Patents
Literature
541 results about "Program counter" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
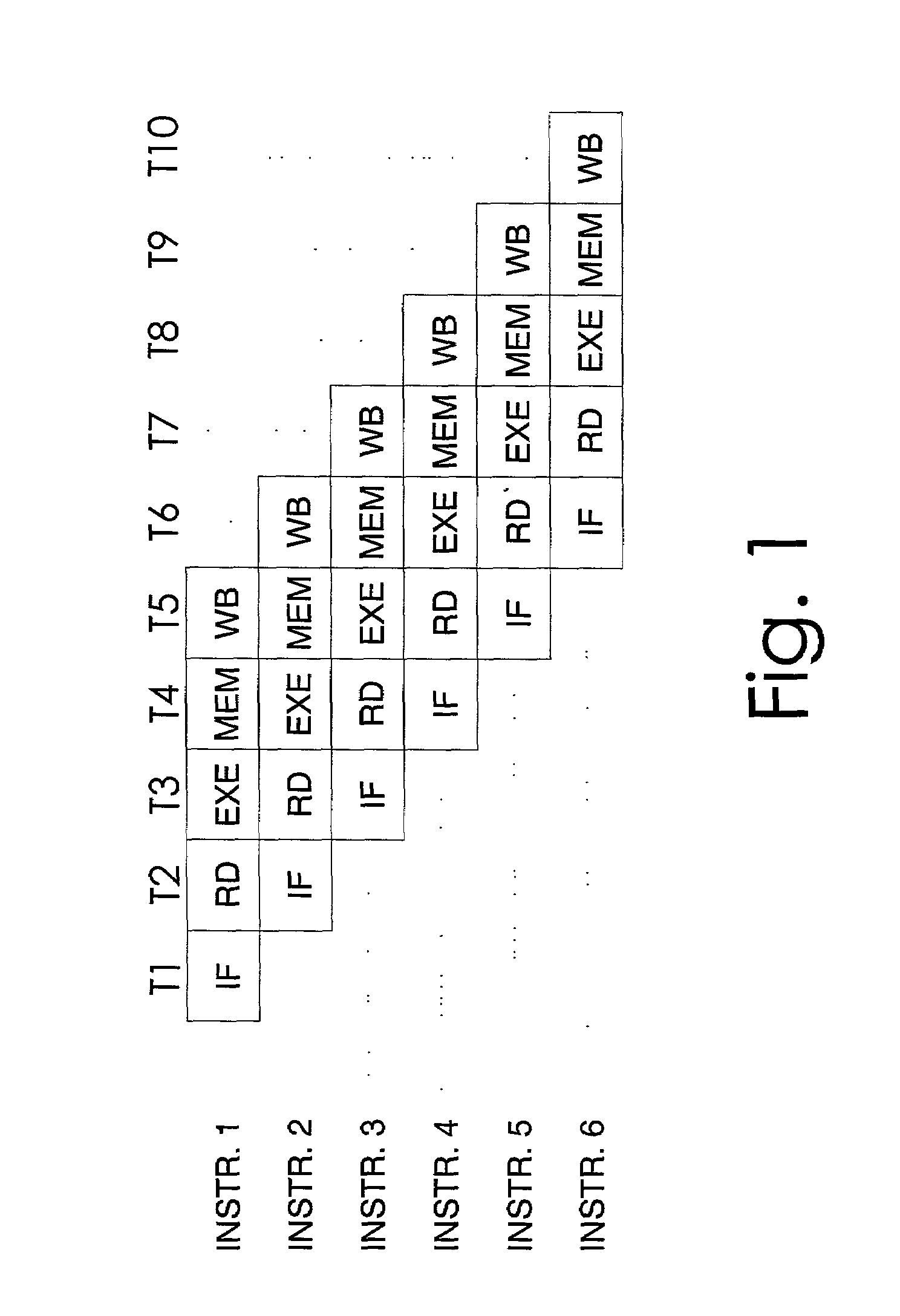
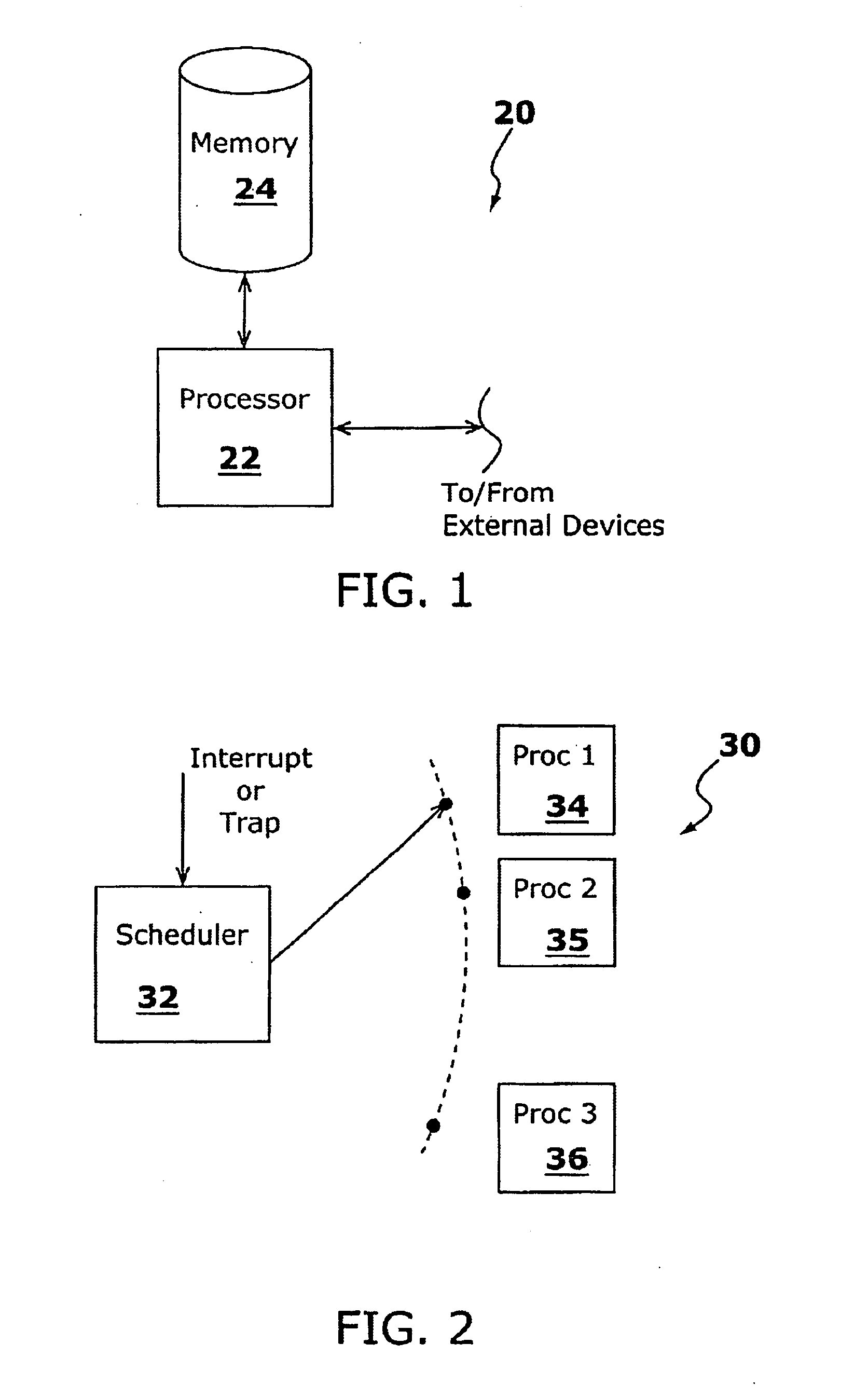
The program counter (PC), commonly called the instruction pointer (IP) in Intel x86 and Itanium microprocessors, and sometimes called the instruction address register (IAR), the instruction counter, or just part of the instruction sequencer, is a processor register that indicates where a computer is in its program sequence.
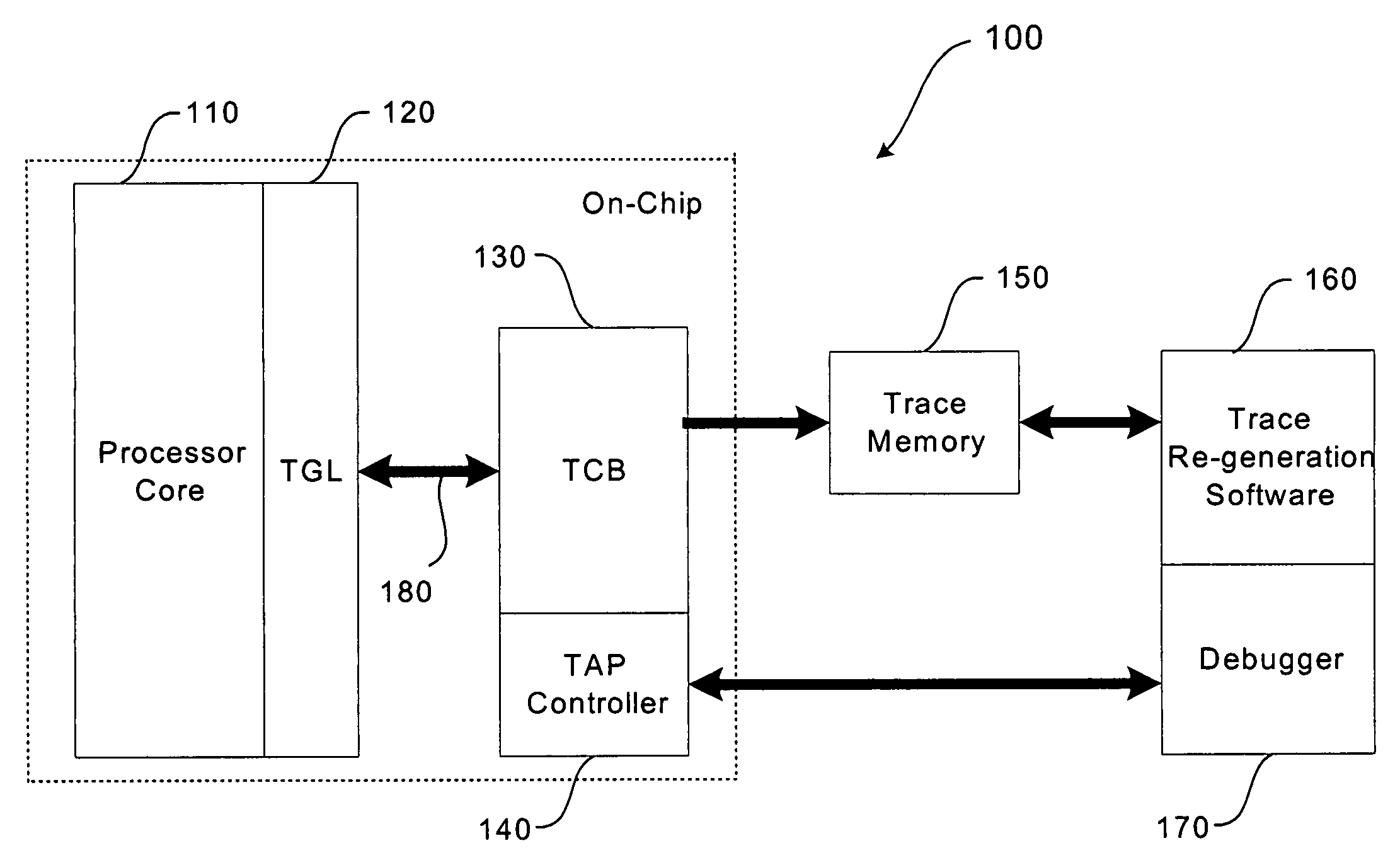
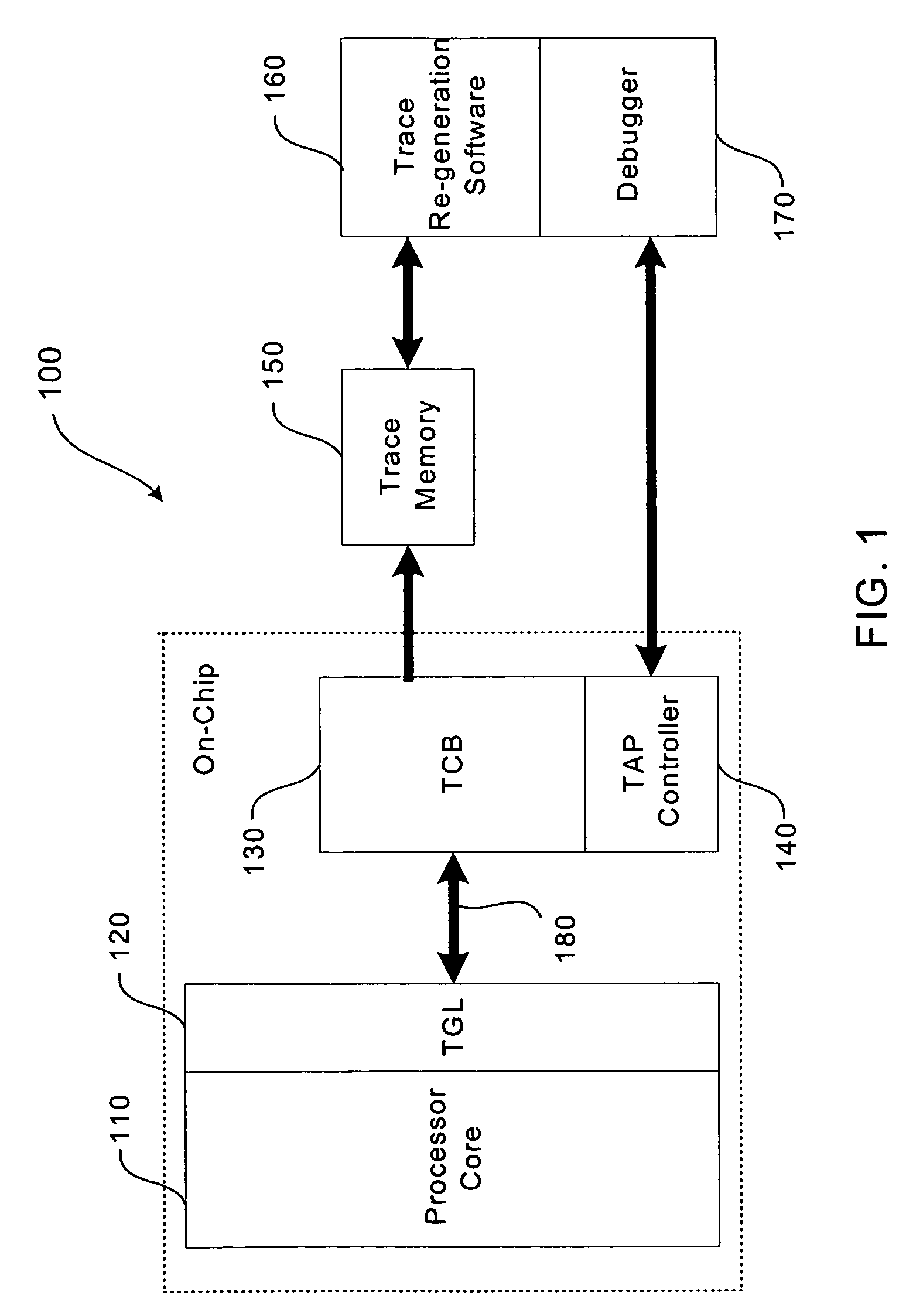
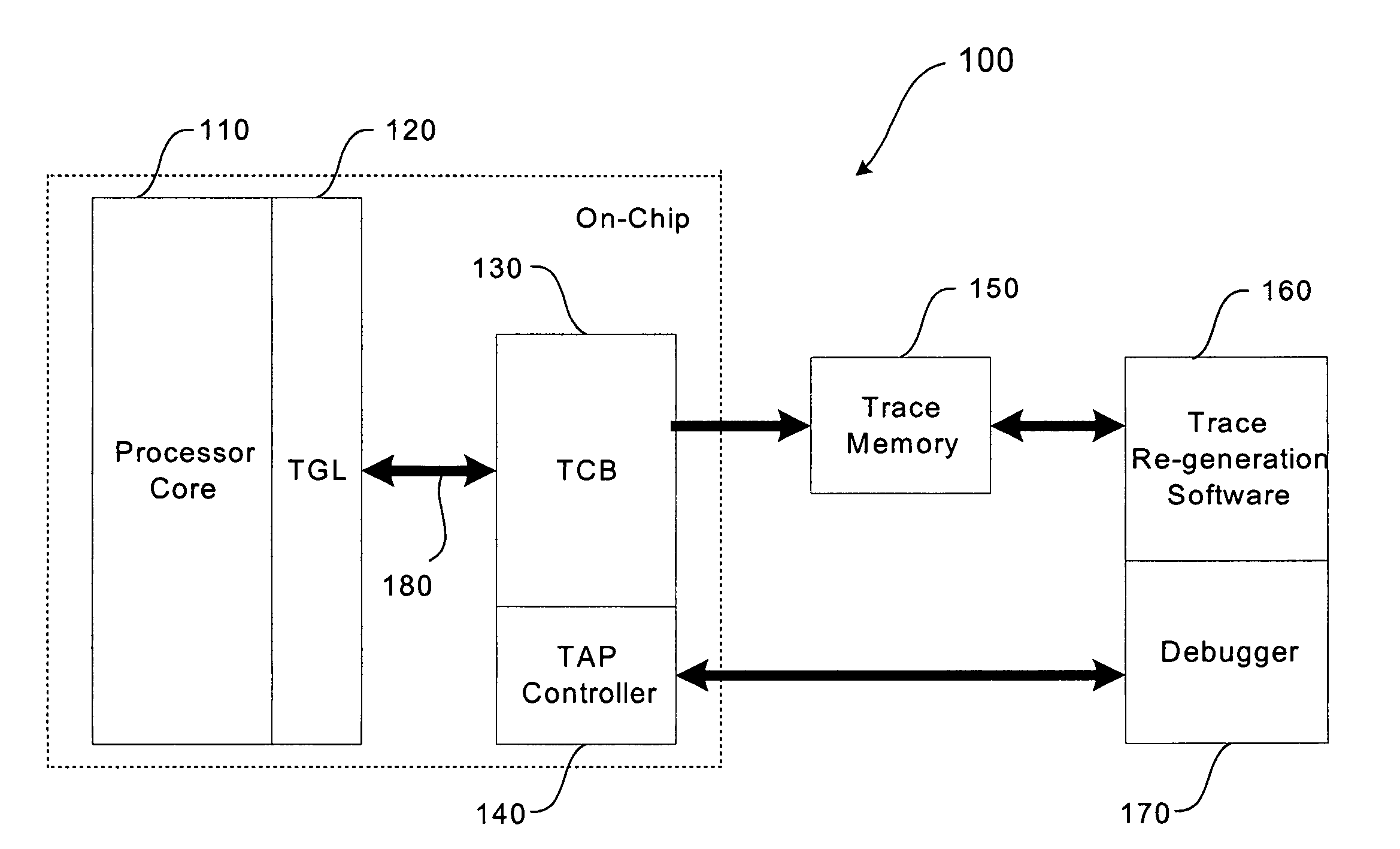
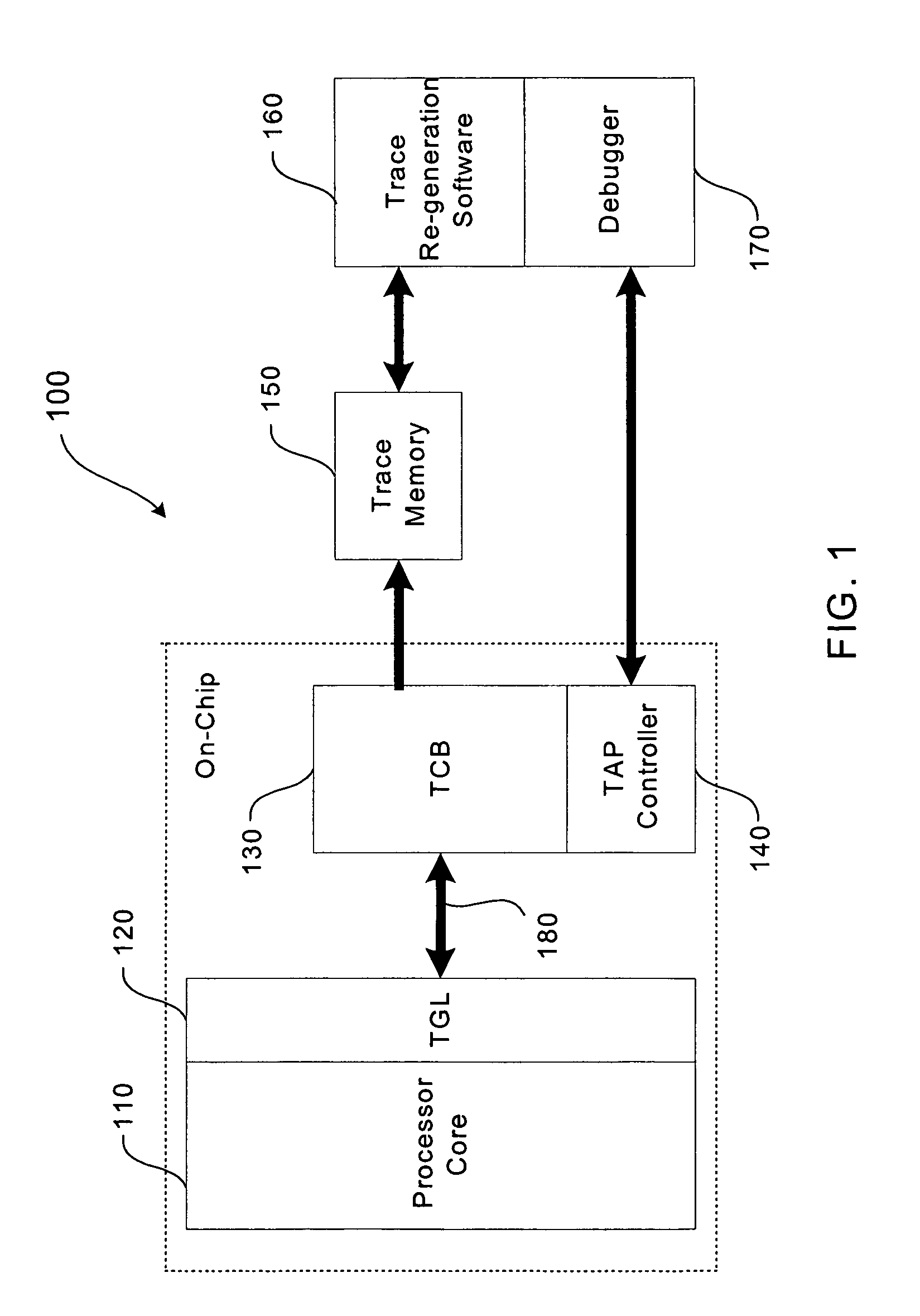
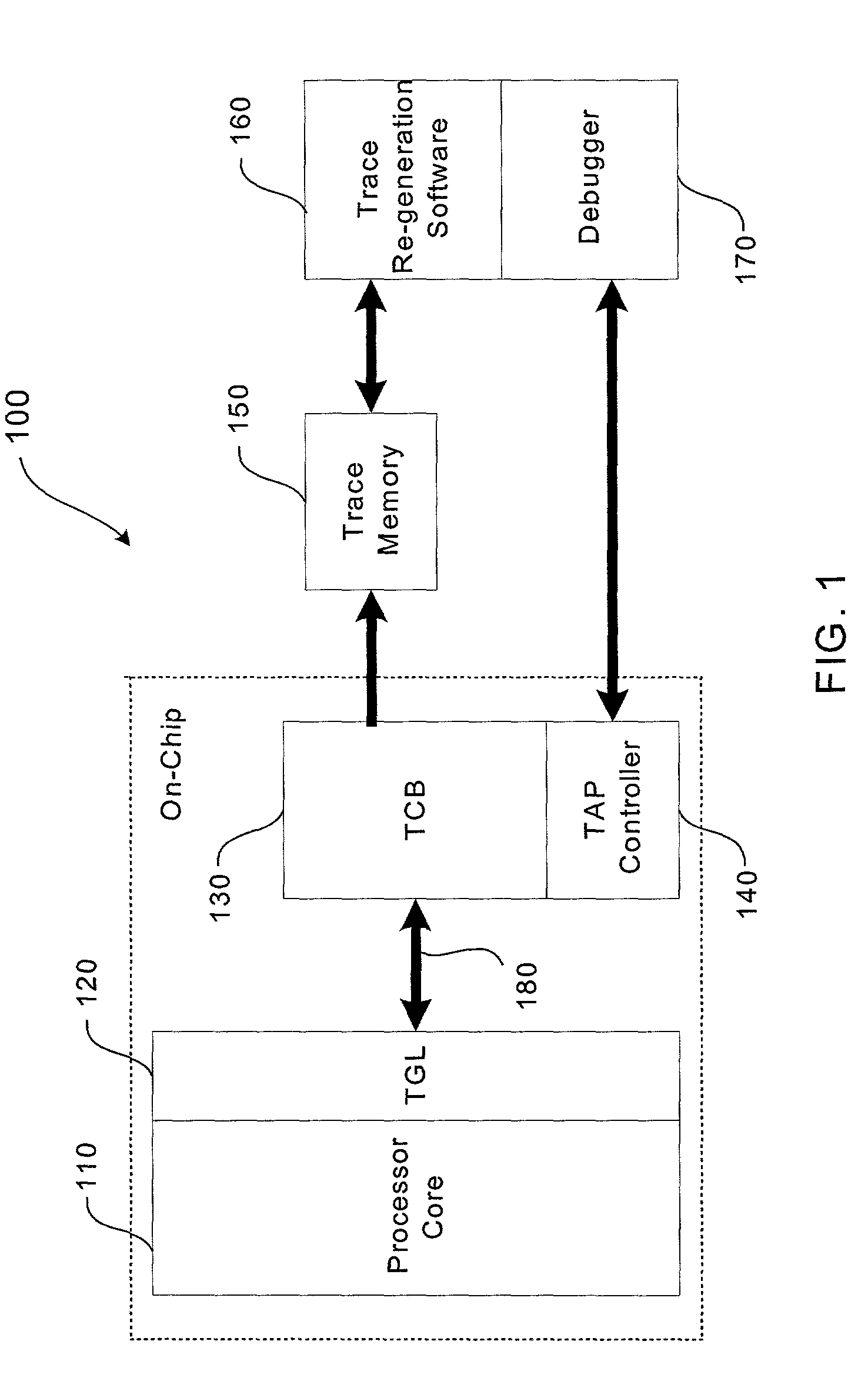
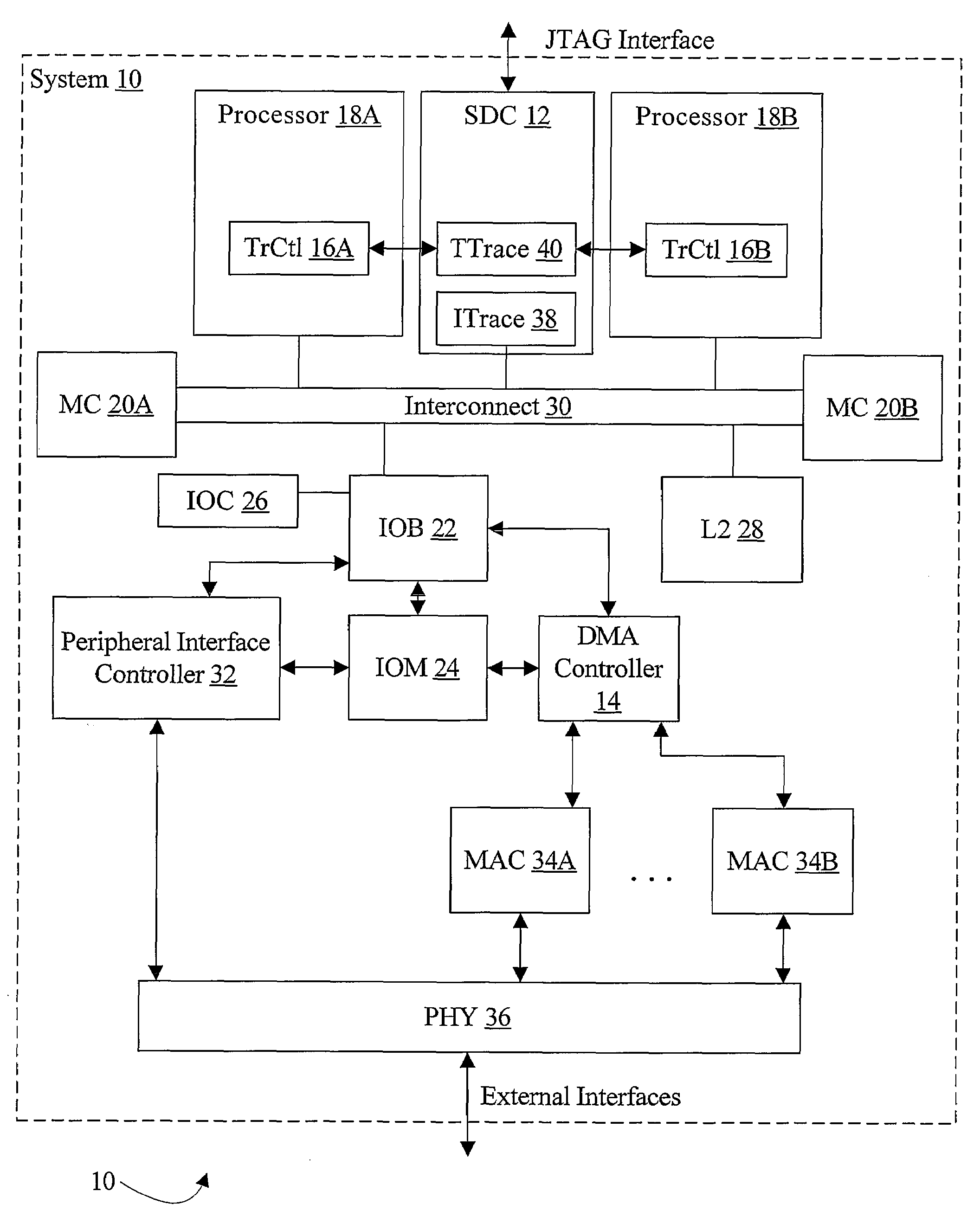
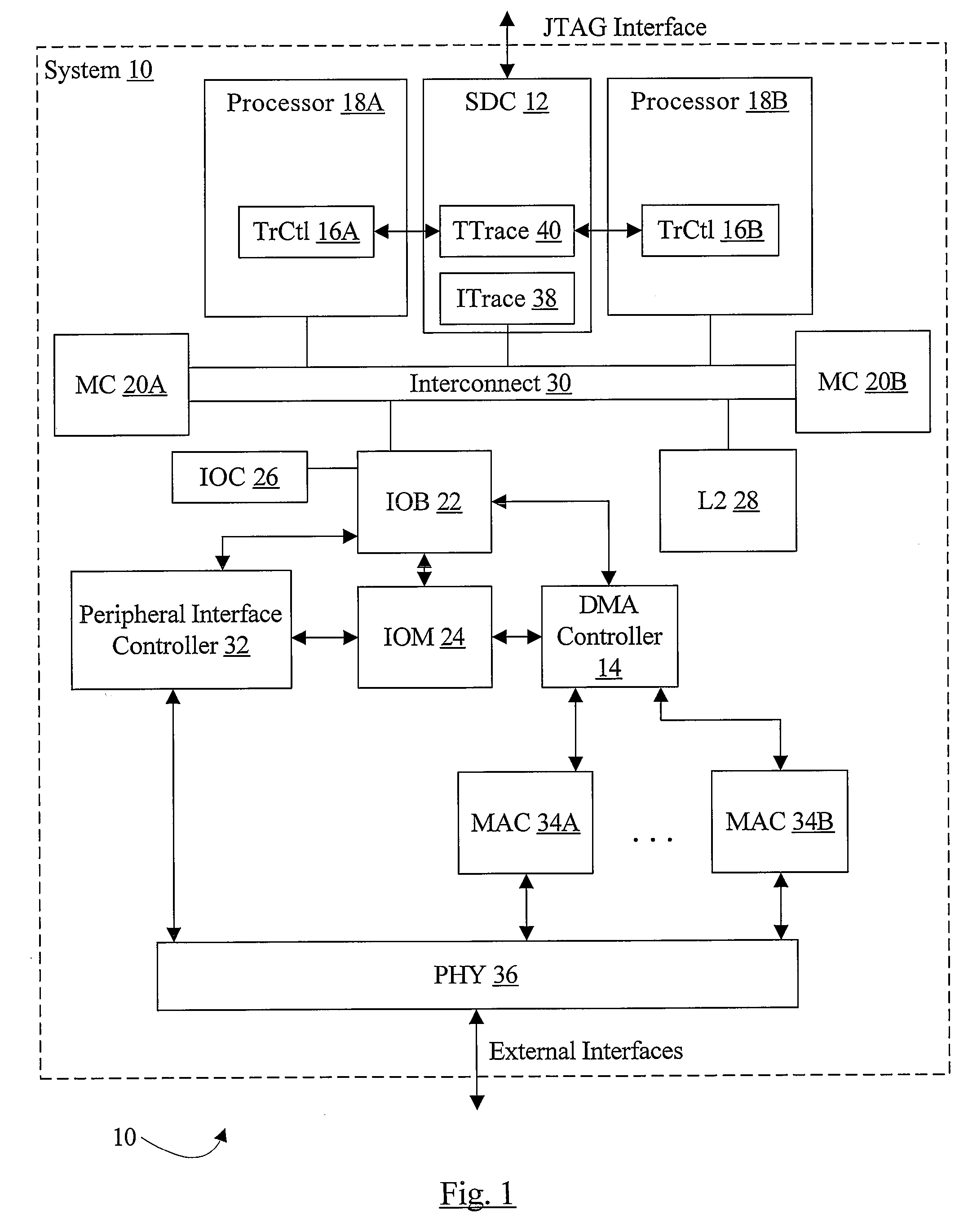
