Patents
Literature
366 results about "Virtual function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
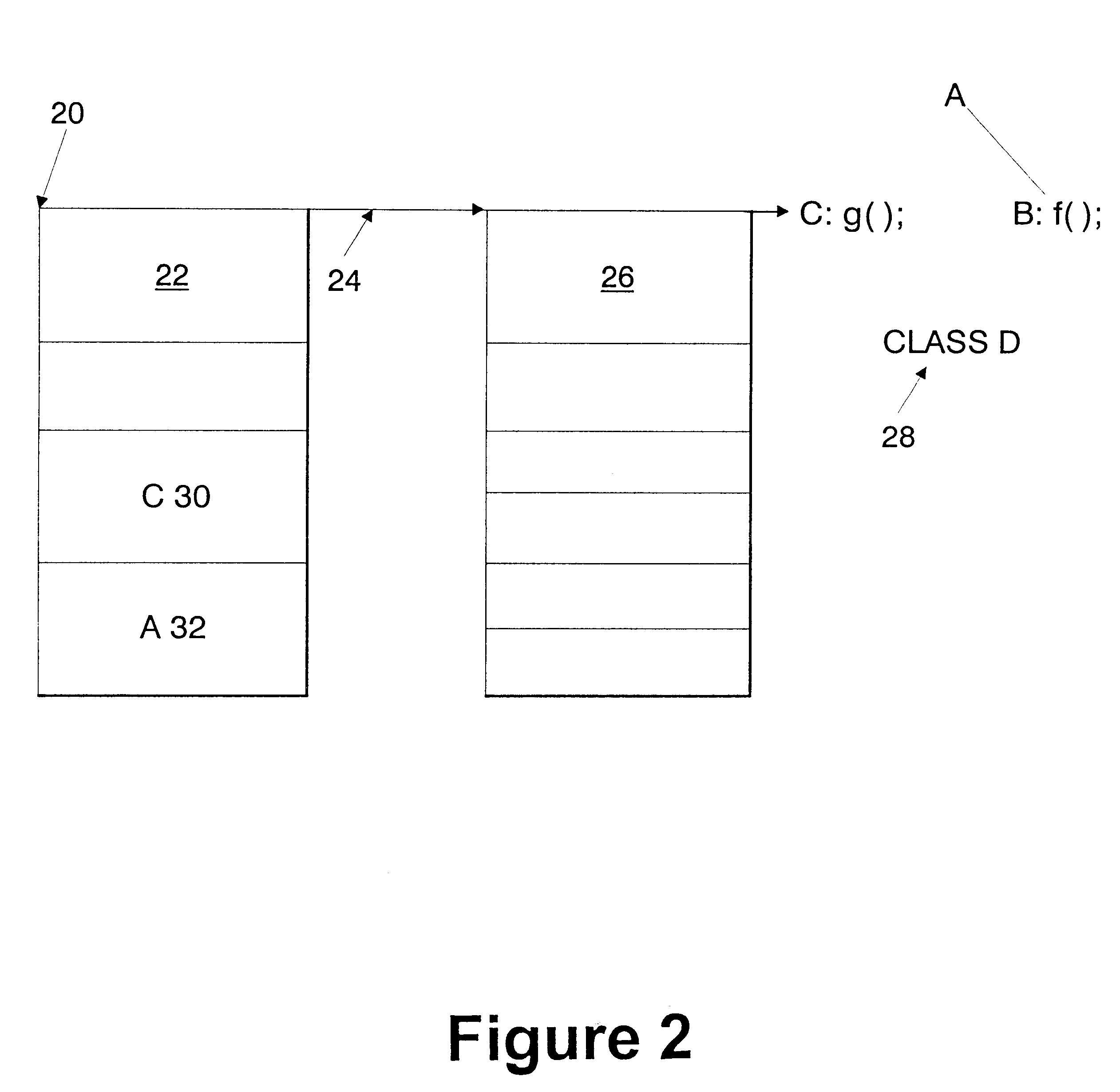
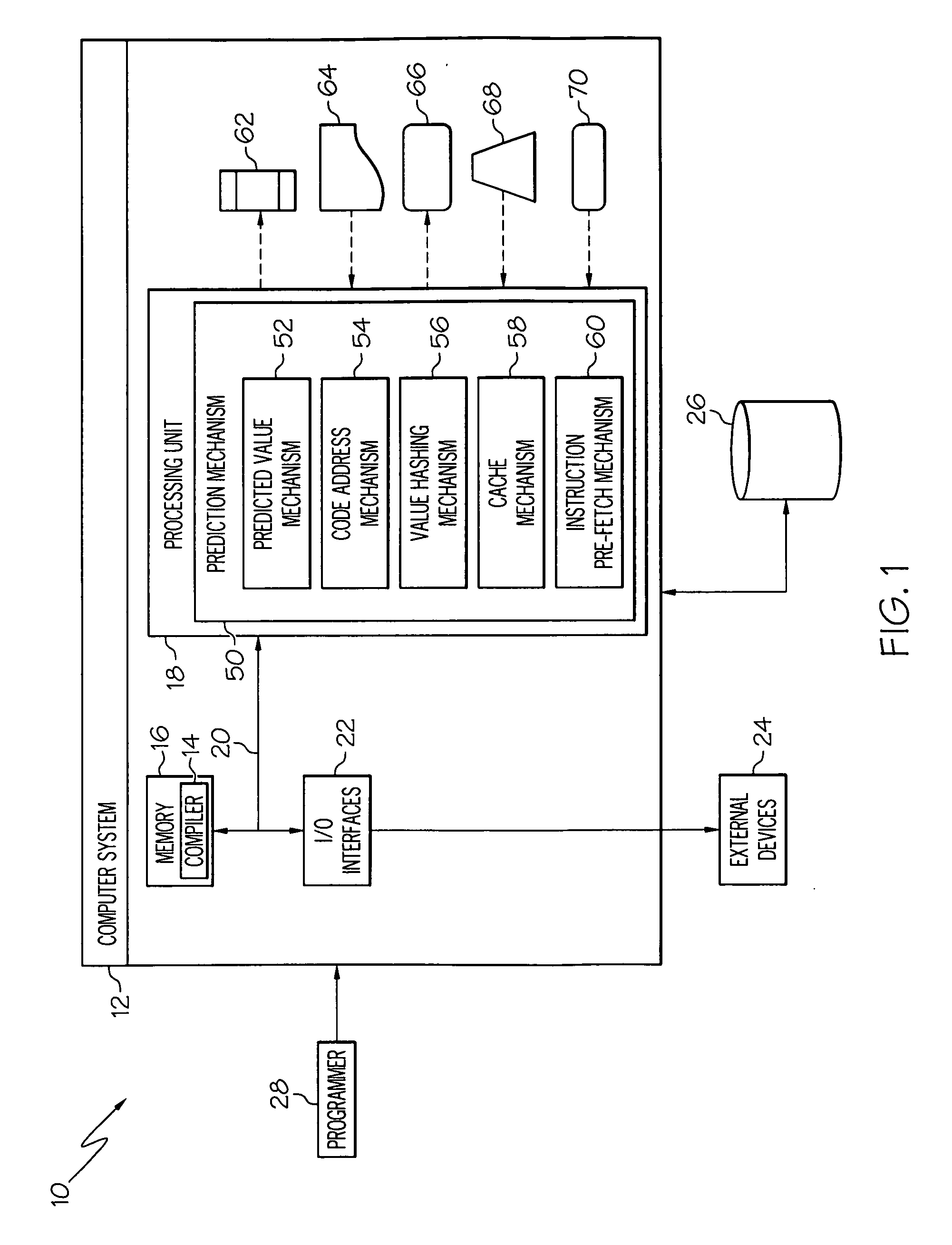
In object-oriented programming, in languages such as C++, and Object Pascal, a virtual function or virtual method is an inheritable and overridable function or method for which dynamic dispatch is facilitated. This concept is an important part of the (runtime) polymorphism portion of object-oriented programming (OOP). In short, a virtual function defines a target function to be executed, but the target might not be known at compile time.
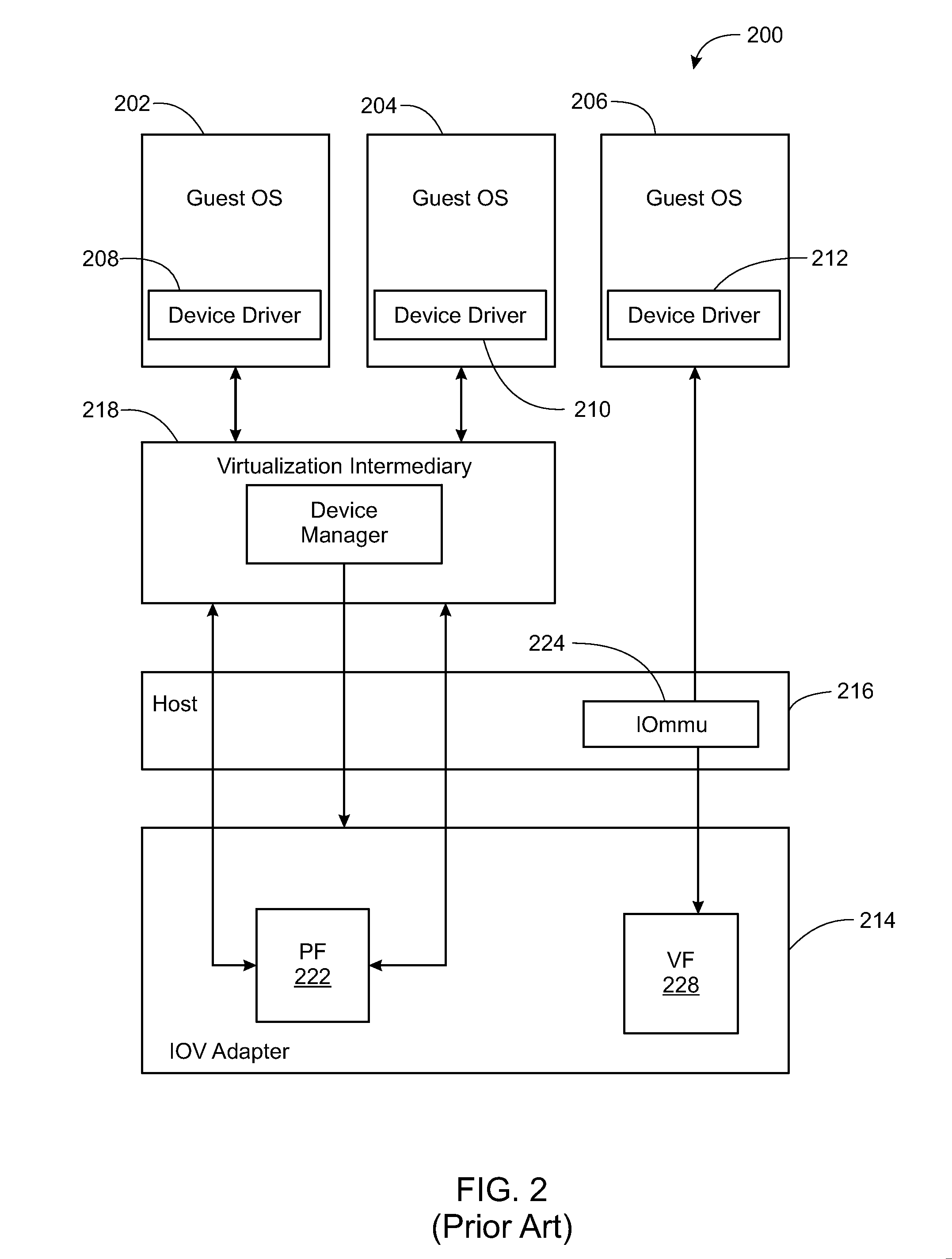
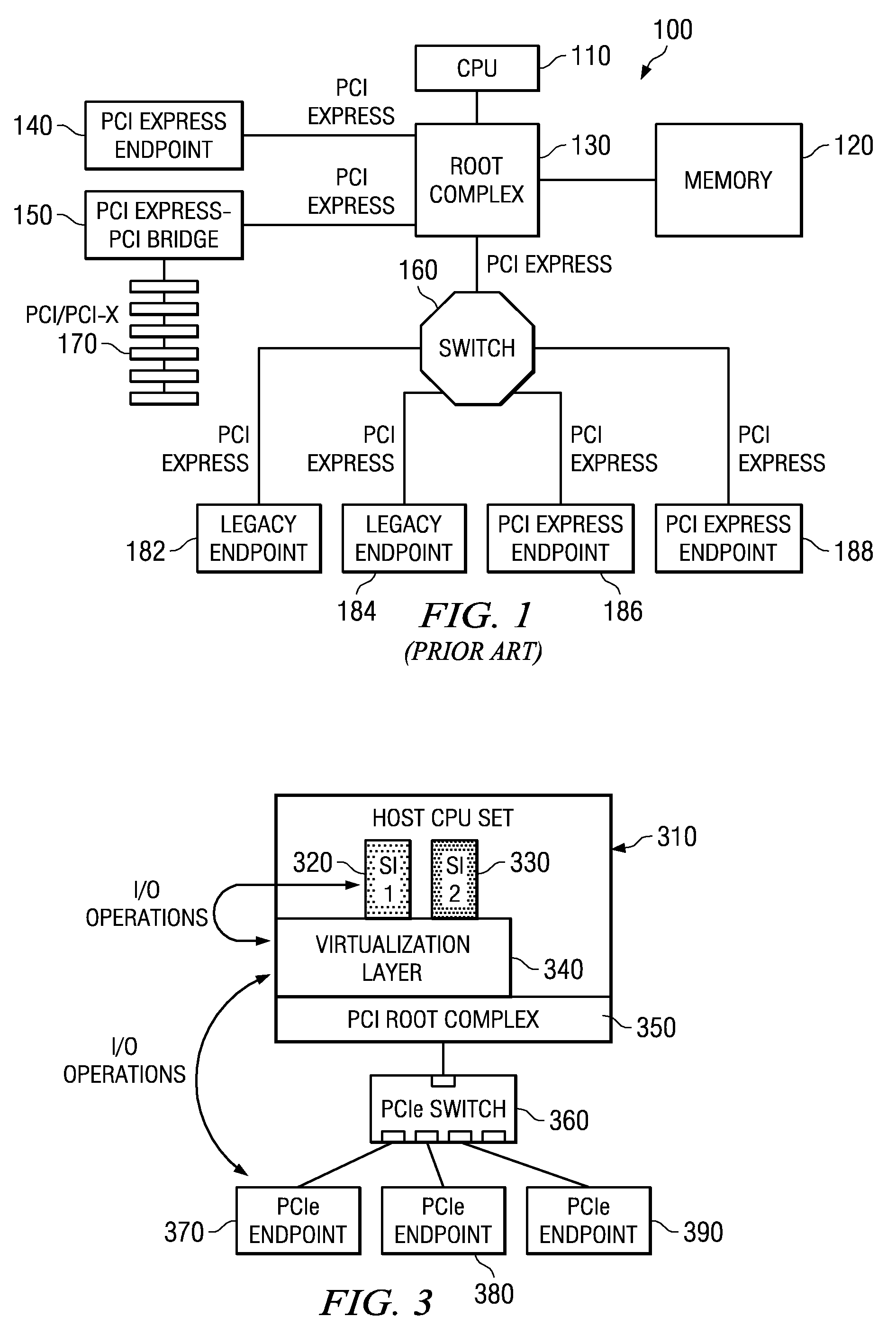
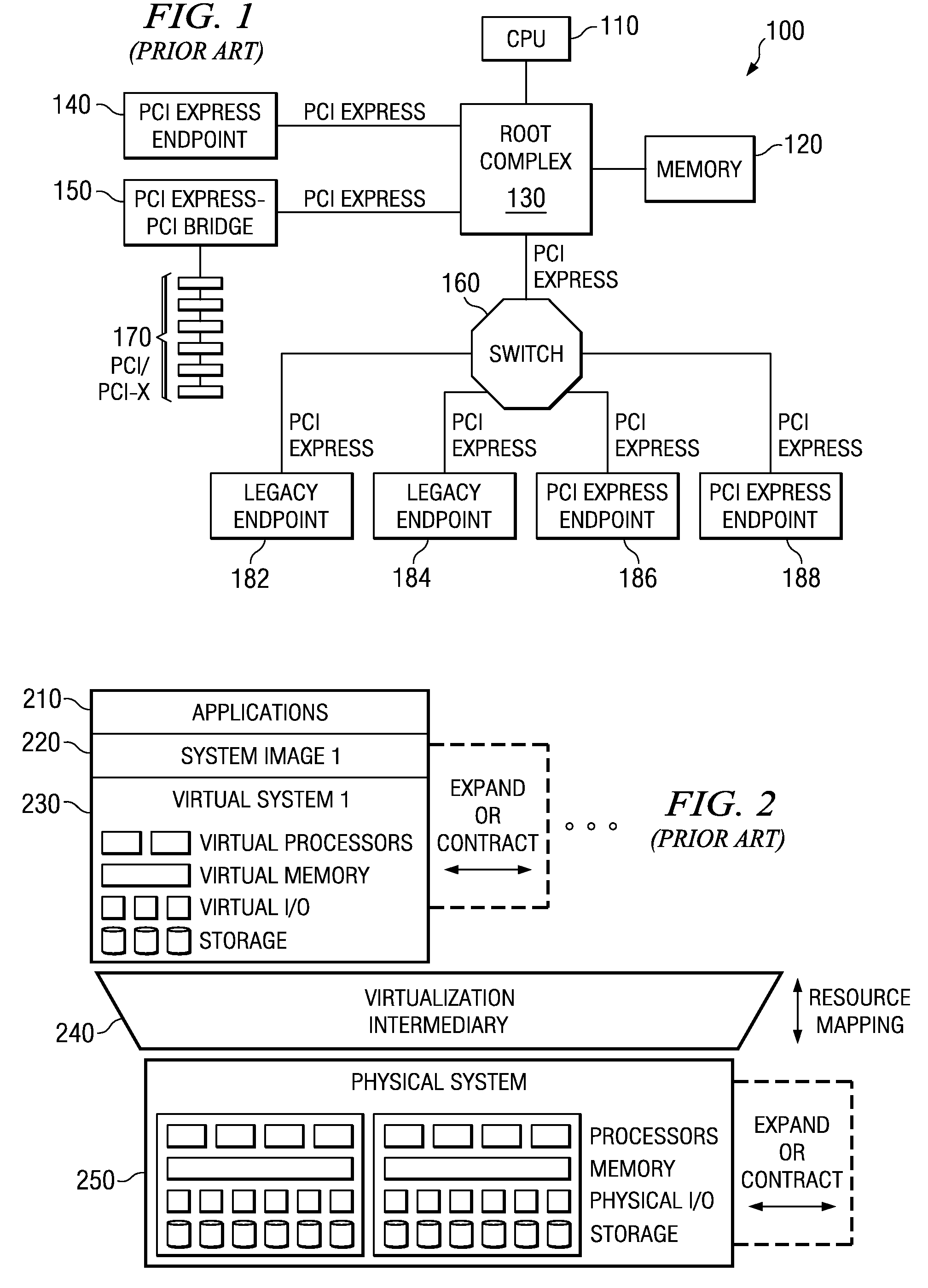
Virtualization intermediary/virtual machine guest operating system collaborative SCSI path management
A method of direct access by a virtual machine (VM) running on a host machine to physical storage via a virtual function (VF) running on an input / output (IO) adapter comprising: providing by a virtualization intermediary running on the host machine an indication of an active path associated with a virtual storage device; obtaining by a guest driver running within a guest operating system of the VM the stored indication of the active path from the shared memory region; dispatching an IO request by the guest driver to the VF that includes an indication of the active path; and sending by the VF an IO request that includes the indicated active path.
Owner:VMWARE INC
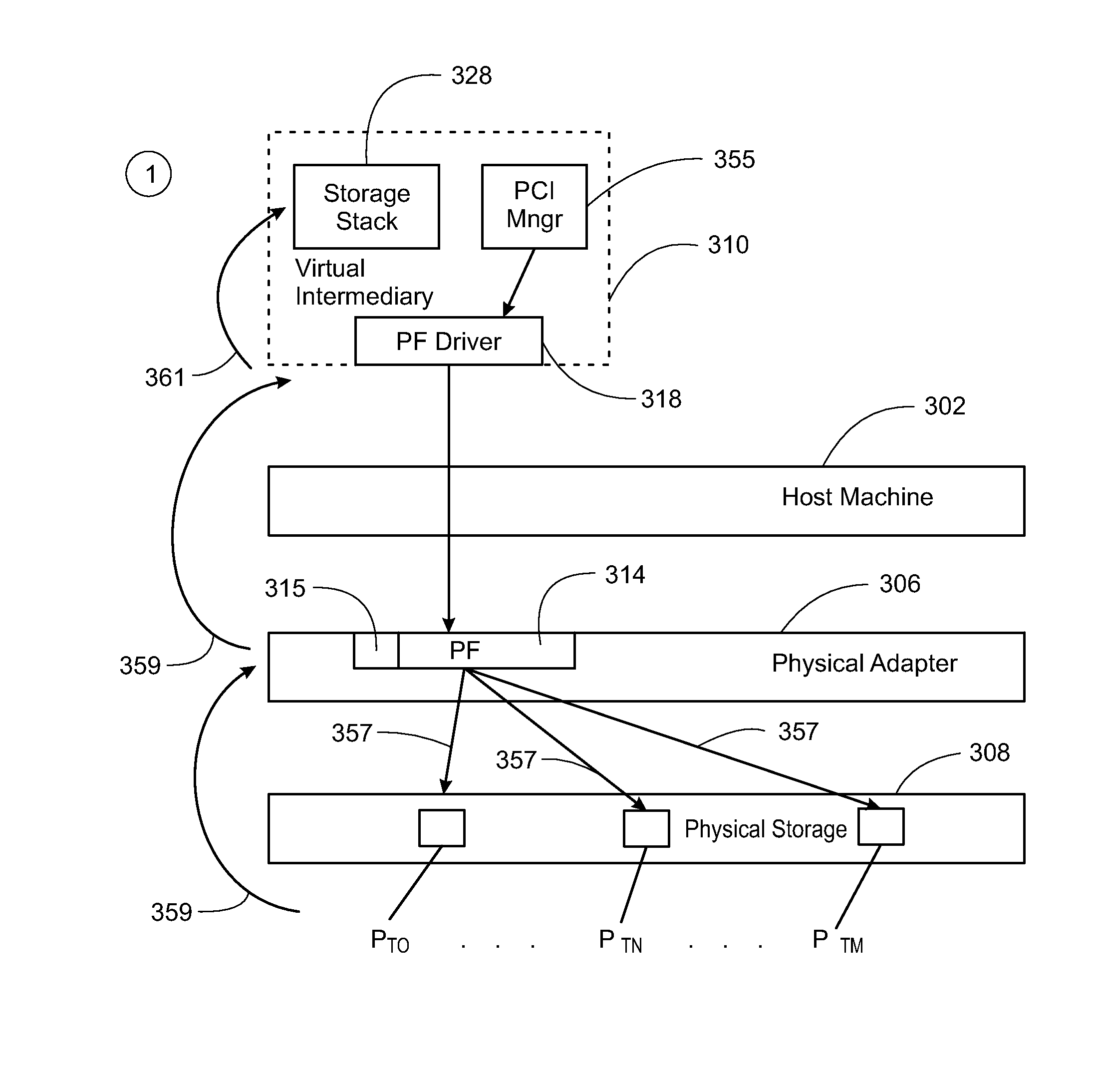
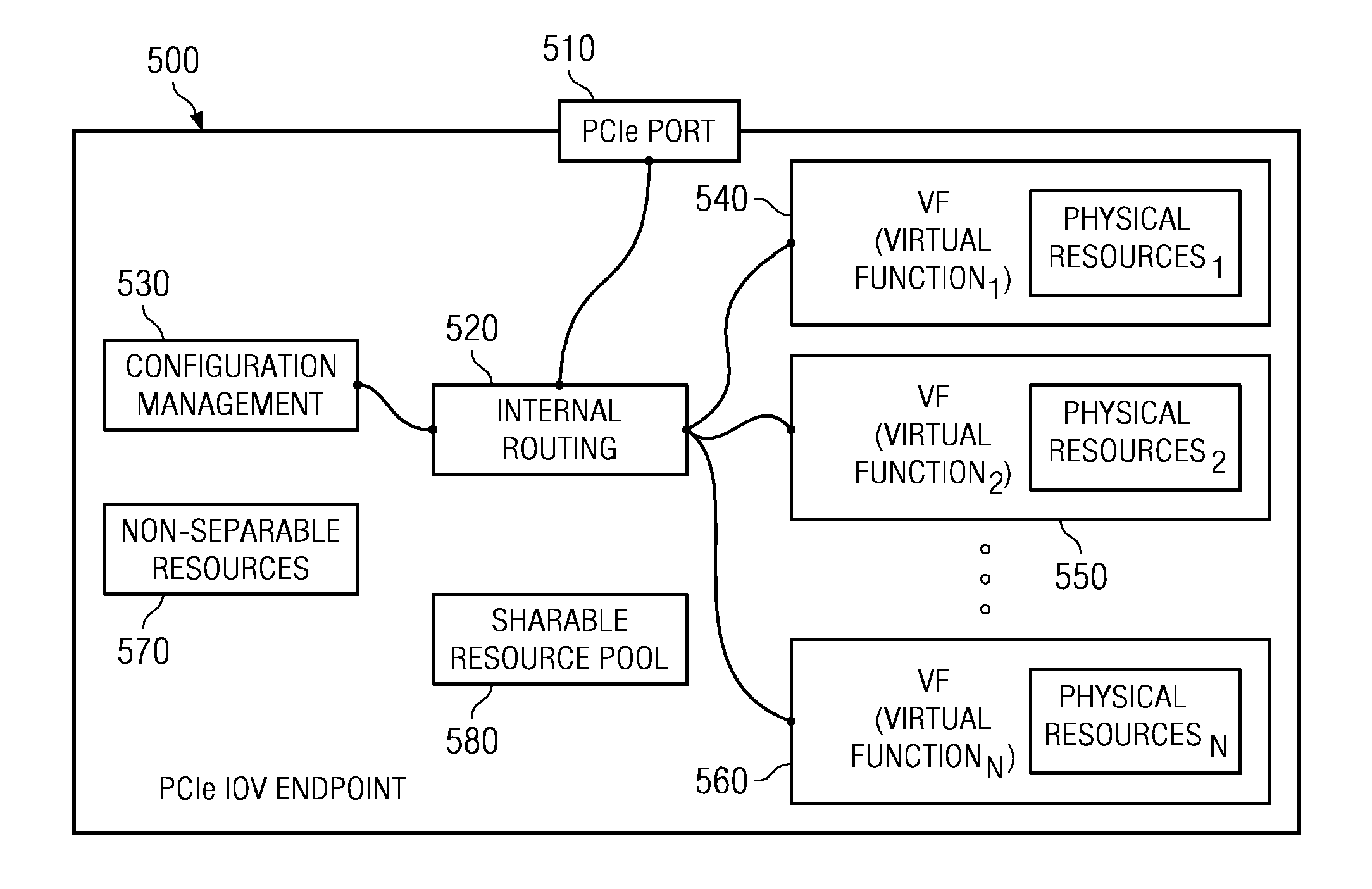
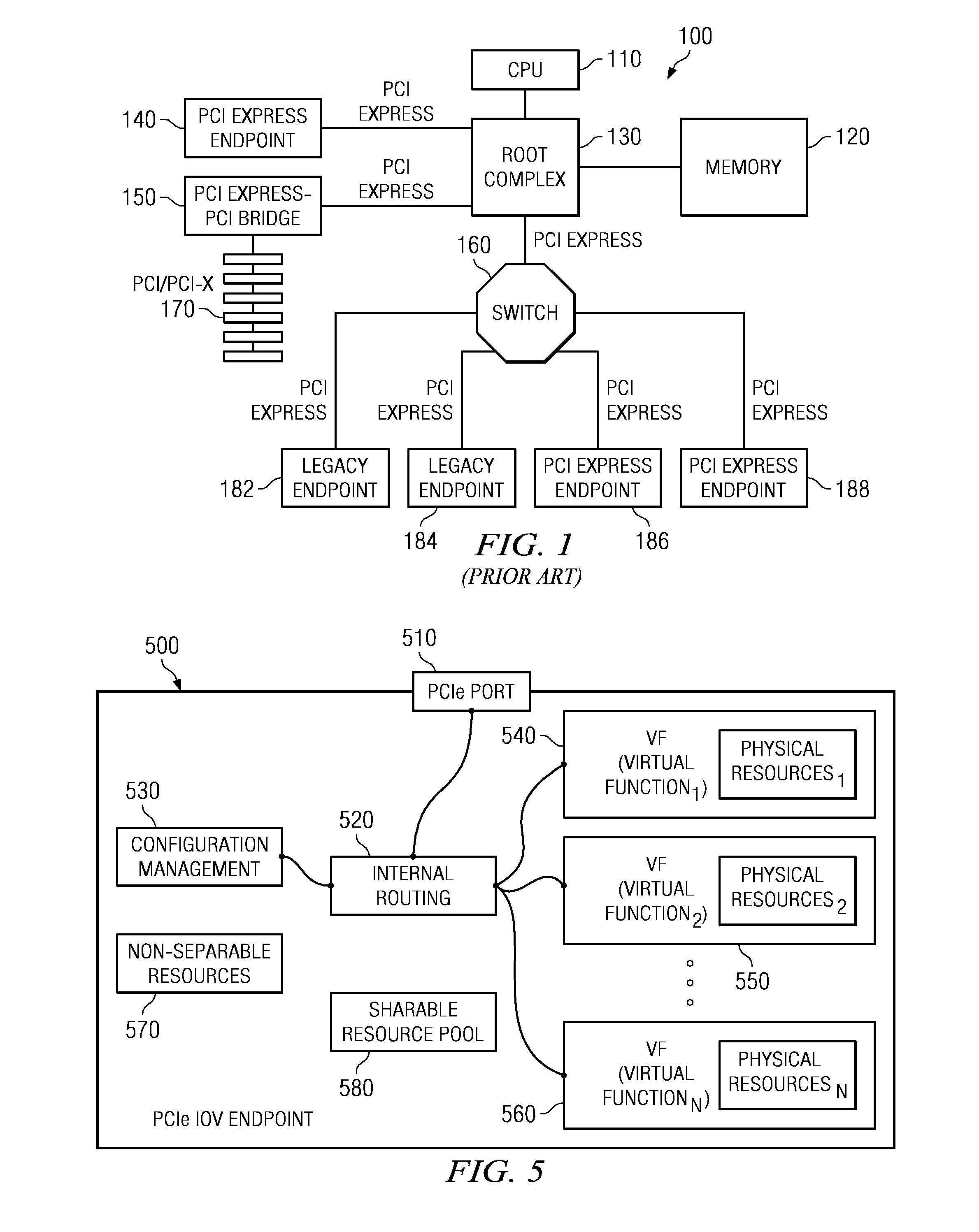
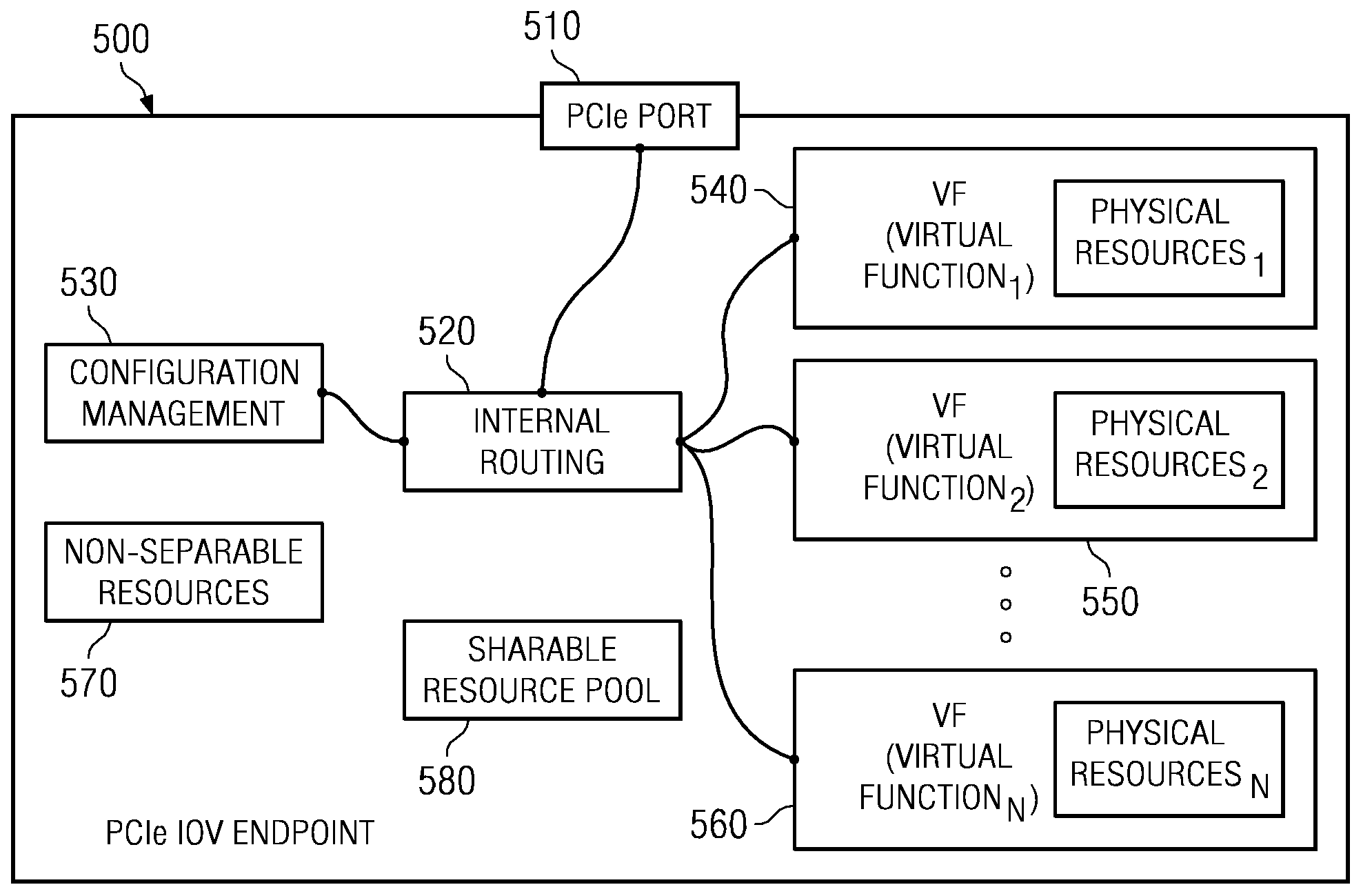
