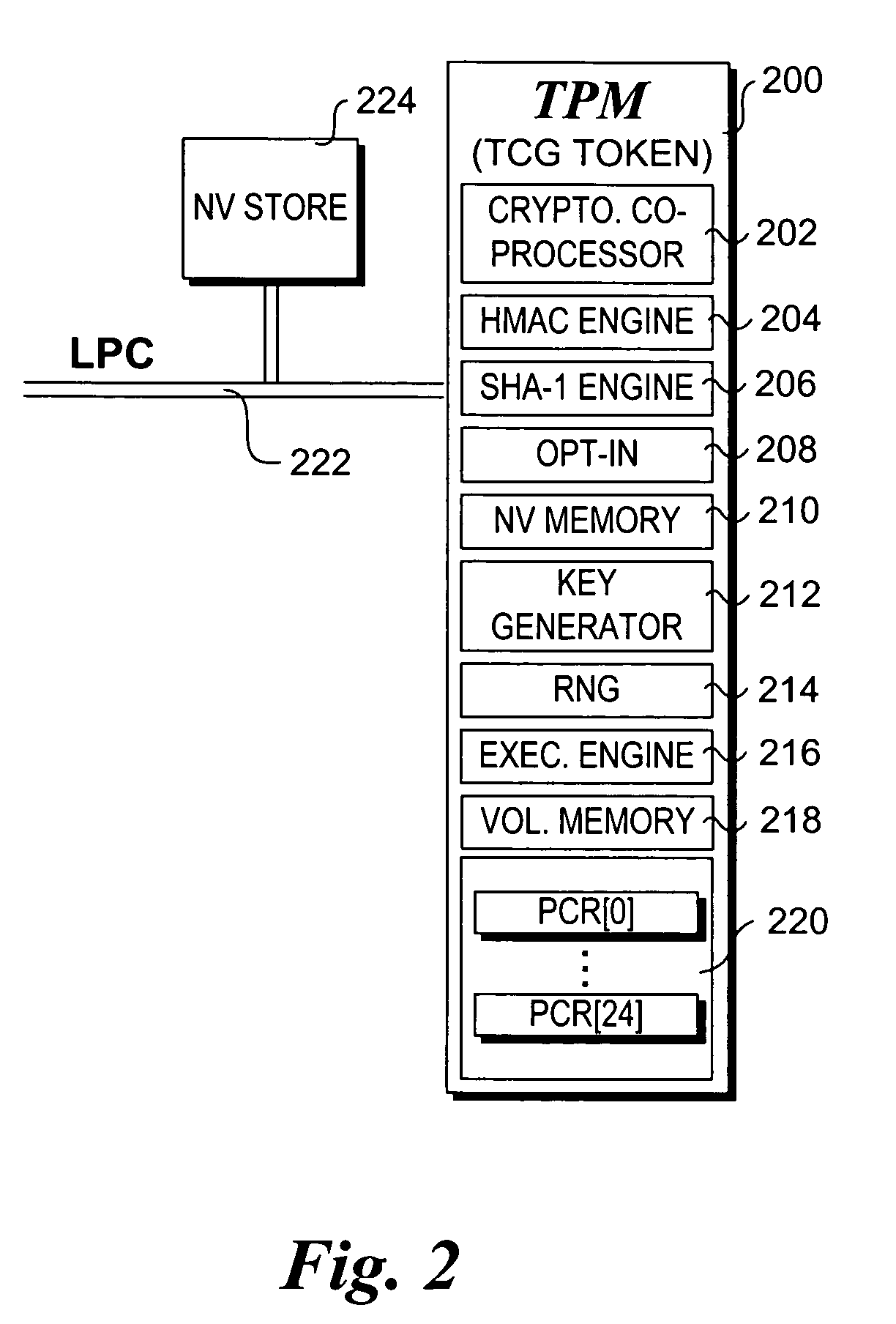
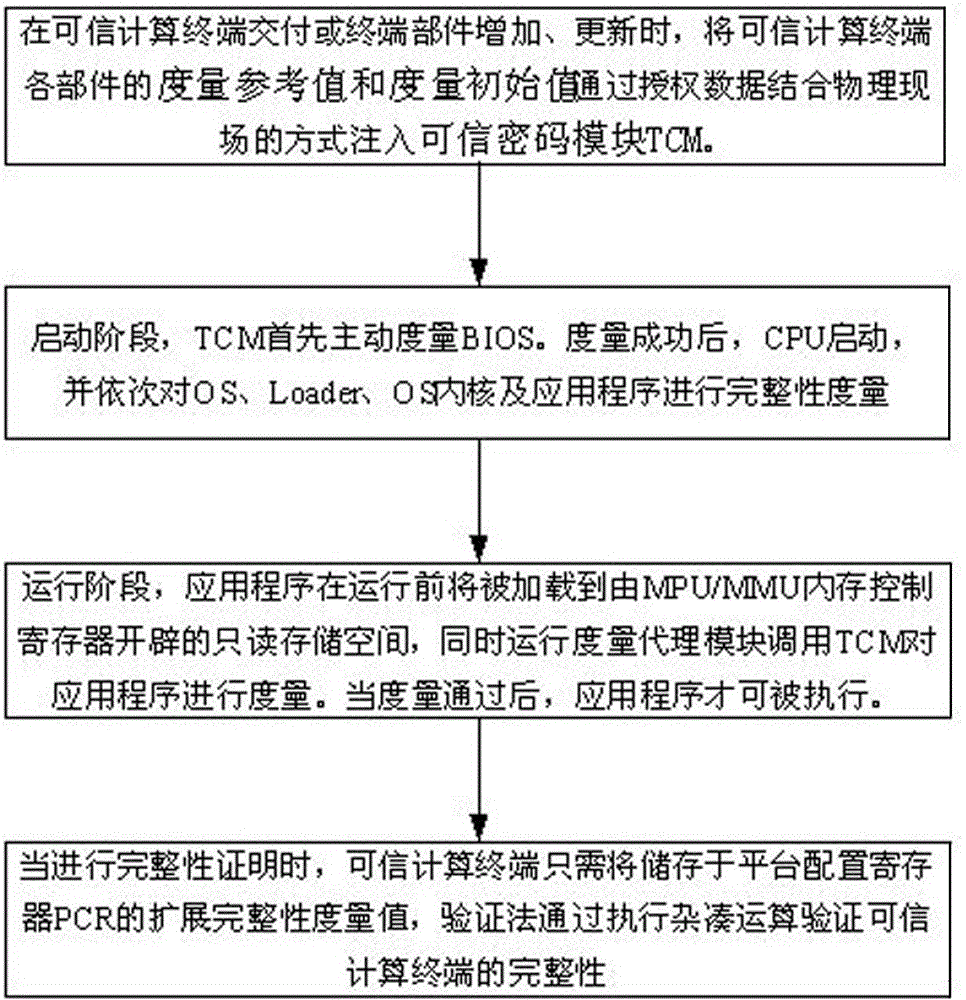
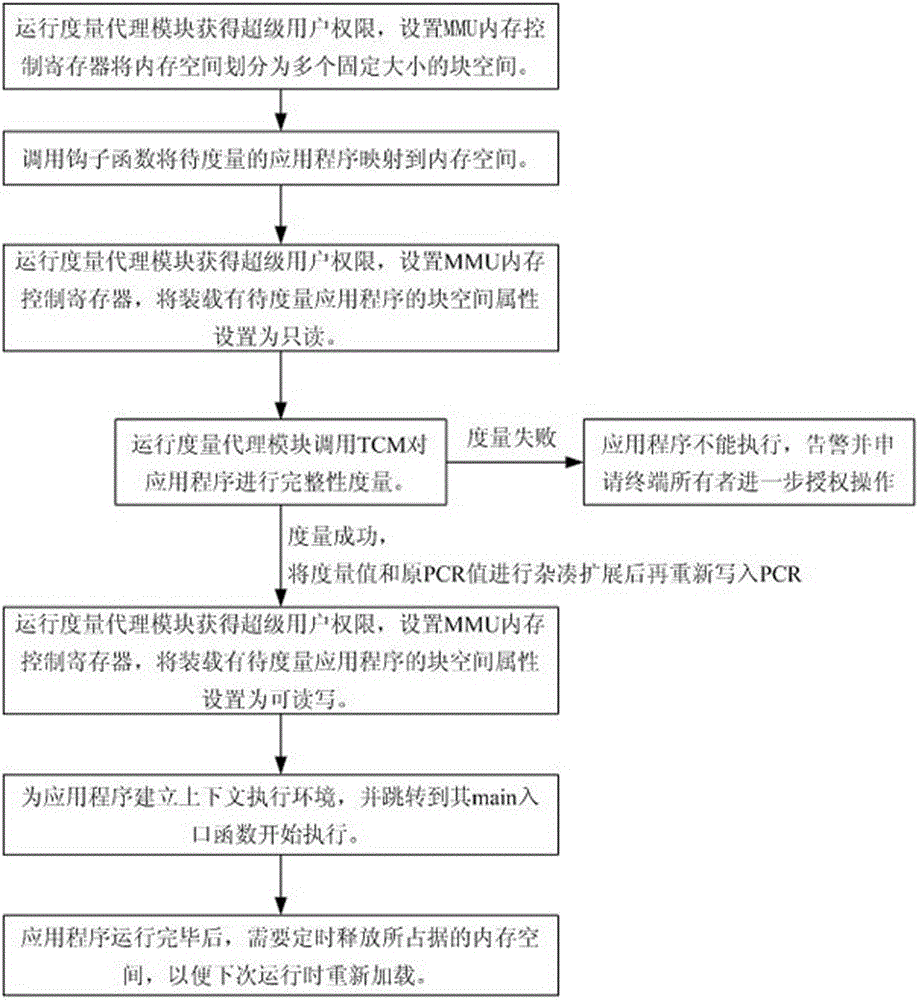
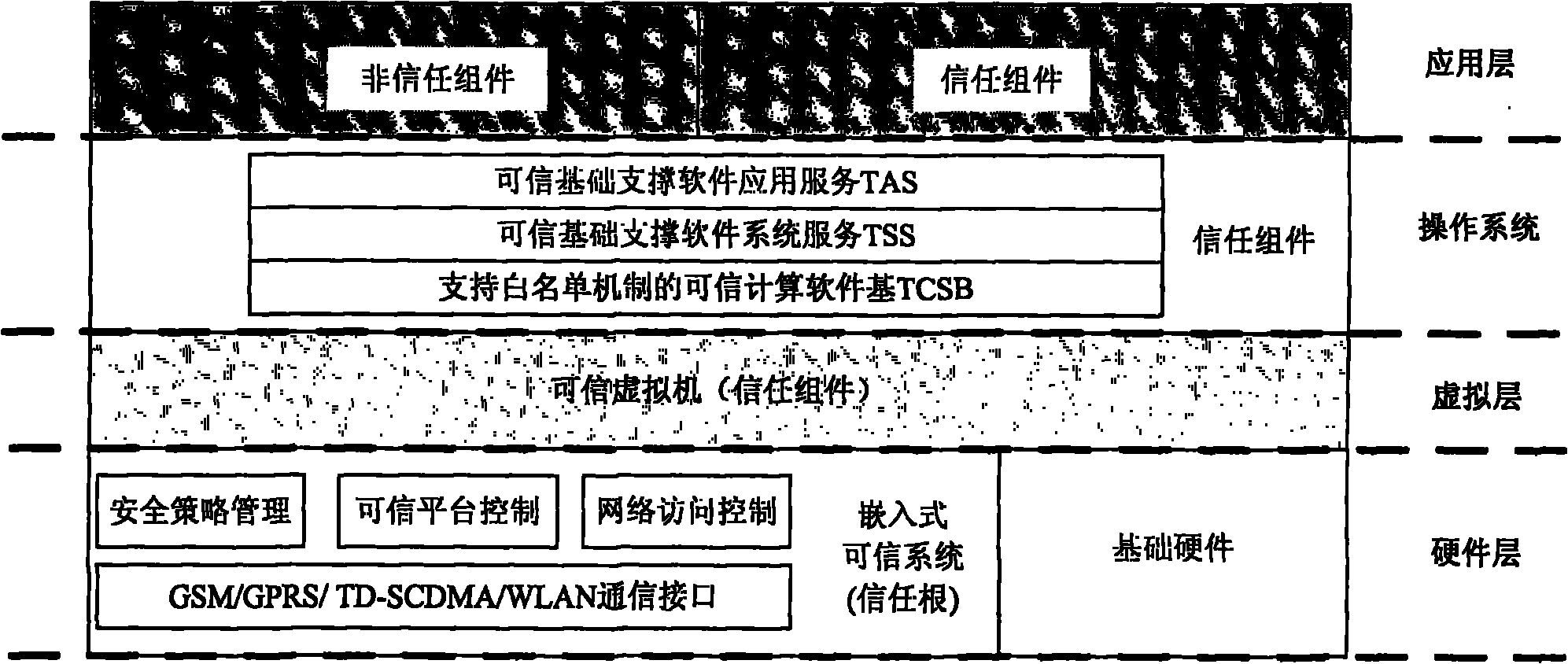
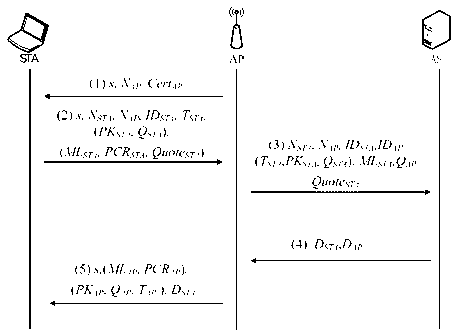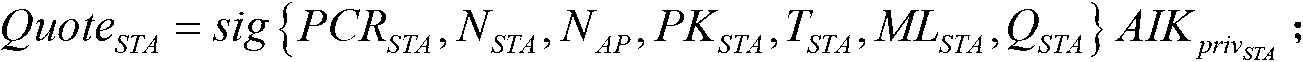Patents
Literature
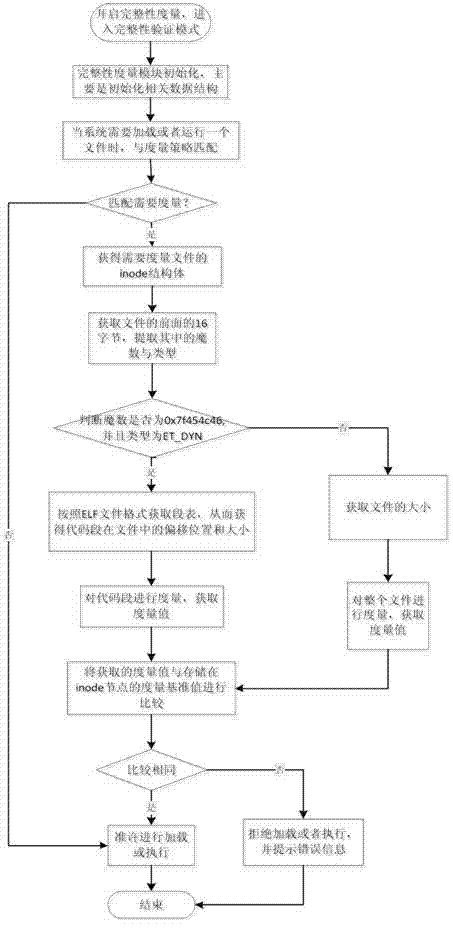
179 results about "Integrity measurement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Integrity is a concept of consistency of actions, values, methods, measures, principles, expectations, and outcomes. In ethics, integrity is regarded as the honesty and truthfulness or accuracy of one’s actions.
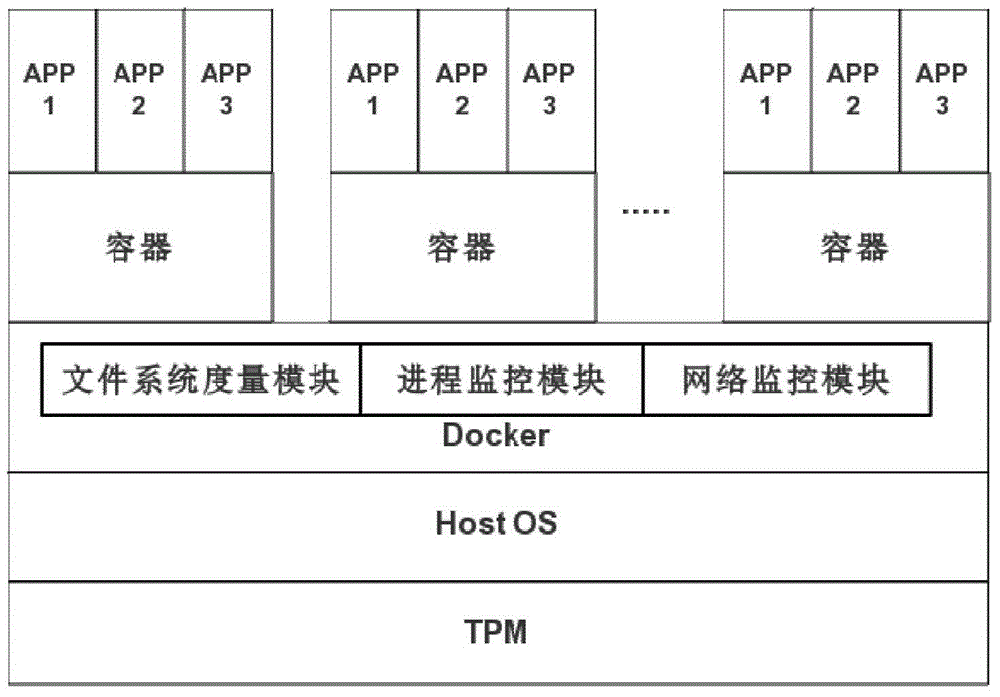
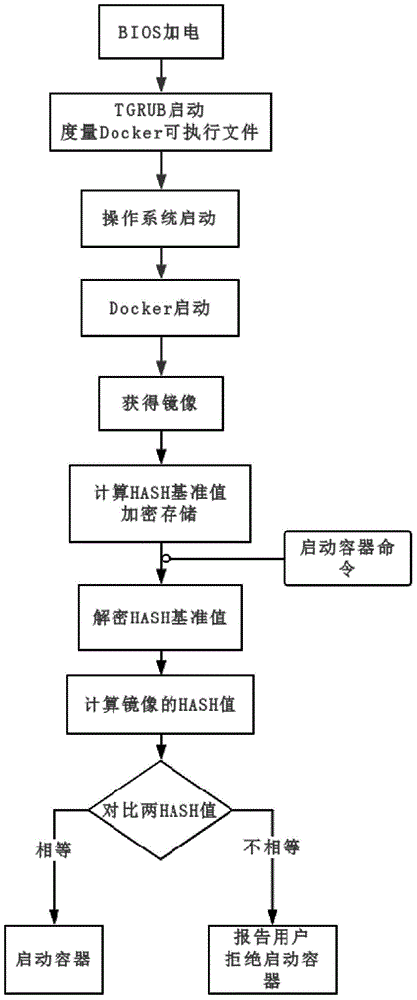
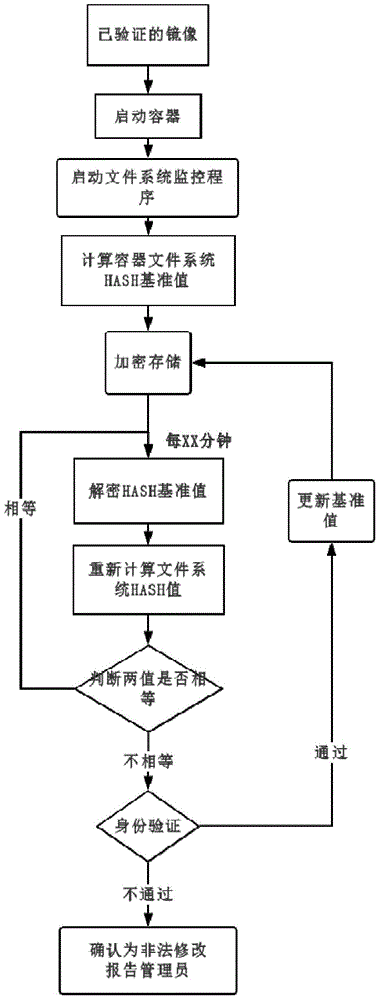
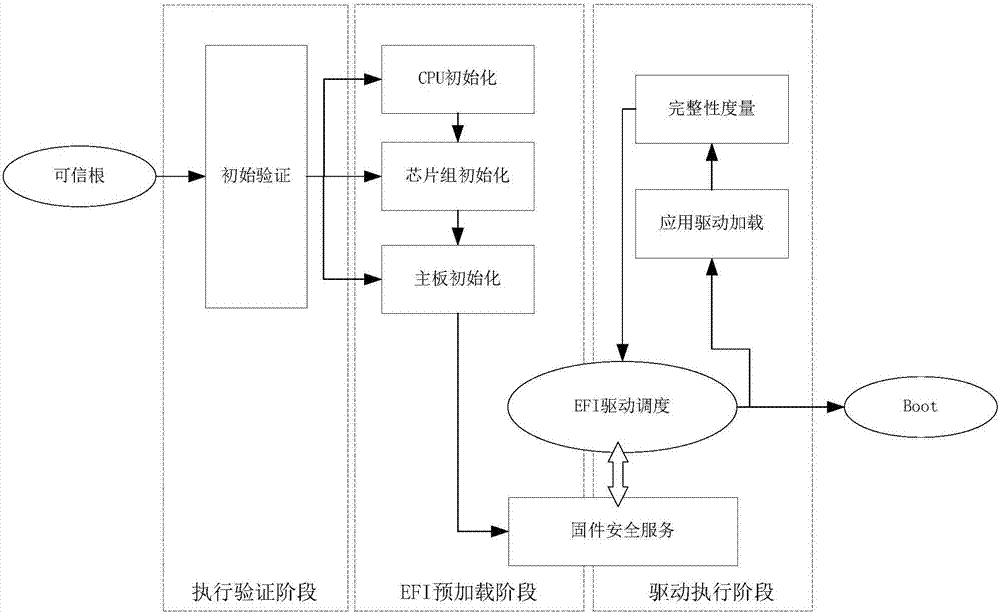
Security reinforcement method for credible container based on Docker
ActiveCN105069353ATrusted bootGuaranteed normal startupPlatform integrity maintainanceNetwork communicationMirror image
The invention discloses a security reinforcement method for a credible container based on Docker used for performing security reinforcement on a Docker container system, and realizes the credible container based on the Docker, as well is applied to a server cluster based on the Docker. The credible container based on the Docker comprises a container program Docker, a container credible measurement module, a progress monitoring module and a network communication monitoring module, wherein the container credible measurement module comprises a credible booting sub-module and a file measurement sub-module. The reinforcement method focuses on the credibility of the Docker container; a credible computing and integrity measurement technology is matched with a real-time monitoring module to reinforce the container system based on the Docker, so that the container and a mirror image are prevented from tampering; and meanwhile, a network communication behavior of the container is limited, and an inner progress of the container is monitored, so as to realize the security reinforced credible container.
