Patents
Literature
55 results about "Indirect branch" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
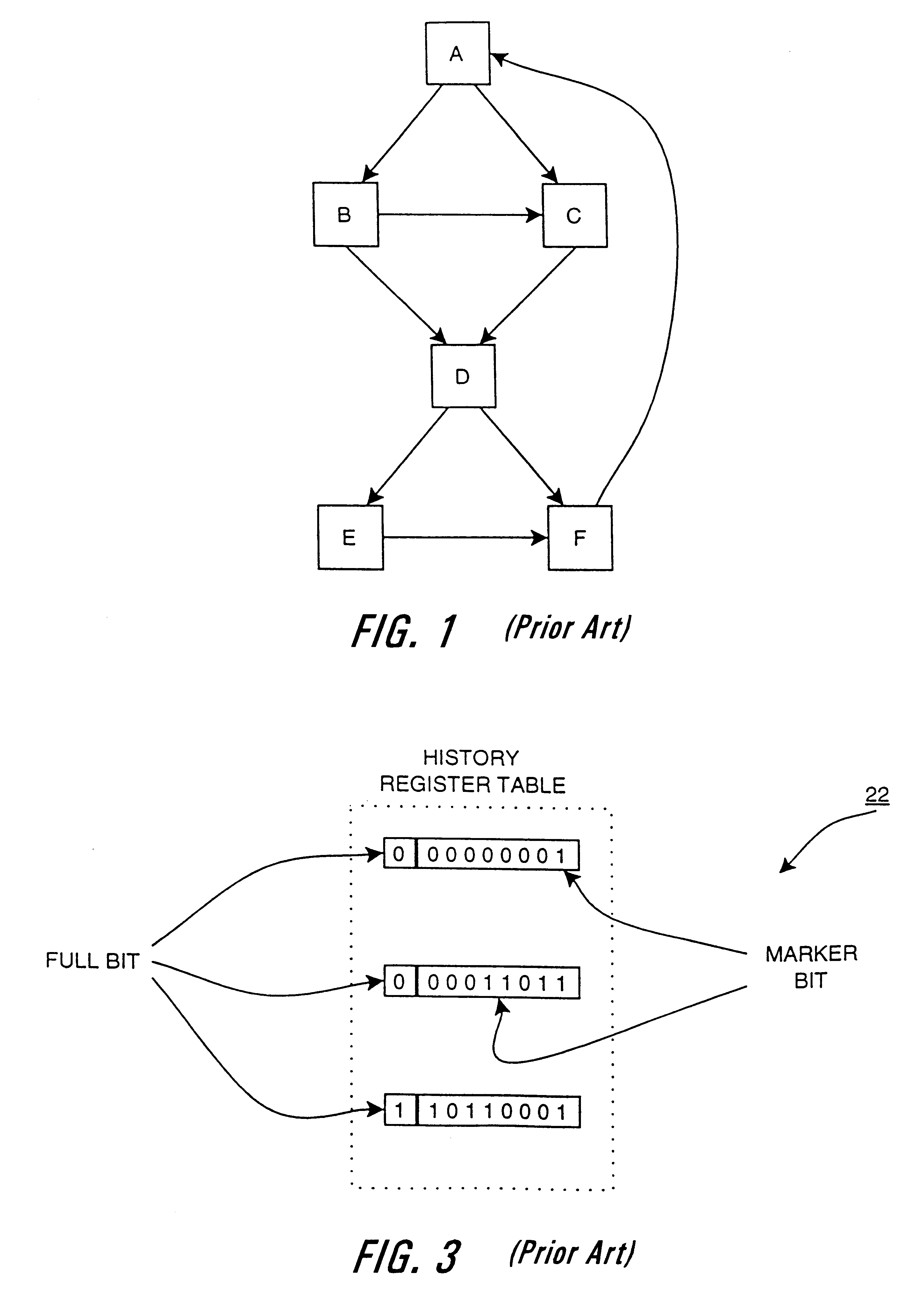
An indirect branch (also known as a computed jump, indirect jump and register-indirect jump) is a type of program control instruction present in some machine language instruction sets. Rather than specifying the address of the next instruction to execute, as in a direct branch, the argument specifies where the address is located. An example is 'jump indirect on the r1 register', which means that the next instruction to be executed is at the address in register r1. The address to be jumped to is not known until the instruction is executed. Indirect branches can also depend on the value of a memory location.
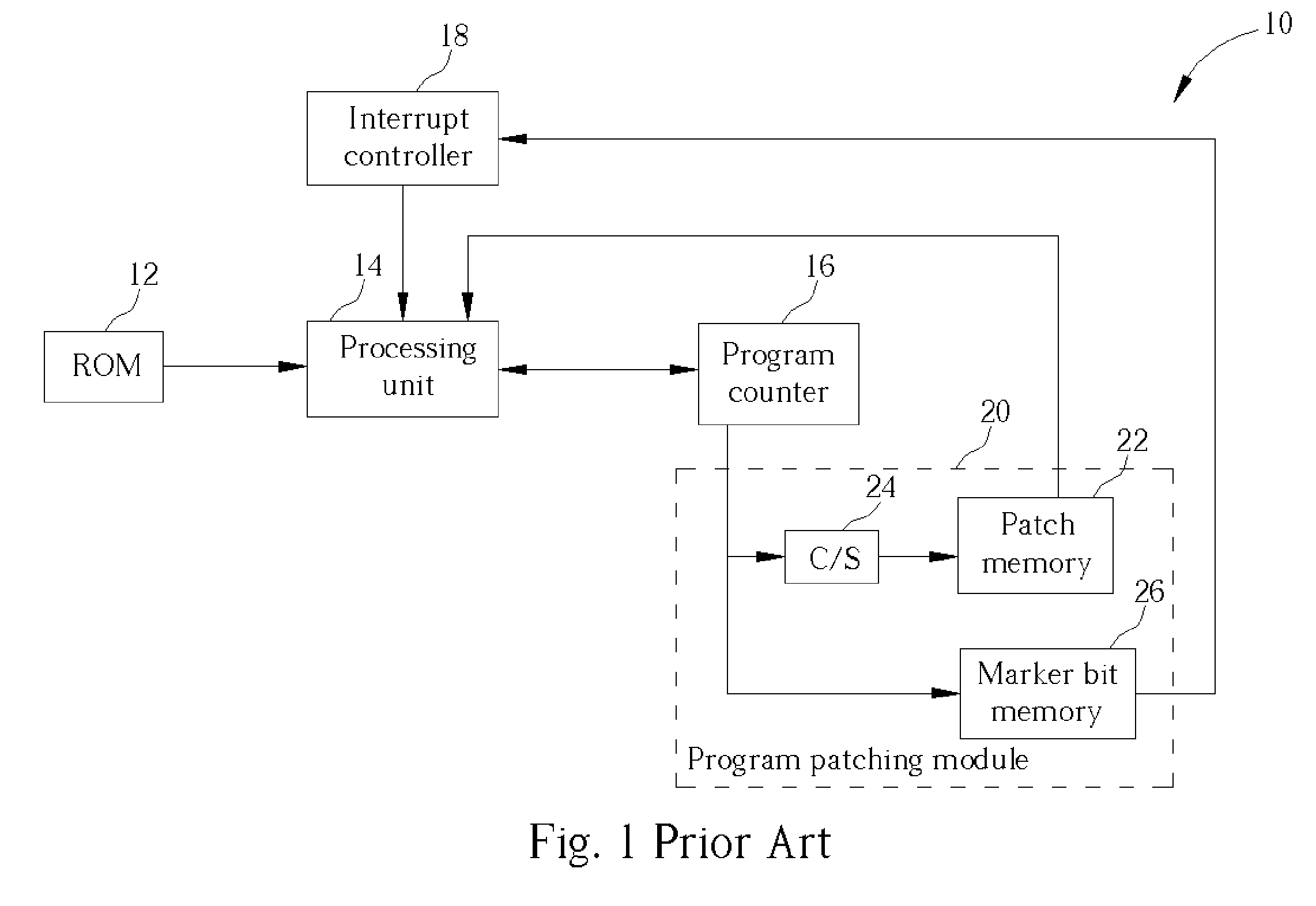
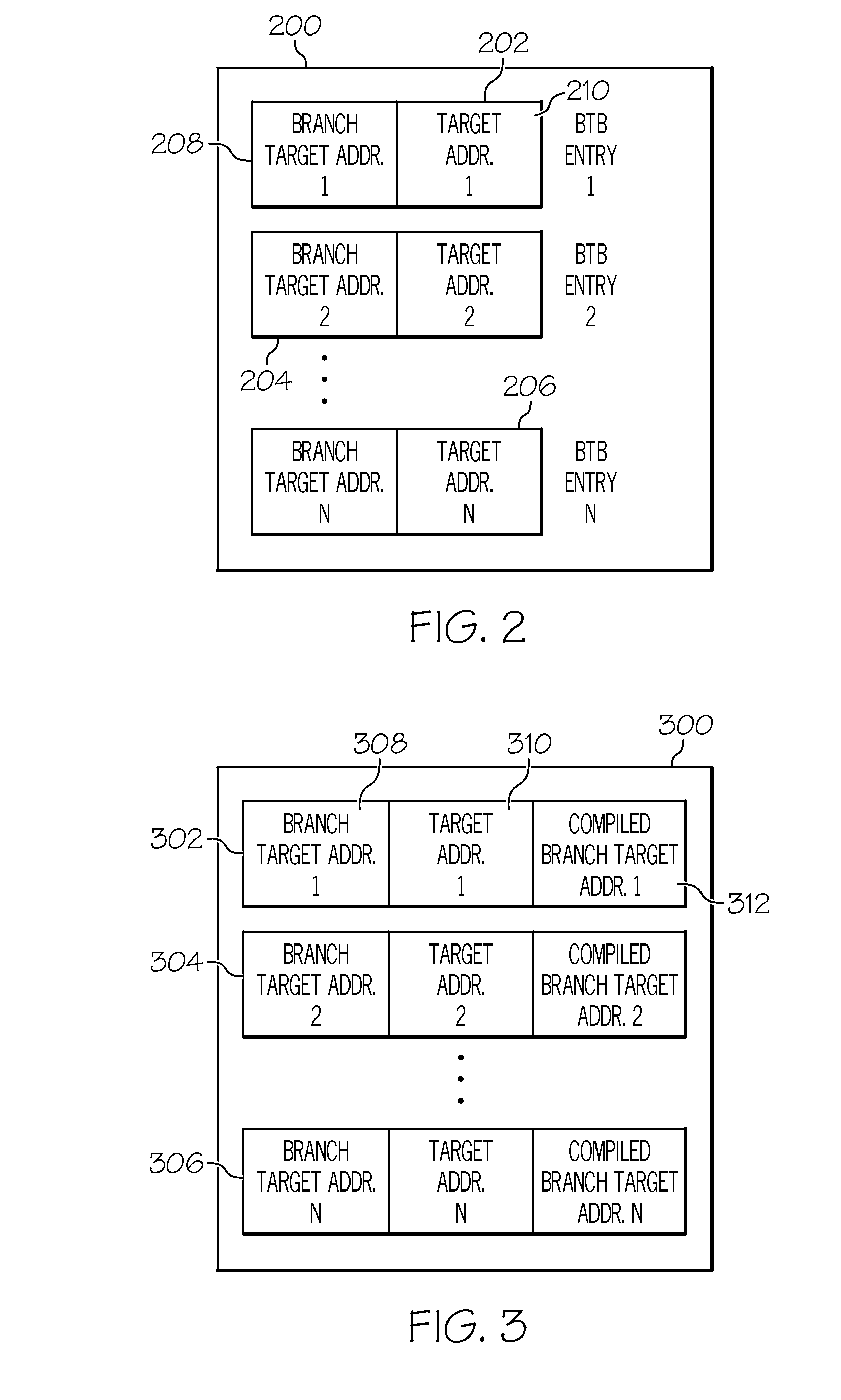
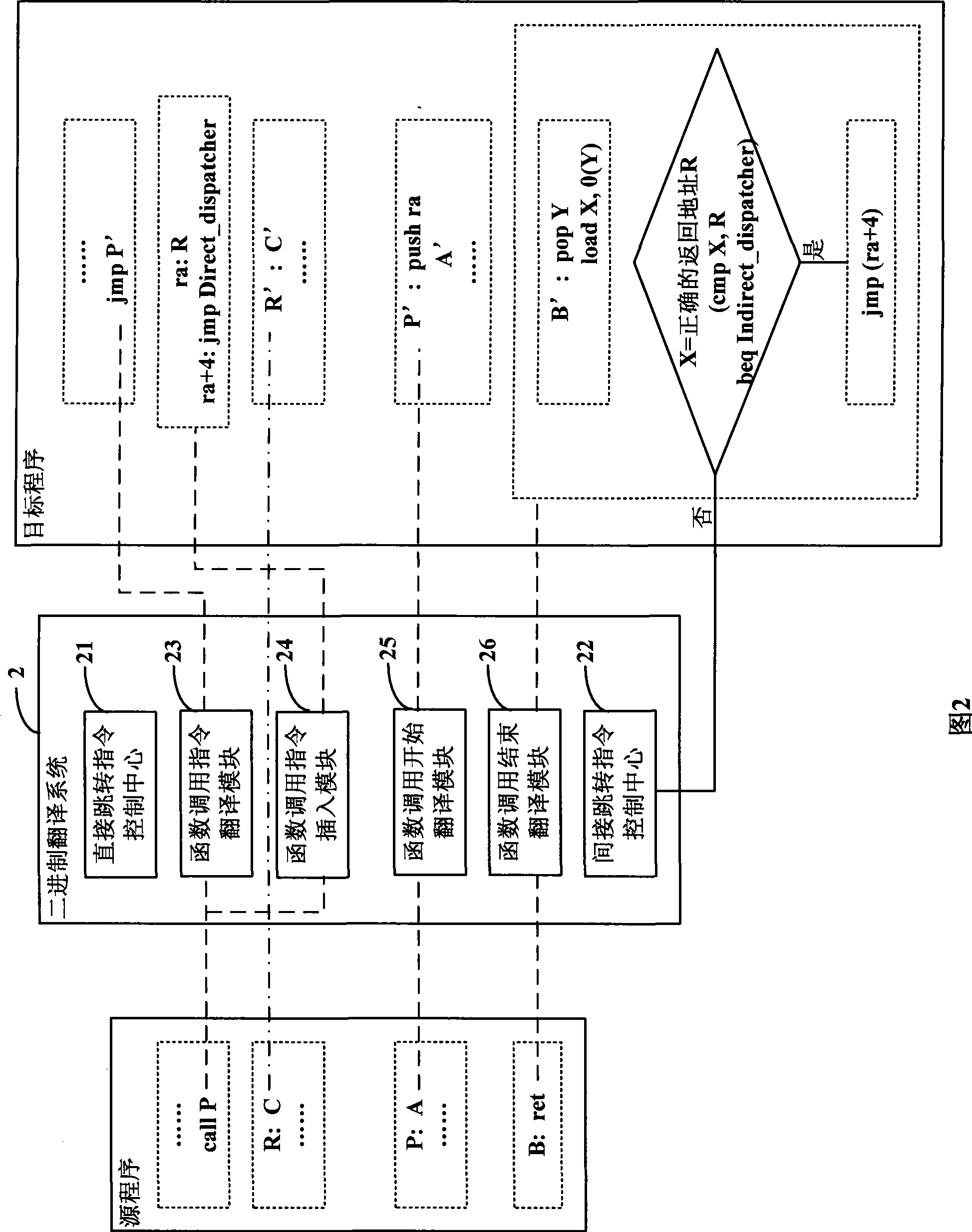
Method for selecting active code traces for translation in a caching dynamic translator
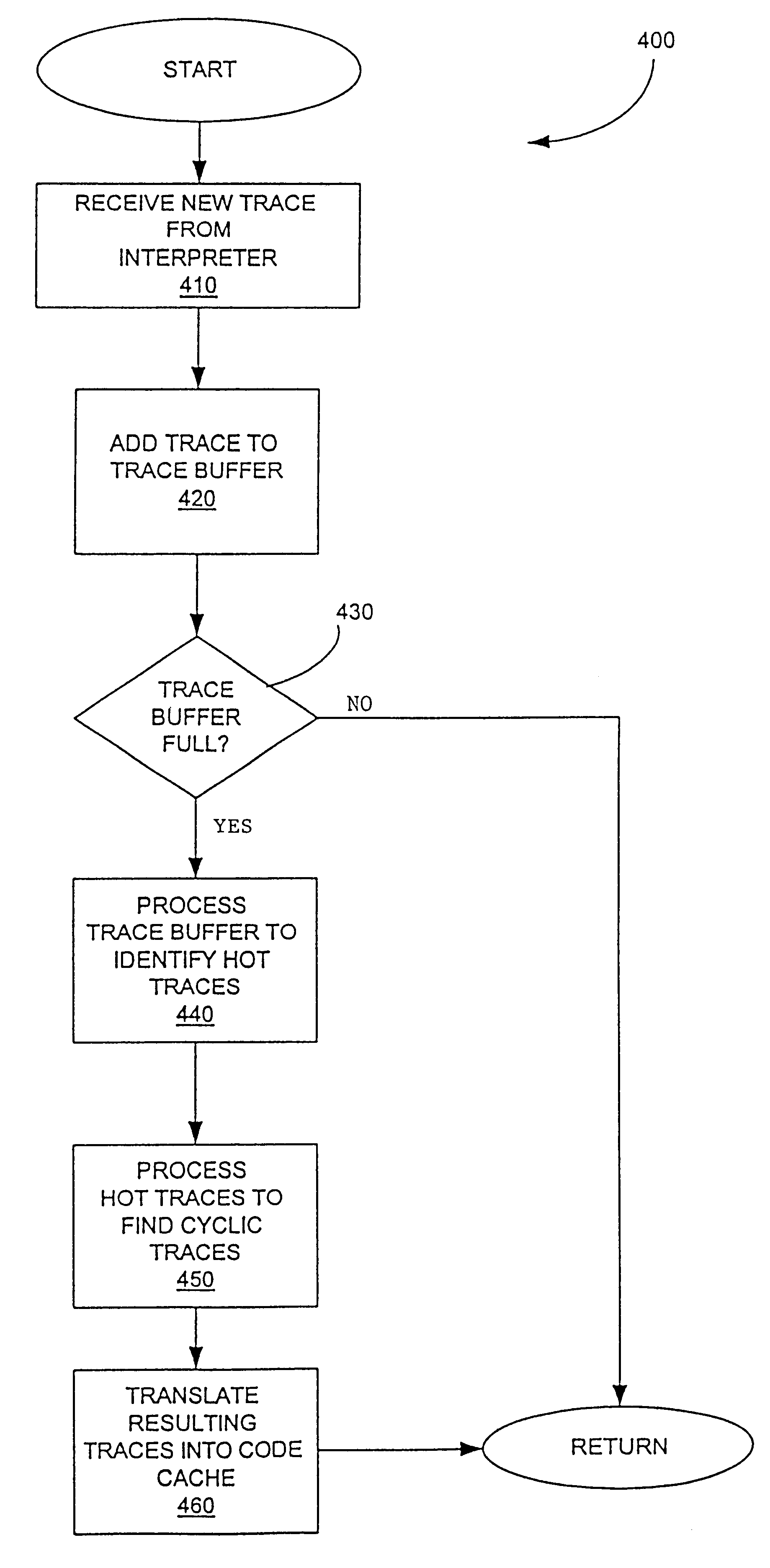
A method is shown for selecting active, or hot, code traces in an executing program for storage in a code cache. A trace is a sequence of dynamic instructions characterized by a start address and a branch history which allows the trace to be dynamically disassembled. Each trace is terminated by execution of a trace terminating condition which is a backward taken branch, an indirect branch, or a branch whose execution causes the branch history for the trace to reach a predetermined limit. As each trace is generated by the executing program, it is loaded into a buffer for processing. When the buffer is full, a counter corresponding to the start address of each trace is incremented. When the count for a start address exceeds a threshold, then the start address is marked as being hot. Each hot trace is then checked to see if the next trace in the buffer shares the same start address, in which case the hot trace is cyclic. If the start address of the next trace is not the same as the hot trace, then the traces in the buffer are checked to see they form a larger cycle of execution. If the traces subsequent to the hot trace are not hot themselves and are followed by a trace having the same start address as the hot trace, then their branch histories are companded with the branch history of the hot trace to form a cyclic trace. The cyclic traces are then disassembled and the instructions executed in the trace are stored in a code cache.
