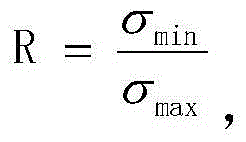Patents
Literature
47results about How to "Avoid frequent updates" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
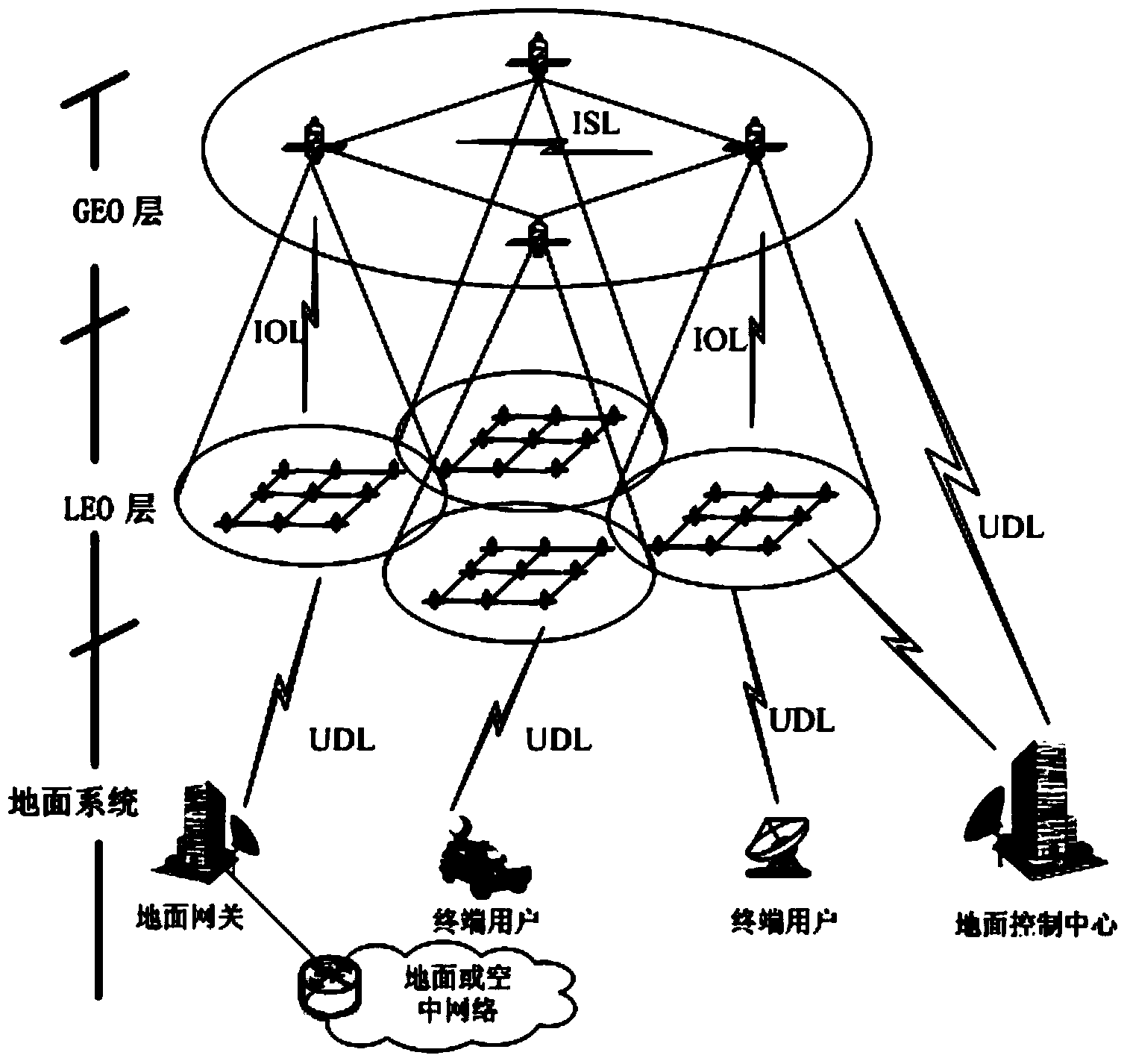
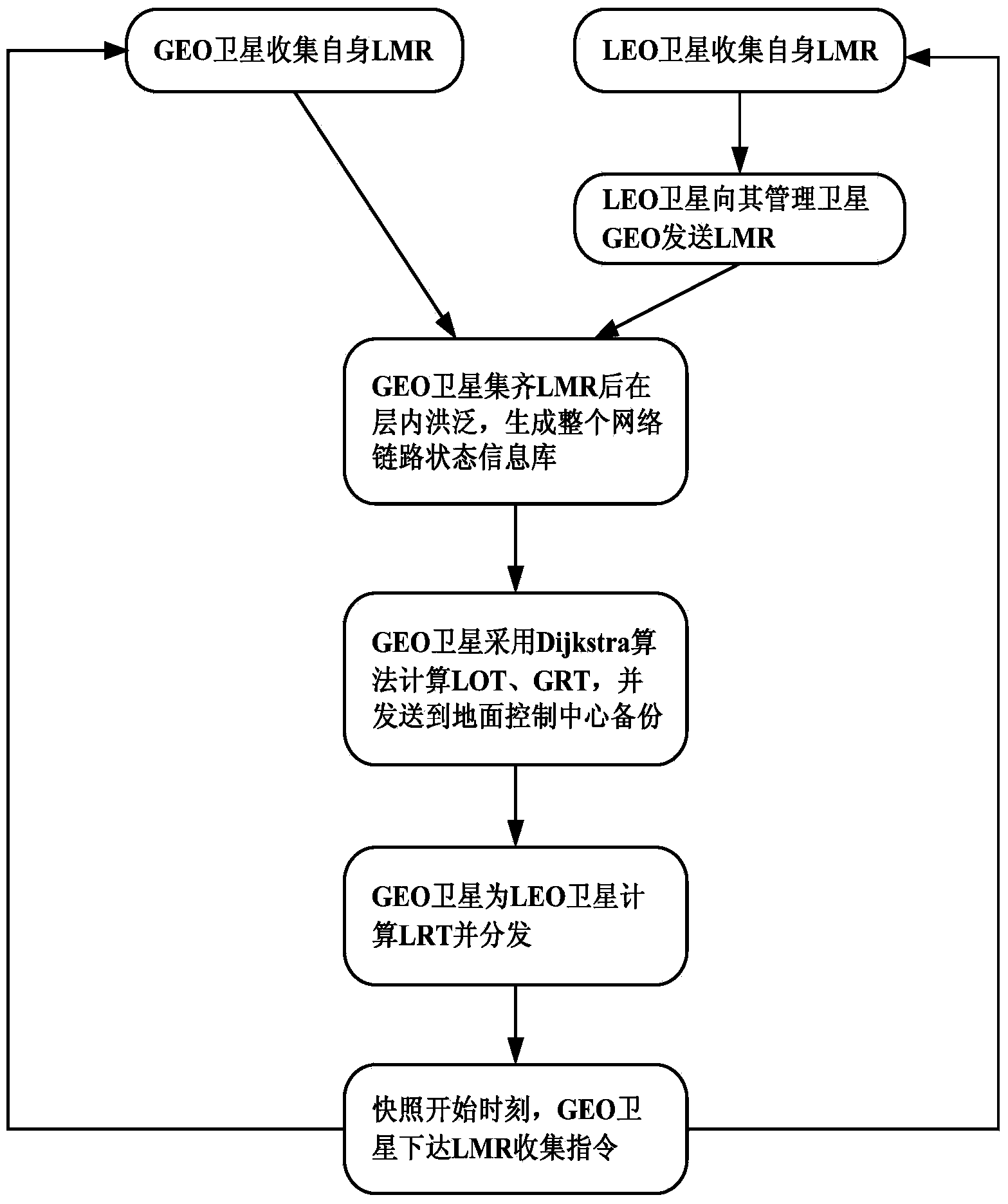
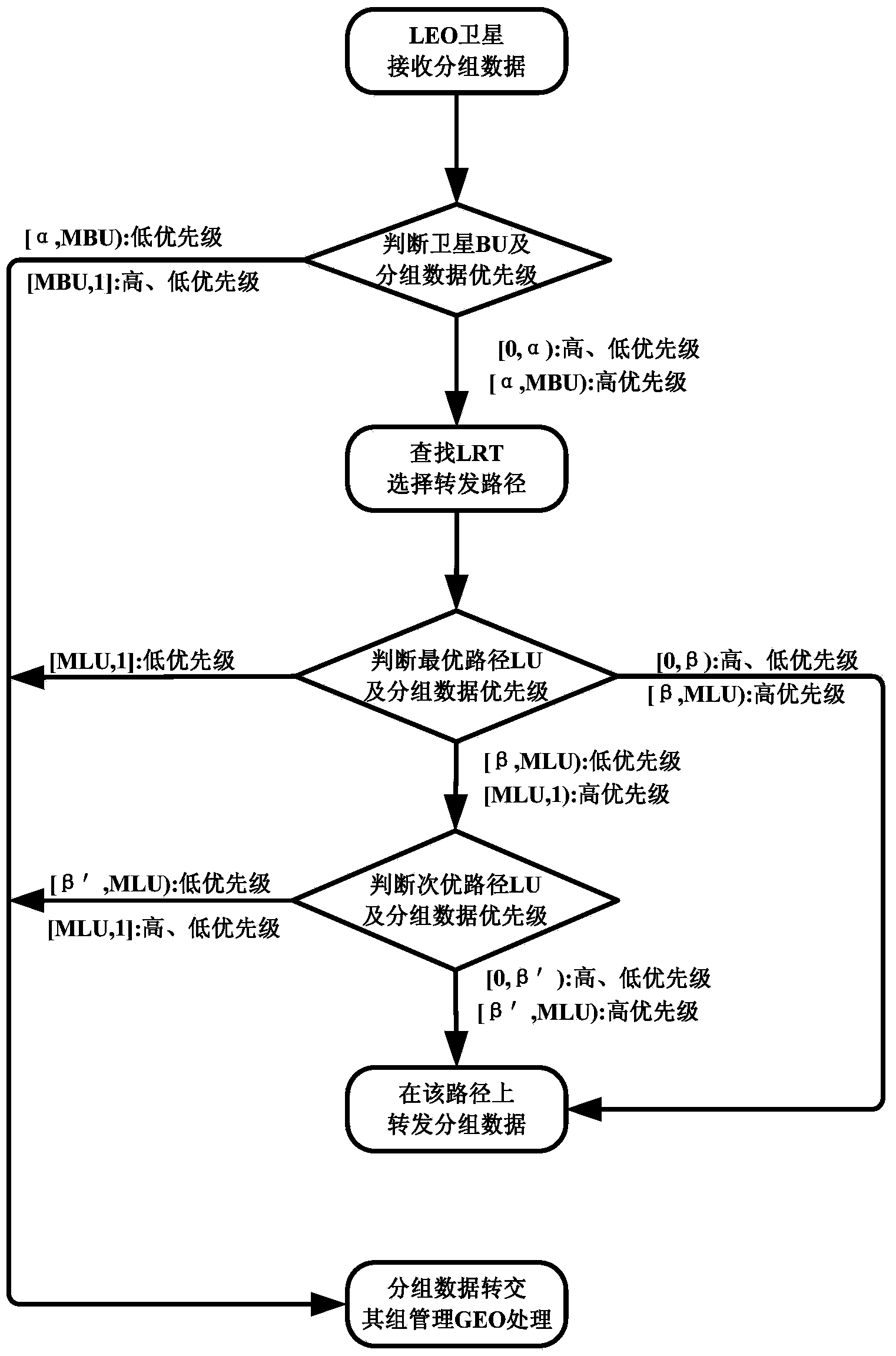
Route exchange method suitable for GEO/LEO double layered constellation network
InactiveCN103905306AReduce overheadShorten convergence timeData switching networksOn boardBoundary values
The invention discloses a route exchange method suitable for a GEO / LEO double layered constellation network. According to the method, a system period is divided into equal-duration time sections based on a dynamic boundary value; a GEO layer satellite high in on-board processing capacity is used for calculating the best route and the second best route for each LEO satellite; in the processes of information transmission and exchange, when loads of the LED satellites are large, the GEO satellite shares part of low priority services in time for the LED satellites, and it is guaranteed that important information is reliably transmitted in real time; when link congestion, node ineffectiveness and other emergency conditions happen in the satellite network, in order to avoid rerouting of the whole network, and the GEO satellite only calculates rerouting for affected routes; after link congestion is eliminated, the LED satellites recover route information in time before congestion in order to avoid link resource waste in the network. In the network that topology time varying happens, links are prone to congestion, on-board resources are limited, continuous high-load flows are prone to being generated, and nodes are prone to being ineffective at the special period, the method can reduce constellation system cost, shorten convergence time, save the on-board resources, increase the utilization rate of the link resources, guarantee that important information is reliably transmitted in real time and improve invulnerability and robustness of the satellite network.
Owner:中国人民解放军西安通信学院
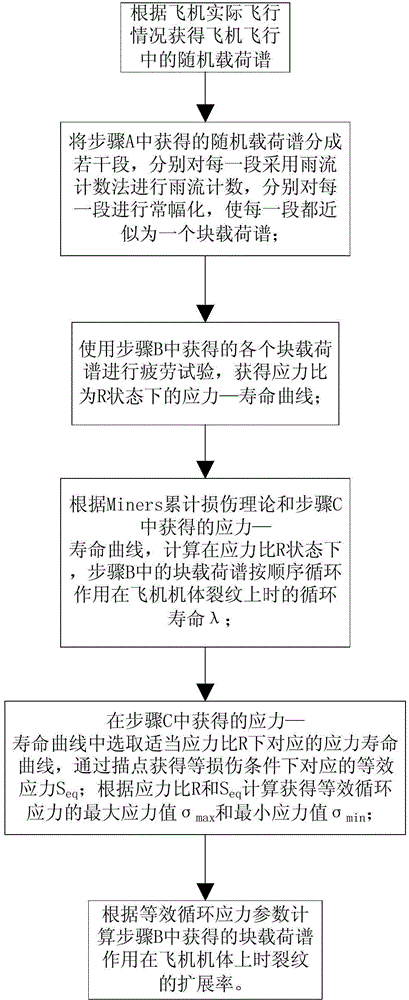
Prediction method of crack propagation life of aircraft body
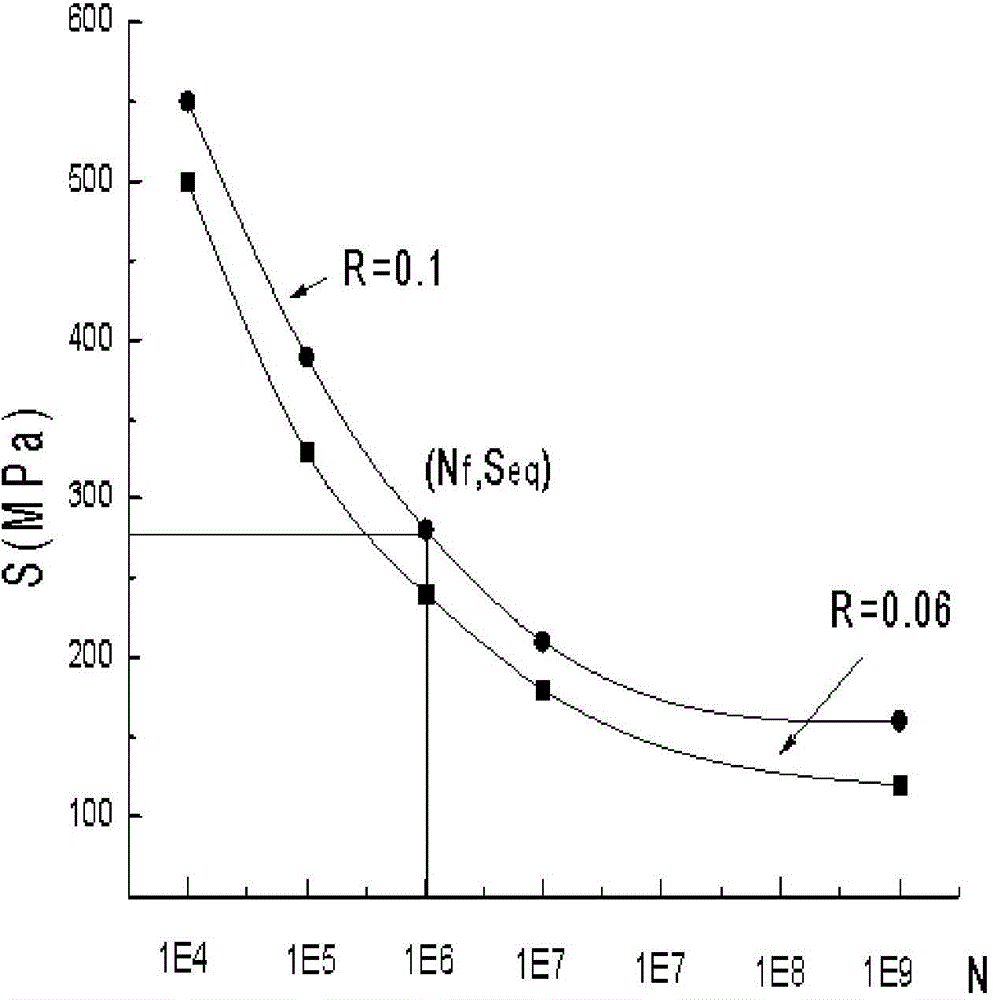
ActiveCN104792633AAvoid frequent updatesAvoid repartitioningMaterial strength using repeated/pulsating forcesStress ratioEngineering
The invention discloses a prediction method of a crack propagation life of an aircraft body. The prediction method comprises the following steps: obtaining a random loading spectrum of an aircraft in flight according to the practical flight situation of the aircraft; dividing the obtained random loading spectrum into a plurality of sections, and respectively performing rain-flow counting and constant amplitude on each section, so that each section is approximated as a block loading spectrum; according to an Miners progressive damage theory, calculating a cycle life lambda effected on a crack of each block loading spectrum under the state of a corresponding stress ratio R, performing a fatigue test under the suitable stress ratio, and obtaining a corresponding stress-life curve; according to an equal defect theory, selecting the correspondence life curve under the suitable stress ratio R in the stress-life curve, and obtaining the equivalent stress Seq corresponding to the same life by a point tracing method; then, according to the R and the Seq, obtaining a maximum stress value sigma max and a minimum stress value sigma min of the equivalent cyclic stress; according to parameters of the equivalent cyclic stress, calculating the propagation rate of the crack when the obtained block loading spectrum is acted on the aircraft body.
Owner:BEIJING AERONAUTIC SCI & TECH RES INST OF COMAC +1
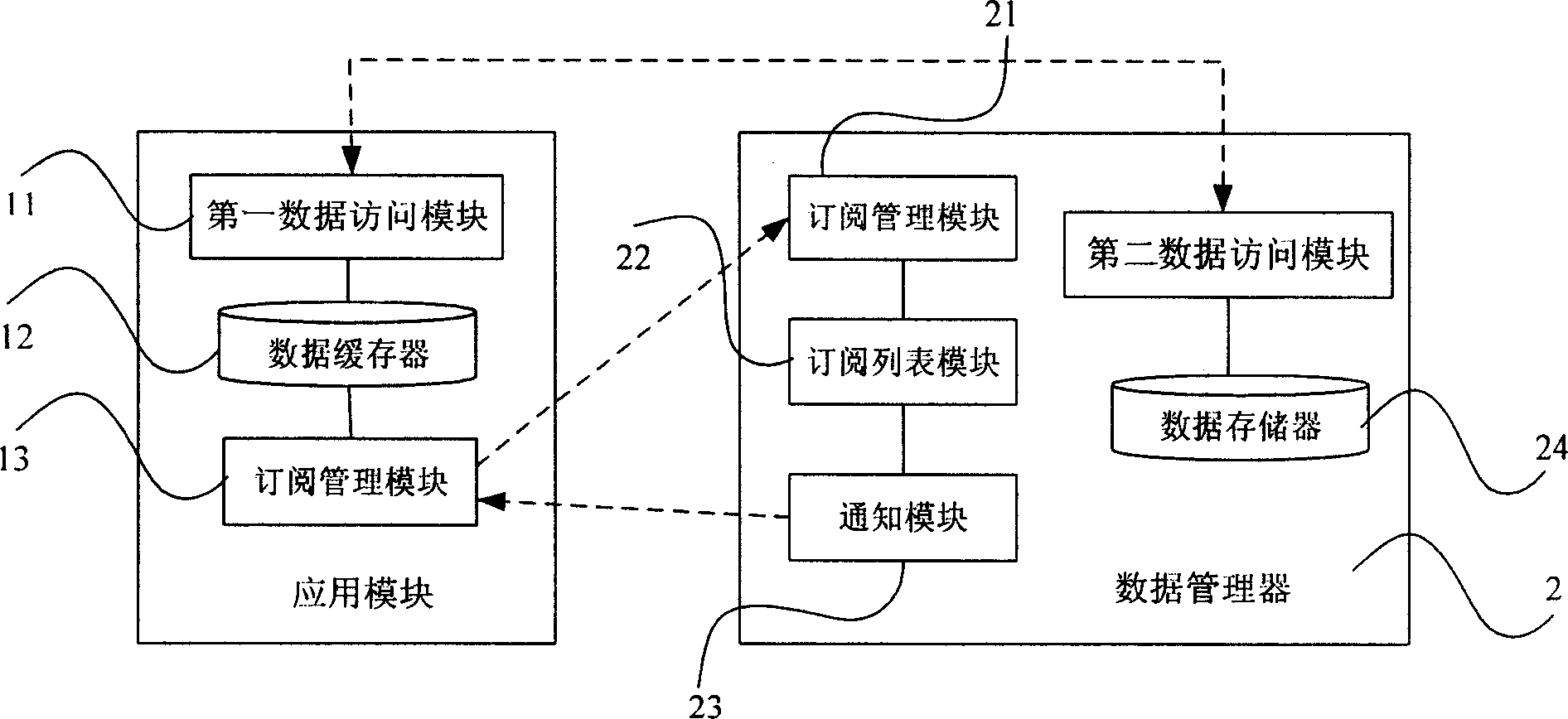
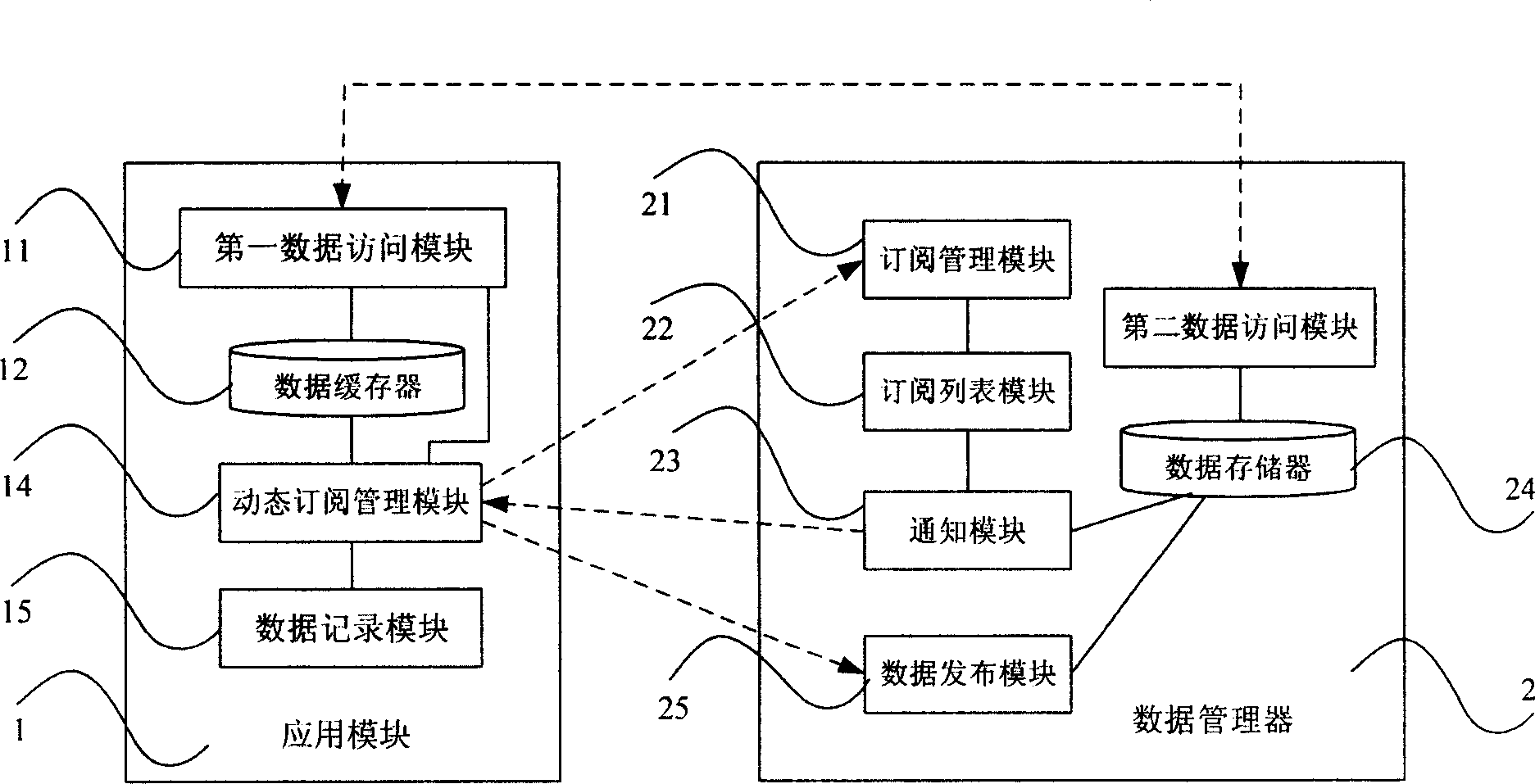
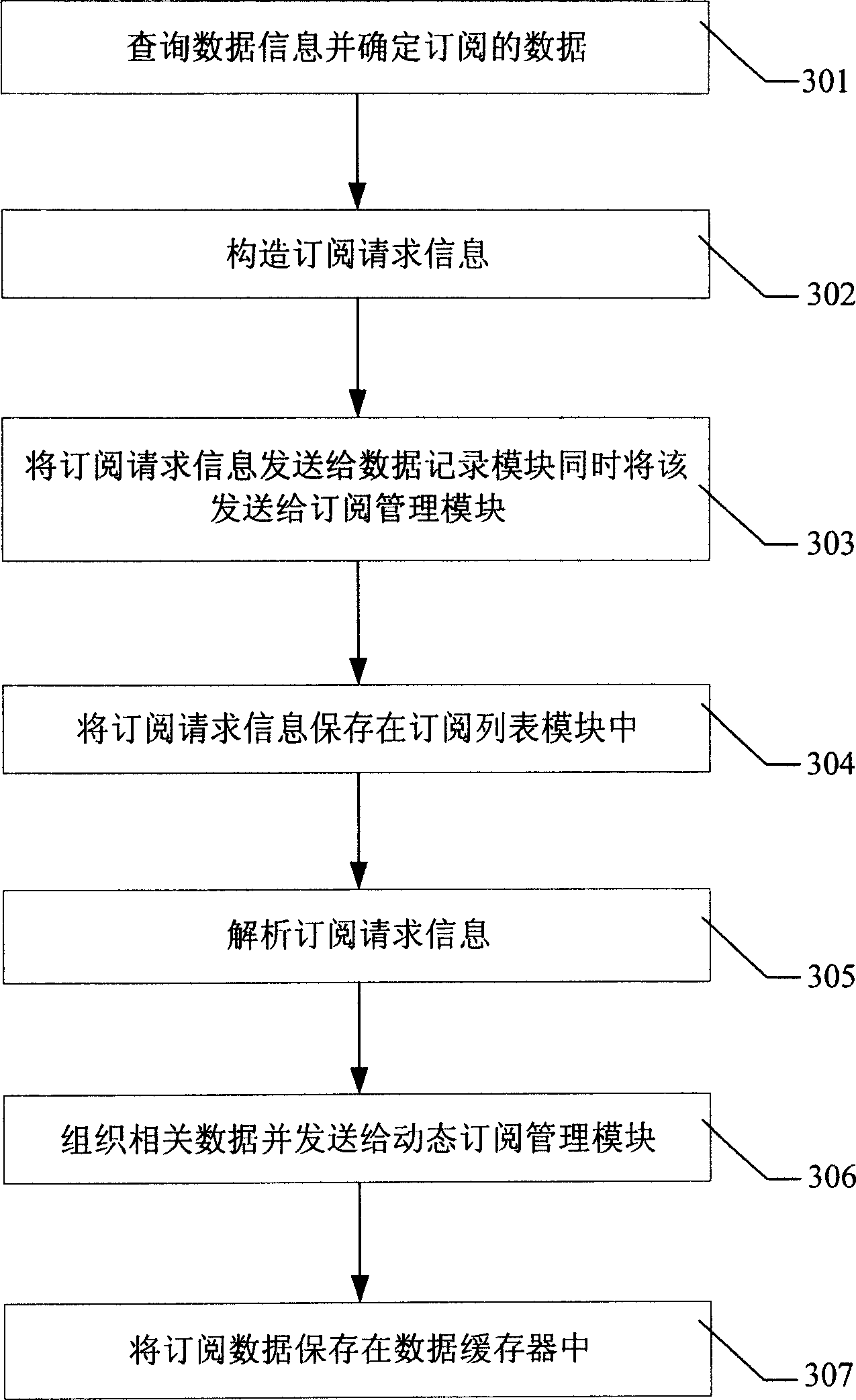
Distributed data management system and its method for dynamically subscribing data
ActiveCN1866833APrecise SubscriptionSubscription timely cancellationData switching networksData accessData management
The invention discloses a distributed data management system, which consists of application module and data supervisor, wherein the application module installs data access module and data buffer; the data supervisor has subscription control module, subscription listing module, notice module and data accumulator; the application module installs dynamic subscription control module and data logging module; the data supervisor installs data distribution module; the data distribution module connects data supervisor; the dynamic subscription control module connects data record module, data buffer and data access module; the subscription control module connects inform module and data issue module. The invention discloses a dynamic subscription data method.
