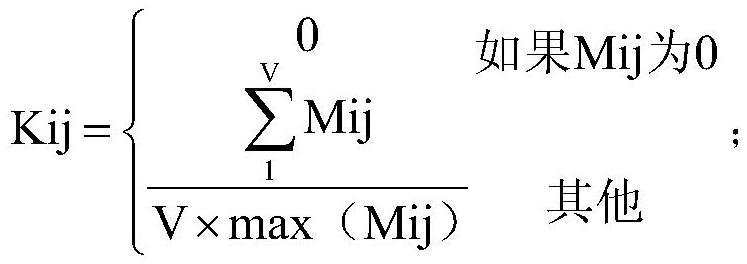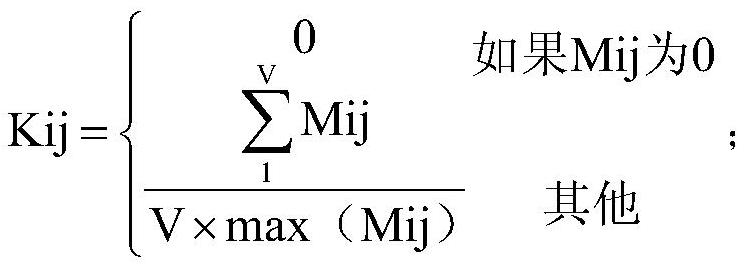Patents
Literature
46results about How to "Prevent deciphering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
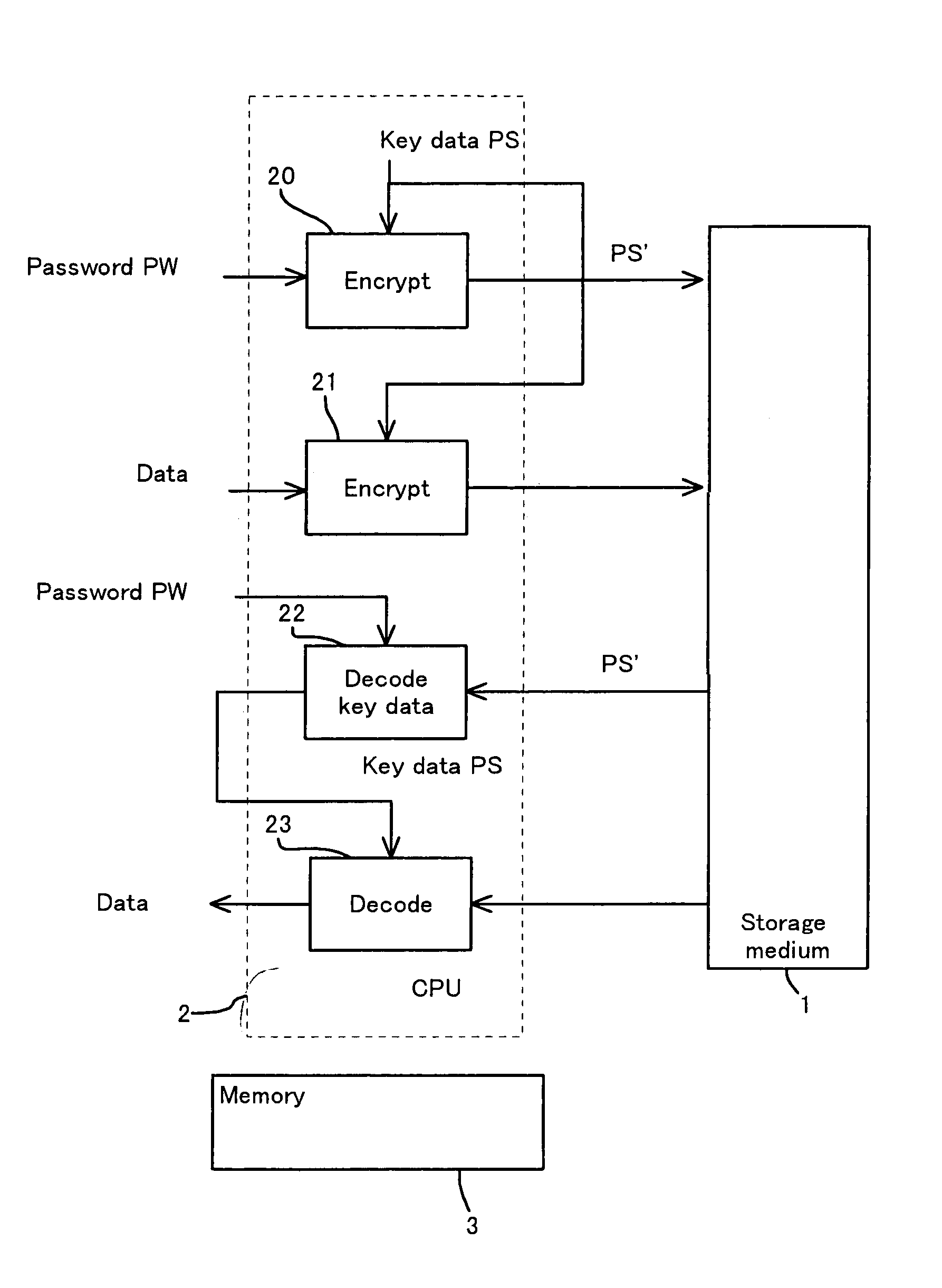
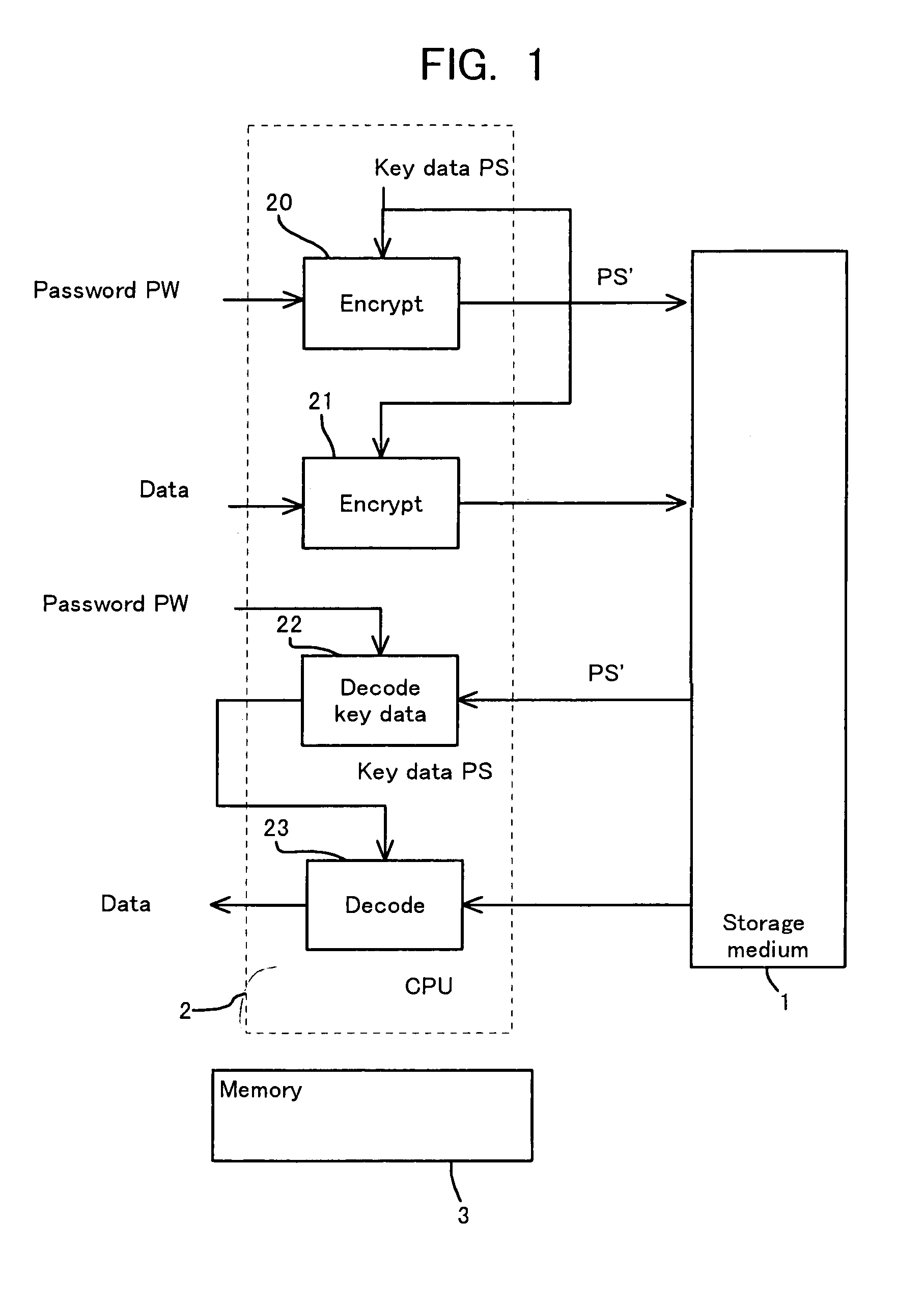
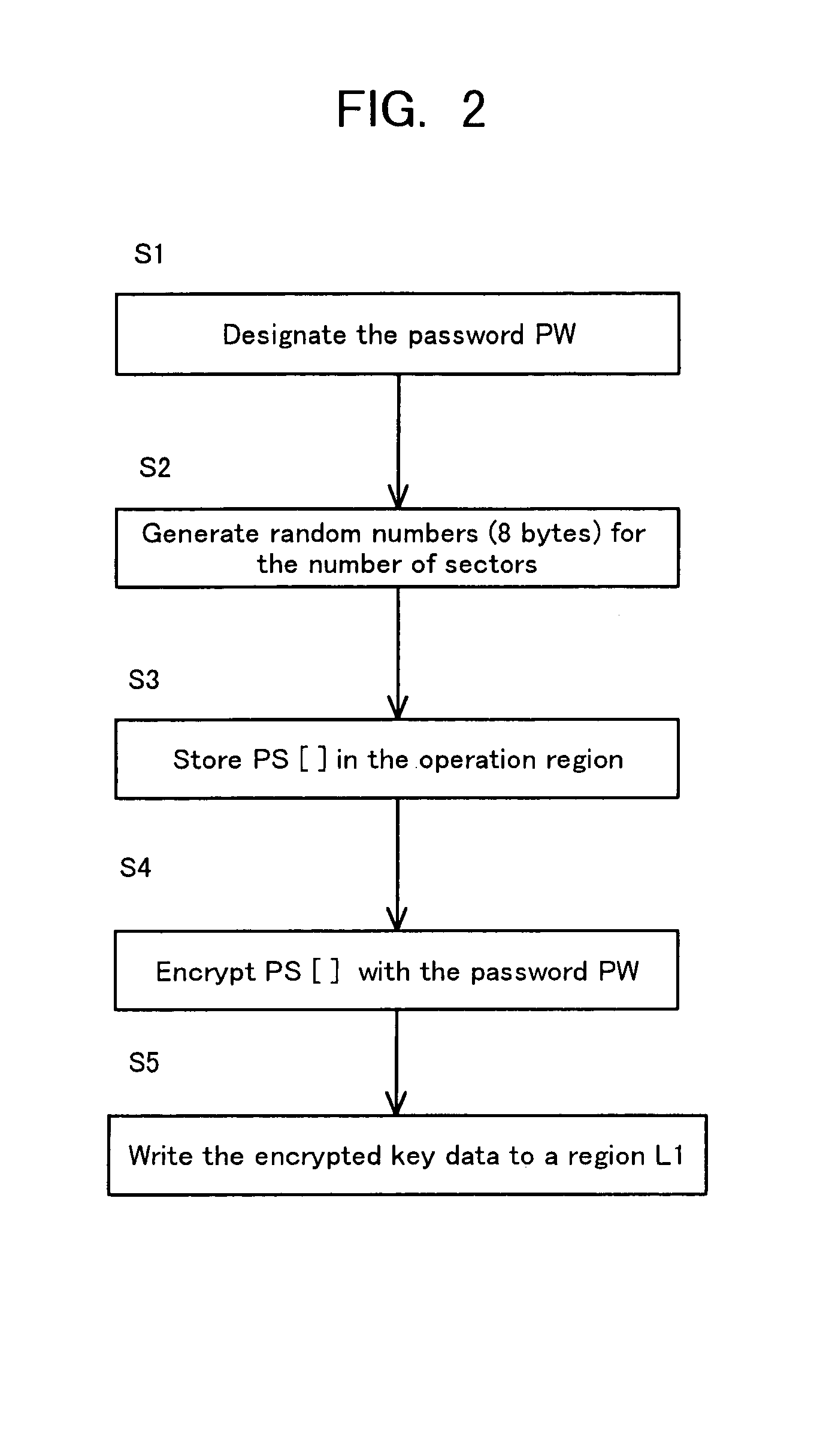
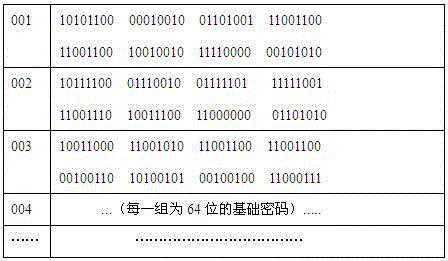
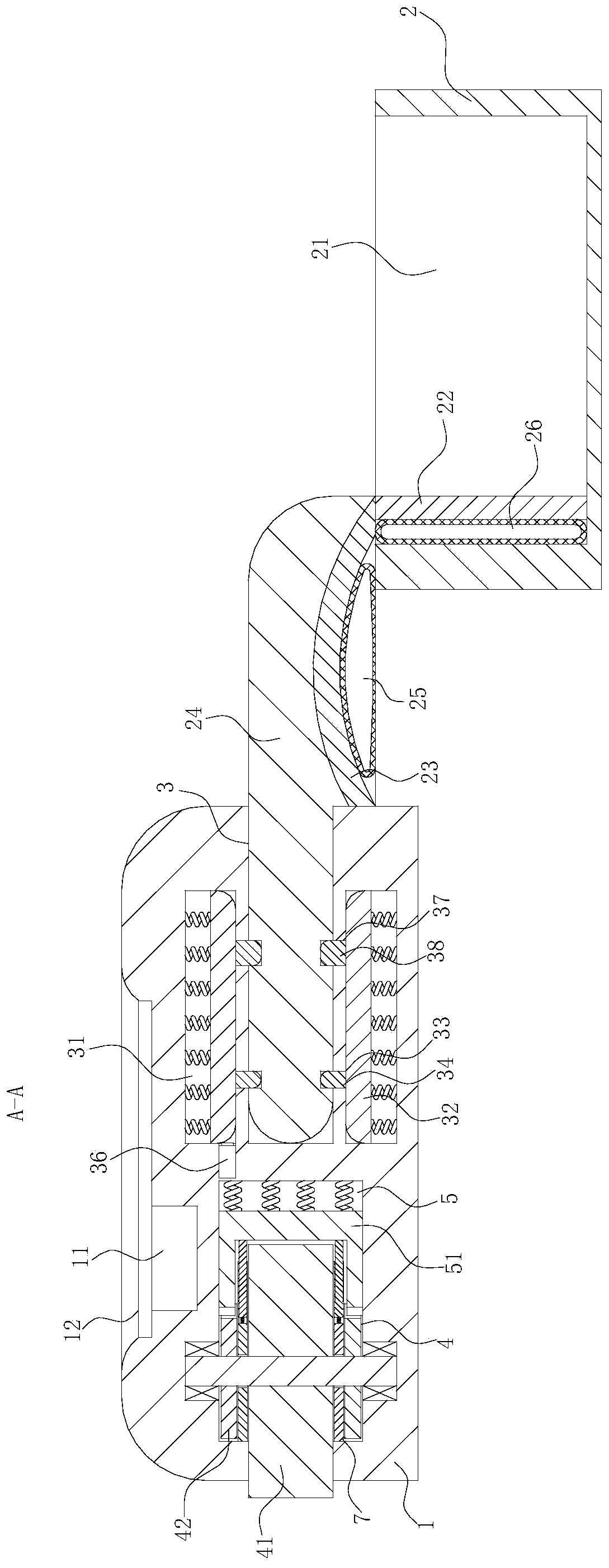
Storage medium and method and apparatus for separately protecting data in different areas of the storage medium
InactiveUS7051213B1Difficult to analyzePrevent decipheringInput/output to record carriersDigital data processing detailsCiphertextPassword
Disclosed are a method and an apparatus for protecting data on a storage medium by encrypting the data to be recorded on the storage medium with a password. This method comprises a step of, generating, for changing key data on each memory unit by one password, the key data, thereafter encrypting the key data with the password and writing the encrypted data to the storage medium, and a step of encrypting the data with the key data and encrypted data to the storage medium. The method further comprises a step of reading the encrypted key data from the storage medium, a step of decoding the encrypted key data with the password, and a step of decoding the data on the storage medium with the decoded key data. The encryption is done by using the key data generated separately from the password, and it is therefore feasible to prevent the password from being analyzed by decoding a cipher text.
Owner:FUJITSU CLIENT COMPUTING LTD
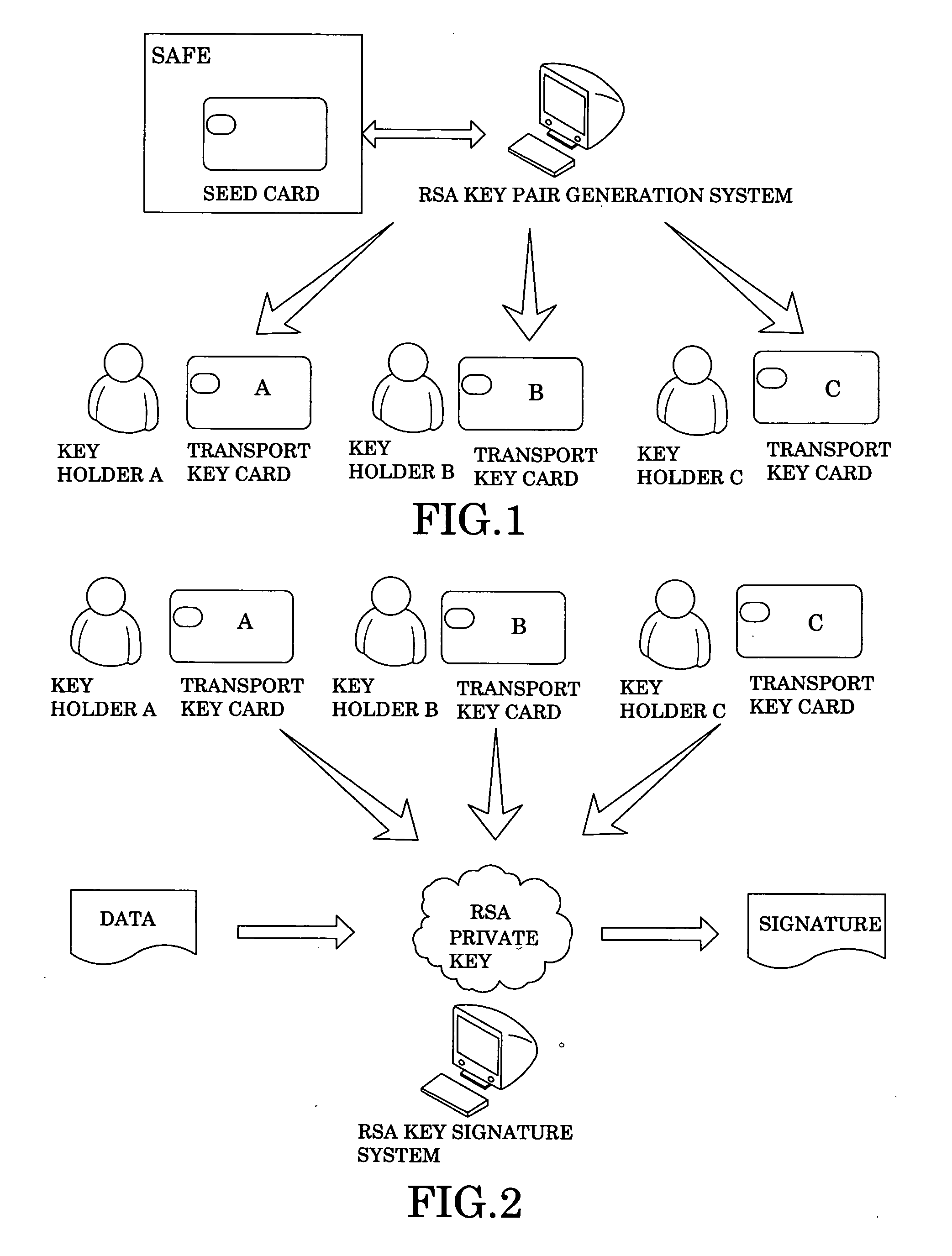
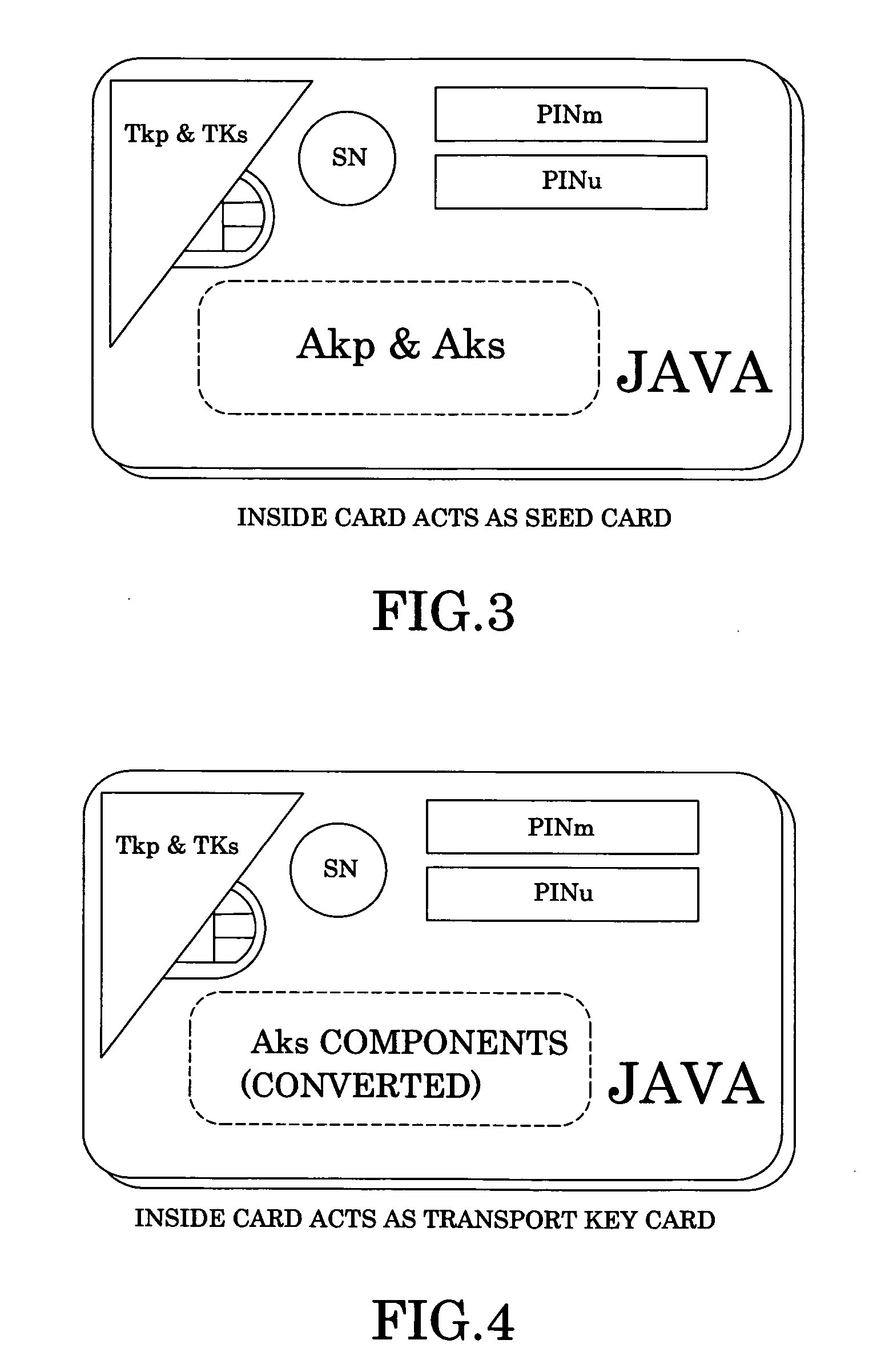
Secure key system
InactiveUS20100172501A1Ensure safetyImprove security levelAcutation objectsSecuring communicationSecurity levelKey Holder
A secure key system includes a key provider for partitioning and converting a private key into a plurality of key components, and a plurality of key holders storing the key components therein respectively for enhancing a security level of the private key, wherein all of the key holders are united to synthesize back the private key from the key components in order for completing a confirmation process so as to ensure the confirmation process being verified by all of the key holders.