Owner:HEWLETT PACKARD DEV CO LP
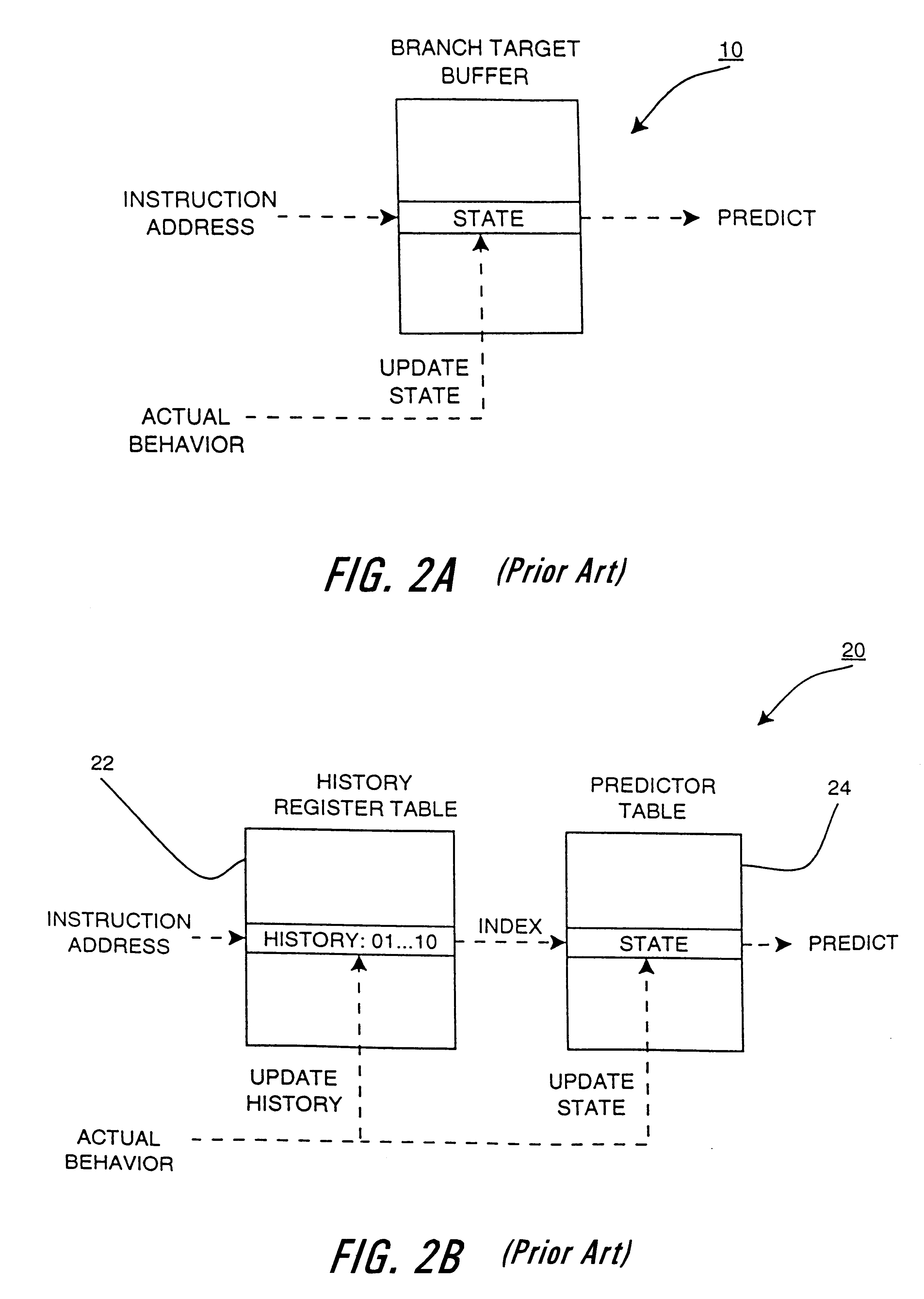
Method and apparatus for profiling of non-instrumented programs and dynamic processing of profile data
InactiveUS6233678B1Digital computer detailsNext instruction address formationProcessor registerParallel computing
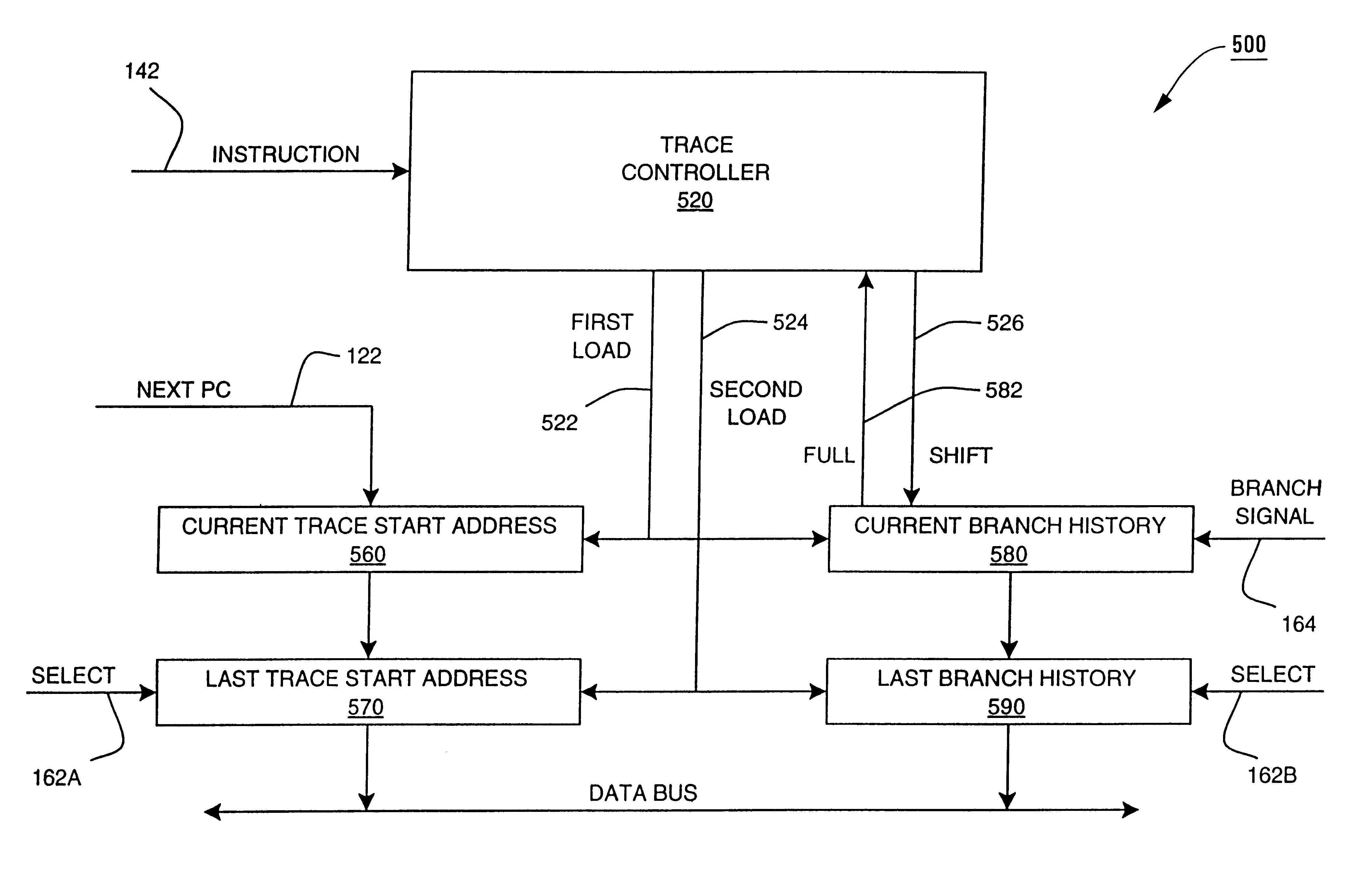
An apparatus and method are shown for collecting a branch history value of a program executing in a processor. A current start address register latches a program count value in response to a trace termination condition, such as an indirect branch instruction. A current branch history register is cleared in response to the trace termination condition and shifts in a branch outcome value of the processor in response to a conditional direct branch instruction. A last trace start address latches the content of the current trace start address and a last branch history register latches the content of the current branch history register when a trace termination condition occurs.
Owner:HEWLETT PACKARD CO
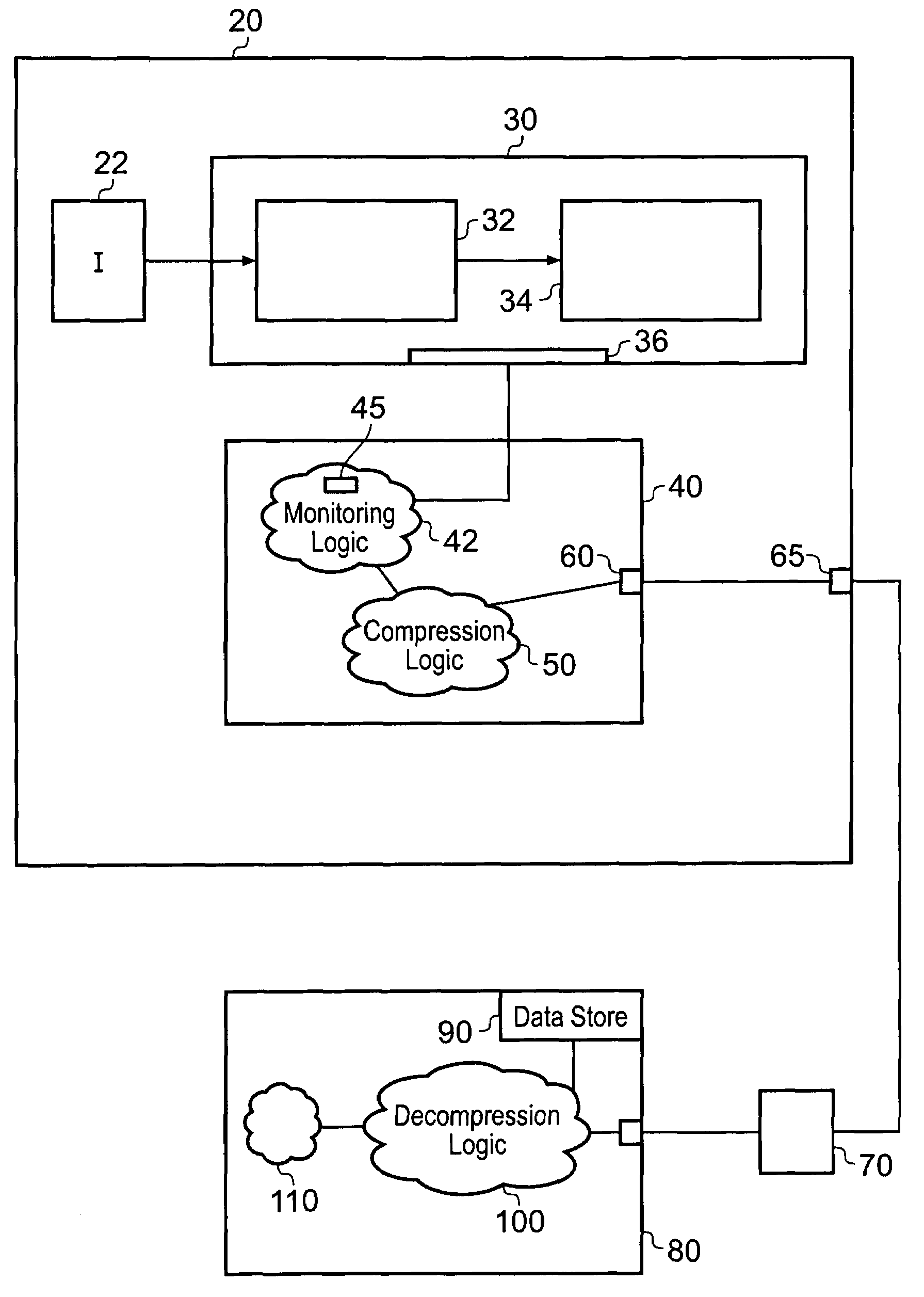
Reducing the size of a data stream produced during instruction tracing
ActiveUS7707394B2Reduce in quantityReduce data volumeEnergy efficient ICTDigital computer detailsProcessing InstructionData stream
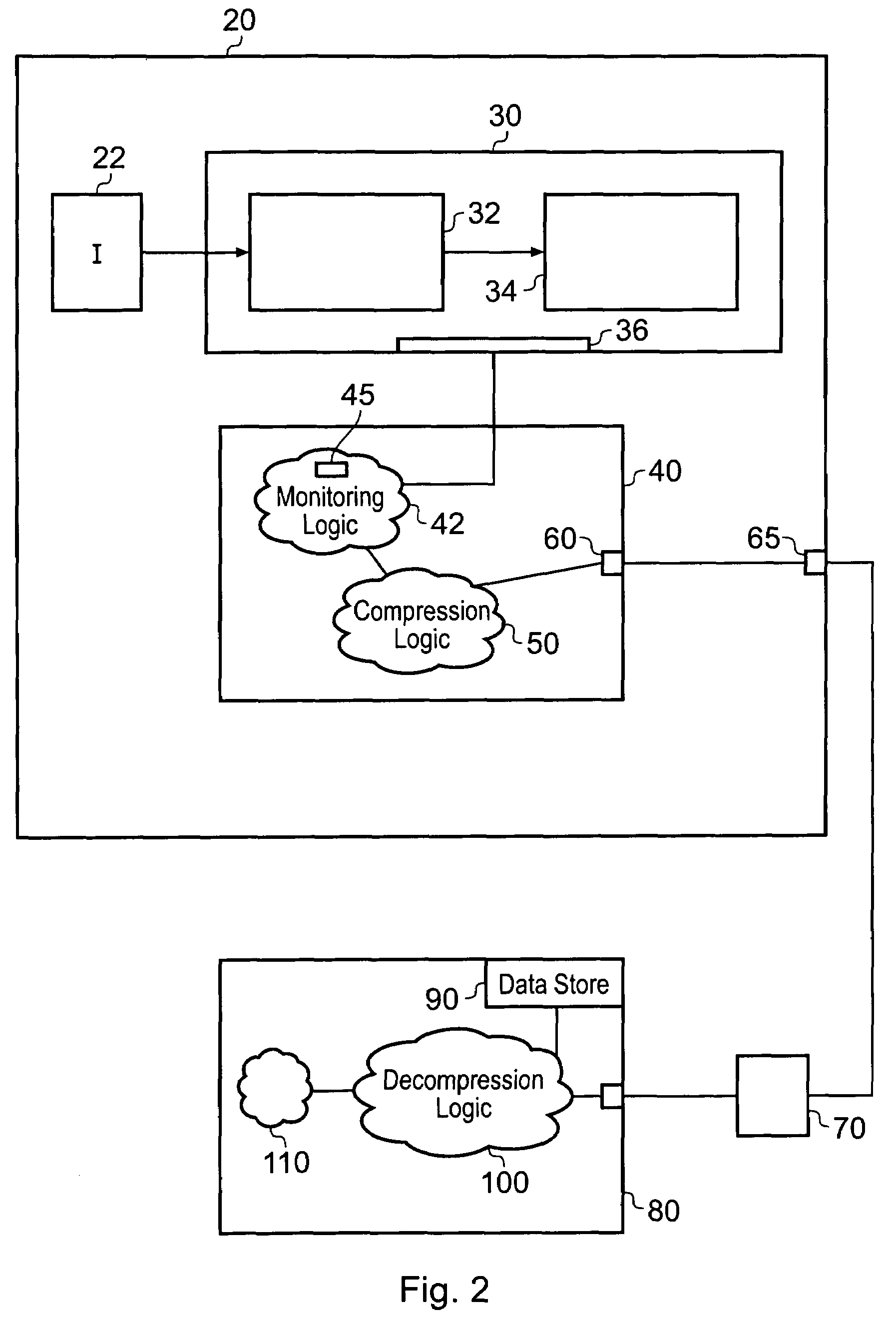
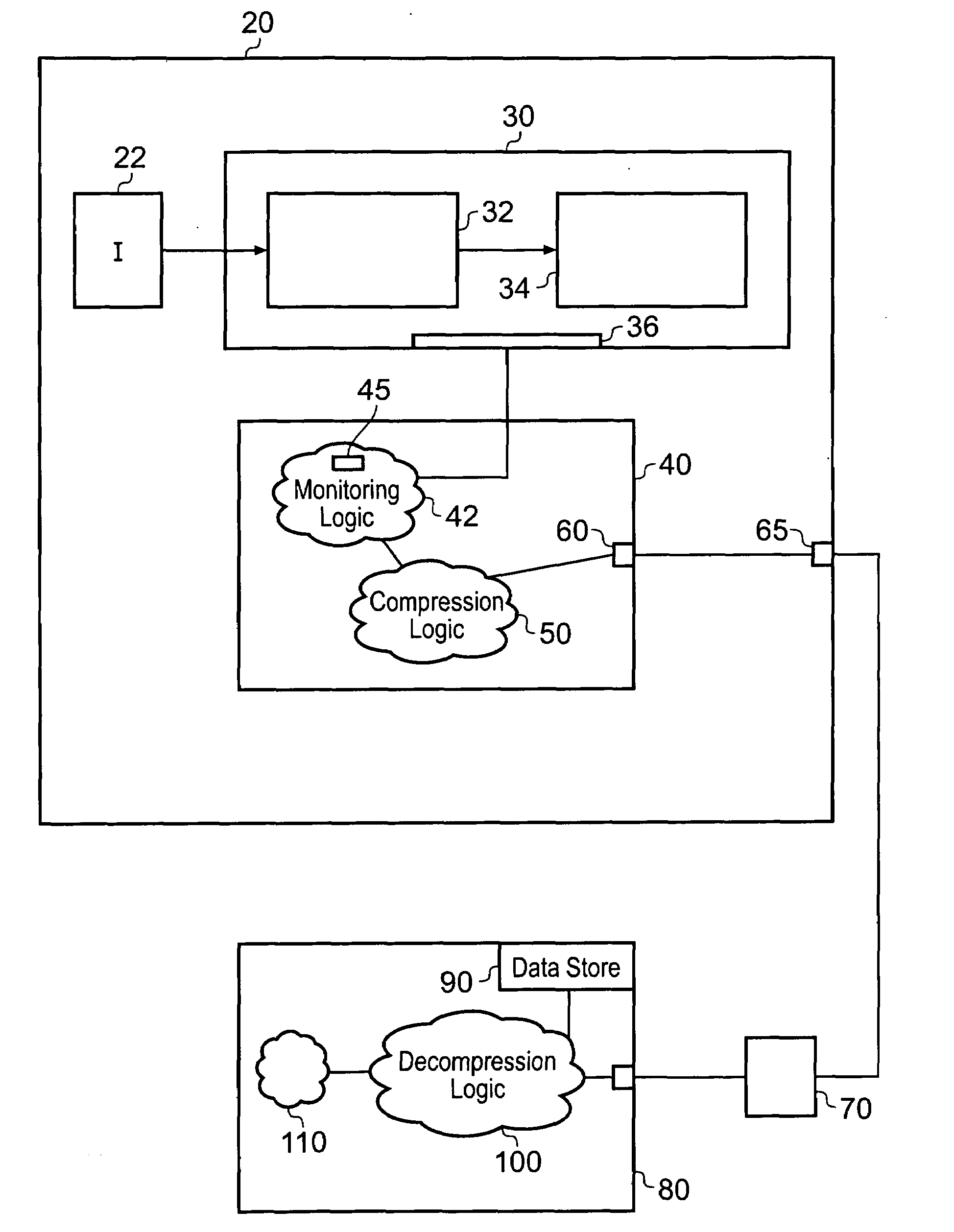
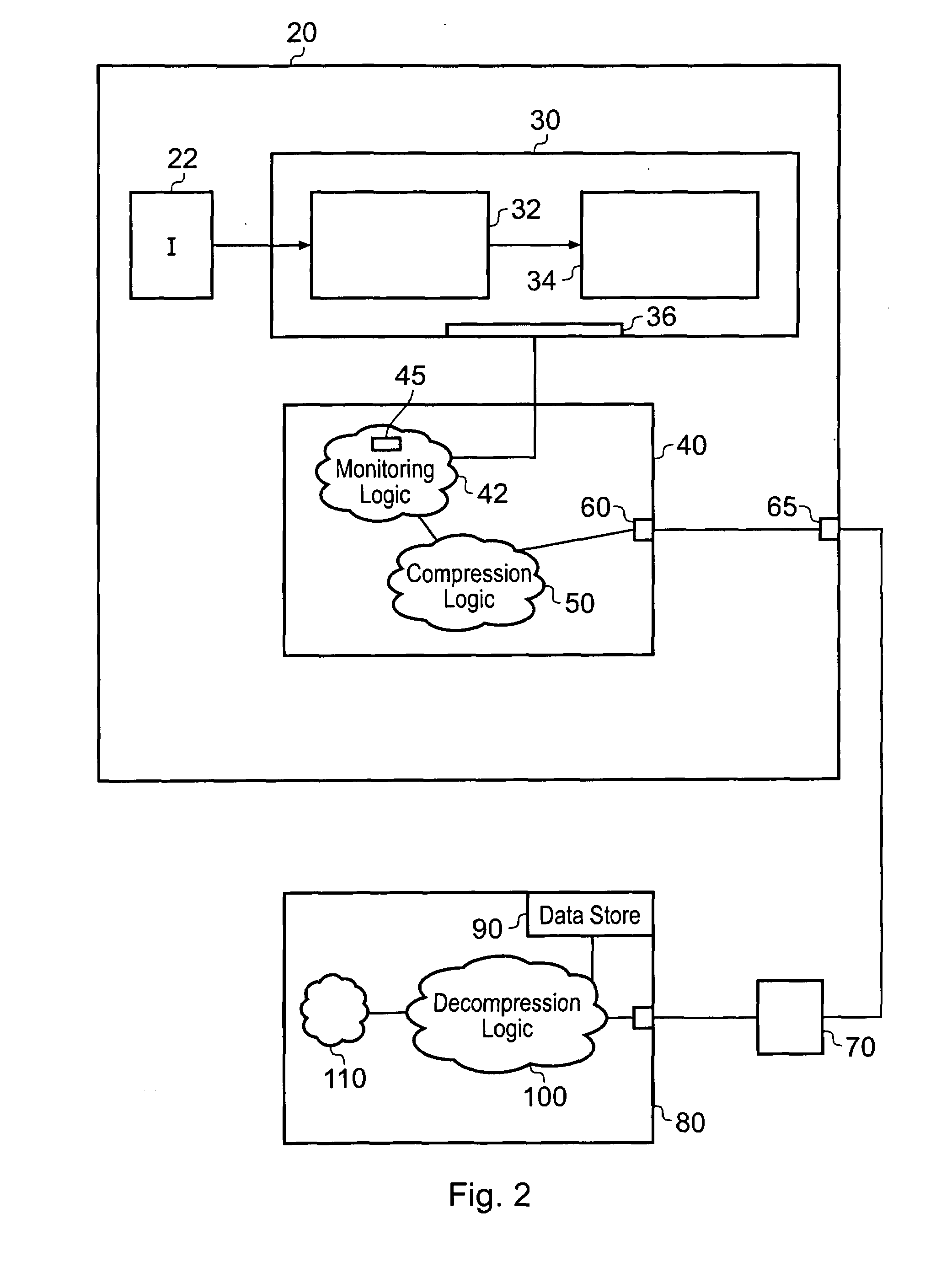
Tracing logic for monitoring a stream of processing instructions from a program being processed by a data processor is disclosed, said tracing logic comprising monitoring logic operable to detect processing of said instructions in said instruction stream; detect which of said instructions in said instruction stream are conditional direct branch instructions, which of said instructions in said instruction stream are conditional indirect branch instructions and which of said instructions in said instruction stream are unconditional indirect branch instructions; said tracing logic further comprising compression logic operable to: designate said conditional direct branch instructions, said conditional indirect branch instructions and said indirect branch instructions as marker instructions; for each marker instruction, output an execution indicator indicating if said marker instruction has executed or a non-execution indicator indicating if said marker instruction has not executed and not output data relating to previously processed instructions that are not marker instructions.
