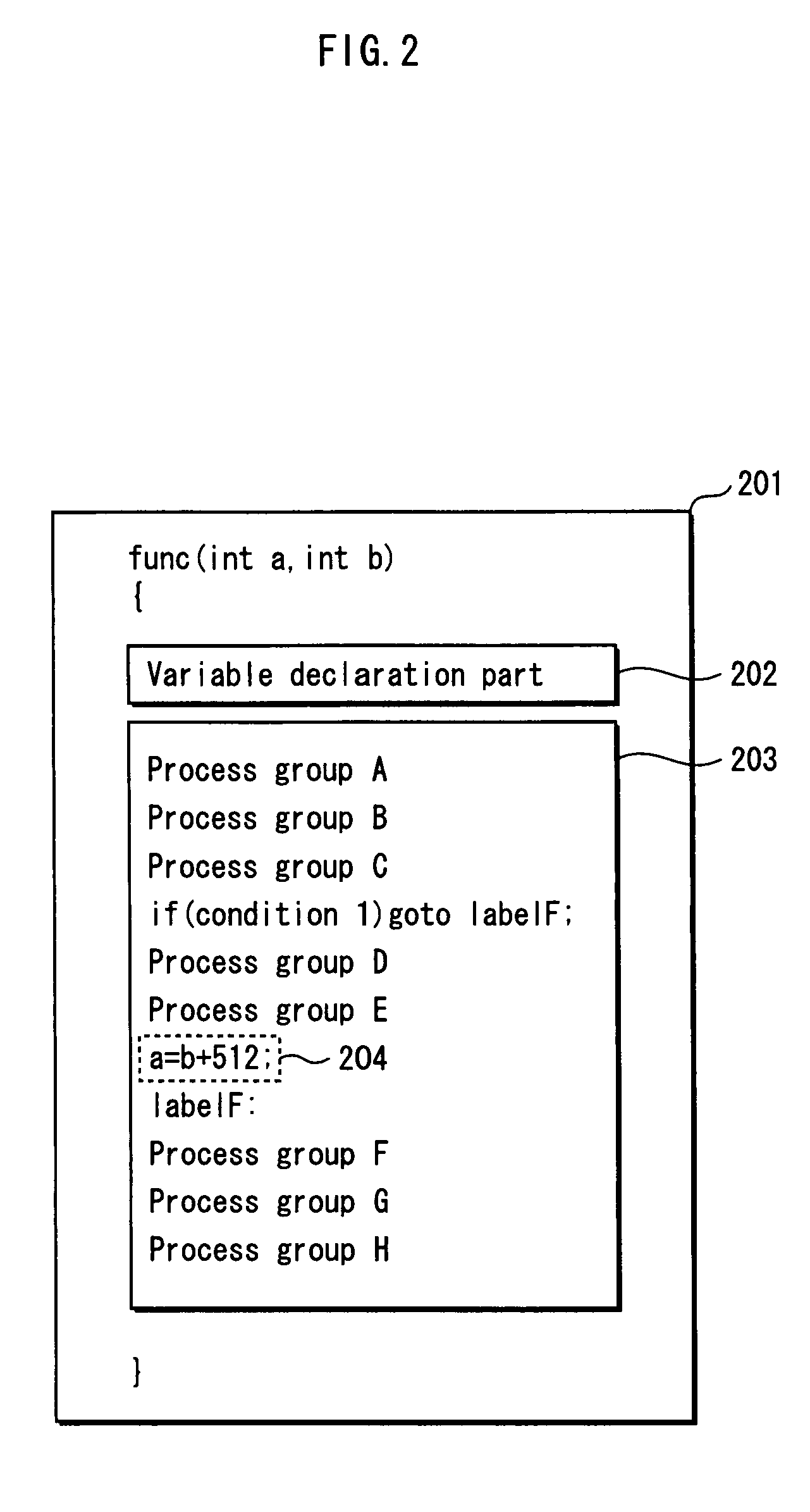
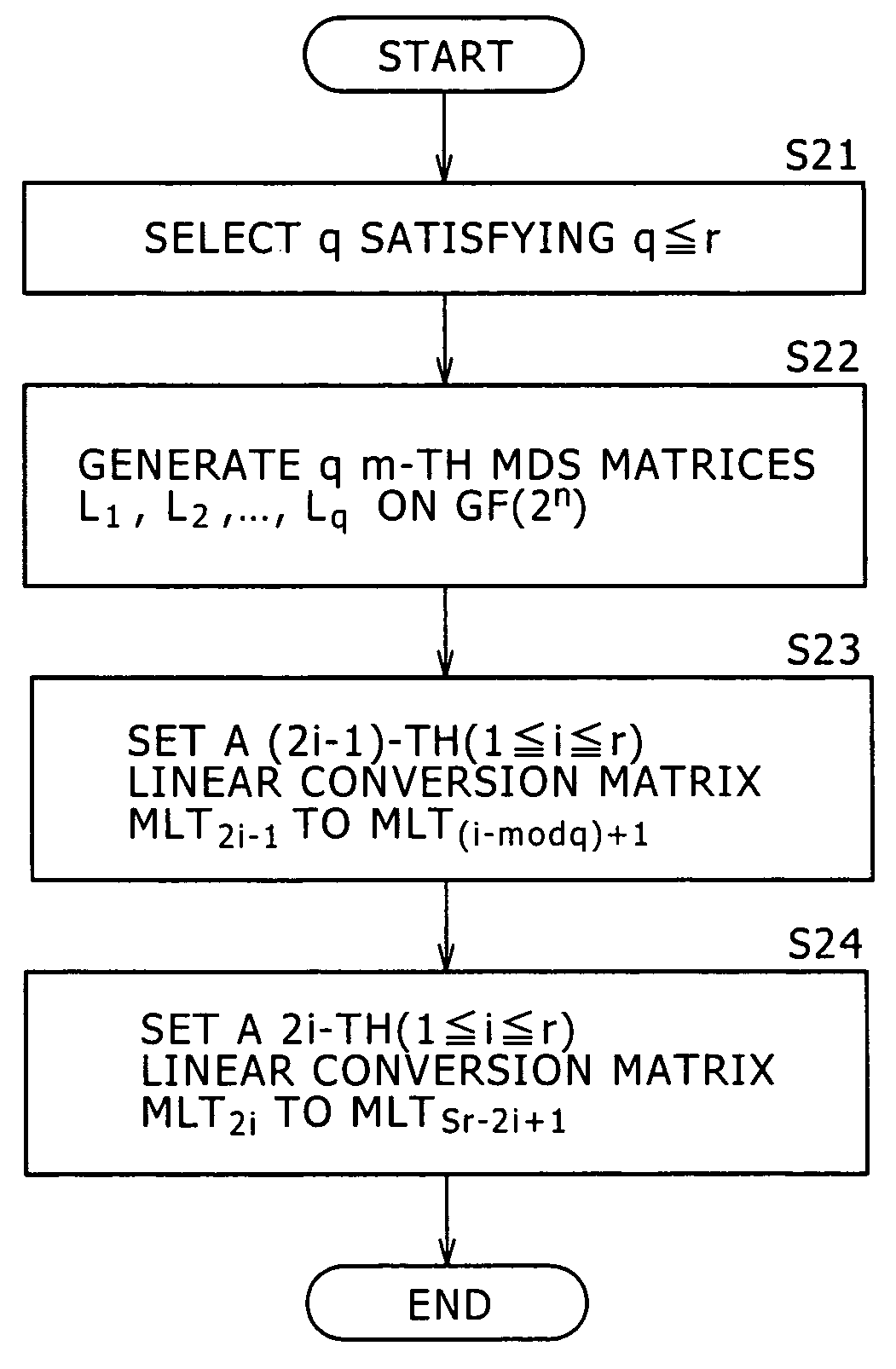
Patents
Literature
61results about How to "Difficult to analyze" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
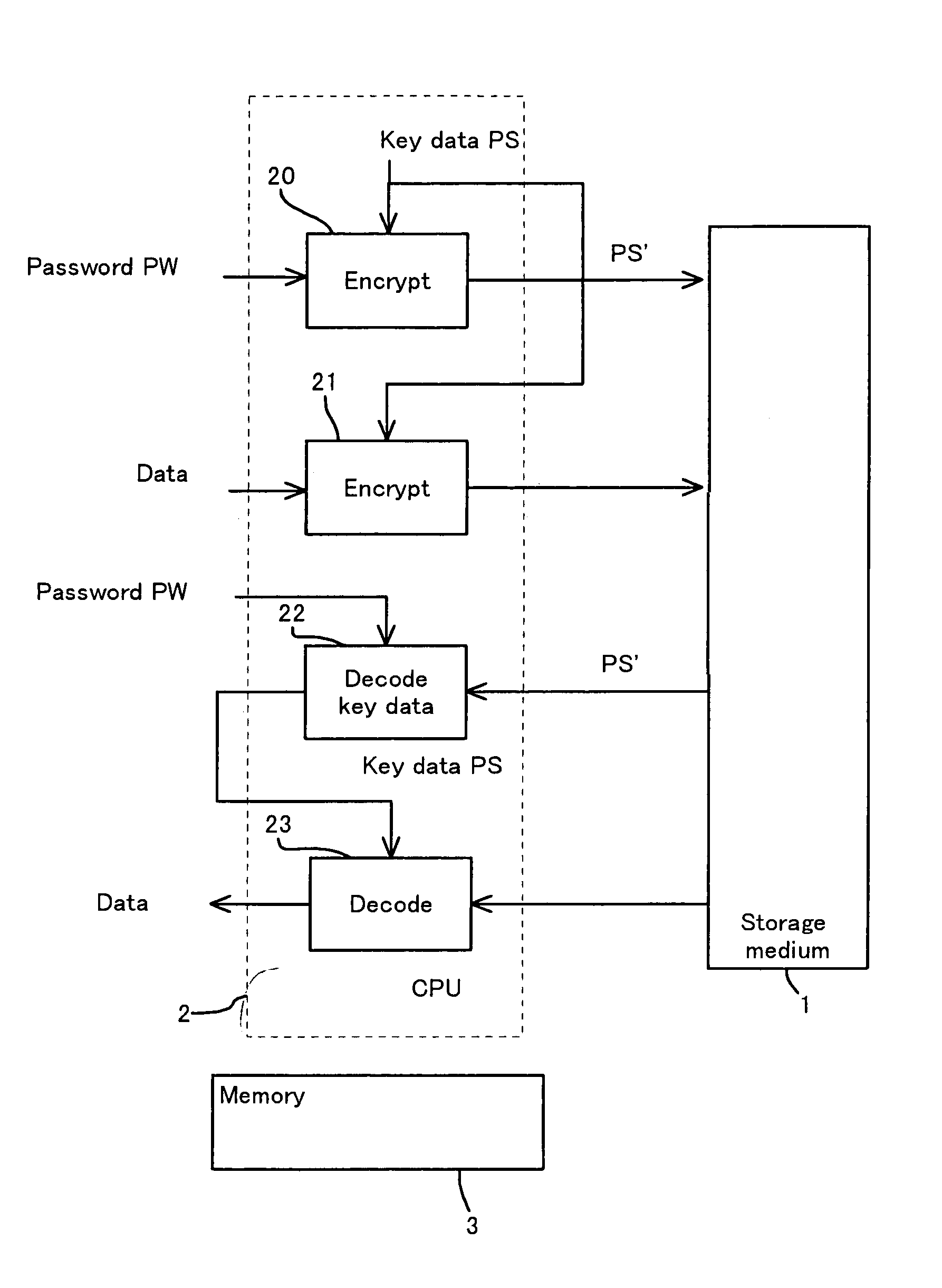
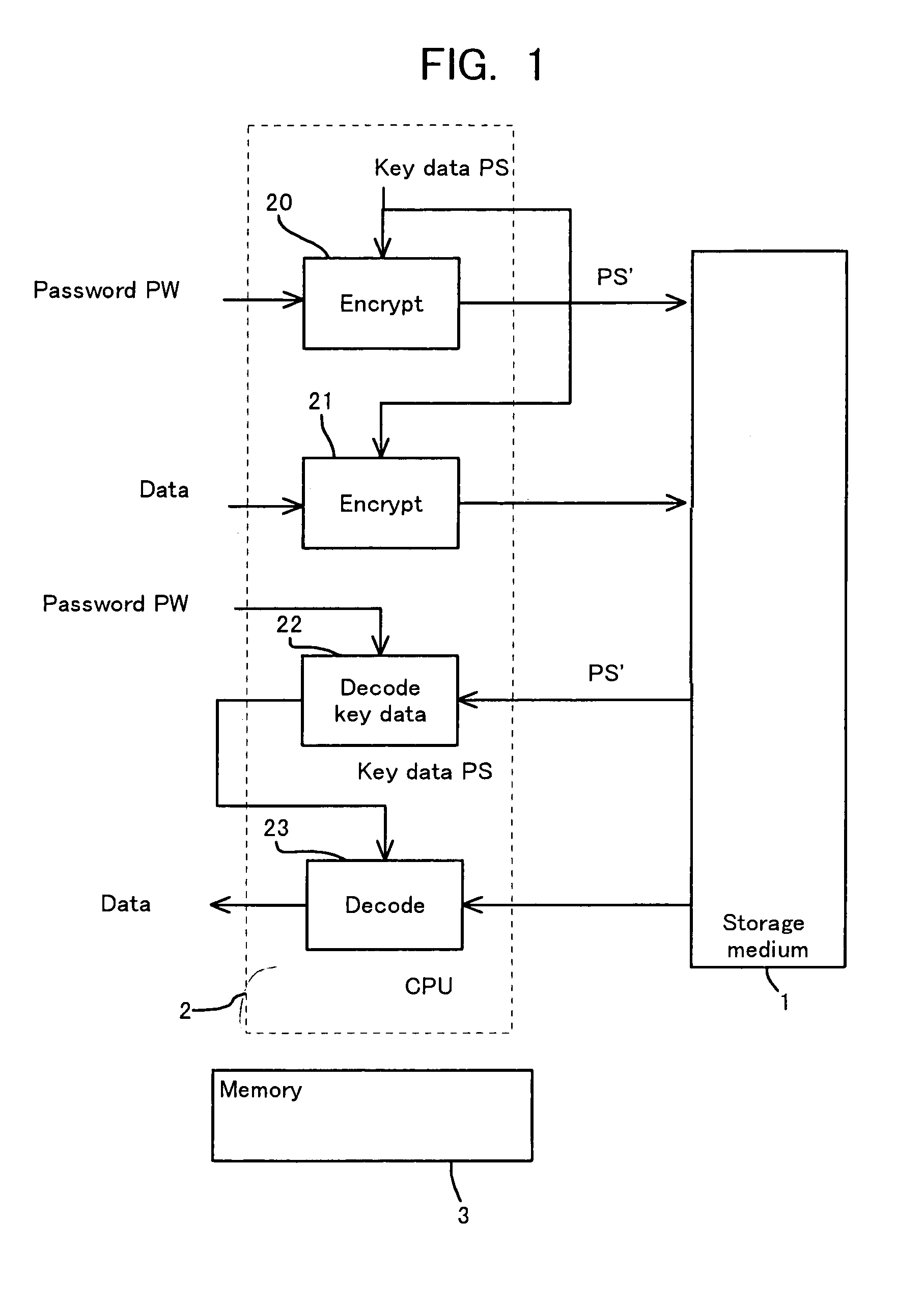
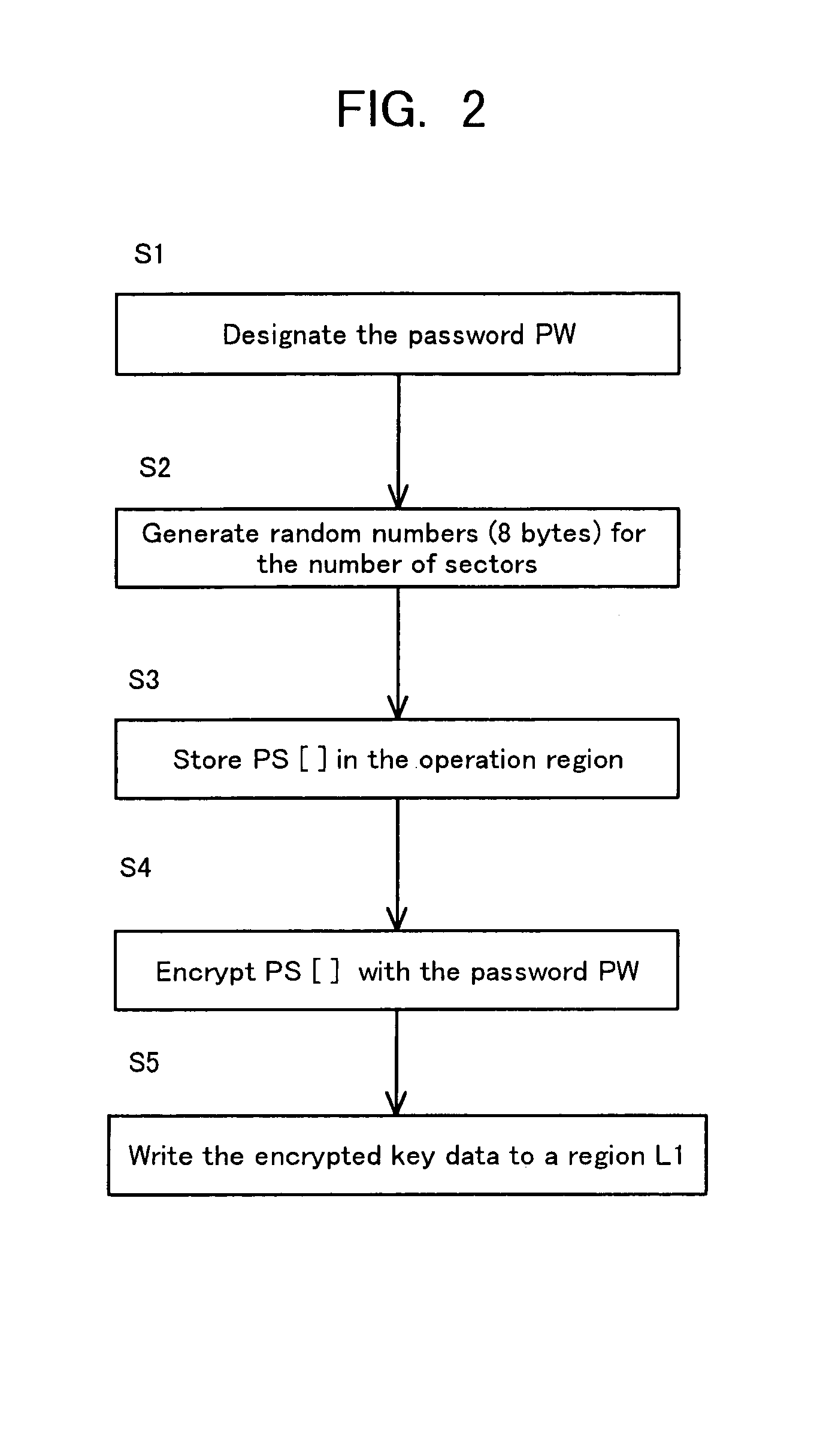
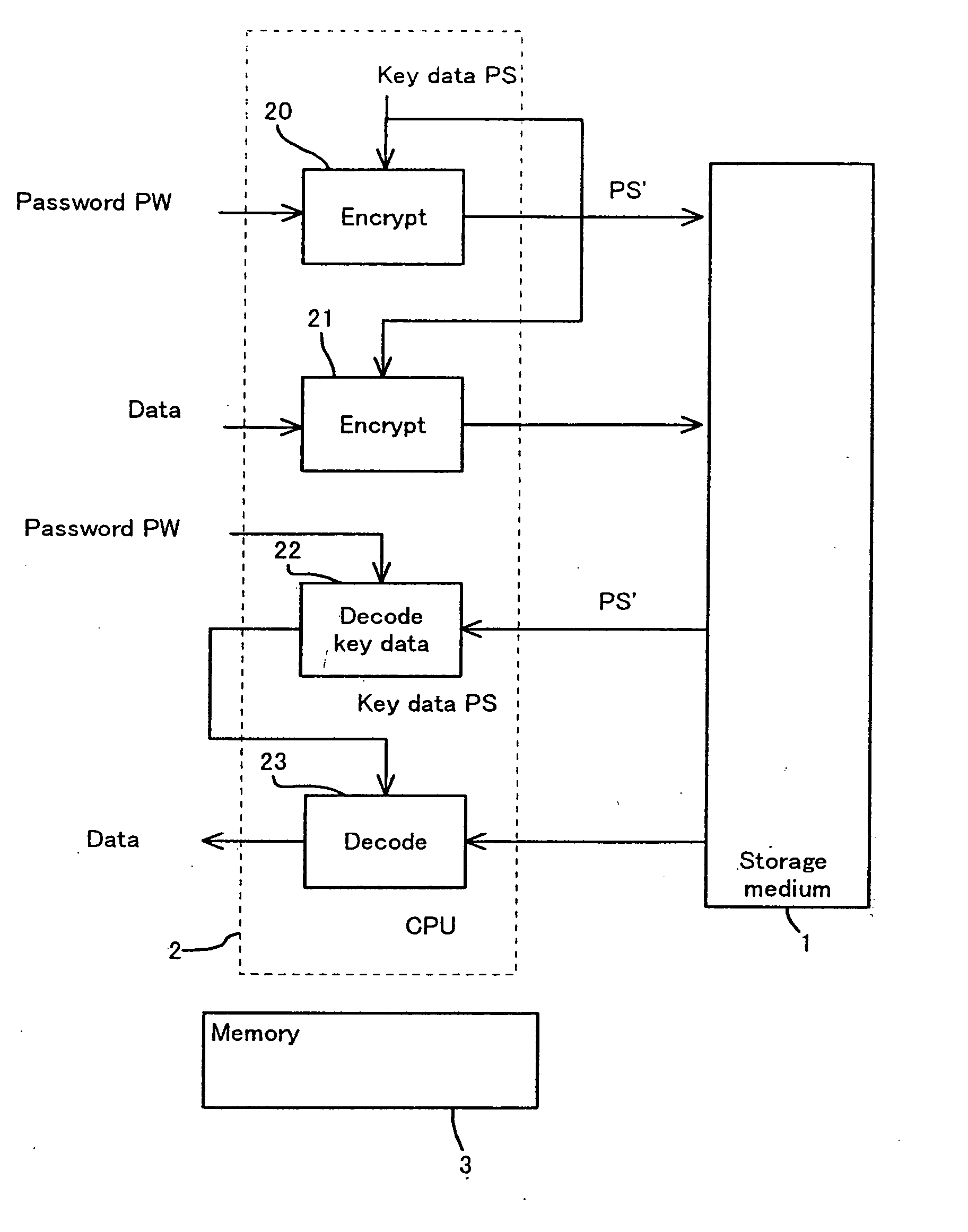
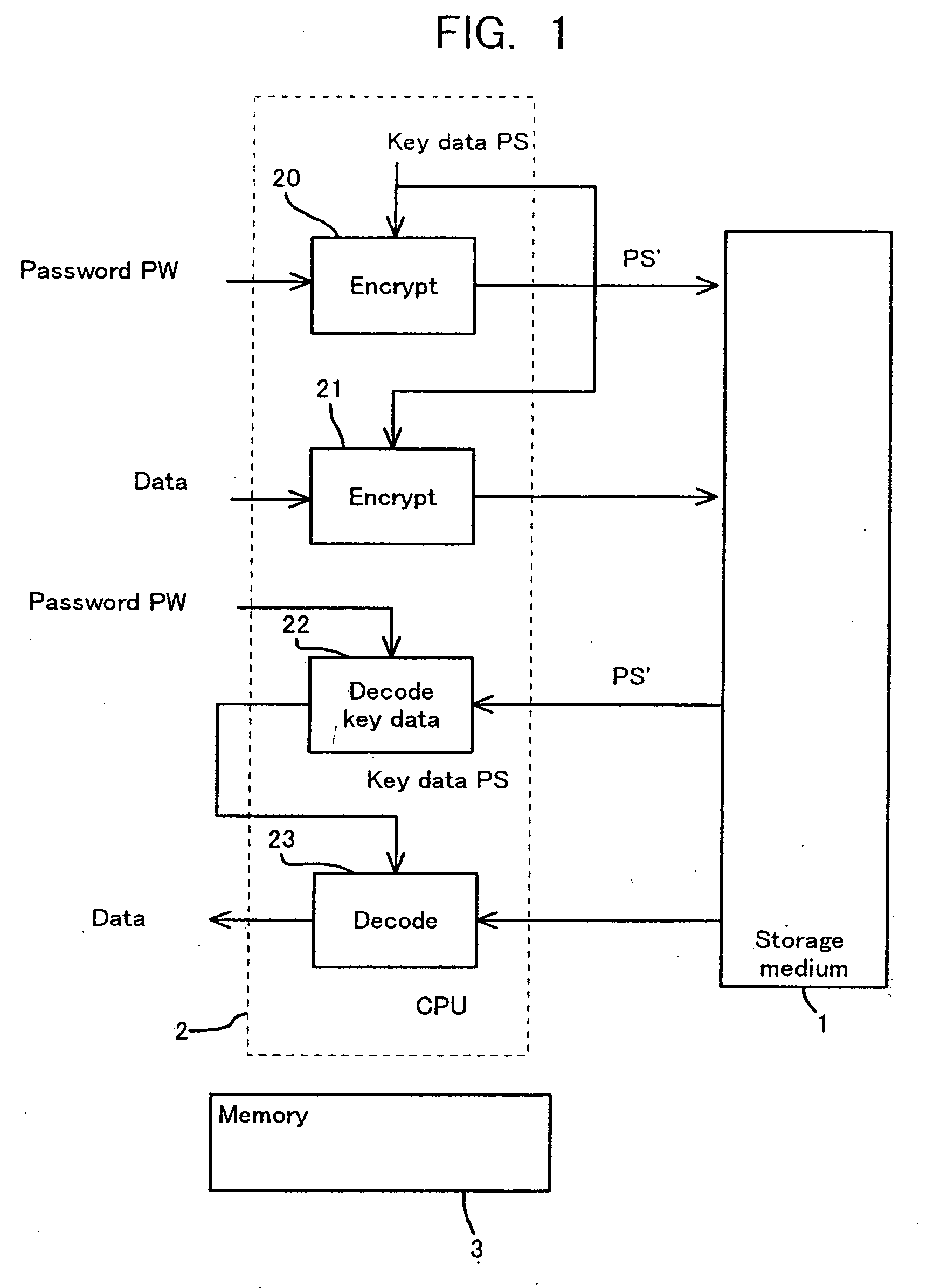
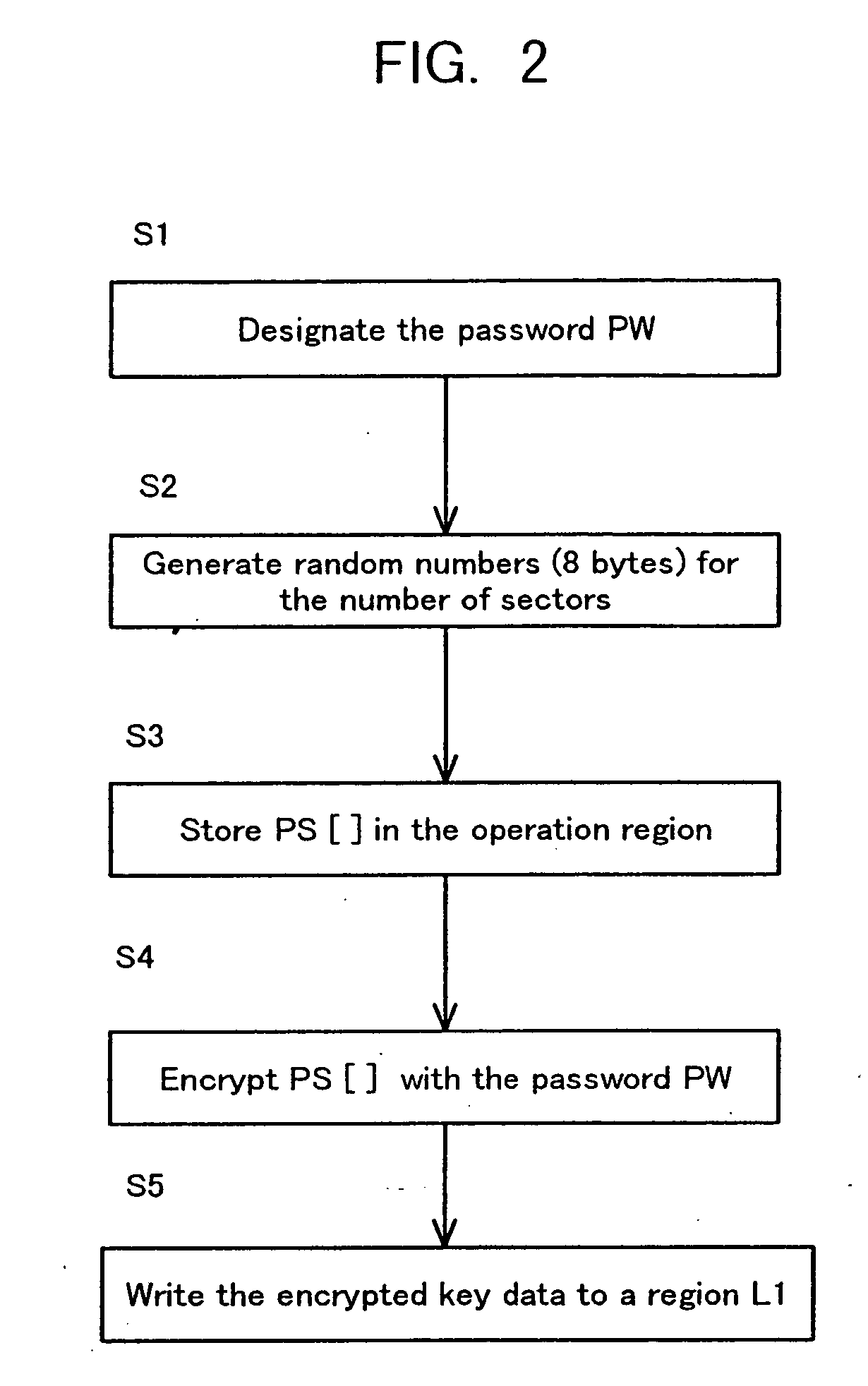
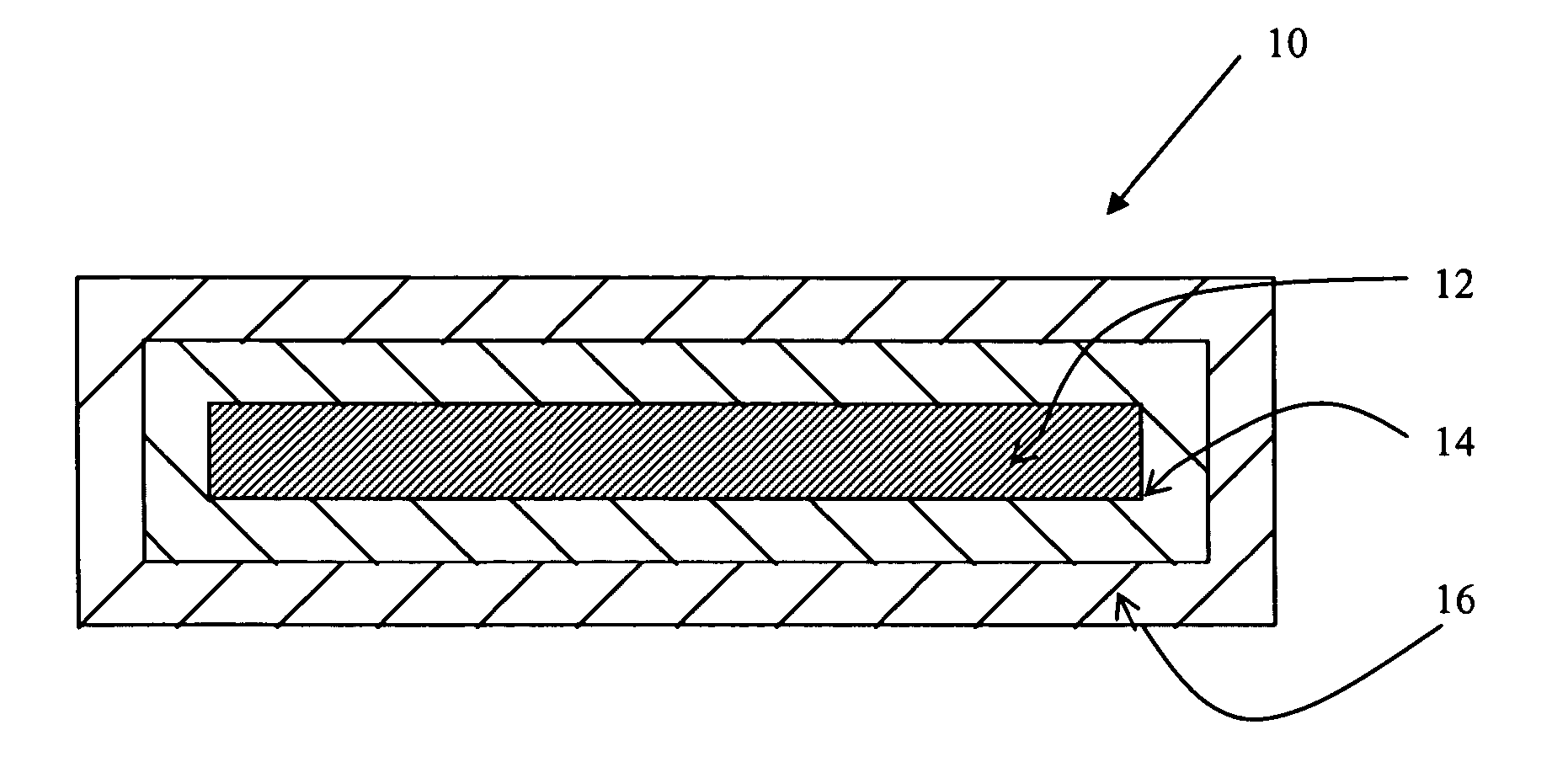
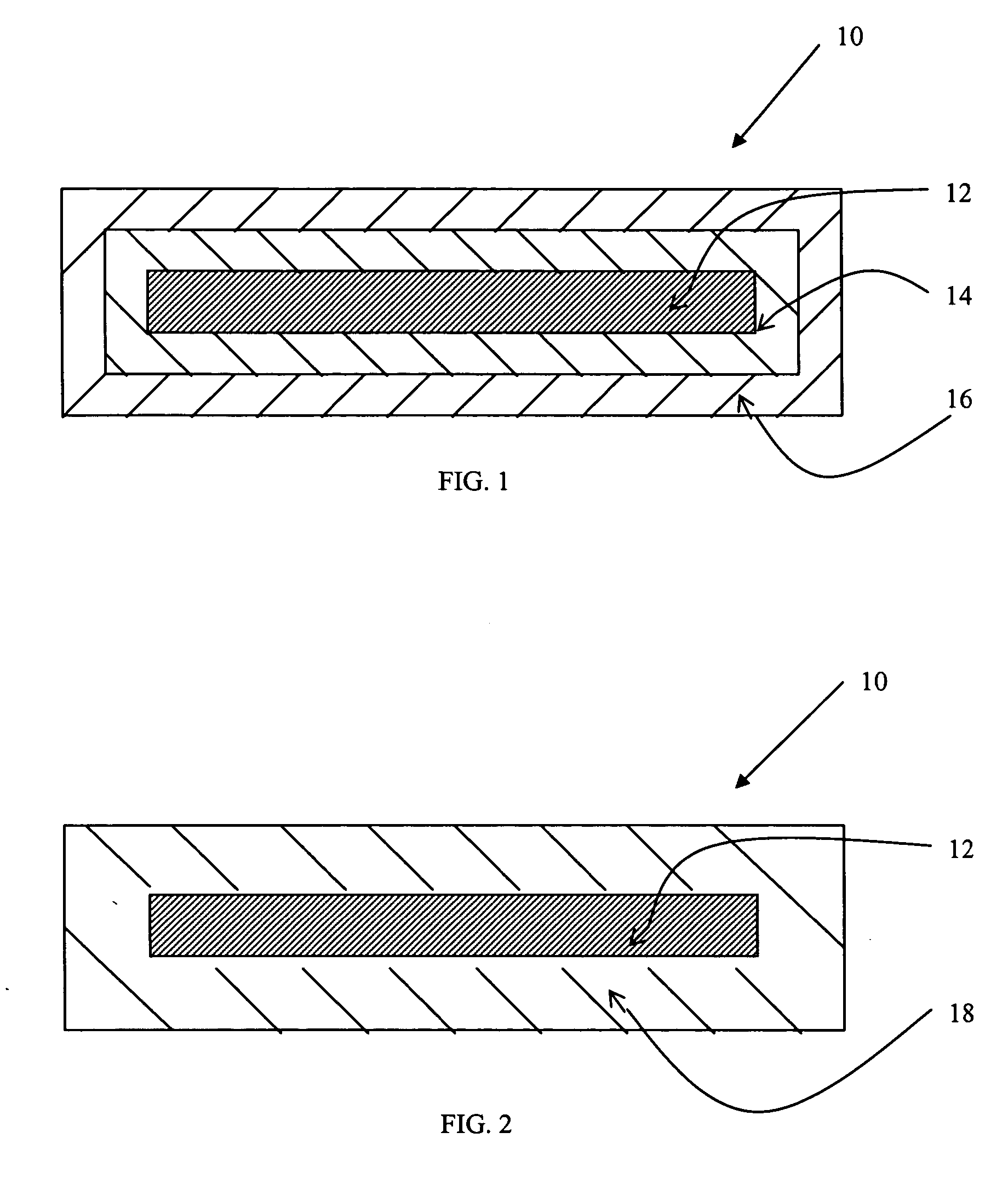
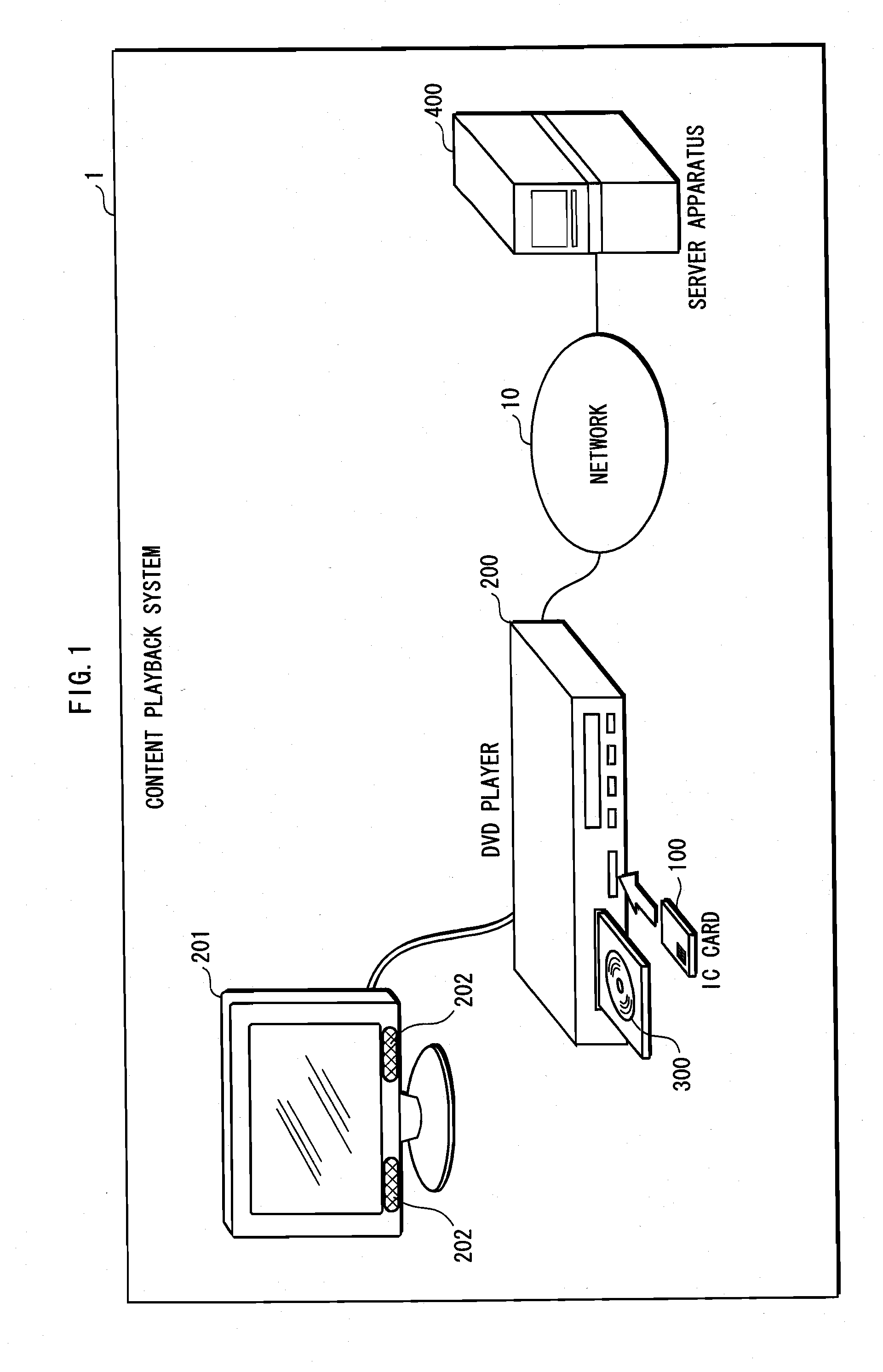
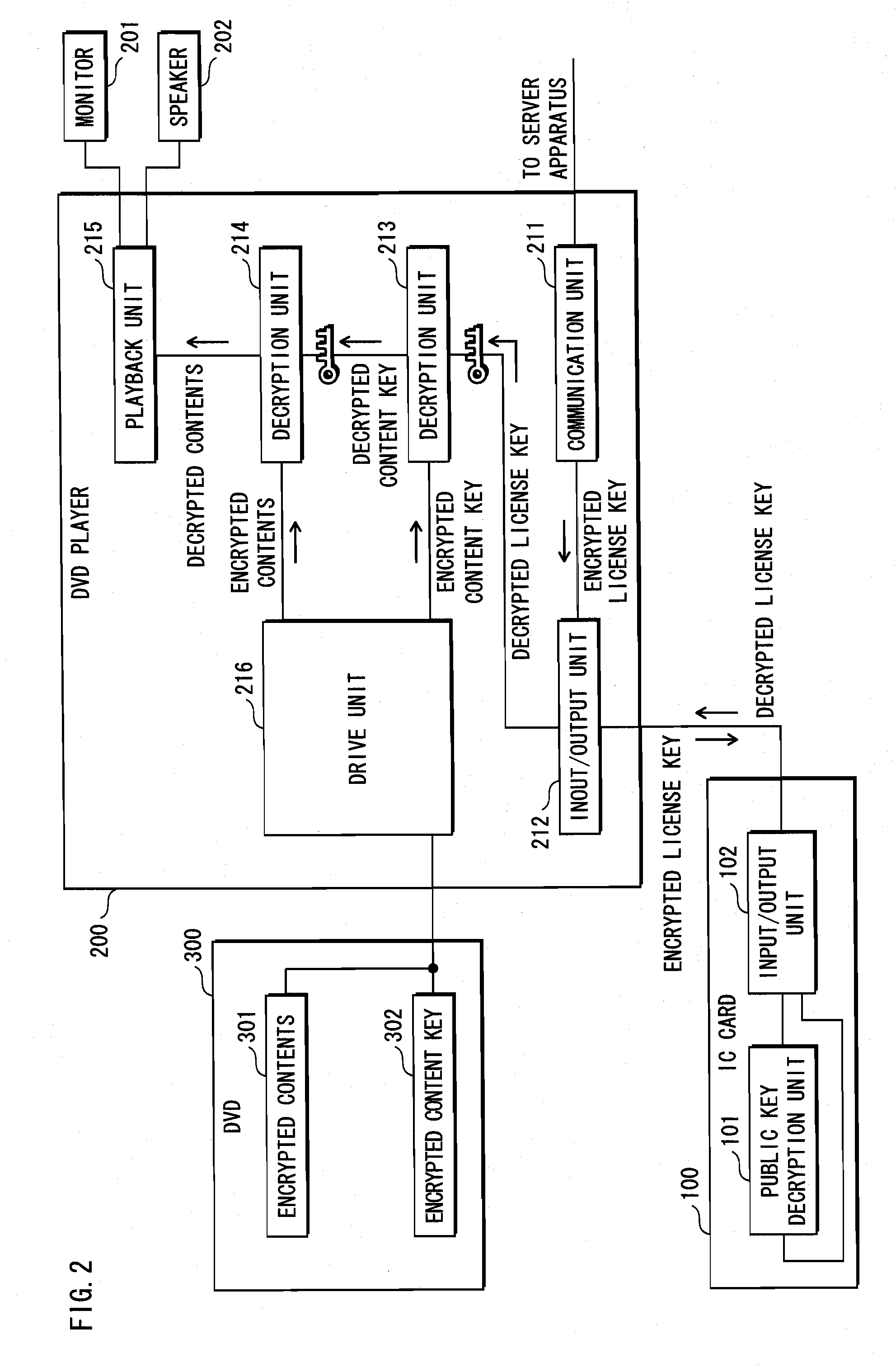
Storage medium and method and apparatus for separately protecting data in different areas of the storage medium
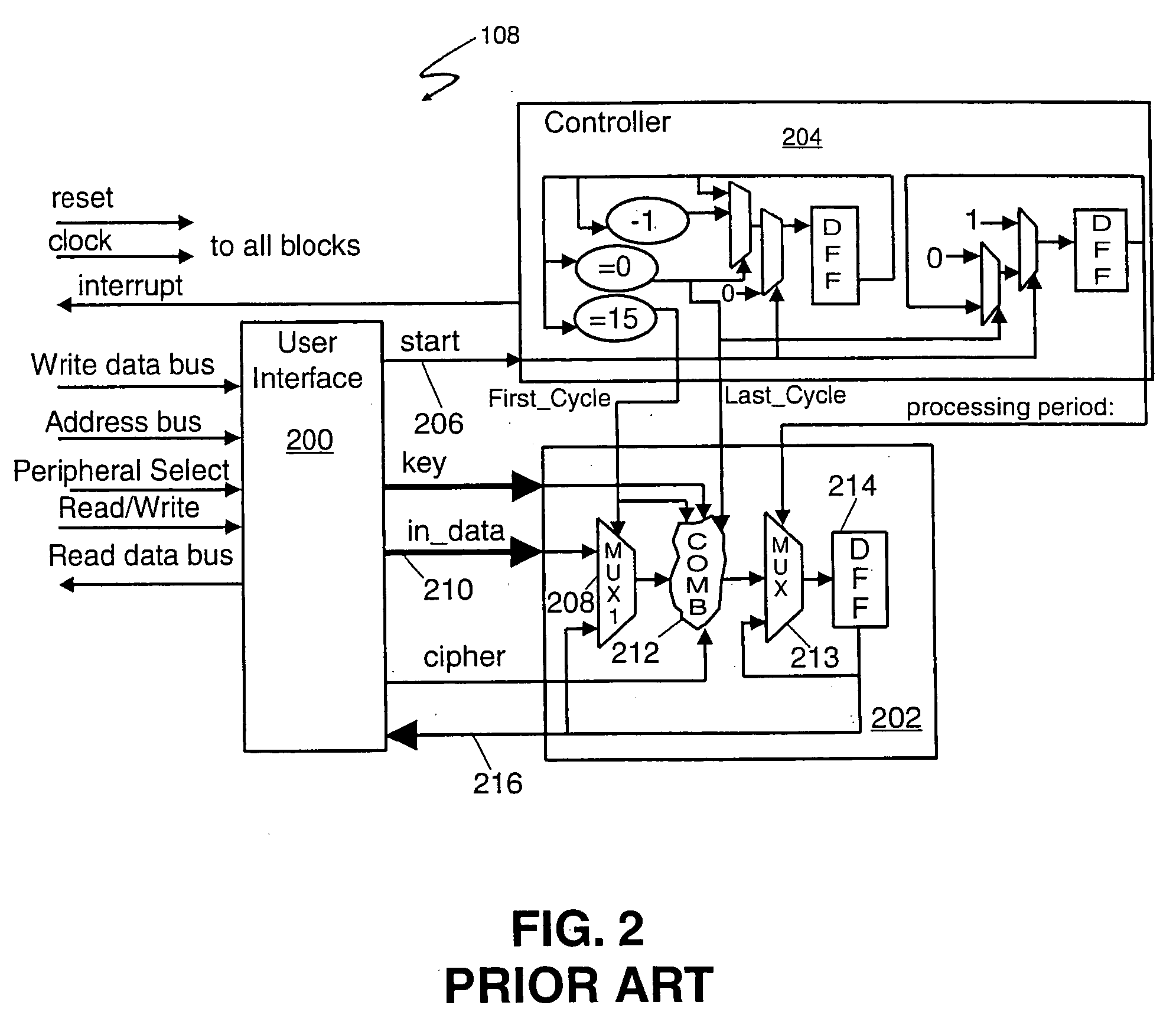
InactiveUS7051213B1Difficult to analyzePrevent decipheringInput/output to record carriersDigital data processing detailsCiphertextPassword
Disclosed are a method and an apparatus for protecting data on a storage medium by encrypting the data to be recorded on the storage medium with a password. This method comprises a step of, generating, for changing key data on each memory unit by one password, the key data, thereafter encrypting the key data with the password and writing the encrypted data to the storage medium, and a step of encrypting the data with the key data and encrypted data to the storage medium. The method further comprises a step of reading the encrypted key data from the storage medium, a step of decoding the encrypted key data with the password, and a step of decoding the data on the storage medium with the decoded key data. The encryption is done by using the key data generated separately from the password, and it is therefore feasible to prevent the password from being analyzed by decoding a cipher text.
Owner:FUJITSU CLIENT COMPUTING LTD
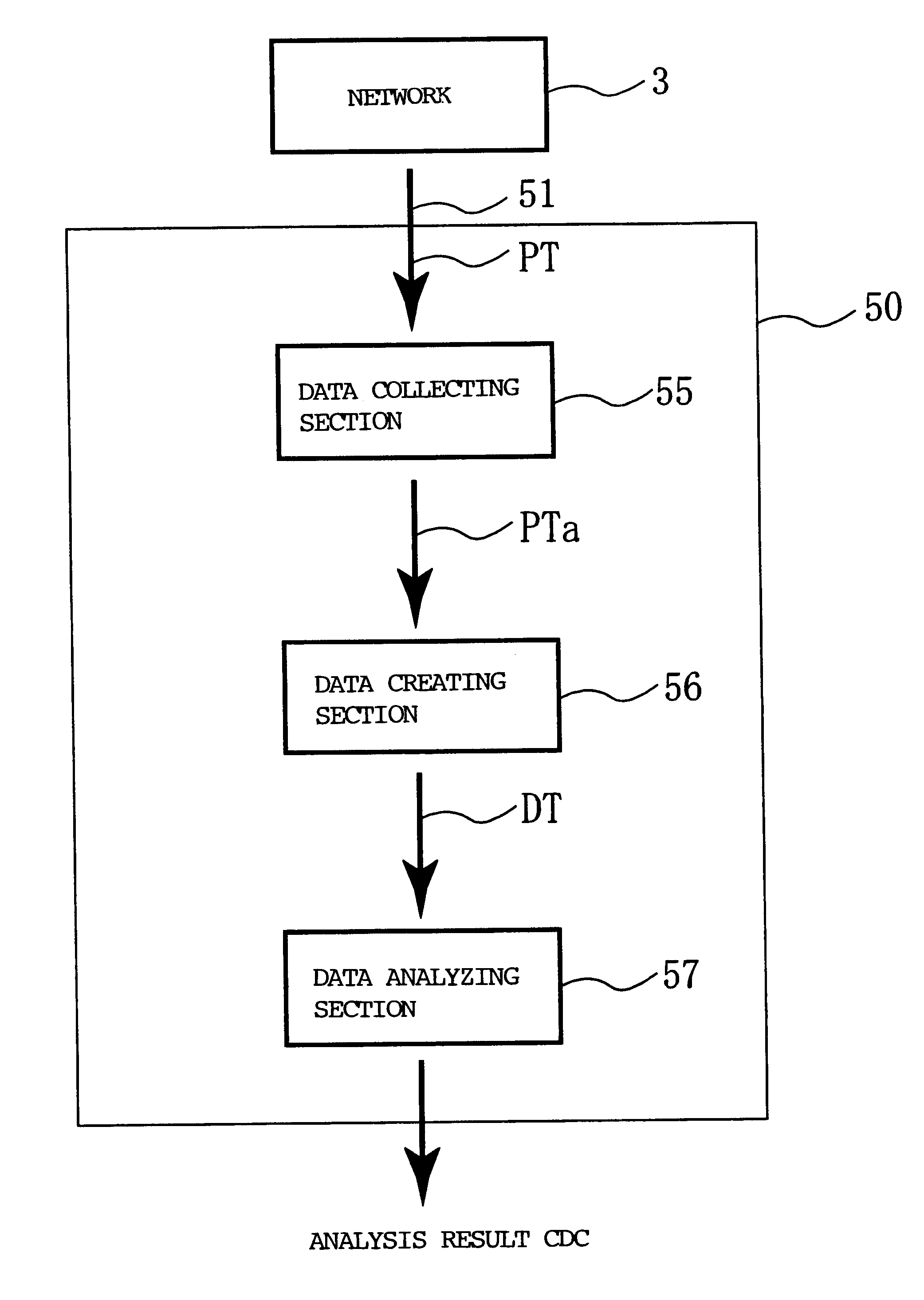
Network unauthorized access analysis method, network unauthorized access analysis apparatus utilizing the method, and computer-readable recording medium having network unauthorized access analysis program recorded thereon
