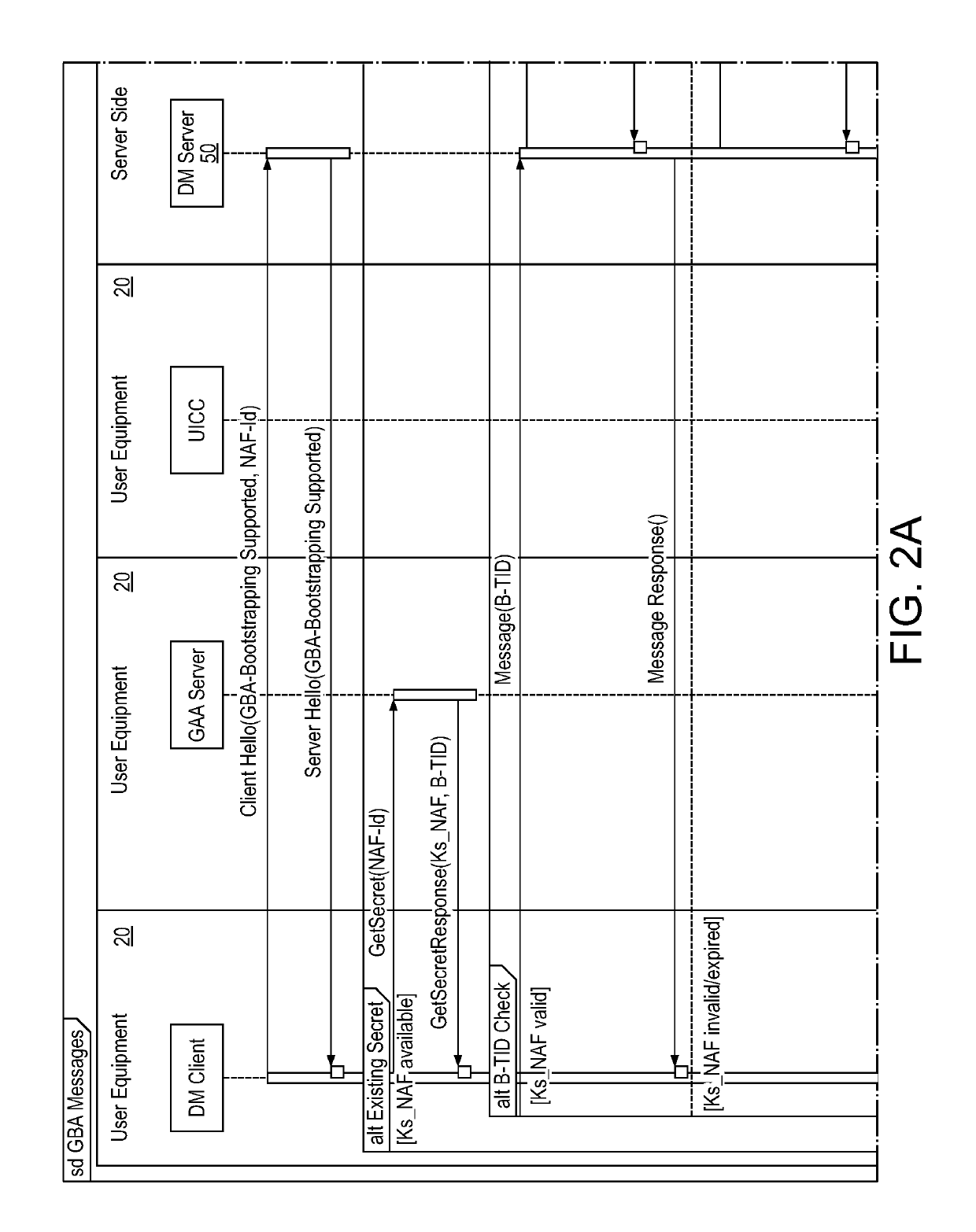
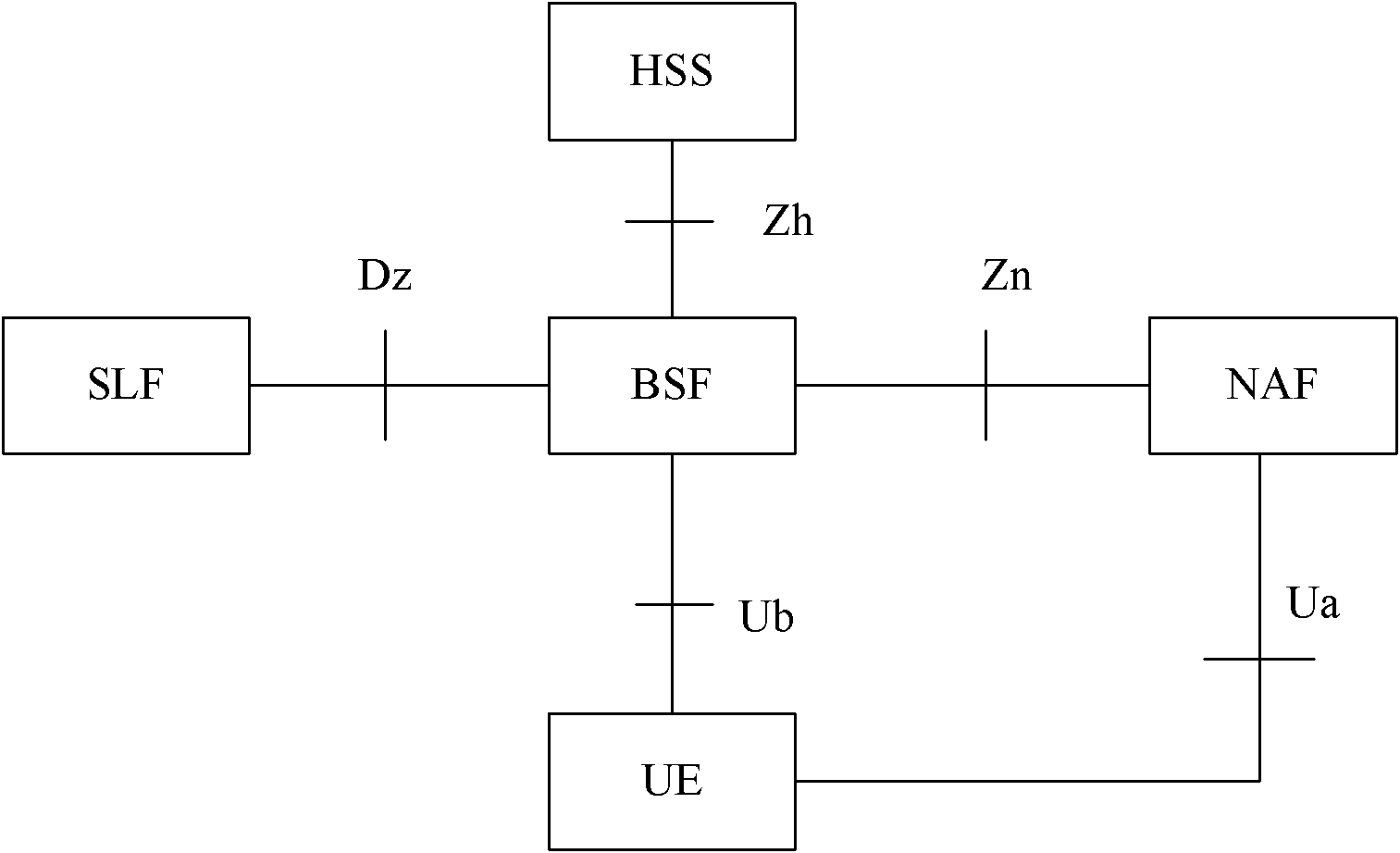
Patents
Literature
40 results about "Generic Bootstrapping Architecture" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
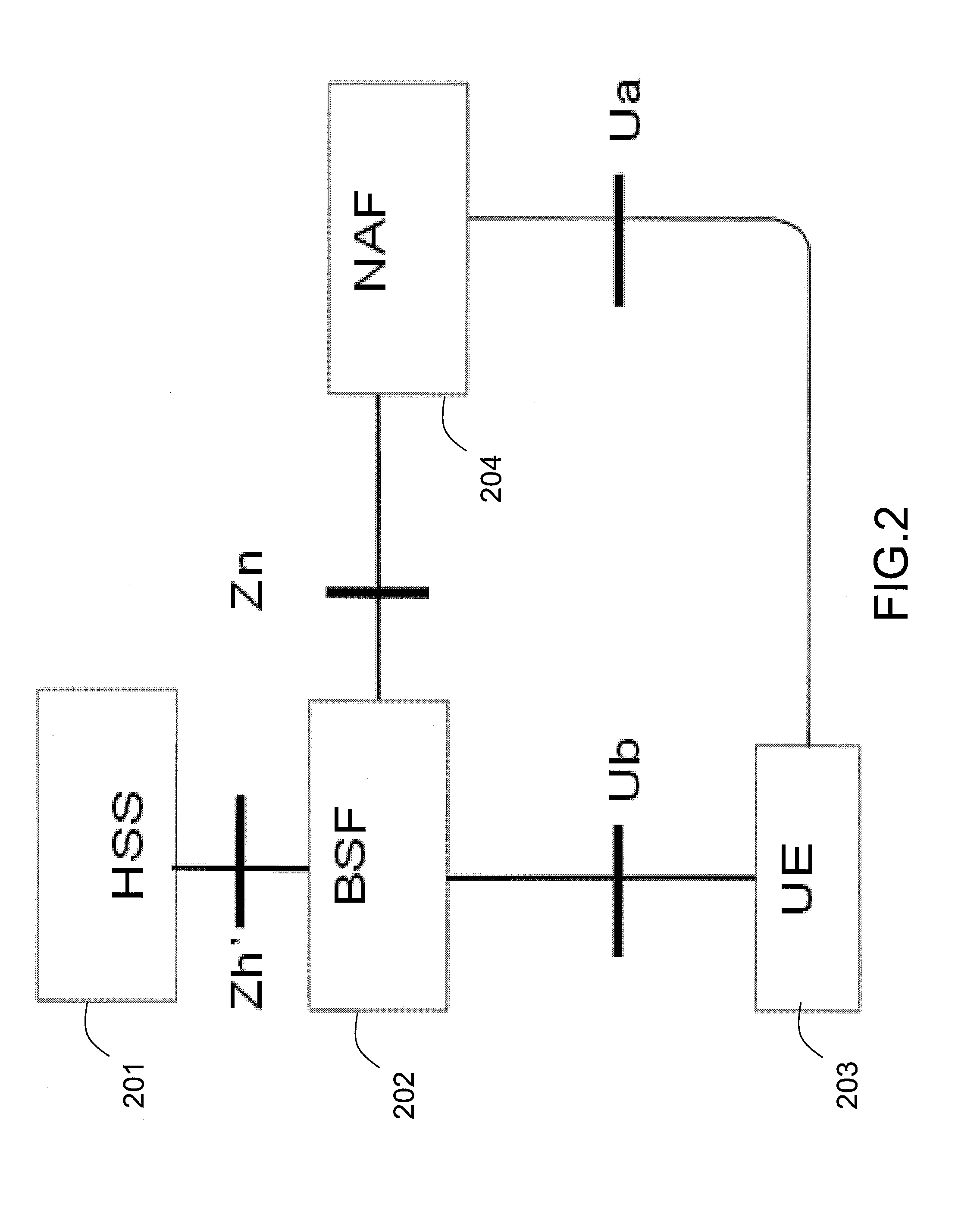
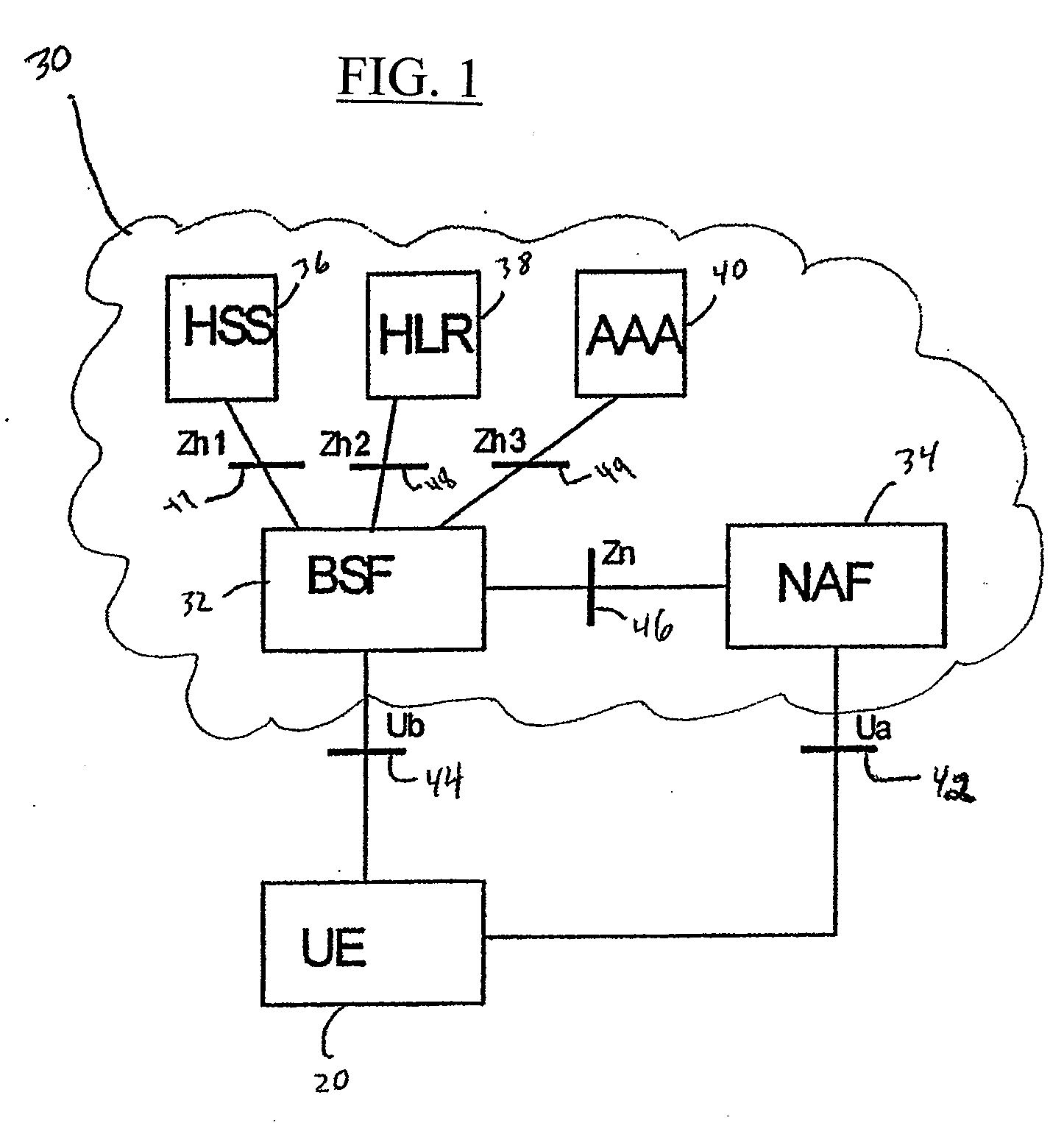
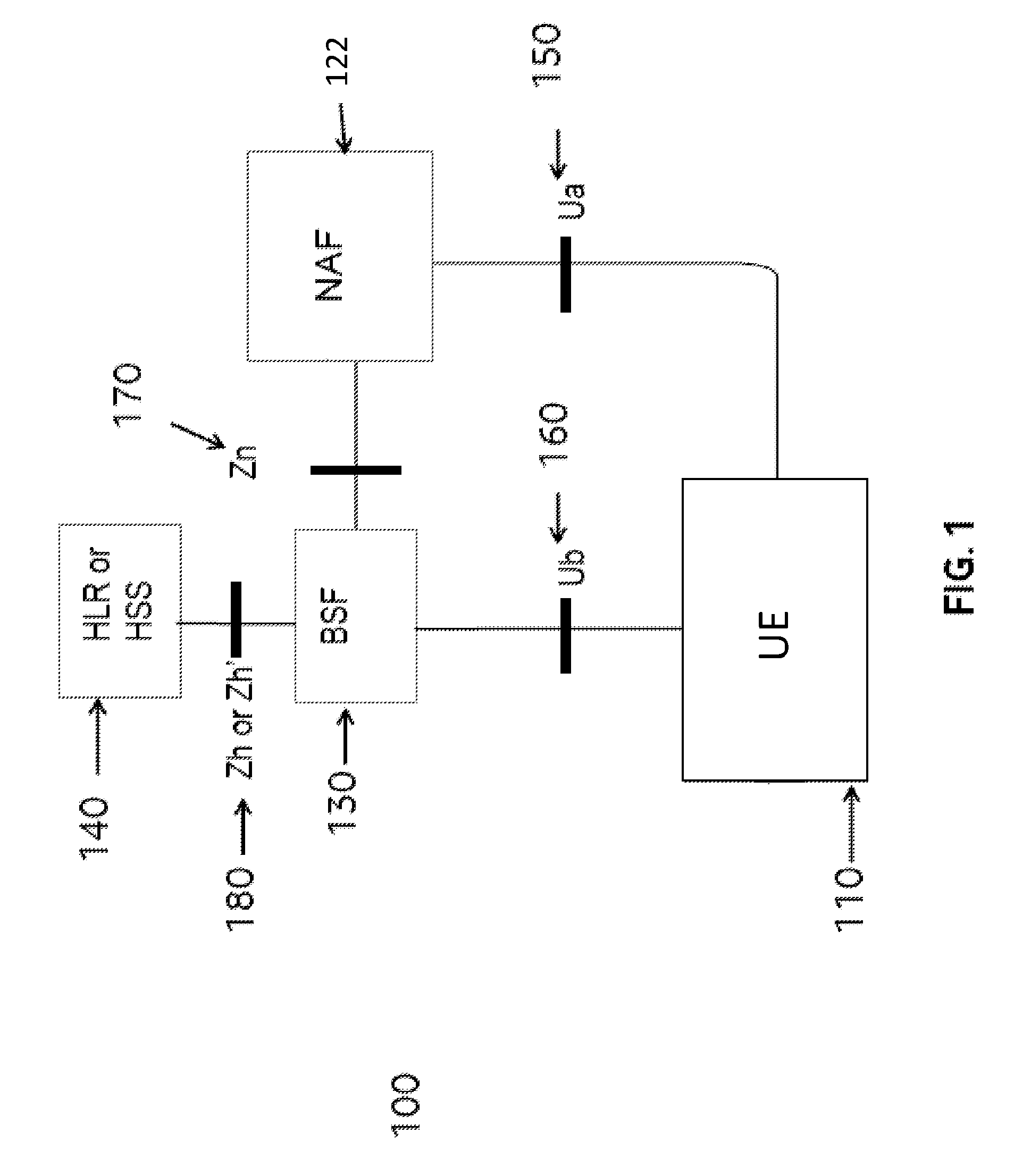
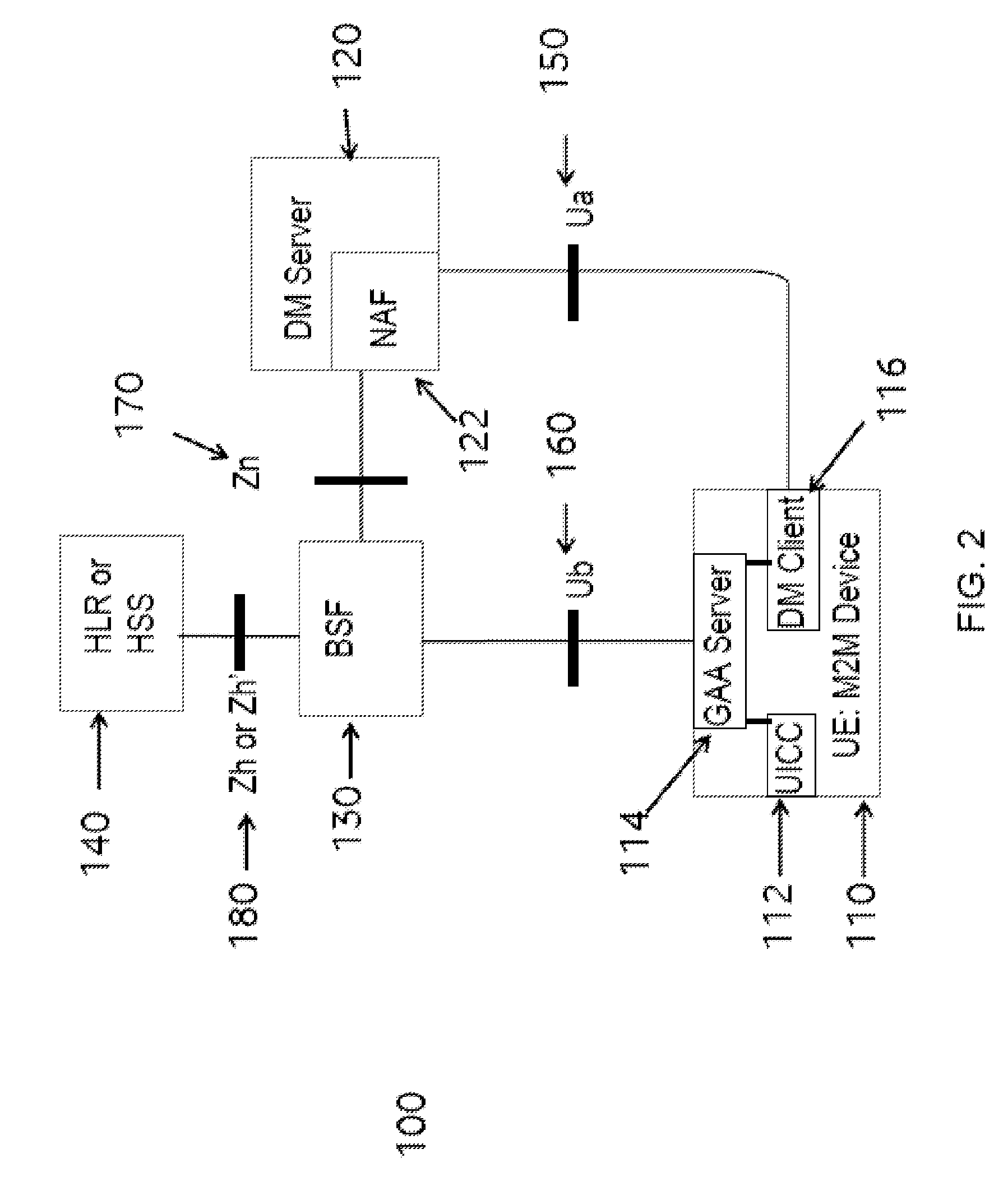
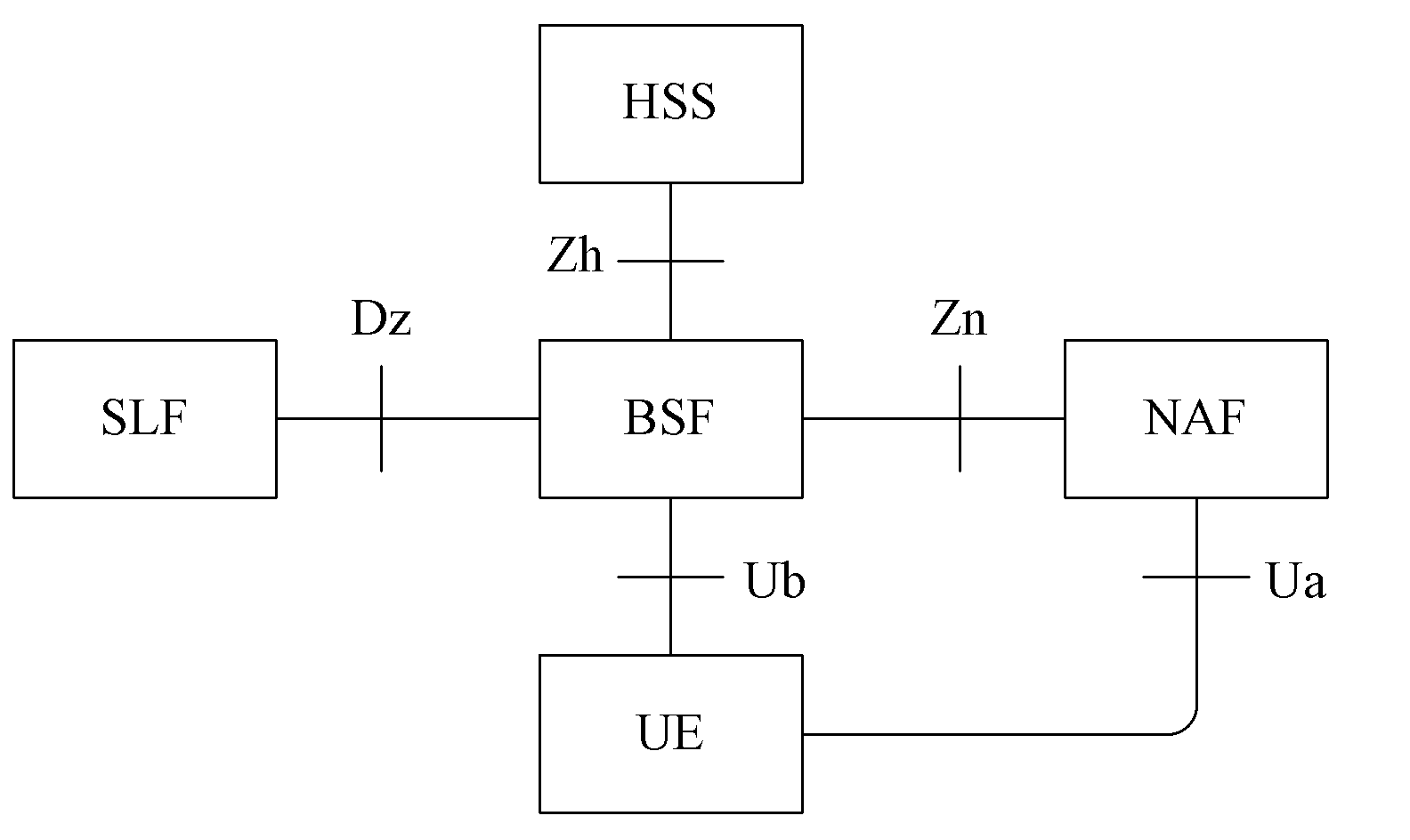
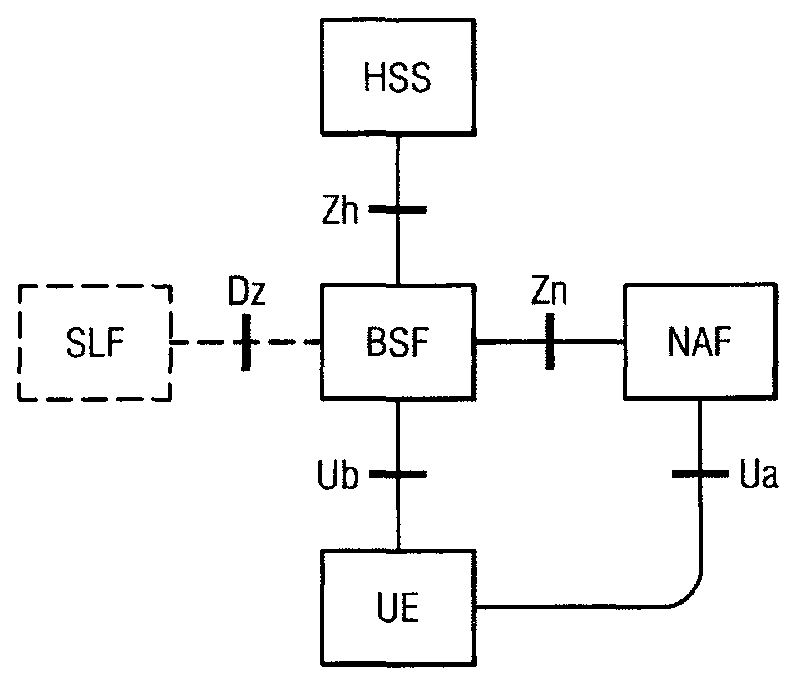
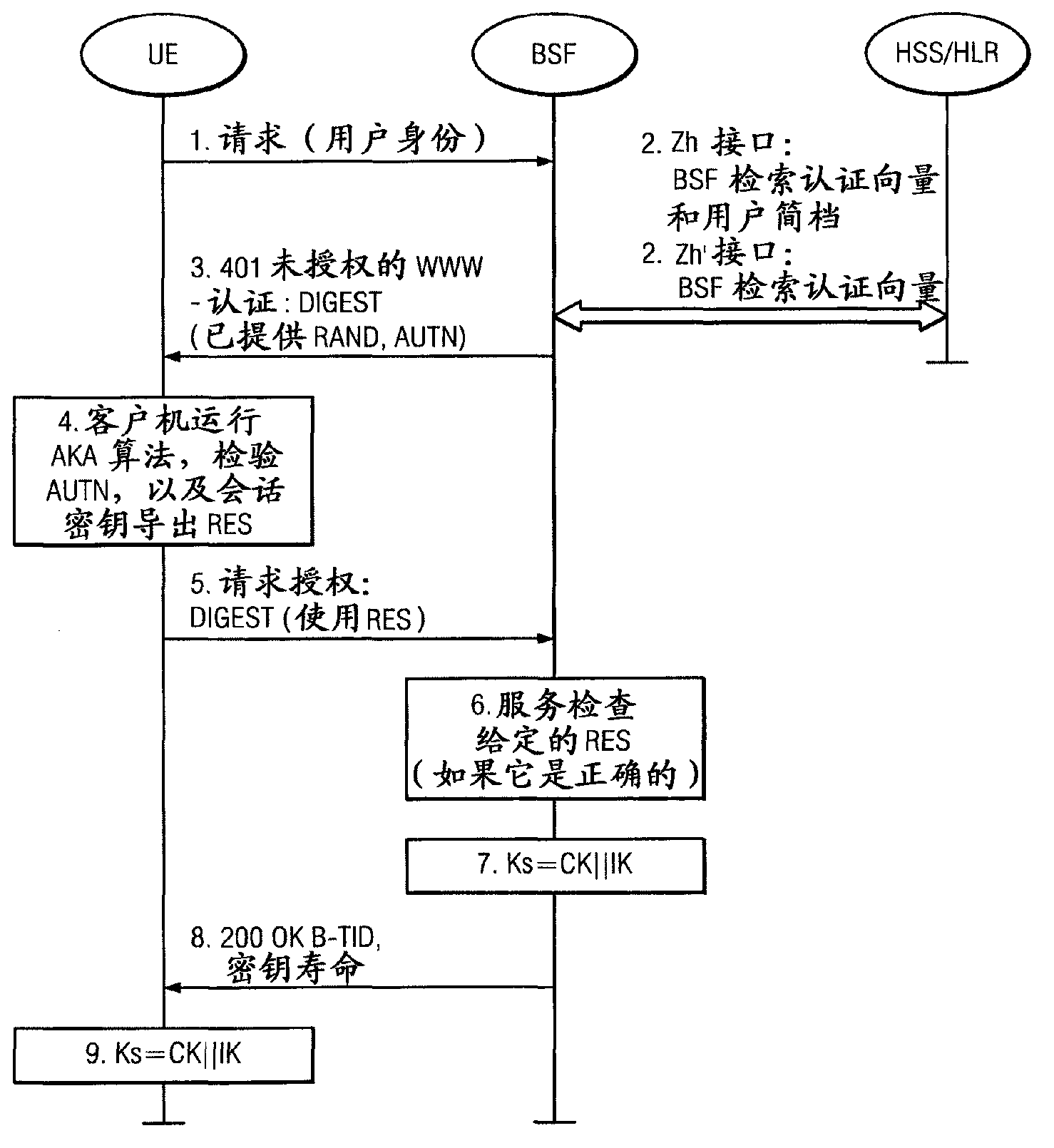
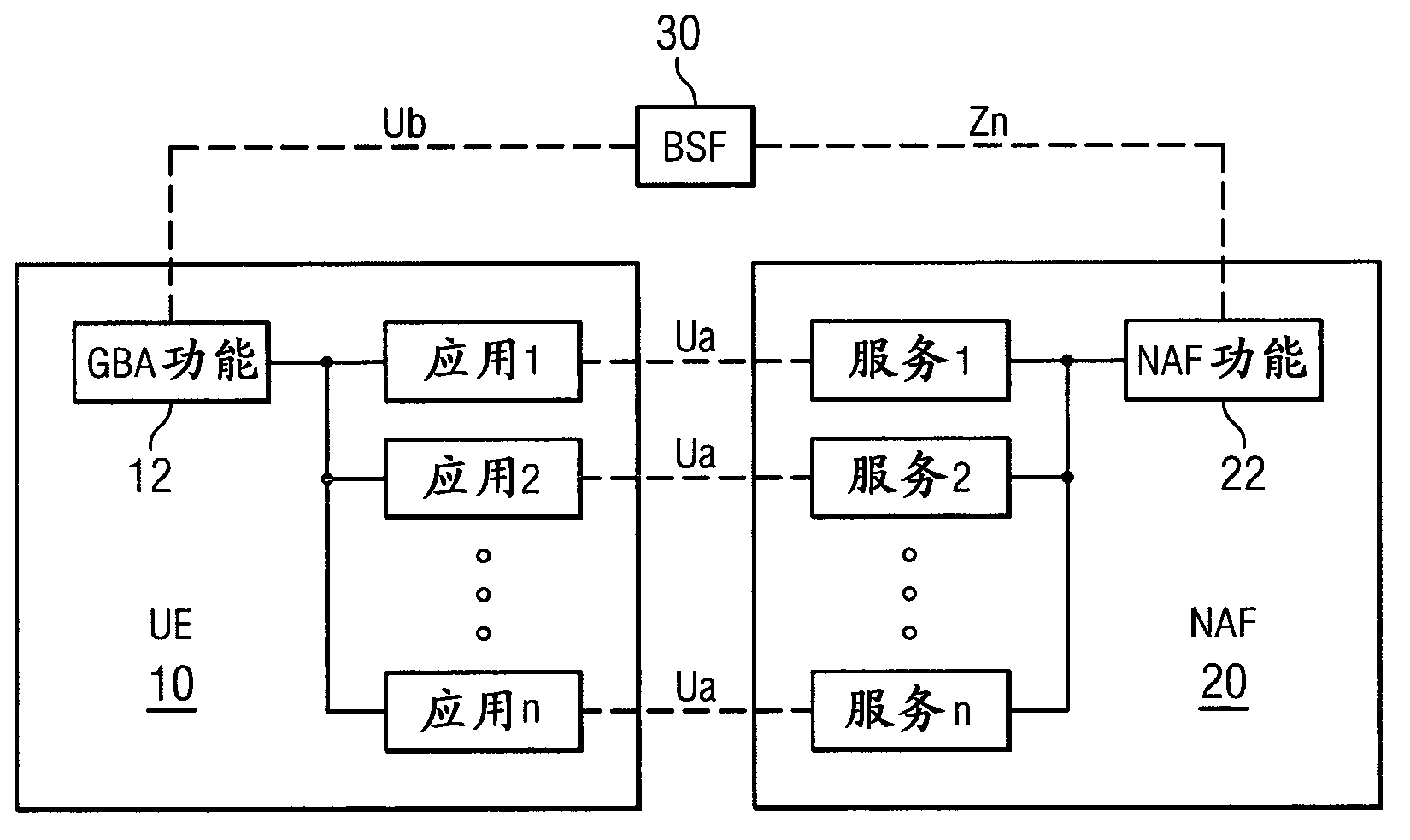
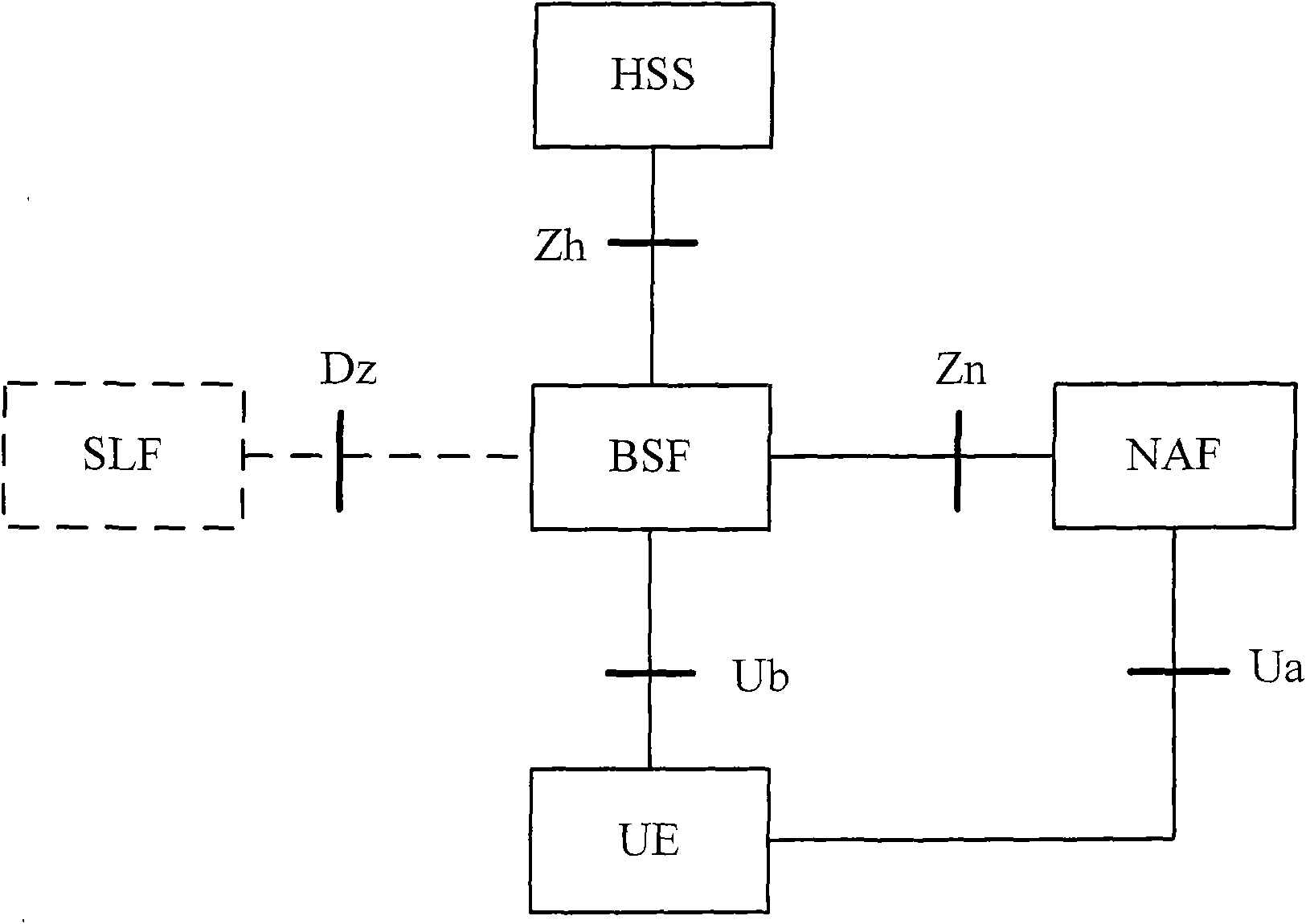
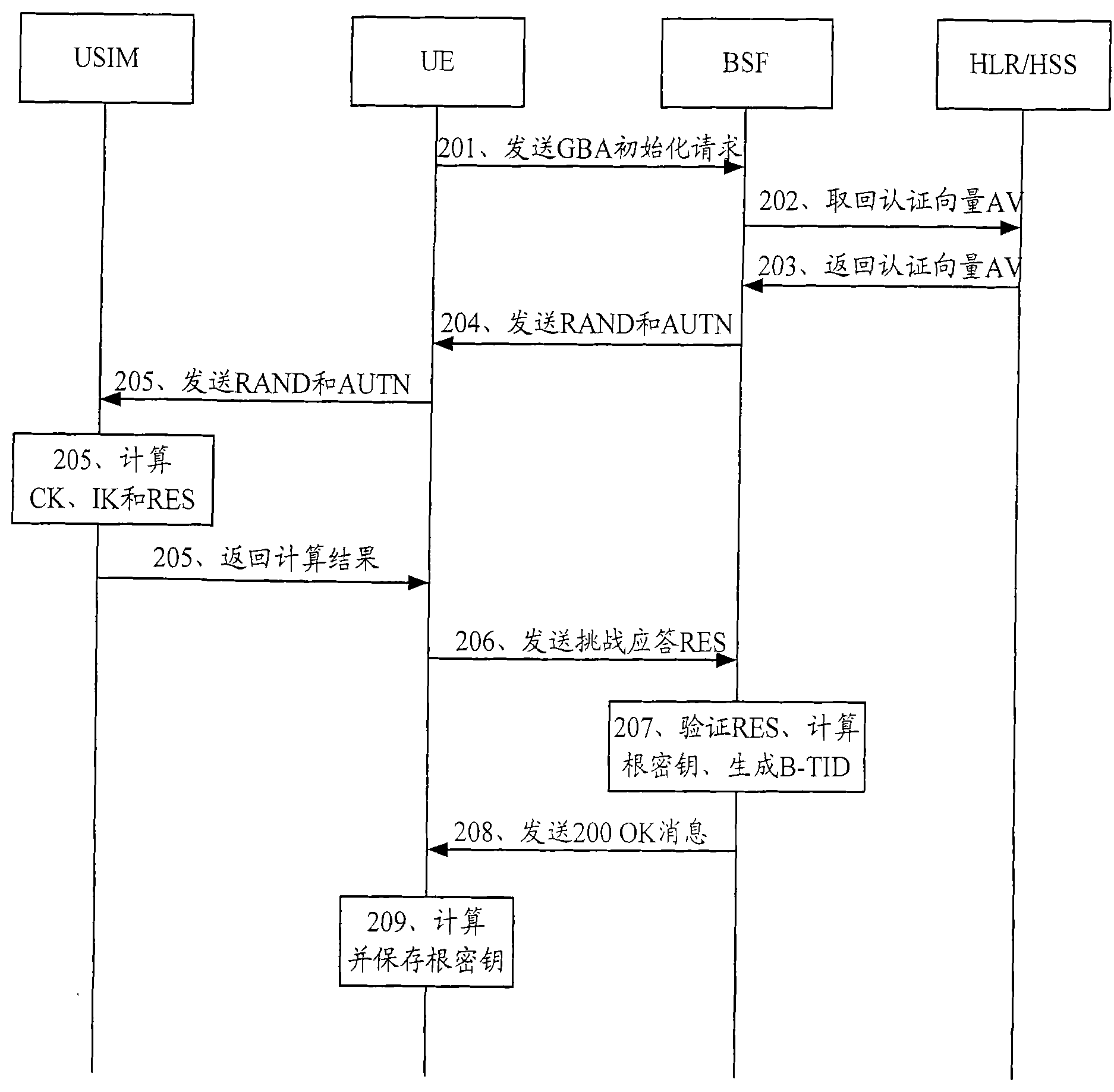
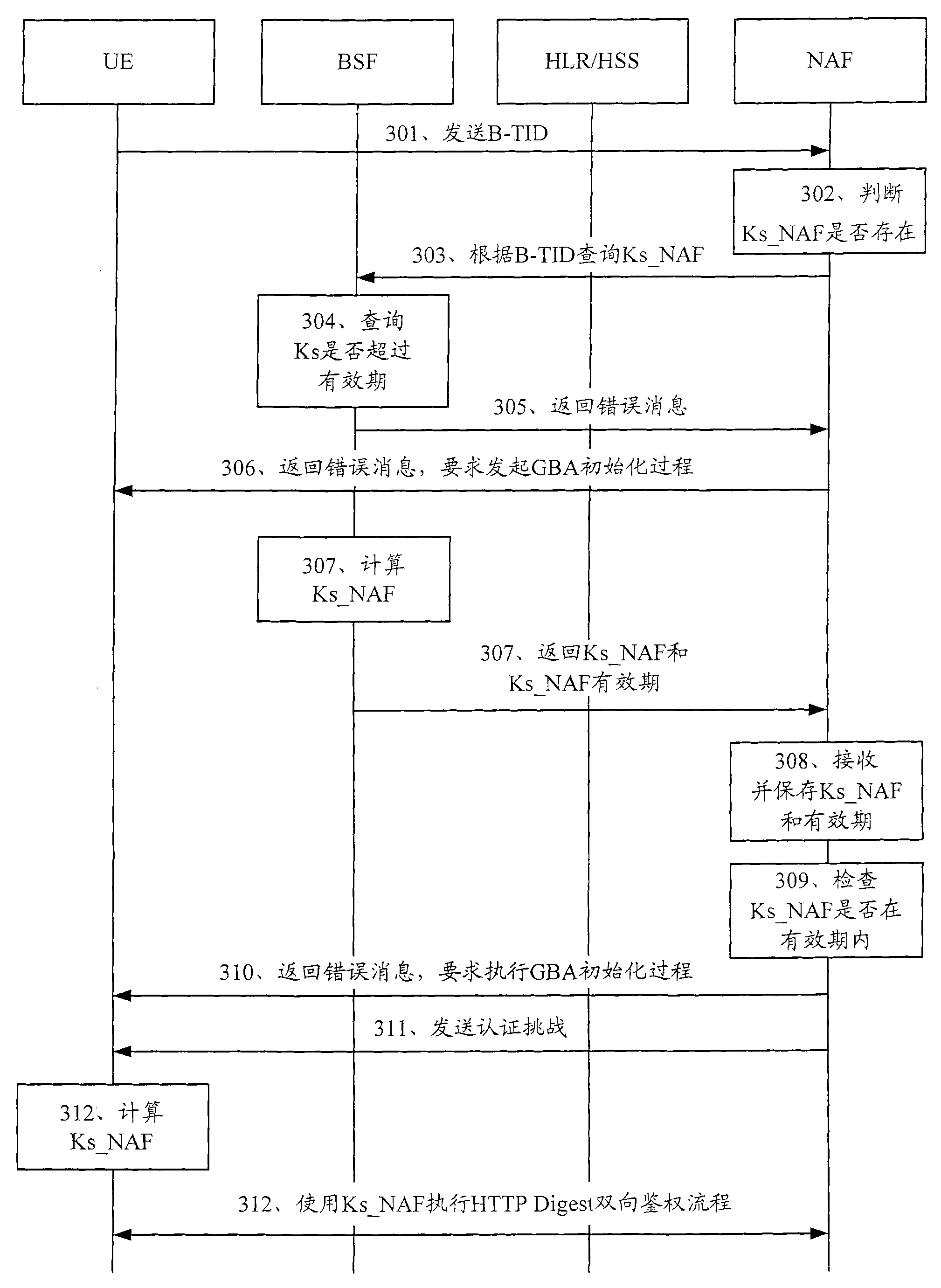
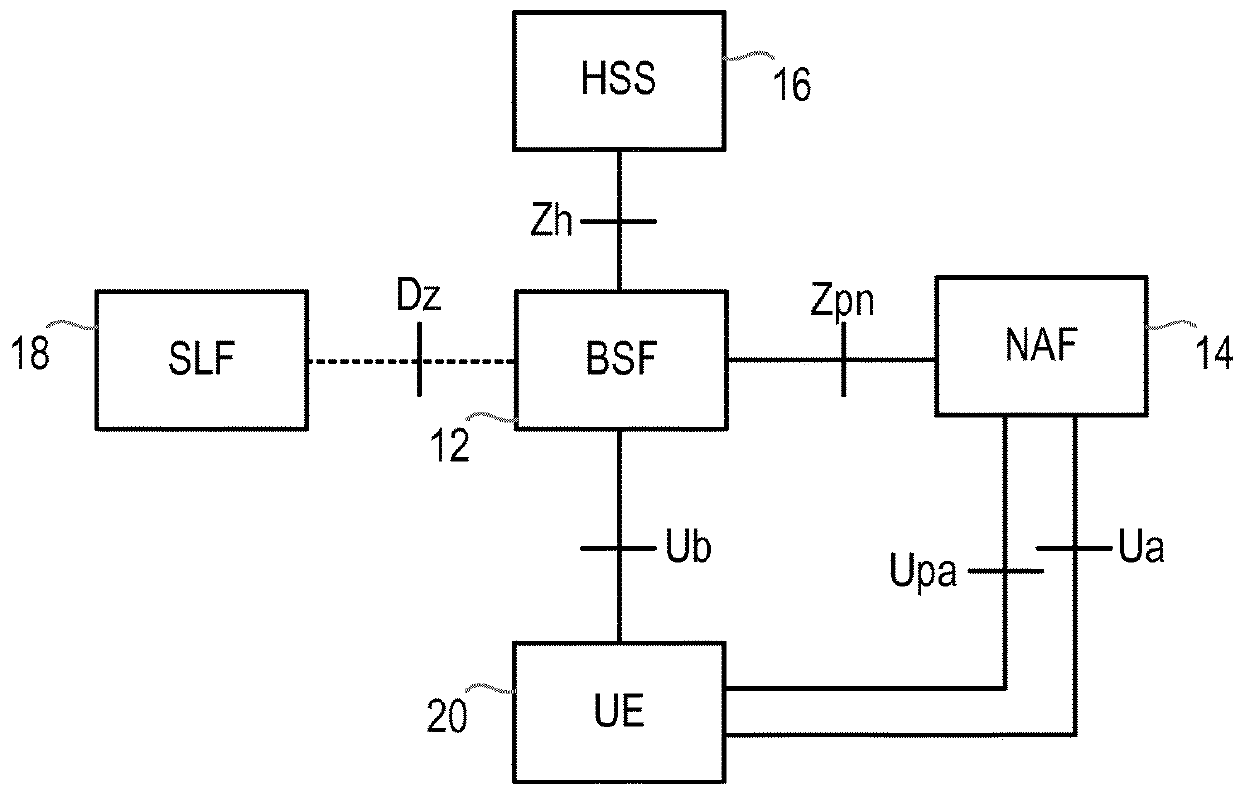
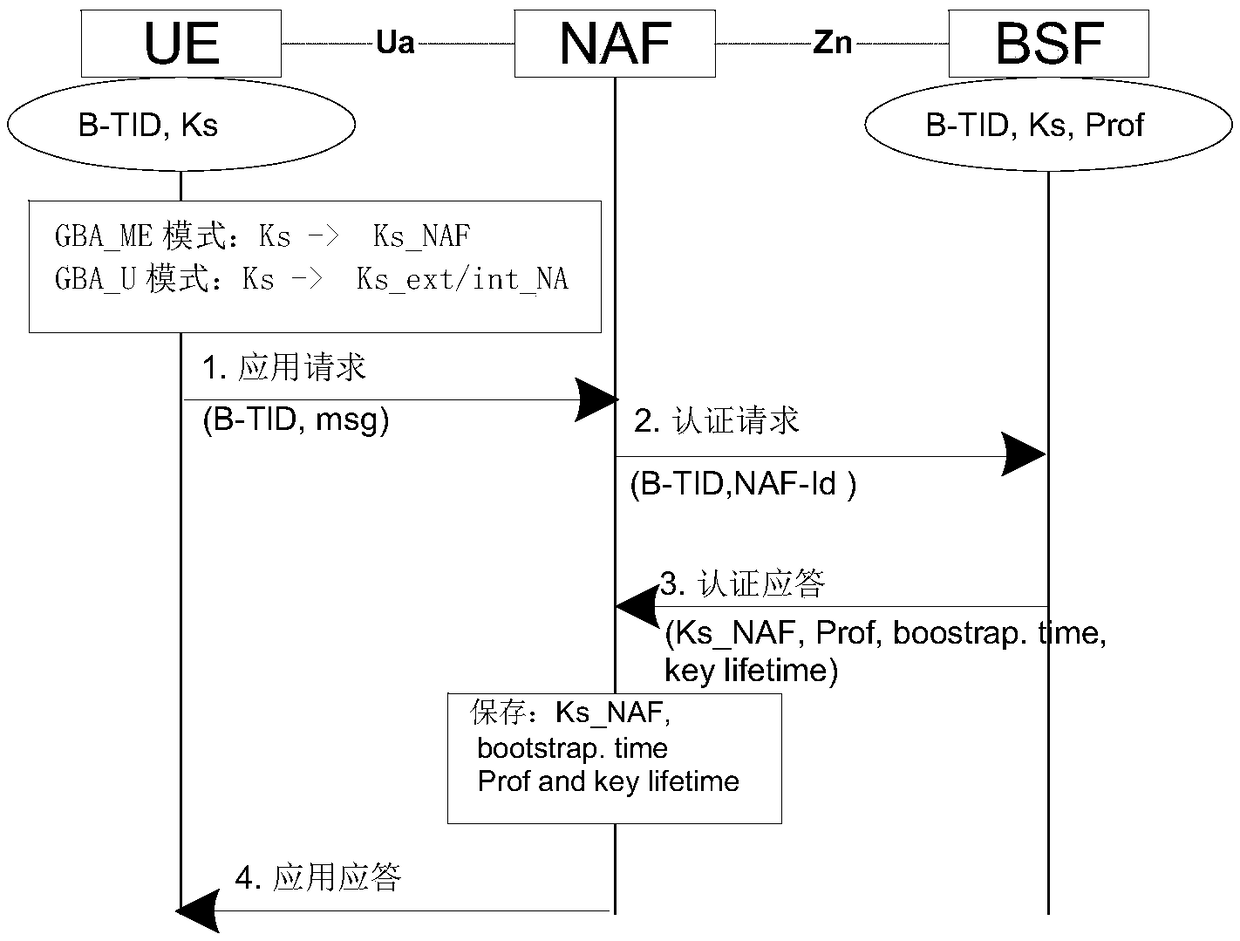
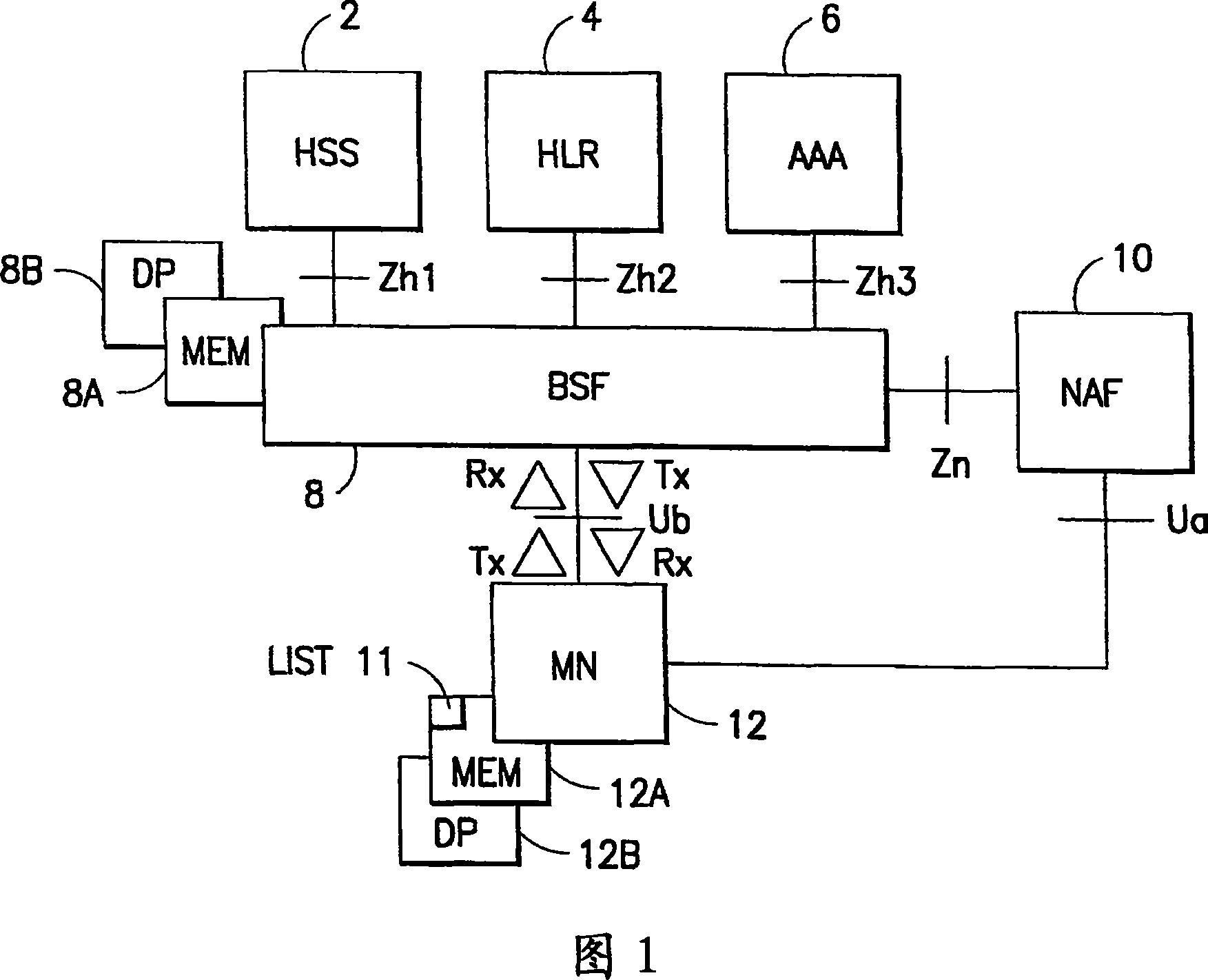
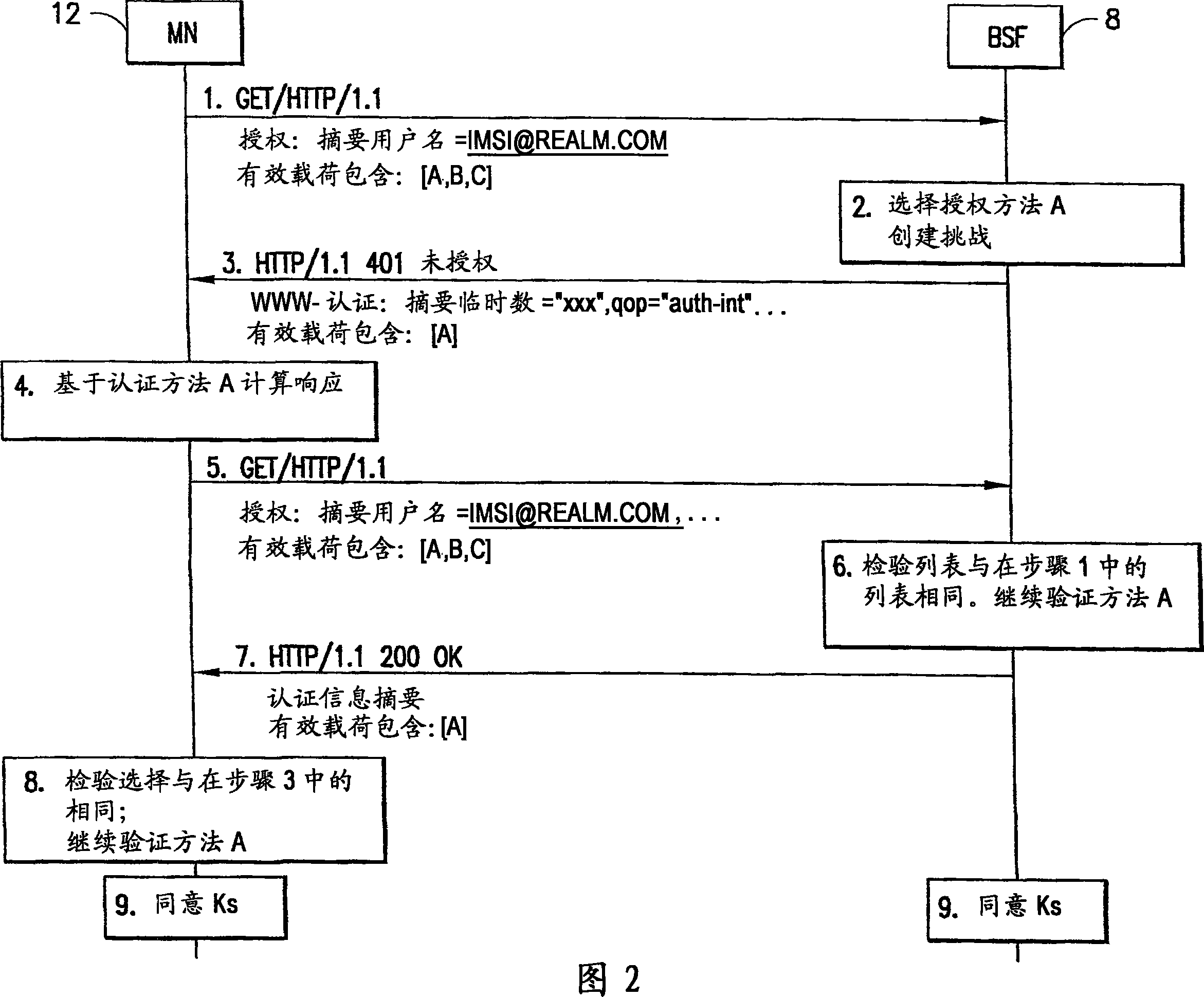
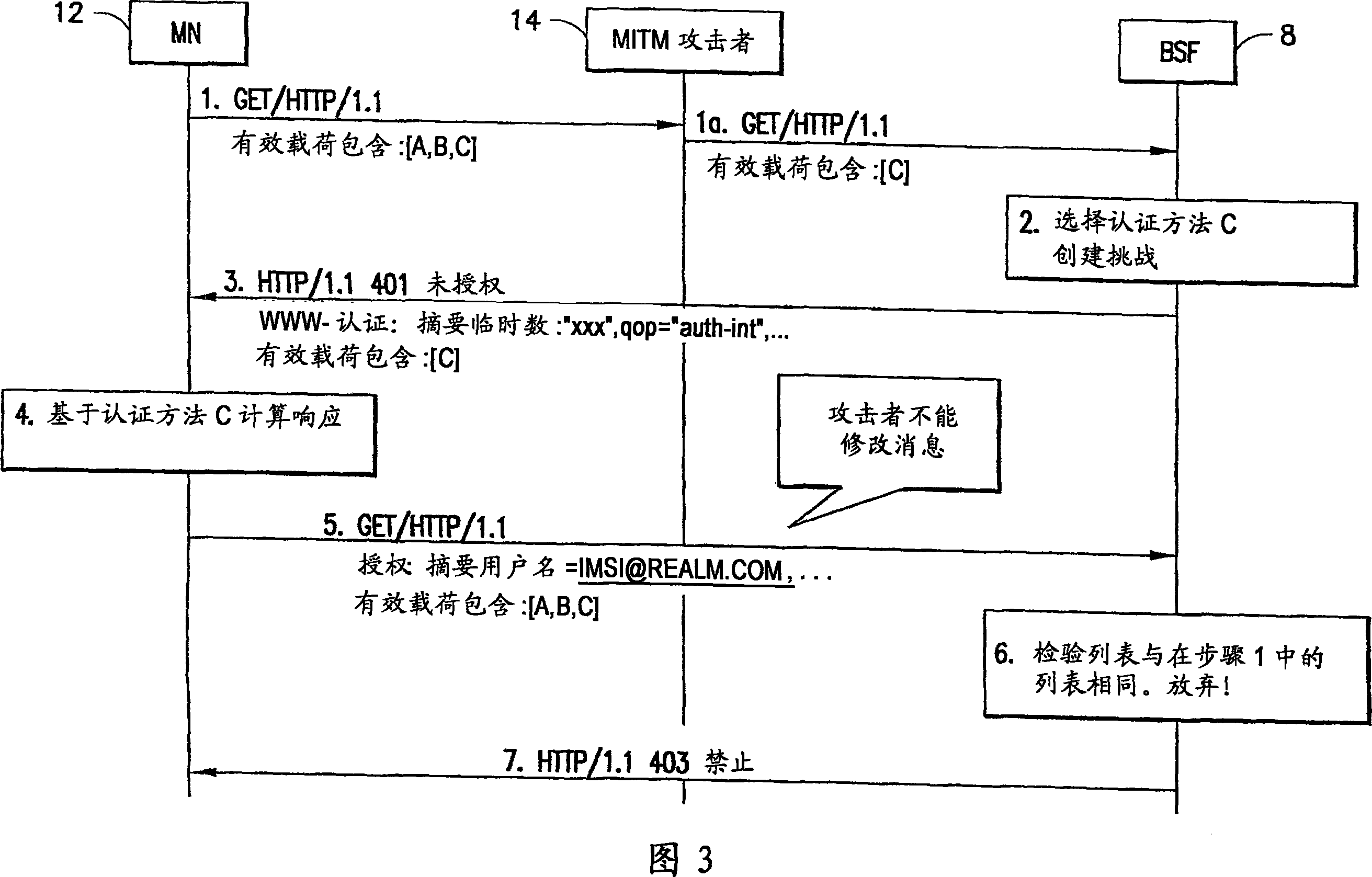