Owner:ARM LTD
Indirect Function Call Instructions in a Synchronous Parallel Thread Processor
ActiveUS20090240931A1Easy to processProvide capabilitySingle instruction multiple data multiprocessorsConcurrent instruction executionSingle instruction, multiple threadsProcessor register
An indirect branch instruction takes an address register as an argument in order to provide indirect function call capability for single-instruction multiple-thread (SIMT) processor architectures. The indirect branch instruction is used to implement indirect function calls, virtual function calls, and switch statements to improve processing performance compared with using sequential chains of tests and branches.
Owner:NVIDIA CORP
Indirect Branch Hint
InactiveUS20110320787A1Minimize the numberImprove performanceDigital computer detailsNext instruction address formationInstruction memoryProcessor register
A processor implements an apparatus and a method for predicting an indirect branch address. A target address generated by an instruction is automatically identified. A predicted next program address is prepared based on the target address before an indirect branch instruction utilizing the target address is speculatively executed. The apparatus suitably employs a register for holding an instruction memory address that is specified by a program as a predicted indirect address of an indirect branch instruction. The apparatus also employs a next program address selector that selects the predicted indirect address from the register as the next program address for use in speculatively executing the indirect branch instruction.
Owner:QUALCOMM INC
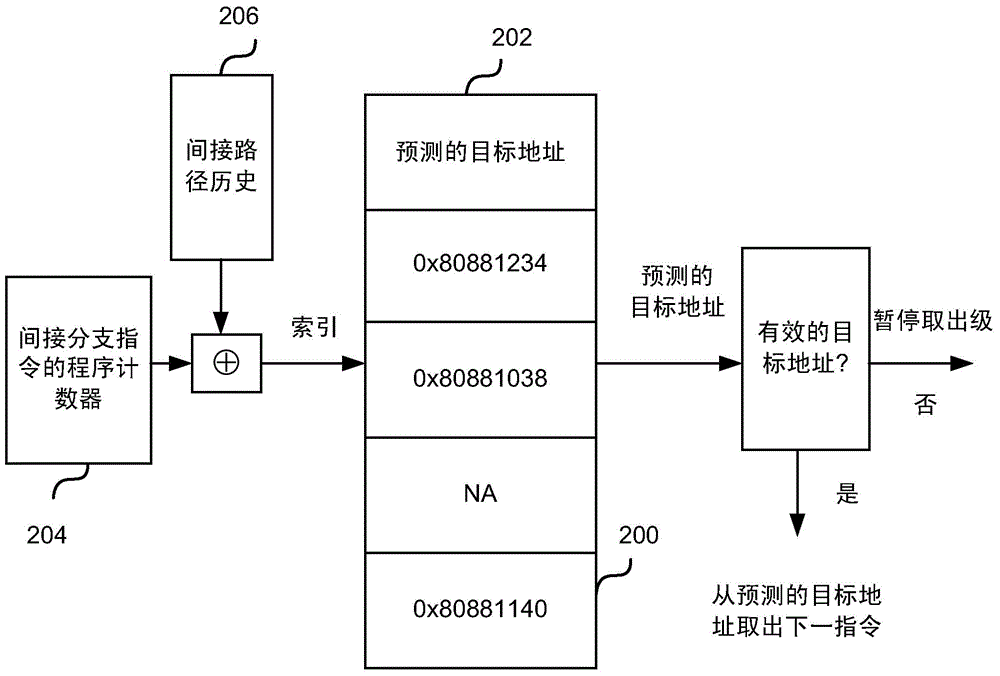
Method and system for branch target prediction using path information
InactiveUS20050262332A1Digital computer detailsConcurrent instruction executionParallel computingIndirect branch
A system and method for predicting a branch target for a current instruction in a microprocessor, the system comprising a cache storing indirect branch instructions and a path register. The path register is updated on certain branches by an XOR operation on the path register and the branch instruction, followed by the addition of one or more bits to the register. The cache is indexed by performing an operation on a portion of the current instruction address and the path register; the entry returned, if any, may be used to predict the target of the current instruction.
Owner:RAPPOPORT LIHU +3
Processing an indirect branch instruction in a SIMD architecture
ActiveUS7761697B1Minimal performance degradationEfficient mechanismDigital computer detailsSpecific program execution arrangementsProgram instructionParallel computing
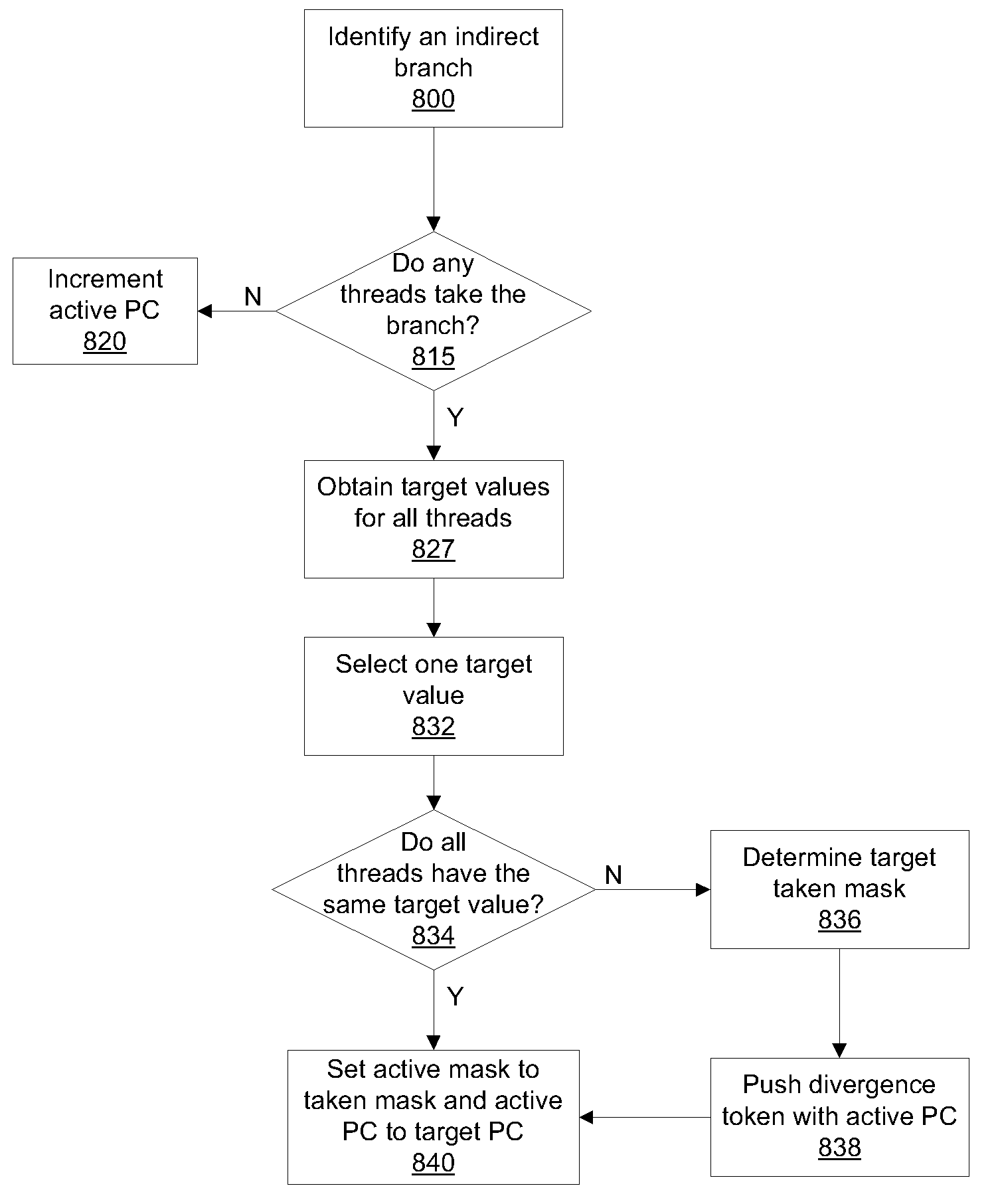
One embodiment of a computing system configured to manage divergent threads in a thread group includes a stack configured to store at least one token and a multithreaded processing unit. The multithreaded processing unit is configured to perform the steps of fetching a program instruction, determining that the program instruction is an indirect branch instruction, and processing the indirect branch instruction as a sequence of two-way branches to execute an indirect branch instruction with multiple branch addresses. Indirect branch instructions may be used to allow greater flexibility since the branch address or multiple branch addresses do not need to be determined at compile time.
Owner:NVIDIA CORP
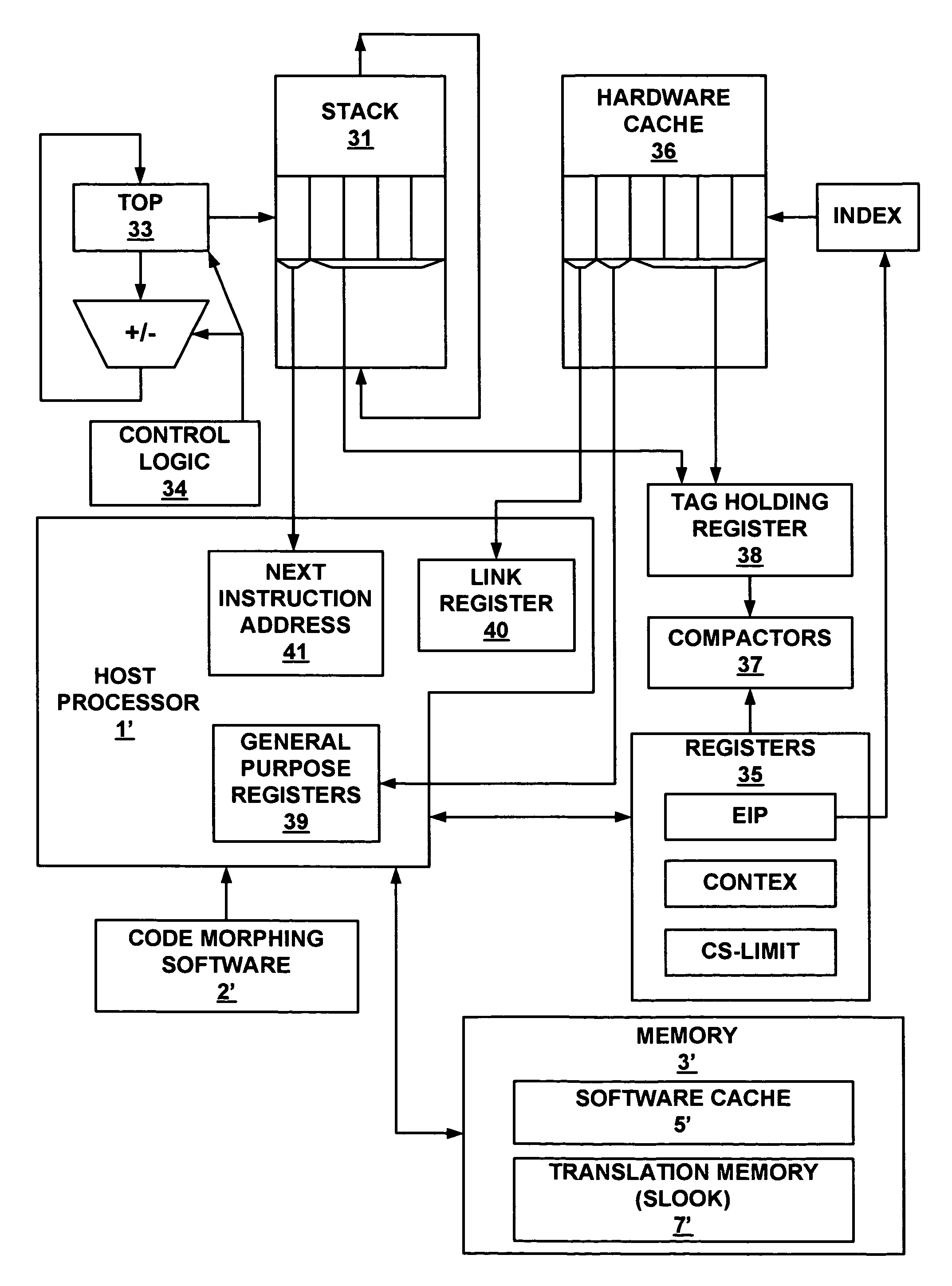
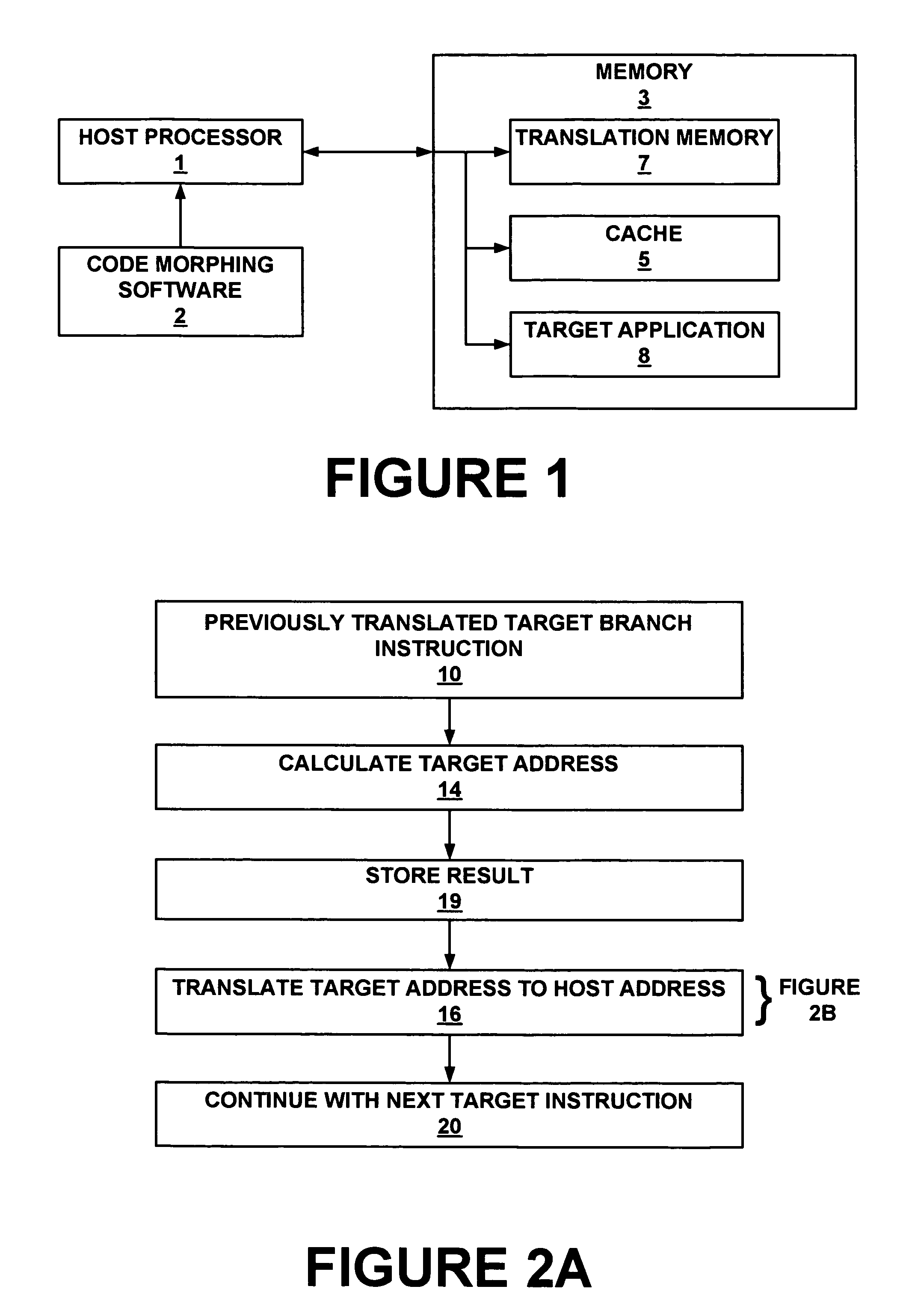
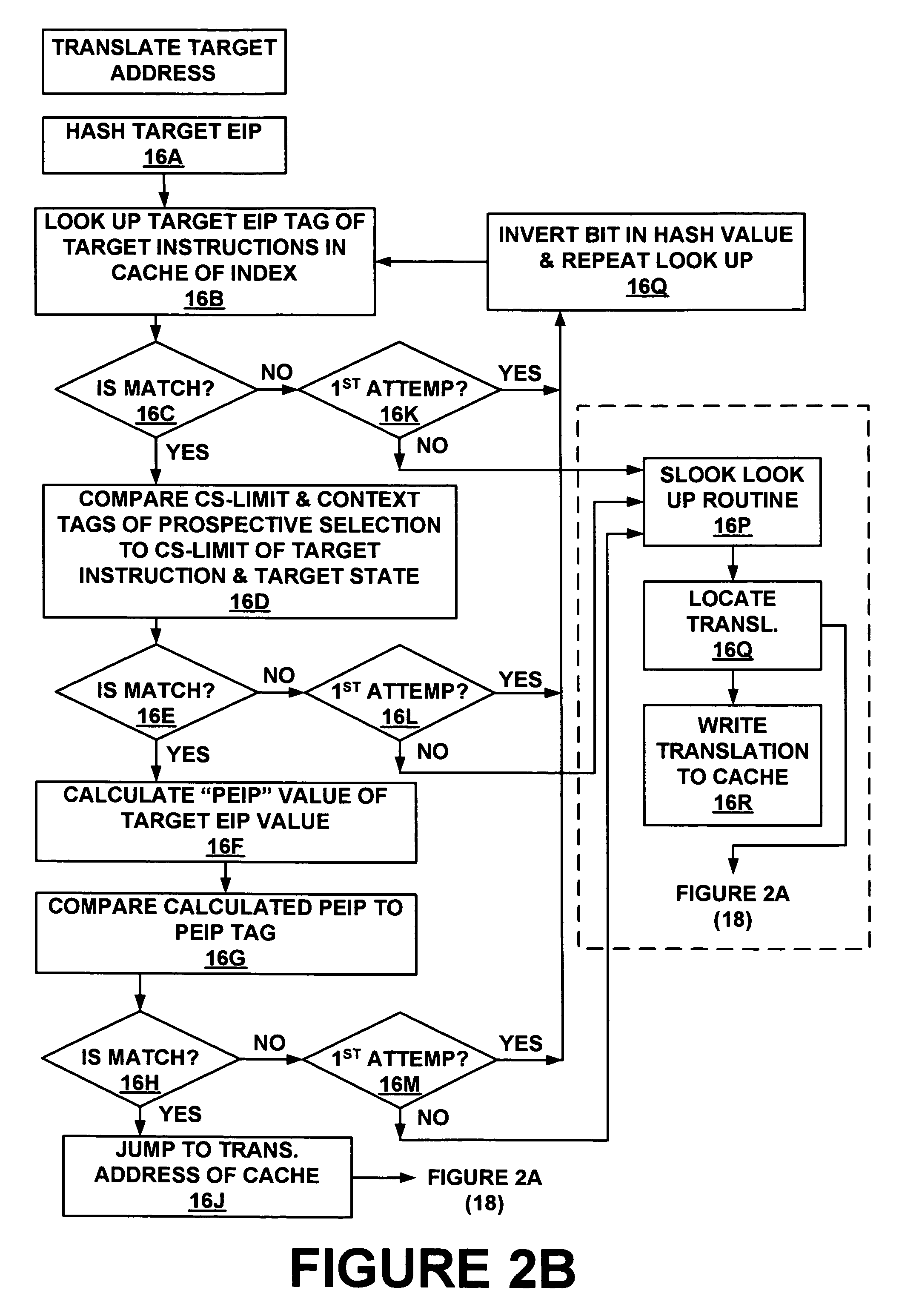
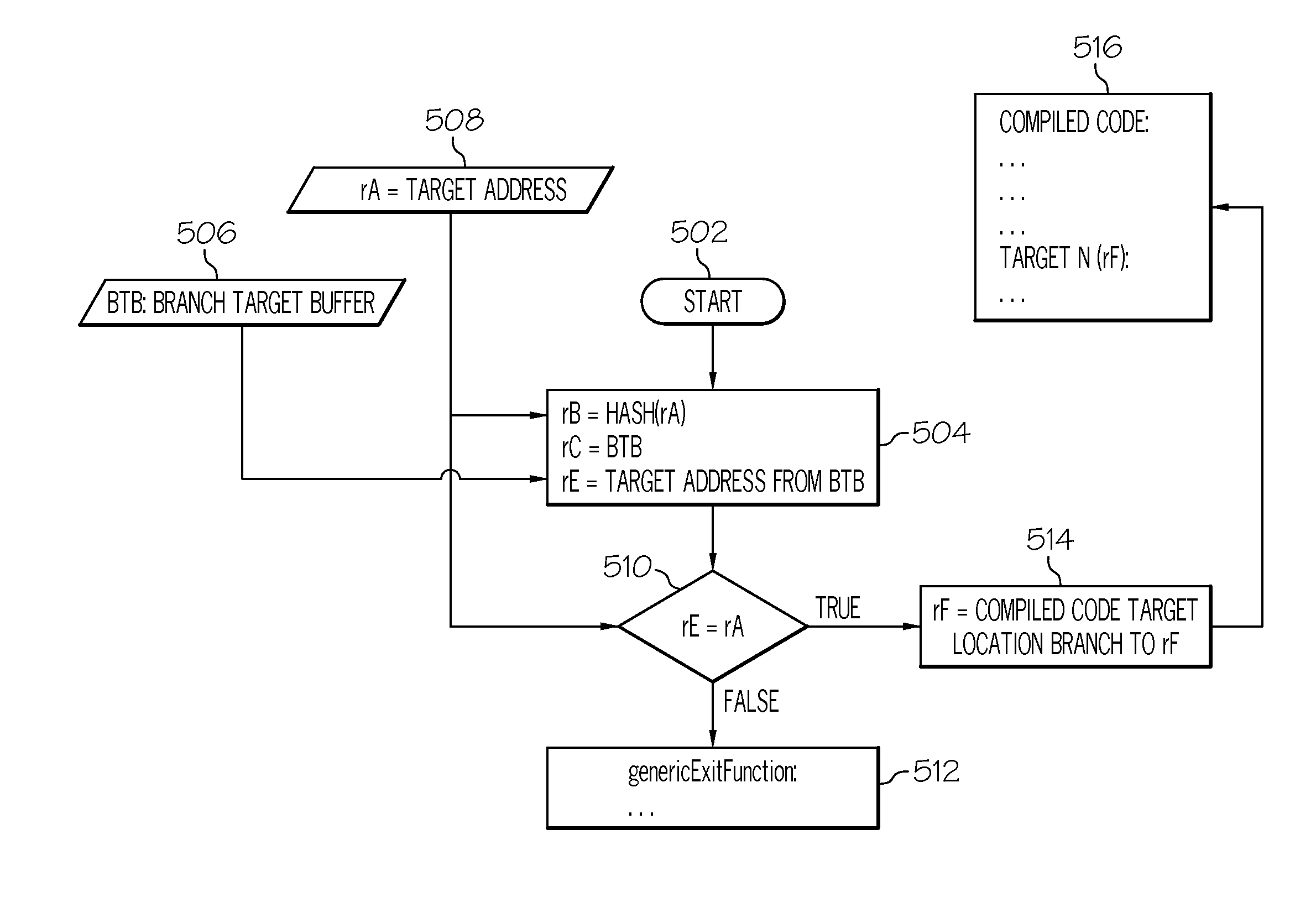
Method and system for storing and retrieving a translation of target program instruction from a host processor using fast look-up of indirect branch destination in a dynamic translation system
InactiveUS7644210B1Fast executionProgram control using stored programsDigital computer detailsProgram instructionParallel computing
Dynamic translation of indirect branch instructions of a target application by a host processor is enhanced by including a cache to provide access to the addresses of the most frequently used translations of a host computer, minimizing the need to access the translation buffer. Entries in the cache have a host instruction address and tags that may include a logical address of the instruction of the target application, the physical address of that instruction, the code segment limit to the instruction, and the context value of the host processor associated with that instruction. The cache may be a software cache apportioned by software from the main processor memory or a hardware cache separate from main memory.
