Patents
Literature
337results about How to "Reduce analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
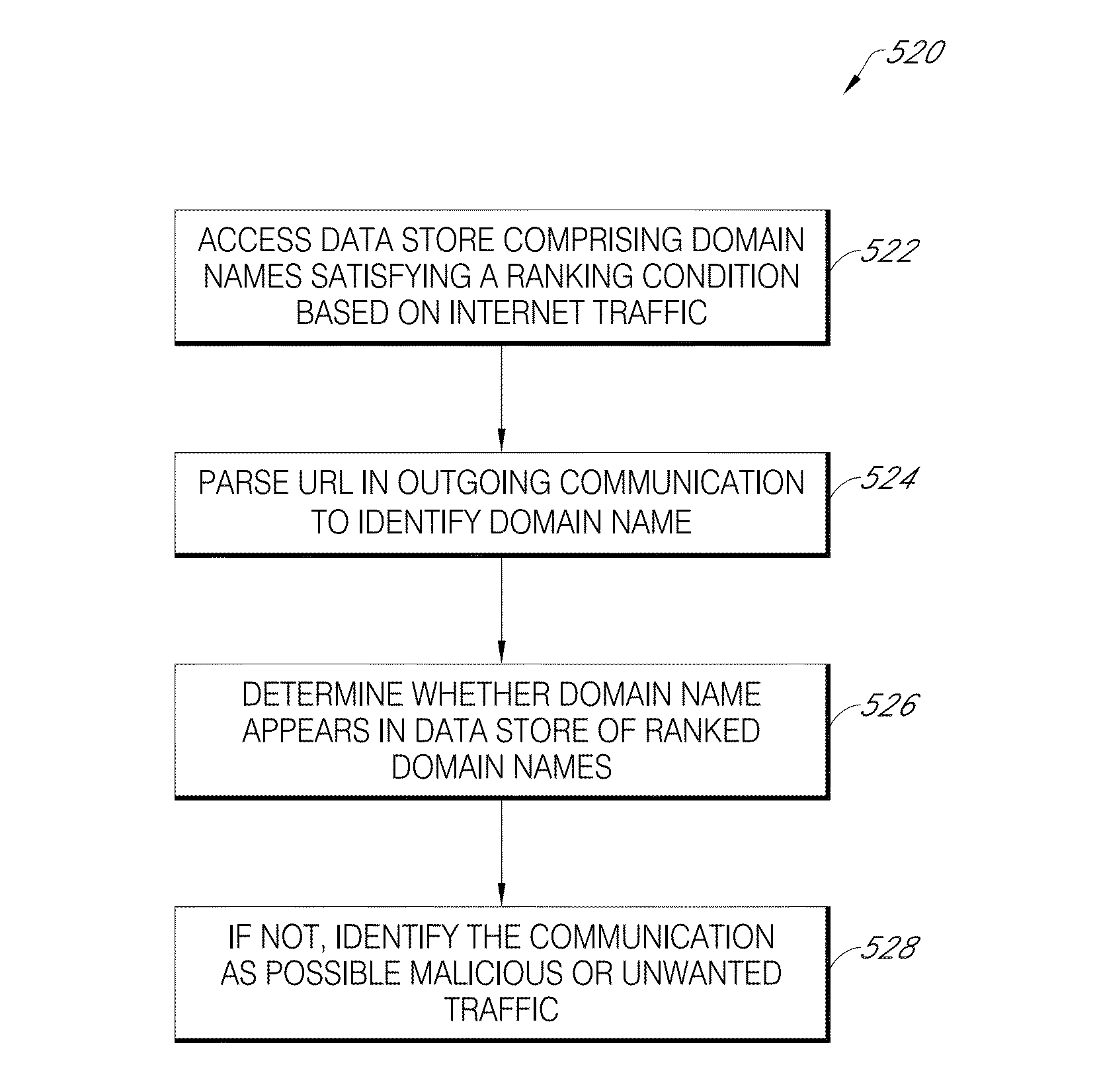
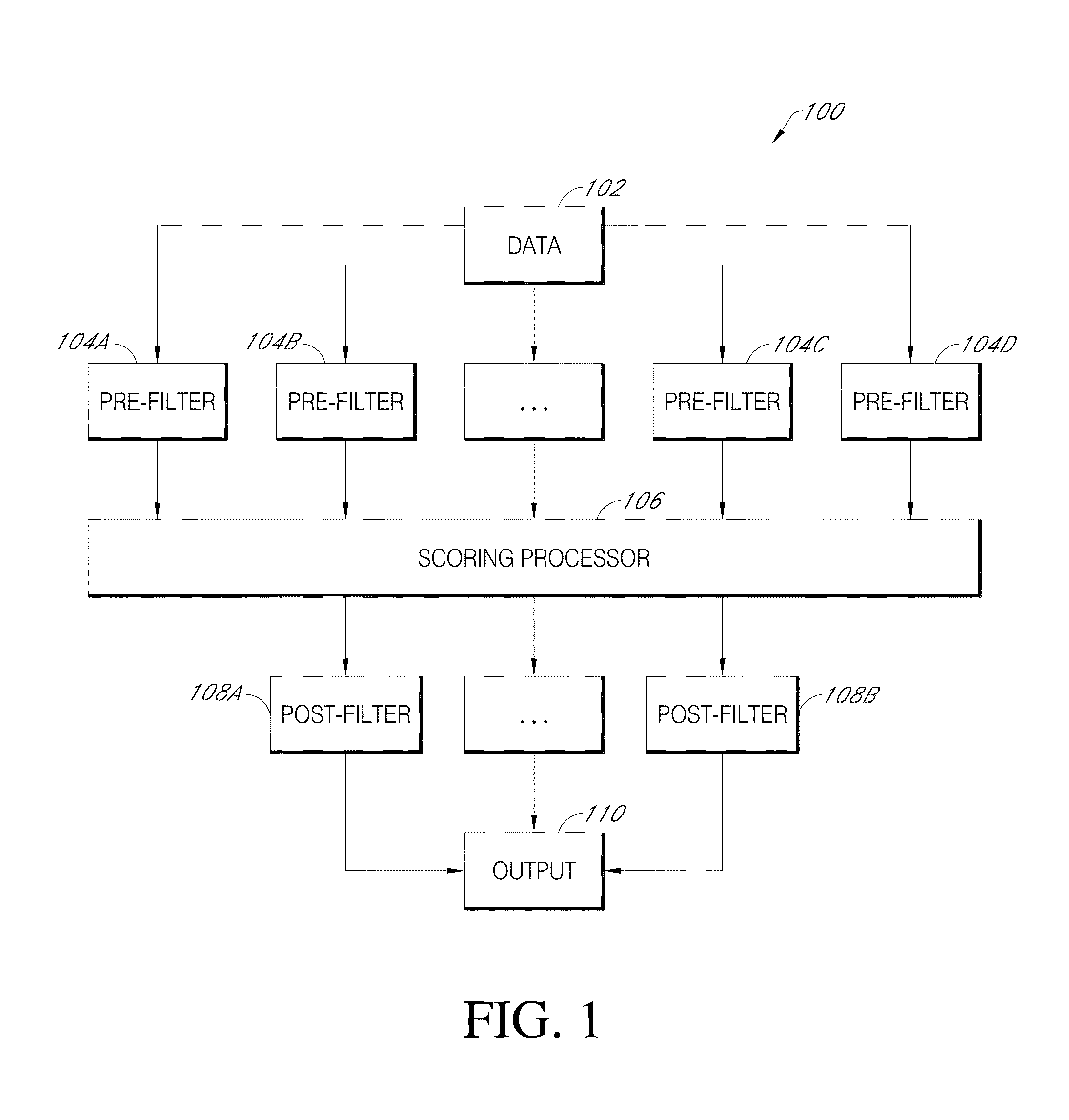
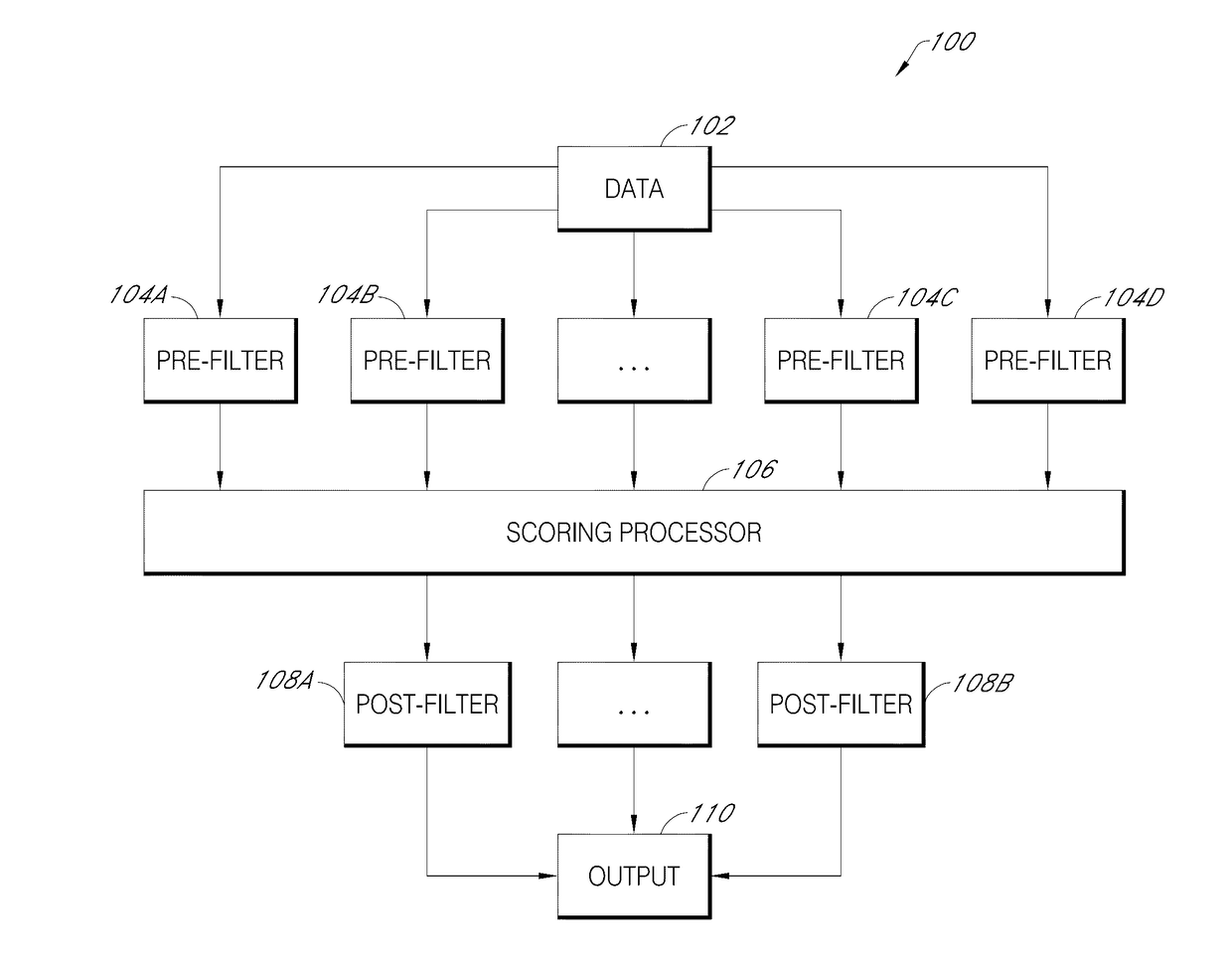
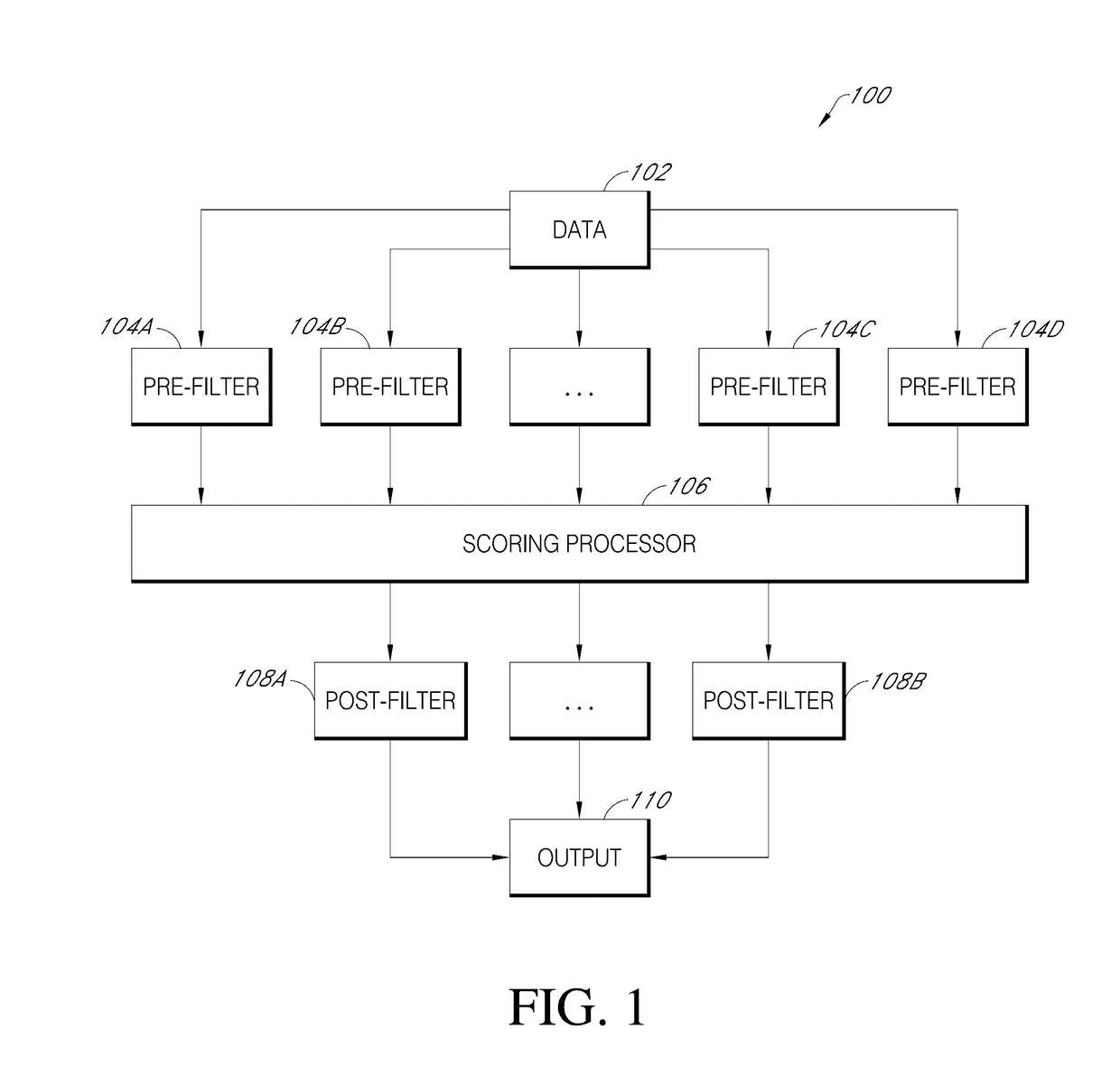
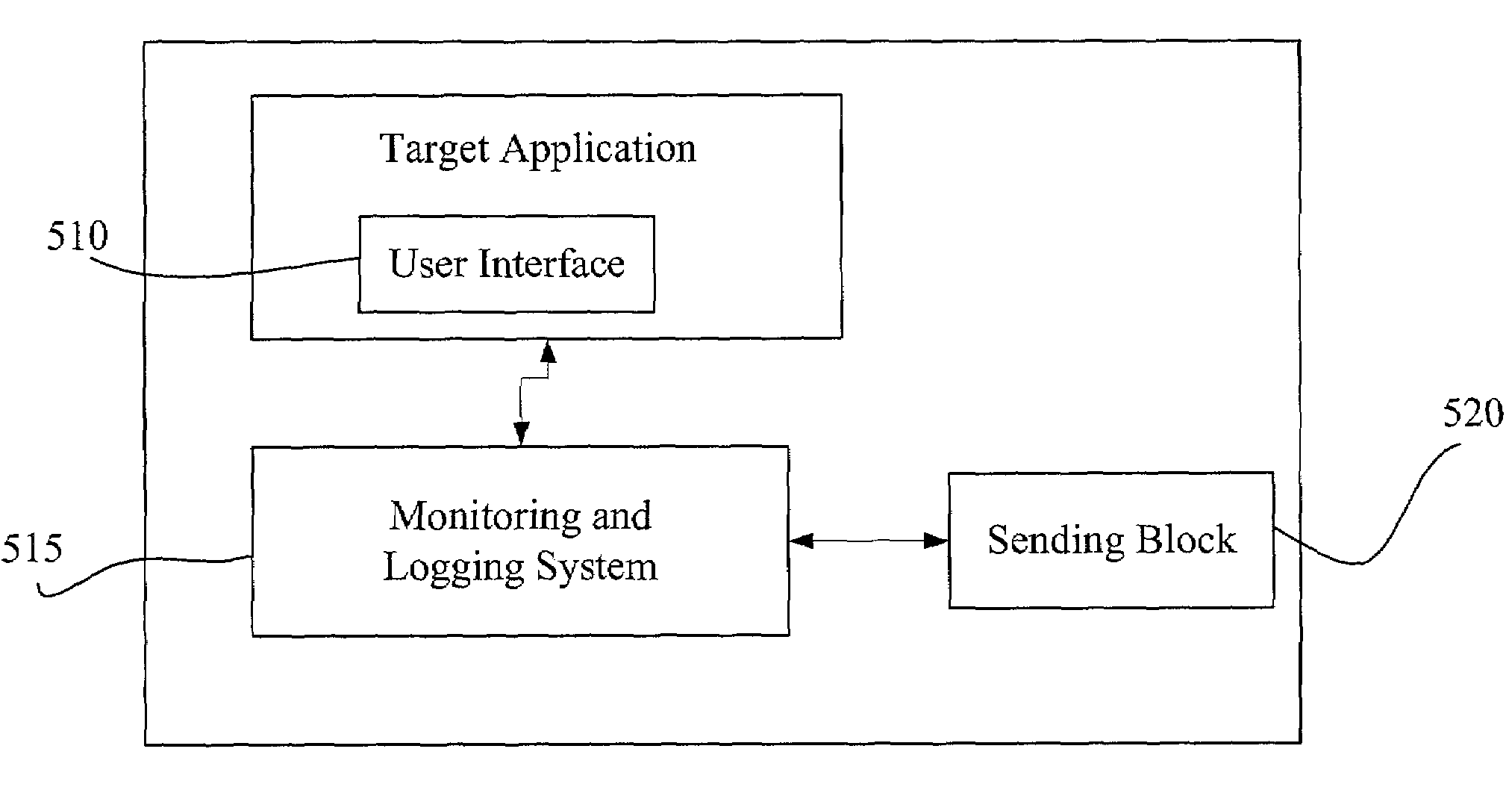
Malicious software detection in a computing system
ActiveUS9043894B1Function increaseConsume significant storageComputer security arrangementsMultiple digital computer combinationsComputerized systemMalware
A computer system identifies malicious Uniform Resource Locator (URL) data items from a plurality of unscreened data items that have not been previously identified as associated with malicious URLs. The system can execute a number of pre-filters to identify a subset of URLs in the plurality of data items that are likely to be malicious. A scoring processor can score the subset of URLs based on a plurality of input vectors using a suitable machine learning model. Optionally, the system can execute one or more post-filters on the score data to identify data items of interest. Such data items can be fed back into the system to improve machine learning or can be used to provide a notification that a particular resource within a local network is infected with malicious software.
Owner:PALANTIR TECHNOLOGIES
Pervasive, domain and situational-aware, adaptive, automated, and coordinated analysis and control of enterprise-wide computers, networks, and applications for mitigation of business and operational risks and enhancement of cyber security
ActiveUS20130104236A1Reduce analysisLower control priorityMemory loss protectionError detection/correctionApplication softwareBusiness process
Real time security, integrity, and reliability postures of operational (OT), information (IT), and security (ST) systems, as well as slower changing security and operational blueprint, policies, processes, and rules governing the enterprise security and business risk management process, dynamically evolve and adapt to domain, context, and situational awareness, as well as the controls implemented across the operational and information systems that are controlled. Embodiments of the invention are systematized and pervasively applied across interconnected, interdependent, and diverse operational, information, and security systems to mitigate system-wide business risk, to improve efficiency and effectiveness of business processes and to enhance security control which conventional perimeter, network, or host based control and protection schemes cannot successfully perform.
Owner:ALBEADO
Robust calculation of crosstalk delay change in integrated circuit design
ActiveUS7359843B1Robust delay change determinationAccurate accountingComputation using non-denominational number representationComputer aided designCapacitanceCapacitive coupling
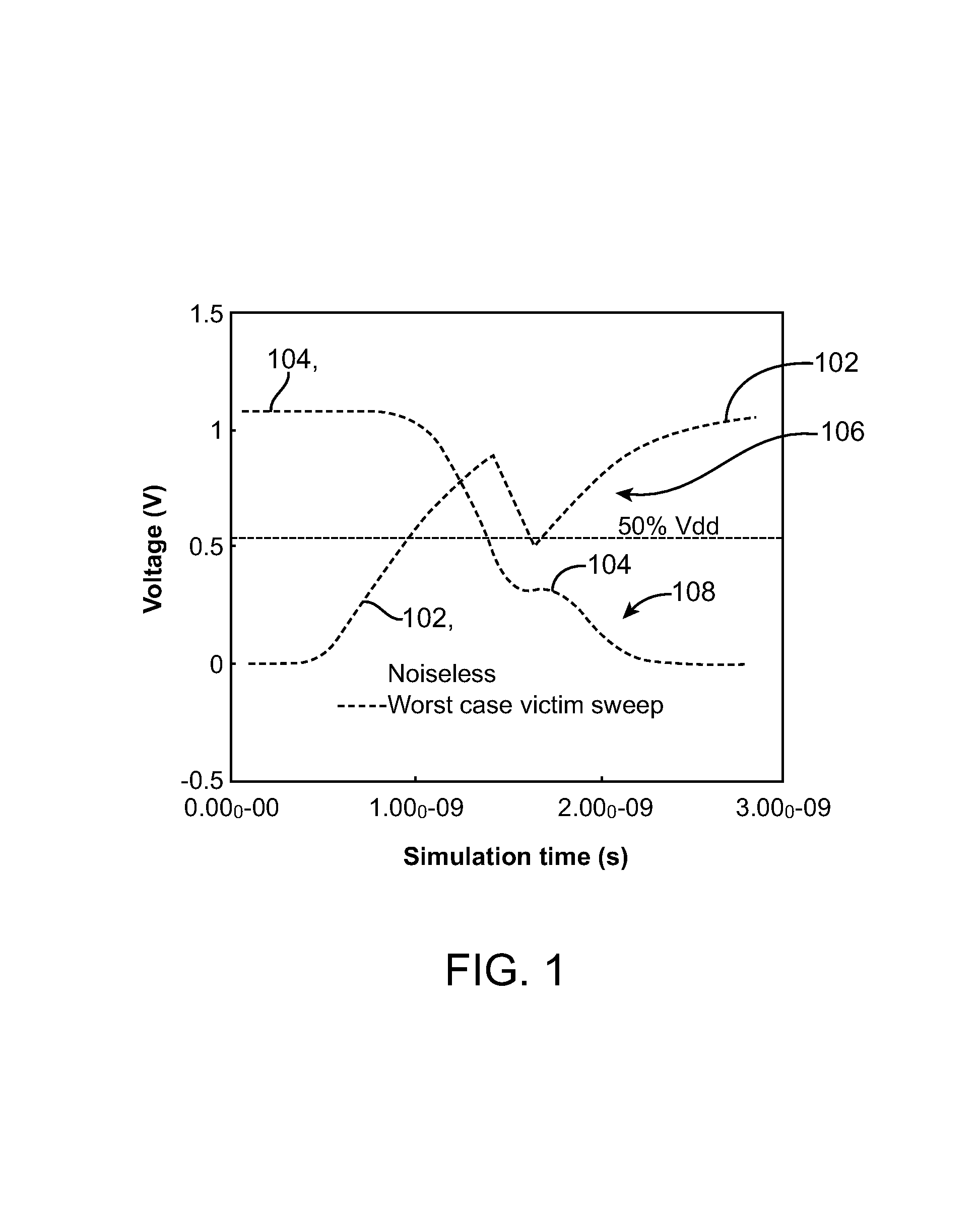
A method of delay change determination in an integrated circuit design including a stage with a victim net and one or more aggressor nets capacitively coupled thereto, the method comprising: determining a nominal (noiseless) victim net signal transition; determining a noisy victim net signal transition; and determining a delay change based upon nominal and noisy victim signal transition arrival times at a victim net receiver output.