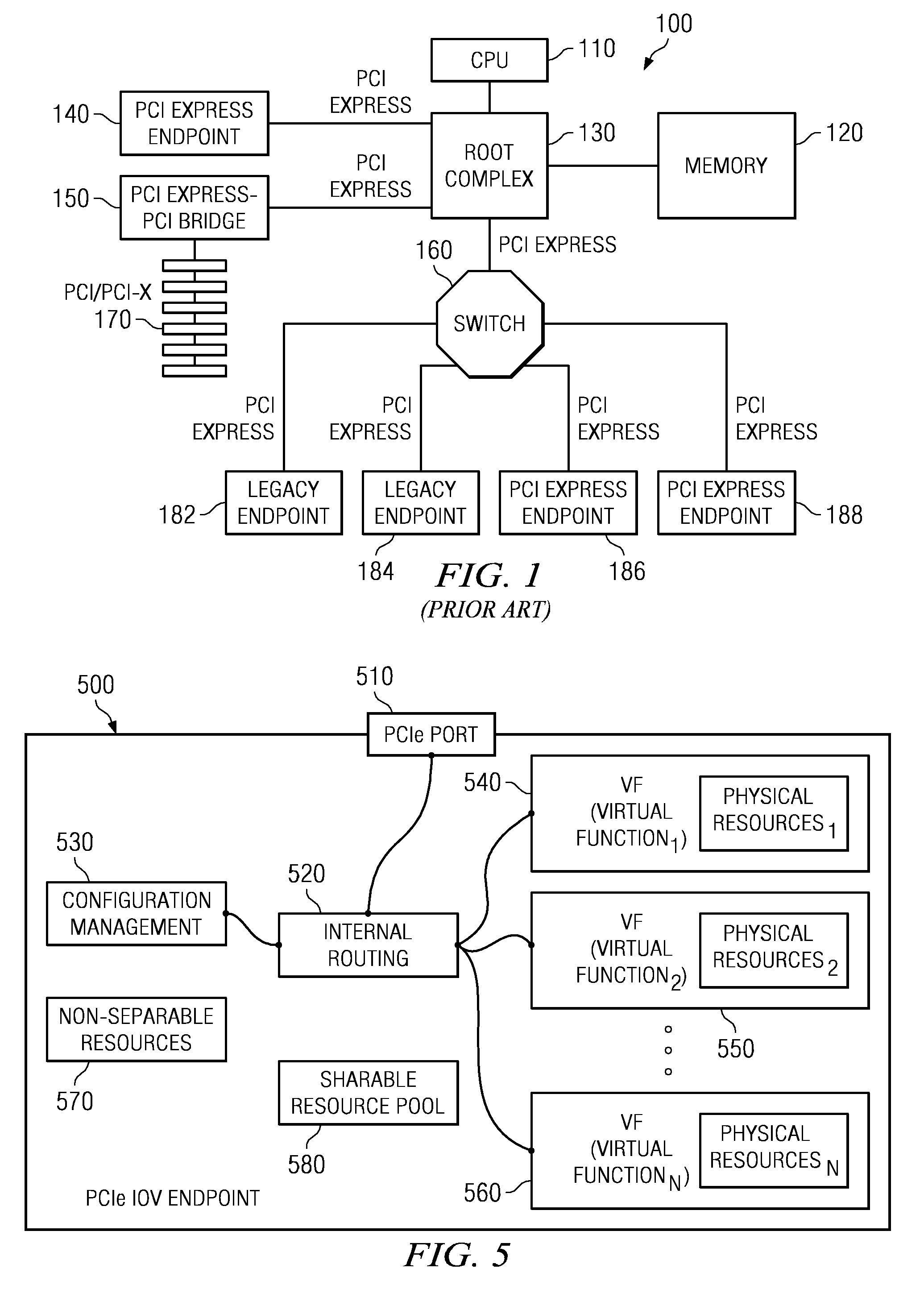
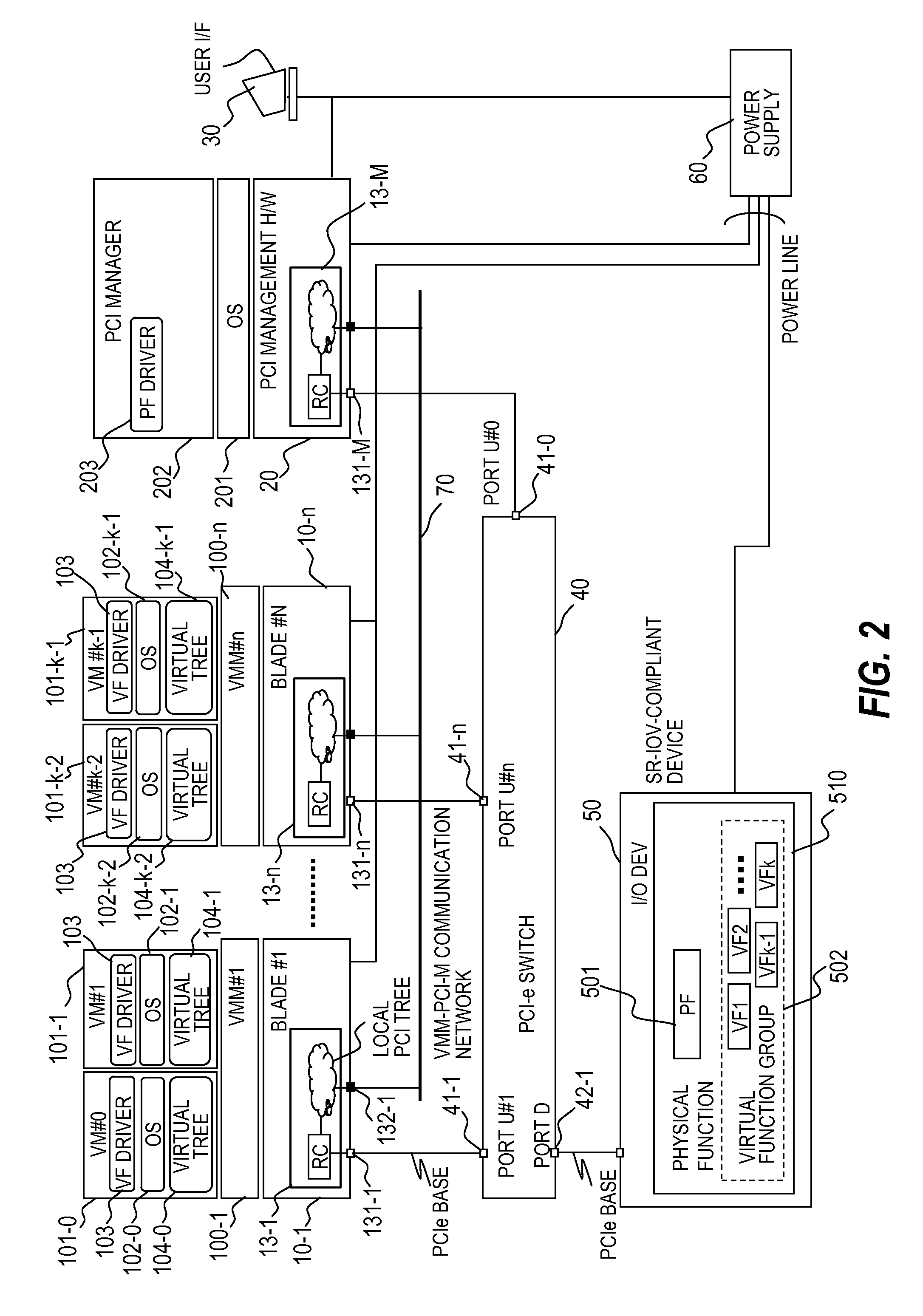
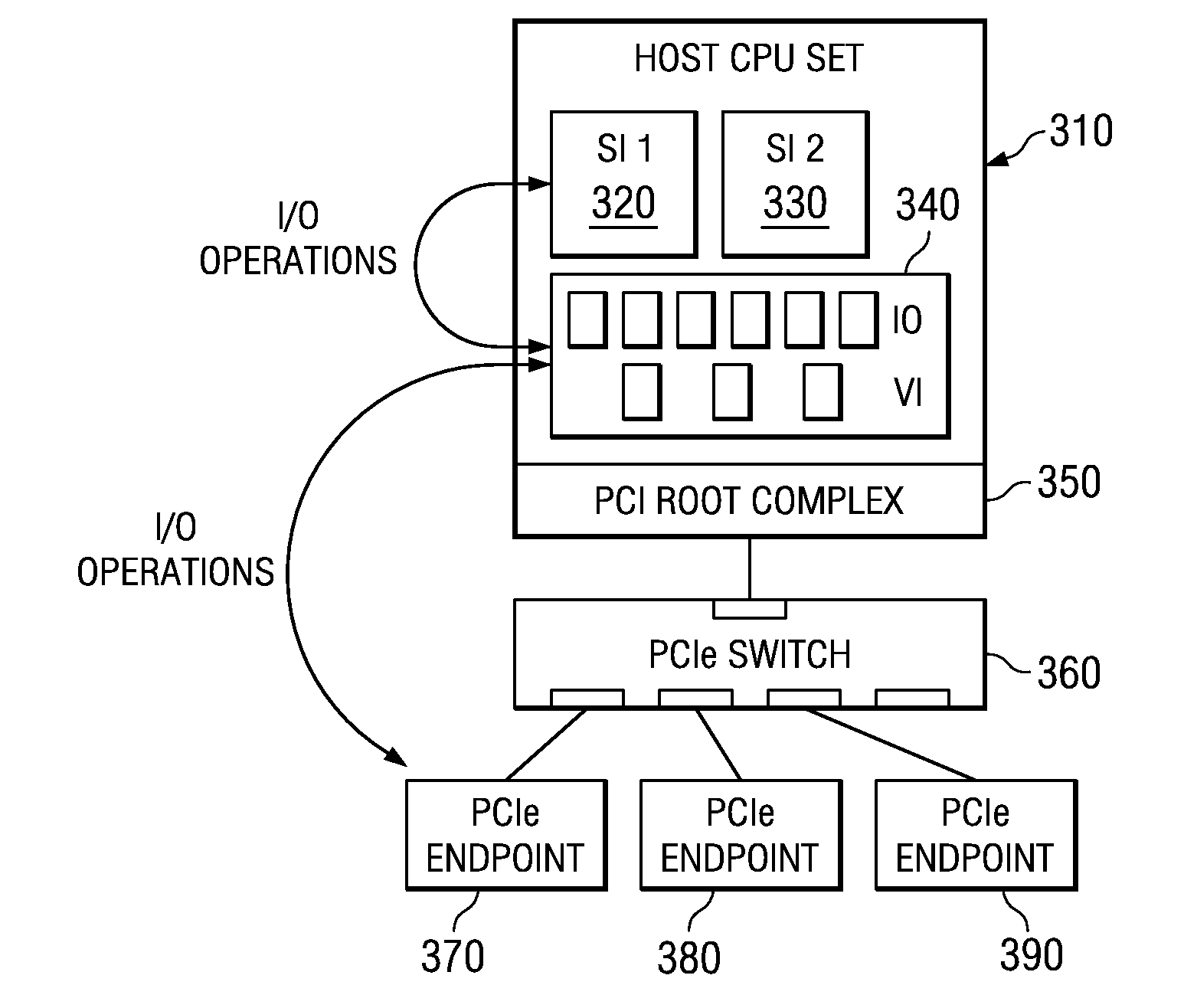
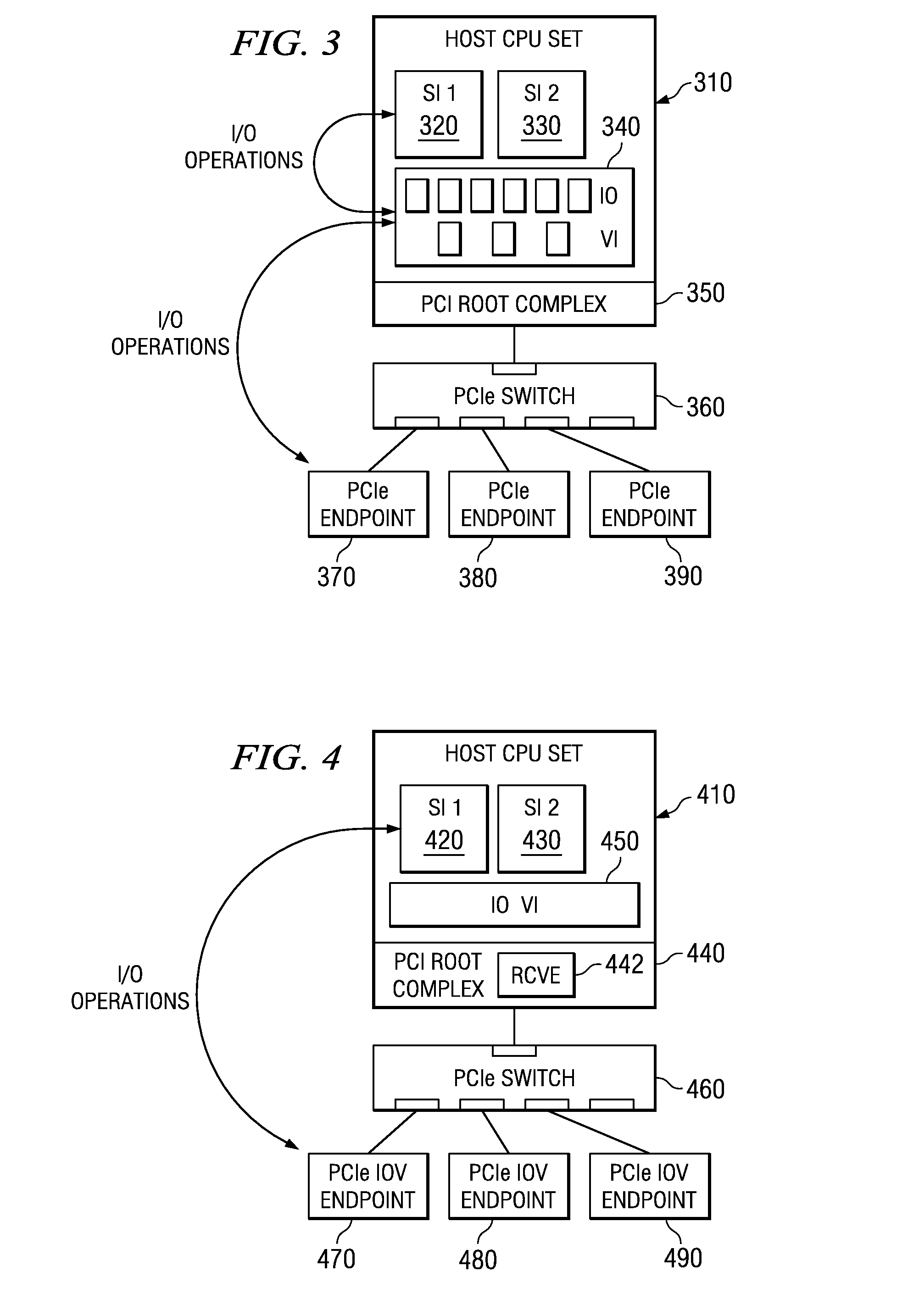
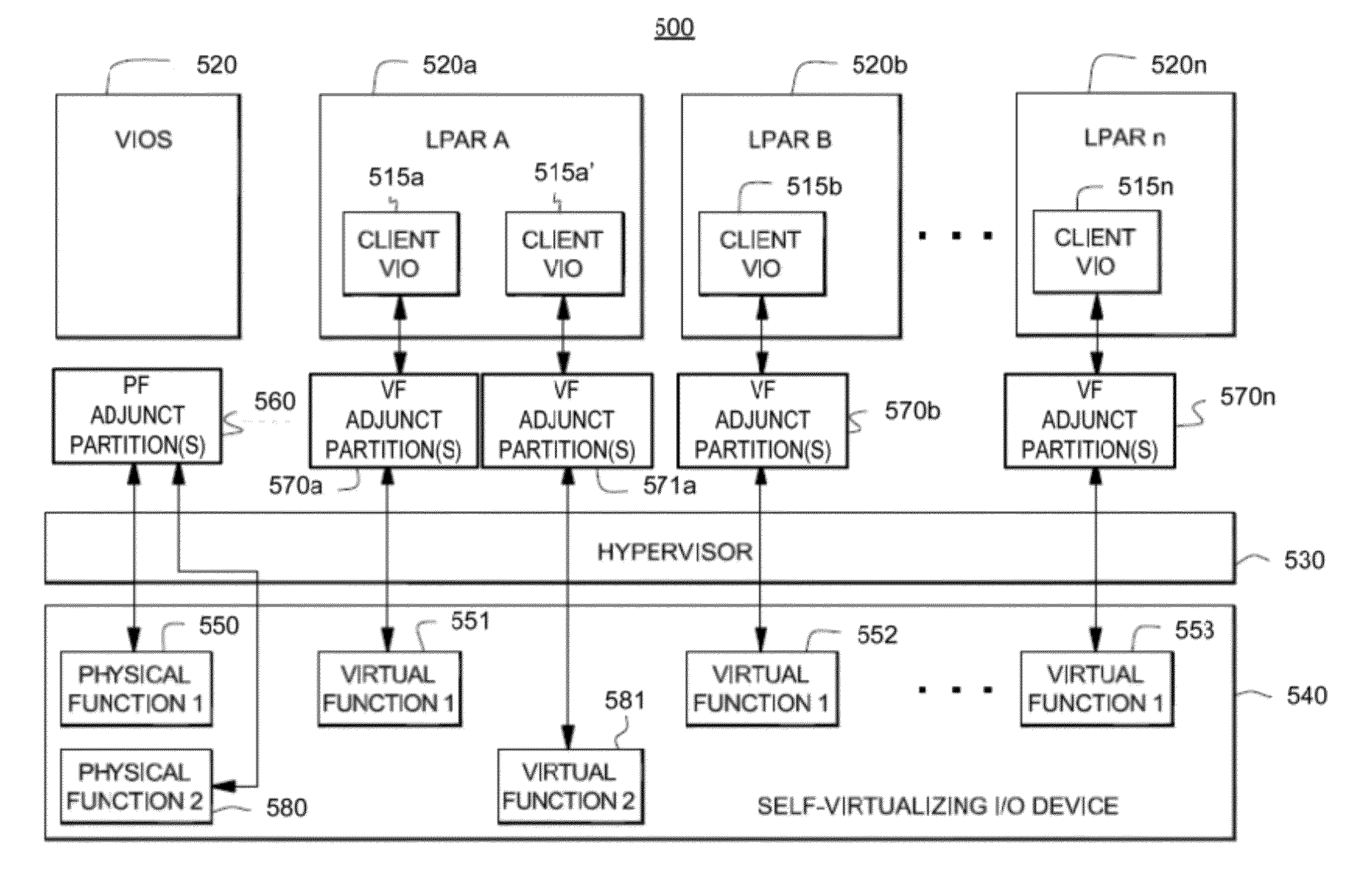
System and method for distribution of resources for an I/O virtualized (IOV) adapter and management of the adapter through an iov management partition
ActiveUS20090144731A1Multiprogramming arrangementsSoftware simulation/interpretation/emulationClient-sideShared resource
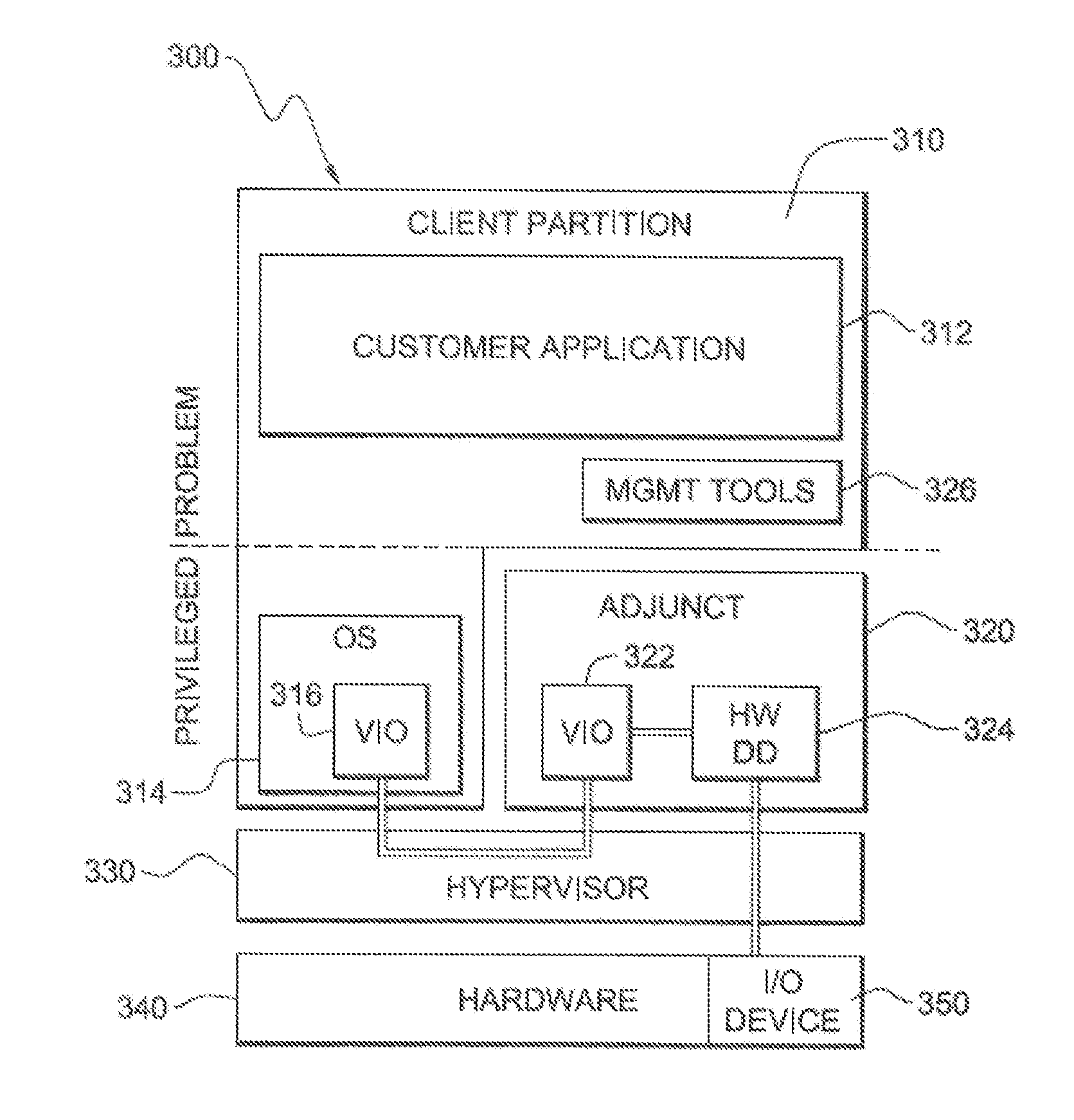
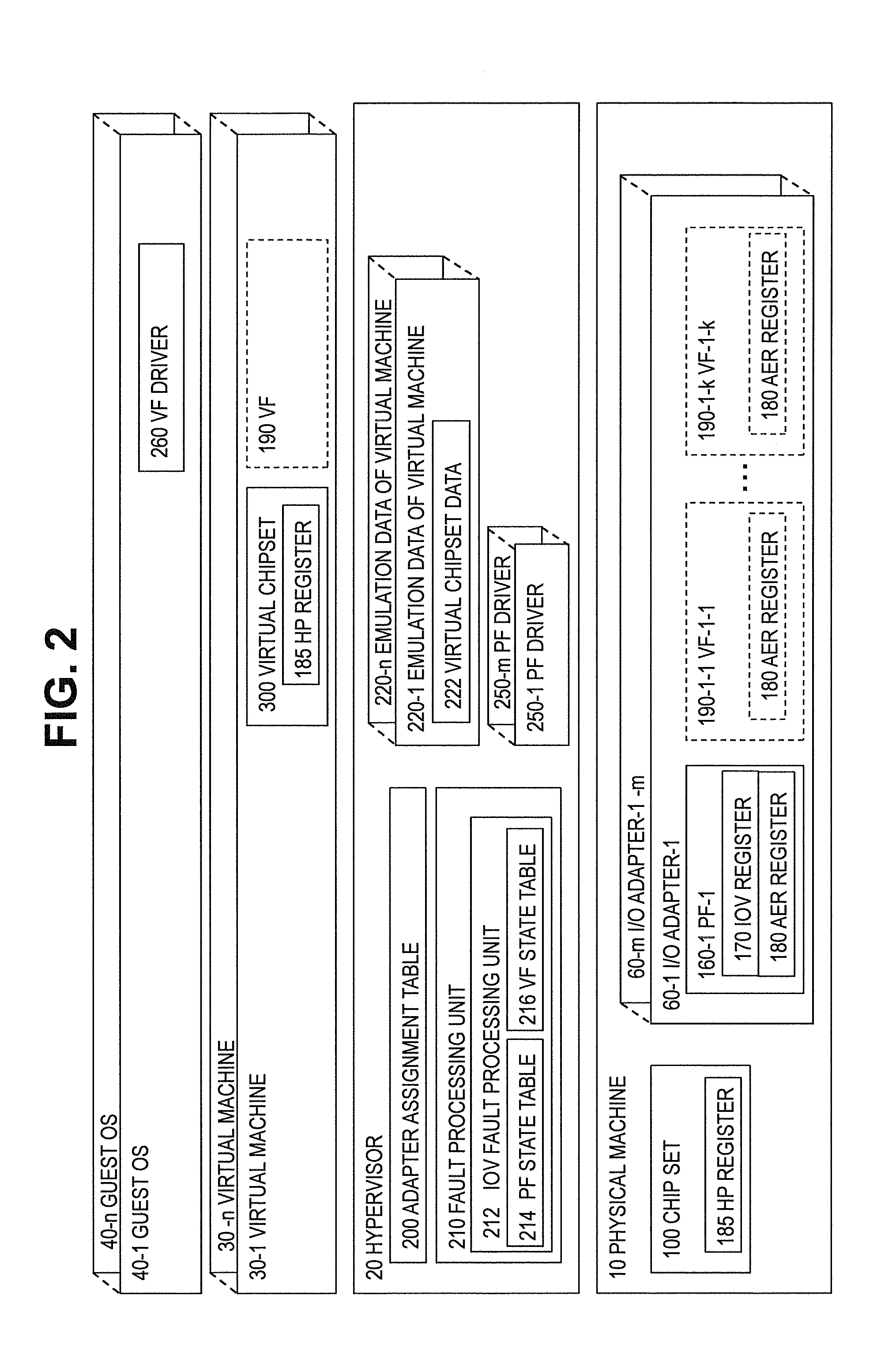
The system and method address the situation where an input / output (I / O) fabric is shared by more than one logical partition (LPAR) and where each LPAR can share with the other LPARs an I / O adapter (IOA). In particular, each LPAR is assigned its own separate address space to access a virtual function (VF) assigned to it such that each LPAR's perception is that it has its own independent IOA. Each VF may be shared across multiple LPARs. Facilities are provided for management of the shared resources of the IOA via a Physical Function (PF) of the IOA by assignment of that PF to an I / O Virtualization Management Partition (IMP). The code running in the IMP acts as a virtual intermediary to the VFs for fully managing the VF error handling, VF reset, and configuration operations. The IMP also acts as an interface to the PF for accessing common VF functionality. Furthermore, the functions of resource assignment and management relative to the VFs and the client partitions that use those VFs, which might normally be done by an entity like a hypervisor, are implemented by this IMP.
