Patents
Literature
228 results about "Application program software" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
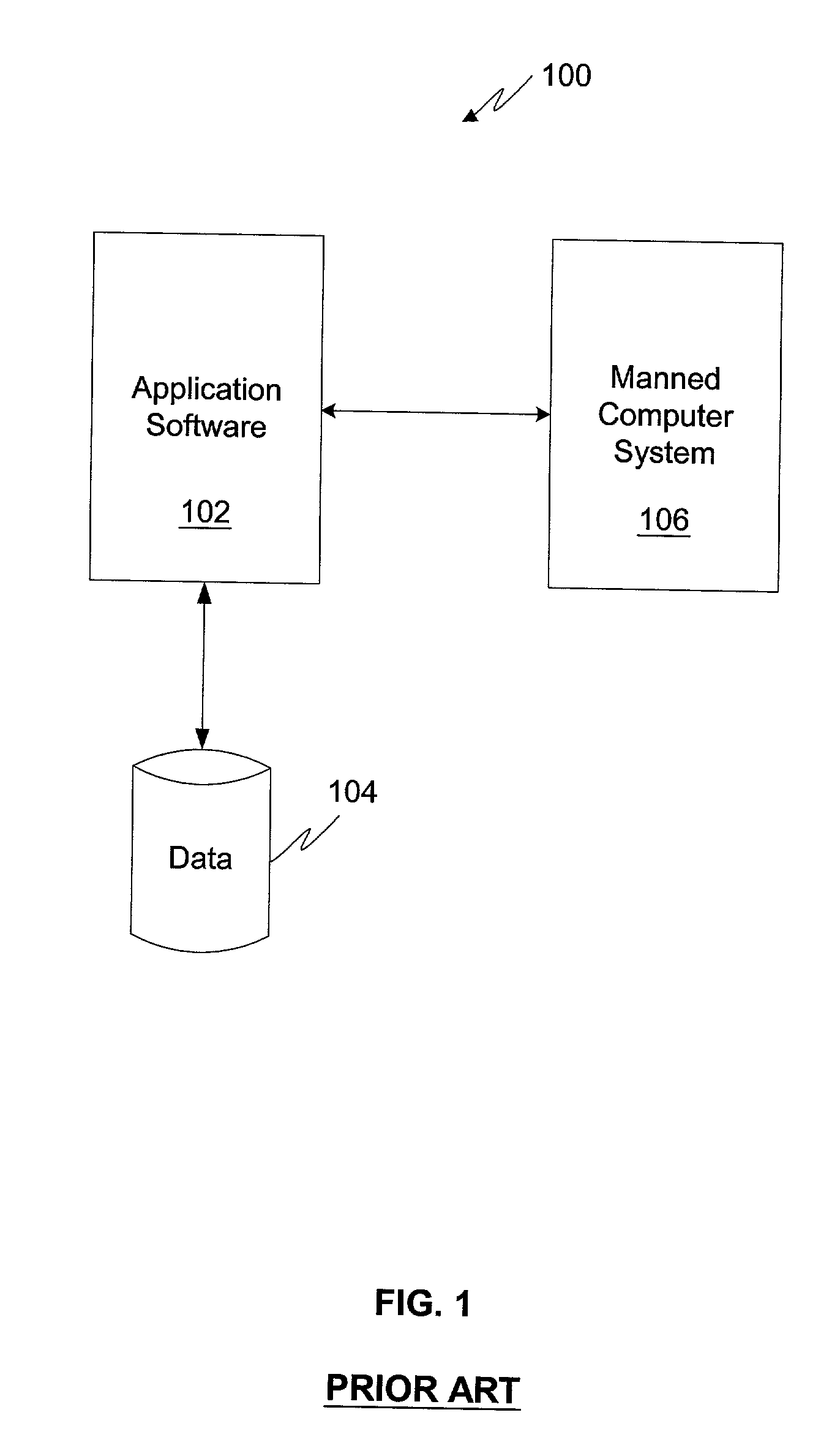
Application software is a program or group of programs designed for end users. These programs are divided into two classes: system software and application software.
System and method for flexible user interfaces
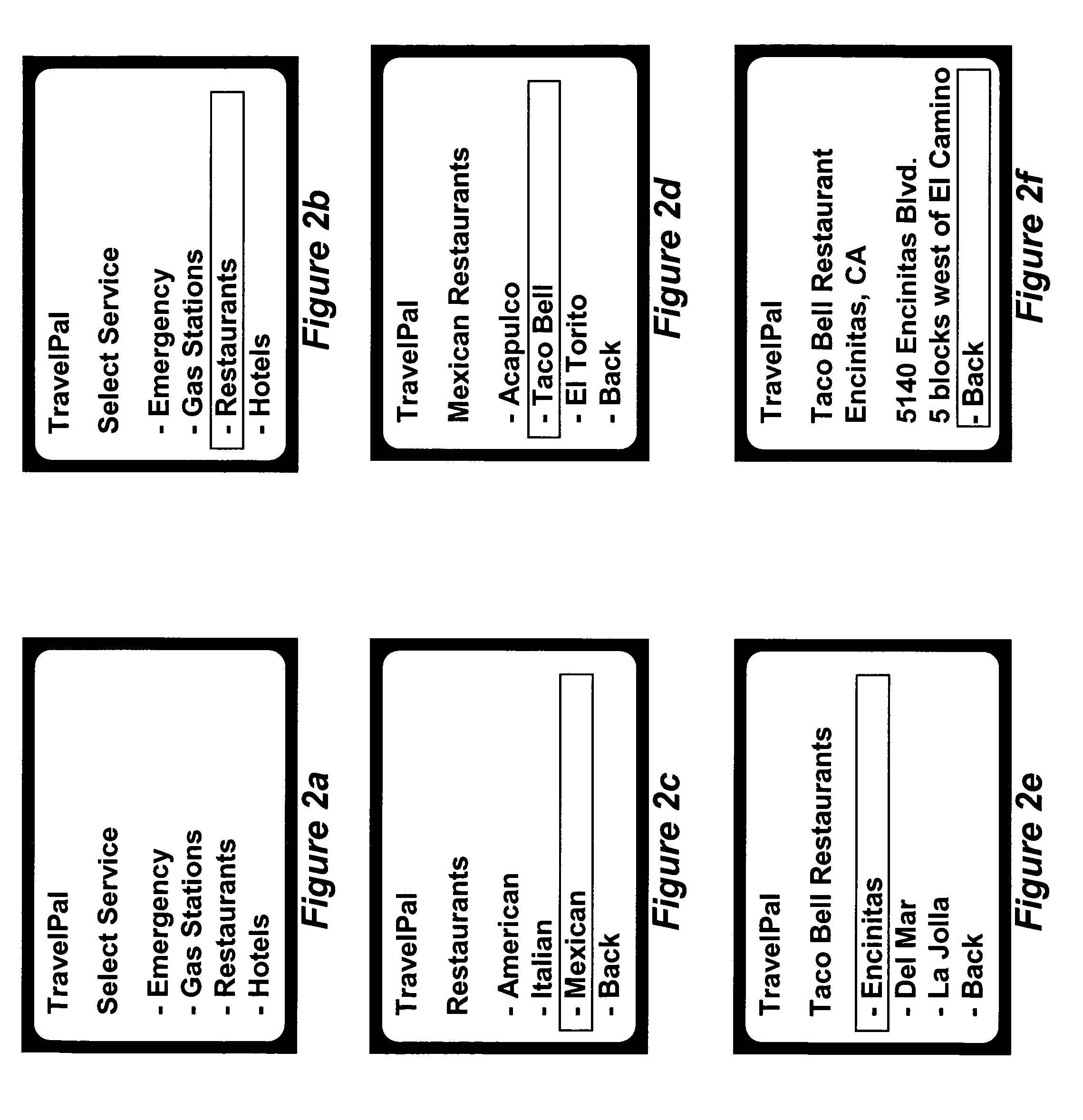
InactiveUS20070061488A1Reduces application software developmentReduce maintenance costsDigital data information retrievalMultiple digital computer combinationsApplication program softwareSoftware update
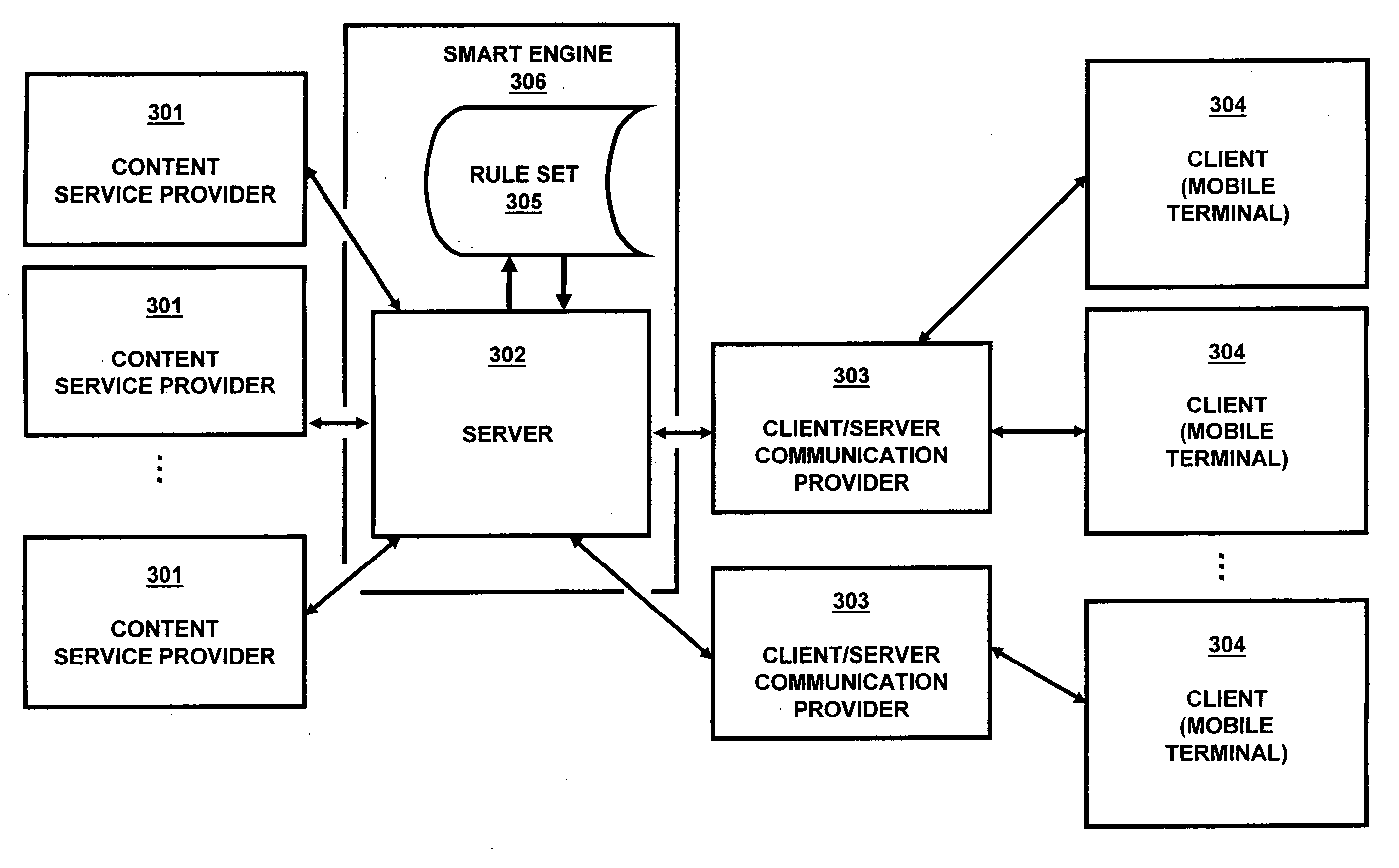
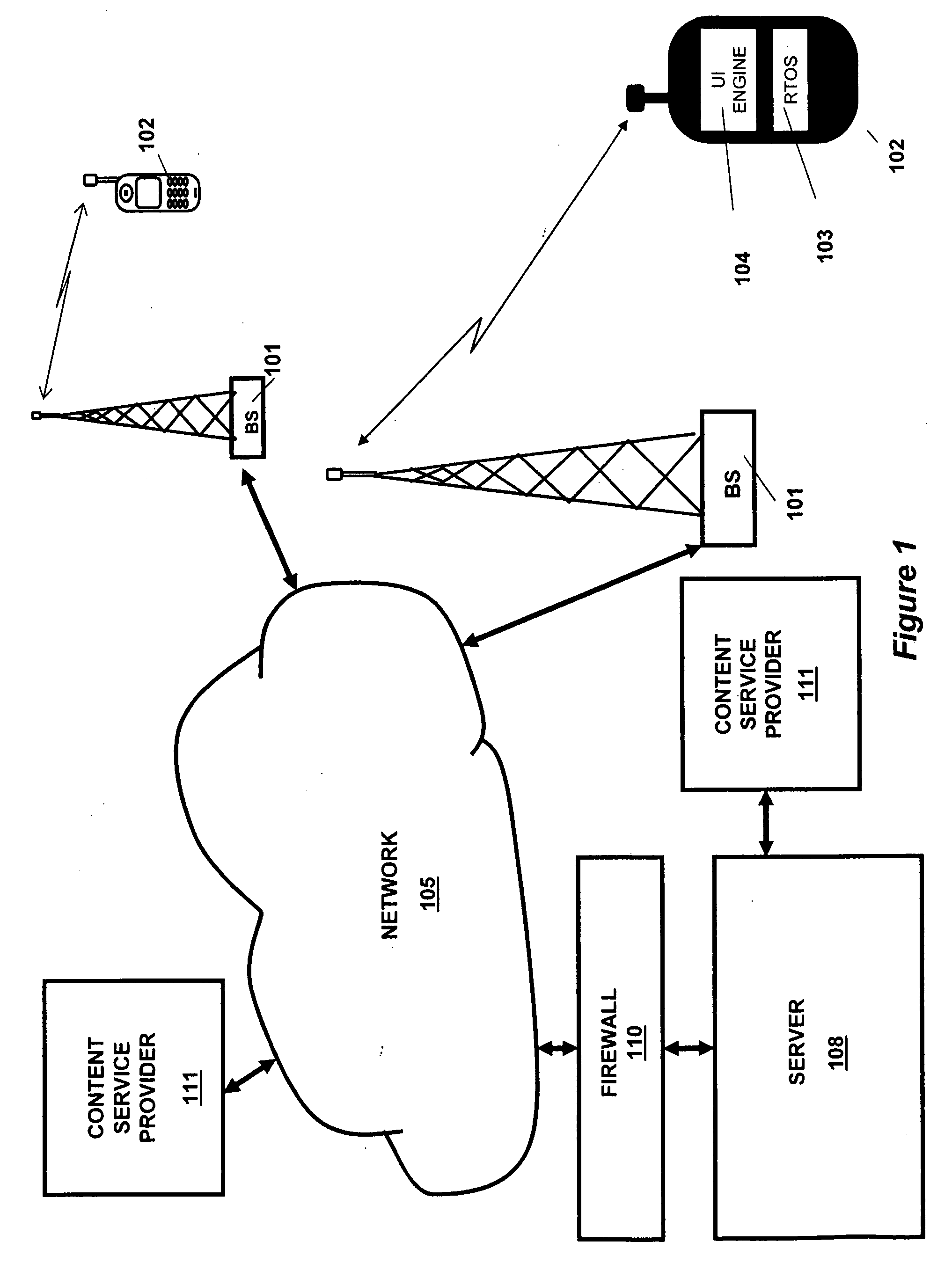
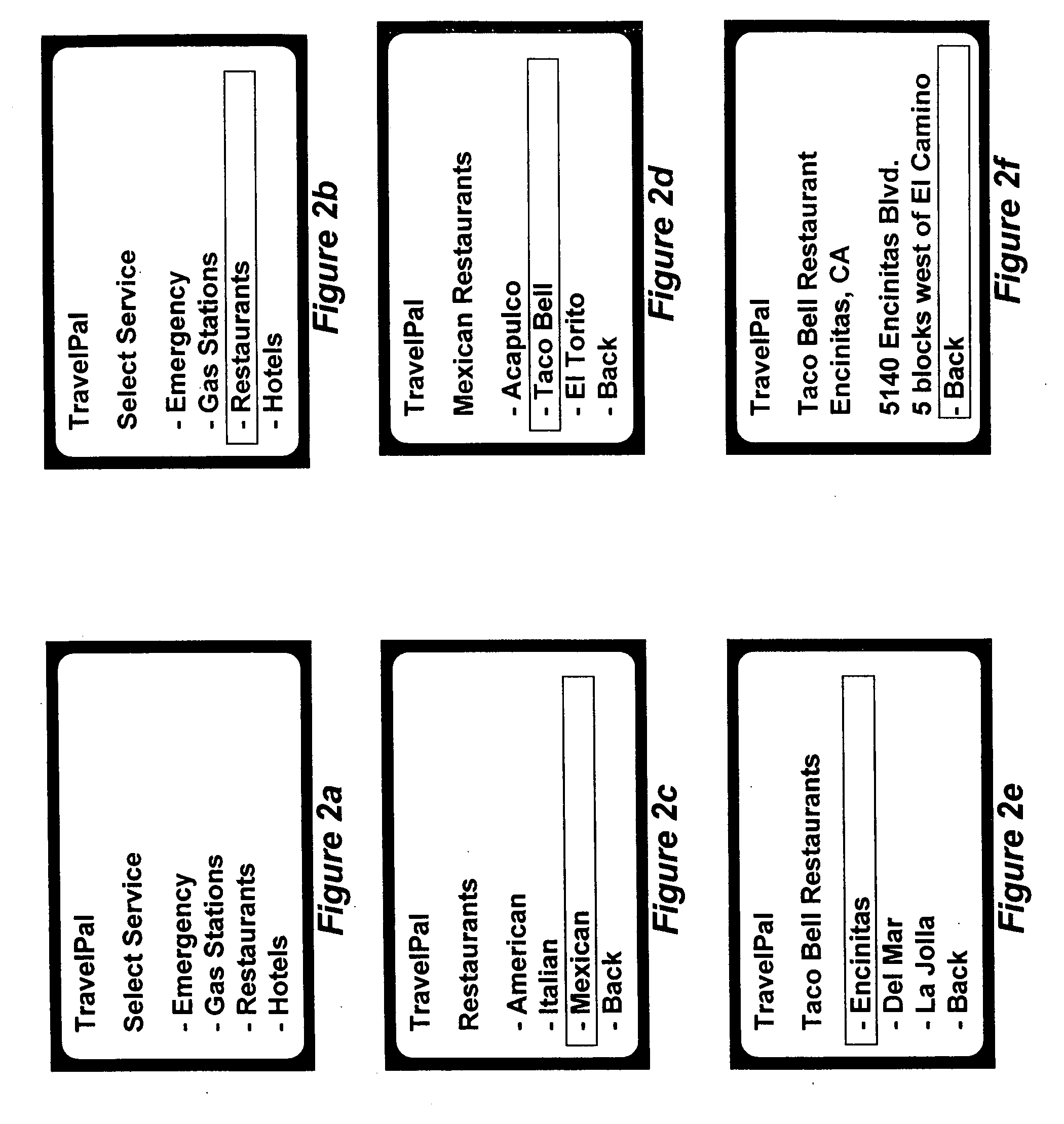
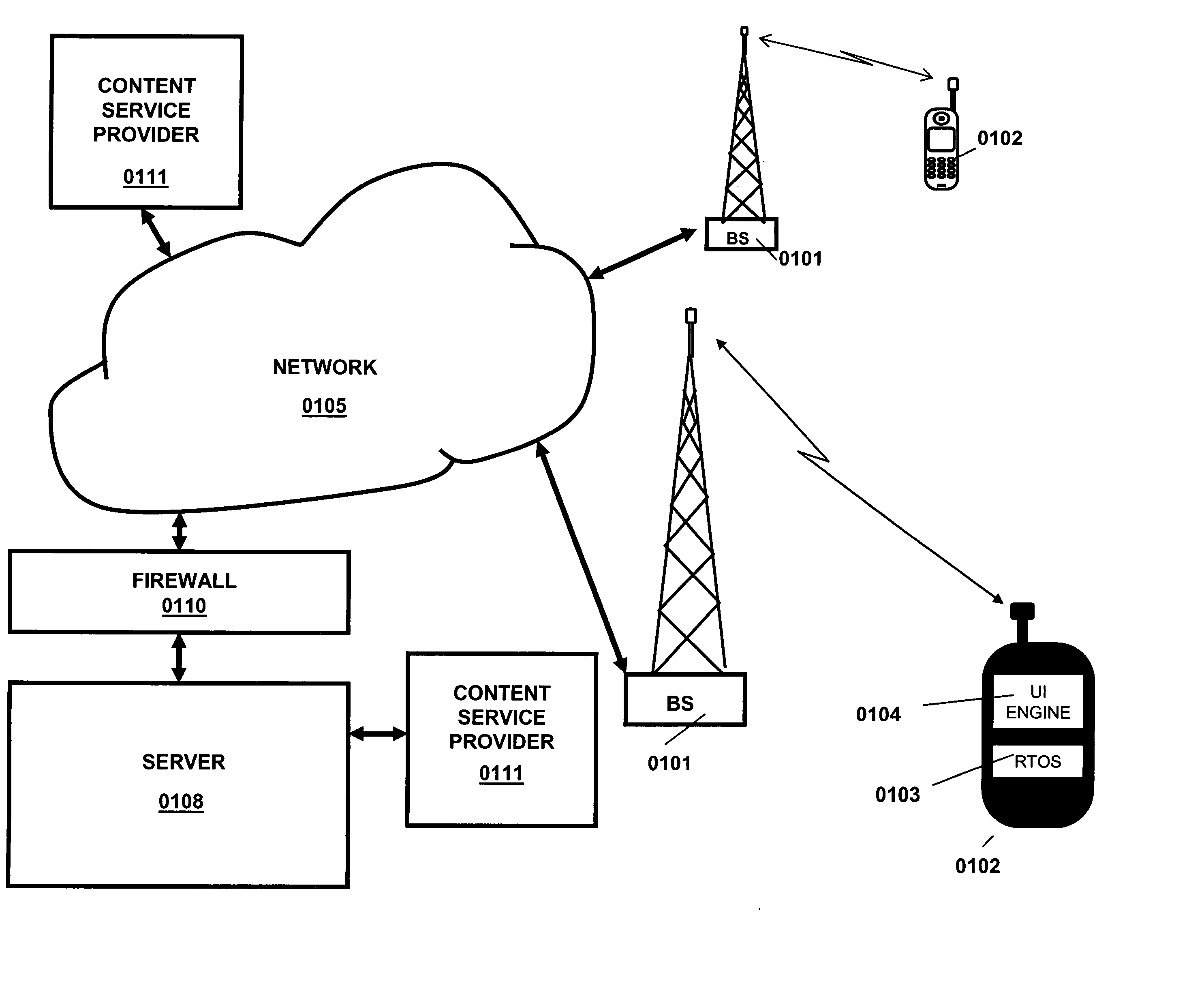
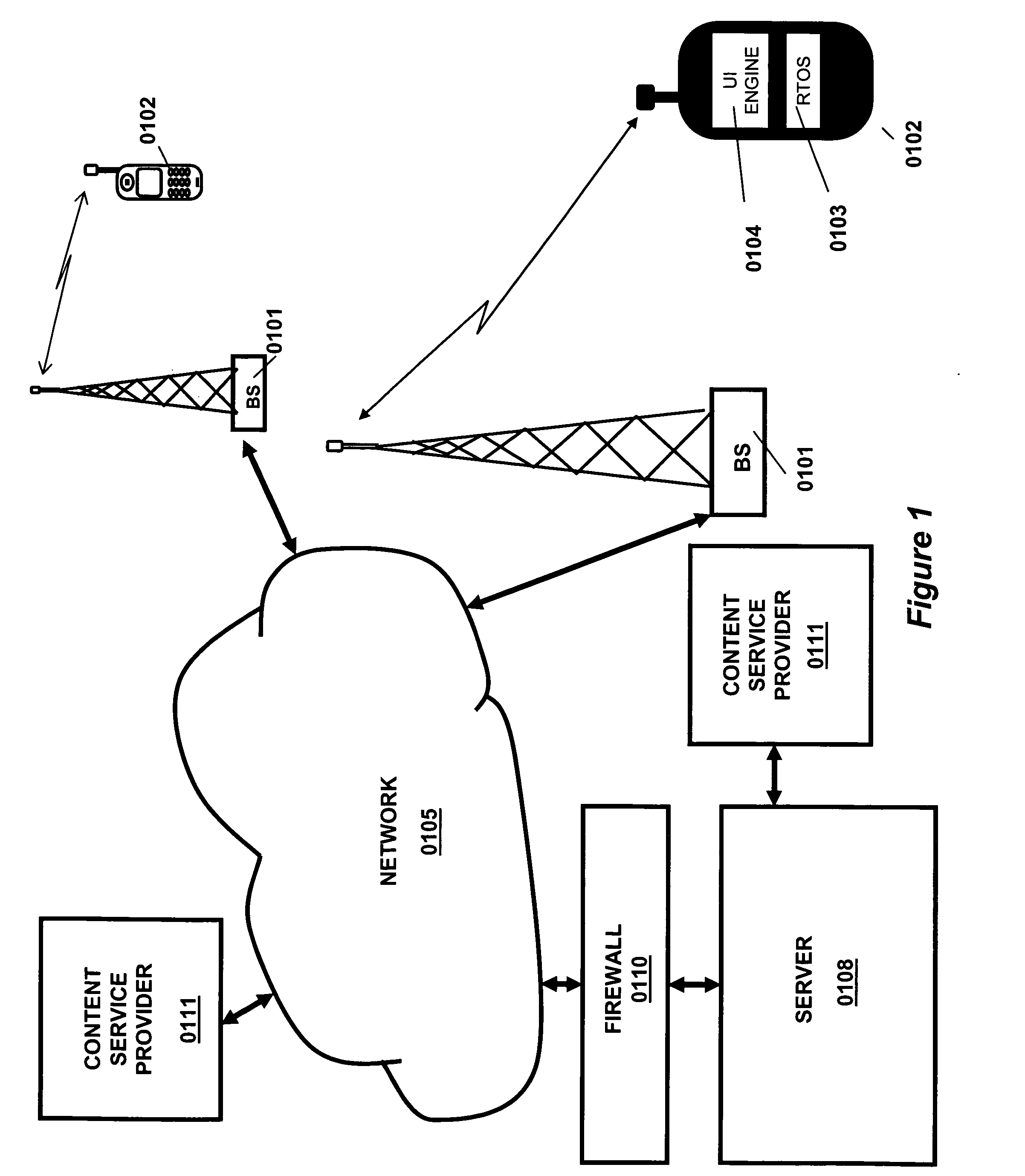
A method and system for implementing a user interface for providing a data service in a mobile client using a server with knowledge of the client's hardware and software capabilities to modify data content and display rules for an improved user interface on the client. Data may be cached on the client to improve application response time and provide a standalone application capability for the client. The automatic conversion of newly developed applications to a plurality of clients with differing hardware and software capabilities reduces application software development and maintenance costs. Software updates and bug fixes can be deployed with the same method and system. An interoperable array of adapters for reporting, billing, and format conversions is also described.
Owner:TRILIBIS
Deploying an application software on a virtual deployment target
InactiveUS20050289538A1Program loading/initiatingMemory systemsApplication program softwareRelevant information
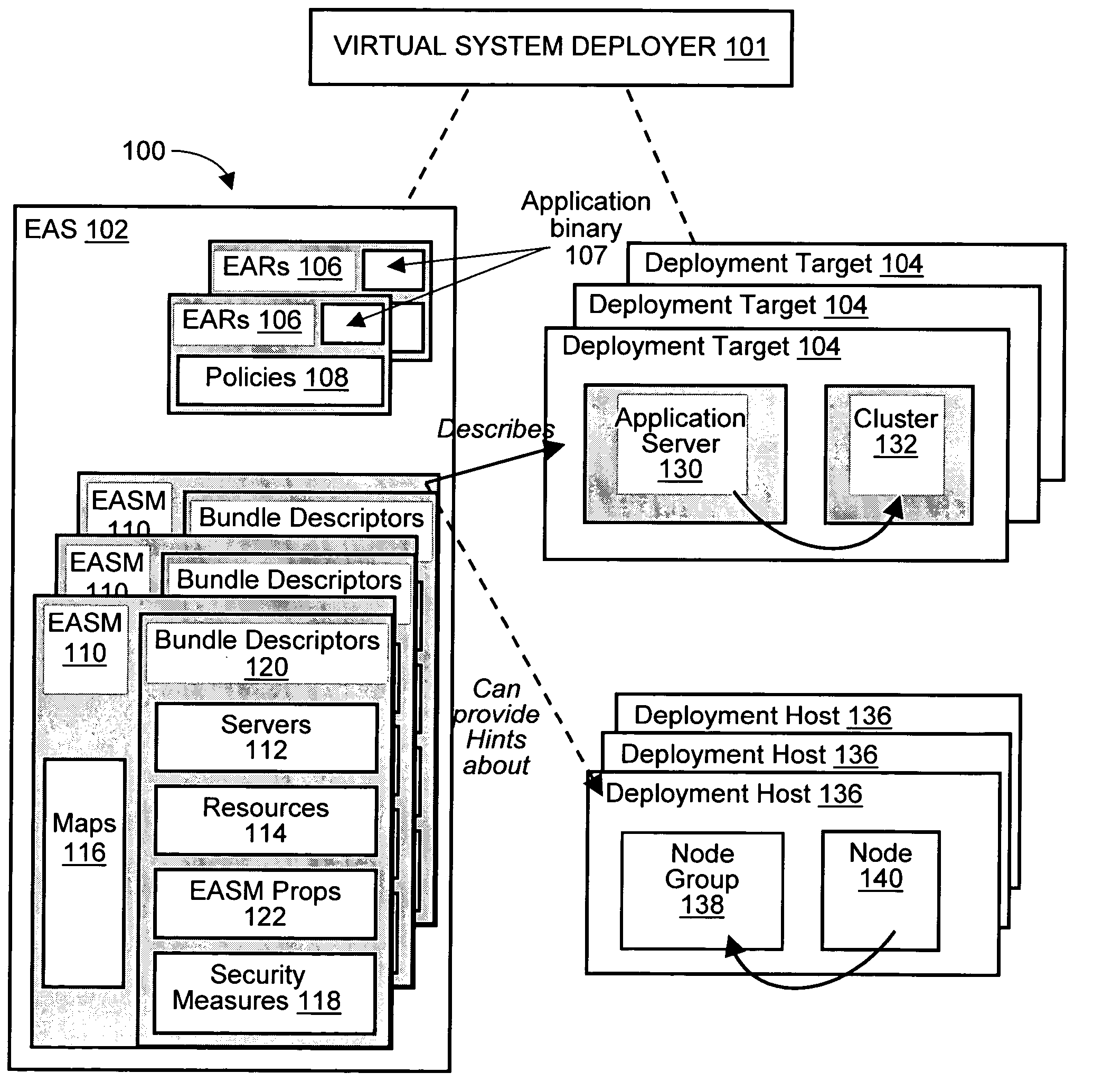
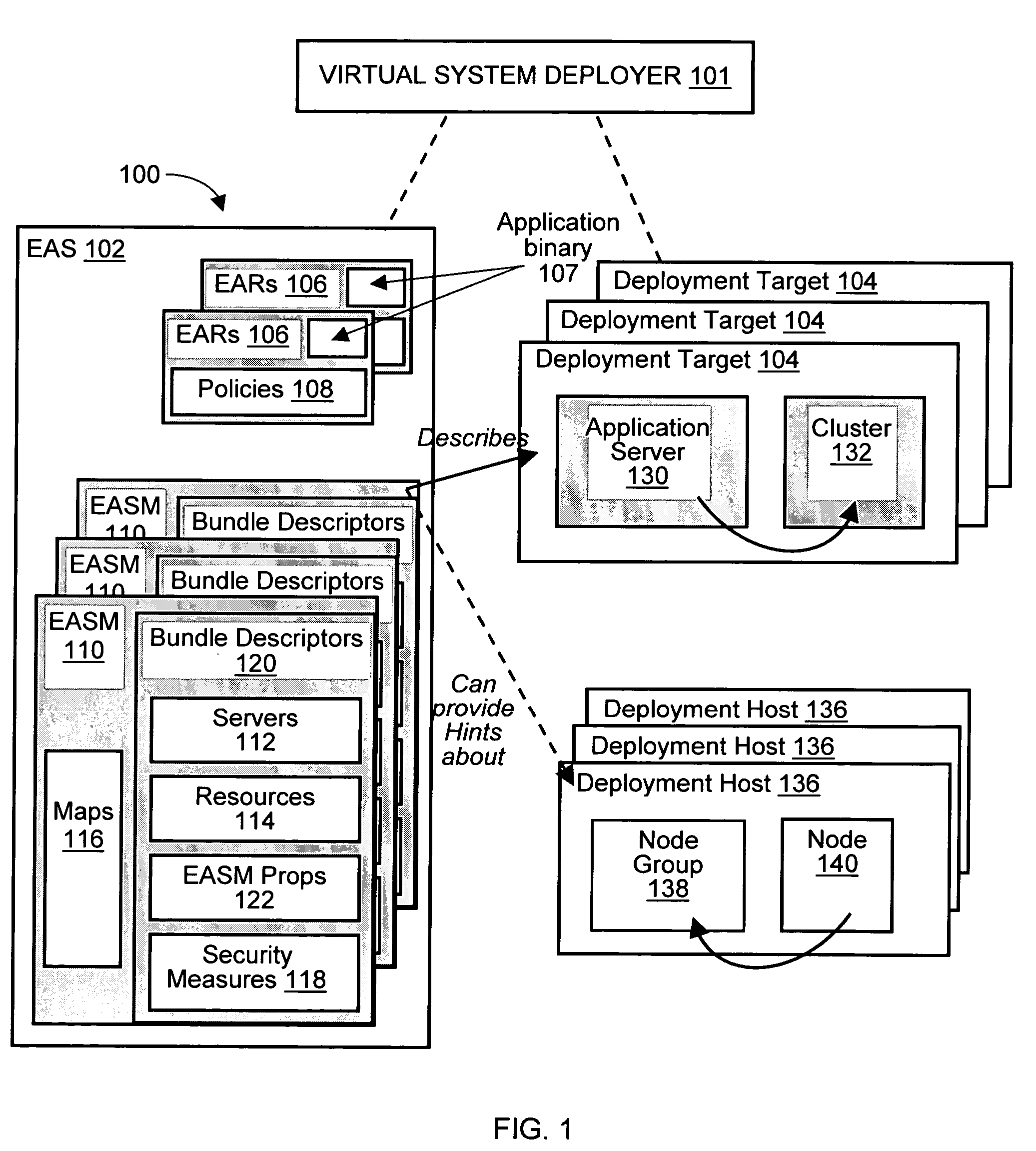
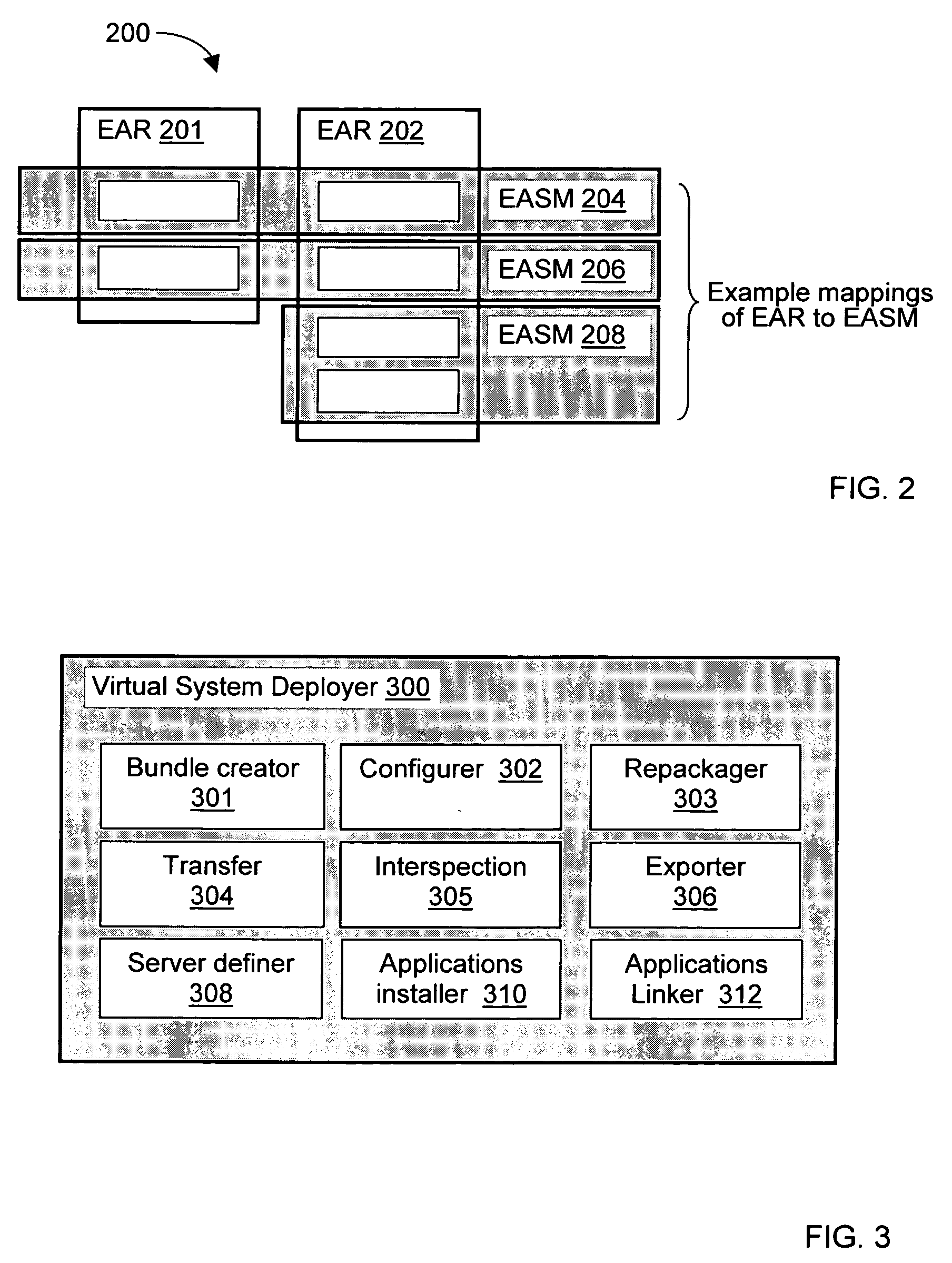
Methods and arrangements to propagate application software to a virtual deployment target are contemplated. More specifically, a user may create multiple virtual deployment targets in a software system such as WebSphere™ and deploy applications to multiple the virtual deployment targets without having to manually fit policy-driven applications into each virtual deployment target. Embodiments are particularly advantageous when the application software is a business solution that needs to be deployed multiple times such as during the development and testing of the business solution. For example, application software of a business solution typically includes a group of applications designed to cooperatively function as a single entity. An application bundle such as an Enterprise Application Solution (EAS) file describes the application software and includes pertinent information about the application software, application configuration data, and runtime configuration data to implement the business solution. Then, the application bundle can be deployed automatically or substantially automatically.