Owner:HUAWEI TECH CO LTD
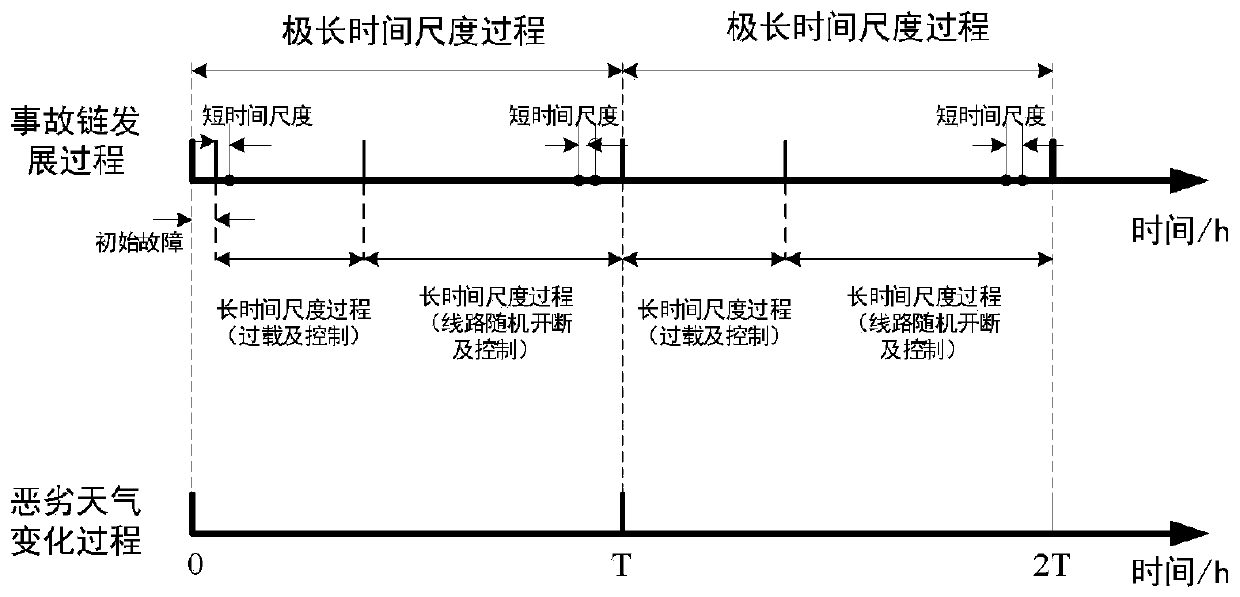
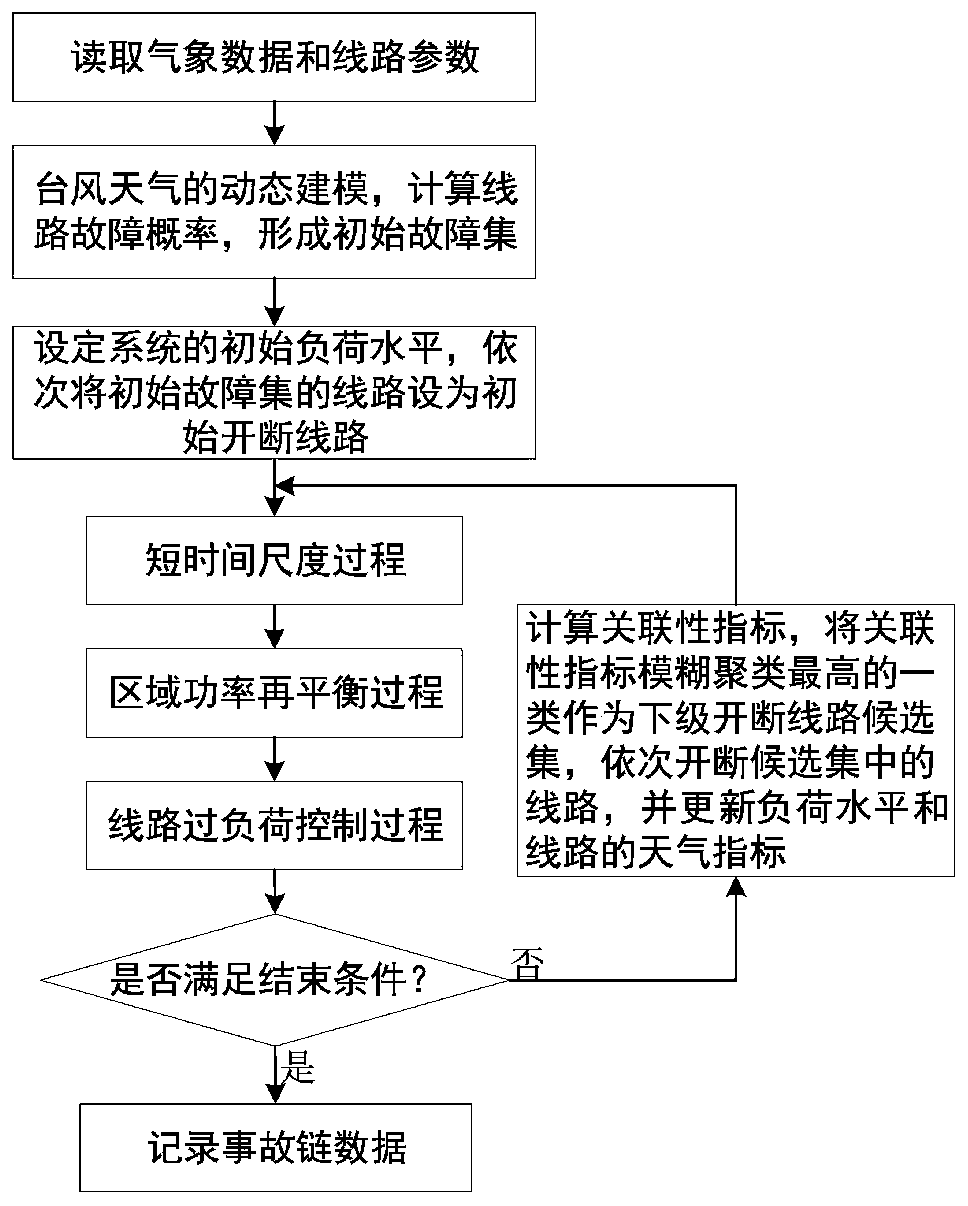
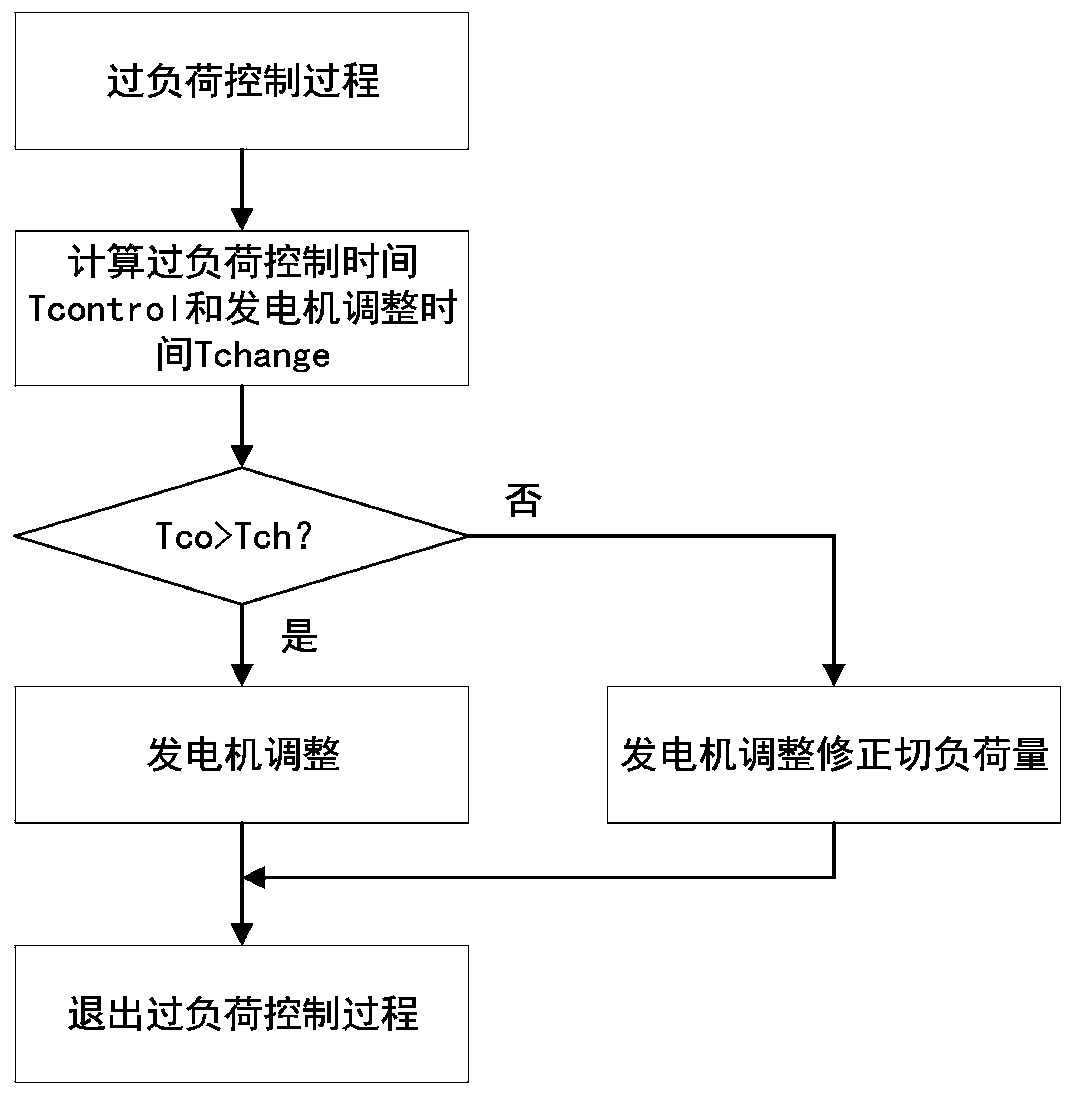
Multi-time scale cascading failure prediction method of power system under typhoon weather condition
ActiveCN109873457AReflect dynamic changesAvoid frequent updatesSingle network parallel feeding arrangementsCascading failureDynamic models
The invention discloses a multi-time scale cascading failure prediction method of a power system under a typhoon weather condition. The method comprises the steps of 1, acquiring meteorological data and line parameters, and building a dynamic model of typhoon weather; 2, calculating initial fault probabilities of lines to form an initial fault set; 3, switching on or off any line of the initial fault set under an initial load level; 4, enabling the power system to sequentially carry out short-time scale judgment and corresponding control process and line overload control process of the short-time scale judgment; 5, carrying out fuzzy clustering on correlation indexes of the line, and taking the class with the highest relevance in a clustering result as an on-off line in the next stage; 6,updating the load level of the power system and weather indexes of the line; 7, repeating the steps 4-6, and until completion conditions are met, recording and outputting accident chain data. According to the method, an accident chain of the power system under the typhoon weather condition can be more really simulated when typhoon comes, so that guidance can be provided for research on cascading failures in typhoon.
Owner:HEFEI UNIV OF TECH
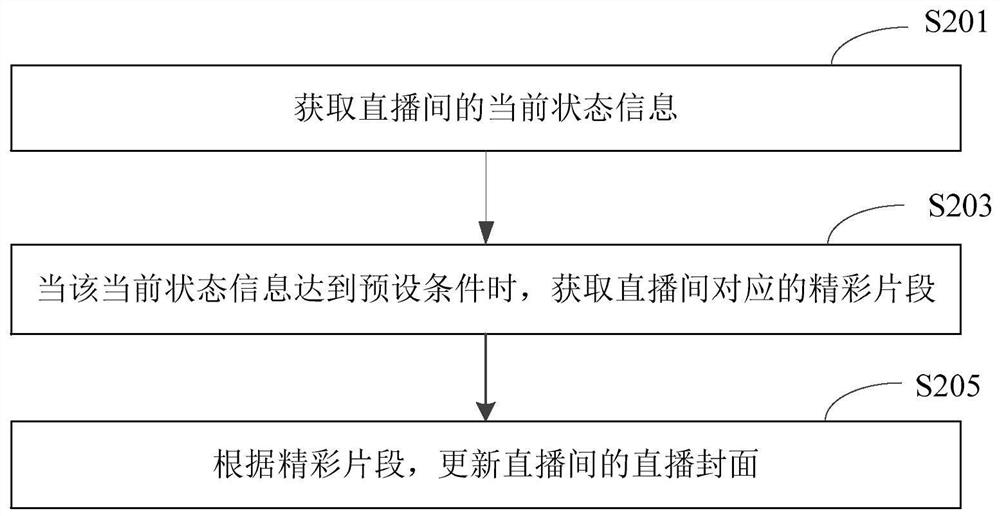
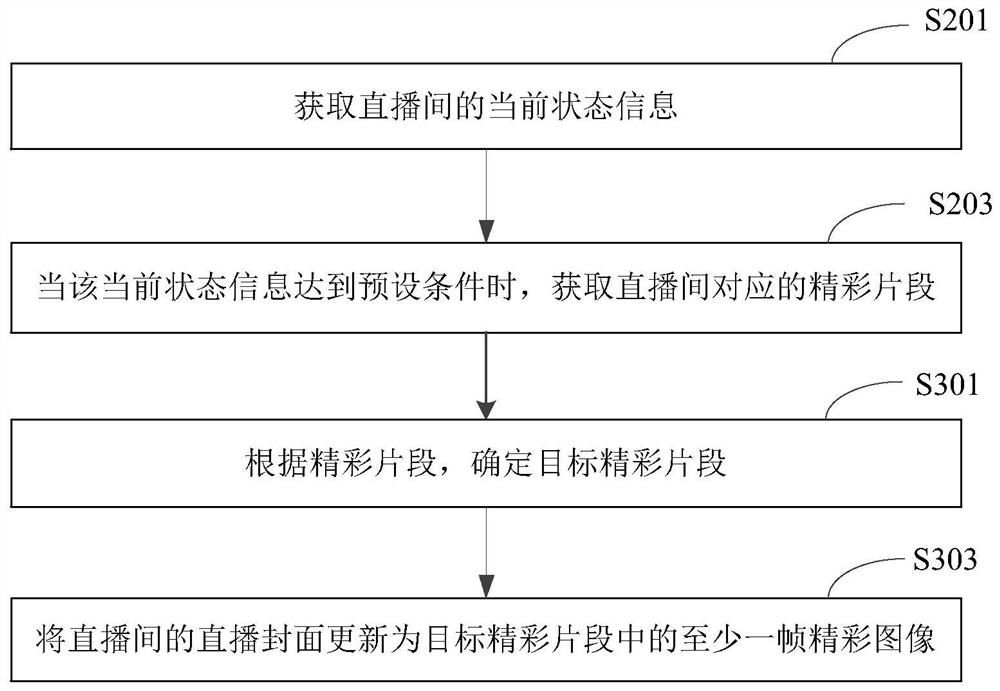
Live broadcast room cover updating method and device, electronic equipment and storage medium
ActiveCN112822504AAvoid frequent updatesTimely drainageNeural architecturesSelective content distributionBroadcastingReal-time computing
The invention relates to a live broadcast room cover updating method and device, electronic equipment and a storage medium. The method comprises the following steps: acquiring current state information of a live broadcasting room; when the current state information reaches a preset condition, acquiring a wonderful fragment corresponding to the live broadcast room; and updating the live broadcast cover of the live broadcast room according to the wonderful fragments. According to the technical scheme disclosed by the invention, the effect of timely drainage can be realized based on the current state information of the live broadcasting room; and the live broadcast room cover can be dynamically updated and can also be prevented from being frequently updated.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