Owner:CADENCE DESIGN SYST INC
System and method for capturing, storing, analyzing and displaying data relating to the movements of objects
ActiveUS20100013931A1Easy to compareSmall amount of memoryImage analysisCharacter and pattern recognitionGraphicsTime segment
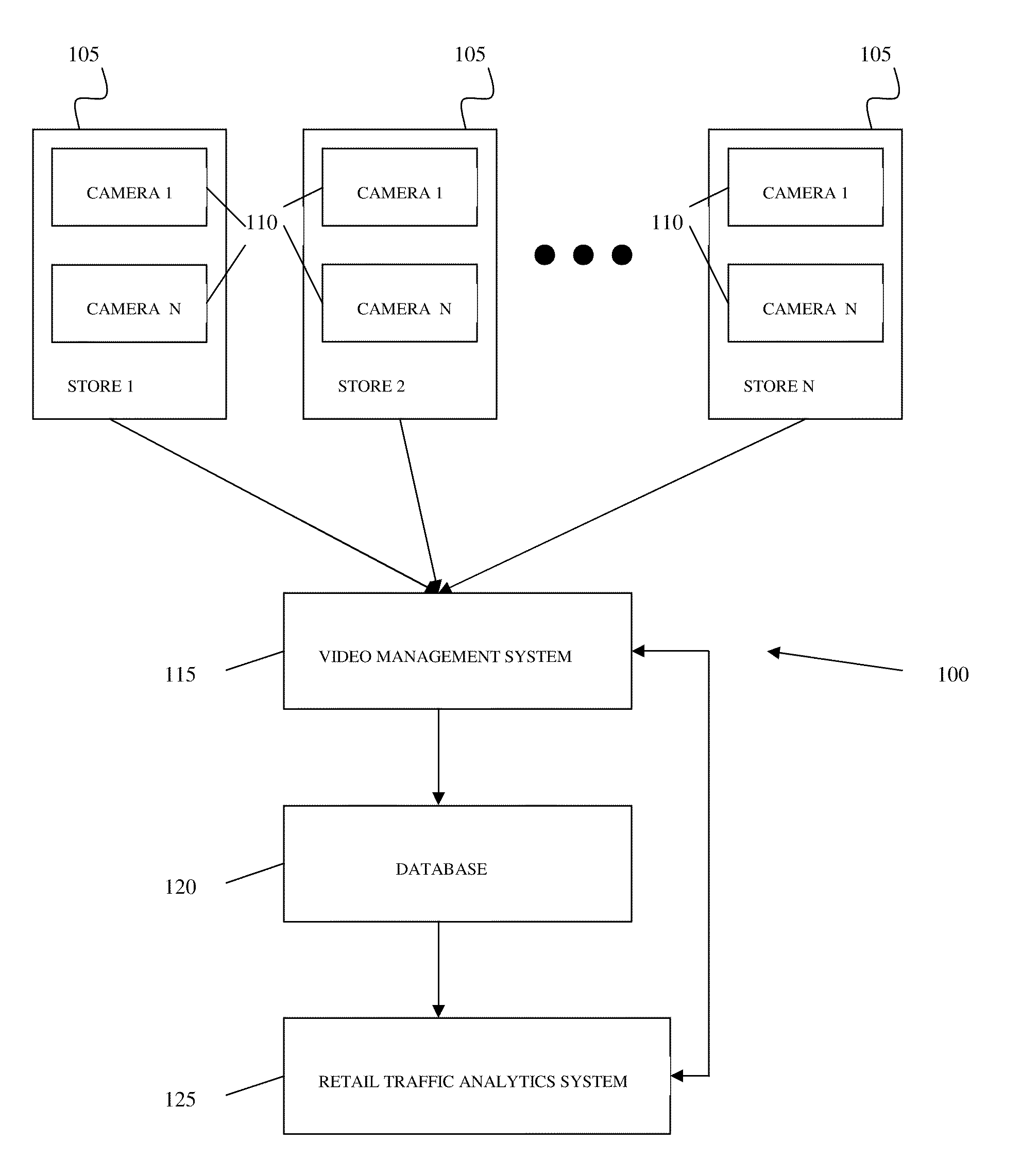
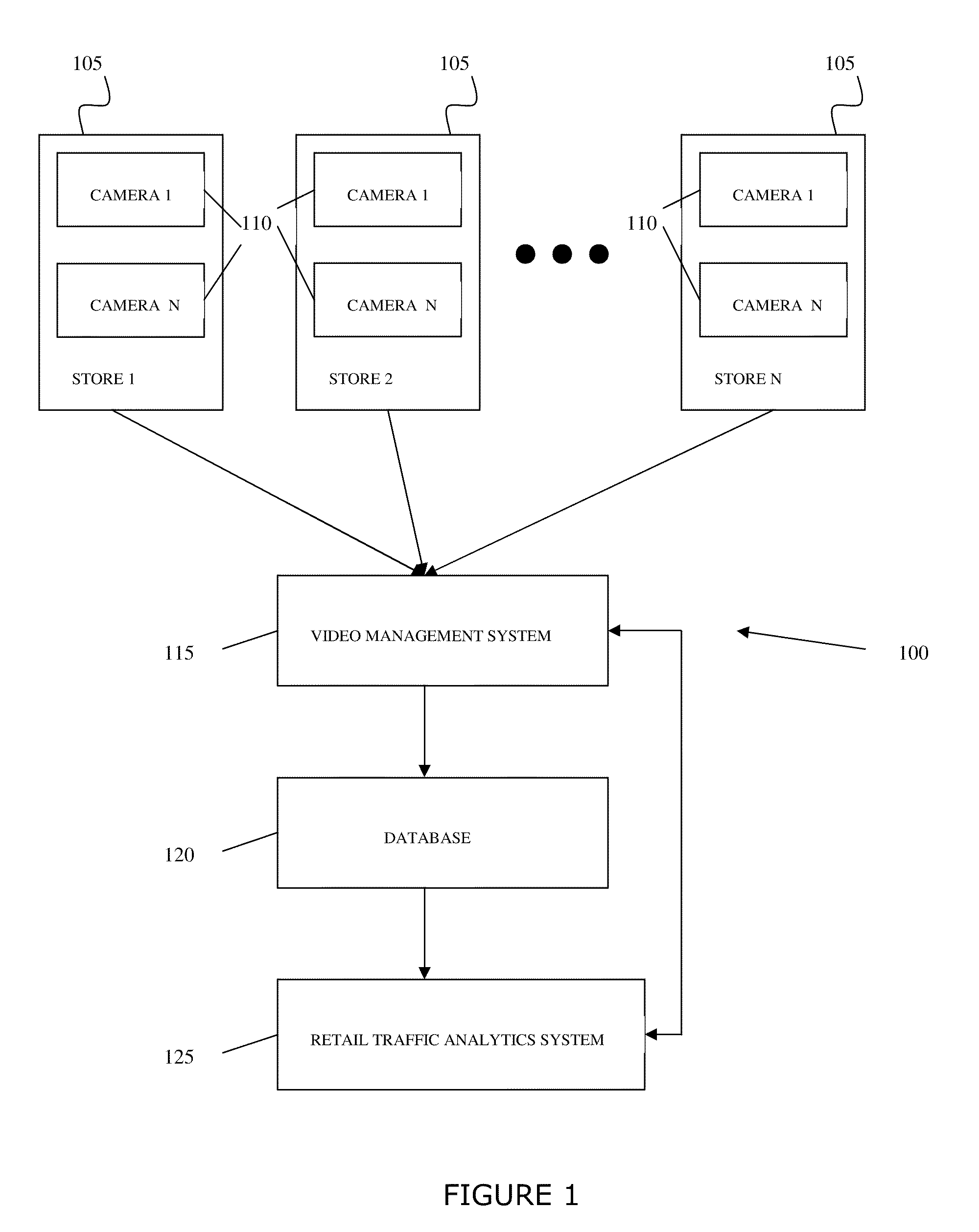
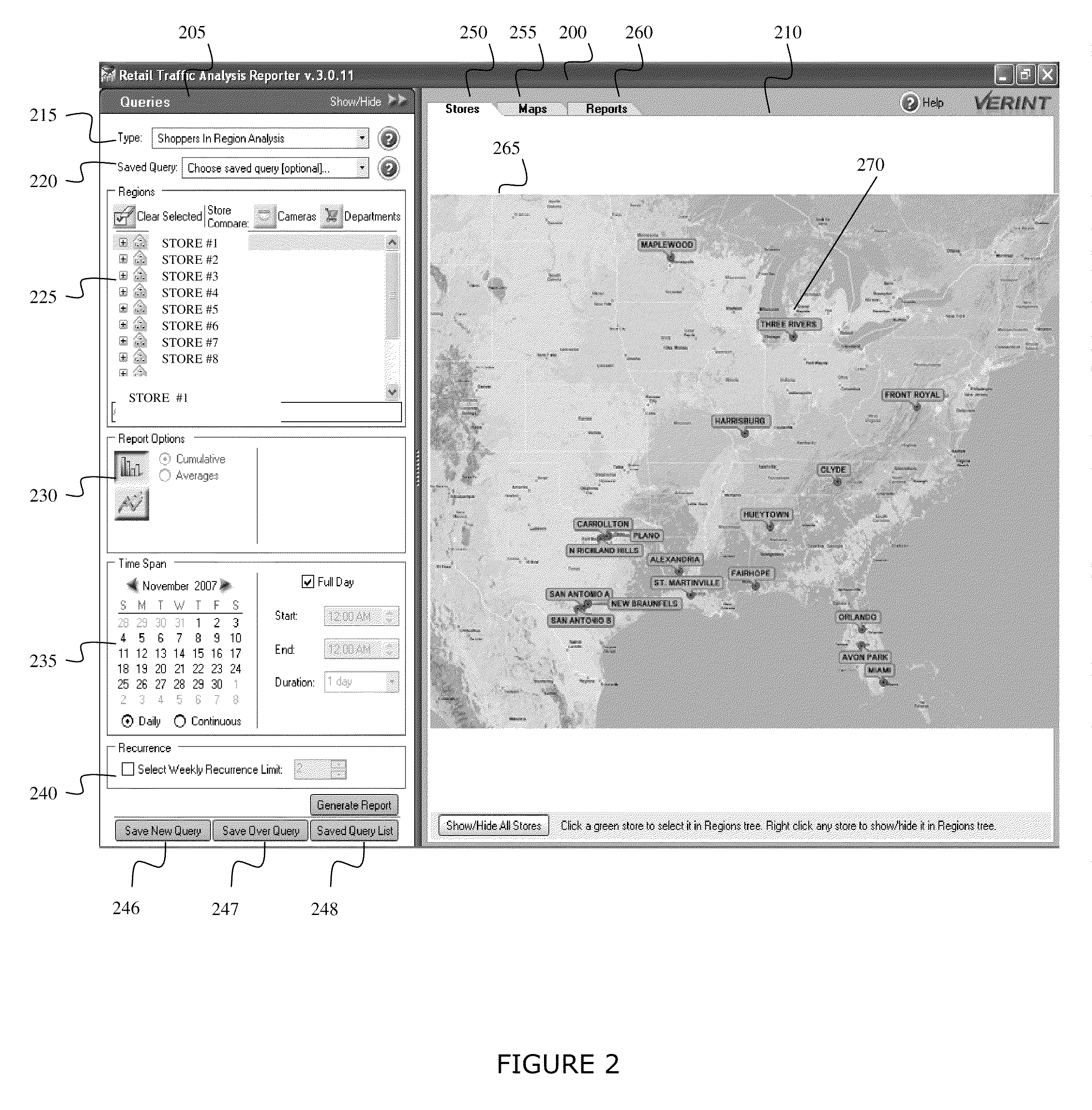
A system and method for the capture and storage of data relating to the movements of objects, in a specified area and enables this data to be displayed in a graphically meaningful and useful manner. Video data is collected and video metadata is generated relating to objects (persons) appearing in the video data and their movements over time. The movements of the objects are then analyzed to detect the movements within a region of interest. This detection of movement allows a user, such as a manager of a store, to make informed decisions as to the infrastructure and operation of the store. One detection method relates to the number of people that are present in a region of interest for a specified time period. A second detection method relates to the number of people that remain or dwell in a particular area for a particular time period. A third detection method determines the flow of people and the direction they take within a region of interest. A fourth detection method relates to the number of people that enter a certain area by crossing a virtual line, a tripwire.
Owner:COGNYTE TECH ISRAEL LTD
Method and apparatus for witness card statistical analysis using image processing techniques
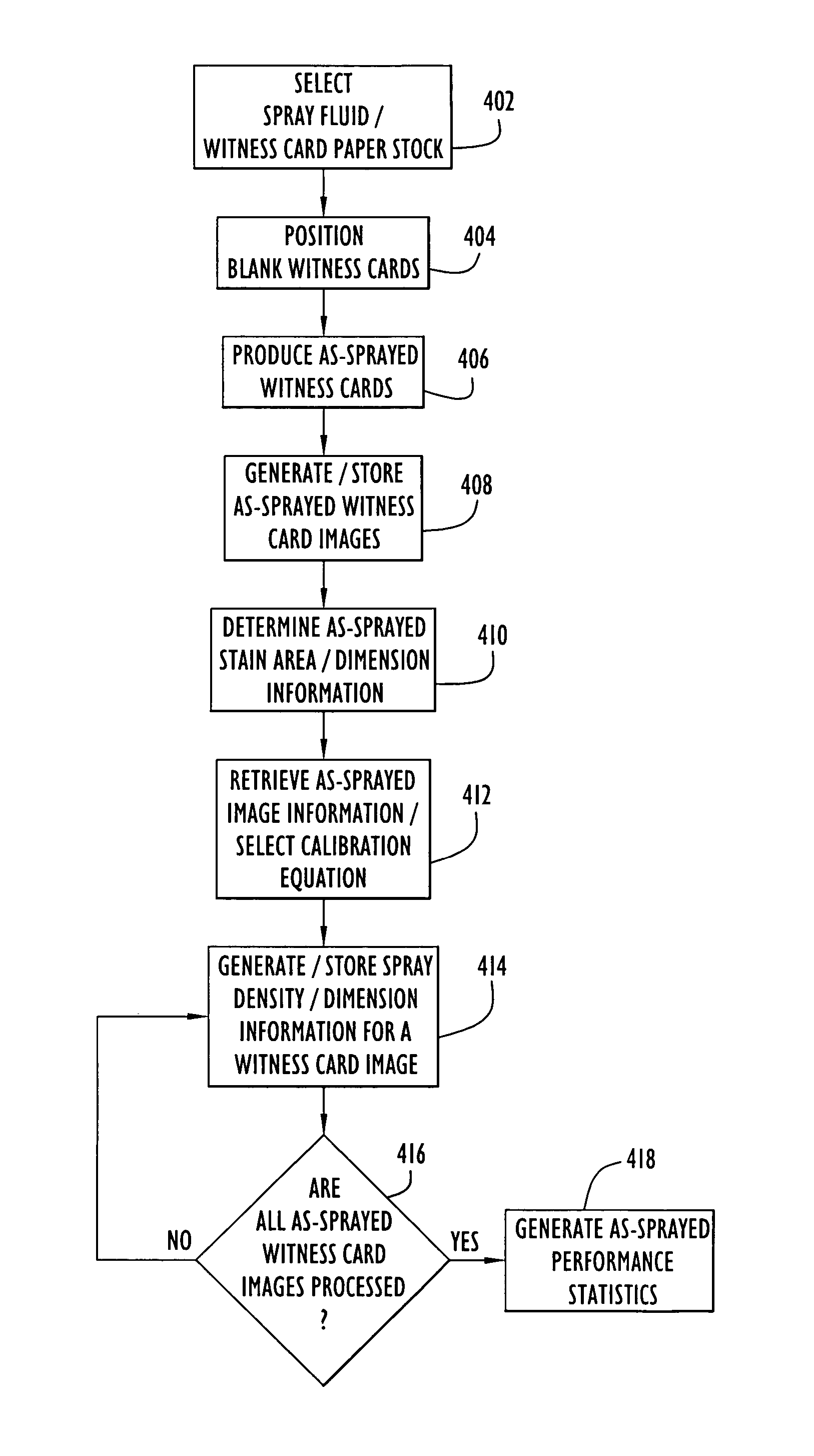
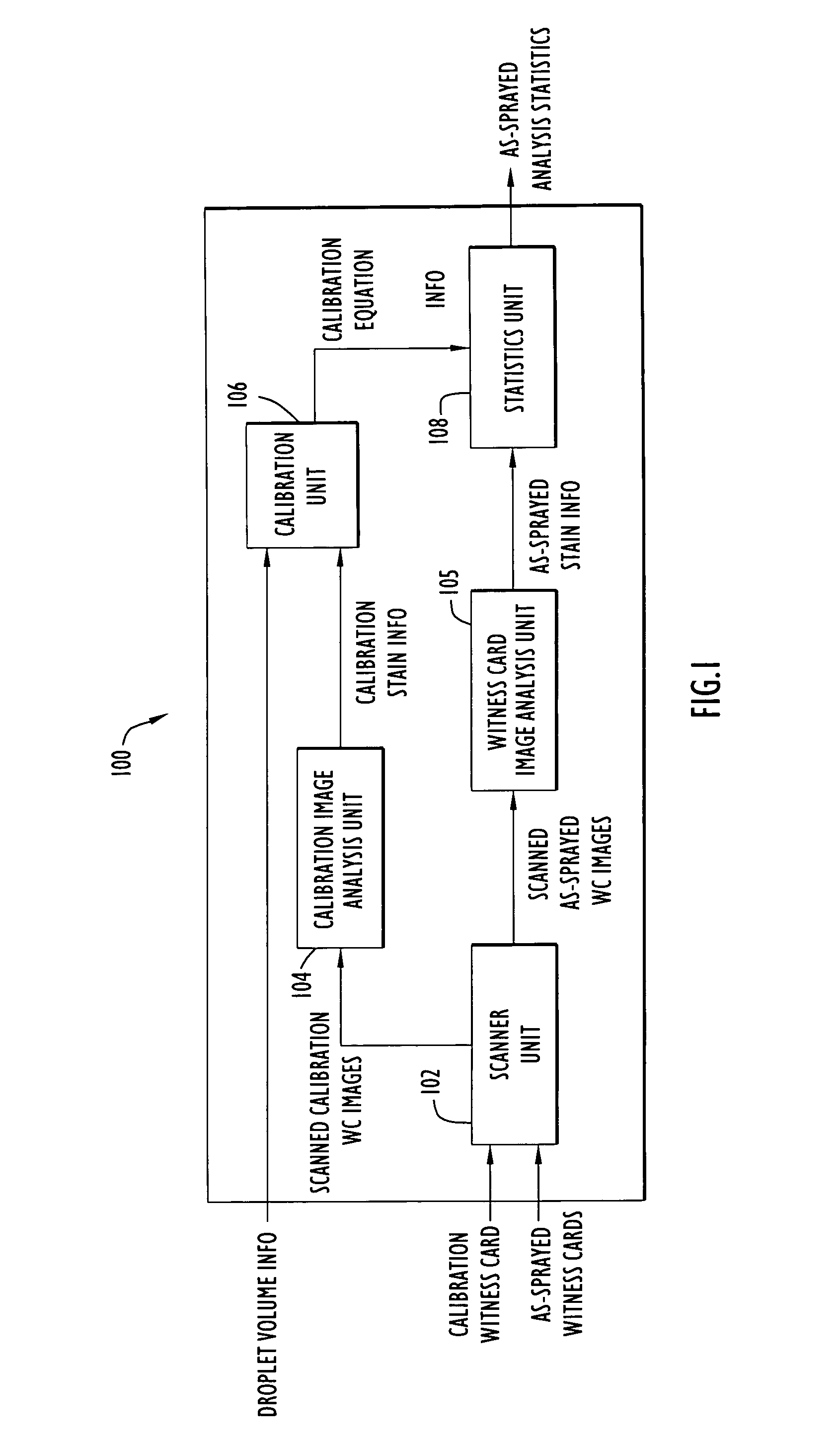
ActiveUS7277570B2Reduce analysisShorten the timeParticle separator tubesMaterial analysis by optical meansImaging processingStatistical analysis
A method and apparatus for performing witness card statistical analysis using image processing techniques to quickly and efficiently generate as-sprayed performance statistics for a spray device, or spray, based upon a comprehensive analysis of as-sprayed witness card stains. Calibration and as-sprayed witness cards are scanned to produce images that are processed using image processing techniques to identify stain areas / dimensions. Calibration stain data is associated with known calibration droplet volumes and used to generate a set of calibration equations that model an observed relationship between the area of calibration stains upon a witness card and the volume of the respective fluid droplets that produced the stains. As-sprayed stain area / dimension information is processed using the developed calibration equations to approximate the volume of as-sprayed droplets. The approach provides a direct quantitative assessment of spray device performance based upon a comprehensive assessment of as-sprayed witness cards, resulting in highly accurate, timely spray device performance statistics.
