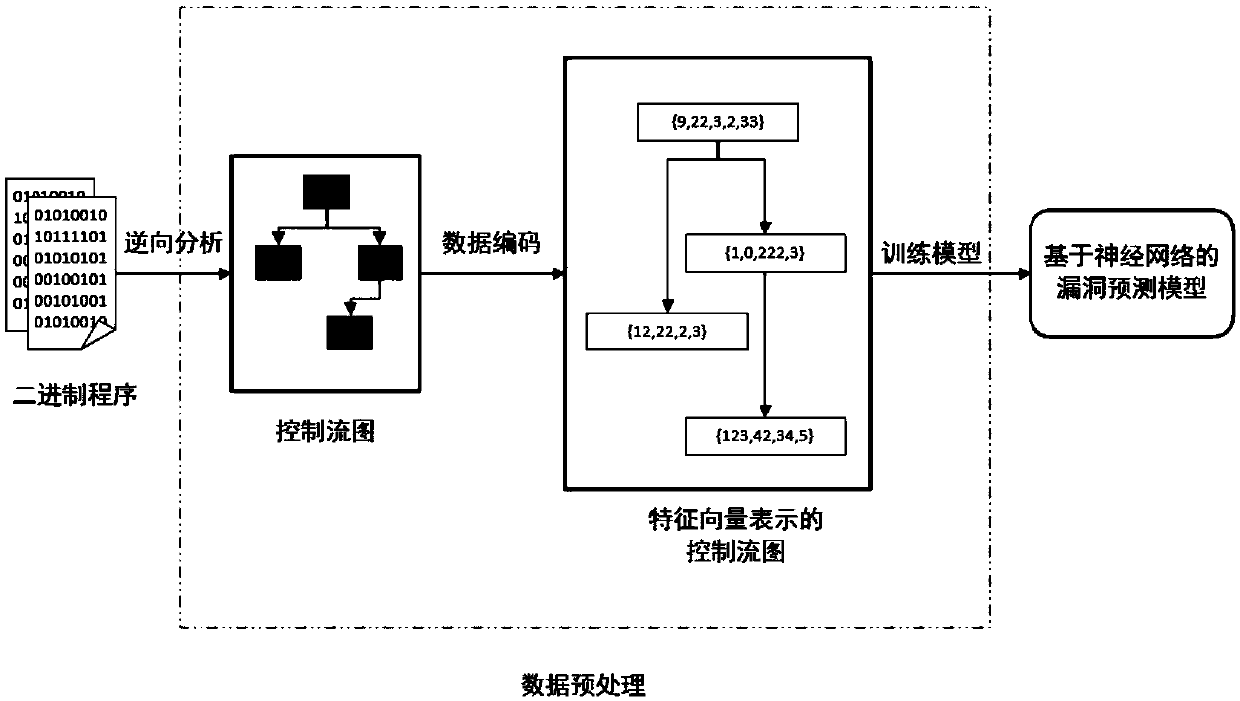
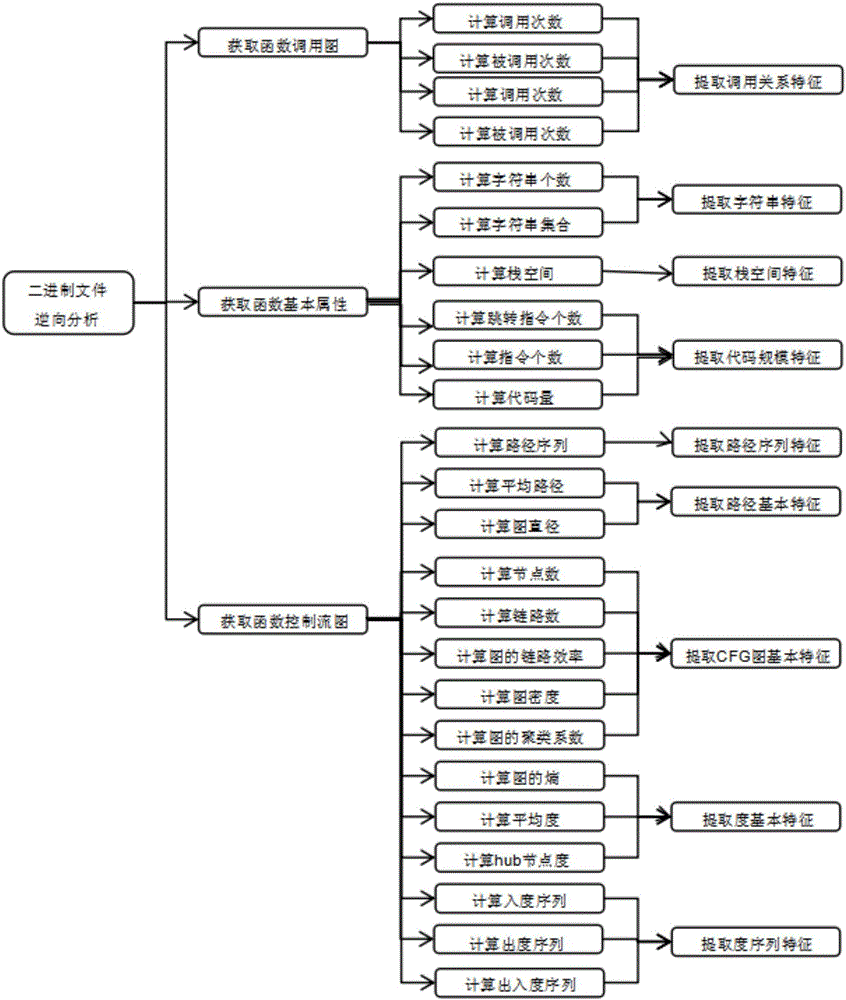
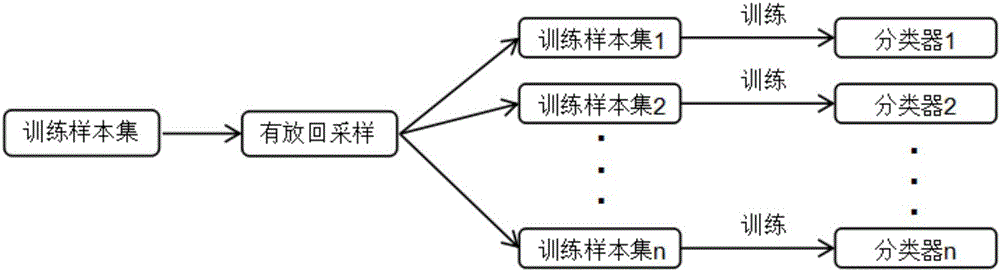
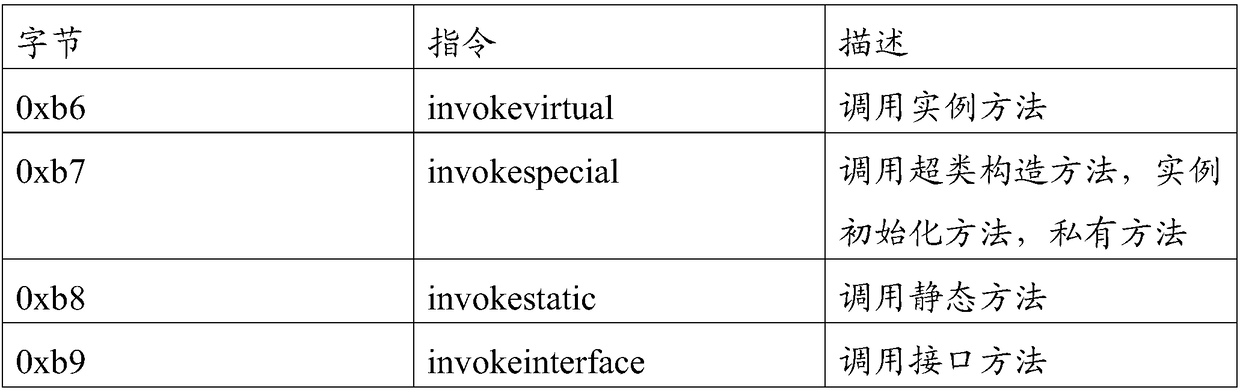
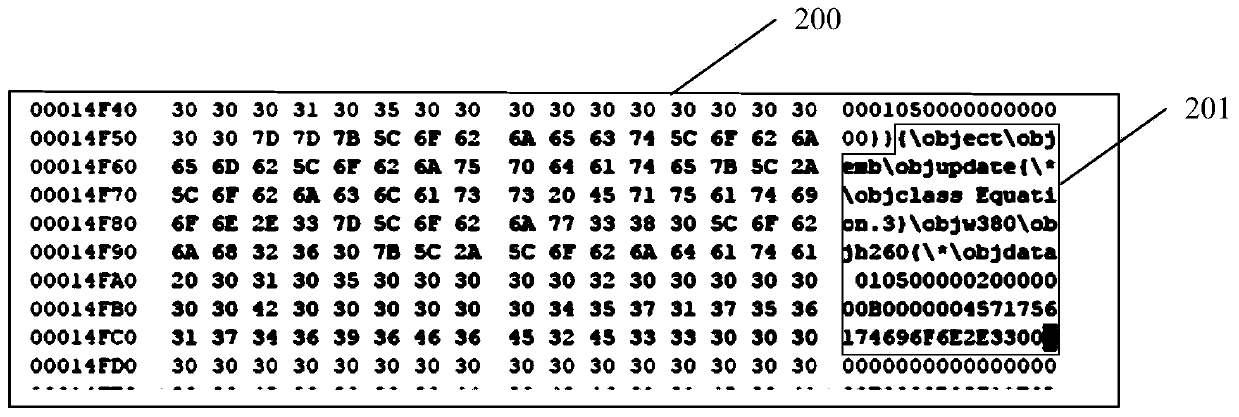
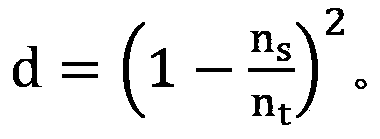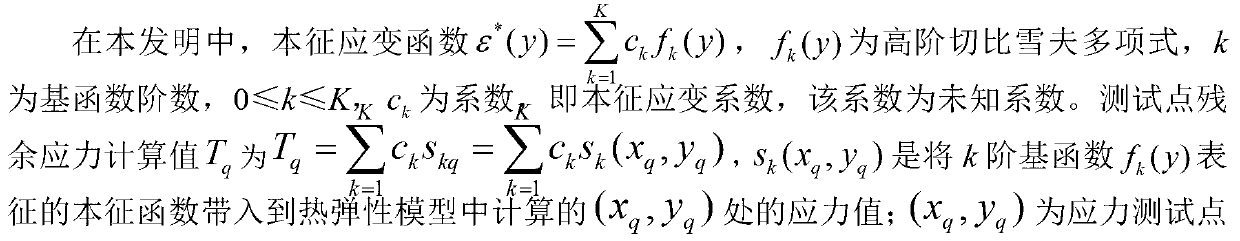Patents
Literature
349 results about "Reverse analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
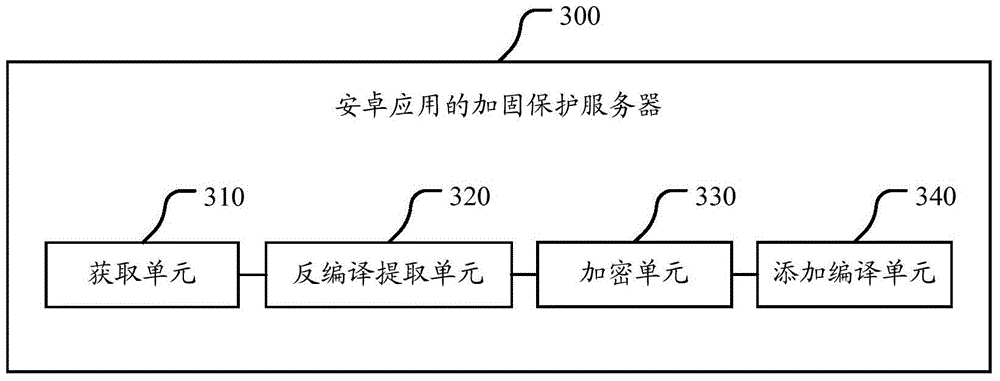
Android platform software protecting system, method and equipment
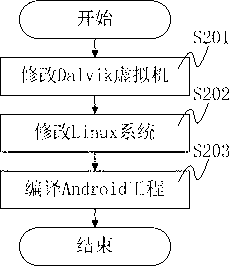
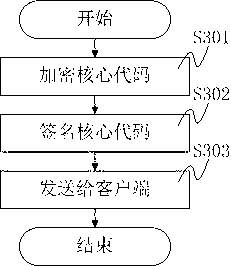
The invention mainly discloses a system and method for protecting application software in an Android system from reverse analysis and decryption. The method mainly comprises the following steps: increasing interfaces for a LiDalvik virtual machine and a Linux system library in the Android system, so that the Android has a capability of directly loading a DEX format file and an SO format file from a memory; storing a core code of the application software in an online server, encrypting and signing the core code, sending the core code to the application software installed at a client end; after receiving the core code, verifying the signature and decrypting the core code by the application software; storing a plaintext into the memory, and directly loading the plaintext into the system; invoking the code; and releasing the memory. The method greatly improves the difficulty in performing reverse analysis and decryption by an attacker, so that the safety of the Android application software can be effectively protected.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
Reinforcement protection method, sever and system for android app
ActiveCN104462959AReduce reverse analysisAvoid gettingPlatform integrity maintainanceProgram controlReverse analysisAndroid app
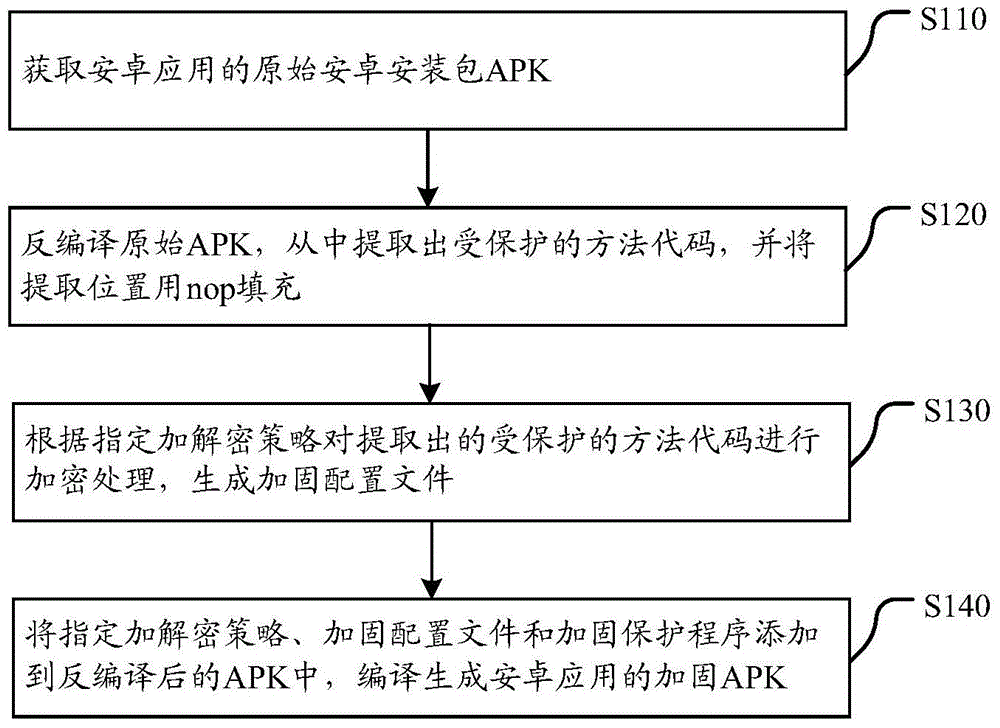
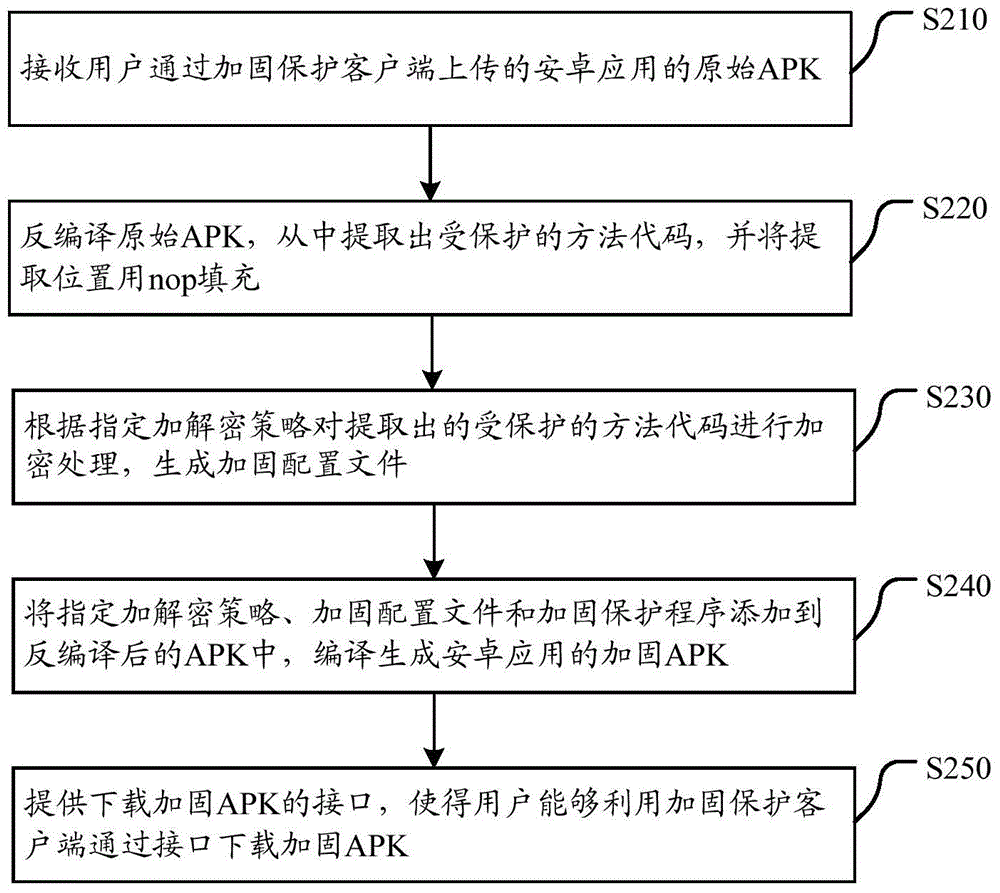
The invention discloses a reinforcement protection method, sever and system for android app. The method comprises the following steps: obtaining an initial android package APK of the android app; decompiling the initial APK, extracting protected method codes from the initial APK, and filling an extraction position with nop; encrypting the extracted protected method codes according to an appointed encryption and decryption strategy to generate a reinforcement configuration file; adding the appointed encryption and decryption strategy, the reinforcement configuration file and a reinforcement protection program into the decompiled APK, and compiling to generate a reinforcement APK of the android app. According to the technical scheme provided by the invention, protected methods can be dynamically encrypted and decrypted, and complete dex mapping does not exist in a memory at any moment, so that a complete dex file is prevented from being obtained in a memory dump manner and the probability of repacking and redistribution of the android app due to reverse analysis is greatly reduced.
Owner:BEIJING QIHOO TECH CO LTD
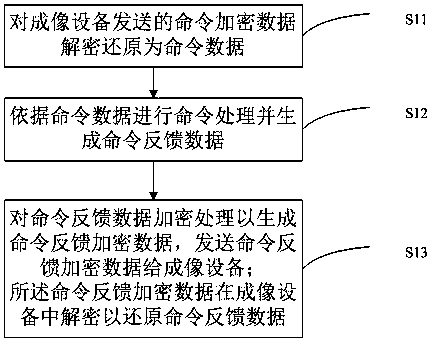
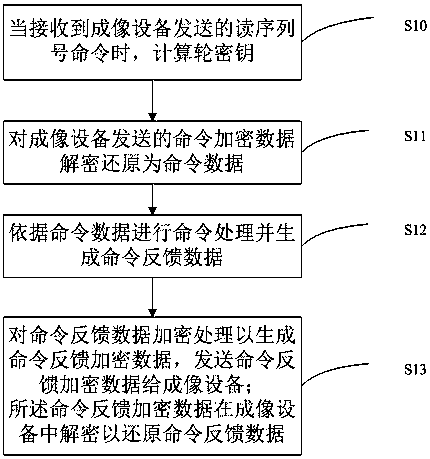
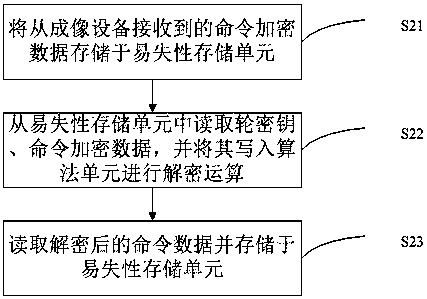
Consumable chip and a communication method thereof, and system and method for communication between consumable chip and imaging device
ActiveCN108819486AAvoid crackingImprove safety and reliabilityDigital data protectionInternal/peripheral component protectionComputer hardwareReverse analysis
The invention, which belongs to the technical field of printer consumables, provides a consumable chip and a communication method thereof, and a system and method for communication between a consumable chip and an imaging device. The communication method comprises: command encrypted data sent by an imaging device are decrypted and restored into command data; command processing is carried out basedon the command data and command feedback data are generated; and the command feedback data are encrypted to generate command feedback encrypted data and the command feedback encrypted data are sent to the imaging device, wherein the command feedback encrypted data are decrypted in the imaging device to restore the command feedback data. The consumable chip comprises a decryption unit for carryingout decryption and restoration on command encrypted data sent by an imaging device, an execution chip for carrying out command processing based on the command data and generating command feedback data, and an encryption unit for encrypting the command feedback data, generating command feedback encrypted data, and sending the command feedback encrypted data to the imaging device. The encrypted communication is simple; and a phenomenon of cracking the communication data by reverse analysis of the communication waveform is avoided.