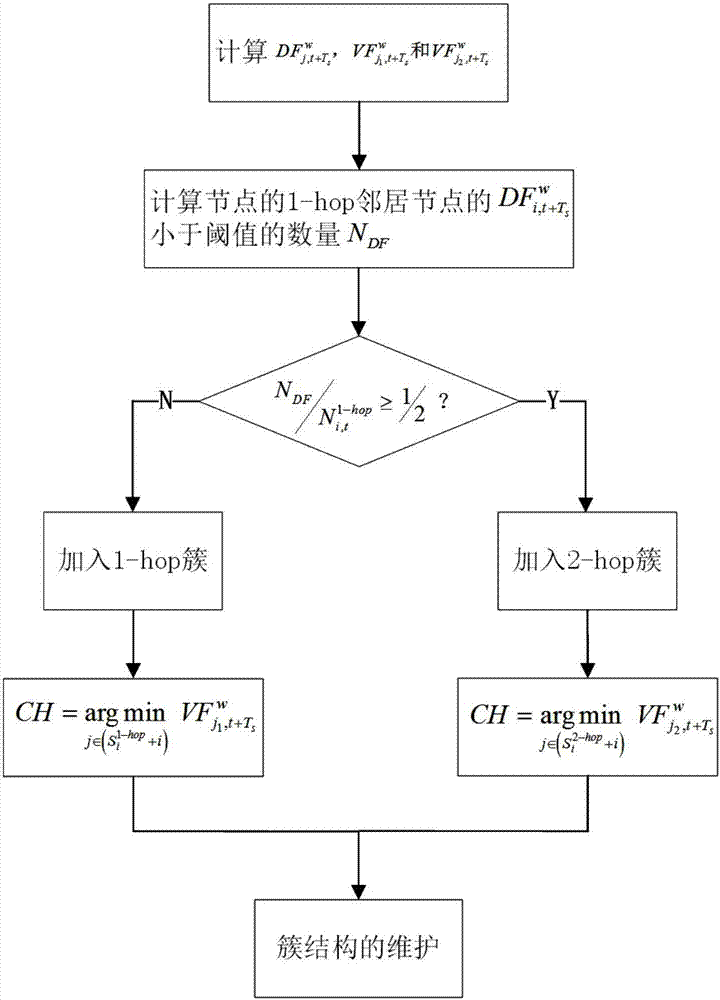
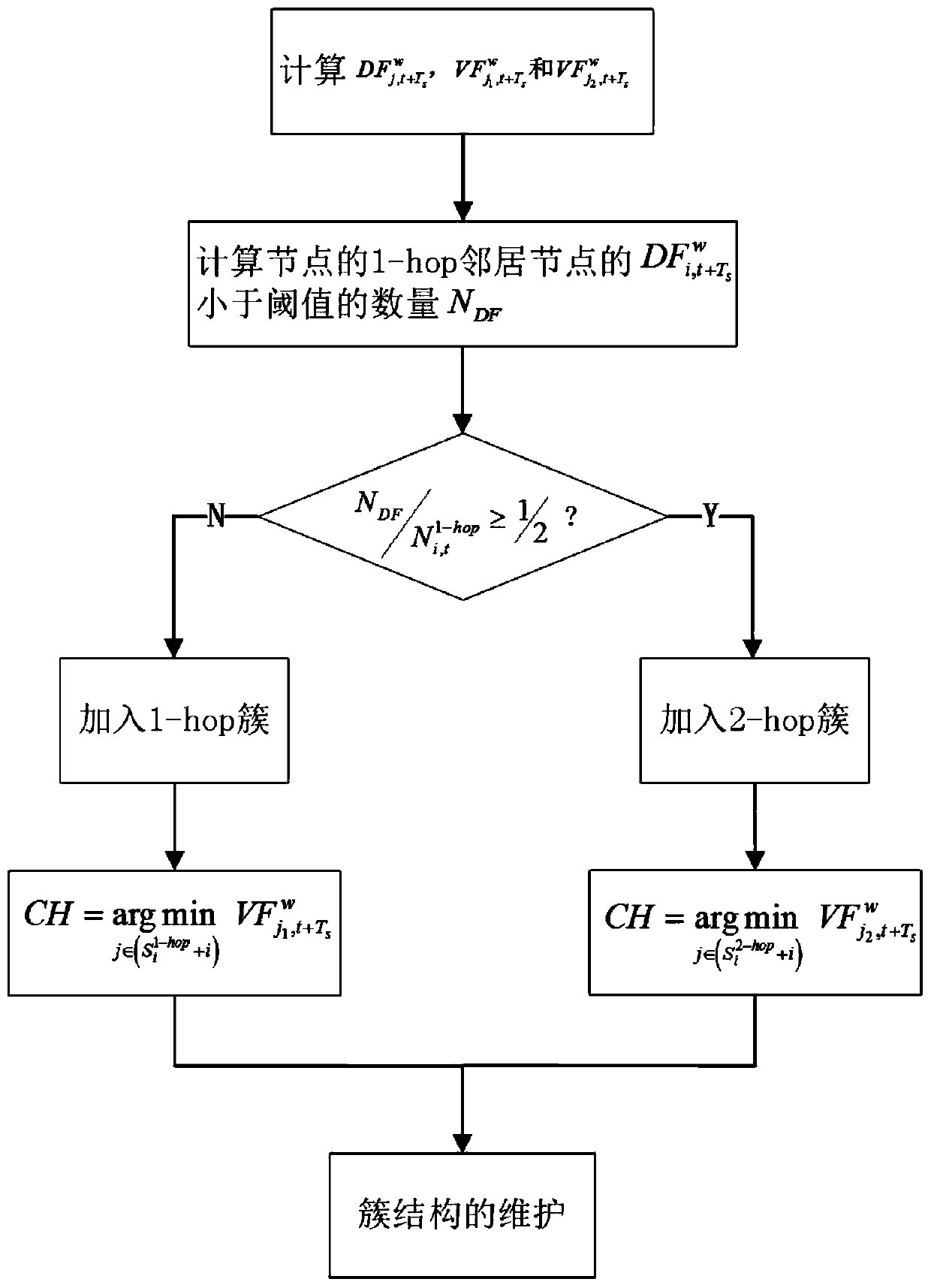
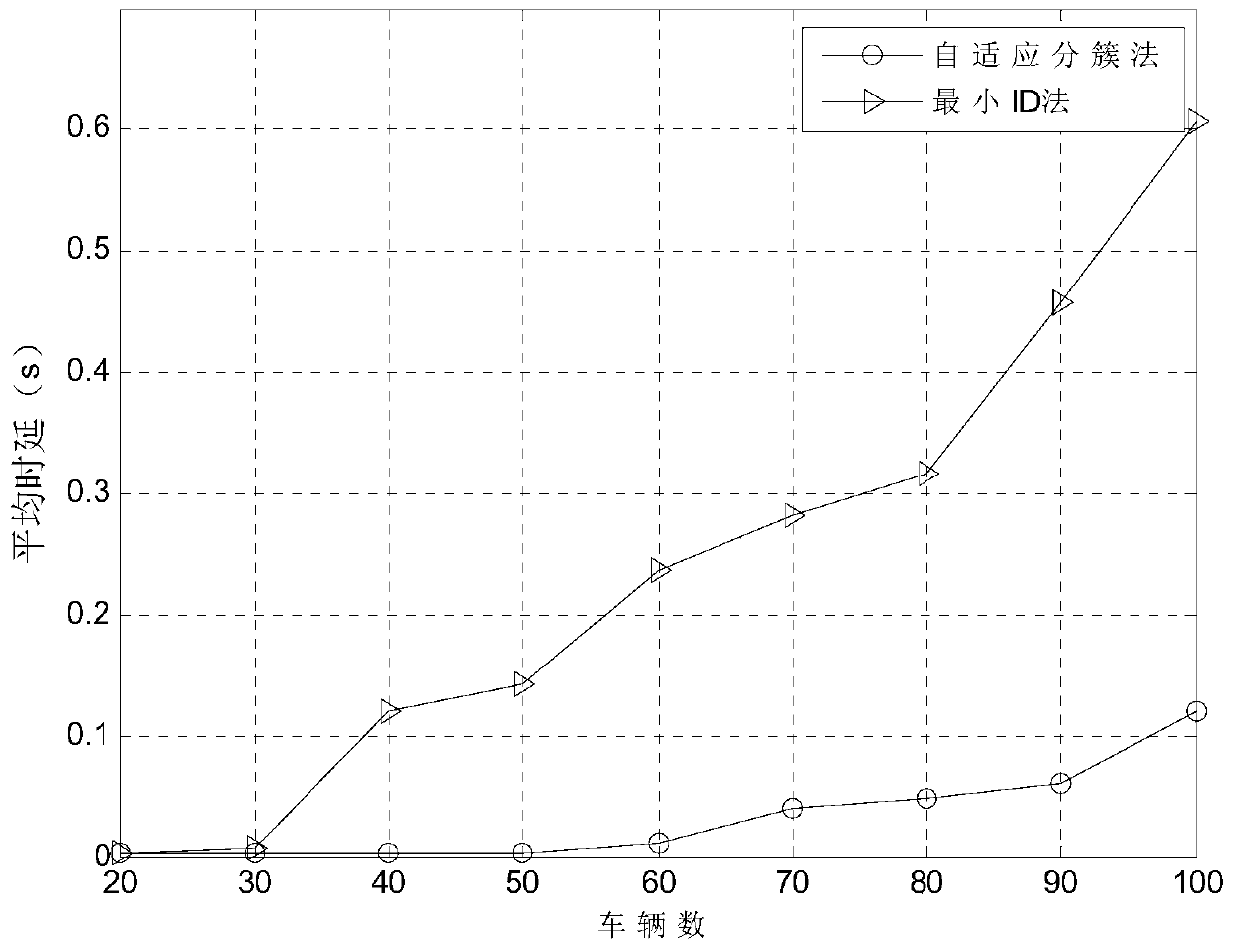
1-hop and 2-hop clusters coexistent adaptive clustering method based on density estimation in VANETs
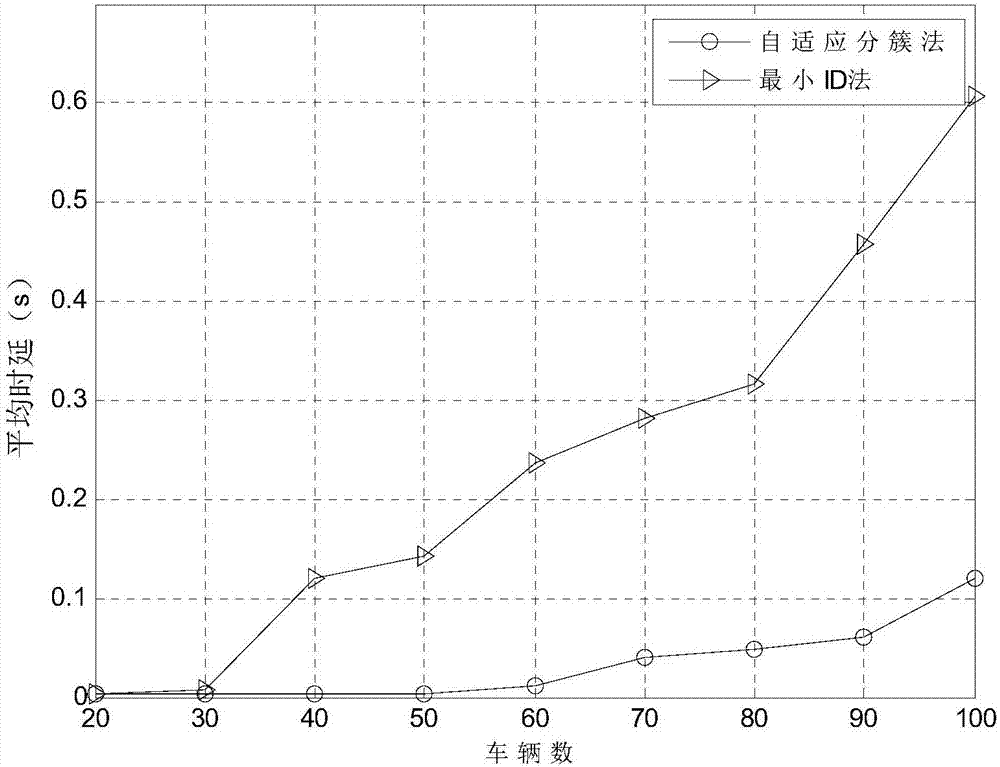
ActiveCN107454649AGuaranteed reasonablenessAvoid frequent updatesNetwork topologiesTransmissionCluster algorithmCurrent velocity
The invention discloses a 1-hop and 2-hop clusters coexistent adaptive clustering method based on density estimation in VANETs. The method comprises the following steps: estimating the 1-hop neighbor node density in the future time, as the formula, based on the current position and current speed of a node, comparing the 1-hop neighbor node density with a threshold, and judging whether the node is suitable to form the 1-hop cluster or the 2-hop cluster, and initializing the node as a cluster head node; in each cluster, selecting a node with the minimum relative mobility, that is the formula is the minimum, as a cluster head, reducing other nodes in the cluster to cluster members, and if there are two or multiple nodes with the minimum relative mobility, then selecting a node with the minimum ID as the cluster head; and performing post maintenance of a cluster structure based on the possible situations in the network. A clustering algorithm disclosed by the invention has the advantages of being low in delay and low in packet loss.
Owner:XI AN JIAOTONG UNIV
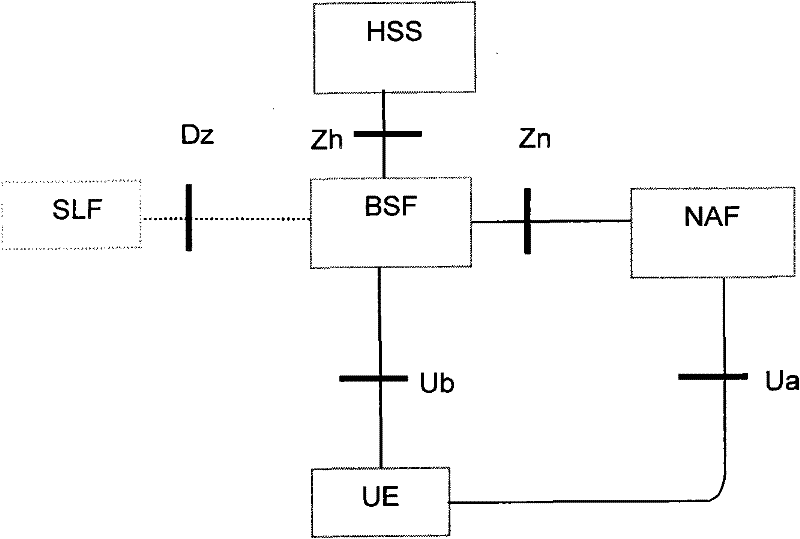
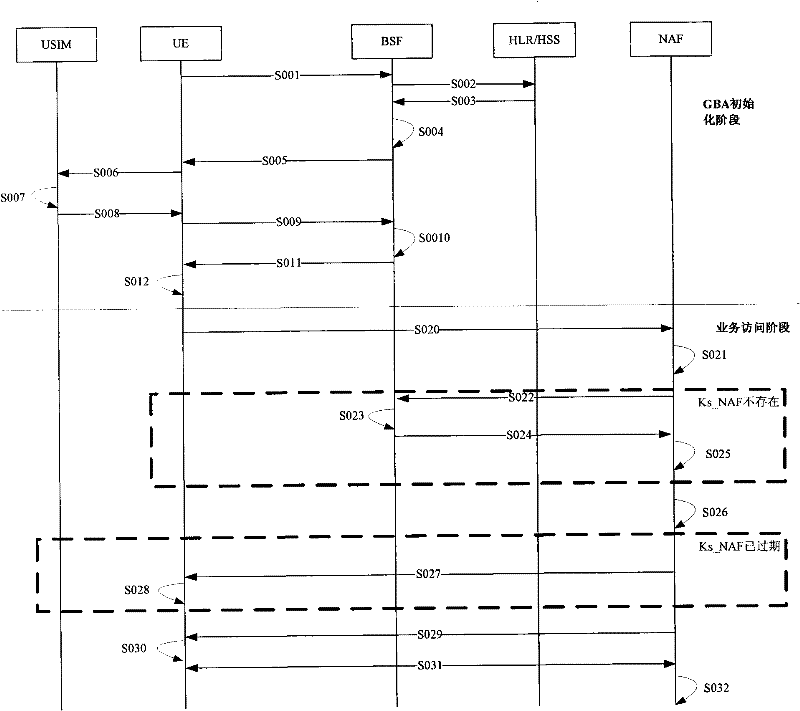
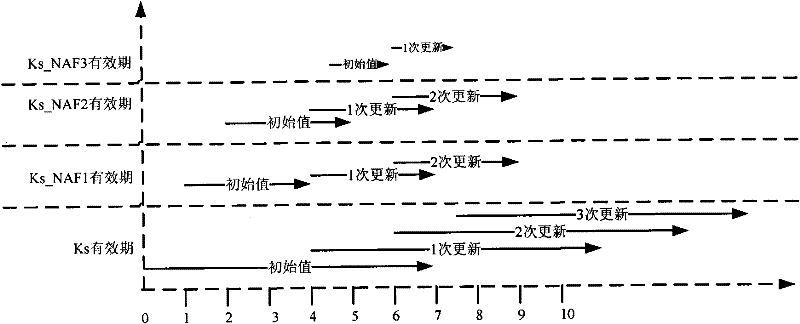
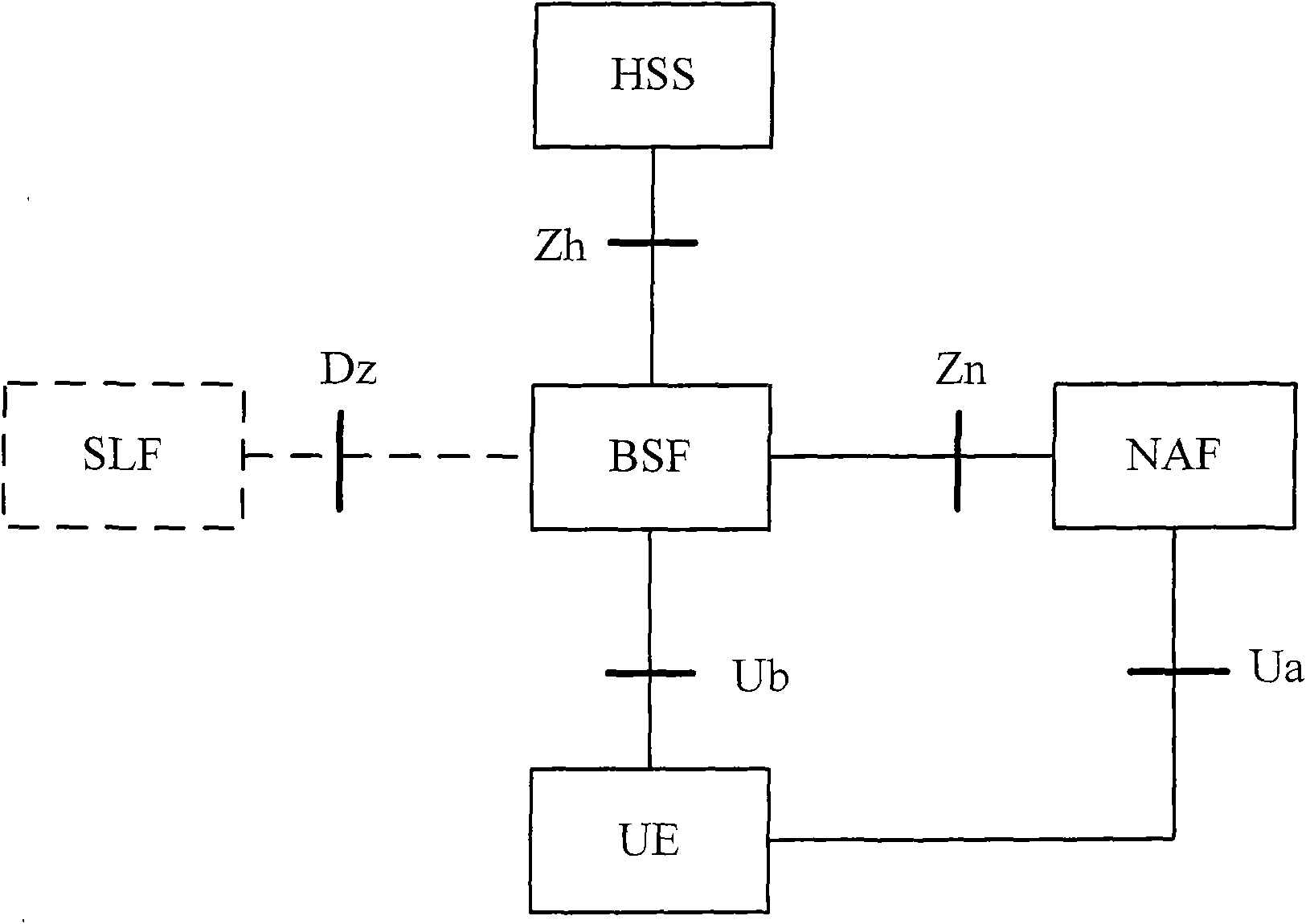
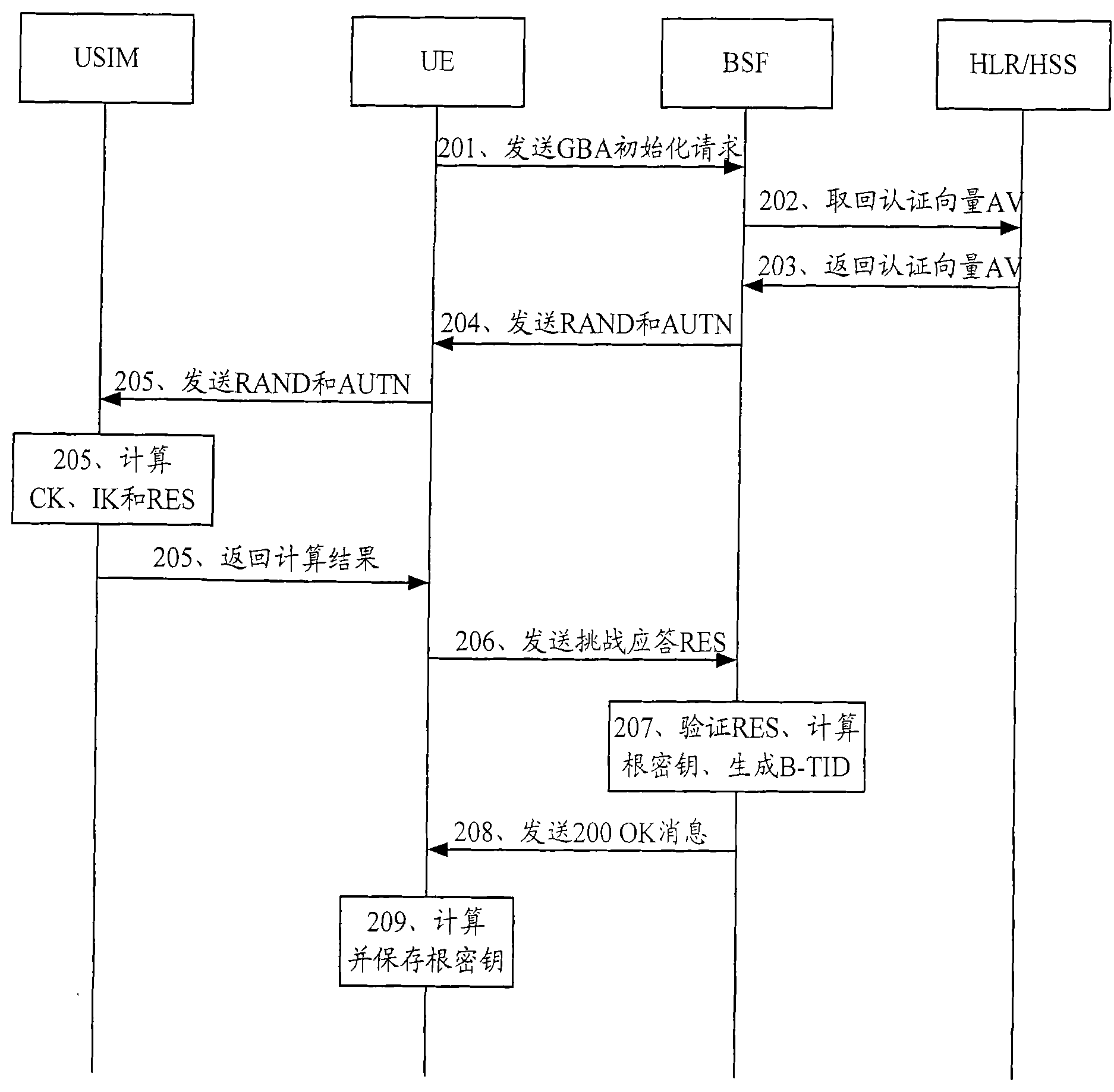
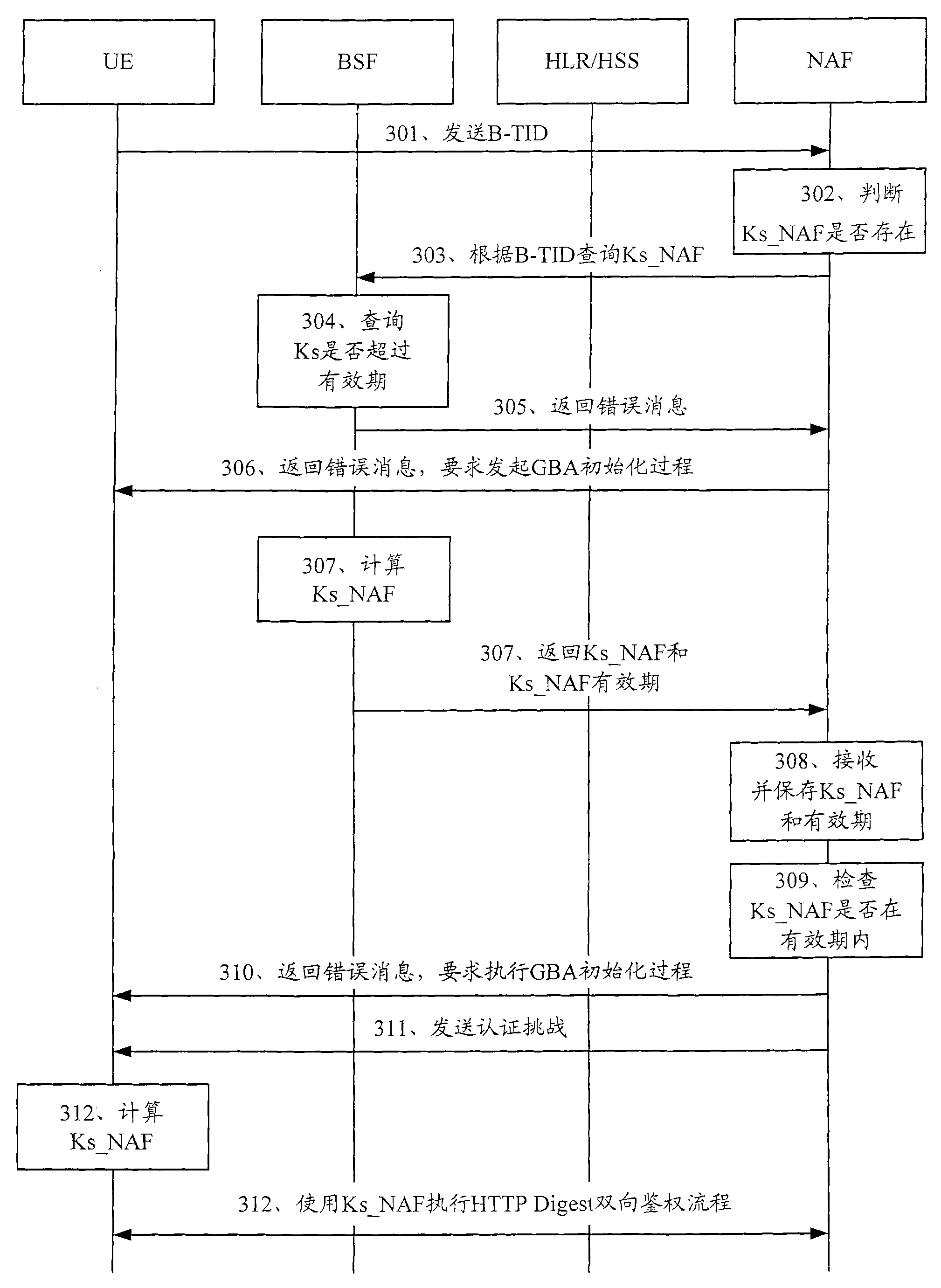
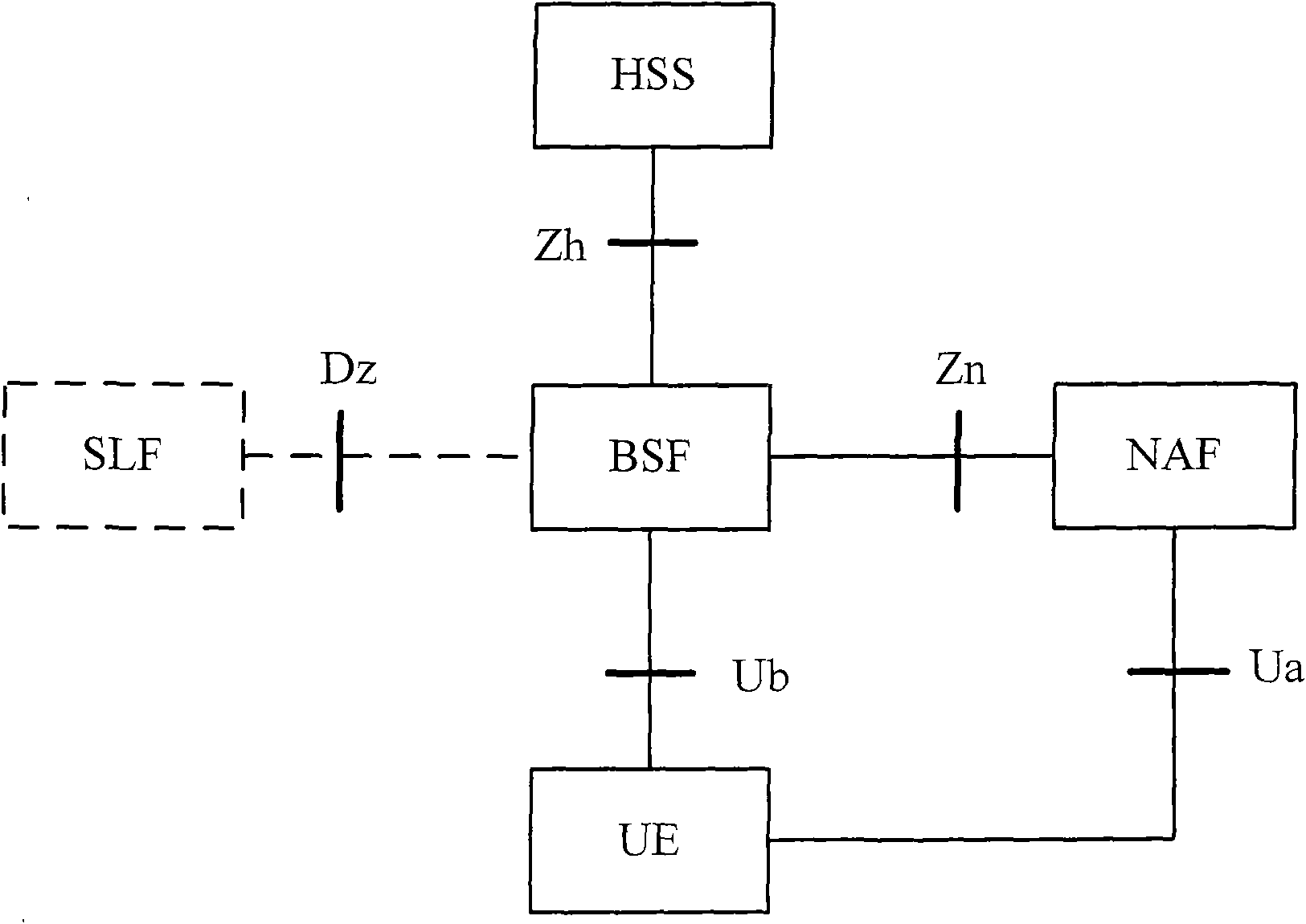
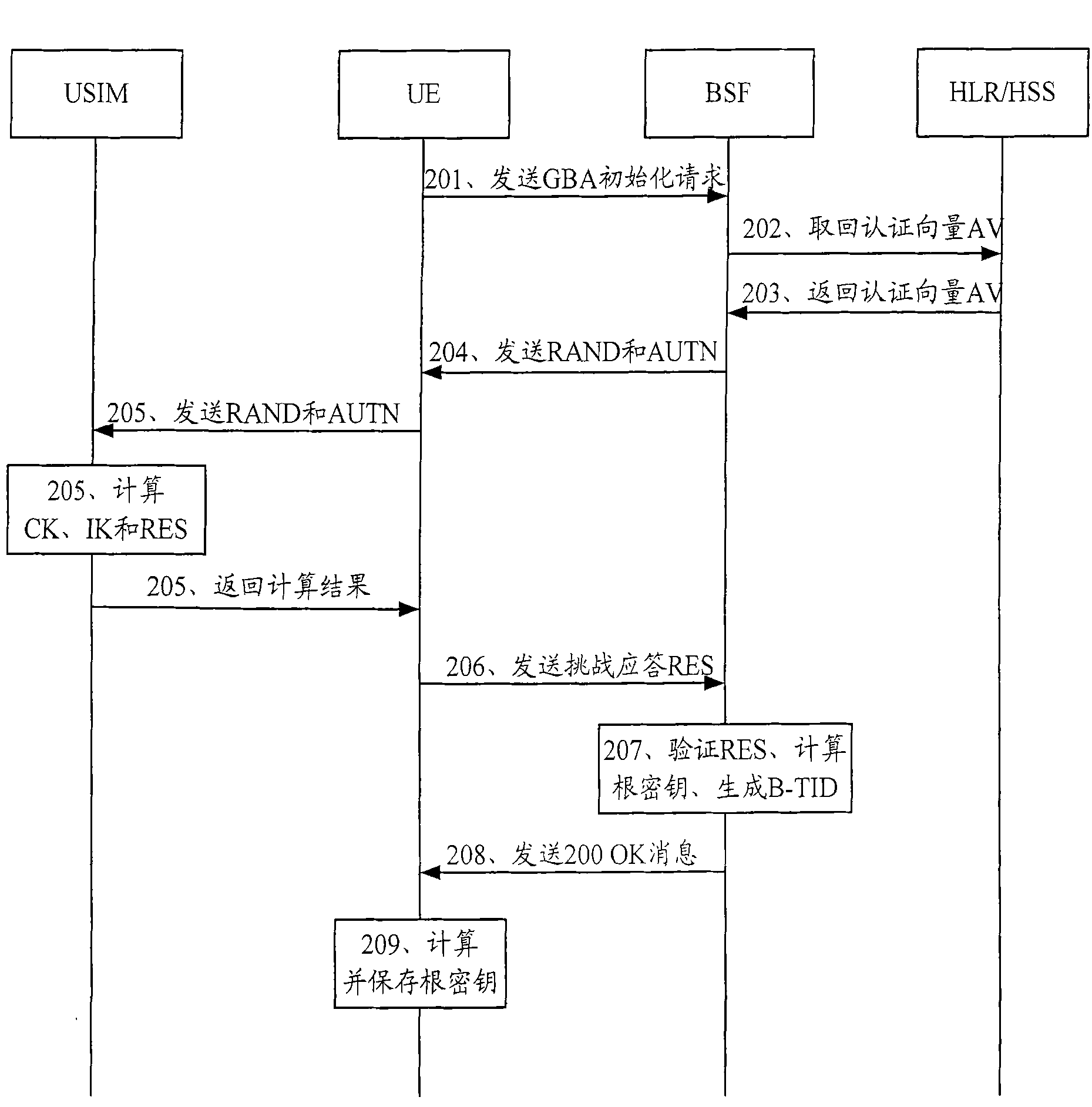
Method, device and system for updating key of general guide architecture
The invention discloses a method, device and system for updating the key of a general guide architecture. The method for updating the key of the general guide architecture comprises the following steps of: receiving a Ks_NAF (Network Application Function) acquisition request with a BSF (Bootstrapping Server Function); obtaining a key parameter, and generating a Ks_NAF according to the formula that Ks_NAF=KDF(Ks, a preset character string, RAND: random, IMPI:IP Multimedia Private Identity, NAF_ID and the key parameter); storing and returning the Ks_NAF and the key parameter. When the method for updating the key of the general guide architecture disclosed by the invention is used for updating a GBA (Genetic Bootstrapping Architecture) key, frequent updating of Ks which is not out of date is avoided, and the key updating load of the BSF and a service platform is reduced.