Owner:PERATON INC
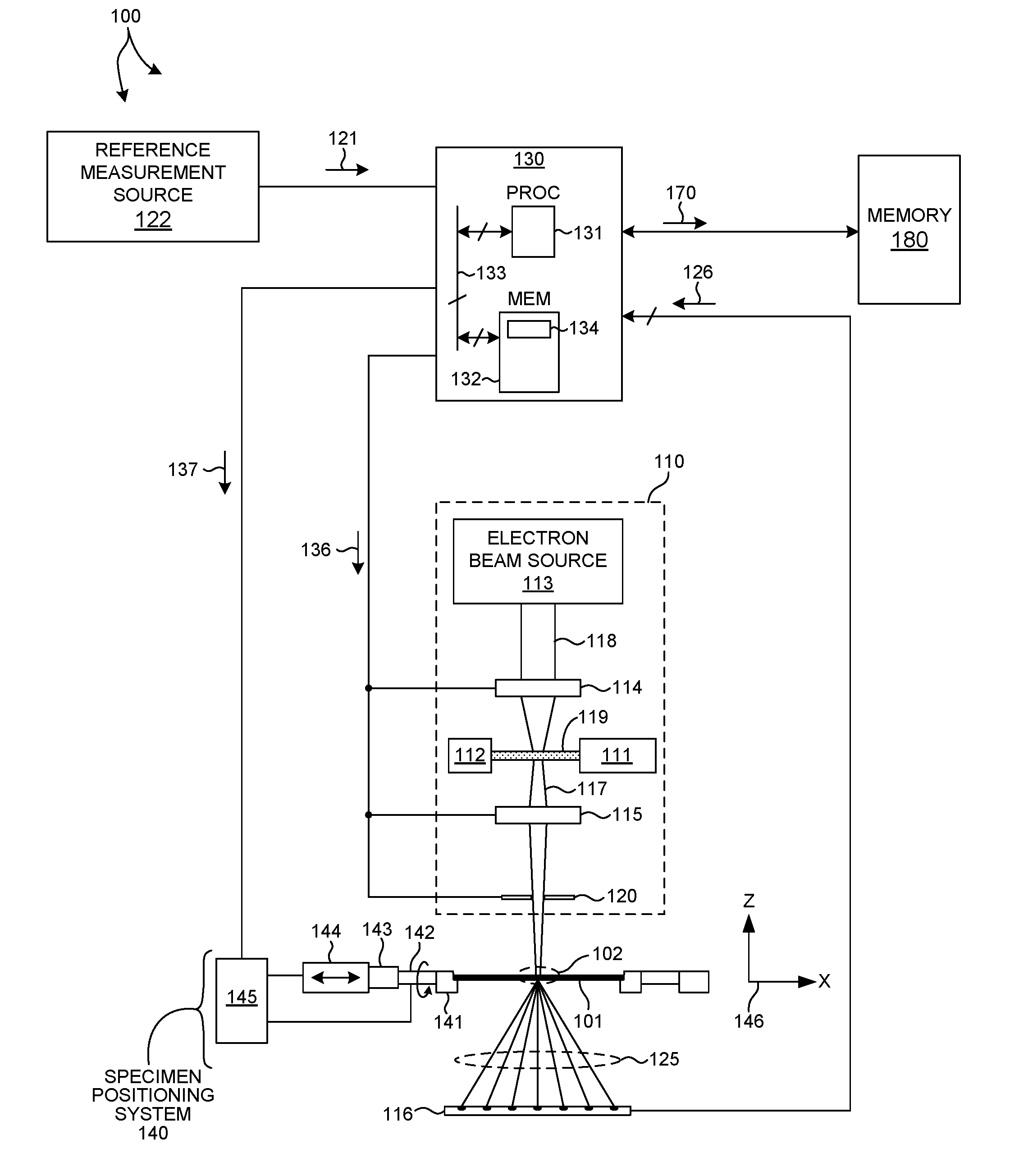
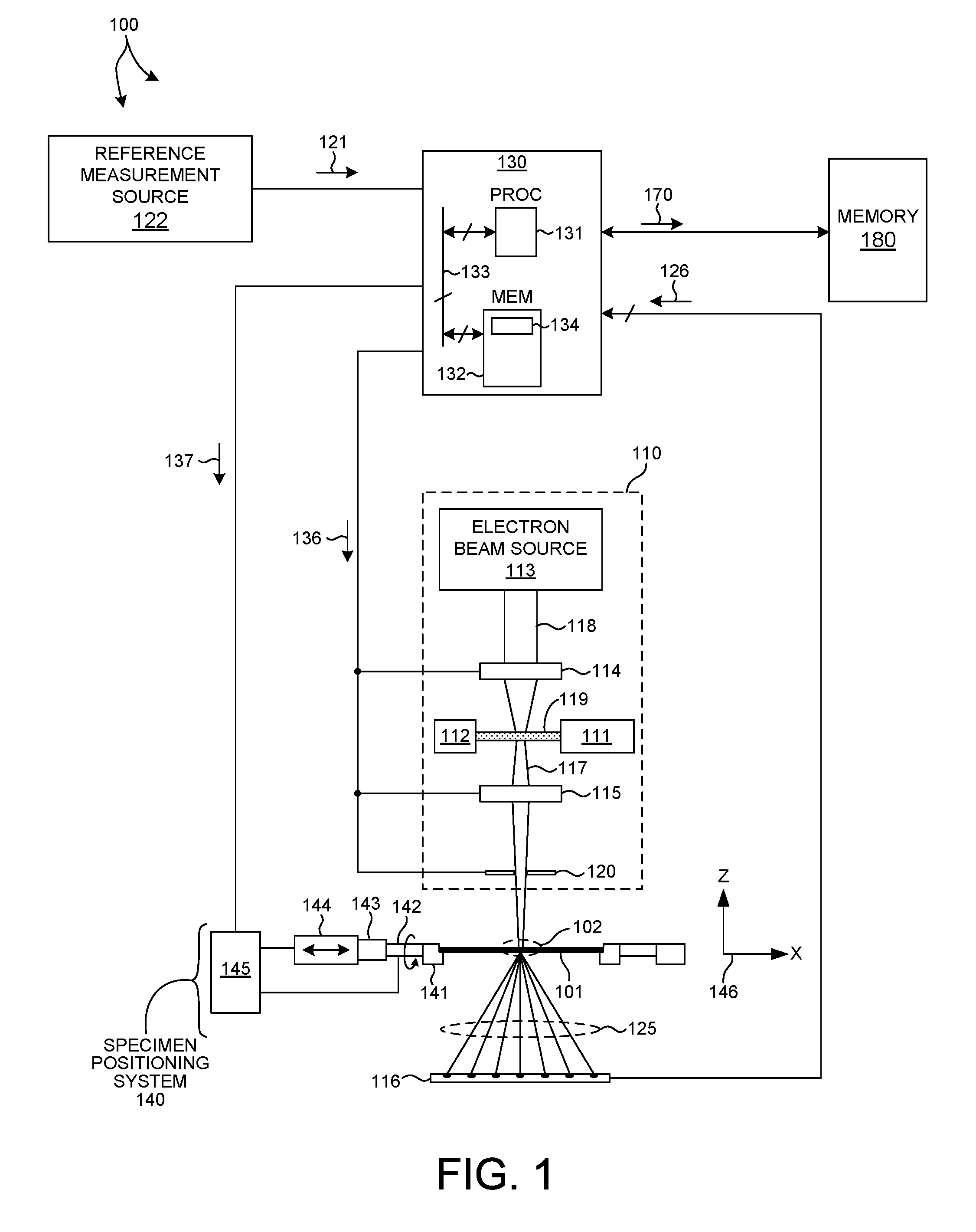
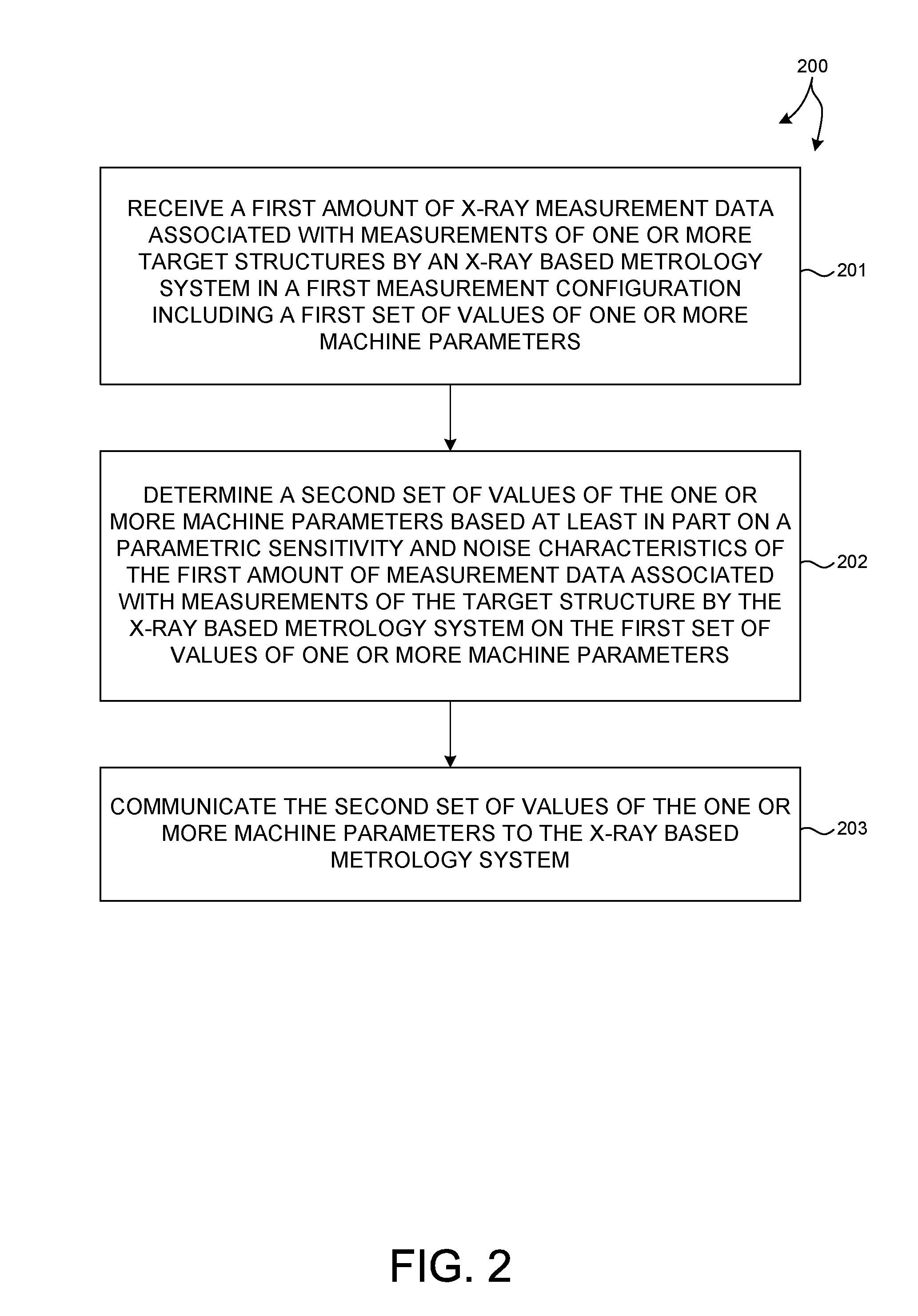
Measurement System Optimization For X-Ray Based Metrology
ActiveUS20160202193A1Maximize precisionMinimize correlationMaterial analysis by optical meansSemiconductor/solid-state device manufacturingSoft x rayMetrology
Methods and systems for optimizing measurement system parameter settings of an x-ray based metrology system are presented. X-ray based metrology systems employing an optimized set of measurement system parameters are used to measure structural, material, and process characteristics associated with different semiconductor fabrication processes with greater precision and accuracy. In one aspect, a set of values of one or more machine parameters that specify a measurement scenario is refined based at least in part on a sensitivity of measurement data to a previous set of values of the one or more machine parameters. The refinement of the values of the machine parameters is performed to maximize precision, maximize accuracy, minimize correlation between parameters of interest, or any combination thereof. Refinement of the machine parameter values that specify a measurement scenario can be used to optimize the measurement recipe to reduce measurement time and increase measurement precision and accuracy.
Owner:KLA TENCOR TECH CORP
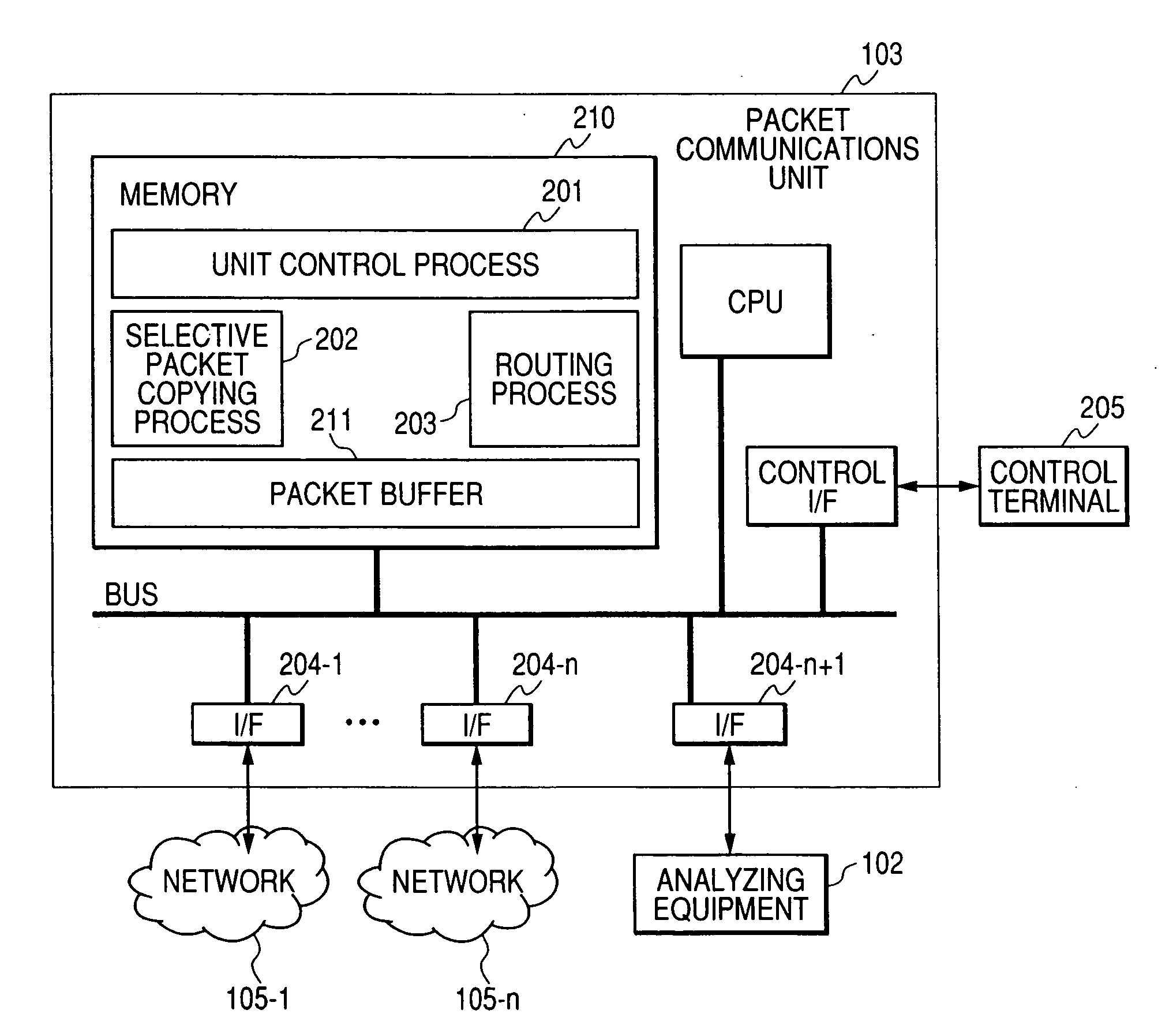
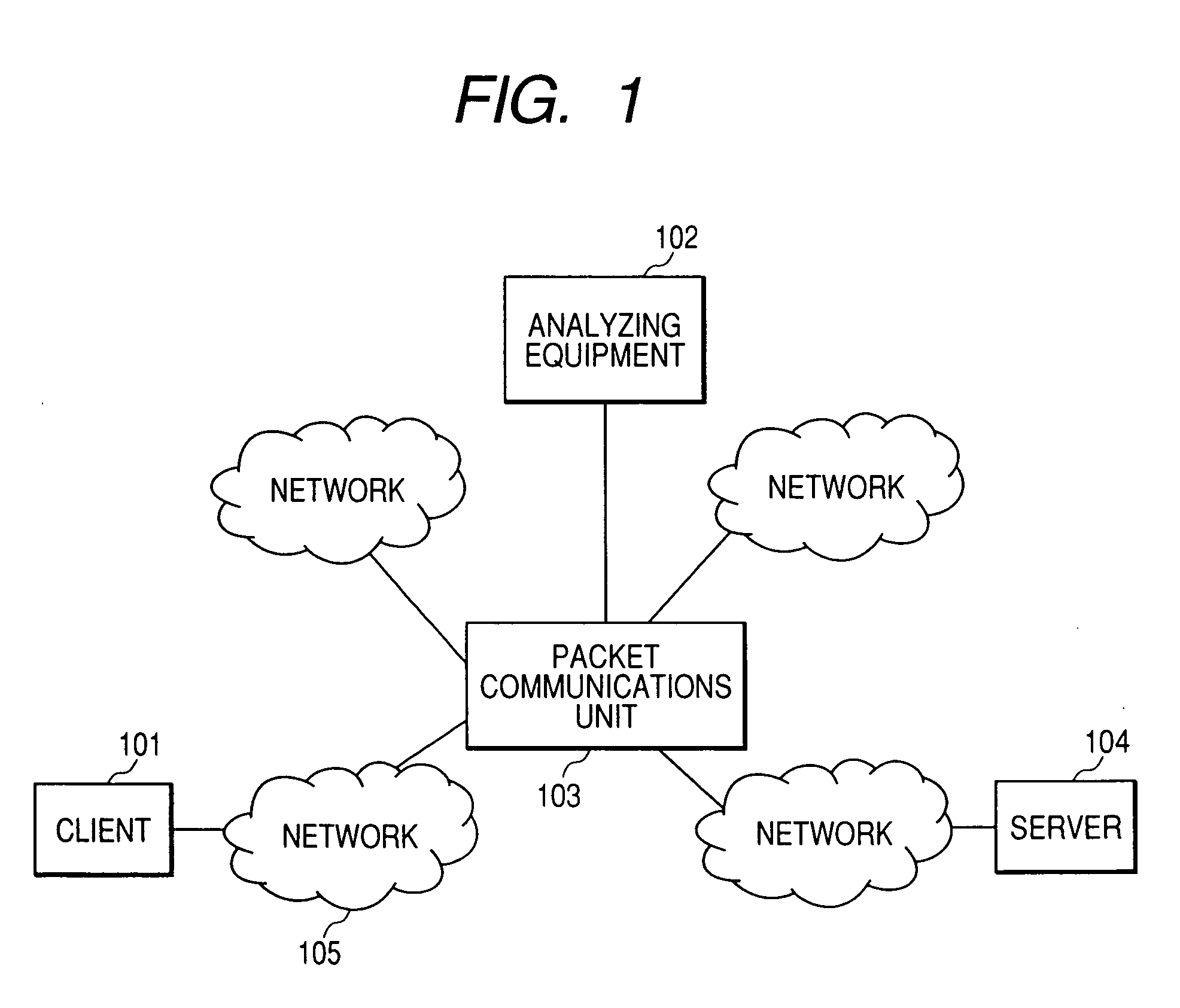
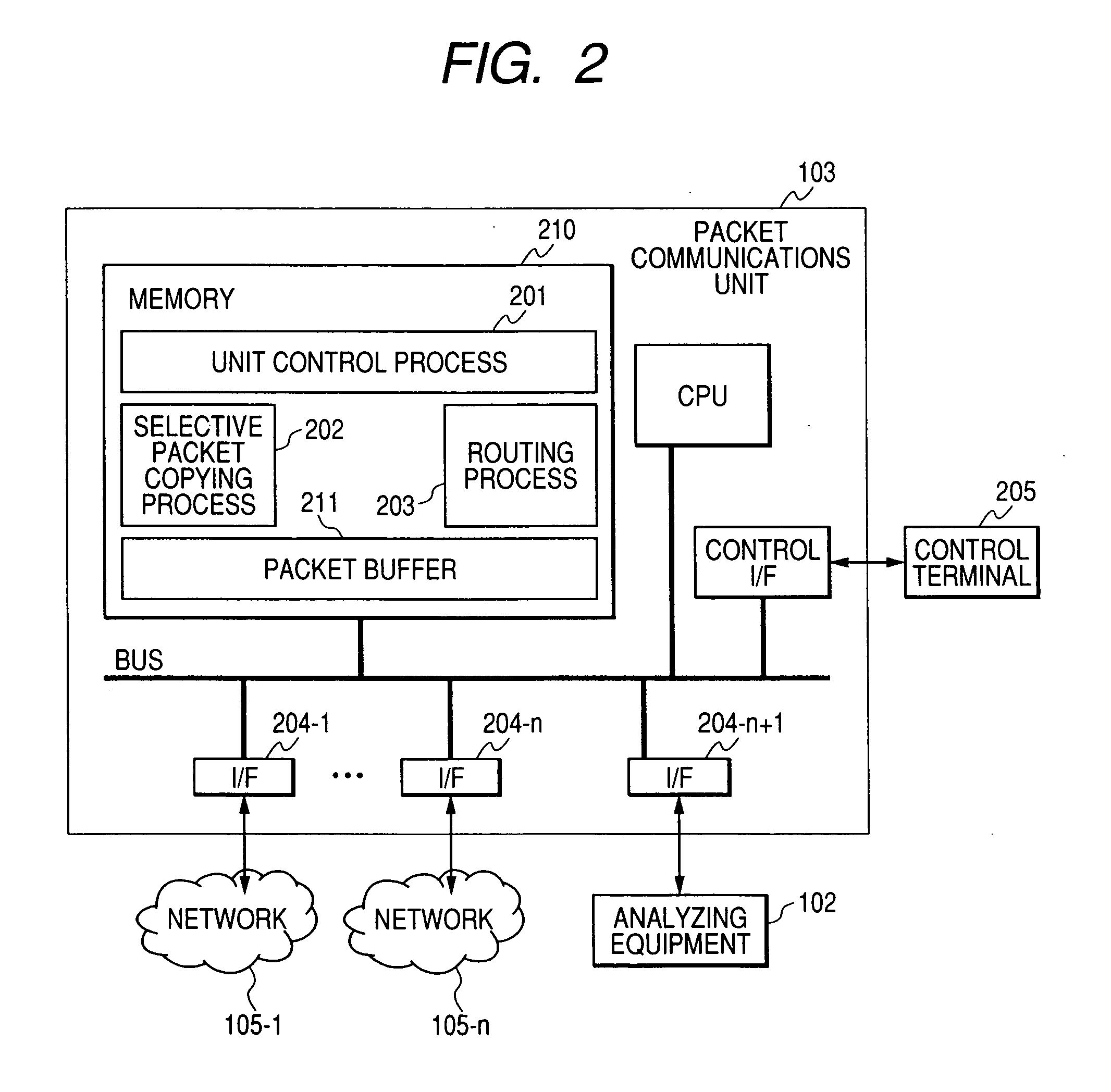
Packet communications unit
InactiveUS20070160073A1Reduce analysisTraffic can be can be increased and reducedError preventionFrequency-division multiplex detailsPacket communicationTraffic capacity
To analyze traffic at an application level, a stream according to TCP or SCTP is required to be reconstructed and to be analyzed. When a packet is transferred to analyzing equipment using a port mirroring function with which a router and a switch are provided, transferred traffic volume increases and exceeds the throughput of the analyzing equipment. As only a part of packets configuring a stream is transferred to the analyzing equipment in transfer to the analyzing equipment using a packet sampling function, analysis at the application level is impossible. To solve the problem, when a packet communication unit recognizes a stream start packet, samples a stream initiated by the packet on a condition and at a rate respectively determined beforehand and generates a condition for copying the packet based upon information of both ends of the stream included in the packet, packets sampled in units of stream can be transferred to the analyzing equipment.
Owner:ALAXALA NETWORKS
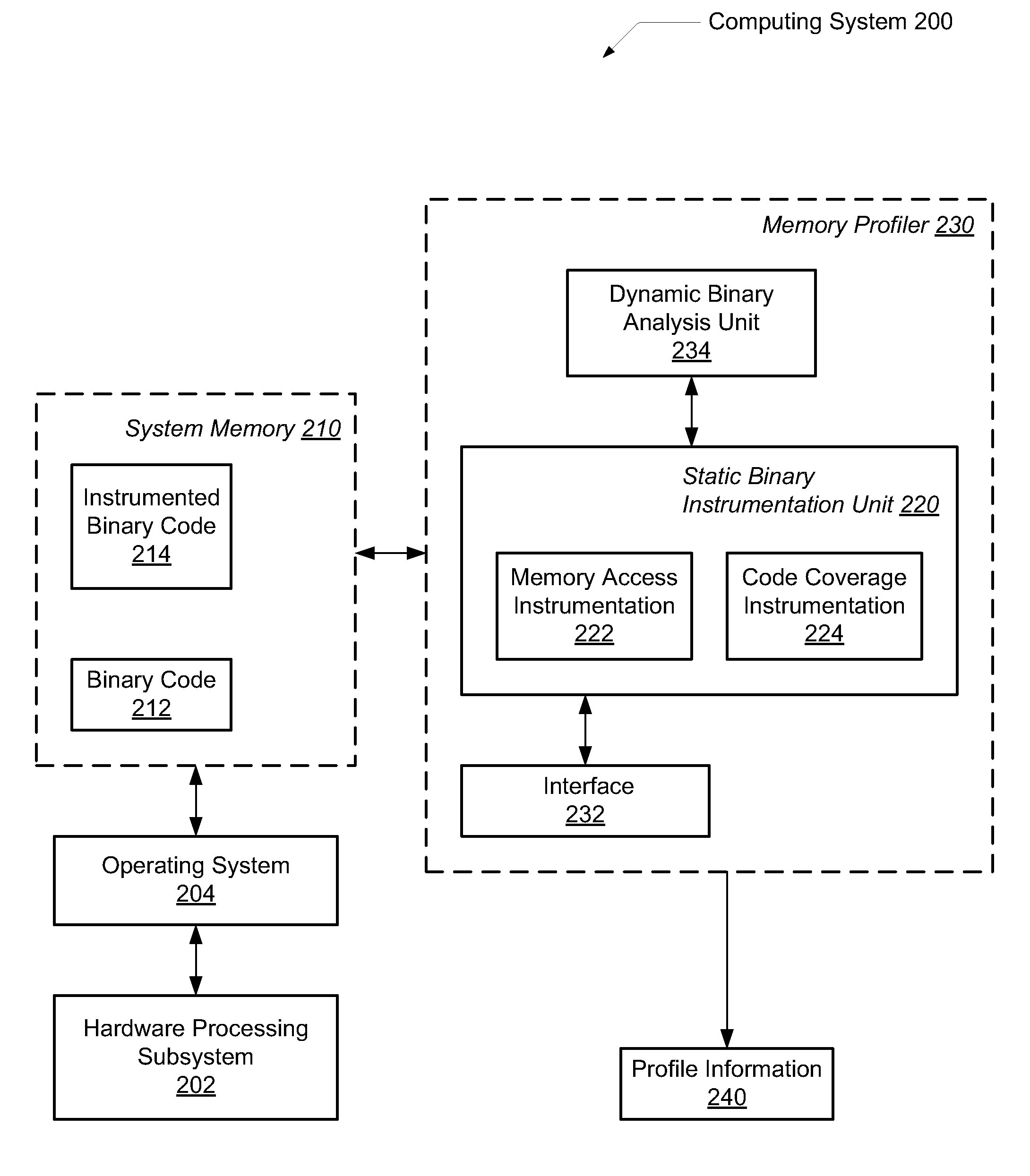
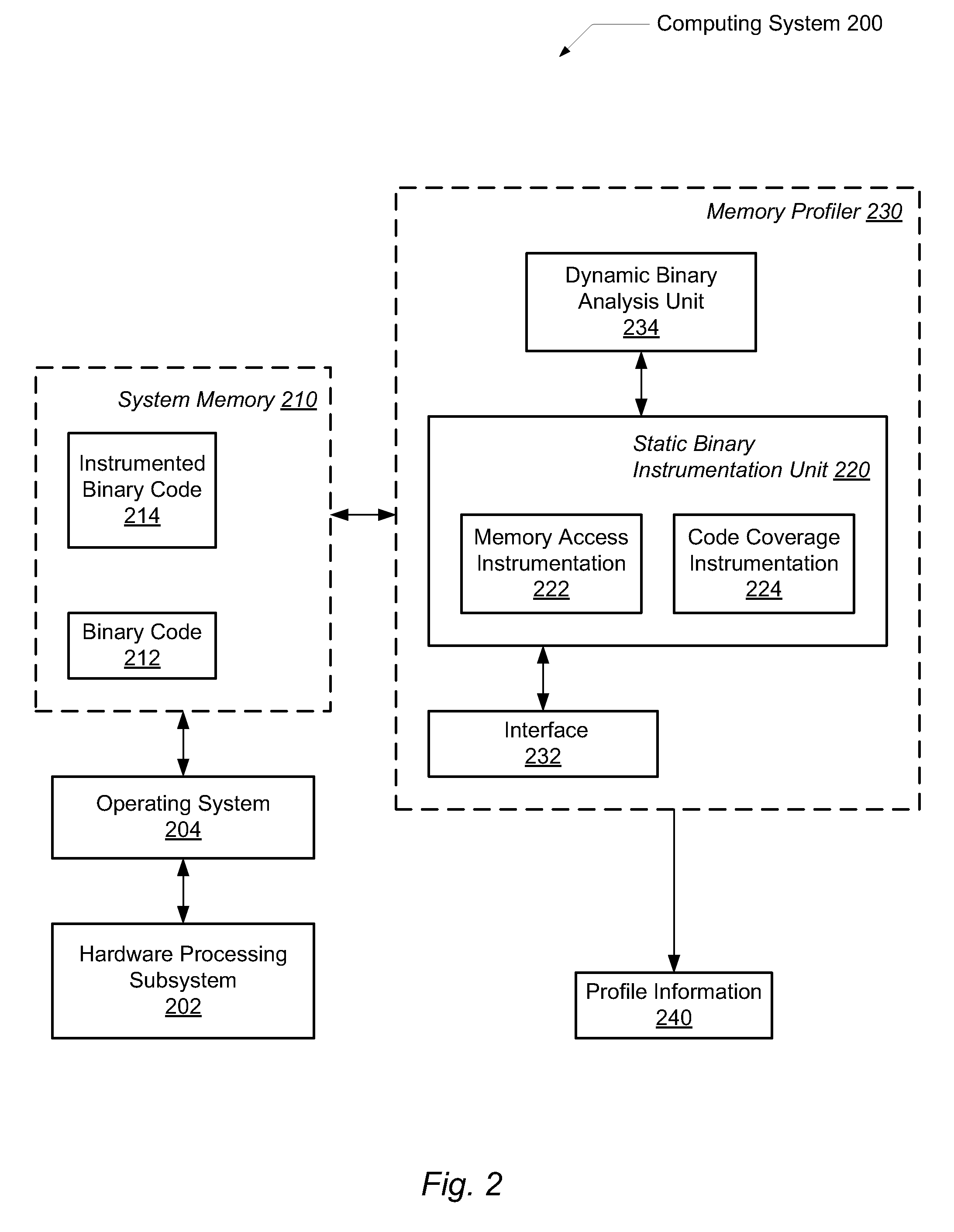
Efficient program instrumentation for memory profiling
ActiveUS20100146220A1Improve system performanceReduce false positiveError detection/correctionSpecific program execution arrangementsMemory profilingLoad instruction
A system and method for performing efficient program instrumentation for memory profiling. A computing system comprises a memory profiler comprising a static binary instrumentation (SBI) tool and a dynamic binary analysis (DBA) tool. The profiler is configured to selectively instrument memory access operations of a software application. Instrumentation may be bypassed completely for an instruction if the instruction satisfies some predetermined conditions. Some sample conditions include the instruction accesses an address within a predetermined read-only area, the instruction accesses an address within a user-specified address range, and / or the instruction is a load instruction accessing a memory location determined from a data flow graph to store an initialized value. An instrumented memory access instruction may have memory checking analysis performed only upon an initial execution of the instruction in response to determining during initial execution that a read data value of the instruction is initialized. Both unnecessary instrumentation and memory checking analysis may be reduced.