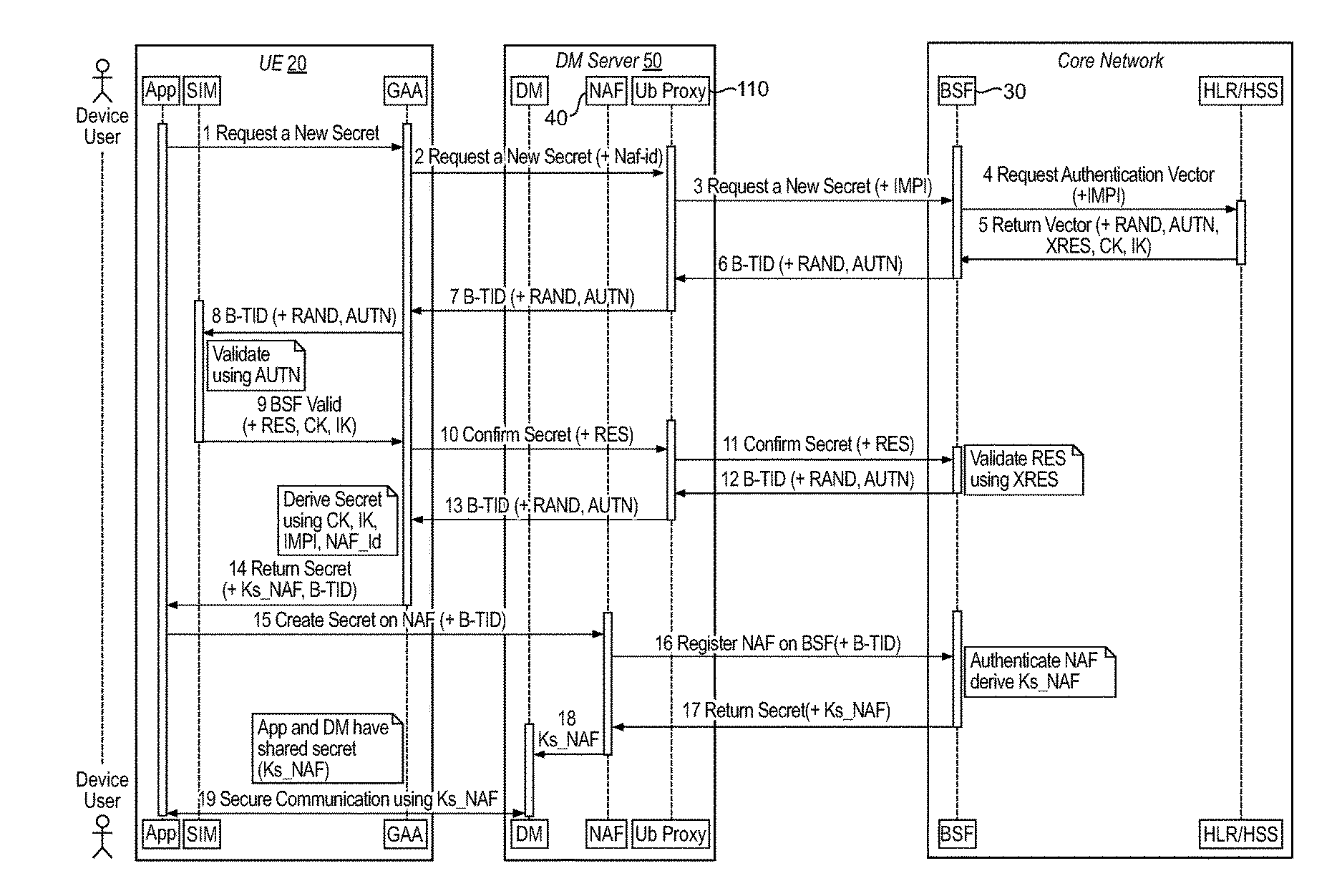
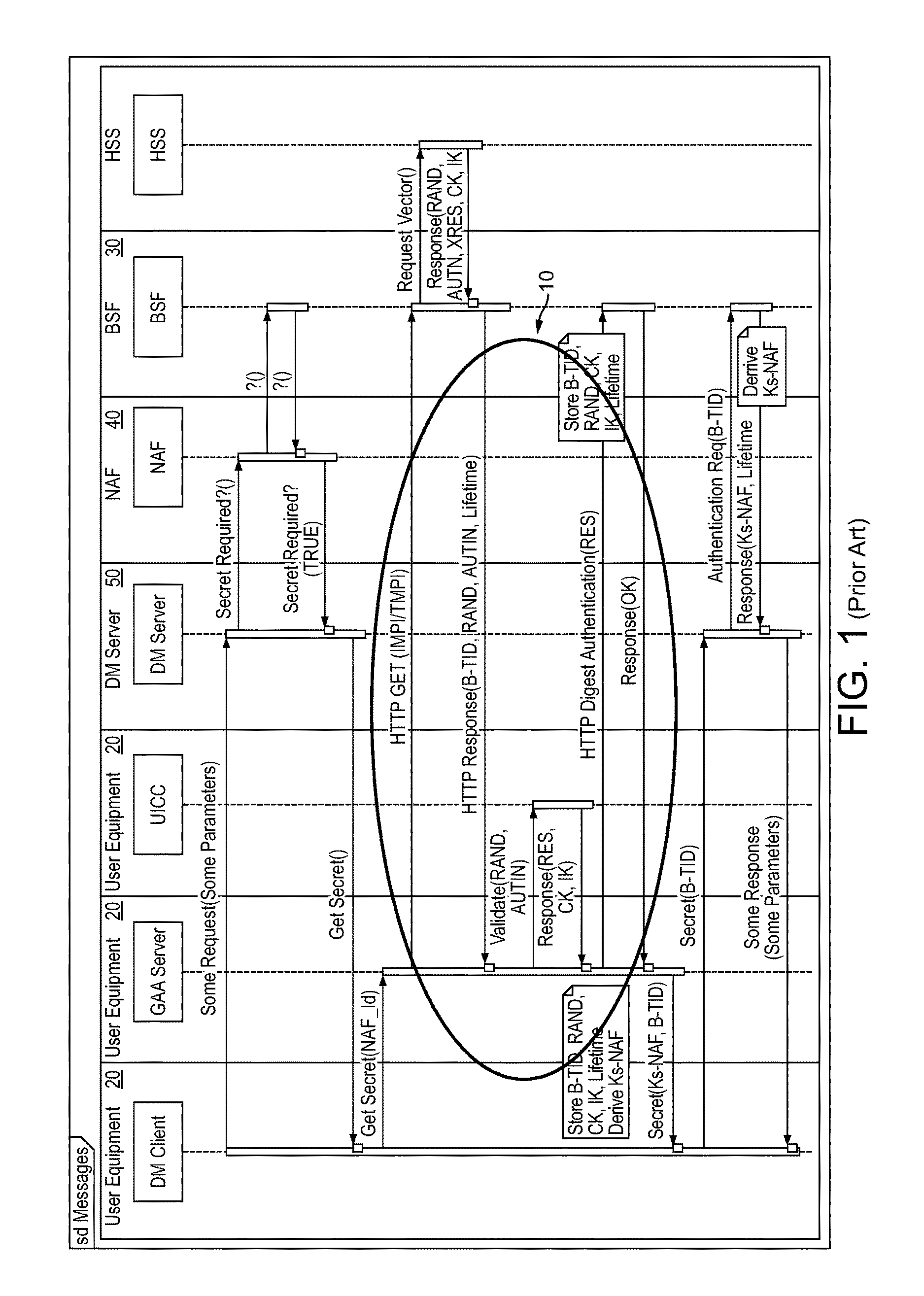
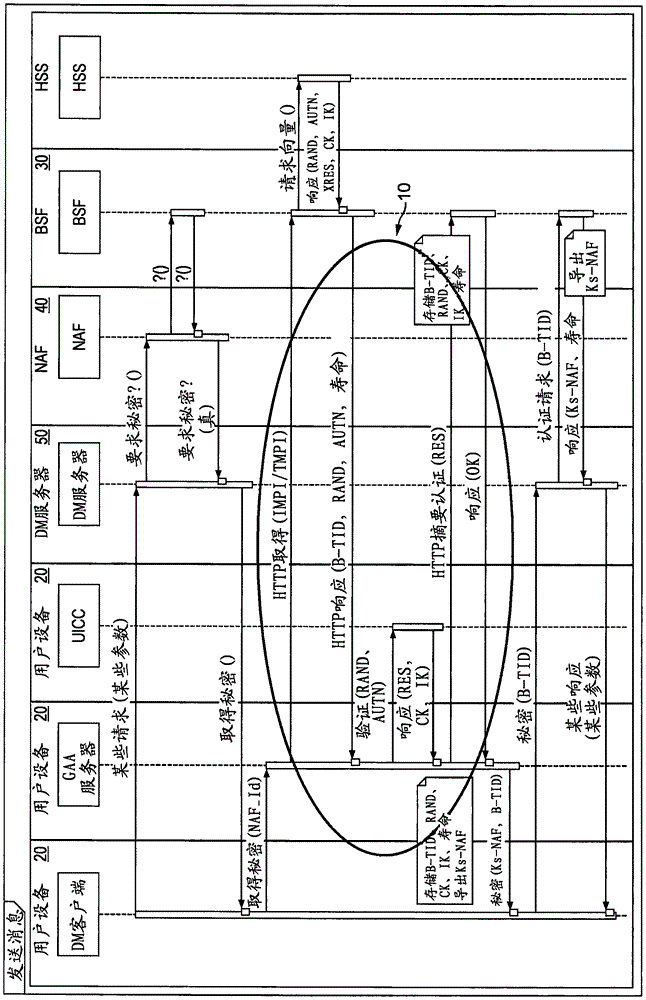
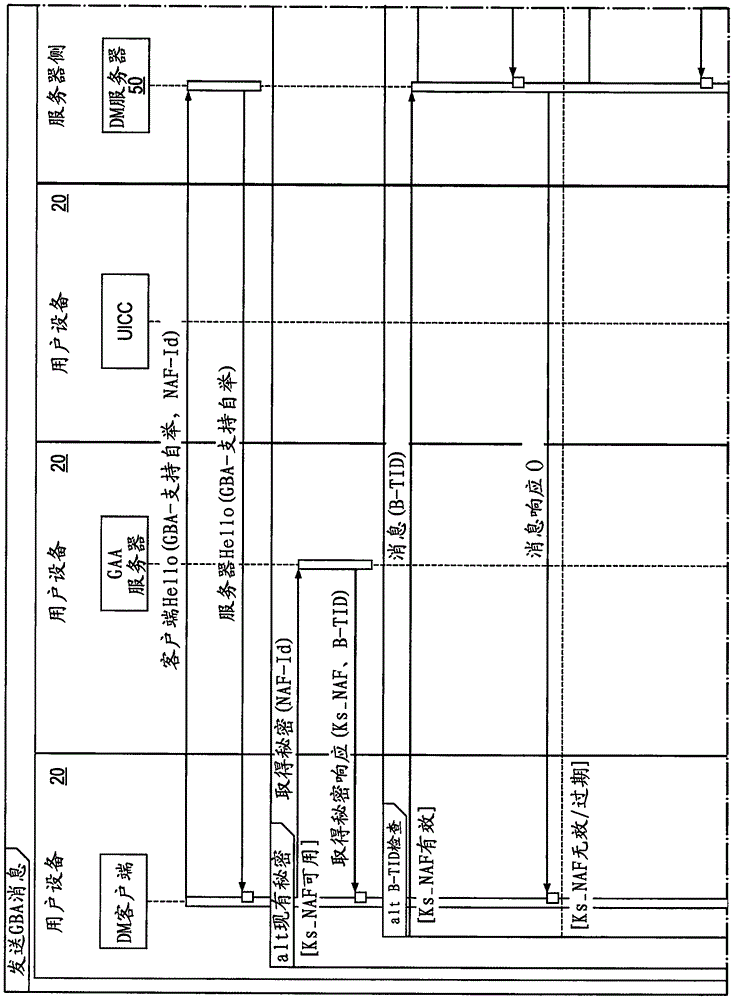
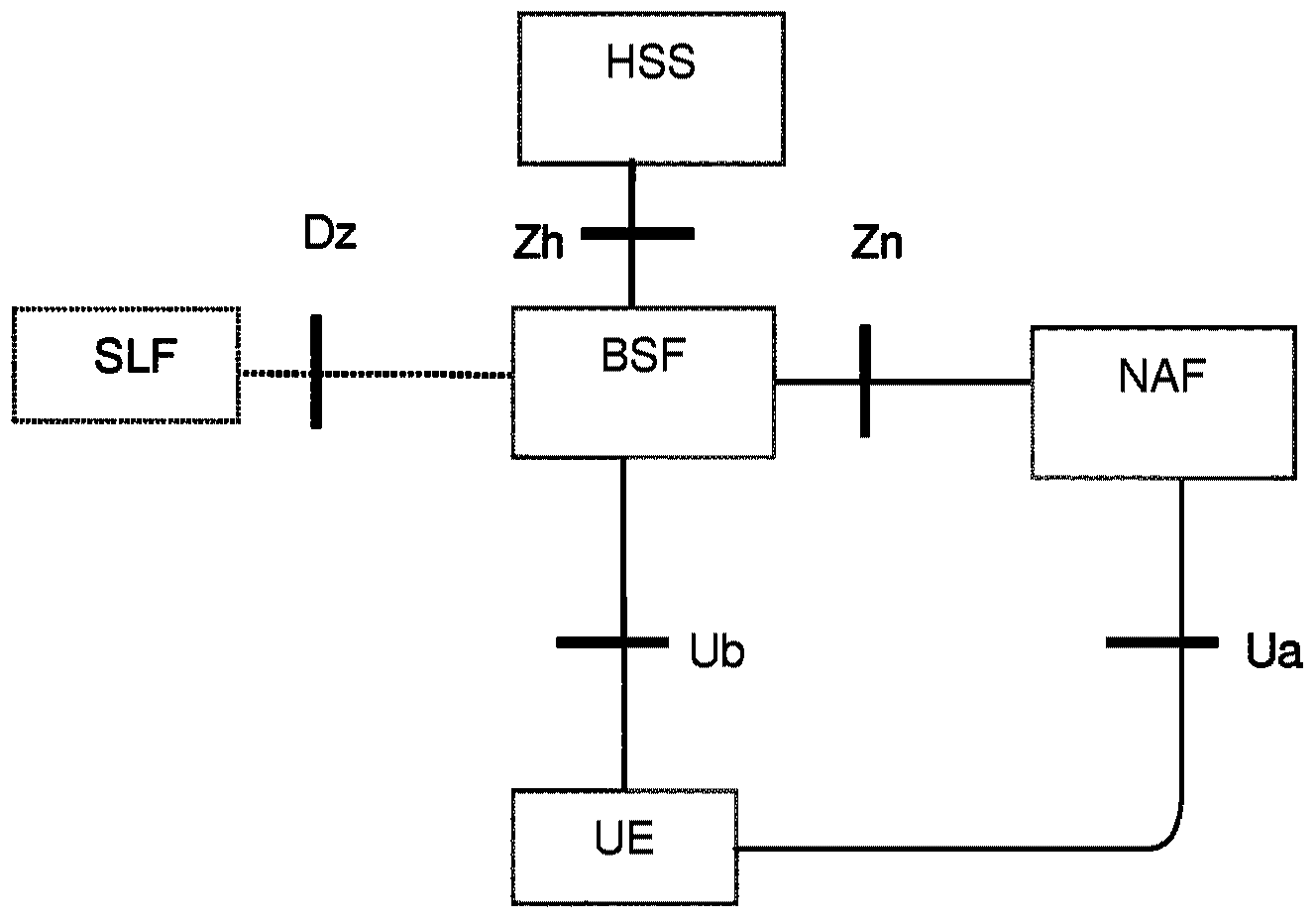
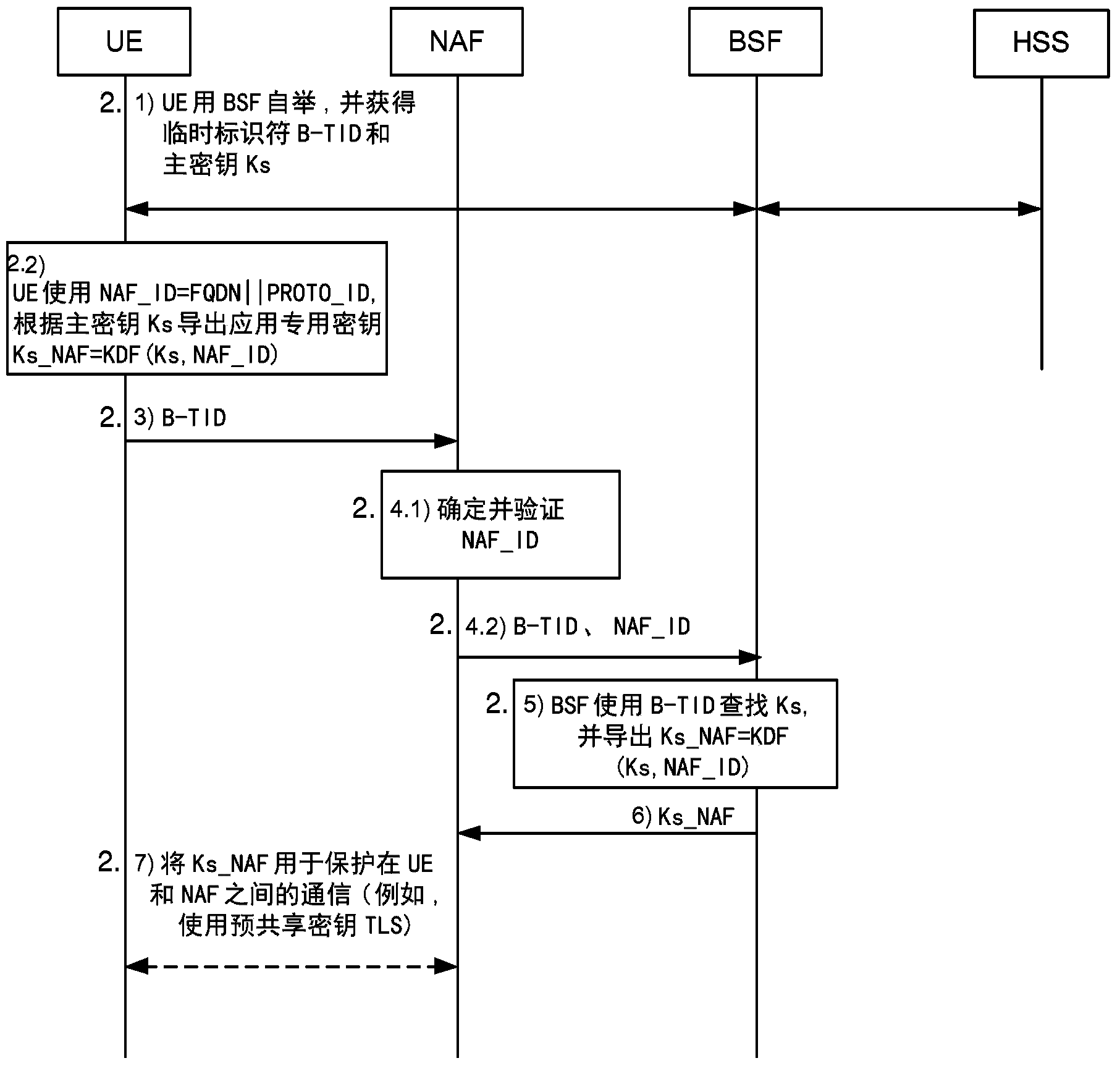
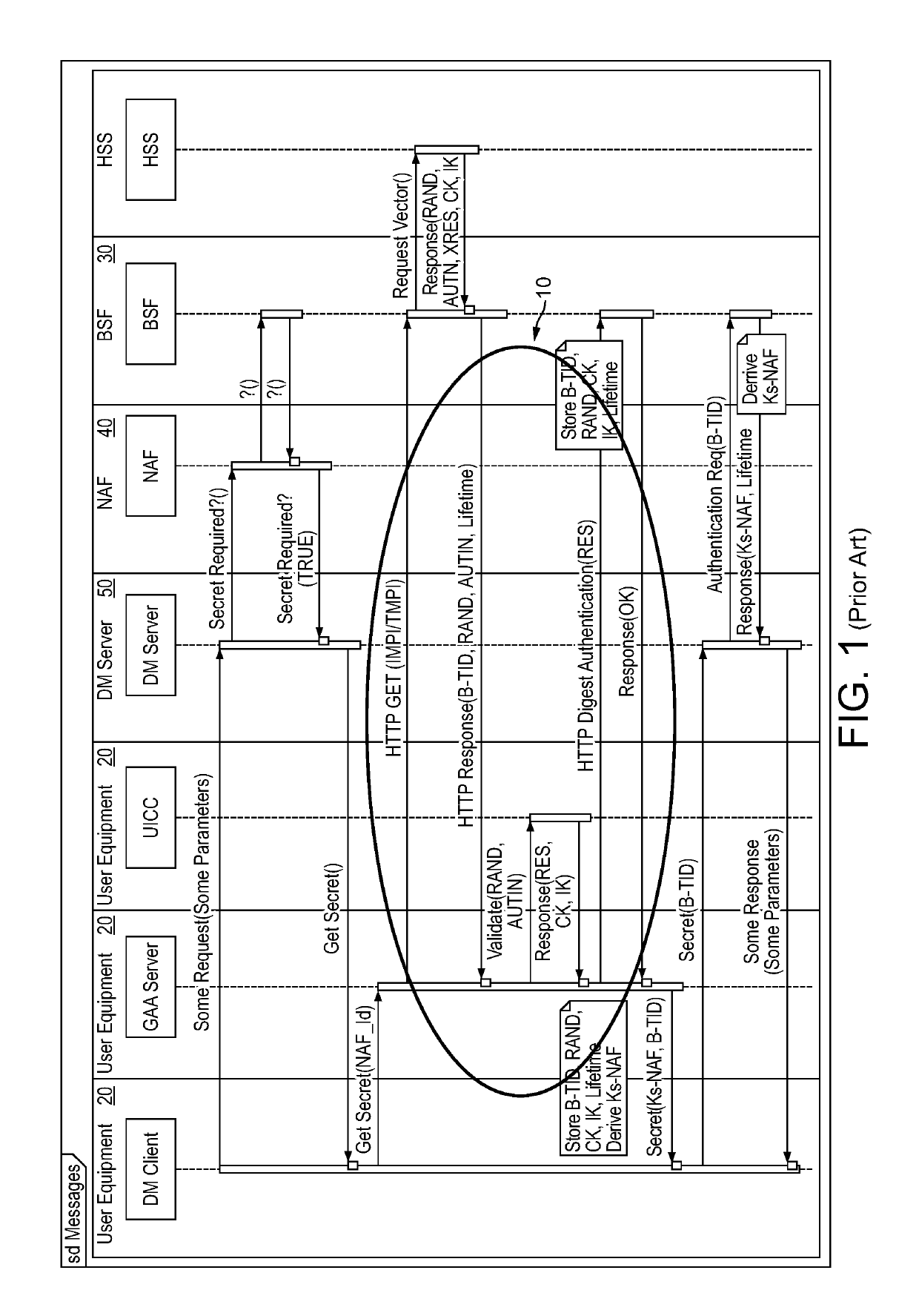
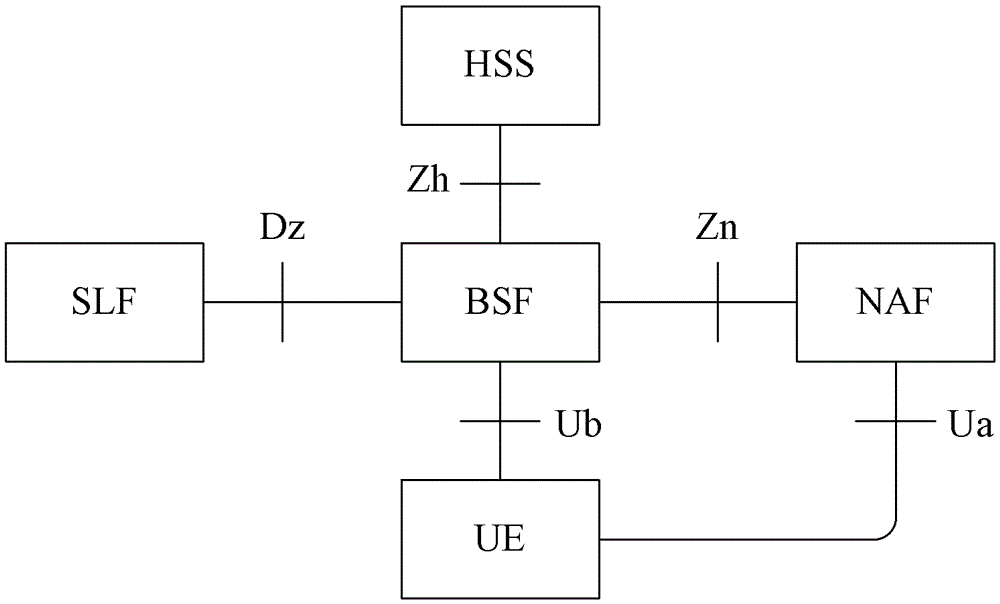
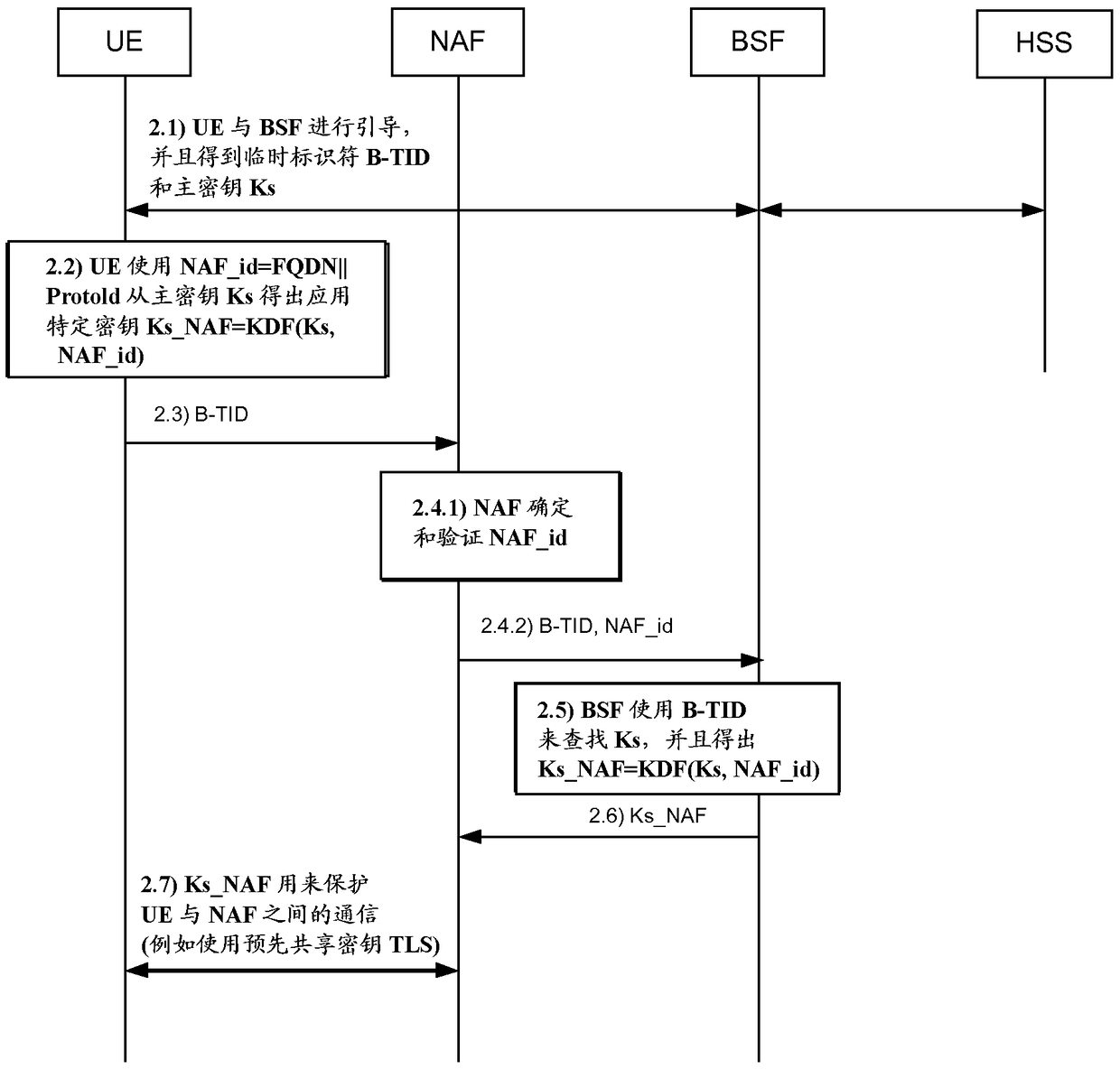
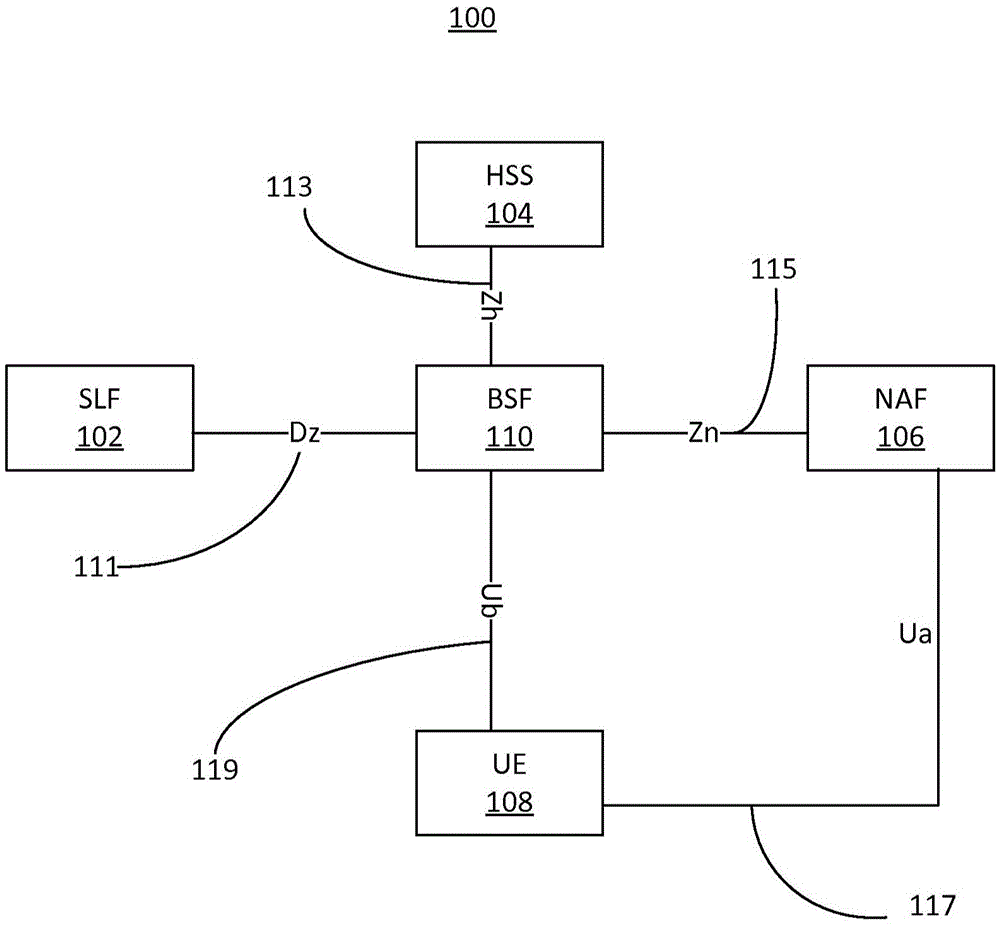
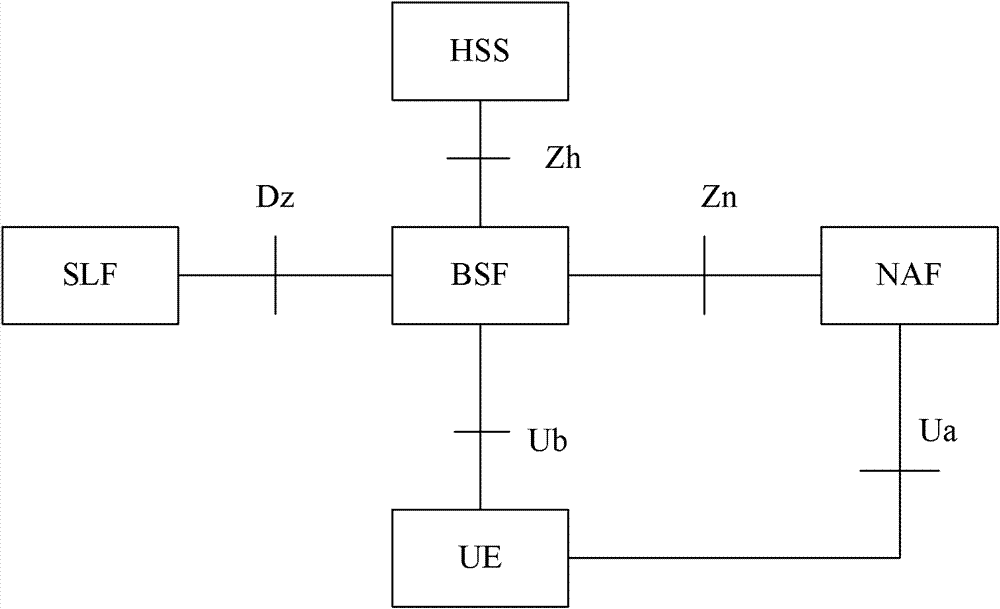
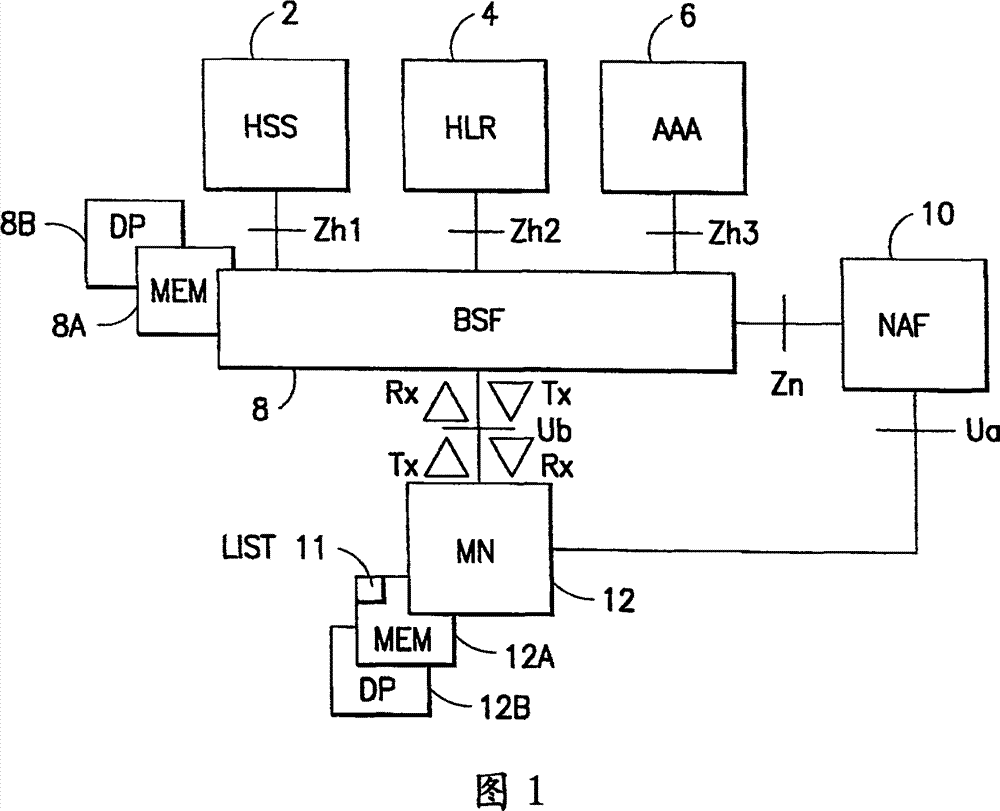
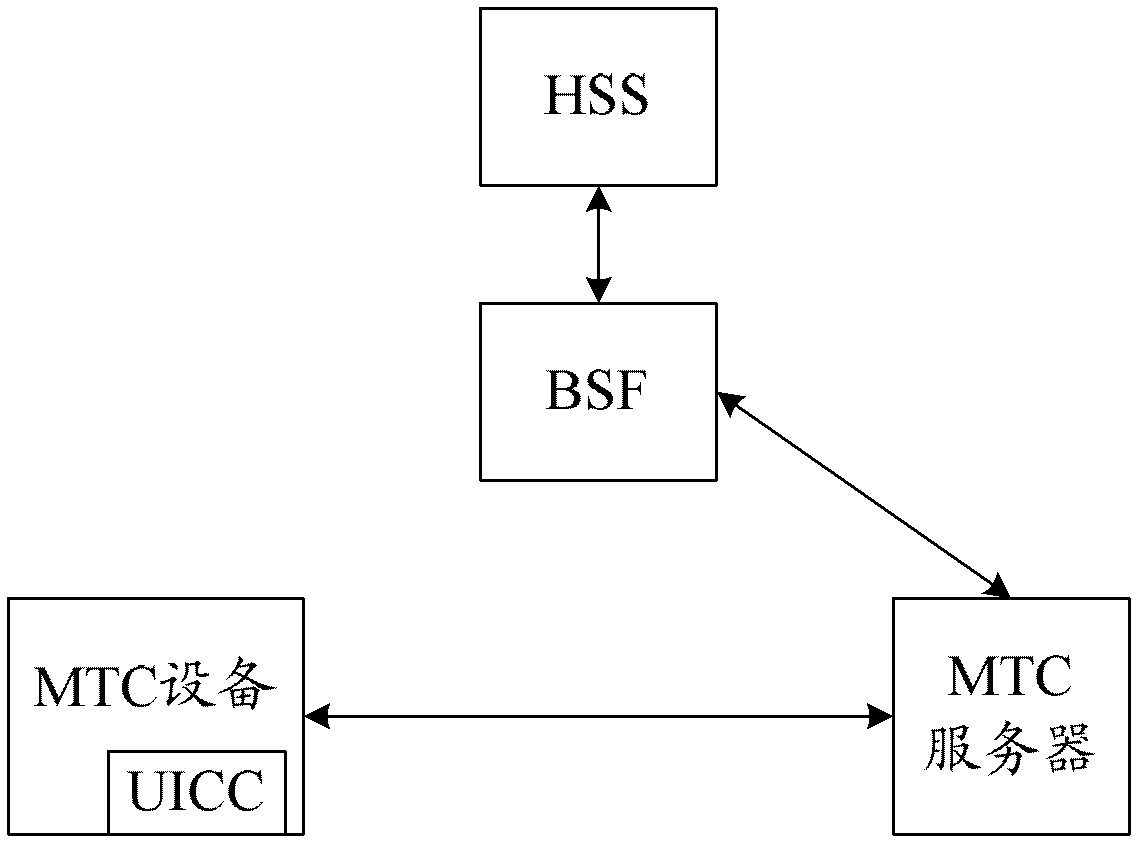
Generic Bootstrapping Architecture (GBA) is a technology that enables the authentication of a user. This authentication is possible if the user owns a valid identity on an HLR (Home Location Register) or on an HSS (Home Subscriber Server).
Authentication method, key distribution method and authentication and key distribution method
InactiveUS20110320802A1Digital computer detailsProgram controlCommunications systemGeneric Bootstrapping Architecture
An authentication method, and a key distribution method, and an authentication and key distribution method are provided. The authentication method is adapted for a machine type communication involved with a wireless communication system, and includes the following steps. At least a user equipment (UE) transmits an application request including at least a first security material to a network application function (NAF), where the at least a first security material is not a key directly obtained through a bootstrapping procedure of a generic bootstrapping architecture. The NAF generates a second security material, which is not the key, either. The NAF replies the UE an application answer with the at least a second security material. In addition, the NAF authenticates the UE by the second security material, or the UE authenticates the NAF by the second security material.
Owner:IND TECH RES INST
Re-Keying in a Generic Bootstrapping Architecture Following Handover of a Mobile Terminal
InactiveUS20070124587A1User identity/authority verificationSecurity arrangementGeneric Bootstrapping ArchitectureRe keying
An apparatus for re-keying a mobile terminal in a foreign network includes a processor. The processor is configured to receive, at the apparatus which is physically located in the foreign network, a request for re-keying from the mobile terminal in the foreign network. The processor is also configured to translate the request for transmission to a home network of the mobile terminal and to transmit the translated request to a bootstrapping server function of the home network.
