Patents
Literature
45results about How to "Effective access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
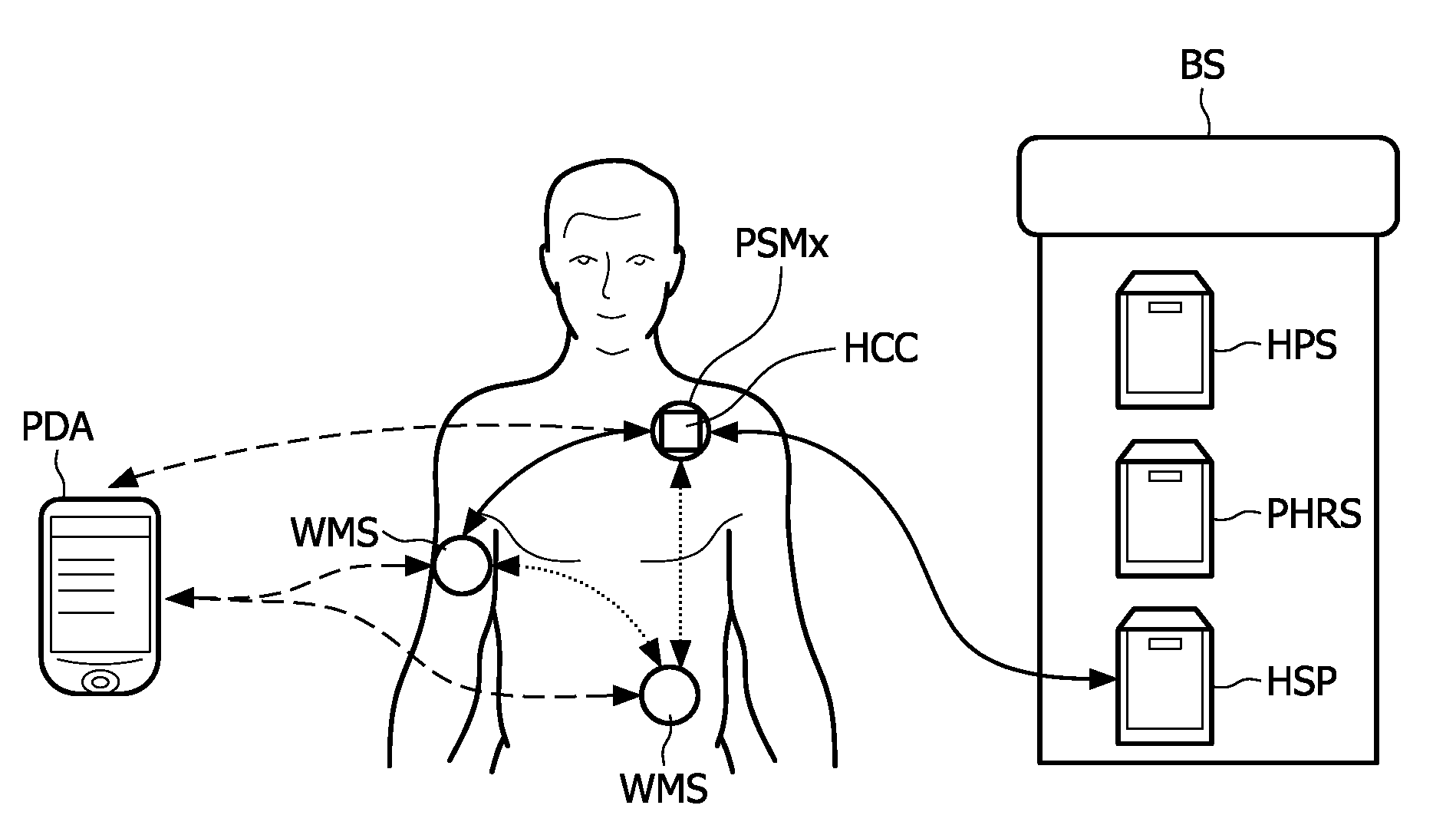
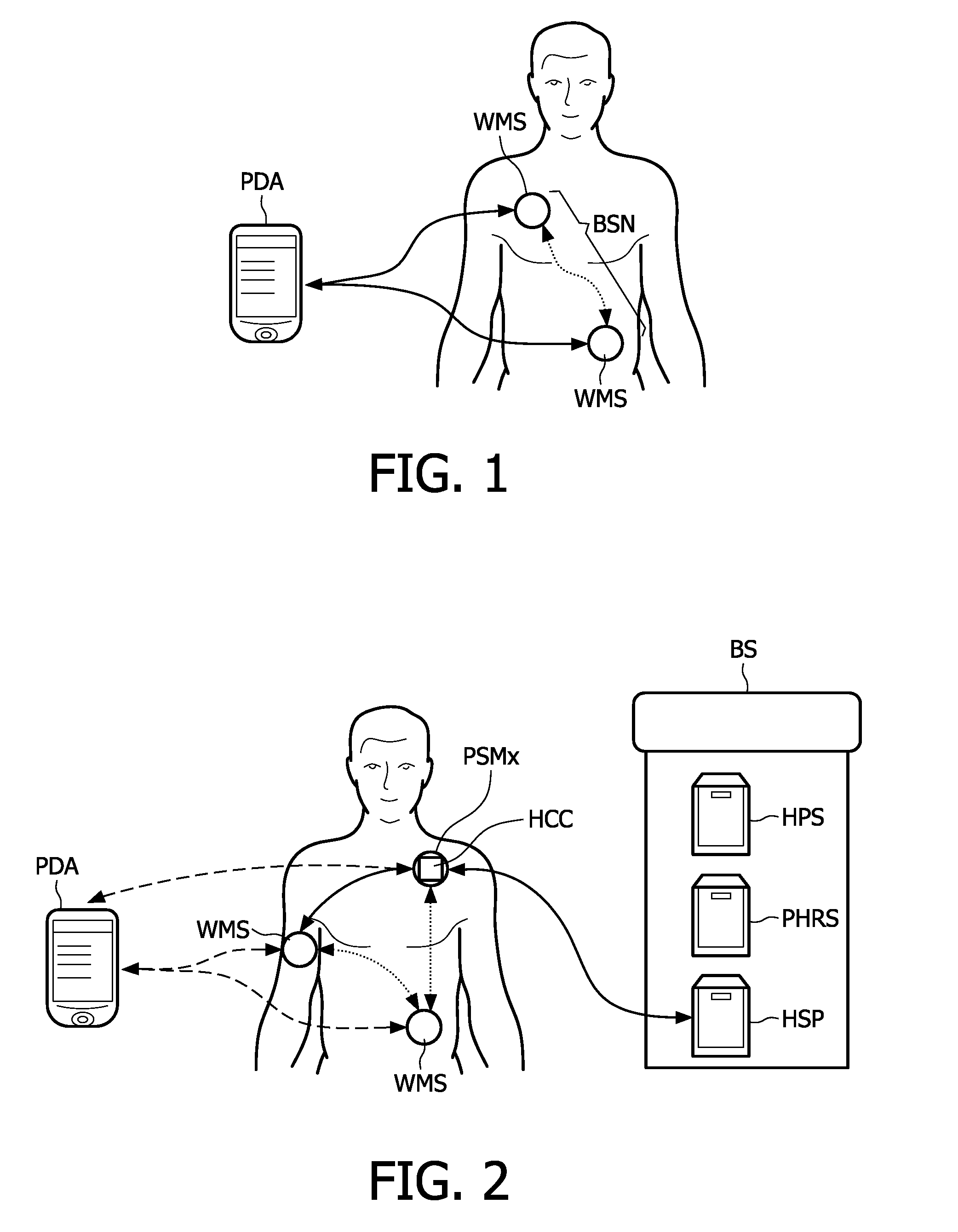
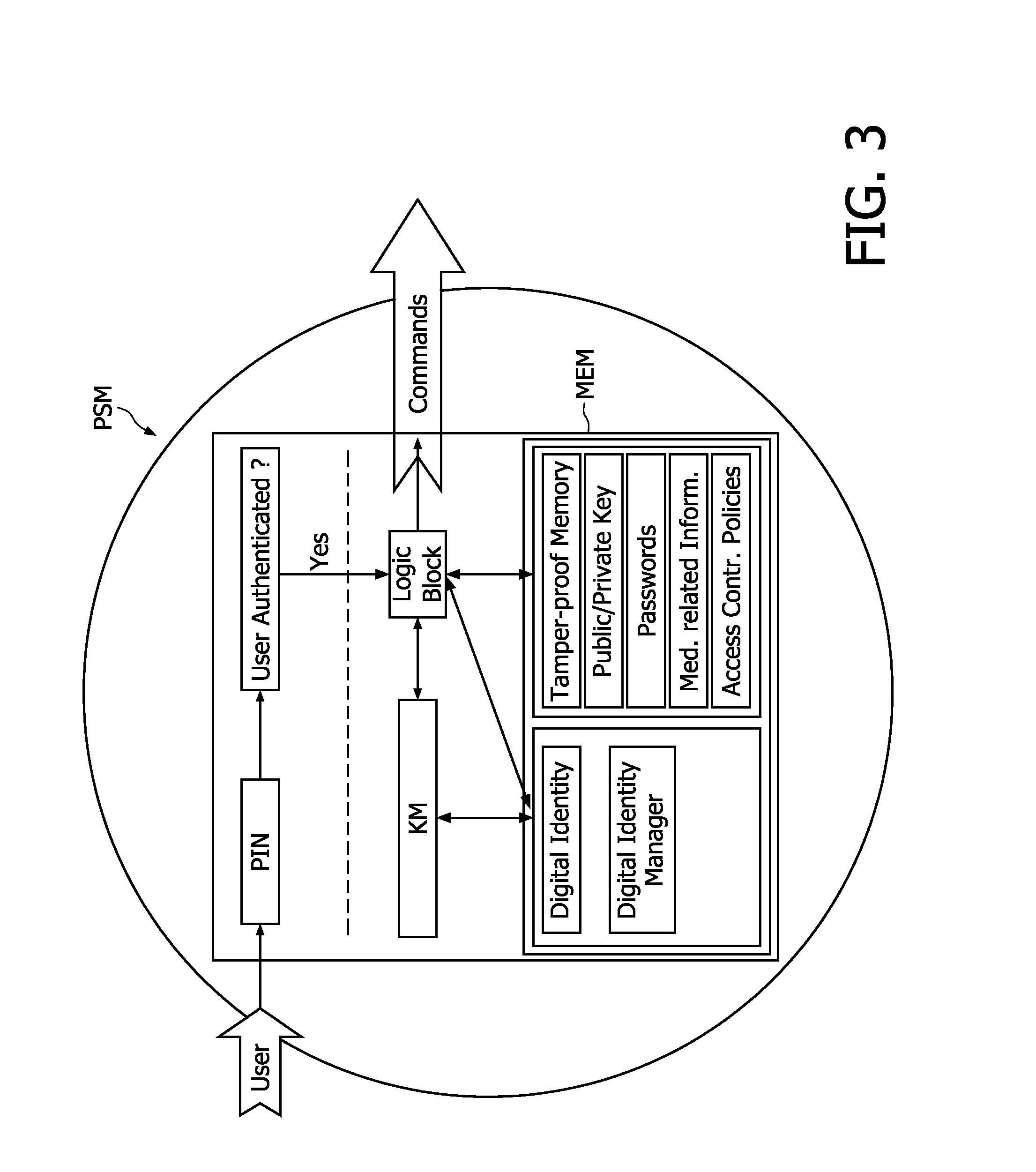
Personal security manager for ubiquitous patient monitoring
ActiveUS20110145894A1Effective and secure accessEffective access controlDigital data processing detailsDigital data protectionSecure communicationPersonal security
The present invention relates to a system and corresponding method for a secure end-to-end patient healthcare system which includes wireless medical sensors adapted to be attached to a patient's body and in communication with each other forming a body sensor network within a wireless medical sensor network including one or more body sensor networks; λ-secure keying means incorporated into each wireless medical sensor for enabling secure communications between the wireless medical sensors, and a personal security manager within the body sensor network and in communication with the wireless medical sensors within the body sensor network, the personal security manager providing secure communications with backend services and providing security relationships within the body sensor network by means of the λ-secure keying means, wherein the λ-secure keying means are such that a coalition of no more than λ compromised wireless medical sensors conceals a pairwise key between any two non-compromised wireless medical sensors and provides protection against node compromise until λ+1 wireless medical sensors have been compromised.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
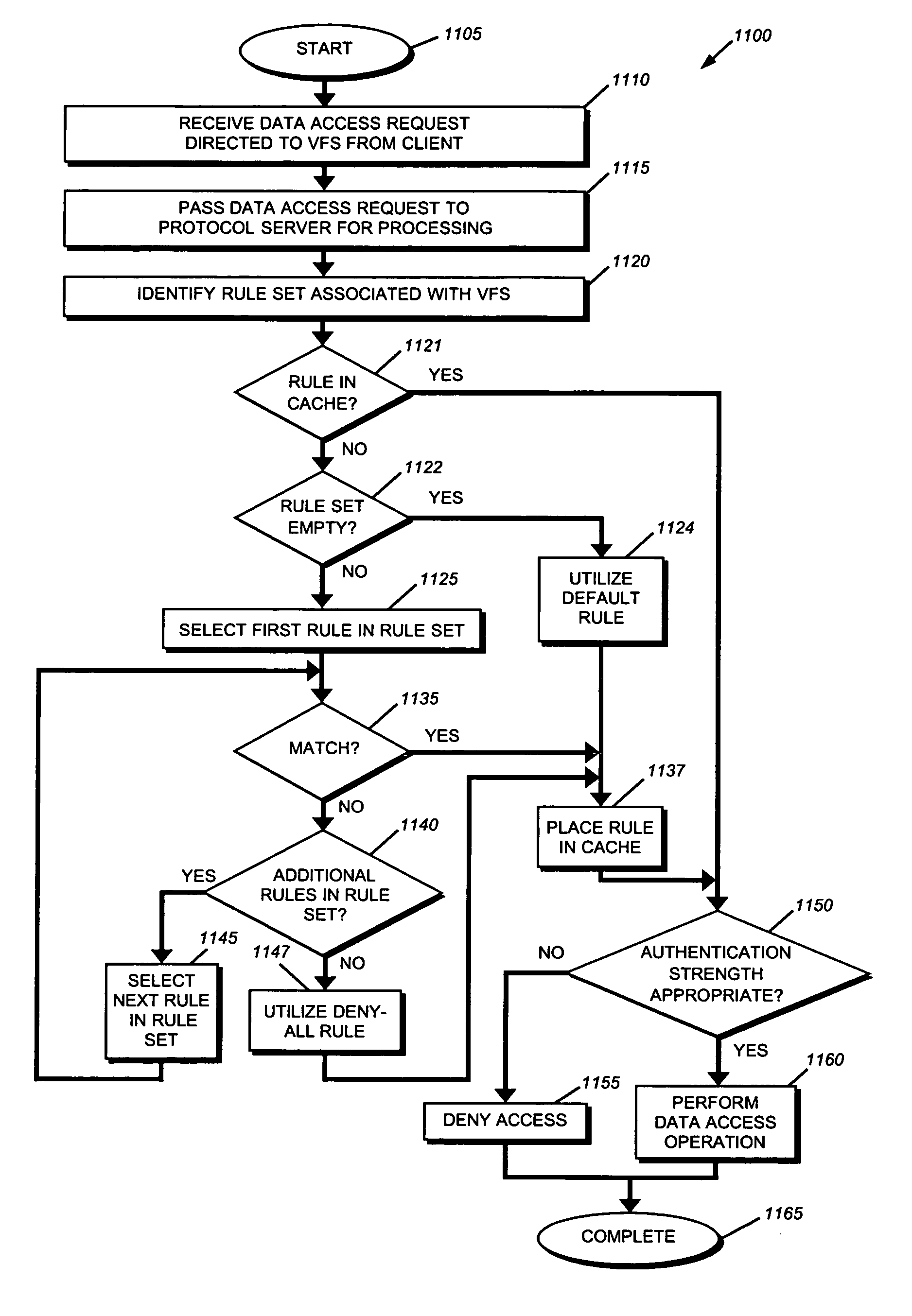
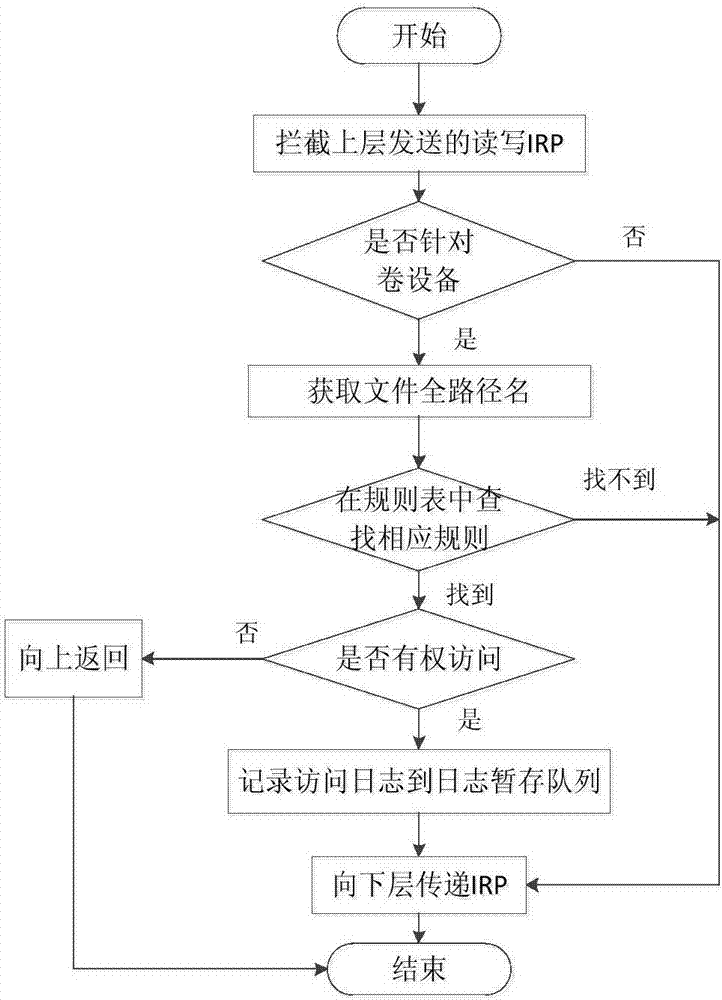
System and method for implementing access controls using file protocol rule sets
ActiveUS7707618B1Effective access controlOvercome disadvantagesDigital data processing detailsAnalogue secracy/subscription systemsVirtual file systemLimited access
A system and method for limiting access using file-level protocol rule sets. A rule set, comprising of an ordered set of rules, is associated with a virtual file system (VFS). When a data access request is received, the network address of the client originating the data access request is utilized to select a matching rule from the rule set for use in determining access to the VFS. The selected rule is then processed to determine if the data access request is permitted.