Owner:INTELLECTUAL VENTURES HOLDING 81 LLC
System and method for optimizing branch logic for handling hard to predict indirect branches
ActiveUS7809933B2Easy to handleImprove processor performanceDigital computer detailsSpecific program execution arrangementsParallel computingIndirect branch
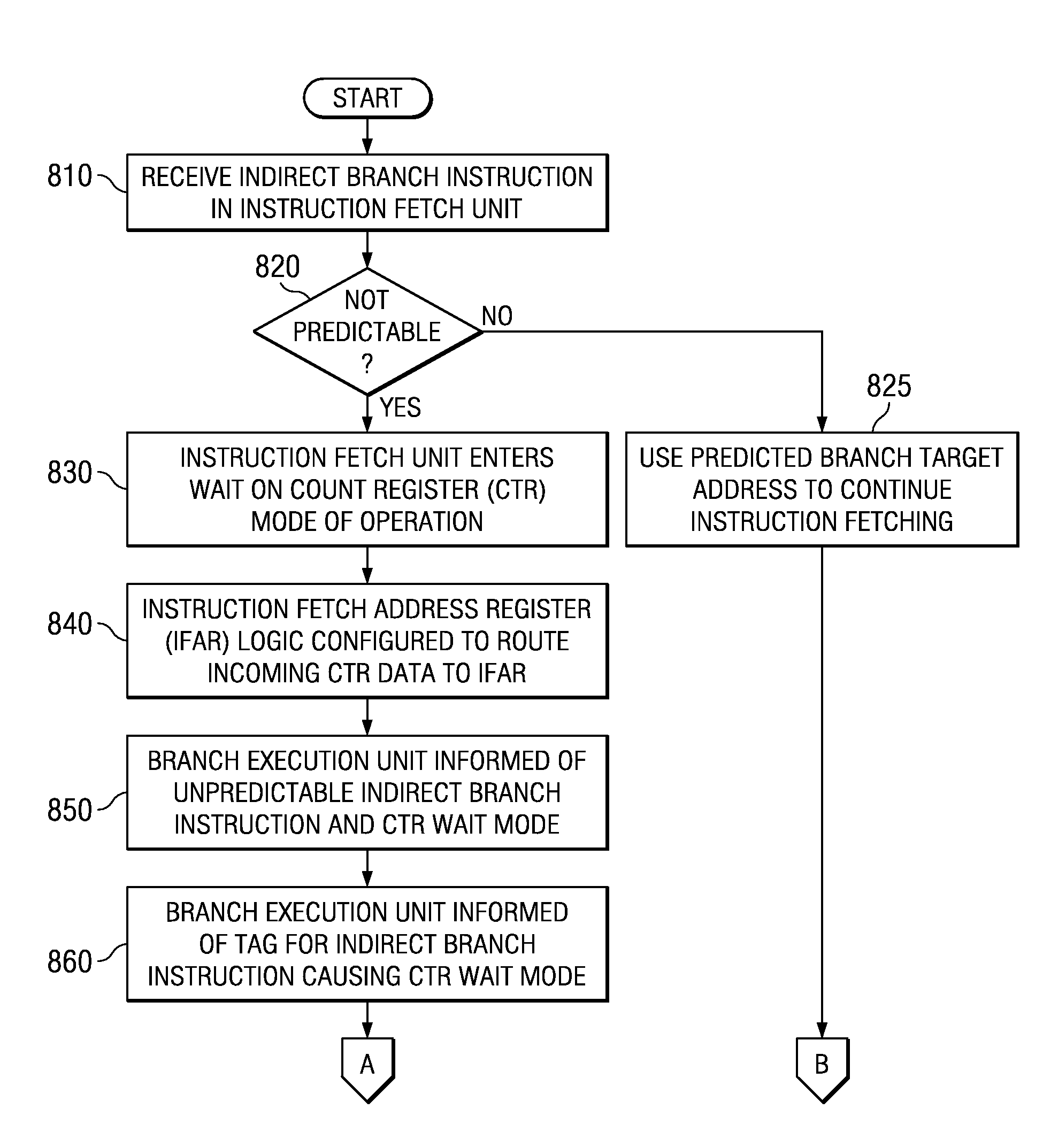
A system and method for optimizing the branch logic of a processor to improve handling of hard to predict indirect branches are provided. The system and method leverage the observation that there will generally be only one move to the count register (mtctr) instruction that will be executed while a branch on count register (bcctr) instruction has been fetched and not executed. With the mechanisms of the illustrative embodiments, fetch logic detects that it has encountered a bcctr instruction that is hard to predict and, in response to this detection, blocks the target fetch from entering the instruction buffer of the processor. At this point, the fetch logic has fetched all the instructions up to and including the bcctr instruction but no target instructions. When the next mtctr instruction is executed, the branch logic of the processor grabs the data and starts fetching using that target address. Since there are no other target instructions that were fetched, no flush is needed if that target address is the correct address, i.e. the branch prediction is correct.
Owner:INT BUSINESS MASCH CORP
Reducing the size of a data stream produced during instruction tracing
ActiveUS20070294592A1Less evenly distributedEasy to compressEnergy efficient ICTError detection/correctionProcessing InstructionData stream
Tracing logic for monitoring a stream of processing instructions from a program being processed by a data processor is disclosed, said tracing logic comprising monitoring logic operable to detect processing of said instructions in said instruction stream; detect which of said instructions in said instruction stream are conditional direct branch instructions, which of said instructions in said instruction stream are conditional indirect branch instructions and which of said instructions in said instruction stream are unconditional indirect branch instructions; said tracing logic further comprising compression logic operable to: designate said conditional direct branch instructions, said conditional indirect branch instructions and said indirect branch instructions as marker instructions; for each marker instruction, output an execution indicator indicating if said marker instruction has executed or a non-execution indicator indicating if said marker instruction has not executed and not output data relating to previously processed instructions that are not marker instructions.
Owner:ARM LTD
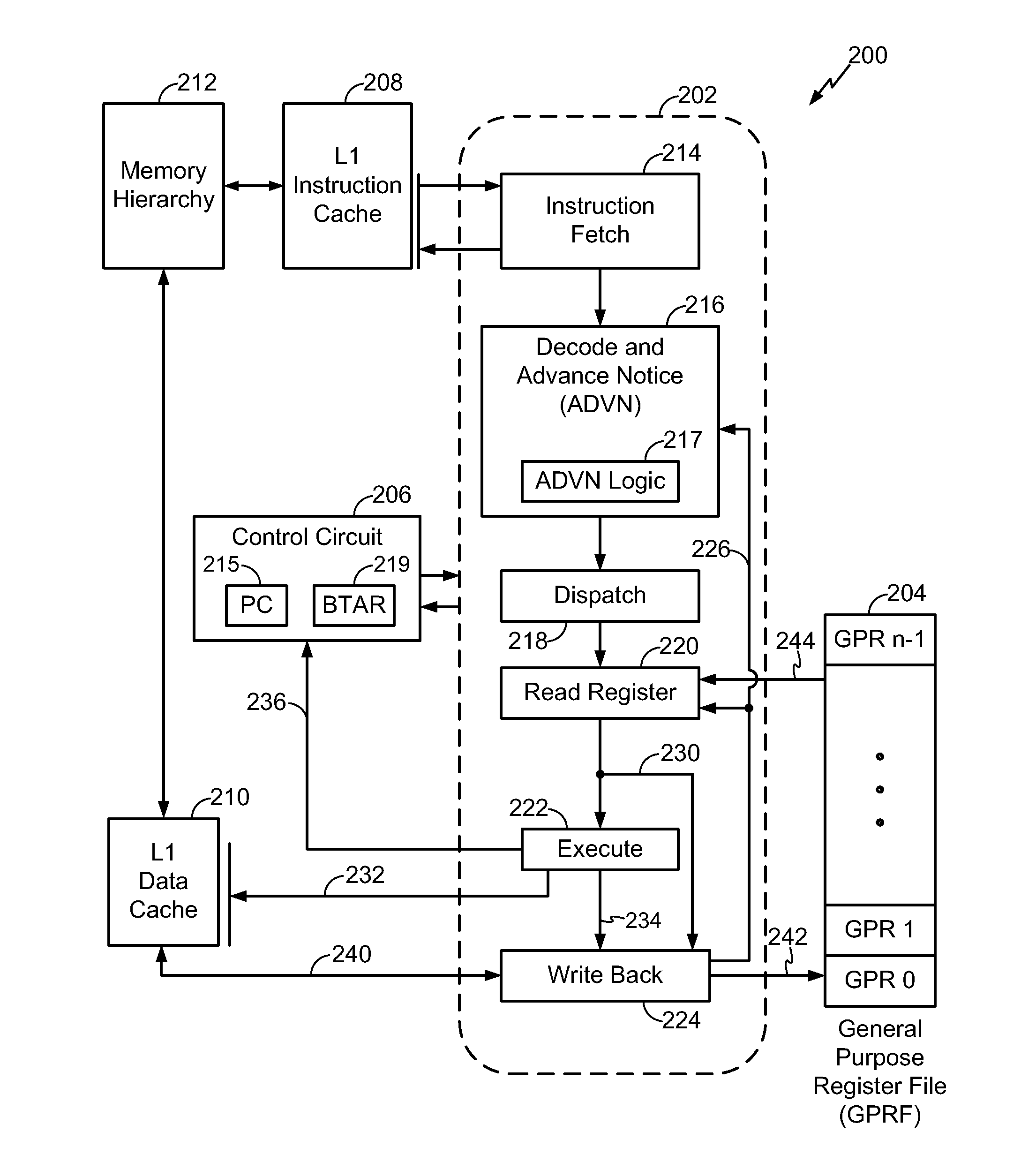
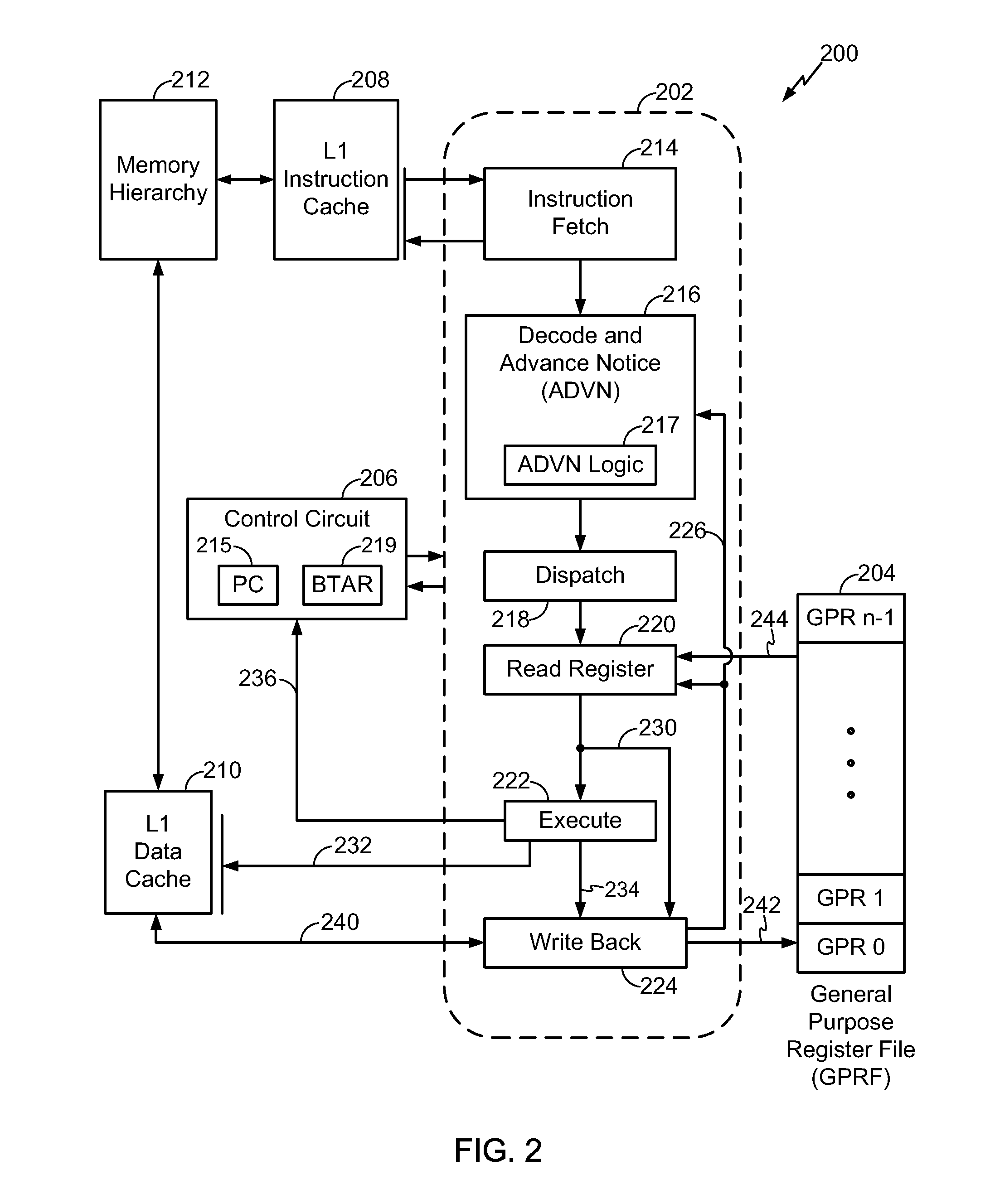
Methods and apparatus for changing a sequential flow of a program using advance notice techniques
InactiveCN102934075ANext instruction address formationConcurrent instruction executionInstruction memoryProcessor register
A processor implements an apparatus and a method for providing advance notice of an indirect branch address. A target address generated by an instruction is automatically identified. A next program address is prepared based on a most current target address before an indirect branch instruction utilizing the most current target address is speculatively executed. The apparatus suitably employs a register for holding an instruction memory address that is specified by a program as a most current indirect address of an indirect branch instruction. The apparatus also employs a next program address selector that selects the most current indirect address from the register as the next program address for use in speculatively executing the indirect branch instruction.
Owner:QUALCOMM INC
Device and method for realizing indirect branch prediction of modern processor
ActiveCN102306093AImprove energy efficiencyUpdate logic is simpleConcurrent instruction executionMass storageParallel computing
The invention discloses a device and a method for realizing the indirect branch prediction of a modern processor. The device comprises a direction predictor, a group-path pointer register and a branch target buffer, wherein the direction predictor selects a first access index and a second access index of a mode historical record while predicting an indirect branch instruction direction, and generates and outputs a corresponding group-path pointer through the mode historical record; the group-path pointer register stores the group-path pointer output by the mode historical record; the branch target buffer establishes subblocks and allocation items; each subblock allocates a destination address item indexed by the group-path pointer to each indirect branch instruction; and each allocation item is used for recording the using condition of the destination address item of each indirect branch instruction. By the device and the method, a prediction effect similar to the effect of direct address prediction can be achieved on the basis that the support of a high-capacity storage structure is not needed, so the energy efficiency of the processor can be improved.
Owner:BEIJING PKUNITY MICROSYST TECH
System and Method for Optimizing Branch Logic for Handling Hard to Predict Indirect Branches
ActiveUS20080307210A1Improve processor performanceImprove performanceDigital computer detailsSpecific program execution arrangementsParallel computingIndirect branch
A system and method for optimizing the branch logic of a processor to improve handling of hard to predict indirect branches are provided. The system and method leverage the observation that there will generally be only one move to the count register (mtctr) instruction that will be executed while a branch on count register (bcctr) instruction has been fetched and not executed. With the mechanisms of the illustrative embodiments, fetch logic detects that it has encountered a bcctr instruction that is hard to predict and, in response to this detection, blocks the target fetch from entering the instruction buffer of the processor. At this point, the fetch logic has fetched all the instructions up to and including the bcctr instruction but no target instructions. When the next mtctr instruction is executed, the branch logic of the processor grabs the data and starts fetching using that target address. Since there are no other target instructions that were fetched, no flush is needed if that target address is the correct address, i.e. the branch prediction is correct.
Owner:IBM CORP
Computer implemented system and method of translation of verification commands of an electronic design
A computer implemented method of translation of verification commands of an electronic design, comprises the steps of receiving the electronic design, receiving at least one analog test harness model having at least one indirect branch contribution statement, translating the at least one indirect branch contribution statement into a plurality of direct branch contribution operators based at least in part upon the at least one analog test harness model and generating a netlist based at least in part upon the translation.
Owner:ZIPALOG
Device and method for realizing indirect branch and prediction among modern processors
ActiveCN102306094AAvoid mistakesImprove forecast accuracyConcurrent instruction executionMass storageParallel computing
The invention discloses a device and a method for realizing indirect branch and prediction among modern processors, wherein the device comprises a branch direction predictor which generates a target pointer according to an indirect branch direction predicted by a plurality of sub-predictors, a target address mapping device which maps the target pointer generated by the branch direction predictor to a virtual address of an indexing branch target buffer, and a branch target buffer which distributes a target address item and a distribution item to an indirect branch instruction; the target address item is indexed through the virtual address; and the distribution item records the use condition of each indirect branch instruction target address item and is indexed through a value of a program counter. On the basis of not needing bulk-storage memory support, both the prediction accuracy and the processor energy efficiency are increased at the cost of time similar to that of the existing indirect branch prediction technique.