Owner:HANGZHOU CHIPJET TECH
Embedded software testing auxiliary system
ActiveCN107562635AImprove construction efficiencyRealize simulationSoftware testing/debuggingTransceiverUsability
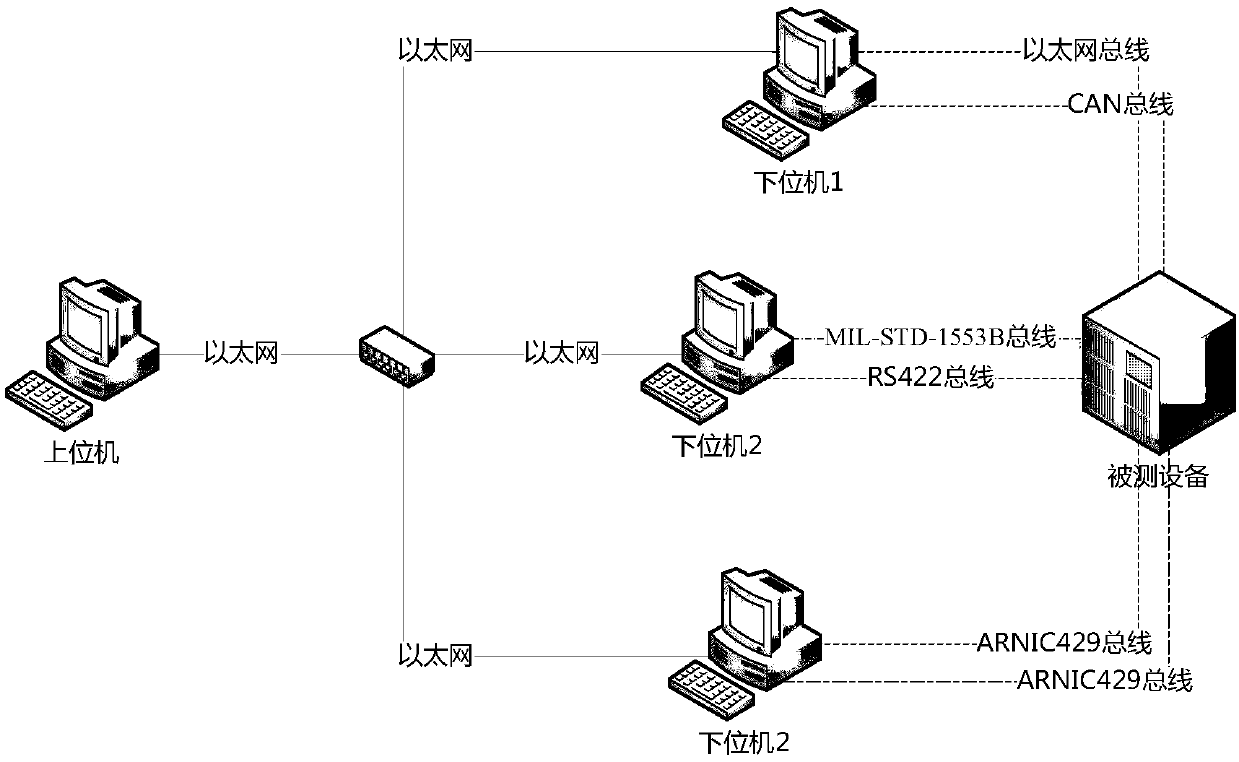
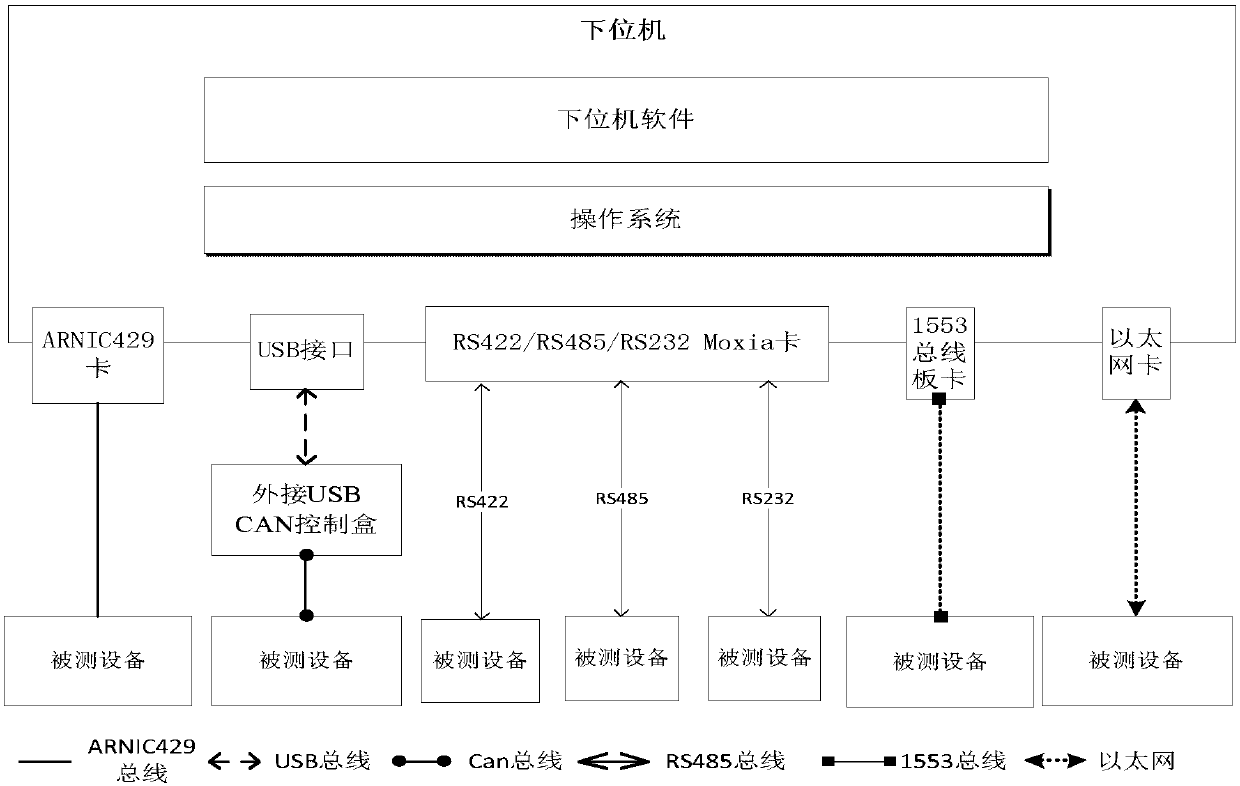
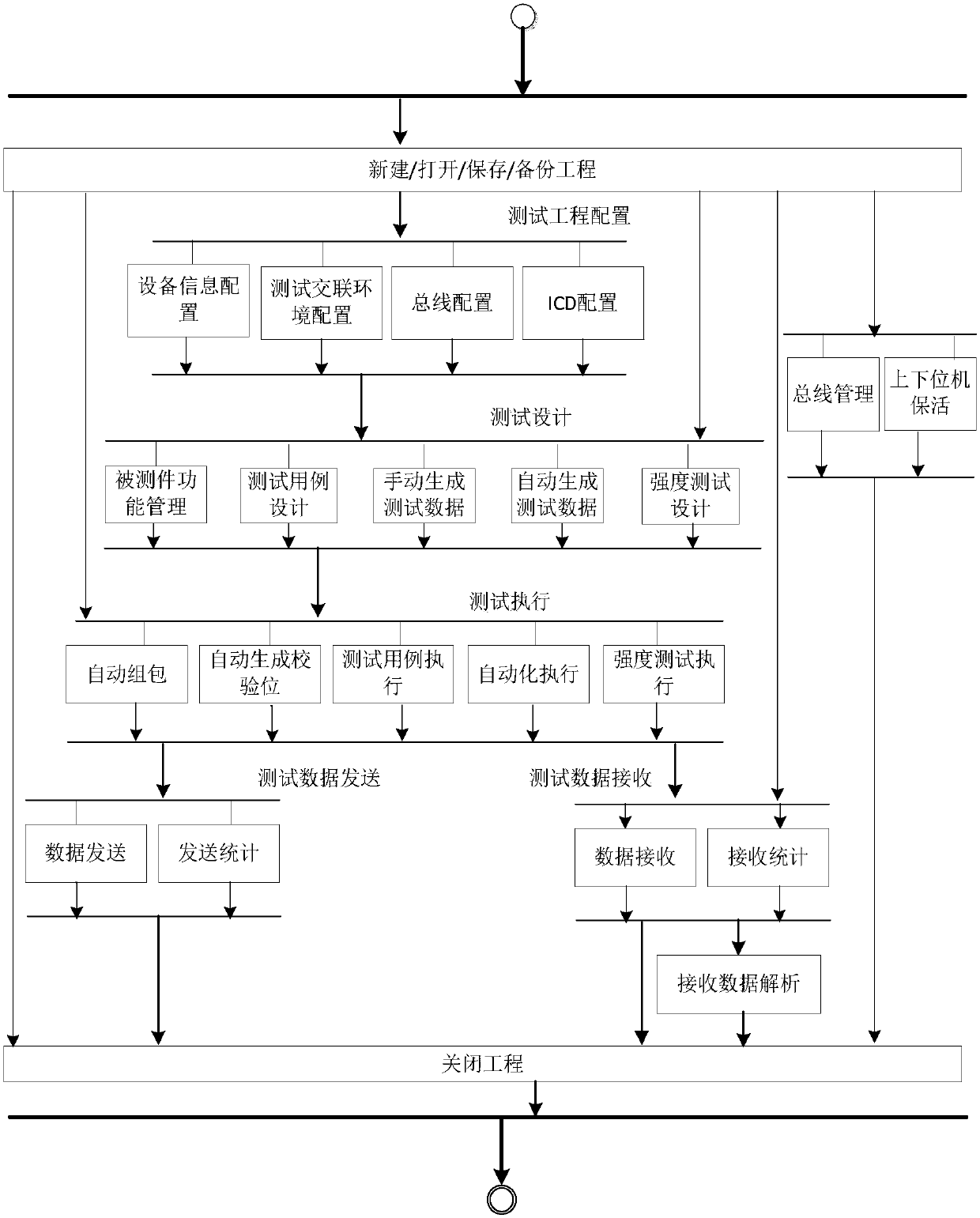
The invention provides an embedded software testing auxiliary system, and aims at providing a software testing auxiliary system which can improve the efficiency of building a testing environment, lower the operation difficulty and improve the usability. According to the technical scheme, an upper computer constructs a testing crosslinking environment of tested equipment and testing equipment, describes bus attributes, an interface control document ICD, testing case preconditions and testing steps, forms control law data according to the preconditions and the testing steps to dispatch testing data, sends, judges and receives the data, and conducts reverse analysis on the received data according to an ICD format; a lower computer cooperates with the upper computer to send the data through adetailed bus, then the data is received, testing cases and design constructed by data simulation and receiving-sending procedure control are automatically executed, and simulation of embedded softwareperipheral equipment and monitoring and detecting of the interaction process of peripheral equipment data are achieved. According to the embedded software testing auxiliary system, the testing casesof controlling a construction testing scene are executed based on the data receiving-sending procedure, and the time for developing a simulation system is shortened.
Owner:10TH RES INST OF CETC
Dynamic taint analysis device and application thereof to document format reverse analysis
InactiveCN103440201AReduce I/O operationsShorten the timeSoftware testing/debuggingData streamReverse analysis
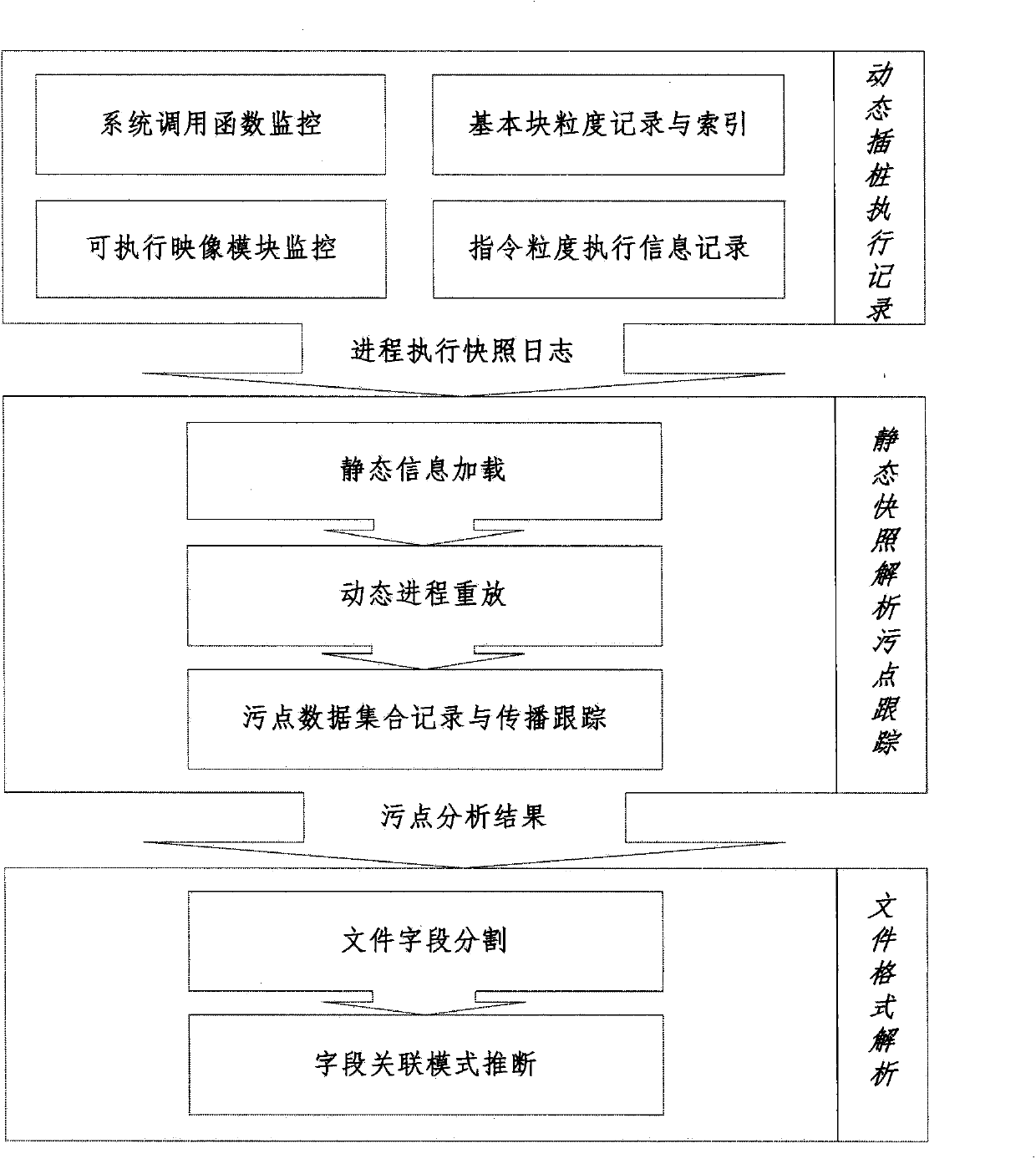
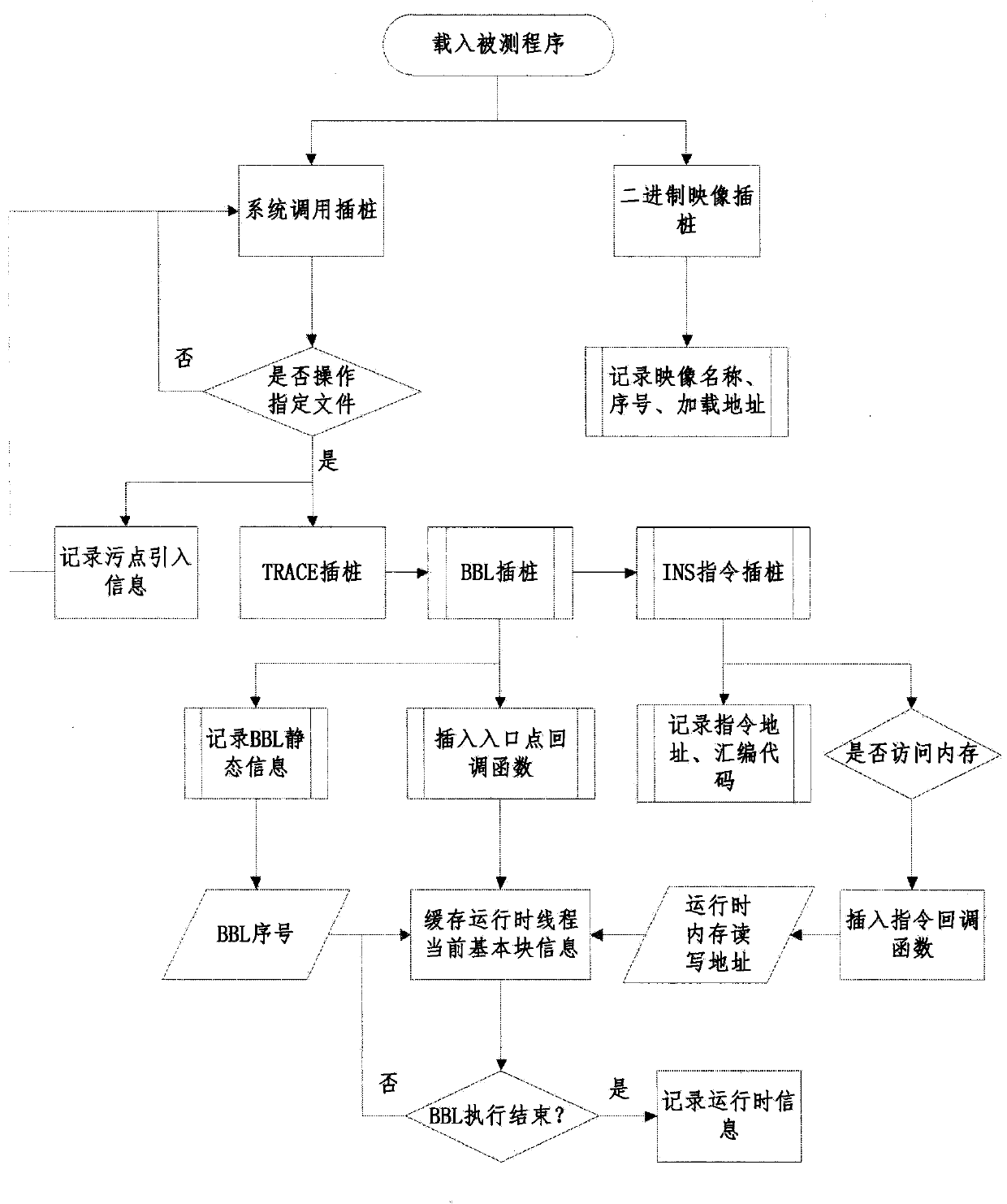
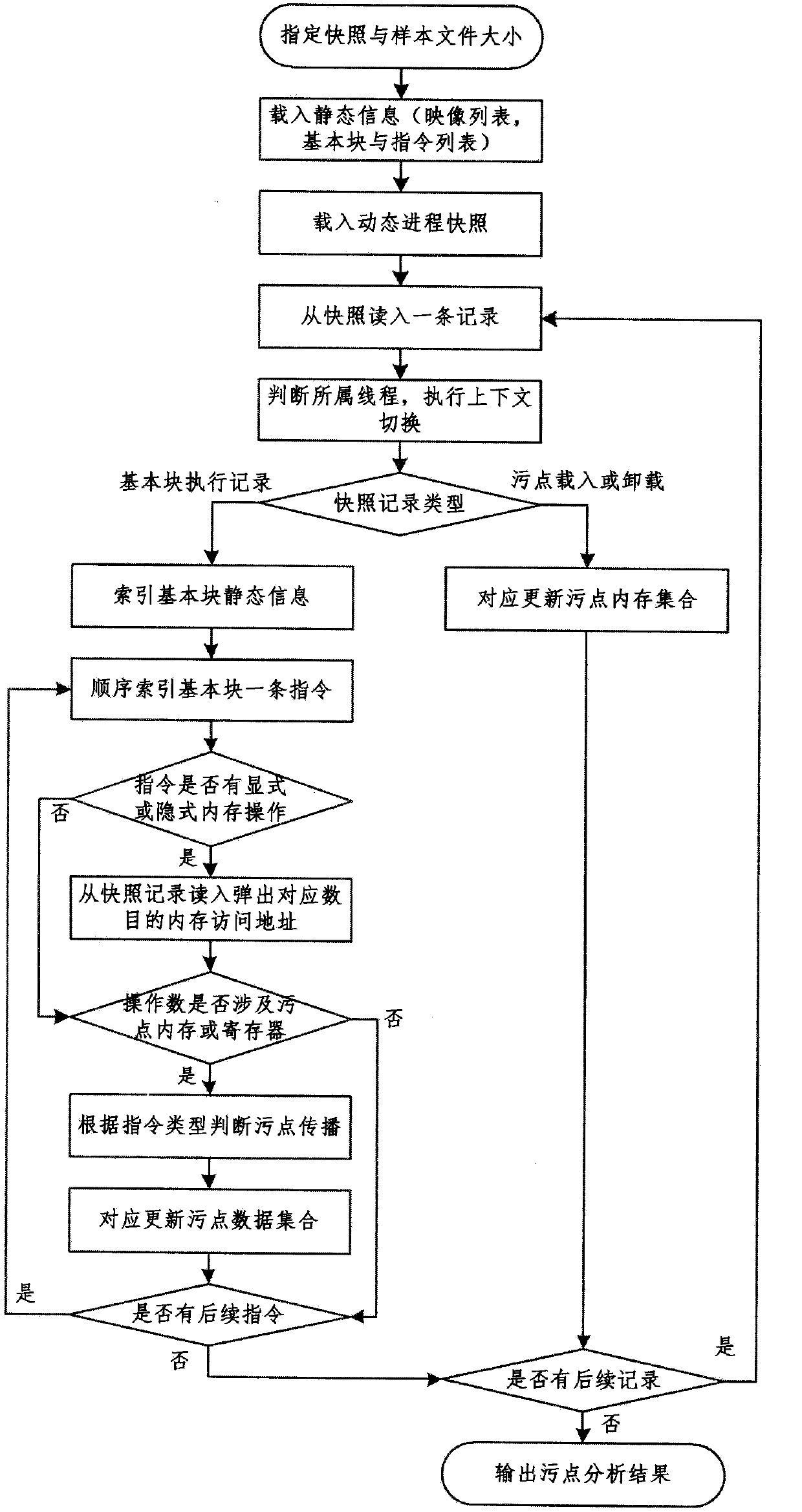
The invention relates to a dynamic taint analysis device and application of the dynamic taint analysis device to document format reverse analysis, wherein the dynamic taint analysis device comprises a dynamic instrumentation executive logging module and a static snapshoot analysis taint tracking module, wherein the dynamic instrumentation executive logging module is used for calling and executing a tested program by using a binary program instrumentation platform, monitoring opening, analyzing and closing behaviors of a data document including original taint data in a process of executing the tested program, and acquiring snapshoot logs of all command processes, context information and memory access information in the process of executing the tested program according to the process of executing the tested program; the static snapshoot analysis taint tracking module is used for analyzing the snapshoot logs and simulating replay execution of a progress according to information obtained by analysis and recording processing and spread information of original taint data in the data document to obtain a taint data stream path. According to the dynamic taint analysis device, I / O (Input / Output), time and space overhead of dynamic taint analysis in a dynamic execution process can be reduced, an extended instruction set can be supported, and the continuity and incidence relation of original taint data can be obtained.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Intelligent fuzzy testing method and system based on vulnerability learning
ActiveCN108647520AEfficient miningSoftware testing/debuggingPlatform integrity maintainanceFeature vectorControl flow
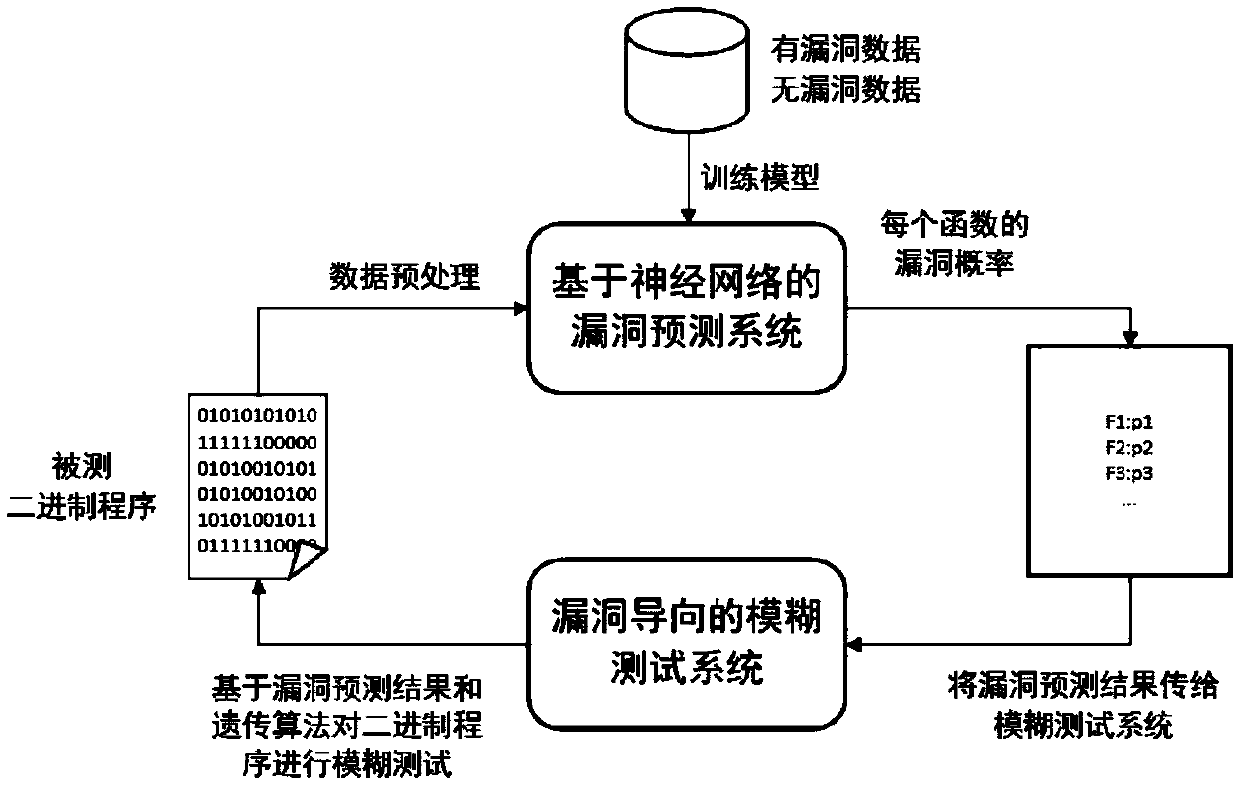
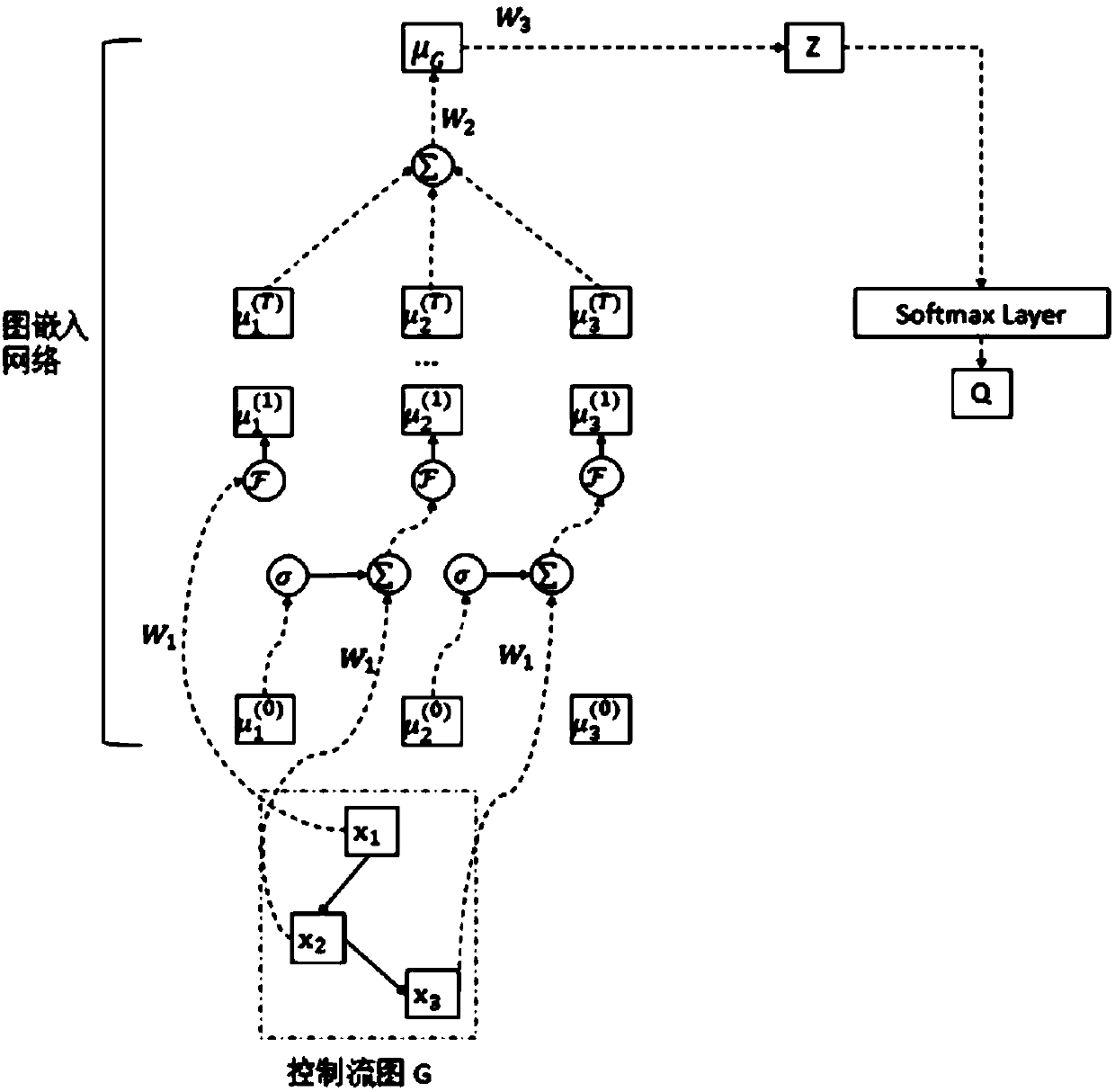
The invention discloses an intelligent fuzzy testing method and system based on vulnerability learning. The intelligent fuzzy testing system comprises a data preprocessing module, a bug prediction module and a bug-oriented fuzzy testing module, wherein the data preprocessing module is used for performing reverse analysis on a to-be-tested binary program to obtain a control flow chart of the to-be-tested binary program and performing feature extraction on each basic block in the control flow chart to obtain a feature vector of each basic block; the bug prediction module is used for predicting the probability of bugs exiting in each function in the program according to the control flow chart of the to-be-tested binary program; and the bug-oriented fuzzy testing module is used for testing theto-be-tested binary program and calculating input fitness scores by combining a certain input execution path, the probability of bugs existing in a function in the execution path and an execution result; input of a high-fitness score is used as a seed to perform heritable variation to generate next-generation input, and the to-be-tested binary program is tested cyclically till testing is over. Through the intelligent fuzzy testing system, the bugs in the binary program can be mined more efficiently.
