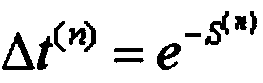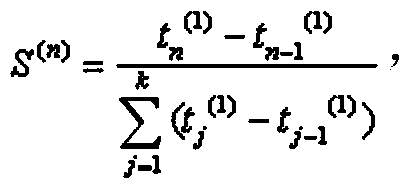Trust evaluation system based on privacy protection and construction method thereof
An evaluation system and privacy protection technology, applied in the field of trust model construction system based on privacy protection, can solve problems such as malicious recommendation, collusion fraud, and trust evaluation results that cannot objectively reflect the trust relationship
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Referring to the accompanying drawings, through the description of the embodiments, the specific implementation of the present invention, such as the interaction process of information between trust nodes, the evaluation method of each trust value, the update method of trust value, etc., will be further described in detail to help the present invention Those skilled in the art have a more complete, accurate and in-depth understanding of the inventive concepts and technical solutions of the present invention, and the specific implementation methods are as follows:
[0023] Such as figure 1 As shown in , a trust evaluation agent node is established between the cloud user and the cloud service provider, that is, the agent is trusted to be a trusted third party for measuring the trust relationship between nodes in the evaluation system. User nodes and service nodes are isolated by trust evaluation agent nodes, and the task of trust evaluation is managed by trust evaluation ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com