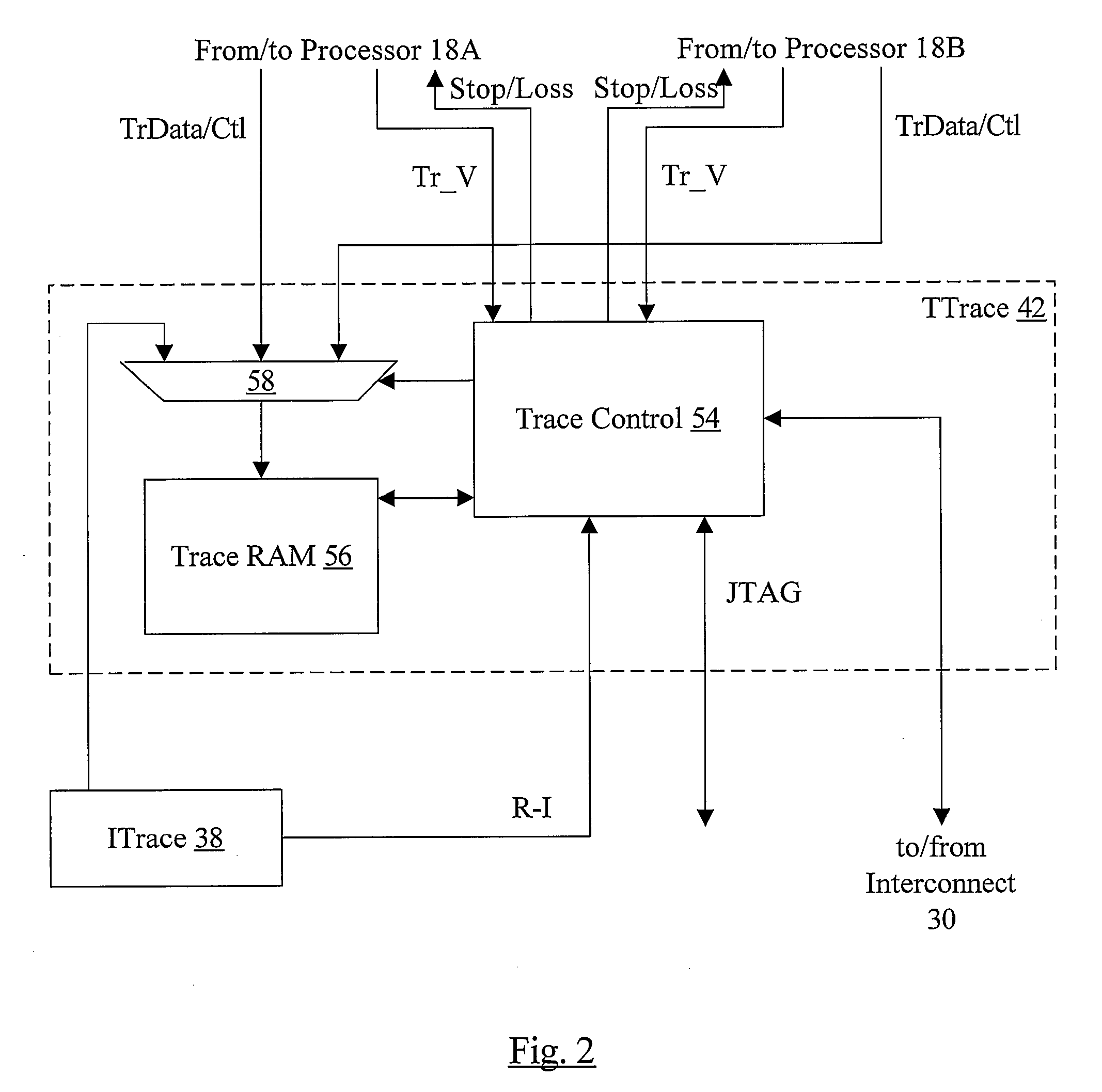
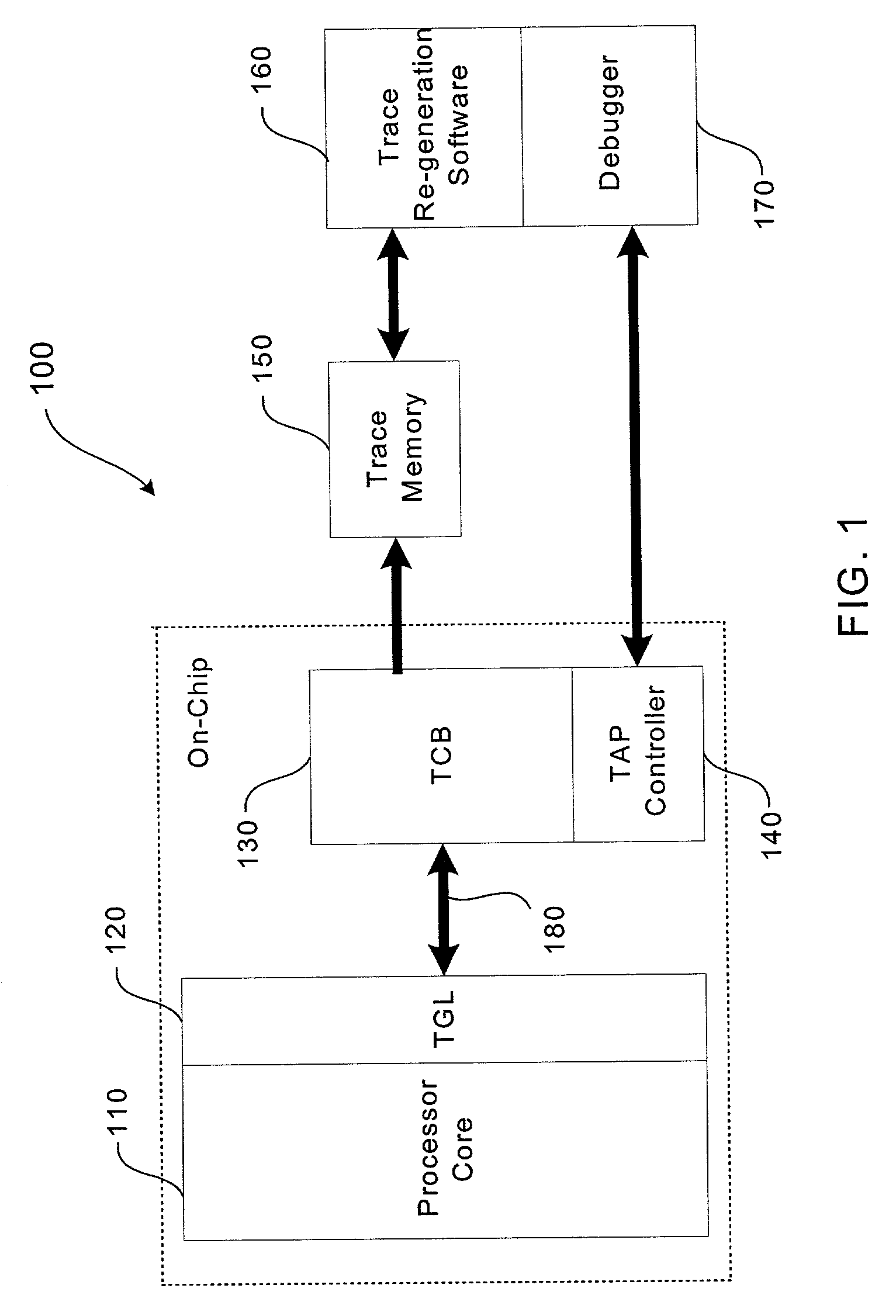
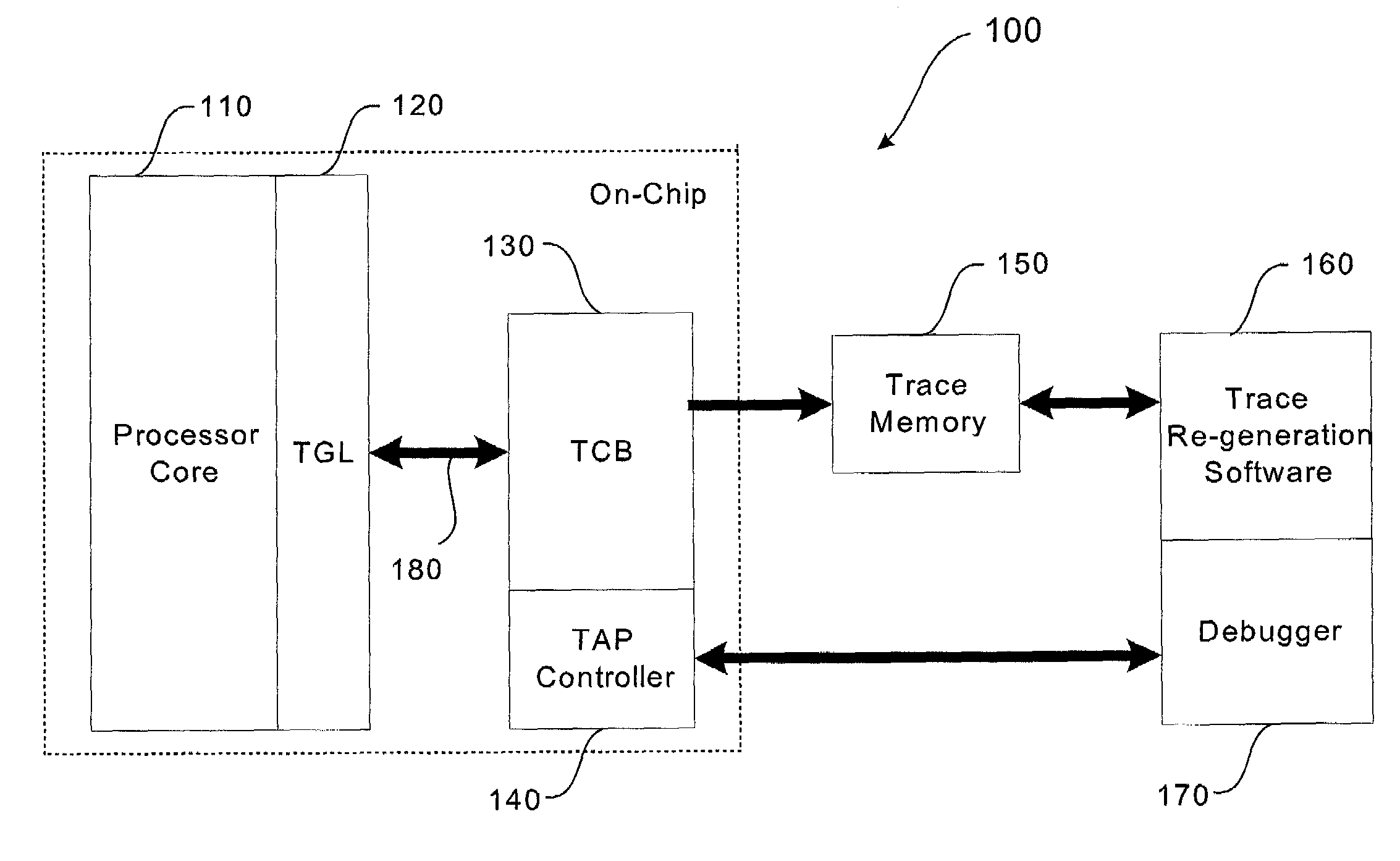
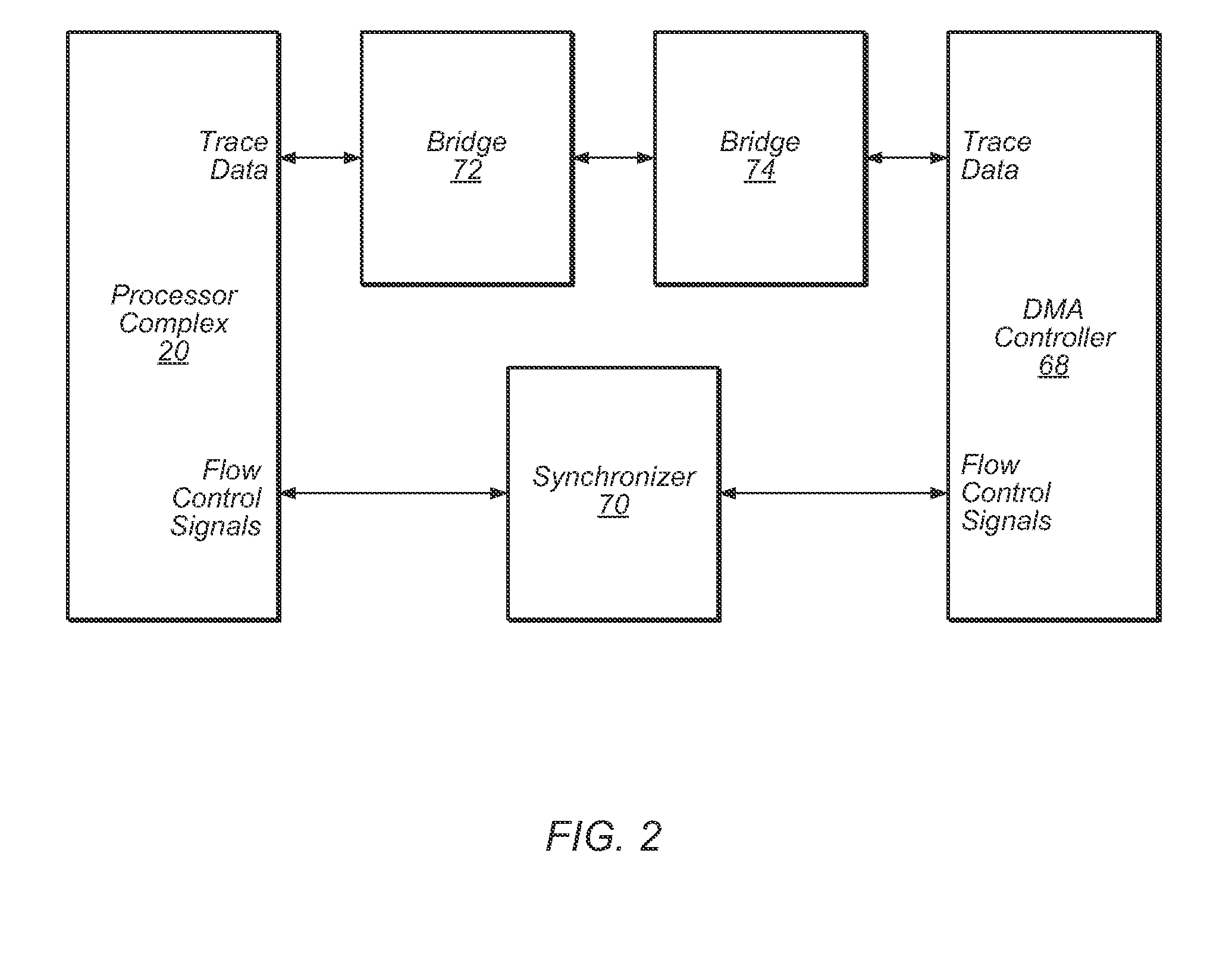
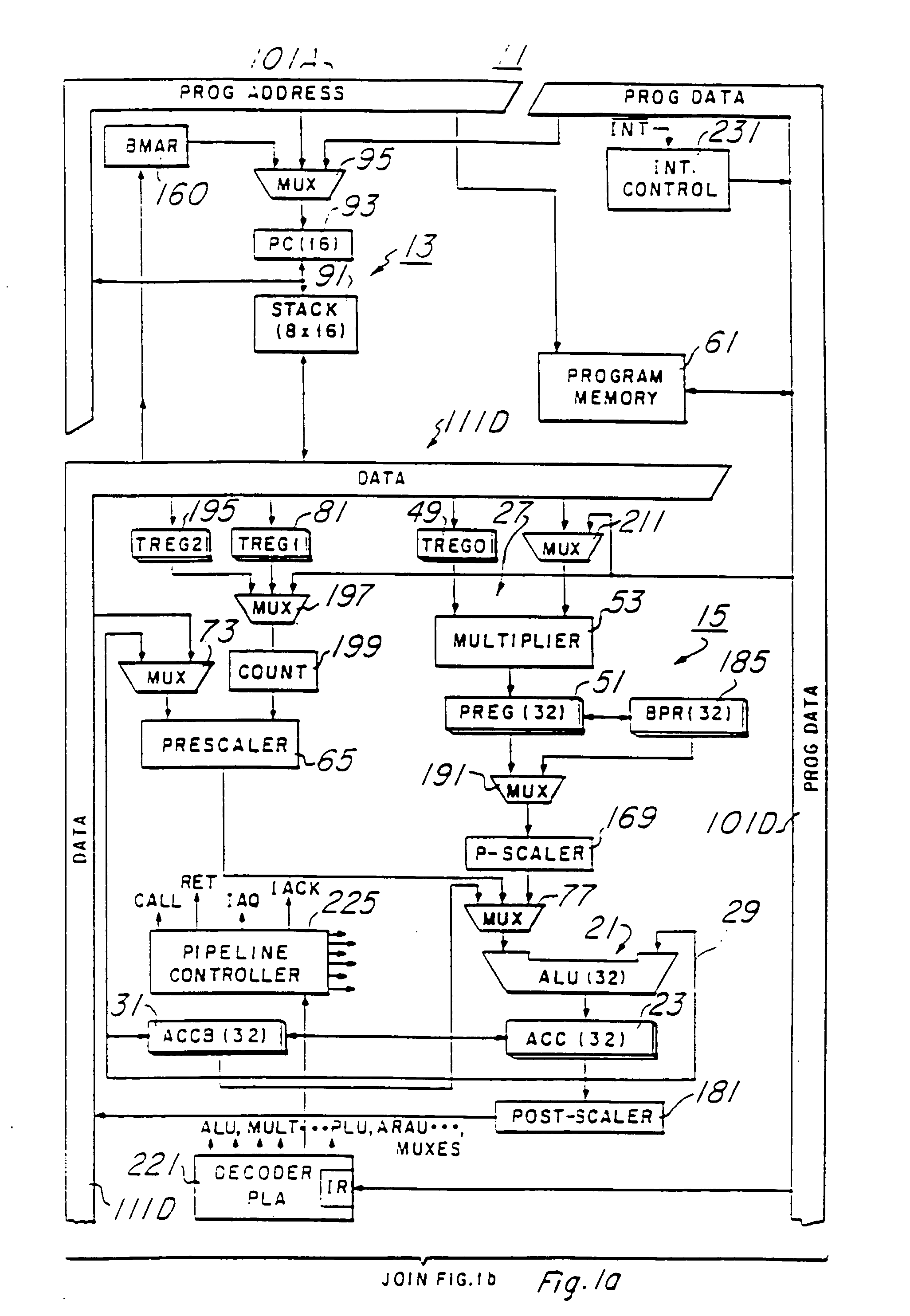
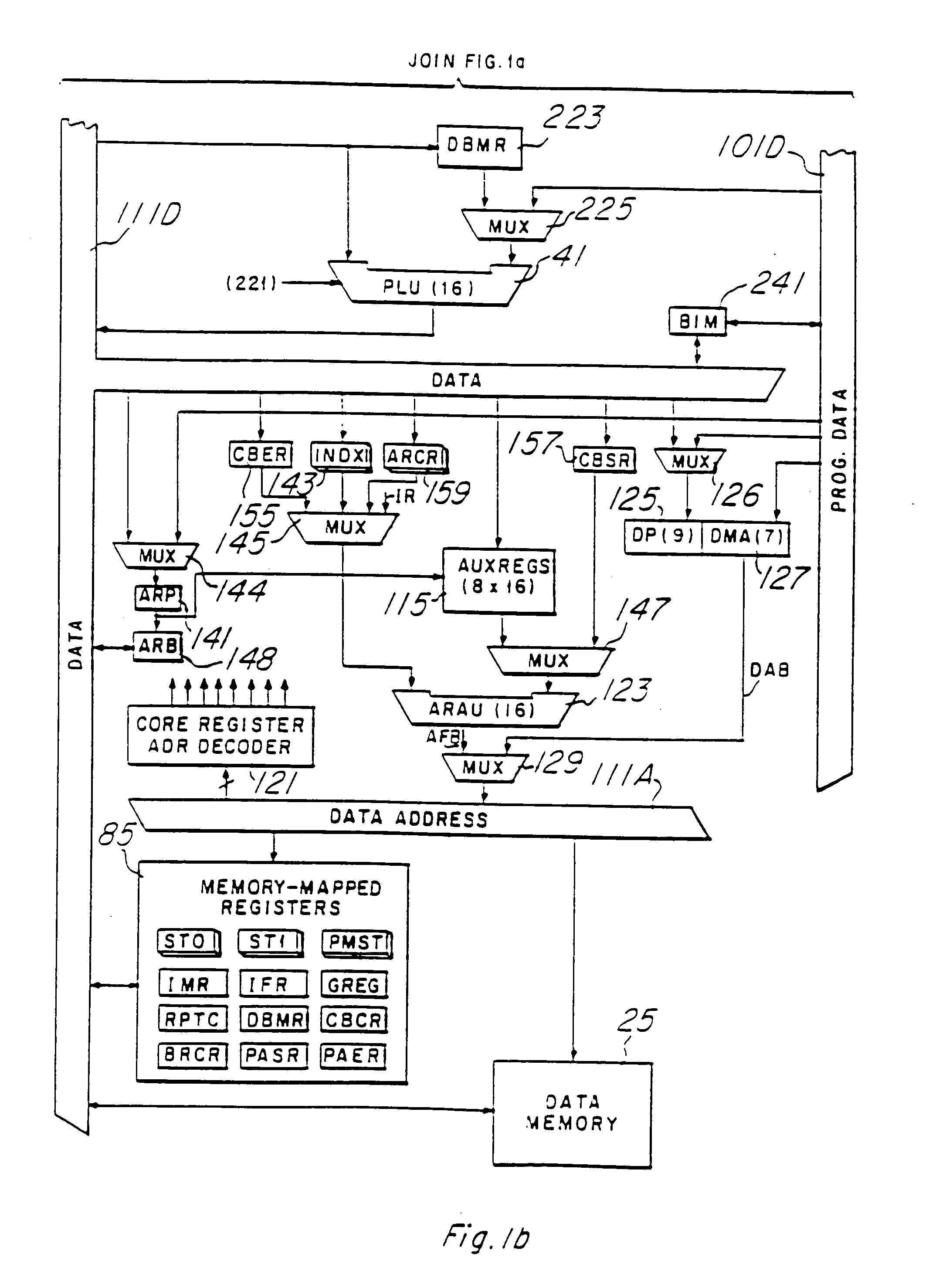
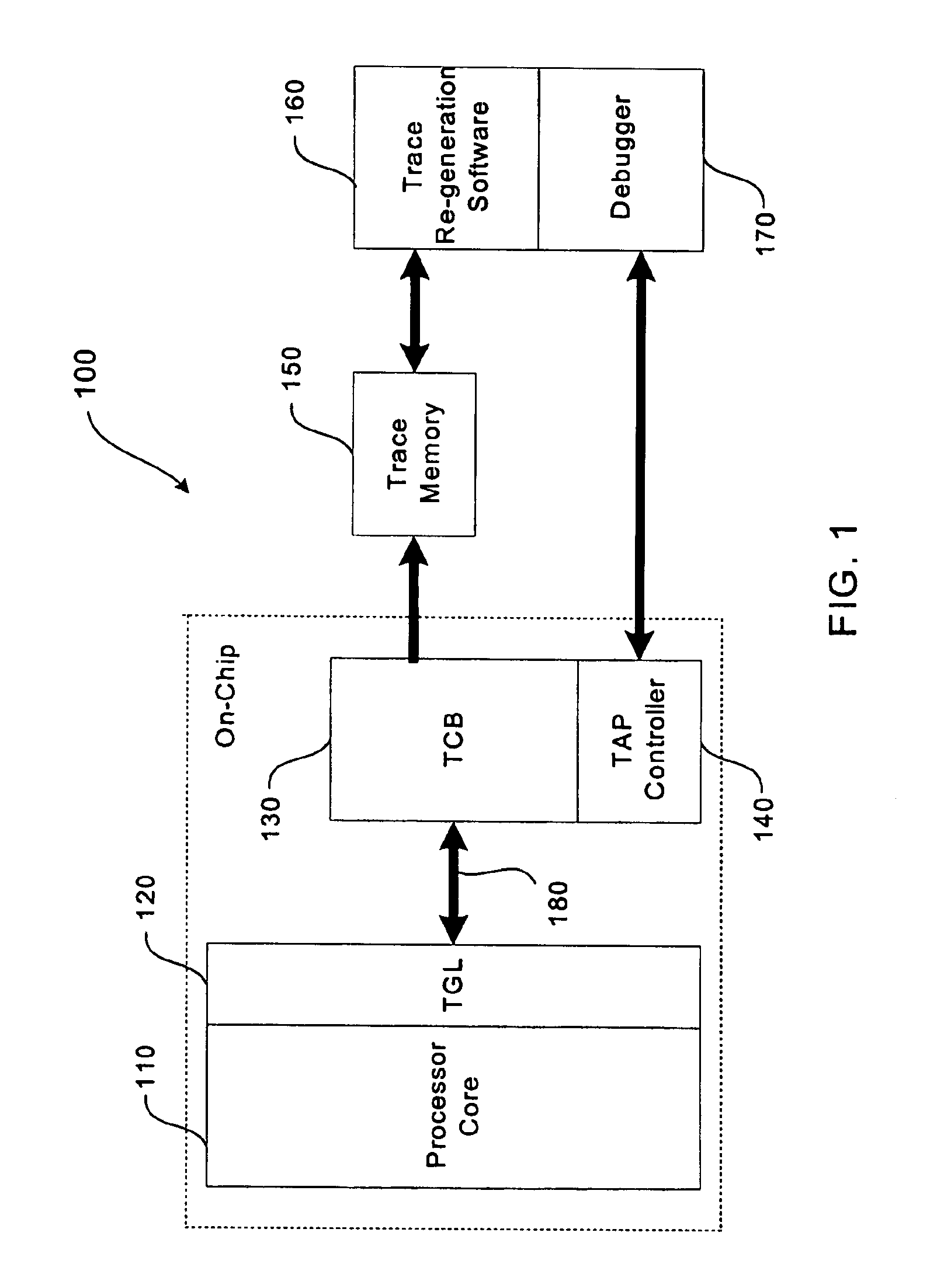
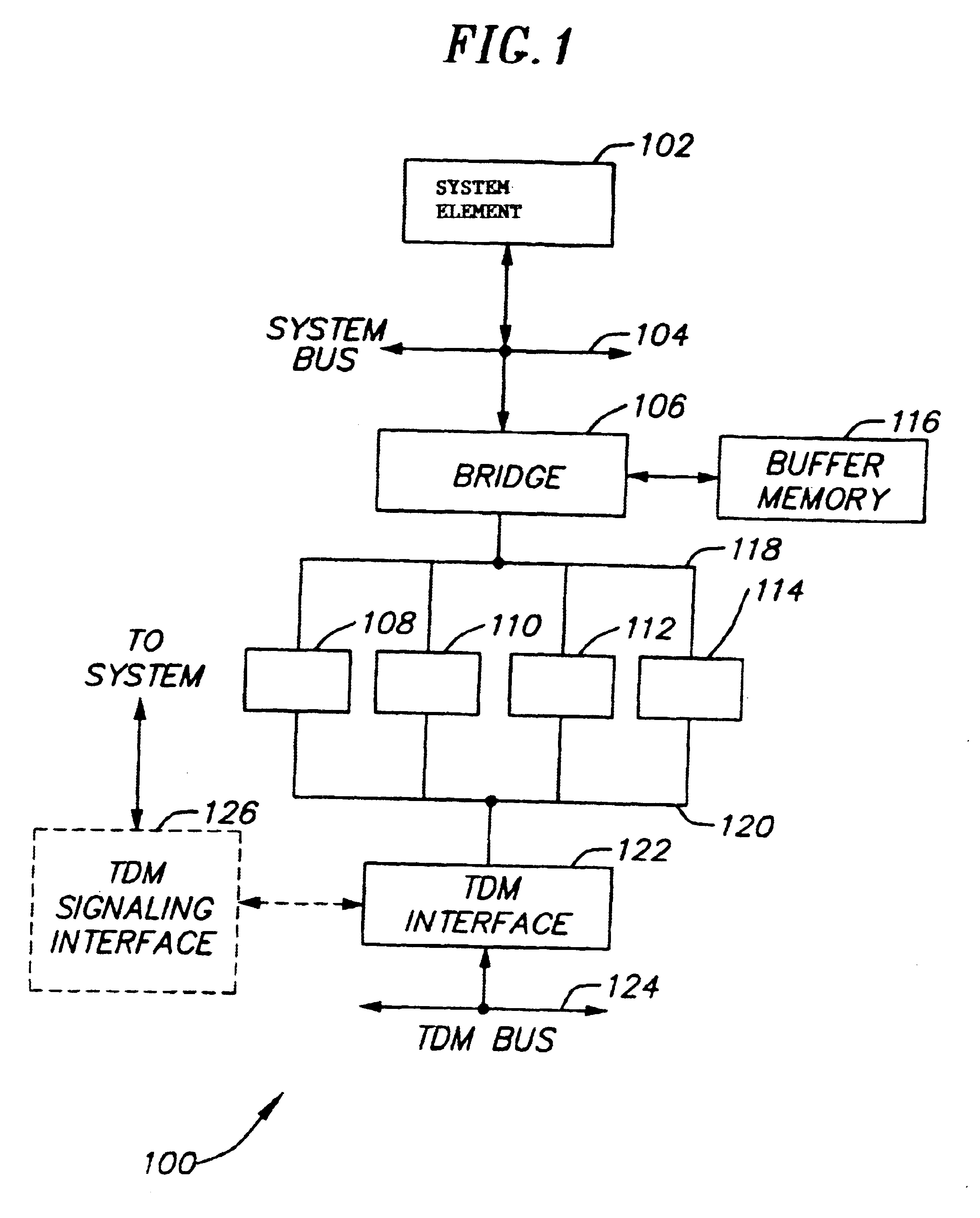
Trace control block implementation and method
InactiveUS7055070B1Error detection/correctionSpecific program execution arrangementsParallel computingProgram counter
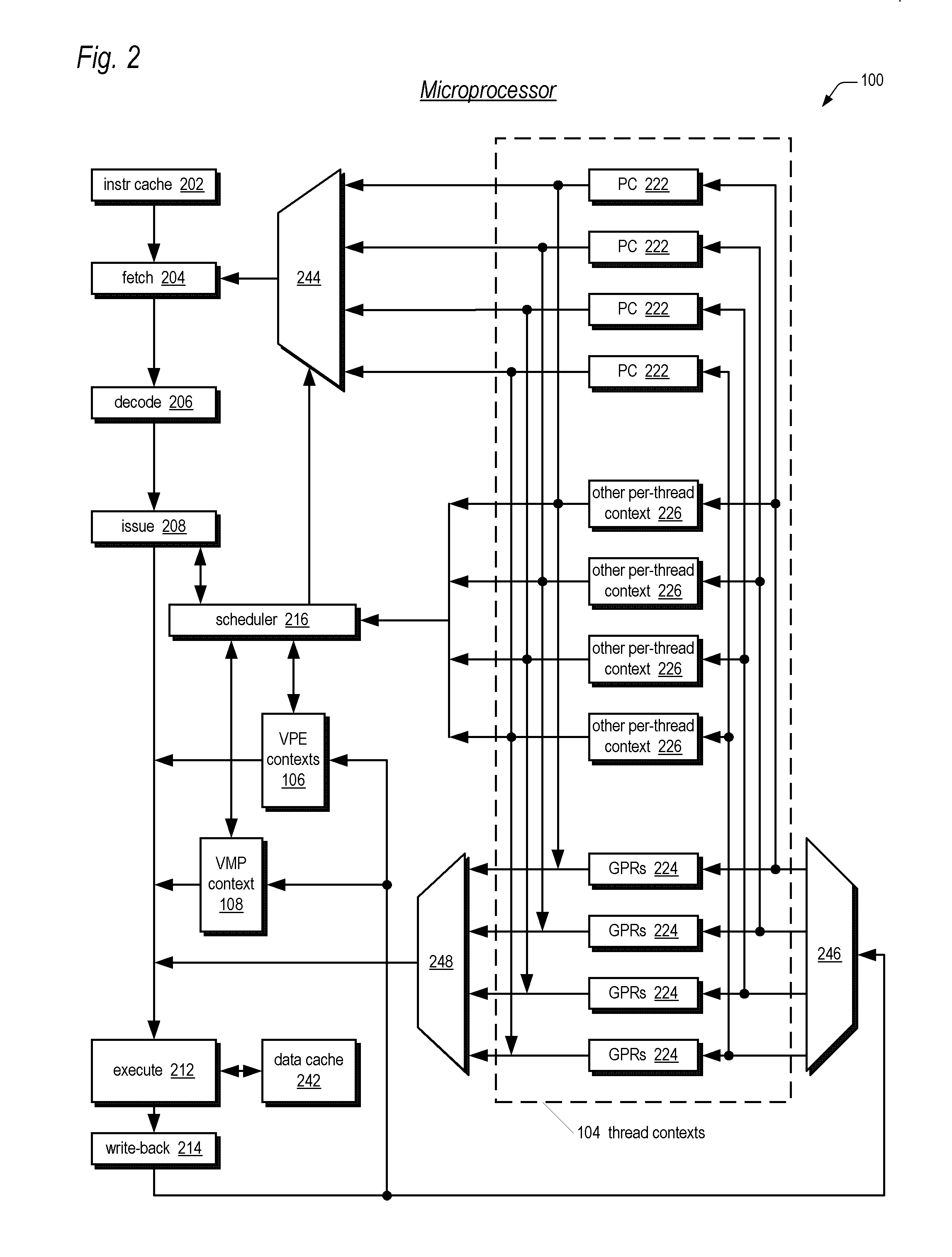
A system and method for program counter and data tracing is disclosed. A trace interface is provided for communication of trace information between a processor core and a trace control block. The trace interface enables various combinations of processor cores and trace control blocks to be implemented.
