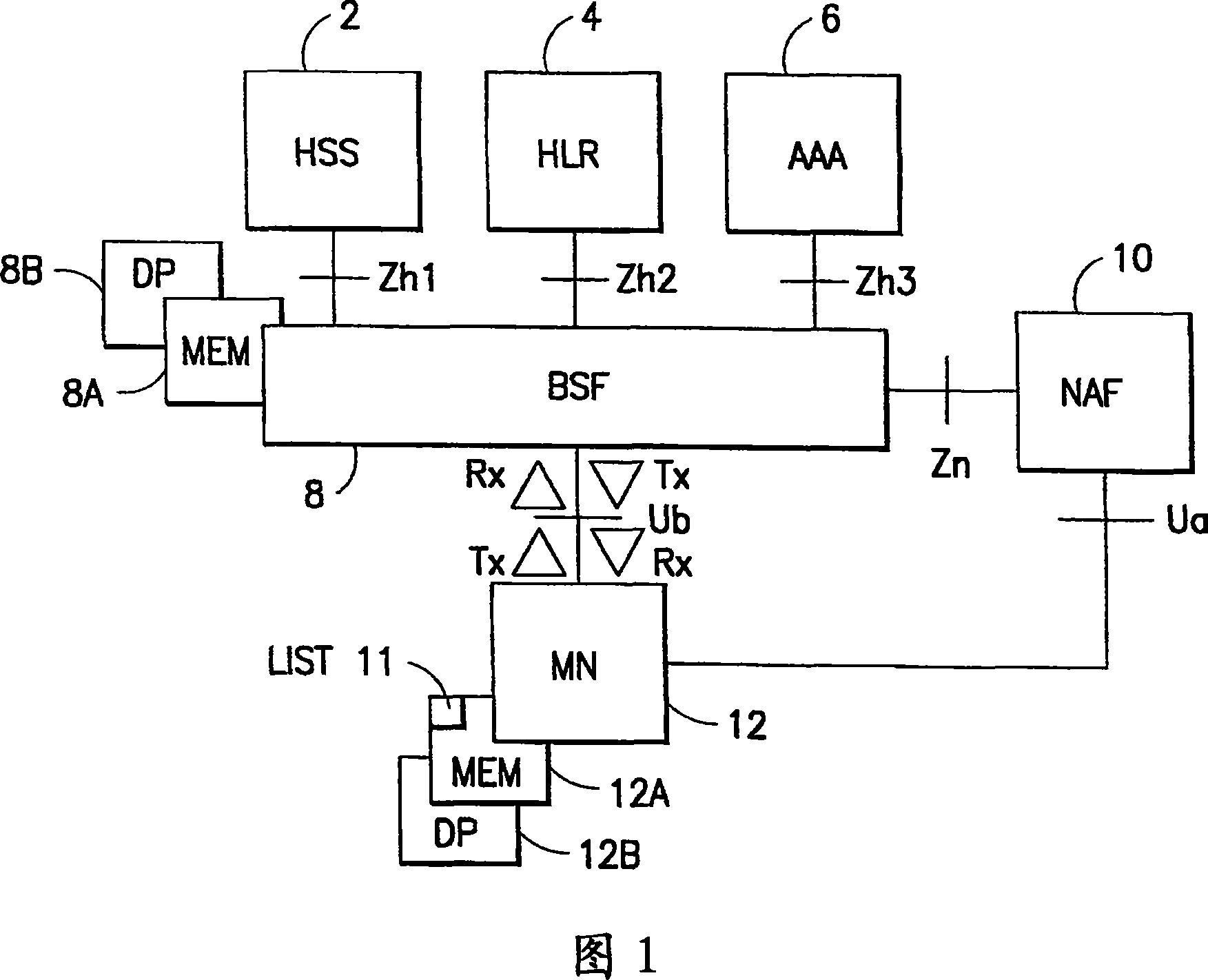
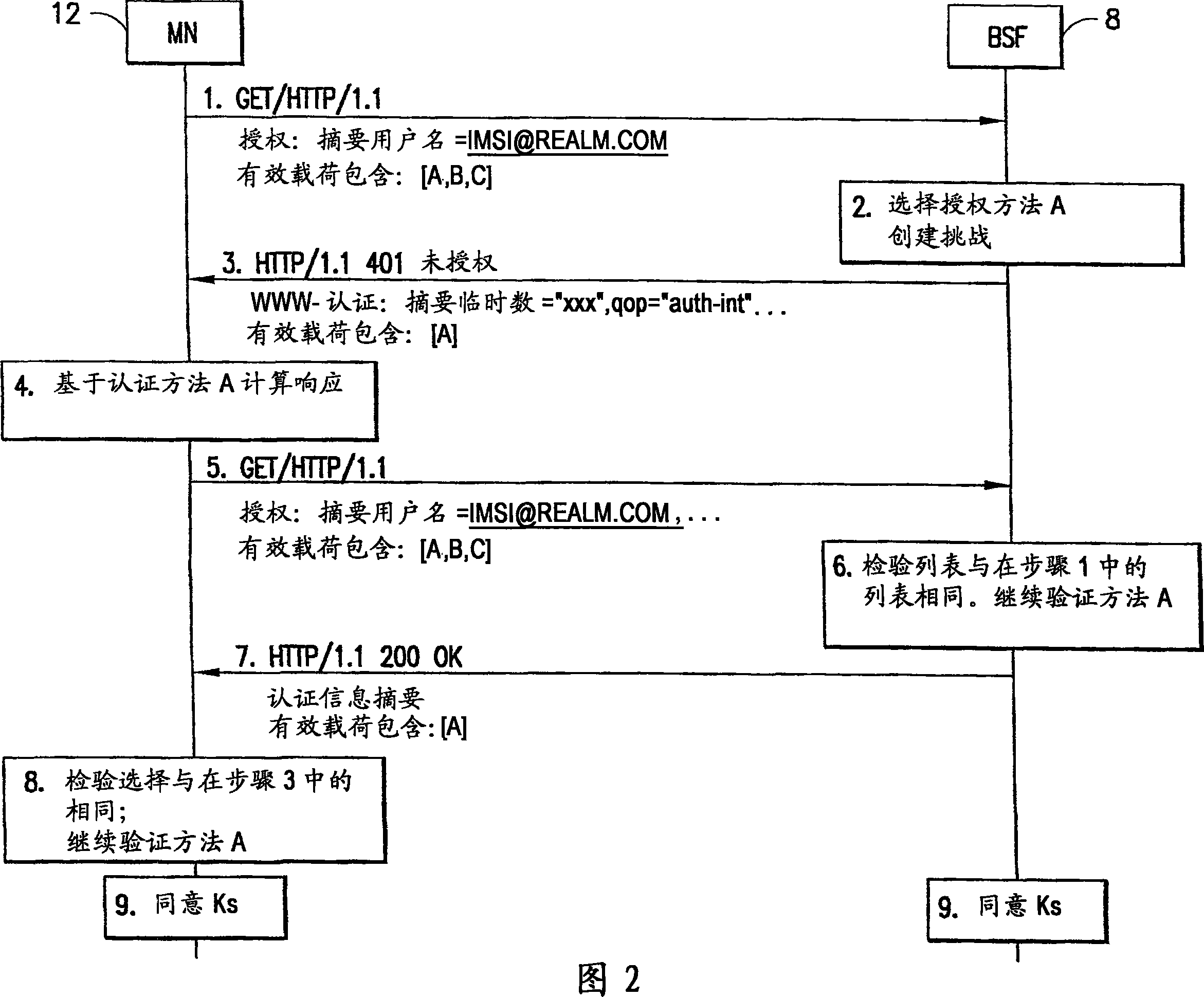
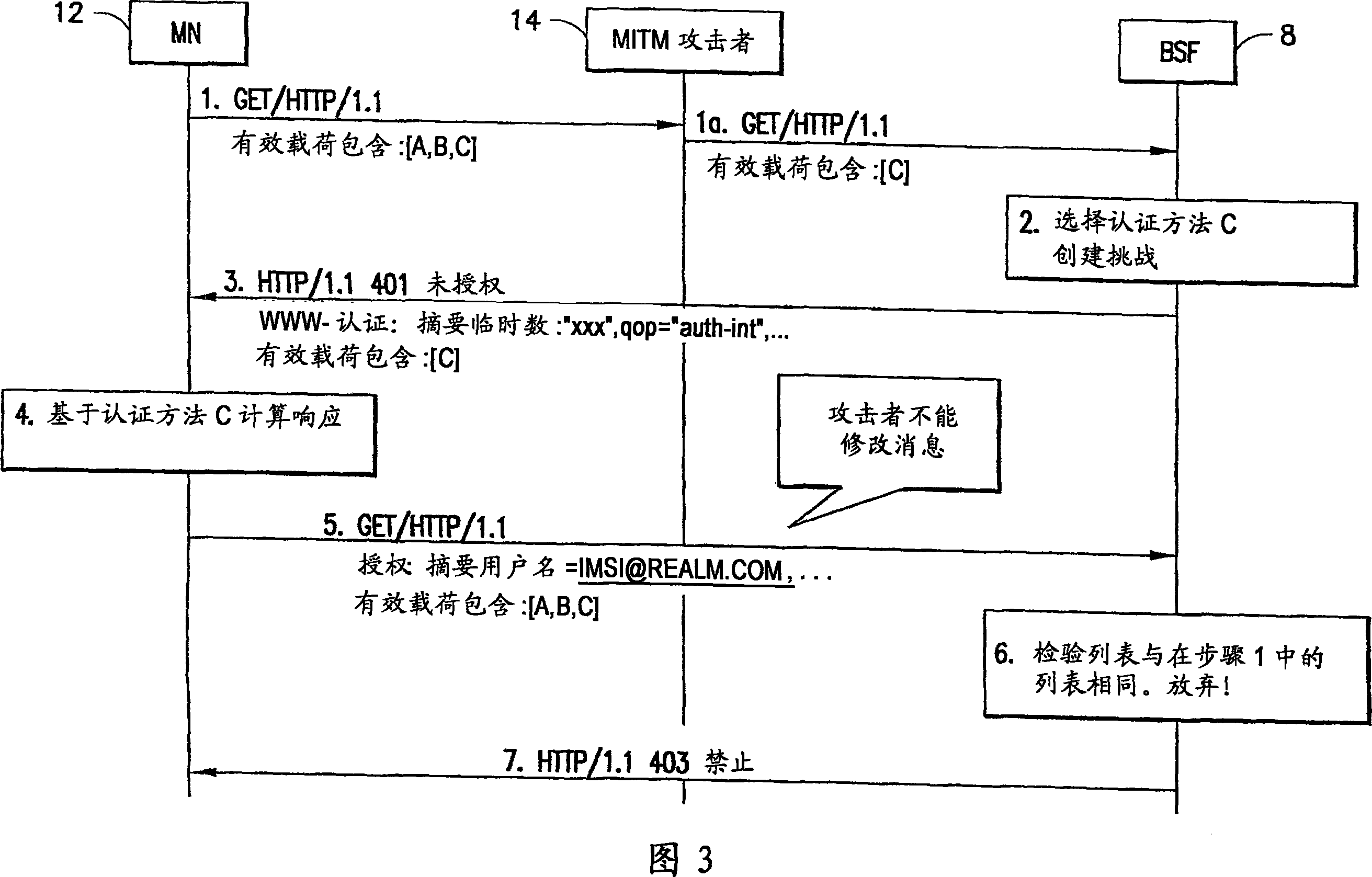
Apparatus, method and computer program product providing mobile node identities in conjunction with authentication preferences in generic bootstrapping architecture (GBA)
A computer program, node technology, applied in authentication and related technical fields, can solve unexpected problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0245] XML scheme 1:
[0246]
[0247]
[0248] xmlns:gba="uri:3gpp2-gba"