Owner:WUHAN UNIV
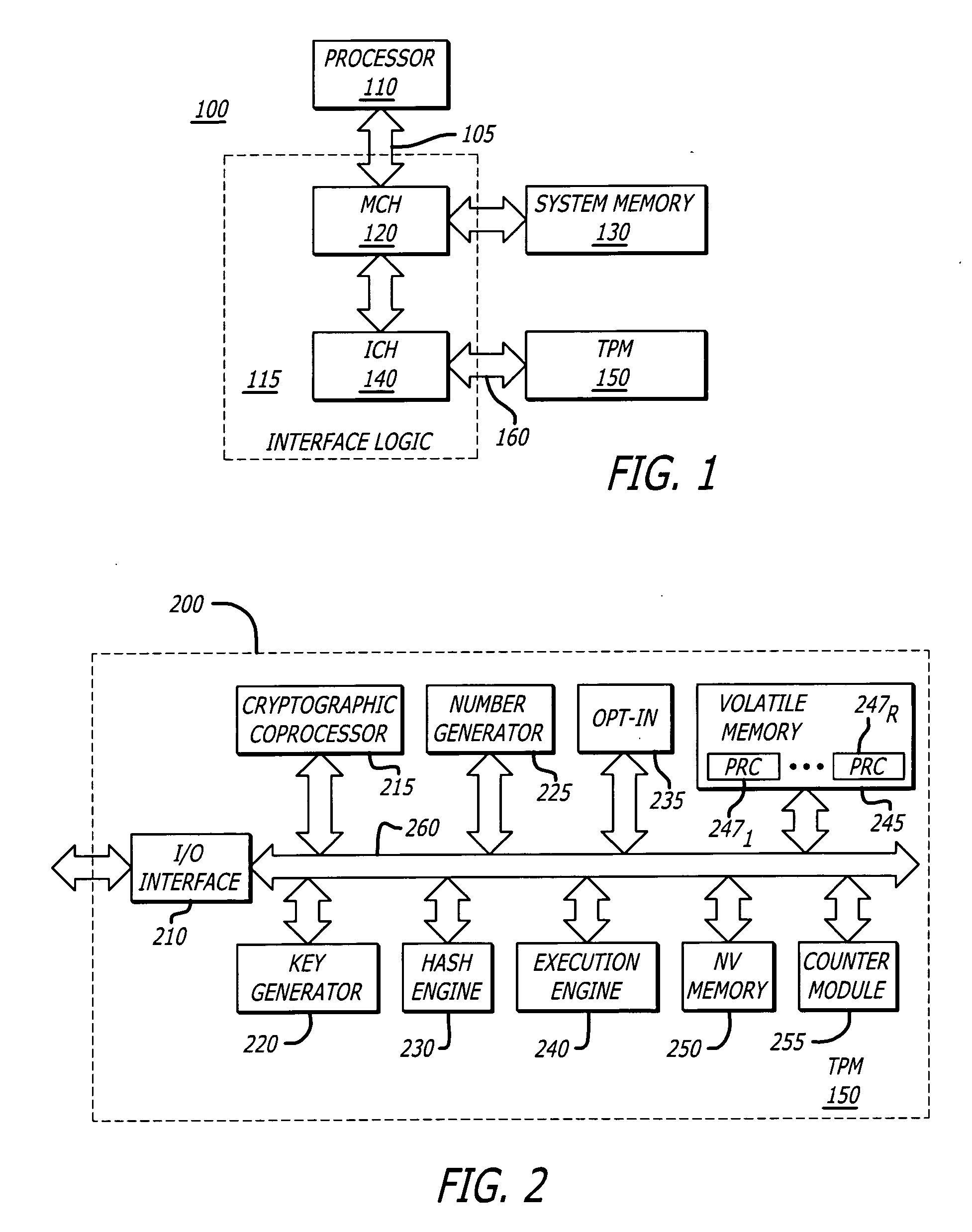
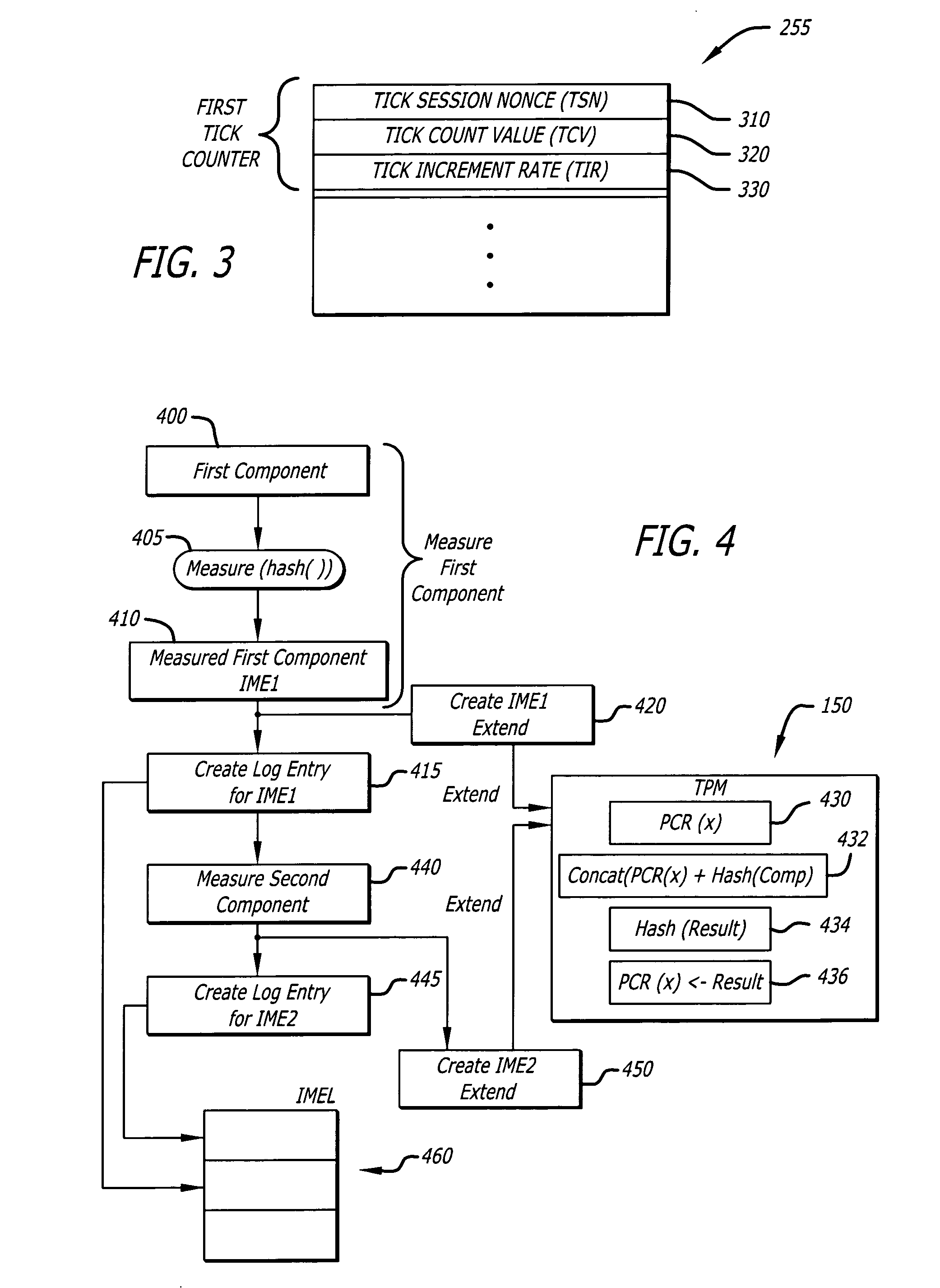
Method for providing integrity measurements with their respective time stamps
InactiveUS20060074600A1Digital computer detailsPlatform integrity maintainanceEngineeringIntegrity measurement
According to one embodiment of the invention, a method comprises conducting a first integrity measurement to produce a first integrity measurement event. Thereafter, an integrity time stamp associated with the first integrity measurement event is created. The integrity time stamp is used to identify the actual time when the first integrity measurement event was produced.
Owner:INTEL CORP
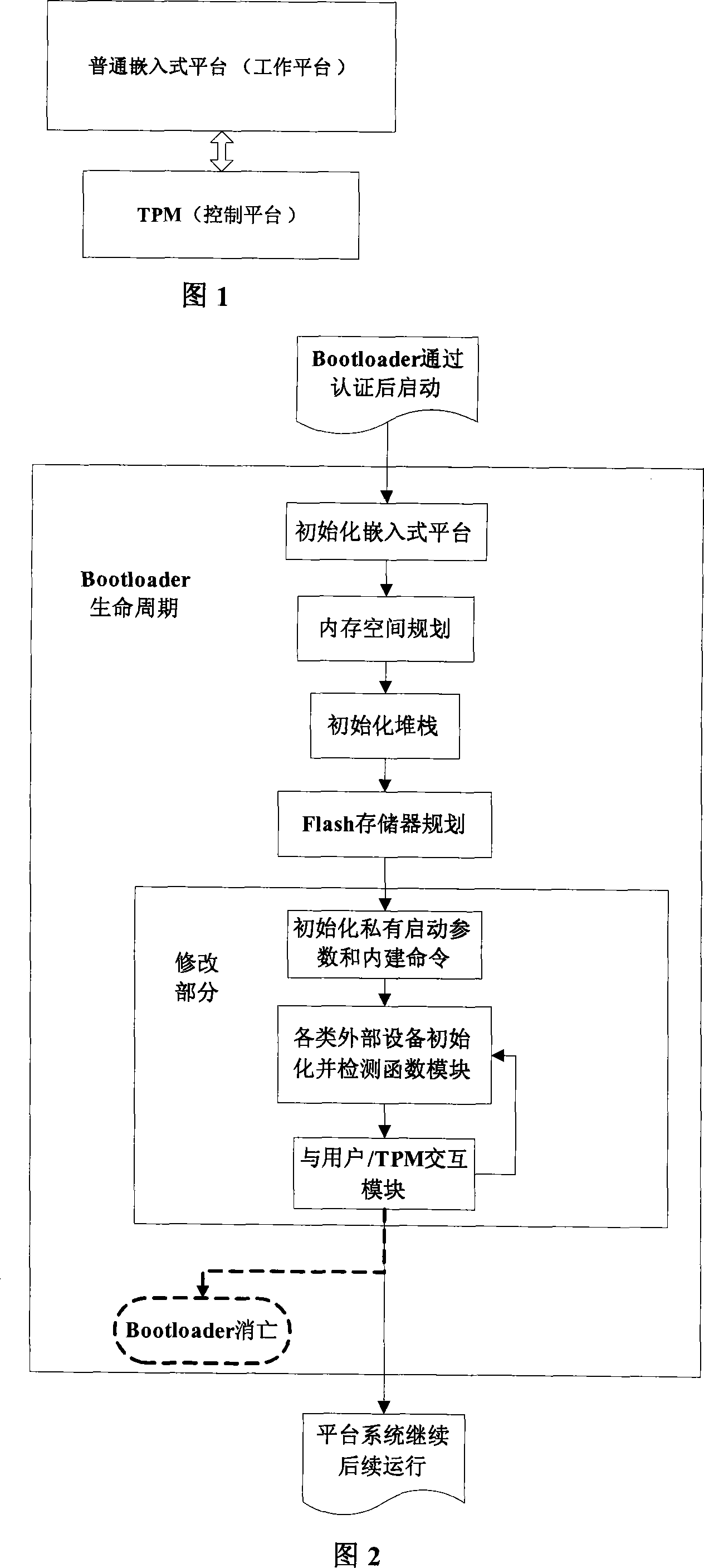
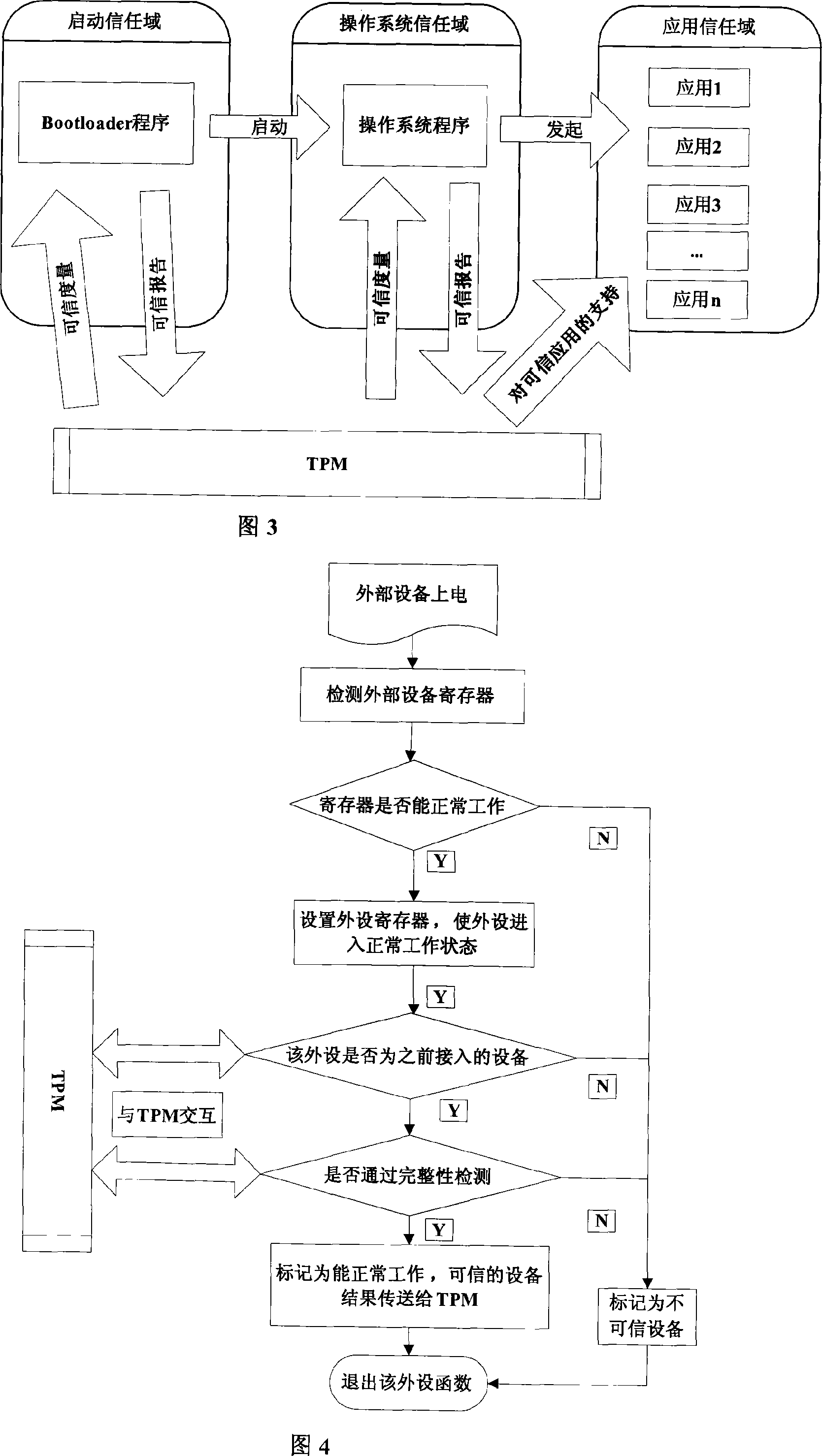
Embed type platform guiding of credible mechanism
InactiveCN101122936AImprove integrityAchieving Trusted MeasurementsDigital data protectionProgram loading/initiatingOperational systemChain structure
The invention discloses an embedded platform guide on a creditable mechanism, i. e.: placing the embedded platform and a TPM together, and using the TPM to support safety and creditability of the embedded platform; In accordance with the creditability completeness measuring roots and prior to running of the CPU of the embedded platform, the TPM carries out completeness verification for the Bootloader and the operation system which are stored in the embedded platform to ensure that the software executable codes in the platform startup chain is not modified, and then permits the CPU of the embedded platform to read the Bootloader for startup; and the TPM controls the startup process and measures completeness and reliability of the appointed external devices as well as initializes the external devices. The invention is used for completeness measuring of the Bootloader executed at the platform in accordance with the creditability chain structure, ensuring good completeness of the Bootloader, and realizing a reporting mechanism in a creditable environment with a TPM monitoring.
Owner:WUHAN UNIV
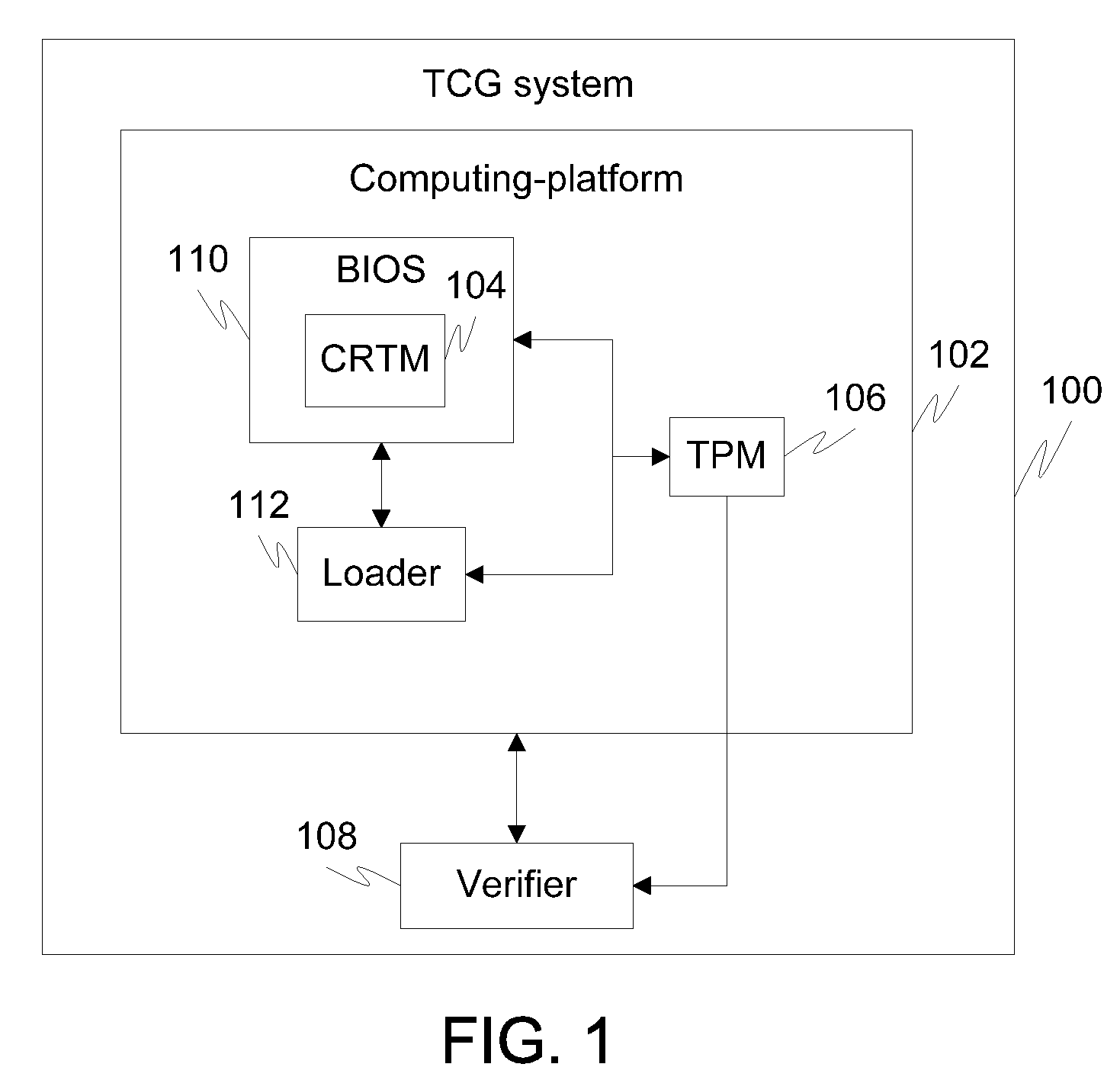
Method and system to authenticate an application in a computing platform operating in trusted computing group (TCG) domain
InactiveUS20080288783A1Verified efficiently and securelyDigital data processing detailsUser identity/authority verificationComputer hardwareApplication software
A method and system for verifying authenticity of an application in a computing-platform operating in a Trusted Computing Group (TCG) domain is provided. The method includes computing one or more integrity measurements corresponding to one or more of the application, a plurality of precedent-applications, and an output file. The output file includes an output of the application, the application is executing on the computing-platform. Each precedent-application is executed before the application. The method further includes comparing one or more integrity measurements with re-computed integrity measurements. The re-computed integrity measurements are determined corresponding to one or more of the application, the plurality of precedent-applications, and the computing-platform.