Owner:NOKIA CORP
Methods and systems for operating a secure mobile device
InactiveUS20160234683A1Reduced or no PKIValidate easilyInternal/peripheral component protectionWireless commuication servicesComputer hardwareGeneric Bootstrapping Architecture
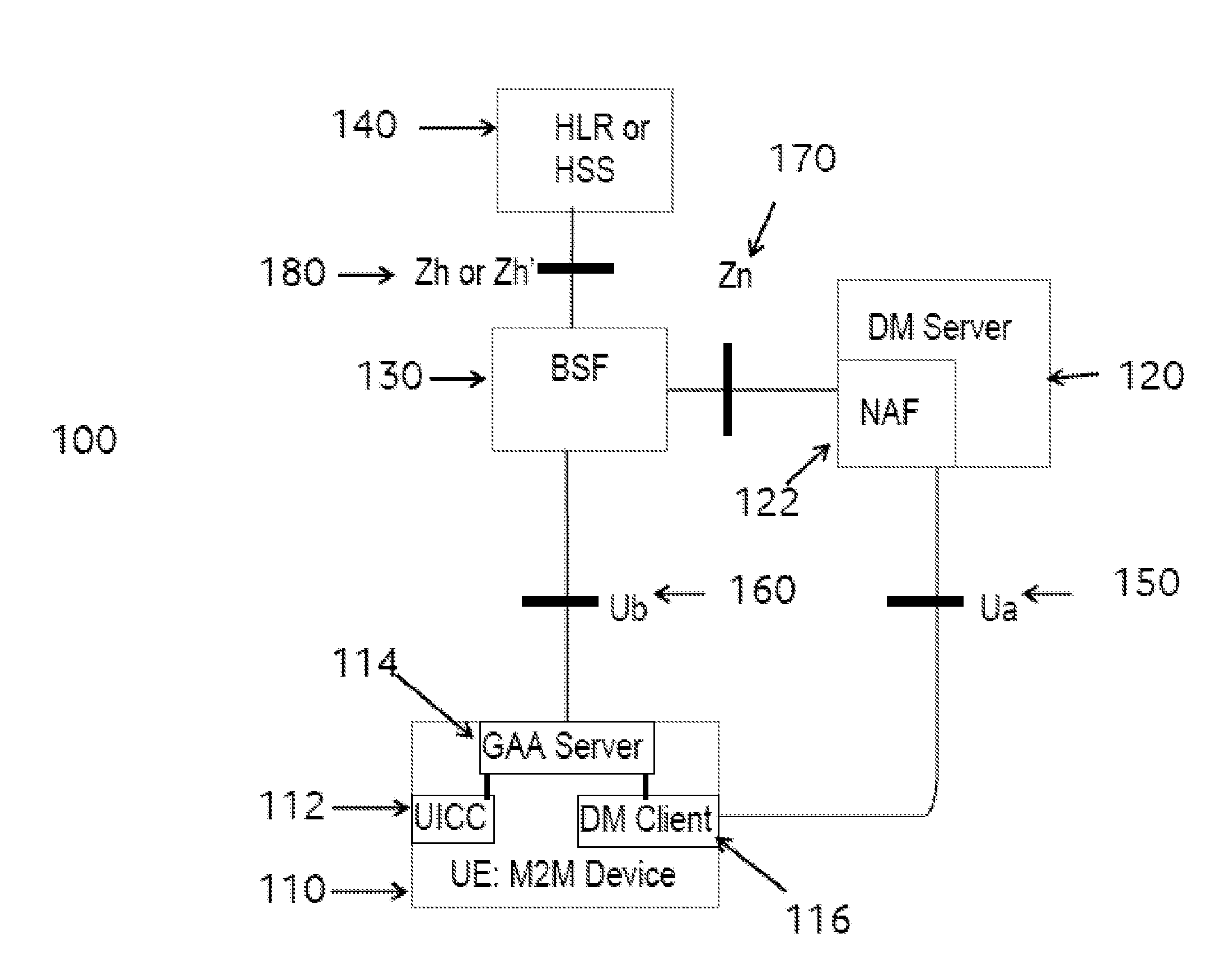
Method and apparatus for communicating with a machine to machine, M2M, device comprising: deriving at a M2M device using generic bootstrapping architecture, GBA, a first key. Sending a second key to the M2M device protected using the first key, wherein the second key is different to the first key. Sending protected data to the M2M device, wherein the protected data is verifiable by the M2M device using the second key.
Owner:VODAFONE IP LICENSING
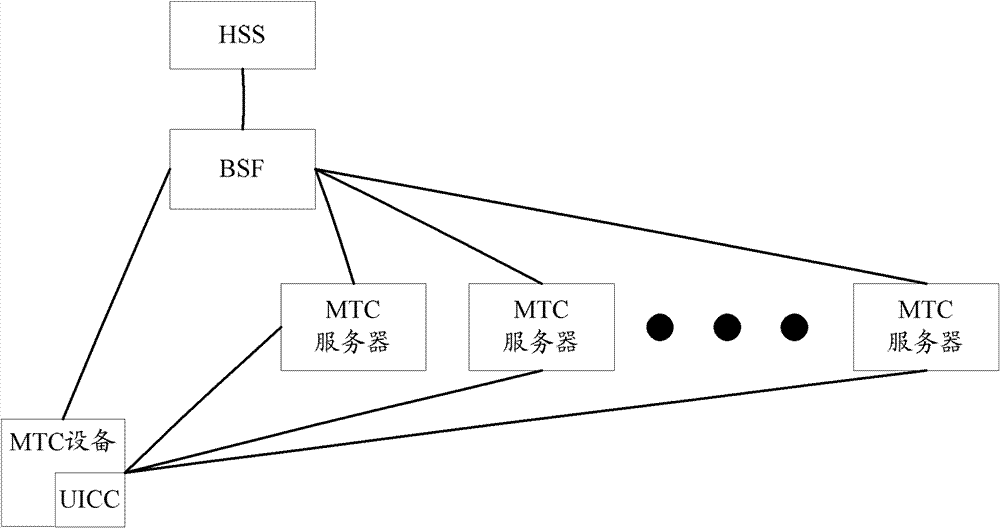
Method and system for managing machine type communication (MTC) equipment based on generic bootstrapping architecture (GBA) in grouping manner
InactiveCN102469455AWireless commuication servicesTransmissionGeneric Bootstrapping ArchitectureCommunication device
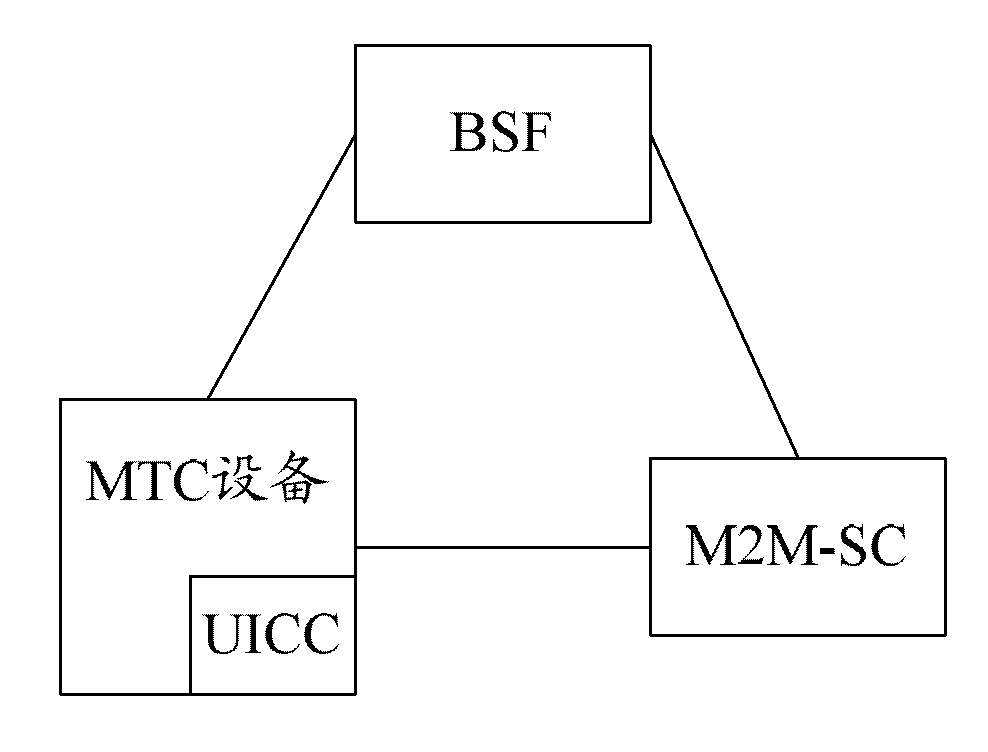
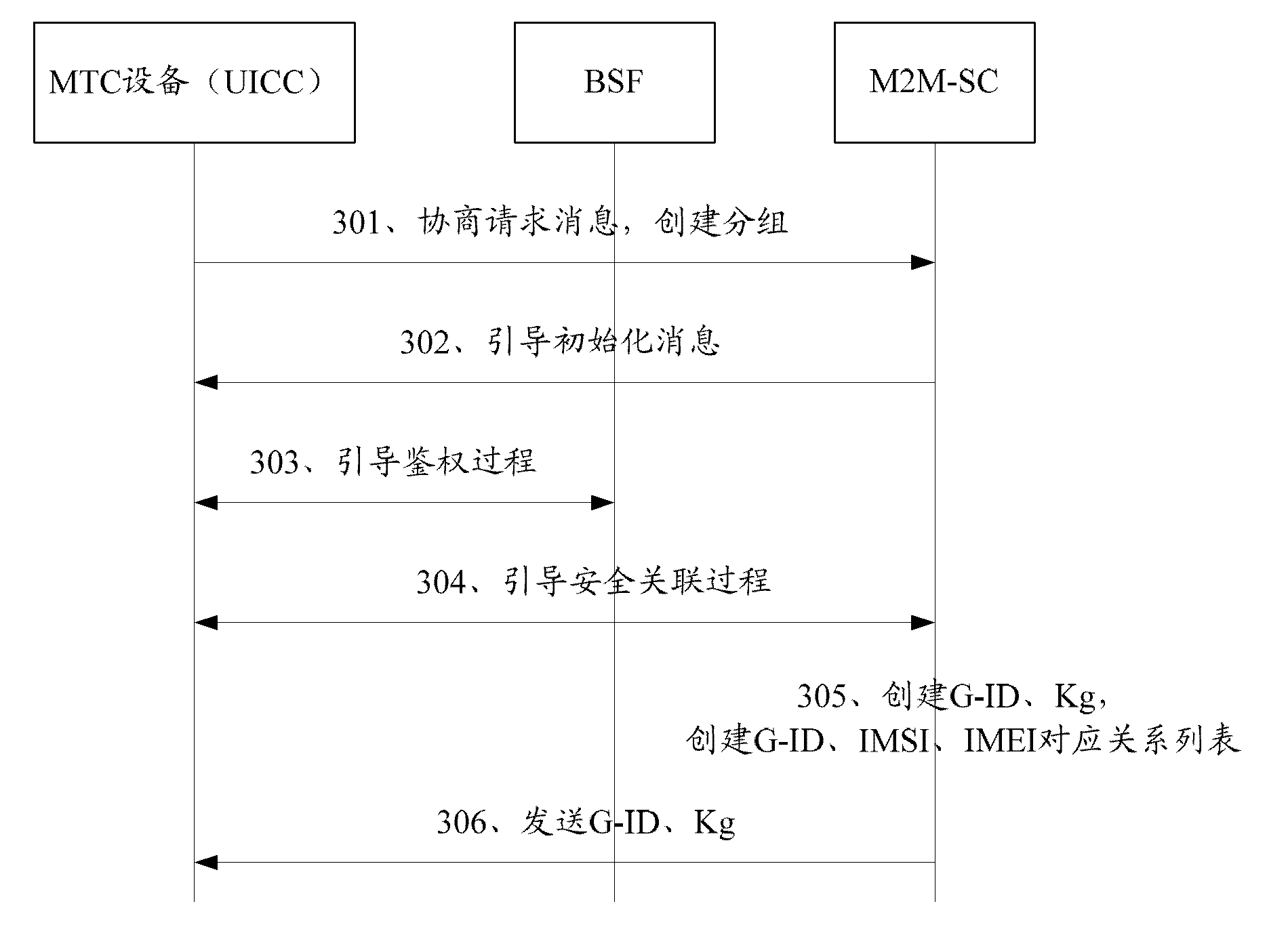
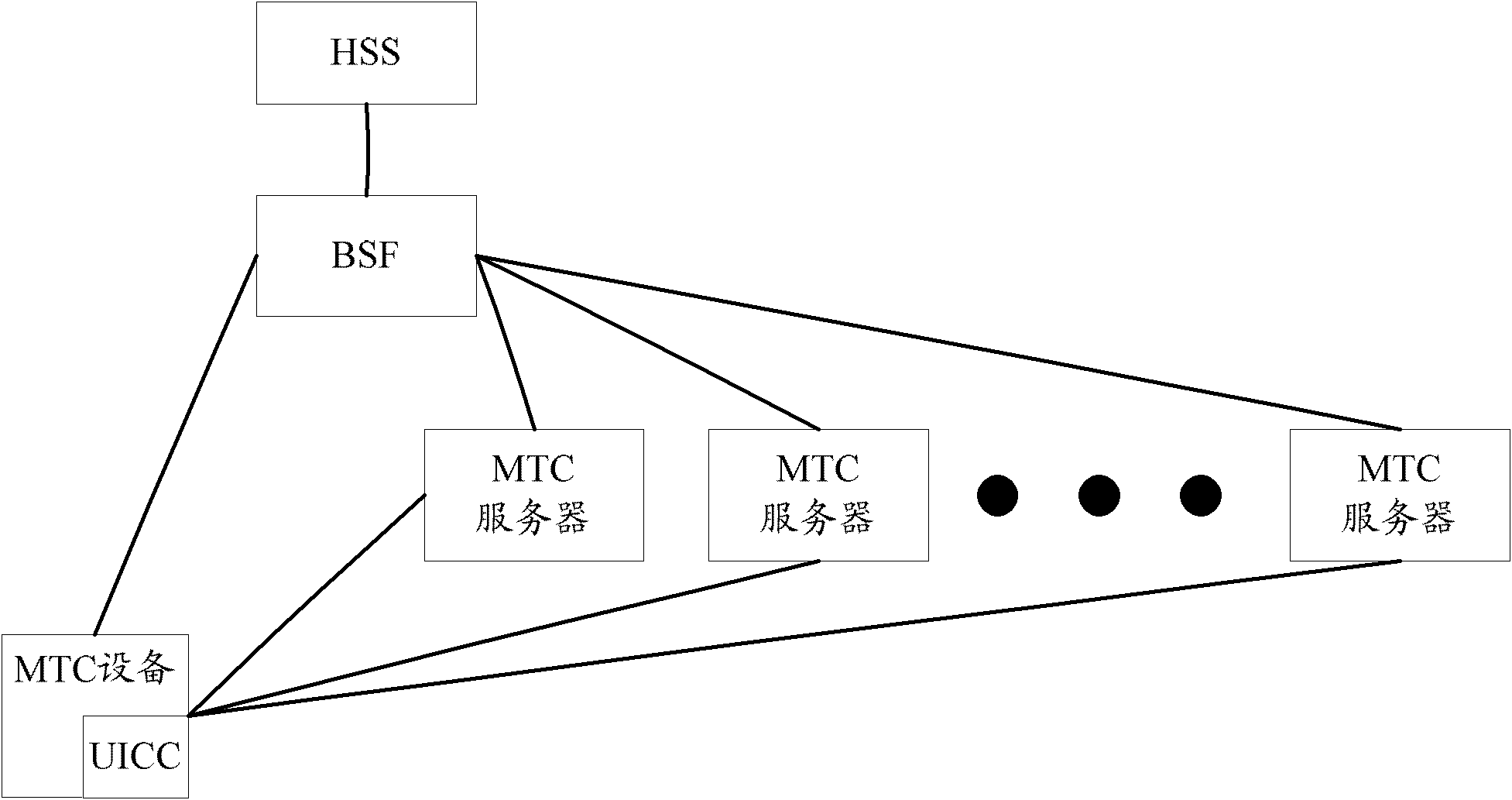
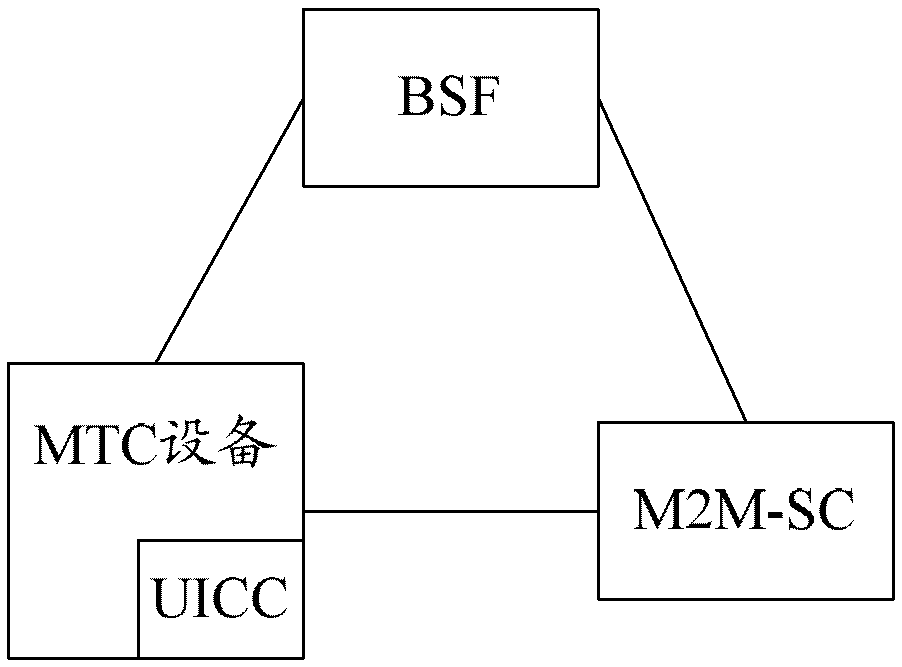
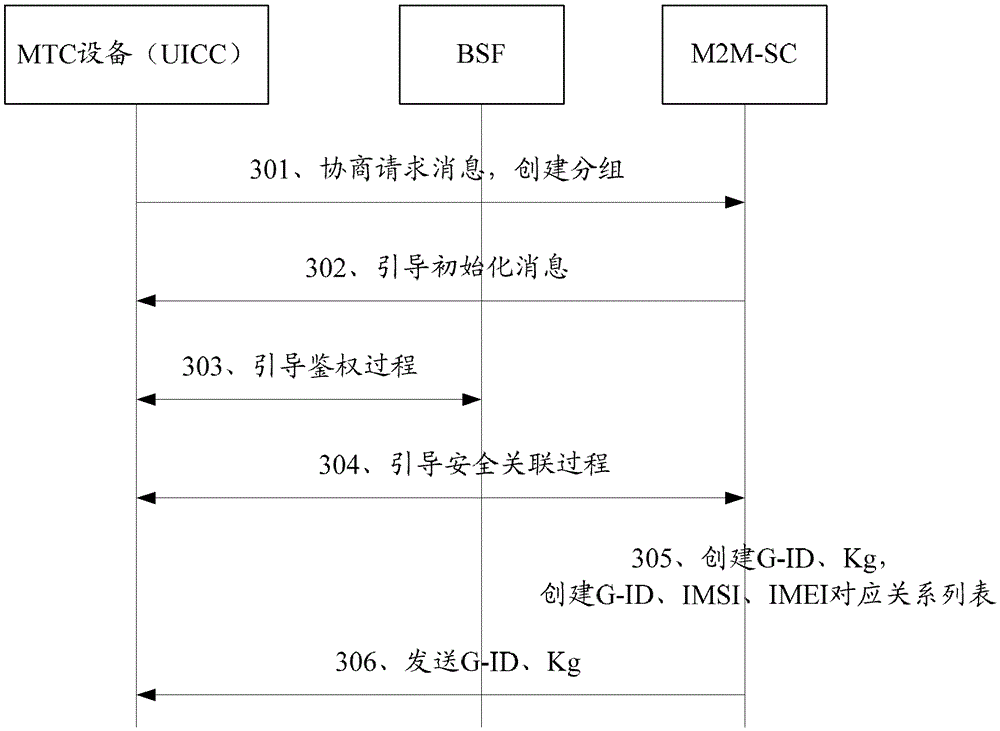
The invention discloses a method for managing machine type communication (MTC) equipment based on a generic bootstrapping architecture (GBA) in a grouping manner. The method is applied to a system which comprises the MTC equipment, a bootstrapping server function (BSF) and a machine to machine service center (M2M-SC), and comprises the following steps that: when the MTC equipment which is determined to be added with a group identifier (G-ID) through the negotiation between first MTC equipment and the M2M-SC is grouped, the first MTC equipment, the BSF and the M2M-SC establish a first session key between the first MTC equipment and the M2M-SC in a first GBA process, and the M2M-SC encrypts the G-ID and a group key Kg which are grouped by the MTC equipment through the first session key and then transmits the encrypted G-ID and group key Kg to the first MTC equipment. By the method, group members in the grouped MTC equipment can be safely managed.
Owner:ZTE CORP
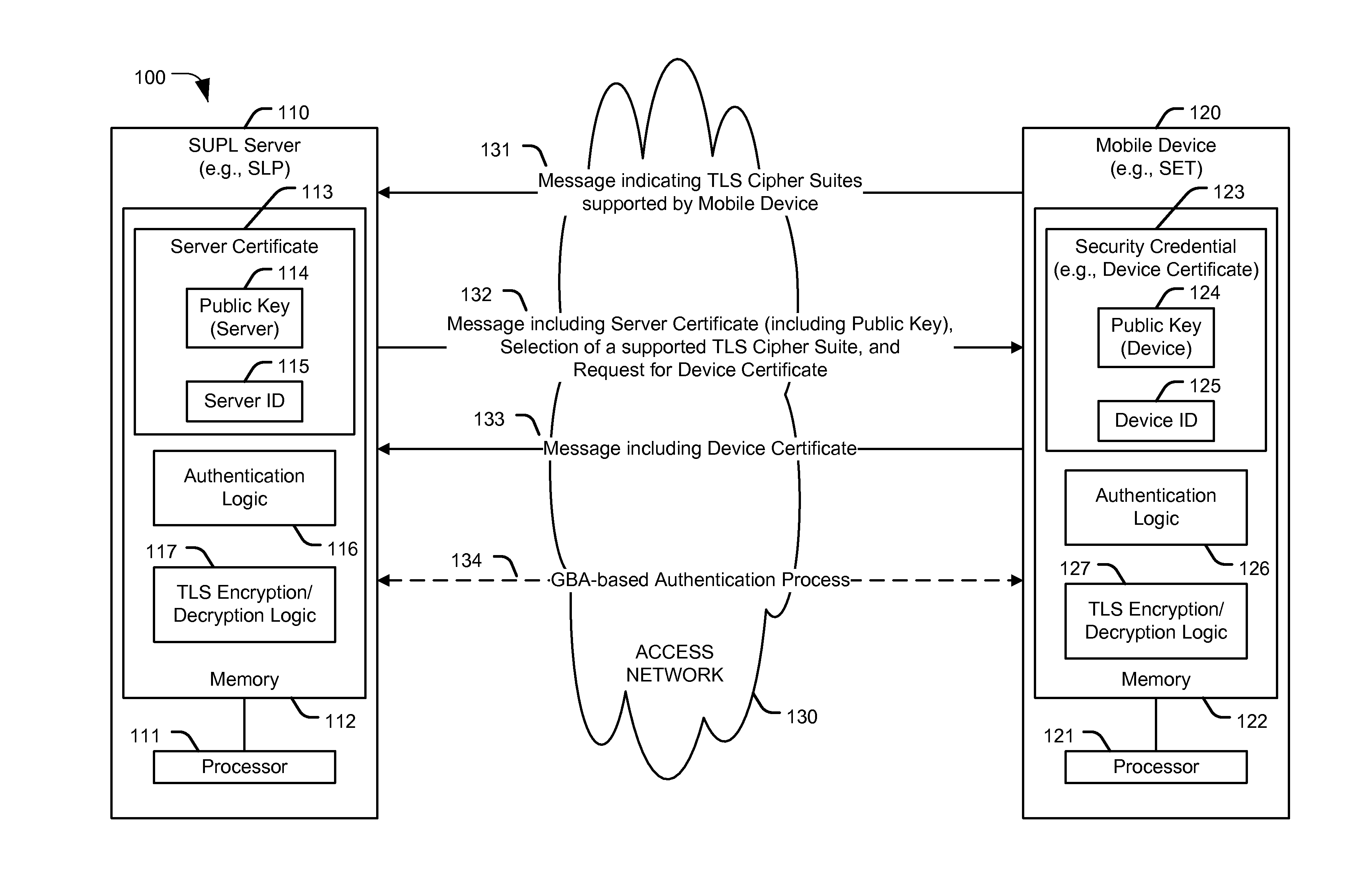
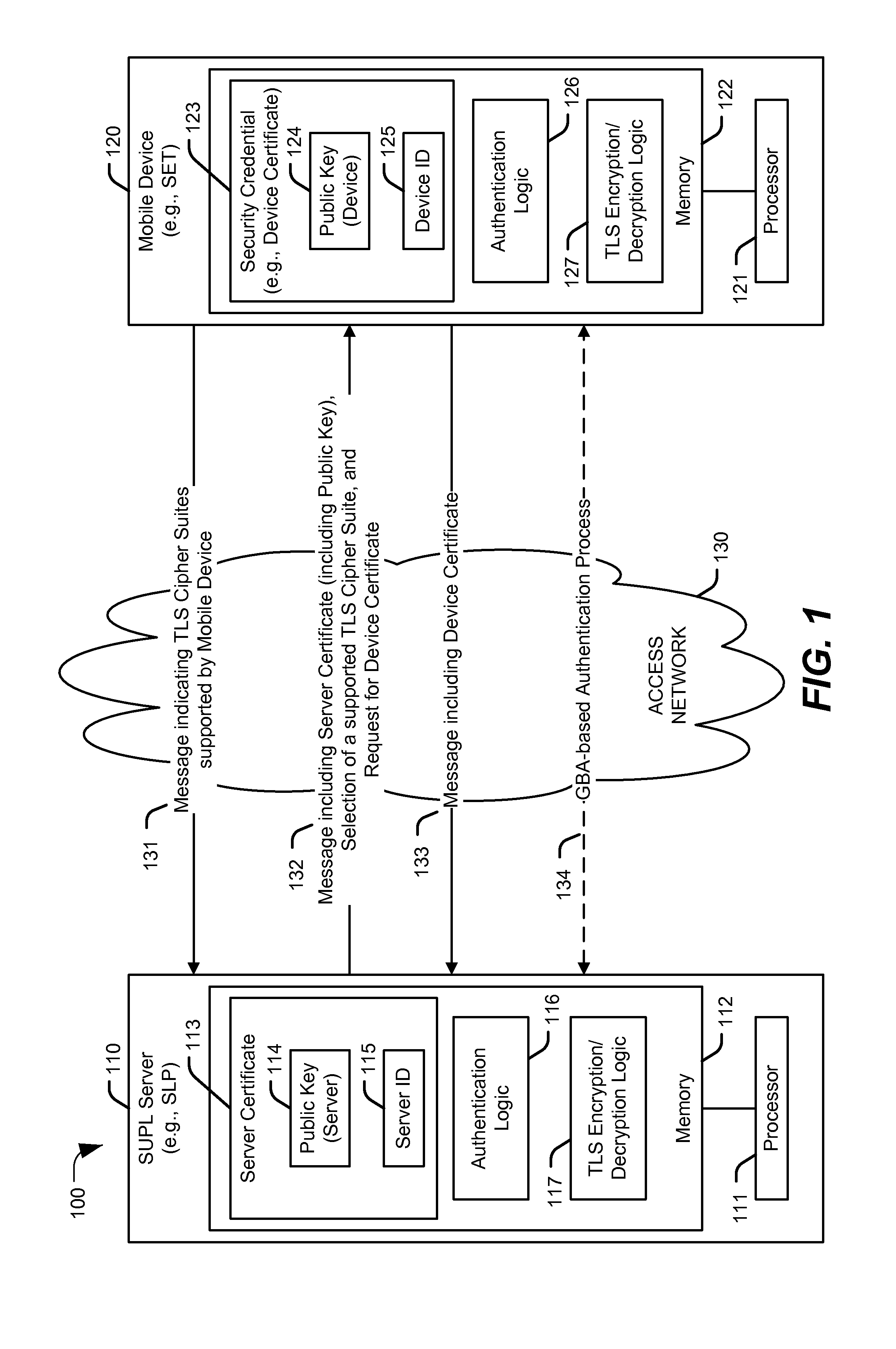
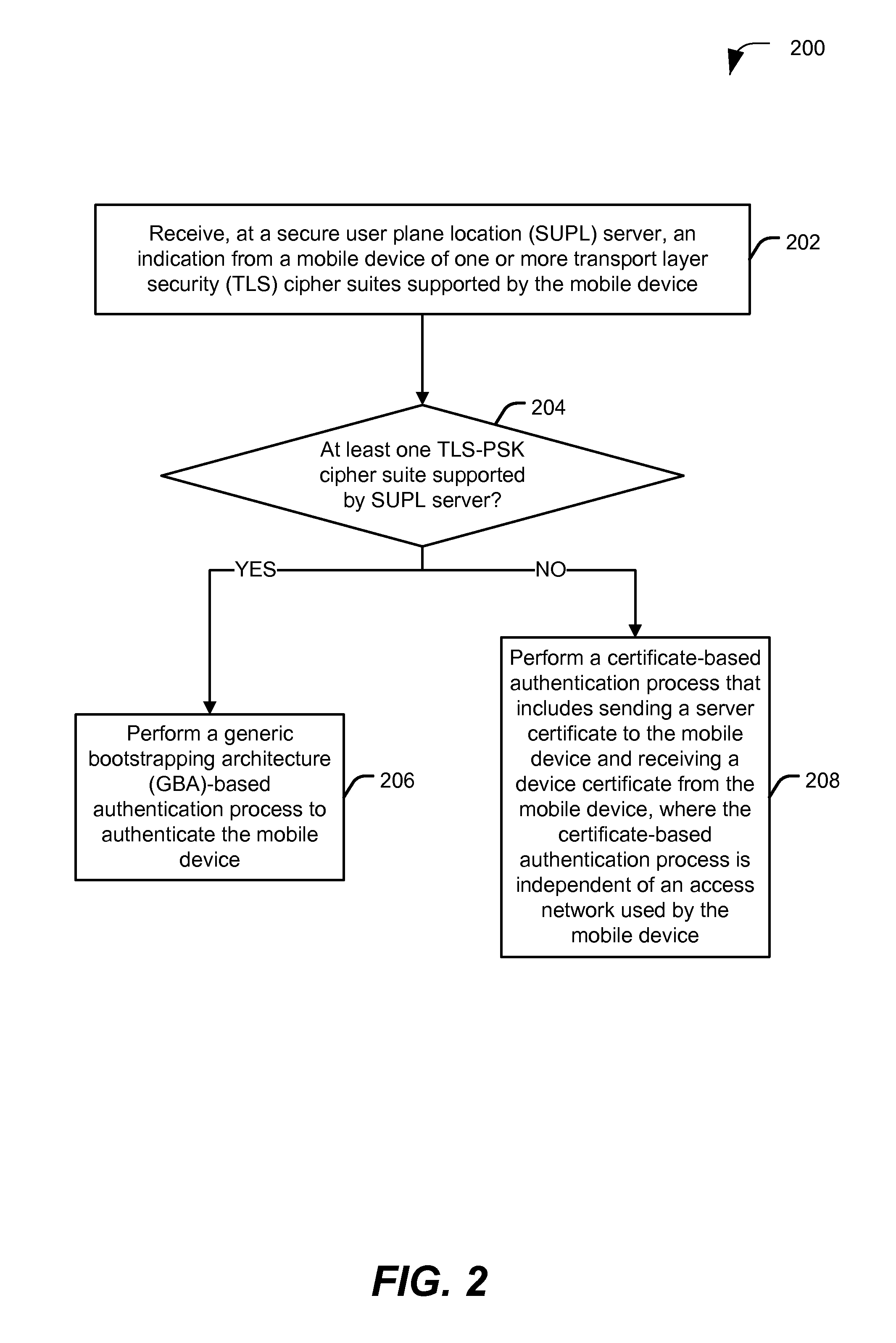
Authentication in secure user plane location (SUPL) systems
A particular method includes receiving, at a secure user plane location (SUPL) server, an indication from a mobile device of one or more transport layer security (TLS) cipher suites supported by the mobile device; determining whether the one or more TLS cipher suites include a TLS pre-shared key (TLS-PSK) cipher suite that is supported by the SUPL server; in response to determining whether the one or more TLS cipher suites include the TLS-PSK cipher suite that is supported by the SUPL server, performing a generic bootstrapping architecture (GBA)-based authentication process to authenticate the mobile device, or determining whether the SUPL server supports a certificate-based authentication method; and in response to determining that the SUPL server supports the certificate-based authentication method, performing the certificate-based authentication method that includes sending a server certificate to the mobile device and receiving a device certificate from the mobile device.