Owner:ORACLE INT CORP
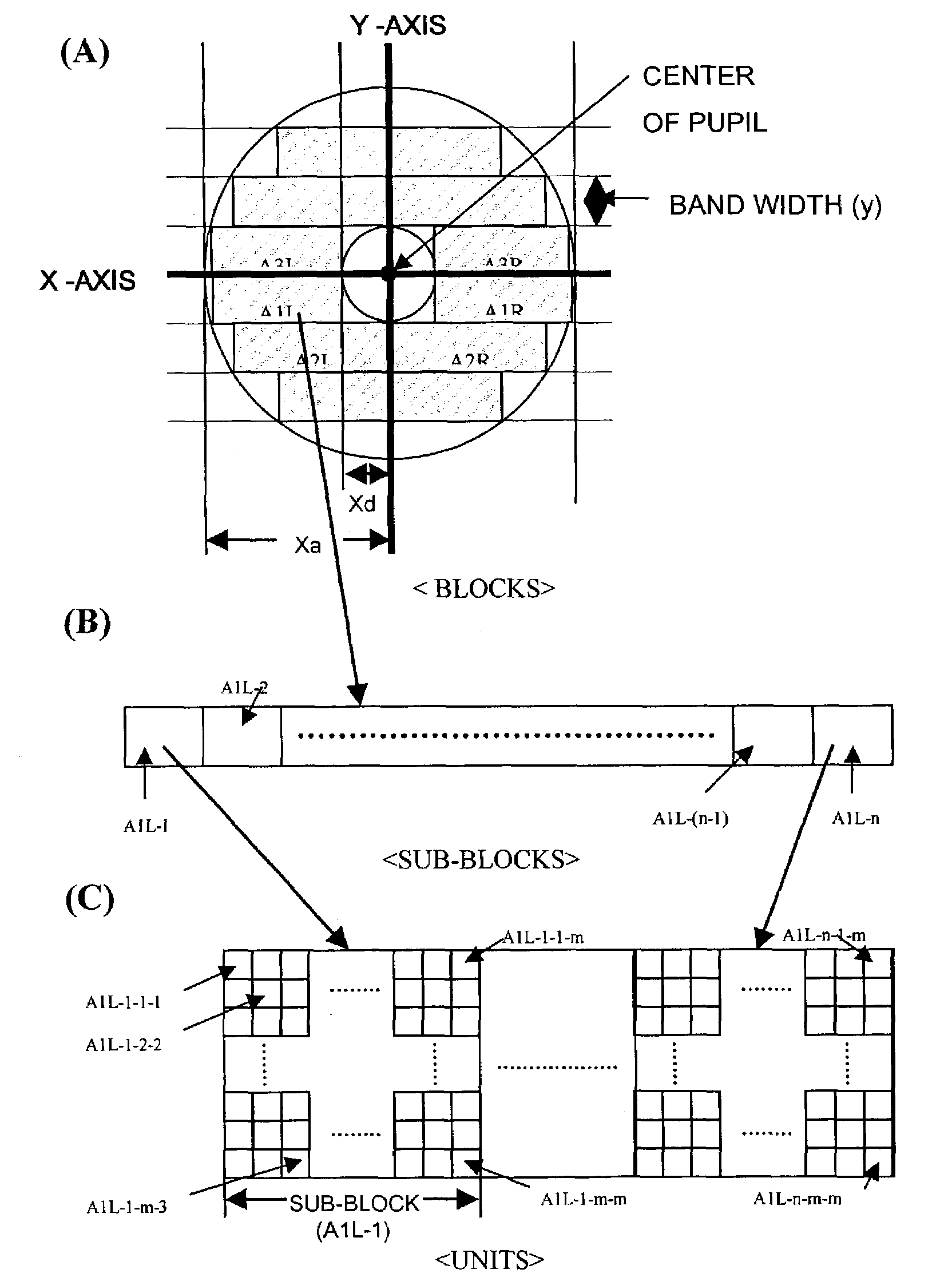
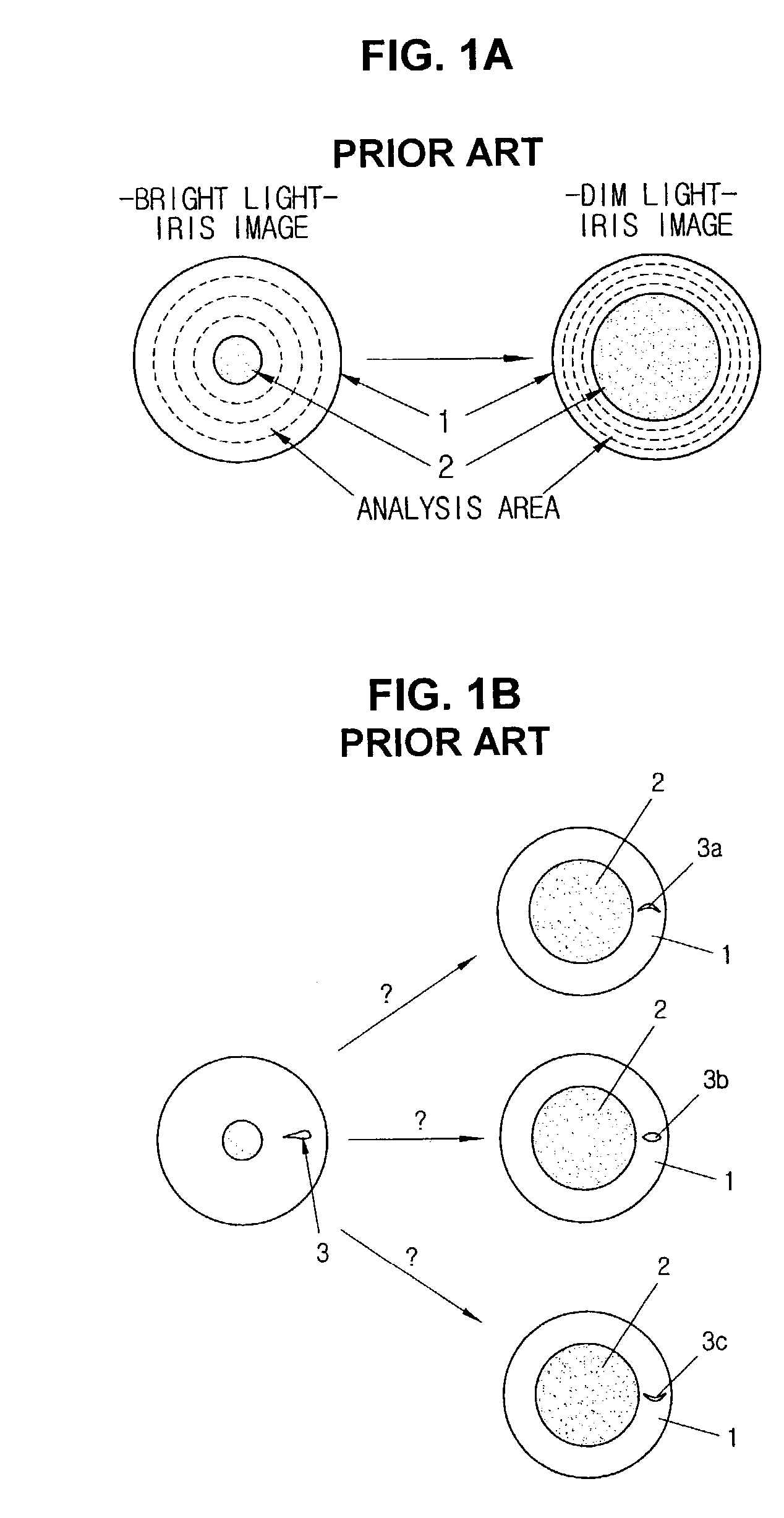
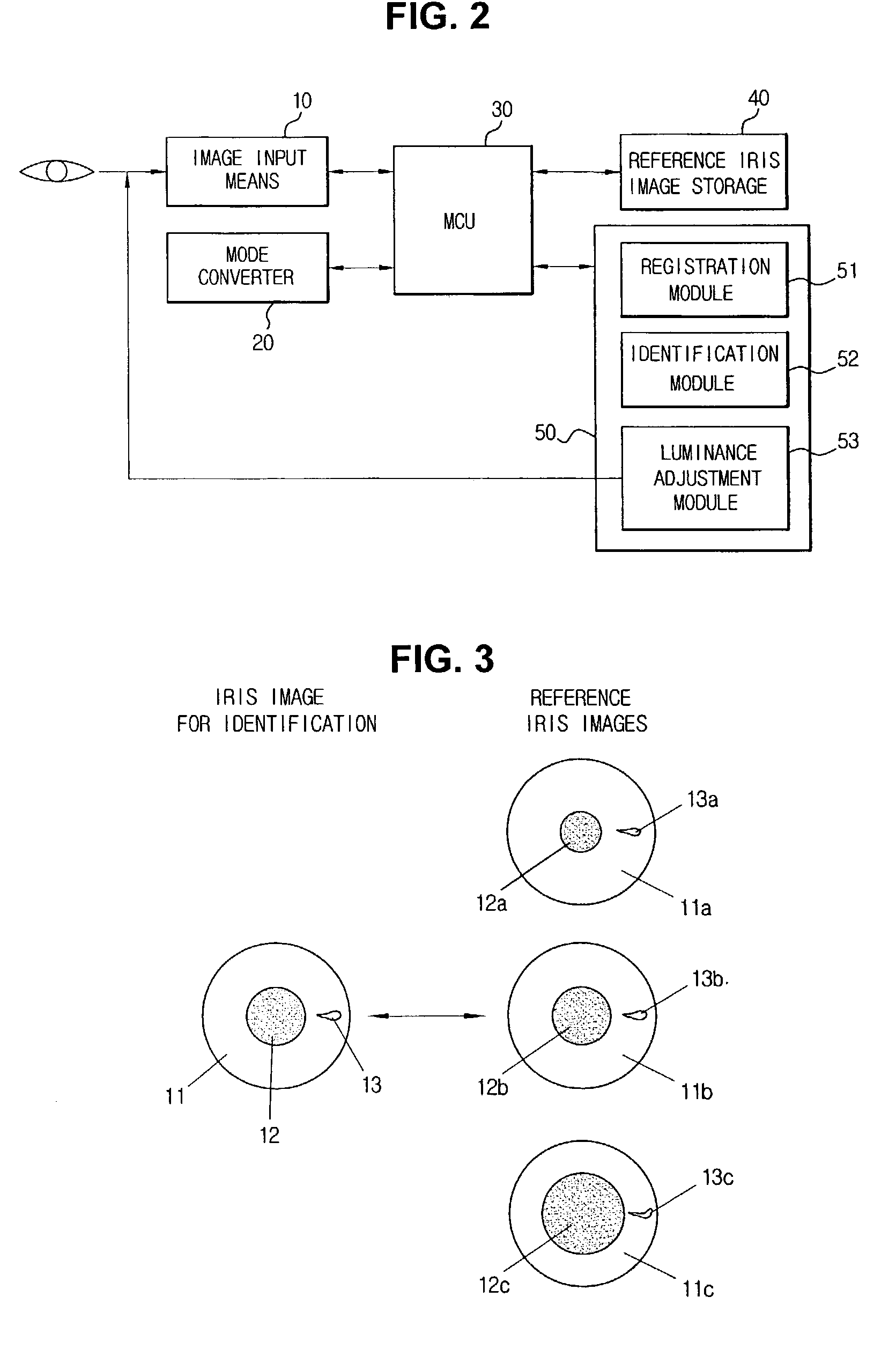
Iris identification
ActiveUS7277561B2Reduce false positive rateReducing analysis error rateCharacter and pattern recognitionPattern recognitionIris image
An iris identification system for confirming identity of a person and method thereof are disclosed. The iris identification system comprises a mode converter for selecting one of registration and identification modes, an image input means, a luminance adjustment module, a registration module, an identification module, a reference iris image storage, and a main control unit. The registration module captures iris images when the registration mode is selected, preprocesses the captured iris image, defines the preprocessed iris image as main, auxiliary, negative main and compensation data, encodes the defined data, and registers the encoded data as data of the reference iris images; The identification module captures an iris image when the identification mode is selected, preprocesses the captured iris image, defines the preprocessed iris image as main, auxiliary, negative main and compensation data, encodes the defined data, and analyzes similarity both data.
Owner:KIM SUNG HYUN +1
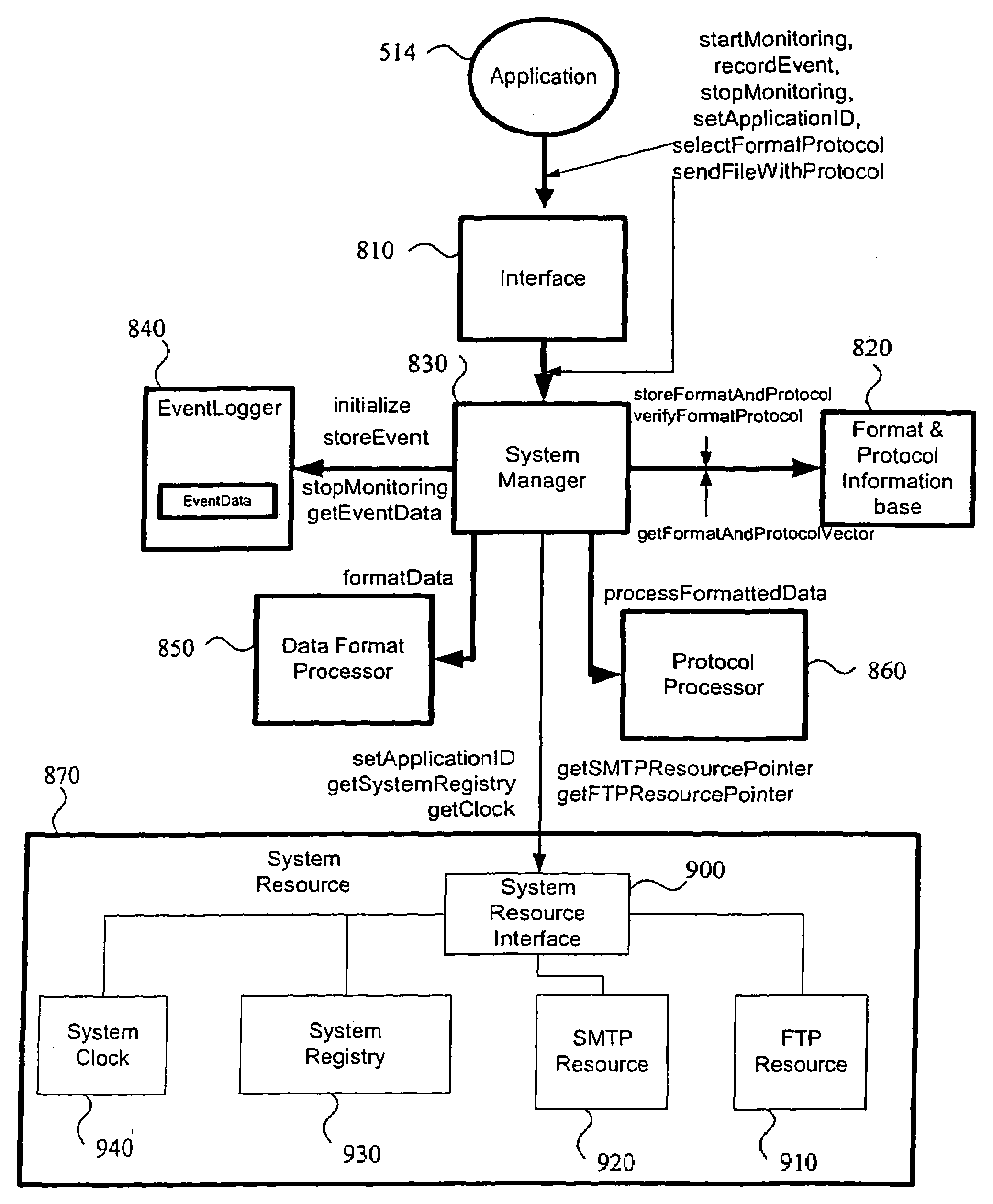
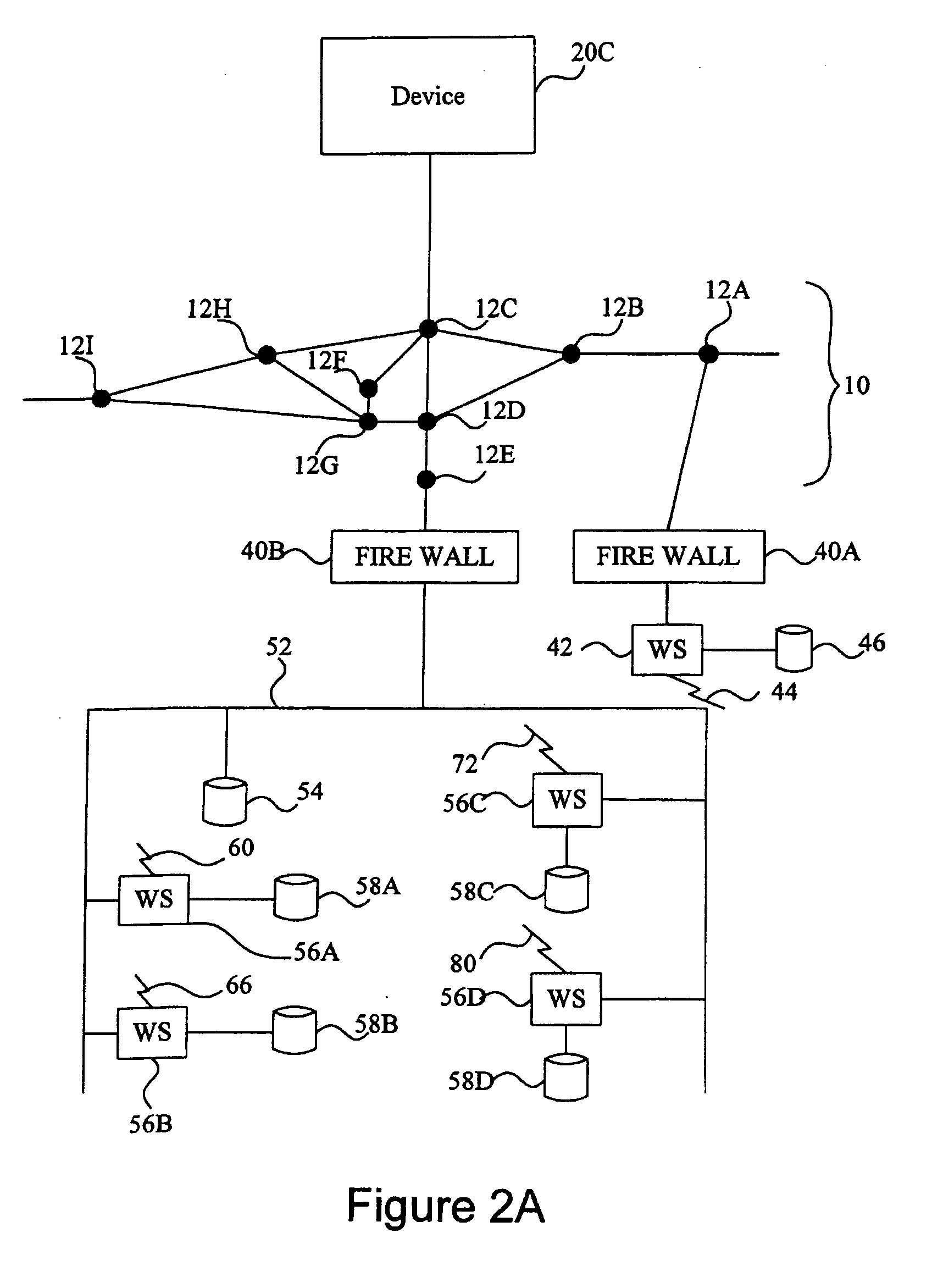
Method and system of remote diagnostic, control and information collection using a dynamic linked library of multiple formats and multiple protocols with restriction on protocol
InactiveUS6988141B1Facilitate configuration and received data analysisReduce analysisMultiple digital computer combinationsTransmissionApplication softwareRemote diagnostics
A method, system and computer program product for (1) collecting information from a remote application unit and / or (2) diagnosing or controlling the remote application unit. By utilizing a shareable computer code device (e.g., a dynamic linked library), a new application can utilize tested, proven code without having to reproduce existing functionality. Moreover, by supporting multiple data formats and / or multiple communication protocols, a computer code device increases the likelihood that a supported format and / or protocol will be either receivable or understandable by a receiver.
