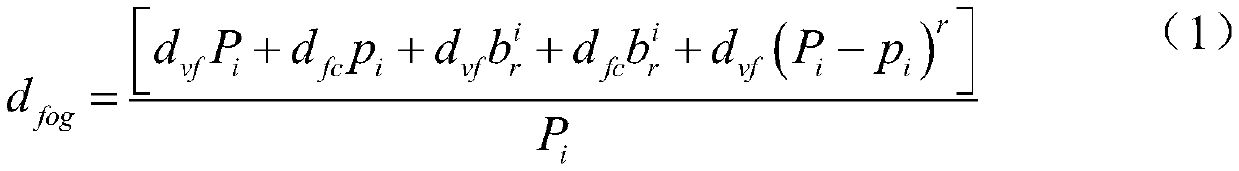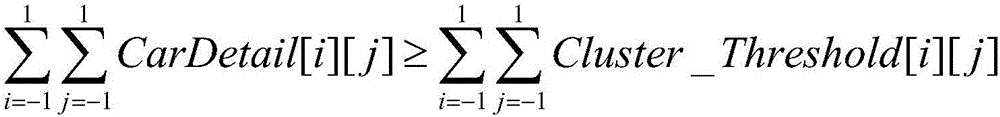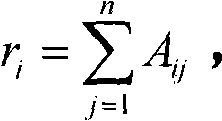Patents
Literature
142 results about "Dependable computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
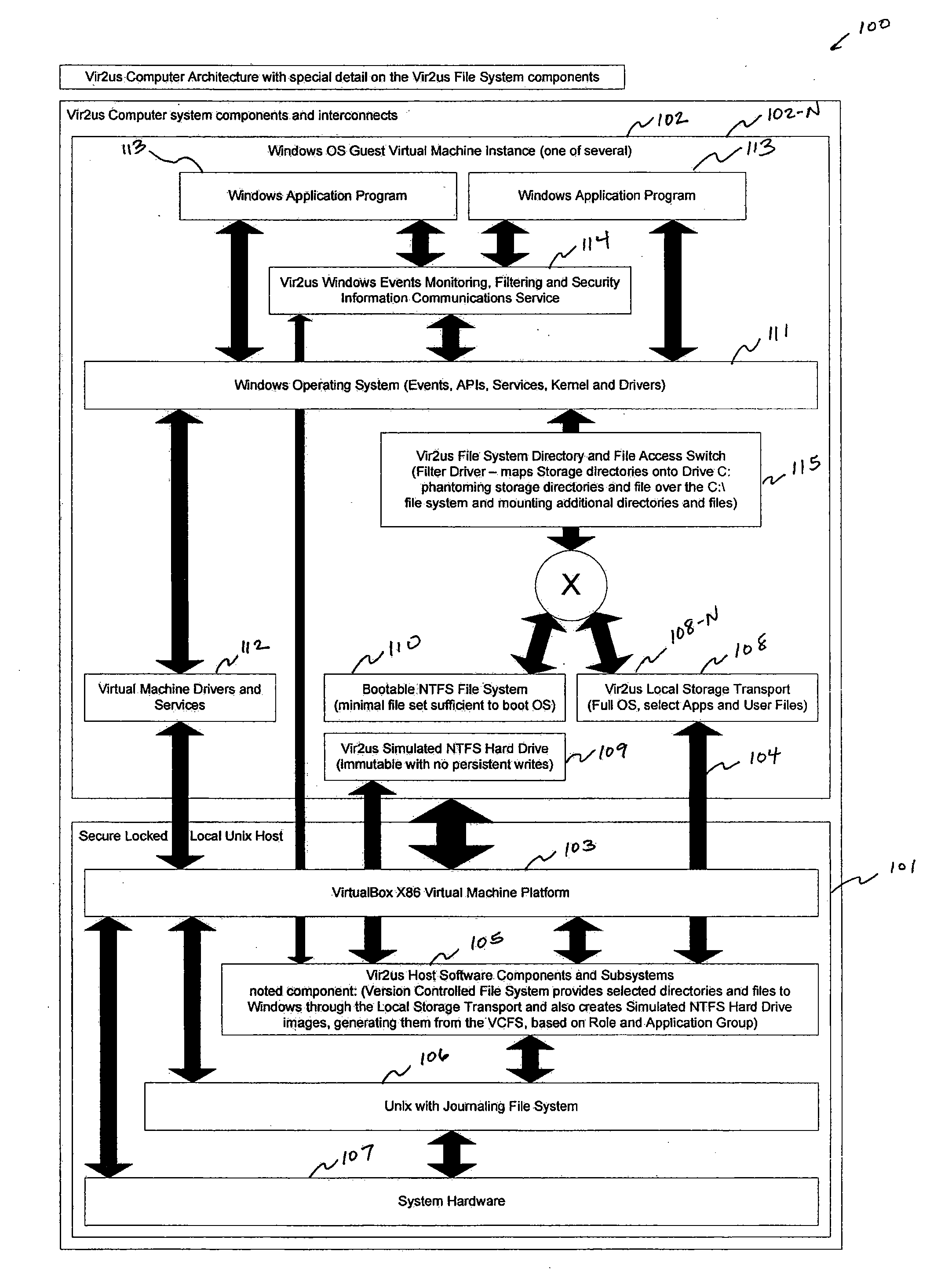
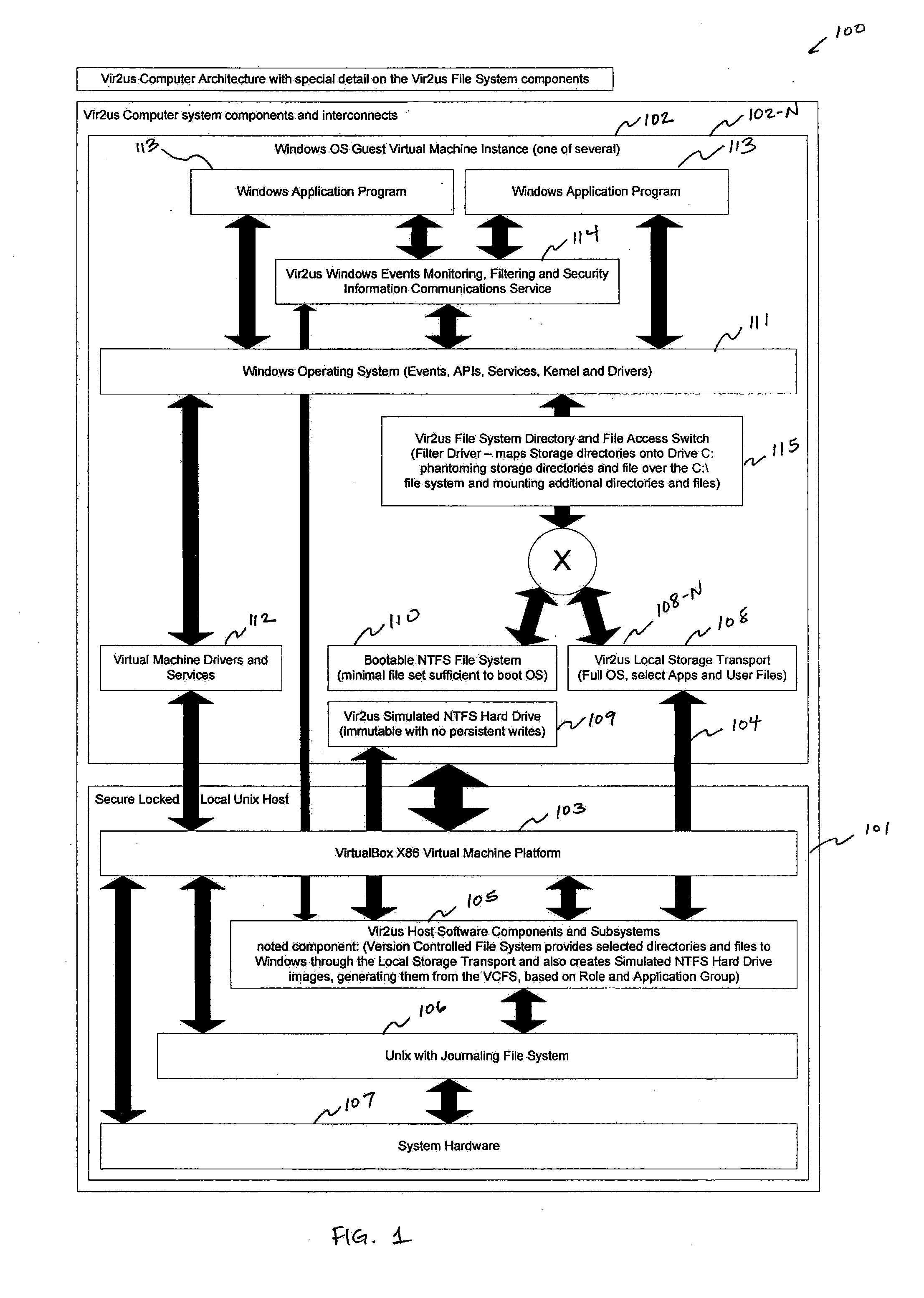
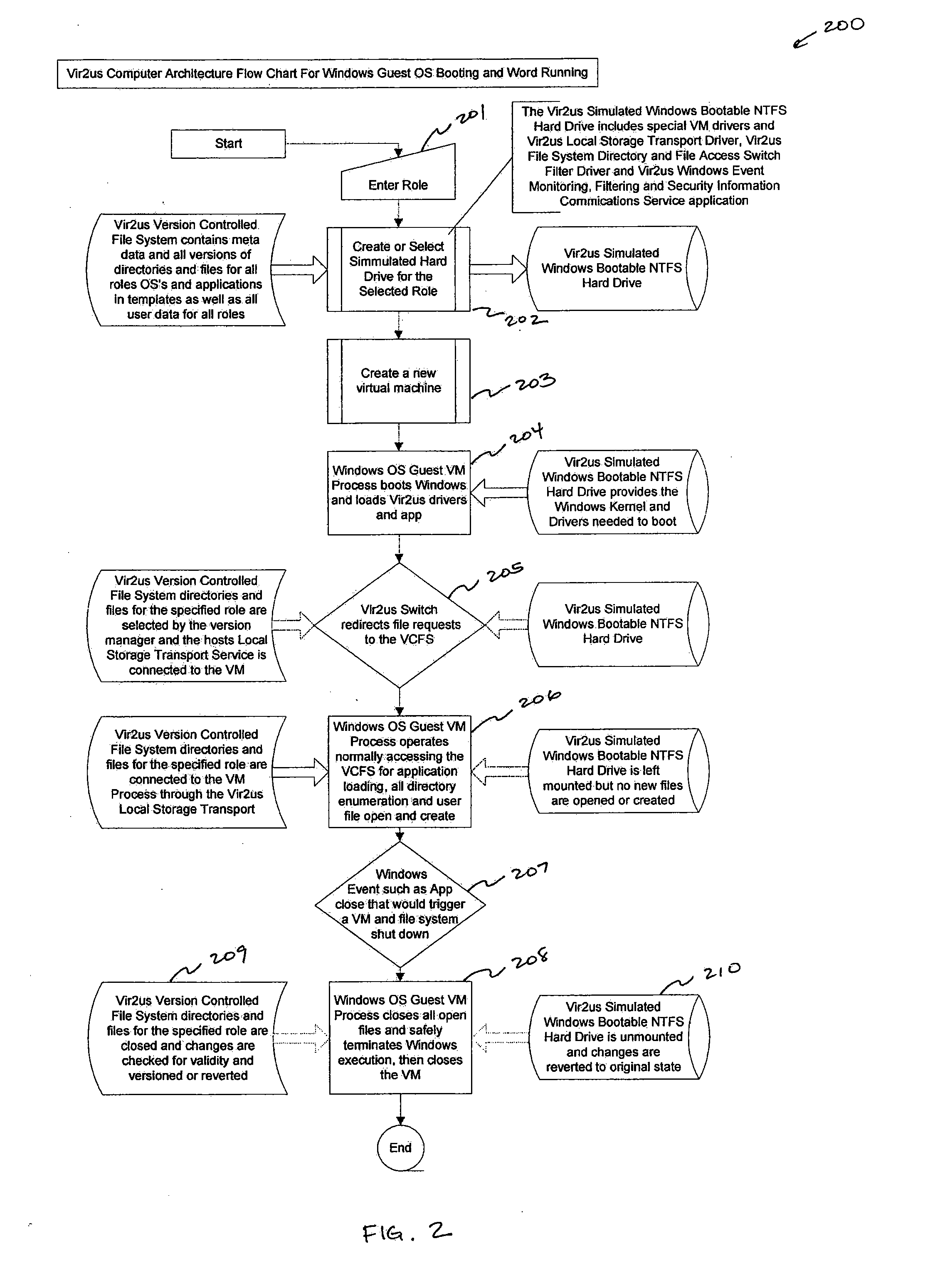
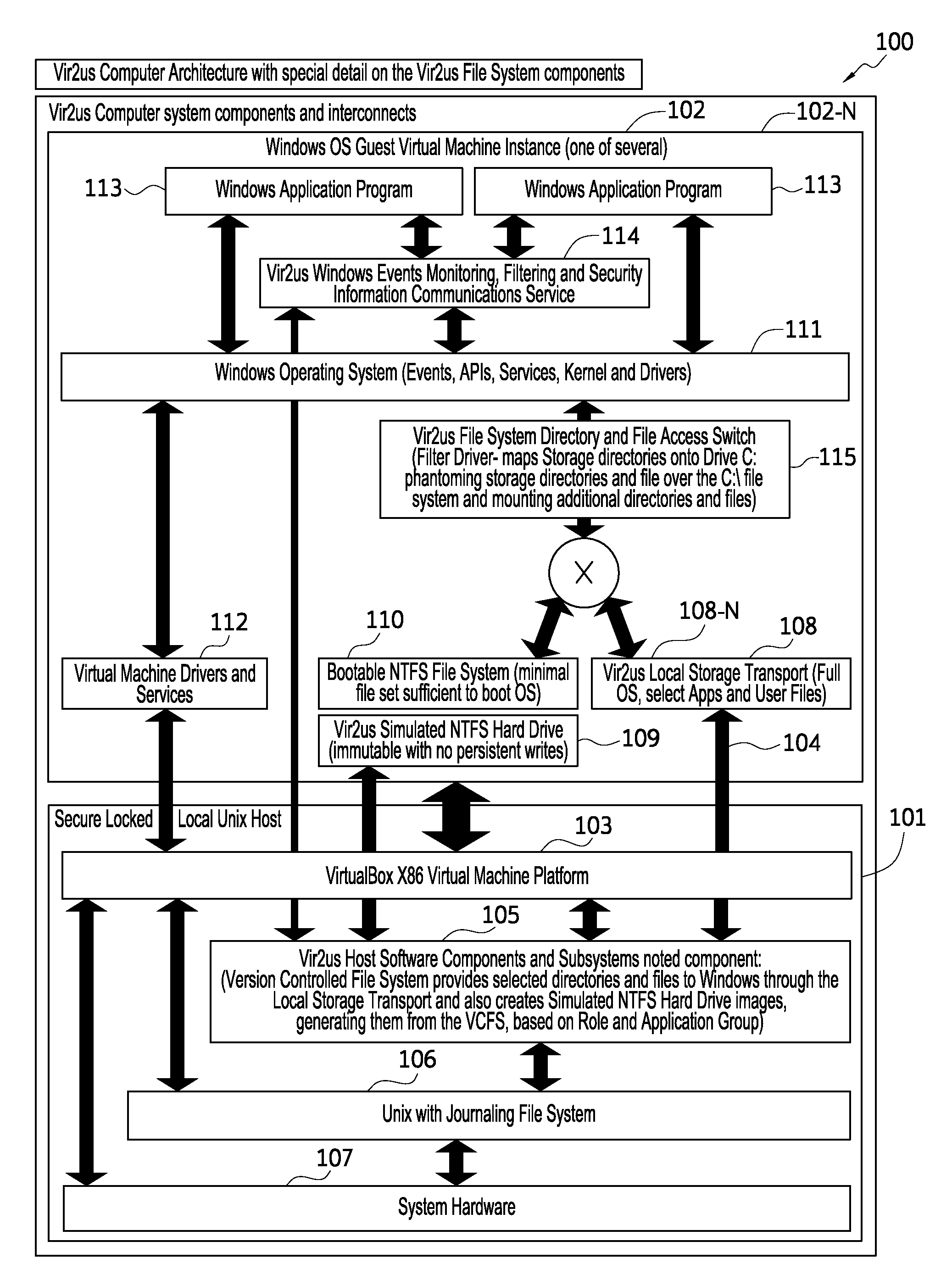
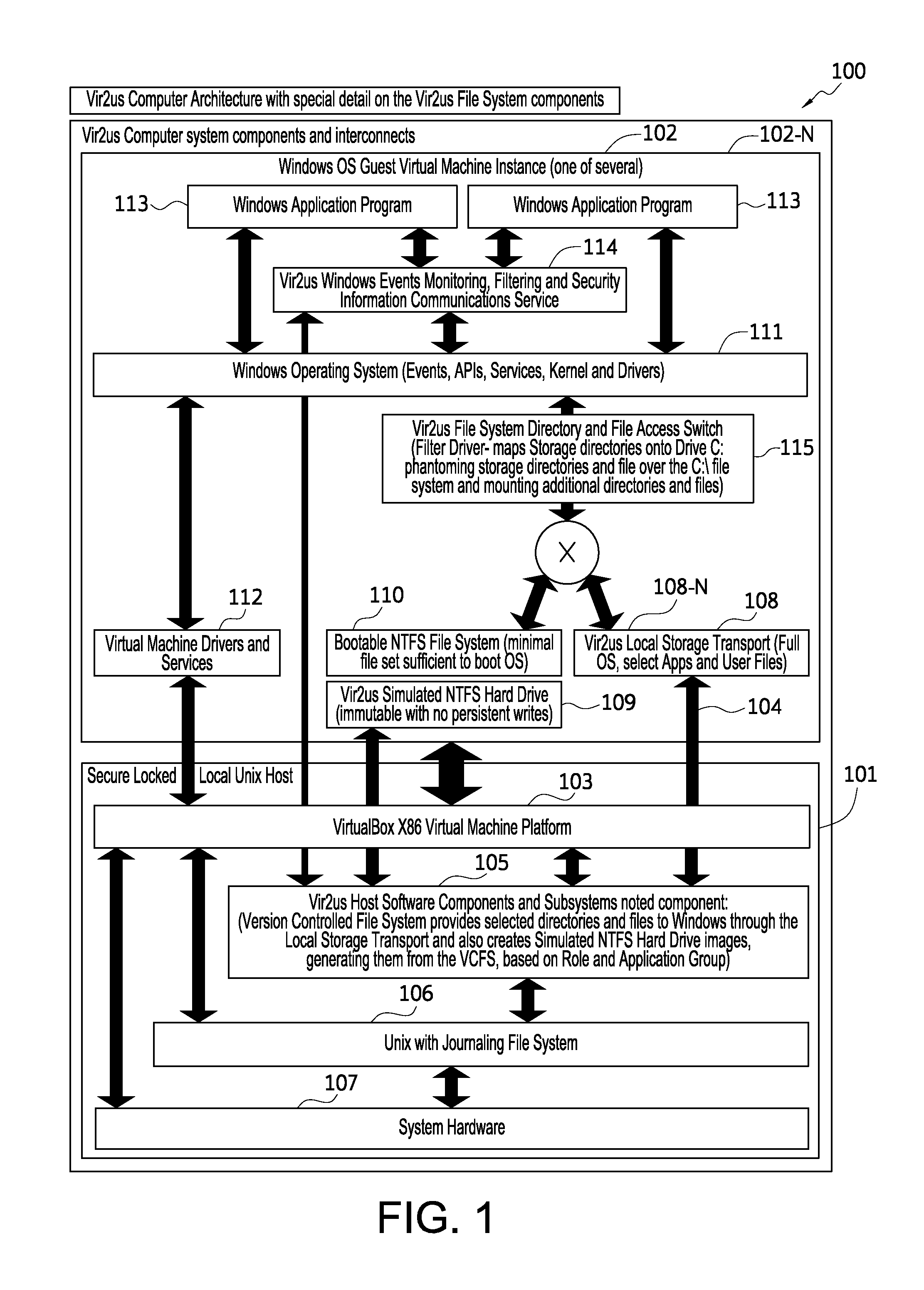
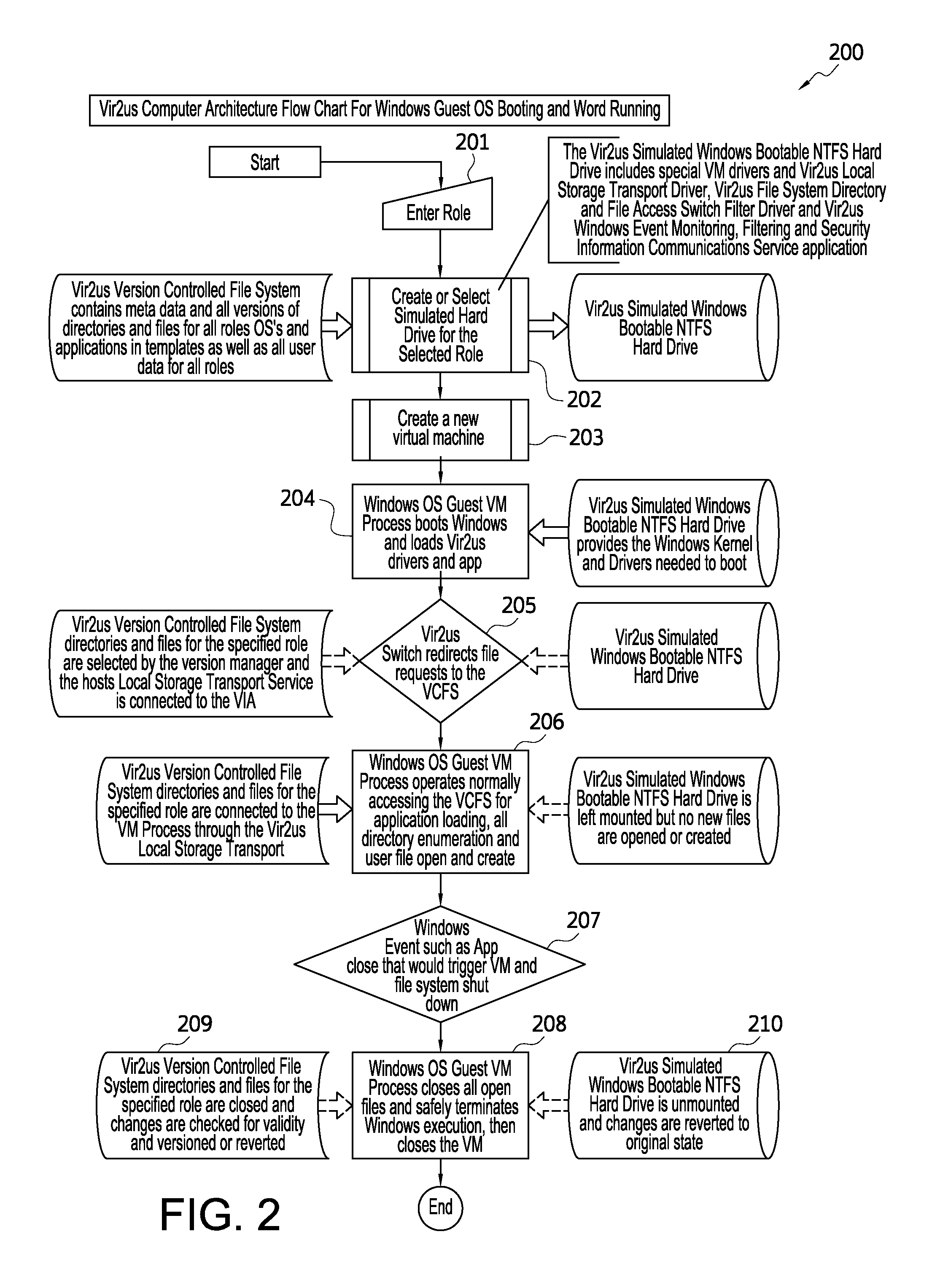
Computer system architecture and method having isolated file system management for secure and reliable data processing
ActiveUS20080184218A1Avoid lostComputer security arrangementsSpecific program execution arrangementsData processing systemReliable computing
System, method, computer, and computer program for secure data processing of potentially malicious code and documents or other data that may contain malicious code. System, method, computer for a secure and reliable computing environment to protect against data loss and / or corruption to provide secure and reliable data processing.