Owner:BEIJING PKUNITY MICROSYST TECH
SPARC V8 system structure based classified type mixed branch prediction system
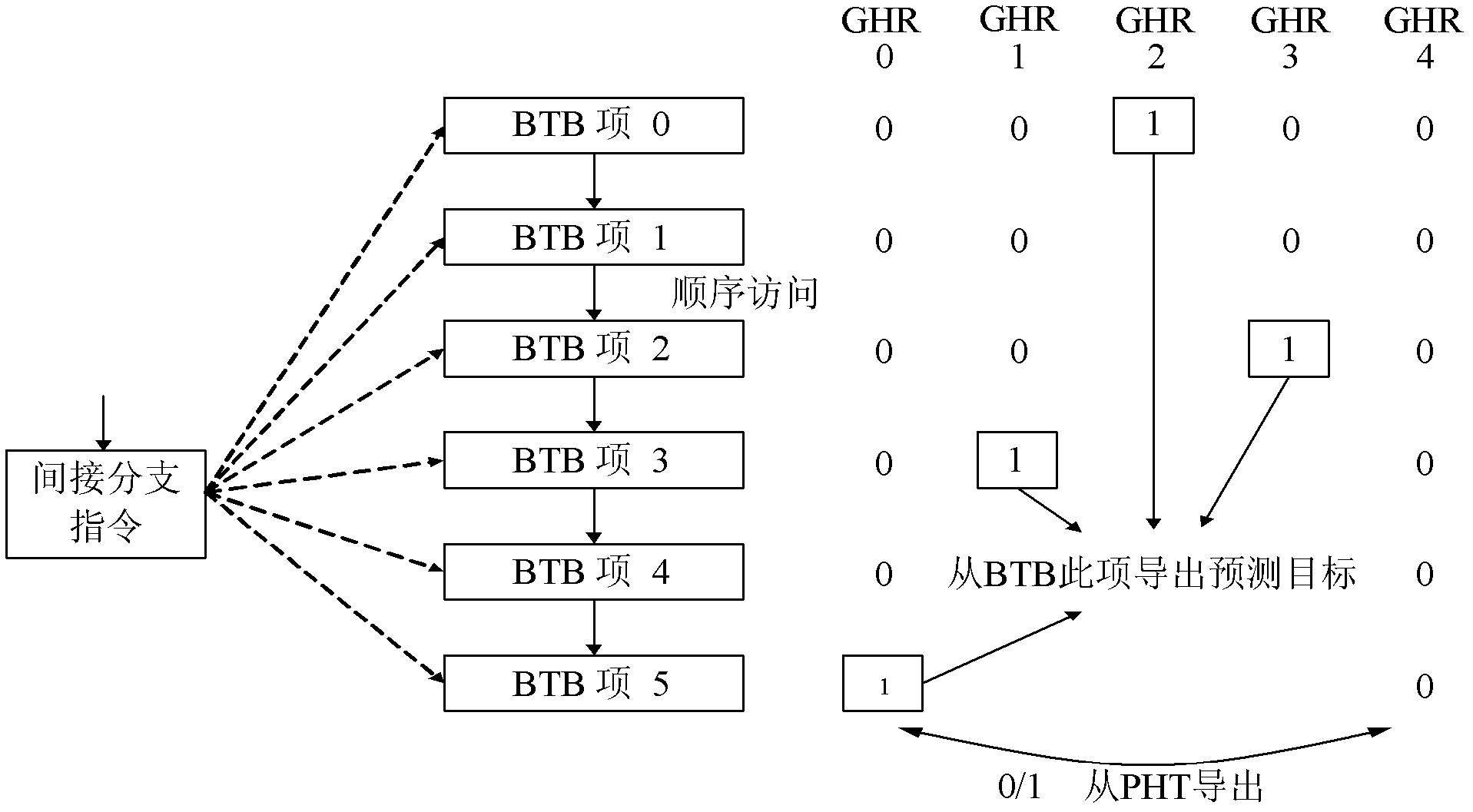
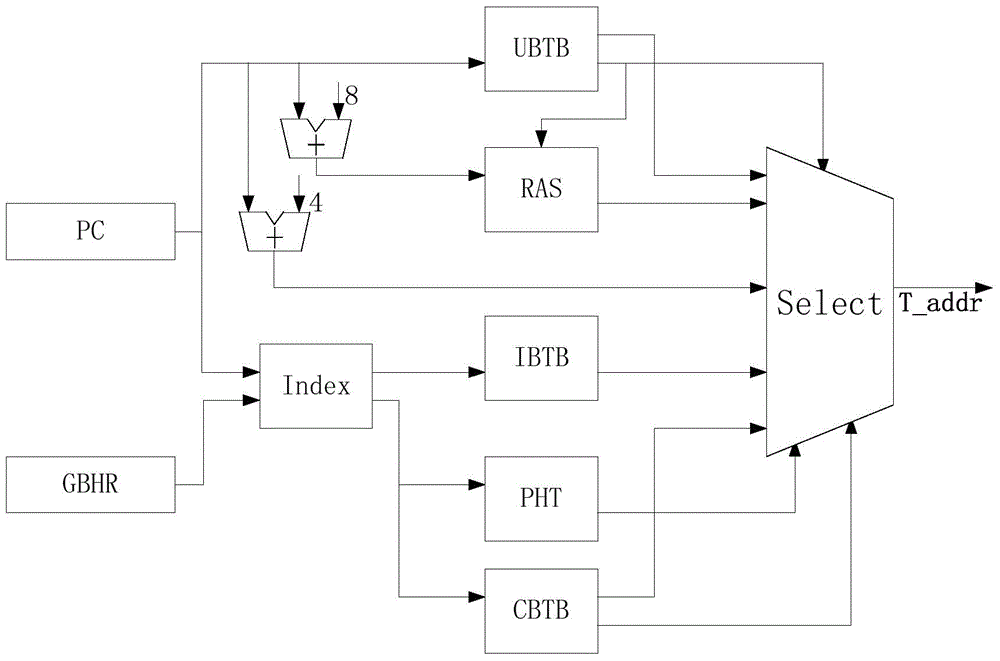
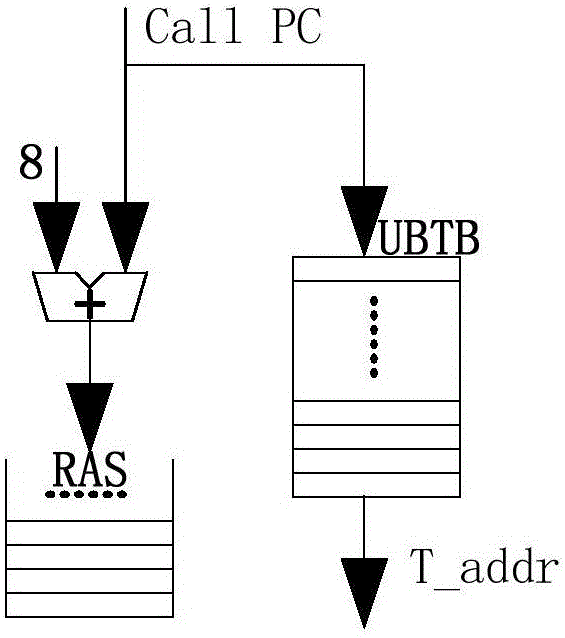
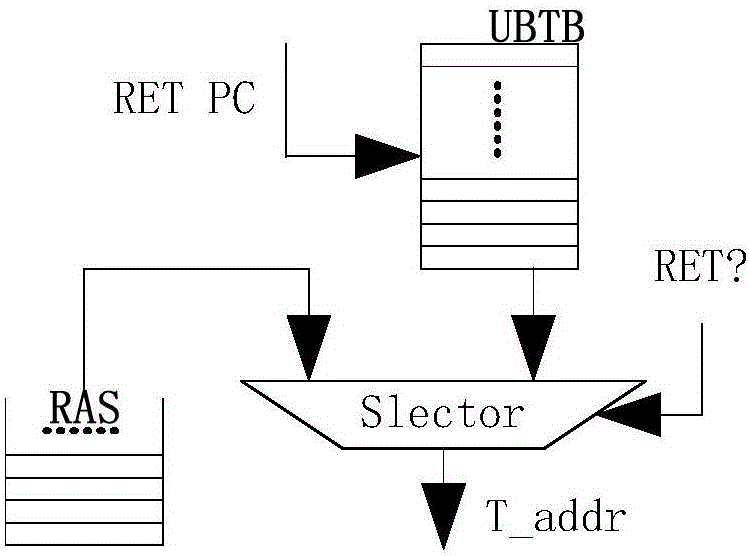
ActiveCN105718241AExpand coverageOptimal Branch Prediction SchemeNext instruction address formationMemory systemsReturn address stackAssembly line
The invention discloses an SPARC V8 system structure based classified type mixed branch prediction system. Firstly, a branch target buffer is queried according to PC values of instructions at an instruction fetching stage to obtain branch instruction types; the branch instructions are dispatched to respective prediction modules; a return address stack (RAS) with a dynamic configuration counter is used in skip branch prediction; a complementary prediction method is used in indirect branch prediction; a tag recording correctness of previous branch prediction in a conditional branch target buffer (CBTB) adopts a partial skip three-state conversion algorithm in conditional branch prediction; decoding result information of the instructions are recorded in a prediction information table (PIT) at a decoding stage; a judgment is made at an execution stage; if a prediction result of the branch instructions is that the skip occurs, the result judgment is made by using a skip prediction result arbiter Arbiter_T; and if the prediction result of the branch instructions is that the skip does not occur, the result judgment is made by using a non-skip prediction result arbiter Arbiter_N. Therefore, the instruction delay influence of the branch instructions on an assembly line is eliminated and the execution efficiency of a processor is improved.
Owner:BEIJING MXTRONICS CORP +1
Predicting indirect branches using problem branch filtering and pattern cache
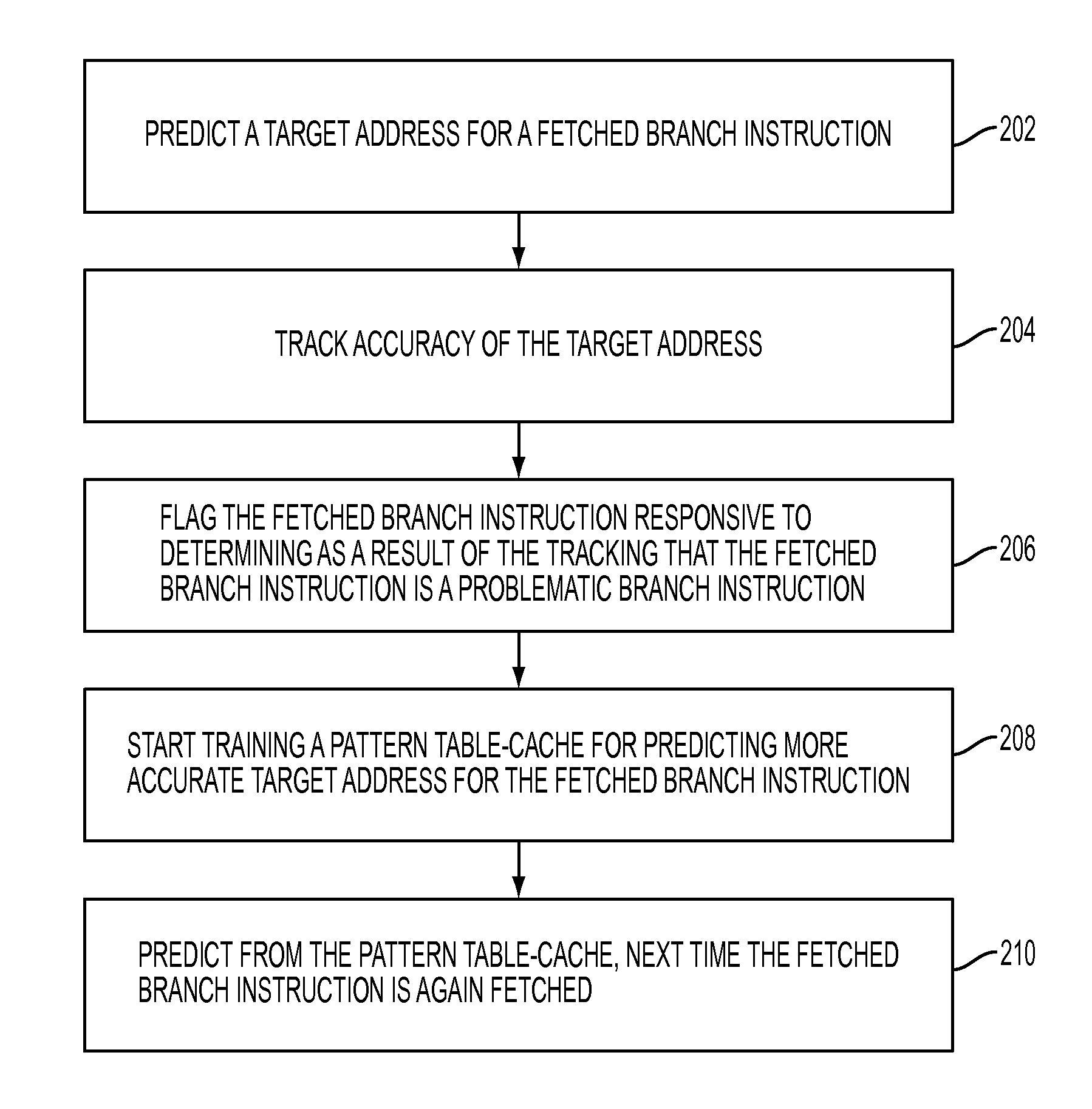
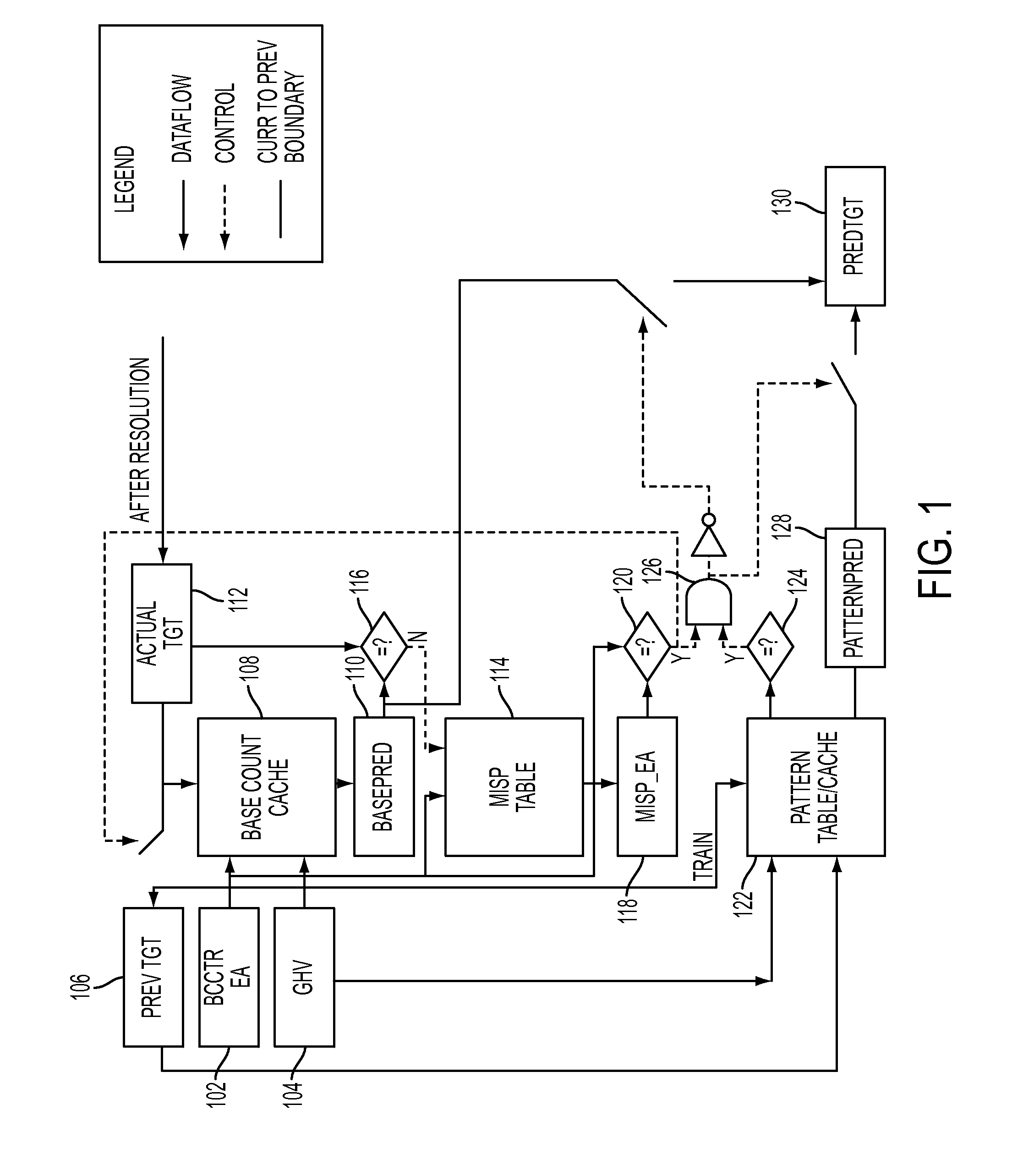
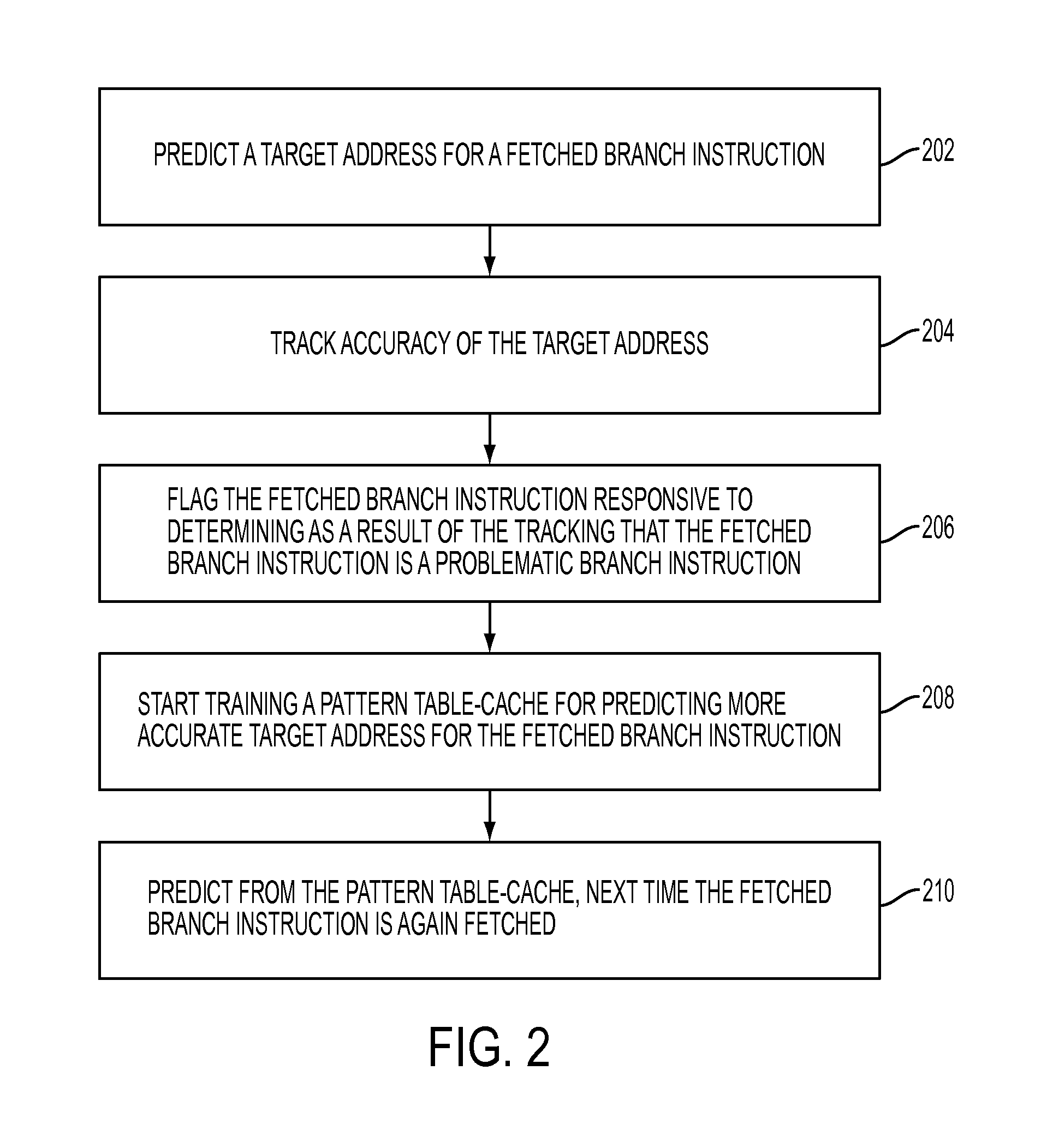
Predicting indirect branch instructions may comprise predicting a target address for a fetched branch instruction. Accuracy of the target address may be tracked. The fetched branch instruction may be flagged as a problematic branch instruction based on the tracking. A pattern cache may be trained for predicting more accurate target address for the fetched branch instruction, and the next time the fetched branch instruction is again fetched, a target address may be predicted from the pattern cache.
Owner:IBM CORP
Method for enabling a branch-control system in a microcomputer apparatus
InactiveUS20050071605A1Reduce the amount of hardwareLow production costDigital computer detailsConcurrent instruction executionMicrocomputerControl system
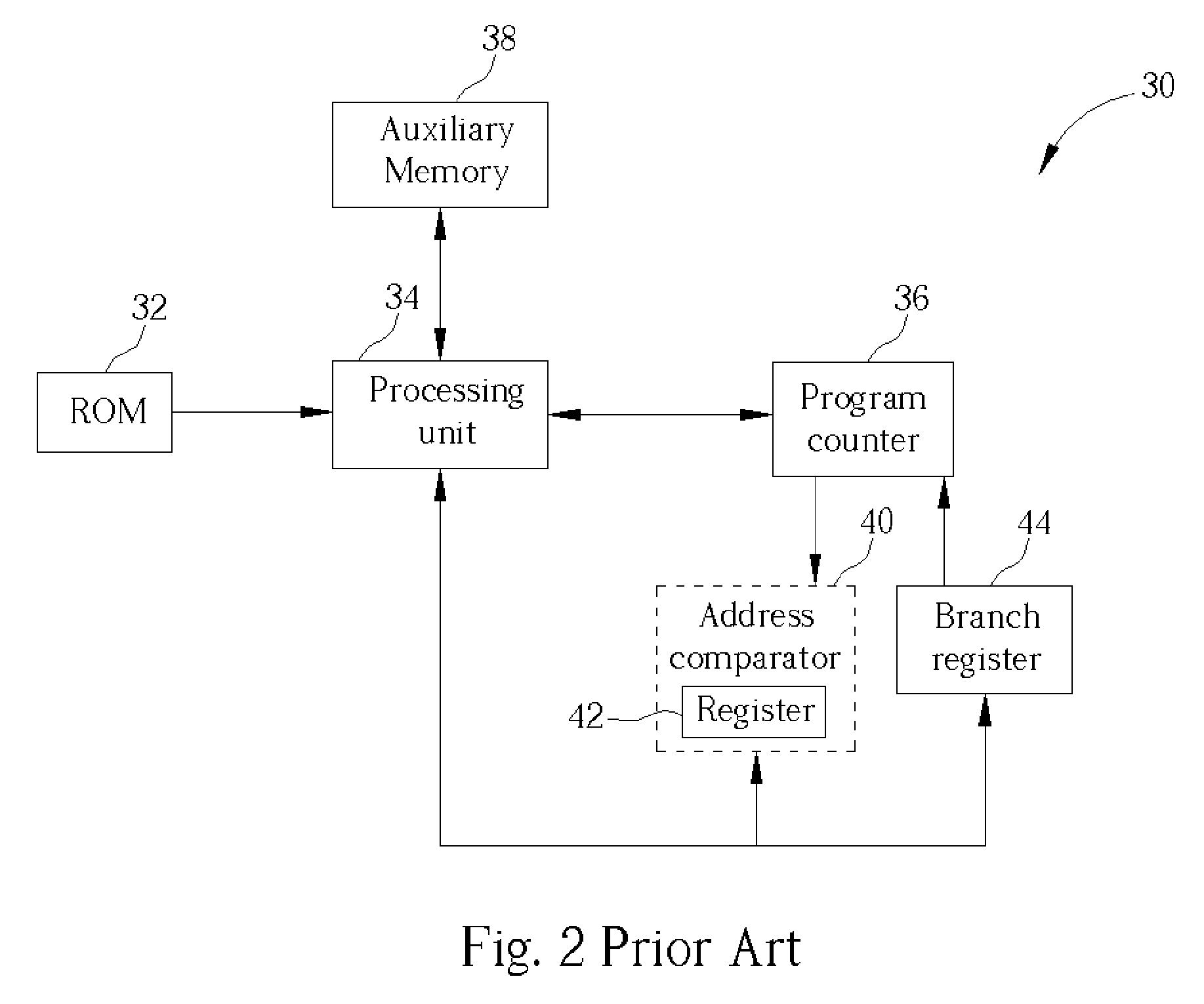
According to the claimed invention, the controller is a chip with a memory connected to the program counter of a microcomputer apparatus. The chip is capable of comparing the value of the program counter against the value stored inside its own memory and issuing an indirect branch instruction with an index upon a match. The indirect branch instruction is capable of searching a table for an entry corresponding to the index and replacing the value of the program counter with the value of the entry in the table.
