Software protection method based on API (Application Program Interface) security attribute hiding and attack threat monitoring
A technology of software protection and security attributes, applied in computer security devices, program/content distribution protection, instruments, etc., can solve the problem of easy removal of threat processing fragments, single type of attack threat, lack of available information, theoretical analysis and research cases, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
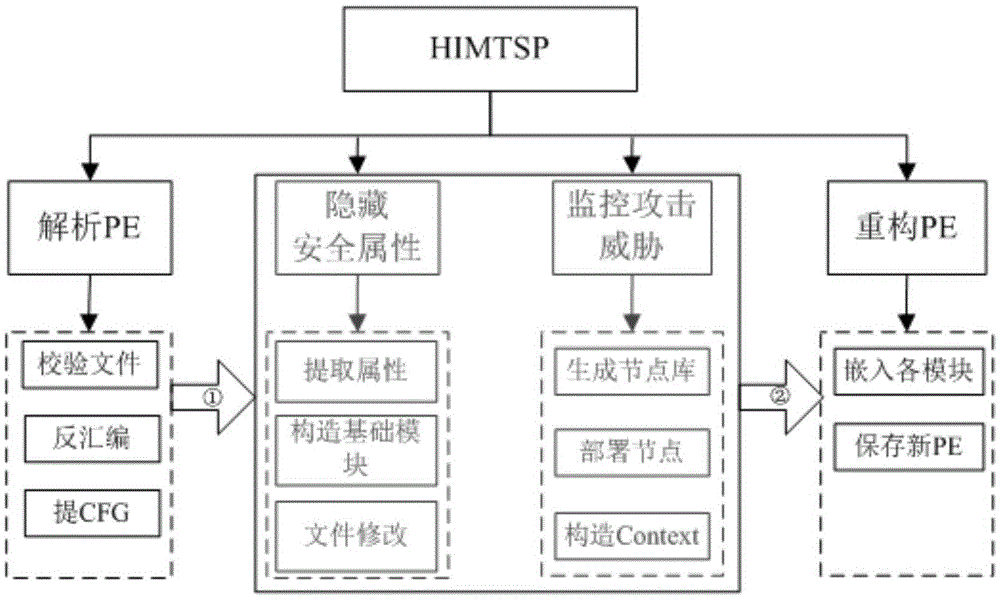
[0058] According to the above technical solution, as shown in the figure, a software protection method based on API security attribute hiding and attack threat monitoring includes the following steps:
[0059] Step 1, extract the DLL file information from the PE file input table to be protected, and record the DLL file information in an input information record table imp_tab;
[0060] The above-mentioned PE file is a portable and executable program file under the Windows platform. According to the structural characteristics of the PE file, find the storage location of the input table, extract each DLL name and its FirstThunk value in the input table in turn, and count the number of APIs in the DLL at the same time, record the length, name (or name) of each API name serial number); the information of each DLL is recorded in the following format of the DLL input information record table imp_tab:
[0061] Table 1 DLL information record table
[0062] First Thunki
D...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com