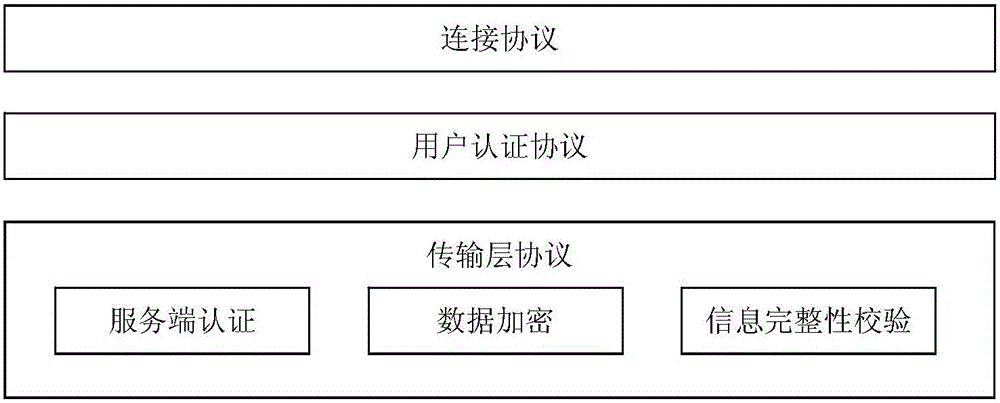
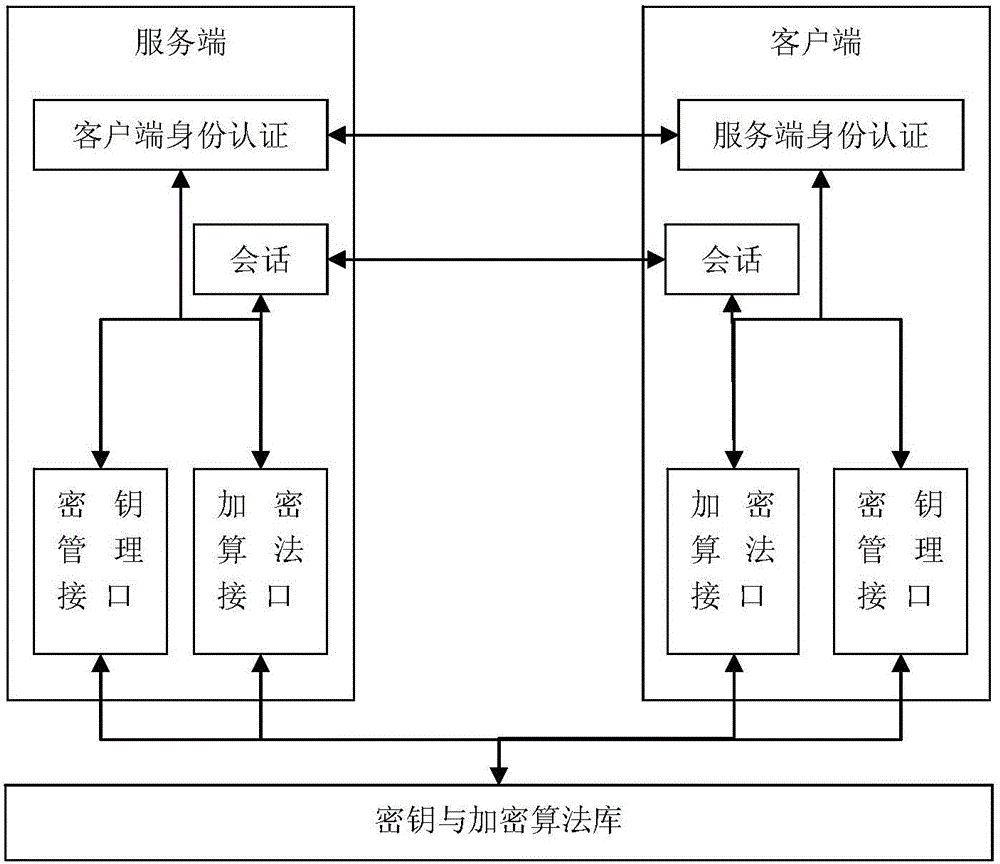
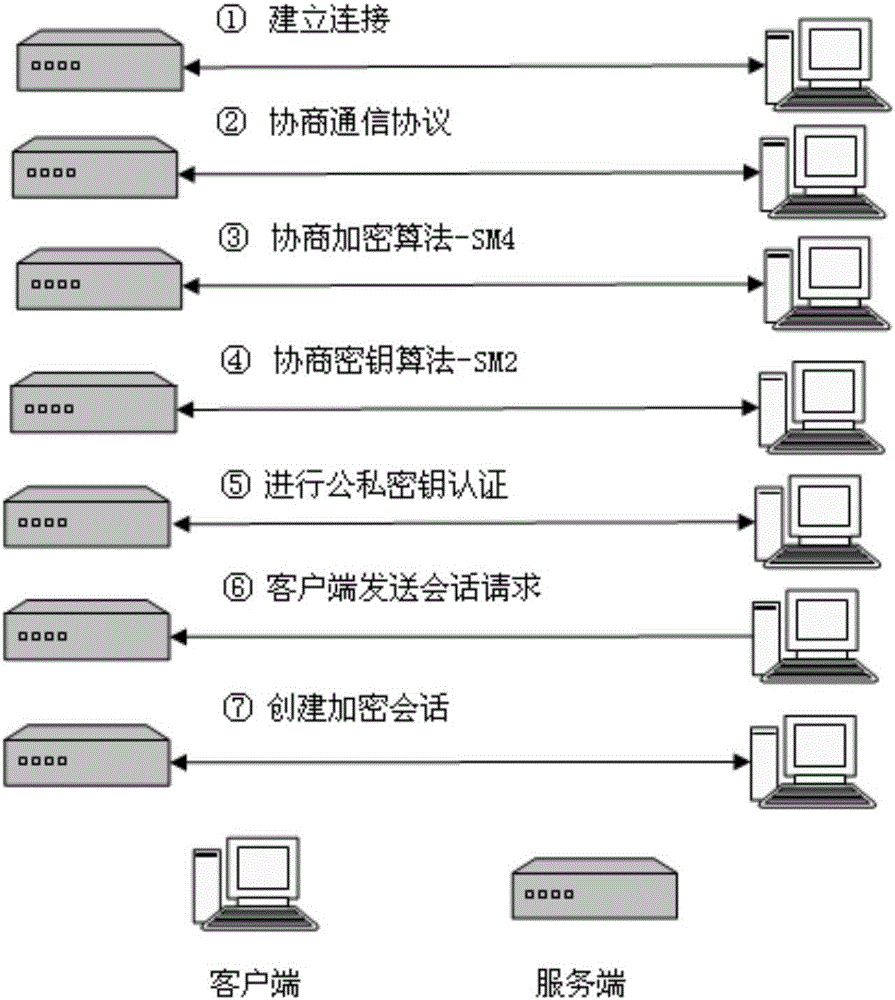
Patents
Literature
176results about How to "Access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
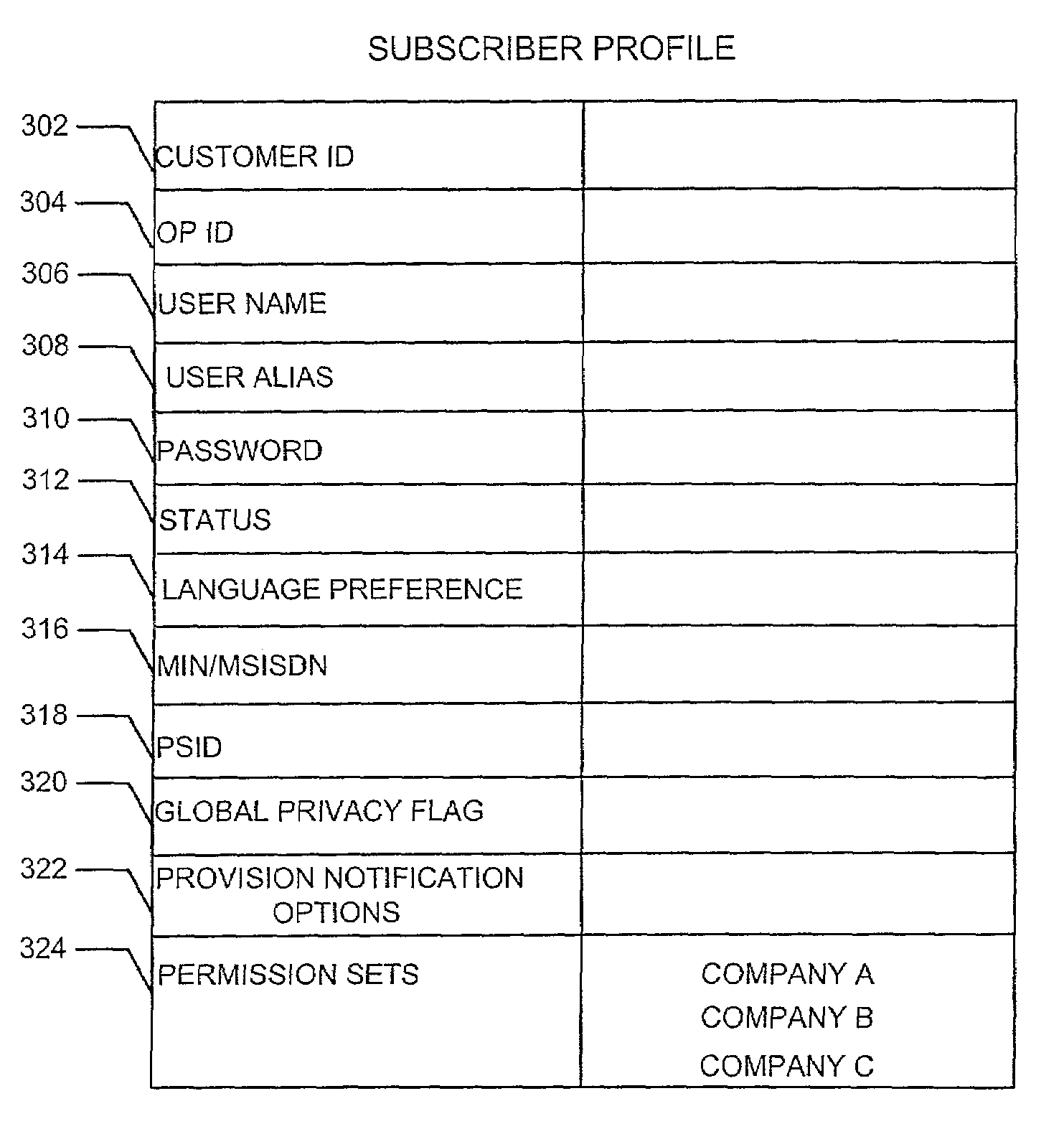
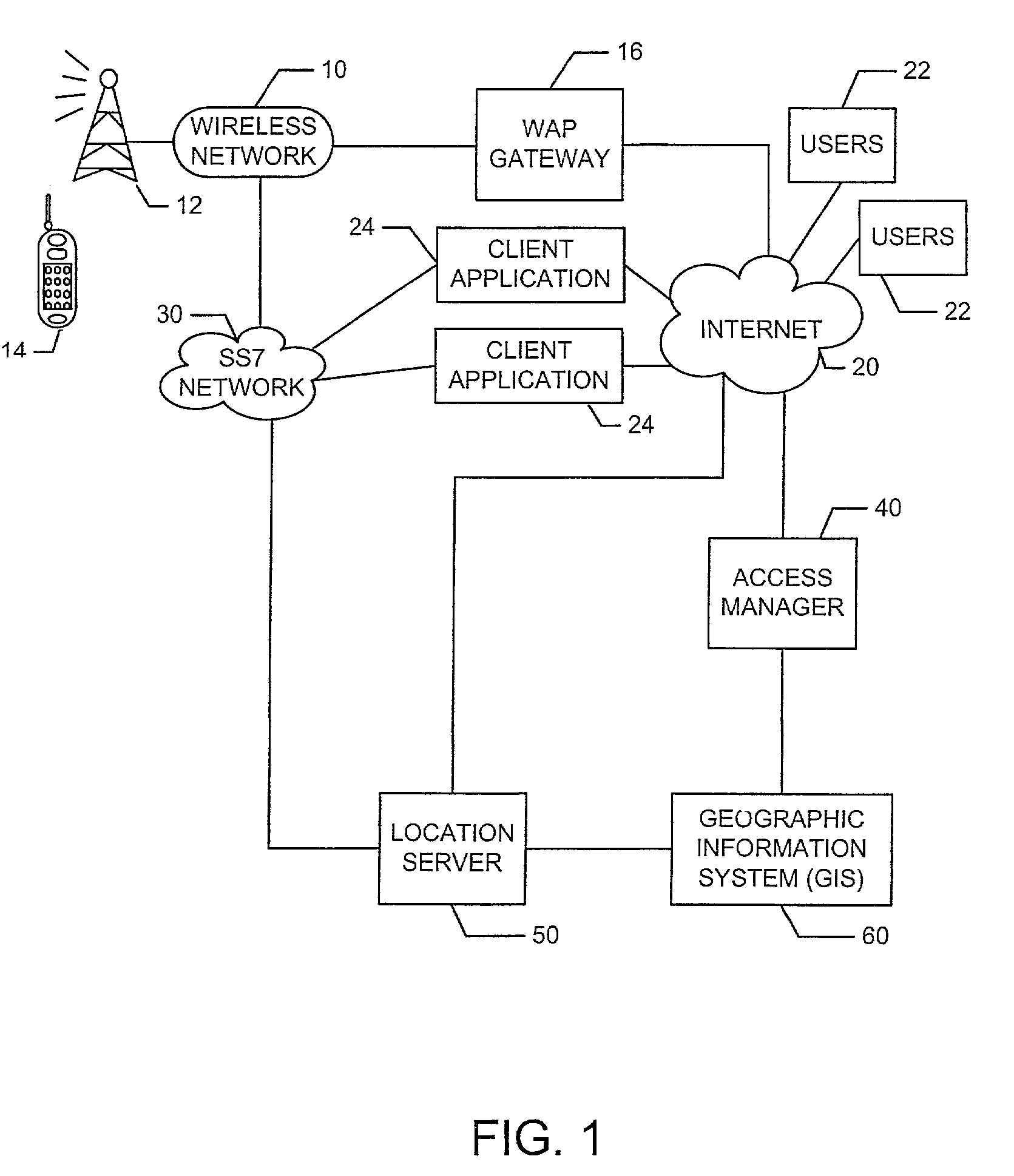
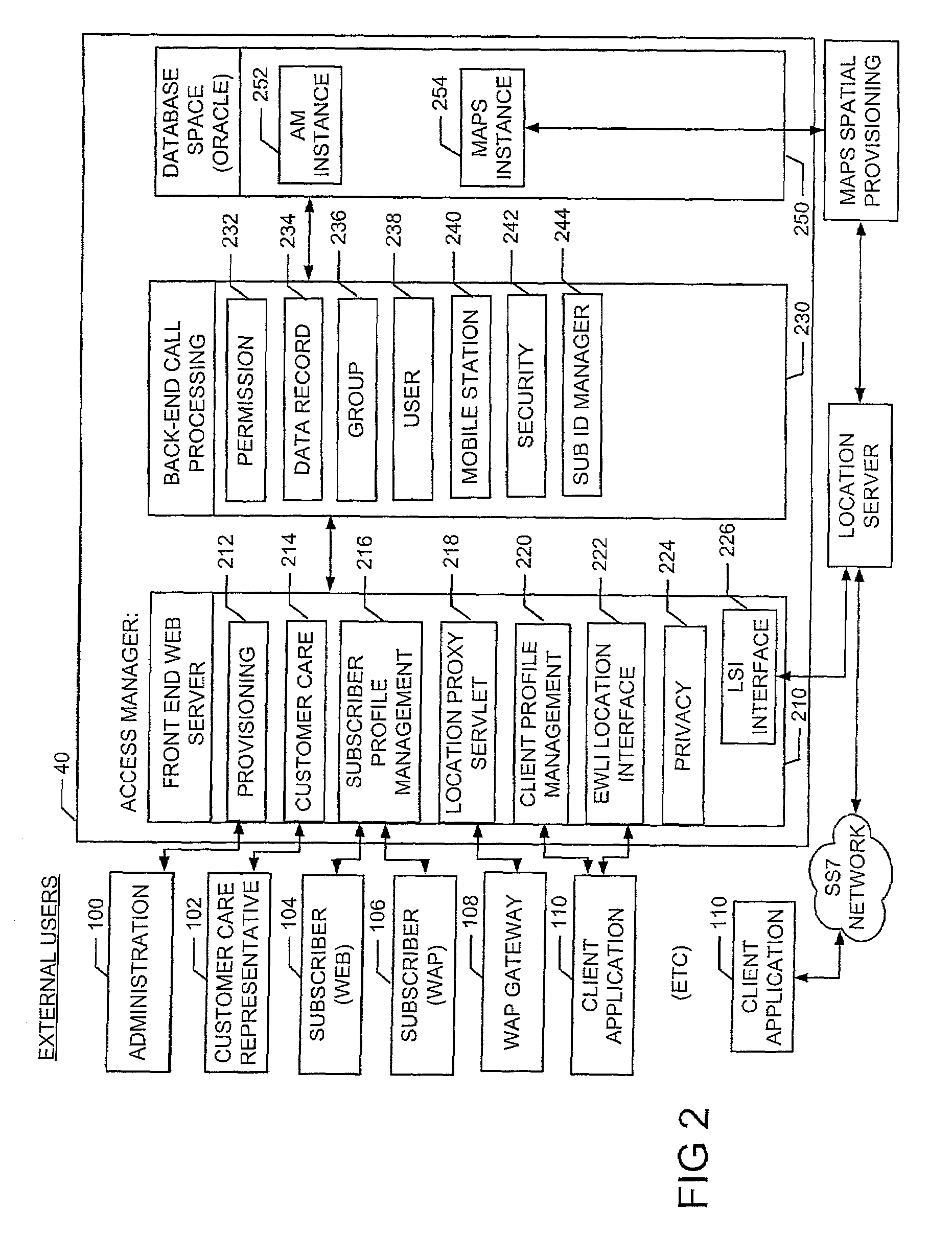
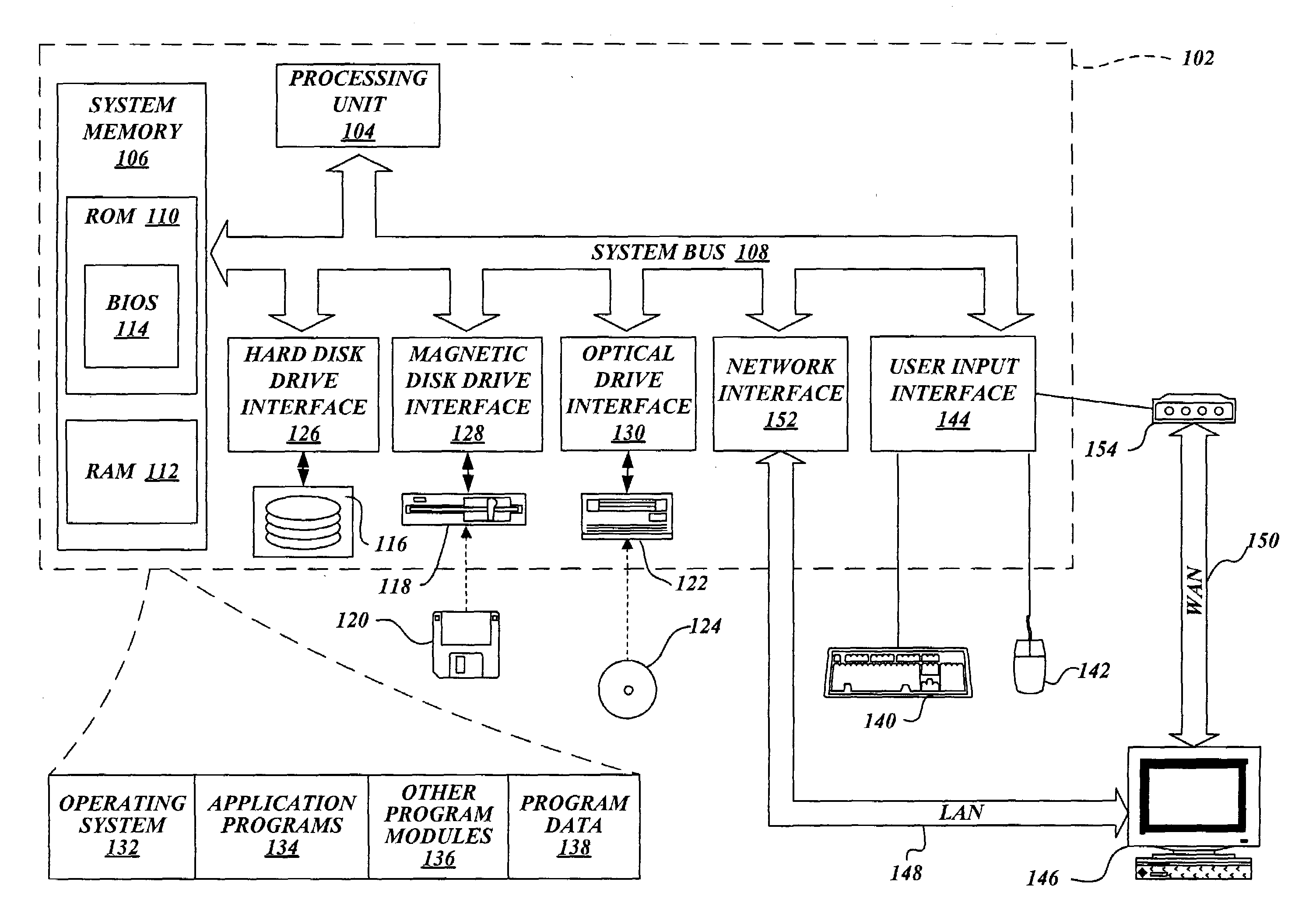
Method and system for managing location information for wireless communications devices
ActiveUS7203752B2Access controlInformation formatSpecial service for subscribersGranularityClient-side
A system and method provide for establishment and use of permission sets for subscribers where client applications in a wireless communication environment are requesting location information for a particular wireless communications device from a provider of such information. The system described herein provides the capability for a wireless communications device operator to establish a profile wherein limitations may be placed on the provision of such location information based on such things as the requesting party, spatial and temporal limitations, as well as granularity. The system described herein may be further configured such that an authentication process is preformed for client application seeking location information which would require the registration of such client applications with a centralized processing system.
Owner:VIDEOLABS
System and method for controlling access to location information
ActiveUS7224987B1Access controlClear instructionsRadio/inductive link selection arrangementsTransmissionGeographic areaUser defined
A system and method for providing location information associated with a location owner to location consumers. A location server includes an owner profile for controlling access to the owner's location information. The owner profile contains information describing a user-defined geographic area. In response to a location consumer requesting the location owner's location information, the location server obtains data describing a current location of the location owner. The server determines if the current location falls within a set of boundaries that defines the user-defined geographic area. If the current location falls within a set of boundaries that defines the user-defined geographic area, the location server transmits the location information to the requesting location consumer.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for authenticating an accessory
ActiveUS20070234420A1Access controlTwo pole connectionsDigital data processing detailsComputer hardwareAuthentication
A method, system, and connector interface for authenticating an accessory. The method includes performing a first authentication operation on the accessory by the media player, where an authentication certificate is validated; and performing a second authentication operation on the accessory by the media player, where an authentication signature is validated. According to the system and method disclosed herein, the media player and accessory may utilize a plurality of commands utilized in a variety of environments such as within a connector interface system environment to control access to the media player.
