Dependable computing based process control method
A process control and trusted computing technology, applied in the field of information security, can solve the problems of no protection, low efficiency, insufficient effect, etc., to prevent the modification of static files, ensure normal operation, and prevent damage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
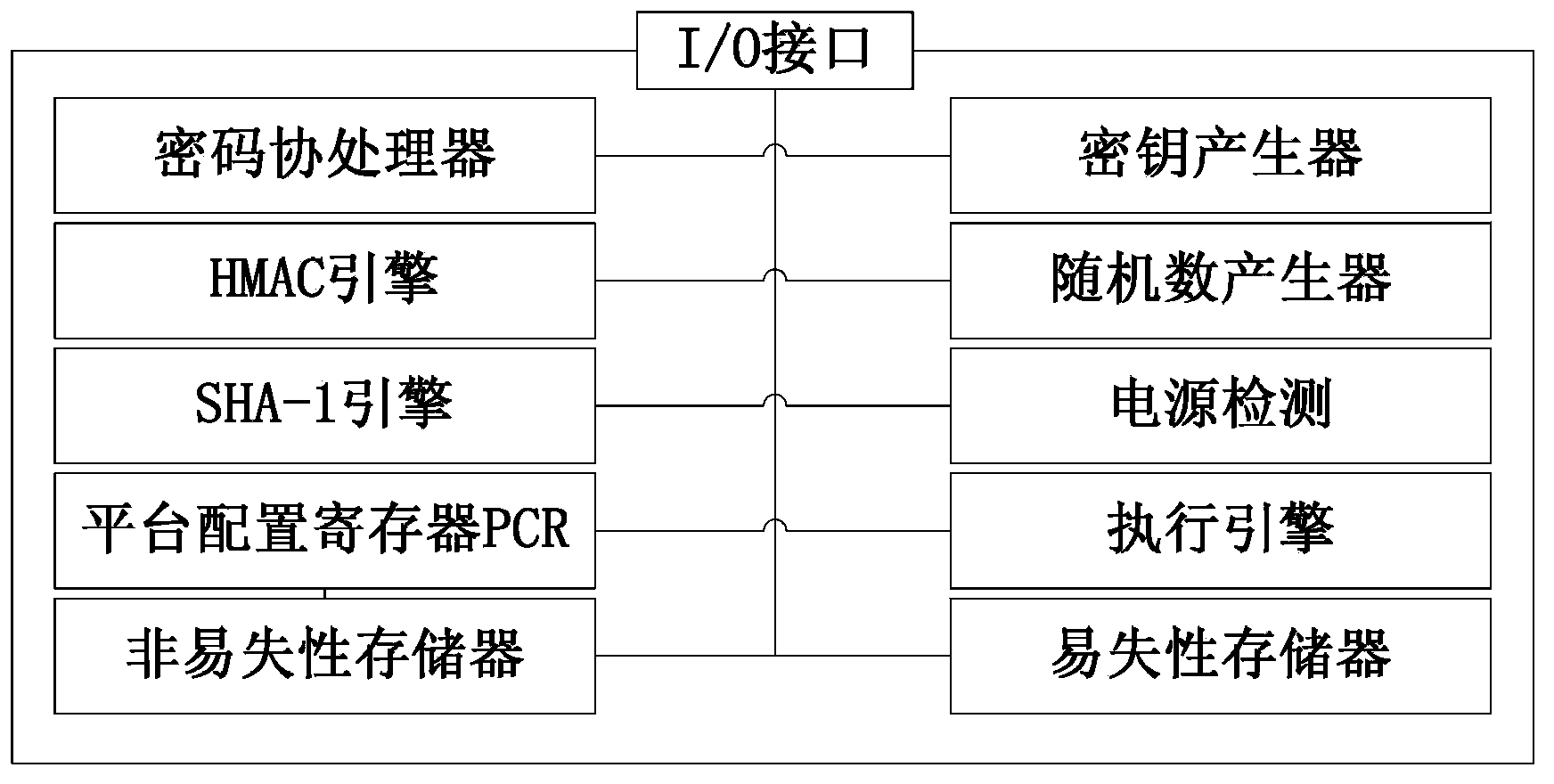
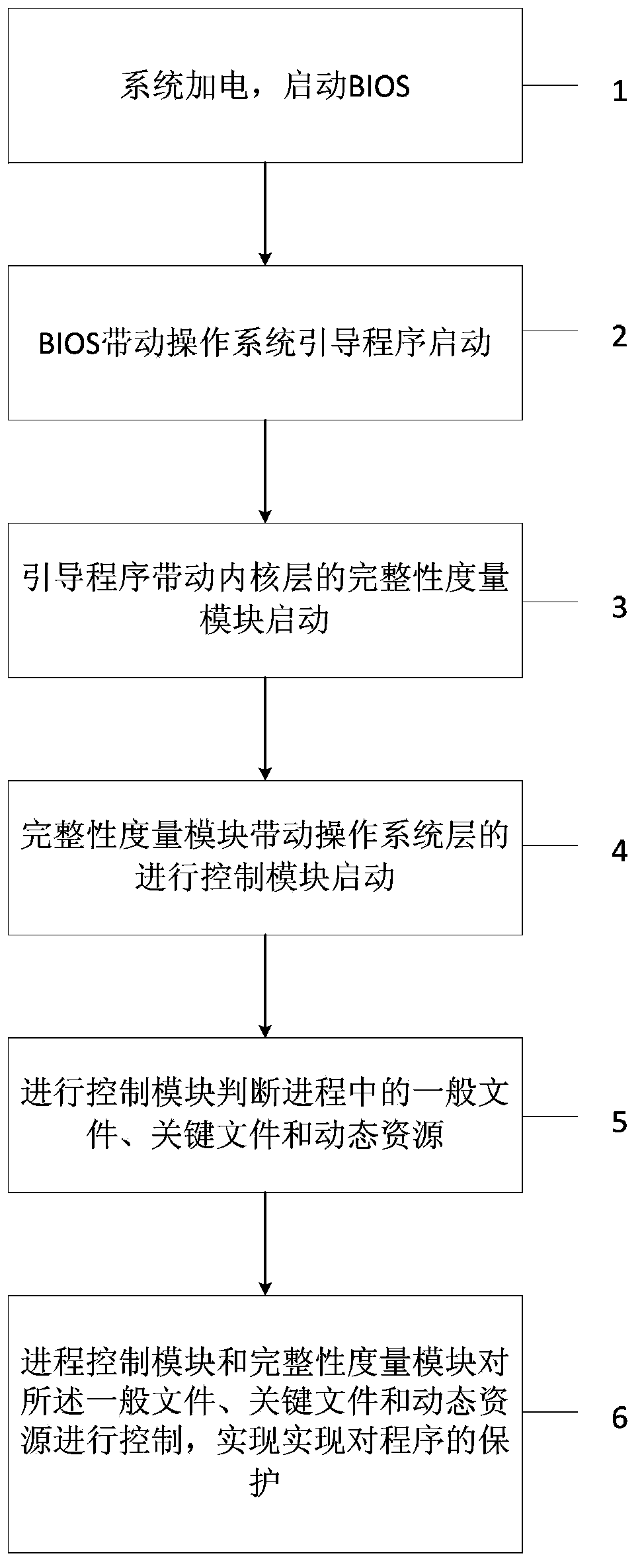
[0050] The process control method provided by the present invention utilizes the measurement algorithm of the cryptographic chip of the trusted platform module to store the static process-related files of the process and the page space dynamically occupied in the memory, and store the integrity values of these various resources in the In the process control module protected by the underlying hardware, it is protected from access and modification by malicious virus programs, thereby ensuring the health of the terminal running programs.