Owner:NETWORK APPLIANCE INC
Method and device for transmitting data unit in WLAN
ActiveUS20160337153A1Effective access controlImprove data throughputNetwork topologiesMulti-frequency code systemsTelecommunications
Owner:LG ELECTRONICS INC
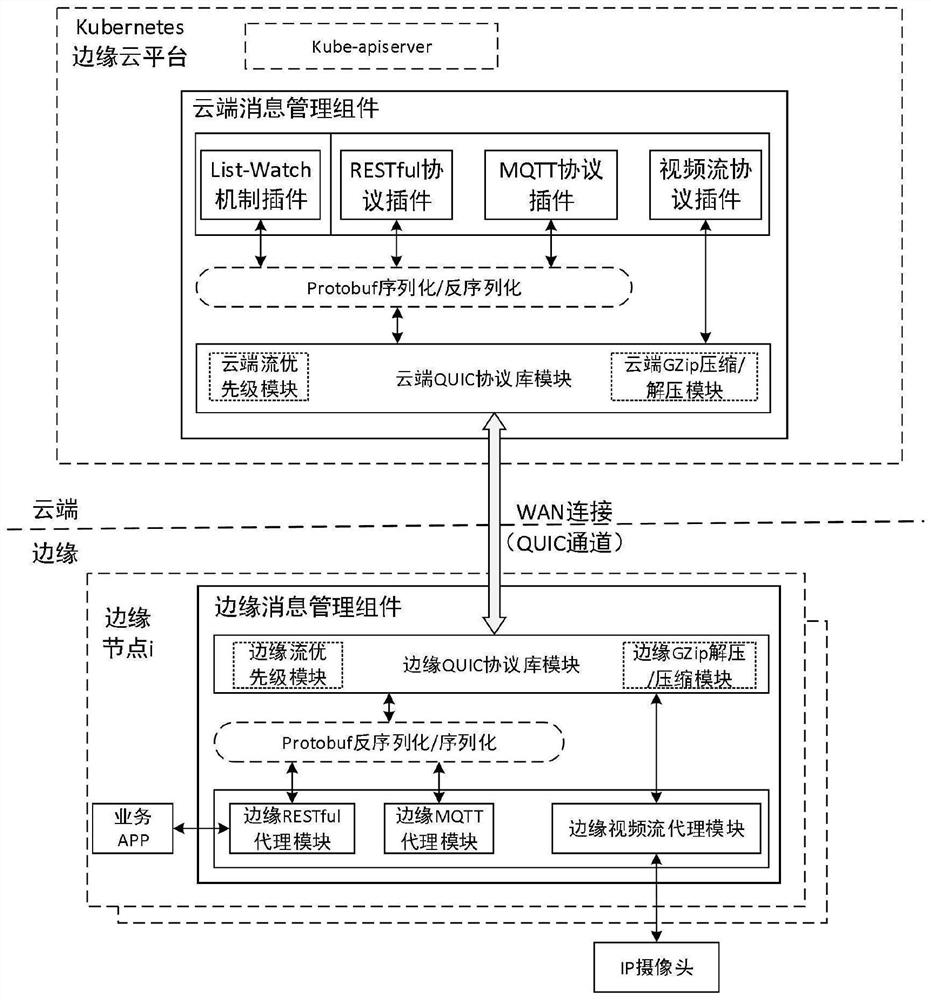
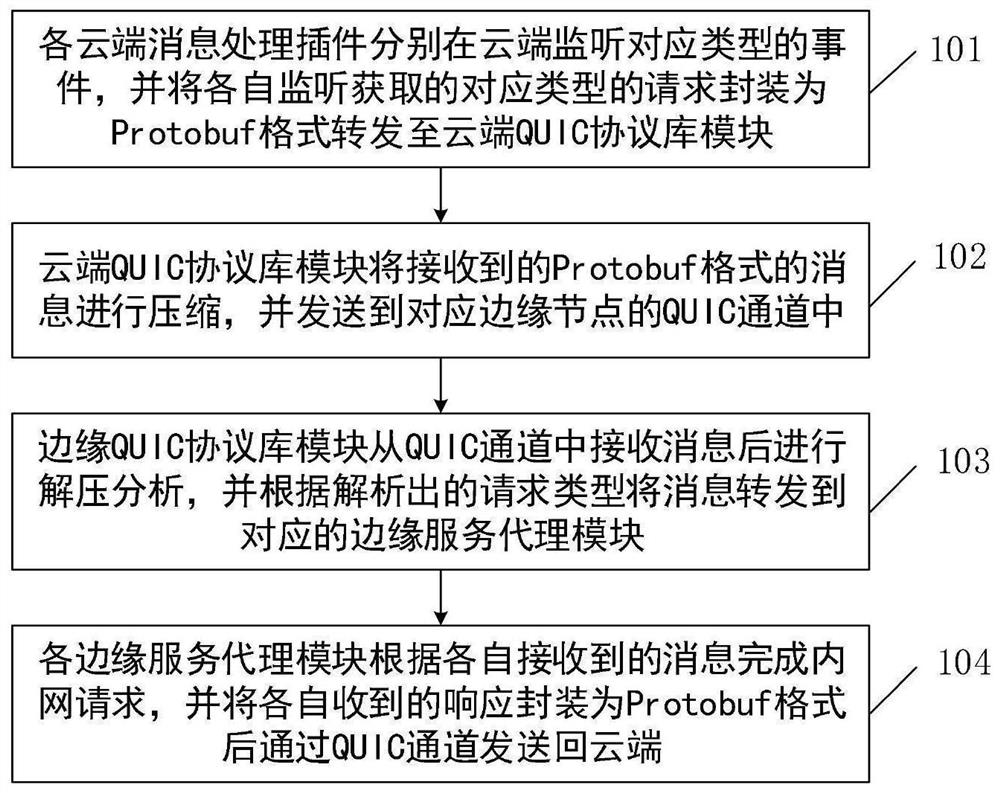
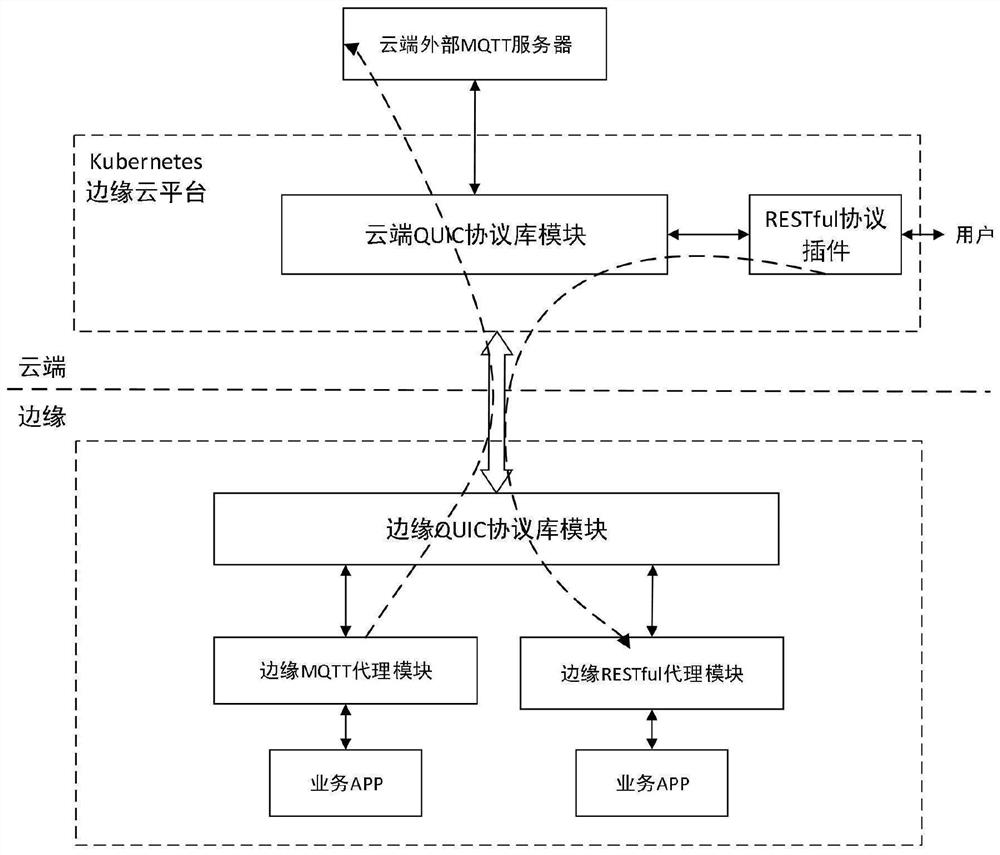
QUIC-based Kubernetes cloud side communication system and method thereof
ActiveCN112769938AImprove interaction efficiencySolve the isolation problemTransmissionHigh level techniquesCommunications systemMessage handling
The invention discloses a QUIC-based Kubernetes cloud side communication system and a method thereof, and the system comprises a cloud message management assembly and an edge message management assembly, the cloud message management assembly comprises a cloud QUIC protocol library module and a plurality of cloud message processing plug-ins, and the edge message management assembly comprises an edge QUIC protocol library module and a plurality of edge service agent modules; each cloud message processing plug-in packages a request monitored and obtained by the cloud message processing plug-in into a Protobuf format and forwards the request to a cloud QUIC protocol library module, and the cloud QUIC protocol library module sends the request to a corresponding QUIC channel; and the edge QUIC protocol library module receives the message from the QUIC channel, analyzes the message and forwards the message to the corresponding edge service agent module, the edge service agent module completes an intranet request and packages a response into a Protobuf format to be sent back to the cloud, and cloud unified scheduling management of a management plane and a service plane can be realized.
Owner:FENGHUO COMM SCI & TECH CO LTD
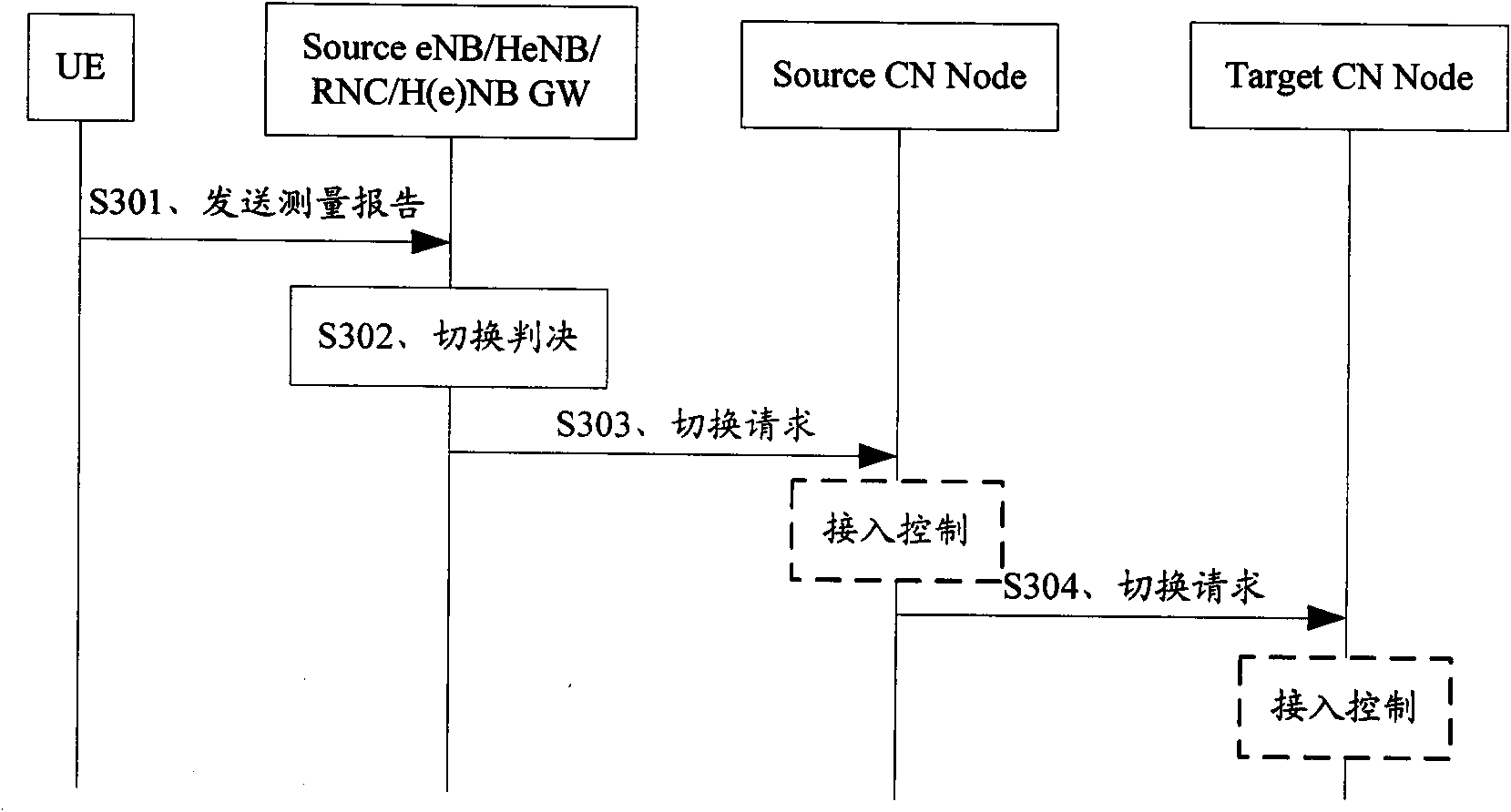
Access control method, access control device and terminal device
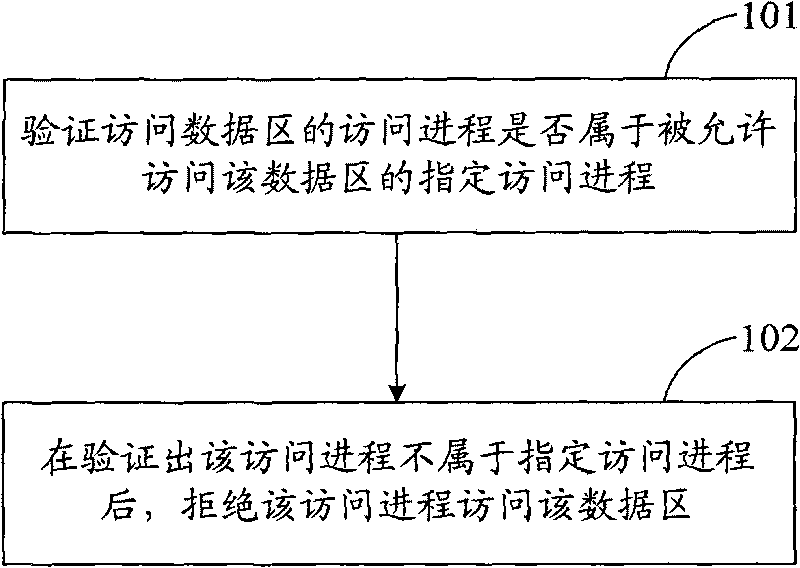
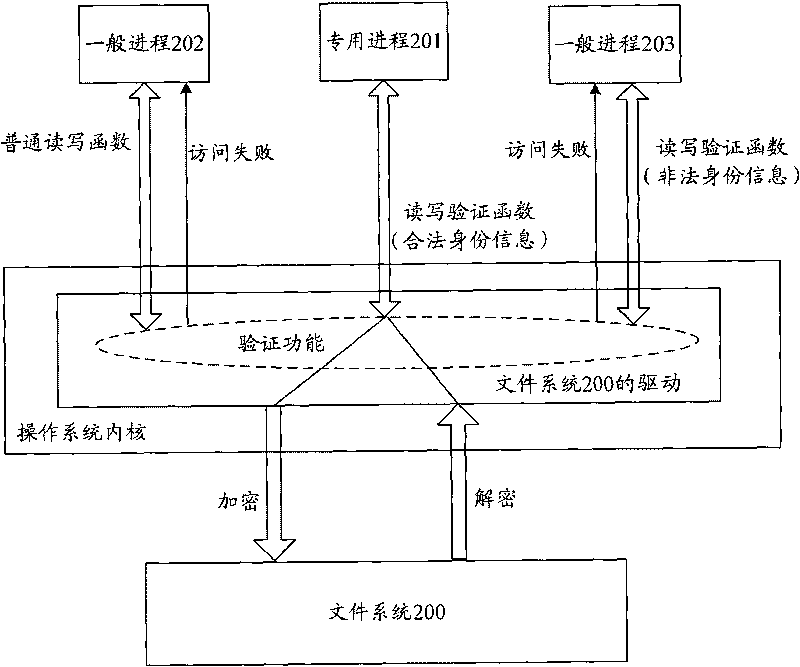
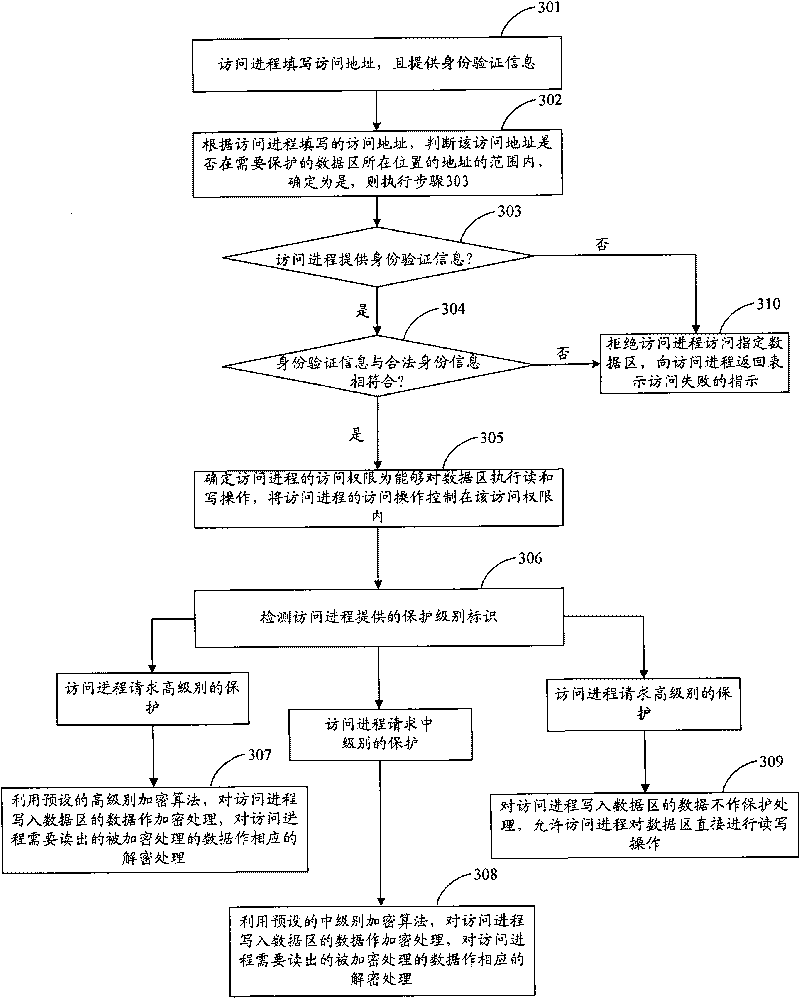
InactiveCN101739361AEffective access controlAccess controlUnauthorized memory use protectionTerminal equipmentAccess control
The implementation of the invention provides an access control method, an access control device and an accessing device. The method includes: whether the access process accessing data area is assigned to the designated access process of the data area allowed to be accessed is verified; the data area is used for storing data; and after the access process is verified not to be assigned to the designated access process, the access process is rejected to access the data area. The technical scheme provided by the implementation of the invention can effectively control the access of access process on data area, reject illegal access process to access the data area and effectively ensure the data of the data area to be safe.
Owner:LENOVO (BEIJING) CO LTD
Terminal, server side, and terminal access management method
ActiveCN105897696AEffective access controlImprove securityTransmissionComputer terminalAccess management
The invention discloses a terminal, a server side, and a terminal access management method. The method comprises: a terminal obtains a token form a server side, information including the token is packaged into an access request message, and then the access request message is sent to the server side; and after the server side receives the access request message, whether the terminal access is allowed is determined based on the access request message. With the method, a secure verification mechanism is provided and thus the server side can carry out effective access controlling on the terminal, so that security of push request connection access is improved.