Owner:ZHEJIANG UNIV
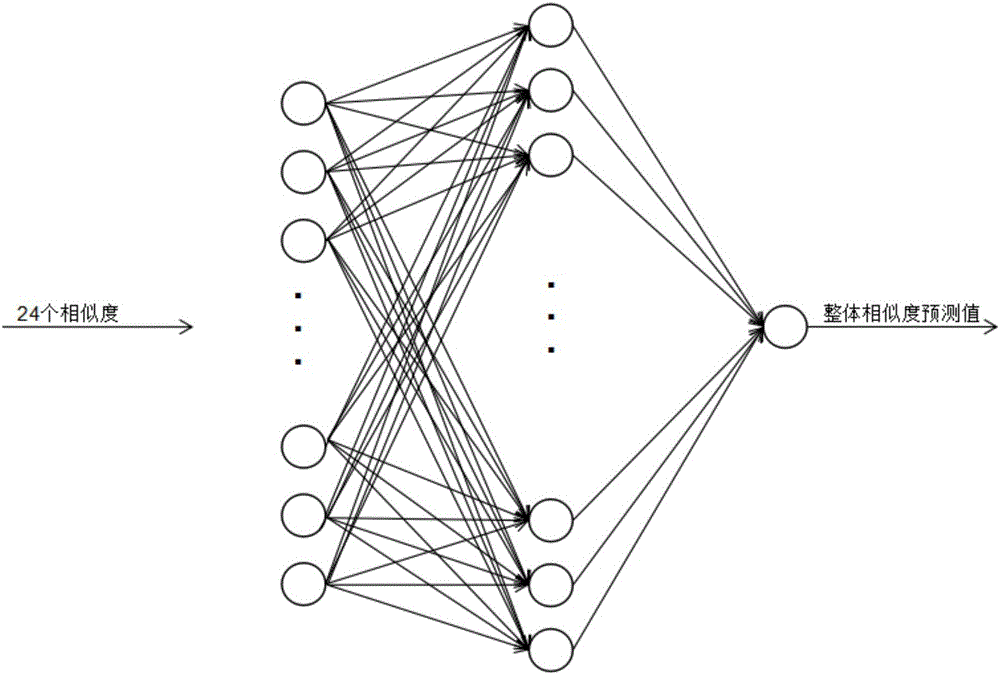
Instruction-set-irrelevant binary code similarity detection method based on neural network
ActiveCN105868108AImplement similarity detectionImprove accuracyCharacter and pattern recognitionSoftware testing/debuggingReverse analysisNeural network classifier
The invention relates to an instruction-set-irrelevant binary code similarity detection method based on a neural network. The method mainly includes the steps that binary files are reversely analyzed, and 24 features on the 9 aspects of call relation features, character string features, stack space features, code scale features, path sequence features, path basic features, degree sequence features, degree basic features and map scale features of functions are extracted. Based on expression forms of the features, the similarity degrees of the 24 features of the two to-be-compared functions are calculated through 3 similarity calculation methods and serve as input vectors of an integrated neural network classifier, and predicted values of the overall similarity between the two functions are acquired and ranked. Compared with the prior art, dependence on specific instruction sets is avoided, similarity detection of binary files of different instruction sets can be achieved, accuracy is high, the technology is simple, and popularization is easy.
Owner:INST OF INFORMATION ENG CAS +1
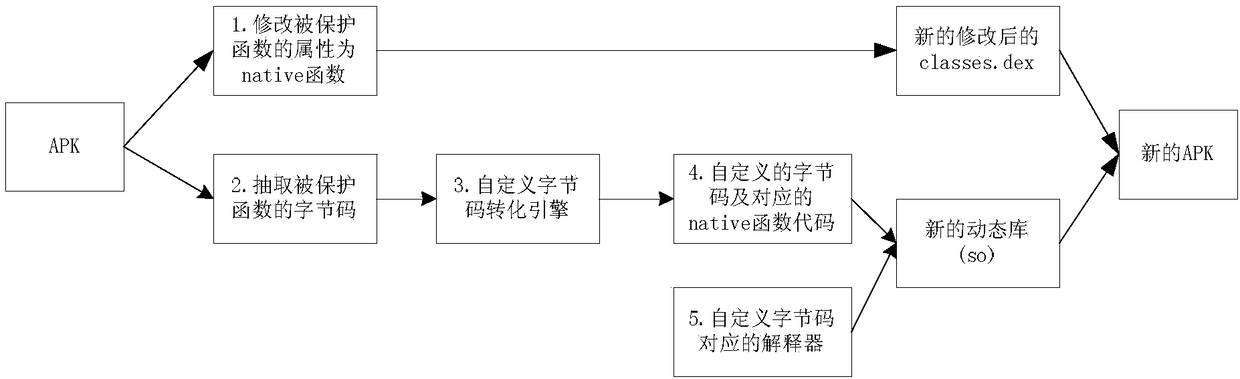
Protection method of executable program on Android platform
ActiveCN108733988AImprove securityIncrease flexibilityProgram/content distribution protectionSpecific program execution arrangementsReverse analysisSoftware engineering
The application provides a protection method of an executable program on an Android platform. The protection method comprises the following steps: determining a function needing to be protected in a classes.dex file in an APK file package, and forming new classes.dex file after the modification; compiling the C / C+ language realization of the function; and compiling the C / C++ language realization of the function as a dynamic library; replacing the original classes.dex file by using the new classes.dex file in the APK file package, and adding the dynamic library in the APK file package. Throughthe protection method provided by the application, the reverse analysis difficulty is increased, and the difficulty of reducing the code is greatly increased.
Owner:BEIJING BANGCLE TECH CO LTD
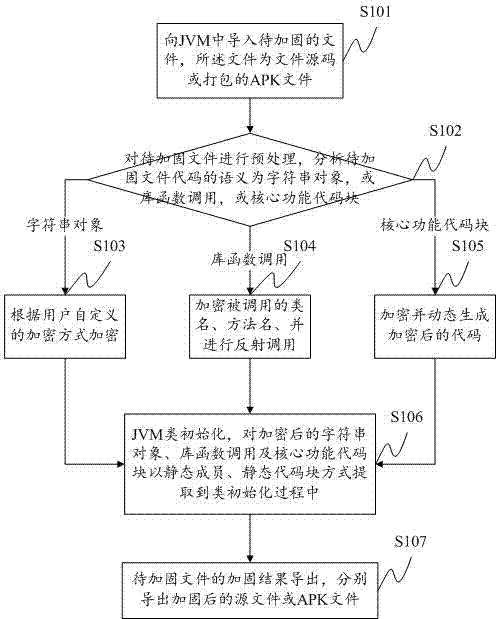
APK application reinforcing method and system
InactiveCN103902858ACopyright protectionReduce the possibility of reverse engineeringProgram/content distribution protectionCoding blockReverse analysis
The invention provides an APK application reinforcing method and system. The method comprises the steps of inputting the source code of files to be reinforced or APK files, preprocessing the files to be reinforced, analyzing the semantics, using different encryption ways according to different objects, conducting JVM class initialization processing on the encrypted objects, extracting the encrypted objects to the class initialization process in the modes of static members, static code blocks and the like, and at last outputting a reinforcing result. Through the APK application reinforcing method, APK application programs under the Android can be reinforced, displaying and calling of any cleartext character string or library functions can not occur to a decompilation result, a core code function is hidden, the difficulty of reverse analysis of the APK files is greatly increased, and therefore the effect of protecting the application codes of a developer is achieved.
Owner:WUHAN ANTIY MOBILE SECURITY
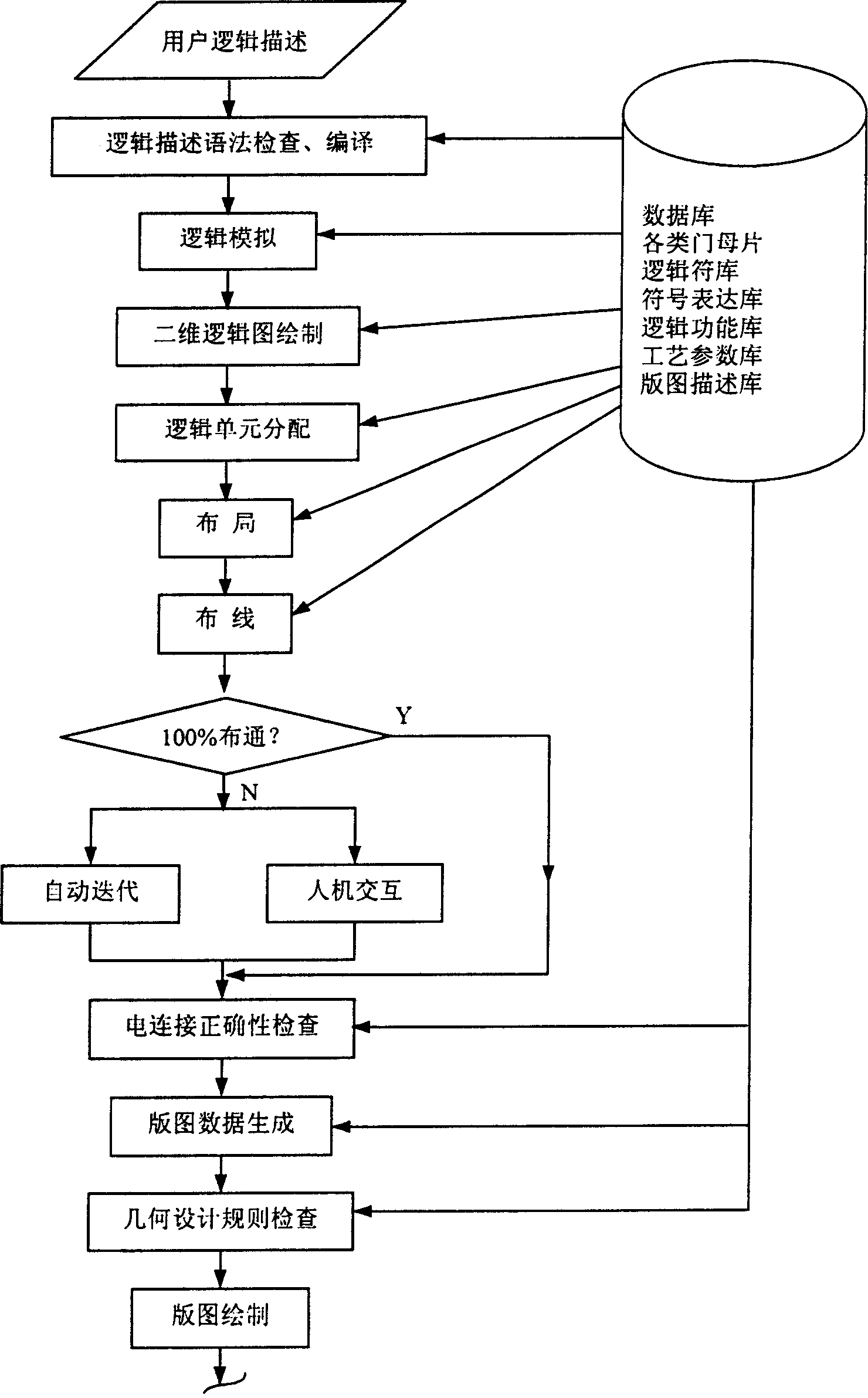
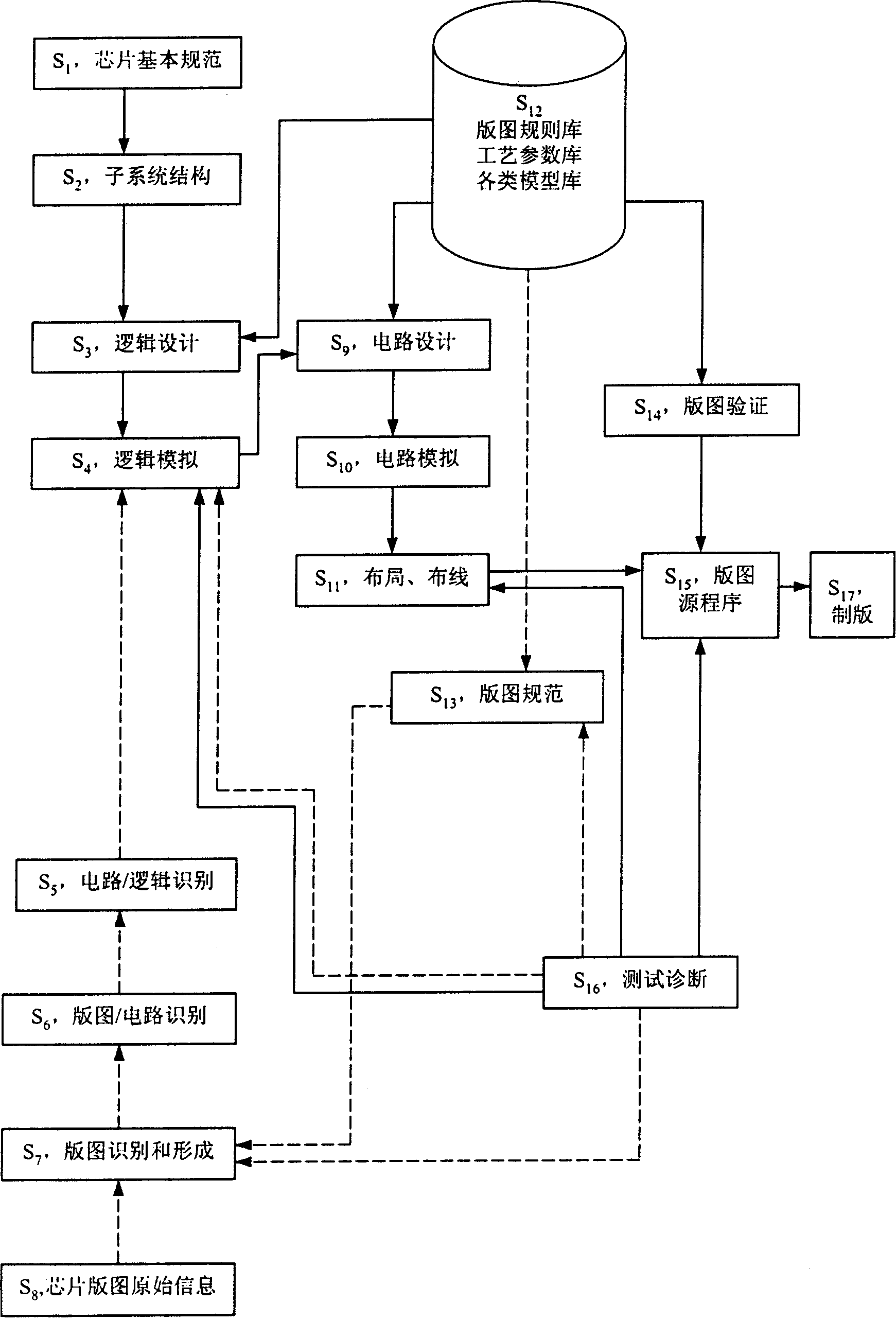
Bidirectional technique system of integrated circuit design
InactiveCN1523660AComplementarySemiconductor/solid-state device manufacturingSpecial data processing applicationsReverse analysisEngineering
This invention puts forward a two-way system for an IC design, a system merging an inverse analysis and positive design. At the present market, an IC analyzer is needed to analyze ready-made chips and the inverse analysis technology is invented for it. On the other hand, the positive design technology is to design chips normally from logic description to the final artwork design. Some parts are compensated and compatible and the invention combines the inverse analysis with the positive design technology to a unified system.