Owner:IBM CORP
Computer system capable of fast switching between multiple operating systems and applications
ActiveUS7356677B1Fast transferFast shutdownDigital data processing detailsDigital computer detailsApplication program softwareOperational system
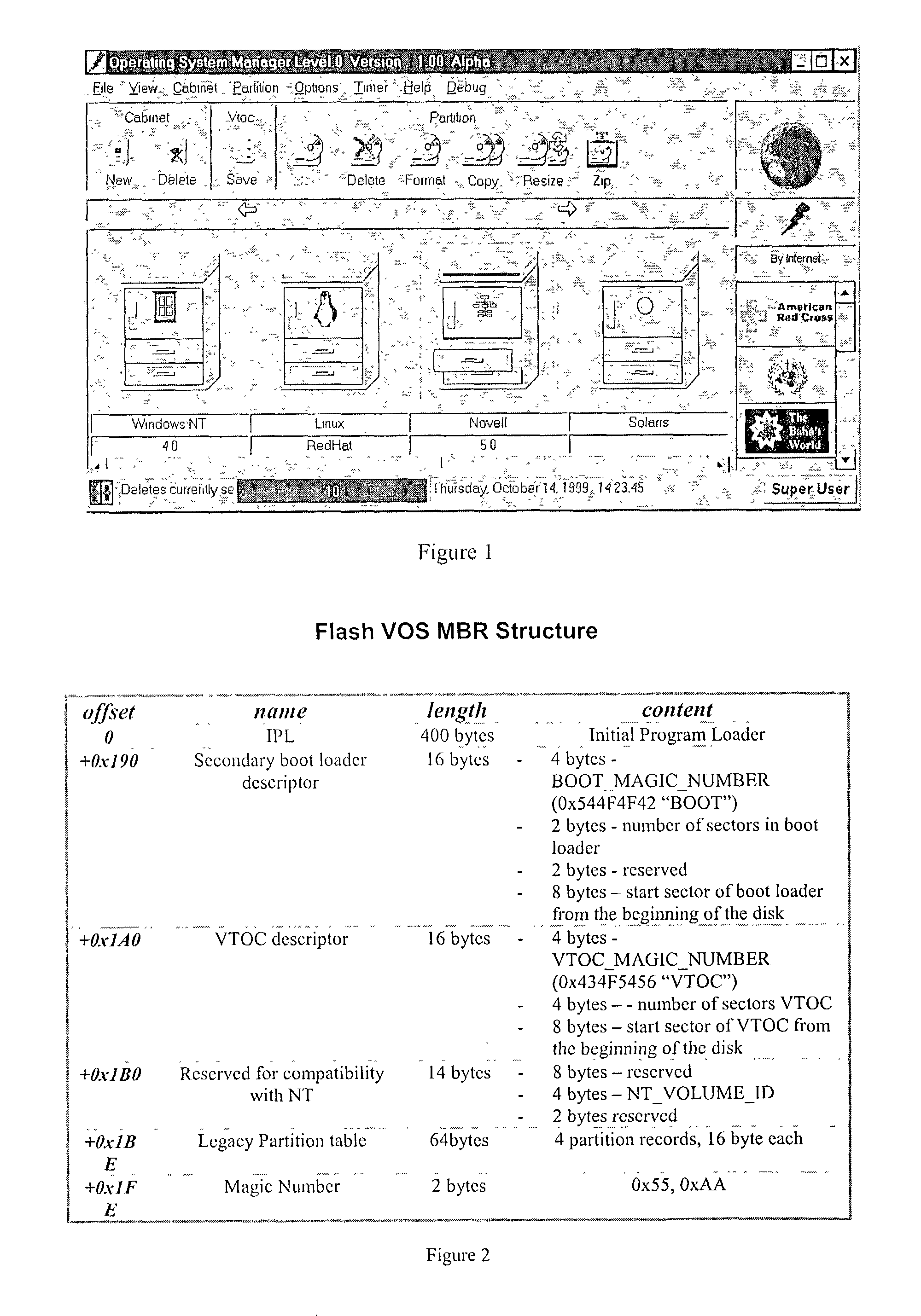
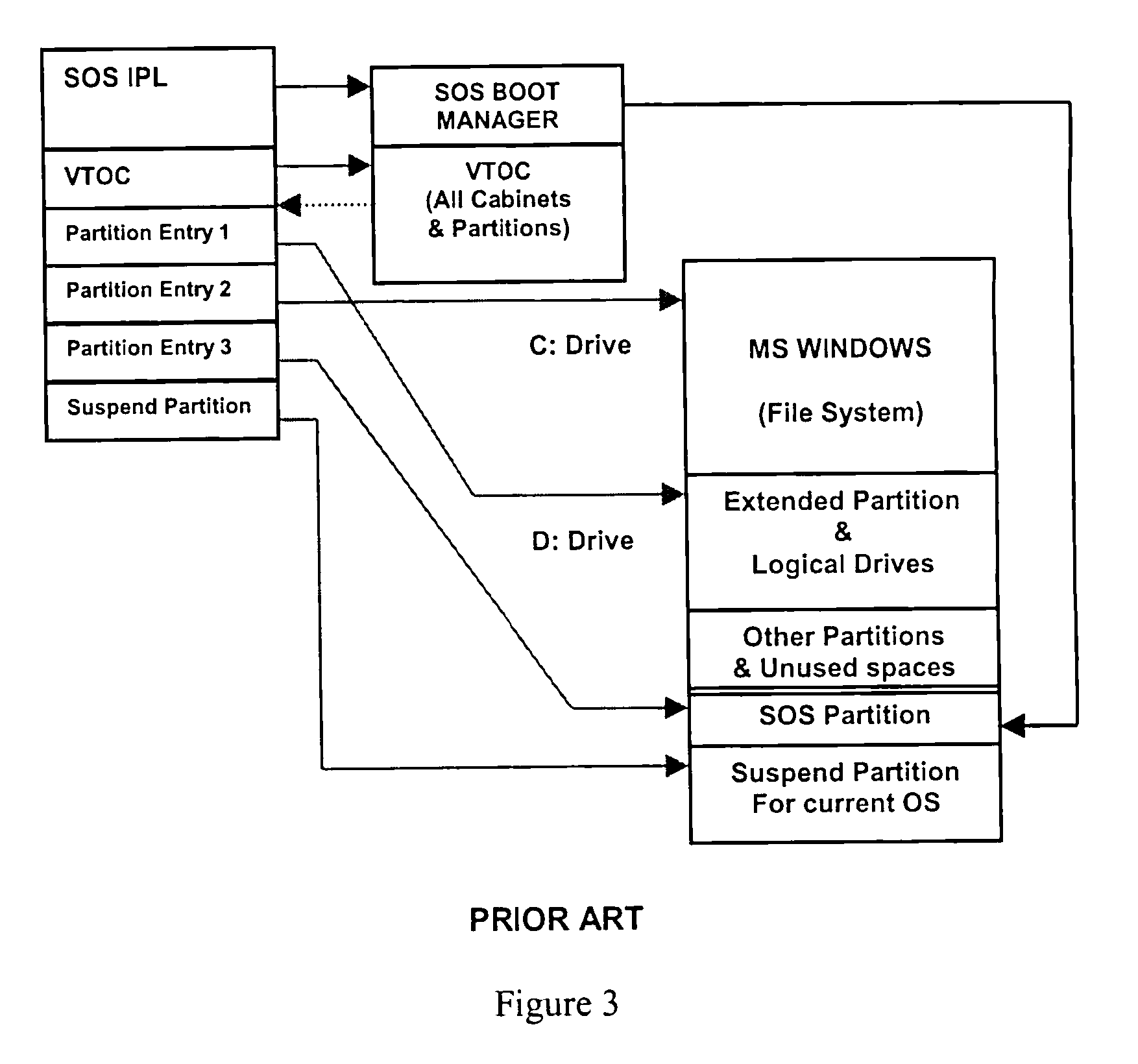
A method and apparatus is presented that allows rapid switching between multiple operating system environments on a single computer, through the use of a Super Operating System operating between the computer system's firmware level and a plurality of bootable operating systems and applications. Relevant data, such as hardware controls, bootable operating systems, and applications software, are grouped onto physical partitions in physical memory. Combinations of compatible partitions can be assigned to a cabinet to create a virtual computer system. A given partition is assignable to multiple cabinets. By operating above the virtual computer systems, the Super Operating System uses the suspend and resume functions of the power management support functions to suspend and hybernate one operating virtual computer system, while activating and operating an alternate virtual computer system on the same computer.
Owner:ONE WORLD LED PTY LTD
Protection of software against use without permit
InactiveUS6266416B1Prevent illegal useKey distribution for secure communicationDigital data processing detailsComputer hardwareApplication program software
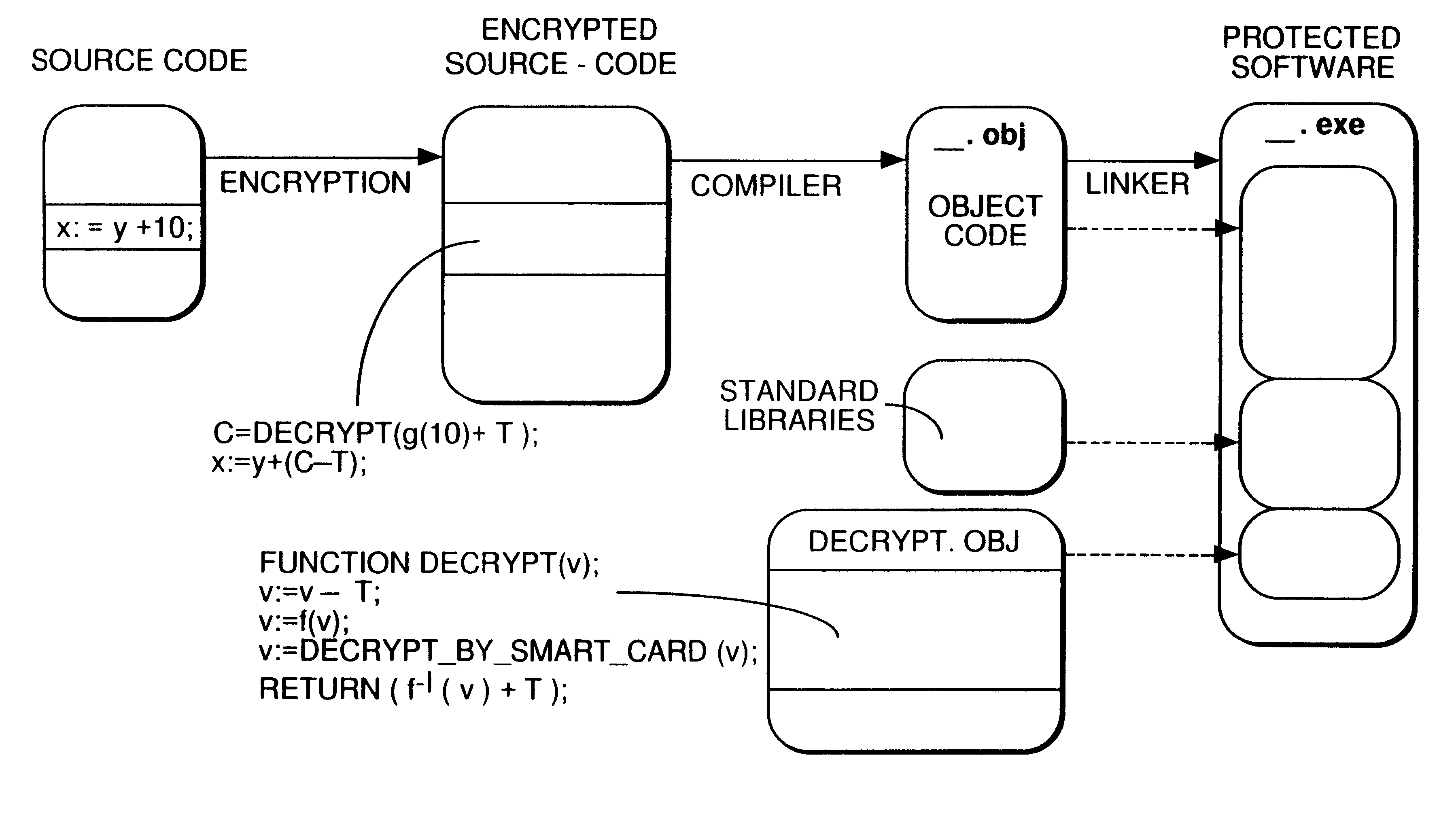
An arrangement to protect software, particularly freely distributed application software, against utilization without permission of the copyright holder. By encrypting the software employing a key (k1) which is different from that key (k2) which is employed in the decryption, better protection is obtained against unauthorized utilization when the decryption key is kept secret to the user. Further improved security is achieved by additionally executing scrambling-descrambling of the communication between the computer in which the software is utilized and the external unit in which the decryption key is stored. Also, the external unit is arranged such that it returns to the host computer, the result from its processing of data received from the host, the result then being utilized in the further execution of the respective program.
Owner:SOSPITA
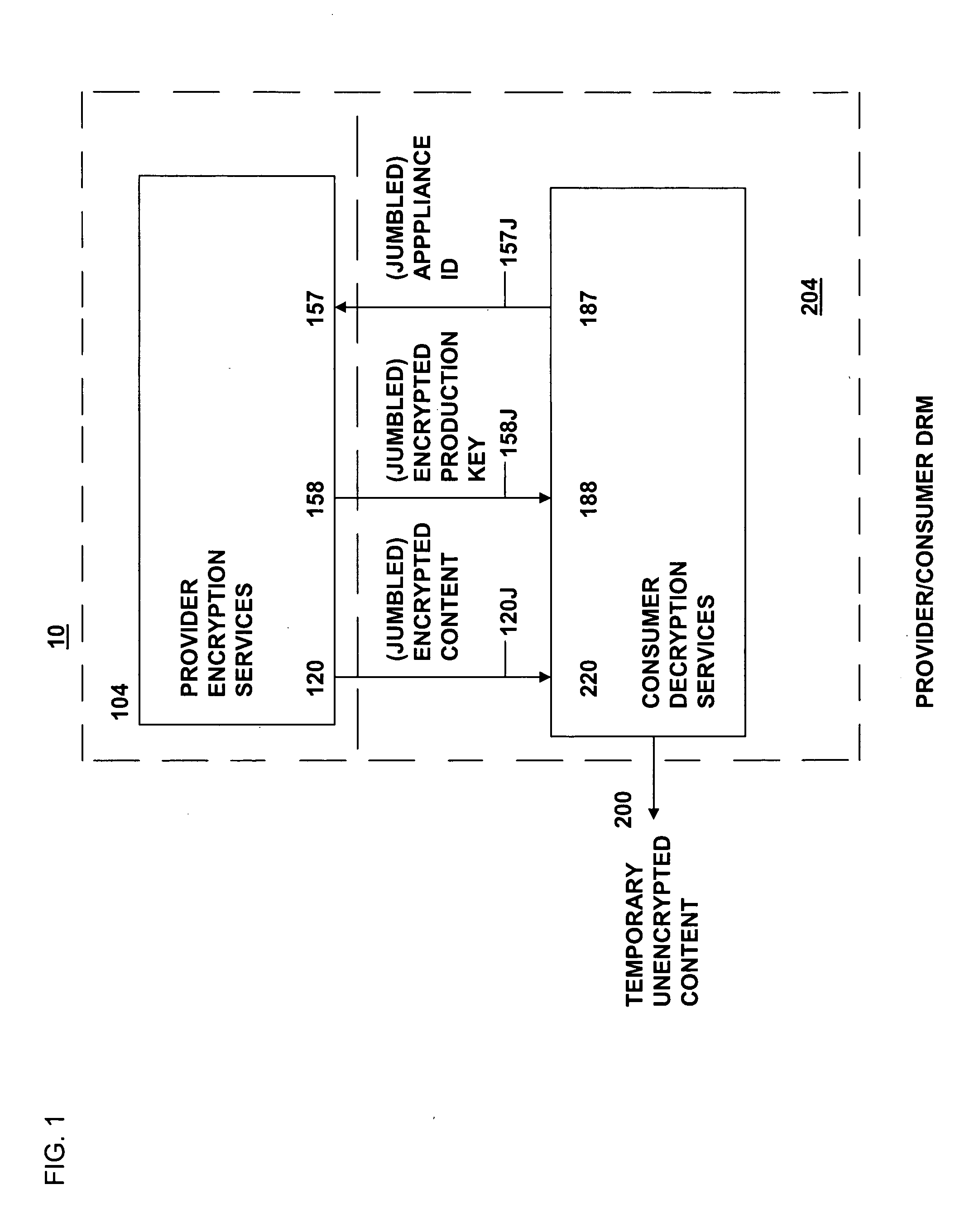
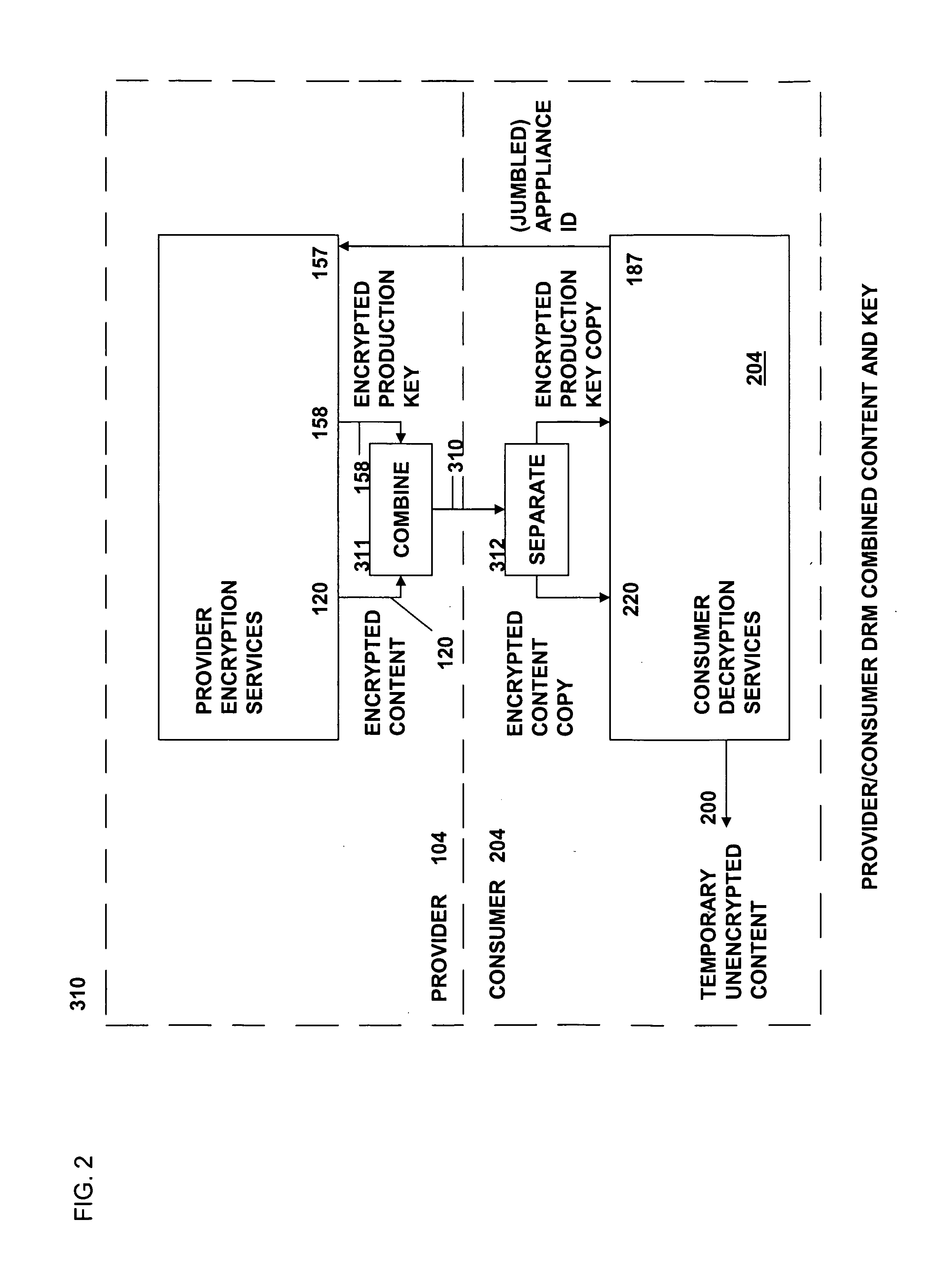
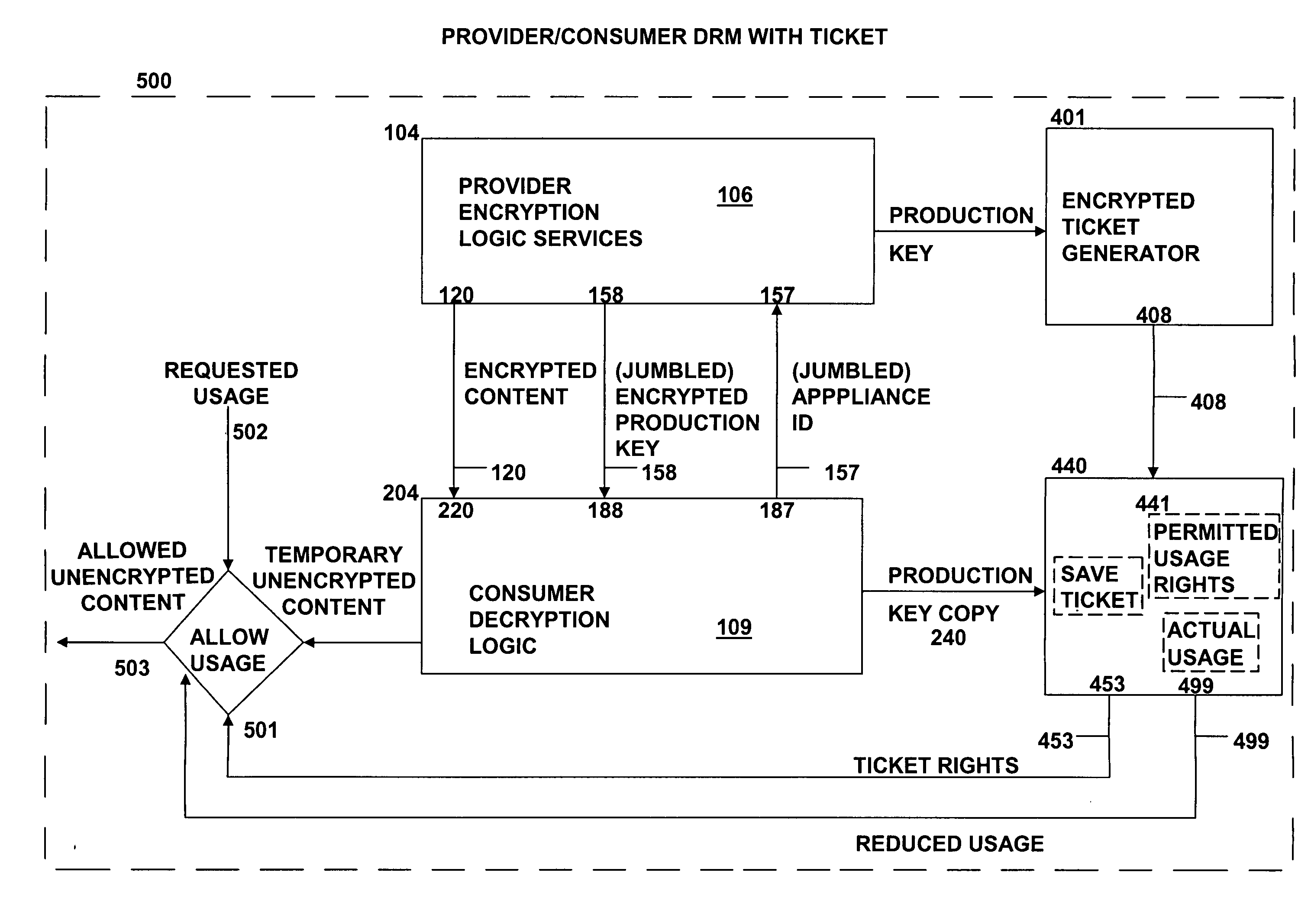
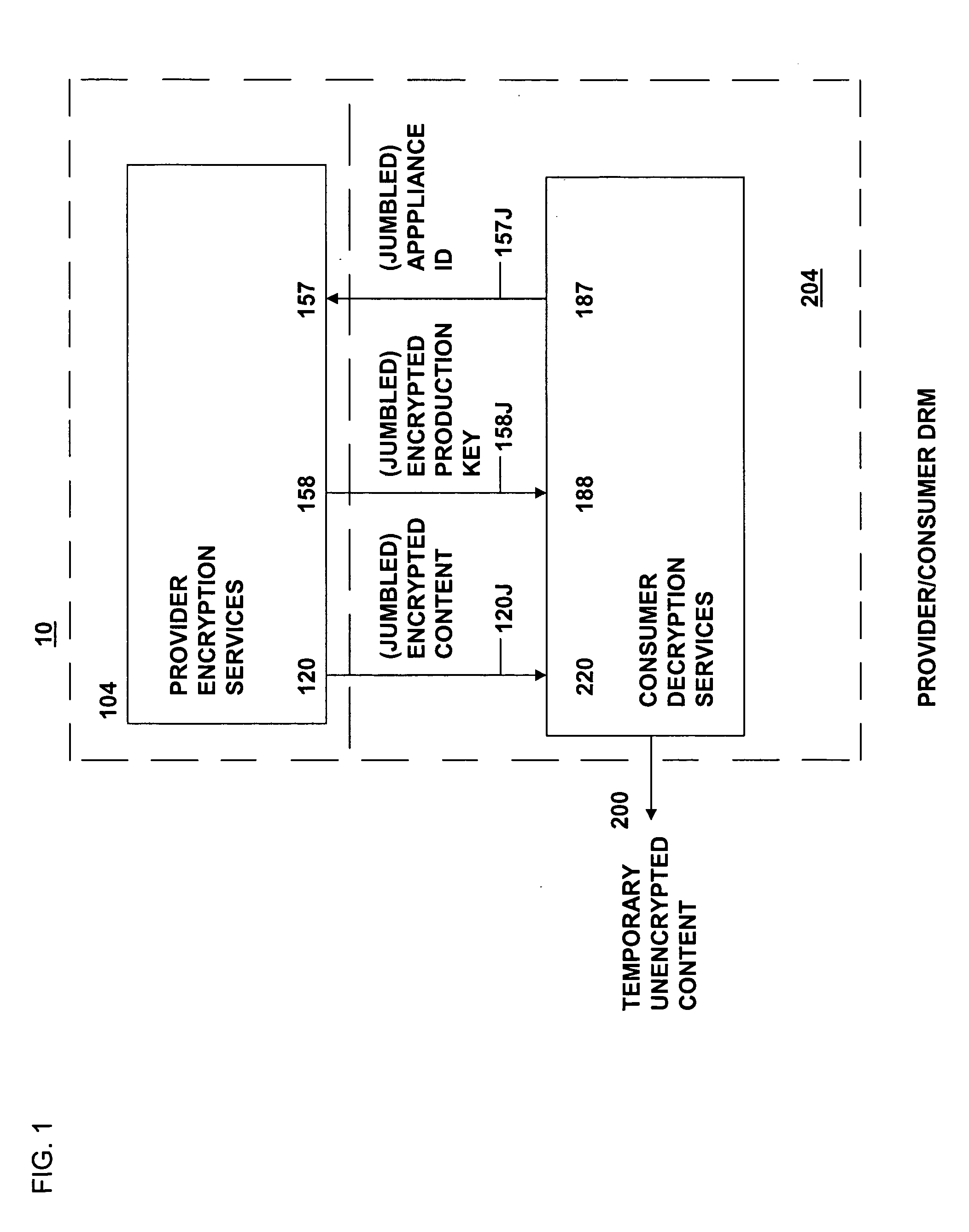
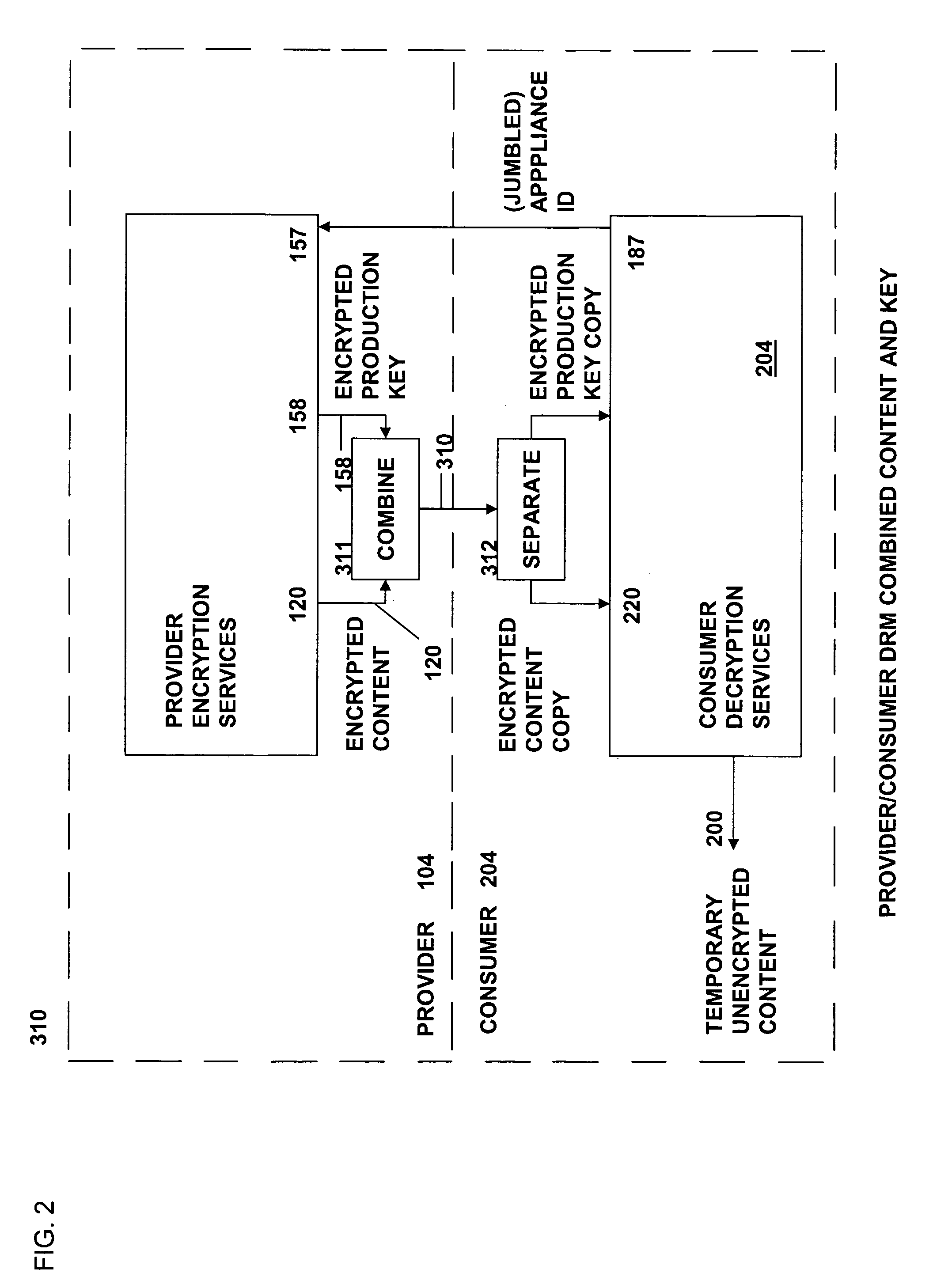
Method and system for secure distribution of selected content to be protected on an appliance-specific basis with definable permitted associated usage rights for the selected content
ActiveUS20080148067A1Unauthorized memory use protectionHardware monitoringApplication program softwareData file
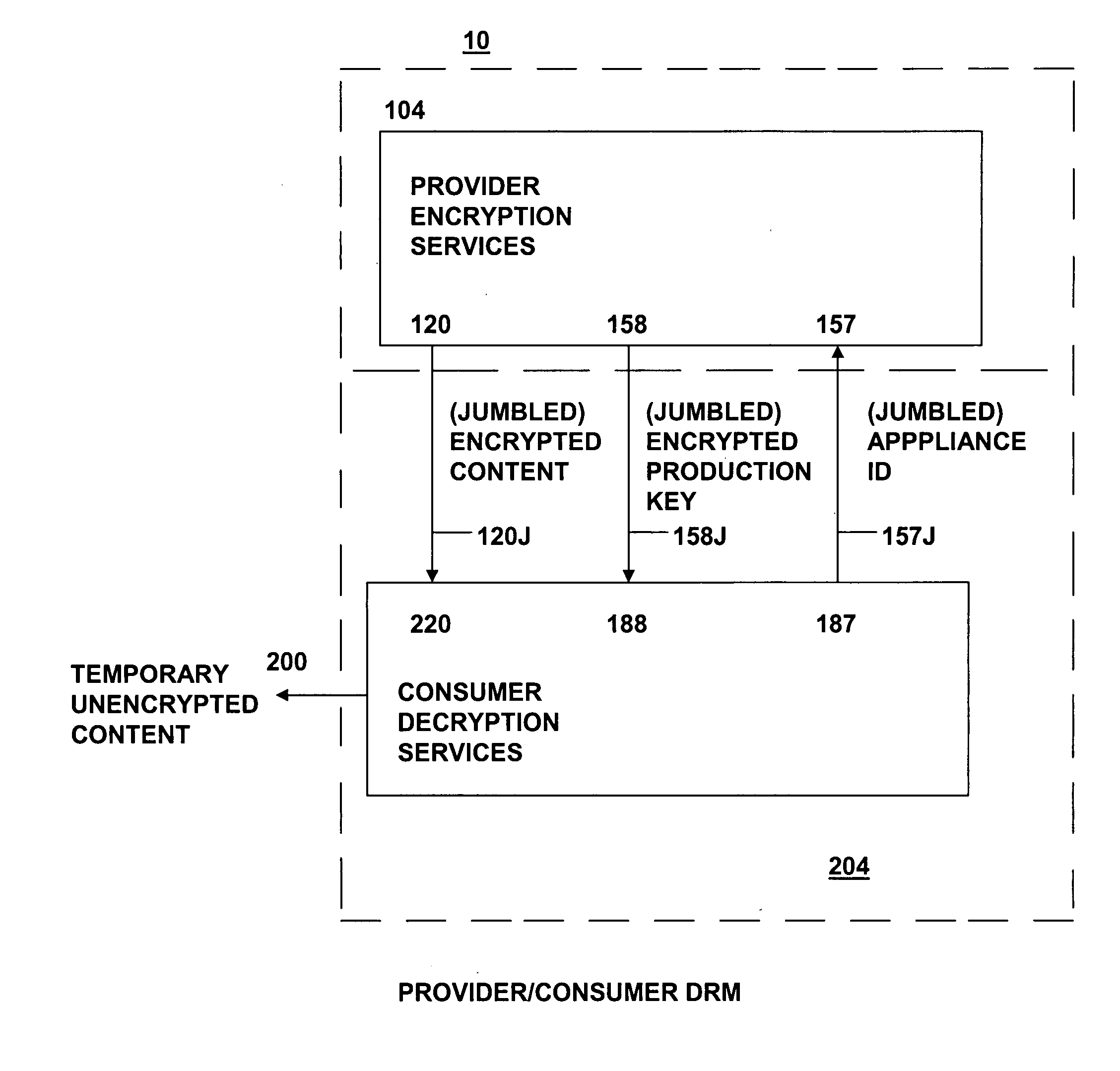
The present invention relates to data rights management and more particularly to a secured system and methodology and production system and methodology related thereto and to apparatus and methodology for production side systems and are consumer side systems for securely utilizing protected electronic data files of content (protected content), and further relates to controlled distribution, and regulating usage of the respective content on a recipient device (computing system) to be limited strictly to defined permitted uses, in accordance with usage rights (associated with the respective content to control usage of that respective content), on specifically restricted to a specific one particular recipient device (for a plurality of specific particular recipient devices), or usage on some or any authorized recipient device without restriction to any one in specific, to control use of the respective content as an application software program, exporting, modifying, executing as an application program, viewing, and / or printing of electronic data files.