Owner:MEDIATEK INC
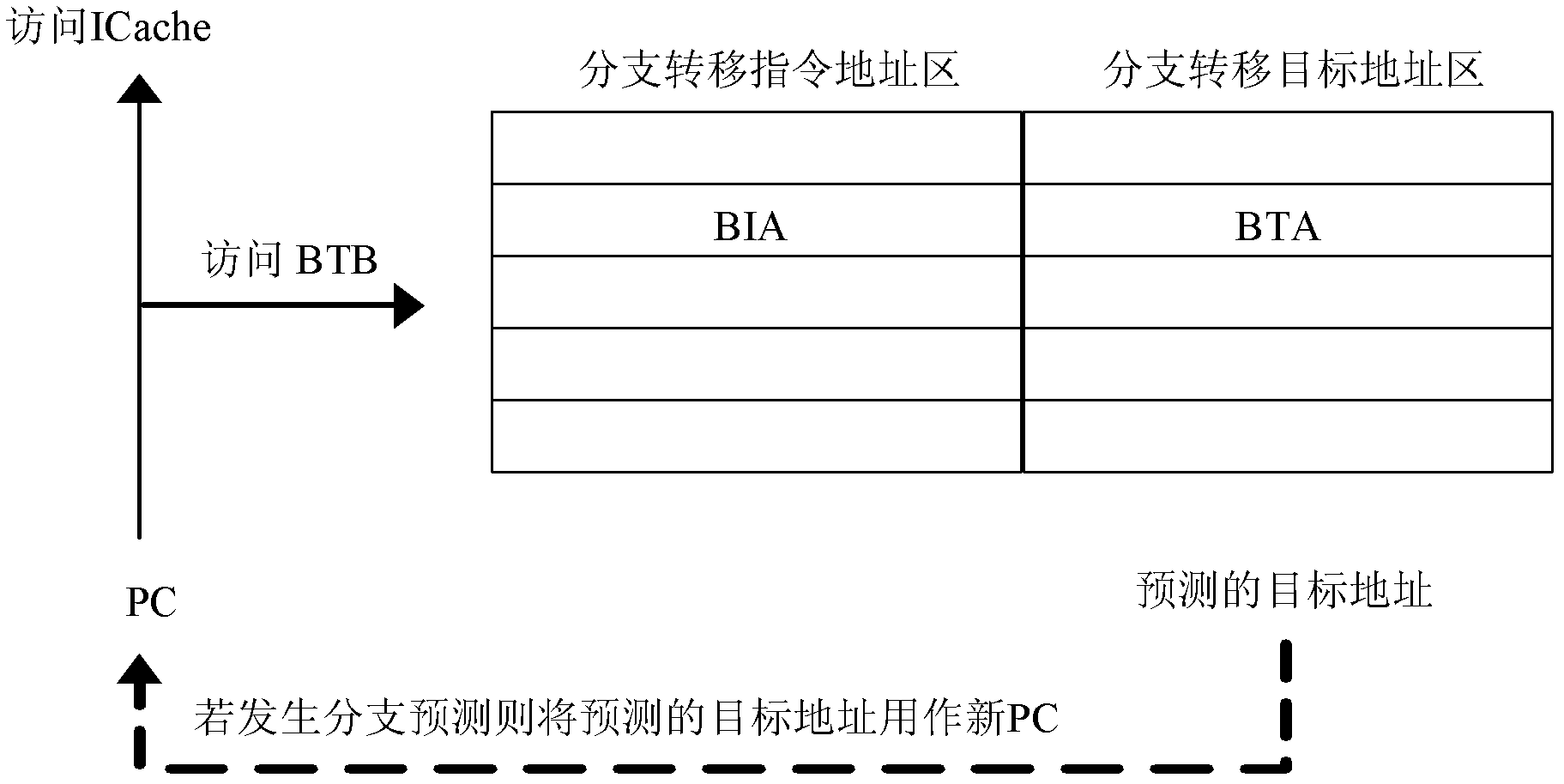
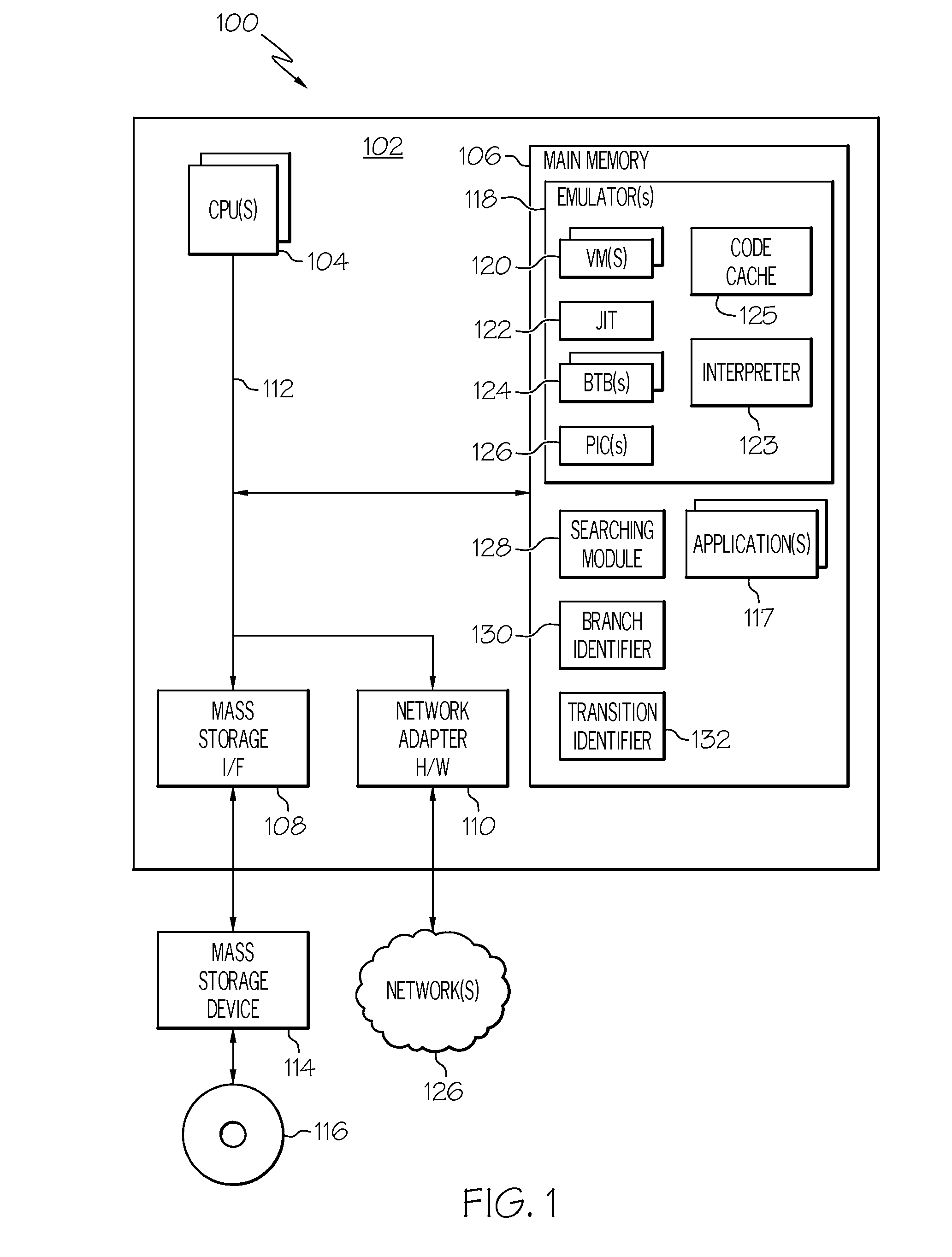
Branch target buffer for emulation environments
ActiveUS20110113223A1Memory architecture accessing/allocationDigital computer detailsData bufferIndirect branch
Branch instructions are managed in an emulation environment that is executing a program. A plurality of entries is populated in a branch target buffer that resides within an emulated environment in which the program is executing. Each of the entries comprises an instruction address and a target address of a branch instruction of the program. When an indirect branch instruction of the program is encountered a processor analyzes one of the entries in the branch target buffer to determine if the instruction address of the one entry is associated with a target address of the indirect branch instruction. If the instruction address of the one entry is associated with the target address of the indirect branch instruction a branch to the target address of the one entry is performed.
Owner:IBM CORP
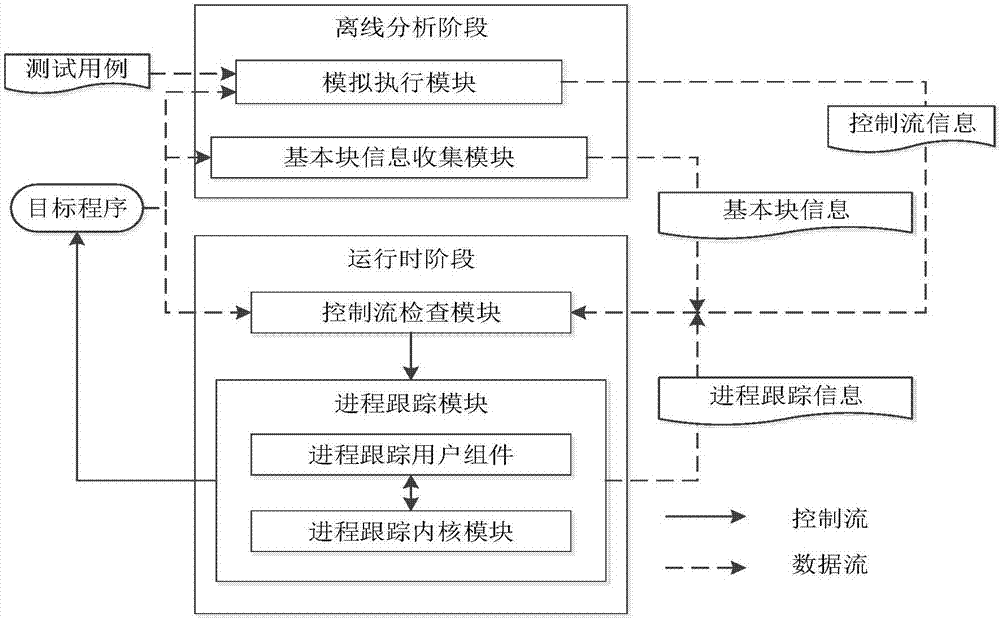
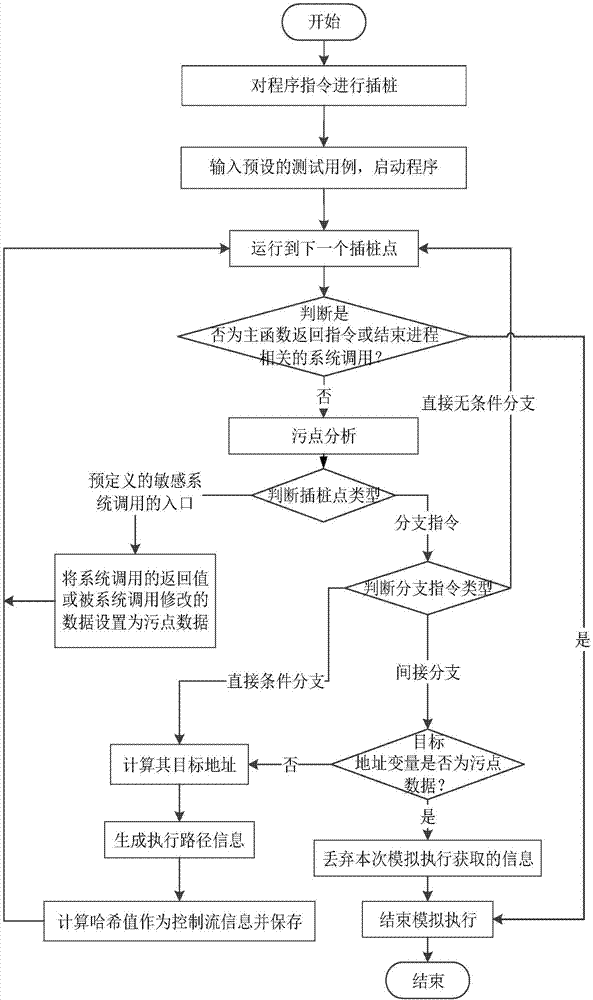
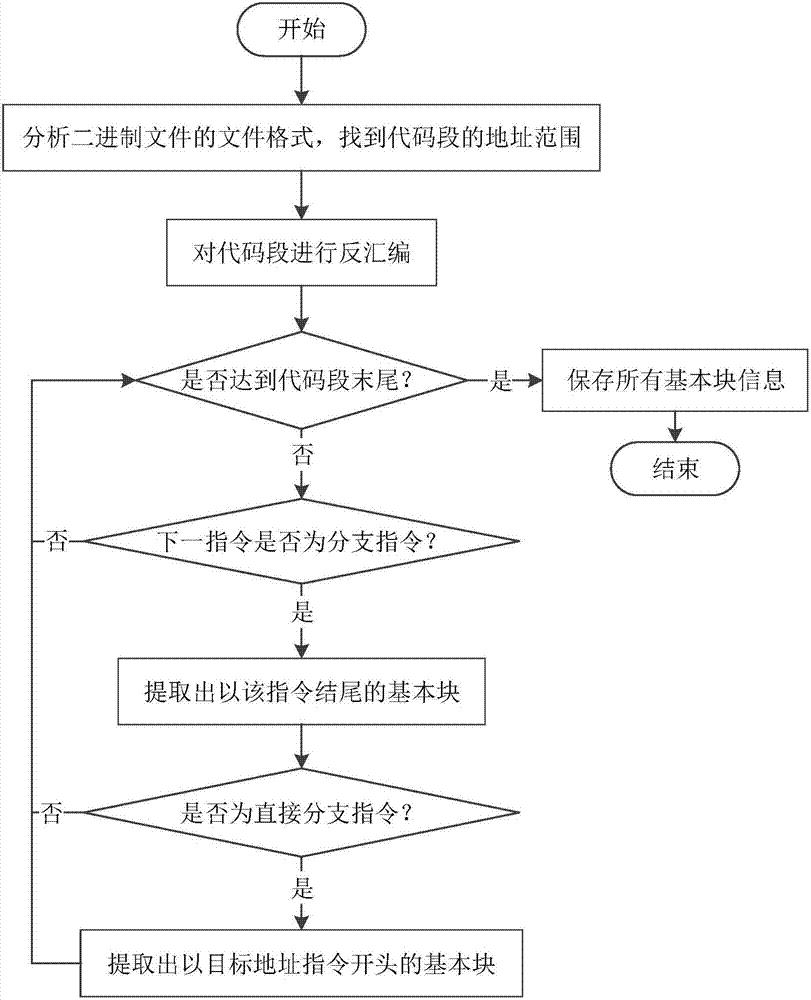
Full context-sensitive program control flow integrity protection method and system
ActiveCN107194252AImplement integrity checksHigh precisionPlatform integrity maintainanceProgram/content distribution protectionControl flowComputer module
The invention discloses a full context-sensitive program control flow integrity protection method and system. According to the method, during an offline analysis stage, control flow information of a program is collected through simulative execution; an executive path is tracked during operation; the executive path, reaching a same indirect branch, of a process is tracked; path information is matched with the control flow information; if the matching succeeds, it is showed that a simulative executive path during offline analysis is the same as a real executive path during operation, and a subsequent legal target address can be judged according to the control flow information in the offline analysis; and if a target address during operation is different from the legal target address, it is judged that the program suffers from control flow hijack attack, so that a control flow check module notifies a process tracking module to stop the process. The invention furthermore discloses the full context-sensitive program control flow integrity protection system. The integrity protection is realized by tracking and checking executive path information, so that the program is prevented from being threatened by the control flow hijack attack.
Owner:HUAZHONG UNIV OF SCI & TECH
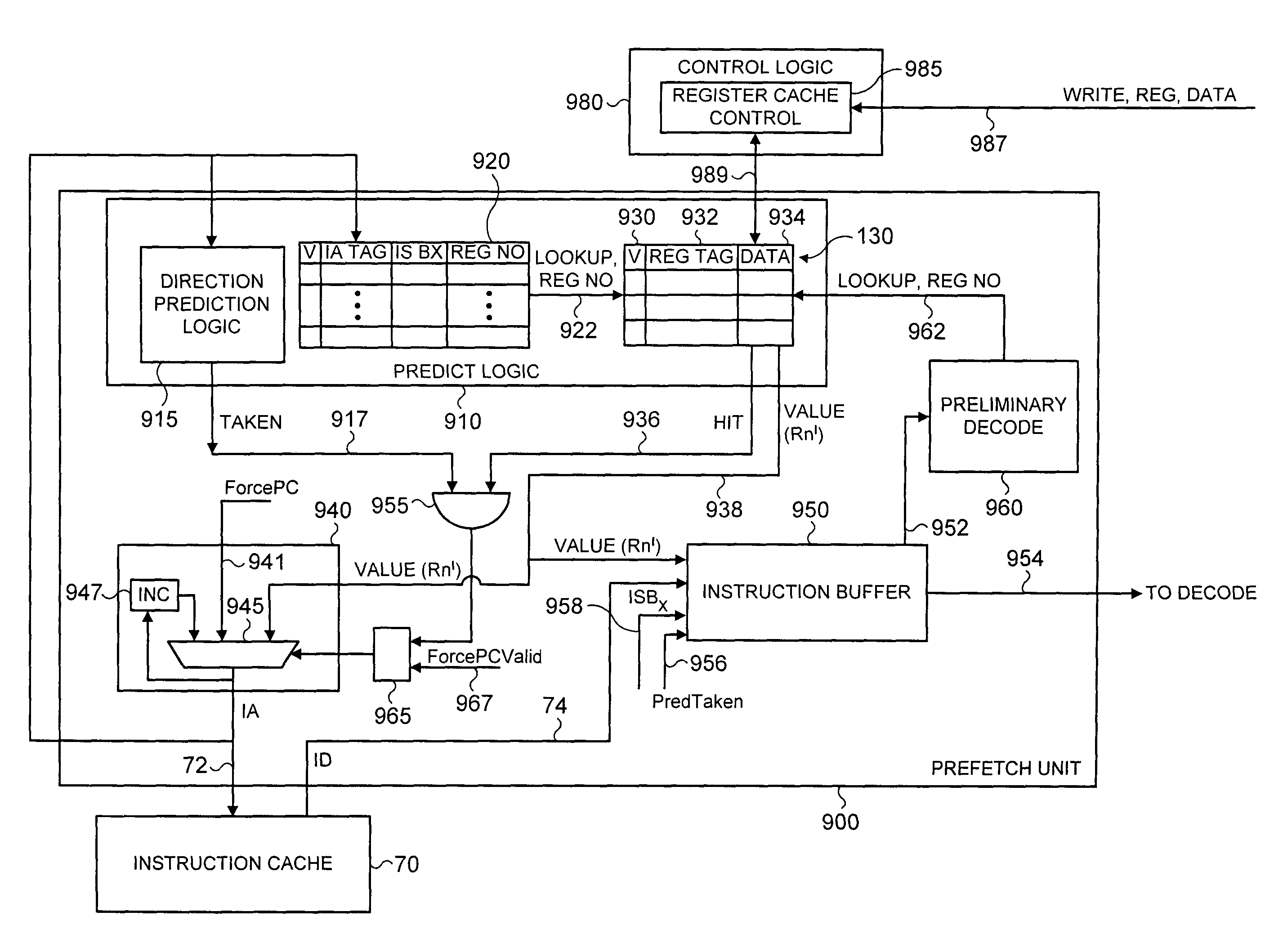
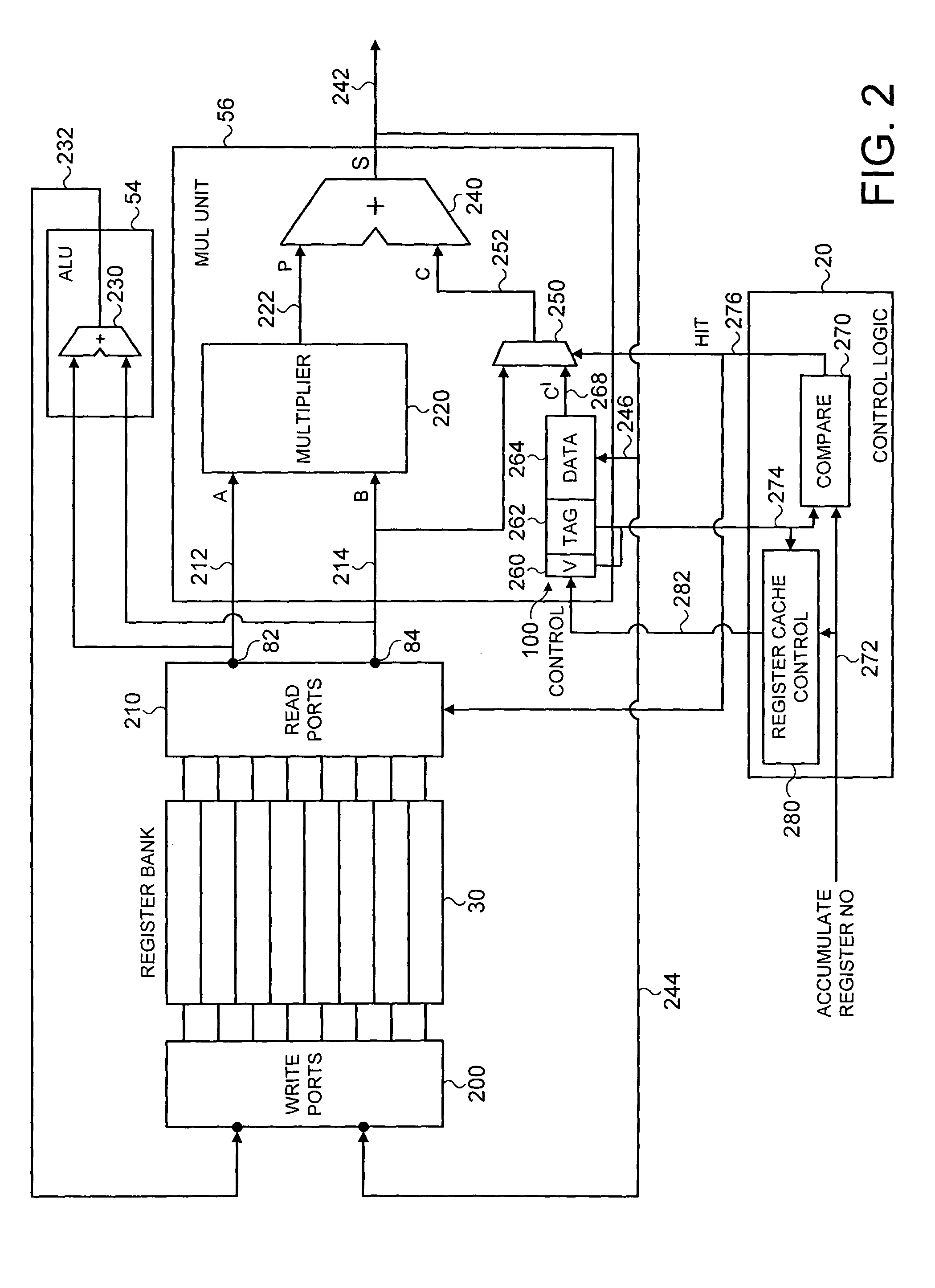
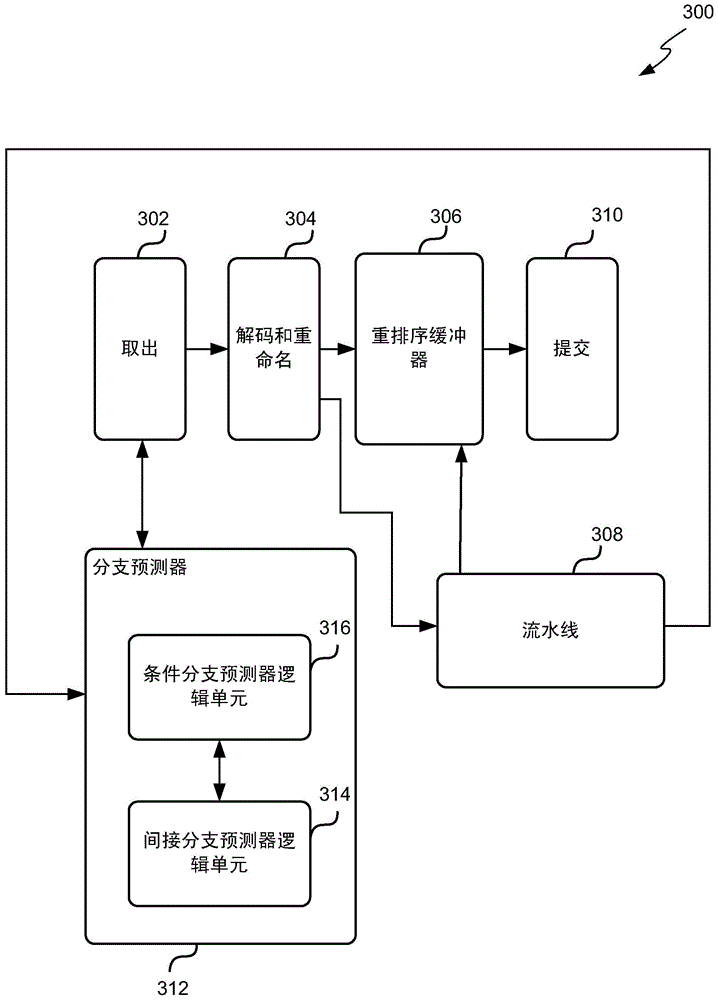
Accessing items of architectural state from a register cache in a data processing apparatus when performing branch prediction operations for an indirect branch instruction
ActiveUS7743238B2Reduce demandAvoid readingRegister arrangementsDigital computer detailsParallel computingIndirect branch
The present invention relates to a data processing apparatus and method for accessing items of architectural state. The data processing apparatus comprises a plurality of registers operable to store items of architectural state, and a plurality of functional units, each functional unit being operable to perform a processing operation with reference to one or more of those items of architectural state. At least one of the functional units has a register cache associated therewith having one or more cache entries, each cache entry being operable to store a copy of one of the items of architectural state, and a register identifier identifying the register containing that item of architectural state. Control logic is operable to determine a subset of the items of architectural state to be copied in the register cache in dependence on the processing operation of the functional unit with which the register cache is associated. This assists in alleviating demands on access ports associated with the registers.