Owner:APPLE INC
Method and system for secure distribution of selected content to be protected
InactiveUS20080092239A1Access controlDigital data processing detailsUser identity/authority verificationSafe systemRights management
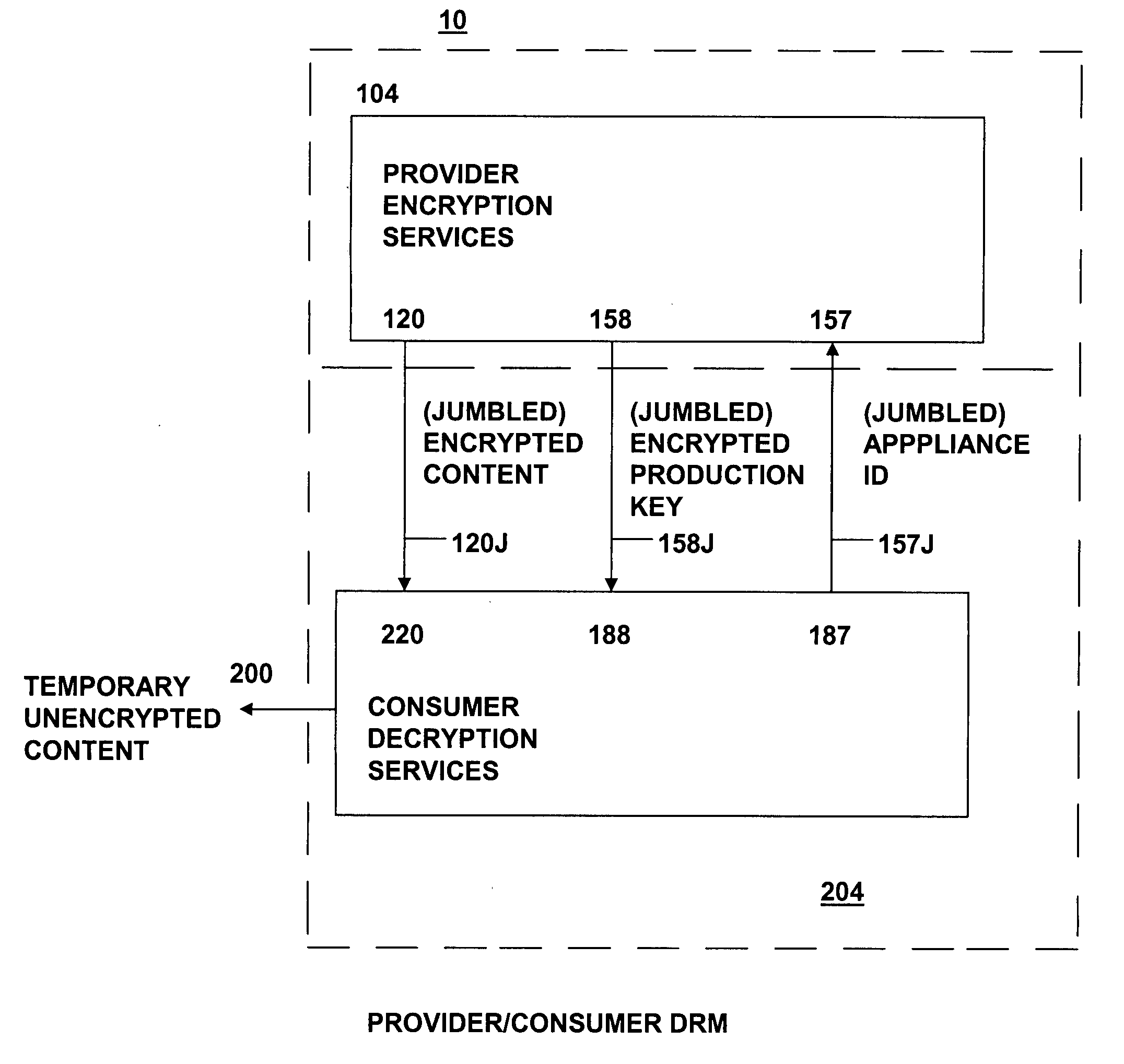
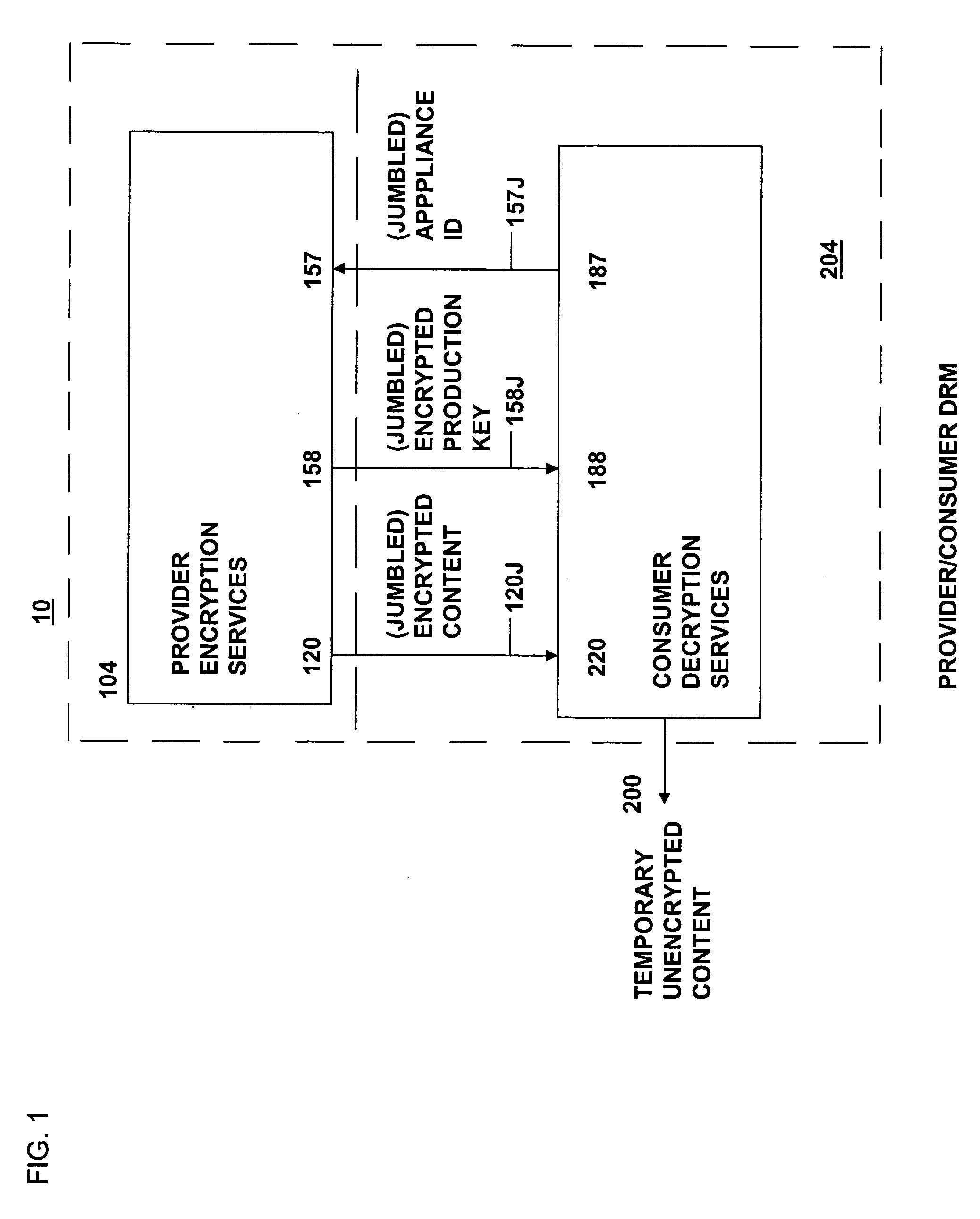
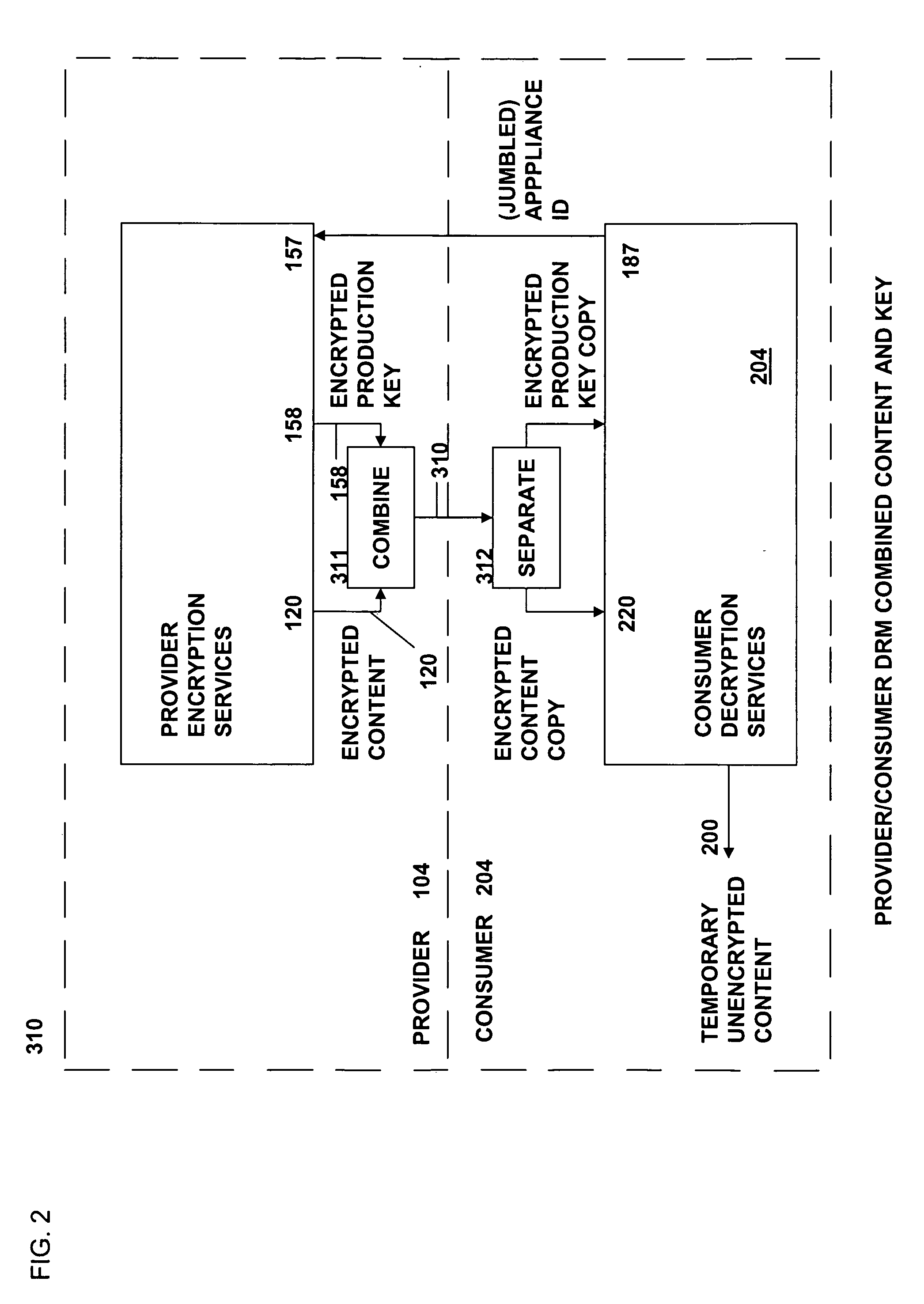
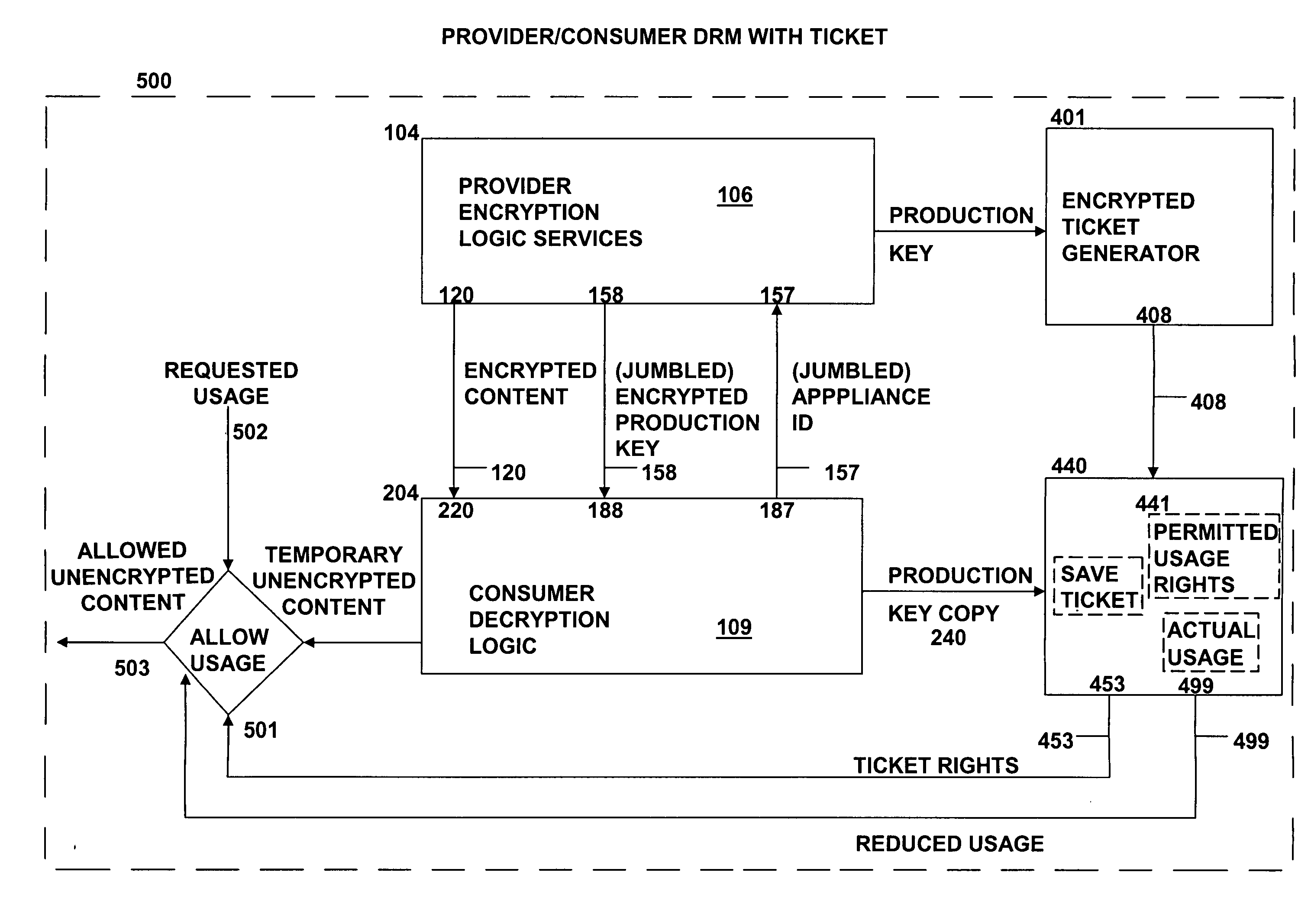
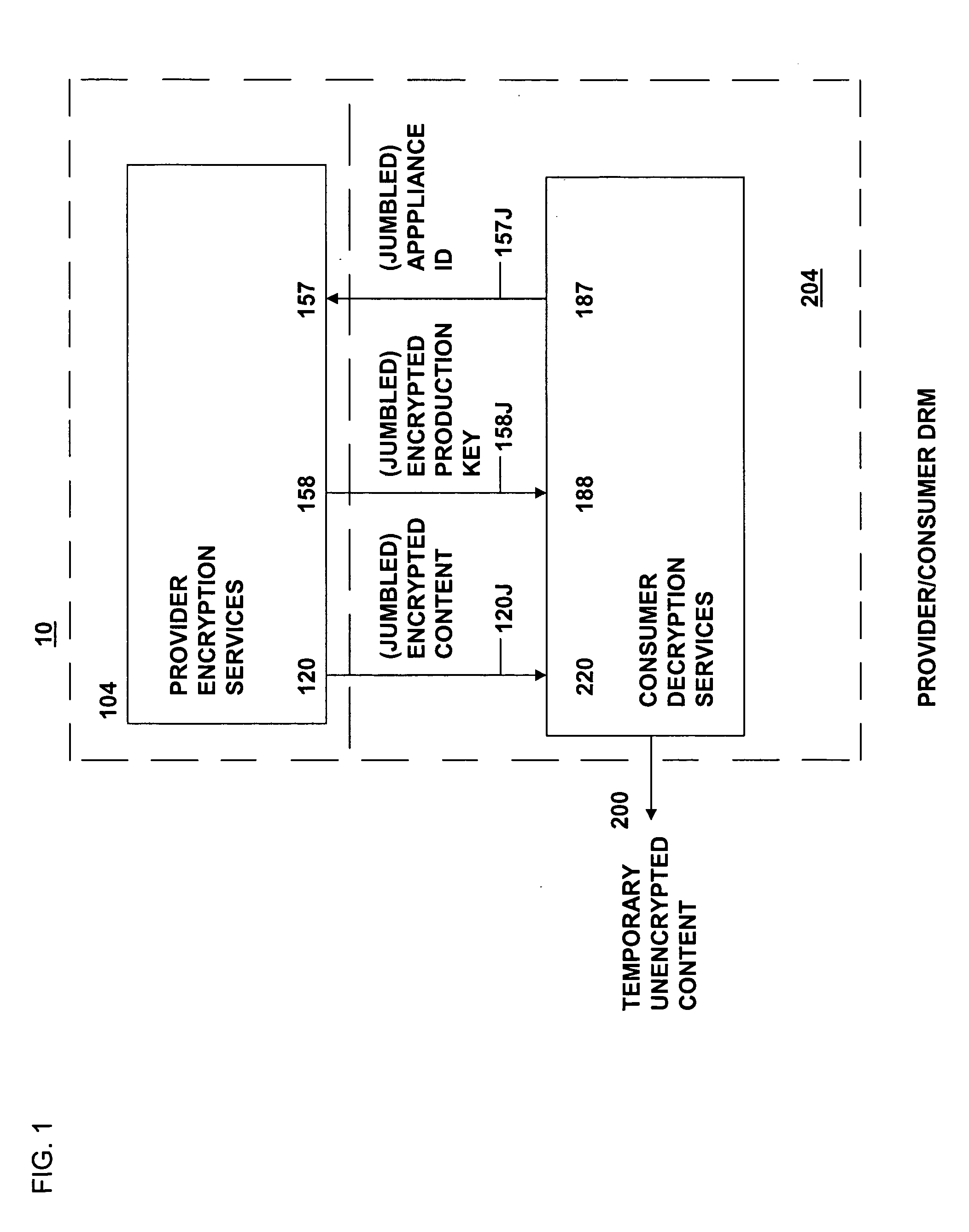
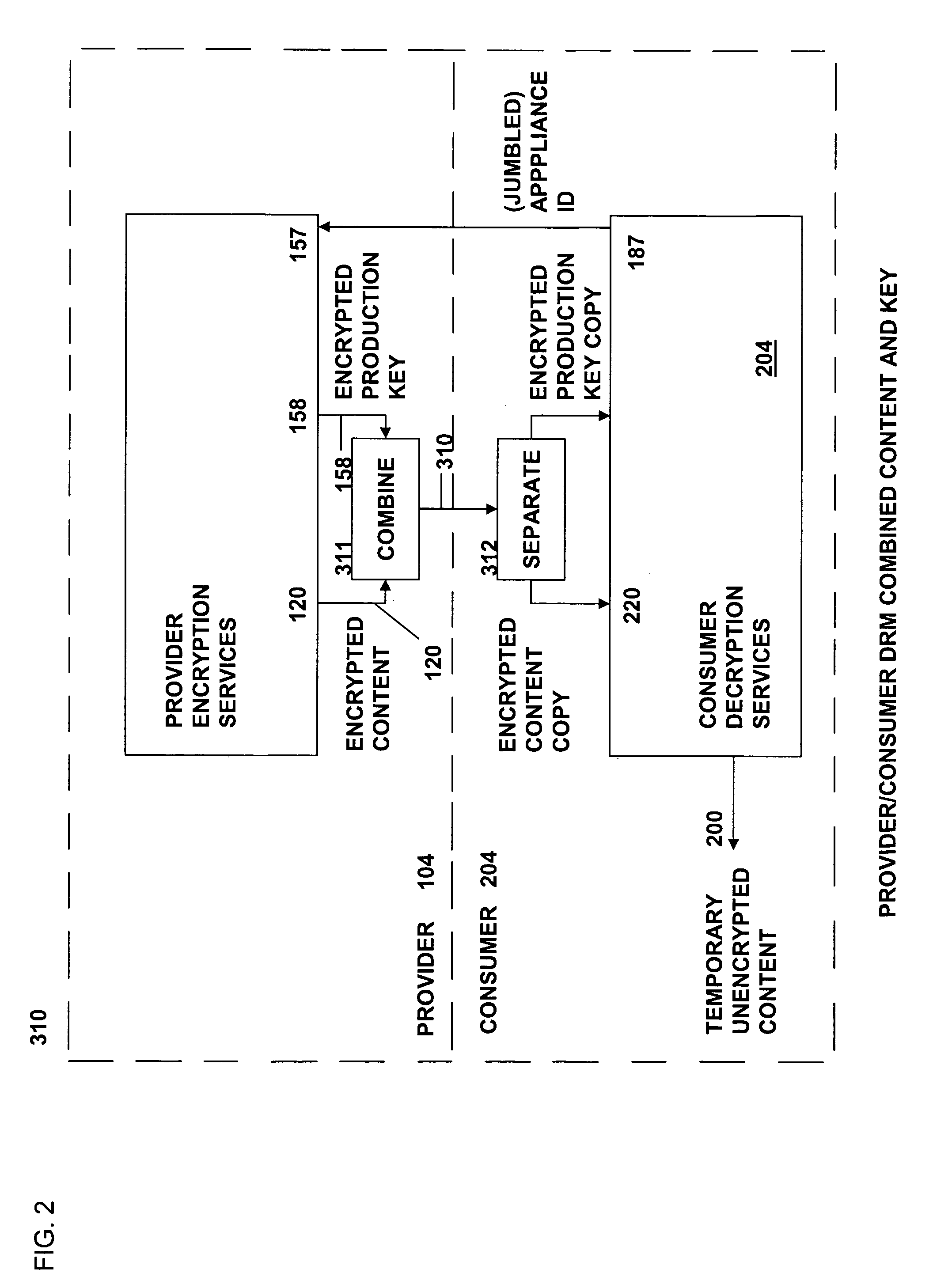
The present invention relates to data rights management and more particularly to a secured system and methodology and production system and methodology related thereto and to apparatus and methodology for production side systems and are consumer side systems for securely utilizing protected electronic data files of content (protected content), and further relates to controlled distribution, and regulating usage of the respective content on a recipient device (computing system) to be limited strictly to defined permitted uses, in accordance with usage rights (associated with the respective content to control usage of that respective content), on specifically restricted to a specific one particular recipient device (for a plurality of specific particular recipient devices), or usage on some or any authorized recipient device without restriction to any one in specific, to control use of the respective content as an application software program, exporting, modifying, executing as an application program, viewing, and / or printing of electronic data files.
Owner:OL SECURITY LIABILITY CO
Method and system for secure distribution of selected content to be protected on an appliance specific basis
ActiveUS20080092240A1Access controlDigital data processing detailsUser identity/authority verificationApplication program softwareData file
The present invention relates to data rights management and more particularly to a secured system and methodology and production system and methodology related thereto and to apparatus and methodology for production side systems and are consumer side systems for securely utilizing protected electronic data files of content (protected content), and further relates to controlled distribution, and regulating usage of the respective content on a recipient device (computing system) to be limited strictly to defined permitted uses, in accordance with usage rights (associated with the respective content to control usage of that respective content), on specifically restricted to a specific one particular recipient device (for a plurality of specific particular recipient devices), or usage on some or any authorized recipient device without restriction to any one in specific, to control use of the respective content as an application software program, exporting, modifying, executing as an application program, viewing, and / or printing of electronic data files.
Owner:DAVID H SITRICK +1
Method, device and system for accessing machine type communication terminal equipment to network
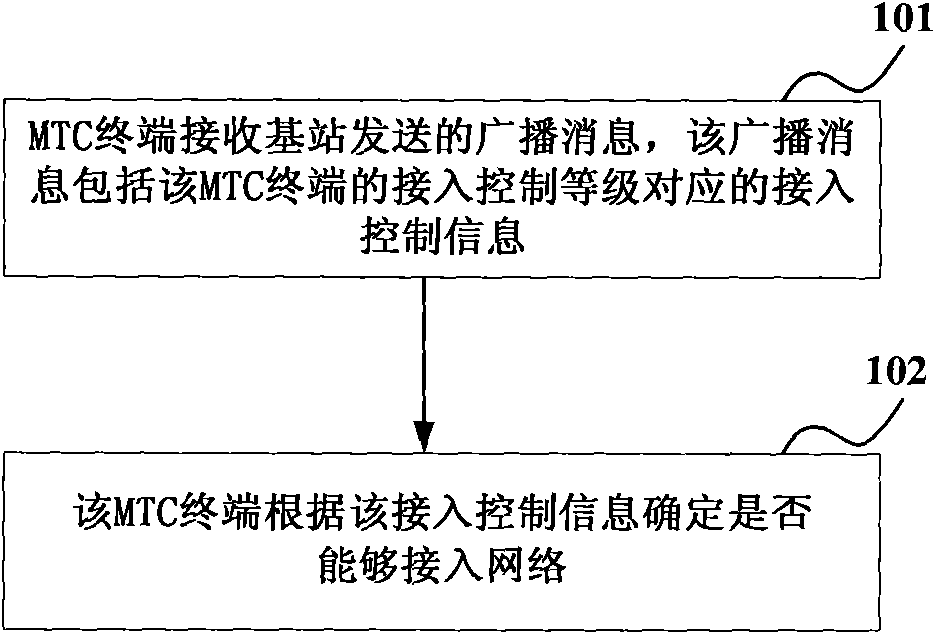
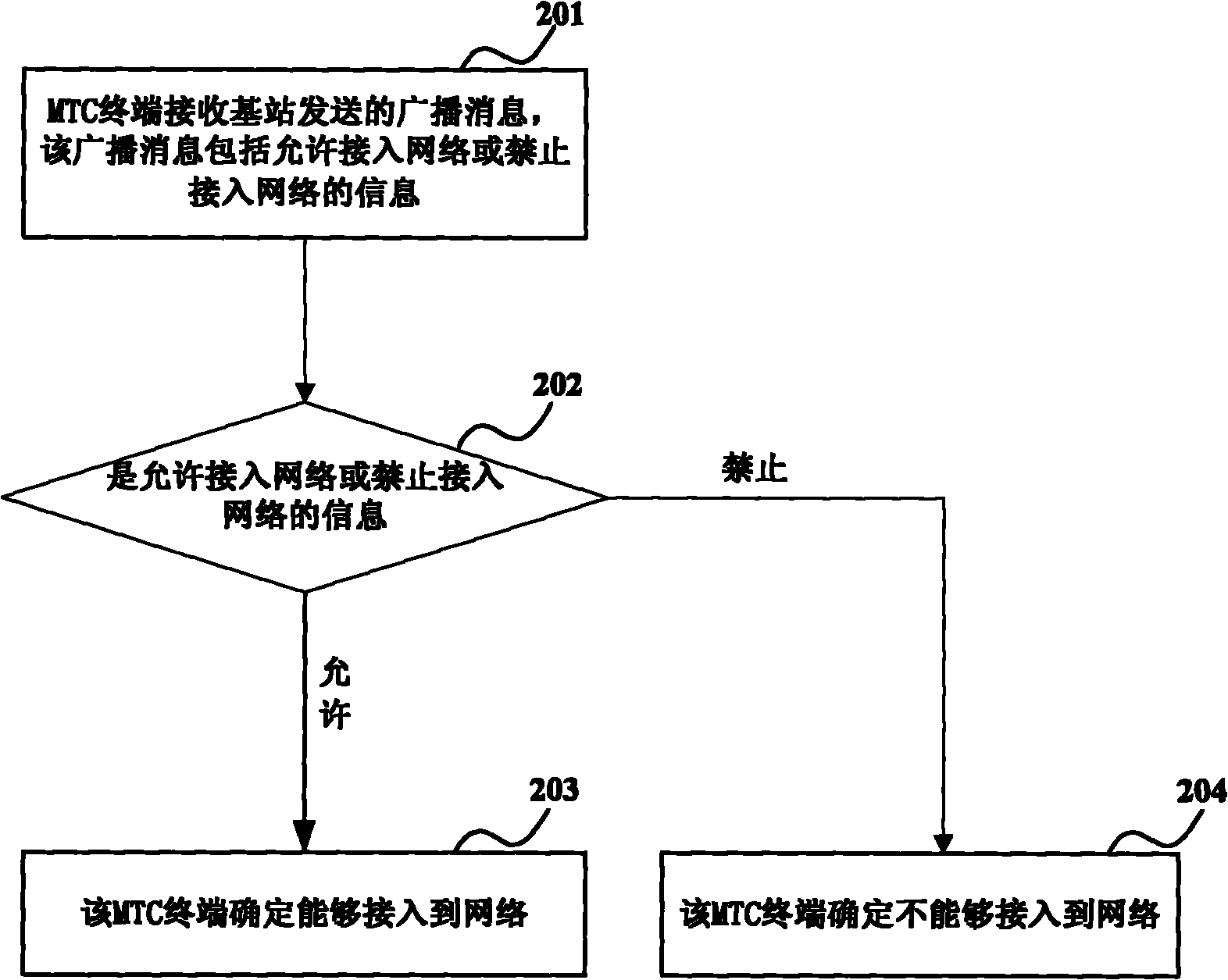
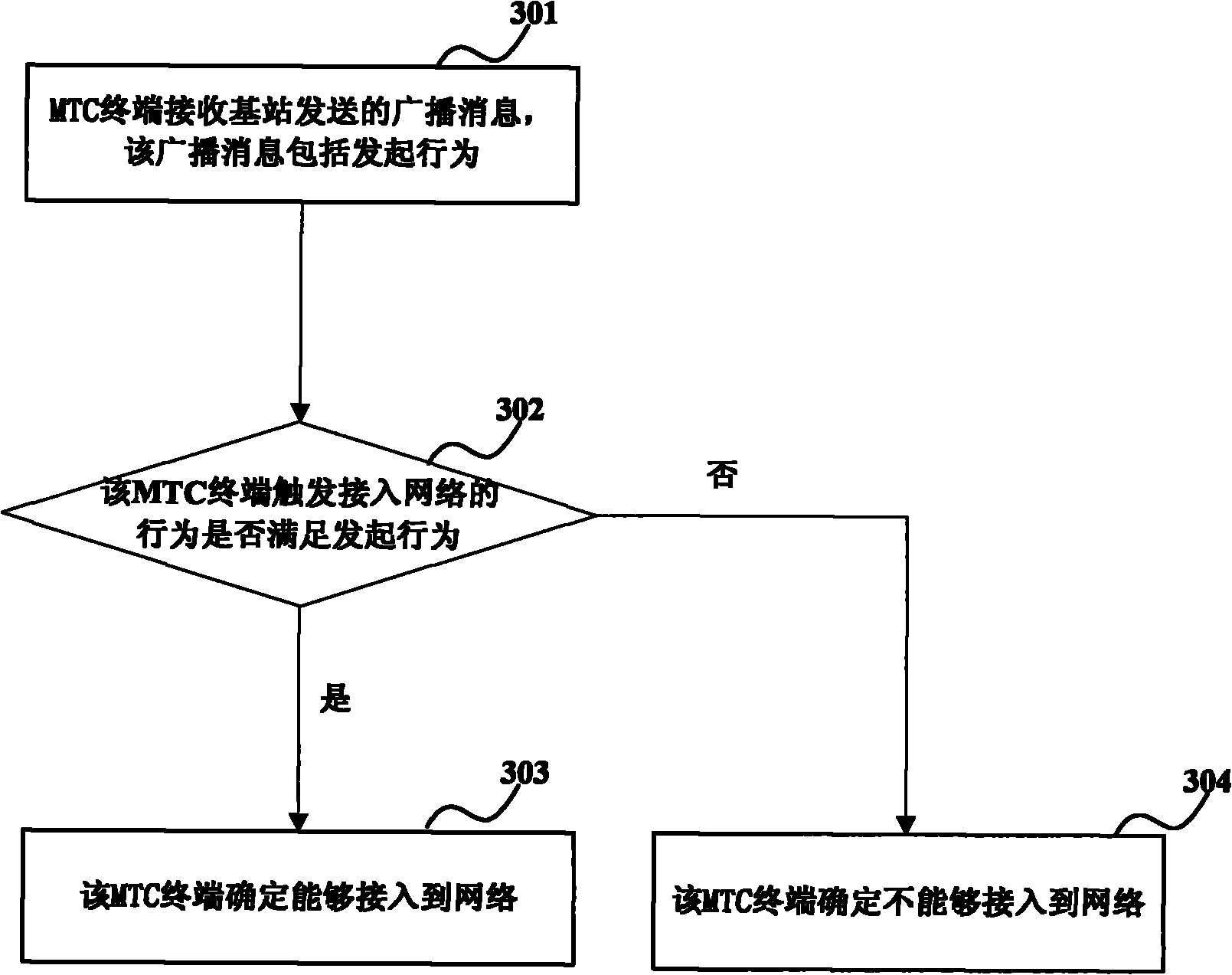
ActiveCN102045810AAccess controlReduce congestionAssess restrictionBroadcast service distributionDevice typeTerminal equipment
The embodiment of the invention provides a method, a device and a system for accessing machine type communication (MTC) terminal equipment to a network. The method comprises the following steps that: the MTC terminal equipment receives a broadcast message sent from a base station, wherein the broadcast message comprises access control information corresponding to the access control level of the MTC terminal equipment, the access control level of the MTC terminal equipment is different from or equal to that of other types of terminal equipment in the network, and the broadcast message also comprises indication parameter numbers to mark the type of the MTC terminal equipment in the access control level and the other types of terminal equipment in the network; and the MTC terminal equipment judges whether the network can be accessed according to the access control information, and executes corresponding access operation. Through the embodiment of the invention, the access of the MTC terminal equipment can be controlled more flexibly, which is helpful for reducing the probability of network congestion.
