Patents
Literature
70 results about "Portable Executable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
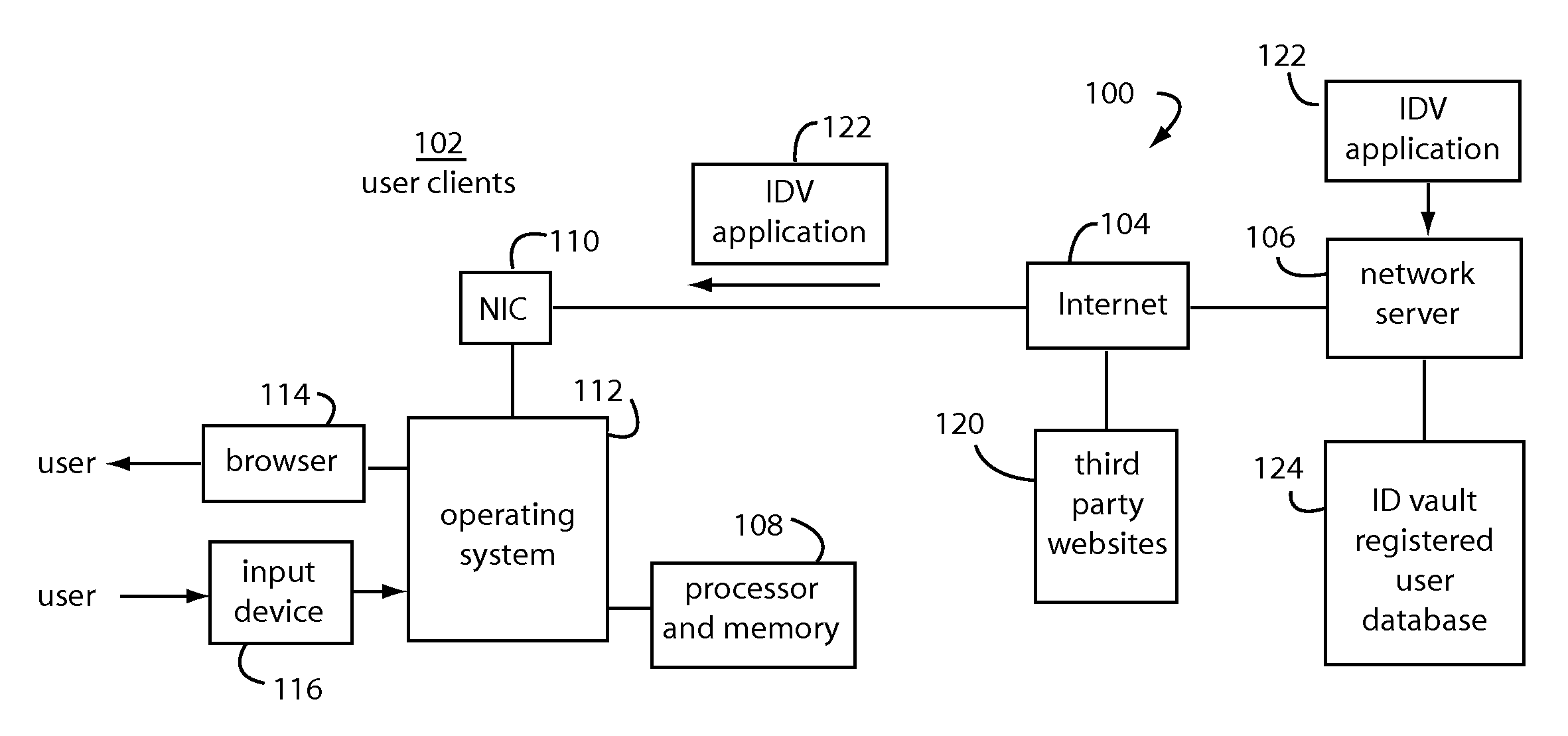
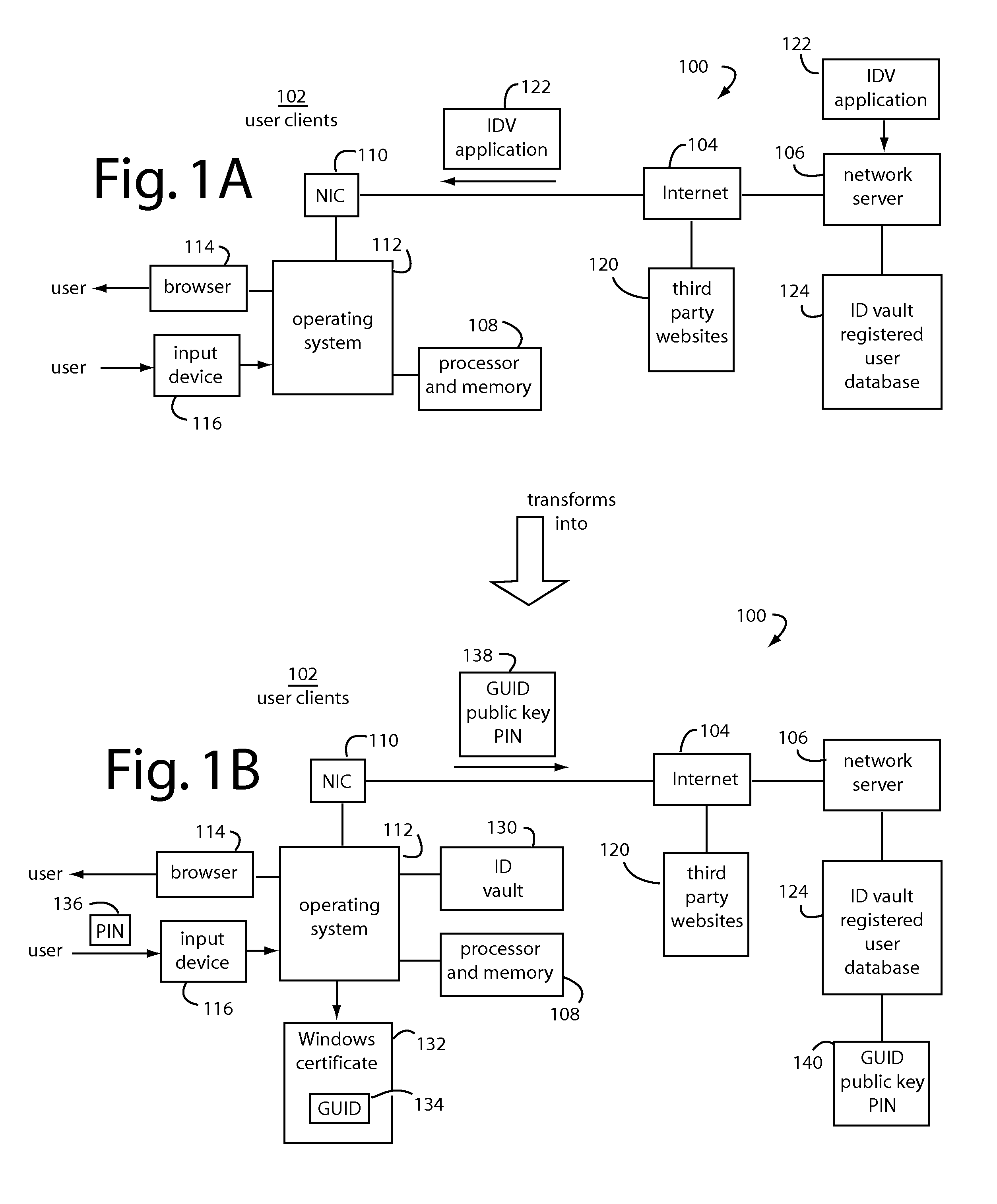
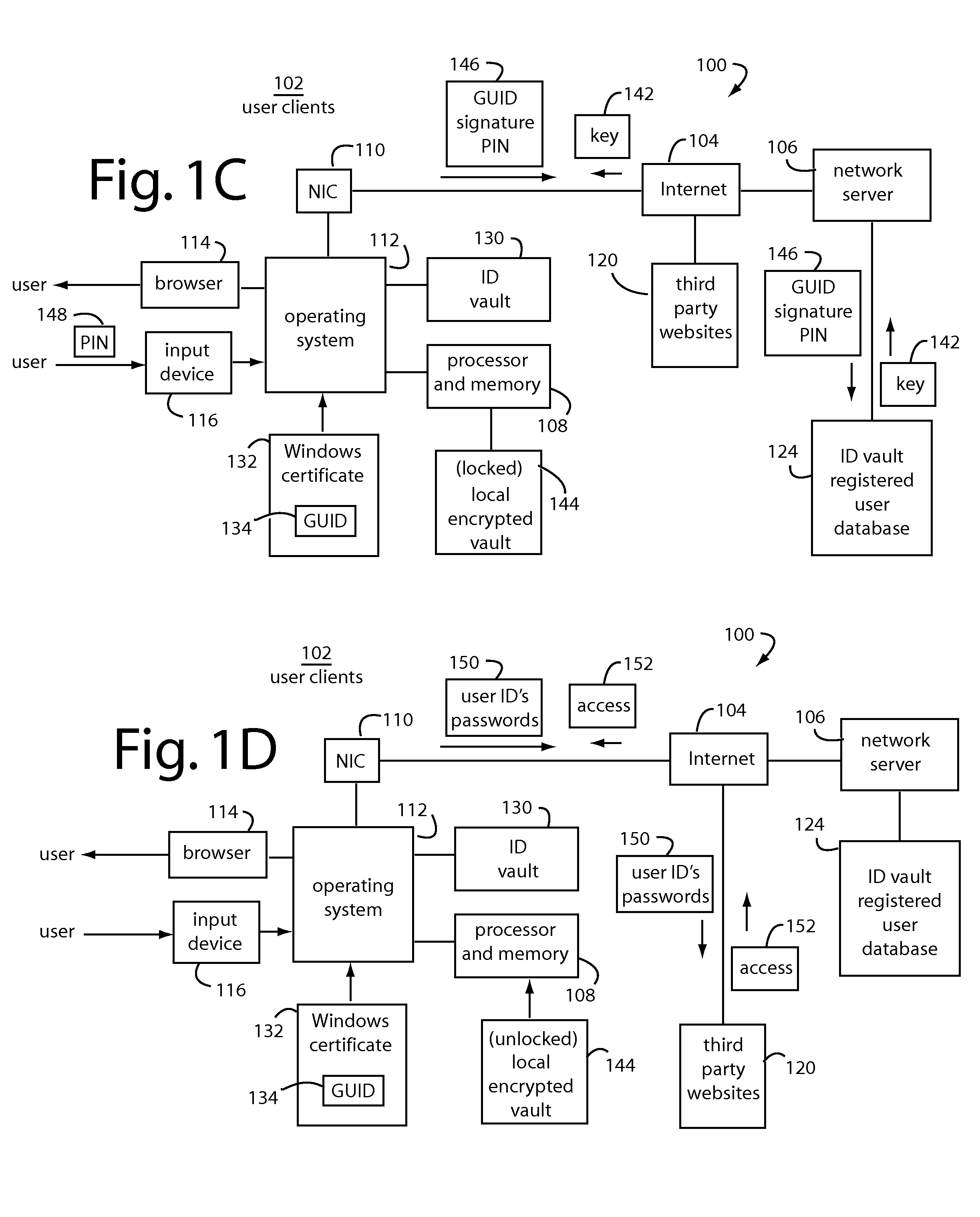
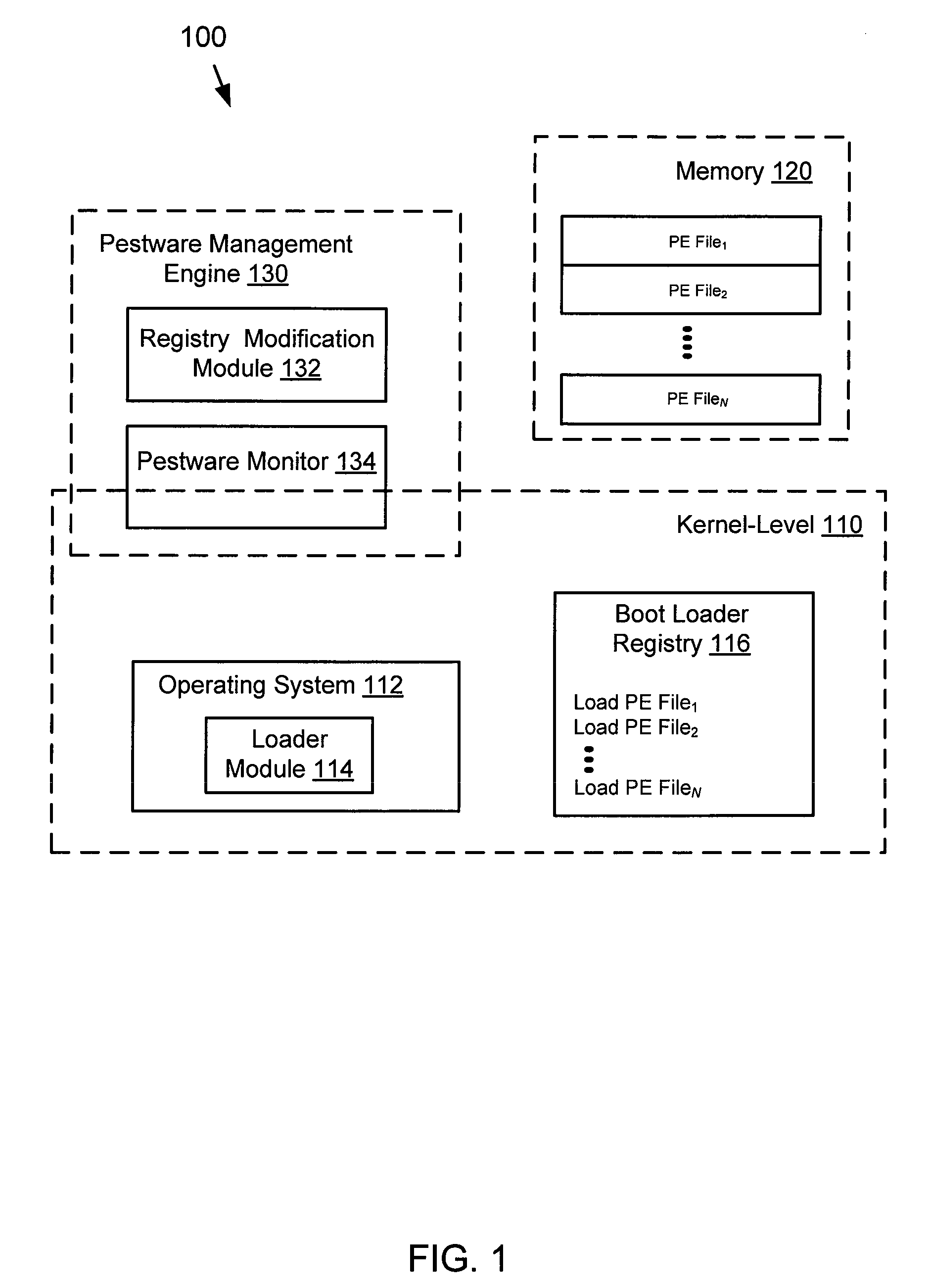
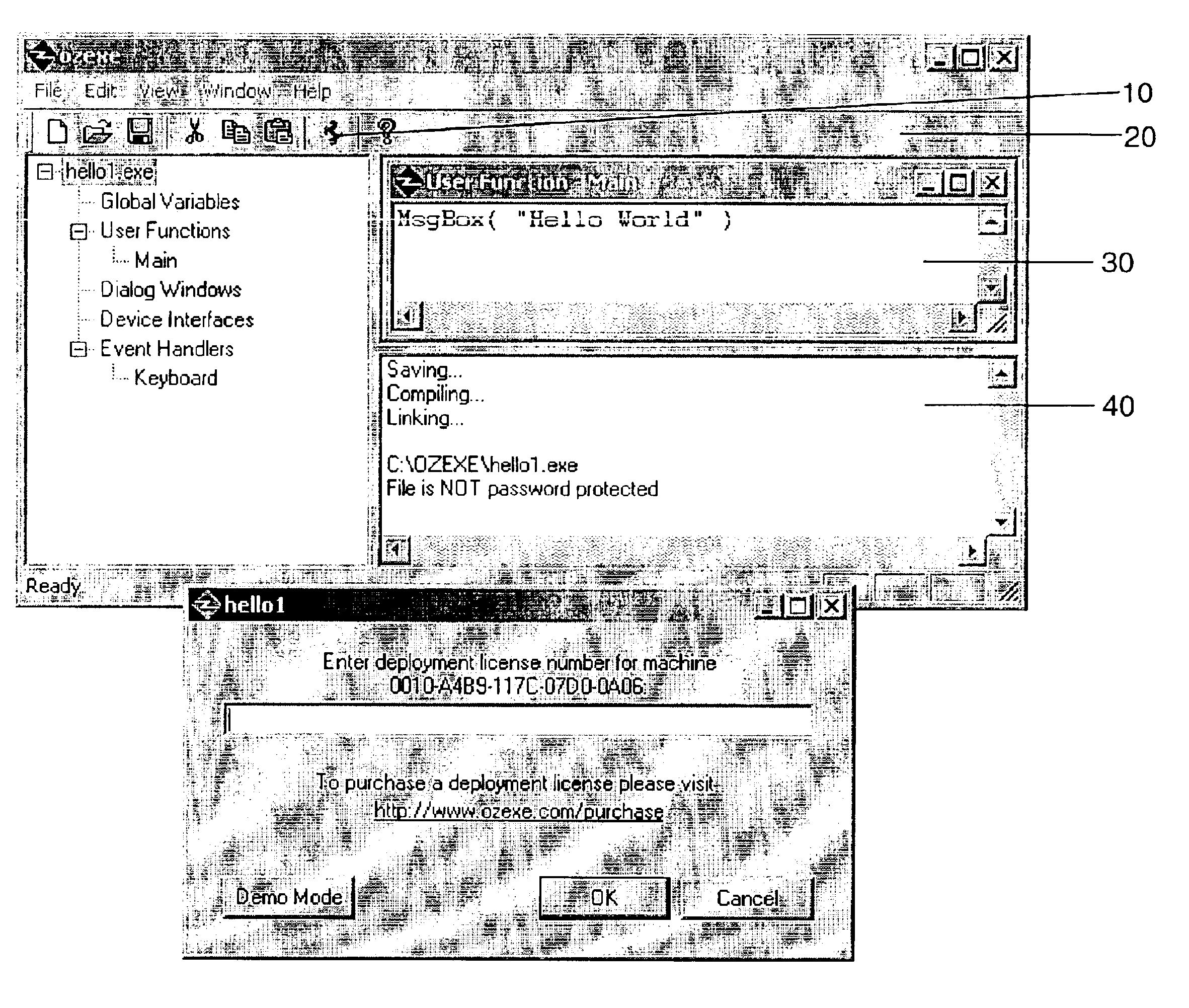
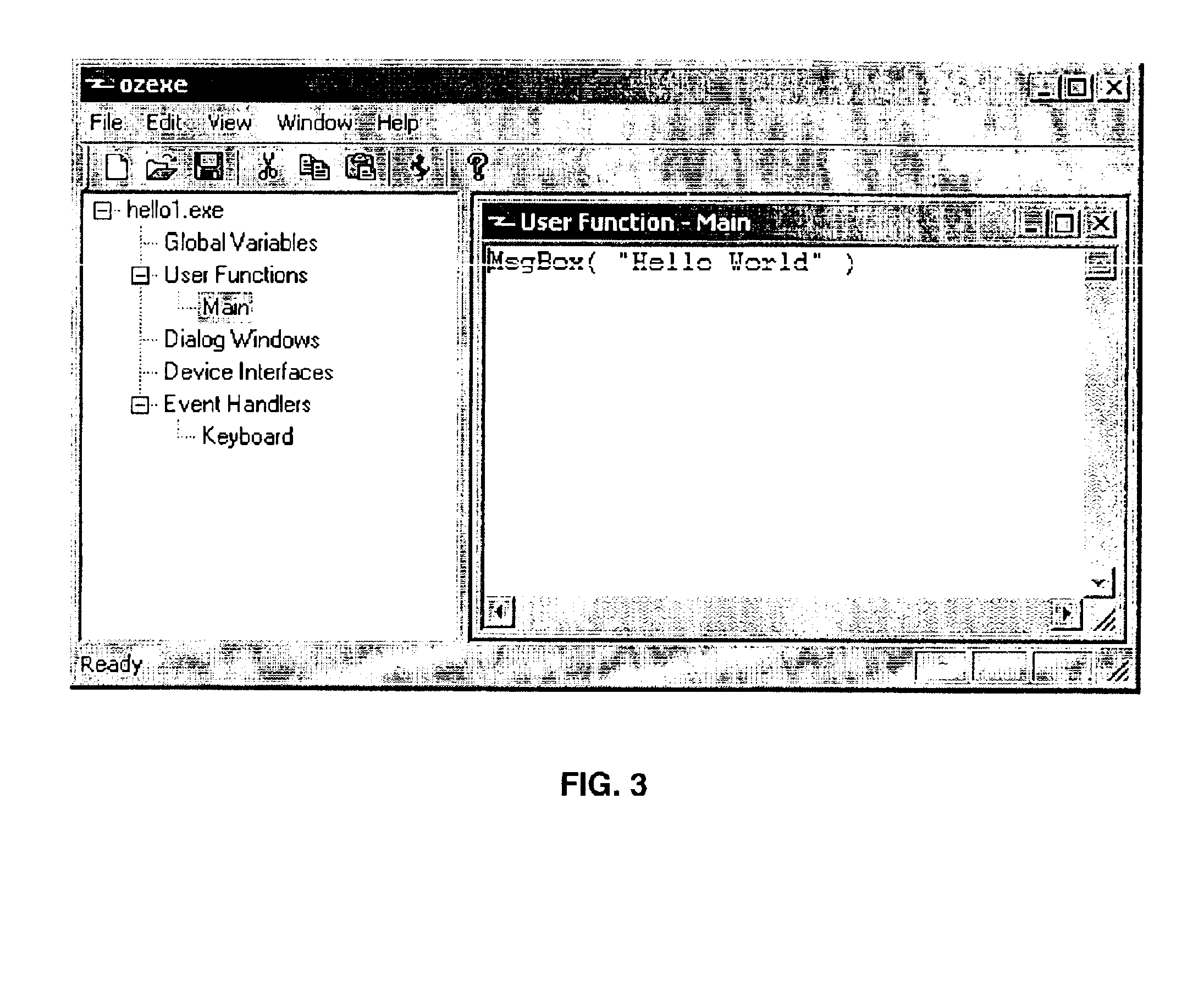
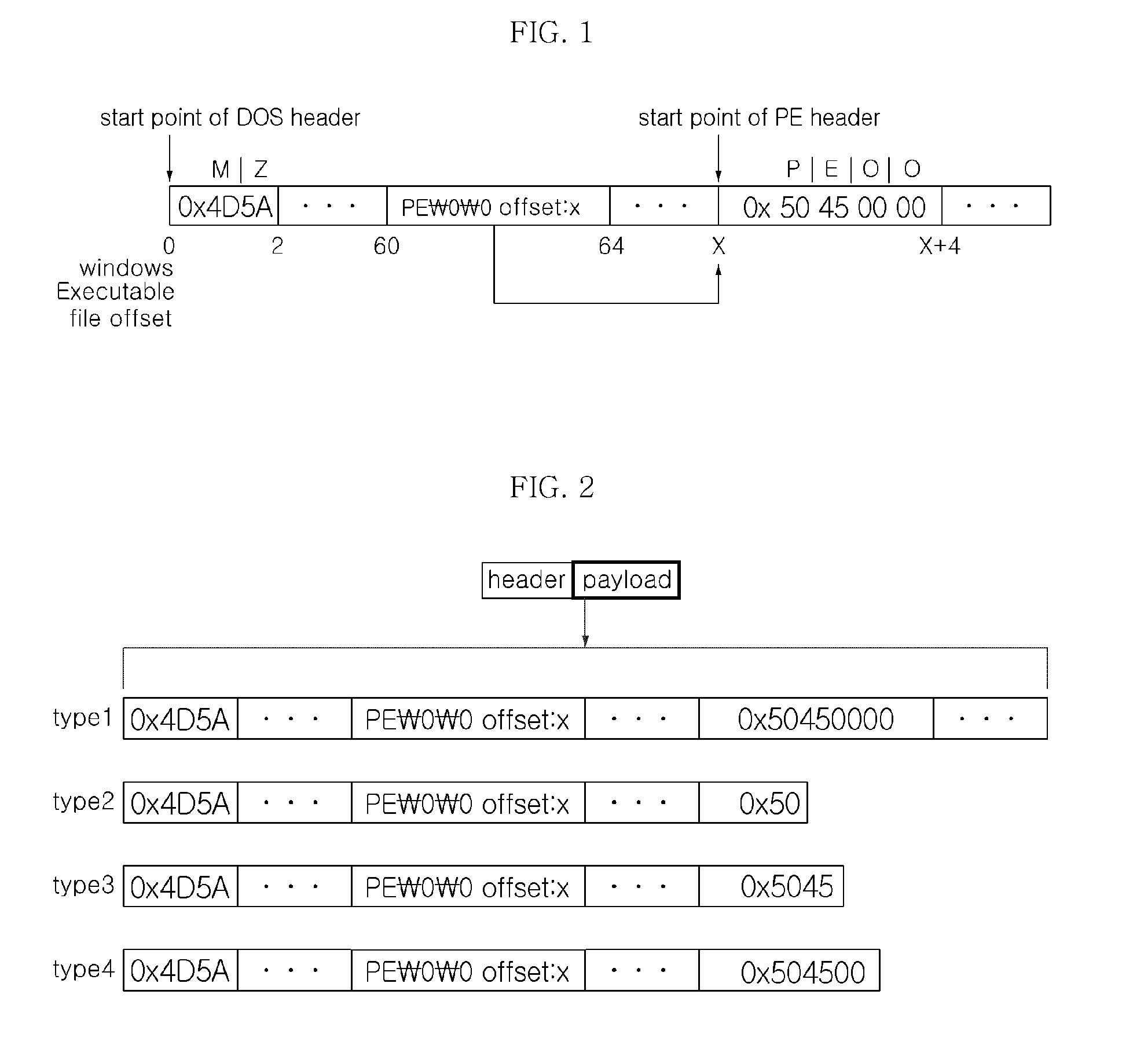
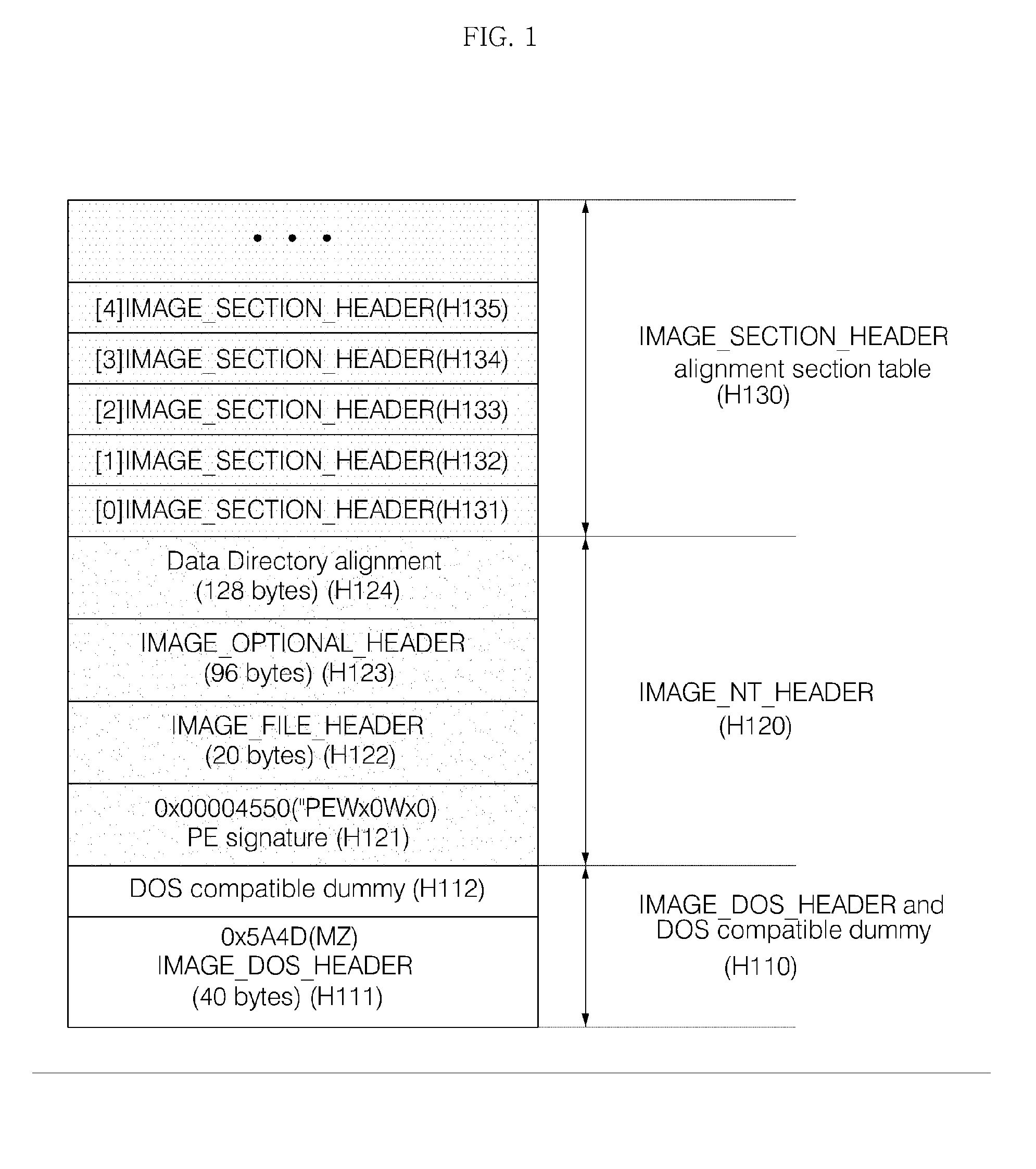
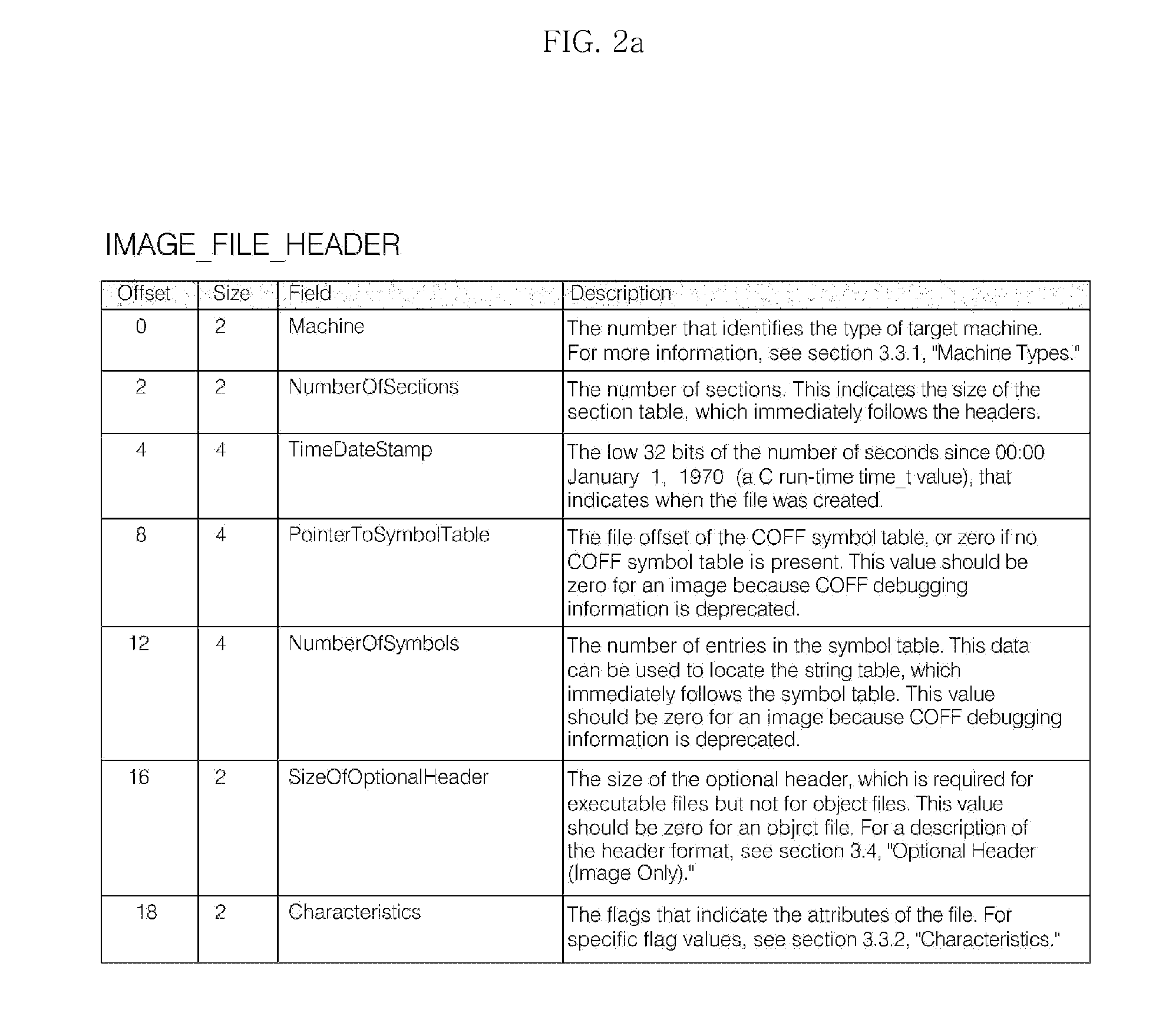
The Portable Executable (PE) format is a file format for executables, object code, DLLs, FON Font files, and others used in 32-bit and 64-bit versions of Windows operating systems. The PE format is a data structure that encapsulates the information necessary for the Windows OS loader to manage the wrapped executable code. This includes dynamic library references for linking, API export and import tables, resource management data and thread-local storage (TLS) data. On NT operating systems, the PE format is used for EXE, DLL, SYS (device driver), and other file types. The Extensible Firmware Interface (EFI) specification states that PE is the standard executable format in EFI environments.