InactiveUS6263444B1Perform communicationEasy to deal withMemory loss protectionError detection/correctionComputer networkAnalysis data
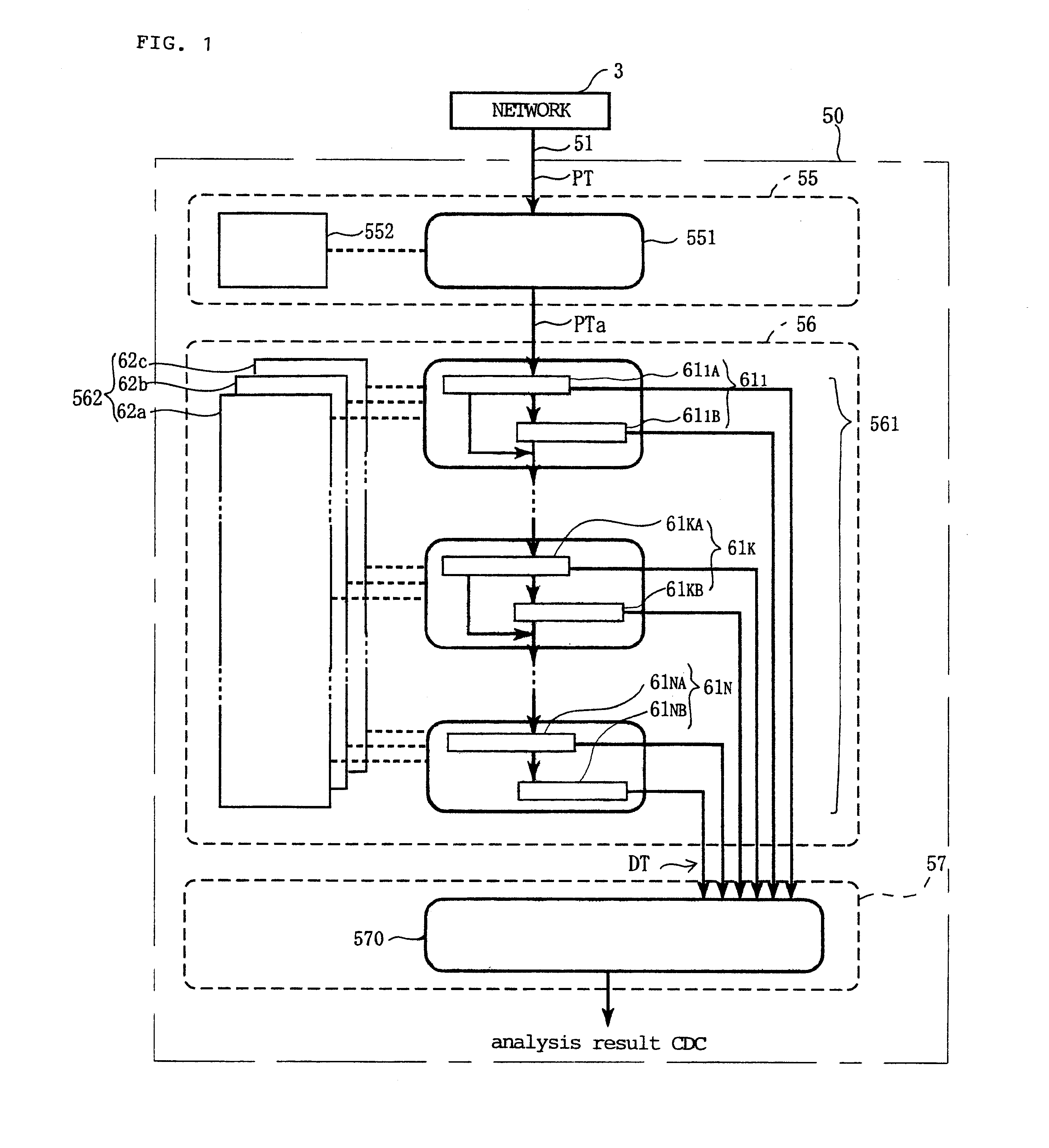
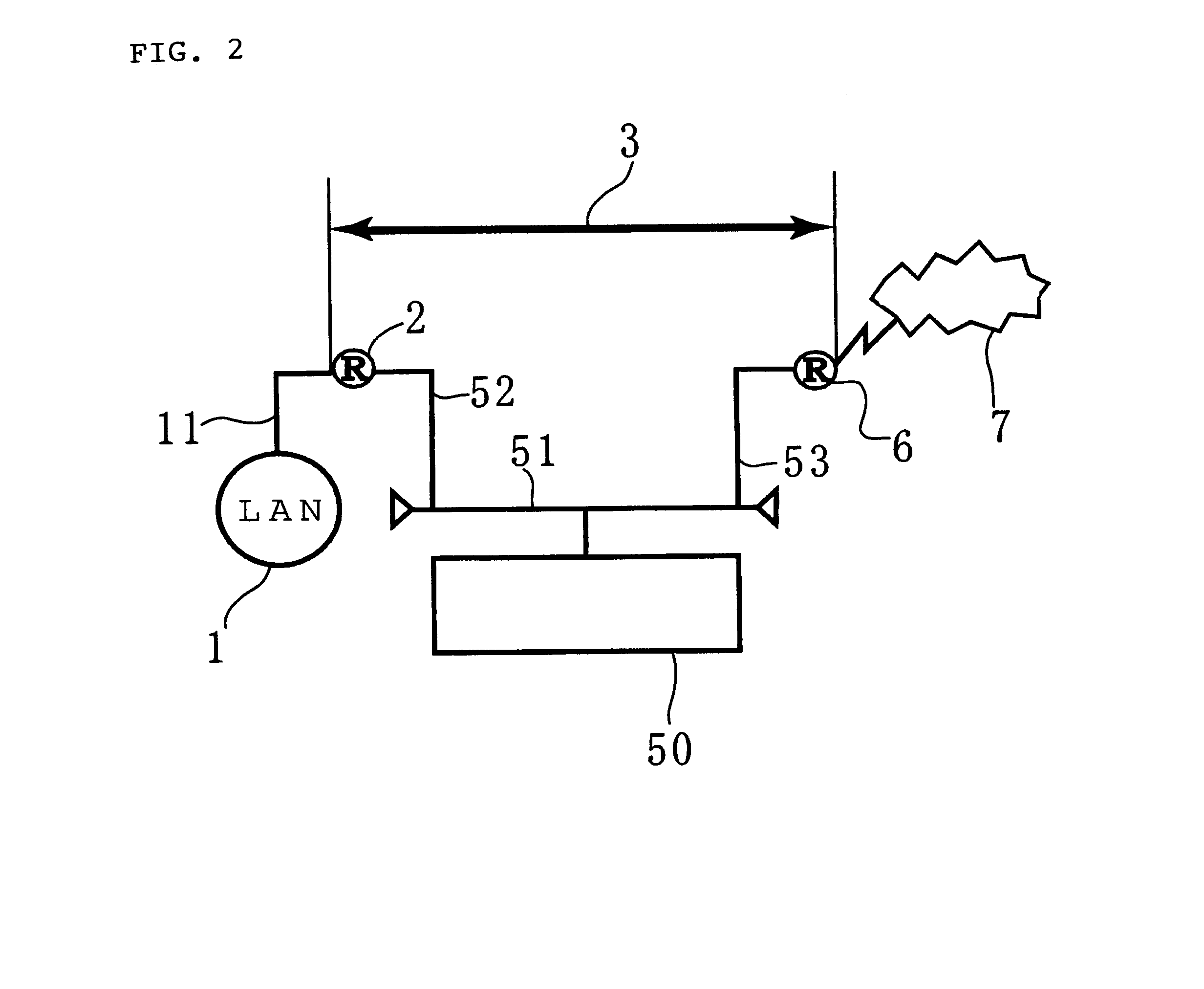
The present invention relates to a network unauthorized access analysis method, a network unauthorized access analysis apparatus utilizing this method and a computer-readable recording medium having a network unauthorized access analysis program recorded thereon, and is capable of processing arbitrary data, performing arbitrary communication between networks, easily dealing with an increase in a number of protocols and coping with arbitrary protocols. A network unauthorized access analysis system 50 for realizing these features analyzes an unauthorized access on a network performing communication between information communication stations by using a layered protocol and includes: a data collecting section 55 for capturing a packet PT transmitted on a network 3; a data creating section 56 for creating analysis data DT by setting parameters of layered modules according to a layered protocol based on information of a previously-read configuration file and processing the packet from the data collecting section by the layered modules; and a data analyzing section 57 for judging whether an unauthorized access is generated in the analysis data DT based on the content described in that file.
Owner:JAPAN AEROSPACE EXPLORATION AGENCY +1
Method and system for implementing machine learning classifications
ActiveUS20160292592A1Difficult to analyzeTask be particularly problematicError detection/correctionText processingData miningAnalysis method
Disclosed is a system, method, and computer program product for implementing a log analytics method and system that can configure, collect, and analyze log records in an efficient manner. Machine learning-based classification can be performed to classify logs. This approach is used to group logs automatically using a machine learning infrastructure.