Owner:ONBEST TECH HLDG
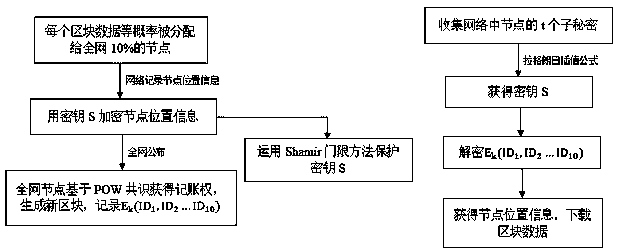
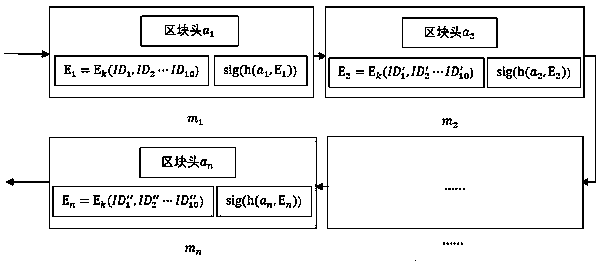
Block chain distributed storage method based on secret sharing
ActiveCN109150968AImprove fault toleranceAvoid attackKey distribution for secure communicationUser identity/authority verificationBlockchainComputer network
The invention discloses a block chain distributed storage method based on secret sharing. The method comprises steps: 1) the network distributes data of each block to nodes in the network according tothe same probability, and the location information of the nodes are recorded; 2) in order to prevent attacks by malicious nodes, a key is used to encrypt the location information of the nodes, the network broadcasts the encrypted location information of the nodes to each node in the whole network, and in order to prevent the opponent from deciphering the key, a Shamir threshold method is used toprotect the key; 3) the nodes in the network acquire accounting rights according to a POW consensus mechanism, and the encrypted location information of the nodes is recorded in the block chain; and 4) when data of a certain block are restored, the sub secrets of the nodes in the network are collected first, and the key is restored according to a Lagrange interpolation formula, the key is used todecrypt the encrypted location information of the nodes, the location information of the node storing the data of the block is acquired, and the block data can be downloaded as long as any node is found out.
Owner:智巡密码(上海)检测技术有限公司
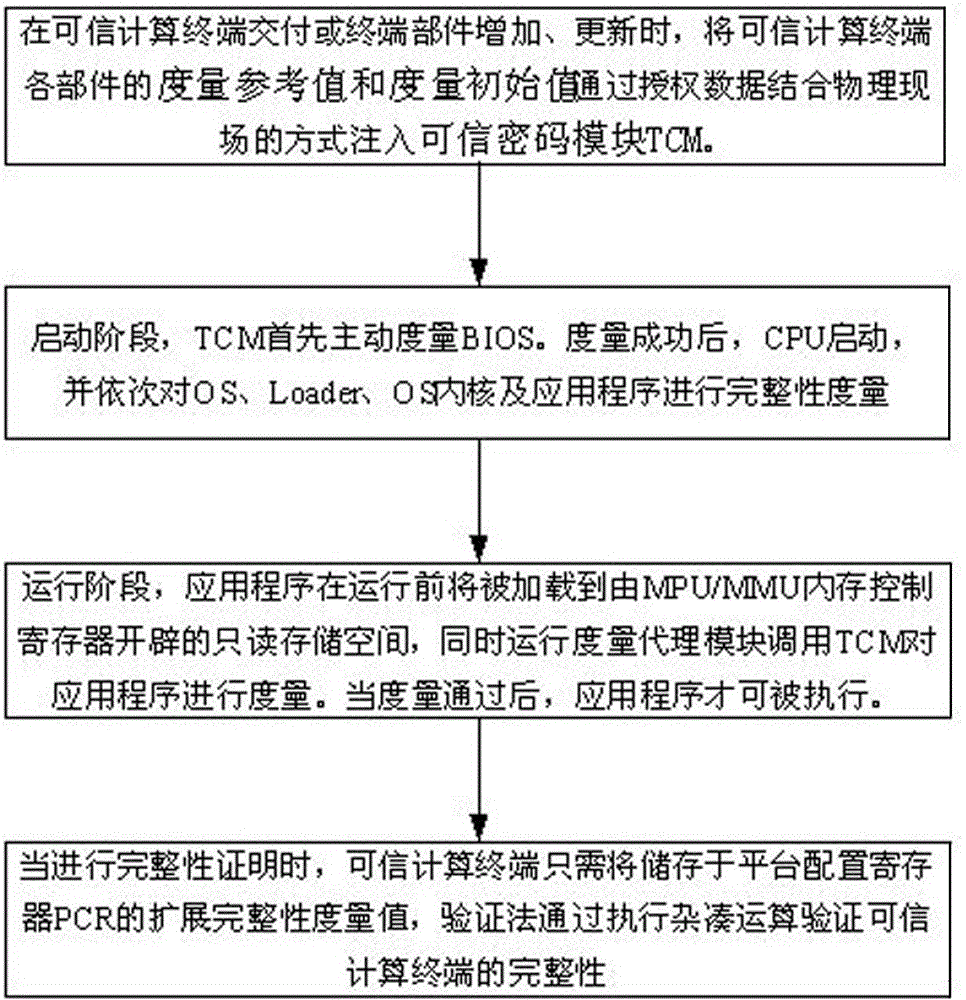
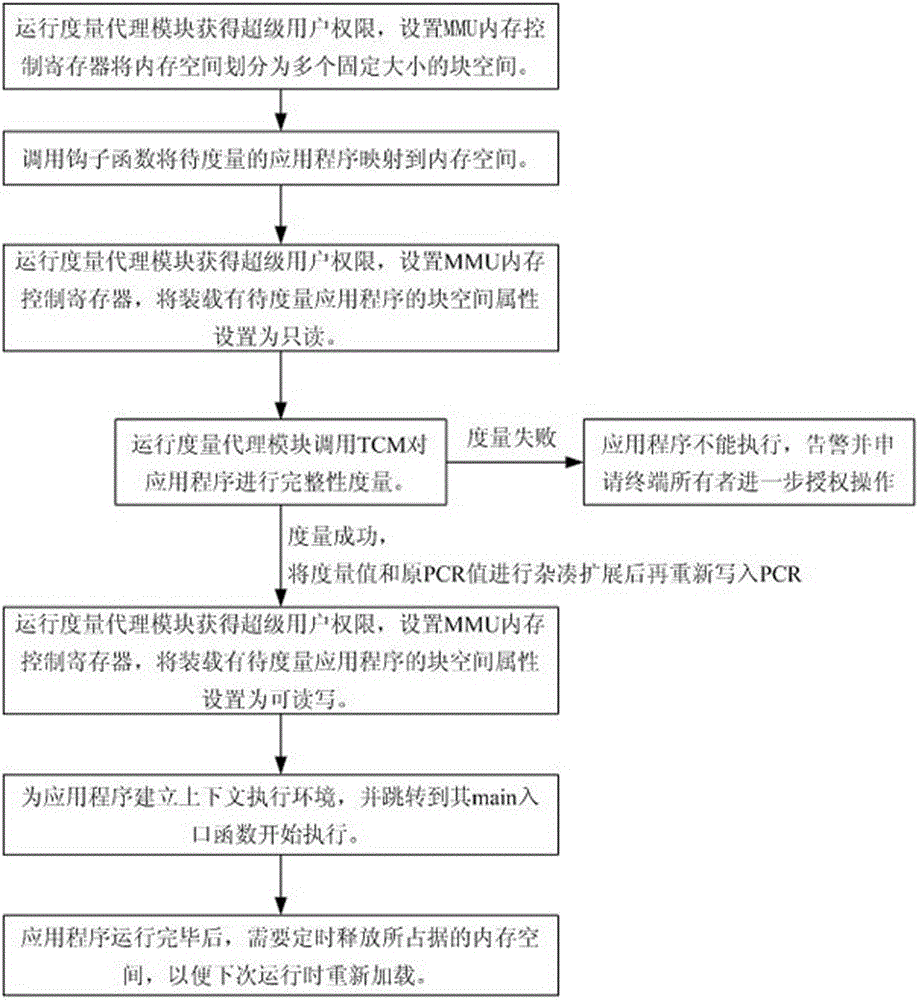
Trusted computing terminal integrity measuring and proving method and device
ActiveCN105608386AResist attackPrevent decipheringInternal/peripheral component protectionPlatform integrity maintainanceApplication softwareTotal measurement
The invention relates to the field of trusted computing, and particularly provides a terminal integrity detecting and proving method and device based on trusted computing for solving problems in the prior art. On the condition of not increasing additional hardware requirements and special instructions, an isolated and safe integrity dynamic measurement environment is built for an application program, and parallel barrier-free operation of other application programs in the measurement process is ensured. In the integrity proving process, the actual measurement value of each component in a computing terminal is concealed, and the problem that a hacker decode the version, configuration, firmware and other information of the terminal through the actual measurement values is effectively prevented; when the trusted computing terminal is subjected to integrity detection, extension integrity measurement values and the total measurement frequency stored in a platform configuration register PCR are sent to a verifier after being signed, and the verifier can detect the integrity of the trusted computing terminal by executing hash operation.
Owner:成都三零嘉微电子有限公司
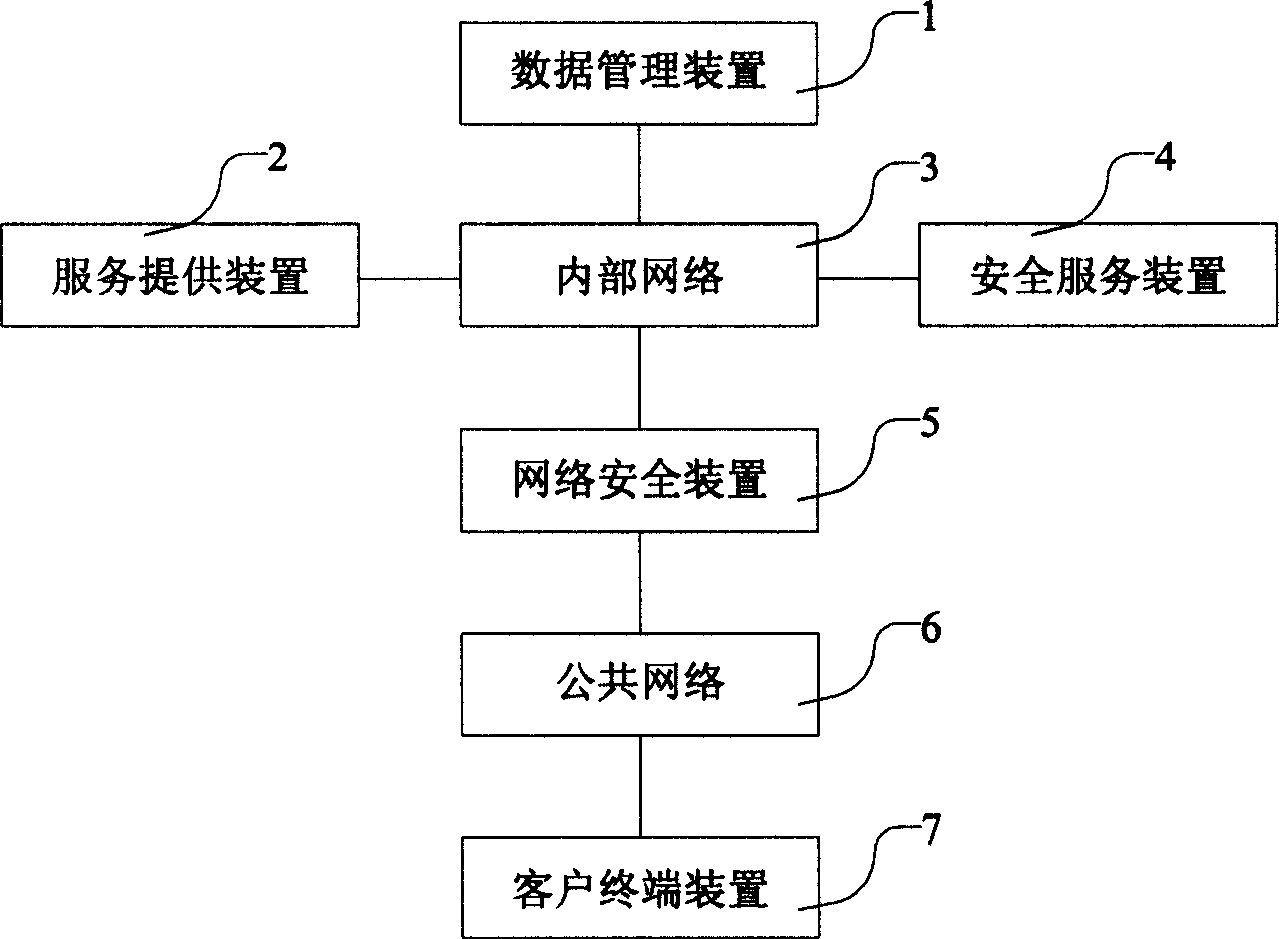
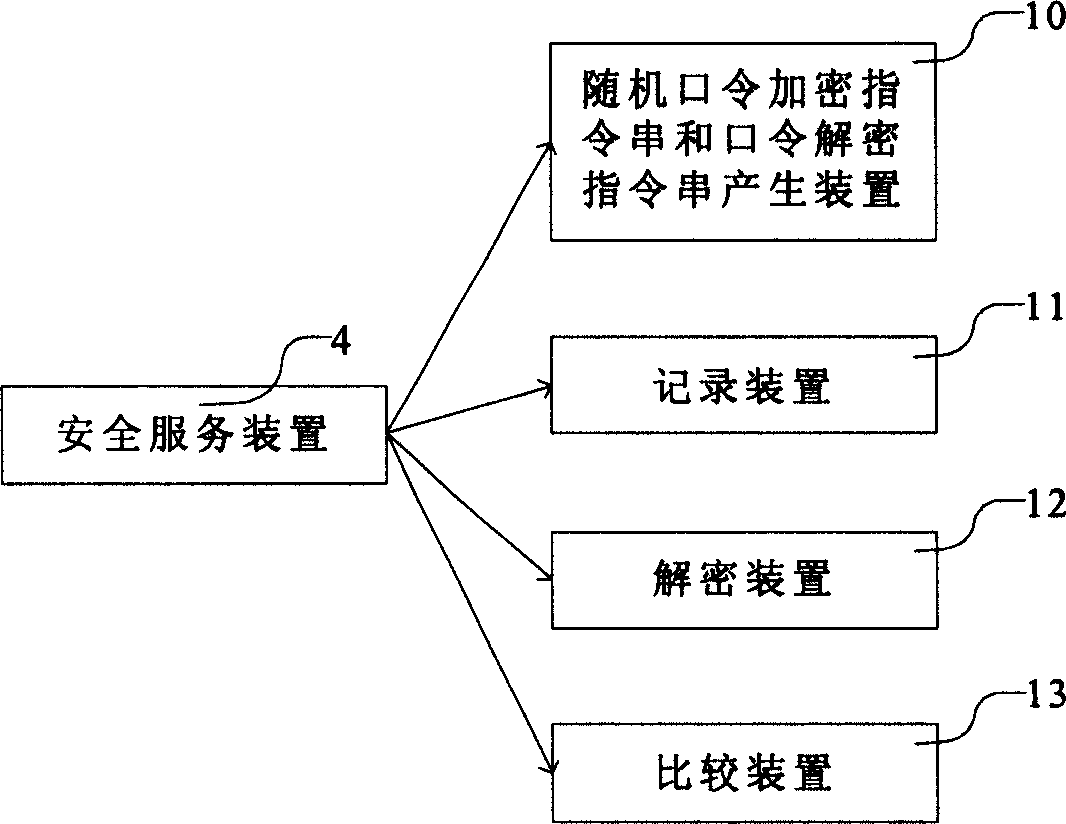
Dynamic encrypting device in network and its password identification method
ActiveCN1588846APrevent decipheringUser identity/authority verificationInput/output processes for data processingUser inputService provision
This invention relates to a dynamic encipheror and its password certification method in a network of data certification field. The device includes a data management device, a service provide device, an internal network, a safety service device, a network safety device, a shared network and a customer end device. The method includes the following steps: The customer end requests for identity certification, a service provide device responds the request to generate initialized data and send it to the customer end which receives the data, checks and downloads the latest edition password input control parts to display its screen, the user inputs the customer identification, clicks a picture region with password character for inputting the password which controller converts the click position to an intermediate value and ciphers it, judges if the input is finished and sends certification data to the service provide device receiving it for certification and returning the result to the customer end which displays the result.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Method and device for improving terminalself-flashing safety through ciphertext handshaking
InactiveCN104065482AImprove securityIncrease the difficulty of crackingUser identity/authority verificationProgram loading/initiatingHandshakingCiphertext
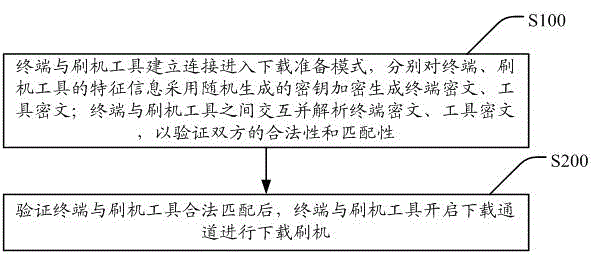
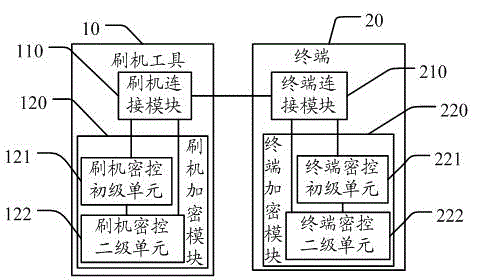
The invention discloses a method and device for improving terminal self-flashing safety through ciphertext handshaking. The method includes the steps that A, a terminal is connected with a flashing tool so as to enter a downloading preparation mode, feature information of the terminal and feature information of the flashing tool are respectively encrypted through secret keys randomly generated, and therefore a terminal ciphertext and a tool ciphertext are generated; the terminal and the flashing tool interact, the terminal ciphertext and the tool ciphertext are analyzed, and therefore legality and matching performance of the terminal and the flashing tool are verified; B, after it is verified that the terminal and the flashing tool are legally matched, a downloading channel is started by the terminal and the flashing tool for downloading and flashing. According to the method and device, after it is verified that the terminal and the flashing tool are legal, the terminal and the flashing tool are controlled to start the downloading channel to conduct downloading and flashing; due to the fact that the secret keys used for encryption each time are generated randomly, the deciphering difficulty is greatly increased, and the ciphertexts can be prevented from being deciphered; meanwhile, downloading and flashing can be conducted only after the terminal and the flashing tool are legally matched, so that safety is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD +1
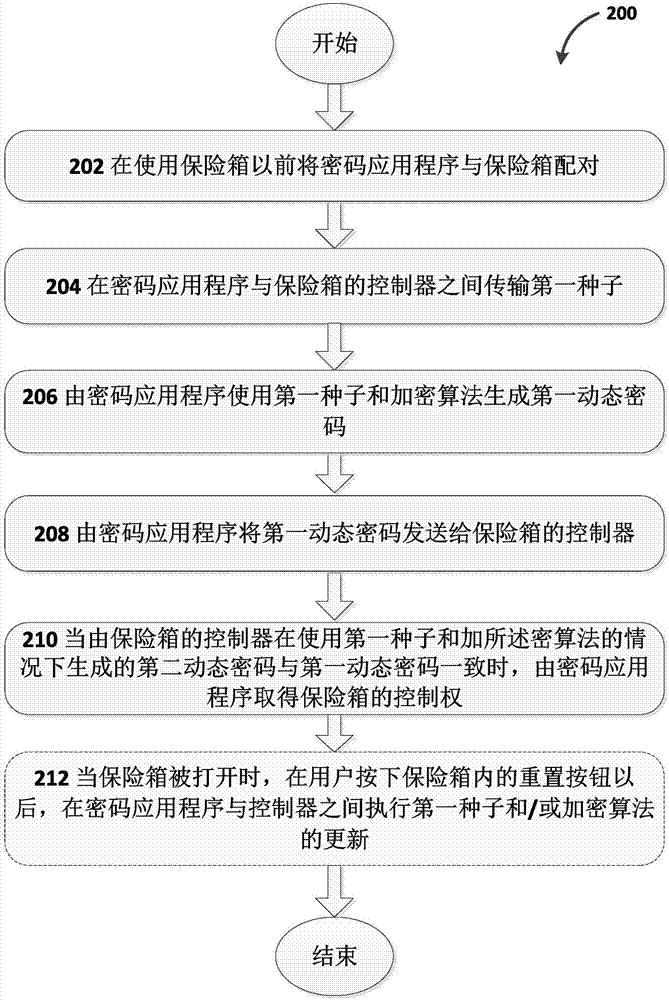
Safe box with dynamic password function
InactiveCN107989514ALow costImprove securityPuzzle locksIndividual entry/exit registersPasswordEncryption
The invention relates to a safe box with a dynamic password function. The safe box is provided with a box body, an electronic lock and a controller, wherein the electronic lock is configured to receive an unlocking signal from the controller so that unlocking can be achieved; and the controller is configured to execute the following actions of receiving a first dynamic password from a user which is generated by a cipherer through a first seed and an encryption algorithm under the condition that the user is legal, generating a second dynamic password through the first seed and the encryption algorithm, comparing the first dynamic password with the second dynamic password, and sending the unlocking signal to the electronic lock under the condition that the first dynamic password and the second dynamic password are consistent. The invention further relates to an operating method of the safe box. By means of the safe box or the method, safety can be improved by using the dynamic passwords,meanwhile, a complex decryption procedure can be avoided, and thus the structure of the controller is simplified and cost is lowered.