Owner:QUALCOMM INC
Method and arrangement for integration of different authentication infrastructures
ActiveCN101569217AWireless network protocolsSecurity arrangementSession managementGeneric Bootstrapping Architecture
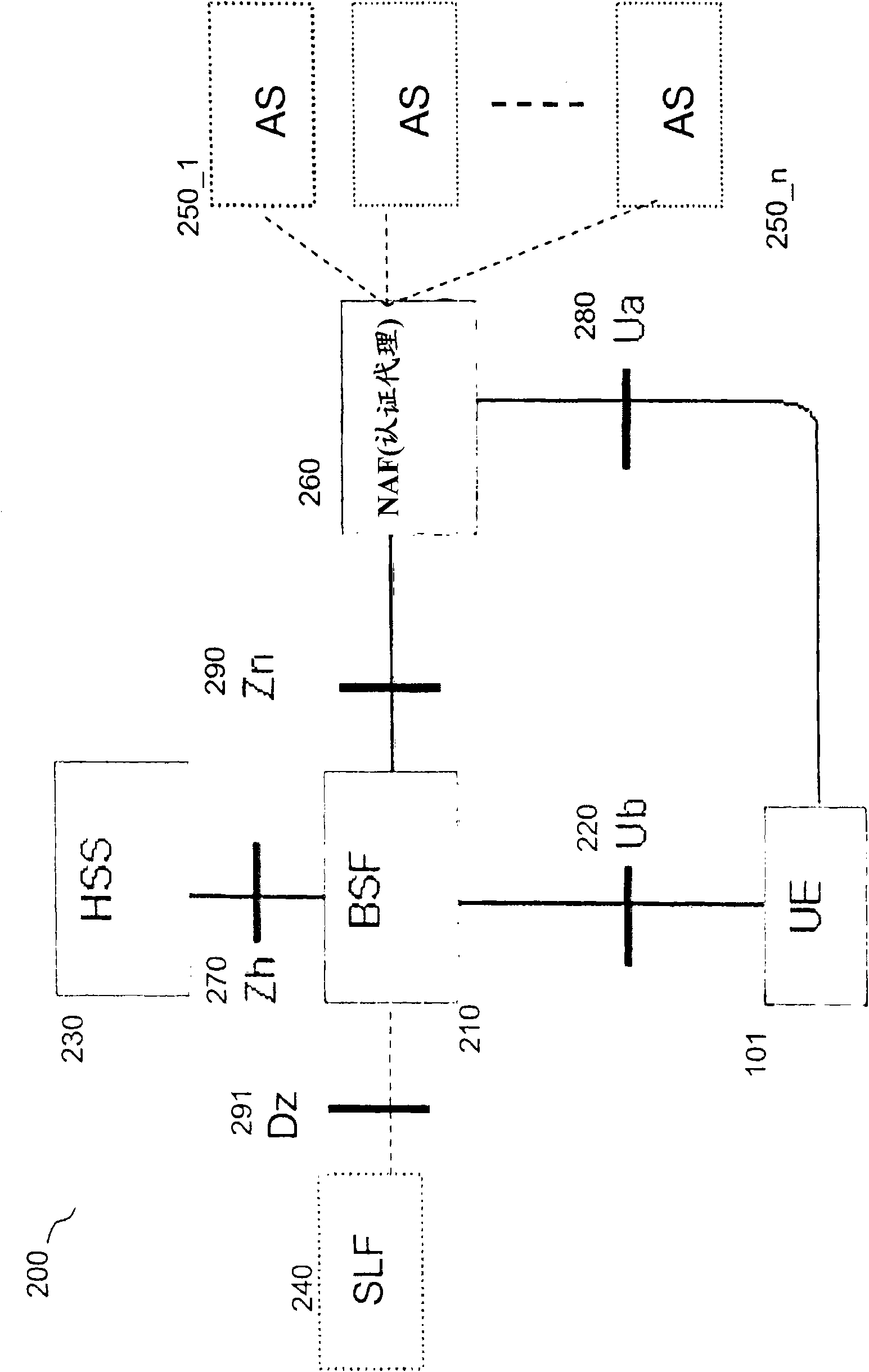
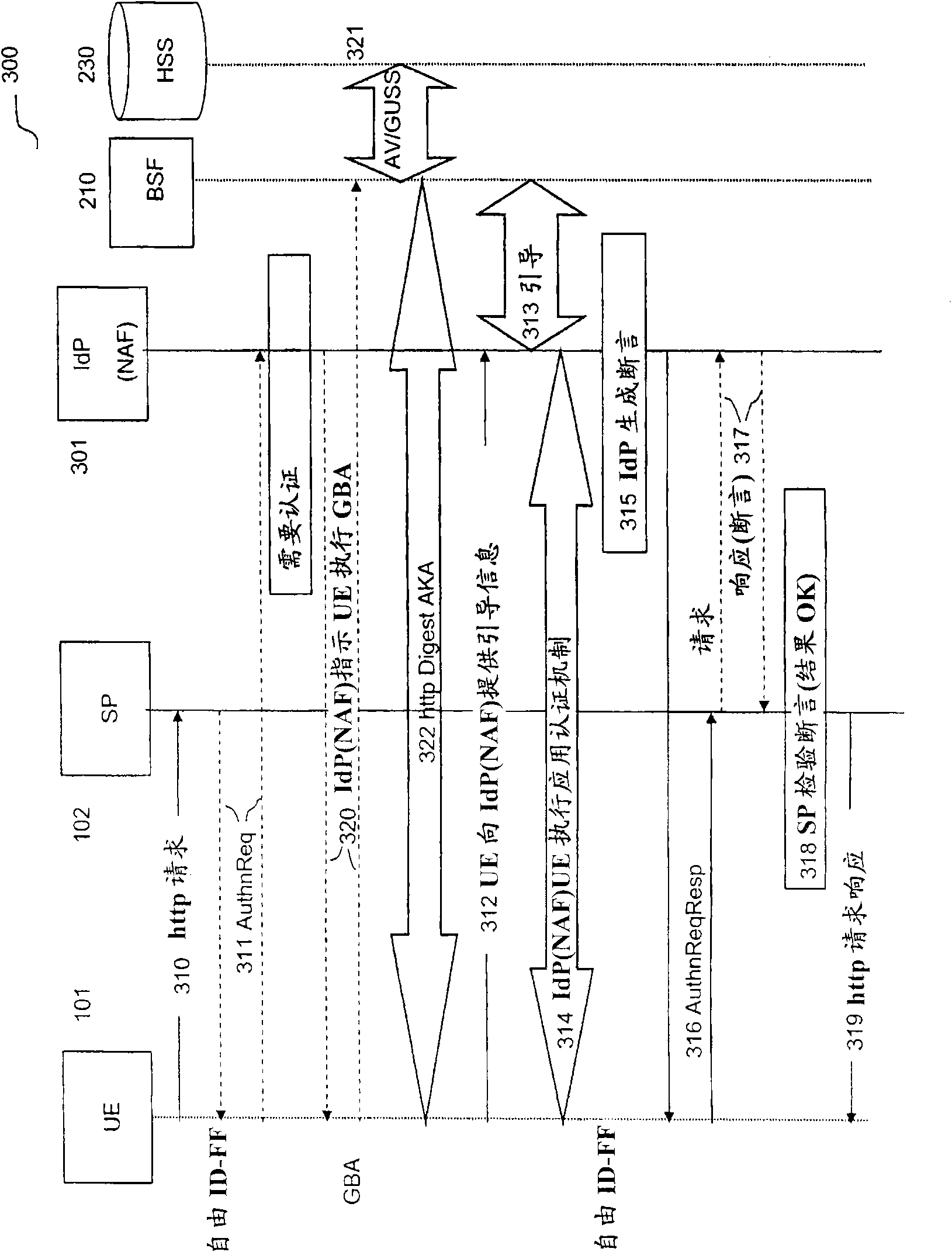
A method is disclosed that provides efficient integration of infrastructure for federated single sign on, e.g. Liberty ID-FF framework, and generic bootstrapping architecture, e.g. 3GPP GAA / GBA architecture. An integrated proxy server (IAP) is inserted in the path between a user and a service provider (SP). The proxy server differentiates type of access and determines corresponding operative state to act as a liberty enabled server or as a GAA / GBA network application function. A Bootstrapping, Identity, Authentication and Session Management arrangement (BIAS) leverages on 3GPP GAA / GBA infrastructure to provide an integrated system for handling Liberty Federated SSO and 3GPP GAA / GBA bootstrapping procedures at the same time. The method and arrangement provides improved use of infrastructure elements and performance for authenticated service access.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method to establish a secure voice communication using generic bootstrapping architecture
InactiveUS20160044505A1Improve securityKnown materialSecret communicationTransmissionVoice communicationGeneric Bootstrapping Architecture
The present invention relates to a method to establish a secure voice communication session between two user equipments with the help of a dedicated Network Application Function (NAF) and at least one Bootstrapping Server Function. A session key is calculated from bootstrapping service derived external or internal NAF keys of the first and the second user equipments. A secured voice communication is established using the calculated session key.
Owner:GEMPLU
Secure session key generation
InactiveCN102037707AImprove securityEncryption apparatus with shift registers/memoriesPublic key for secure communicationGeneric Bootstrapping ArchitectureComputer science
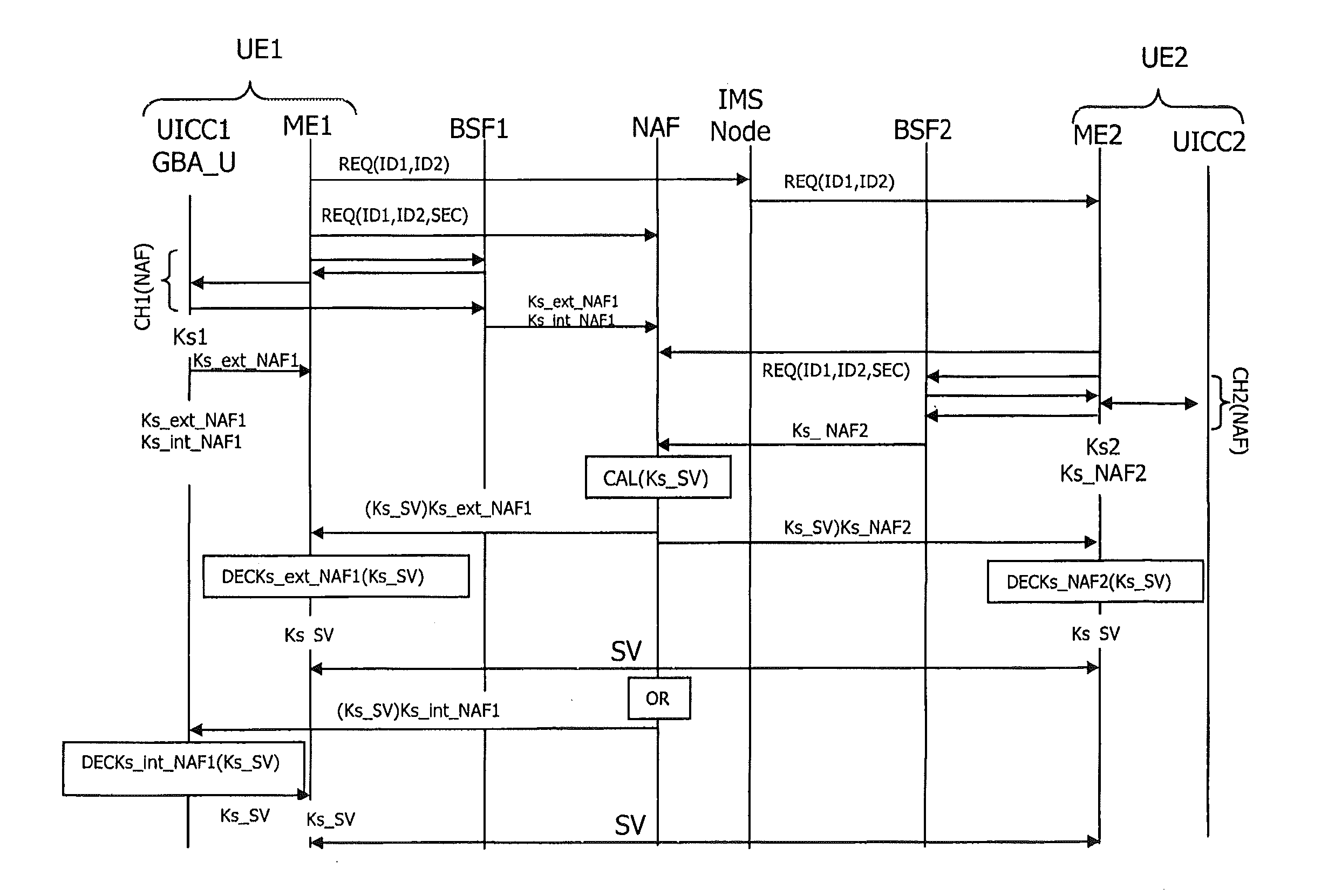
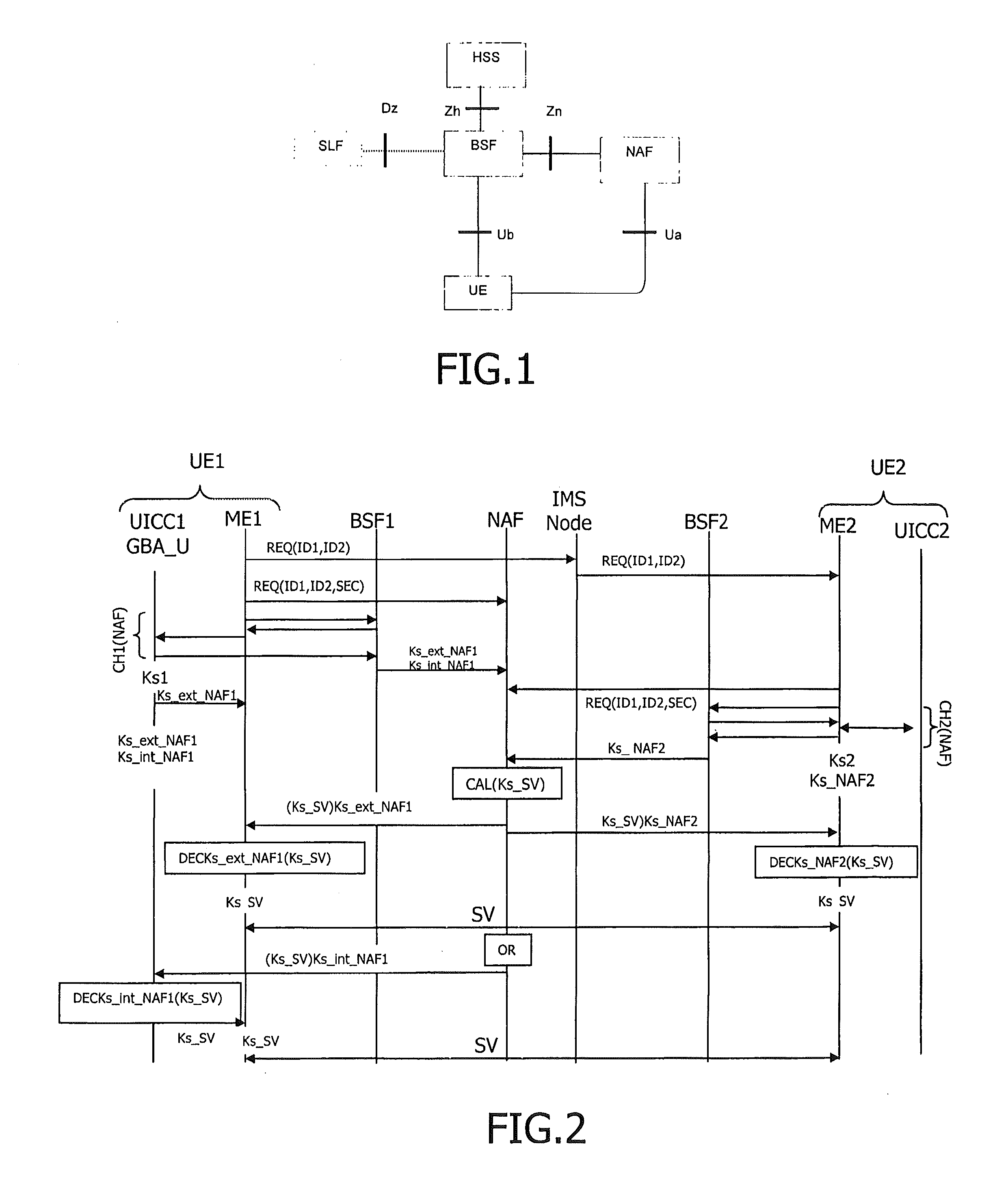
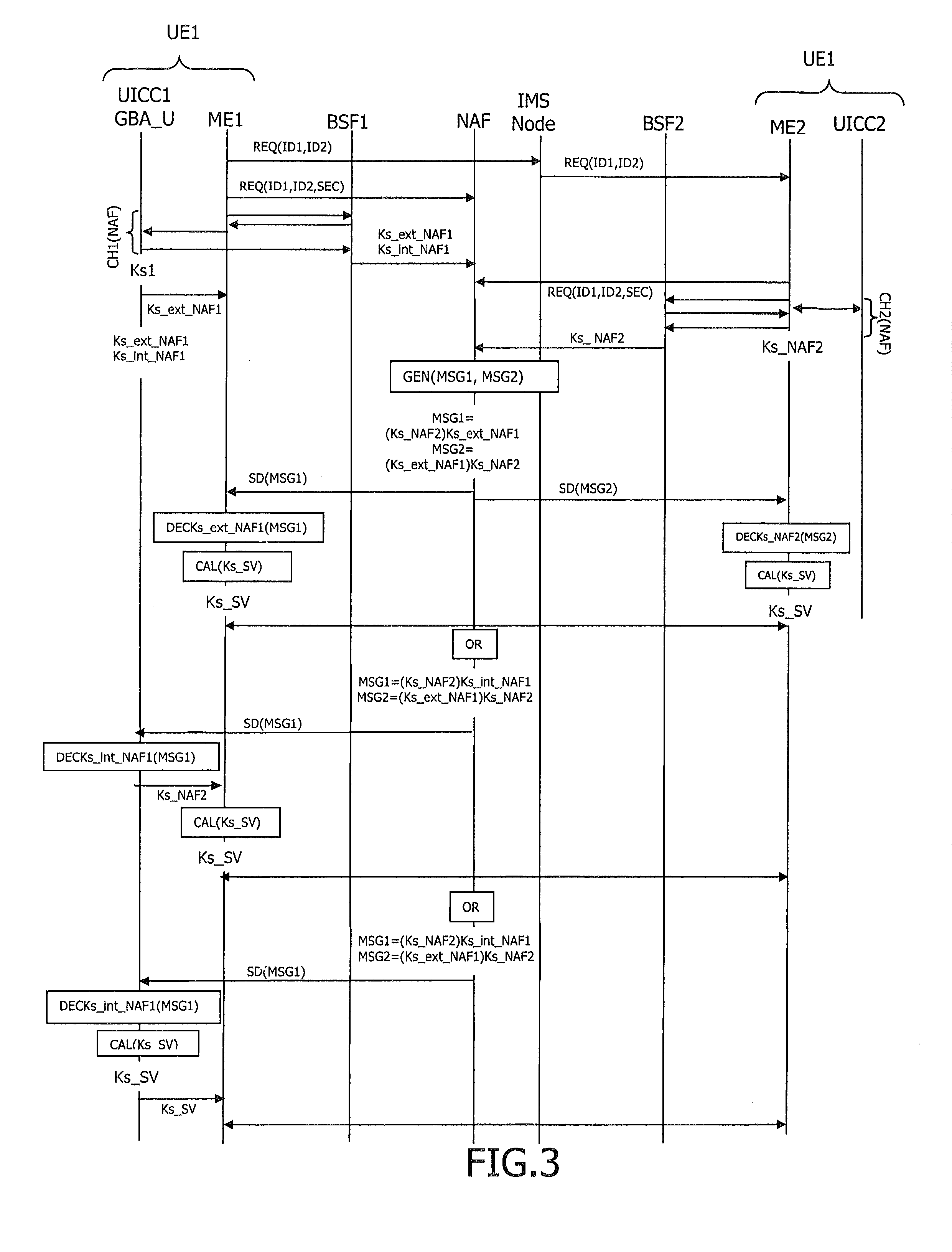
A method and apparatus for securing the interface between a Universal Integrated Circuit Card (UICC) and a Terminal in wireless communications is disclosed. The security of Authentication and Key Agreement (AKA) and application level generic bootstrapping architecture (GBA) with UICC-based enhancements (GBA_U) procedures is improved. A secure shared session key is used to encrypt communications between the UICC and the Terminal. The secure shared session key generated using authenticating or non-authenticating procedures.
Owner:INTERDIGITAL PATENT HLDG INC
Generic bootstrapping architecture usage with web applications and web pages
ActiveCN103004244AKey distribution for secure communicationUser identity/authority verificationDomain nameFully qualified domain name
A method includes receiving at a network application function a request related to a generic bootstrapping architecture key originated from a user equipment (1). The received request includes a network application function identifier that includes a uniform resource locator, where the network application function has a fully qualified domain name. The method further includes causing a generic bootstrapping architecture key to be generated for the user equipment based at least in part on the uniform resource locator that is part of the network application function identifier (5). Apparatus and computer programs for performing the method are also disclosed.
Owner:NOKIA TECHNOLOGLES OY
Method, device and system for updating key
ActiveCN102065421AReduce update loadAvoid frequent updatesSecurity arrangementComputer hardwareGeneric Bootstrapping Architecture
The embodiment of the invention discloses a method for updating a key. The method comprises the following steps: receiving a bootstrapping service identifier from network application function (NAF) and inquiring whether a root key is in the valid period according to the bootstrapping service identifier; if the root key is not in the valid period, returning the error message to user equipment (UE) by NAF and ensuring NAF to initiate generic bootstrapping architecture (GBA) with the UE; and if the root key is in the valid period, generating a random number, obtaining a service key according to the random number, sending the service key, the valid period of the service key and the random number to NAF and ensuring NAF to carry out two-way authentication with the UE according to the service key and the random number. The embodiment of the invention reduces the load of bootstrapping server function (BSF) and the load of a service server. The embodiment of the invention also discloses a device and system applying the method.