Owner:HUAWEI TECH CO LTD
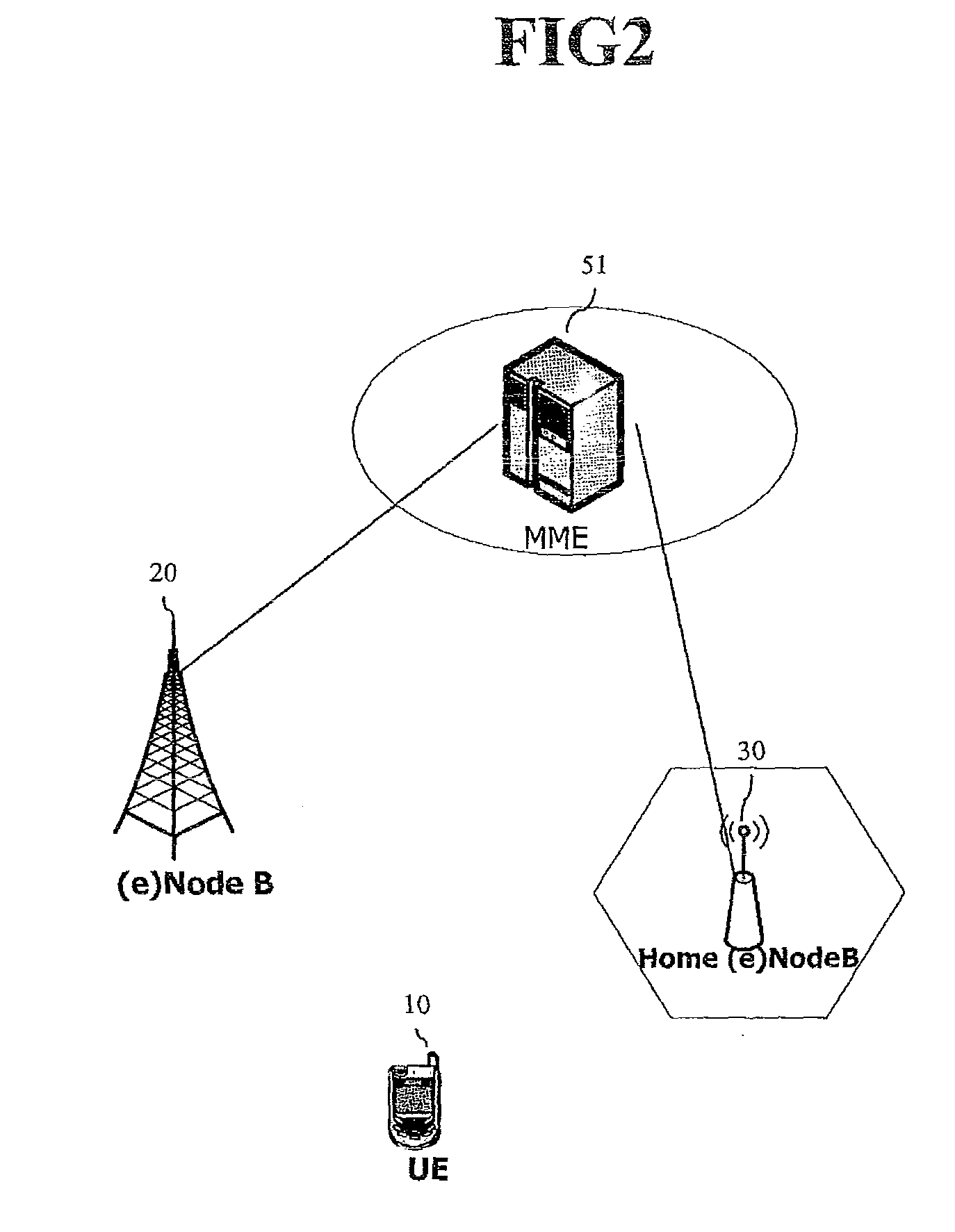
Method for controlling access of terminal to home (e)nodeb
ActiveUS20100238858A1Reduce amount of resourceAccess controlAssess restrictionNetwork topologiesTelecommunicationsUser group
A method for controlling access of a terminal to a Home (e)NodeB by a network entity, the terminal accessed to the Home (e)NodeB operated in a closed access mode or a hybrid access mode by using a specific closed subscriber group (CSG) ID, the method comprises: recognizing by the network entity, that an allowed access timer of the specific CSG ID with respect to the Home (e)NodeB has expired; transmitting an Update Bearer Request message to other network entity in order to change a membership of the expired CSG ID; transmitting a Bearer Modify Request message to the Home (e)NodeB in order to change a membership of the expired CSG ID; and updating a bearer with said other network entity, and a bearer with the Home (e)NodeB.
Owner:LG ELECTRONICS INC
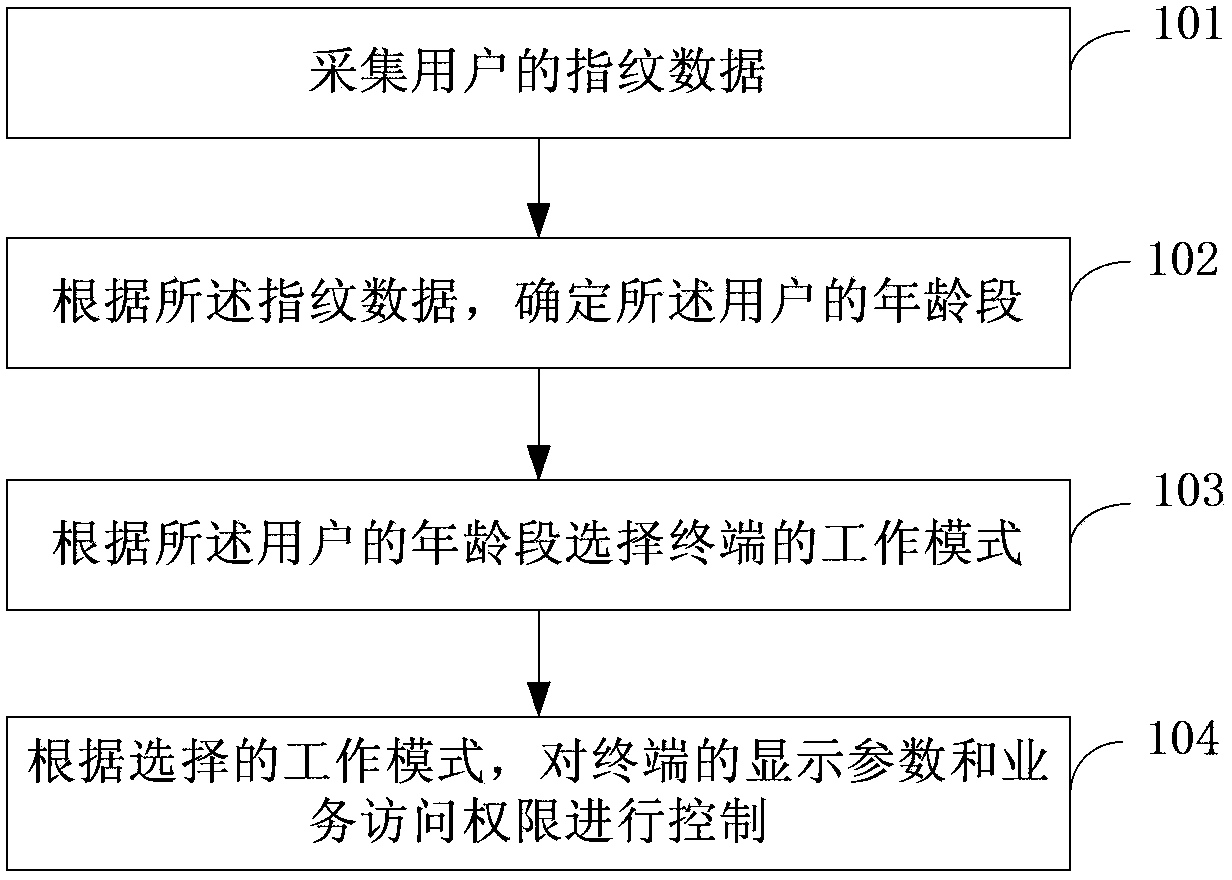
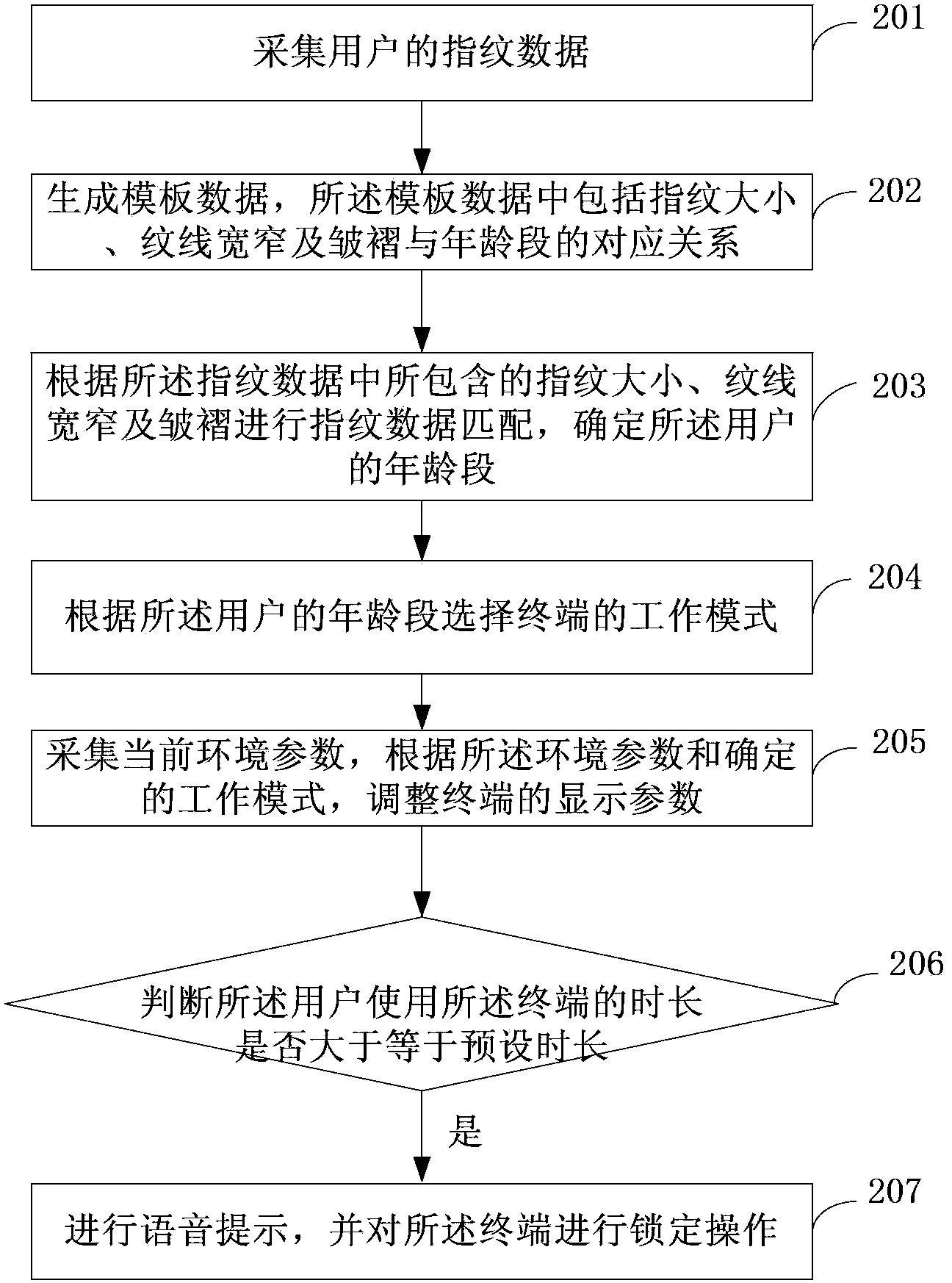
Method and system for terminal mode selection based on fingerprint identification
InactiveCN103353928AAccess controlReasonable control of access rightsDigital data authenticationTerminal operationMode selection
The invention provides a method and a system for terminal mode selection based on fingerprint identification. The method comprises the following steps: acquiring user fingerprint data; determining user age group according to the fingerprint data; selecting working mode of a terminal according to the user age group; controlling the display parameter and the business access permission of the terminal according to the selected working mode. The technical scheme of the invention realizes automatic identification of the terminal operation main body, and adjusts the display parameter of the terminal and controls the business access permission of the terminal according to different operation main bodies.
Owner:BEIJING BENY WAVE SCI & TECH
Control method and system of network access authority in WLAN
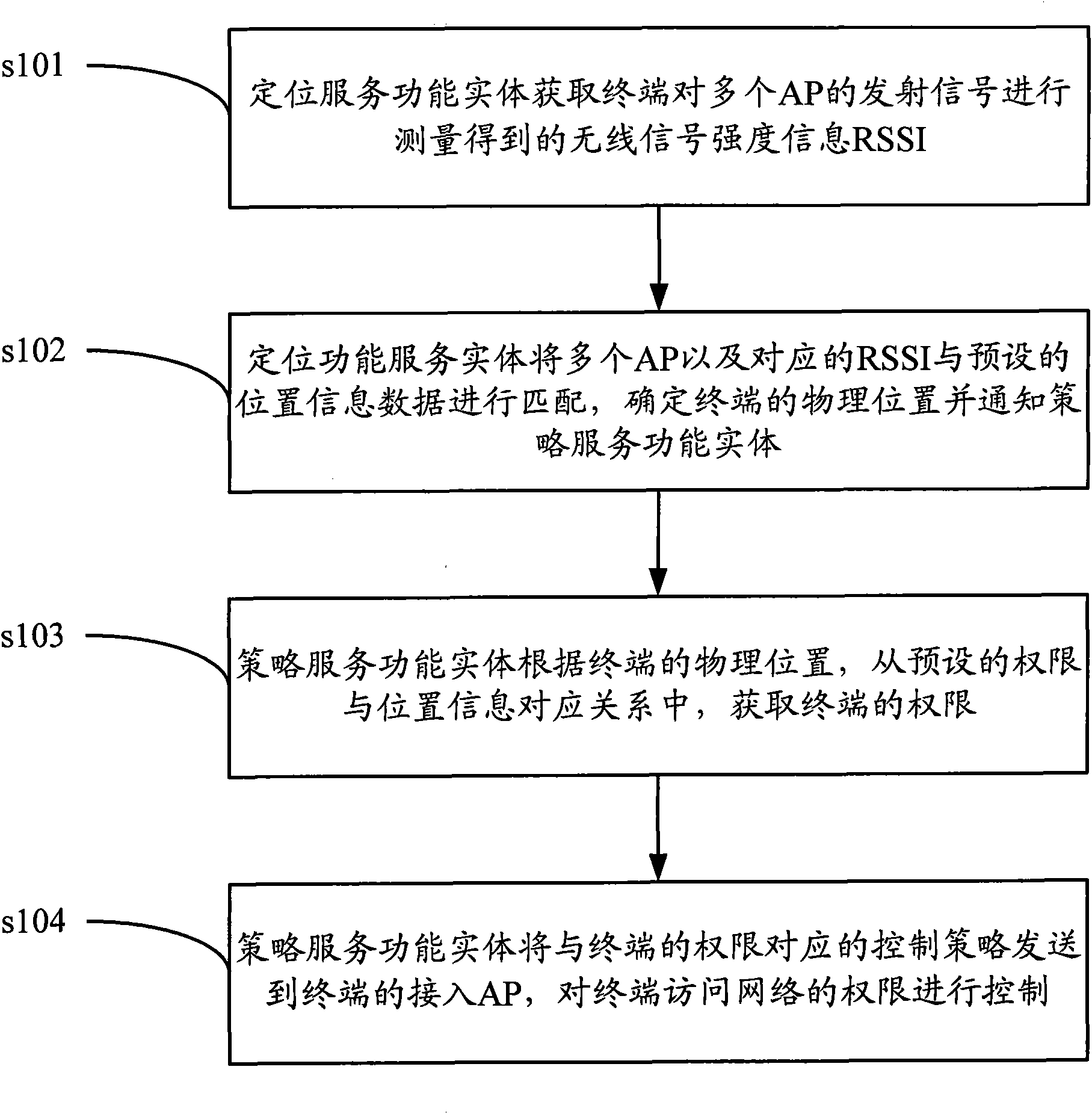
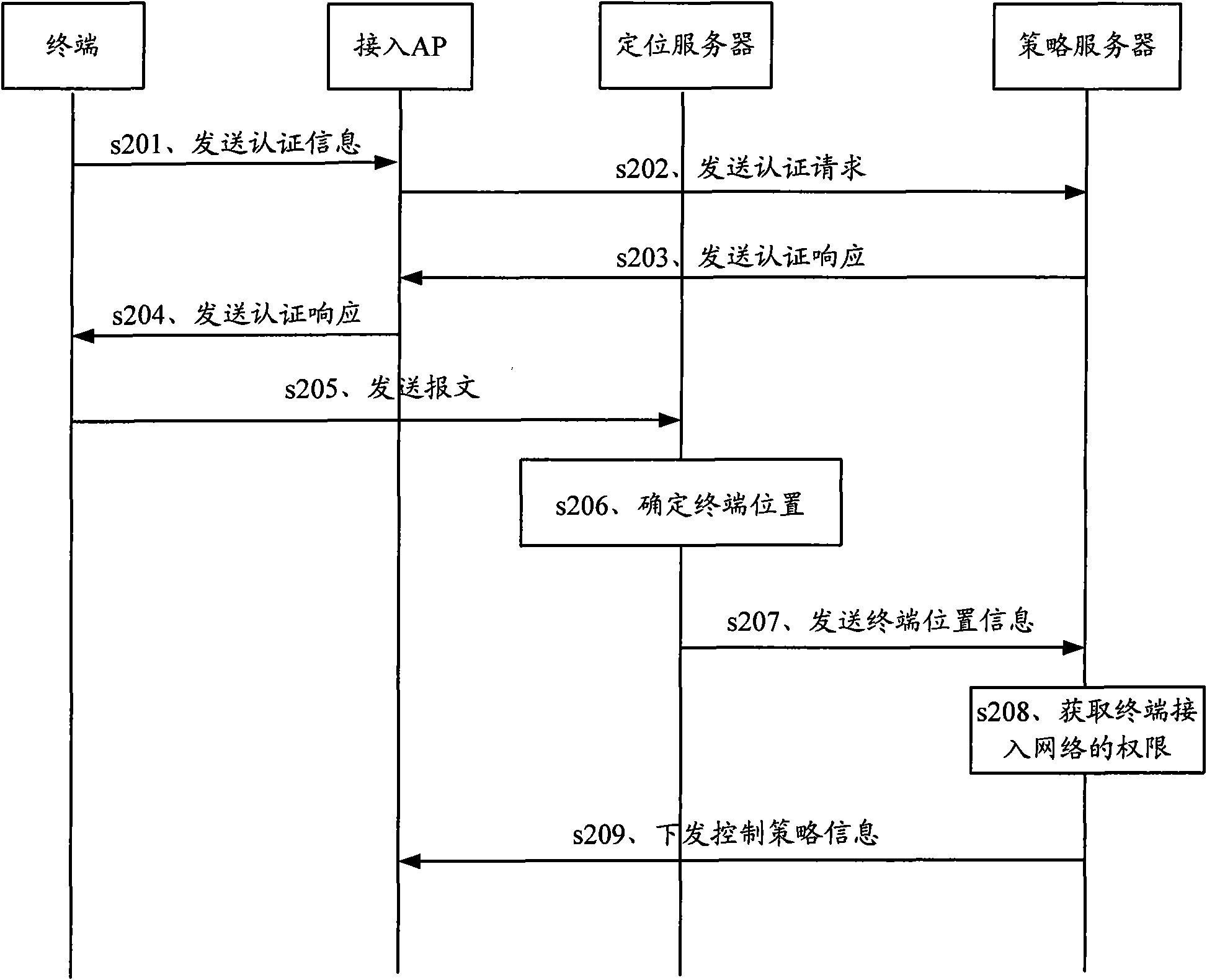
InactiveCN101668293AAccess controlNetwork topologiesSecurity arrangementComputer networkInformation data
The invention discloses a control method and a system of the network access authority in a WLAN. Wherein, the control method comprises the steps of obtaining wireless signal intensity information RSSIwhich is obtained by measuring a plurality of emission signals of AP of a terminal, carrying out matching with preset position information data and determining the physical position of the terminal;and further obtaining the authority which corresponds to the physical position, and generating the corresponding strategy according to the authority for controlling the network access authority of theterminal. The use of the control method and the system can realize the control of the network access authority of the terminal based on the physical position located by the terminal in the WLAN.