Owner:NINGBO YAOLONG SOFTWARE TECH CO LTD
Method and system for remotely controlling vehicle
InactiveCN105721541AEnsure data securityPrevent decipheringEncryption apparatus with shift registers/memoriesMultiple encryptionComputer terminal
The invention discloses a method and system for remotely controlling a vehicle. In a communication control process of a mobile terminal and a vehicular-mounted equipment end, a rolling code type method is employed, i.e., multiple groups of ciphers and multiple encryption and decryption algorithms are simultaneously replaced uninterruptedly, so that decoding caused by interception of information by a decoder in the communication process is prevented, the data security when the mobile terminal and the vehicular-mounted equipment end communicate is guaranteed, the security factor is improved, and the method has the advantages of high simplicity, convenient operation, reasonable design, convenient application and the like.
Owner:DALIAN ROILAND SCI & TECH CO LTD
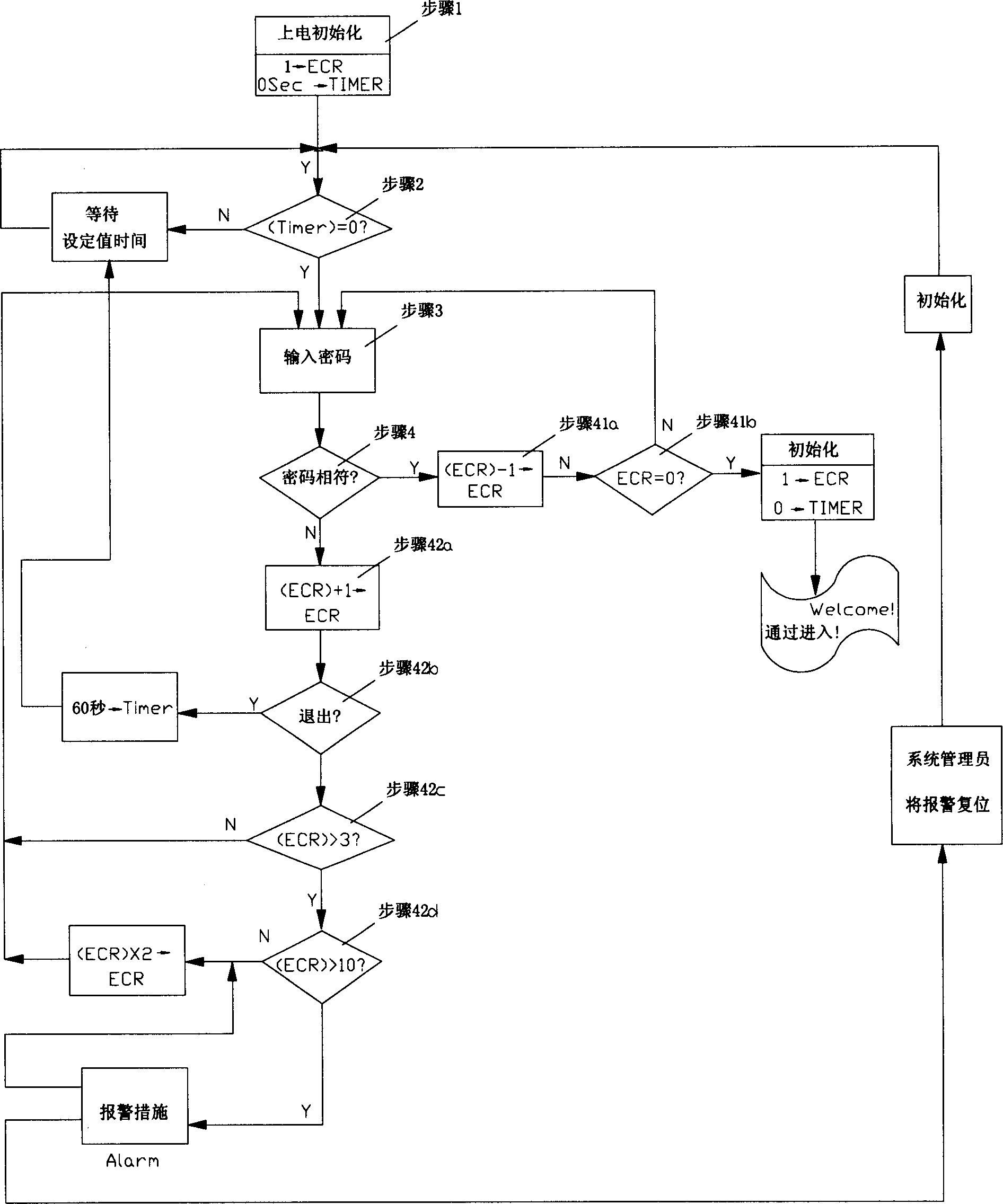
Cipher safe protecting method for preventing intelligent device input cipher from being decrypted
InactiveCN1773414APrevent decipheringDigital data processing detailsUser identity/authority verificationElectricityProcessor register
The present invention relates to a cryptogram safety protection method for preventing the intelligent device inputted cryptogram from being decrypted. Said invention utilizes the devices of register and timer, etc. and adopts two programs of first cryptogram safety control program and second cryptogram safety control program to prevent the intelligent device inputted cryptogram from being decrypted. Said invention also provides the concrete steps of said protection method.
Owner:SHANGHAI ELECTRICGROUP CORP +1
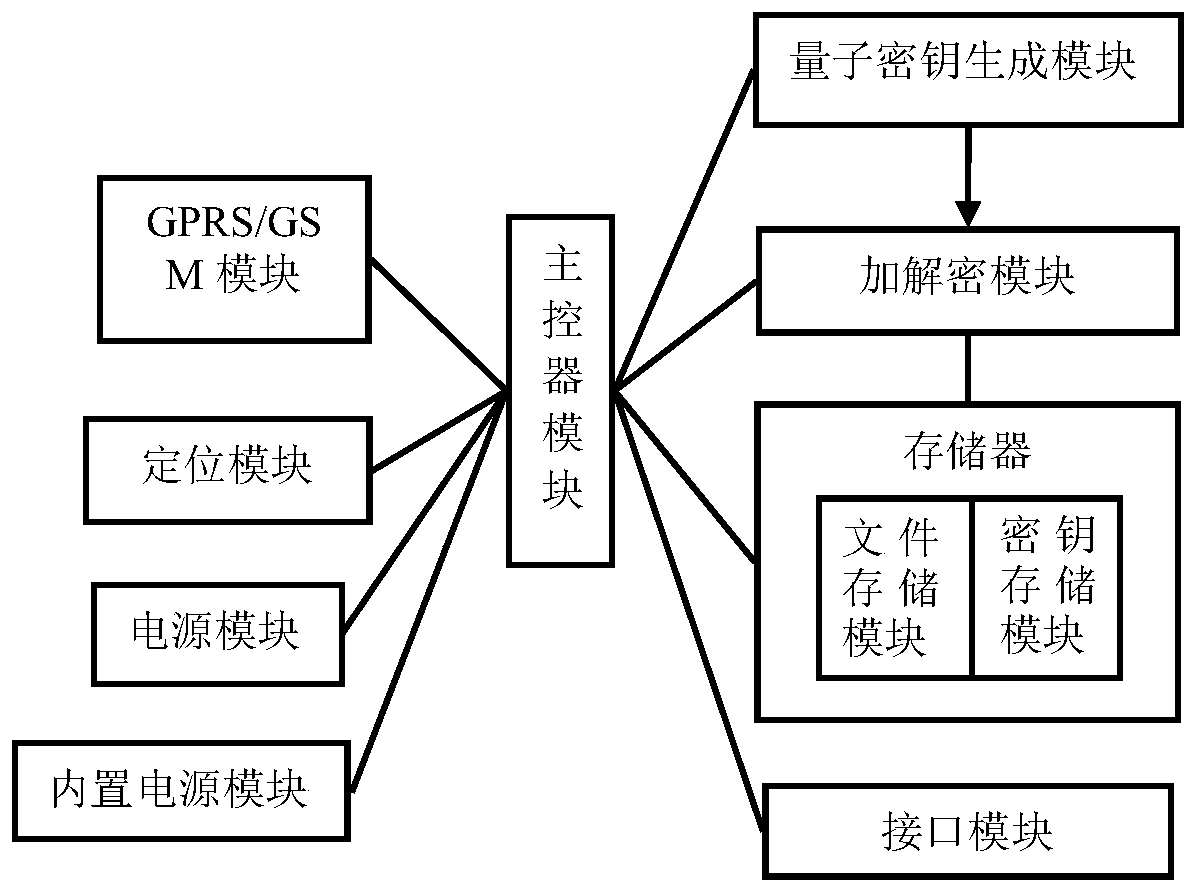
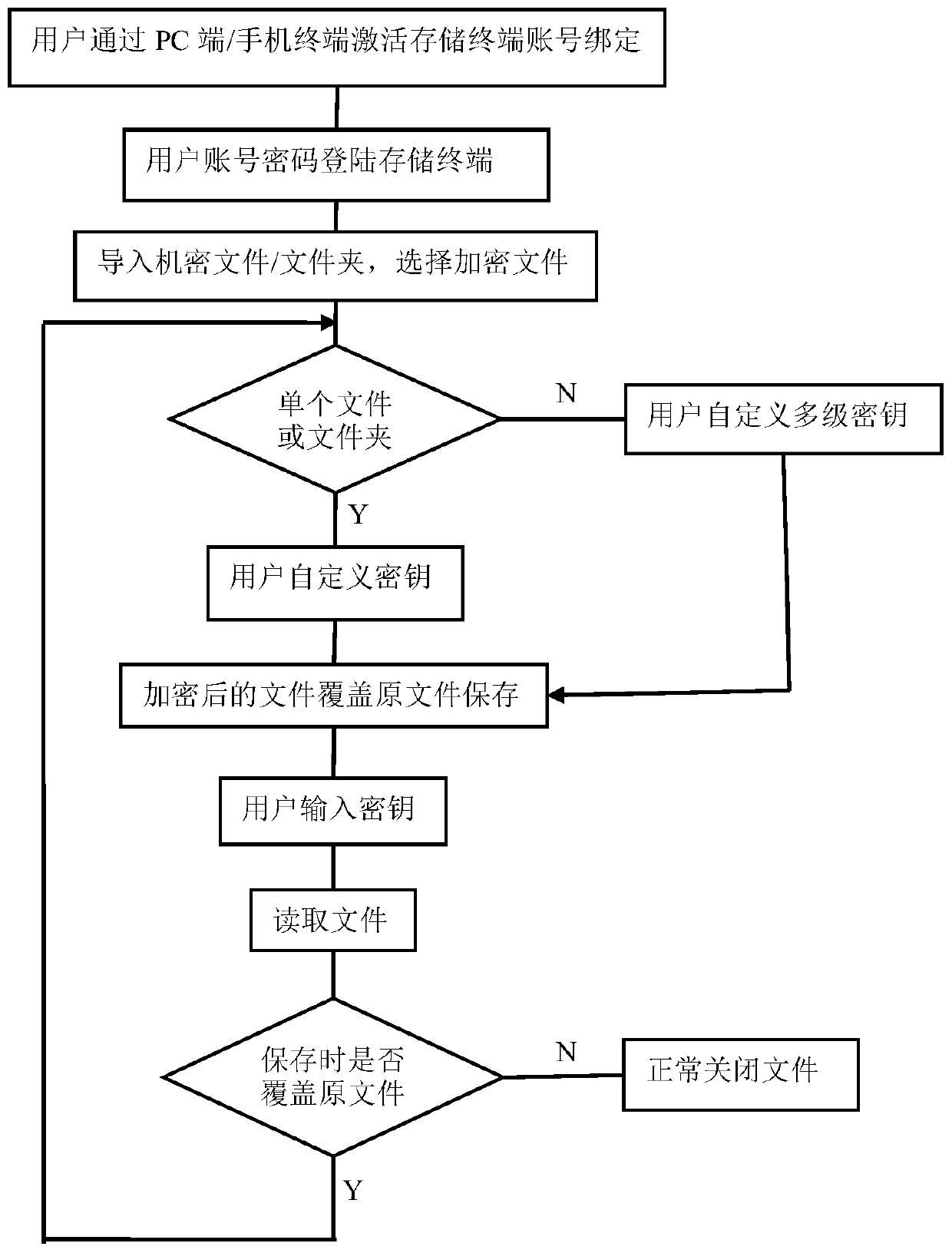
Mobile data storage terminal based on quantum key encryption
PendingCN110188564APrevent decipheringHigh data encryption securityKey distribution for secure communicationDigital data protectionElectricityComputer terminal
The invention discloses a mobile data storage terminal based on quantum key encryption. The device comprises a main controller module, an interface module, a memory, an encryption and decryption module and a power supply module, the system is characterized by further comprising a quantum key generation module, the quantum key generation module is electrically connected to the master controller module and the memory and used for generating quantum keys, and the encryption and decryption module carries out encryption and decryption operation on a single file or all files in a folder based on thequantum keys. According to the mobile data memory, the quantum key with quantum true randomness is used for encryption, so that the mobile data memory can be effectively prevented from being decodedby a computer with ultra-strong computing power, and higher-level data encryption security is achieved.
Owner:HENGTONG QASKY QUANTUM INFORMATION RES INST CO LTD
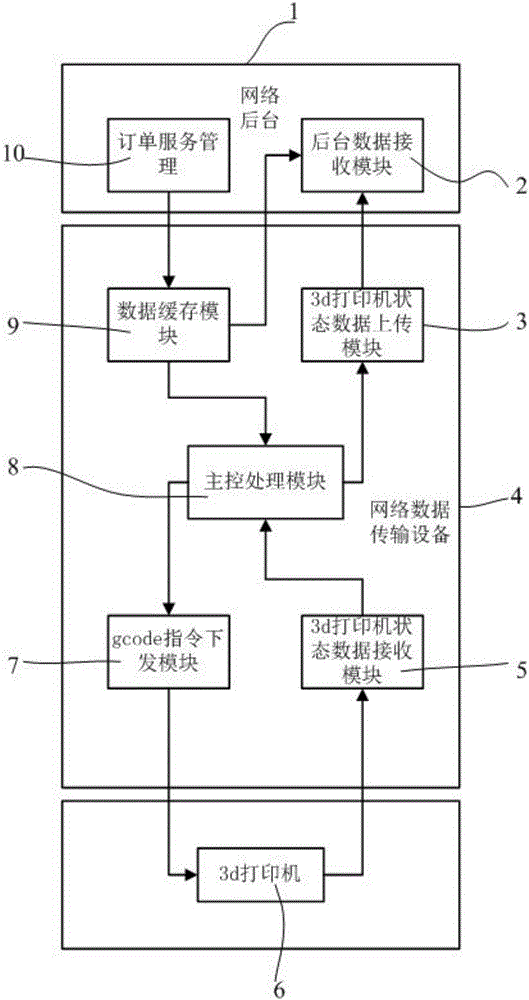
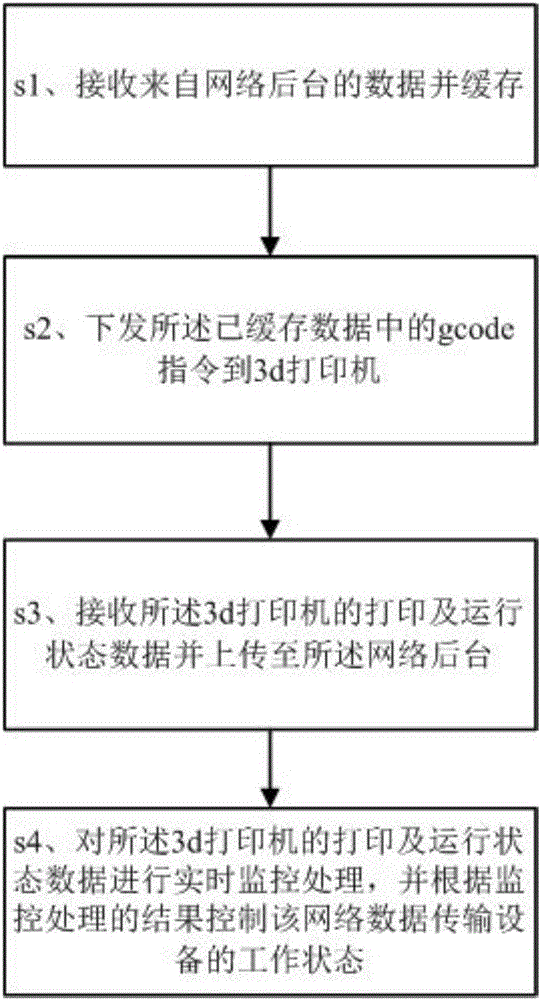
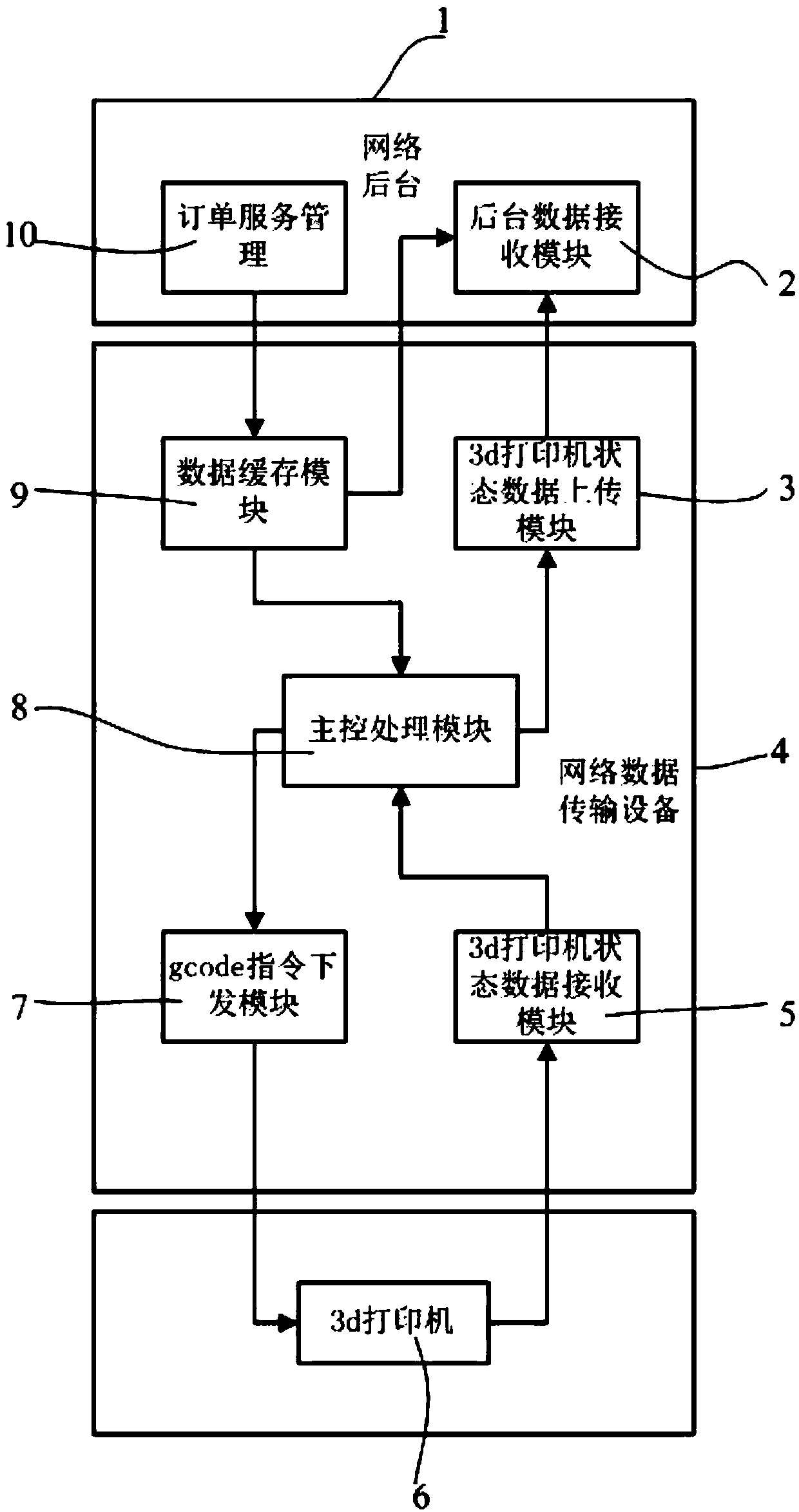
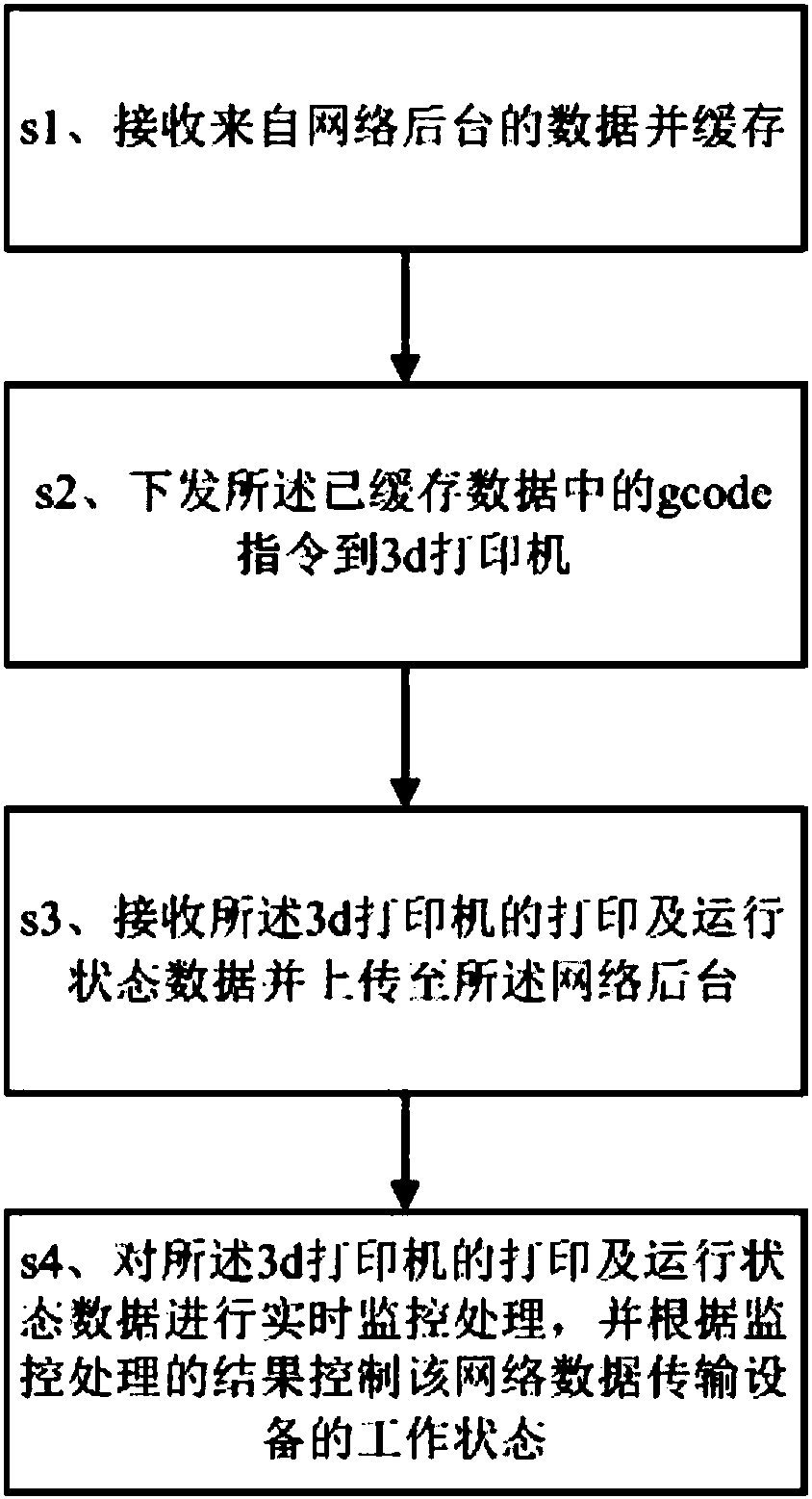
Network data transmission device and method for 3d printer
ActiveCN105856563APrevent decipheringAvoid storageAdditive manufacturing apparatusComputer moduleNetwork data
The invention discloses a network data transmission device and method for a 3d printer. The network data transmission device comprises a background data receiving module, a data-caching module, a gcode instruction issuing module, a 3d printer status data receiving module, a 3d printer status data uploading module and a main control processing module, wherein the background data receiving module is used for receiving data coming from a network background; the data-caching module is used for caching the received data coming from the network background; the gcode instruction issuing module is used for issuing a gcode instruction in the cached data coming from the data-caching module to the 3d printer; the 3d printer status data receiving module is used for receiving printing and operation status data of the 3d printer; the 3d printer status data uploading module is used for uploading the printing and operation status data of the 3d printer to the network background; and the main control processing module is used for conducting real-time monitoring process on the printing and operation status data of the 3d printer and controlling the working state of the 3d printer. The network data transmission device and method for the 3d printer have the advantages that operation is easy, the copyright of the gcode instruction is protected, and meanwhile the state of the printer can be obtained by the network background successfully.