Owner:ARM FINANCE OVERSEAS LTD
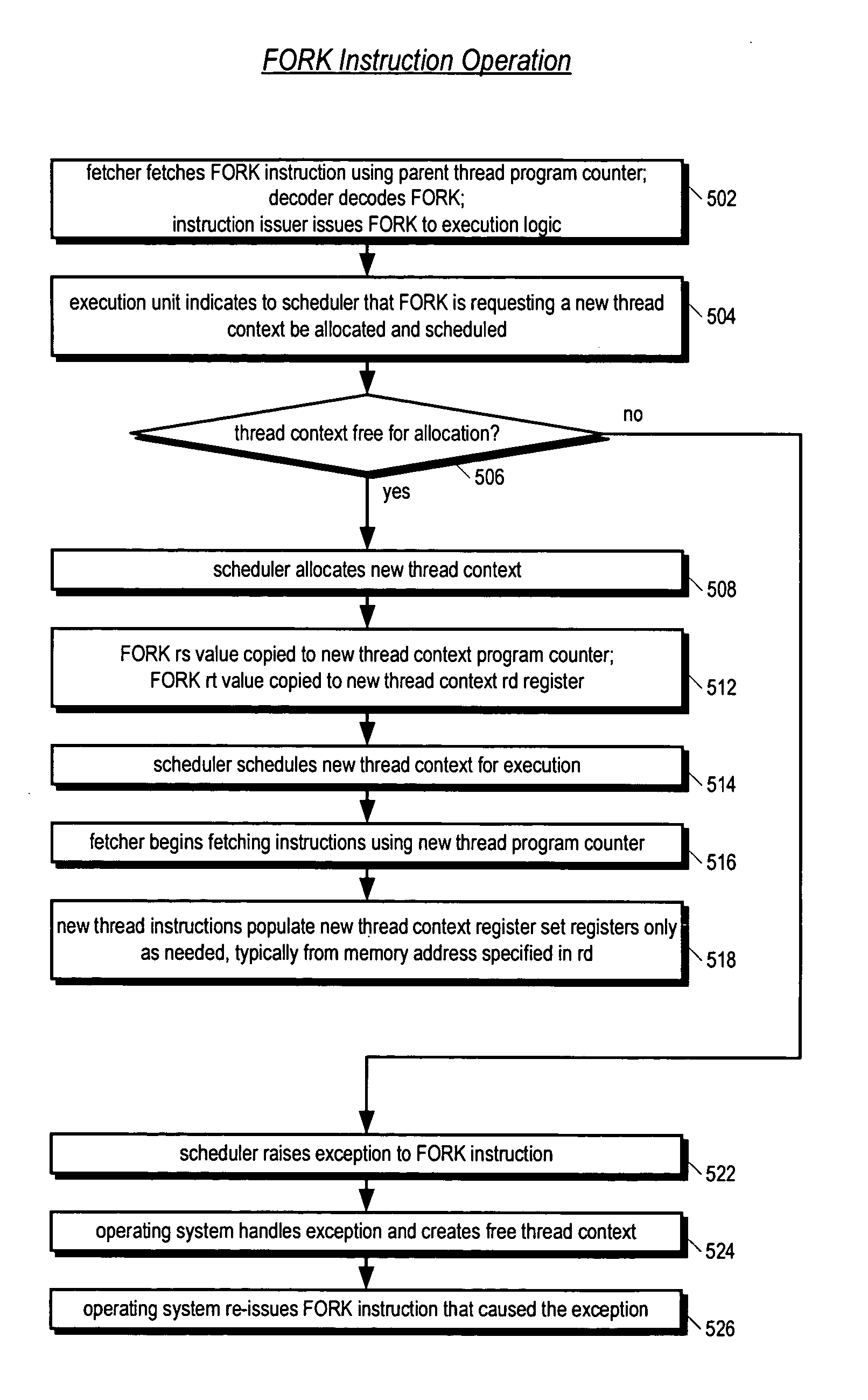
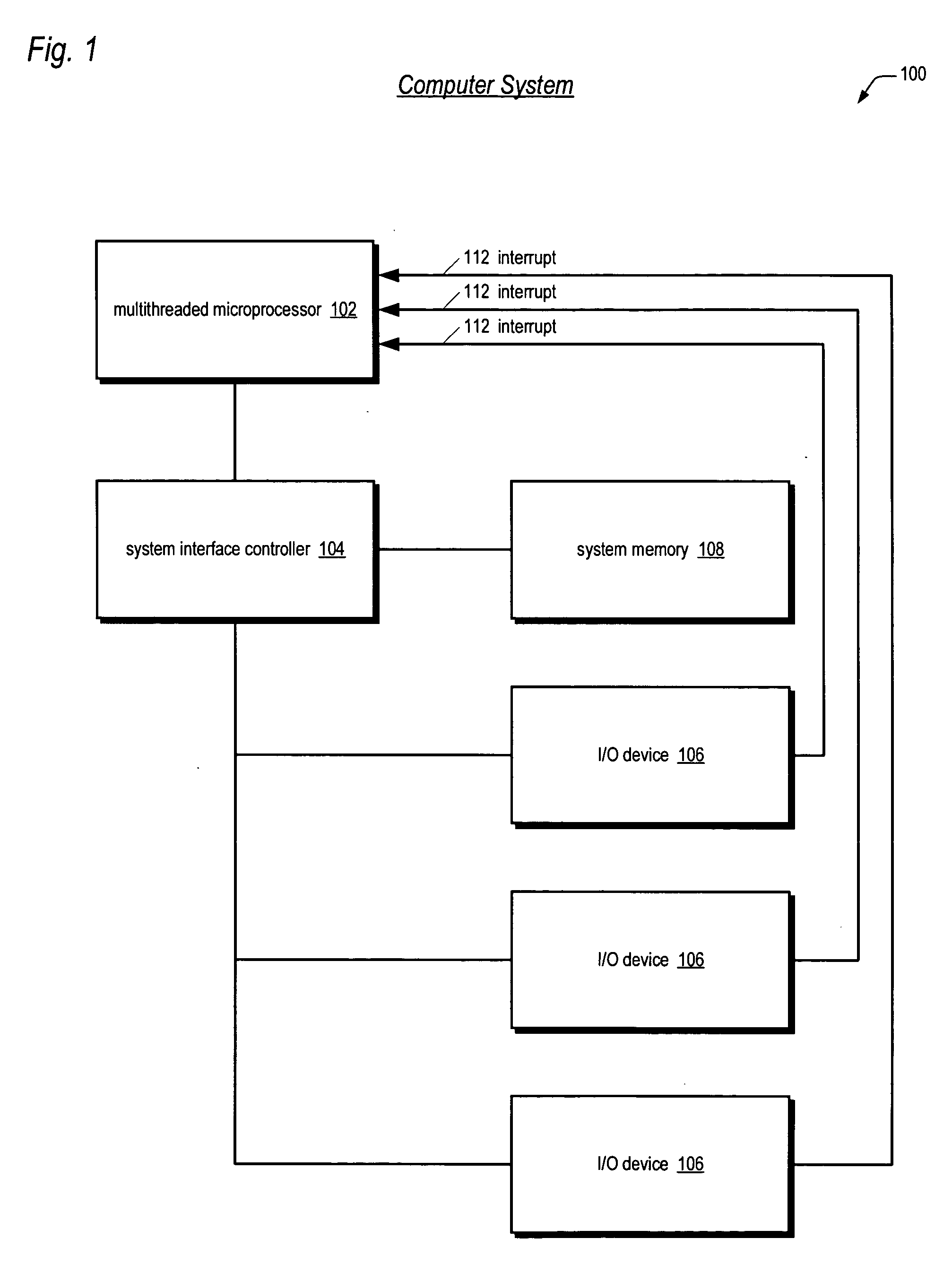
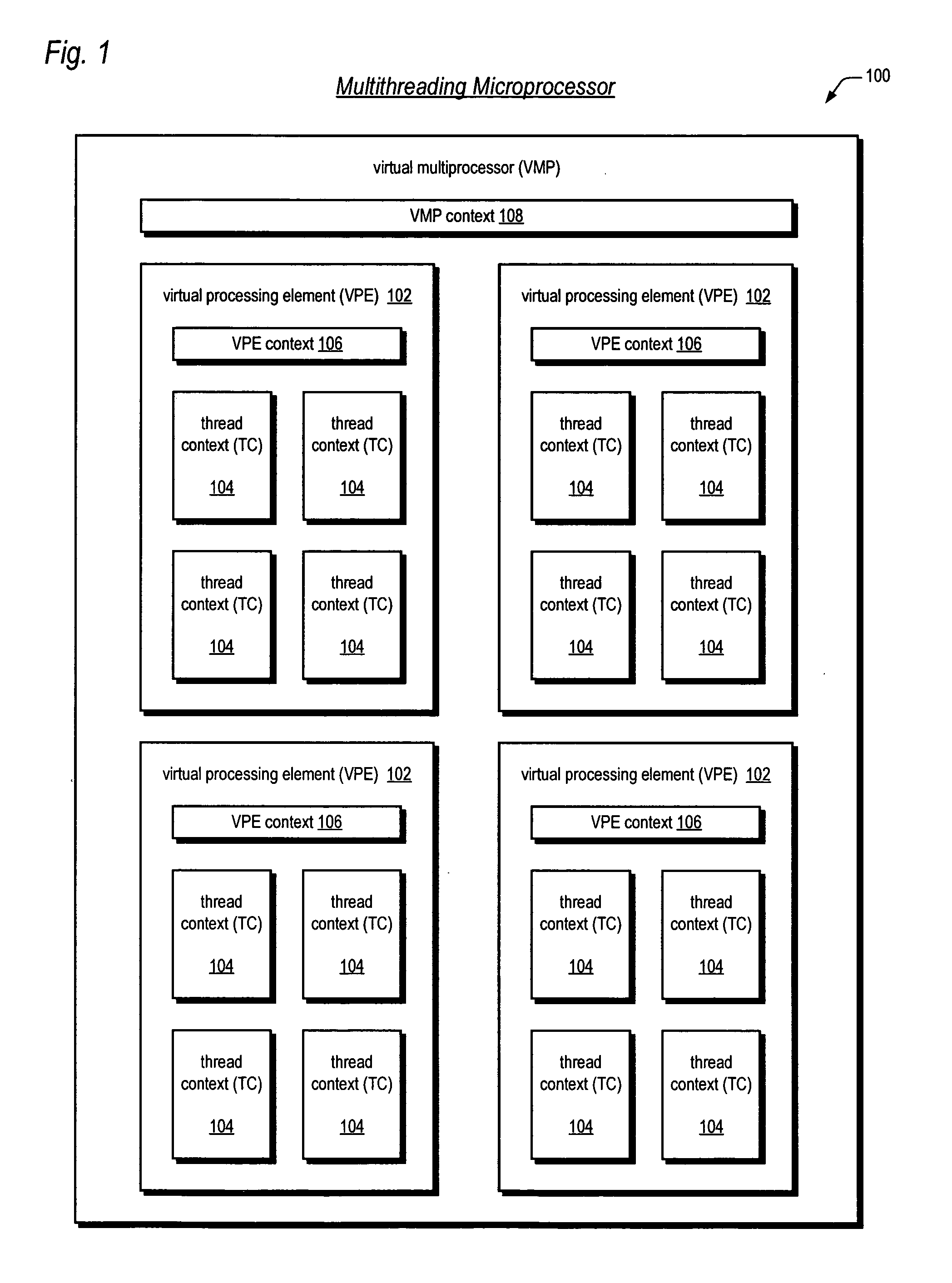
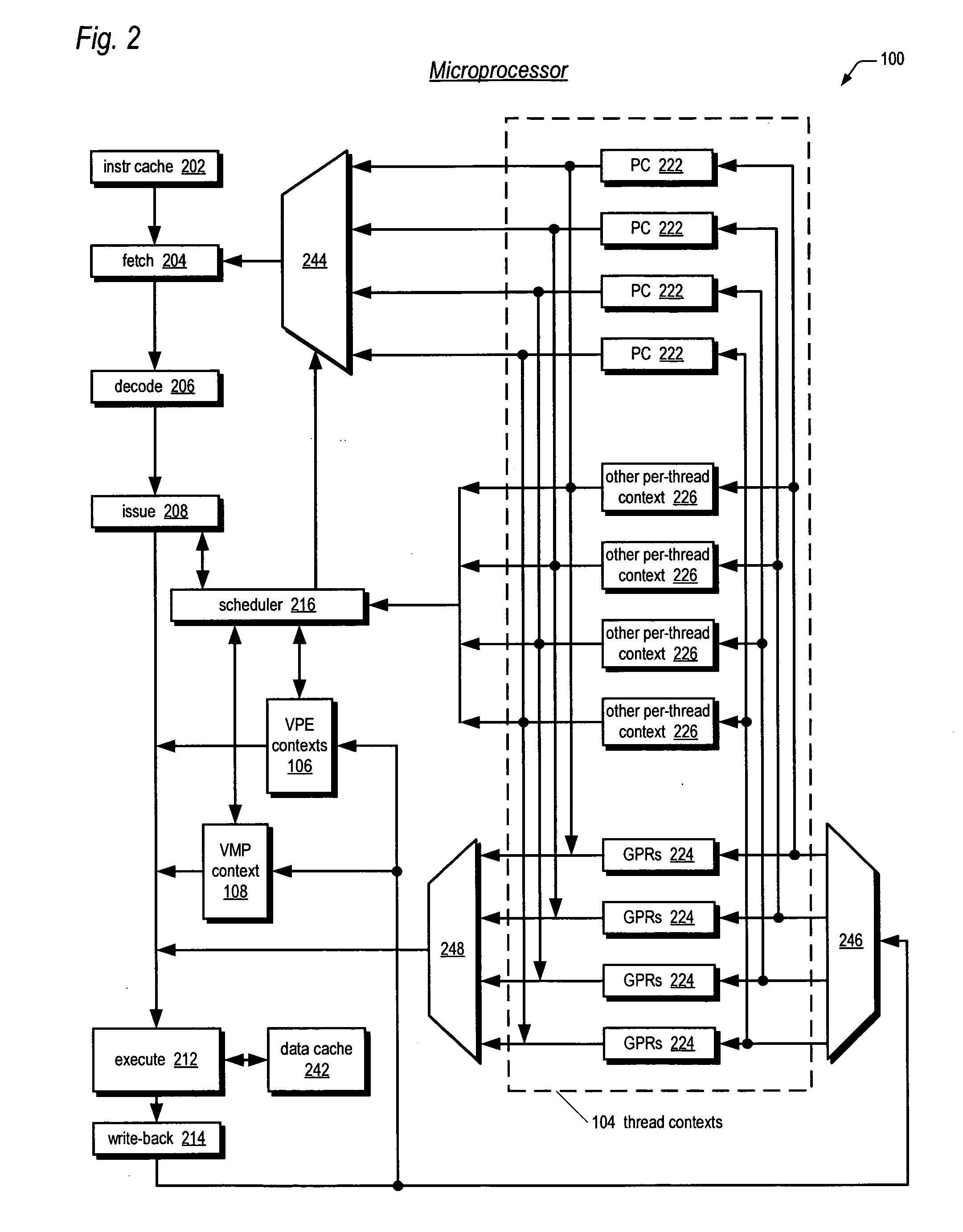
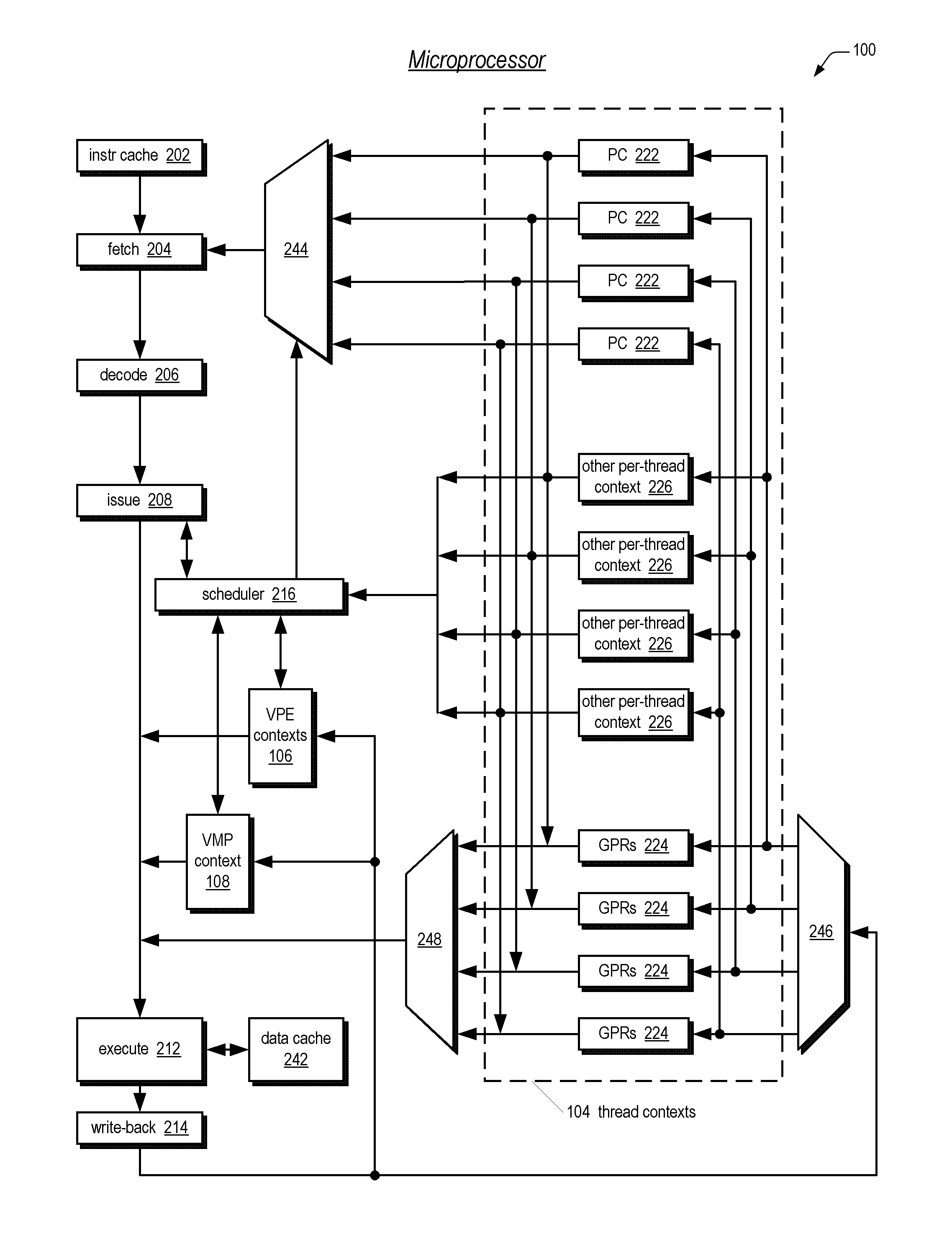
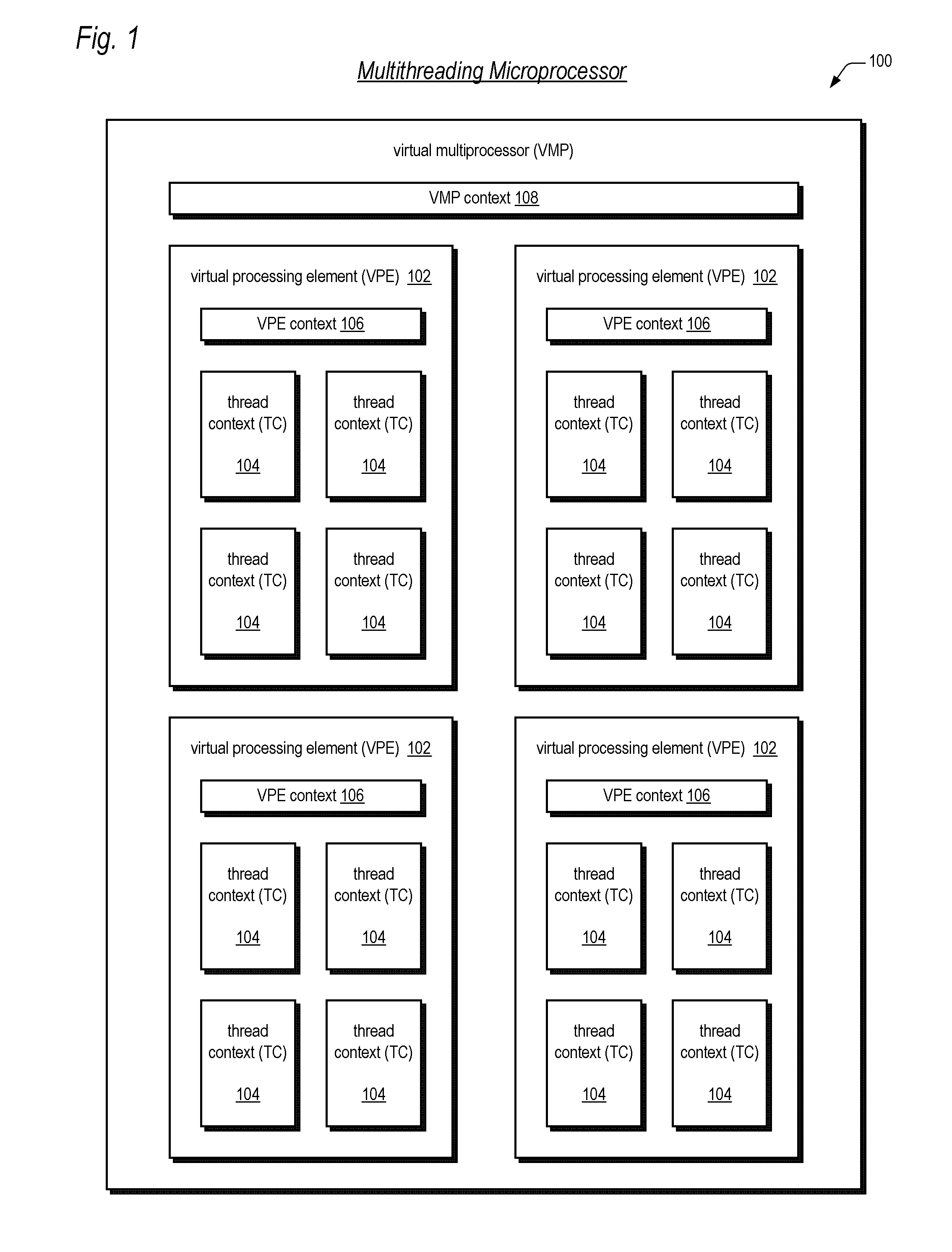
Apparatus, method, and instruction for initiation of concurrent instruction streams in a multithreading microprocessor
ActiveUS20050120194A1Reduce overheadAvoid wasting energyProgram initiation/switchingSoftware engineeringGeneral purposeComputer architecture
A fork instruction for execution on a multithreaded microprocessor and occupying a single instruction issue slot is disclosed. The fork instruction, executing in a parent thread, includes a first operand specifying the initial instruction address of a new thread and a second operand. The microprocessor executes the fork instruction by allocating context for the new thread, copying the first operand to a program counter of the new thread context, copying the second operand to a register of the new thread context, and scheduling the new thread for execution. If no new thread context is free for allocation, the microprocessor raises an exception to the fork instruction. The fork instruction is efficient because it does not copy the parent thread general purpose registers to the new thread. The second operand is typically used as a pointer to a data structure in memory containing initial general purpose register set values for the new thread.
Owner:MIPS TECH INC
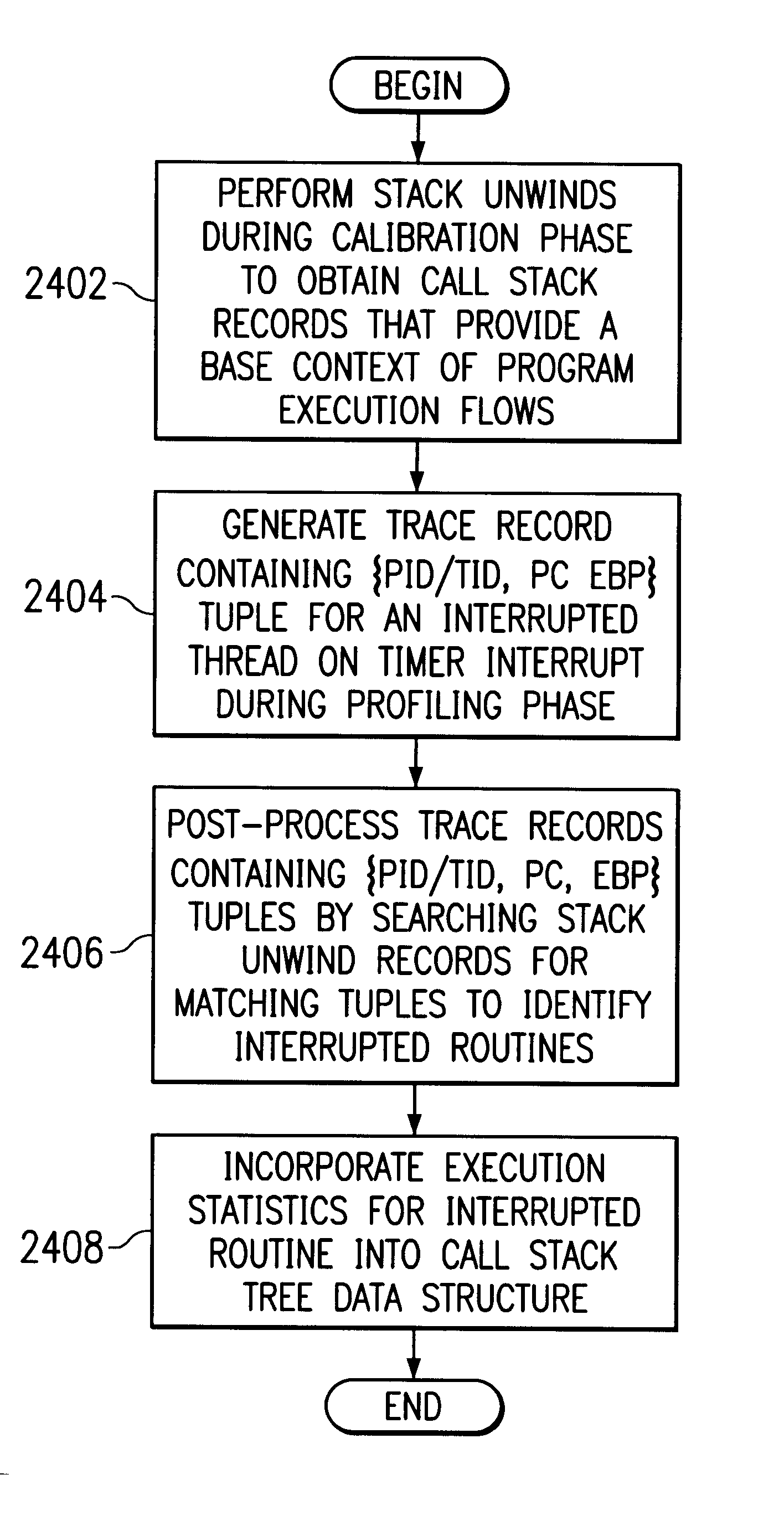
Minimizing profiling-related perturbation using periodic contextual information
InactiveUS6662358B1Digital data information retrievalError detection/correctionCall stackProgram counter
A method and system for monitoring performance of a program is provided. A trace record containing a call stack associated with the program is periodically generated. An occurrence of a selected event or a timer interrupt is detected, and in response, an execution context sample is obtained that contains a process identifier, a thread identifier, a program counter, and a stack pointer. A trace record containing the execution context sample data is generated. During post-processing, the execution context samples are compared with a call stack to identify the routine associated with the execution sample data.
Owner:IBM CORP
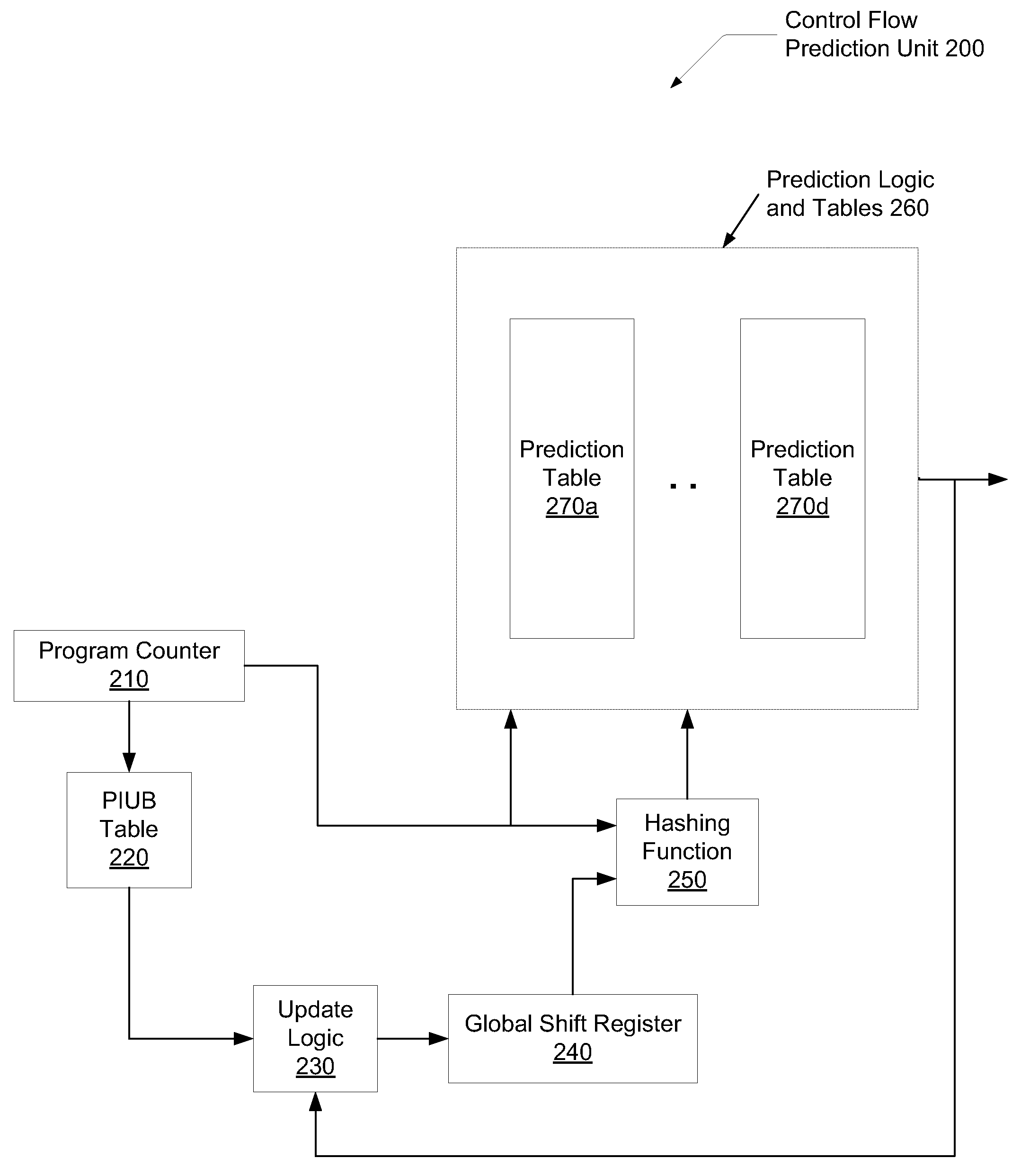
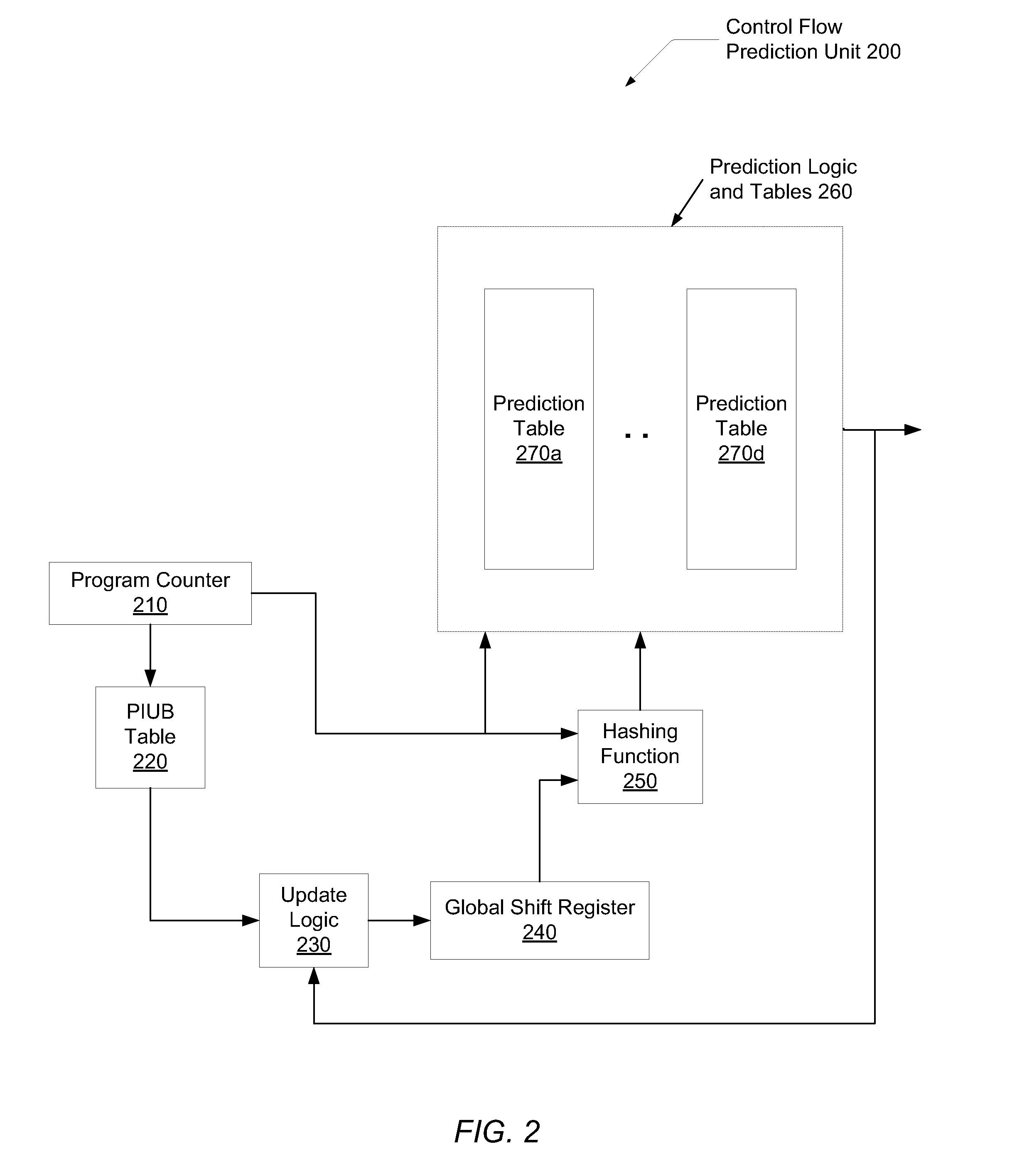
Branch history with polymorphic indirect branch information
ActiveUS20090164766A1Improve accuracyImprove forecast accuracyDigital computer detailsConcurrent instruction executionTarget arrayShift register
A system and method for efficient improvement of branch prediction in a microprocessor with negligible impact on die-area, power consumption, and clock cycle period. It is determined if a program counter (PC) register contains a polymorphic indirect unconditional branch (PIUB) instruction. One determination may be searching a table with a portion or all of a PC of past PIUB instructions. If a hit occurs in this table, the global shift register (GSR) is updated by shifting a portion of the branch target address into the GSR, rather than updating the GSR with a taken / not-taken prediction bit. The stored value in the GSR is input into a hashing function along with the PC in order to index prediction tables such as a pattern history table (PHT), a branch target buffer (BTB), an indirect target array, or other. The updated value due to the PIUB instruction improves the accuracy of the prediction tables.