Owner:OL SECURITY LIABILITY CO
User interface system and method for implementation on multiple types of clients
InactiveUS20060077941A1Reduces application software developmentReduce maintenance costsInformation formatContent conversionApplication program softwareSoftware update
A method and system for implementing a user interface for providing a data service in a mobile client using a server with knowledge of the client's hardware and software capabilities to modify data content and display rules for an improved user interface on the client. Data may be cached on the client to improve application response time and provide a standalone application capability for the client. The automatic conversion of newly developed applications to a plurality of clients with differing hardware and software capabilities reduces application software development and maintenance costs. Software updates and bug fixes can be deployed with the same method and system.
Owner:TRILIBIS
Secure Application Acceleration System, Methods and Apparatus
ActiveUS20170206034A1Less timeEasy to deployInput/output to record carriersDigital data protectionApplication program softwareData set
An improved storage controller that enables the acceleration of datacenter software, by making it easier to deploy application software portions (applets) onto storage devices, in a manner that best supports runtime performance acceleration of storage-network-latency-throttled applications. Means are defined for how server hosted applications cause to have provisioned, initiate execution of, and work with a multitude of applets on a multitude of storage devices, proximate to storage contents. This invention supports the multi-exabyte growth of data storage, by scaling performance acceleration linearly with the growth in the number of storage devices. This in turn supports the evolving cloud and Enterprise Cognitive Computing datacenter by providing the infrastructure necessary for accelerating applications that face enormous heterogeneous datasets. This includes Big Data Analytics of problems that have eluded successful analysis.
Owner:FETIK RICHARD
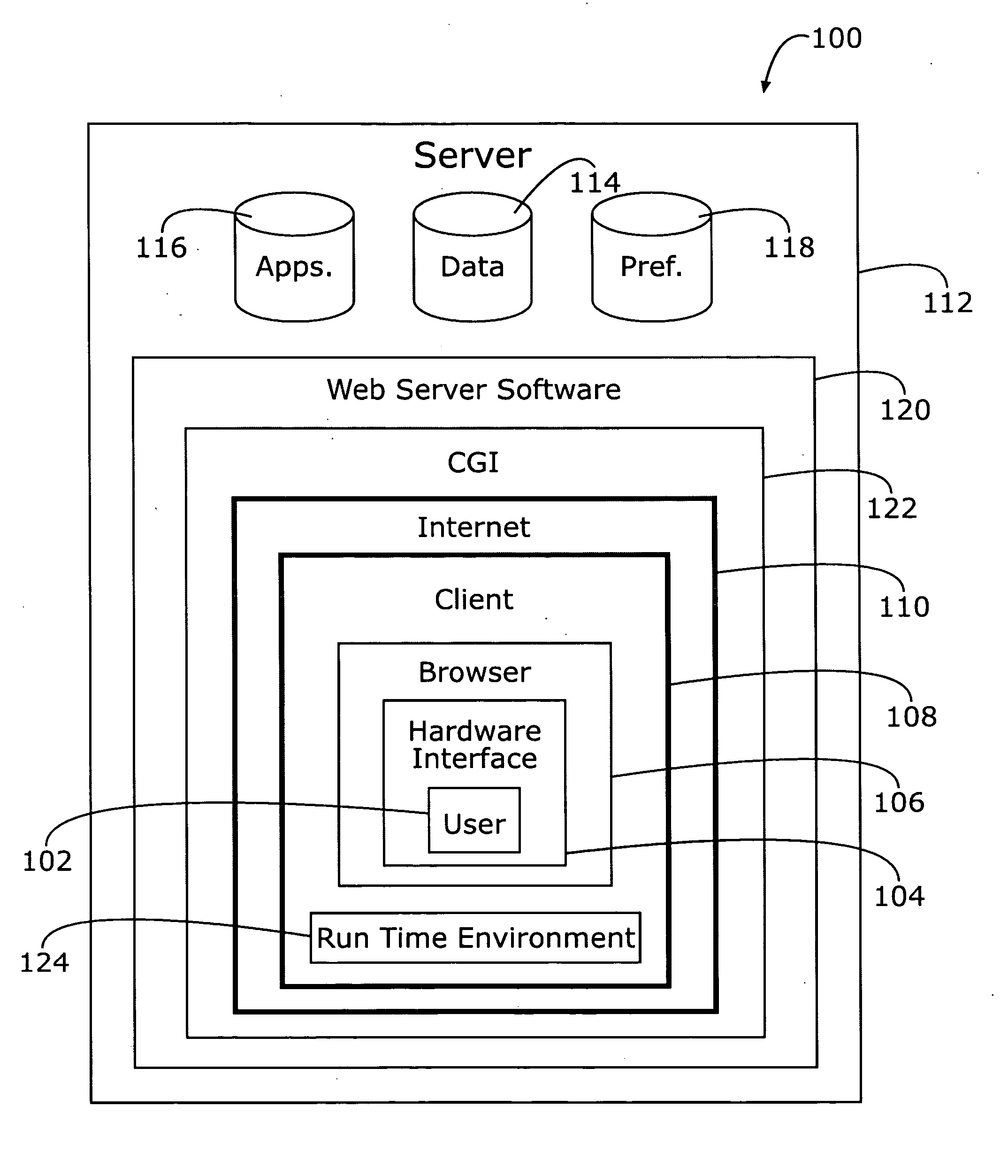
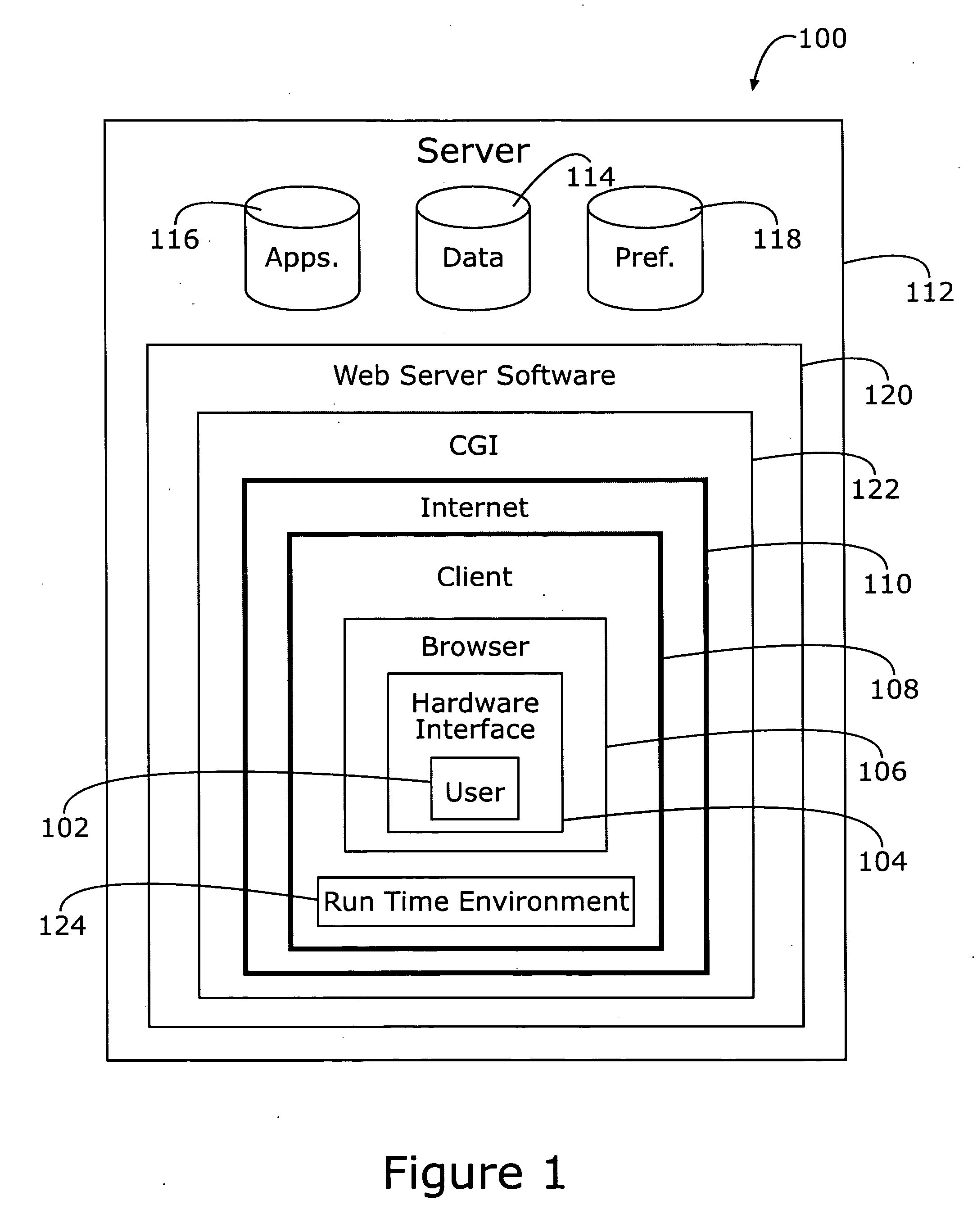
Internet operating system
InactiveUS20060259592A1Easy to buildOvercome problemsInterprogram communicationMultiple digital computer combinationsOperational systemData access
An Internet-based operating system whereby use of data and application software stored on a server may be selectively downloaded to a client device upon request therefrom allowing server-based applications to be accessed and executed on the client device. Because secure communication may readily be established between the server and the client device, many traditional problems of remote data access are overcome. Application software, typically Java code, provides an inherently virus-proof programming language. The end user, operating a client device may access a wide variety of application software with no need to purchase, install, and maintain the software on his machine. Using an easy-to-use GUI, a user selects an application, opens existing or creates new files. The application executable code is identified by a link embedded in a stream of markup language, typically XML. The operating system allows complex applications to be executed on thin clients having limited memory / storage capacity.
Owner:ANGELINE BRENT J
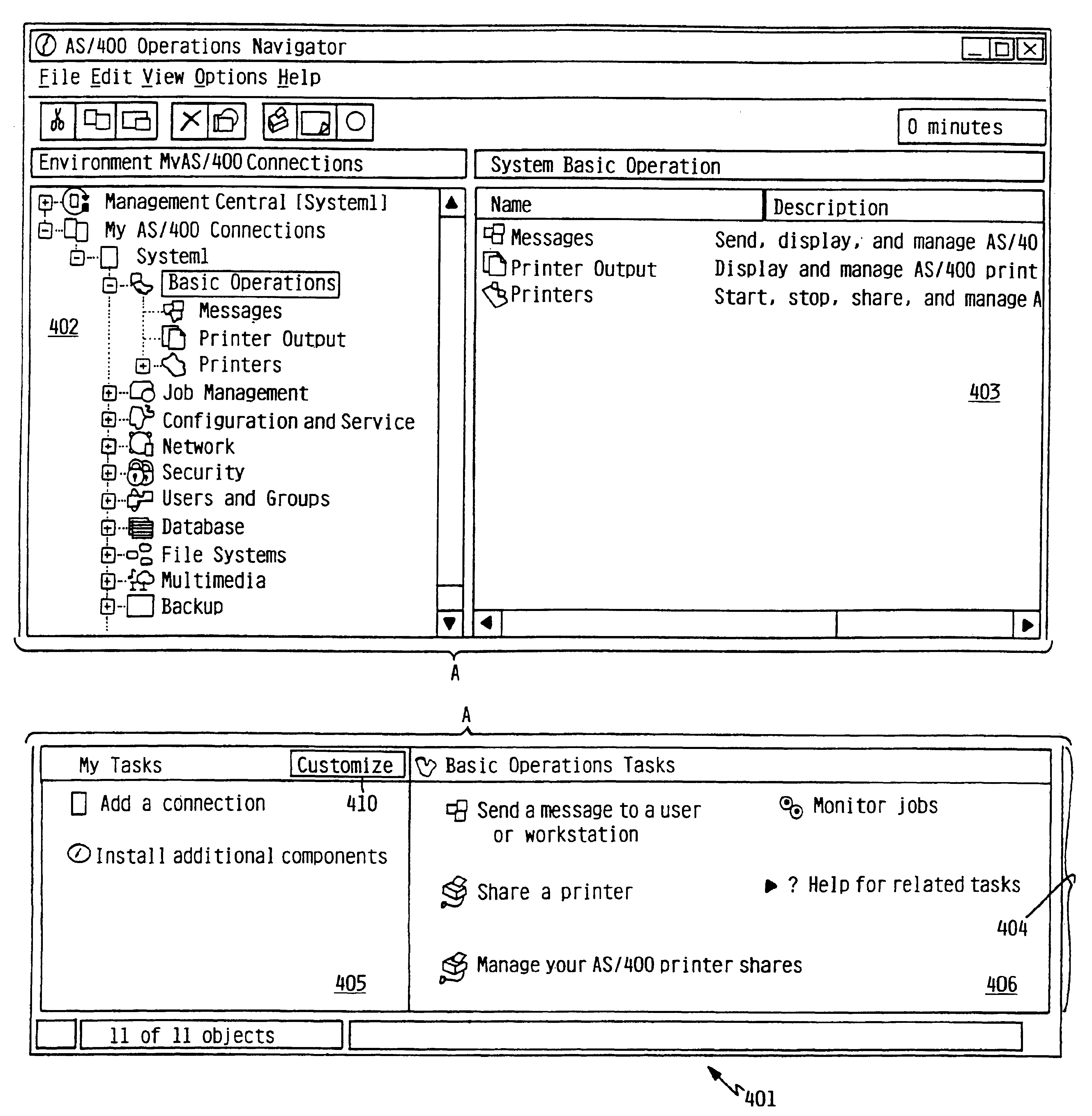
Hybrid task and file oriented user interface
InactiveUS6925609B1Easy to switchExecution for user interfacesInput/output processes for data processingApplication program softwareApplication software
An interactive process navigation window is a hybrid of a file-based paradigm and a task-based paradigm. The window contains multiple panes, in which at least one pane (object pane) lists objects, while another pane lists tasks which are applicable to a selected object in the object pane, and which serves as a launchpad for various application software. A root object pane is placed in the upper left portion of the window, displaying groupings and sub-groupings of objects. A content object pane is placed in the upper right portion, the content pane displaying the contents of a group selected from the root pane. A task pane occupies the bottom of the window, the task pane displaying tasks applicable to the group selected from the root pane. In one embodiment, the task pane is divided into two parts, one of which displays tasks related to a selected group from the root pane, as described above, while the other displays a user-configurable list of frequently performed tasks, which does not vary with the contents of the object pane(s). The navigation window described herein provides diverse users with an interface which is both task-oriented and object-oriented, making it easy to switch from one paradigm to the other, depending on user preference, the type of task to be performed, or other appropriate factors.
Owner:IBM CORP
Protecting software from unauthorized use by applying machine-dependent modifications to code modules
ActiveUS7188241B2Prevents illegal copyingEliminating opportunityDigital data processing detailsUser identity/authority verificationCode moduleApplication program software
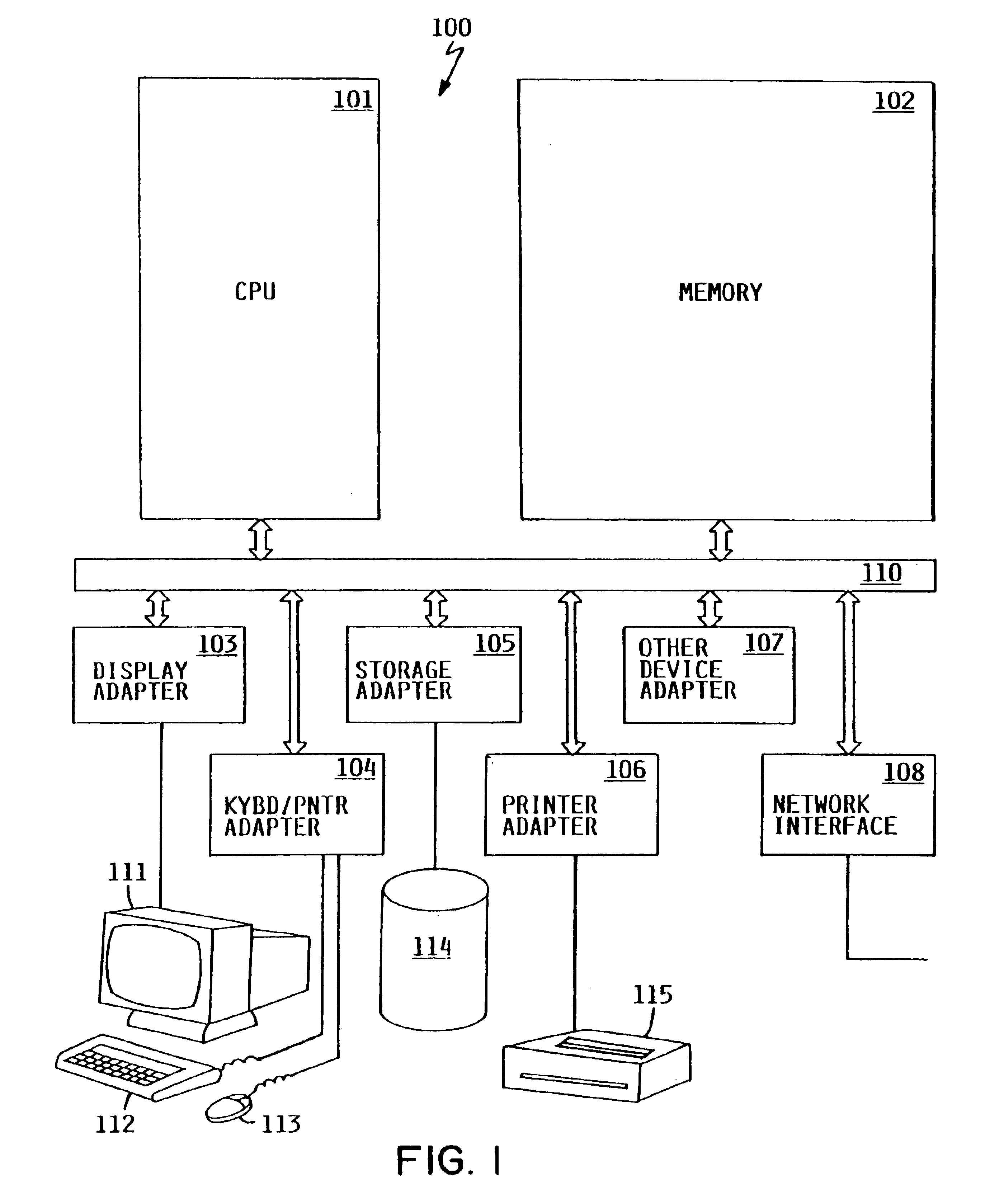
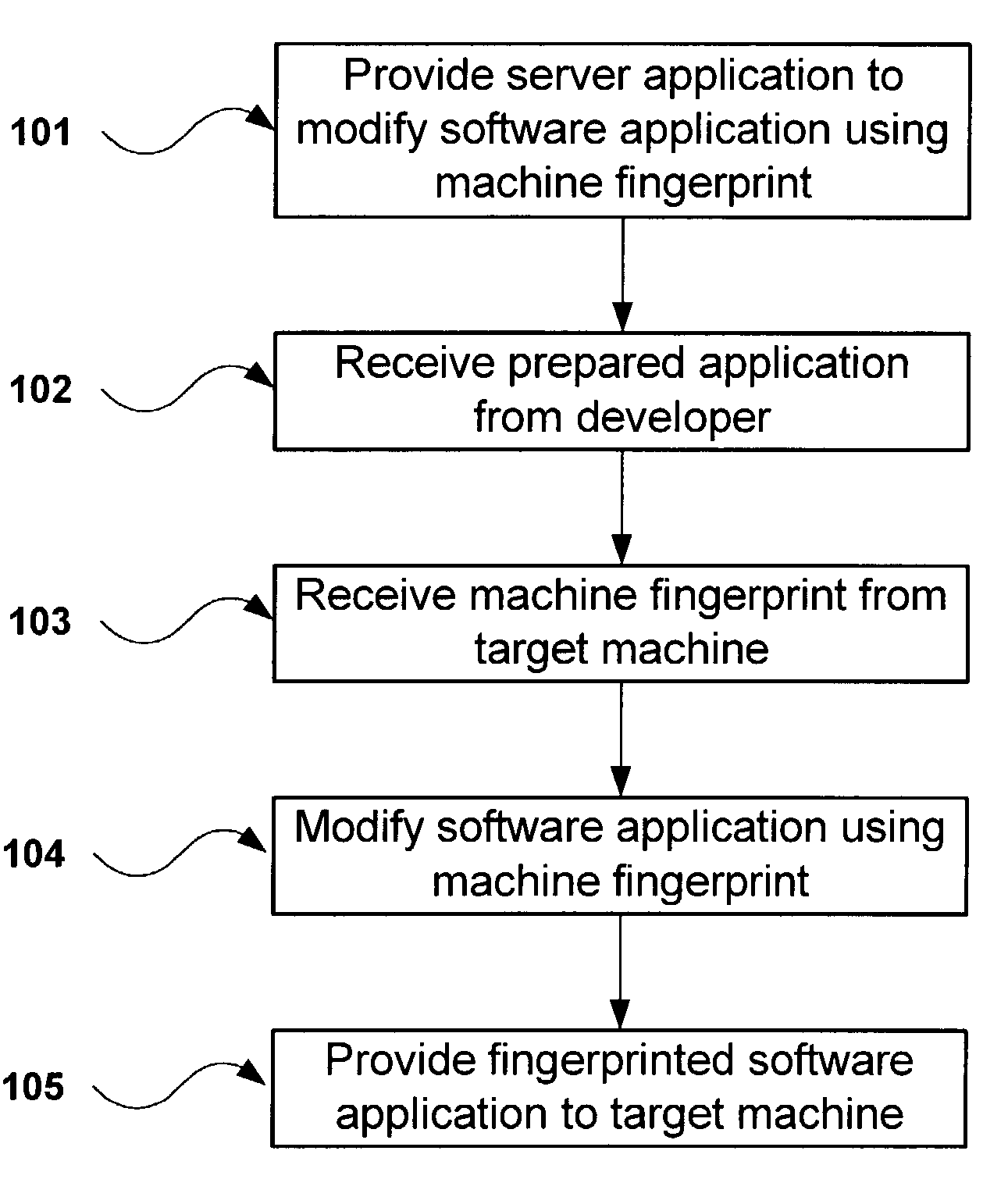
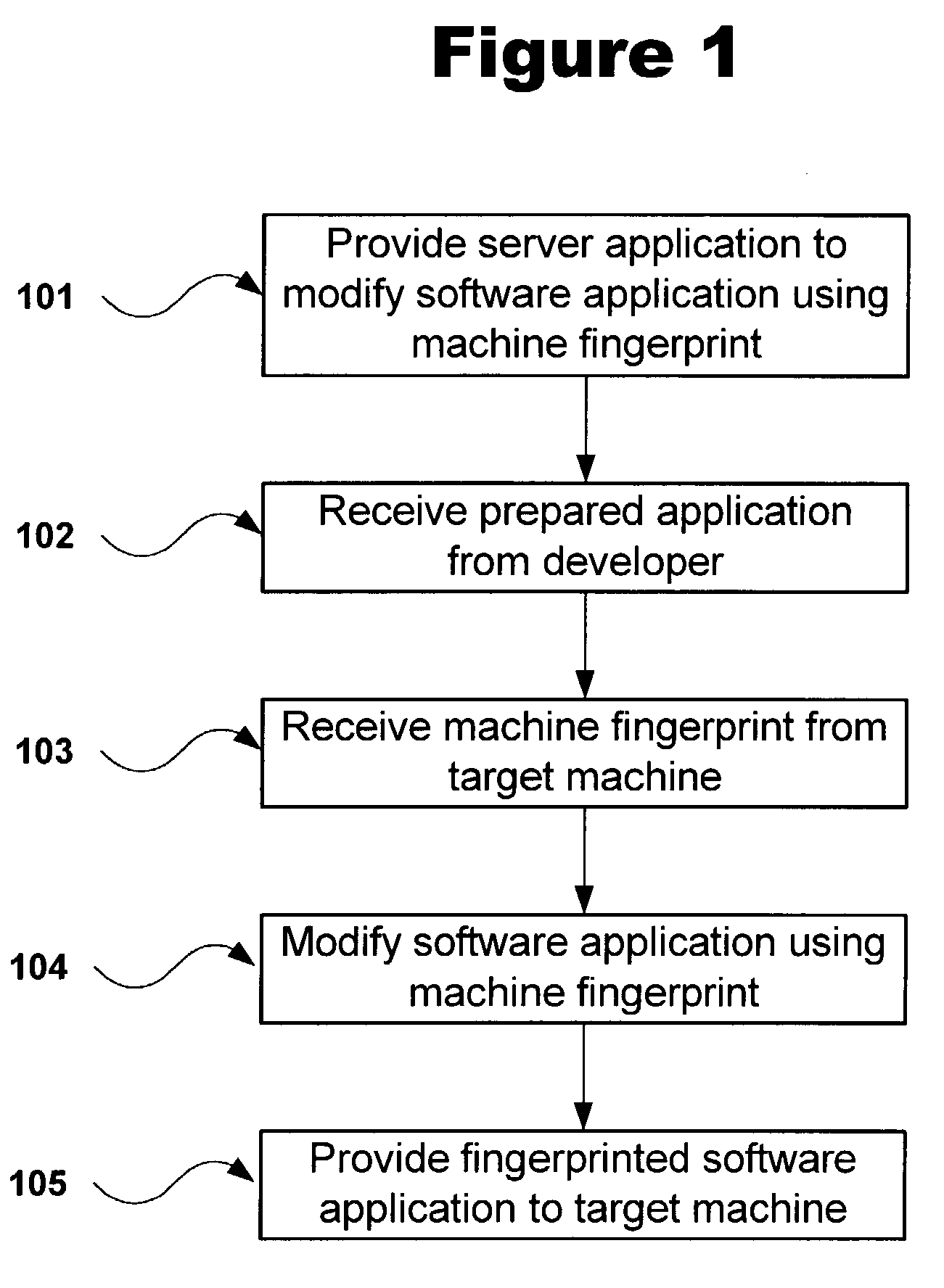
A method and system for providing anti-piracy protection to a software application on a server connected to a target machine over a network is described. The method includes providing a server with a server application for modifying the application software based on a machine fingerprint of the target machine, and for receiving and storing the application software. The server application receives the target machine fingerprint in conjunction with a license transaction between the server and the target machine. The server then modifies the application software using the received machine fingerprint, and provides the resulting modified software to the target machine, wherein the supplied software will only operate correctly on the target machine.