Owner:上海芯华微电子有限公司 +2
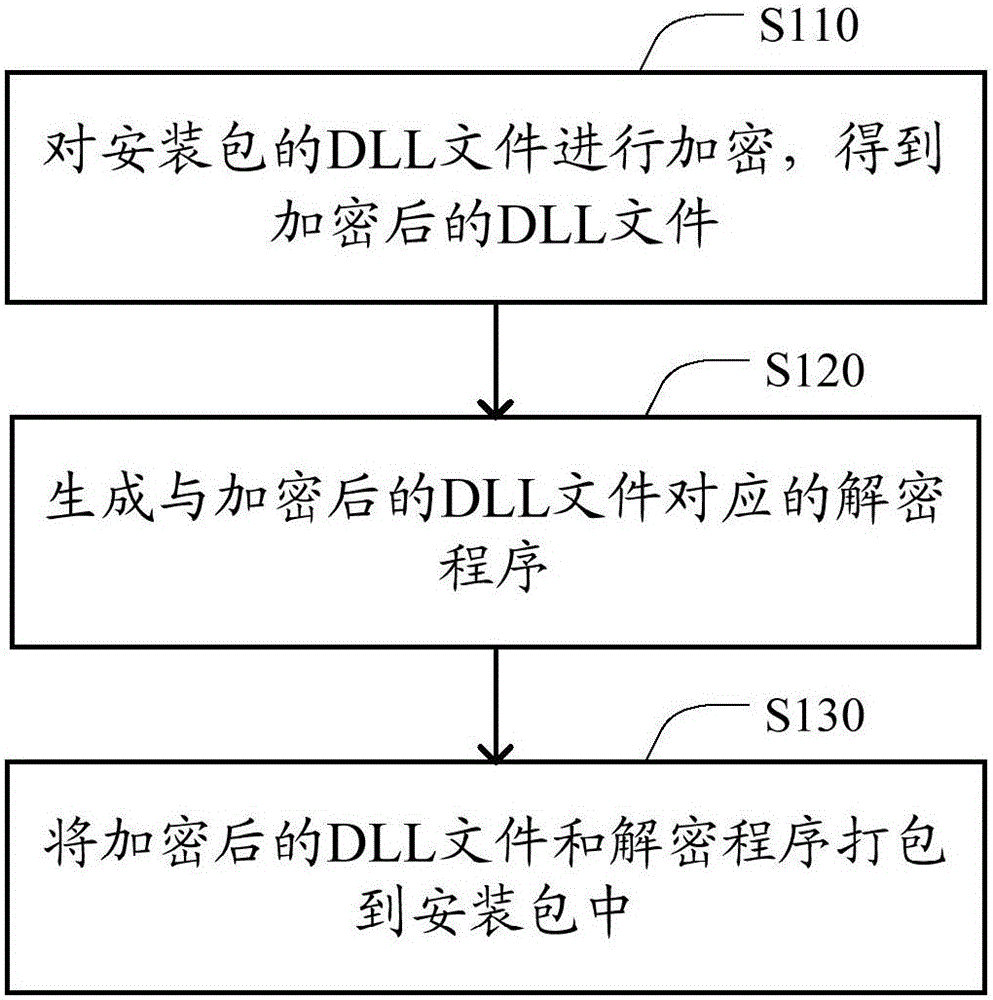
Method and device for reinforcing dynamic link library (DLL) file of installation package
ActiveCN106295370ATo achieve reinforcementEffective protectionDigital data protectionReverse analysisOperating system
The method discloses a method and device for reinforcing a dynamic link library (DLL) file of an installation package. The method includes the steps that the DLL file of the installation package is encrypted, and the encrypted DLL file is obtained; a decryption program corresponding to the encrypted DLL file is generated; the encrypted DLL file and the decryption program are packaged in the installation package. According to the technical scheme, the DLL file is reinforced through the decryption program independent of the DLL file, cracking of the DLL file is difficult to achieve through a reverse analysis method, therefore, the DLL file is effectively protected, and the requirements of a developer for protecting the DLL file are met.
Owner:BEIJING QIHOO TECH CO LTD +1
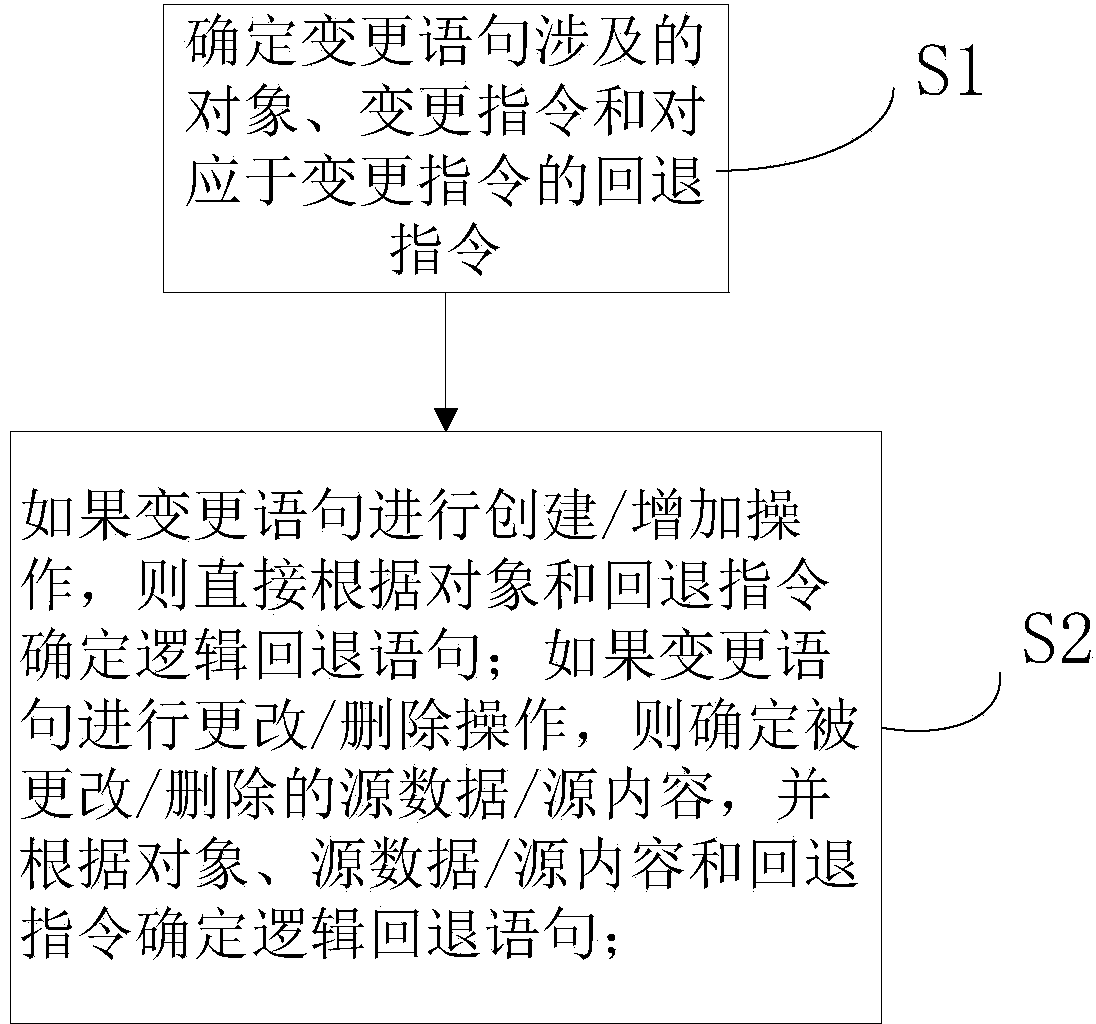
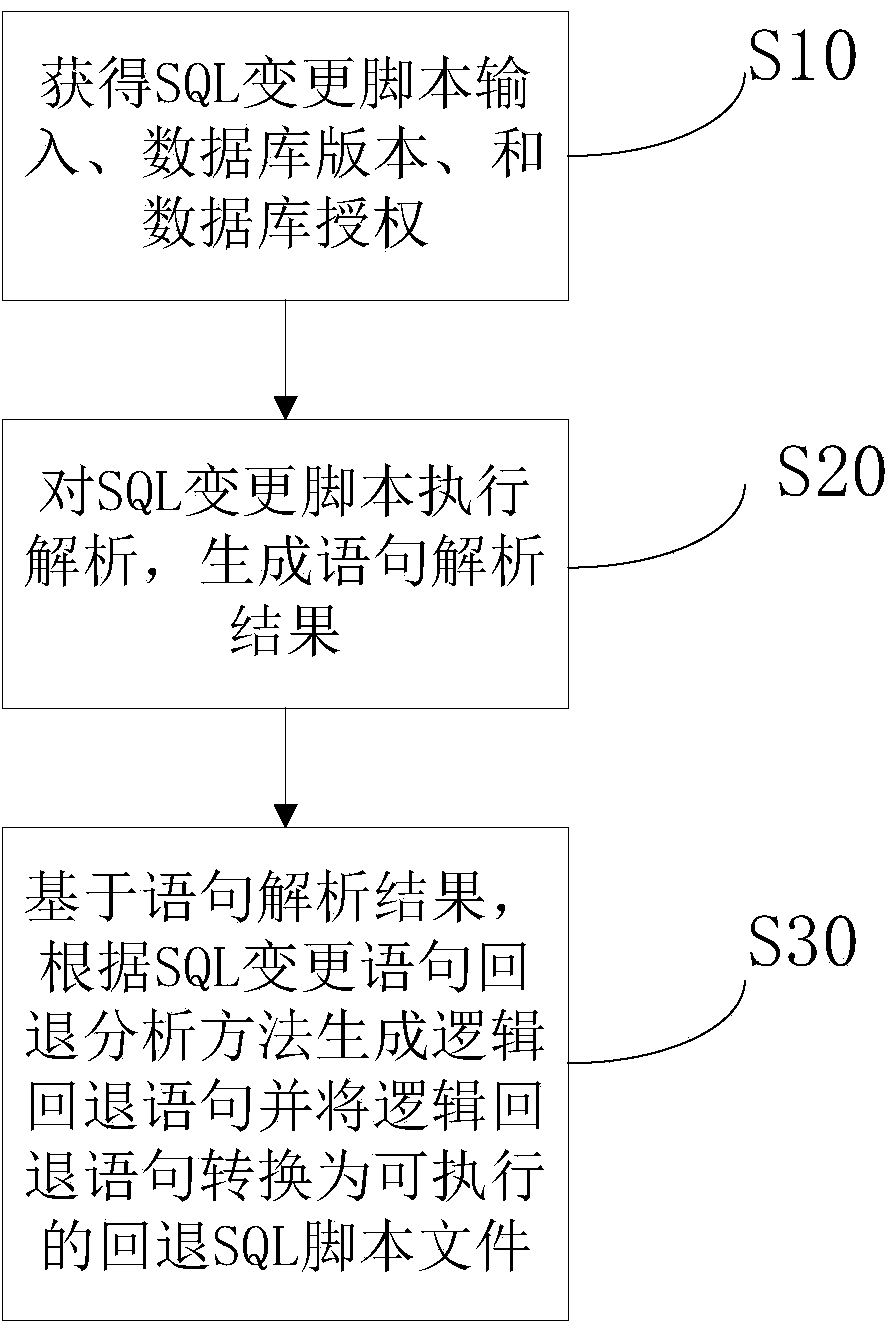
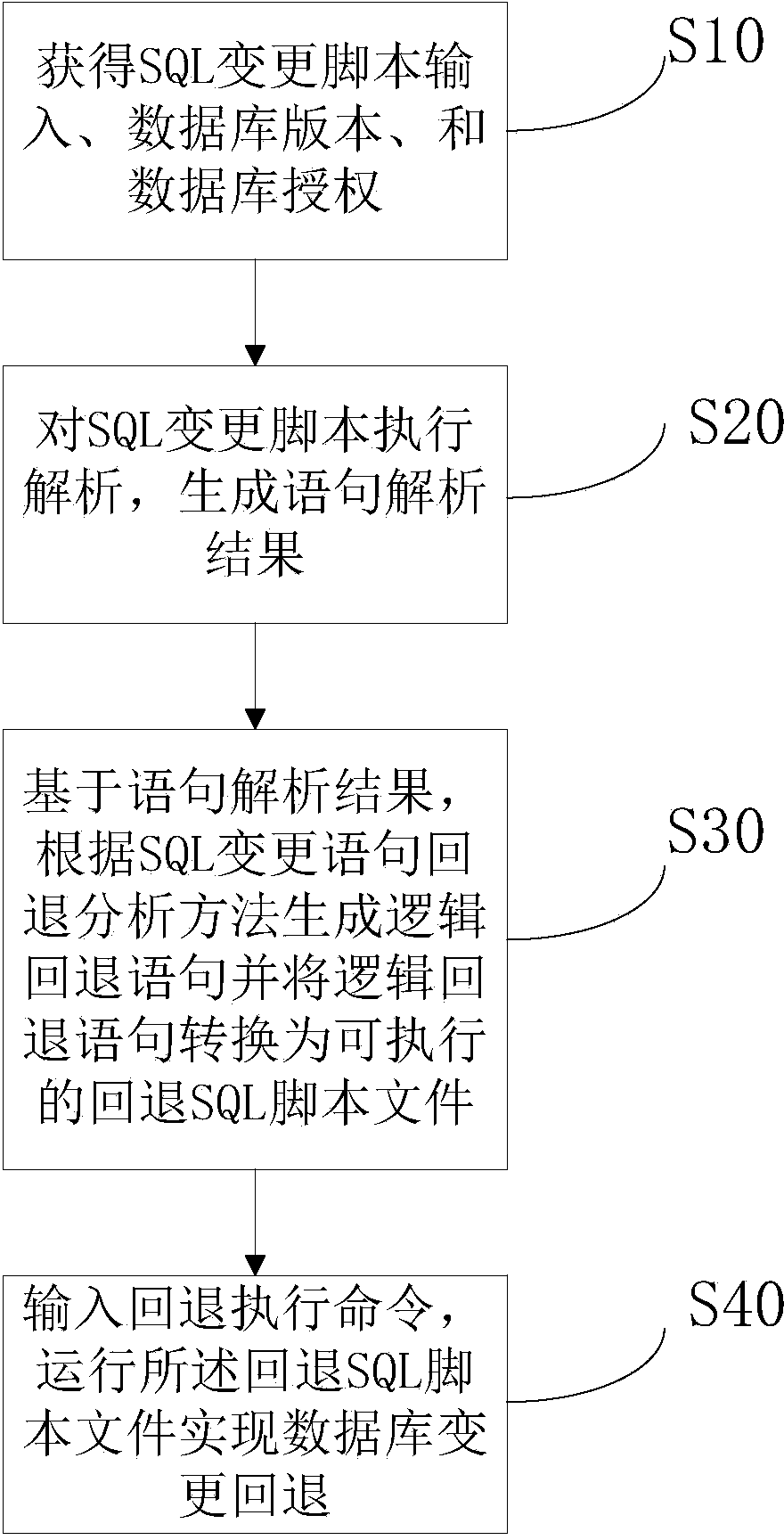
Alternation statement reverse analysis method, database alternating and backspacing method and database alternating and backspacing system
ActiveCN103678532AStrong targetingEasy to operateDatabase management systemsSpecial data processing applicationsReverse analysisTheoretical computer science
The invention discloses an alternation statement reverse analysis method, a database alternating and backspacing method and a database alternating and backspacing system. The reverse analysis method includes S1, determining objects and alternation commands both involved in an alternation statement and backspacing commands corresponding to the alternation commands; S2, in case of creating / adding of the alternation statement, directly determining a backspacing statement according to the objects and the backspacing commands, and in case of changing / deleting of the alternation statement, determining changed / deleted source data / content, and determining the backspacing statement according to the objects, the source data / content and the backspacing commands. The backspacing method includes S10, acquiring input, database version and database authorization of an SQL (structured query language) alternation script; S20, analyzing the SQL alternation script to generate a statement analysis result; S30, based on the statement analysis result, generating the backspacing statement and transforming the backspacing statement into an executable backspacing SQL script file according to the alternation statement reverse analysis method. The backspacing method has the advantages of wide application range, high operability, safety and high automation.
Owner:中移信息技术有限公司
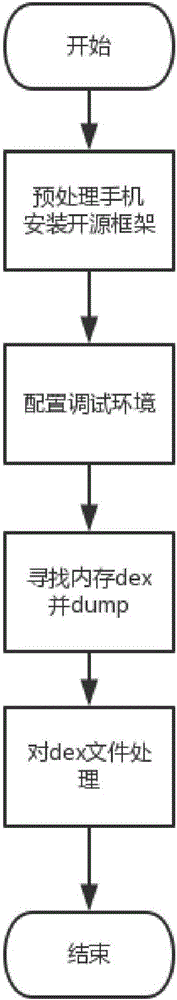
Dynamic shelling method for Android application
InactiveCN105930692ARealize security protectionNormal program functionProgram/content distribution protectionReverse analysisApplication software
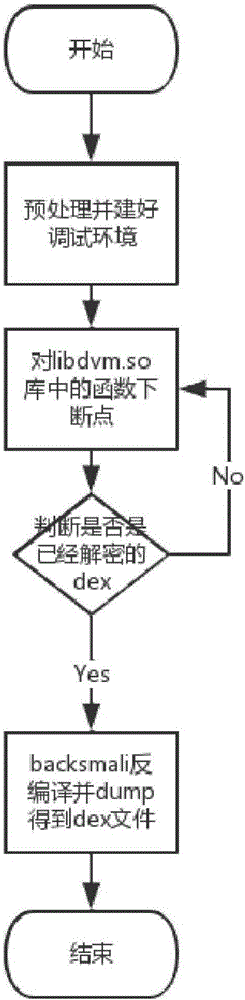
The invention discloses a dynamic shelling method for an Android application. A reinforced Android application is taken as a target program, and a dex file of the target program is obtained by utilizing an Xposed framework, so that the target program can be subjected to shelling. The dynamic shelling method comprises an Android mobile phone preprocessing process, a target program debugging process, a target program shelling process and a process of extracting the dex file in the target program and repairing the program. A library Libdvm.so in an Android system contains a function with a function parameter being the dex file, such as an openDexFile function, dex subjected to shelling serves as a parameter and is transmitted to the openDexFile function, and the dex subjected to the shelling is obtained by making a breakpoint at the openDexFile function. By utilizing the technical scheme provided by the method, a malicious Android program can be effectively subjected to reverse analysis to obtain a source code of the program so as to realize security protection of the system.
Owner:北京鼎源科技有限公司
Reversible electroencephalogram analysis method
In recent years, a great advancement on the electroencephalogram detection and classification feature extraction technology is obtained, various behavior activities of a person are detected from epilepsy morbidities, in a traditional mode, an electroencephalogram is used for authority brain disease studying and definite diagnosis making, and a classification data resource is used for judging human thinking activities and limb, face and eye activities at present; analysis of the electroencephalogram is more and more important in the fields. The invention provides a new electroencephalogram analysis method; and through analysis on the electroencephalogram, on the basis that the classification accuracy is guaranteed, the reversible analysis method is provided. The method can be finally used for definite diagnosis making of clinical experience, the human brain state stage can be judged, and difficulties of electroencephalogram accurate quantitative analysis are avoided; meanwhile, reverse analysis on quantitative analysis results can be carried out, verification with the clinical medicine experience is finally achieved, and more scientific conclusions are obtained
Owner:CHONGQING UNIV
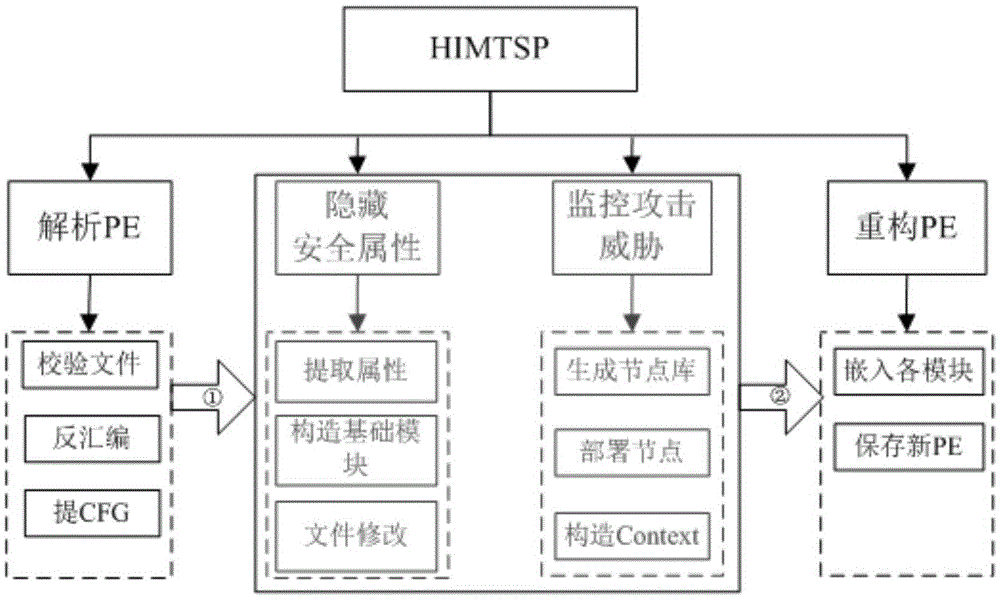
Software protection method based on API (Application Program Interface) security attribute hiding and attack threat monitoring
The invention discloses a software protection method based on API (Application Program Interface) security attribute hiding and attack threat monitoring. The software protection method comprises the following steps: obtaining the original input information record chart of a file to be protected, extracting the execution control flow graph of the file, extracting an API calling point, extracting an API parameter passing code block, extracting an API returned value decryption point, dumping a DLL (Dynamic Link Library), calculating a new API entry address, constructing a springboard function block, inserting an exception instruction in the returned value decryption point, constructing a node, generating a node library, deploying a node network, constructing a node background, constructing a returned value decryption processing function, and reconstructing a PE (Portable Executable) file. From internal and external aspects, software is protected so as to analyze the function of API boundary information in a reverse analysis process from an angle of the reverse engineering of the attackers, the API security attribute which needs to be hidden and a detection node library are put in a program new node, and a new node entry is subjected to encryption processing to further prevent the attackers from carrying out reverse analysis on the protected PE file.