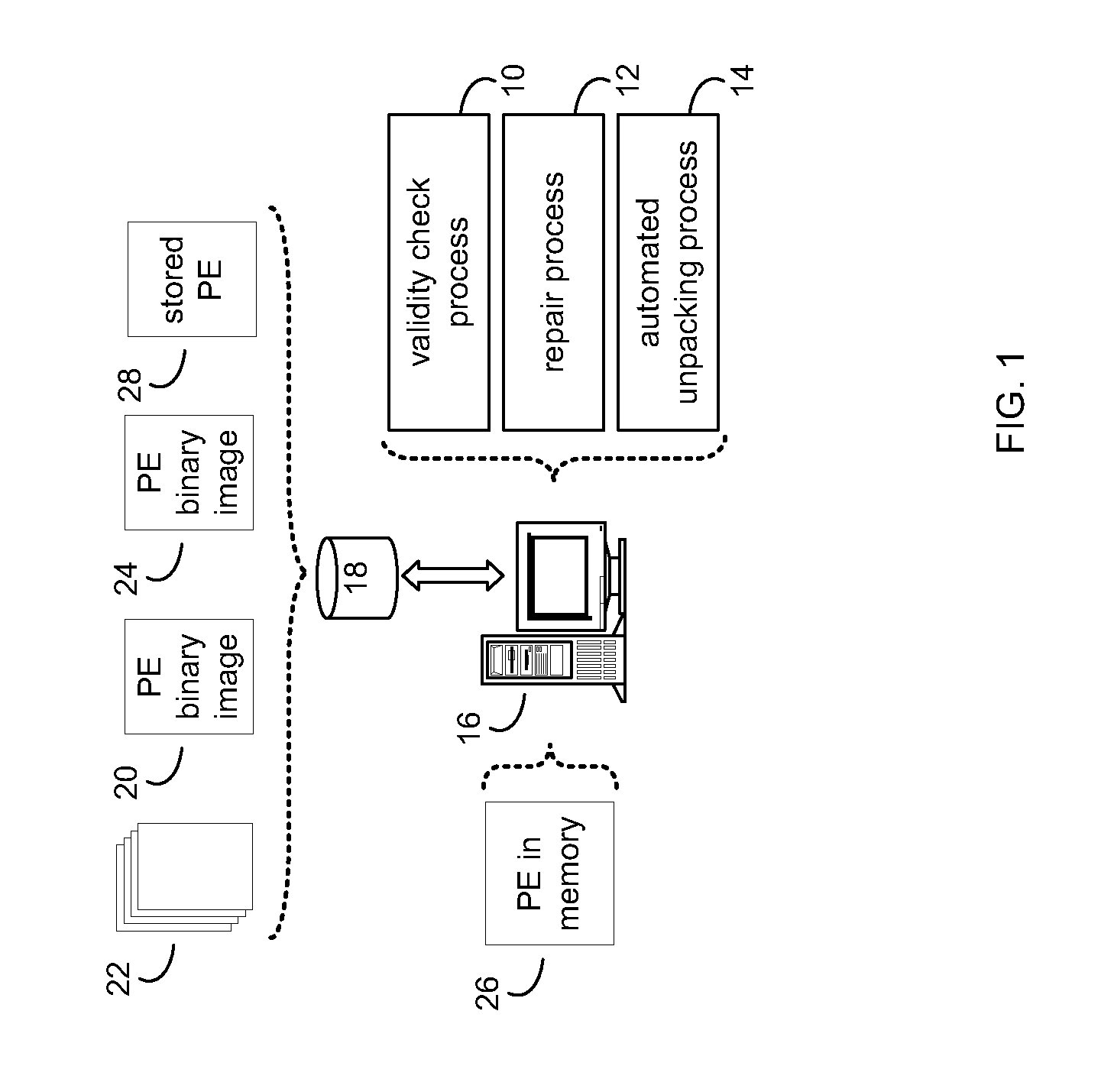
Securing portable executable modules
InactiveUS20120036569A1Digital data processing detailsUser identity/authority verificationProgramming languageOperational system
An import address table (IAT) and dynamic linked libraries (DLLs) security mender process is configured to store nominal IAT table entries and in-process binary images, from either a priori data and / or from computed values. Particular IAT table entries and in-process binary images are fetched for comparison with expected values. These particular IAT table entries and / or in-process binary images are then overwritten with nominal values for the IAT table entries and in-process binary images. The IAT-DLL security mender runs in parallel with the operating system and has access to its IAT and inline code in system memory.
Owner:WHITE SKY
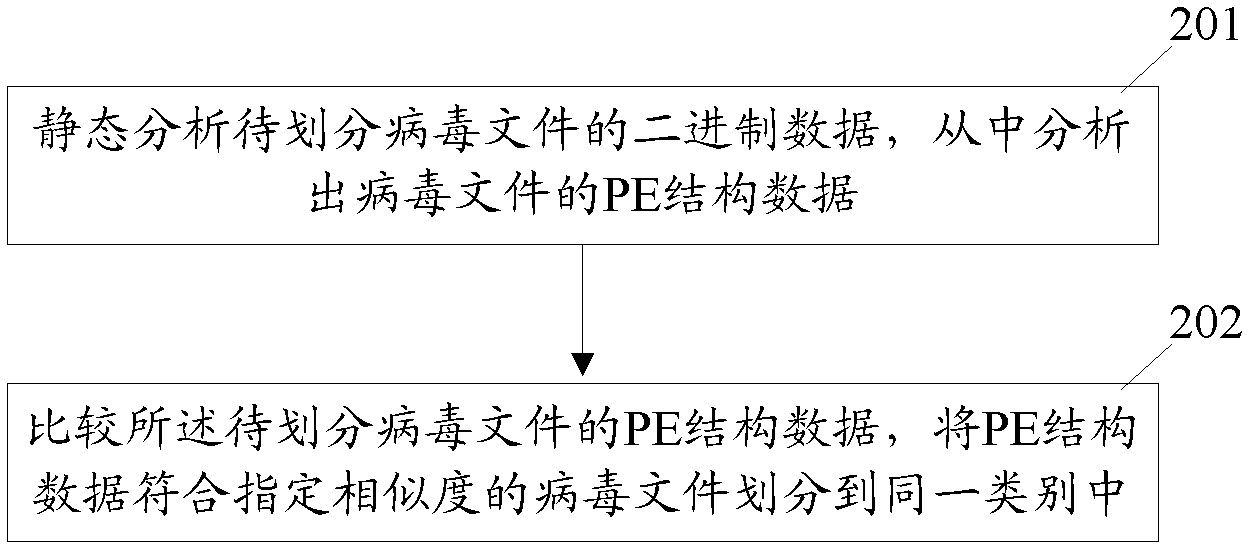
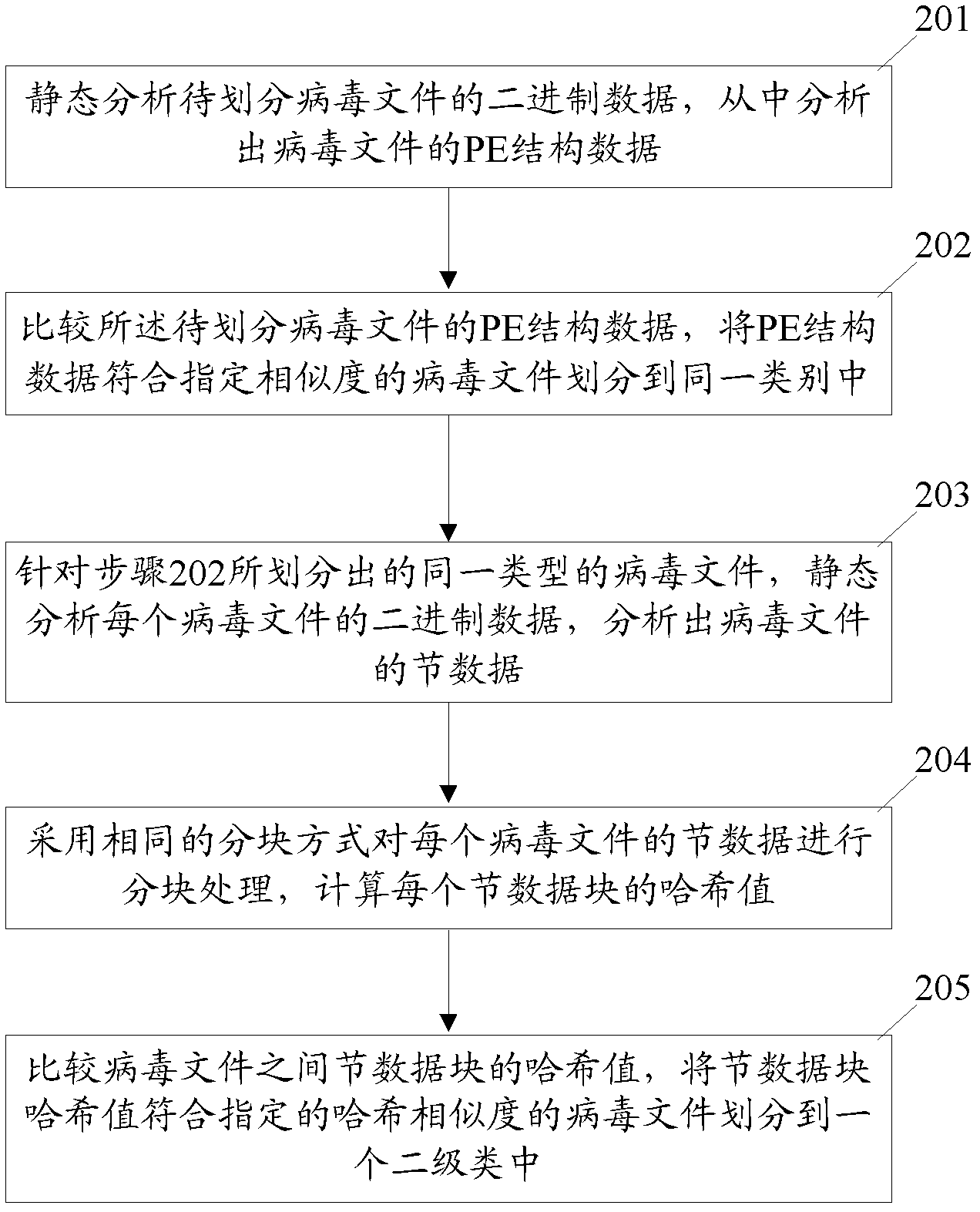
Cluster partitioning processing method and cluster partitioning processing device for virus files
ActiveCN102930206AImprove clustering efficiencyReduce consumptionPlatform integrity maintainanceResource consumptionData profiling
The invention discloses a cluster partitioning processing method and a cluster partitioning processing device for virus files. The method comprises the following steps of: (A) statically analyzing binary data of virus files to be partitioned, and analyzing portable executable (PE) structure data of the virus files from the binary data; and (B) comparing the PE structure data of the virus files to be partitioned, and partitioning the virus files with the PE structure data according with appointed similarity into the same category. The device comprises a first data analyzing module and a first cluster partitioning module, wherein the first data analyzing module is used for statically analyzing the binary data of the virus files to be partitioned and extracting the PE structure data of the virus files from the binary data; and the first cluster partitioning module is used for comparing the PE structure data of the virus files to be partitioned and partitioning the virus files with the PE structure data according with the appointed similarity into the same category. By the cluster partitioning processing method and the cluster partitioning processing device for the virus files, the cluster partitioning efficiency of the virus files of a computer can be improved, resource consumption is reduced, and the virus catching risk caused by the virus files which run dynamically is eliminated.
Owner:TENCENT TECH (SHENZHEN) CO LTD
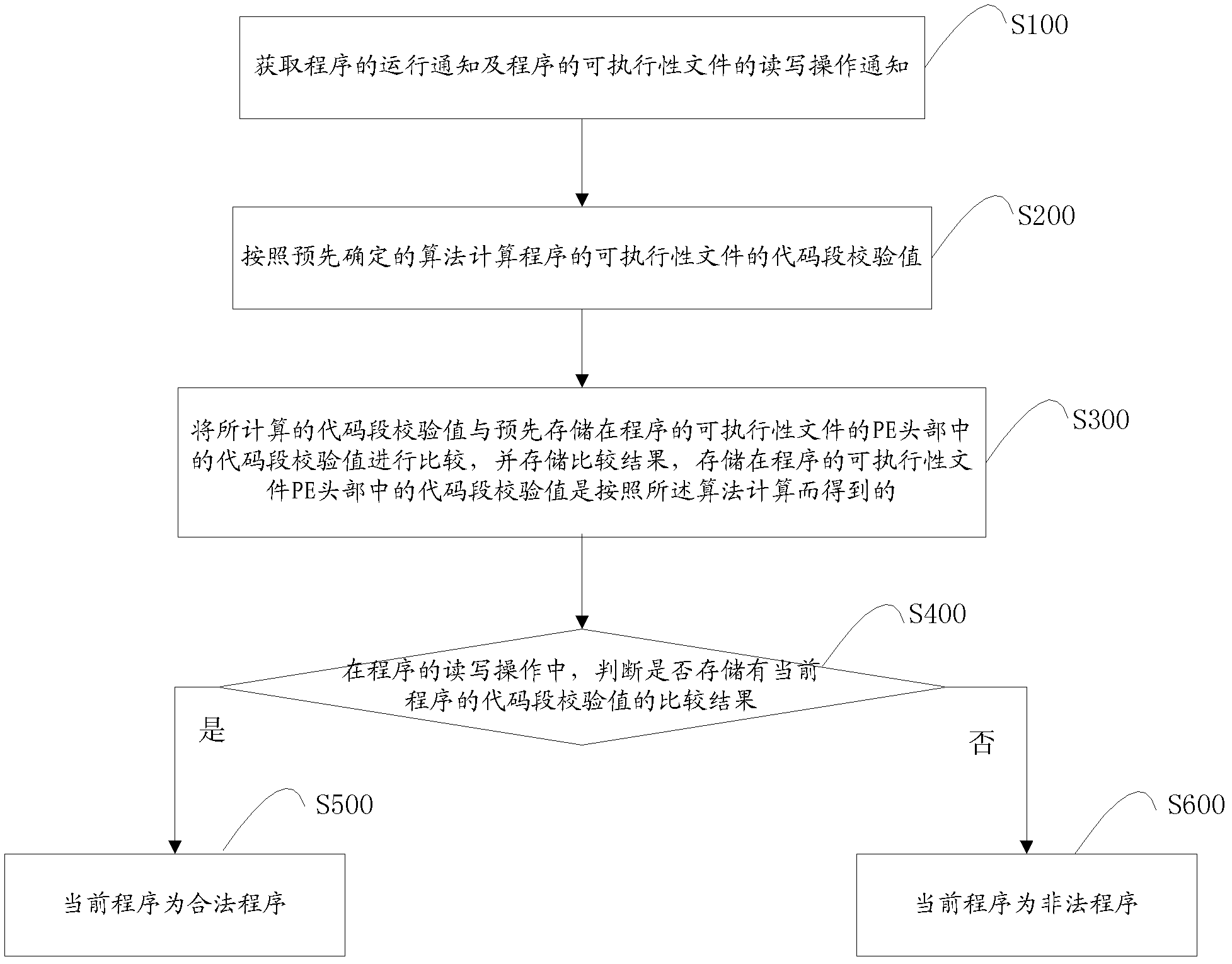
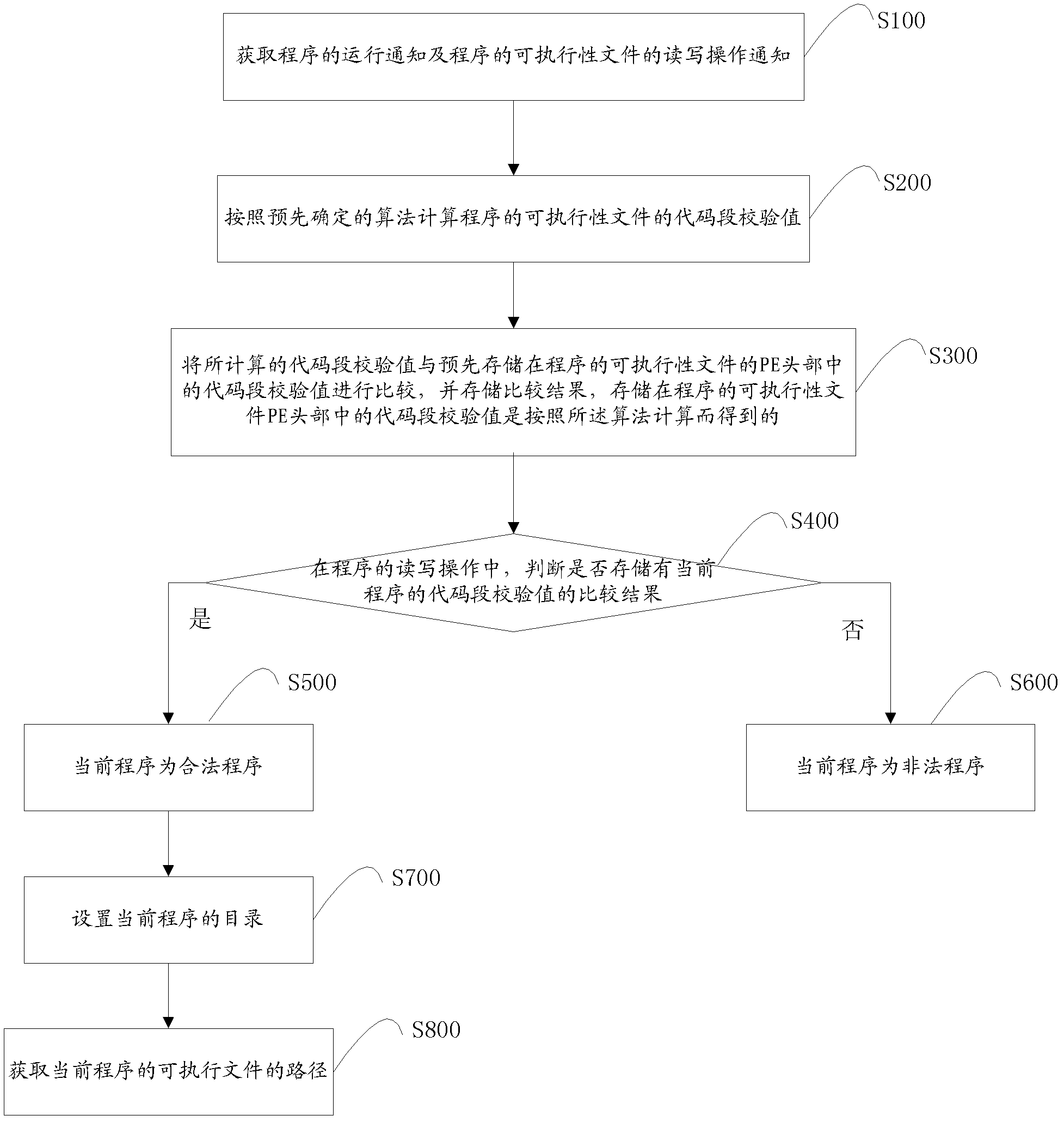
Program validity verification method and system
ActiveCN102509049AImprove user experienceWill not seriously affect the running speedPlatform integrity maintainanceOperational systemValidation methods
The invention discloses a program validity verification method and a system. The program validity verification method includes steps of acquiring running notices and read-write operation notices of executable documents of programs, calculating verification values of code segments of the executable documents of the programs according to the preset algorithm, comparing verification values of code segments in the PE (portable executable) header of the executable documents stored in the programs in advance with the calculated verification values of the code segments and storing the comparison results; and judging whether the comparison results of the verification values of the code segments of the current program or not during read-write operation of the program, is so, the current program is valid, or if not, the current program is invalid. The invention further provides a program validity verification system. According to the technical scheme, even when more programs of validity verification are required and document operation controls of running programs of users are required to be responded in real time, running speed of the operating system cannot be affected seriously and using experiences of the users are improved greatly.
Owner:SURFILTER NETWORK TECH
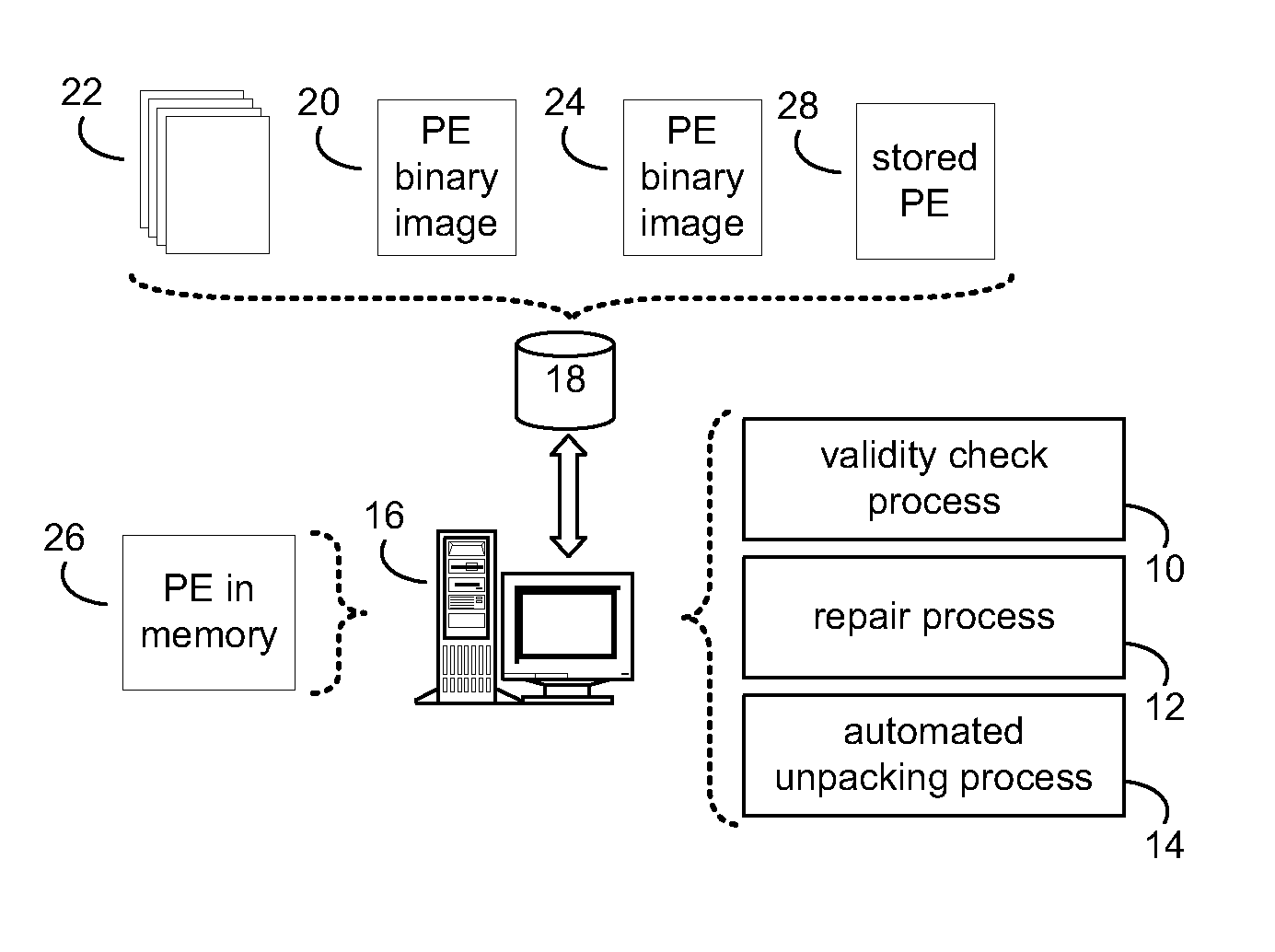
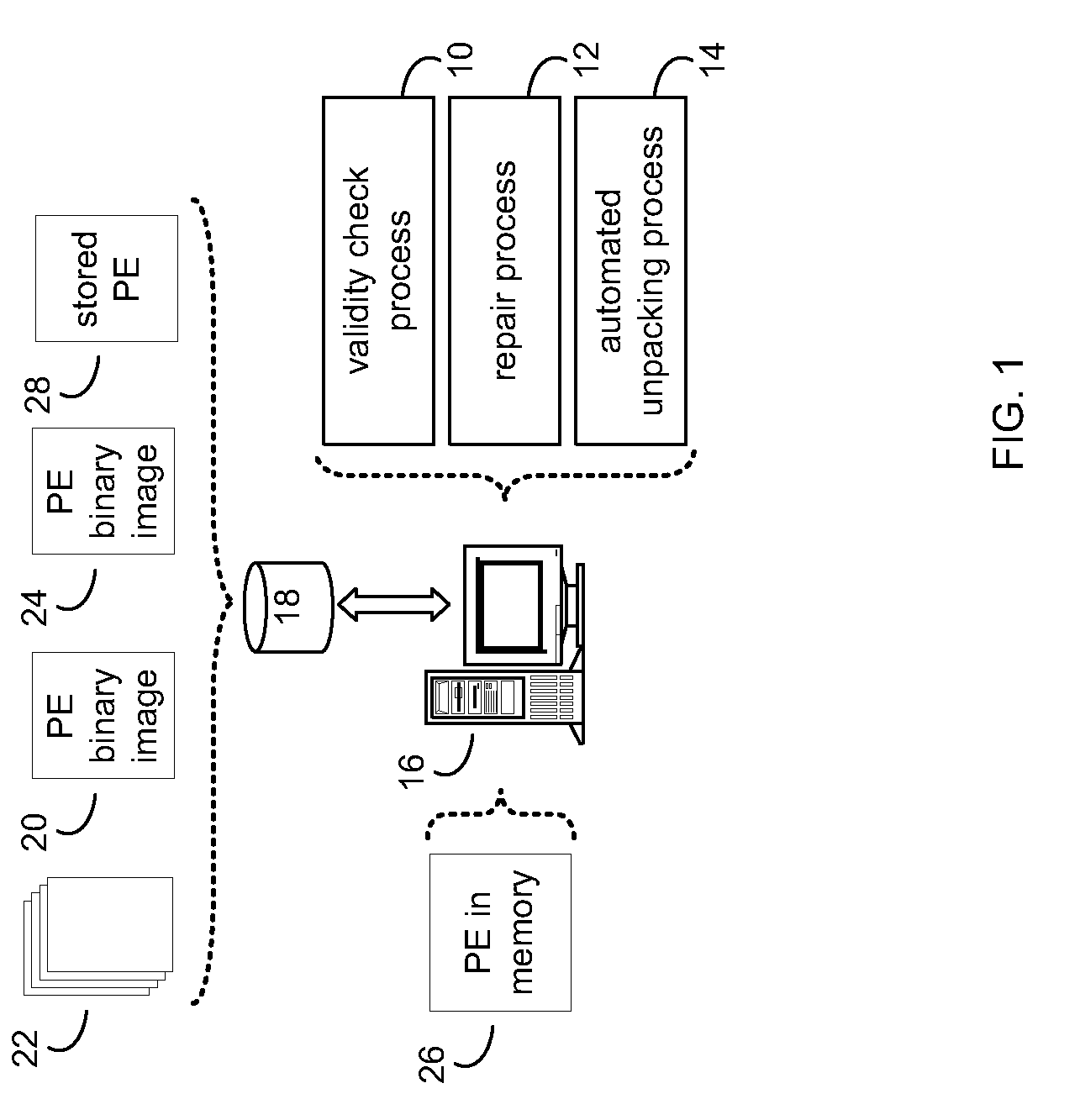
Repairing portable executable files
ActiveUS20110029805A1Digital data processing detailsReverse engineeringComputer hardwarePortable Executable
A portable executable file can be repaired by identifying an invalid field of a portable executable file. A likelihood of repairing the invalid field of the portable executable file is determined. A repair model for repairing the invalid field of the portable executable file is generated, and the invalid field of the portable executable file is repaired based upon, at least in part, the repair model.