Owner:NEW H3C TECH CO LTD
Method and apparatus to facilitate secure network communications with a voice responsive network interface device
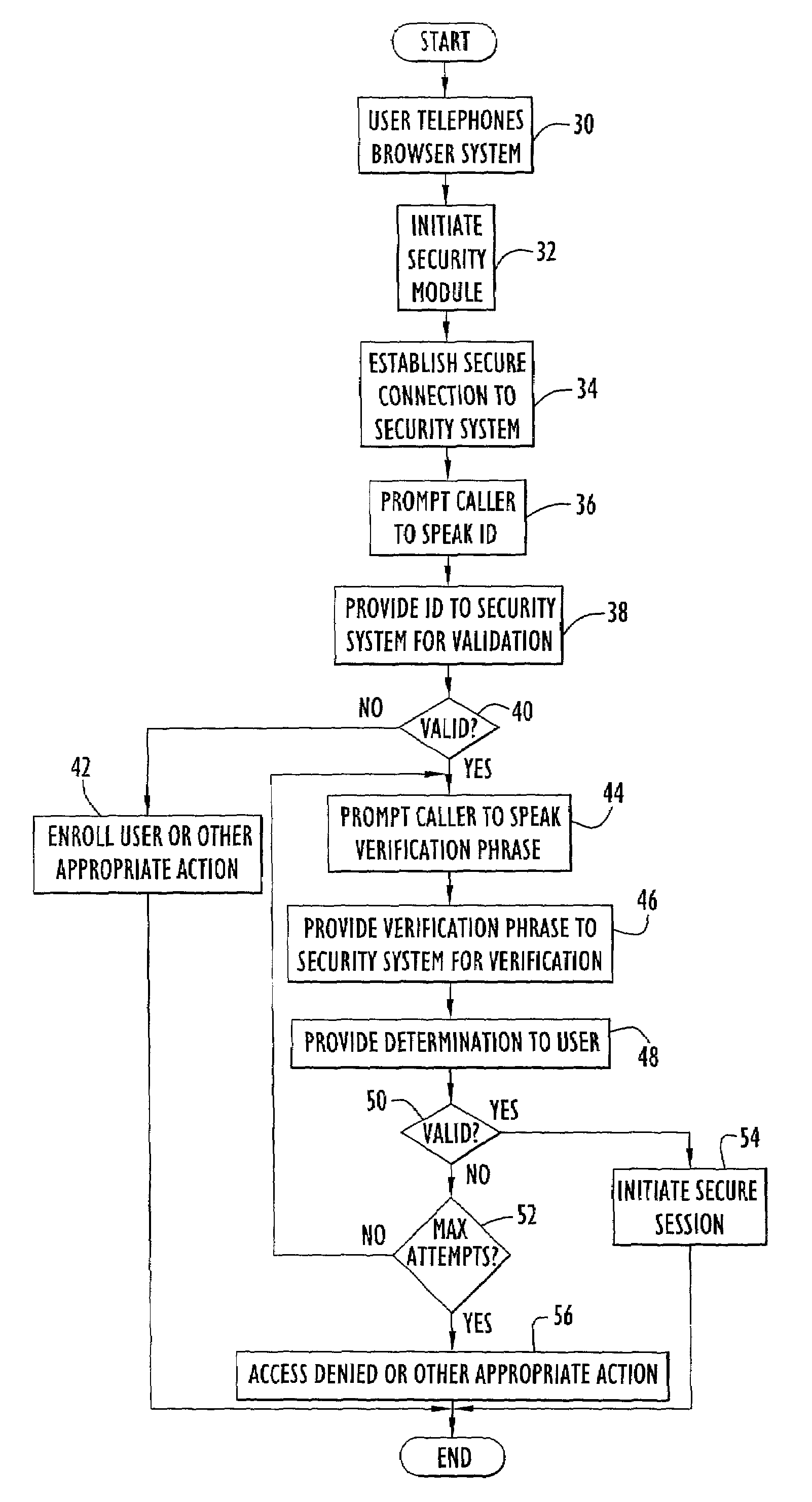
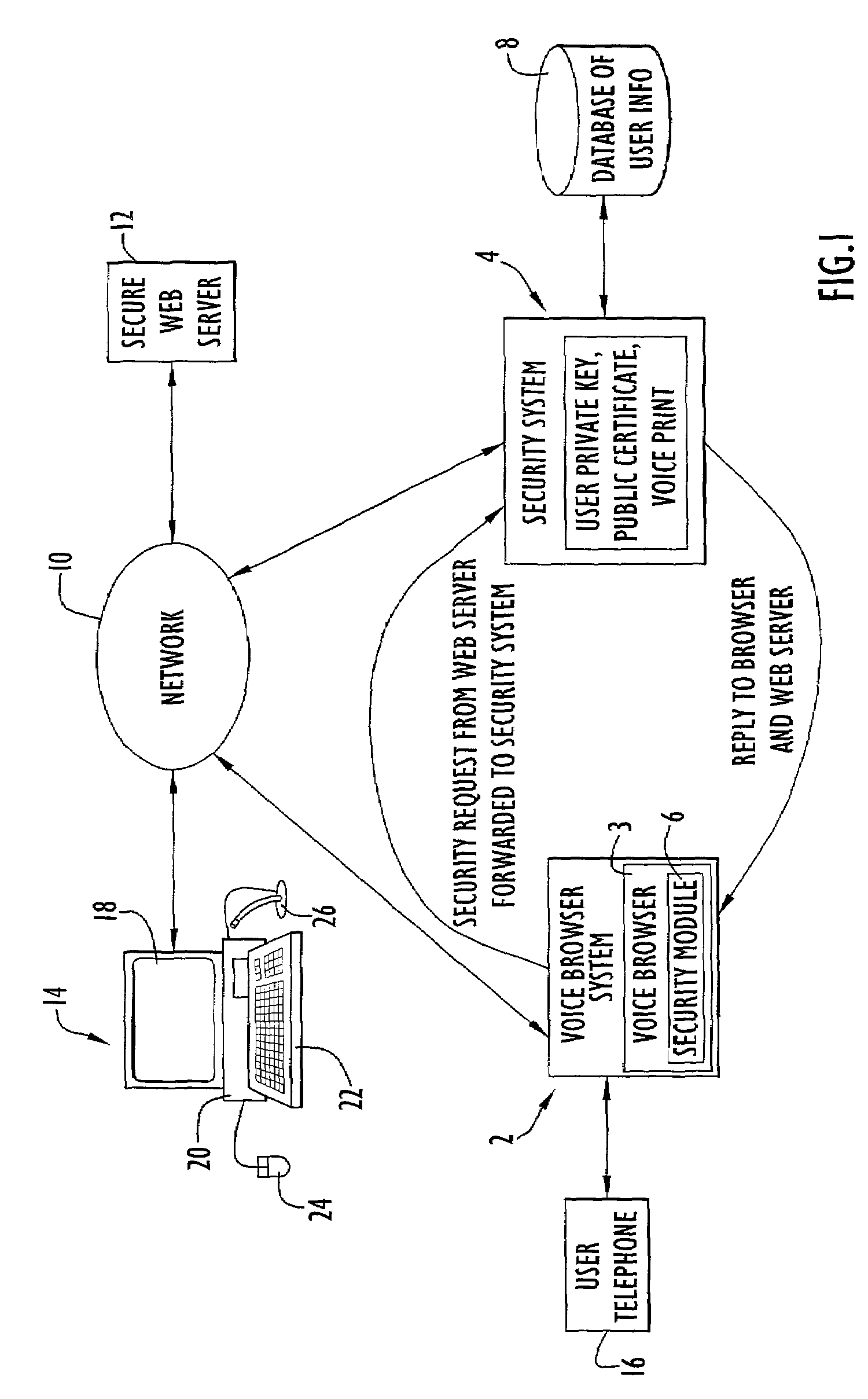
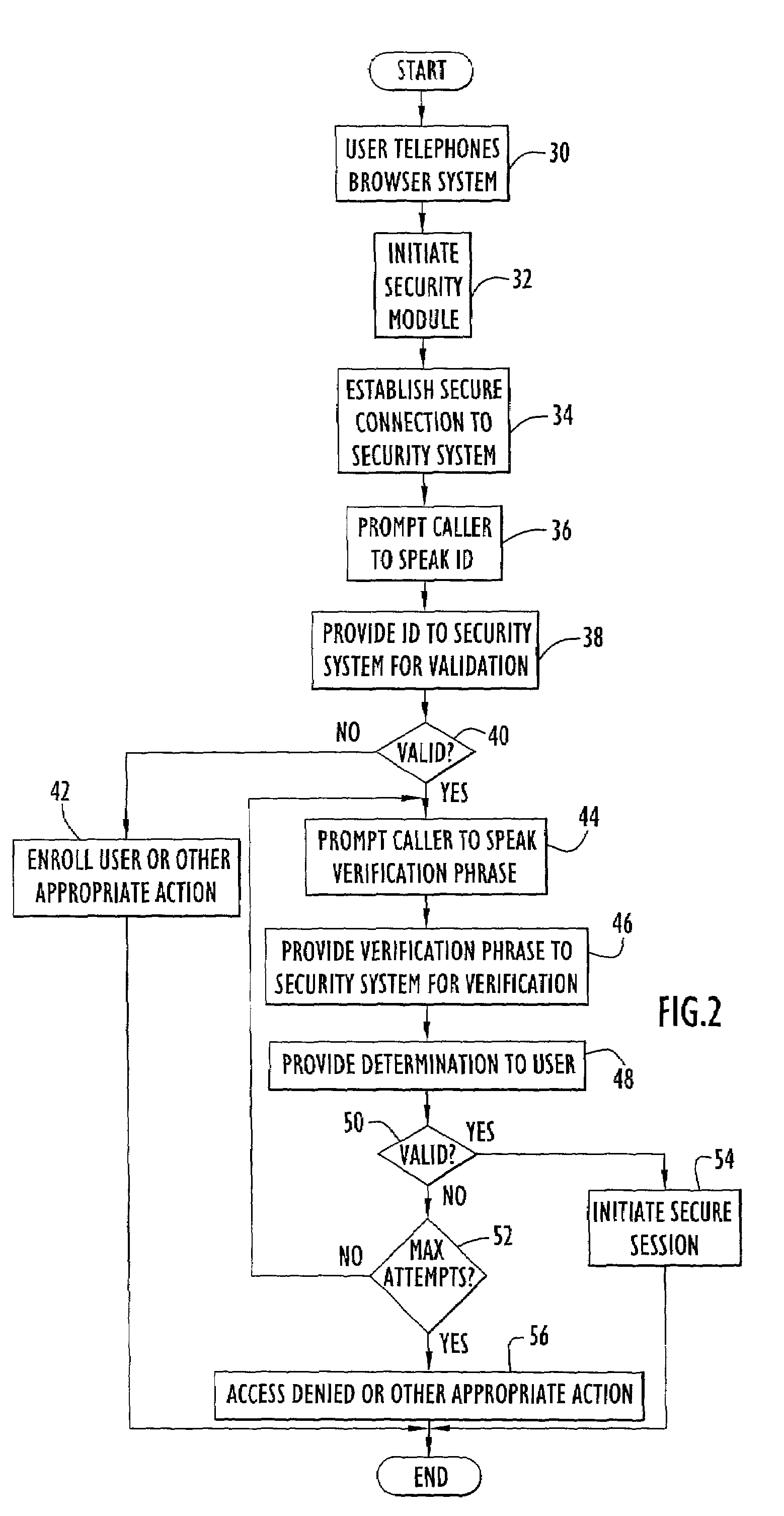
InactiveUS7185197B2Access controlSecure CommunicationsKey distribution for secure communicationDigital data processing detailsVoice browserSoftware modules
A system for facilitating secure network communications includes a security computer system and corresponding software. The security system is utilized in conjunction with a voice browser residing on a server system. A user accesses the network by placing a call to the voice browser system. The voice browser includes a software module that creates a secure connection to the security system. The user provides an identification to the voice browser system that is transferred to and verified by the security system. Once the identification is verified, the user is prompted by the voice browser system to speak a phrase for voice verification. The verification speech signals are transferred from the voice browser system to the security system to verify those speech signals against speech signals of a particular authorized user associated with the identification and stored in a database. When the user is verified, the security system retrieves a user private key and certificate from the database. In response to the user subsequently accessing a web site residing on a secure server, the secure server and voice browser system initiate a secure key exchange. During the key exchange, data packets containing security information are transferred from the voice browser system to the security system for processing, while security information from the security system is transferred to the secure server via the voice browser system. The resulting session key is securely transferred to the voice browser system to facilitate secure communications between the voice browser system and secure server.
Owner:EXCELIS INC
Method of controlling network access amount and server
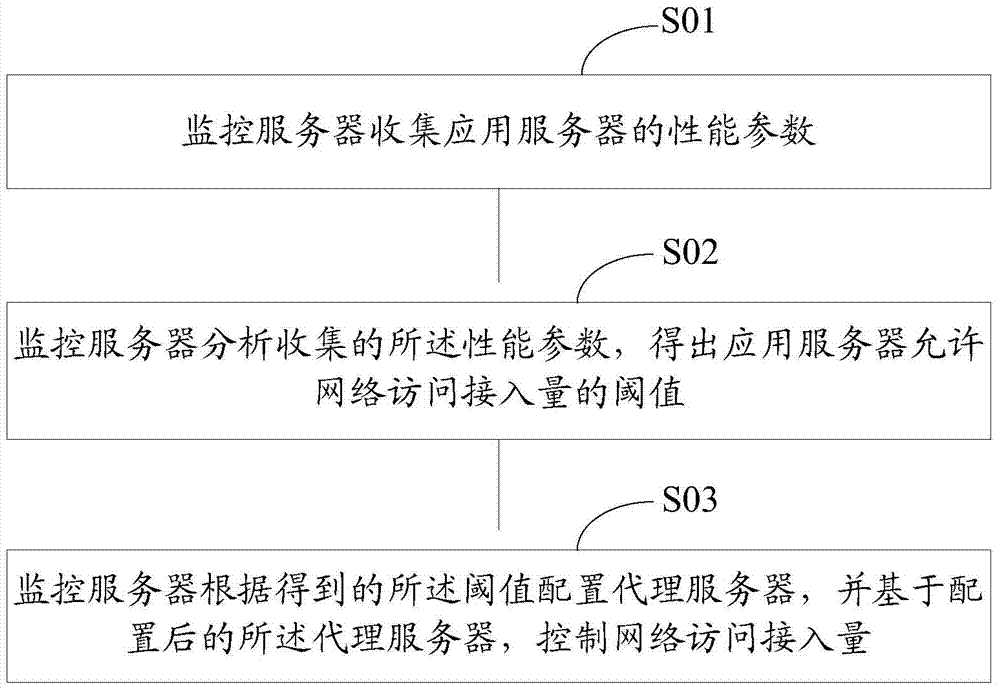
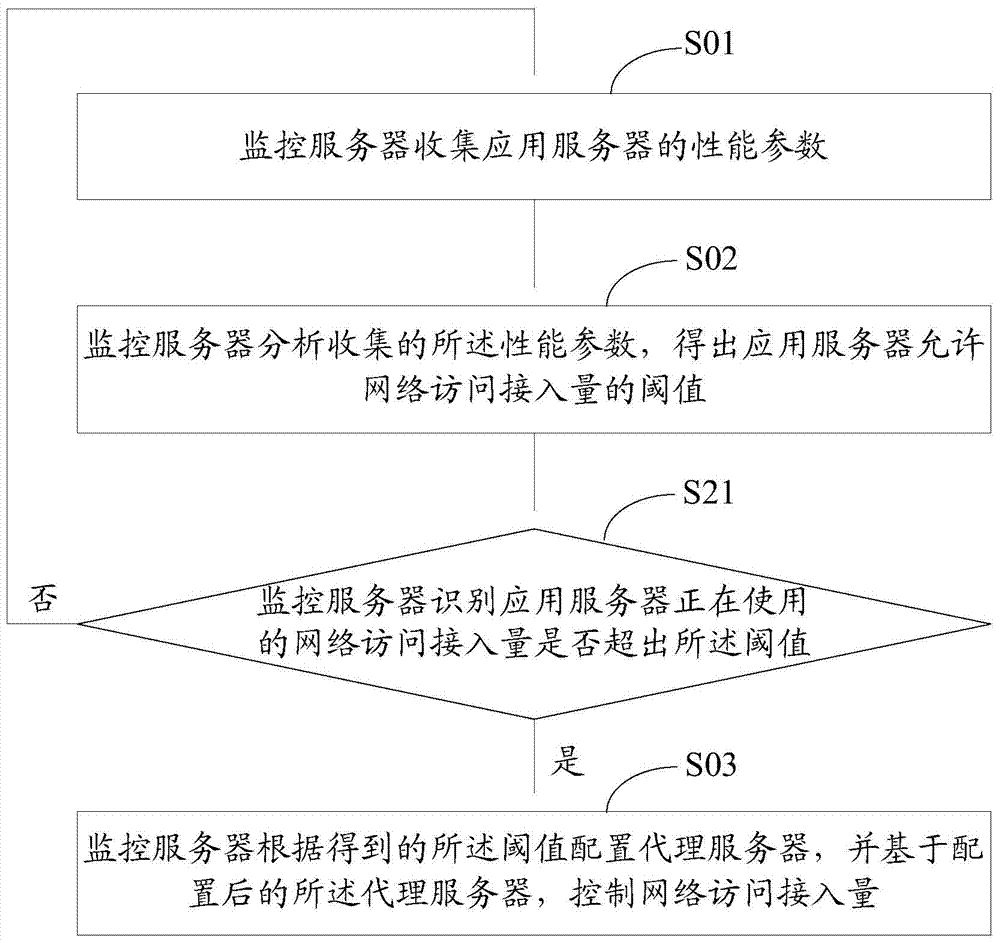
ActiveCN104767689AAccess controlDynamic adjustment of access volumeHybrid transportApplication serverBack end server
The present invention discloses a network access traffic control method and server, in embodiments of the present invention, a monitoring server collects performance parameters of an application server; the monitoring server analyzes the collected performance parameters, to obtain a threshold of network access traffic allowed by the application server; and the monitoring server configures an agent server according to the obtained threshold, and controls network access traffic based on the configured agent server. Compared with the prior art in which a traffic limiting threshold is not set or is set only according to experience regardless of actual conditions in most websites, the embodiments of the present invention have beneficial effects of dynamically adjusting network access traffic according to an actual running condition of a network: and further, in the embodiments of the present invention, stable performance of a back-end server is ensured, and a network resource of the server is used appropriately.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and devices for handling access authorities
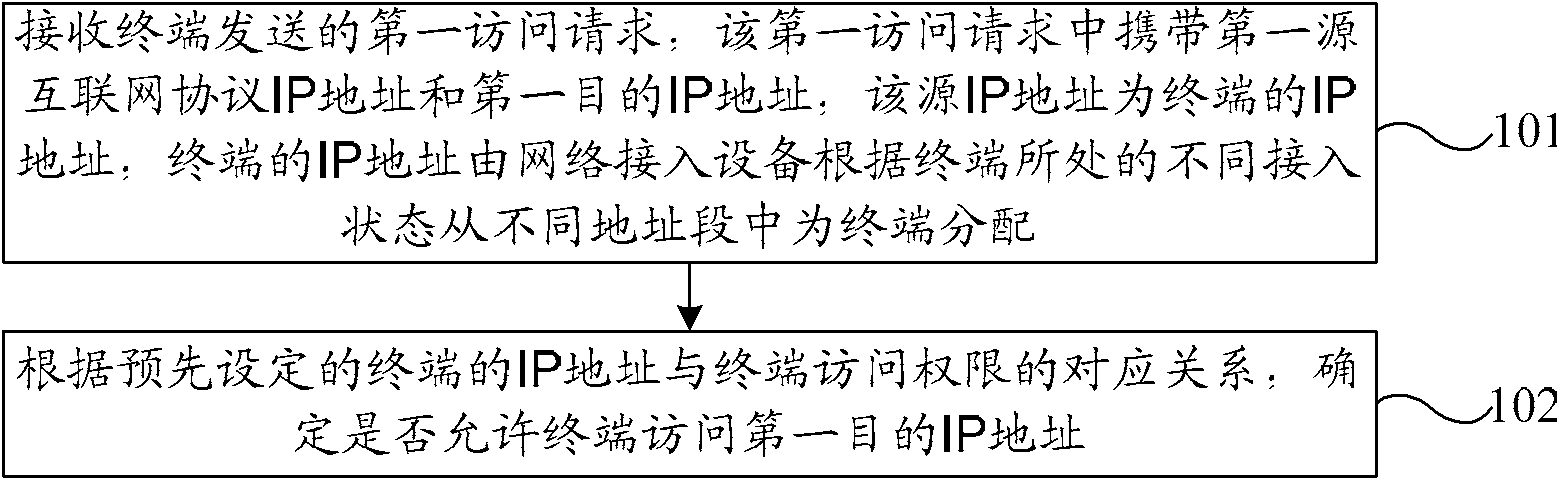
The invention relates to a method and devices for handling access authorities. The method includes receiving the first access request from terminal, which contains the first source internet protocol (IP) address and the first destination IP address, the former being the terminal address. Then based on preset correspondence between the terminal IP address and the terminal access authority, decisions will be made as for whether to allow the terminal to visit the first destination IP address. This invention aims at saving storage resources of NAD to ensure its control over terminal access authorities.
Owner:HUAWEI TECH CO LTD
Traffic management architecture
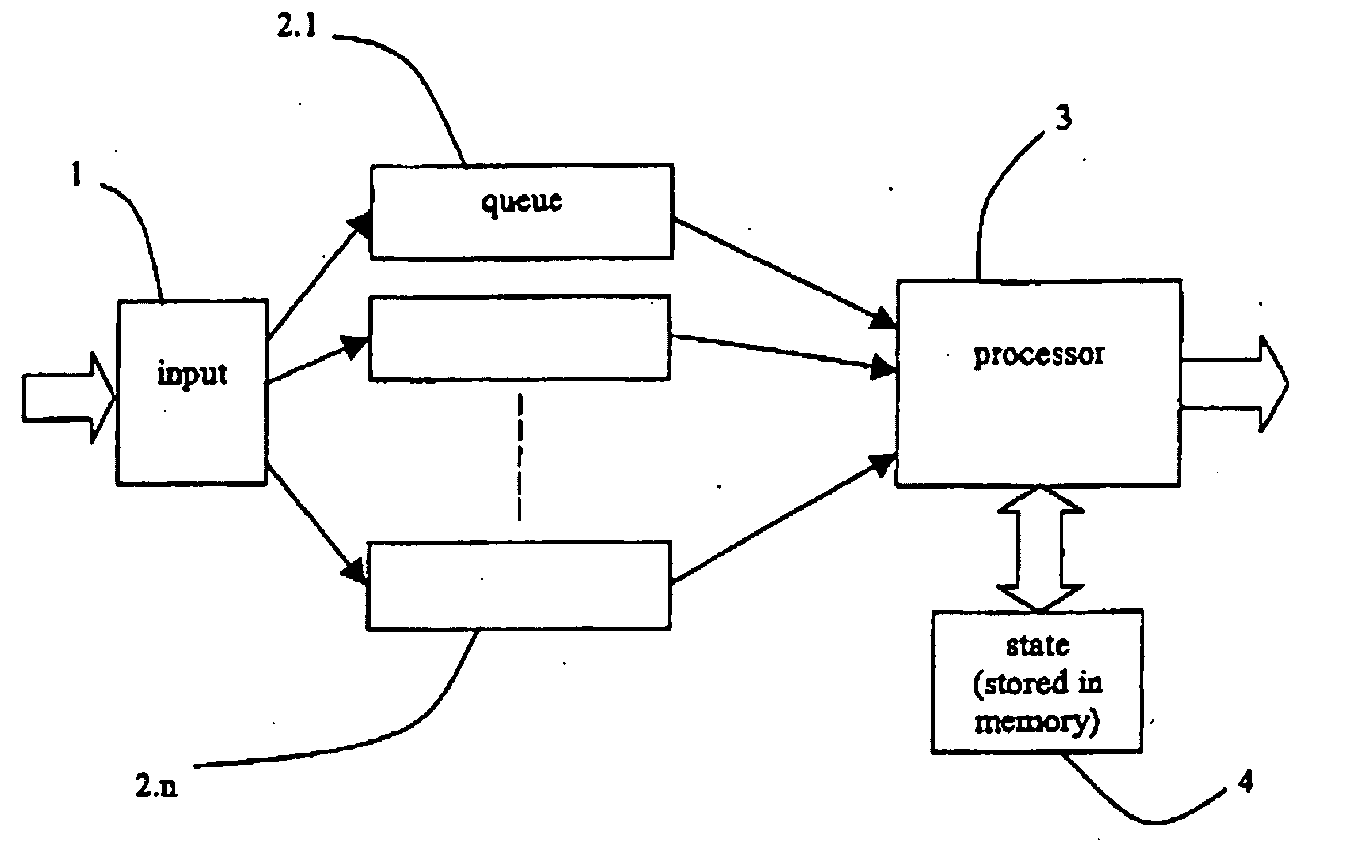
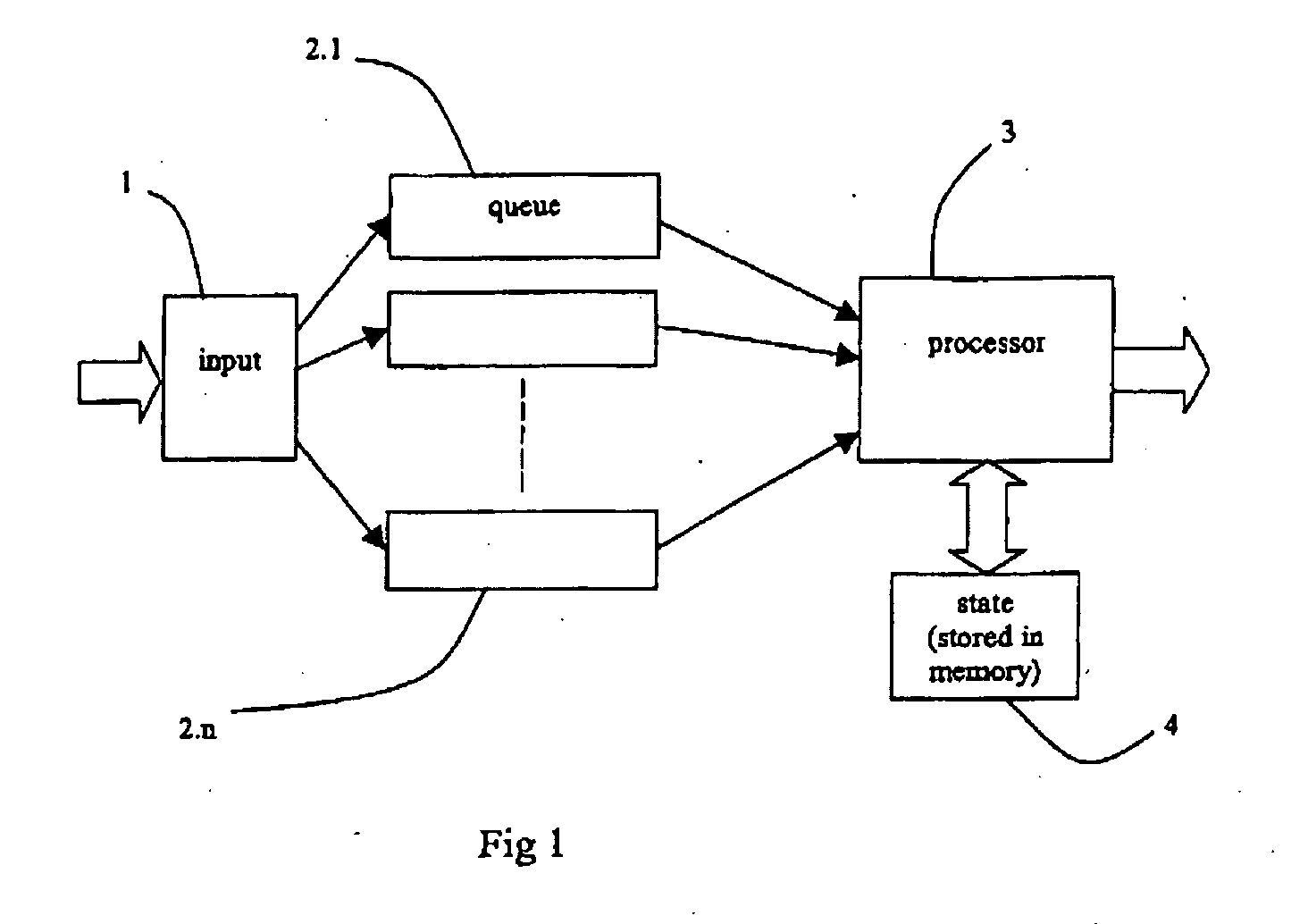
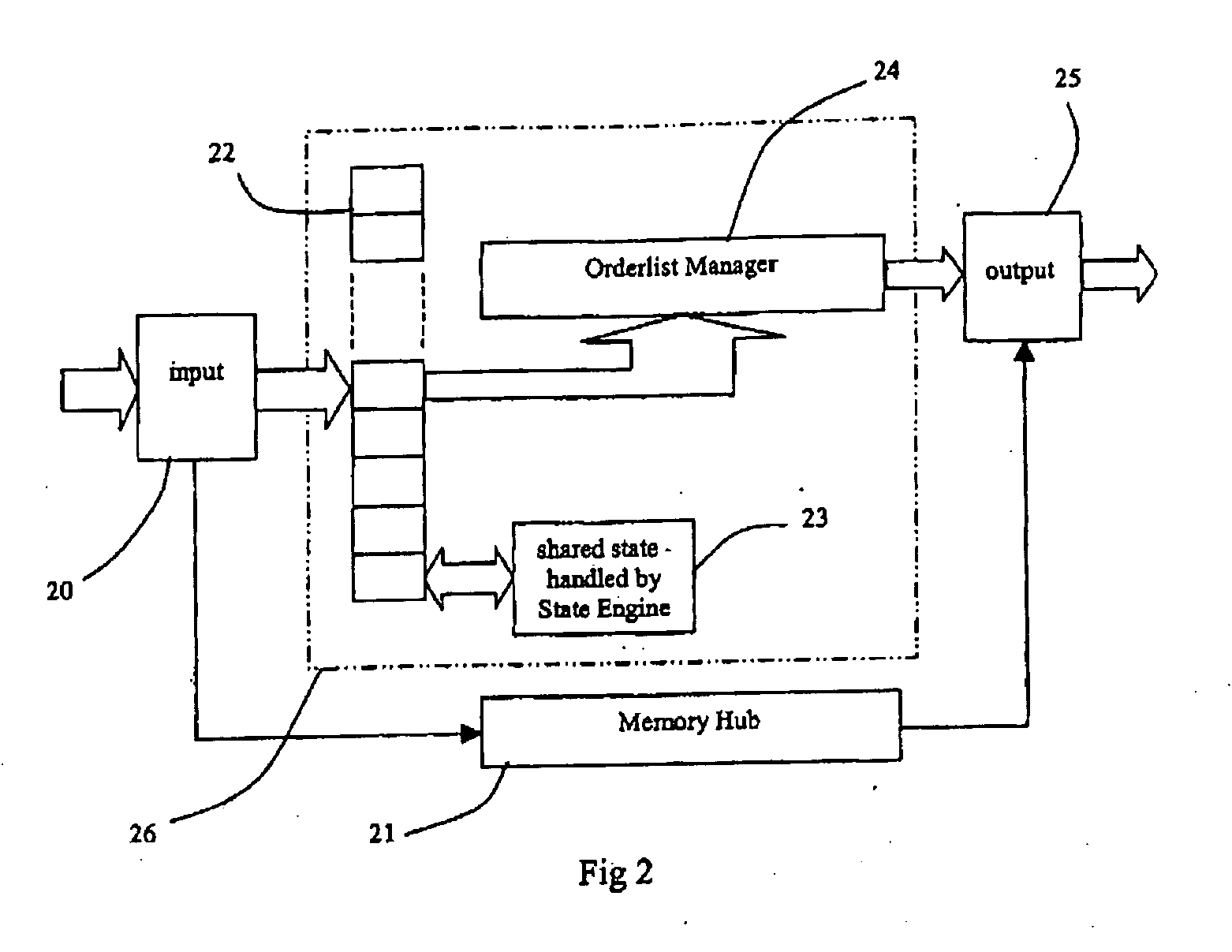
InactiveUS20050243829A1Access controlData switching by path configurationStore-and-forward switching systemsRapid processingRapid access
An architecture for sorting incoming data packets in real time, on the fly, processes the packets and places them into an exit order queue before storing the packets. This is in contrast to the traditional way of storing first then sorting later and provides rapid processing capability. A processor generates packet records from an input stream and determines an exit order number for the related packet. The records are stored in an orderlist manager while the data portions are stored in a memory hub for later retrieval in the exit order stored in the manager. The processor is preferably a parallel processor array using SIMD and is provided with rapid access to a shared state by a state engine.