Owner:IBM CORP
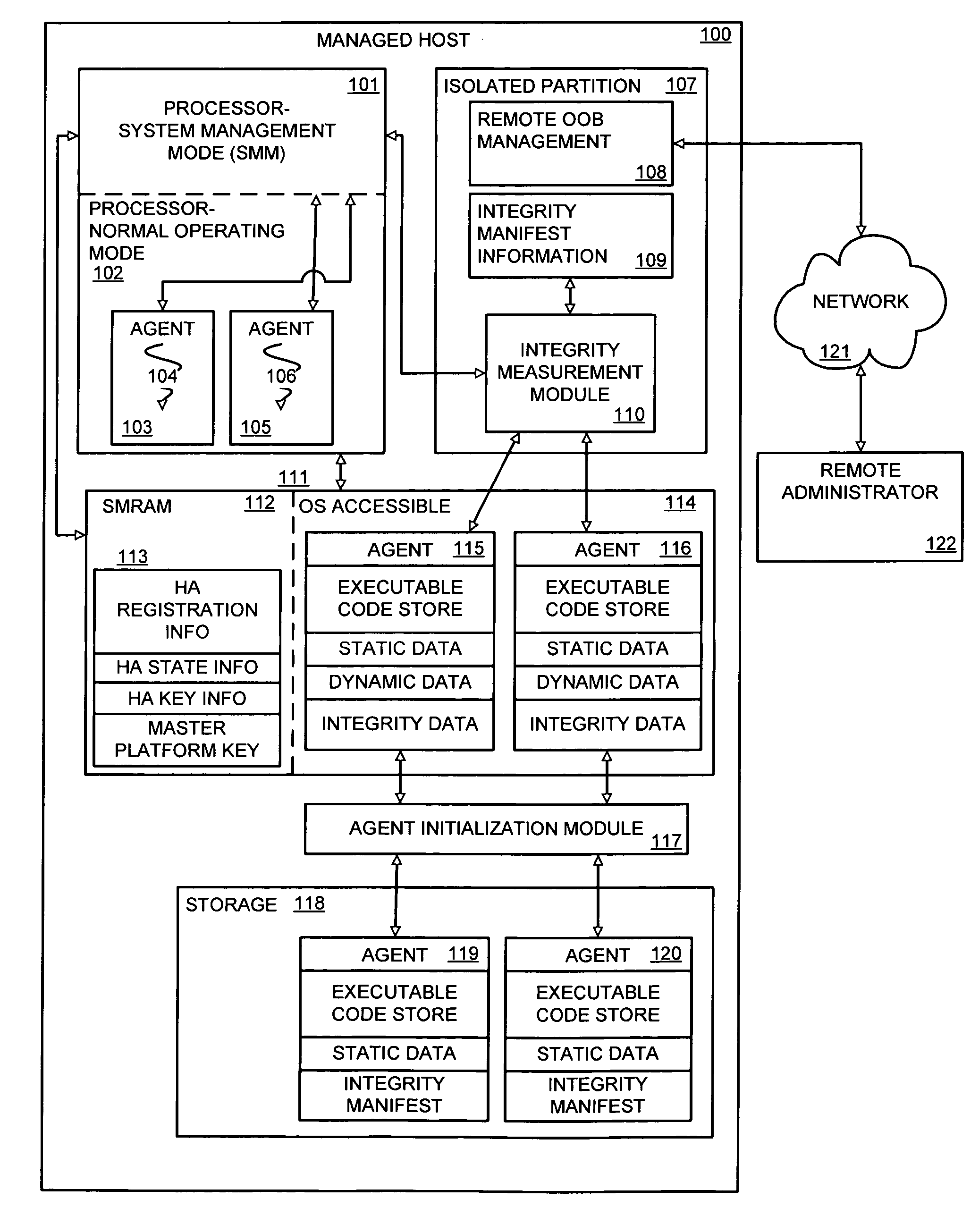
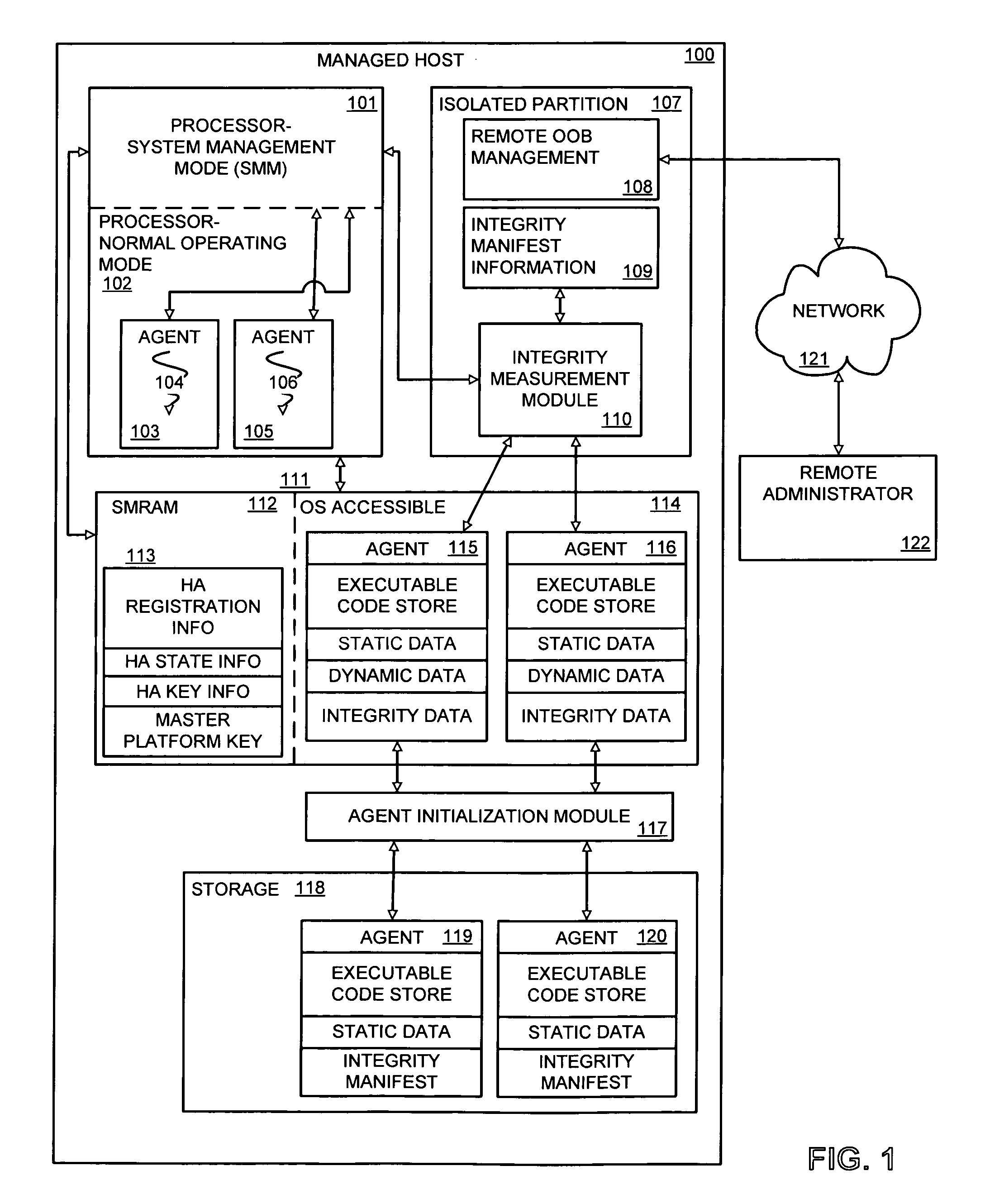
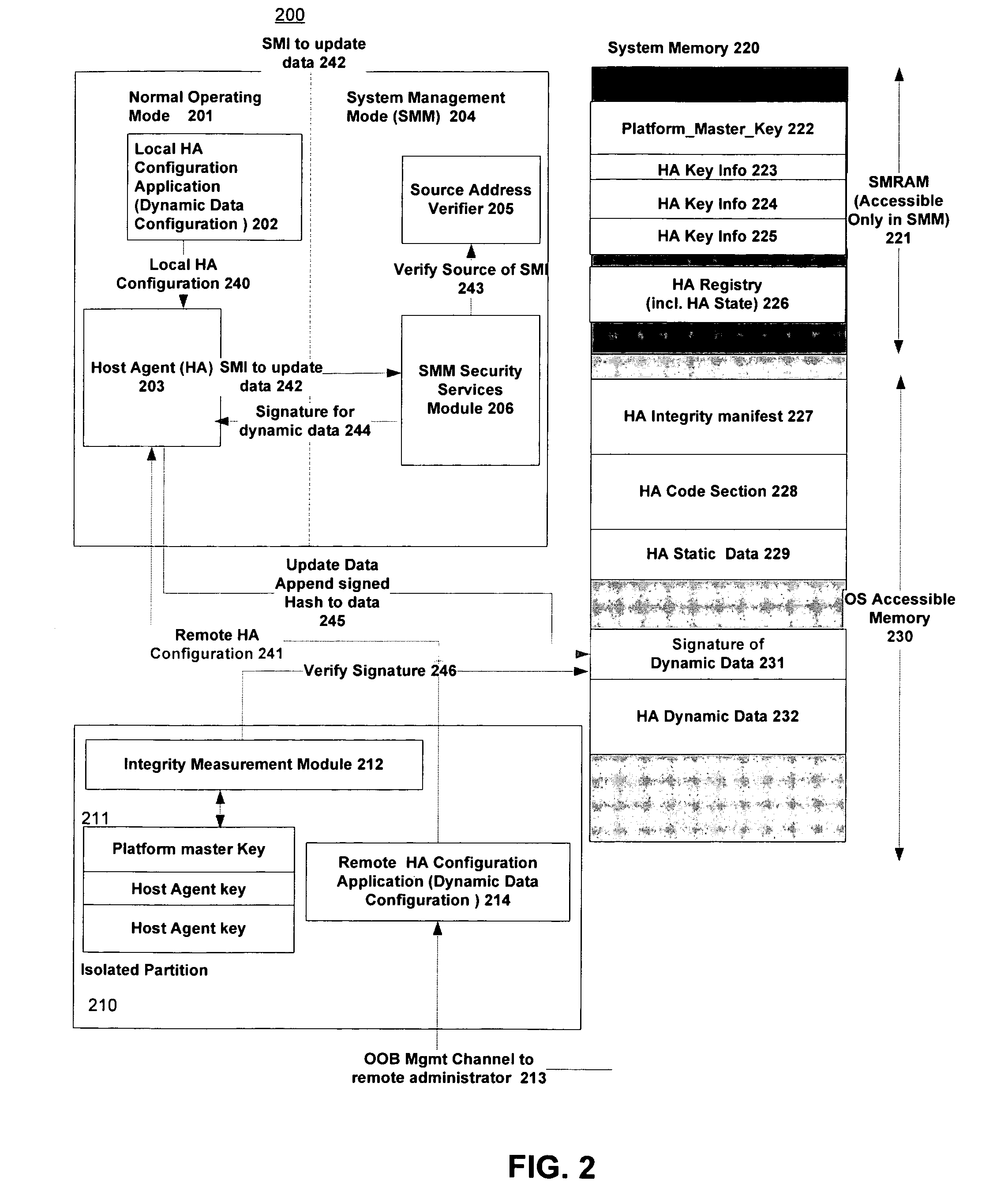
Tamper-resistant method and apparatus for verification and measurement of host agent dynamic data updates
InactiveUS20080134321A1Digital data processing detailsUser identity/authority verificationDynamic dataComputer security
A platform for verifying the validity of changes to dynamic data modifiable during the runtime execution of an agent. In one embodiment, a management mode of a processor uses key information to generate a signature for a set of dynamic data, the signature to verify the validity of the state of the dynamic data to an integrity measurement agent.
Owner:RAJAGOPAL PRIYA +5
Method for designing domestic BMC (Baseboard Management Controller) chip trusted firmware
InactiveCN106127056AIntegrity guaranteedEnsure crediblePlatform integrity maintainanceElectricityComputer module
The invention discloses a method for designing trusted firmware of a domestic BMC chip. The method adds a trusted function module to the guide layer, kernel layer, middleware and software layer of the BMC firmware, and updates the kernel program during the BMC power-on and start-up process. , application program and BIOS key code to measure the integrity to ensure the integrity of the program, thus establishing a trusted execution environment for the system platform. The method of the present invention measures the integrity of each functional component during the start-up operation of the BMC, ensures the integrity of the program and does not have malicious codes implanted, establishes a complete chain of trust in the BMC start-up process, and ensures the reliability of the system platform execution environment. This will help improve the core competitiveness of domestic BMC chips.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
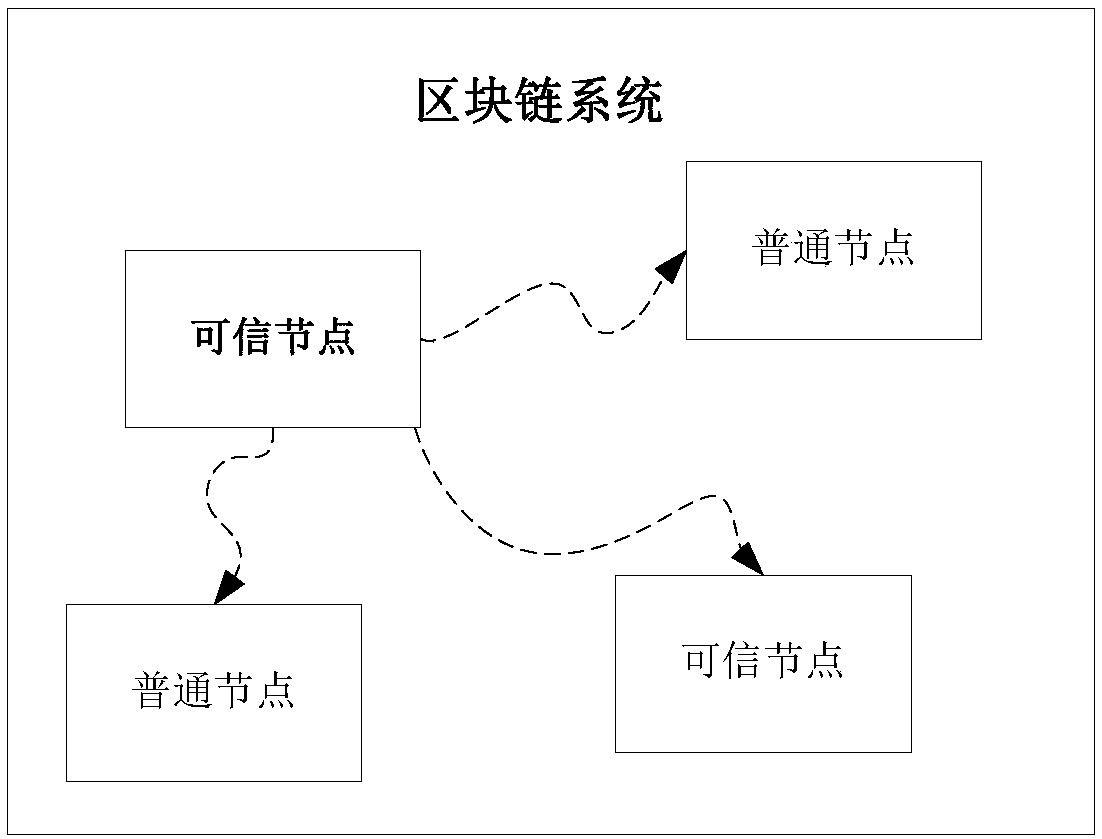
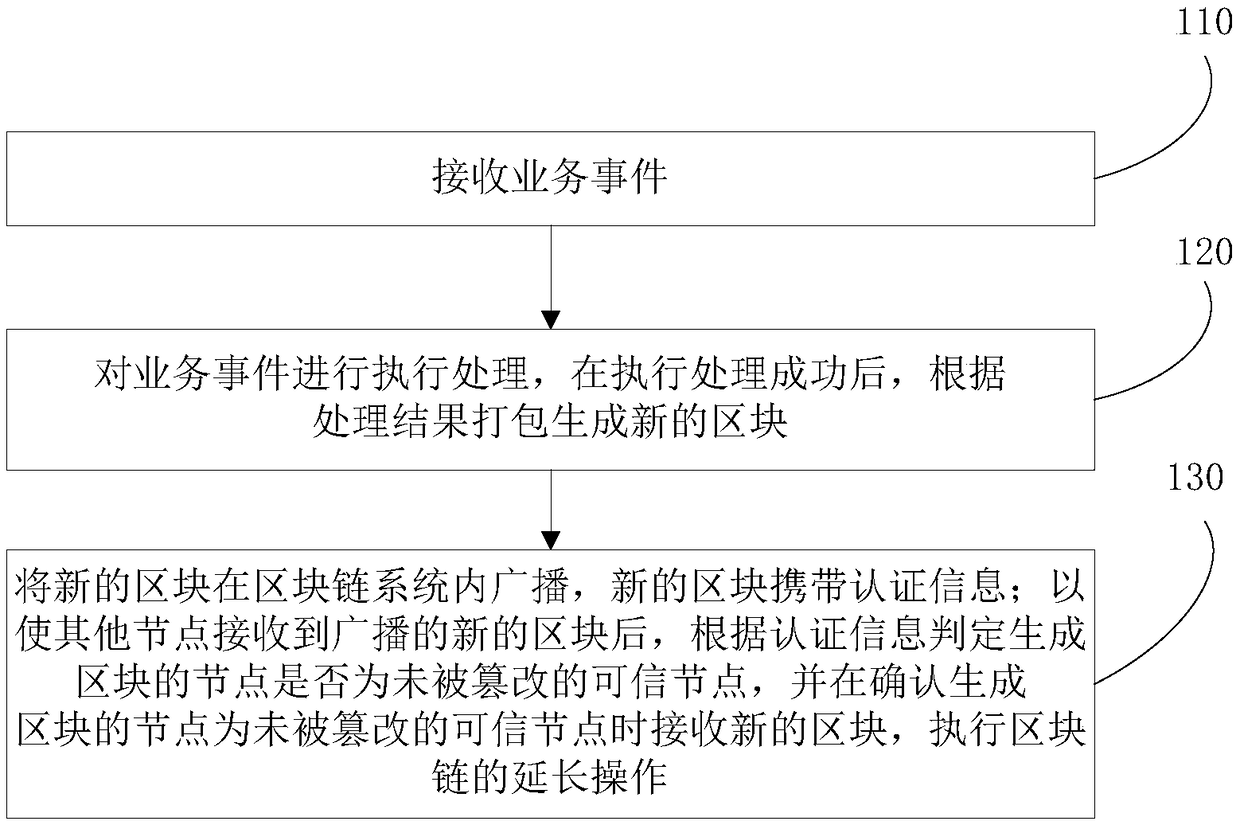
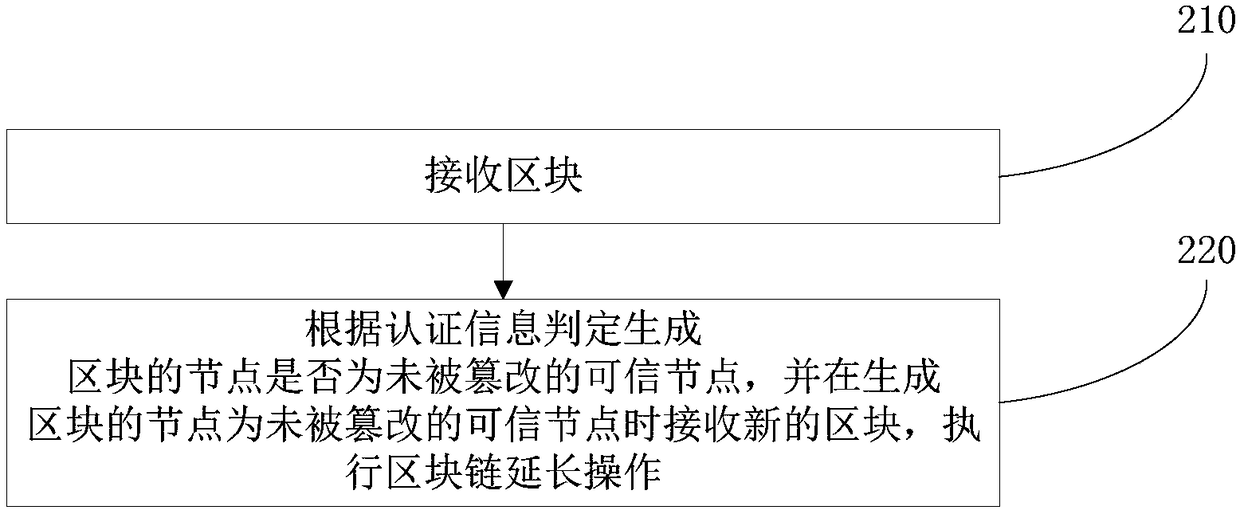
Block chain system and block consensus method and device
InactiveCN108320160ASingle point of processingEasy to handleTransmissionProtocol authorisationChain systemParallel processing
The embodiment of the invention provides a block chain system and a block consensus method and device. According to the invention, a trusted node for generating a block attaches authentication information thereof, namely, a signature of the block and an integrity measurement value of the trusted node, to the generated new block and broadcasts the new block into the block chain system. A block receiving node can determine the credibility of the block by only checking the authentication information carried by the block, and does not need to execute business events included in the block any more,thereby realizing single-point processing for the business events, thus enabling the other nodes to concurrently process other business events, and improving the processing ability of the whole network nodes for the business events. Meanwhile, the nodes need not to independently execute the same business event, so that the nodes do not generate repeated calling when external equipment is requiredto be called, and a technical problem that it is impossible to realize calling outside the chain in the prior art is overcome.
Owner:张超
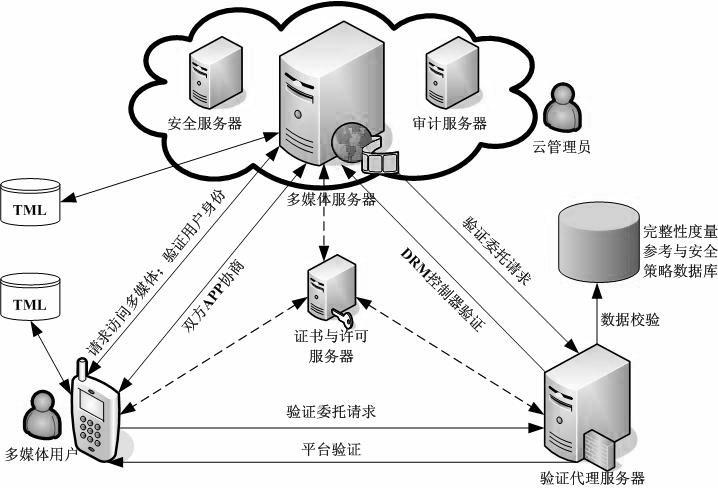
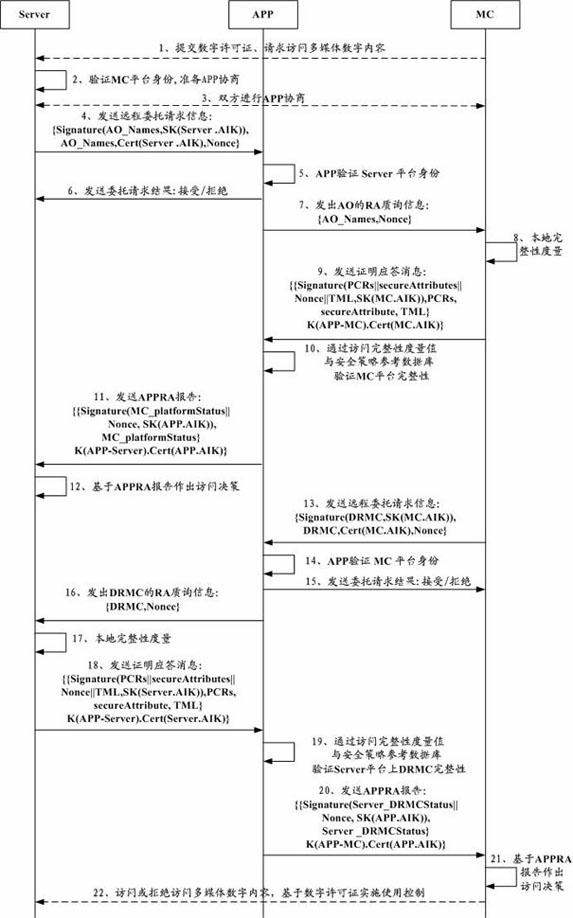
Digital content trusted usage control method based on cloud computing
The invention discloses a digital content trusted usage control method based on cloud computing. The system framework comprises a multimedia server, a mobile terminal, a verification agent server, a certificate and license server, an integrity measurement reference and security policy database and a trust measurement log, wherein the mobile terminal uses the multimedia digital content on the multimedia server through a graphical user interface of a DRM (digital rights management) controller; a multimedia server platform runs the DRM controller and performs usage control on the DRM controller through a DRM license; the mobile terminal and the multimedia server determine a verification agent through negotiation; and by adopting a remote proof method and a bidirectional integrity verification security protocol, which support the verification agent, the bidirectional trust relationship between the multimedia content provider and the terminal user is guaranteed, and the secrete privacy data on the terminal equipment of the user is protected as well. In the invention, as the DRM controller is configured on the multimedia server, the possibility of malicious attack such as breaking, tampering and the like, performed by an illegal user, is avoided.