Owner:REVERSINGLABS INT
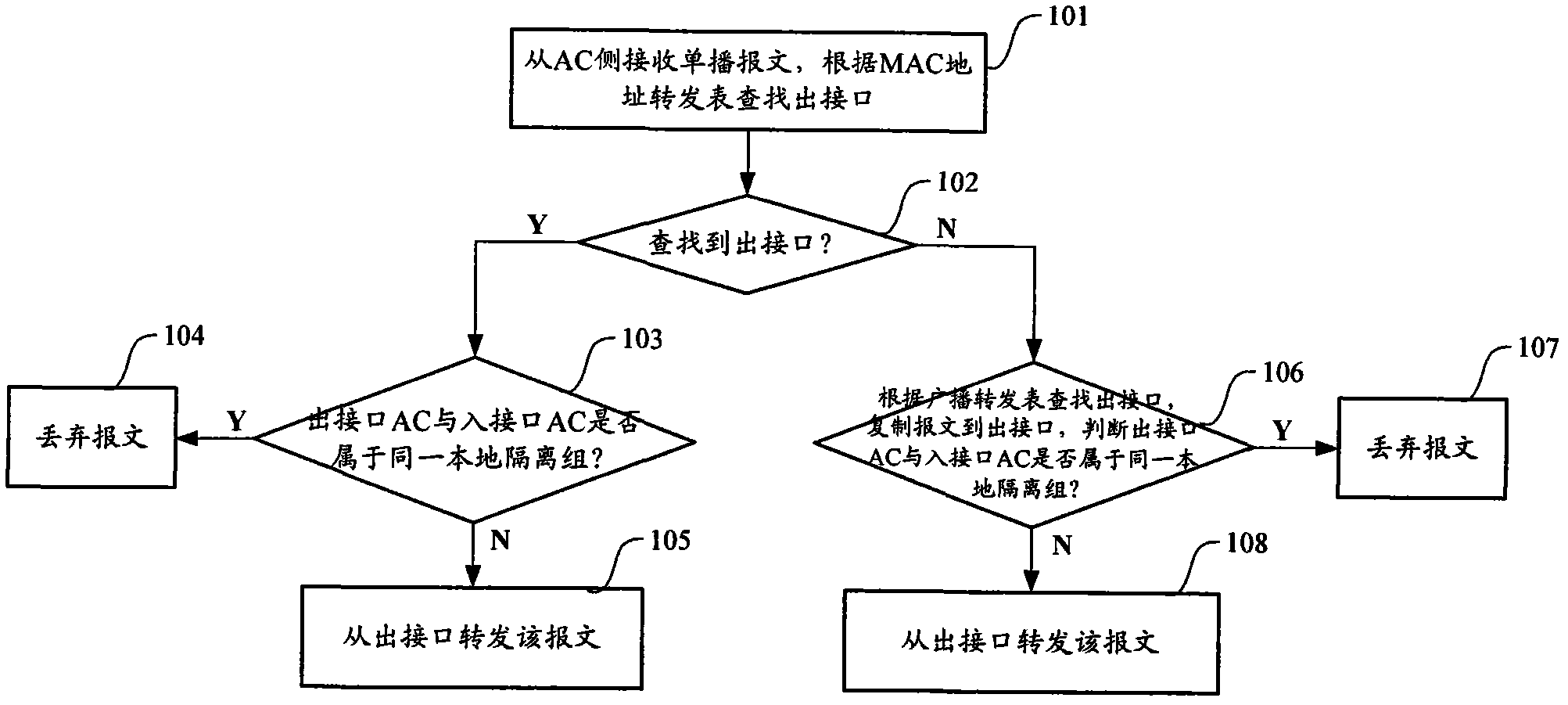
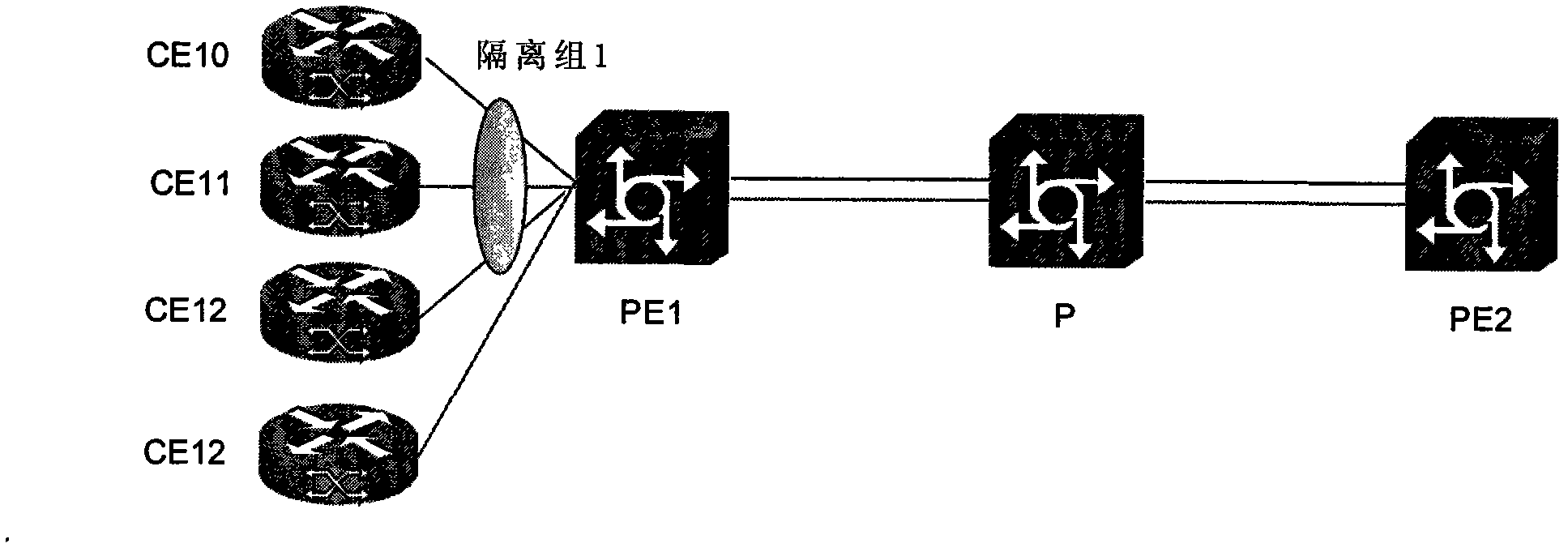
Network isolation method in VPLS (Virtual Private Lan Service) and device thereof
ActiveCN102255785AAchieve isolationFlexible accessNetworks interconnectionComputer hardwareNetwork isolation
The invention discloses a network isolation method in a VPLS (Virtual Private LAN Service) and a device thereof. The network isolation method comprises the following steps: configuring a local isolation set on a PE (Portable Executable) device; adding local ACs (Attachment Circuits) of the PE device, which belong to the same VPLS example but are needed to be isolated, into the same local isolation set; and in a message forwarding process, limiting the forwarding of the message on the basis of a VPLS source filter principle when a message output interface AC and a message input interface AC belong to the same local isolation set, thereby realizing the isolation among the local ACs of the PE device. In the invention, a global insulation set is respectively arranged on PE devices at the local and an opposite end; ACs which are on the PE devices at the local end and the opposite end, belong to the same VPLS example but are needed to be isolated are added to the same global isolation set; and in a message forwarding process, on the basis of the VPLS source filter principle, the forwarding of the message is limited when a message output interface AC and a message input interface AC belong to the same global isolation set on the PE device at a message receiving end, thus the isolation between a local AC and a far-end AC of the PE device.
Owner:XINHUASAN INFORMATION TECH CO LTD
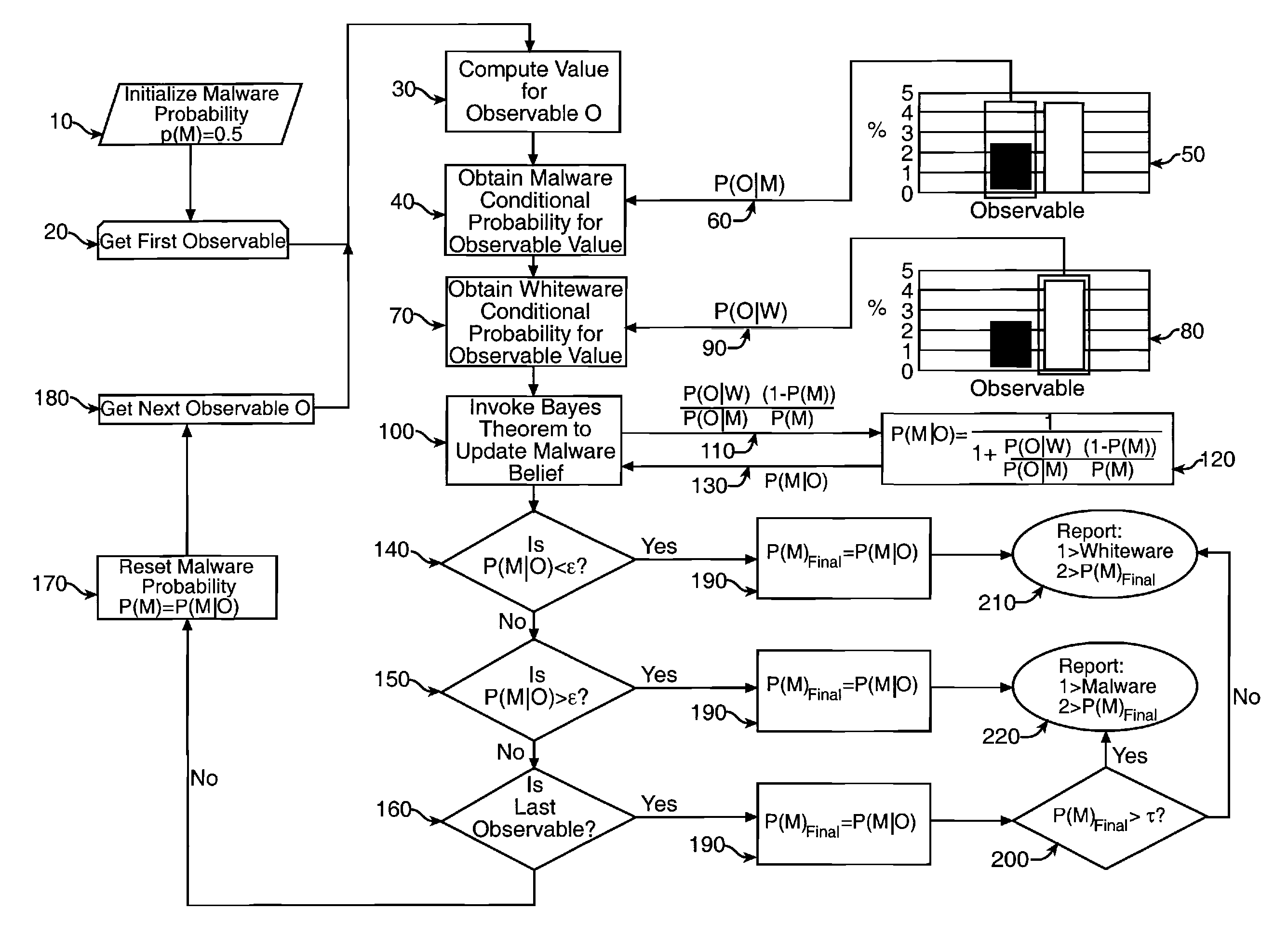
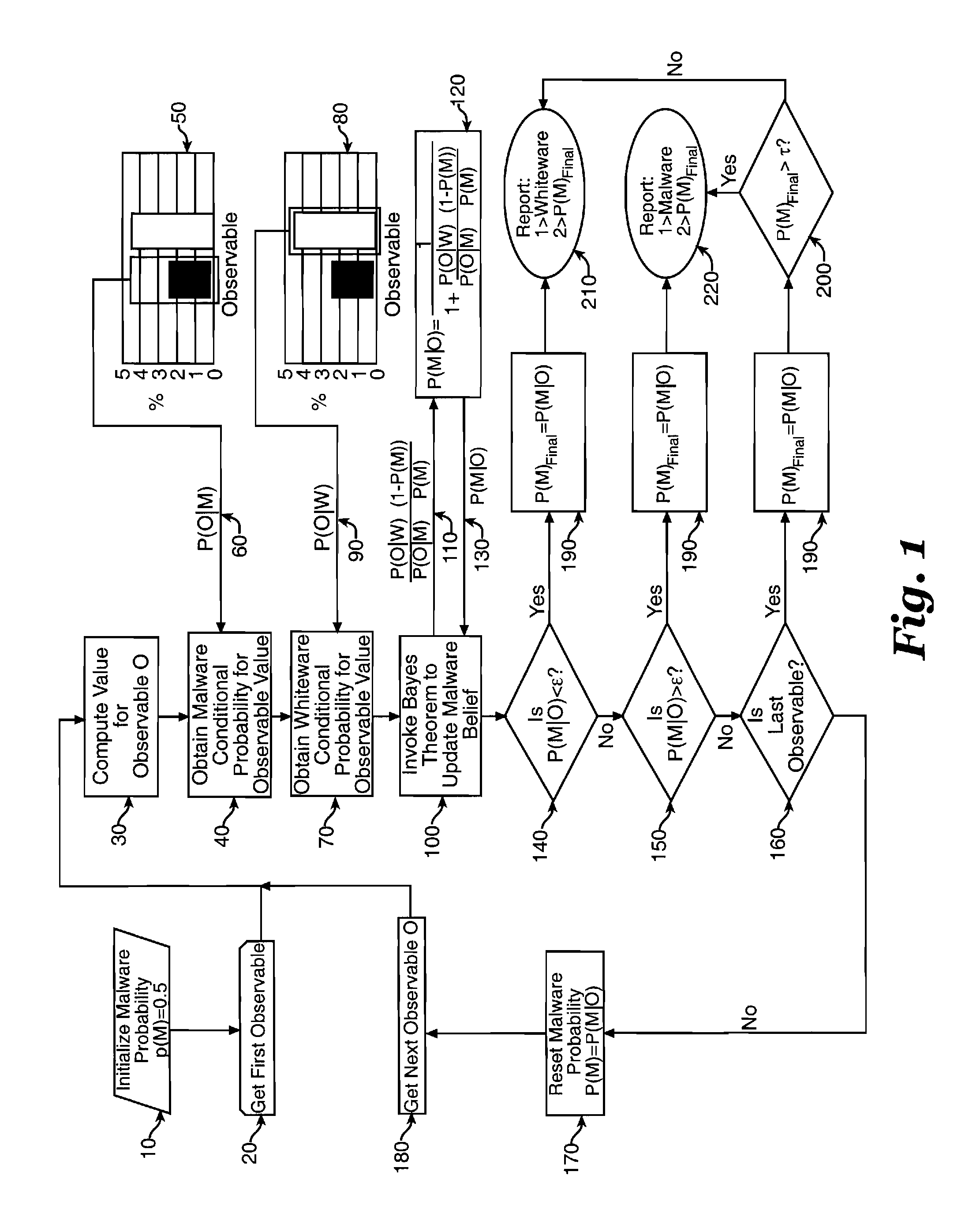
Classifying portable executable files as malware or whiteware
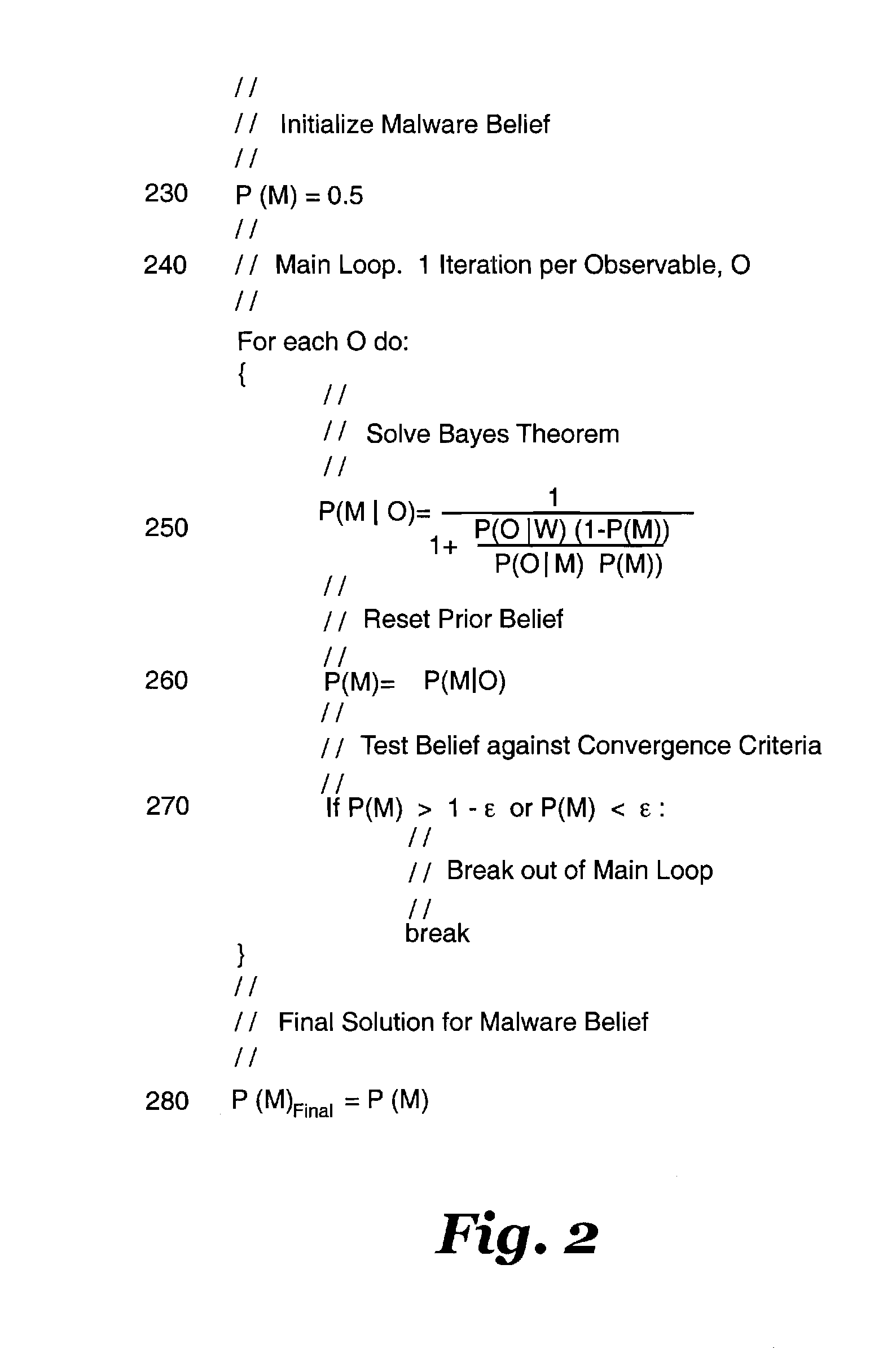
ActiveUS8549647B1Maximize accuracyRapid determinationMemory loss protectionError detection/correctionBayes' theoremPortable Executable
An improved approach for classifying portable executable files as malicious (malware) or benign (whiteware) is disclosed. The invention classifies portable executable files as malware or whiteware after using Bayes Theorem to evaluate each observable feature of each file with respect to other observable features of the same portable executable file with reference to statistical information gathered from repositories of known whiteware and malware files.
Owner:AIR FORCE US SEC
Methods, systems, and computer program products for integrating legacy applications into a platform-independent environment
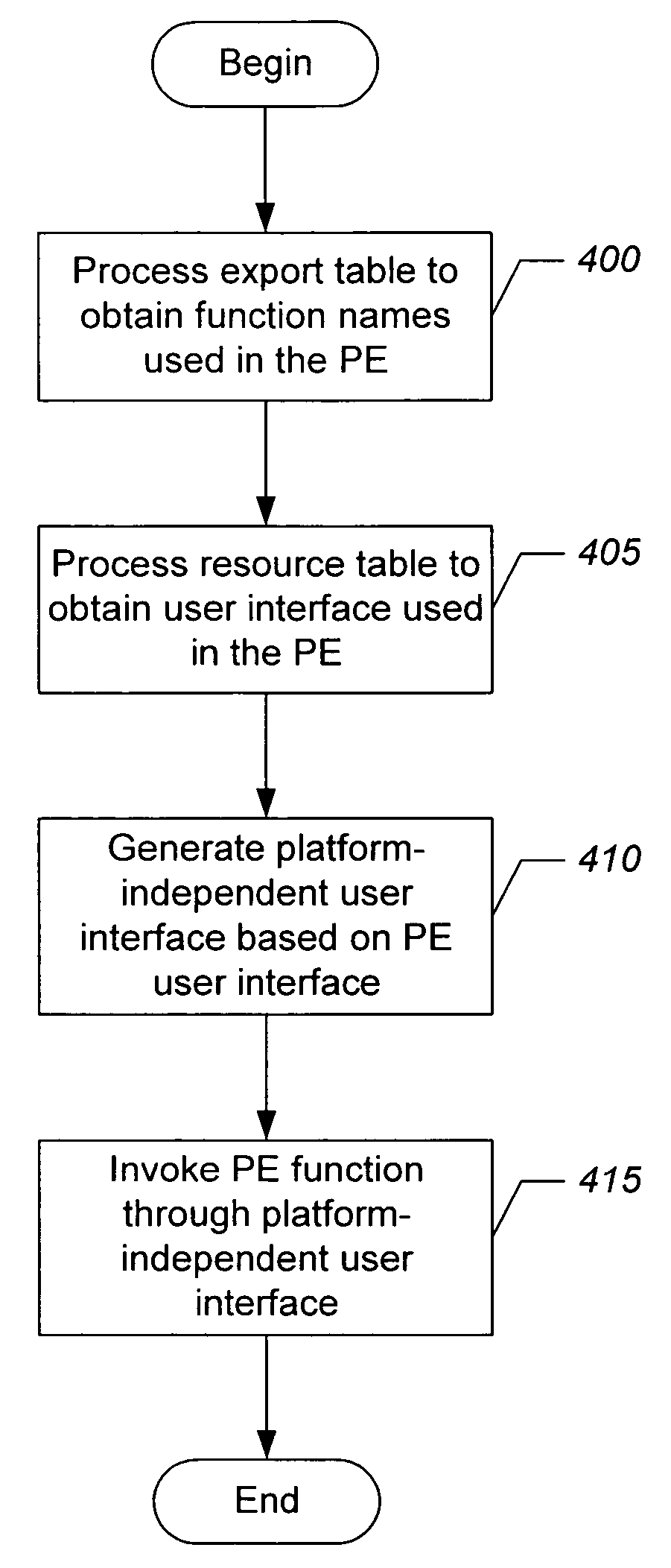
InactiveUS20050172263A1Execution for user interfacesMemory systemsApplication softwareComputer science
A portable executable (PE) is invoked through a platform-independent interface by processing an export table in the PE to obtain the function names used in the PE. A resources table in the PE is processed to obtain a user interface used in the PE. A platform-independent user interface is generated based on the user interface used in the PE. At least one of the functions used in the PE is invoked through the platform-independent user interface.
Owner:IBM CORP
Software development system for editable executables
InactiveUS20040088679A1Simple but powerful programming languageSimple grammarUnauthorized memory use protectionHardware monitoringIndependent functionObject code
The invention provides a Software Development Program having a compiled programming language, Compiler for that language, and a built-in text Editor. The programming language has a block structure and simple syntax. The Software Development Program is distributed free to developers, but programs created with the Software Development Program must be licensed. In addition to machine-readable Object Code, Executable Files created with the Compiler include the embedded Source Code (including independent function libraries that help form an Executable Shell) from which they were created. Separate Source Code and Object Code files are not required. The Compiler edits the Executable Files directly, thereby eliminating the need for source code control.
Owner:THE DESCARTES SYST GROUP
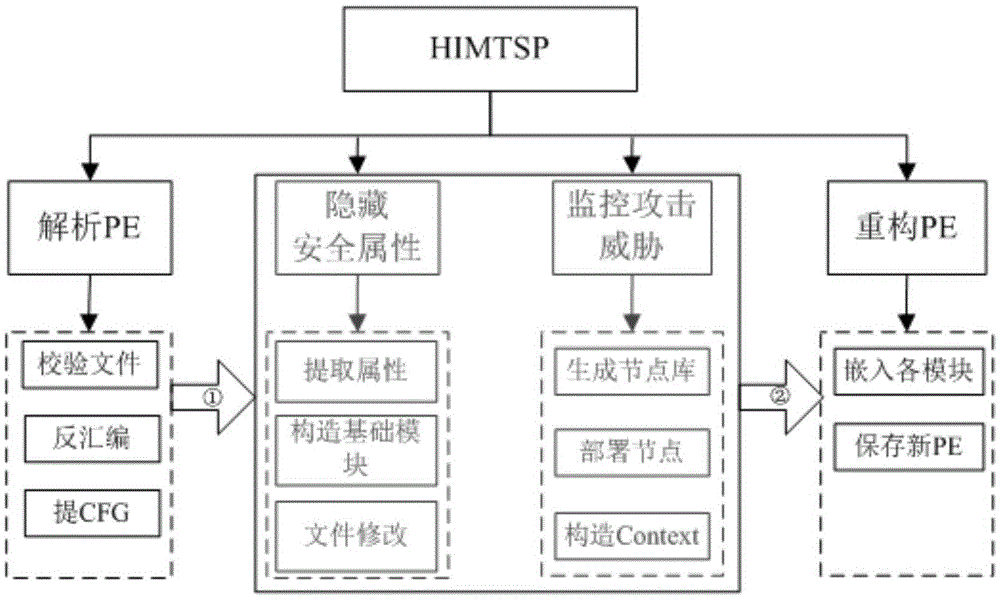
Software protection method based on API (Application Program Interface) security attribute hiding and attack threat monitoring
The invention discloses a software protection method based on API (Application Program Interface) security attribute hiding and attack threat monitoring. The software protection method comprises the following steps: obtaining the original input information record chart of a file to be protected, extracting the execution control flow graph of the file, extracting an API calling point, extracting an API parameter passing code block, extracting an API returned value decryption point, dumping a DLL (Dynamic Link Library), calculating a new API entry address, constructing a springboard function block, inserting an exception instruction in the returned value decryption point, constructing a node, generating a node library, deploying a node network, constructing a node background, constructing a returned value decryption processing function, and reconstructing a PE (Portable Executable) file. From internal and external aspects, software is protected so as to analyze the function of API boundary information in a reverse analysis process from an angle of the reverse engineering of the attackers, the API security attribute which needs to be hidden and a detection node library are put in a program new node, and a new node entry is subjected to encryption processing to further prevent the attackers from carrying out reverse analysis on the protected PE file.
