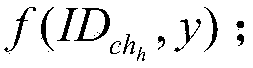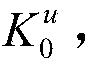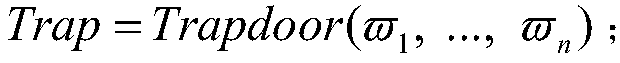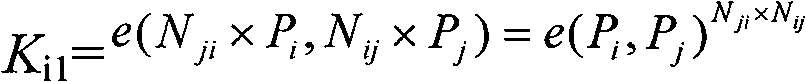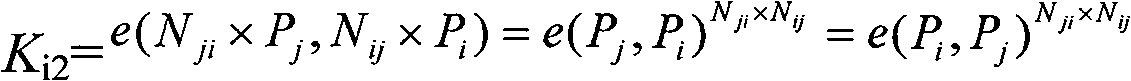Patents
Literature
44 results about "Pairwise key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
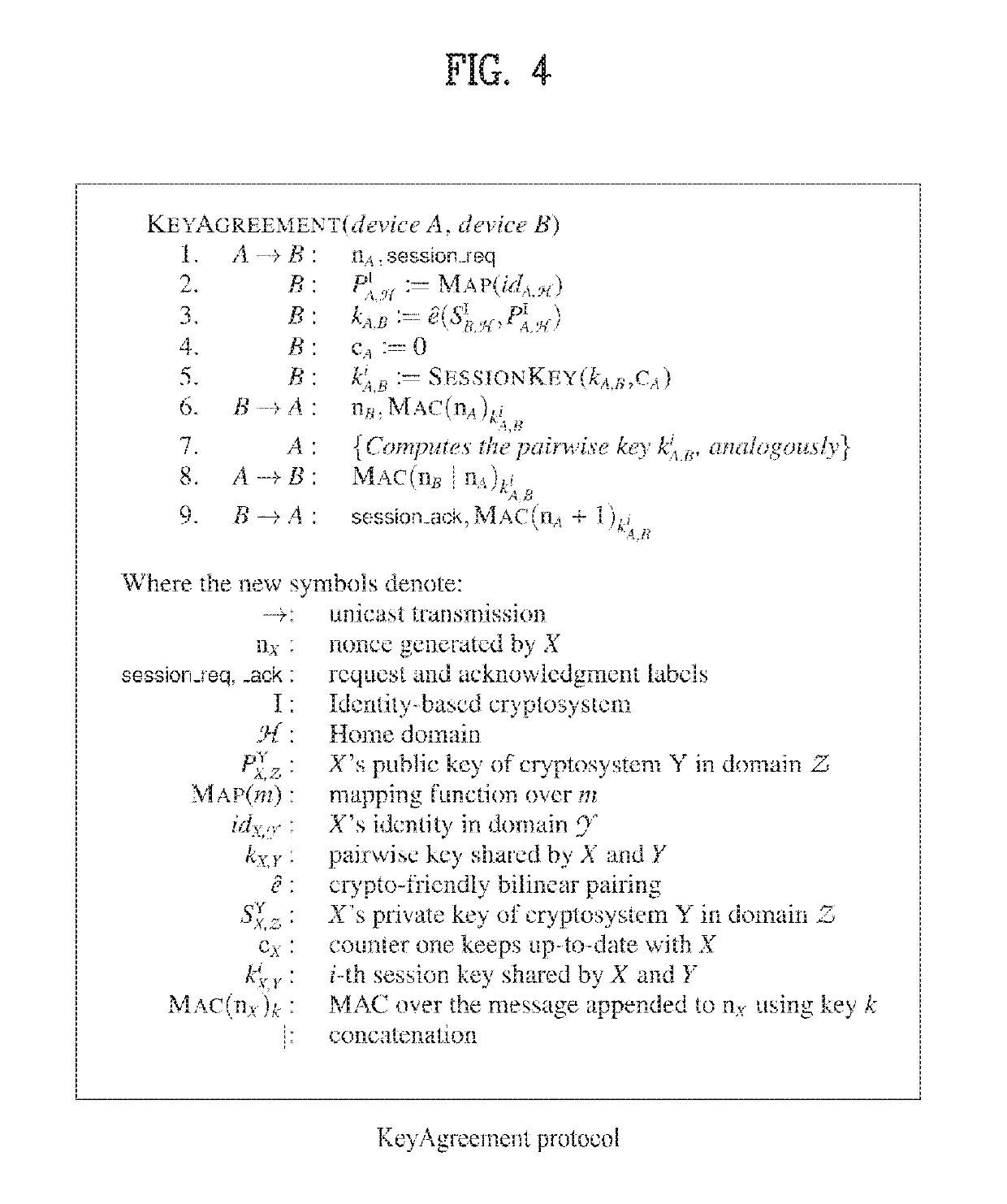
Method and apparatus for generating pairwise cryptographic transforms based on group keys
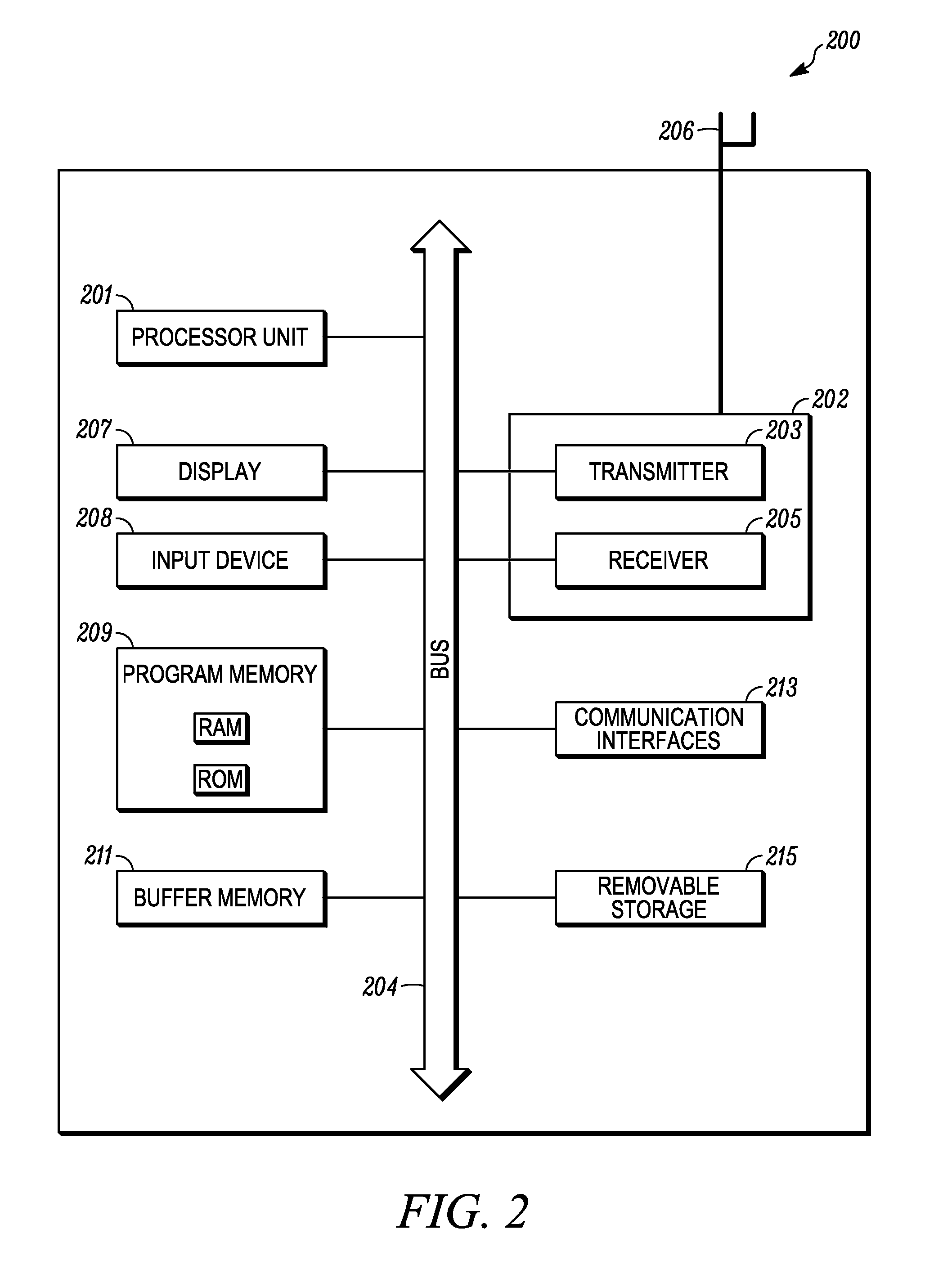
ActiveUS7234058B1Key distribution for secure communicationDigital data processing detailsPairwise keyComputer security
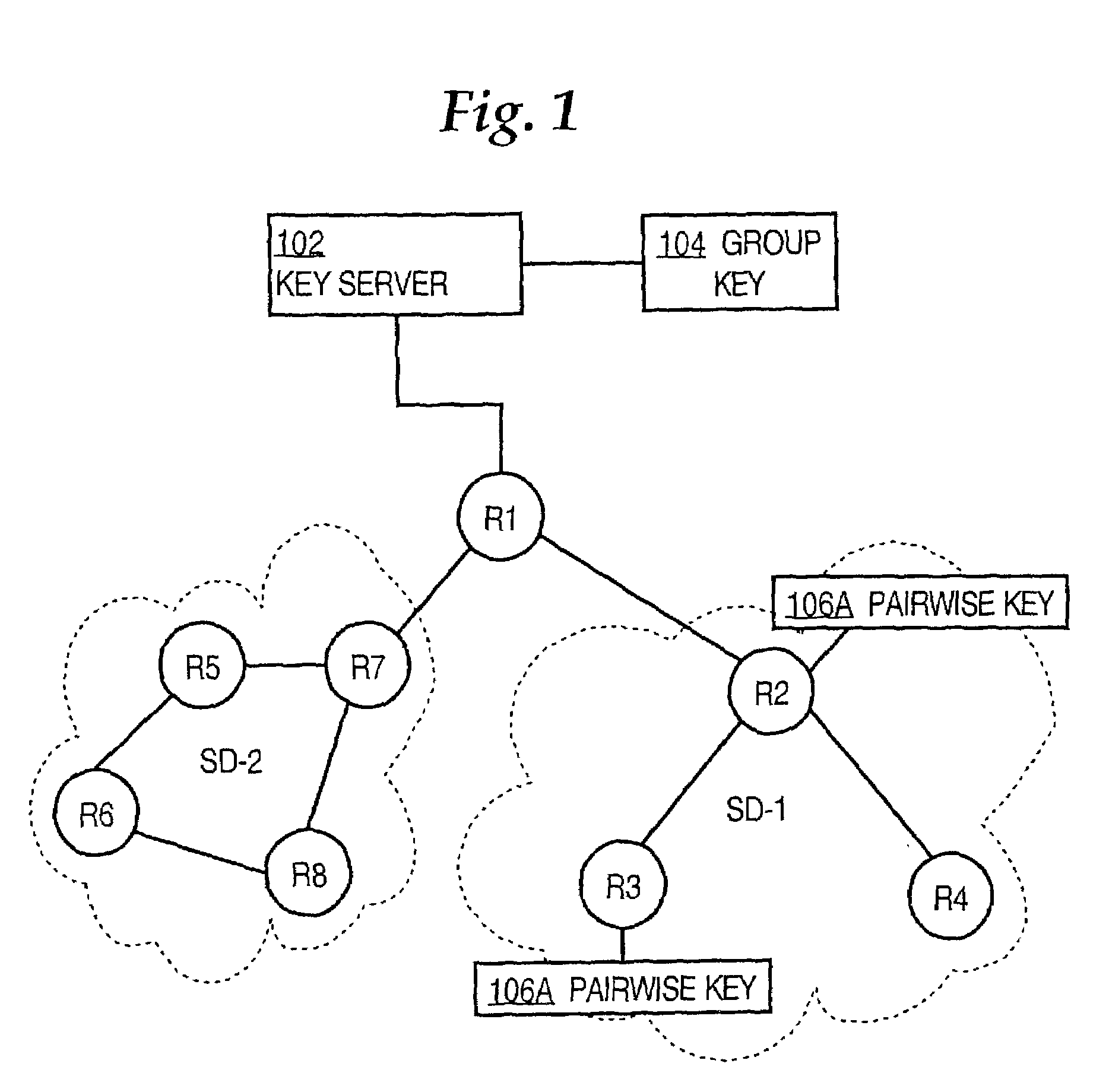
Group key management techniques are applied to generating pair-wise keys for point-to-point secure communication applications. Nodes participating in a secure communication group each receive