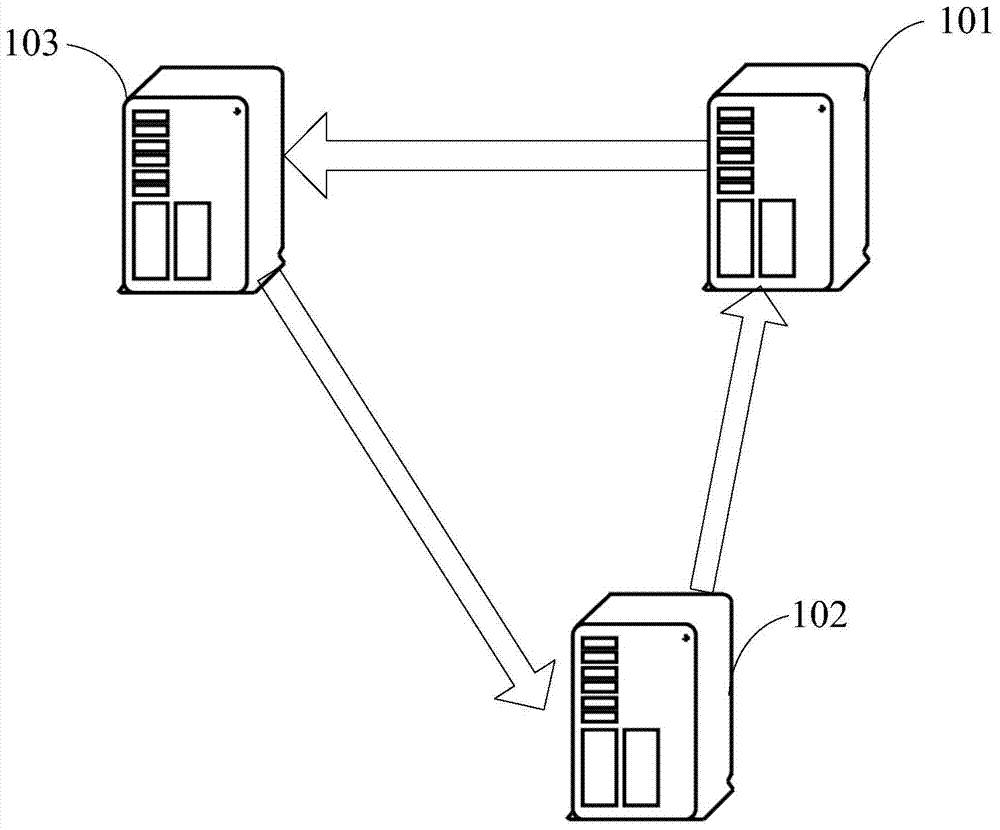
Method of controlling network access amount and server
A technology for accessing and controlling the network, applied in the Internet field, it can solve the problems of insufficient intelligence, high system load, adverse effects on merchants, etc., and achieve the effect of improving intelligence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
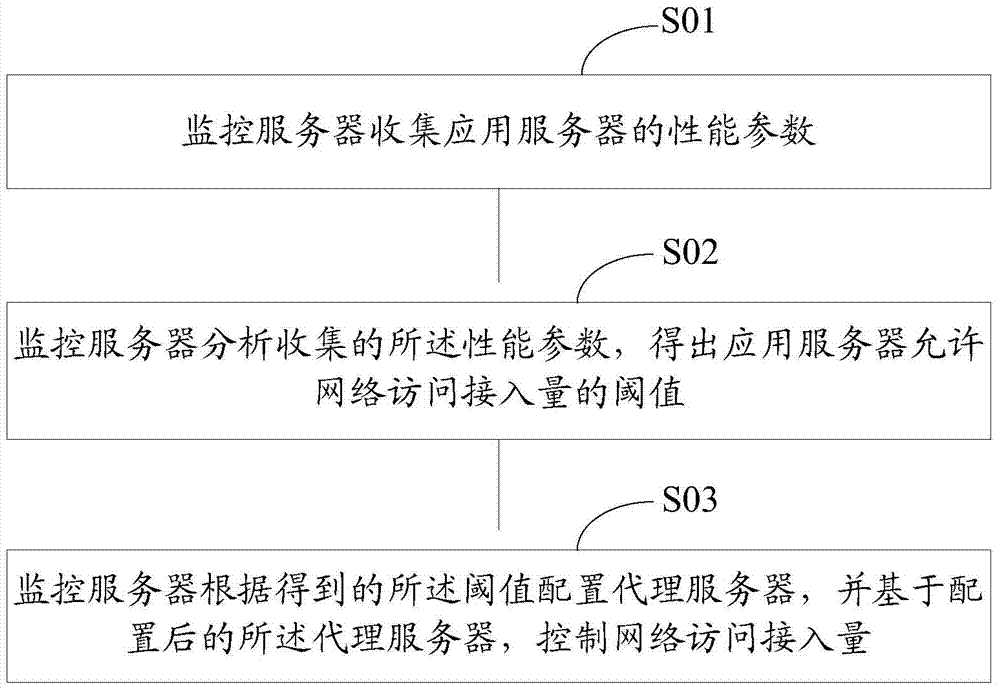
[0025] based on figure 1 For a description of the examples, please refer to figure 2 , figure 2 It is a schematic flow chart of the first embodiment of the method for controlling the amount of network access in the present invention; figure 2 As shown, the method for controlling the amount of network access in the present invention comprises the following steps:
[0026] Step S01, the monitoring server collects performance parameters of the application server;
[0027] The monitoring server collects the status of each functional module of the back-end server, that is, the application server in real time, such as collecting the CPU (Central Processing Unit, central processing unit) load and IO (Input / Output, input and output) interface corresponding to the website server, database, cache, etc. The usage status of the application server and the usage status of the memory are used to obtain the performance parameters corresponding to the above functional modules of the appl...