Owner:RICOH KK
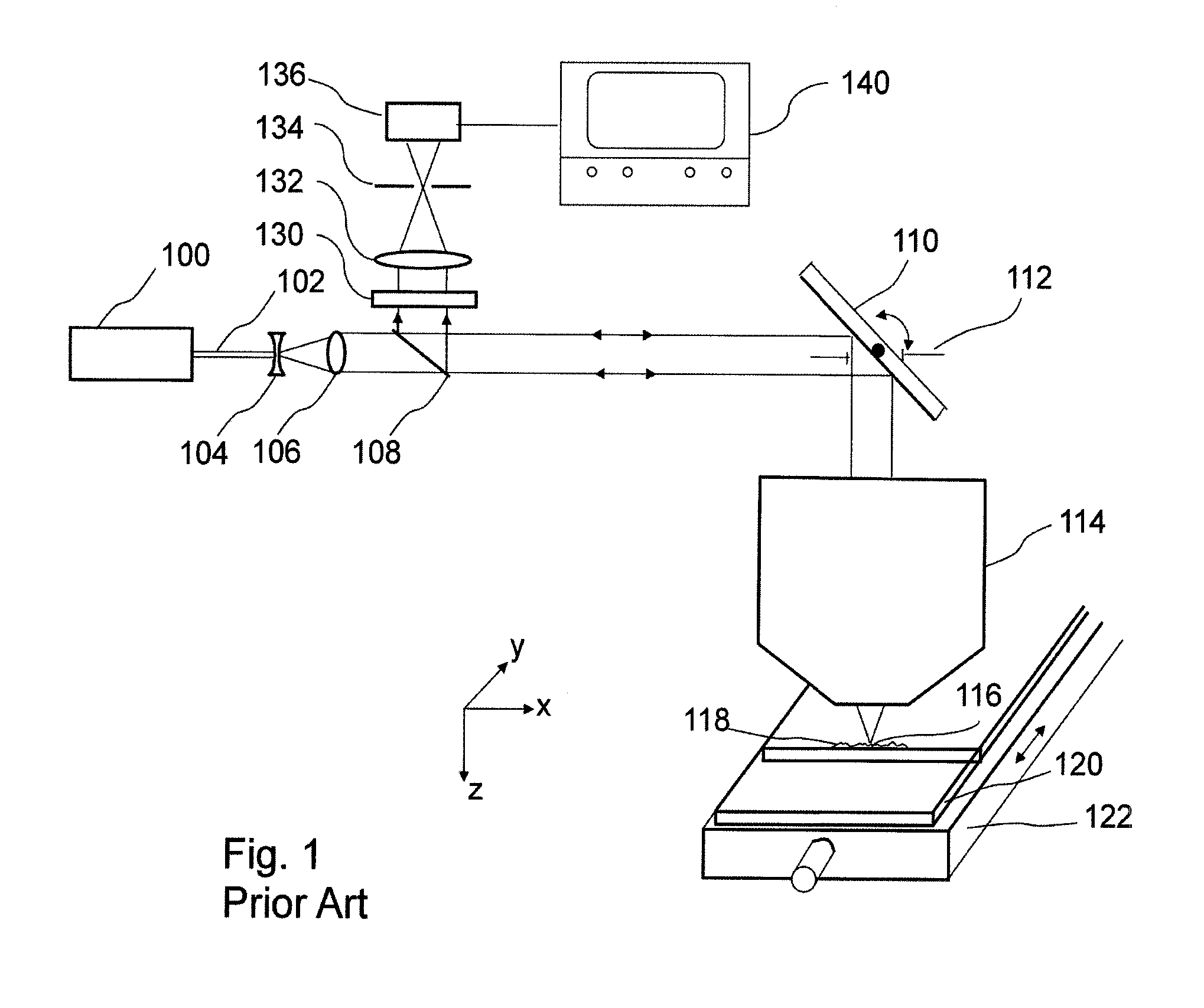
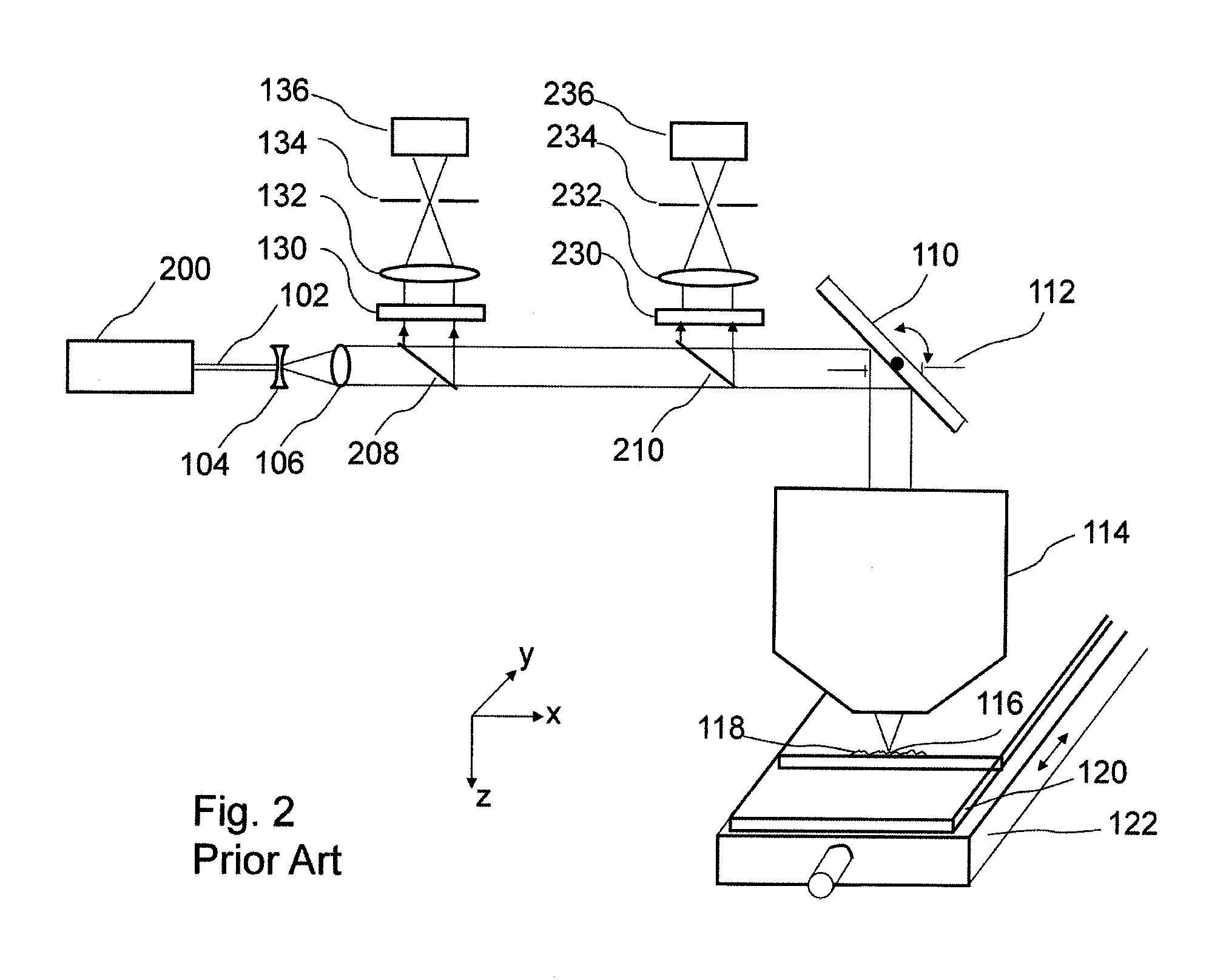
Laser-based maintenance apparatus
ActiveUS20070157730A1Shorten the timeEfficient and effectiveAnalysing solids using sonic/ultrasonic/infrasonic wavesNuclear energy generationOptoelectronicsLaser light
A laser maintenance apparatus is provided with a laser system including a laser light source and an optical system and emitting a laser light, a light transmitting device for generating the laser light emitted from the laser system, and a laser irradiation device for irradiating the laser light generated by the light transmitting device to an object portion. The laser system includes an element for changing an irradiation condition of the laser light.
Owner:KK TOSHIBA
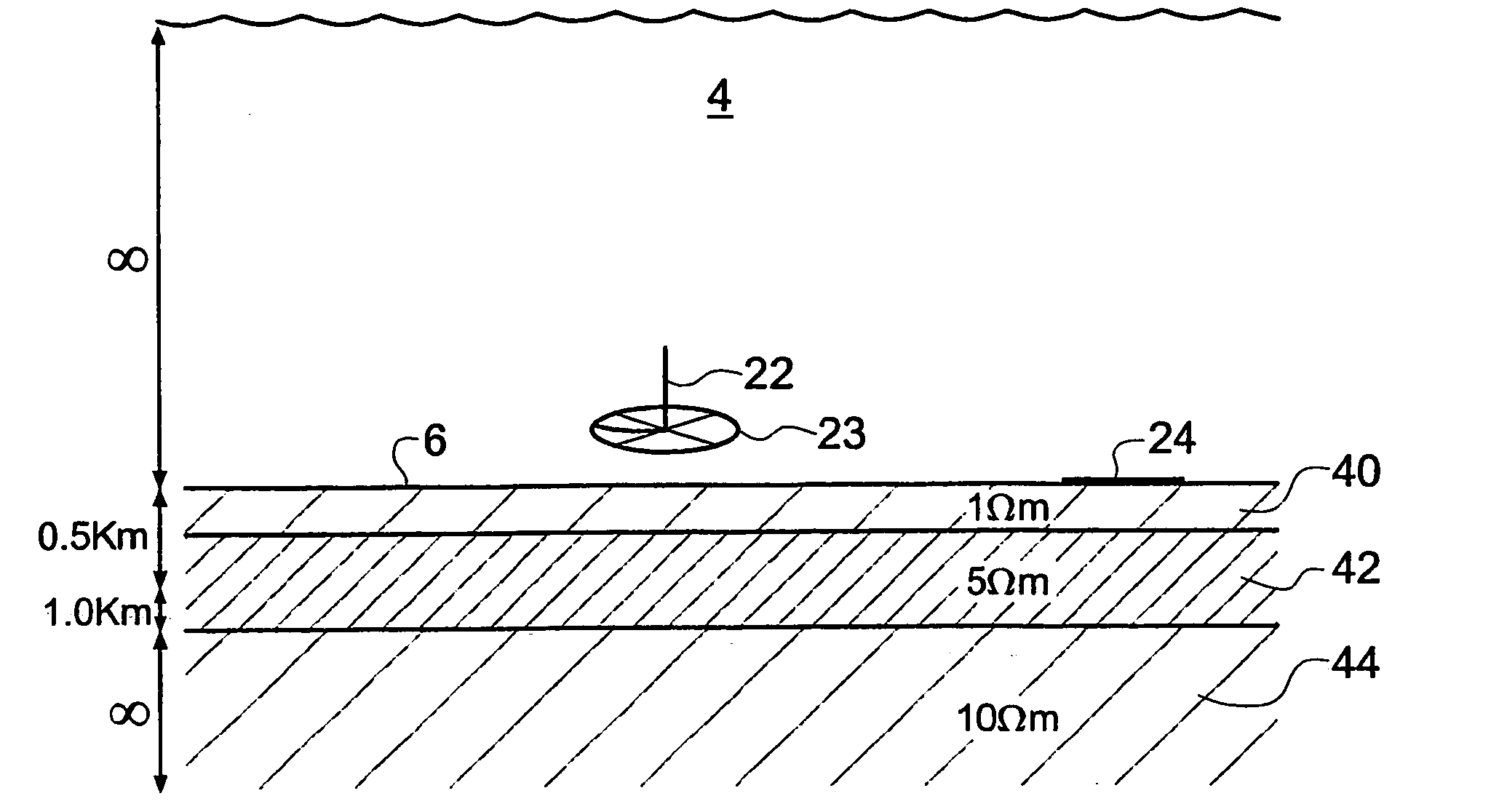
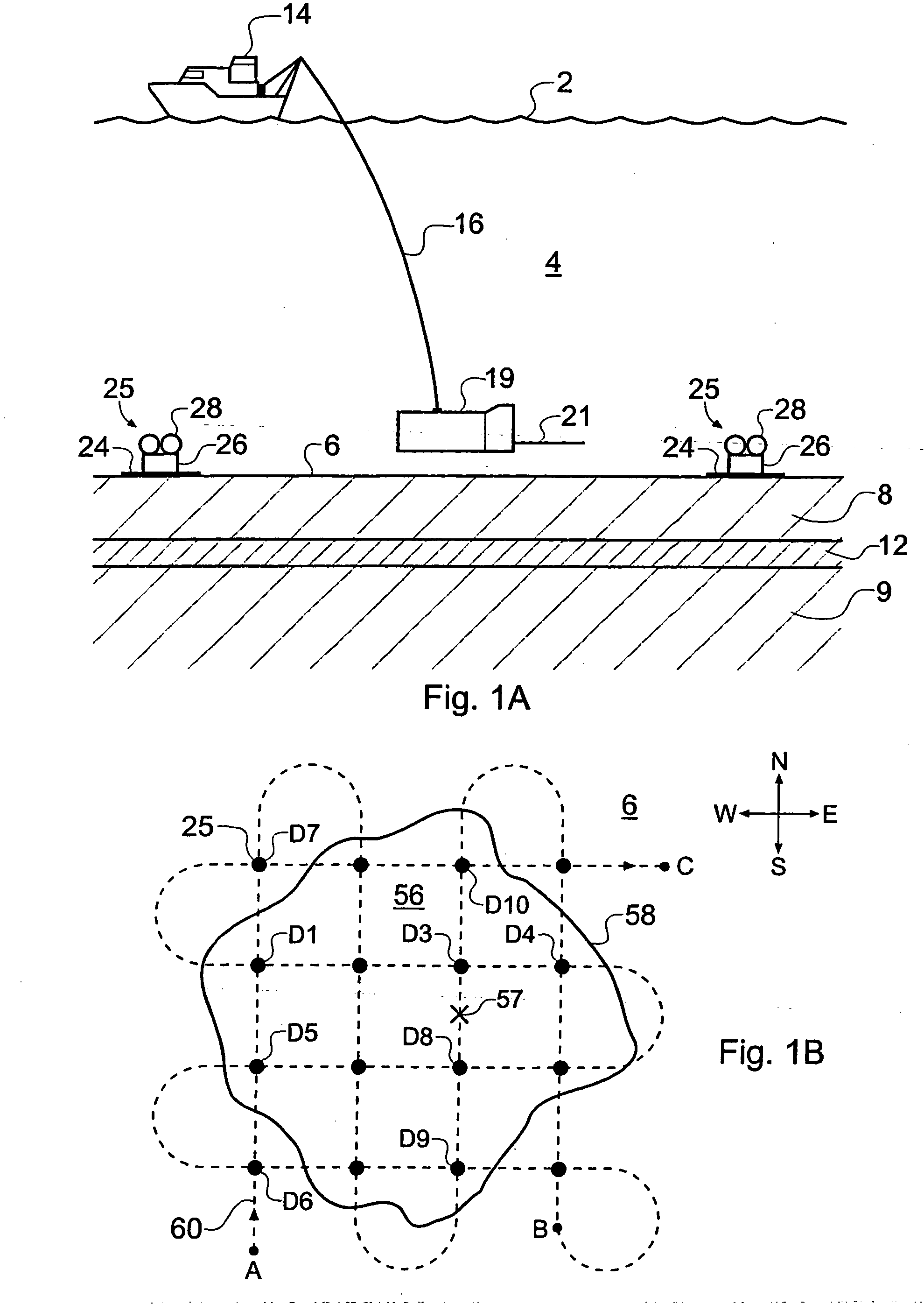
Electromagnetic surveying for resistive or conductive bodies
ActiveUS20060186889A1Reduce analysisWater resource assessmentDetection using electromagnetic wavesElectrical resistance and conductanceElectricity
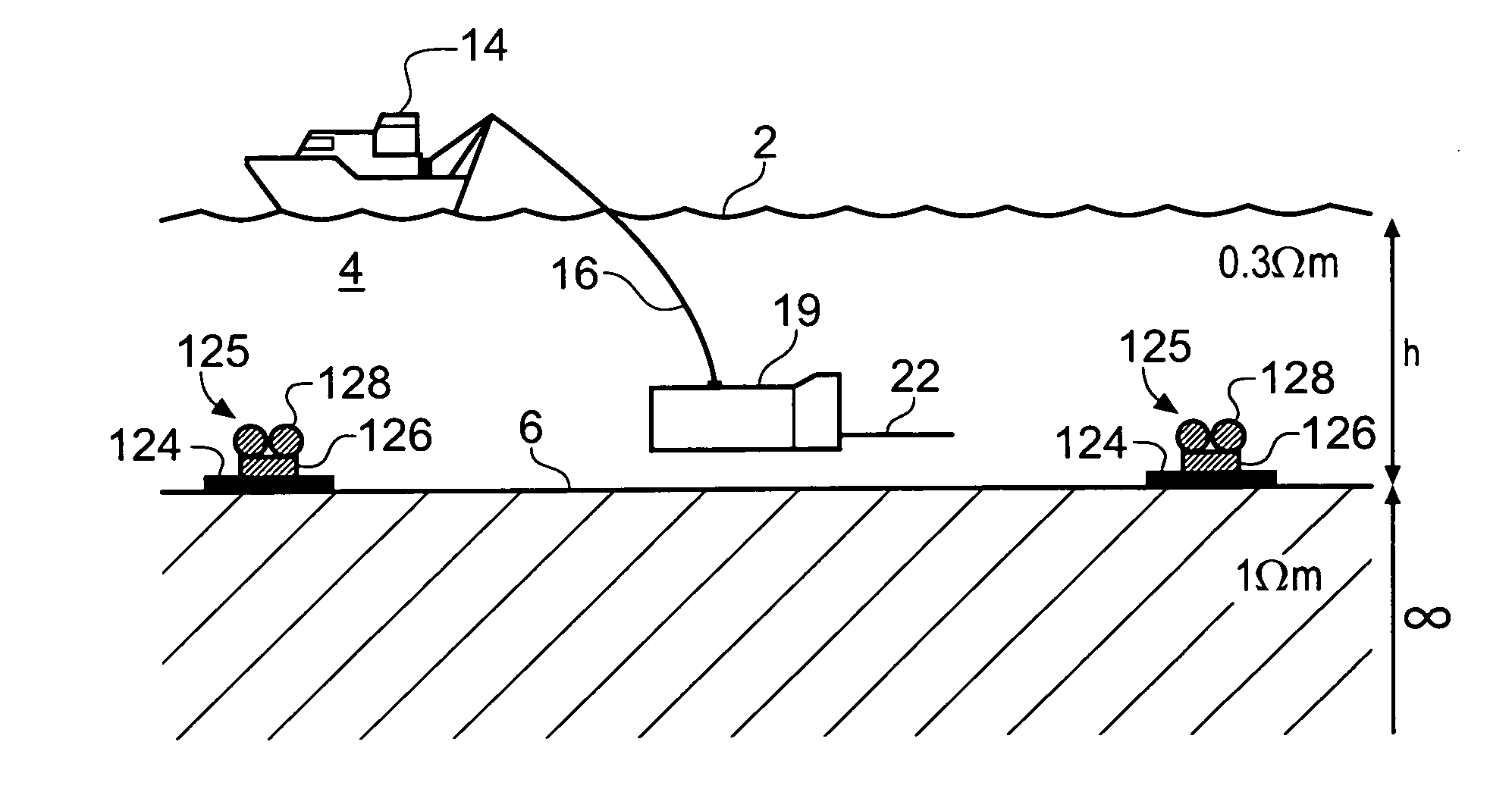
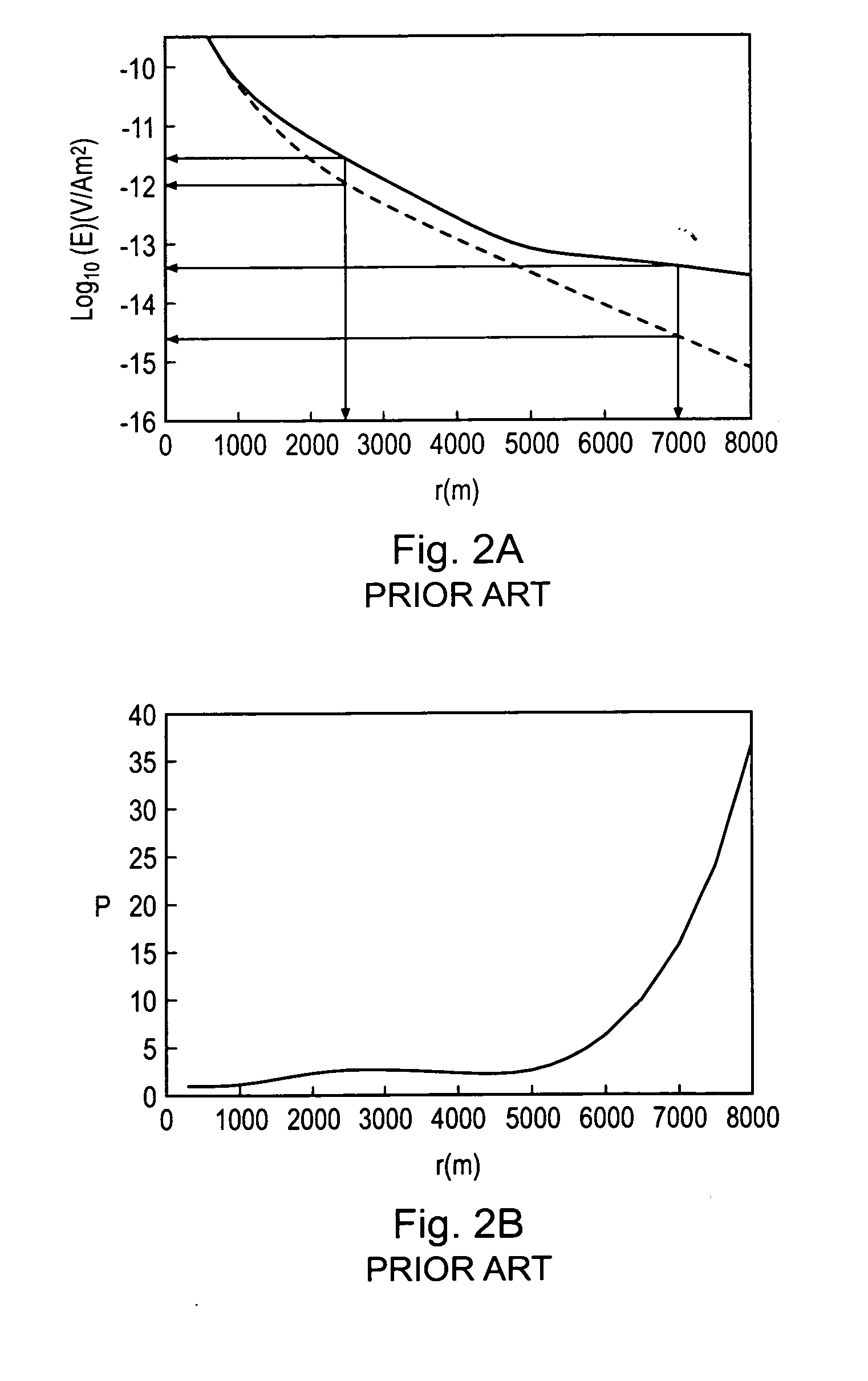
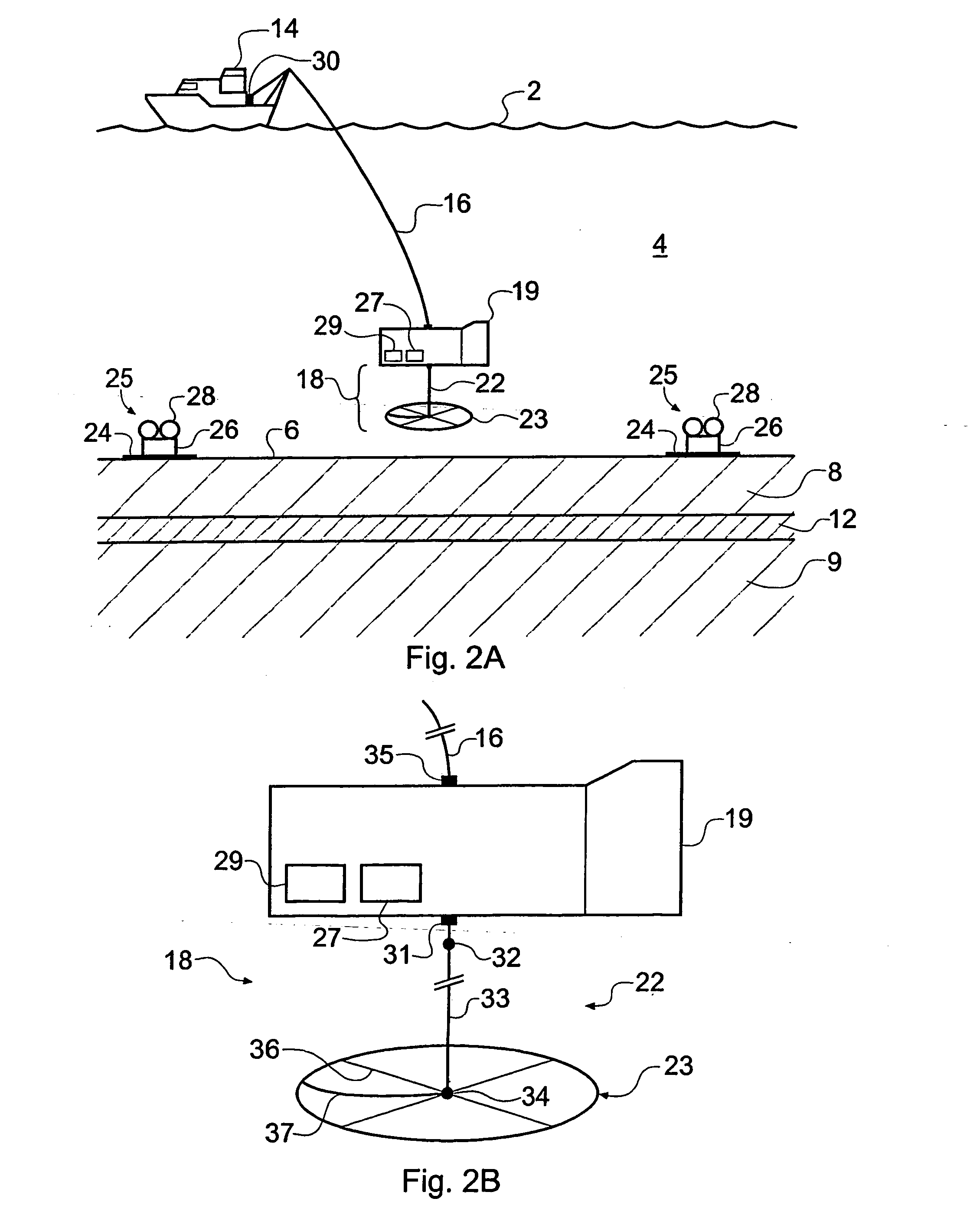
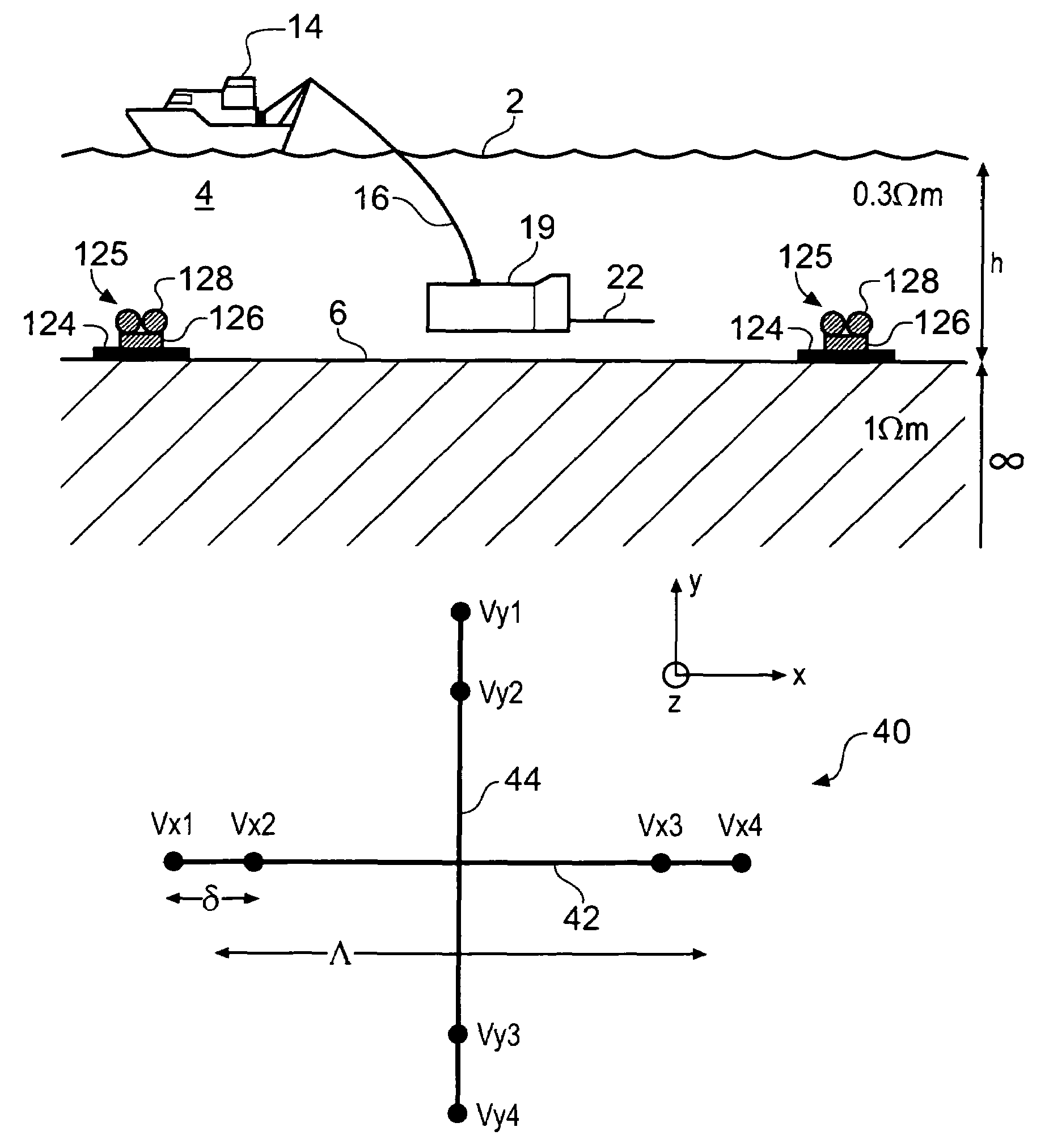
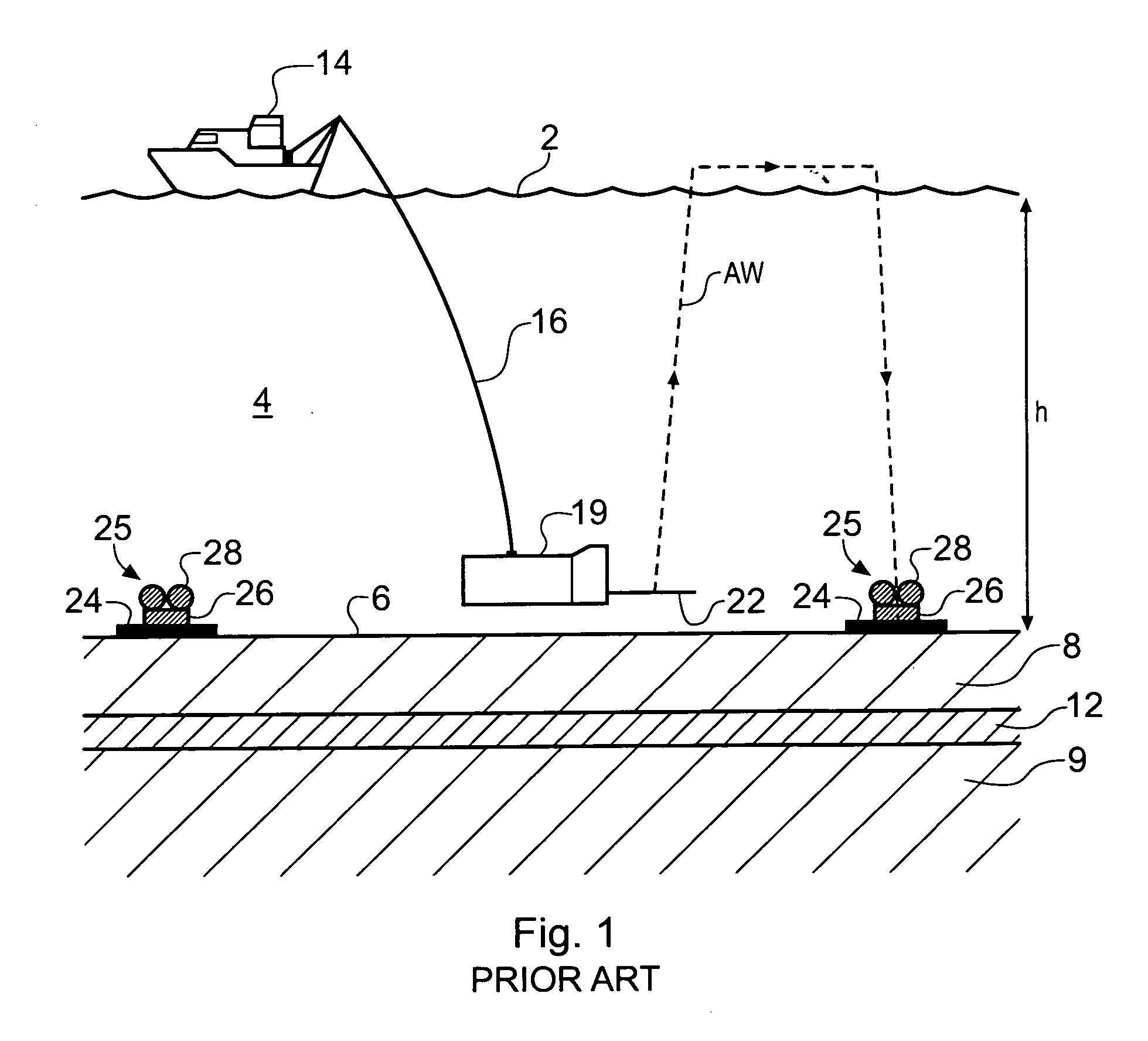
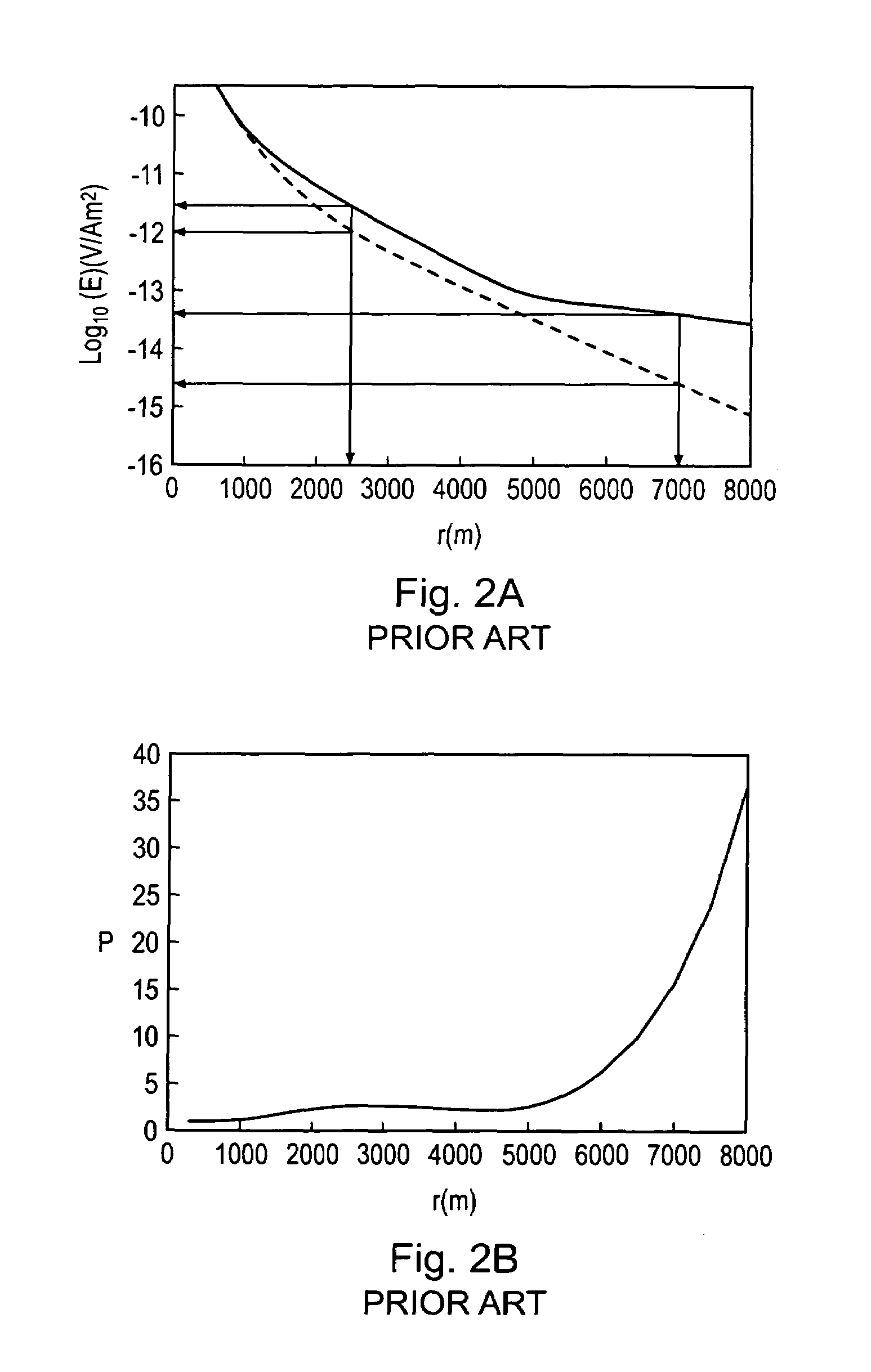