Owner:HENAN UNIV OF SCI & TECH
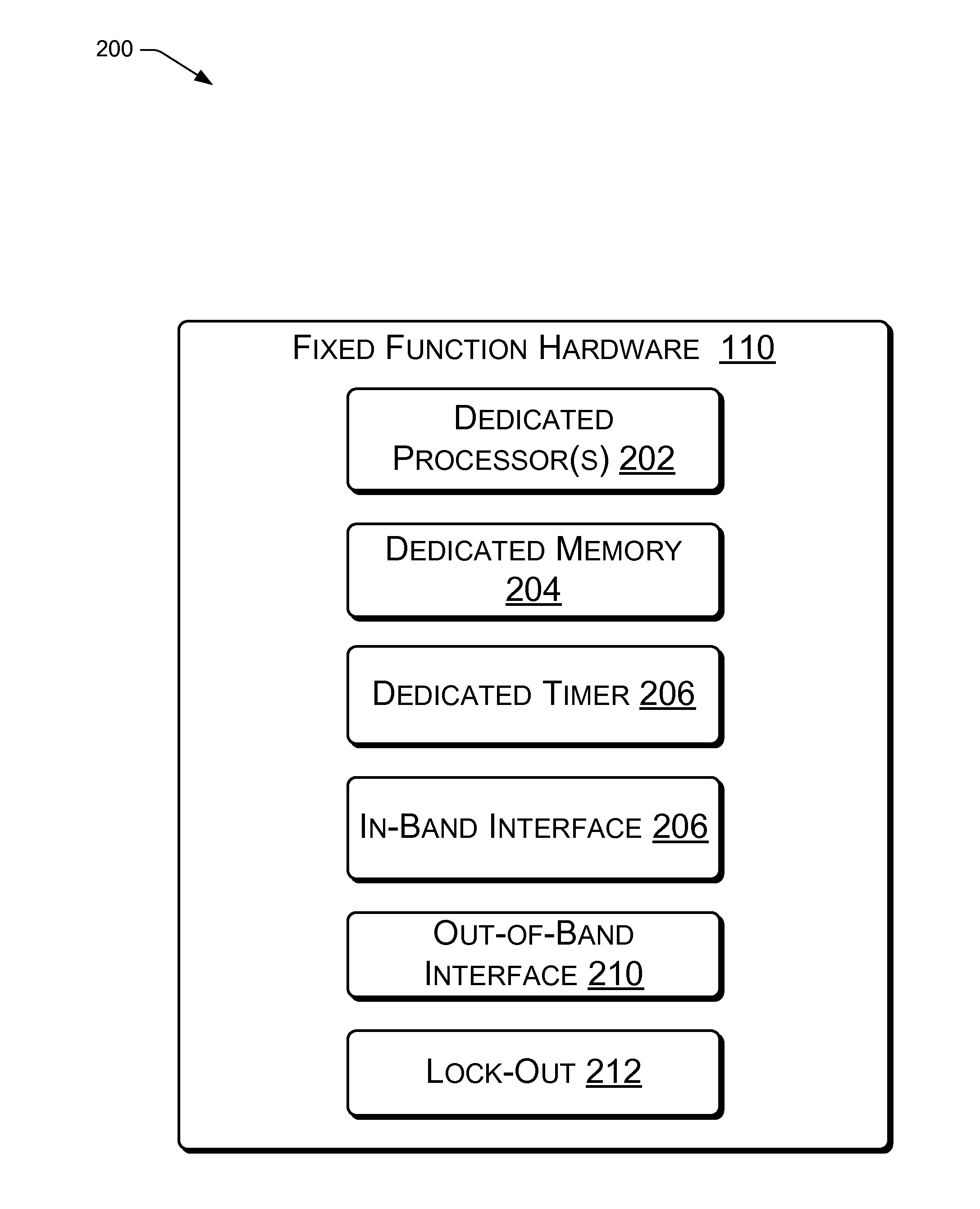
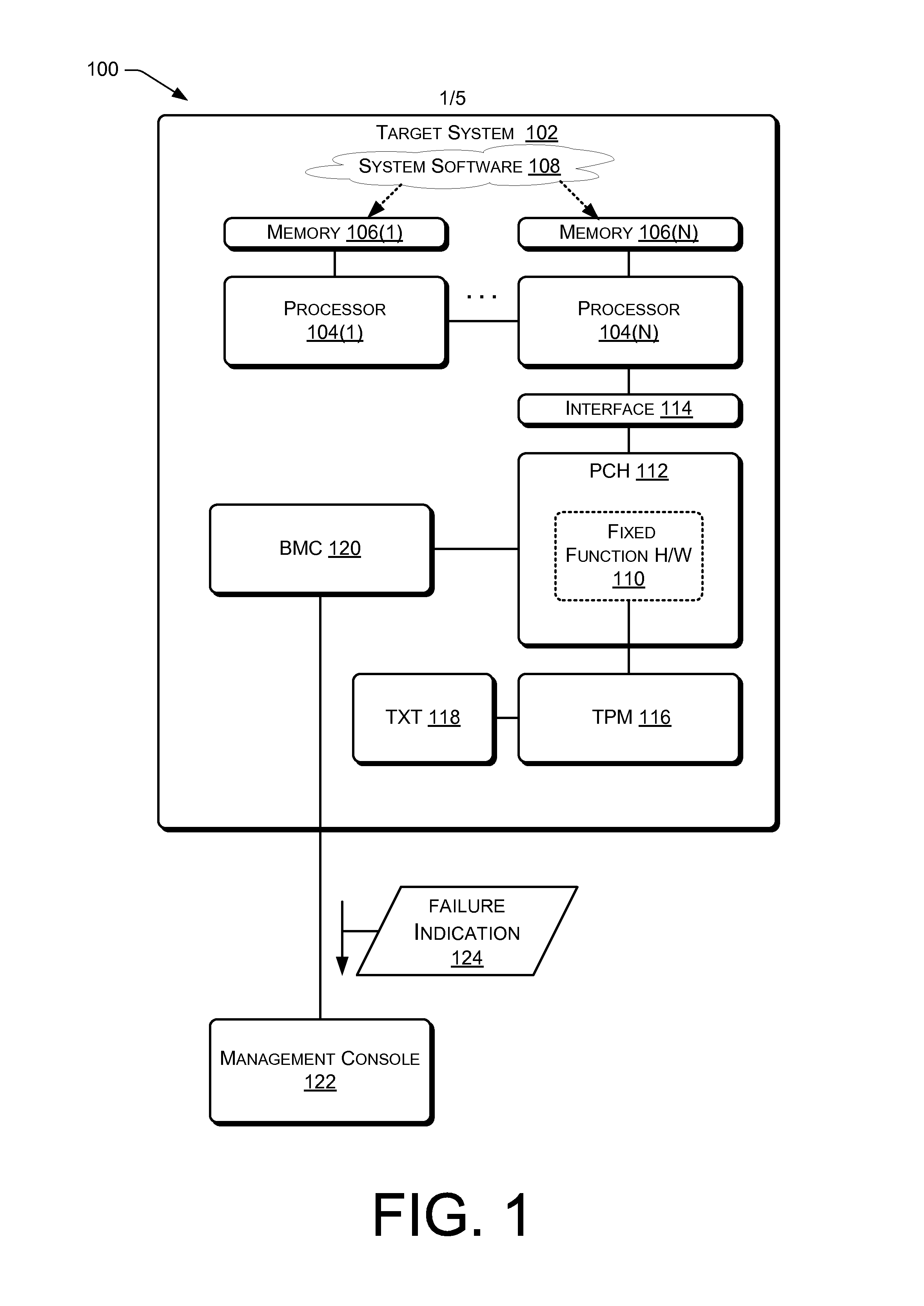
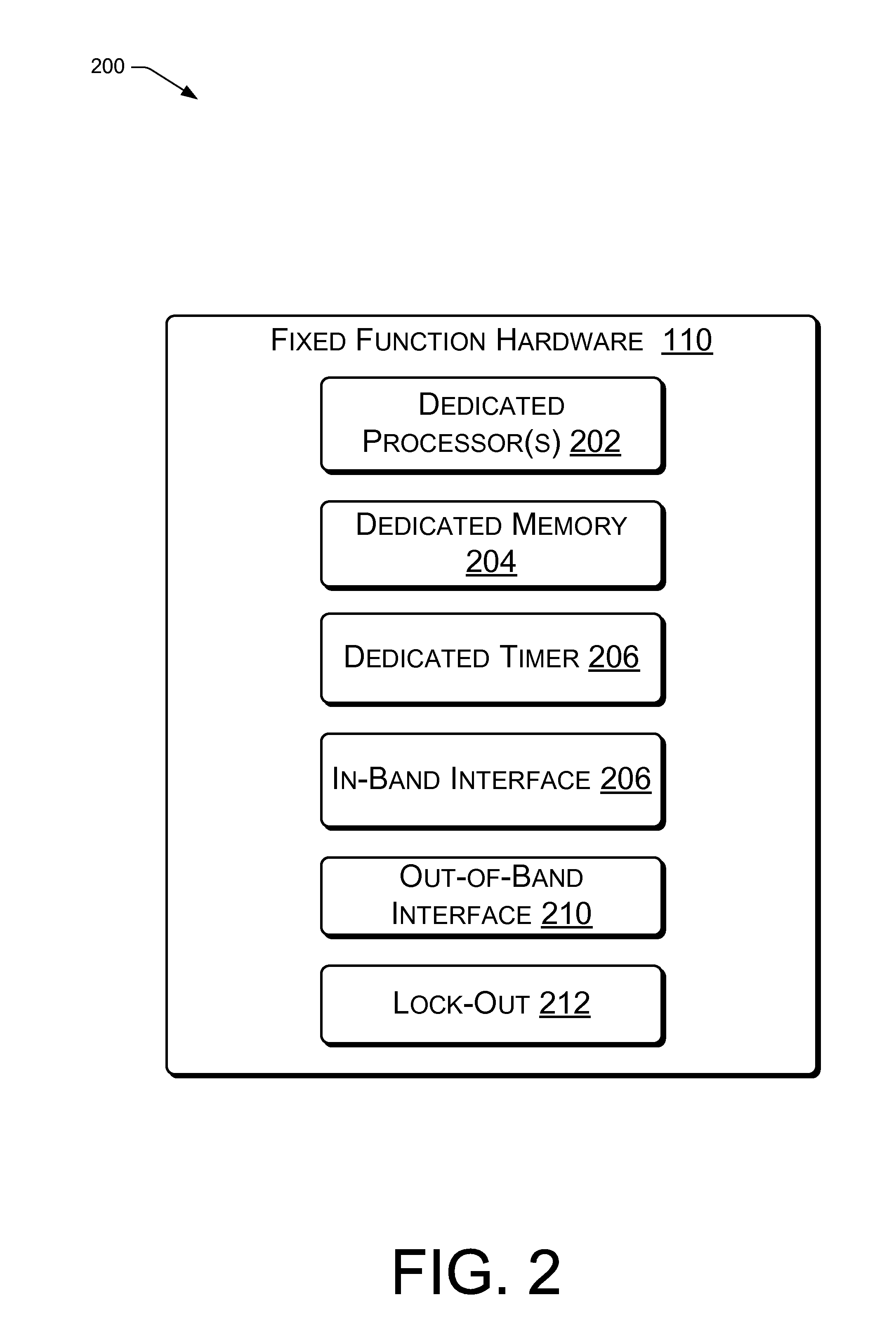
Apparatus for hardware accelerated runtime integrity measurement
InactiveUS20140359239A1Memory architecture accessing/allocationFault responseFixed-functionMemory address
Techniques are described for providing processor-based dedicated fixed function hardware to perform runtime integrity measurements for detecting attacks on system supervisory software, such as a hypervisor or native Operating System (OS). The dedicated fixed function hardware is provided with memory addresses of the system supervisory software for monitoring. After obtaining the memory addresses and other information required to facilitate integrity monitoring, the dedicated fixed function hardware activates a lock-out to prevent reception of any additional information, such as information from a corrupted version of the system supervisory software. The dedicated fixed function hardware then automatically performs periodic integrity measurements of the system supervisory software. Upon detection of an integrity failure, the dedicated fixed function hardware uses out-of-band signaling to report that an integrity failure has occurred.The dedicated fixed function hardware provides for runtime integrity verification of a platform in a secure manner without impacting the performance of the platform.
Owner:INTEL CORP
Methods and system for program execution integrity measurement
ActiveUS7904278B2Facilitates partial re-measurementFlexible policy enforcementNuclear monitoringDigital computer detailsOperational systemOperating system
Owner:UNITED STATES GOVERNMENT AS REPRESENTED BY THE NAT SECURITY AGENCY
Wireless local area network trusted security access method
ActiveCN103024743AImprove integrityGood measure of integritySecurity arrangementAccess methodCryptosystem
A wireless local area network trusted security access method includes five steps of an access activation stage, an access request stage, a certificate authentication request stage, a certificate authentication response stage and an access response stage. Integrality measurement of terminals is achieved by using an integrality measuring chip, identity authentication is achieved by using a digital certificate technology, and negotiation of session keys is achieved by using a certificateless public key system. According to the wireless local area network trusted security access method, integrality authentication, identity authentication and key negotiation processes are fully integrated, only five times of interactions are required for achieving access processes, and the method is high in security and simultaneously capable of saving system overhead.
Owner:BEIHANG UNIV
Method and apparatus to authenticate base and subscriber stations and secure sessions for broadband wireless networks
InactiveUS7747862B2Key distribution for secure communicationUser identity/authority verificationTrusted Platform ModuleBroadband
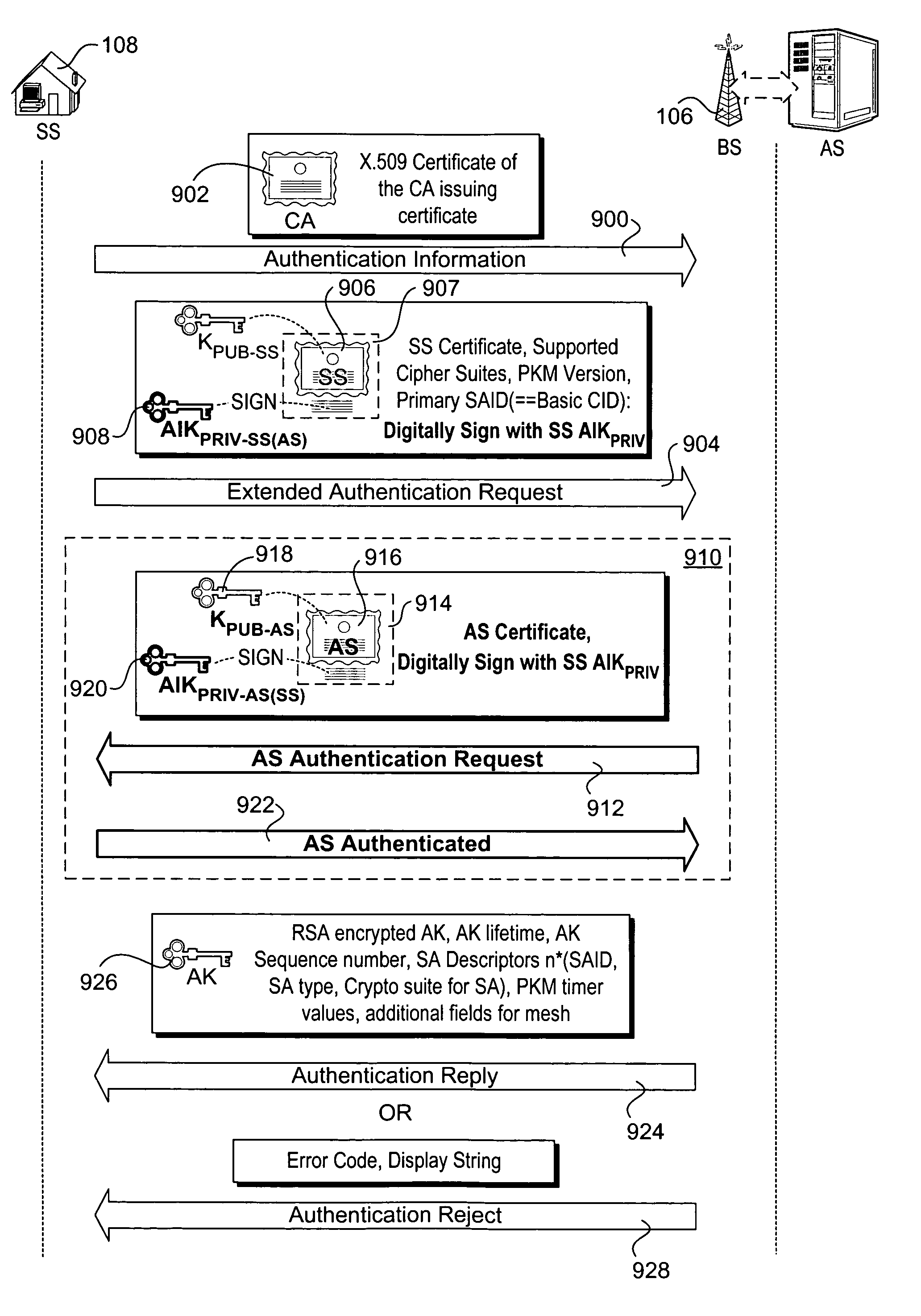
Methods and apparatus to authenticate base and subscriber stations and secure sessions for broadband wireless networks, such as IEEE P802.16-based networks. The apparatus employs a trusted platform module (TPM) to generate security keys, including attestation identity keys (AIKs). A subscriber station (SS) generates an AIK key pair for a specific authentication server (AS) operated by a broadband wireless network, and sends the public AIK key to the AS during a one-time service signup process. In response to an access request, the SS sends authentication information including a manifest signed with the SS's private AIK key. The SS may then be authenticated by the AS via use of the SS's public AIK key. The AS may be authenticated by the SS using a similar process, thus supporting mutual authentication via AIK keys. The TPM may also be used to verify a current configuration of a subscriber station platform is an authorized configuration. Integrity measurements are made via the TPM, and corresponding configuration identifiers are sealed to the TPM and sent to the authentication server during the signup process. During a subsequent access request, an attempt is made to unseal a configuration identifier, which can only proceed if a corresponding configuration has not changed.
Owner:INTEL CORP
Trusted computing terminal integrity measuring and proving method and device
ActiveCN105608386AResist attackPrevent decipheringInternal/peripheral component protectionPlatform integrity maintainanceApplication softwareTotal measurement
The invention relates to the field of trusted computing, and particularly provides a terminal integrity detecting and proving method and device based on trusted computing for solving problems in the prior art. On the condition of not increasing additional hardware requirements and special instructions, an isolated and safe integrity dynamic measurement environment is built for an application program, and parallel barrier-free operation of other application programs in the measurement process is ensured. In the integrity proving process, the actual measurement value of each component in a computing terminal is concealed, and the problem that a hacker decode the version, configuration, firmware and other information of the terminal through the actual measurement values is effectively prevented; when the trusted computing terminal is subjected to integrity detection, extension integrity measurement values and the total measurement frequency stored in a platform configuration register PCR are sent to a verifier after being signed, and the verifier can detect the integrity of the trusted computing terminal by executing hash operation.
Owner:成都三零嘉微电子有限公司
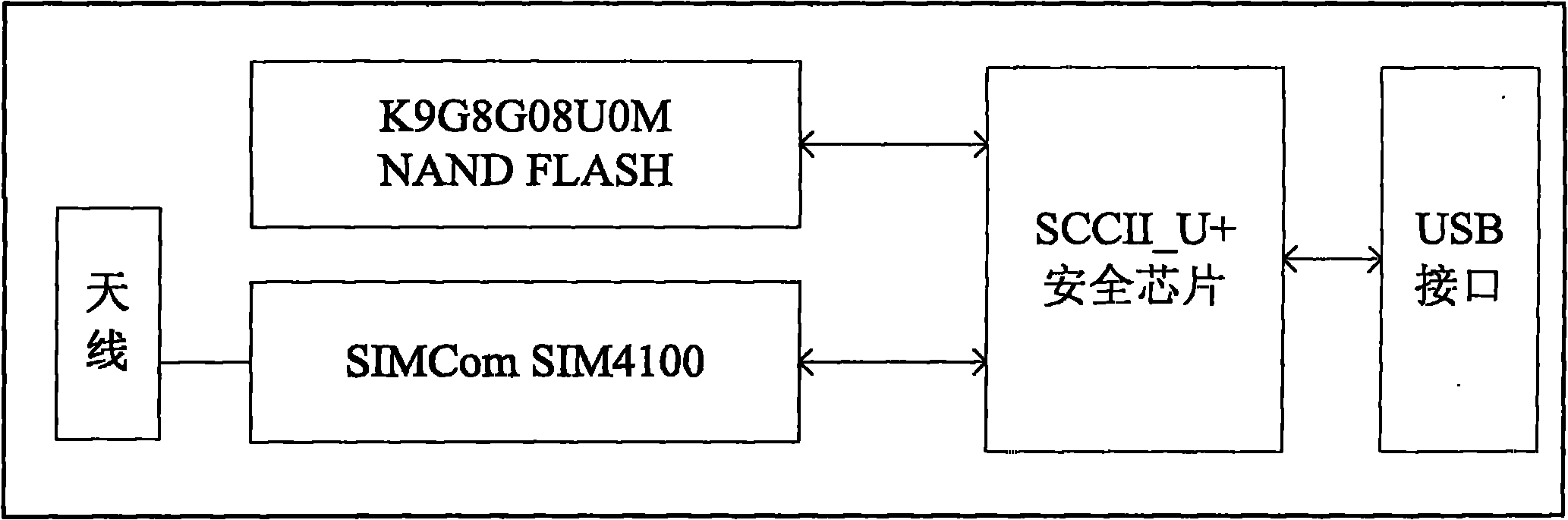
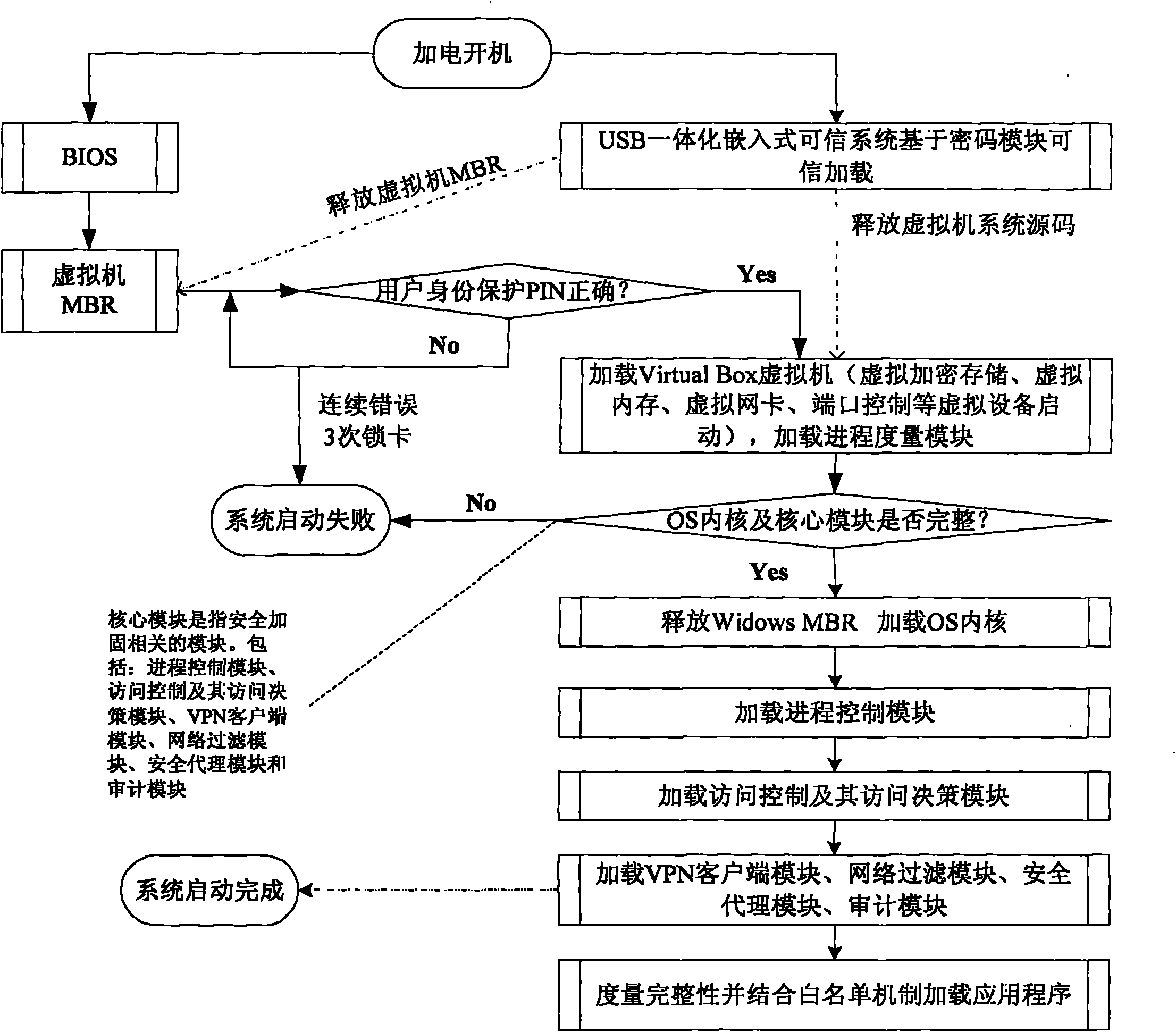
Security terminal reinforcing model and reinforcing method of tolerable non-trusted component
ActiveCN102004876APrevent leakageUniqueness guaranteedDigital data protectionPlatform integrity maintainanceAccess networkConfidentiality
The invention relates to a security terminal reinforcing model and reinforcing method of a tolerable non-trusted component, which can ensure the security of the computing environment of the terminal equipment in an access network. A universal serial bus (USB) integrated embedded trusted system is used as a trusted root of a terminal; the behavior control of the non-trusted component is realized based on a virtual machine; the trusted computing software supporting a white list mechanism ensures that services and applications listed in the white list mechanism can be started without integrity measurement to tolerate the loading and the running of the non-trusted component; and especially, under the condition that the component running on the terminal is not trusted, the predictability and the controllability of the final result are ensured, the confidentiality of the related information when the access terminal accesses the network is ensured, and the confidentiality and the integrity of the local information of the terminal are ensured. The invention is matched with the existing trusted computing and other information security technologies to construct a terminal computing environment with a predictable security result.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Space information network roaming and trusted security access method
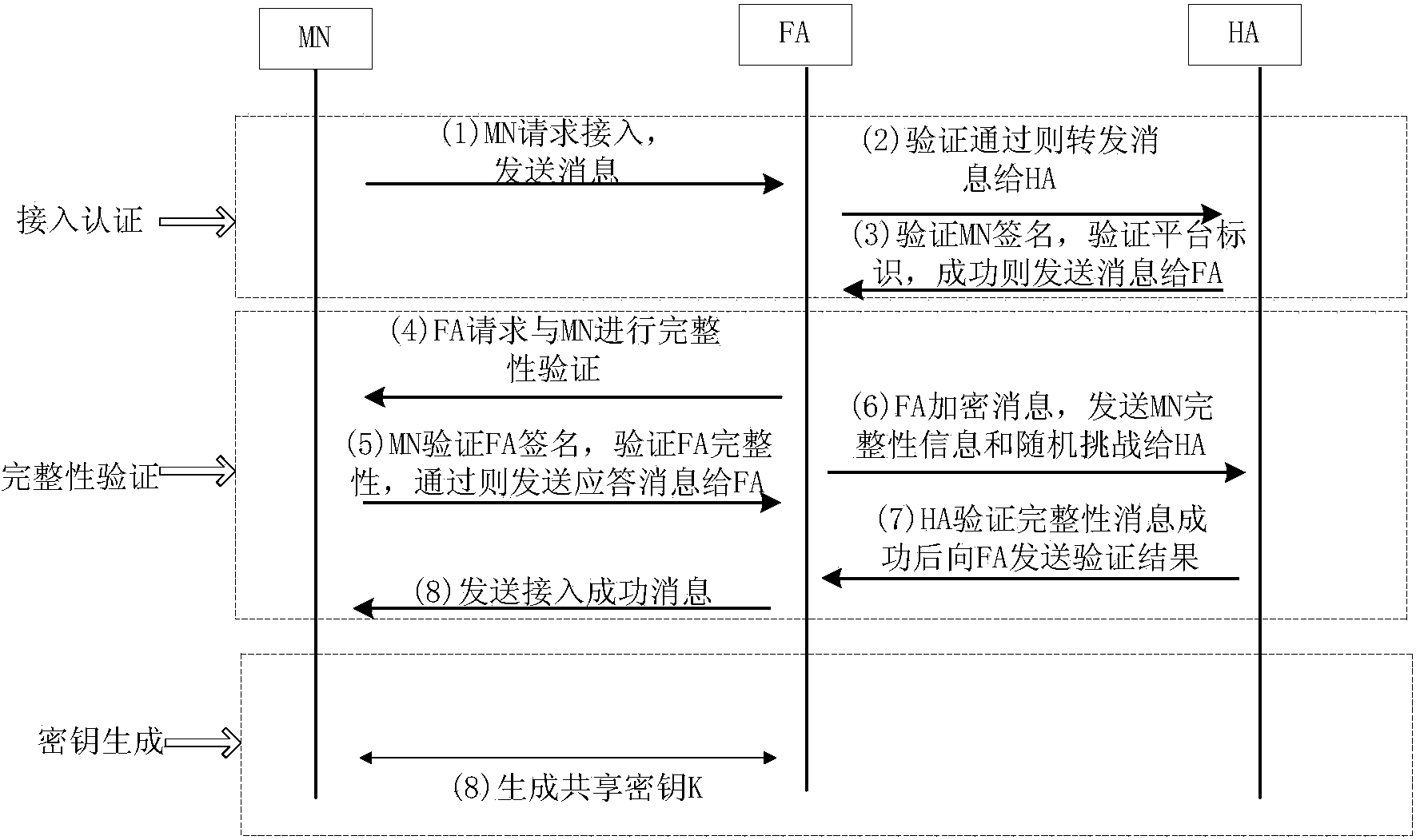
ActiveCN103634796AImprove integrityGood measure of integrityNetwork topologiesSecurity arrangementAccess methodInformation networks
The invention discloses a space information network roaming and trusted security access method. The space information network roaming and trusted security access method includes a node registration stage, a request access stage, an identity authentication stage, an integrity verification stage and a key generation stage. Session key negotiation among terminal access nodes MN and a non-local security domain authentication server FA is completed, procedures of the integral space information network roaming and trusted security access method are completely completed at the moment, mutual identity authentication and integrity measurement among the terminal access nodes MN and the non-local security domain authentication server FA are implemented, and the terminal access nodes MN, the non-local security domain authentication server FA and a local security domain authentication server HA participate in the session key negotiation among the terminal access nodes MN and the non-local security domain authentication server FA. The space information network roaming and trusted security access method has the advantages that the interaction round number is low, session keys are high in security, a trusted computing related technology is utilized, the integrity of the terminal access nodes can be measured, and the problem of easy network attack due to poor integrity and trustworthiness of terminals can be solved.