Owner:VIR2US
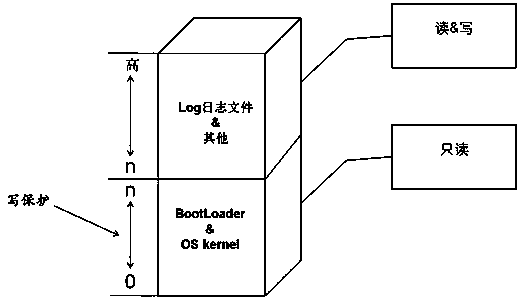
Dependable computing system capable of protecting BIOS and method of use thereof
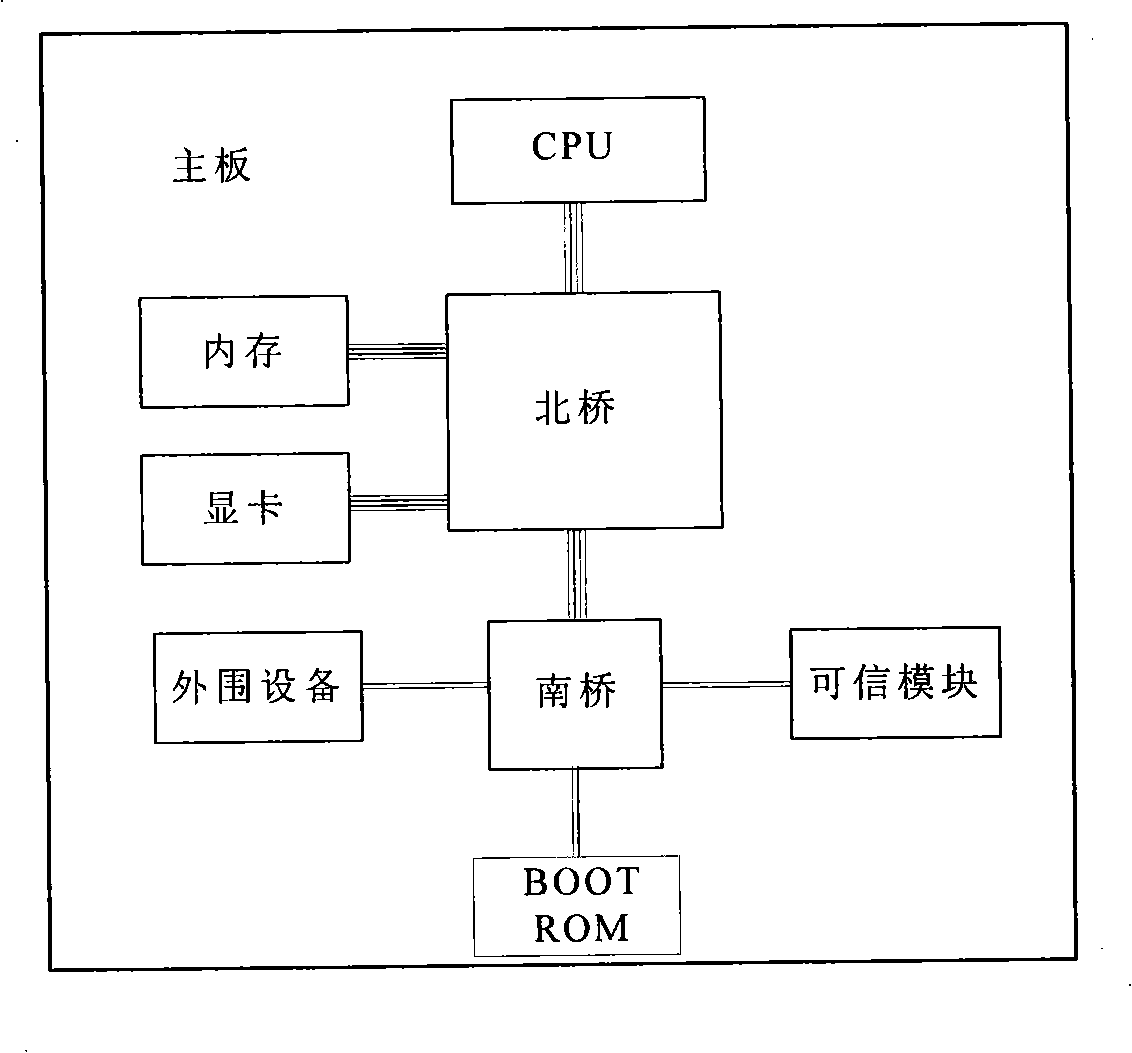
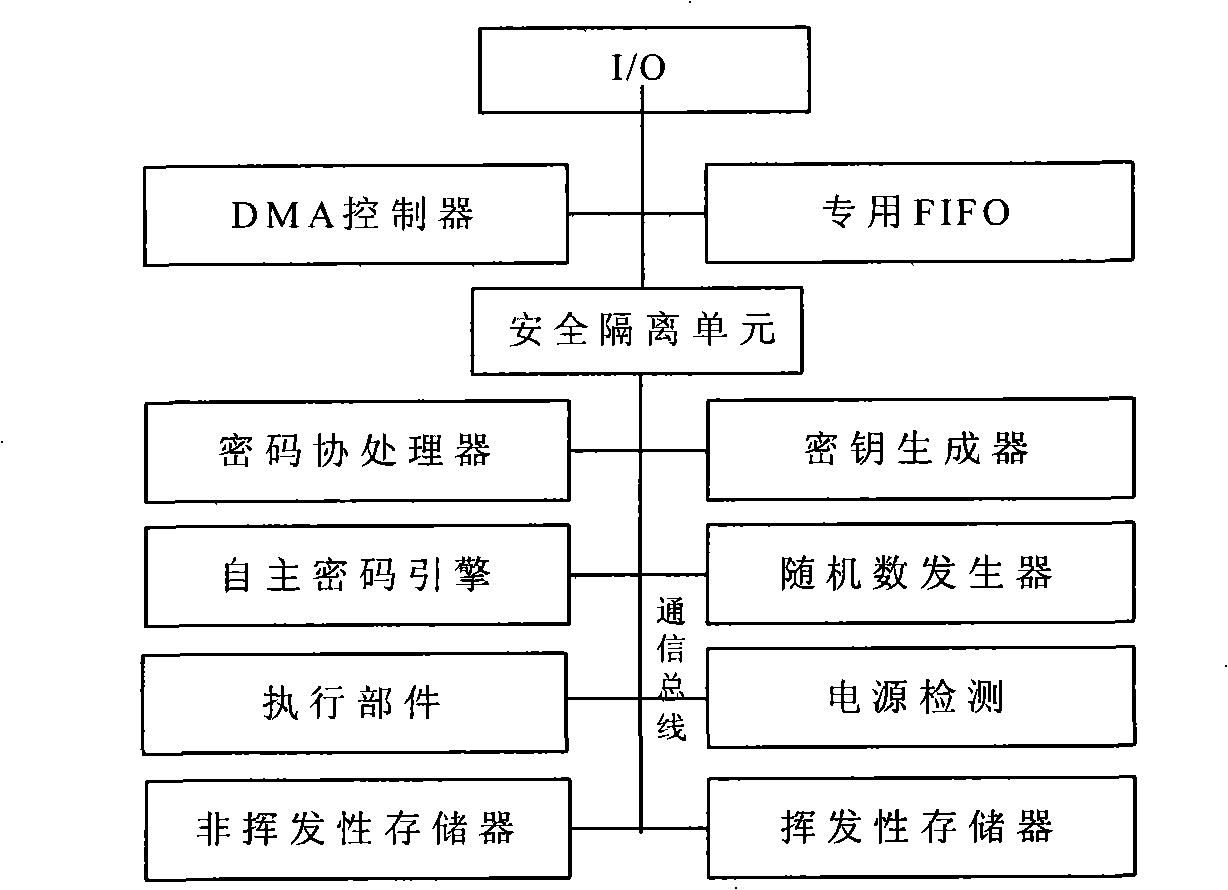
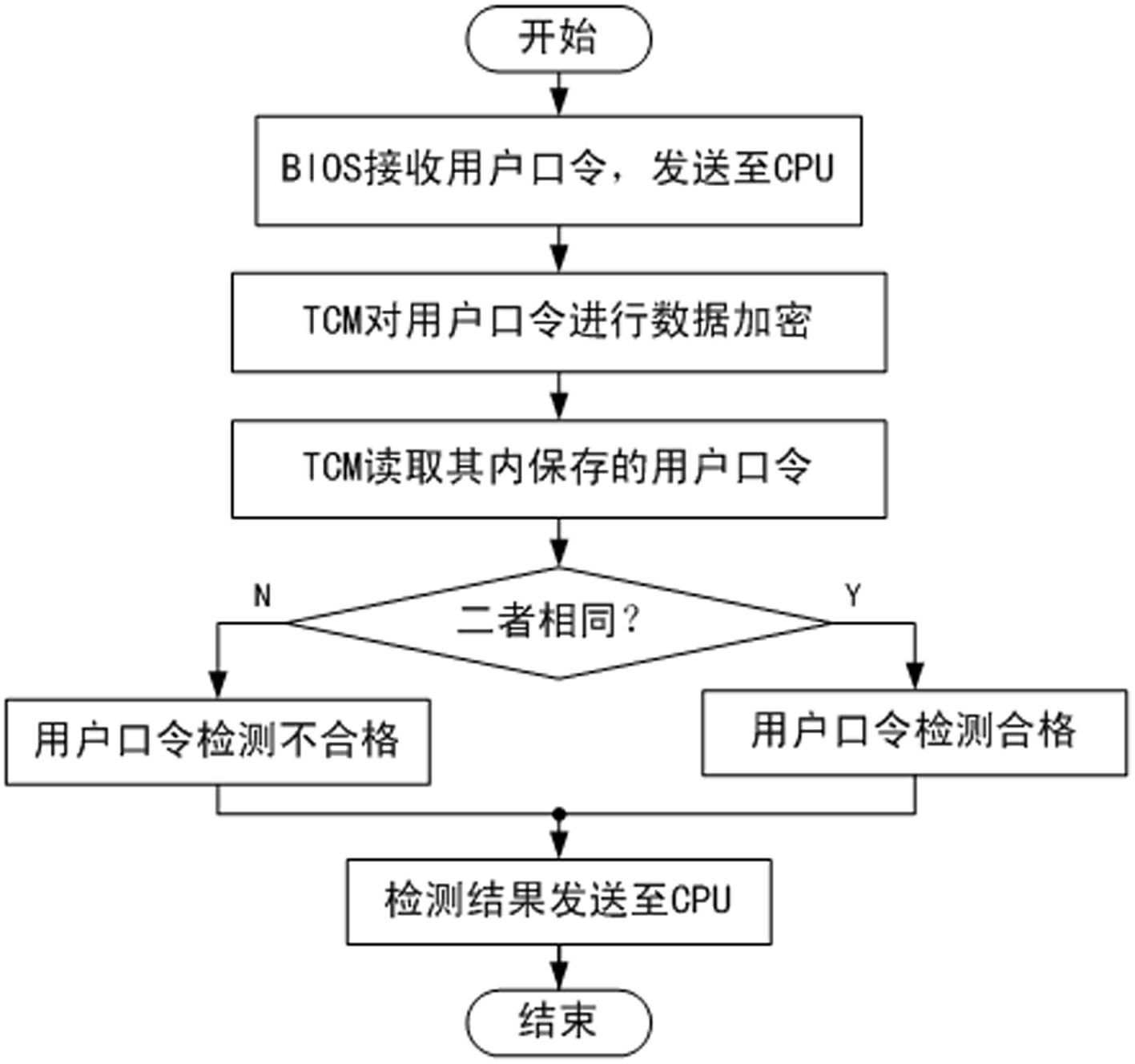
InactiveCN101281577ABuild a Trusted Computing EnvironmentProgram loading/initiatingProgram/content distribution protectionPasswordTrusted Computing
The invention provides a trusted computer system for protecting BIOS and the application method thereof, belonging to the field of information security. The invention is characterized in the physical connective way of a trusted computing module and a BOOT ROM, wherein the trusted computing module is connected to a system mainboard, and the BOOT ROM is connected to the trusted computing module by a communication bus. The trusted computing module comprises a DMA controller, a FIFO unit and a security isolation unit; the DMA controller is used for reading BIOS code to the FIFO unit of the trusted computing module or reading the BIOS code from the FIFO unit to the I / O bus of the trusted computing module; the FIFO unit is used for temporally storing BIOS code to be processed; the security isolation unit is used for preventing vicious procedures outside the trusted computing module from reading confidential information in memory cell inside the trusted computing module. The read / write and update of BIOS code need the identity authentication and password authentication of a current user, ensuring the security of BIOS key code; the equipment access control is realized by hardware method, reaching the effect of active control of mainboard peripheral equipment.
Owner:BEIJING UNIV OF TECH
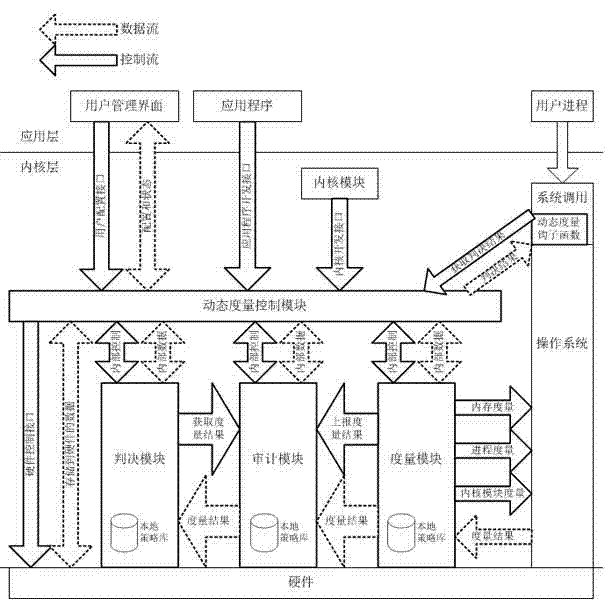
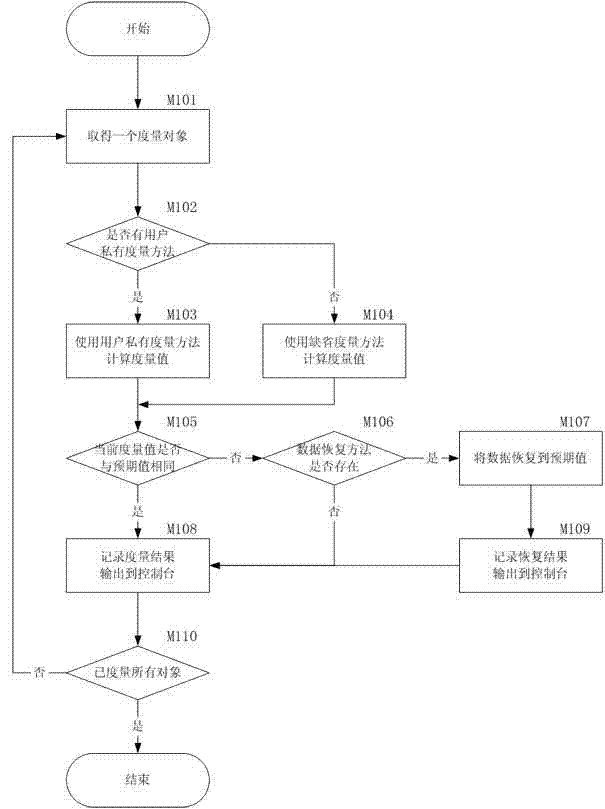
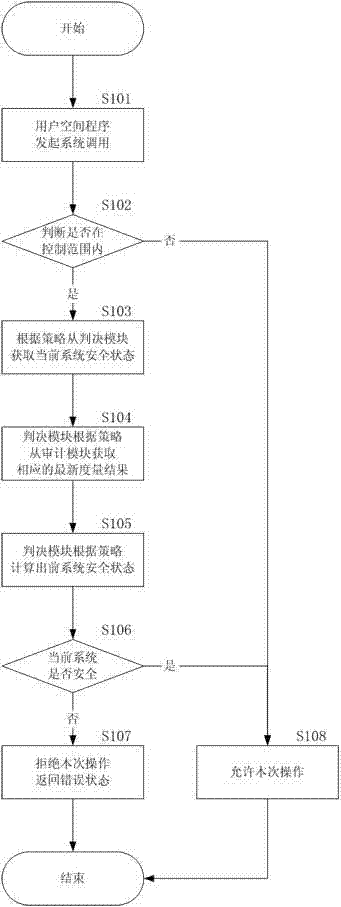
Dynamic measuring method based on dependable computing and management system
ActiveCN103577748AIntegrity guaranteedIncrease credibilityPlatform integrity maintainanceOperational systemTrusted Computing
The invention discloses a dynamic measuring method based on dependable computing and a management system. The management system interacts with a user through a user management interface of an operation system and application programs. The management system comprises a dynamic measurement control module interacting with the operation system, wherein the dynamic measurement control module controls a judgment module, an audit module and a measuring module, the judgment module obtains a latest measurement result from the audit module and judges whether the operation system is dependable or not according to a strategy, the measuring module is responsible for detecting the dependable state of the operation system in operation, the audit module is responsible for calculating, storing and reporting measurement results in a classified mode, the control module is responsible for configuring external management programs to other modules, sending system state information to the external management programs and providing access ports of trusted software special hardware for the modules. The management system works in a kernel layer, the system can guarantee integrity of the modules once starting static measurement, and credibility and safety are improved.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
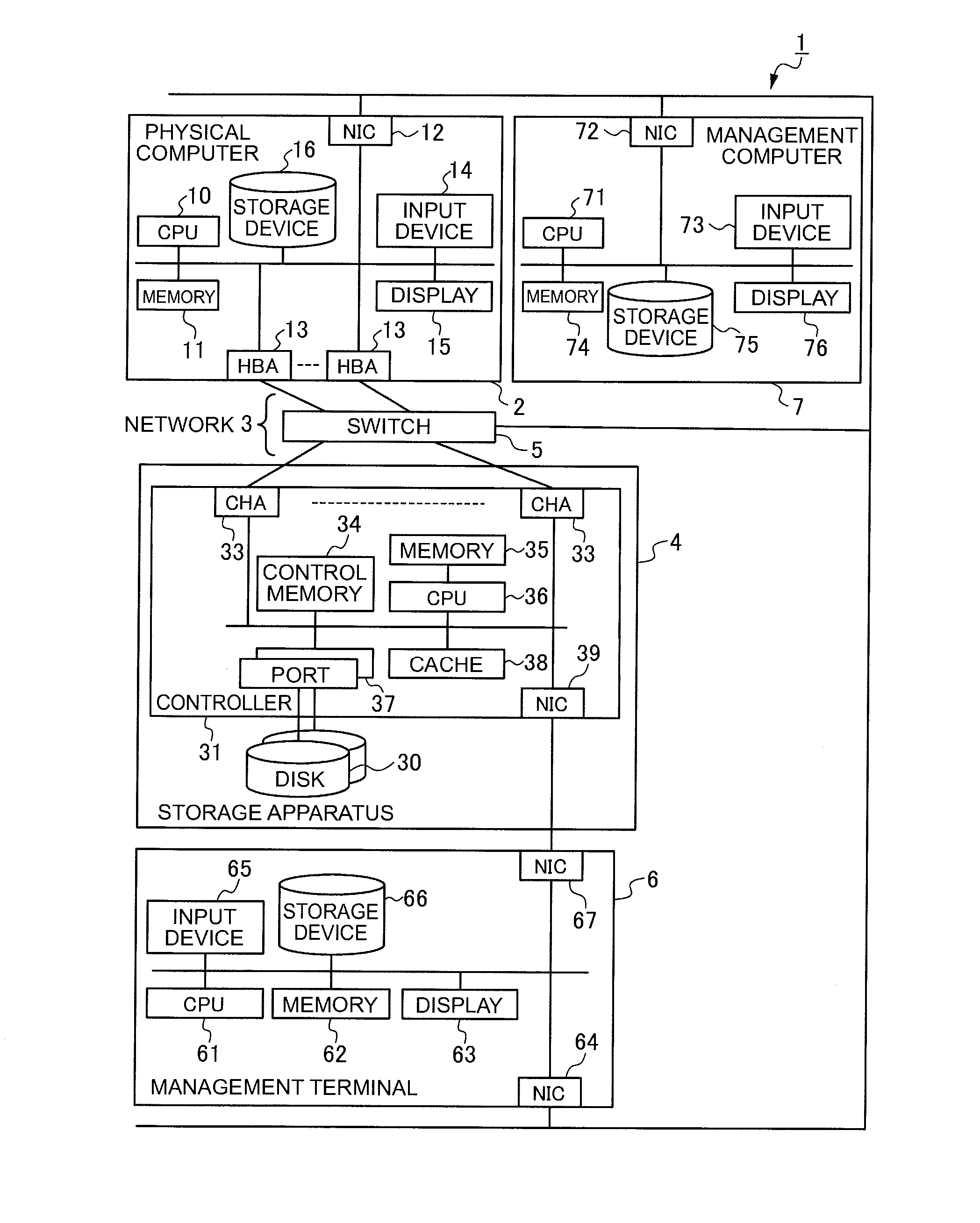
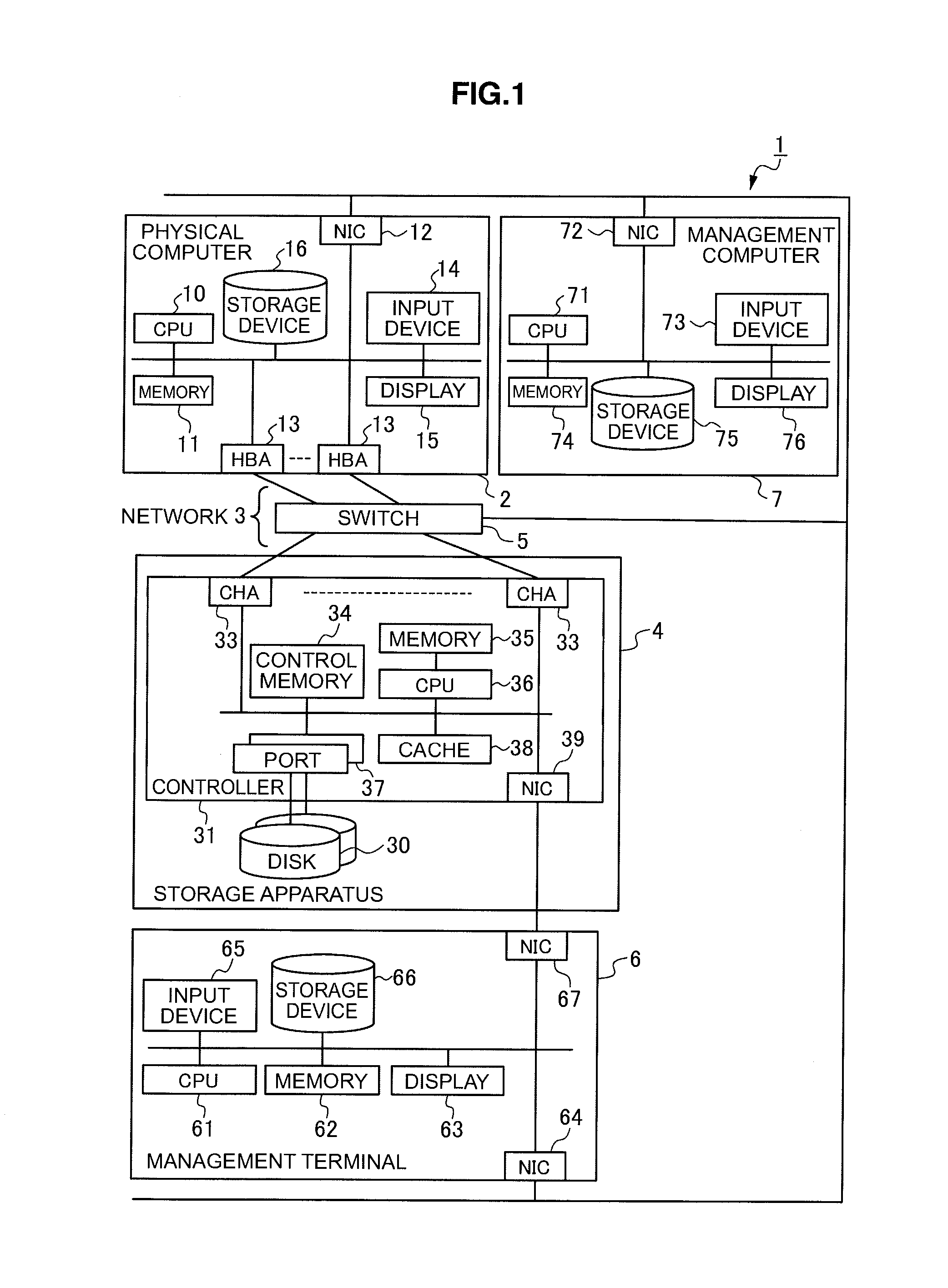
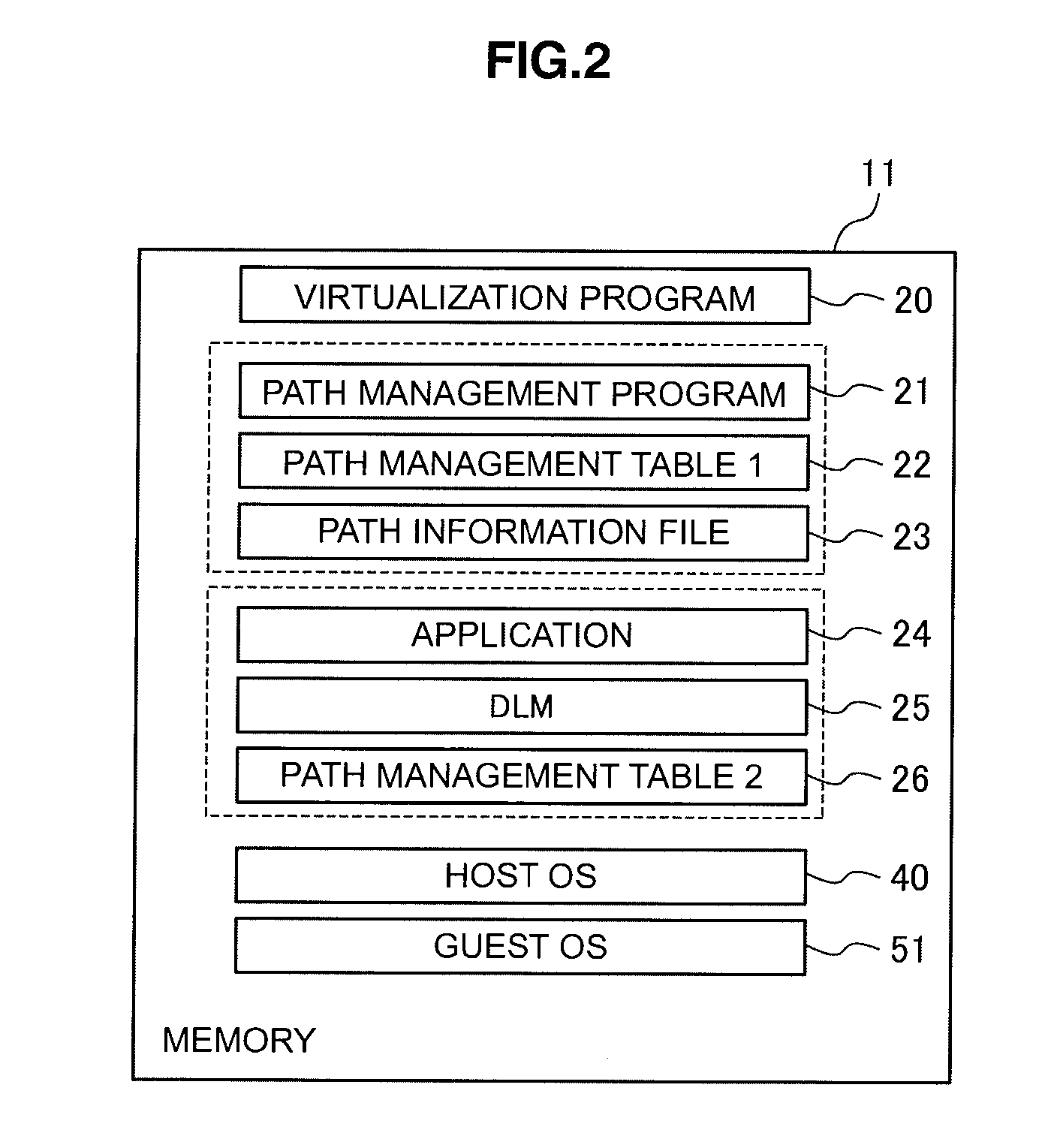
Computer apparatus and path management method
InactiveUS20110004708A1Avoid delayReduce impactError detection/correctionInput/output processes for data processingManagement unitVirtual computing
A highly-reliable computer apparatus and path management method capable of reducing the impact of a failure in a physical I / O device on the entire virtual computer system is suggested.If a first path management unit detects a failure in a virtual HBA, it notifies a second path management unit of the failure; and in response to the failure notice, the second path management unit gives an instruction to the first path management unit corresponding to each virtual computer having another virtual HBA that uses a physical HBA corresponding to the virtual HBA in which the failure has been detected, to block the other virtual HBA; and if the first path management unit receives the instruction from the second path management unit to block the virtual HBA, it blocks the designated virtual HBA.