Owner:PACE ANTI PIRACY
Three-dimensional application program framework structure and a method for implementing an application program based on the same, and an automatic testing system based on a three-dimensional application software framework and a method therefor
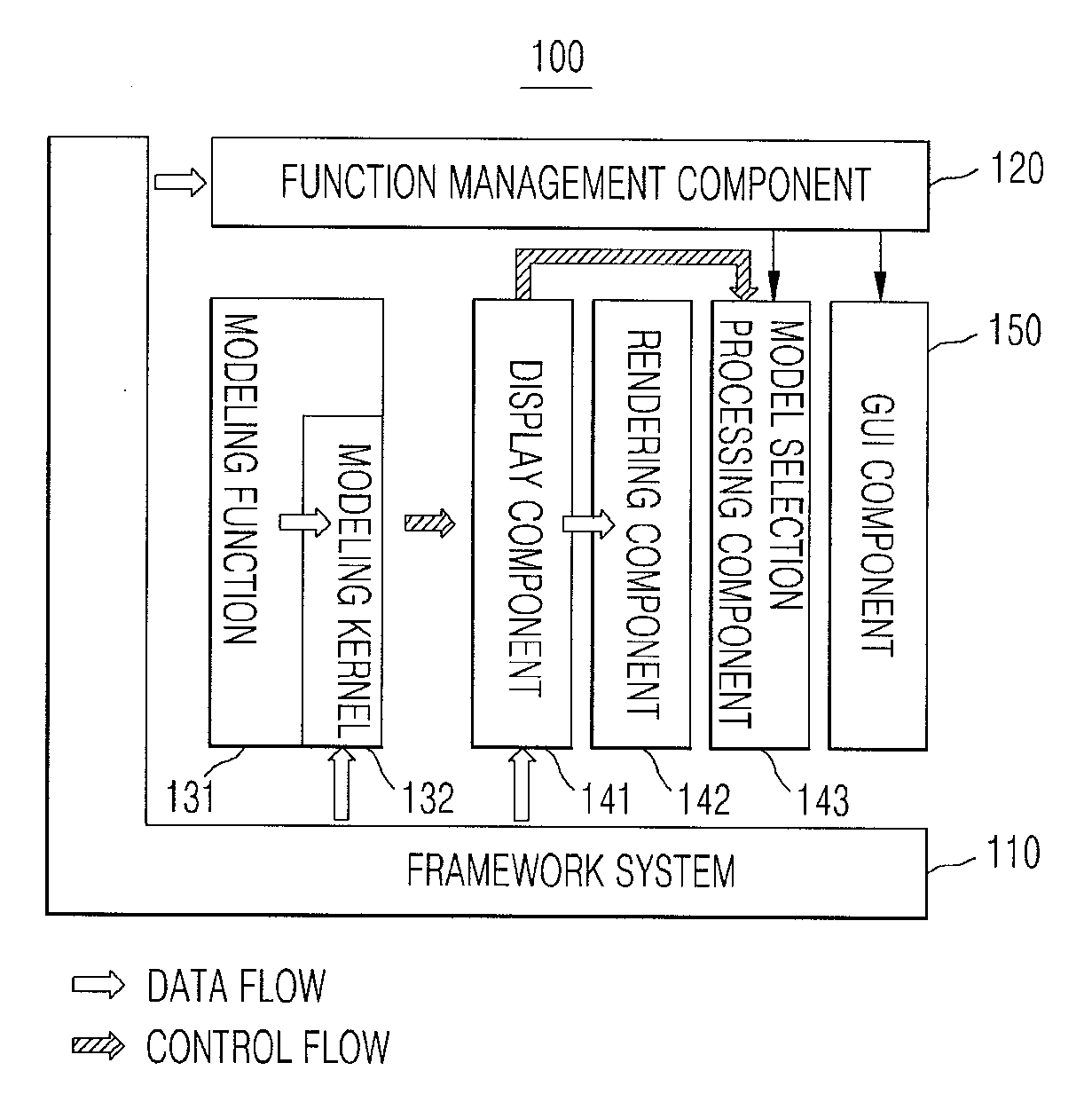
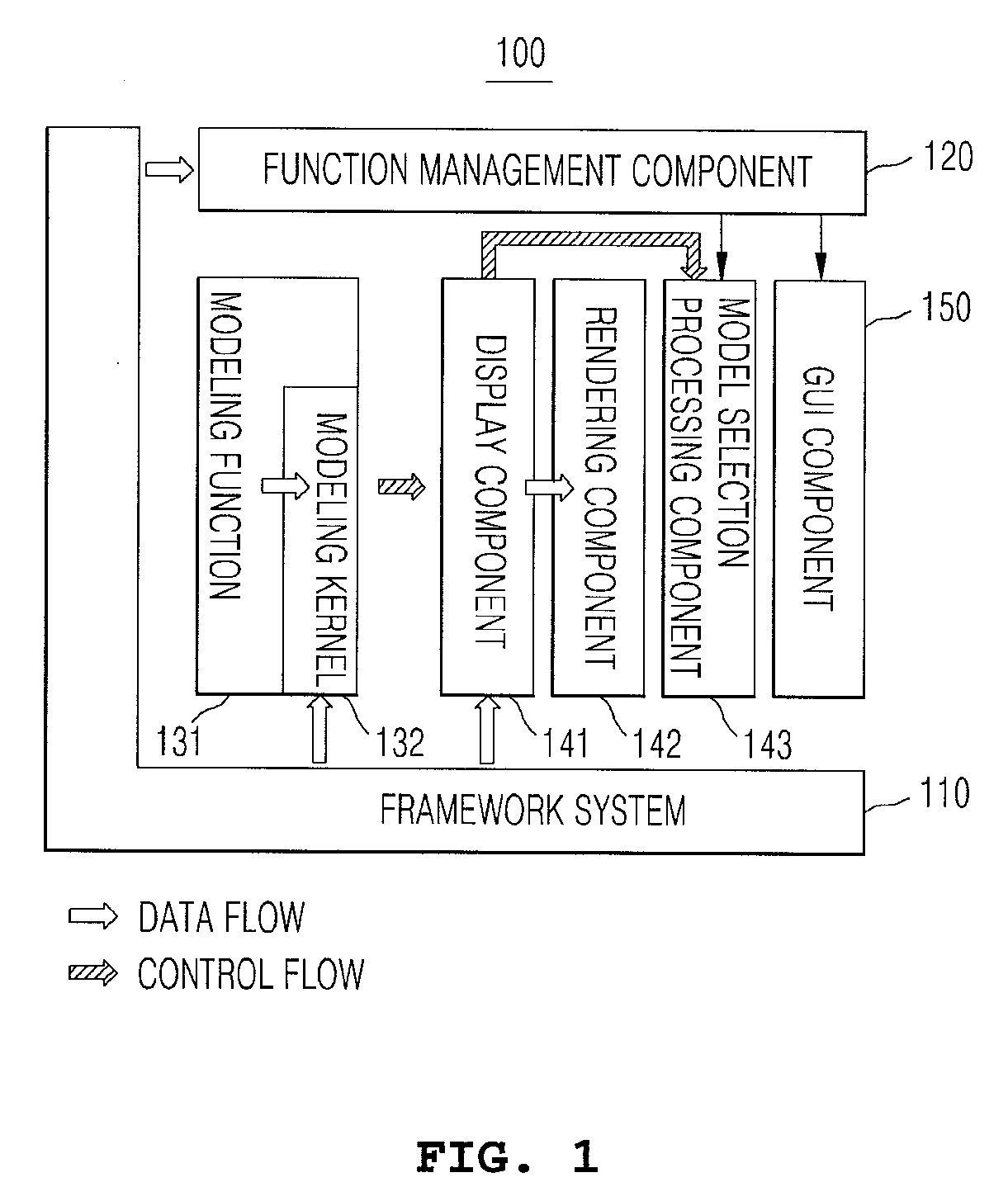
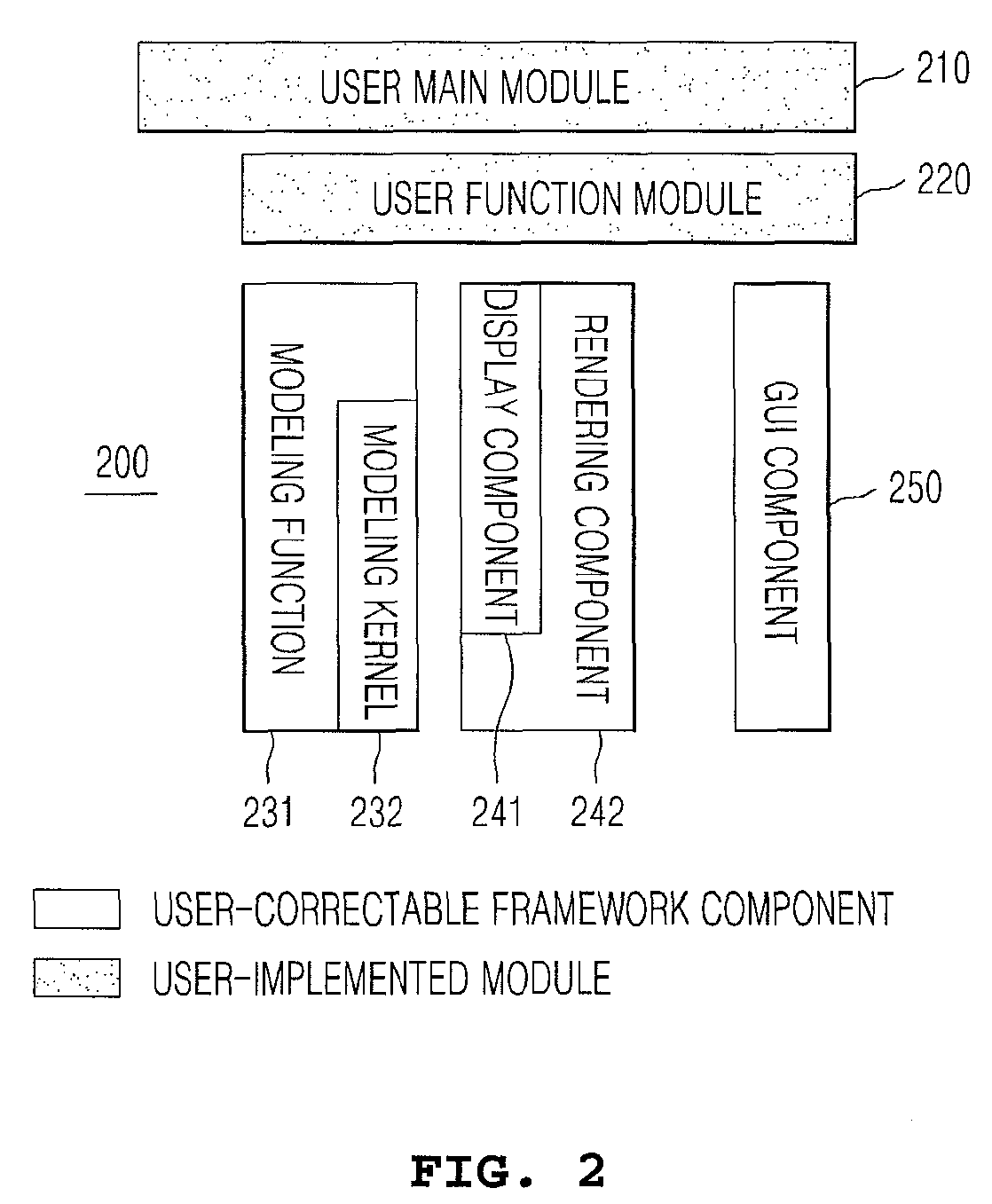
InactiveUS20110125448A1Ensure stable executionMaintain relatively stableError detection/correctionElectrical measurementsGraphicsFrame based
A three-dimensional application program framework structure; a method for implementing an application program based on the same; and an automatic testing system based on a three-dimensional application software framework and a method therefor. The three-dimensional application program framework structure provides a framework comprising functions and management of the environment of the system and events to be implemented by the user (developer), and the developer can easily expand the graphic user interface (GUI) and an actual modeling function as required, and user model. In addition, by using an automatic test system based on the framework, it is possible to record the function-execution history of the user and to automatically generate a test case, and to thereby test the functioning of the application software through the use of the test case regardless of changes in the source code and the GUI.
Owner:CODESE
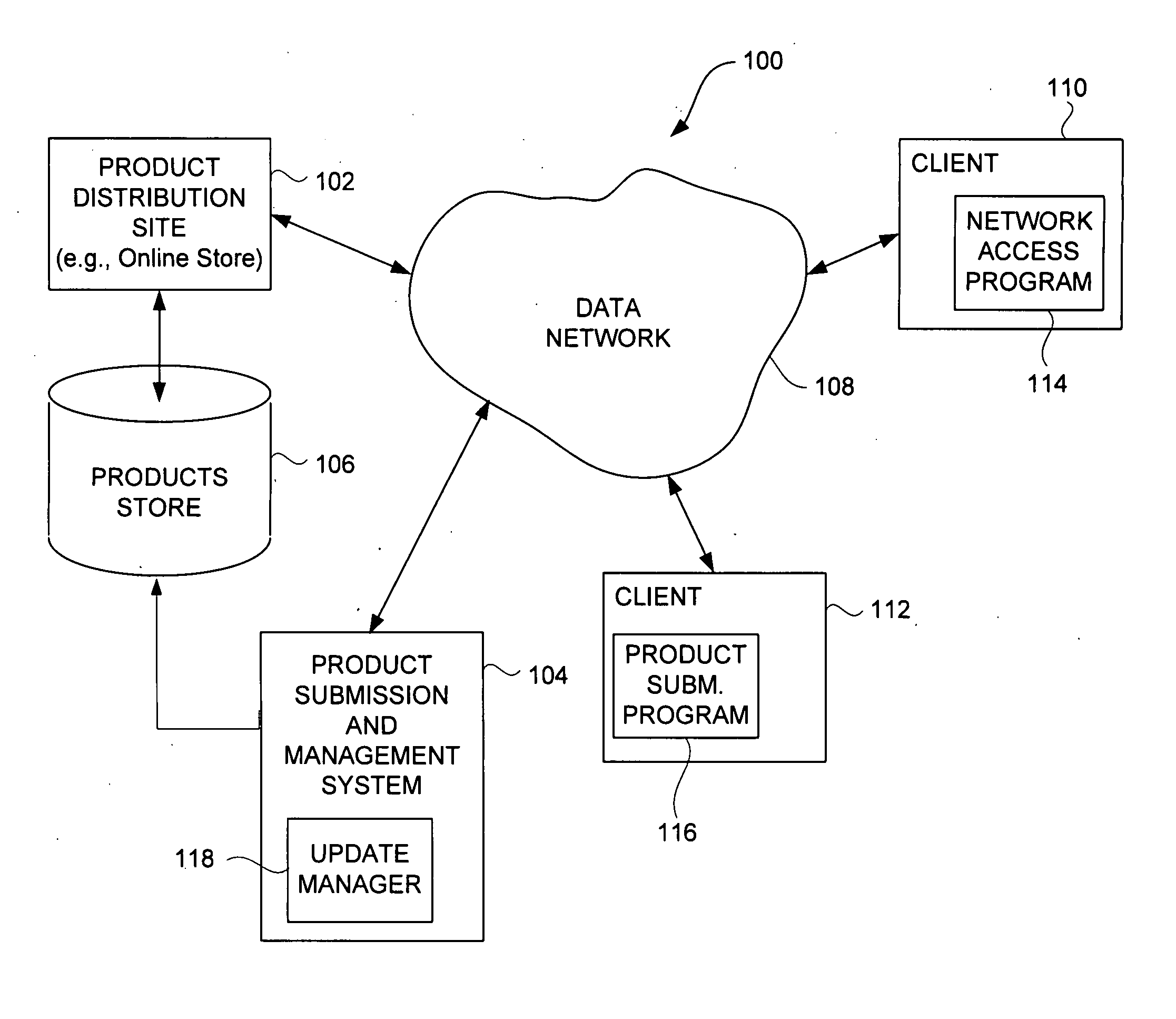
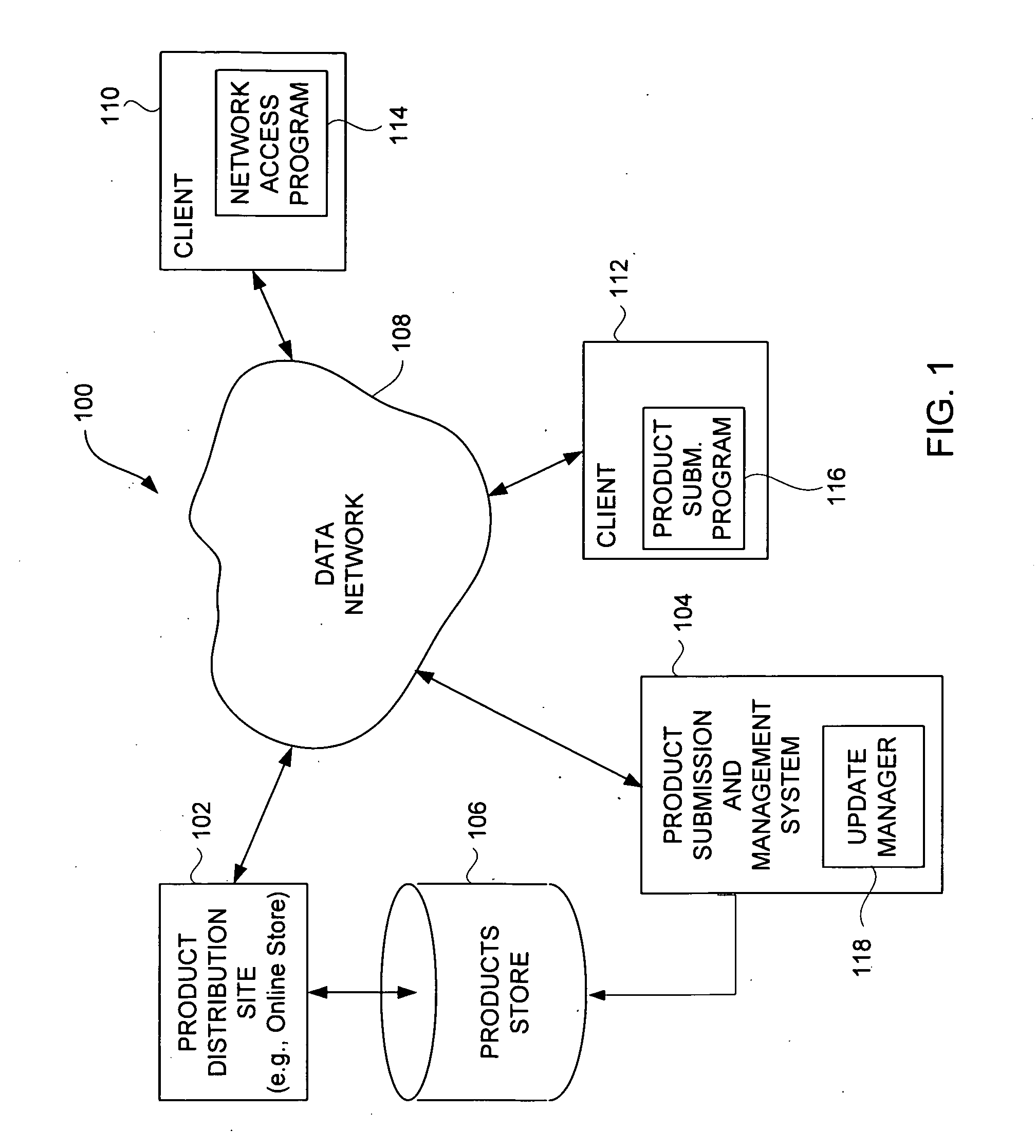
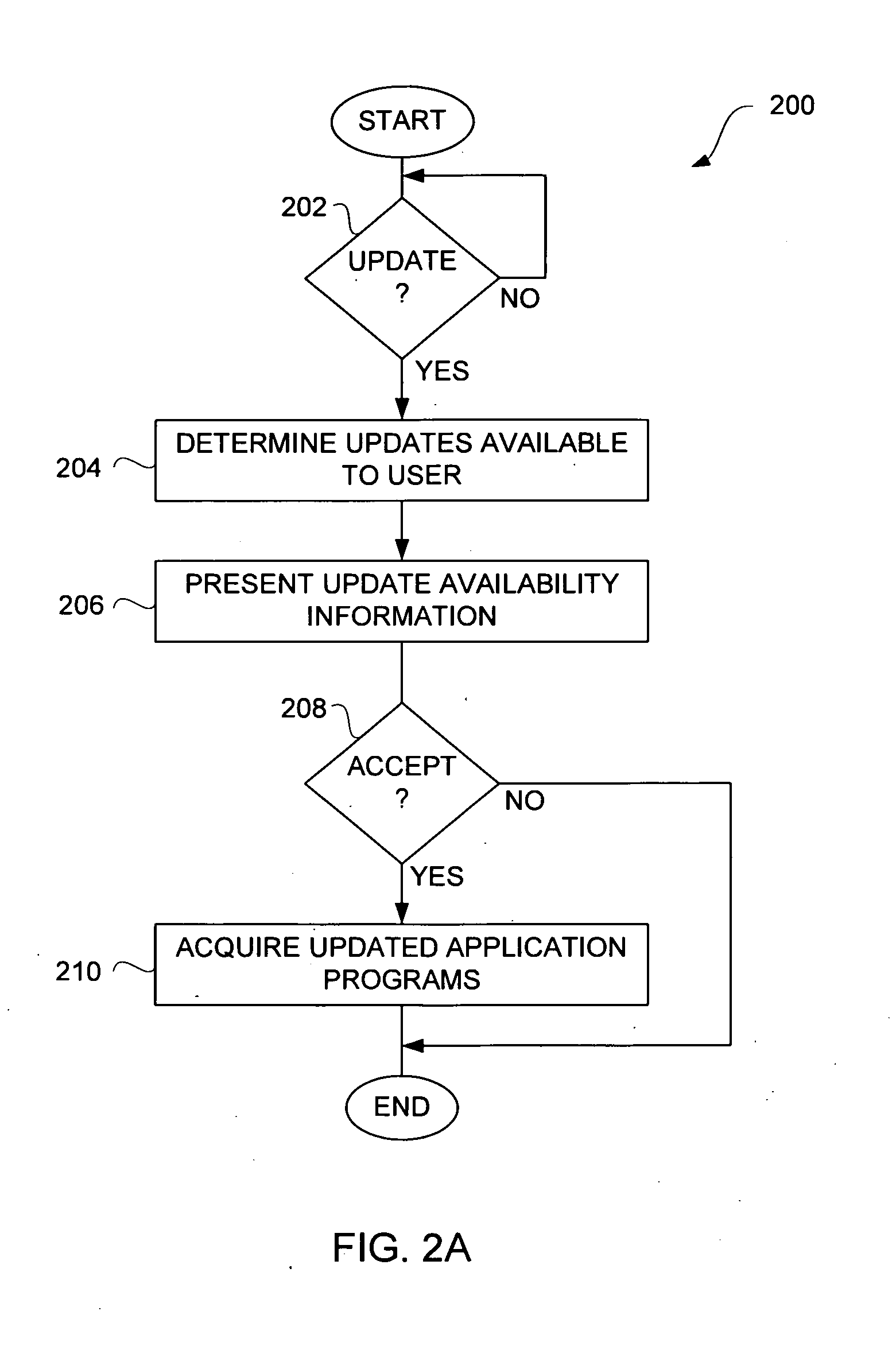
Techniques for Acquiring Updates for Application Programs
InactiveUS20090307682A1Effective distributionDigital computer detailsProgram loading/initiatingComputer-aidedApplication software
Improved approaches for submission, management and / or distribution of updates to digital products, such as application programs (software programs), with respect to an online product distribution site are disclosed. Updates to numerous digital products can be centrally managed in a uniform and computer-assisted manner so that updates can be efficiently distributed to appropriate users.
Owner:APPLE INC
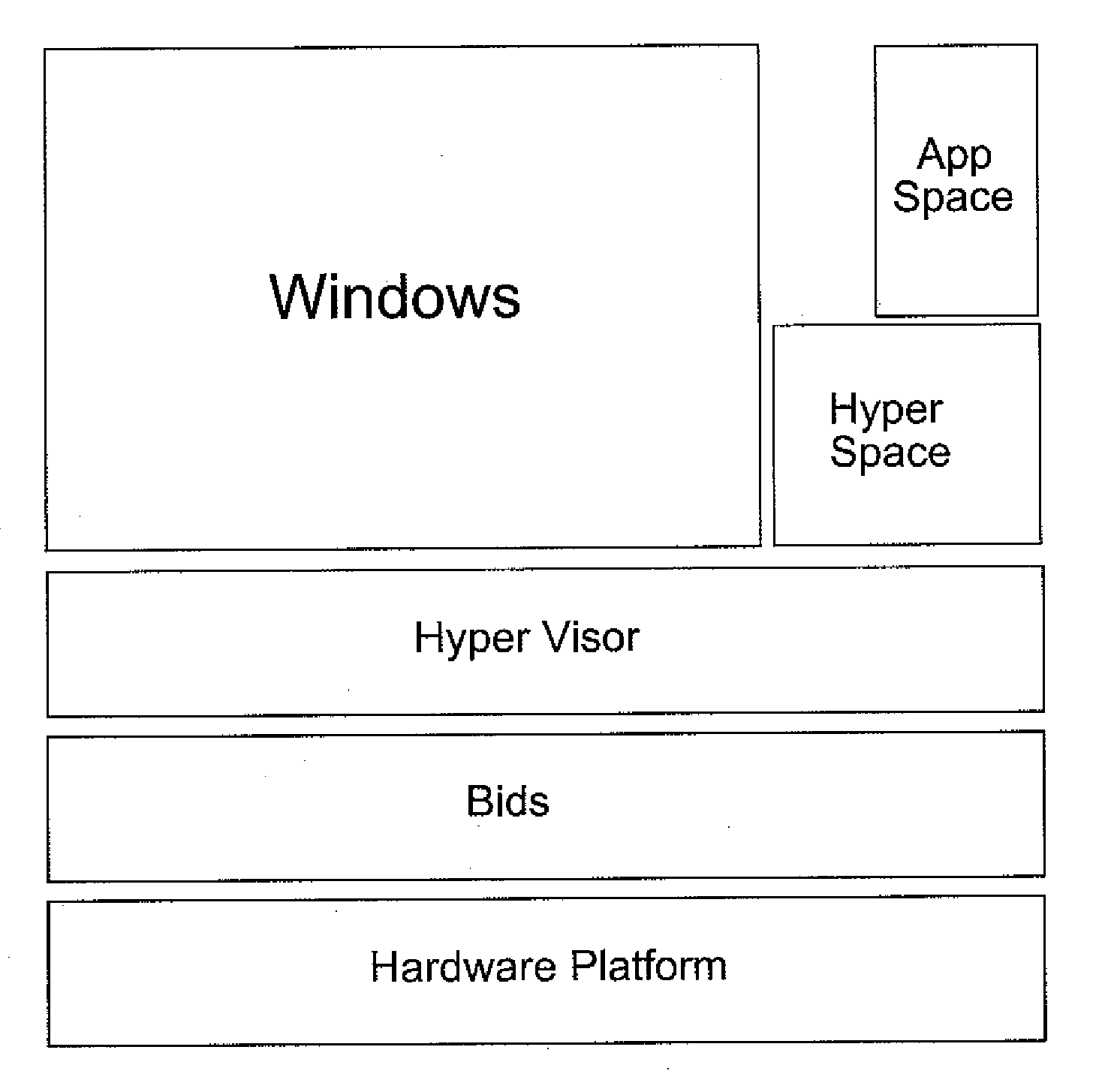
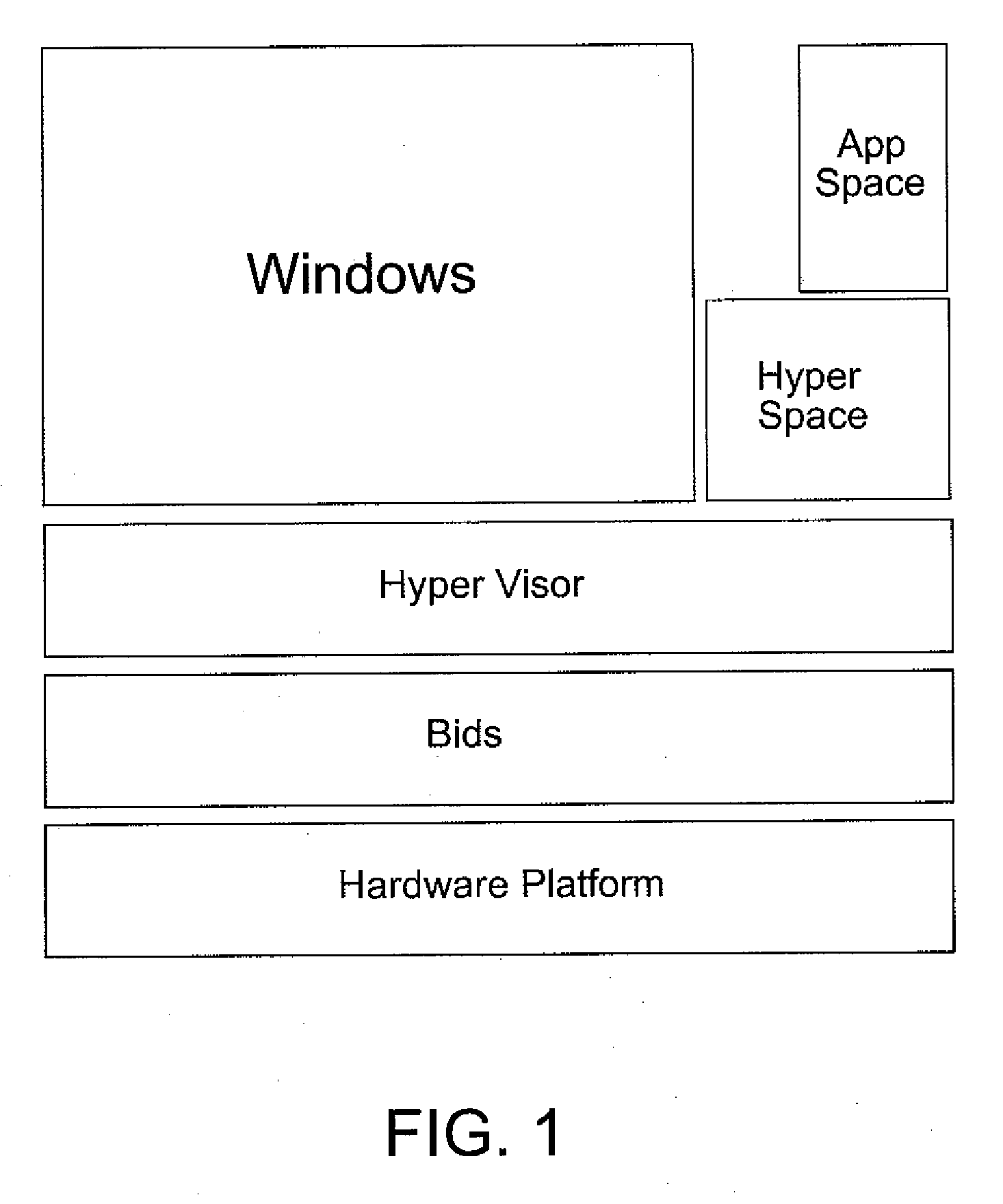
Hypervisor and virtual machine ware
InactiveUS20090287571A1Digital computer detailsSoftware simulation/interpretation/emulationApplication program softwareGraphics
An apparatus, system and method for an instant-on environment. The apparatus, system and method may include a hypervisor instantiated by a BIOS, at least one application space instantiated by the hypervisor in parallel to, and prior to complete boot of, at least one main operating system, and a graphical user interface including at least one application software, which at least one application software includes at least one embedded content, launched within said at least one application space.
Owner:MATTEL INC
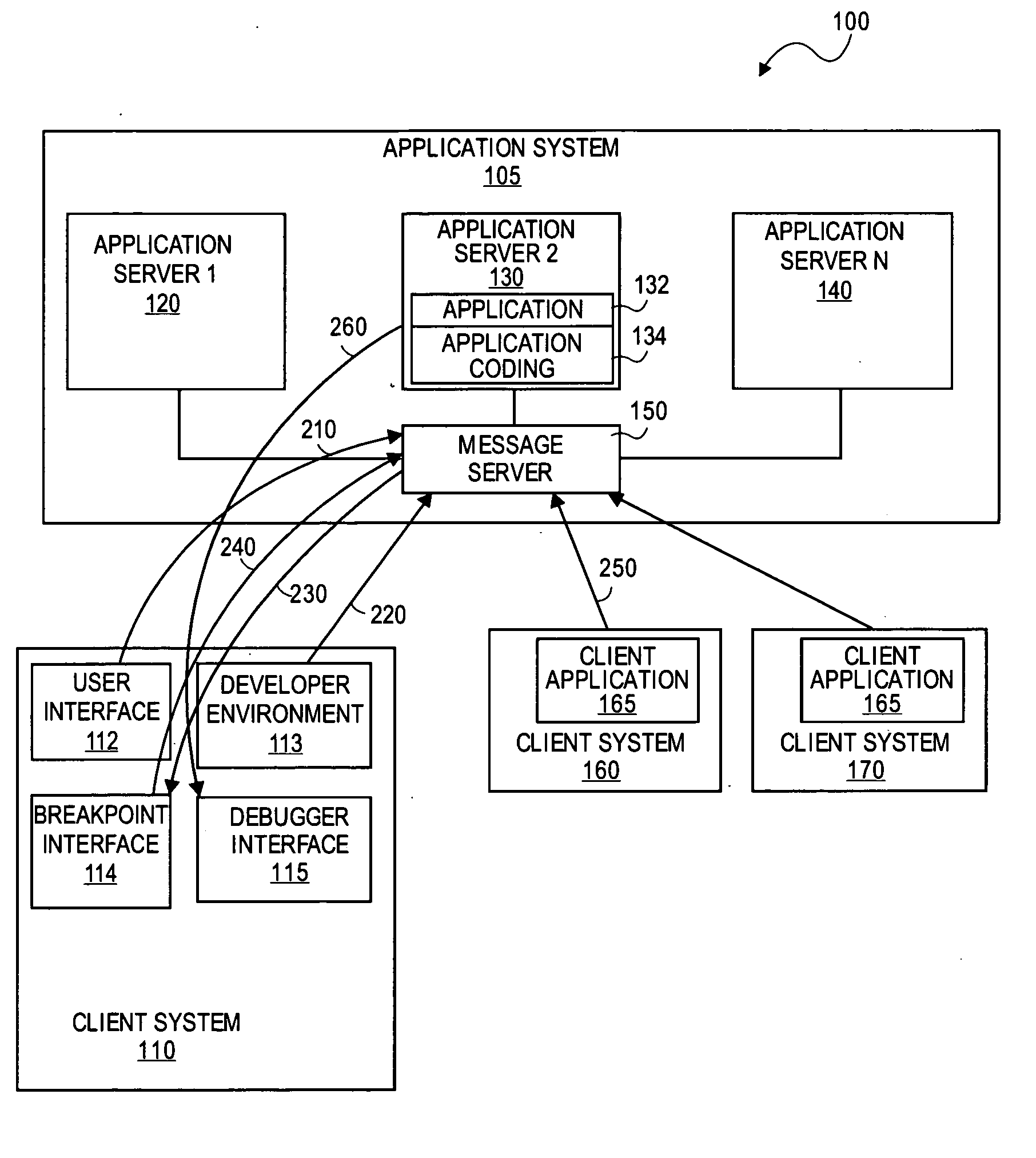
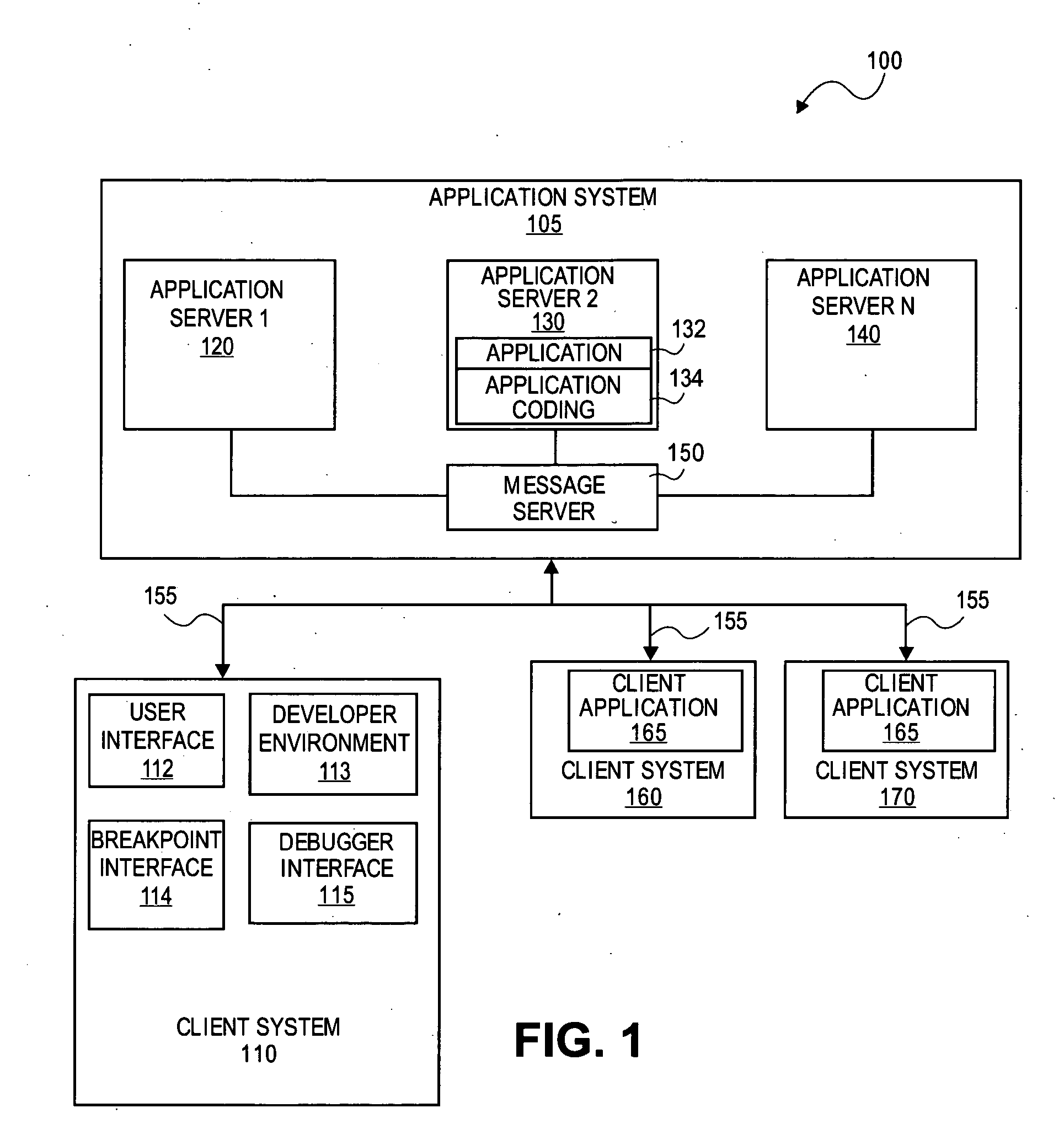
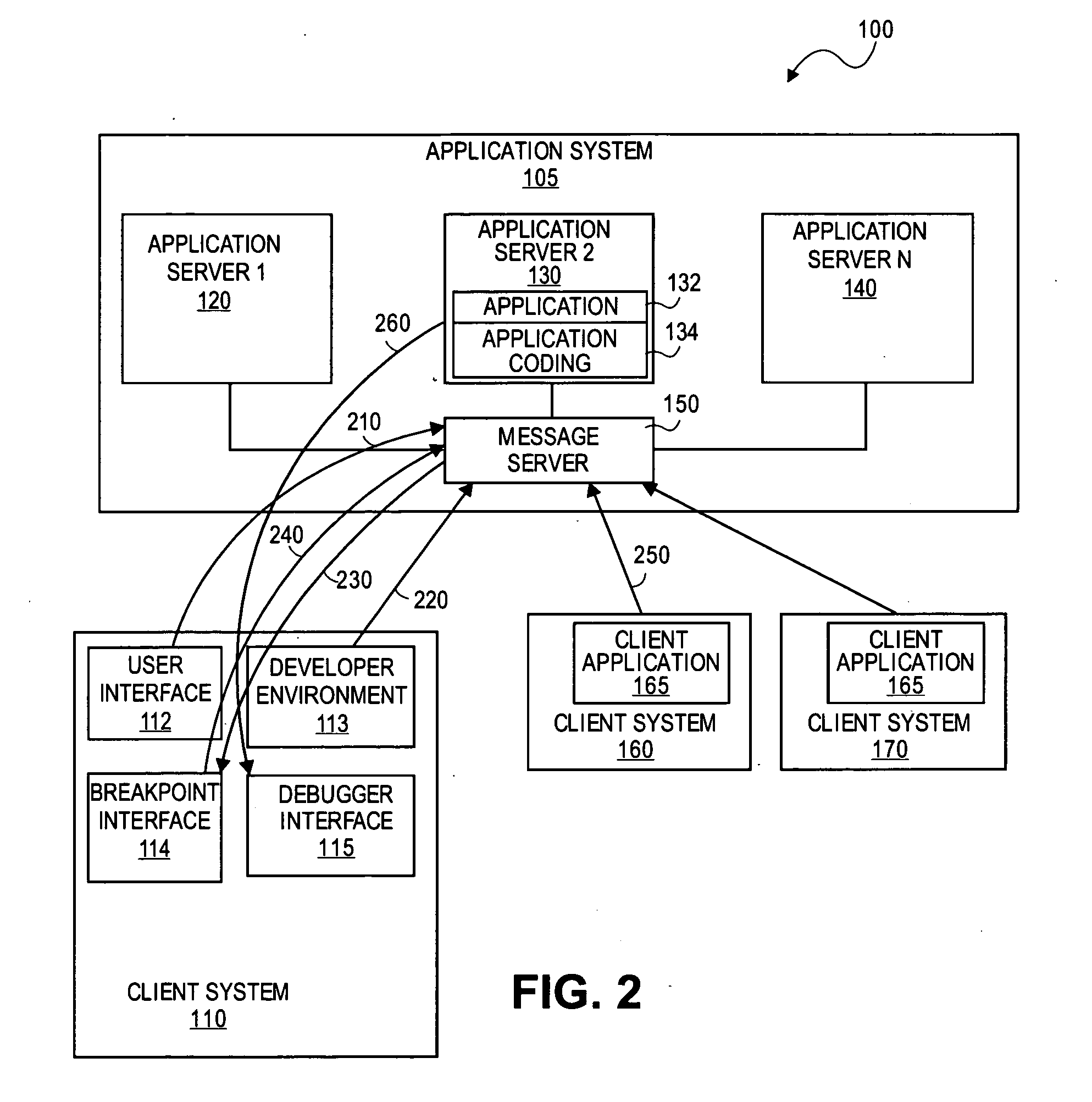
Debugging of remote application software on a local computer
InactiveUS20070168997A1Error detection/correctionSpecific program execution arrangementsGraphicsApplication program software
Methods and systems are provided for facilitating remote debugging from a local computer with a graphical user interface for debugging application in a computer system comprising an application system and one or more clients. The server receives a request from the local computer to monitor an application invoked by a client and running on the application system. Breakpoint information may be set via a breakpoint user interface initiated at the local computer by the server. Breakpoint information will be sent to one or more computer of the server system. The graphical user interface is provided to the local computer via a debugger interface initiated at the local computer by the server.