Owner:NUBIA TECHNOLOGY CO LTD
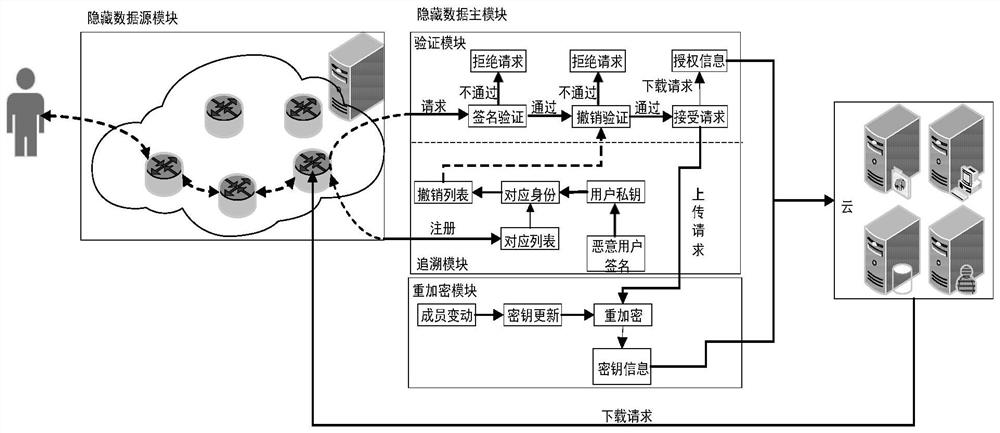
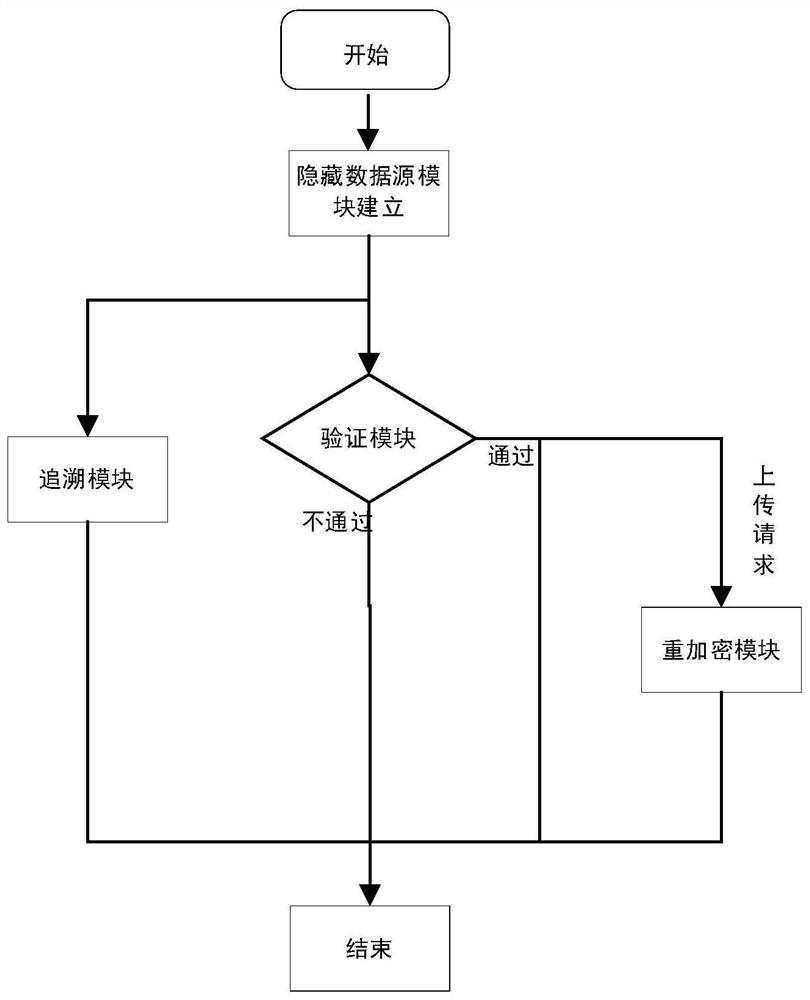
Anonymous data sharing method and system based on data source and data main hiding
ActiveCN111600875APrivacy protectionReduce overheadKey distribution for secure communicationIp addressData source
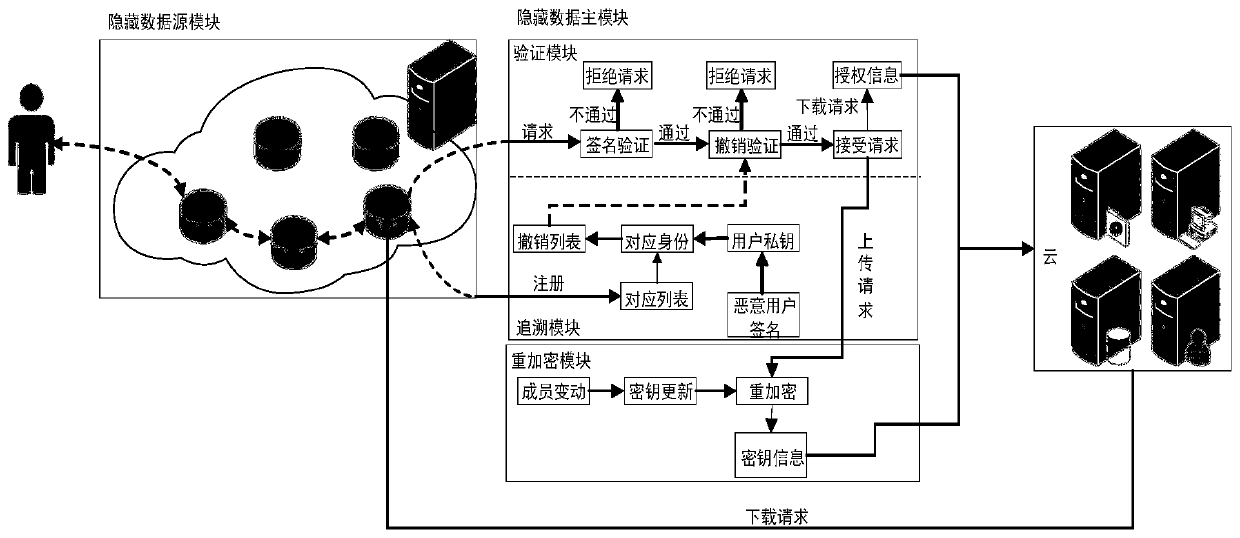
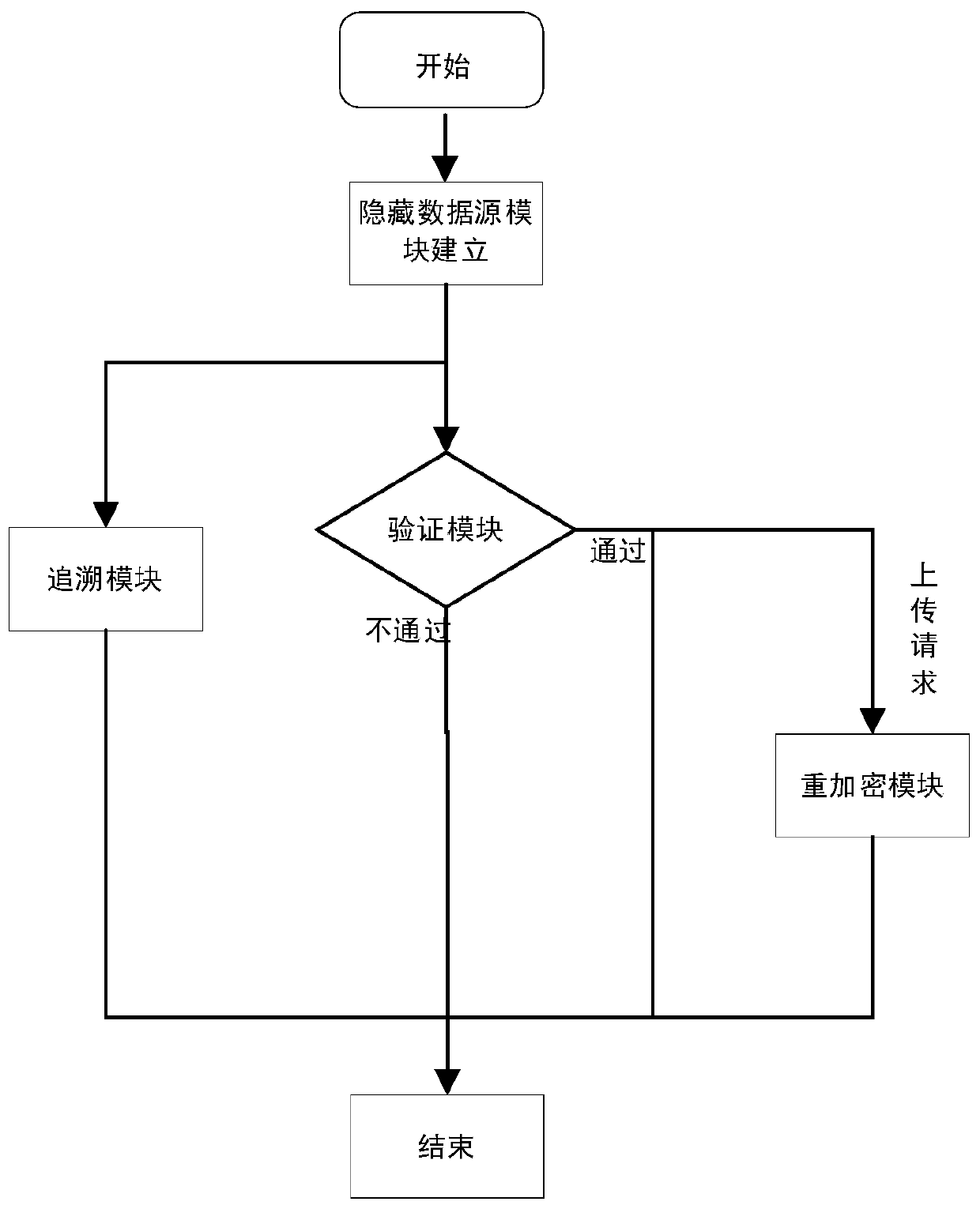
The invention discloses an anonymous data sharing method and system based on a data source and data main hiding. In the stages of registration and request initiating, effective access control is achieved through group signature, anonymous authentication is completed to protect user identity privacy, and meanwhile the problem that the user identity is associated due to leakage of the user IP address is solved by hiding the user IP address through onion routing. In the file uploading stage, the group administrator re-encrypts the uploaded file by using a re-encryption technology and generates key information; in the file downloading stage, after revocation verification and signature verification are completed, a group administrator generates authorization information for a user, so that theuser can obtain a decryption and re-encryption key from key information, and the forward security of the scheme is ensured; and in the group dynamic stage, the group administrator performs key updating and updates encryption of the cloud file, so that the expenditure of the user side is greatly reduced.
Owner:JIANGSU UNIV
Permission determination method and device for storage cluster, equipment and storage medium
ActiveCN110909379AAvoid abuseEffective access controlDigital data protectionEngineeringAuthority control
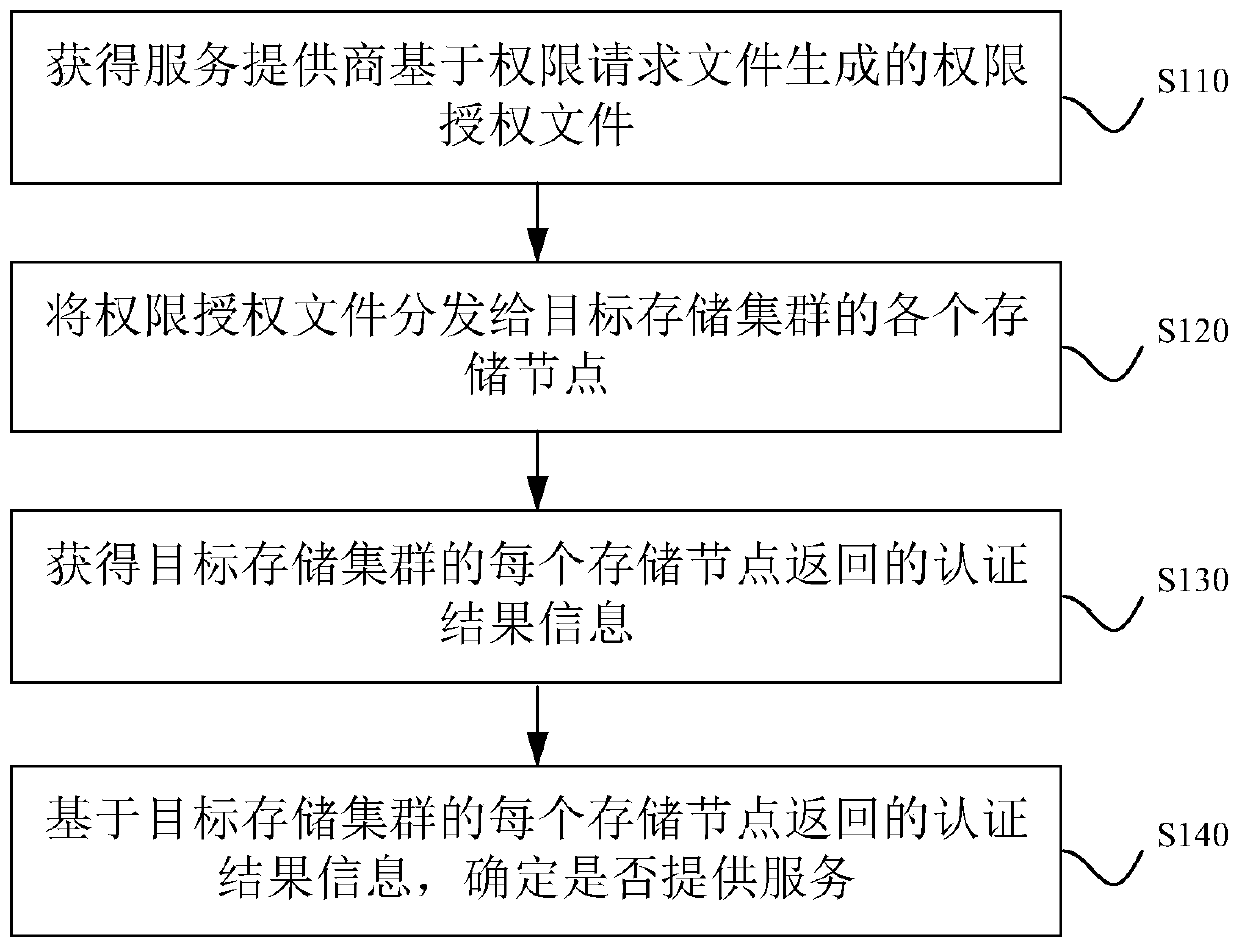
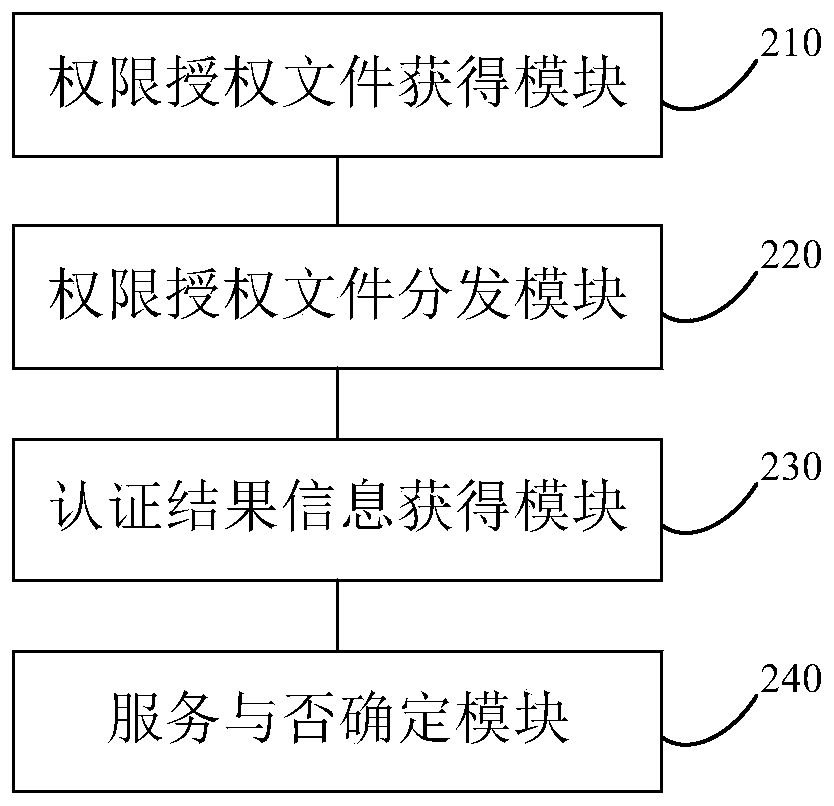
The invention discloses a permission determination method for a storage cluster, and the method comprises the following steps: obtaining a permission authorization file generated by a service providerbased on a permission request file, the permission authorization file comprising a cluster identifier of an authorized storage cluster and a node identifier of each storage node in the authorized storage cluster; distributing the authority authorization file to each storage node of the target storage cluster; obtaining authentication result information returned by each storage node of the targetstorage cluster, wherein the authentication result information is information that each storage node of the target storage cluster determines whether authentication is passed or not according to a cluster identifier and a node identifier contained in the authority authorization file; and determining whether to provide a service based on the authentication result information. By applying the technical scheme provided by the embodiment of the invention, authority control can be effectively carried out, and authority abuse is avoided. The invention furthermore discloses a storage cluster permission determination device, storage cluster permission determination equipment and a storage medium, which have corresponding technical effects.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
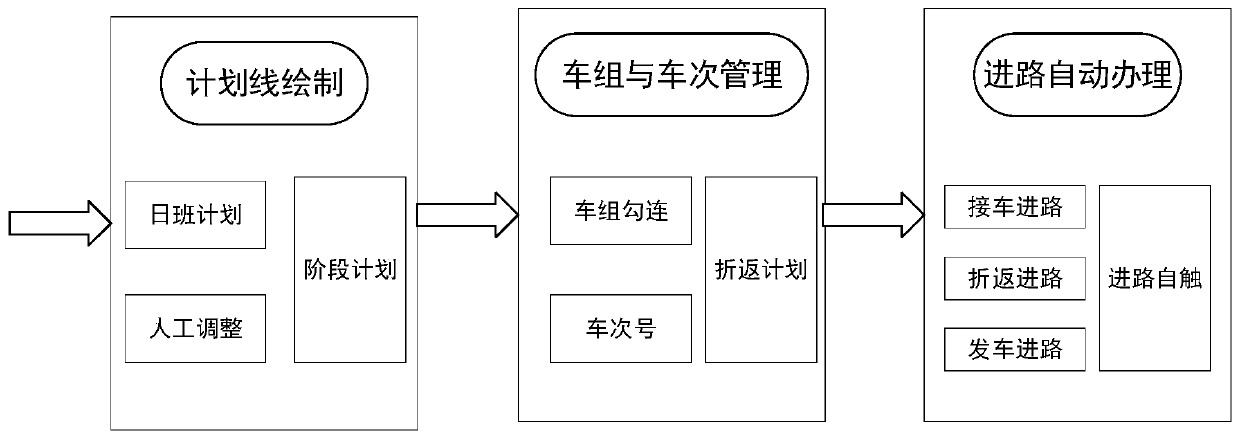
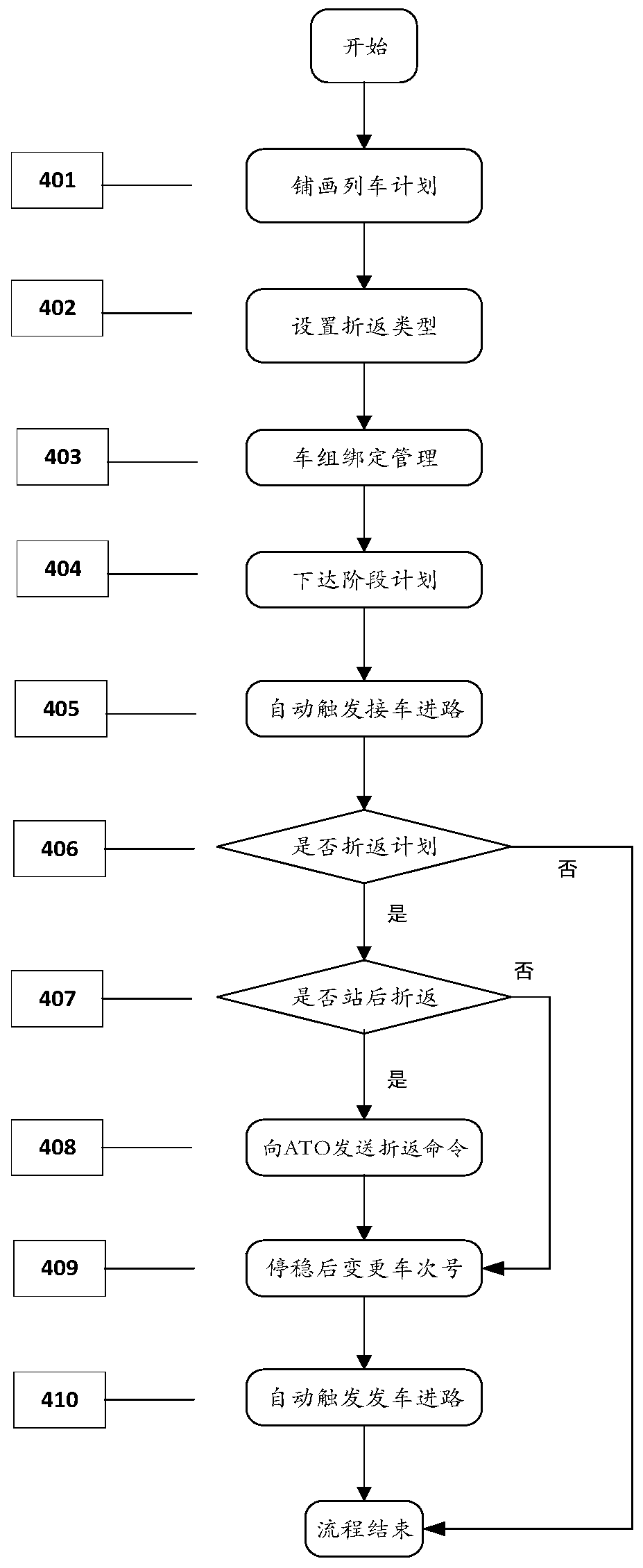
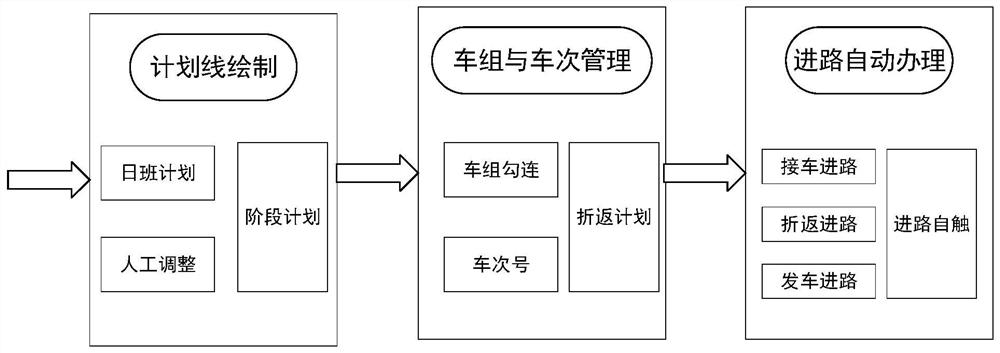
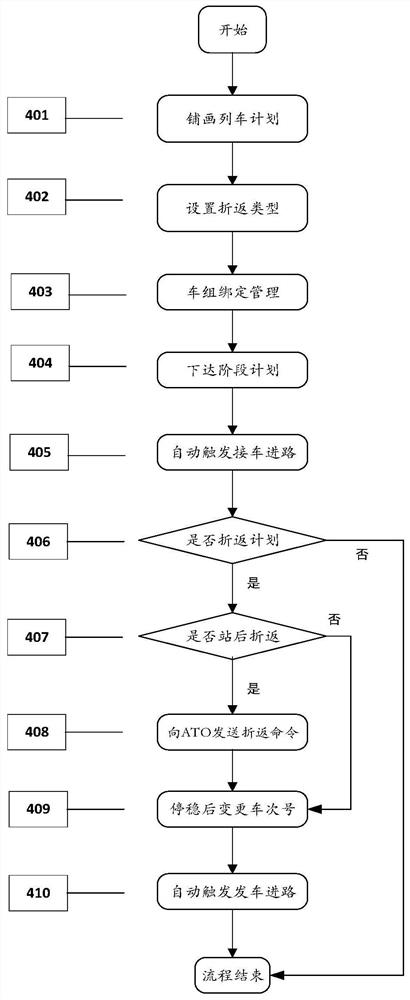
CTC route control method for automatic inter-city railway reentry operation
The invention relates to a CTC route control method for automatic inter-city railway reentry operation. The CTC route control method comprises the steps that firstly train set binding management is performed on a train operation plan line in which reentry operation occurs in a prepared adjustment plan, a hooking relationship is formed and then transmitted to train station equipment, and the station equipment automatically changes the number of a reentry train according to the received hooking relationship in combination with the type of the reentry operation, and automatically triggers the route of the reentry train. Compared with the prior art, the CTC route control method has the advantages of reducing the workload of manual intervention, improving the degree of automation of the systemand the like.