Embodiment 2
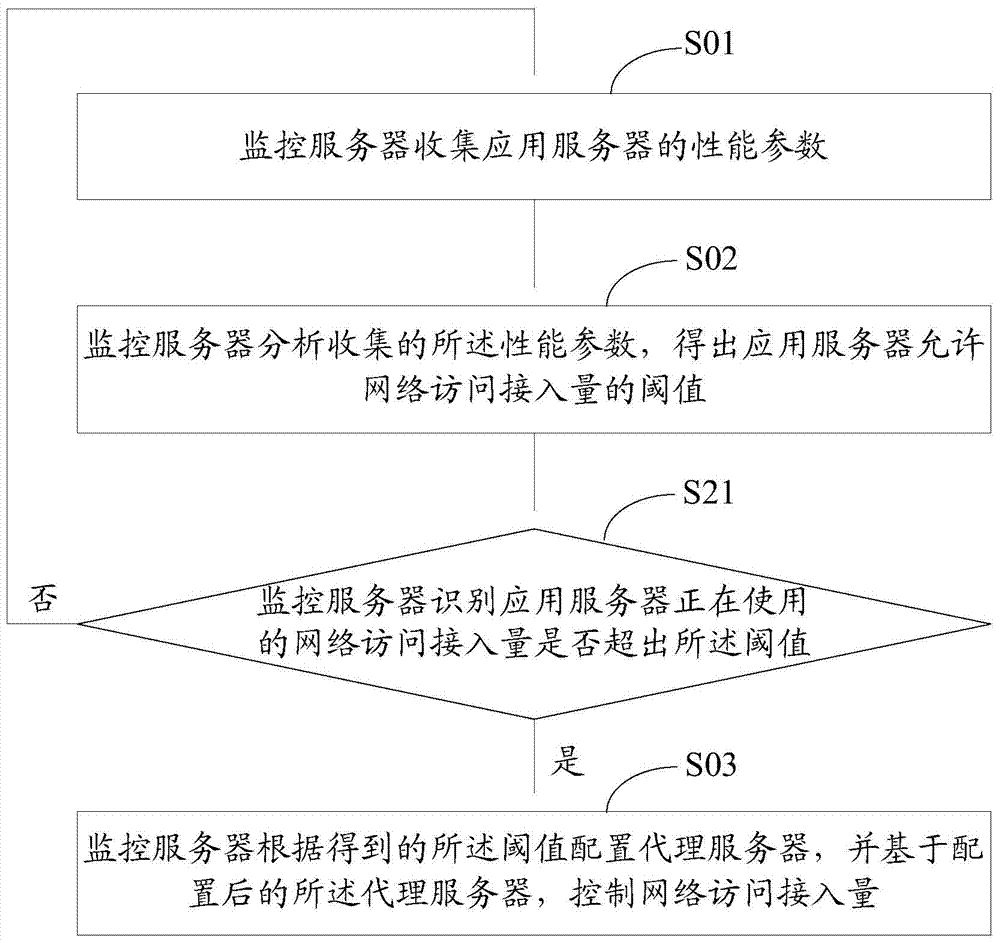
[0038] image 3 It is a schematic flow chart of the second embodiment of the method for controlling the amount of network access in the present invention; the embodiment of the present invention is the same as figure 2 The difference between the above embodiments is that before the monitoring server configures the proxy server, it must first identify whether the network access volume being used by the application server exceeds the threshold value of the network access volume allowed by the application server.
[0039] based on figure 2 The specific description of said embodiment, such as image 3 As shown, the method for controlling the amount of network access in the present invention is in step S02, the monitoring server analyzes the collected performance parameters, obtains the threshold value of the network access amount allowed by the application server, and then further includes:
[0040] Step S21, the monitoring server identifies whether the network access volume b...
Embodiment 3
[0046] Figure 4 It is a schematic flow chart of the third embodiment of the method for controlling the amount of network access in the present invention; the embodiment of the present invention is the same as figure 2 or image 3 The difference between the above embodiments is that before the monitoring server collects the performance parameters of the application server, the monitoring server obtains the resource configuration table; the method for the monitoring server to obtain the resource configuration table includes: when the monitoring server is initialized, obtain the resource configuration table; or, The monitoring server obtains the resource configuration table configured by the user side such as background maintenance personnel.
[0047] based on image 3 The specific description of said embodiment, such as Figure 4 As shown, the method for controlling the amount of network access in the present invention also includes before step S01, the monitoring server co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com