Owner:RAMBUS INC
Resource sharing method and service providing system
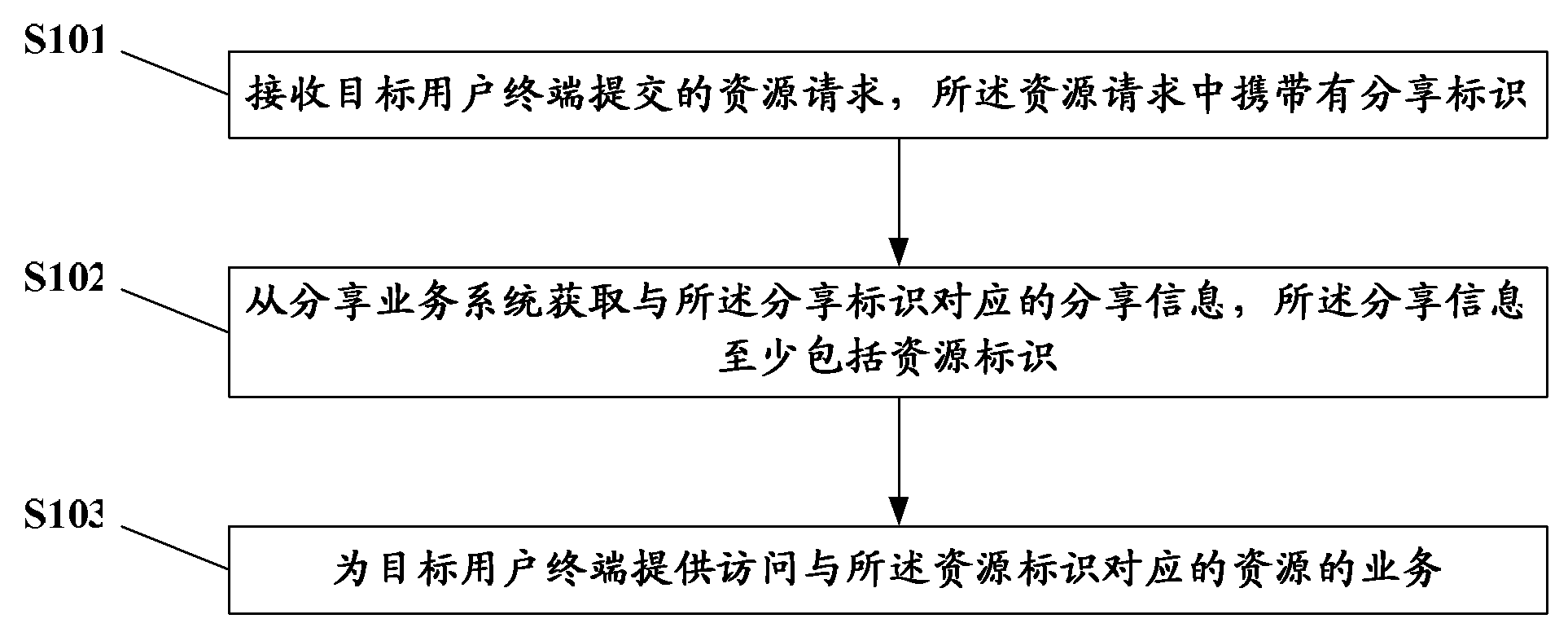
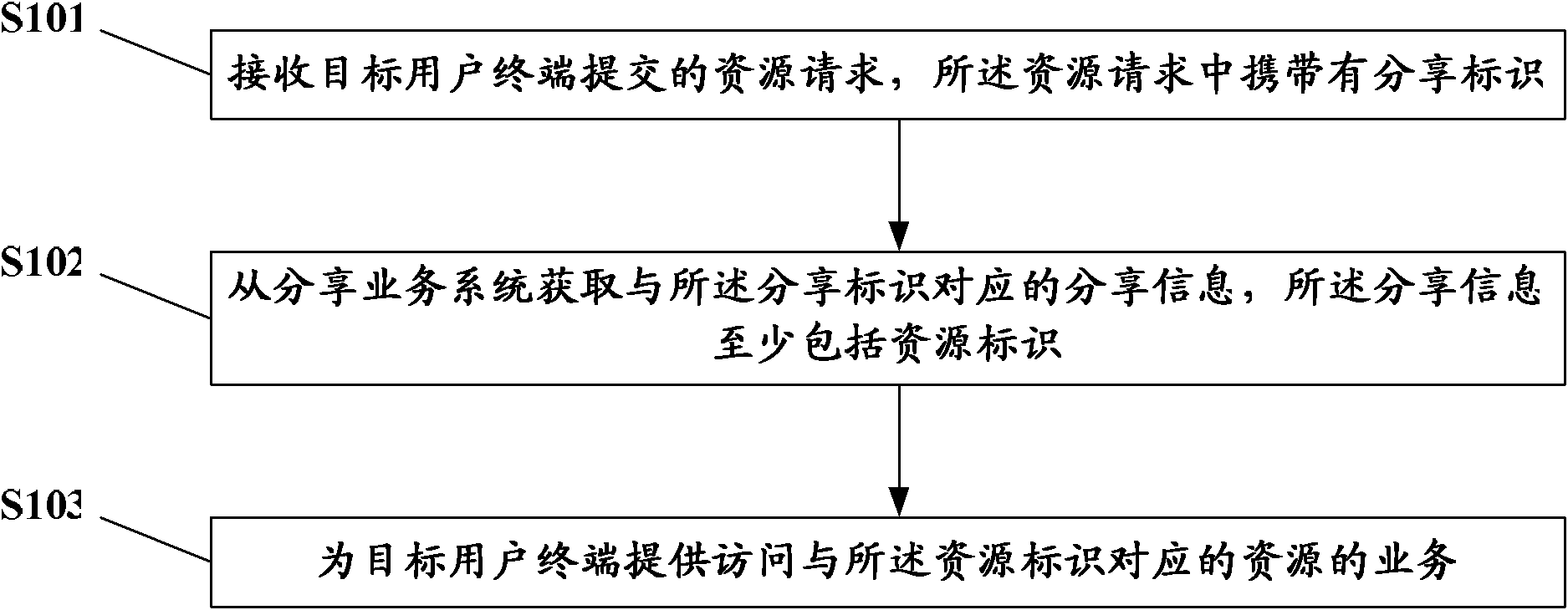
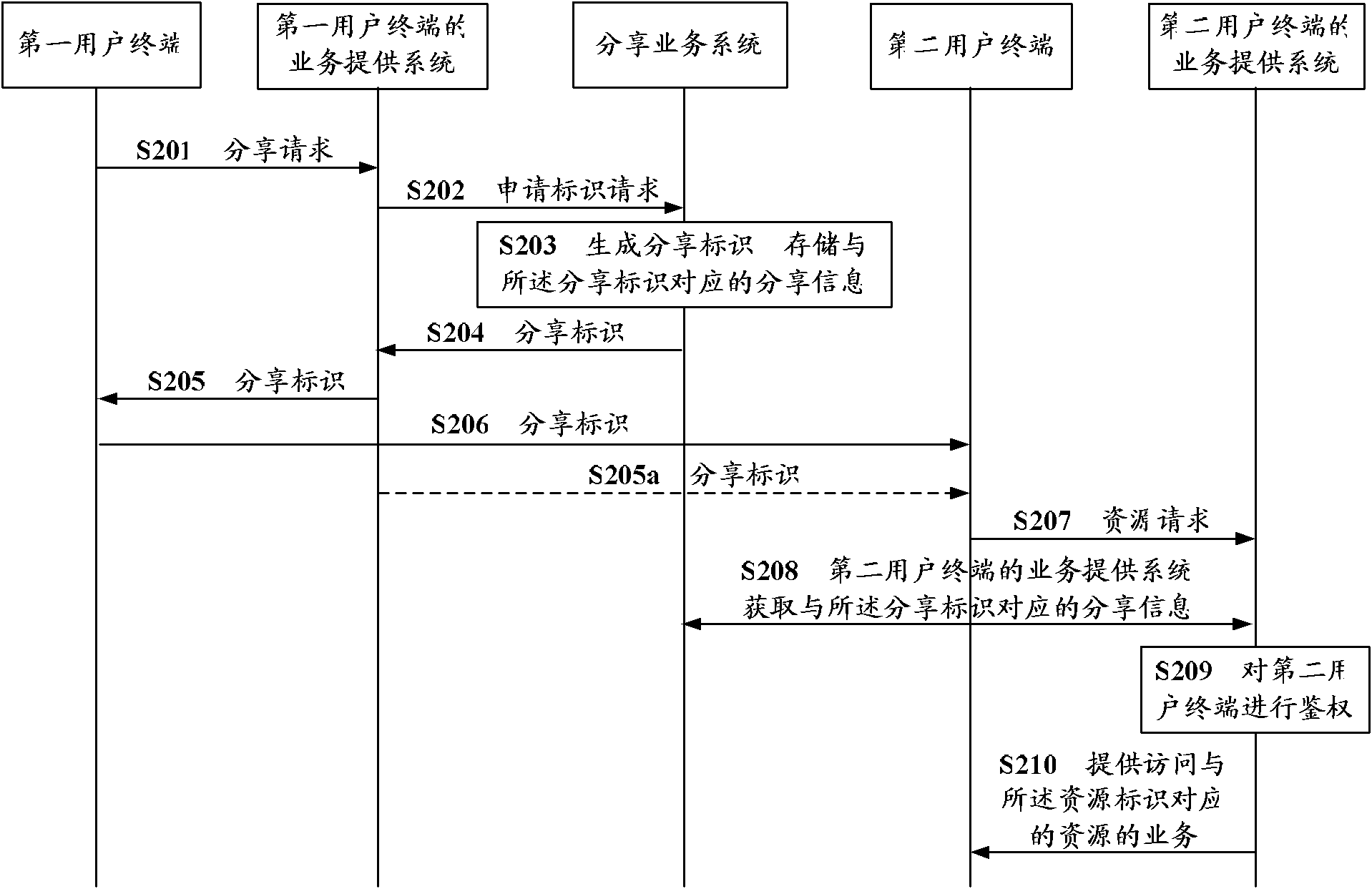
InactiveCN102098345AAccess controlSolve the problem of uncontrolled spreadTransmissionResource identifierDistributed computing
The invention discloses a resource sharing method and a service providing system. The method comprises the following steps of: receiving a resource request submitted by a target user terminal, wherein the resource request carries a sharing identifier; acquiring sharing information which corresponds to the sharing identifier from a sharing service system, wherein the sharing information at least comprises a resource identifier; and providing a service for accessing a resource which corresponds to the resource identifier for the target user terminal. The service providing system allows the user terminal to access resources and does not directly transmit the resources to the user terminal, so that the access of certain resources by the user terminal can be controlled once the resources are deleted by the service providing system.
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD
Write-protection blocks for non-volatile semiconductor memory device
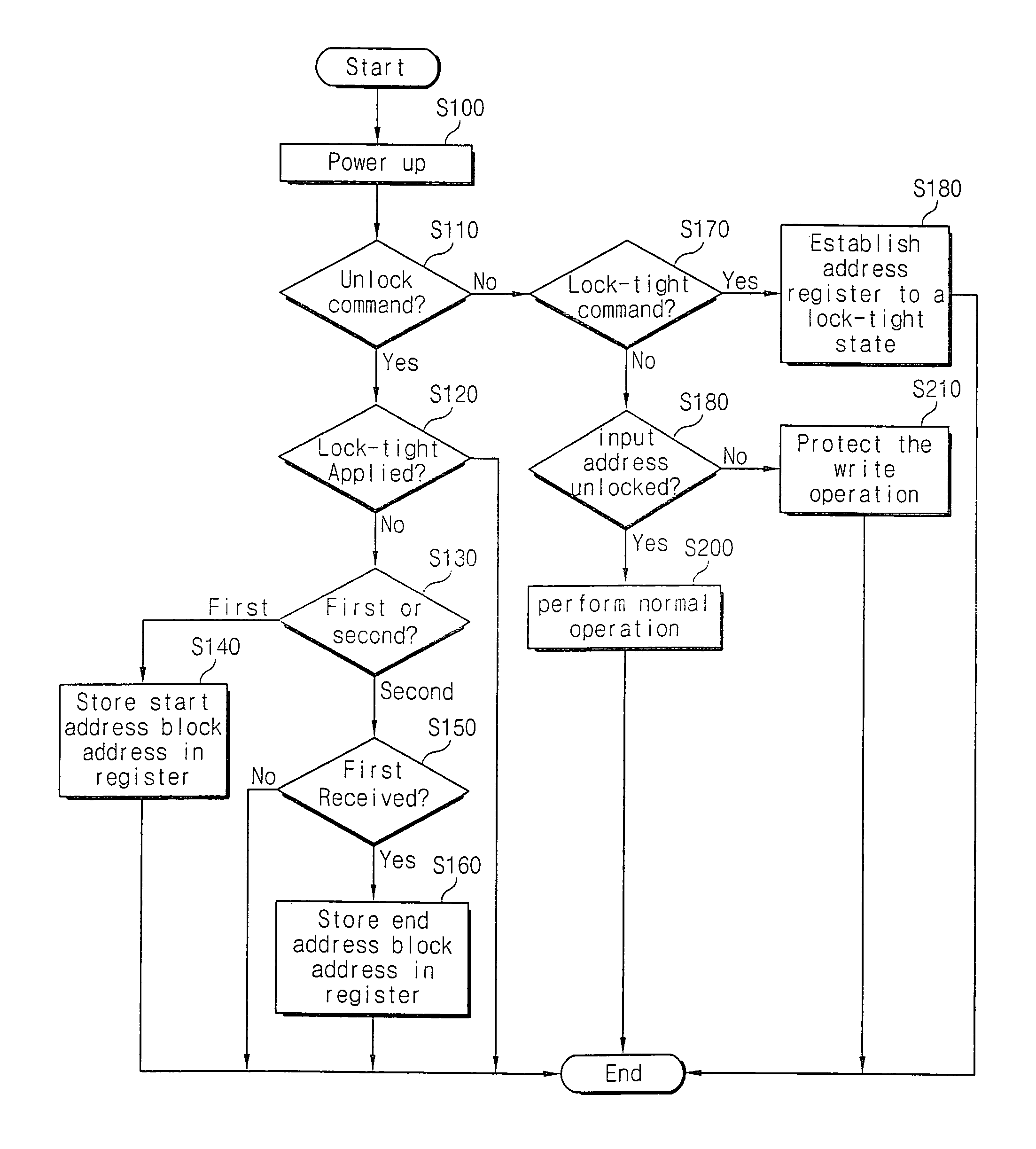
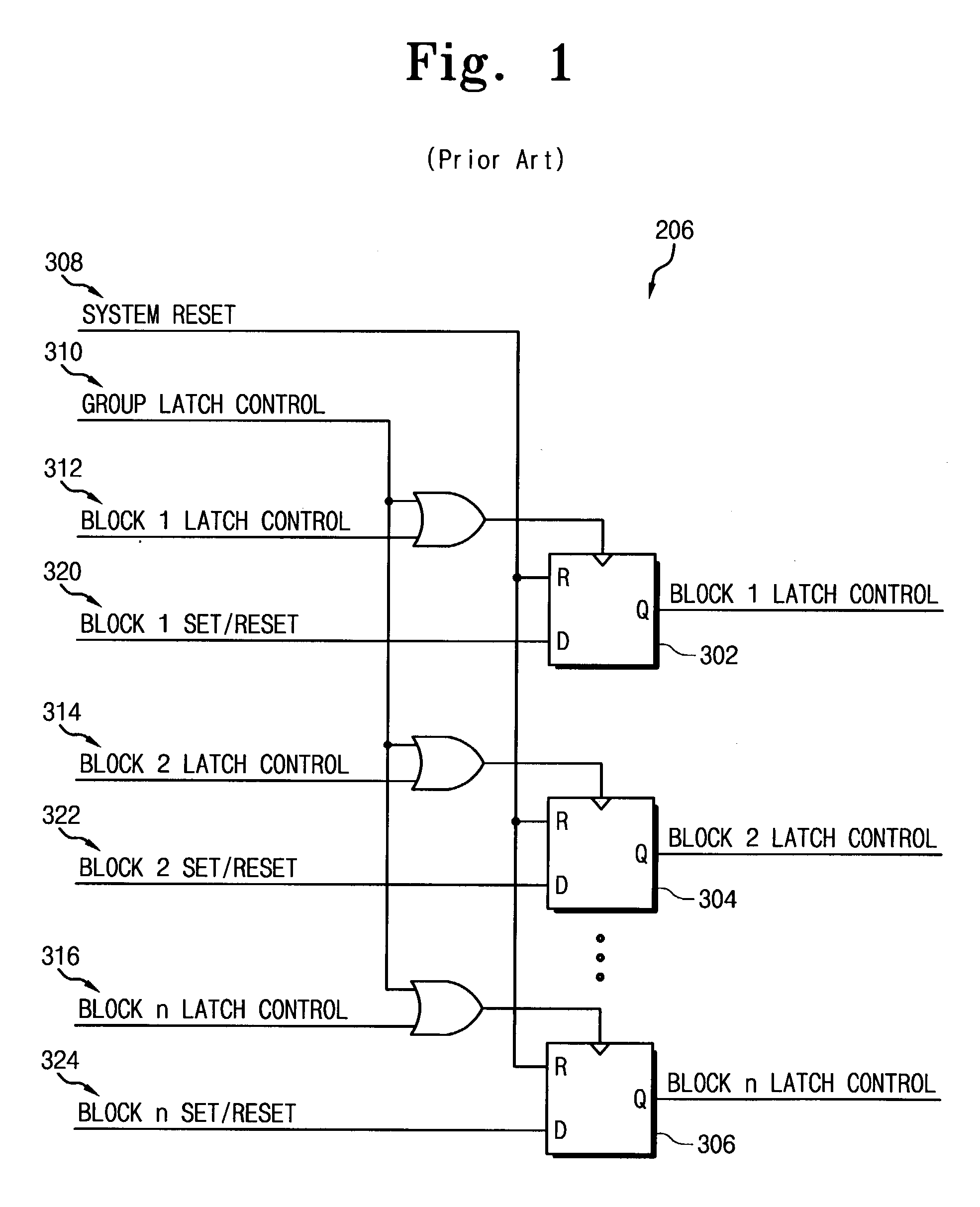
ActiveUS7210012B2Access controlMemory loss protectionRead-only memoriesSemiconductor memoryWrite protection
A non-volatile semiconductor memory device and / or a data processing system include a non-volatile memory array having a plurality of memory blocks and a write-protection control circuit that controls access to blocks of memory based on a start block address and an end block address. The write-protection control circuit may store start and end block addresses of an unlock region of the non-volatile memory array, and selectively activate a write enable signal according to the relationship between a write address and the start and end block addresses.
Owner:SAMSUNG ELECTRONICS CO LTD
Apparatus and method to control access to logical volumes using one or more copy services
InactiveUS20050114465A1Access controlError detection/correctionDigital computer detailsInformation storageDatabase
A method to control access to logical volumes disposed in one or more information storage and retrieval systems when using copy service relationships. The method provides a first information storage and retrieval system, a second information storage and retrieval system, and a plurality of host computers capable of communicating with the first information storage and retrieval system. The method forms (N) host computer group, and assigns each of the plurality of host computers to the a host computer group. The method forms (N) logical volume groups, and assigns one or more of the plurality of first logical volumes to a logical volume group. The method receives a request from a host computer assigned to the (i)th host computer group to establish a copy service relationship between a source logical volume and a target logical volume. The method determines if both the source and target logical volumes are assigned to the (i)th logical volume group. If both the source and target logical volumes are assigned to the (i)th logical volume group, then the method establishes the requested copy service relationship.