Owner:HITACHI LTD
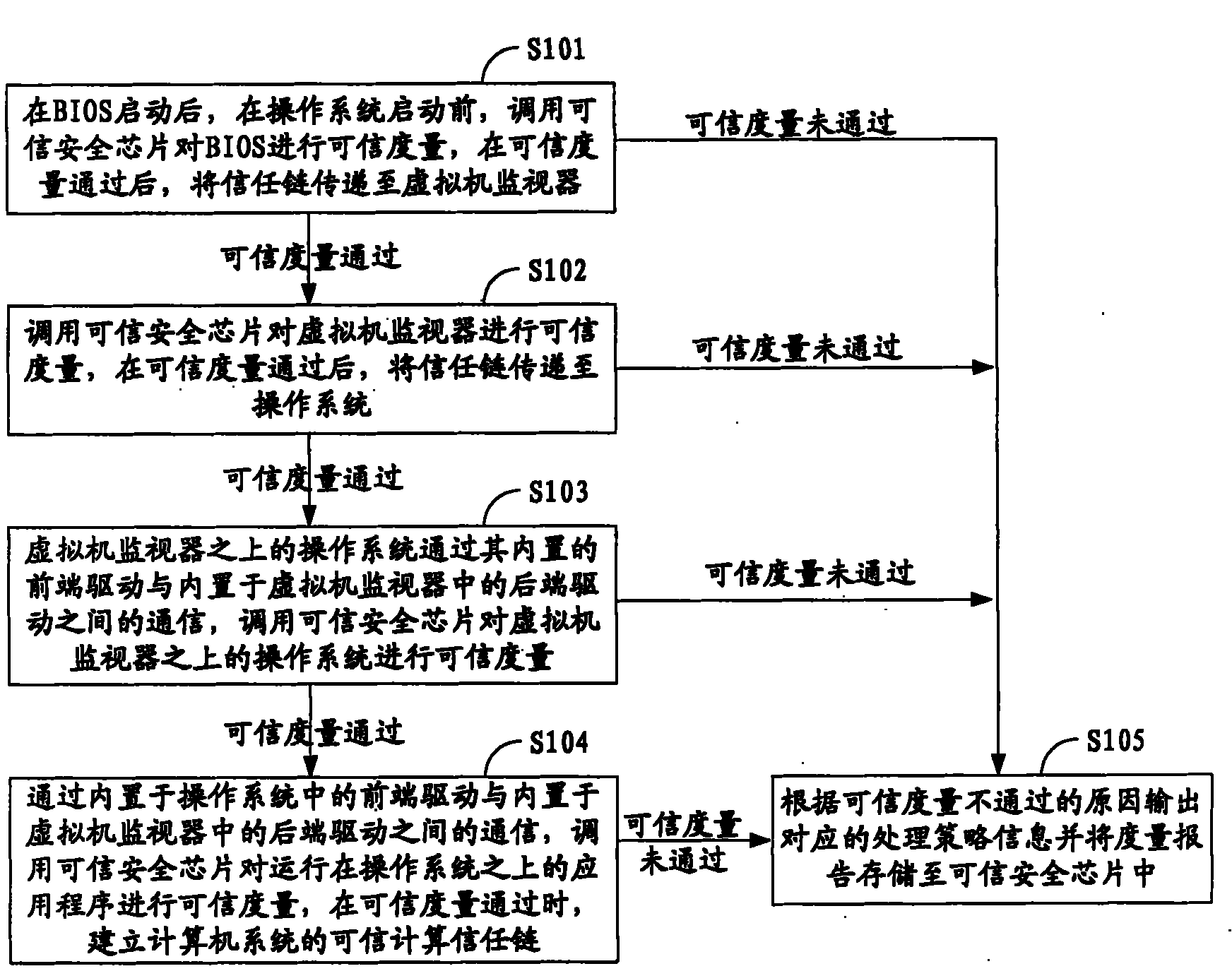
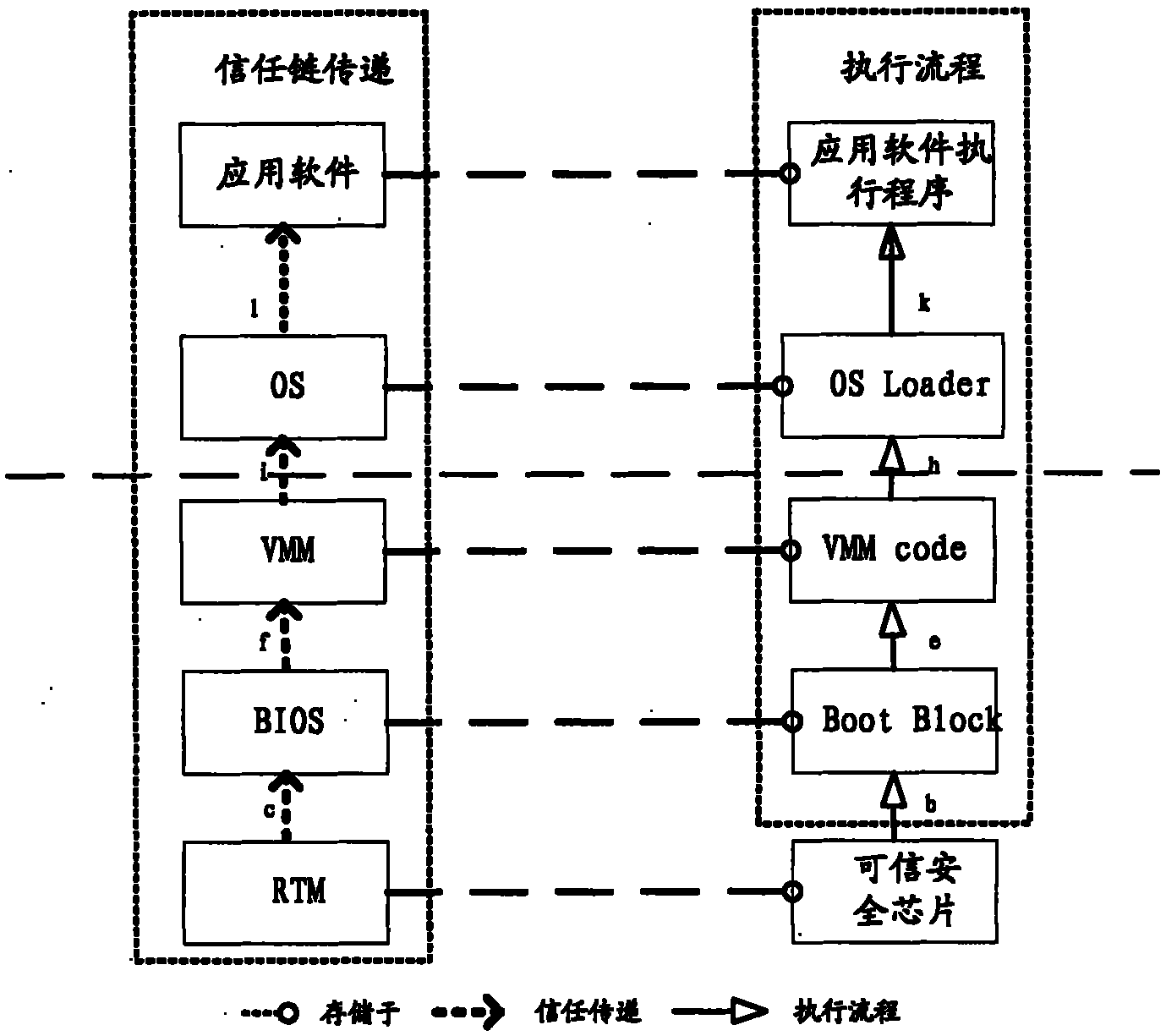
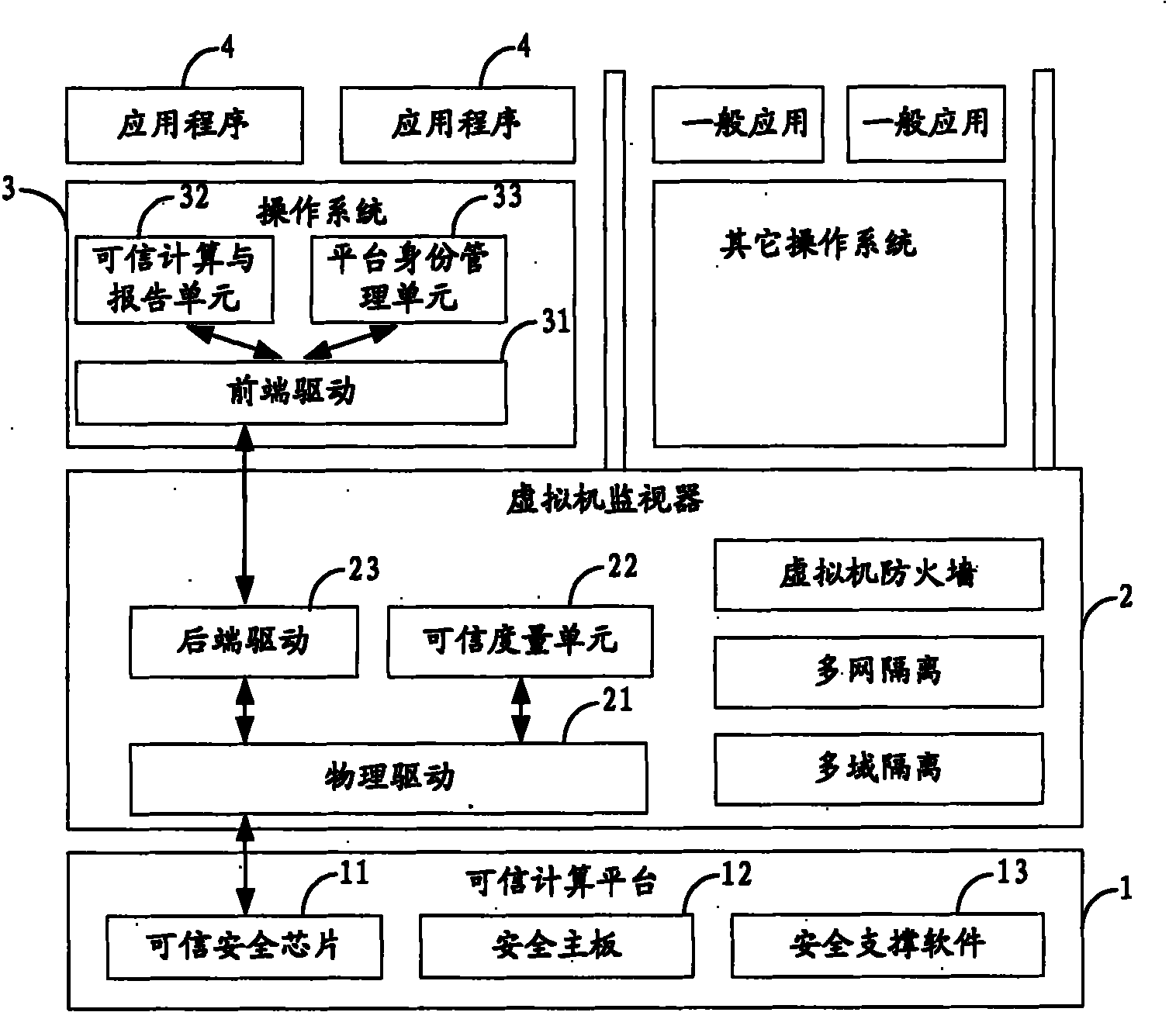
Computer system and measuring method thereof
ActiveCN102136043AImprove securityHardware monitoringInternal/peripheral component protectionOperational systemComputerized system
The invention is suitable for the field of computer application and provides a computer system and a measuring method thereof. The method comprises the following steps of: after the startup of a BIOS (Basic Input Output System) and before the startup of an operating system, calling a credible security chip to perform measurement of trust on the BIOS and transmitting a trust chain to a virtual machine monitor after the measurement of trust passes; calling the credible security chip to perform measurement of trust on the virtual machine monitor and transmitting a trust chain to the operating system after the measurement of trust passes; calling the credible security chip to perform measurement of trust on the operating system and transmitting a trust chain to an application program running on the operating system after the measurement of trust passes; and calling the credible security chip to perform measurement of trust on the application program running on the operating system and establishing a dependable computing trust chain of the computer system when the measurement of trust passes. By adopting the embodiment of the invention, the security of the computer system can be greatly enhanced.
Owner:天津长城计算机系统有限公司
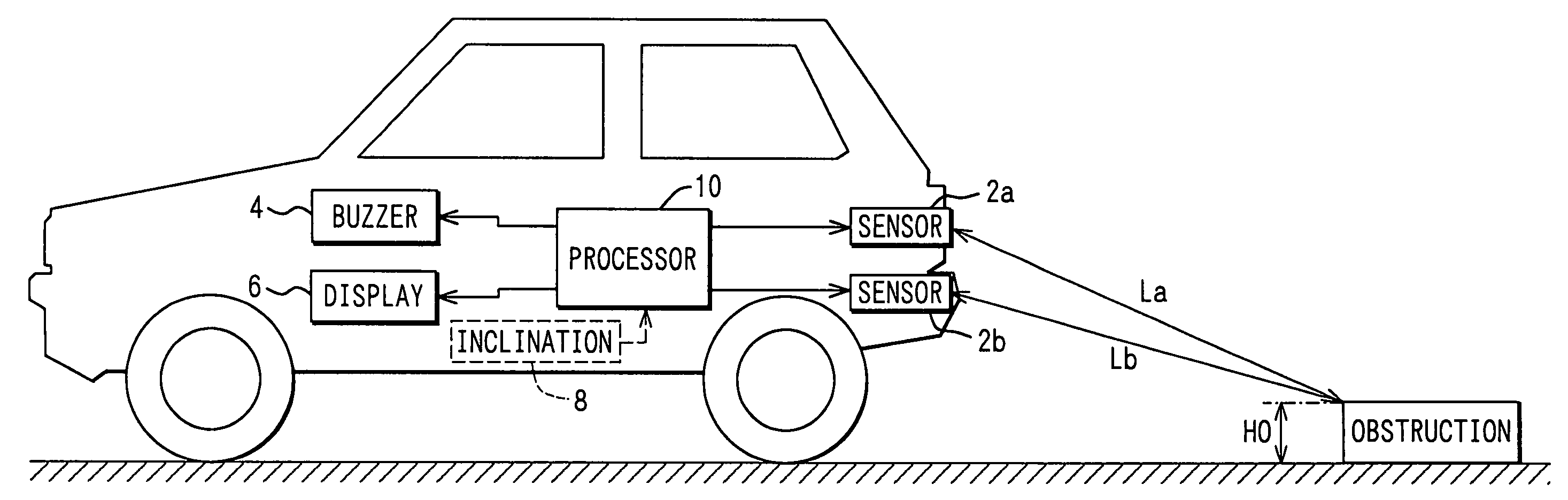
Driving assisting apparatus for vehicles
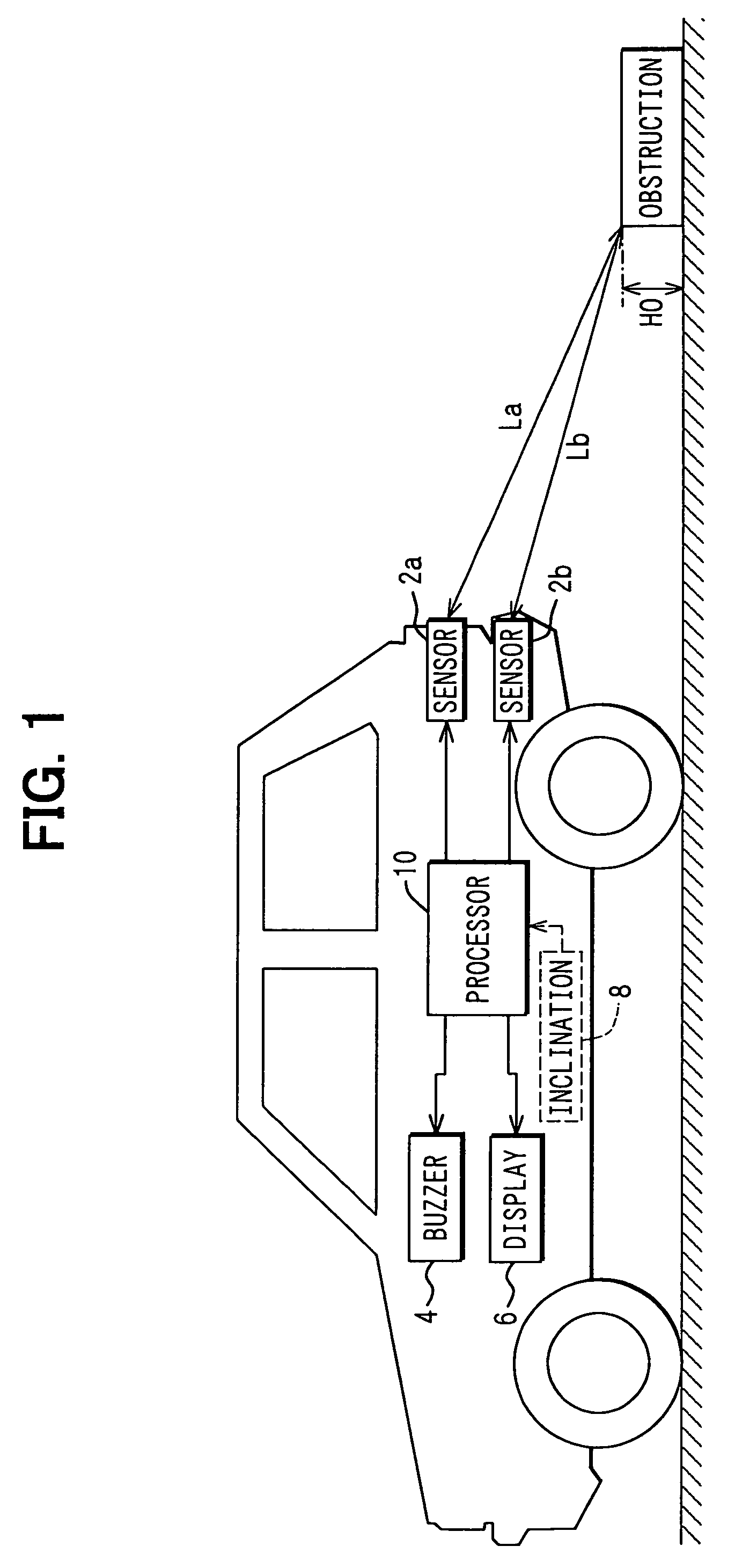
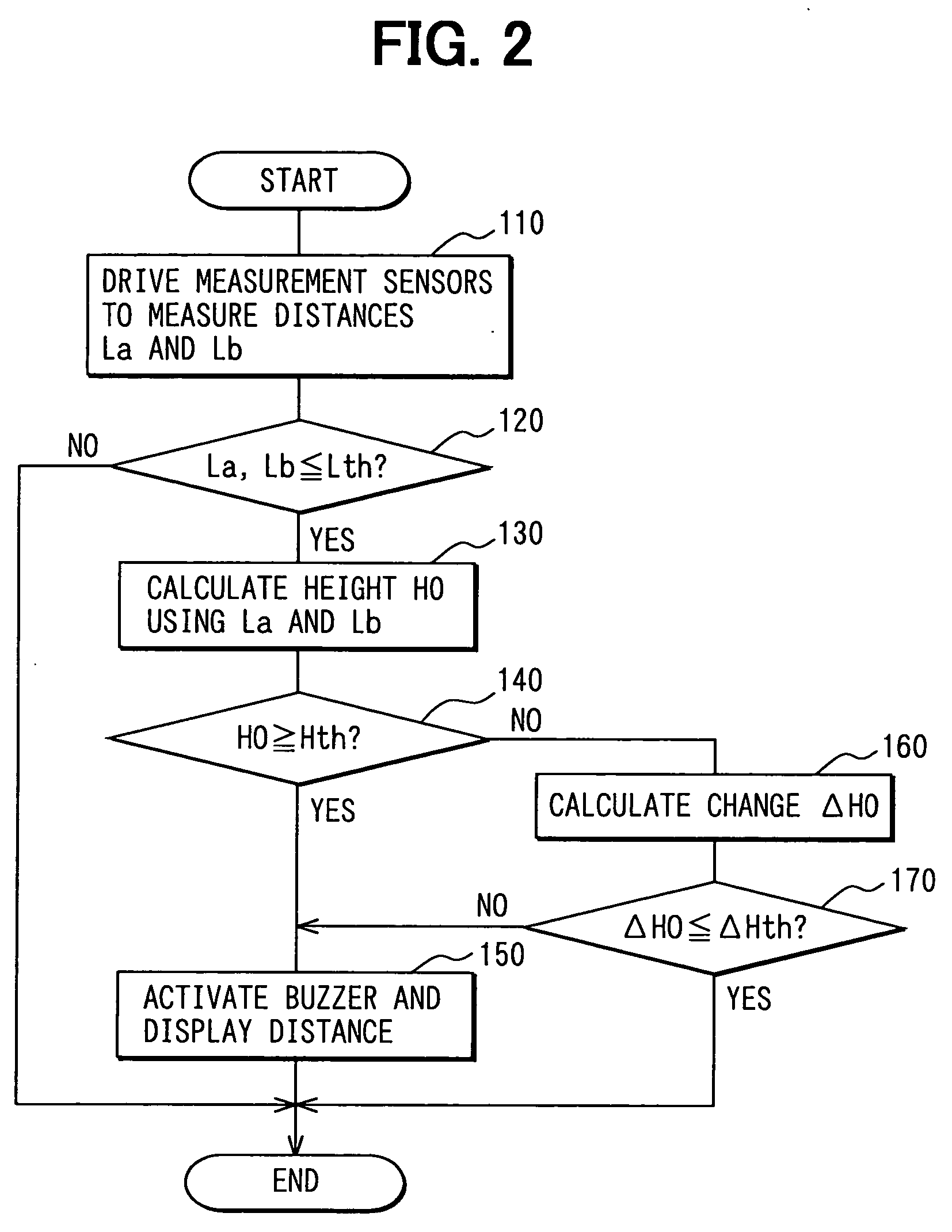
InactiveUS20050110620A1Reduce stepsDigital data processing detailsPedestrian/occupant safety arrangementDriver/operatorEngineering
A pair of distance measurement sensors provided at different heights measures distances to an obstruction. When the measured distances are shorter than a threshold distance, the height of the vehicle is found based on the measured distances. When the height of the vehicle is found greater than a threshold height, the existence of the obstruction is reported to the driver. When the height of the vehicle is found smaller than the threshold height, on the other hand, a change in obstruction height is found and compared with a threshold. When the change in obstruction height is greater than the threshold, the existence of the obstruction is reported to the driver since the height is determined to be an unreliable result of computation.
Owner:DENSO CORP
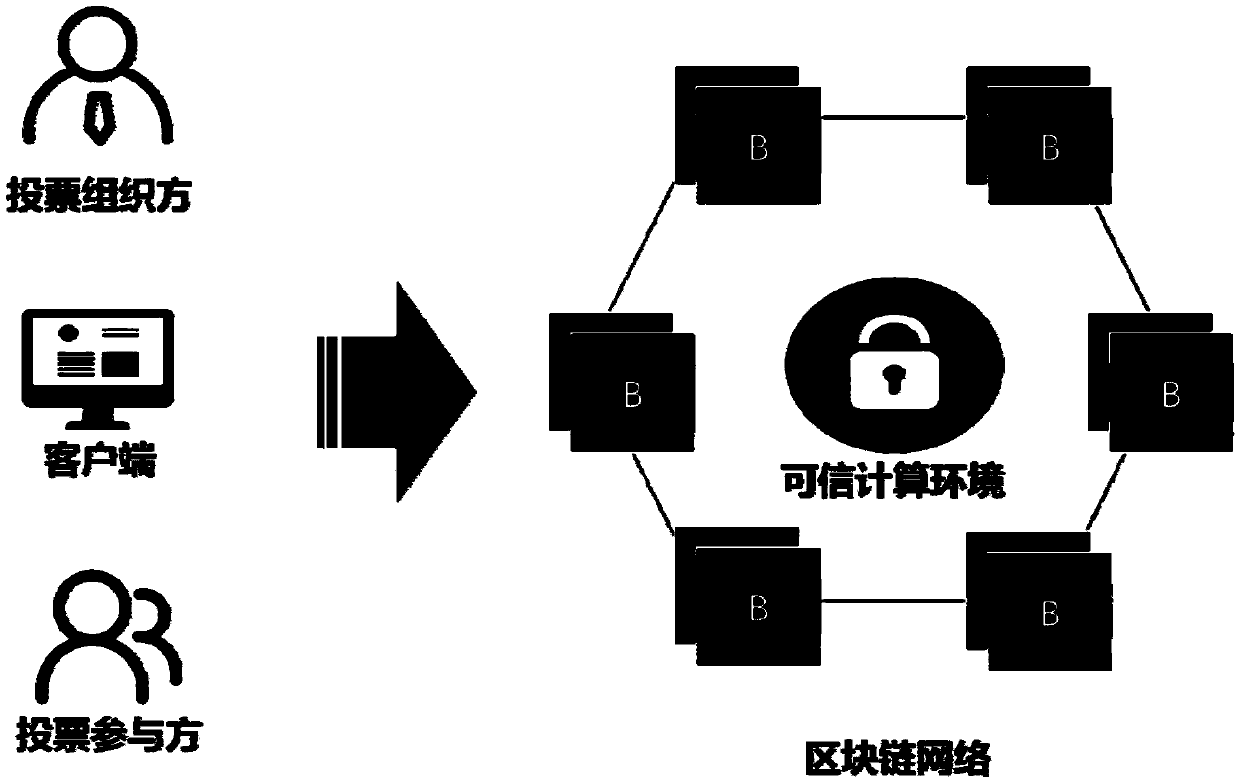
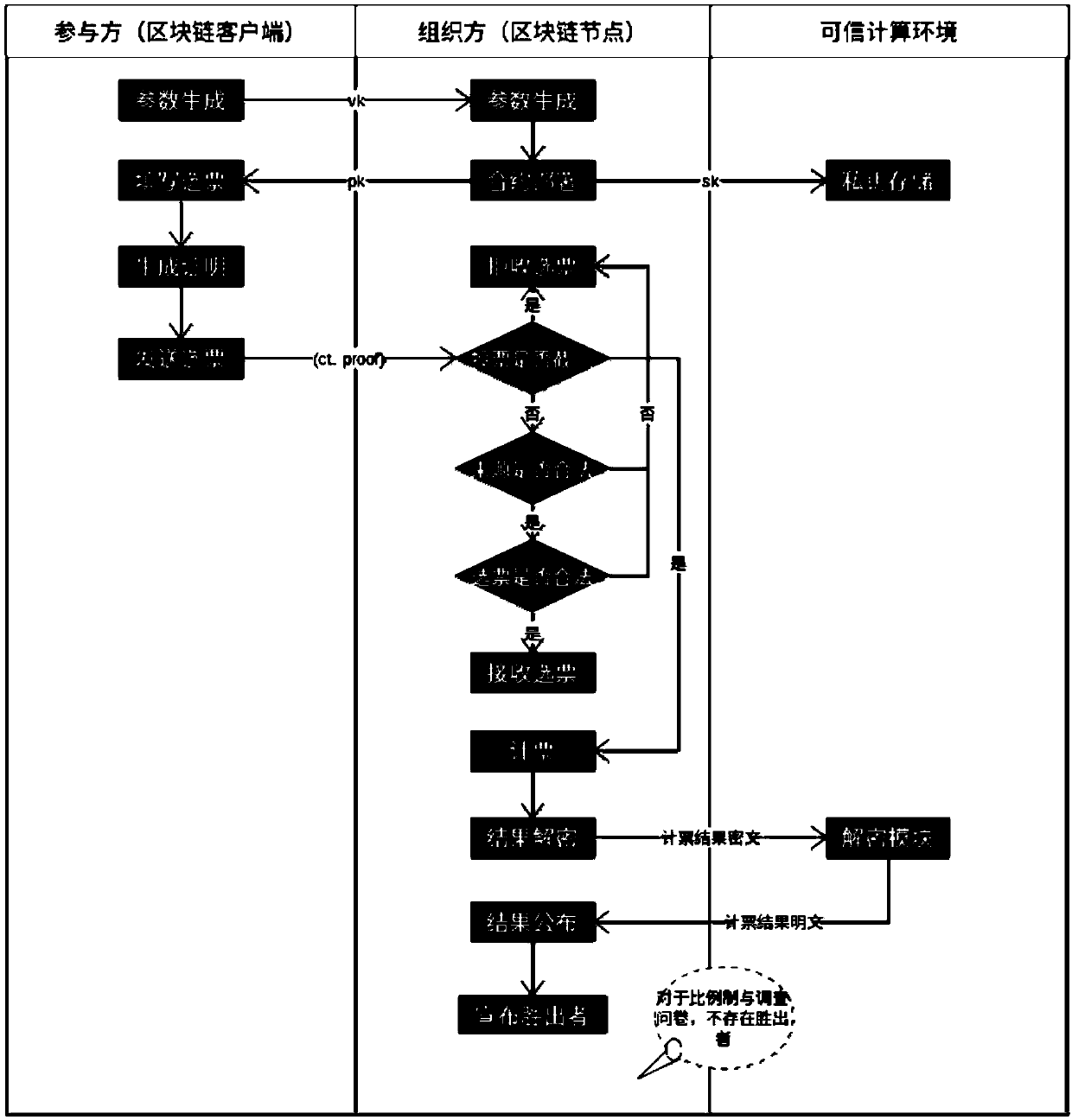
Anonymous electronic voting method based on blockchain technology
ActiveCN109523683ALow costImprove efficiencyVoting apparatusCommunication with homomorphic encryptionTrusted ComputingZero-knowledge proof
The invention discloses an anonymous electronic voting method based on a blockchain technology. According to the anonymous electronic voting method, voting contents are hidden through a homomorphic encryption algorithm, meanwhile, vote validity is ensured through a zero-knowledge proof technology, vote collecting, and the vote counting process and result disclosure are all conducted on a blockchain system, wherein voting results are decrypted through a dependable computing environment, the problem that a private key makes contact with a network in the voting result decrypting process under a traditional way is solved, and the anonymous attribute of voting is protected in the true sense.
Owner:HANGZHOU QULIAN TECH CO LTD
Trust evaluation system based on privacy protection and construction method thereof
ActiveCN103746957AMeet individual needsImprove interaction success rateTransmissionPersonalizationComputer network
A trust evaluation system based on privacy protection and a construction method thereof relate to the field of dependable computing in information safety. The system comprises a service node, a trust evaluation proxy node and a user node. The trust evaluation proxy node dynamically deploys a trust evaluation method to measure the trust relationship between the user node and the service node. The user node and the trust evaluation proxy node transmit and receive information mutually and evaluate the service node. The system and its construction method aim to objectively, accurately and justly quantify the trust relationship between the user node and the service node, effectively inhibit malicious acts such as conspired fraud, malevolent recommendation and the like, raise interactive success rate of the user node and the service node and meet requirements of user node individuation to the maximum.
