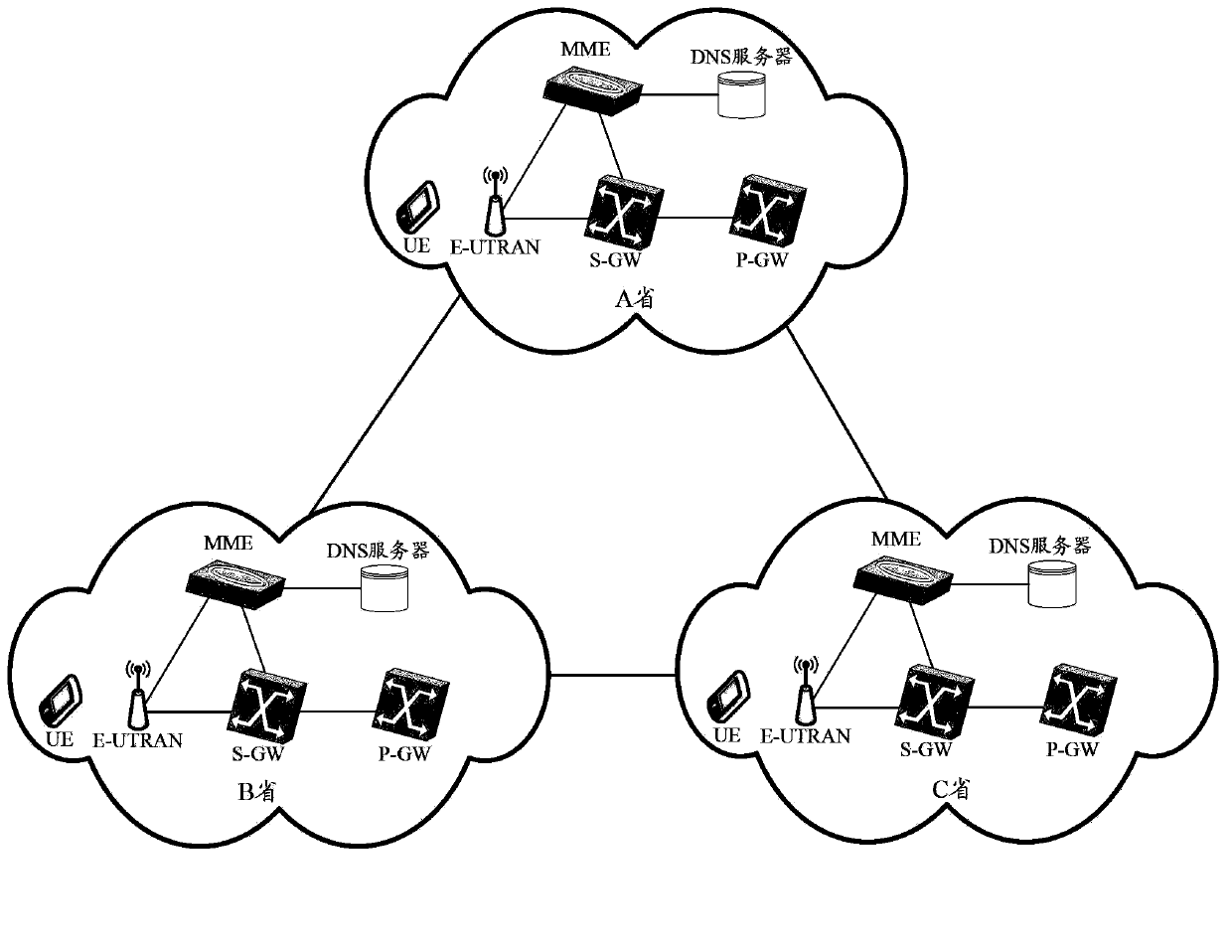
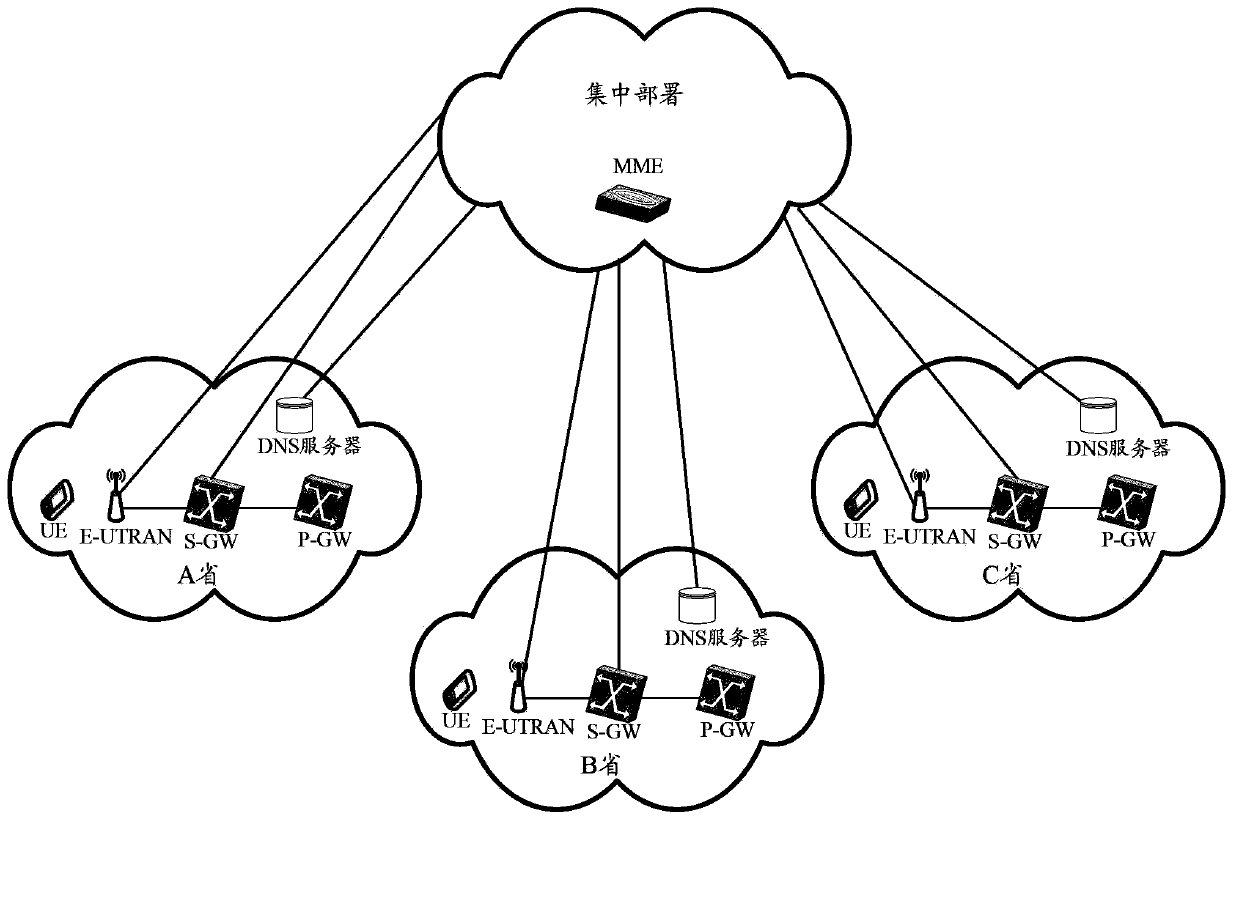
ActiveCN103974237AImplement Mobility ManagementNetwork traffic/resource managementNetwork data managementFully qualified domain nameManagement process
The invention provides a mobile management method and entity applied to an LET (long term evolution) network of MME (mobile management entity) centralized deployment. The method includes: configuring a corresponding relation, between location information of UE (user equipment) and an IP (internet protocol) address of an DNS (domain name system) server in the area of the UE, on the MME; receiving a mobile management message, carrying the location information of the UE, sent from the UE by the MME, and searching the IP address of the matched DNS server through the MME according to the location information of the UE; creating an FQDN (fully qualified domain name) through the MME according to related information of the UE, sending an N-record query request message, carrying the FQDN, to the matched DNS server, selecting an S-GW (serving-gateway) or P-GW (packet data network gateway) according to an S-GW or P-GW list and local rules returned by the DNS server, and initiating an A-record query request to the DNS server so as to acquire an IP address of the selected S-GW or P-GW; initiating a mobile management process to the selected S-GW or P-GW through the MME. Mobile management in the LET network of the MME centralized deployment is realized.
Owner:CHINA MOBILE COMM GRP CO LTD
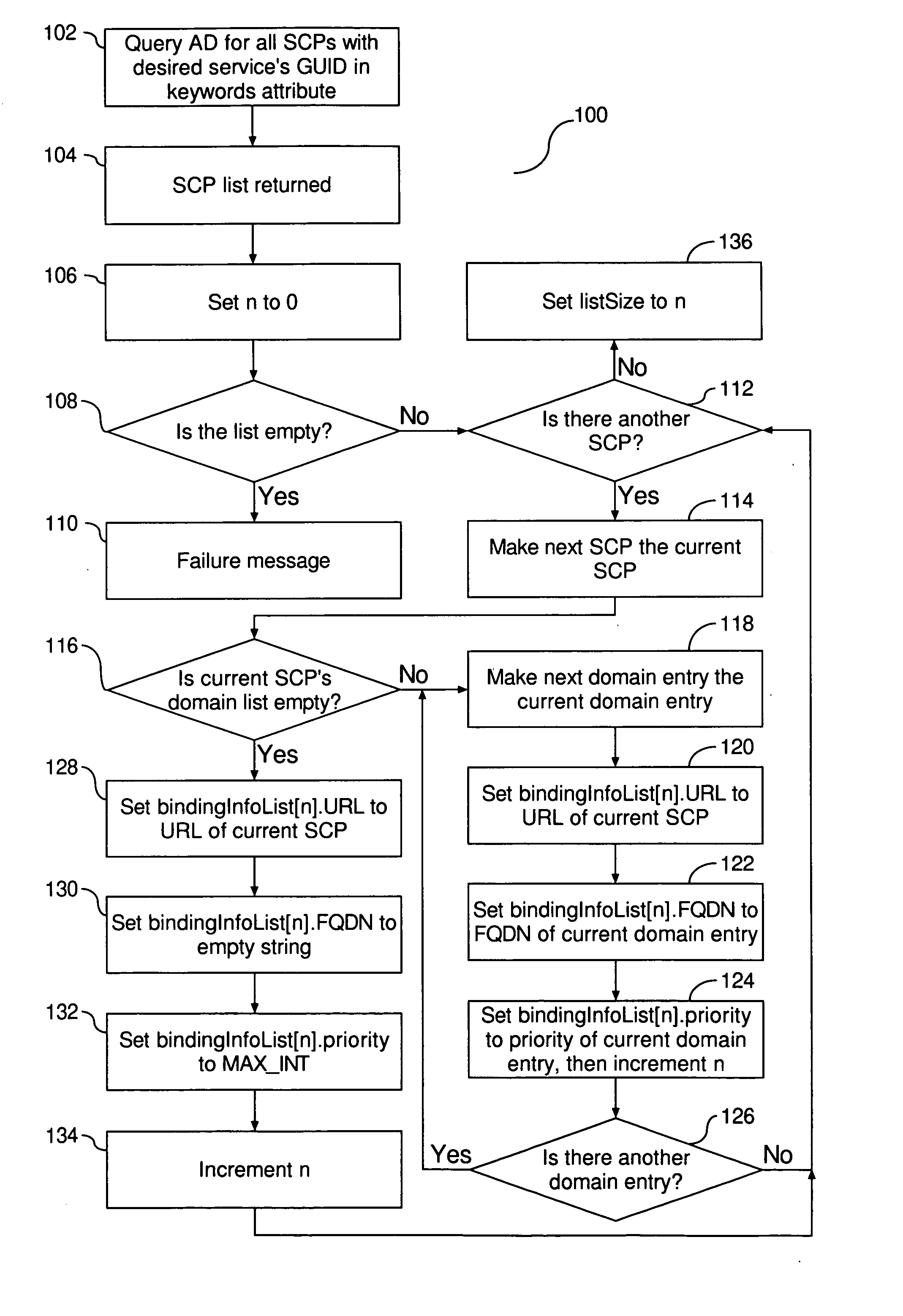
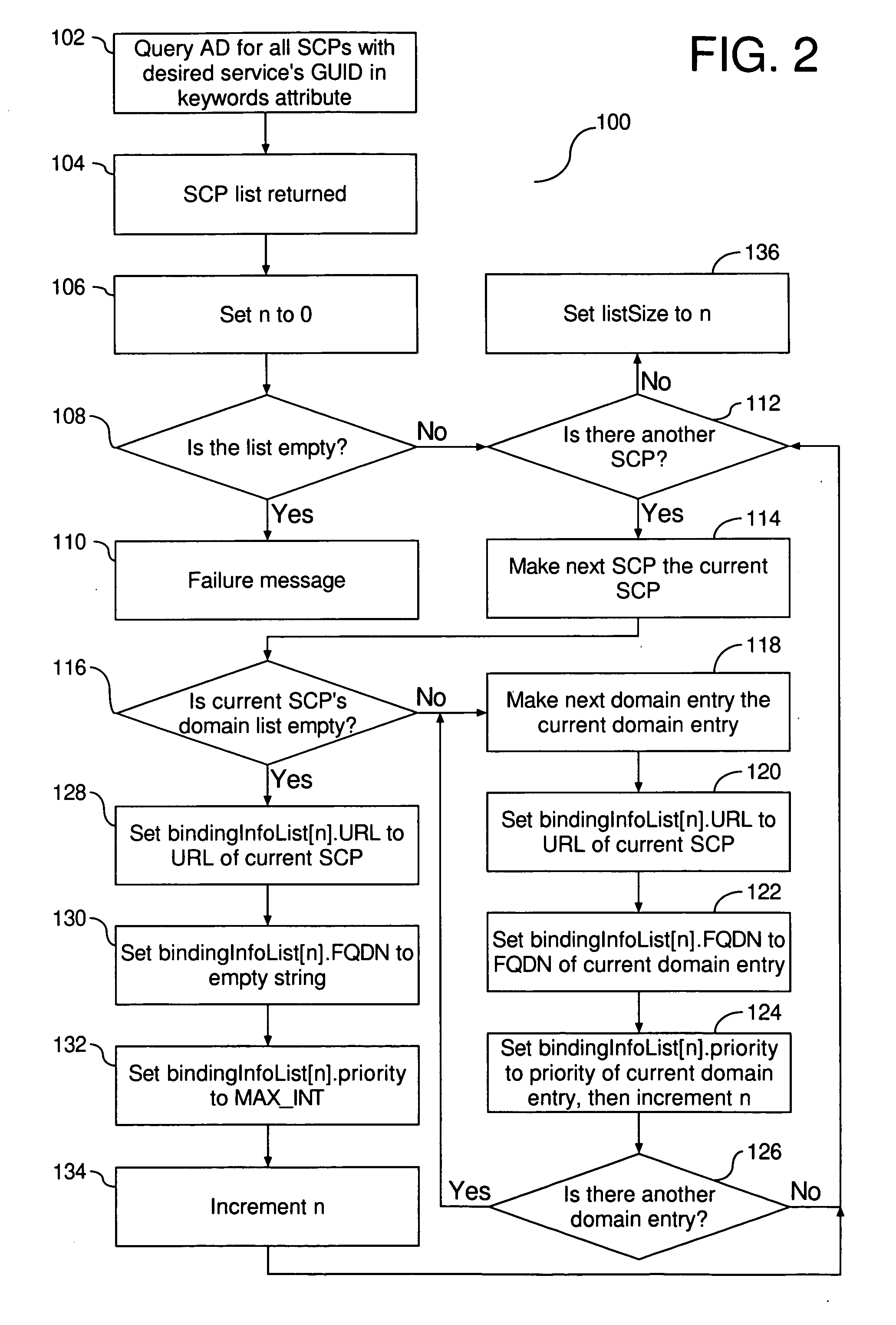
Priority based LDAP service publication mechanism
ActiveUS20070050331A1Data processing applicationsMultiple digital computer combinationsFully qualified domain nameClient-side
A method and system are provided for directing a client to a preferred service instance. At creation of a service instance, the service binding attribute of the created instance is extended to include assigned domains and associated priorities. There are then two phases to directing a client to the preferred service instance. The first phase is compilation of a list of domains and priorities for the service in response to a query. Upon completion of the first phase, a second phase is executed to determine a preferred service for the client by comparing fully qualified domain name entries and assigned priority entries.