Owner:ADVANCED MICRO DEVICES INC
Distributed pipeline memory architecture for a computer system with even and odd pids
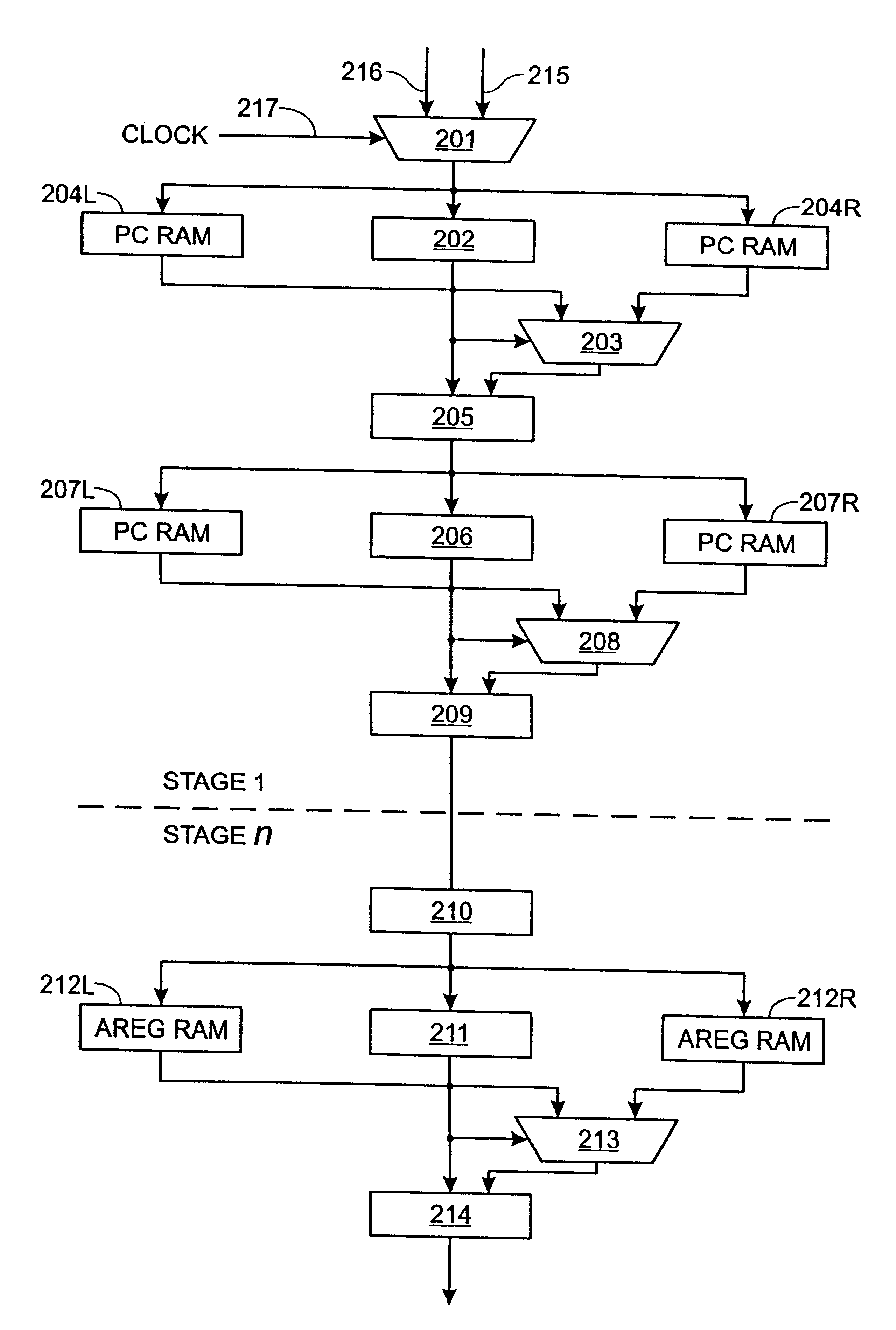
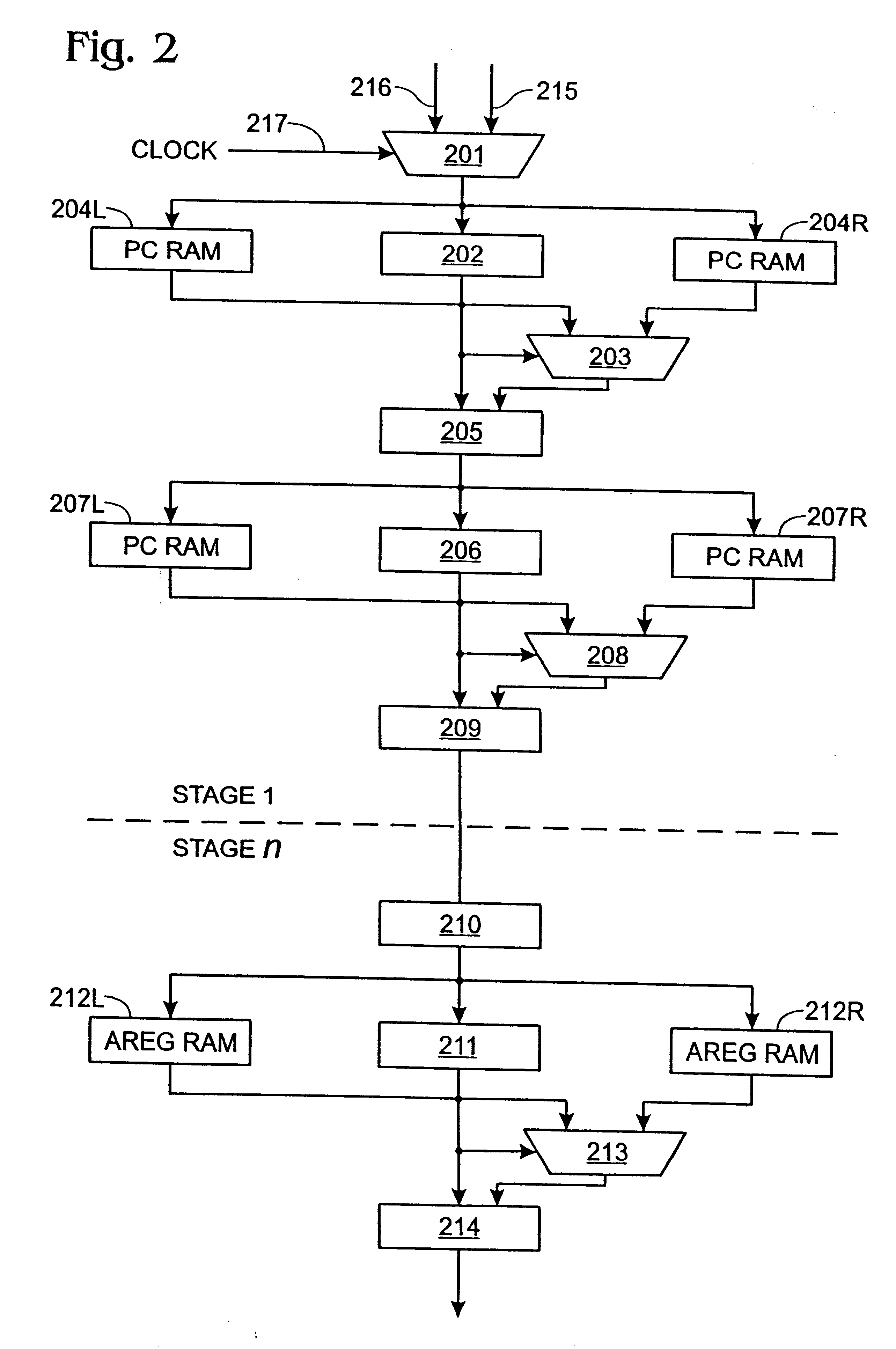
InactiveUS6209020B1General purpose stored program computerMultiprogramming arrangementsAccess timeComputerized system
A computer system architecture in which each processor has its own memory, strategically distributed along the stages of an execution pipeline of the processor, to provide fast access to often used information, such as the contents of the address and data registers, the program counter, etc. Memory storage is strategically located in close physical proximity to a stage in an execution pipeline at which memory is commonly or repeatedly accessed. Coupled to the pipeline at various stages are small memory cells for storing information that is consistently and repeatedly requested at that stage in the execution pipeline. The speed of the execution pipeline in a processor is critical to overall performance of the processor and the computer architecture of the present invention as a whole. To that end, the clock cycle time at which the pipeline is operated is increased as much as the operating characteristics of the logic and associated circuitry will allow. Generally, access times for memory are slower than the clock cycle times at which the pipeline logic can operate. Thus, there is a point of diminishing return at which increasing the clock cycle time of the pipeline is less advantageous if the pipeline must wait for memory access to complete. Thus, there is provided two sets of strategically located memory cells distributed along the execution pipeline of a processor, and alternately accesses the memory cells.
Owner:NORTEL NETWORKS LTD
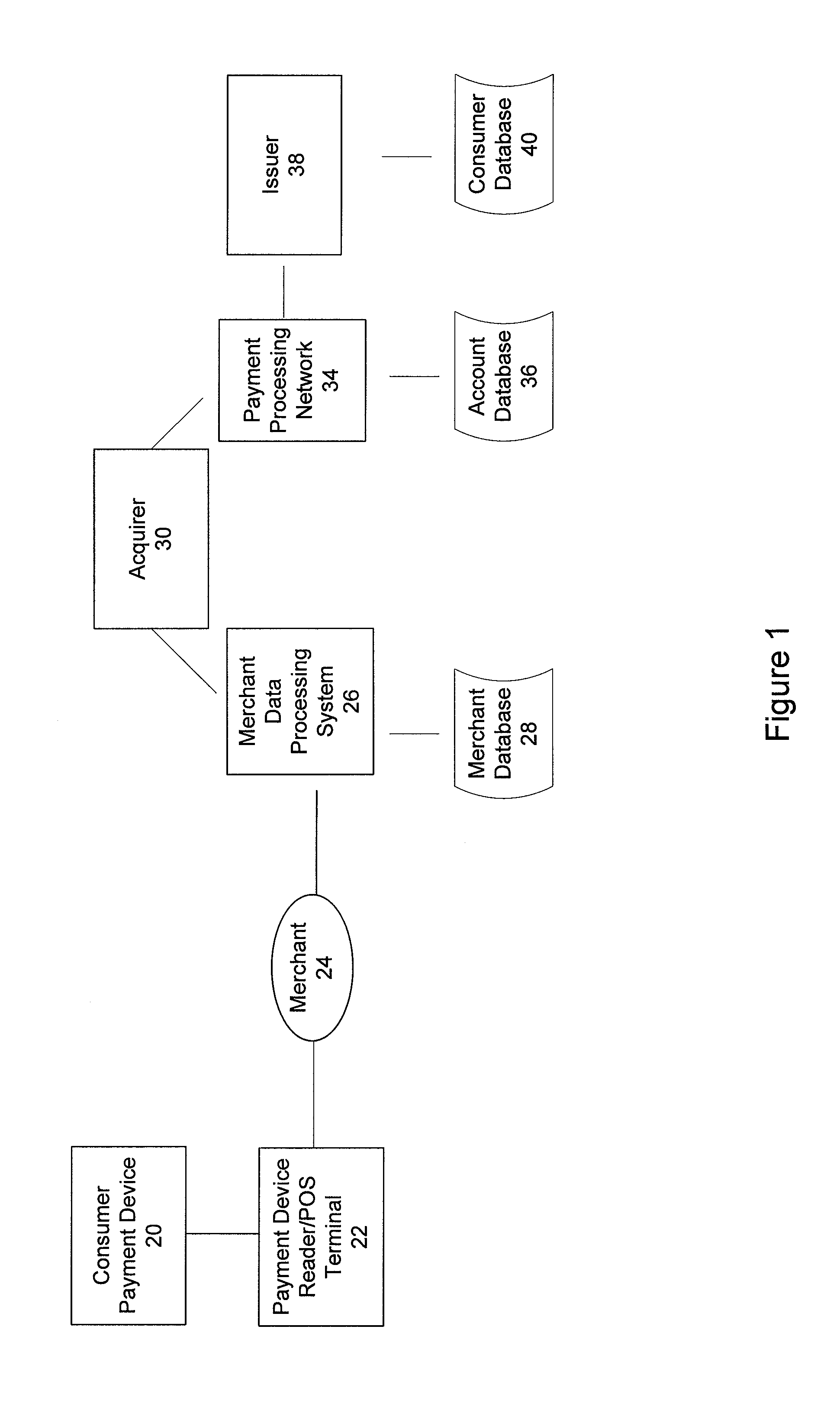
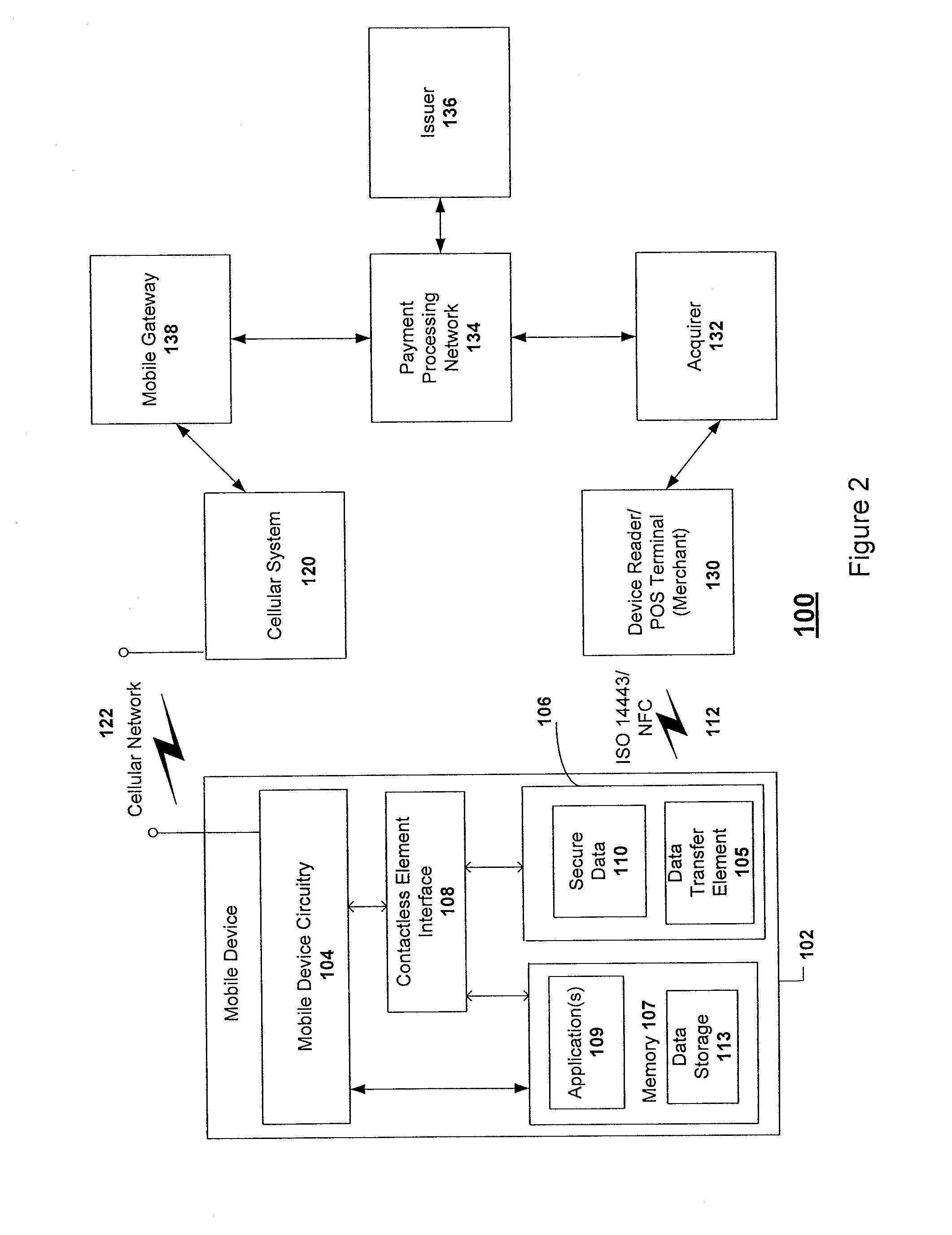
Method of performing transactions with contactless payment devices using pre-tap and two-tap operations
ActiveUS20100211504A1Minimize impactNear-field transmissionFinanceProcessor registerPayment transaction
A system, apparatus, and method for processing payment transactions that are conducted using a mobile payment device that includes a contactless element, such as an integrated circuit chip. The invention enables one or more of the operations of activation of a payment application, transfer of transaction data, updating of account records, setting or re-setting of a payment application counter or register, or transfer or processing of a script, command, or instruction, with these functions being performed with minimal impact on a consumer. This is accomplished by introducing a pre-tap and / or two-tap operation prior to, or as part of, the transaction flow.
Owner:VISA INT SERVICE ASSOC
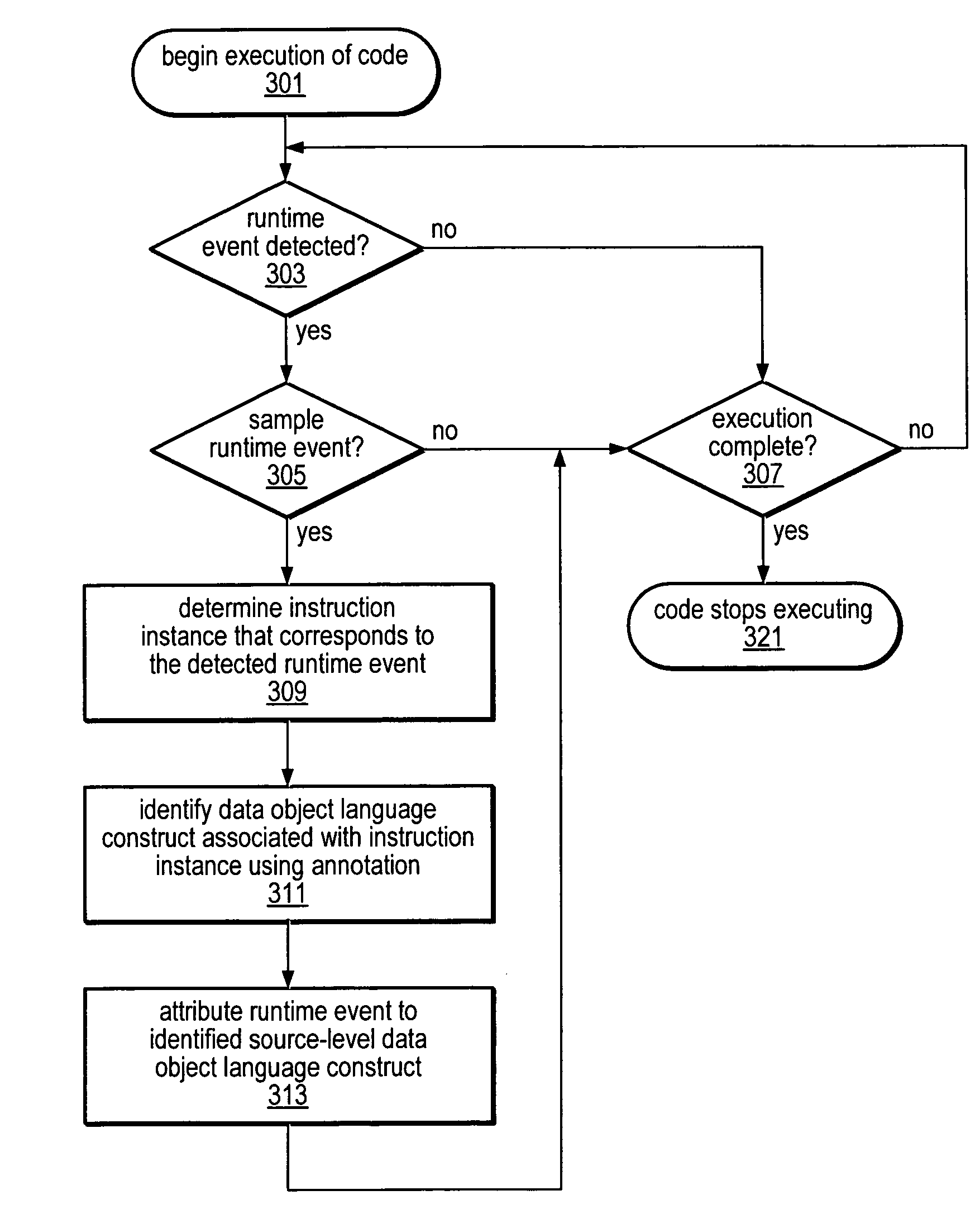
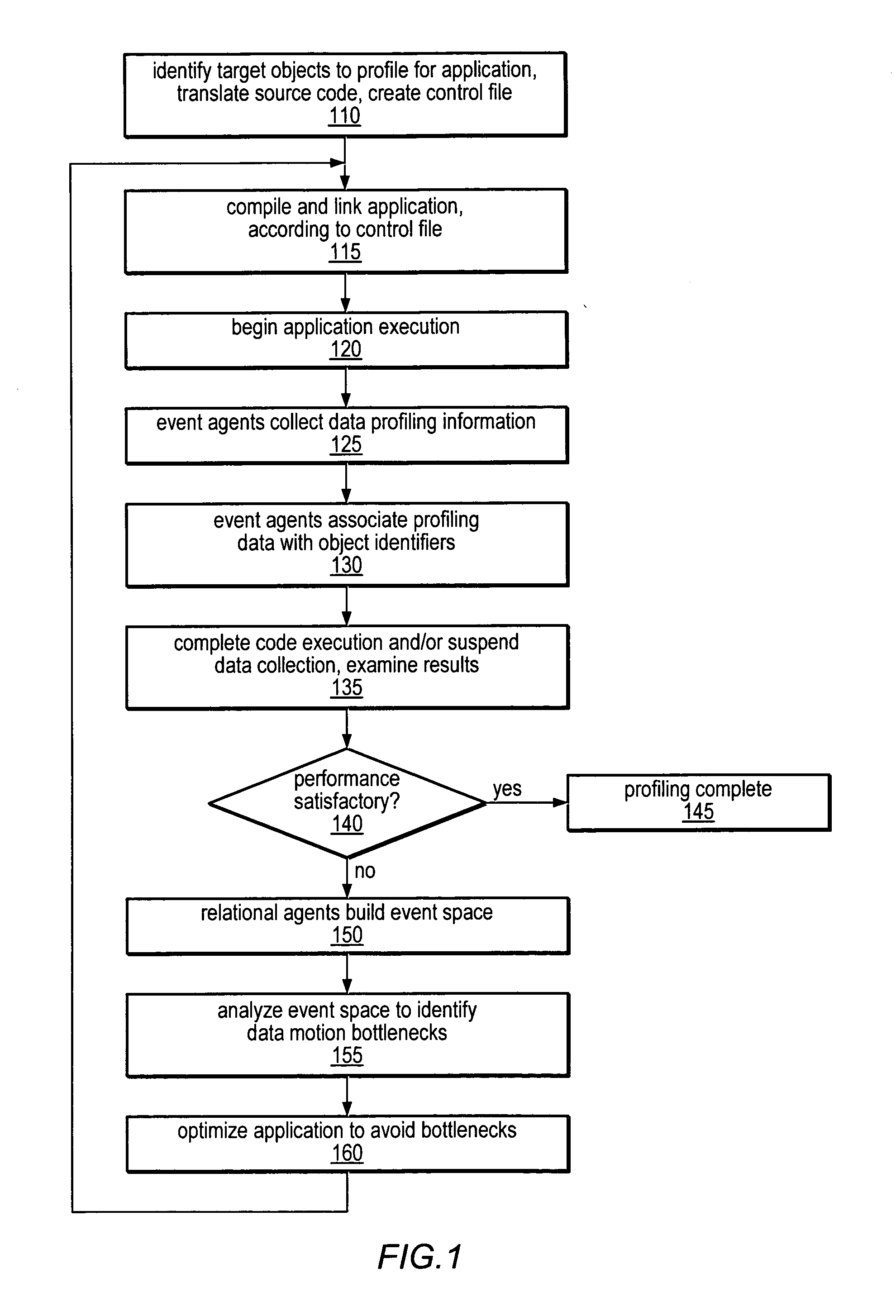
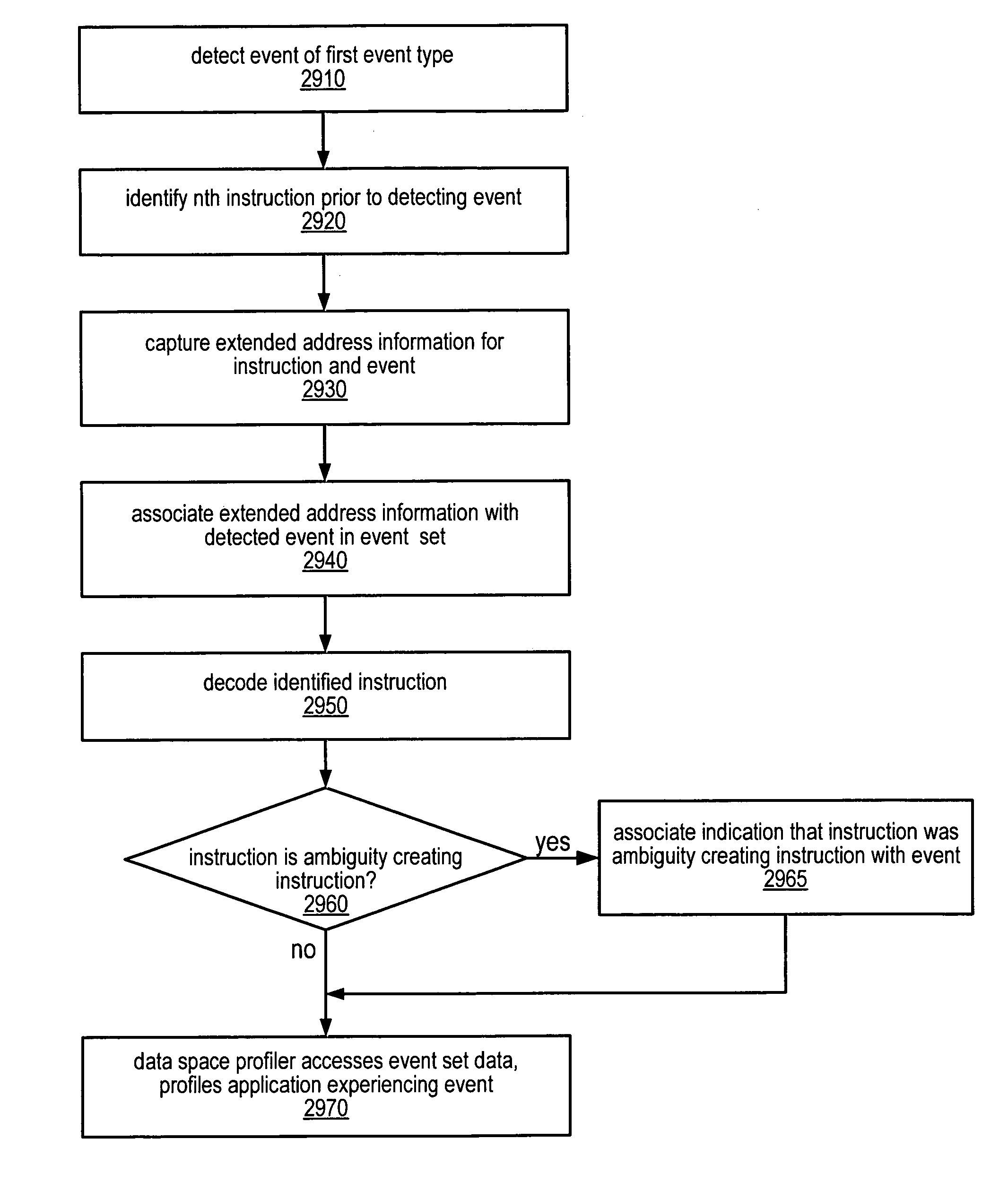
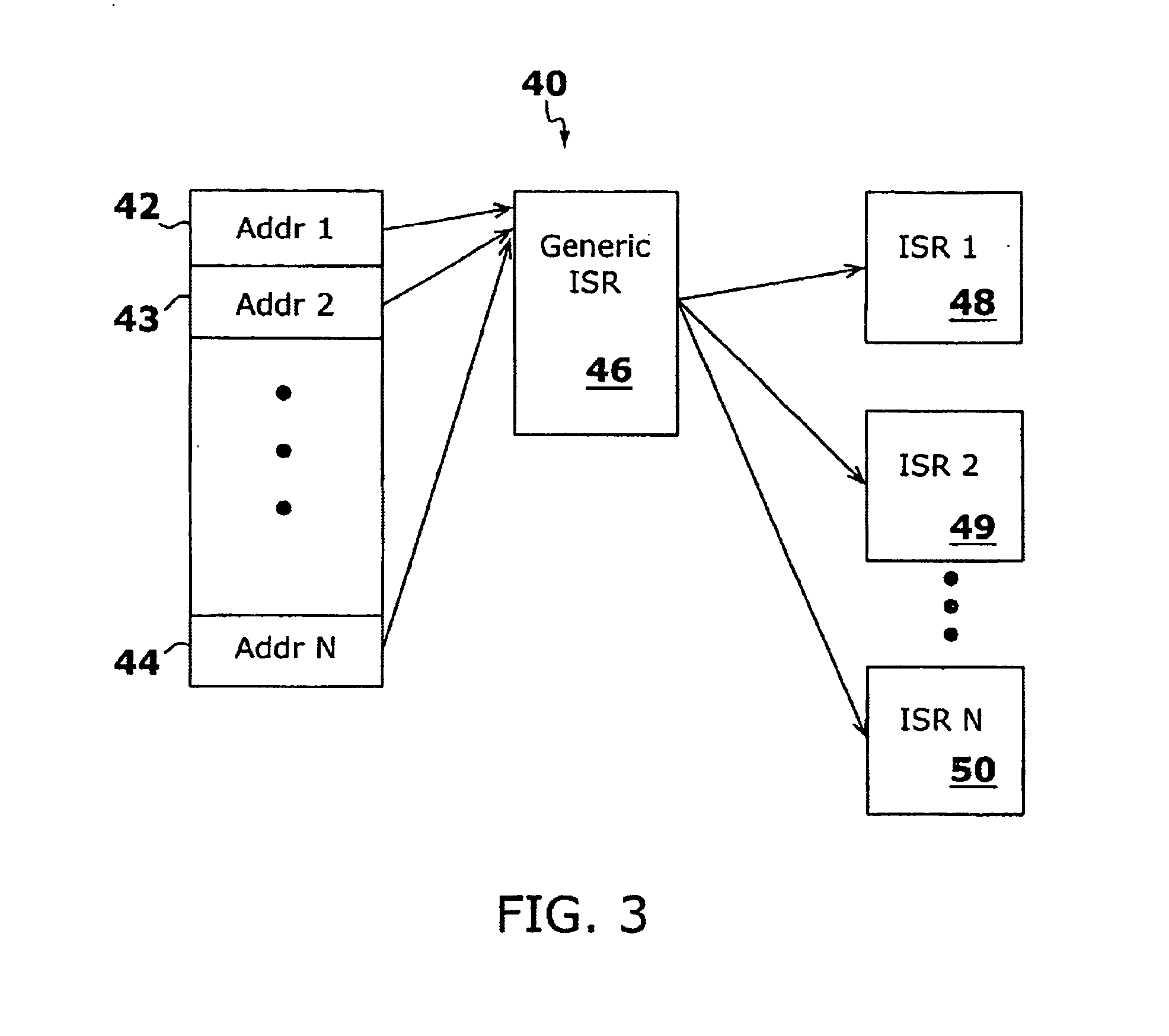
Method and apparatus for identifying instructions associated with execution events in a data space profiler
ActiveUS20080127120A1Error detection/correctionSpecific program execution arrangementsEvent typeData space
A system and method for profiling a software application may include means for capturing profiling information corresponding to an instruction identified as having executed coincident with the occurrence of a runtime event, and for associating the profiling information with the event in an event set. In some embodiments, the identified instruction, which may have triggered the event, may be located in the program code sequence at a predetermined position relative to the current program counter value at the time the event was detected. The predetermined relative position may be fixed dependent on the processor architecture and may also be dependent on the event type. The predetermined relative position may be zero, indicating that when the event was detected, the program counter value corresponded to an instruction associated with the event. If the identified instruction is an ambiguity-creating instruction, an indication of ambiguity may be associated with the event.