Owner:汉兴同衡科技集团有限公司
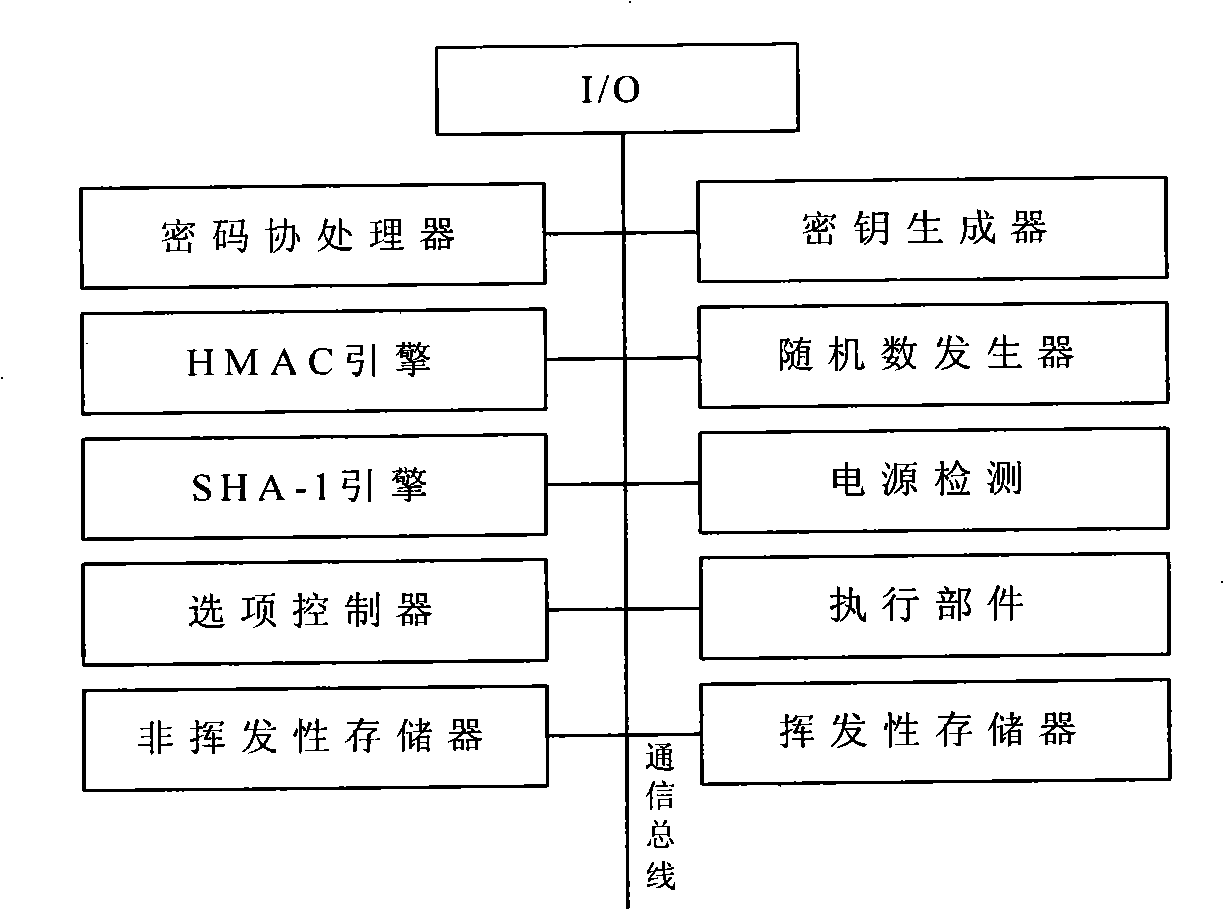
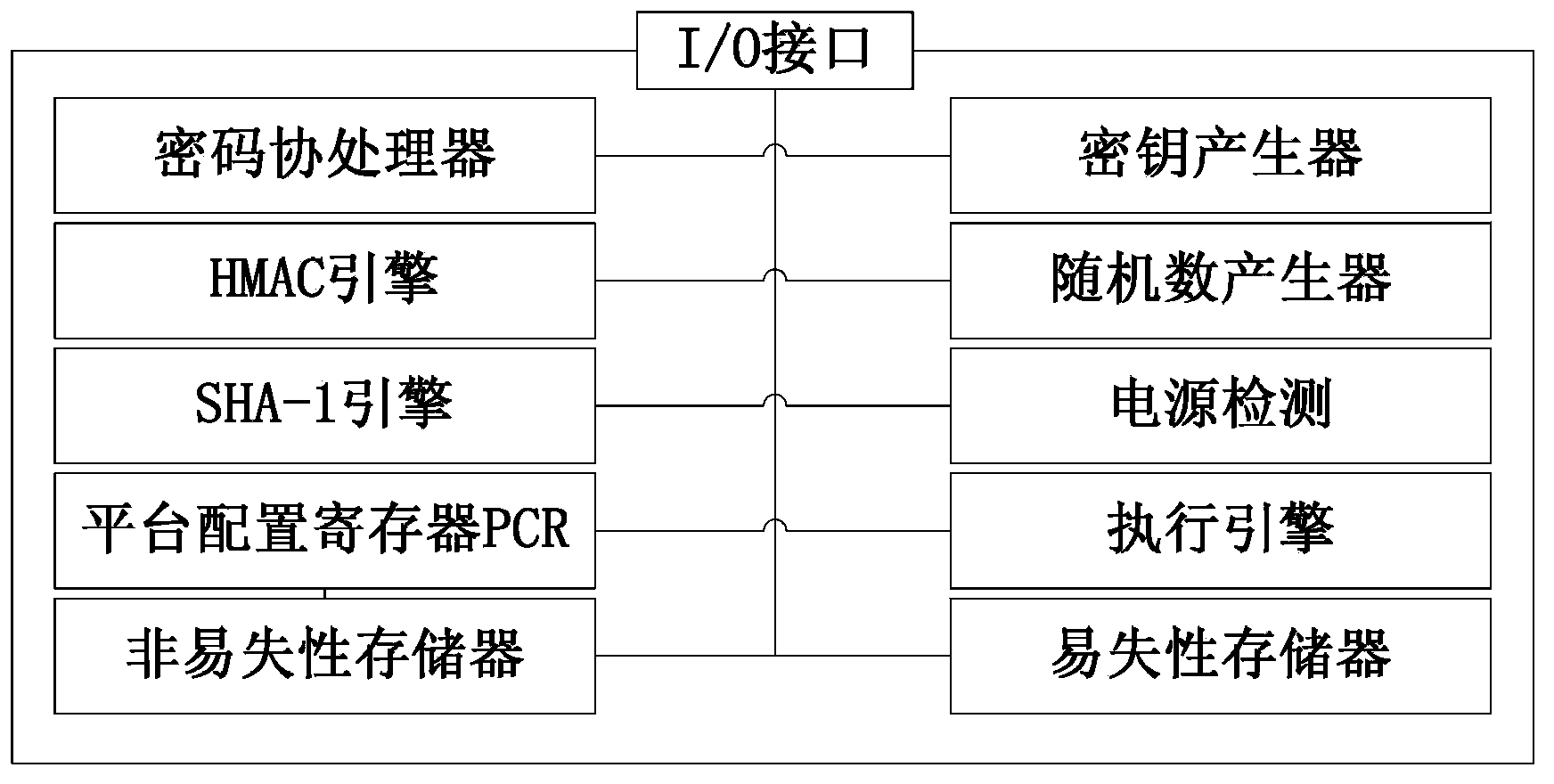
Dependable computing unit based on homemade TCM and operation method thereof
InactiveCN106991329AImprove computing speedVersatilePlatform integrity maintainanceOperational systemInformation security
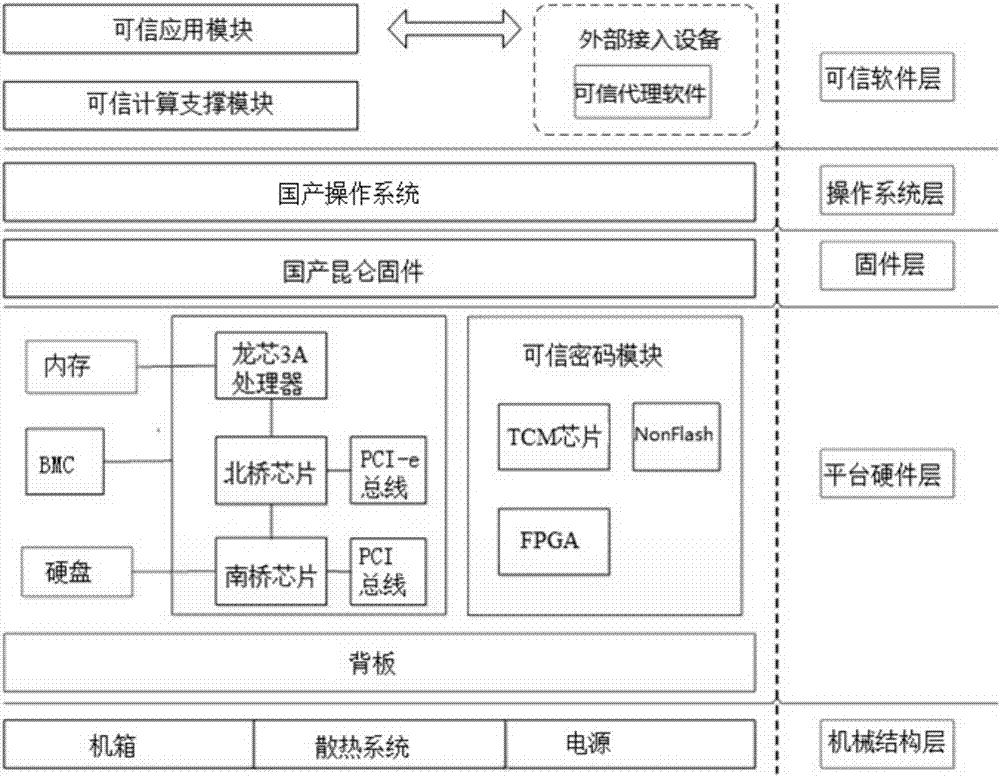
The invention relates to a dependable computing unit based on a homemade TCM and an operation method thereof. The dependable computing unit comprises a mechanical structure layer, a platform hardware layer, a firmware layer, an operation system layer and a dependable software layer; the mechanical structure layer comprises a case, a heat dissipating system and a power source; the firmware layer comprises firmware; the operation system layer comprises an operation system; the platform hardware layer comprises a backboard, a computing unit module and a dependable code module; the dependable software layer comprises a dependable application module and a dependable computing supporting module. The dependable computing unit is complete in function, high in algorithm computing efficiency and large in concurrence work capacity; serving as the dependable computing unit, the unit can provide high-performance data encryption / decryption service for an information safety transmission system and serve as main code equipment and core member of a host data safety storage system, an identity authentication system and a symmetric and asymmetrical secret key management system, and has wide system application potentiality.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Method for realizing dependable SSH based on dependable computing
InactiveCN101741842AAvoid security threatsProtection against replay attacksKey distribution for secure communicationUser identity/authority verificationKey exchangeMan-in-the-middle attack
The invention provides a method for realizing dependable SSH based on dependable computing. The method integrates remote authentication of the dependable computing with key exchange of an SSH protocol so as to closely combine platform status information verification with session key negotiation; and the method enhances the security of data at a communication end point on the premise that safe transmission of the data is ensured. The method requires that both a server and a client are provided with dependable security chips; and the platform status can be measured by a measurement module and a dependable operating system. The method can not only effectively prevent the security threat that the communication with an unknown end point by using a security channel may undergo various attacks in the SSH protocol, but also effectively protect against replay attack, impersonation attack and man-in-the-middle attack.
Owner:BEIJING JIAOTONG UNIV
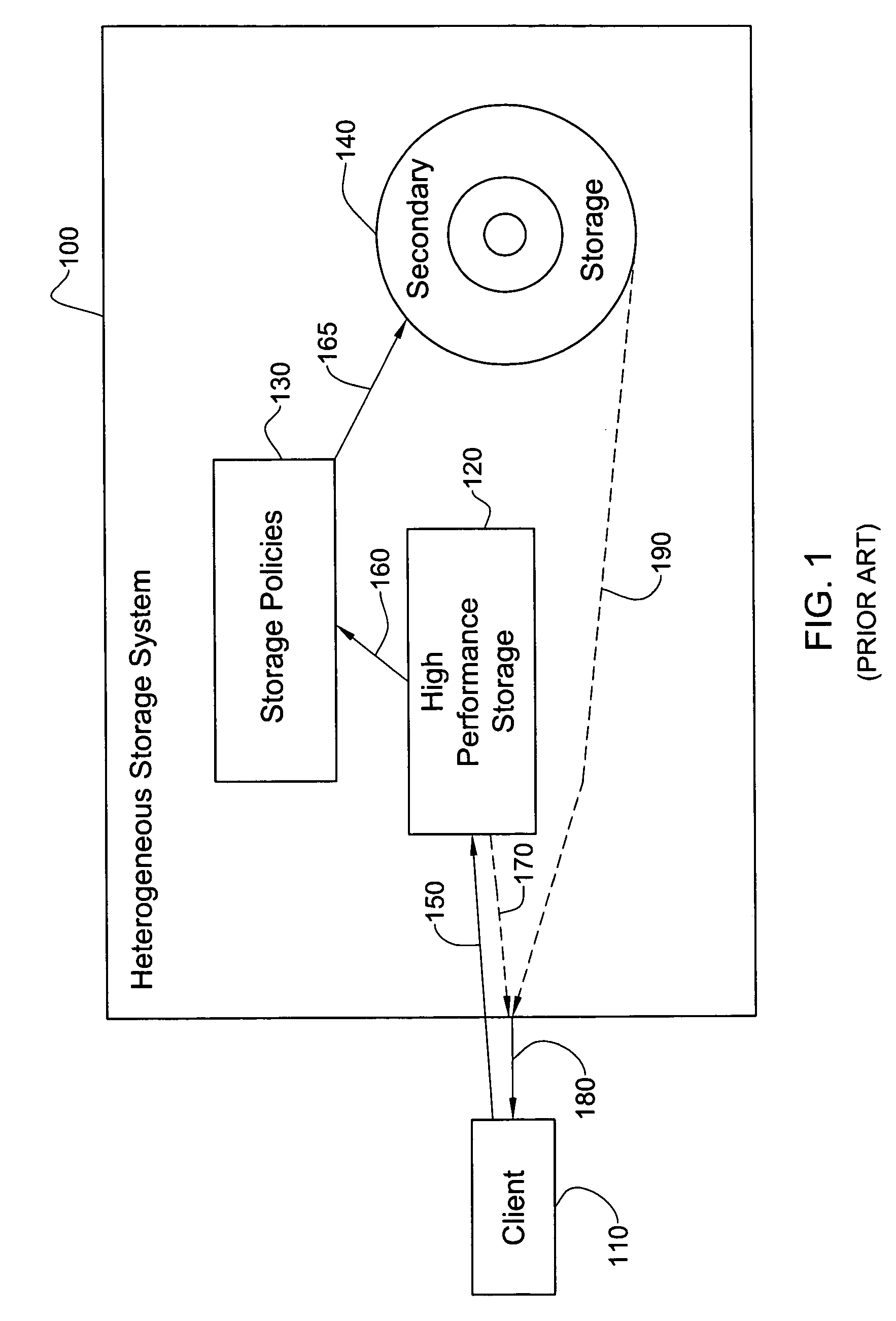
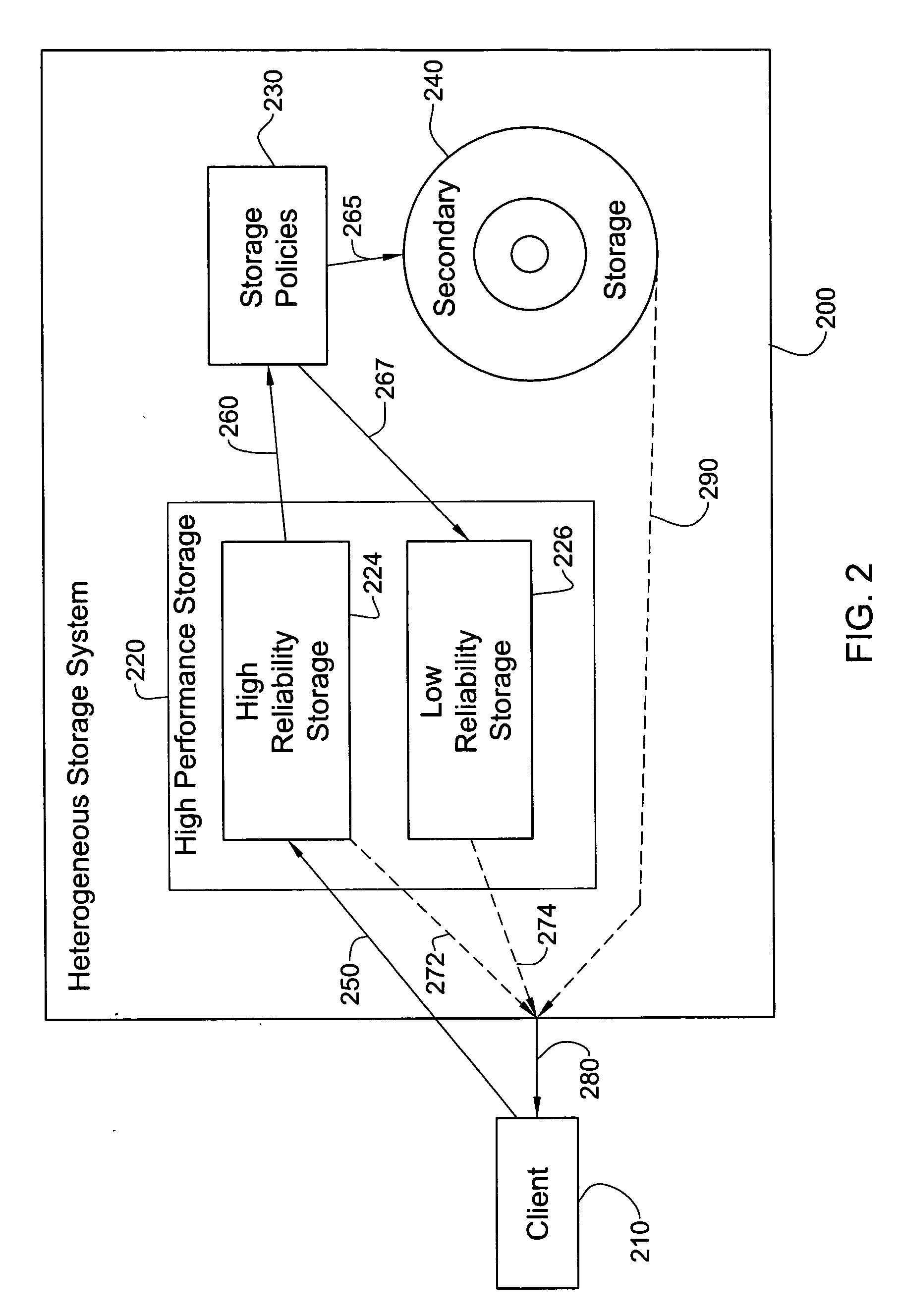
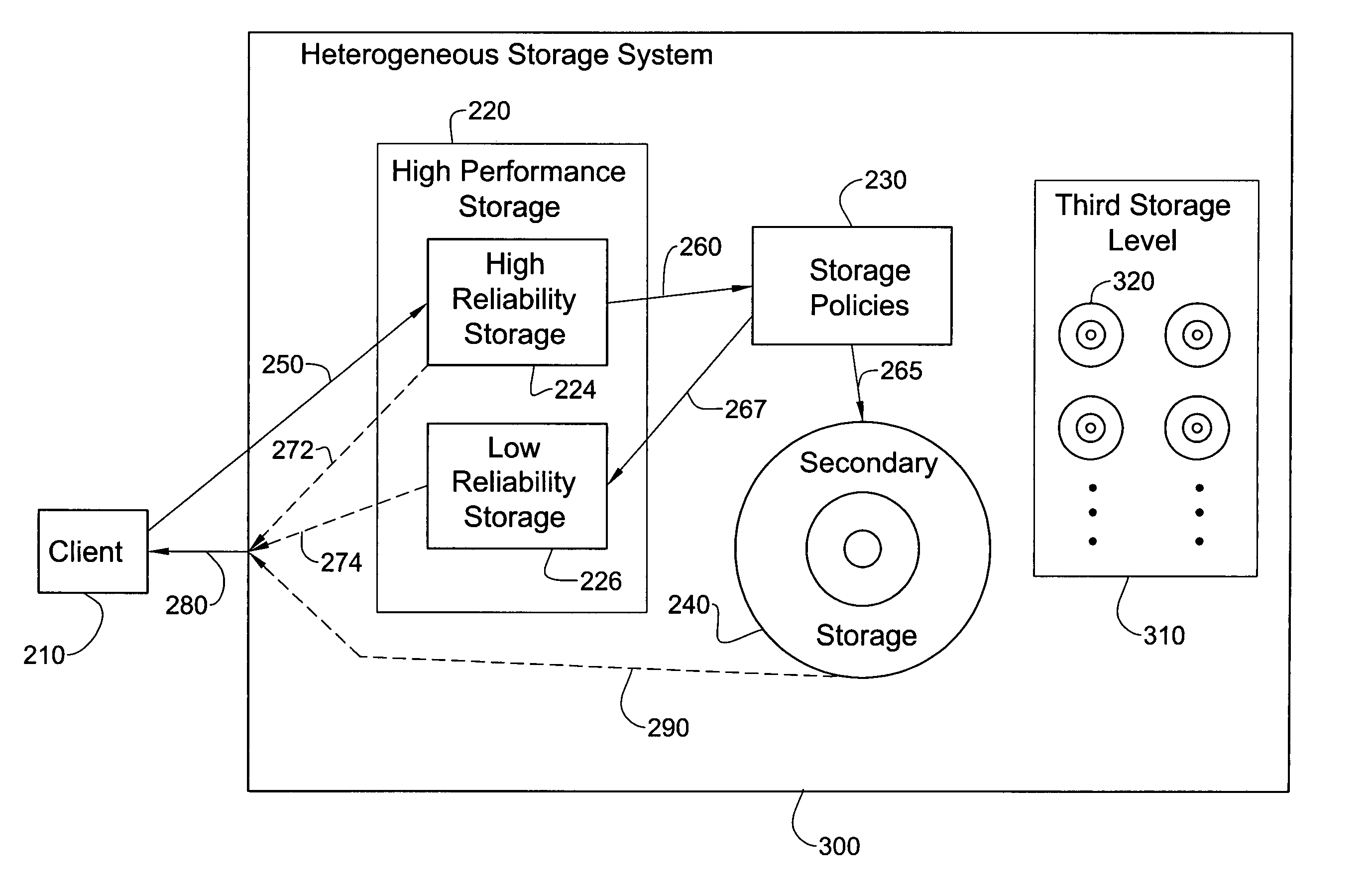
Inexpensive reliable computer storage via hetero-geneous architecture and a staged storage policy
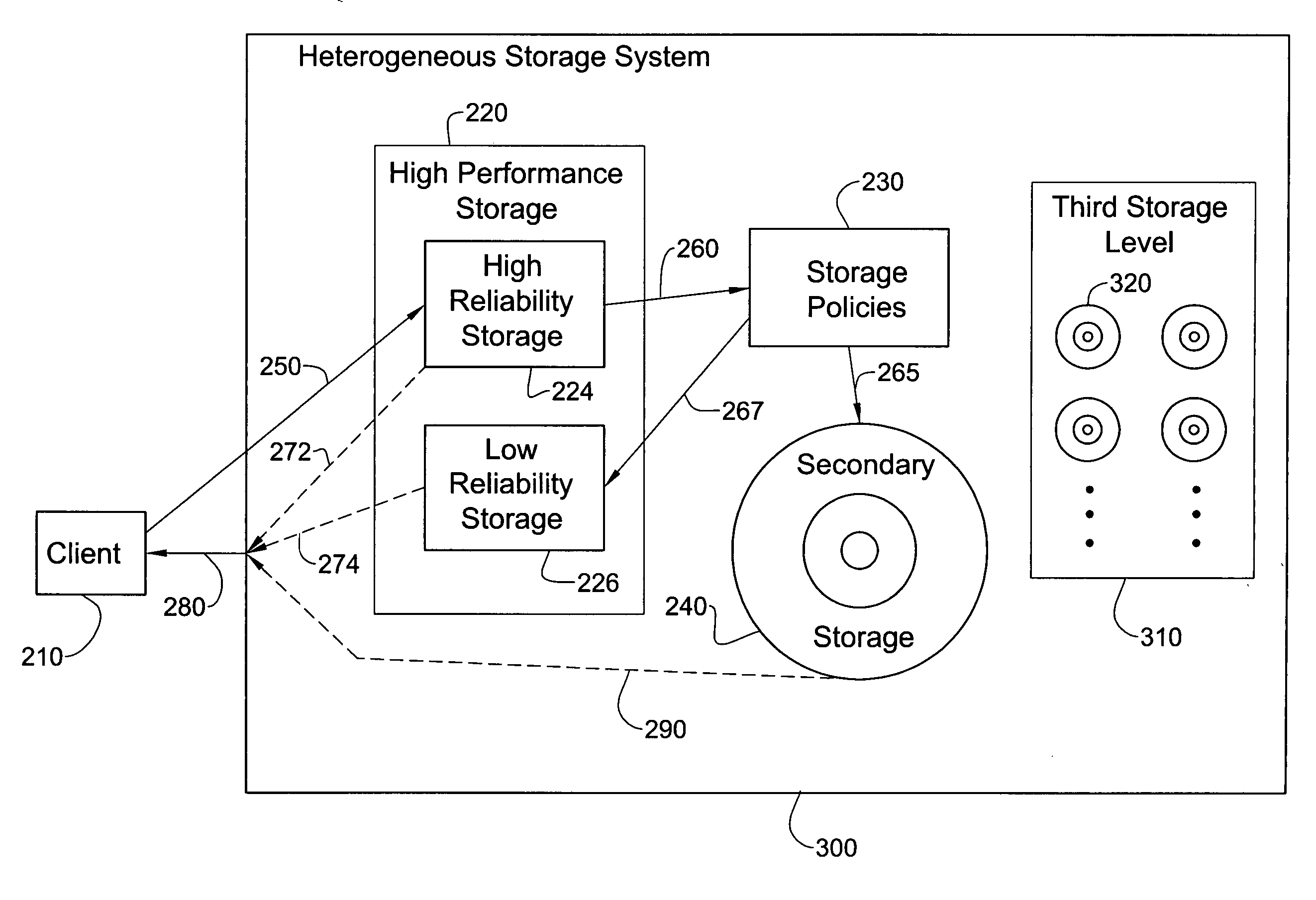
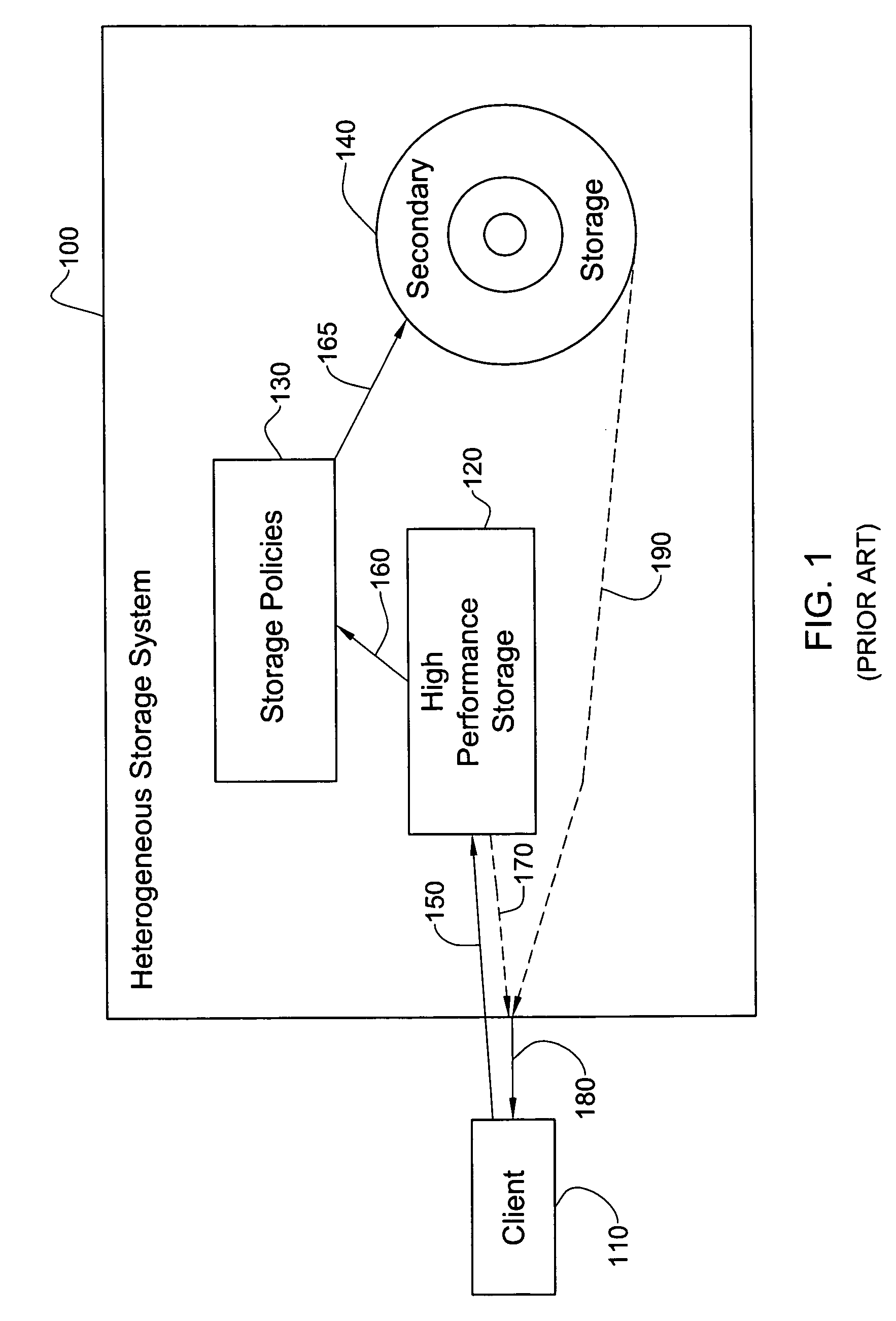
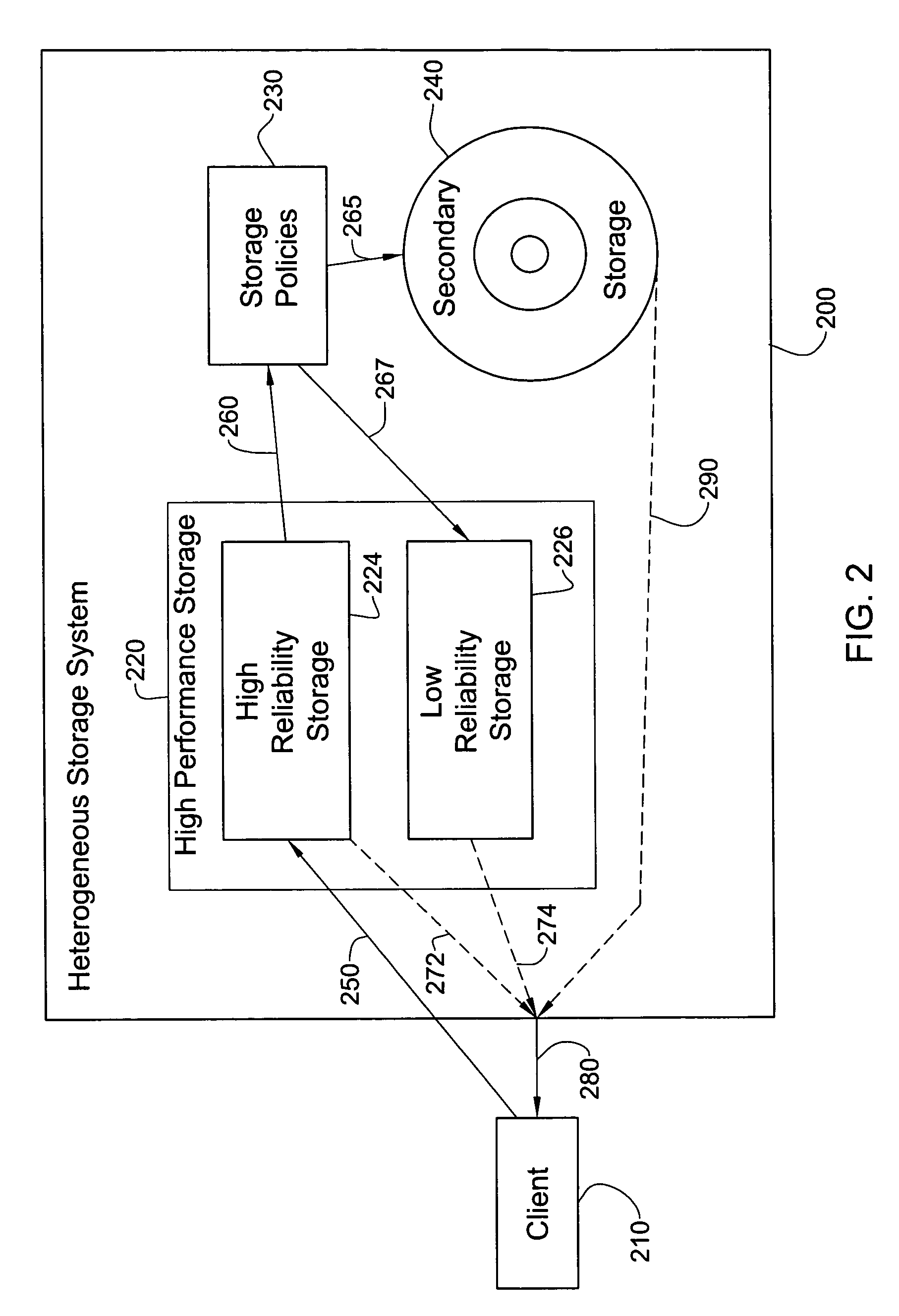
InactiveUS20050097287A1Improve performanceLow reliabilityData processing applicationsMemory loss protectionData storeComputer science
An inexpensive storage system is disclosed along with methods of managing such a system. In one preferred embodiment, the system includes a high performance high reliability storage medium configured for initial storage of data, a low performance high reliability storage medium configured for backup of data initially stored on the high performance high reliability storage medium, and a high performance low reliability storage medium, configured to receive data transferred from the high performance high reliability storage medium, after the data has been backed up on the low performance high reliability storage medium. This significantly reduces the cost of the system without substantially comprising performance. Reliability is likewise maintained owing to the high reliability backup.