Owner:MAPLEBEAR INC
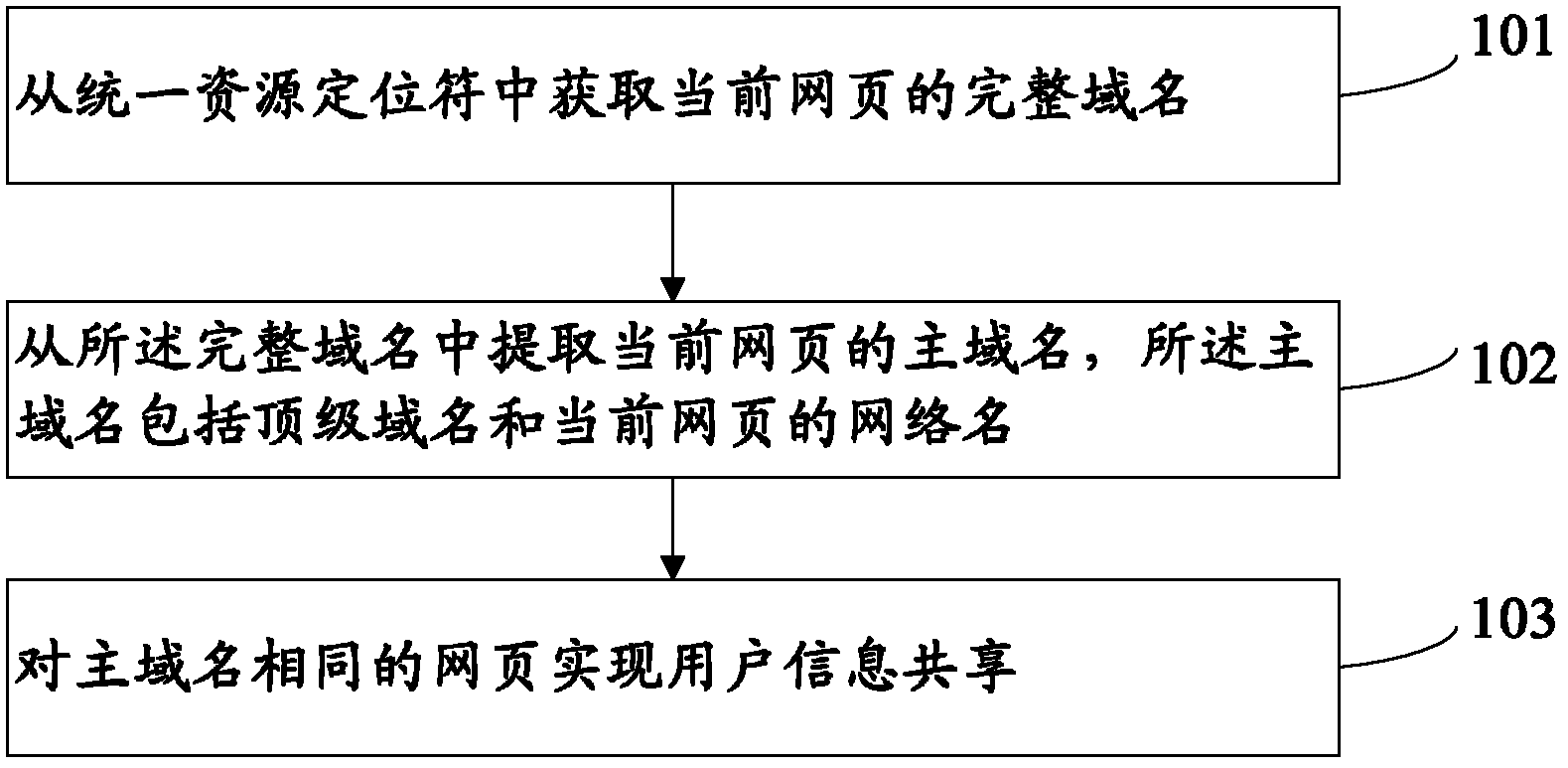
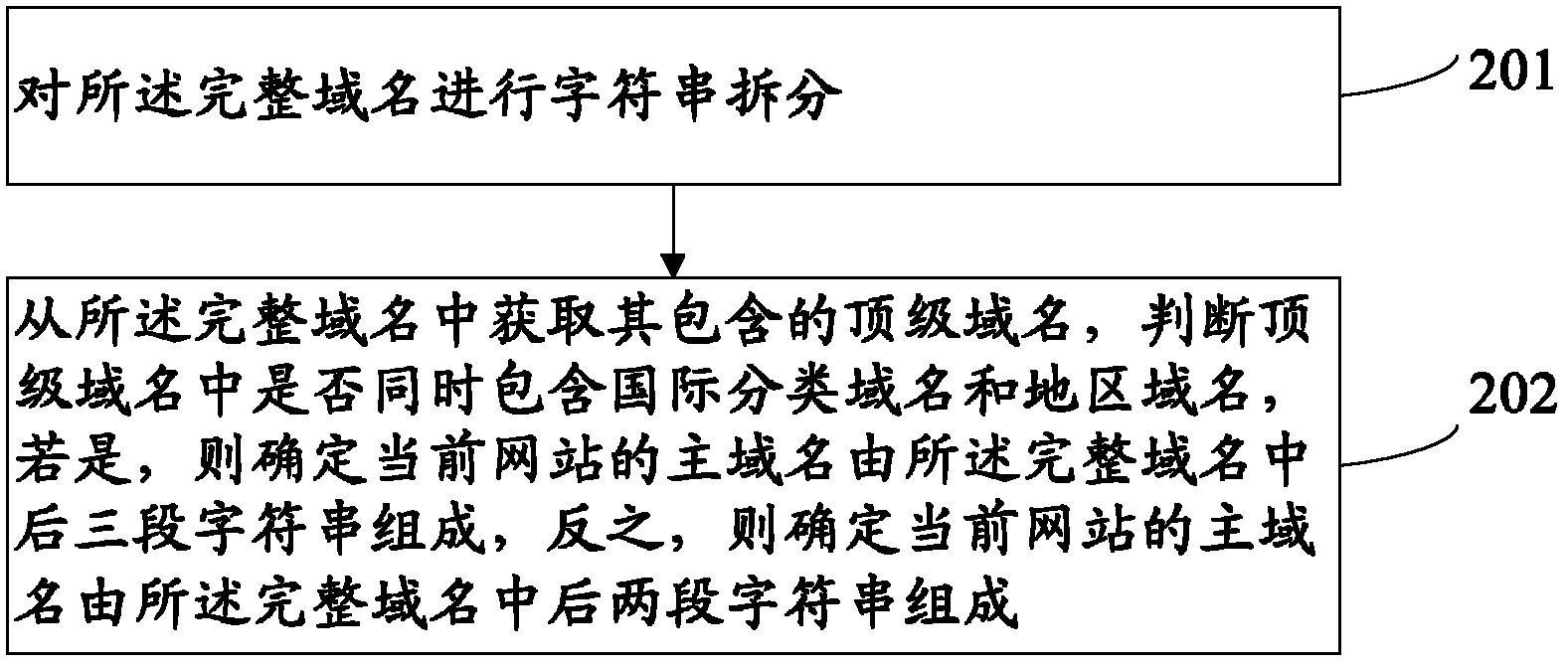
Method and system for user information sharing
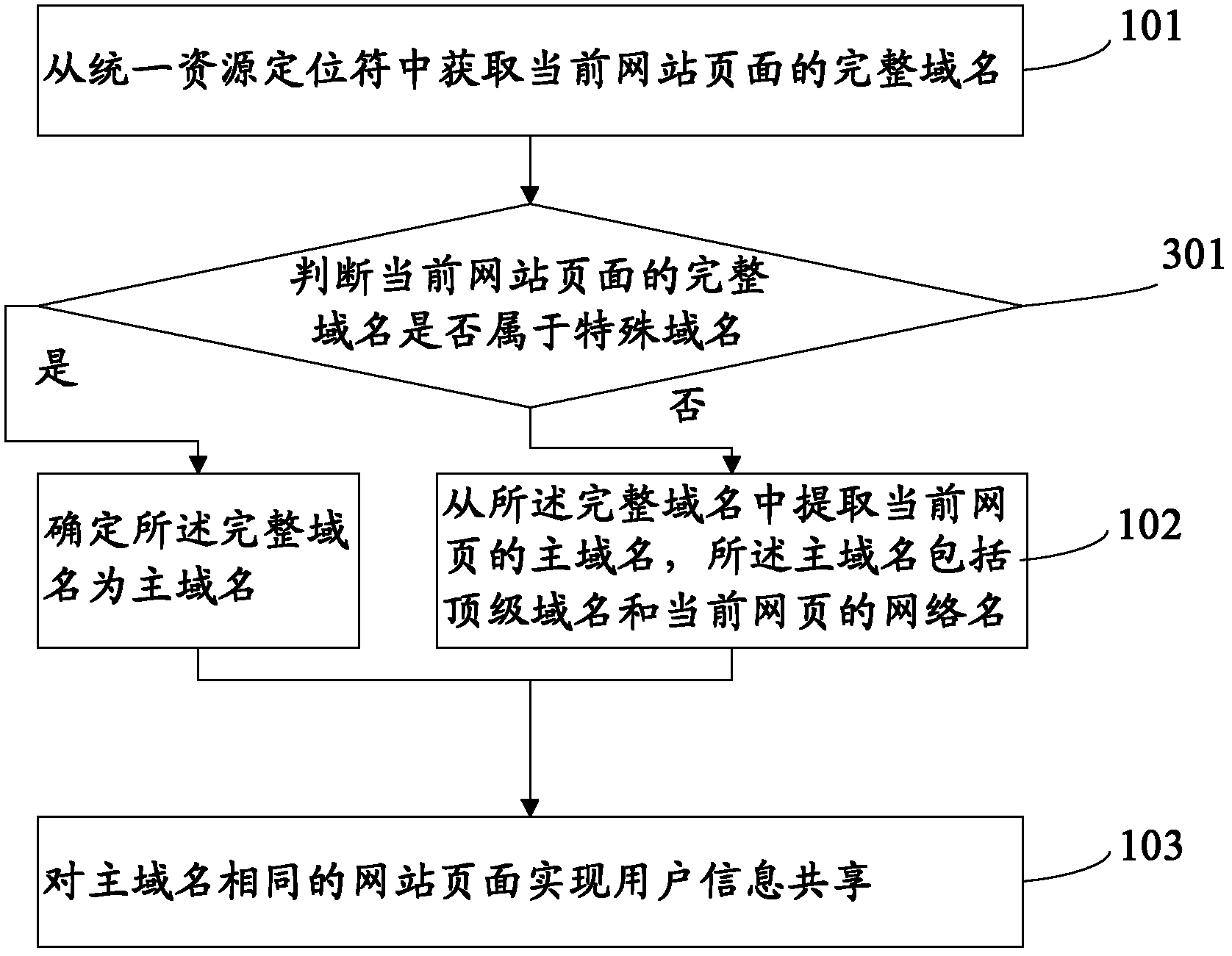
ActiveCN102664926AAchieve sharingReduce storageTransmissionInformation sharingFully qualified domain name
The application provides a user information sharing method, comprising the following steps: obtaining a complete domain name of a current webpage from a uniform resource locator; extracting a main domain name of the current webpage from the complete domain name, wherein the main domain name includes a top level domain name and a network name of the current webpage; and realizing user information sharing for webpages with same main domain names. In addition, the application also discloses a user information sharing system for realizing the method. According to the method and the system for user information sharing, occupation of system resources by user information records can be reduced; and sharing of user information can be realized.
Owner:BEIJING QIHOO TECH CO LTD
Method and arrangement for terminal reporting
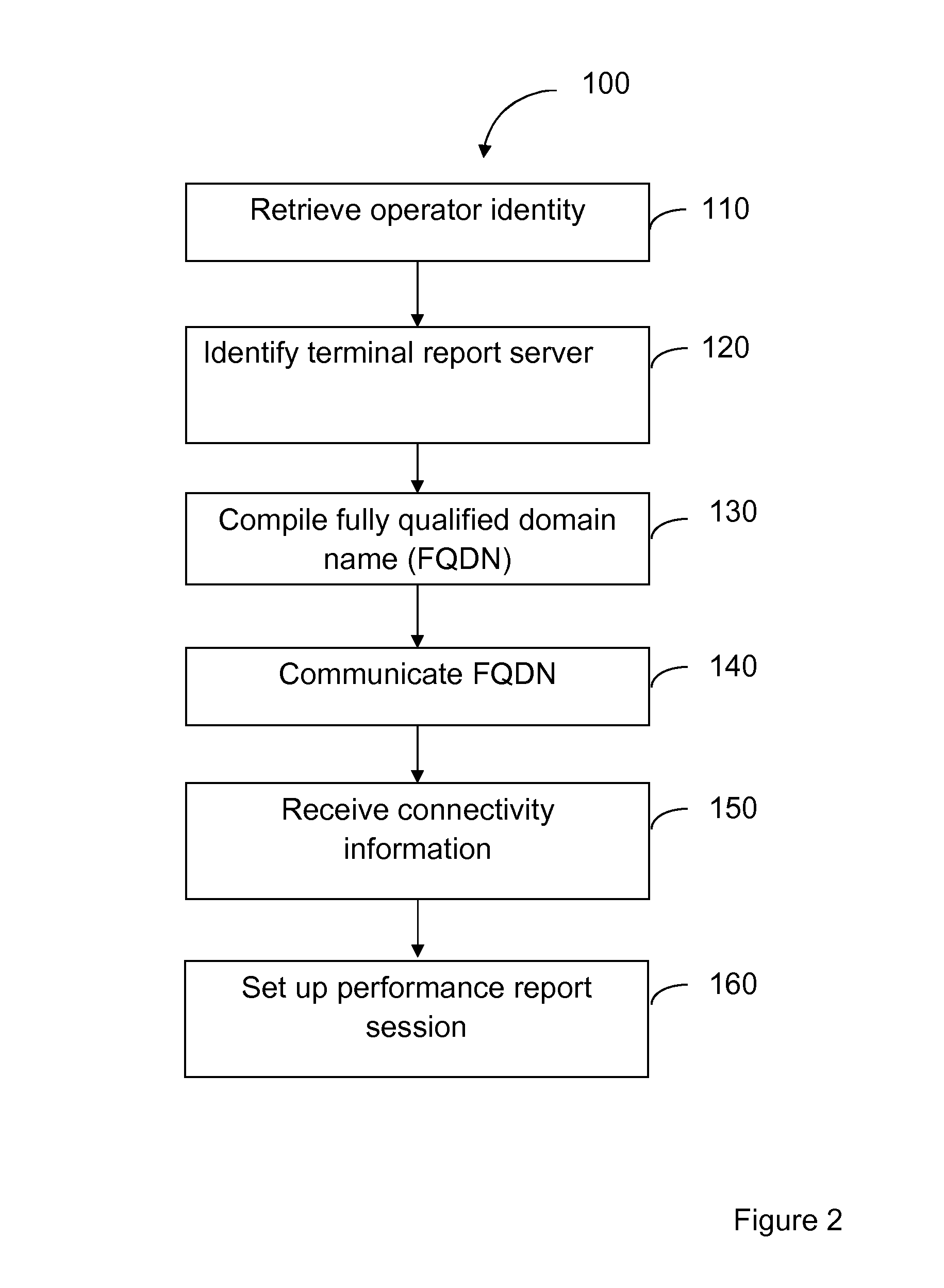
ActiveUS20140295864A1Broaden their knowledgeReduce needConnection managementTransmissionDomain nameFully qualified domain name
The invention relates to a method for performance reporting in a wireless network, wherein at least one terminal is associated to a terminal report server by means of information in the terminal. Prior to initiating the performance report, information on operator identity is retrieved. The operator identity is combined with information identifying the associated terminal report server to compile a fully qualified domain name. Connectivity information to the terminal server report is requested and received from a domain name server, whereupon a performance report session to the terminal report server is initiated using the received connectivity information. The invention also relates to a terminal wherein the inventive method is applied.
Owner:TELEFON AB LM ERICSSON (PUBL)
Computer networks with unique identification
InactiveUS20110264806A1Function increaseDigital computer detailsData switching networksData packDomain name
A computer network is described in which the data-link layer address, e.g. MAC address, of the network cards of client nodes are used to uniquely identify the nodes in the provision of network to application layer services. A link layer aware router may determine the MAC address of a client node from a data packet transmitted by the client node, and determines the services to provide to the user, e.g. a proxy redirect of the packet, based on a database of client node MAC addresses to user attributes. By determining MAC addresses, the router can also identify unregistered MAC addresses, and can forward a HTTP request by an unregistered user to a remote configuration web page for registering the user or to a security warning web page. The router may also support Network Address Translation and Domain Name System services using the MAC addresses, with a fully qualified domain name, hostname or the like being assigned to the MAC addresses.