Owner:SHENZHEN 7TH TECH CO LTD
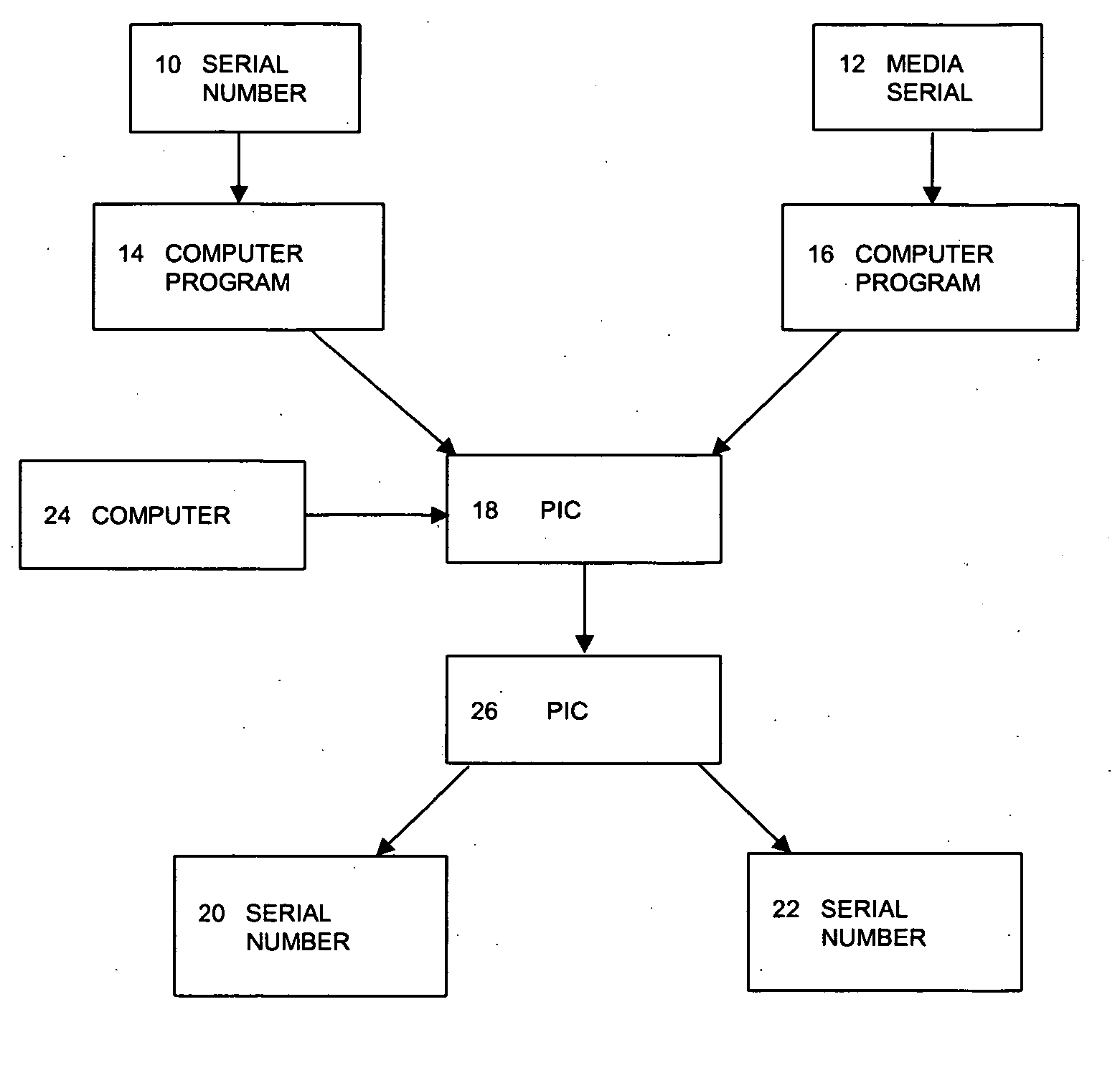
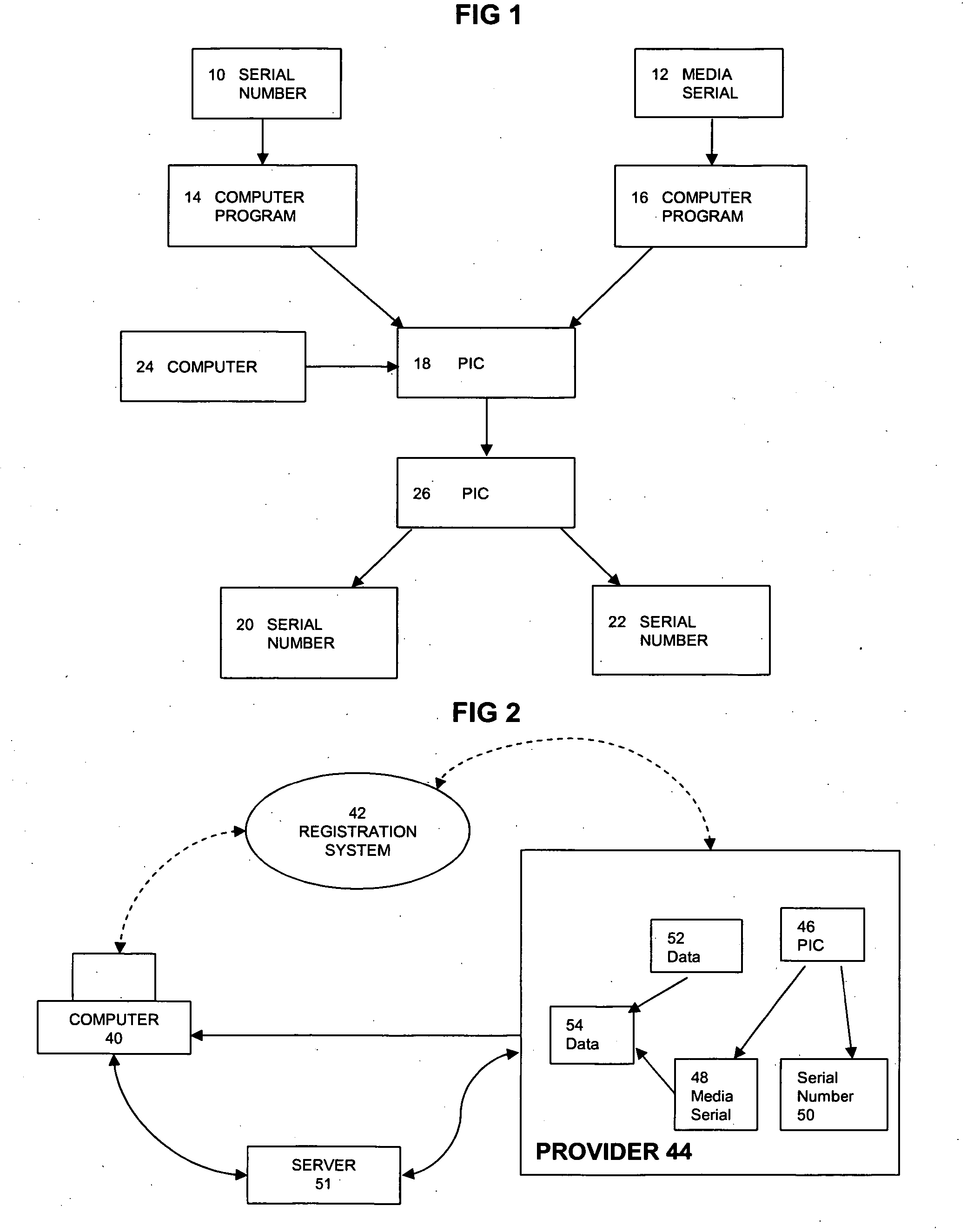
Method of manufacturing application software
InactiveUS20070073623A1Prevent decipheringLow costProgram/content distribution protectionSecuring communicationPersonalizationApplication software
A method for manufacturing an application software by providing data comprising the software content and data comprising at least media serial code specific to the application. The media serial code is used to provide a personalized application software. The method also provides data comprising a primary computer program, which is used to authenticate the media serial code.
Owner:E ON SOFTWARE
CPU instruction protection method and system suitable for function and information security chip
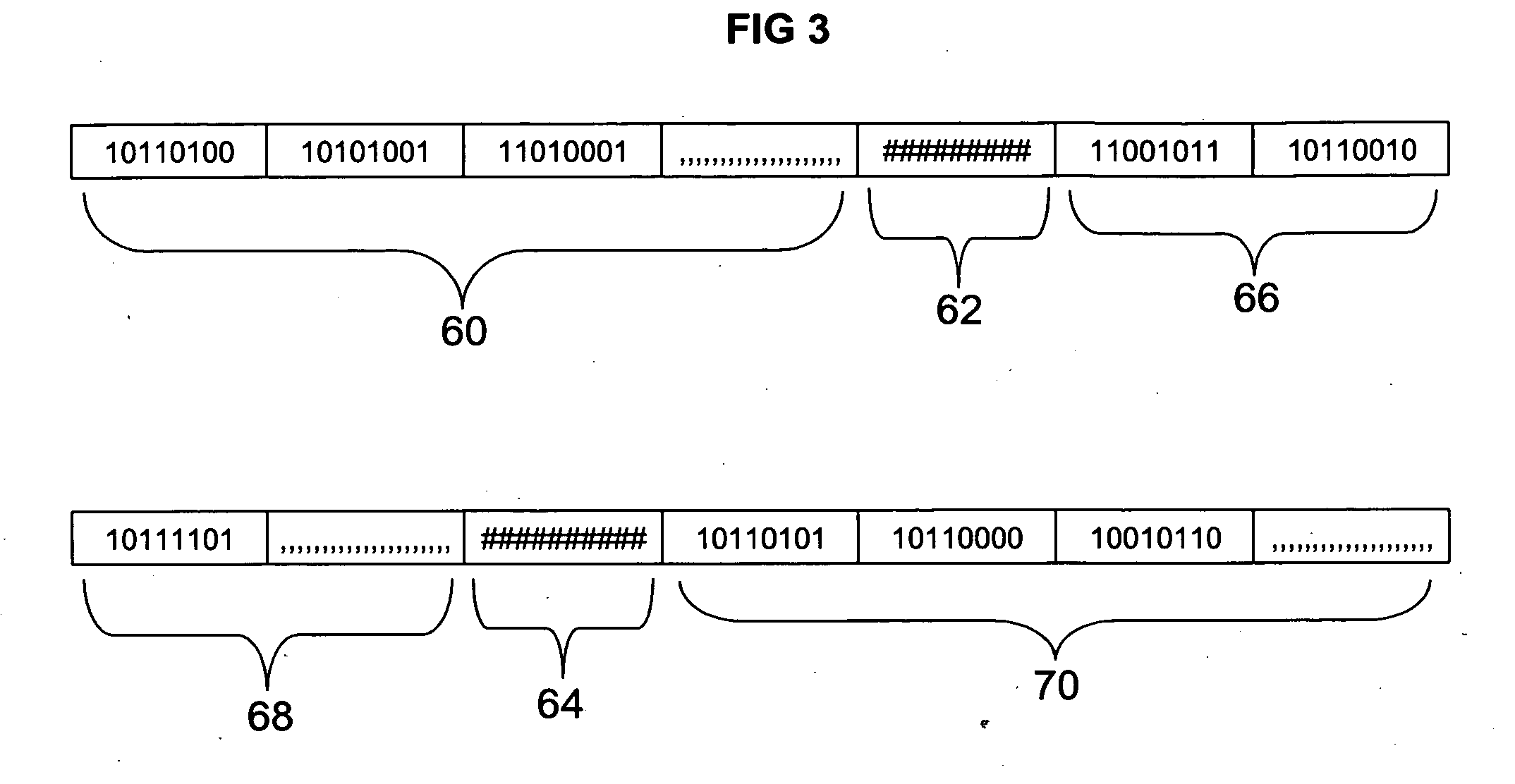
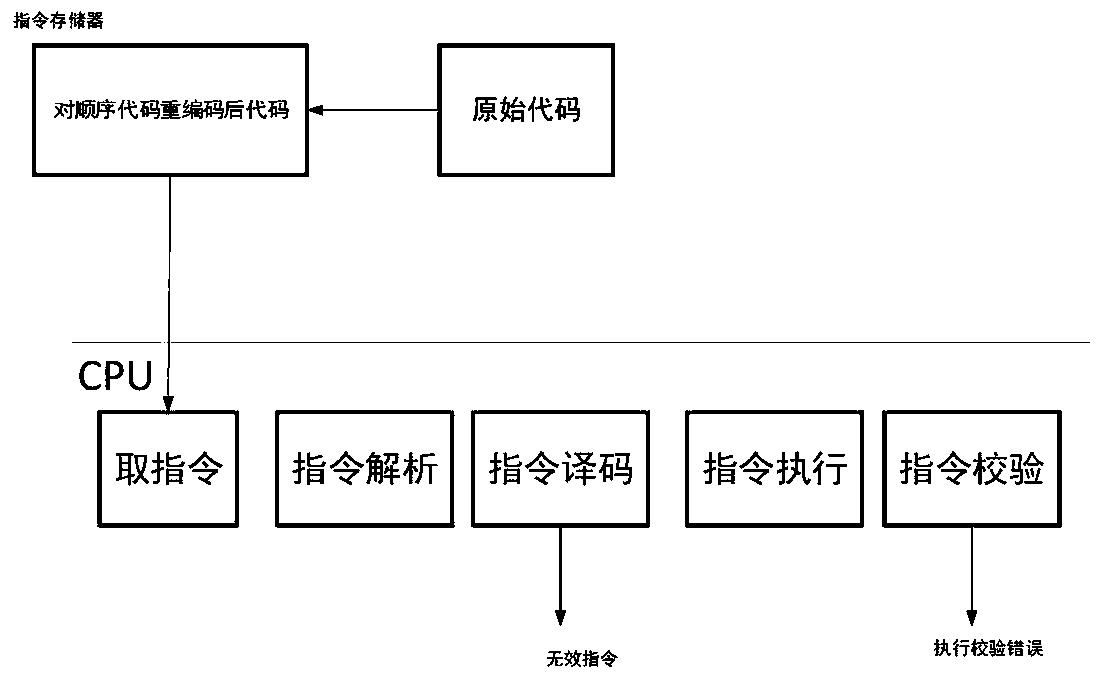
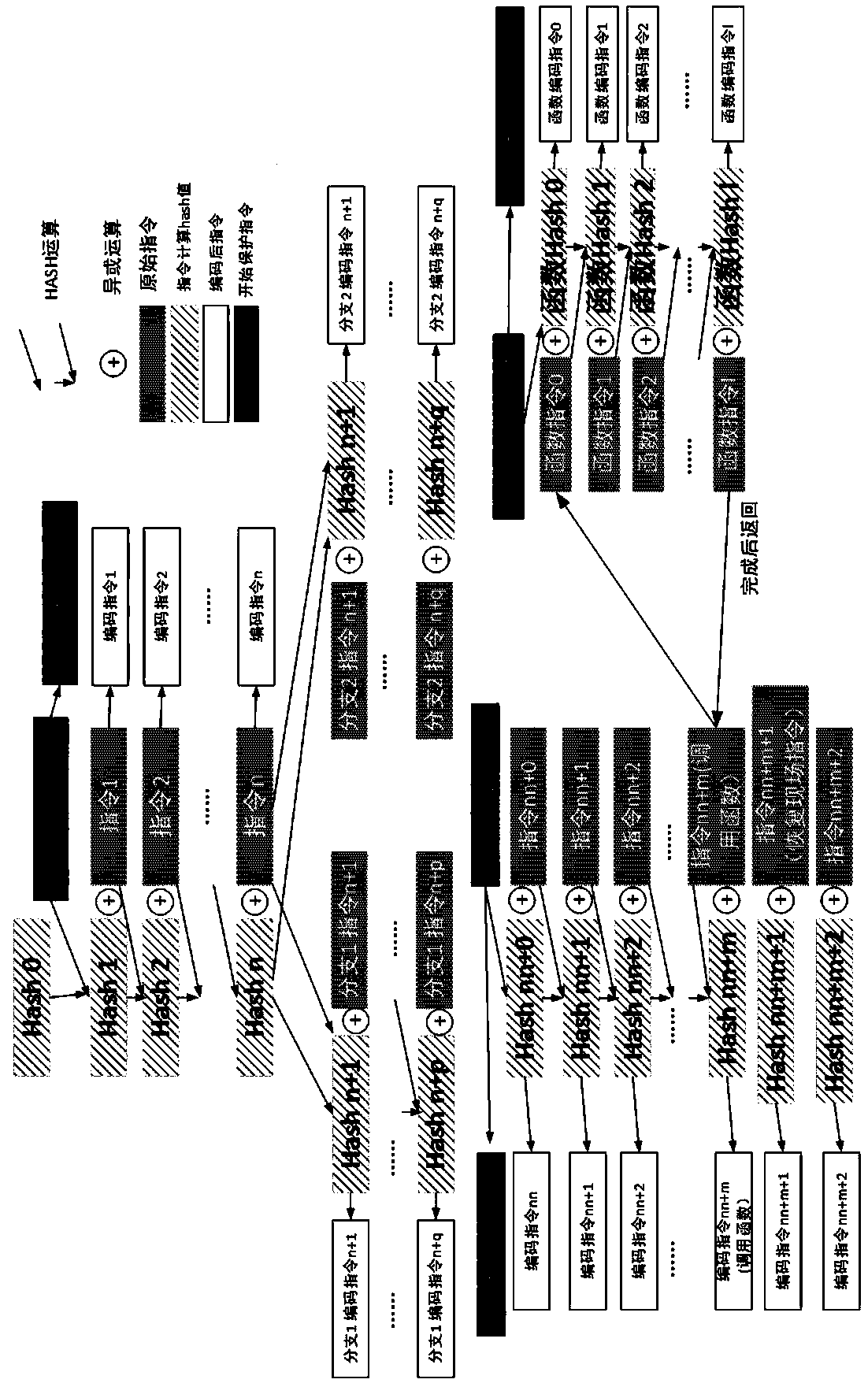
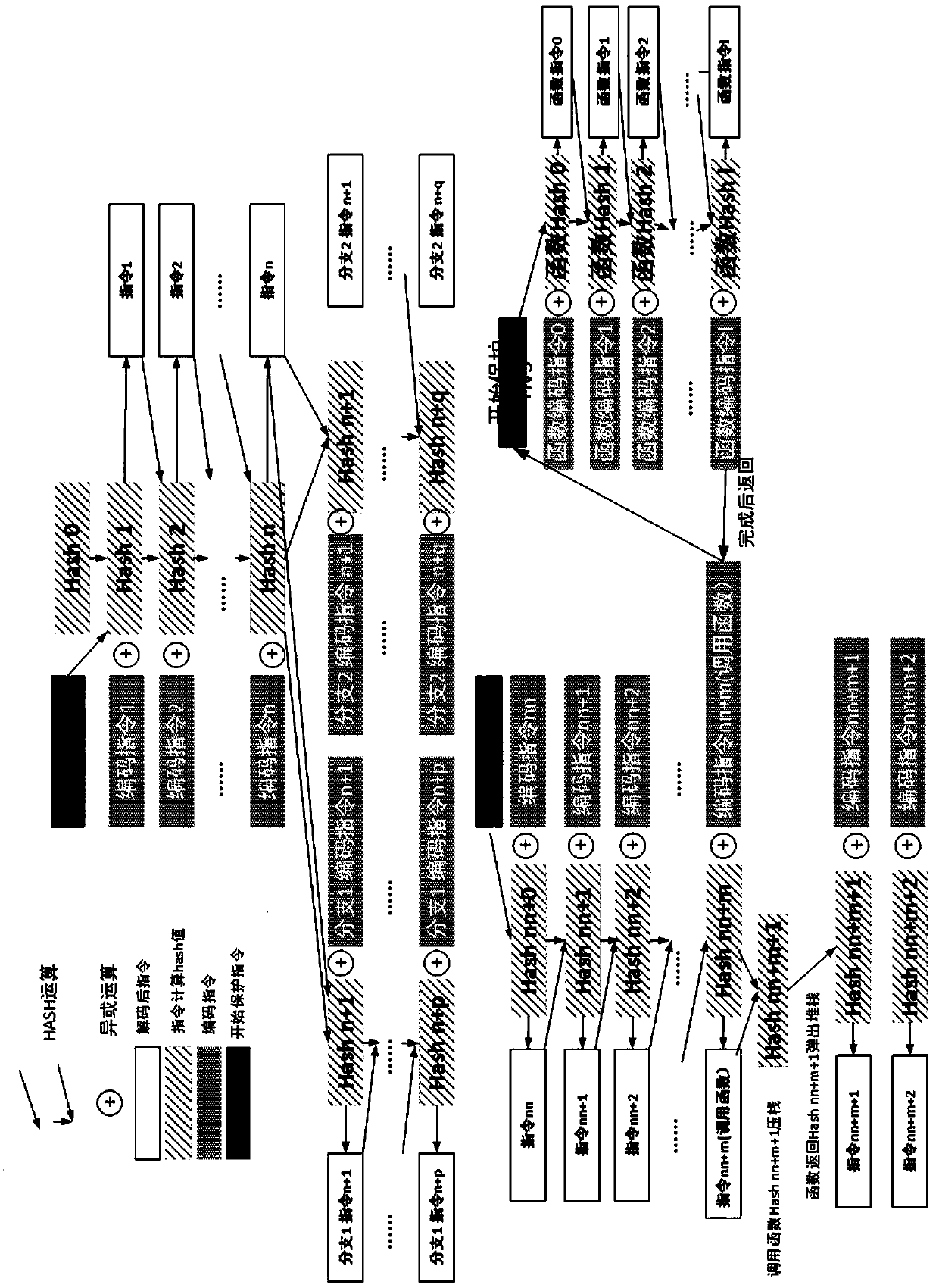
ActiveCN111475868ARealize detectionDetection securityInternal/peripheral component protectionHash functionParallel computing
The invention provides a CPU instruction protection method and system suitable for a function and information security chip. According to the invention, a hash function is utilized to generate an encoding random value and a corresponding decoding random value, and the encoding random value and the original instruction or the encoding instruction value are utilized to perform encoding operation ordecoding operation, so that recoding and decoding of an instruction are correspondingly realized. The output of each round of hash function comprises the information of each previous round of instruction, so that an error in any step will influence all subsequent encoding and decoding processes. Therefore, the encoding random value and the decoding random value among the instructions have corresponding continuity, the exception occurring in any step can be continued to the subsequent steps, so that the detection of the function security and the information security of a chip is realized, the instructions can be recoded and compared after being executed, and the function security and the information security of the CPU instruction storage, reading, decoding and execution processes are protected.