Owner:CHINA MOBILE COMM GRP CO LTD
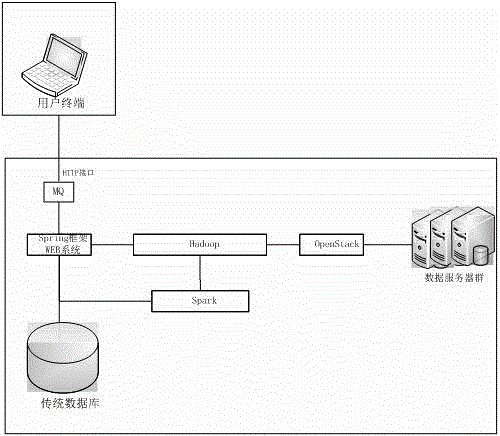
High-efficiency real-time electronic map fence realization method based on big data
InactiveCN106484752AImprove efficiencyIncrease flexibilityGeographical information databasesSpecial data processing applicationsMessage queueElectronic map
The invention discloses a high-efficiency real-time electronic map fence realization method based on big data. Distributed storage of high-efficiency real-time electronic map fence information is realized through adoption of architecture of big data; the electronic map fence information is searched through distributed computation; and information indicating that a user terminal enters or exits an electronic map is triggered. The method comprises the steps that when the electronic map fence information is added to a system, the electronic map fence information is stored in a distributed storage component Hadoop, and an index is added to the electronic map fence information; when an information queue of the system receives position information of the user terminal, the position information is transmitted to a distributed computation component Spaprk for processing and the distributed storage component Hadoop for information backup; and the distributed computation component Spaprk receives the position information of the user terminal, the electronic map fence information around users is searched rapidly and corresponding temporary files are generated; and when the system detects that a certain user terminal enters or exits a certain electronic map fence, corresponding information is triggered to be sent to the user terminal.
Owner:杨庆磊
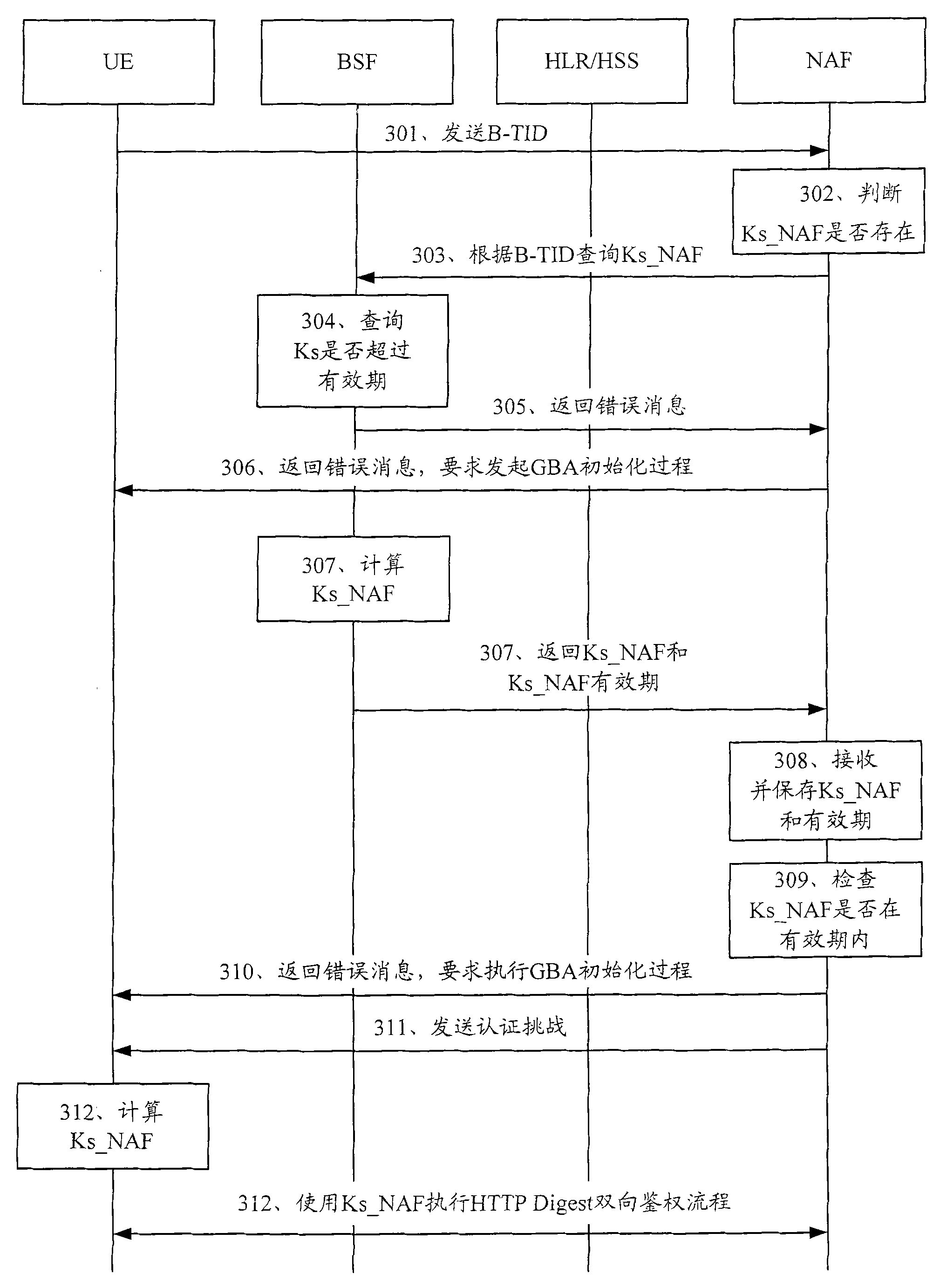
Method, device and system for updating key
ActiveCN102065421AReduce update loadAvoid frequent updatesSecurity arrangementComputer hardwareGeneric Bootstrapping Architecture
The embodiment of the invention discloses a method for updating a key. The method comprises the following steps: receiving a bootstrapping service identifier from network application function (NAF) and inquiring whether a root key is in the valid period according to the bootstrapping service identifier; if the root key is not in the valid period, returning the error message to user equipment (UE) by NAF and ensuring NAF to initiate generic bootstrapping architecture (GBA) with the UE; and if the root key is in the valid period, generating a random number, obtaining a service key according to the random number, sending the service key, the valid period of the service key and the random number to NAF and ensuring NAF to carry out two-way authentication with the UE according to the service key and the random number. The embodiment of the invention reduces the load of bootstrapping server function (BSF) and the load of a service server. The embodiment of the invention also discloses a device and system applying the method.
Owner:CHINA MOBILE COMM GRP CO LTD
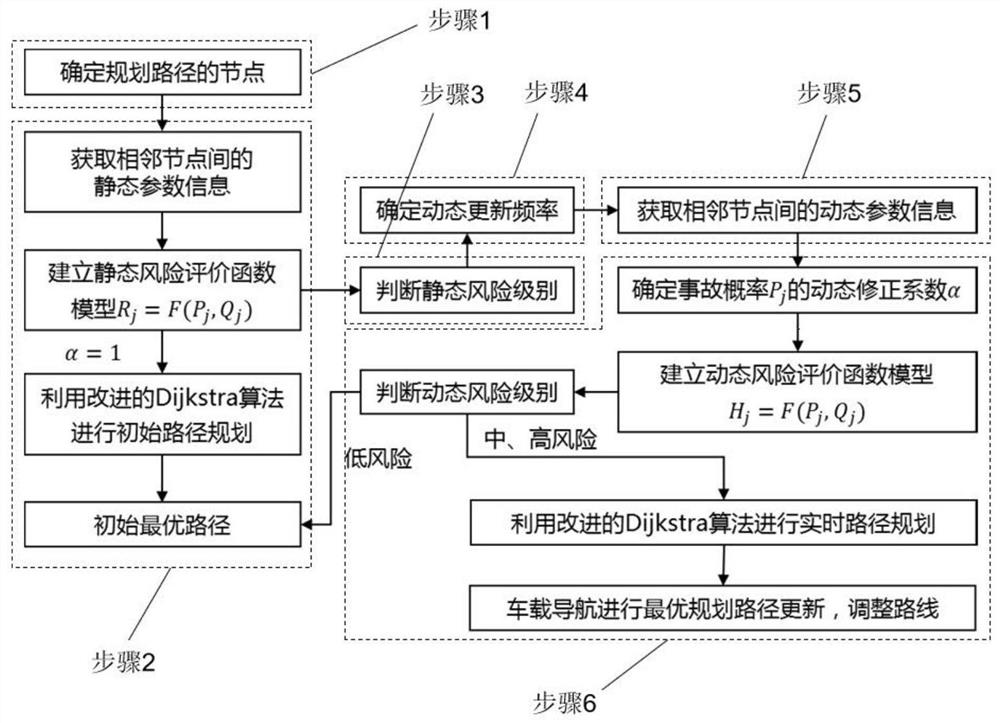
Risk minimization-based hazardous waste transportation path real-time planning method
PendingCN113361997ARich pathGuaranteed accuracyResourcesLogisticsEnvironmental resource managementSystems engineering
According to the risk minimization-based dangerous waste transportation path real-time planning method provided by the embodiment of the invention, risk factors are incorporated into an optimal path planning process, dangerous waste vehicles, road parameters, environmental parameters, traffic information and driving behaviors are comprehensively considered, a transportation risk evaluation function model is constructed, and the risk minimization-based dangerous waste transportation path real-time planning method is provided. And the risk of dangerous waste transportation is subjected to refined evaluation, so that the planned path is more comprehensive and more objective.
Owner:NANJING UNIV
Virtual private network access method and device for mobile user
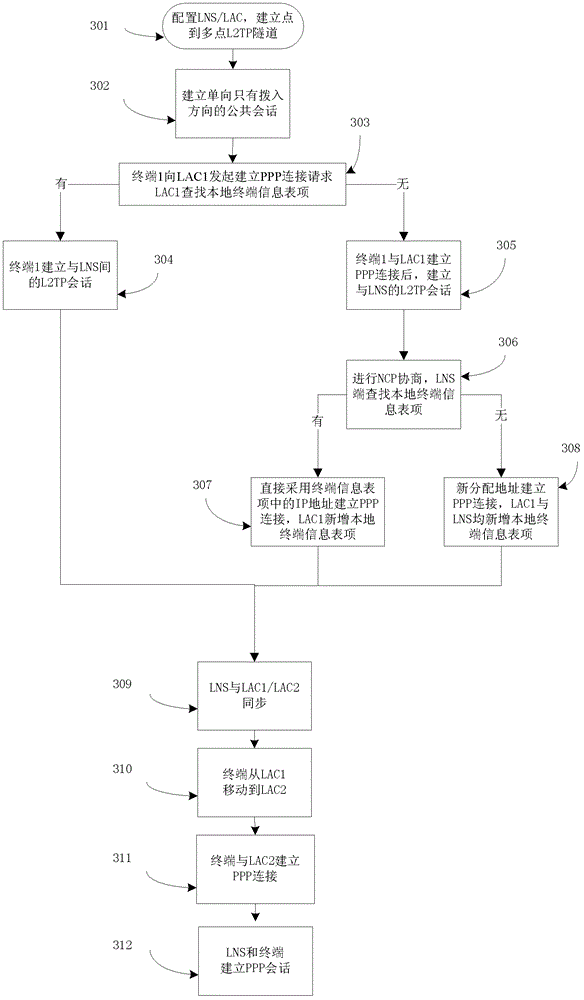
ActiveCN102724767AQuick buildAvoid long interruptionsConnection managementNetworks interconnectionAccess methodPrivate network
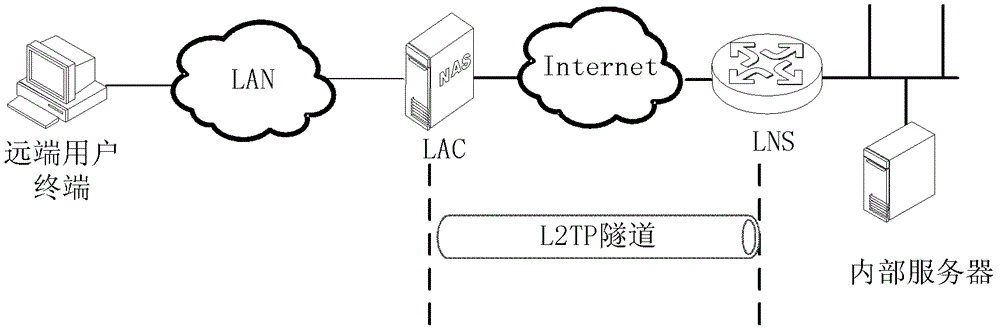
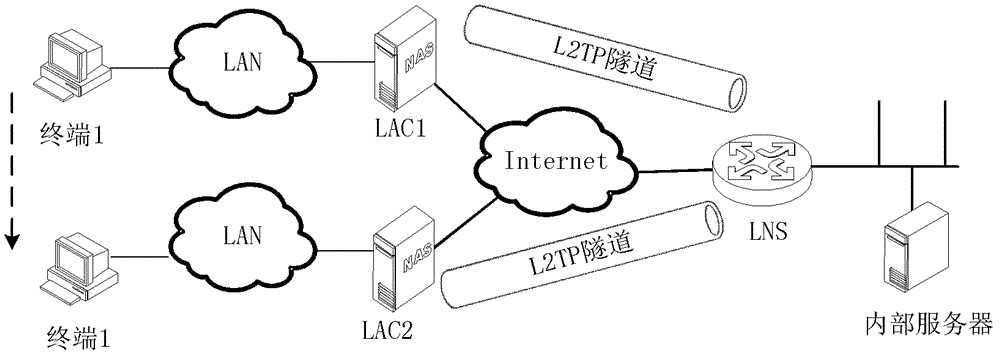
The invention discloses a virtual private network access method and a virtual private network access device for a mobile user. The method and the device support the mobile user to access the virtual private network. The method comprises the following steps of: establishing a permanent layer 2 tunneling protocol (L2TP) channel between an L2TP network server (LNS) and a first L2TP access concentrator (LAC), and also establishing the permanent L2TP channel between the LNS and a second LAC in an LAC active initiation way; establishing a public session and synchronizing the second LAC after an L2TP session between a terminal and the first LAC is established; and when the terminal moves from a first LAC network into a second LAC network, rapidly accessing the LNS and establishing the L2TP session without changing an Internet protocol (IP) address of the terminal. The LACs and the LNS are provided with a terminal information table entry and a revocation timer, the LNS is also provided with a message synchronization device for conveniently realizing LAC information synchronization. By the method and the device, the terminal can access the virtual private network by using the same IP address when the terminal moves, so that all service applications based on network IP and network rights are not changed during roaming.