Owner:NORTHWEST UNIV(CN)
Bug excavation method based on executable code conversed analysis
InactiveCN101482846AMake up for blindnessMake up for one-sidednessSoftware testing/debuggingReverse analysisProgram instruction
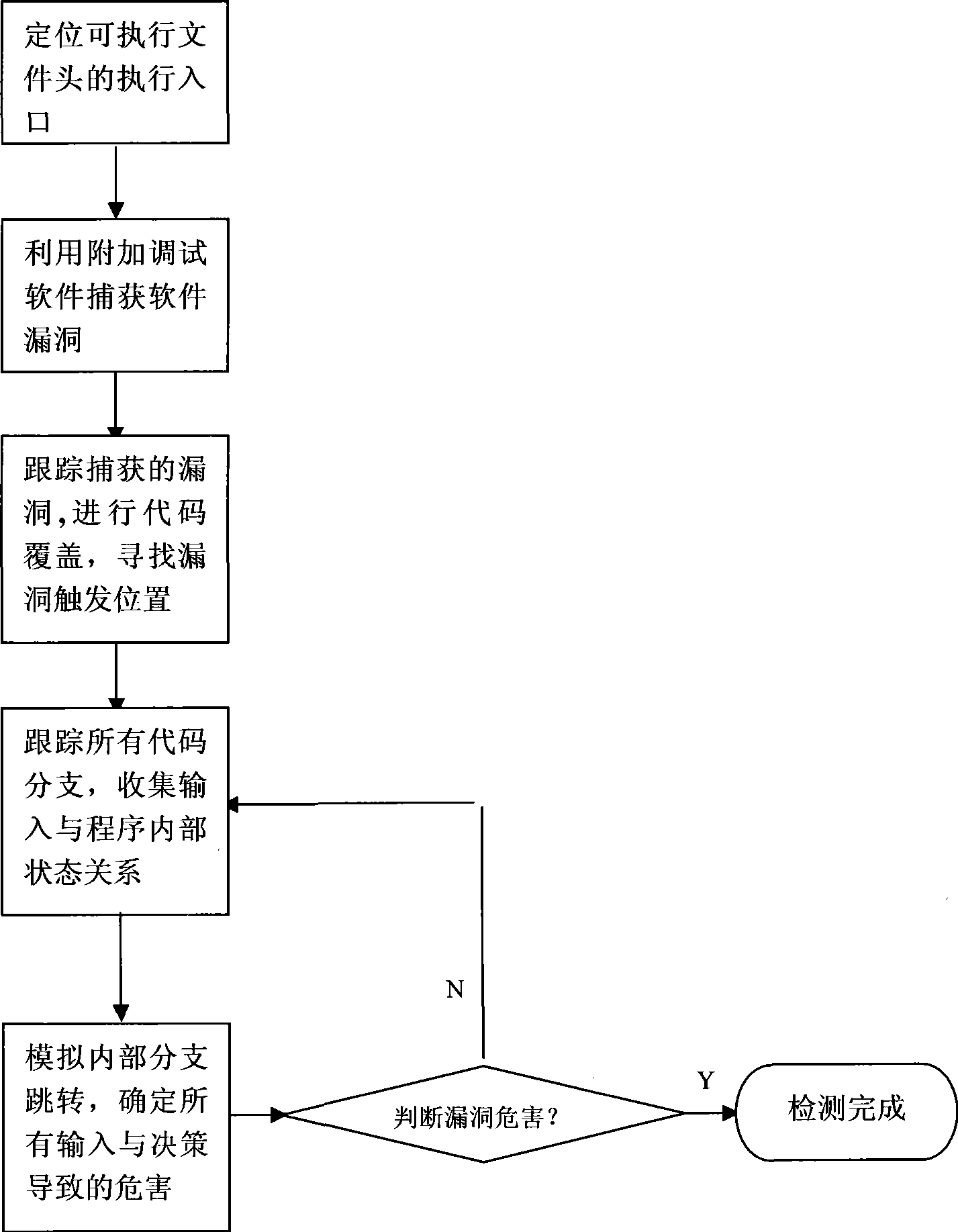
The present invention relates to a vulnerability evaluation method which is in the technical field of software engineering and is based on reverse analysis of executable code. Specially, a gray box detecting method is adopted for the PE format document in the Windows system. The vulnerability information of program is captured with debugging software. The alternated data and decision are dynamically analyzed through analyzing the specific code when the program is away from the safety state by the vulnerability and reversely analyzing the program instruction flow and inputting decision information. The inherent and logical vulnerabilities in the program are evaluated. The harm of vulnerability is confirmed thereby obtaining the purpose of detecting vulnerability. The vulnerability evaluation method of the invention has higher detecting efficiency, and can evaluate the logical vulnerability which is likely to be leaked from being detected in the program more successfully.
Owner:SHANGHAI JIAO TONG UNIV
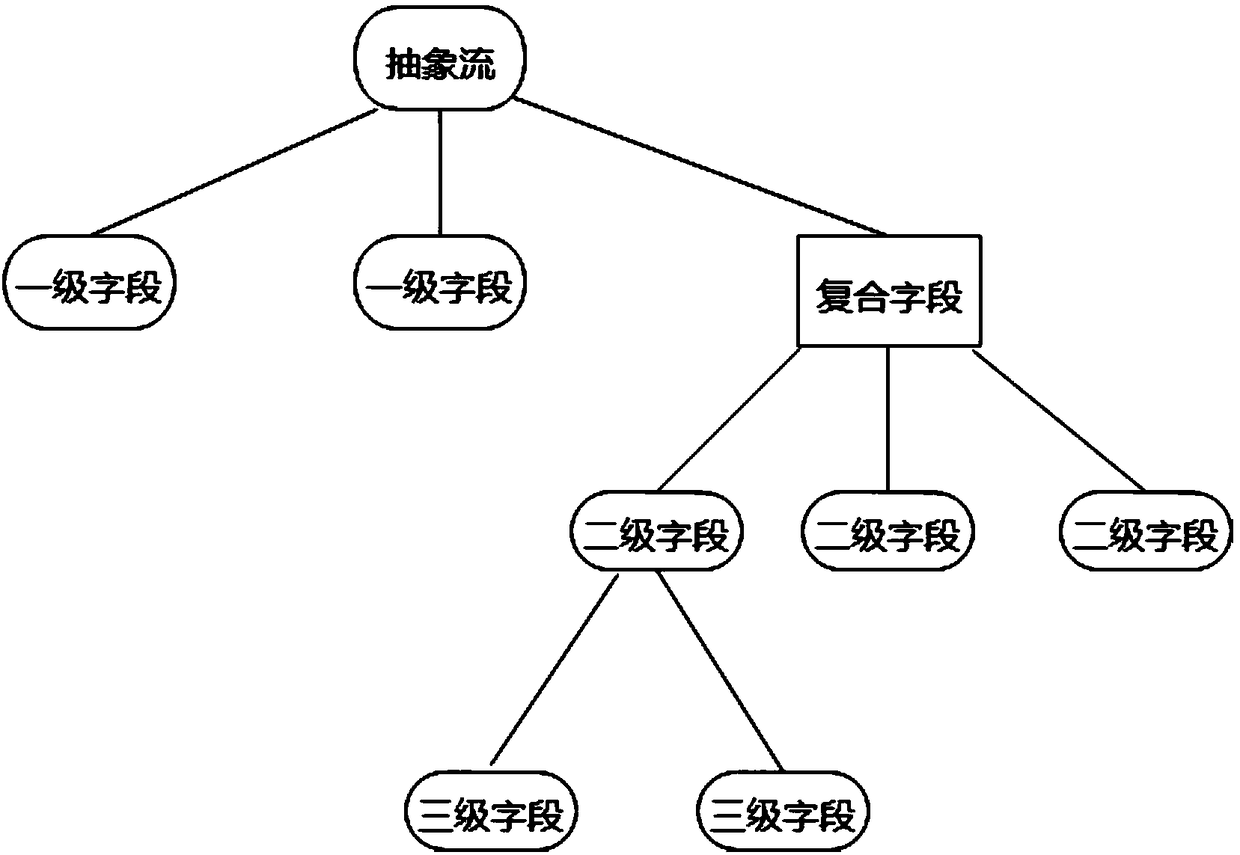
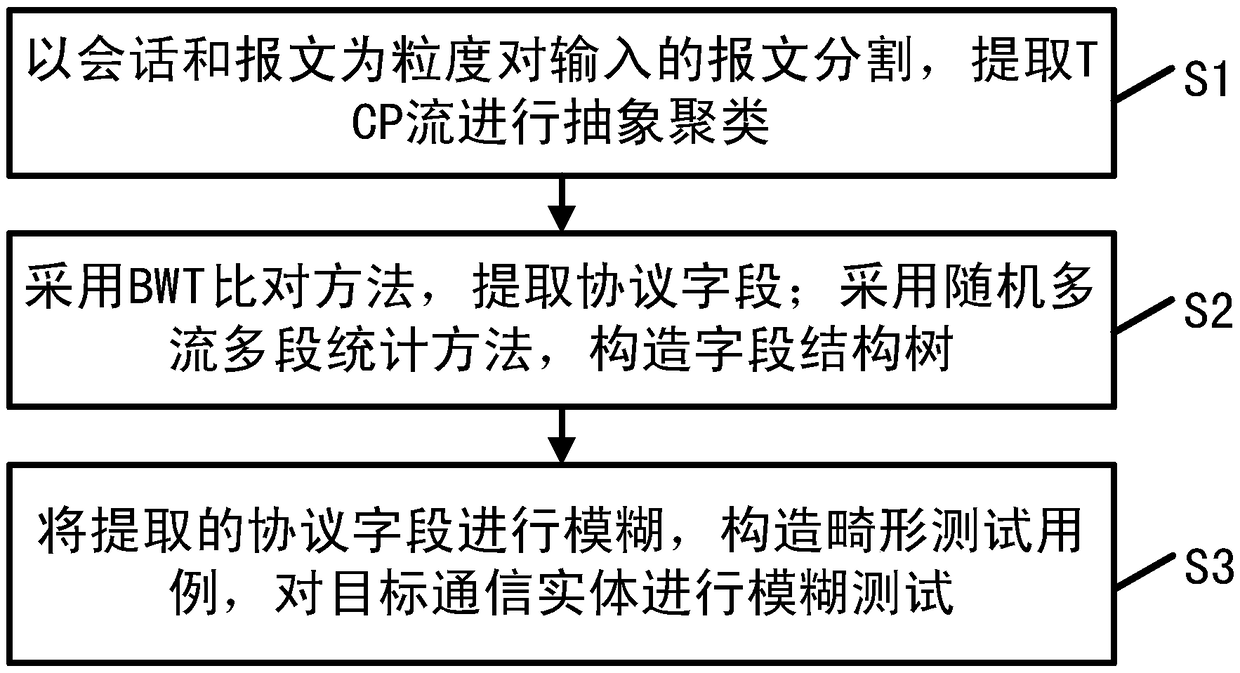
A protocol field inverse analysis system and method based on BWT
ActiveCN109040081AQuick searchImprove design flexibilityData switching networksHigh level techniquesReverse analysisMulti stream
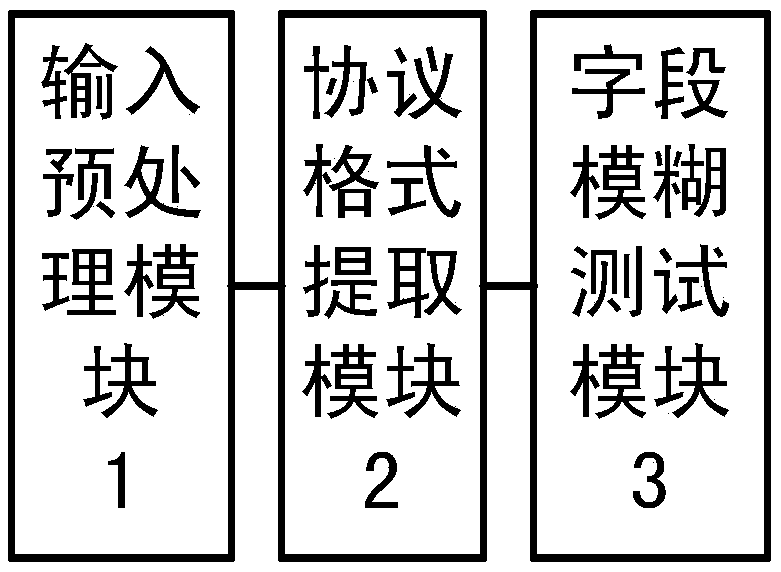
The invention provides a protocol field reverse analysis system and method based on BWT. Specific suffix index is constructed, so that specific substring matching only needs to be completed once in each alignment process. Moreover, the alignment algorithm based on suffix index is flexible in design, consumes less space in the index stage, and the length of subsequence is variable, protocol fieldscan be quickly identified. After the fixed field is identified, the invention counts the fields with high frequency through a random multi-stream multi-segment matching method, constructs a grammar tree according to the field position and the number of the fields, extracts the field structure, and thus realizes the inverse of the field format. After being classified, the reverse field is used asthe input of the fuzzy test tool, a large number of deformity test cases is sent to the target communication entity, and at the same time, the debugger is combined with the sniffer to carry out abnormal monitoring on the target communication entity, the abnormality is found and analyzed, so as to subsequently improve the safety of the target communication entity.
Owner:HARBIN INST OF TECH AT WEIHAI
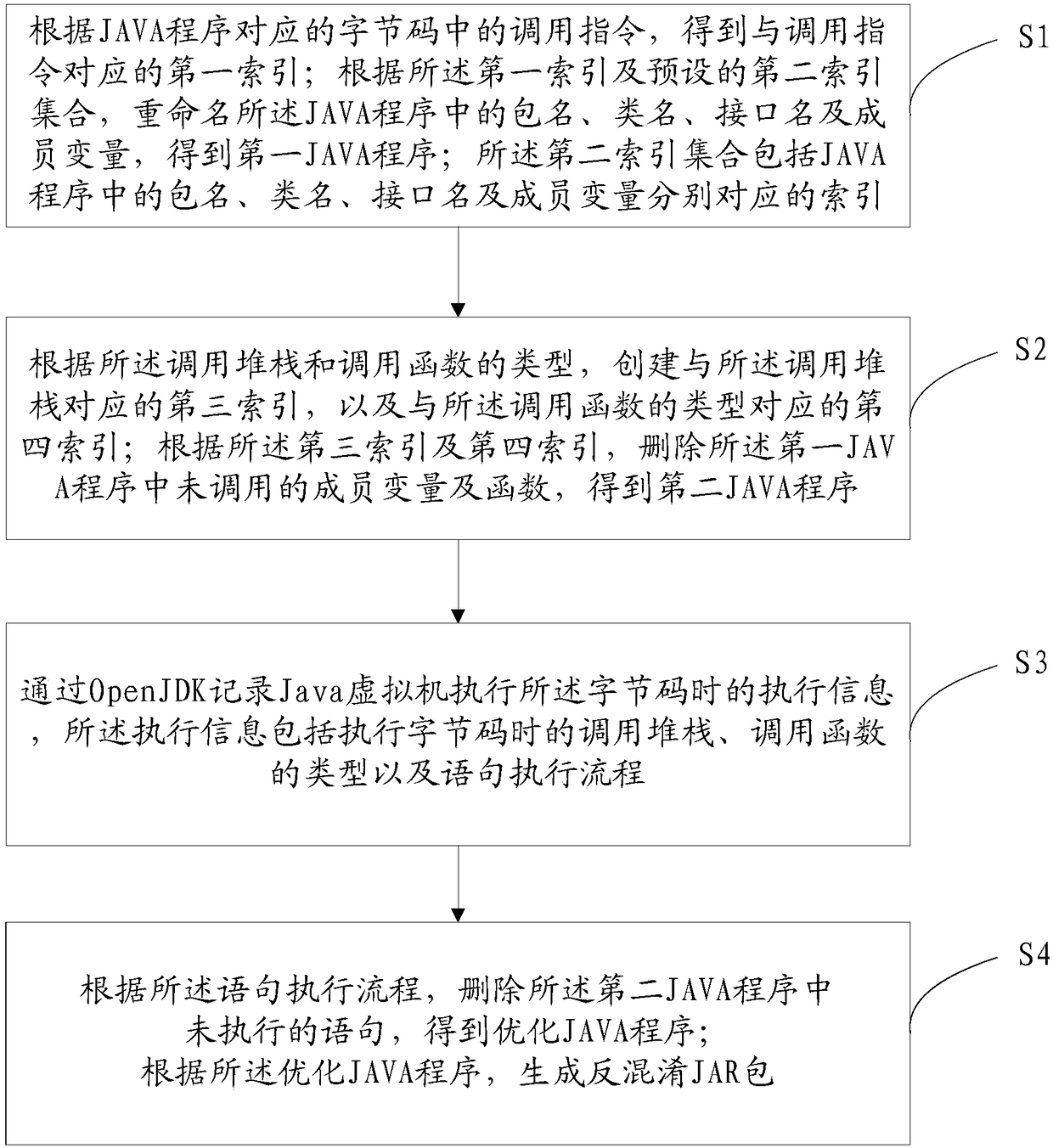
JAVA program anti-obfuscation method and terminal
ActiveCN108153518AFix bugsLow costDecompilation/disassemblySoftware designReverse analysisObfuscation
The invention provides a JAVA program anti-obfuscation method and a terminal. According to a first index and a preset second index set, a package name, a class name, an interface name and member variables are renamed to obtain a first JAVA program, execution information when a Java virtual machine executes a bytecode is recorded through OpenJDK, the uncalled member variables of the first JAVA program and a function are deleted to obtain a second JAVA program, according to a statement execution process in the execution information, the unexecuted statemenTS in the second JAVA program are deleted to obtain an optimized JAVA program. According to the method, the problem is solved that in the original confused Jar package, the package name, class name, method in the JAVA program are replaced with meaningless names, much confusion can be produced when the meaningless names are viewed in reverse analysis, resulting in that the reverse analysis process is very time-consuming.
Owner:XIAMEN MEIYA PICO INFORMATION
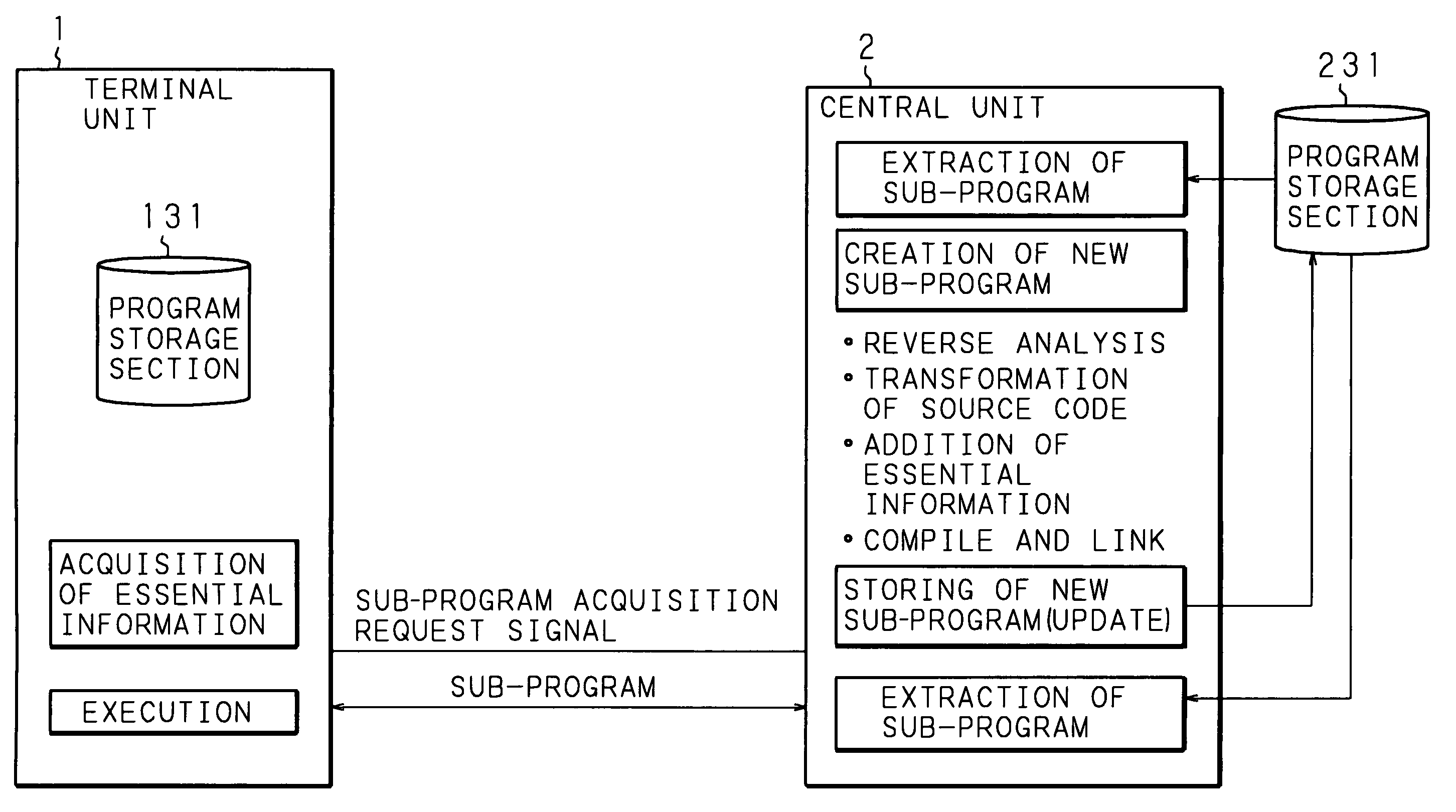
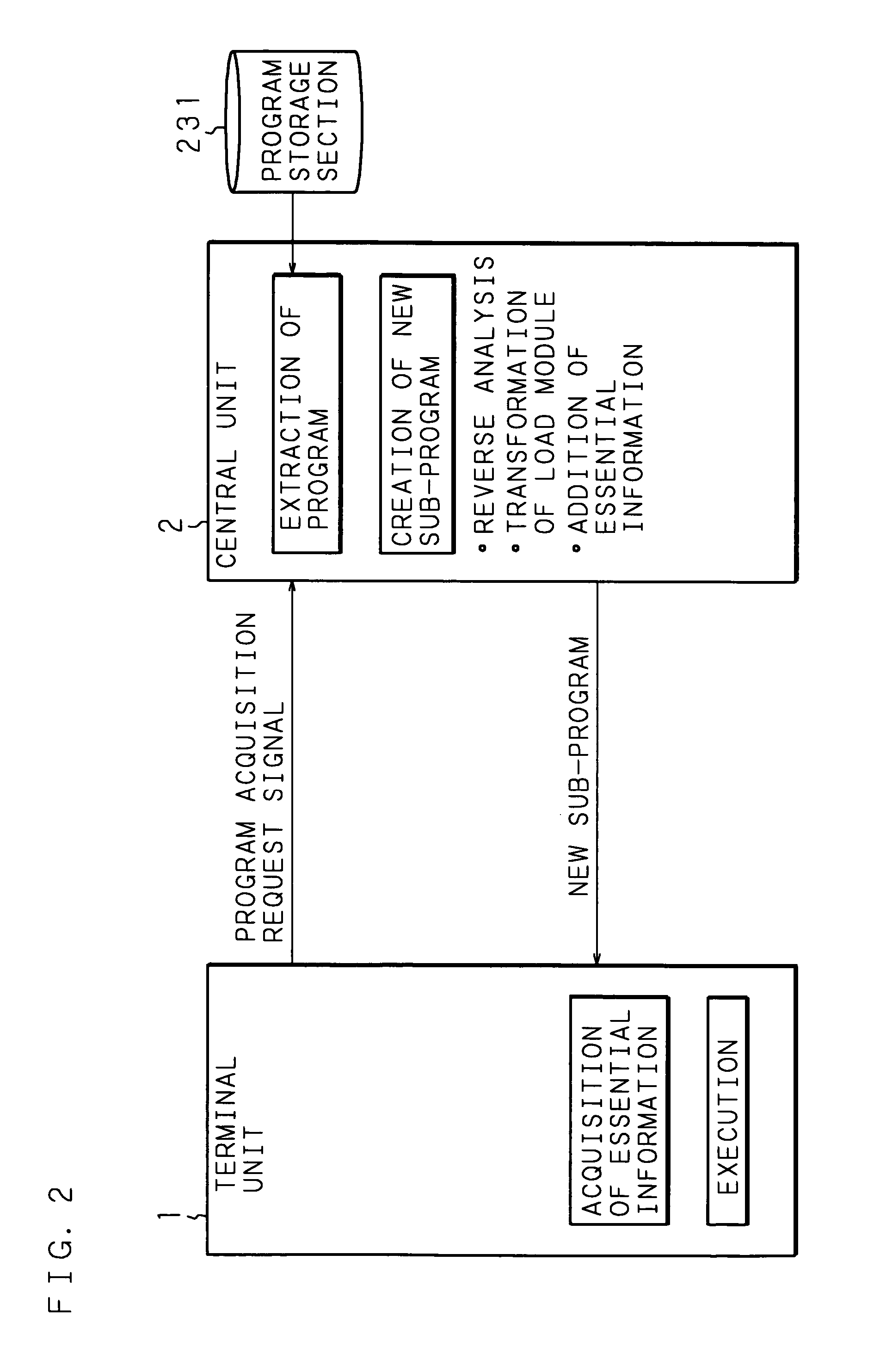
Computer system, central unit, and program execution method
InactiveUS7865961B2Improve securityDifficult to executeDigital data processing detailsUnauthorized memory use protectionThird partyReverse analysis
In a program execution method in which a program to be executed is stored in a central unit and a terminal unit acquires the program from the central unit and executes the program, when the central unit receives an acquisition request from the terminal unit, it creates a load module different from the program, which produces the same computation results and differs in the location where essential information is to be embedded, and transmits the load module to the terminal unit together with the essential information necessary for executing the program. The terminal unit receives the program, stores the program on a memory, and executes the program based on the embedded essential information. This method makes it difficult for malicious third parties to illegally execute the program by reverse analysis, and enhances the security of the load module to be executed.