Owner:ORACLE INT CORP
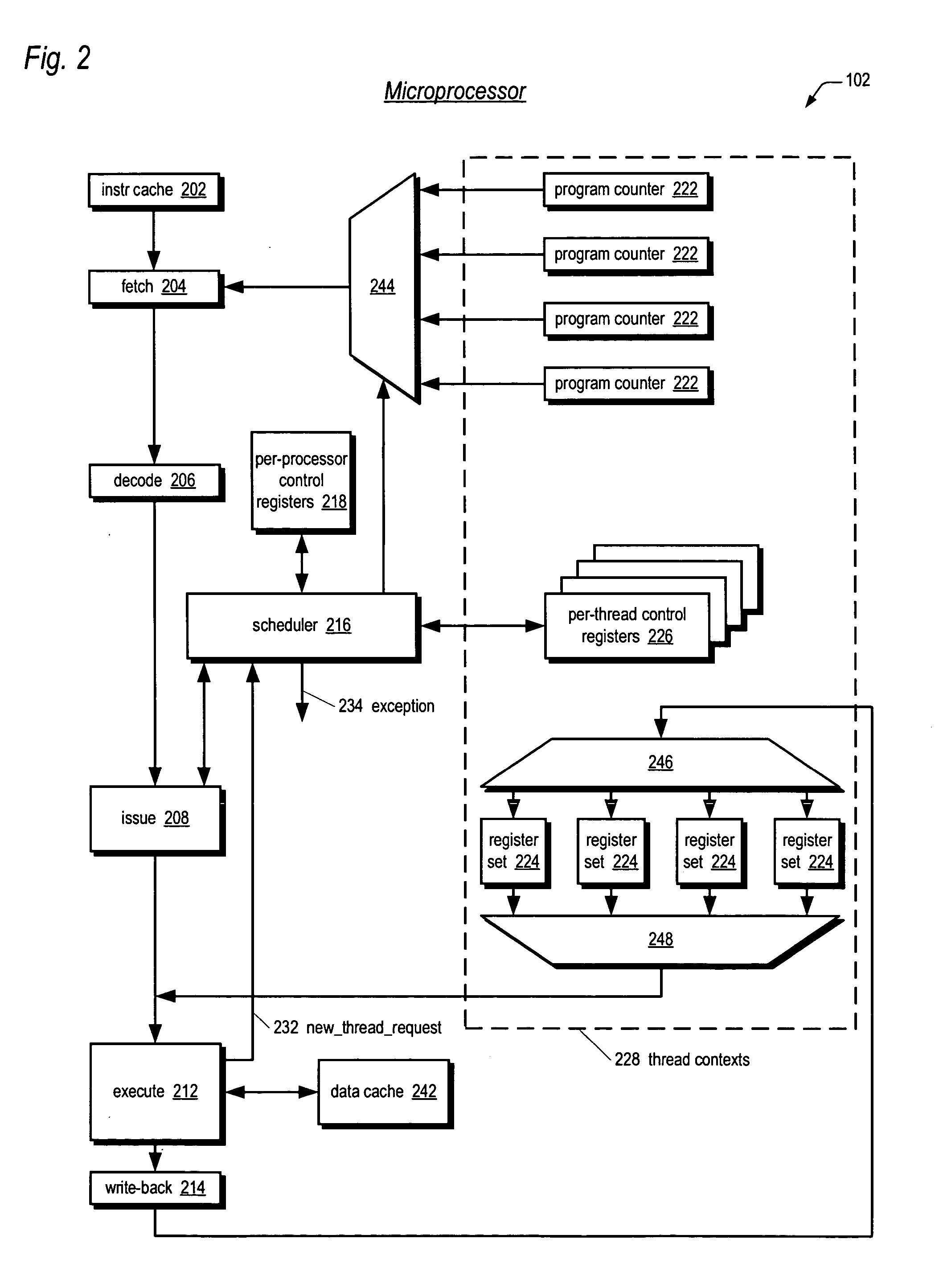
Software emulation of directed exceptions in a multithreading processor
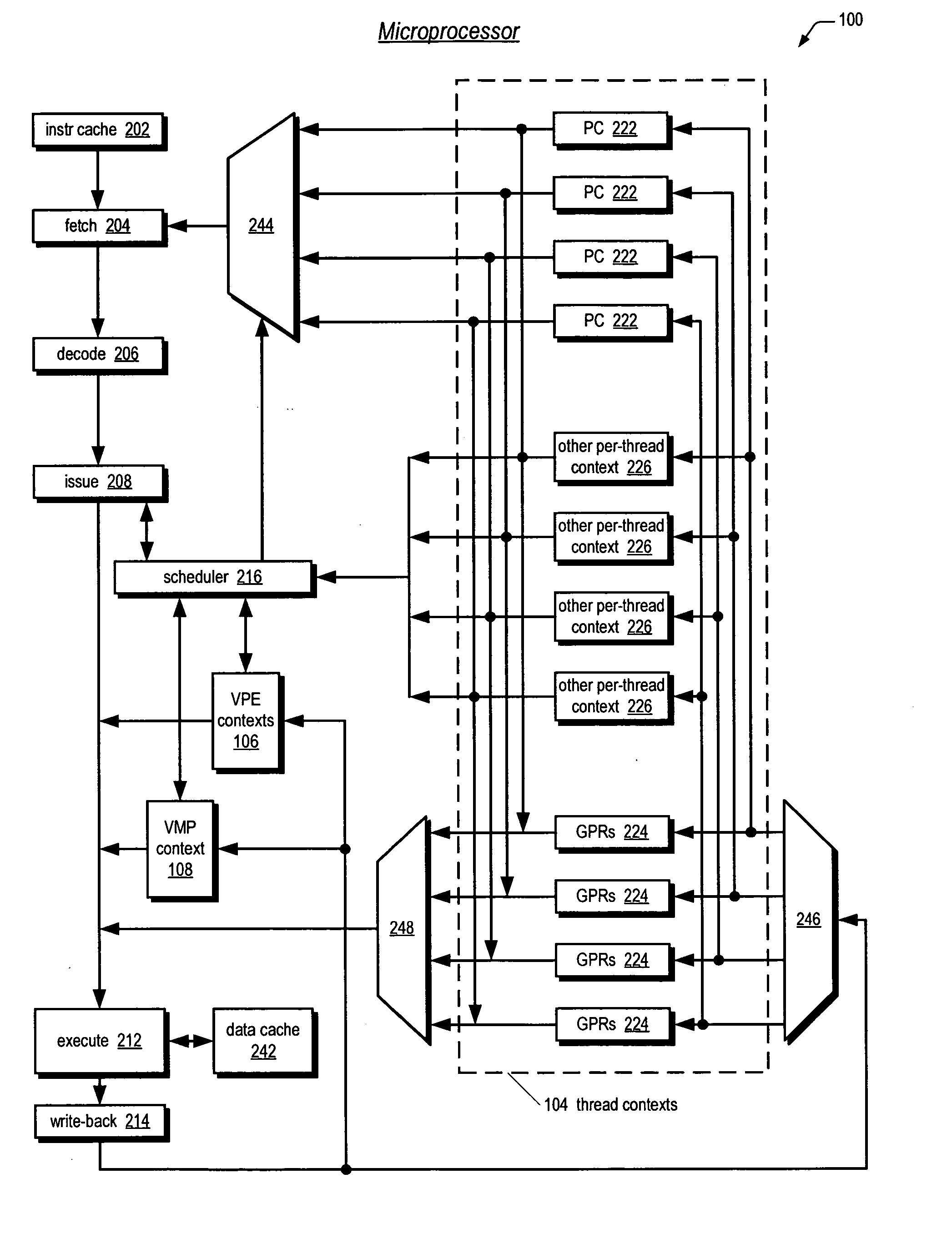
ActiveUS20060161421A1More scalableSave areaDigital computer detailsSoftware simulation/interpretation/emulationGeneral purposeSoftware emulation
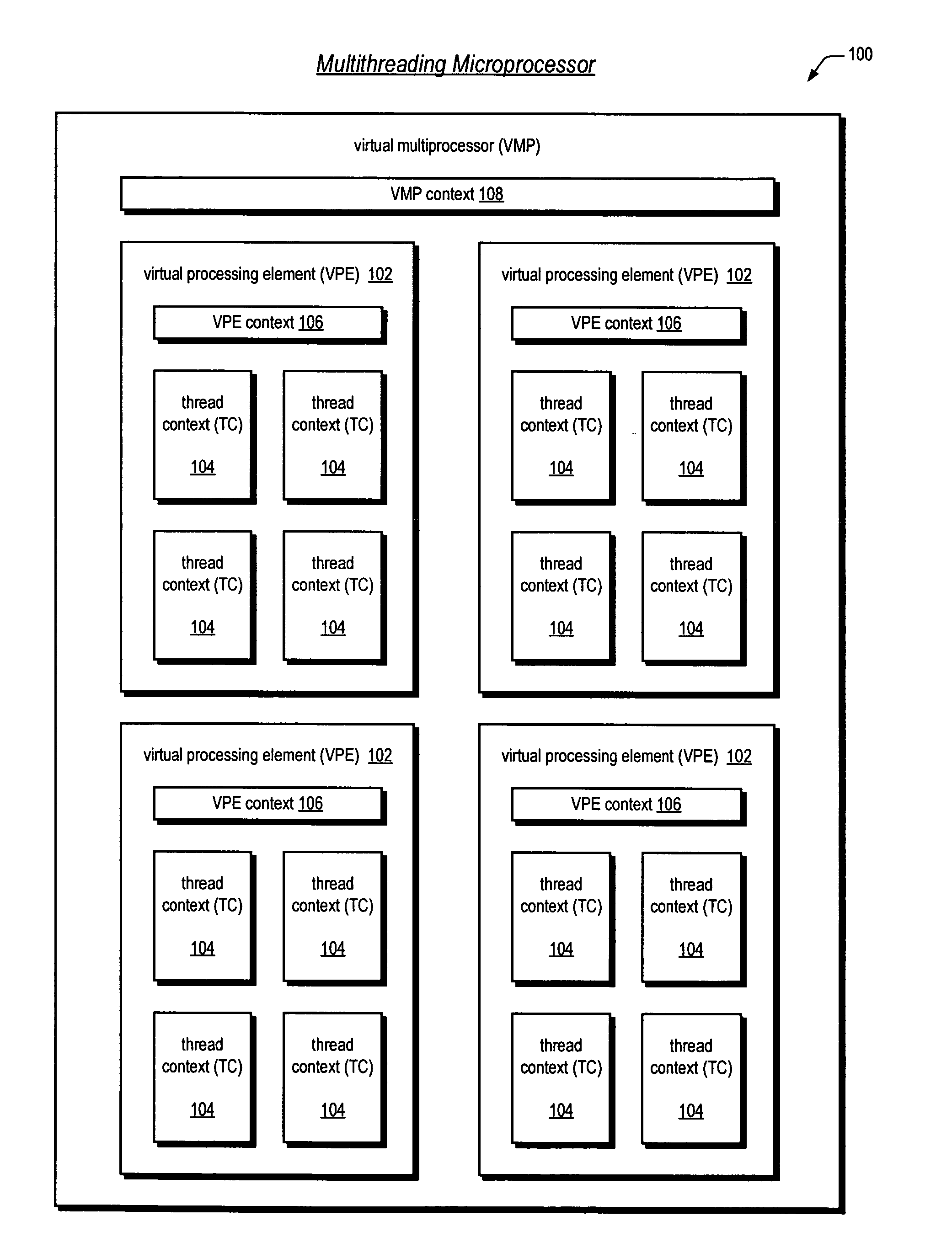
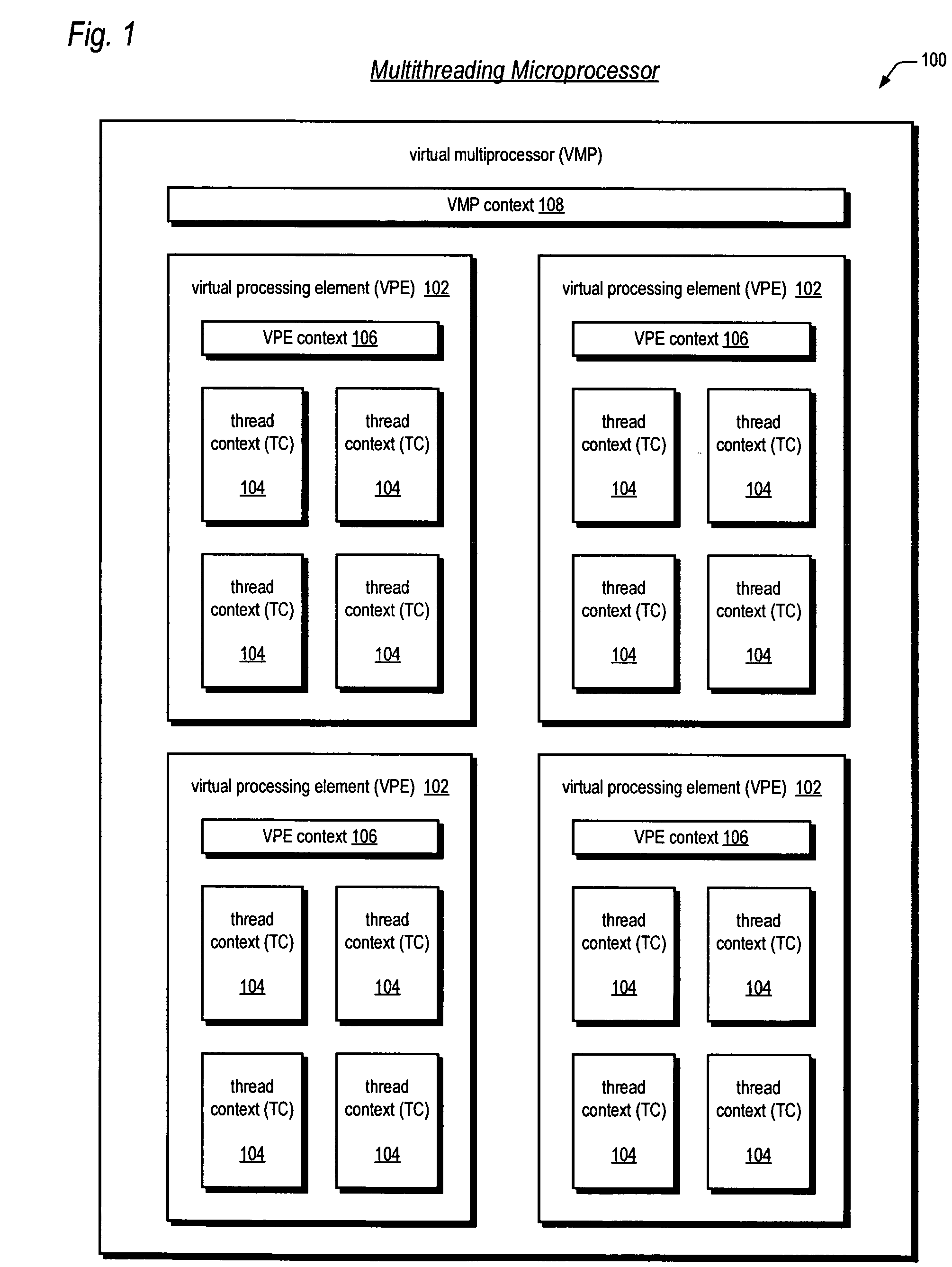
A multithreading microprocessor has a plurality of thread contexts (TCs) each including sufficient state, such as general purpose registers and program counter, to execute a separate thread of execution as one of a plurality of symmetric processors controlled by a multiprocessor operating system. However, the microprocessor hardware does not support the ability for one TC to direct an exception to another TC, i.e., to specify to which of the other TCs the exception is directed. A first thread running on a first TC of the operating system executes architected instructions to halt a second thread (either user or kernel thread) running on a second TC, save state of the second TC, write the second TC state to emulate an exception—including writing a restart register with the address of an exception handler, and unhalt the second TC to execute the exception hander.
Owner:MIPS TECH INC
Thread ending method and device and parallel processor system
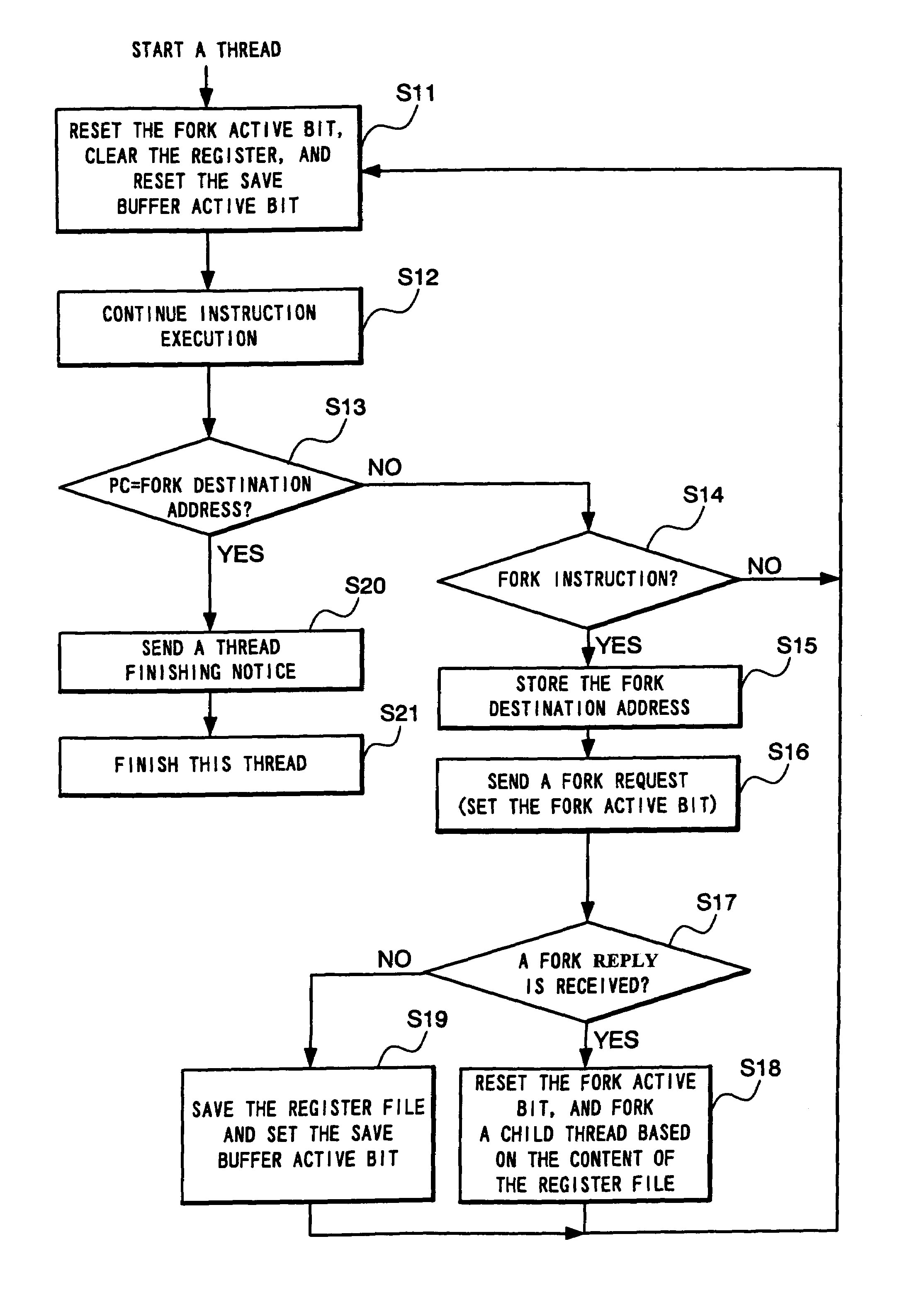
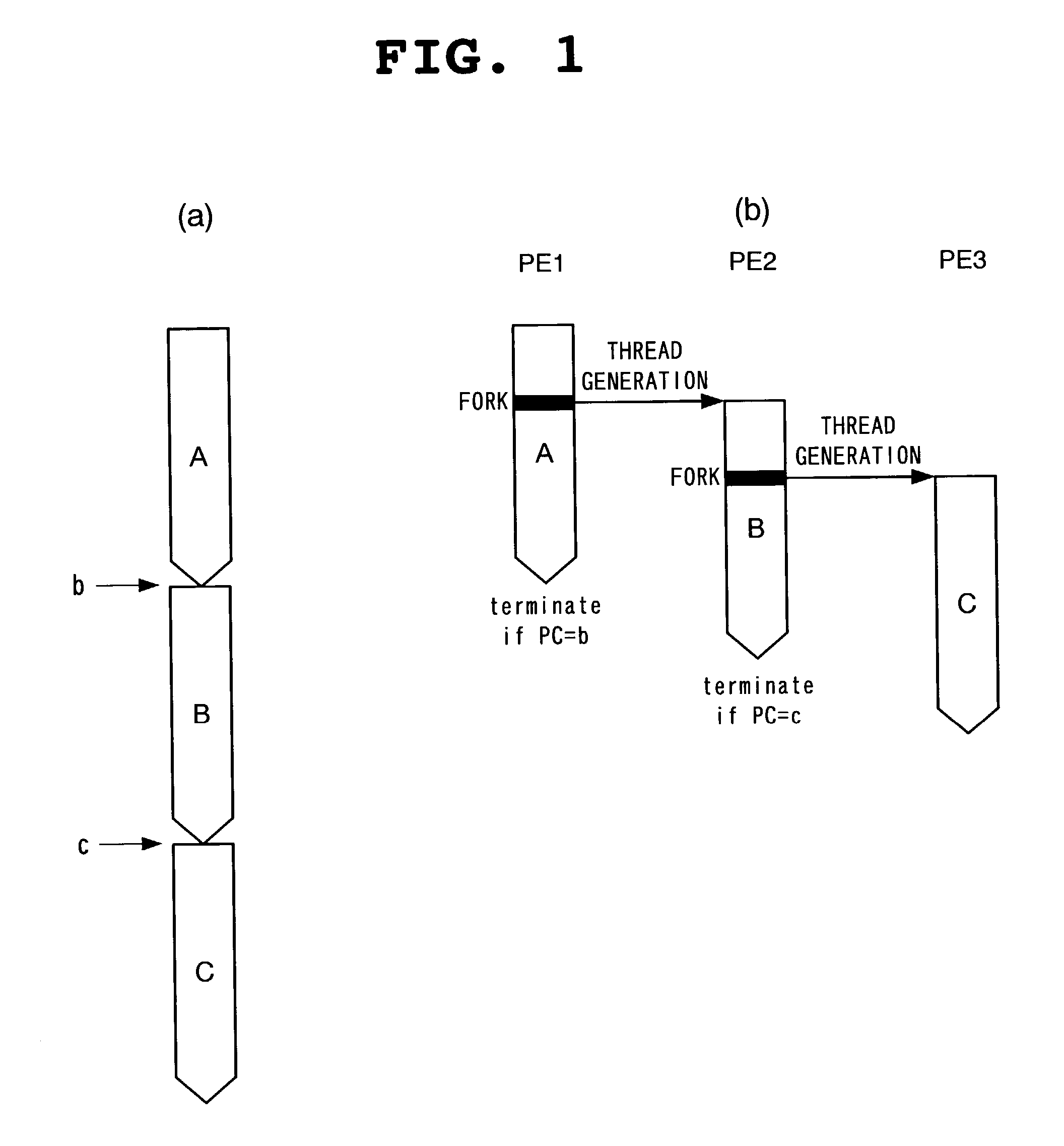
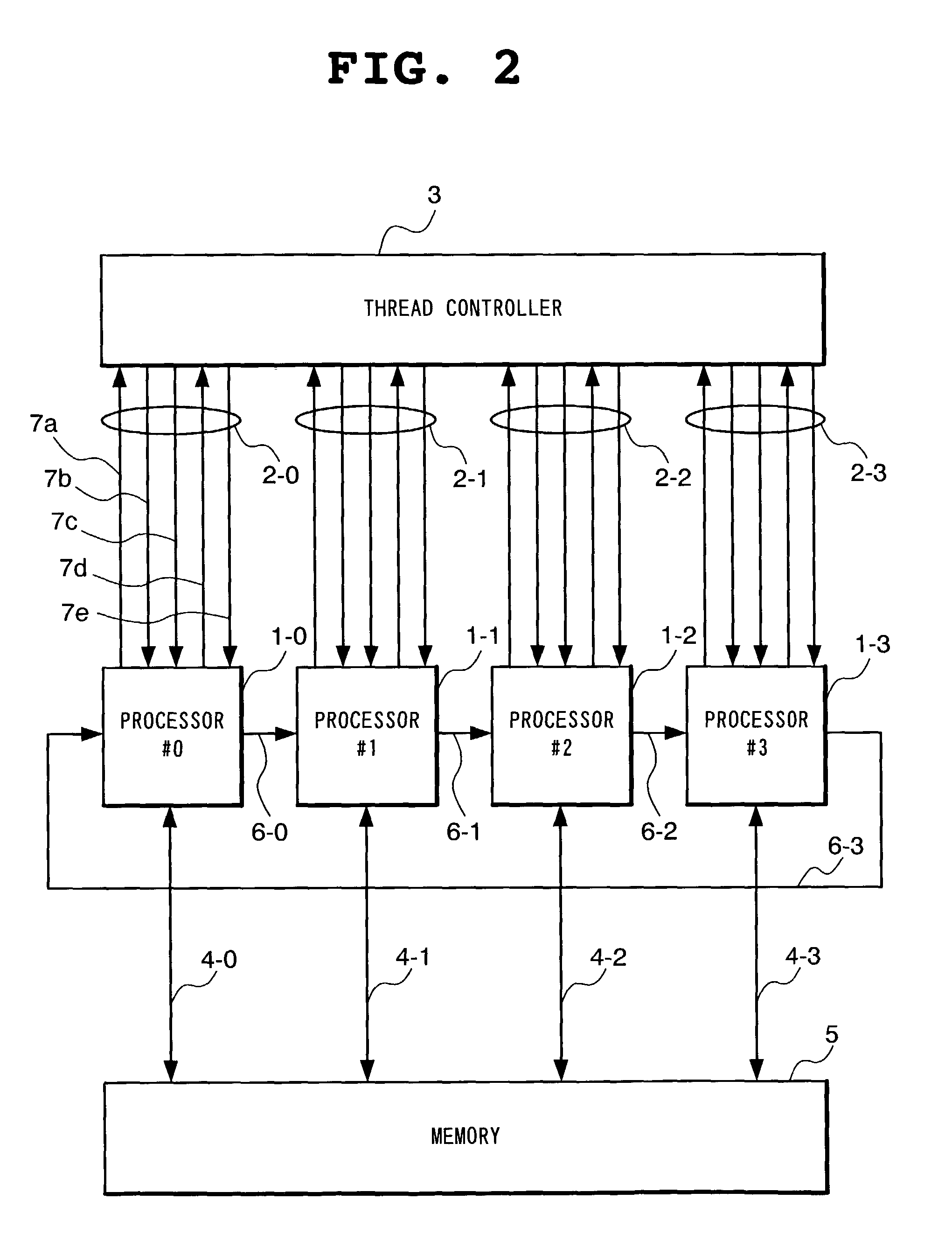
InactiveUS7134124B2Reduce instructionReduce the numberProgram initiation/switchingResource allocationProcessor registerProgram counter
Each processor comprises a register for storing start address of a forked child thread and a comparator for detecting that the value of its own program counter is coincident with the start address stored in this register. Each processor sends a thread stop notice to a thread controller when the value of its own program counter is coincident with the start address of the forked child thread and ends the execution of a parent thread when receiving a thread end permission from the thread controller.
Owner:NEC CORP
Symmetric multiprocessor operating system for execution on non-independent lightweight thread contexts
InactiveUS20060195683A1Lightweight in of areaLightweight in of powerEnergy efficient ICTDigital computer detailsGeneral purposeUser Privilege
A multiprocessing system is disclosed. The system includes a multithreading microprocessor including a plurality of thread contexts (TCs), each having a program counter and a general purpose register set for executing a thread. The microprocessor also includes a shared privileged resource, shared by the plurality of TCs rather than being replicated for each of the plurality of TCs, and privileged to be managed only by operating system-privileged threads rather than by user-privileged threads. The system also includes a multiprocessor operating system (OS), configured to manage the shared privileged resource, and to schedule execution of both the operating system-privileged threads and the user-privileged threads on the plurality of TCs.
Owner:MIPS TECH INC
Trace control from hardware and software
InactiveUS7185234B1Error detection/correctionSpecific program execution arrangementsVisibilityProgram counter
A system and method for program counter and data tracing is disclosed. The tracing mechanism of the present invention enables increased visibility into the hardware and software state of the processor core.
Owner:ARM FINANCE OVERSEAS LTD
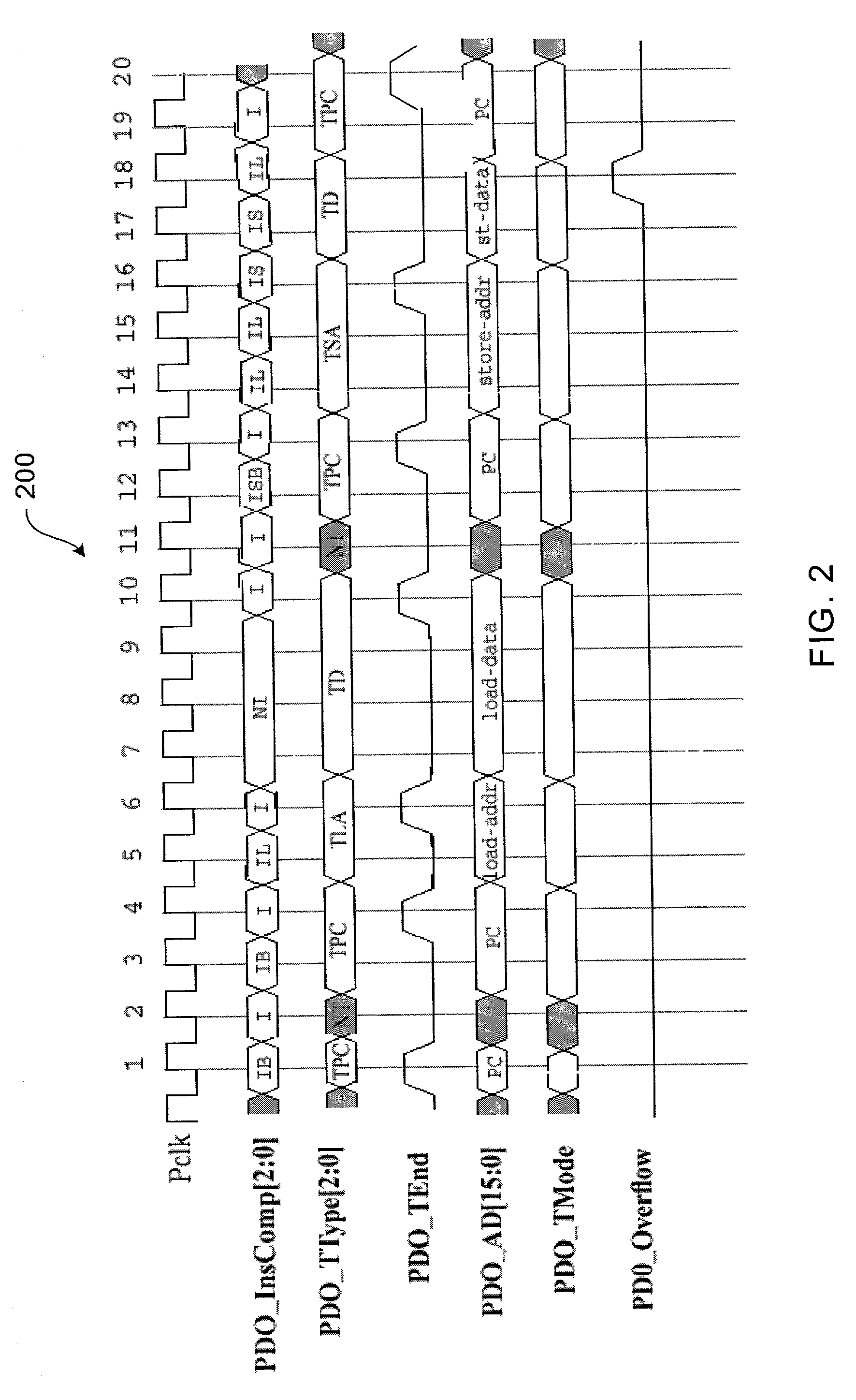
Optimized external trace formats
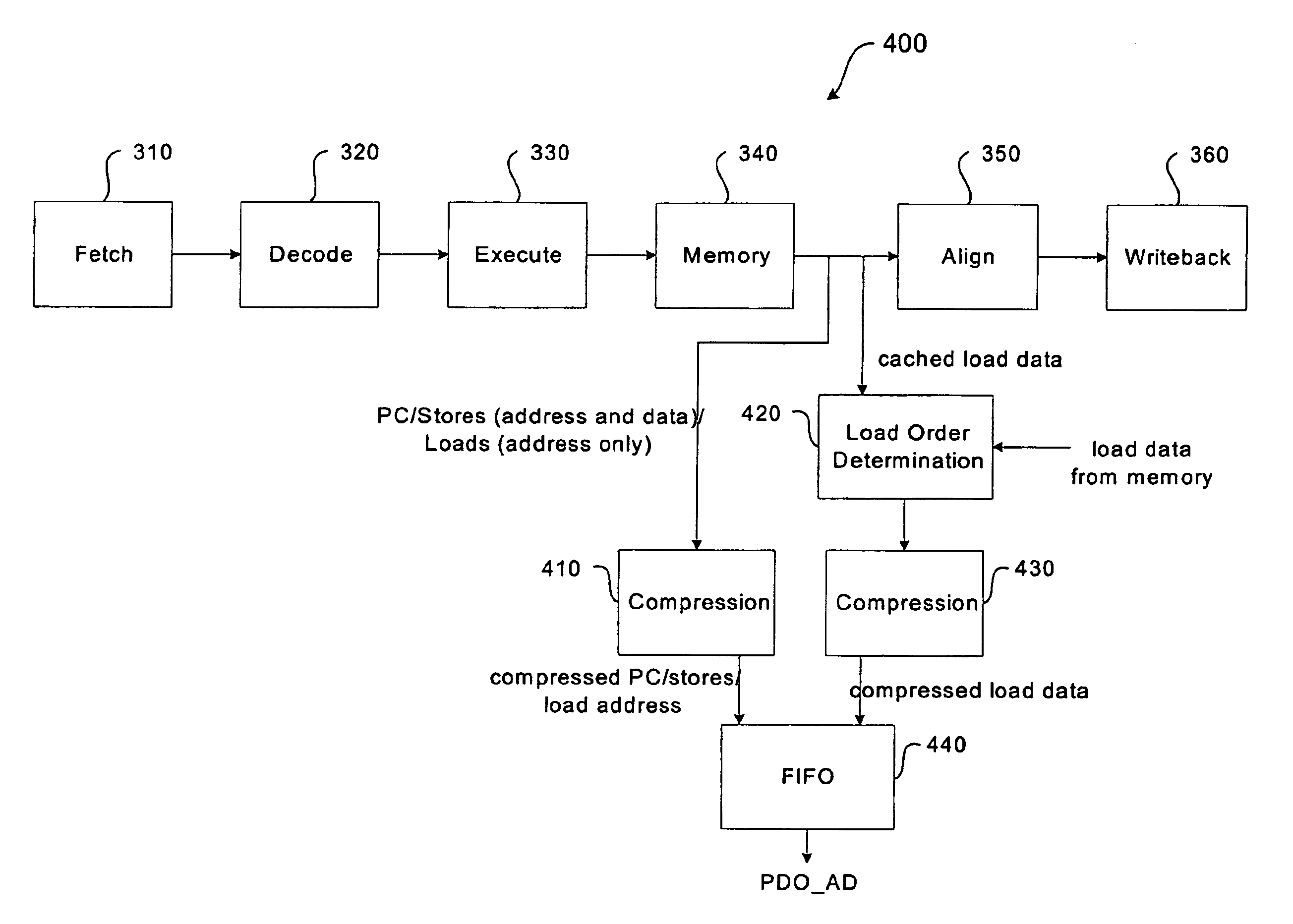
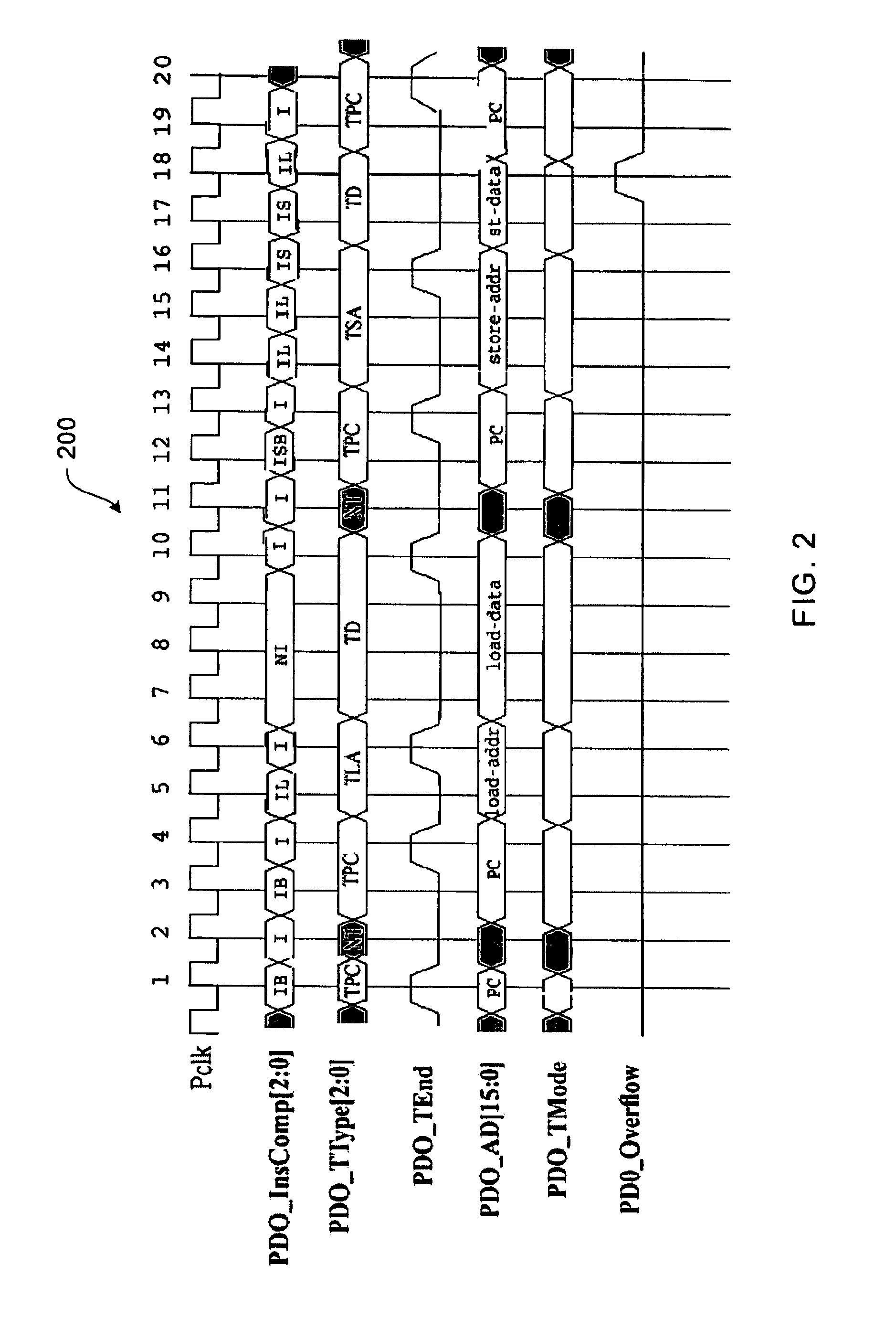
A system and method for program counter and data tracing is disclosed. Generated trace messages are included within a trace word format and stored in trace memory, thereby enabling a reduction in the amount of trace storage required.
