Gateway and method for phishing defense
A technology for phishing and phishing websites, which is applied in the field of gateways to defend against phishing, and can solve problems such as inability to defend against phishing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
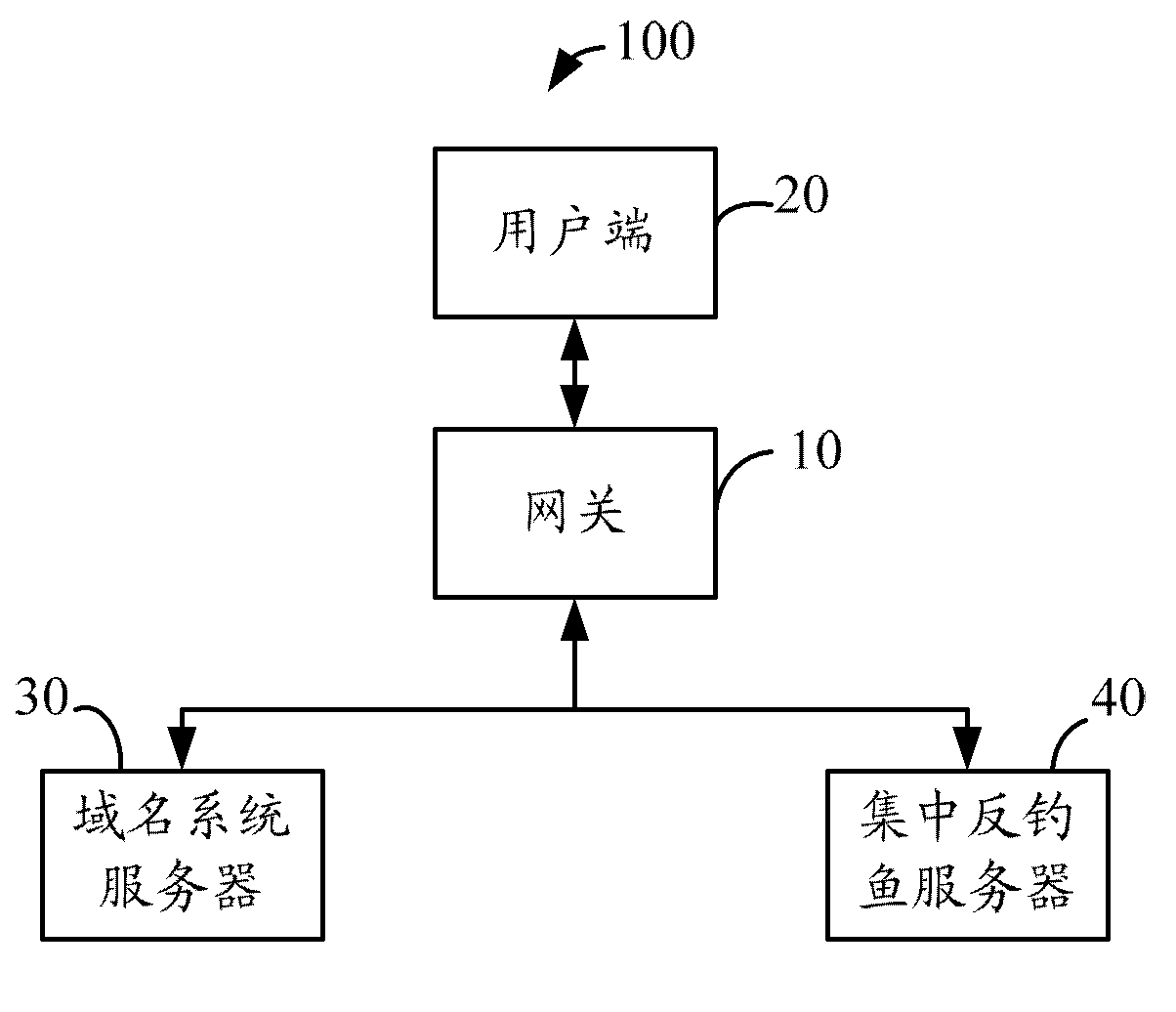
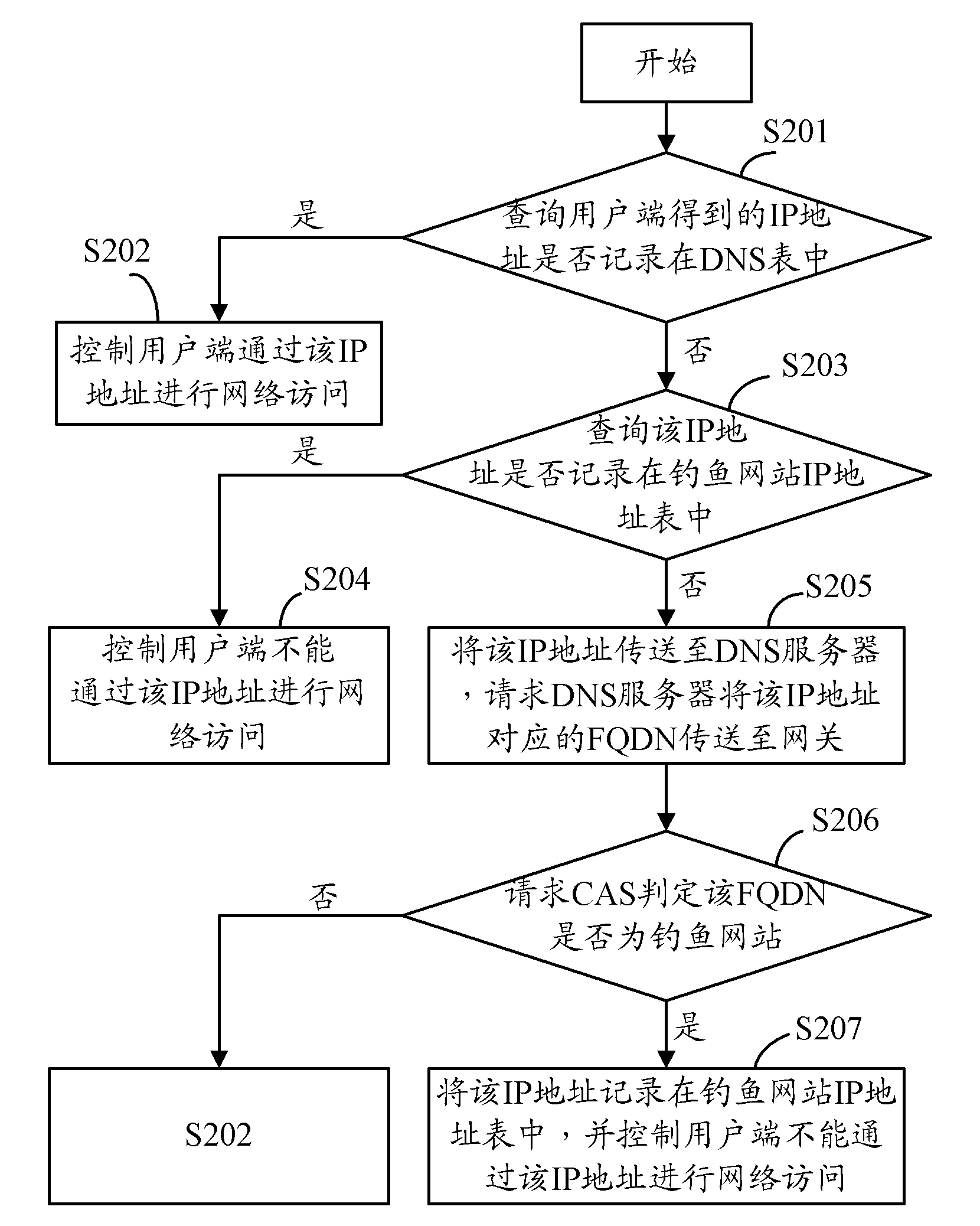
[0012] Please refer to figure 1 The anti-phishing system 100 of the present invention includes a gateway 10 and a client 20 connected to the gateway 10, a domain name system (Domain Name System, DNS) server 30 and a centralized anti-phishing server (Centralized Anti-phishing Server, CAS) 40. The DNS server 30 is used to convert the domain name request sent by the client 20 into an IP address, and then feeds back the IP address to the gateway 10, and according to the request of the gateway 10, sends the fully qualified domain name (Fully Qualified Domain Name, FQDN) to the gateway 10. The CAS40 can judge whether the website that the user terminal 20 will visit is a phishing website according to the FQDN input by the user terminal 20 .
[0013] The gateway 10 stores a DNS table and a phishing website IP address table. The DNS table records the IP address obtained by DNS server 30 performing domain name resolution according to the domain name request sent by client 20 . The IP...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com