Owner:CASCO SIGNAL
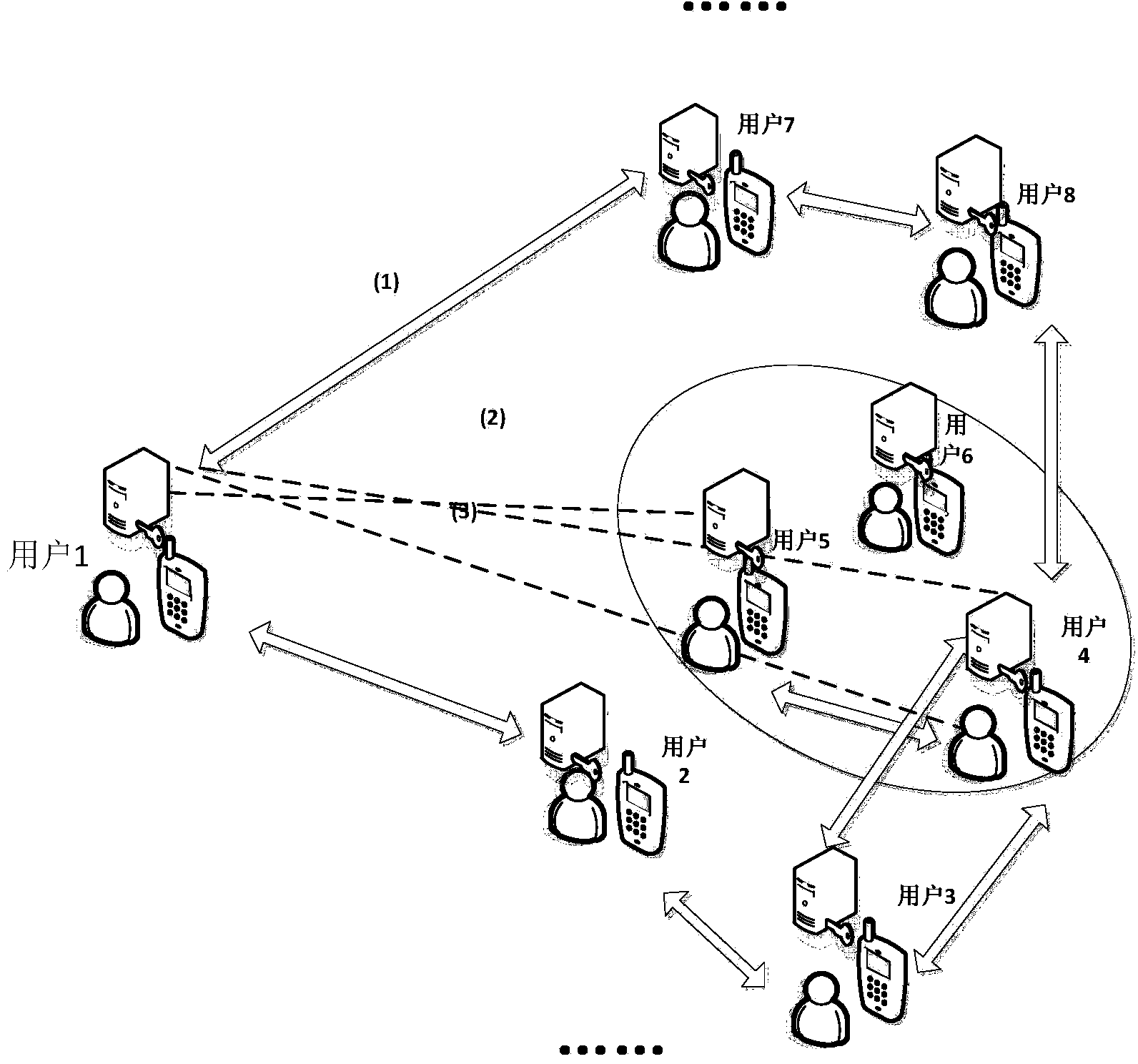
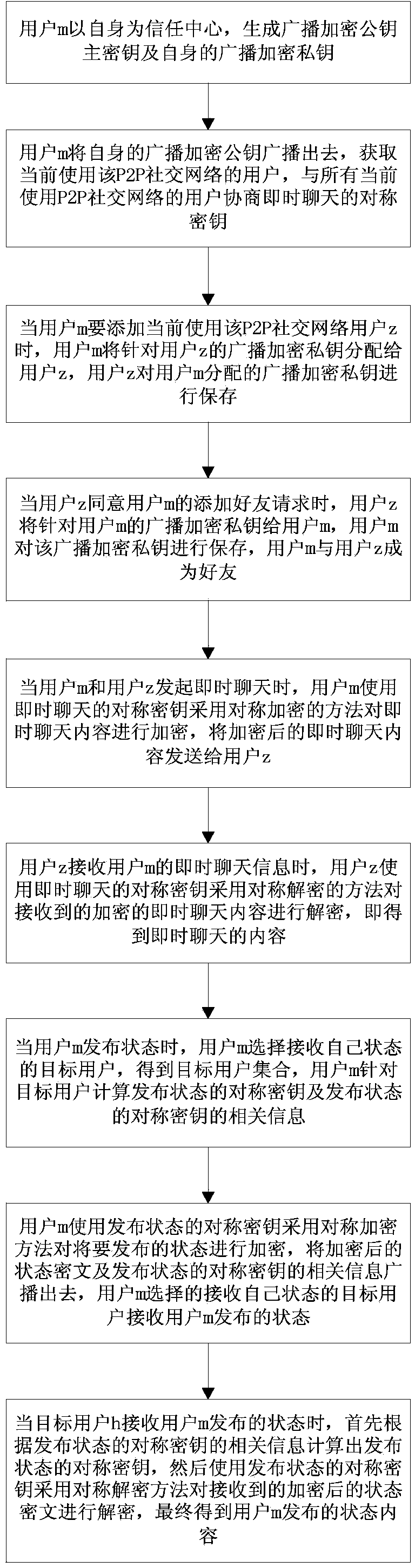
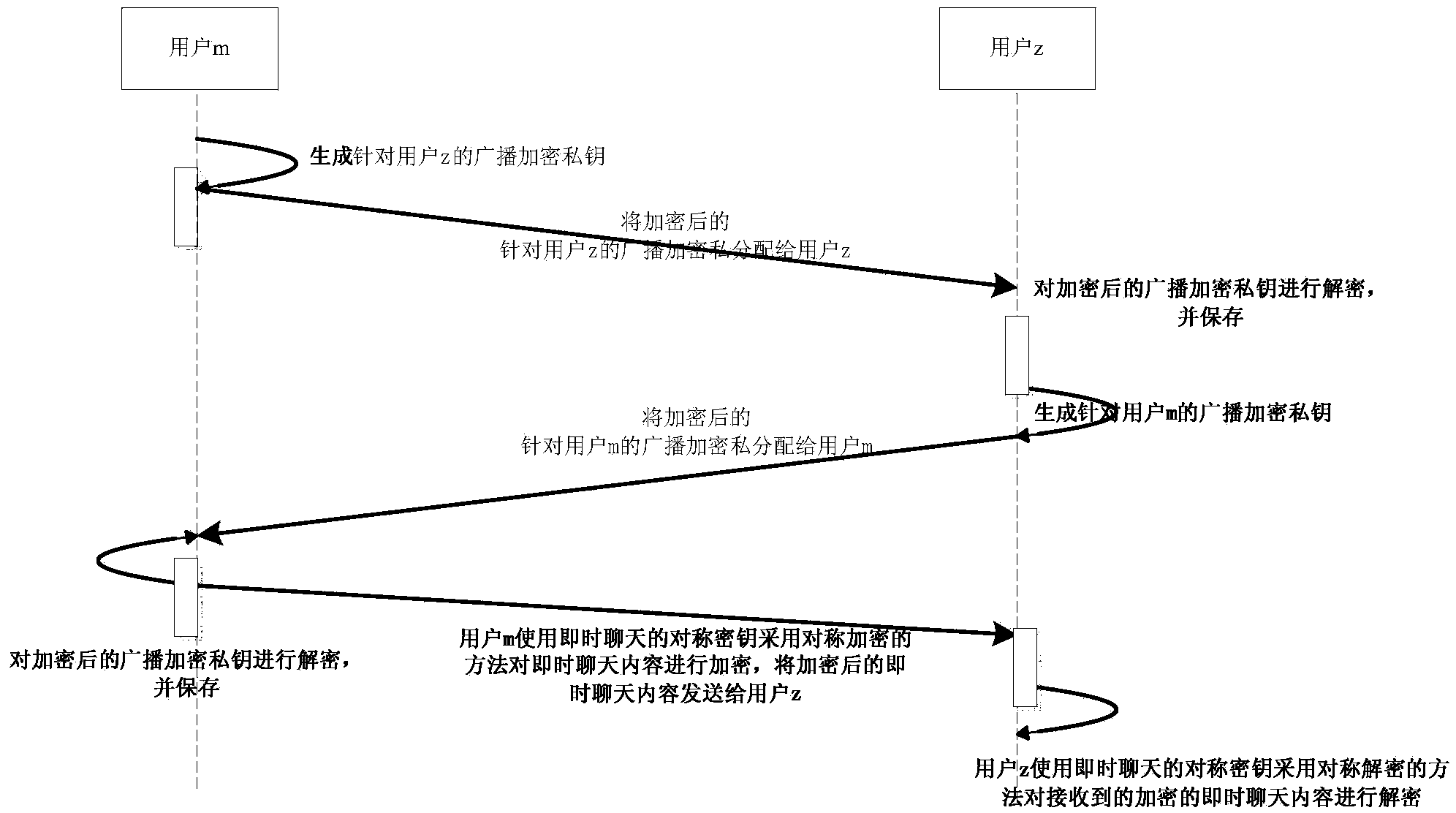
Privacy protection system and method used for P2P social network and based on broadcast encryption
ActiveCN104301327AEffective access controlReduce transfer volumeTransmissionPrivacy protectionInformation transfer
The invention relates to a privacy protection system and method used for a P2P social network and based on broadcast encryption. The system comprises a key agreement module, a symmetrical encryption communication module and an encryption and decryption module for broadcast encryption. The key agreement module is used for conducting key agreement when instant chats are established between users in the current P2P social network and other users. The symmetrical encryption communication module is used for encrypting and decrypting broadcast encryption private keys when the users in the current P2P social network add friends and encrypting and decrypting sent instant chat information in the instant chat process. The encryption and decryption module for broadcast encryption is used for selecting the users receiving the state when the users in the current P2P social network issue the state and broadcasting the encrypted issued state, and the users receiving the state receive the information through decryption. On the basis of the P2P social network, effective access control over the social network is achieved, the information transmission amount in the social network is reduced, and the safety of user information is enhanced.
Owner:NORTHEASTERN UNIV
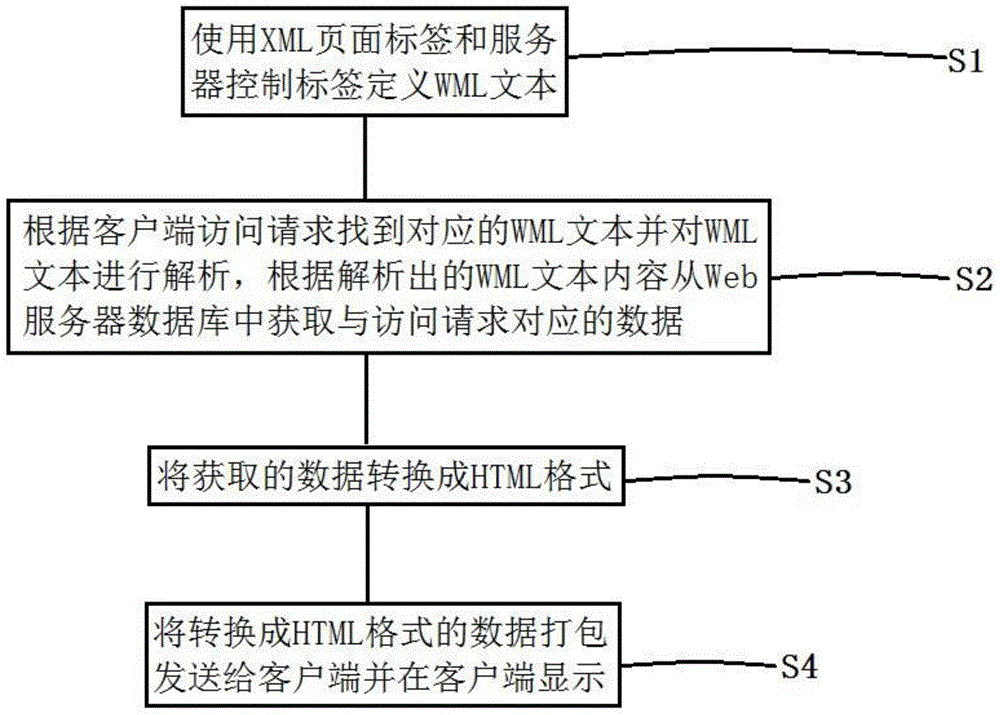
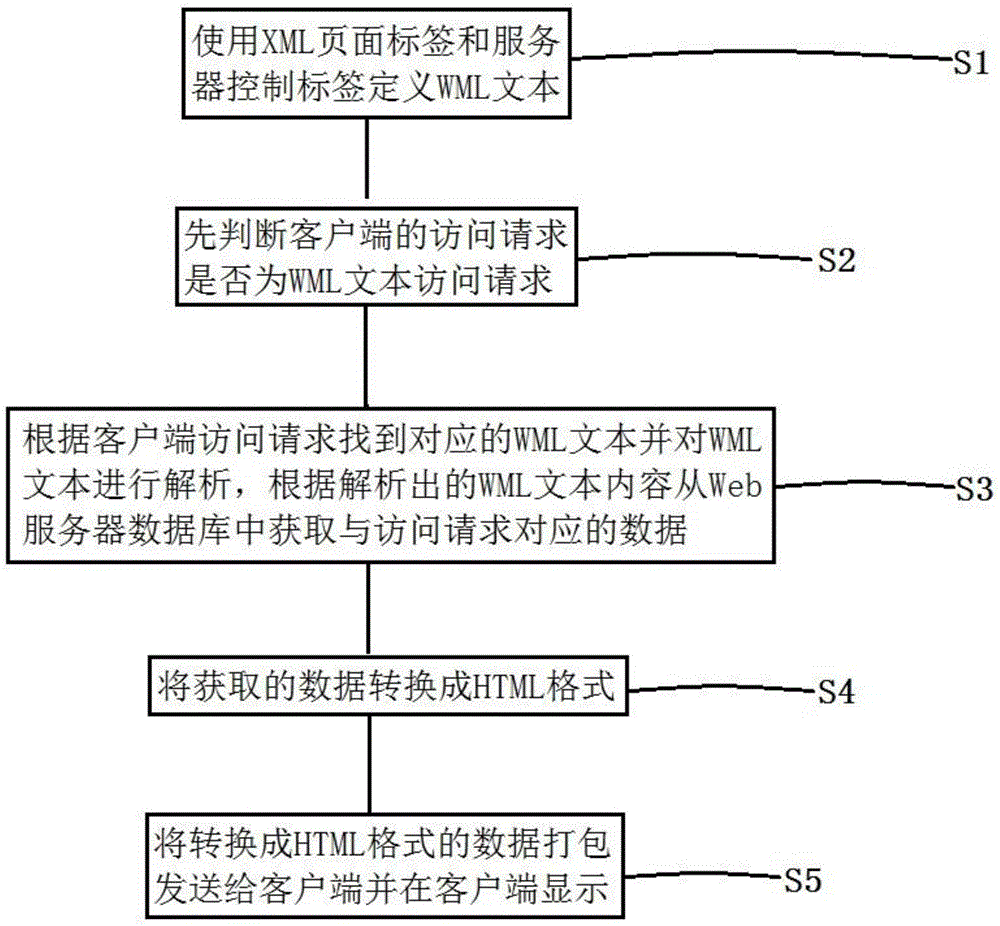
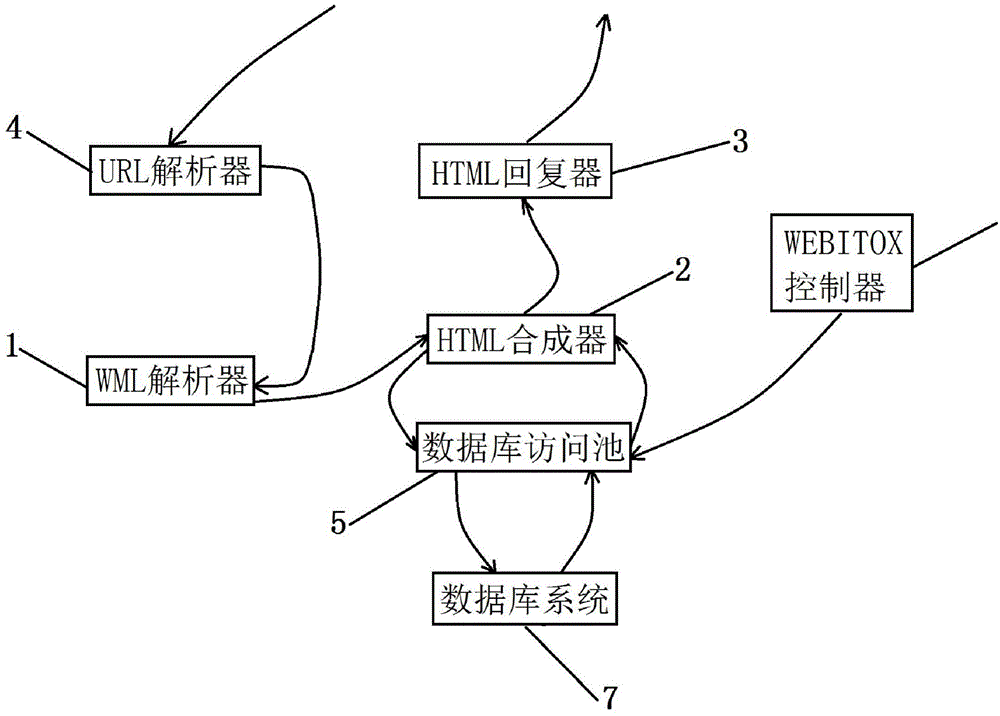
Web page data generation method, WEBITOX server and Web application system
ActiveCN105989010AAchieve seamless connectionSimplify the development processSpecial data processing applicationsWeb applicationWeb service
The invention discloses a Web page data generation method, a WEBITOX server and a Web application system. The method comprises following steps: using an XML page label and the server to control a label-defined WML text; finding a corresponding WML text according to the access requirement of a client and analyzing the WML text and obtaining data corresponding to the access requirement from a Web server database according to the analyzed WMML text content; converting obtained data into an HTML format; and packaging data in the HTML format to send it to the client and display data in the client. The invention further provides the Web server and the Web application system. The Web page data generation method, the Web server and the Web application system provided by the invention have following beneficial effects: seamless connection between the database and the Web server is achieved; development and management of the application system for the database are simplified such that a company can easily transplant applications to the WEB server; access and release of shared data and exclusive data can be effectively controlled and performance of the system is improved and convenience of data access is enhanced.