Owner:BEIHANG UNIV
Star trust chain supporting embedded platform application program integrality verification method
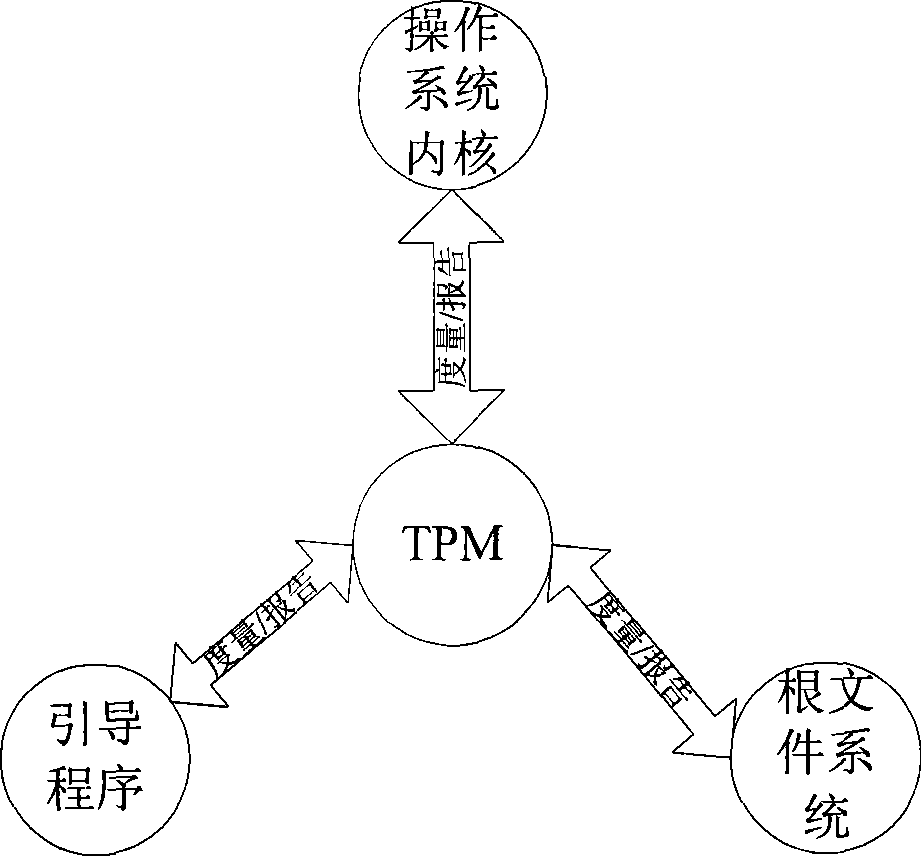
InactiveCN101504704AIntegrity Metric ImplementationConvenience and Credibility MetricsPlatform integrity maintainanceOperational systemValidation methods
The invention discloses an application program integrity verification method for an embedded platform supported by a star trust chain. The embedded platform is provided with a TPM realized by an independent hardware which is taken as a trusted measurement of the whole platform, and the TPM uses a hardwire to control the operation of the embedded platform; the inside of the TPM is integrated with a trusted computing root, a trusted storage root and a trusted report root by adopting a physical mode so as to have physical protection on the TPM and a connecting circuit; and the TPM forms star trust relationship with the embedded platform Bootloader, an operating system kernel and a root file system. The method is characterized in that an integral application program which needs trust expansion in the root file system is subjected to trusted measurement by the trusted computing root of the TPM, and an obtained trusted measurement value is saved in the trusted storage root of the TPM; and the application program is subjected to integrity measurement during the starting of an operating system, then an obtained measurement value is compared with the trusted measurement value, and the integrity verification of the application program passes if the obtained measurement value is consisted with the trusted measurement value, otherwise, the integrity verification fails.
Owner:WUHAN UNIV
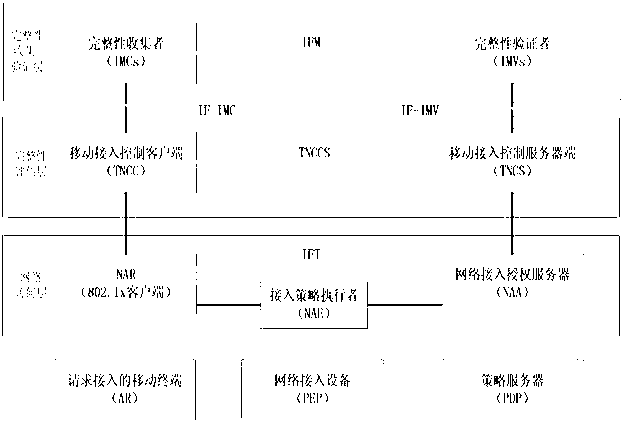
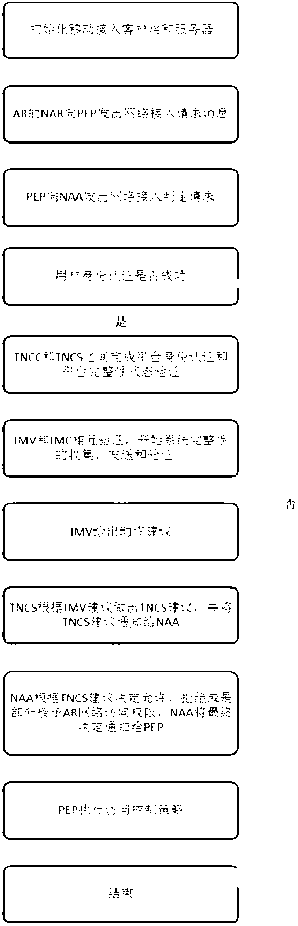
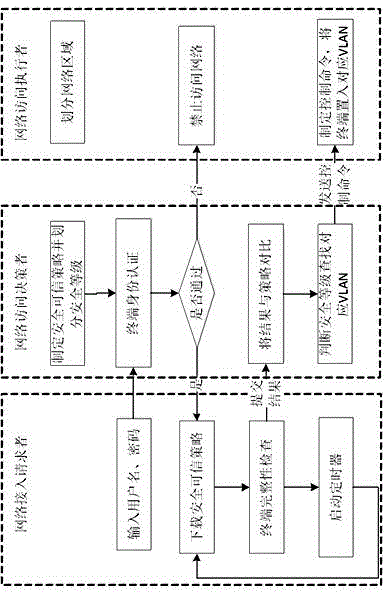
Trusted network access method and system for mobile terminal
The invention discloses a trusted network access method and a trusted network access system for a mobile terminal, and belongs to the technical field of trusted network access. The method comprises the following steps that: 1) the mobile terminal loads an integrity measurement collector and detects the integrity of the integrity measurement collector, and a policy decision point loads an integrity measurement verifier and detects the integrity of the integrity measurement verifier; 2) the mobile terminal transmits a network access request to a policy enforcement point; 3) after receiving the network access request, the policy enforcement point transmits a network access judgment request to the policy decision point, and authenticates the user identity of the mobile terminal; 4) after the user identity passes authentication, platform identity authentication is performed between the policy decision point and the mobile terminal, the policy decision point and the mobile terminal mutually authenticate system integrity, and a platform trust relationship between the policy decision point and the mobile terminal is established; and 7) the policy decision point transmits a suggestion indicating whether to access the policy enforcement point according to the platform trust relationship, and the policy enforcement point authorizes network access permission to the mobile terminal according to the suggestion. By the method and the system, network resources can be well protected.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
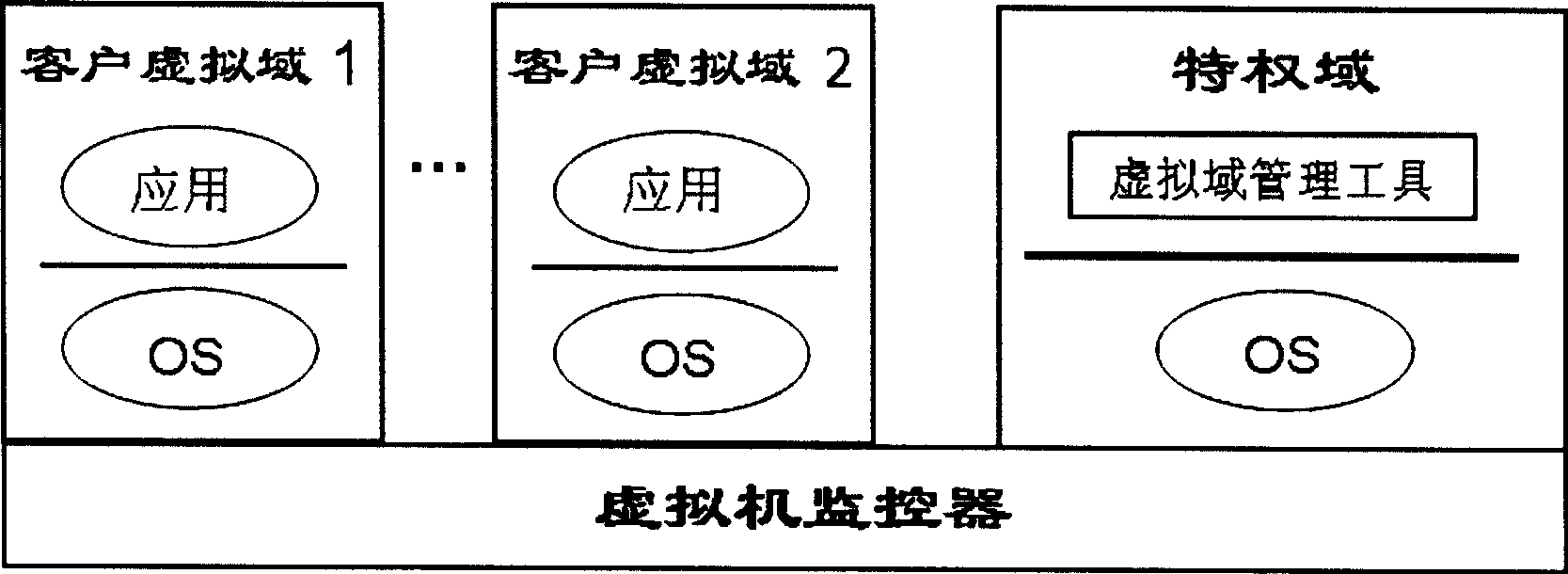
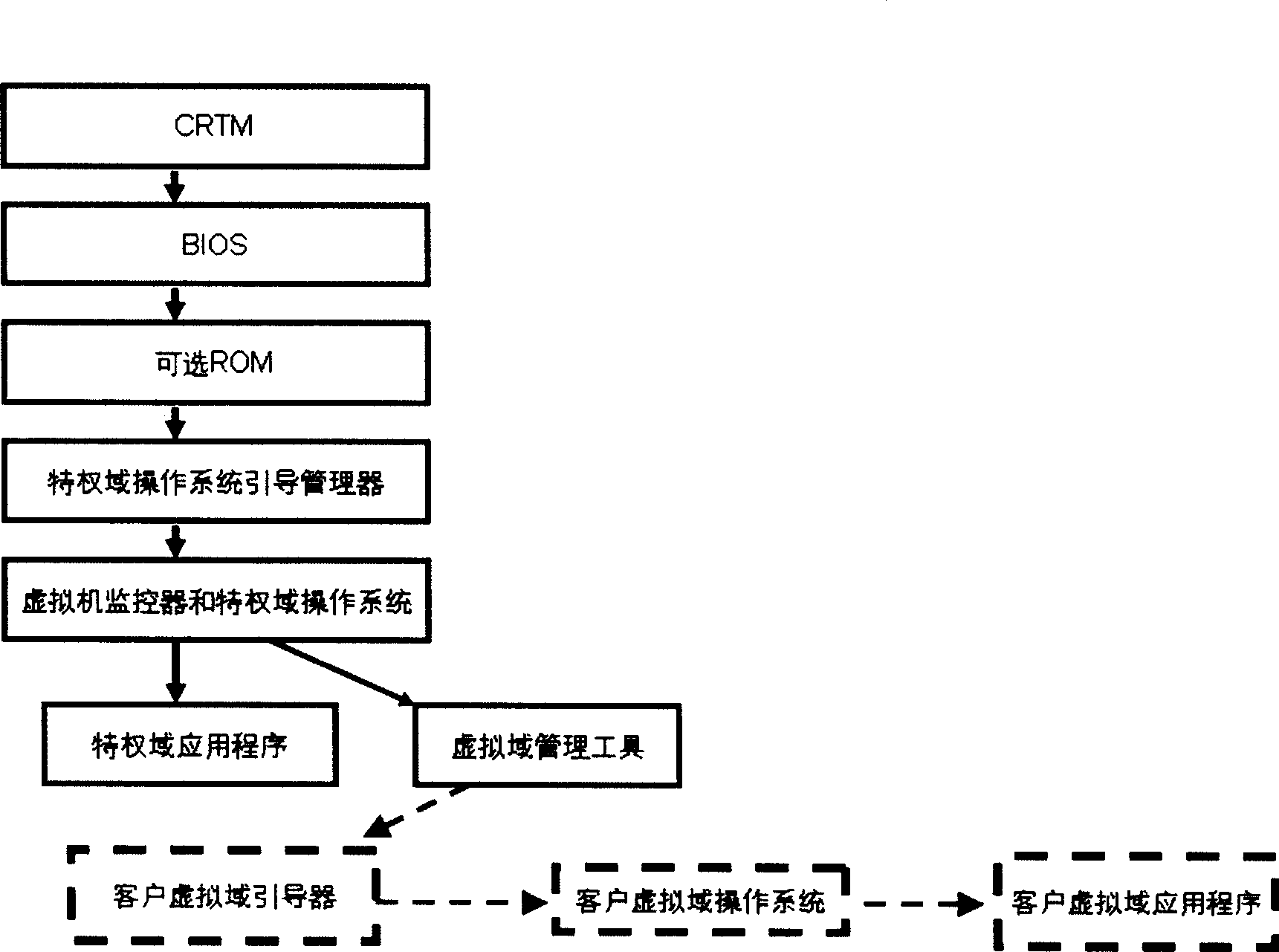
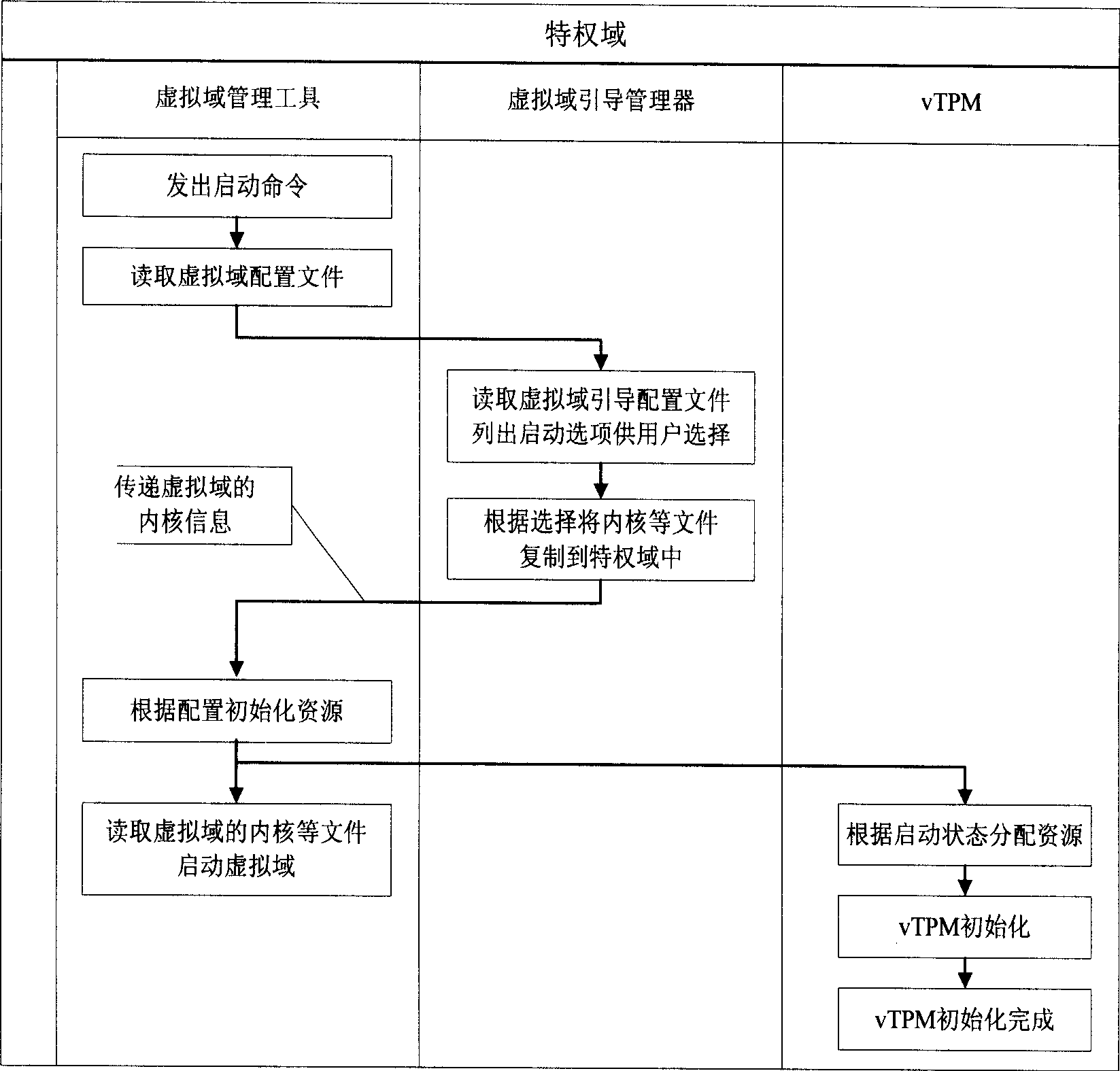
Method for measuring completeness of credible virtual field start-up files supporting non-delaying machine
InactiveCN101488173AReduced integrityShorten the timePlatform integrity maintainanceProgram loading/initiatingVirtual fieldManagement tool
The invention relates to a method for supporting the integrity measurement of boot files in trusted virtual domain of a zero-downtime machine. Management tool and boot manager of the virtual domain in privilege domain are modified to realize that the integrity measurement of the system boot files in the trusted virtual domain is just carried out when the system boot files are loaded, therefore, the safety and extensible problems for carrying out the integrity measurement of the system boot files in the trusted virtual domain when booting computer are overcome and the system flexibility are improved, and the arrangement of the trusted virtual domain including re-customizing or updating kernel system of virtual domain can be carried out dynamically during running process of computer, and data service of other virtual domain in the same hardware platform is not interrupted when booting trusted virtual domain. The measurable boot files comprise configuration files of virtual domain, boot configuration files of virtual domain and the files that are needed to be measured are designated by the boot configuration files of virtual domain. The method can cooperate with other trusted computing technology in virtual environment to build a complete virtual domain boot trusted chain.