Owner:NANJING SEMIDRIVE TECH CO LTD
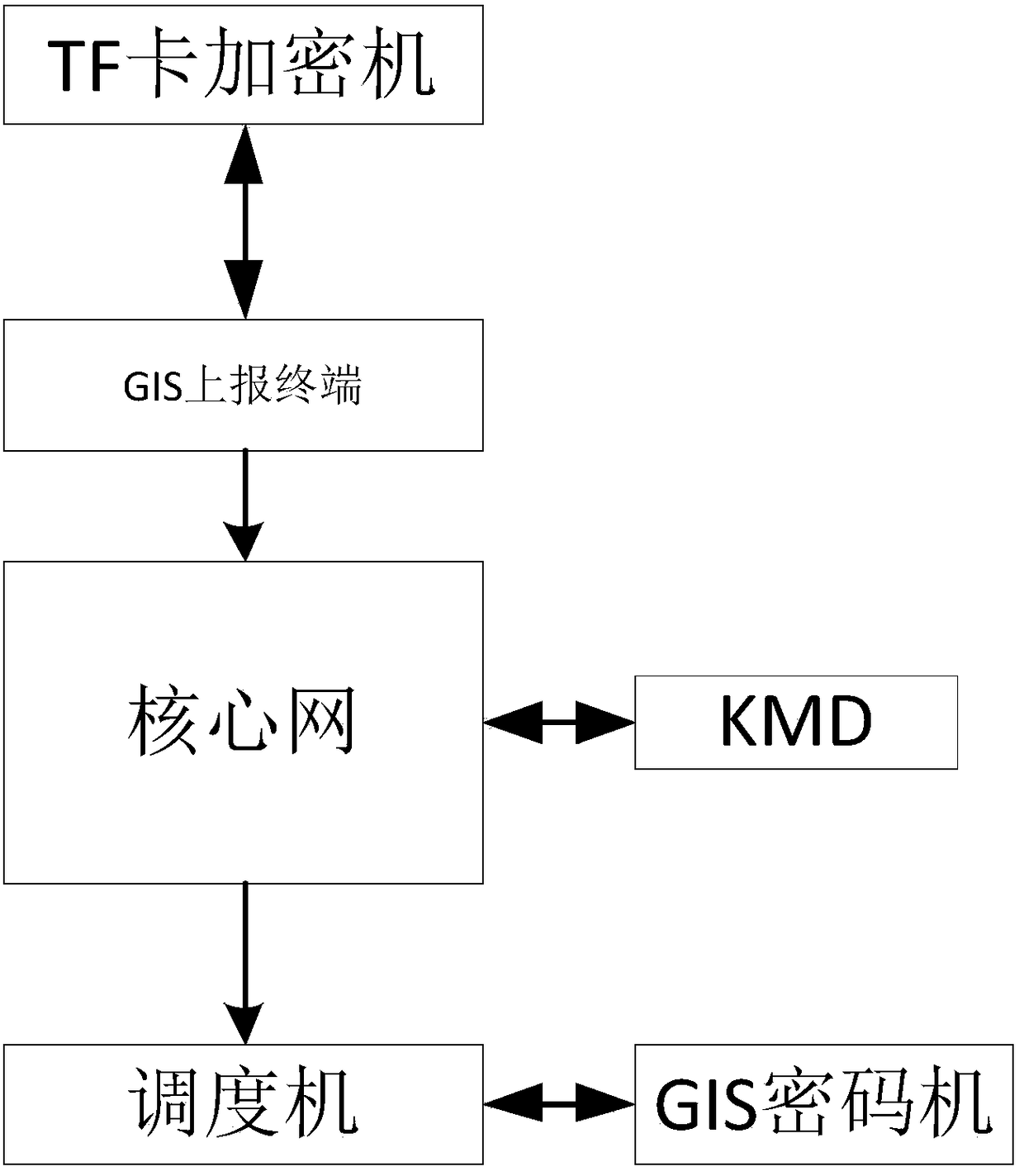
GIS position information transmission encryption method and device in trunking communication
ActiveCN108174344AEnsure safetyGuaranteed confidentialityLocation information based serviceSecurity arrangementInformation processingInformation transmission
The invention relates to the field of information processing in trunking communication, and in particular relates to a GIS position information transmission encryption method and device in trunking communication. The GIS position information transmission encryption method in trunking communication comprises the steps that: a core network receives GIS position information encrypted for one time, and puts the GIS position information encrypted for one time in a KMD data frame format packet; a KMD analyzes and decrypts the KMD data frame format packet, so that the GIS position information is obtained; then, the GIS position information is encrypted for the second time; then, the GIS position information encrypted for the second time forms a packet according to a protocol stack format; a dataframe format packet of the core network is formed, and transmitted to the KMD; the core network analyzes the transmitted data frame format packet of the core network, so that the GIS position information encrypted for the second time is obtained; then, information is forwarded to a corresponding dispatcher according to the KMS forwarded by the number of a subscriber; after receiving KMD forwardinginformation, the dispatcher performs KMD forwarding information decryption through a GIS cryptographic machine, so that the GIS position information is obtained; and the dispatcher sends the GIS position information to the corresponding dispatcher, namely the subscriber, according to the number of the subscriber.
Owner:成都三零瑞通移动通信有限公司
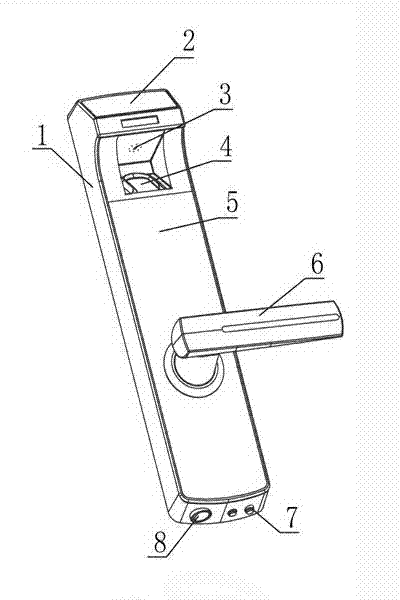
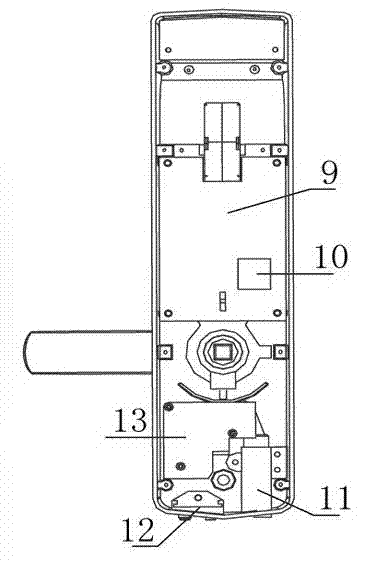
Novel fingerprint lock
InactiveCN102278009BAvoid safety hazardsPrevent peepingCharacter and pattern recognitionElectric permutation locksLiquid-crystal displayPassword
The invention discloses a fingerprint lock. A housing comprises a panel (1), a liquid crystal display screen (2) is arranged at the uppermost side of the front face of the panel (1), a buzzer (3) is arranged below the liquid crystal display screen (2), a fingerprint recognition system (4) is arranged below the buzzer (3), a touch screen (5) is arranged below the fingerprint recognition system (4), a lever handle (6) is arranged below the touch screen (5); the bottom of the panel (1) is provided with an external power supply column (7) and a mechanical key hole (8); a circuit board (9) is arranged above the inside of the panel (1), a chip (10) is arranged below the circuit board (9), a shaft of the lever handle (6) is arranged below the chip (10), a motor (13) is arranged below the shaft of the lever handle (6), and an external power supply base (12) and a mechanical key housing (11) are respectively arranged at the left and the right of the downside of the motor (13). The novel fingerprint lock can be opened by adopting one or combination of fingerprints, touch screen passwords and traditional mechanical keys.
Owner:兰溪市卓越电子有限公司
Inkpad for anti-counterfeiting by using single nucleotide polymorphous biogenetic marker
InactiveCN101891986ALong durationPrevent decipheringMicrobiological testing/measurementInksGene bankNucleotide
The invention relates to an inkpad for anti-counterfeiting by using a single nucleotide polymorphous biogenetic marker. The inkpad comprises a common inkpad and is characterized by further comprising 0.1 to 10 weight percent of target gene segment PCR amplification product mixture and 0.001 to 0.1 weight percent of solution of a DNA enzyme inhibitor, wherein the target gene segment PCR amplification product is obtained by amplifying a SNP locus-containing gene segment. The inkpad amplifies part of segments from a complicated genome DNA by searching a sequence where the conventional known SNP locus is in a gene bank and by designing a gene segment of a specificity amplification individual of a primer and effectively prevents other people from decoding and counterfeiting. At the same time, the DNA is stable and can be stored for a long time, even for thousands of years.
Owner:叶欣
RFID variable current density technology module manufacture method
InactiveCN101169835APrevent decipheringSecure transmissionRecord carriers used with machinesComputer hardwareArithmetic circuits
A RFID variable stream encryption technical module manufacture method is characterized in that the RFID variable stream encryption technical module in a RFID module includes a sub-module A(1) capable of realizing stream encryption arithmetic circuit; the technical module also includes a sub-module B(5) capable of realizing variable stream encryption arithmetic configuration circuit. Interface A-1(2) of the sub-module A(1) is connected with the interface B-1(3) of the sub-module B(5) to connect the sub-module A(1) with the sub-module B(5), wherein A-1(2) changes along with B-1(3) to change stream encryption circuit of A(1) along with configurable parameters stored in B-2(4) of B(5), thereby realizing configurable variation of stream encryption arithmetic of A(1) by data storage operation of B-2(4).
Owner:上海正诺电子技术有限公司
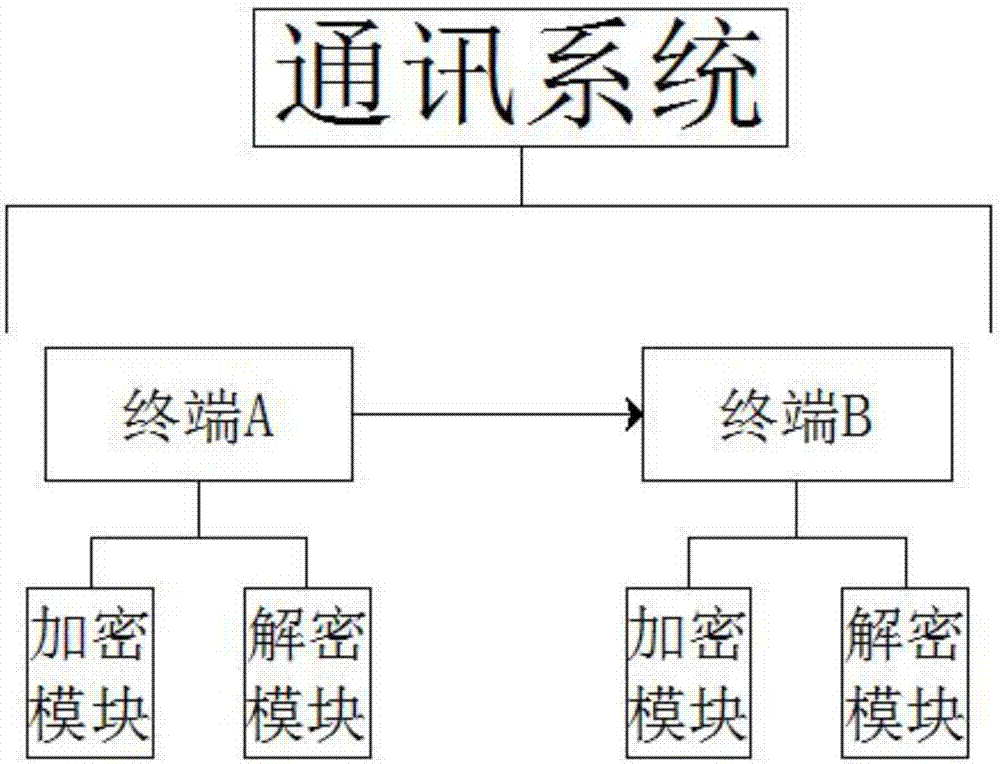
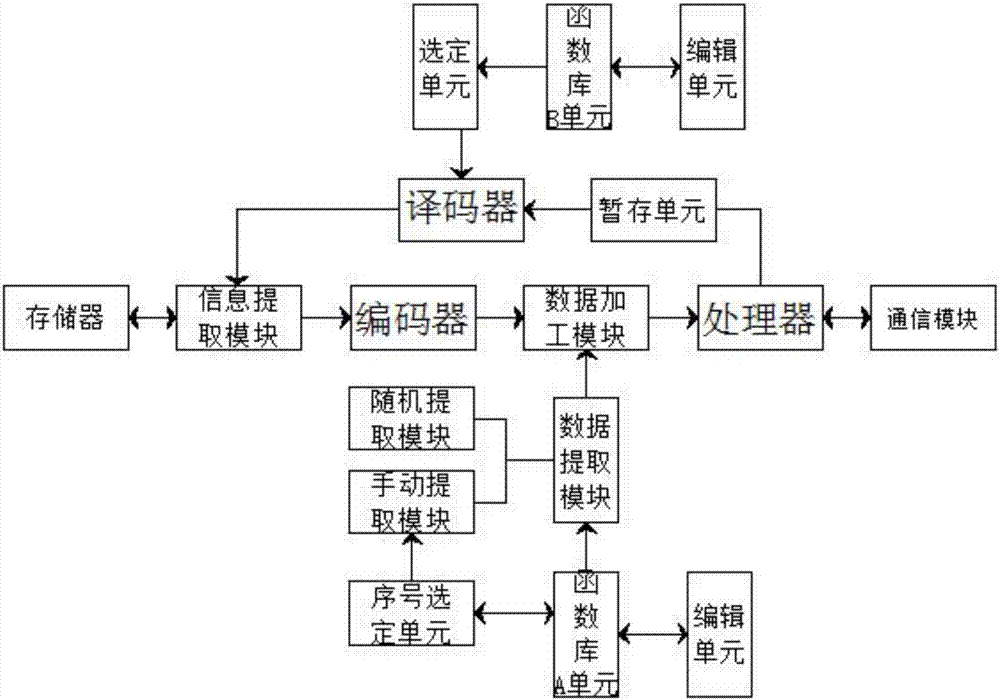
Information encryption system
InactiveCN107181587AEasy to useStable performanceMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesData transmissionEncryption system
The invention discloses an information encryption system and relates to the information encryption technology field. The system comprises a communication system, a function database A unit and a function database B unit. The communication system comprises a terminal A and a terminal B, the terminal A and the terminal B being connected through a data transmission module. The terminal A and the terminal B each comprise an encryption module and a decryption module. Each encryption module comprises a memory, an encoder and a data processing module, wherein the memory is connected with the encoder through an information extracting unit, and the encoder and the data processing module are connected through a data transmission unit. The function database A unit is connected with a data encryption module through a data extracting module. Each decryption module comprises a processor, a decoder and an information extracting module which are connected together, wherein the processor is connected with the decoder through a temporary storage unit. The function database B unit is connected with the decoder through a selection unit. Coding rearrangement is conducted through information transmitted by a random selection algorithm, so the encryption intensity of information is further improved.
Owner:合肥左成传媒科技有限公司
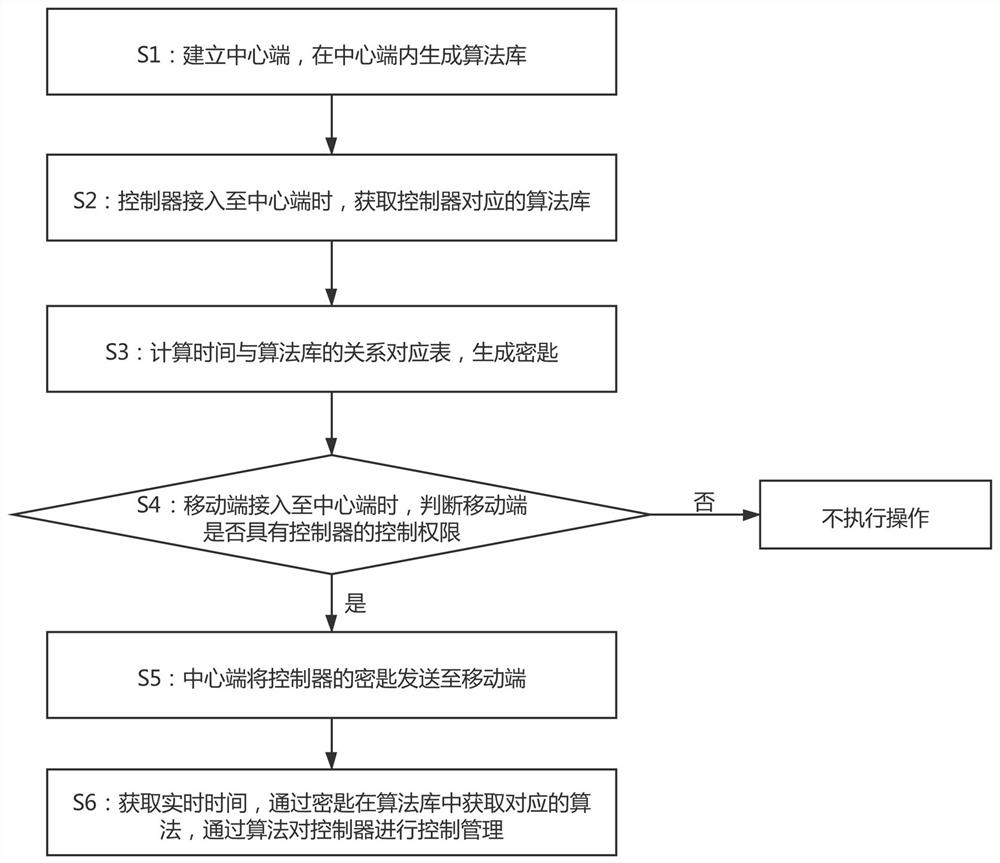
Anti-decoding Bluetooth broadcast roller shutter door control method
PendingCN112135298AReduce the risk of being intercepted simulating door openingsImprove securityKey distribution for secure communicationSecurity arrangementAlgorithmMobile end
The invention provides an anti-decoding Bluetooth broadcast roller shutter door control method, and relates to the technical field of control, and the method comprises the following steps: S1, building a central end, and generating an algorithm library in the central end; S2, acquiring the algorithm library corresponding to the controller when the controller is accessed to the central end; S3, calculating a relation corresponding table of time and the algorithm library, and generating a key; S4, when the mobile terminal is accessed to the central end, judging whether a mobile terminal has thecontrol authority of the controller or not, if so, executing S5, otherwise, not executing the operation; S5, enabling the central end to send the key of the controller to the mobile terminal; S6, acquiring the real time, obtaining a corresponding algorithm in the algorithm library through the key, and performing the control and management of the controller through the algorithm. The anti-decodingBluetooth broadcast roller shutter door control method is good in safety, decoding can be effectively prevented, the risk that a wireless signal is intercepted to simulate door opening is effectivelyreduced, the control mode is novel, the method can be used in cooperation with an APP, and financial safety is guaranteed.