Owner:IBM CORP
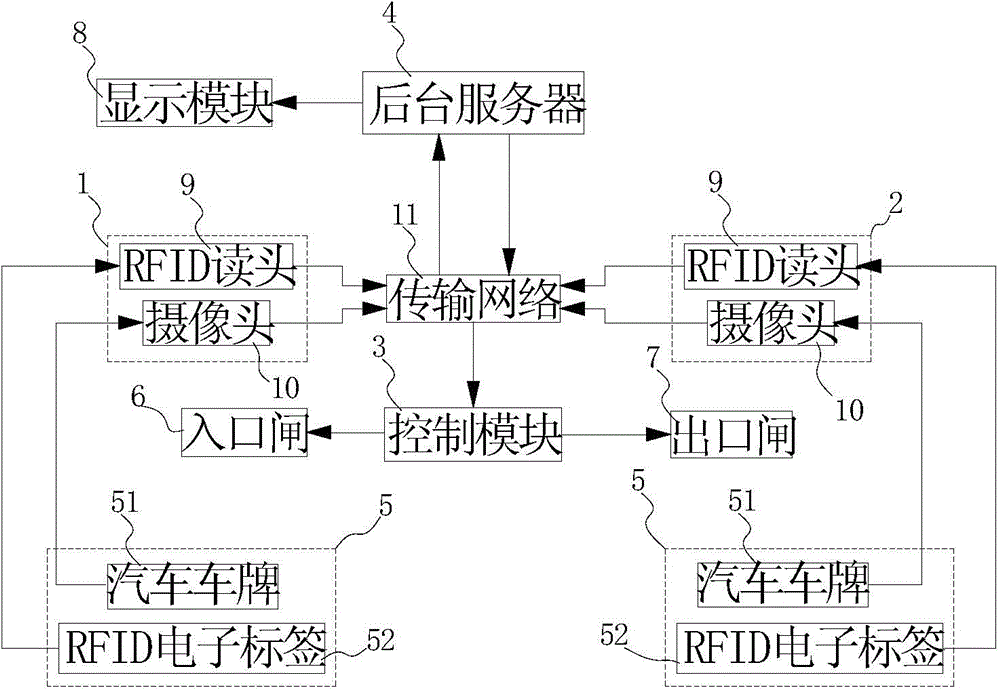
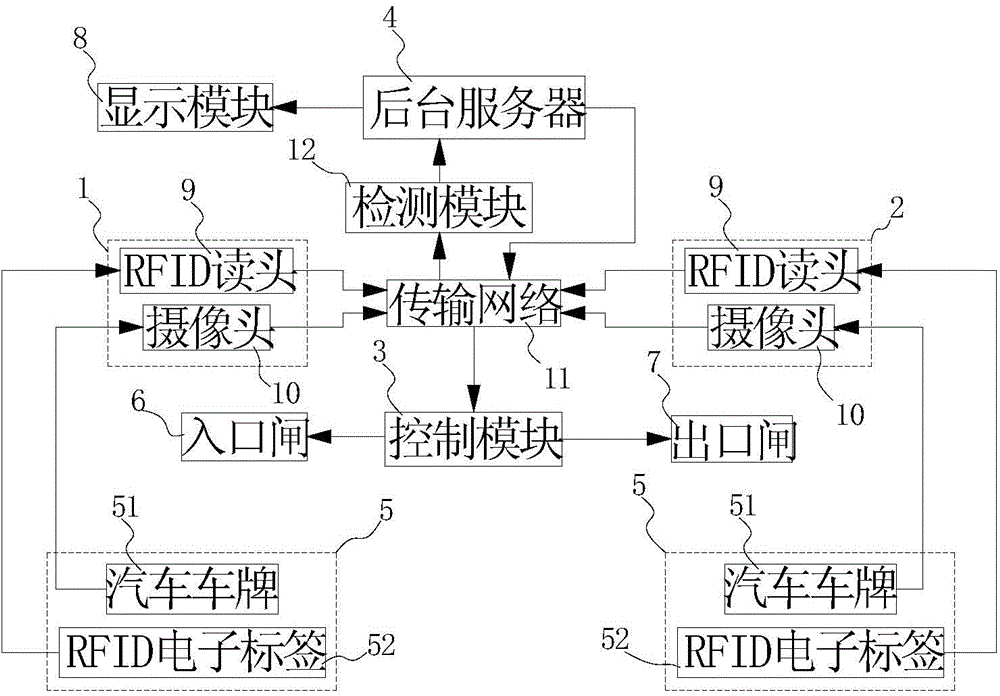
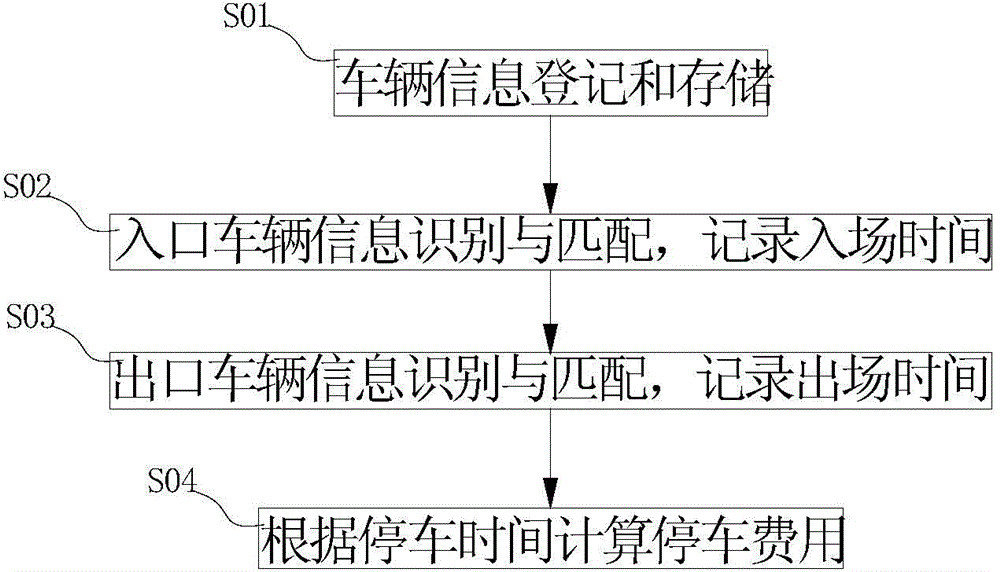
Parking charging and payment systems and parking charging and payment methods thereof
InactiveCN104809763AImprove entry and exit efficiencyNo management confusionTicket-issuing apparatusCo-operative working arrangementsEntry timeComputer science
The invention discloses parking charging and payment systems and parking charging and payment methods thereof. A background server prestores vehicle information and generates a related payment account, a first identification module identifies the vehicle information at an entrance and sends identification information to the background server, the background server performs correct matching verification and records vehicle entry time, a second identification module identifies the vehicle information at an exit and sends identification information to the background server, and the background server performs correct matching verification and records vehicle exit time, thus vehicle parking time is calculated, parking fare is calculated according to the rate, and the related fare is removed from the payment account related to the vehicle information. Charging and payment when the vehicle enters and exits from a parking lot are completed via the systems automatically, and vehicle entry and exit efficiency is improved; the vehicle information is prestored in the background server, identification and matching accuracy is high, and disordered vehicle management cannot be caused.
Owner:SHENZHEN EPARKING TECH
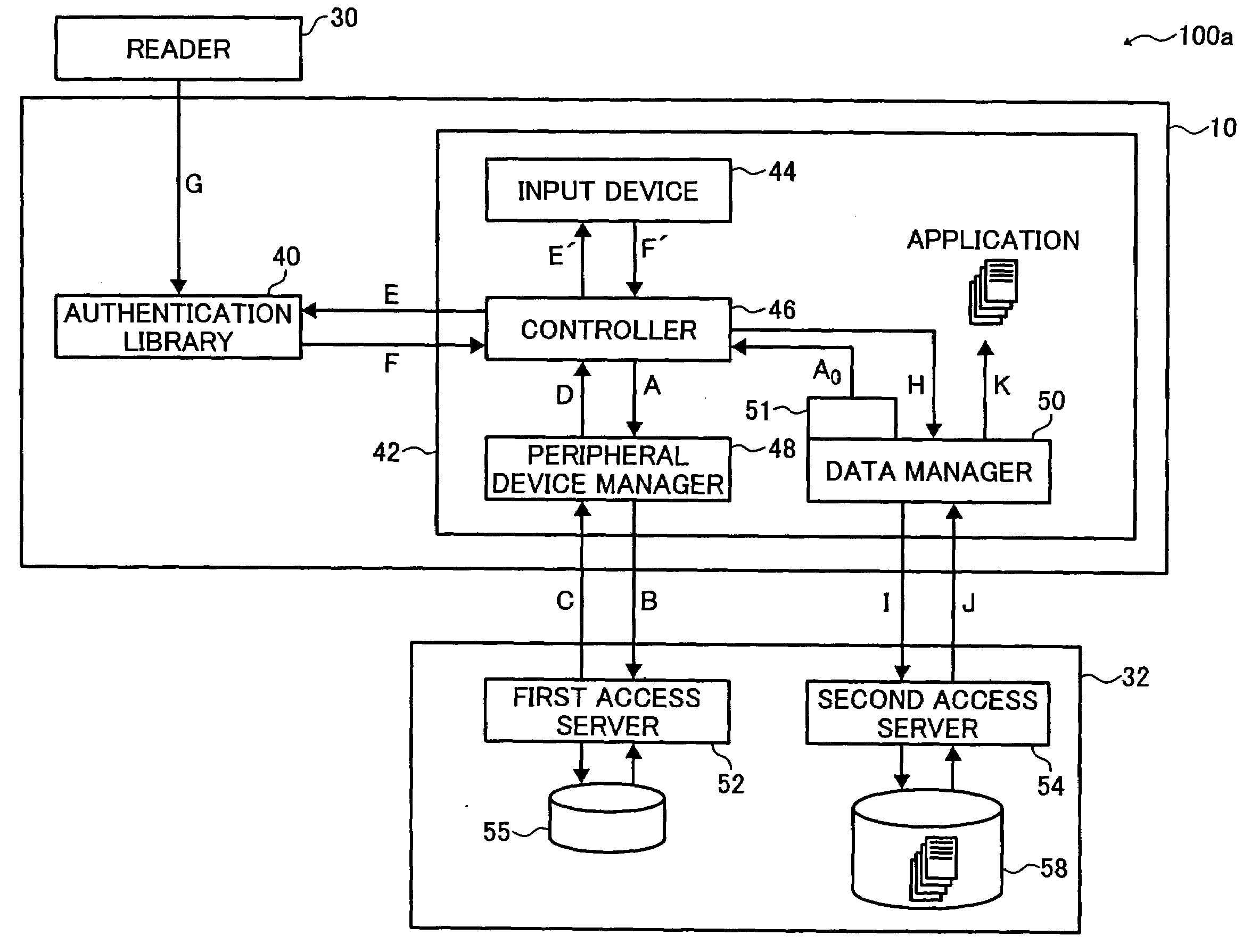
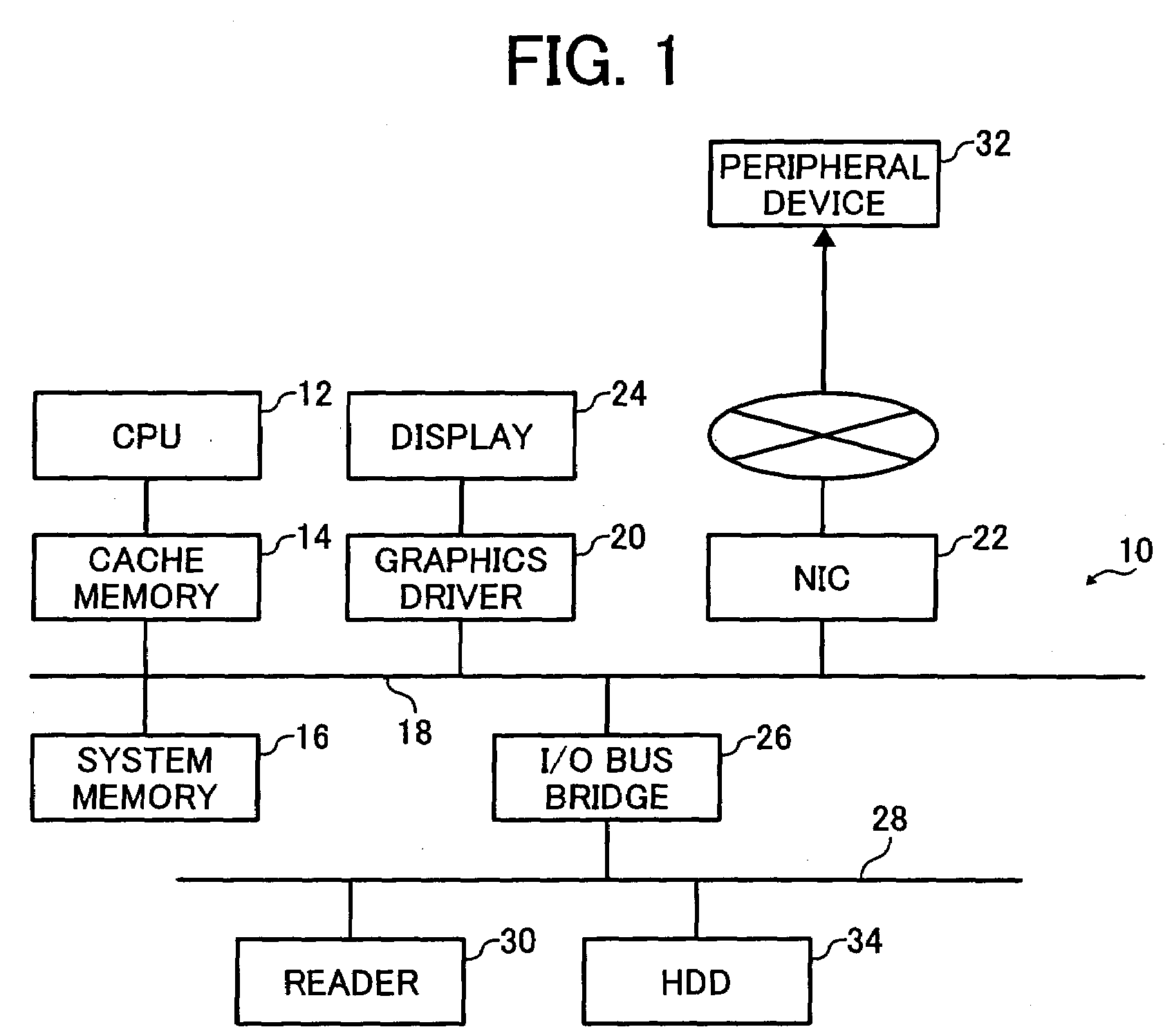
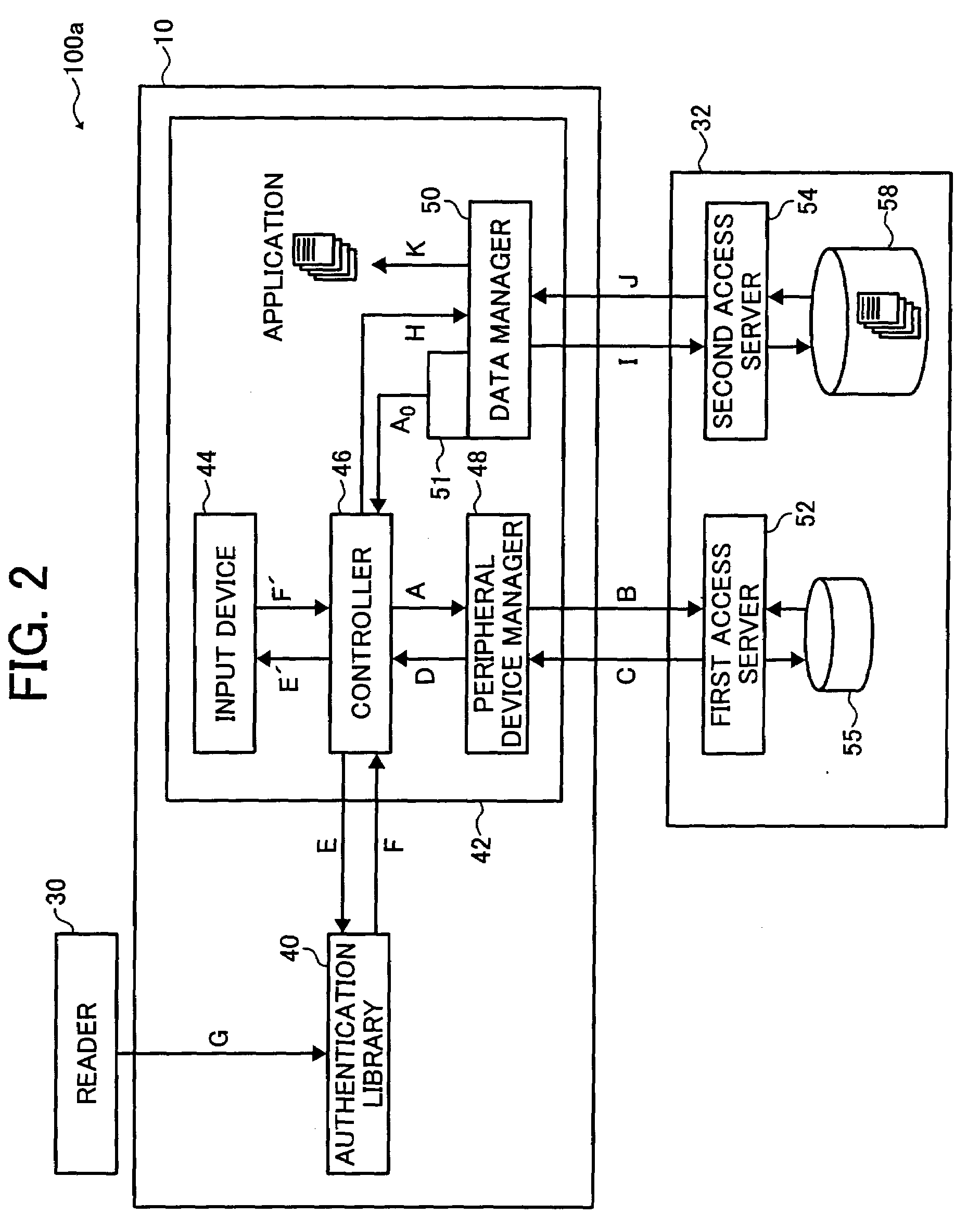
Data processor, peripheral device, and recording medium used herewith
InactiveUS20080060059A1Access controlLimited accessDigital data processing detailsUser identity/authority verificationNetwork connectionData storing
A data processor connected to a peripheral device via a network includes an interceptor, a controller, and a peripheral device manager. The interceptor intercepts an access request for data stored in the peripheral device to issue a message indicating the interception and transmit the access request to the peripheral device. The controller determines, upon receipt of the message from the interceptor, whether to perform authentication based on configuration information of the peripheral device. Additionally, the controller determines, when authentication is to be performed, a mode for obtaining authentication data depending on whether an authentication library is installed. The peripheral device manager retrieves the configuration information from the peripheral device and transmits the configuration information to the controller.
Owner:RICOH KK
Intelligent medical service method based on undistinguishable confusion
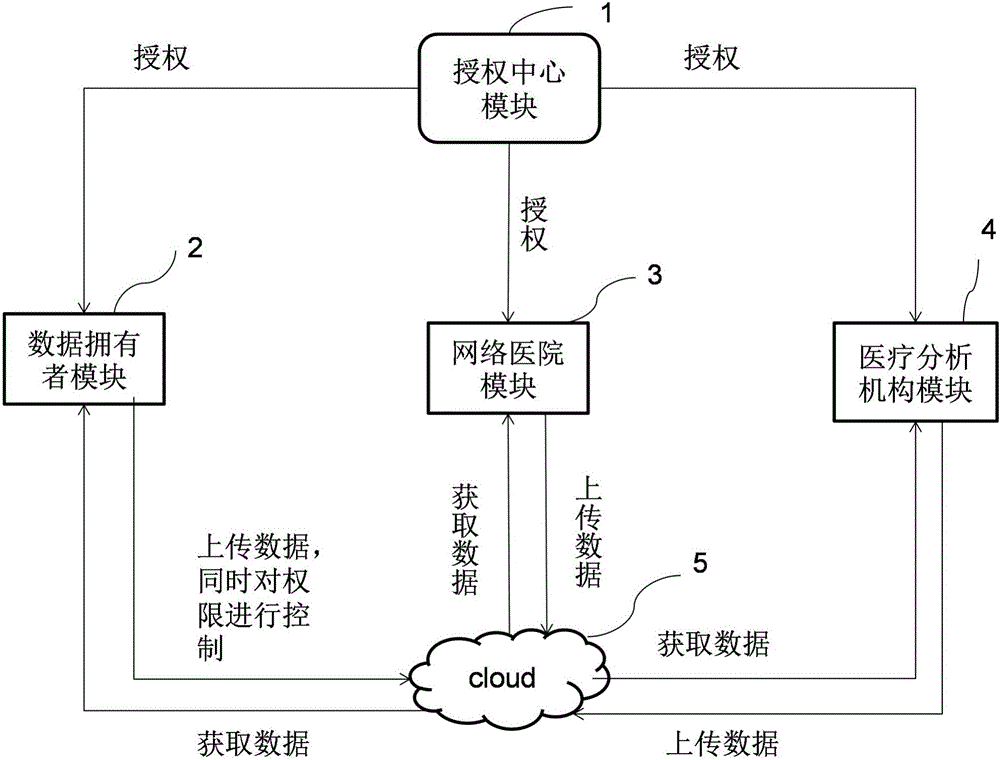
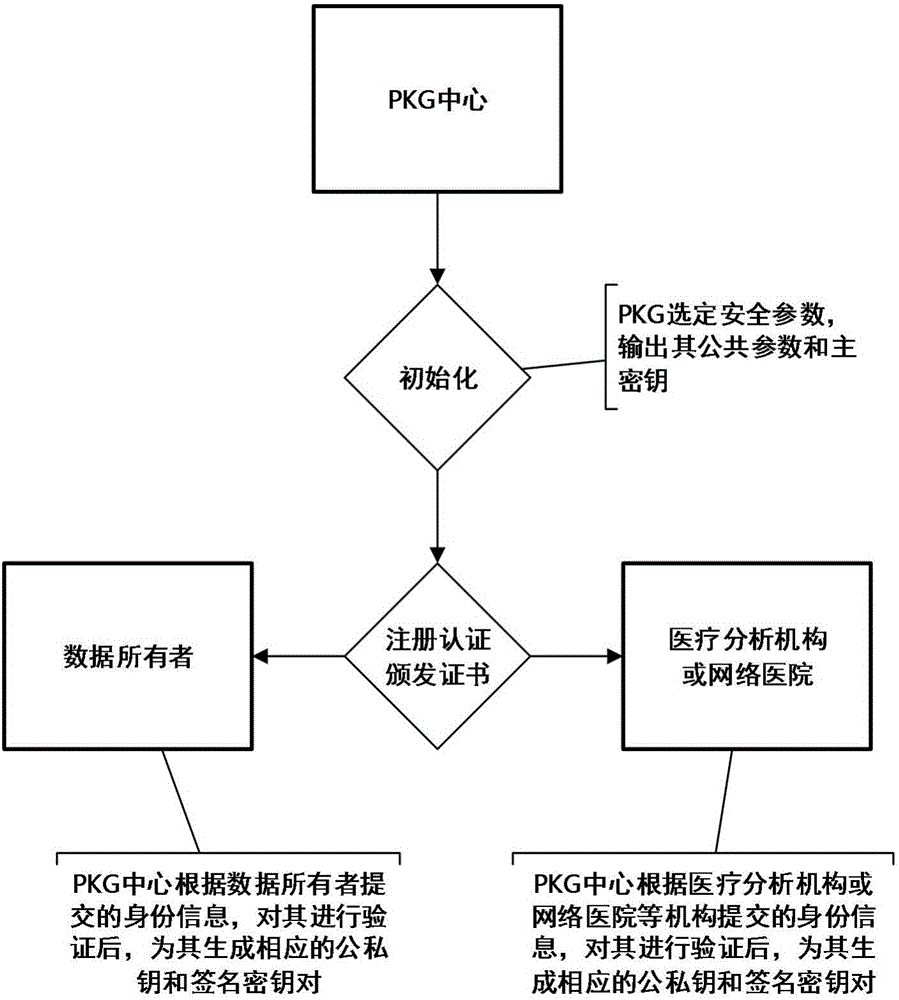
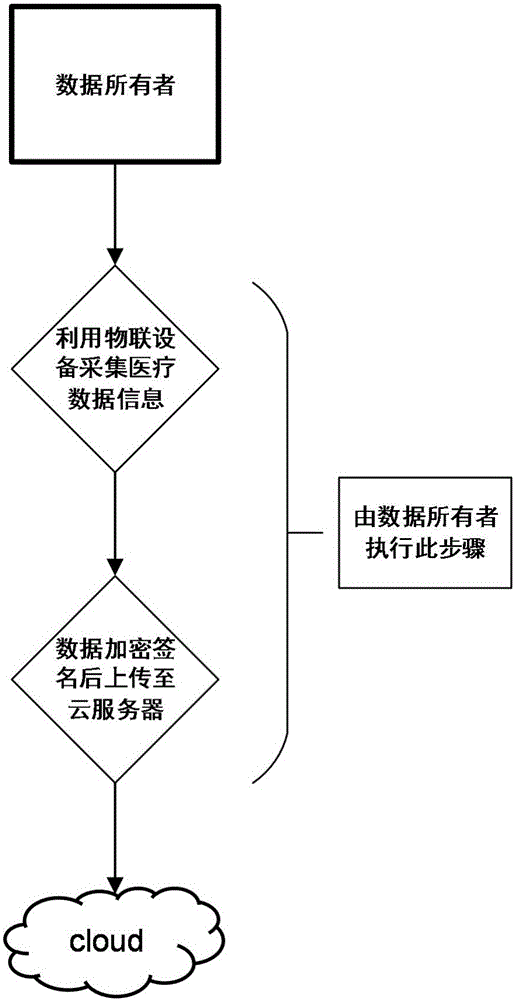
ActiveCN105978854AFlexible Control AllocationAssignment Convenience ControlKey distribution for secure communicationData processing applicationsCiphertextData access
The invention discloses an intelligent medical service method based on undistinguishable confusion, which is characterized in that a data owner independently decides allocation for the medical data access authority through carrying out security symmetric encryption on medical information uploaded to a cloud server; a medical data analysis mechanism carries out confusion on a medical data analysis program by using an undistinguishable confusion technology, the confused program is deployed to the cloud server, and security analysis is carried out on the medical data by using a confusion program so as to acquire a correct medical analysis result; and the access authority of other related mechanisms for a ciphertext can be controlled conveniently without changing the ciphertext structure by using a key sharing scheme. According to the invention, the privacy of data is realized, interaction of keys is reduced, and storage and management of a great number of keys are avoided; the integrity and the effectiveness of data can be verified; and the access type of medical data is decided by the user, the overall structure of an algorithm is not change at the same time, and the expansibility of the scheme is enhanced.