Owner:IBM CORP
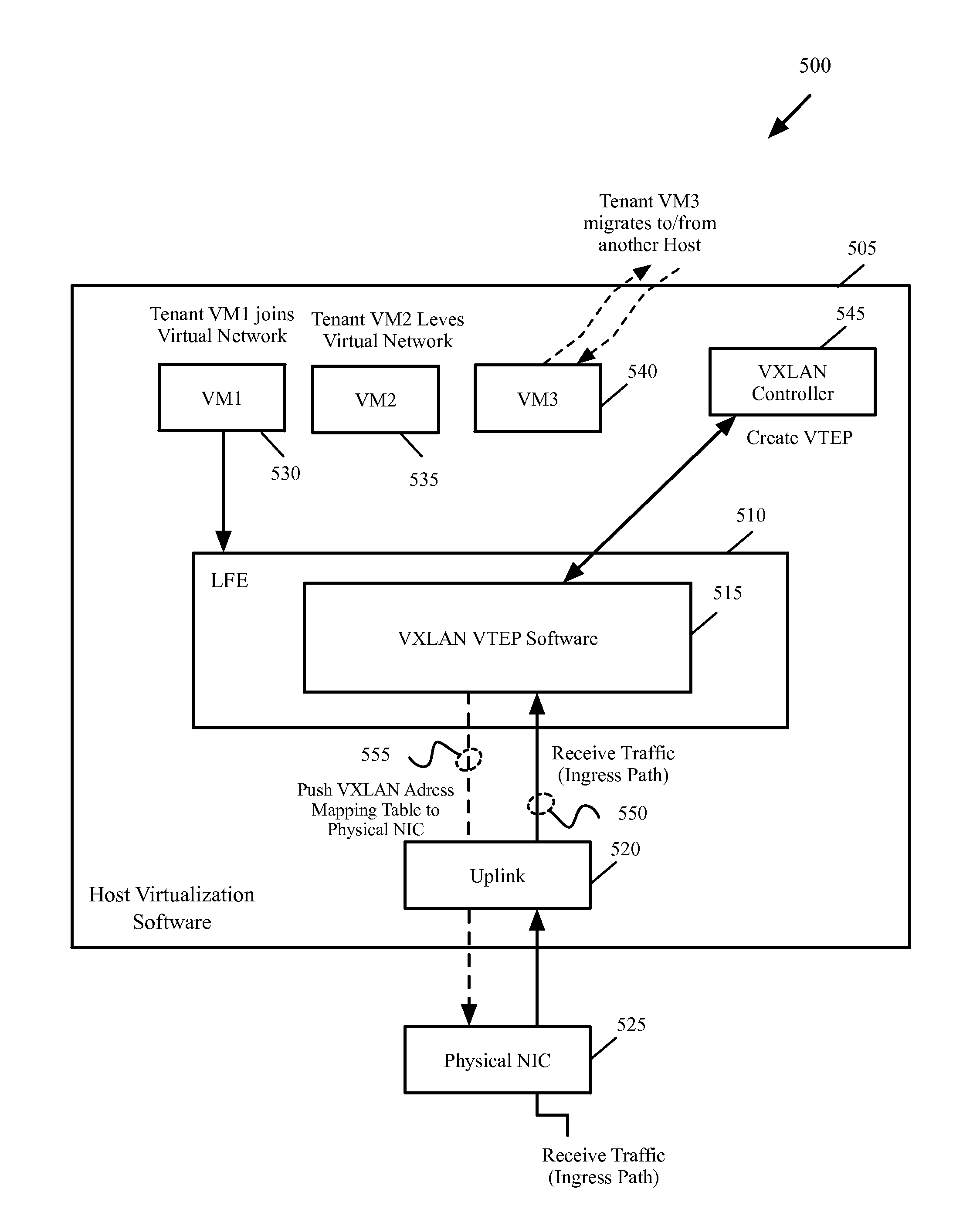
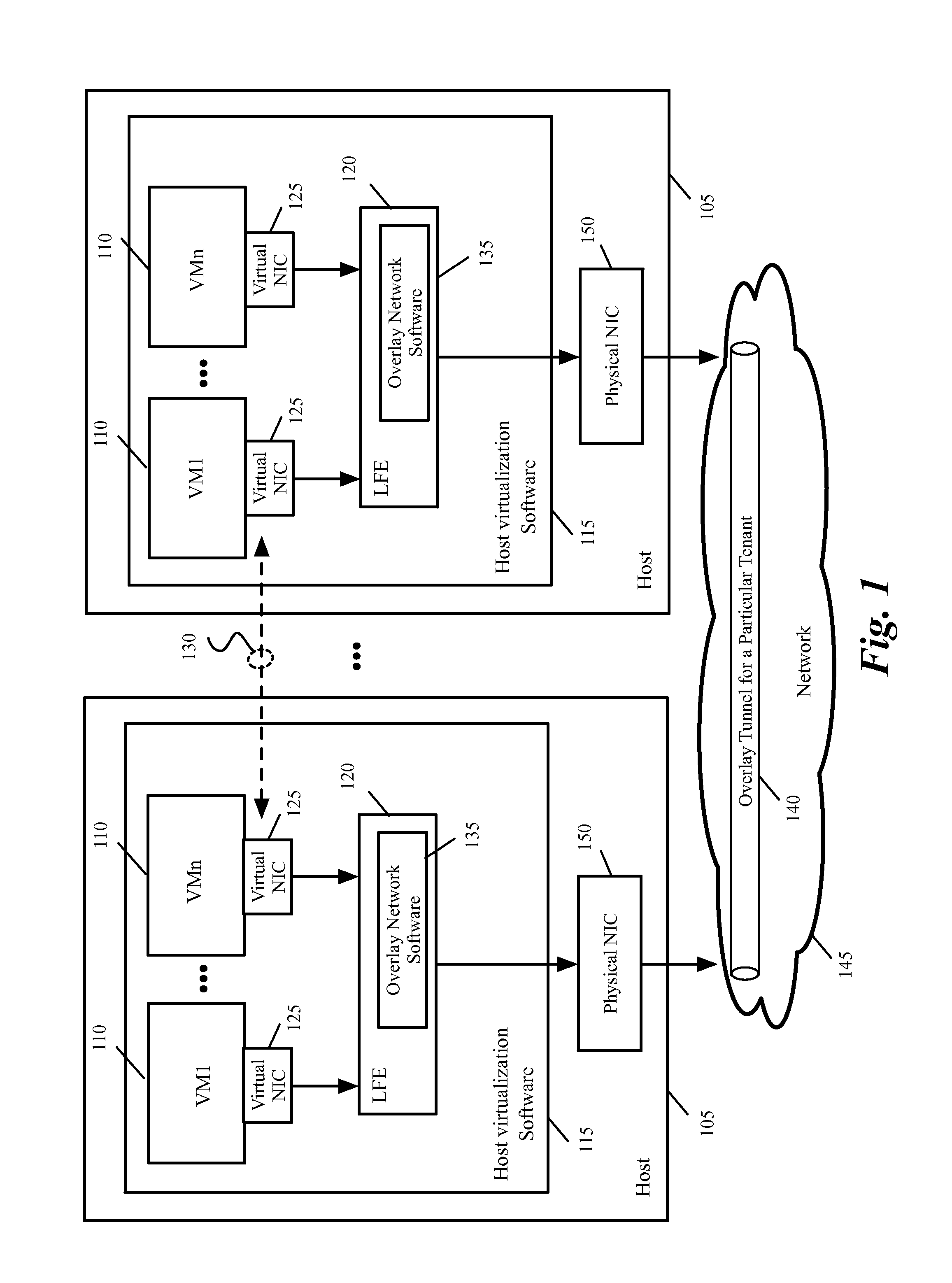
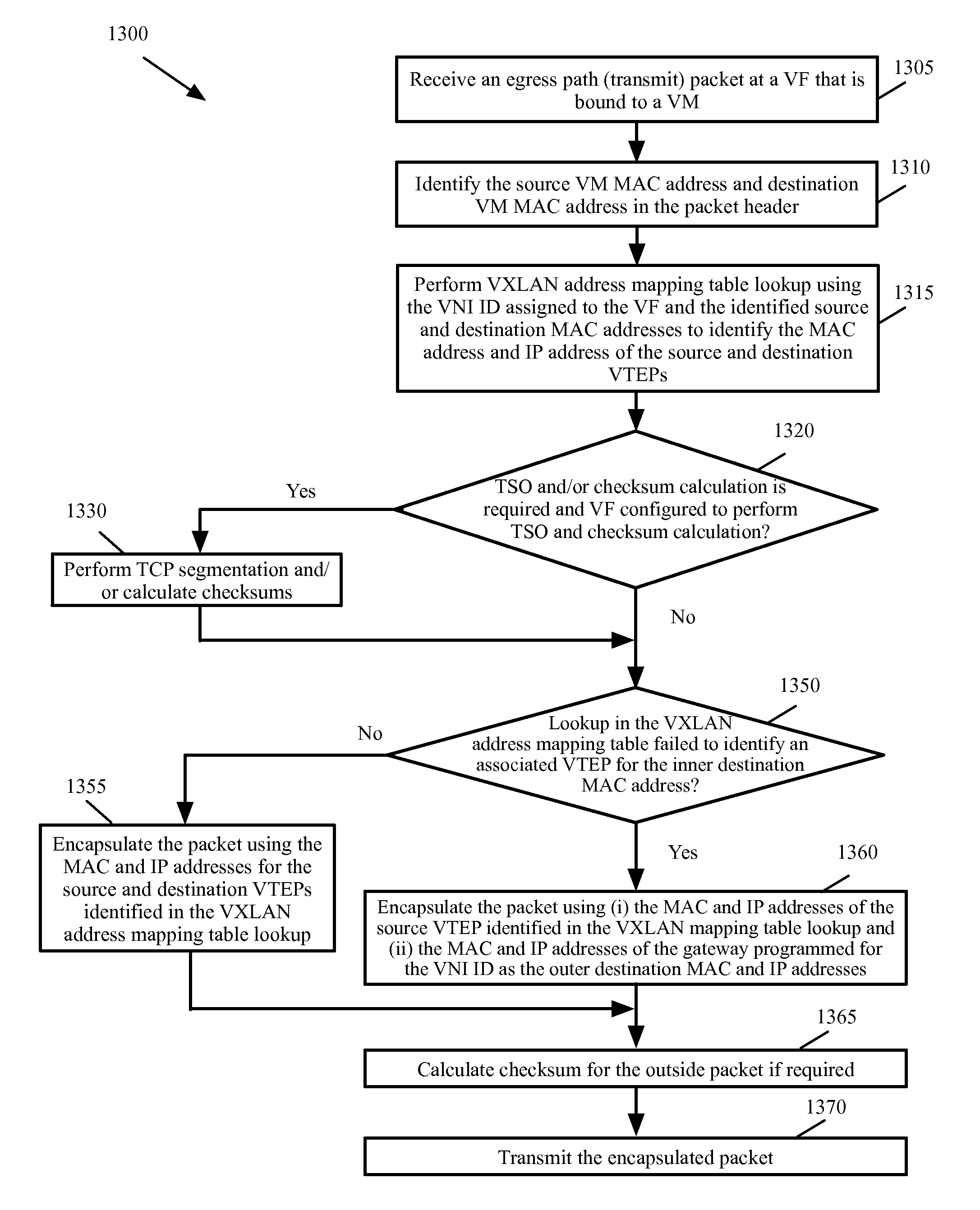
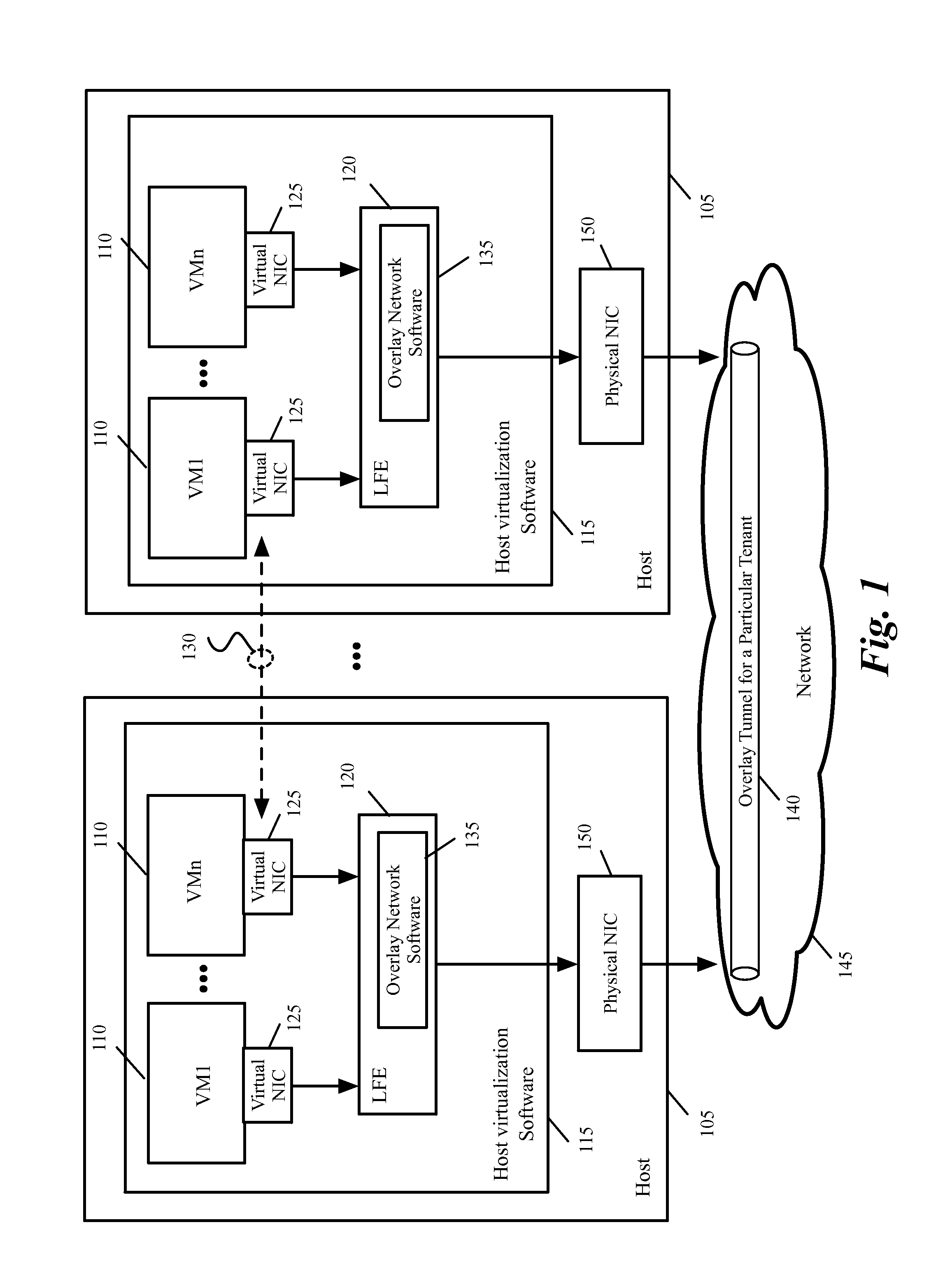
Methods and systems for providing multi-tenancy support for single root I/O virtualization
ActiveUS20150381495A1Data switching by path configurationProgram controlVirtualizationI/O virtualization
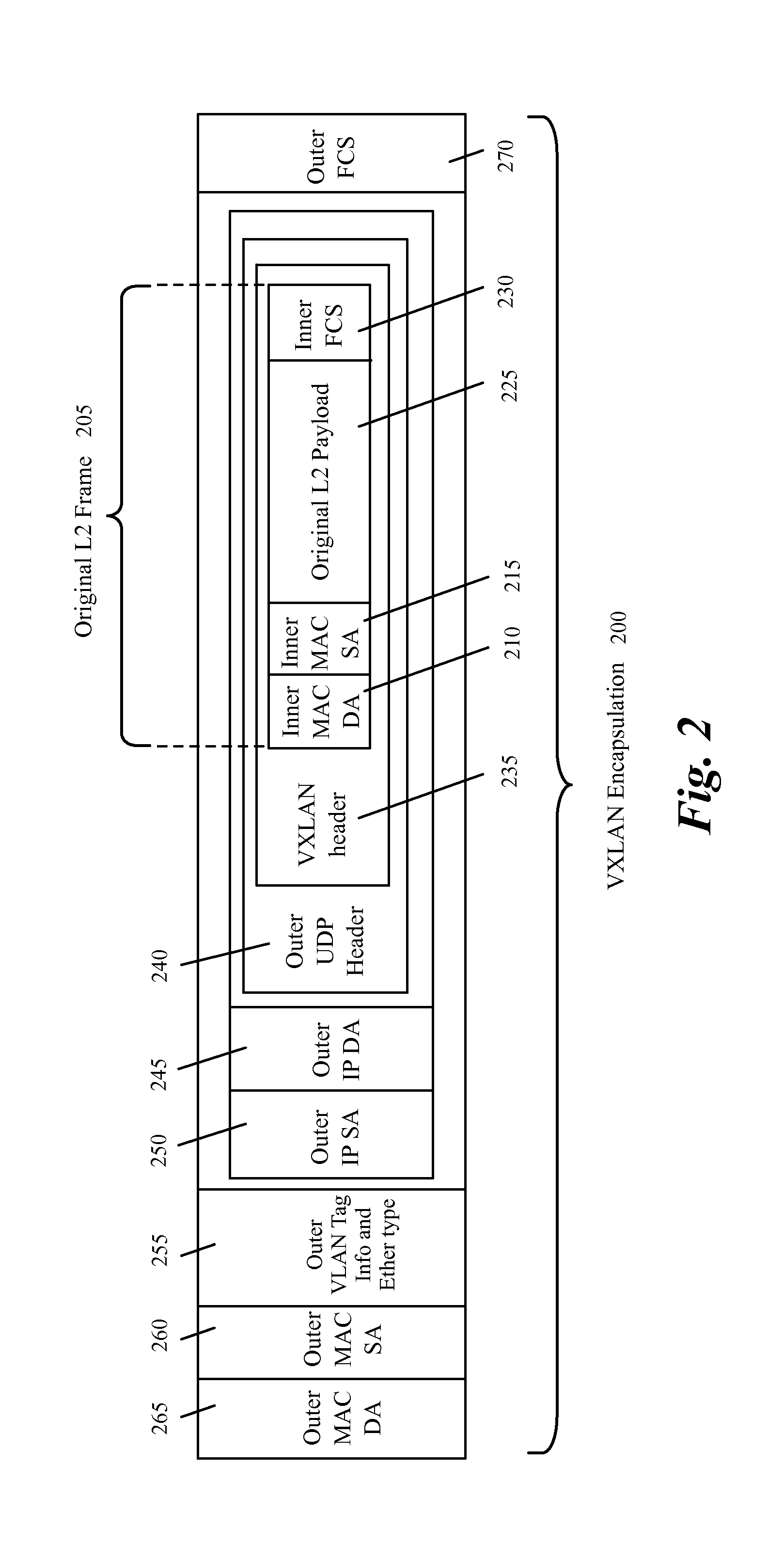
A method for providing support for multi-tenancy in single root input / out virtualization (SR-IOV) enabled physical network interface controller (NIC) is provided. The NIC is associated with a host. The SR-IOV provides a physical function (PF) and a set of virtual functions (VFs) for the NIC. The method at a VF of the physical NIC, receives a mapping table of an overlay network which associates an identification of each of a set of virtual machine (VM) of a tenant on the host to an identification of a tunnel end point on the overlay network. The method receives a transmit packet from a VM connected to the VF and performs a lookup in the mapping table to identify source and destination tunnel end points associated with source and destination VMs in the packet. The method encapsulates the packet, for transmission through the tunnel end point associated with the source VM.
Owner:NICIRA
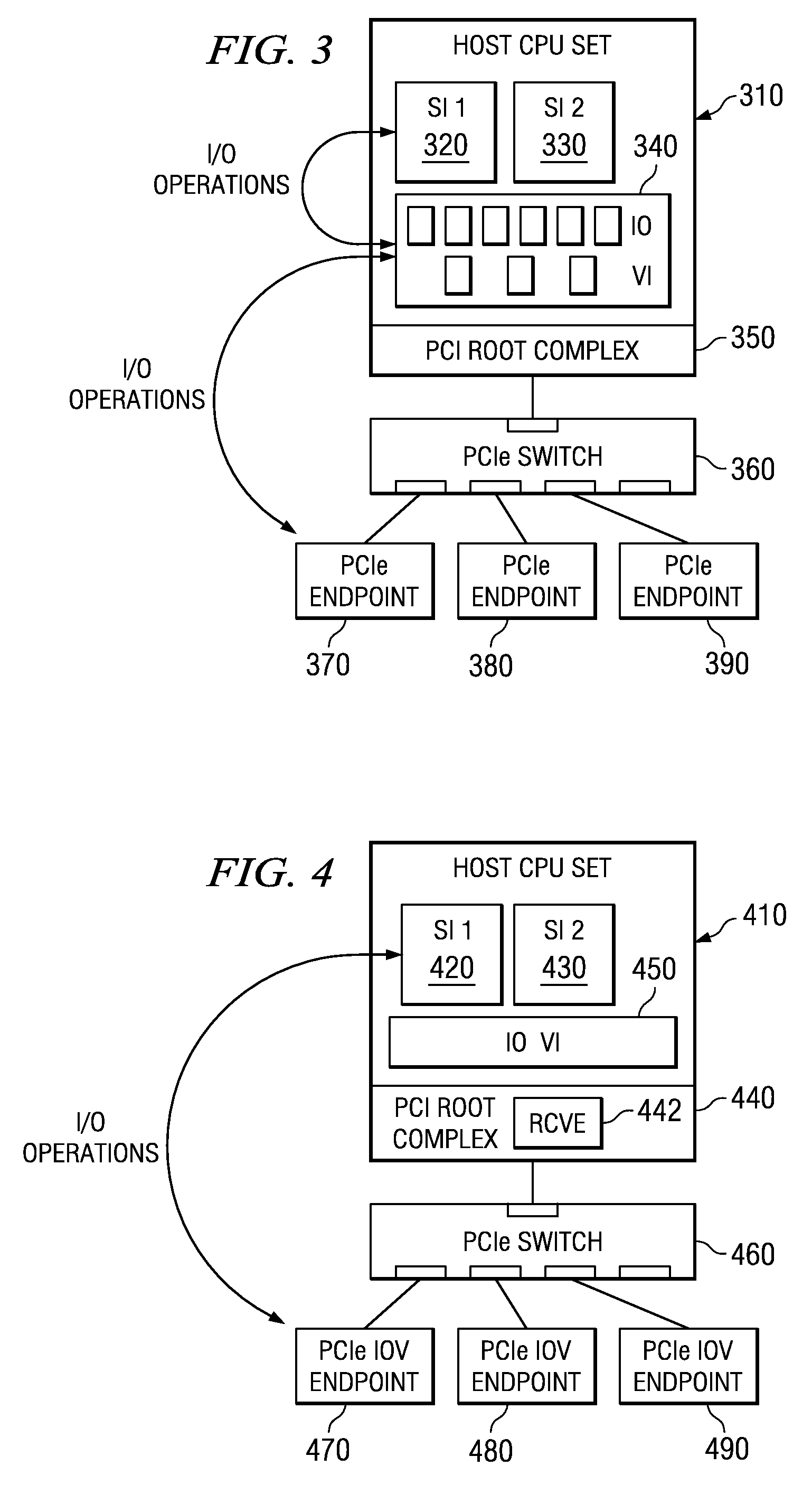
System and method for management of an iov adapter through a virtual intermediary in a hypervisor with functional management in an iov management partition
ActiveUS20090133028A1Avoid resourcesMultiprogramming arrangementsSoftware simulation/interpretation/emulationCapability managementFunctional management
A system and method which provide a mechanism for an I / O virtualization management partition (IMP) to control the shared functionality of an I / O virtualization (IOV) enabled I / O adapter (IOA) through a physical function (PF) of the IOA while the virtual functions (VFs) are assigned to client partitions for normal I / O operations directly. A hypervisor provides device-independent facilities to the code running in the IMP and client partitions. The IMP may include device specific code without the hypervisor needing to sacrifice its size, robustness, and upgradeability. The hypervisor provides the virtual intermediary functionally for the sharing and control of the IOA's control functions.
Owner:IBM CORP
Vendor-independent resource configuration interface for self-virtualizing input/output device
ActiveUS20120297379A1Software simulation/interpretation/emulationMemory systemsVirtualizationOutput device
A vendor-independent resource configuration interface automatically maps virtual functions to physical functions in a self-virtualizing IO resource using the concept of a logical port that maps to a particular physical port and protocol in the self-virtualizing IO resource. A user wishing to provide a logical partition access to a self-virtualizing IO resource typically creates or configures a logical port for the logical partition by mapping the logical port to a particular physical port and protocol defined for the self-virtualizing IO resource, and an appropriate virtual function mapped to an appropriate physical function on an appropriate self-virtualizing IO resource is automatically selected, typically without requiring the user to have a detailed understanding of the numbers of supported virtual functions, physical functions and protocols supported by specific resources.
Owner:IBM CORP
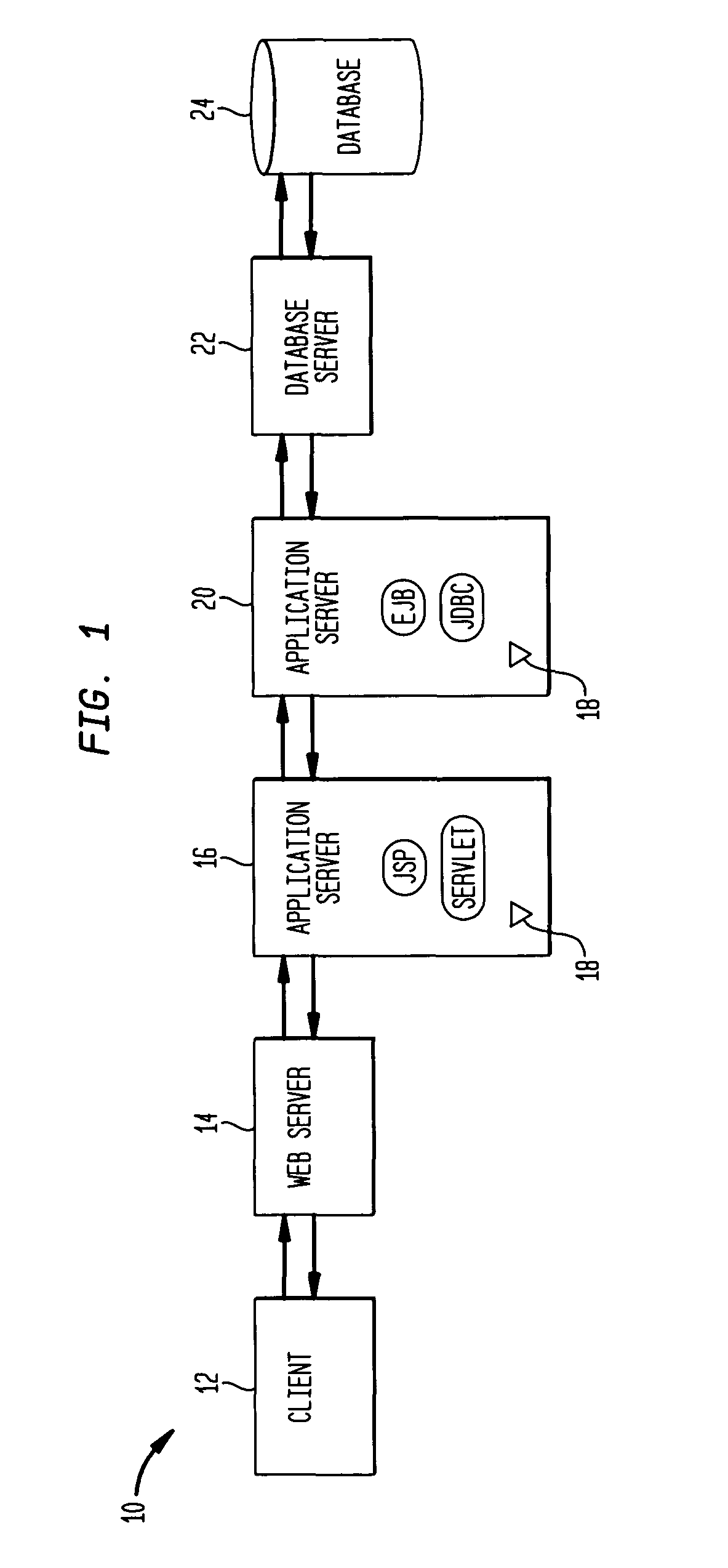
Propagating web transaction context into common object model (COM) business logic components
ActiveUS20050039190A1Error detection/correctionSpecific program execution arrangementsStart timeTime mark
Owner:MICRO FOCUS LLC
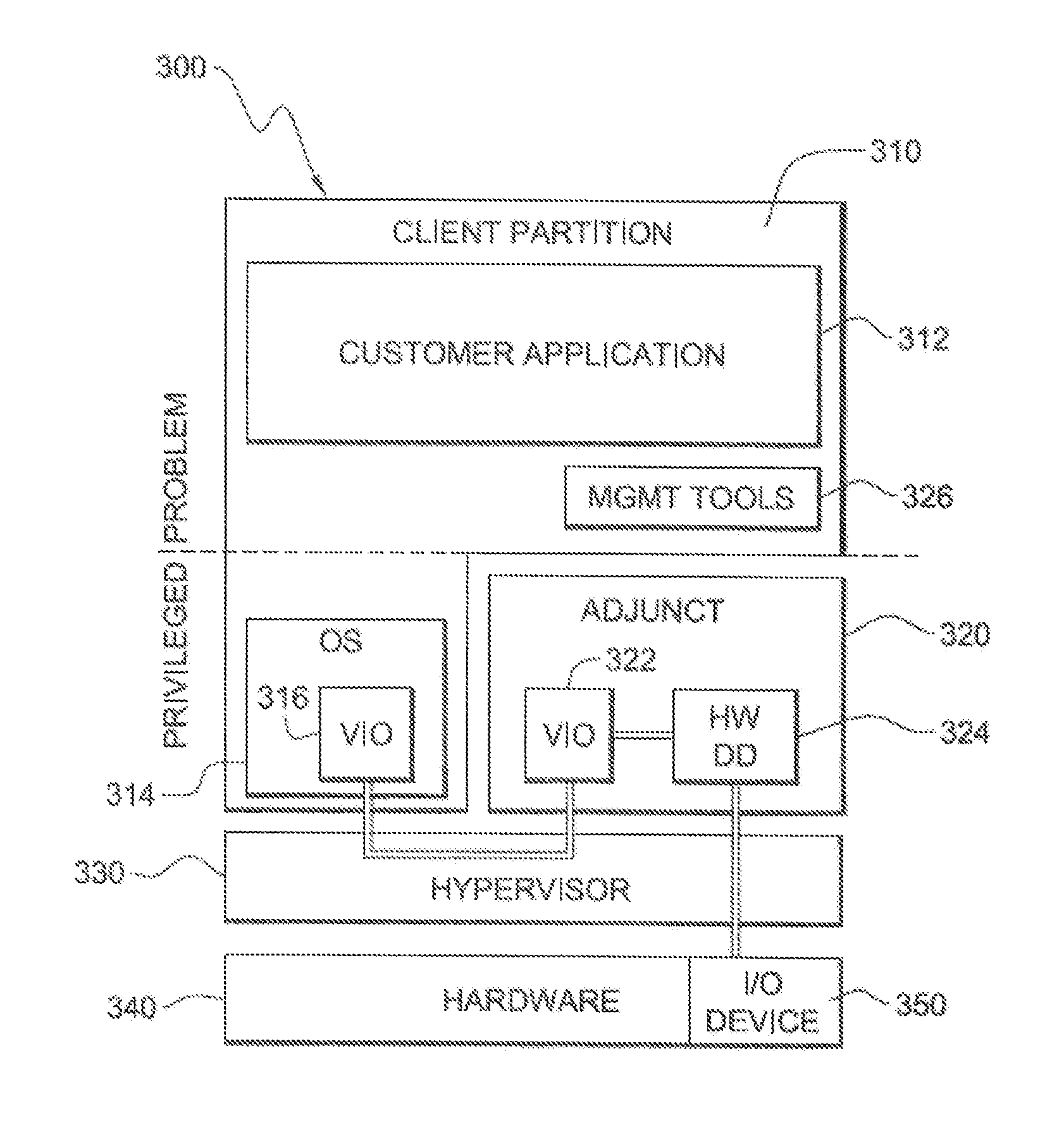
Enhanced error handling for self-virtualizing input/output device in logically-partitioned data processing system
ActiveUS20120159245A1Simplified error handlingAvoid the needNon-redundant fault processingRedundant operation error correctionVirtualizationData processing system
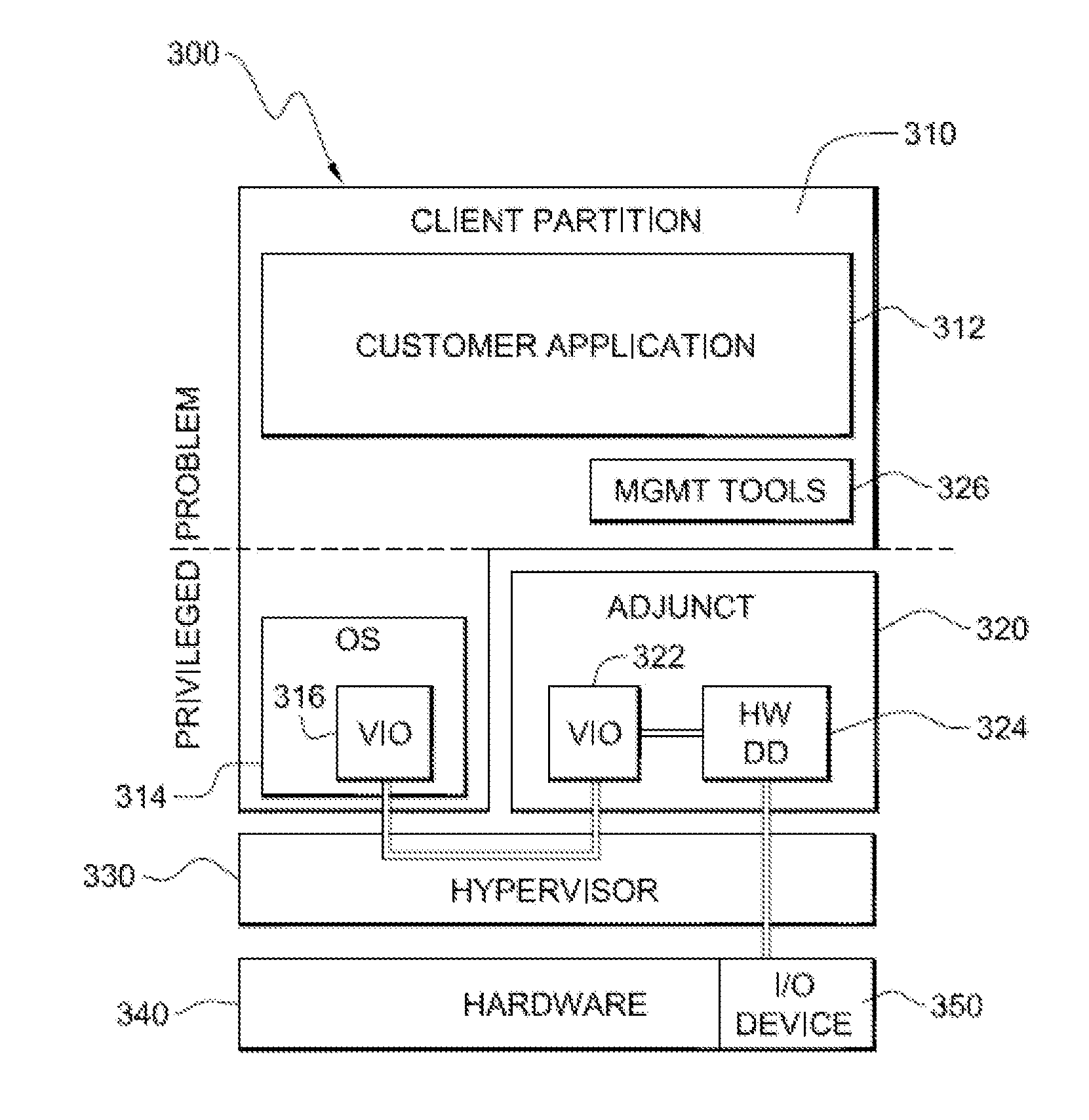
Error handling is simplified for a self-virtualizing IO resource that utilizes a physical function adjunct partition for a physical function in the self-virtualizing IO resource to coordinate error recovery for the self-virtualizing IO resource, by restarting each virtual function adjunct partition associated with that physical function to avoid the need to coordinate error recovery within the logical partitions to which such virtual function adjunct partitions are assigned.