Owner:CHINA MOBILE COMM GRP CO LTD
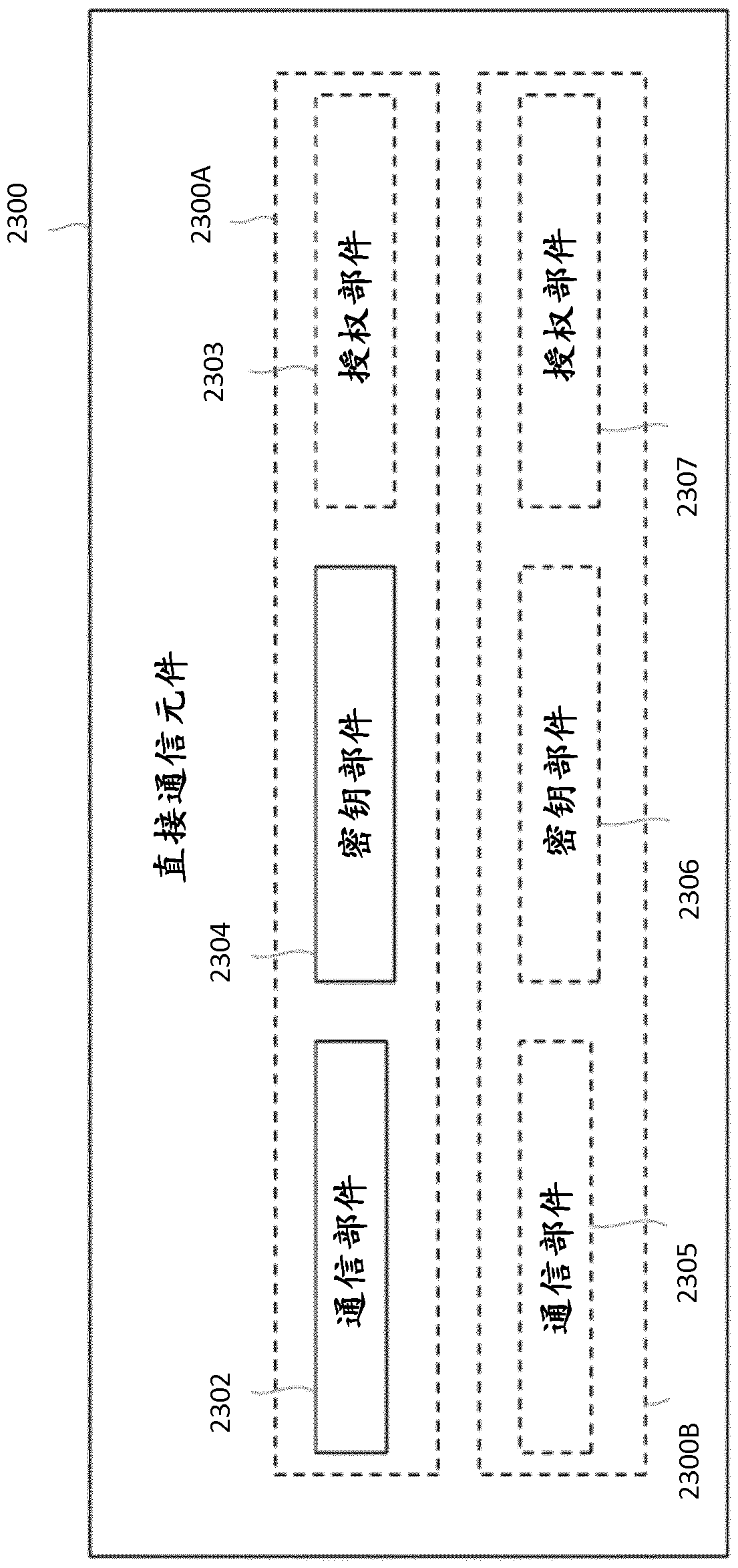
Methods and apparatus for direct communication key establishment
ActiveUS20180279120A1Address be challengeKey distribution for secure communicationConnection managementGeneric Bootstrapping ArchitectureEngineering
Methods And Apparatus For Direct Communication Key Establishment Methods (100, 200, 300) and apparatus (400, 500, 600, 700, 800, 900) are disclosed for establishing a key for direct communication between a User Equipment device, UE, and a device. The methods and apparatus cooperate to form a system for securing direct communication between a UE and a device over an interface. The system comprises a UE (20), a device (30) and a Direct Communication Element (40). The Direct Communication Element (40) is configured to obtain a shared session key and Generic Bootstrapping Architecture Push Information, GPI, to derive a direct communication key from at least the shared session key, and to send the direct communication key and the GPI to the device (30). The device (30) is configured to send the GPI to the UE (20). The UE (20) is configured to derive the shared session key from at least the GPI and to derive the direct communication key from the shared session key. Also disclosed are a computer product operable to carry out methods according to the present invention and a computer program product comprising a computer readable medium having such a computer product stored thereon.
Owner:TELEFON AB LM ERICSSON (PUBL)
Client registration and secret key sharing method, device and system based on GBA
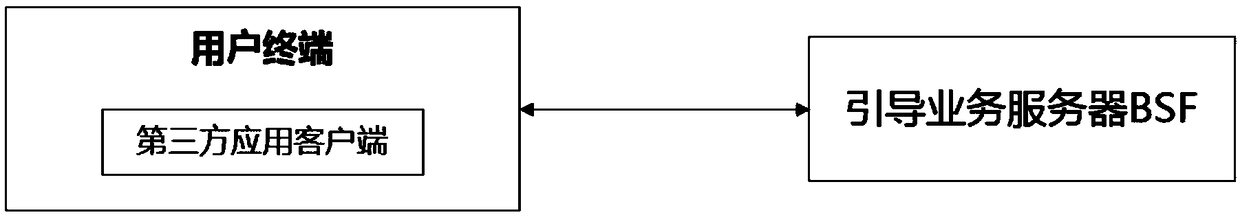
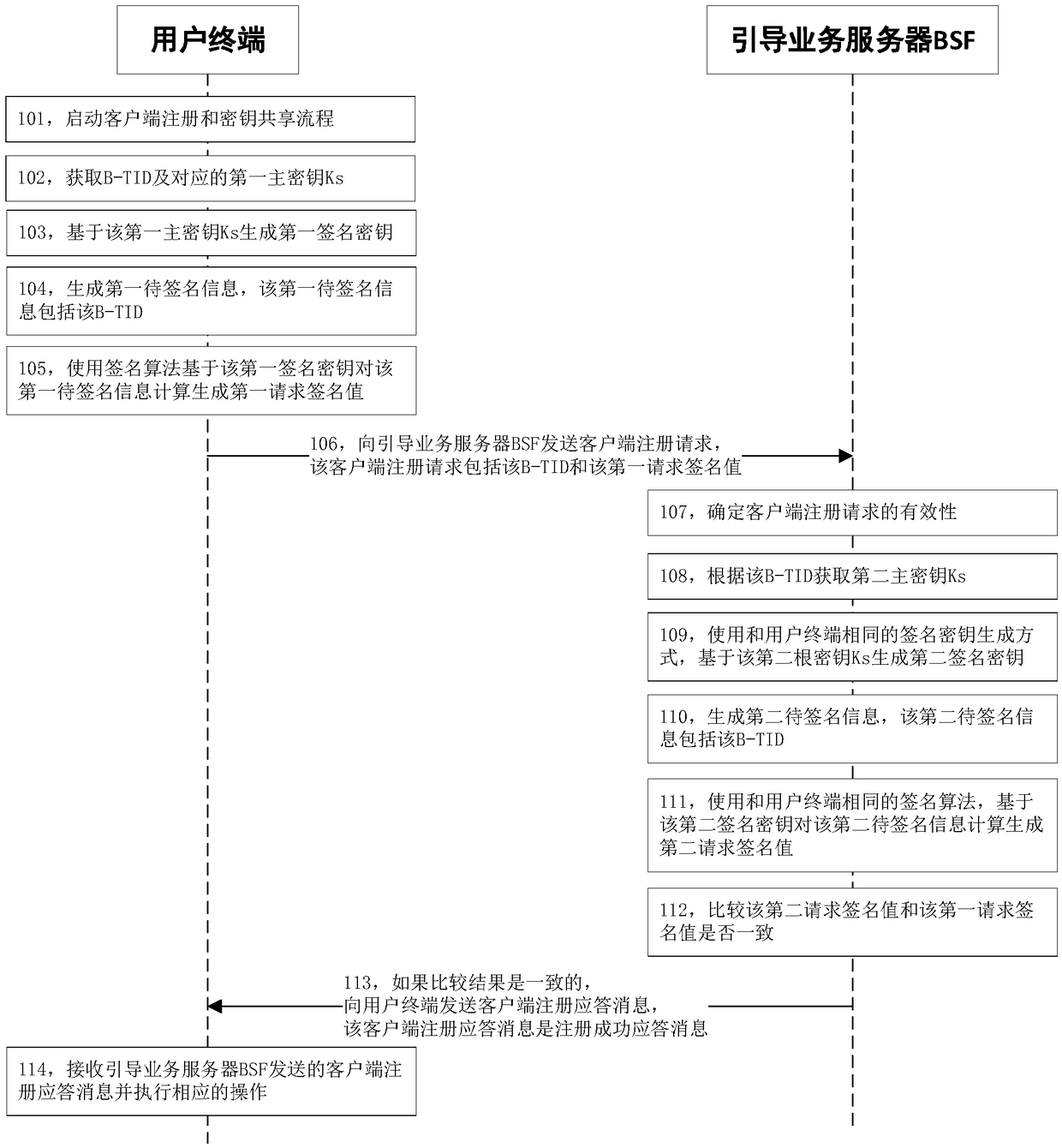
InactiveCN109121135AOvercoming technical deficienciesSecurity arrangementSecuring communicationThird partyGeneric Bootstrapping Architecture
The present invention discloses a client registration and secret key sharing method, device and system based on GBA (Generic Bootstrapping Architecture). The method comprises the steps of: operating auser terminal with a third-party application client to send a client registration request to a guidance business server BSF (Bootstrapping Server Function), wherein the client registration request comprises a B-TID (Bootstrapping Transaction Identifier) and a first request signature value; and verifying the validness of the first request signature value in the client registration terminal according to the B-TID and the corresponding secret key, and after the verification is valid, providing safe registration information and service for the third-party application client after, and generatingan application secret key for the third-party application client.
Owner:刘高峰
Method and apparatus for direct communication key establishment
InactiveCN108141755AService provisioningNetwork topologiesAir interfaceGeneric Bootstrapping Architecture
A method, performed by a User Equipment device (UE), for obtaining a key for direct communication with a device over an air interface, wherein the UE has previously acquired a transaction identifier received from a Bootstrapping Server Function (BSF), in a Generic Bootstrapping Architecture (GBA), procedure, is provided. The method comprises storing the transaction identifier, sending the transaction identifier to the device and requesting key generation for direct communication with the device. If the transaction identifier is invalid, the method further comprises receiving from the device adevice identifier and key generation information, deriving a session shared key from at least the key generation information, and deriving a direct communication key from at least the session shared key and the device identifier.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and apparatus for securing a connection in a communications network
ActiveCN104756458ASecurity arrangementSecuring communicationSecure communicationGeneric Bootstrapping Architecture
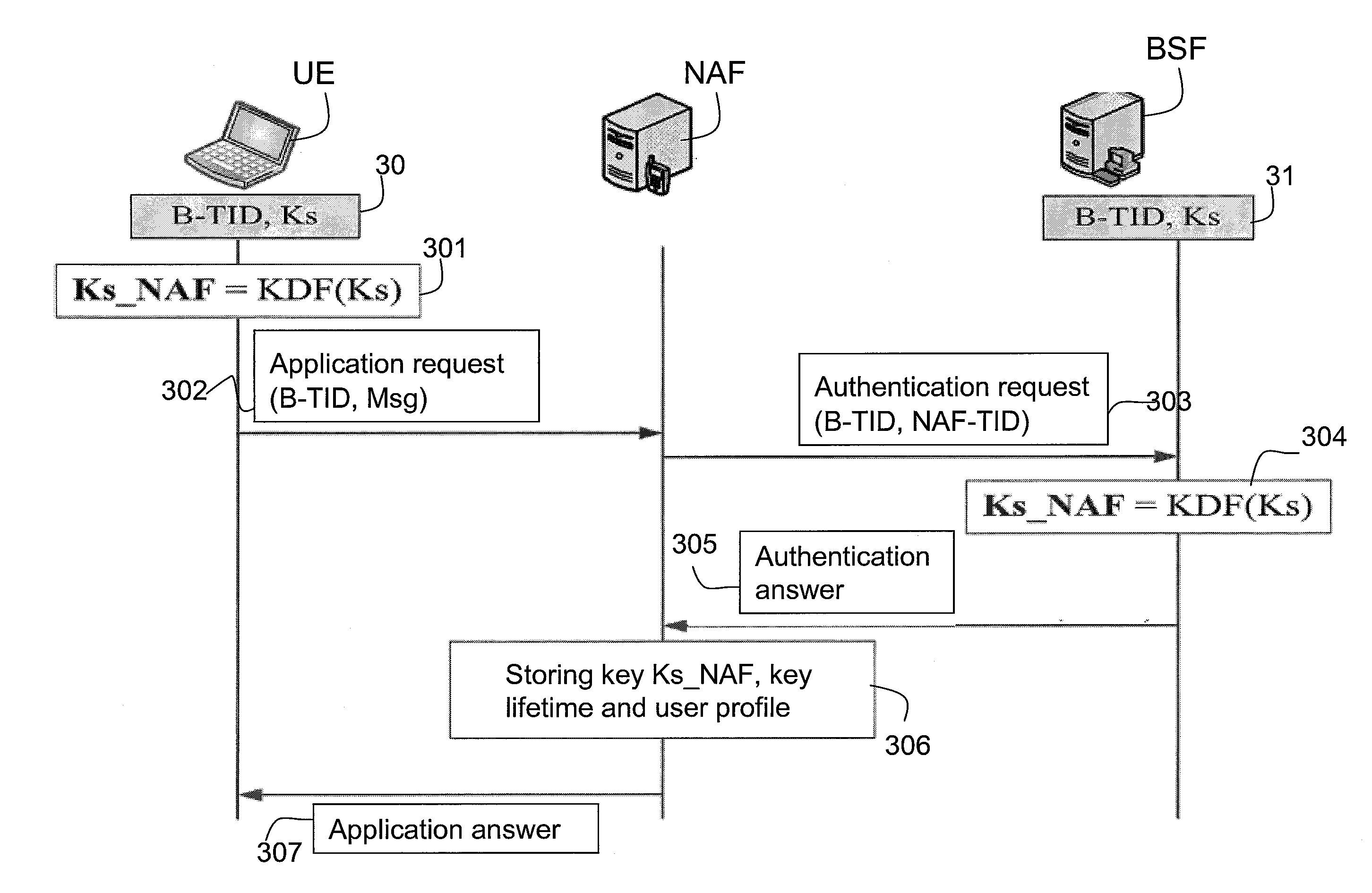
A method of securing a session between a Network Application Function, NAF, and a User Equipment, UE, connected to a network. The NAF is assigned a NAF identifier, NAF_id, using the Generic Bootstrapping Architecture, GBA, or a similar architecture and a shared secret is established between the UE and the NAF (S7.1). An application request containing a bootstrapping transaction identifier is sent to the NAF from the UE (S7.2) and an authentication request comprising the bootstrapping transaction identifier, the NAF_id, and information derived from the shared secret is sent to a Bootstrapping Server Function, BSF, from the NAF (S7.4).The BSF and the UE determine a NAF key, Ks_NAF, by using a modified parameter in place of or in addition to an original parameter in a key derivation function, the modified parameter being derived from the shared secret and the original parameter of the key derivation function (S7.5). This NAF key is transmitted from the BSF to the NAF (S7.6) and used to secure communications between the NAF and the UE (S7.7). Also provided are apparatus to act as a NAF, UE, and BSF in the method above.
Owner:TELEFON AB LM ERICSSON (PUBL)
User identity management for permitting interworking of a bootstrapping architecture and a shared identity service
ActiveCN102550001ATransmissionSecurity arrangementGeneric Bootstrapping ArchitectureService provision
A method, apparatus and computer program product are provided to facilitate authentication of a request, such as by a mobile terminal, while also supplying information about the user to a service, website, application or the like A method, apparatus and computer program product may provide for interworking a bootstrapping architecture, such as Generic Bootstrapping Architecture, and a shared identity service, such as OpenID architecture In this regard, a method, apparatus and computer program product may provide for a secure session with a service provider through Generic Bootstrapping Architecture while being able to supply the service provider with the user information and / or accessing a user account using OpenID architecture.
Owner:NOKIA TECHNOLOGLES OY
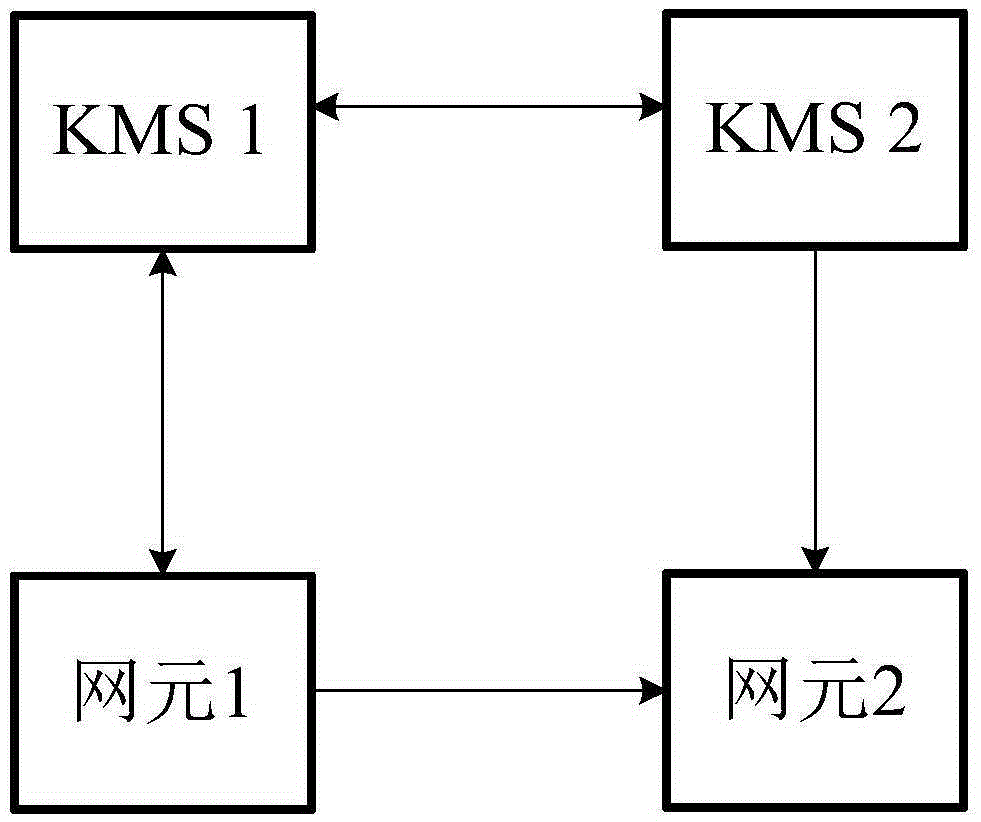
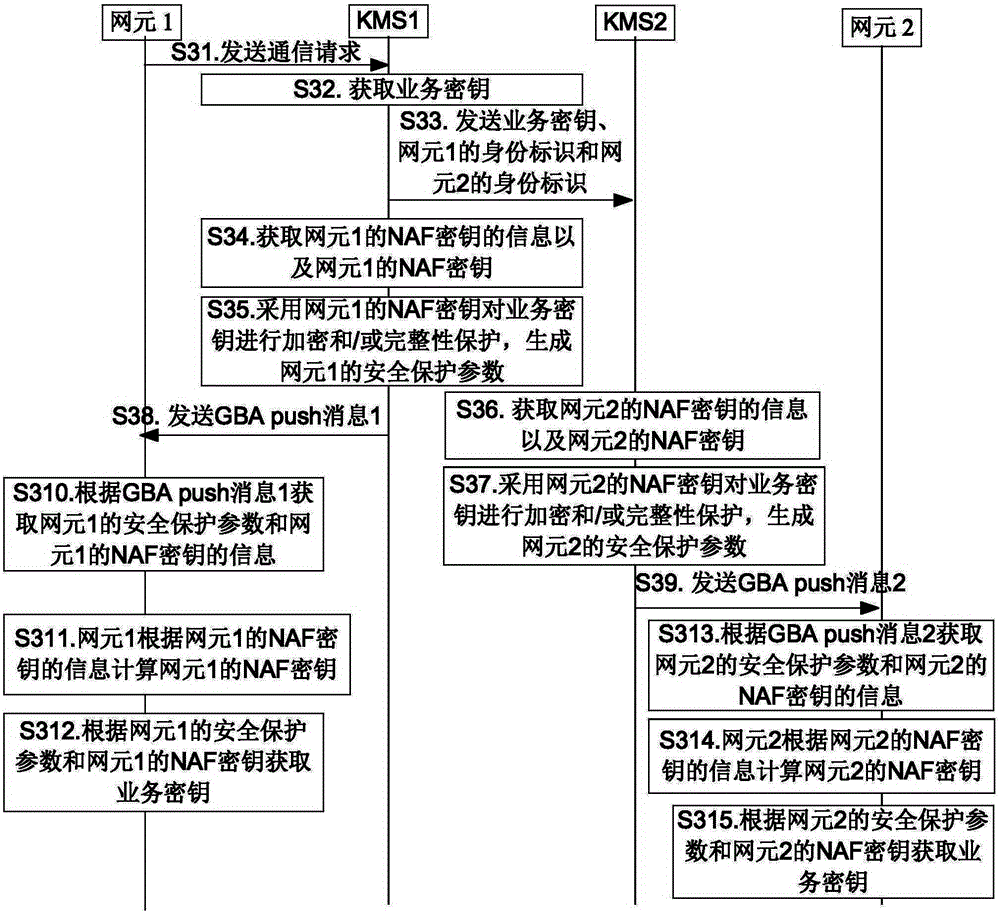
Key distribution and reception method, key management center, and first and second network elements
ActiveCN106487501AEnsure safetyAvoid eavesdropping attacksKey distribution for secure communicationMultiple keys/algorithms usageGeneric Bootstrapping ArchitectureKey distribution
The embodiment of the invention discloses a key distribution and reception method, a key management center, and first and second network elements. The key distribution and reception method disclosed by the embodiment comprises the steps: a first key management center obtains information of an NAF key of the first network element and the NAF key of the first network element, the information of the NAF key of the first network element being the information necessary for obtaining the NAF key of the first network element; the first key management center obtains a service key, the service key being used for performing encryption and / or integrity protection on communication data when the first network element communicates with the second network element; the first key management center performs encryption and / or integrity protection on the service key by adopting the NAF key of the first network element and generates a first safety protection parameter; and the first key management center sends a first GBA (Generic Bootstrapping Architecture) push message to the first network element, wherein the first GBA push message carries the first safety protection parameter and the information of the NAF key of the first network element. The embodiment can prevent data from suffering from eavesdropping attack in a transmission process.
Owner:HUAWEI TECH CO LTD
Apparatus, method and computer program product providing mobile node identities in conjunction with authentication preferences in generic bootstrapping architecture (GBA)
ActiveCN101228769ARadio/inductive link selection arrangementsTransmissionGeneric Bootstrapping ArchitectureAuthentication
In one exemplary and non-limiting aspect thereof a method is provided that includes sending a wireless network (WN) a first message that includes a list of authentication mechanisms supported by a node and, in association with each authentication mechanism, a corresponding identity; determining in the WN an authentication mechanism to be used for bootstrapping, based at least on the list received from the node; and including information in a second message that is sent to the node, the information including the determined authentication mechanism in conjunction with a corresponding identity. The method further includes protecting at least the list of authentication mechanisms supported by the node and the corresponding identities and sending a second message to the network, the second message including at least the list of authentication mechanisms and the corresponding identities. The method further includes receiving a second response message from the network that is at least partially integrity protected, where the second response message includes an indication of the selected authentication mechanism and the corresponding identity.
Owner:NOKIA TECHNOLOGLES OY
Generic bootstrapping architecture protocol
ActiveUS20170041785A1Improve securityReduce the numberMessaging/mailboxes/announcementsSecurity arrangementGeneric Bootstrapping ArchitectureProxy server
Method and system for communicating securely with a user equipment, UE, using generic bootstrapping architecture, GBA, the system comprising a bootstrapping server function, BSF. A proxy server configured to receive messages from a user equipment, UE, in a first format. Convert the received messages from the first format to a second format. Transmit the received UE messages to a bootstrapping server function, BSF, in the second format. Receive messages from the BSF, in a third format. Convert the messages received from the BSF from the third format to a fourth format. Transmit the received BSF messages to the UE in the fourth format.