Owner:ADVANCED NETWORK TECH LAB
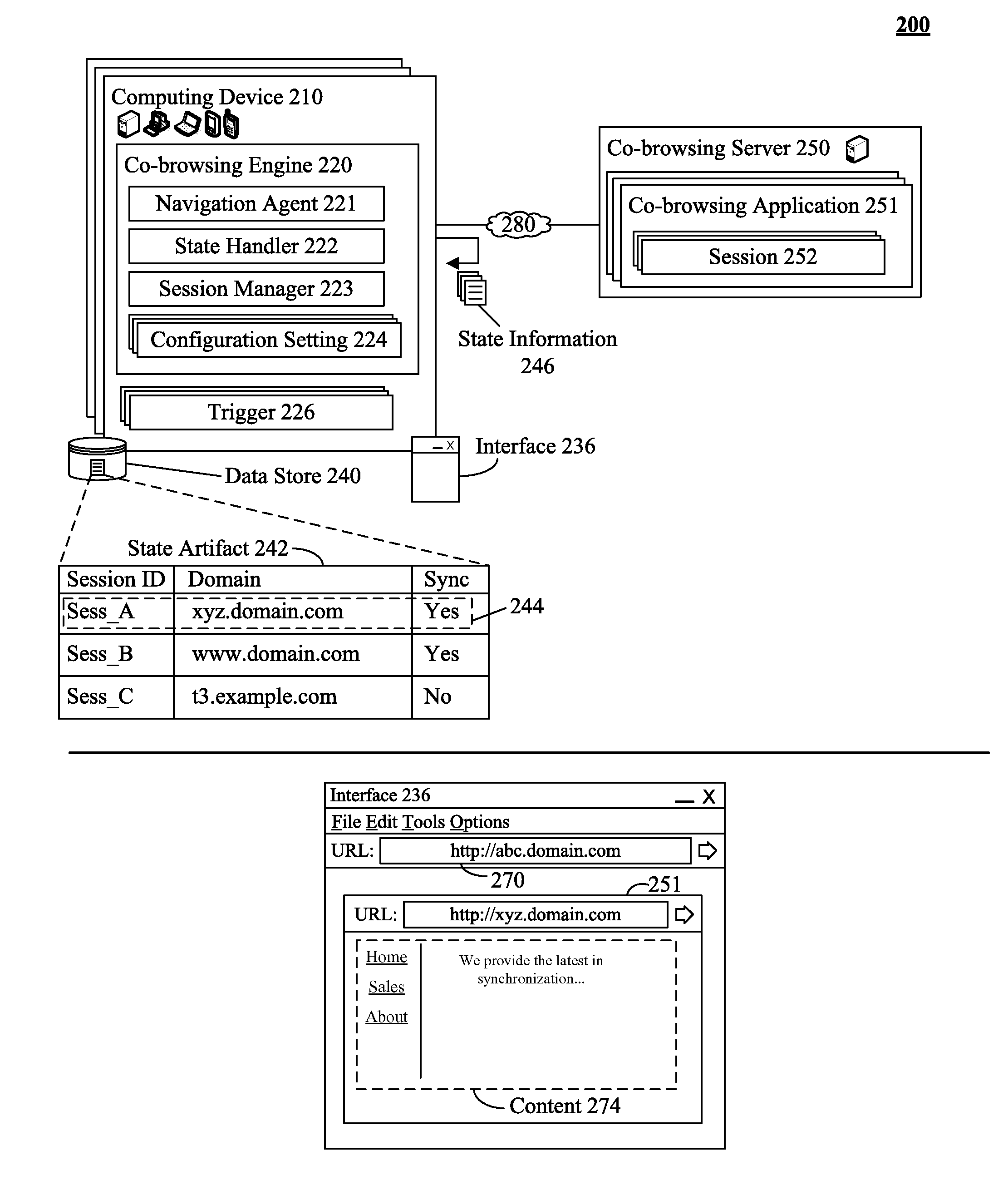
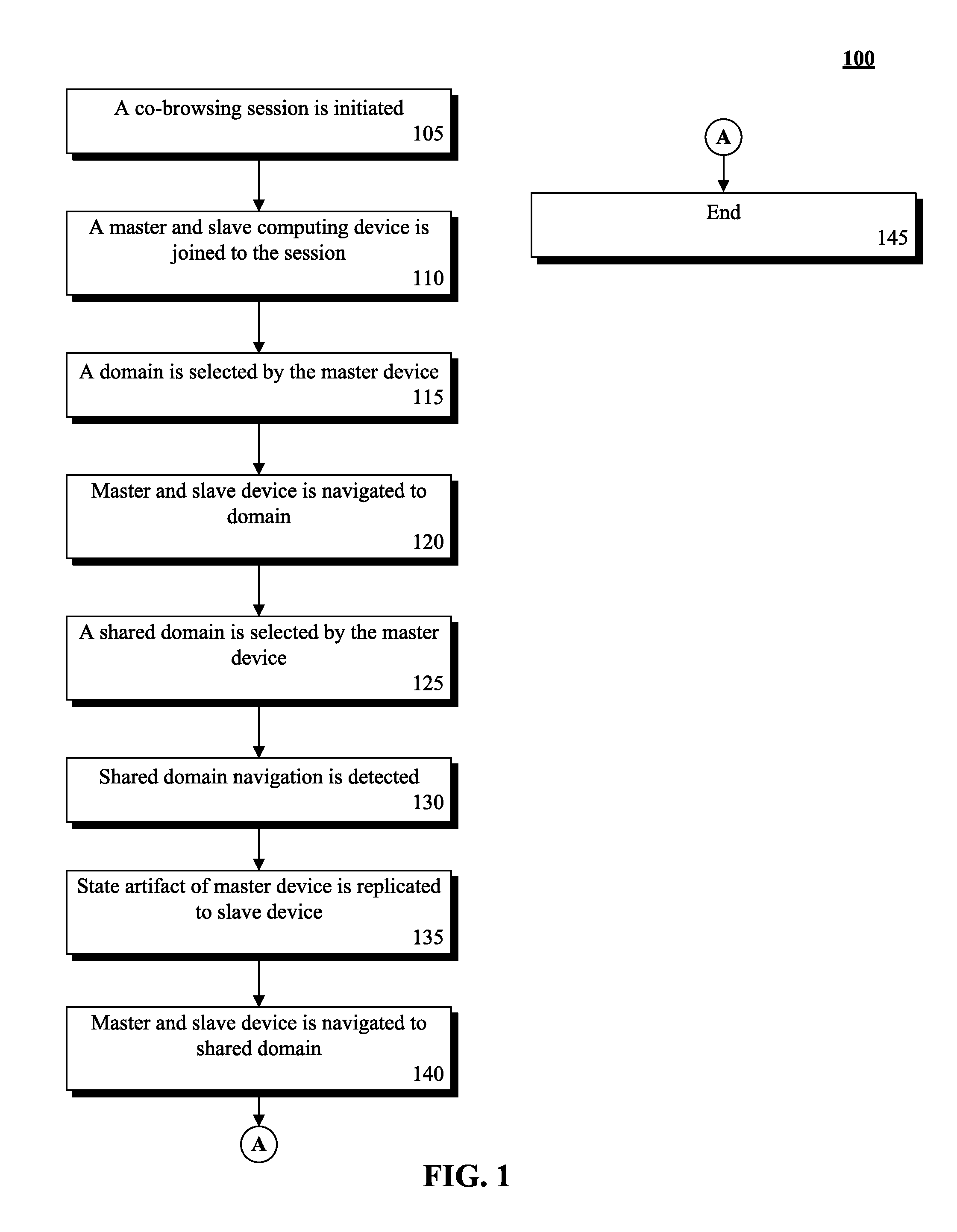
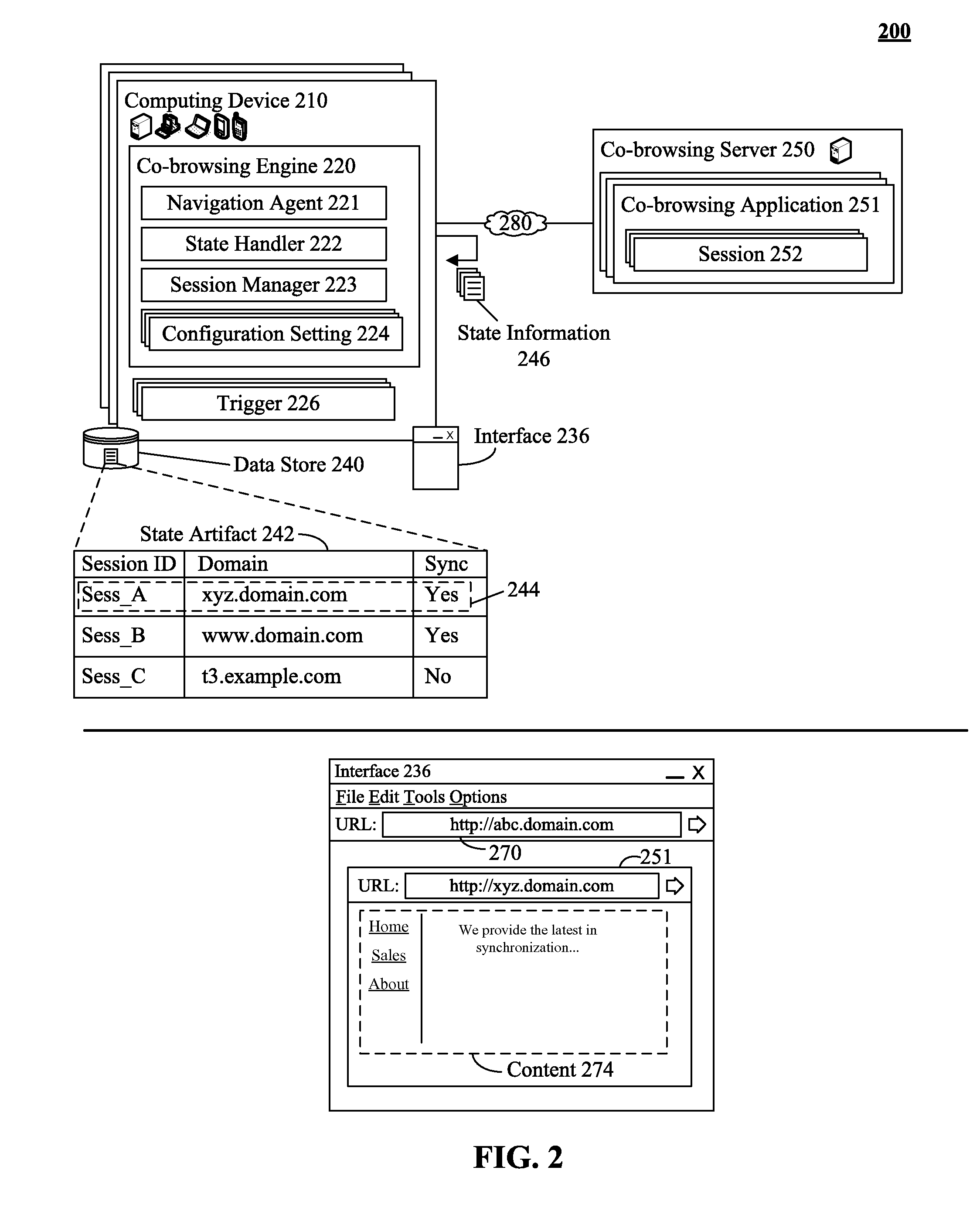
Multi-domain co-browsing utilizing localized state management
InactiveUS20120297007A1Improving multi-domain co-browsingMultiple digital computer combinationsTransmissionDomain nameFully qualified domain name
A master and a slave computing device within a co-browsing session can be identified. The devices can be associated with a first Unified Resource Identifier (URI) where a portion of the URI is a fully qualified domain name of a Domain Name System (DNS) hierarchy. The devices can be associated with a co-browsing application. A request associated with a second URI from the master computing device can be detected. The second URI can share a root domain with the first URI. A portion of a master artifact associated with the master device can be conveyed to the slave device. The master artifact can be associated with state information of the session. A portion of a slave artifact linked to the slave device can be modified with the portion of the master artifact. The devices can be navigated to the second URI in response to the request.
Owner:IBM CORP
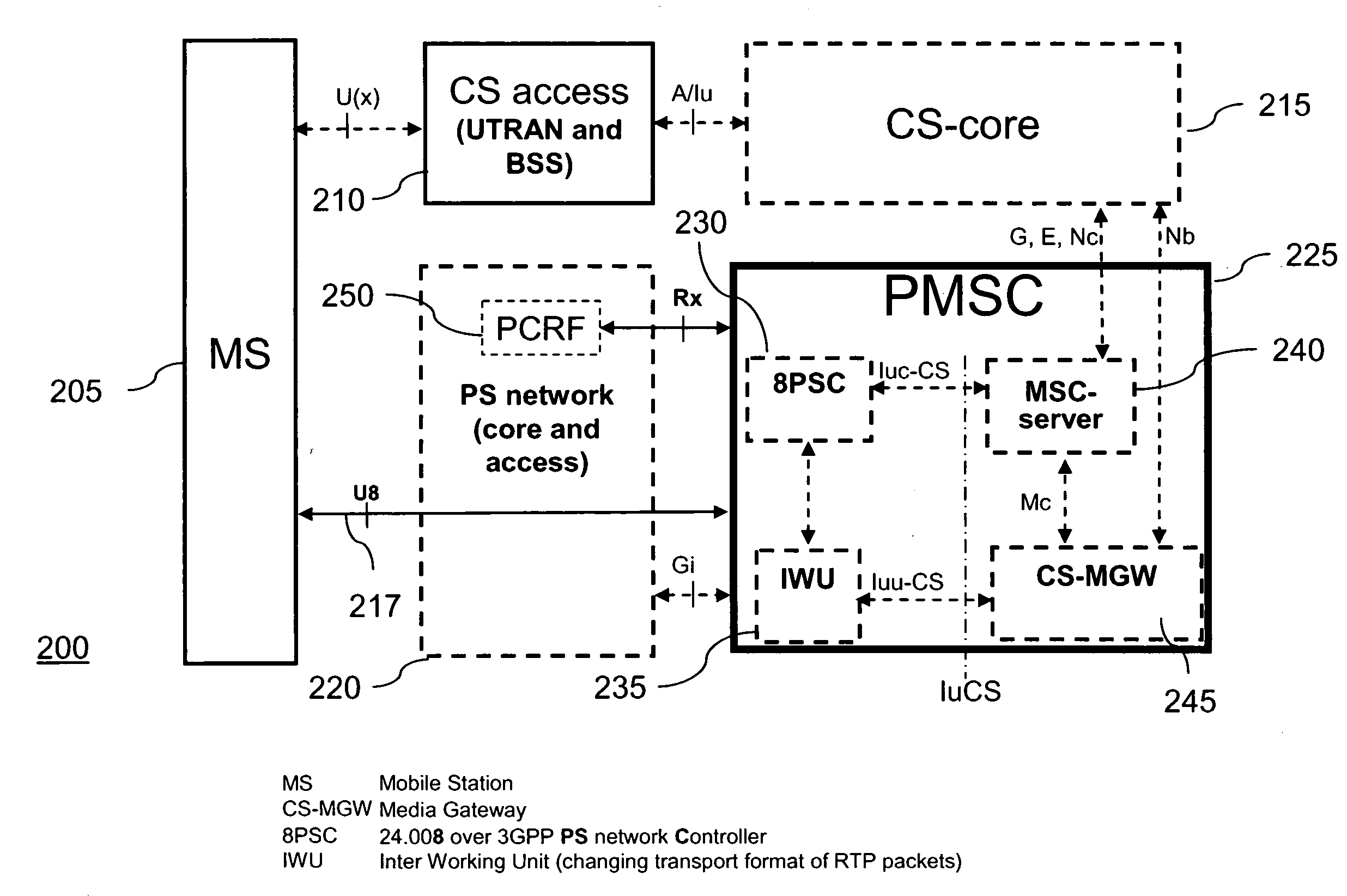
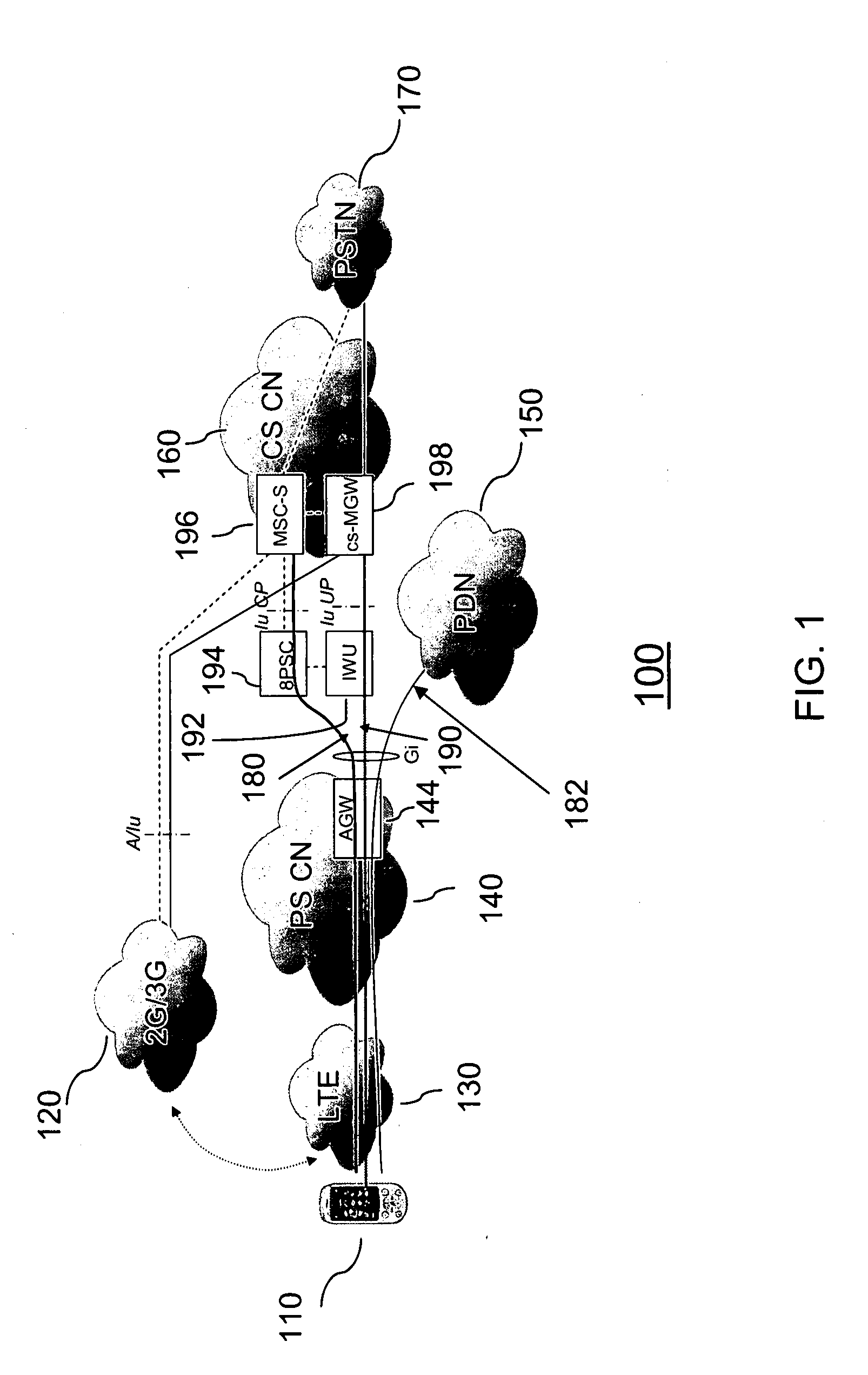
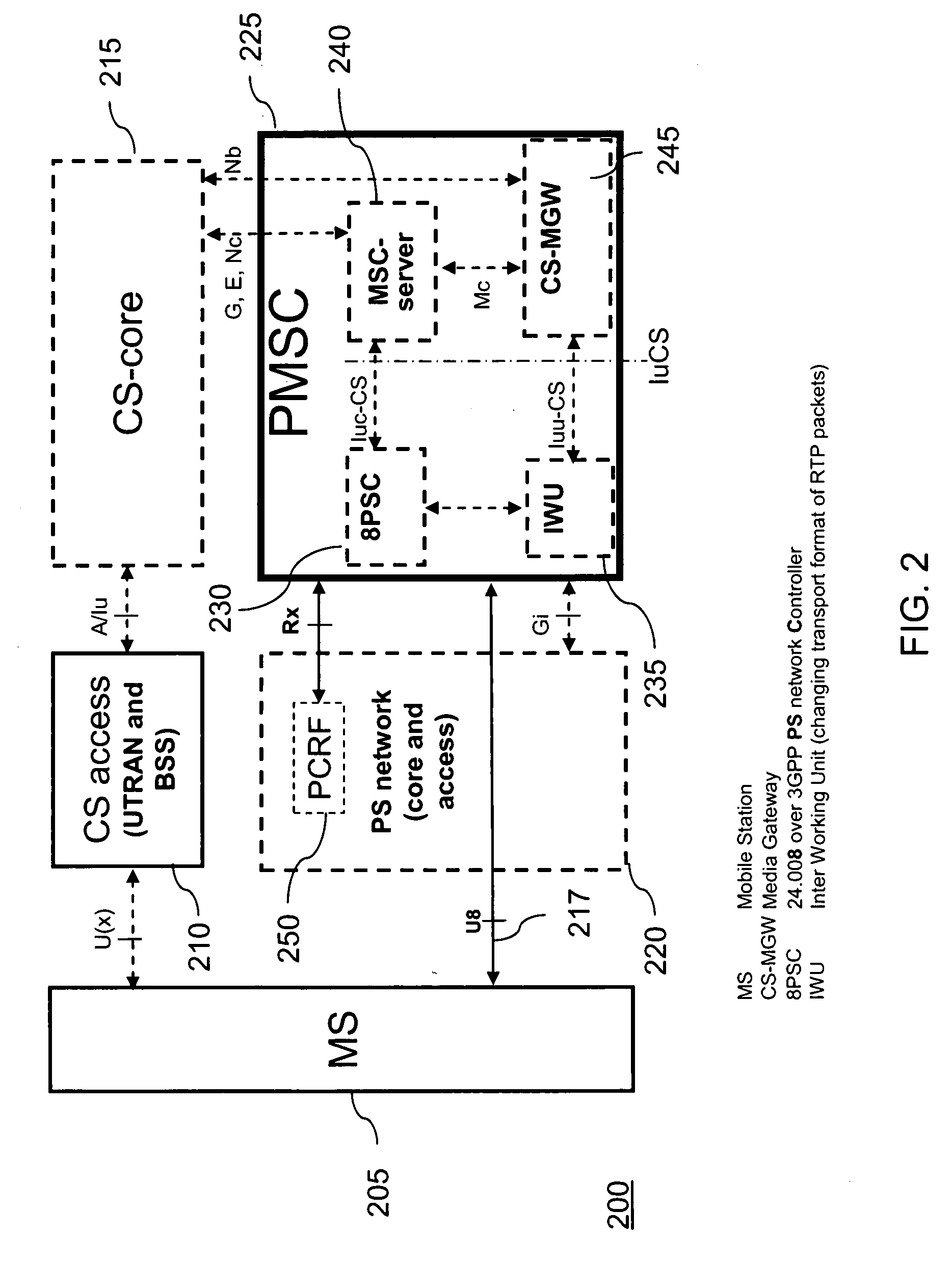
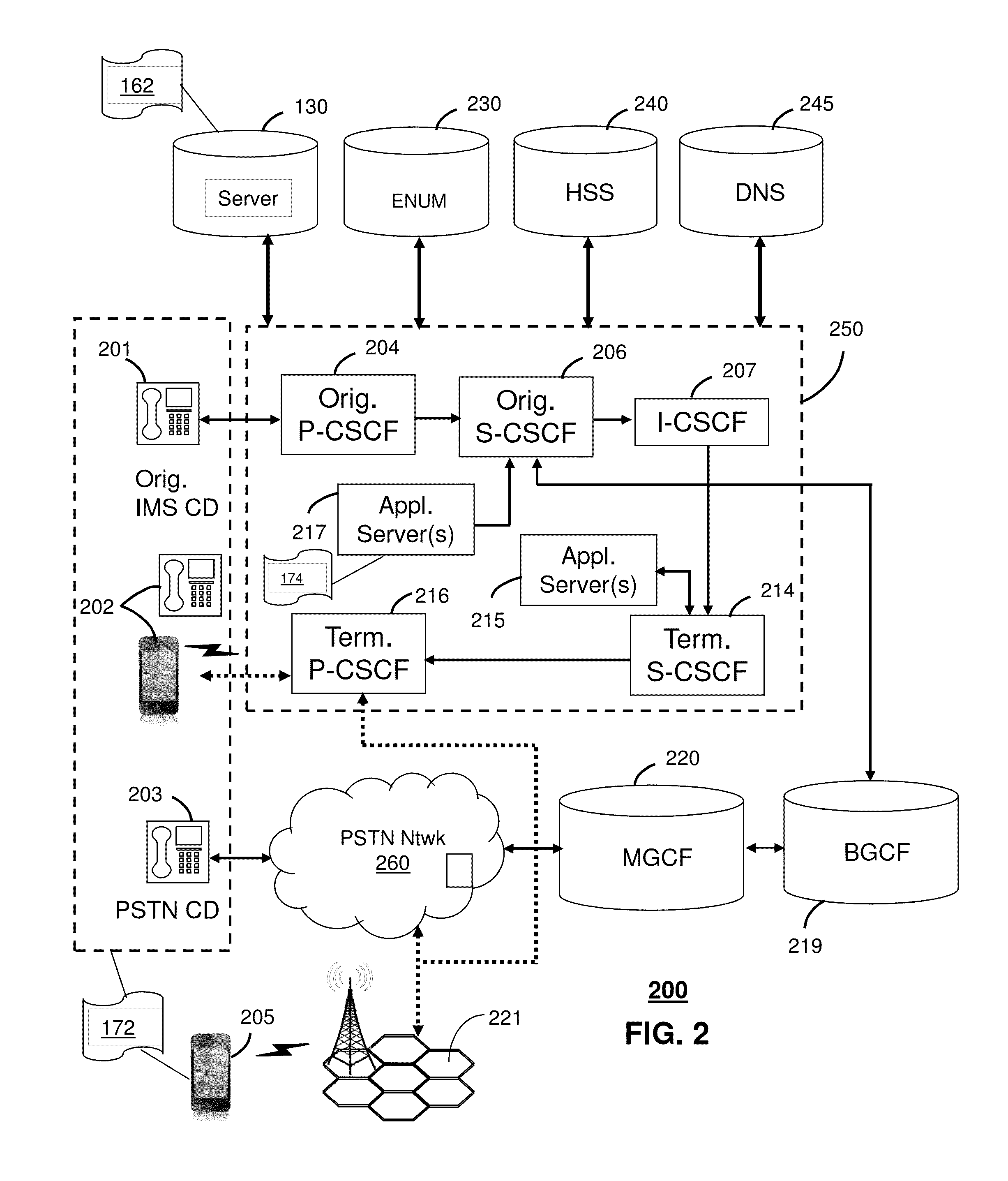
Method and apparatus for providing circuit switched domain services over a packet switched network