Owner:IBM CORP
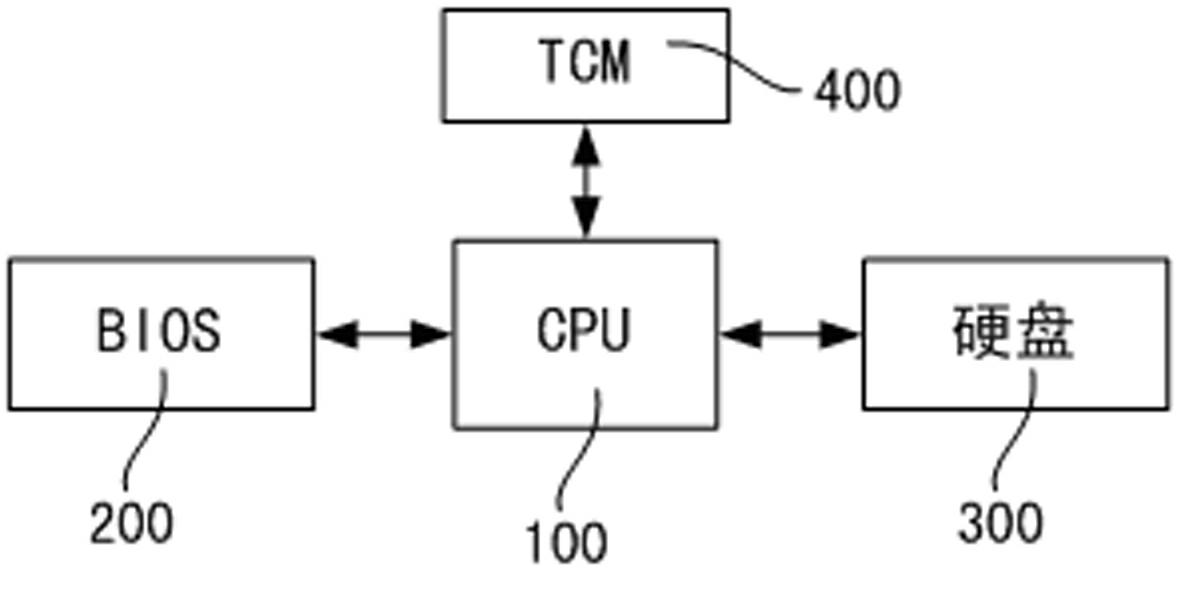
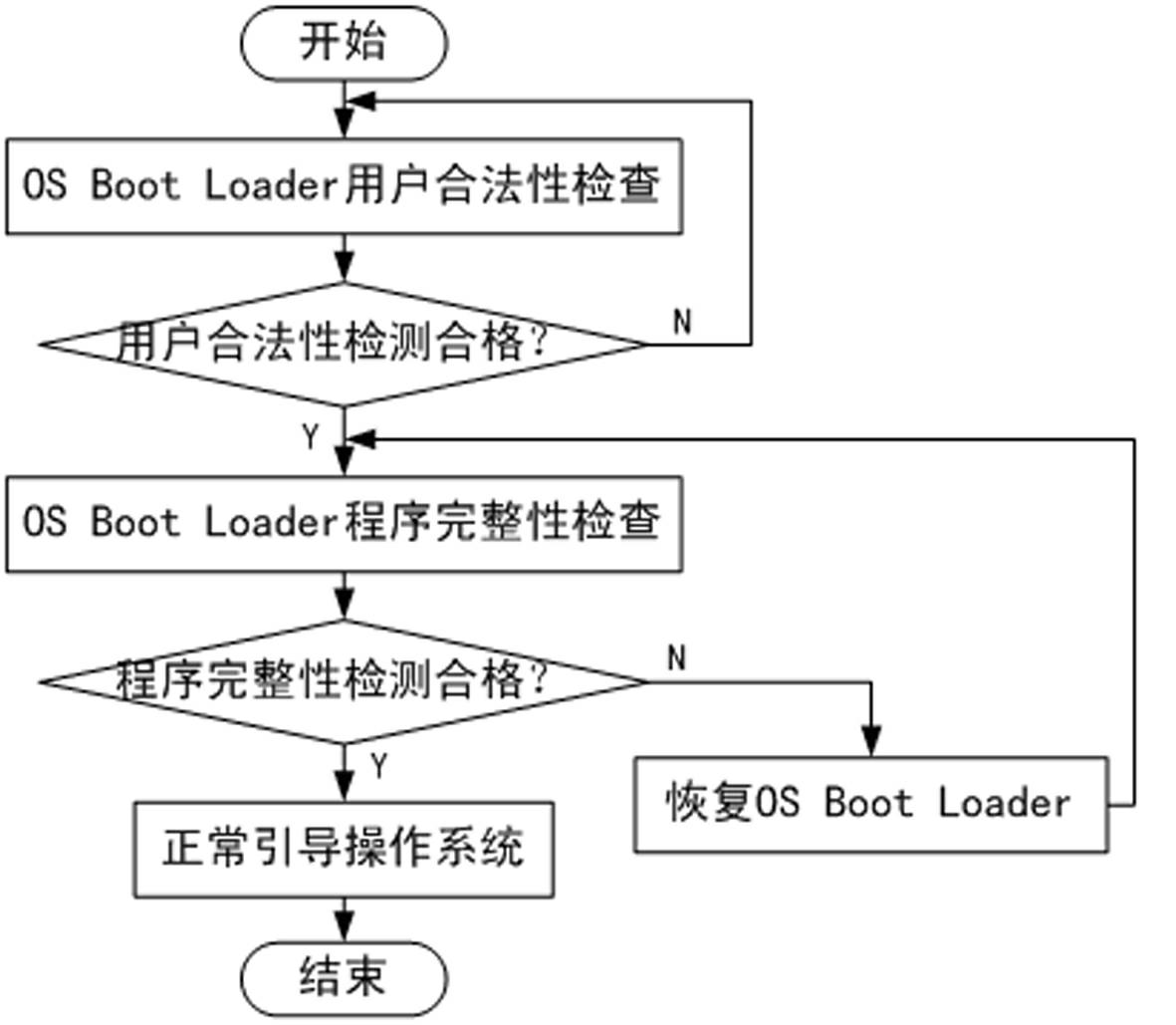
Operation system security bootstrap device and bootstrap device
InactiveCN102650944ANot be tampered with maliciouslyImplement backupProgram loading/initiatingRedundant operation error correctionTrusted ComputingOperating system security
The invention discloses an operation system security bootstrap device, which includes a base input and output system, a central processing unit and a hard disk. The central processing unit is connected with the base input and output system and the hard disk; a bootstrap program is stored in the hard disk to realize the bootstrap to an operation system. Particularly, the bootstrap device further includes a dependable computing cryptographic module which is connected with the central processing unit. The central processing unit controls the dependable computing cryptographic module to verify the legality of an operator and detect the completeness of the bootstrap program, and backups the bootstrap program to realize the restorability of the bootstrap program. The invention further provides a security bootstrap method utilizing the device. Before the operation system is started, the identity of the operator is subjected to legality verification, so as to ensure that the operator is authorized legally; the hard disk bootstrap program is subjected to completeness detection, so as to ensure that the bootstrap program to be not maliciously interpolated; and the backup and restoring mechanism of the bootstrap program can continue the correct bootstrap to the operation system under the condition that the bootstrap program is interpolated.
Owner:NATIONZ TECH INC
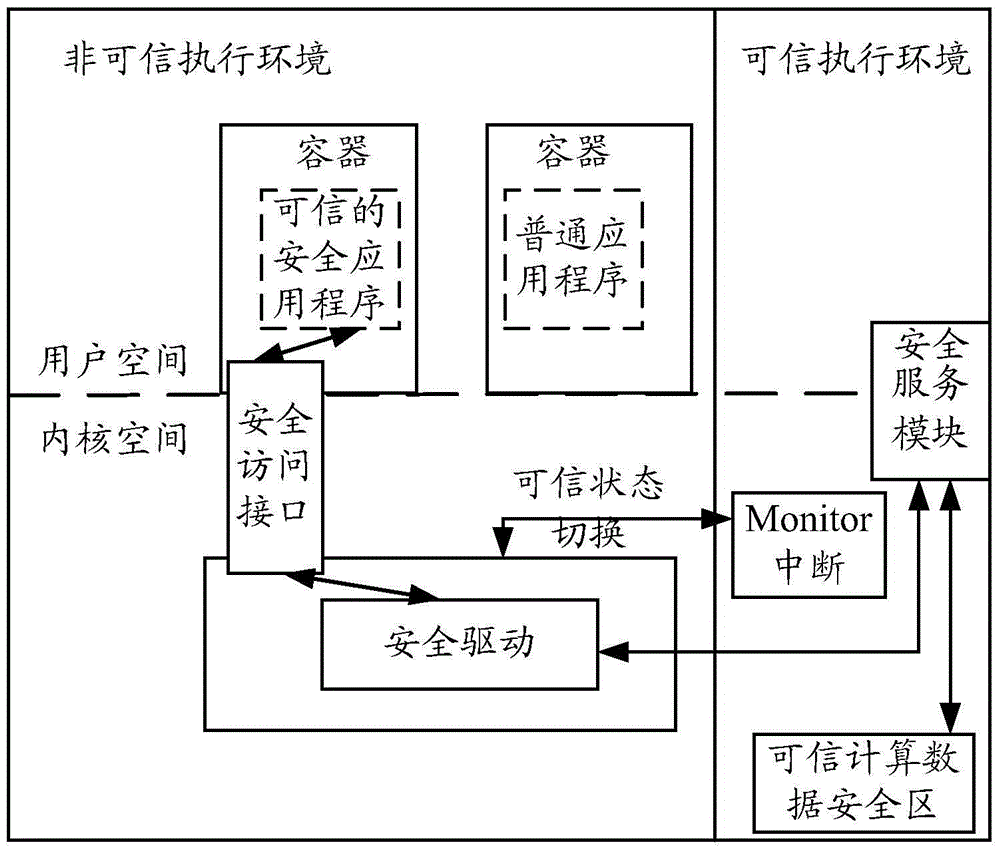
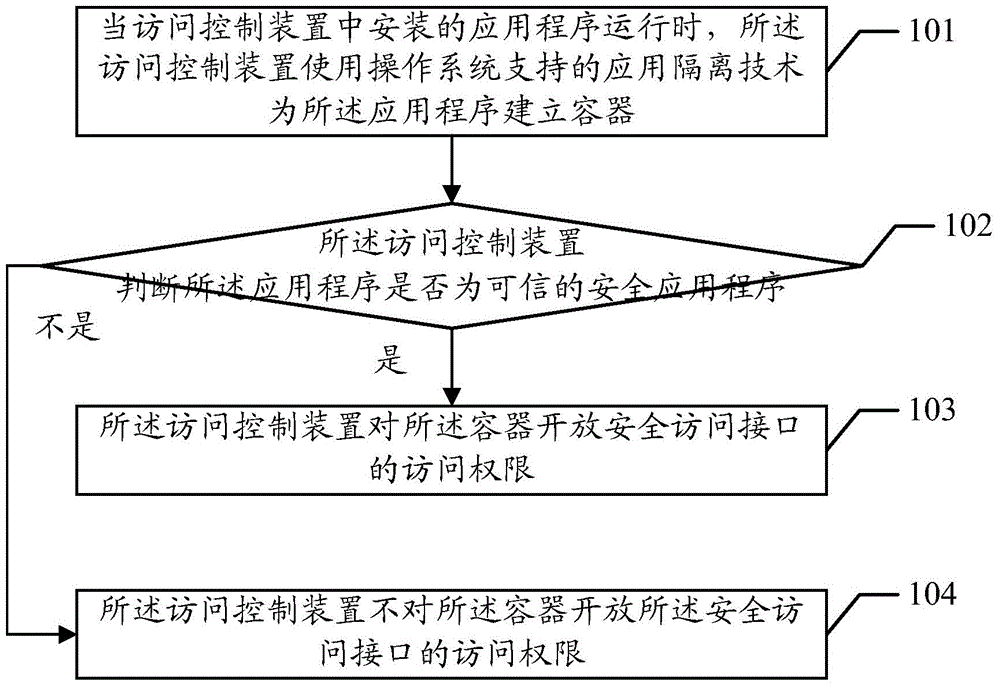
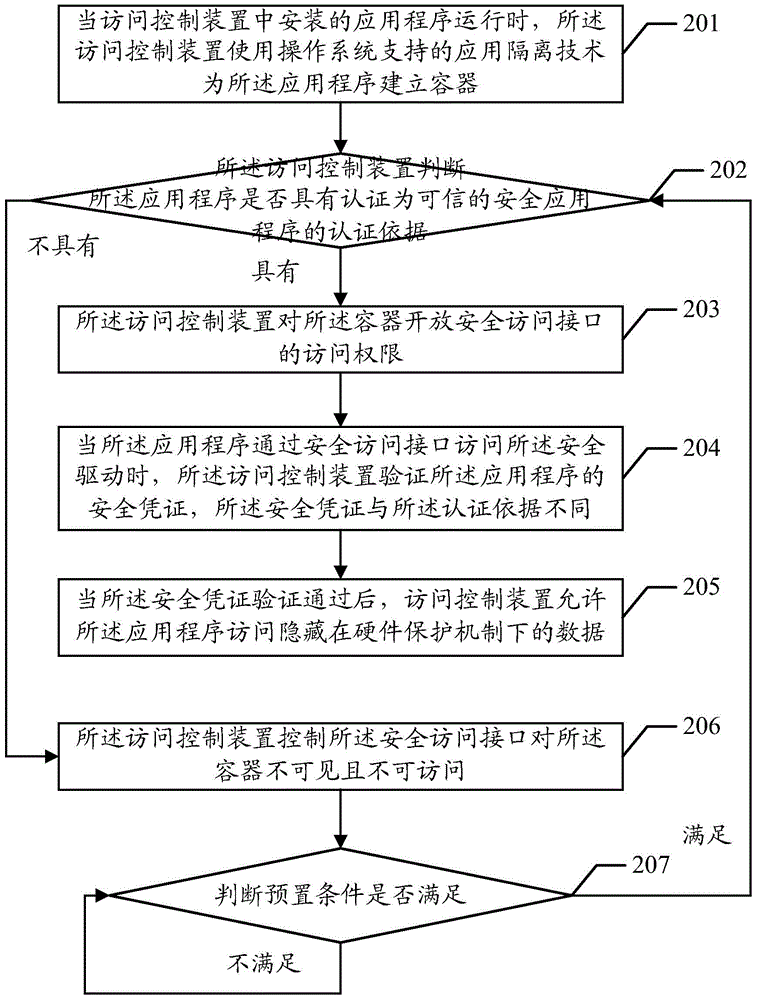
Access control method and device
ActiveCN105138904AImprove securityAvoid direct contactPlatform integrity maintainanceProtection mechanismTrusted Computing
The embodiment of the invention discloses an access control method and device. The access control method and device are used for reinforcing protection over data concealed under a hardware protection mechanism of a dependable computing platform and preventing violent cracking by a malicious application program. The method comprises the steps that a container is established for the running application program, then whether the application program is a dependable security application program or not is judged, and if the circumstance that the application program is the dependable security application program cannot be confirmed, the access permission of a safety access interface is not released for the container.
Owner:HUAWEI TECH CO LTD
Key encrypting and storing method based on tree structure
InactiveCN101582760AEasy accessImprove securityKey distribution for secure communicationUnauthorized memory use protectionRelationship - FatherTrusted Computing
The invention relates to a key encrypting and storing method based on a tree structure, which belongs to the technical field of dependable computing. A binary tree layering and encrypting technology is adopted to convert the protection for many data encrypting keys into the protection for a main key and comprises four parts of binary tree initialization, data encrypting key insertion, deletion and reading. A root node of a binary tree represents the main key and is stored in a dependable crypto module, and keys represented by other nodes are stored in an external memory, wherein a leaf node represents the data encrypting keys, and when a non-root node is stored, a father node of an upper layer is always used for encrypting the non-root node, thus when used, the data encrypting keys must be reduced. The method saves the memory space of the dependable crypto module, can store large numbers of keys and can be widely applied to a computer information system of a high safety class.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
Computer system architecture and method having isolated file system management for secure and reliable data processing
ActiveUS8775369B2Avoid lostDigital data processing detailsComputer security arrangementsData processing systemSystems management
System, method, computer, and computer program for secure data processing of potentially malicious code and documents or other data that may contain malicious code. System, method, computer for a secure and reliable computing environment to protect against data loss and / or corruption to provide secure and reliable data processing.
Owner:VIR2US
Inexpensive reliable computer storage via hetero-geneous architecture and a staged storage policy
InactiveUS7225308B2Quick searchLow costData processing applicationsMemory loss protectionComputer scienceDependable computing
An inexpensive storage system is disclosed along with methods of managing such a system. In one preferred embodiment, the system includes a high performance high reliability storage medium configured for initial storage of data, a low performance high reliability storage medium configured for backup of data initially stored on the high performance high reliability storage medium, and a high performance low reliability storage medium, configured to receive data transferred from the high performance high reliability storage medium, after the data has been backed up on the low performance high reliability storage medium. This significantly reduces the cost of the system without substantially comprising performance. Reliability is likewise maintained owing to the high reliability backup.
Owner:INT BUSINESS MASCH CORP
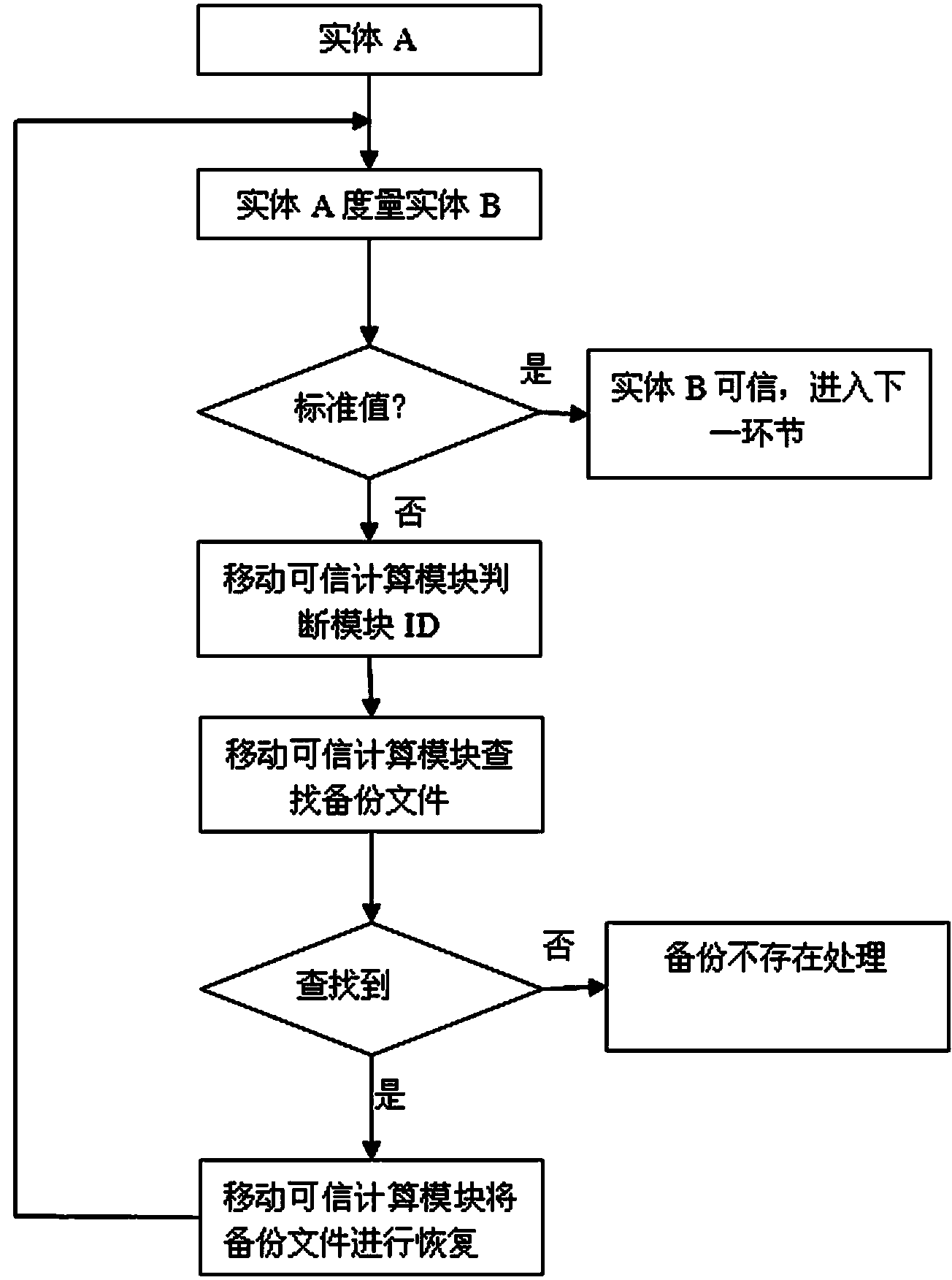
Embedded terminal dependable starting method based on mobile dependable computing module
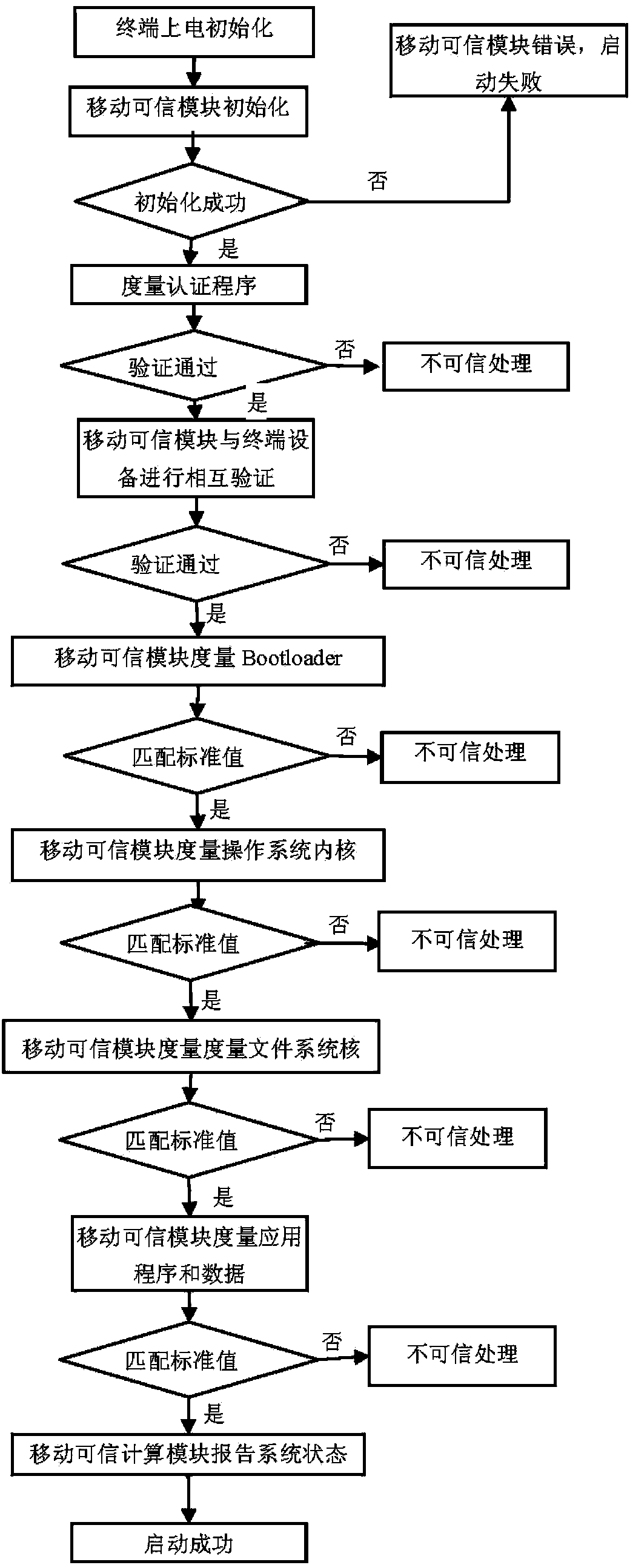
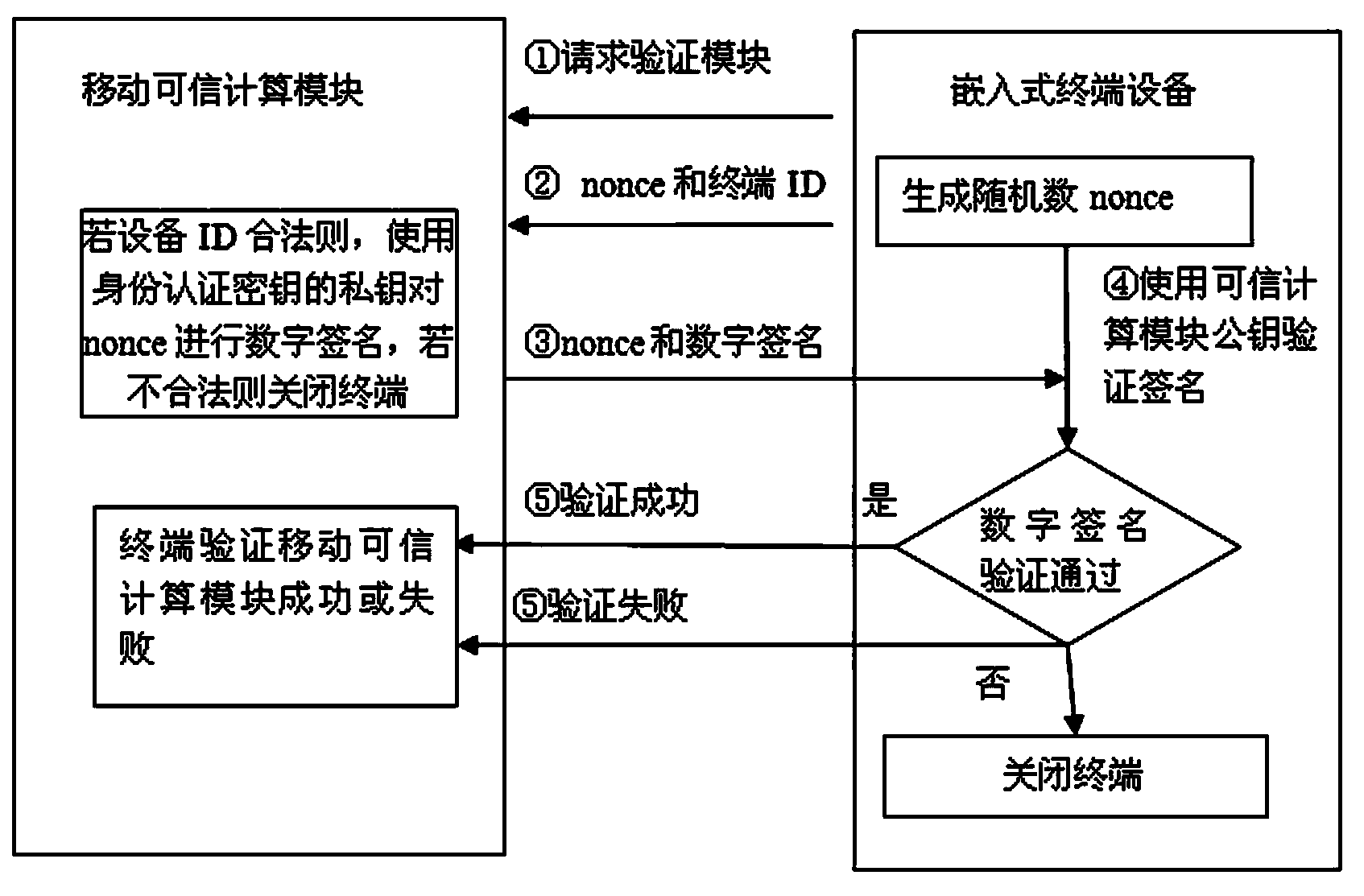
ActiveCN103530548AMake up for the disadvantages of limited computing powerGuaranteed safe operationDigital data authenticationBootstrappingTrusted ComputingSafe operation
The invention discloses an embedded terminal dependable starting method based on a mobile dependable computing module. Segmentation is carried out on a starting procedure, measurement is carried out on partial content of the starting procedure, although the safety is reduced to some extent, the starting speed is improved greatly, and the defect that the computing capability of embedded type equipment is limited is compensated effectively. After a system is started, measurement of the remaining part is carried out, the computing capability is no longer the pure embedded type equipment, it is ensured that all the verification can be completed in a short time, and safe operation of the embedded terminal is effectively ensured due to the verification of all content as a whole.