Owner:NORTHWEST UNIV(CN)
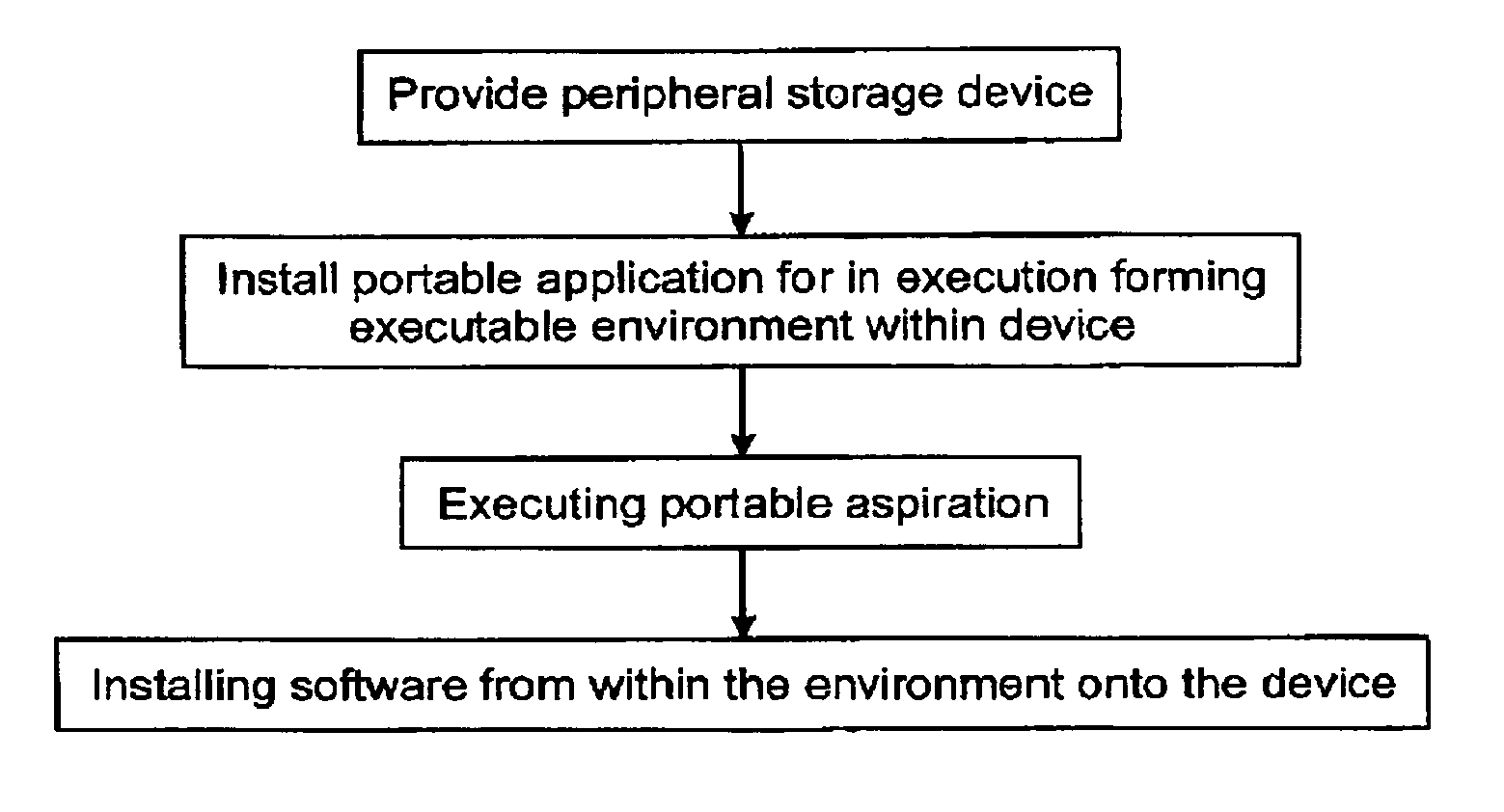
Method and system for installing portable executable applications
According to the invention, a first executable environment is provided. The first executable environment is for execution within an operating system environment of a host computer system. The first executable environment is not an emulator for emulating any of another processor and another operating system. A software application is provided for installation and execution within the operating system environment. The software application is for fixed installation and not for installation in a portable fashion for being ported from one host computer system to another. The software application is then installed within the first executable environment, the installed software application installed within a removable peripheral memory storage device for execution within the first executable environment.
Owner:KINGSTON DIGITAL CO LTD
Method and system for realizing malicious code marking
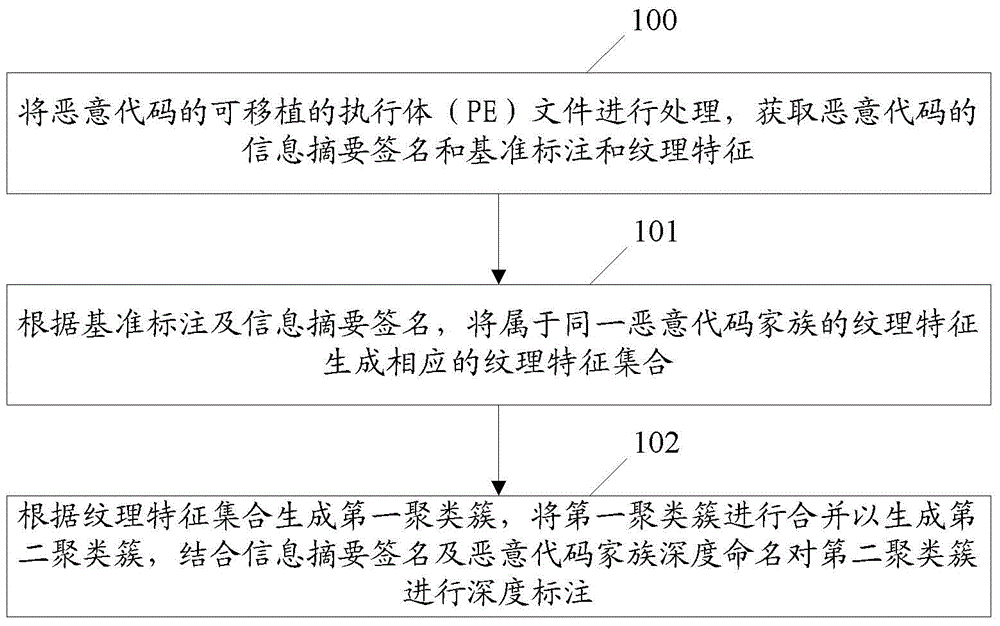
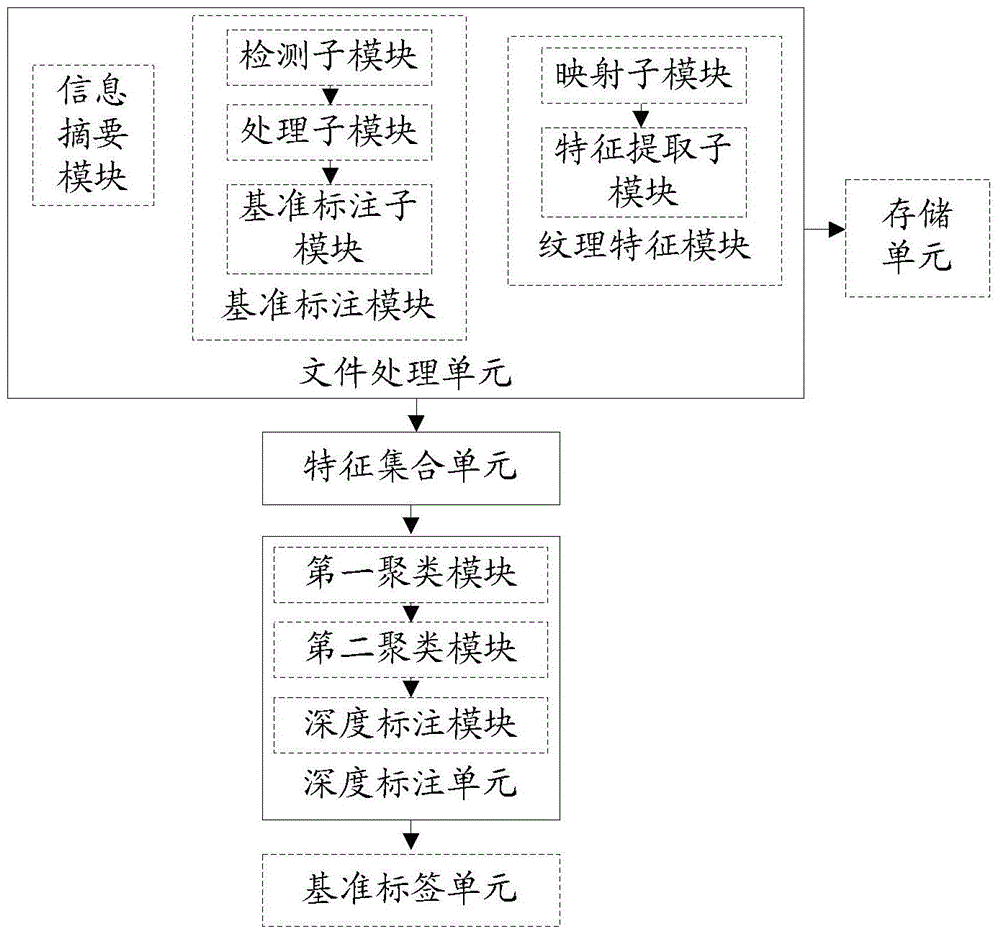
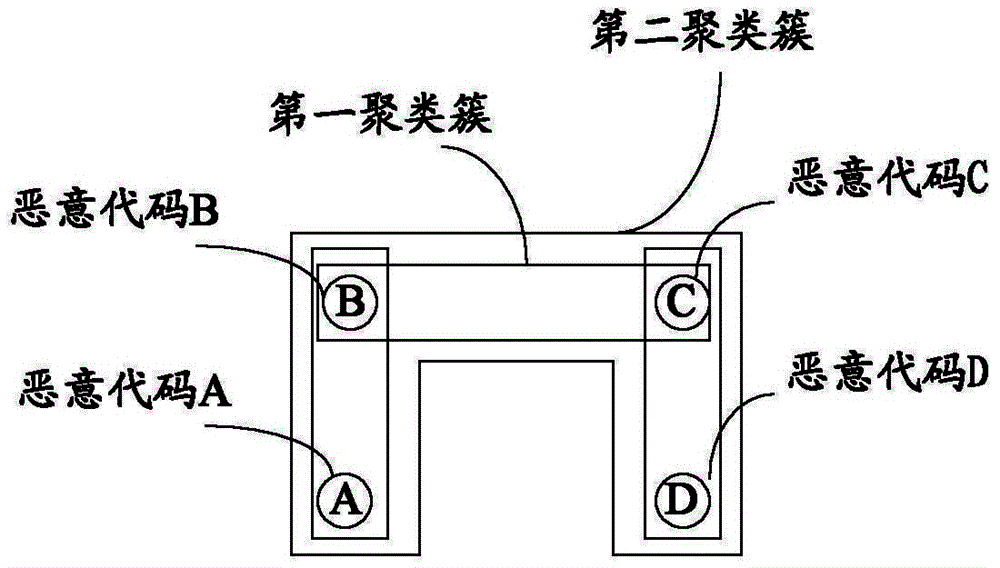
ActiveCN104978521AImprove accuracyImprove versatilityPlatform integrity maintainanceFeature setSoftware engineering
The invention discloses a method and a system for realizing malicious code marking. The method comprises the following steps of: processing a PE (Portable Executable) file of a malicious code to obtain an information abstract signature, datum dimension and vein features of the malicious code; enabling the vein features belonging to the same malicious code family to generate a corresponding vein feature set according to the datum dimension and the information abstract signature; generating a first clustering cluster according to the vein feature set; merging the first clustering cluster to generate a second clustering cluster; and combining the information abstract signature and the malicious code family deep naming to perform deep marking on the second clustering cluster. The malicious code is subjected to datum dimension and deep marking; the information abstract signature and the malicious code family deep naming are used; the marking method of each malicious code family is specified; and the accuracy and the universality of the malicious code marking are improved.
Owner:BEIJING VENUS INFORMATION SECURITY TECH +1
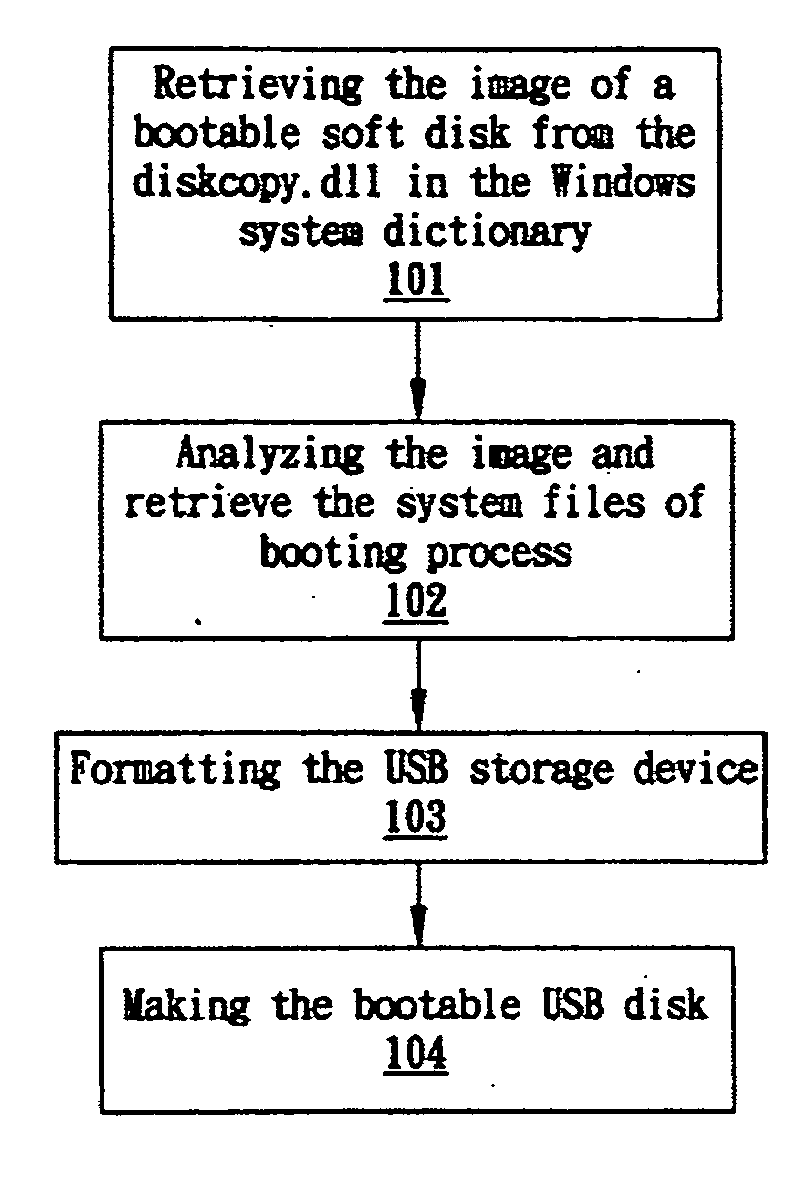
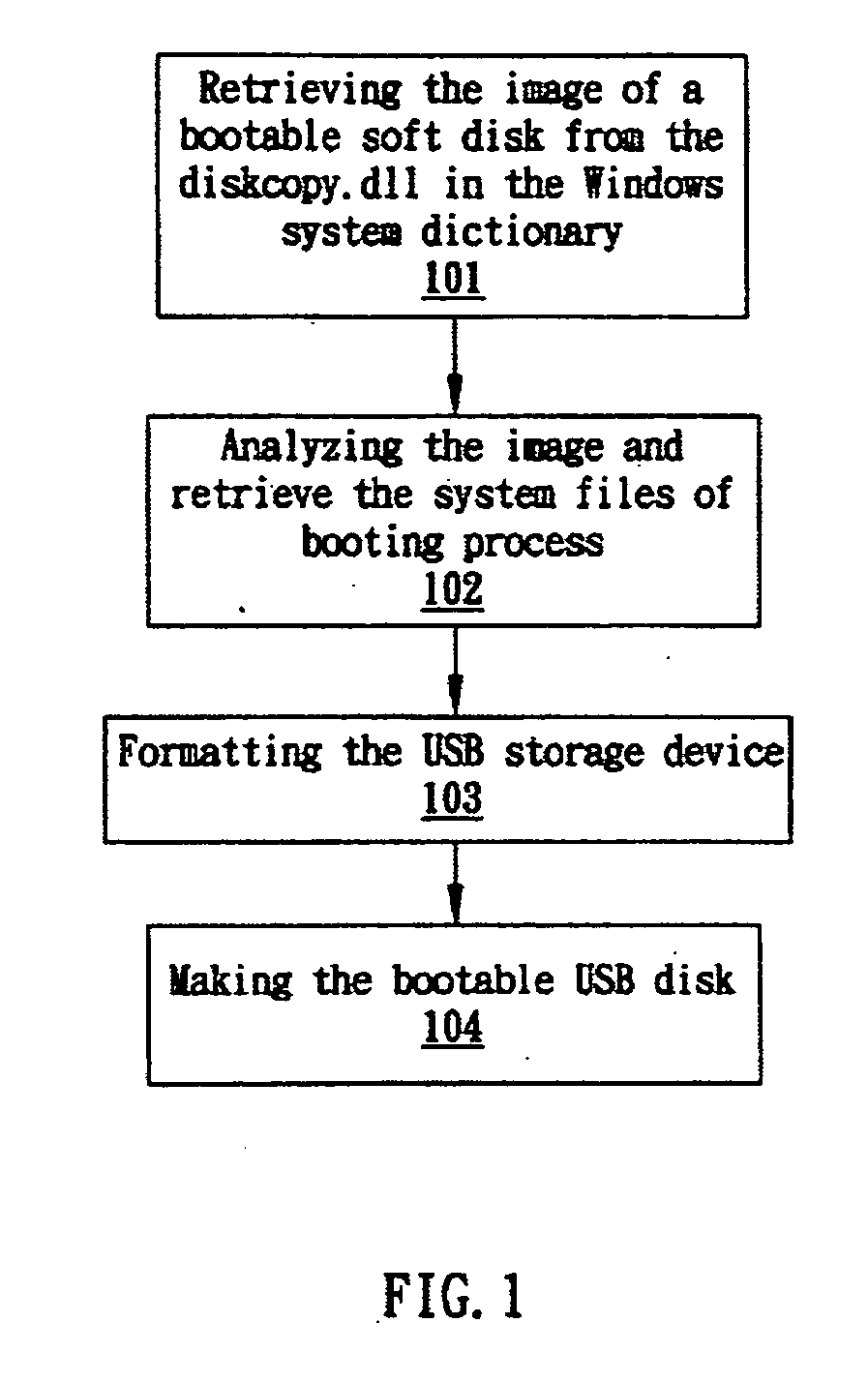
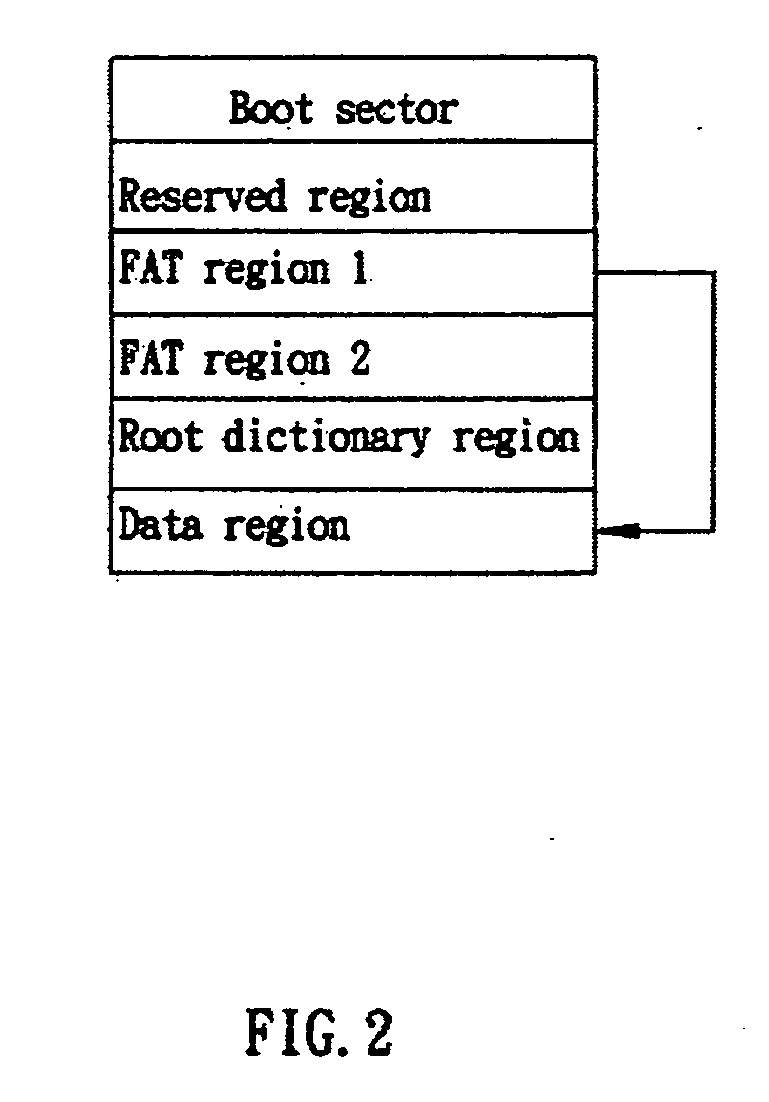
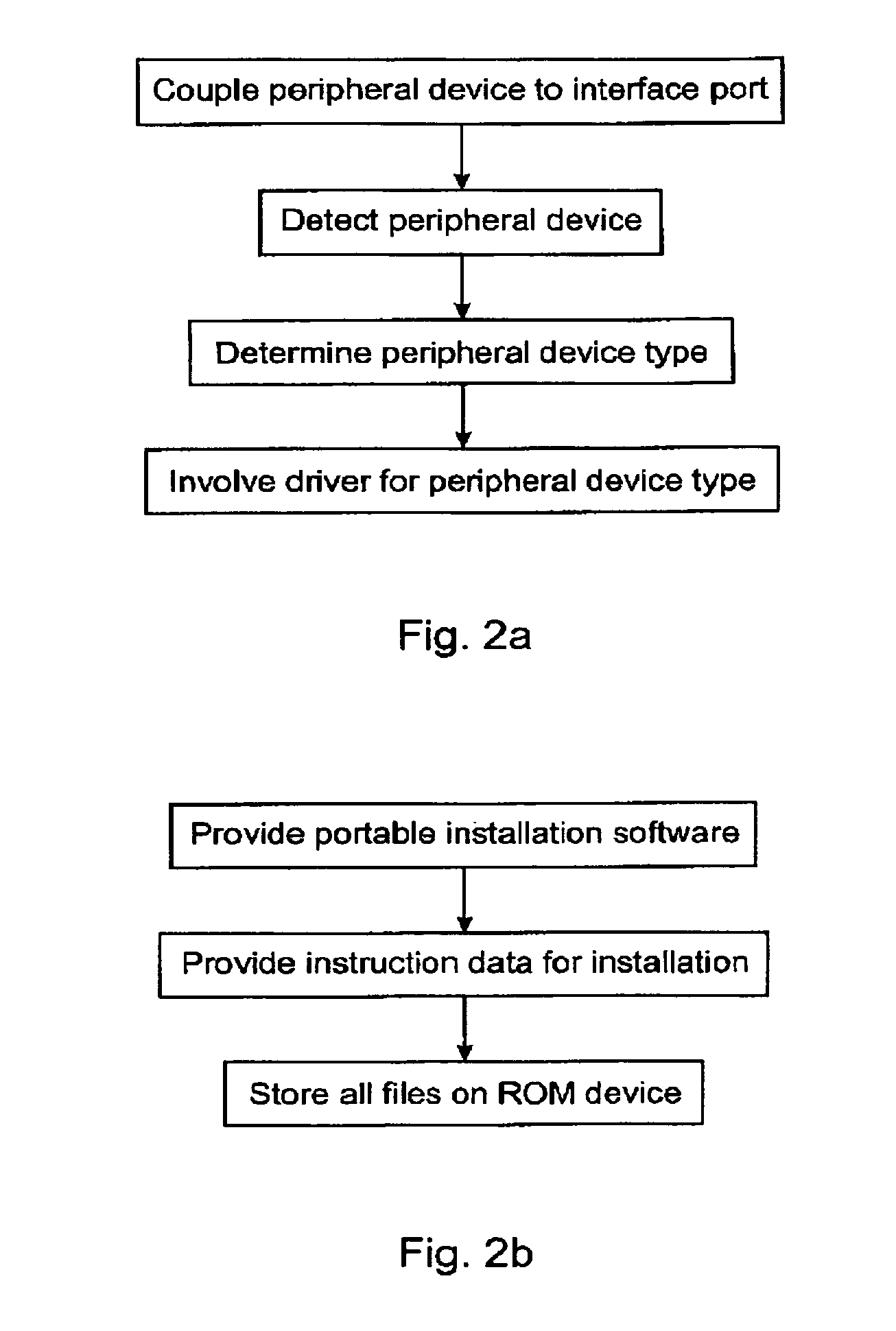
Method for making a bootable USB storage device
The invention provides a method for making a bootable USB storage device of Windows XP operation system, which provides external bootup, can be disabled and removed after booting, and wherein the operation mode is command line. In one embodiment, the method comprises: analyzing the portable executable file in Windows XP and retrieving the image of boot disk in the PE file; analyzing the image of boot disk and retrieving the system files required by the booting process; and making the boot disk.
Owner:WISTRON CORP
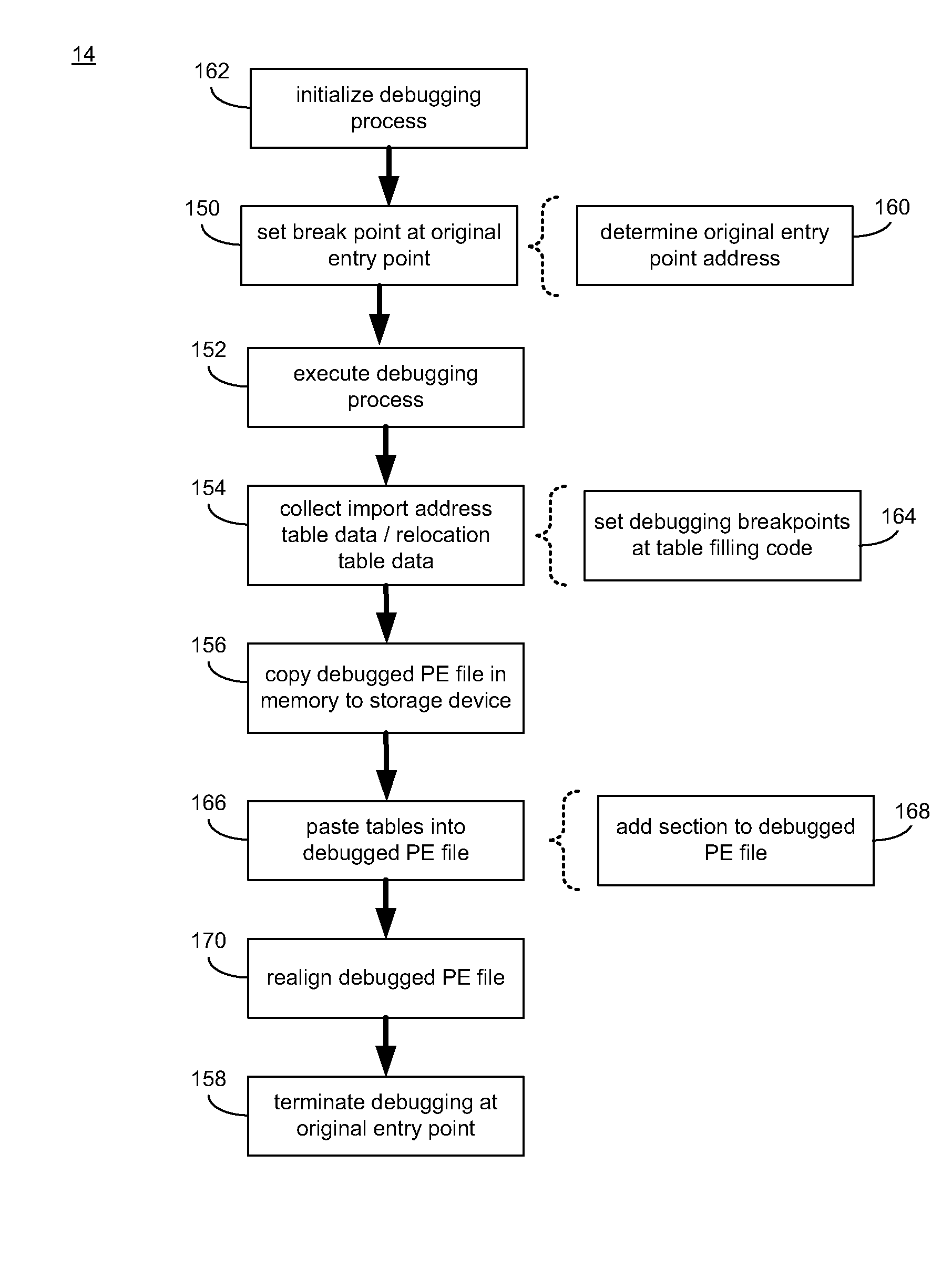
Automated Unpacking of Portable Executable Files
Automated unpacking of a portable executable file includes setting a debugging breakpoint at an original entry point address of a packed portable executable file. A debugging process is executed for the packed portable executable file to obtain a debugged portable executable file in memory. One or more of import address table data and relocation table data are collected during execution of the debugging process for the packed portable executable file. The debugged portable executable file in memory is copied to a storage medium, and the debugging process is terminated.