A method of determining a domain mode for a mobile station operating in either a circuit-switched domain or a packet-switched domain. A first domain mode is determined, and then a determination is made whether to rove from the first domain mode to a second domain mode. The determination may be made by a Packet Mobile Switching Center (PMSC) when, for example, the mobile station moves between Routing Areas. Alternatively, the mobile station may make the determination based, for example, on pre-provisioned selection criteria. The mobile station derives a Fully Qualified Domain Name (FQDN) based on a cell identifier of a current cell and uses the FQDN in a DNS query to obtain the IP address of the PMSC.
Owner:TELEFON AB LM ERICSSON (PUBL)
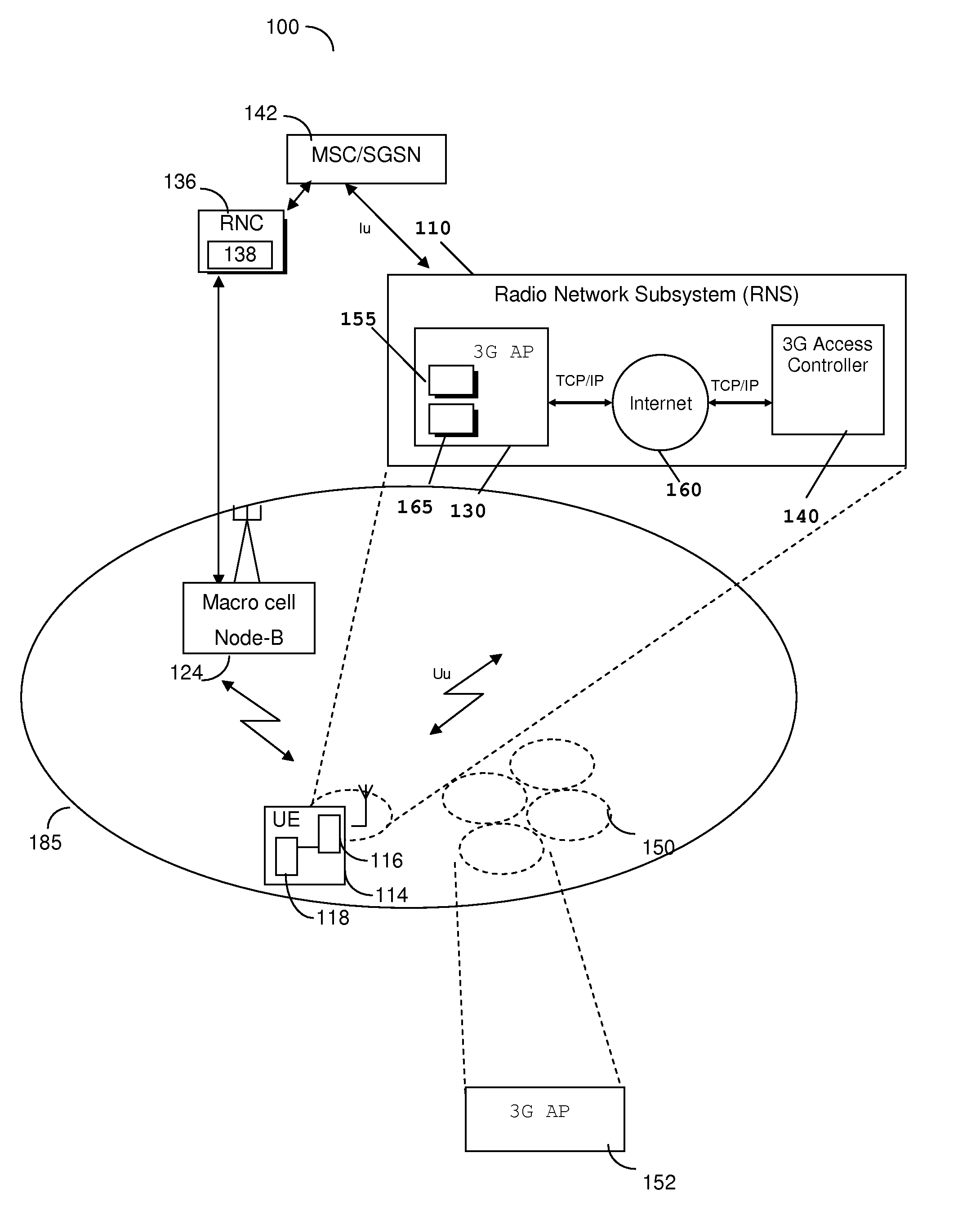
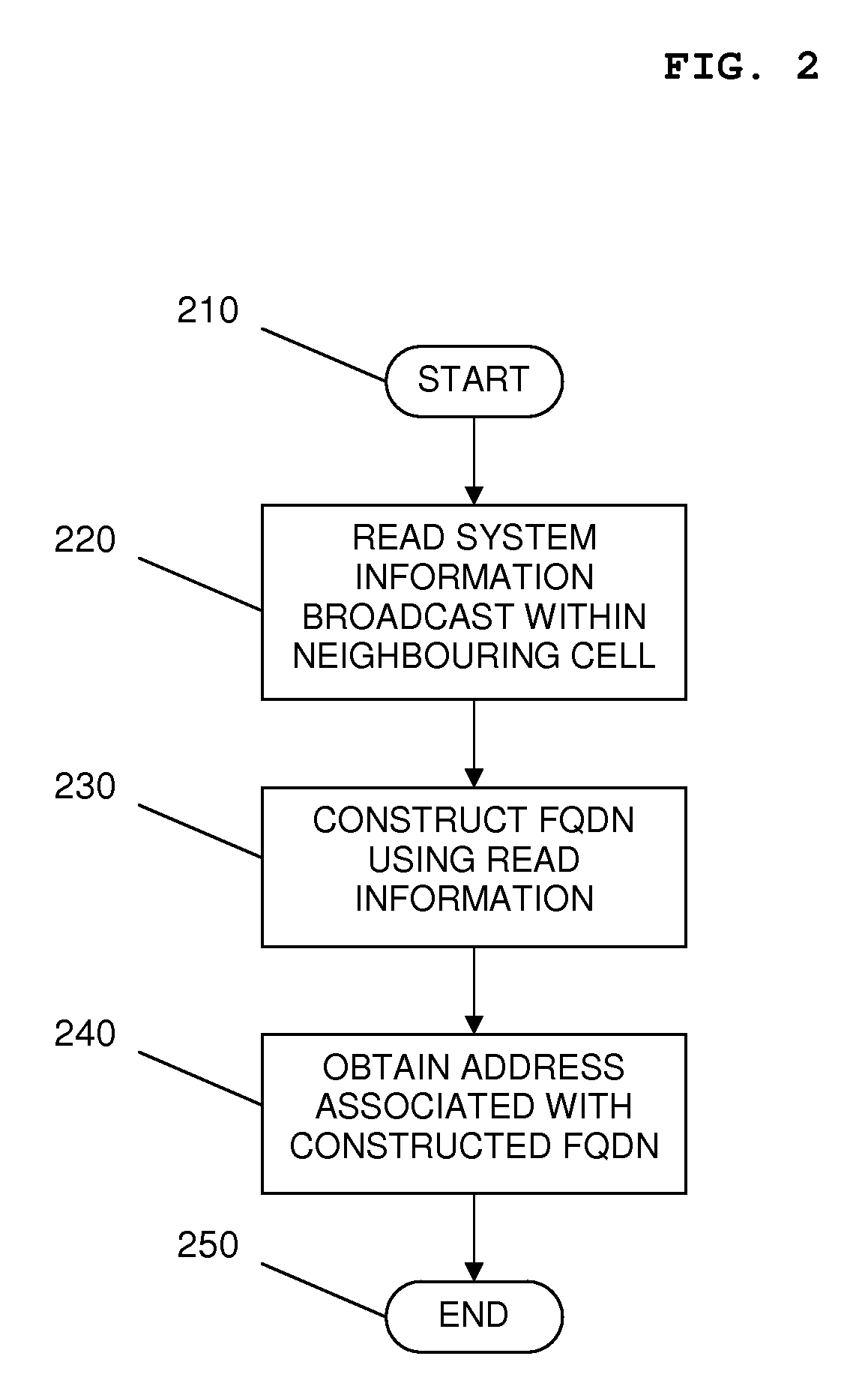
Method and apparatus for obtaining an address associated with a neighbouring cell of a cellular communication network
InactiveUS20090310532A1Mitigate, alleviate or eliminate one orReduce needAssess restrictionNetwork topologiesDomain nameTransceiver
A network element (110) for supporting communications in a communication cell of a cellular communication network (100) can comprise transceiver circuitry arranged to enable communication with one or more wireless communication units (114) located within the general vicinity of the communication cell, and signal processing logic. The signal processing logic is arranged to read (220) system information broadcast within a neighbouring cell, construct (230) a Fully Qualified Domain Name (FQDN) using the read system information, and to obtain (240) an address associated with the constructed FQDN.