Owner:上海飞维信息技术有限公司
Controllable information access storage device, information access control method and information protection method
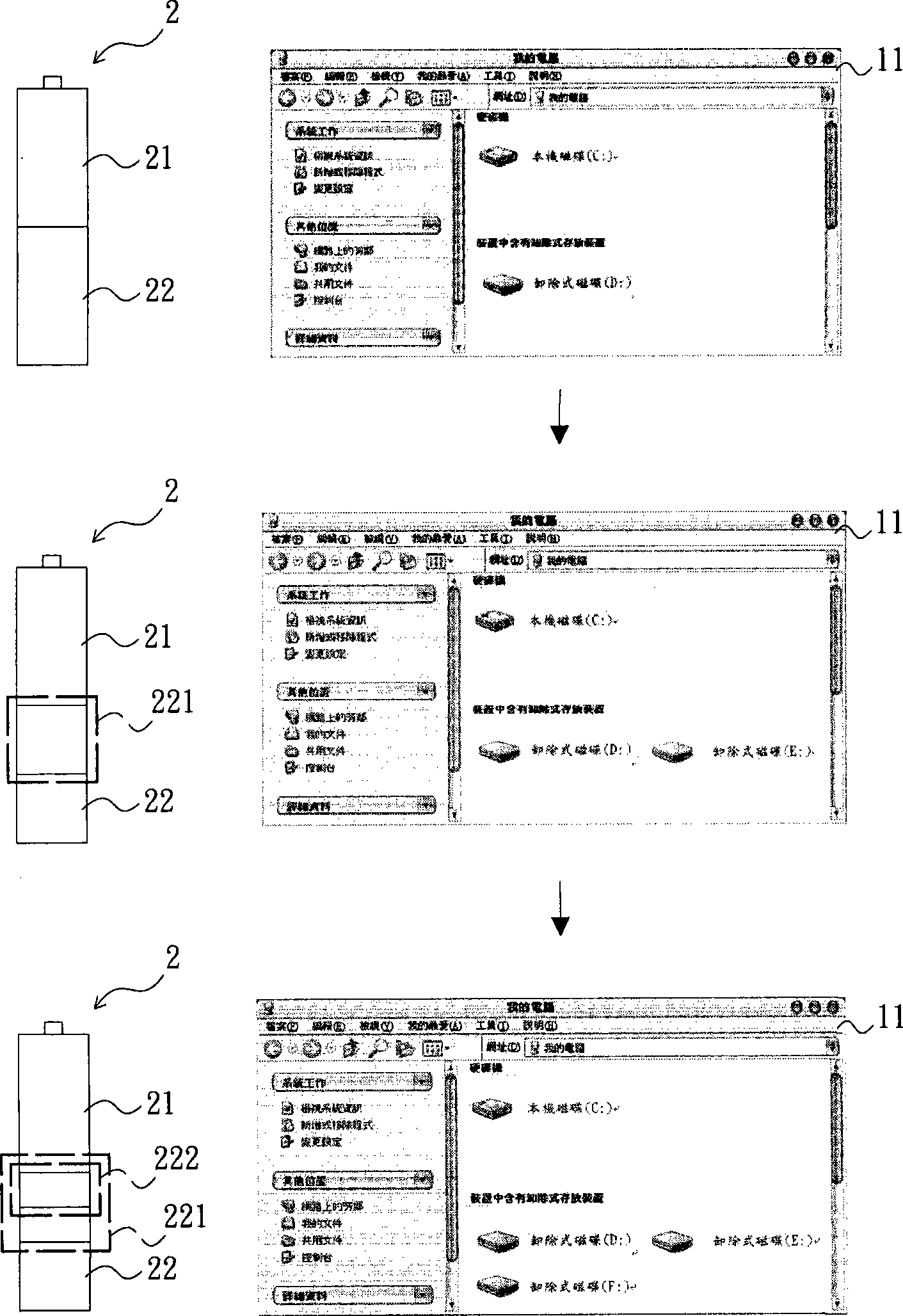
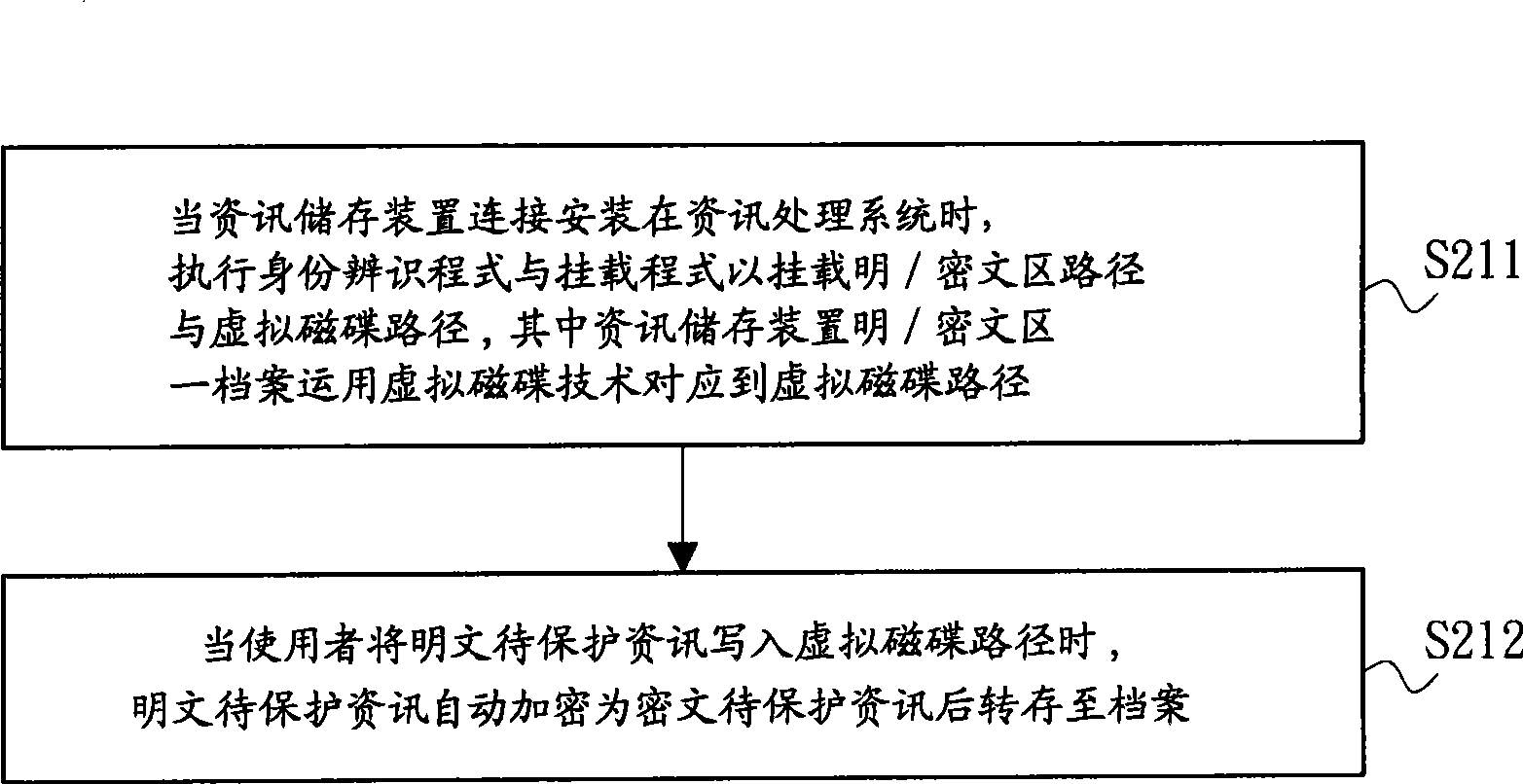
ActiveCN101499038AImplement protection mechanismEffective access controlUnauthorized memory use protectionInternal/peripheral component protectionPlaintextInformation processing
The invention relates to a controllable access information storage device, an information access control method and an information protection method. The controllable access information storage device has a program area and a hidden area. A file in a plaintext / cryptograph area of the hidden area is corresponded to a virtual disc path by a virtual disc technology. When the information storage device is mounted to an information processing system and executes an identity identification and loading program, the plaintext / cryptograph area path and the virtual disc path are loaded via correct verification and execution result. The plaintext protection information is automatically encrypted to cryptograph protection information when written to the virtual disc path and then uploaded to the file. Operation of the user to the virtual disc path is operation of the file substantially. Therefore, propose and function of securing and managing the confidentiality of the file.
Owner:FINEART TECH CO LTD
Acquiring method and equipment of ACL (Allowable Closed Subscriber Group List)
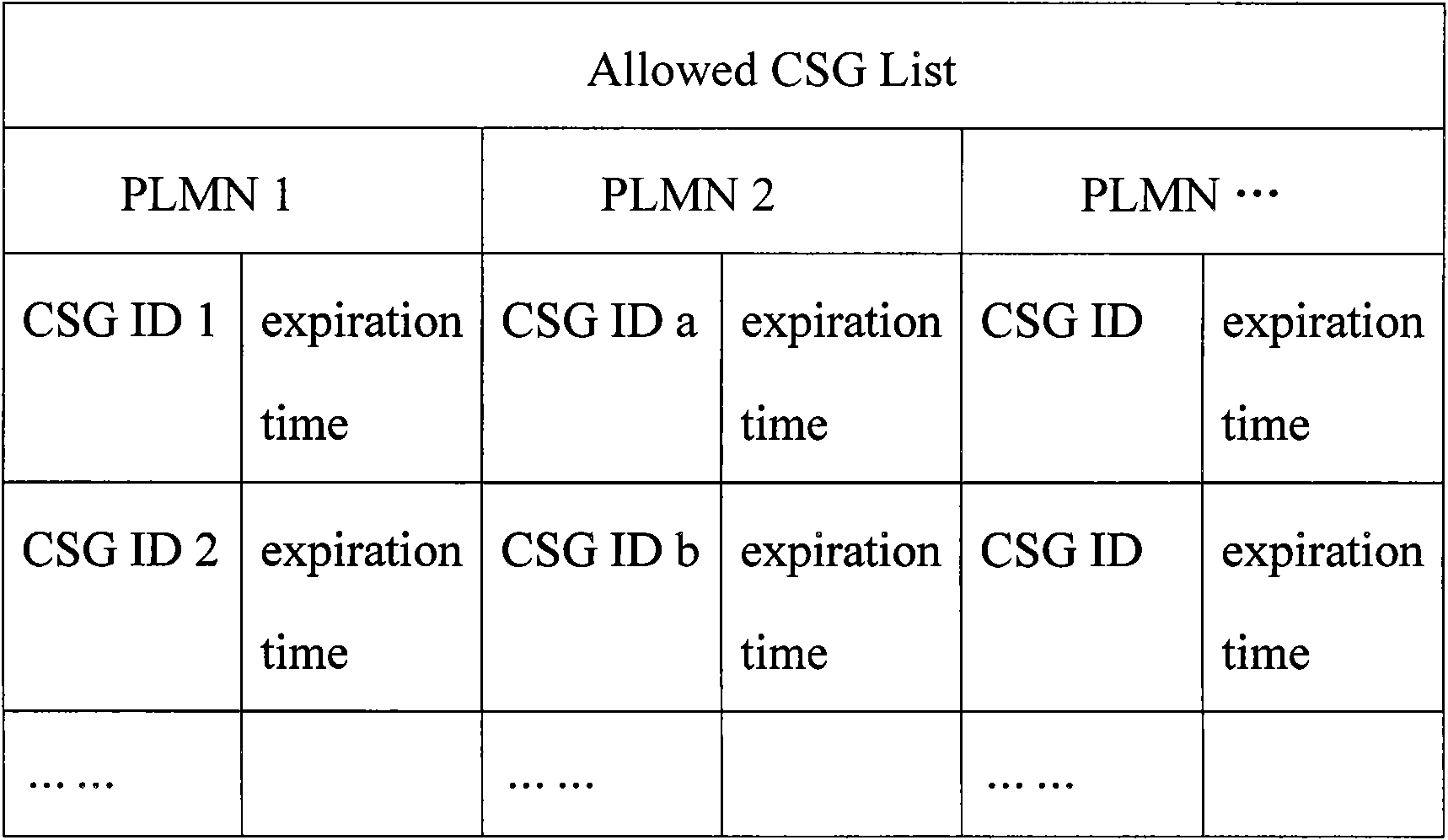
ActiveCN101938733AEffective access controlImprove the efficiency of access managementAssess restrictionNetwork data managementNODALTelecommunications
The invention discloses an acquiring method and equipment of an ACL (Allowable Closed Subscriber Group List). The acquiring method of the ACL comprises the following steps of: sending an ACL request message containing PLMN (Public Land Mobile Network) identifying information to network equipment storing the ACL by a network node carrying out access control in a current network system; and receiving an ACL response message sent by the network equipment by the network node, wherein the ACL response message contains the ACL of a destination PLMN which corresponds to the PLMN identifying information. In the invention, the network node can acquire the ACL of the corresponding destination PLMN, thereby effectively carrying out the access control of a subscriber, enhancing the efficiency of the access management of the subscriber and ensuring the safety of the network system.
Owner:DATANG MOBILE COMM EQUIP CO LTD
An auditing and playback system for an https/http protocol
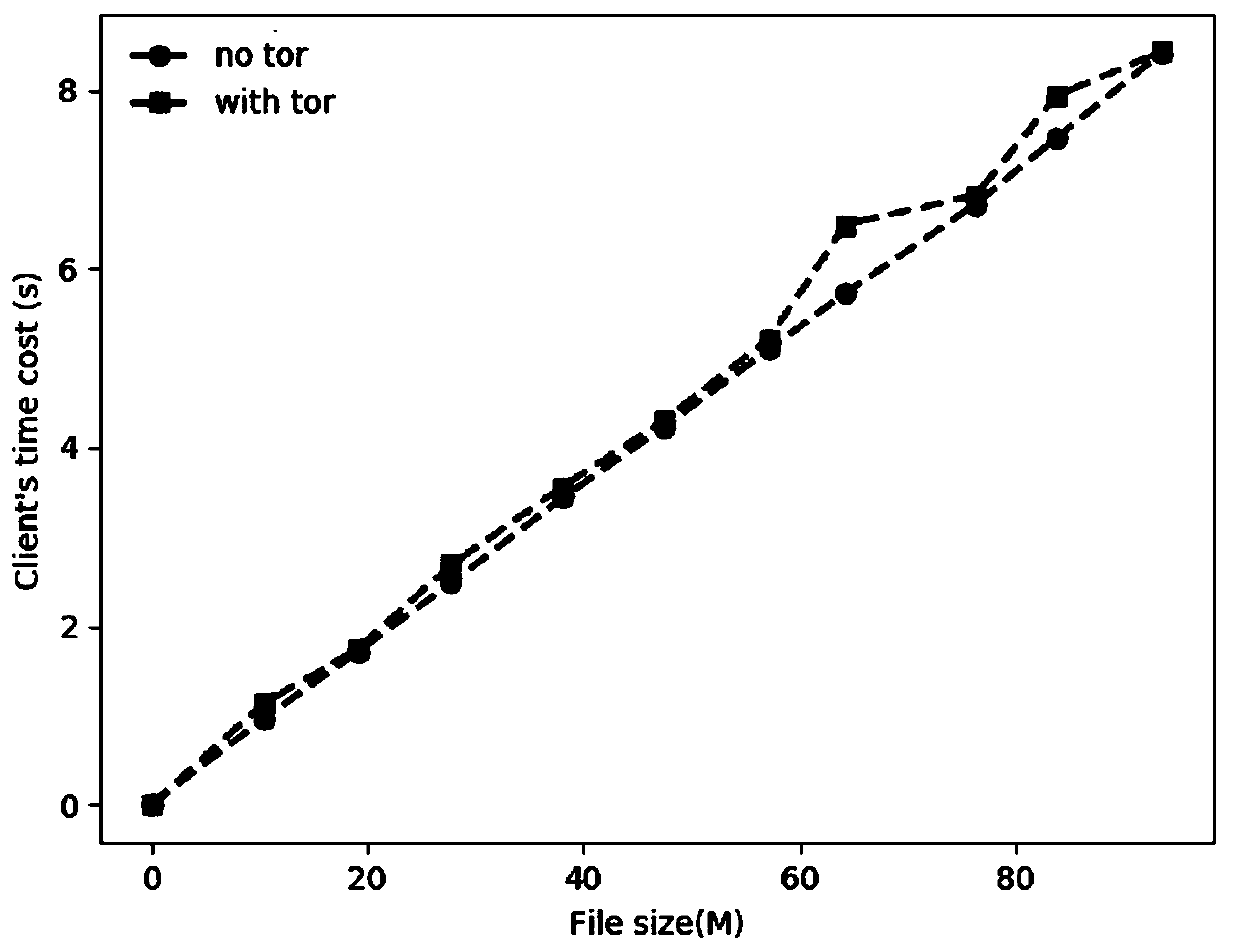
InactiveCN109743302AEffective access controlDetailed Visual AuditTransmissionReverse proxyClient-side
The invention discloses an auditing and playback system of an https / http protocol. The auditing and playback system comprises an https / http proxy unit, and the https / http proxy unit comprises a connection forwarding module which supports at least a forward proxy mode and a reverse proxy mode and is used for establishing connection between a client and a server and forwarding a request of the client to the server through an http / https proxy; The data recording module which is used for storing and recording the url address which is visited by the client side and passes through the http / https agency and the request and response message data of the http returned by the response; And the auditing and playback module which is used for loading the response html and the resource file returned by the server corresponding to the url address from the file of the storage record according to the url address of the storage record so as to play back and display a real page accessed by the client previously, thereby realizing the visual auditing of the access of the client. According to the invention, a user does not need to additionally install client software, so that the user experience is greatly improved.
Owner:中电福富信息科技有限公司
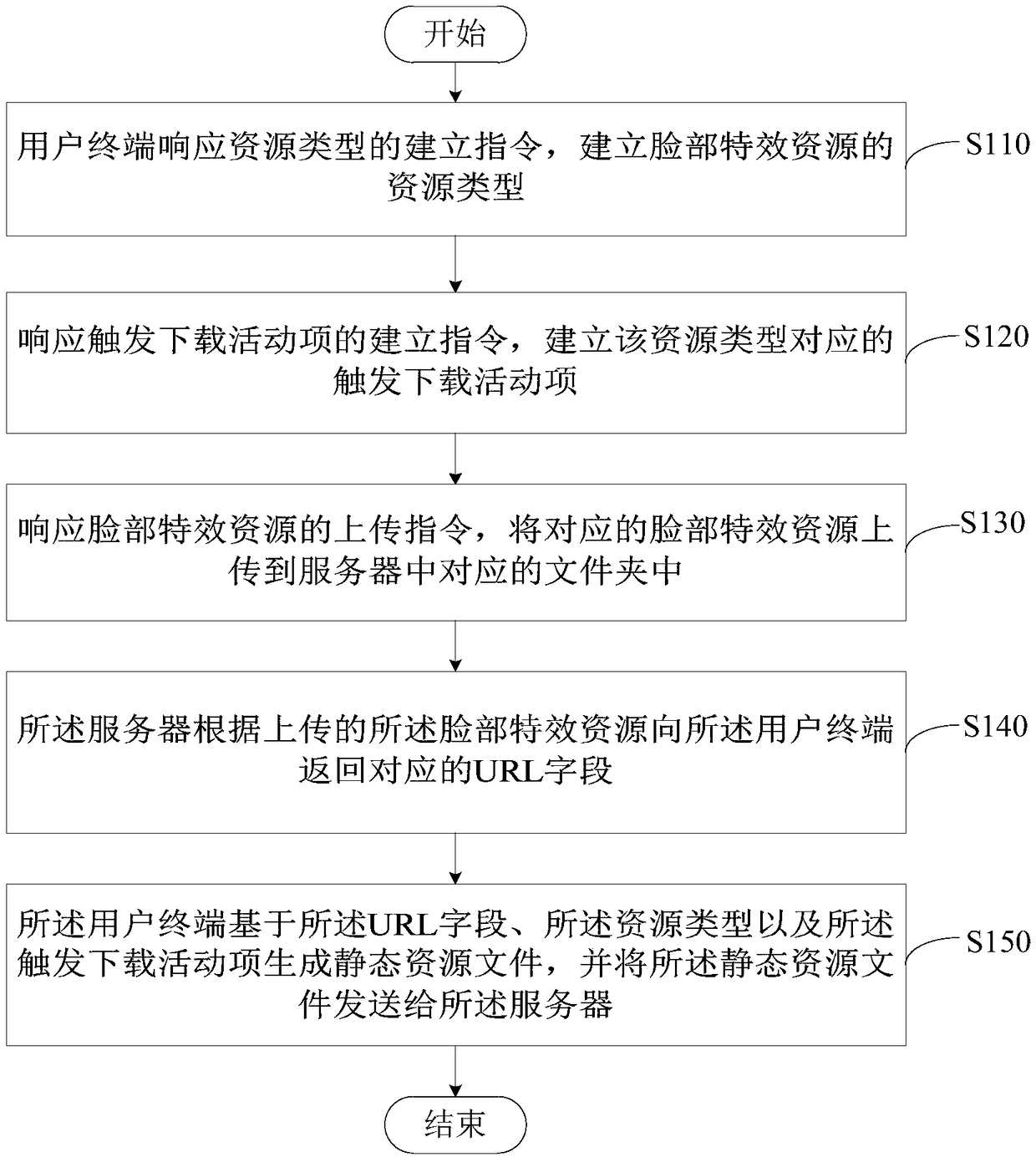
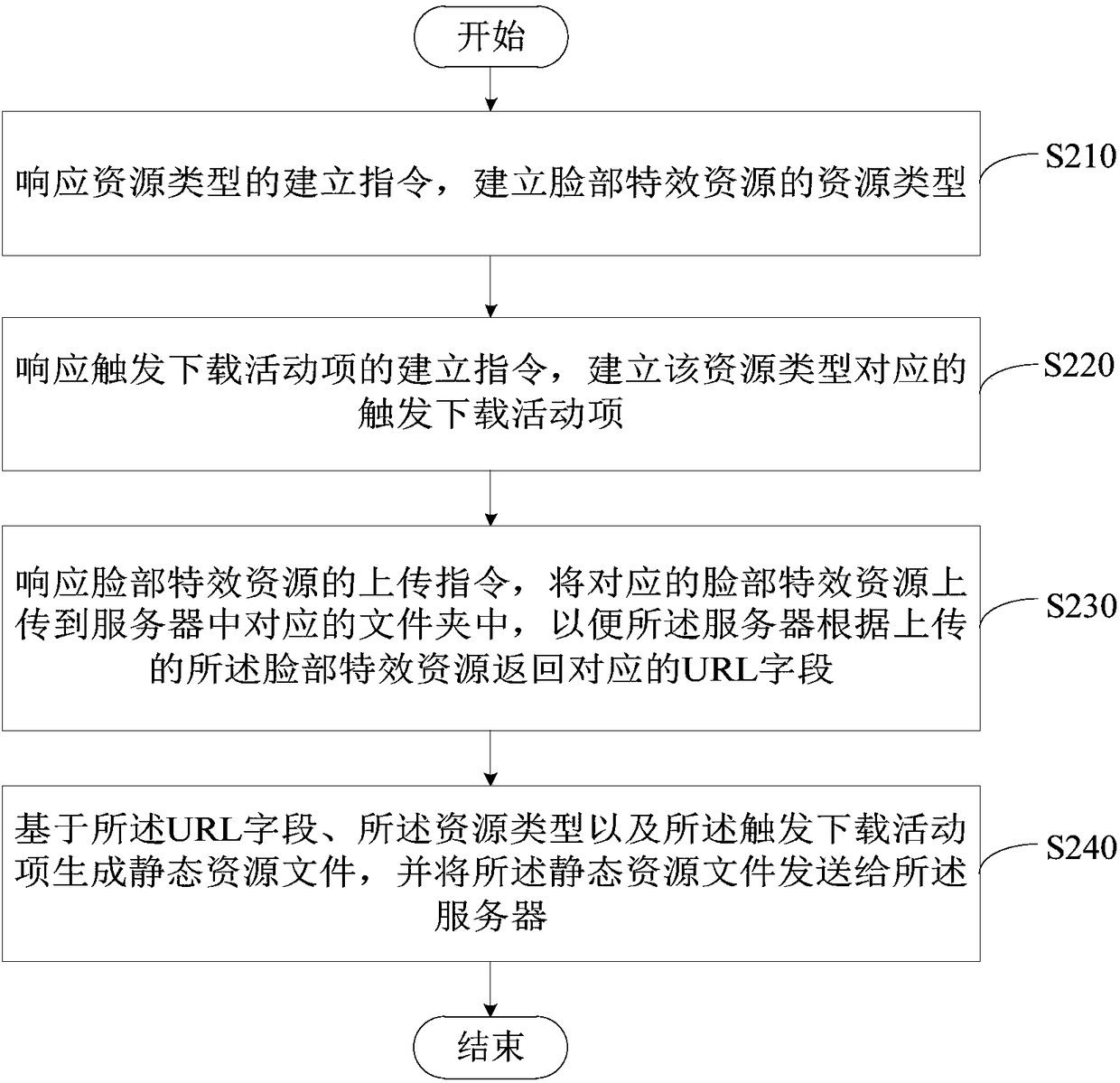
Method, device and system for generating facial effect resource, and readable storage medium
ActiveCN108418890AReduce trafficEffective access controlTelevision system detailsColor television detailsTraffic volumeSpecial effects
Embodiments of the invention provide a method, a device and a system for generating a facial effect resource, and a readable storage medium. The method comprises the following steps of: establishing aresource type of the facial effect resource by a user terminal in response to an establishment instruction of the resource type; establishing a trigger download activity item corresponding to the resource type in response to the establishment instruction of the trigger download activity item; uploading the corresponding facial effect resource to the corresponding folder in the server in responseto an upload instruction of the facial effect resource; returning a corresponding URL field to the user terminal according to the uploaded facial effect resource by the server; and, by the user terminal, generating a static resource file based on the URL field, the resource type and the trigger download activity item, and sending the static resource file to the server. Therefore, the traffic access can be effectively controlled during the peak traffic period, and the facial effect resources can be provided in a static manner, which can reduce the access traffic of the server and effectively provide the facial special effects resources used by the mobile terminal.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
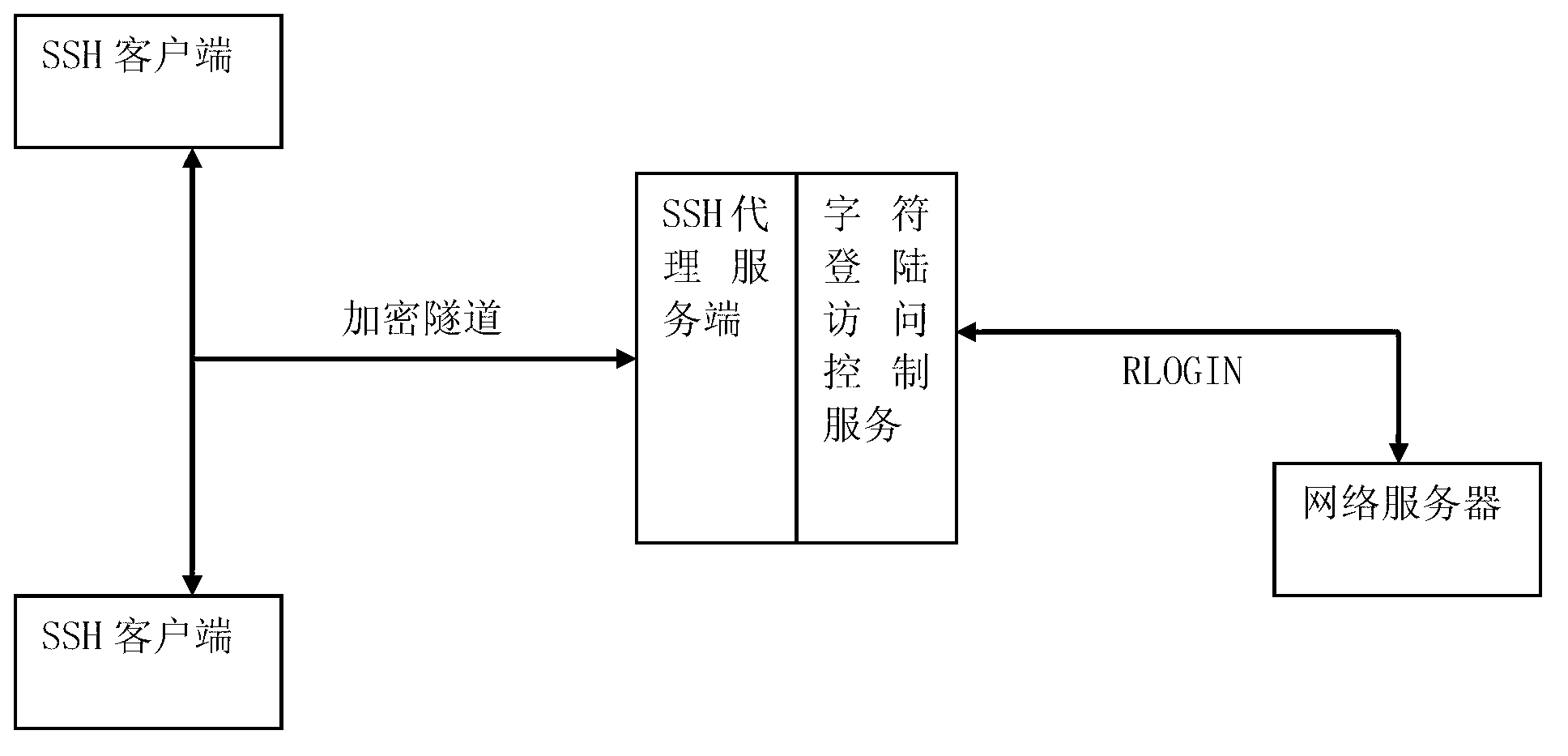
Safety accessing system and safety accessing method for character terminal RLOGIN protocol
InactiveCN103237061AEnsure safetyProtect equipment investmentSecuring communicationProtocol for Carrying Authentication for Network AccessProxy service
The invention belongs to the technical field of computer network security, and discloses a safety accessing system and a safety accessing method for a character terminal RLOGIN protocol. The safety accessing system for the character terminal RLOGIN protocol comprises an SSH (secure shell) agency service terminal and a character login access control service terminal, wherein the SSH agency service terminal is used for SSH connection from client sides to login an internal network, verifying identifications and selecting equipment requiring to be accessed, and the character login access control service terminal is used for connecting an RLOGIN protocol to a selected UNIX / LINUX server, converting data between encrypted data and unencrypted data, simultaneously monitoring keywords of an instruction, and performing instruction blocking as required. On the basis of not changing existing network environment and operation habits as far as possible, the safety accessing system and the safety accessing method for the character terminal RLOGIN protocol guarantees safety of access links, and can effectively manage network equipment and servers requiring to be accessed.