Owner:IBM CORP
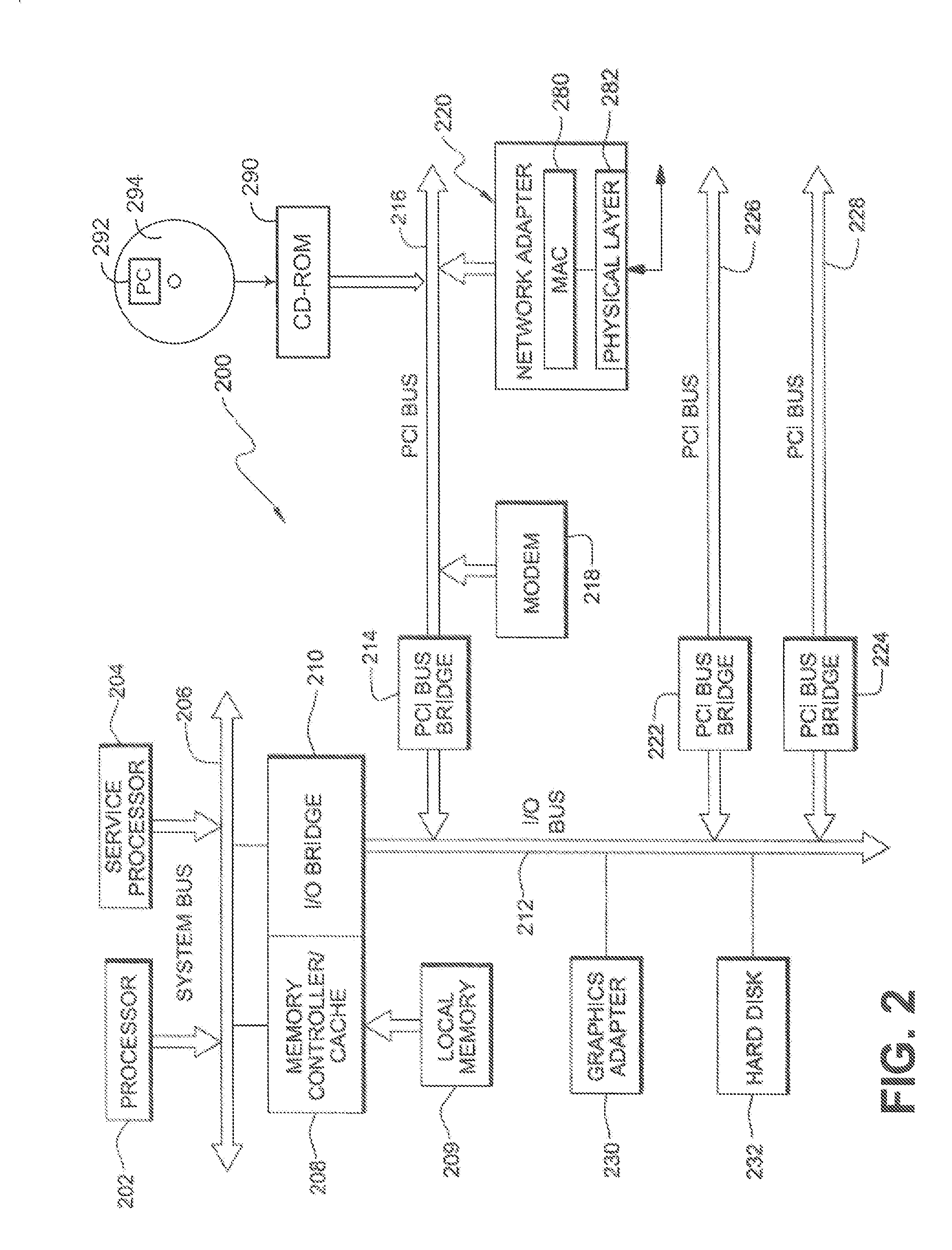
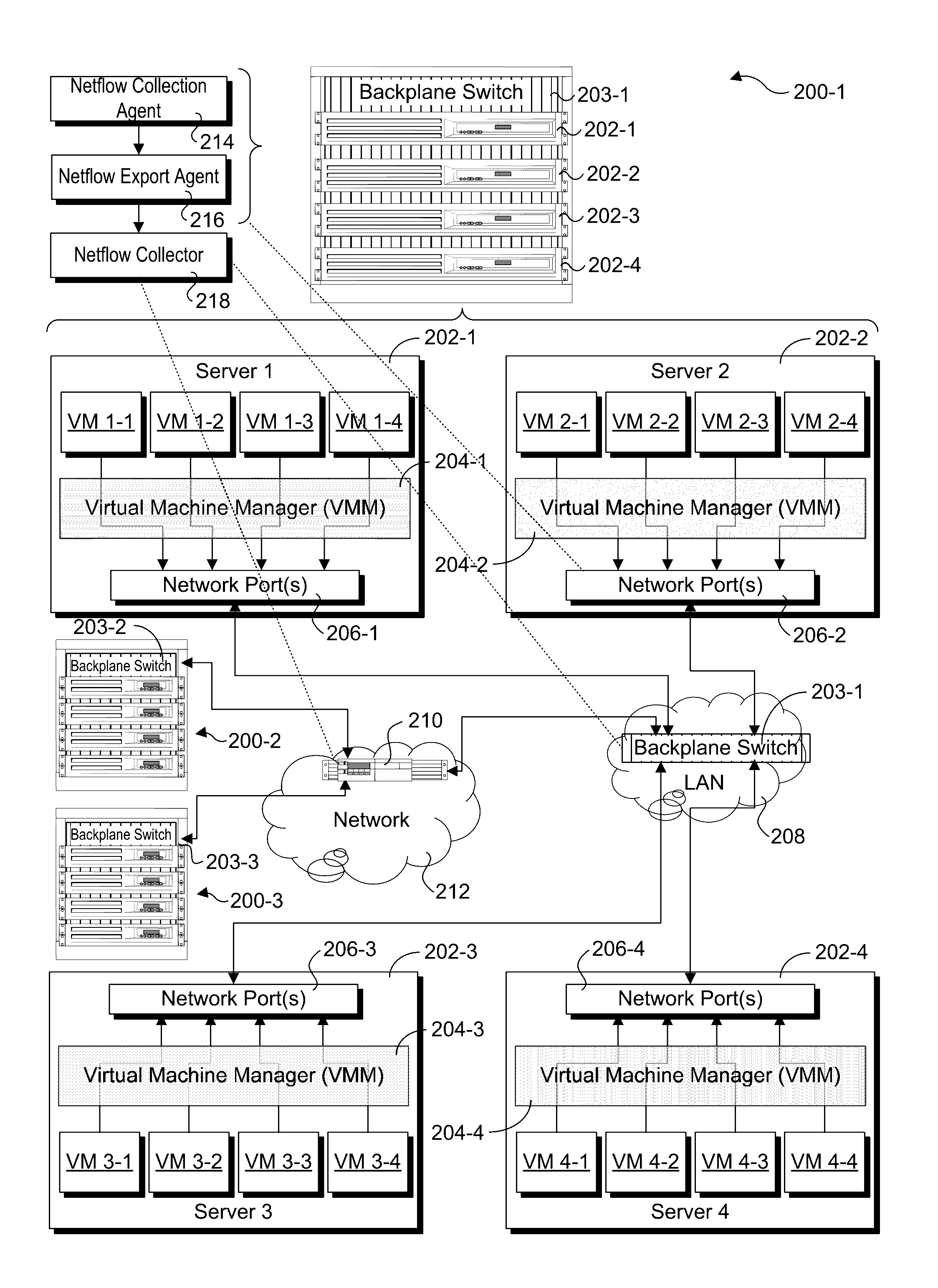
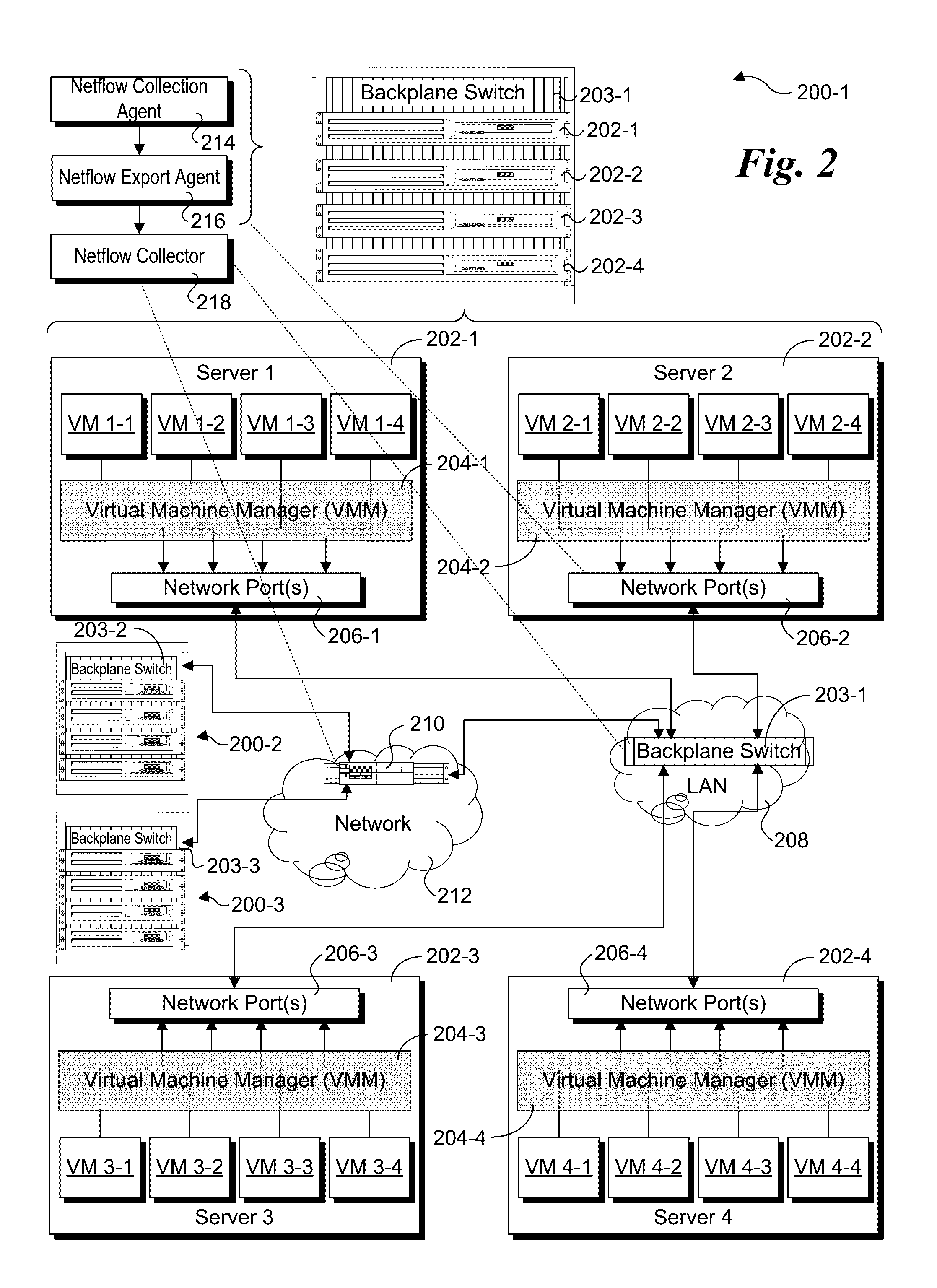
Netflow collection and export offload using network silicon
Methods and apparatus for collection of Netflow data and export offload using network silicon. In accordance with aspects of the embodiments, the Netflow export and collection functions are offloaded to the network silicon in the chipset, System on a Chip (SoC), backplane switch, disaggregated switch, virtual switch (vSwitch) accelerator, and Network Interface Card / Controller (NIC) level. For apparatus implementing virtualized environments, one or both of the collection and export functions are implemented at the Physical Function (PF) and / or Virtual Function (VF) layers of the apparatus.
Owner:INTEL CORP
System and Method for Management of an IOV Adapter Through a Virtual Intermediary in an IOV Management Partition
InactiveUS20090133016A1Multiprogramming arrangementsSoftware simulation/interpretation/emulationI/O virtualizationShared resource
The system and method address the situation where an input / output (I / O) fabric is shared by more than one logical partition (LPAR) and where each LPAR can share with the other LPARs an I / O adapter (IOA). In particular, each LPAR is assigned its own separate address space to access a virtual function (VF) assigned to it such that each LPAR's perception is that it has its own independent IOA. Each VF may be shared across multiple LPARs. Facilities are provided for management of the shared resources of the IOA via a Physical Function (PF) of the IOA by assignment of that PF to an I / O Virtualization Management Partition (IMP). The code running in the IMP acts as a virtual intermediary to the VFs for fully managing the VF error handling, VF reset, and configuration operations. The IMP also acts as an interface to the PF for accessing common VF functionality.
Owner:IBM CORP
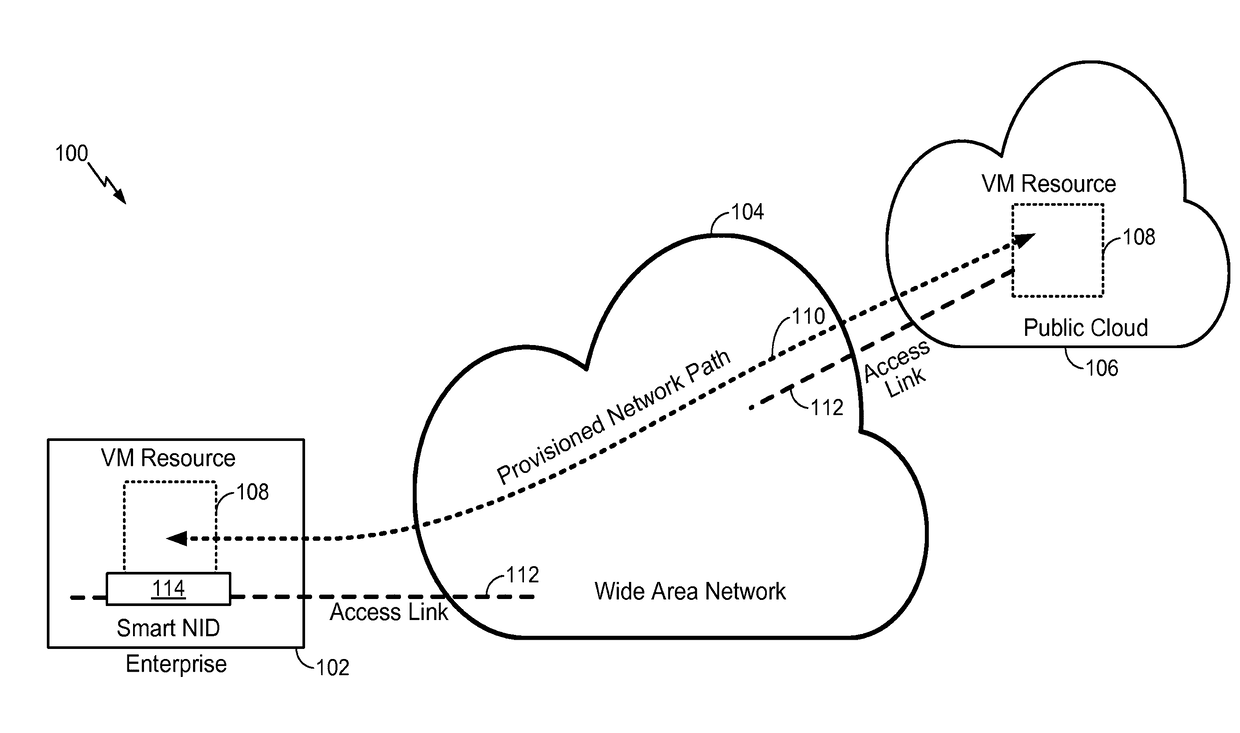
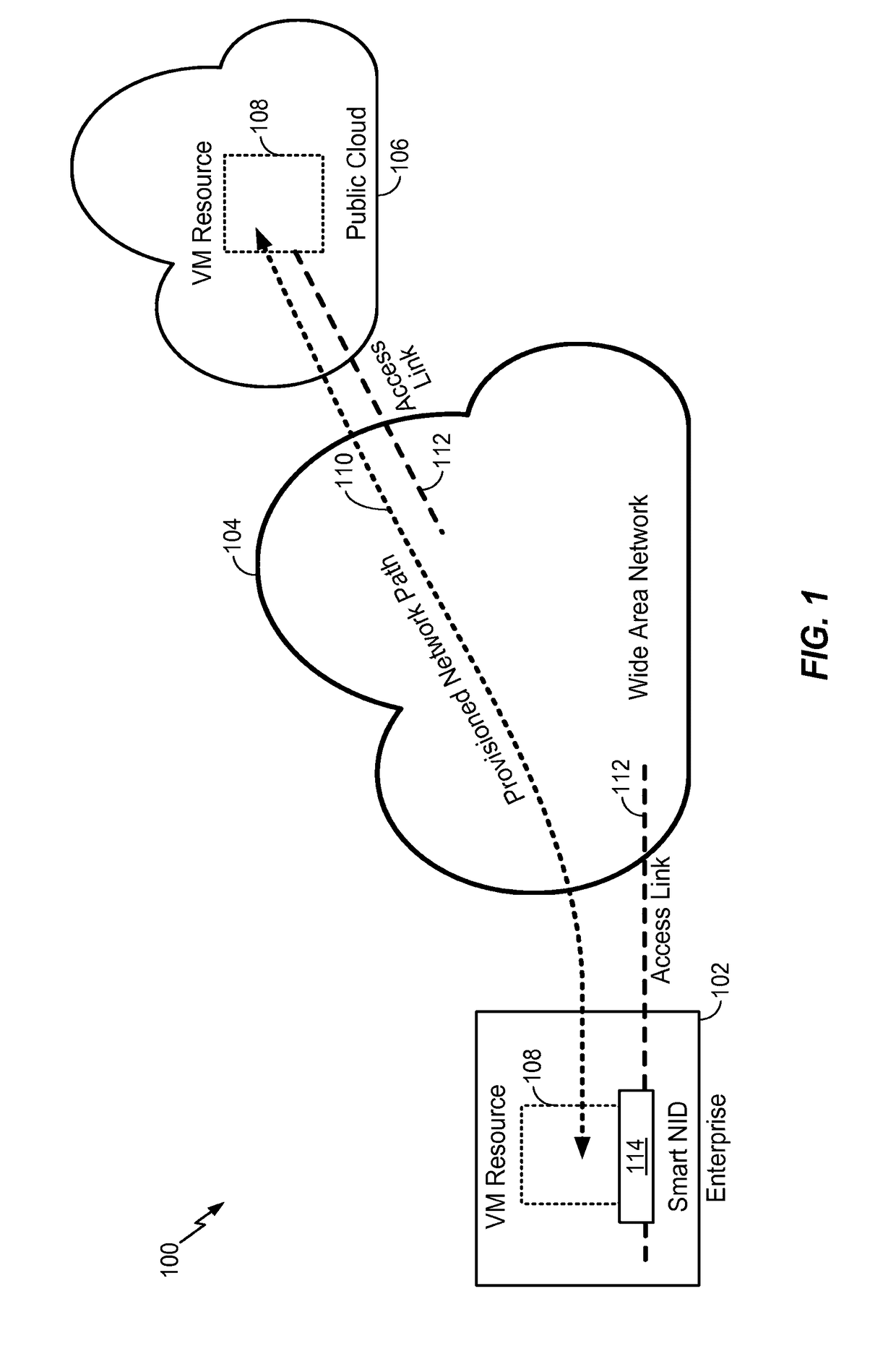
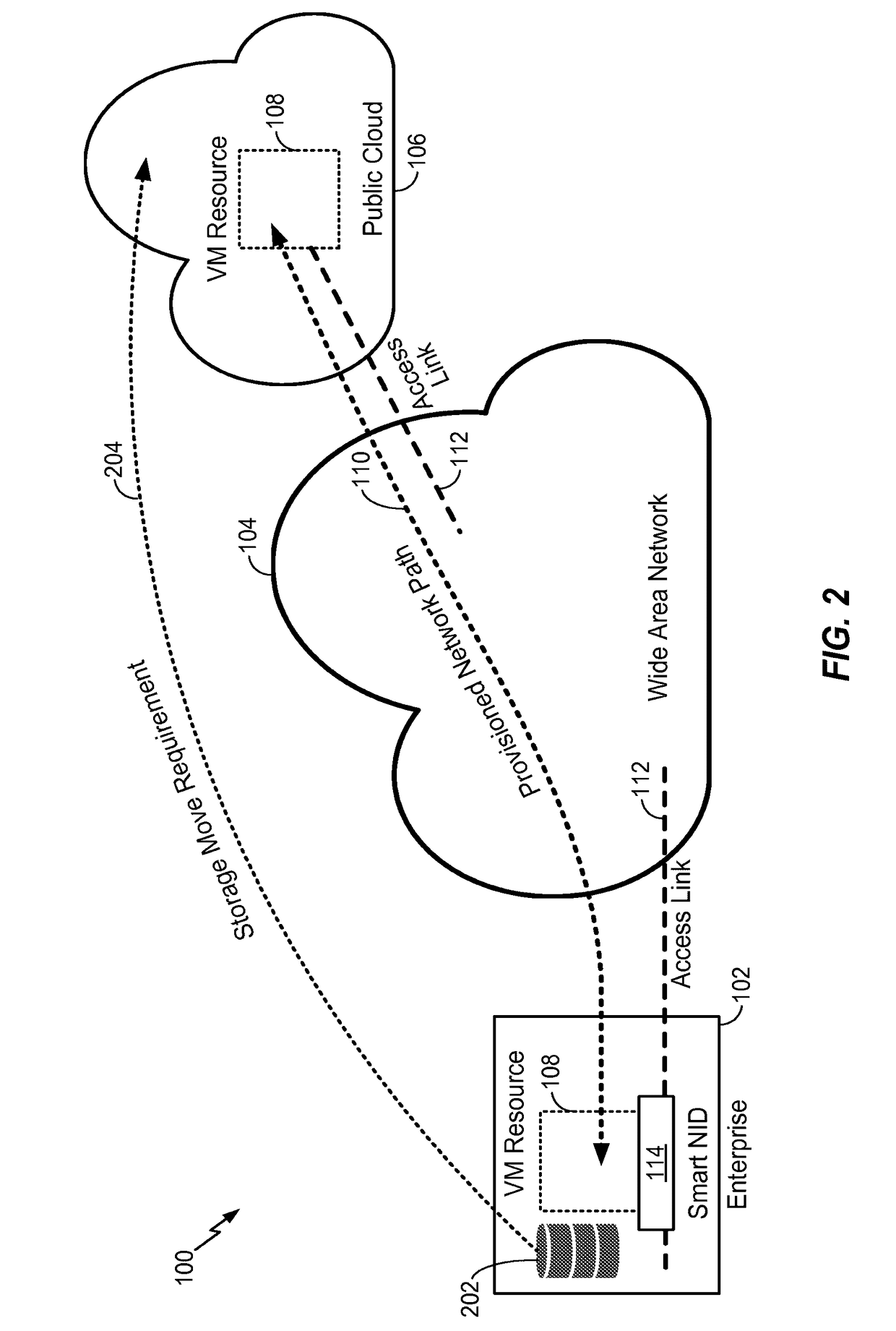
Method and apparatus for provisioning virtual network functions from a network service provider
A method and apparatus facilitates an enterprise to lease virtual appliances from network services provider. The method operates by deploying a converged networking and computing device at a service location, downloading a virtual network function to the converged networking and computing device, activating the virtual network function by a service in the wide area network, and connecting the virtual network function to a provisioned network path over the wide area network. Different virtual network functions can be deployed to different locations. The same virtual network function scan be deployed to different locations. Moreover, more than one virtual network function may be deployed to more than one service location. The virtual network functions can be realized through virtual machines, software containers, etc.