Owner:FUJITSU LTD
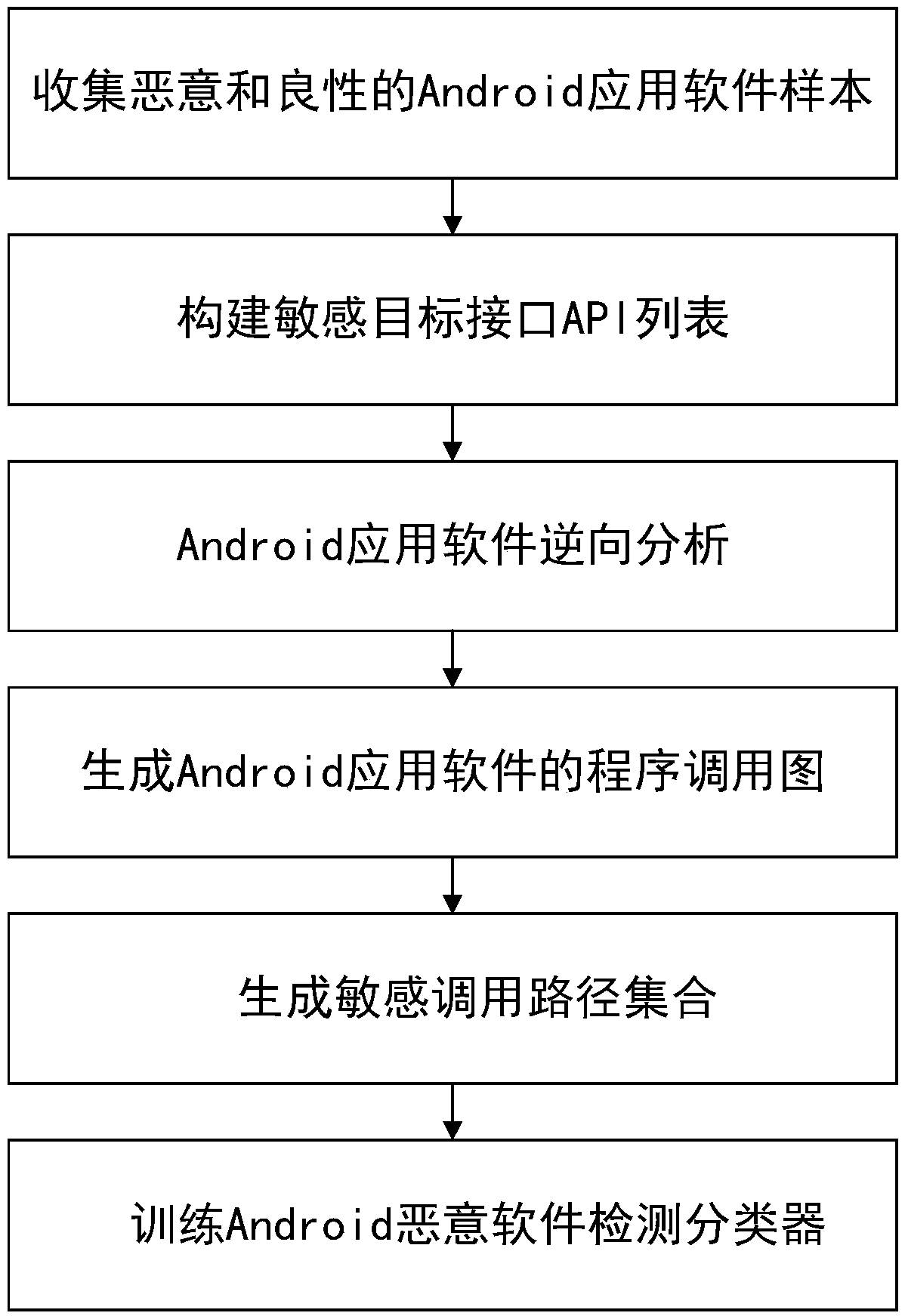
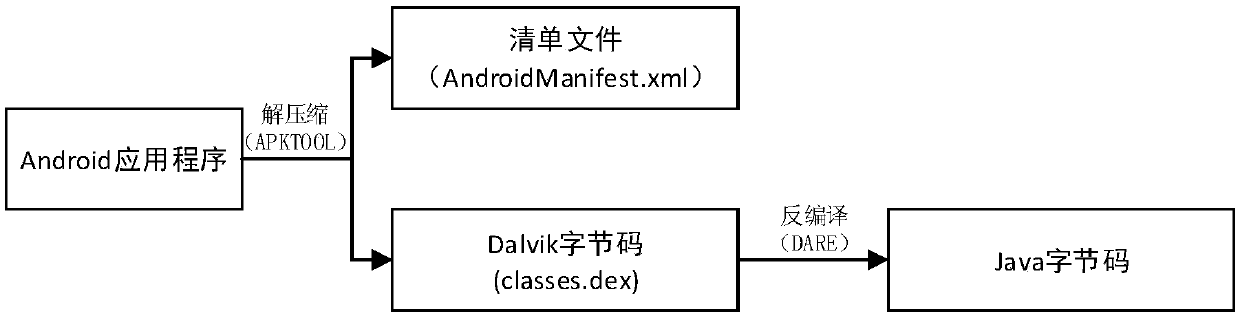
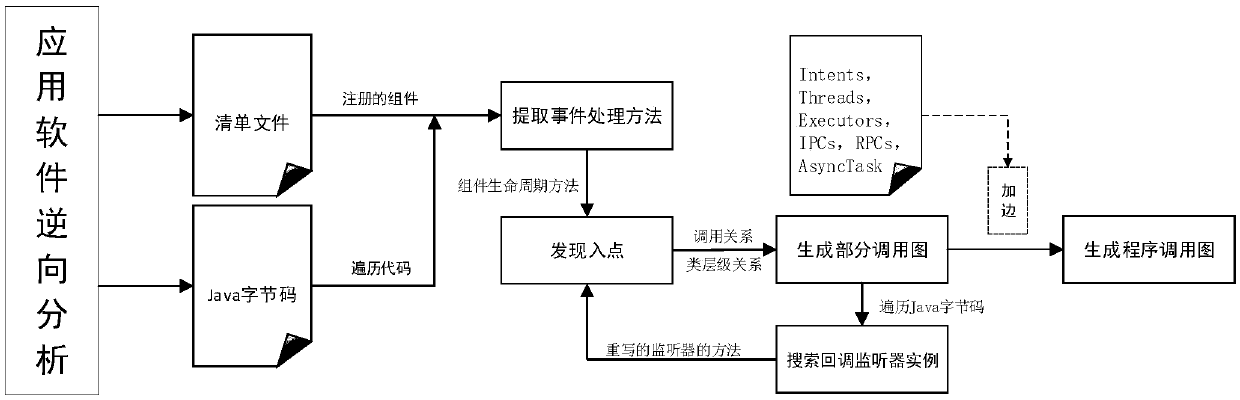
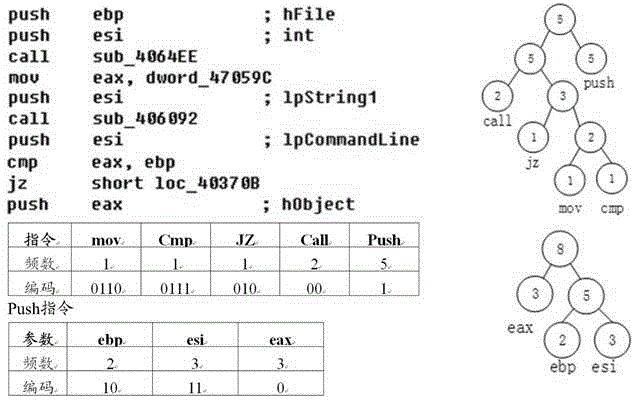
An Android malicious software detection method based on a sensitive calling path
ActiveCN109684840AAccurate identificationHigh precisionCharacter and pattern recognitionPlatform integrity maintainanceFeature vectorReverse analysis
The invention discloses an Android malicious software detection method based on a sensitive calling path, and mainly solves the problem that an existing scheme is low in malicious software detection accuracy. According to the scheme, a sensitive target interface API list is constructed through a natural language processing technology; Generating a sensitive calling path set by using the Android application software subjected to reverse analysis; Taking the sensitive calling path as a feature, and establishing an Android sensitive calling path feature library by analyzing a large number of benign software and malicious software data sets; Processing the sensitive calling path set of the sample into a feature vector, and training a classifier model by adopting a supervised machine learning algorithm by utilizing the feature vector; And detecting whether the Android application software with unknown security is malicious software or not by using the trained classifier model. The method ishigh in precision, easy to expand and remarkable in intelligence, and can be used for automatic detection of the mobile terminal and examination and analysis of the Android application market.
Owner:XIDIAN UNIV
Confusing method and device of executable application
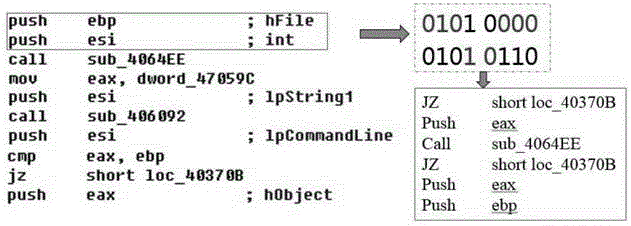
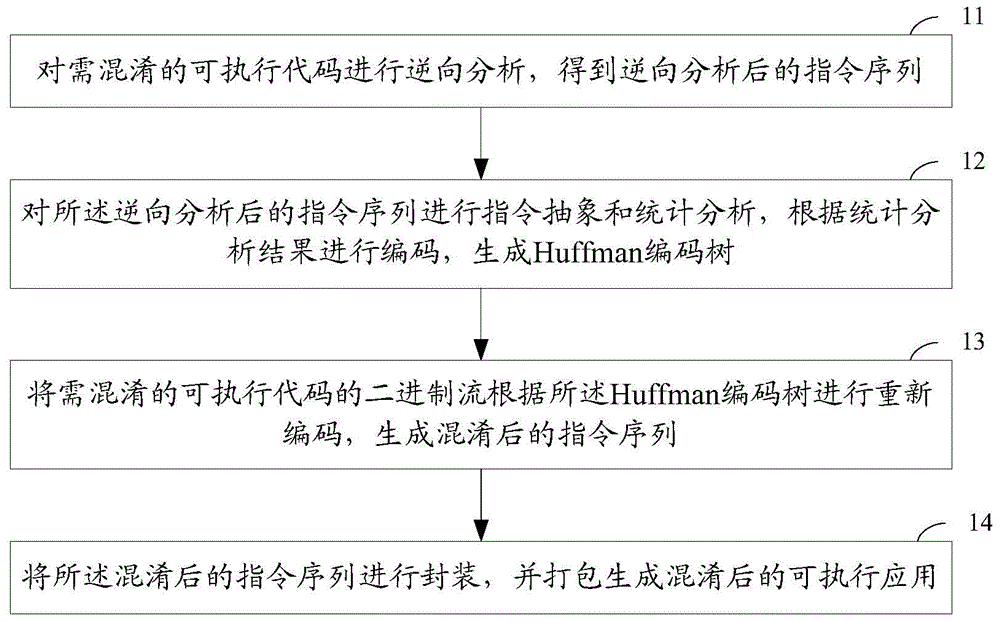
ActiveCN104573427AReduced ability to recognizeIncrease the difficultyProgram/content distribution protectionProgramming languageStatistical analysis
The invention provides a confusing method and device of executable application, wherein the method comprises the following steps: A, reversely analyzing executable codes need to be confused, so as to obtain a reversely analyzed instruction sequence; B, applying instruction abstract and statistic analysis to the reversely analyzed instruction sequence, coding based on the result of the statistic analysis in order to generate a Huffman coding tree; C, recoding binary flow of the executable codes need to be confused based on the Huffman coding tree, so as to generate a confused instruction sequence; D, packaging the confused instruction sequence, and packing into the confused executable application. By utilizing the confusing method and device of executable application, the ability of automated tools for identifying the confusing method can be reduced, thereby increasing the difficulty of reading codes and cracking applications for attackers.
Owner:BEIJING UNIV OF POSTS & TELECOMM
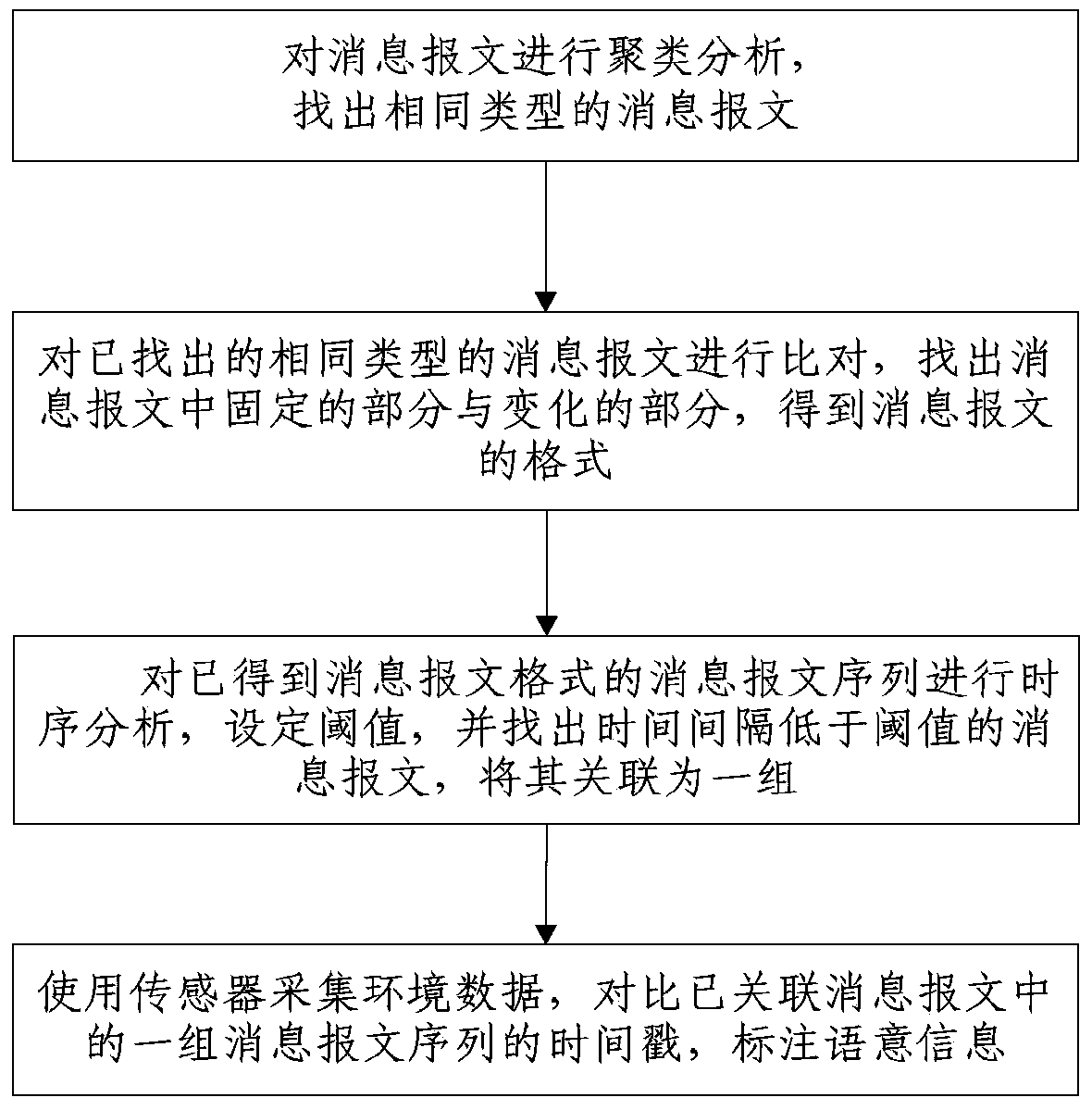
Method and device for protocol automatic reverse analysis of embedded equipment
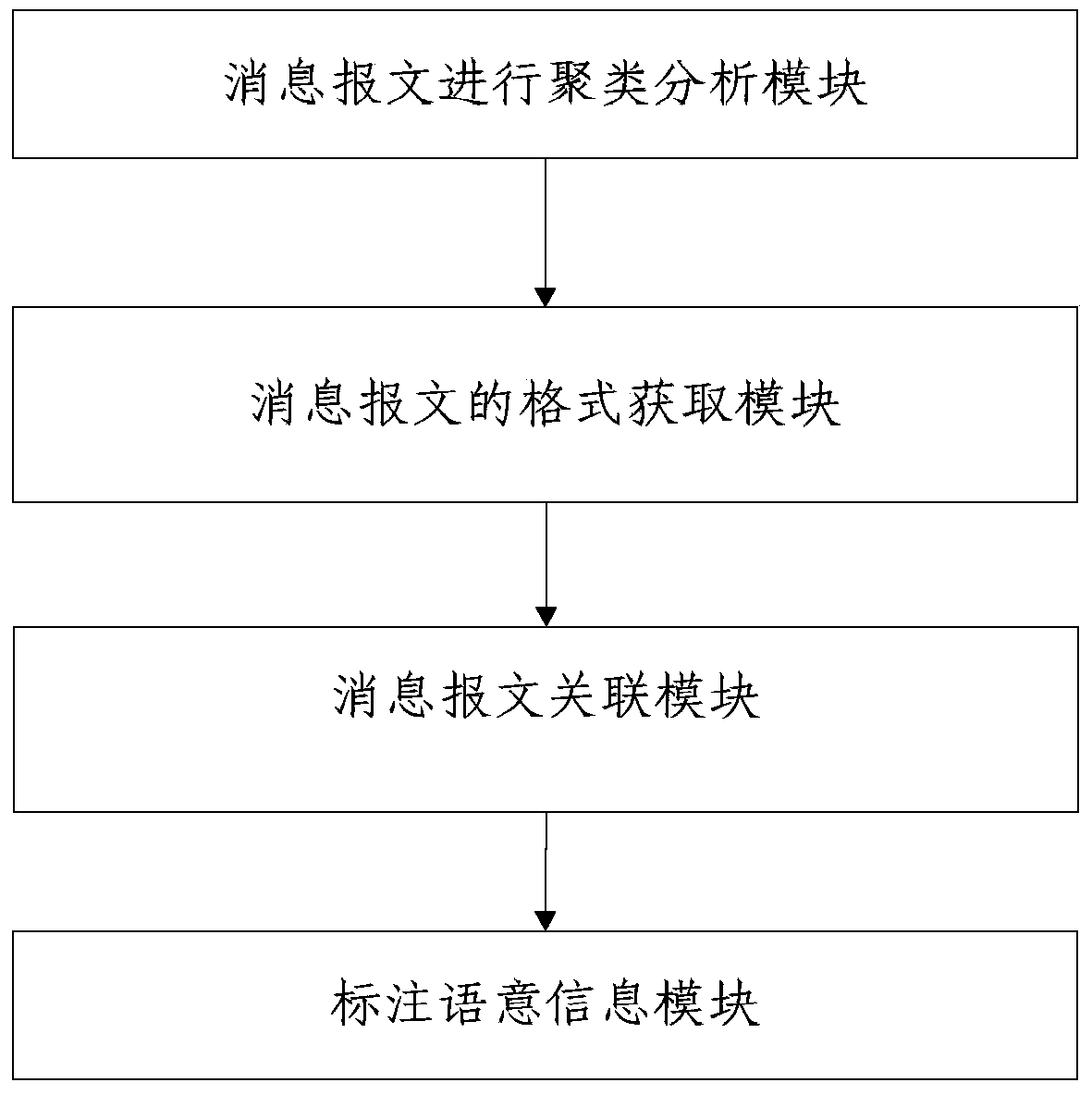
The invention discloses a method for protocol automatic reverse analysis of embedded equipment. The method for the protocol automatic reverse analysis of the embedded equipment comprises the following steps that clustering analysis is conducted on information messages, and the information messages of the same type are found; the information messages are compared with the information messages which are the same in type and are already found, the fixed part of the information messages and the changing part of the information messages are found, and the format of the information messages are obtained; timing sequence analysis is conducted on the information message sequence with the information message format being already found, a threshold value is set, and the information messages with the time intervals lower than the threshold value are found and are associated in one set; sensors are used for collecting environment data, timestamps of one set of information message sequence in the associated information messages are compared, and language information is labeled. Meanwhile, the invention further discloses a device for the protocol automatic reverse analysis of the embedded equipment, and the device for the protocol automatic reverse analysis of the embedded equipment comprises the following modules: an information message clustering analysis module, an information message format acquiring module, an information message association module and a semantic information labeling module.