Owner:福建安麟机电科技有限公司
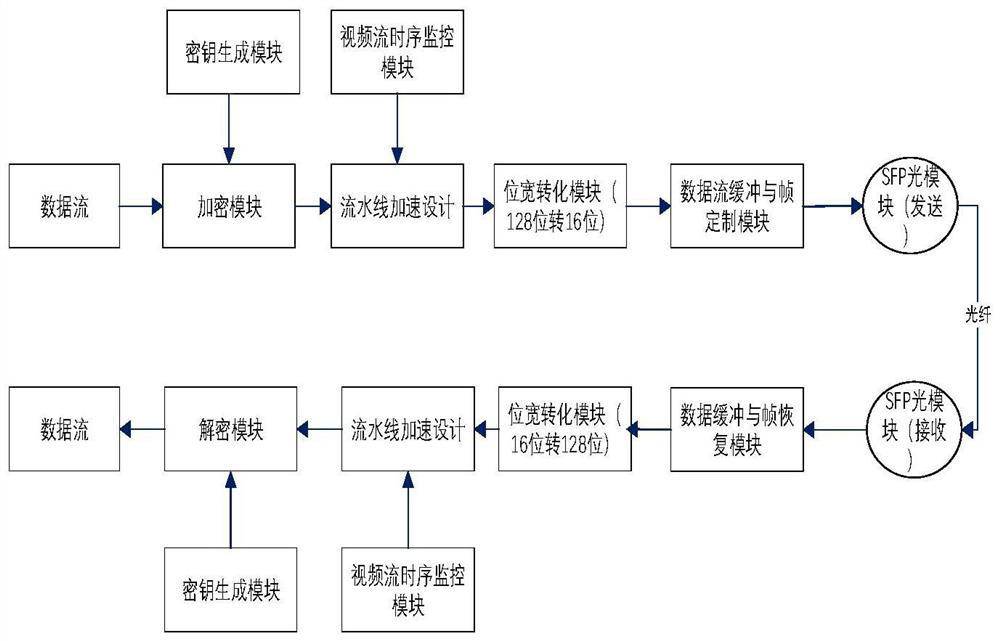
A Fiber Encryption Method Based on FPGA
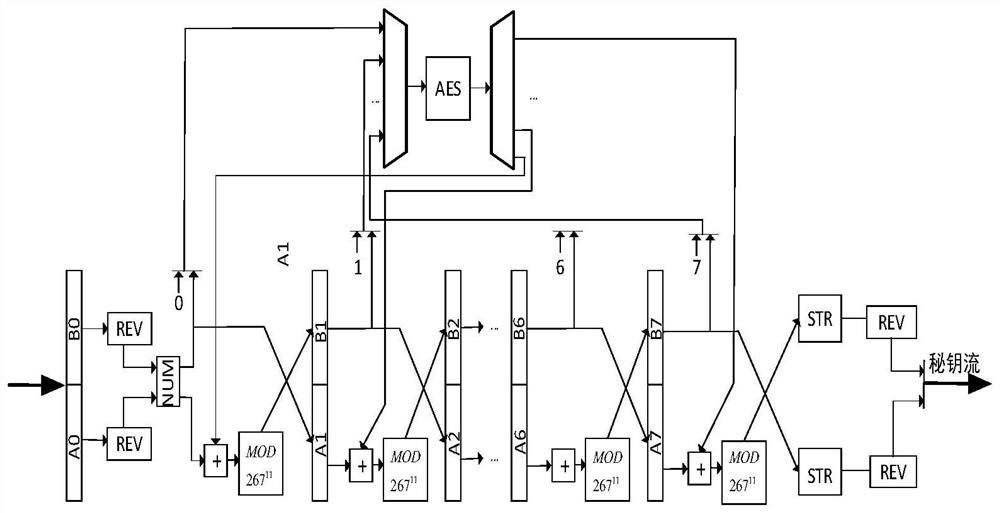
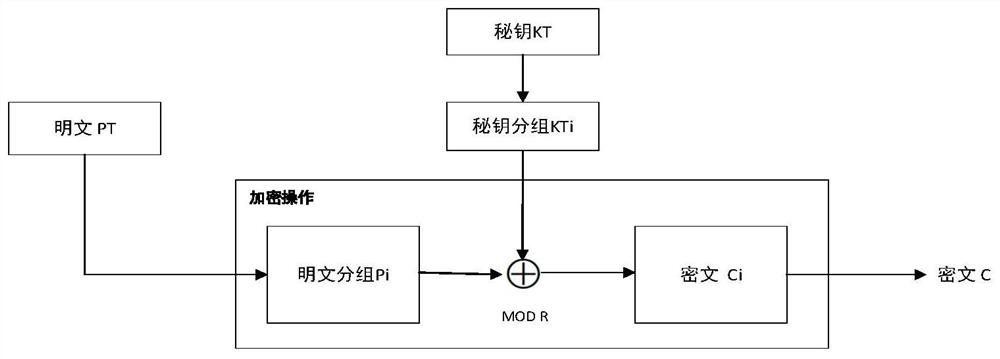
ActiveCN113037390BEnsure link securityPrevent decipheringMultiplex system selection arrangementsWavelength-division multiplex systemsComputer hardwarePlaintext
The invention discloses an FPGA-based optical fiber encryption method, comprising the following steps: (1) obtaining plaintext PT; (2) obtaining a key KT of an FPE encryption mode with a Logistic model; (3) encrypting the plaintext PT with the key KT, Obtain ciphertext C; (4) Pipeline accelerated ciphertext C; (5) Convert the bit width of ciphertext C data; (6) Send data using the frame structure customized by Aurora protocol; (7) The receiving end buffers the received data and strips Frame structure; (8) The receiver decodes the ciphertext C to obtain the plaintext PT. The invention effectively guarantees the link security of the communication, avoids the deciphering and eavesdropping of the video stream data; the overall communication rate can reach 6.25Gpbs.
Owner:NANJING UNIV OF POSTS & TELECOMM
Intelligent electronic lock
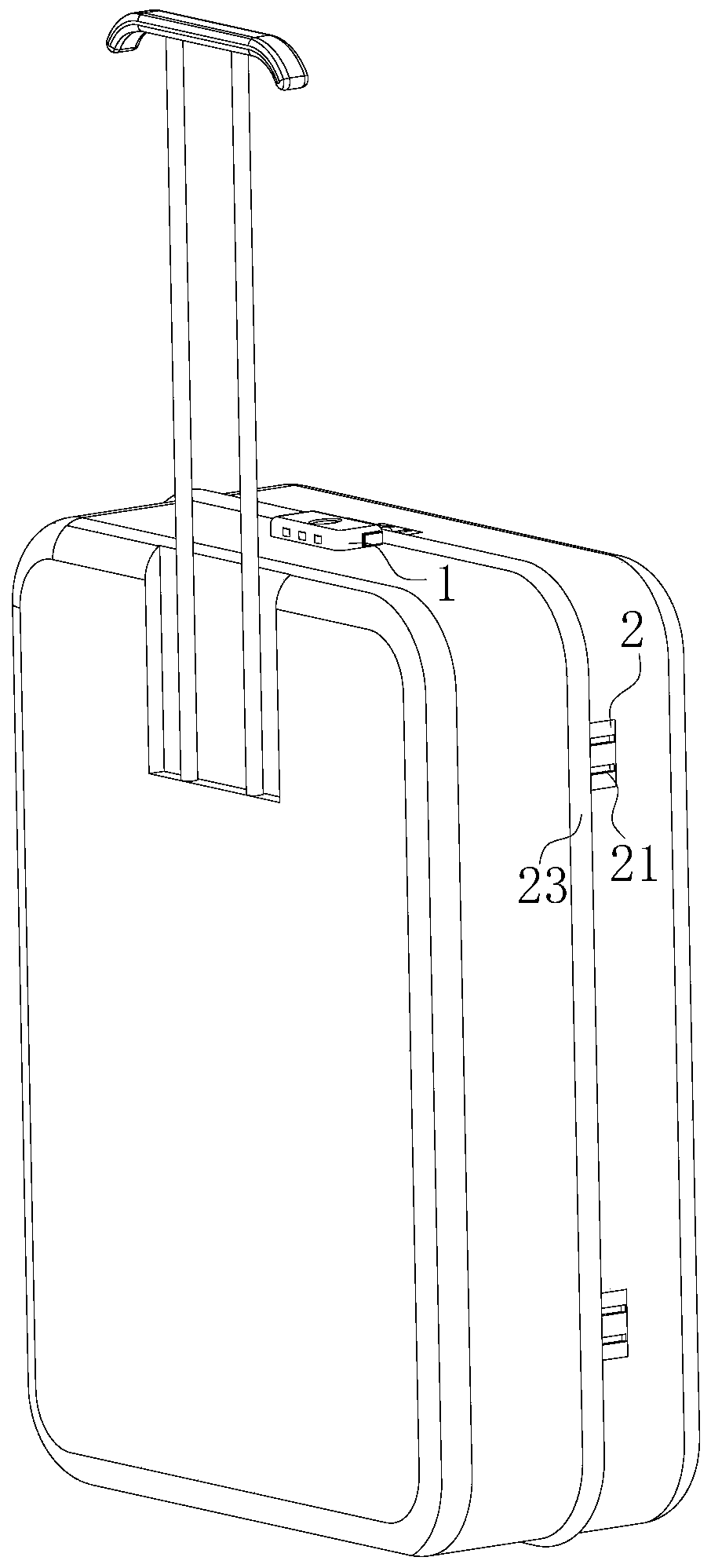
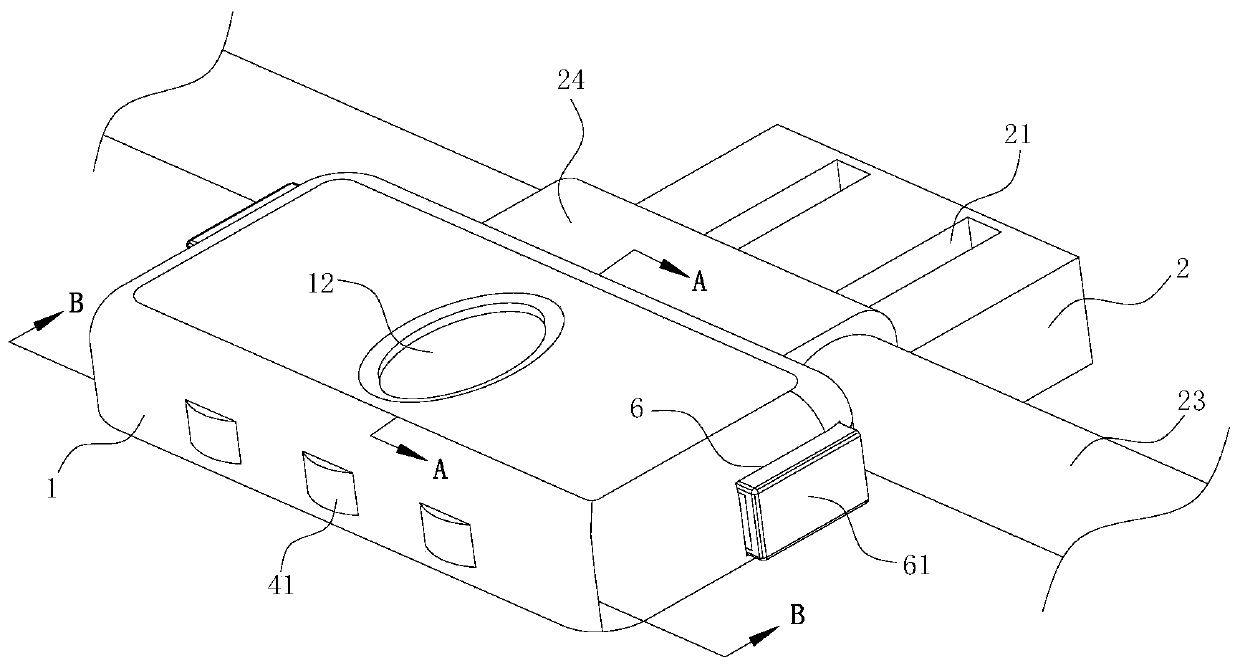
InactiveCN111520005AIncreased chance of breakageImprove securityNon-mechanical controlsOther accessoriesTrunk compartmentMechanical engineering
The invention belongs to the technical field of safety locks, and particularly relates to an intelligent electronic lock. The intelligent electronic lock comprises a lock head, a positioning block andan intelligent regulator, the lock head is of a rectangular structure, the lock head is fixedly connected to one side, close to a pull rod, of a luggage case top, wherein the luggage case is a commonbox-shaped structure body which is folded through a zipper, the intelligent regulator is mounted on one side of the lock head, a fingerprint identifier is fixedly connected to the surface of one side, far away from the luggage case, of the lock head, the fingerprint identifier is used for identifying fingerprints and is electrically connected with the intelligent regulator, the positioning blockis embedded into one side, far away from the pull rod, of the luggage case folding part, the positioning blocks are uniformly distributed along the direction of the luggage case zipper, and symmetrically-designed first grooves are formed in the surface of the positioning block. Through the arrangement of the fingerprint recognizer and the intelligent regulator, the output of the unlocking instruction is completed through the input of the fingerprint of a user, so that the recognition mechanism of the intelligent electronic lock is more rigorous, and the unlocking mechanism of the luggage caseis more perfect.
Owner:张圆圆
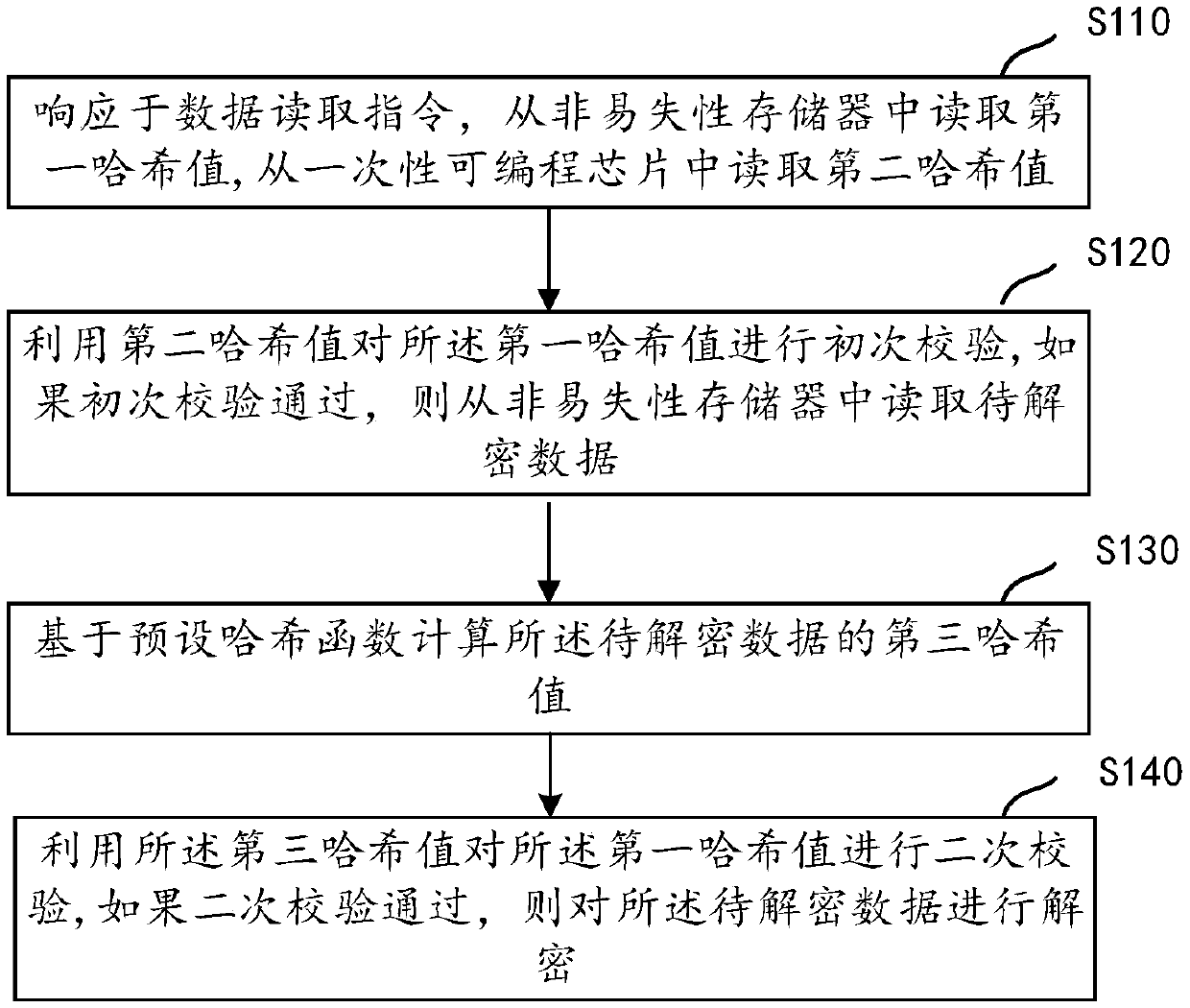
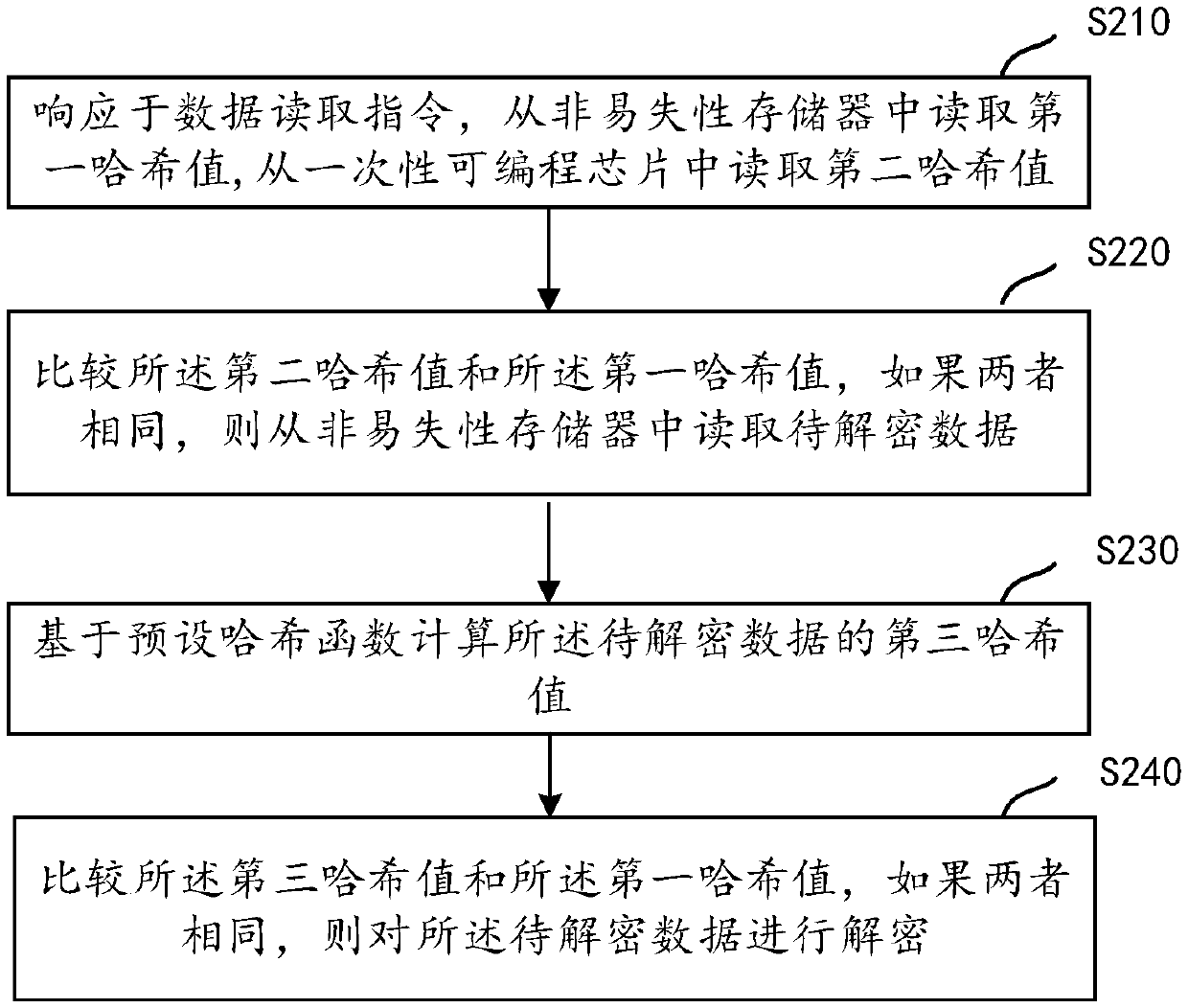
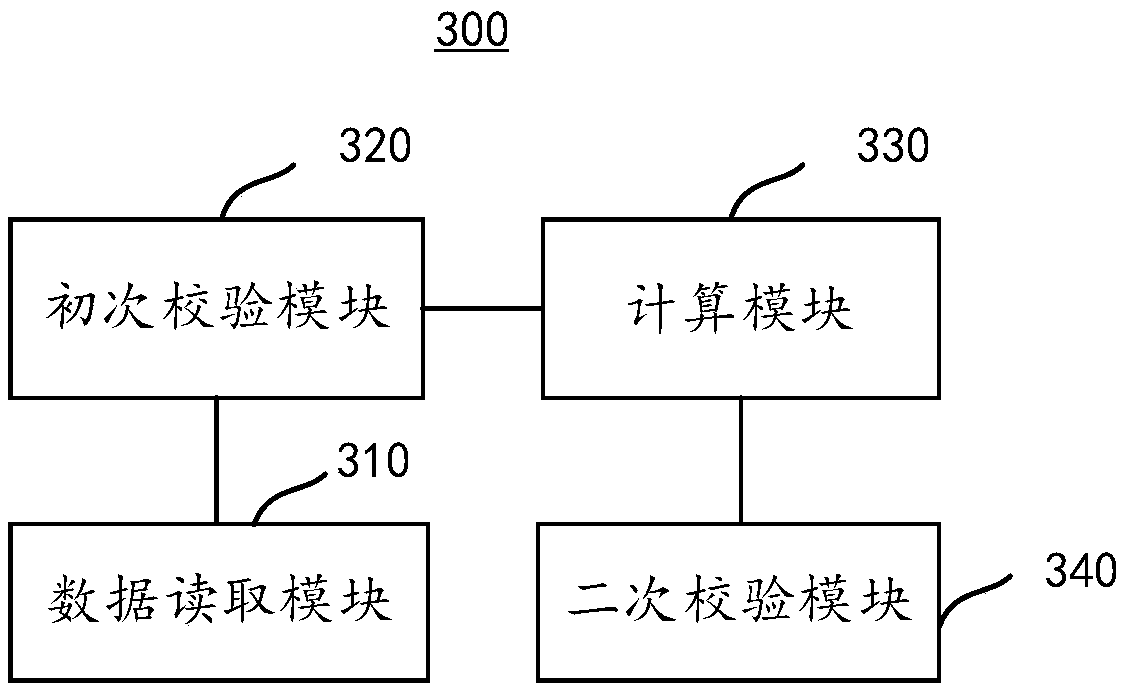
Data decryption method and device and computer readable storage medium
PendingCN111143904AIntegrity guaranteedPrevent decipheringInternal/peripheral component protectionData integrityHash function
The invention provides a data decryption method and device, and a computer readable storage medium. The method comprises the steps of reading a first hash value from a nonvolatile memory; reading a second hash value from the one-time programmable chip; performing primary verification on the first hash value by utilizing the second hash value; if the first verification is passed, reading the to-be-decrypted data from the nonvolatile memory; calculating a third hash value of the to-be-decrypted data based on a preset hash function; performing secondary verification on the first hash value by utilizing the third hash value; and if the secondary verification is passed, decrypting the to-be-decrypted data. According to the method and the device, the to-be-decrypted data is subjected to secondary verification to verify the integrity of the to-be-decrypted data, and then the to-be-decrypted data is decrypted under the condition of ensuring the integrity of the to-be-decrypted data, so that the to-be-decrypted data is effectively prevented from being decrypted in a bypass attack mode to obtain the key of the encryption algorithm.