Owner:XIDIAN UNIV
Neighborhood access method in heterogeneous network, wireless access control center and system
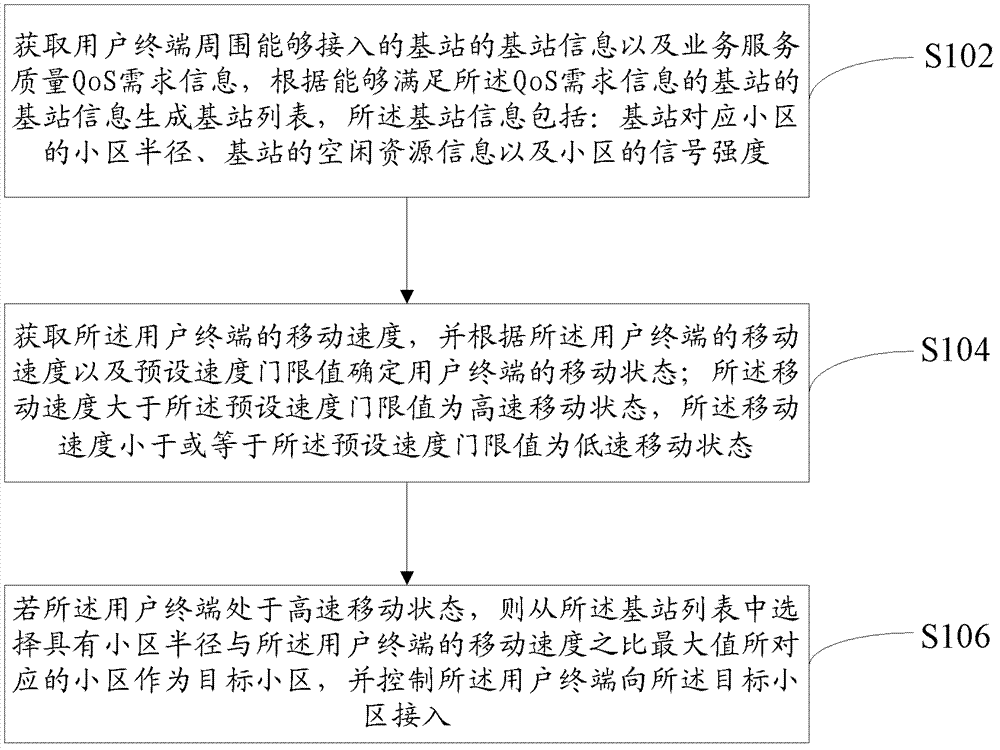
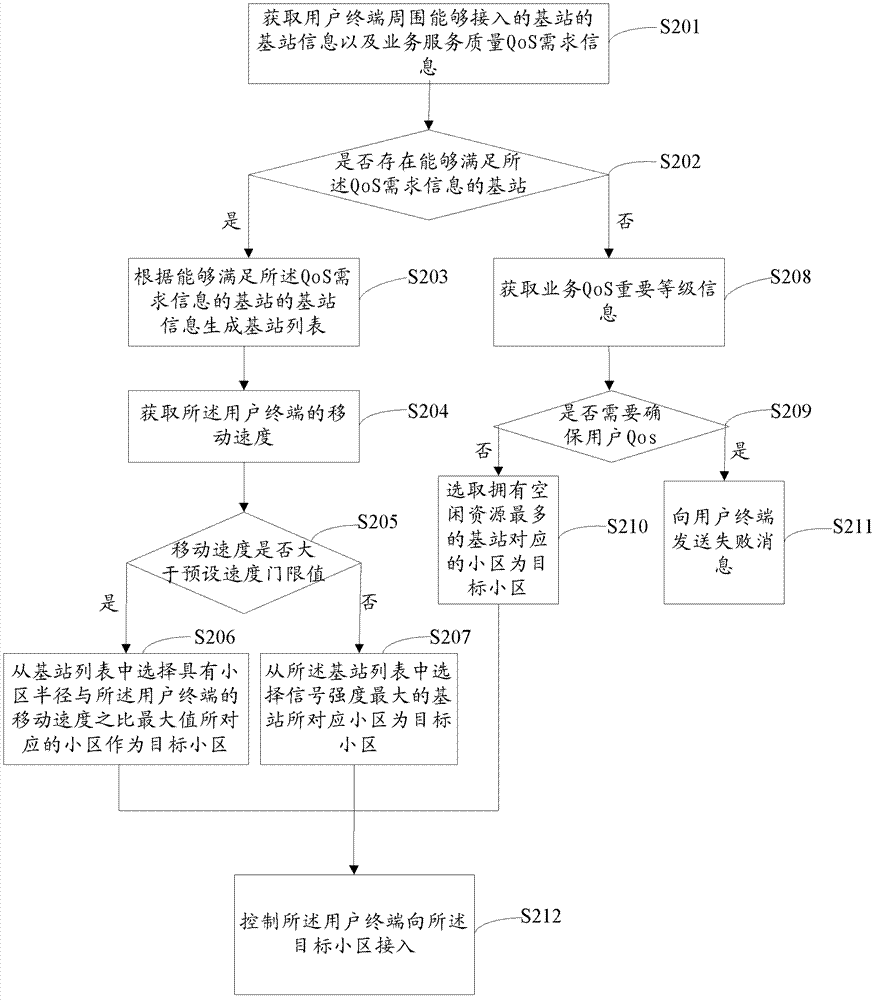
ActiveCN102711222AAccess controlAssess restrictionConnection managementQuality of serviceAccess method
The invention provides a neighborhood access method in the heterogeneous network, a wireless access control center and a system. The neighborhood access method in the heterogeneous network includes acquiring base station information and request information of QoS (quality of service) of base stations around a user terminal and generating base station lists according to the base station information capable of meeting the request information of the QoS; acquiring moving speed of the user terminal, and determining moving states of the user terminal according to the moving speed of the user terminal and preset speed threshold value; selecting a neighborhood corresponding to the maximum value of the ratio of the diameter of the neighborhood to the moving speed of the user terminal as a target neighborhood if the user terminals are at high speed moving state, and controlling the user terminal to access to the target neighborhood. By the neighborhood access method, the user terminal can be provided with the optimum target neighborhood to access according to the request information of the QoS of users and the base station information when the user terminal launches service requests.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
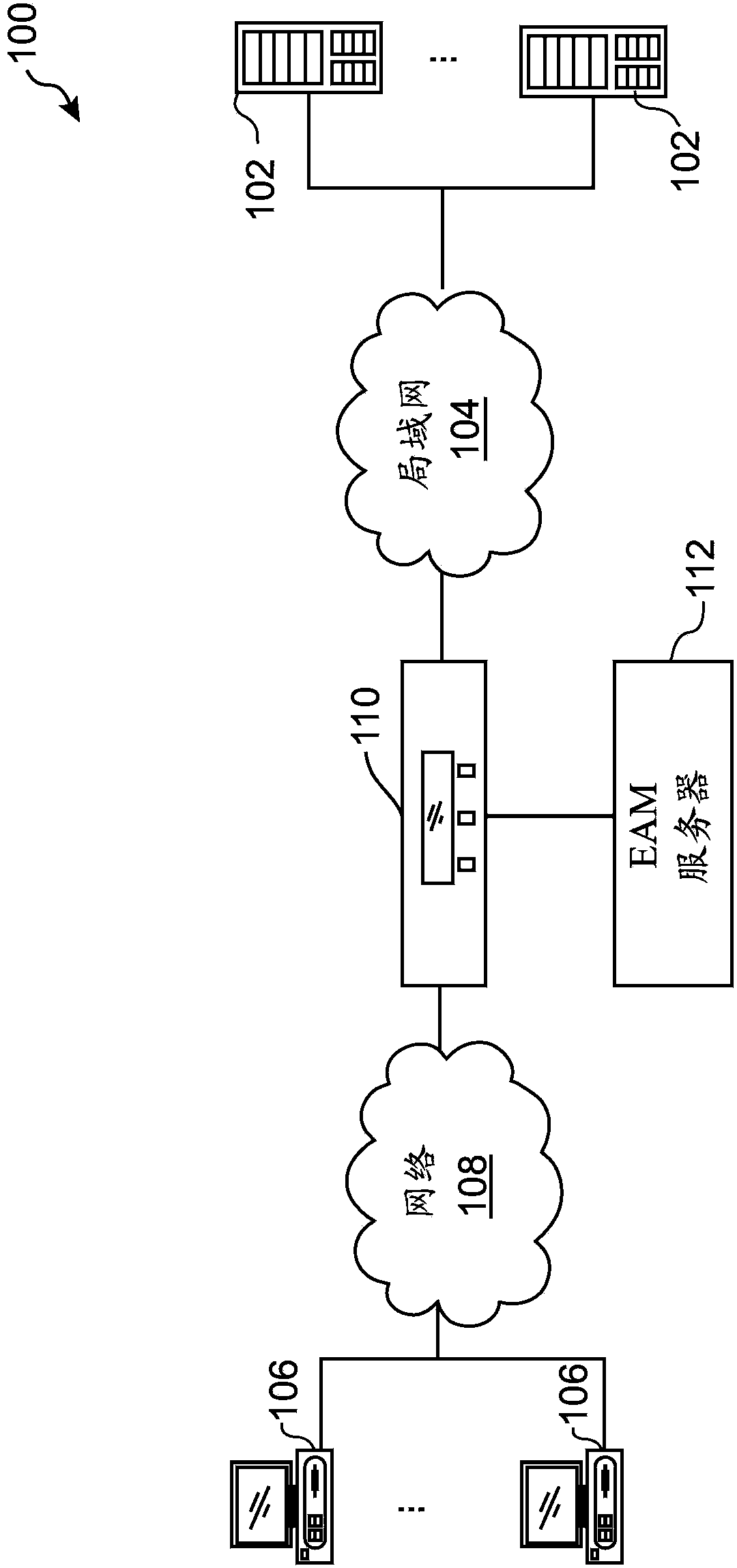
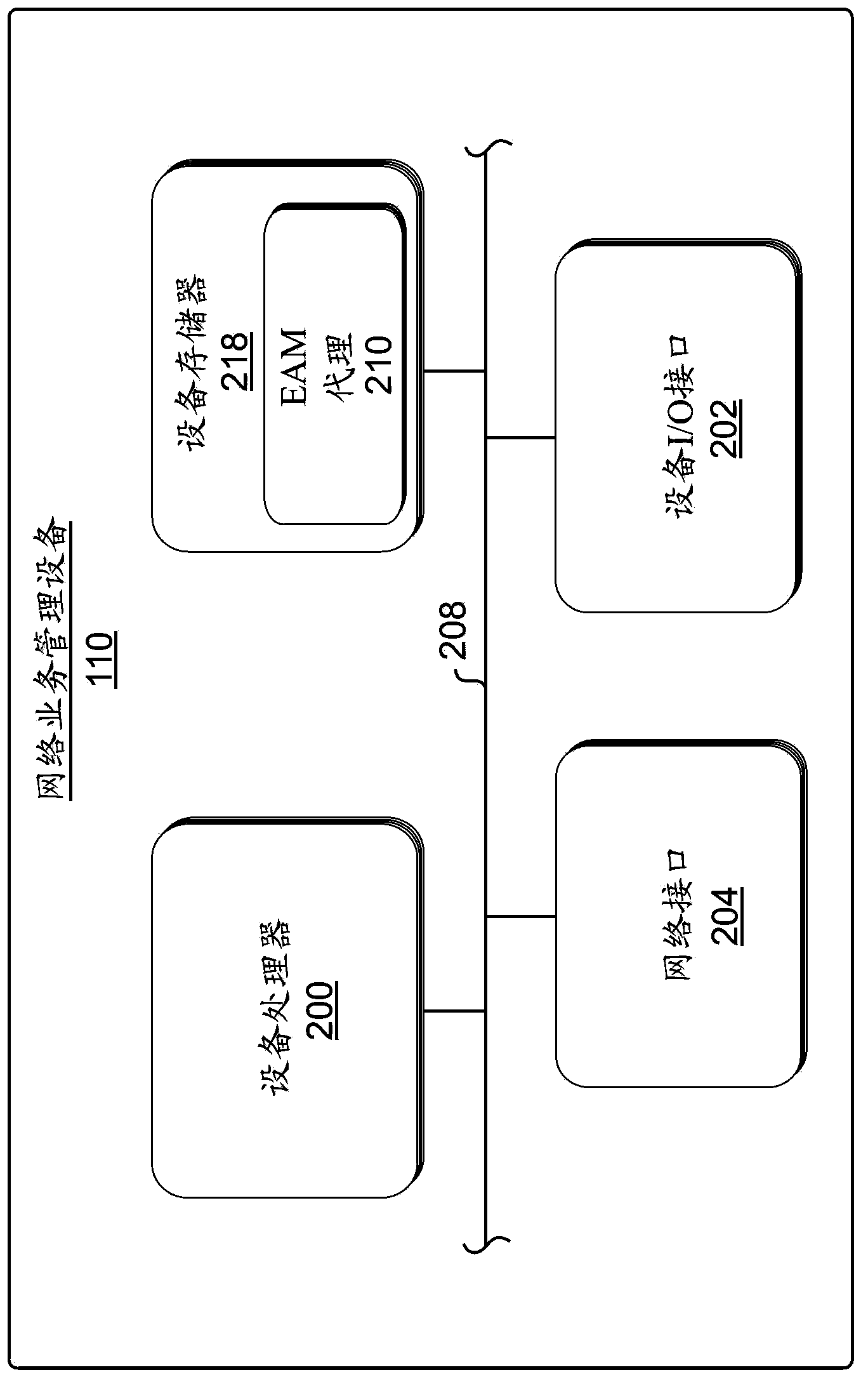
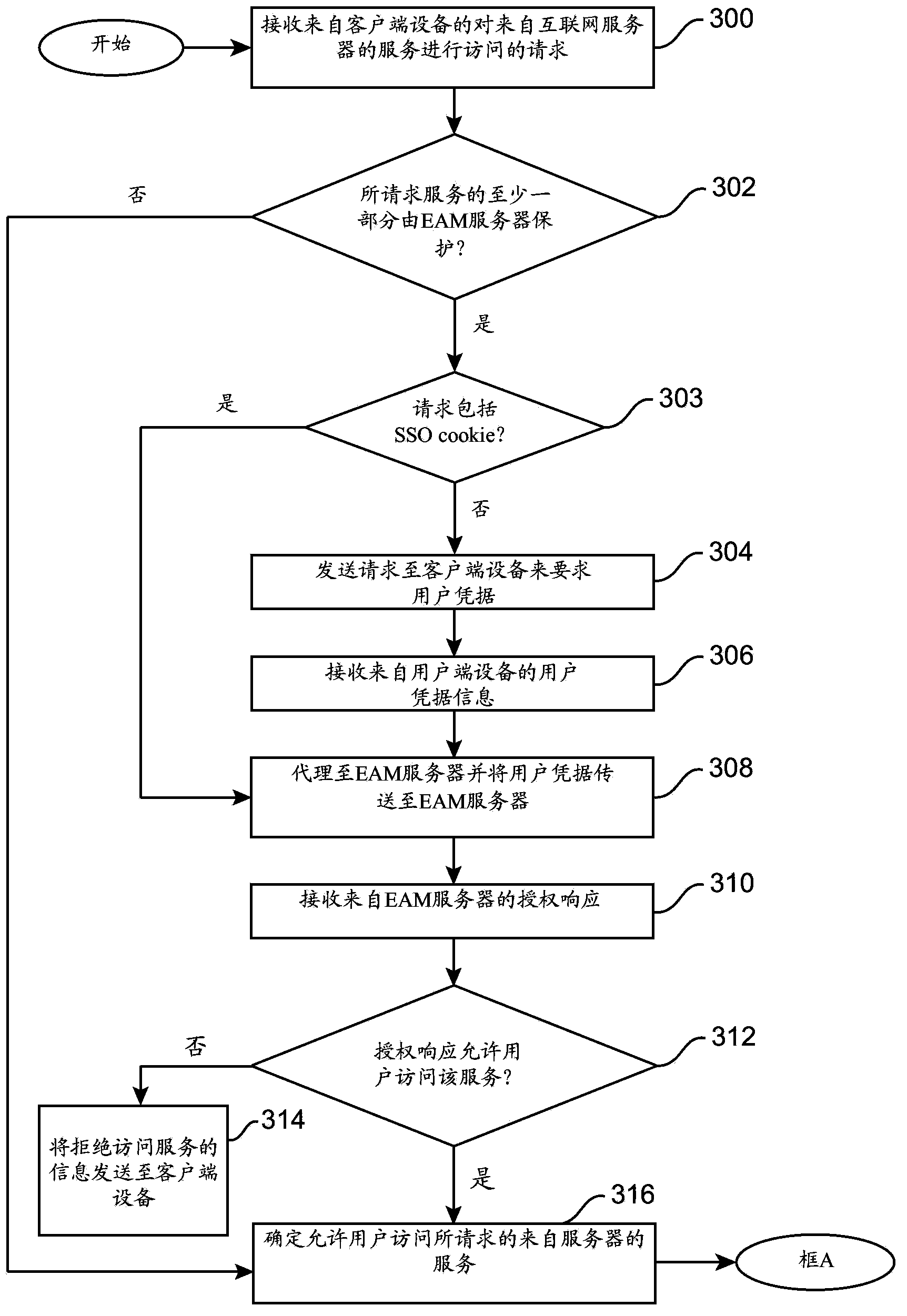
System and method for combining an access control system with a traffic management system
A system and method for handling a request from a client device to access a service from a server. The method comprises receiving a request from a user using a client device to access a service from a server. The request is received by a network traffic management device having a local external access management (EAM) agent. The EAM agent directly communicates with an EAM server that provides authentication policy information of a plurality of users able to at least partially access the server. User credential information is sent from the EAM agent to the EAM server, whereby the EAM agent receives access policy information of the user from the EAM server. The system and method selectively controls access of the user's request to the server in accordance with the received access policy information at the network traffic management device.
Owner:F5 NETWORKS INC
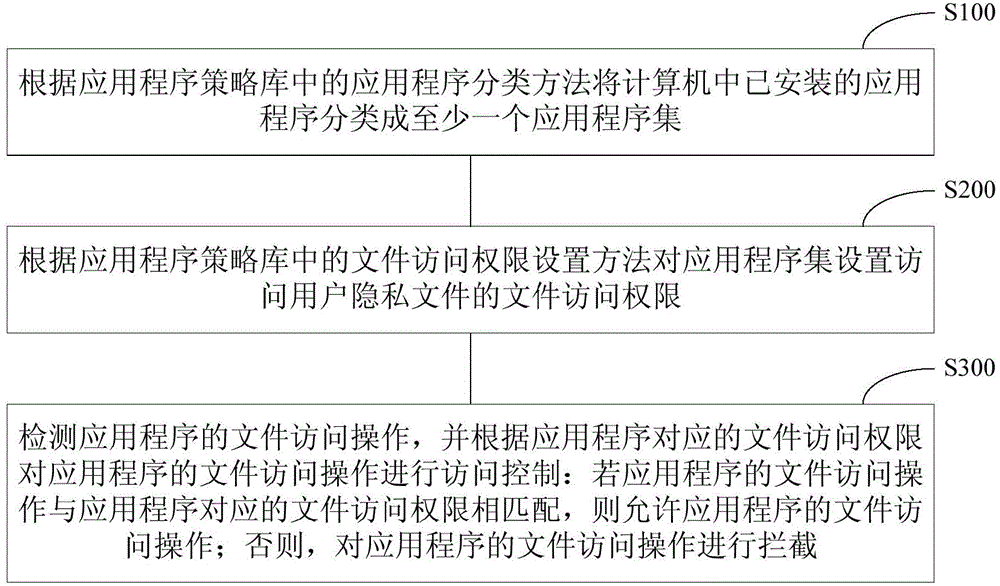
Method and system for protecting user privacy in computer
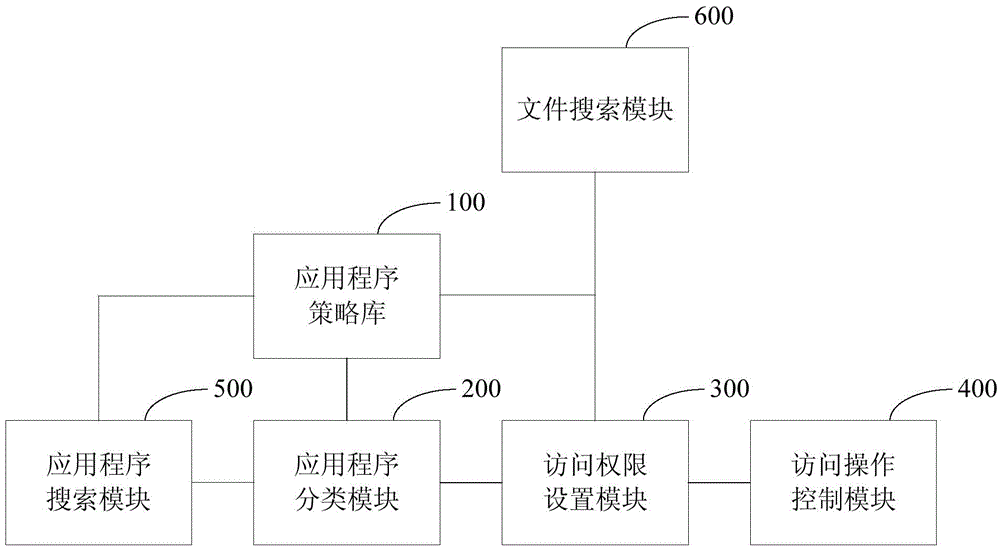
The invention discloses a method for protecting the user privacy in a computer. The method comprises the following steps that application programs are classified into an application program set according to an application program classification method in an application program strategy base; the file access authority is set for the application program set according to a file access authority setting method in the application program strategy base; the file access operation of the application programs is detected, and in addition, the file access operation of the application programs is subjected to access control according to the file access authority in accordance with the application programs; if the file access operation of the application programs is matched with file access authority corresponding to the corresponding programs, the file access operation of the application programs is allowed; otherwise, the file access operation of the application programs is intercepted. The invention also provides a system for protecting the user privacy in the computer. The method and the system for protecting the user privacy in the computer have the advantages that the loss of the private data of the user can be effectively prevented, and in addition, higher practicability is realized.
Owner:BEIJING RISING NETWORK SECURITY TECH CO LTD
Method and apparatus for selecting public land mobile-communication network for network access
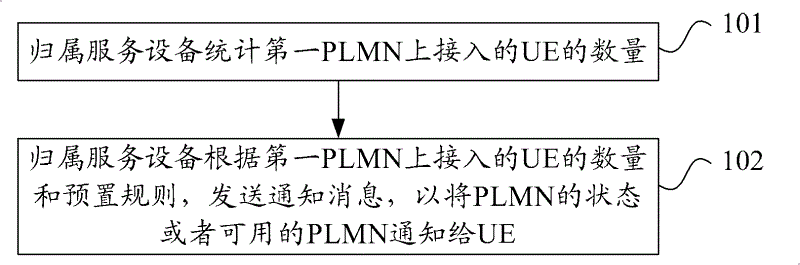
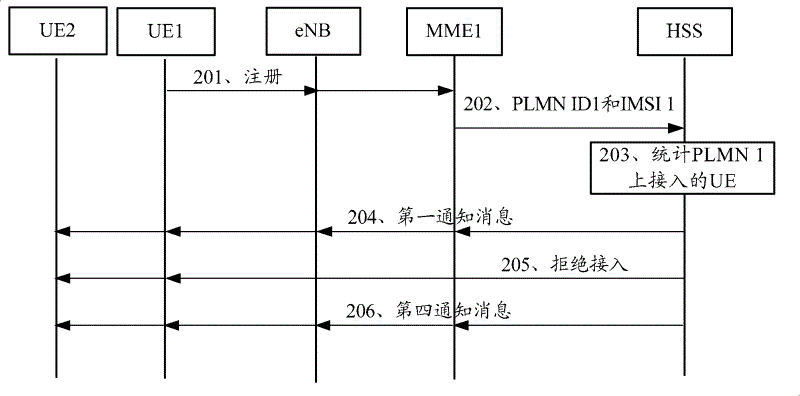
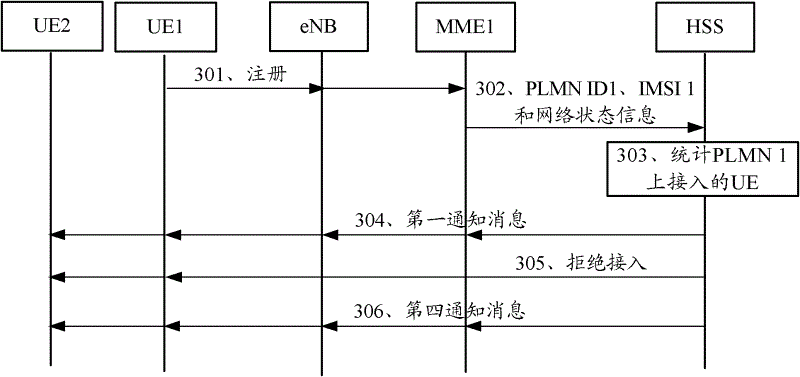
ActiveCN102625418AAccess controlAssess restrictionWireless commuication servicesNetwork access serverTelecommunications
The embodiments of the invention provide a method and an apparatus for selecting public land mobile-communication network (PLMN) for network access. The method comprises the following steps that: home service equipment carries out statistics on the number of UE with access to a first PLMN; and according to the number of UE with access to the first PLMN and a preset rule, the home service equipment sends a notification message, thereby notifying the state of the first PLMN or an available PLMN to the UE. According to the embodiments of the invention, when the number of UE with access to the first PLMN exceeds a threshold value or the number of UE with access to the first PLMN exceeds the threshold value and the network state information of the PLMN is abnormal, the home service equipment or a machine type communication (MTC) service platform can notify the UE that the access to the PLMN is restricted currently, so that the UE can select other PLMN access; therefore, it is realized that access to a network through the available PLM by a user can be effectively controlled when there is a network problem on the PLMN or it is necessary to satisfy a requirement of a current PLMN network.