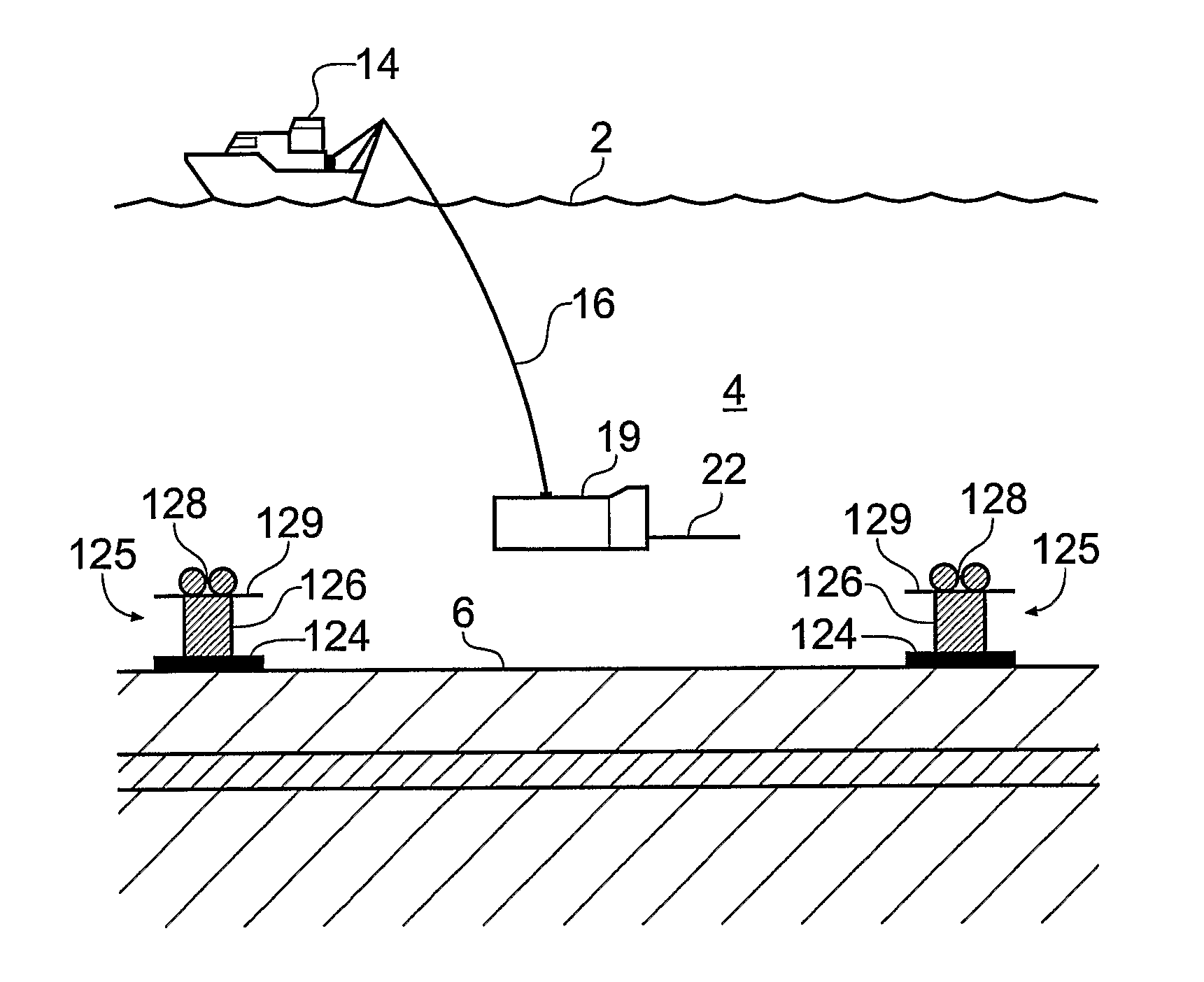
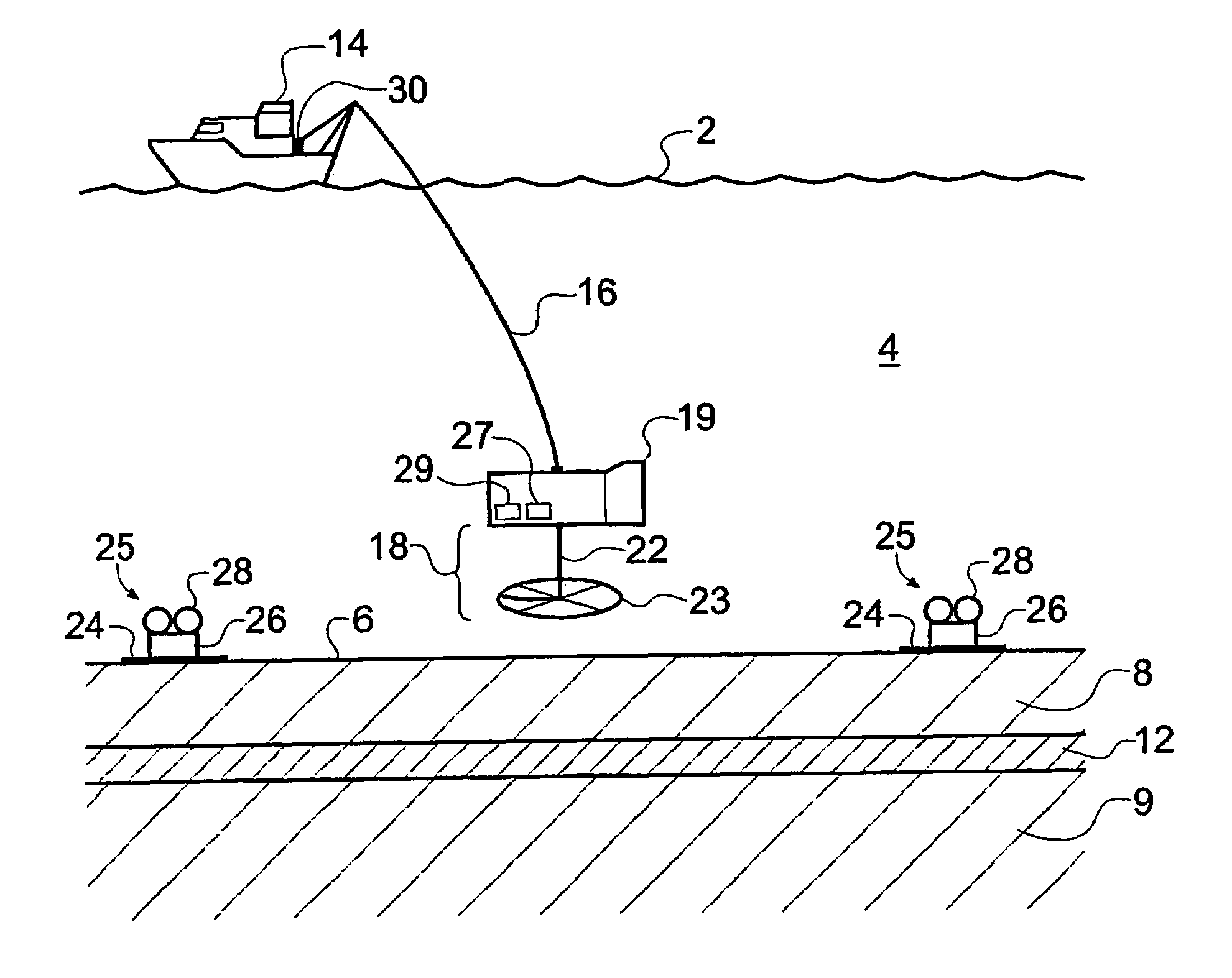
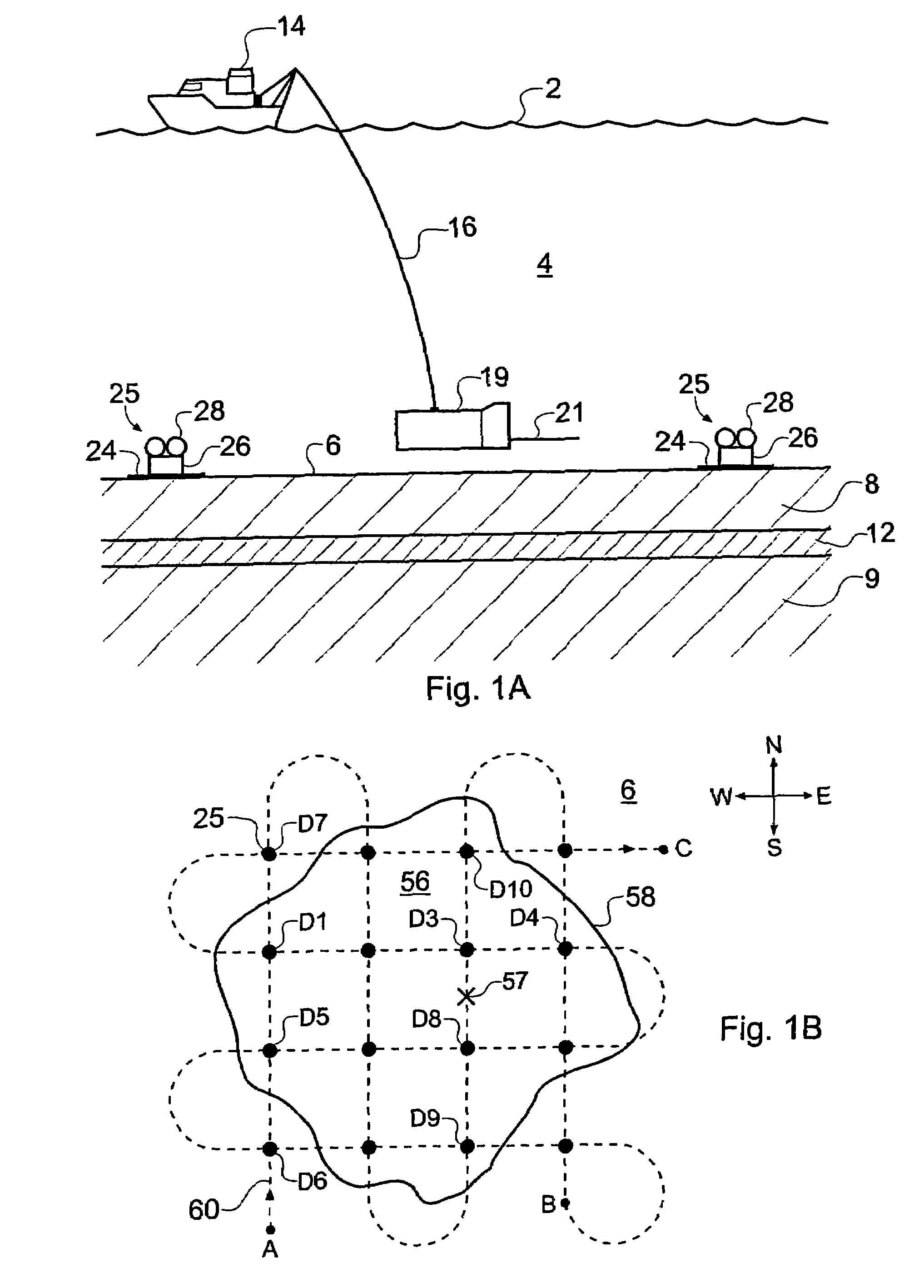
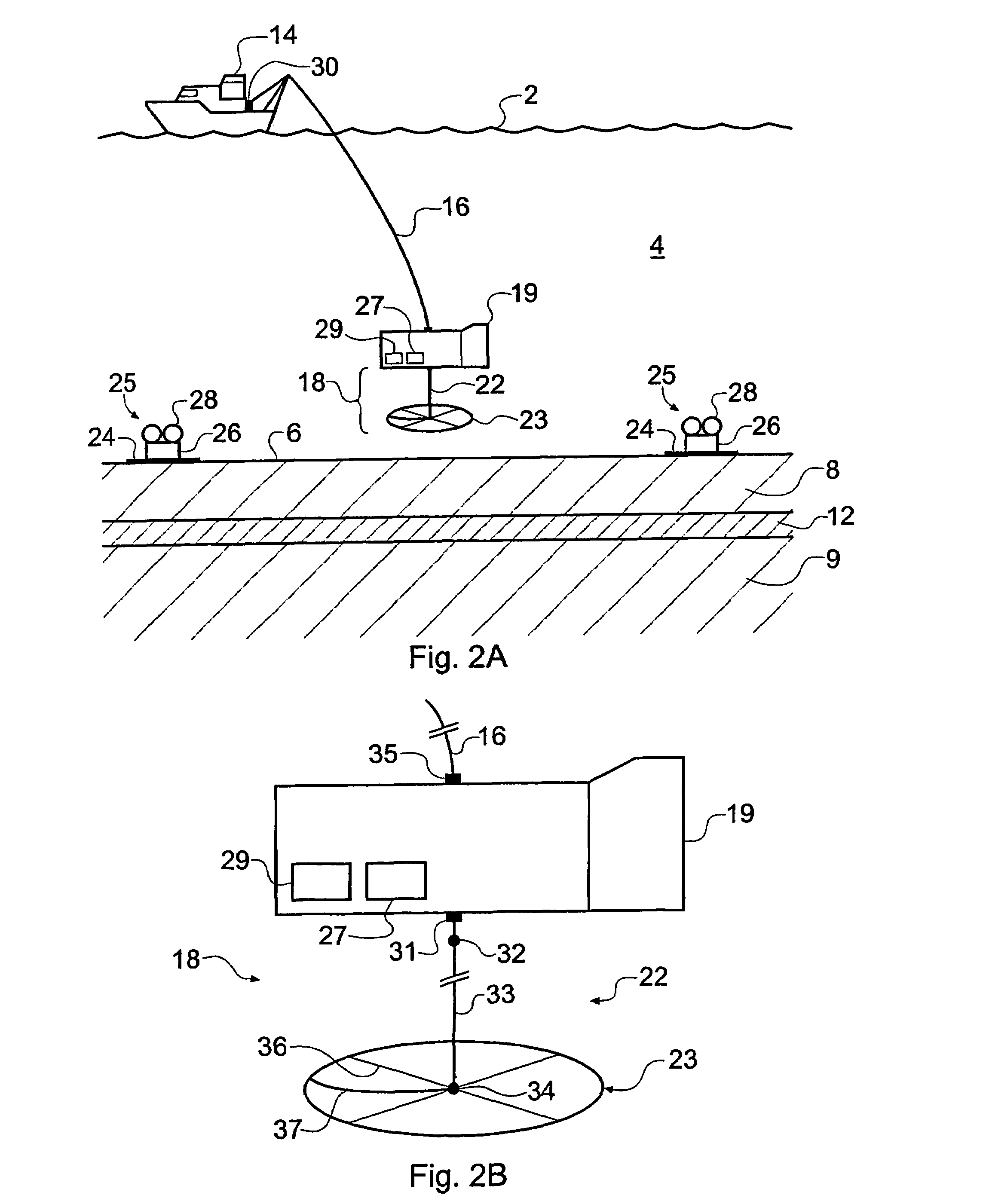
A method of analyzing electromagnetic survey data from an area of seafloor 6 that is thought or known to contain a resistive or conductive body, for example a subterranean hydrocarbon reservoir 12, is described. The method includes providing horizontal electromagnetic field data obtained by at least one receiver 125 from at least one horizontal electric dipole transmitter 22. Horizontal gradients in the electromagnetic field data are determined for a first component of the electromagnetic field data along a first direction and for a second component of the electromagnetic field data along a second direction. The first and second components can be the electric field along the first and second directions, or the magnetic field perpendicular to the first direction and second directions. The gradients are then combined to provide combined response data. Because the combined response data are relatively insensitive to the transverse electric (TE) mode component of the transmitted signal, the method allows hydrocarbon reservoirs to be detected in shallow water where the TE mode component interacting with the air would otherwise dominate.