Owner:ORACLE INT CORP
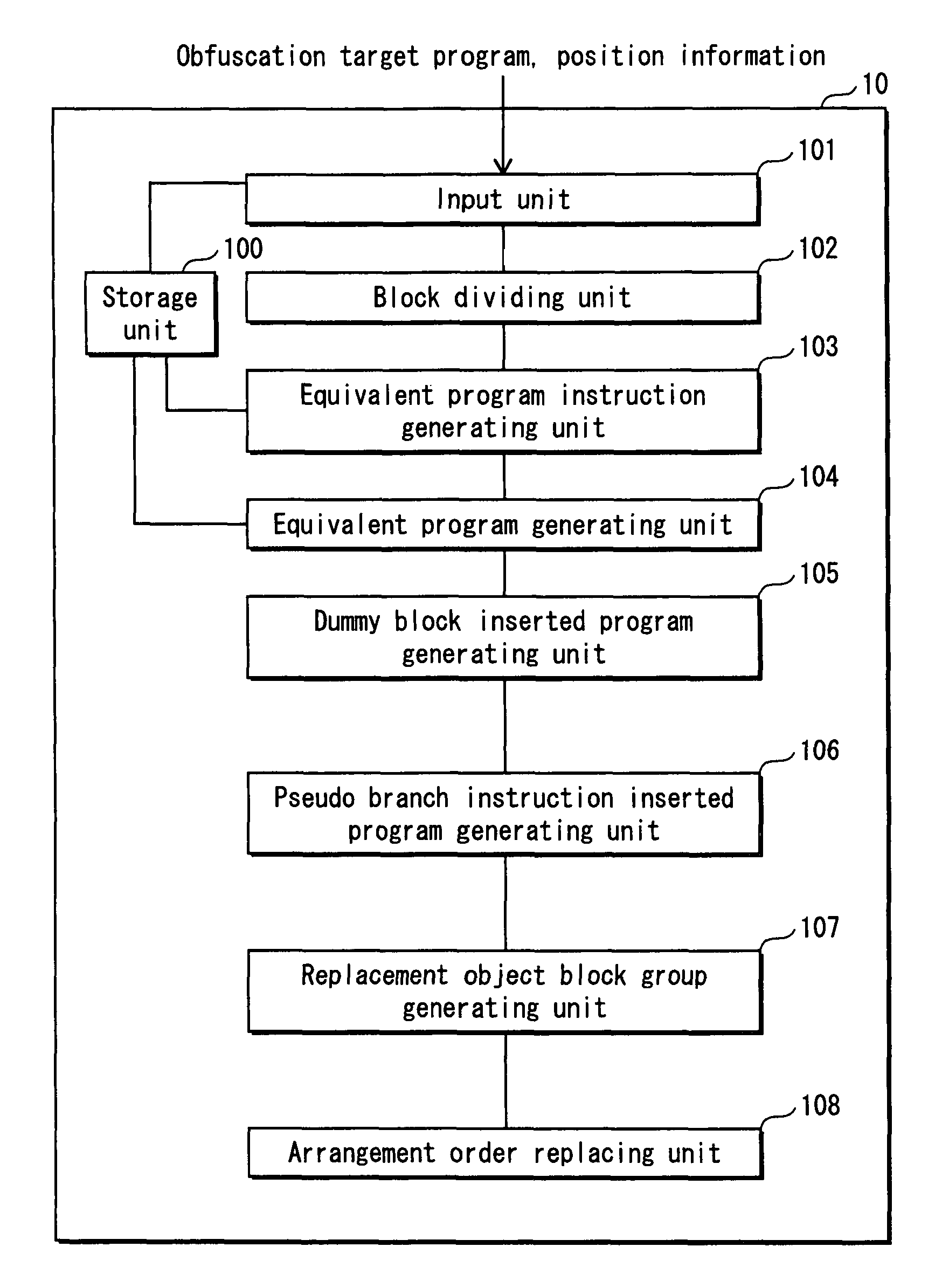
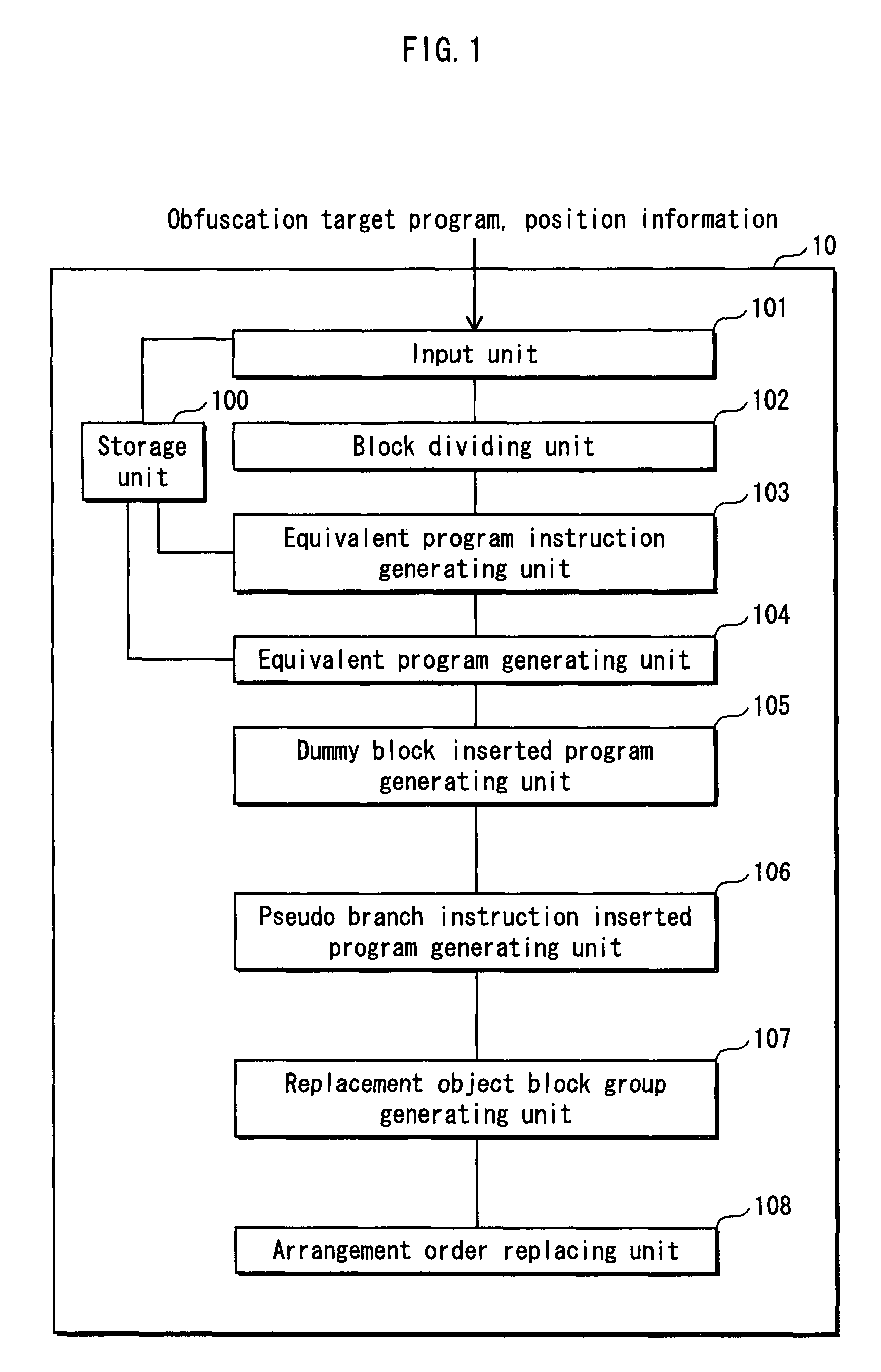
Program illegiblizing device and method
ActiveUS20090083521A1Obtain confidential informationDifficult to analyzeDigital computer detailsProgram/content distribution protectionProcessing InstructionProgram instruction
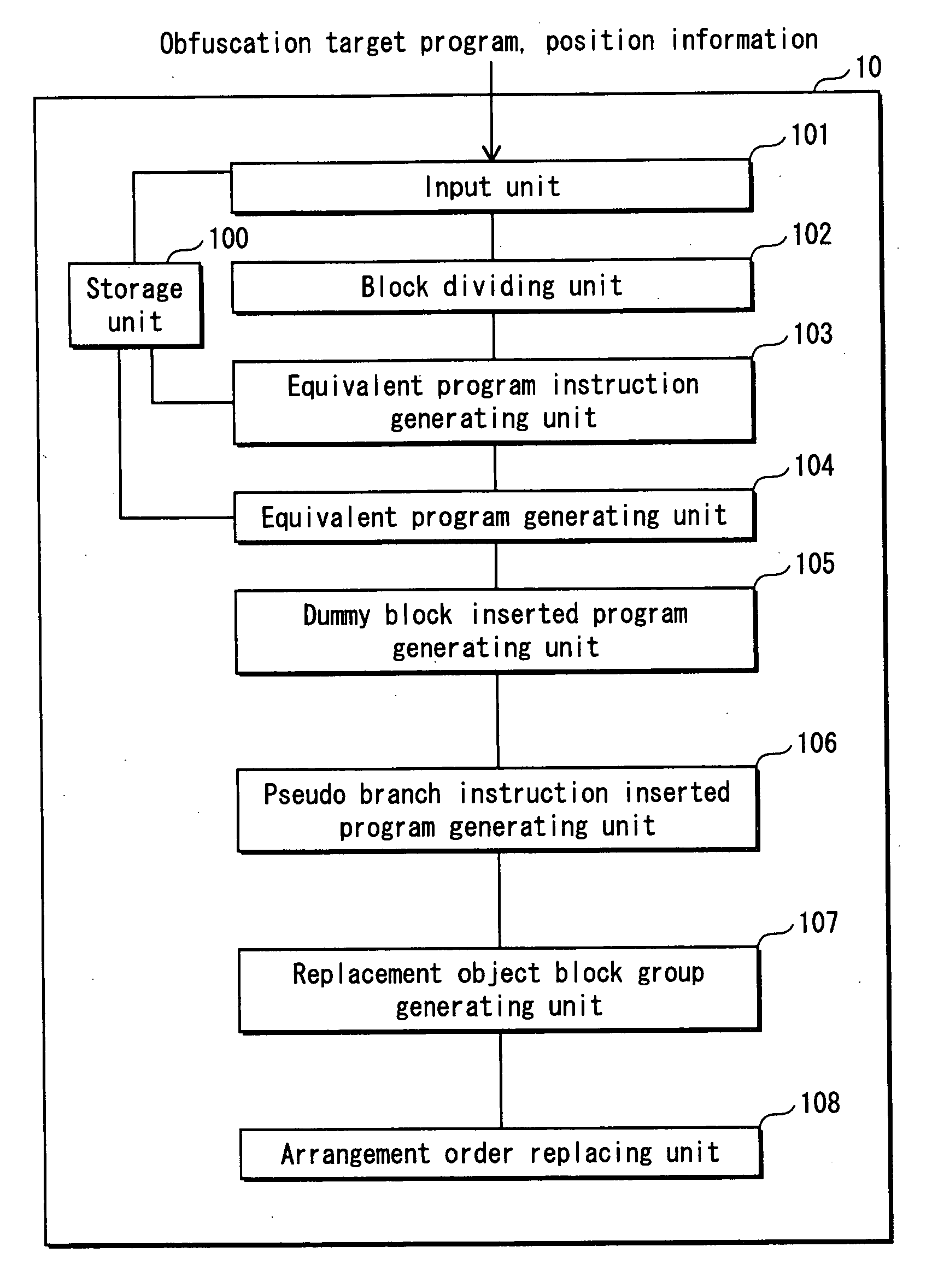
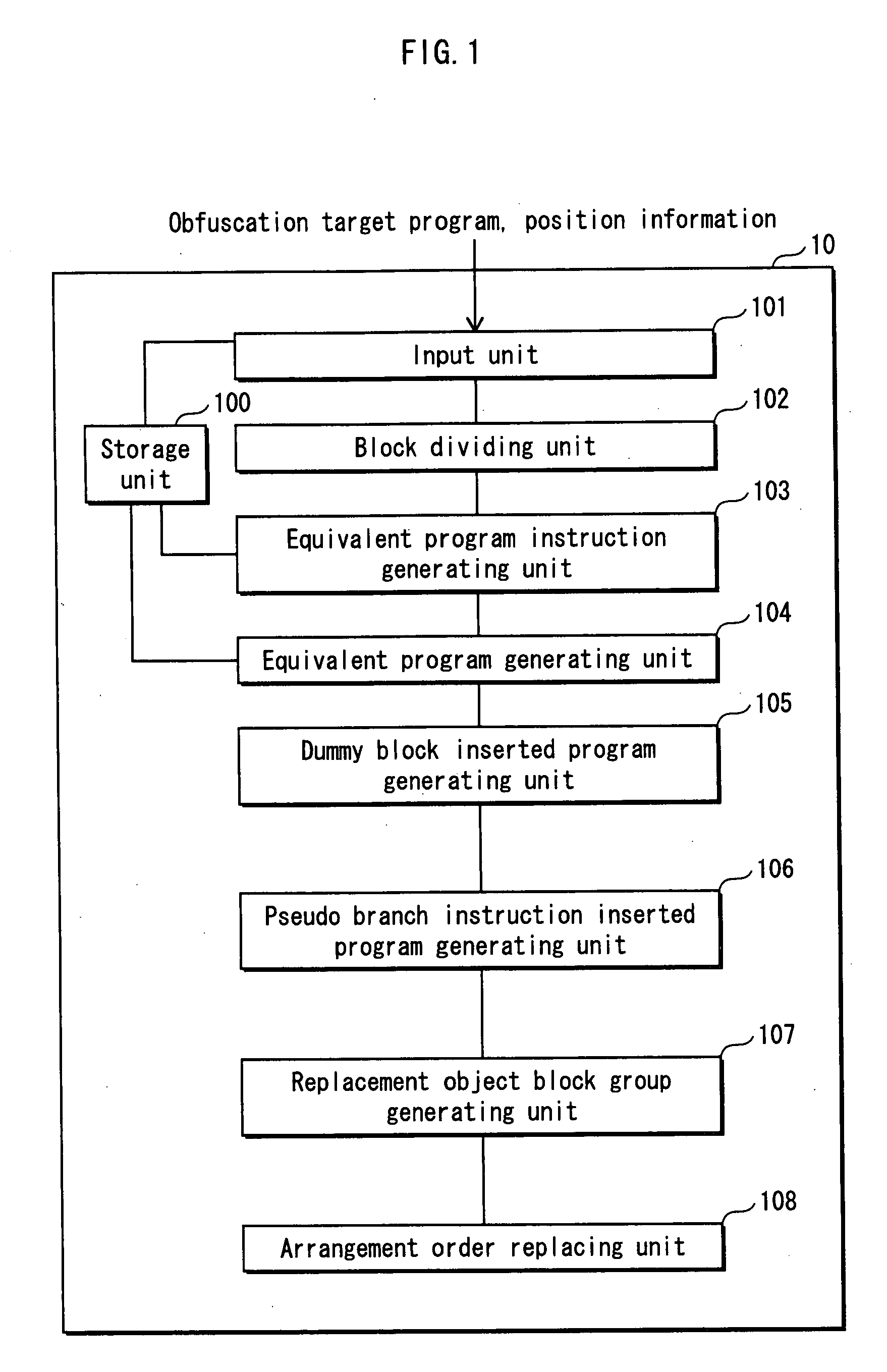
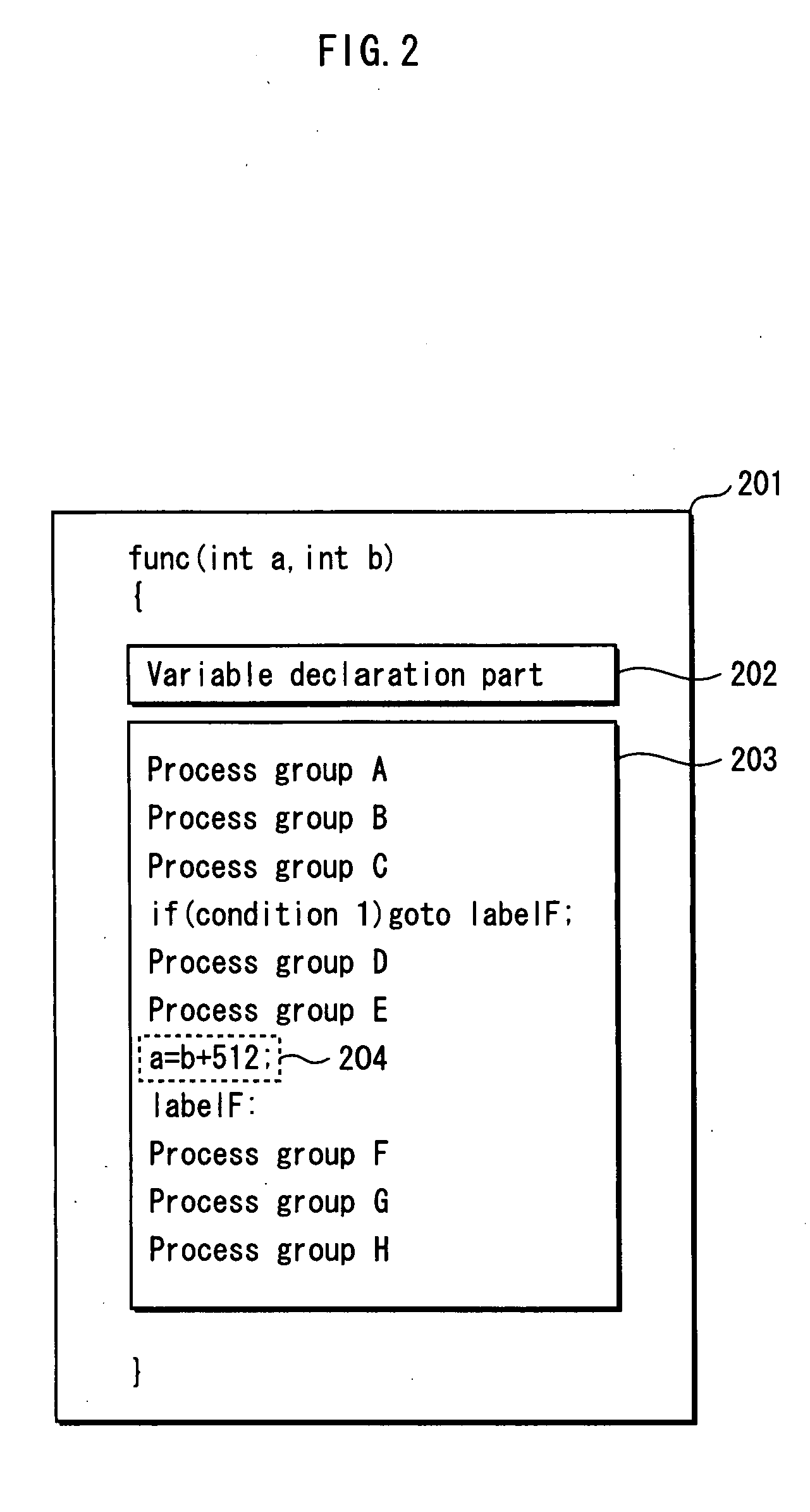
A program obfuscating device for generating obfuscated program from which unauthorized analyzer cannot obtain confidential information easily. The program obfuscating device stores original program that contains authorized program instructions and confidential process instruction group containing confidential information that needs to be kept confidential, generates process instructions which, when executed in predetermined order, provide same result, with execution of last process instruction thereof, as the confidential process instruction group, inserts the process instructions into the original program at position between start of the original program and the confidential process instruction group so as to be executed in the predetermined order, in place of the confidential process instruction group, generates dummy block as dummy of the process instructions, and inserts the dummy block and control instruction, which causes the dummy block to be bypassed, into the original program, and inserts branch instruction into the dummy block.
Owner:PANASONIC CORP
Encryption Processing Apparatus, Encryption Processing Method, and Computer Program
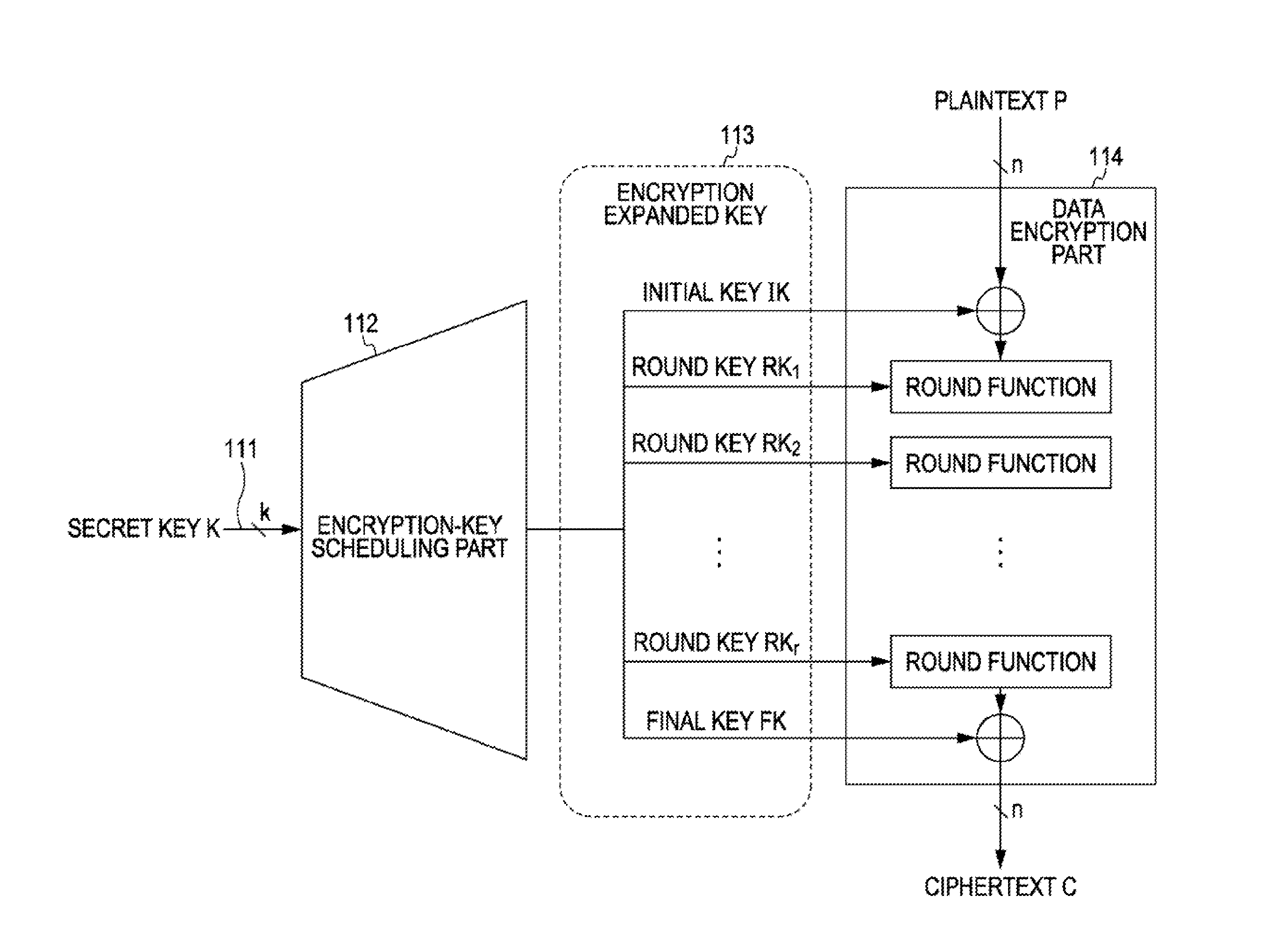
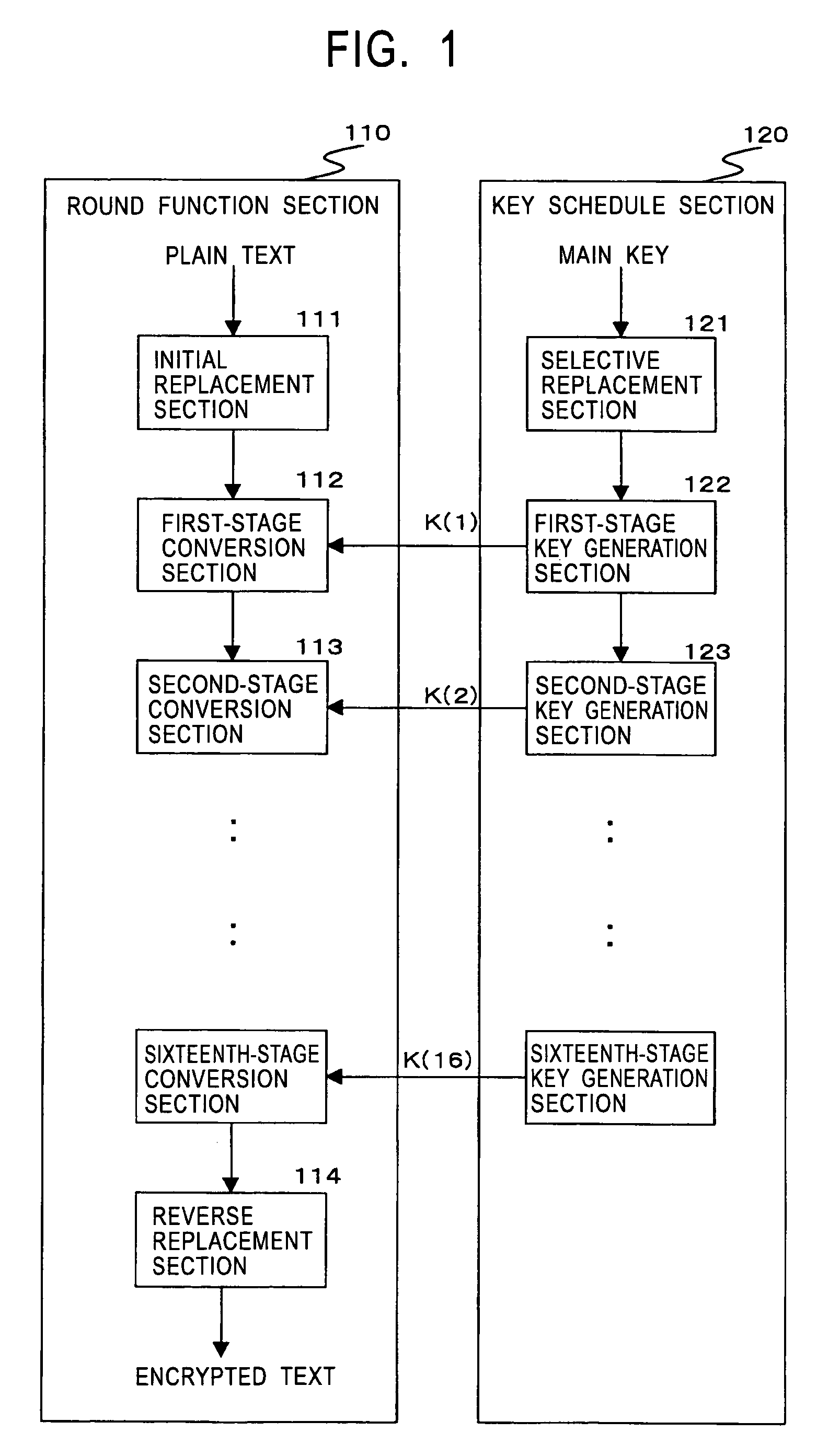
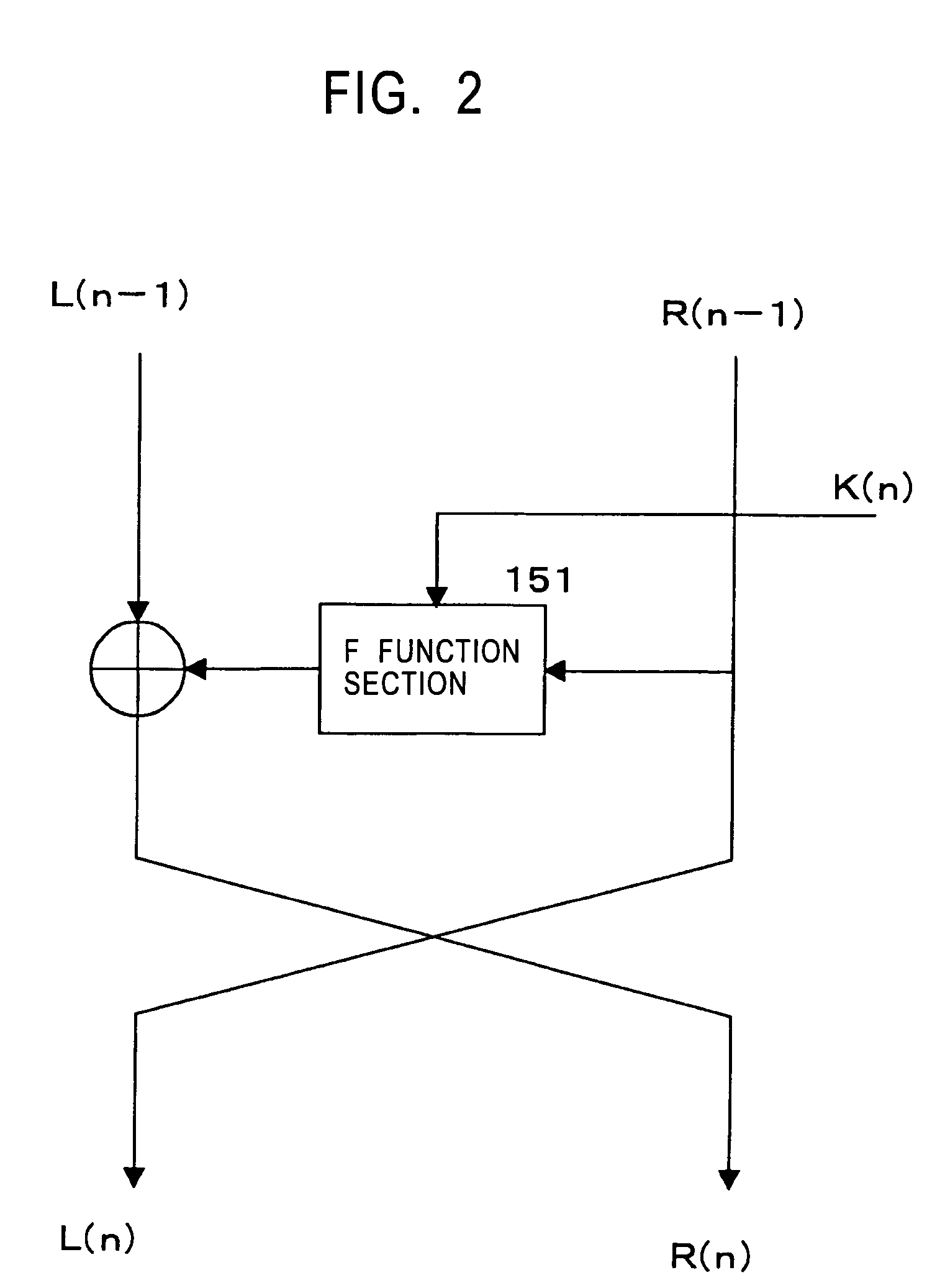
InactiveUS20080056490A1Great difficulty of key analysisGreat difficulty of cryptanalysisSecret communicationCryptographic attack countermeasuresRound functionData transformation
An encryption processing apparatus for performing common-key blockcipher processing, the encryption processing apparatus includes an encryption processing part that performs data transformation in which a round function is iterated for a plurality of rounds; and a key scheduling part that generates round keys used to execute the round function. The key scheduling part is configured to repeatedly apply an xs times multiplication over an extension field GF( 2m), generated by an m-th order irreducible polynomial f(x) defined over GF(2), to an m-bit intermediate key generated by transformation of a secret key to generate a plurality of different round intermediate keys serving as data for generating a plurality of different round keys.
Owner:SONY CORP
Storage medium and method and apparatus for separately protecting data in different areas of the storage medium
InactiveUS20050251866A1Difficult to analyzeImprove data confidentialityInput/output to record carriersDigital data processing detailsCiphertextPassword
Disclosed are a method and an apparatus for protecting data on a storage medium by encrypting the data to be recorded on the storage medium with a password. This method comprises a step of, generating, for changing key data on each memory unit by one password, the key data, thereafter encrypting the key data with the password and writing the encrypted data to the storage medium, and a step of encrypting the data with the key data and encrypted data to the storage medium. The method further comprises a step of reading the encrypted key data from the storage medium, a step of decoding the encrypted key data with the password, and a step of decoding the data on the storage medium with the decoded key data. The encryption is done by using the key data generated separately from the password, and it is therefore feasible to prevent the password from being analyzed by decoding a cipher text.
Owner:FUJITSU LTD
Apparatus and method for automatic inspection of through-holes of a component
ActiveUS20130163849A1Avoid irregularitiesShorten test timeImage enhancementImage analysisInfra red radiationDigital image
An apparatus and a method for automatic inspection of through-holes of a component is provided. The proposed apparatus includes an imaging module, an image processing module and an analysis module. The imaging module generates a thermographic image of the component by passing a medium through the through-holes and capturing infra-red radiation emitted from the component while the medium is flowing through the through-holes. The image processing module fits the thermographic image on a digital image obtained from geometrical data of the component. The image processing module is further masks the fitted thermographic image using a digital image mask to extract regions corresponding to through-holes in the thermographic image. The digital image mask is computed based on a determination of positions of through-holes on the digital image. The analysis module evaluates the masked thermographic image to determine an irregularity or blockage in one or more of the through-holes.
Owner:SIEMENS ENERGY GLOBAL GMBH & CO KG
Substrate with alloy finish and method of making
InactiveUS20060286400A1Difficult to analyzeDifficult to controlNatural mineral layered productsThin material handlingCyanide compoundElectroplating
Substrates having an alloy finish and methods of producing the same. The finished product according to one embodiment of the present invention is a substrate having an alloy finish comprising two or more metals, and is made by the method of the present invention. Generally, the method of the present invention comprises provision of a substrate, electroplating two or more metals onto the substrate, and then baking the plated substrate to result an alloy of the plated metals through diffusion. Substrates made according to the present invention can be covered with a variety of types of alloy finishes, and a variety of characteristics of such finishes can be achieved. The method of the present invention uses steps of electroplating and heating that are well-known in the art, and does not require the use of toxic, cyanide-based plating baths.