Owner:IP ACCESS LTD
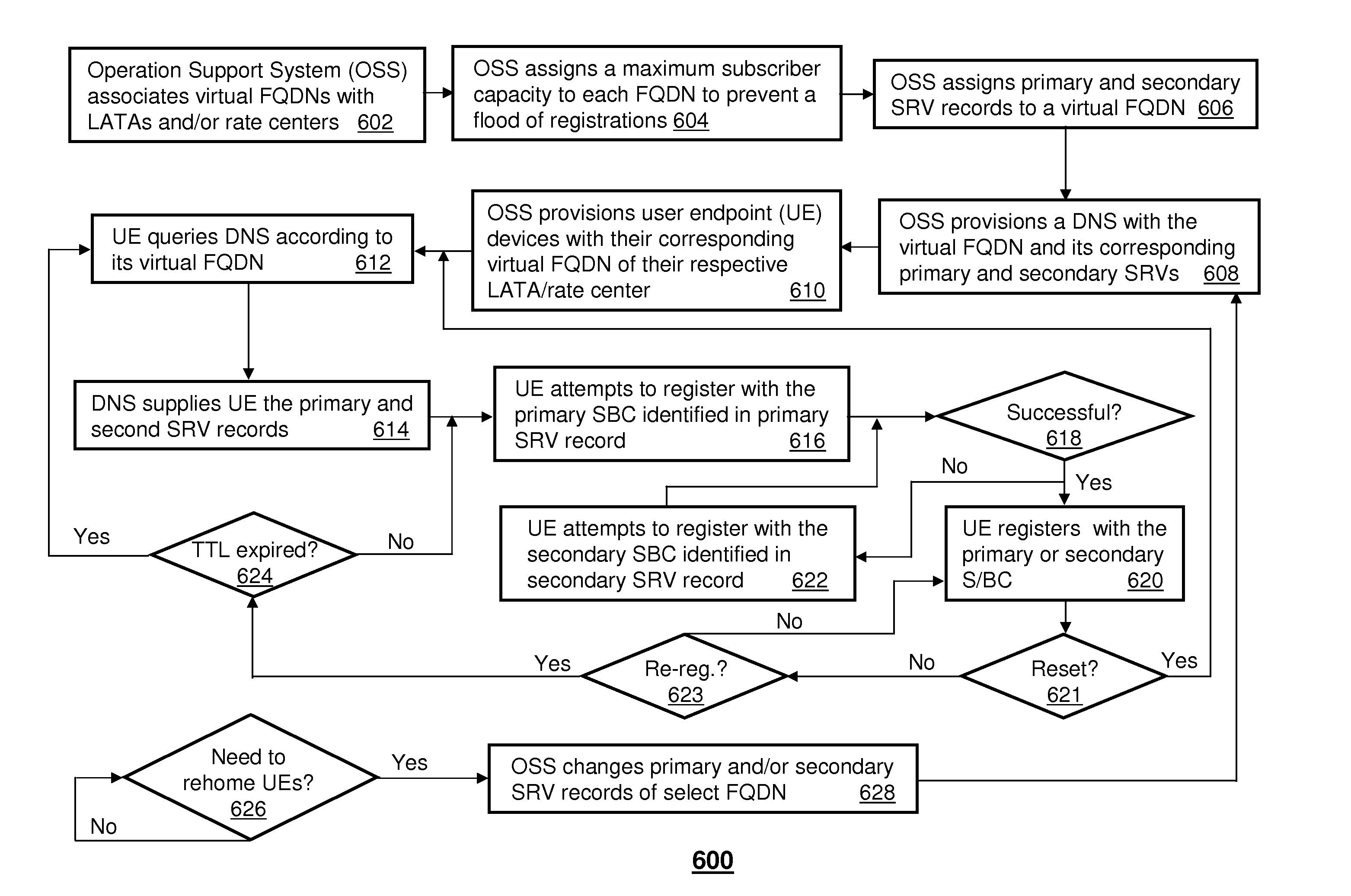
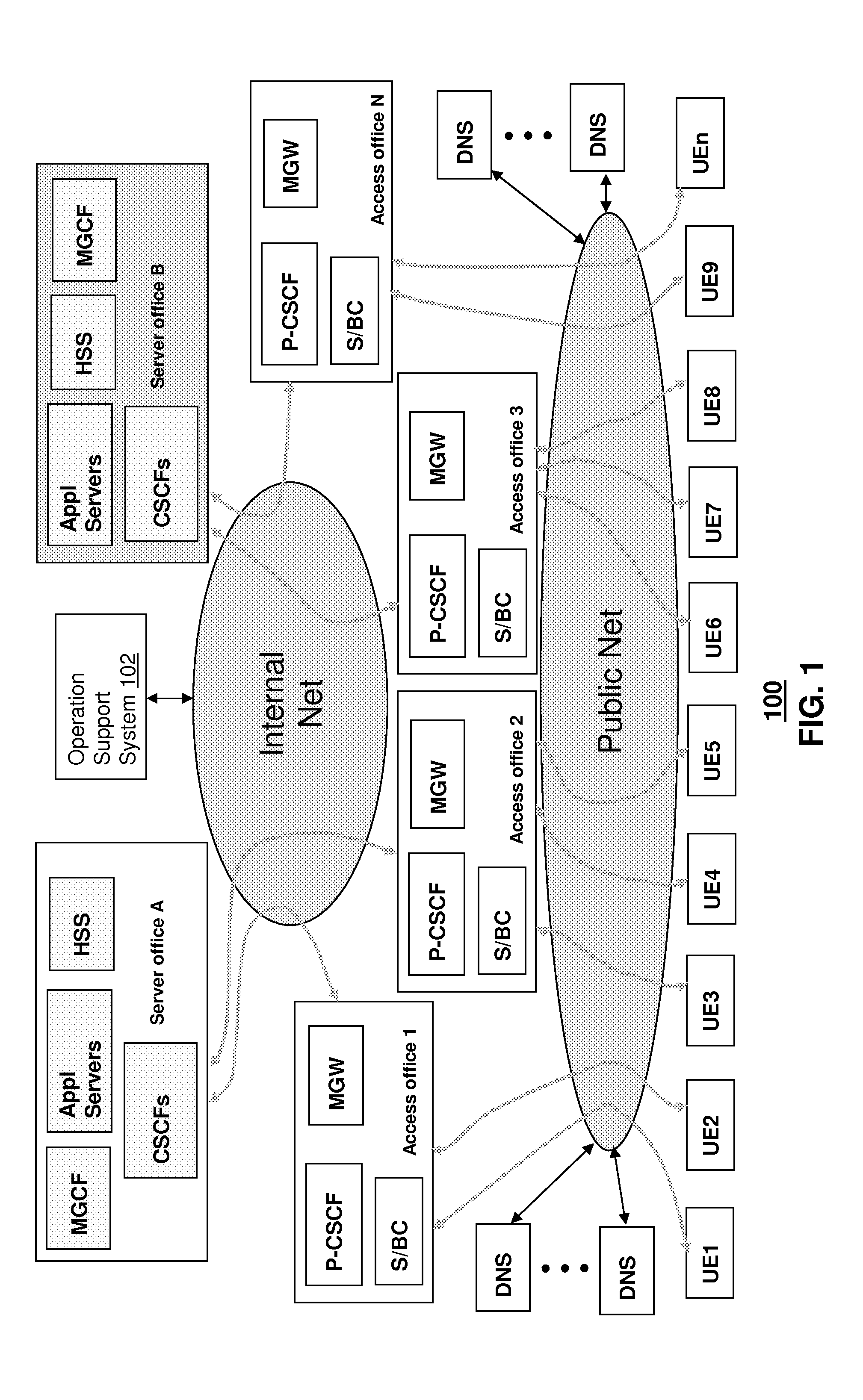
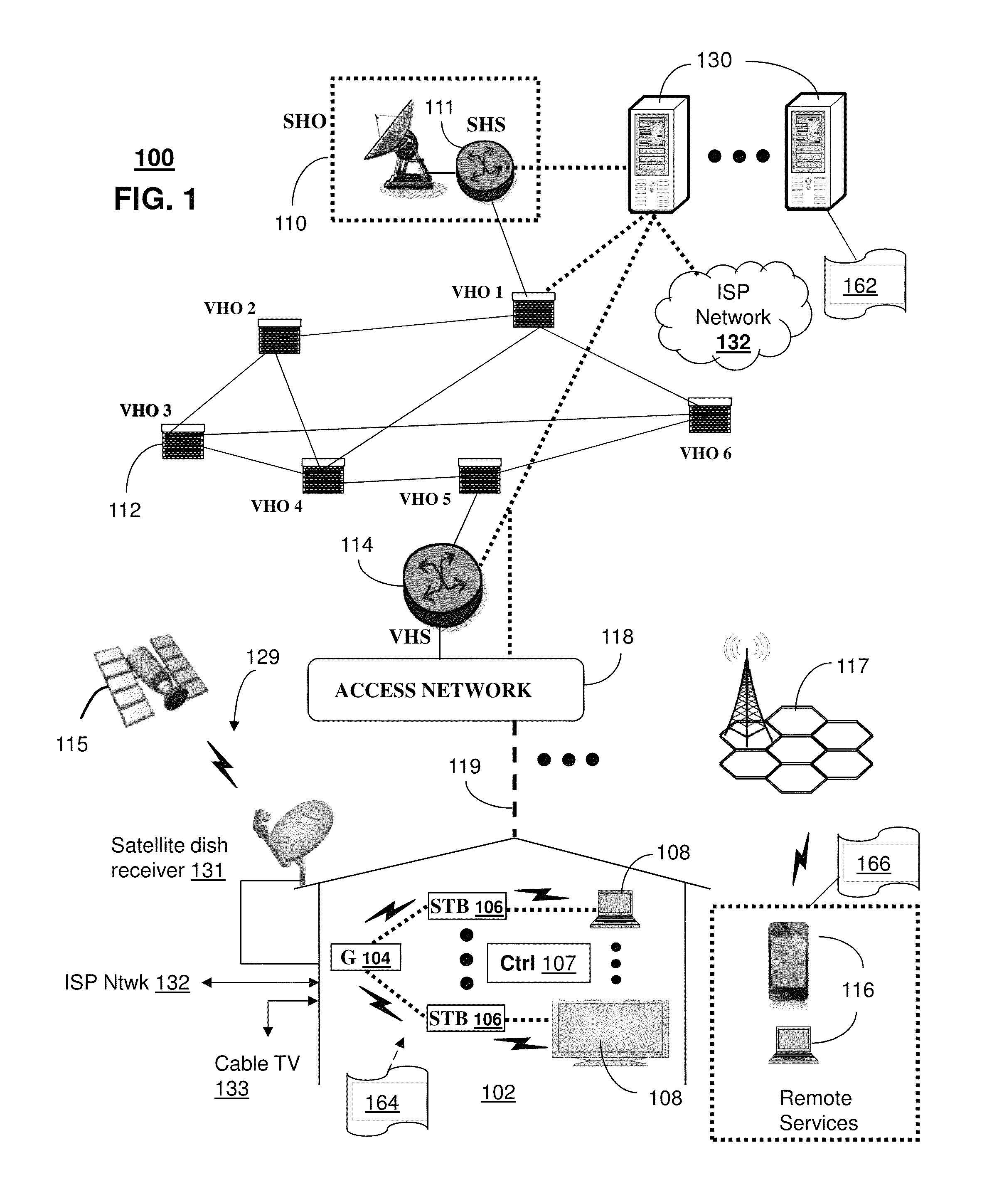
Method and apparatus for managing user endpoint devices in a communication network
ActiveUS8543640B2Multiple digital computer combinationsTransmissionDomain nameFully qualified domain name
A system that incorporates teachings of the present disclosure may include, for example, a user endpoint device having a controller to submit a query to a Domain Name System (DNS) for information associated with a Fully Qualified Domain Name (FQDN) assigned to at least one of a Local Access Transport Area (LATA) or rate center of the user endpoint device, and receive from the DNS one or more descriptors of one or more session border controllers, wherein the one or more descriptors are associated with the FQDN of the user endpoint device. Additional embodiments are disclosed.
Owner:AT&T INTPROP I L P
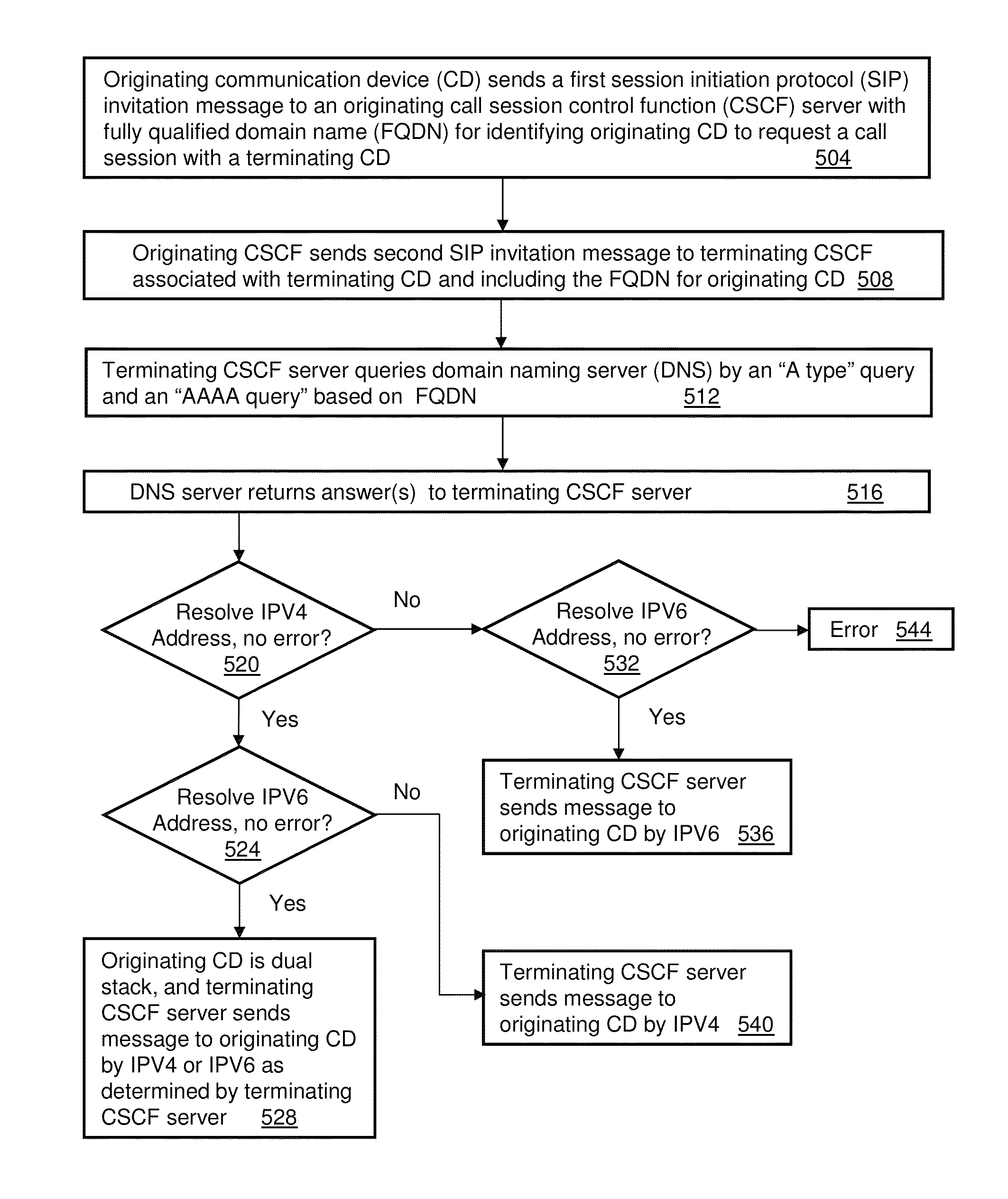
Apparatus and methods for flexible communicatons in a network
InactiveUS9015327B2Multiple digital computer combinationsTransmissionDomain nameSession Initiation Protocol
A method that incorporates teachings of the subject disclosure may include, for example, transmitting a first query to a domain naming server responsive to receiving a session initiation protocol message comprising a fully qualified domain name. The first query can include one of an internet protocol version 4 address query or an internet protocol version 6 address query associated with the fully qualified domain name. The method can include receiving at least one answer from the domain naming server. The at least one answer can include at least one of an internet protocol version 4 address having no errors, a second internet protocol version 6 address having no errors, or both. The method can also include transmitting a message to a communication device. The message can include information associated with the at least one answer.