Owner:NEW H3C TECH CO LTD
Method of controlling security of terminal set top box applied under environment of living broadcast and broadcast on demand
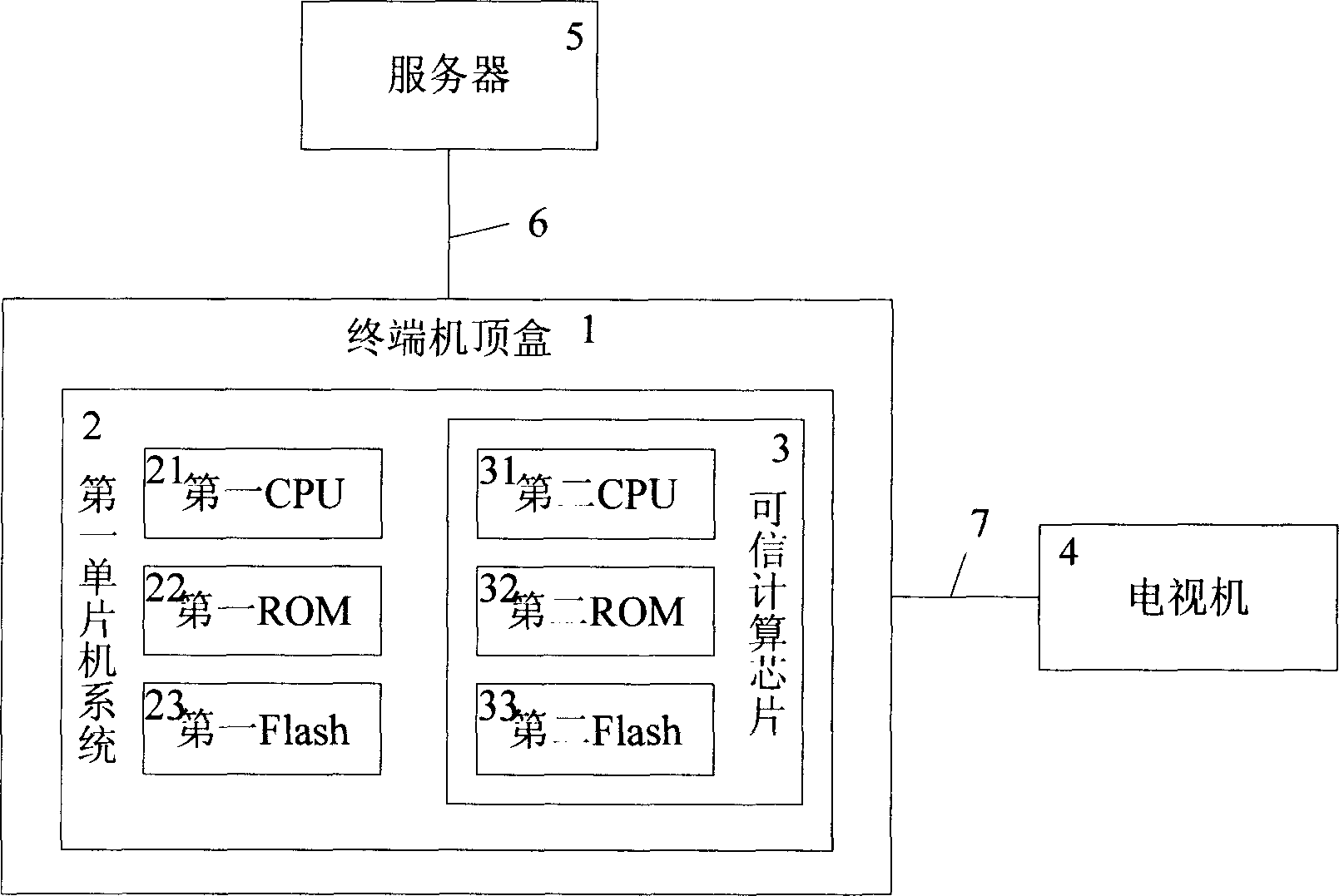
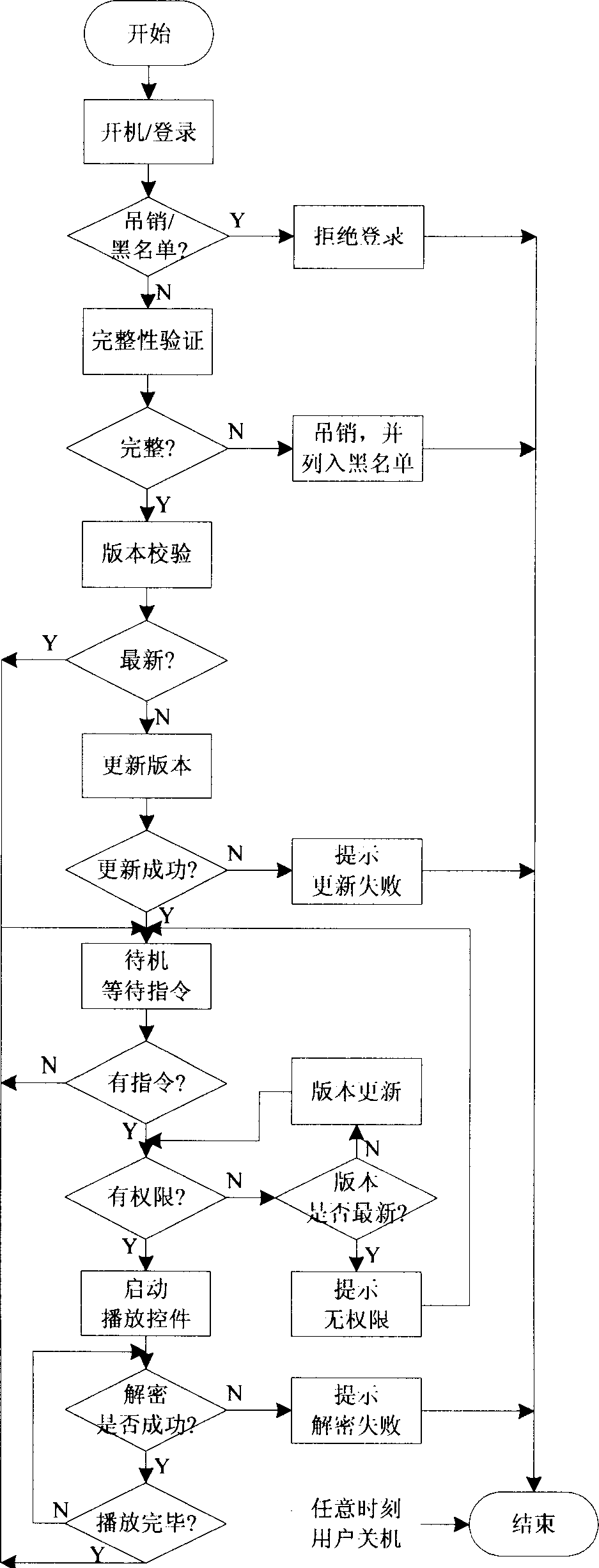
InactiveCN1917563AAvoid frequent updatesSecurity controls are effectiveTelevision system detailsColor television detailsTrusted ComputingDigital television
The method comprises: embedding a dependable computing chip into a digital set-top box; the right object of digital media content, decrypt key and decrypt program are packaged into the dependable computing chip; with digital right management technology, each operation in the dependable computing chip can be effectively supervised and controlled to ensure that the digital media content can not be illegally used. In addition, the frequent renew of decrypt key can be avoided, and the renew operation time period can be reduced to 3-6 months.
Owner:上海文广互动电视有限公司
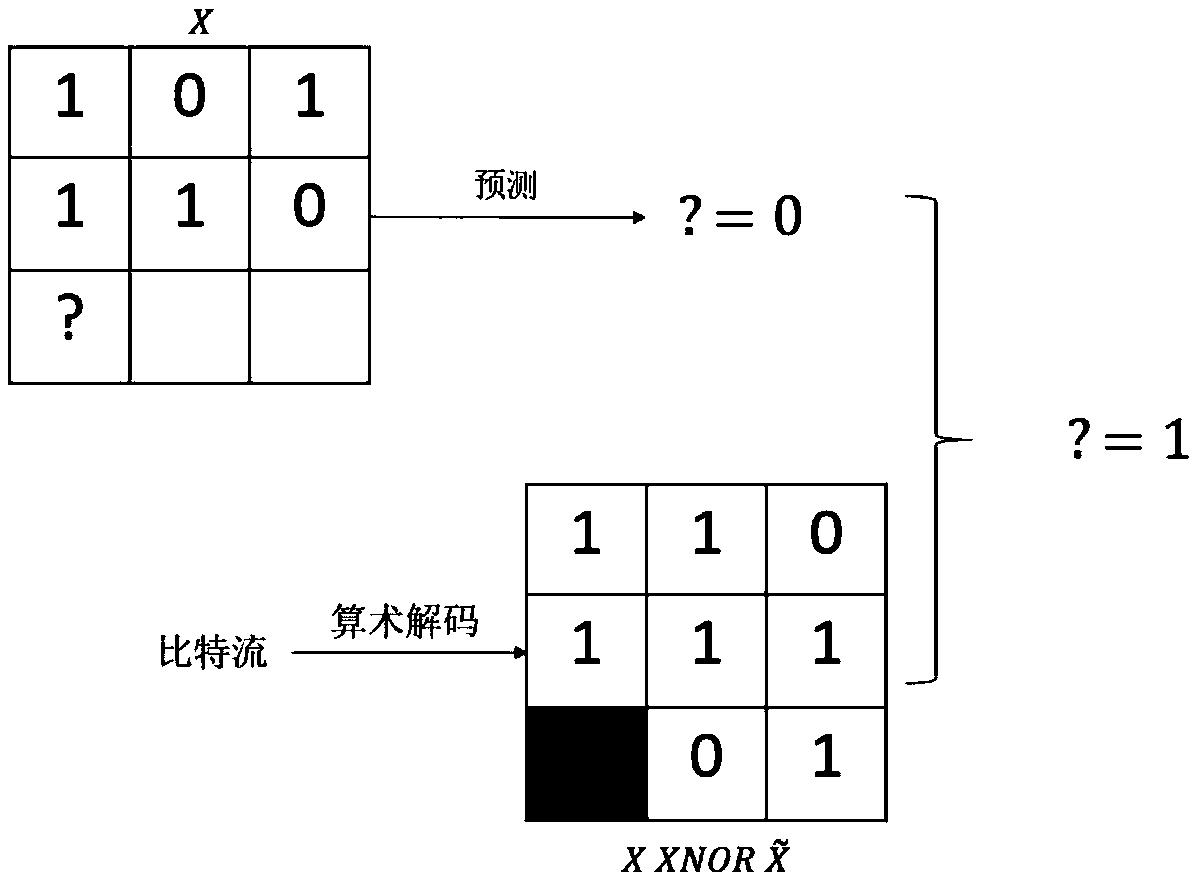
Binary image coding method through combination of bit operation and probability prediction
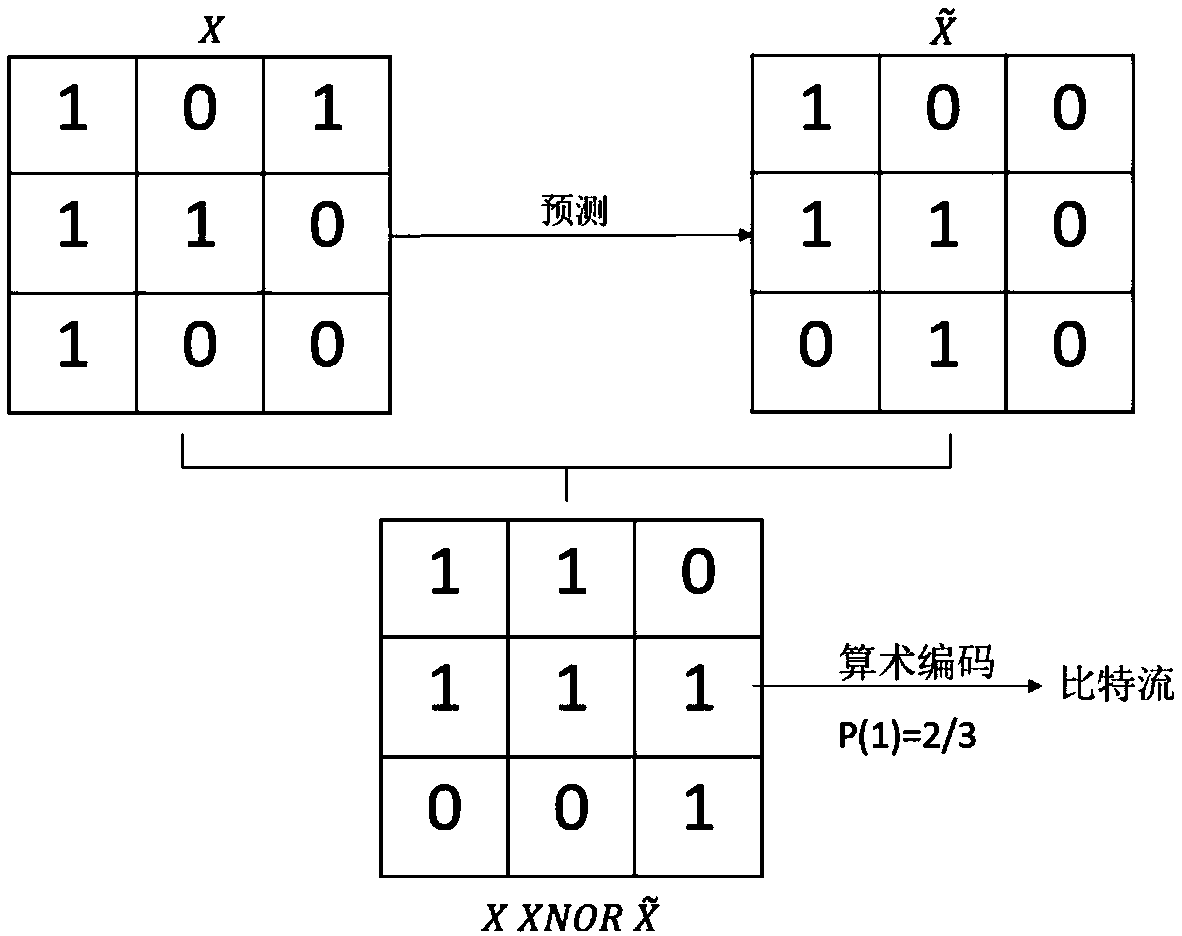
ActiveCN108632630AAvoid frequent updatesReduce complexityDigital video signal modificationEncoding algorithmArithmetic coding
The invention discloses a binary image coding method through combination of bit operation and probability prediction. The method comprises a coding process and a decoding process. The decoding processis an inverse process of the coding process. The coding process comprises the following steps of predicting a value of a current pixel based on coded pixels in a binary image; carrying out bit operation on a predicted value and a true value of the current pixel to obtain a residual, and obtaining prediction accuracy; and coding the residual into a bit stream through utilization of a entropy coding algorithm, and taking the prediction accuracy as a global context probability model of a binary arithmetic coding algorithm if the binary arithmetic coding algorithm in the entropy coding algorithmis employed. A fixed coding interval is employed, and the complexity of the coding process is greatly reduced.
Owner:UNIV OF SCI & TECH OF CHINA
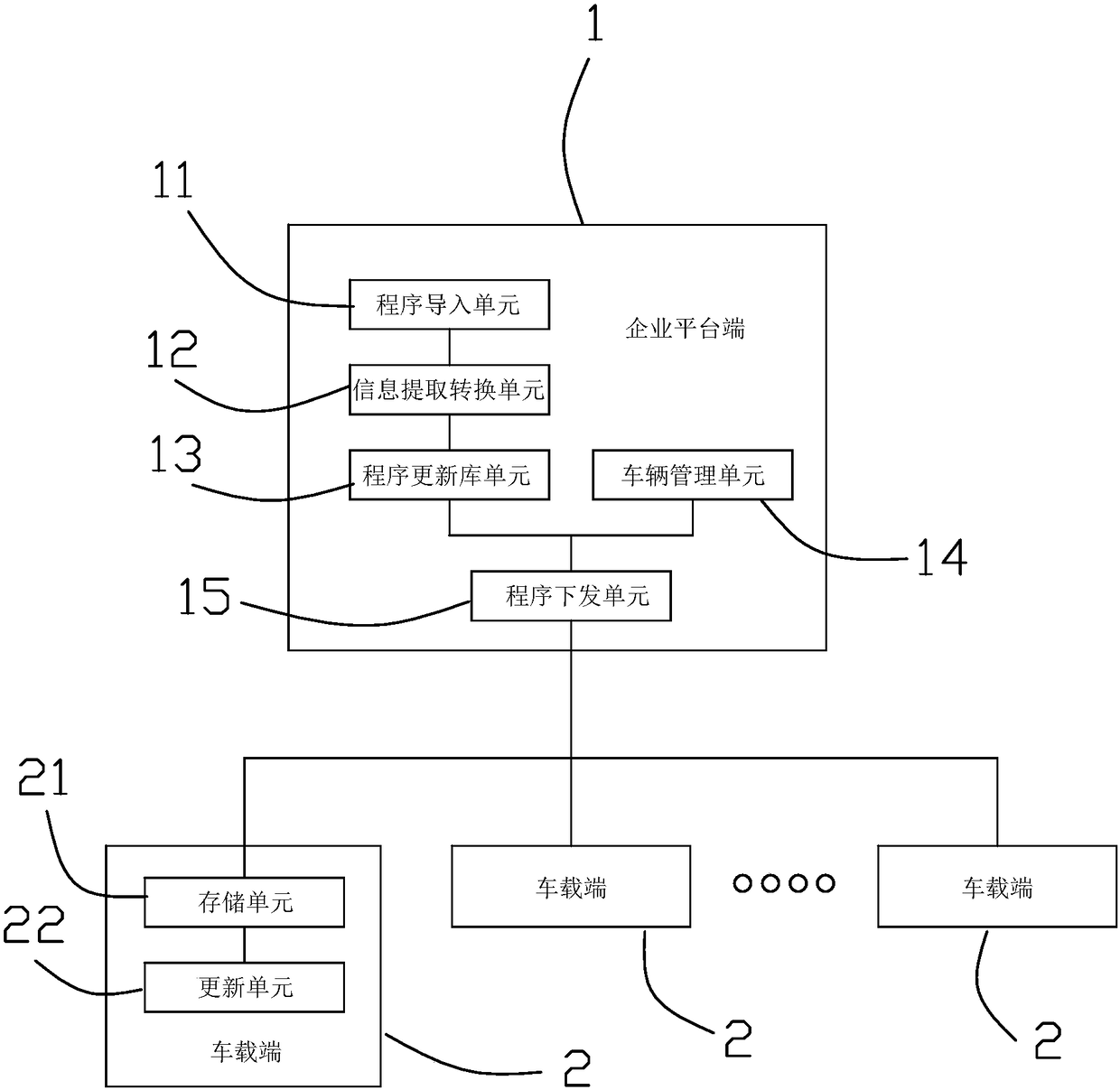
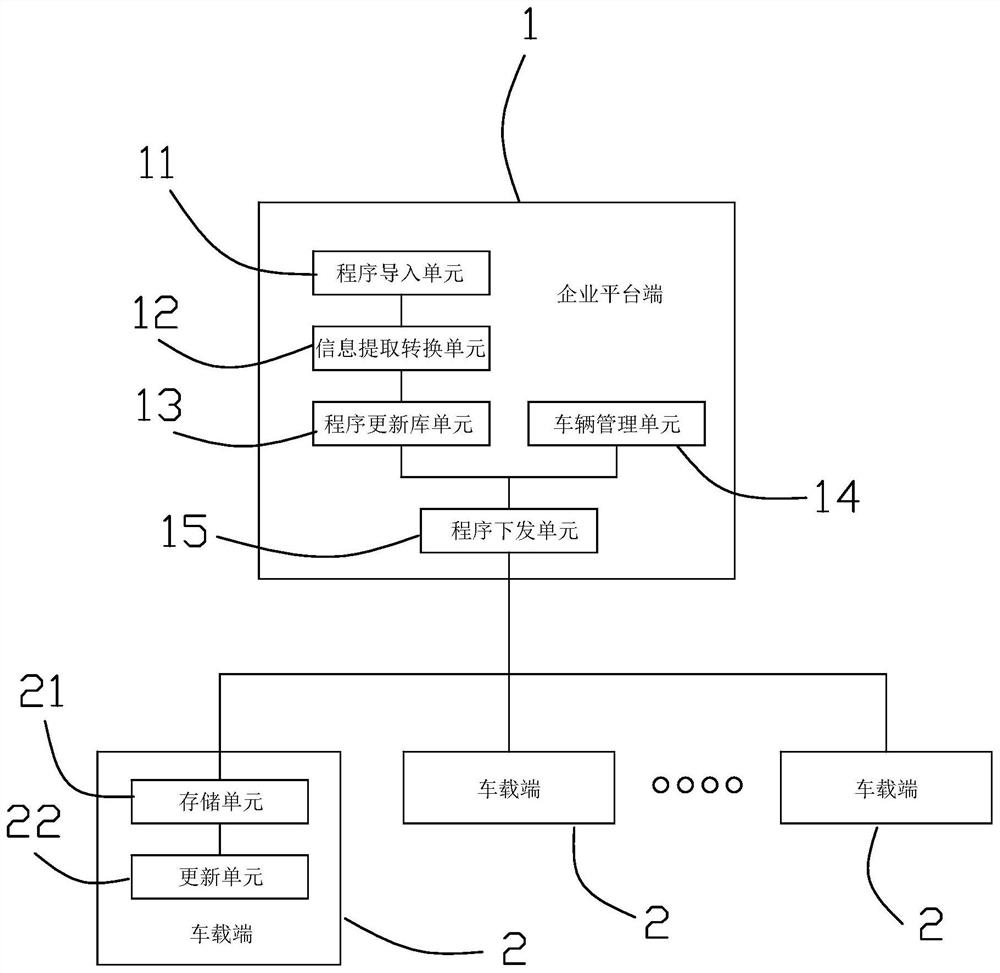
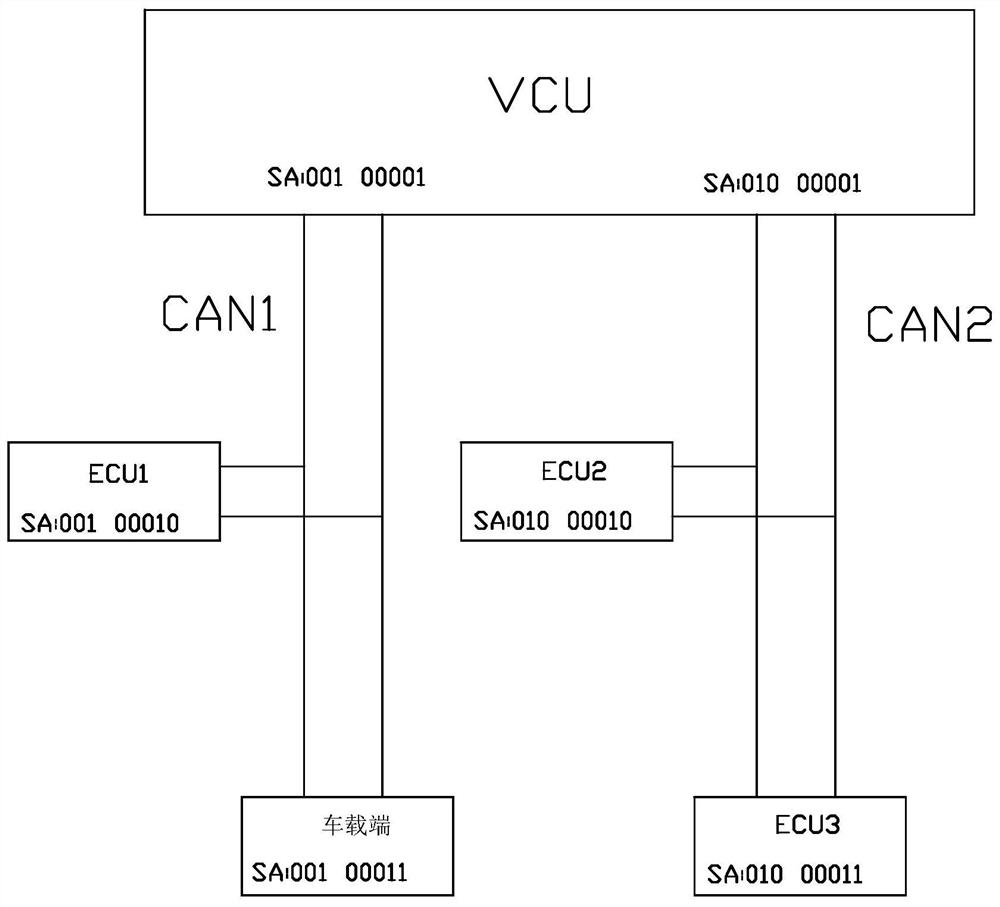
New-energy vehicle ECU remote program updating management system and method
ActiveCN108153562ARealize remote program updateNo need to add additional hardware facilitiesProgram loading/initiatingProgram/content distribution protectionManagement unitManagement process
The invention discloses a new-energy vehicle ECU remote program updating management system and method. The system comprises an enterprise platform side and a vehicle-mounted terminal, and the enterprise platform side comprises a program importing unit, an information extraction conversion unit, a program updating library unit, a vehicle management unit and a program issuing unit; the vehicle-mounted terminal comprises a storage unit and an updating unit which are connected; according to the updating management process, an updating program is imported and converted into a standard format, the updating program is issued to a vehicle owner side according to the vehicle ECU model and ECU program version number matching state, and the vehicle-mounted side under the enable state is subjected toprogram updating. The updating program adopTS the universal format, the requirement for vehicle-mounted terminal hardware is lowered, and the cost is lowered; due to the method for controlling the program updating opportunity jointly by a VCU and an ECU needing to be updated, the imponderable risk caused by program updating in the vehicle using process is avoided; ECU program updating among different CAN sub-neTS of vehicles is achieved, and illegal program updating is avoided.