Owner:JARDEN ZINC PRODS LLC
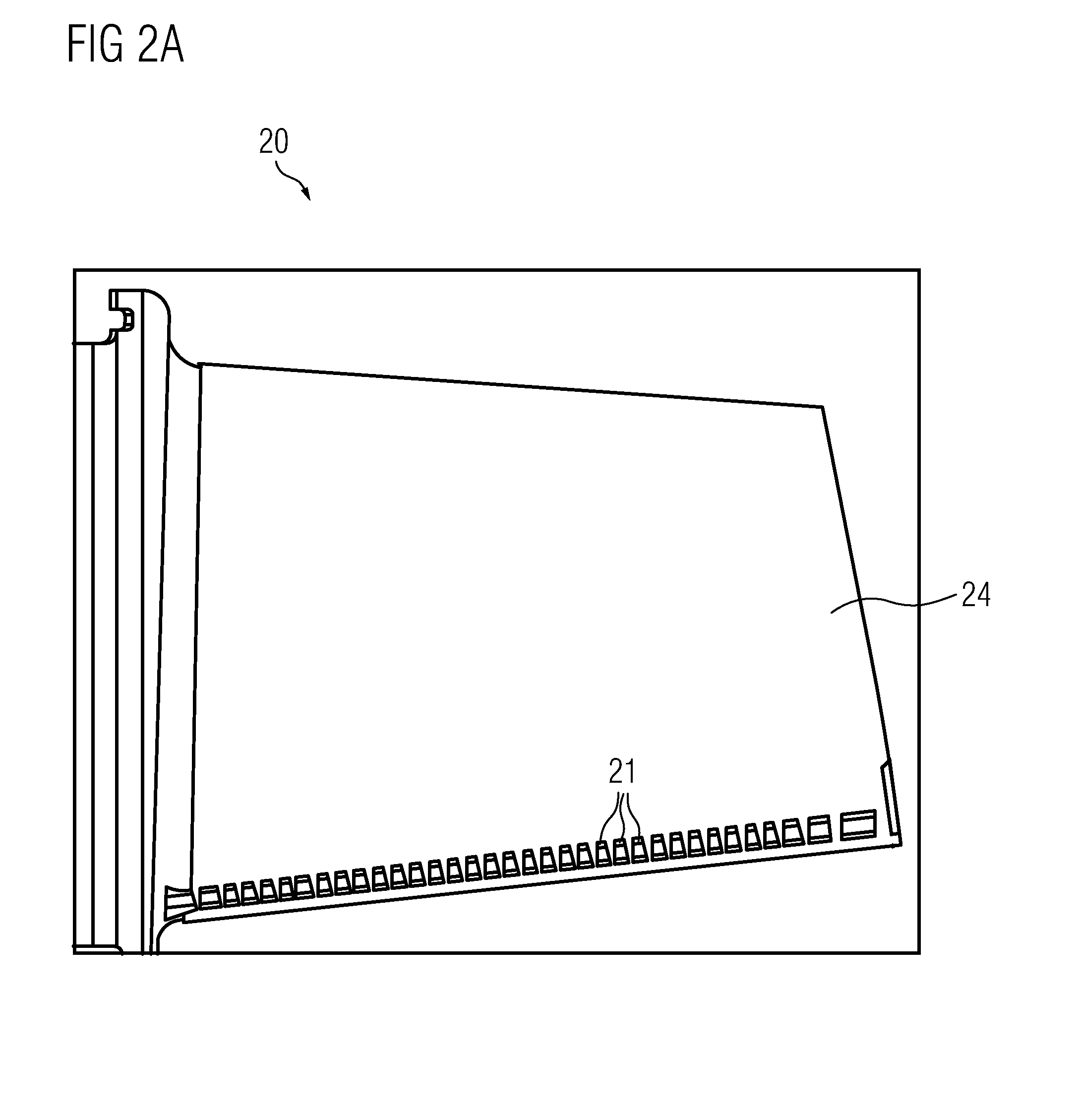
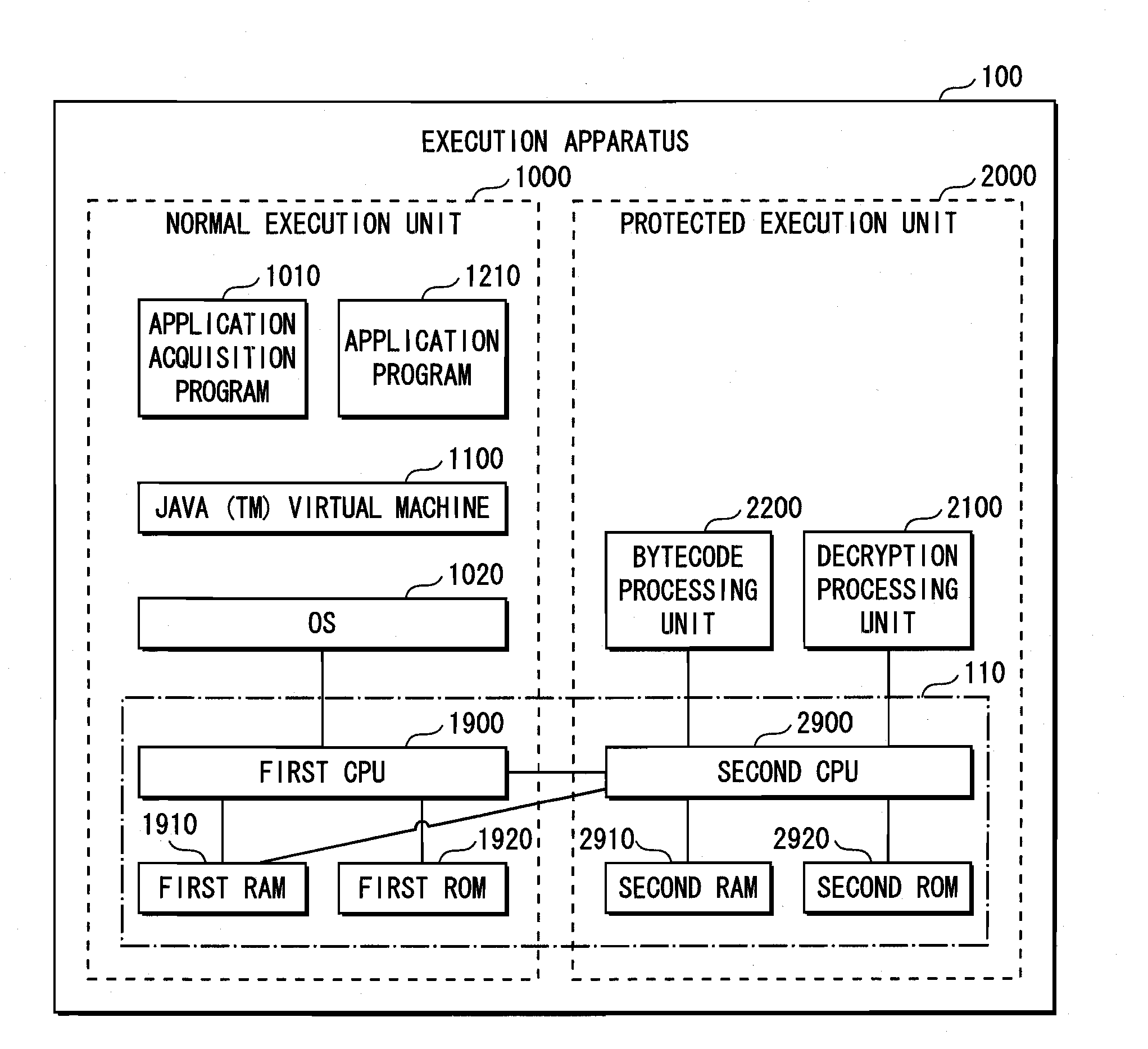
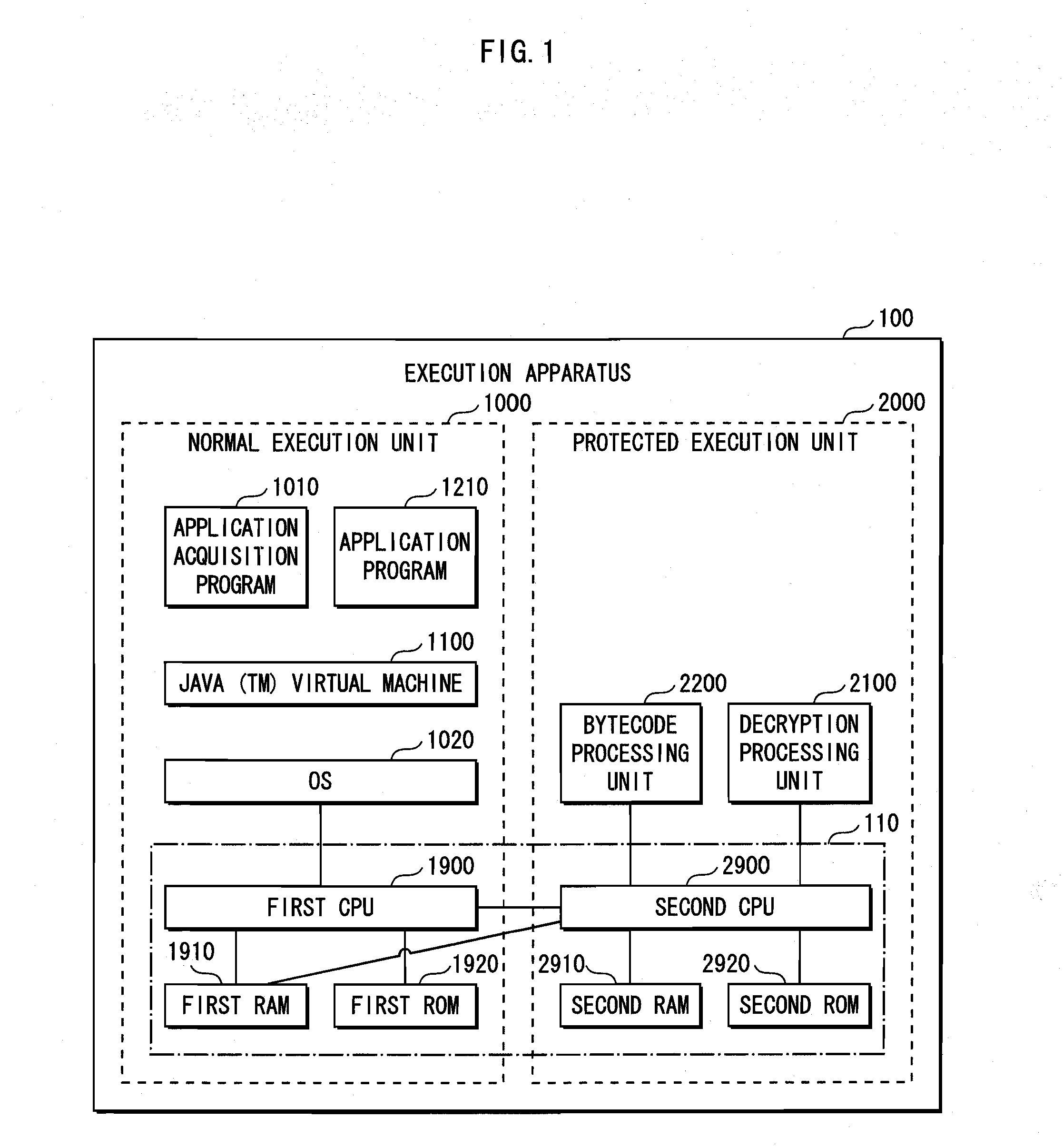
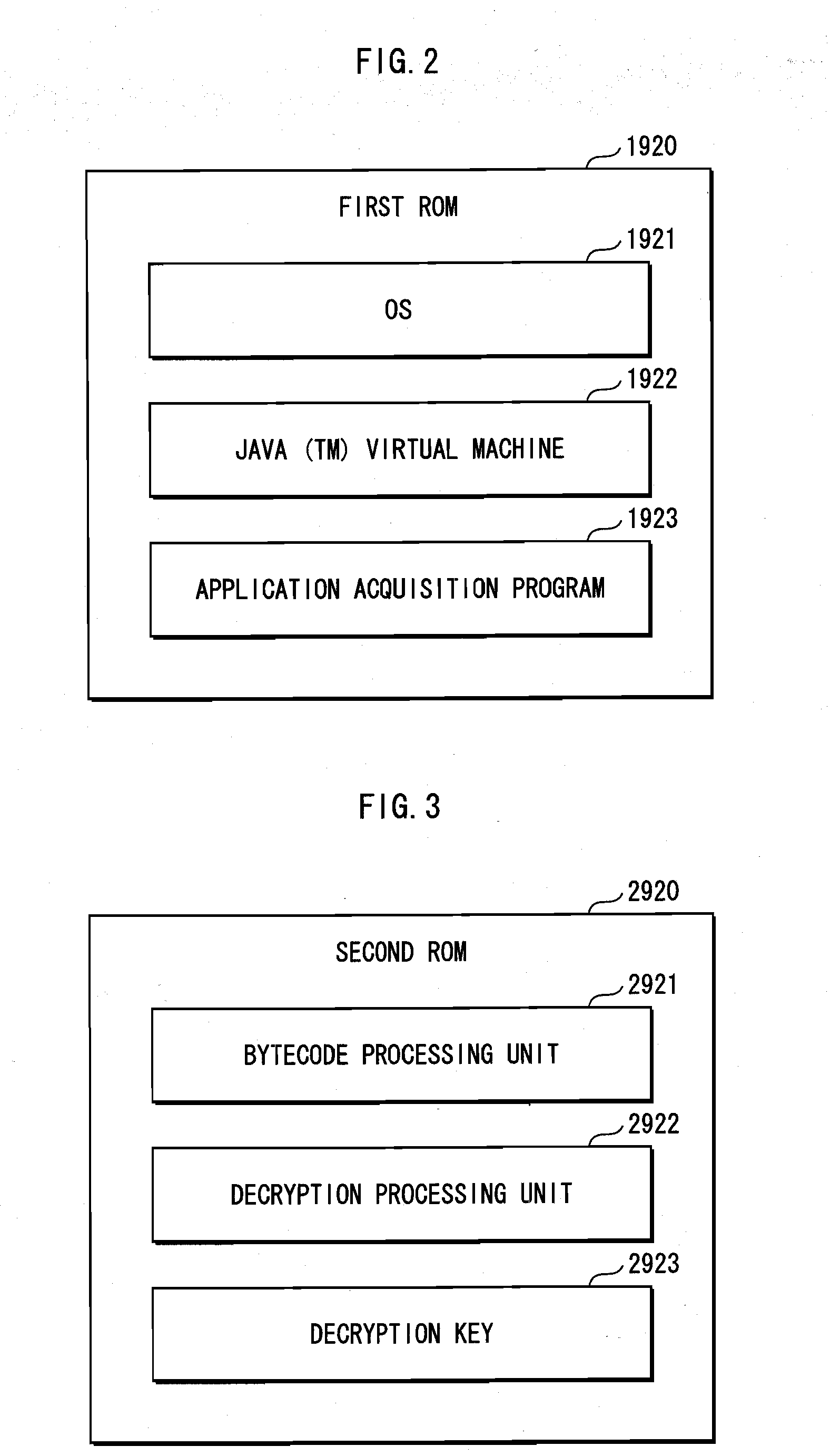
Execution device
InactiveUS20100146304A1Small sizeNot possible to executeUnauthorized memory use protectionHardware monitoringApplication softwareExecution model
A program execution device is a device for executing an application program having at least one class including an execution code created by an object directivity language. The program execution device includes a first execution device having a memory and a processor and a tamper-resistant second execution device having a memory and a processor. When a class is executed, a loader loads an execution code of the class in the memory of the second execution device and loads a portion of the class other than the execution code loaded in the memory of the second execution device, in the memory of the first execution device.
Owner:PANASONIC CORP
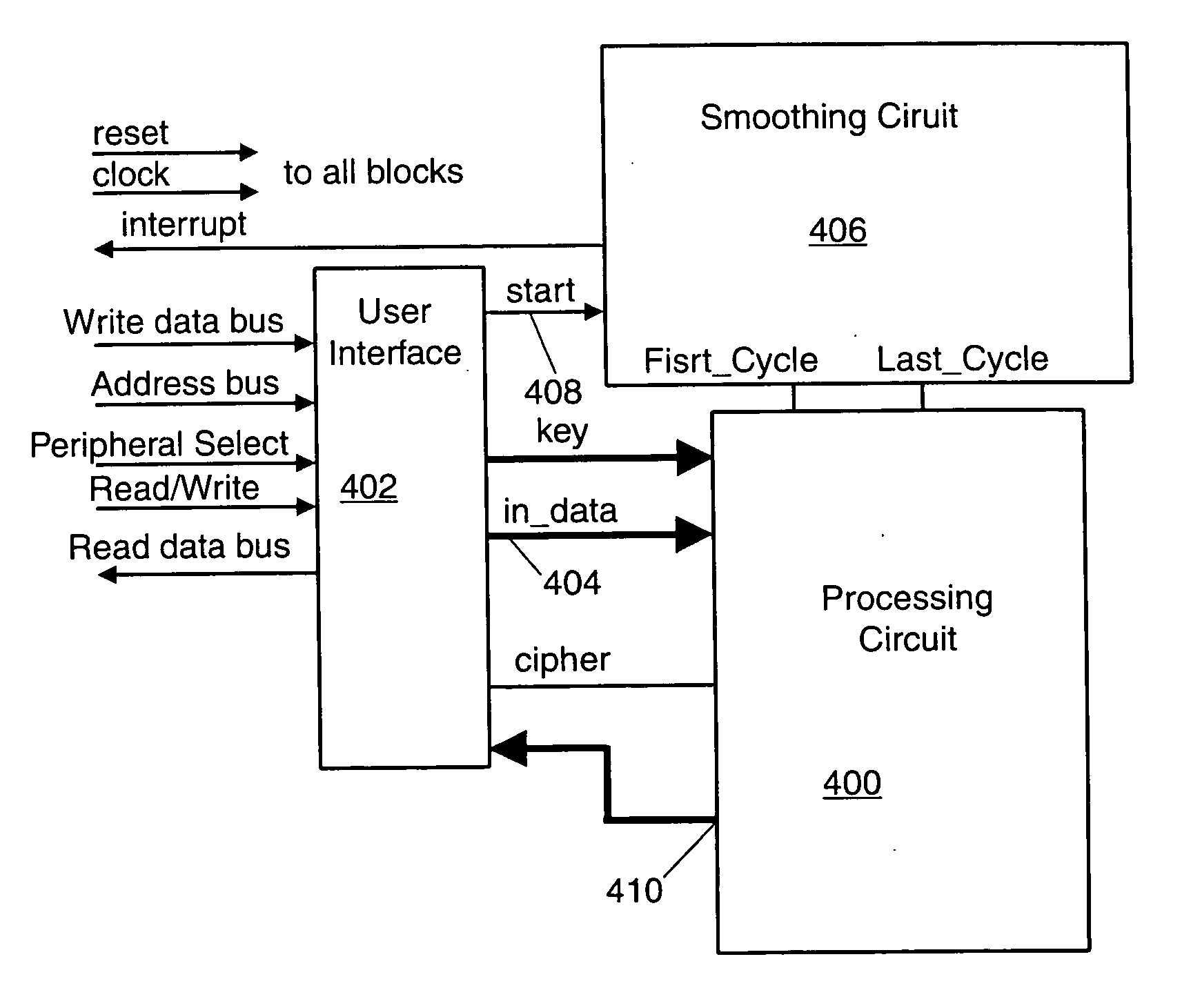
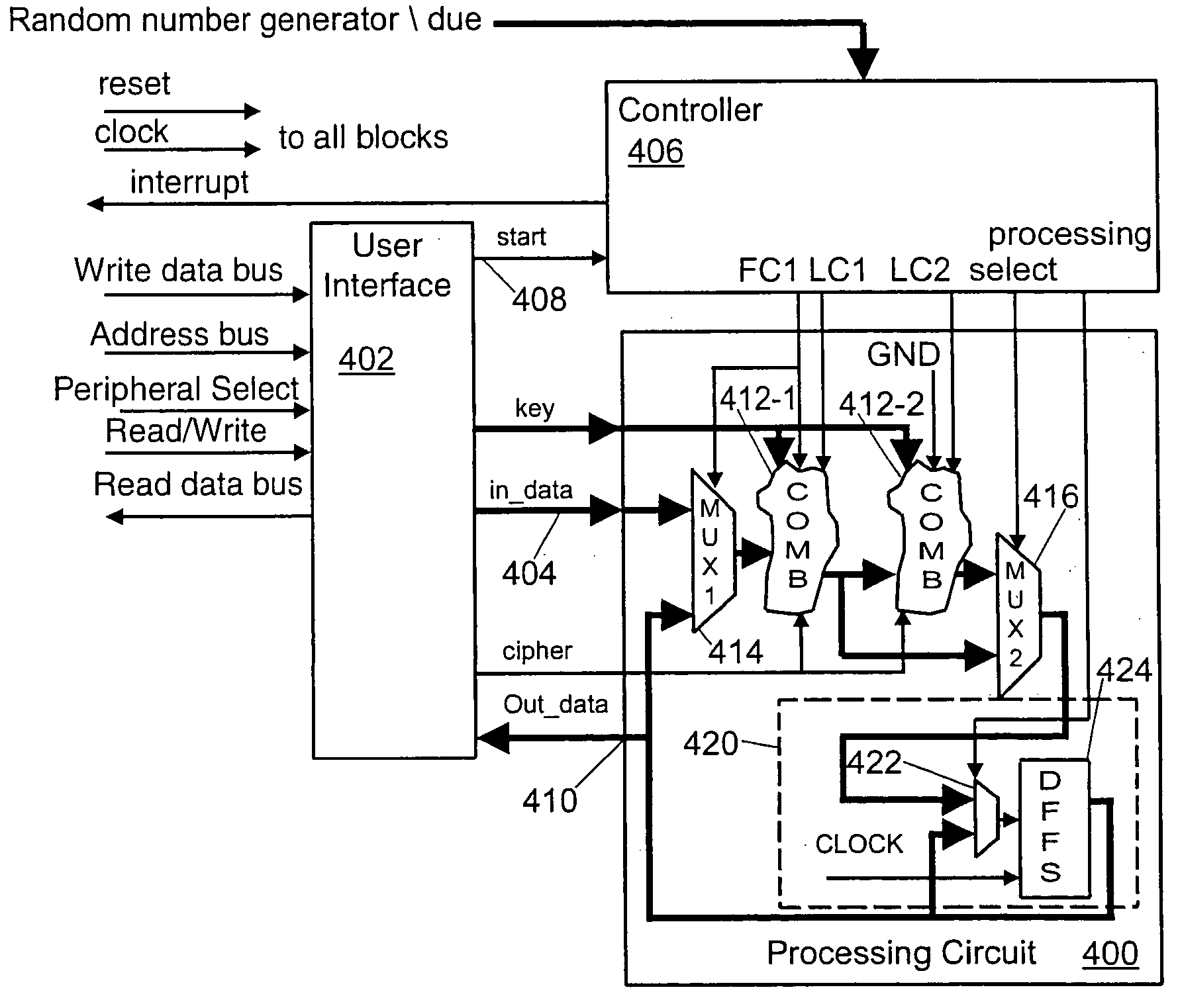
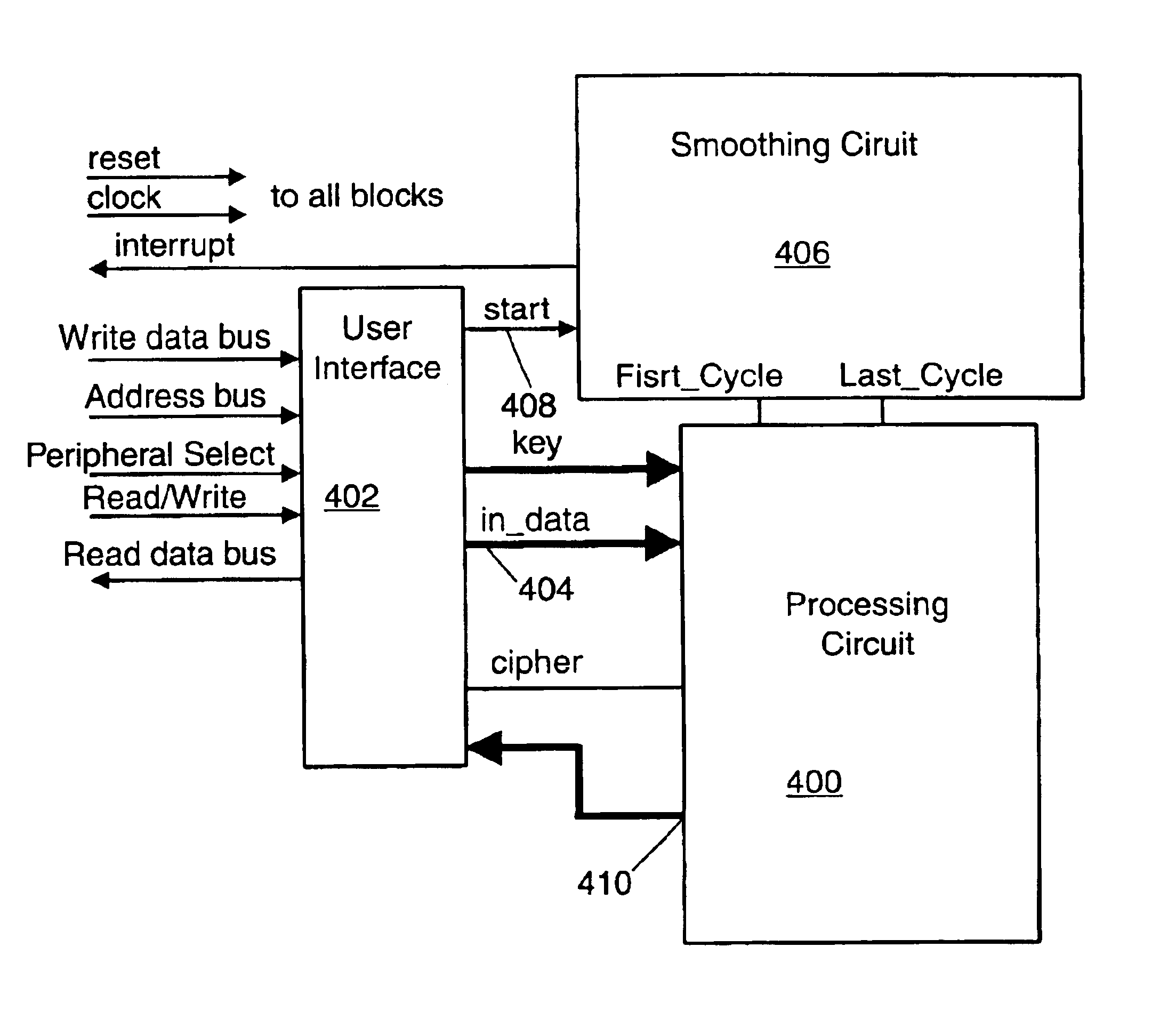
Method and apparatus for smoothing current consumption in an integrated circuit
InactiveUS20050027471A1Difficult to analyzeResistance/reactance/impedenceVolume/mass flow measurementEngineeringCurrent consumption
The invention includes a system for smoothing current consumption in a digital logic module. A processing circuit is configured to receive an input and manipulate the input during a processing time period to produce an output. A non-processing time period follows production of the output. The processing circuit is further configured to draw an active range of current during the processing time period and an inactive range of current during the non-processing time period. The system comprises a smoothing circuit coupled to the processing circuit and configured to engage the processing circuit during the non-processing time period. The smoothing circuit is also configured to cause the processing circuit to draw an active range of current during the non-processing time period.
Owner:ATMEL CORP
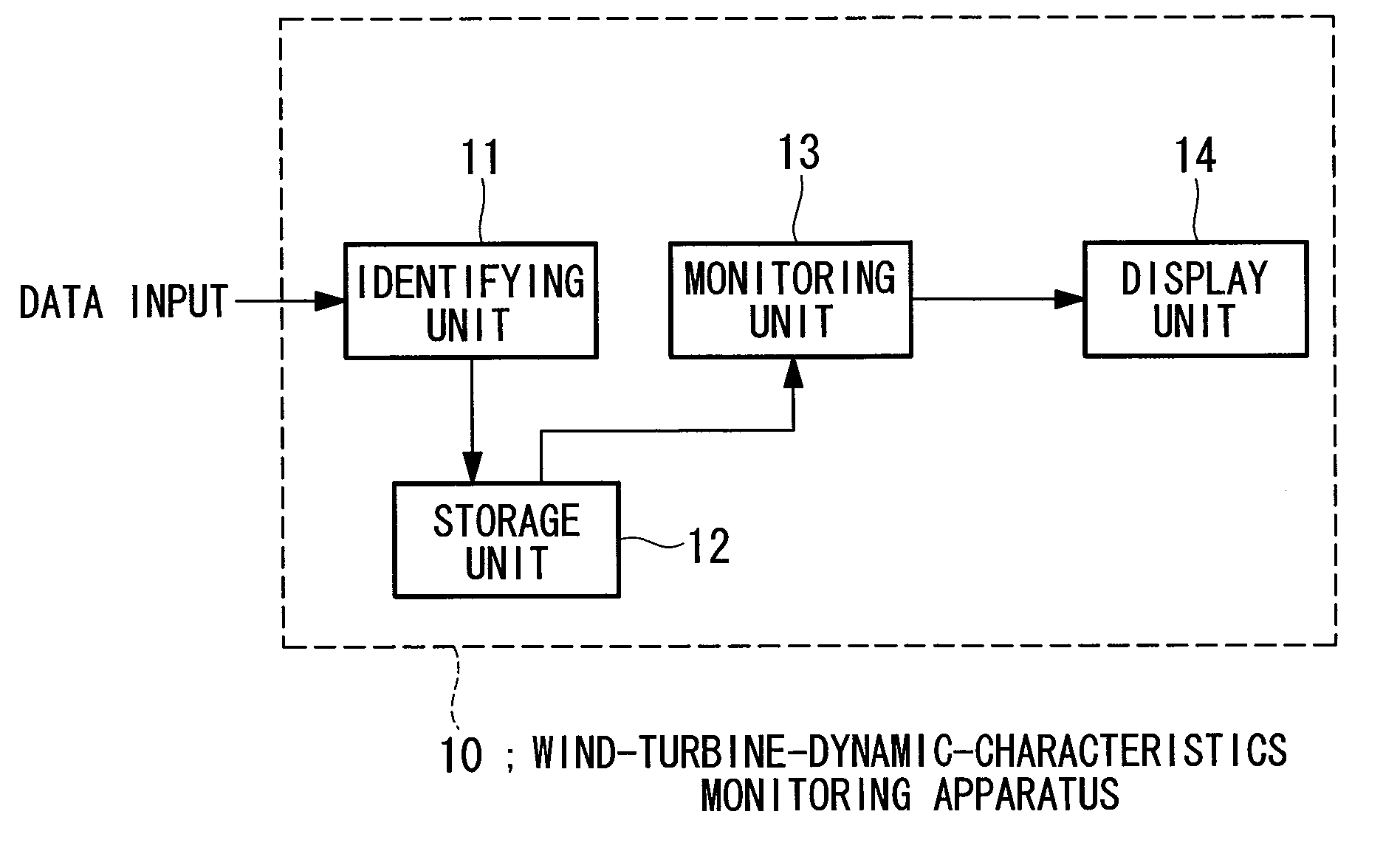
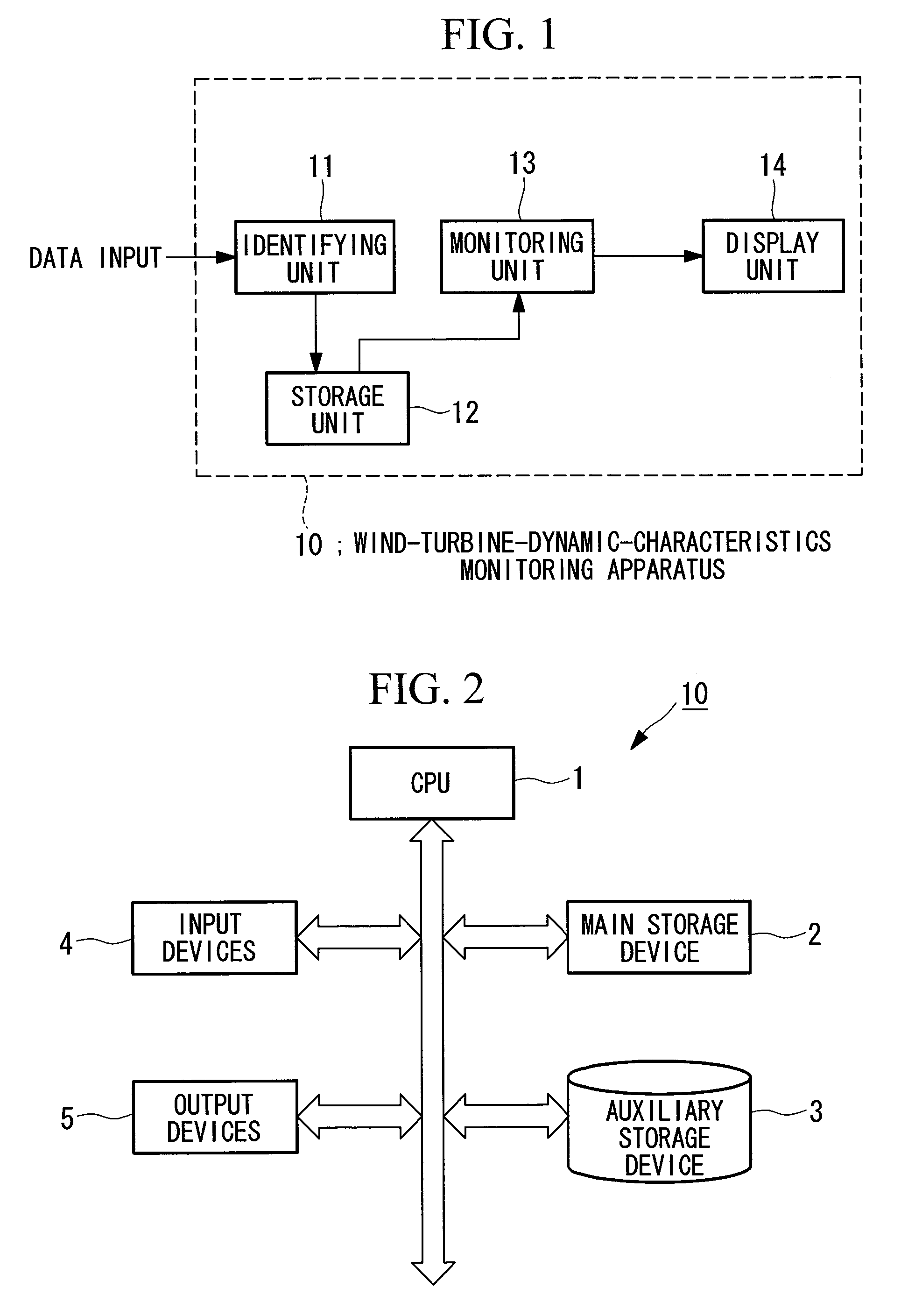
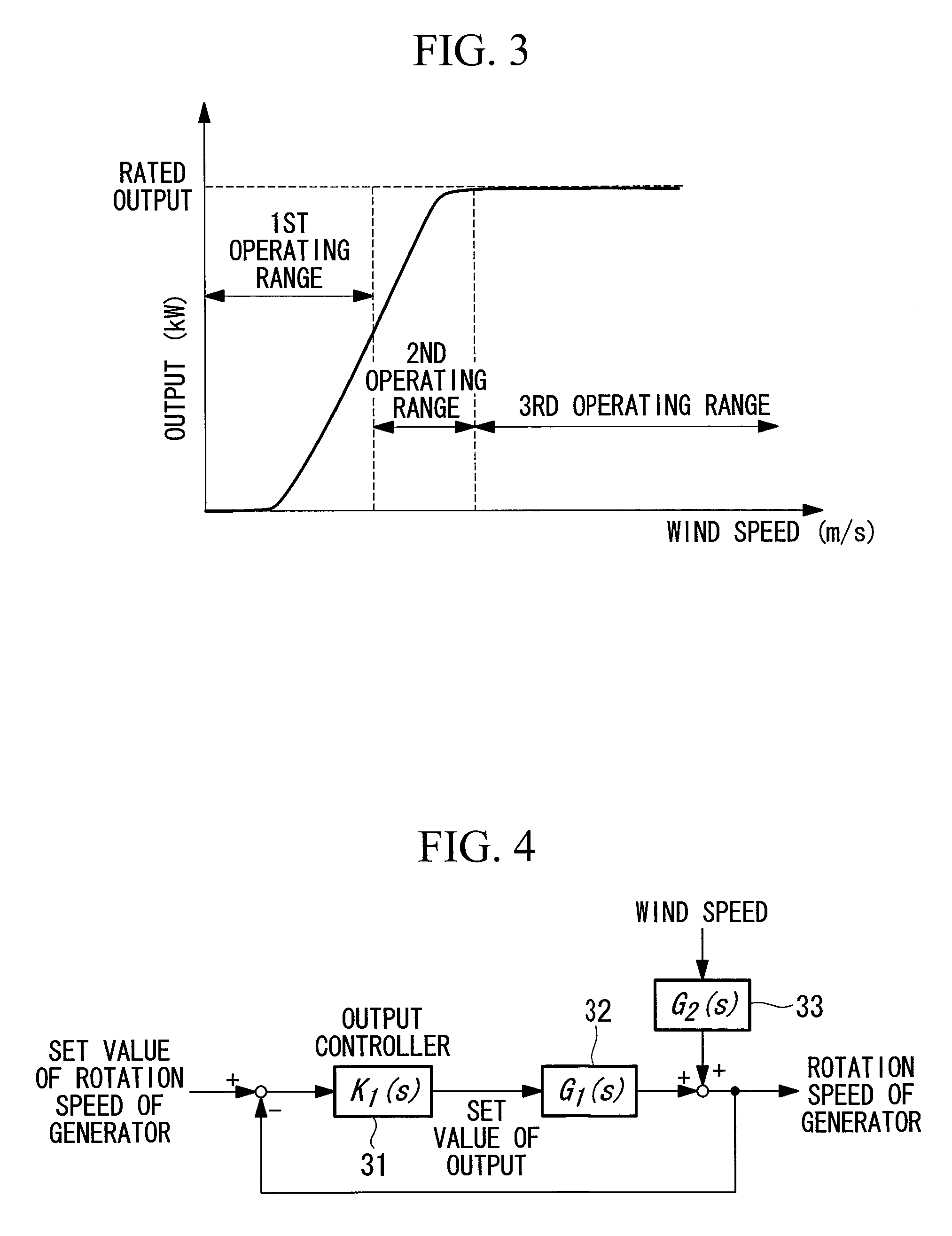
Wind-turbine-dynamic-characteristics monitoring apparatus and method therefor
ActiveUS20100301606A1Convenient winding operationMaintain controlWind motor controlWind motor combinationsEngineeringTurbine
It is an object to enable stable operation of a wind turbine and to change a control parameter of the wind turbine at an appropriate timing. A dynamic-characteristics model of a wind turbine is identified for each of a plurality of ranges that are determined in accordance with wind speed, and the identified dynamic-characteristics model is monitored for each of the ranges.