Owner:PGS GEOPHYSICAL AS
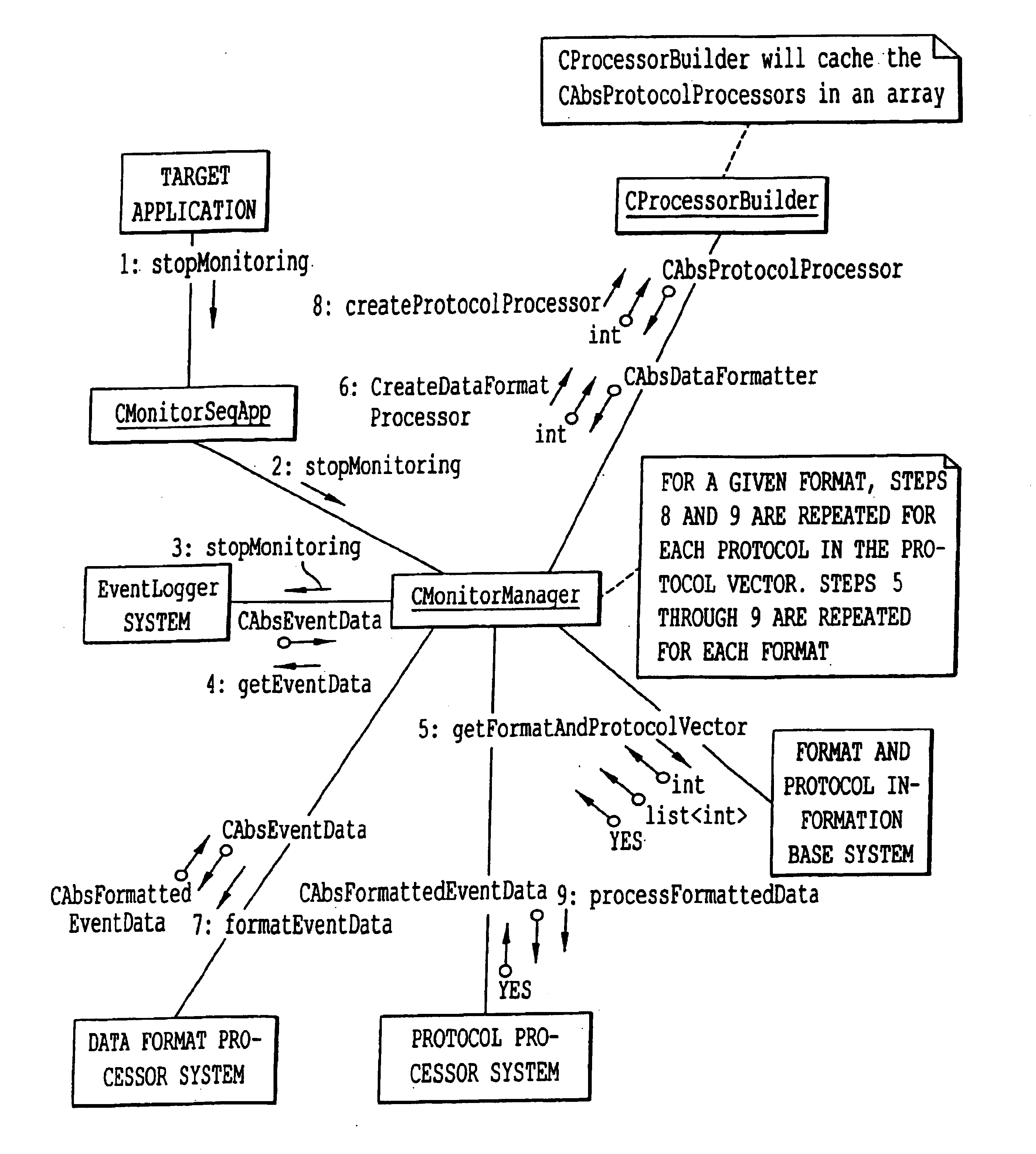
Method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols with delegating protocol processor
InactiveUS7047293B2Easy to analyzeEasy to configureInput/output to record carriersError detection/correctionProtocol processingNetwork Communication Protocols
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. The event information for a particular target application is formatted and transmitted according to a combination of a data format and communication protocol requested by the target application. The transmission of data representing the event information is handled in at least two levels of software classes, with at least one abstract software class having a declared virtual function and two or more software classes derived from the at least one abstract class and having definitions of the function for communicating the event information through specified communication protocols. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
Malicious software detection in a computing system
ActiveUS20170134397A1Function increaseReduce impactDigital data information retrievalComputer security arrangementsComputerized systemMalware
A computer system identifies malicious Uniform Resource Locator (URL) data items from a plurality of unscreened data items that have not been previously identified as associated with malicious URLs. The system can execute a number of pre-filters to identify a subset of URLs in the plurality of data items that are likely to be malicious. A scoring processor can score the subset of URLs based on a plurality of input vectors using a suitable machine learning model. Optionally, the system can execute one or more post-filters on the score data to identify data items of interest. Such data items can be fed back into the system to improve machine learning or can be used to provide a notification that a particular resource within a local network is infected with malicious software.
Owner:PALANTIR TECHNOLOGIES
Electromagnetic surveying for hydrocarbon reservoirs
InactiveUS20060129322A1Reduce analysisEasy to separateElectric/magnetic detection for well-loggingPermeability/surface area analysisOcean bottomData set
An electromagnetic survey method for surveying an area of seafloor that is thought or known to contain a subterranean hydrocarbon reservoir, comprising obtaining a first survey data set with a vertical electric dipole (VED) antenna for generating vertical current loops and a second survey data set with a vertical magnetic dipole (VMD) antenna for generating horizontal current loops. In an alternative embodiment, the VMD antenna is dispensed with and the horizontal electromagnetic field is derived from the naturally occurring magnetotelluric (MT) electromagnetic field. In another alternative embodiment, the VED data is compared with a background geological model instead of VMD or MT data. The invention also relates to a survey apparatus comprising VED and VMD antennae, to planning a survey using this method, and to analysis of survey data taken using this survey method. The first and second survey data sets allow the galvanic contribution to the detector signals collected at a detector to he independently contrasted with the inductive effects. This is important to the success of using electromagnetic surveying for identifying hydrocarbon reserves and distinguishing them from other classes or structure.
Owner:OHM
Method and software system for modularizing software components for business transaction applications
InactiveUS7007266B1Reduces design analysisReduce effortSoftware designOffice automationData setApplication server
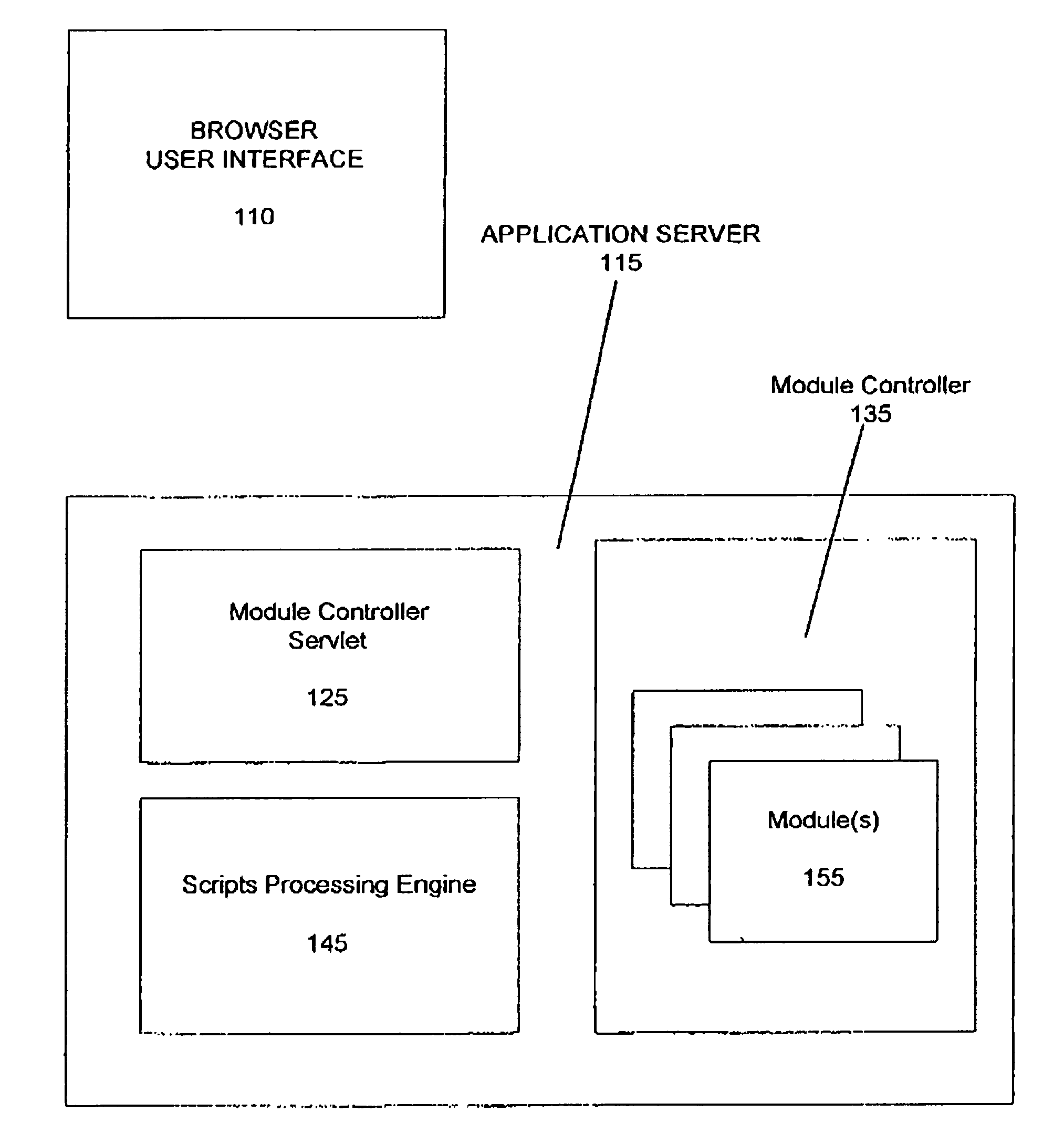
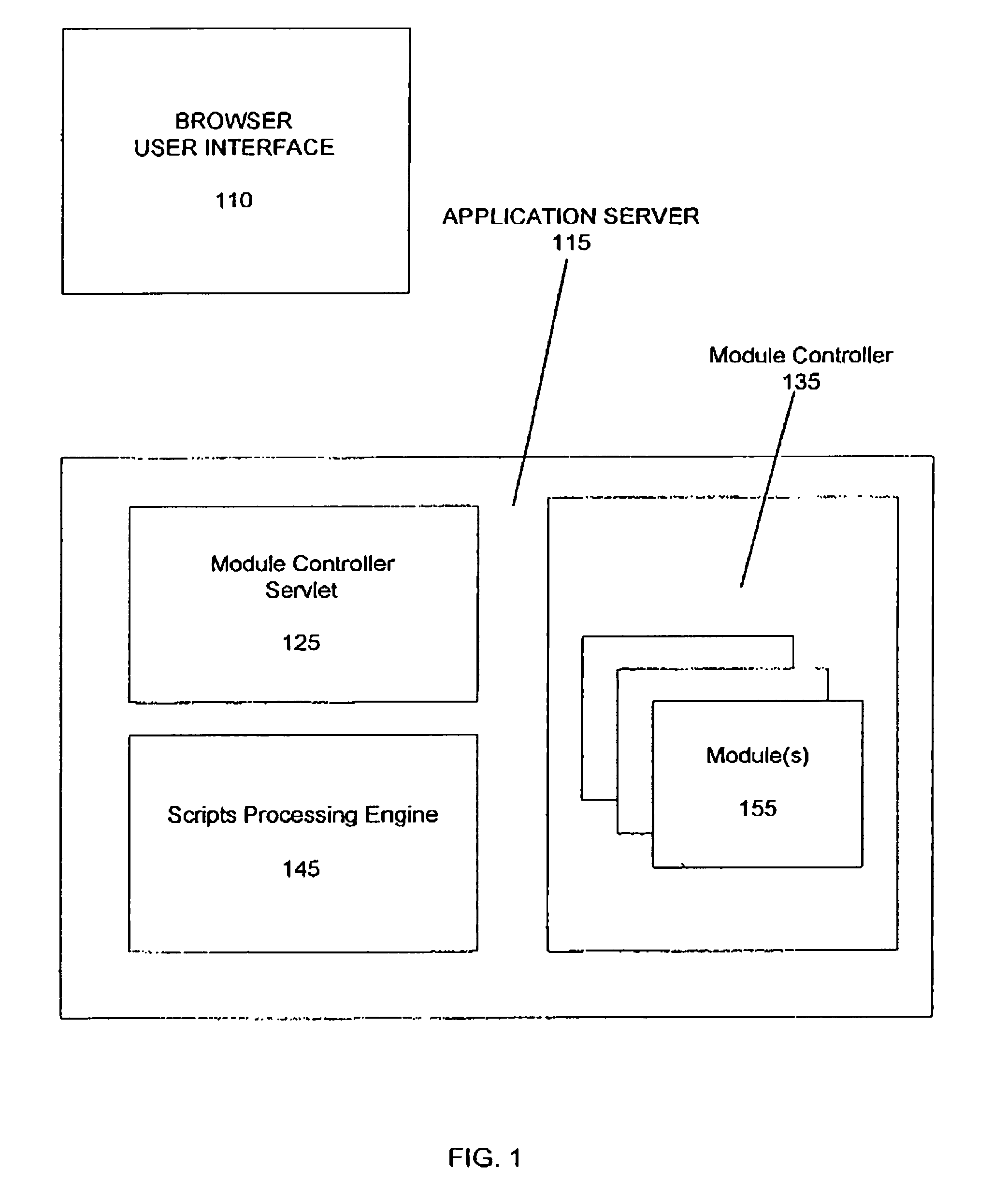
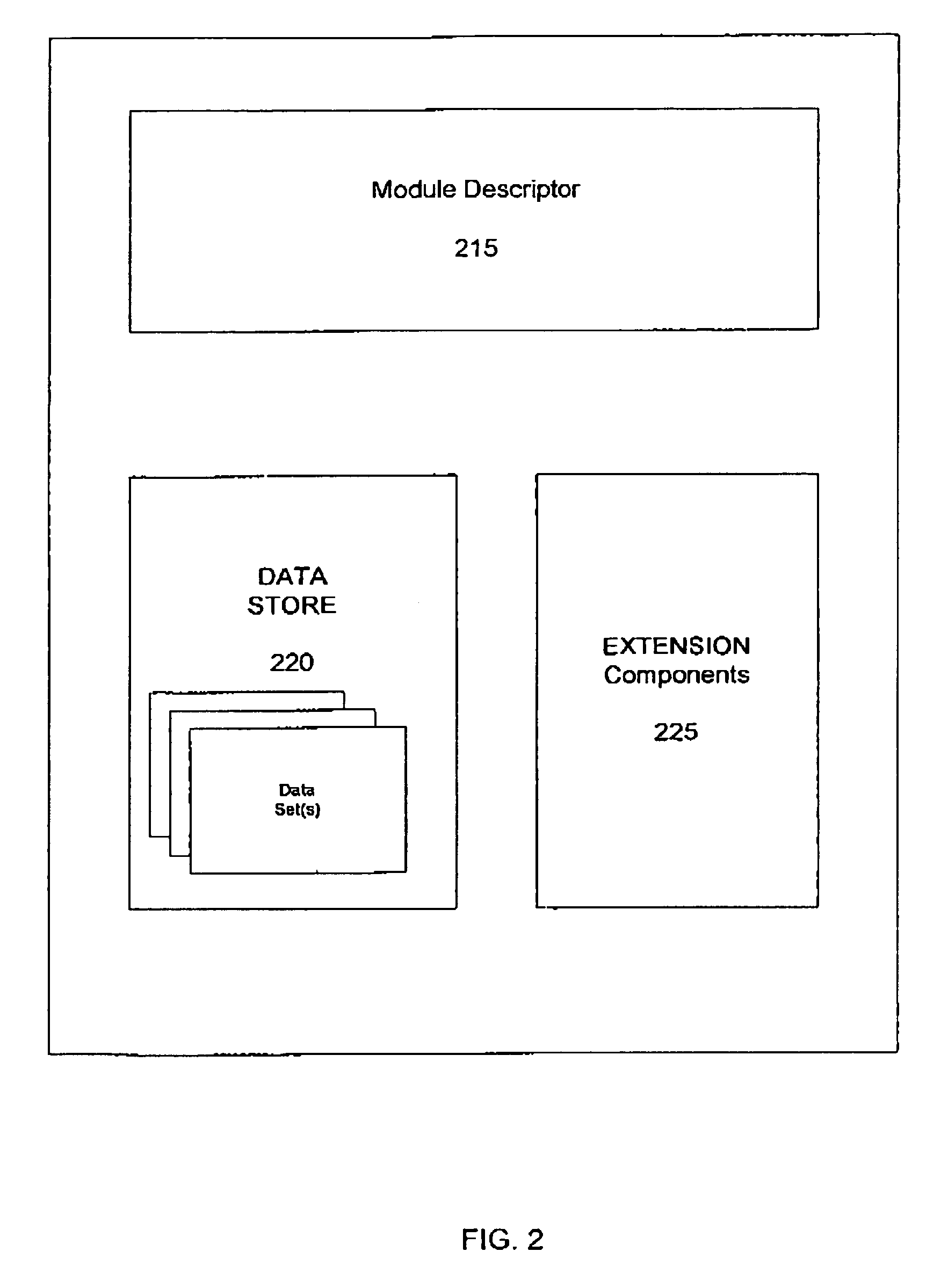
A system for modularizing a business application, the system including a computer having a first computer-readable medium encoded with a browser and an application server. The browser manages a user presentation interface for the business application and is configured to support client-side scripting. The application server is coupled to the computer and includes a second computer-readable medium that is encoded with a server-side script processing engine for processing scripts submitted by the browser and a Module Controller Servlet for opening, closing and managing at least one Module associated with the business application. A Module is a dynamic, configurable software element which includes at least one Extension component and a Data Store. The Extension component defines at least one particular business method function associated with the business application and is invoked as required by the business application. The Data Store includes at least one associated data set which contains data associated with the business application.
Owner:ROGUE WAVE SOFTWARE
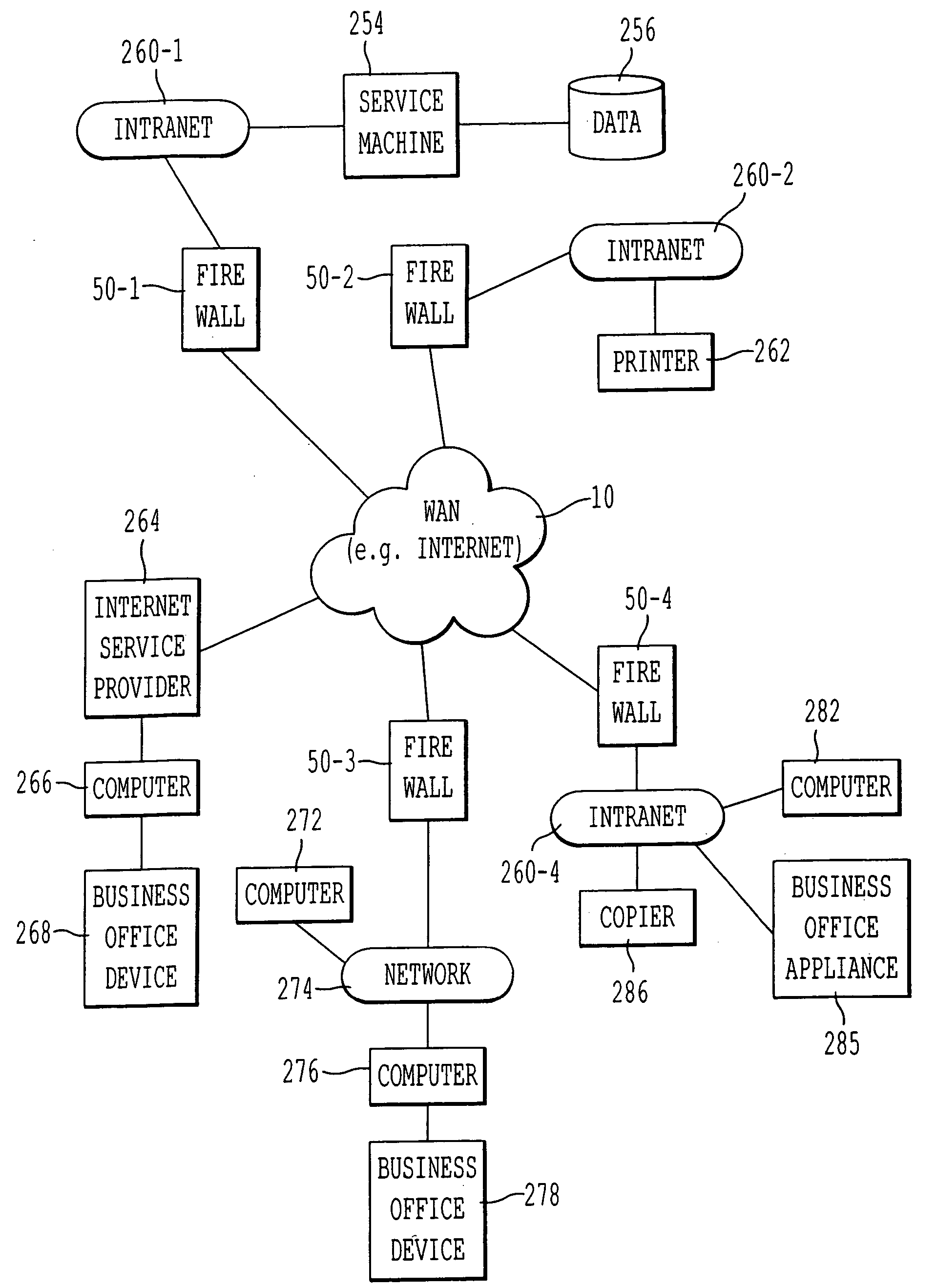
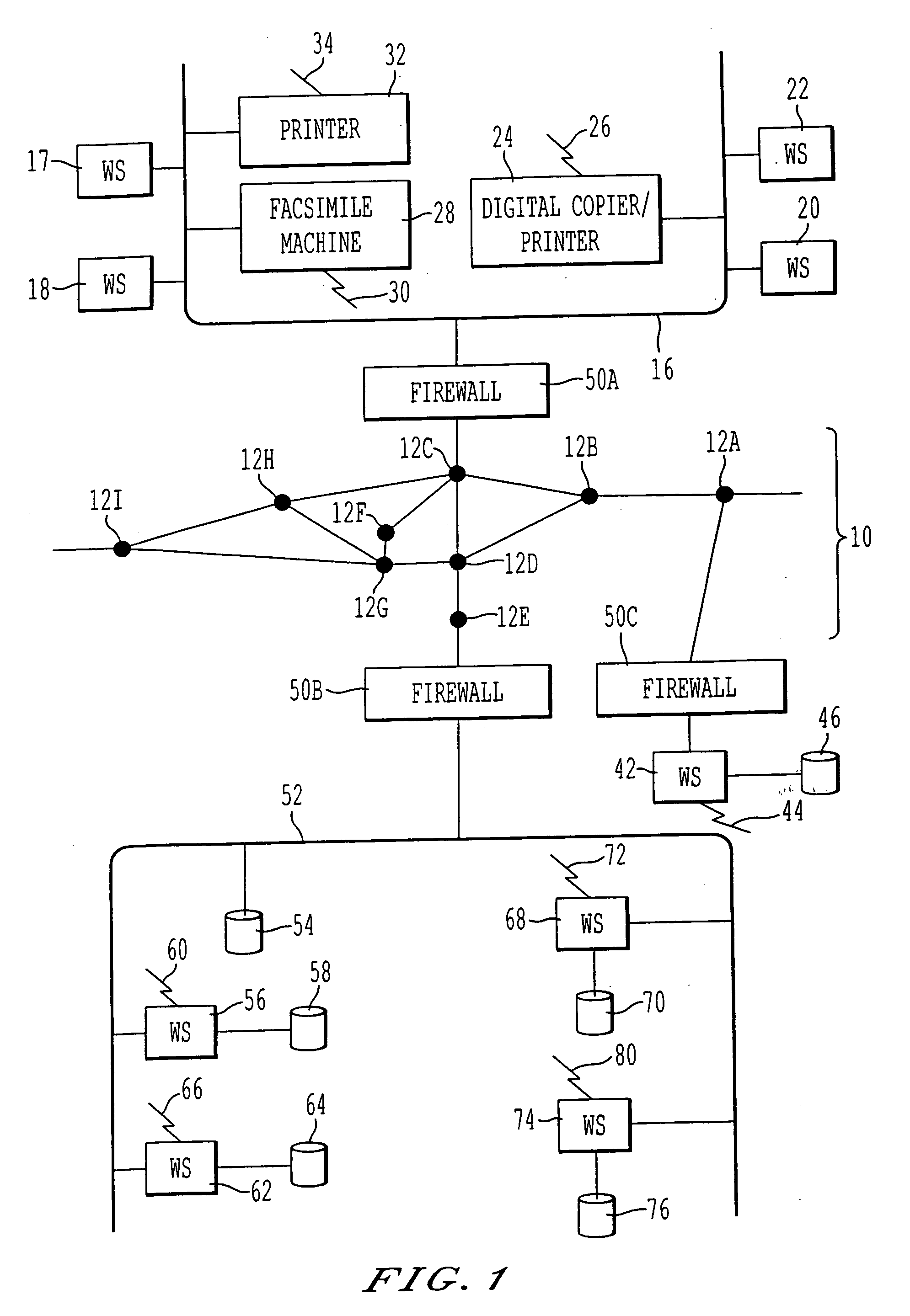
Object-oriented method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols
ActiveUS7533333B2Low costEasy to analyzeData processing applicationsData switching networksThree levelInformation Harvesting
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. The event information for a particular target application is formatted and transmitted according to a combination of a data format and communication protocol requested by the target application. The formatting of data representing the event information is handled in at least three levels of software classes, with two levels of abstract classes and one concrete software class. The formatting of information to be transmitted through the requested communication protocol is handled in at least three levels of software classes, with one abstract class and two levels of concrete classes. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
Mass-sensitive chemical preconcentrator
InactiveUS7168298B1Improve dynamic rangeHigh-precision detectionVibration measurement in solidsAnalysing fluids using sonic/ultrasonic/infrasonic wavesElectrical resistance and conductanceAnalyte
A microfabricated mass-sensitive chemical preconcentrator actively measures the mass of a sample on an acoustic microbalance during the collection process. The microbalance comprises a chemically sensitive interface for collecting the sample thereon and an acoustic-based physical transducer that provides an electrical output that is proportional to the mass of the collected sample. The acoustic microbalance preferably comprises a pivot plate resonator. A resistive heating element can be disposed on the chemically sensitive interface to rapidly heat and release the collected sample for further analysis. Therefore, the mass-sensitive chemical preconcentrator can optimize the sample collection time prior to release to enable the rapid and accurate analysis of analytes by a microanalytical system.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
Method and system of remote diagnostic, control and information collection using a dynamic linked library of multiple formats and multiple protocols with intelligent formatter
InactiveUS7287085B1Facilitate configuration and received data analysisReduce analysisMultiple digital computer combinationsTransmissionSoftware engineeringRemote diagnostics
A method, system and computer program product for (1) collecting information from a remote application unit and / or (2) diagnosing or controlling the remote application unit. By utilizing a shareable computer code device (e.g., a dynamic linked library), a new application can utilize tested, proven code without having to reproduce existing functionality. Moreover, by supporting multiple data formats and / or multiple communication protocols, a computer code device increases the likelihood that a supported format and / or protocol will be either receivable or understandable by a receiver.