Owner:HUAWEI TECH CO LTD
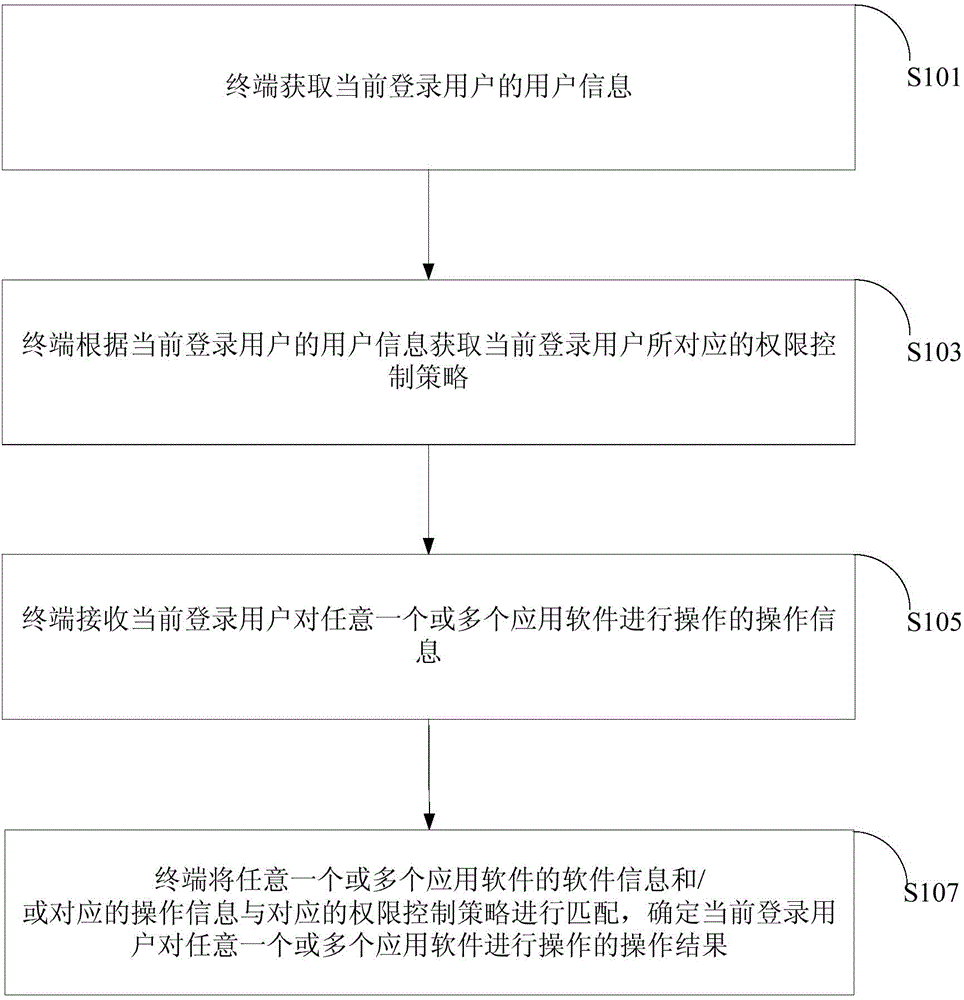
Application software authority control method and system
ActiveCN104820791AAccess controlEffective control of authorityProgram/content distribution protectionSoftware engineeringApplication software
The invention discloses an application software authority control method and an application software authority control system. The method comprises the following steps that: a terminal obtains user information of a current login user; the terminal obtains an authority control strategy corresponding to the current login user according to the user information of the current login user; the terminal receives operation information for operating any one or a plurality of pieces of application software by the current login user; the terminal matches software information of any one or the plurality of pieces of application software and / or the corresponding operation information with the corresponding authority control strategy; and an operating result of operating any one or the plurality of pieces of application software by the current login user is determined. The application software authority control method and the application software authority control system solve the problem of control incapability on the authorities of the application software under the condition with the plurality of pieces of application software in the prior art.
Owner:DATANG NETWORK CO LTD
Distribution system and method
A system for dispensing items comprises trays each adapted to support items to be dispensed. A casing comprises a restocking volume receiving trays with items thereon for subsequent storage. A storage volume accommodates the trays in storage. An outlet is used to dispense any selected items on the trays. An arm displaces trays within the casing, and displaces items from the trays to the outlet. A controller unit receives an identification of each item in the trays when positioned in the restocking volume, and monitors a position of each identified item within the trays in the casing to control the actuation of the arm to dispense items through the outlet as a function of an order entered through the user interface.
Owner:PLANNING TECH INT
Building video intercom method, device and system
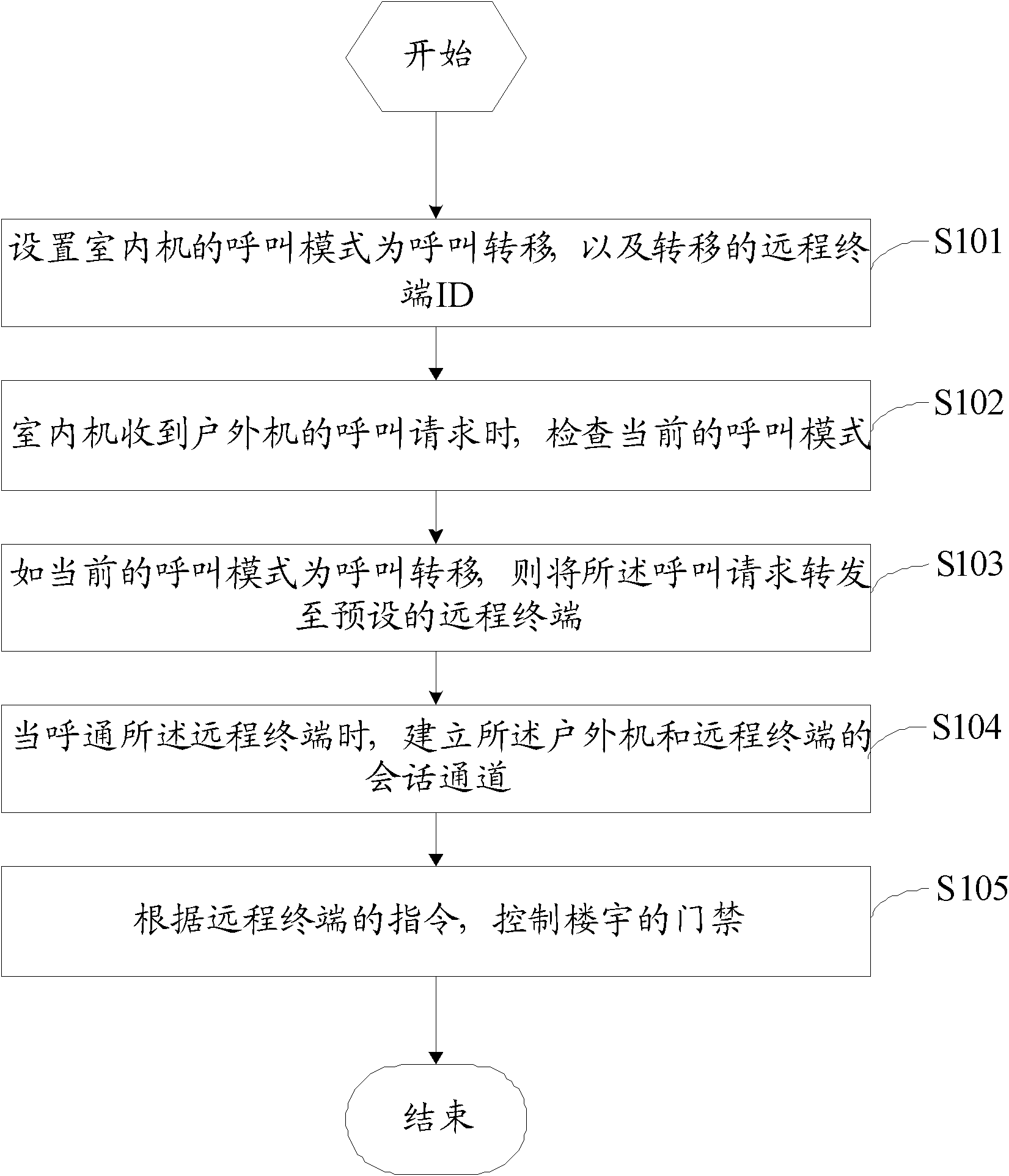
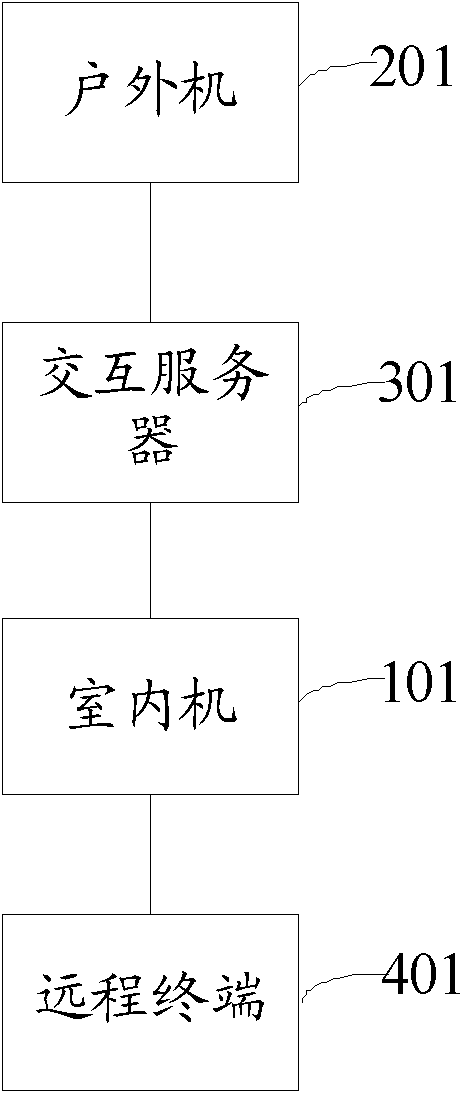
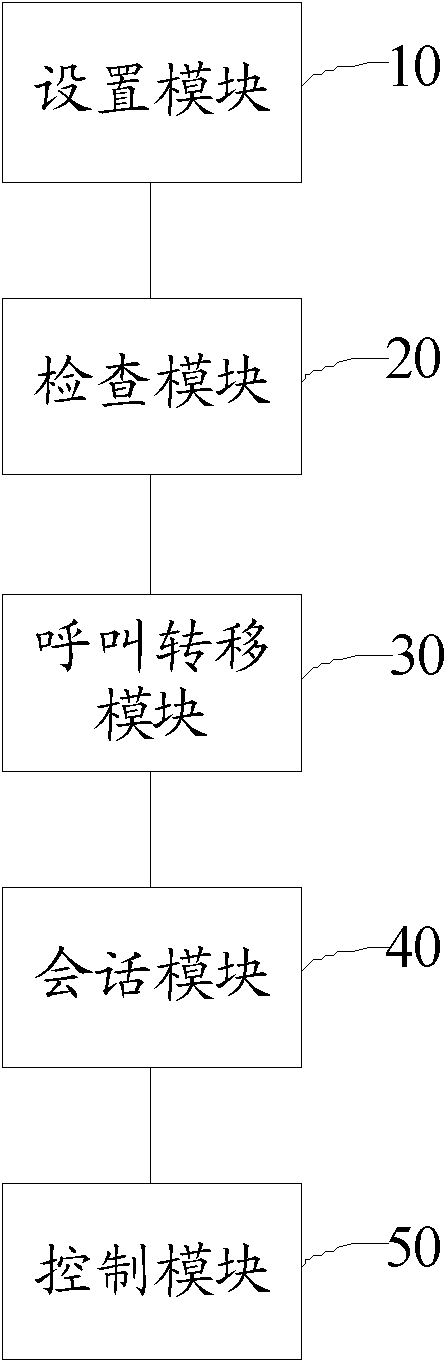
InactiveCN102300072AAccess controlTwo-way working systemsStations for two-party-line systemsSoftswitchCall forwarding
The invention discloses a building video intercom method, which includes: when an indoor unit receives a call request from an outdoor unit, checks the current call mode; if the current call mode is call transfer, then forwards the call request to a preset The remote terminal provided; when the remote terminal is called, a conversation channel between the outdoor unit and the remote terminal is established. The invention also proposes corresponding devices and systems. A building video intercom method, device and system proposed by the present invention install a softswitch system in the indoor unit, and the softswitch system can still communicate with the outdoor unit when the resident is not near the indoor unit, and further control Building access control.
Owner:兴旺
Safety login method based on domestic cryptographic algorithm
The invention discloses a safety login method based on a domestic cryptographic algorithm. Service-end login software and client-end login software are installed on an embedded device and a debugging computer respectively. The embedded device is connected with the debugging computer through a network interface. A client end remotely logs in a device through a network. The login software uses a secret key verification method. A user may log in the device just after a client-end secret key and a service-end secret key pass respective identity verification so as to perform encrypted session. The safety login software is installed on the client end. On the premise that an original function of the device is not changed, a new authentication mode is used and plaintext transmission is converted into cryptograph transmission. Thus, a risk bug in the conventional remote login software is solved, communication security between the network equipment and external environment is improved, and malicious attack to network management is effectively defended.
Owner:成都卫士通信息产业股份有限公司
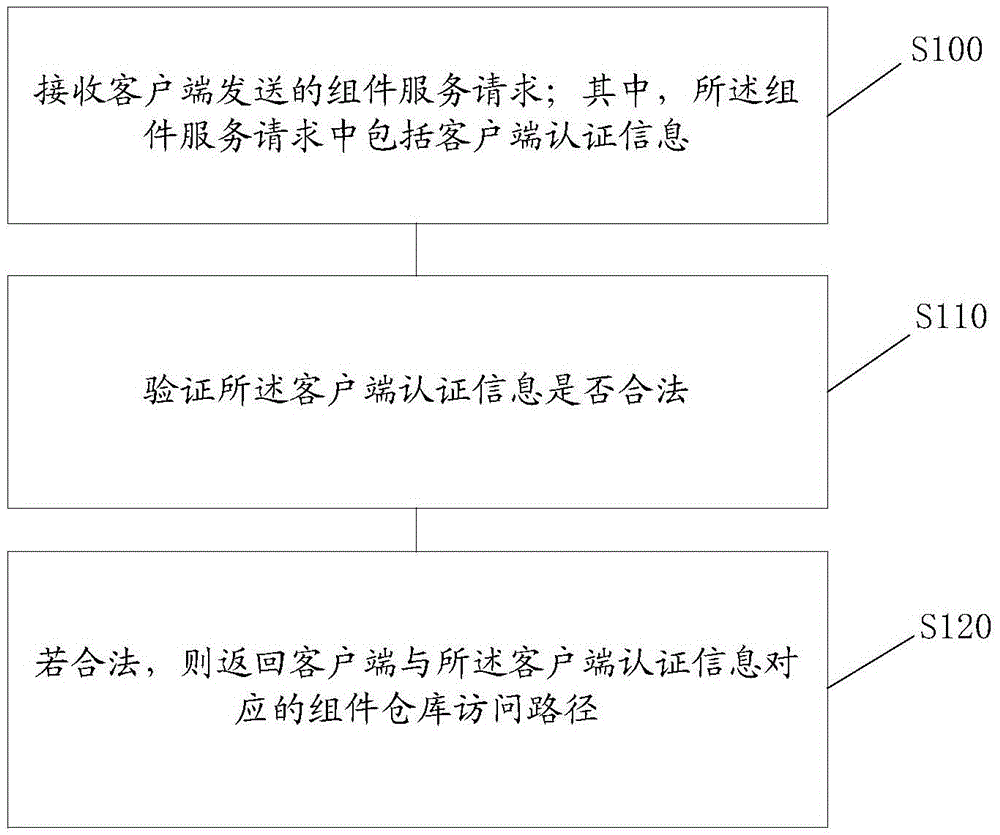
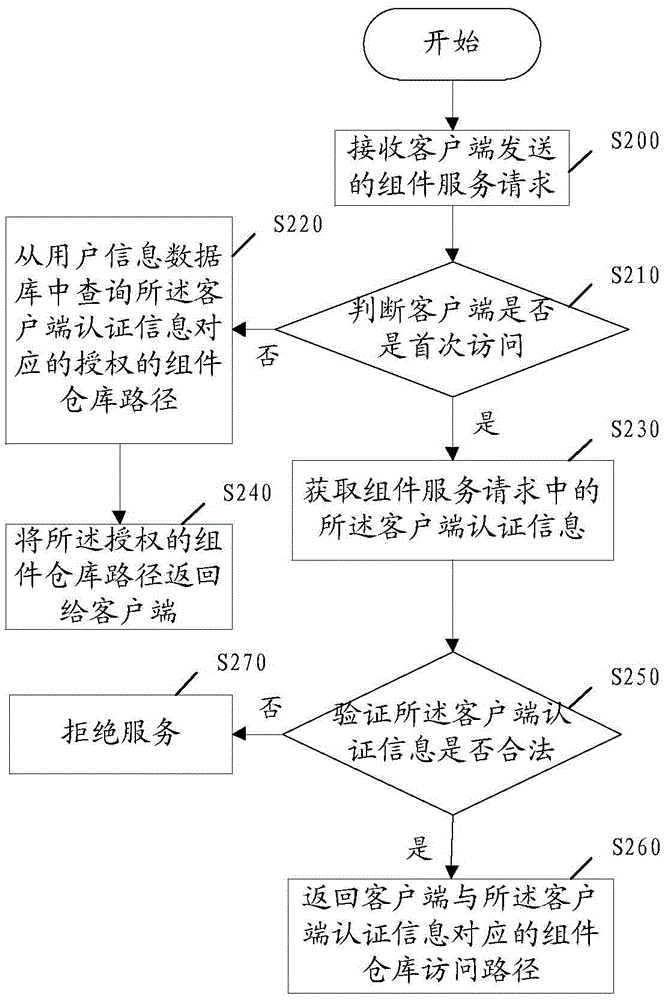
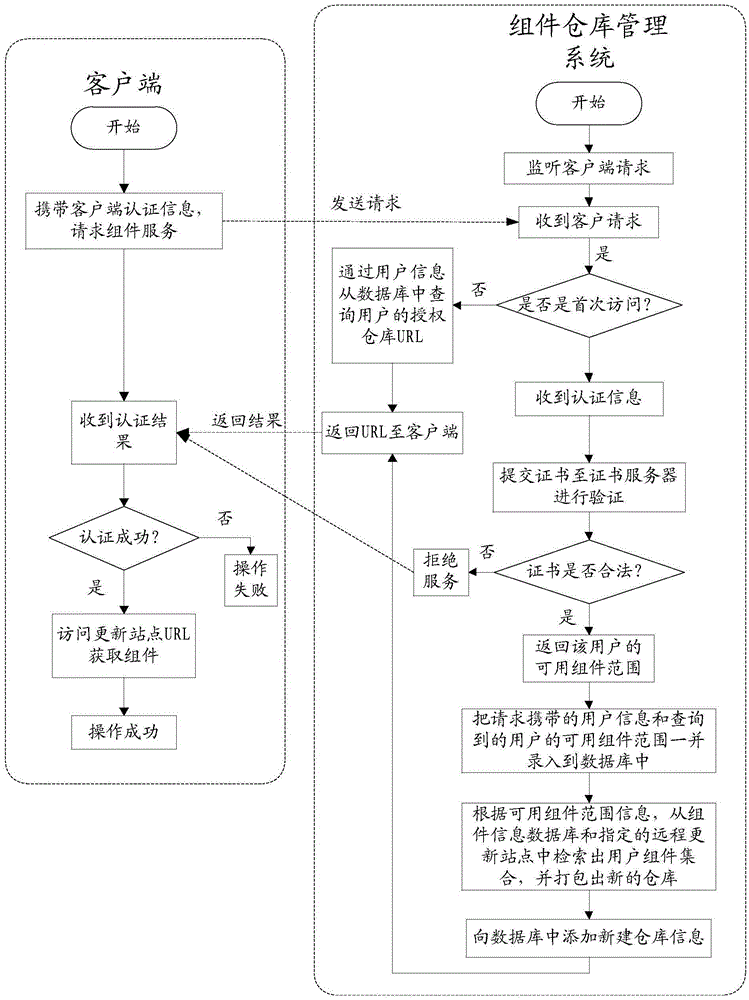
Component repository management method and system
InactiveCN105653901AAvoid infringementAccess controlDigital data protectionProgram/content distribution protectionClient-sideDatabase
The invention discloses a component repository management method, comprising the steps of receiving a component service request sent by a client, wherein the component service request comprises client authentication information; verifying whether the client authentication information is valid or not; and if valid, returning a component repository access path corresponding to the client authentication information to the client. The method can conveniently and quickly control the client, namely a user, to acquire the authority of a repository component, and can prevent a customized component or a charged component from being infringed. The invention further discloses a component repository management system.
Owner:SHENZHEN KEMANDA INTELLIGENT MANAGEMENT SCI &TECH
Recovery method of flexible solar assembly
ActiveCN105895731AEfficient separationSolve the difficult problem of separation and purificationLight-sensitive devicesFinal product manufactureRecovery methodState of art
The invention relates to a recovery method of a flexible solar assembly. The method comprises the steps including cryogenic separation, coating material separation and coating material gathering successively. According to the method, a chip of the solar assembly is separated from other layers in the cryogenic method, the problem that a coating material on the recovery chip is hard to separate from materials of the other layers or is hard to recover after separation in the prior art is solved, and the high-value material in the flexible solar assembly can be recovered at low cost; The recovery method is simple in steps, low in operation difficulty, low in comprehensive cost, high in recovery efficiency, friendly to the environment and wide in application prospects.
Owner:HANERGY MOBILE ENERGY HLDG GRP CO LTD
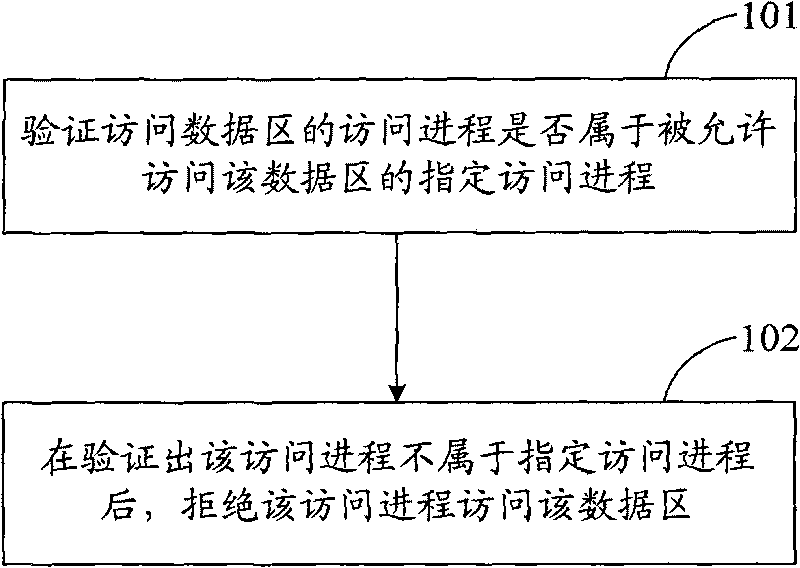
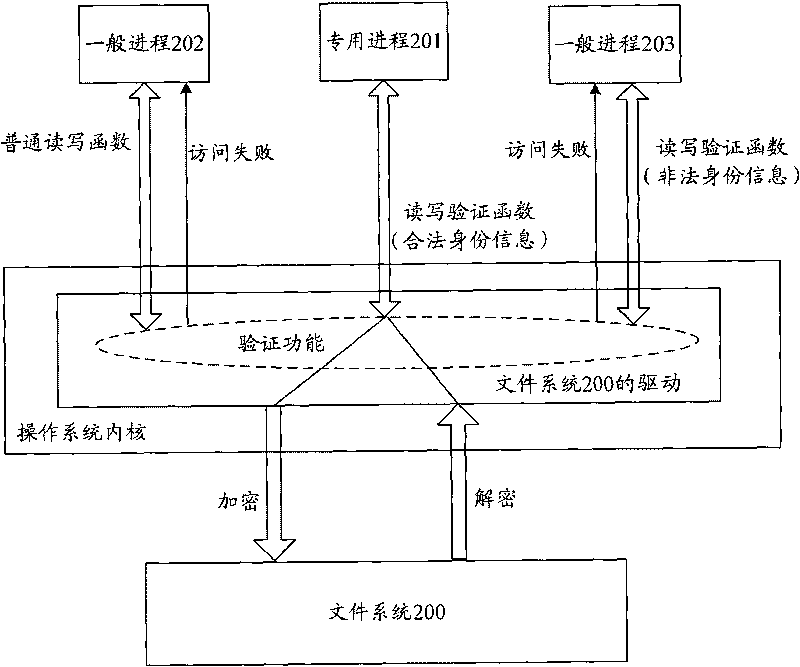
Access control method, access control device and terminal device
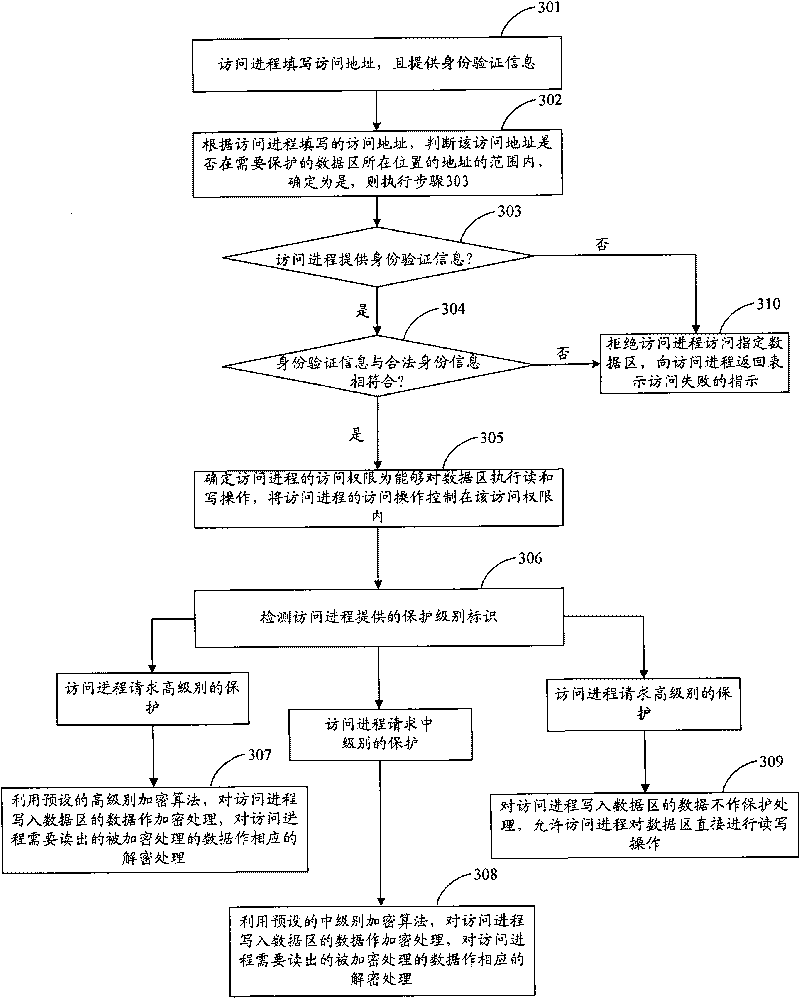
InactiveCN101739361AEffective access controlAccess controlUnauthorized memory use protectionTerminal equipmentAccess control
The implementation of the invention provides an access control method, an access control device and an accessing device. The method includes: whether the access process accessing data area is assigned to the designated access process of the data area allowed to be accessed is verified; the data area is used for storing data; and after the access process is verified not to be assigned to the designated access process, the access process is rejected to access the data area. The technical scheme provided by the implementation of the invention can effectively control the access of access process on data area, reject illegal access process to access the data area and effectively ensure the data of the data area to be safe.
Owner:LENOVO (BEIJING) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com