Owner:ARM LTD
Indirect function call instructions in a synchronous parallel thread processor
ActiveUS8312254B2Easy to processProvide capabilitySingle instruction multiple data multiprocessorsConcurrent instruction executionSingle instruction, multiple threadsParallel computing
An indirect branch instruction takes an address register as an argument in order to provide indirect function call capability for single-instruction multiple-thread (SIMT) processor architectures. The indirect branch instruction is used to implement indirect function calls, virtual function calls, and switch statements to improve processing performance compared with using sequential chains of tests and branches.
Owner:NVIDIA CORP
Instruction and Logic for a Binary Translation Mechanism for Control-Flow Security
InactiveUS20150278126A1Memory architecture accessing/allocationRuntime instruction translationControl flowParallel computing
A processor includes a front end, an execution pipeline, and a binary translator. The front end includes logic to receive an instruction and to dispatch the instruction to a binary translator. The binary translator includes logic to determine whether the instruction includes a control-flow instruction, identify a source address of the instruction, identify a target address of the instruction, determine whether the target address is a known destination based upon the source address, and determine whether to route the instruction to the execution pipeline based upon the determination whether the target address is a known destination based upon the source address. The target address includes an address to which execution would indirectly branch upon execution of the instruction.
Owner:INTEL CORP
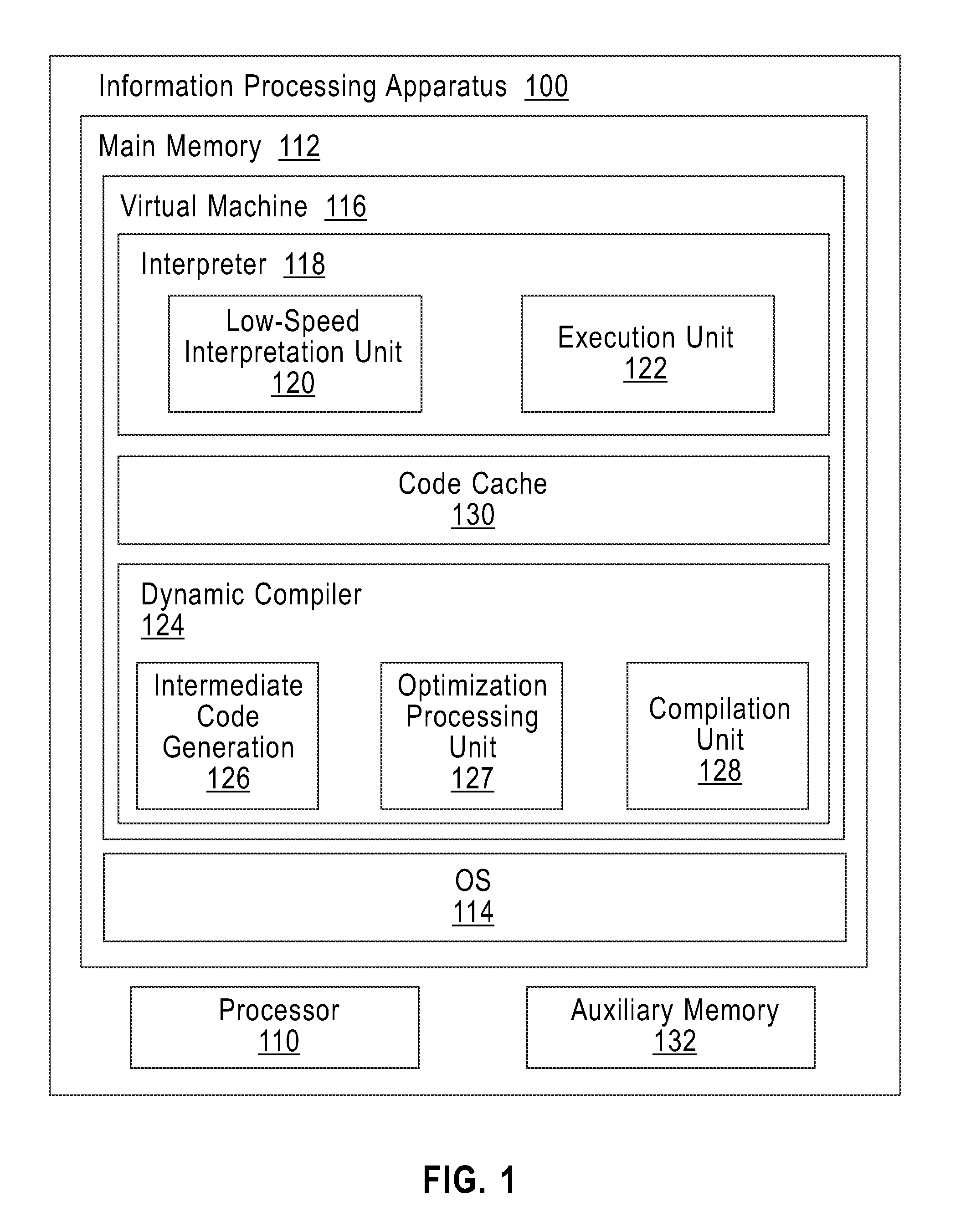
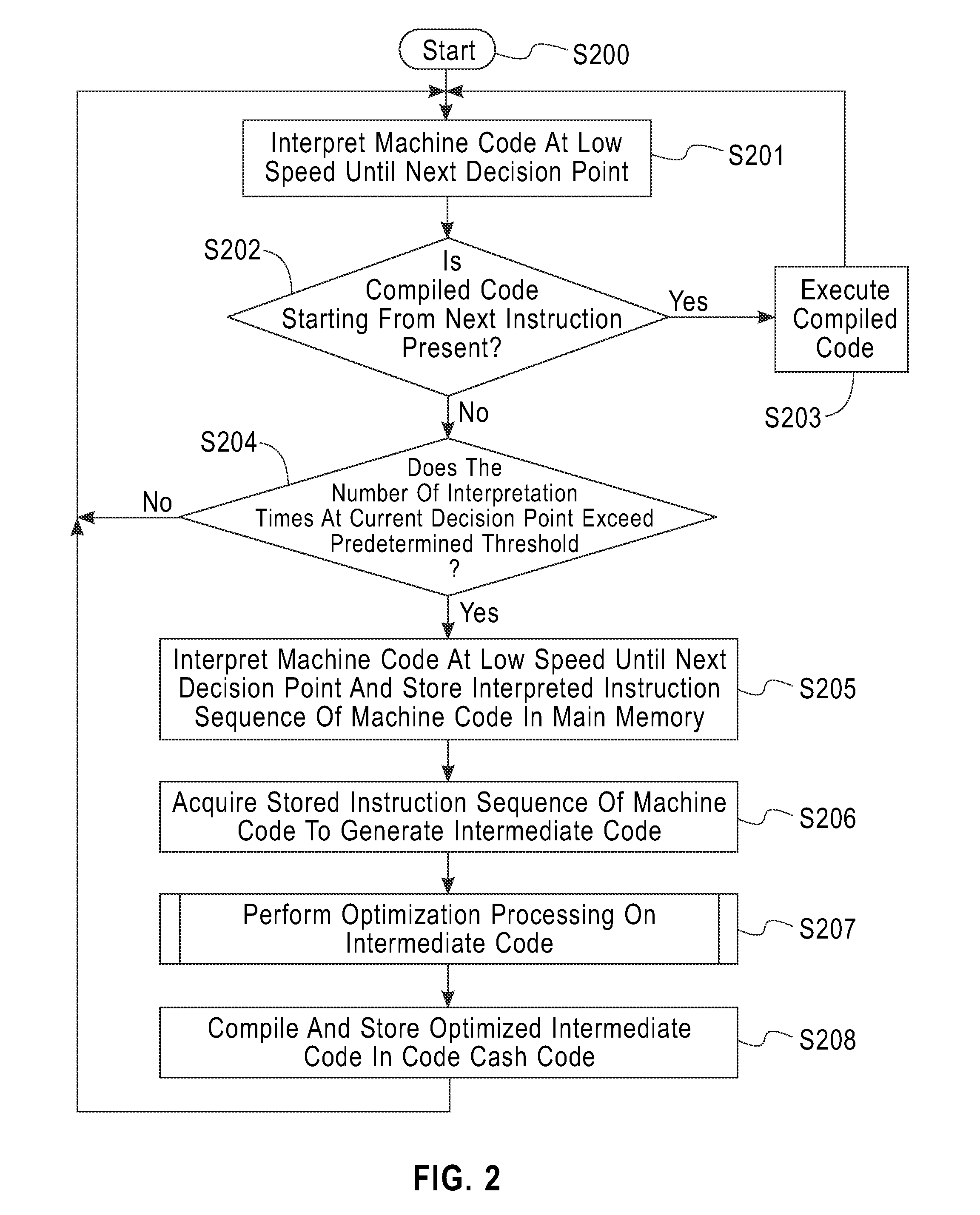
Compiling method, program, and information processing apparatus
InactiveUS20130198498A1Low average CPU loadReduce memory consumptionSoftware engineeringDigital computer detailsDynamic compilationInformation processing
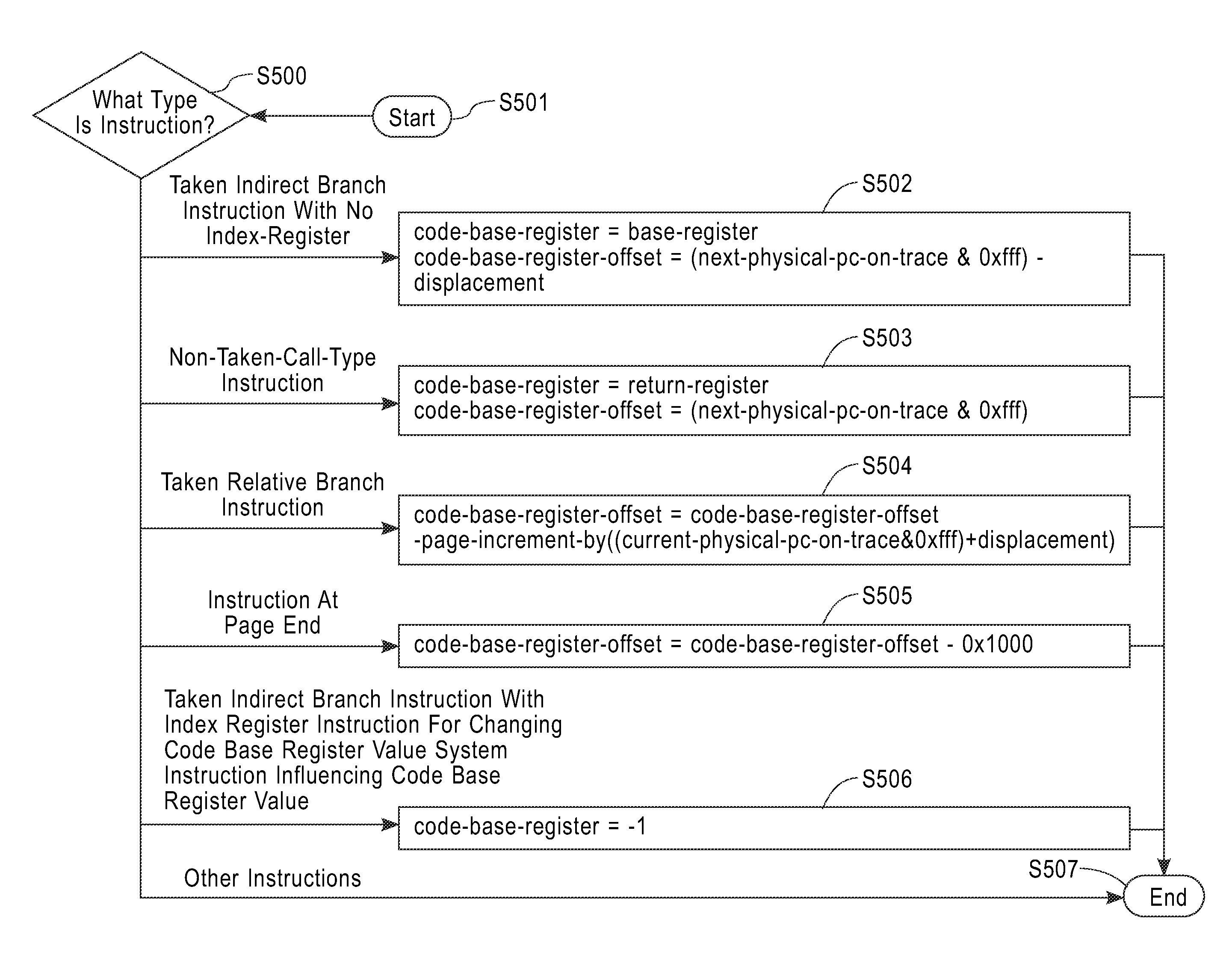
A method, program, and apparatus for optimizing compiled code using a dynamic compiler. The method includes the steps of: generating intermediate code from a trace, which is an instruction sequence described in machine language; computing an offset between an address value, which is a base point of an indirect branch instruction, and a start address of a memory page, which includes a virtual address referred to by the information processing apparatus immediately after processing a first instruction; determining whether an indirect branch instruction that is subsequent to the first instruction causes processing to jump to another memory page, by using a value obtained from adding the offset to a displacement made by the indirect branch instruction; and optimizing the intermediate code by using the result of the determining step.
Owner:IBM CORP
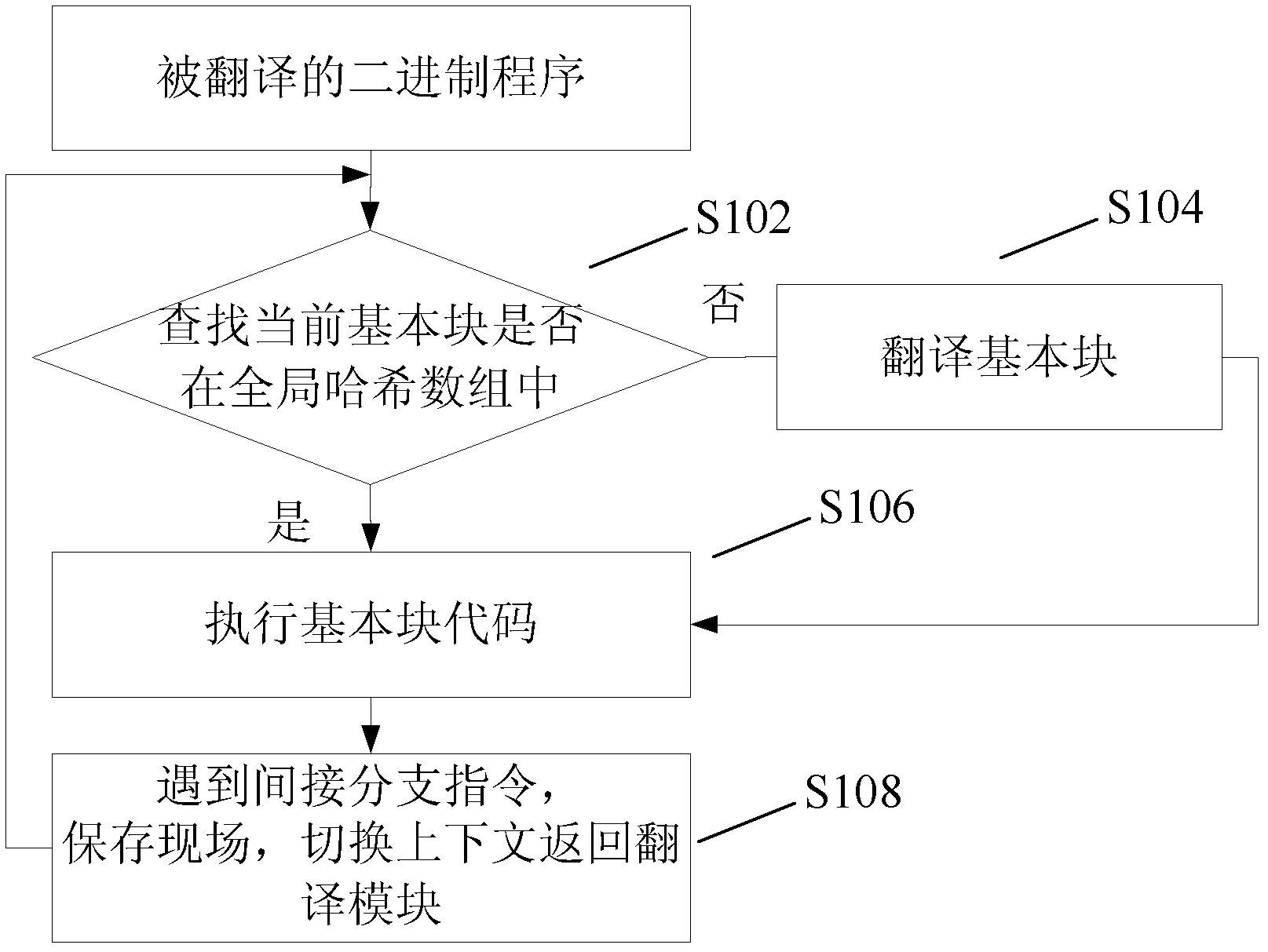
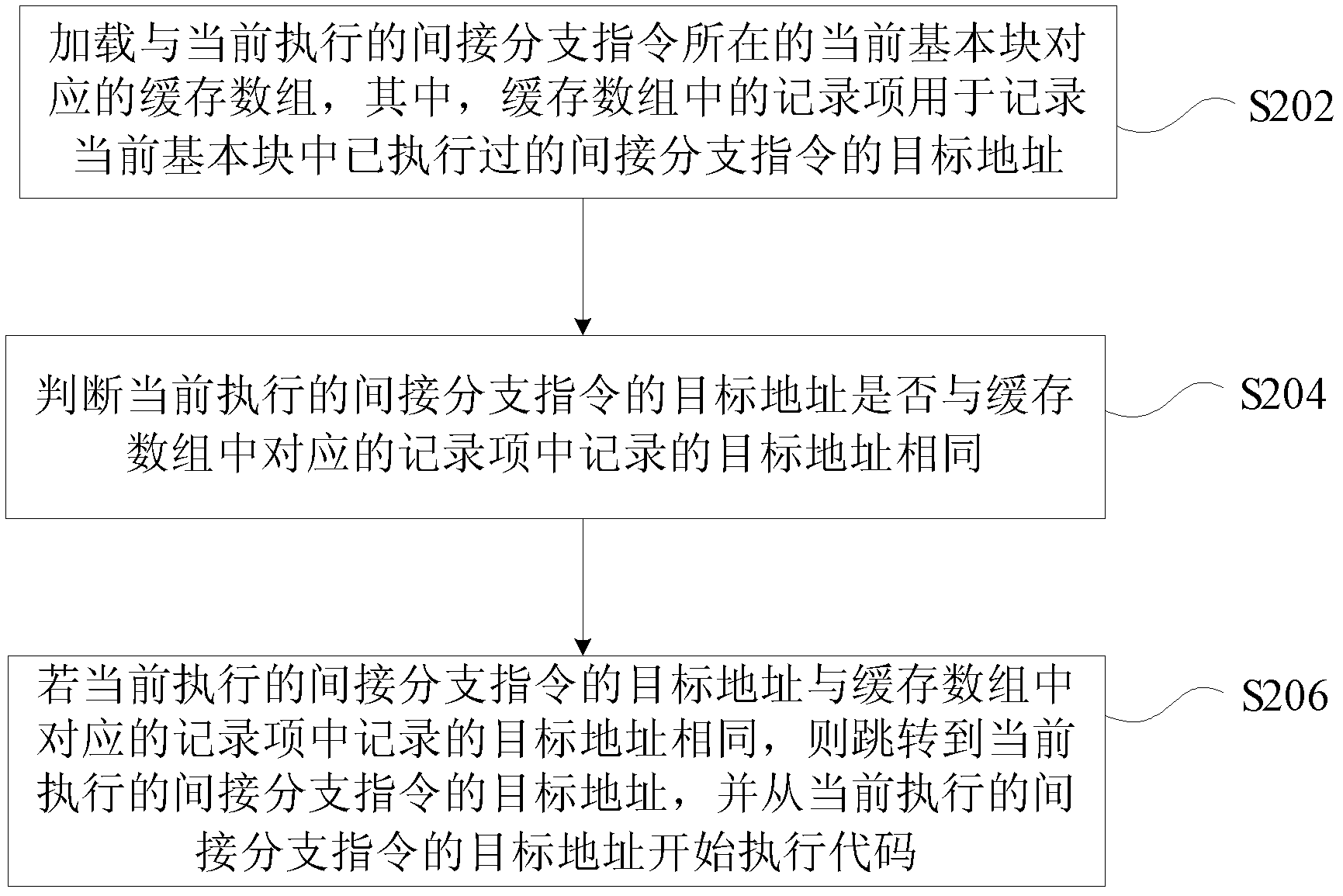
Indirect branch instruction processing method and device
ActiveCN102662631ALow efficiencyImprove efficiencyProgram controlMemory systemsArray data structureIndirect branch
The invention discloses an indirect branch instruction processing method and an indirect branch instruction processing device, wherein the method comprises the steps: loading caching array corresponding to a current basic block in which an indirect branch instruction currently executing is, wherein a record item in the caching array is used for recording a target address of the executed indirect branch instruction in the current basic block; judging whether the target address of the indirect branch instruction currently executing is identical with the recorded target address of the corresponding record item in the caching array, if yes, skipping to the target address of the indirect branch instruction currently executing, and starting executing codes from the target address of the indirect branch instruction currently executing. According to the method, the problem that context switches are excessive in binary translation process to cause low translation efficiency can be solved, and the effect of improving the efficiency of a binary translation system is achieved.