Owner:CIENA
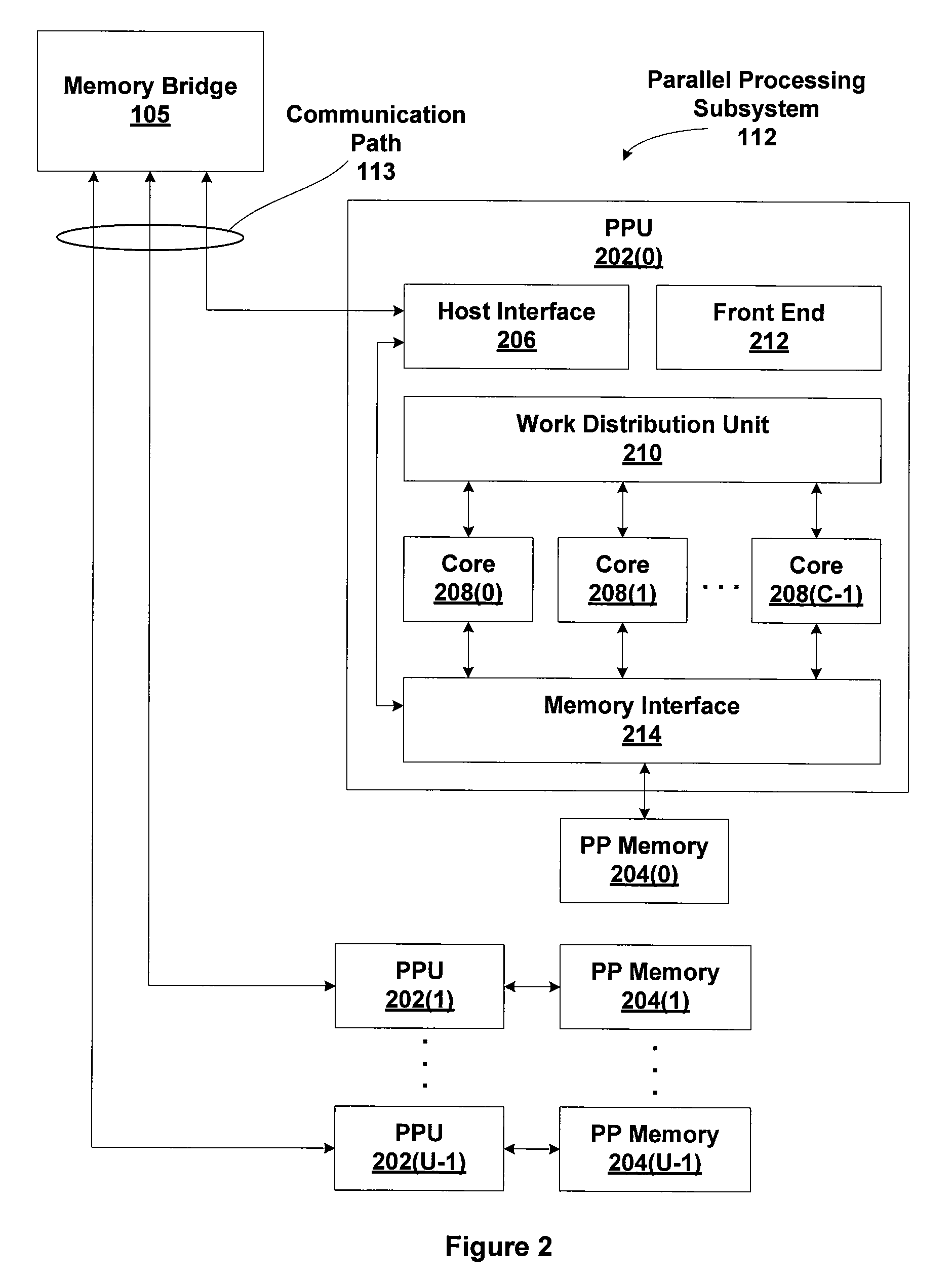
Indirect Function Call Instructions in a Synchronous Parallel Thread Processor
ActiveUS20090240931A1Easy to processProvide capabilitySingle instruction multiple data multiprocessorsConcurrent instruction executionSingle instruction, multiple threadsProcessor register
An indirect branch instruction takes an address register as an argument in order to provide indirect function call capability for single-instruction multiple-thread (SIMT) processor architectures. The indirect branch instruction is used to implement indirect function calls, virtual function calls, and switch statements to improve processing performance compared with using sequential chains of tests and branches.
Owner:NVIDIA CORP
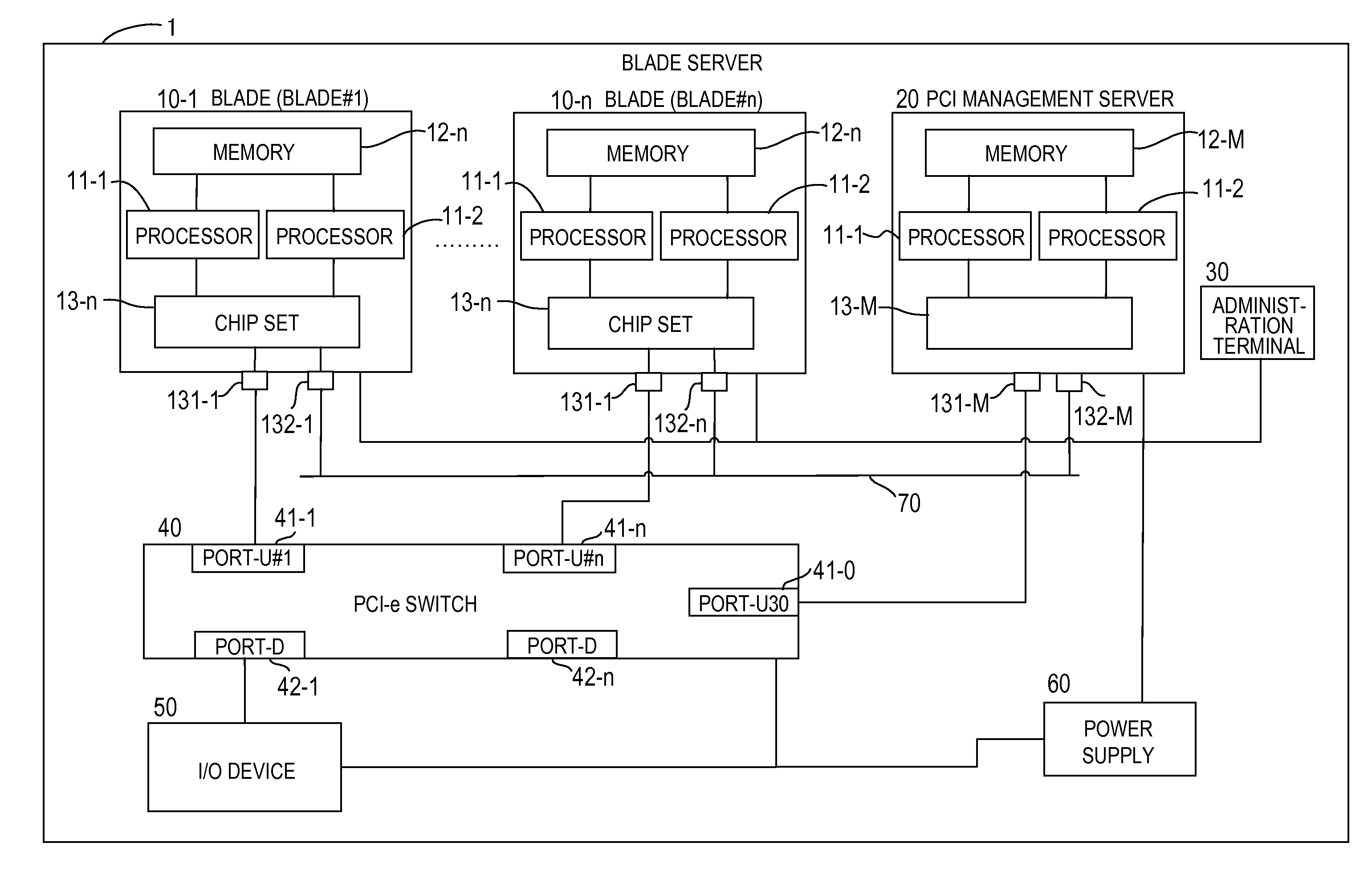
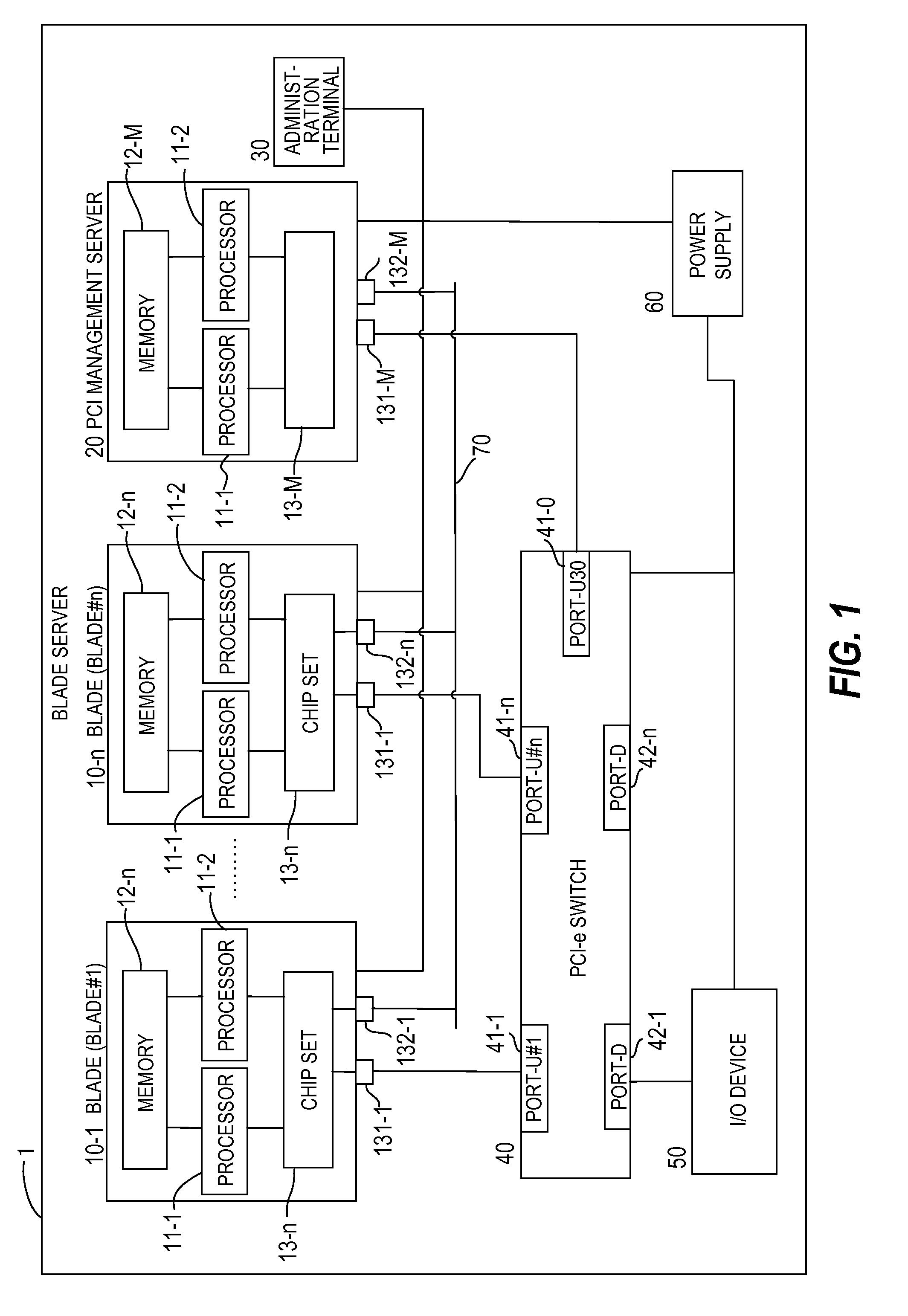
Computer system and method for sharing PCI devices thereof
InactiveUS20100082874A1Low costInput/output processes for data processingFinancial transactionOperating system
In order to provide an inexpensive way to share an I / O device loaded in an I / O drawer among a plurality of blades, in a server system including a plurality of servers, a PCI device, and a manager for initializing a PCI switch, the PCI device has a plurality of virtual functions (VFs). The PCI switch, which has VF allocation information which indicates association between the servers and the VFs, is configured to: receive a transaction from one of the servers or from the PCI device; when the received transaction is a transaction sent from the one of the servers, remove a server identifier with which a sender server is identified and transfer the received transaction to the PCI device; and when the received transaction is a transaction sent from the PCI device, attach a server identifier that is determined based on the VF allocation information.
Owner:HITACHI LTD
Sharing multiple virtual functions to a host using a pseudo physical function
ActiveUS20120167085A1Multiprogramming arrangementsData switching by path configurationComputer hardwareStructure of Management Information
A method is provided comprising: enumerating a group of available virtual functions corresponding to the physical function; mapping the group of available virtual functions to a non-transparent port of the switch by creating a copy of a configuration space for the physical function while assigning unique vendor and device identifications for different classes of devices, wherein the mapping creates a pseudo physical function exposing a subset of the SR-IOV capability from the configuration space for the physical function; receiving a request to access the physical function from the single host; and providing the pseudo physical function to the single host for loading on the single host, in response to the receiving of the request, wherein the pseudo physical function is designed to call management functions of the single host to enable the group of available virtual functions in a local hierarchy of the single host.
Owner:AVAGO TECH INT SALES PTE LTD
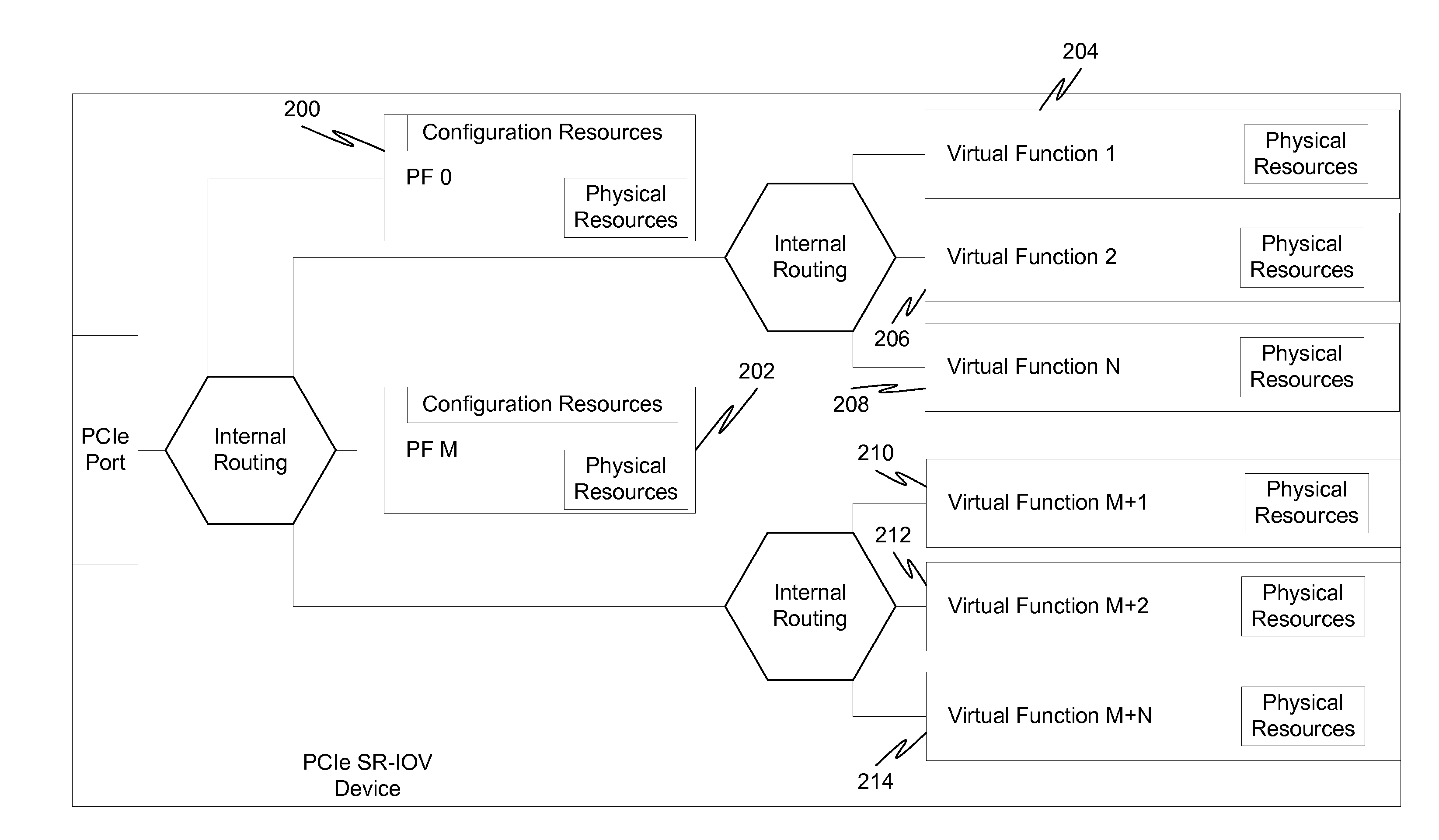
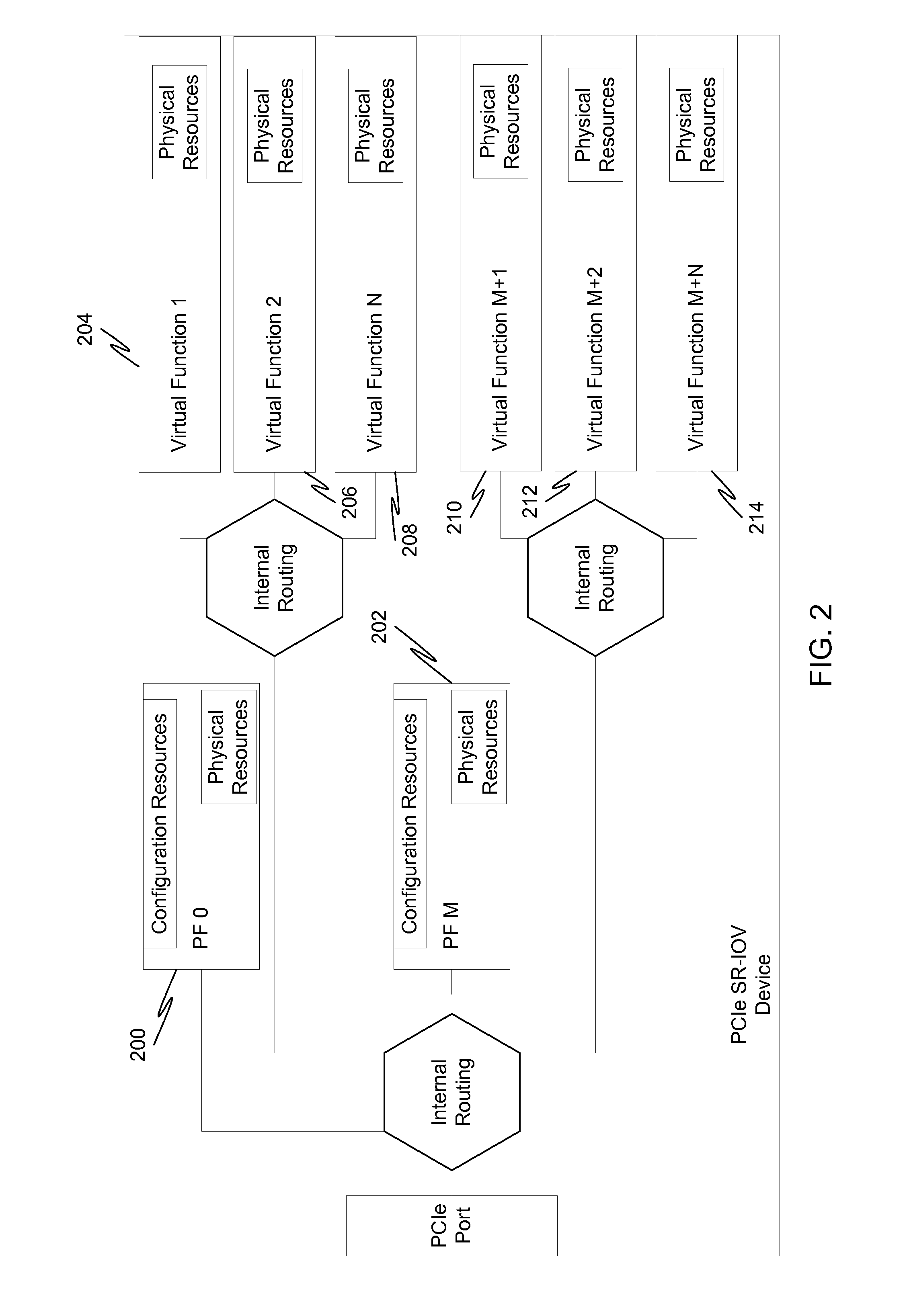
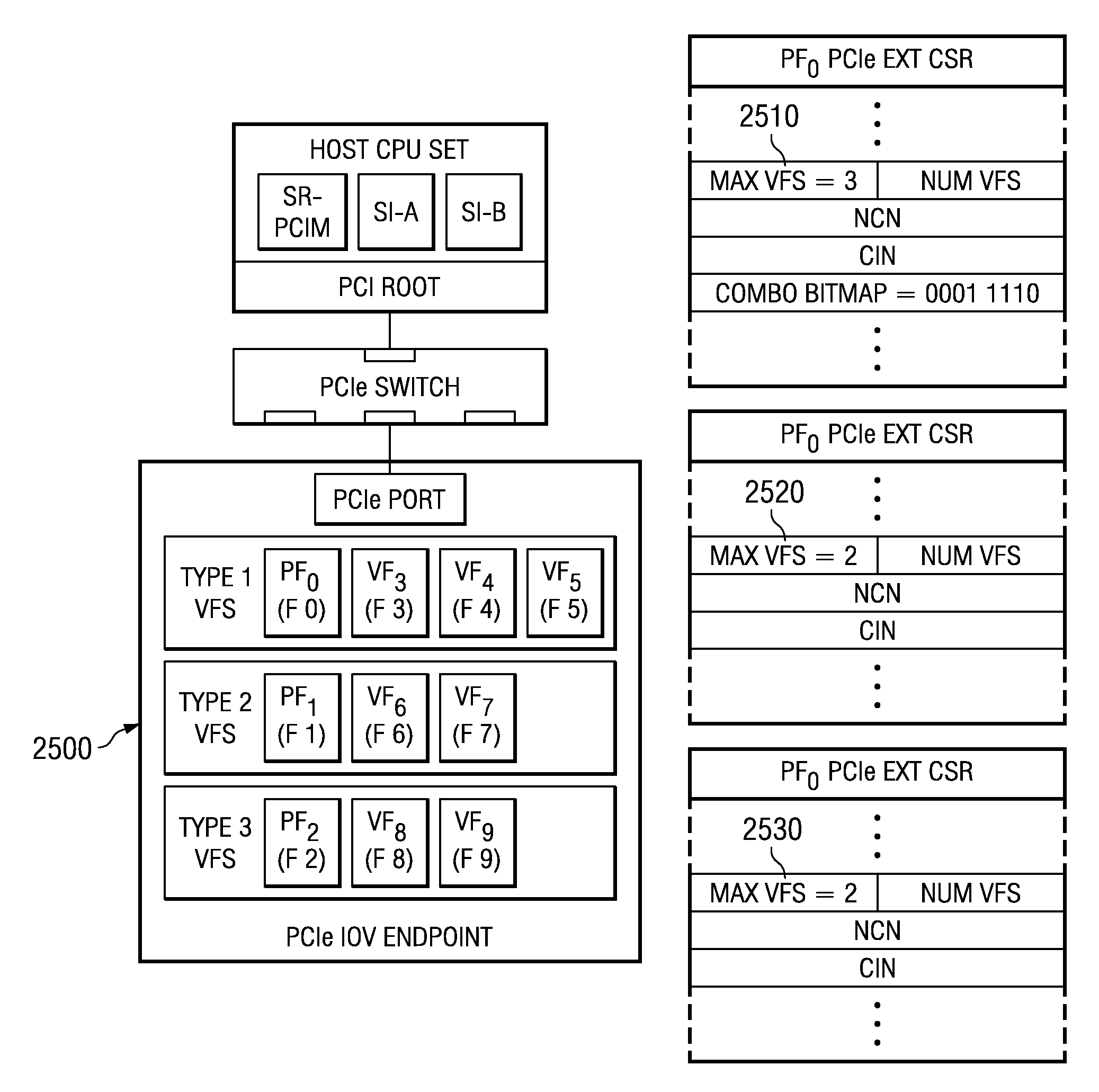
System and method for configuring an endpoint based on specified valid combinations of functions
Owner:INT BUSINESS MASCH CORP
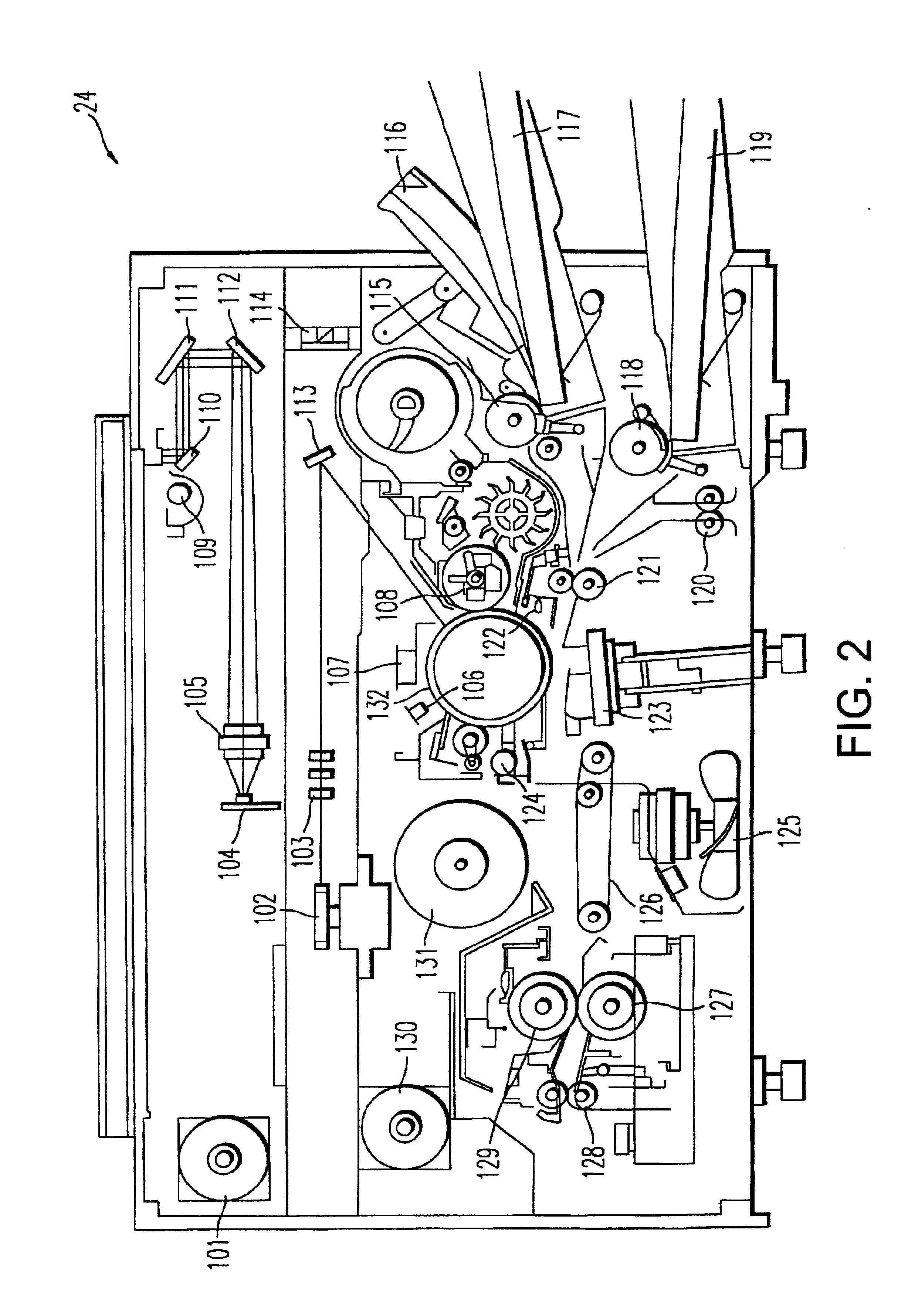
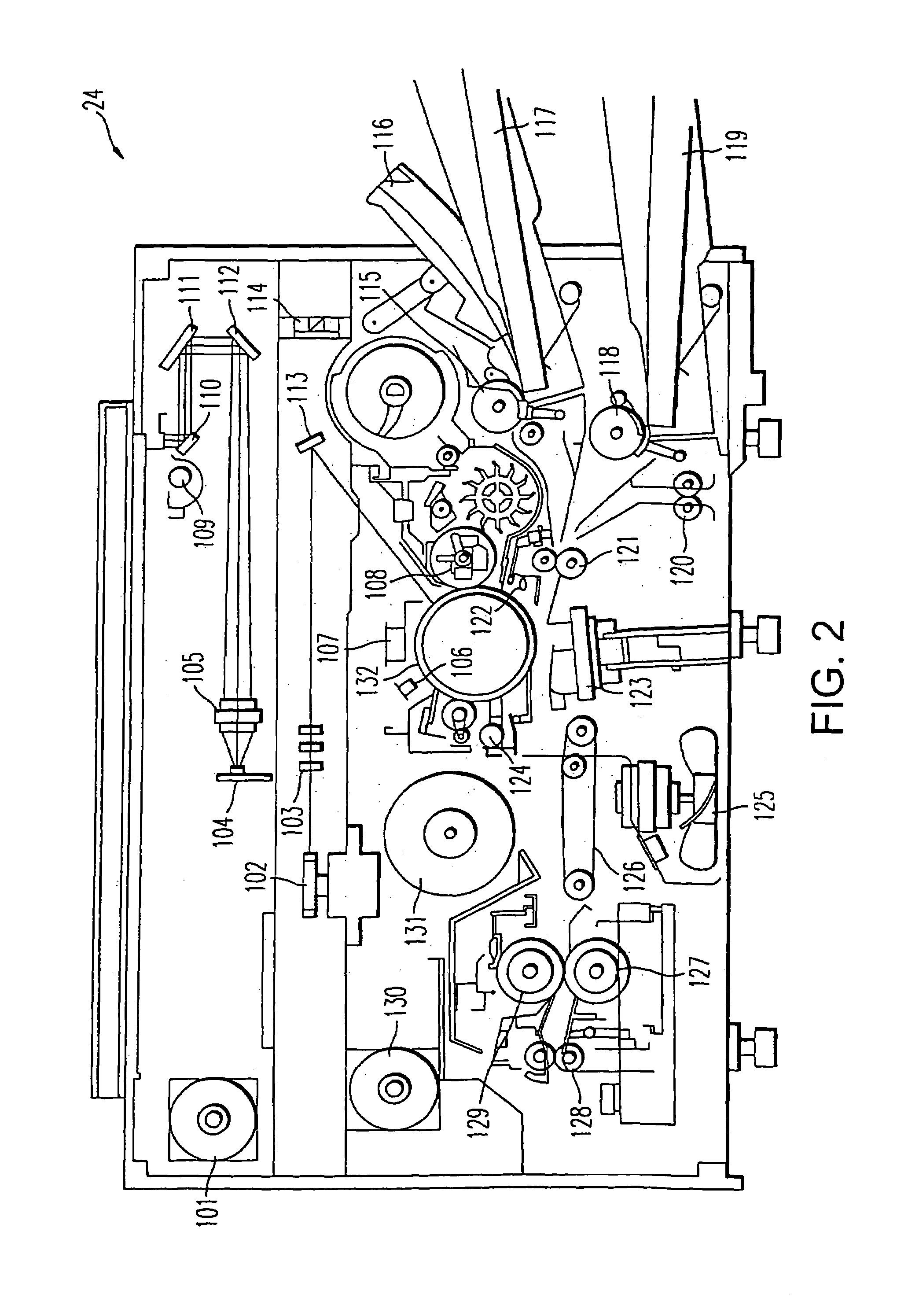
Method and system of remote monitoring and support of devices, using POP3 and decryption using virtual function
ActiveUS6925571B1Quickly and easily changeEasy to doMemory loss protectionUser identity/authority verificationProcess moduleComputer module
A method involves retrieving from an email message, information concerning at least one remotely monitored device. The method involves obtaining a line of the email message containing the information, decoding the line obtained from the email message if it has been encoded, and decrypting the decoded line. The decrypting involves using an abstract decrypter class configured to perform a virtual function and using any one of a plurality of derived decrypter classes each of which is configured as a derived class of the abstract decrypter class. The abstract decrypter class and the any one of the derived decrypter classes are collectively configured to decrypt the decoded email message, using the any one of the derived decrypter classes with the abstract decrypter class without having to modify the abstract decrypter class. An exemplary system for remotely monitoring devices uses the SMTP email protocol to send status, configuration, or other information concerning at least one of the devices in a MIME attachment of an email message. A POP3 processing module in the receiver of the email has a class structure. An interface class accesses an email server and obtain the email message including the MIME attachment. An extractor class extracts the MIME attachment from the email message, and a decoder class performs Base64 decoding of the attachment. An abstract decrypter class and each of plural derived decrypter classes configured as a derived class thereof, permit flexibility in adopting new decryption processes without having to modify the abstract decrypter class.