Owner:MITSUBISHI HEAVY IND LTD
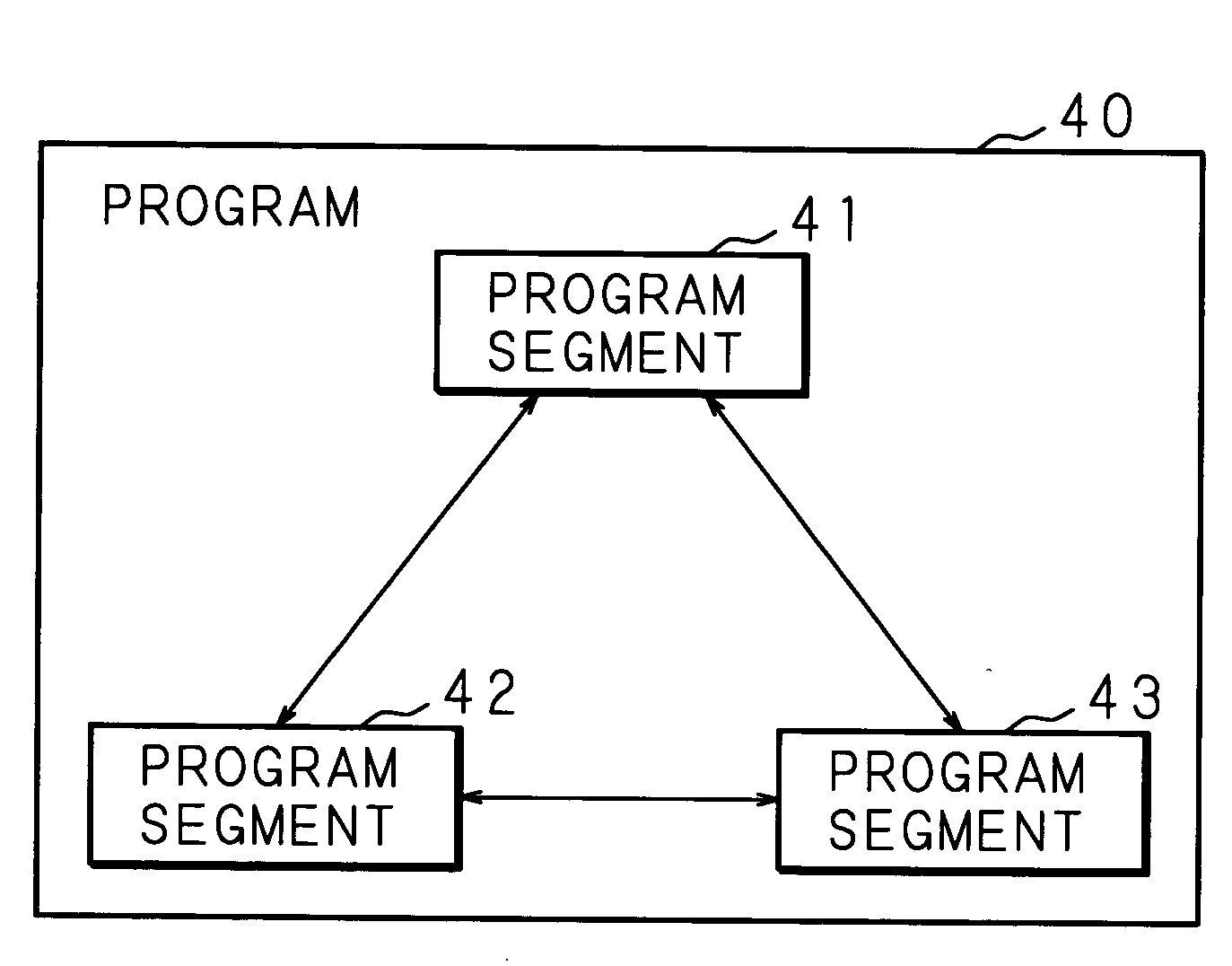
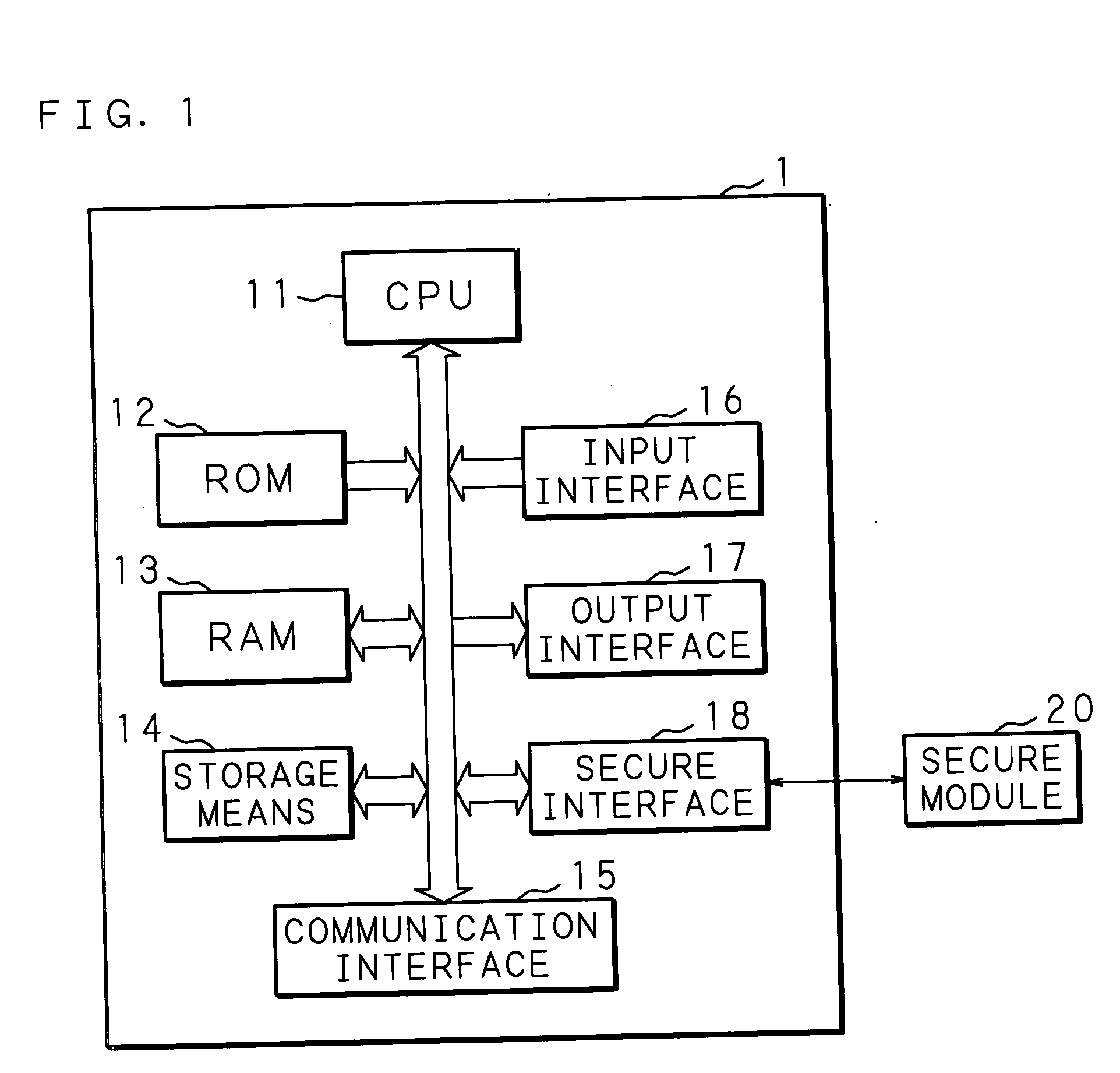
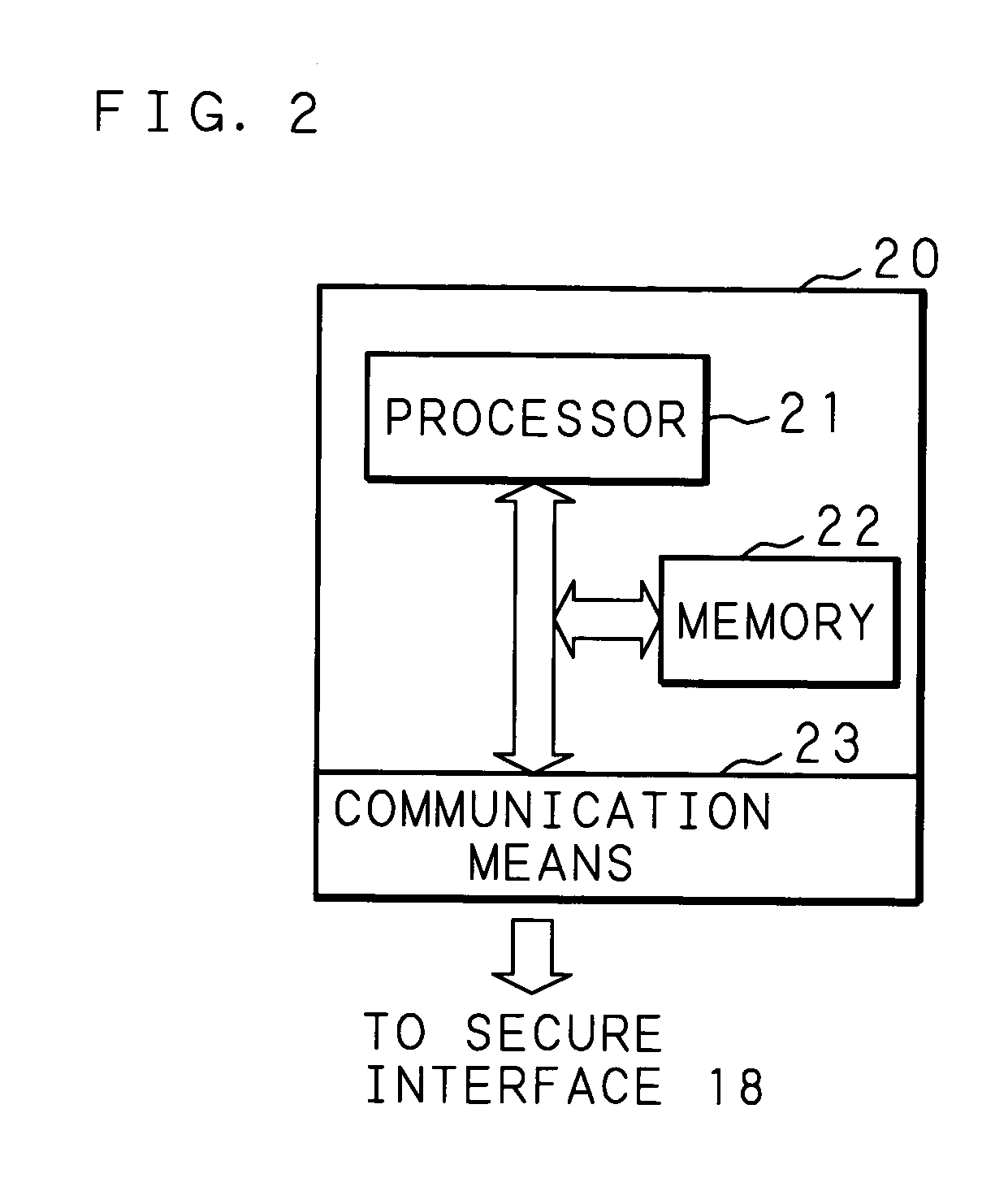
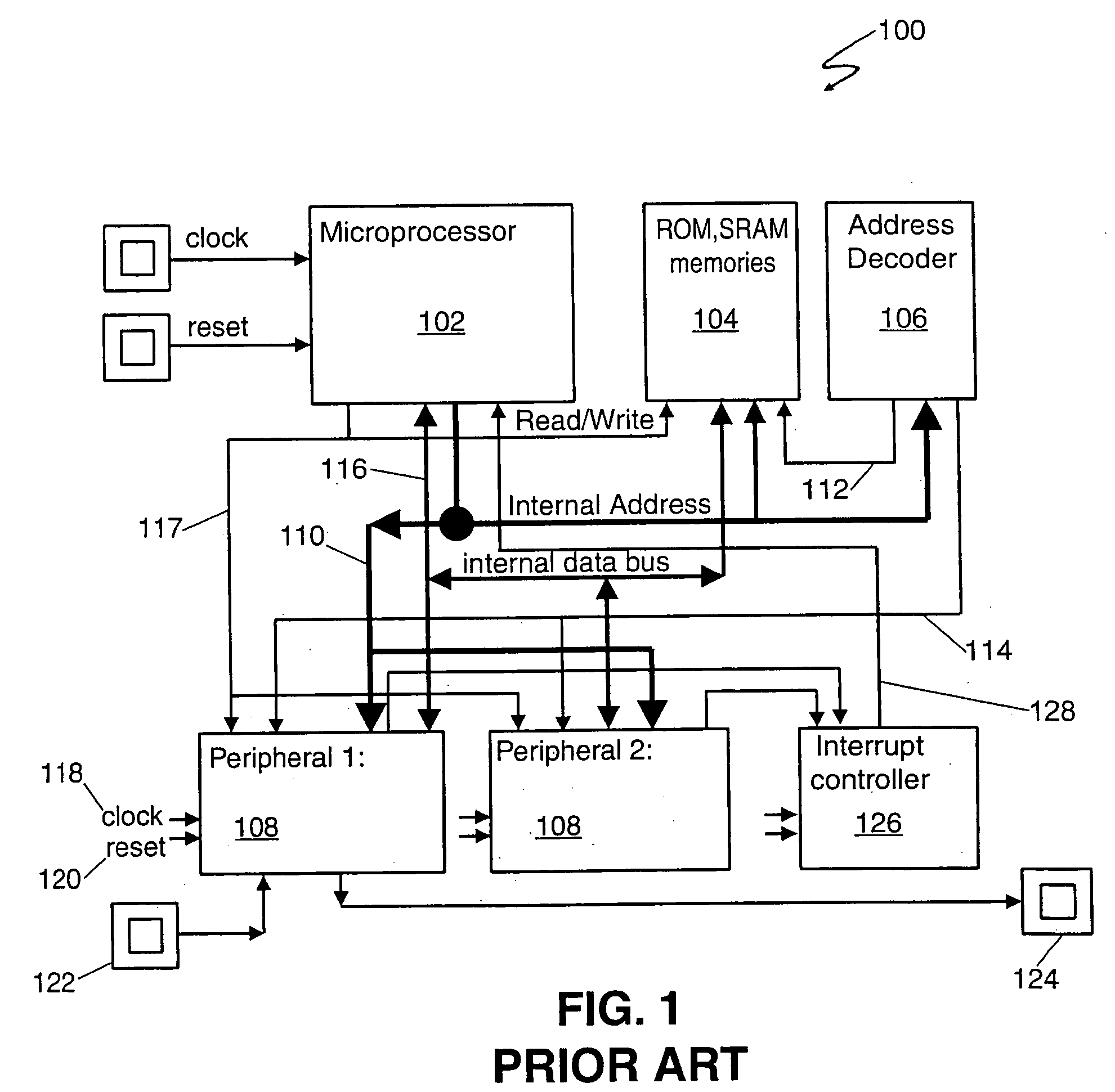
Information processing apparatus
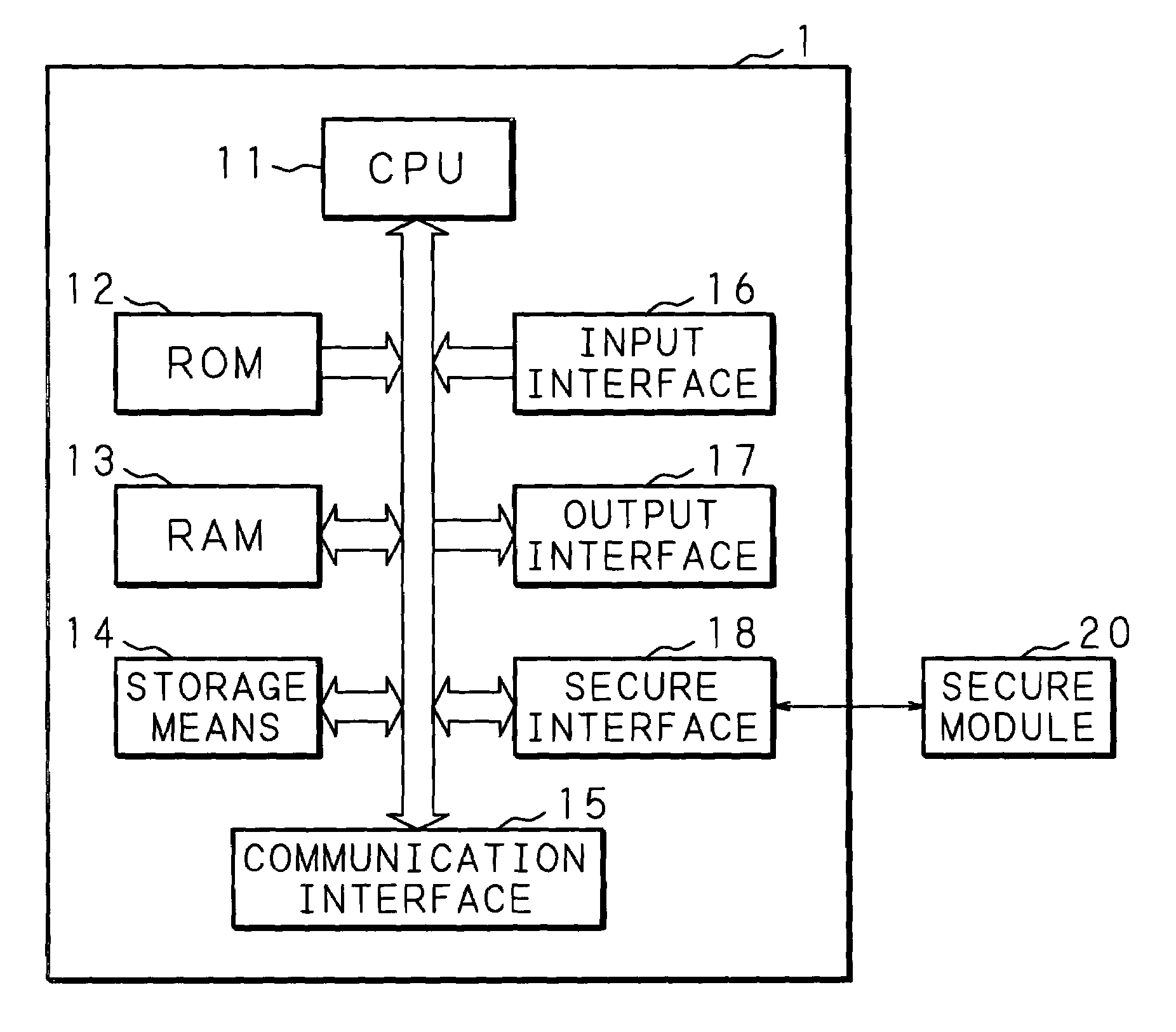
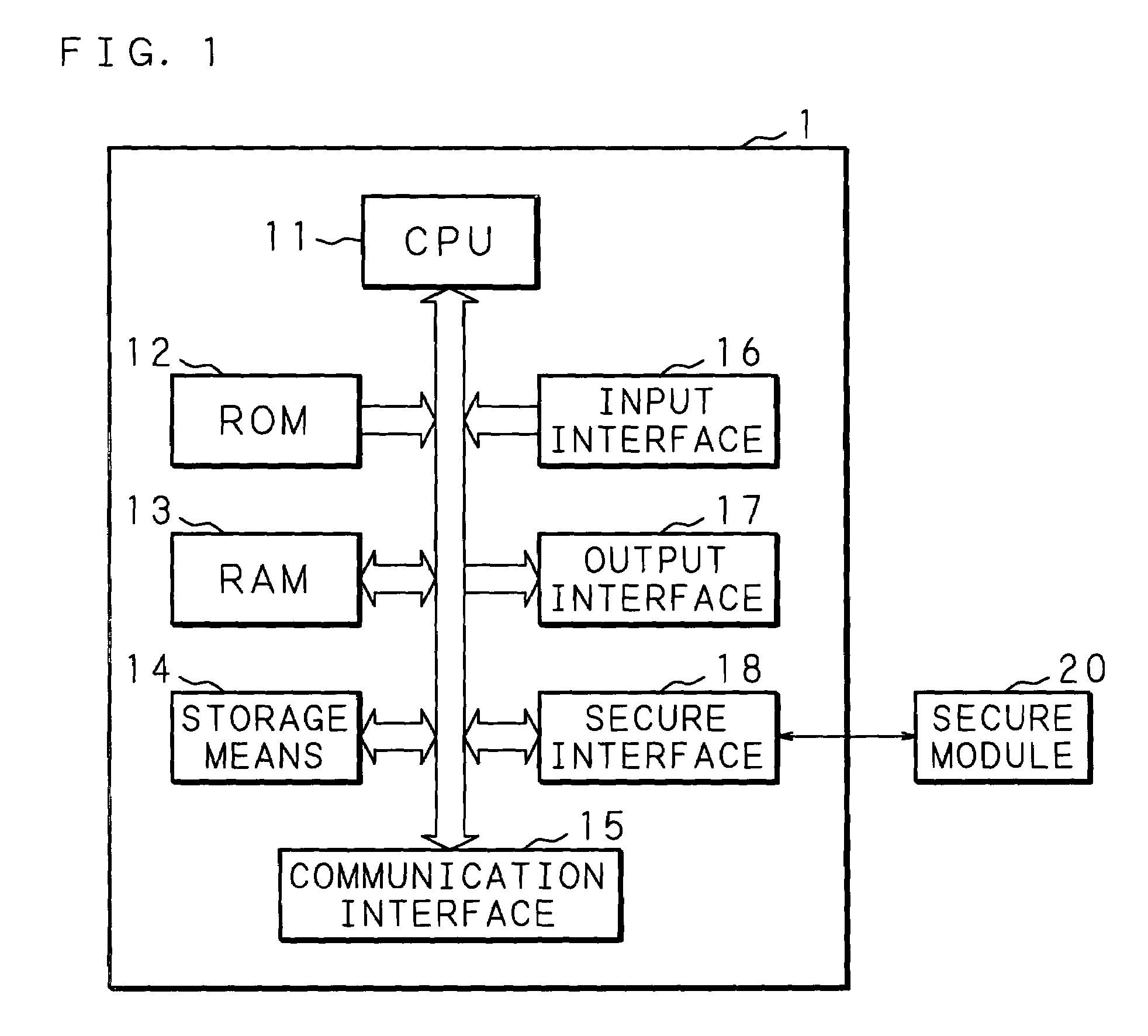
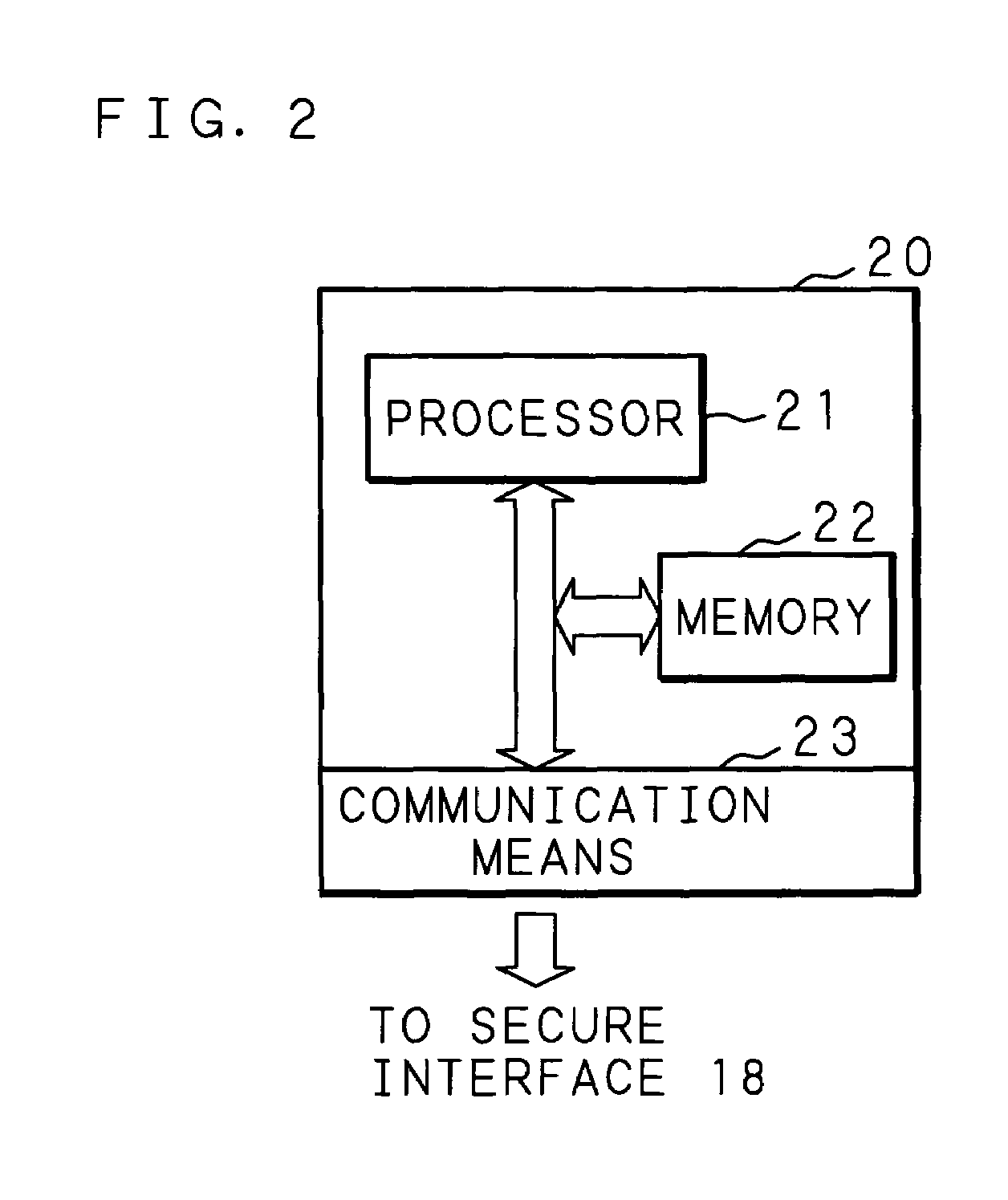
InactiveUS20050097524A1Improve securityReduce overheadDigital data processing detailsUnauthorized memory use protectionComputer hardwareInformation processing
An information processing apparatus has: a memory 13; CPU for executing a program written in the memory 13; a secure module 20; and storage means for storing a plurality of encrypted programs into which a program is divided. The CPU transmits the program stored in the storage means to the secure module 20. The secure module 20 has: means for receiving the program stored in the storage means, means for returning the received program to an executable state; means for writing the program, which has been returned to the executable state, in the memory 13 in a sequence for CPU to execute, and means for deleting the program from the memory 13 by CPU after execution is completed. When executing the program, the information processing apparatus can make reverse analysis by a malicious third party difficult, and enhance security of a load module to be executed.