Owner:DATCENT TECH
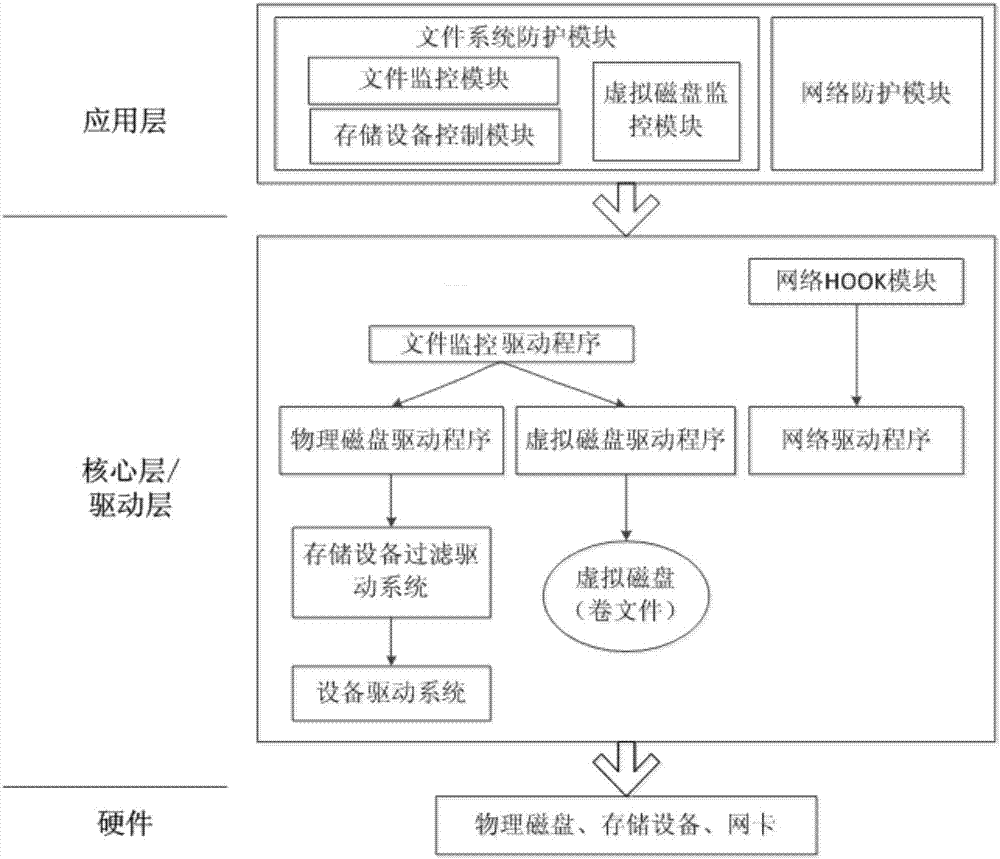
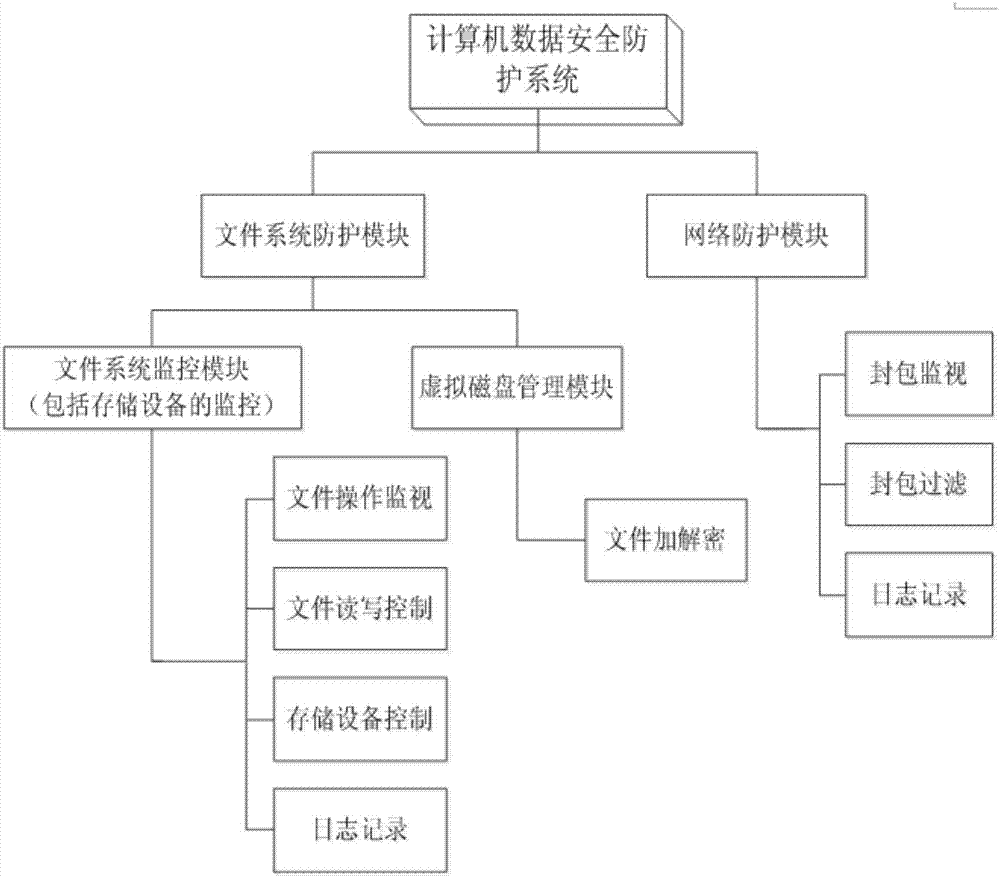
Interconnection information safety protective system of electric automobile
InactiveCN107247907AImplement access controlRealize transparent encryption and decryptionDigital data protectionTransmissionConfidentialityFile system
The invention discloses an interconnection information safety protective system of an electric automobile. The system comprises a network protection module and a document system protection module, wherein the network protection module is used to filter a network package, manage and control networking actions and record detailed information of network actions; the document system protection module comprises a document monitoring module, a storage equipment control module and a virtual magnetic disk control module; the document monitoring module is used to monitor document operations, record operation information of a document and control document reading and writing according to an access permission of the document; the storage equipment control module is used to control reading and writing of storage equipment; and the virtual magnetic disk control module is used to establish a virtual magnetic disk, load / unload the virtual magnetic disk and control reading and writing of the virtual magnetic disk. According to the invention, an information safety protective system is achieved to monitor and protect an electric automobile information platform effectively; confidentiality and integrity of computer data can be maintained better; and a better and reliable protection service can be provided for personal information.
Owner:NARI TECH CO LTD +3
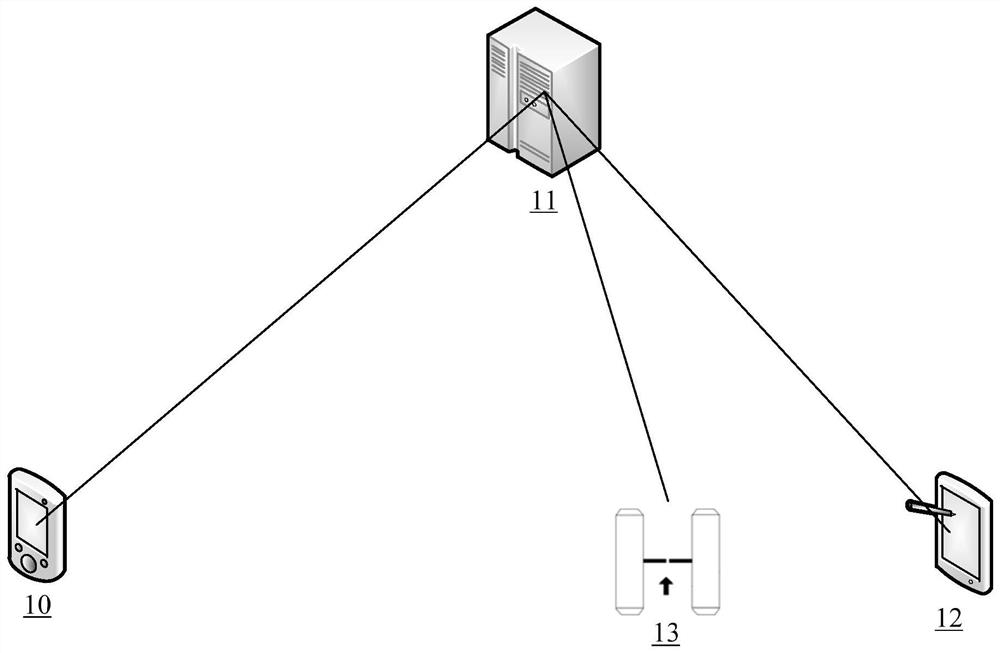
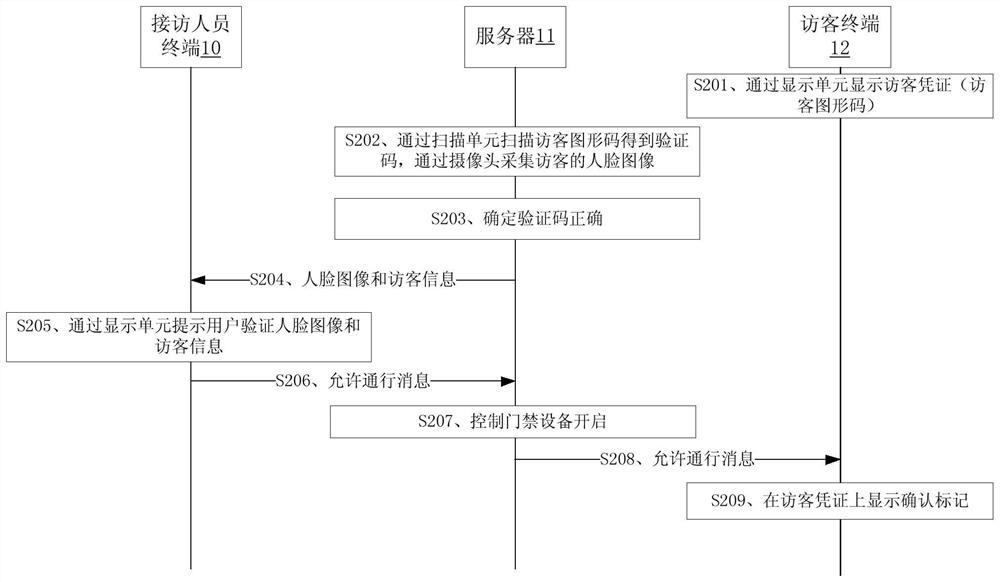
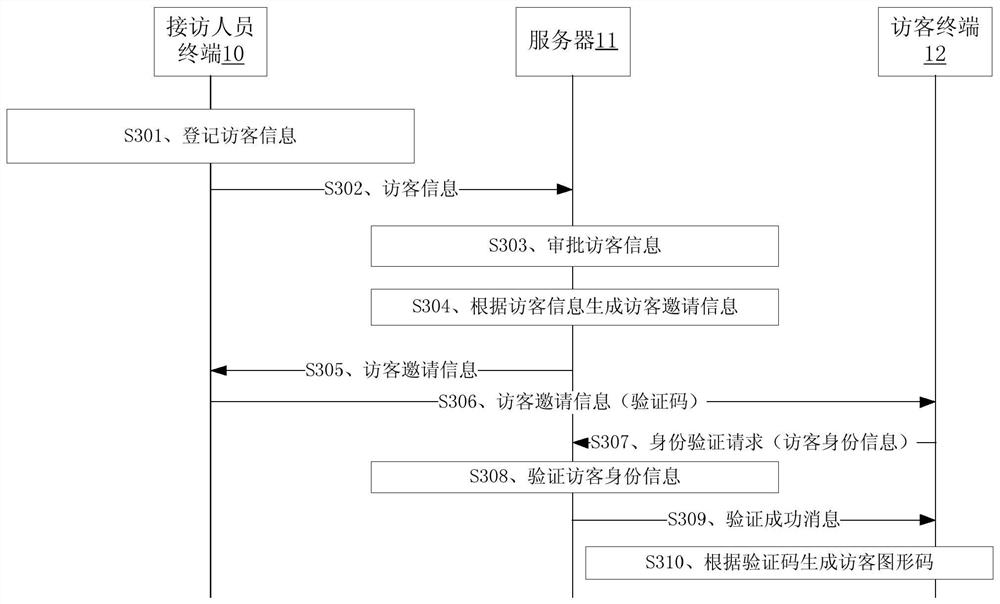
Visitor management method, related equipment, storage medium and system
PendingCN112530067AEfficient accessEffective access controlIndividual entry/exit registersGraphicsComputer science
The embodiment of the application discloses visitor control, a visitor control device, a storage medium and related equipment. The visitor management method comprises the following steps: scanning a visitor graphic code in a visitor certificate displayed on a visitor terminal through a scanning unit to obtain a verification code; collecting a face image of a visitor through a camera; after the verification code is verified to be correct, sending the face image and the visitor information of the visitor to a visitor receiving personnel terminal; and after a confirmation instruction of the visitor receiving terminal for the face image and the visitor information is received, sending a passage permission message to the visitor terminal. The visitor passage efficiency of the provided method can be improved by being compared with manual verification of the visitor information in related technologies.