Owner:浙江中科正方电子技术有限公司
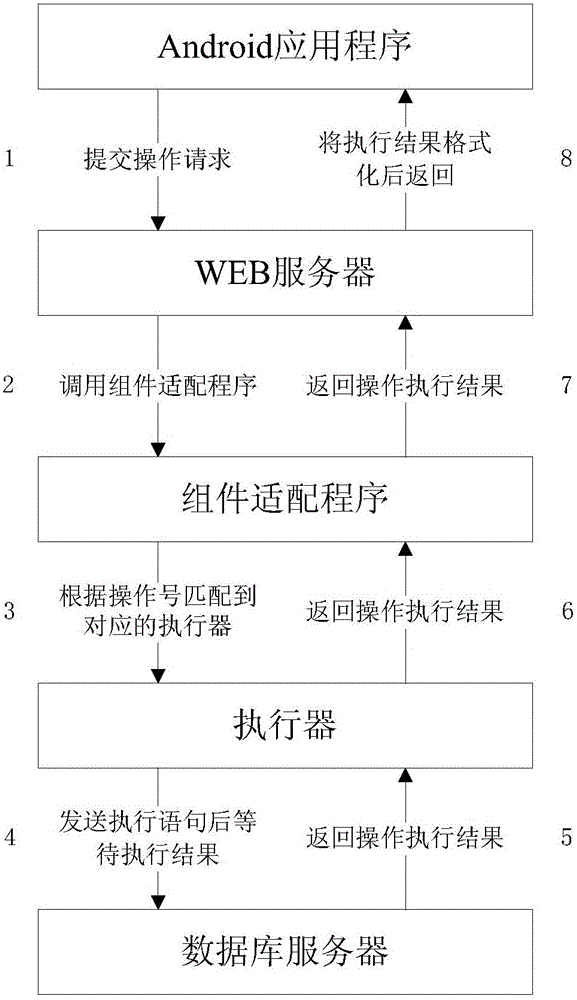
Method for Android application to access database
InactiveCN105956160AEasy to callAchieve real-timeDigital data authenticationProgram loading/initiatingWeb serviceDatabase server
The invention provides a method for an Android application to access a database. A Web server, an assembly adaption program, an executor and a database server are arranged, an Android application program is communicated with the Web server through a wireless network, and the Web server is communicated with the database server through the network; and the Web server is matched with the corresponding executor according to an operation number requested by the Android application program to operate the database, and a processing result is returned to the Android application program after the operation is finished. Since operation commands on the database are uniformly processed by the same server, the Android application program only needs to send the operation number to the Web server to carry out the corresponding operation on the database, jamming communication is carried out through a server side, the operation commands can be subjected to centralized management to achieve operation instantaneity, use convenience is embodied, and the operation instantaneity and safety of the database is guaranteed.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
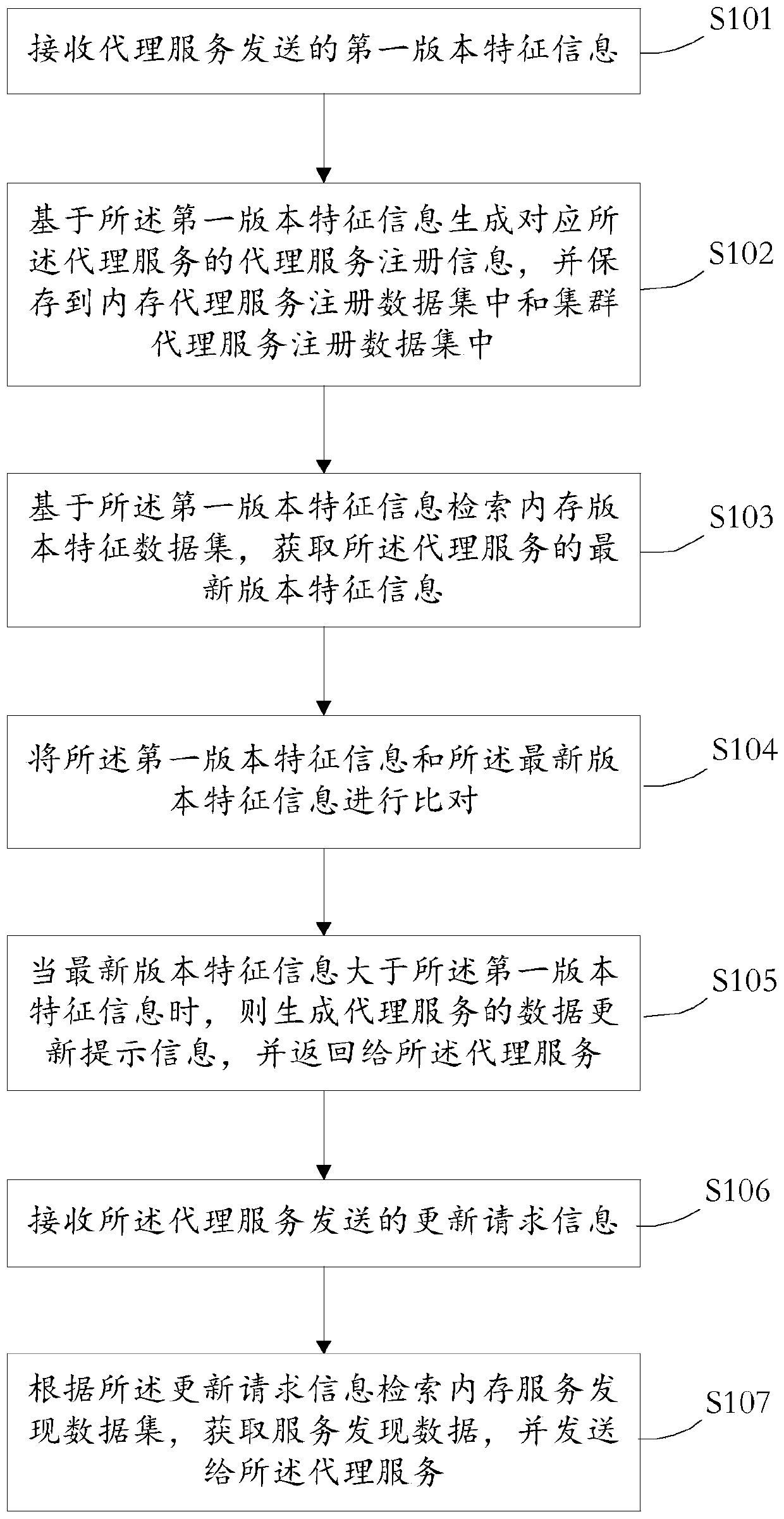
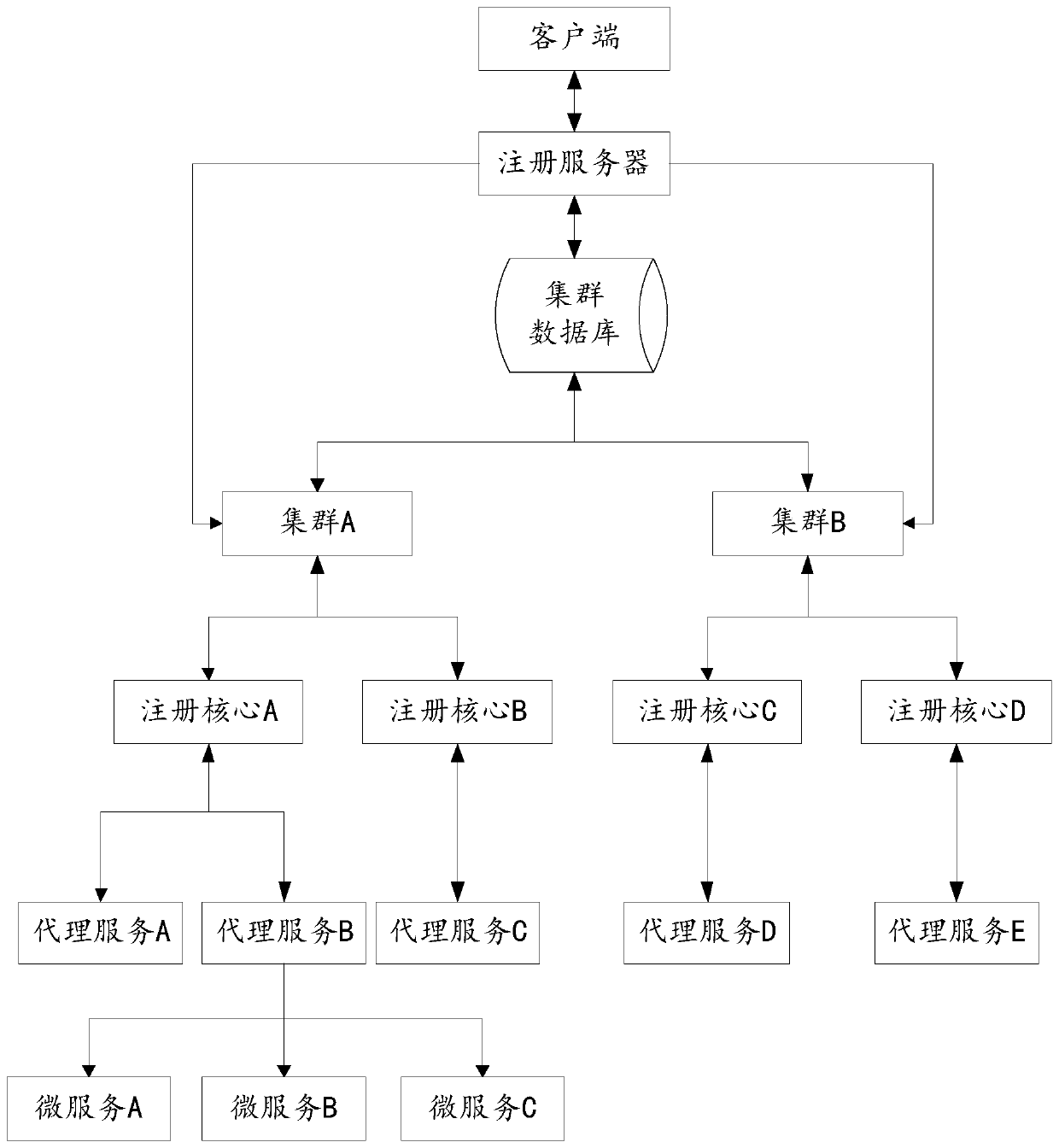
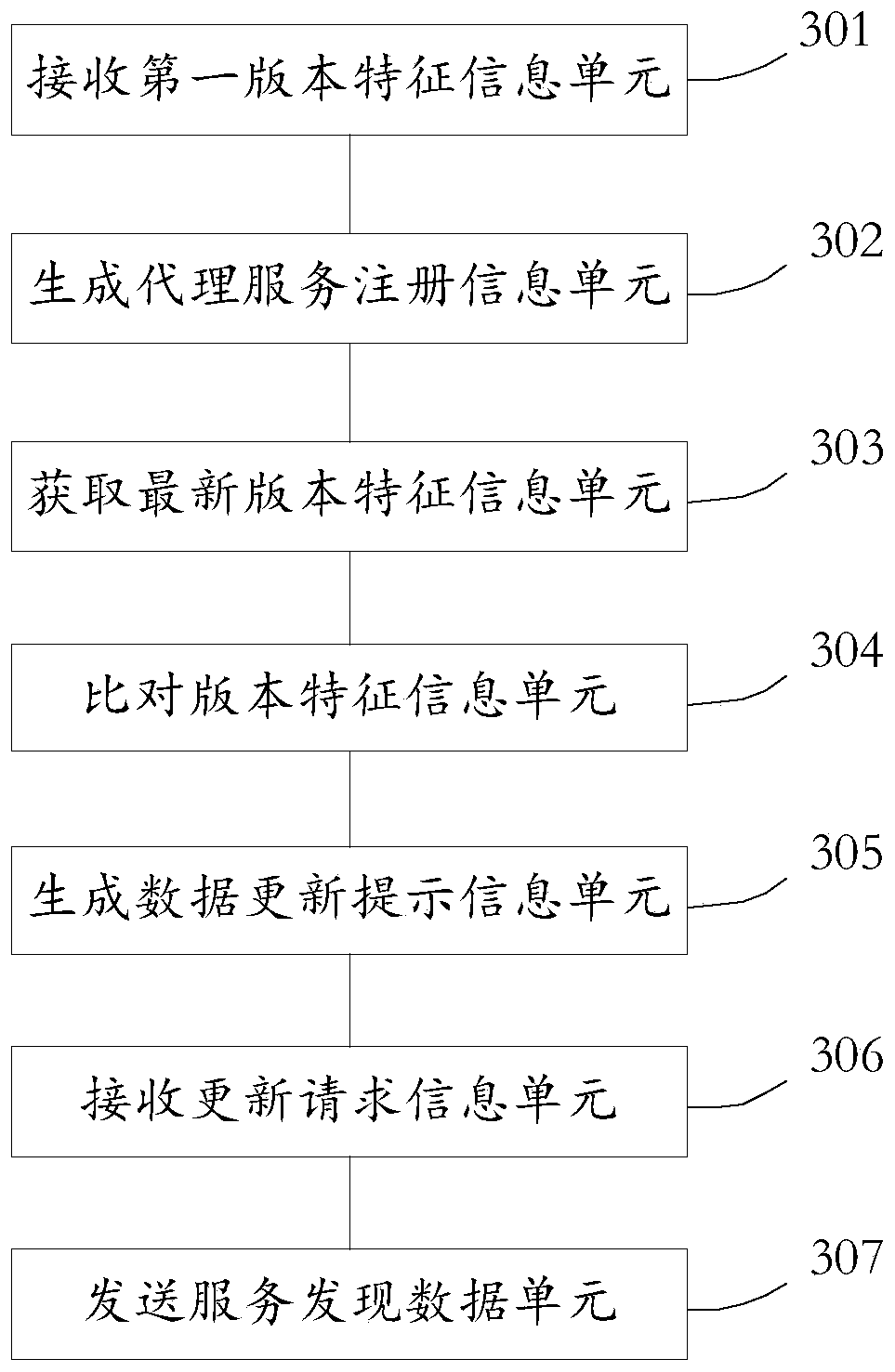
Registration core management method and device, medium and electronic equipment
ActiveCN111309366ACapable of horizontal expansionHave diversityVersion controlTerm memoryService discovery
The invention provides a registration core management method and device, a medium, electronic equipment and a registration core management system. According to the network scheme provided by the invention, the registration core of the cluster connection has a transverse capacity expansion capability, so that the proxy service has diversity. According to the method and the device, a live detectionfunction, a data upgrading function during starting and a regular interception upgrading function are provided, so that the consistency of data in clusters, registration cores and proxy services is ensured, and effective work of service discovery is ensured. The registration core stores the data of service discovery in the memory, so that the data processing capability of the service discovery isimproved. And the processing logic code is dynamically issued to the proxy service, so that frequent updating of the proxy service is avoided, and the adaptability and flexibility of the proxy serviceare improved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
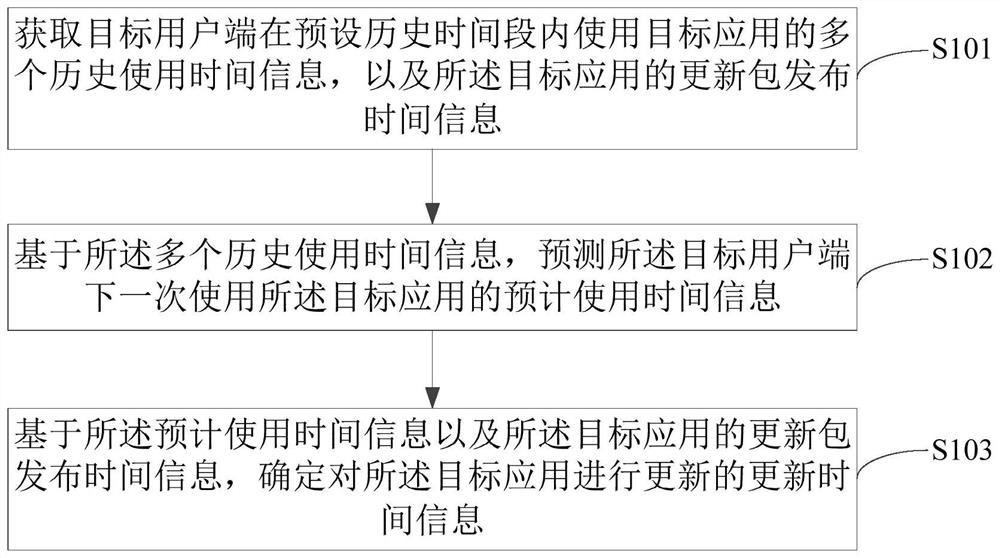
Application updating method and device, computer equipment and storage medium
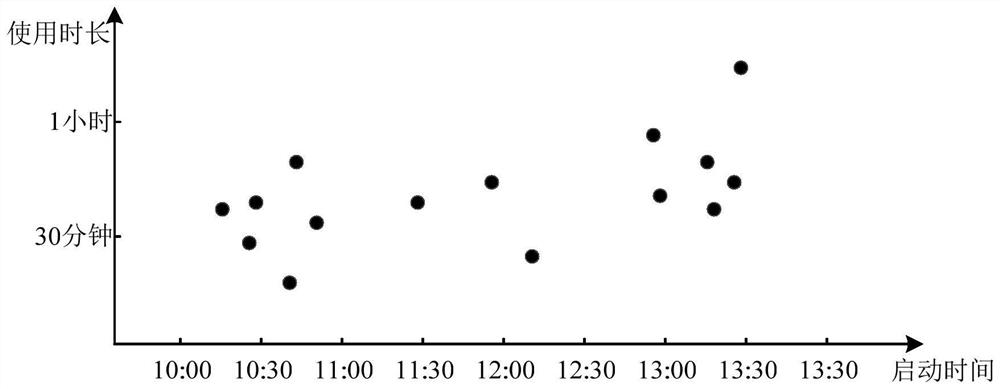
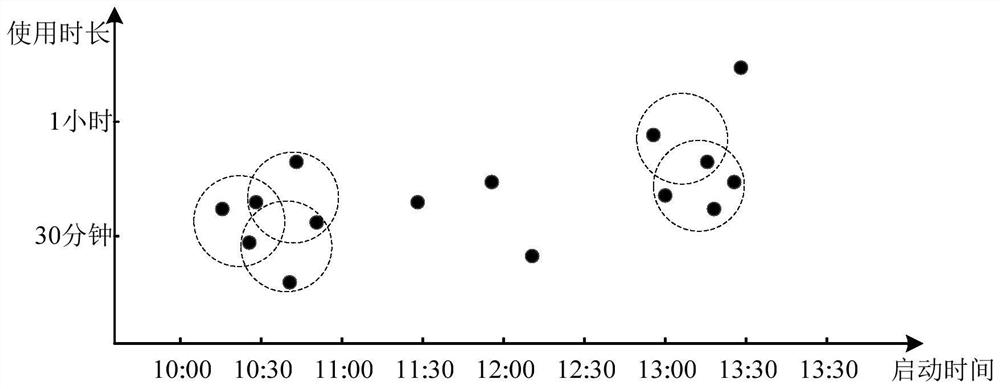
PendingCN114579157AReduce updateGood application serviceCharacter and pattern recognitionSoftware deploymentUse of timeComputer equipment
The invention provides an application updating method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining multiple pieces of historical use time information of using a target application by a target user side in a preset historical time period, and obtaining update package release time information of the target application; predicting predicted use time information of using the target application next time by the target user side based on the plurality of pieces of historical use time information; and determining update time information for updating the target application based on the predicted use time information and the update package release time information of the target application. According to the embodiment of the invention, the use rule of each target application and the update package release time rule are combined, so that not only can unnecessary update be reduced, but also the target user side can be effectively ensured to be in the latest version when using each target application, and better application service can be provided for a user.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Router-based express delivery method and system
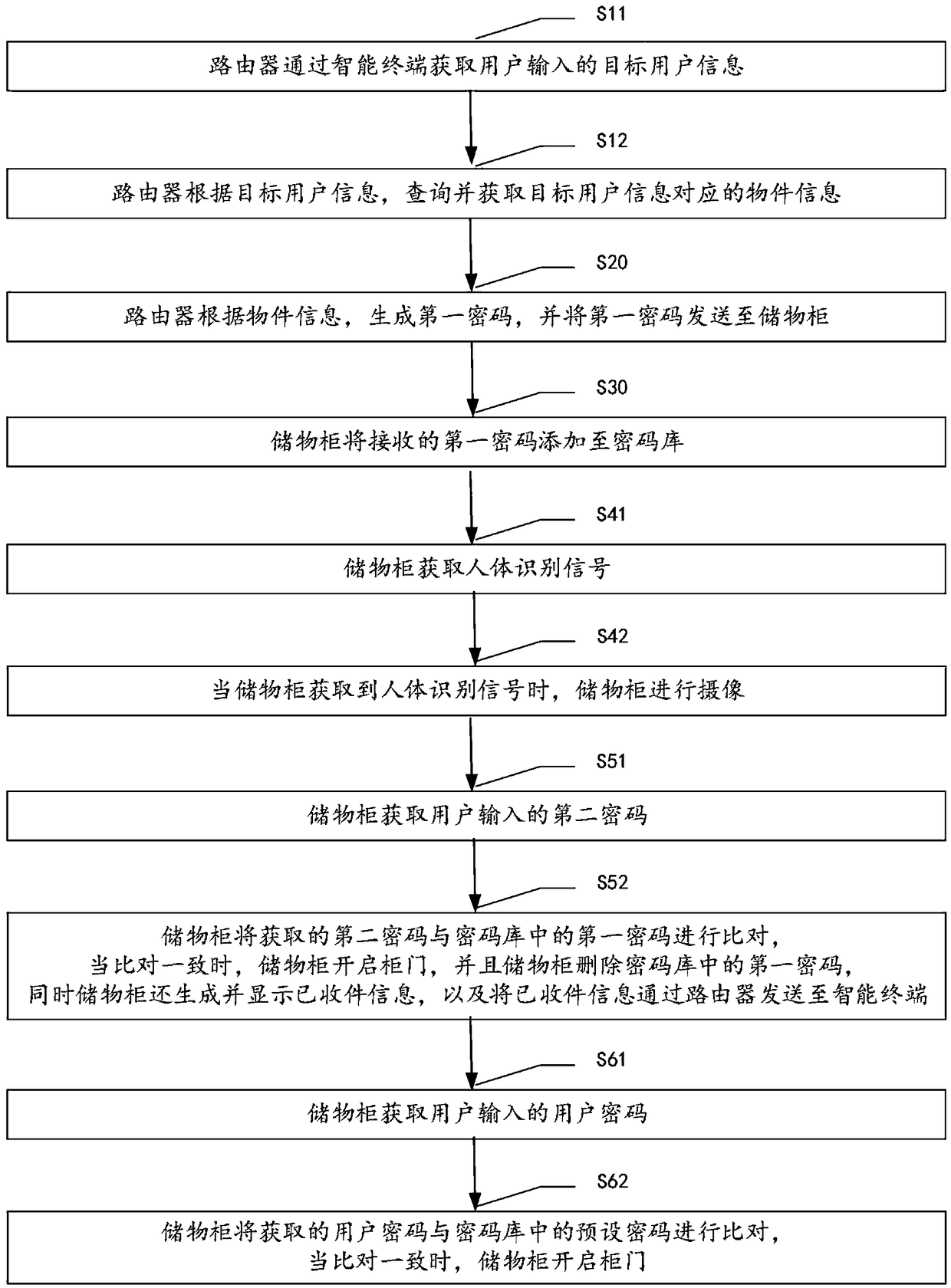
InactiveCN108648365AEasy to manageReduce deliveryApparatus for meter-controlled dispensingIndividual entry/exit registersPasswordUser input
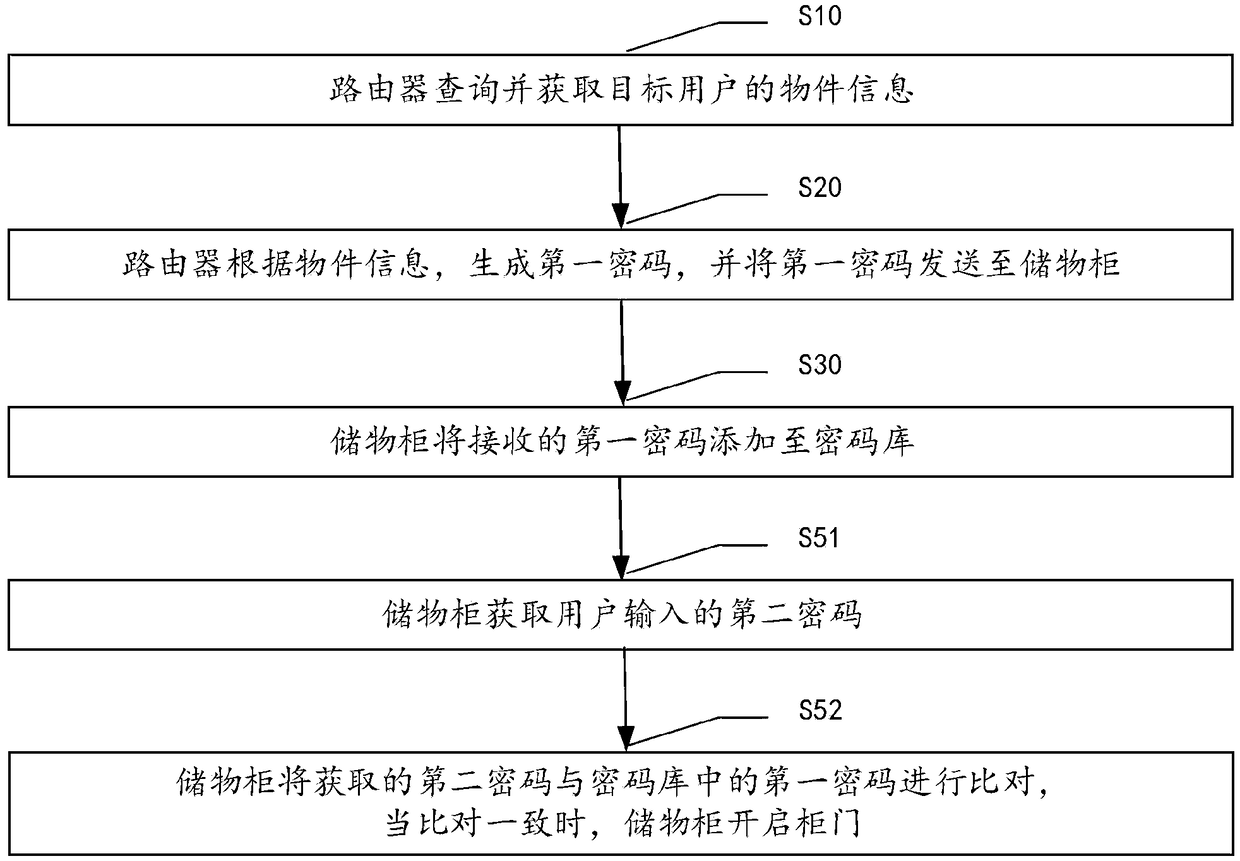
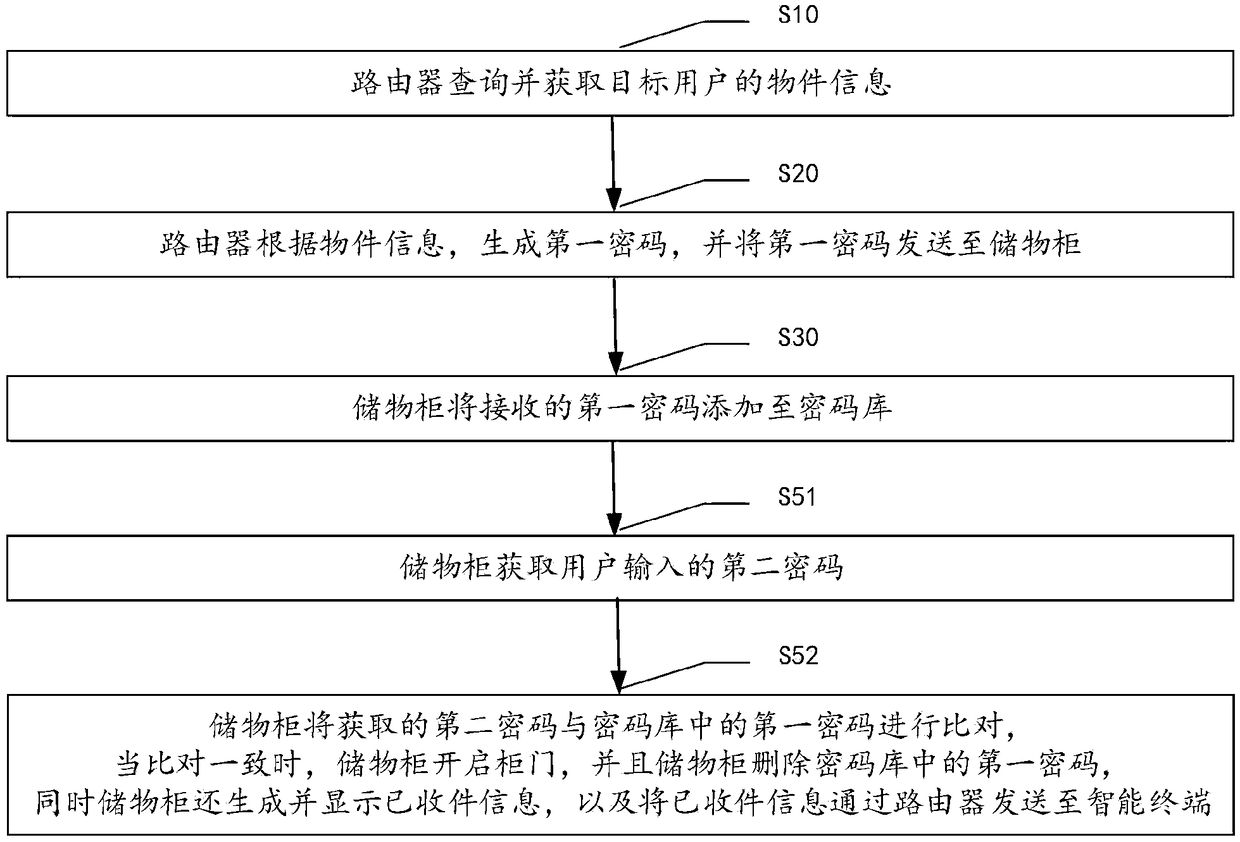
The invention provides a router-based express delivery method and system. The method includes the steps that step S10, a router queries and acquires object information of a target user; step S20, therouter generates a first password according to the object information, and sends the first password to a storage cabinet; step S30, the storage cabinet adds the received first password to a password library; step S51, the storage cabinet acquires a second password input by a user; step S52, the second password obtained by the storage cabinet is compared with the first password in the password library, and when the comparison is consistent, a cabinet door of the storage cabinet is opened. The system comprises an integrated information inquiry module, a password generation module, the router ofa first communication module, an integrated second communication module, a password addition module, a password acquisition module, a password comparison module and the storage cabinet of a cabinet door opening module. The method achieves the intelligent management of an express delivery cabinet by using an express delivery number as a dynamic password for opening the express delivery cabinet.