Owner:CANAAN BRIGHT SIGHT CO LTD
Integrated module for controlling opening and closing of box body
InactiveCN106703541APrevent decipheringReduce volumeElectric permutation locksIndividual entry/exit registersFingerprintIntegrated circuit
The invention relates to an integrated module for controlling the opening and closing of a box body. The integrated module comprises a box body door sheet and an operation panel; the operation panel and an integrated circuit control box are connected into a whole; the box body door sheet is located between the operation panel and the integrated circuit control box; and the integrated circuit control box is internally provided with a control circuit board connected with the operation panel. The integrated module has the characteristics that the universal performance is good, installation space of an electronic lock is saved greatly, storage space is increased, the operation is convenient, and since a fingerprint sensor is located in a safe box, the fingerprint sensor can not be cracked by a person through electronic equipment easily, and the safety of the safe box is improved.
Owner:NINGBO ANGEL ELECTRONICS TECH
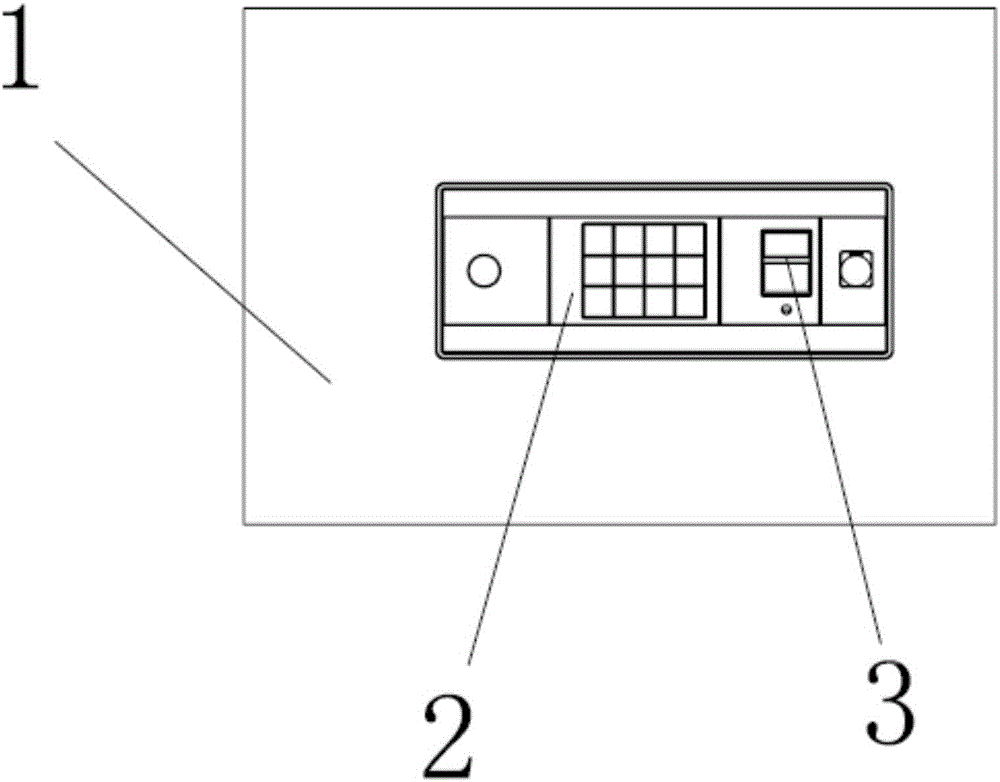
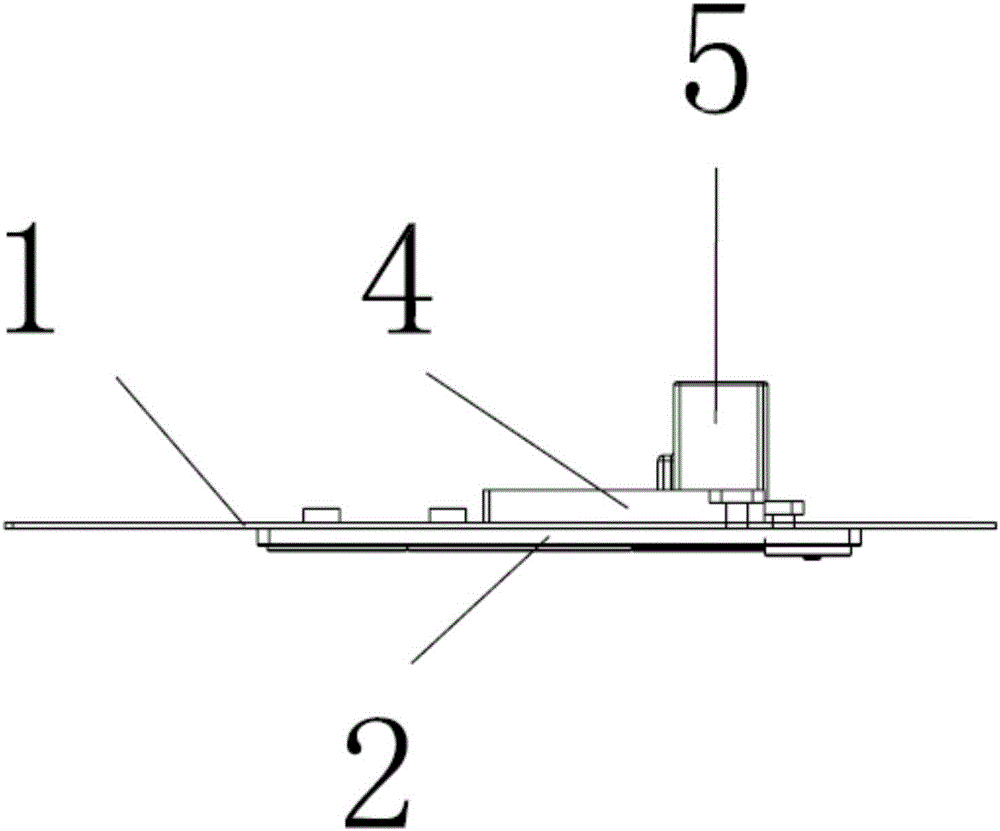
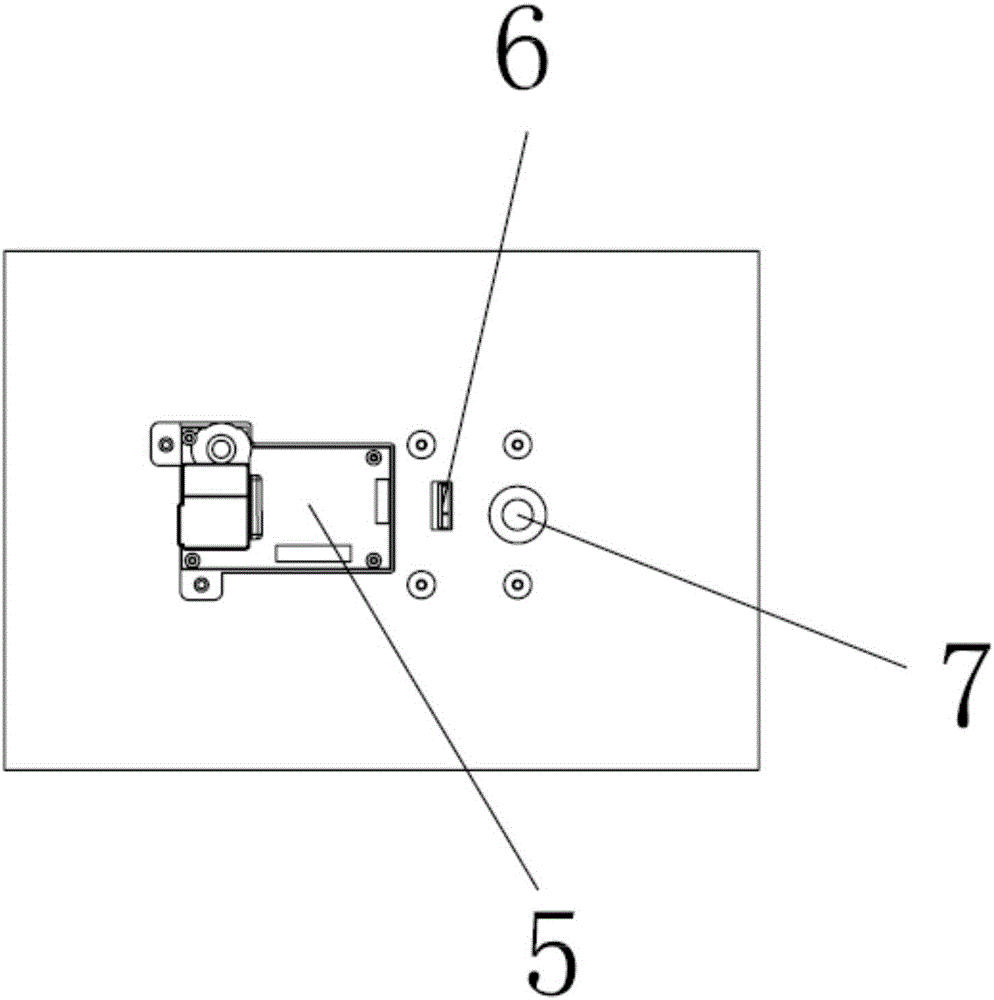
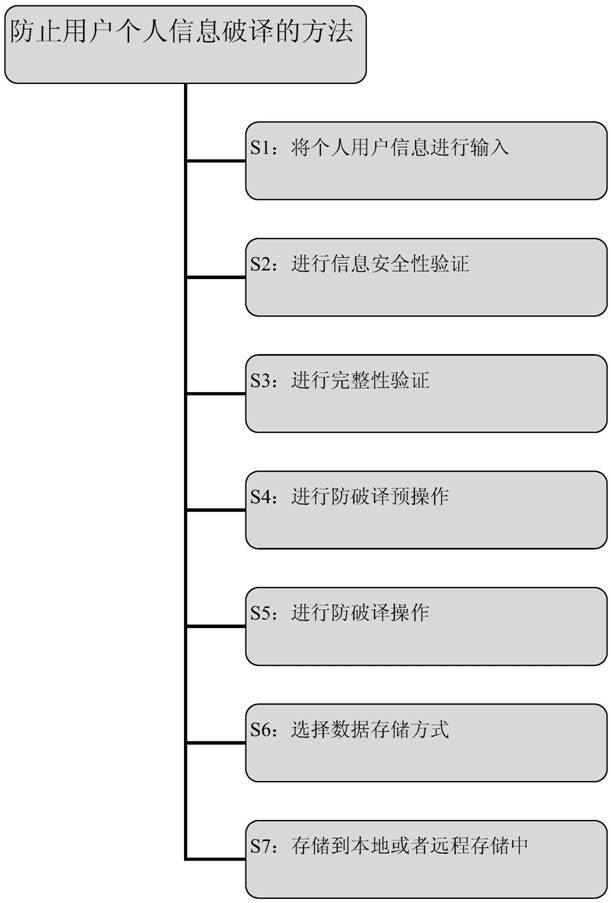
A method to prevent deciphering of user's personal information
ActiveCN107026872BIncrease the difficultyReduce the probability of being decipheredKey distribution for secure communicationInternet privacyEngineering
A method for preventing deciphering of user personal information, comprising: inputting personal user information through an energy-saving monitoring switch; performing information security verification on the input personal user information; performing integrity verification on the personal user information after the security verification; Perform anti-deciphering pre-operation on the personal user information subject to integrity verification; perform anti-deciphering operation on the personal user information subject to integrity verification; select the data storage method; or in remote storage. The method can significantly improve the difficulty of deciphering the user's personal information and reduce the probability of being deciphered; and it does not occupy too much space on the carrier where the user's personal information is stored, thereby improving the subsequent storage of the information by the user's personal information operator with proper authority. At the same time, it makes the whole circuit more compact, takes up less physical space, and can effectively reduce the power consumption of the whole system.
Owner:宁波潮涌道投资合伙企业(有限合伙)
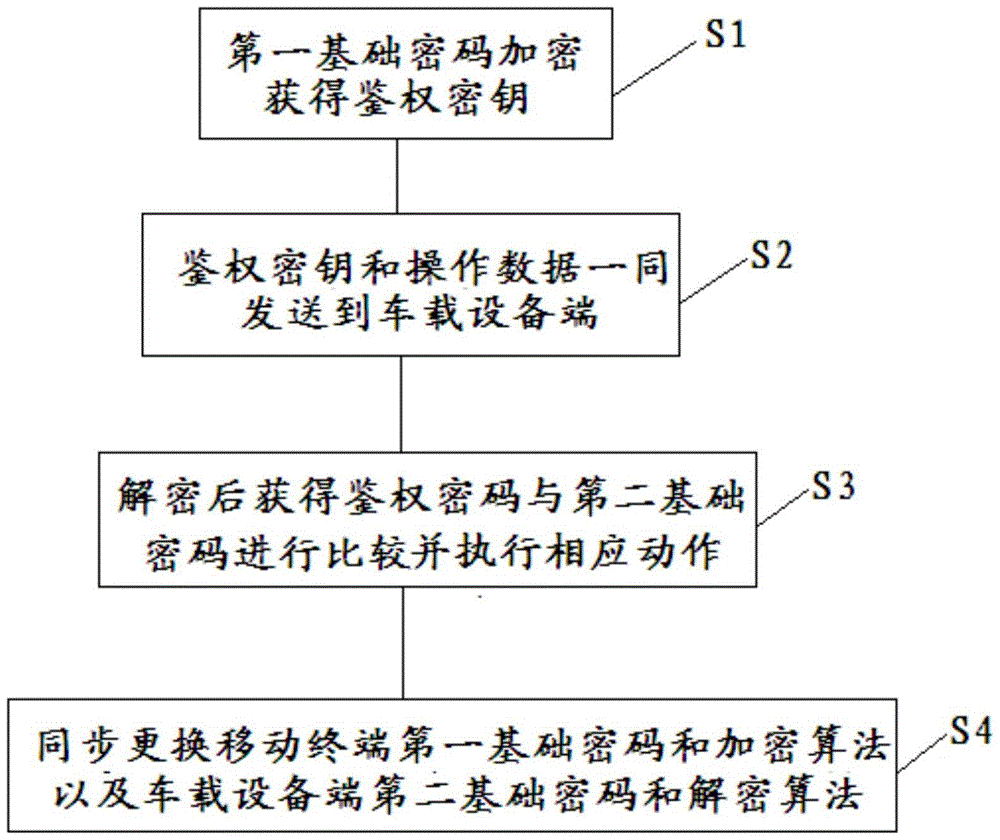
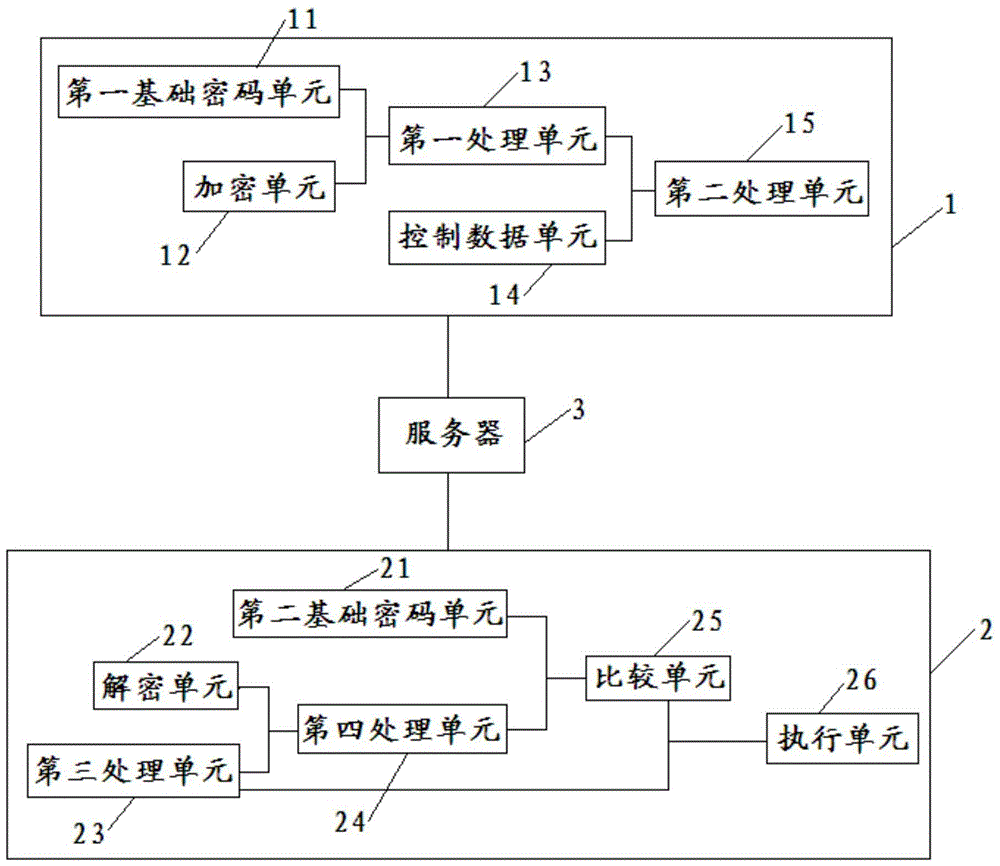
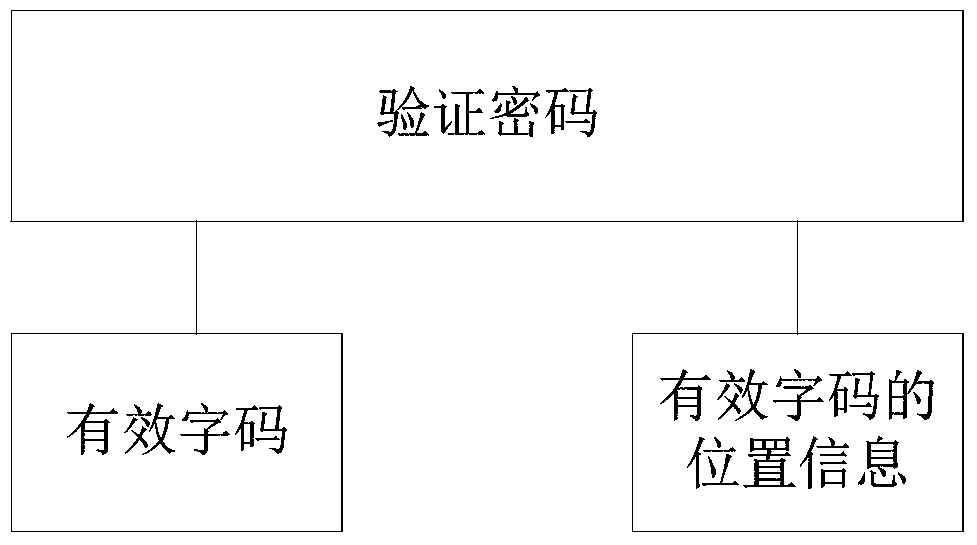
Security password setting and verification method
ActiveCN104537300BPrevent decipheringEnter your password in a secure wayDigital data authenticationPasswordCipher
The invention relates to a safe password setting and verifying mode. The safe password setting and verifying mode is characterized by comprising the following steps: (A) basic passwords are set by a user and are composed of a plurality of orderly character codes; (B) an encryption principle is set, encryption operation is carried out on the basic passwords according to the encryption principle to form verifying passwords including valid character codes capable of being used for verifying the user identity and / or position information of the valid character codes, and encryption input prompts coincident with the encryption principle are given to the user; (C) composition of the input passwords is appointed, wherein the input passwords comprise valid codes needing character code value verifying and / or character code value position verifying and interference codes which are at least one bit in length and are used for hiding the positions of the valid codes; (D) when character code values of the valid codes in the passwords input by the user at present and / or the character code position information are / is coincident with information included by the verifying passwords, it is judged that the current passwords is correctly input by the user, and verification of the passwords is successful. By means of the safe password setting and verifying mode, the password inputting safety can be greatly improved, and the passwords are effectively prevented from being stolen and decoded.