Owner:SHANDONG SYNTHESIS ELECTRONICS TECH
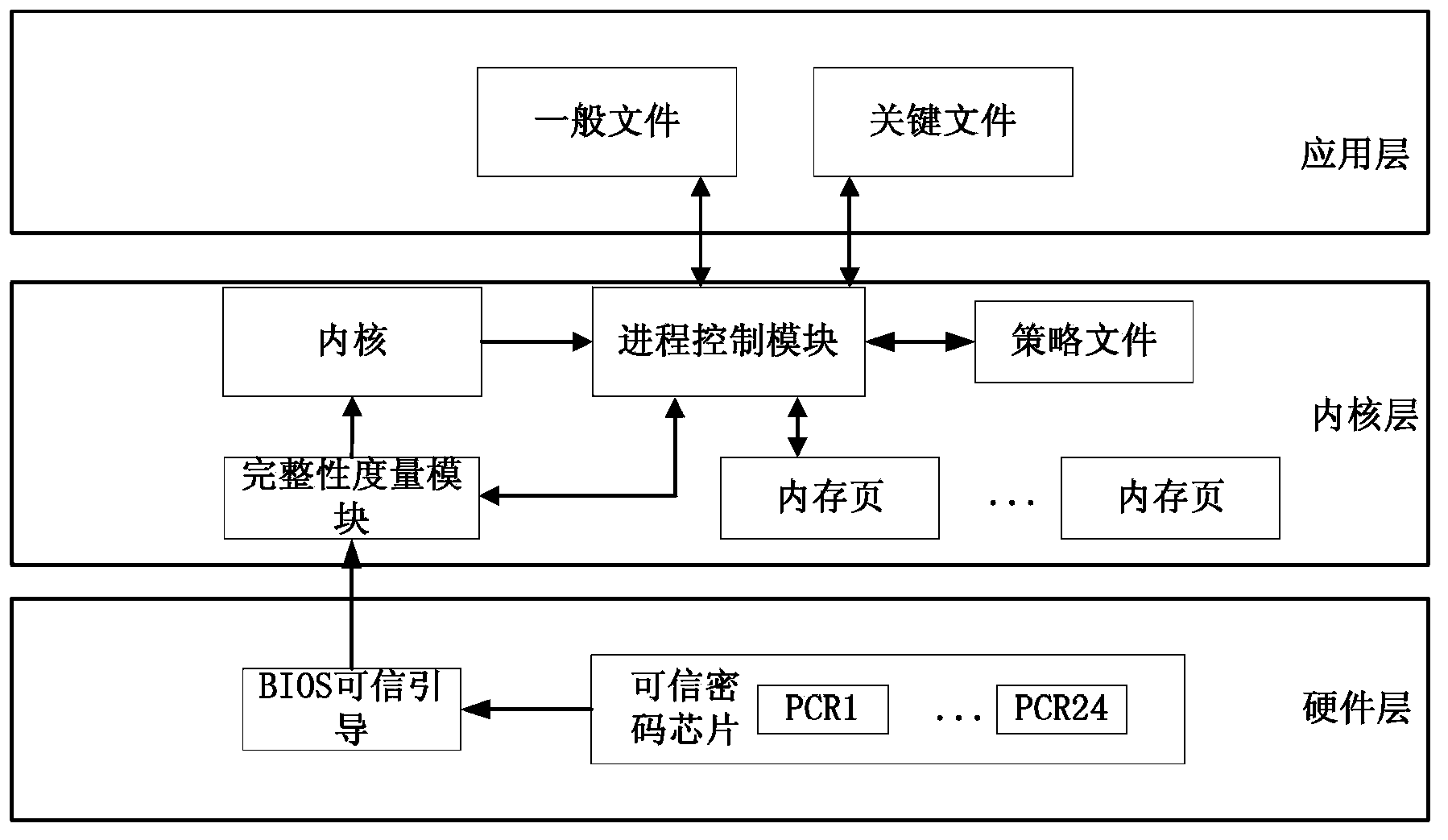
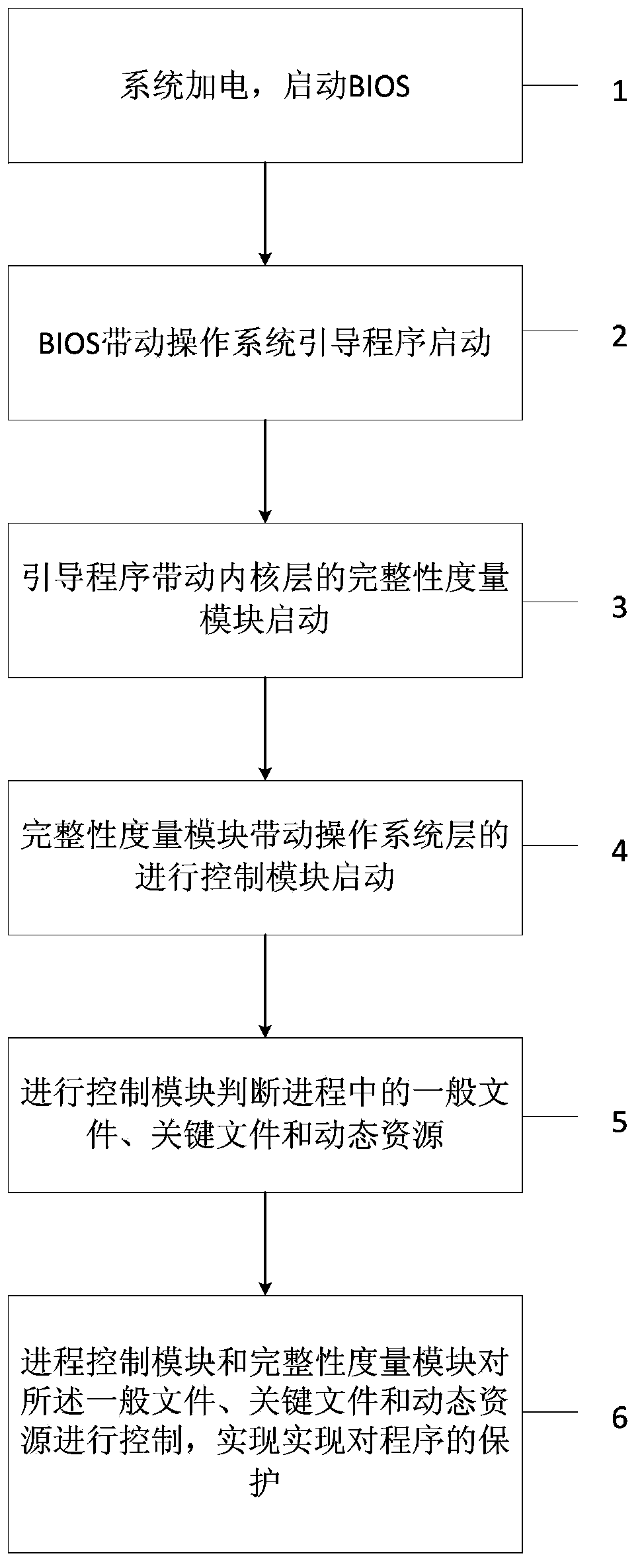
Dependable computing based process control method
ActiveCN103455756AAvoid destructionGuaranteed uptimePlatform integrity maintainanceOperational systemDynamic resource
The invention provides a dependable computing based process control method. The process control method includes that a system is powered and a BIOS (basic input / output system) is started; the BIOS drives an operating system bootstrap program to start; the bootstrap program drives an integrity measurement module in an inner nuclear layer to start; the integrity measurement module drives a process control module in an operating system layer to start; the process control module is used for judging ordinary files, critical files and dynamic resources in process; the process control module and the integrity measurement module are used for controlling the ordinary files, the critical files and the dynamic resources to realize protection of the program. By the method, the files related to process operation are subjected to protection based on the dependable computing platform hardware algorithm, static files and the dynamic files are protected, permission of accessed files and mapping relation label pages are defended, and protective means are stereo and include the aspects of direct encryption storage, and inputting credibility quantity into a dependable computing platform register and the like, so that the process can be effectively controlled.
Owner:STATE GRID CORP OF CHINA +5
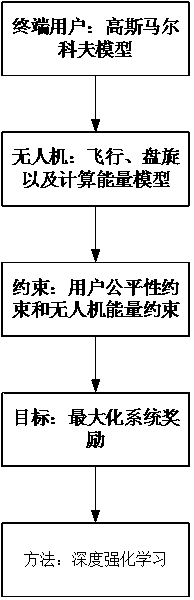
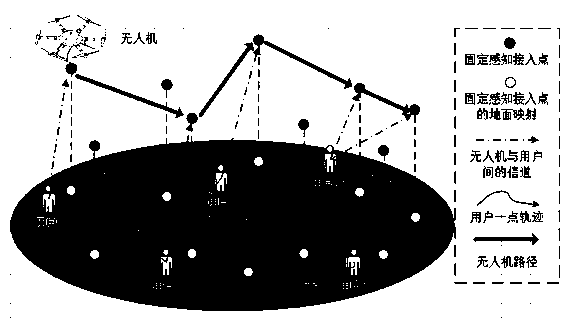
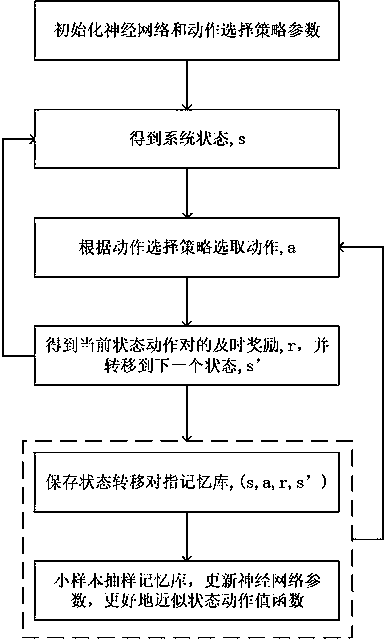
Method for maximizing system benefits in dynamic environment based on deep reinforcement learning
InactiveCN110428115APrevent overfittingForecastingNeural learning methodsDisaster areaReinforcement learning algorithm
The invention designs an unmanned aerial vehicle path planning method for providing a low-delay and high-reliability calculation service for a dynamic user under a mobile edge calculation architecturebased on deep reinforcement learning. Considering that the unmanned aerial vehicle has a convenient infrastructure, a communication channel can be quickly built in a remote or disaster area, and computing resources can also be erected to provide services for a terminal mobile user, the unmanned aerial vehicle is considered to serve as a mobile computing server, and efficient interaction servicesare provided for the terminal mobile user above the terminal mobile user. According to the invention, the real-time movement of the terminal user is considered; the method comprises the following steps: establishing a Gaussian-Markov mobile model by modeling, establishing a user position state, an unmanned aerial vehicle position state, an unmanned aerial vehicle battery capacity state and a channel state between an unmanned aerial vehicle and a user, and planning an unmanned aerial vehicle path by combining a deep reinforcement learning algorithm to maximize the long-term benefit of the system.
Owner:NANJING UNIV OF SCI & TECH
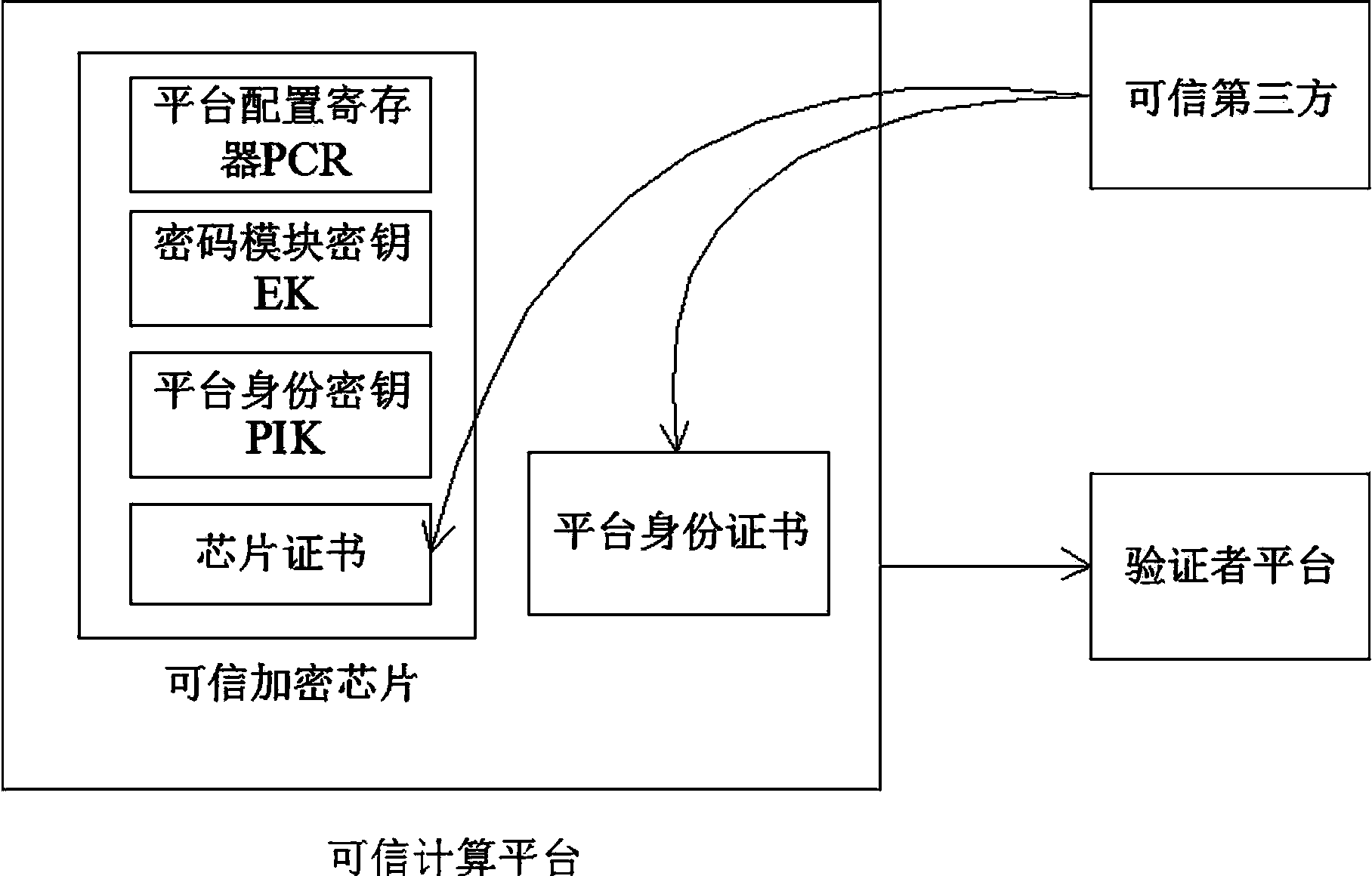
Platform integrity verification method
InactiveCN104270376AProof of integrityValid proof of integrityTransmissionRelevant informationTrusted Computing
The invention discloses a platform integrity verification method. The method includes the specific steps that the integrity of a dependable computing platform is reported by the dependable computing platform, and a verifier finishes the verification process after a verifier platform receives the relevant information. Compared with the prior art, according to the platform integrity verification method, a safe dependable encryption chip is adopted, the platform can provide an integrity report for an external entity, a receiver judges the credibility of the platform according to the reported metric, the practicability is high, and the safety, integrity and effectiveness of the platform are guaranteed effectively.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Method for calculating temperature, pressure and dryness of injected steam and nitrogen mixture
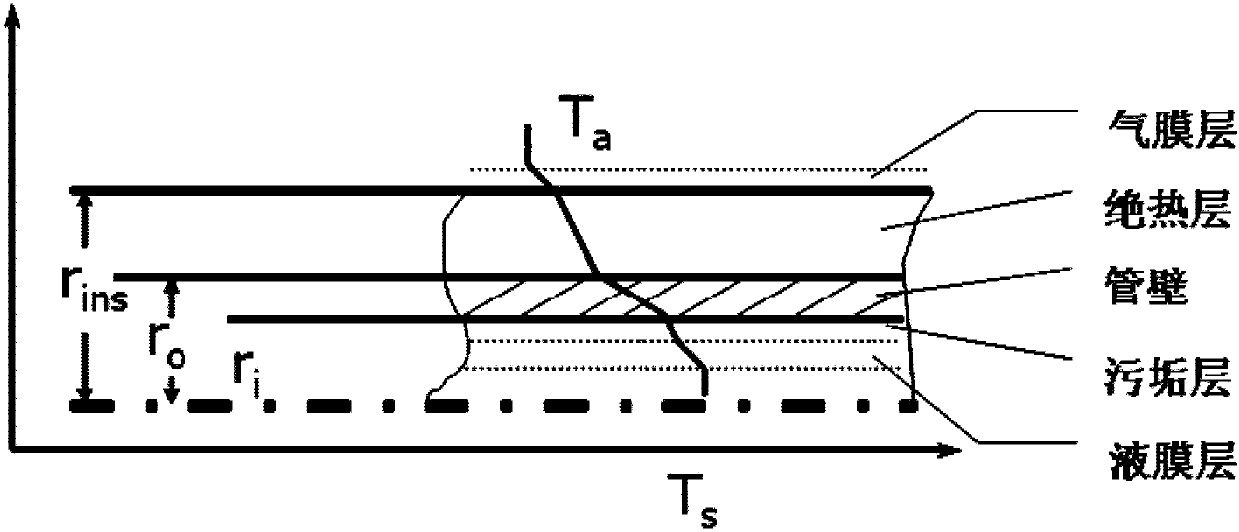
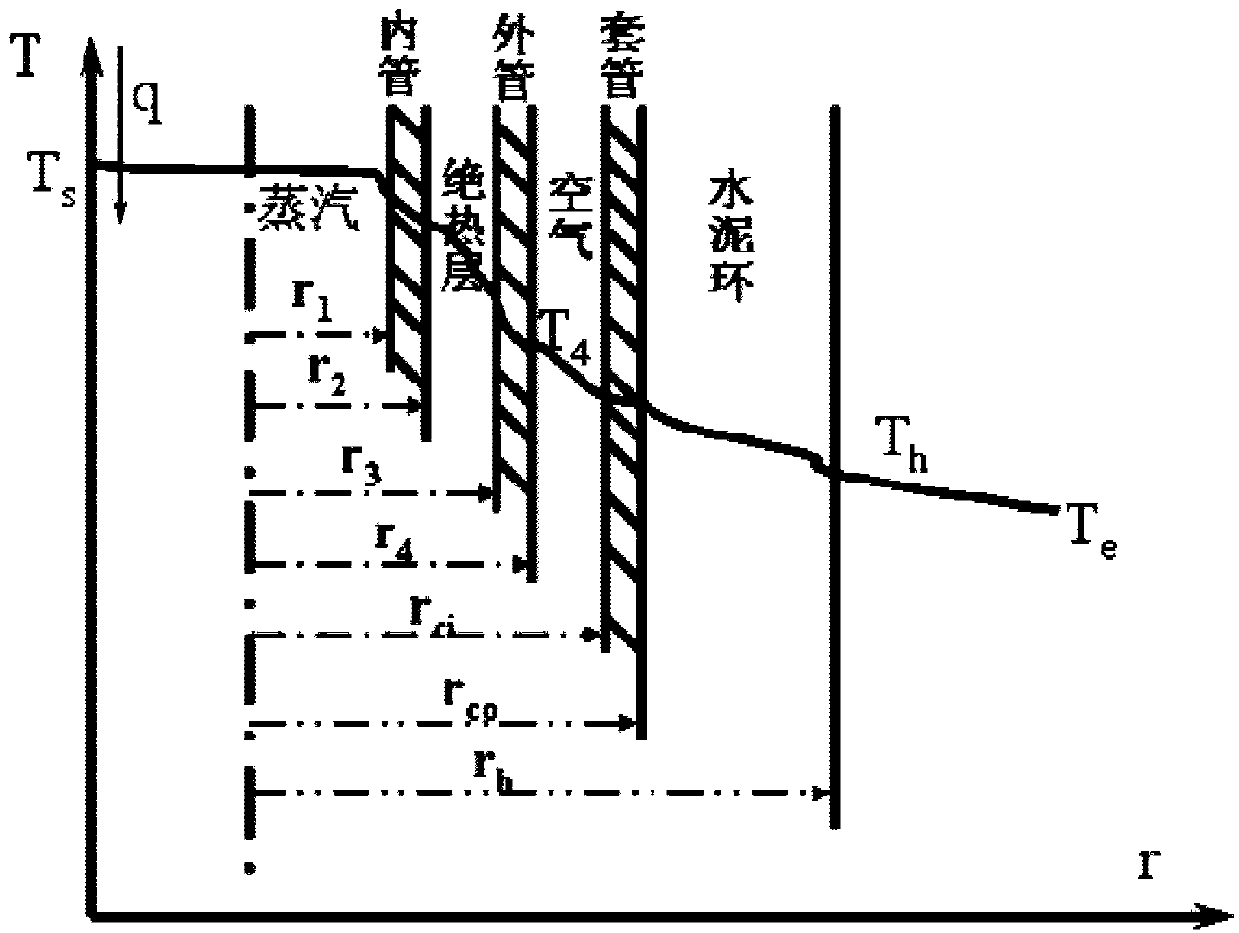
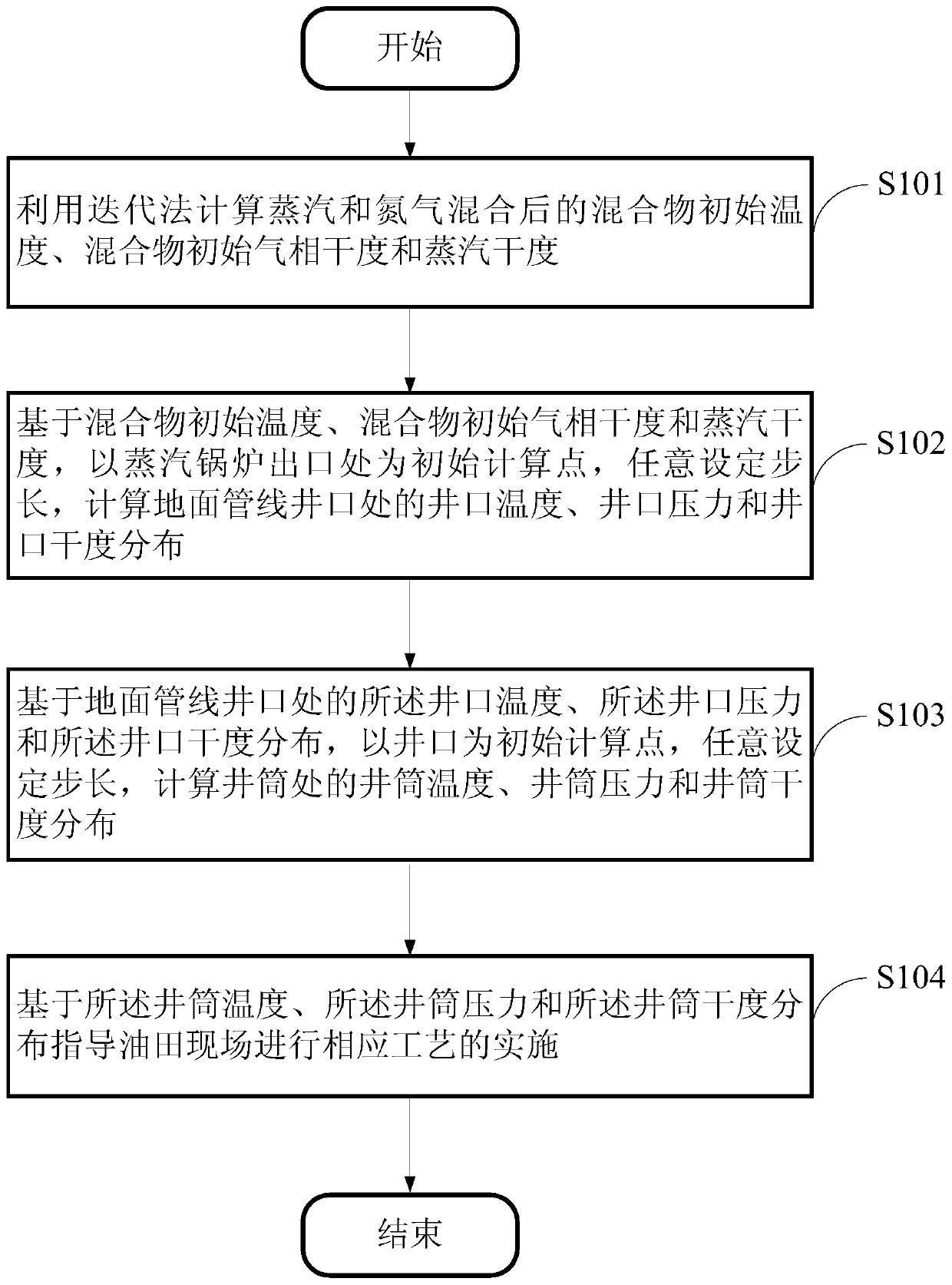
ActiveCN104850681AGood calculation stabilityImprove calculation accuracySurveyConstructionsNitrogenEngineering
The invention provides a method for calculating temperature, pressure and dryness of an injected steam and nitrogen mixture. The method comprises the steps as follows: calculating initial temperature, initial gaseous dryness and initial steam dryness of a mixture after steam is mixed with nitrogen; calculating wellhead temperature, wellhead pressure and wellhead dryness distribution of a surface pipeline wellhead with randomly set step length by using the outlet of a steam boiler as an initial calculating point; calculating wellbore temperature, wellbore pressure and wellbore dryness distribution with randomly set step length by using the wellhead as an initial calculating point; and providing guidance for the implementation of the corresponding technology in an oil field site based on the wellbore temperature, the wellbore pressure and the wellbore dryness distribution. The method of the invention has excellent computational stability and higher computational accuracy, and provides reliable calculation means for optimal design of wellbore injecting parameters of a stream and nitrogen mixed system.