Owner:TSINGHUA UNIV
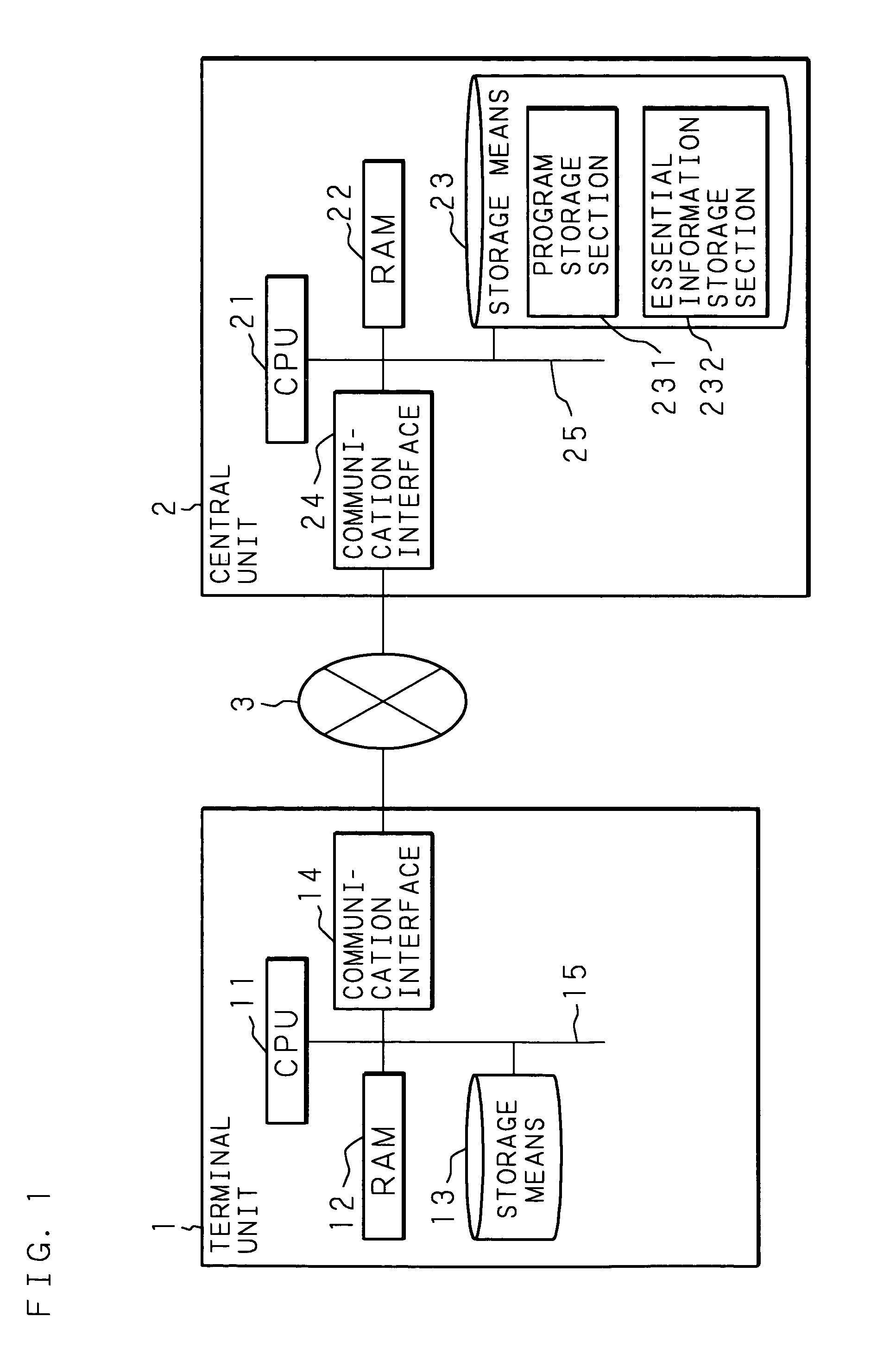
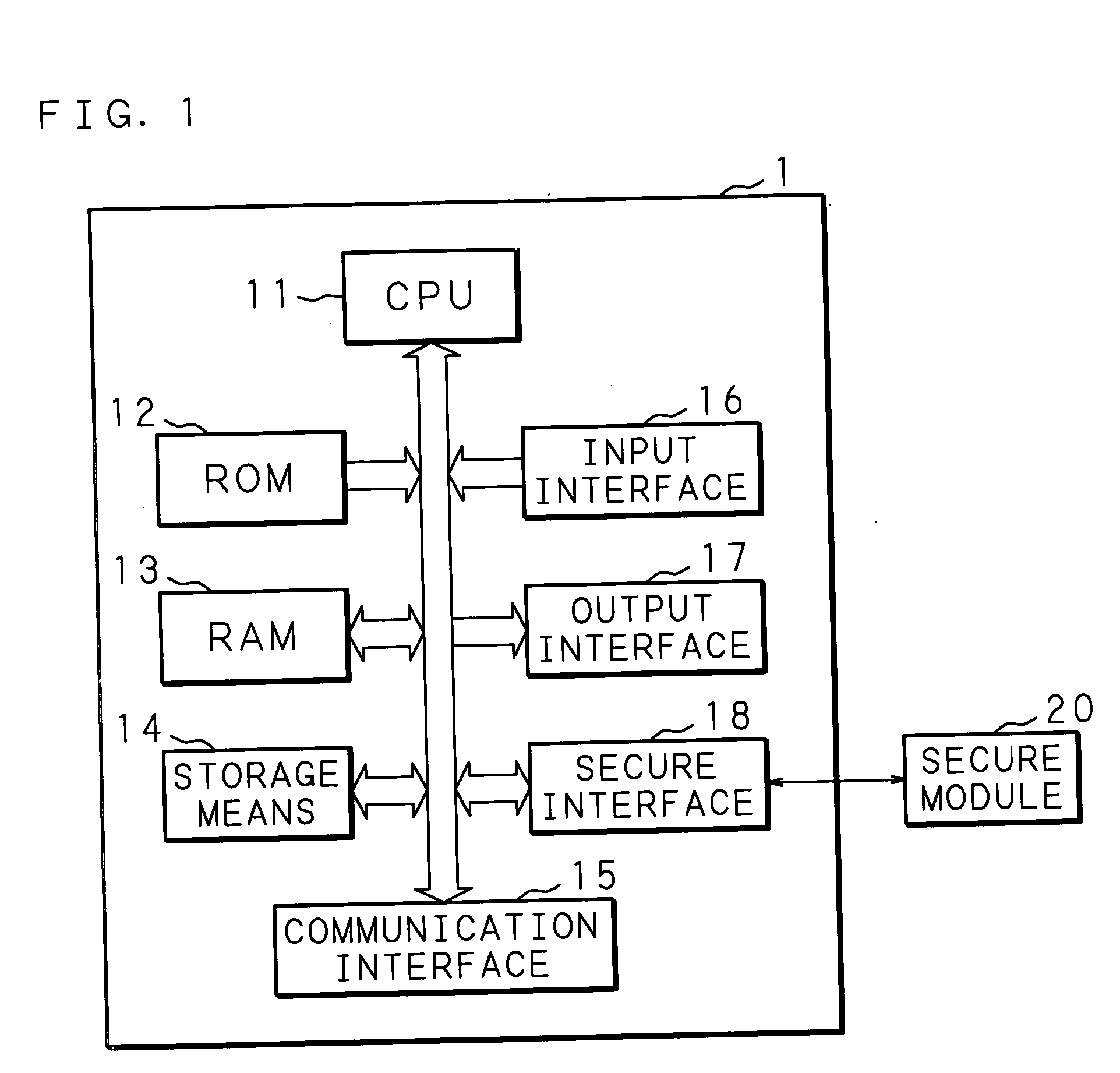
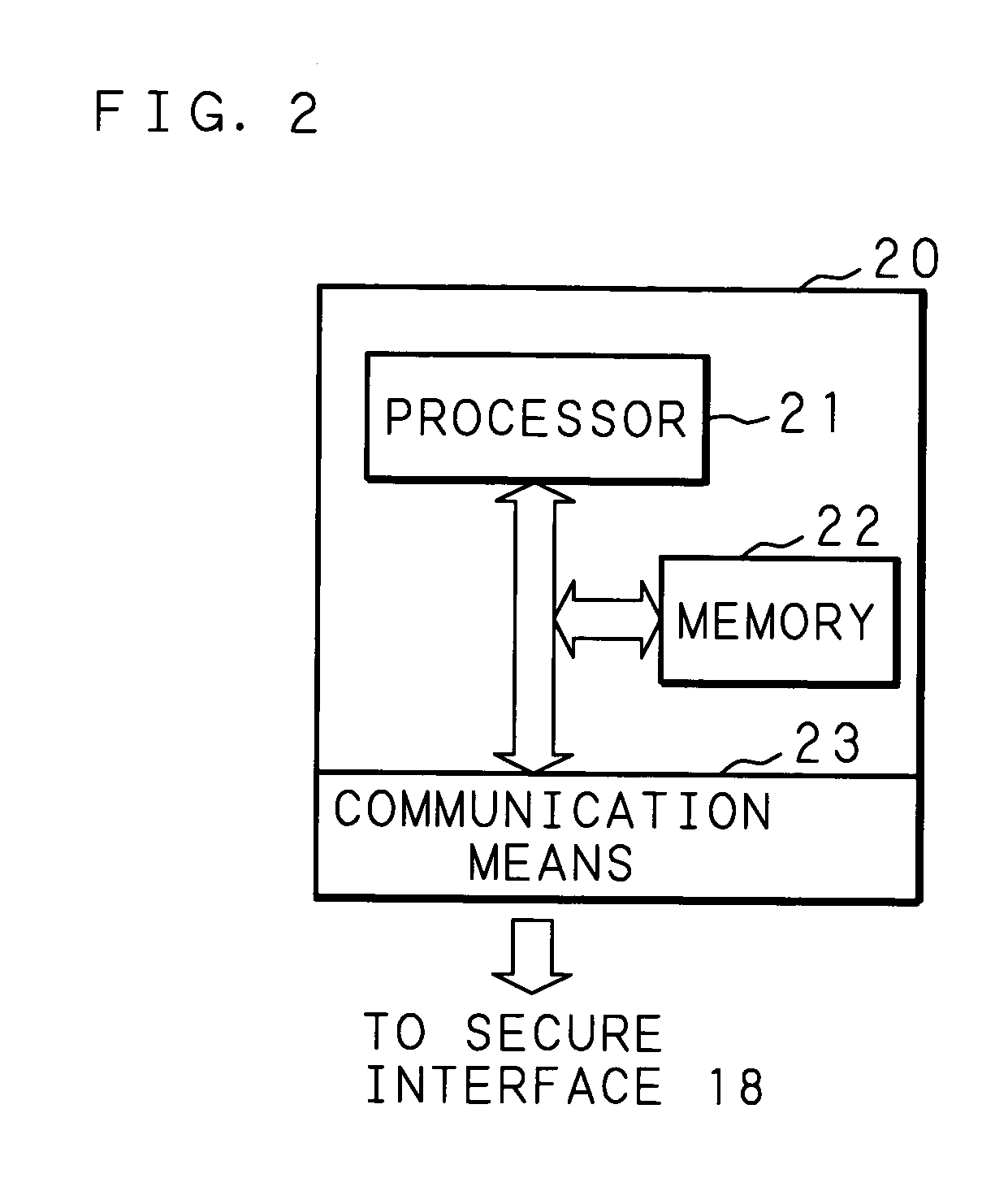
Information processing apparatus
InactiveUS20050097524A1Improve securityReduce overheadDigital data processing detailsUnauthorized memory use protectionComputer hardwareInformation processing
An information processing apparatus has: a memory 13; CPU for executing a program written in the memory 13; a secure module 20; and storage means for storing a plurality of encrypted programs into which a program is divided. The CPU transmits the program stored in the storage means to the secure module 20. The secure module 20 has: means for receiving the program stored in the storage means, means for returning the received program to an executable state; means for writing the program, which has been returned to the executable state, in the memory 13 in a sequence for CPU to execute, and means for deleting the program from the memory 13 by CPU after execution is completed. When executing the program, the information processing apparatus can make reverse analysis by a malicious third party difficult, and enhance security of a load module to be executed.
Owner:FUJITSU LTD
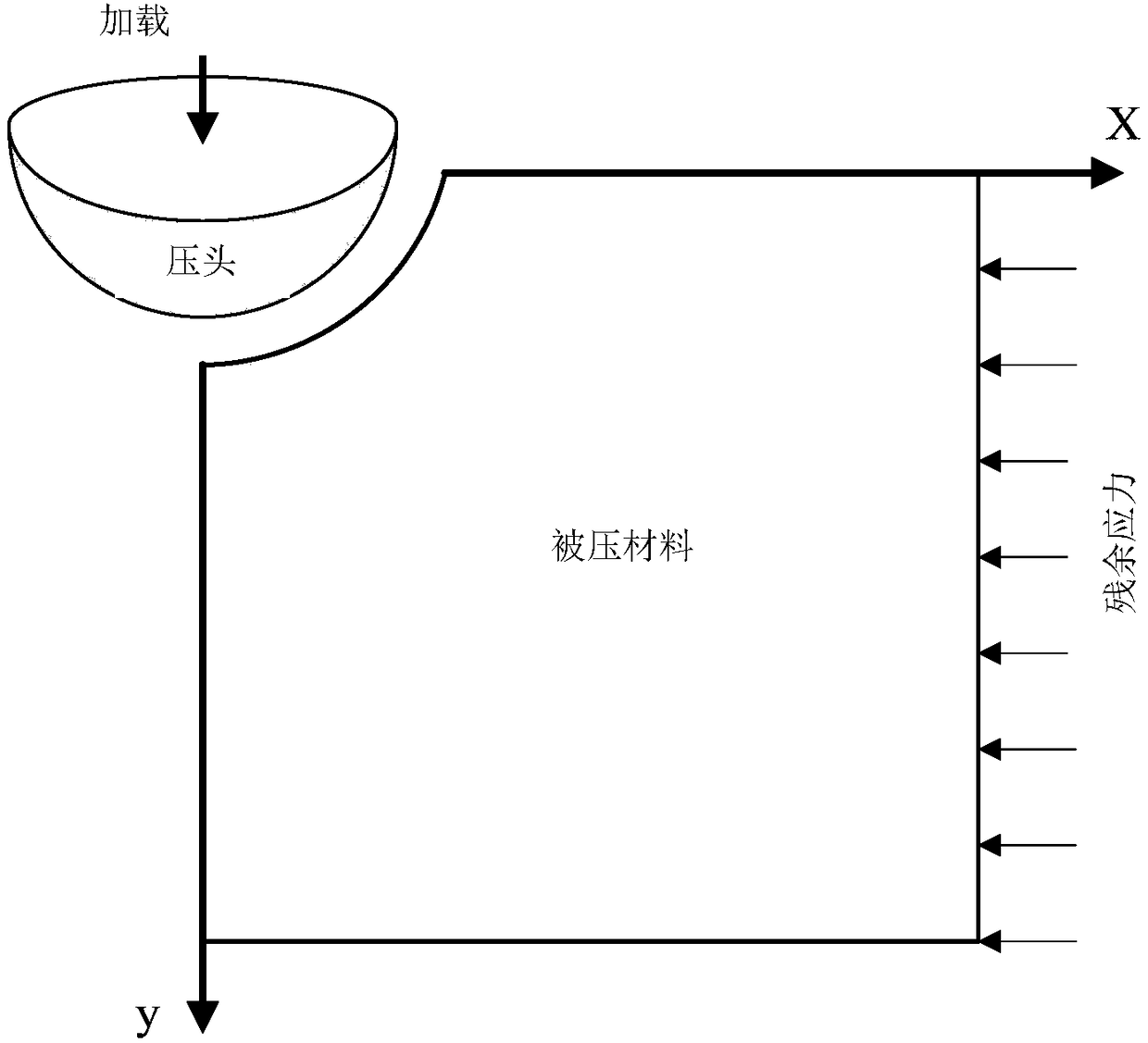
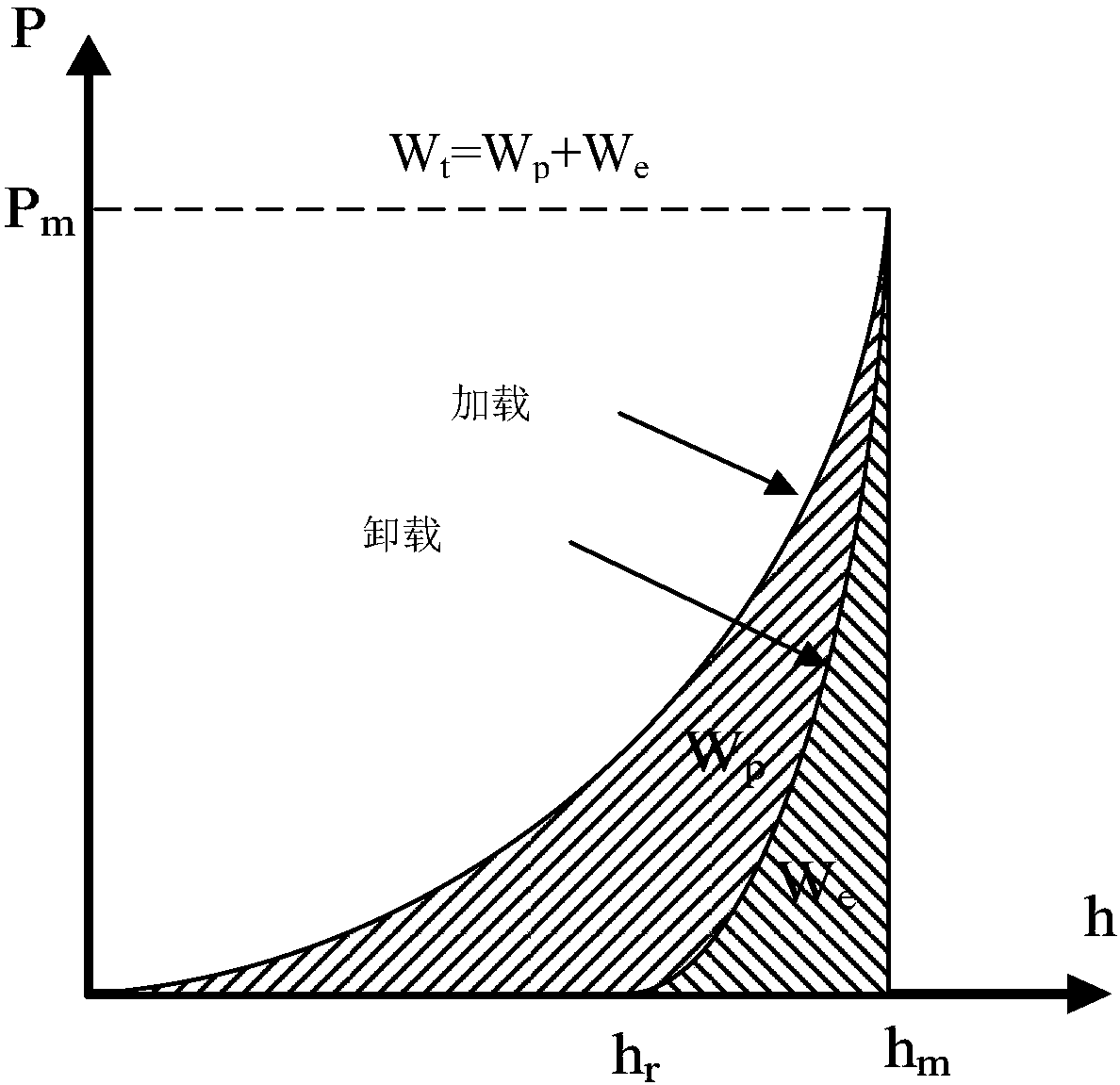
Method for measuring residue stress and metal material elastic-plastic mechanical property by continuous press mark method
InactiveCN108387470AConvenient and accurate simulationImprove experimental efficiencyGeometric CADDesign optimisation/simulationReverse analysisTest sample
The invention discloses a method for measuring the residue stress and metal material elastic-plastic mechanical property by a continuous press mark method. The residue stress is simulated by exertingtransverse load onto a test sample without residue stress; continuous ball press mark experiments are performed; a dimensionless function expression between the press mark power ratio and the metal material mechanical property at different depth is built; the press mark experiment is performed on materials to be tested; the real press mark power ratio is obtained from a load-displacement curve; bya reverse analysis solving method, three groups of different press-in depths or more are selected so that the total sum of the error absolute value between the inversion press mark power ratio and the real press mark power ratio is minimum; at the moment, the values of the yield strength, residue stress and strain hardening indexes are solved values.