Owner:SAP AG
Method and system for secure distribution of selected content to be protected on an appliance specific basis
ActiveUS20080092240A1Access controlDigital data processing detailsUser identity/authority verificationApplication program softwareData file
The present invention relates to data rights management and more particularly to a secured system and methodology and production system and methodology related thereto and to apparatus and methodology for production side systems and are consumer side systems for securely utilizing protected electronic data files of content (protected content), and further relates to controlled distribution, and regulating usage of the respective content on a recipient device (computing system) to be limited strictly to defined permitted uses, in accordance with usage rights (associated with the respective content to control usage of that respective content), on specifically restricted to a specific one particular recipient device (for a plurality of specific particular recipient devices), or usage on some or any authorized recipient device without restriction to any one in specific, to control use of the respective content as an application software program, exporting, modifying, executing as an application program, viewing, and / or printing of electronic data files.
Owner:DAVID H SITRICK +1
Application instrumentation and monitoring
ActiveUS20060123101A1Cost effectiveAvoid the needDigital computer detailsComputer security arrangementsApplication softwareData store
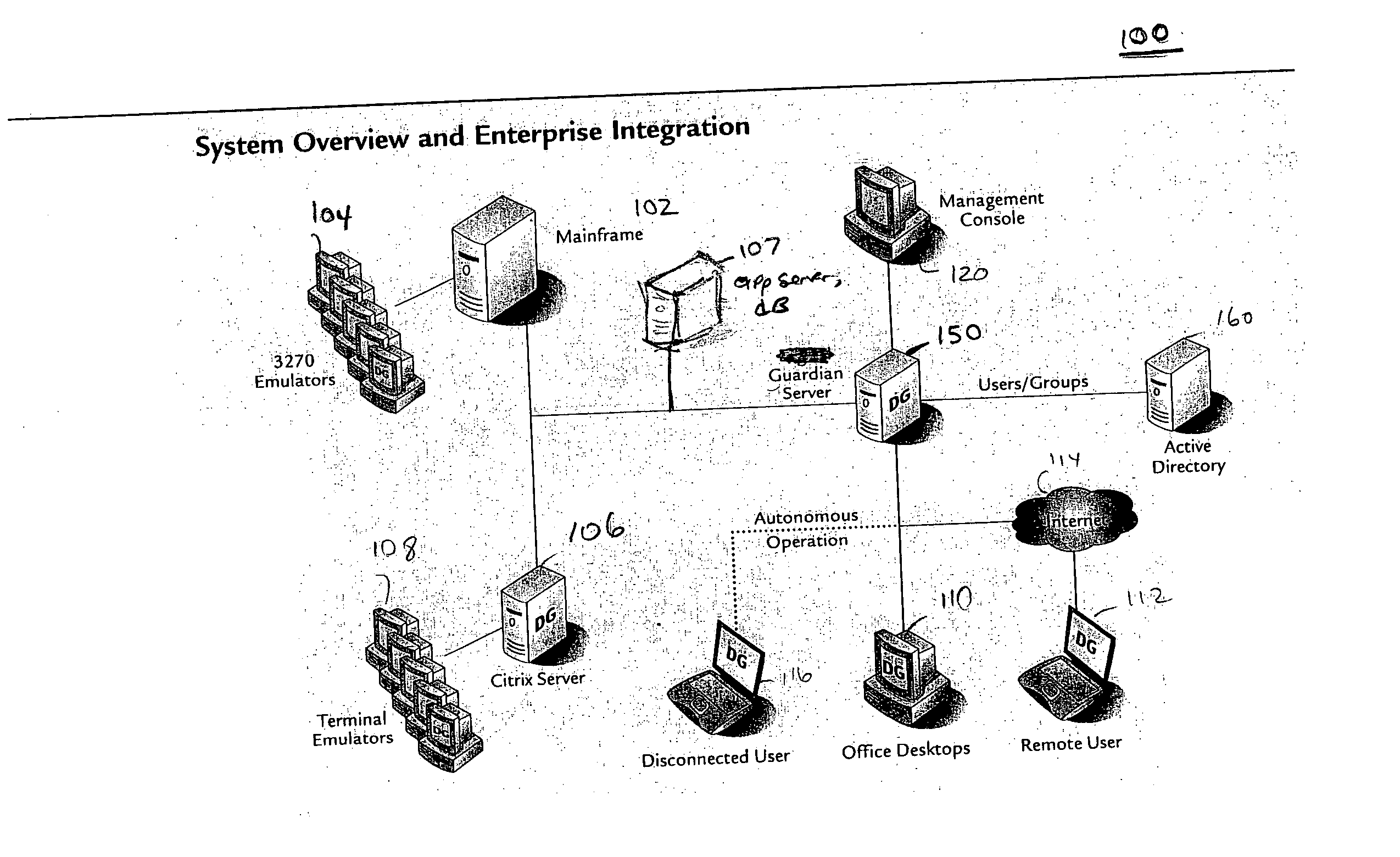
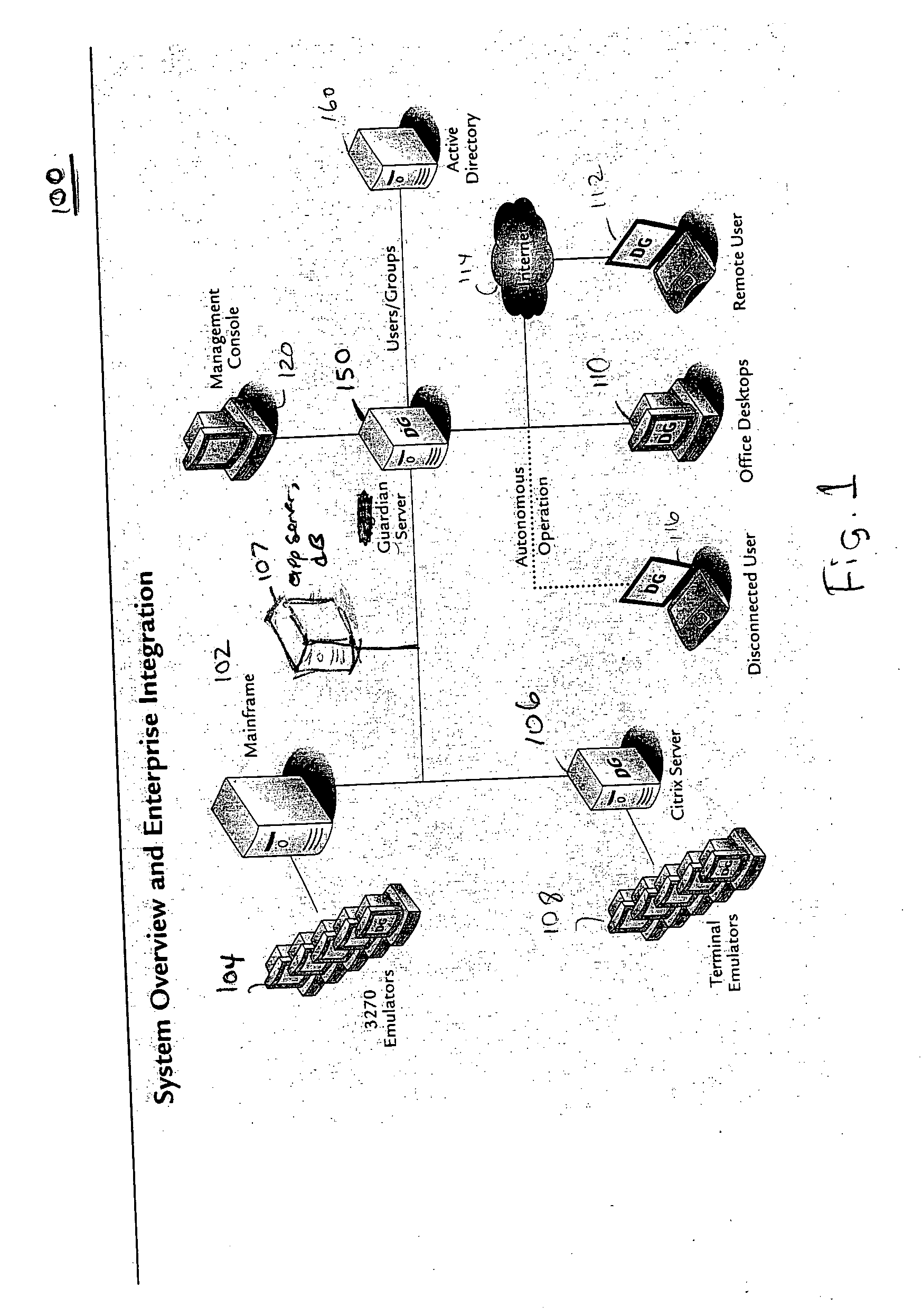
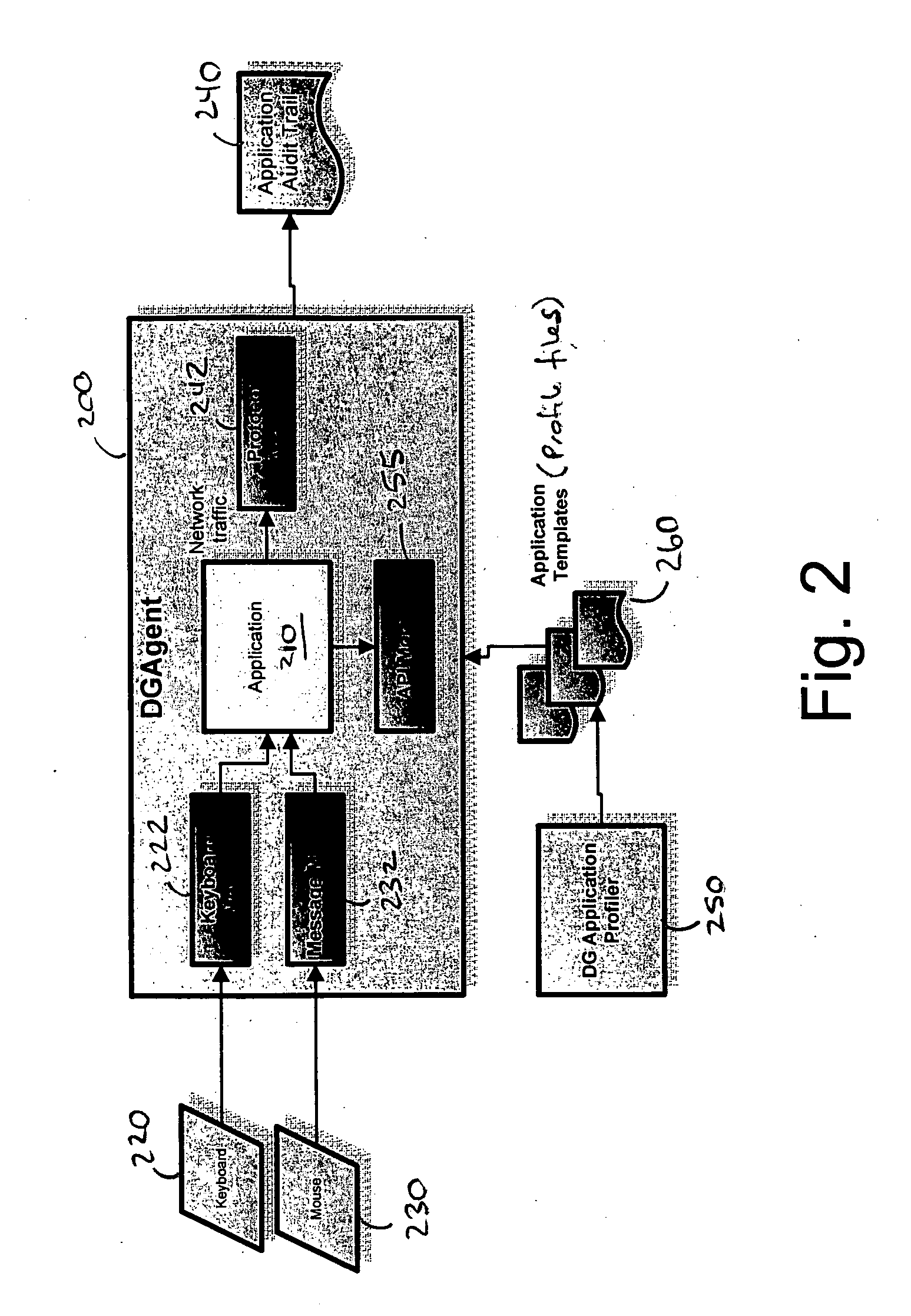
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
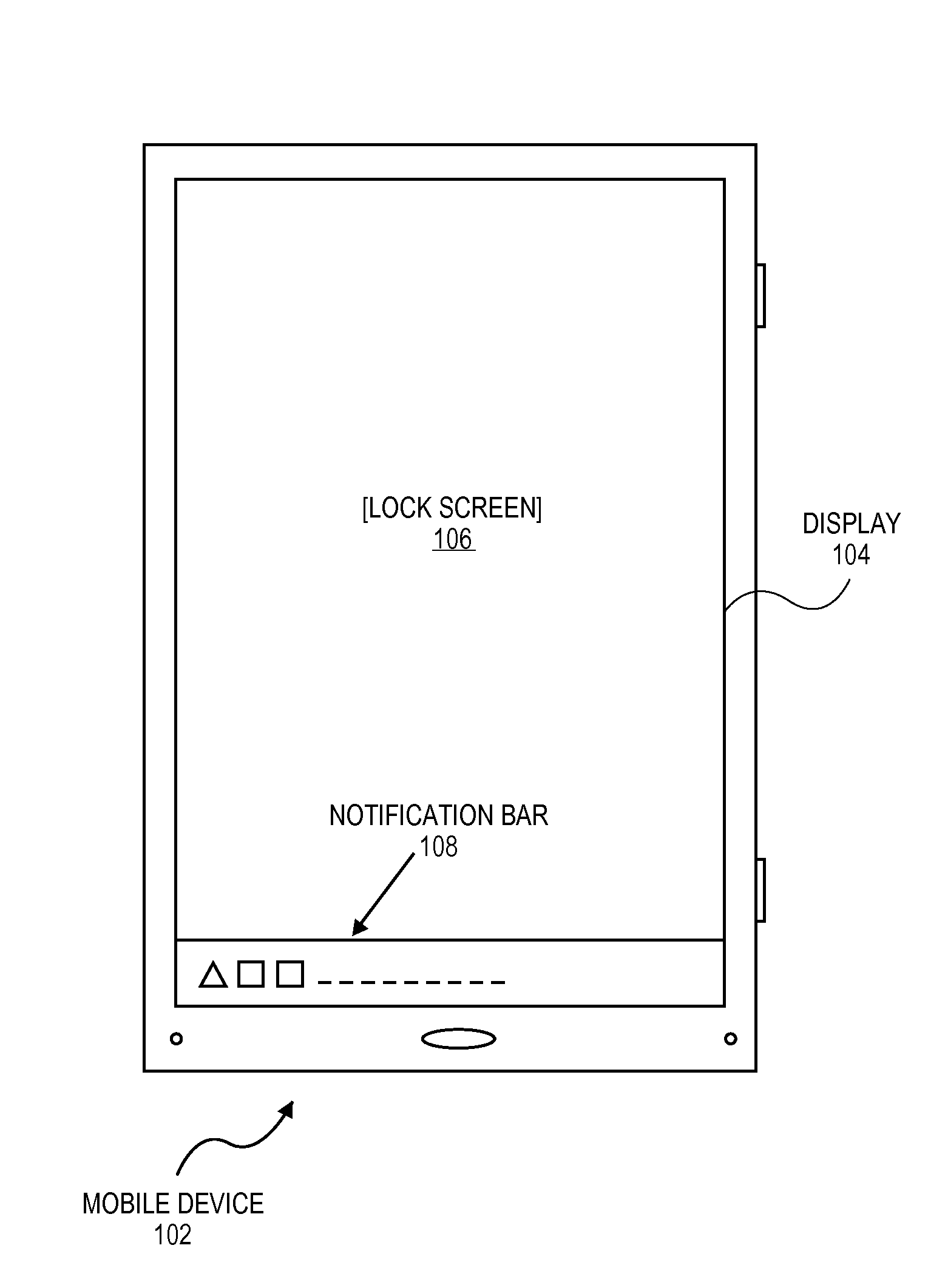
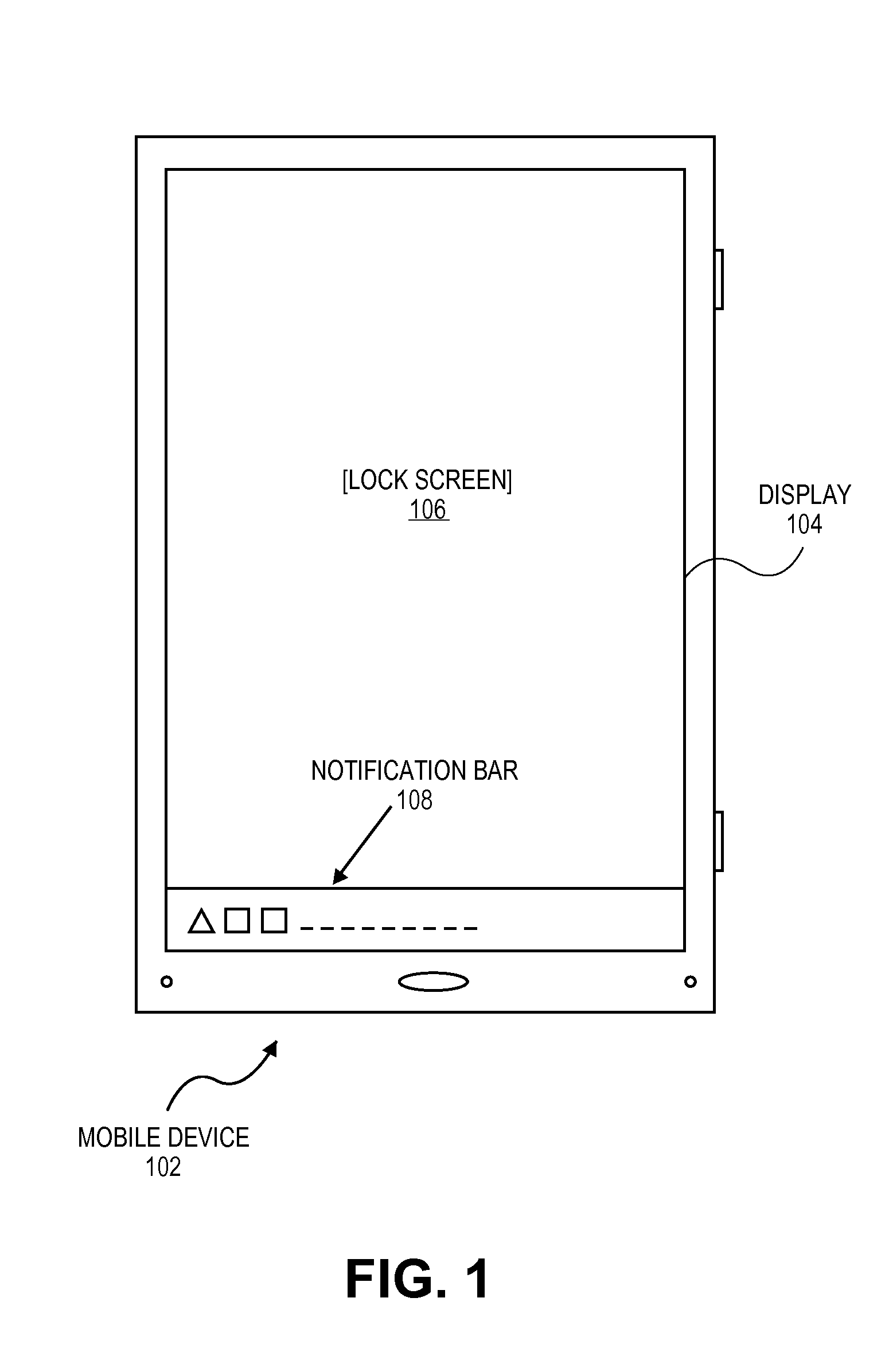
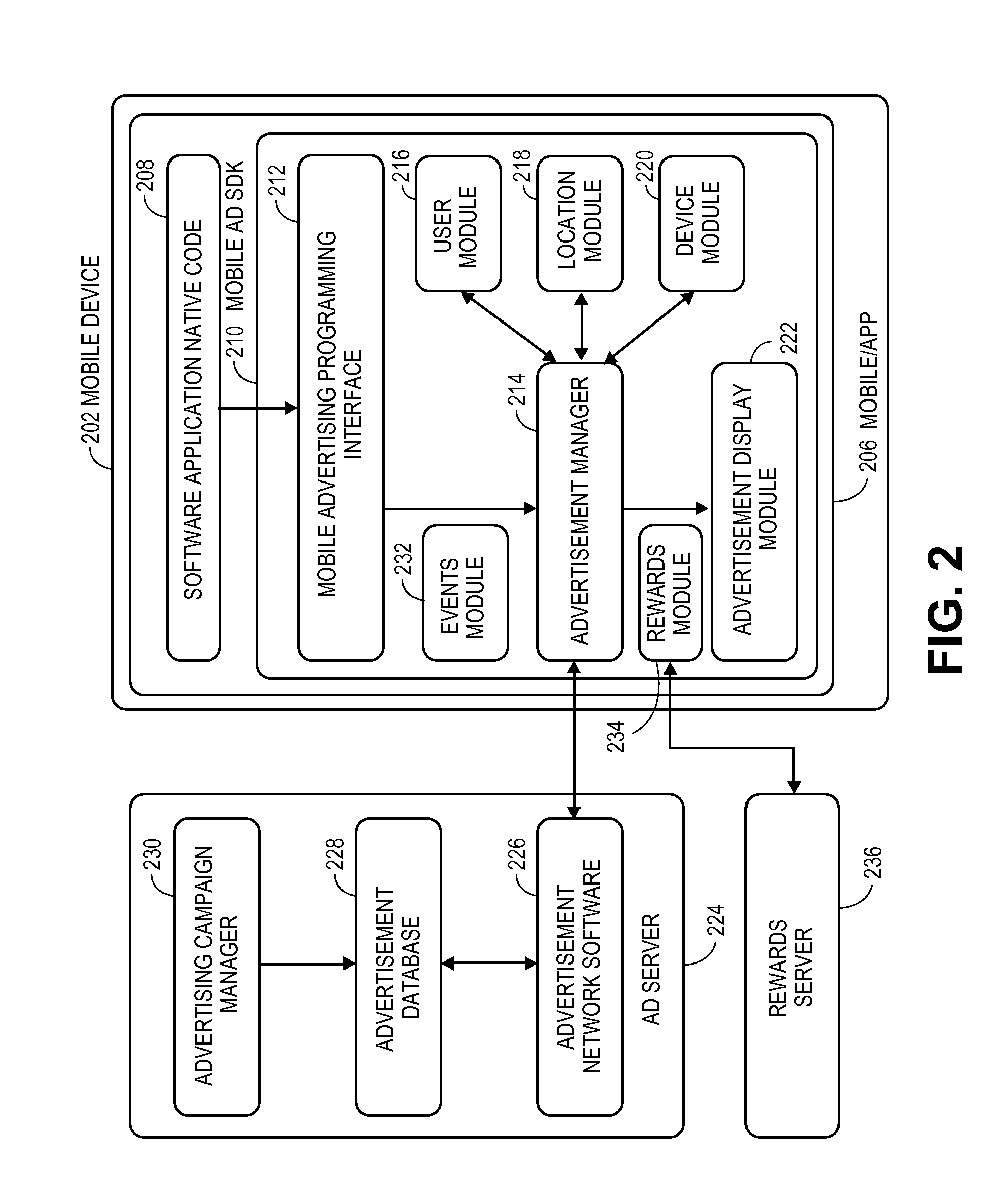
Extending mobile applications to the lock screen of a mobile device
ActiveUS20160044091A1Discounts/incentivesSoftware maintainance/managementApplication program softwareGeolocation
App content, such as an app notification, is displayed on a lock screen or home screen of a mobile device even when the app is closed. In contrast to present app content, the content may be full-screen, engaging, interactive, and media-rich. An app content SDK is inserted into an app and works directly with native app software. The content SDK determines whether the app has permission to display content on, for example, a lock screen. It may also determine whether the app has priority in displaying the content. The content itself is retrieved either from a content server or from the app itself. In either case, the retrieval and display of the content is coordinated and managed by the SDK which may use other constraints, such as date / time, geographic location, and device motion patterns to determine which content should be displayed.
Owner:ADENDA MEDIA
Method and system for remote browsing of computer files using a bar code reader
InactiveUS20050223389A1Easy to adaptReduce the burden onCo-operative working arrangementsConnection managementApplication program softwareTransport layer
A method of integrating host application software with data collection devices (e.g., bar code scanners) located on remote, wireless terminals. A data collection object executes on the host computer, using a predetermined interface between the host application software and the data collection object. That interface, and the communications between the host application software and the data collection object, are configured so that to the host application software the data collection device appears to be local hardware on the host computer. The data collection object creates and executes threads of execution for controlling operation of the data collection device, with the threads communicating with the remote terminals via a host computer transport layer, the wireless link, and a remote computer transport layer at the remote terminals. A data collection device driver on the remote terminal receives communications from the data collection object, and returns information to the data collection object, over the remote computer transport layer, wireless link, and host computer transport layer.