Owner:YGSOFT INC
Registration control method of mobile terminal for accessing call center and system thereof
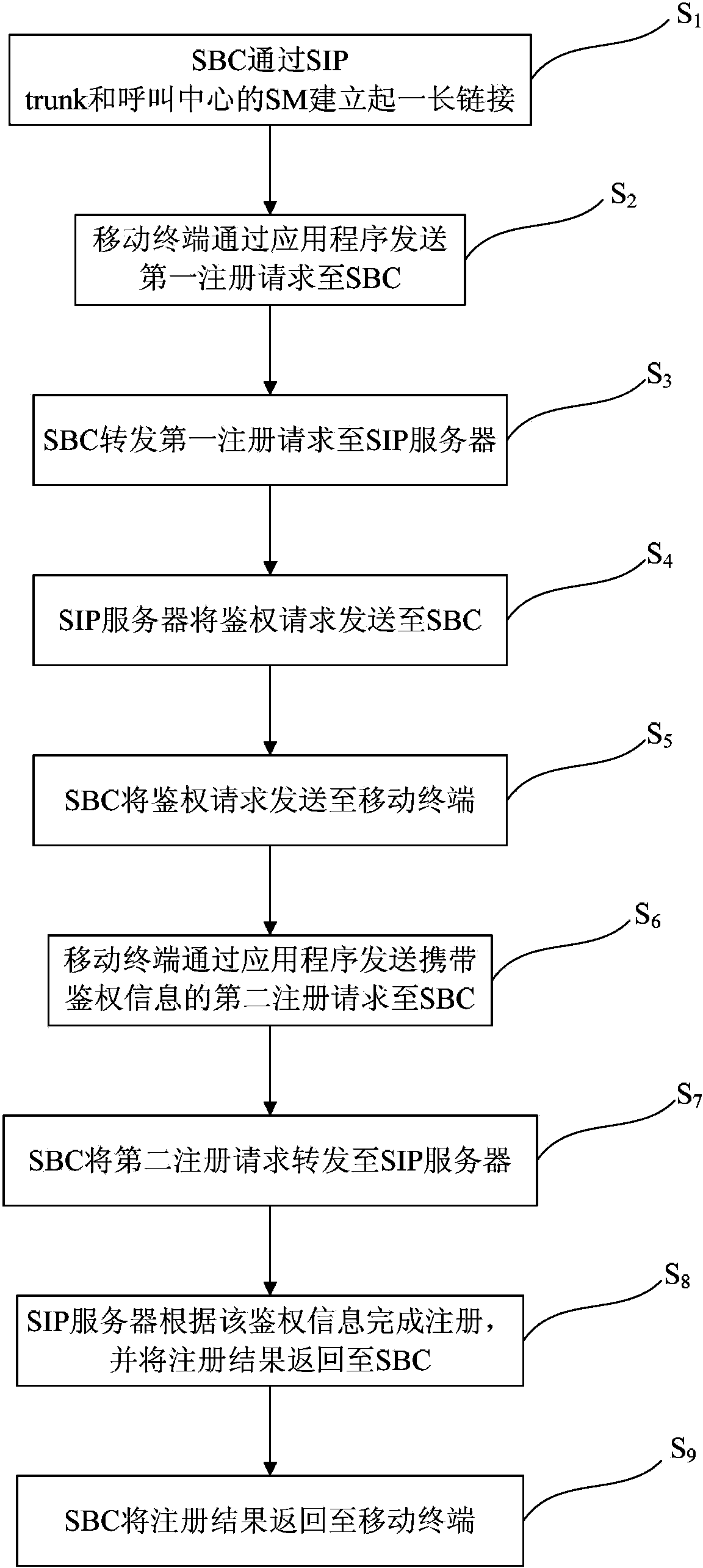
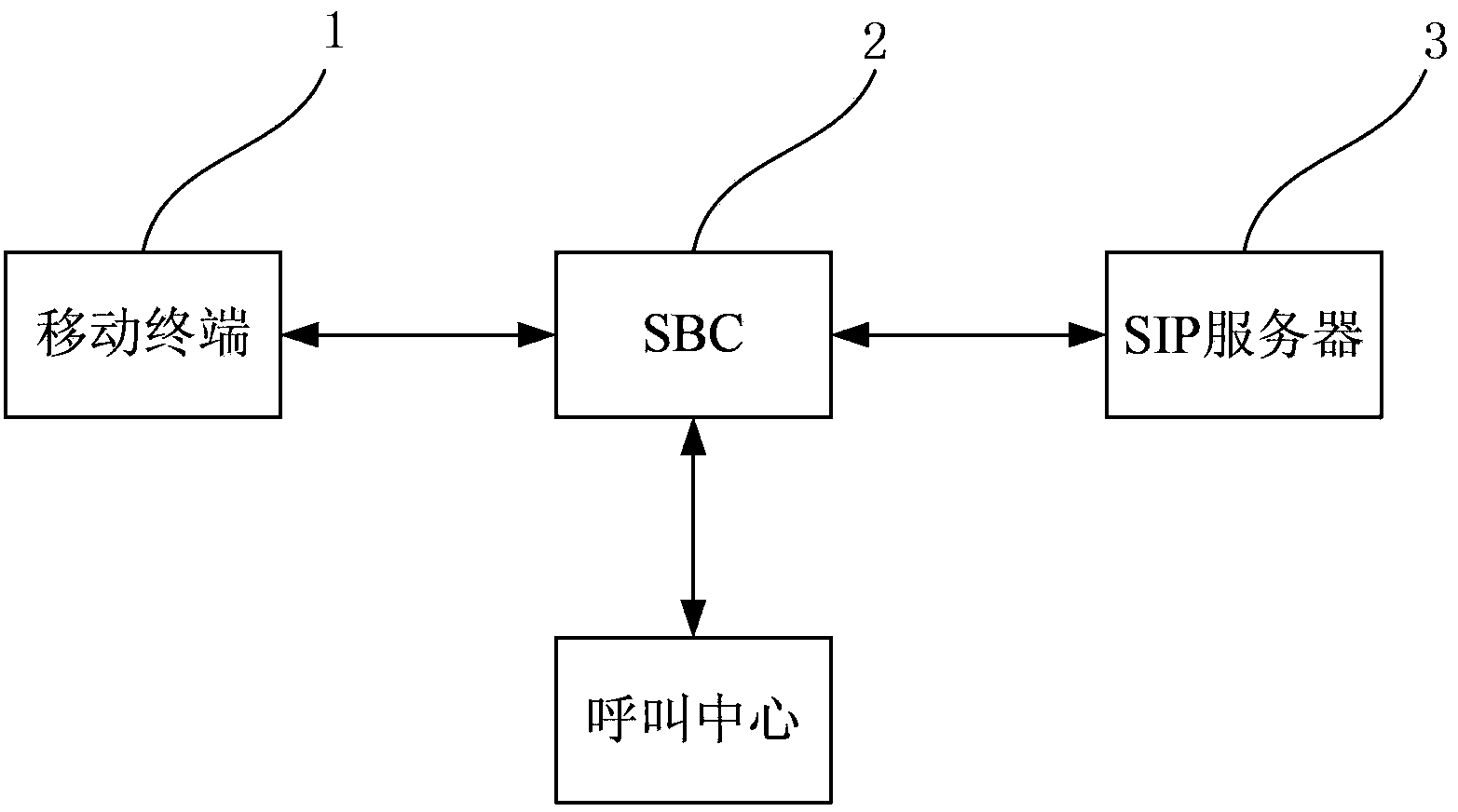
InactiveCN104348784AThe registration method is stableEasy to useTransmissionSecurity arrangementComputer terminalApplication software
The invention discloses a registration control method of a mobile terminal for accessing a call center and a system thereof. The registration control method comprises the steps that a long link is established by an SBC via an SIP trunk and the SM of the call center; the mobile terminal sends a first registration request to the SBC via an application program; the SBC forwards the first registration request to an SIP server; the SIP server sends an authentication request to the SBC; the SBC sends the authentication request to the mobile terminal; the mobile terminal sends a second registration request carrying authentication information to the SBC via the application program; the SBC forwards the second registration request to the SIP server; the SIP server completes registration according to the authentication information and returns the registration result to the SBC; and the SBC returns the registration result to the mobile terminal. The mobile terminal is registered via the SBC. Compared with methods in the prior art, the registration method is relatively stable, reliable and practical.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
Data access method, device and system, electronic equipment and computer readable medium
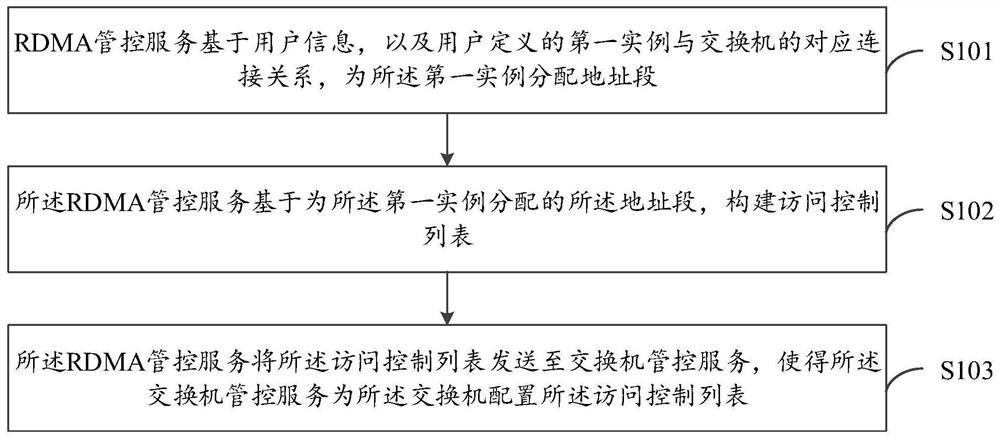
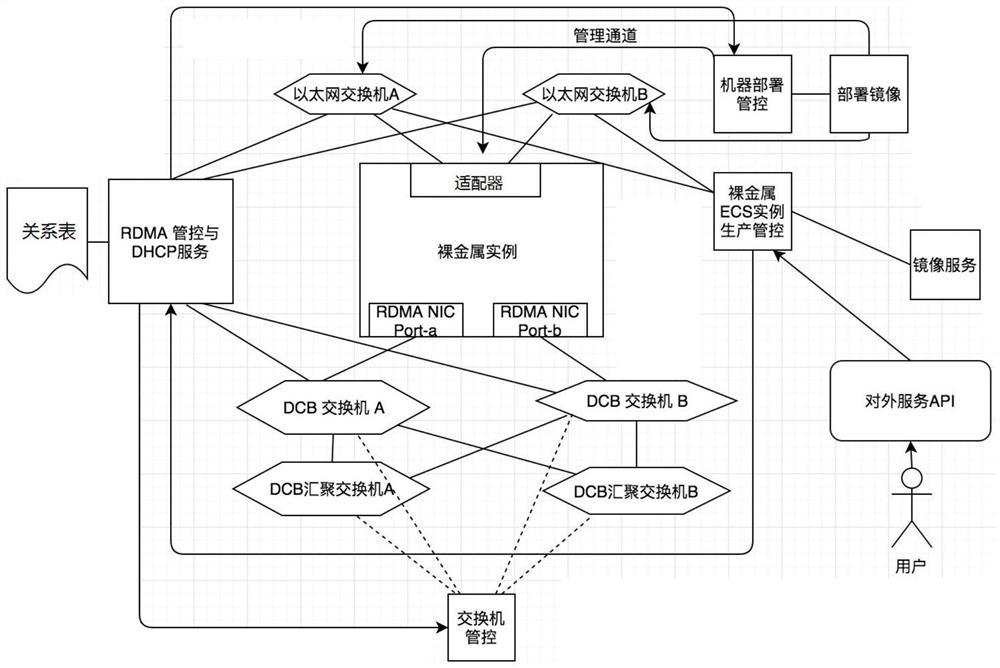
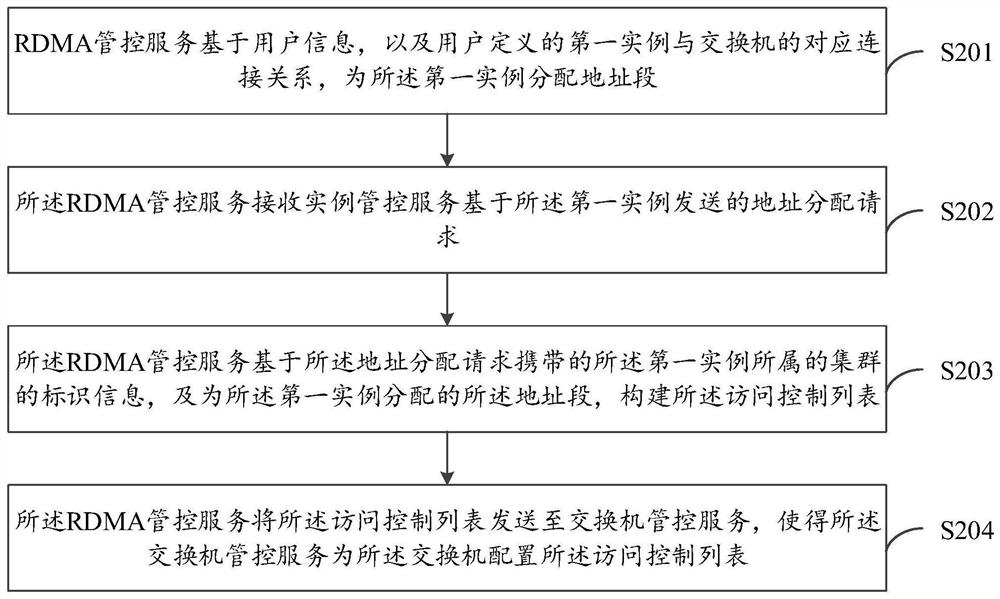
ActiveCN112565158AEffective access controlSolve the problem of access isolationSecuring communicationData accessEngineering
The embodiment of the invention provides a data access method, device and system, electronic equipment and a computer readable medium, and relates to the field of data access. The method comprises thefollowing steps: an RDMA management and control service allocates an address field to a first instance based on user information and a corresponding connection relationship between the first instancedefined by a user and a switch; the RDMA management and control service constructs an access control list based on the address fields allocated to the first instances, and the access control list isused for controlling access between different first instances defined by a user; and the RDMA management and control service sends the access control list to the switch management and control service,so that the switch management and control service configures the access control list for the switch. According to the embodiment of the invention, the access among different instances defined by thesame user can be effectively controlled, so that the problem of access isolation of different users accessing the RDMA network node is effectively solved.
Owner:ALIBABA CLOUD COMPUTING LTD
Method and device for establishing access relationship, electronic equipment and storage medium
PendingCN114866258ACanonical Access ControlLegal access controlEncryption apparatus with shift registers/memoriesUser identity/authority verificationInternet privacyIdentity recognition
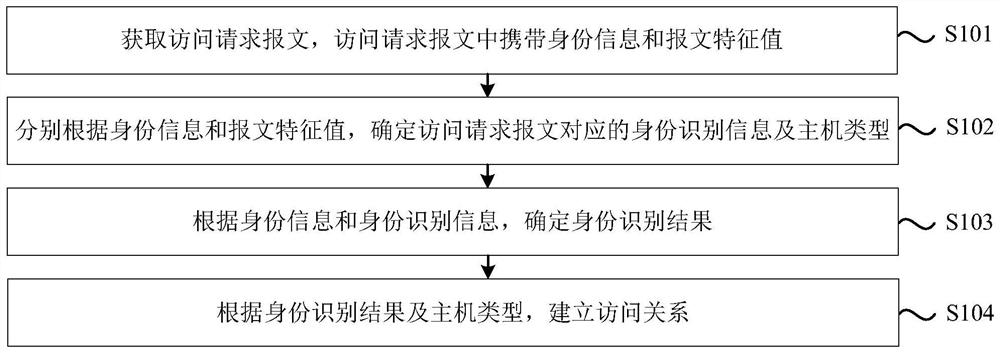
The invention discloses an access relationship establishment method and device, electronic equipment and a storage medium. The method comprises the following steps: acquiring an access request message, wherein the access request message carries identity information and a message feature value; determining identity identification information and a host type corresponding to the access request message according to the identity information and the message feature value; determining an identity recognition result according to the identity information and the identity recognition information; and establishing an access relationship according to the identity recognition result and the host type. According to the technical scheme, the identity information and the message feature value in the access request message are confirmed, and whether the access relation is established or not is determined based on the identity recognition information and the host type, so that operations such as identity counterfeiting, malicious permission utilization and unauthorized access can be effectively avoided, and normative, legal, effective and safe access control is realized.
Owner:海恒数字科技(青岛)有限公司 +2
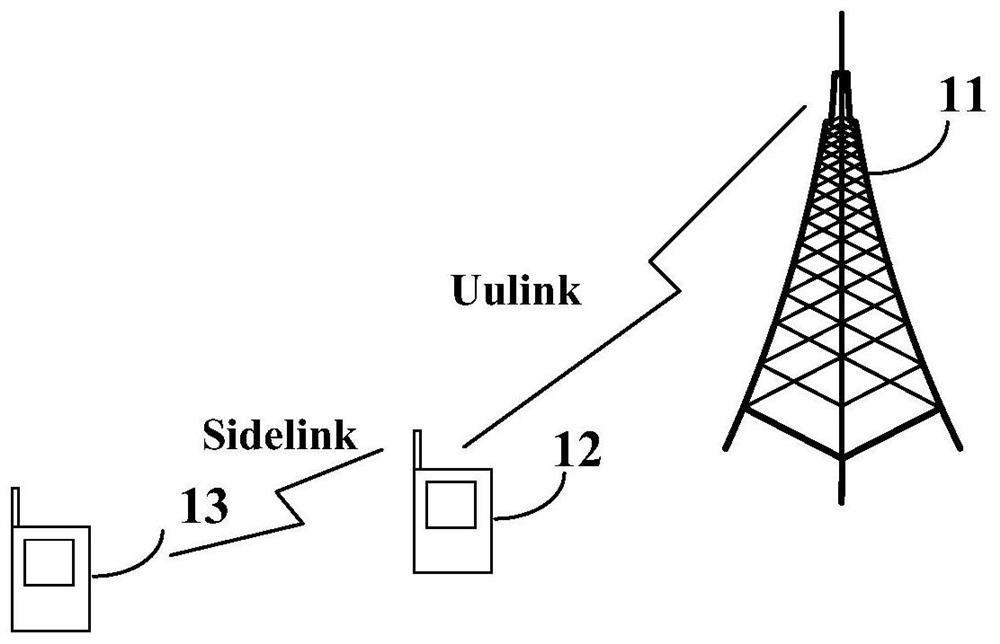
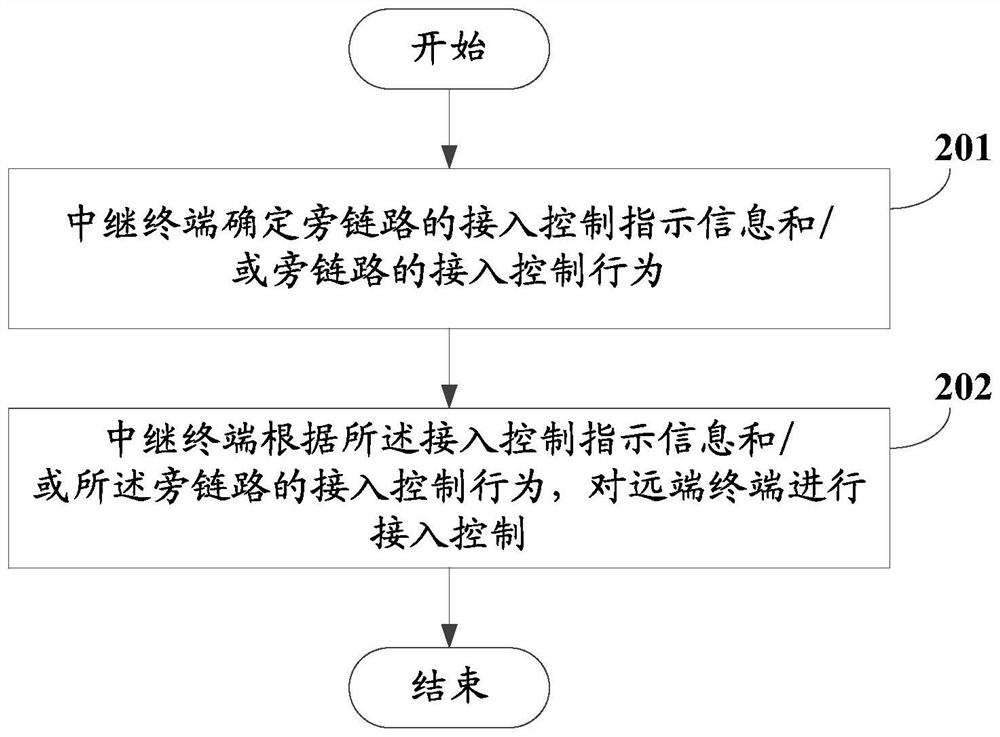
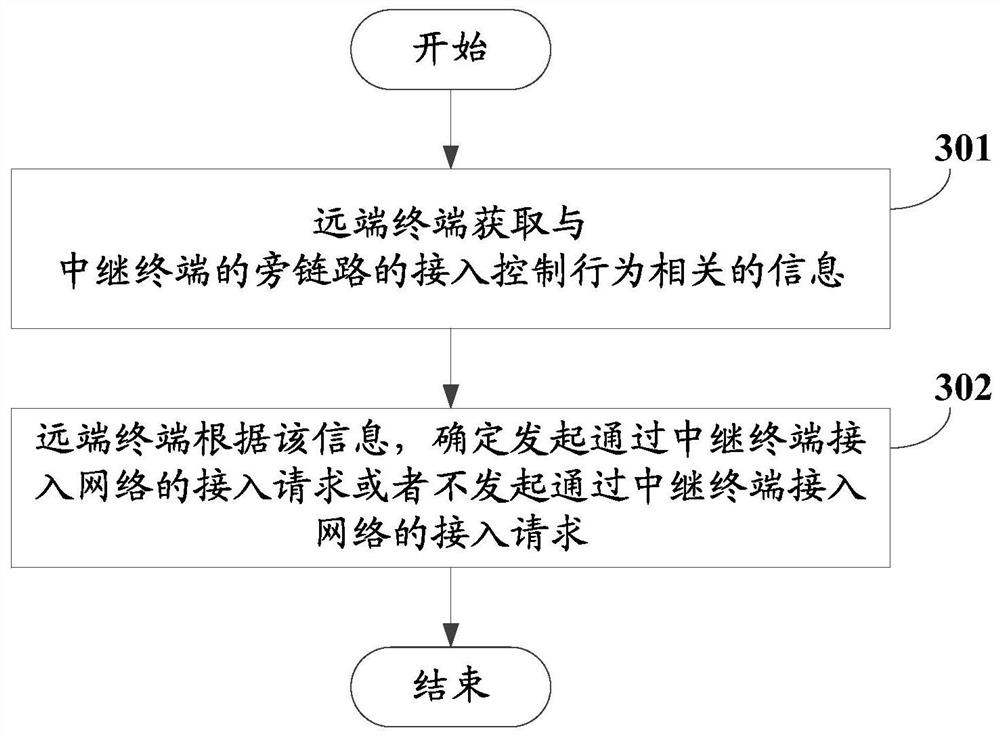
Access control method and device
The invention discloses an access control method and device. The method comprises the following steps: a relay terminal determines access control indication information of a side link and / or an access control behavior of the side link; and the relay terminal performs access control on a remote terminal according to the access control indication information and / or the access control behavior of the side link. In the embodiment of the invention, the relay terminal can perform access control on the far-end terminal according to the determined access control indication information and / or the access control behavior of the side link, so that when the relay terminal provides a relay transmission service between the far-end terminal and the network side equipment, network access control can be effectively performed, and aggravation of network congestion or increase of signaling overhead is avoided.
Owner:VIVO MOBILE COMM CO LTD
Computer firewall device based on cloud database and using method
The invention discloses a computer firewall device based on a cloud database and a use method, and the method comprises the following steps: S1, application protocol intelligent recognition control: automatically recognizing a DBA protocol, an operation and maintenance protocol, hacker access and application software, carrying out the comprehensive monitoring of all interface access of the database, and achieving the effective access control; S2, precise interception: performing blocking based on various conditions such as IP addresses, time, operations, keywords, database accounts, statementlengths, column names, table names, line numbers and injection feature libraries, and precise access control is realized; S3, APT attack prevention: according to the combination of access behaviors, the statistical model quickly verifies and blocks complex and continuous violation operation and malicious attack behaviors; S4, built-in AI: a built-in intelligent learning module, machine intelligentlearning, automatic modeling and automatic generation of a blocking rule base for actively defending unknown security threats; S5, bypass blocking.