Owner:RICOH KK
Method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols with delegating protocol processor
ActiveUS20060164683A1Easy to analyzeEasy to configureDigitally marking record carriersError detection/correctionProtocol processingSystems approaches
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. The event information for a particular target application is formatted and transmitted according to a combination of a data format and communication protocol requested by the target application. The transmission of data representing the event information is handled in at least two levels of software classes, with at least one abstract software class having a declared virtual function and two or more software classes derived from the at least one abstract class and having definitions of the function for communicating the event information through specified communication protocols. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
Method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols with verification of formats and protocols
InactiveUS7171670B2Low costEasy to analyzeHardware monitoringMultiprogramming arrangementsReliable transmissionNetwork Communication Protocols
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. A combination of a data format and communication protocol requested by a target application is verified for validity. If the requested combination is invalid, a valid combination is substituted for more reliable transmission. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
Imaging system with dynamic range maximization
ActiveUS20110064296A1Small rangeMaximize dynamic rangeMaterial analysis by optical meansCharacter and pattern recognitionComputer scienceImage system
A method of operating an instrument that is a macroscope, microscope, or slide scanner is provided where the instrument has a larger dynamic range for measurement than a dynamic range required in the final image of a specimen. In the method, data is measured from a specimen using the instrument, and the dynamic range of the measured data is contracted in the final image file during scanning.
Owner:HURON TECH INT
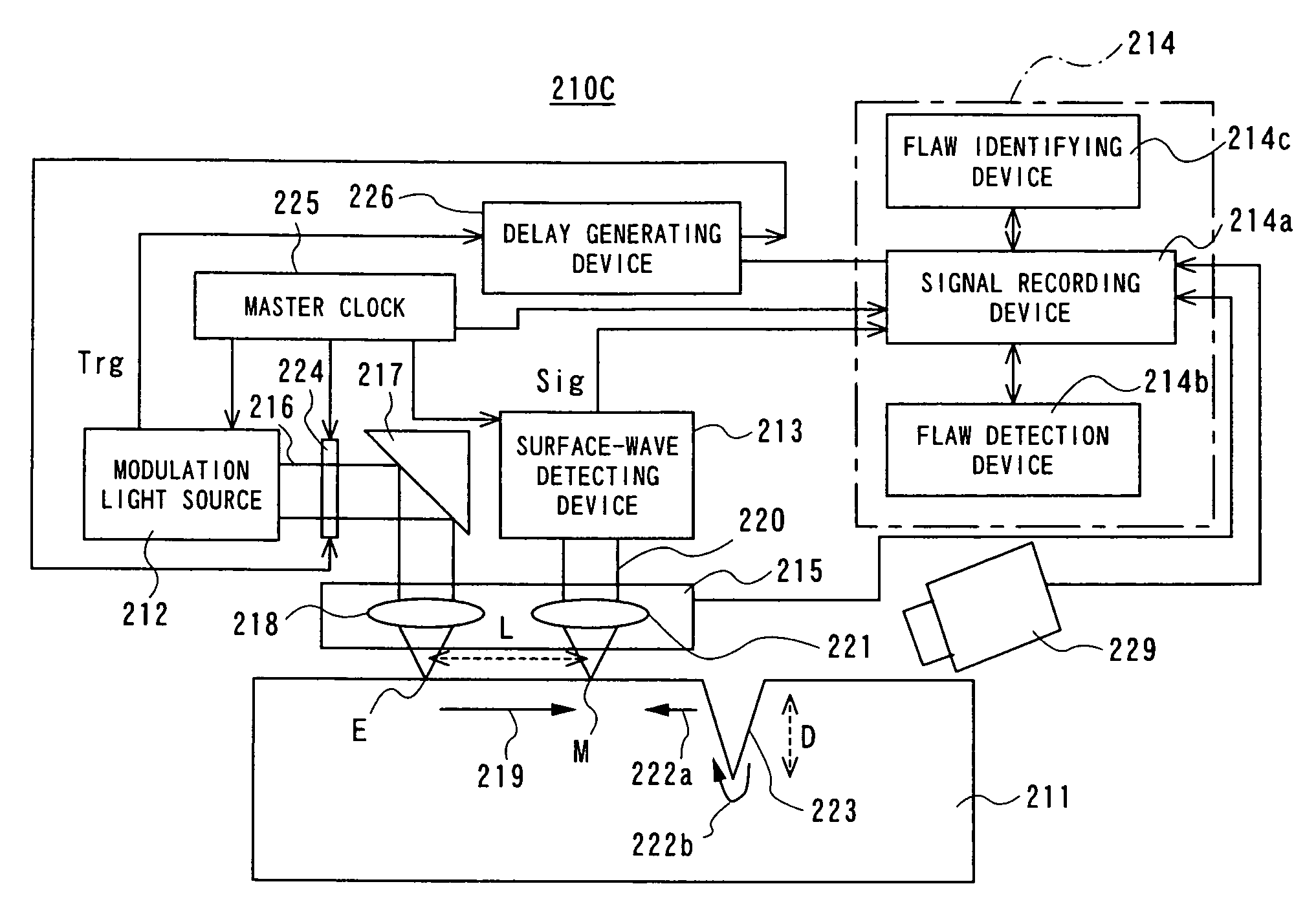
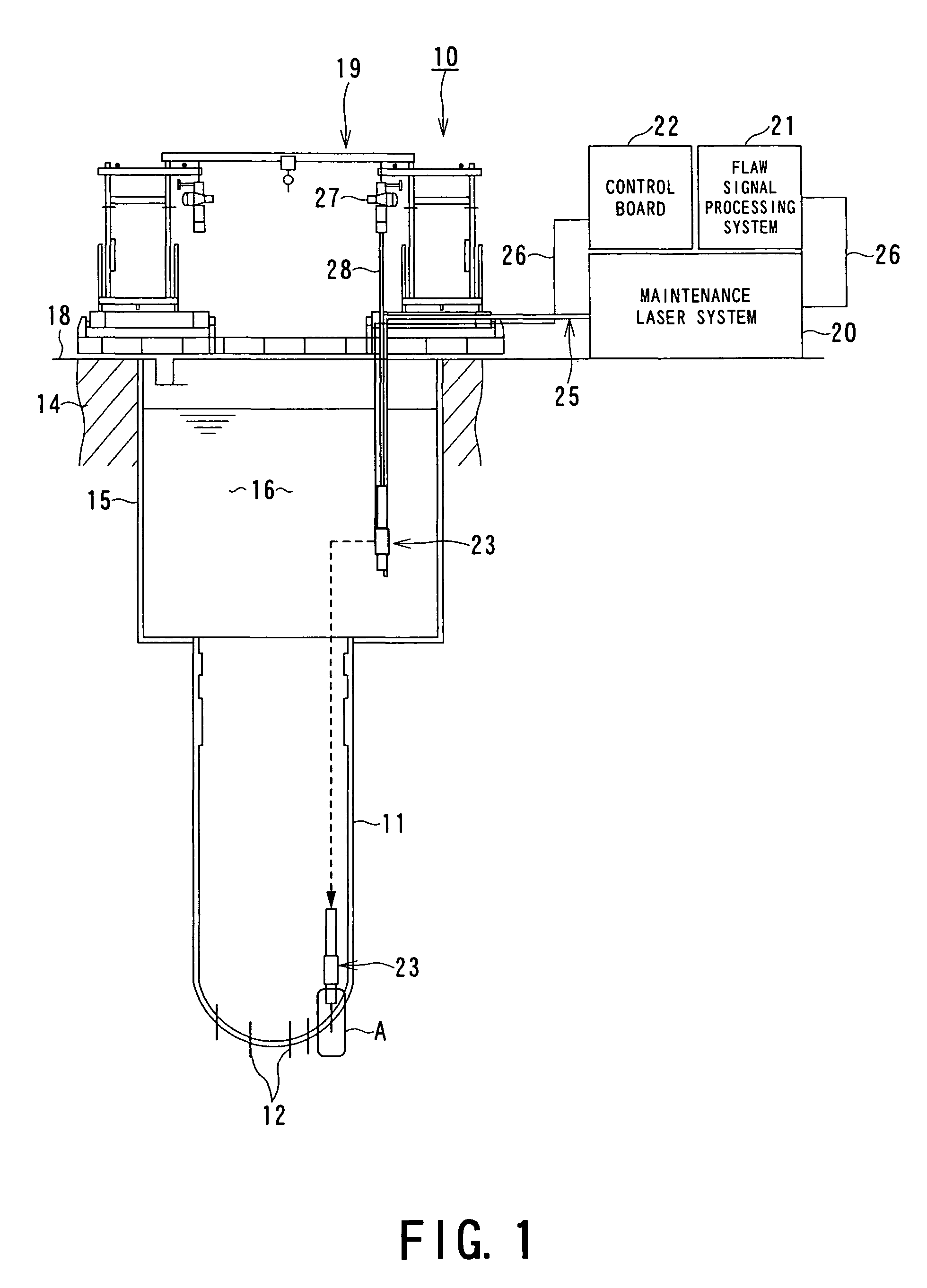
Laser-based maintenance apparatus
ActiveUS7728967B2Easy to insertEasy to removeAnalysing solids using sonic/ultrasonic/infrasonic wavesNuclear energy generationOptoelectronicsLaser light
A laser maintenance apparatus including a laser system which includes an optical system for emitting, in a first irradiation condition, a generation laser beam for generating an ultrasonic wave in a portion of an object on which maintenance is to be performed, and including a laser source configured to generate and detect a detection laser beam which interacts with the ultrasonic wave generated by the laser light beam in the first condition. The laser maintenance apparatus also includes a light transmitting device for transmitting laser light emitted from the laser system, a laser irradiation device for irradiating laser light transmitted by the light transmitting device to the object portion, and a transporting / scanning mechanism for transporting the light transmitting device and the laser irradiation device to a portion near the object portion, and scanning over an arbitrary range at the object portion.
Owner:KK TOSHIBA
Manufacturing design and process analysis and simulation system
InactiveUS7239991B2Facilitate design and production and measurement taskReduce analysisSimulator controlElectric controllersProcess dimensionProcess simulation
A process simulation system that simulates the operation of the manufacturing and measurement systems used to produce and measure the articles being analyzed relative to engineering design targets, engineering design tolerances, producibility and / or quality. In one embodiment, the user is able to assess, without risk or production cost while accelerating speed-to-market, the effect of contemplated changes (i.) to engineering design targets, (ii.) to engineering design tolerances, (iii.) to tooling, (iv.) to part pre-process dimensions and (v.) to the measurement system—on manufactured part dimensions, producibility and quality (i.) without modifying tooling, (ii.) without changing part pre-process dimensions, (iii.) without producing new parts, (iv.) without measuring article characteristics on the new parts and (v.) without changing the measurement system. The simulation functionalities, according to embodiments of the present invention, enable the user to verify whether or not the contemplated changes will have the desired effect without incurring the time and expense involved in actually making the changes, producing parts, measuring part characteristics, changing the measurement system and then determining whether the changes accomplished the desired objectives.
Owner:TUSZYNSKI STEVE W
Electromagnetic surveying for resistive or conductive bodies
ActiveUS7362102B2Reduce analysisWater resource assessmentDetection using electromagnetic wavesOcean bottomElectrical resistance and conductance
A method of analyzing electromagnetic survey data from an area of seafloor 6 that is thought or known to contain a resistive or conductive body, for example a subterranean hydrocarbon reservoir 12, is described. The method includes providing horizontal electromagnetic field data obtained by at least one receiver 125 from at least one horizontal electric dipole transmitter 22. Horizontal gradients in the electromagnetic field data are determined for a first component of the electromagnetic field data along a first direction and for a second component of the electromagnetic field data along a second direction. The first and second components can be the electric field along the first and second directions, or the magnetic field perpendicular to the first direction and second directions. The gradients are then combined to provide combined response data. Because the combined response data are relatively insensitive to the transverse electric (TE) mode component of the transmitted signal, the method allows hydrocarbon reservoirs to be detected in shallow water where the TE mode component interacting with the air would otherwise dominate.
Owner:PGS GEOPHYSICAL AS
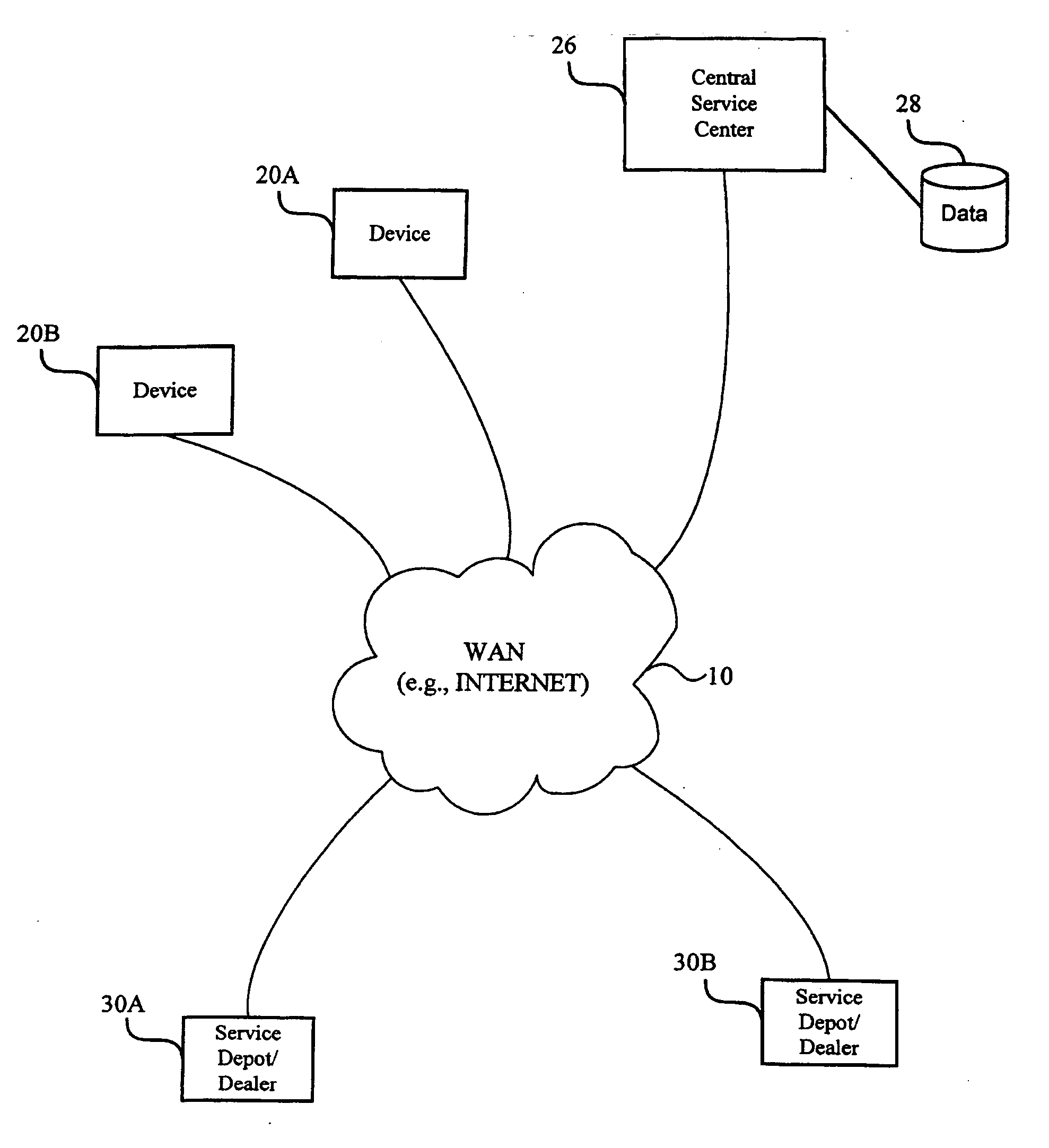
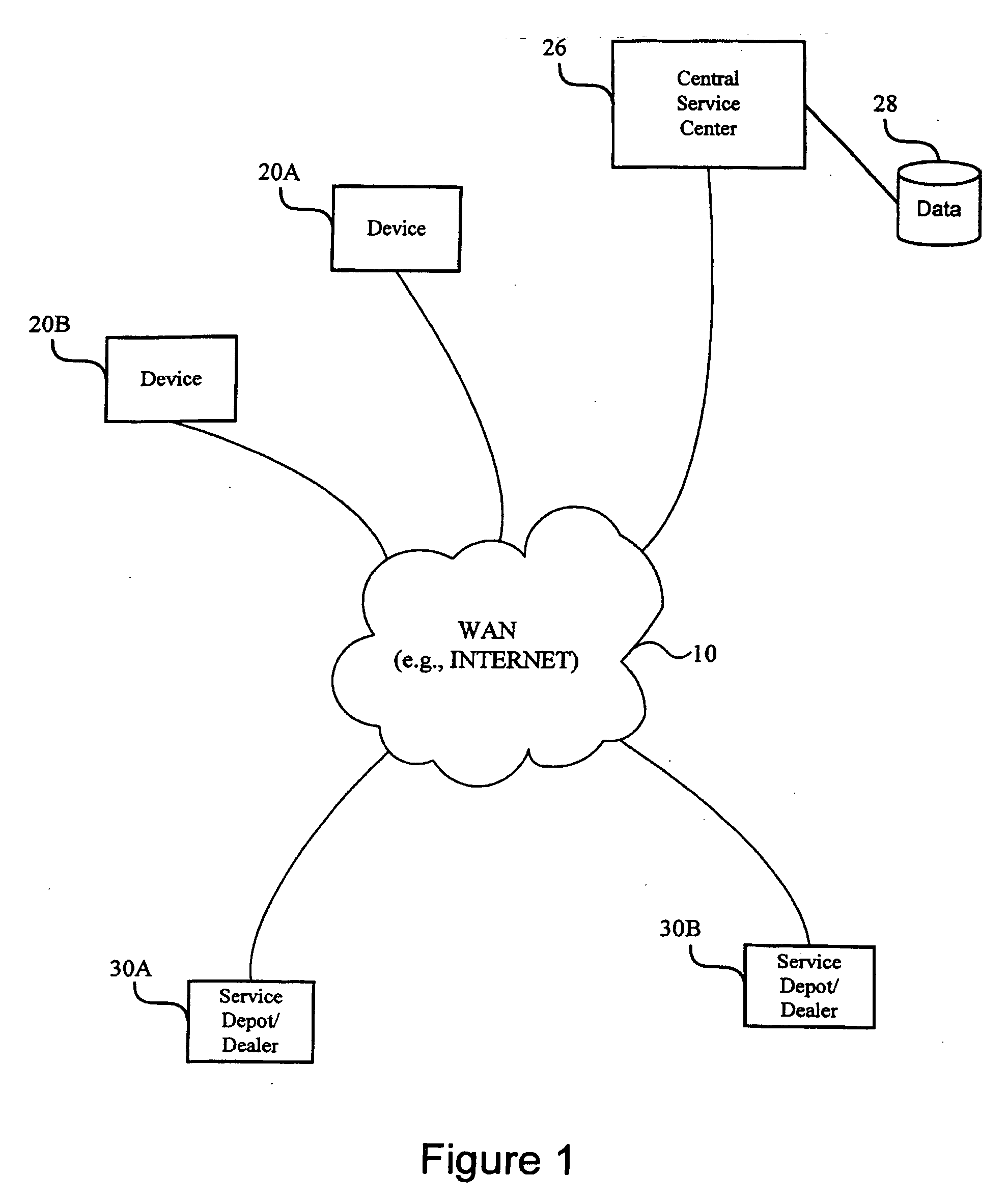
Method and system for diagnosing, collecting information and servicing a remote system
InactiveUS20070033266A1Reduce analysisEfficient communicationMultiple digital computer combinationsTransmissionRemote systemMonitoring system
A monitoring system, method, and computer-program product tracks events and device states in a device and sends those events and states to a remote central service center using an Internet access module. The remote central service center monitors the received events and states for errors or warnings. The monitoring software (e.g., a dynamic link library) supports multiple data formats and multiple protocols to more effectively communicate the event and state information.
Owner:RICOH KK
Method and system of remote diagnostic, control and information collection using a dynamic linked library of multiple formats and multiple protocols with restriction on protocol
InactiveUS20060031538A1Facilitate configuration and received data analysisReduce analysisMultiple digital computer combinationsTransmissionData formatRemote diagnostics
A method, system and computer program product for (1) collecting information from a remote application unit and / or (2) diagnosing or controlling the remote application unit. By utilizing a shareable computer code device (e.g., a dynamic linked library), a new application can utilize tested, proven code without having to reproduce existing functionality. Moreover, by supporting multiple data formats and / or multiple communication protocols, a computer code device increases the likelihood that a supported format and / or protocol will be either receivable or understandable by a receiver.
Owner:RICOH KK
Electromagnetic Surveying for Resistive or Conductive Bodies
ActiveUS20070288211A1Reduce analysisSuitable for collectionElectric/magnetic detection for well-loggingSurveyHydrocotyle bowlesioidesTransmitter
A method of analysing electromagnetic survey data from an area of seafloor (6) that is thought or known to contain a conductive or resistive body, such as a subterranean hydrocarbon reservoir (12), is described. The method includes providing electric field data and magnetic field data, for example magnetic flux density, obtained by at least one receiver (25) from a horizontal electric dipole (HED) transmitter (22) and determining a vertical gradient in the electric field data. The vertical gradient in the electric field data and the magnetic field data are then combined to generate combined response data. The combined response data is compared with background data specific to the area being surveyed to obtain difference data sensitive to the presence of a subterranean hydrocarbon reservoir. Because the combined response data are relatively insensitive to the transverse electric (TE) mode component of the transmitted signal, the method allows hydrocarbon reservoirs to be detected in shallow water where the TE mode component interacting with the air would otherwise dominate. Furthermore, because there is no mixing between the TE and transverse magnetic (TM) modes in the combined response data, data from all possible transmitter and receiver orientations may be used. The background data may be provided by magneto-telluric surveying, controlled source electromagnetic surveying or from direct geophysical measurement.
Owner:PGS GEOPHYSICAL AS
Method for bonding prepared substrates for roadways using a low-tracking asphalt emulsion coating
A method for bonding together an existing substrate layer and a pavement layer, such that a strong adhesive bond is formed by using a tack coat, provided by an asphalt emulsion, in between the layers as the bond coat. The tack coat layer is a low-tracking coating which cures quickly such that the pavement layer may be applied to the substrate, hours to days after the emulsion is applied to the substrate. The asphalt emulsion comprises at least a first phase of from about 30% to about 70% of an asphalt composition, about 30% to about 70% water, and about 0.1% to about 3.0% emulsifying agent, stabilizer and / or additives, or 0.1% to about 30% if polymeric or other additives are also included.
Owner:BLACKLIDGE IP
Electromagnetic surveying for hydrocarbon reservoirs
InactiveUS7337064B2Reduce analysisEasy to separateElectric/magnetic detection for well-loggingPermeability/surface area analysisOcean bottomData set
An electromagnetic survey method for surveying an area of seafloor that is thought or known to contain a subterranean hydrocarbon reservoir, comprising obtaining a first survey data set with a vertical electric dipole (VED) antenna for generating vertical current loops and a second survey data set with a vertical magnetic dipole (VMD) antenna for generating horizontal current loops. In an alternative embodiment, the VMD antenna is dispensed with and the horizontal electromagnetic field is derived from the naturally occurring magnetotelluric (MT) electromagnetic field. In another alternative embodiment, the VED data is compared with a background geological model instead of VMD or MT data. The invention also relates to a survey apparatus comprising VED and VMD antennae, to planning a survey using this method, and to analysis of survey data taken using this survey method. The first and second survey data sets allow the galvanic contribution to the detector signals collected at a detector to he independently contrasted with the inductive effects. This is important to the success of using electromagnetic surveying for identifying hydrocarbon reserves and distinguishing them from other classes or structure.
Owner:OHM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com