Owner:KLEIN JOHN +2
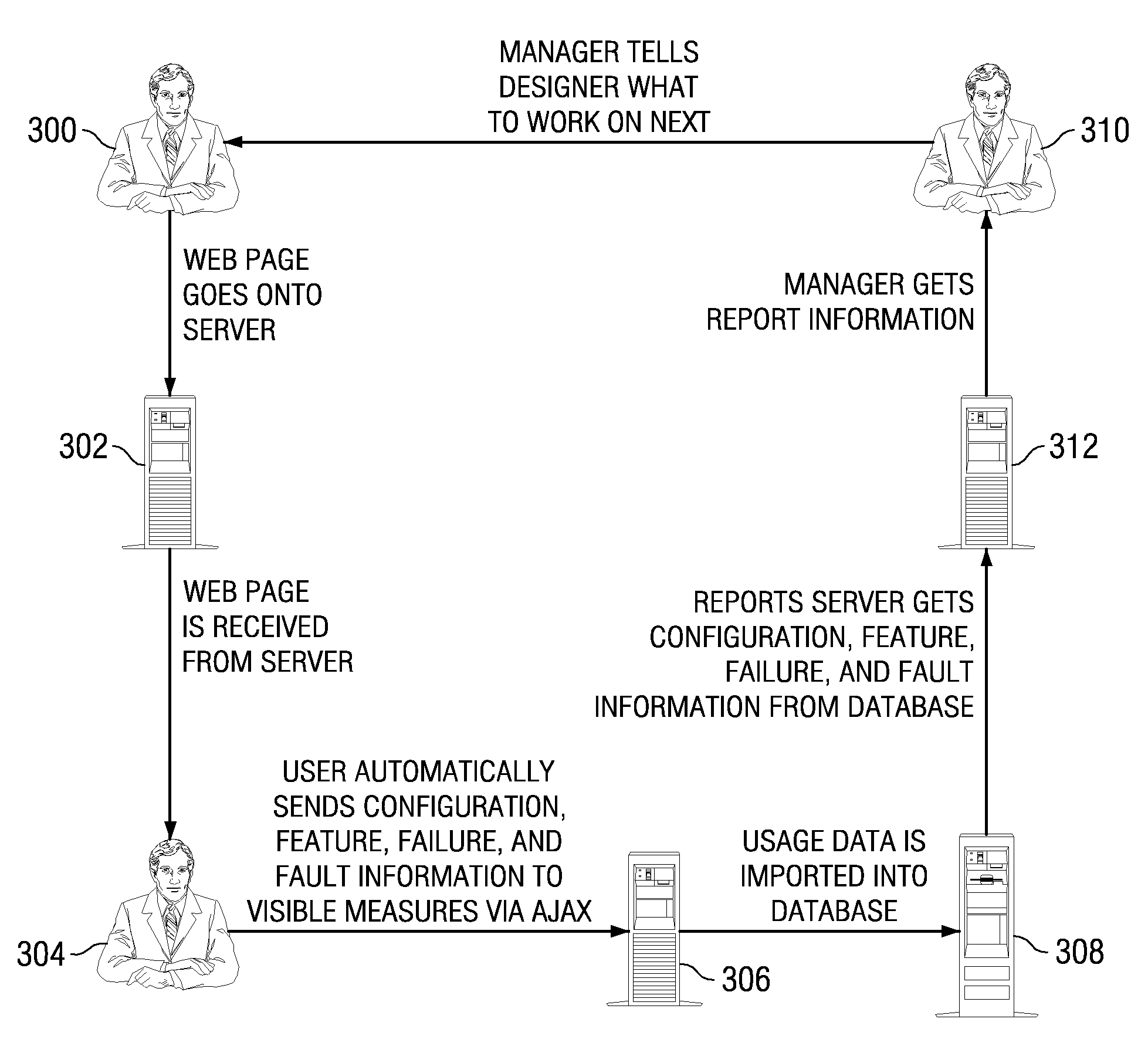
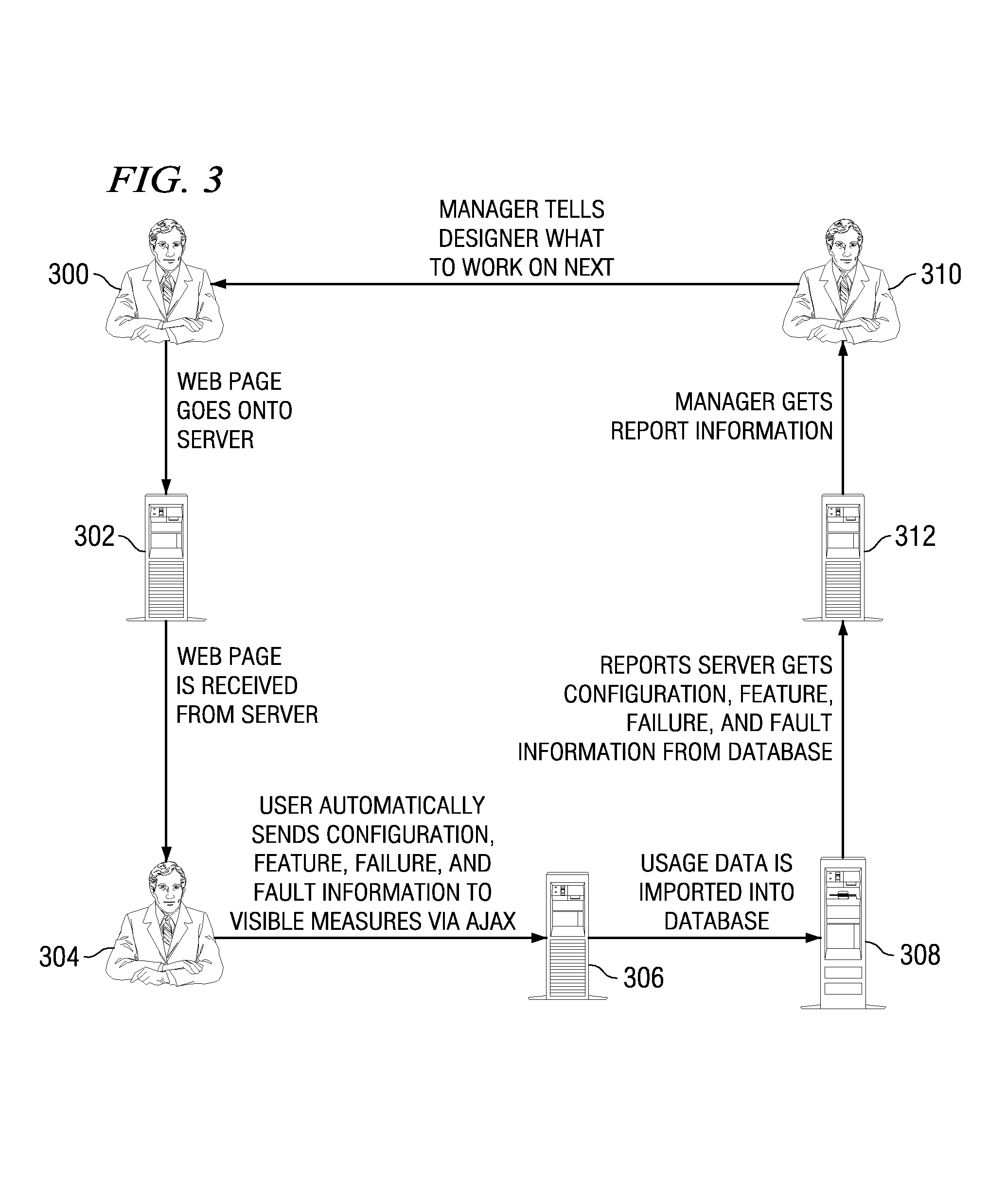
Distributed capture and aggregation of dynamic application usage information
ActiveUS7356590B2Quality improvementReliable transportationError detection/correctionMultiple digital computer combinationsApplication program softwareFile system
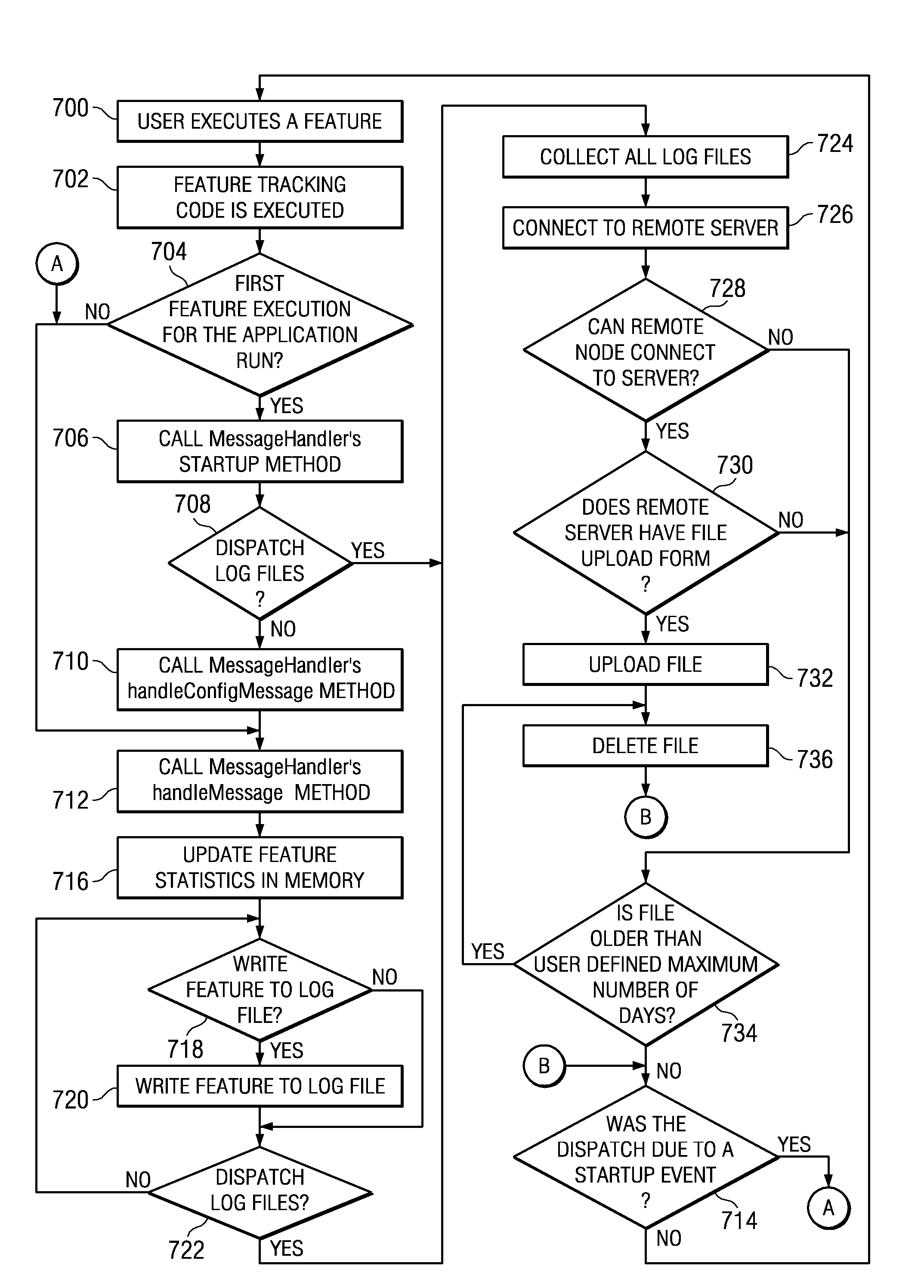
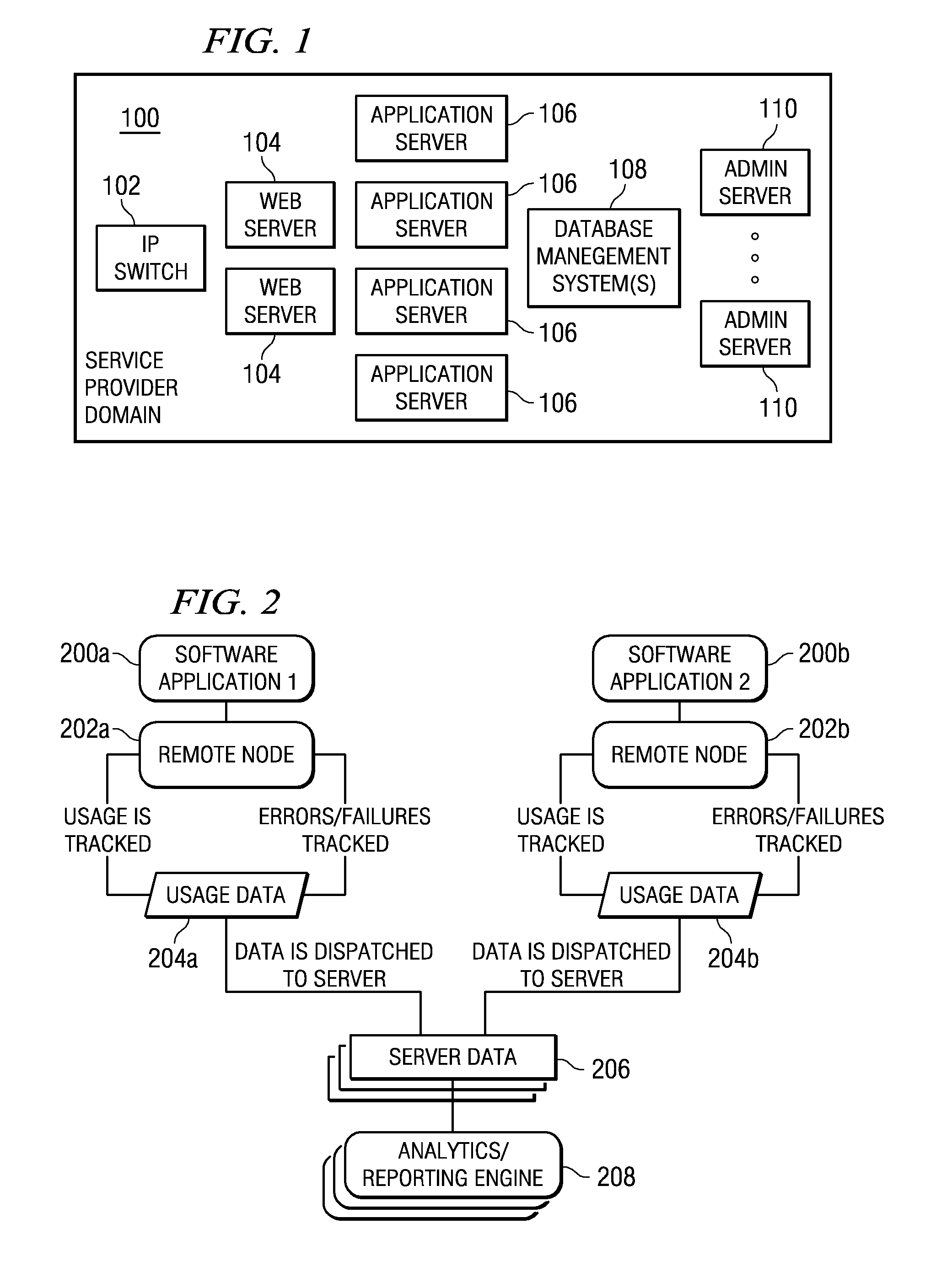
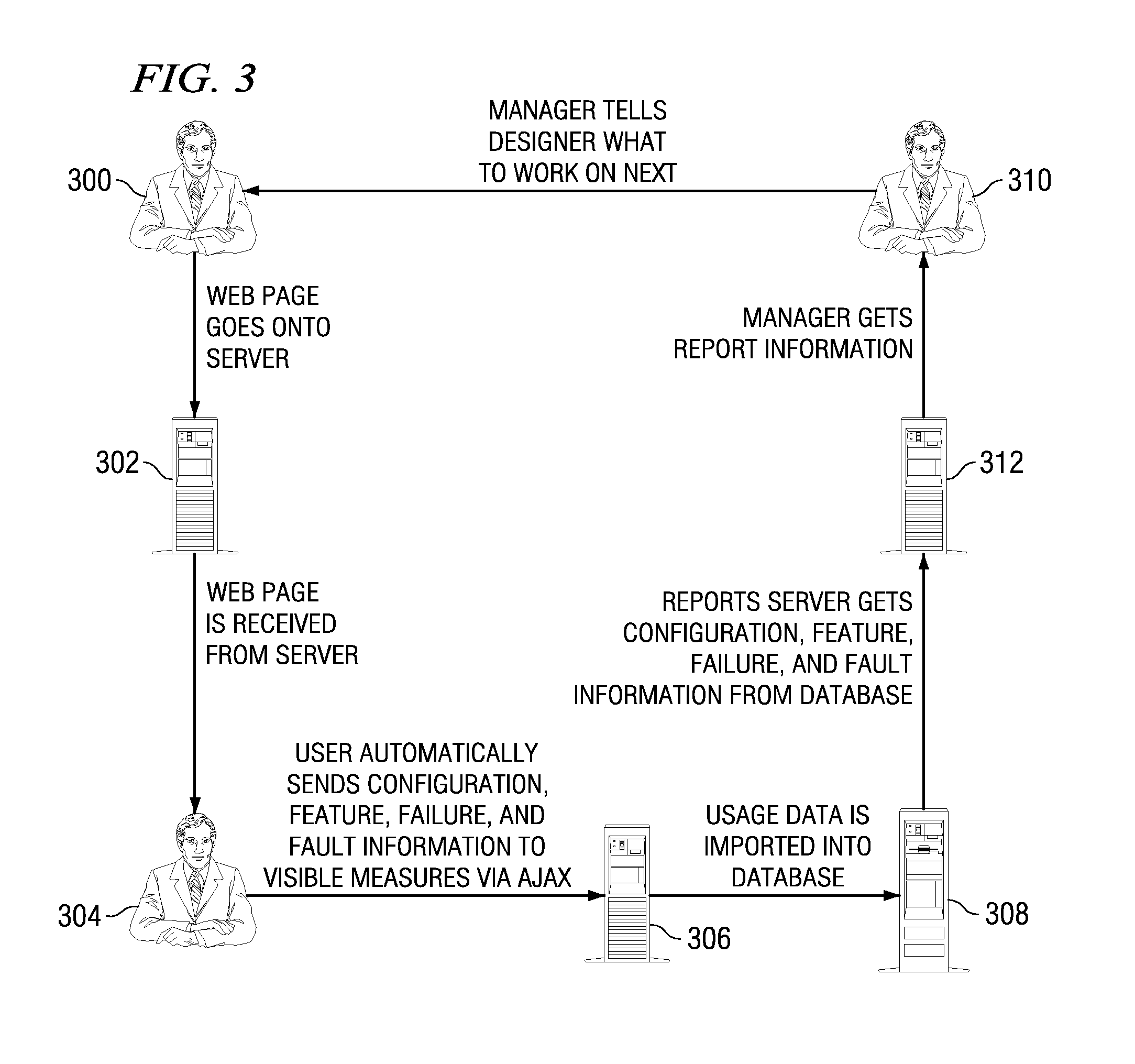
A web-based hosted solution through which application developers create, manage and monitor application usage analytics in an online manner. Preferably, an application under test is one of: application software, a script-enabled web application, or a rich Internet application (RIA). During the development process, a usage monitoring API is integrated into the application and the application is deployed. As users interact with the application, a log file is generated, typically in one of two ways. If the application is able to write to a local file system (in the user's machine), usage information is gathered in a log file local to the deployed application and then dispatched to an upload server for processing in a batch manner. If the application is not able to write to the user machine's local file system, the usage information is sent to a remote logging server, preferably on a just-in-time basis, and then the log file is generated on the logging server. In either case, preferably the usage information that is tracked comprises “features,”“faults” and “failures” of the application, independent of platform, location, and number of deployed application instances.
Owner:ACUITYADS US INC
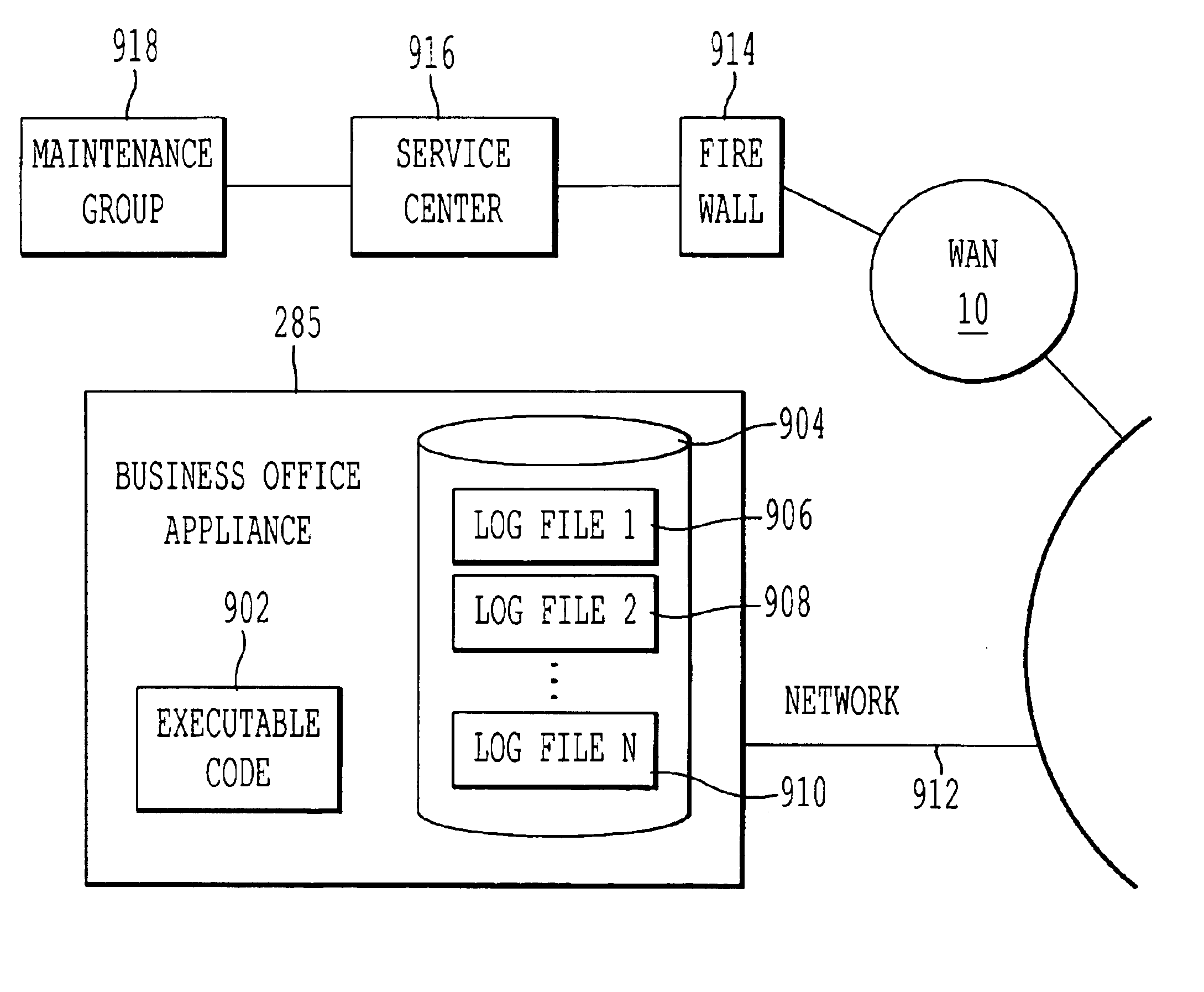
Method and system for maintaining the business office appliance through log files
InactiveUS6915342B1Telemetry/telecontrol selection arrangementsDetecting faulty computer hardwareApplication program softwareLogbook
A method and system for monitoring a business office appliance by a remote service center using logs that are transferred to the remote service center. When the service center analyzes the data in the logs, it can detect warning messages or error messages from application software controlling the monitored appliances and remotely diagnose or fix those monitored appliances.
Owner:RICOH KK
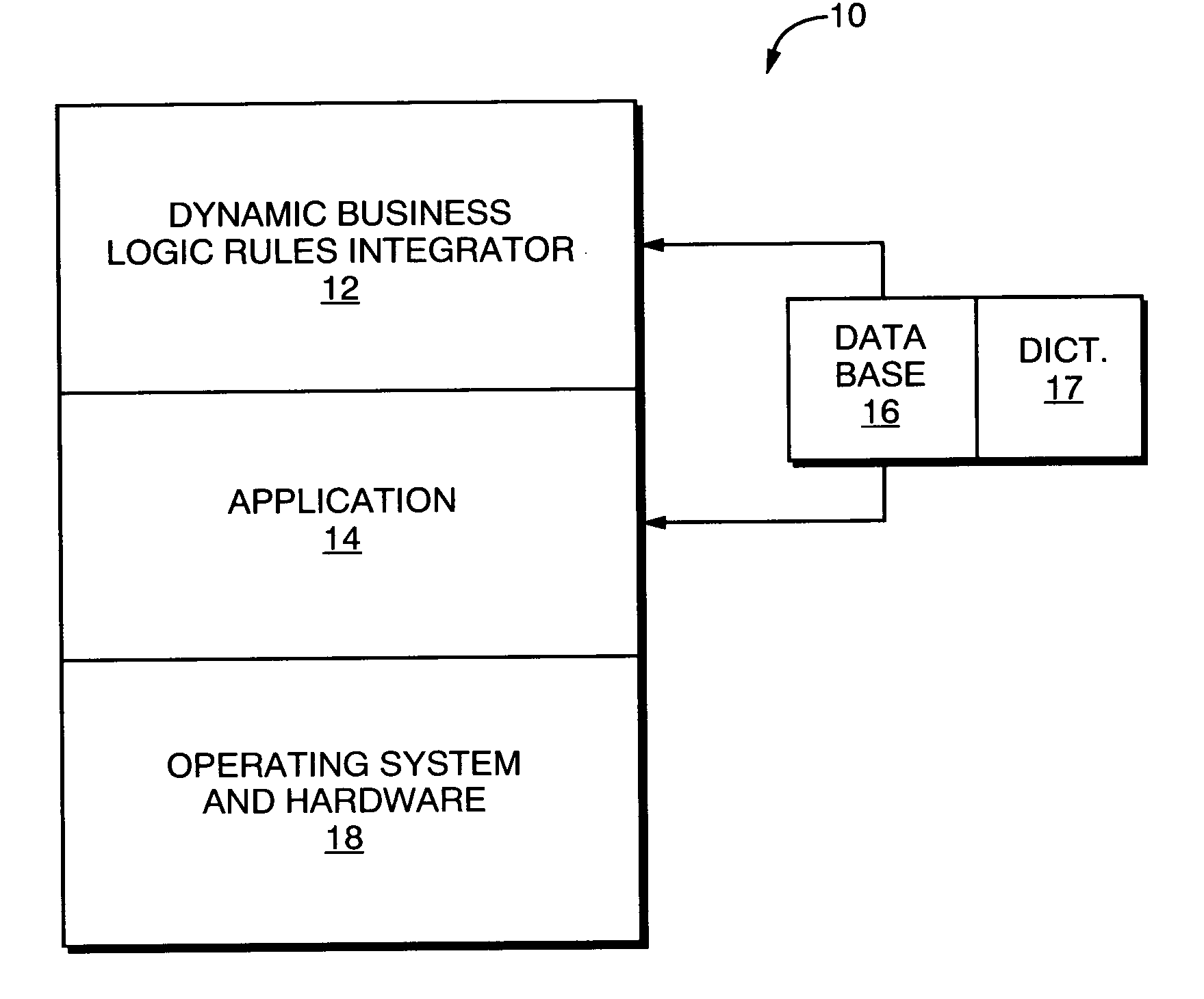
System and method for dynamic business logic rule integration
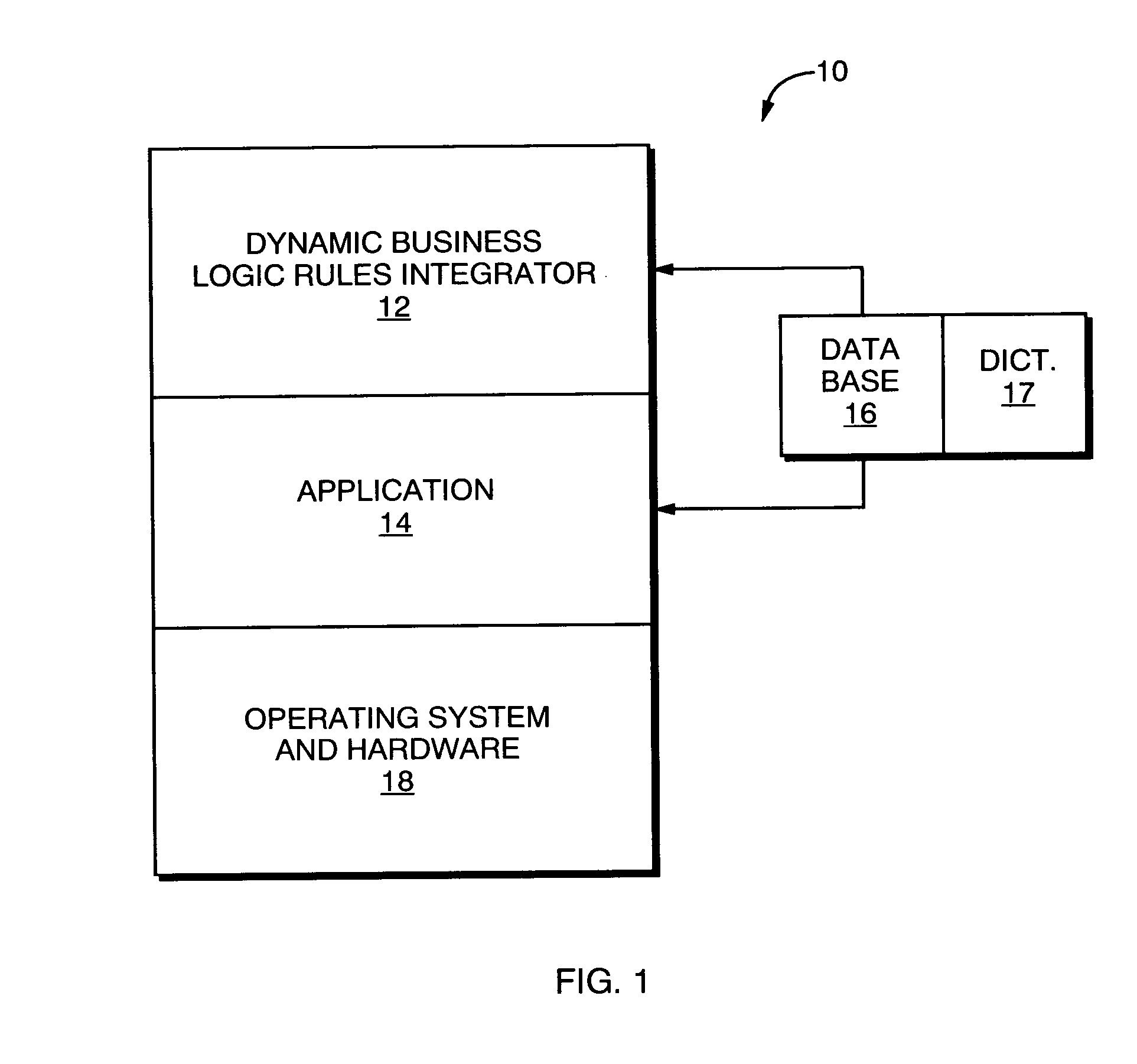
ActiveUS7124145B2Process less efficientEasy to handleOffice automationSpecial data processing applicationsApplication program softwareIntegrator
A system for dynamically integrating changes in rules governing business operations into a rule-implementing application program includes a dynamic business logic rule integrator (“DBLRI”) that provides rules to the application software as executable routines. The DBLRI presents to a user one or more GUIs through which the user writes functional-language expressions for the rules. The GUIs provide menus of associated functions, operators and parameters that are available for use. The set of parameters associated with a given GUI is dynamically updated, to correspond to changes in the underlying business logic rules. The user writes and / or edits the expressions by selectively combining the available functions, operators and parameters. The DBLRI evaluates the functional expressions and produces associated executable parse trees or DLLs, which the application software then calls at appropriate times. The DBLRI operates also with a dynamically configurable database that provides parameters required for the rules as the rules are updated, added and / or revised.
Owner:MILLENNIUM IT USA
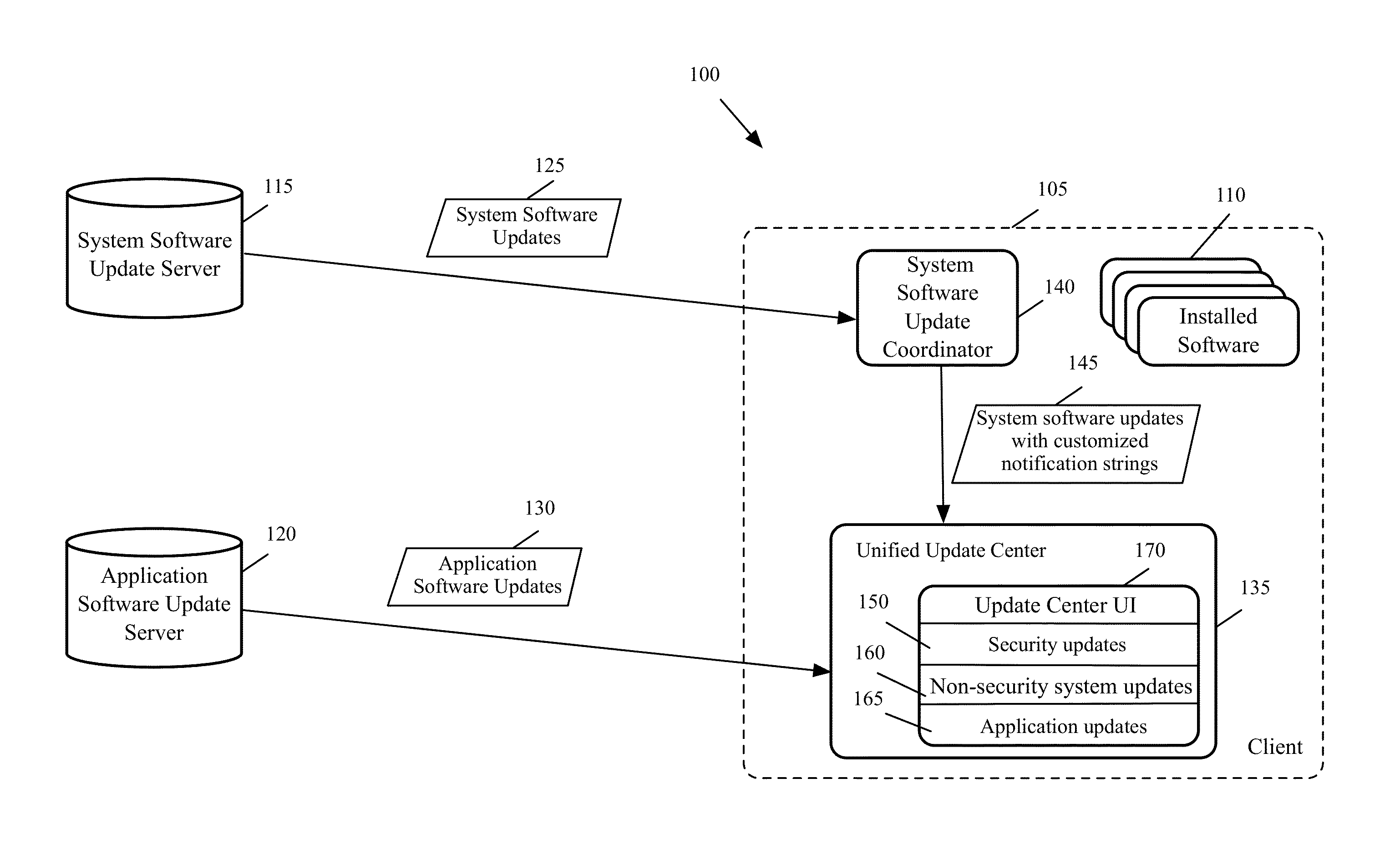
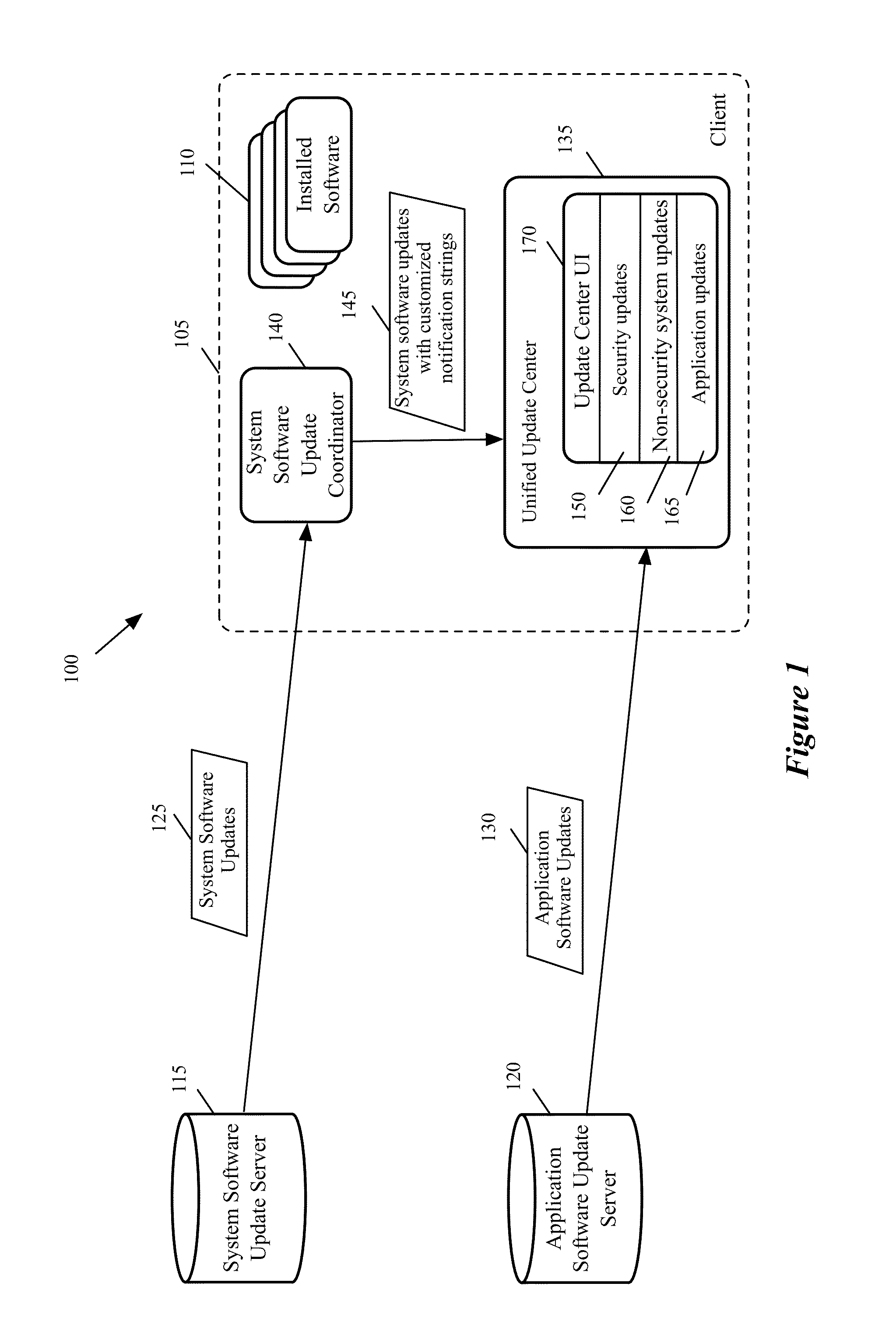
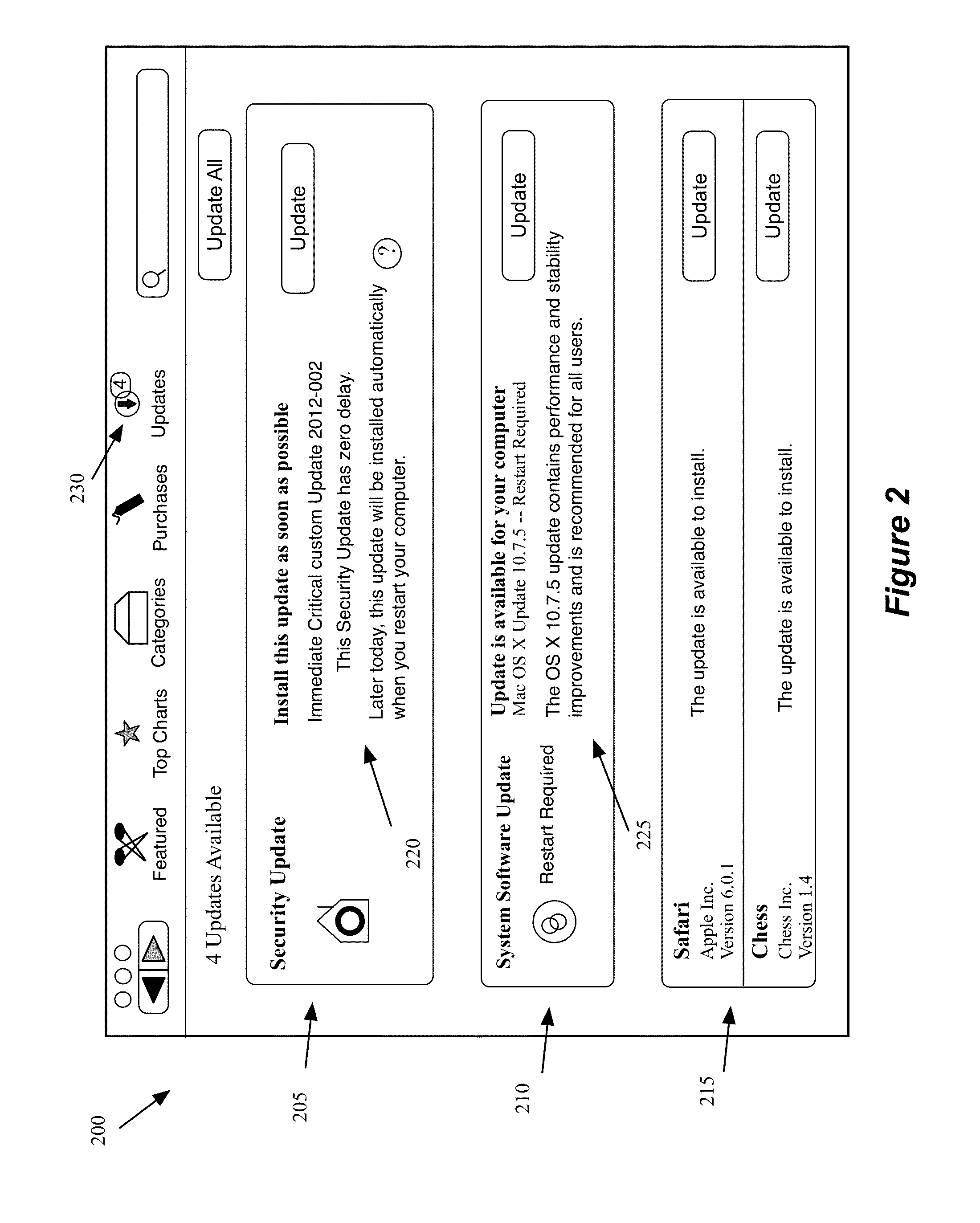
Providing A Unified Update Center for Security Software Updates and Application Software Updates
A graphical user interface (GUI) for a unified software update display center is provided. The GUI includes a first display area for displaying a set of available security system software updates. The GUI includes a second display area for displaying a set of available non-security system software updates. The GUI includes a third display area for displaying a set of available application software updates. The GUI includes a single selection tool for installing all available security updates without installing any updates displayed in the second and third display areas. The GUI includes individual selection tools for installing individual updates displayed in the second and third display areas. The GUI includes a selection tool to receive further updates from a system update server and an application update server. The critical security updates are displayed with different display attributes or in different sections to distinguish them from other types of updates.