Owner:BEIJING JIAOTONG UNIV
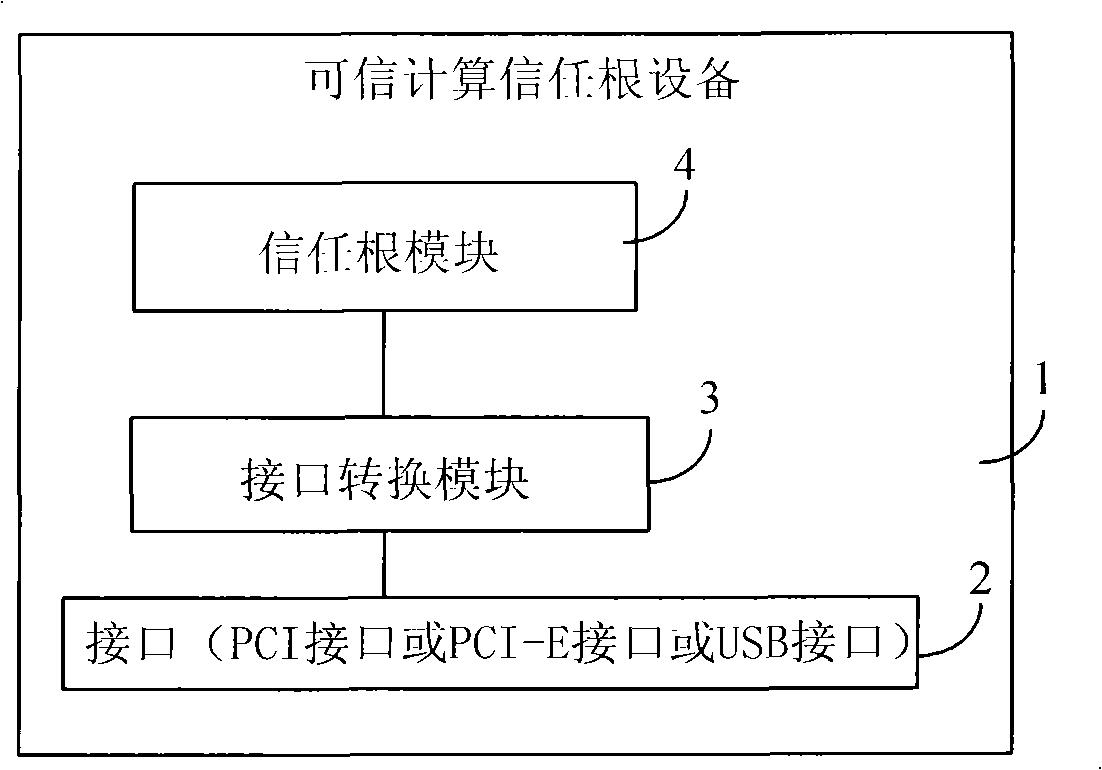
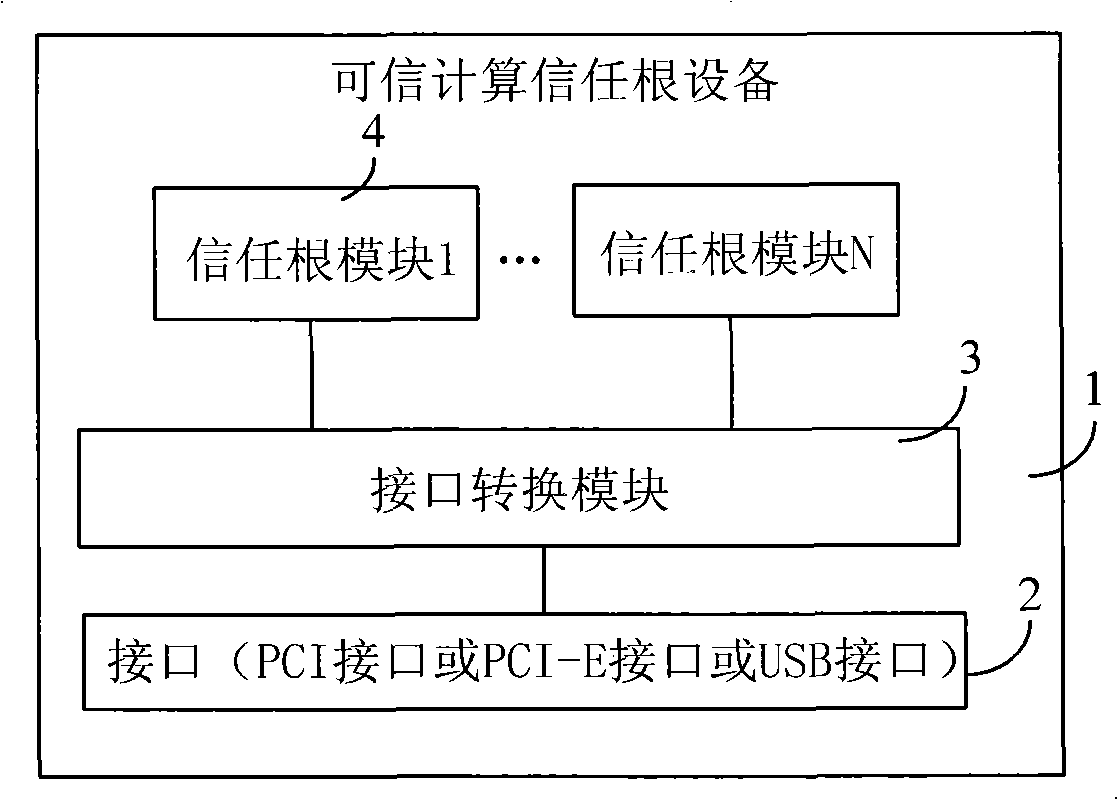
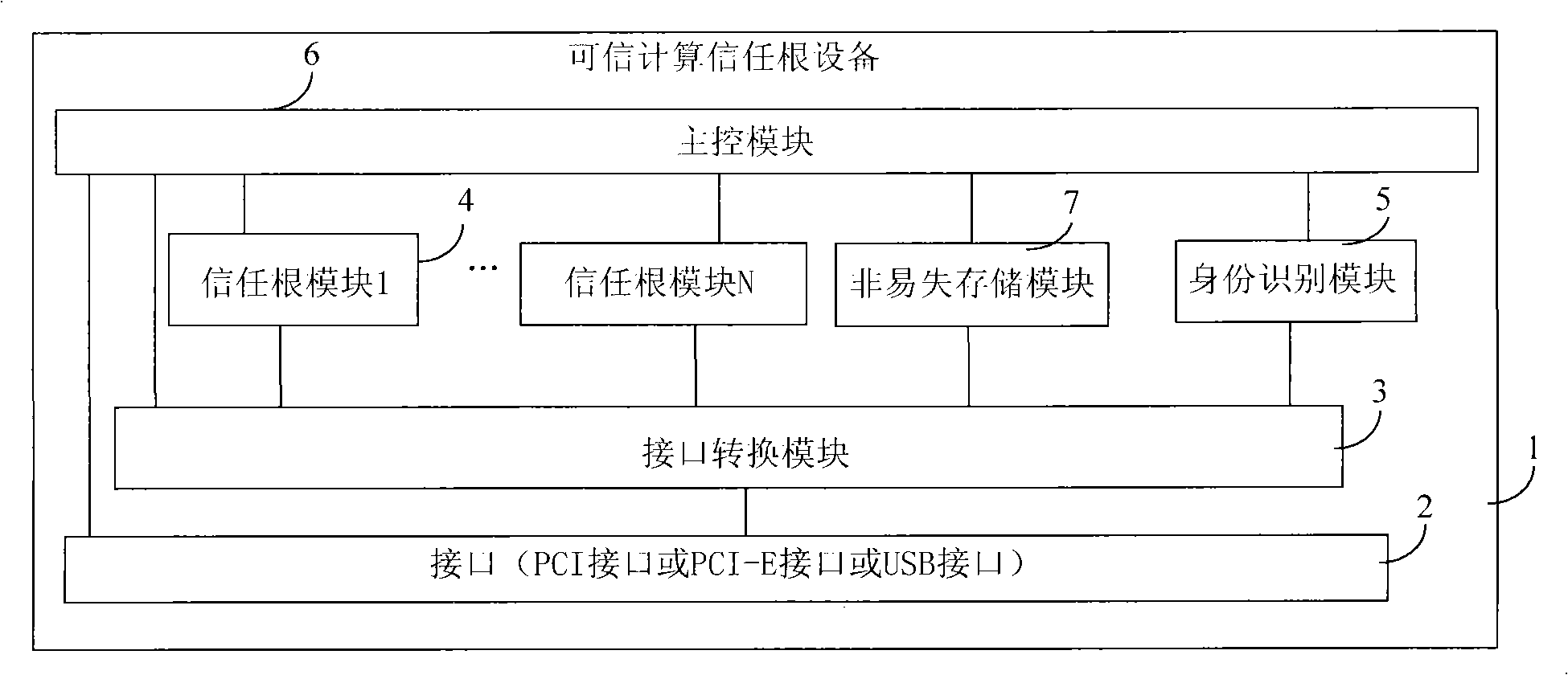
Trusted computation trust root device for computer and computer
InactiveCN101794362AAdd trusted computing functionSafeInternal/peripheral component protectionCommunication interfaceSERCOS interface
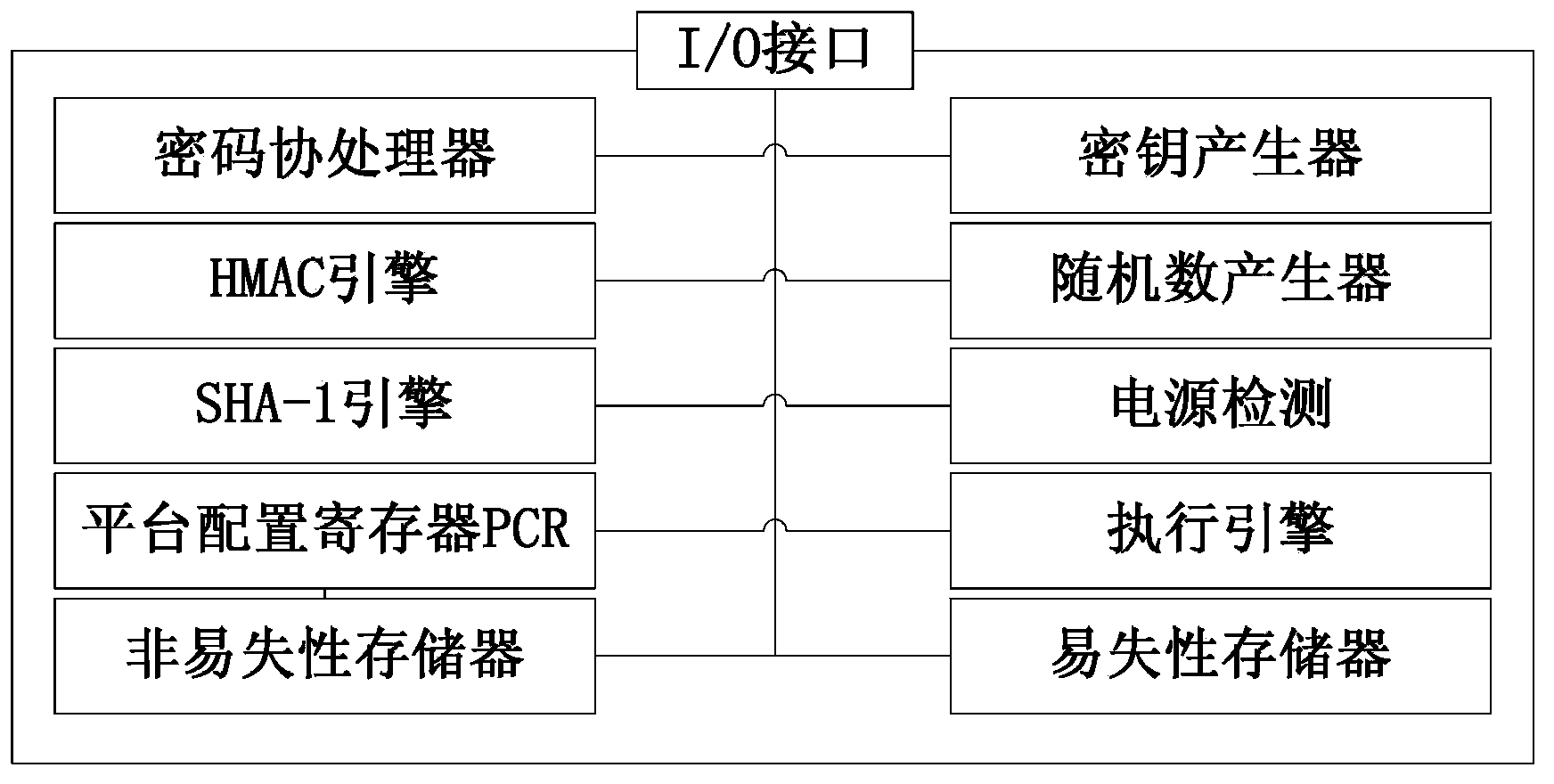
The embodiment of the invention provides a trusted computation trust root device for a computer and the computer. The device comprises a circuit board, an interface conversion module and at least one trust root module, wherein the circuit board is connected with an interface, the interface is matched with a PCI (Programmable Communication Interface), a PCI-E interface or a USB interface of a computer motherboard, the interface conversion module and the trust root module are both arranged on the circuit board, the interface conversion module is used for exchanging data between the interface of the circuit board and the PCI interface, the PCI-E interface or the USB interface of the computer, and the trust root module is used for carrying out secret key production and encryption and decryption treatment, storing a secret key and sensitive data and supplying integrity measurement, data safety protection and identity authentication information. The device can be used for an ordinary computer to enable the ordinary computer to have the safety of a trusted computer.
Owner:华北计算技术研究所
Dependable computing based process control method
ActiveCN103455756AAvoid destructionGuaranteed uptimePlatform integrity maintainanceOperational systemDynamic resource
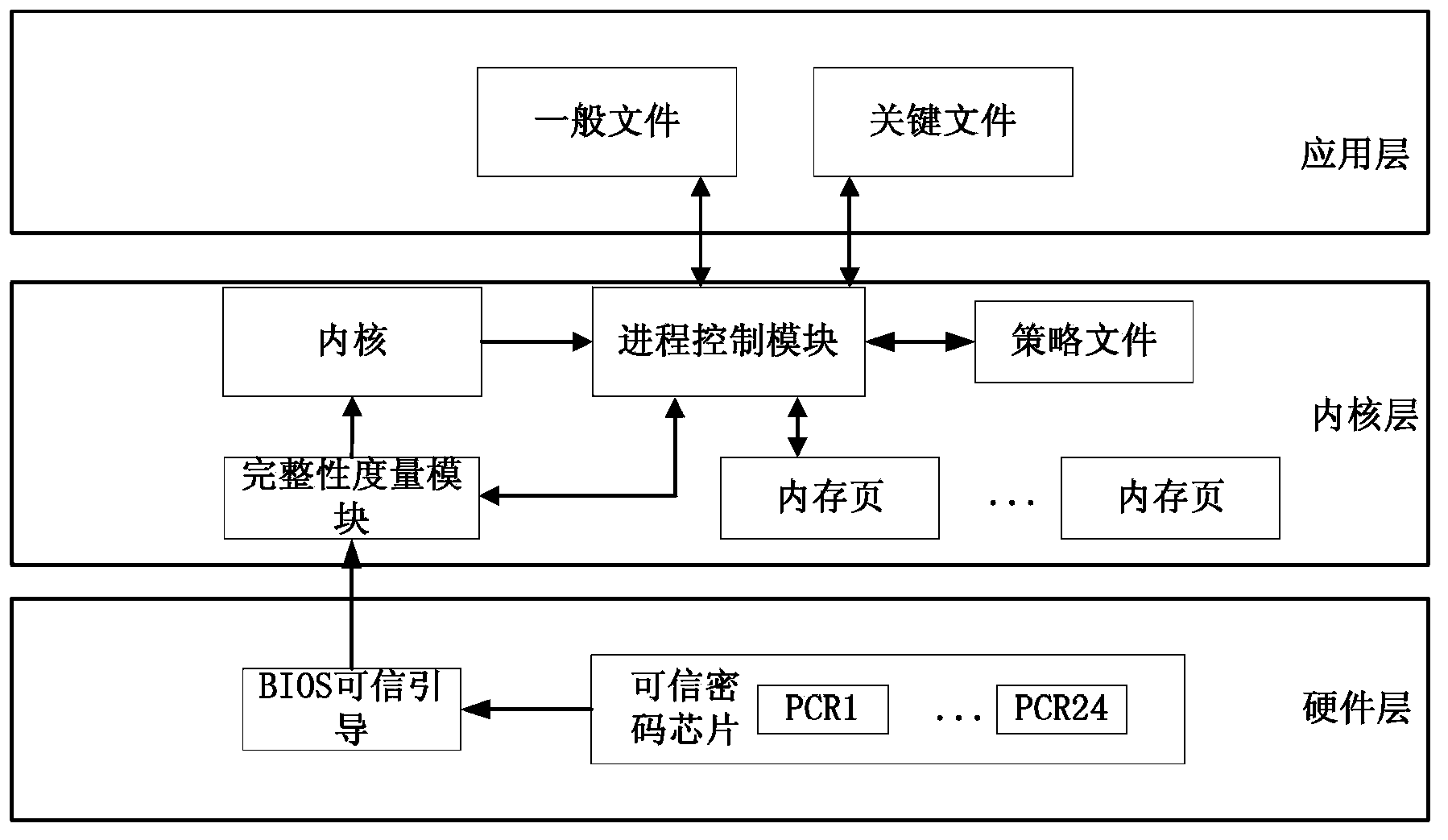
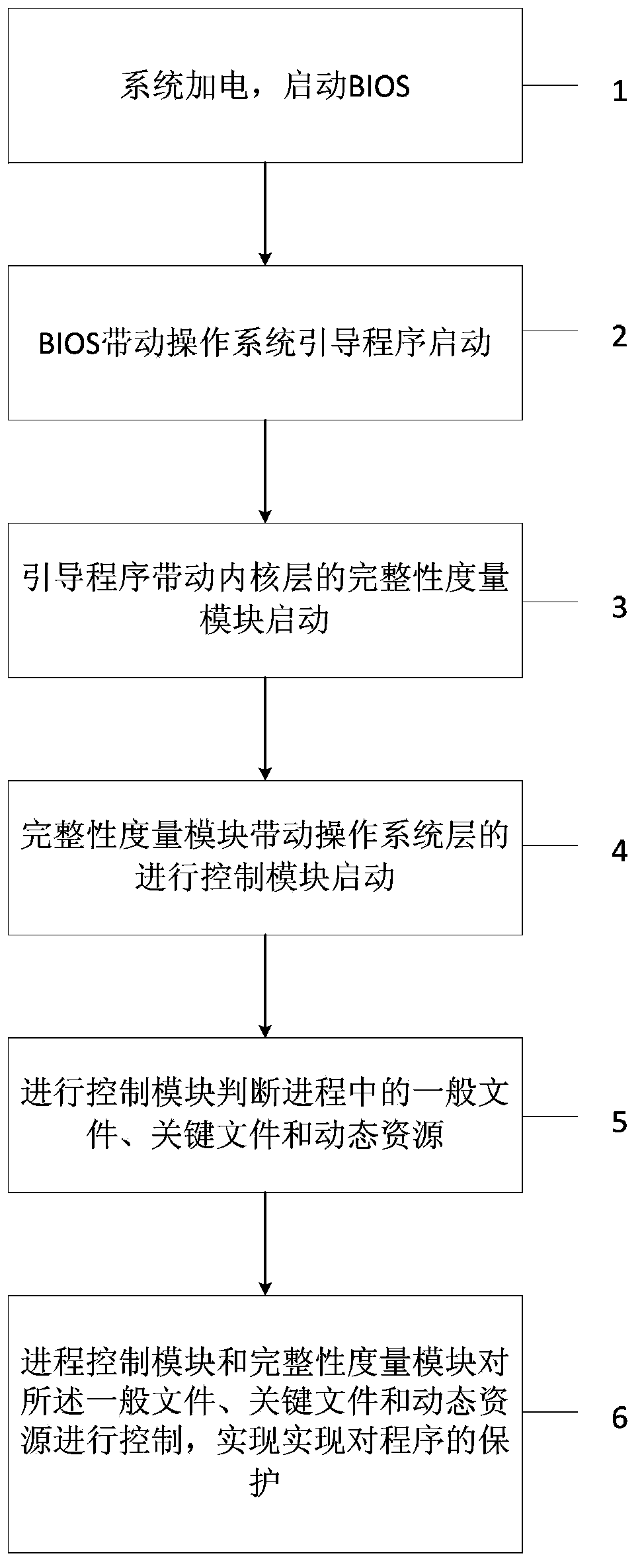
The invention provides a dependable computing based process control method. The process control method includes that a system is powered and a BIOS (basic input / output system) is started; the BIOS drives an operating system bootstrap program to start; the bootstrap program drives an integrity measurement module in an inner nuclear layer to start; the integrity measurement module drives a process control module in an operating system layer to start; the process control module is used for judging ordinary files, critical files and dynamic resources in process; the process control module and the integrity measurement module are used for controlling the ordinary files, the critical files and the dynamic resources to realize protection of the program. By the method, the files related to process operation are subjected to protection based on the dependable computing platform hardware algorithm, static files and the dynamic files are protected, permission of accessed files and mapping relation label pages are defended, and protective means are stereo and include the aspects of direct encryption storage, and inputting credibility quantity into a dependable computing platform register and the like, so that the process can be effectively controlled.