Owner:AT&T INTPROP I LP
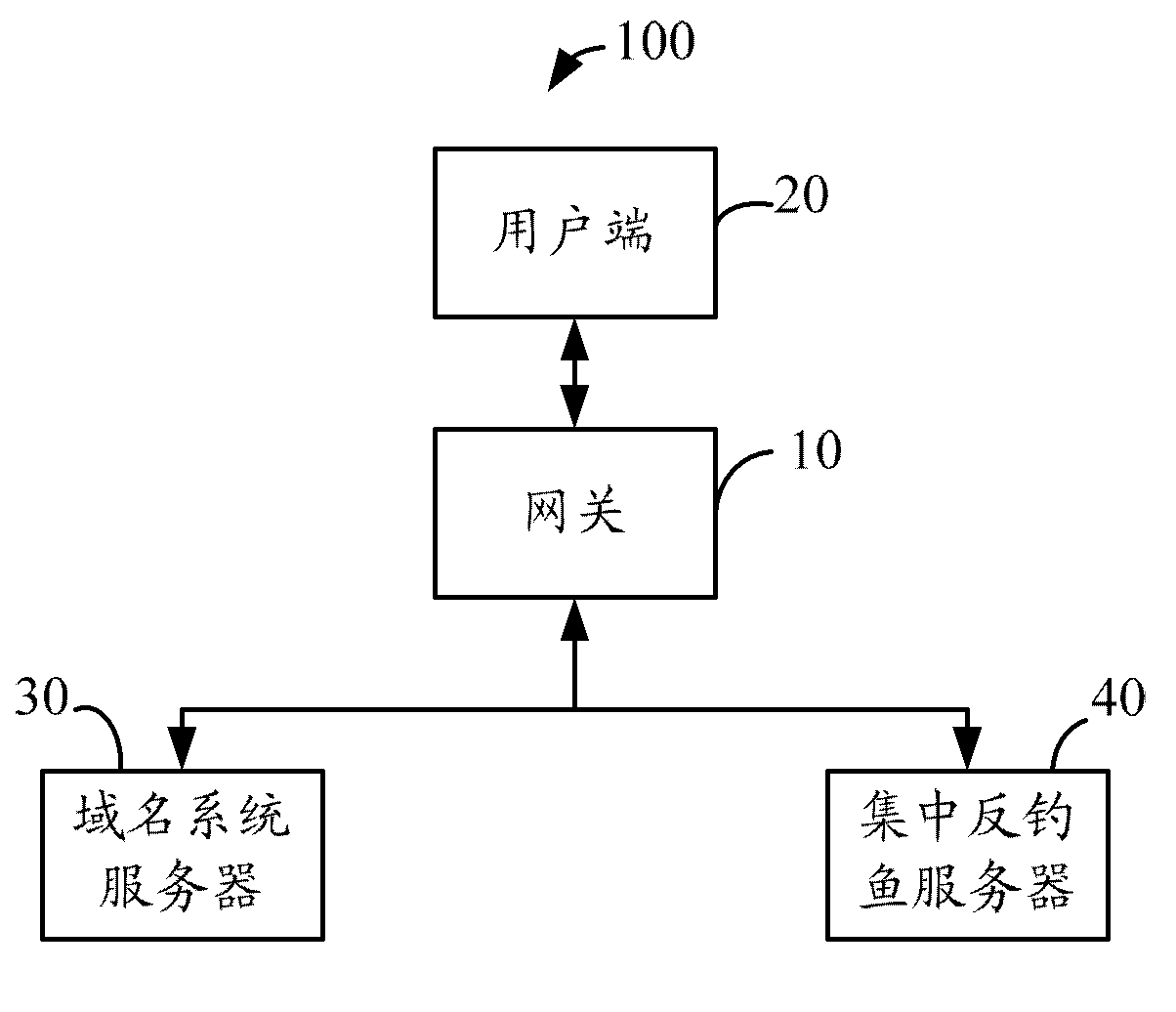
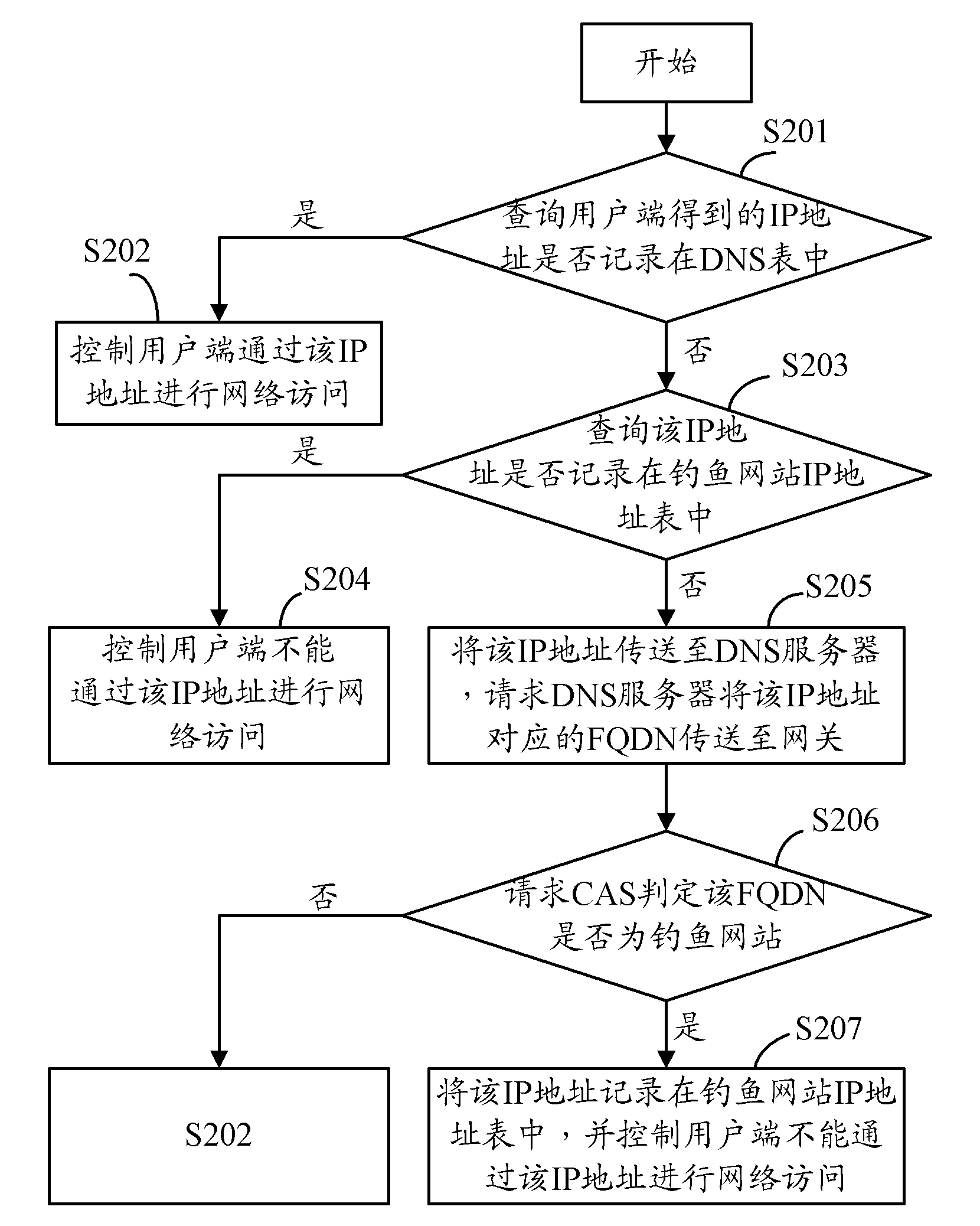
Gateway and method for phishing defense
InactiveCN102761500ASolve the problem of not being able to defend against phishingNetwork connectionsDomain nameFully qualified domain name
The invention provides a gateway and method for phishing defense. The method is applied to the gateway, and the gateway implements the following steps: when an IP (internet protocol) address obtained by the gateway after a domain name request is transmitted by a client does not exist in a DNS (domain name service) list and a phishing website IP address list, the IP address is transmitted to a DNS server for requesting the DNS server to transmit an FQDN (fully qualified domain name) corresponding to the IP address to the gateway, the IP address obtained by the DNS server through domain name resolution according to the domain name request transmitted by the client is recorded in the DNS list, and the IP address of at least one phishing website is recorded in the phishing website IP address list; and the gateway requests to centralize anti-phishing websites and judges whether the FQDN corresponding to the IP address is the phishing website or not, and when the FQDN corresponding to the IP address is not the phishing website, the gateway is used for controlling the client to perform network access through the IP address. The gateway can realize phishing defense by judging whether the IP address is the correct IP address, and further solve the problem that the phishing defense can not be realized through an existing centralized anti-phishing system when the client is attacked by a hacker in the prior art.
Owner:AMBIT MICROSYSTEMS (SHANGHAI) LTD
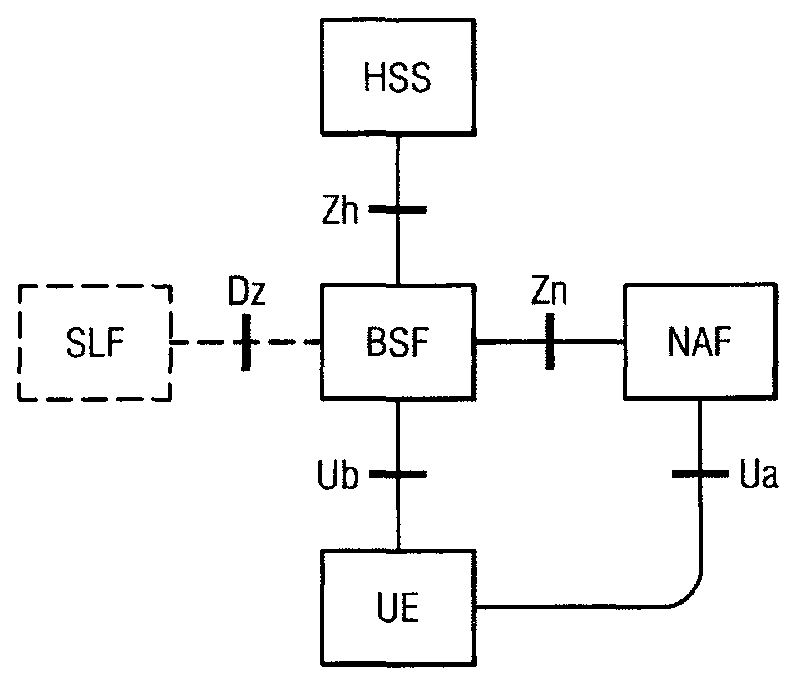
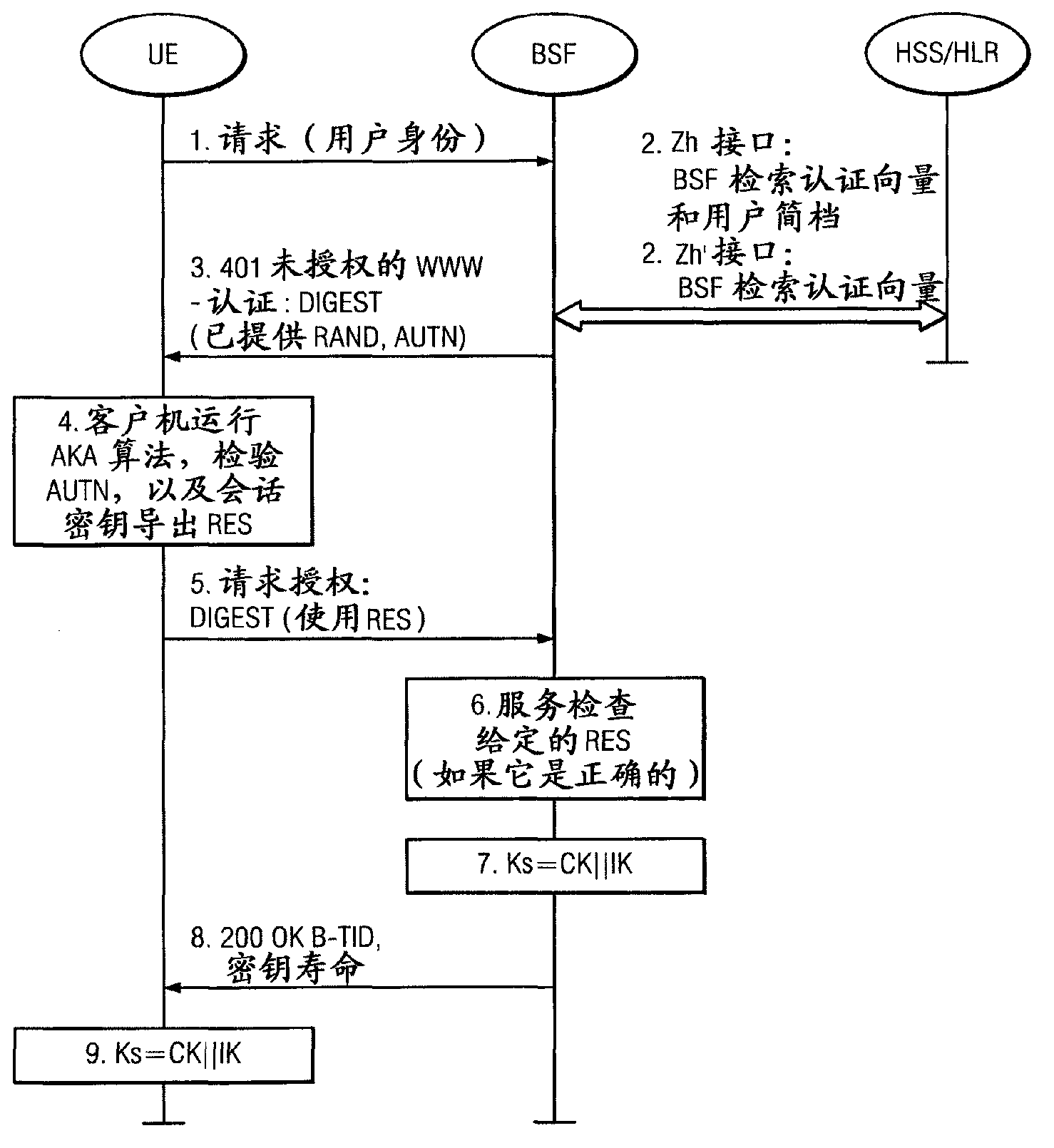
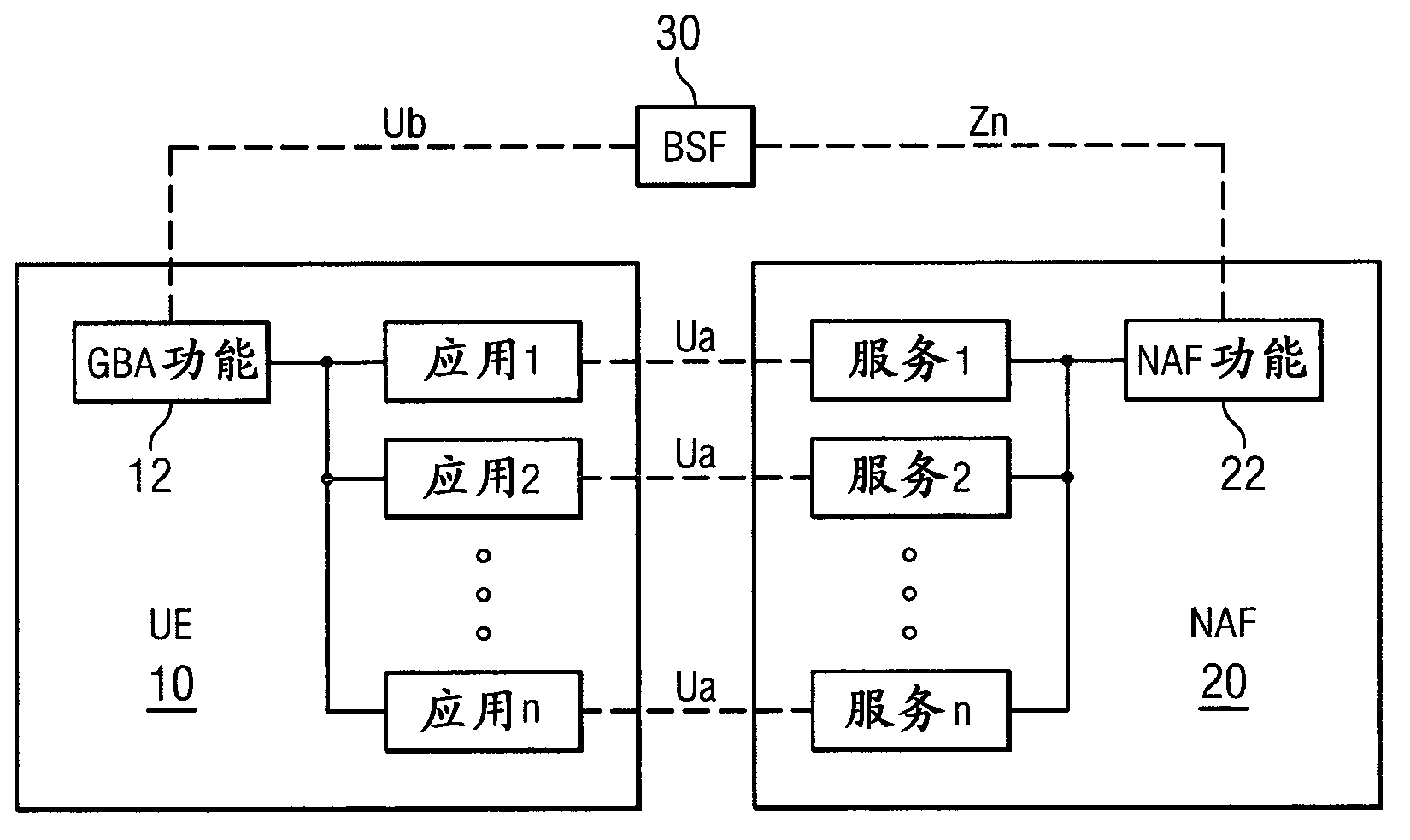
Generic bootstrapping architecture usage with web applications and web pages
ActiveCN103004244AKey distribution for secure communicationUser identity/authority verificationDomain nameFully qualified domain name
A method includes receiving at a network application function a request related to a generic bootstrapping architecture key originated from a user equipment (1). The received request includes a network application function identifier that includes a uniform resource locator, where the network application function has a fully qualified domain name. The method further includes causing a generic bootstrapping architecture key to be generated for the user equipment based at least in part on the uniform resource locator that is part of the network application function identifier (5). Apparatus and computer programs for performing the method are also disclosed.