Owner:南京哈佳智能科技有限公司
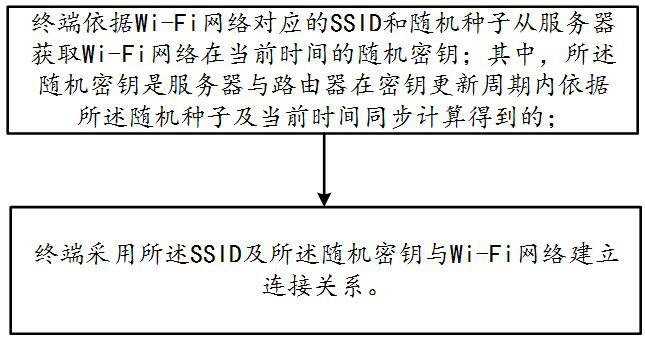
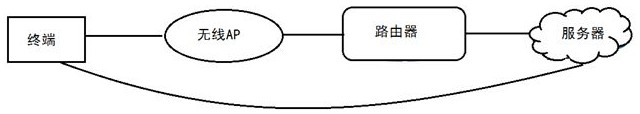
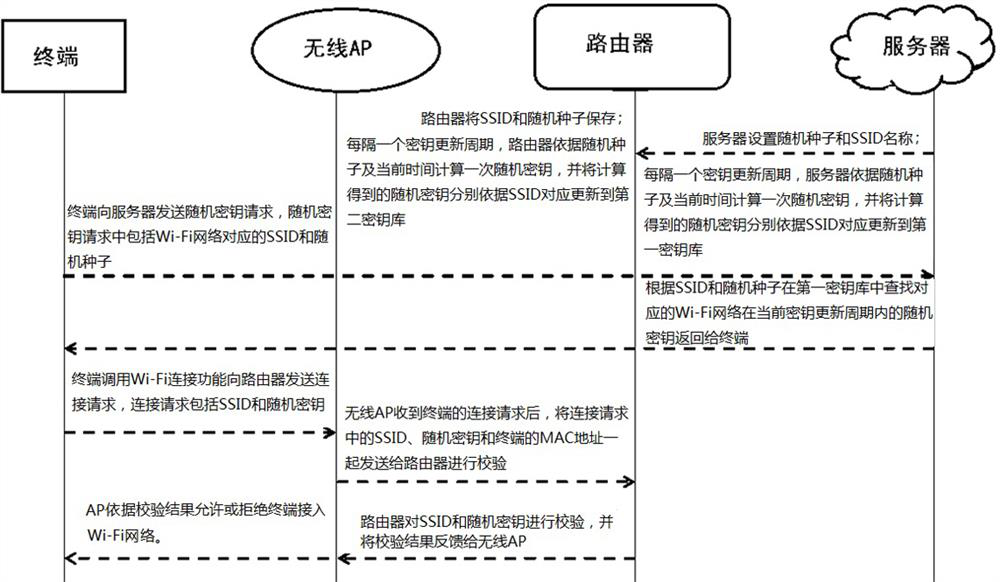
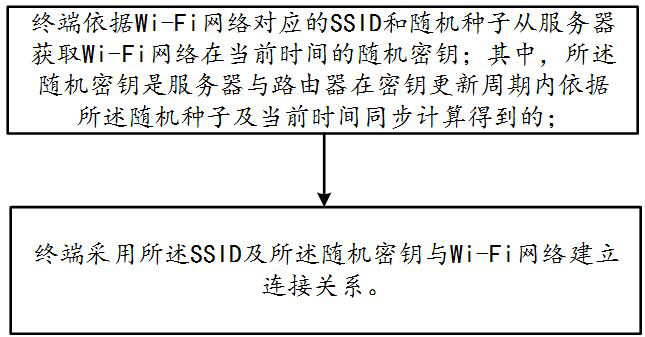
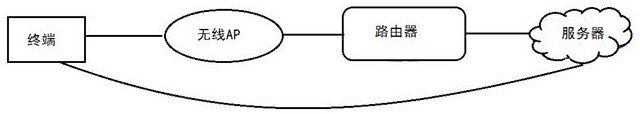
Wi-Fi connection management method, terminal and system
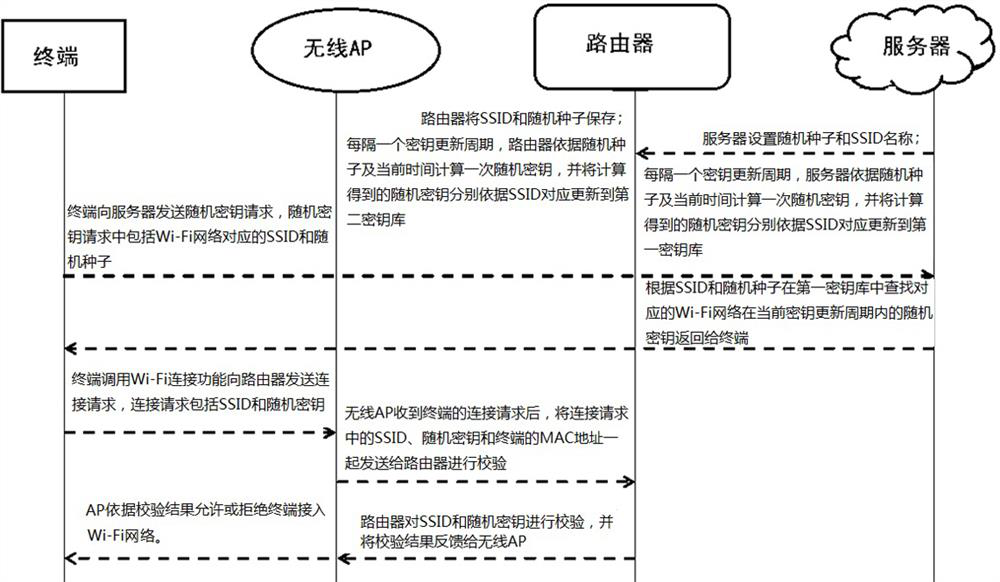
ActiveCN111800788AImprove securityEnsure safetyConnection managementSecurity arrangementRandom seedEngineering
The invention discloses a Wi-Fi connection management method, a terminal and a system, and the method comprises the steps that the terminal obtains a random secret key of a Wi-Fi network at the current time from a server according to an SSID corresponding to the Wi-Fi network and a random seed; wherein the random key is obtained by synchronous calculation of the server and a router according to the random seed and the current time in a key updating period; and the terminal uses the SSID and the random key to establish a connection relationship with a Wi-Fi network. The terminal and the systemadopt the method to solve the problems of low Wi-Fi connection management security and low maintenance cost in the prior art.
Owner:QUANXUN HUIJU NETWORK TECH BEIJING CO LTD
Method, terminal and system for wi-fi connection management
ActiveCN111800788BImprove securityEnsure safetyConnection managementSecurity arrangementRandom seedEngineering
The present invention discloses a method, terminal and system for Wi-Fi connection management, wherein the method includes: the terminal acquires a random key of the Wi-Fi network at the current time from a server according to the SSID corresponding to the Wi-Fi network and a random seed; Wherein, the random key is calculated by the server and the router according to the random seed and the current time during the key update period; the terminal uses the SSID and the random key to establish a connection relationship with the Wi-Fi network. The terminal and the system adopt the above-mentioned method to solve the problems of low Wi-Fi connection management security and maintenance cost in the prior art.
Owner:QUANXUN HUIJU NETWORK TECH BEIJING CO LTD
Transmission method of multicast preview services
ActiveCN102546195BEffective access controlSolve management problemsSpecial service provision for substationMultiplex system selection arrangementsManagement objectAuthorization
The present invention provides a method and a device for transmitting a multicast preview service, wherein the method includes the following steps: looking up, in a management object and / or attributes of the management object, an attribute carried in a multicast joining request message according to a predetermined sequence, wherein the management object and / or the attributes of the management object includes at least one of the following: Multicast Operations Profile (MOP), an authorization group of Extension Multicast Operations Profile (EMOP), an Allowed preview groups table of Multicast Subscriber Control (MSC), and a preview group of EMOP (S102); forwarding or stopping forwarding to a user a service requested by the multicast joining request message according to a lookup result (S104). The present invention solves the problem in conventional art that multicast services of multiple Service Providers (SPs) cannot be managed, and improves the multicast control method.
Owner:ZTE CORP
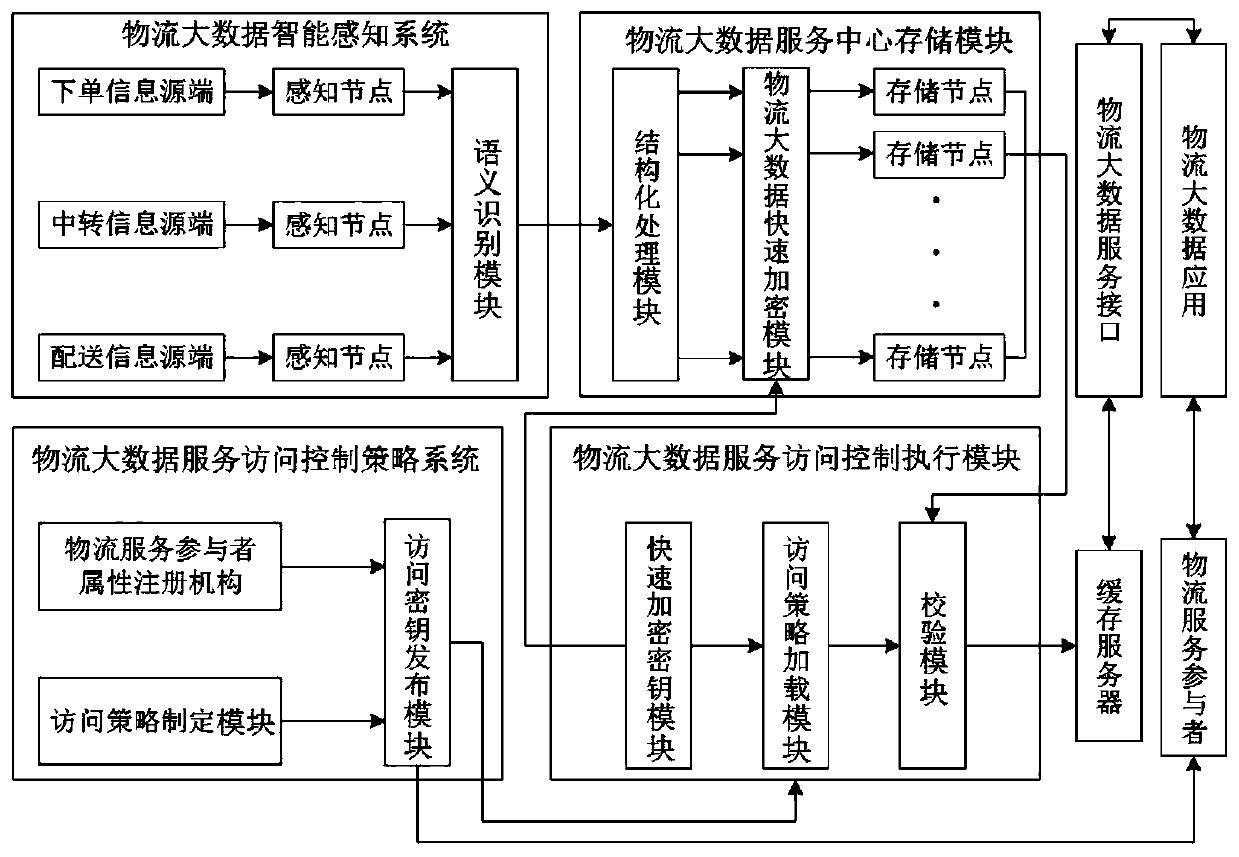
A logistics big data information security access control system
ActiveCN107196967BEnsure safetyGuarantee high efficiencyTransmissionLogistics managementData access control
The invention relates to a logistics big data information security access control system. Email sending information big data are encrypted, and user access is strictly controlled, thereby ensuring the secure storage and access of the email sending information big data; all mail information bid data are structurally processed and are stored in a data center, the detail information corresponding to each mail is marked with security labels of different levels, which is conducive to effectively controlling the user access of privacy data, and ensuring the security and high efficiency of access control.
Owner:蜻蜓农业研究院(江苏)有限公司
The ctc approach control method for the automatic reentry operation of the intercity railway
ActiveCN110203259BEffective access controlReduce workloadAutomatic systemsControl engineeringReliability engineering
The invention relates to a CTC approach control method for automatic turn-back operation of intercity railways. In the method, firstly, the train group binding management is carried out on the train operation plan line with turn-back operation in the prepared adjustment plan, and after forming a link relationship, it is issued to the station. Equipment, the station equipment automatically changes the turn-back train number according to the received connection relationship and the turn-back operation type, and automatically triggers the route of the turn-back operation train. Compared with the prior art, the invention has the advantages of reducing the workload of manual intervention, improving the degree of system automation and the like.
Owner:CASCO SIGNAL
Anonymous data sharing method and system based on data source and data master hiding
ActiveCN111600875BPrivacy protectionReduce overheadKey distribution for secure communicationIp addressData source
Owner:JIANGSU UNIV
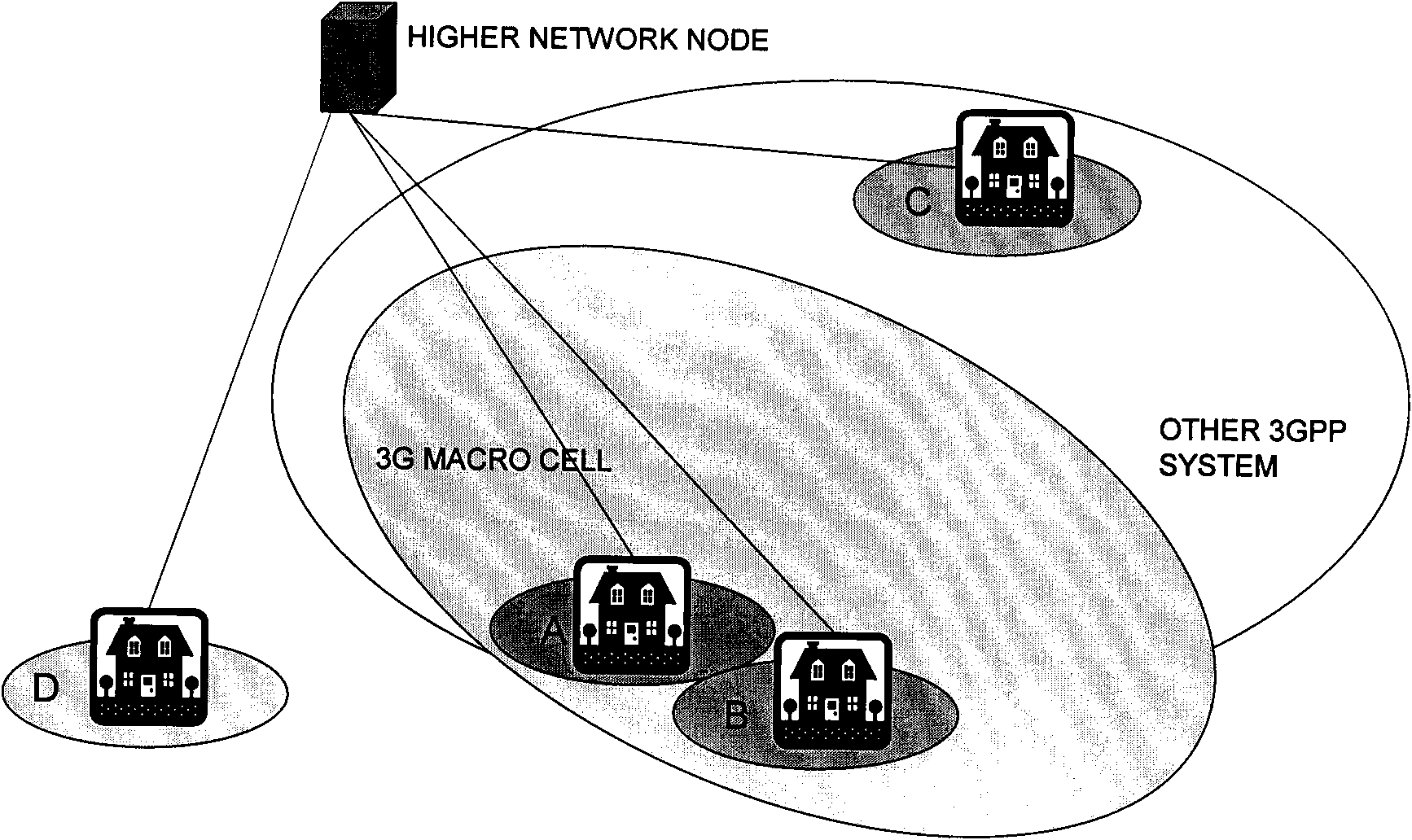
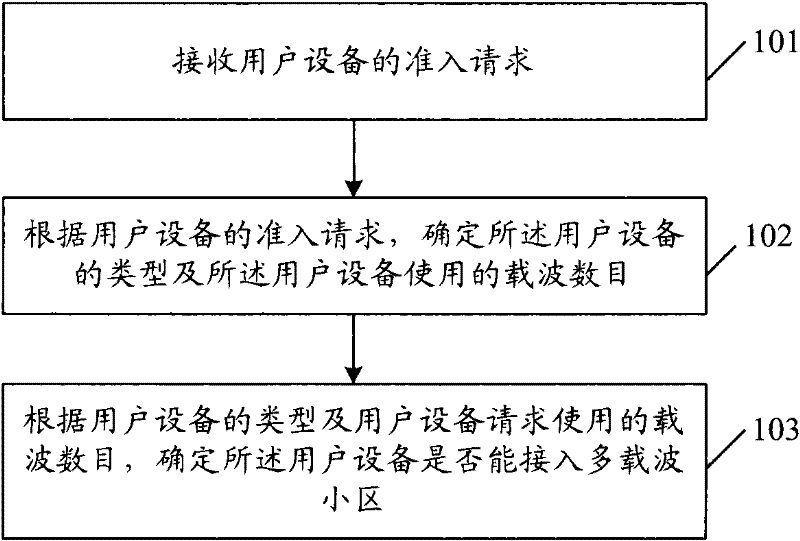
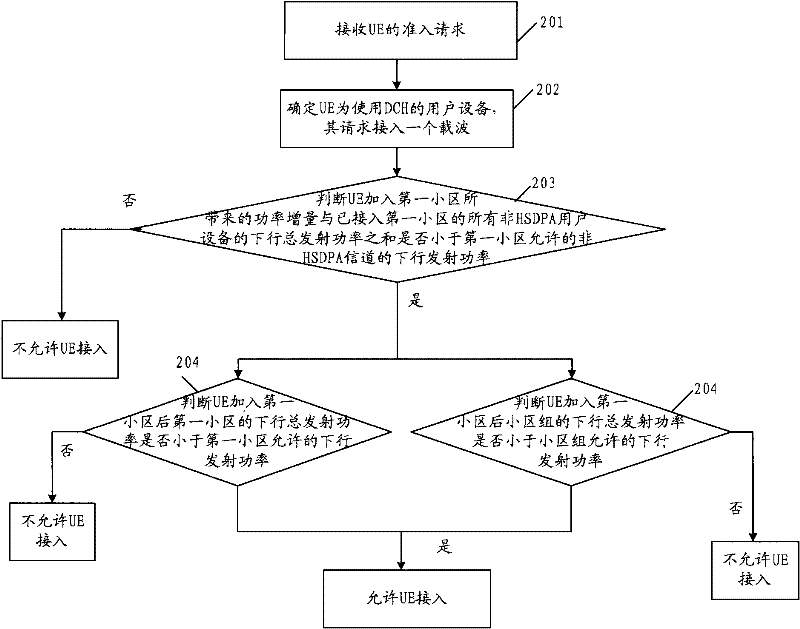
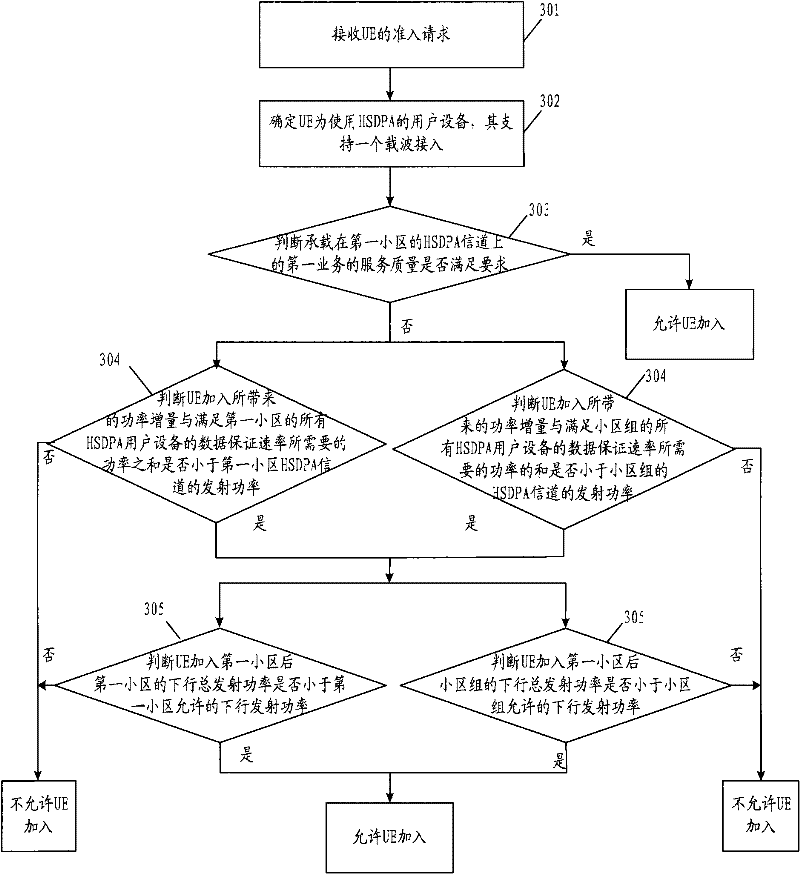
Method and device for user equipment admission control in multi-carrier cell
Embodiments of the present invention provide an admission control method, control device, and network system for a multi-carrier cell, wherein the admission control method for a multi-carrier cell includes: receiving an admission request from a user equipment; , determining the type of the user equipment and the number of carriers used by the user equipment; determining whether the user equipment can access the multi-carrier cell according to the type of the user equipment and the number of carriers used by the user equipment. Using the technical solutions provided by the embodiments of the present invention, effective admission control is performed on users joining multi-carrier cells.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com