Owner:RICOH KK
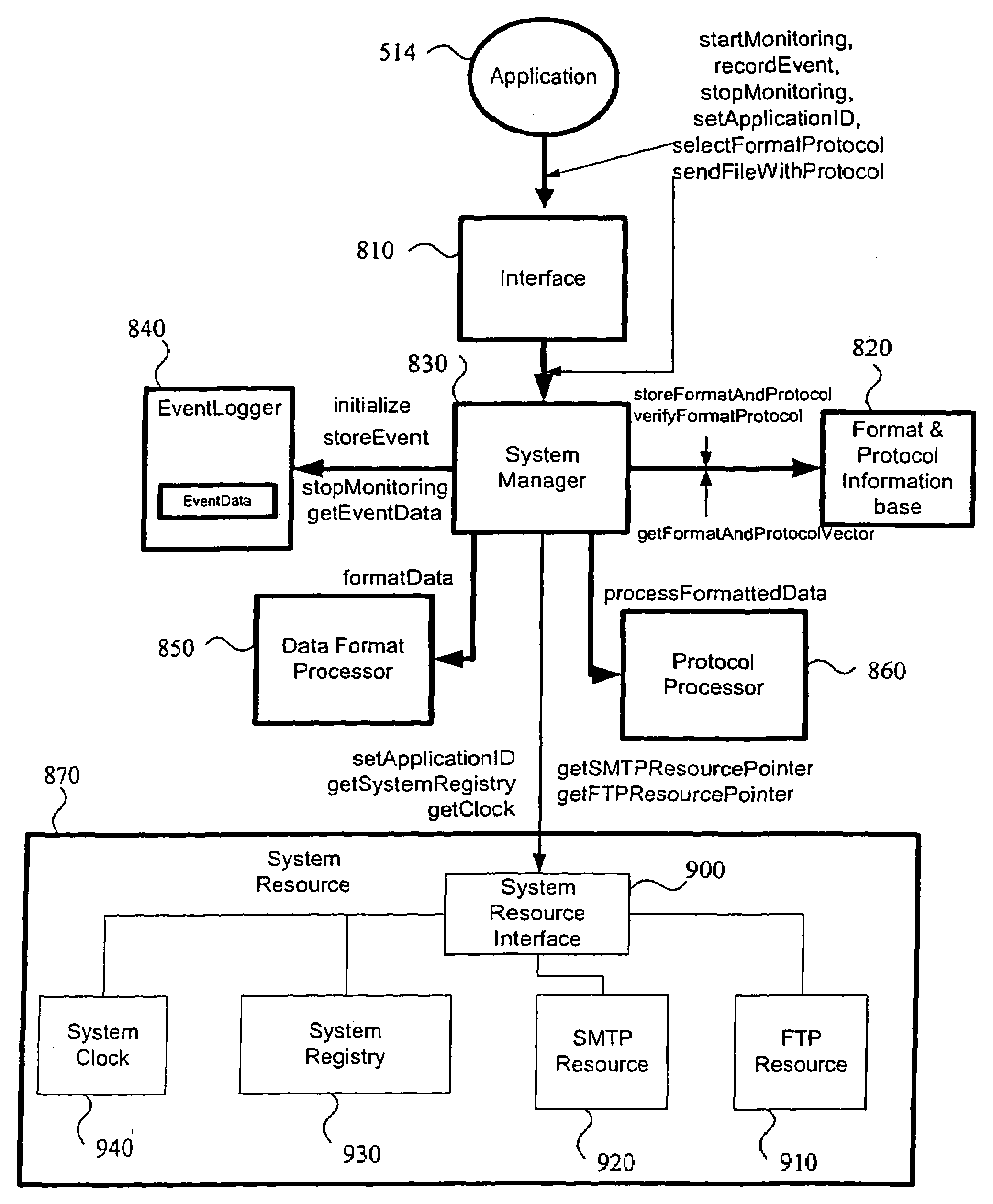
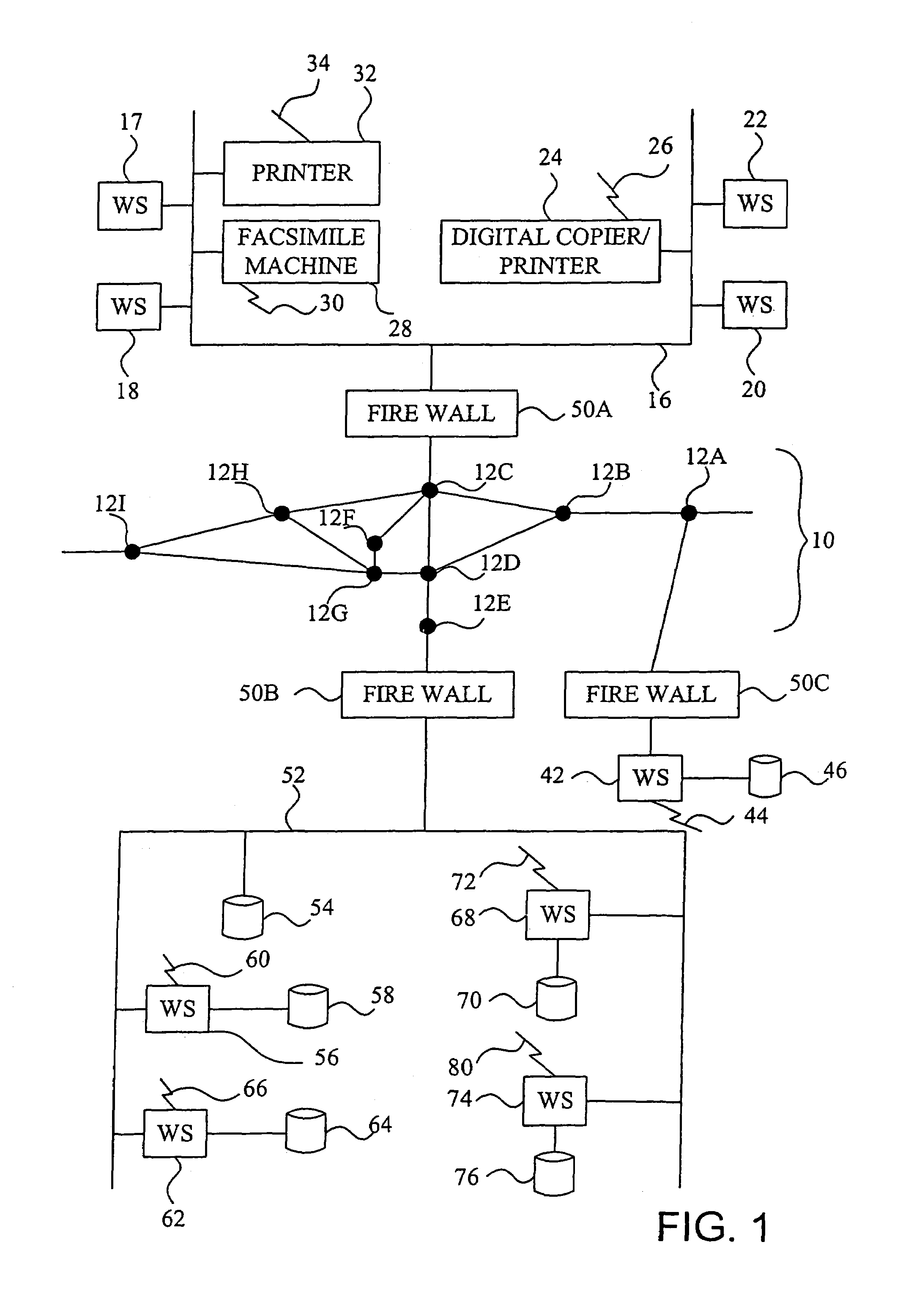
Method and system of remote diagnostic, control and information collection using multiple formats and multiple protocols with delegating protocol processor
InactiveUS7047293B2Easy to analyzeEasy to configureInput/output to record carriersError detection/correctionProtocol processingNetwork Communication Protocols
A system, method and program product for diagnosing, controlling and collecting information from devices. Information regarding events of each one of a plurality of target applications executing in an application unit is collected and formatted into one of multiple data formats for transmission through one of multiple communication protocols at the request of each of the target applications, through an interface. The event information for a particular target application is formatted and transmitted according to a combination of a data format and communication protocol requested by the target application. The transmission of data representing the event information is handled in at least two levels of software classes, with at least one abstract software class having a declared virtual function and two or more software classes derived from the at least one abstract class and having definitions of the function for communicating the event information through specified communication protocols. The formatted data is transmitted through, e.g., e-mail or FTP to a predetermined destination or may be saved to local storage, e.g., a local disk. By sharing resources, code duplication is reduced or eliminated.
Owner:RICOH KK
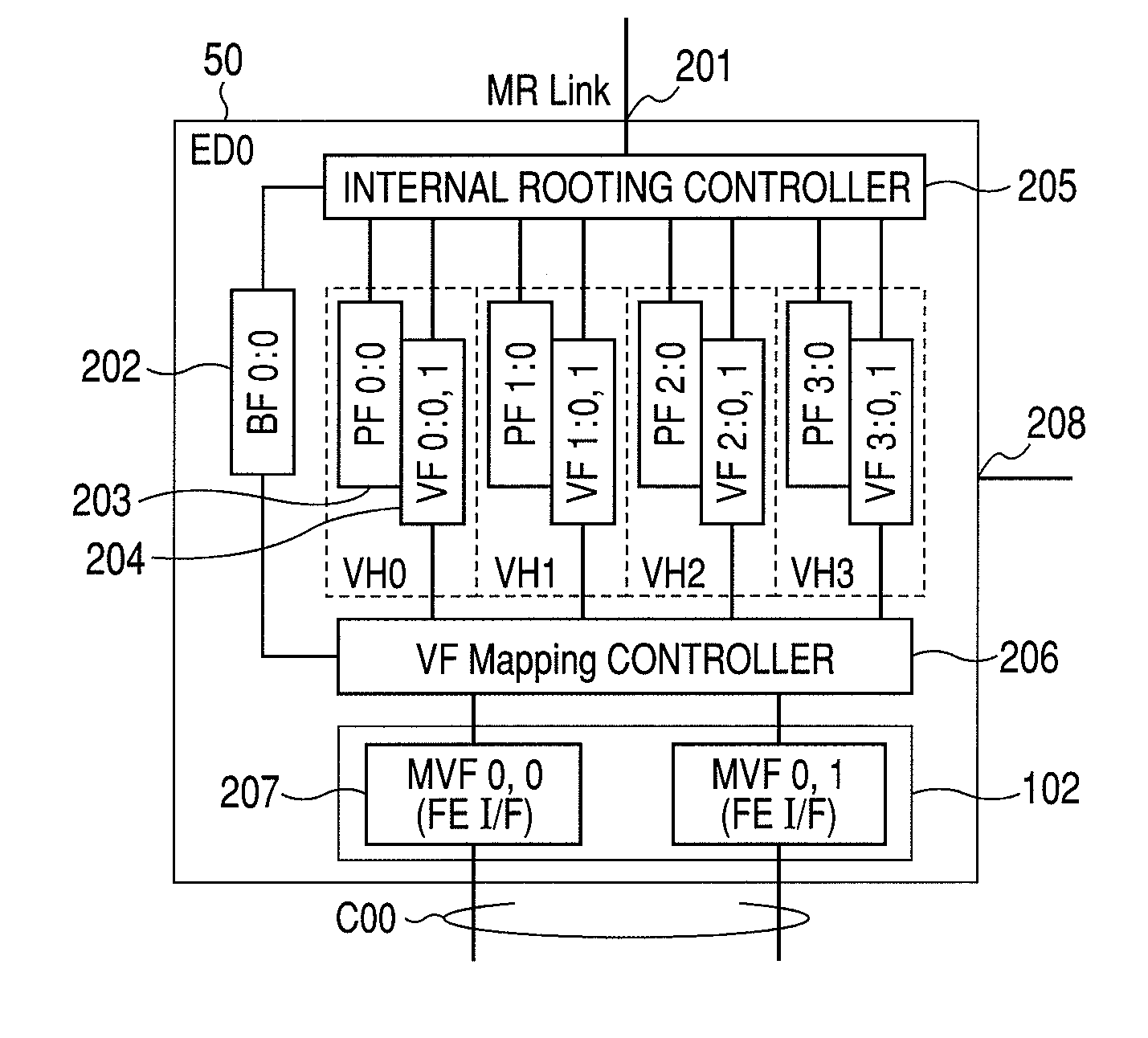
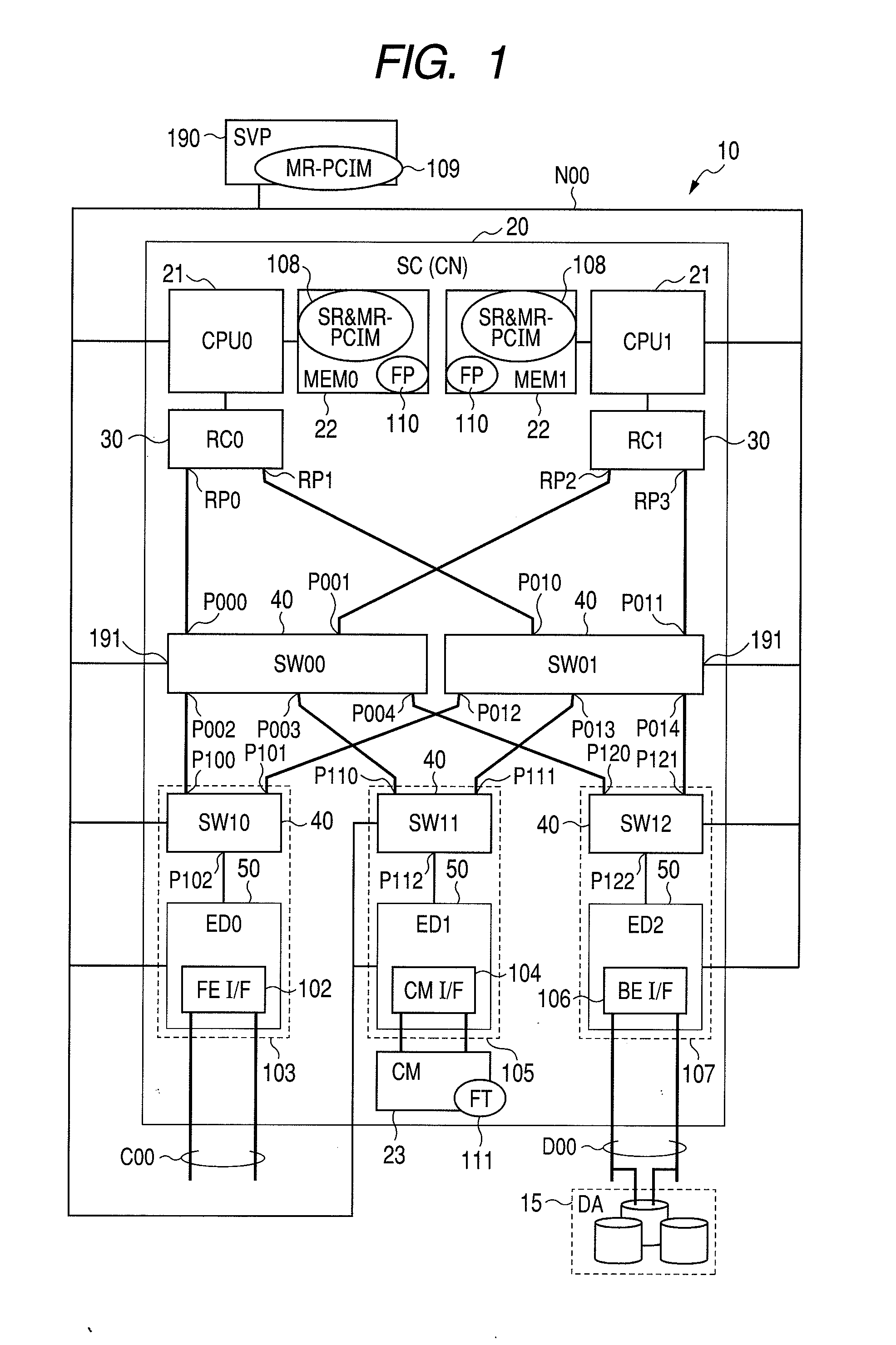
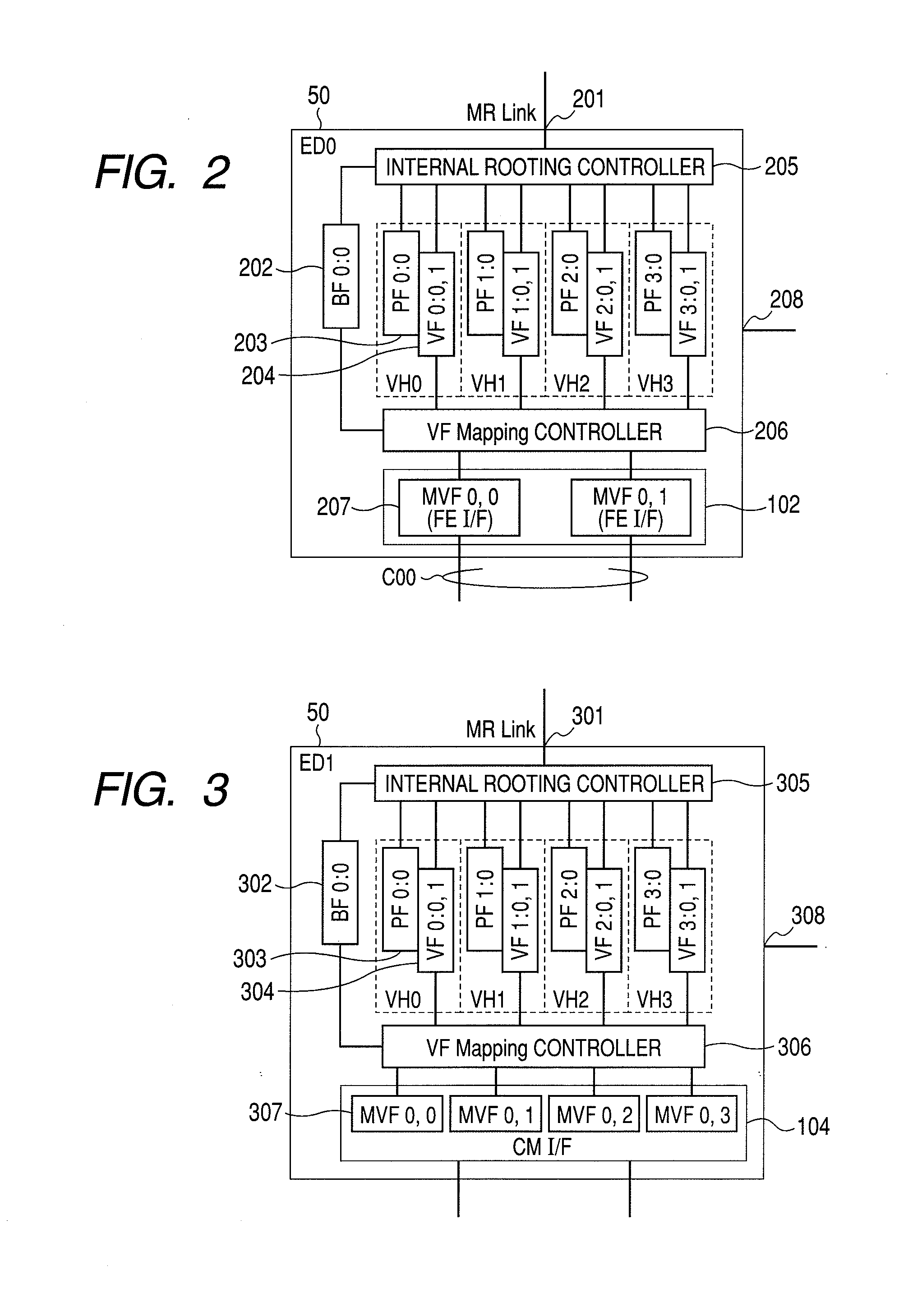
Storage Device, and Data path Failover Method of Internal Network of Storage Controller
InactiveUS20100115329A1Improve reliabilityMemory adressing/allocation/relocationComputer security arrangementsFailoverControl store
A storage device in which the MR-IOV is applied to an internal network of a storage controller. Data path failover can be executed in the storage device. The internal network of the storage controller is configured to enable the access of a virtual function (VF) “VF 0:0, 1” of each endpoint device (ED0-ED2) from a root port RP0. Likewise, “VF 1:0, 1” of each endpoint device can be accessed from a root port RP1. In a first data path from the RP0 to ED0 in a normal state, “VF 0:0, 1” and “MVF 0, 0” are connected by VF mapping. When a failure occurs on the first data path, the MR-PCIM executes the VF migration, whereby in the second data path from the RP1 to ED0,“VF 1:0, 1” and “MVF 0, 0” are connected by VF mapping. As a result, failover to the second data path is realized.
Owner:HITACHI LTD
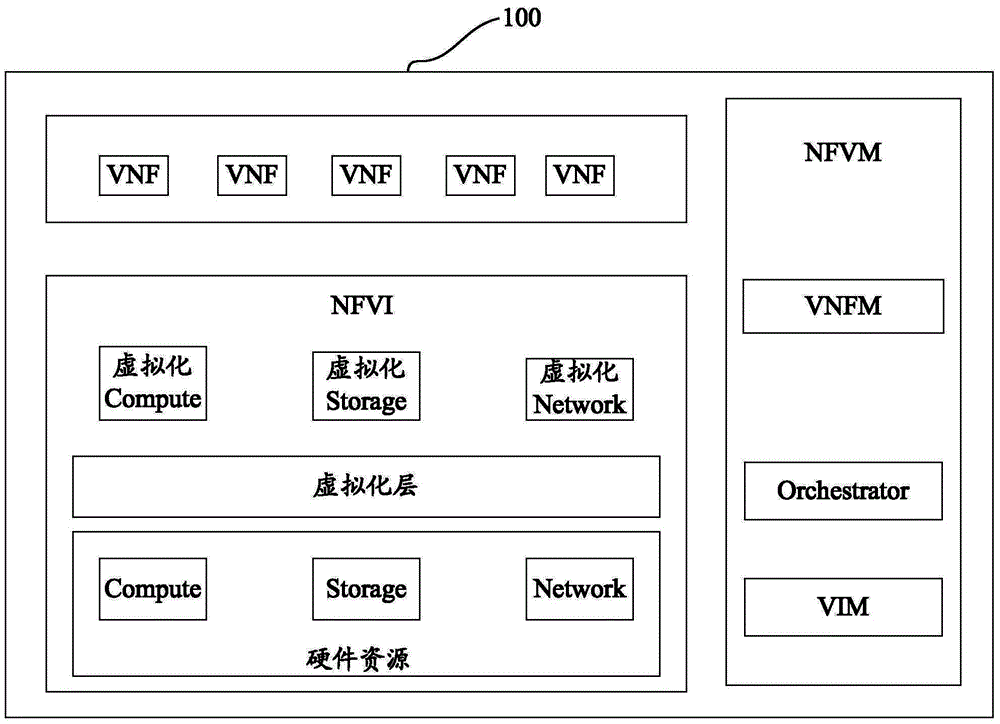
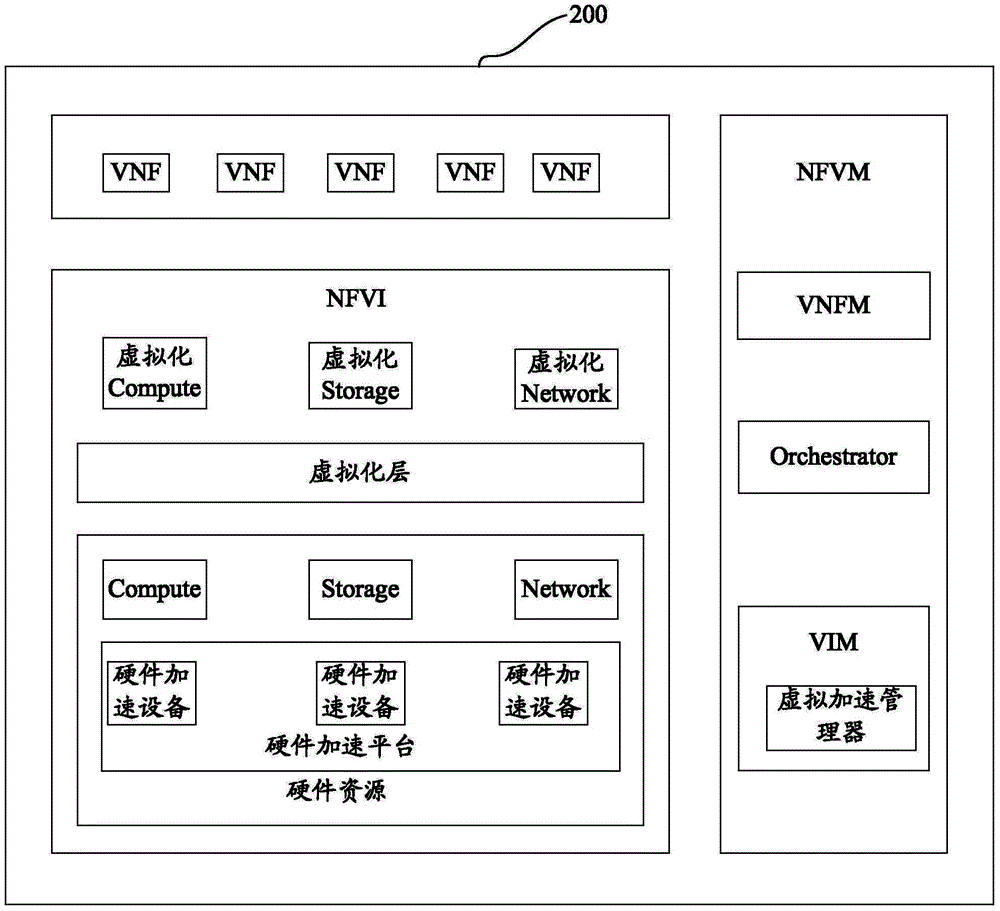
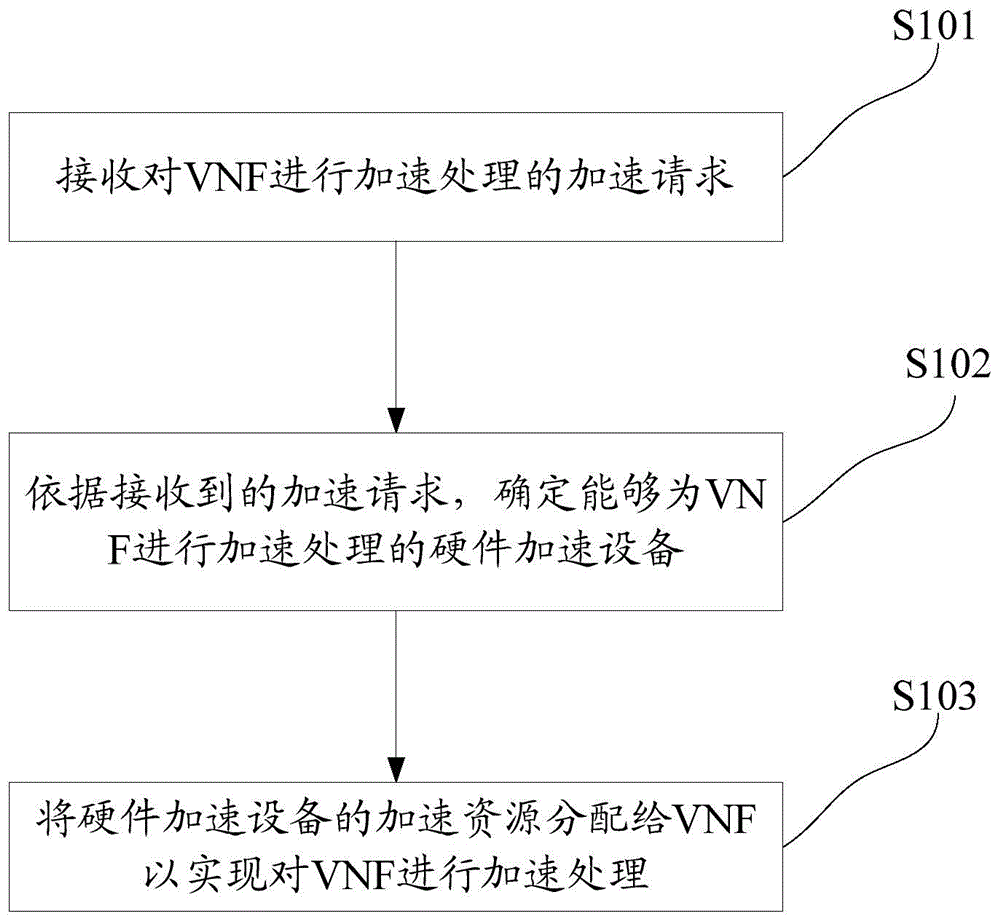
VNF (virtual network function) acceleration method and device
ActiveCN104951353AAchieve accelerated processingImplement virtualization managementSoftware simulation/interpretation/emulationResource utilizationComputer science
Disclosed are a method and an apparatus for implementing acceleration processing on a virtual network function (VNF). In the present invention, an acceleration request for performing acceleration processing on the VNF is received; a hardware acceleration device that can perform acceleration processing on the VNF is determined according to the acceleration request; an acceleration resource of the hardware acceleration device is allocated to the VNF for performing the acceleration processing on the VNF. The present invention can dynamically select and allocate the corresponding hardware acceleration device for the VNF, thereby implementing virtual management of the hardware acceleration device and improving resource utilization.
Owner:HUAWEI TECH CO LTD
Methods and systems for providing multi-tenancy support for Single Root I/O Virtualization
ActiveUS9419897B2Data switching networksSoftware simulation/interpretation/emulationVirtualizationI/O virtualization
A method for providing support for multi-tenancy in single root input / out virtualization (SR-IOV) enabled physical network interface controller (NIC) is provided. The NIC is associated with a host. The SR-IOV provides a physical function (PF) and a set of virtual functions (VFs) for the NIC. The method at a VF of the physical NIC, receives a mapping table of an overlay network which associates an identification of each of a set of virtual machine (VM) of a tenant on the host to an identification of a tunnel end point on the overlay network. The method receives a transmit packet from a VM connected to the VF and performs a lookup in the mapping table to identify source and destination tunnel end points associated with source and destination VMs in the packet. The method encapsulates the packet, for transmission through the tunnel end point associated with the source VM.