Owner:NOKIA TECHNOLOGLES OY
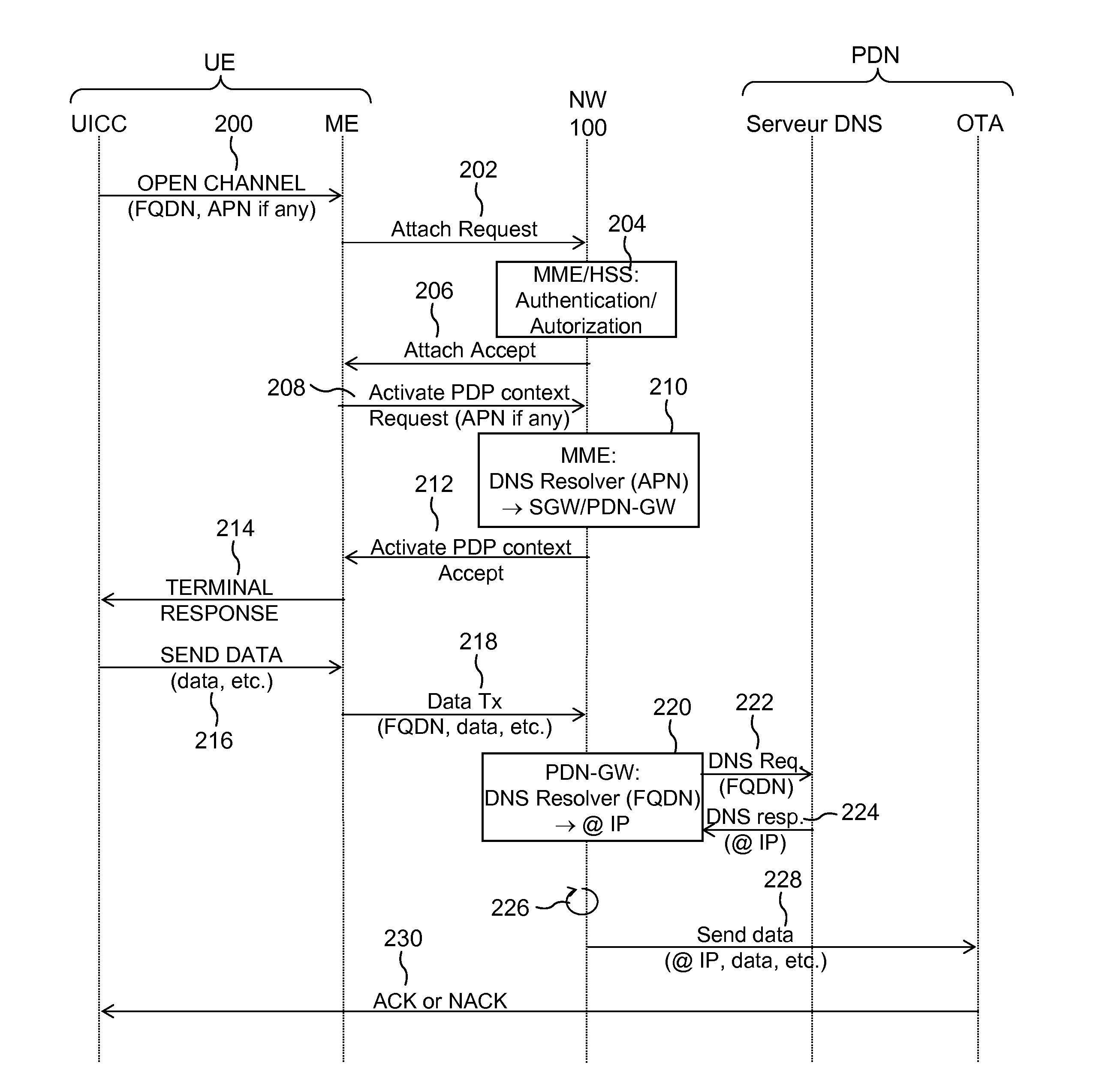
Method of establishing an IP connection in a mobile network and various corresponding equipment items
ActiveUS20140146747A1Efficiently distributedWaste of resourceWireless commuication servicesTransmissionDomain nameFully qualified domain name
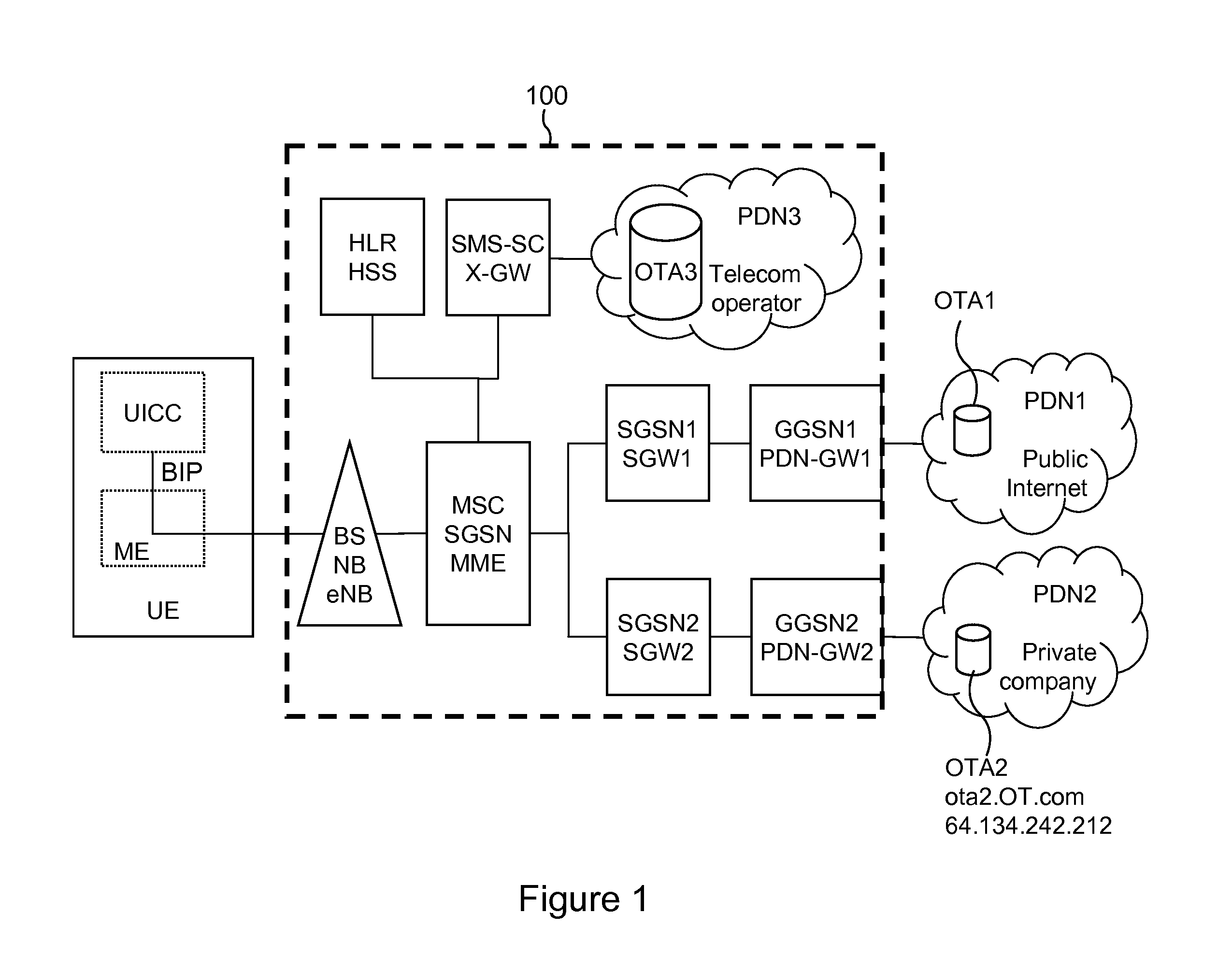
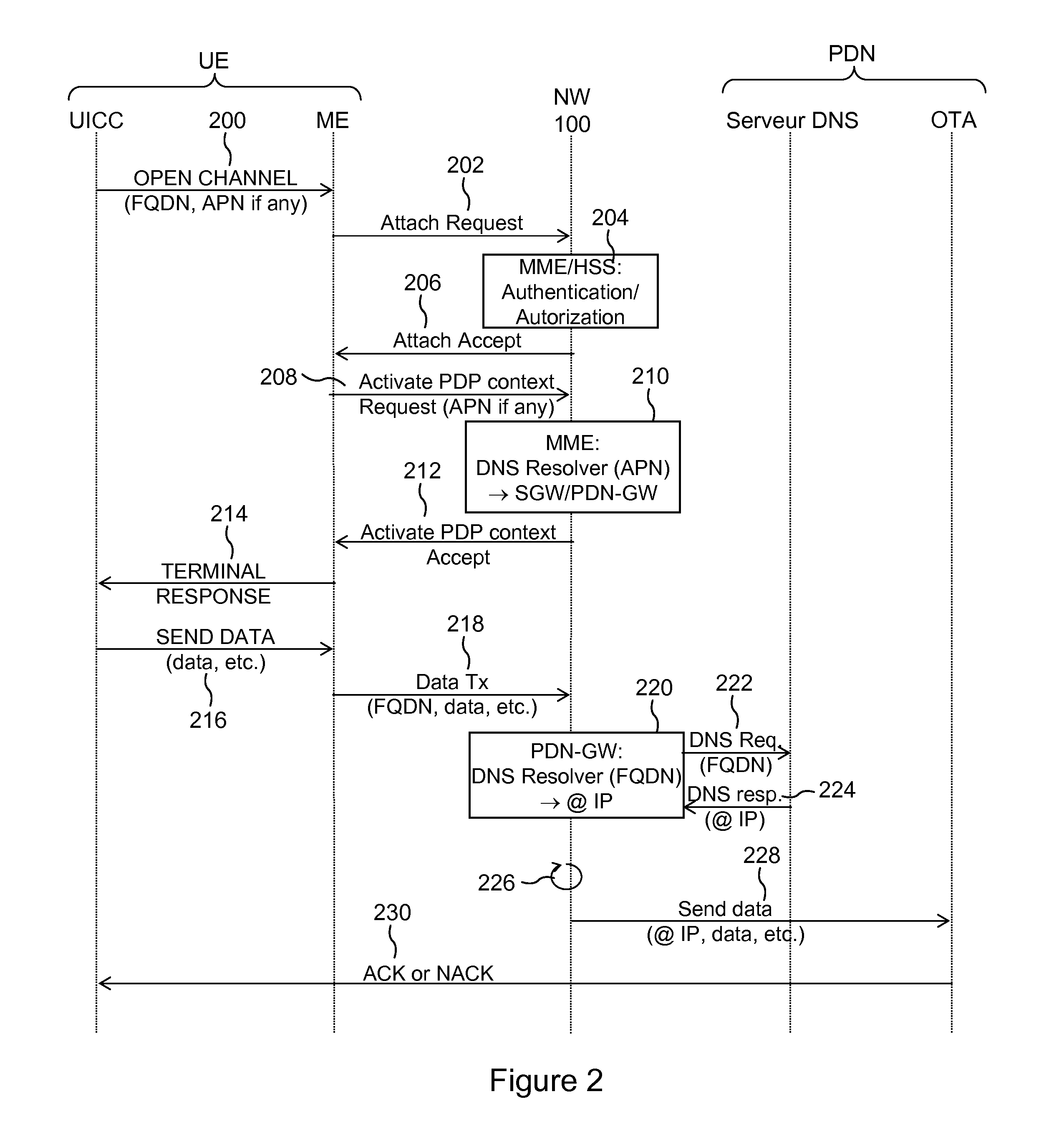
The disclosure relates to the field of wireless communications, and more particularly a method of establishing an IP connection through a 3GPP mobile network, at least partially of IP type, a network equipment item, MME or PDN-GW, of that mobile network, a mobile network infrastructure, a mobile terminal and a corresponding system. The method includes the following steps, on a first equipment item, MME or PDN-GW, of the mobile network other than a mobile equipment item UE of the mobile network: receiving a fully qualified domain name, FQDN, sent by a mobile equipment item, UE, of the mobile network, the FQDN identifying a target data server; and on reception of the FQDN, triggering the resolution of the FQDN into an IP address of the target data server. Thus, a mobile user equipment item provided with a UICC card may be produced at low cost without incorporating DNS resolution mechanisms.