Owner:FUJITSU LTD
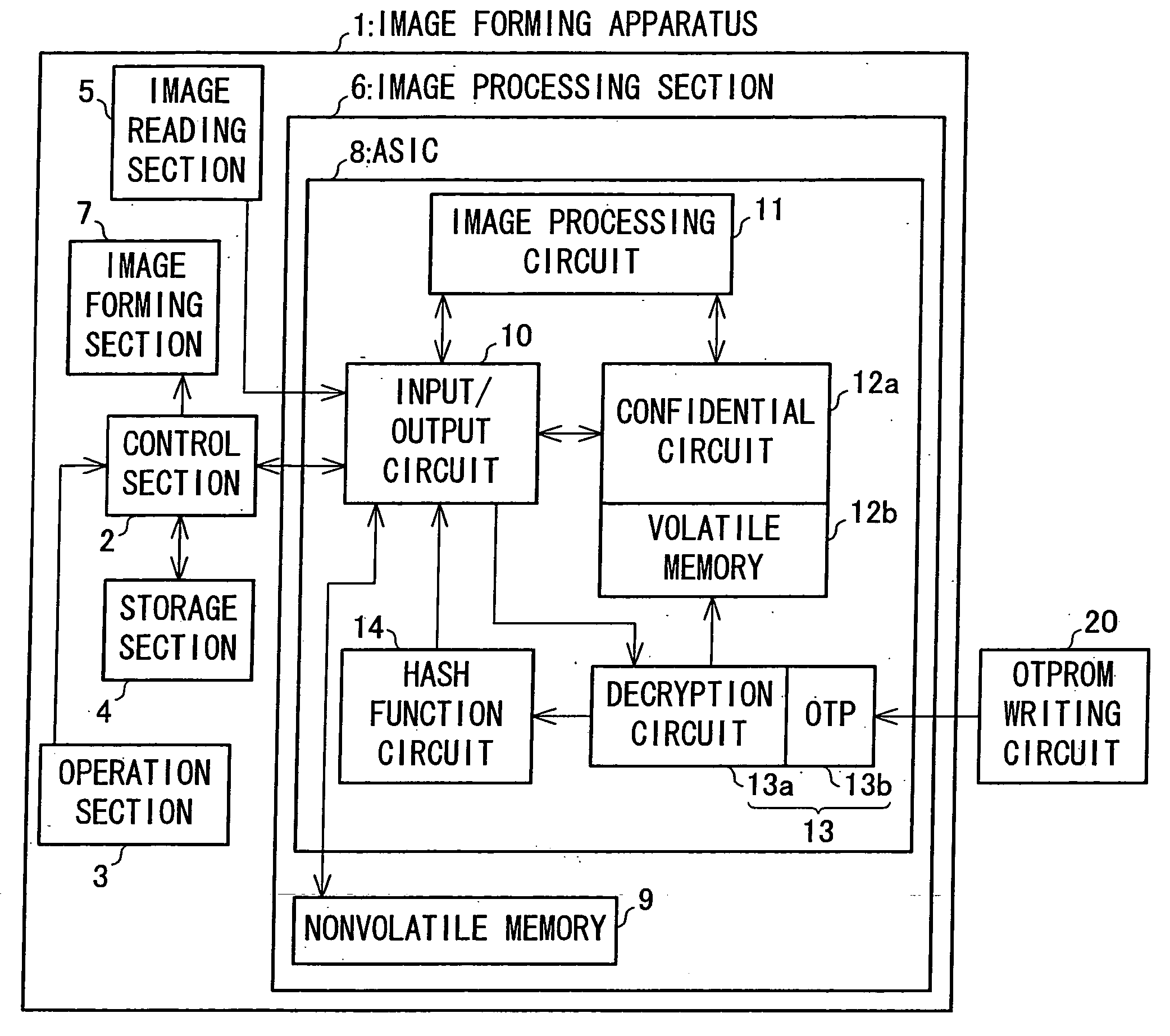
Semiconductor device and electronic apparatus
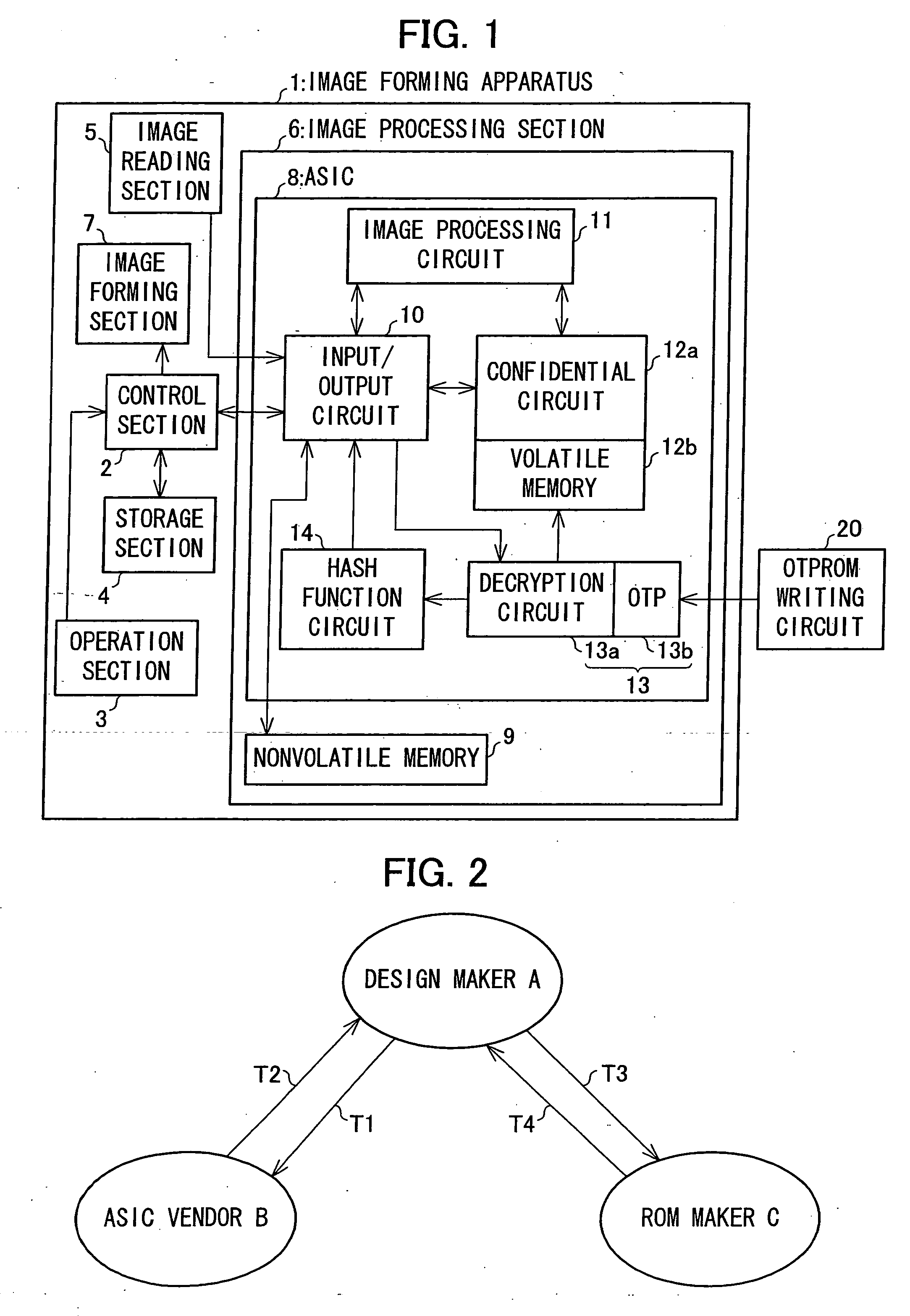
InactiveUS20050198404A1Difficult to analyzeReduce usageSolid-state devicesSemiconductor/solid-state device manufacturingImaging processingSemiconductor
An ASIC (semiconductor device) of an image processing section is provided with an input / output circuit for performing input and output to and from an image processing circuit and a confidential circuit. The input / output circuit performs output to outside of the ASIC at a timing shifted from a timing of output from the confidential circuit, for example, so as to hide the processing of the confidential circuit. With this arrangement, it is possible to hide an algorithm in the confidential circuit. Further, the ASIC is provided with a decryption circuit for decrypting an encrypted program stored in a nonvolatile memory provided separately from the ASIC. The decryption circuit is caused to function as a decryption section upon later-writing into an OTP.
Owner:SHARP KK
Apparatus and method for automatic inspection of through-holes of a component
ActiveUS9310312B2Component with highDifficult to analyzeImage enhancementImage analysisImaging processingDigital image
Owner:SIEMENS ENERGY GLOBAL GMBH & CO KG
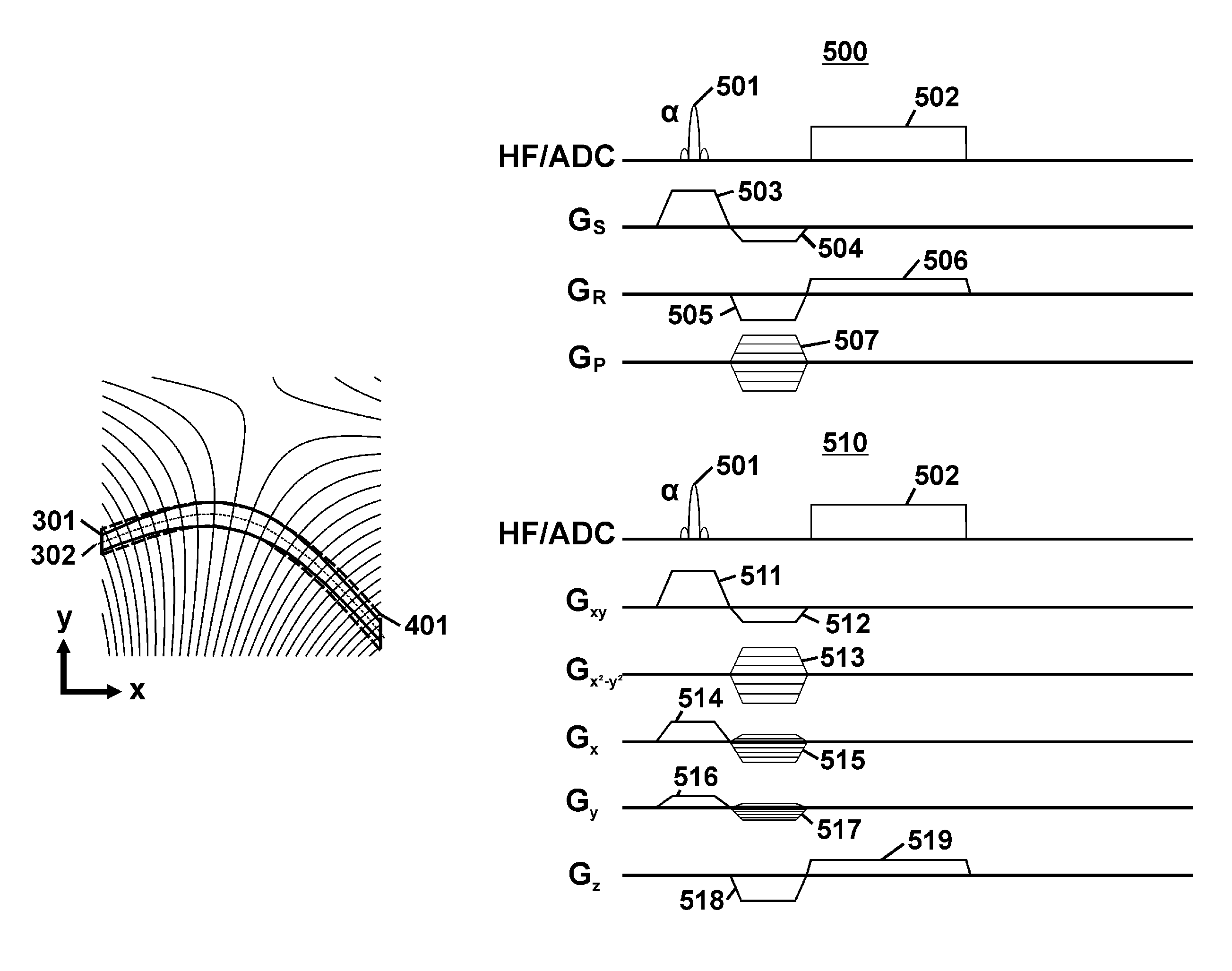
Method of magnetic resonance imaging for the selection and recording of curved slices
InactiveUS20120262171A1Fast and efficientImprove spatial resolutionMeasurements using NMR imaging systemsElectric/magnetic detectionAngle dependenceResonance
A method of MR imaging applies a magnetic field Bgrad1 having a spatially non-linear dependence to select a volume of at least one curved slice. The slice is described by its midsurface AM, a volume of the selected slice being made up of nν partial volumes in each of which gradients of at least one pair of remaining superimposed magnetic fields Bgradi (i>1) exhibit an angle dependence of 70° to 110° with respect to one another and with respect to the normal of the midsurface AM. At least one superimposed magnetic field of the respective pair exhibits a spatially non-linear dependence and combinations of these pairs are used for spatial encoding. In this way, curved surfaces can be mapped efficiently in high resolution and the method can be adapted to the slice shape.
Owner:UNIVERSITATSKLINIKUM FREIBURG
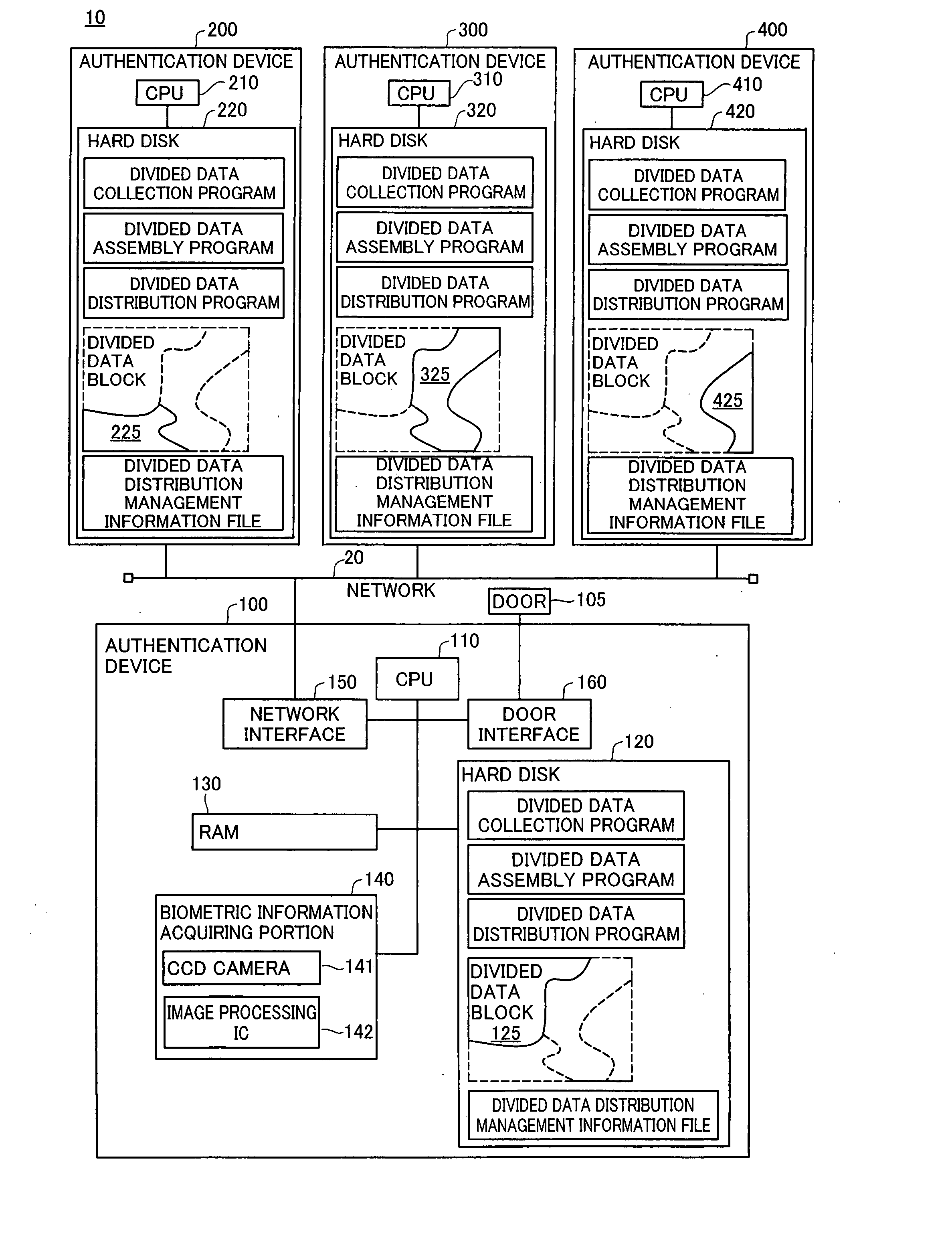
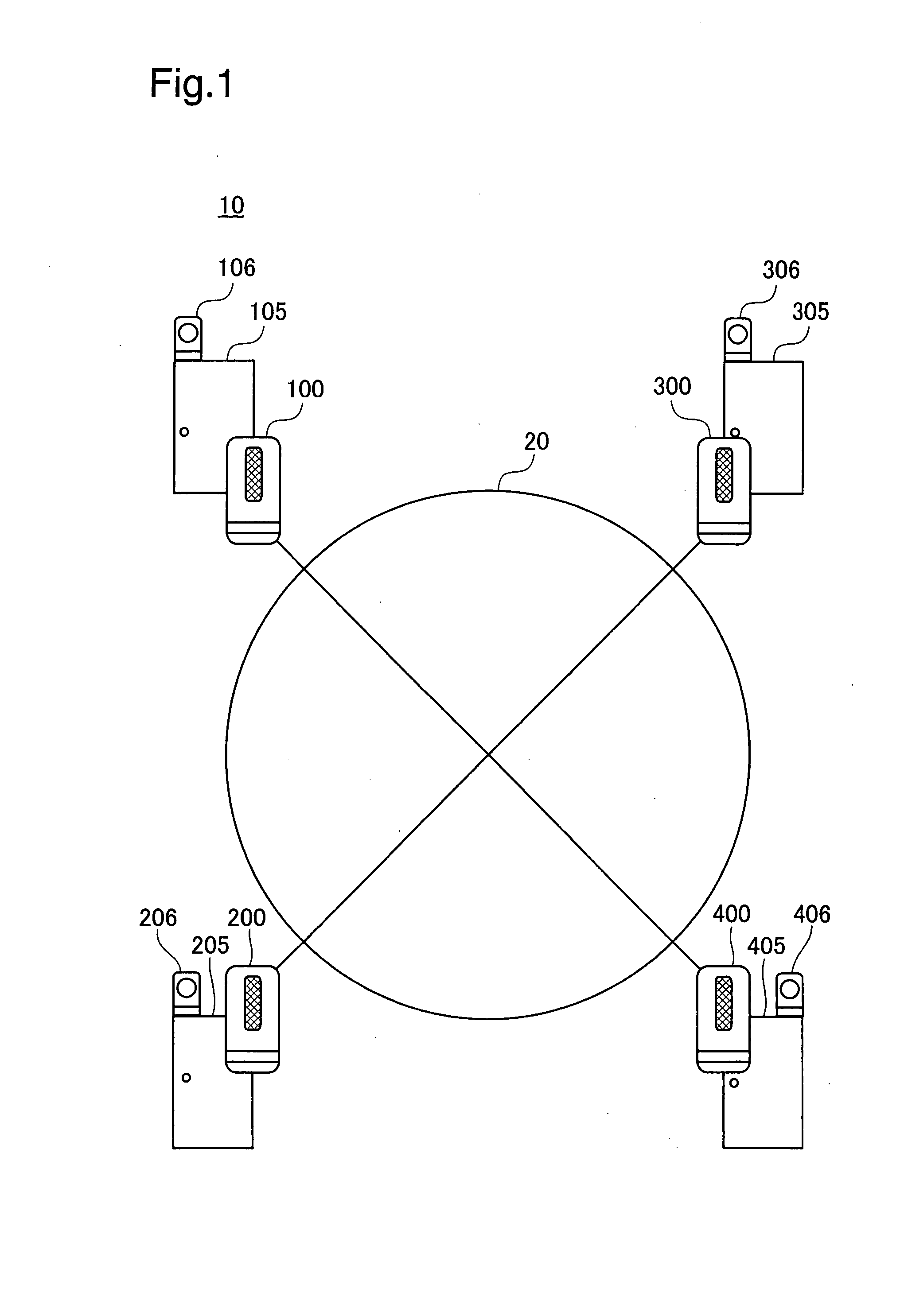
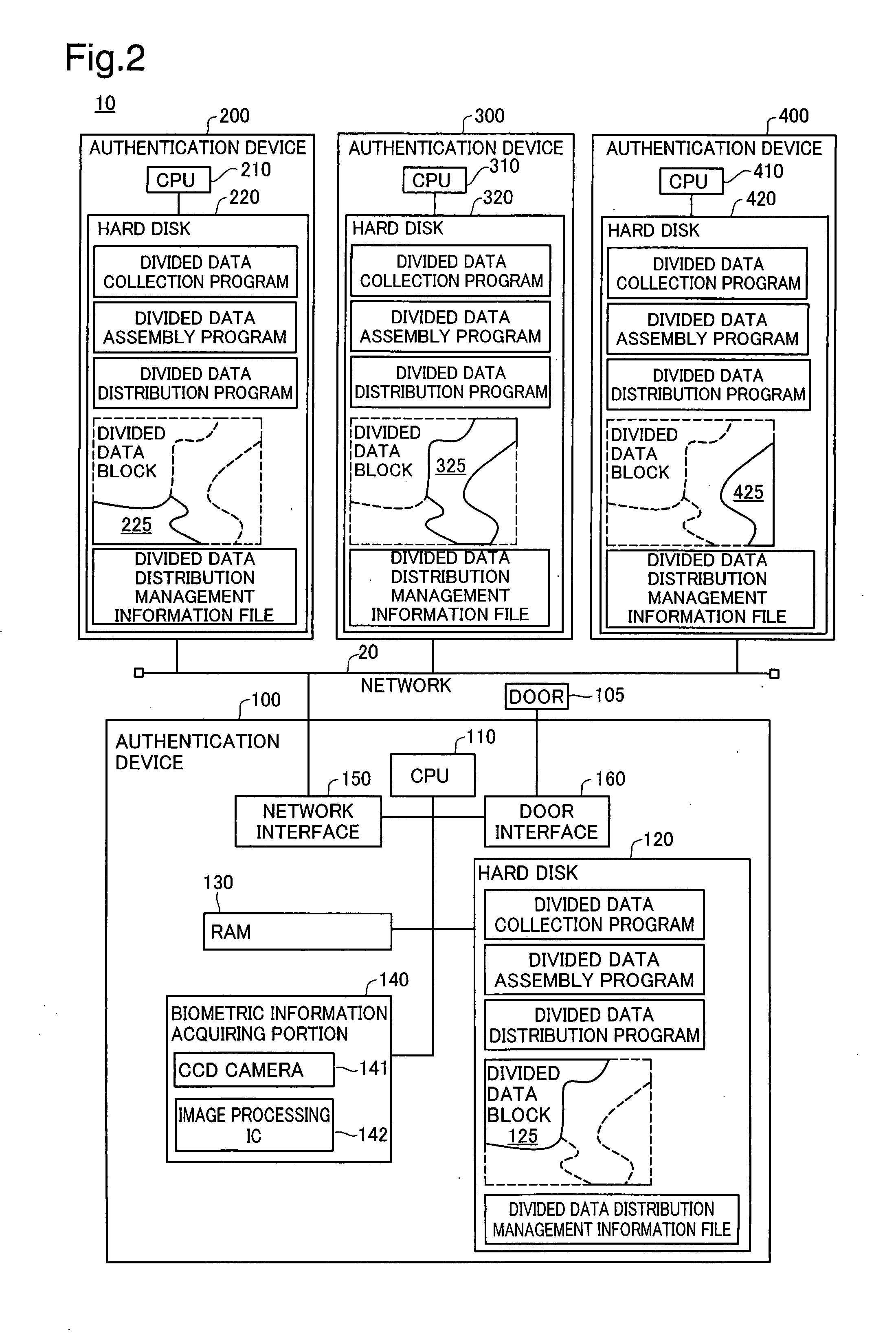
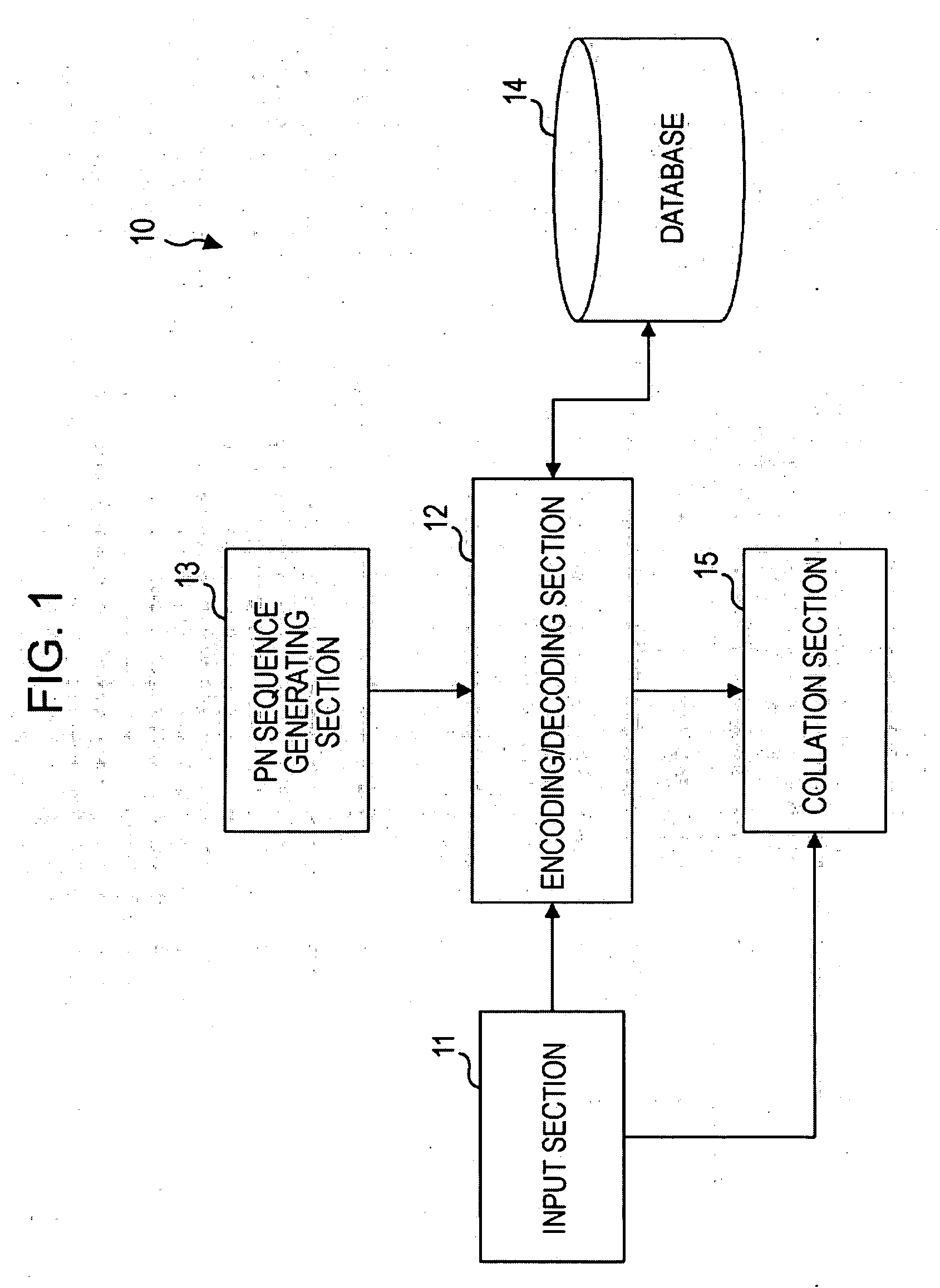
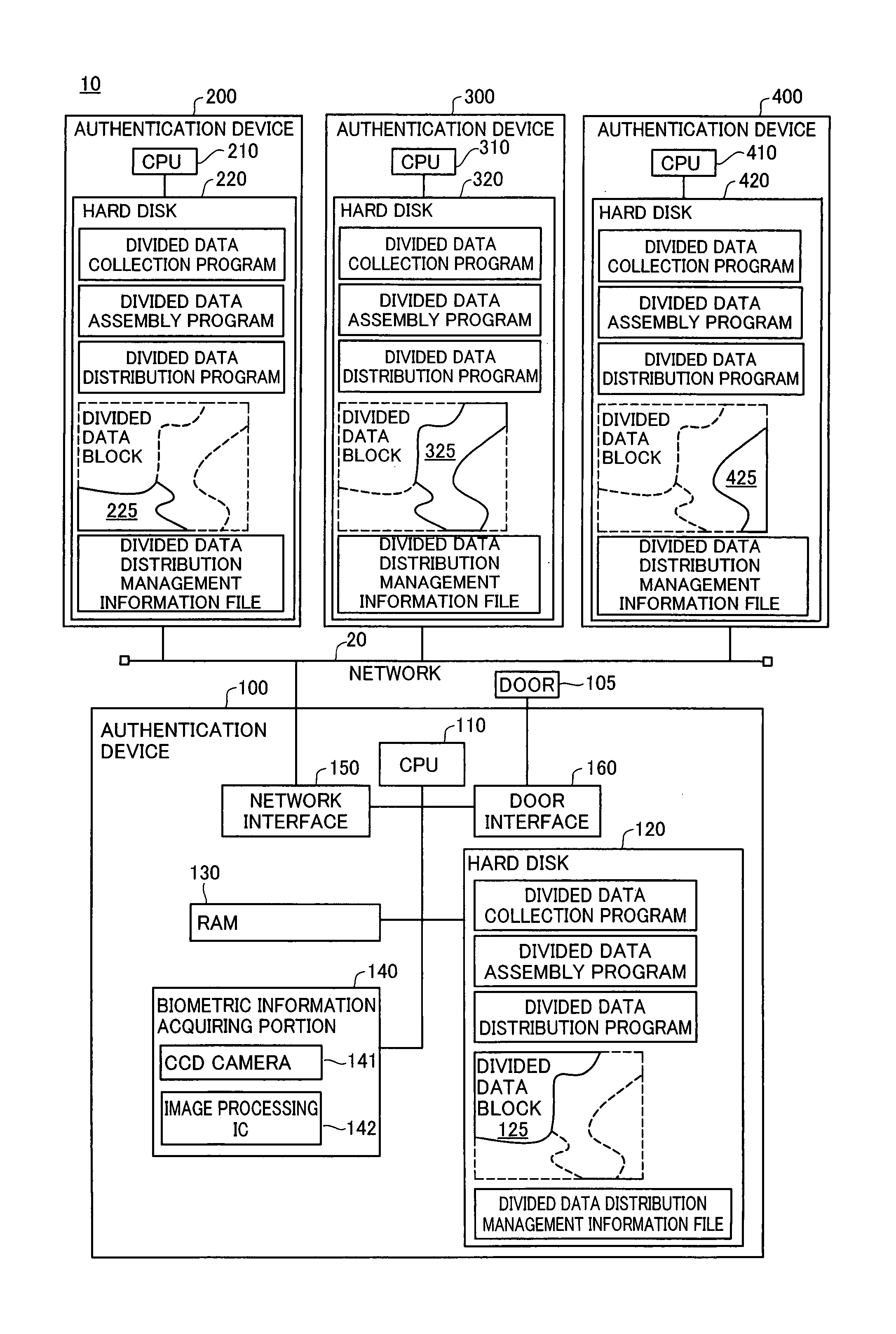
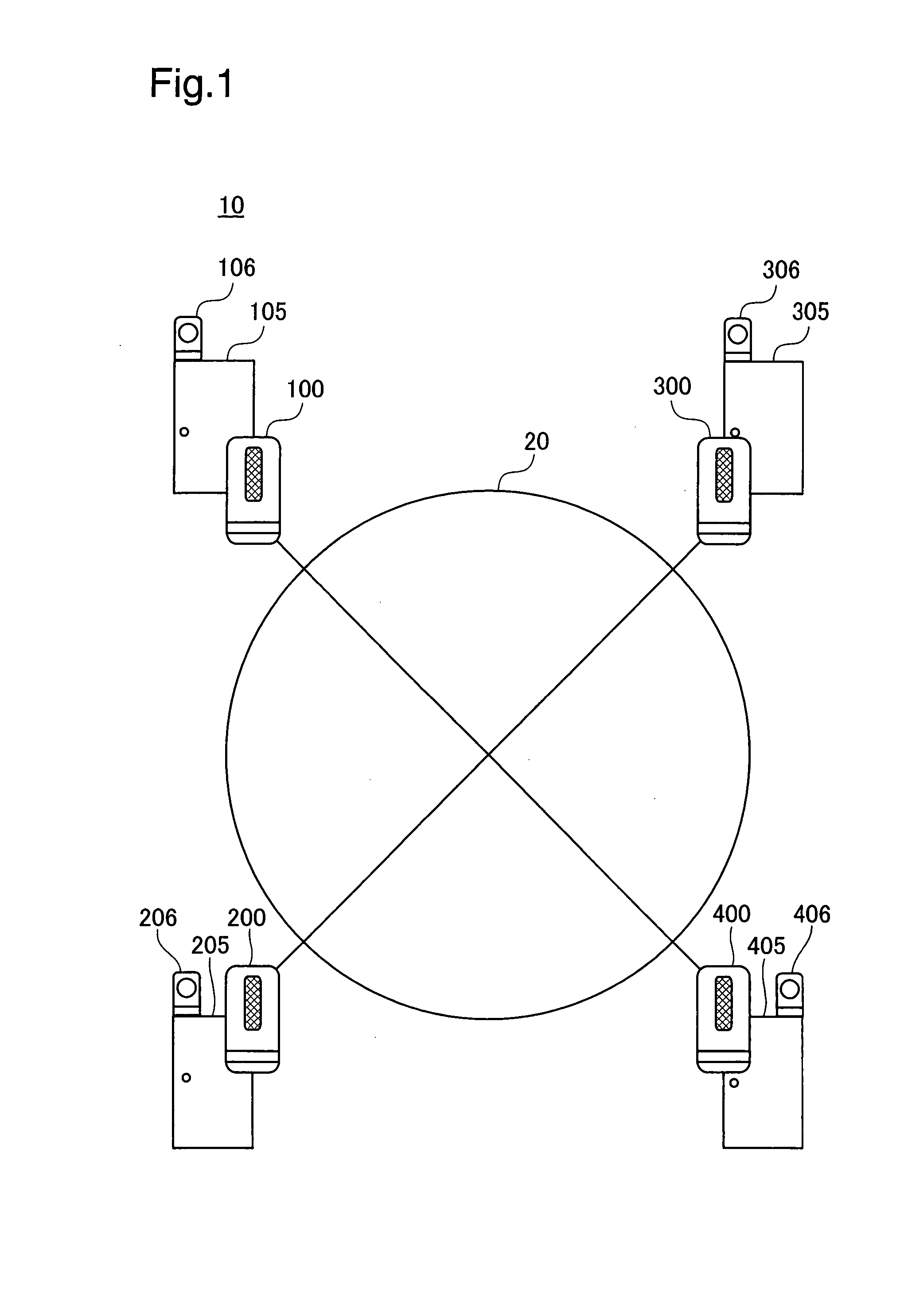
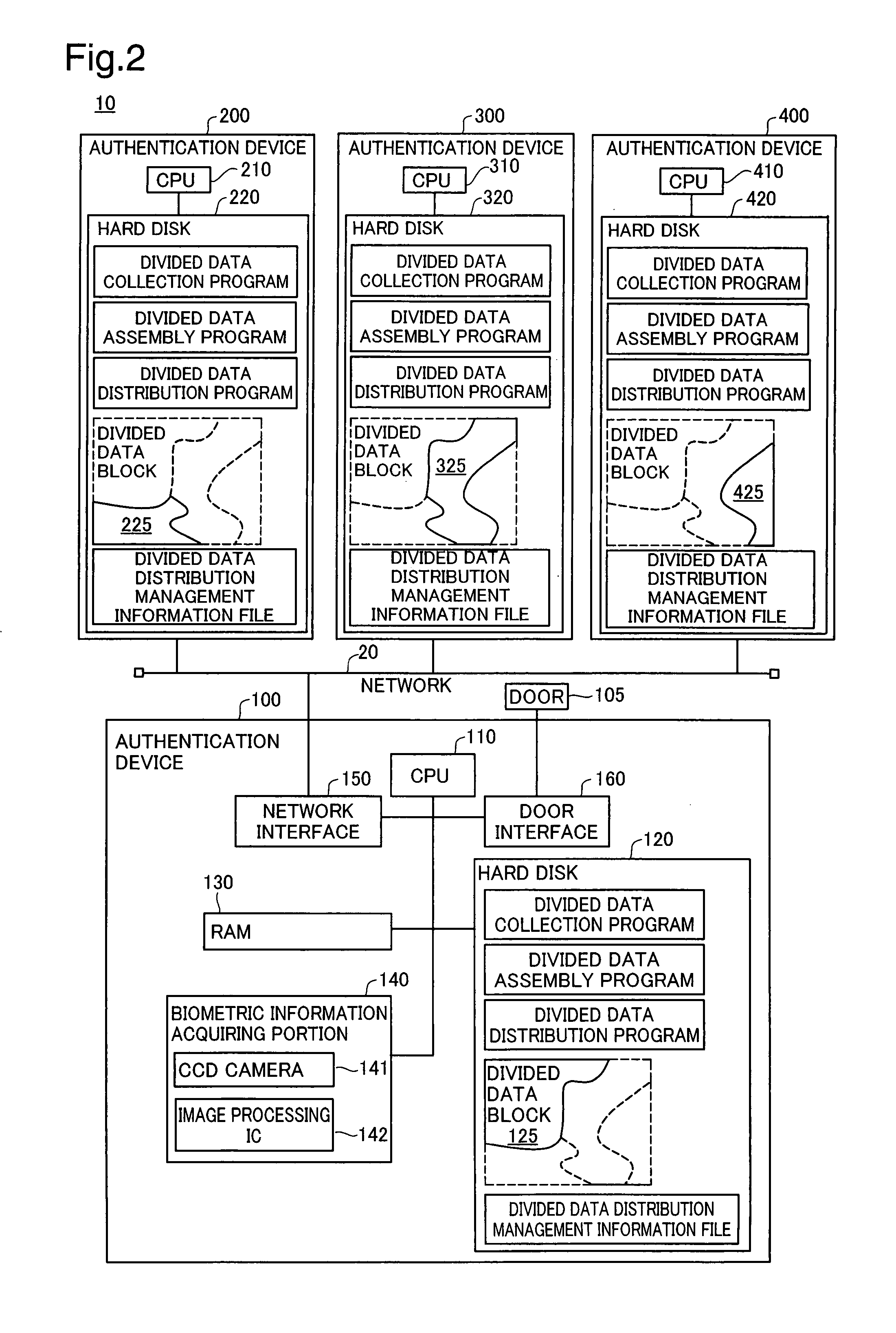
Authentication device, authentication system, and verification method for authentication device
InactiveUS20070300293A1Avoid authenticationAvoid analysisSpecial service provision for substationDigital data processing detailsValidation methodsAuthentication system
At startup, divided data blocks are received from other authentication devices and are assembled together with the local divided data block to reconstitute first authentication data. After a prescribed time interval, divided data blocks are again received from other authentication devices and are assembled together with the local divided data block to reconstitute second authentication data. The first authentication data and the second authentication data are cross-checked, and the legitimacy of the other authentication devices is decided; in the event that the other authentication devices are legitimate devices, one authentication device among the multiplicity of authentication devices re-divides the second authentication data into a multiplicity of divided data blocks for re-distribution, and a process of reconstituting the authentication data from the divided data, cross-checking the reconstituted data with the first authentication data, and deciding whether the other authentication devices are legitimate devices is repeated at prescribed intervals.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
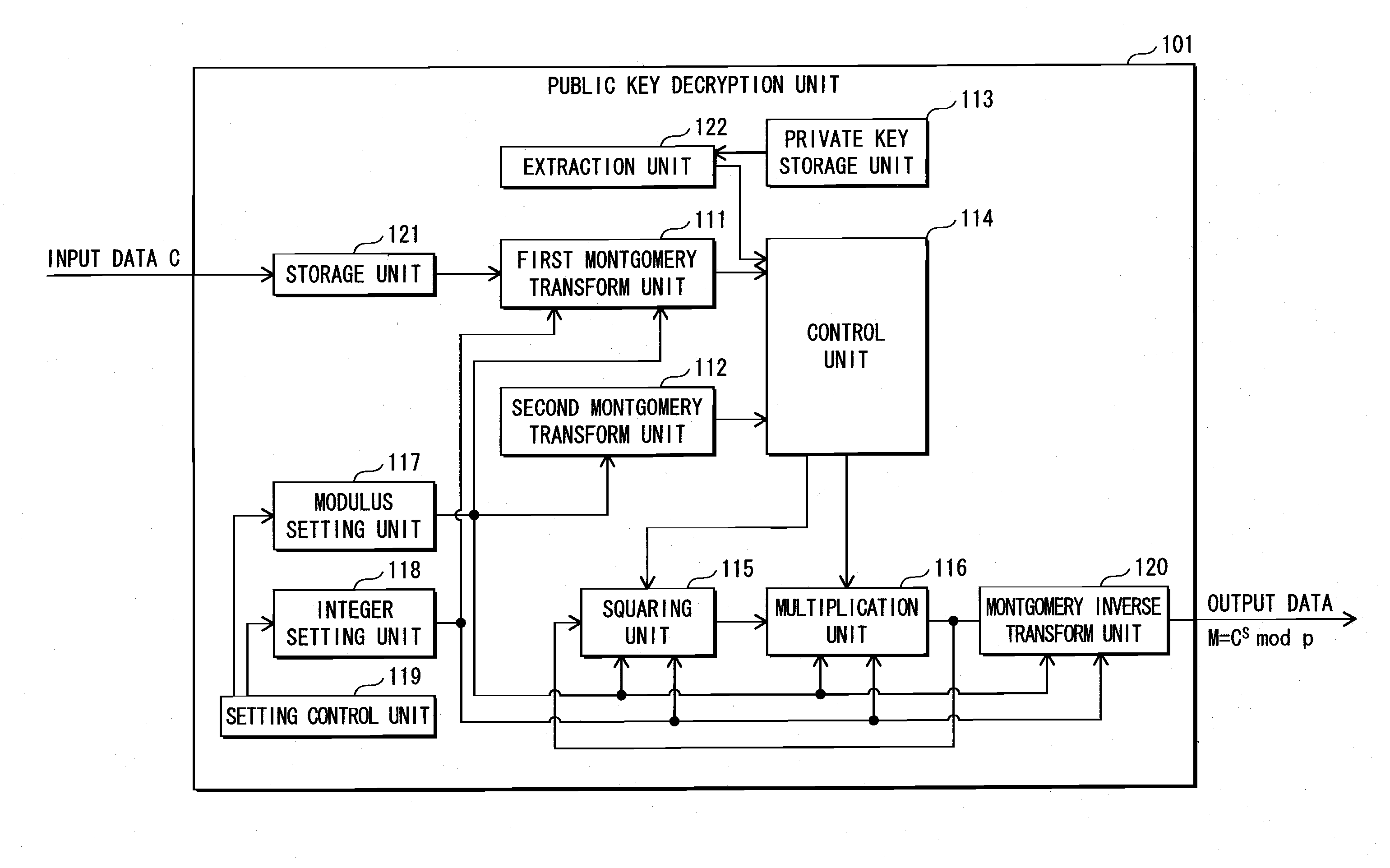
Information security device, information security method, computer program, computer-readable recording medium, and integrated circuit
ActiveUS20100064142A1Avoid weightDifficult to analyzeDigital data processing detailsUnauthorized memory use protectionPower analysisCryptosystem
The present invention aims to provide an information security apparatus that counters a simple power analysis attack (SPA) on an information security apparatus such as an RSA cryptosystem. The information security apparatus uses a multiplication with 1 in a Montgomery domain. 1 in the Montgomery domain is determined depending on a modulus and an integer k, which is greater than a number of bits of a modulus p. Therefore, it is hard for attackers who do not know p or k to analyze. Also, even if an analyzer can predict the Hamming weight, it is possible to further improve the safety against the SPA by modifying k or the modulus at random.