Owner:STATE GRID CORP OF CHINA +5
Dynamic link library integrity measuring method under perlink mechanism
ActiveCN104751048ADoes not affect startup speedPerformance is not affectedComputer security arrangementsPrelinkCode segment
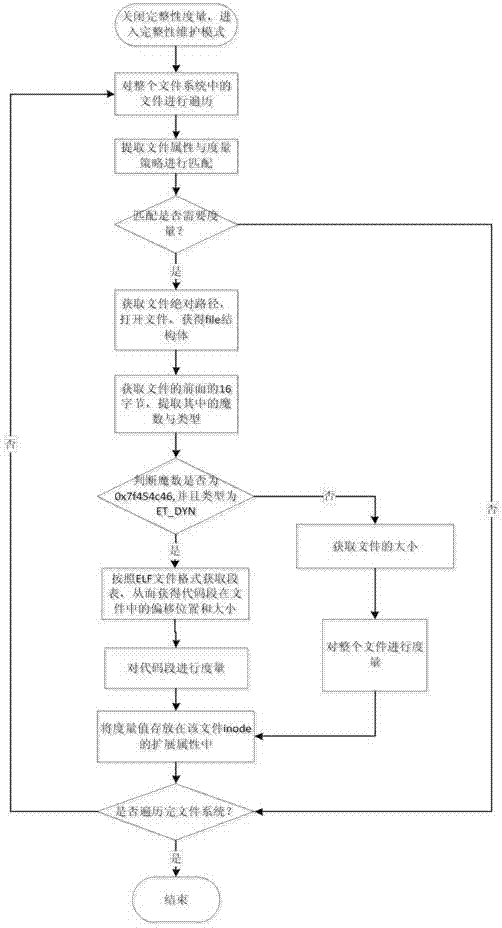
The invention discloses a dynamic link library integrity measuring method under a perlink mechanism. The method comprises the steps that firstly, a Linux integrity measuring enabling switch is turned off, an integrity maintaining mode is achieved, and a file to be measured is extracted; secondly, whether the measured file belongs to a dynamic link library file or not is detected, and if yes, the displacement position and length of a code segment in the dynamic link library file in the file are extracted and sent to a measurement function, and the reference measurement value is calculated and stored; thirdly, an integrity verification mode is achieved, when a file loaded by the system is the file to be measured, whether the file belongs to the dynamic link library file or not is detected, if yes, the displacement position and length of a code segment in the dynamic link library file in the file are extracted and sent to the measurement function, the measurement value is calculated and compared with the reference measurement value, if the measurement value is matched with the reference measurement value, loading executing is allowed, and if the measurement value is not matched with the reference measurement value, loading executing is refused. The integrity measurement can be carried out on the dynamic link library file without closing a prelink tool.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Method and server for integrity measurement based on BMC and TCM
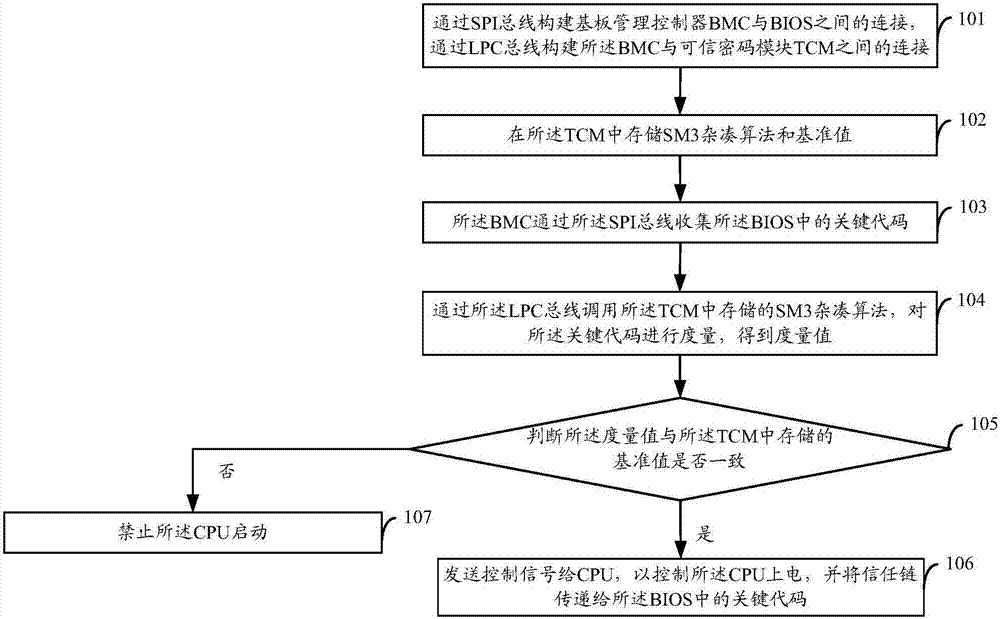
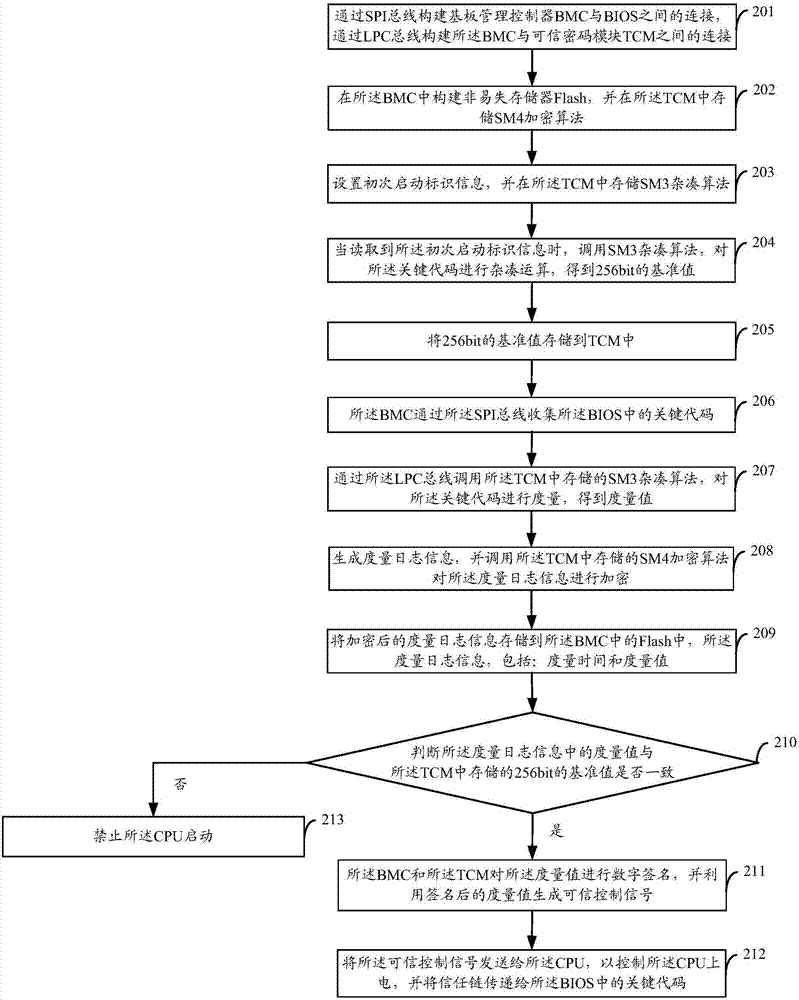
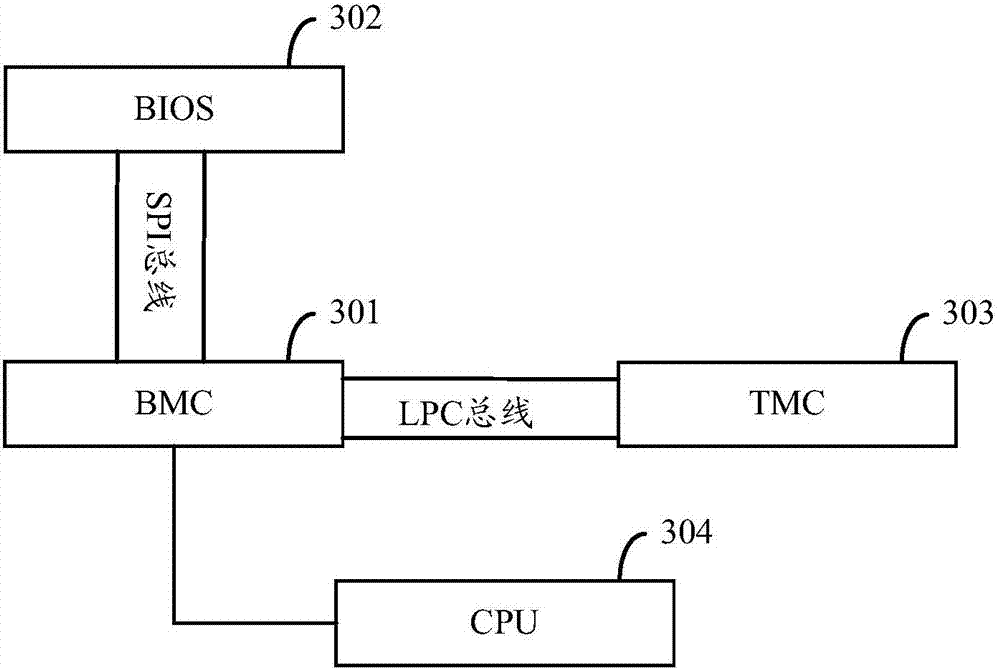
InactiveCN107169379ARealize trust transferEncryption apparatus with shift registers/memoriesDigital data protectionControl signalBIOS
The invention provides a method and server for integrity measurement based on BMC and TCM. The method comprises: building connection between baseboard management controller BMC and BIOS through the SPI bus, building connection between BMC and trusted cryptography module TCM through the LPC bus and storing SM3 hash algorithms and reference values in the TCM; the BMC collects key codes in the BIOS through the SPI bus; the SM3 hash algorithms stored in the TCM are called through the LPC bus for measuring the key codes to obtain measurement values; determining whether the measurement values are consistent with the reference values stored in the TCM; if the measurement values are consistent with the reference values, sending control signals to the CPU to control the power-on of the CPU and transmitting a trust chain to the key codes in the BIOS; otherwise, forbidding the start of the CPU. The technical scheme of the invention realizes trust deliver.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
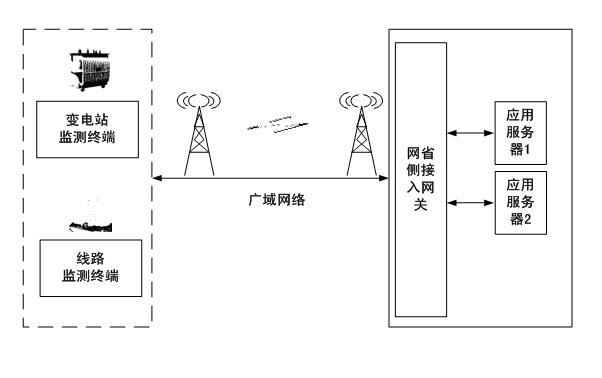
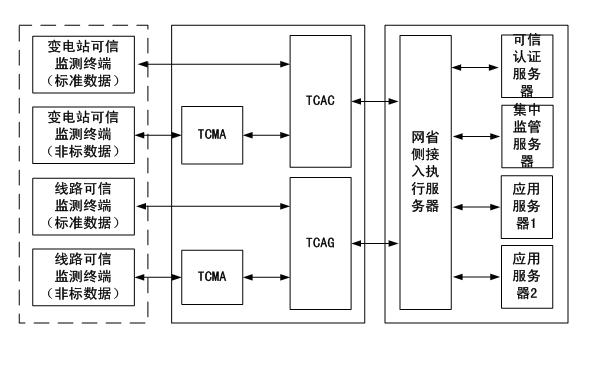
Power transmission and transformation equipment state monitoring system security protection method based on trust chain transmission
Owner:STATE GRID ELECTRIC POWER RES INST
Creditability detection method of computer
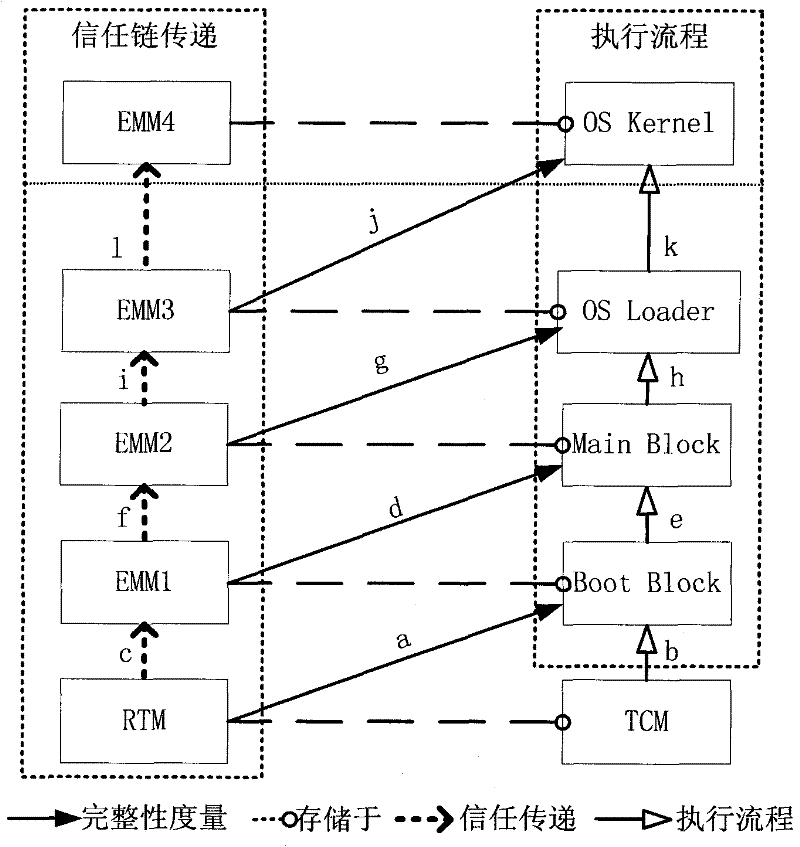
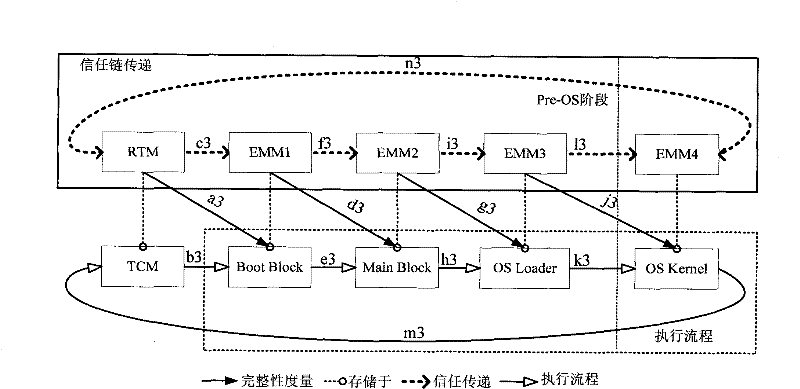
ActiveCN102214278AImprove securityIncrease flexibilityPlatform integrity maintainanceComputerized systemChain of trust
The invention relates to a creditability detection method of a computer. The method comprises the following steps of: building an annular trust chain, wherein the annular trust chain has end points which sequentially are a trusted cryptography module (TCM), a boot block of a basic input output system (BIOS), a main block, an operating system (OS) loader and an OS kernel; initializing integrity measurement from any one of the end points on the annular trust chain, and sequentially carrying out the integrity measurement along a clockwise direction or an anticlockwise direction of the annular trust chain until the measurement of all end points on the annular trust chain is finished; and after the measurement of the last end point which is subjected to the integrity measurement is finished, transmitting trust to the TCM, and finishing a final creditability report of a computer platform by the TCM. By the creditability detection method of the computer, the safety and validation flexibilityof the computer platform are improved, the maintenance updating cost of a computer system is reduced, and the expansion of the computer system can be facilitated.
Owner:NATIONZ TECH INC
Device and method for implementing credible embedded system on existing embedded equipment
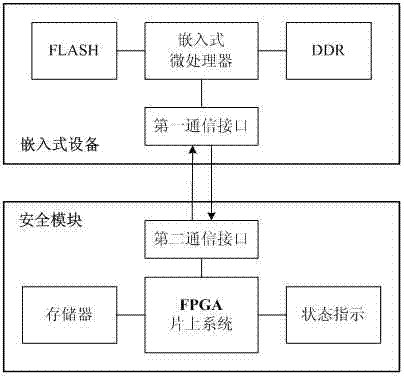
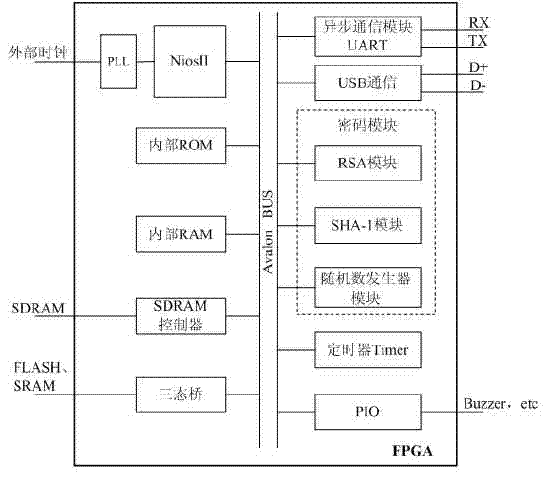
InactiveCN102819706ASimple compositionIncrease flexibilityComputer security arrangementsHardware structureSpecific function
The invention discloses a credible embedded system on the basis of a safety module and aims to solve the technical problem of improving the safety of the existing embedded equipment. The credible embedded system disclosed by the invention comprises embedded equipment and the safety module. The embedded equipment is physically connected with the safety module by a serial bus, wherein the embedded equipment is an embedded system platform for implementing specific functions; and the safety module uses a FPGA (Field Programmable Gate Array) SOC (System On Chip) as a core and is used for providing functions of encryption and decryption operation of data, integrity measurement and the like for the embedded equipment and improving the safety of the embedded equipment in the process from start to operation. Compared with the prior art, an additional program storage is not added for the embedded equipment; an original hardware structure of the embedded equipment does not need to be changed; the safety module has simple circuit composition; and the credible embedded system has strong flexibility and simple application mode, is easy to implement and has general applicability.
Owner:CHONGQING UNIV
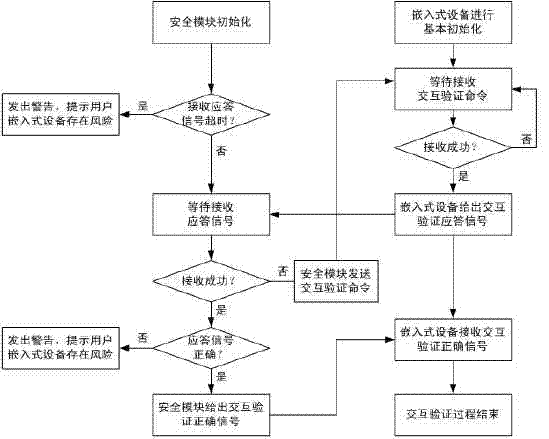
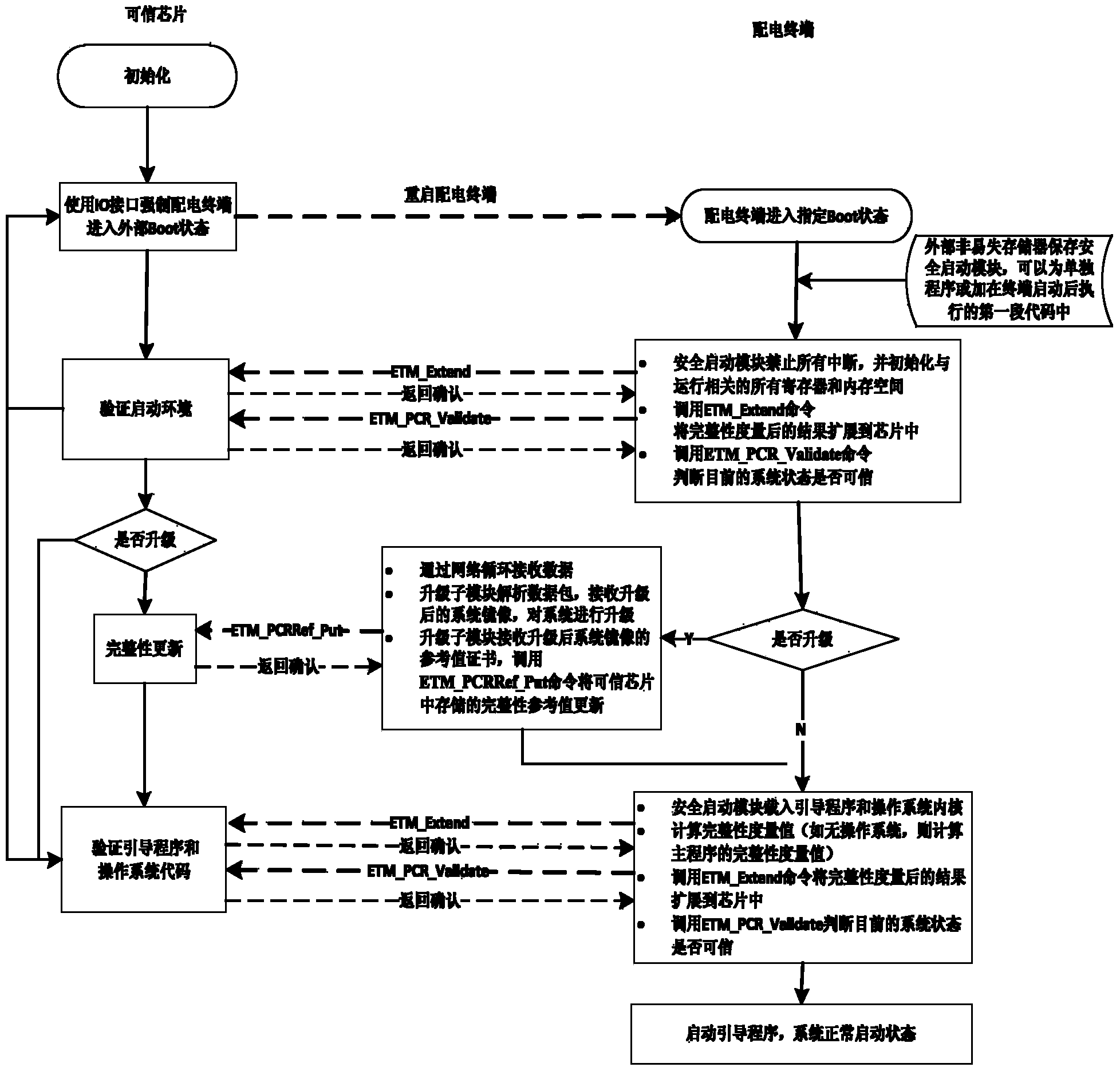
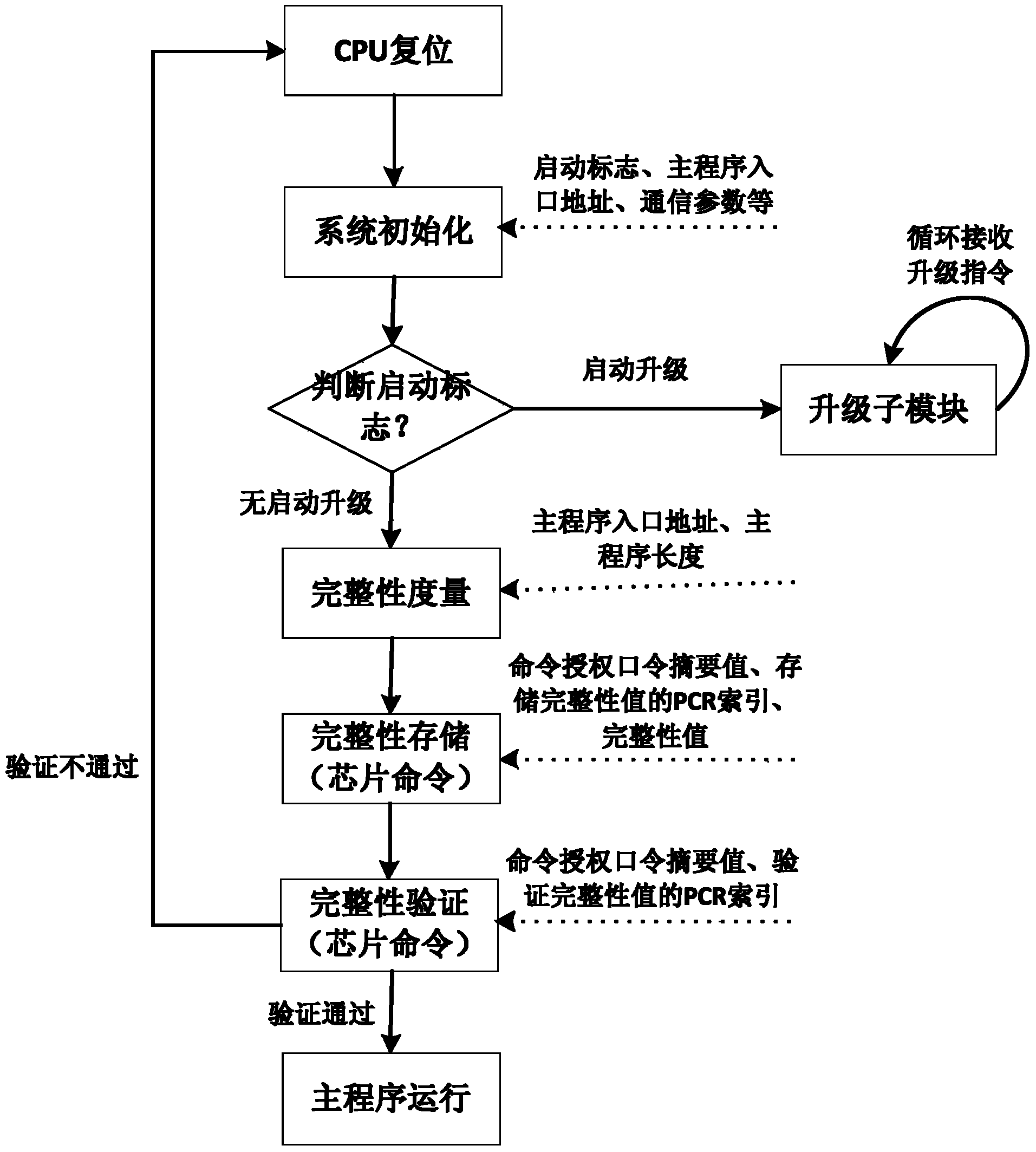
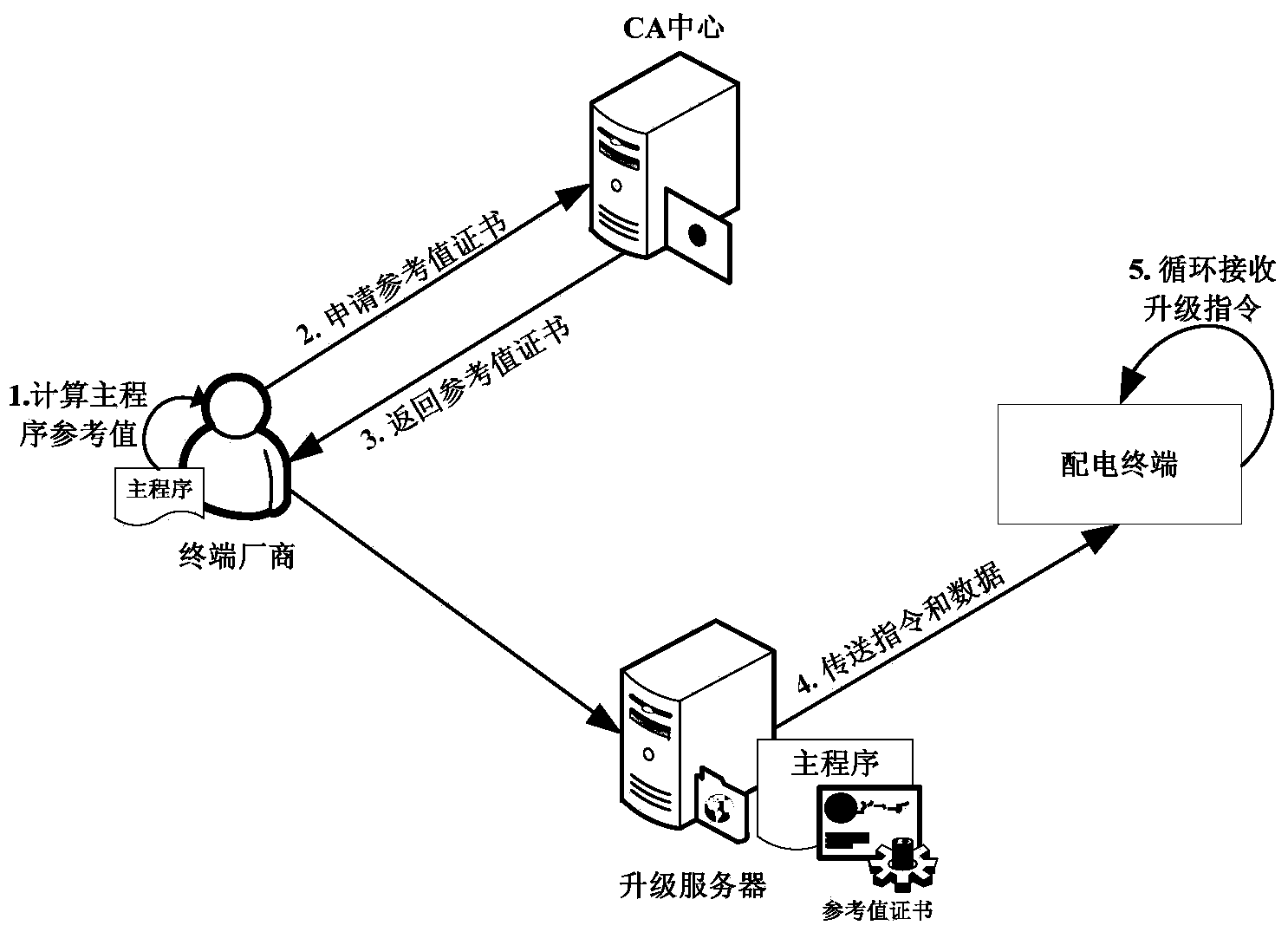
Method for establishing trusted environment in power distribution terminal
ActiveCN103646214AEnable Trusted BootImprove integrityPlatform integrity maintainanceEngineeringMalware
The invention provides a method for establishing a trusted environment in a power distribution terminal. A trusted chip is added in the power distribution terminal to be used as a hardware trust root, pre-configured integrity reference values are stored inside, and then a secure startup module is added in a system to be used as an initial operation module of the system. During startup of the system, integrity measurements are performed on a system state and a critical system image, so that the integrity of the operation system on the power distribution terminal is protected, trust is established, the trusted operation environment can be established finally, the ability of malicious software to destroy the integrity of the system is restrained from the source, and the security level of the system of the power distribution terminal is increased.