Owner:SICHUAN FEIXUN INFORMATION TECH CO LTD
Task execution method of robot, control equipment, robot and storage medium
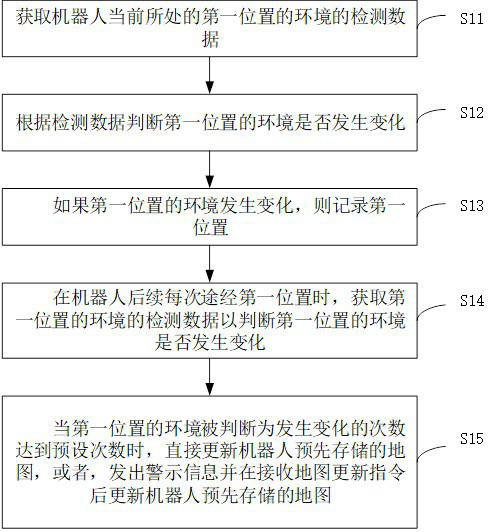
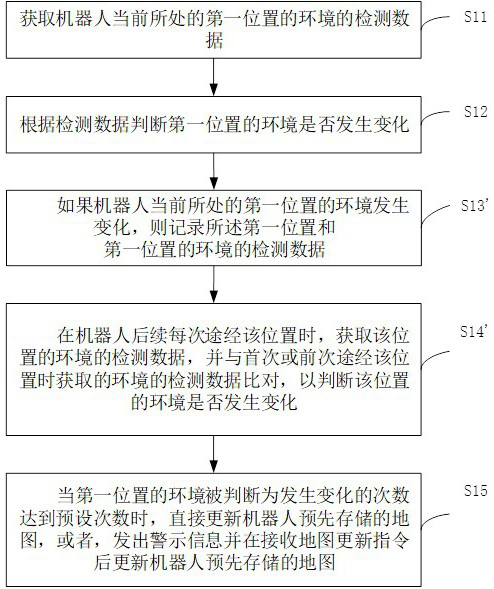
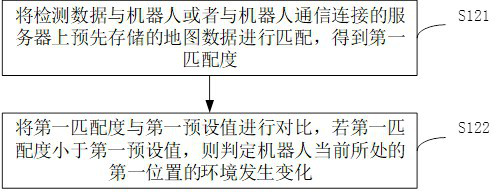
ActiveCN112198882AAvoid frequent updatesEasy to confirm manuallyDigital data information retrievalSpecial data processing applicationsSimulationIndustrial engineering
The invention relates to a task execution method of a robot, control equipment, the robot and a storage medium. The task execution method comprises the steps of: acquiring detection data of an environment of a first position where the robot is located currently; judging whether the environment of the first position is changed or not according to the detection data; if the environment of the firstposition changes, recording the first position; when the robot subsequently passes through the first position every time, acquiring detection data of the environment of the first position to judge whether the environment of the first position is changed or not; and directly updating a map pre-stored by the robot when the environment of the first position is judged to be changed for a preset numberof times, or sending warning information and updating the map pre-stored by the robot after receiving a map updating instruction. The problems of inaccurate positioning and path planning incapabilitydue to untimely map updating can be solved, the condition of temporary environment change is eliminated, and a reliable basis is provided for deciding whether the map needs to be updated or not.
Owner:SUZHOU USTAR ROBOT CO LTD
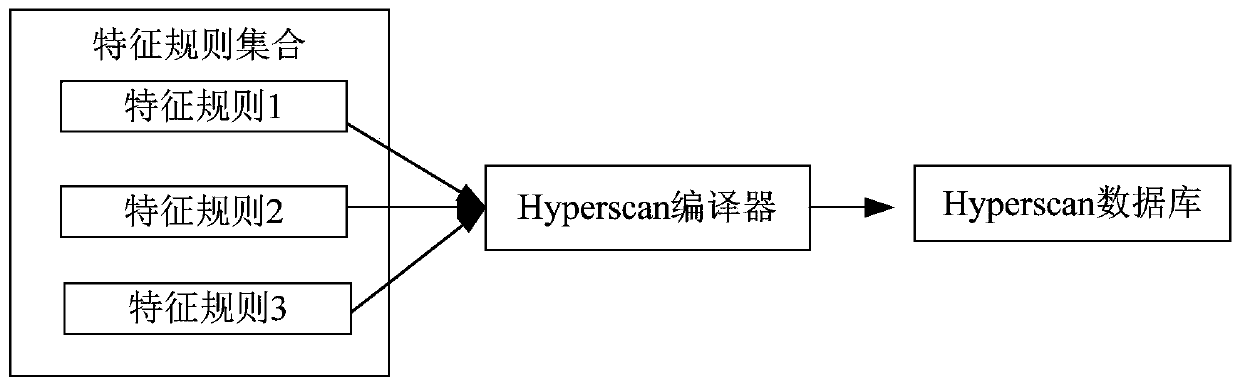
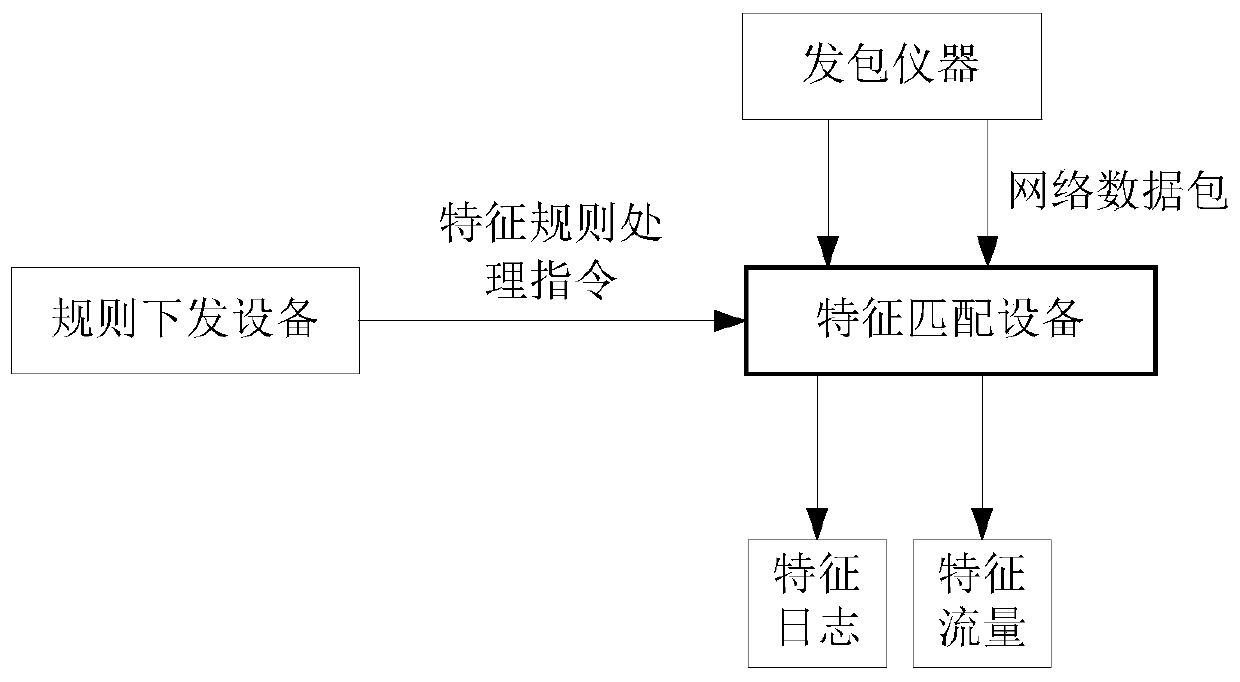
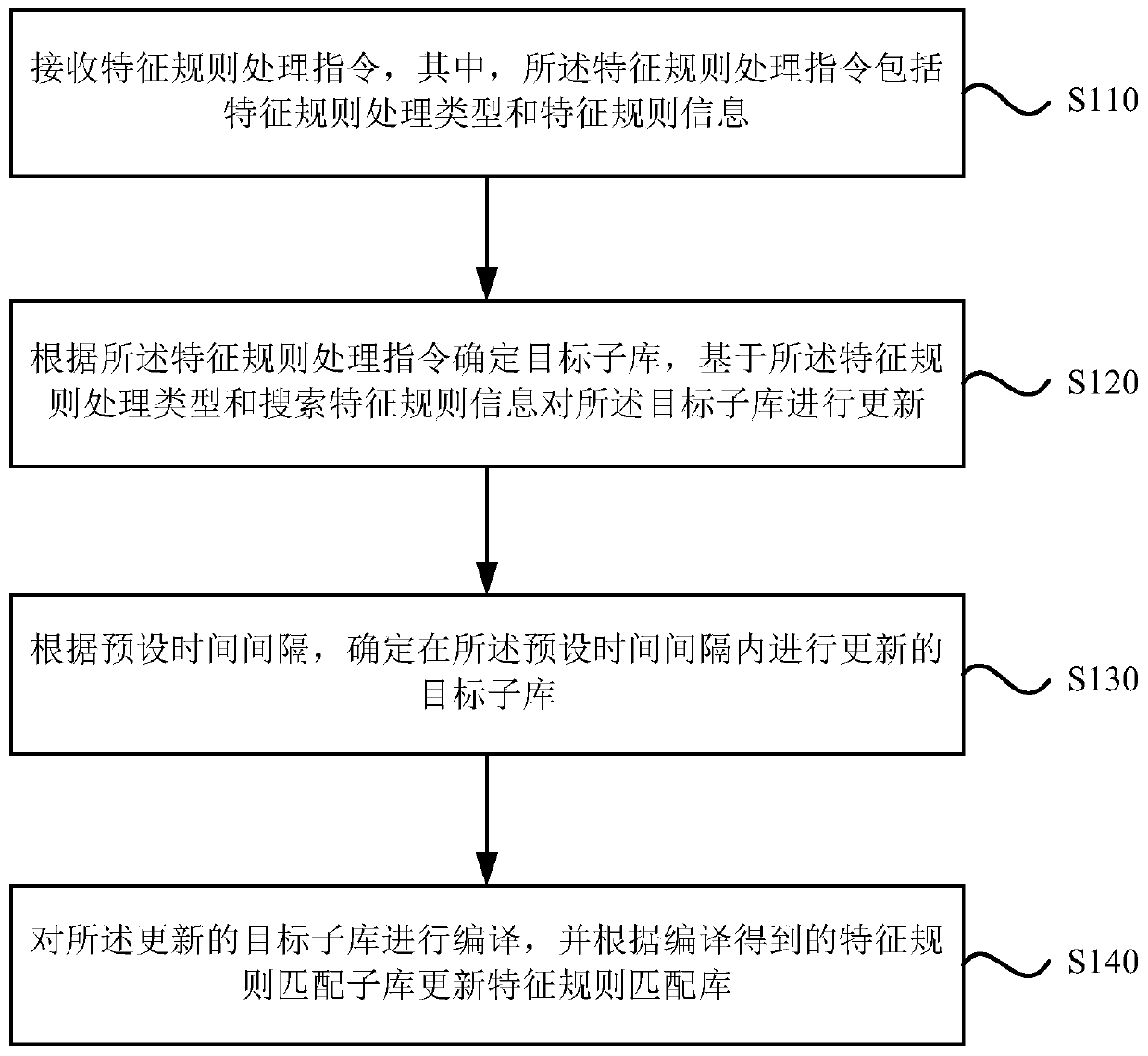
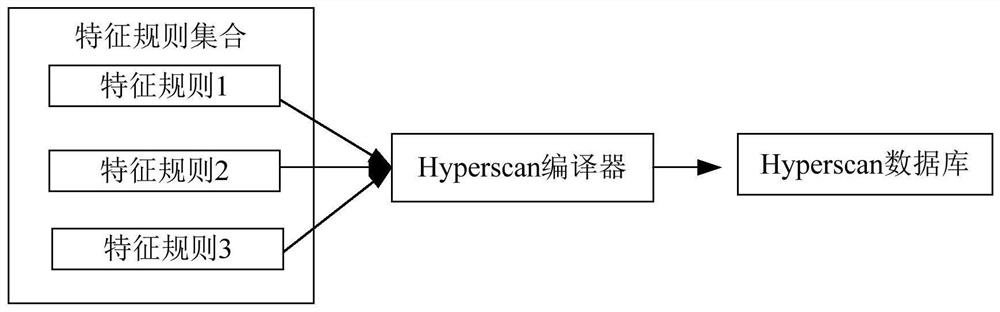
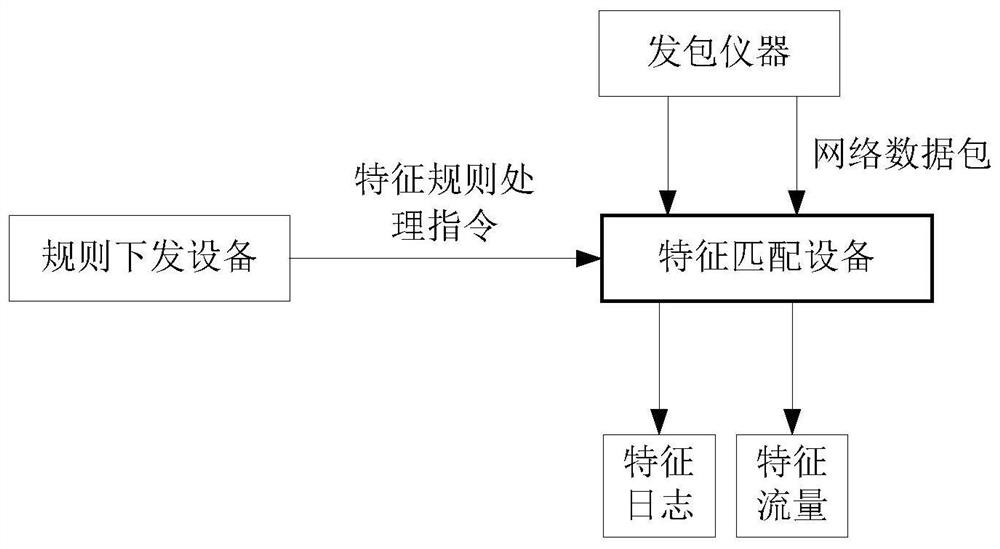
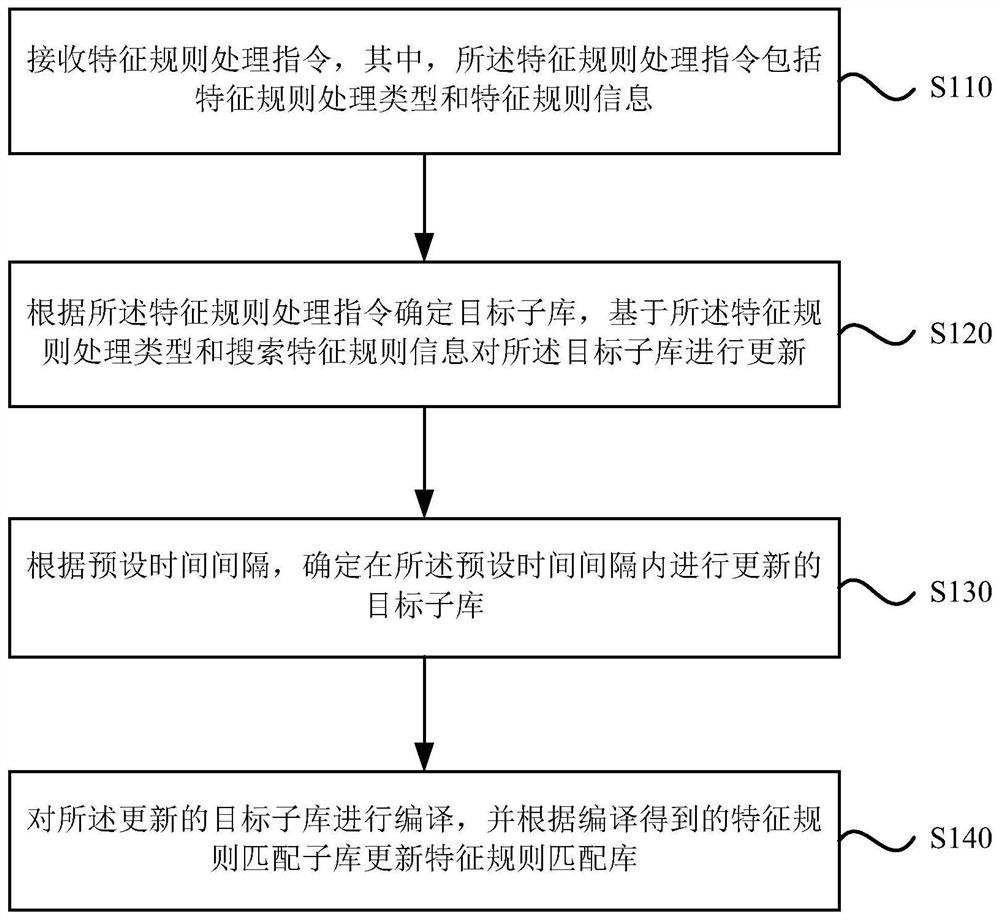
Feature rule matching library updating method, device, storage medium and electronic equipment
ActiveCN110716946AReduce capacityCompile fastDatabase updatingSpecial data processing applicationsProgramming languageDatabase
The invention discloses a feature rule matching library updating method, a feature rule matching library updating device, a storage medium and electronic equipment. The method comprises the followingsteps: receiving a feature rule processing instruction which comprises a feature rule processing type and feature rule information; determining a target sub-library according to the feature rule processing instruction, and updating the target sub-library based on the feature rule processing type and the feature rule information; determining a target sub-library updated in a preset time interval according to the preset time interval; and compiling the updated target sub-library, and updating a feature rule matching library according to the compiled feature rule matching sub-library. The space for storing the feature rules is divided into the multiple independent sub-libraries, the sub-libraries are small in capacity and high in compiling speed, the sub-libraries are independent of one another and can be compiled in parallel, compiling time is shortened, compiling efficiency of the feature rule matching library is improved, and compiling real-time performance of the feature rule matchinglibrary is improved.
Owner:RUN TECH CO LTD BEIJING
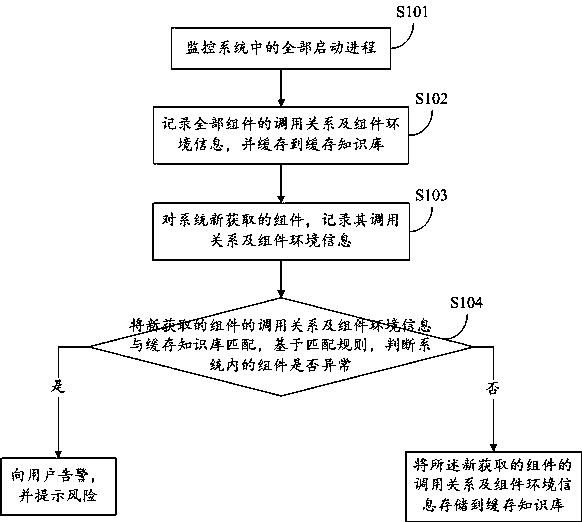
APT heuristic detection method and system based on abnormal component association
InactiveCN108073809AIncrease attack costReduce concealmentPlatform integrity maintainanceSoftware engineeringMatch rule
The invention provides an APT heuristic detection method and system based on abnormal component association. The method includes the steps of monitoring all startup processes in the system; recordingcall relations and component environment information of all components and buffering the call relations and the component environment information into a cache knowledge base; recording call relationsand component environment information of components newly acquired by the system; matching the call relations and the component environment information of the newly-acquired components with the cacheknowledge base, and determining whether the components in the system are abnormal based on matching rules; if yes, making an alarm to users and performing risk prompting, or else storing the call relations and the component environment information of the newly-acquired components into the cache knowledge base. The invention further provides a corresponding system and a storage medium. Through themethod, detect modularization, engineering, high concealment and complex APT attacks can be effectively detected.
Owner:HARBIN ANTIY TECH
Adaptive Clustering Algorithm Based on Density Estimation for Coexistence of 1-hop and 2-hop Clusters in Vanets
ActiveCN107454649BGuaranteed reasonablenessAvoid frequent updatesNetwork topologiesTransmissionCluster algorithmPacket loss
The invention discloses a 1-hop and 2-hop clusters coexistent adaptive clustering method based on density estimation in VANETs. The method comprises the following steps: estimating the 1-hop neighbor node density in the future time, as the formula, based on the current position and current speed of a node, comparing the 1-hop neighbor node density with a threshold, and judging whether the node is suitable to form the 1-hop cluster or the 2-hop cluster, and initializing the node as a cluster head node; in each cluster, selecting a node with the minimum relative mobility, that is the formula is the minimum, as a cluster head, reducing other nodes in the cluster to cluster members, and if there are two or multiple nodes with the minimum relative mobility, then selecting a node with the minimum ID as the cluster head; and performing post maintenance of a cluster structure based on the possible situations in the network. A clustering algorithm disclosed by the invention has the advantages of being low in delay and low in packet loss.