Owner:PANASONIC CORP
Program illegiblizing device and method
ActiveUS8312297B2Obtain confidential informationDifficult to analyzeMemory loss protectionDigital data processing detailsProcessing InstructionProgram instruction
A program obfuscating device for generating obfuscated program from which unauthorized analyzer cannot obtain confidential information easily. The program obfuscating device stores original program that contains authorized program instructions and confidential process instruction group containing confidential information that needs to be kept confidential, generates process instructions which, when executed in predetermined order, provide same result, with execution of last process instruction thereof, as the confidential process instruction group, inserts the process instructions into the original program at position between start of the original program and the confidential process instruction group so as to be executed in the predetermined order, in place of the confidential process instruction group, generates dummy block as dummy of the process instructions, and inserts the dummy block and control instruction, which causes the dummy block to be bypassed, into the original program, and inserts branch instruction into the dummy block.
Owner:PANASONIC CORP
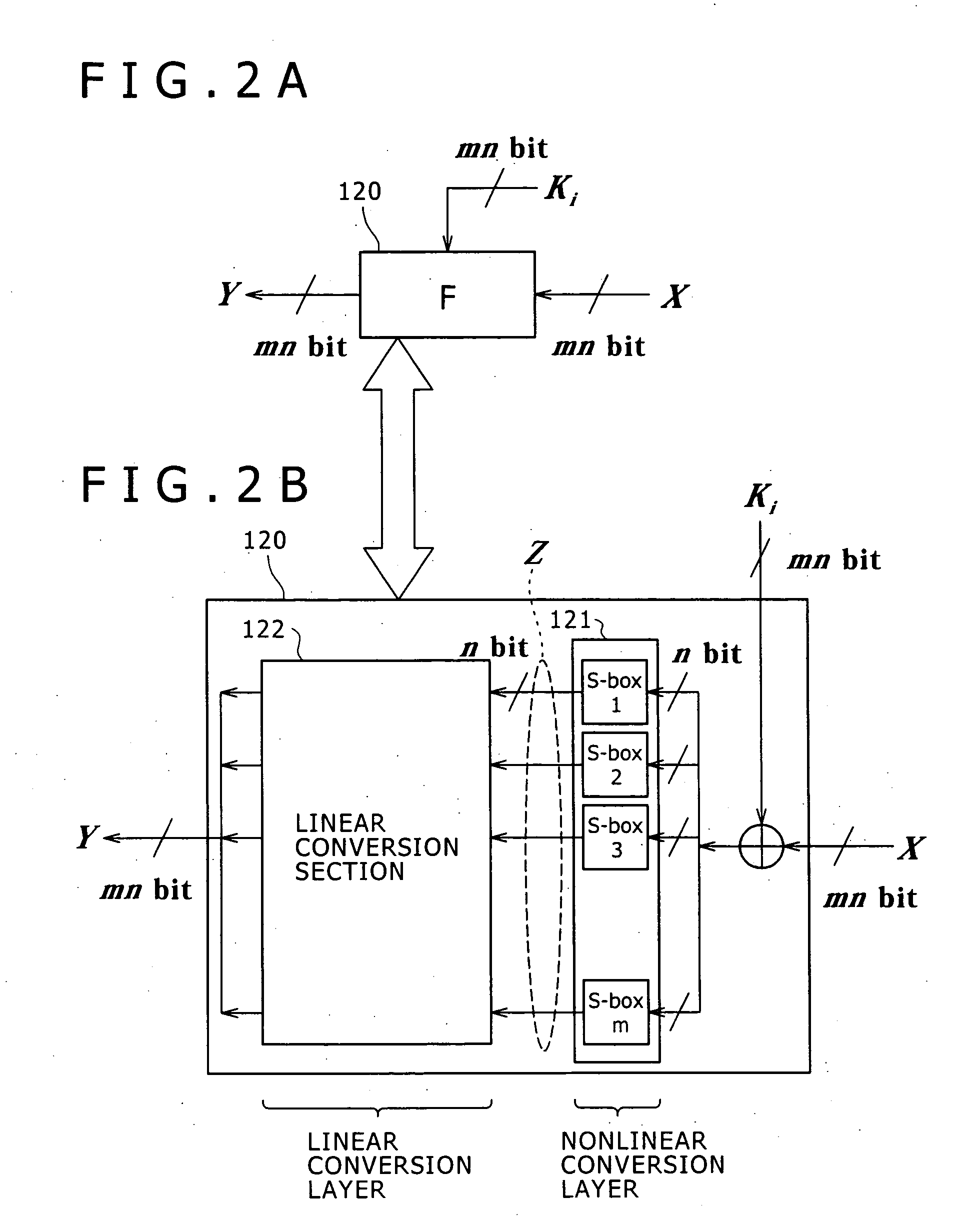
Encryption device, encryption method, and computer program
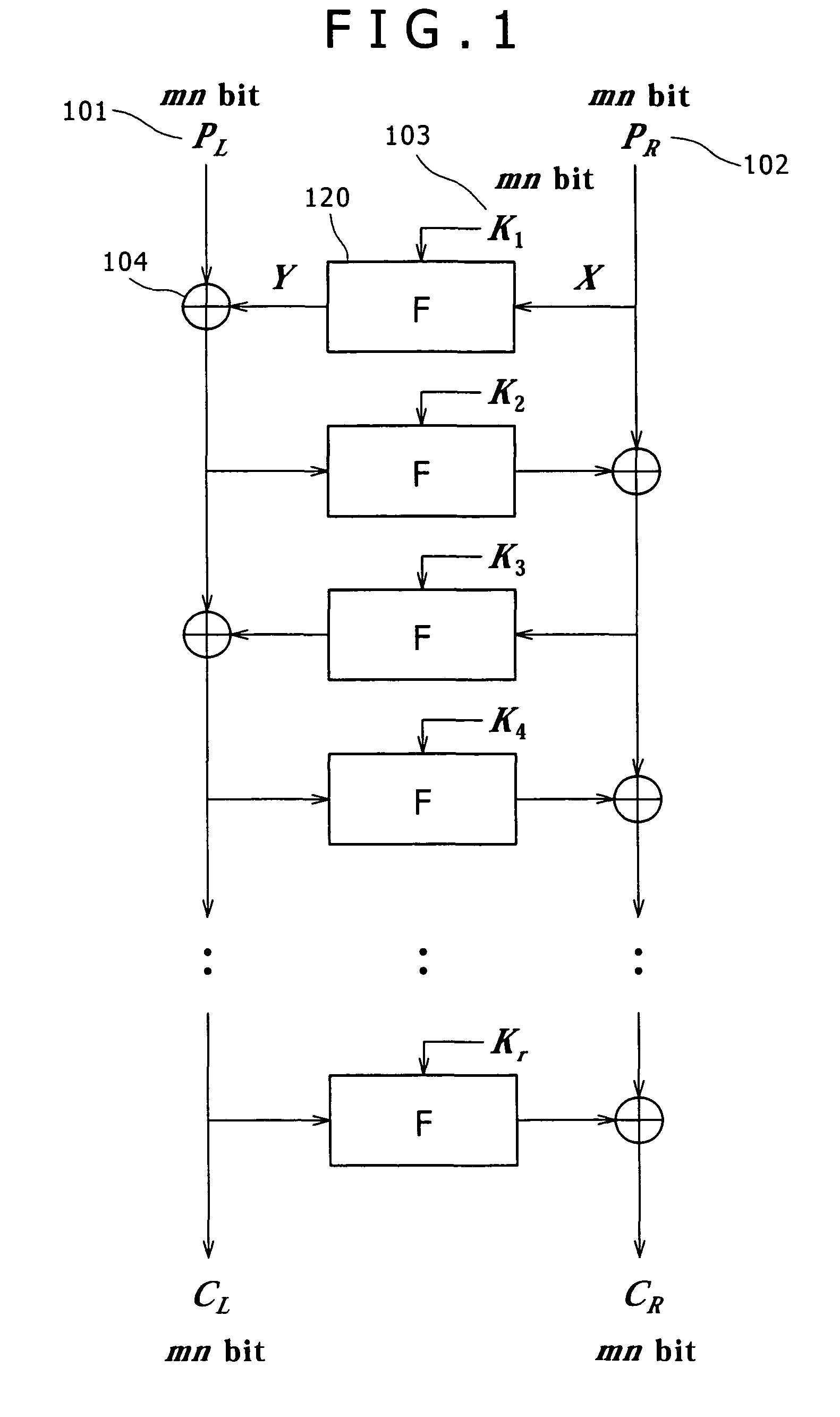
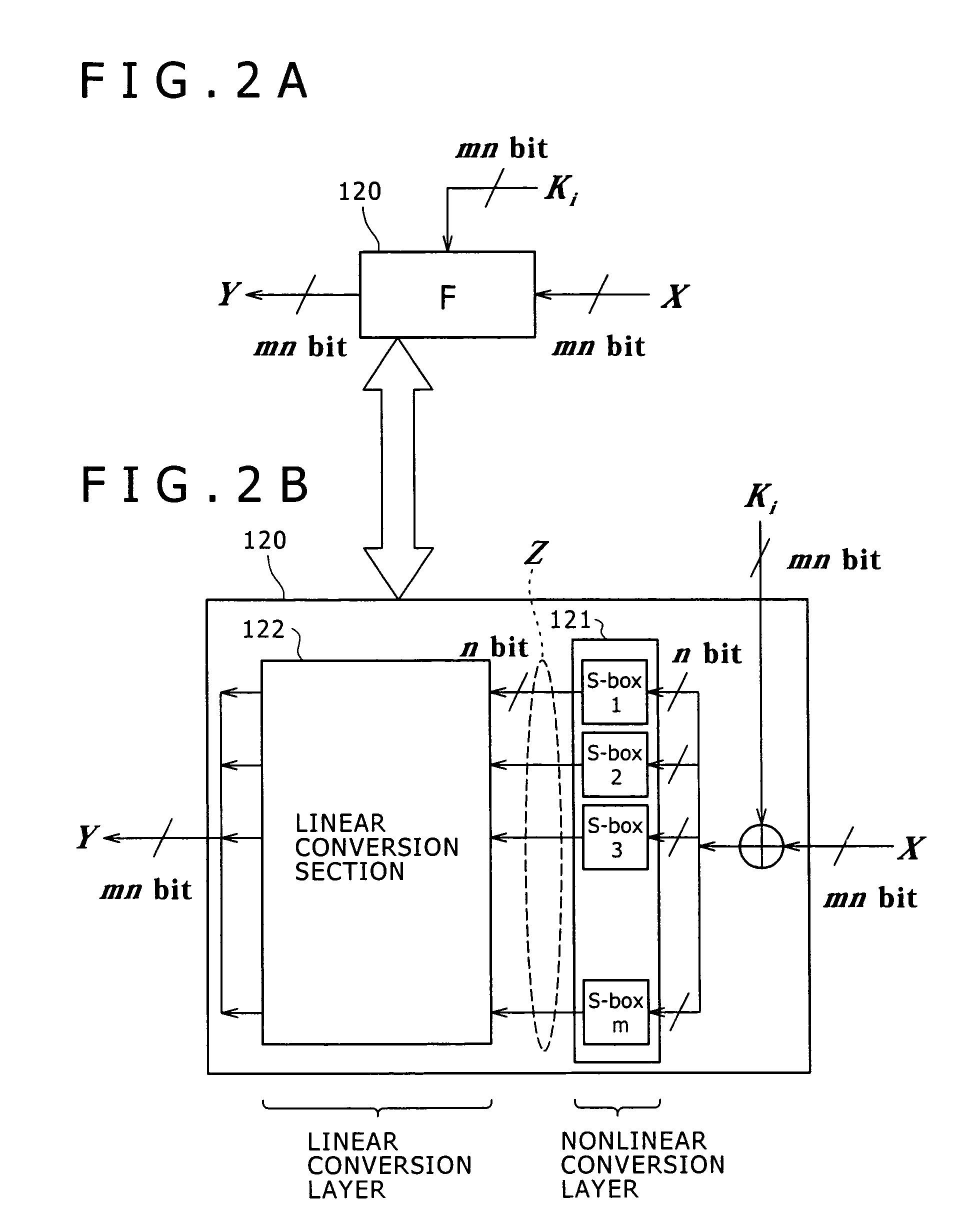
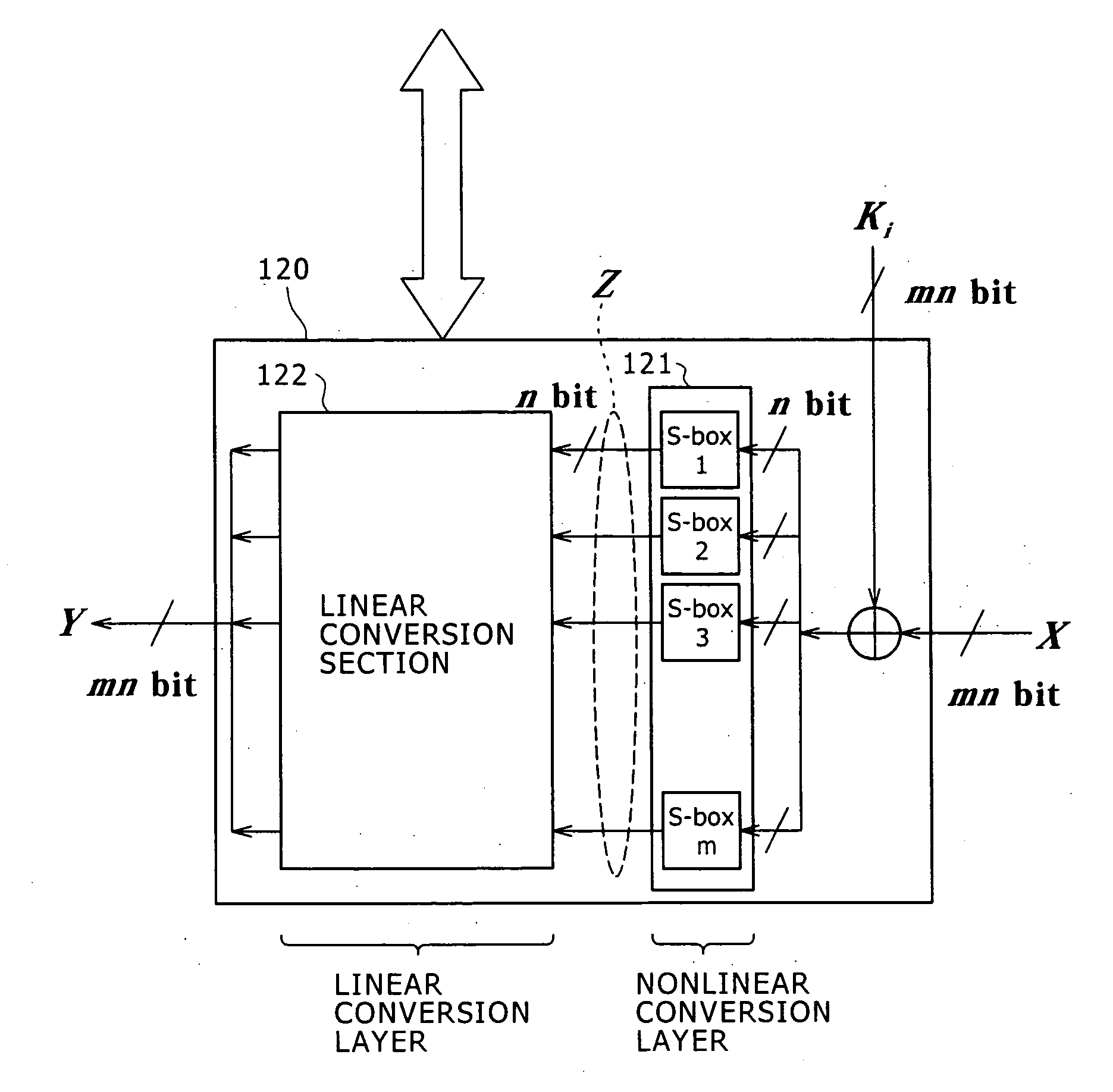
ActiveUS7747011B2Difficult to analyzeImprove the immunityMultiple keys/algorithms usageUnauthorized memory use protectionComputer hardwareMDS matrix
The invention realizes a high-security cryptographic processing apparatus that increases difficulty in analyzing its key and a method therefor. In Feistel-type common-key-block cryptographic processing that repeatedly executes an SPN-type F-function having the nonlinear conversion section and the linear conversion section over a plurality of rounds, Linear conversion processing of an F-function corresponding to each of the plurality of rounds is carried out by linear conversion processing that applies square MDS (Maximum Distance Separable) matrices. The invention uses a setting that arbitrary m column vectors included in inverse matrices of square MDS matrices being set up at least in consecutive even-numbered rounds and in consecutive odd-numbered rounds, respectively, constitute a square MDS matrix. This structure realizes cryptographic processing whereby resistance to linear cryptanalysis attacks in the common-key-block cipher is improved.
Owner:SONY CORP
Method of magnetic resonance imaging for the selection and recording of curved slices
InactiveUS9097777B2Fast and efficientImprove spatial resolutionMeasurements using NMR imaging systemsElectric/magnetic detectionAngle dependenceResonance
A method of MR imaging applies a magnetic field Bgrad1 having a spatially non-linear dependence to select a volume of at least one curved slice. The slice is described by its midsurface AM, a volume of the selected slice being made up of nν partial volumes in each of which gradients of at least one pair of remaining superimposed magnetic fields Bgradi (i>1) exhibit an angle dependence of 70° to 110° with respect to one another and with respect to the normal of the midsurface AM. At least one superimposed magnetic field of the respective pair exhibits a spatially non-linear dependence and combinations of these pairs are used for spatial encoding. In this way, curved surfaces can be mapped efficiently in high resolution and the method can be adapted to the slice shape.
Owner:UNIVERSITATSKLINIKUM FREIBURG
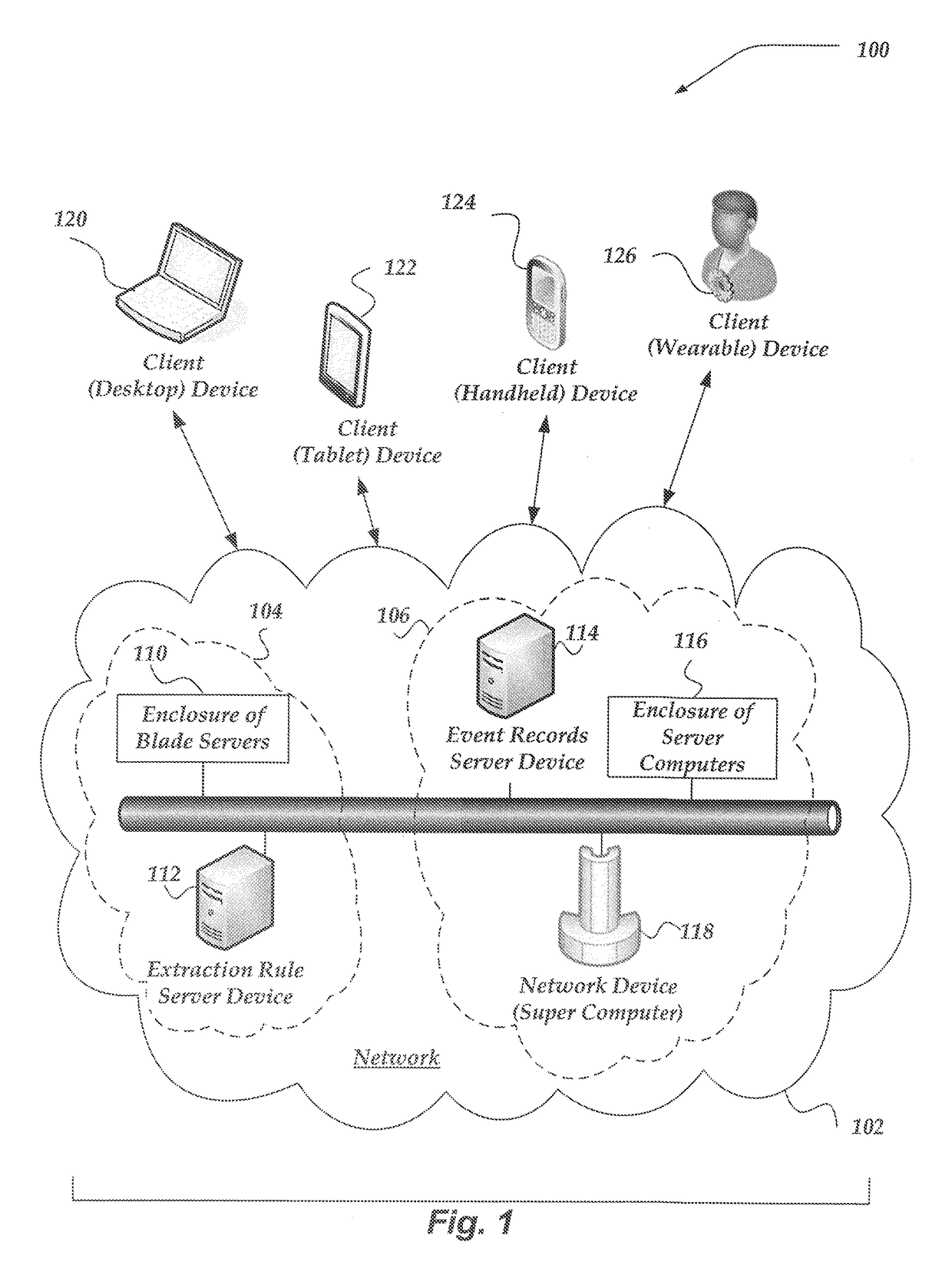
Providing an extraction rule associated with a selected portion of an event
ActiveUS20180293051A1Easy to collectIncrease productionDigital data information retrievalData sortingReal time displayData mining
Embodiments are directed towards real time display of event records with an indication of previously provided extraction rules. A plurality of extraction rules may be provided to the system, such as automatically generated and / or user created extraction rules. These extraction rules may include regular expressions. A plurality of event records may be displayed to the user, such that text in a field defined by an extraction rule is emphasized in the display of the event record. The same emphasis may be provided for text in overlapping fields, or the emphasis may be somewhat different for different fields. The user interface may enable a user to select a portion of text of an event record, such as by rolling-over or clicking on an emphasized part of the event record. By selecting the portion of the event record, the interface may display each extraction rule associated with the selected portion.
Owner:SPLUNK INC
Method and apparatus for a variable processing period in an integrated circuit
ActiveUS20050089060A1Increased power consumptionDifficult to makeEncryption apparatus with shift registers/memoriesConcurrent instruction executionComputer scienceLogic module
The invention is a system for modifying the processing period in a digital logic module. The invention comprises the following. A processing circuit is configured to receive an input in order to create an output. A controller is coupled to the processing circuit and is configured to track L manipulations, wherein L is an integer. The controller is further configured to send a select signal to the processing circuit and to cause the processing circuit to manipulate the input over N clock cycles. N is an integer and N is less than or equal to L. N varies over the plurality of processing time periods. An output port is coupled to the processing circuit and is configured to convey the output.
Owner:ATMEL CORP
Information processing apparatus
InactiveUS7805758B2Improve securityReduce overheadMemory loss protectionError detection/correctionThird partyInformation processing
An information processing apparatus has: a memory 13; CPU for executing a program written in the memory 13; a secure module 20; and storage means for storing a plurality of encrypted programs into which a program is divided. The CPU transmits the program stored in the storage means to the secure module 20. The secure module 20 has: means for receiving the program stored in the storage means, means for returning the received program to an executable state; means for writing the program, which has been returned to the executable state, in the memory 13 in a sequence for CPU to execute, and means for deleting the program from the memory 13 by CPU after execution is completed. When executing the program, the information processing apparatus can make reverse analysis by a malicious third party difficult, and enhance security of a load module to be executed.
Owner:FUJITSU LTD
Method and apparatus for smoothing current consumption in an integrated circuit
InactiveUS6954866B2Difficult to analyzeResistance/reactance/impedenceVolume/mass flow measurementEngineeringCurrent consumption
The invention includes a system for smoothing current consumption in a digital logic module. A processing circuit is configured to receive an input and manipulate the input during a processing time period to produce an output. A non-processing time period follows production of the output. The processing circuit is further configured to draw an active range of current during the processing time period and an inactive range of current during the non-processing time period. The system comprises a smoothing circuit coupled to the processing circuit and configured to engage the processing circuit during the non-processing time period. The smoothing circuit is also configured to cause the processing circuit to draw an active range of current during the non-processing time period.