Owner:LOONGSON TECH CORP
Processing method for calling and returning function, and binary translation method and system
InactiveCN101452395AImprove operational efficiencyEasy to implementProgram controlMemory systemsReturn functionIndirect branch
The invention discloses a processing method for function call and return and a method and a system for binary translation. The processing method comprises: taking a return address of function call of a source program as a dummy order and storing the dummy order behind a function call order of an object program; storing an address of the dummy order in a stack at the beginning of the function callof the object program; taking out an address stored in the top of the stack when the function call of the object program is finished; and skipping behind the dummy order when the value of the addresstaken out from the stack top is equal to the return address of function call of the source program. The processing method can realize quick return after the function call and can avoid the problem oflow efficiency caused by Hash collision, thereby reducing the overhead of return-type indirect branch and improving performance of binary translation.
Owner:JIANGNAN INST OF COMPUTING TECH
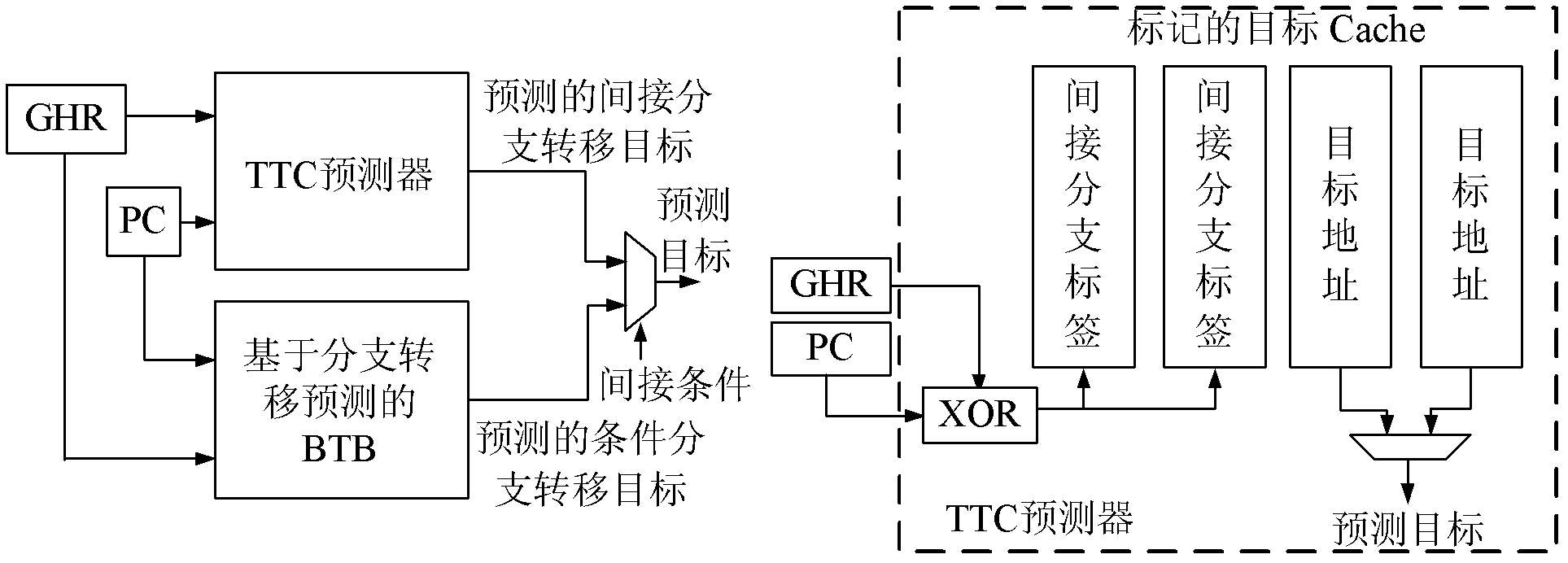
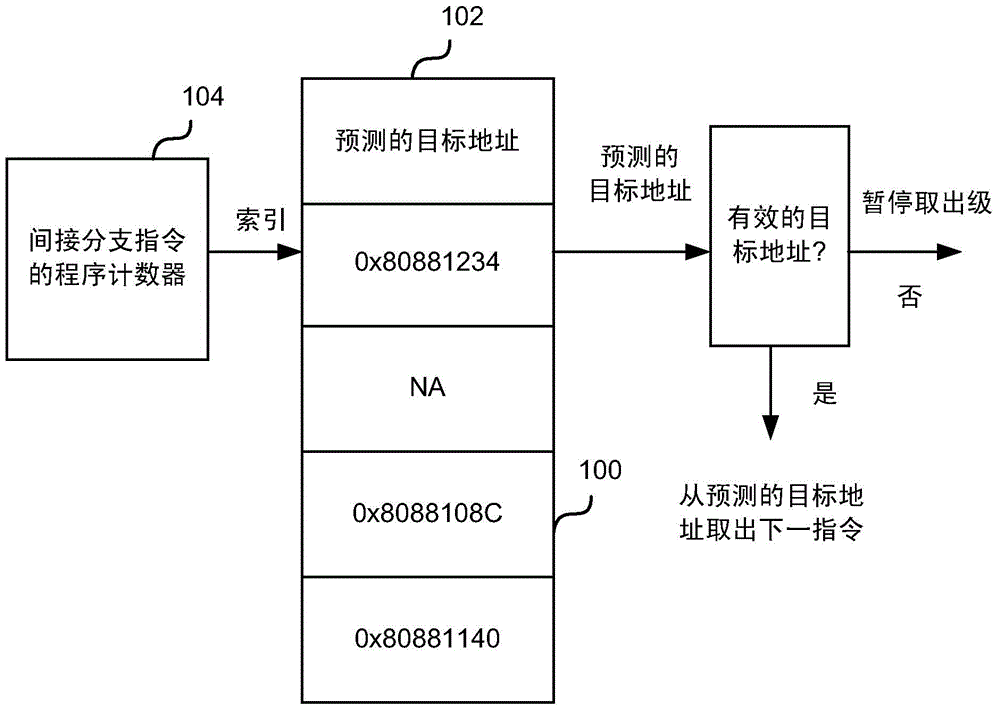
Indirect branch prediction
Provided are a method and indirect branch predictor logic units to predict the target addresses of indirect branch instructions. The method comprises storing in a table predicted target addresses for indirect branch instructions indexed by a combination of the indirect path history for previous indirect branch instructions and the taken / not-taken history for previous conditional branch instructions. When a new indirect branch instruction is received for prediction, the indirect path history and the taken / not-taken history are combined to generate an index for the indirect branch instruction. The generated index is then used to identify a predicted target address in the table. If the identified predicted target address is valid, then the target address of the indirect branch instruction is predicted to be the predicted target address.
Owner:MIPS TECH INC
Techniques for predicting a target address of an indirect branch instruction
ActiveUS20170315810A1Memory architecture accessing/allocationMemory systemsParallel computingIndirect branch
A technique for operating a processor includes identifying a difficult branch instruction (branch) whose target address (target) has been mispredicted multiple times. Information about the branch (which includes a current target and a next target) is learned and stored in a data structure. In response to the branch executing subsequent to the storing, whether a branch target of the branch corresponds to the current target in the data structure is determined. In response to the branch target of the branch corresponding to the current target of the branch in the data structure, the next target of the branch that is associated with the current target of the branch in the data structure is determined. In response to detecting that a next instance of the branch has been fetched, the next target of the branch is utilized as the predicted target for execution of the next instance of the branch.
Owner:IBM CORP
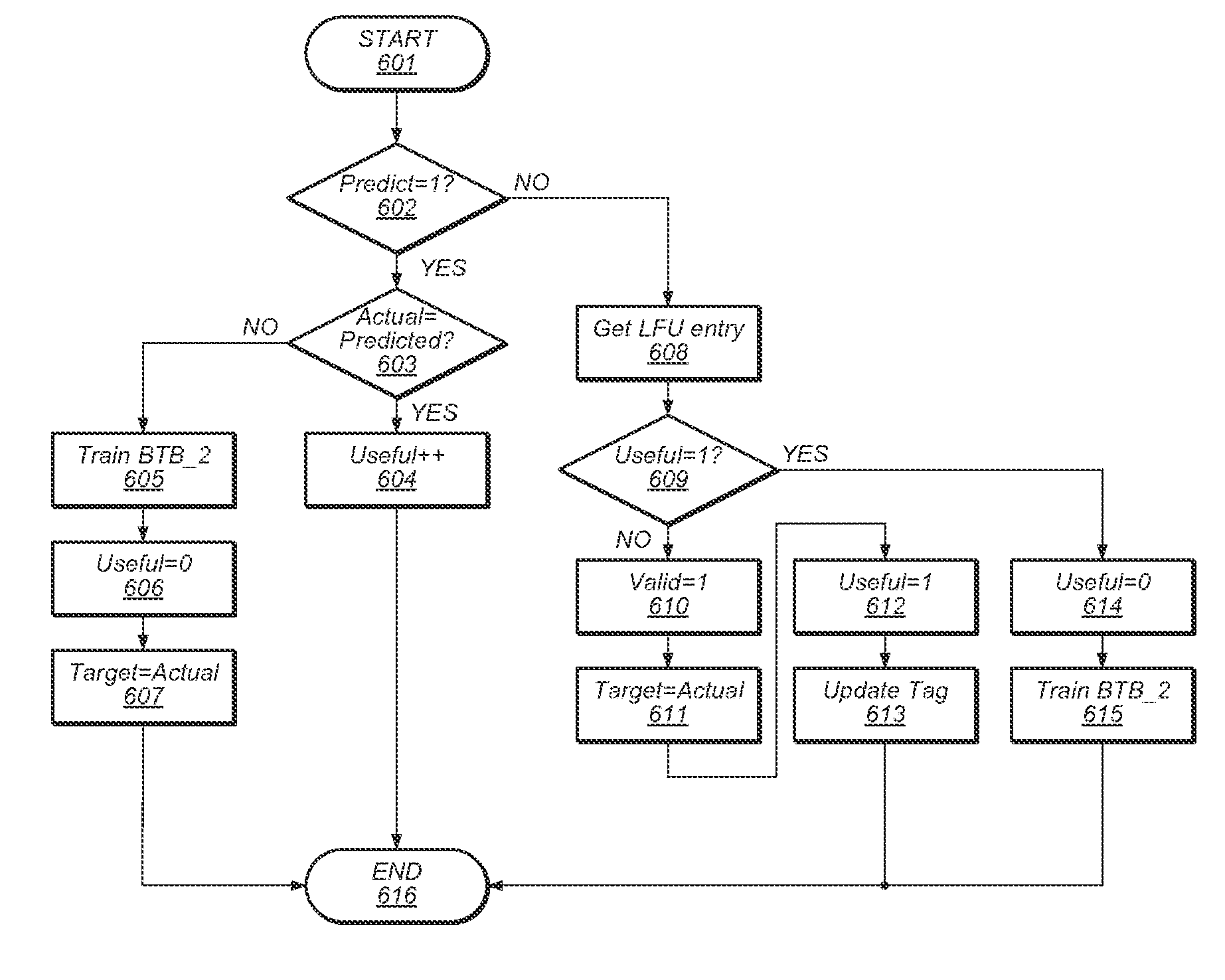
Usefulness Indication For Indirect Branch Prediction Training
ActiveUS20140195789A1Digital computer detailsConcurrent instruction executionParallel computingIndirect branch
A circuit for implementing a branch target buffer. The branch target buffer may include a memory that stores a plurality of entries. Each entry may include a tag value, a target value, and a prediction accuracy value. A received index value corresponding to an indirect branch instruction may be used to select one of entries of the plurality of entries, and a received tag value may then be compared to the tag value of the selected entries in the memory. An entry in the memory may be selected in response to a determination that the received tag does not match the tag value of compared entries. The selected entry may be allocated to the indirect instruction branch dependent upon the prediction accuracy values of the plurality of entries.
Owner:APPLE INC
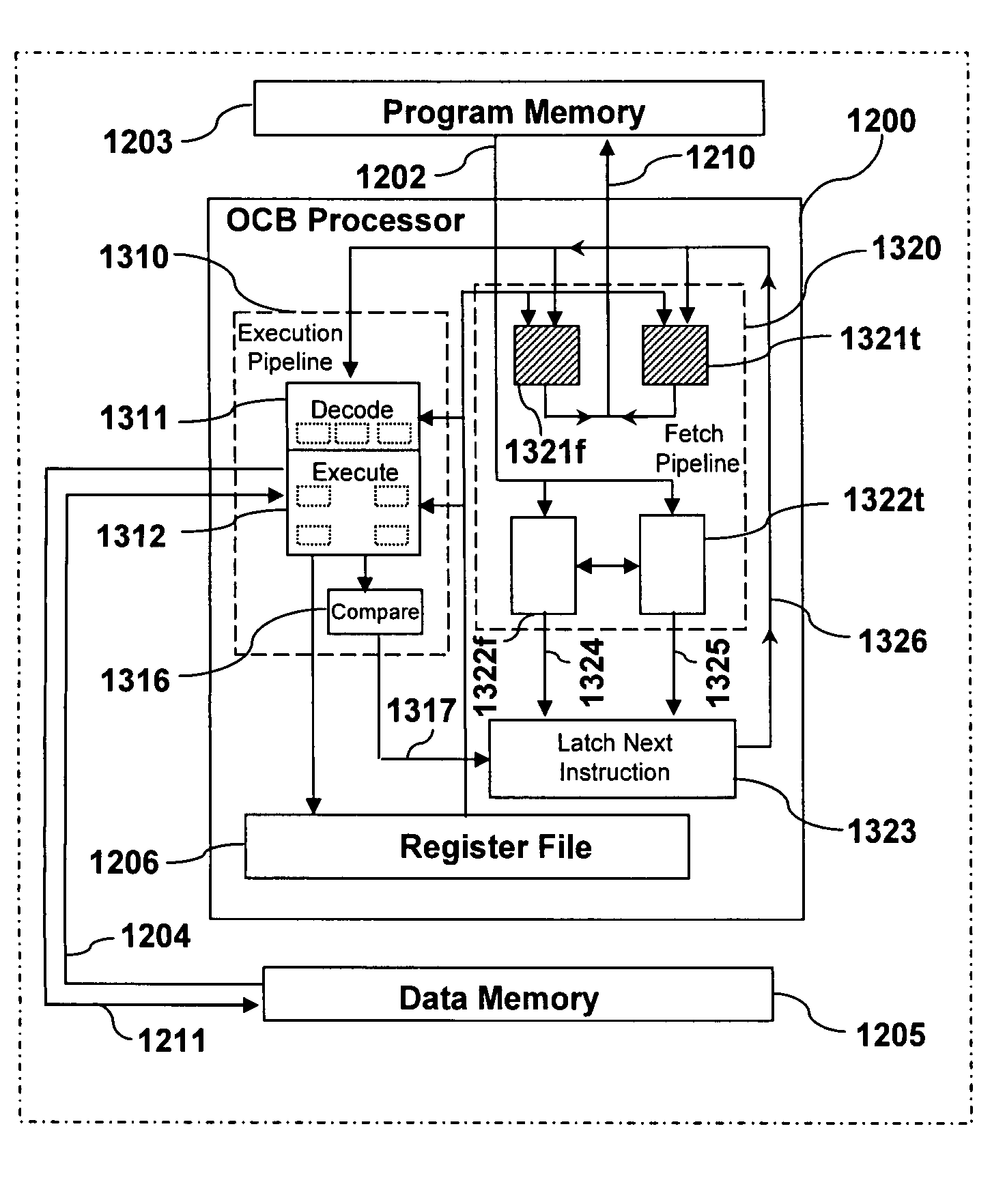
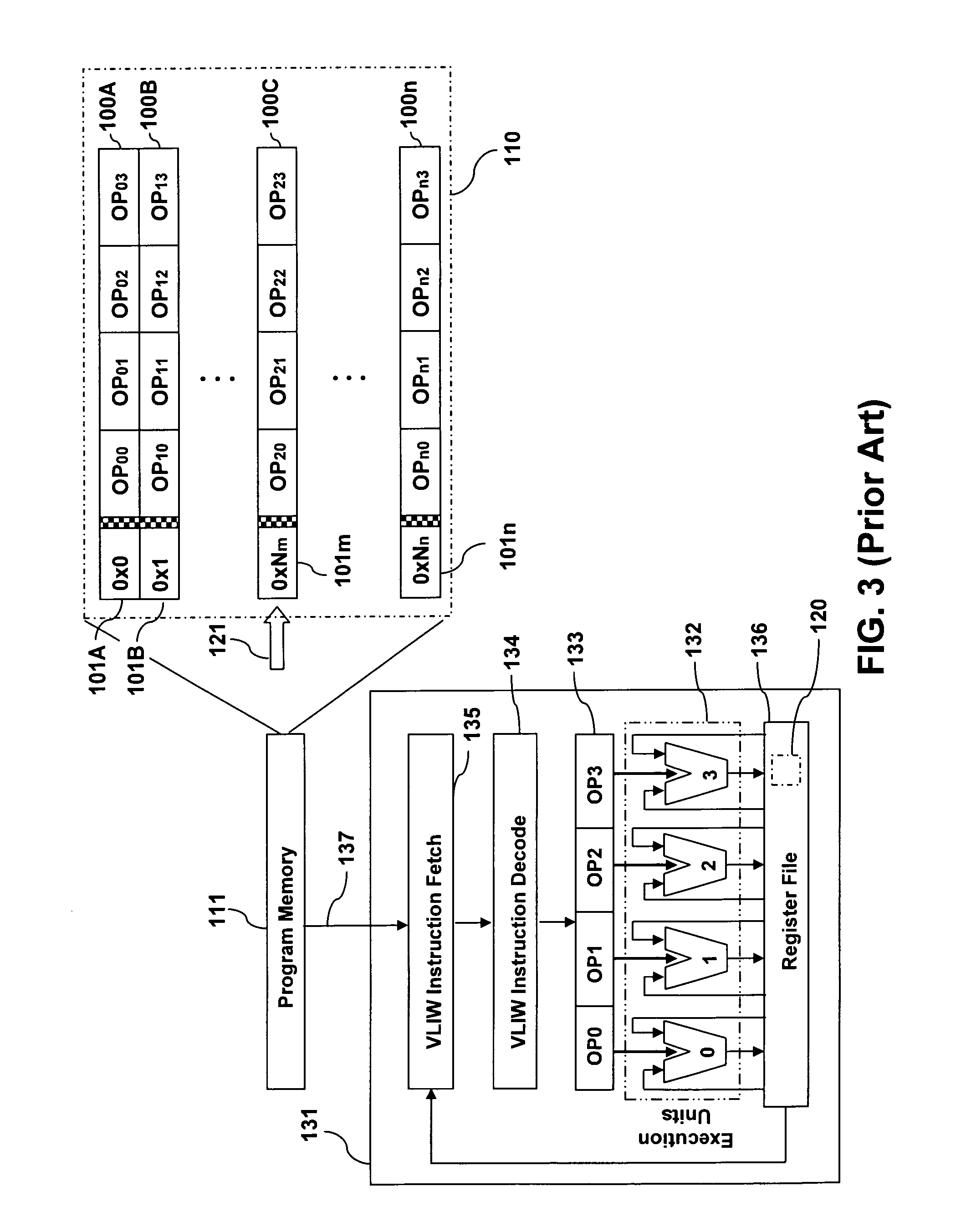
Operation, compare, branch VLIW processor
InactiveUS7818552B2Eliminates branch penaltyWithout performanceDigital computer detailsProgram/content distribution protectionParallel computingIndirect branch
A VLIW processor is provided with an architecture which includes fetching and executing circuitry which when combined with operation, compare, branch (OCB) instructions realizes no processing branch penalties. The OCB instructions are provided with two direct branch fields or with two indirect branch fields.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com