Owner:ARM FINANCE OVERSEAS LTD
Method and apparatus for identifying instructions associated with execution events in a data space profiler
ActiveUS8176475B2Error detection/correctionSpecific program execution arrangementsProgram counterComputer science
Owner:ORACLE INT CORP
System, method and apparatus of securing an operating system
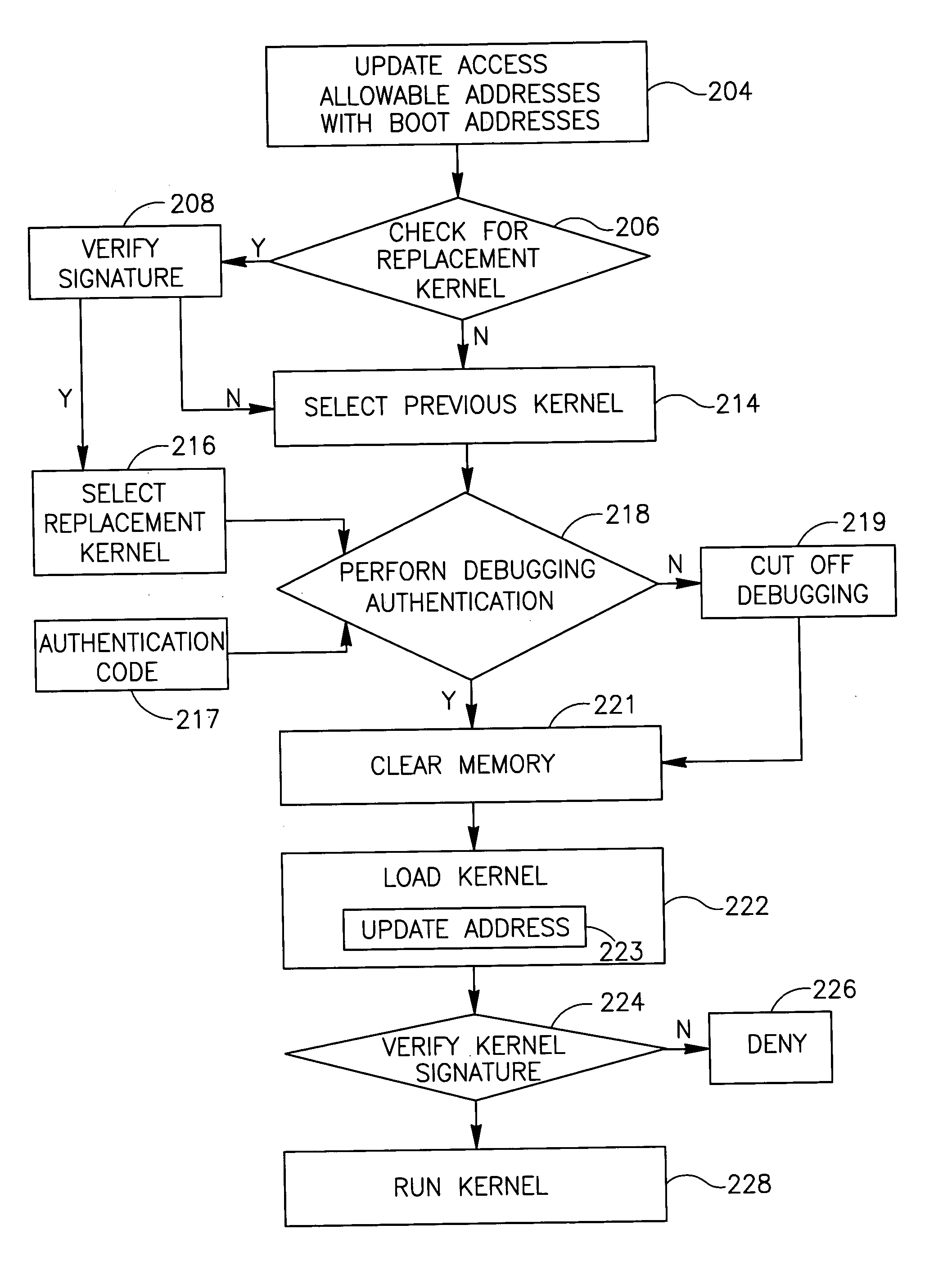
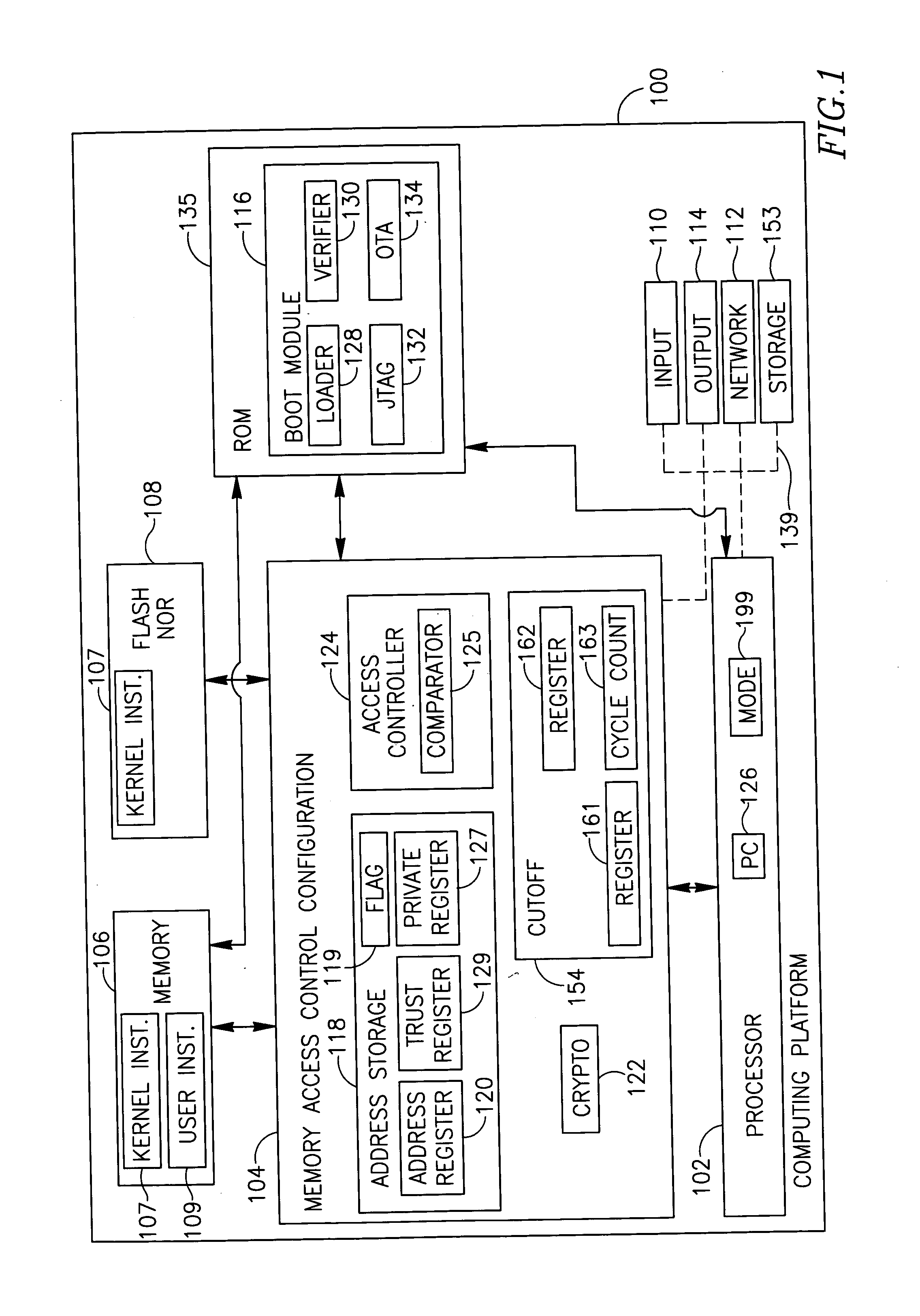
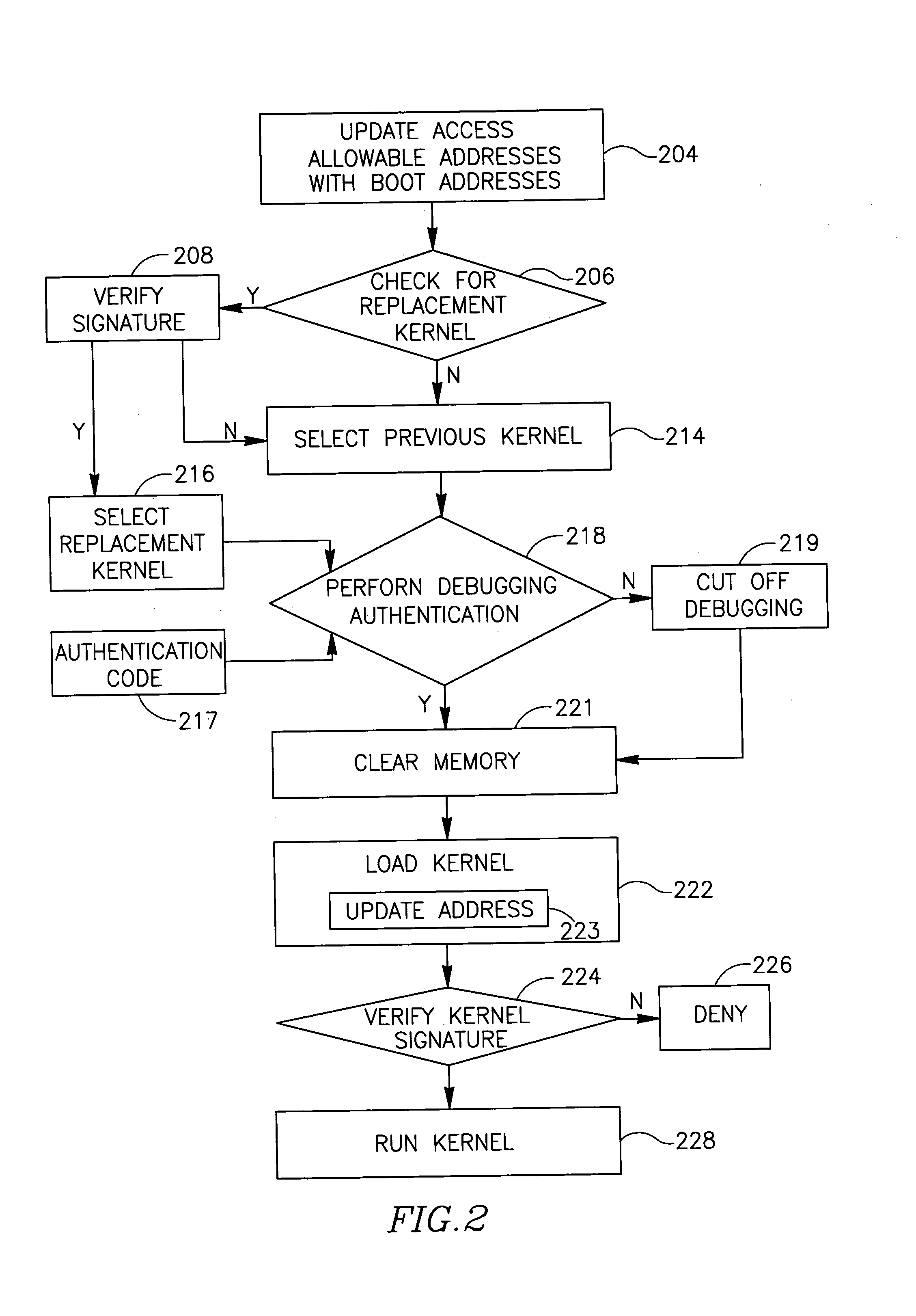
InactiveUS20060112241A1Digital computer detailsInternal/peripheral component protectionOperational systemProgram counter
Embodiments of the present invention provide a method, apparatus and system of securing an operating system. The apparatus, according to some demonstrative embodiments of the invention, may include a memory access controller to receive from a processor a program counter representing a requested address of a memory to be accessed by the processor during a kernel mode of operation, and to selectively enable the processor to access the requested address based on a comparison between the requested address and one or more allowable addresses. Other embodiments are described and claimed.
Owner:DISCRETIX TECH
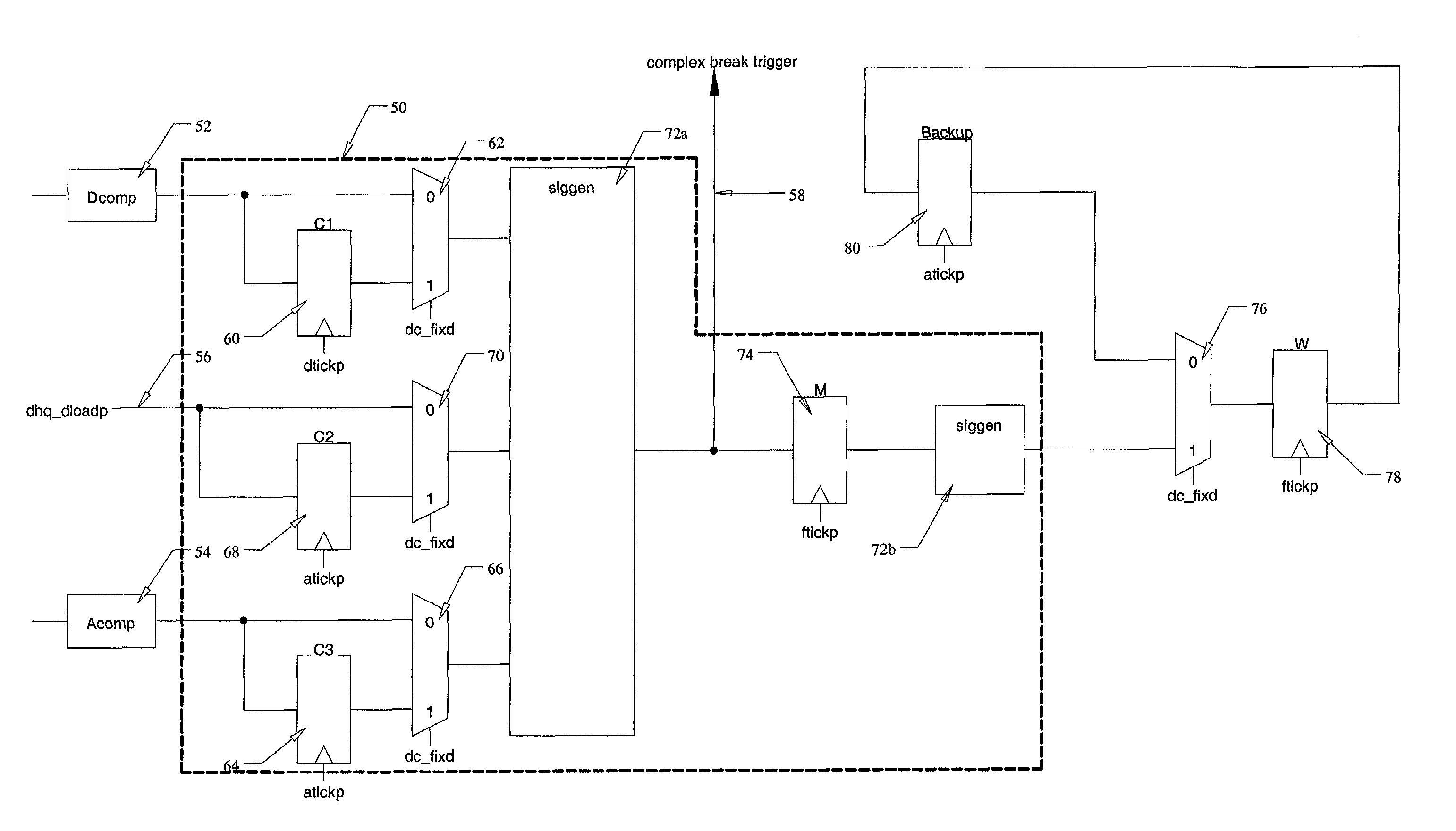
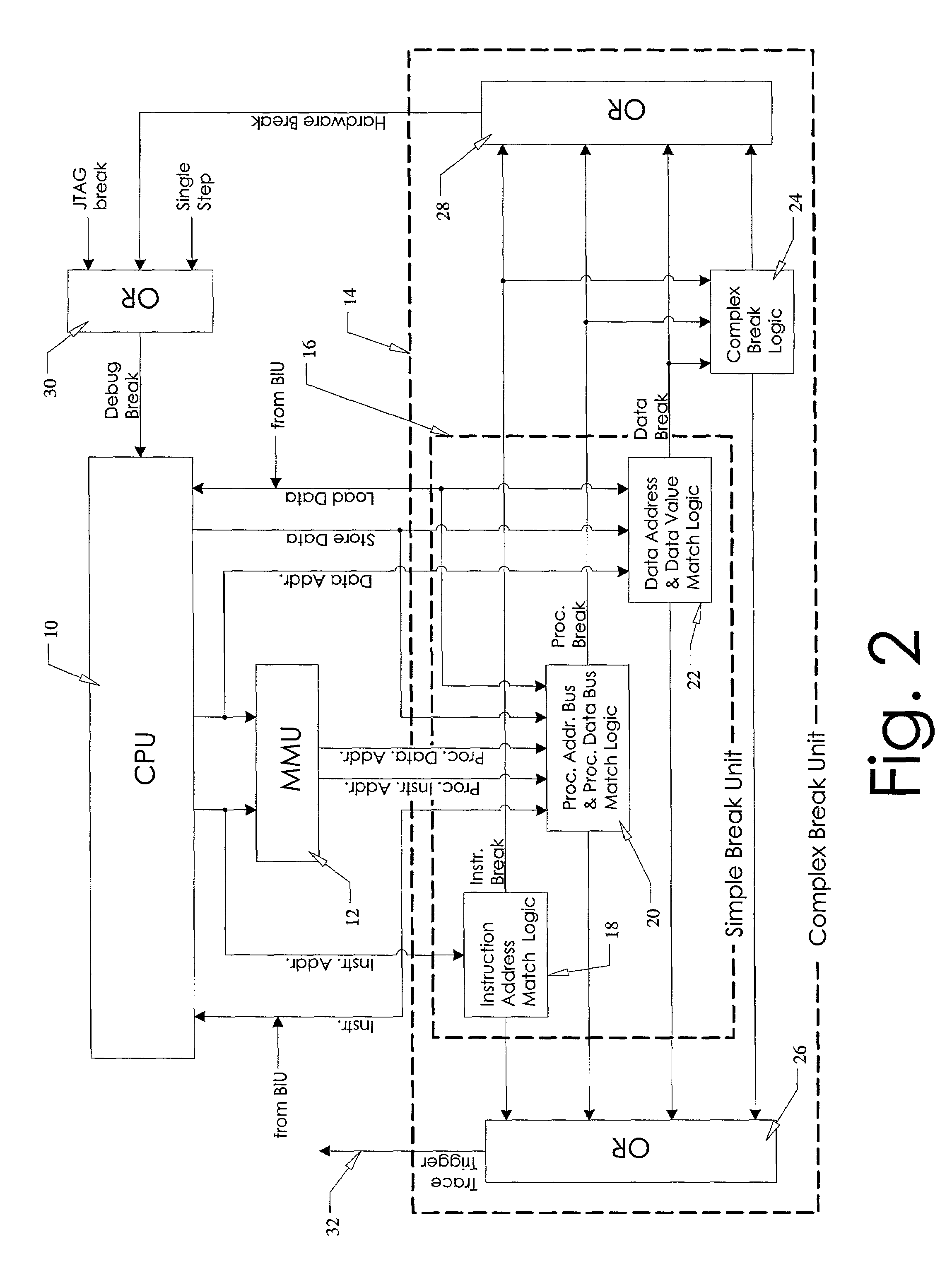
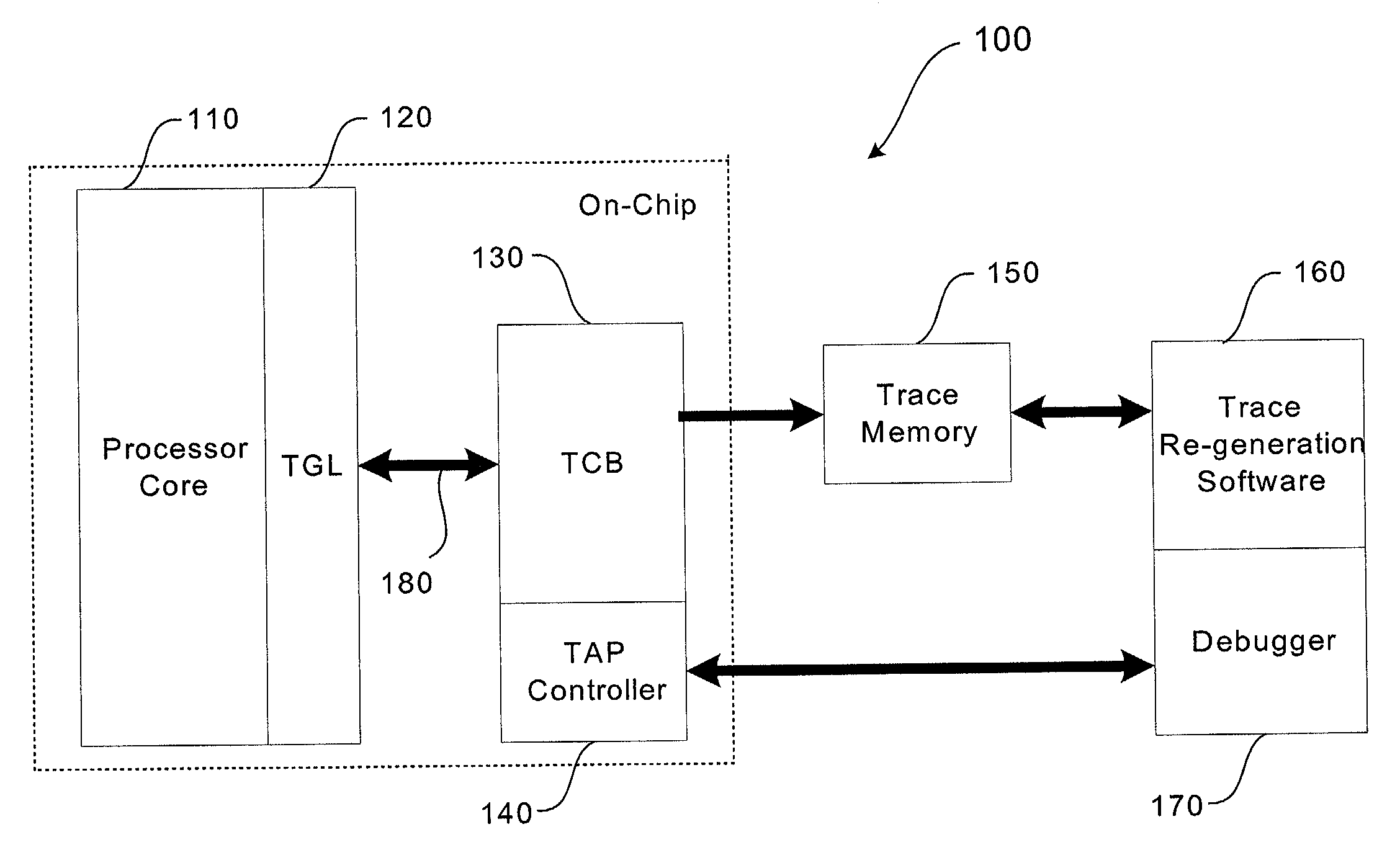
System and method for state restoration in a diagnostic module for a high-speed microprocessor
InactiveUS7043416B1Data processing applicationsAnalogue computers for electric apparatusProgram counterComputer science
A system and method are presented for saving and restoring the state of a diagnostic module in a microprocessor. The diagnostic module contains a complex break state machine, capable of halting the microprocessor at specified breakpoints. These breakpoints are based on combinations of instruction locations and / or data values, along with previous machine states. A problem occurs with prior art diagnostic modules when the processor returns from an exception occurring during a fix-up cycle inserted to handle a data load miss associated with an instruction located in a branch delay slot (the location immediately following a conditional branch instruction). Under these circumstances, the exception handler restores the program counter to the location of the branch instruction, causing the branch to be re-executed. The prior art state machine erroneously updates its internal state a second time when the branch is re-executed. According to the system and method disclosed herein, at each state change the previous machine state saved. Thus, when a branch instruction is re-executed, the complex break state machine of the present invention is restored to its previous state, thereby correcting the error.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Tree-based thread management
ActiveUS20150205607A1Increase speedAvoid bad consequencesDigital computer detailsSpecific program execution arrangementsMulti processorParallel computing
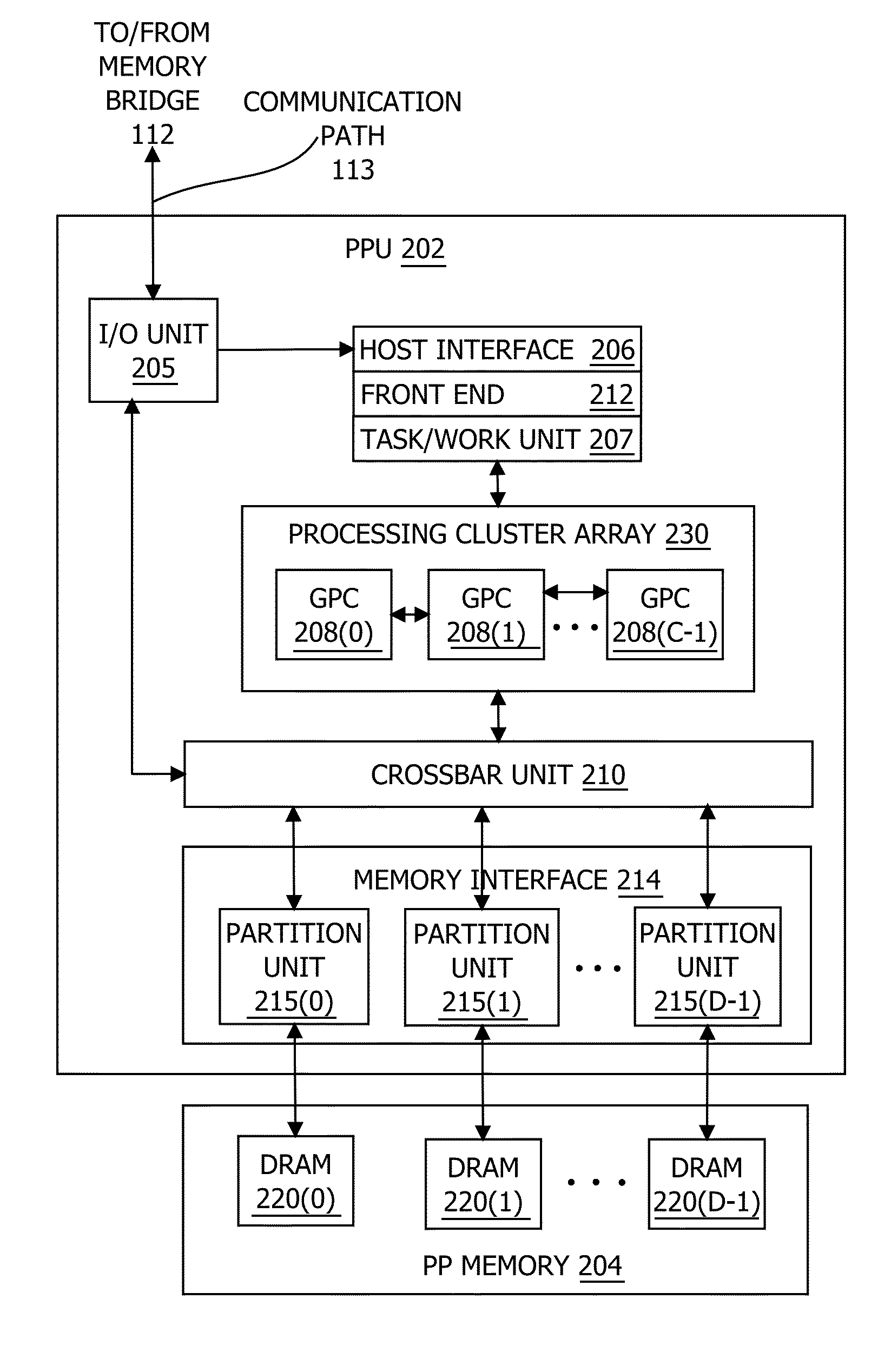
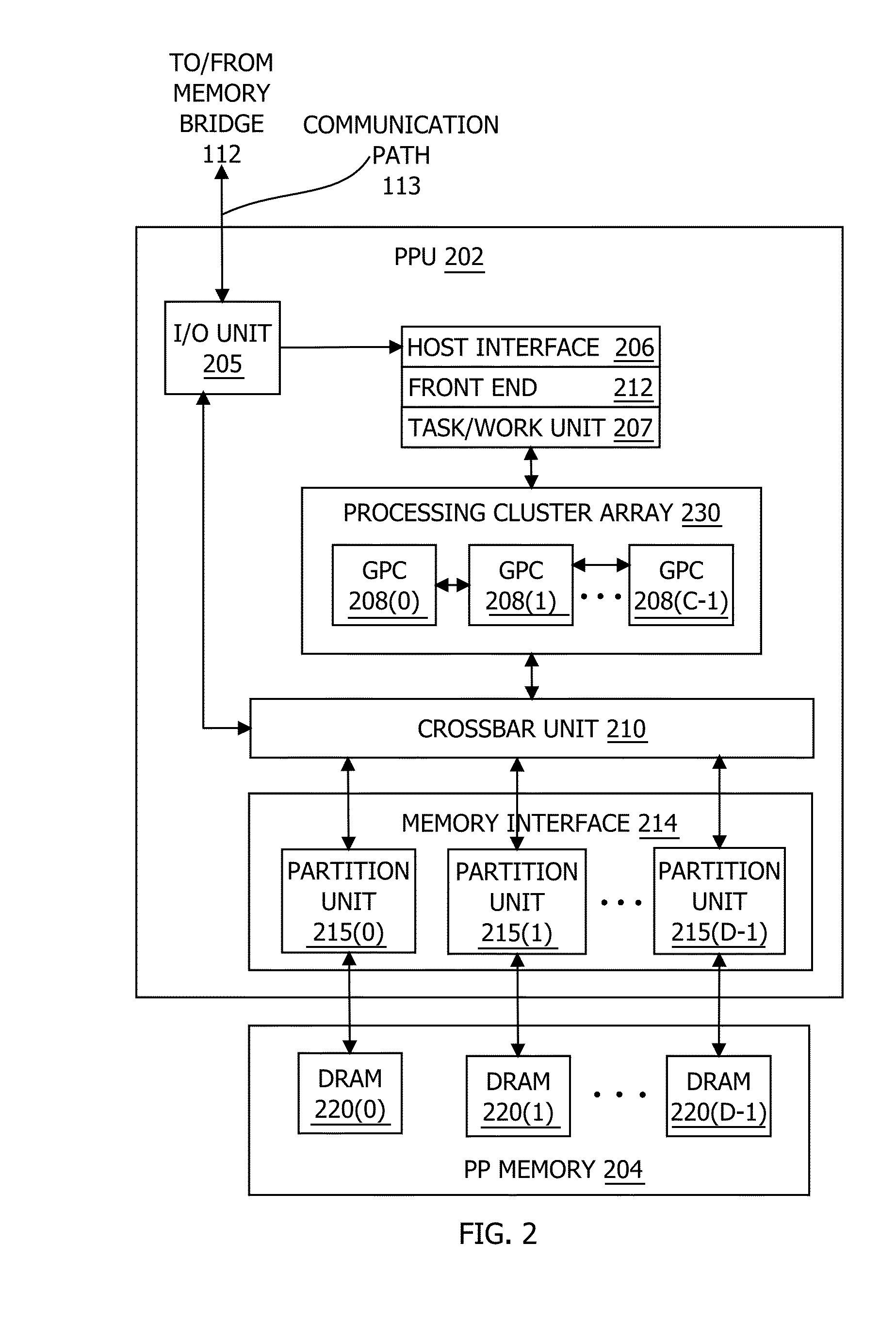
In one embodiment of the present invention, a streaming multiprocessor (SM) uses a tree of nodes to manage threads. Each node specifies a set of active threads and a program counter. Upon encountering a conditional instruction that causes an execution path to diverge, the SM creates child nodes corresponding to each of the divergent execution paths. Based on the conditional instruction, the SM assigns each active thread included in the parent node to at most one child node, and the SM temporarily discontinues executing instructions specified by the parent node. Instead, the SM concurrently executes instructions specified by the child nodes. After all the divergent paths reconverge to the parent path, the SM resumes executing instructions specified by the parent node. Advantageously, the disclosed techniques enable the SM to execute divergent paths in parallel, thereby reducing undesirable program behavior associated with conventional techniques that serialize divergent paths across thread groups.