Owner:PETROCHINA CO LTD
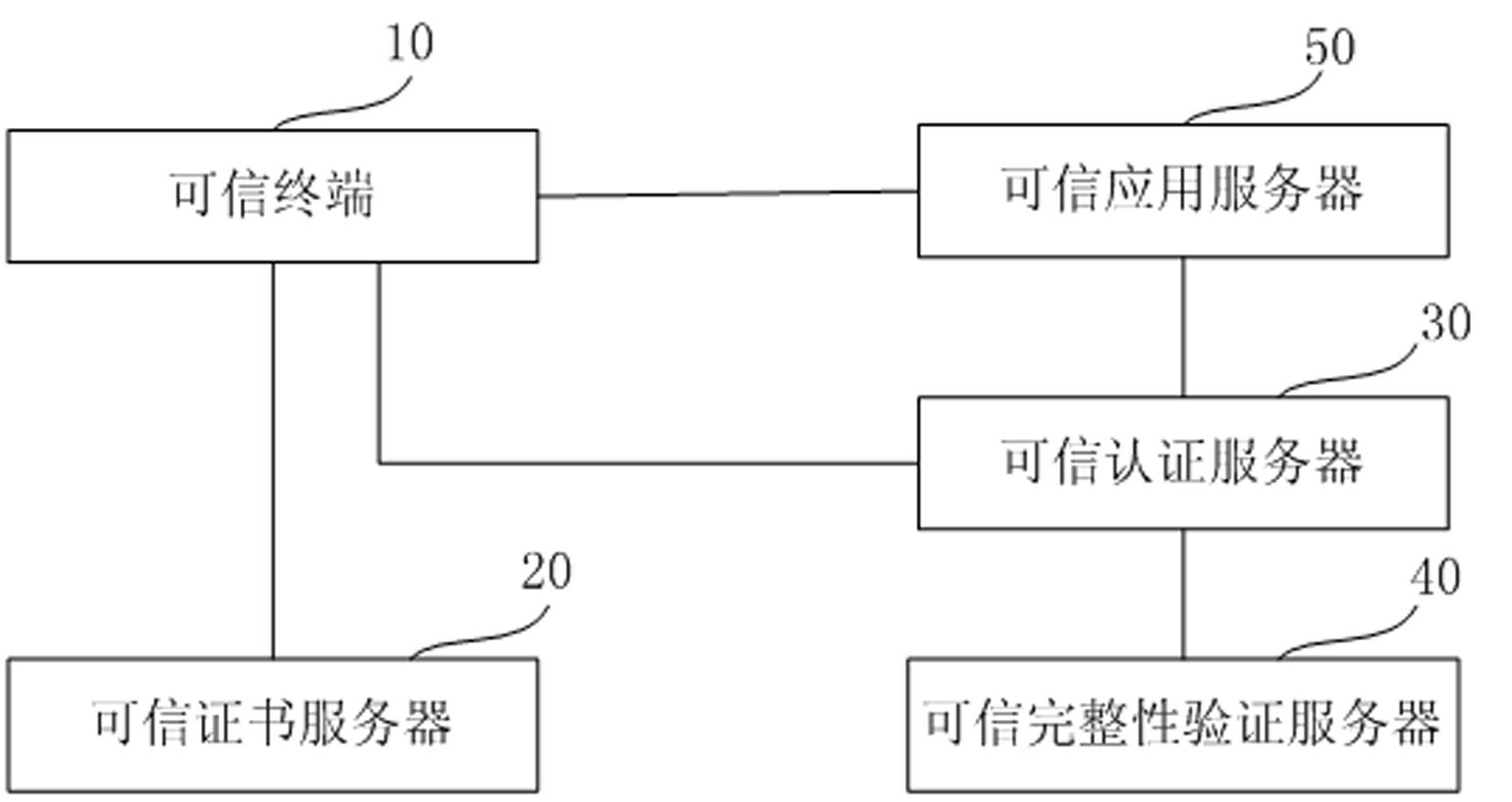
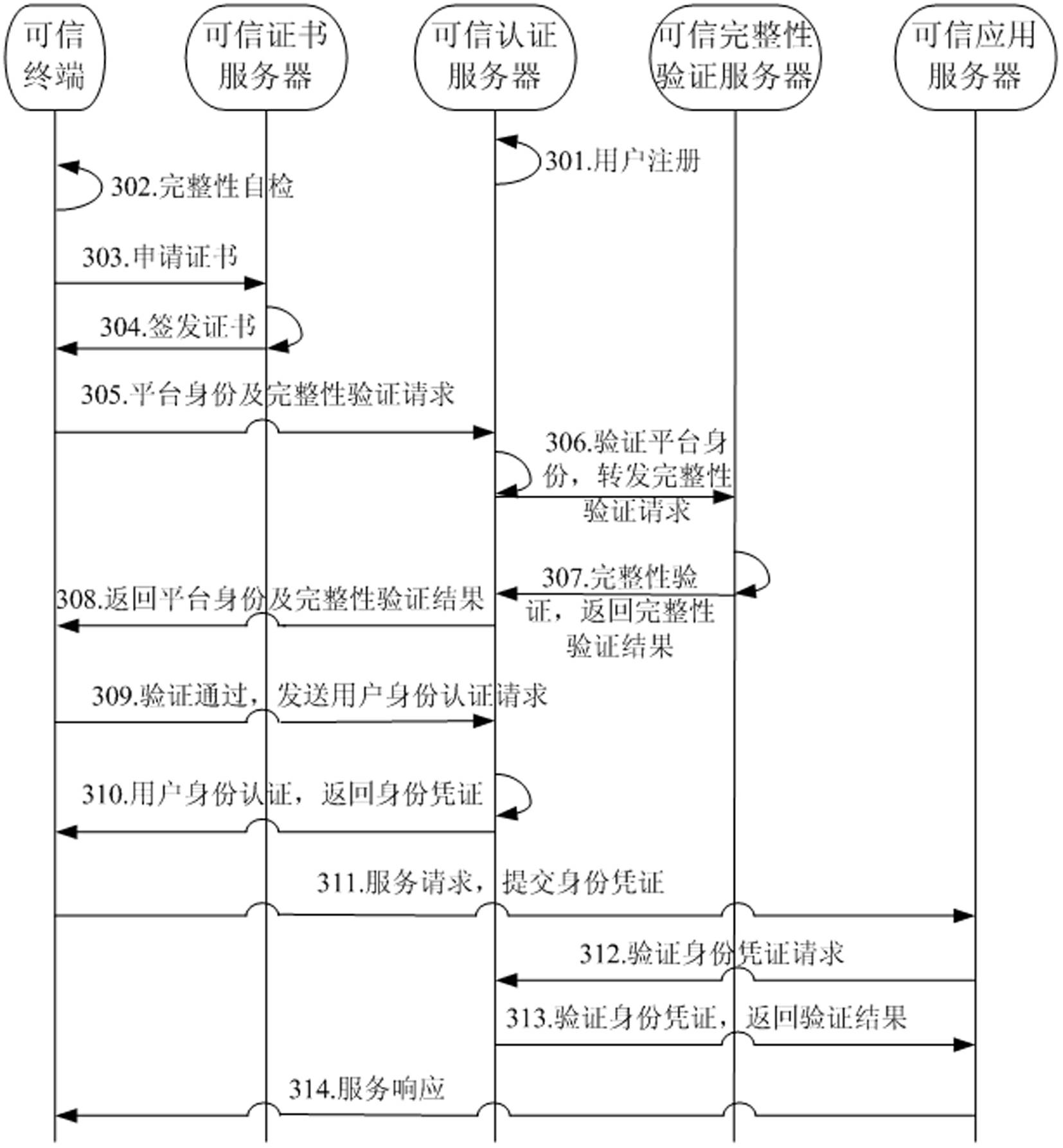
Authentication system and method based on dependable computing
The present invention relates to an authentication system and a method based on dependable computing. The authentication system based on dependable computing comprises a dependable terminal, a dependable certificate server, and a dependable authentication server. Each of the dependable terminal, the dependable certificate server and the dependable authentication server has a dependable computing module. According to the authentication system and the method based on dependable computing provided by the invention, PKI digital certificate technology and a dependable computing platform are combined, the security of a network and a server terminal is ensured, at the same time, terminal can be ensured to be dependable, the security of a whole network is raised greatly, and creditability and security of computer network certification are raised.
Owner:NATIONZ TECH INC
A vehicle big data computing and unloading method based on a fog network
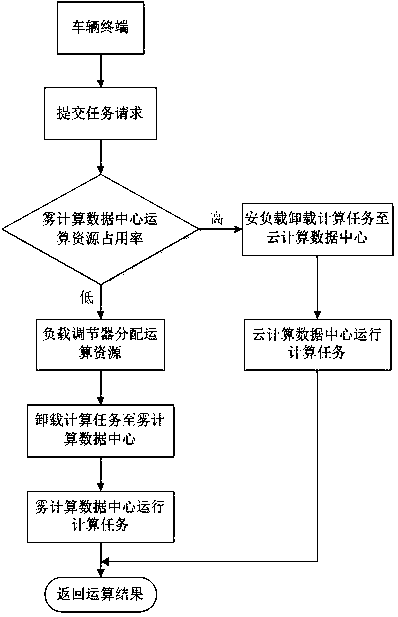
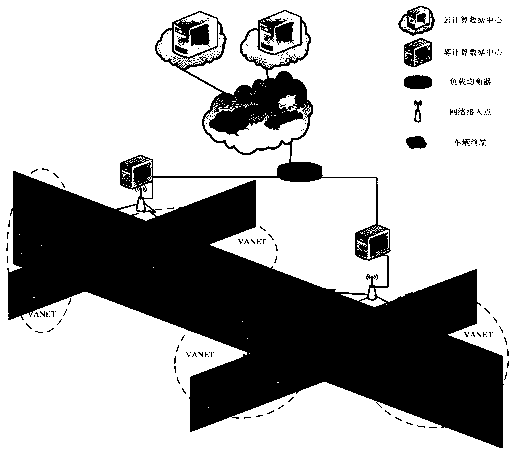
ActiveCN109947574ALess number of task failuresLess number of failed tasksResource allocationParticular environment based servicesReliable computingFog computing
The invention discloses a vehicle big data computing and unloading method based on a fog computing network. According to the invention, a more efficient and reliable computing environment can be provided for analyzing vehicle big data. Firstly, a fog computing network system architecture is provided, a network delay model is further established, then a task generation model is established, a fog computing resource optimization model is established, and finally a load balancing computing resource effective task unloading algorithm is used. Efficient Task Offloading Algorithm with Load Balancing, CRETOA) is used for managing computing resources for load balancing of the fog computing network, and a road vehicle terminal request computing task is allocated to the optimal fog computing resources.
Owner:NANJING UNIV OF POSTS & TELECOMM
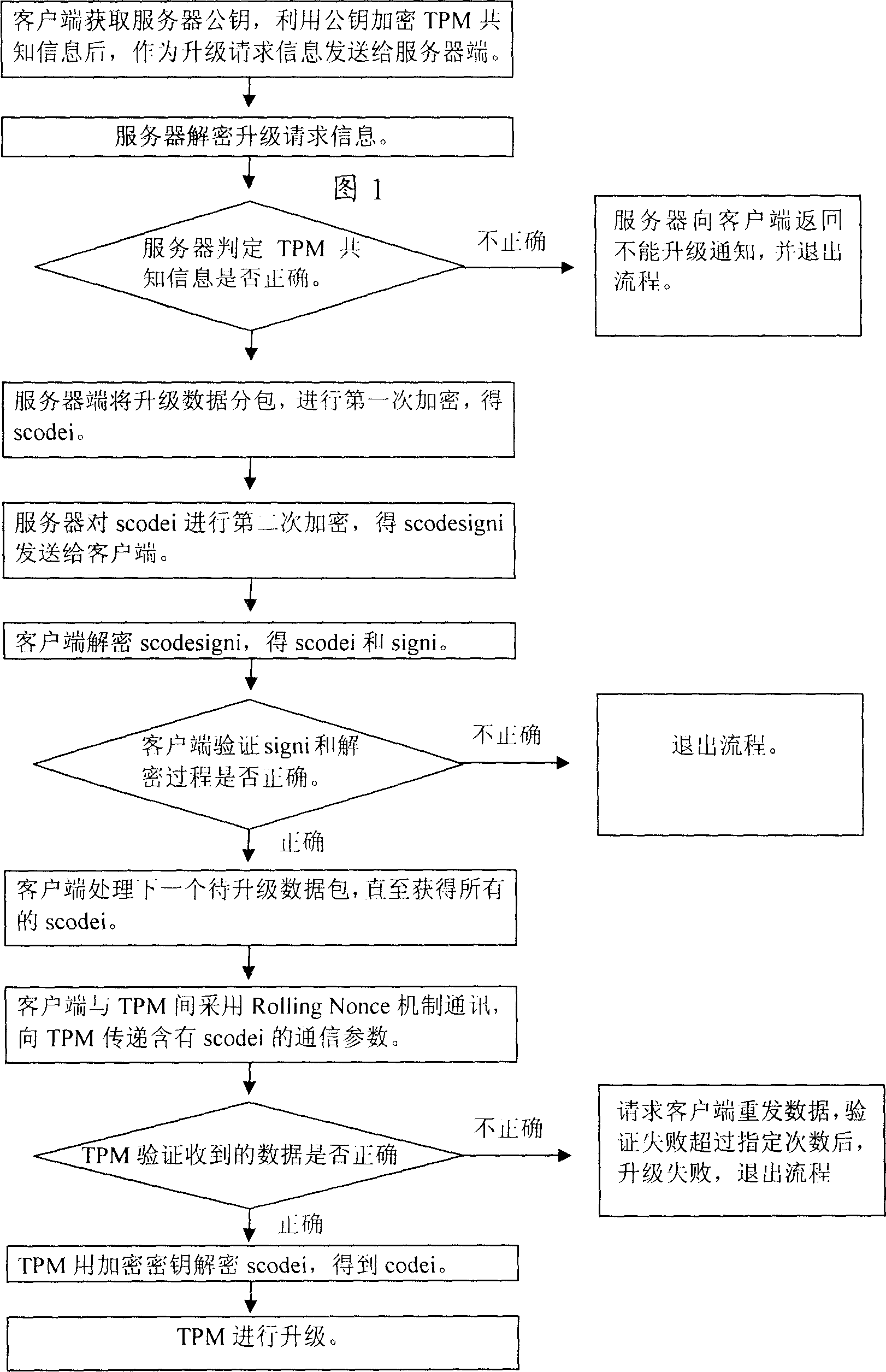
Method for upgrading function of creditable calculation modules
ActiveCN1917424ASimple methodMultiple keys/algorithms usagePublic key for secure communicationTrusted ComputingComputer module
The method comprises: a server side for providing data update, a client side comprising a dependable computing module and a dependable computing module are provided; using the code of the dependable computing module as the secret information shared by the update provider and the dependable computing, by which the mutual authentication mechanism and encryption communication are established between the server side and client side in order to download the update data to client side; the secret communication also be set between the client side and TPM, and when the TPM conforms the correction of update data from the client side, it make update.
Owner:SHENZHEN SINOSUN TECH
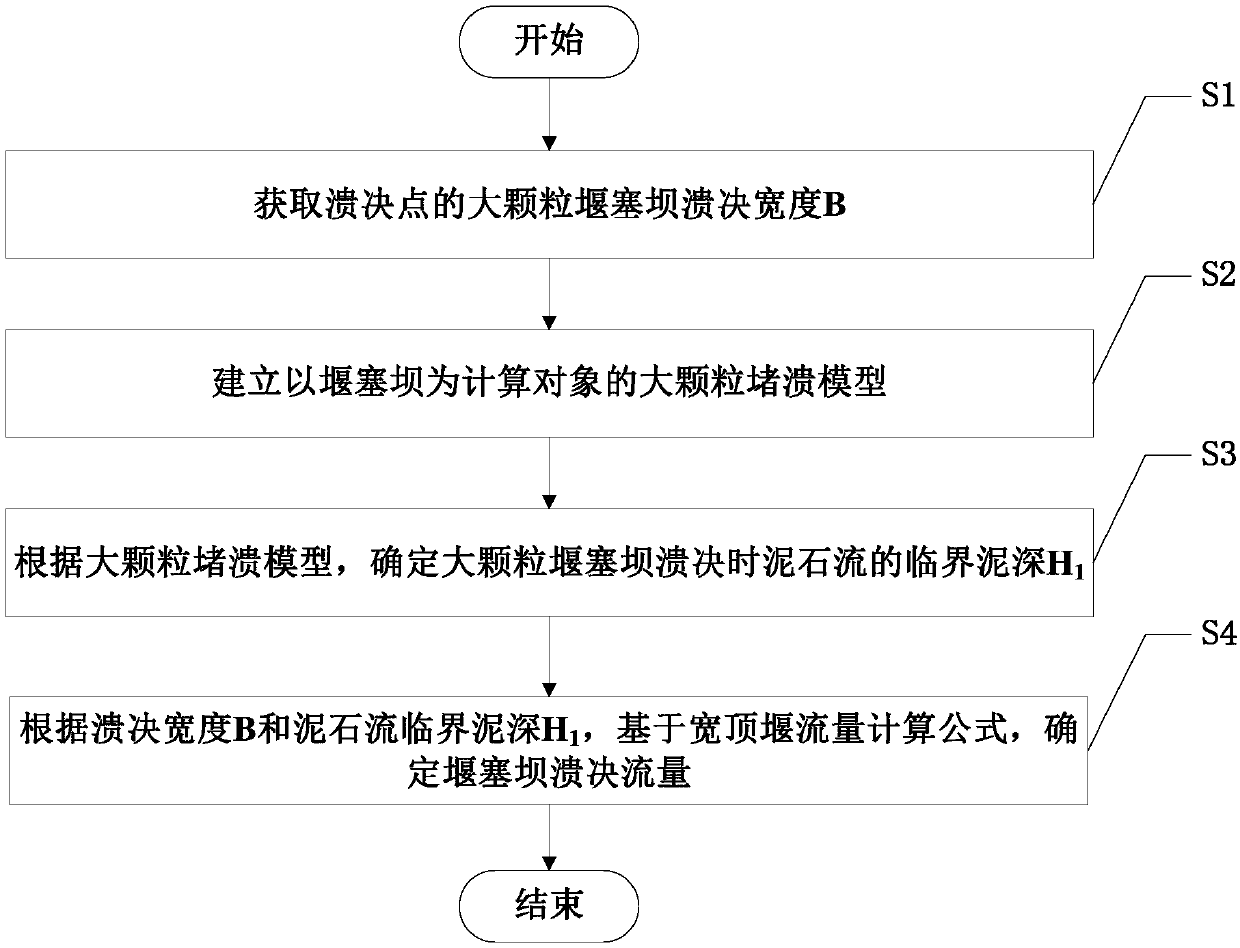
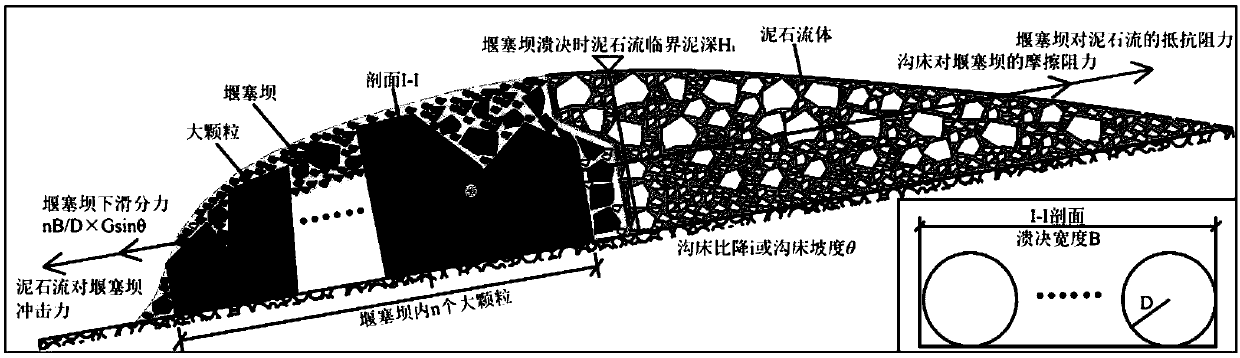
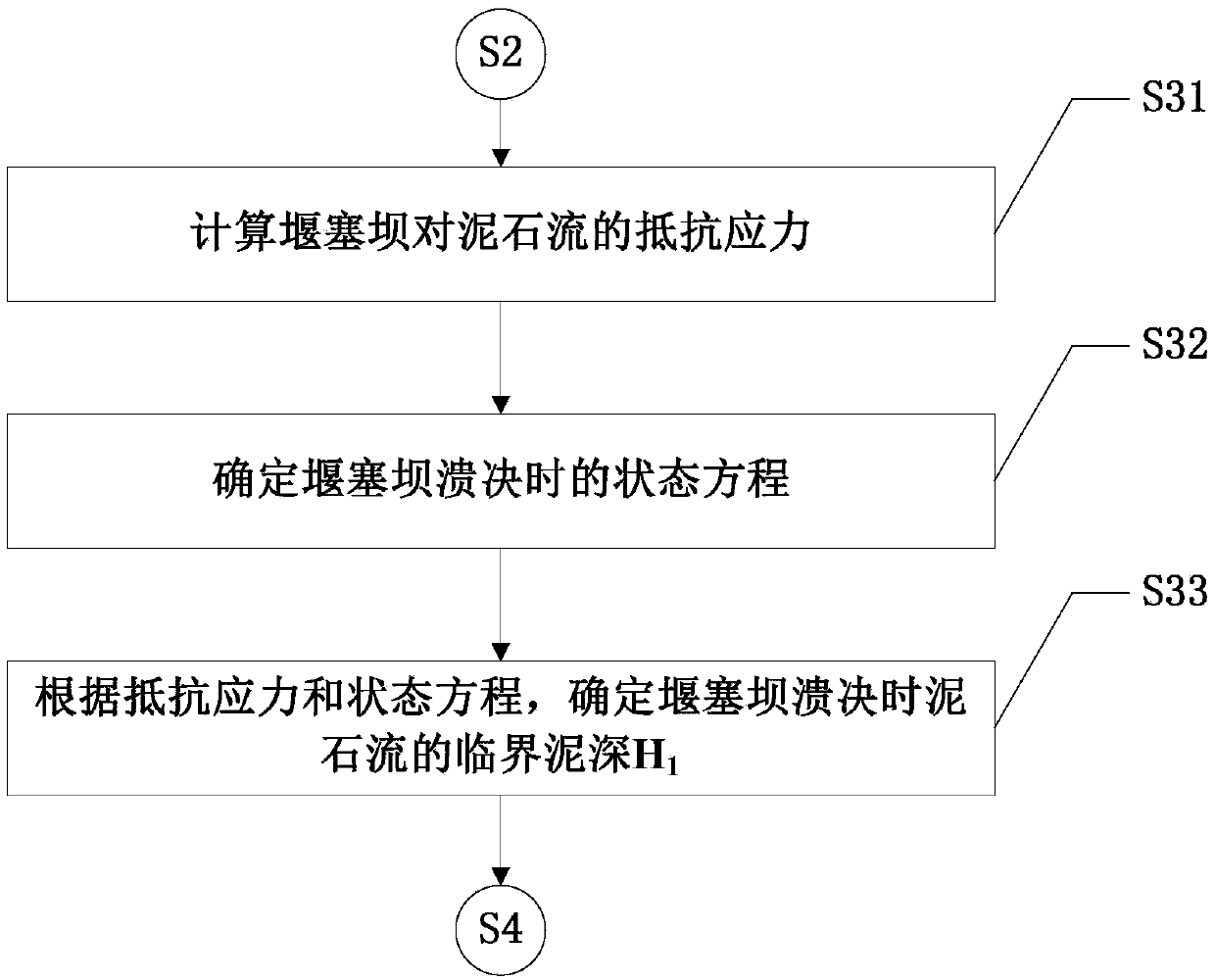
Calculation method of outburst discharge of large particle weir and plug dam under impact of outburst viscous debris flow
ActiveCN108984962AVerify reliabilityGeometric CADSpecial data processing applicationsDebris flowCalculation methods
A calculation method of outburst discharge of a large granular weir and a plug dam under the impact of outburst viscous debris flow is disclosed. Through analysis of the static equilibrium relationship of large particles in a weir-plug dam under the impact of viscous debris flow, the formulas for calculating the critical mud depth of debris flow and the maximum particle diameter in weir-plug dam are derived, then the calculation model of weir plug dam outburst discharge and maximum particle diameter is established by using the calculation formula of weir plug dam outburst discharge, and the reliability of the model is verified by an example, and thus an accurate and reliable calculation method is provided for determining the outburst discharge in debris flow prevention and control engineering.
