Terminal dependable computing and data static safety system and method
A static security and data technology, applied in the field of remote desktop systems, can solve problems such as security risks, cost, computing power, unsatisfactory graphical desktop experience, and difficulty in improving information security capabilities of network protocols and operating system kernels.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to have a clearer understanding of the technical features, purposes and effects of the present invention, the specific implementation manners of the present invention will now be described with reference to the accompanying drawings.
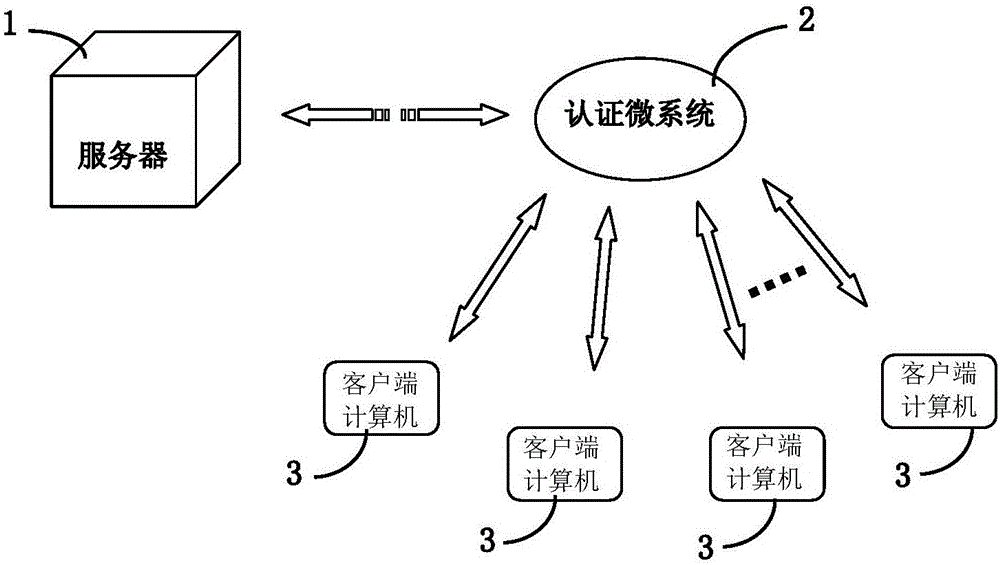
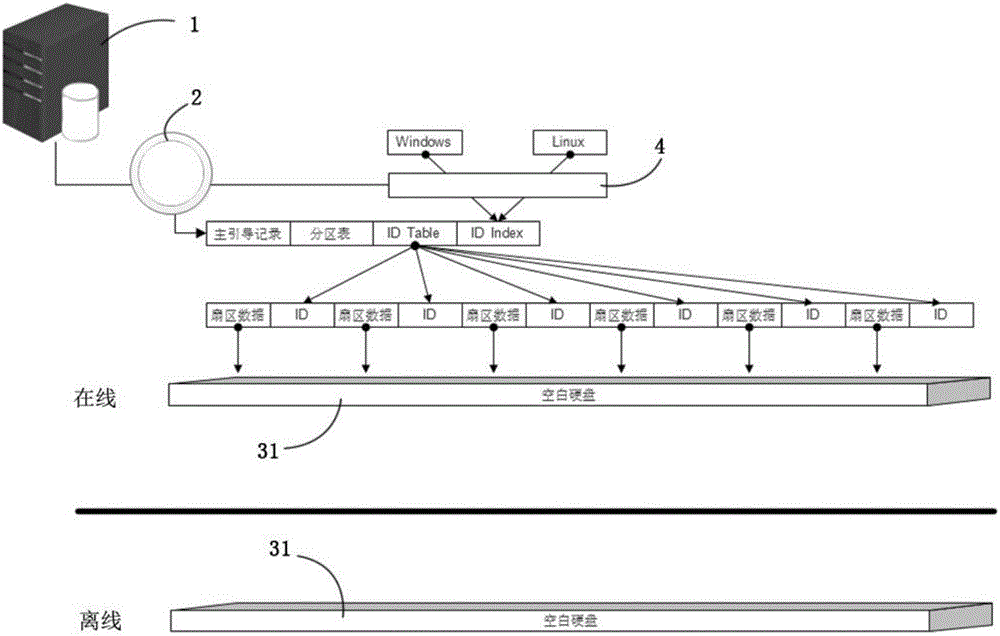
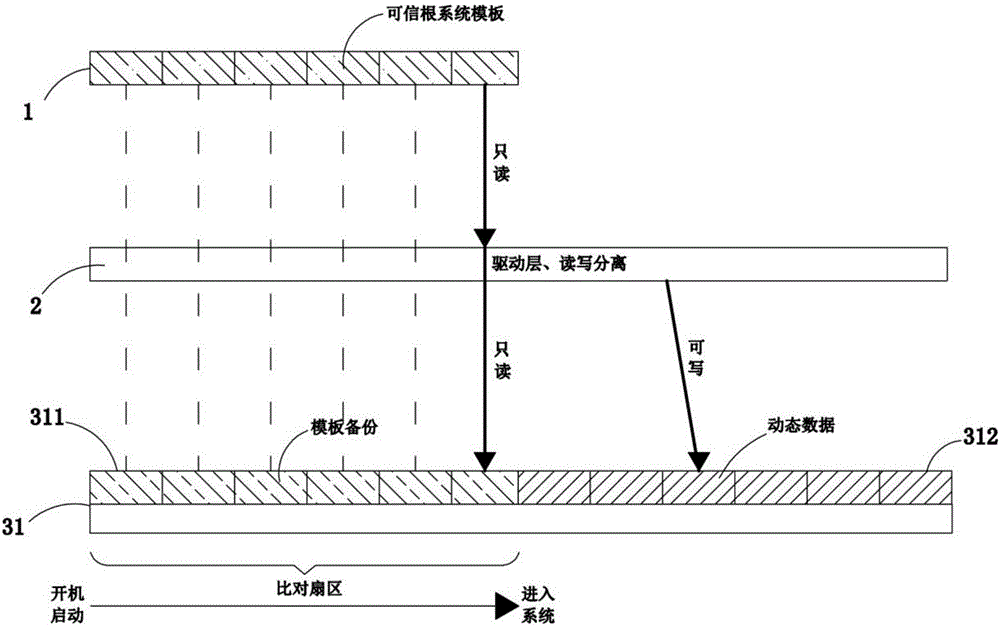
[0028] The terminal trusted and data static security system of the present invention is a trusted remote desktop system that can provide remote security monitoring. By establishing a set of security control measures between the hardware of the client computer and the operating system software, the user's The operating application system performs unified back-end management, and assigns each user a trusted desktop running computing environment. Utilizing the security architecture of the terminal trusted and data static security system of the present invention, the operating system and data are stored on the local hard disk in a sector structure, and the data pointer technology of the sector can effectively prevent attacks from tool...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com