Owner:APPLE INC
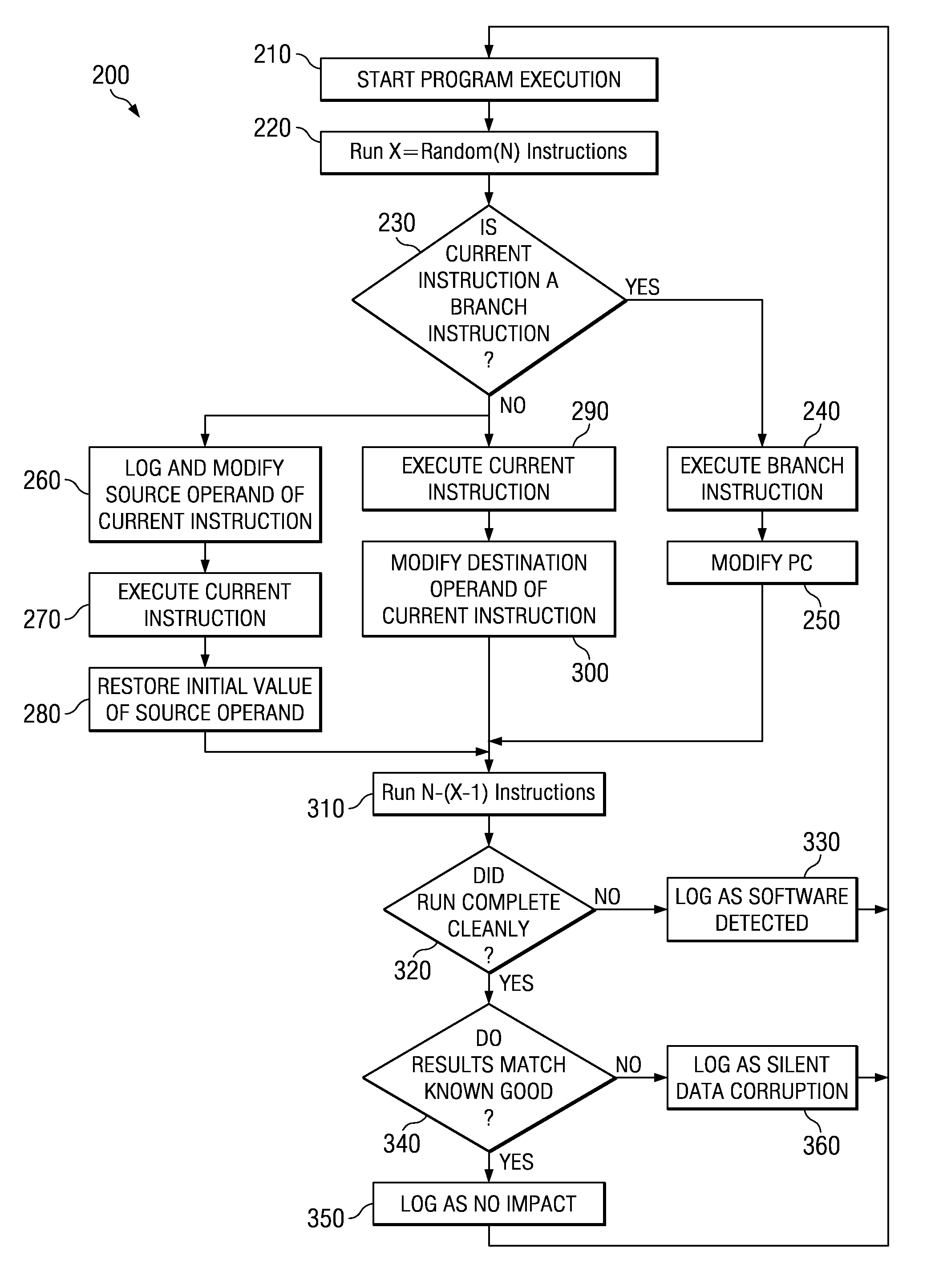
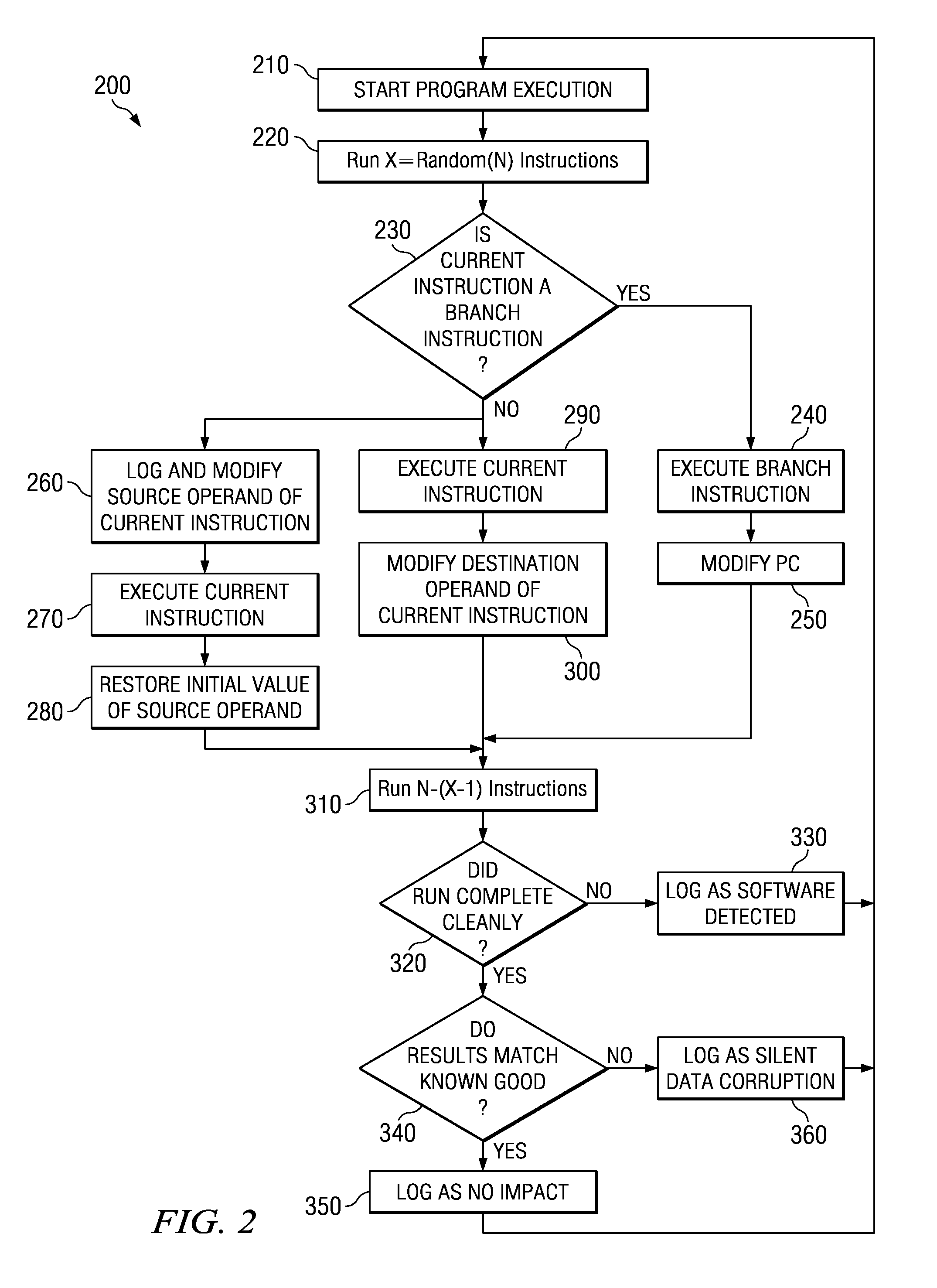
Method and Apparatus for Testing Soft Error Rate of an Application Program
InactiveUS20090249301A1Software testing/debuggingSpecific program execution arrangementsApplication program softwareOperational system
Techniques are provided for determining consequences of an injected fault on a system running a given application program or operating system, in order to measure the software impact of a hardware soft error on the application program / operating system. The application program software is emulated instruction-by-instruction, where source operands are randomly modified before an instruction is executed, and destination operands are randomly modified after an instruction is executed, in order to mimic hardware soft errors. In addition, a program counter is randomly modified after execution of a branch instruction. The resulting consequences of such modifications are monitored such that a fault of an instruction being executed is modeled in order to determine a soft error rate (SER) for a software application program or operating system.
Owner:IBM CORP
Method for assuring integrity of mobile applications and apparatus using the method
InactiveUS20140150096A1Memory loss protectionError detection/correctionApplication program softwareMobile apps
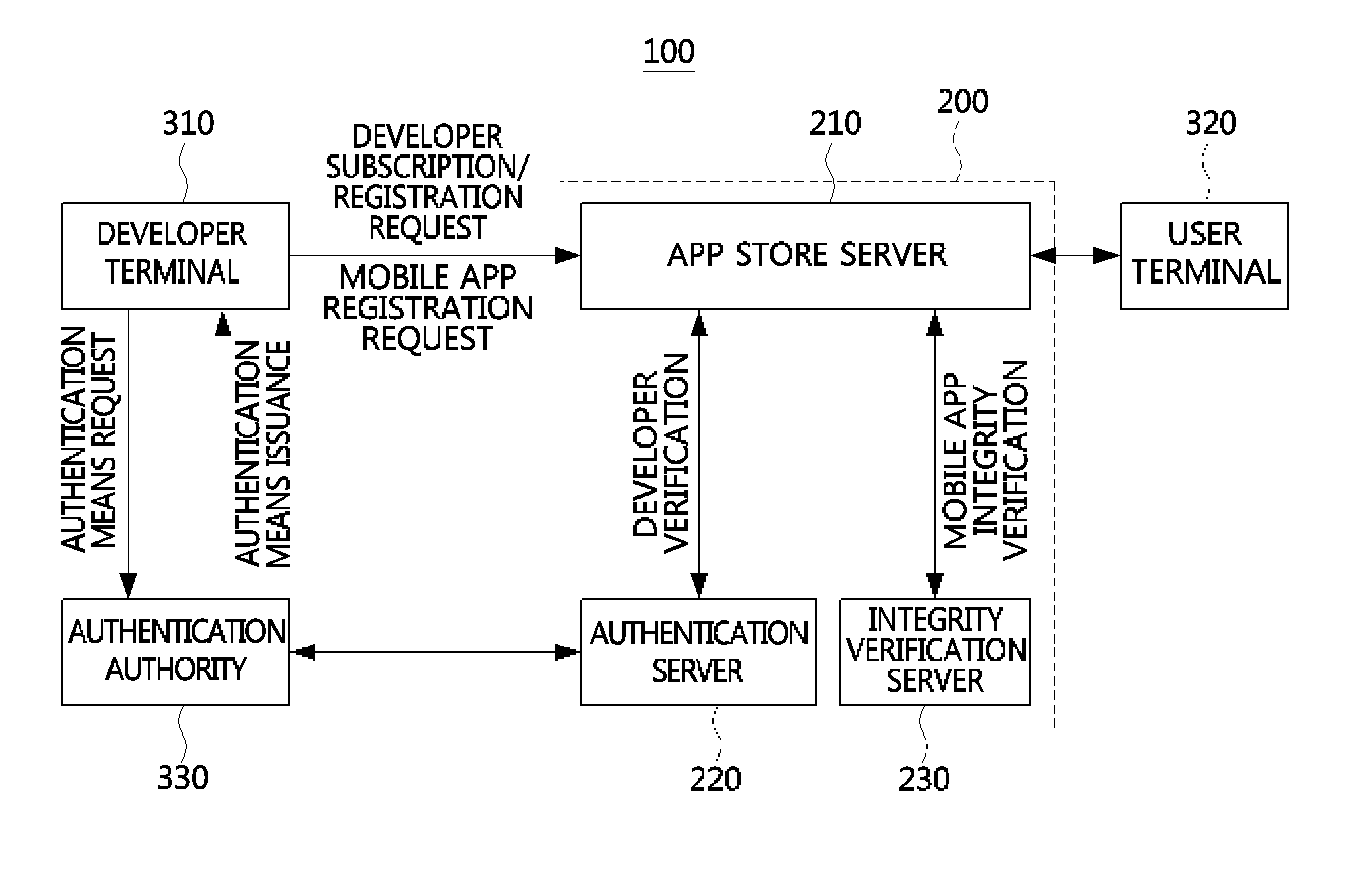
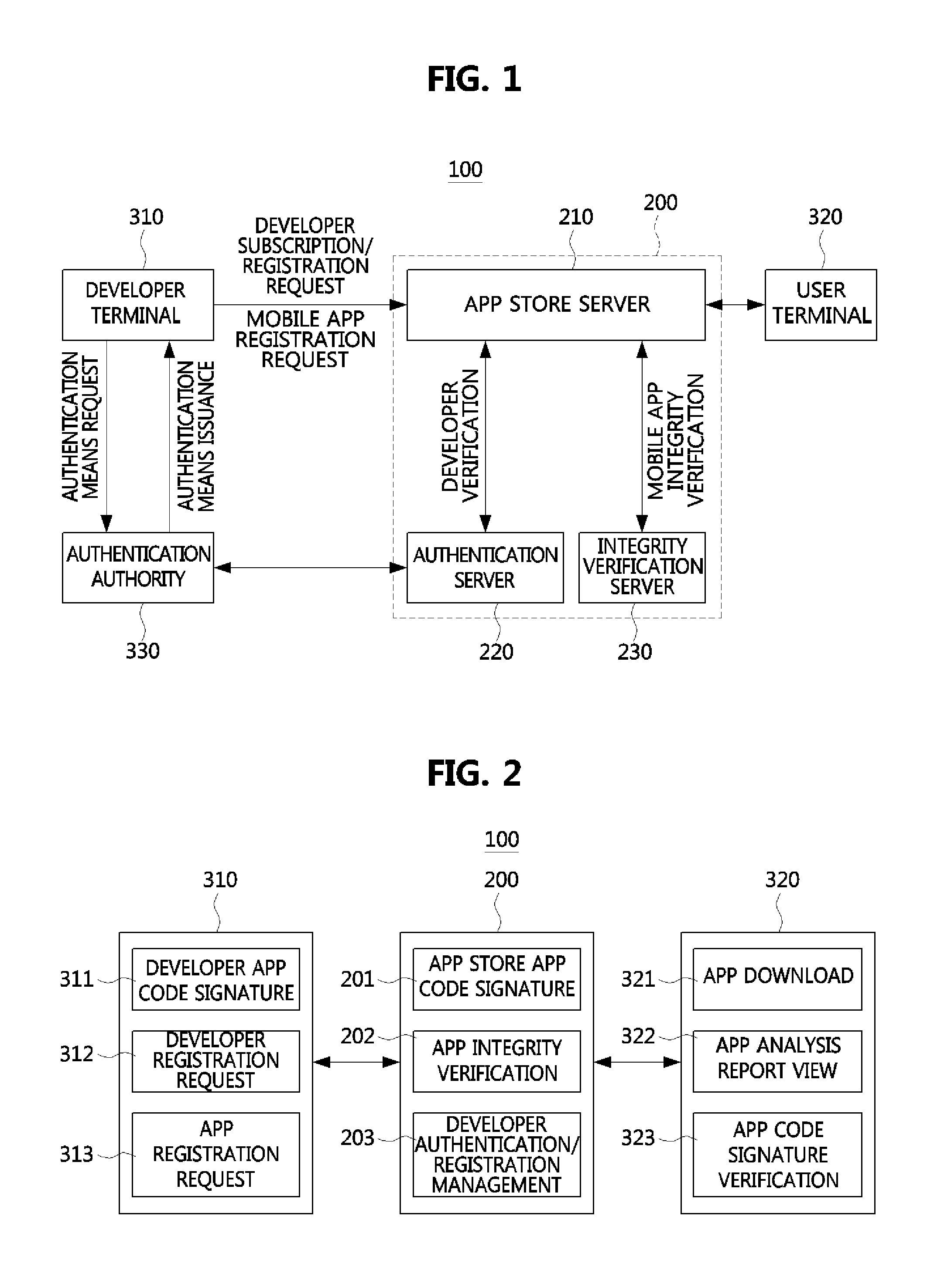
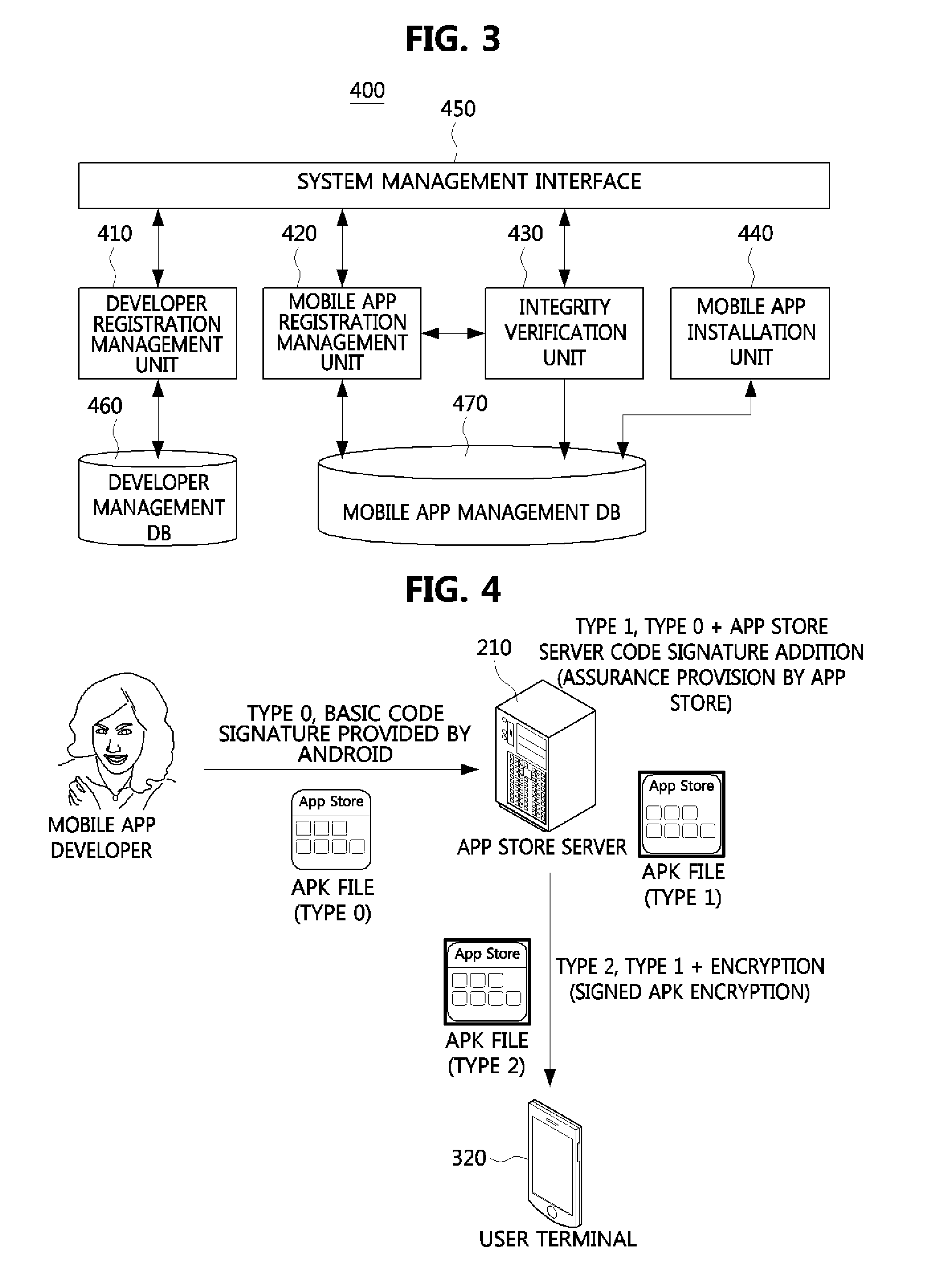
An apparatus for assuring integrity of a mobile application or application software (app) includes a developer registration management unit configured to authenticate a mobile app developer based on an authentication means in response to a subscription and registration request of the mobile app developer, and an integrity verification unit configured to verify whether the mobile app has the integrity by unpackaging the mobile app uploaded to an app store server in a packaged state and determine whether to write a code signature of the app store server to the mobile app based on an integrity verification result. Thus, a secure mobile ecosystem can be constructed.
Owner:ELECTRONICS & TELECOMM RES INST
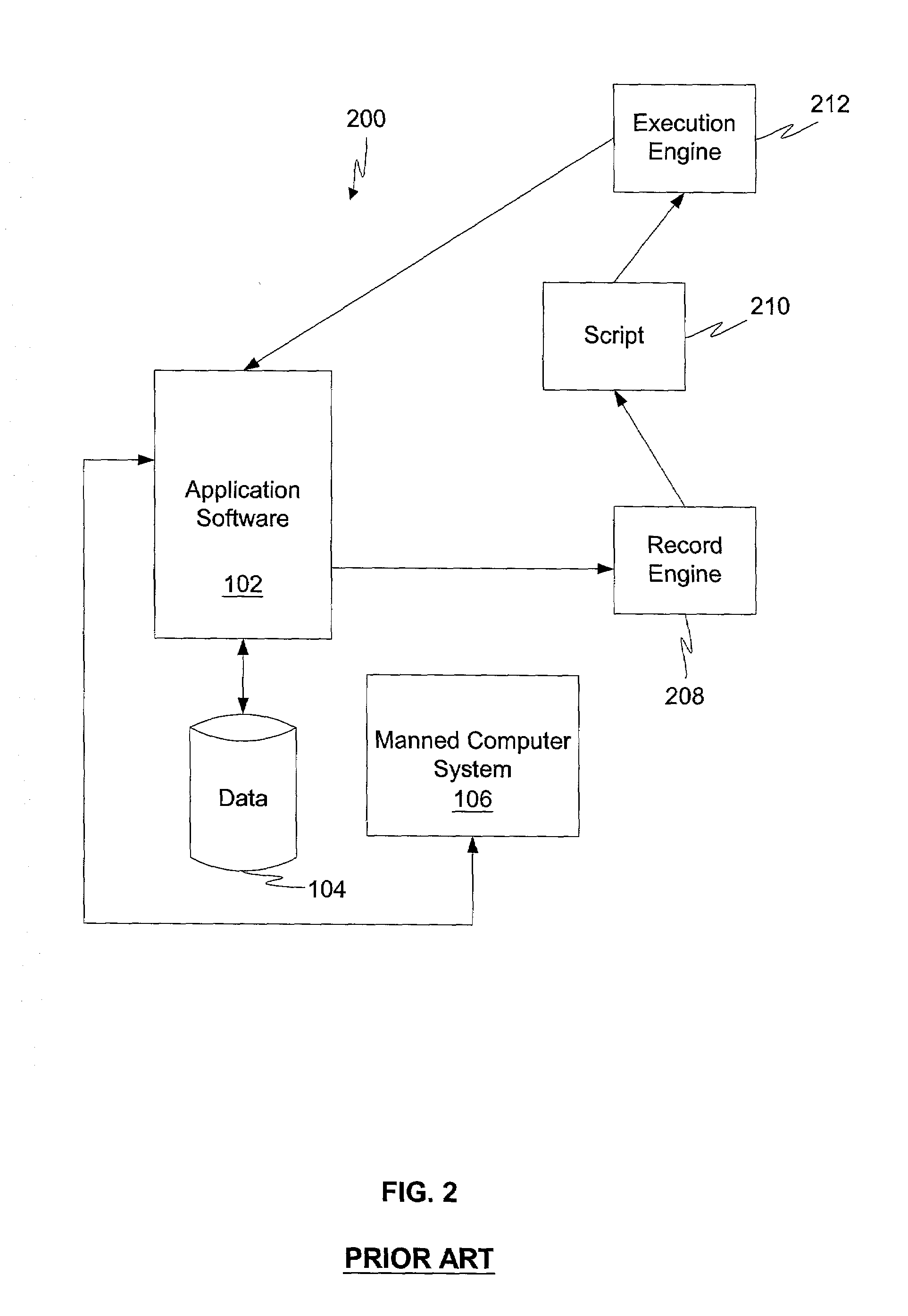
System and method for automatically generating a script for testing software
ActiveUS7039899B1Facilitates automatically generating a scriptEasy to testError detection/correctionSpecific program execution arrangementsApplication program softwareElectronic form
A script generator facilitates the testing of software, such as application software or other software. The script generator automatically generates a script from metadata that includes code defining the application software. The script contains logic for the application software. The script is used in conjunction with a second set of data, such as a spreadsheet, that is extracted from application data and metadata by the script generator or is created manually. An execution engine uses the script and corresponding second set of data to simulate an end user's potential use of the application software. The application software is thus efficiently tested in this manner.
Owner:ORACLE INT CORP
Simulation testing method for partition application software of embedded system
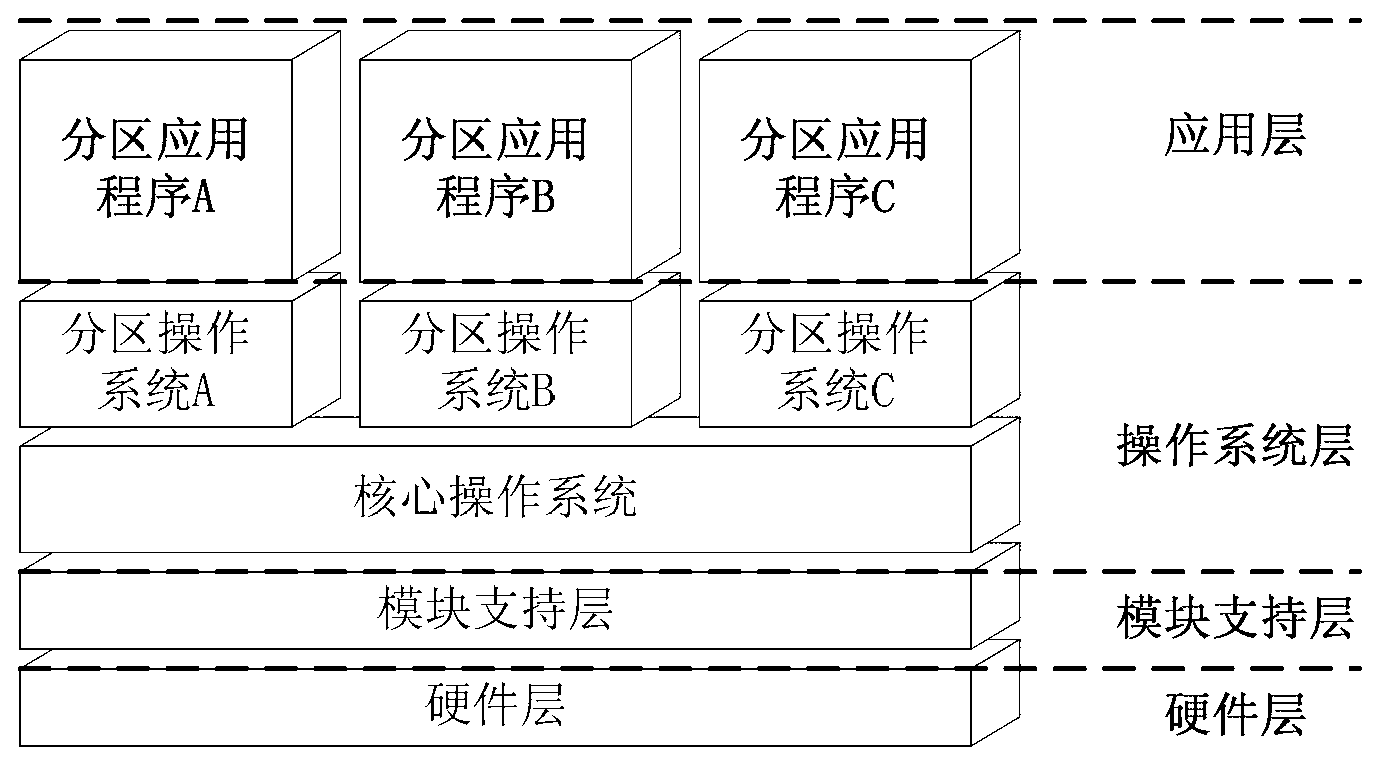
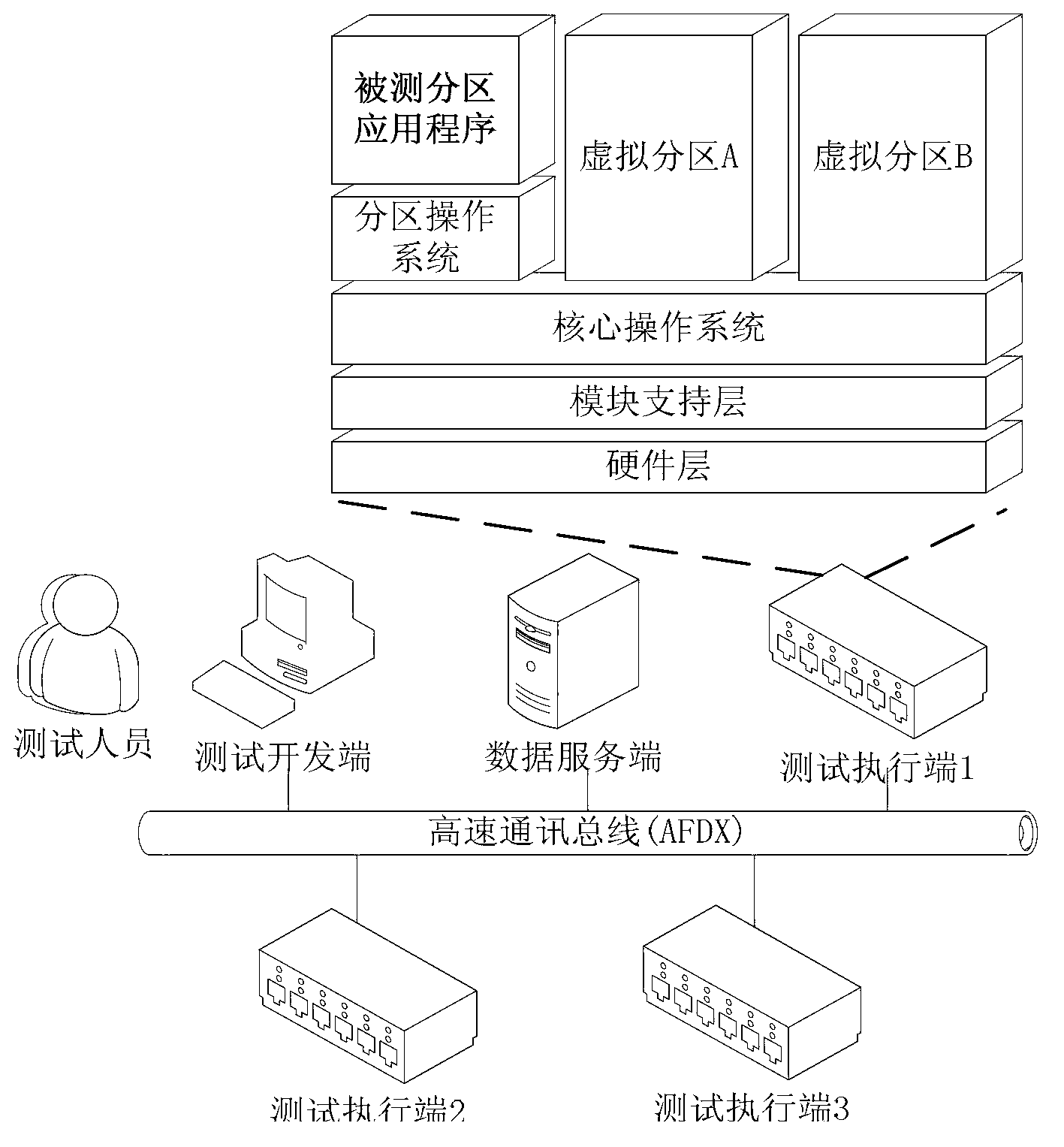
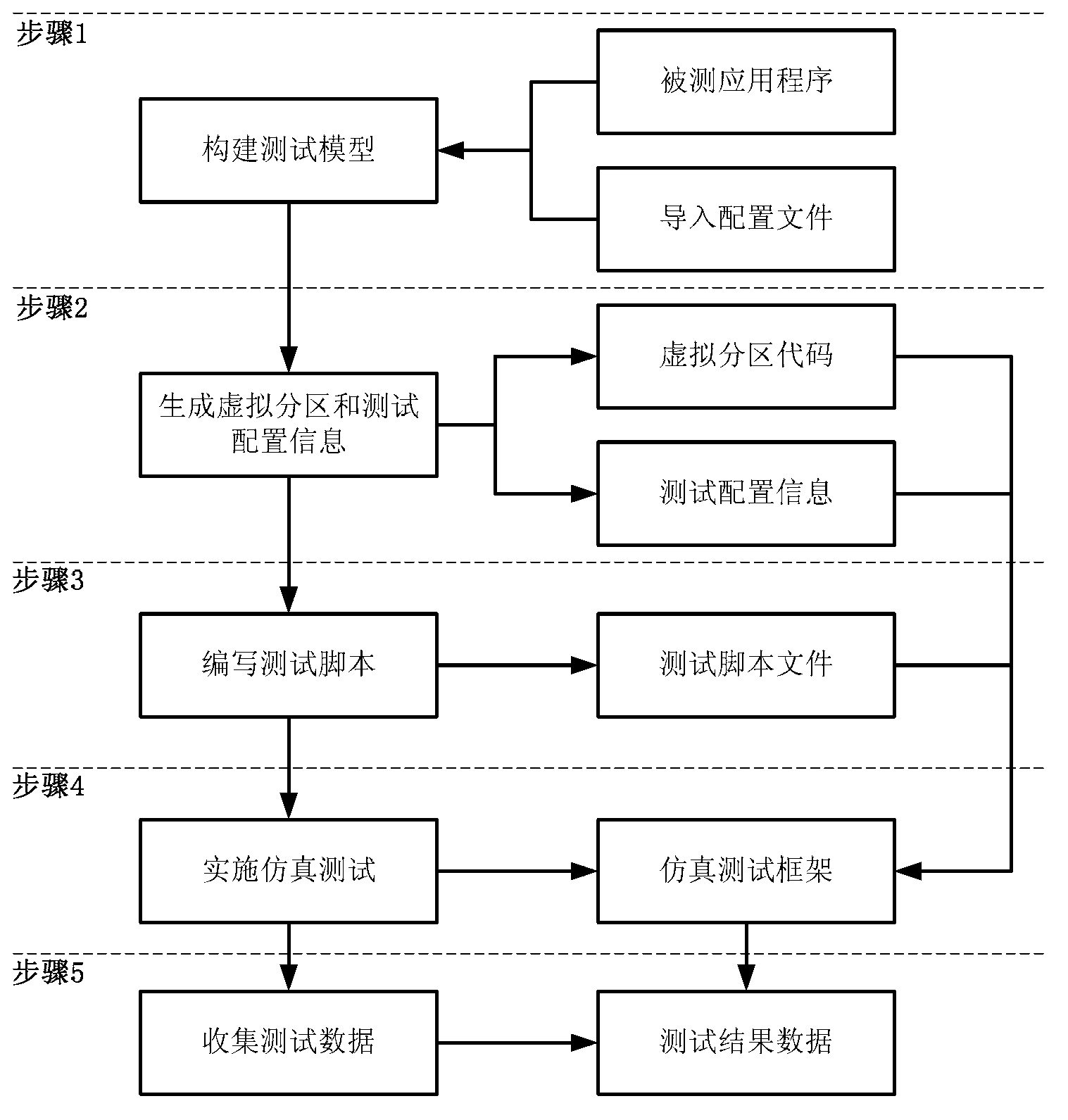
ActiveCN103235756AReduce development costsHigh simulationSoftware testing/debuggingApplication program softwareEmbedded software
A simulation testing method for partition application software of an embedded system comprises five steps: step one, building a testing model; step two, generating testing configuration information and a virtual partition code according to the testing model; step three, writing a testing script, and writing a response action for an allocated event occurring during the testing process; step four, performing testing on a partition application to be tested; and step five, collecting and analyzing the testing data. The simulation testing method for the partition application software of the embedded system can be implemented in a development and integration test phase of a partition embedded software applicationand can test or verify the execution sequence, the scheduling performance and the interface communication function of the partition embedded software application. The technical scheme of the simulation testing method for the partition application software of the embedded system comprises the steps of utilizing a calculation and storage unit of a core operating system, simulating the dynamic behaviors of other partition applications on line through a virtual partition mode, and exerting testing actuation to the application to be tested and receiving response. The simulation testing method for the partition application software of the embedded system has a broad application prospect in the technical field of software testing.