[0249] xmlns:xs="http:∥www.w3.org / 2001 / XMLSchema">
[0250]
[0251]
[0252]
[0253]
[0254]
[0255]
[0256]
[0257] minOccurs="0" / >
[0258]
[0259] minOccurs="0" / >
[0260]
[0261] minOccurs="0" / >
[0262]
[0263]
[0264]
[0265]
[0266] type="gba:authInfo" minOccurs="1" / >
[0267]
[0268]
[0269]
[0270]
...
example 2
[0306] XML scheme 2:
[0307]
[0308]
[0309] xmlns:gba="uri:3 gpp2-gba"
[0310] xmlns:xs="http:∥www.w3.org / 2001 / XMLSohema">
[0311]
[0312]
[0313]
[0314]
[0315]
[0316]
[0317]
[0318] minOccurs="0" / >
[0319]
[0320] minOccurs="0">
[0321]
[0322] minOccurs="0" / >
[0323]
[0324]
[0325]
[0326]
[0327] type="gba:authInfo" minOccurs="1" / >
[0328]
[0329]
[0330]
[0331]
[0332]
[0333] ...
example 3
[0359] XML scheme 3:
[0360]
[0361]
[0362] xmlns:gba="uri:3gpp2-gba"
[0363] xmlns:xs="http:∥www.w3.org / 2001 / XMLSchema">
[0364]
[0365]
[0366]
[0367]
[0368]
[0369]
[0370]
[0371] minOccurs="0" / >
[0372]
[0373] minOccurs="0" / >
[0374]
[0376]
[0377]
[0378]
[0379]
[0380]
[0381]
[0382]
[0383]
[0384]
[0385]
[0386]
[0387]
[0388]
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com