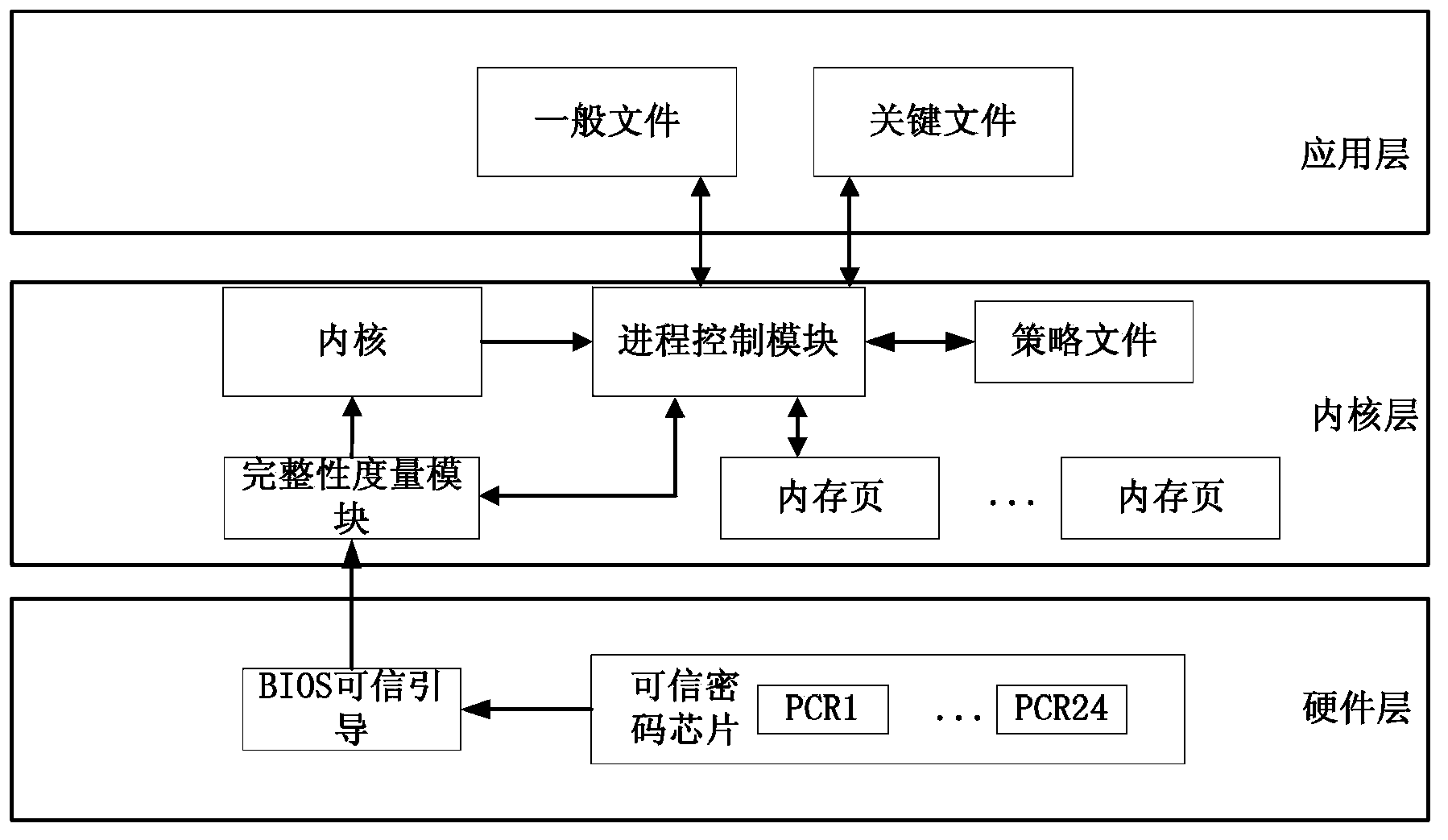
[0051] Specifically, the implementation of the process control method of this embodiment depends on the system architecture diagram, such as figure 2 As shown, the keys include the process control module, the integrity measurement module, and the policy file storing the integrity measu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com