Owner:NVIDIA CORP
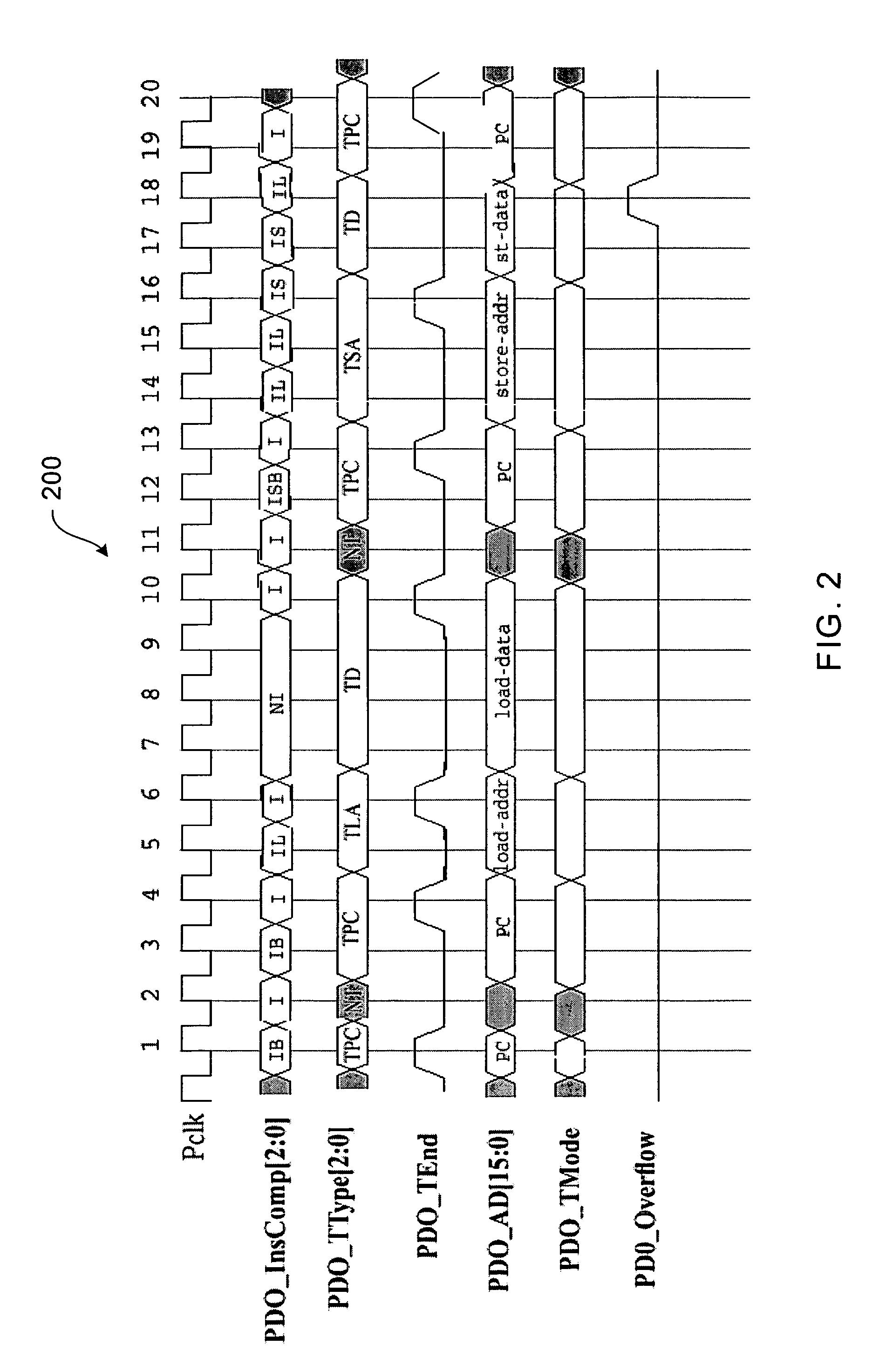
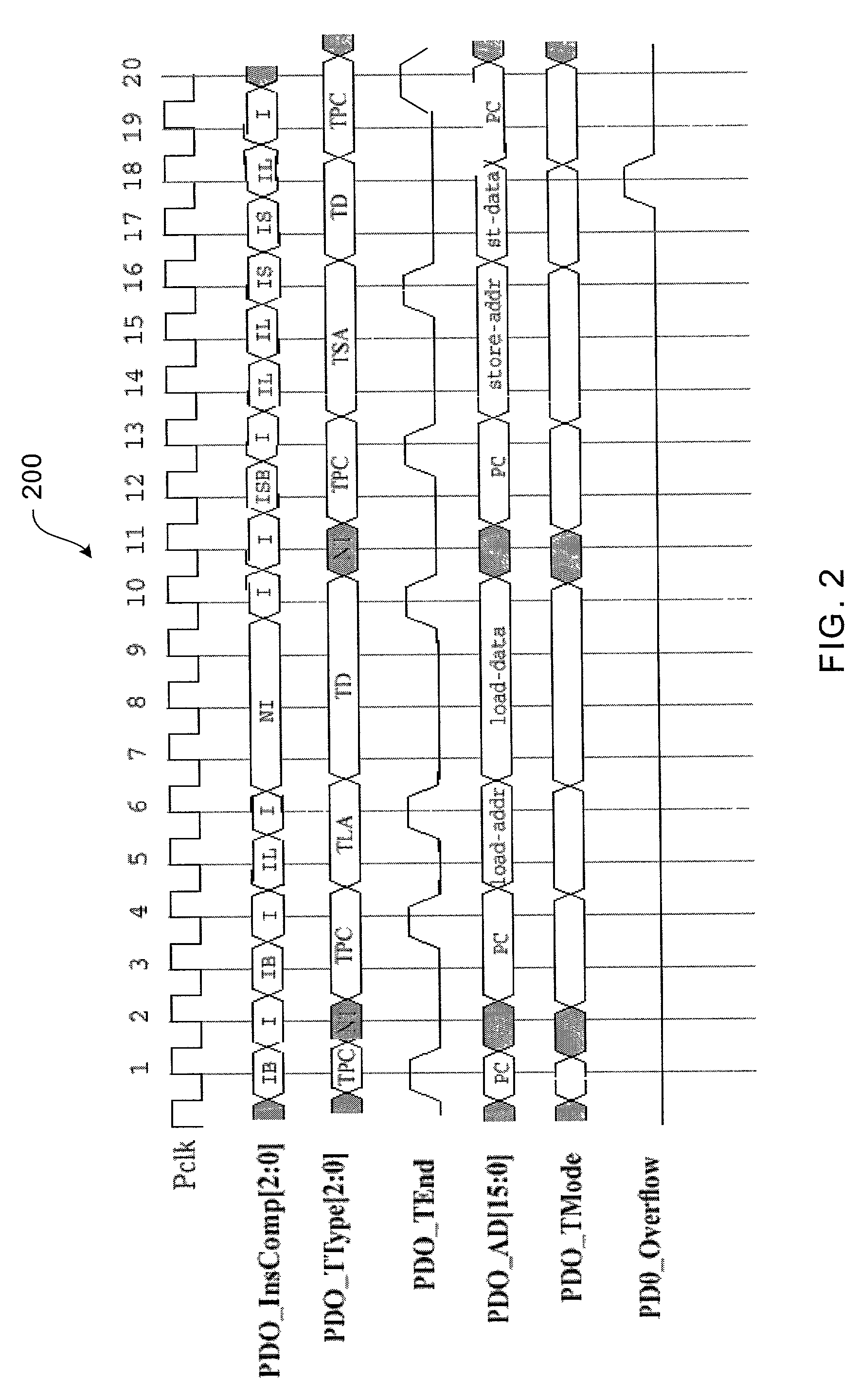
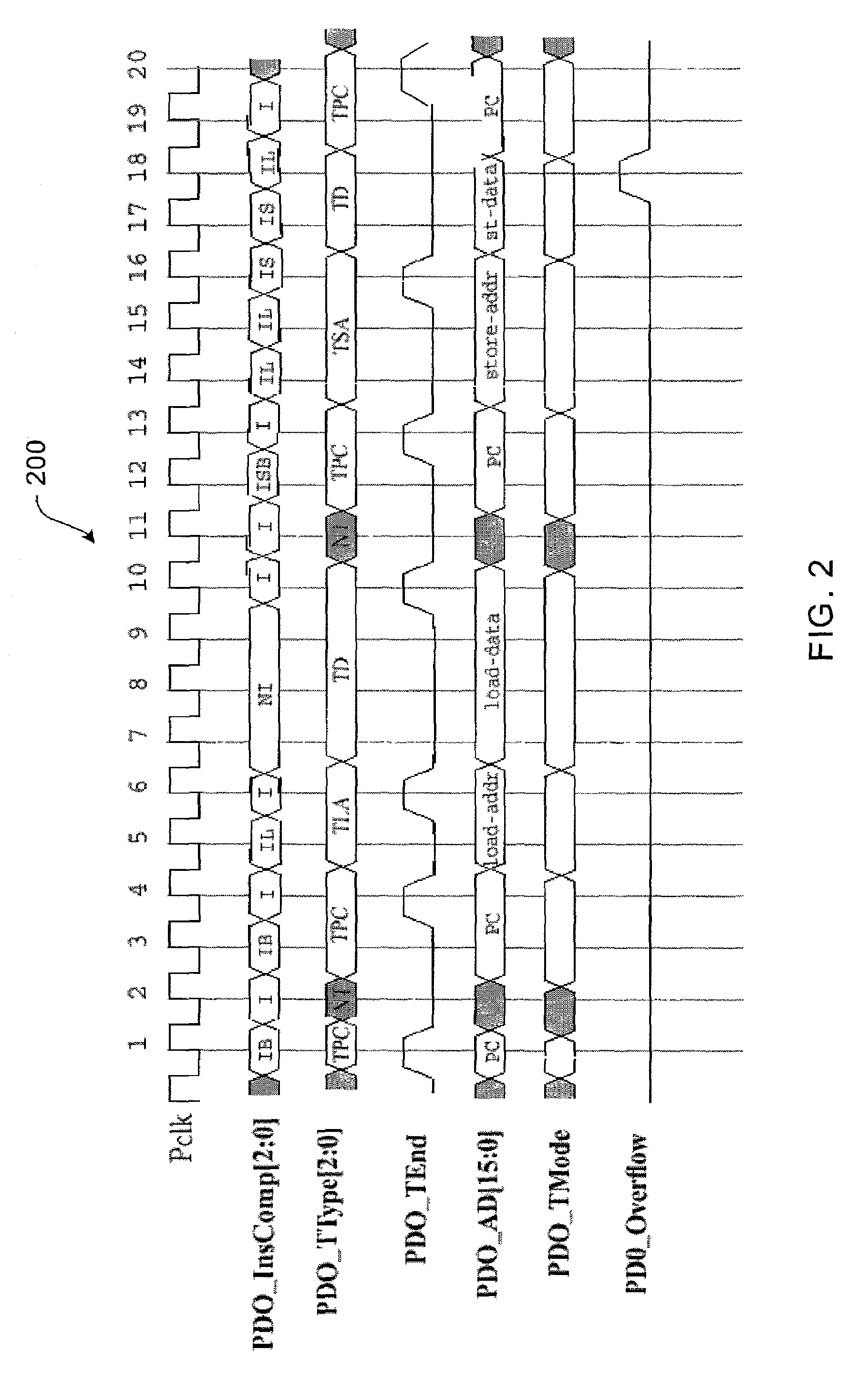
Program Counter (PC) Trace
In one embodiment, an integrated circuit comprises a first processor configured to output program counter (PC) trace records, wherein PC trace records provide data indicating the PCs of instructions retired by the first processor. The integrated circuit further comprises a second source of trace records, and a trace unit coupled to receive the PC trace records from the first processor and the trace records from the second source. The trace unit comprises a trace memory into which the trace unit is configured to store the PC trace records and trace records from the second source. The trace unit is configured to interleave the PC trace records and the trace records from the second source in the trace memory according to the order of receipt of the records.
Owner:APPLE INC
Trace control based on a characteristic of a processor's operating state
A system and method for program counter and data tracing is disclosed. The tracing mechanism of the present invention enables increased visibility into the hardware and software state of the processor core.
Owner:ARM FINANCE OVERSEAS LTD
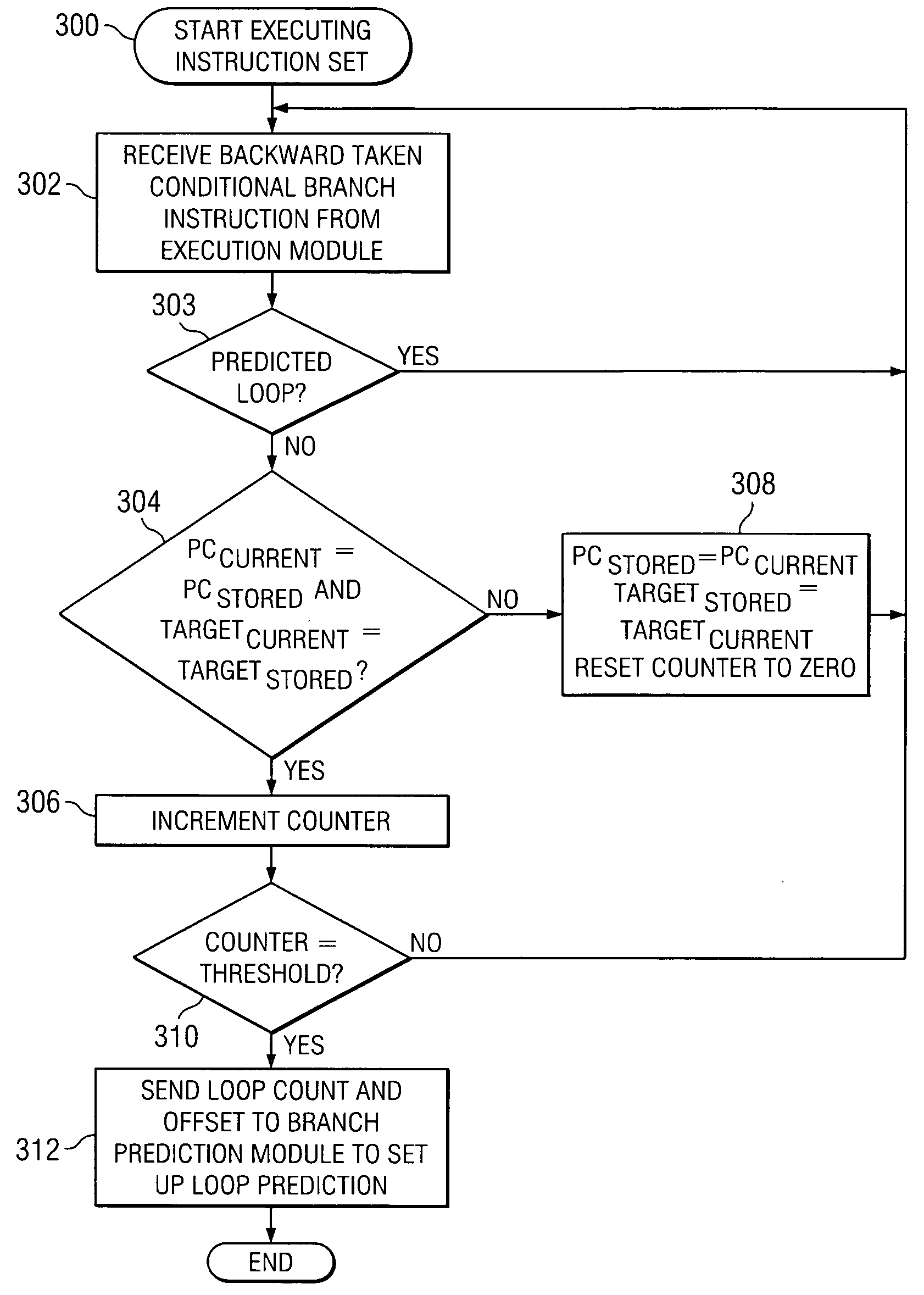
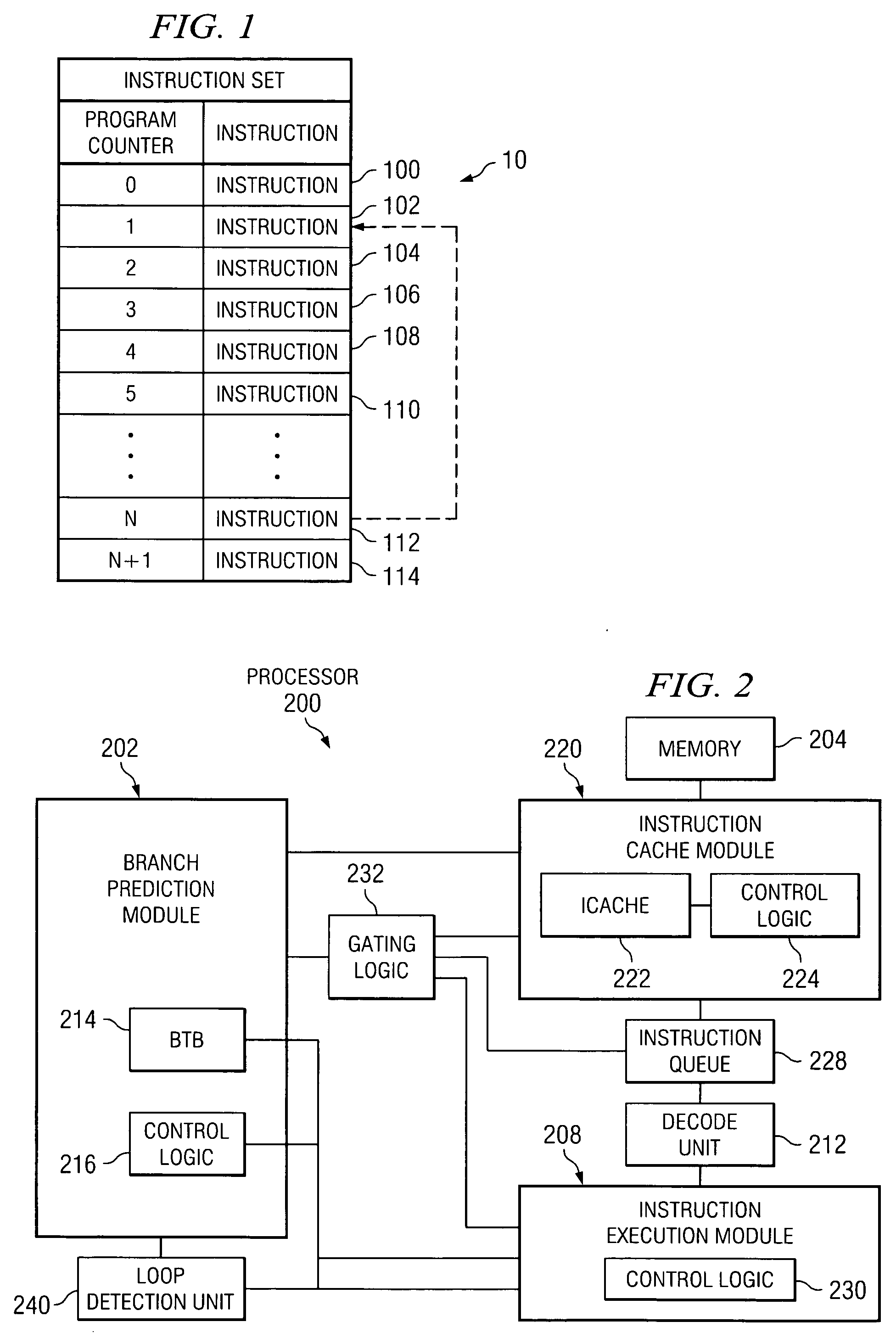
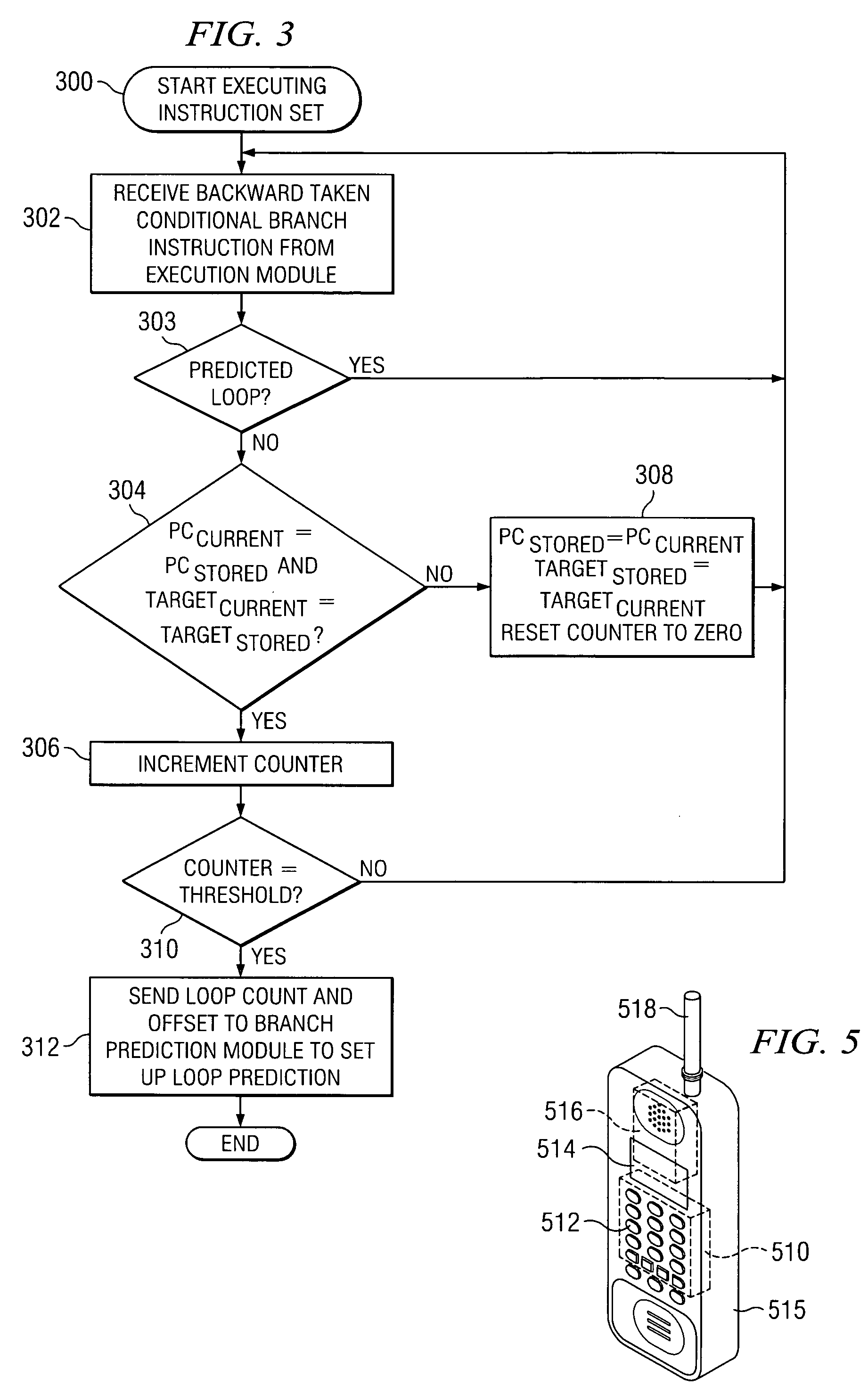
Loop detection and capture in the intstruction queue
ActiveUS20070113059A1Digital computer detailsSpecific program execution arrangementsProgram counterCycle detection
A system and a method to identify a conditional branch instruction having a program counter and a target address, and increment a loop count each time the program counter and the target address equal a stored program counter and a target address. The system and method additionally includes assignment of a start loop pointer and an end loop pointer, based on an offset, when the loop count is equal to a threshold value, and capturing instructions for a loop, as defined by the start loop pointer and the end loop pointer, in an instruction queue.
Owner:TEXAS INSTR INC
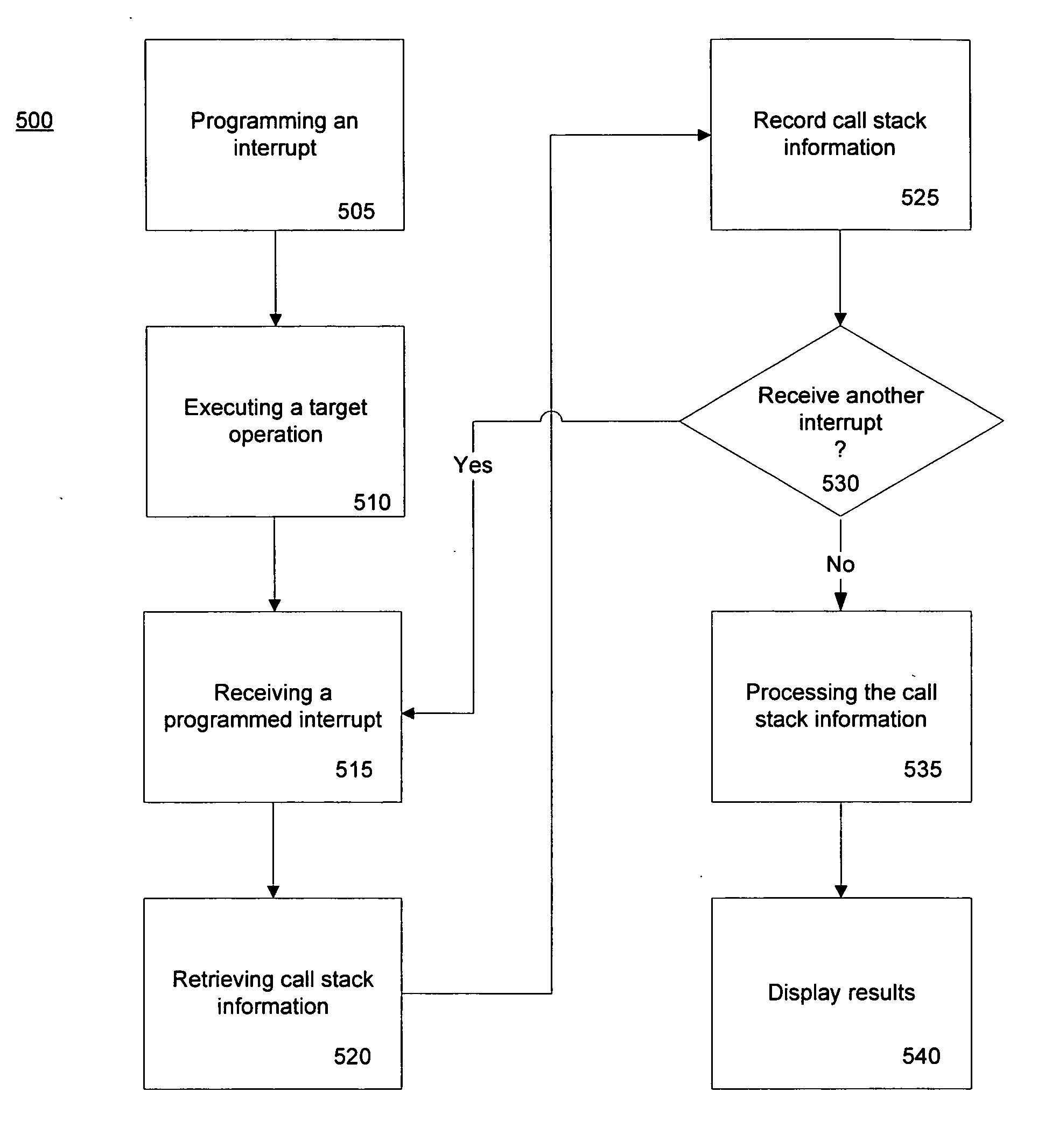
Method and system for a call stack capture
InactiveUS20060075386A1Reduces effect of profilingEliminate the effects ofError detection/correctionSpecific program execution arrangementsCall stackOperational system
A method of acquiring software profile information of a target software application includes receiving a programmed interrupt while executing an application in a computer system, servicing the interrupt such that call stack information is acquired and processing the call stack information to produce statistical information concerning function calls. The call stack information includes program counter and other information which is derived from the target application as well as operating system. Some or all of the call stack information may be recorded. The statistical information includes statistics concerning the number of samples wherein a series of functions calls are included in the call stack information and the number of samples wherein a set of function calls are at the top of the call stack information.
Owner:MICROSOFT TECH LICENSING LLC
External trace synchronization via periodic sampling
InactiveUS7134116B1Error detection/correctionSpecific program execution arrangementsVisibilityParallel computing
A system and method for program counter and data tracing is disclosed. The tracing mechanism of the present invention enables increased visibility into the hardware and software state of the processor core.