Owner:XI AN JIAOTONG UNIV
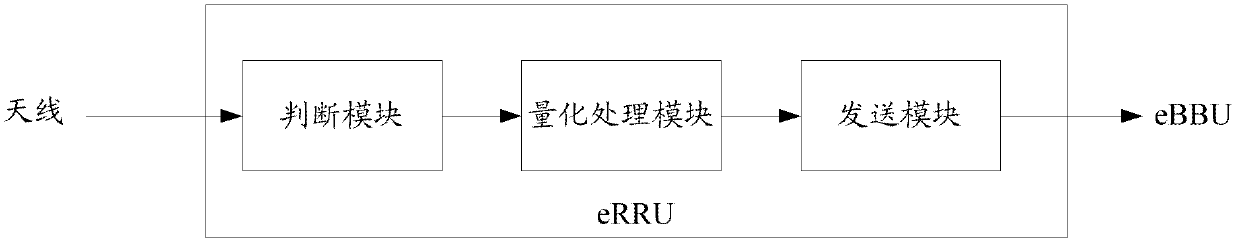
Same-phase IQ(In-phase Quadrate) data compression method and device
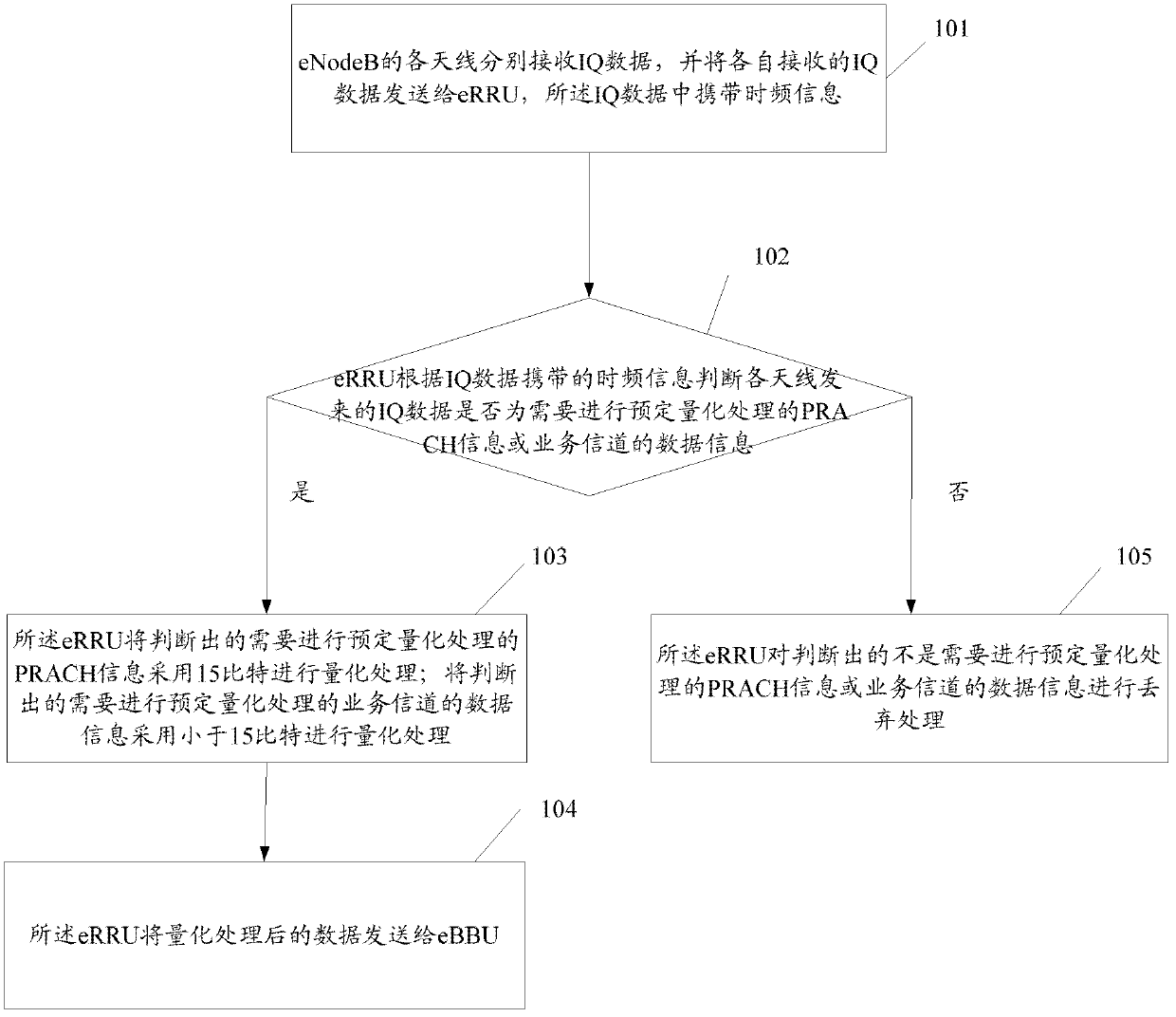
InactiveCN102340823BReduce bit widthReduce rateError preventionNetwork traffic/resource managementData compressionData information
Disclosed is a method for compressing in-phase quadrature (IQ) data, which comprises: an evolved radio remote unit (eRRU), according to time-and-frequency information carried in IQ data sent from each antenna, determining whether the IQ data is physical random access channel (PRACH) information or data information of a service channel that requires predetermined quantization processing; performing quantization processing using 15 bits on the PRACH information that requires predetermined quantization processing, and performing quantization processing using 15 bits on the data information of the service channel that requires predetermined quantization processing; and sending the data after quantization processing to an evolved building baseband unit (eBBU). Also disclosed are an eRRU and an evolved base station (eNodeB). The embodiments of the present invention can reduce the rate of an air interface and avoid frequent replacement of devices.
Owner:ZTE CORP
Method, device, storage medium and electronic device for updating feature rule matching library
ActiveCN110716946BReduce capacityCompile fastDatabase updatingSpecial data processing applicationsSoftware engineeringComputer engineering
The invention discloses a method, device, storage medium and electronic equipment for updating a feature rule matching library, wherein the method includes receiving a feature rule processing instruction, wherein the feature rule processing instruction includes a feature rule processing type and feature rule information; according to the The feature rule processing instruction determines the target sub-library, and updates the target sub-library based on the feature rule processing type and the feature rule information; according to a preset time interval, determines the target to be updated within the preset time interval A sub-library: compiling the updated target sub-library, and updating the feature rule matching library according to the compiled feature rule matching sub-library. By dividing the space for storing feature rules into multiple independent sub-libraries, the capacity of the sub-libraries is small, the compilation speed is fast, and each sub-library is independent of each other, and can be compiled in parallel, which reduces the compilation time and improves the feature rule matching library. The compilation efficiency is improved, and the real-time performance of feature rule matching library compilation is improved.
Owner:RUN TECH CO LTD BEIJING
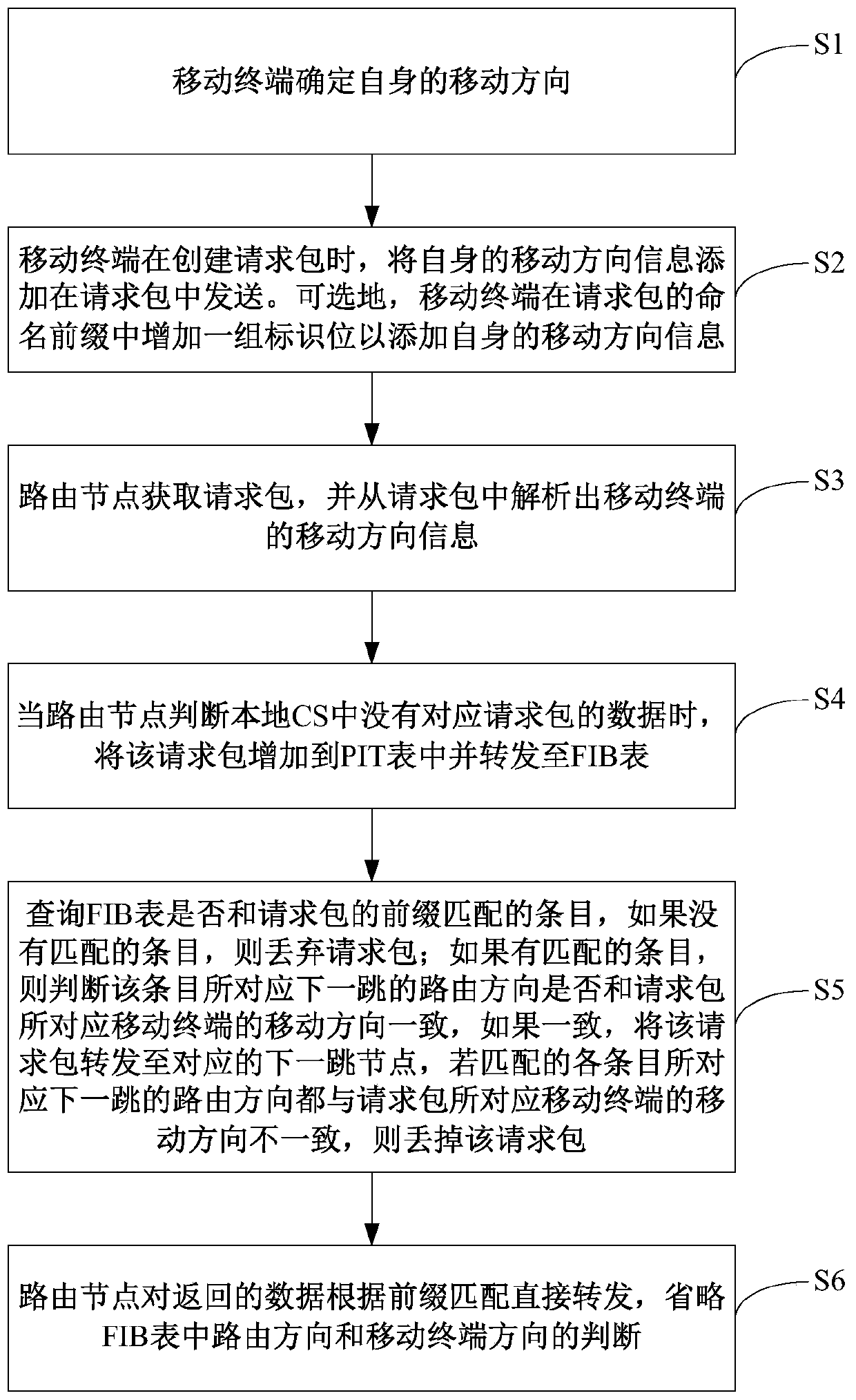
Direction-aware forwarding method, device and system based on NDN network architecture
ActiveCN107040471BReduce the number of retweetsAvoid frequent updatesData switching networksNetwork data managementTelecommunicationsNetwork architecture
The invention relates to the field of communication technologies, and discloses a direction-aware forwarding method, device and system based on an NDN network architecture. The system of the present invention includes: a mobile terminal, which is used to add its own moving direction information to the request packet when creating a request packet; a routing node is used to parse out the moving direction information of the mobile terminal from the request packet; when judging the local CS If there is no data corresponding to the request packet, add the request to the PIT table and forward it to the FIB table; then check whether the FIB table has an entry matching the prefix of the request packet; if there is a matching entry, determine the entry corresponding to the next Whether the routing direction of a hop is consistent with the mobile terminal corresponding to the request packet, if it is consistent, forward the request packet to the corresponding next hop node, if the routing direction of the next hop corresponding to each matching entry is consistent with the request If the moving direction of the mobile terminal corresponding to the packet is inconsistent, the request packet is discarded.
Owner:CENT SOUTH UNIV
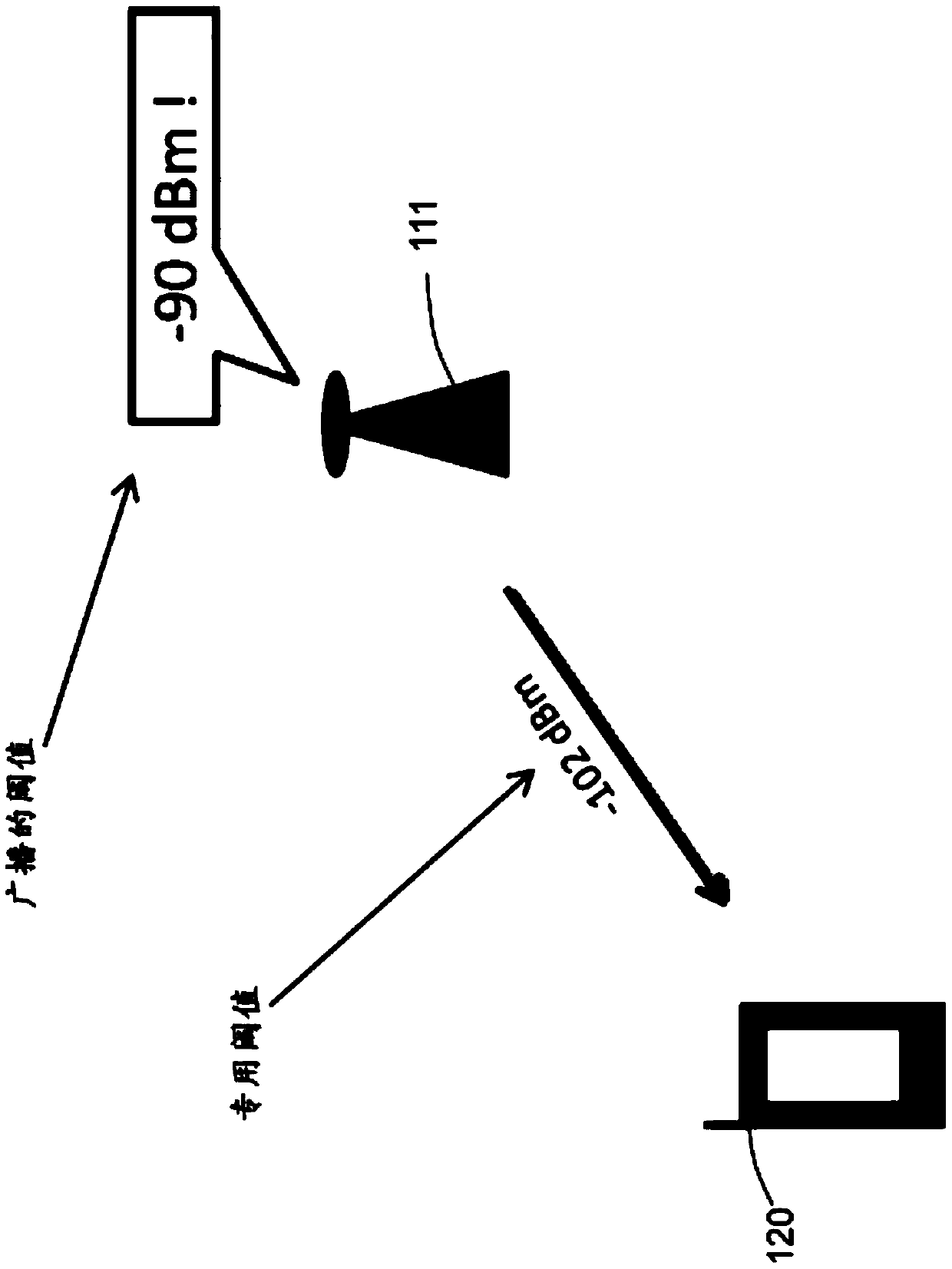
Terminal and method for inter RAT access selection in a communications network
ActiveCN105519199AAvoid frequent updatesAvoid heavily loaded control channelsAssess restrictionBroadcast service distributionSwitched communication networkBroadcasting
Owner:TELEFON AB LM ERICSSON (PUBL)
A new energy vehicle ecu remote program update management system and method
ActiveCN108153562BRealize remote program updateNo need to add additional hardware facilitiesProgram loading/initiatingProgram/content distribution protectionIn vehicleNew energy
Owner:浙江中科正方电子技术有限公司
A method, device and system for renewing keys
ActiveCN102065421BReduce update loadAvoid frequent updatesSecurity arrangementEngineeringComputer science
The embodiment of the present invention discloses a method for renewing a key, which includes the following steps: receiving the guidance service identification from the network application function NAF, and querying whether the root key is within the validity period according to the guidance service identification; if the root key If it is not within the validity period, return an error message to the user equipment through the NAF, and perform a general bootstrap architecture GBA initialization with the user equipment; if the root key is within the validity period, generate a random number, and obtain the root key according to the random number service key, and send the service key, the validity period of the service key, and the random number to the NAF, so that the NAF communicates with the user equipment according to the service key and the random number Perform two-way authentication. The embodiments of the present invention reduce the load of the BSF and the load of the service server. The embodiment of the present invention also discloses a device and a system for applying the above method.
Owner:CHINA MOBILE COMM GRP CO LTD
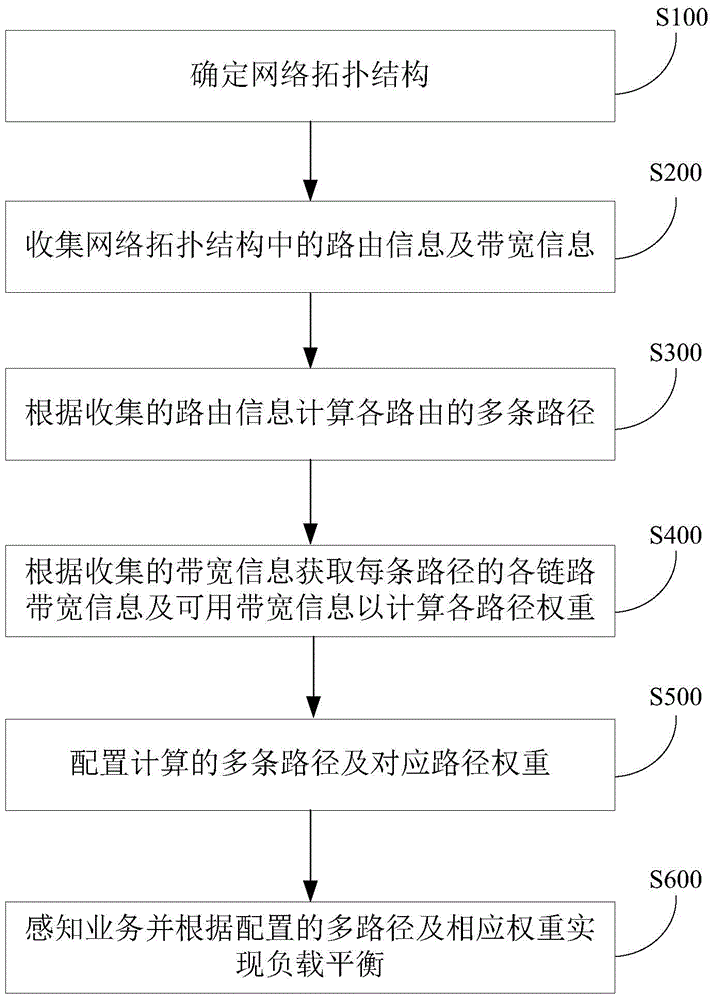
Multi-path load balancing method based on business perception
ActiveCN103685054BAvoid frequent updatesAvoid congestionData switching networksTraffic capacityNetwork topology
The invention provides a multipath load balancing method based on service awareness. The method is used for balancing loads according to path weight and aware service traffic. The load balancing method includes the following steps that a network topology structure is determined; routing information and bandwidth information of the network topology structure are collected; according to the collected routing information, multiple paths of all routes are calculated; according to the collected bandwidth information, all link bandwidth information and available bandwidth information of all the paths are acquired so as to calculate weight of all the paths; the calculated multiple paths and the corresponding path weight are configured; load balance is achieved by the aware service through the configured multiple paths and the corresponding weight. The multipath load balancing method based on service awareness follows up the bandwidth of links so that the multiple paths and the corresponding path weight can be calculated, frequent updating of the routes is avoided, when the loads are balanced, bandwidth allocation is performed according to the weight of all the paths, meanwhile traffic is in awareness, and therefore load balancing is performed according to the aware traffic and the weight of the multiple paths.
Owner:FENGHUO COMM SCI & TECH CO LTD
Laser radar simulation method and device
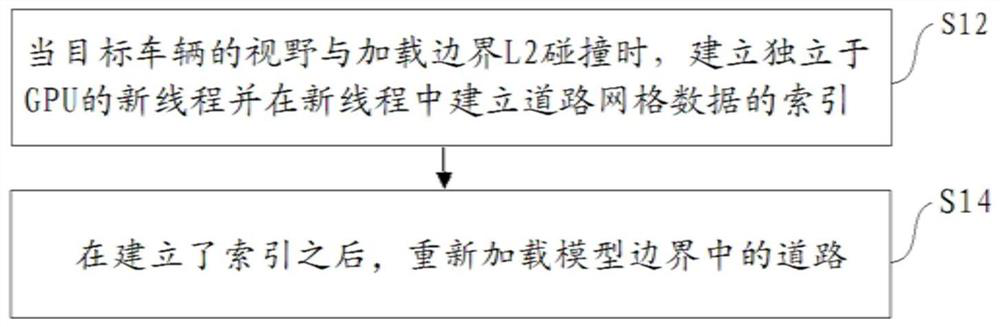
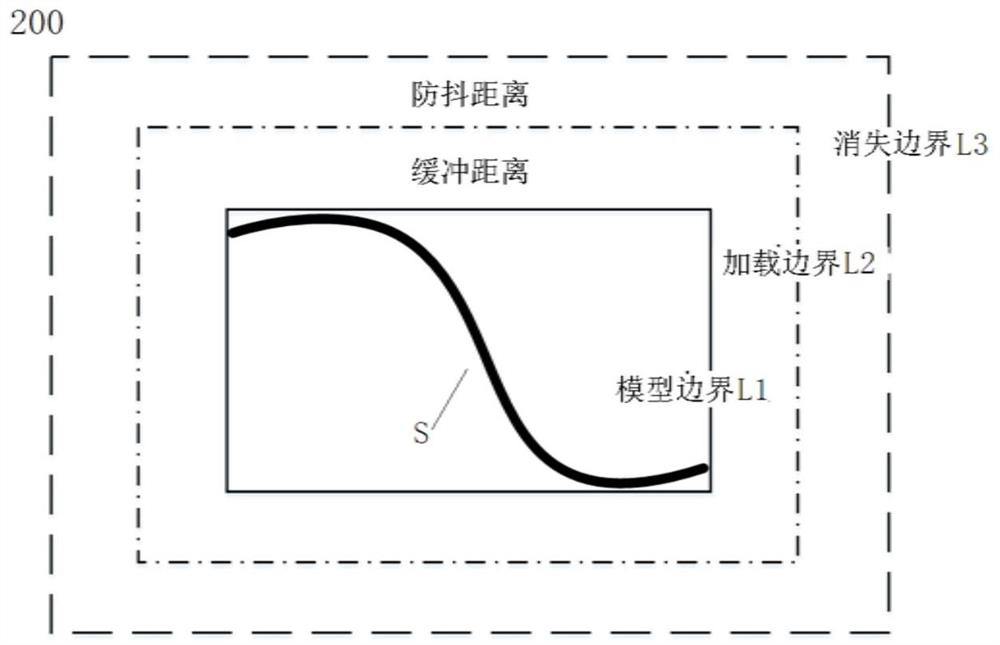
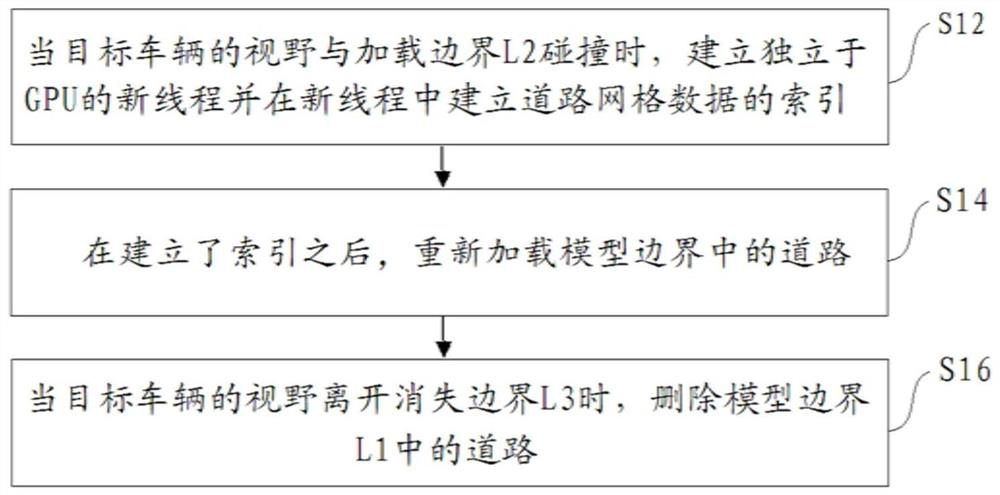
PendingCN111812674AAvoid CatonTake advantage ofElectromagnetic wave reradiationSimulationRoad networks
The invention discloses a laser radar simulation method and device. A road model comprises a model boundary and a loading boundary located outside the model boundary. The laser radar simulation methodcomprises the following steps of: when the field of view of a target vehicle collides with the loading boundary, establishing an index of road grid data, wherein the index is a data structure used for managing grids; and after the index is established, updating the road information in the road model. The road model further comprises a vanishing boundary located outside the loading boundary, and when the field of view of the target vehicle leaves the vanishing boundary, a road in the model boundary is deleted. According to the laser radar simulation method and the device, the jamming phenomenon of the laser radar during road updating can be avoided at least; and the situation of frequent road updating can be avoided by increasing the disappearance boundary.
Owner:BEIJING JINGWEI HIRAIN TECH CO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com