Owner:STATE GRID CORP OF CHINA +5
System and method for dynamic cross-domain access control based on trusted network connection
ActiveCN104618395AGuaranteed secure and trusted accessRealize dynamic controlTransmissionNetwork connectionTrust level
The invention discloses a system for dynamic cross-domain access control based on trusted network connection. The system comprises a trusted network access requester, a network access decision-maker and a network access controller, wherein the network access decision-maker moves the requester into different safety trusted domains according to the state of the network access requester, so as to achieve dynamic cross-domain access control. The invention further discloses a method for dynamic cross-domain access control based on trusted network connection, and according to the method, platform identity authentication and integrity measurement are carried out by using a domestic TCM chip to rank the network according to safety trusted levels, and the access of the network by a terminal is limited according to the terminal identity authentication and integrity measurement results. According to the invention, dynamic cross-domain access control is set up on the basis of trusted network connection, and the terminal is put in the network domains of different safety levels in a dynamic manner according to the safety trusted status of the terminal in time, so that the safe and trusted access of the network is guaranteed.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Safe remote loading method of operating system
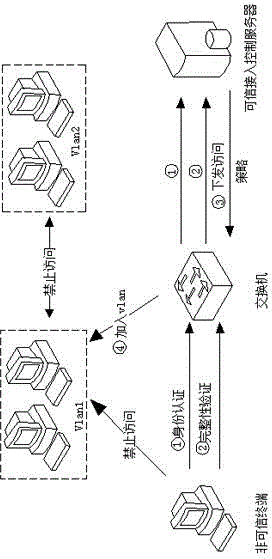
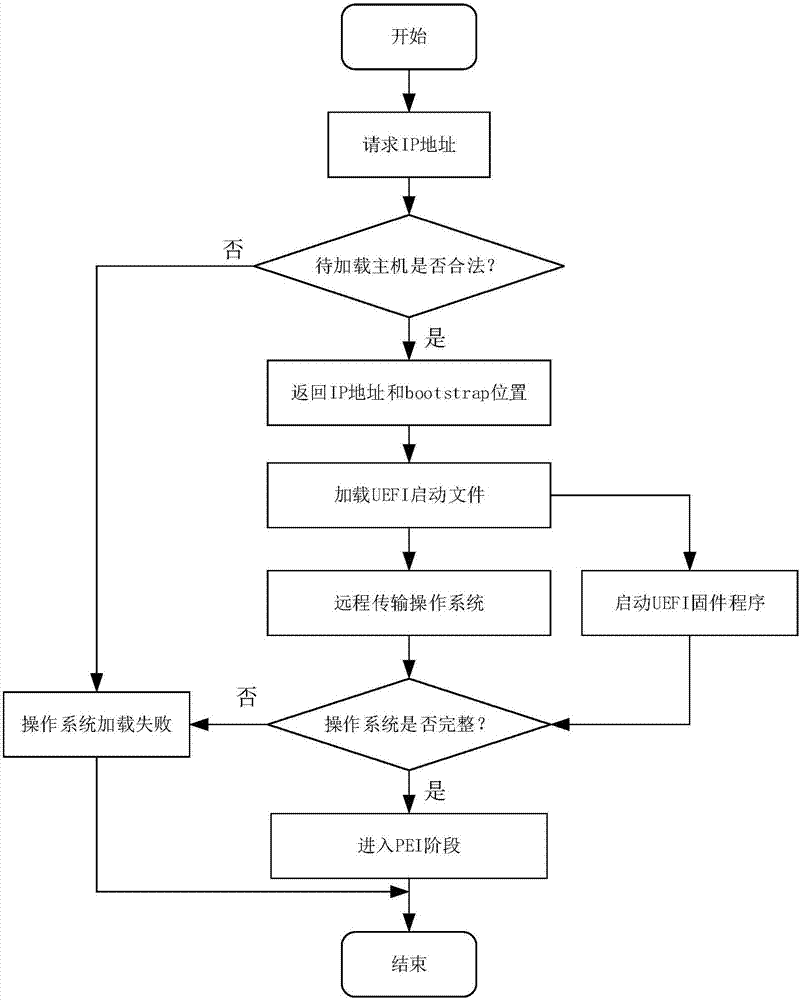
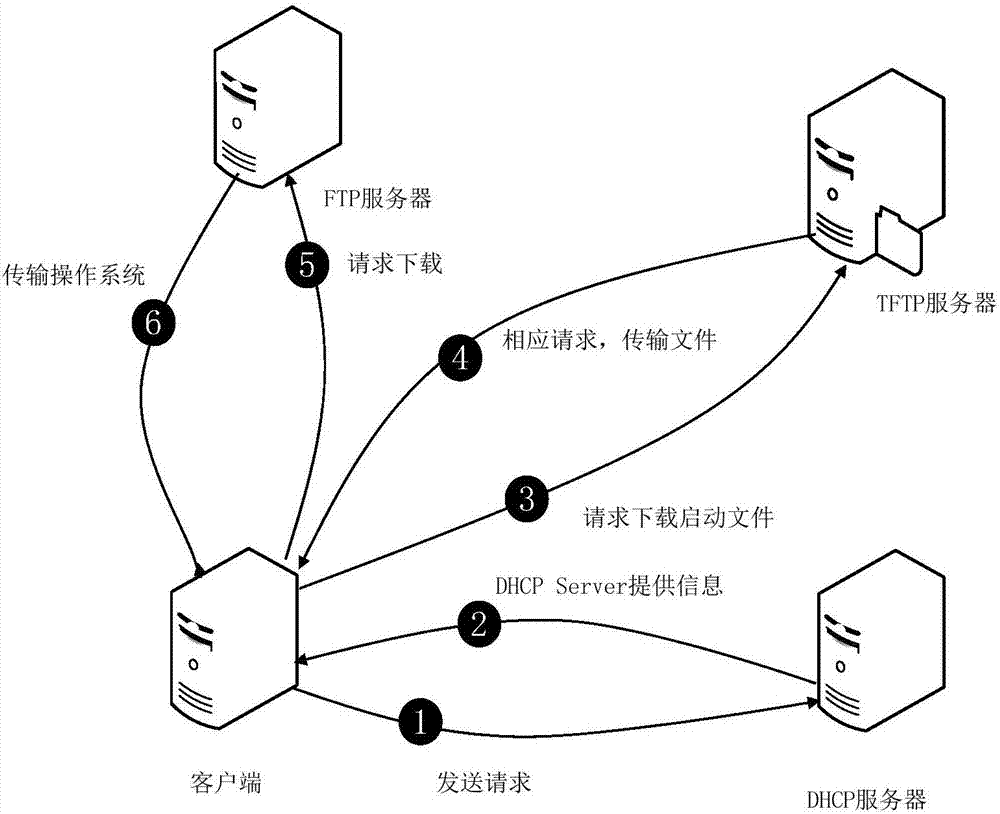
ActiveCN106940769AEnsure safetyDigital data authenticationTransmissionOperational systemSecurity software
The invention discloses a safe remote loading method of an operating system. The safe remote loading method comprises the following steps: (1) a legality verification step of a computer to be subjected to loading; (2) a remote loading step of the operating system; (3) an integrity measurement step of the operating system in a loading process. Aiming at the problem that current security software cannot process operating system-level malicious programs, the integrity of the operating system can be measured before the operating system is started up, so that the environment security before startup is guaranteed.
Owner:GUANGZHOU UNIVERSITY
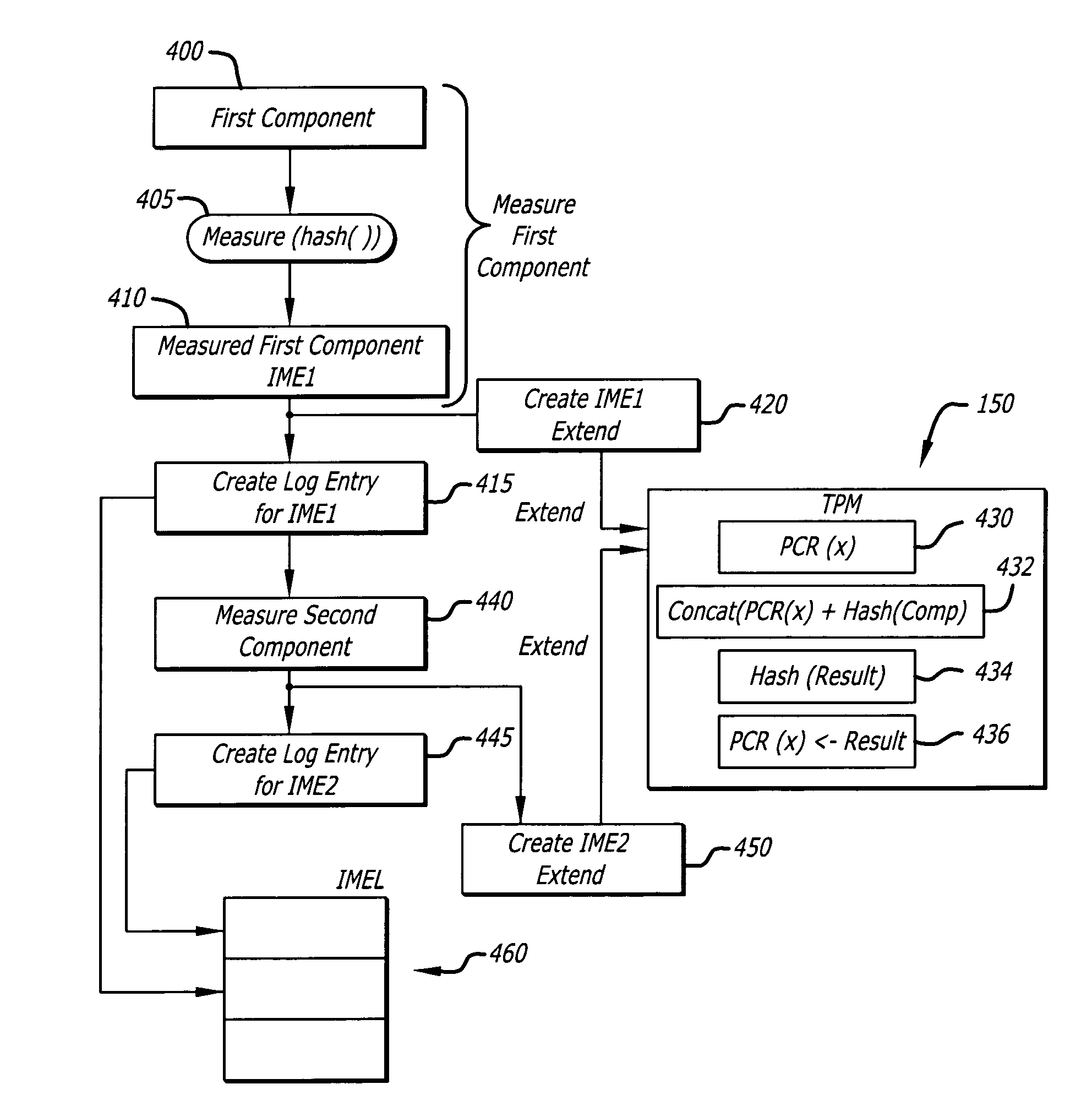
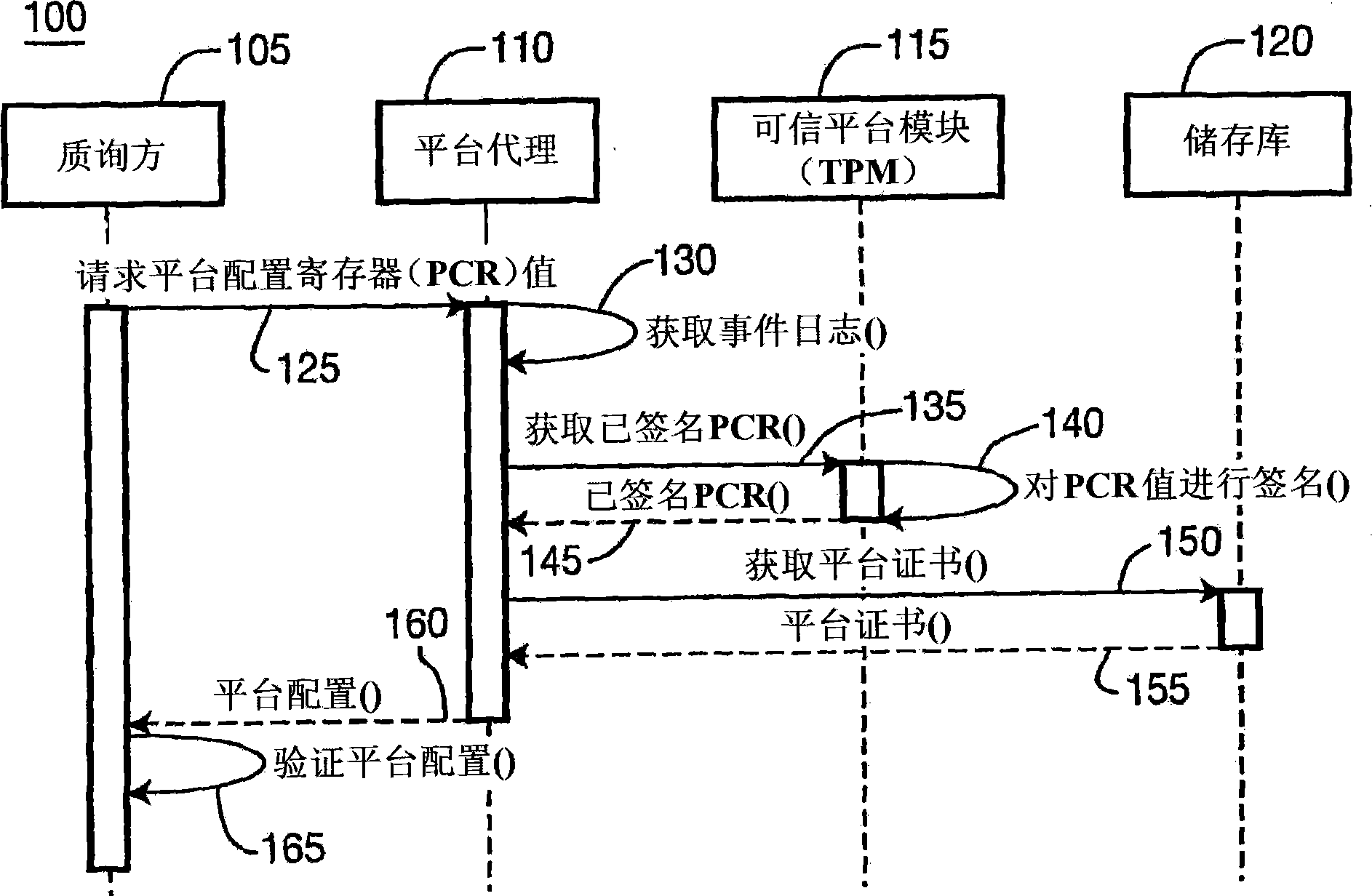
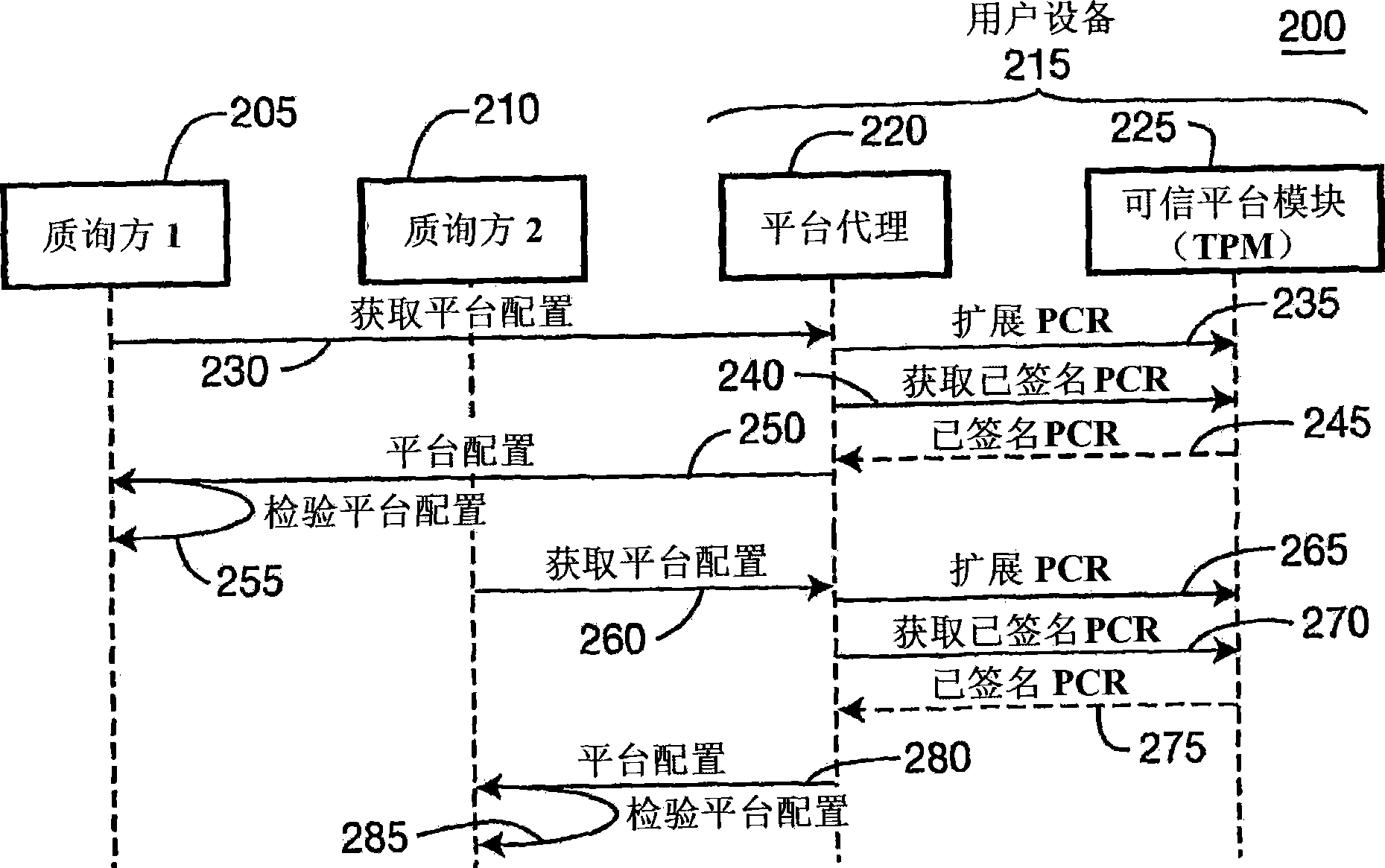
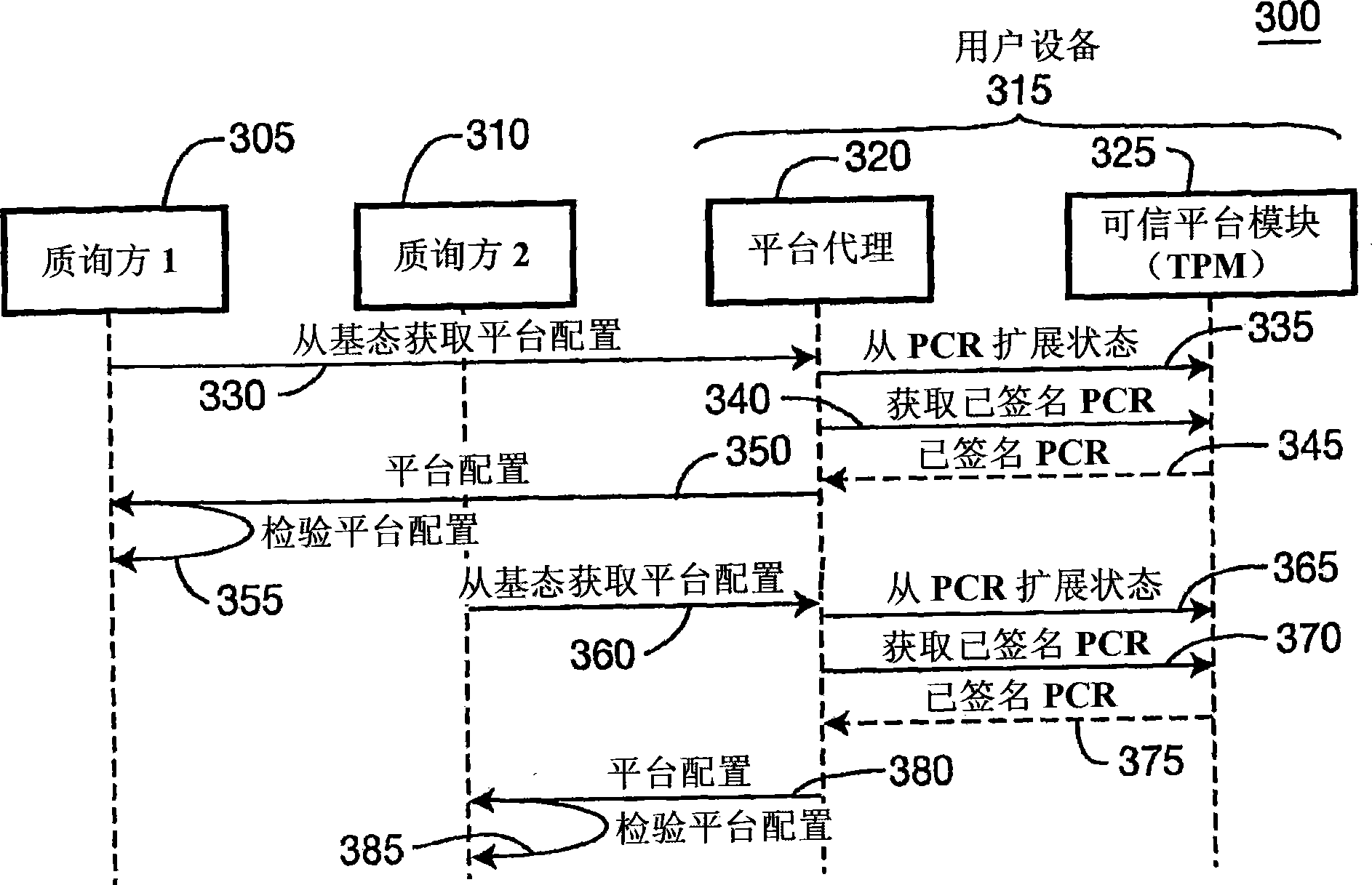
Apparatus and methods for performing trusted computing integrity measurement reporting
An apparatus and methods that use trusted platform modules (TPM) to perform integrity measurements of multiple subsystems are disclosed. The state of platform configuration registers (PCRs) after boot up are stored as the base state of the system. In another embodiment, an application that is to be verified requests that its state be extended from the base state of the system. When such a requestis received, the state of the system is extended directly from the base state PCR contents and not from the system state. In another embodiment, a virtual PCR is used, where such a virtual PCR uses alarger memory space than a conventional TPM provides for a physical PCR, by use of encrypted storage on external, protected memory.
Owner:INTERDIGITAL TECH CORP
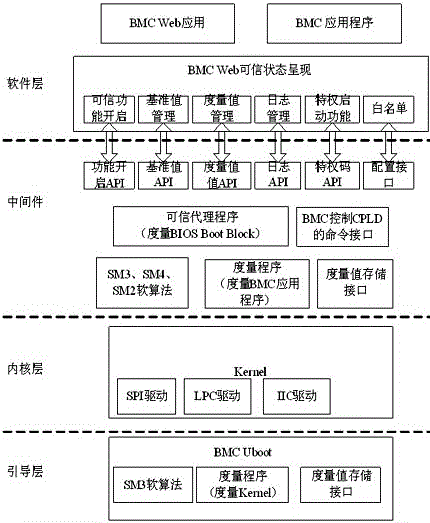
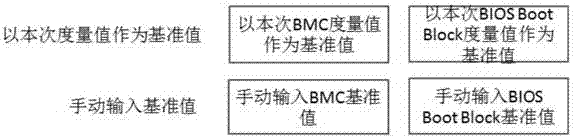
Method for BMC reliable configuration with access control function
InactiveCN107145788AIntegrity guaranteedEnsure crediblePlatform integrity maintainanceElectricityComputer module
The invention provides a method for BMC reliable configuration with an access control function. A reliable function module is added in a BMC Web management interface; the reliable function module is started; a standard value is configured; a reliable state of BMC firmware is presented; and a BIOS reliable state is presented. During electric starting of BMC, integrity measurement is conducted on the BMC firmware and BIOS key codes, so that program integrity can be ensured, and thus a reliable execution environment of a system platform can be established. In this way, the BMC can be consolidated; the integrity measurement is conducted on the BMC firmware and the BIOS during the BMC start running, so that program integrity can be ensured, and implantation of malicious codes can be avoided; a complete trust chain of the BMC start course is established; and reliability of the execution environment of the system platform is ensured.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com