Owner:ARM FINANCE OVERSEAS LTD
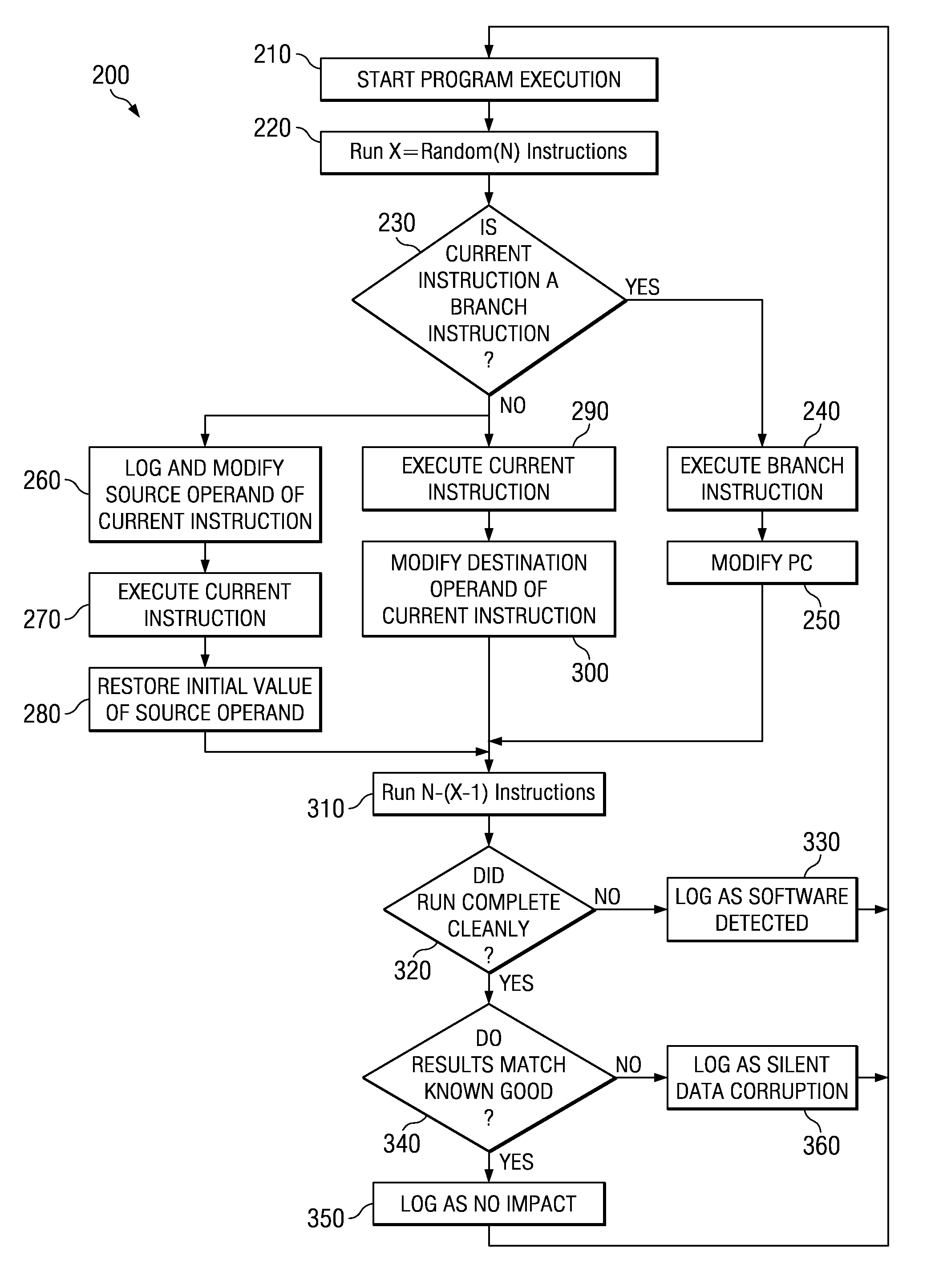
Method and Apparatus for Testing Soft Error Rate of an Application Program
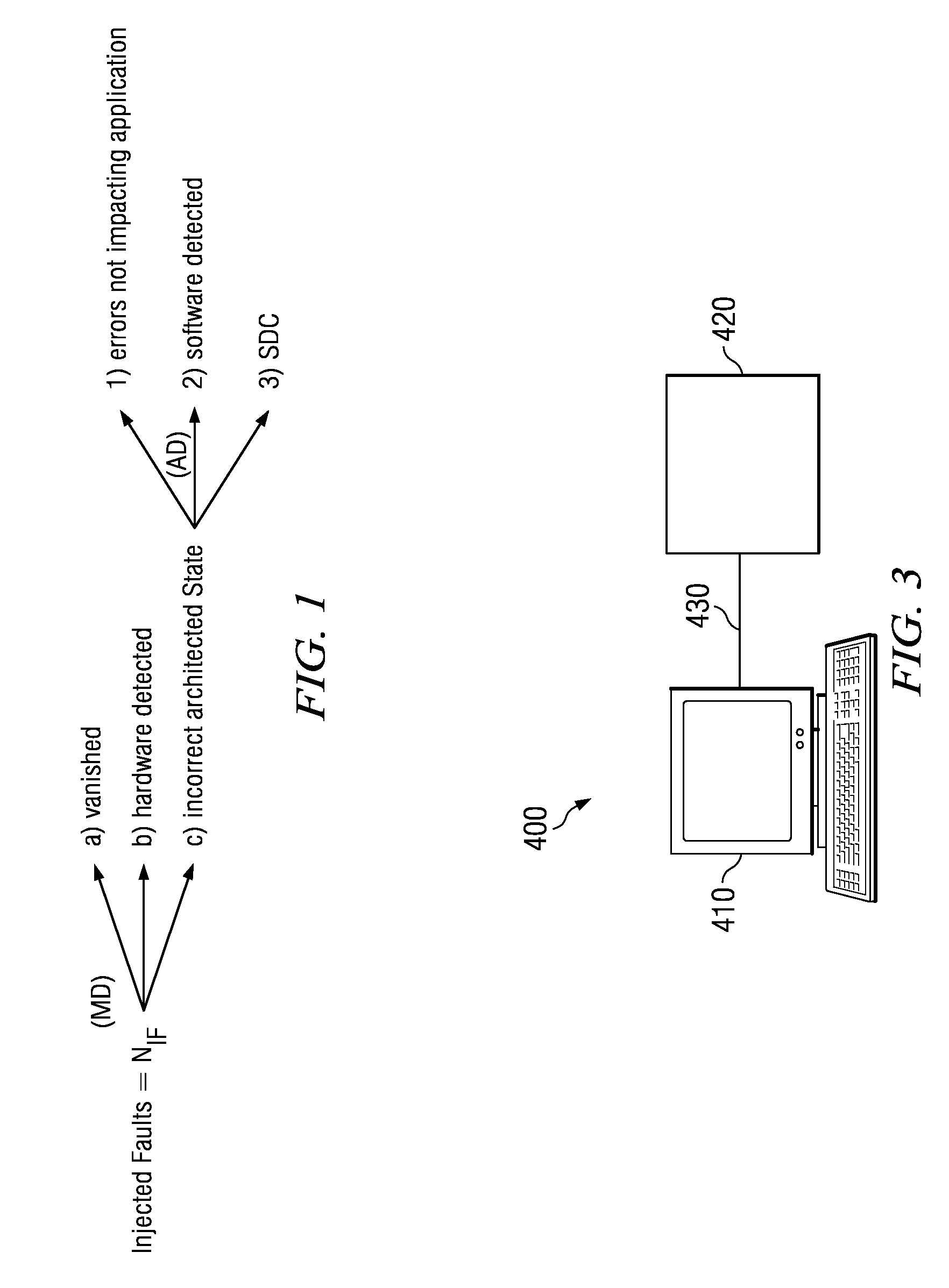
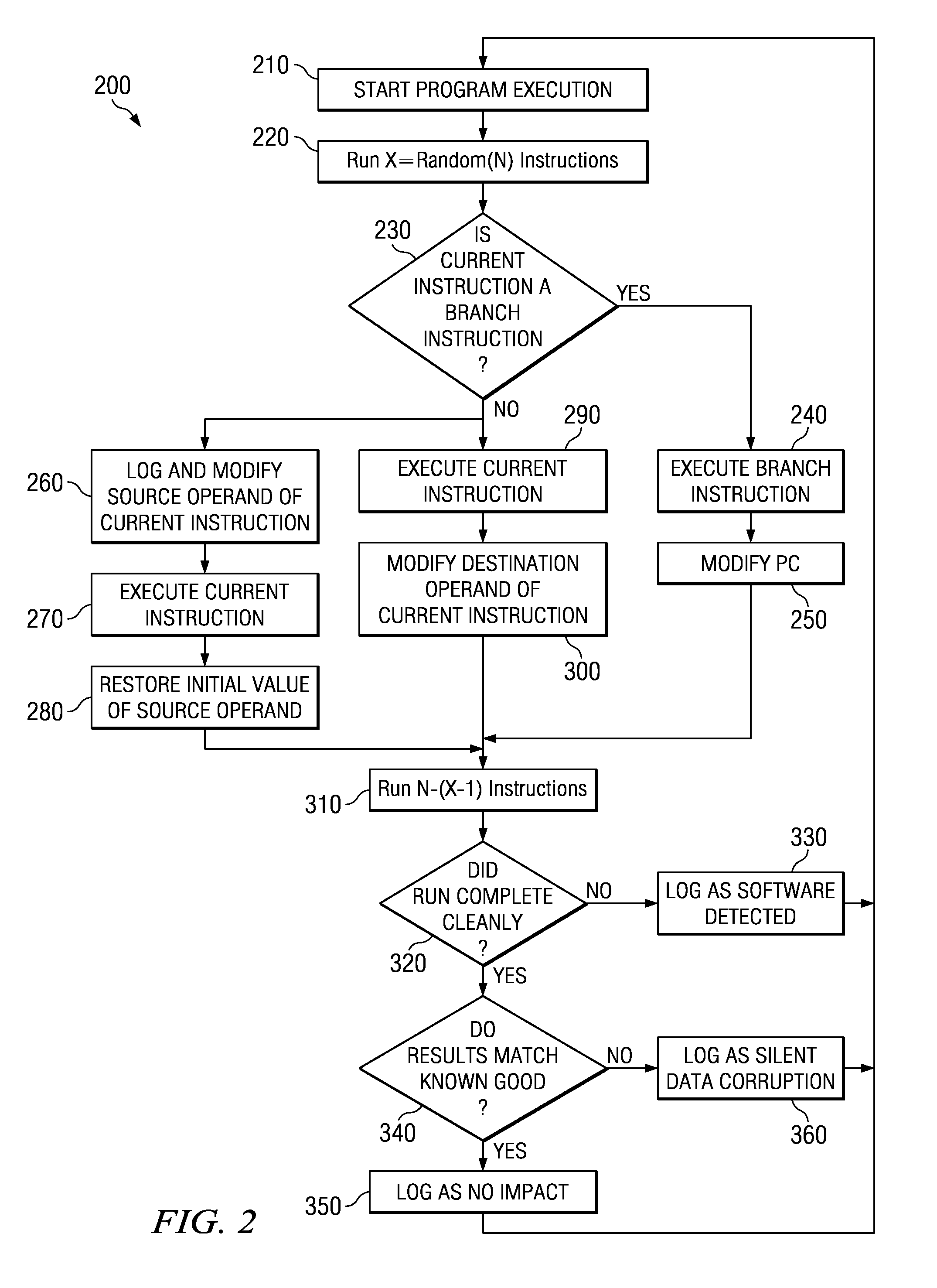
InactiveUS20090249301A1Software testing/debuggingSpecific program execution arrangementsApplication program softwareOperational system
Techniques are provided for determining consequences of an injected fault on a system running a given application program or operating system, in order to measure the software impact of a hardware soft error on the application program / operating system. The application program software is emulated instruction-by-instruction, where source operands are randomly modified before an instruction is executed, and destination operands are randomly modified after an instruction is executed, in order to mimic hardware soft errors. In addition, a program counter is randomly modified after execution of a branch instruction. The resulting consequences of such modifications are monitored such that a fault of an instruction being executed is modeled in order to determine a soft error rate (SER) for a software application program or operating system.
Owner:IBM CORP
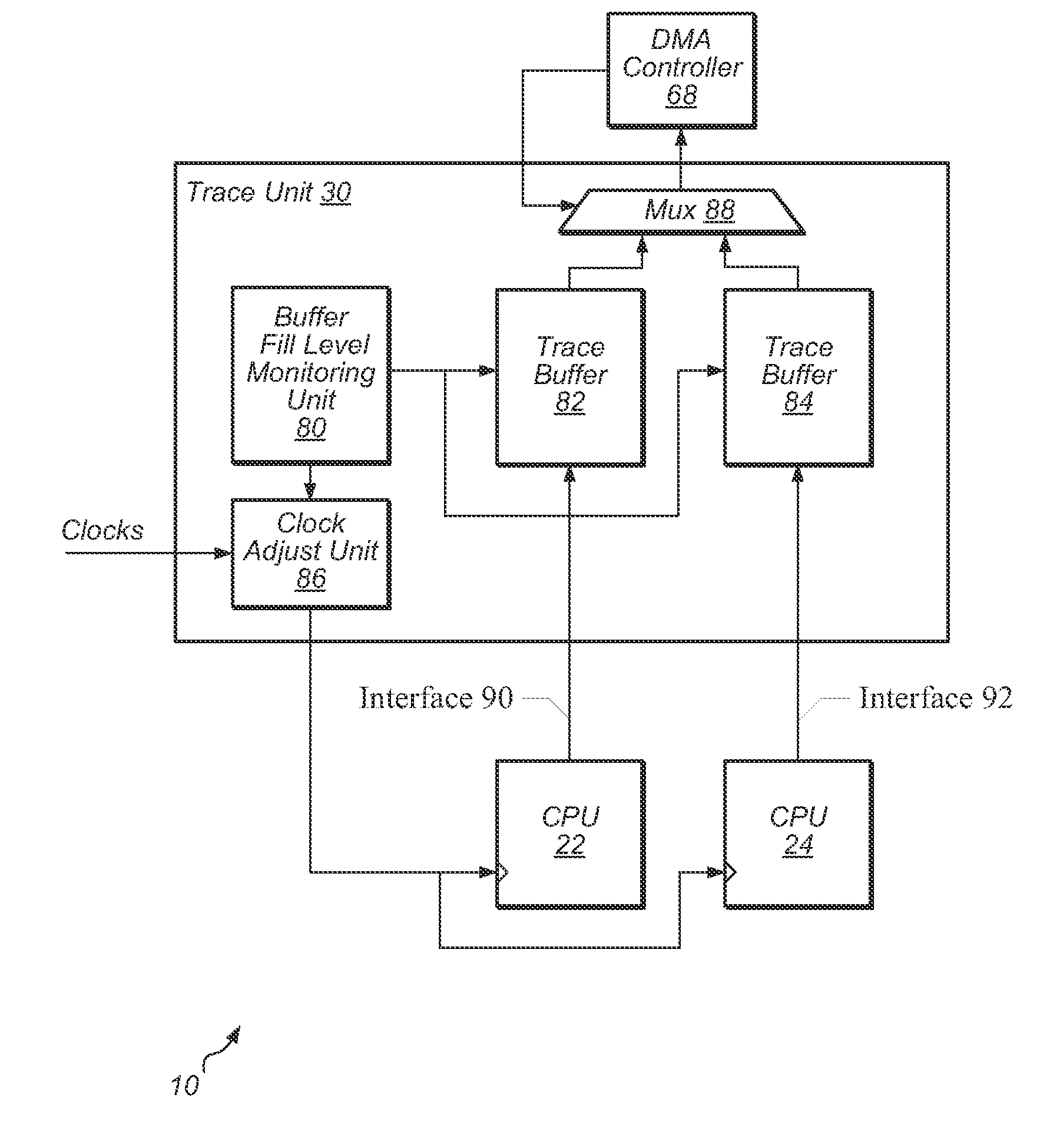
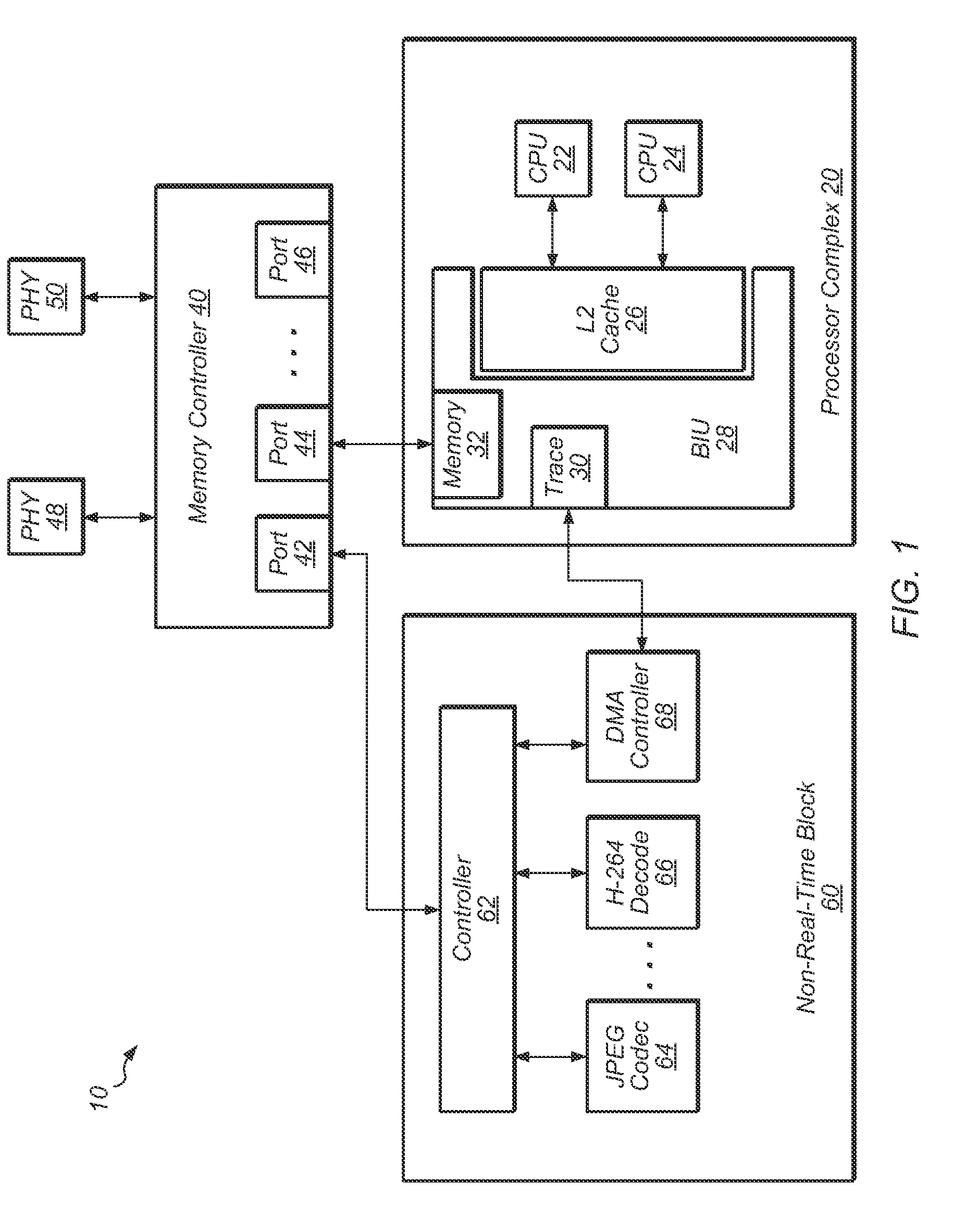
Non-intrusive processor tracing
A system, apparatus, and method for writing trace data to storage. Trace data is captured from one or more processors, and then the trace data is written to a trace buffer. The trace data includes program counters of instructions executed by the processors and other debug data. A direct memory access (DMA) controller in a non-real-time block of the system reads trace data from the trace buffer and then writes the trace data to memory via a non-real-time port of a memory controller.
Owner:APPLE INC
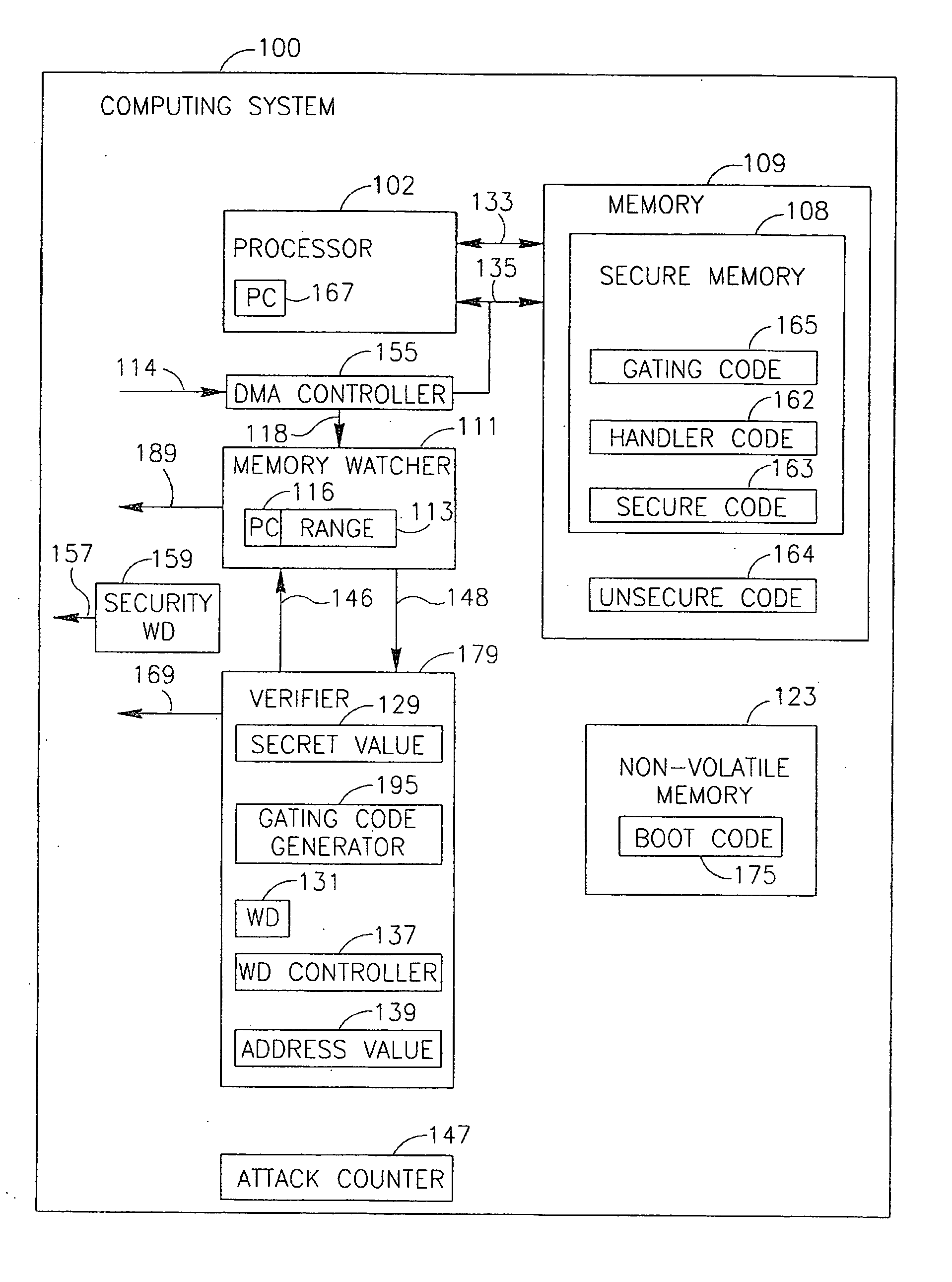
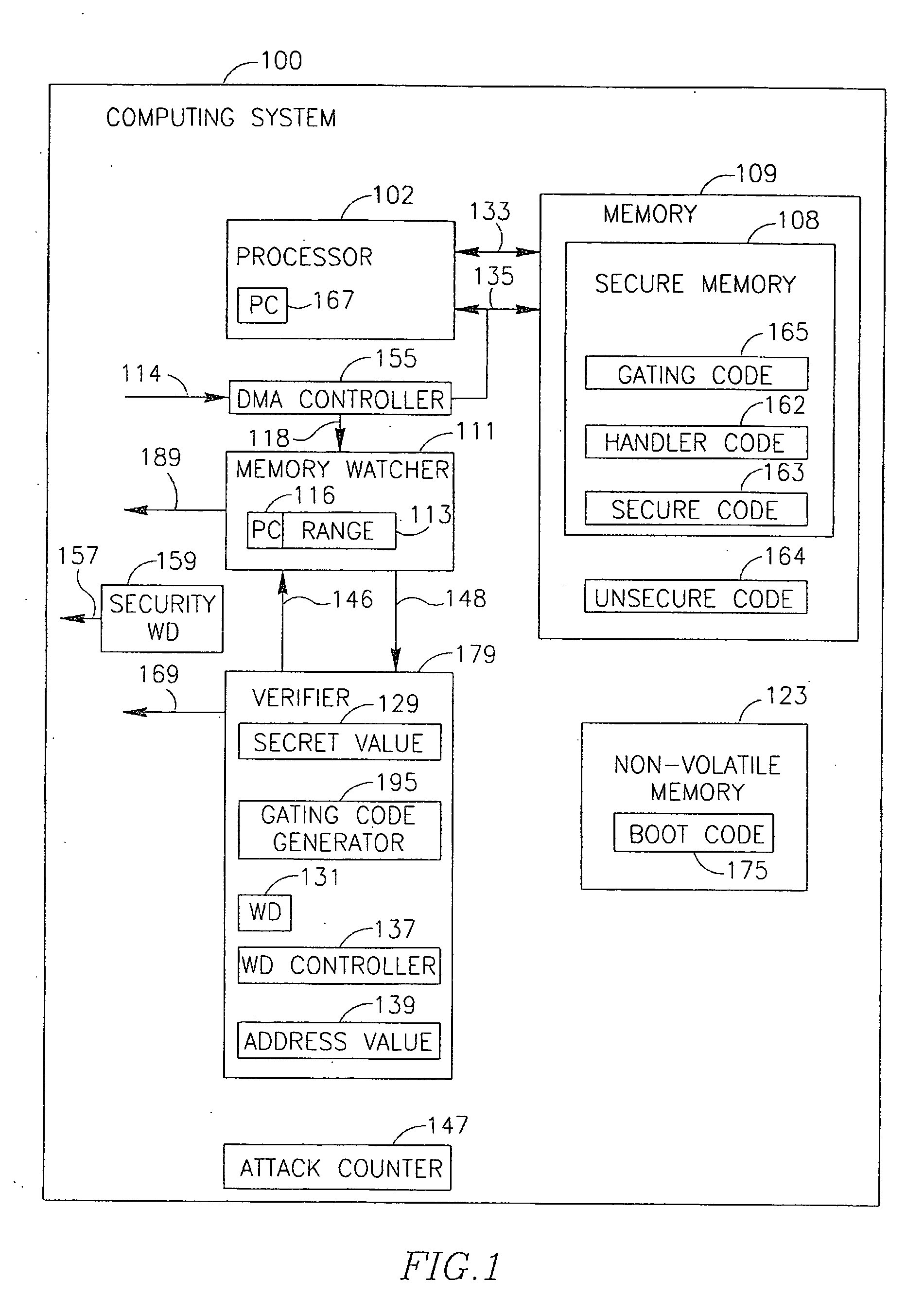
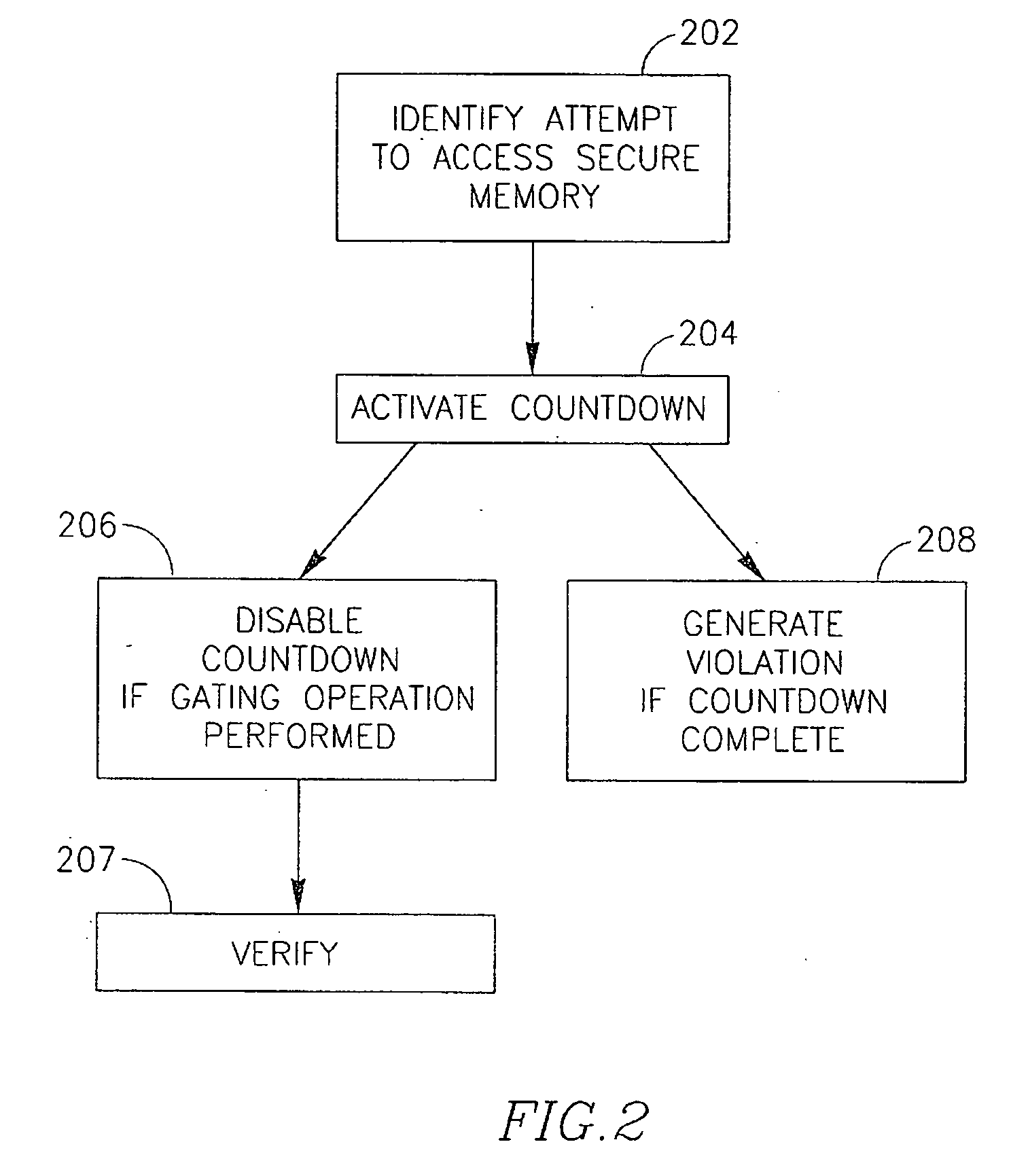
System, device and method of verifying that a code is executed by a processor
InactiveUS20070016832A1Access is disabledError detection/correctionInternal/peripheral component protectionEntry pointProgram counter
Some demonstrative embodiments of the invention include a method, device and / or system of verifying that a secure code is executed by a processor. The device may include, for example, a memory to store a secure code; a processor intended to execute a gating code, wherein the gating code, when executed by the processor, results in the processor to perform at least one operation and set a program counter of the processor to point to an entry point of the secure code; and a verifier to verify that the processor had executed the gating code only if the processor performs the at least one operation. Other embodiments are described and claimed.
Owner:ARM LTD +1
Method and apparatus for changing microcode to be executed in a processor
InactiveUS6691308B1Runtime instruction translationGeneral purpose stored program computerComputer architectureEngineering
A Central Processing Unit (CPU) hotpatch circuit compares the run-time instruction stream against an internal cache. The internal cache stores embedded memory addresses with associated control flags, executable instruction codes, and tag information. In the event that a comparison against the current program counter succeeds, then execution is altered as required per the control flags. If no comparison match is made, then execution of the instruction that was accessed by the program counter is executed.
Owner:MICROELECTRONIC INNOVATIONS LLC
Devices, systems and methods for conditional instructions
A data processing device includes a circuit having status conditions wherein a particular set of the status conditions can occur in operation of the circuit. An instruction register operates to hold a branch instruction conditional on a particular set of the status conditions. A decoder is connected to the instruction register and the circuit. A program counter is coupled to the decoder wherein the decoder is operable to enter a branch address into the program counter in response to the branch instruction when the particular set of the status conditions of the circuit are present. Other data processing devices, systems and methods are also disclosed.
Owner:BOUTAUD FREDERIC +1
Symmetric multiprocessor operating system for execution on non-independent lightweight thread contexts
InactiveUS20070043935A2Lightweight in of areaLightweight in of powerDigital computer detailsEnergy efficient computingGeneral purposeUser Privilege
A multiprocessing system is disclosed. The system includes a multithreading microprocessor including a plurality of thread contexts (TCs), each having a program counter and a general purpose register set for executing a thread. The microprocessor also includes a shared privileged resource, shared by the plurality of TCs rather than being replicated for each of the plurality of TCs, and privileged to be managed only by operating system-privileged threads rather than by user-privileged threads. The system also includes a multiprocessor operating system (OS), configured to manage the shared privileged resource, and to schedule execution of both the operating system-privileged threads and the user-privileged threads on the plurality of TCs.
Owner:MIPS TECH INC
Dynamic selection of a compression algorithm for trace data
InactiveUS7069544B1Error detection/correctionSpecific program execution arrangementsVisibilityParallel computing
A system and method for program counter and data tracing is disclosed. The tracing mechanism of the present invention enables increased visibility into the hardware and software state of the processor core.
Owner:ARM FINANCE OVERSEAS LTD
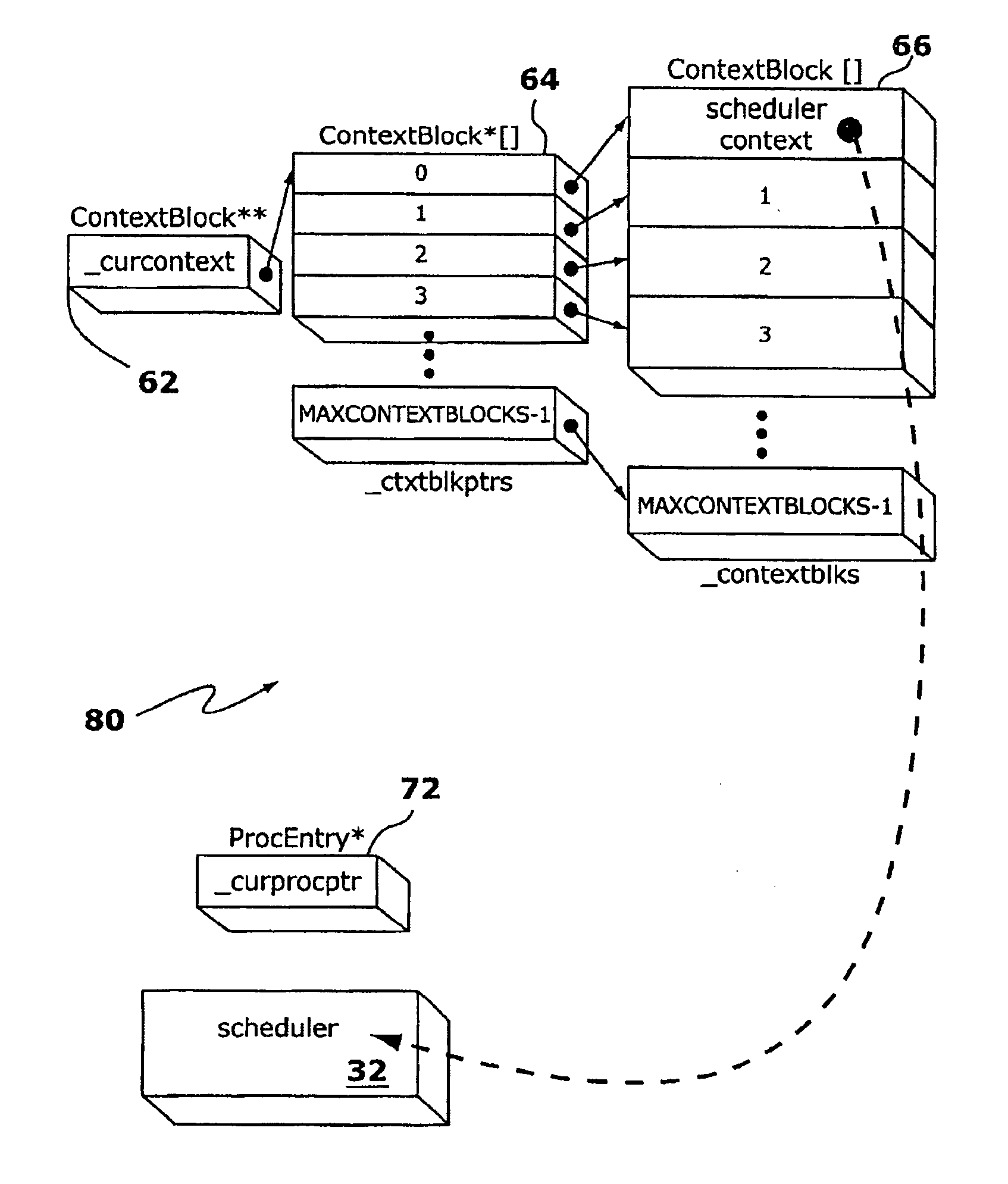
Replaceable scheduling algorithm in multitasking kernel
InactiveUS7296271B1Reduce needEnhancing kernel portabilityProgram synchronisationDigital computer detailsPowerPCProgram counter
Disclosed is providing one of a plurality of schedulers for a multitasking system for a processor that includes choosing a particular one of the schedulers, setting a program counter to an address corresponding to code of the particular one of the schedulers, and the processor executing code at an address corresponding to the program counter. Also included may be setting a stack pointer to an address corresponding to stack space for the particular one of the schedulers and the processor using the stack space at the stack pointer after executing code at the address corresponding to the program counter. The system described herein provides a small kernel that can run on a variety of hardware platforms, such as a PowerPC based Symmetrix adapter board used in a Symmetrix data storage device provided by EMC Corporation of Hopkinton, Ma. The core kernel code may be written for the general target platform, such as the PowerPC architecture. Since the PowerPC implementation specific modules are well defined, the system may be quite portable between PowerPC processors (such as the 8260 and 750), and should prove relatively easy to port to any PowerPC based Symmetrix adapter board / CPU combination. The kernel may also be ported to run on other RISC machines (Hitachi SH series) and can be ported to CISC architectures.
Owner:EMC IP HLDG CO LLC
Multi-channel, multi-service debug on a pipelined CPU architecture
InactiveUS6934937B1Digital computer detailsSoftware testing/debuggingCpu architectureParallel computing
A method and system for debugging an executing service on a pipelined CPU architecture are described. In one embodiment, a breakpoint within an executing service is set and a minimum state of the executing service is saved. In addition, a program counter of the executing service is altered. The program counter is restored and the state of the executing service is restored.
Owner:AVAGO TECH INT SALES PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com