Owner:ATMEL CORP
Data Processing Apparatus, Data Processing Method, and Computer Program
InactiveUS20080222204A1Reduce possibilityDifficult to analyzeRandom number generatorsSpecial data processing applicationsData processingTheoretical computer science
A data processing apparatus includes an input section configured to receive data to be encoded, a first pseudo-random-number generating section configured to generate a first pseudo-random number, a second pseudo-random-number generating section configured to a second pseudo-random number, an address determining section configured to determine matrix address candidate values on the basis of a bit string of the second pseudo-random number generated by the second pseudo-random-number generating section, a matrix generating section configured to generate a matrix in which pixel values based on constituent bit values of the first pseudo-random number generated by the first pseudo-random-number generating section are set at matrix positions designated on the basis of the matrix address candidate values, and an encoding section configured to generate encoded data by executing exclusive OR operations between corresponding positional data in the matrix generated by the matrix generating section and the received data.
Owner:SONY CORP
Authentication device, authentication system, and verification method for authentication device
InactiveUS7941832B2Avoid analysisAvoid authenticationSpecial service provision for substationDigital data processing detailsValidation methodsAuthentication system
At startup, divided data blocks are received from other authentication devices and are assembled together with the local divided data block to reconstitute first authentication data. After a prescribed time interval, divided data blocks are again received from other authentication devices and are assembled together with the local divided data block to reconstitute second authentication data. The first authentication data and the second authentication data are cross-checked, and the legitimacy of the other authentication devices is decided; in the event that the other authentication devices are legitimate devices, one authentication device among the multiplicity of authentication devices re-divides the second authentication data into a multiplicity of divided data blocks for re-distribution, and a process of reconstituting the authentication data from the divided data, cross-checking the reconstituted data with the first authentication data, and deciding whether the other authentication devices are legitimate devices is repeated at prescribed intervals.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
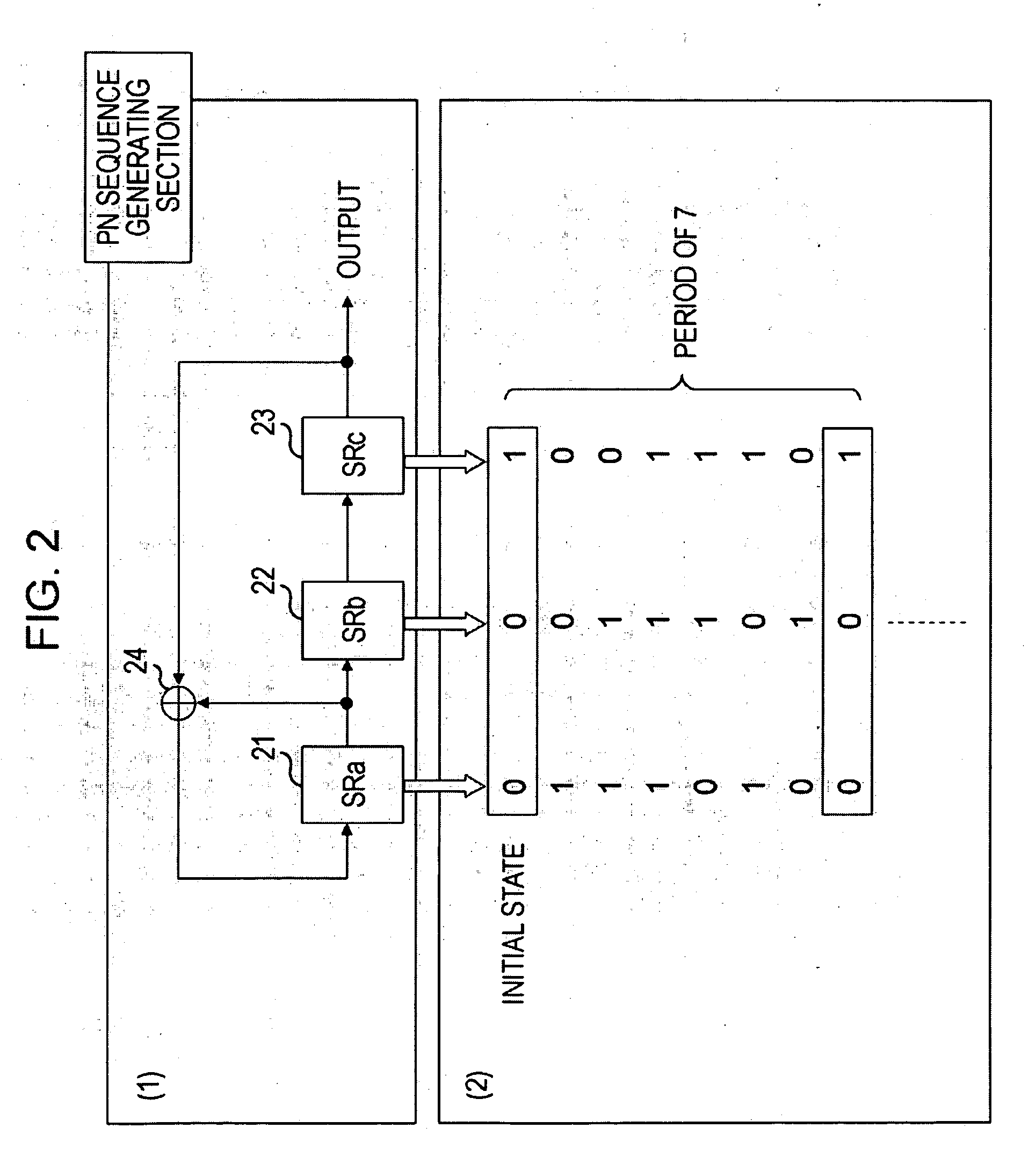
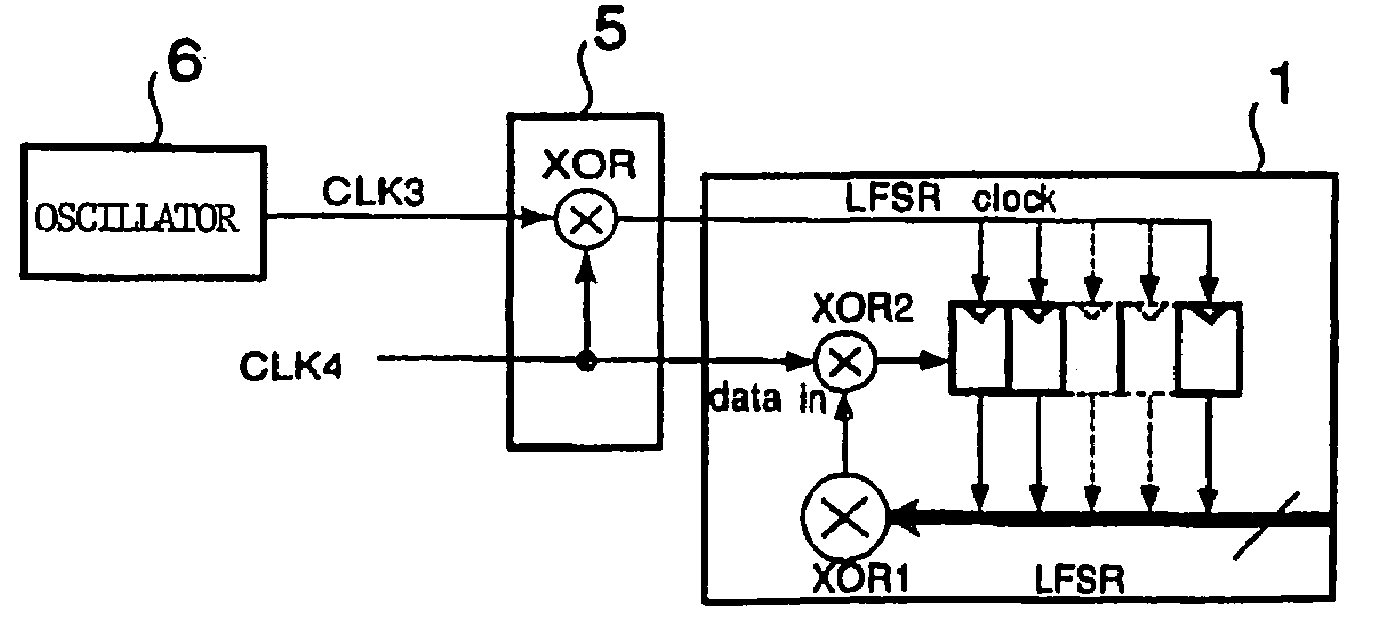
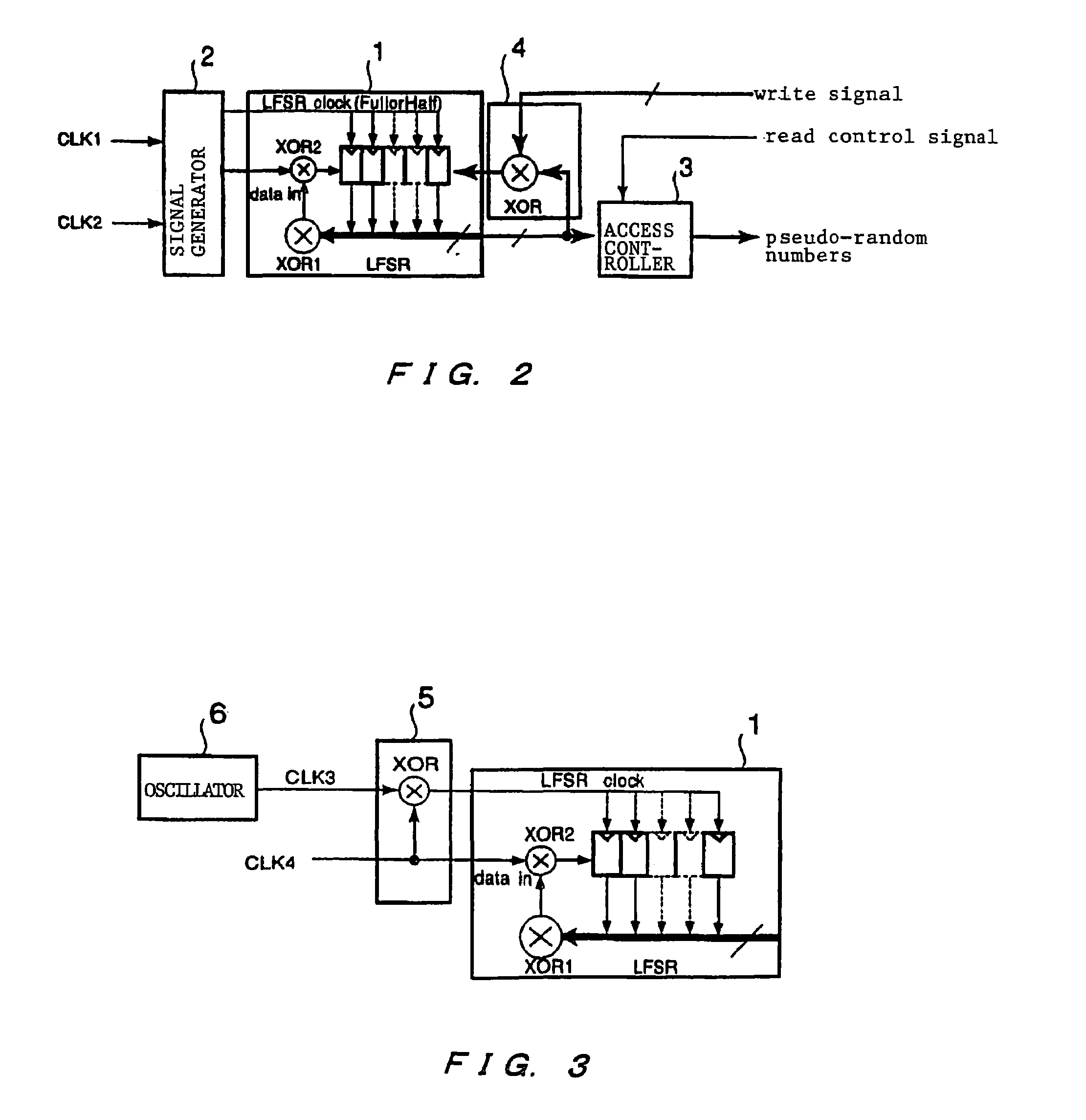
Pseudo-random number generator
InactiveUS7376687B2High randomnessDifficult to analyzeRandom number generatorsCoding/ciphering apparatusRandom number generationPseudorandom number generator
A pseudo-random number generator comprises a linear feedback register for generating pseudo-random numbers; and a signal generator for generating a shift clock for operating a linear feedback register and predetermined input data. The linear feedback register has a plurality of registers connected in series, a first logical operation circuit for taking logical operation of output data from predetermined registers to deliver the result thereof, and a second logical operation circuit for taking logical operation of input data supplied from the outside and output data of the first logical operation circuit to supply the result thereof to any one of the registers.
Owner:RENESAS ELECTRONICS CORP
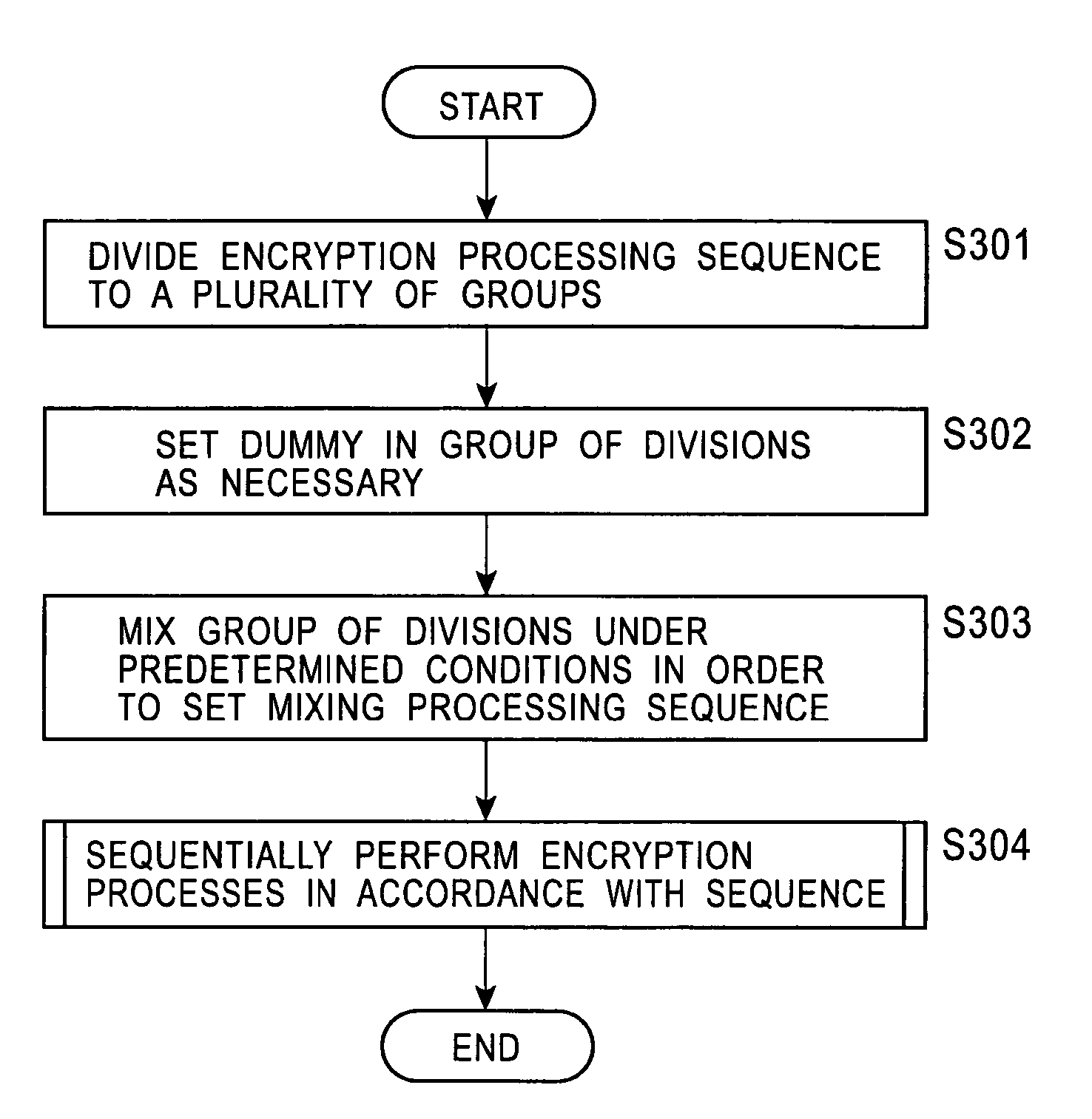
Encryption processing apparatus and encryption processing method for setting a mixed encryption processing sequence
InactiveUS7984305B2Difficult to analyzeIncrease the difficultyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwarePower analysis
An encryption processing apparatus and method in which the difficulty of encryption analysis based on power analysis can be increased considerably are provided. By dividing an original encryption processing sequence into a plurality of groups and by mixing the processing sequence by setting dummies as necessary, several hundreds to several thousands of types of different mixed encryption processing sequences can be set, and a sequence selected from a large number of these settable sequences is performed. According to this configuration, consumption power variations which are completely different from consumption power variations caused by a regular process possessed by the original encryption processing sequence can be generated, and thus the difficulty of encryption analysis based on power analysis can be increased considerably.
Owner:SONY CORP
Encryption device, encryption method, and computer program
ActiveUS20090103714A1Difficult to analyzeImprove the immunityMultiple keys/algorithms usageUnauthorized memory use protectionComputer hardwareMDS matrix
The invention realizes a high-security cryptographic processing apparatus that increases difficulty in analyzing its key and a method therefor. In Feistel-type common-key-block cryptographic processing that repeatedly executes an SPN-type F-function having the nonlinear conversion section and the linear conversion section over a plurality of rounds, Linear conversion processing of an F-function corresponding to each of the plurality of rounds is carried out by linear conversion processing that applies square MDS (Maximum Distance Separable) matrices. The invention uses a setting that arbitrary m column vectors included in inverse matrices of square MDS matrices being set up at least in consecutive even-numbered rounds and in consecutive odd-numbered rounds, respectively, constitute a square MDS matrix. This structure realizes cryptographic processing whereby resistance to linear cryptanalysis attacks in the common-key-block cipher is improved.
Owner:SONY CORP
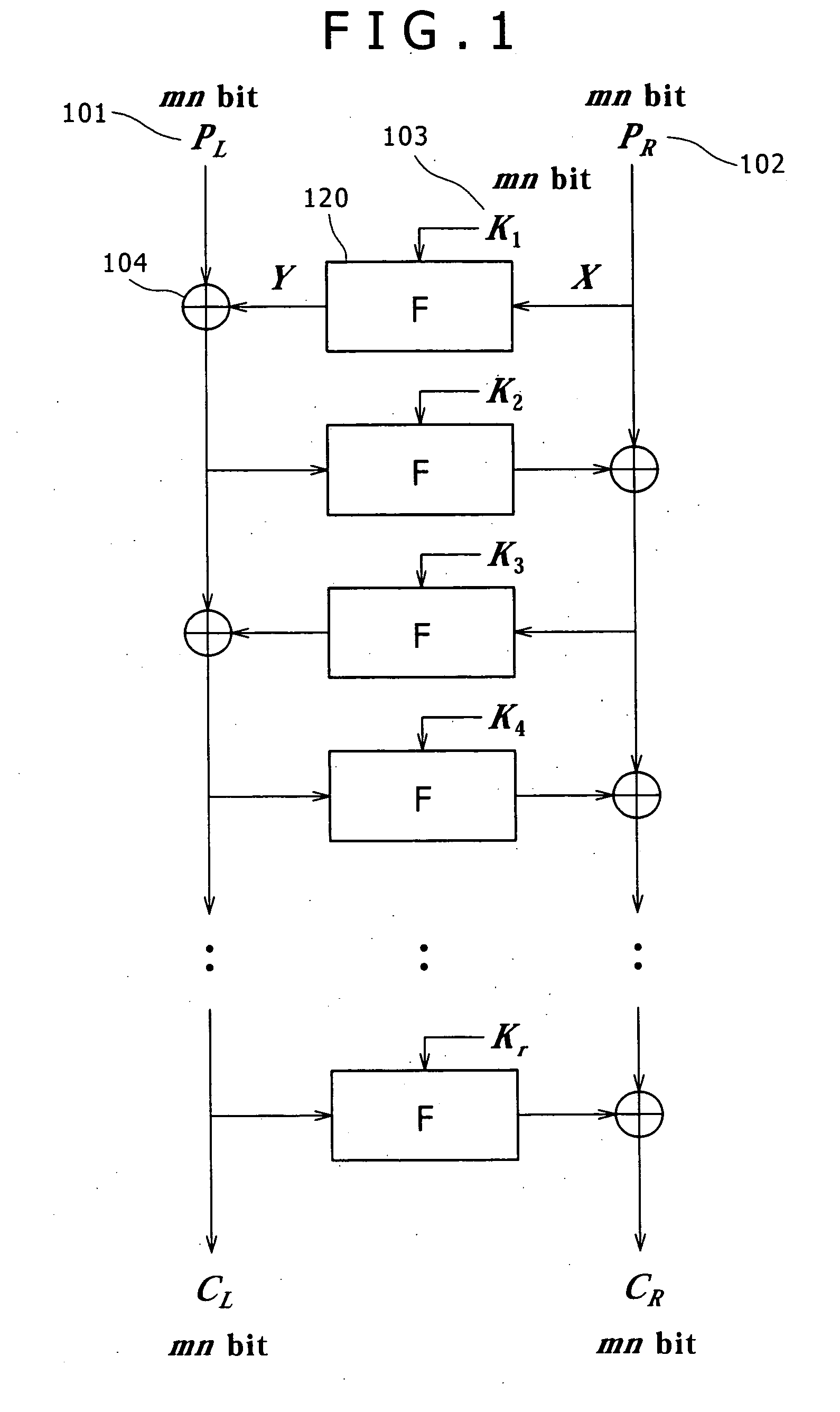
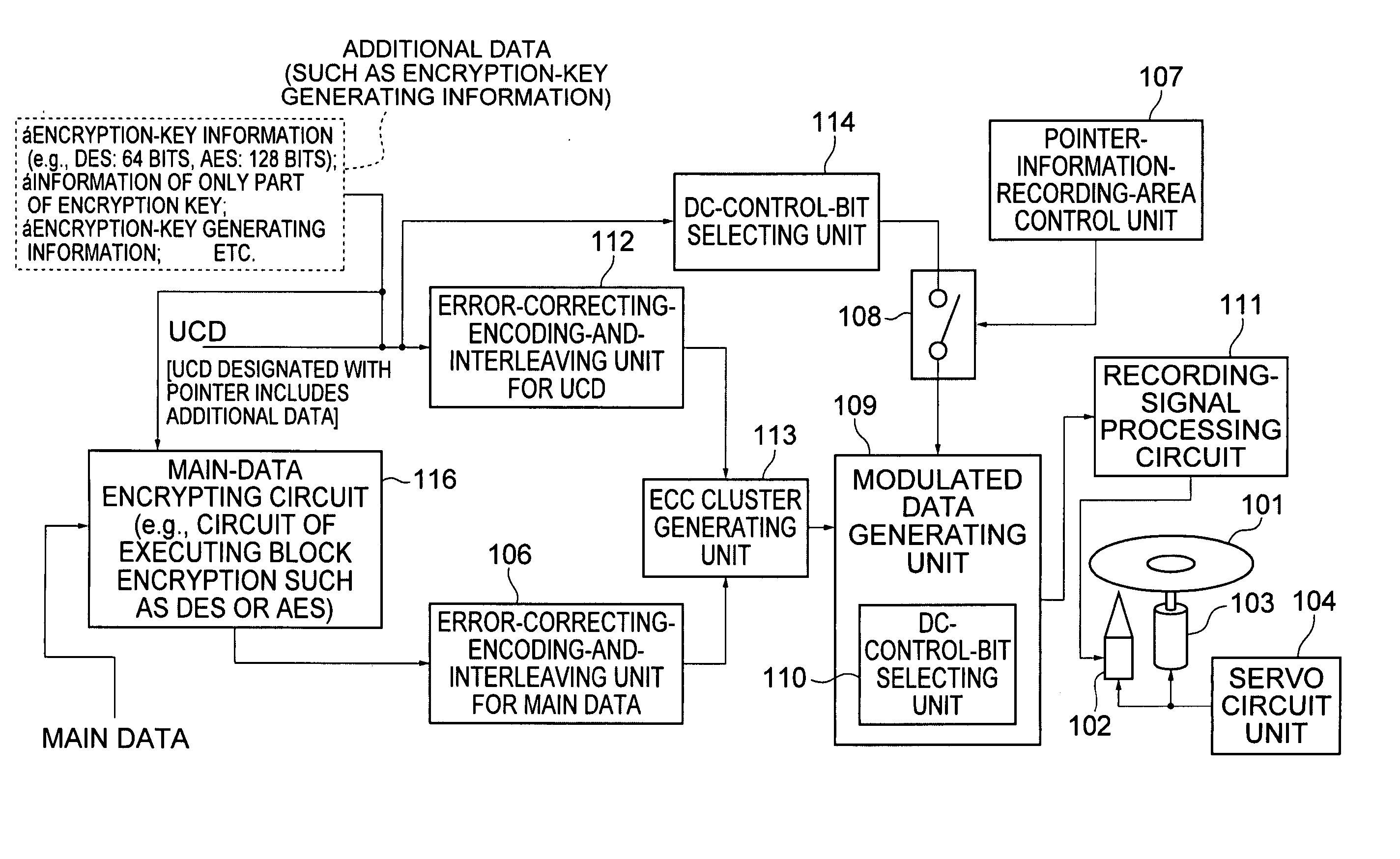
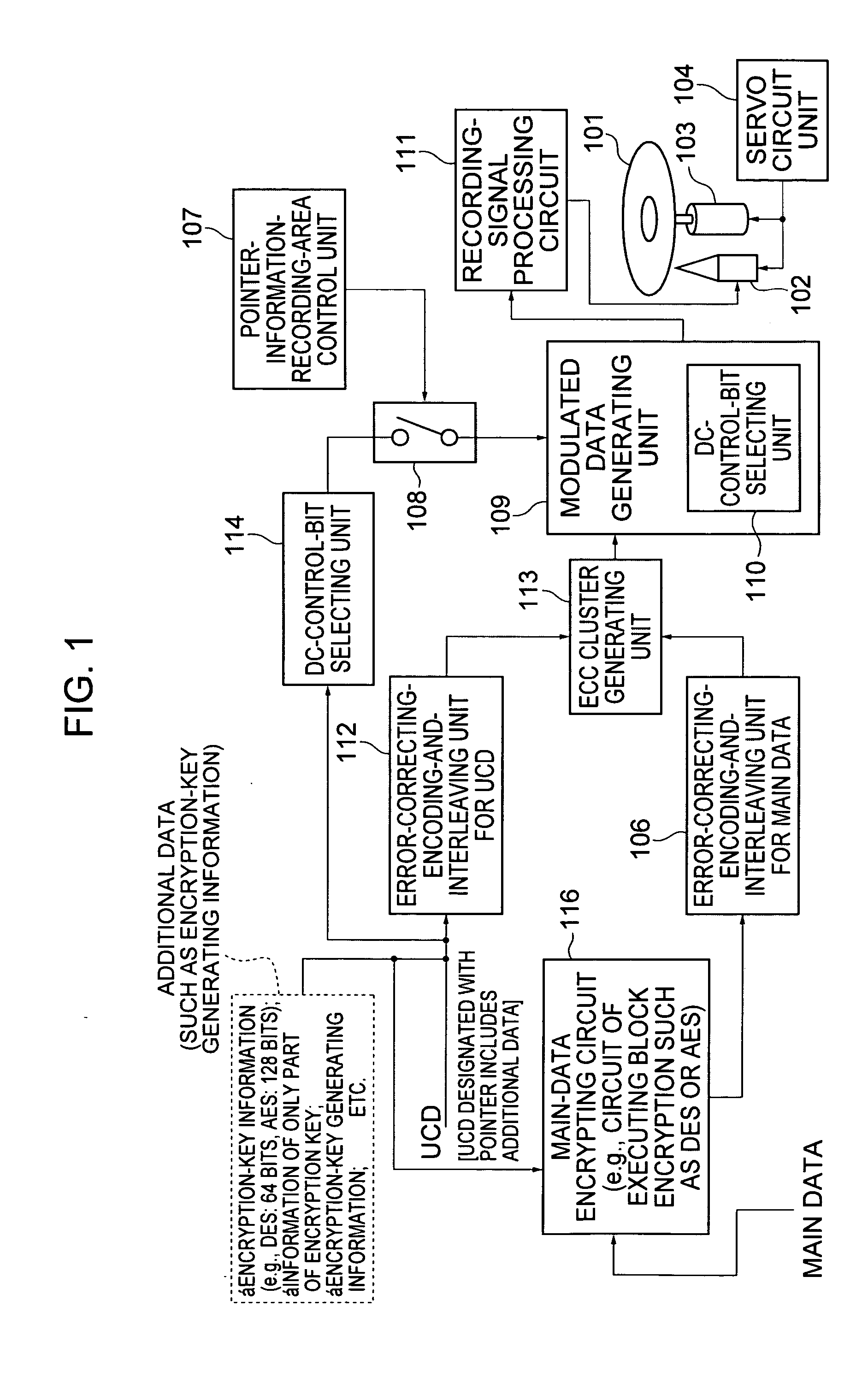
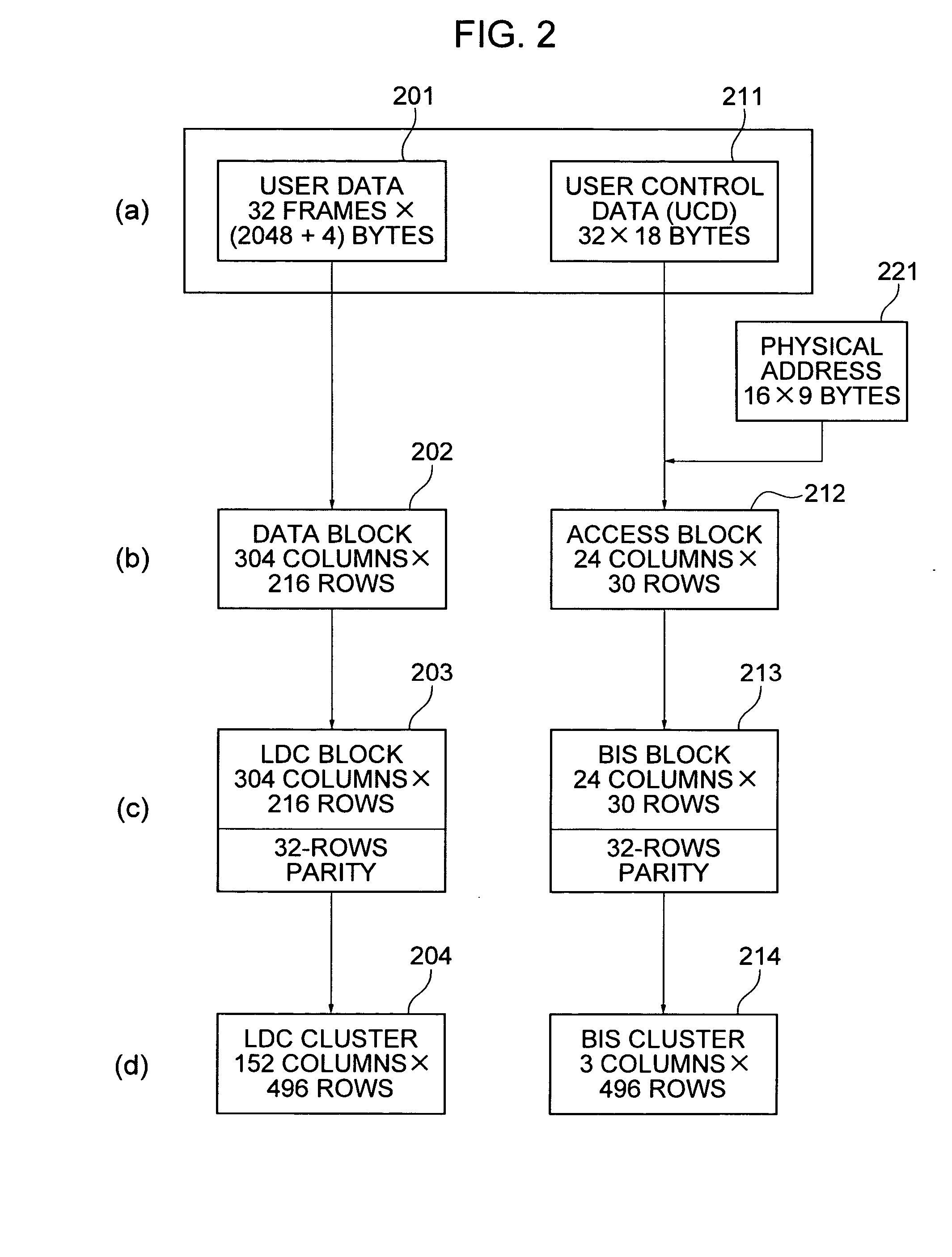
Information recording processor, information playback processor, method therefor, and information recording medium and computer program used therewith
InactiveUS20050123271A1Difficult to analyzeTelevision system detailsColor television signals processingComputer hardwareUser control
In an information recording processor, component bits of additional data to be recorded on an information recording medium are stored in specific user control data. Pointer information representing row and column numbers used as identification information of the user control data is set as the values of DC control bits in a user-control-data-pointer-information-set recording frame selected from recording data. In an information playback processor, from the DC control bits in the recording frame, the row and column numbers of the user control data are acquired. The user control data is acquired and the additional data is acquired.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com