Owner:NANJING UNIV OF TECH
Method for machining bolt holes in hanging subassembly of aircraft engine by using numerical control equipment
InactiveCN103785874AImprove production efficiencyHigh degree of assembly automationNumerical controlReverse analysis
The invention belongs to the field of numerical control machining methods, and particularly relates to a method for machining bolt holes in a hanging subassembly of an aircraft engine by using mechanical control equipment. The method comprises the following steps of preassembling the hanging subassembly by using an assembling tool; positioning the hanging subassembly on a special machining supporting clamp; performing measurement and reverse analysis and adjusting numerical control machining programs; positioning the subassembly and the clamp on a machine tool in an integrated manner; automatically forming holes by using the machine tool and examining a machining result; preassembling the hanging subassembly by using a small number of bolts; establishing a measuring benchmark on the product under aircraft axes; positioning the product on the special machining supporting clamp and then examining the appearance error and the location degree of the product; performing reverse modeling and analysis by using CATIA (computer-graphics aided three-dimensional interactive application) software; adjusting a normal tolerance point of a curved surface of the subassembly; correcting a hole-forming machining program; and positioning the whole pre-assembled hanging subassembly by using the benchmark of the special machining clamp on the machine tool as a tool setting benchmark and using the measuring benchmark established on the subassembly as an examination point, and then forming the holes on the subassembly in a machining manner.
Owner:AVIC SAC COMML AIRCRAFT
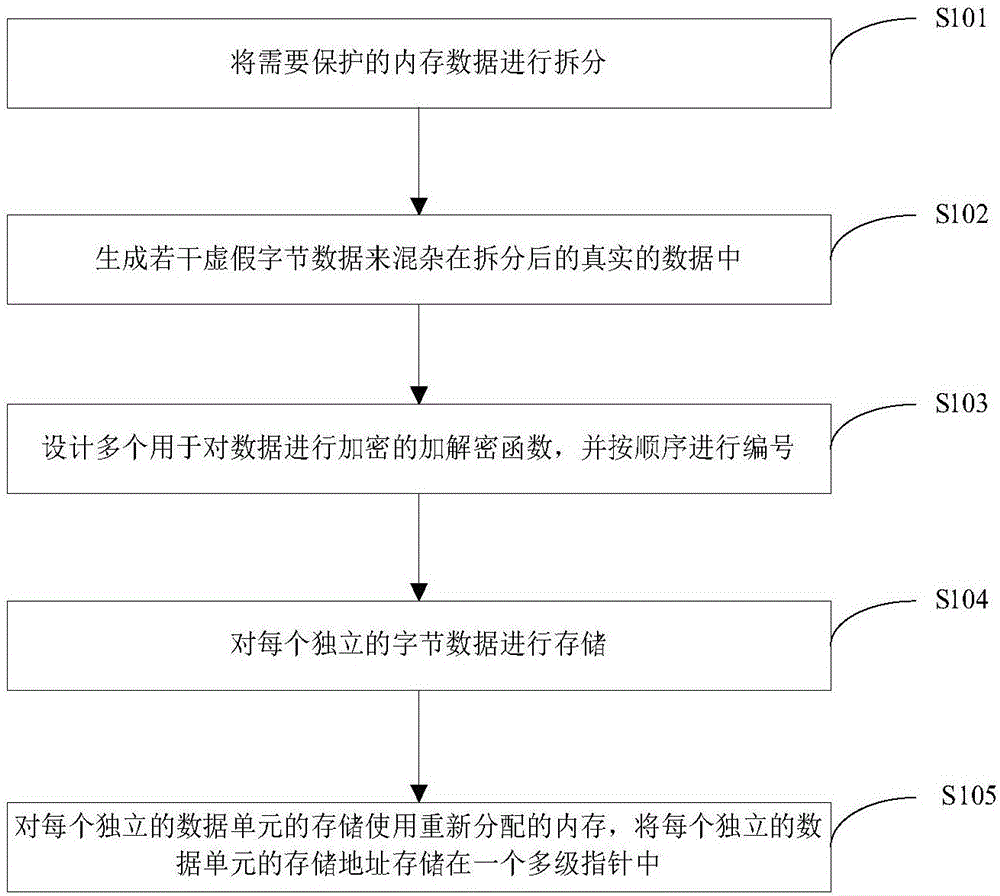
Secure memory data protection method and device
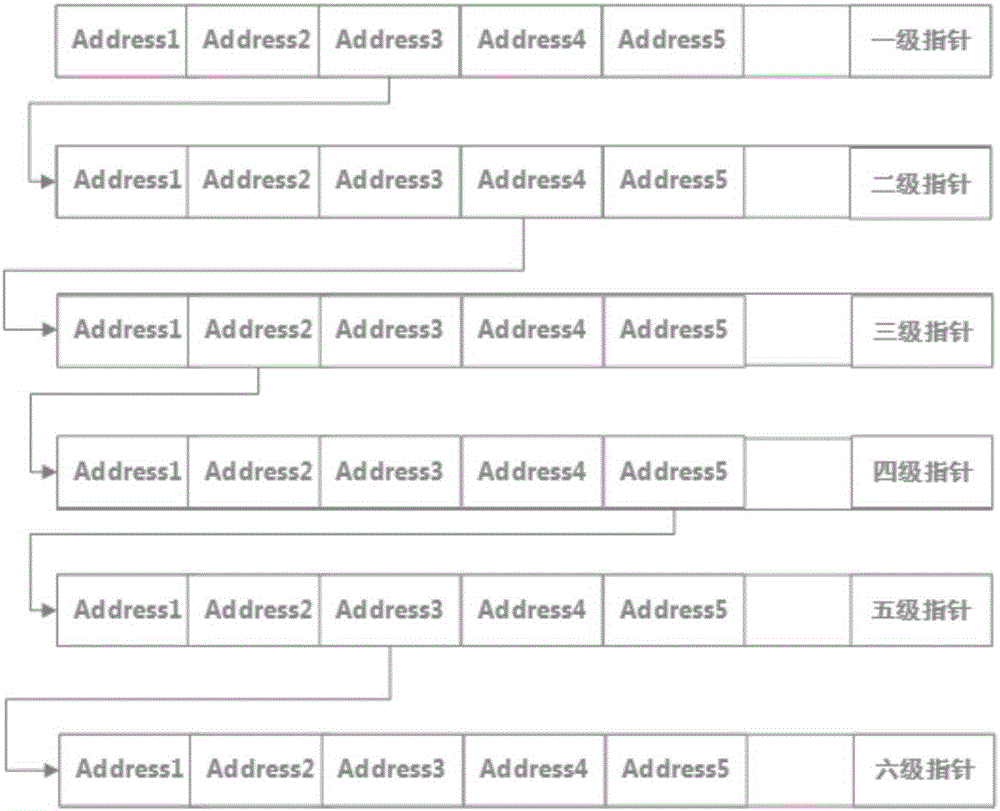
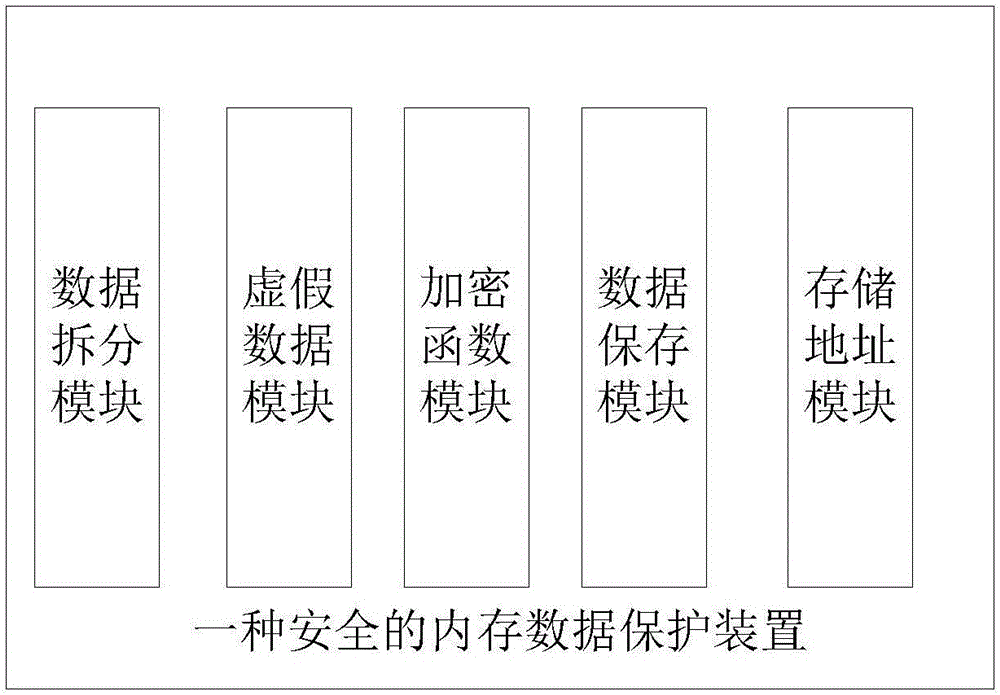
ActiveCN106598882ASafety protectionPlay a role in confusingUnauthorized memory use protectionDigital data protectionReverse analysisByte
The invention discloses a secure memory data protection method and device. The method comprises the following steps: (1) splitting memory data to be protected into independent byte data one by one; (2) generating a plurality of false byte data, and mixing into split real data; (3) designing a plurality of encryption and decryption functions for encrypting the data, and numbering the functions in sequence; (4) storing each independent byte data, wherein a storage format includes the following field information; and (5) storing each independent data unit with a redistributed memory, and storing a storage address of each independent data unit into a multilevel pointer. The secure memory data protection method is designed under the consideration of data encryption from an angle of inconvenient HACK reverse analysis, so that the data can be protected more securely, and the method is easy to implement.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Reverse-based intrusion detection system and reverse-based intrusion detection method
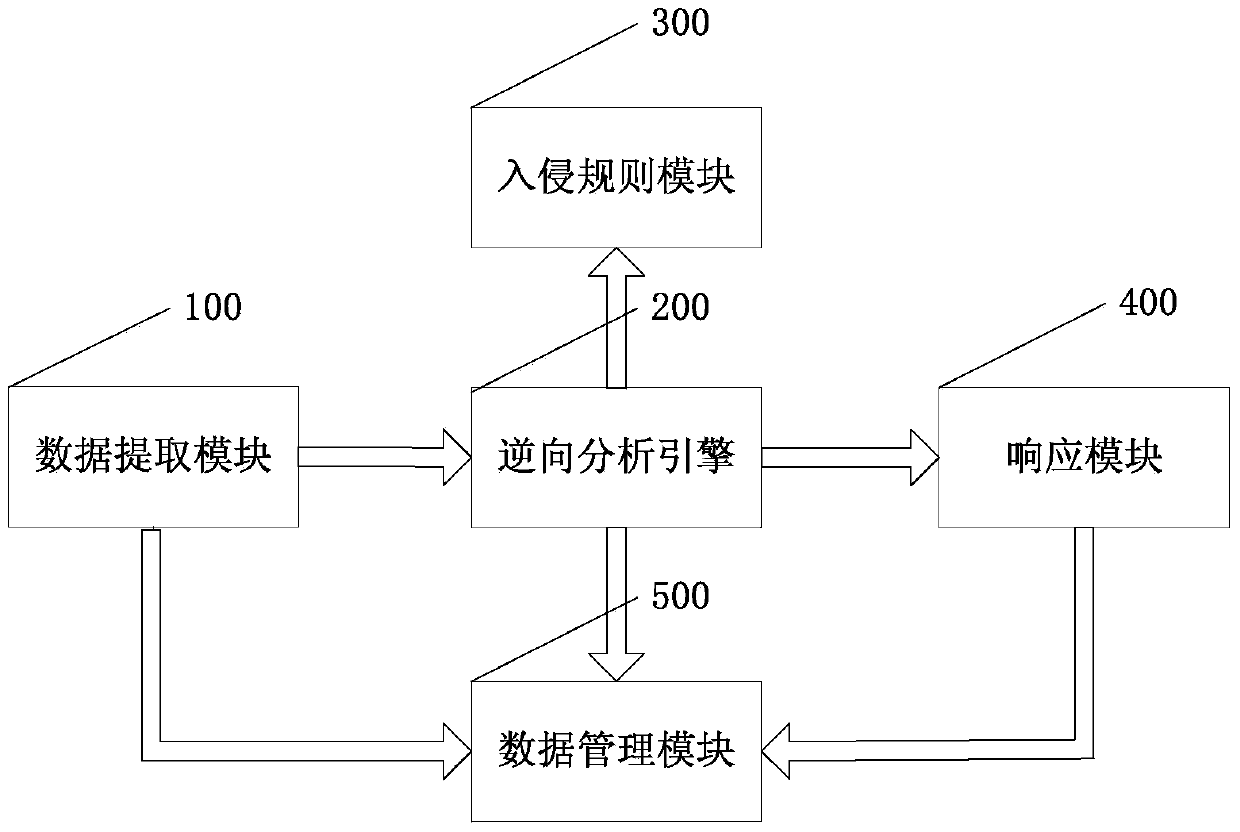
ActiveCN103746992ADoes not interfere with normal operationReduce overheadTransmissionData packReverse analysis
The invention discloses a reverse-based intrusion detection system and a reverse-based intrusion detection method and relates to the field of network encryption protocols. The system comprises a data extraction module, a reverse analysis module, an intrusion rule module, a response module and a data management module. The method comprises the following steps: (1) capturing all network data packages running through an Android phone by the data extraction module, sending to a reverse analysis engine, acquiring network processes and user behaviors by the data extraction module to generate a system log and a weblog, and sending the system log and the weblog to the data management module; (2) identifying intrusion behaviors by the reverse analysis engine through the TCP / IP (transmission control protocol / Internet protocol) analysis technology and the apk decompilation reverse technology by combining the system log and the weblog; (3) performing warning and recording on the intrusion behaviors identified by the reverse analysis engine through the response module; (4) storing all information of a user in the data management module so as to facilitate later evidence collection and lookup. The reverse-based intrusion detection system and the reverse-based intrusion detection method disclosed by the invention have safety, timeliness, expandability and advancement.
Owner:WUHAN HONGXU INFORMATION TECH
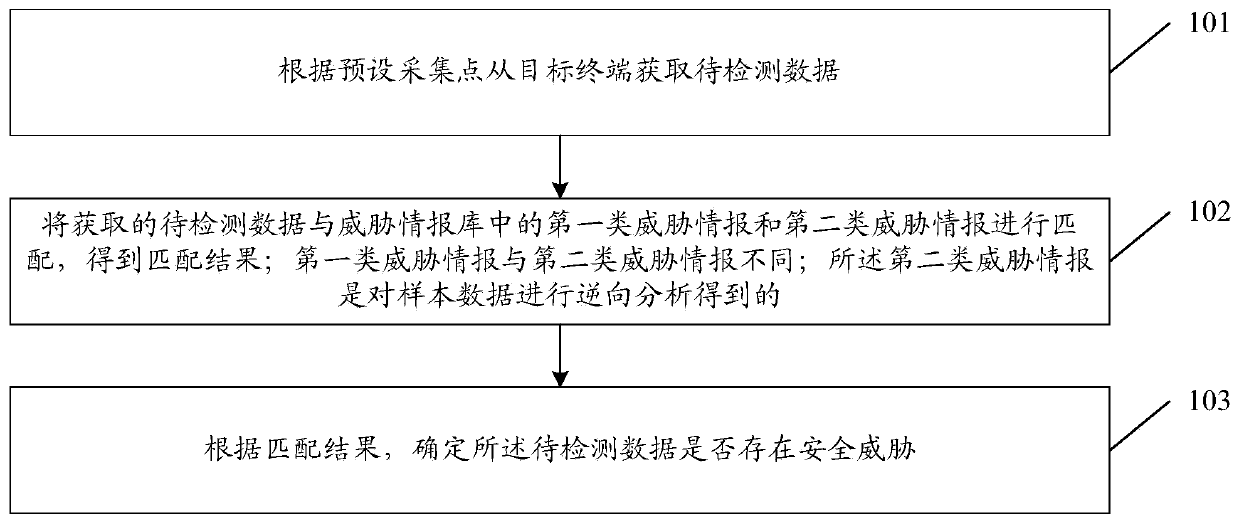
Data detection method and device and storage medium
The invention discloses a data detection method and device and a storage medium. The method comprises the steps of obtaining to-be-detected data from a target terminal according to a preset collectionpoint; matching the obtained to-be-detected data with a first type of threat information and a second type of threat information in a threat information library to obtain a matching result, wherein the first type of threat information is different from the second type of threat information, and the second type of threat information is obtained by performing reverse analysis on sample data; and determining whether the to-be-detected data has security threats or not according to the matching result. By adopting the scheme of the invention, more security threats can be found in the to-be-detected data, so that the accuracy of detecting the security threats for the user terminal is improved, and the user experience is further improved.
Owner:SANGFOR TECH INC
Processor structure and instruction system representation method based on multi-dimensional variable description table
InactiveCN101645005ATo achieve compilation workScalableSpecific program execution arrangementsReverse analysisProcessor register
The invention relates to the field of reverse analysis of computer softwares, in particular to a processor structure and an instruction system representation method based on a multi-dimensional variable description table. The method adopts a multi-layer triple nested table (Table) to construct a structural characteristic library and an instruction system description template of processors, the Table is represented as [<Tp1, Ts1, Ti1>, <Tp2, Ts2, Ti2>, ..., <Tpn, Tsn, Tin>], each triple <Tpn, Tsn, Tin> represents one processor, Tpn performs the classification, indexing and screening on the processors, Tsn provides register structure information, interruption structure information, reset address information and storage space distribution information, Tin provides a machine code, an assemblyexpression and the mapping relation between the machine code and the assembly expression, data in the Table is extracted from an information database of the processors, and the information database ofthe processors can be managed and maintained. The method has strong universality, and can be used for most of the prior processors.
Owner:THE PLA INFORMATION ENG UNIV
Method for constructing light gauge welding residual stress field on basis of small-hole process tested data
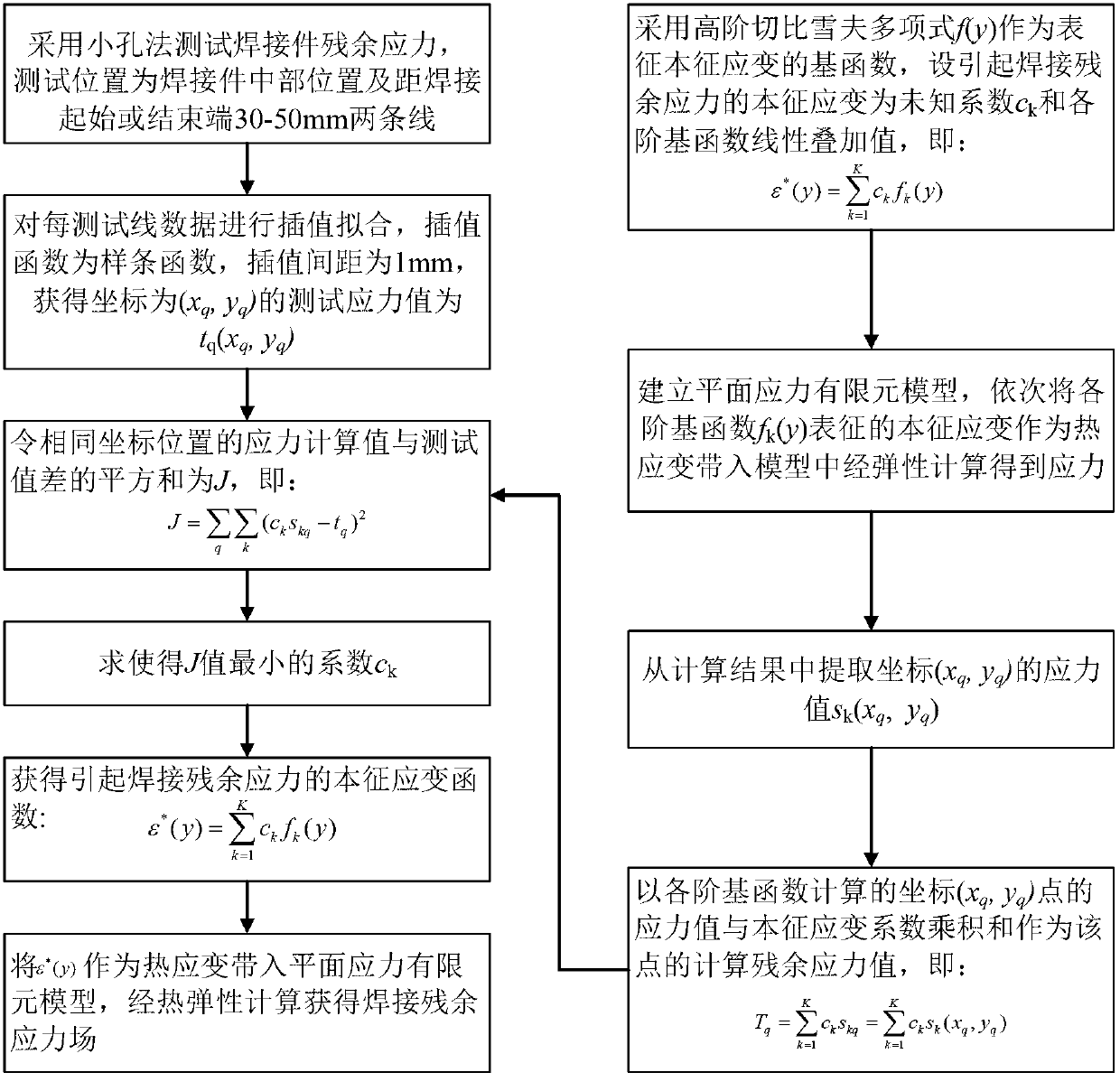
InactiveCN103344555AEasy to operateImprove efficiencyUsing mechanical meansMaterial analysisEigenstrainElement model
The invention discloses a method for constructing a light gauge welding residual stress field on the basis of small-hole process tested data. The method comprises the following steps of: firstly, testing a residual stress of a weld assembly by adopting a small hole process, carrying out interpolation fitting on the tested stress values, then sequentially substituting each first-order polynomial in a finite element model by using a high-order Chebyshev polynomial as a primary function of representing unknown intrinsic strain causing the welding residual stress, carrying out calculation of elasticity to obtain calculated stress values of coordinate points with same tested stresses, selecting a coefficient enabling the quadratic sum of differences of the calculated stress values and the fitted tested stress values to be minimum as an intrinsic strain coefficient, multiplying the intrinsic strain coefficient by corresponding all order polynomials and then linearly overlapping to be used as an intrinsic strain, and finally obtaining a welding residual stress field through a finite element process. On the basis of the small hole process tested data, the intrinsic strain causing the welding residual stress is constructed by using a thermo-elasticity finite element method and a reverse analysis method, therefore, the distribution of the light gauge welding residual stress field is obtained; and the method is convenient to operate and high in efficiency.
Owner:JIANGSU UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com