Owner:广东金融资产交易中心股份有限公司
Anti-attack data transmission method and device
InactiveCN107948185AGet goodAvoid the problem of accidental damage to the data flow of normal transmissionTransmissionComputer hardwareData field
The invention discloses a method and device for anti-attack data transmission, which solves the problem that the prior art cannot solve the problem of anti-attack. This application obtains the communication protocol message to be transmitted; Anti-attack preprocessing is performed on the data on the information bit to generate processing information; the above processing information is stored in the extension bit of the above-mentioned communication protocol message in the above-mentioned message header, and the converted communication protocol message is obtained, wherein, The above-mentioned message header of the above-mentioned communication protocol message includes the above-mentioned information bits and the above-mentioned extension bits; the above-mentioned converted communication protocol message is sent to the receiving device; this application is applicable to the field of data attack defense.
Owner:高伟红
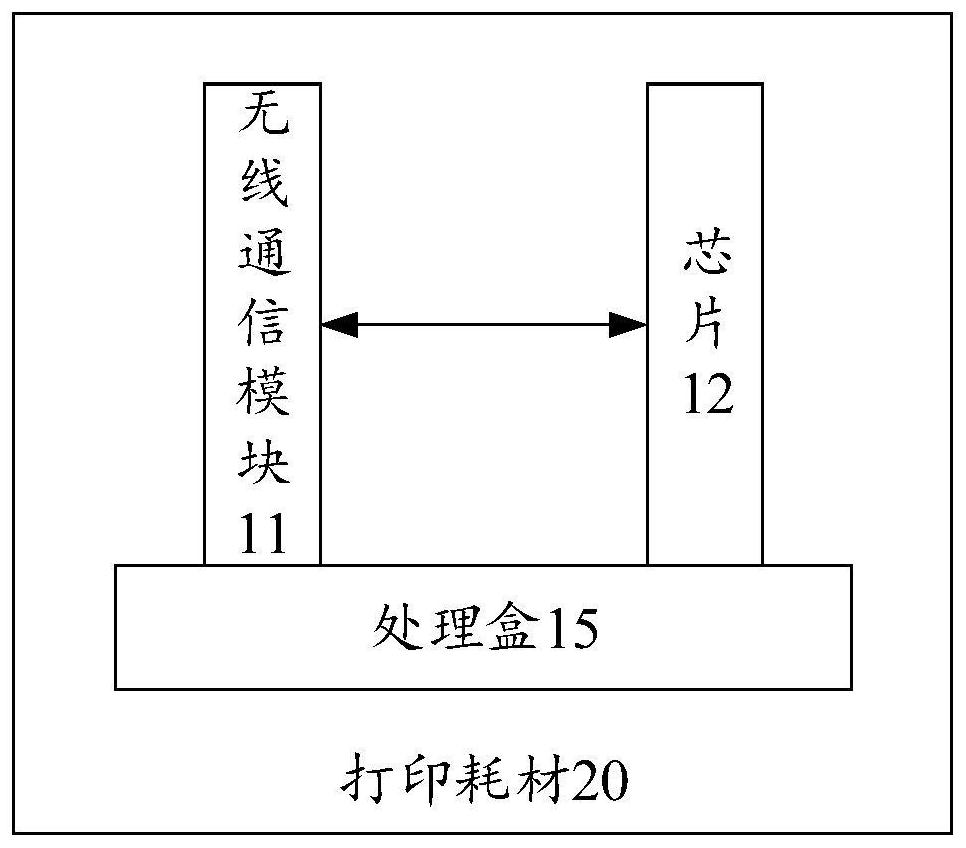
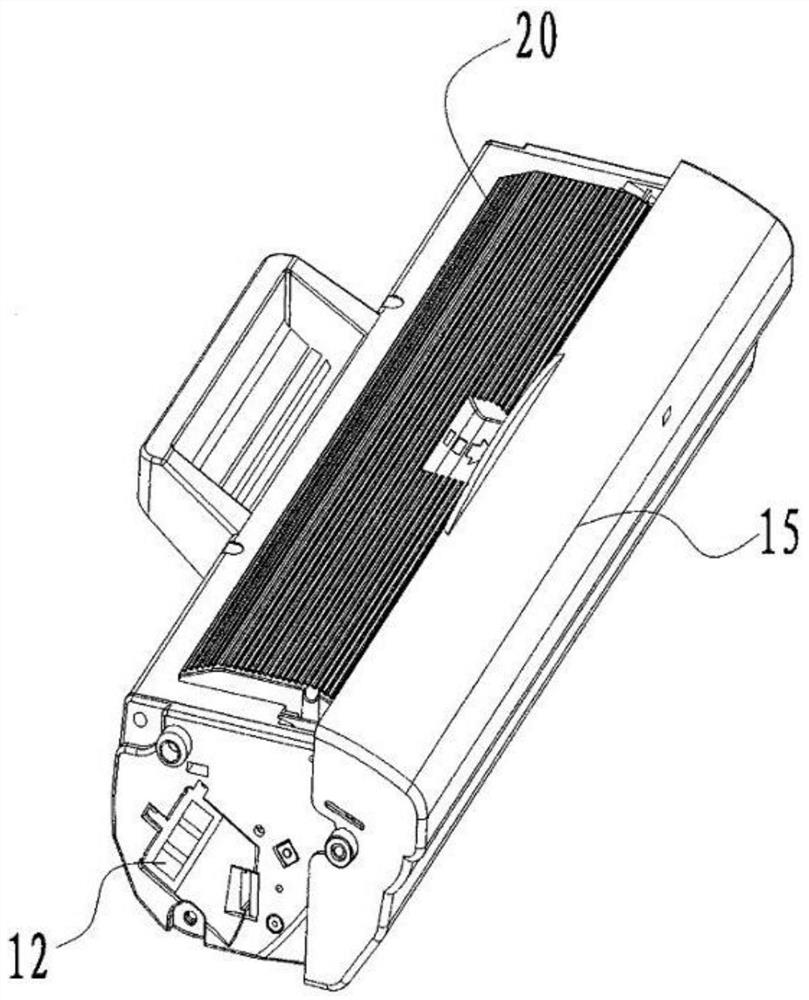
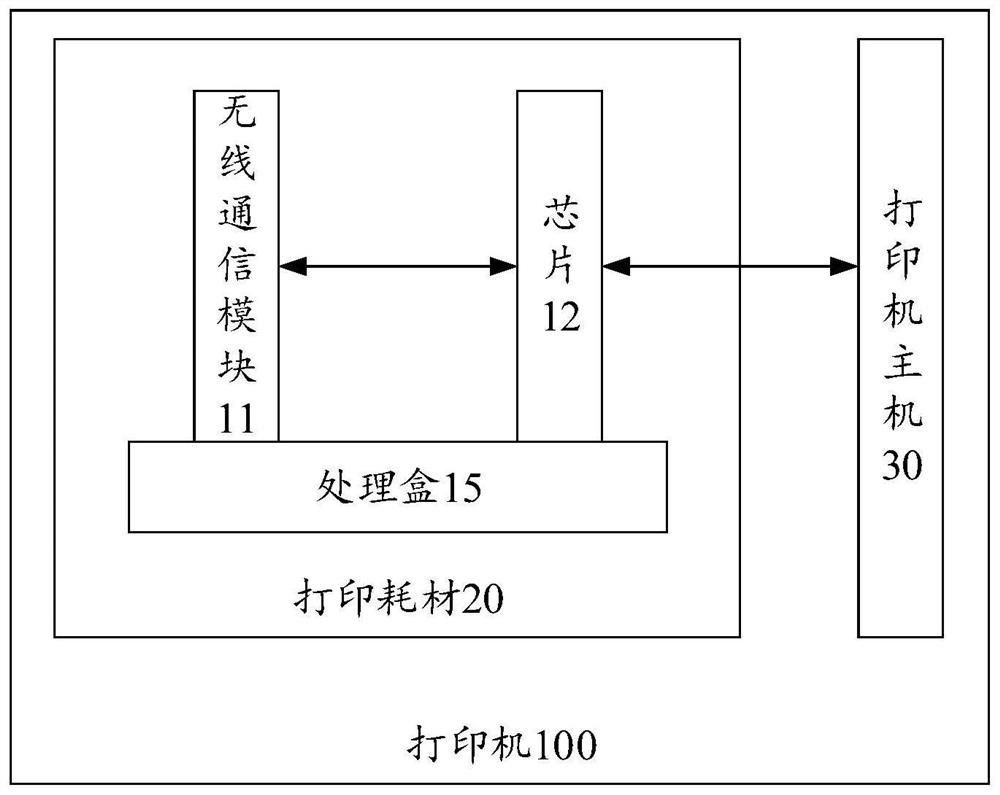
A kind of wireless communication module, printing consumables and printer
ActiveCN110497696BPrevent imitationPrevent decipheringTransmissionOther printing apparatusComputer printingEngineering
The present invention provides a wireless communication module, printing consumables and a printer. The wireless communication module is detachably installed on a printer host and / or a processing box of the printing consumables, and is used for wirelessly sending the identification information of the printing consumables To the verification center for legality verification, and receive the legality verification result information fed back by the verification center, and forward the legality verification result information to the printer host, so that the printer host determines whether to execute the printing job according to the legality verification result information. The present invention realizes the method of remote legality verification of printing consumables by the verification center, because the verification work of the present invention is completed by the verification center, and the verification center can combine the latest and most authoritative verification technology to verify the legality of the printing consumables. Carry out verification to prevent illegal production and imitation of printing consumables. At the same time, the wireless communication module of the present invention can be reused, thereby reducing the verification cost of printing consumables.
Owner:前海联大(深圳)技术有限公司
A network data transmission device and method for 3D printers
ActiveCN105856563BPrevent decipheringAvoid storageAdditive manufacturing apparatusManufacturing data aquisition/processingNetwork data3d printer
The invention discloses a network data transmission device and method for a 3d printer. The network data transmission device comprises a background data receiving module, a data-caching module, a gcode instruction issuing module, a 3d printer status data receiving module, a 3d printer status data uploading module and a main control processing module, wherein the background data receiving module is used for receiving data coming from a network background; the data-caching module is used for caching the received data coming from the network background; the gcode instruction issuing module is used for issuing a gcode instruction in the cached data coming from the data-caching module to the 3d printer; the 3d printer status data receiving module is used for receiving printing and operation status data of the 3d printer; the 3d printer status data uploading module is used for uploading the printing and operation status data of the 3d printer to the network background; and the main control processing module is used for conducting real-time monitoring process on the printing and operation status data of the 3d printer and controlling the working state of the 3d printer. The network data transmission device and method for the 3d printer have the advantages that operation is easy, the copyright of the gcode instruction is protected, and meanwhile the state of the printer can be obtained by the network background successfully.
Owner:SHENZHEN 7TH TECH CO LTD
Method and system for reciprocally encrypting data, equipment and storage medium
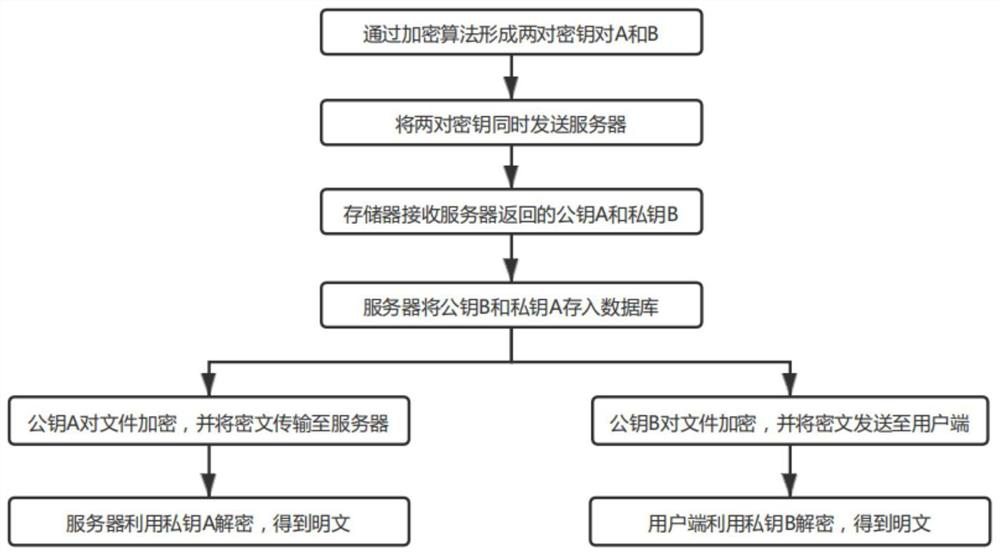
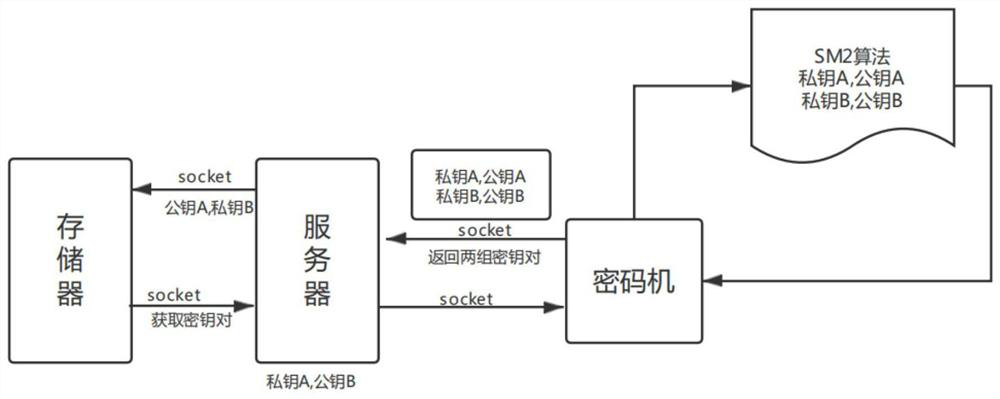
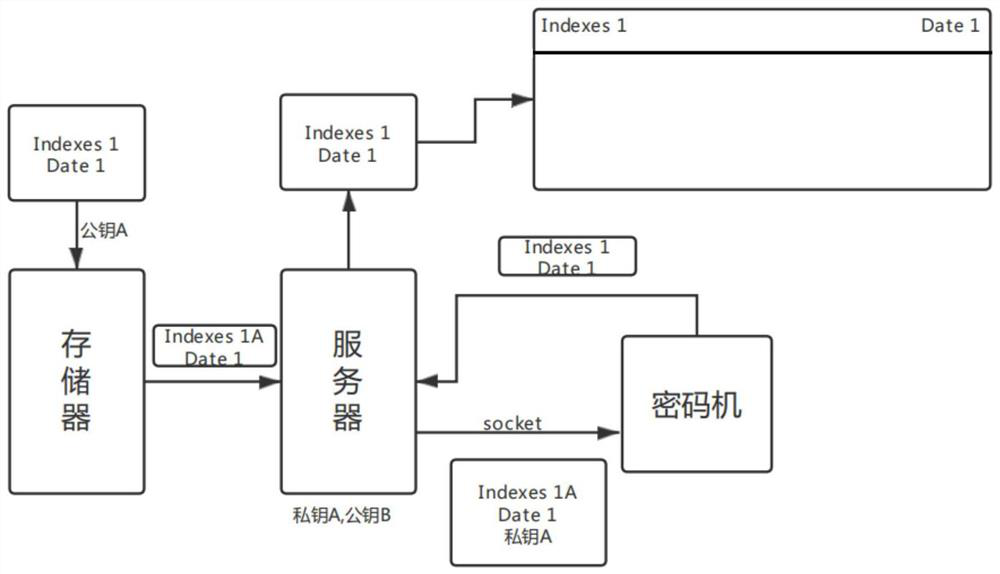
PendingCN113347144AImprove securityIncrease storage capacityKey distribution for secure communicationMultiple keys/algorithms usageCiphertextData transport
The invention belongs to the technical field of data encryption, and particularly discloses a method and system for reciprocally encrypting data, equipment and a storage medium. The method comprises the following steps: a cipher machine randomly forms two key pairs through an encryption algorithm, namely a private key A, a public key A, a private key B and a public key B, stores the public key A and the private key B in a local user side, and stores the private key A and the public key B in a server; the public key A encrypts a file; after receiving a ciphertext, the server decrypts the ciphertext through the private key A; the server encrypts the file through the public key B, and a client decrypts the file through the private key B when the receiving the ciphertext. The invention provides a reciprocal storage index query data mode, so that the data transmission process is effectively prevented from being tampered and decoded. The data security transmission performance and storage performance are effectively improved.
Owner:西安慧博文定信息技术有限公司
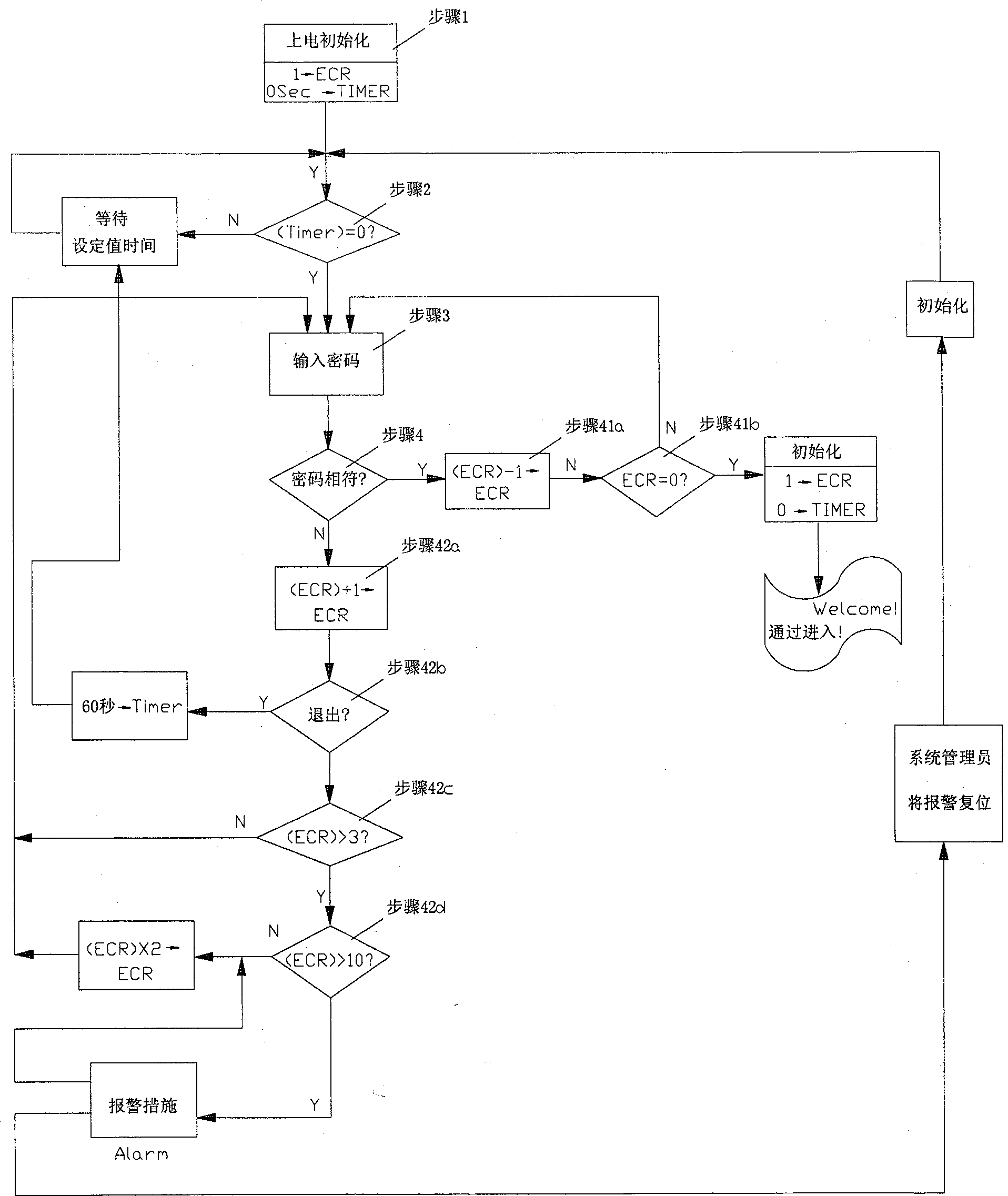
Cipher safe protecting method for preventing intelligent device input cipher from being decrypted
InactiveCN100498641CPrevent decipheringDigital data processing detailsUser identity/authority verificationElectricityProcessor register
The present invention relates to a cryptogram safety protection method for preventing the intelligent device inputted cryptogram from being decrypted. Said invention utilizes the devices of register and timer, etc. and adopts two programs of first cryptogram safety control program and second cryptogram safety control program to prevent the intelligent device inputted cryptogram from being decrypted. Said invention also provides the concrete steps of said protection method.
Owner:SHANGHAI ELECTRICGROUP CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com