Owner:REVERSINGLABS INT
Method and system for installing portable executable applications
According to the invention, a first executable environment is provided. The first executable environment is for execution within an operating system environment of a host computer system. The first executable environment is not an emulator for emulating any of another processor and another operating system. A software application is provided for installation and execution within the operating system environment. The software application is for fixed installation and not for installation in a portable fashion for being ported from one host computer system to another. The software application is then installed within the first executable environment, the installed software application installed within a removable peripheral memory storage device for execution within the first executable environment.
Owner:KINGSTON DIGITAL CO LTD
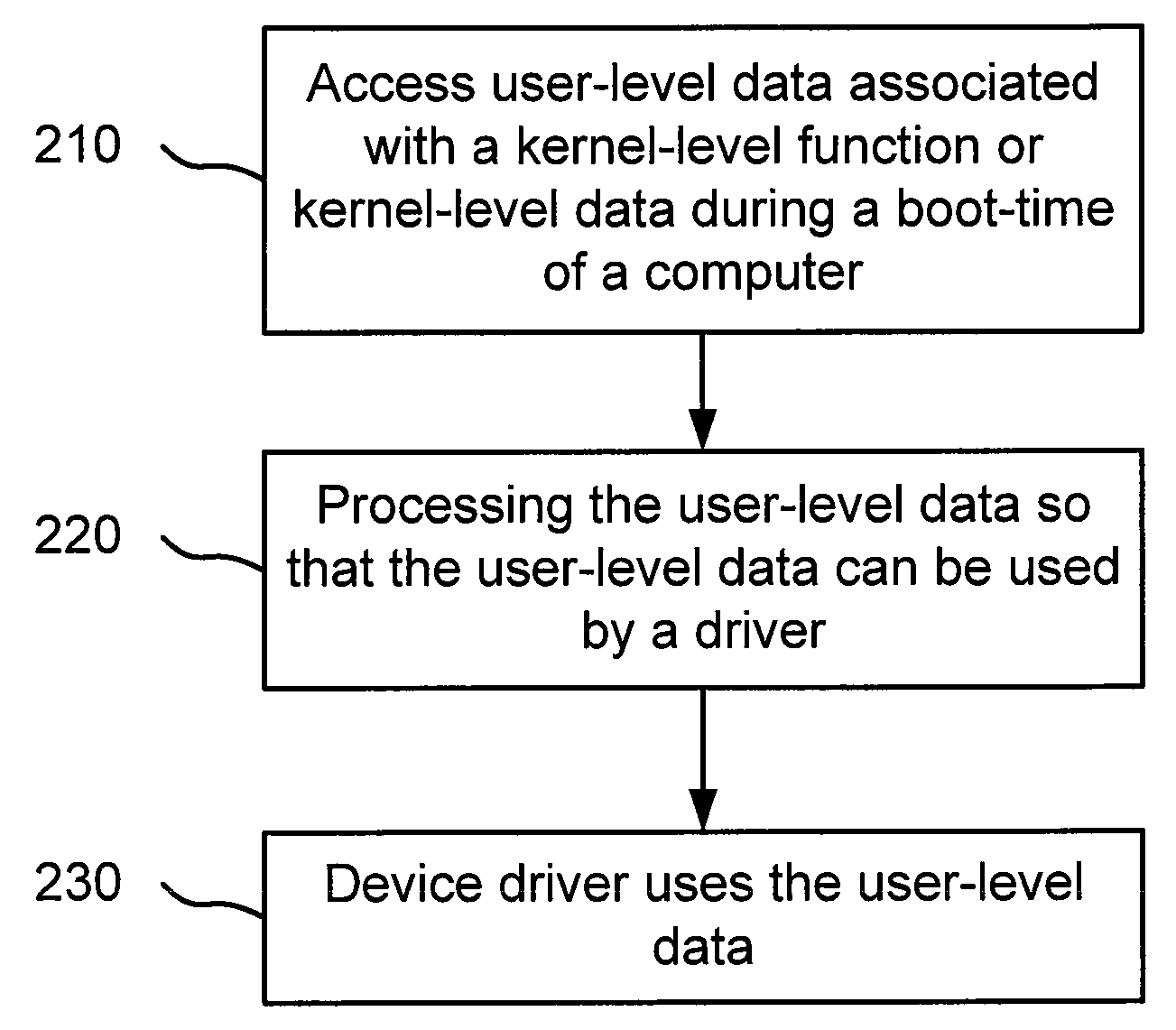
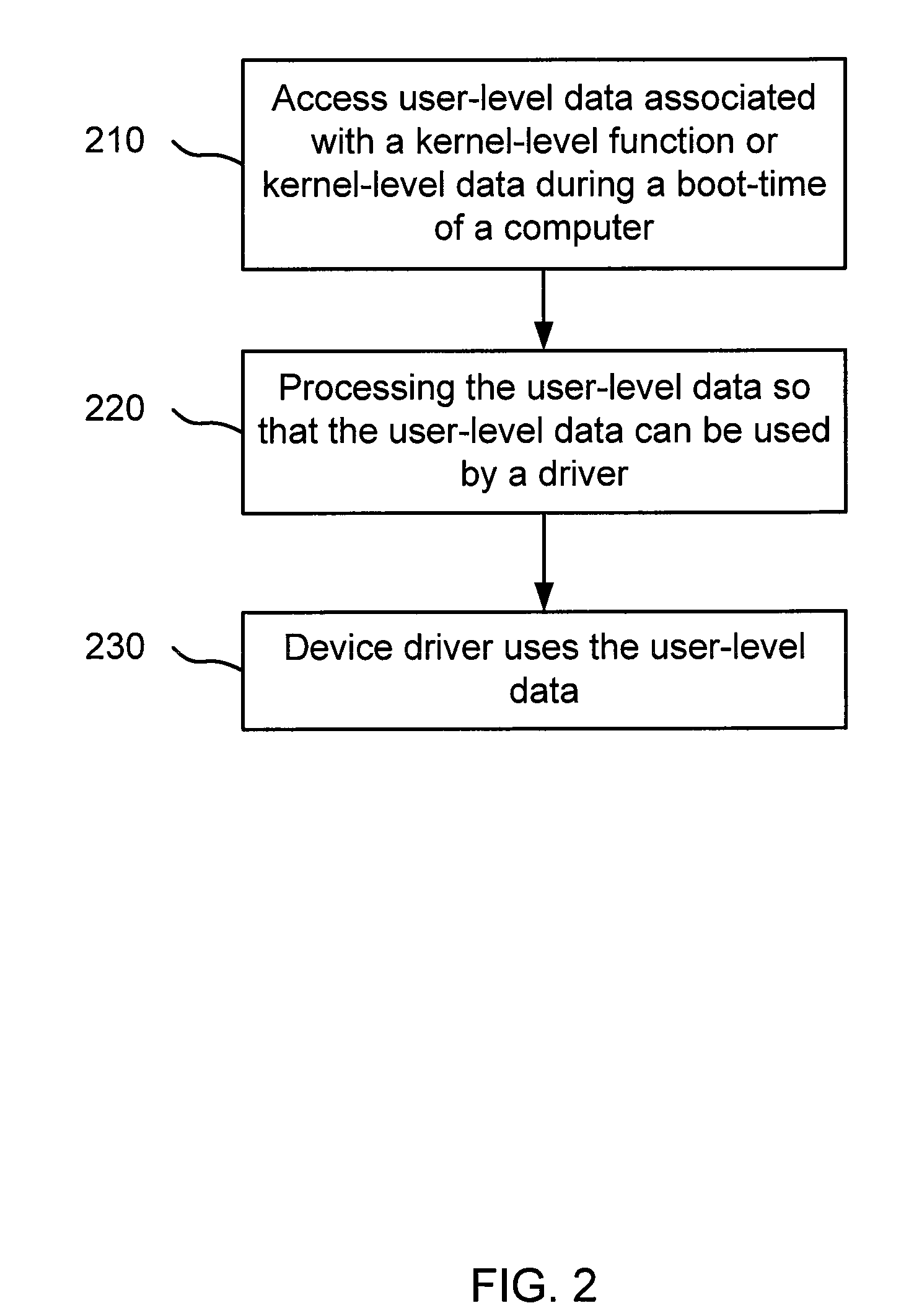
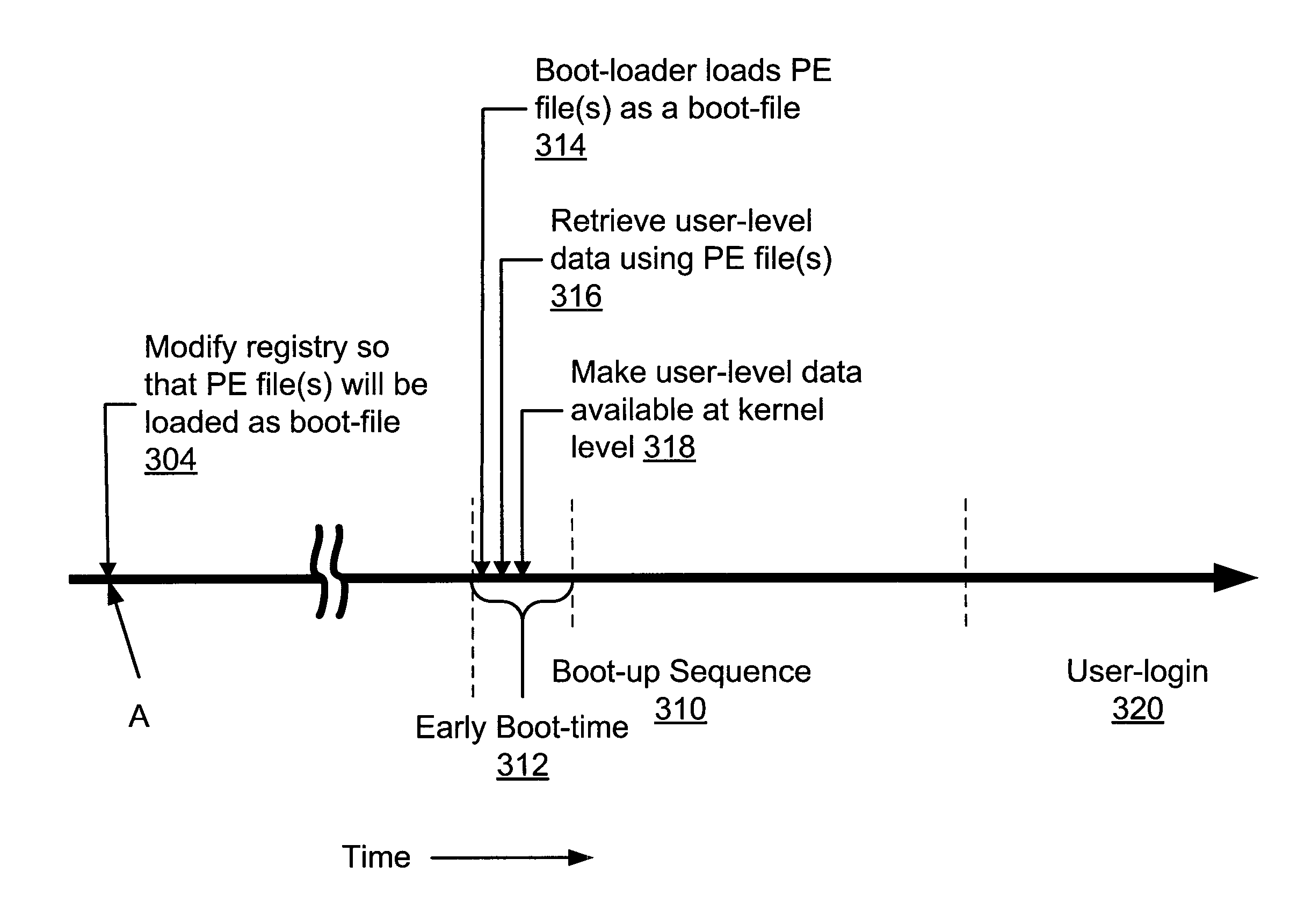
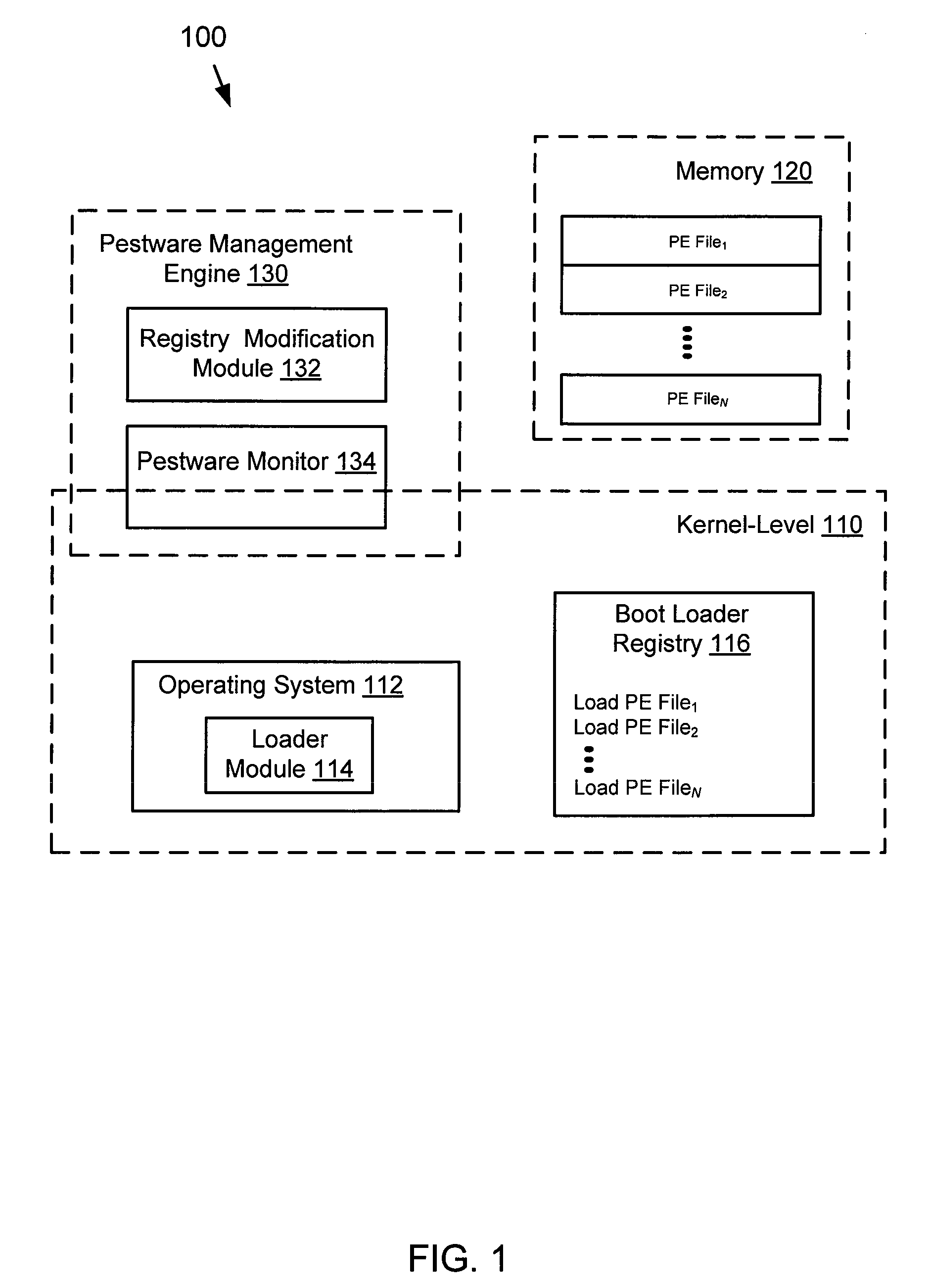
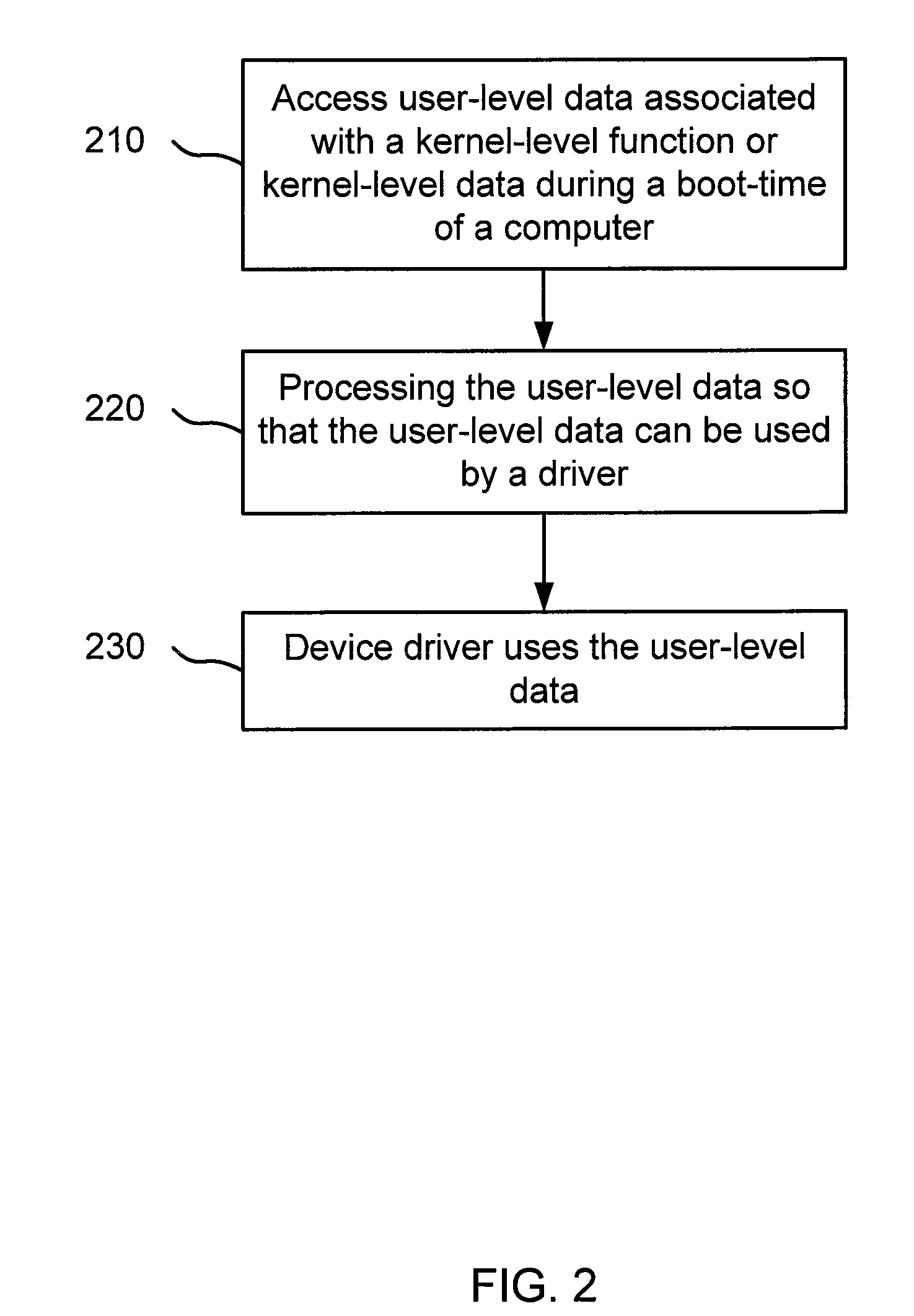
File manipulation during early boot time
A system and method for enabling access to user-level data is described. One embodiment includes accessing user-level data associated with a kernel-level function using a portable executable (PE) file. The user-level data is accessed during a boot-time of a computer. In this embodiment, the PE file is also accessed using the computer.
Owner:OPEN TEXT CORPORATION
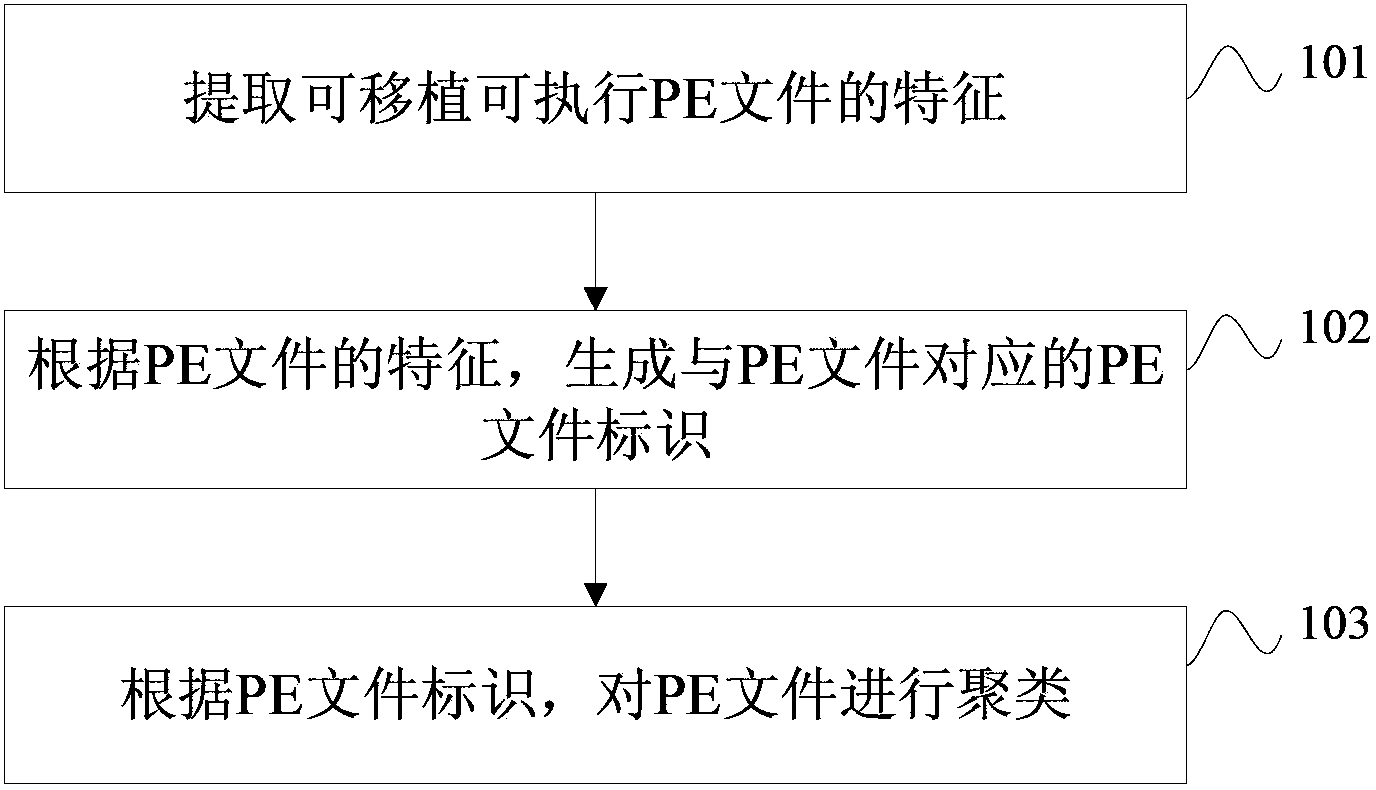
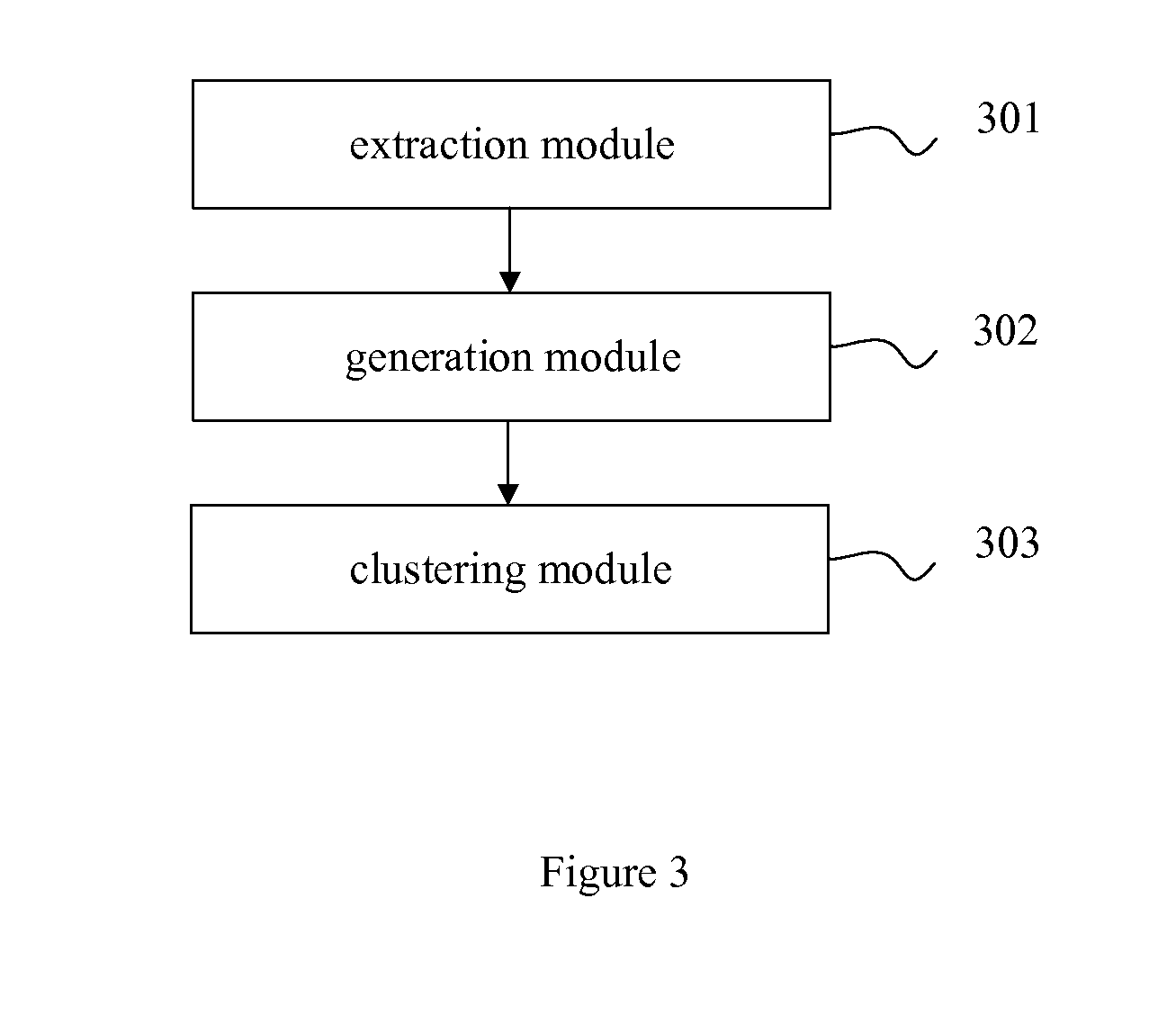
Clustering method and device of portable execute (PE) files
InactiveCN103679012AReduce in quantityReduce storage costsPlatform integrity maintainanceSpecial data processing applicationsNetwork communicationPortable Executable
The invention discloses a clustering method and device of portable execute (PE) files, and belongs to the field of network communication. The clustering method comprises the steps that features of the PE files are extracted, PE file identifications corresponding to the PE files are generated according to the features of the PE files, and the PE files are clustered according to the PE file identifications. The clustering device comprises an extraction module, a generation module and a clustering module. According to the features extracted from the PE files, the PE file identifications corresponding to the PE files are generated, the PE files are clustered according to the PE file identifications, and the clustering method and device of the PE files reduce the number of the PE files of a virus analysis end and a virus searching and killing server, cluster the irregular PE files to form regular categories, reduce storage cost, improve matching efficiency, and improve the capacity of resisting variant virus PE files and the early warning capacity.