Owner:NICIRA
Memory virtualized management method based on metadata server
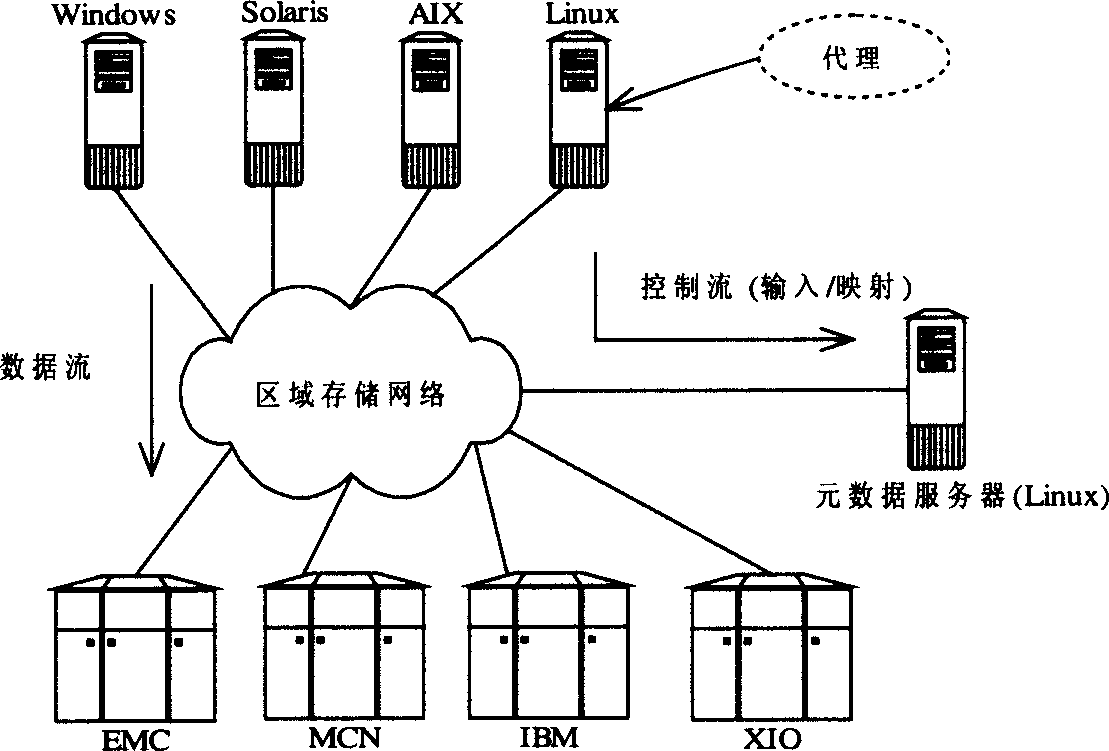
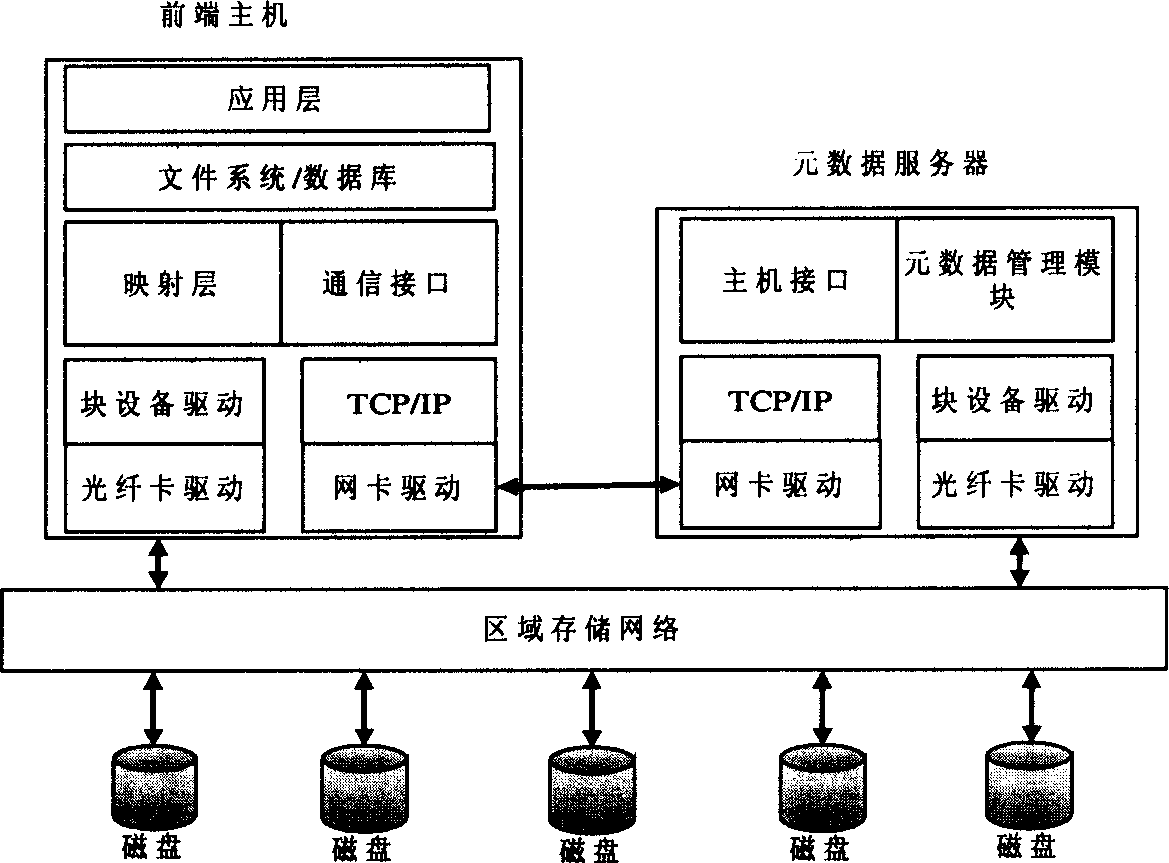
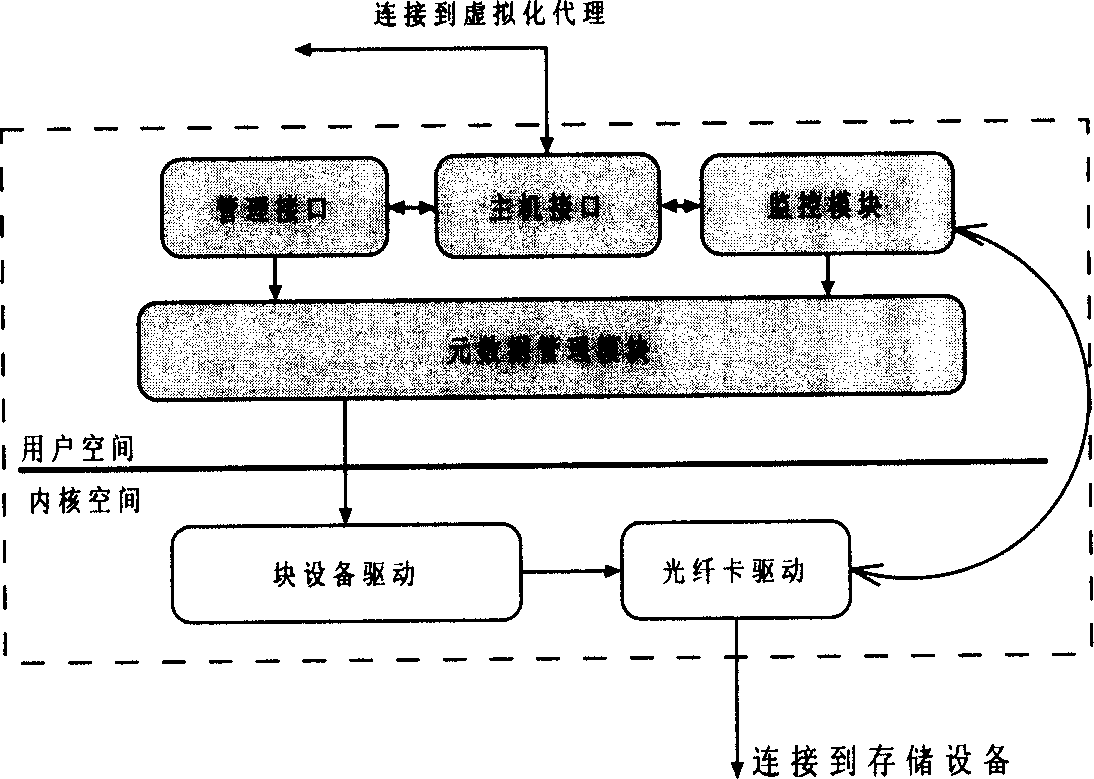
InactiveCN1664793AImprove scalabilityAchieving a single point of managementInput/output to record carriersMemory adressing/allocation/relocationVirtualizationStorage area network
This invention relates to a store virtualization manage method based on metadata server belonging to store area net virtualization realm, characterized by the followings: virtual proxy module of each front-end host computer actualizing the shift from virtual logic reel to actual physical reel; one or multiple metadata servers forming physical reel with different storage device by global unique identifier and building storage pool to reflect metadata constructing reel of storage device; using managing module to actualize the control to metadata; building communicating association of virtual proxy module supplied with metadata information and managing module jointed with previously received identifier information to constitute corresponding virtual device via Ethernet. It can accomplish various virtual function, and ignore the effect of system throughput ratio and respond time.
Owner:TSINGHUA UNIV
System and method for migration of a virtual endpoint from one virtual plane to another
InactiveUS20080147943A1Data switching by path configurationMemory systemsVirtualizationApplication software
A system and method for migration of a virtual endpoint from one virtual plane to another are provided. With the system and method, when a management application requests migration of a virtual endpoint (VE) from one virtual plane (VP) to another, a fabric manager provides an input / output virtualization intermediary (IOVI) with an interrupt to perform a stateless migration. The IOVI quiesces outstanding requests to the virtual functions (VFs) of the VE, causes a function level reset of the VFs, deconfigures addresses in intermediary switches corresponding to the VP, and informs the fabric manager that a destination migration is requested. The fabric manager sends an interrupt to the destination IOVI which performs a function level reset of the destination VFs and reprograms the intermediary switches with the addresses of the destination VP. The destination VFs may then be placed in an active state.
Owner:IBM CORP
Virtualization of vendor specific network interfaces of self-virtualizing input/output device virtual functions
InactiveUS20120124572A1Effectively abstract awayInterprogram communicationSoftware simulation/interpretation/emulationVirtualizationOperational system
A vendor independent partition interface between a logical partition and an adjunct partition associated with a self-virtualizing IO resource is used to effectively abstract away vender-specific interface details for the self-virtualizing IO resource. By doing so, vender-specific implementation details may be isolated from the operating systems resident in logical partitions, thus requiring only changes in vendor specific firmware in order to support new or revised self-virtualizing IO resources.
Owner:IBM CORP
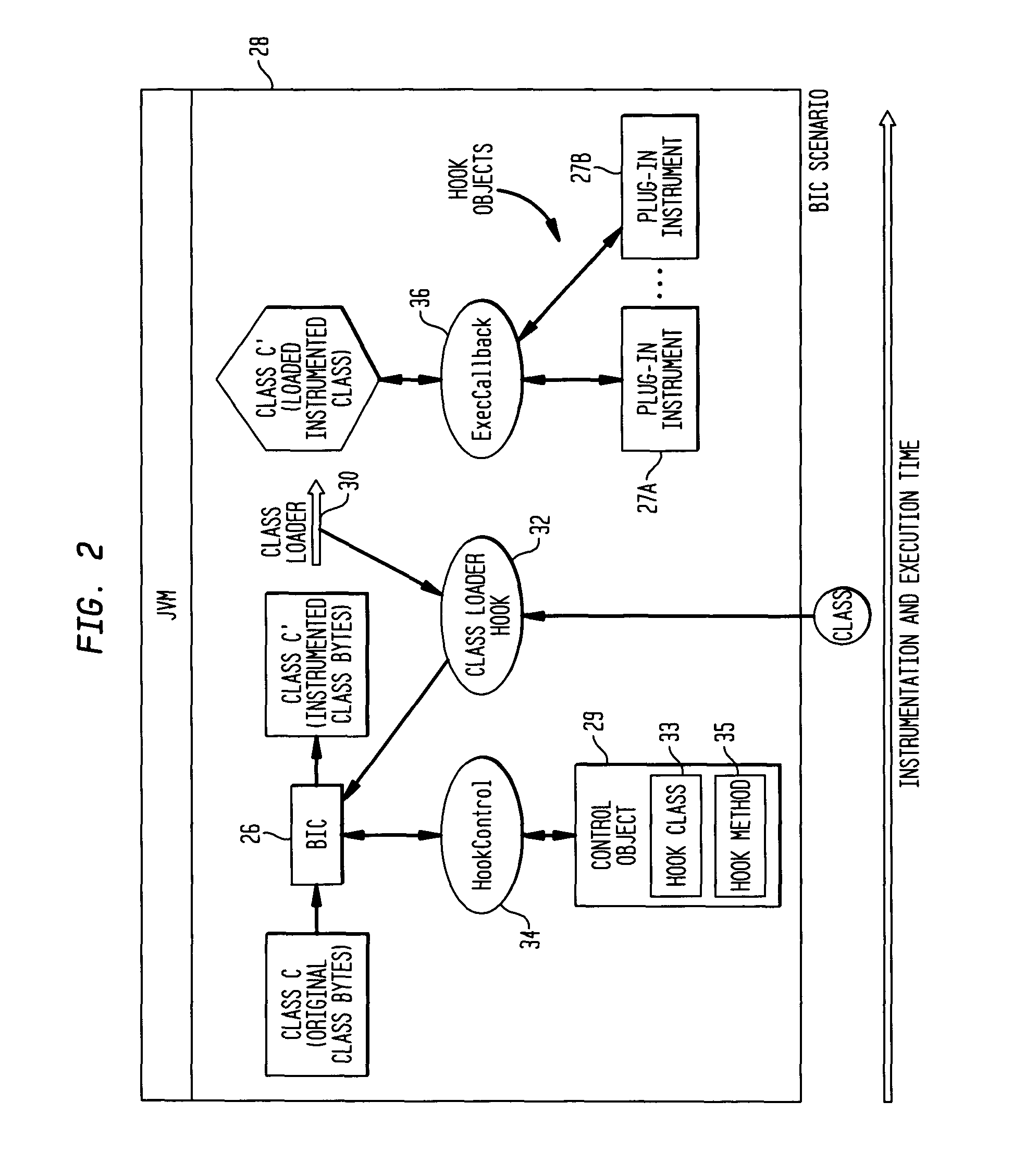
Setting instance breakpoints in object oriented computer programs
InactiveUS6240545B1Software testing/debuggingSpecific program execution arrangementsBase classClass hierarchy
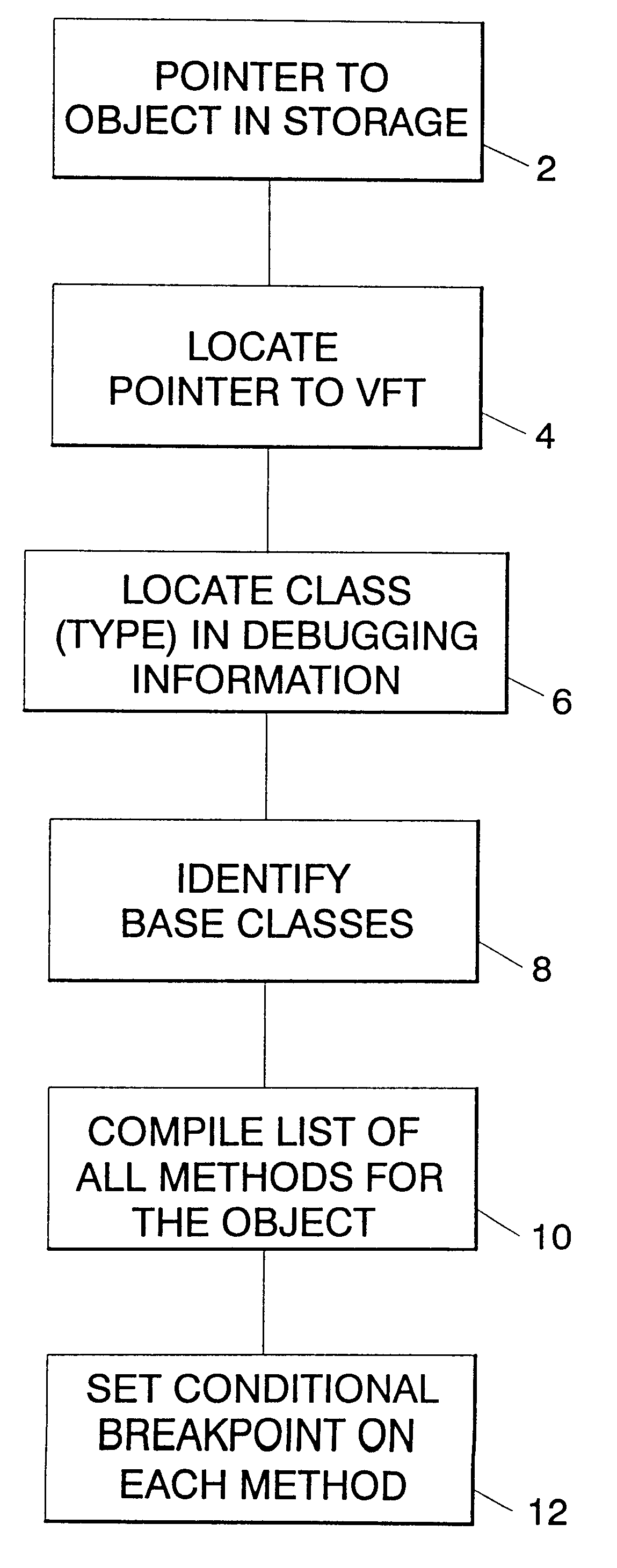
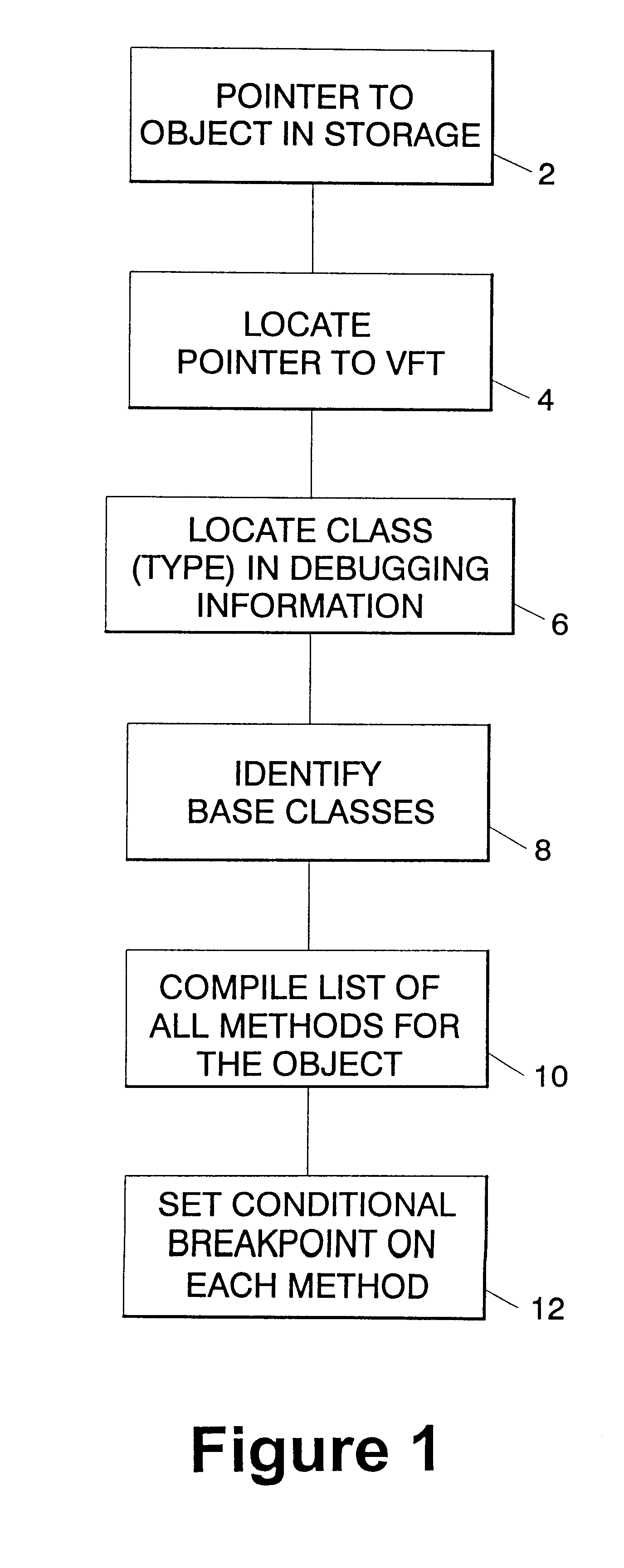
A mechanism for setting a conditional breakpoint on all methods called by a specific instance of a class. To set the instance breakpoint, the debugger determines all of the methods that can be applied to the object type or class. In an environment in which full debugging information includes the correspondence between virtual function tables and specific classes, and full class hierarchy information, the methods are located by locating the pointer to the type's virtual function table, and from the virtual function table, locating the specific class in the debugging information. Identifying the specific type permits all of the base classes of the type to be identified in the debugging information, and from the class hierarchy information, all methods for objects of the type can be compiled. The debugger then sets a conditional breakpoint on each method, the condition specifying that the breakpoint should cause program execution to automatically stop only if the method is being called for the particular object or instance for which the instance breakpoint was set.
Owner:IBM CORP
Simplified DMA mappings for self-virtualizing input/output device virtual functions
InactiveUS20120151473A1Facilitate data communicationMultiprogramming arrangementsSoftware simulation/interpretation/emulationVirtualizationMapping algorithm
Multiple TCE entries at the same indices in multiple, same size TCE tables are mapped to facilitate data communication between a self-virtualizing IO resource and a logical partition. First and second TCE tables used by an adjunct partition that interfaces a self-virtualizing IO resource with a logical partition may be identically sized, so that whenever a DMA operation between the self-virtualizing IO resource and the logical partition is desired the same TCE entries in the first and second TCE tables may be used to perform a redirected DMA operation, and without the need to perform hashing or other mapping algorithms to map to the respective TCE entries in the respective TCE tables.
Owner:IBM CORP
Method and system for managing interconnection of virtual network functions
ActiveUS20150295750A1Resource allocationDigital computer detailsStructure of Management InformationConnection manager
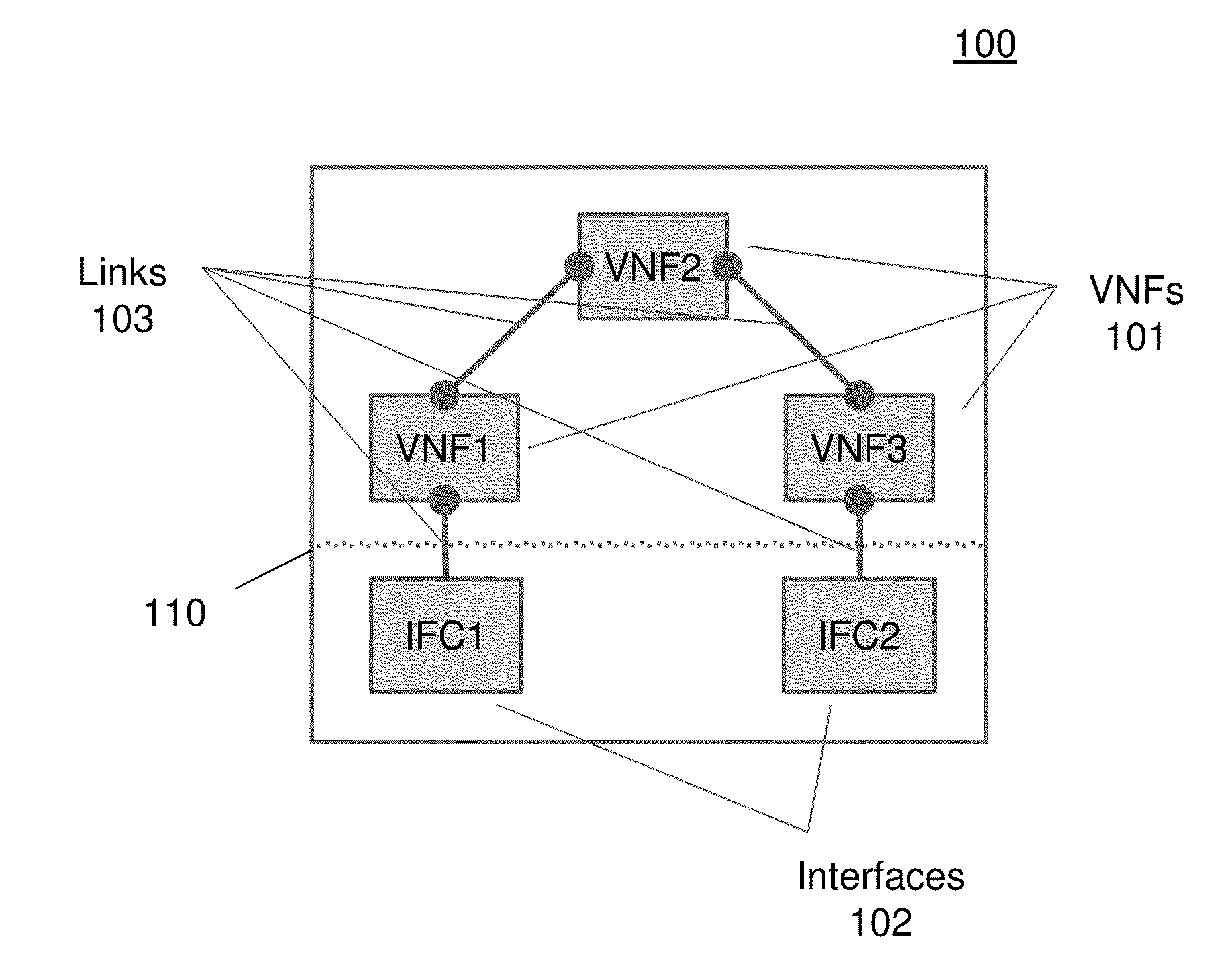
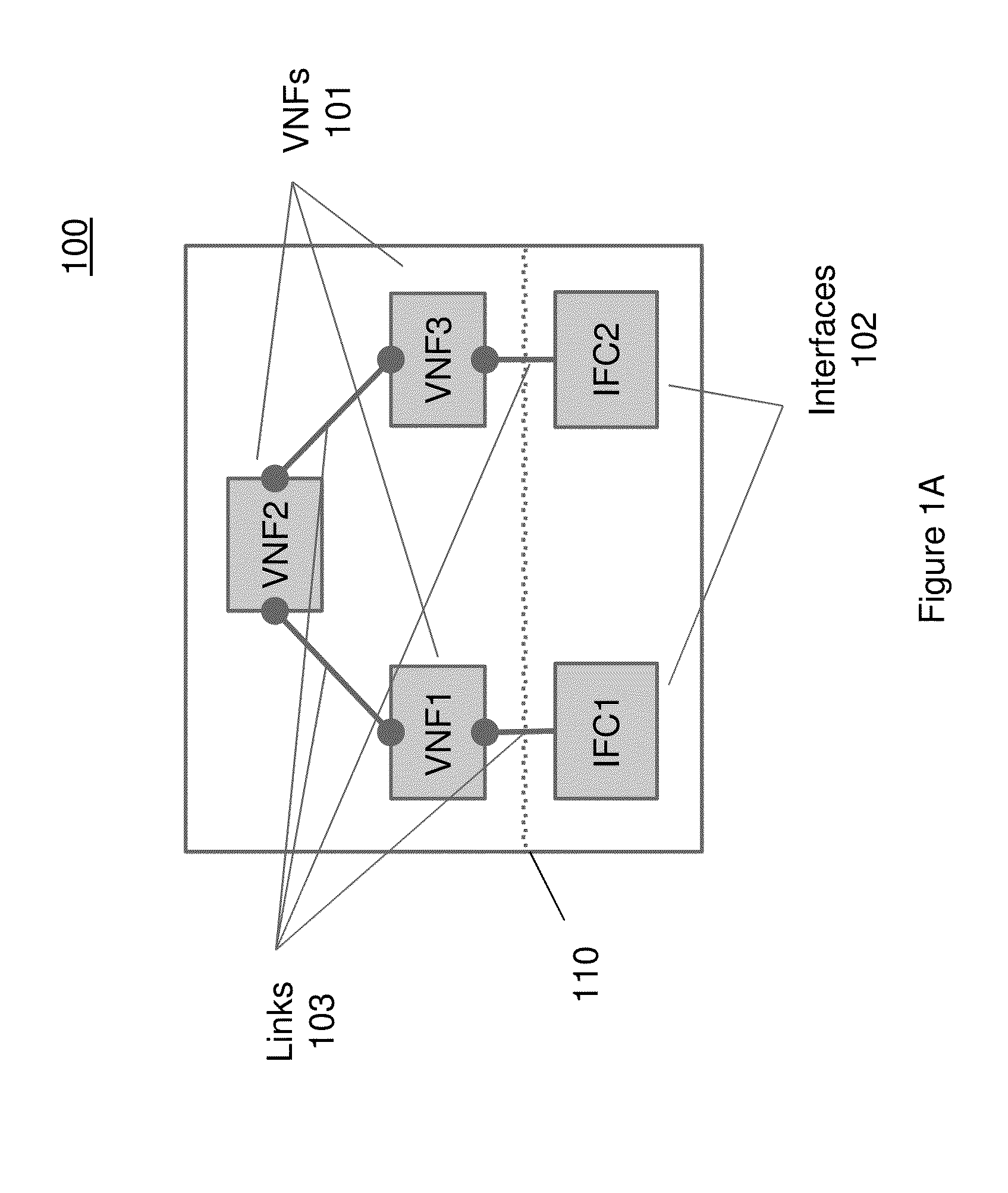
A method and apparatus is disclosed herein for use of a connectivity manager and a network infrastructure including the same. In one embodiment, the network infrastructure comprises one or more physical devices communicably coupled into a physical network infrastructure or via the overlay provided by the physical servers; and a virtual network domain containing a virtual network infrastructure executing on the physical network infrastructure. In one embodiment, the virtual network domain comprises one or more virtual network functions connected together through one or more links and executing on the one or more physical devices, and one or more interfaces coupled to one or more network functions via one or more links to communicate data between the virtual network domain and at least one of the one or more physical devices of the physical network infrastructure while the virtual network domain is isolated from other virtual infrastructures executing on the physical network infrastructure.
