Monitoring device and method for protecting user privacy based on iPhone operating system (iOS)
A user privacy and operating system technology, applied in the field of mobile application security monitoring, can solve problems such as insufficient security research, mobile phone data security leakage, and threats to user data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
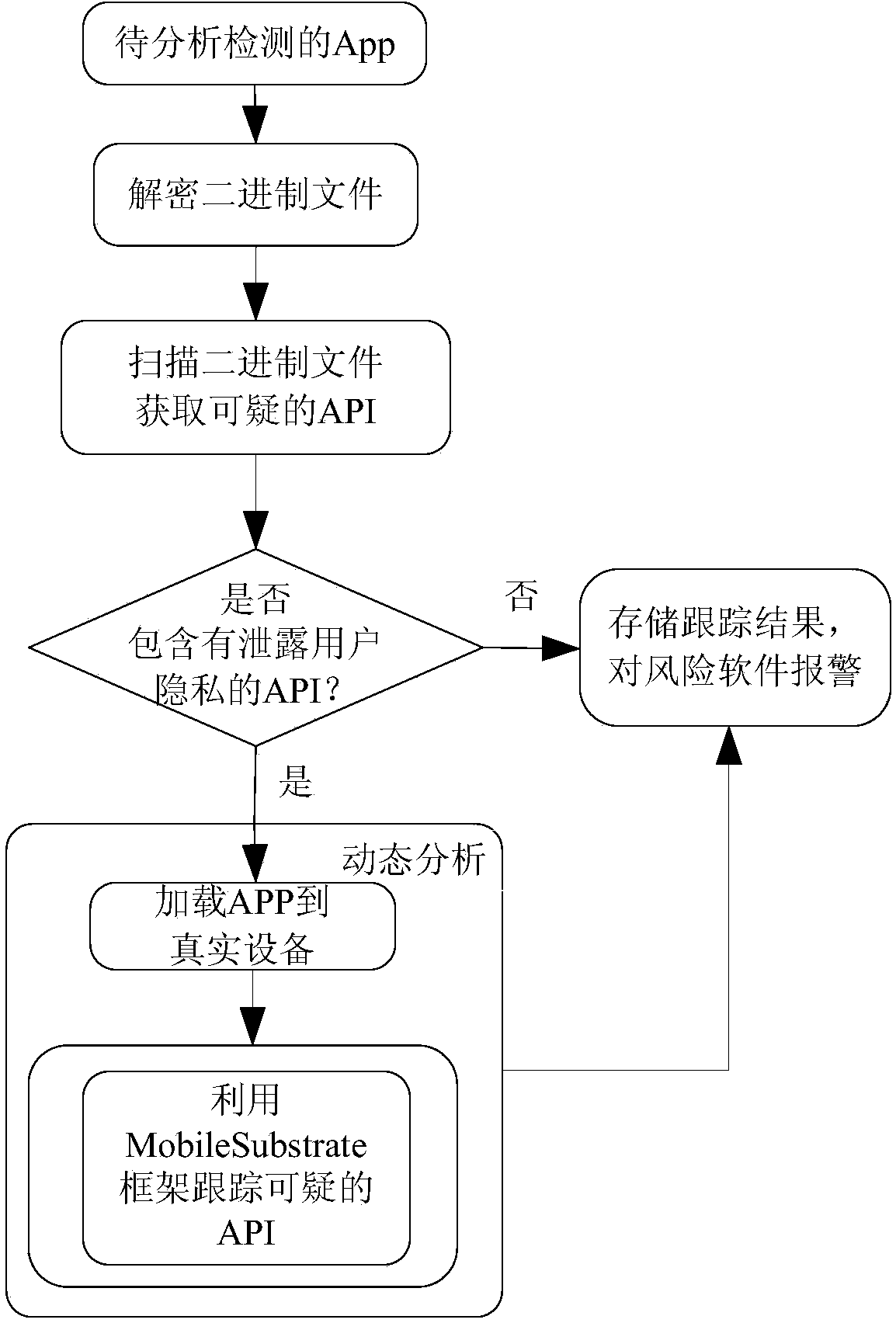
[0033] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
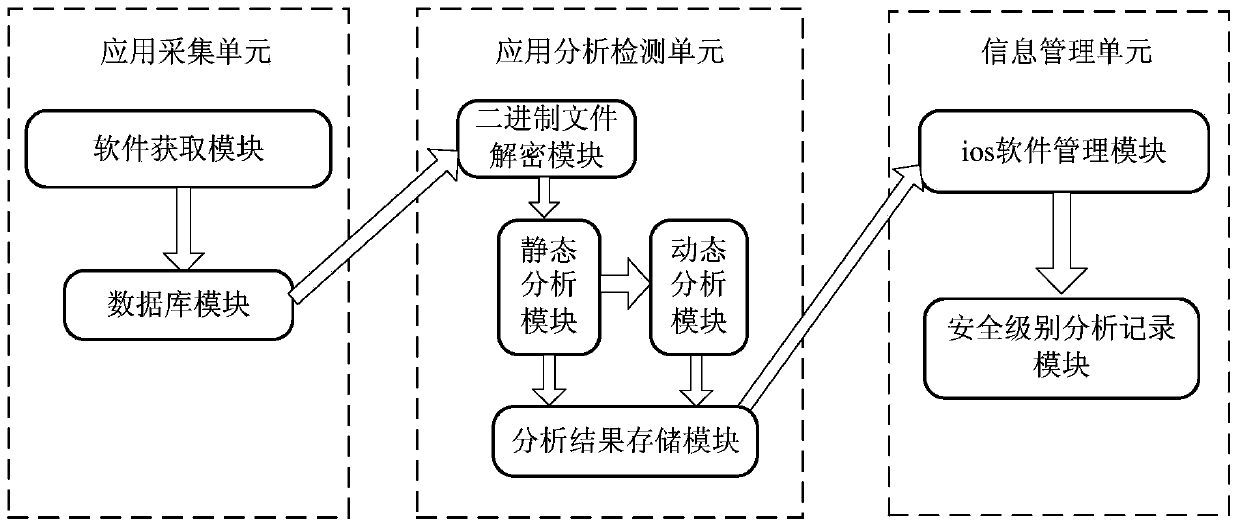
[0034] refer to figure 1 , introduces the composition and structure of the monitoring device based on the Apple mobile phone operating system iOS to protect user privacy: there are three components: an application collection unit, an application analysis and detection unit, and an information management unit. in:
[0035] (A) Application collection unit: used to automatically download the latest or commonly used application software APP (APPlication) in the iOS software source of the iPhone operating system, or receive the APP to be tested sent by the testing organization or individual, and send it into the software The acquisition module stores the downloaded or received APP in the database, which consists of two modules: a software acquisition module and a data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com