Owner:TENCENT TECH (SHENZHEN) CO LTD
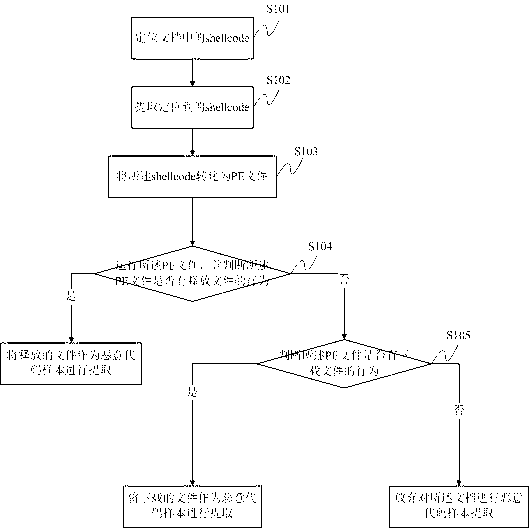
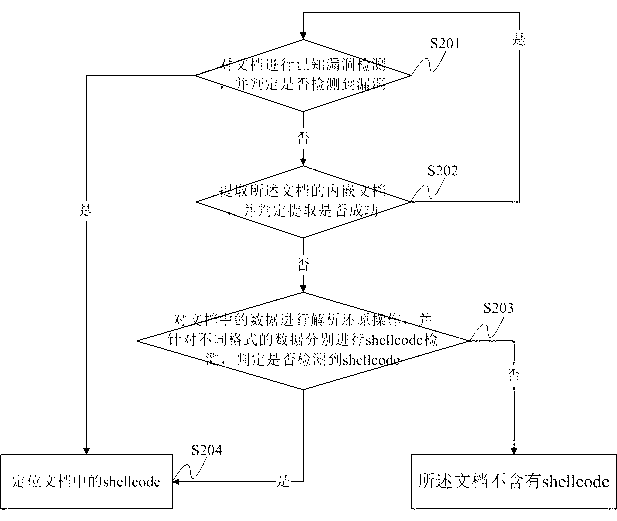
Malicious code sample extraction method and system based on document type bug
ActiveCN103294951AEasy extractionHigh speedPlatform integrity maintainanceDocument Type CodeShellcode
The invention discloses a malicious code sample extraction method and a system based on a document type bug. The method comprises the steps that a shellcode in a document is positioned; the positioned shellcode is extracted, and then converted into a PE (Portable Executable) file; the PE file is operated; whether the PE file releases a file is judged; if so, the released file serves as a malicious code sample to be extracted; if not, whether the PE file downloads a file is judged; if so, the downloaded file serves as a malicious code sample to be extracted; and if not, malicious code sample extraction on the document is abandoned. Compared with the traditional culture method, the method extracts more accurately, quickly and conveniently.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
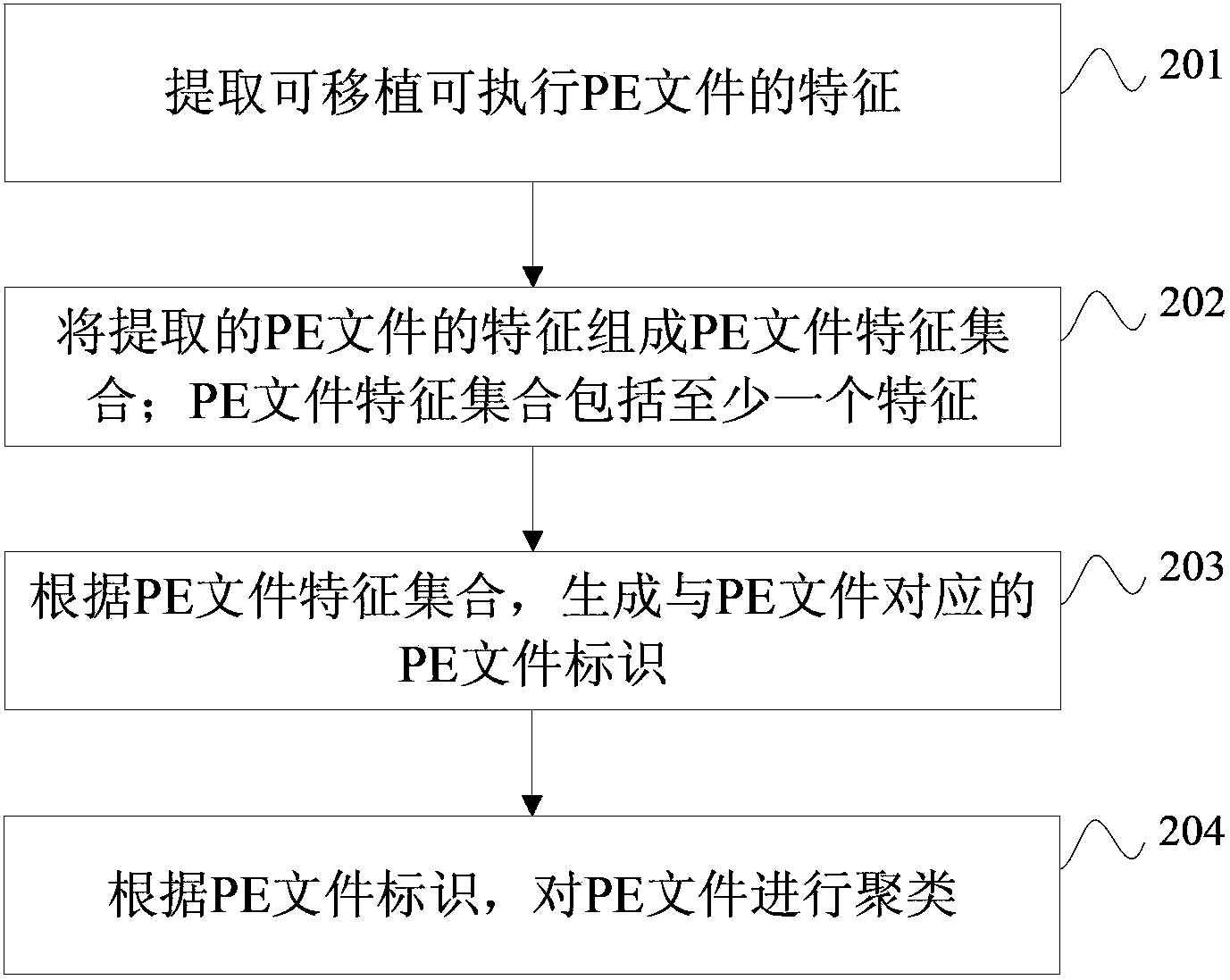
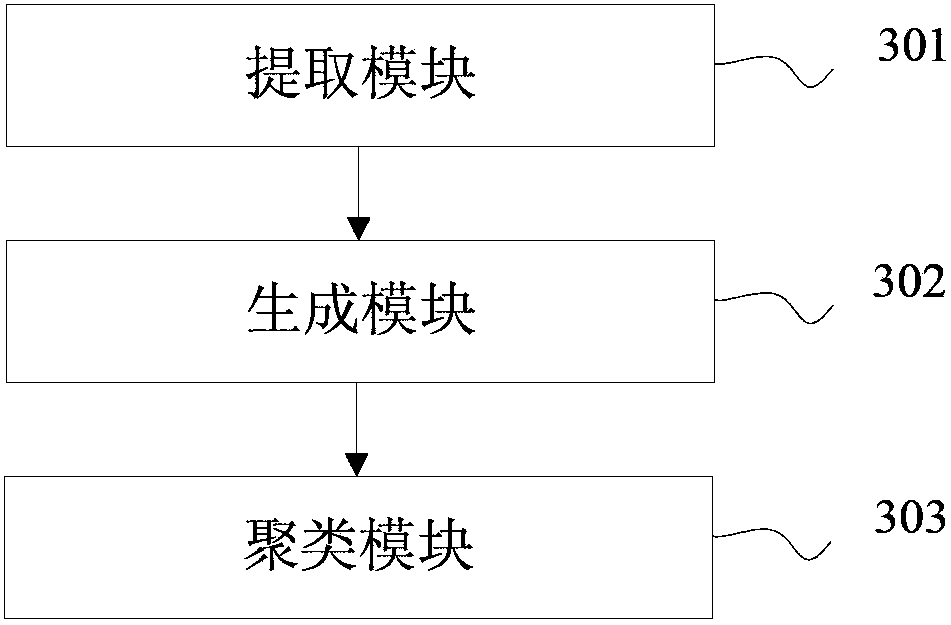
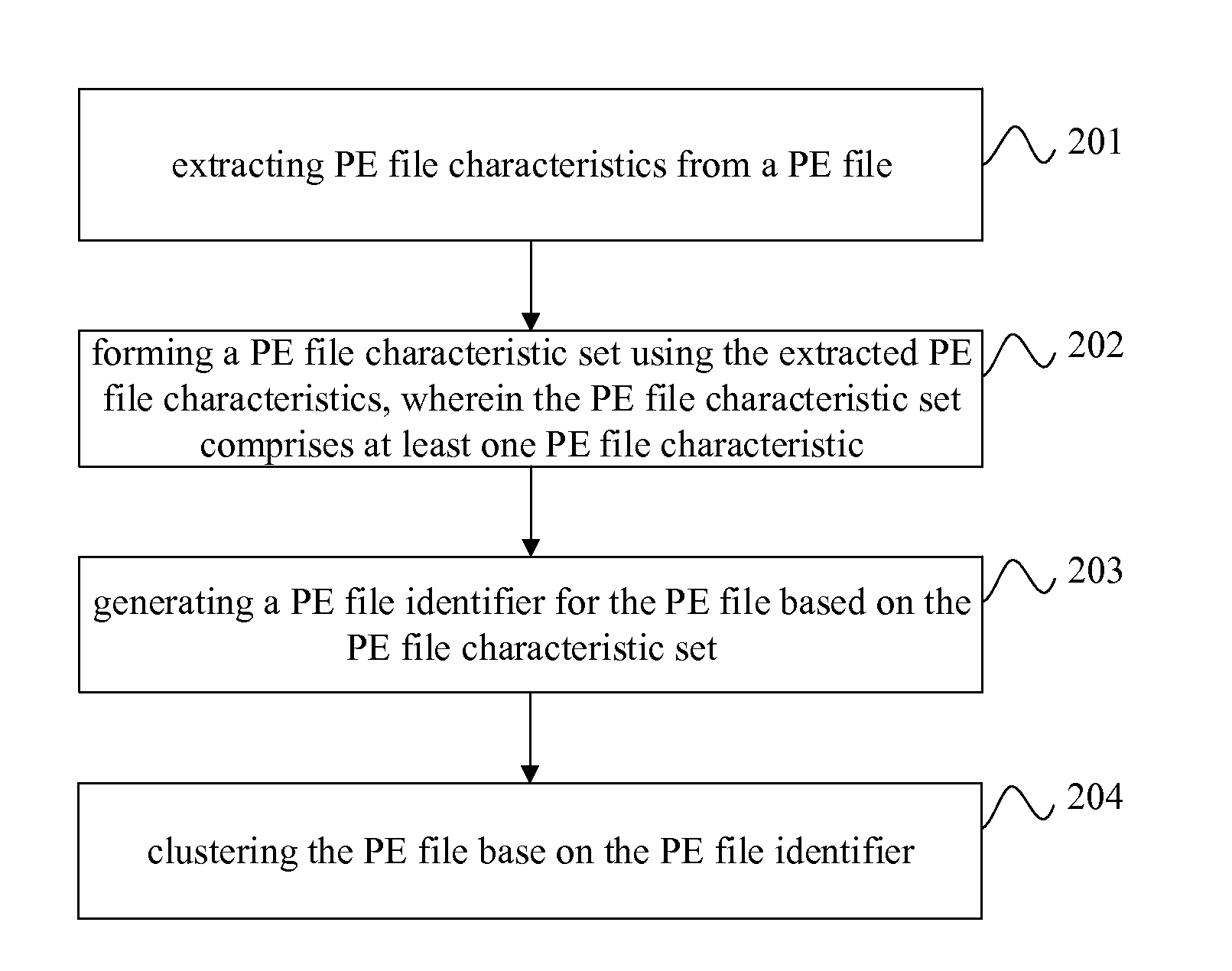
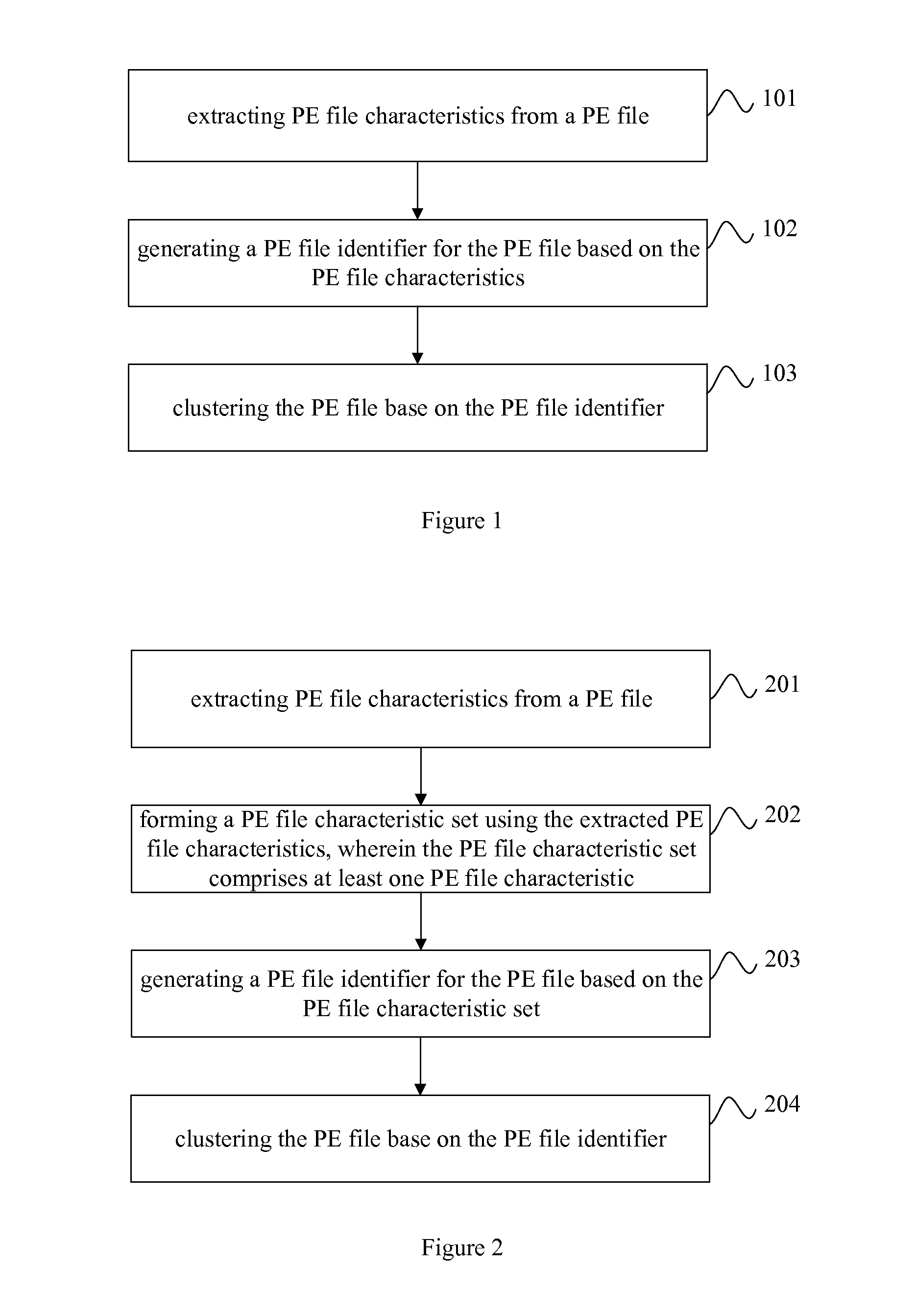
Method and apparatus for clustering portable executable files
InactiveUS20150178306A1Reduce storage costsImprove matching efficiencyDigital data information retrievalDigital data processing detailsThe InternetCluster based
The present invention relates to Internet and communication technologies, and discloses a method and apparatus for clustering portable executable (PE) files. The method comprises: extracting PE file characteristics from a PE file; generating a PE file identifier for the PE file based on the PE file characteristics; and clustering the PE file base on the PE file identifier. The apparatus comprises an extraction module, a generation module, and a clustering module. In accordance with embodiments of the present invention, a PE file identifier is generated for the PE file based on PE file characteristics extracted from the PE file, and the PE files are clustered based on the PE file identifier. Thus, random PE files are clustered into ordered classes, and the number of PE files to be processed by the antivirus clients and servers are reduced, which reduces storage costs, improves matching efficiency and the ability to detect and combat PE virus variants.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Identification method and system of malicious sample type on the basis of characteristics
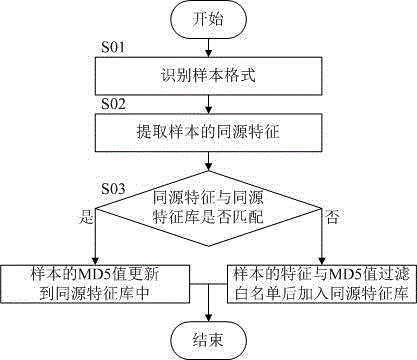
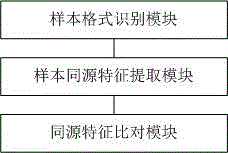
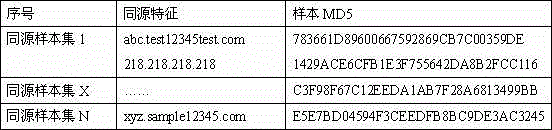
InactiveCN105488408AHave homologous propertiesPlatform integrity maintainancePattern recognitionDocumentation
The invention belongs to the field of the information security technology, and particularly relates to an identification method and system of a malicious sample type on the basis of characteristics. The method comprises the following steps: firstly, identifying the format of a sample to identity a PE (Portable Executable) sample, an OFFICE document sample or an EML (Equal Matrix Language) mail sample; then, extracting the homology characteristics of the sample, comparing the homology characteristics with a homology characteristic library, and if characteristics are matched, updating the MD5 (Message Digest 5) value of the sample to the homology characteristic library; and if the characteristics are not matched, after the characteristics of the sample and the MD5 value are subjected to whitelist filtering, adding the characteristics and the MD5 value of the sample into the homology characteristic library. The method prevents the samples from being isolated, and the samples have the homology. In addition, after the samples have the homology, the common attack event of the samples with the homologous attribute can be conveniently found. Meanwhile, homology characteristic analysis assists in detecting unknown malicious codes.
Owner:中国信息安全认证中心 +1
Software development system for editable executables
InactiveUS6904591B2Unauthorized memory use protectionHardware monitoringIndependent functionObject code
The invention provides a Software Development Program having a compiled programming language, Compiler for that language, and a built-in text Editor. The programming language has a block structure and simple syntax. The Software Development Program is distributed free to developers, but programs created with the Software Development Program must be licensed. In addition to machine-readable Object Code, Executable Files created with the Compiler include the embedded Source Code (including independent function libraries that help form an Executable Shell) from which they were created. Separate Source Code and Object Code files are not required. The Compiler edits the Executable Files directly, thereby eliminating the need for source code control.
Owner:THE DESCARTES SYST GROUP
Updating system and method of portable executable programs
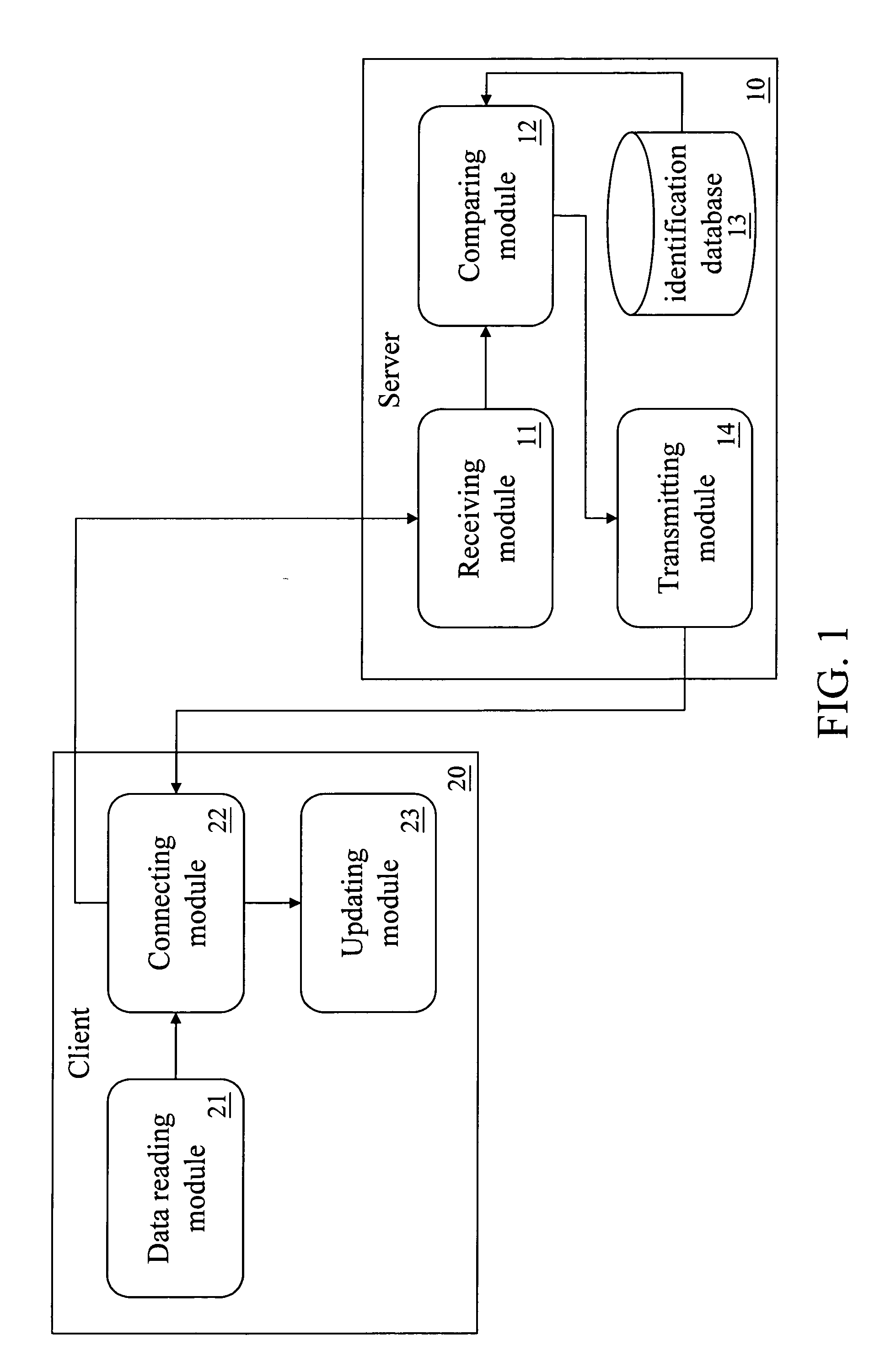
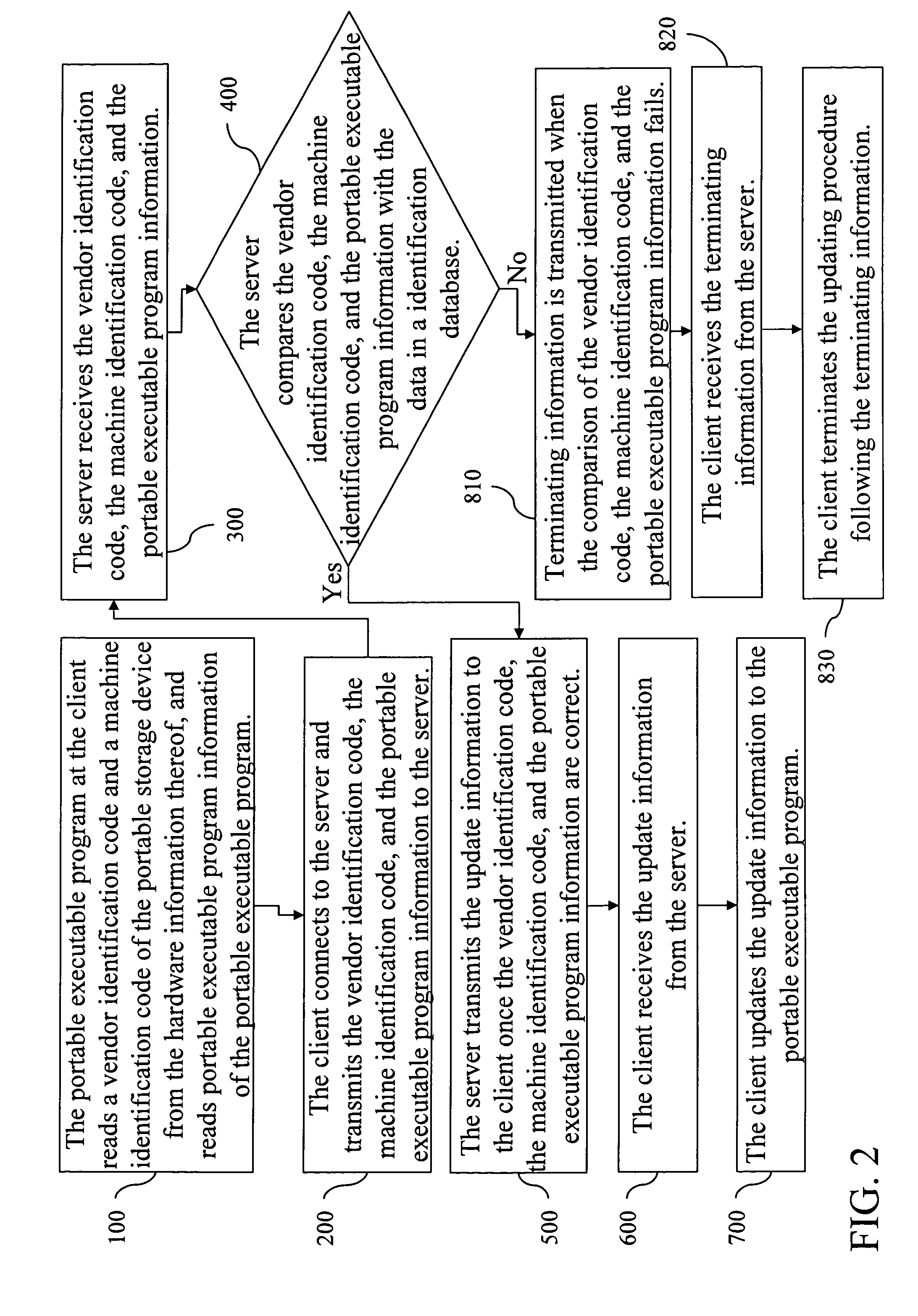
InactiveUS20100050166A1Updating of informationMultiple digital computer combinationsSpecific program execution arrangementsPortable ExecutableOperating system
An update system of a portable executable program and the method thereof are provided. By verifying a vendor identification code and machine identification code and checking information of the portable executable program, the system can update the portable executable program in a portable storage device. This solves the inconvenience problem in updating a portable executable program in a portable storage device that requires repeated registrations. Using the system and method, the portable executable program in a portable storage device can be updated without involving repeated registrations.