Owner:NICIRA
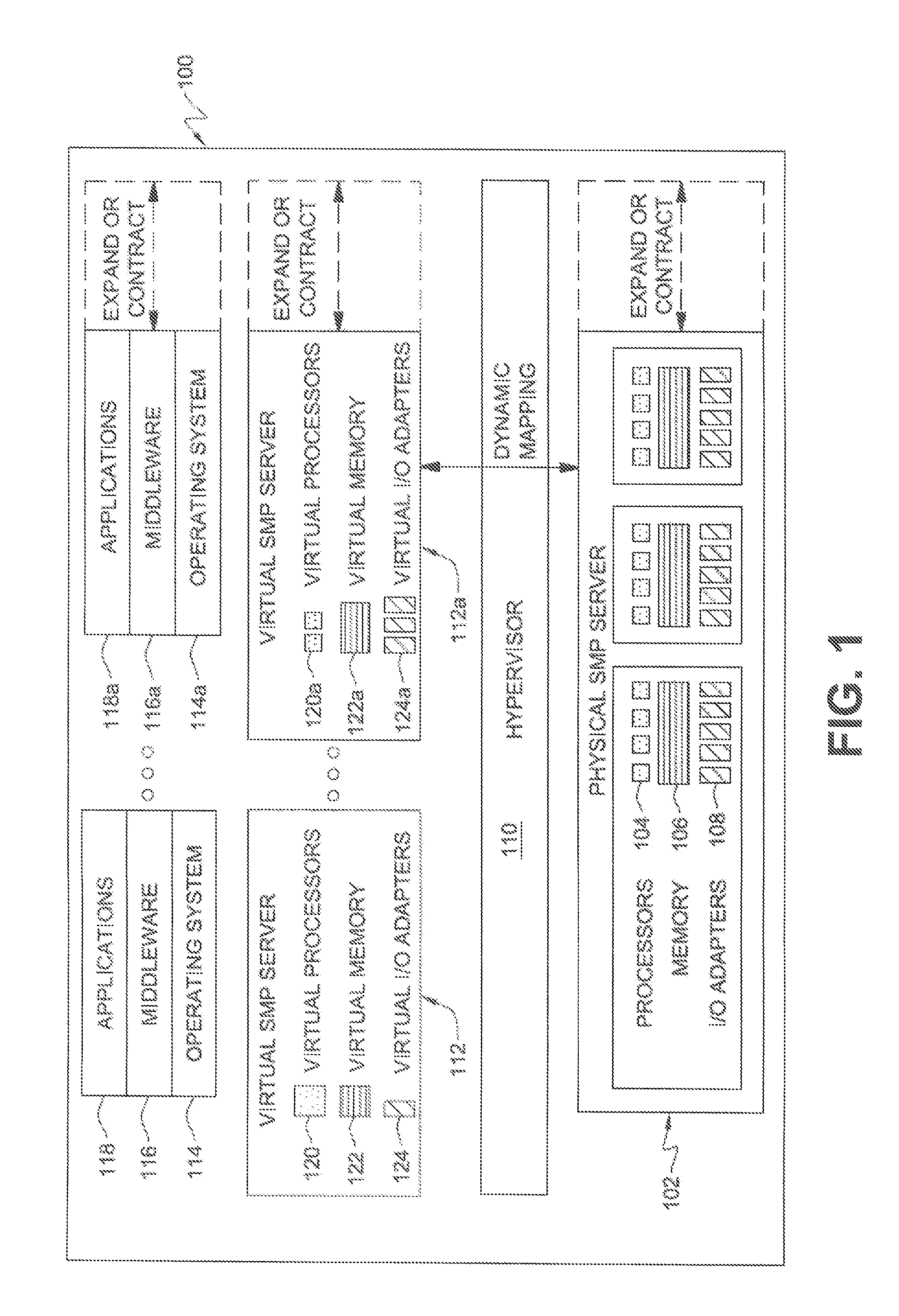
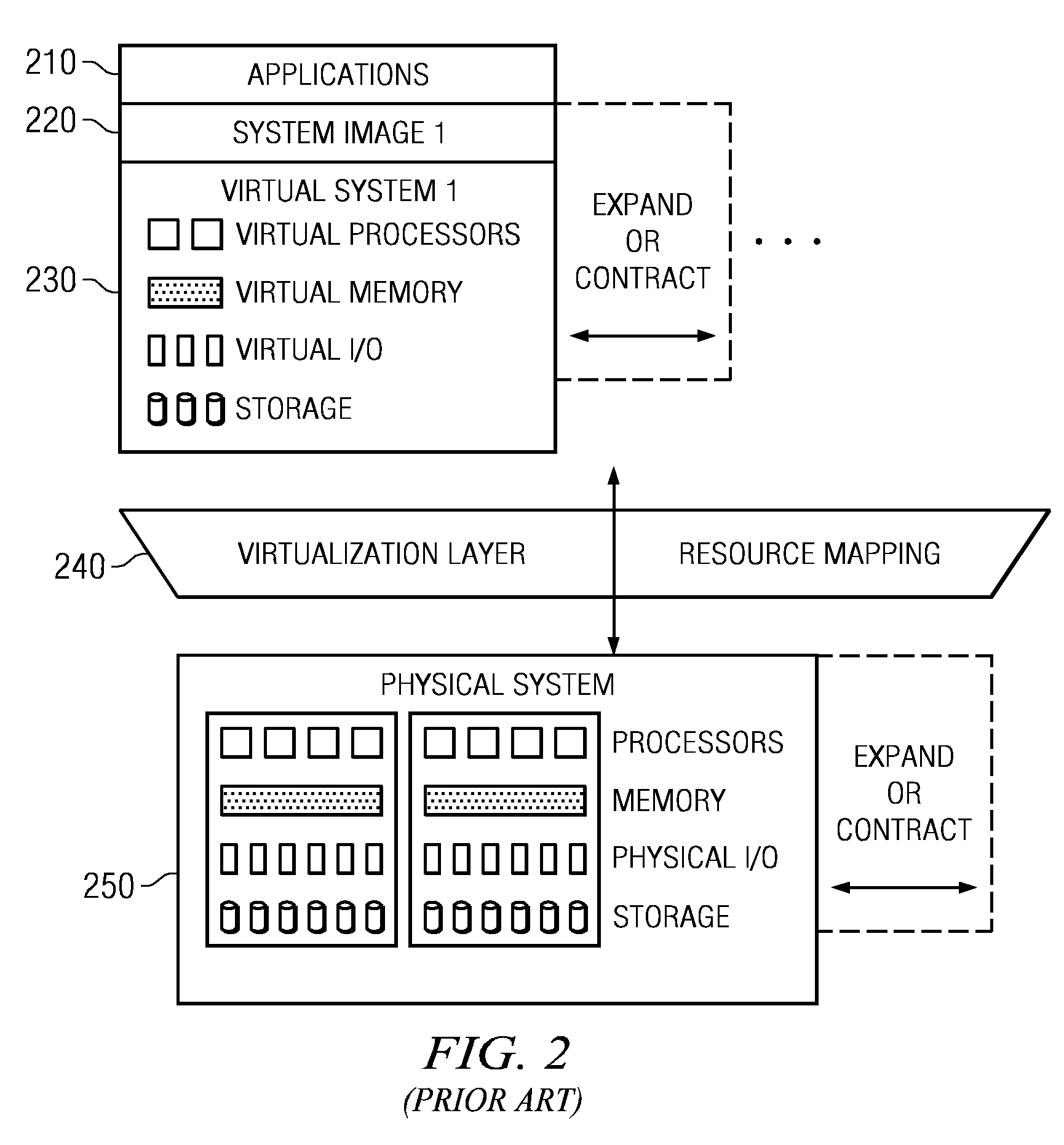
Virtual computer system and controlling method of virtual computer
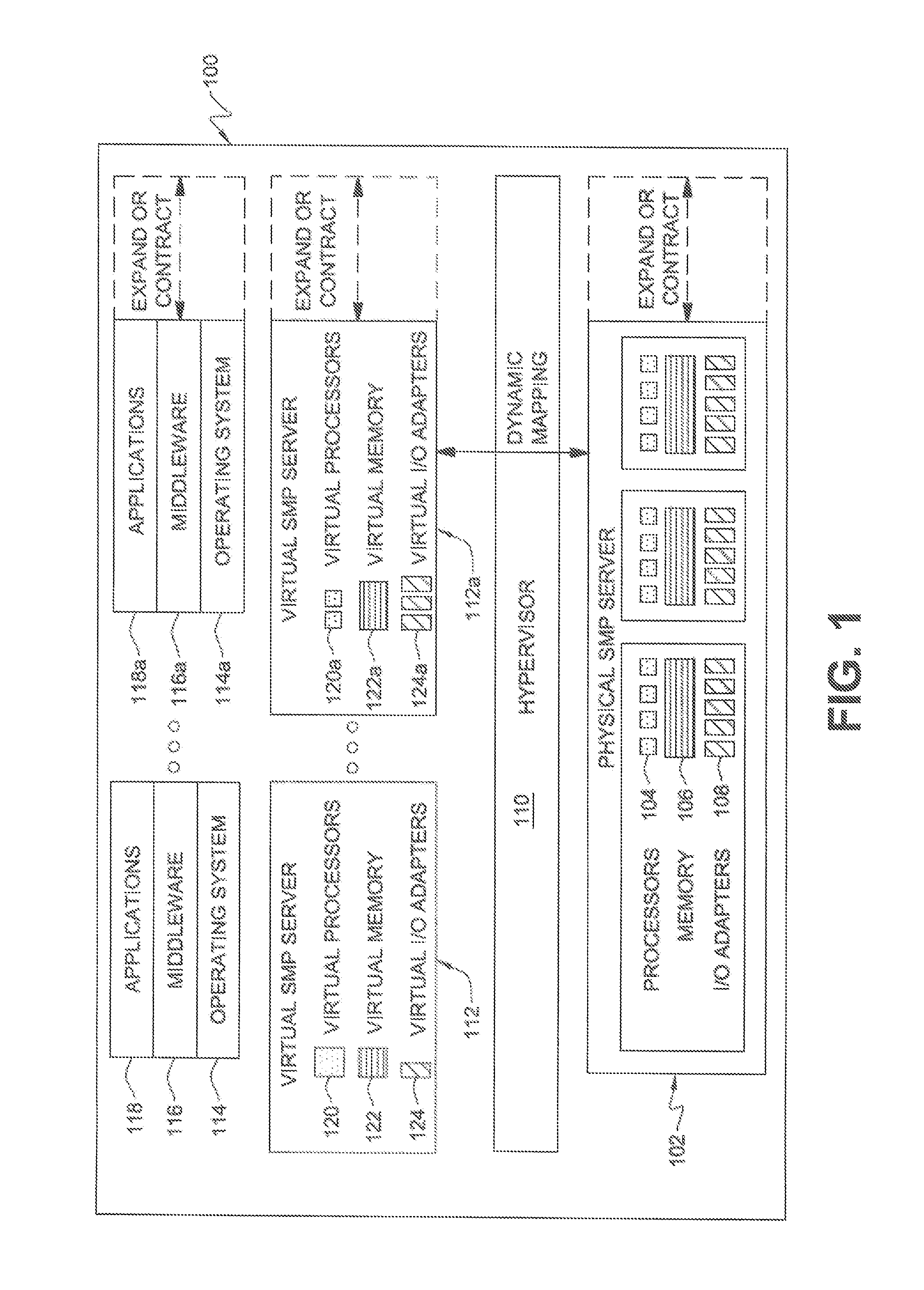
InactiveUS20120246644A1Improve performanceImprove reliabilitySoftware simulation/interpretation/emulationMemory systemsComputer resourcesVirtualization
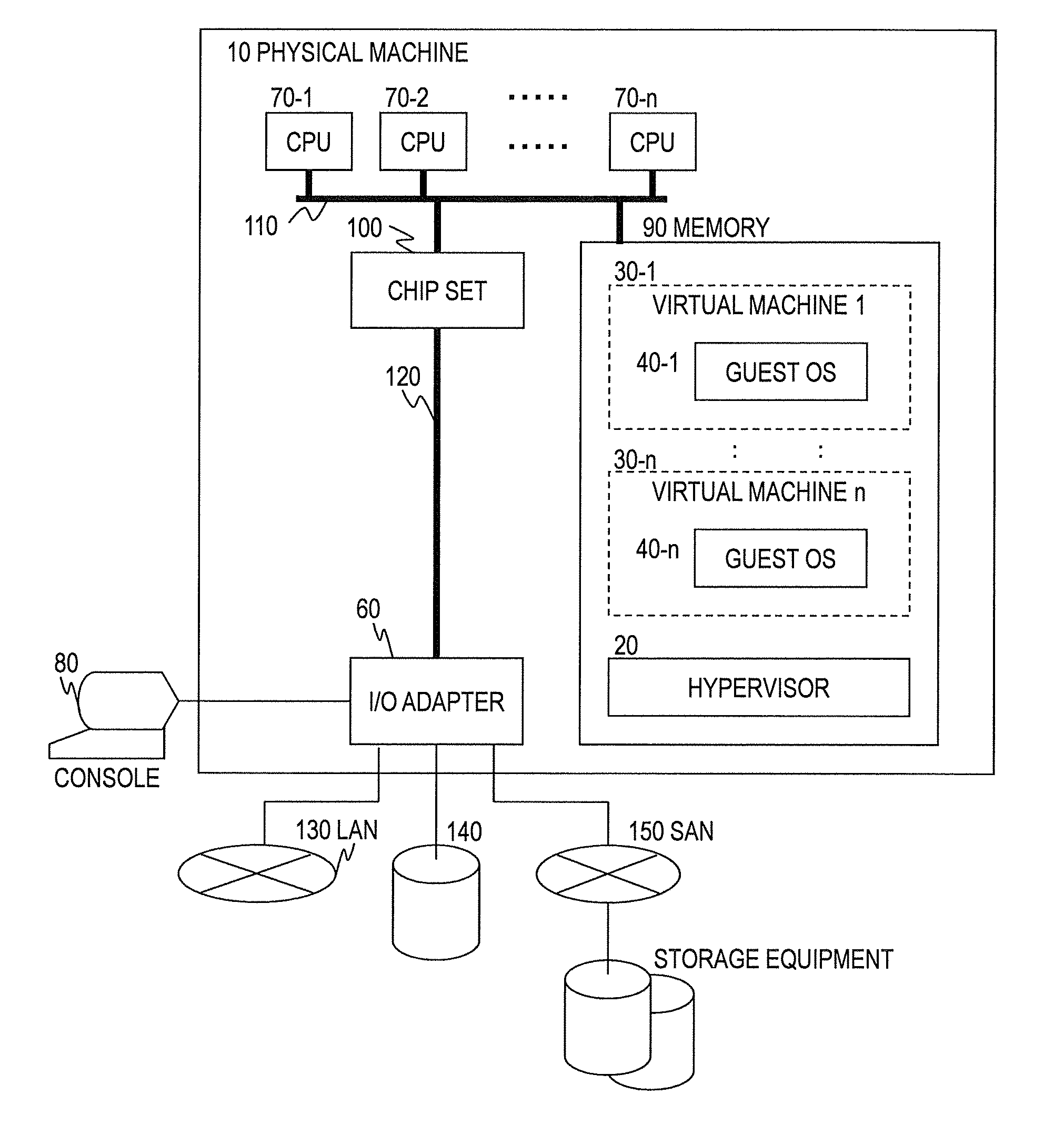
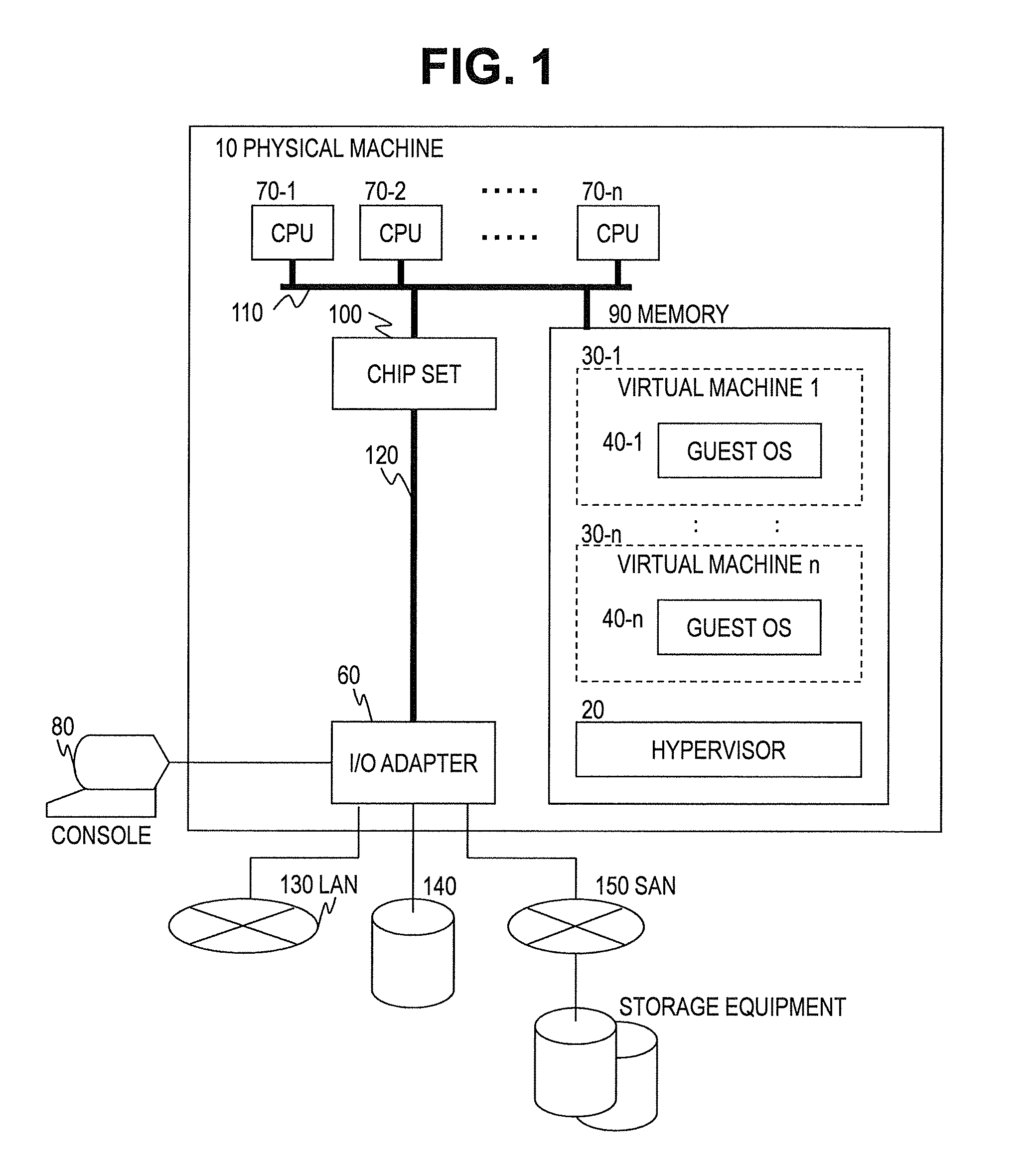
A method of controlling a virtual machine of a computer, the computer comprising: a physical machine comprising an I / O adapter having a physical function that creates a virtual function; a virtualization unit that provides computer resources of the physical machine to the virtual machine; and an OS that is executed on the virtual machine, the virtualization unit creating a virtual machine to which the virtual function is assigned, the virtual machine running the OS thereon, the method comprising: a first step of detecting, by the virtualization unit, a state change of the I / O adapter; a second step of identifying, by the virtualization unit, when a state of the I / O adapter becomes a predetermined state, the virtual machine to which the virtual function is assigned; and a third step of notifying, by the virtualization unit, the OS running on the identified virtual machine of the state of the I / O adapter.
Owner:HITACHI LTD
PRESERVING TRAFFIC CLASS PRIORITY QoS WITH SELF-VIRTUALIZING INPUT/OUTPUT DEVICE
InactiveUS20120180047A1Preserve QoS prioritizationError preventionTransmission systemsTraffic capacityOutput device
Owner:IBM CORP
Method and device for establishing link between virtual network functions
ActiveCN104734931ARealize automatic creationProgram controlNetworks interconnectionIp addressSoftware engineering
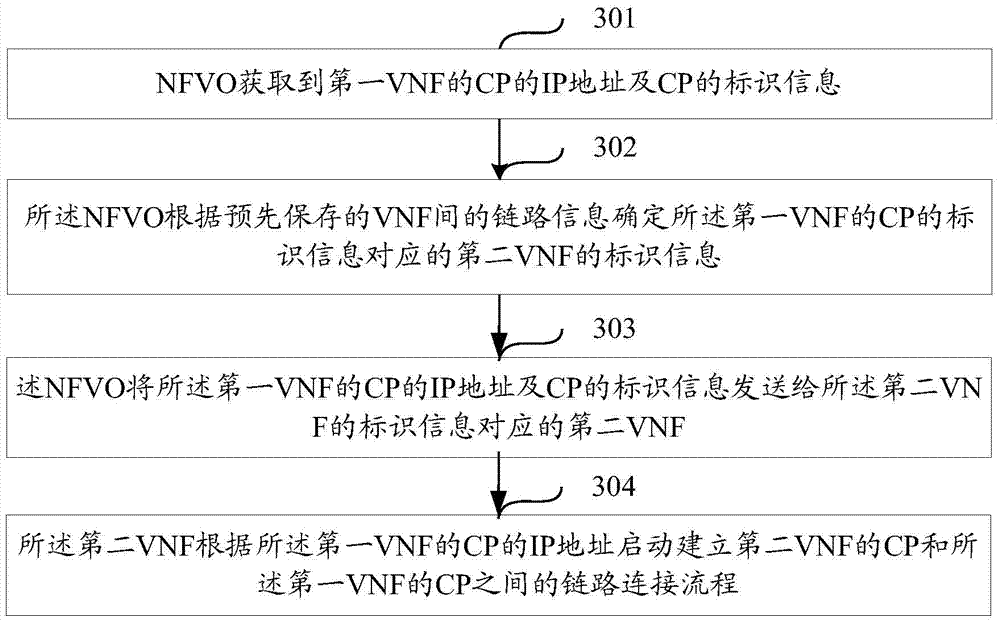
The invention discloses a method and device for establishing a link between virtual network functions to solve the problem that a link between VNFs cannot be automatically established. The method comprises the steps that an NFVO obtains an IP address and identification information of a CP of a first VNF; the NFVO determines the identification information, corresponding to the CP identification information of the first VNF, of the second VNF according to the link information between the VNFs; the link information comprises the corresponding relation of CP identification information of all the VNFs and the corresponding relation of the identification information of all the CPs and the identification information of all the VNFs; the NFVO sends the IP address and the identification information of the CP of the first VNF to the second VNF corresponding to the identification information of the second VNF, and the second VNF starts to establish a link connecting procedure between the CP of the second VNF and the CP of the first VNF according to the IP address of the CP of the first VNF.
Owner:HUAWEI TECH CO LTD
Best fit mapping of self-virtualizing input/output device virtual functions for mobile logical partitions
InactiveUS20120159481A1Software simulation/interpretation/emulationMemory systemsComputer architectureGoal system
A virtual function mapping process, which is capable of being used in connection with the migration of a logical partition to a target system, creates candidate lists for virtual functions assigned to the logical partition, which are populated with candidate physical ports from a target system that are capable of being mapped to such virtual functions. Candidate physical ports are assigned weights based upon their suitability to be mapped to a particular virtual function, and as candidate physical ports are selected for virtual functions, weights for other candidate physical ports for other virtual functions are recalculated to reflect the impact of the selection of candidate physical ports on the suitability of the remaining physical ports for other virtual functions.
Owner:IBM CORP
Computer-implemented method and processing unit for predicting branch target addresses
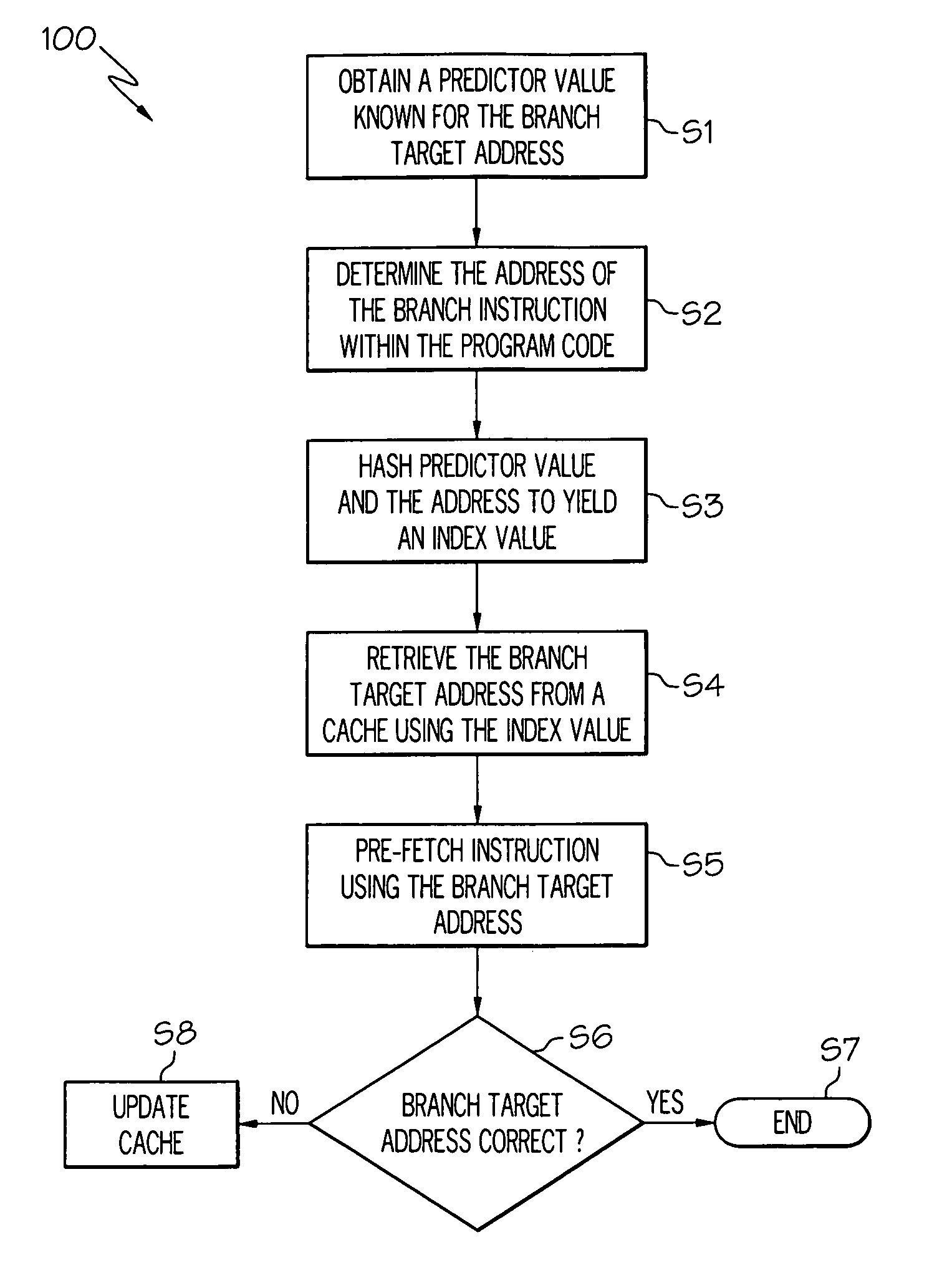
InactiveUS20070088937A1Accurate predictionDigital computer detailsSpecific program execution arrangementsOperandProcessing element
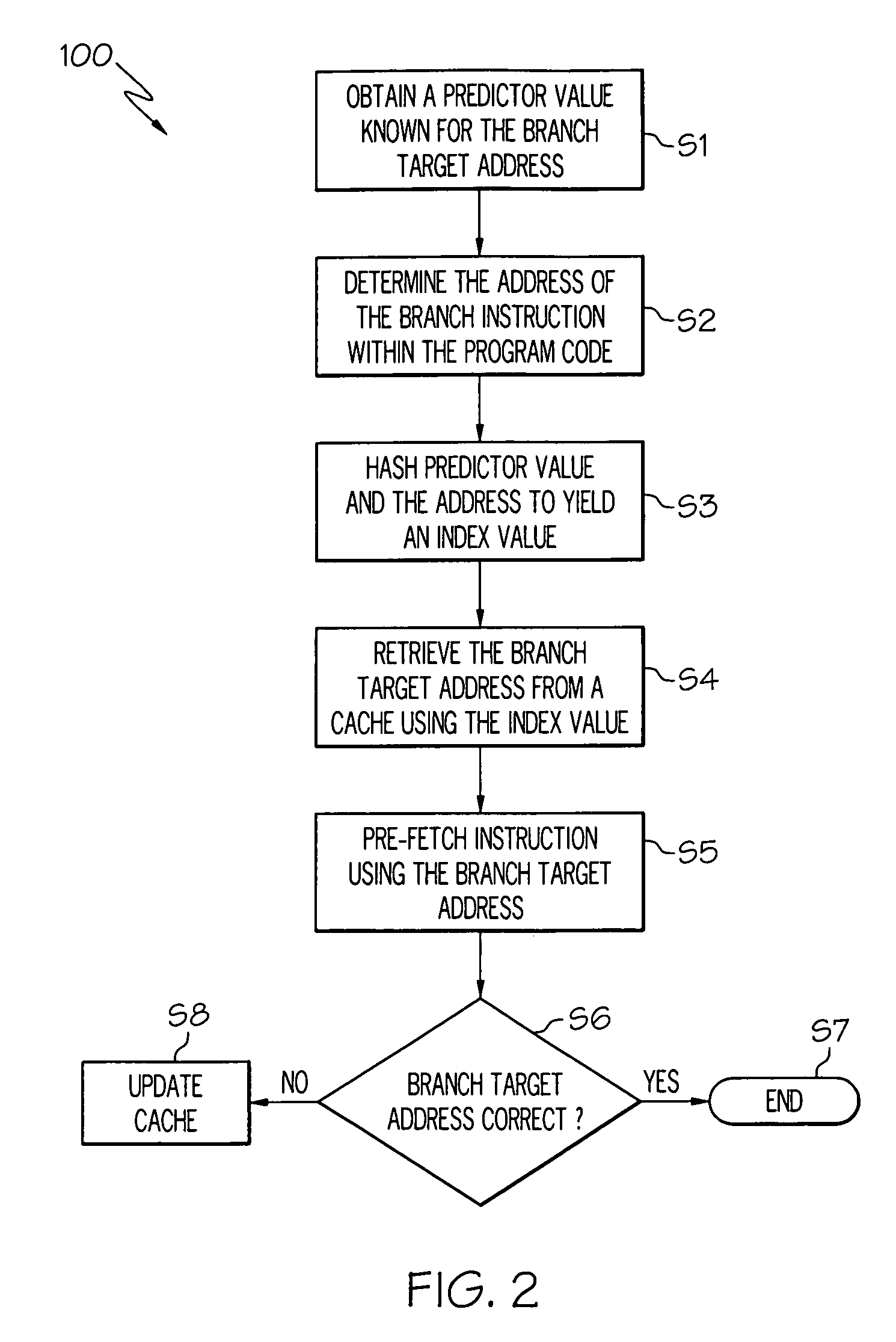
Under the present invention, a branch target address corresponding to a target instruction to be pre-fetched is predicted based on two values. The first value is a “predictor value” that is known for the branch target address. The second value is the address of the branch instruction from which the target instruction is branched to within the program code. Once these two values are provided, they can be processed (e.g., hashed) to yield an index value, which is used to obtain a predicted branch target address from a cache. This technique is generally implemented for branch instructions such as switch statements or polymorphic calls. In the case of the former, the predictor value is a selector operand, while in the case of the latter the predictor value is a class object address (in JAVA) or a virtual function table address (in C++).
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com