Owner:SICHUAN UNIVERSITY OF SCIENCE AND ENGINEERING
Method for predicting optimal release point of airdropped material
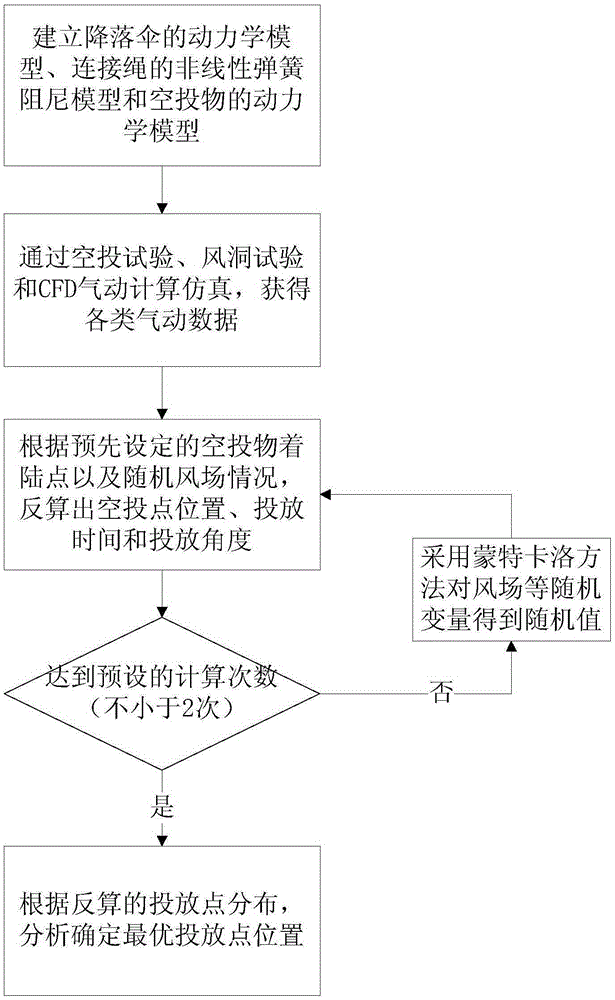
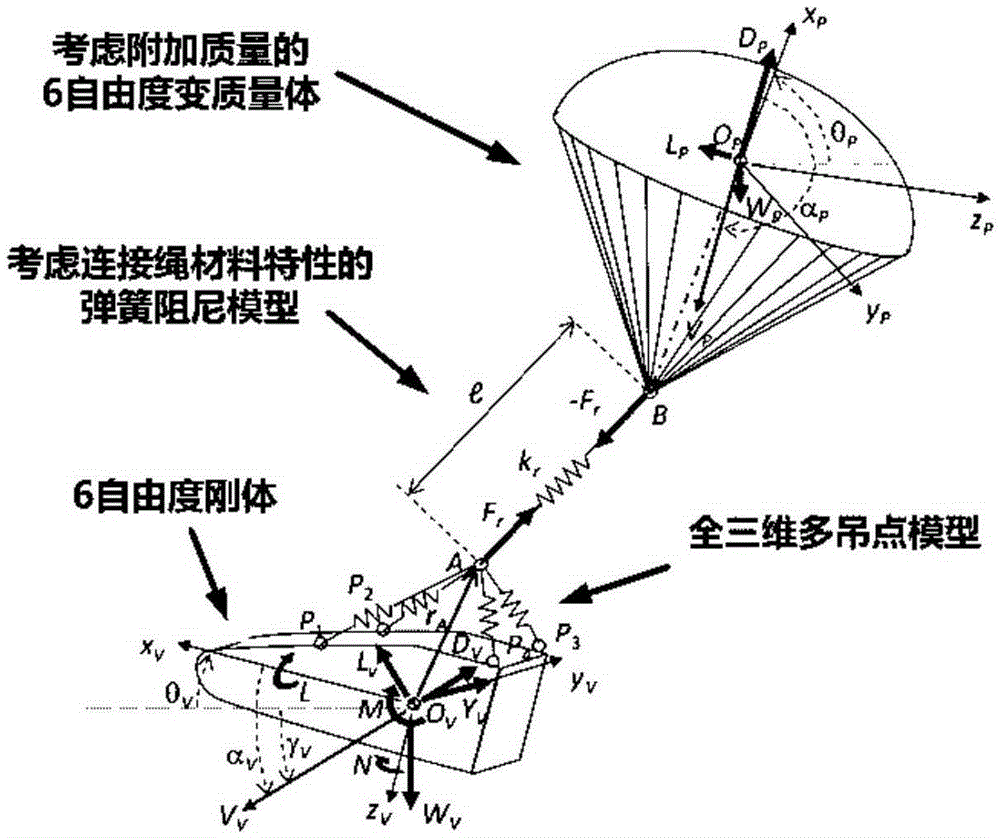
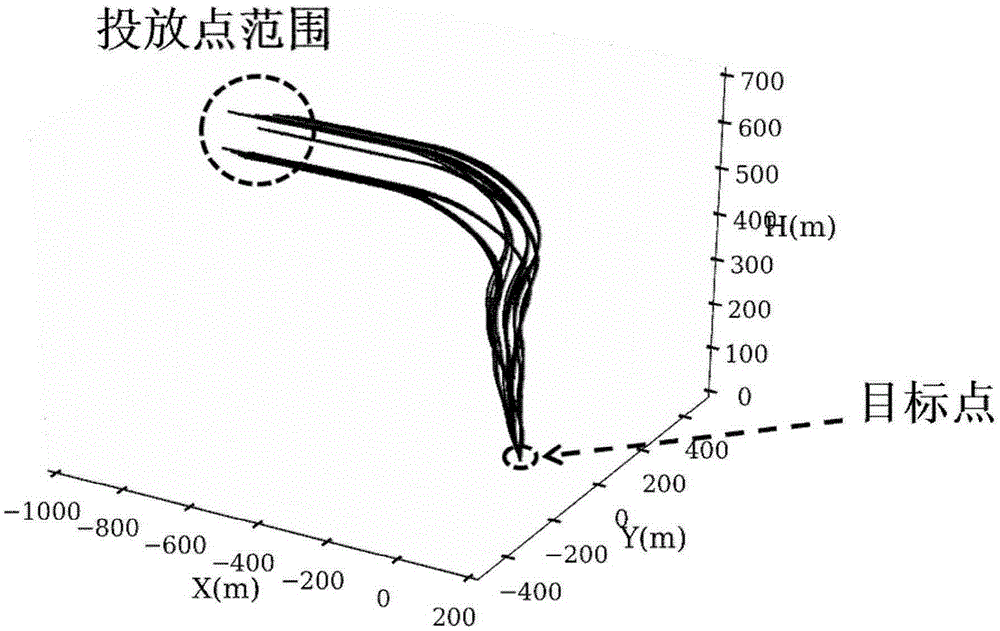
InactiveCN105260508AThe calculation is close to the actual situationReliable calculationSpecial data processing applicationsDynamic modelsRelease time
The invention discloses a method for predicting an optimal release point of an airdropped material. The method comprises: performing calculation by regarding a parachute as a three-dimensional 6-degree-of-freedom variable mass body, analyzing a motion characteristic of the airdropped material in a parachute opening and stable descent process according to an actual parachute descent working procedure, establishing a reliable dynamic model of a goods and materials airdropping process, simulating a motion track of the airdropped material after leaving from an aircraft, and calculating a parachute descent trajectory; and calculating and analyzing optimal release point, release time and release angle of the airdropped material with a Monte Carlo method according to a known target release point. With the method, the parachute descent airdropping process is subjected to high-precision dynamic modeling and solving, so that an airdropping point in a specified airdropping condition can be calculated reliably and a theoretical reference is provided for accurately mastering a release opportunity in a parachute descent implementation process to enable goods and materials to land in a predetermined landing site.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS +1
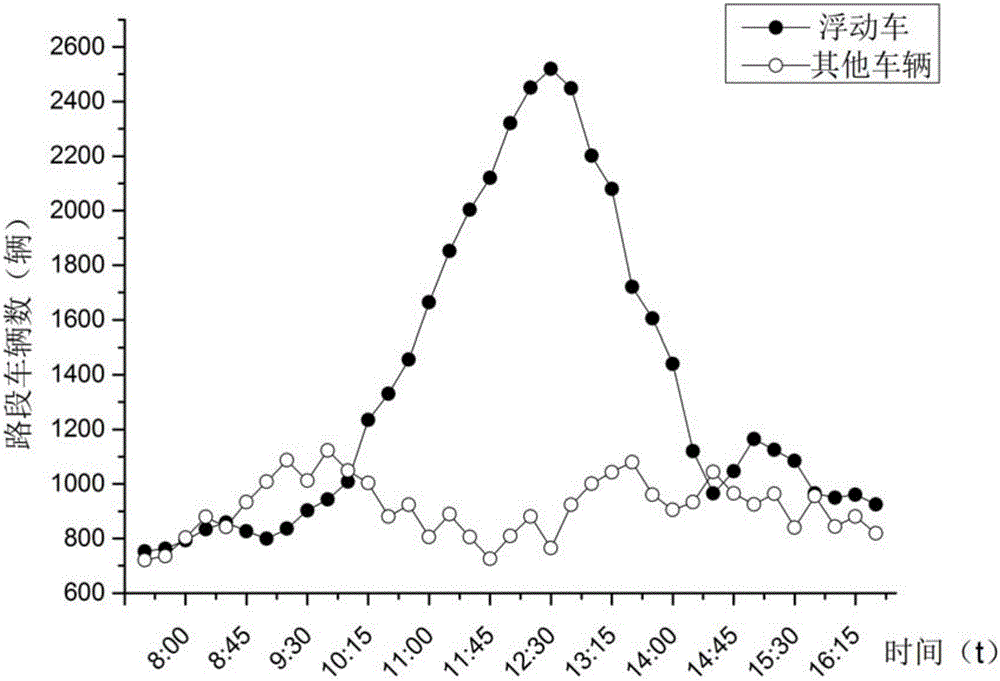
Floating car aggregation detection method based on multivariate data fusion
ActiveCN106530704AMeet application needsImprove accuracyDetection of traffic movementSimulationDependable computing
The invention discloses a floating car aggregation detection method based on multivariate data fusion. According to the method, a region in need of analysis is mapped to a virtual grid, GPS data and bayonet data of the floating cars are combined to form a high-efficiency and reliable calculation platform. Through use of the multivariate data, the calculation can be ensured to be more accurate, and thus, the floating car aggregation detection accuracy and the efficiency can be improved.
Owner:HANGZHOU DIANZI UNIV
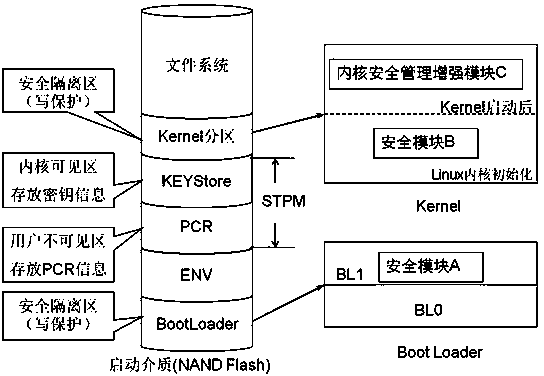
Method for constructing STPM of android system
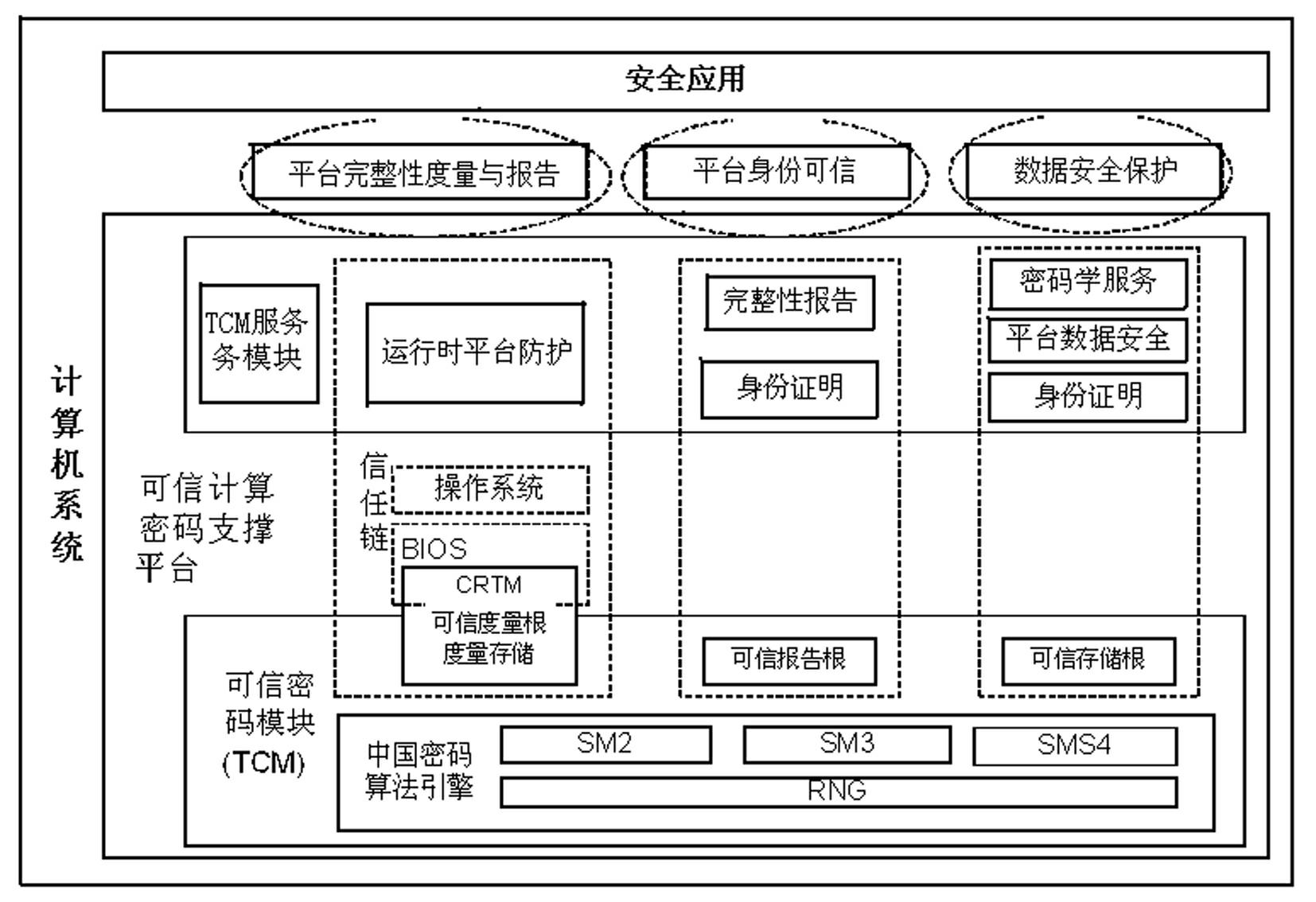
ActiveCN103530578AImplement secure bootAchieve securityDigital data protectionInternal/peripheral component protectionHardware architectureTrusted Platform Module
The invention discloses a method for constructing an STPM of an android system. According to the dependable computing conception, on the basis that an existing handheld device hardware architecture is not changed, the TPM technology idea and the divide-and-conquer conception are adopted, and the functions of dependable storage, dependable measurement, three-layer key management and the like of the STPM are respectively achieved in the android system; the STPM is constructed to provide a basis for secondary safe development on mobile devices, and on the basis, developers can further achieve the development of various safety functions such as safe start of the system, measurement on start of upper-layer application programs and protection on private data of users. The method provides the basis for system safety of the mobile devices and privacy of the private data of the users from the bottom layer of the system. The method mainly has the advantage that the construction of the STPM overcomes the defect that the existing mobile devices lack a TPM and provides the basis for safe development of the mobile devices.
Owner:WUHAN UNIV
Method for calculating damage effect of target of conventional facility
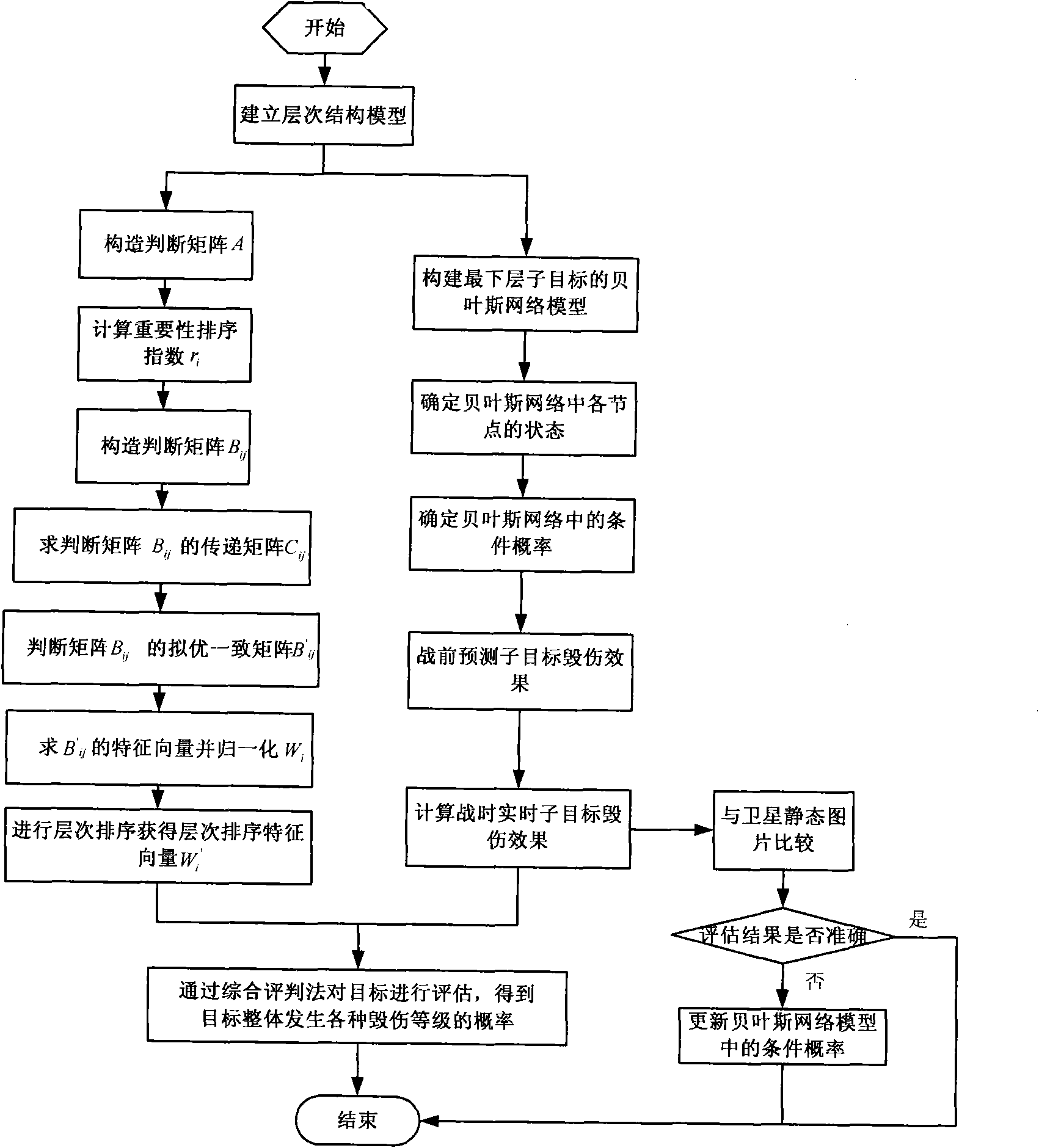
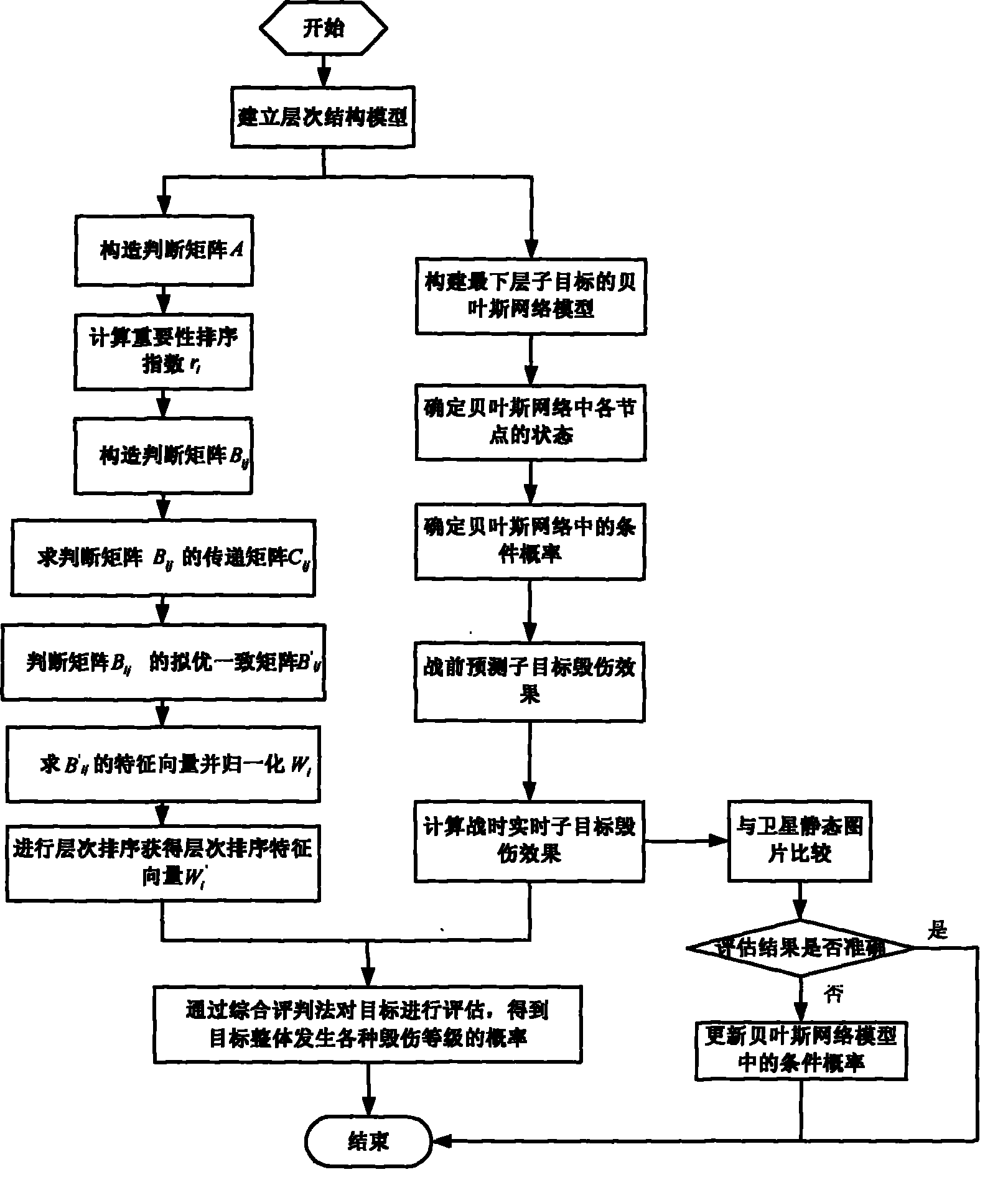
InactiveCN101807227AMeet the consistency inspection requirementsImprove reliabilitySpecial data processing applicationsComputing MethodologiesEffect assessment
The invention discloses a method for calculating the damage effect of the target of a conventional facility, belonging to the field of the technology for assessing and calculating the damage effect of the target of the conventional facility. The method for calculating the damage effect of the target of a conventional facility comprises the following steps: dividing the target into various types of sub-targets on various layers according to the combat task and the characteristic of the target; constructing the judgment matrix of a hierarchical structure model from top to bottom with the improved analytic hierarchy process; calculating the weight of the same type of sub-targets on the same layer relative to the sub-targets on the upper layer; calculating the damage effect of the sub-targets on the bottommost layer by a Bayesian network decision-making model; and calculating the whole damage effect of the target with the comprehensive assessment method. The method can be used for rapidly and reliably calculating the damage effect of the complex target and the target in the real wartime though less or no more accurate damage information is available.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
Terminal dependable computing and data static safety system and method
ActiveCN106502927AAchieve securityEnsure safetyUnauthorized memory use protectionPlatform integrity maintainanceData informationNetwork connection
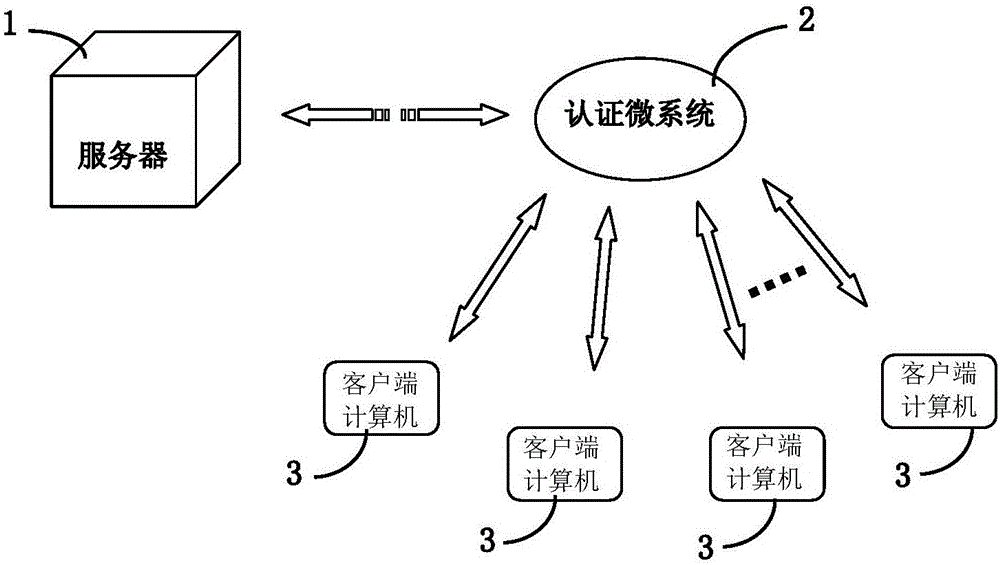
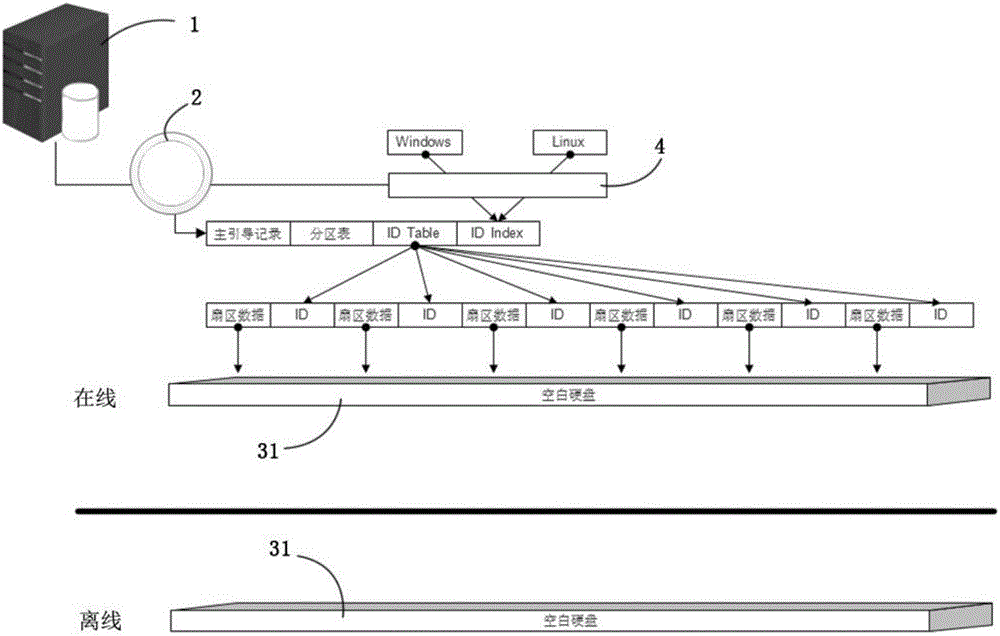
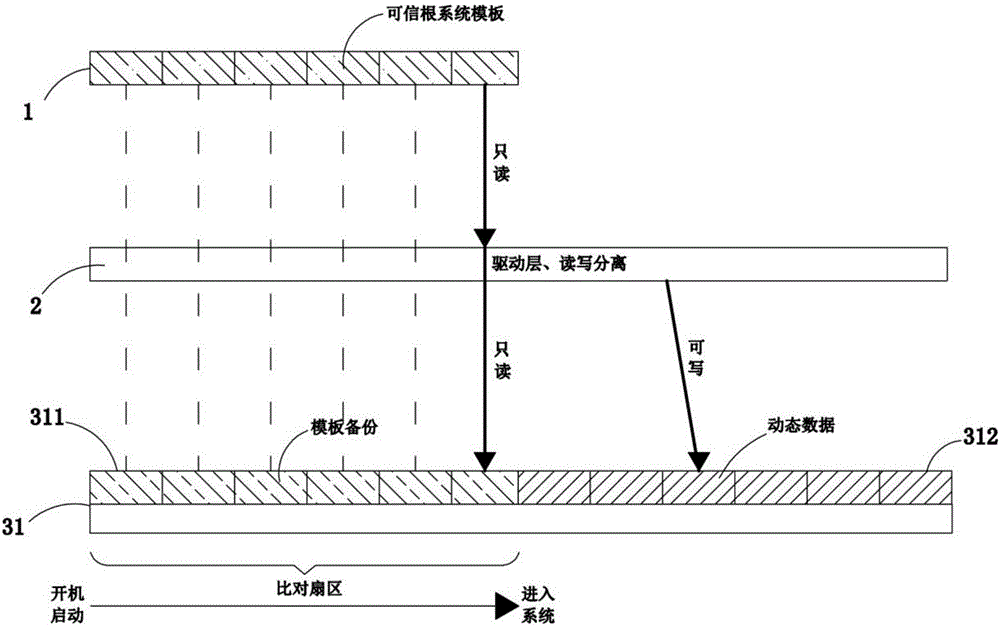
The invention provides a terminal dependable computing and data static safety system. The system comprises a server, a client computer and an authenticated microsystem module. The server is connected with the client computer through the network, and a template file of a dependable root system and a data pointer file from the client computer are stored in the server; a dependable authenticated microsystem is stored in the authenticated microsystem module and used for comparing data information of the server with that of the client computer, and after the client computer passes the hardware dependable authentication, the data pointer file, stored in the server, of the client computer is mapped to the hardware of the client computer; the authenticated microsystem module compares the data of the dependable root system tagged by the data pointer file with the corresponding data of a dependable root system of a storage sector of a hard disk; if the data is inconsistent, it is determined that the client computer is not dependable. The invention further discloses a terminal dependable computing and data static safety method. Real-time dependable monitoring is achieved before a remote terminal enters a system layer, and data safety is protected.
Owner:山东微创软件有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com