Owner:VODAFONE IP LICENSING
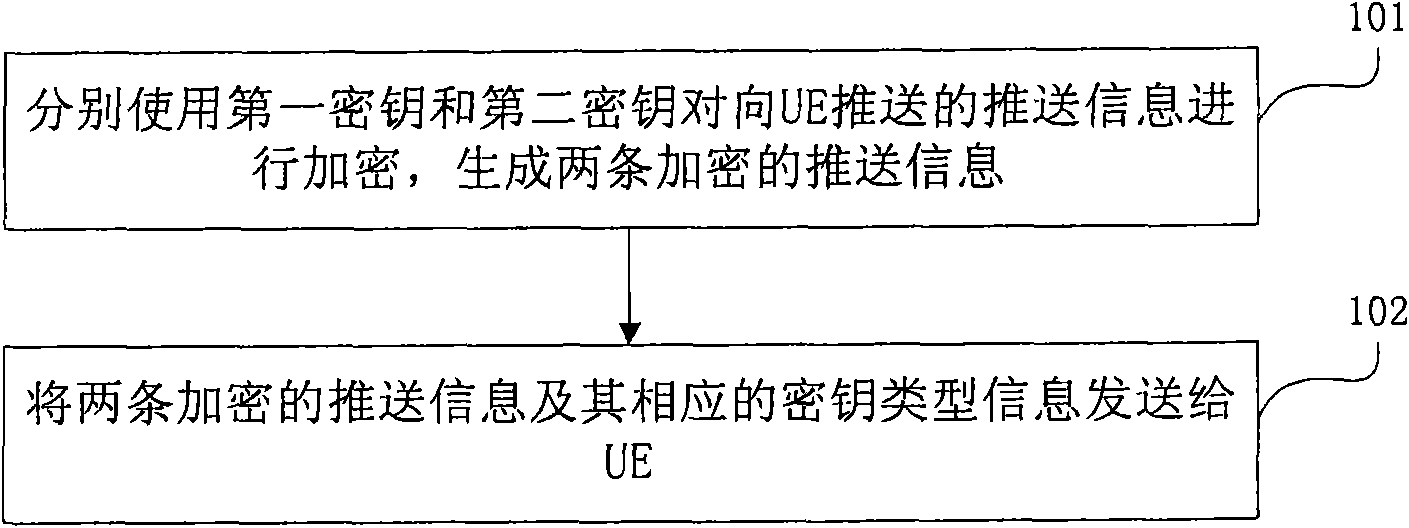
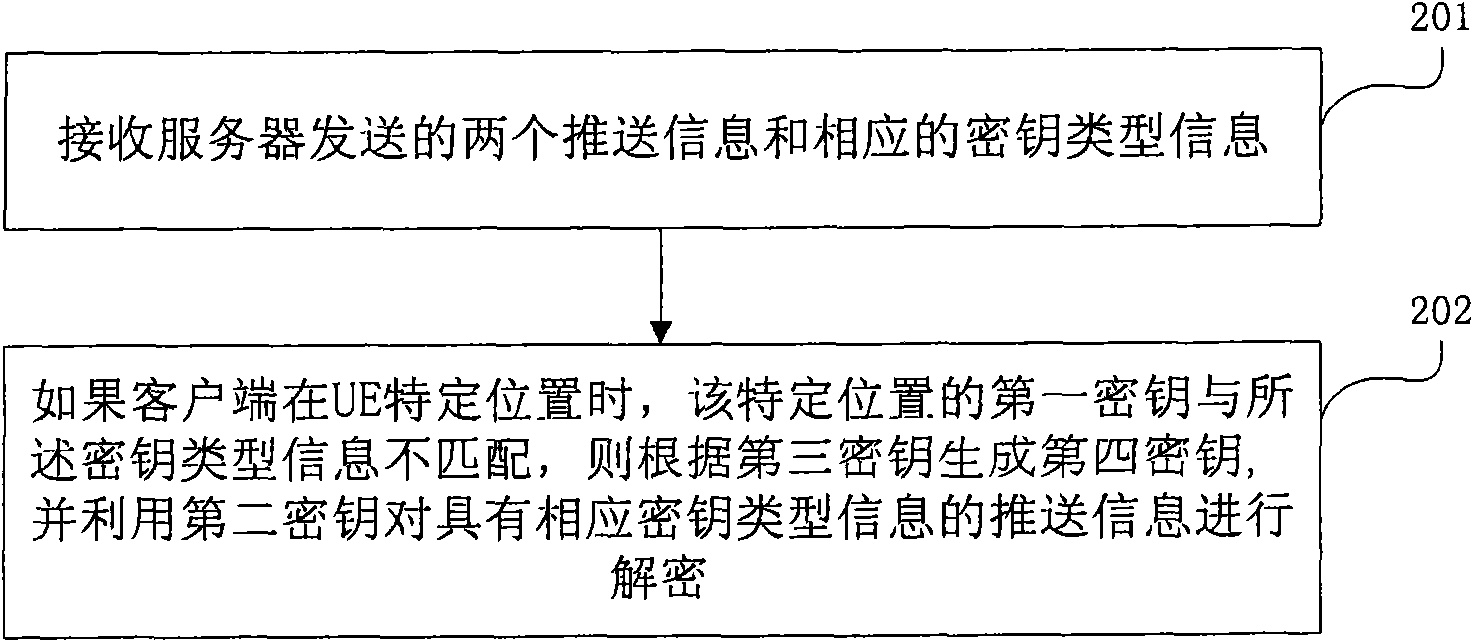
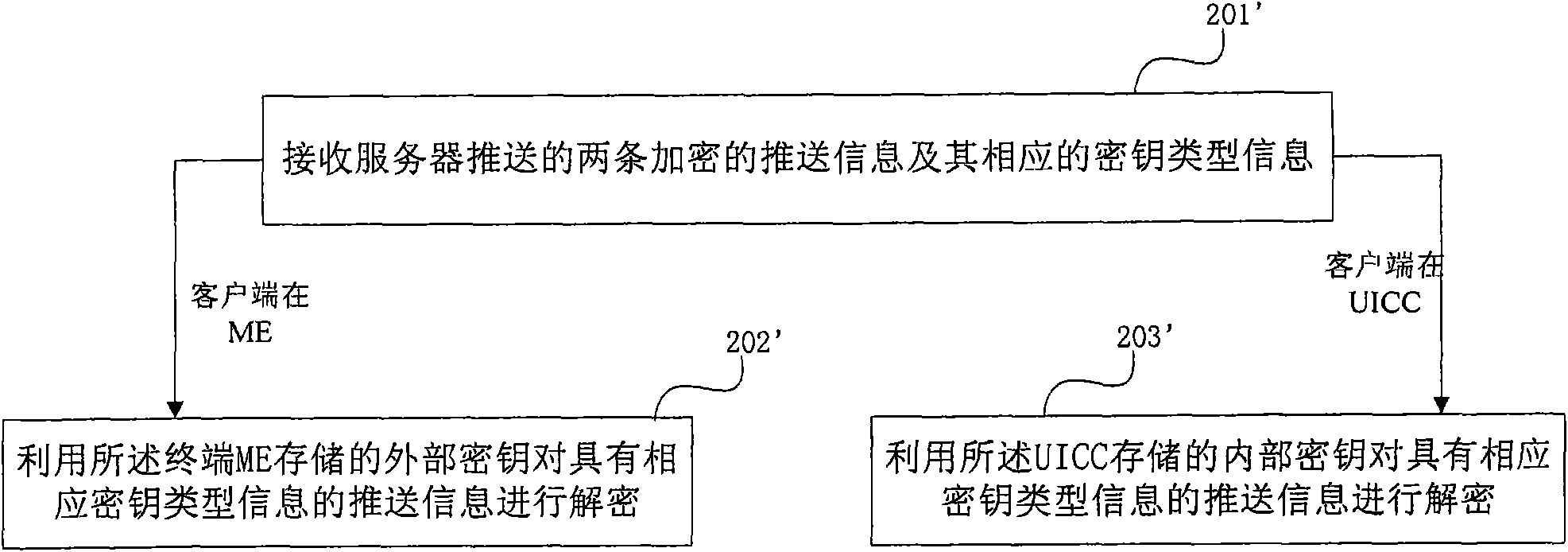
Secret key notification and decryption method and device in GBA (Generic Bootstrapping Architecture) Push
ActiveCN101877834ASolve the problem that the push information cannot be decryptedMessaging/mailboxes/announcementsTransmissionComputer hardwareGeneric Bootstrapping Architecture
The embodiment of the invention provides secret key notification and decryption method and device in generic bootstrapping architecture push (GBA Push). The secret key notification method comprises the steps of: encrypting push information to be pushed to user equipment (UE) respectively by using a first secret key and a second secret key so as to generate two encrypted push information; and sending the two encrypted push information and corresponding secret key type information thereof to the UE. Therefore, the problem that the UE cannot decrypt the push information during GBA Push due to the inconsistency between the secret key type pushed by a server and a secret key type supported by the UE is solved.
Owner:HUAWEI TECH CO LTD
Generic bootstrapping architecture protocol
ActiveCN106714154AMessaging/mailboxes/announcementsSecurity arrangementGeneric Bootstrapping ArchitectureSchema for Object-Oriented XML
Owner:VODAFONE IP LICENSING
Network application function authorisation in a generic bootstrapping architecture
InactiveCN104247485AComputer security arrangementsSecurity arrangementTelecommunicationsGeneric Bootstrapping Architecture
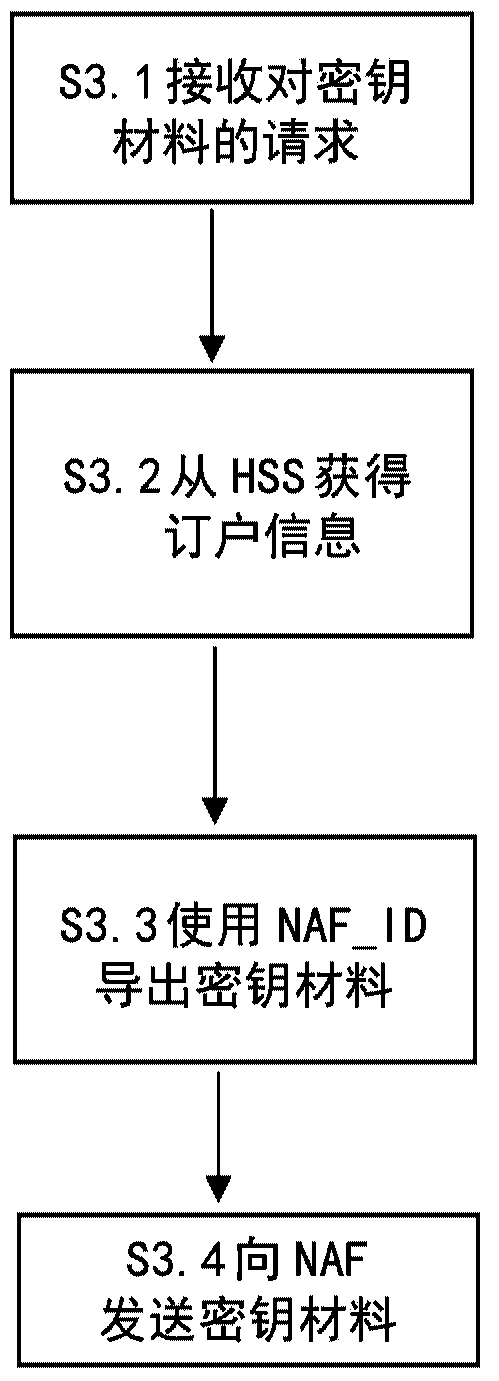
There is provided a method of authorising a subscriber user equipment to access a Network Application Function, NAF, in a Generic Bootstrapping Architecture, GBA. The method comprises, at a Bootstrapping Server Function, BSF, receiving a request for key material for the subscriber user equipment from the NAF, wherein the NAF is associated with one or more NAF identifiers, NAF_IDs, obtaining subscriber information from a Home Subscriber System, HSS, the information including one or more NAF_IDs that are valid for the subscriber, authorising the subscriber user equipment on the basis of the identity of said NAF and the NAF_ID(s) included within the subscriber information. In the event that the subscriber user equipment is authorised, key material is derived using a NAF_ID that is contained within said subscriber information; and the key material is sent to said NAF.
Owner:TELEFON AB LM ERICSSON (PUBL)
Generic bootstrapping architecture protocol
ActiveUS10484869B2Improve securityReduce the numberKey distribution for secure communicationMessaging/mailboxes/announcementsGeneric Bootstrapping ArchitectureProxy server
Method and system for communicating securely with a user equipment, UE, using generic bootstrapping architecture, GBA, the system comprising a bootstrapping server function, BSF. A proxy server configured to receive messages from a user equipment, UE, in a first format. Convert the received messages from the first format to a second format. Transmit the received UE messages to a bootstrapping server function, BSF, in the second format. Receive messages from the BSF, in a third format. Convert the messages received from the BSF from the third format to a fourth format. Transmit the received BSF messages to the UE in the fourth format.
Owner:VODAFONE IP LICENSING
Method and system for MTC (Machine Type Communication) servers to share key
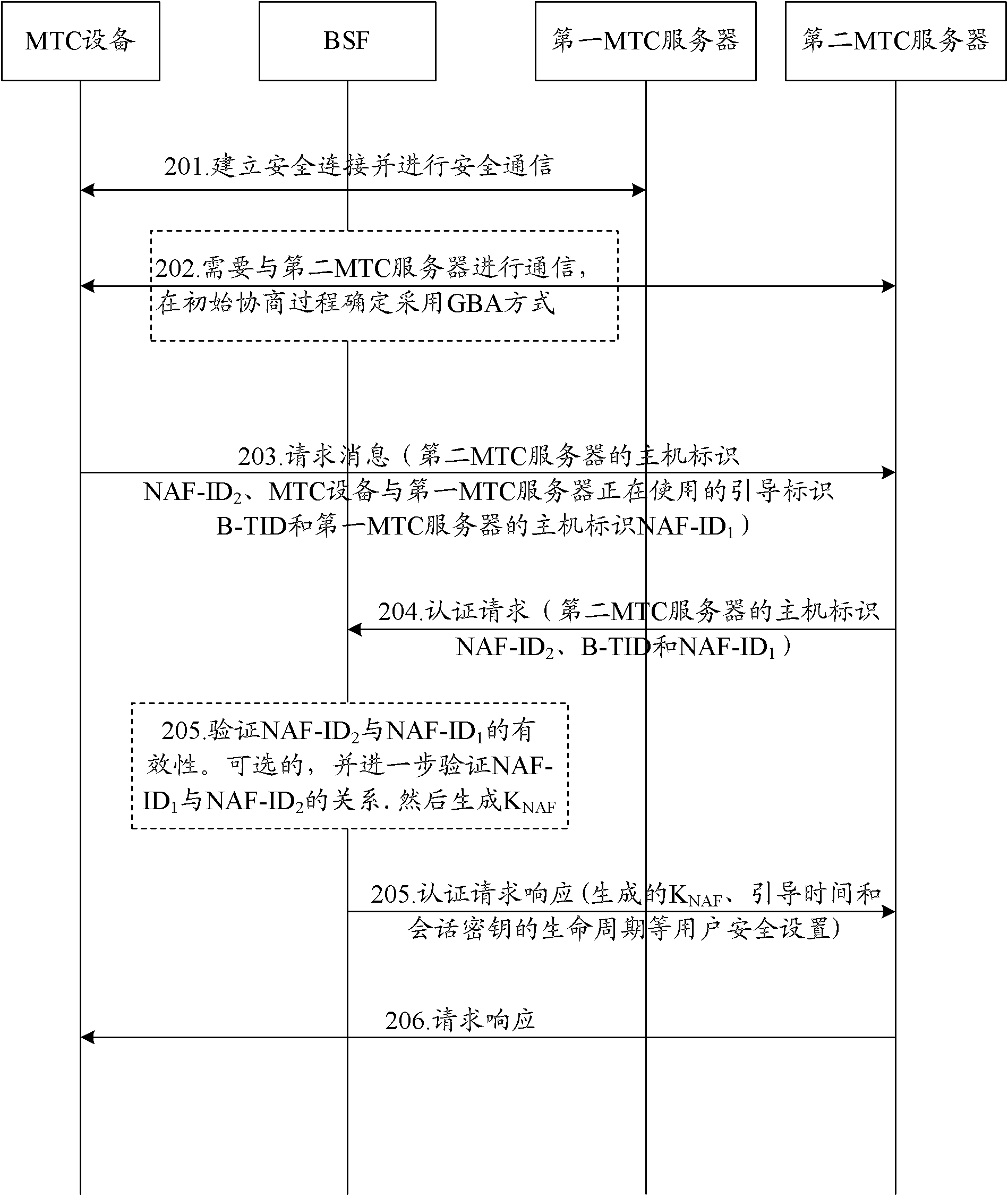
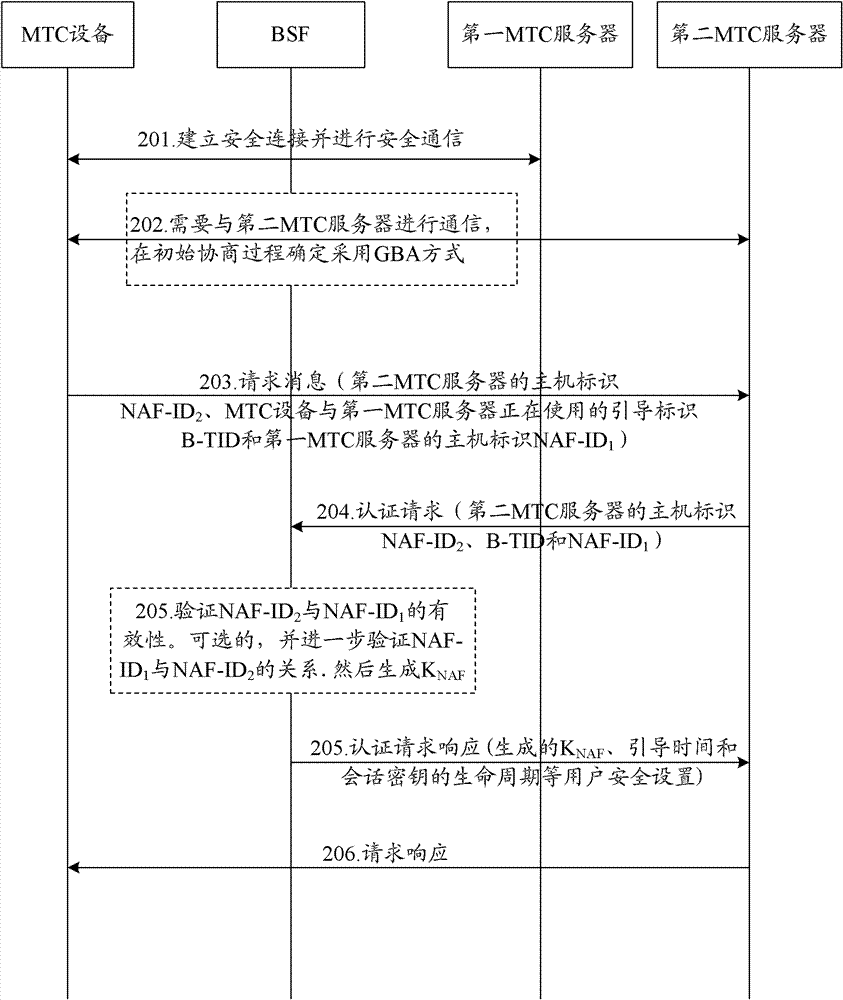
InactiveCN102595389AImprove efficiencyService provisioningSecurity arrangementSecure communicationGeneric Bootstrapping Architecture
The invention discloses a method for MTC (Machine Type Communication) servers to share a key. The method comprises the following steps of: sending request information, which comprises a boot identity B-TID used by an MTC device and a first MTC server right now and a host identity NAF (Network Application Function)-ID1 of the first MTC server, to a second MTC server when security connection is established and security communication is carried out by the MTC device and the first MTC server through a GBA (Generic Bootstrapping Architecture) process; sending an authentication request, which comprises a host identity NAF-ID2, the B-TID and the NAF-ID1 of the second MTC server, to a BSF (Bootstrapping Server Function) by the second MTC server; and generating a session key KNAF according to the B-TID and the NAF-ID1 after the NAF-ID2 and the NAF-ID1 are verified to be effective by the BSF, and sending the session key KNAF to the second MTC server. The invention also correspondingly discloses a system for the MTC servers to share the key. According to the method and the system which are disclosed by the invention, the security communication between the MTC device and multiple MTC servers can be carried out simultaneously, and the use rate of a network resource can be increased.
Owner:ZTE CORP
Method and system for group management of machine-type communication equipment based on general guidance architecture
InactiveCN102469455BTransmissionSecurity arrangementGeneric Bootstrapping ArchitectureComputer science
The invention discloses a GBA-based MTC equipment group management method, which is applied to a system including MTC equipment, BSF and M2M-SC. The method includes: when the first MTC equipment negotiates with the M2M-SC and determines to join the group When the MTC devices identified as G-ID are grouped, the first session key is established between the first MTC device and the M2M-SC through the first GBA process between the first MTC device, the BSF and the M2M-SC, and the M2M-SC The G-ID and group key Kg of the MTC device group are encrypted by the first session key and sent to the first MTC device. By adopting the present invention, the group members in the MTC equipment grouping can be safely managed.
Owner:ZTE CORP
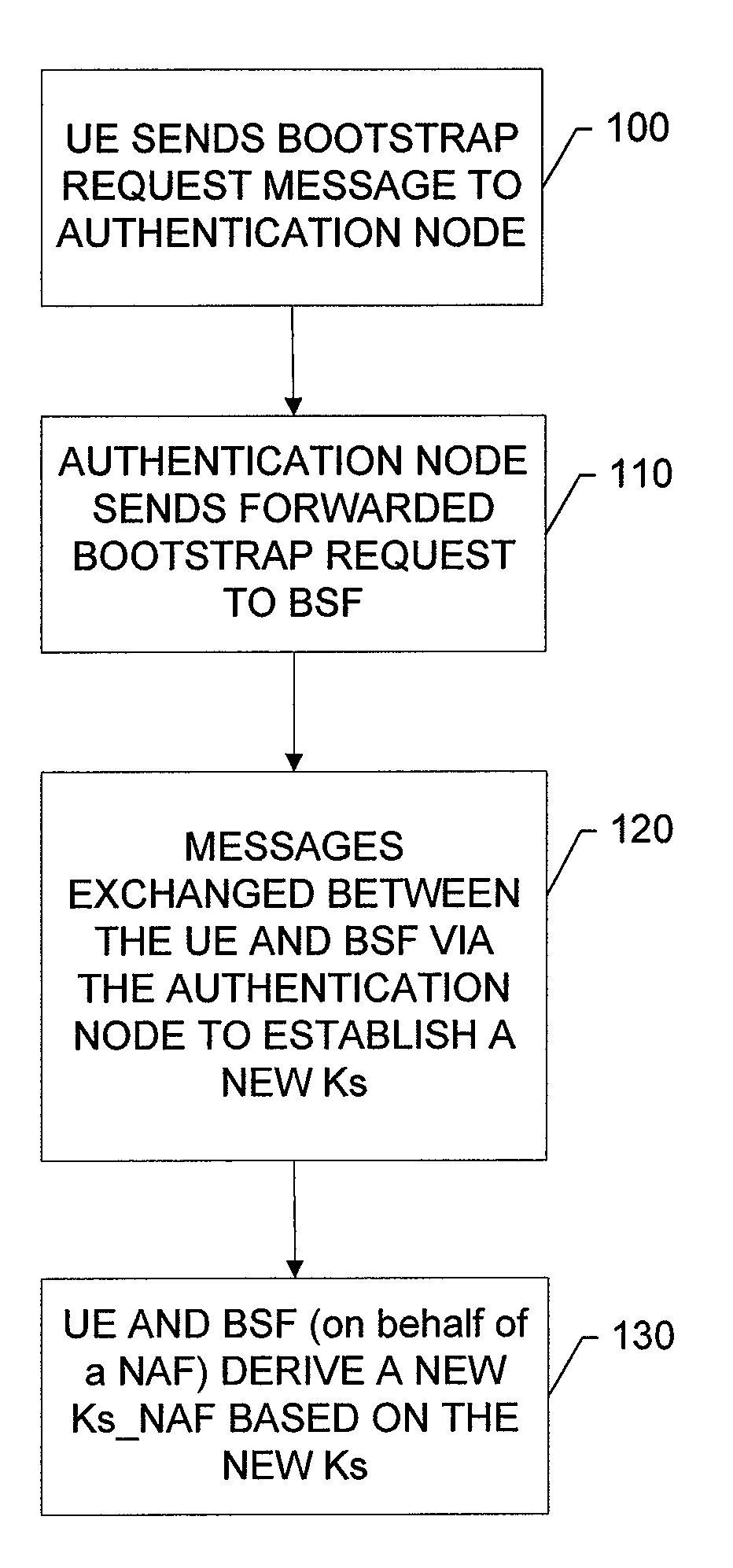
Implementing a common bootstrap architecture type security association for terminals in a mobile telecommunications network
ActiveCN103563419BEasy to useReduce signalingTransmissionSecurity arrangementNetwork access serverTelecommunications network
The invention relates to a method for implementing a GBA type security association for a terminal, comprising the following steps performed in a network access server after receiving a request to attach to a network from a terminal: dispatching a request for security association (E2) to the initiating function server, receiving (E5) a response containing the security association parameters from the initiating function server, and dispatching (E5) a message containing the security association parameters to the terminal.
Owner:ORANGE SA (FR)
Method and device for securing connections in a communication network
ActiveCN104756458BSecurity arrangementSecuring communicationGeneric Bootstrapping ArchitectureEngineering
Method and Apparatus for Securing a Connection in a Communications Network A method of operating a user equipment (UE) using a Generic Bootstrapping Architecture (GBA) is provided. The method includes establishing a shared secret between the UE and a Network Application Function (NAF). An authentication request is sent to a Bootstrapping Server Function (BSF) by the UE. An original parameter intended for a key derivation function and a bootstrapping transaction identifier is received from the BSF. An application request, including the bootstrapping transaction identifier, is sent by the UE to the NAF. A modified parameter is derived by the UE from the secret and the original parameter intended for the key derivation function. A cryptographic key is determined using said modified parameter in place of or in addition to the original parameter in the key derivation function, and communications with the NAF are secured using the key.
Owner:TELEFON AB LM ERICSSON (PUBL)
Access network assisted bootstrapping
The Generic Bootstrapping Architecture is used in a method for assigning the bootstrapping transaction ID so that a machine-to-machine server or other device can locate and communicate with a bootstrapping server function. The bootstrapping server function assigns the bootstrapping transaction ID and updates a DNS server with an entry that maps the bootstrapping transaction ID to a network node IP Address.
Owner:INTERDIGITAL PATENT HLDG INC
A method and system for mtc server shared key
InactiveCN102595389BImprove efficiencyService provisioningSecurity arrangementSecure communicationGeneric Bootstrapping Architecture
The invention discloses a method for MTC servers to share keys. When an MTC device establishes a secure connection with a first MTC server through a GBA process and performs secure communication, it can send request information to a second MTC server (including the MTC device and the first MTC server). The host identification NAF-ID1 of the boot identification B-TID and the first MTC server being used); The second MTC server sends an authentication request to the BSF (including the host identification NAF-ID2, B-TID and NAF-ID1 of the second MTC server ); After the BSF verifies that NAF-ID2 and NAF-ID1 are valid, it generates a session key KNAF according to B-TID and NAF-ID1, and sends it to the second MTC server. The present invention also correspondingly discloses a system for MTC servers to share keys. Through the present invention, MTC equipment can be safely communicated with multiple MTC servers at the same time, and the use efficiency of network resources is improved.
Owner:ZTE CORP
Apparatus, method and computer program product providing mobile node identities in conjunction with authentication preferences in generic bootstrapping architecture (GBA)
In one exemplary and non-limiting aspect thereof a method is provided that includes sending a wireless network (WN) a first message that includes a list of authentication mechanisms supported by a node and, in association with each authentication mechanism, a corresponding identity; determining in the WN an authentication mechanism to be used for bootstrapping, based at least on the list receivedfrom the node; and including information in a second message that is sent to the node, the information including the determined authentication mechanism in conjunction with a corresponding identity. The method further includes protecting at least the list of authentication mechanisms supported by the node and the corresponding identities and sending a second message to the network, the second message including at least the list of authentication mechanisms and the corresponding identities. The method further includes receiving a second response message from the network that is at least partially integrity protected, where the second response message includes an indication of the selected authentication mechanism and the corresponding identity.
Owner:NOKIA TECH OY
Method and system for triggering machine type communication (MTC) equipment
ActiveCN102869015ARealize security protectionFirmly connectedNetwork traffic/resource managementConnection managementComputer networkGeneric Bootstrapping Architecture
The invention discloses a method and system for triggering machine type communication (MTC) equipment. The method comprises the following steps: sending a request message to a bootstrapping server function (BSF) by an MTC server, wherein the request message contains generic bootstrapping architecture push information (GPI) request information and trigger request information; generating GPI by the BSF via a GPI request handling process, adding trigger instruction parameter information to the GPI according to the trigger request information, sending the GPI containing the trigger instruction parameter information to the MTC server; sending the GPI containing the trigger instruction parameter information to the MTC equipment to be triggered by the MTC server; and implementing trigger by the MTC equipment according to the trigger instruction parameter information in the received GPI. In the invention, security protection for an MTC equipment triggering process is implemented; and meanwhile, secure connection between the MTC equipment and the MTC server can be ensured.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com