Owner:IDEMIA FRANCE
Method for managing data sharing among application programs
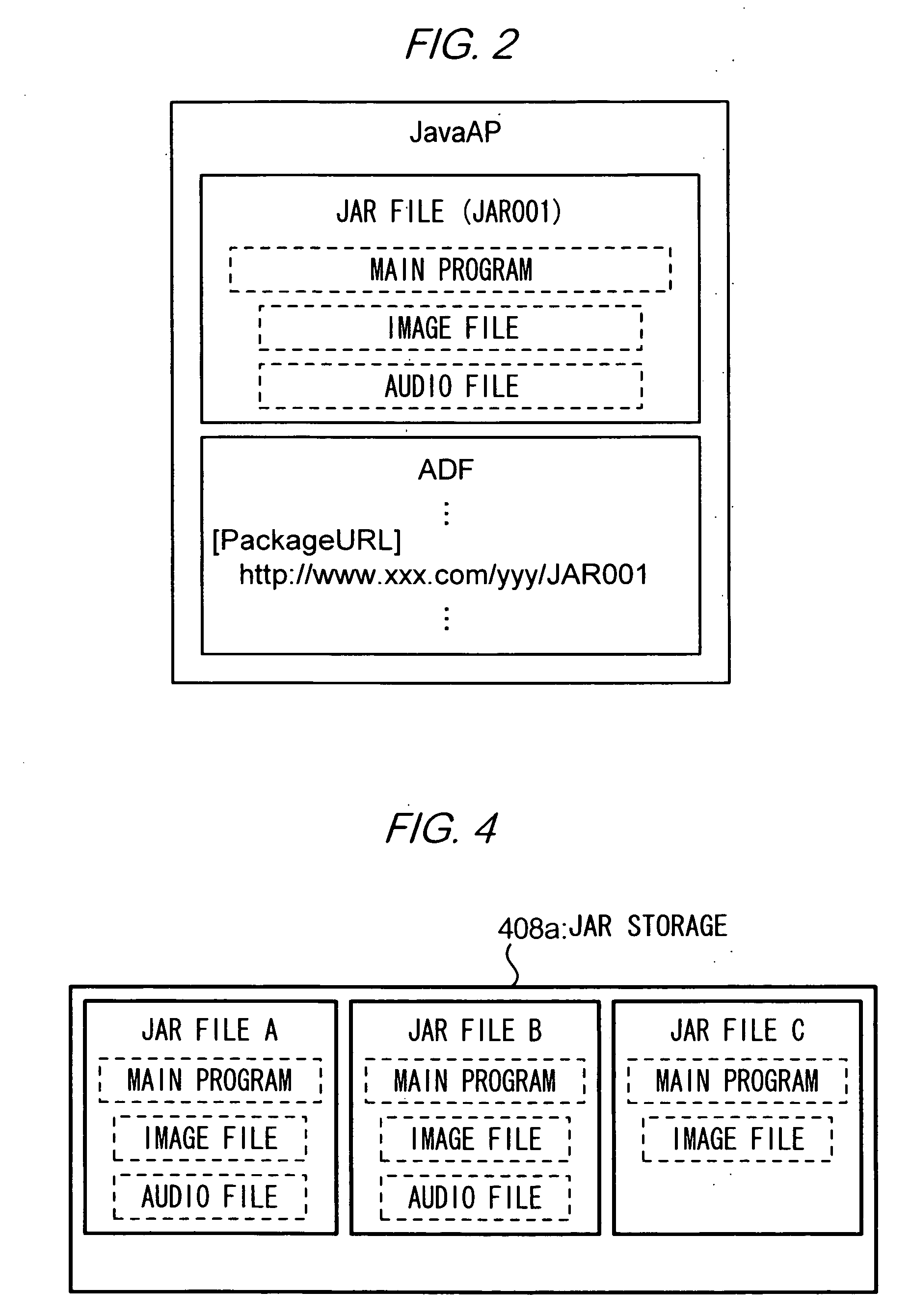
InactiveUS20050021792A1Keep data safeDigital data processing detailsUnauthorized memory use protectionFully qualified domain nameData transport
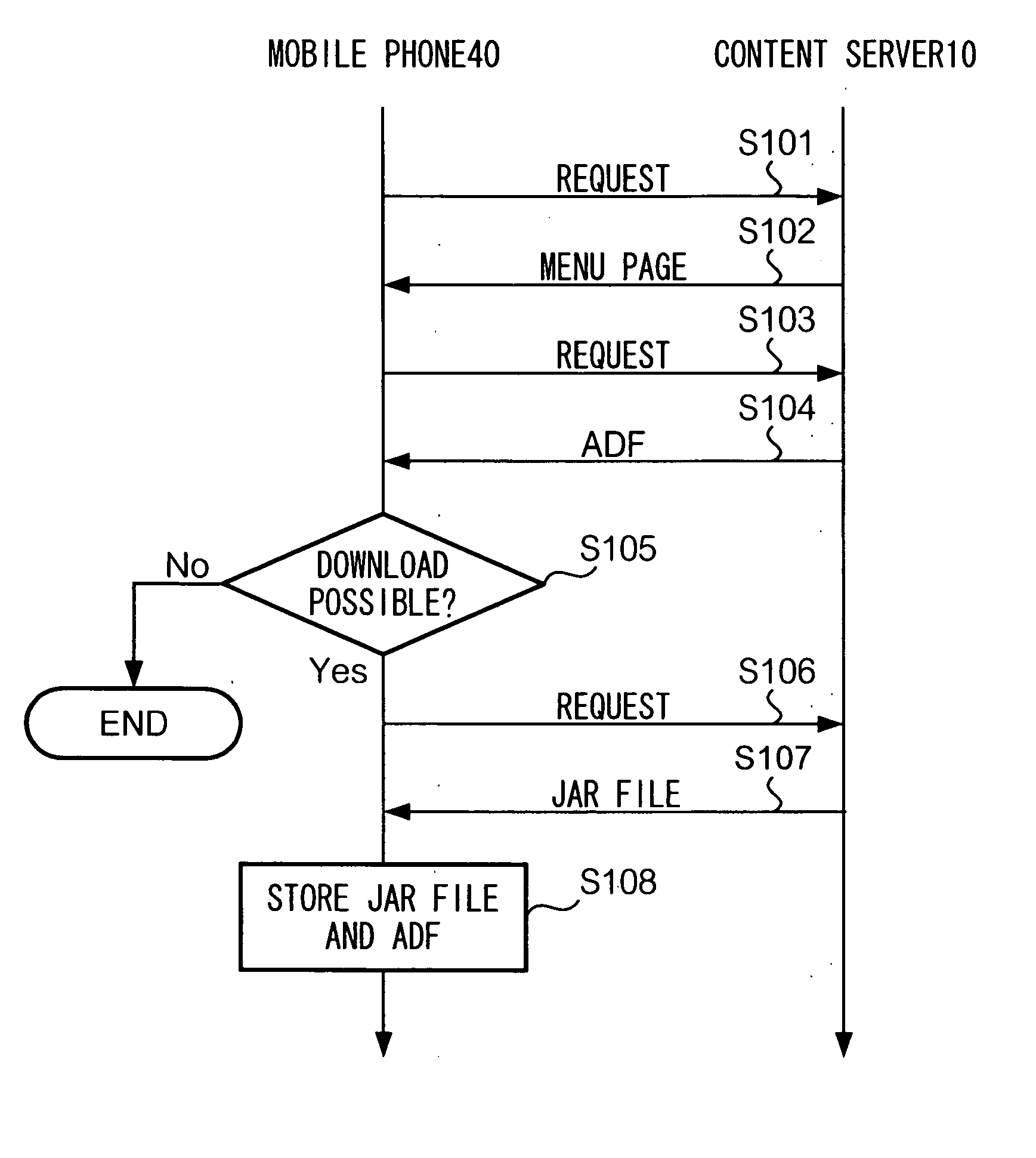
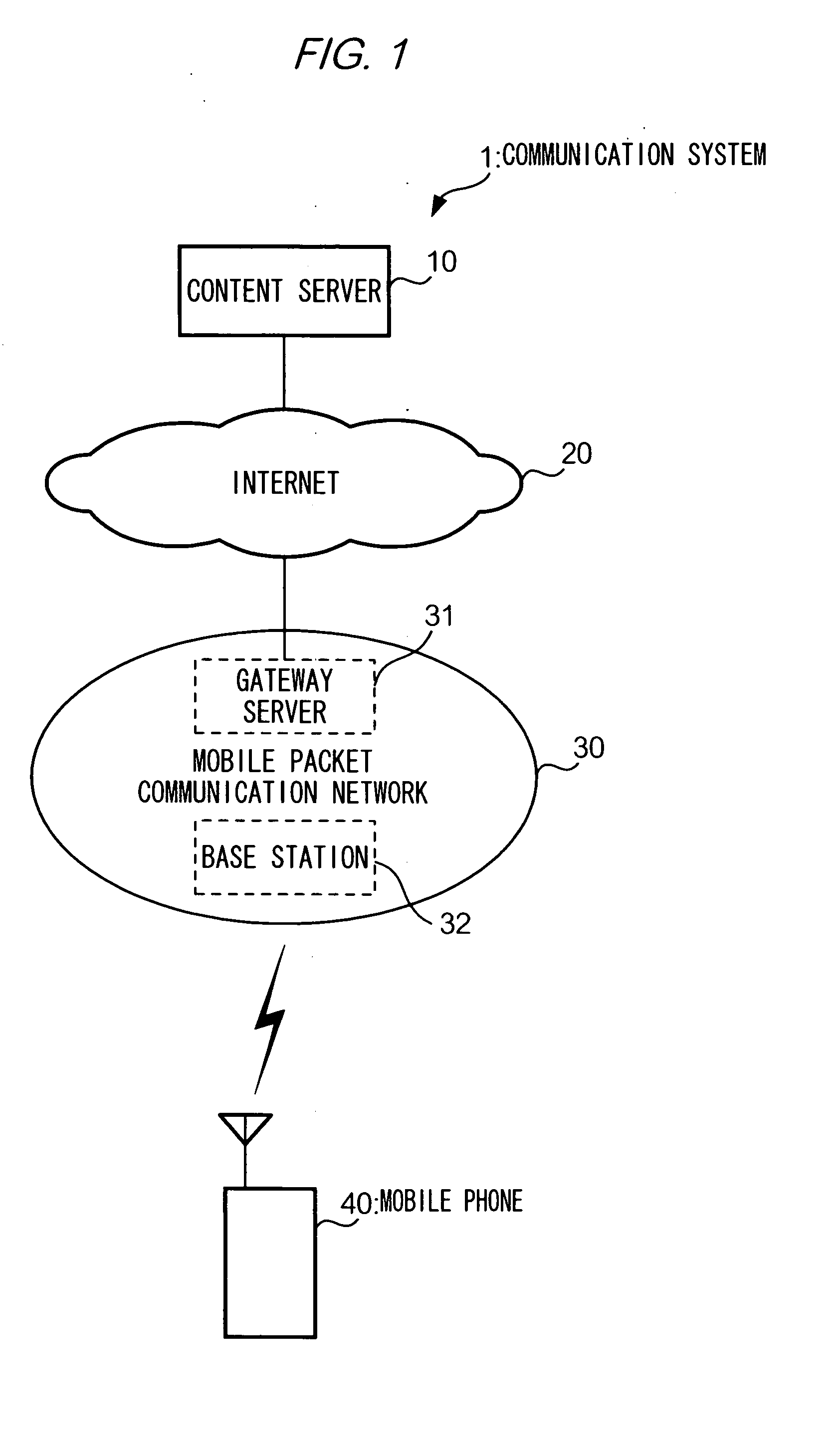
A mobile phone compares a URL of a provider of an original Java application (JavaAP) with a URL of a provider of a destination JavaAP, to determine whether a FQDN (Fully Qualified Domain Name) of the URLs are identical. Only if the FQDNs are identical, the mobile phone permits the destination JavaAP to use data relating to the original JavaAP. In this way, appropriate management of transferring data from an application to another will be effected, thereby improving data security against an unauthorized application.
Owner:NTT DOCOMO INC
Method for automatic heterogeneous platform file synchronization and puppet server
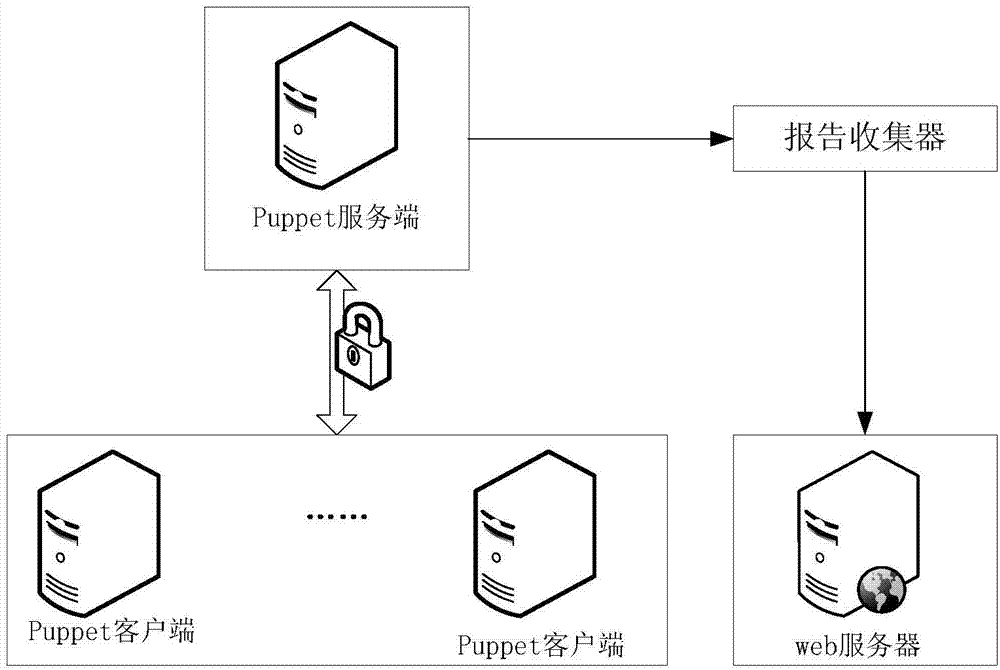
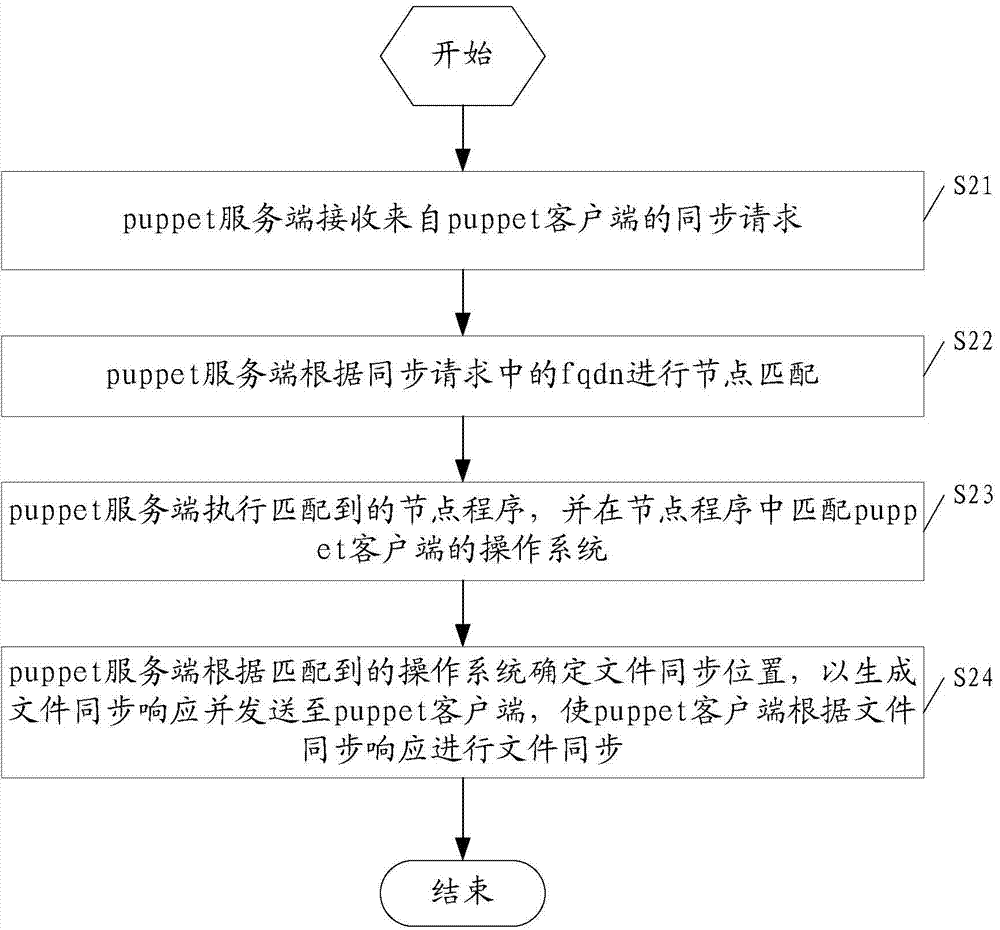
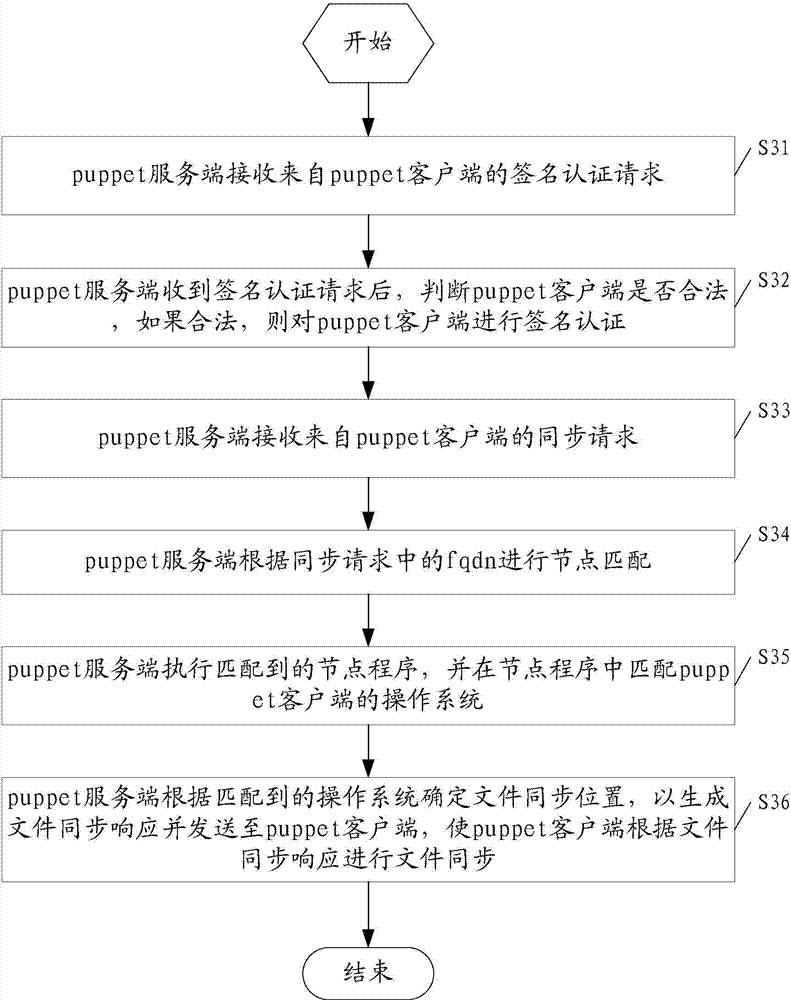
ActiveCN104519100AImprove reusabilityAchieve synchronizationSecuring communicationFile synchronizationFully qualified domain name
The embodiment of the invention discloses a method for automatic heterogeneous platform file synchronization and a puppet server. The method comprises the following steps: the puppet server receives a file synchronization request from a puppet client, wherein the file synchronization request at least contains the operating system and the fully qualified domain name fqdn of the puppet client; the puppet server carries out node matching according to the fqdn in the file synchronization request; the puppet server executes a matched node program, and matches the operating system of the puppet client in the node program; and the puppet server determines the file synchronization position according to the matched operating system, generates a file synchronization response and sends the file synchronization response to the puppet client so that the puppet client can carry out file synchronization according to the file synchronization response. By adopting the method and the puppet server disclosed by the embodiment of the invention, efficient automatic heterogeneous platform file synchronization can be realized.
Owner:NEW SINGULARITY INT TECHN DEV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com