Owner:BEIHANG UNIV
Distributed capture and aggregation of dynamic application usage information
ActiveUS20100030785A1Quality improvementReliable transportationError detection/correctionDigital computer detailsApplication program softwareFile system
A web-based hosted solution through which application developers create, manage and monitor application usage analytics in an online manner. Preferably, an application under test is one of: application software, a script-enabled web application, or a rich Internet application (RIA). During the development process, a usage monitoring API is integrated into the application and the application is deployed. As users interact with the application, a log file is generated, typically in one of two ways. If the application is able to write to a local file system (in the user's machine), usage information is gathered in a log file local to the deployed application and then dispatched to an upload server for processing in a batch manner. If the application is not able to write to the user machine's local file system, the usage information is sent to a remote logging server, preferably on a just-in-time basis, and then the log file is generated on the logging server. In either case, preferably the usage information that is tracked comprises “features,”“faults” and “failures” of the application, independent of platform, location, and number of deployed application instances.
Owner:ACUITYADS US INC
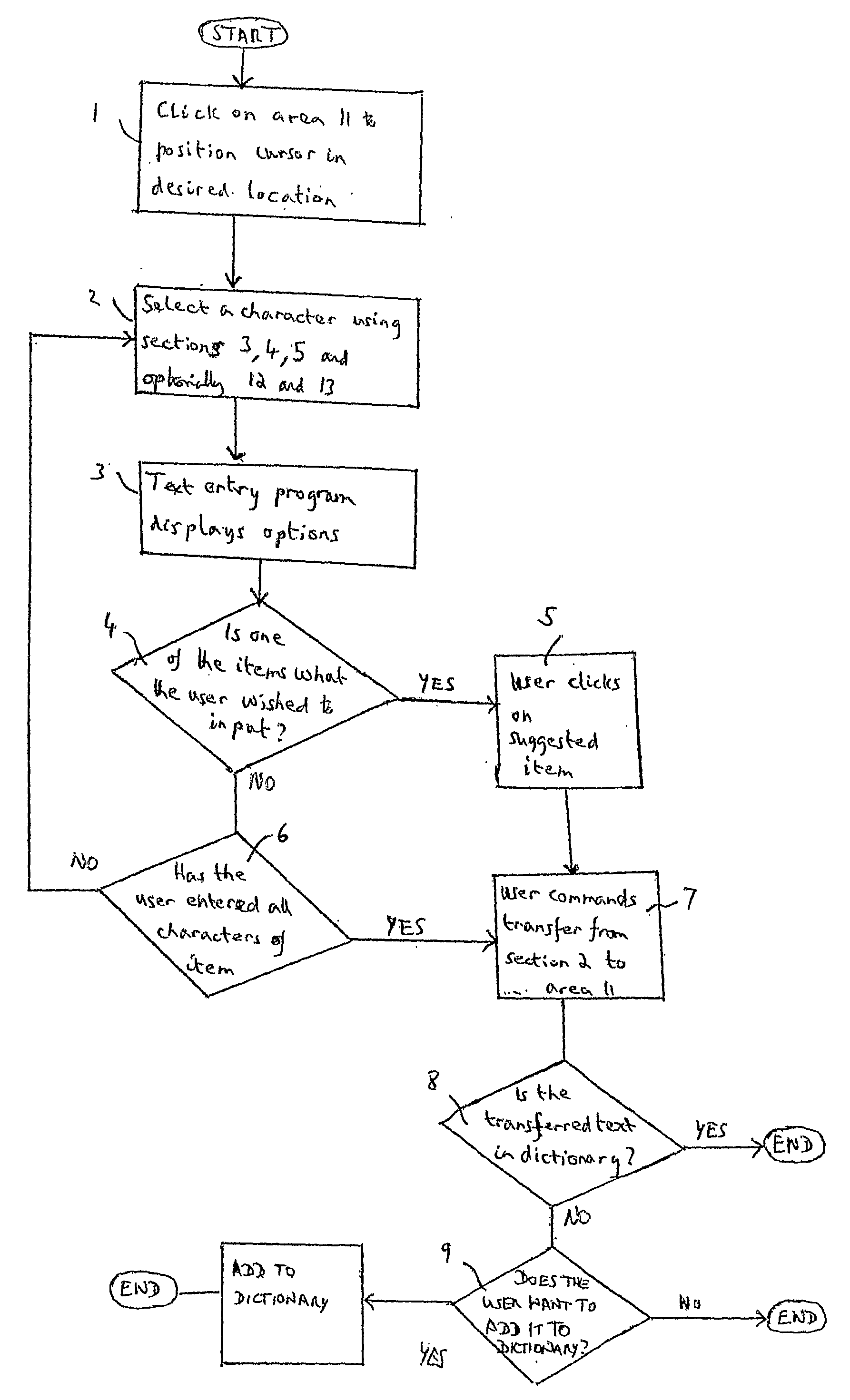
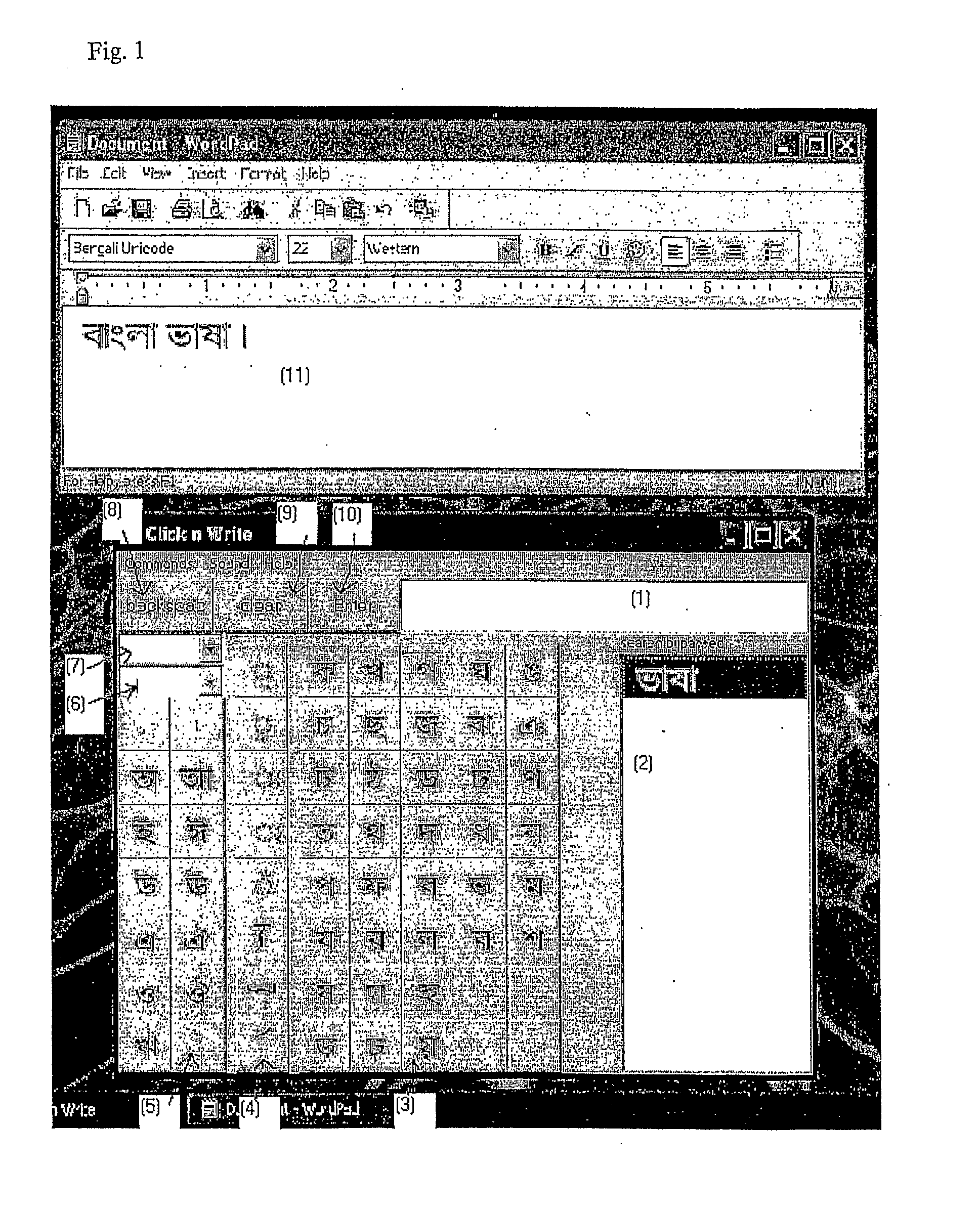
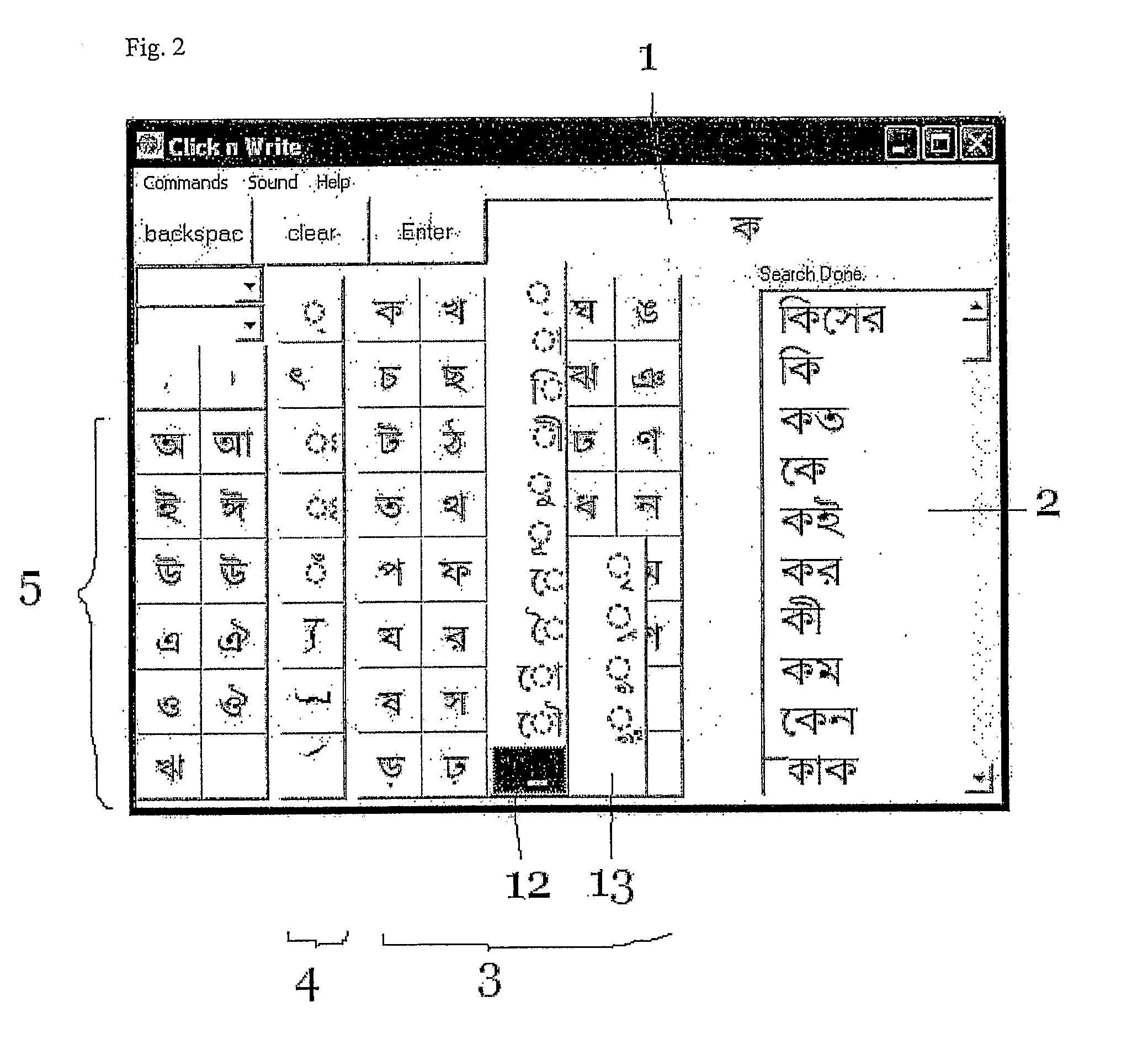
Method of data entry for indic languages
InactiveUS20070156394A1Input/output for user-computer interactionNatural language data processingGraphicsGraphical user interface
An Indic text entry program is proposed which runs on a computer system simultaneously with application software adapted to receive Indic text. The Indic text entry program provides a graphical user interface on a screen of the computer system. A user selects successive Indic characters using a mouse. The successively selected characters are presented in the graphical user interface until, in response to a command from the user, the characters are transferred to the application software. Thus, Indic text can be input to the application software without use of a specially adapted keyboard. The program at each time suggests items from a dictionary consistent with the characters selected so far. If one of the suggestions matches what the user wished to type, the user can select that item rather than typing the rest of the word.
Owner:BANERJEE AROOP KUMAR +1
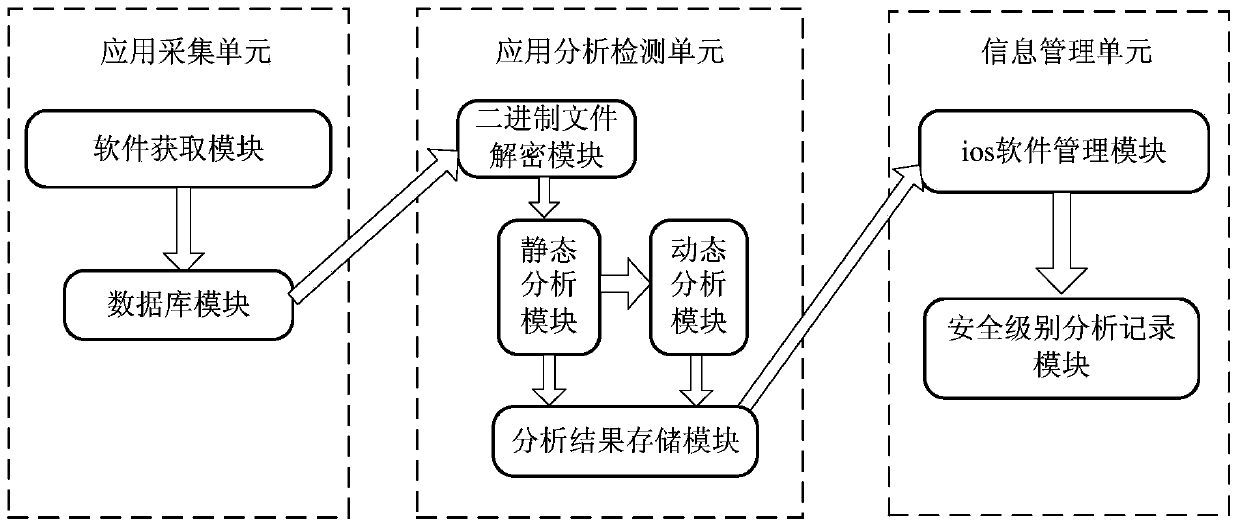
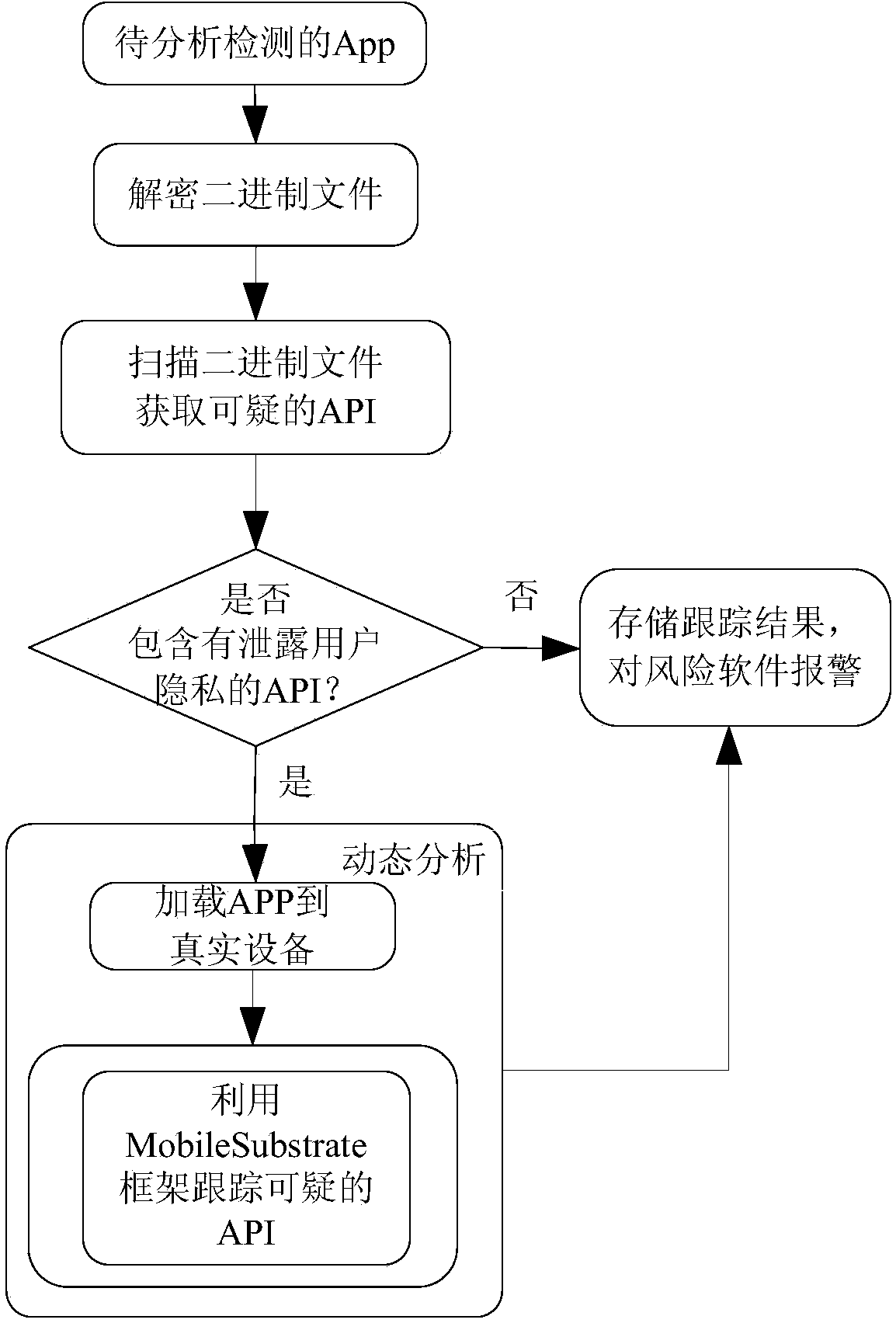
Monitoring device and method for protecting user privacy based on iPhone operating system (iOS)
InactiveCN104200155ASimple structureIngenious designPlatform integrity maintainanceApplication program softwareOperational system
The invention discloses a monitoring device and method for protecting user privacy based on an iPhone operating system (iOS). The monitoring device is provided with an application collection unit, an application analysis detection unit and an information management unit. The monitoring device can be used for conducting monitoring and early warning on whether application program software (APP) leaks user privacy (comprising contact information, mobile phone numbers, positions of mobile phones, short messages, user accounts, passwords, call records, photos, favorites, history, email addresses, contents of emails and the like), reminding a user of the potential risk of the software, and storing and analyzing the monitored result, and then conducts software security level evaluation on the application program according to a software security level research algorithm. The mobile phone security monitoring device is simple in structure, ingenious in design, simple in operating steps, easy to learn and master and safe in use, and has application and popularization prospects.
Owner:INST OF INFORMATION ENG CAS
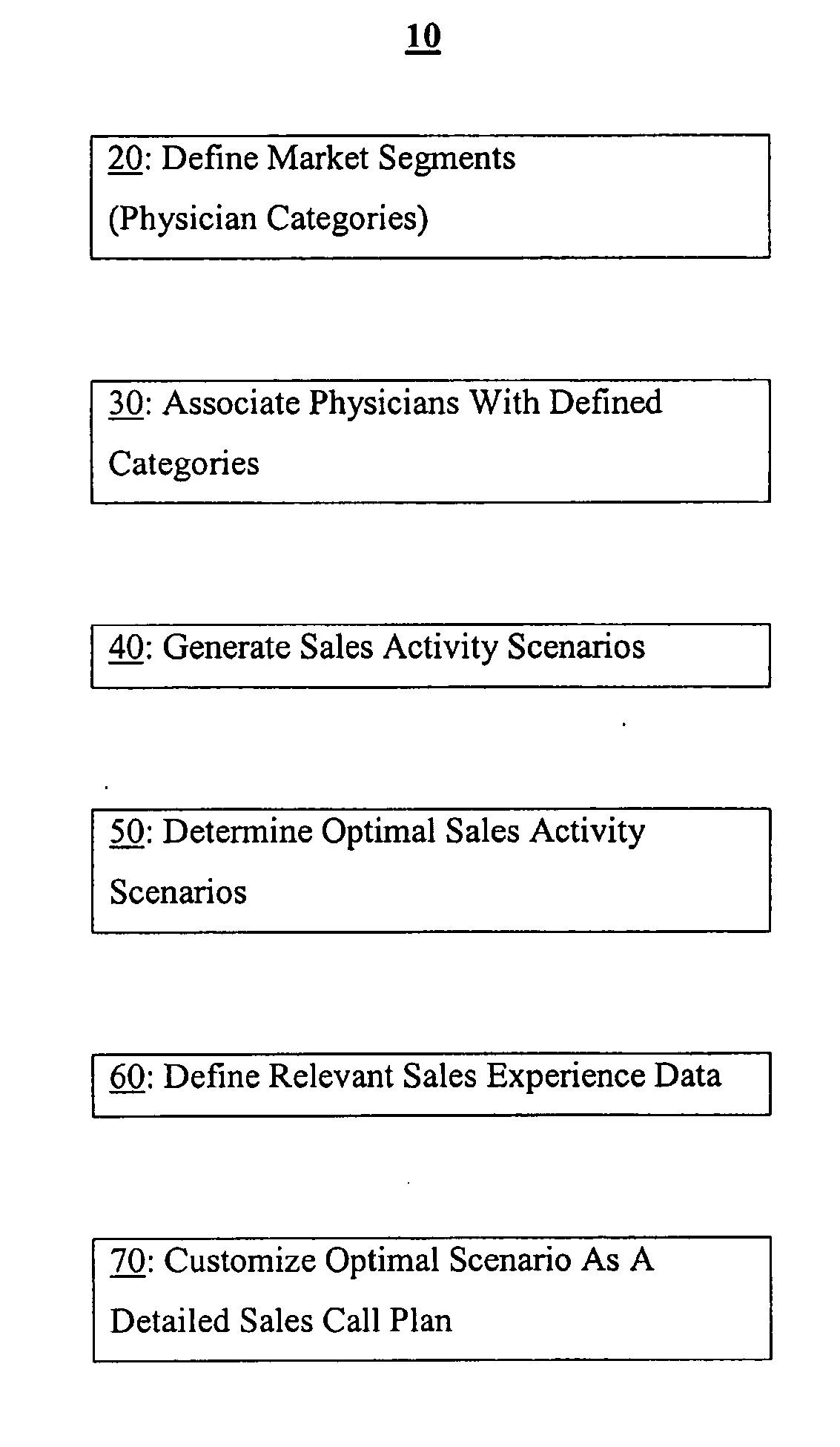
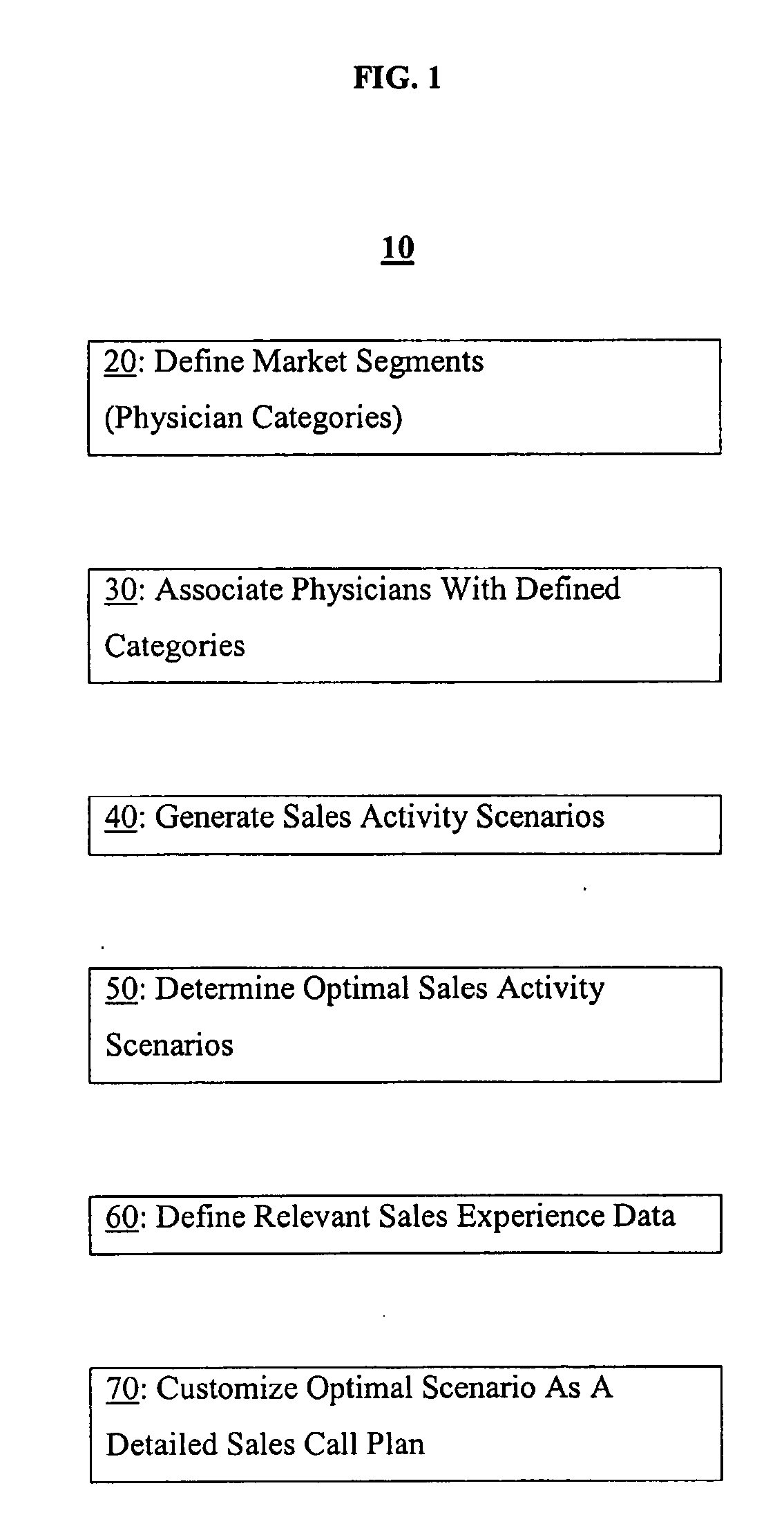
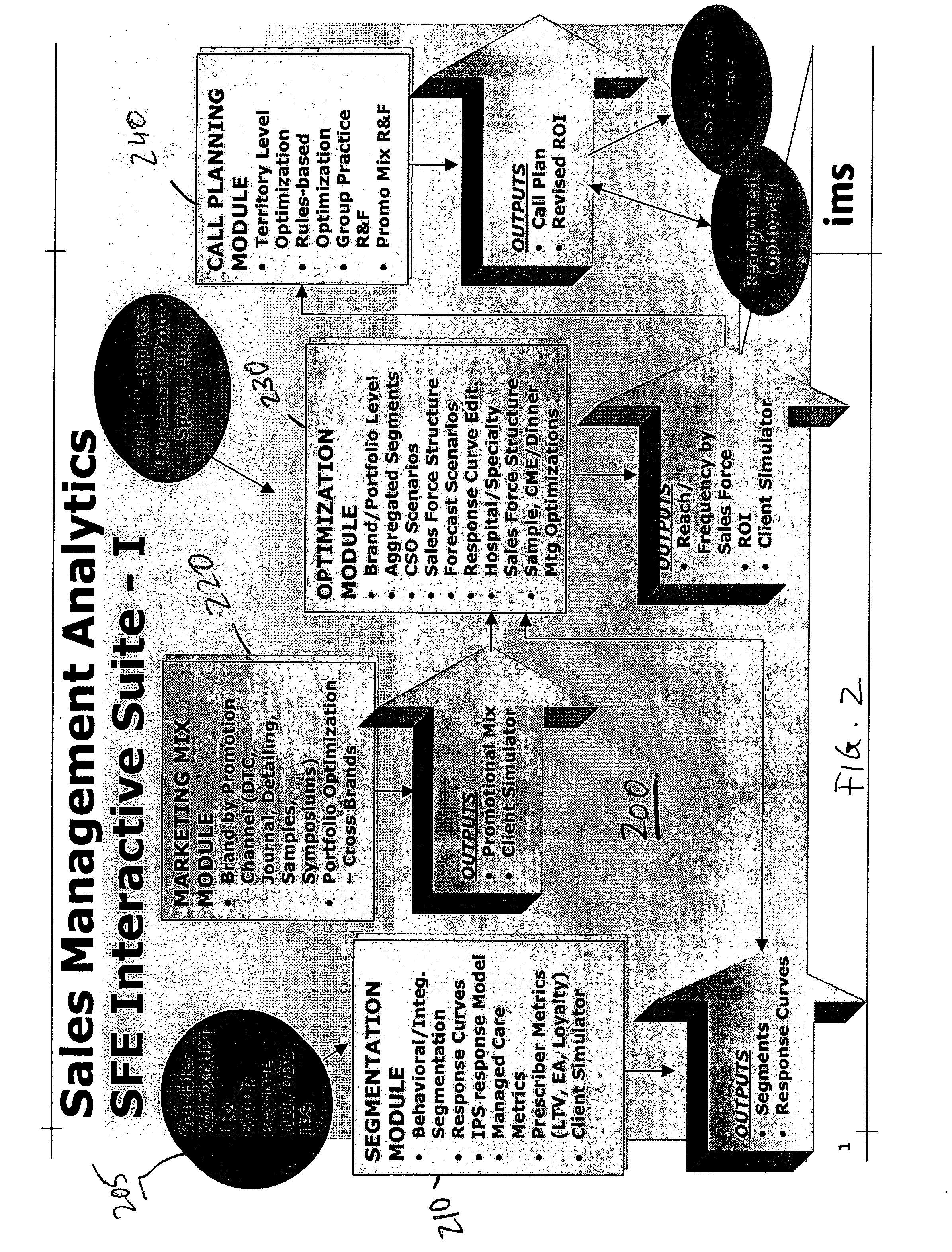
Methods and software arrangements for sales force effectiveness
InactiveUS20060129447A1Market predictionsResourcesApplication program softwarePharmaceutical industry
A business planning solution for sales force effectiveness in promoting products in a target market is provided. The planning solution analyzes sales and market data to identify target market segments that are likely to respond to sales force activity. Business resources can then be allocated to optimize sales force activity. Detailed sales call plans can be generated. The business planning solution may be implemented as a computer software application on conventional stand alone or networked computer arrangements. For pharmaceutical industry applications, the software application is configured to process pharmaceutical market research data.
Owner:IMS SOFTWARE SERVICES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com