Owner:INVENTEC CORP
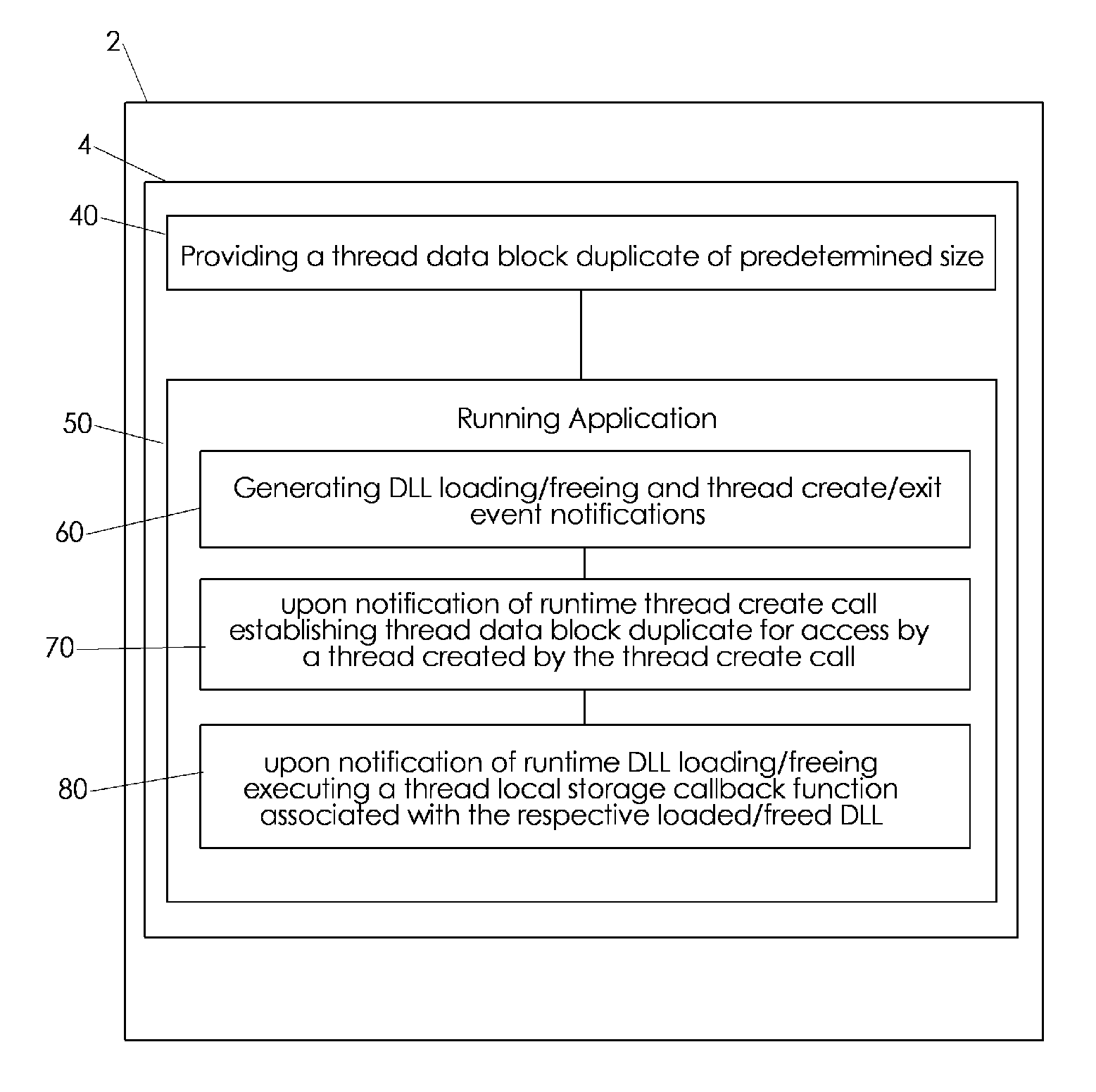
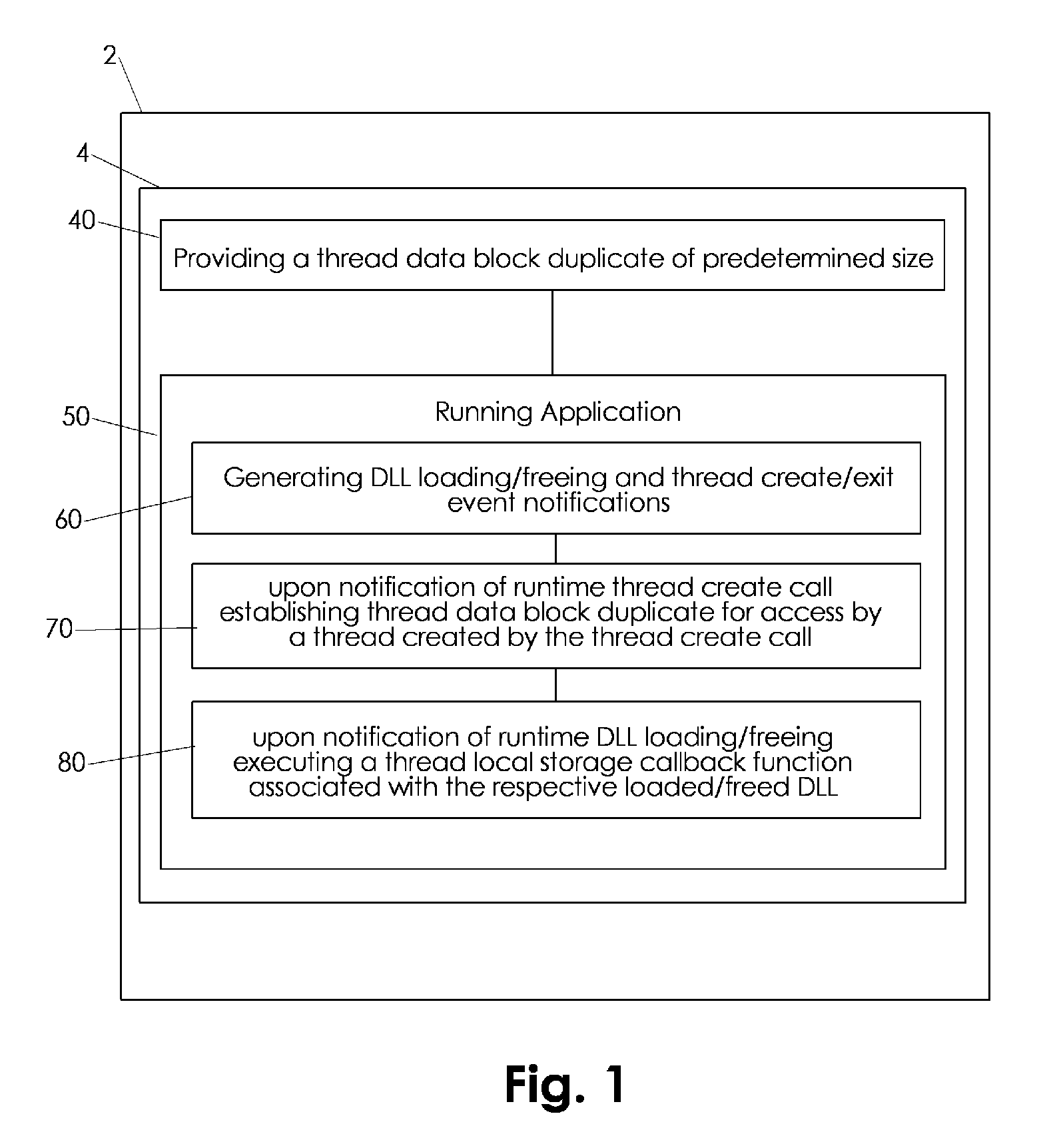
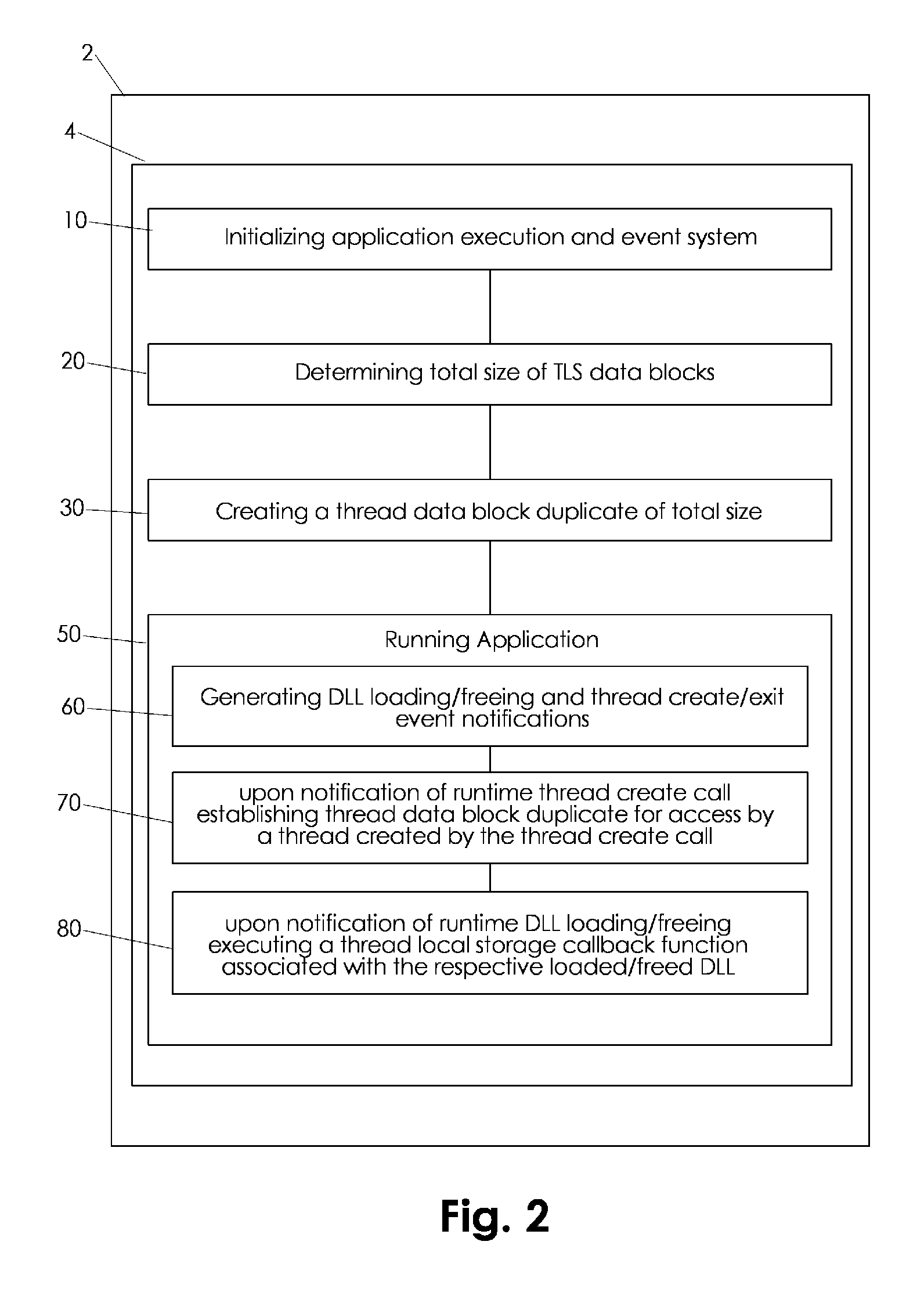
Runtime emulating static thread local storage of portable executable software code
A Windows™ process loader is emulated for dynamic TLS data allocation during respective application runtime. A total required TLS data block size is initially calculated and corresponding data block duplicates are created preferably after initializing of the application. An event notification system such as a hooking system intercepts DLL loading and freeing activity as well as thread creation and exiting and provides event notifications for dynamic allocation of corresponding TLS data block duplicates.
Owner:VMWARE INC
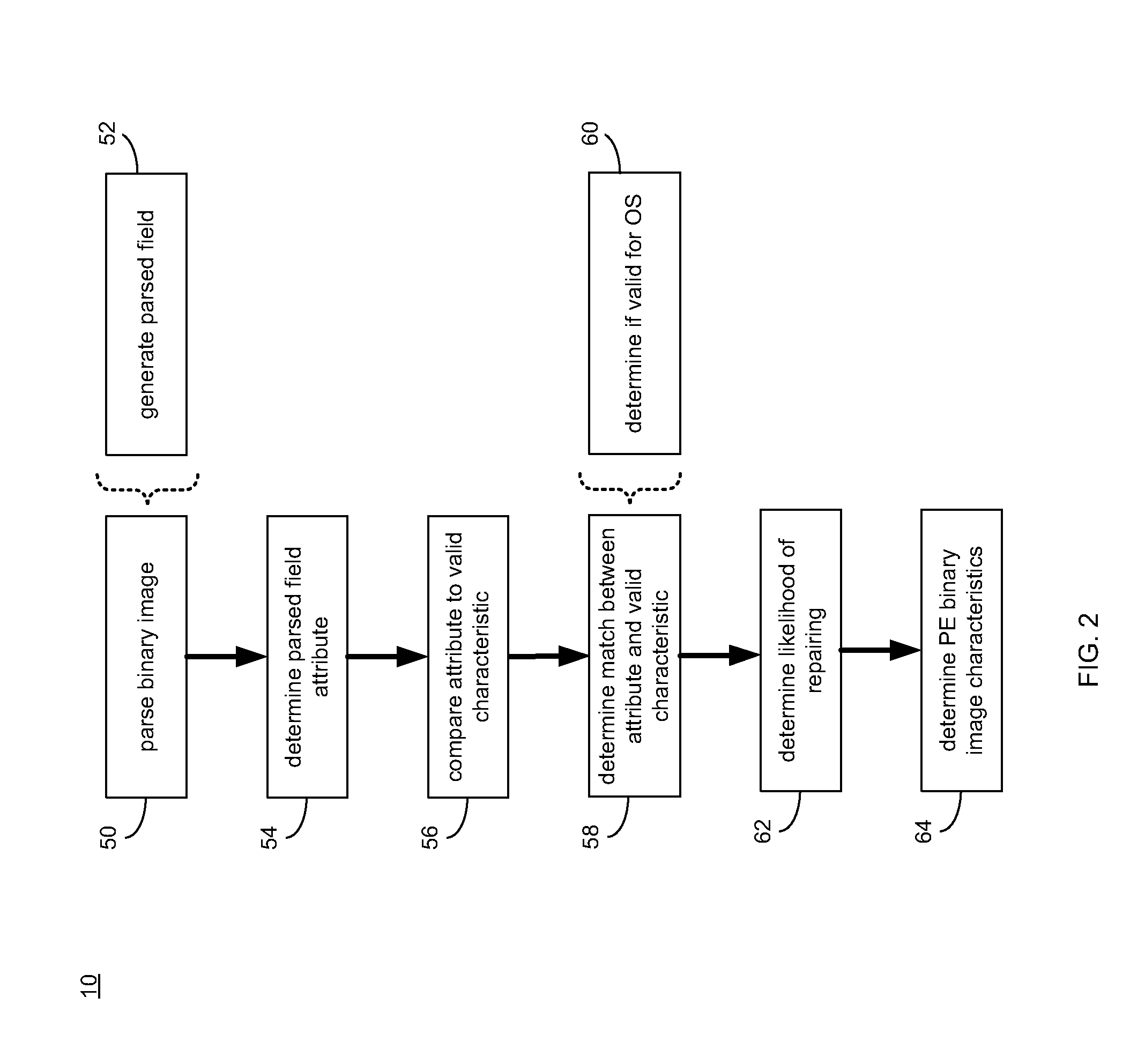
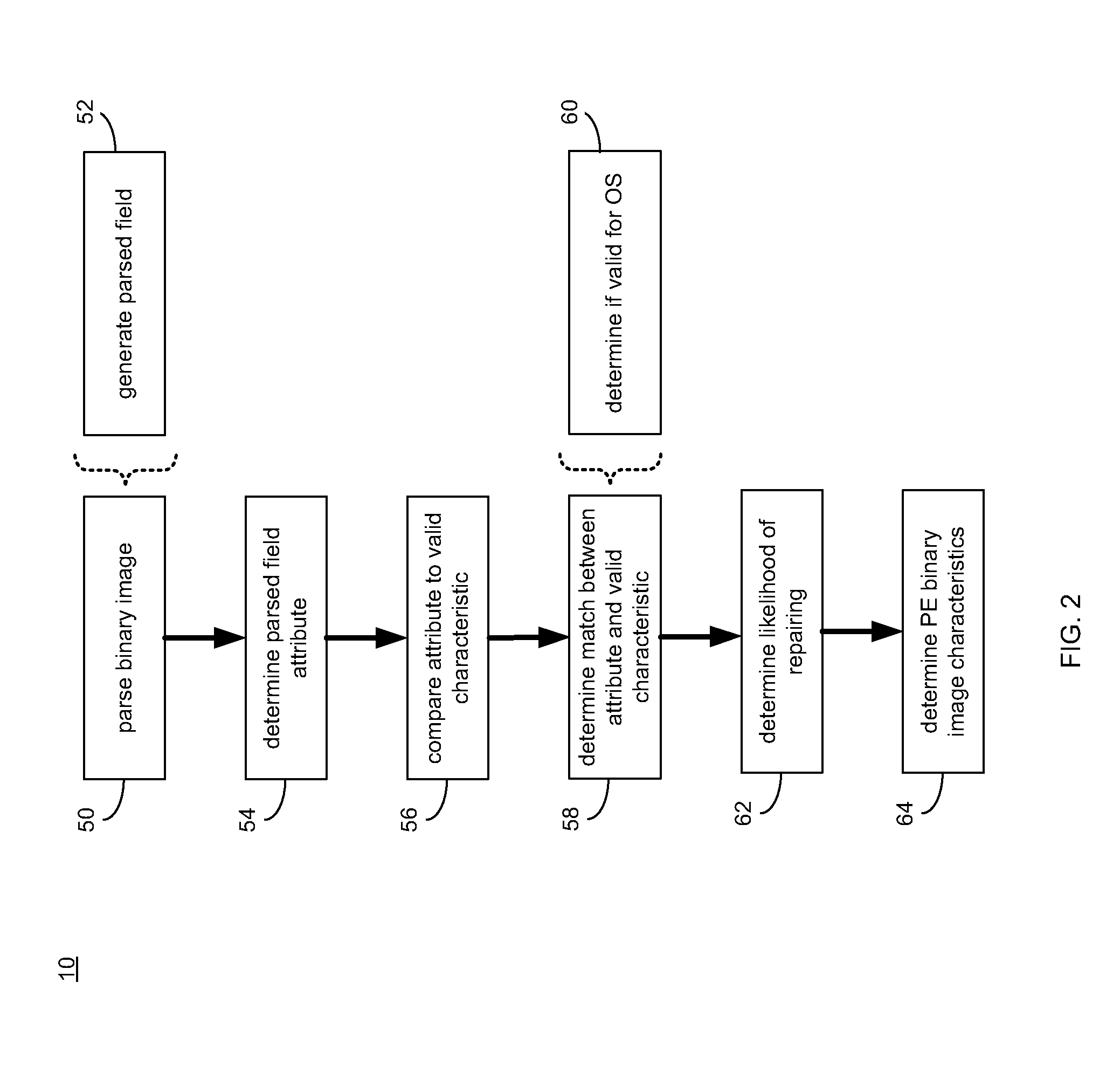
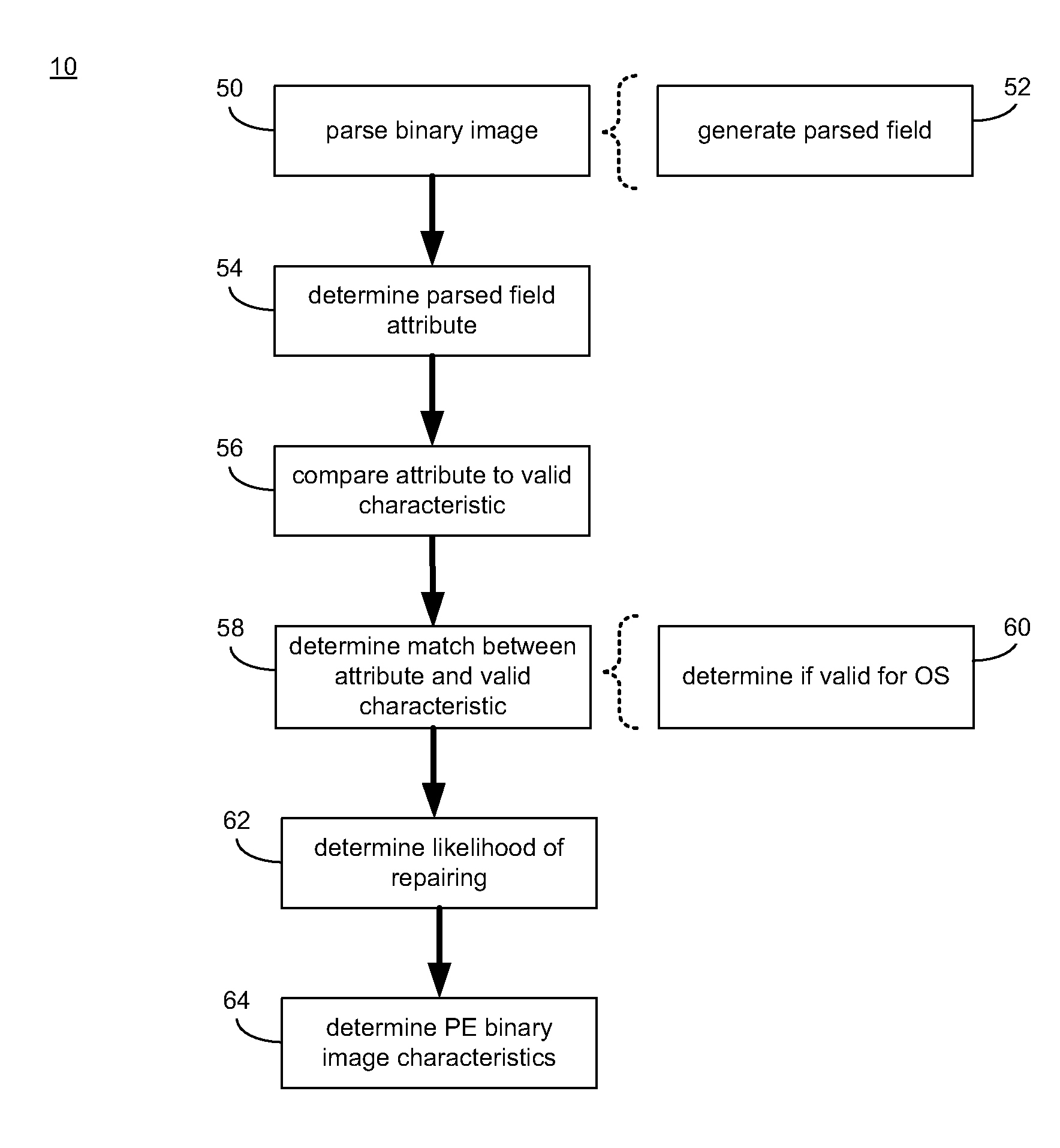
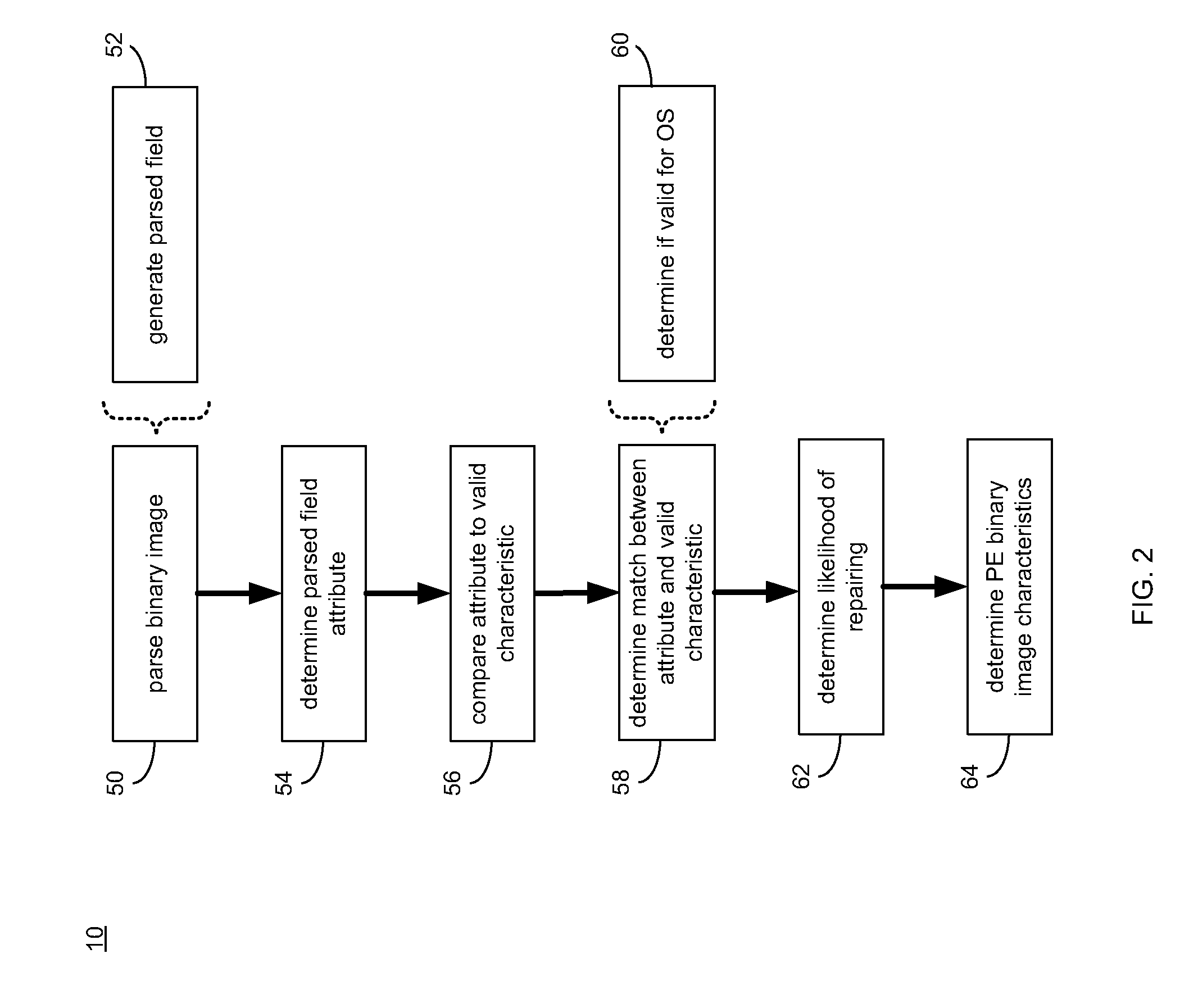
Portable executable file analysis
ActiveUS20110066651A1Digital data processing detailsReverse engineeringPortable ExecutableField based
A portable executable file is analyzed by parsing a binary image of the portable executable file to generate a parsed field. An attribute of the parsed field is determined. The attribute of the parsed field is compared to a valid characteristic of a valid corresponding field based upon, at least in part, a portable executable file format specification. It is determined if the attribute of the parsed field matches the valid characteristic of the valid corresponding field.
Owner:REVERSINGLABS INT
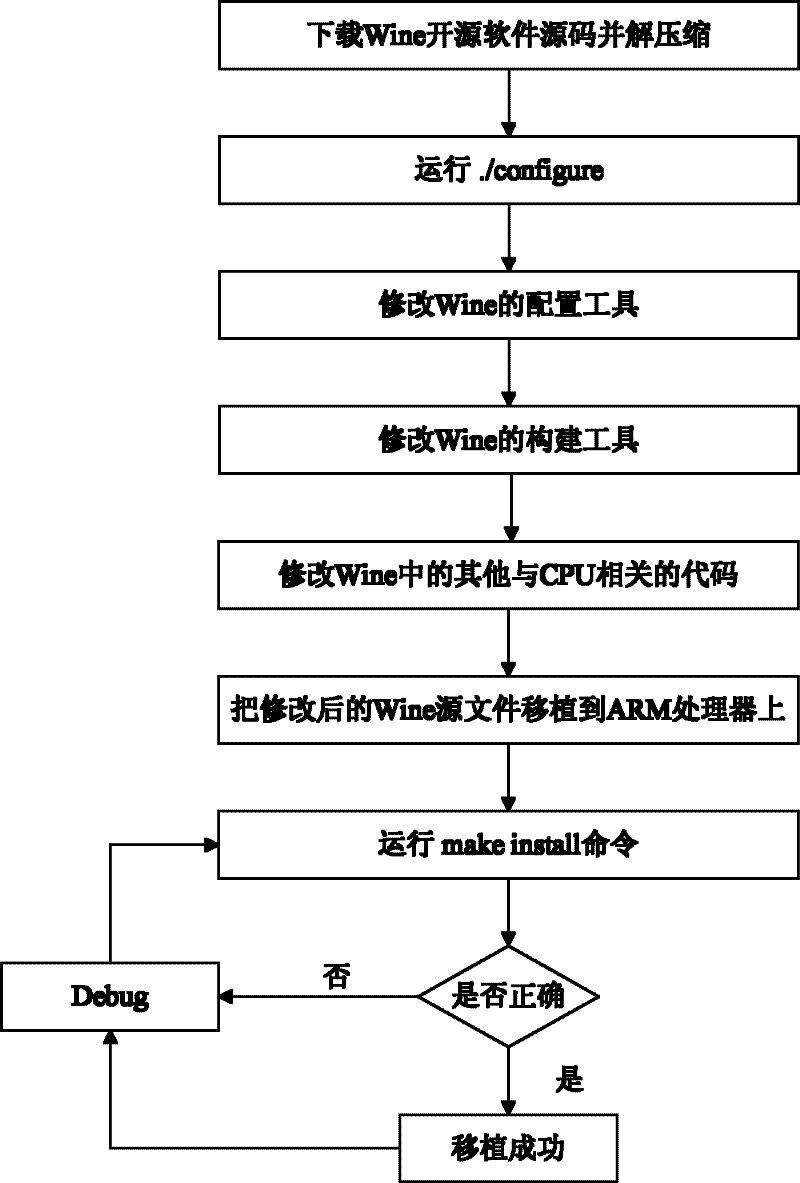
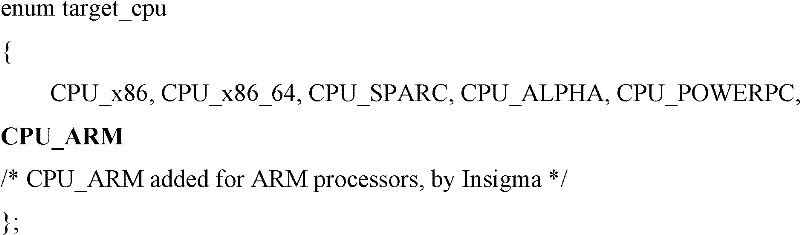
Method for realizing Wine construction tool transplanting on ARM (Advanced RISC Machines) processor
The invention discloses a method for realizing Wine construction tool transplanting on an ARM (Advanced RISC Machines) processor, which comprises the following steps of: (1) modifying a configuration tool of Wine to replace a gcc (GNU Compiler Collection) compiler and library under an X86 platform by a cross compiler of arm-linux and a library file of arm-linux; (2) modifying a construction tool of Wine so that a windows target application program generates PE (Portable Executable) format mapping corresponding to the ARM processor; (3) modifying other codes which are relevant to a CPU (Central Processing Unit) in the Wine so that all the codes of Wine are adapted to the ARM processor; and (4) installing the modified Wine source code on the ARM processor. The method is used for realizing the transplanting of Wine and ensuring that the Wine can run on an OMS (Open Mobile System) intelligent mobile phone.
Owner:INSIGMA TECHNOLOGY CO LTD
Method and device for accelerating starting of application program
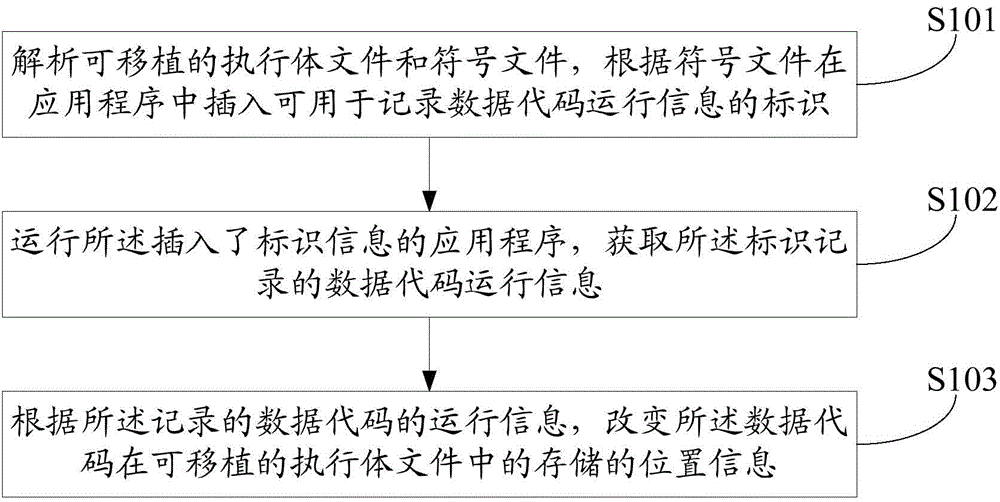
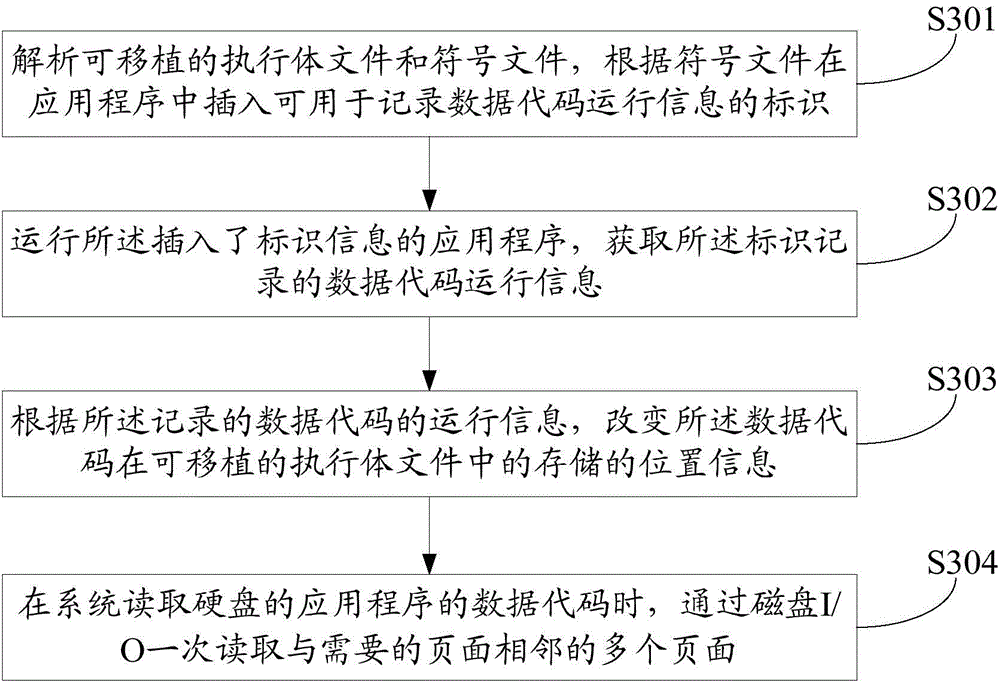
ActiveCN104572139AFast startupReduce the number of jumpsProgram loading/initiatingThe InternetActuator
The invention is suitable for the field of the Internets and provides a method for accelerating the starting of an application program. The method comprises the following steps: receiving and analyzing the transplantable actuator file of the application program and the symbol file of the application program, and inserting identifiers capable of being used for recording the data code running information of the application program in the application program according to the symbol file; running the application program in which identifier information is inserted, and obtaining the data code running information that the identifiers record; changing the position information of data codes stored in the transplantable actuator file according to the recorded running information of the data codes. The memory position of the data codes is correspondingly changed through recording the running information of program codes, so that when the application program runs, the I / O skip times of a hard disk can be effectively reduced, and the efficiency of reading the data of the hard disk is improved. Therefore, the purpose of raising the starting speed of the application program is achieved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
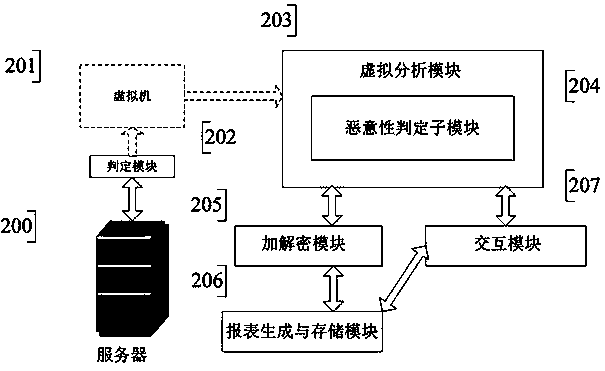
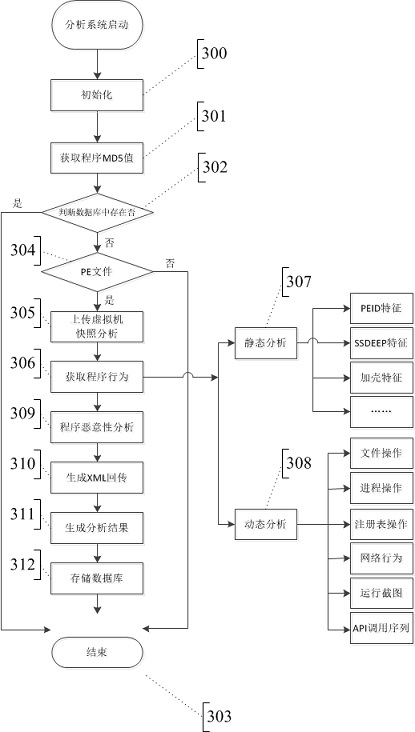
Trojan horse decision system based on dynamic code sequence tracking analysis
InactiveCN104346570AAvoid identificationAvoid escape damagePlatform integrity maintainanceDecision systemData transmission
The invention provides a Trojan horse decision system based on dynamic code sequence tracking analysis. The system comprises an interaction module, a decision module, a virtual analysis module, a malicious intention decision sub-module, an encrypting / decrypting module and a report generating and storing module. The interaction module is a carrier of the interaction between a user and a server; the decision module is used for deciding whether a program uploaded by the user is a portable executable (PE) program or not, and whether the program is analyzed or not; the virtual analysis module is used for statically and dynamically analyzing behavior operation of suspicious programs and deciding the malicious intentions and classifications of the programs; the malicious intention decision sub-module is used for completing the decision of the malicious intention of the programs to be detected; the encrypting / decrypting module is used for encrypting / decrypting the files and data transmitted between the virtual analysis module and a server system; the report generating and storing module is used for generating an analysis report and storing the analysis report data and analyzed suspicious program samples. The Trojan horse decision system provided by the invention realizes the efficient detection, and has an effect of recognizing new varied Trojan horses.
Owner:XIAN UNIV OF POSTS & TELECOMM +1
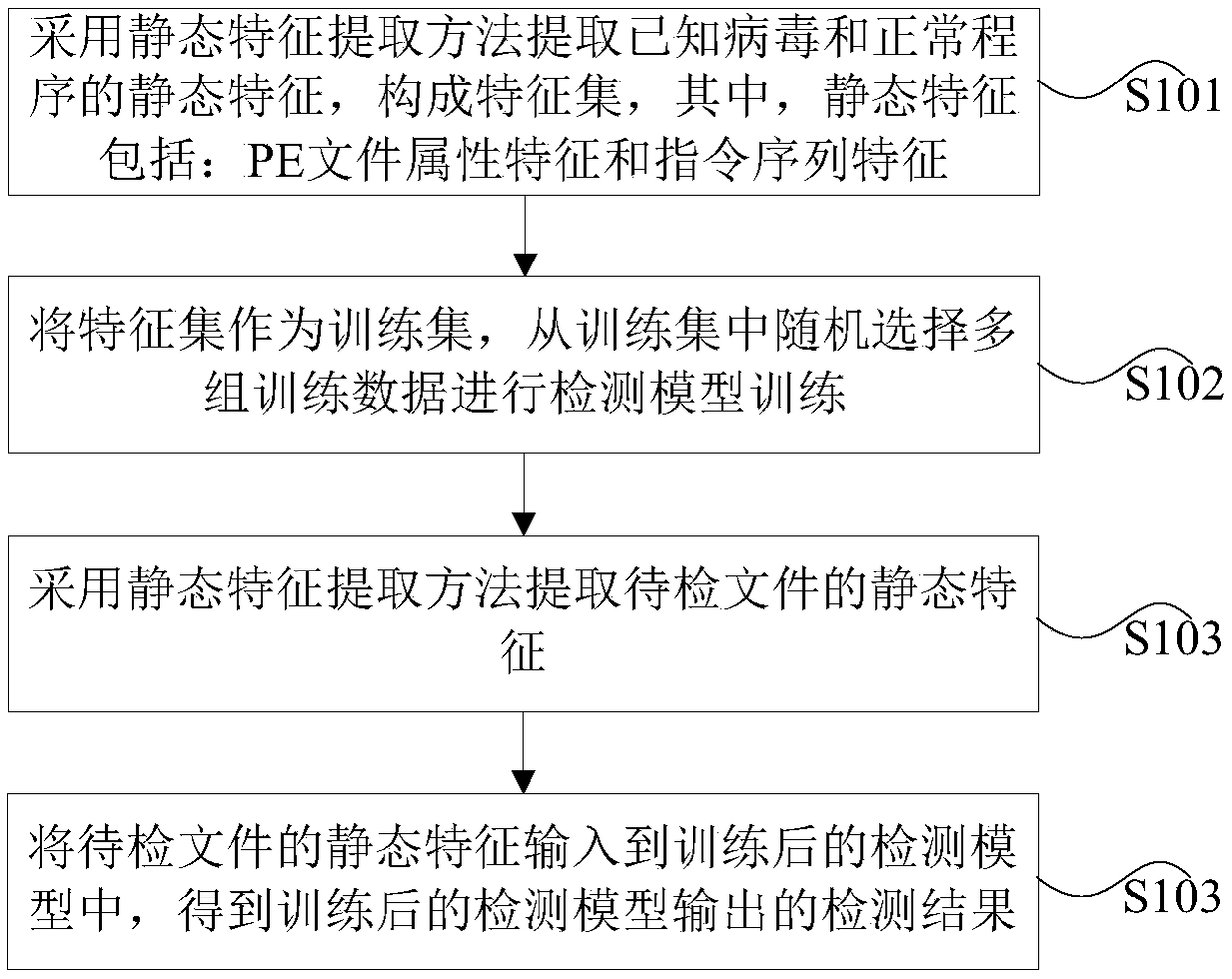
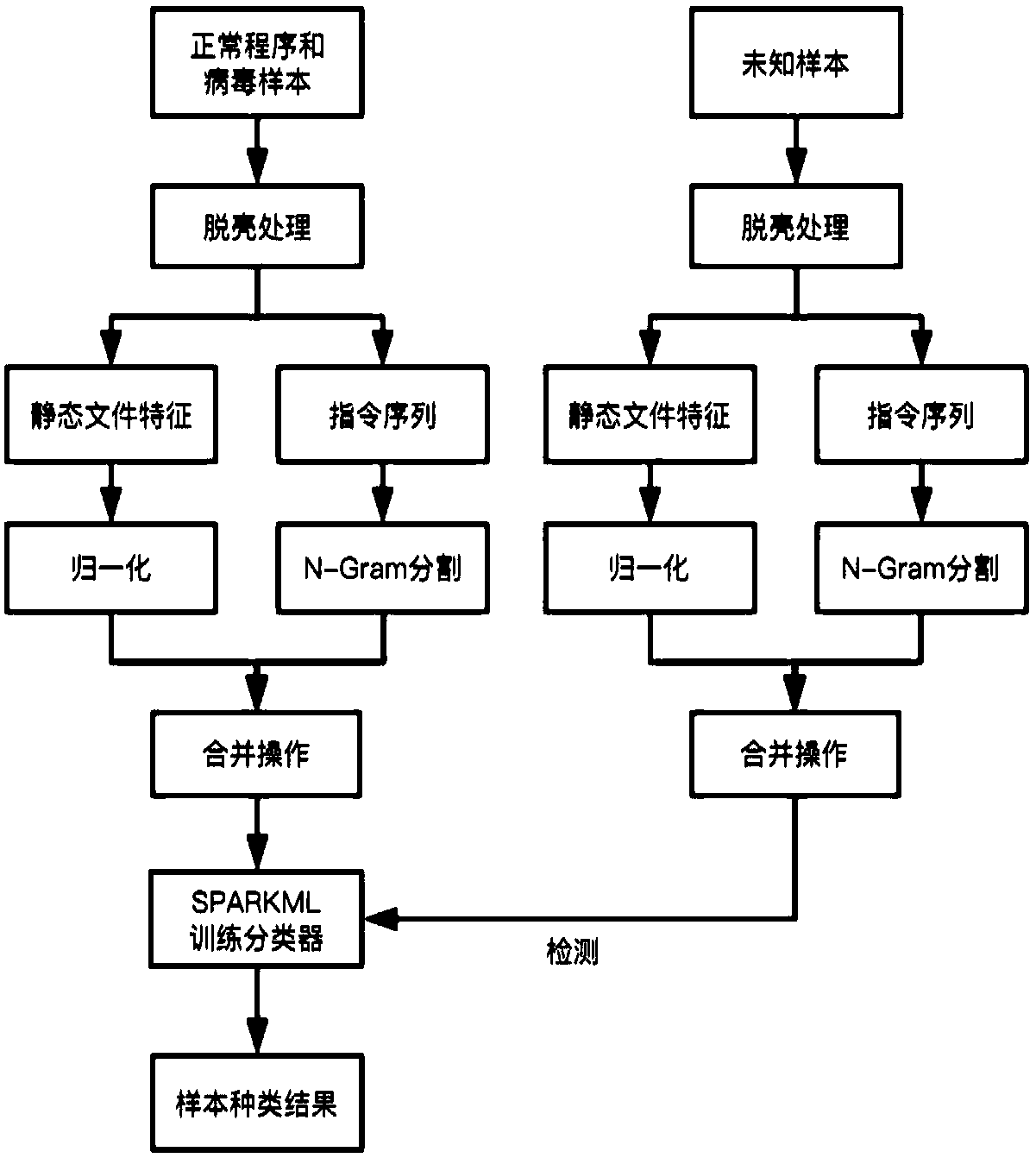
Virus detection method, apparatus, device and medium for portable executable file
InactiveCN109063478ASolve the hysteresisInstant detectionPlatform integrity maintainanceHysteresisFeature set
The invention provides a virus detection method, an apparatus, a device and a medium of a portable executable file. The method comprises the following steps: extracting static features of known viruses and normal programs by using a static feature extraction method to form a feature set, wherein, the static features include: PE file attribute features and instruction sequence features; The featureset is used as training set, and multiple groups of training data are randomly selected from the training set to train the detection model. The static feature extraction method is used to extract thestatic feature of the document to be checked. The static characteristics of the documents to be inspected are inputted into the detection model after training, and the detection results output by thedetection model after training are obtained. The invention solves the problem that the traditional virus detection has hysteresis, and realizes the technical effect that the new virus or the virus variant can be detected immediately.
Owner:中国人民解放军61660部队
File manipulation during early boot time
Owner:OPEN TEXT CORPORATION
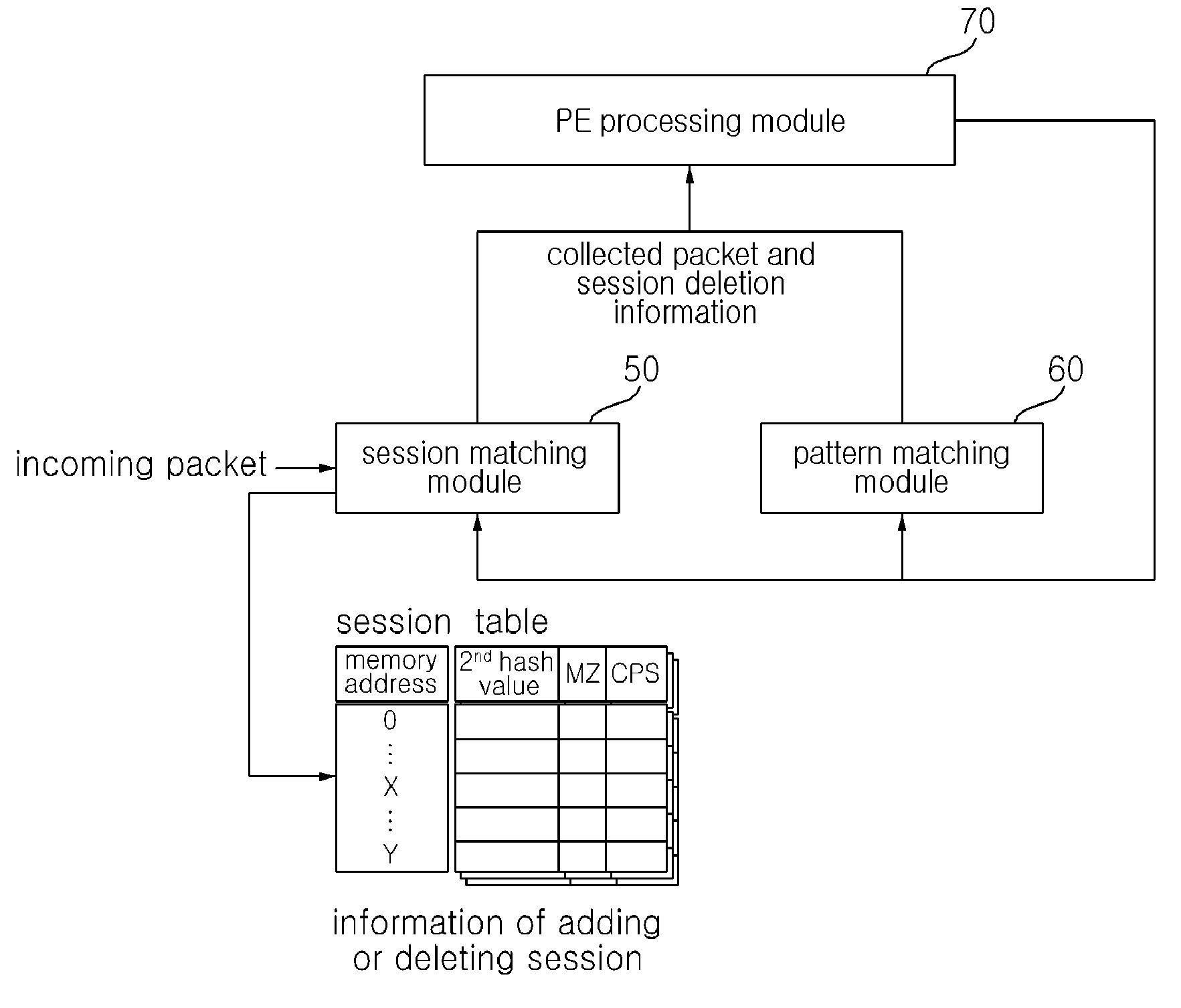
Method of extracting windows executable file using hardware based on session matching and pattern matching and appratus using the same
InactiveUS20100146621A1Memory loss protectionError detection/correctionPattern matchingNetwork packet
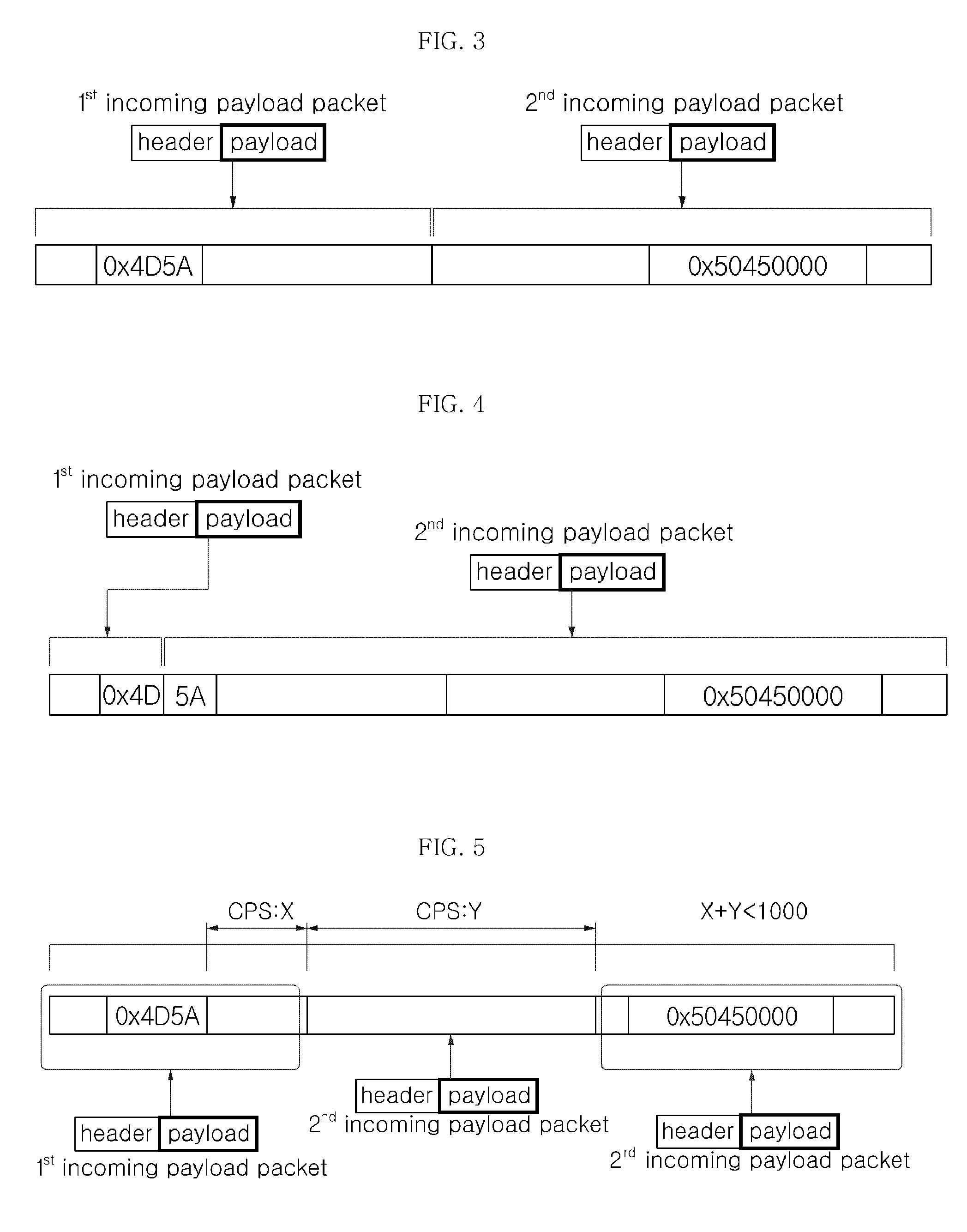
A method and apparatus for extracting a windows executable file that can search for a pattern related to windows executable files among a large quantity of network packets using a hardware-based session tracking and pattern matching technology and that can extract all packets included in the corresponding session are provided. The method of extracting a windows executable file includes: collecting incoming packets having a payload according to a session of a reference packet having an MZ pattern; performing a portable executable (PE) pattern matching for the collected incoming packets; and forming a PE file based on at least one incoming packet satisfying the PE pattern matching.
Owner:ELECTRONICS & TELECOMM RES INST
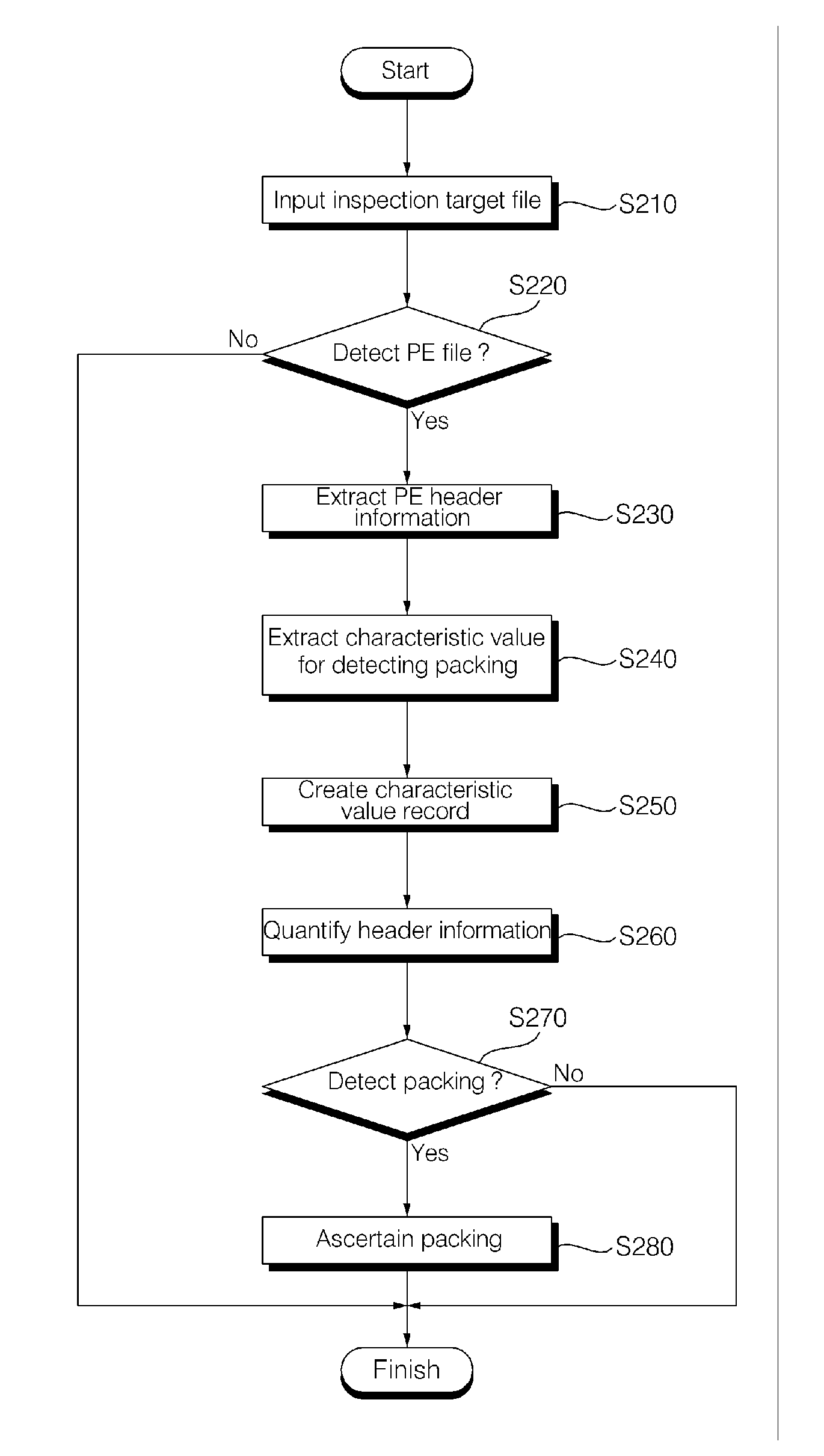
Device and method for detecting packed pe file
InactiveUS20100153421A1Improve detection efficiencyReduce analysisDigital data information retrievalSpecial data processing applicationsPortable ExecutableDatabase
The present invention discloses a device and method for detecting a packed PE (portable executable) file. In the device and method for detecting a packed PE file, information for detecting packing are extracted by analyzing the header of a target file, and a record containing characteristic values shown only in a packed PE file is created by using the extracted information. The packing of the target file is detected by calculating the similarity with a PE file which is not packed based on the created record and comparing it with a derived threshold value. Therefore, a packed PE file can be detected even if it is packed by a packing method which is not well-known.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com