a group key and associated policy information. When a first node wishes to establish a secure point-to-point connection to a second node, the first node derives a pairwise key from the group key and policy information, for example, by hashing the group key and information identifying the two nodes. As a result, a pairwise key is generated without exchanging negotiation messages among the two nodes and without expensive asymmetric cryptographic computation approaches.
Owner:CISCO TECH INC
Non-Interactive Hierarchical Identity-Based Key-Agreement
InactiveUS20090225986A1Less mobileImprove securityKey distribution for secure communicationBandwidth constraintPairwise key
A pairwise key-agreement scheme is provided for creating key agreements non-interactively between pairs of nodes disposed in a hierarchy of nodes. The scheme is non-interactive so that any two nodes can agree on a shared secret key without interaction. In addition, the scheme is identity-based so that any given node only needs to know the identity of peer nodes to compute the shared secret key. All of the nodes are arranged in a hierarchy where an intermediate node in the hierarchy can derive the secret keys for each of its children from its own secret key and the identity of the child. Accordingly, the scheme is fully resilient against compromise of any number of leaves in the hierarchy and of a threshold number of nodes in the upper levels of the hierarchy. The scheme is well-suited for environments such as mobile ad-hoc networks (MANETs), which are very dynamic, have acute bandwidth-constraints and have many nodes are vulnerable to compromise.
Owner:IBM CORP
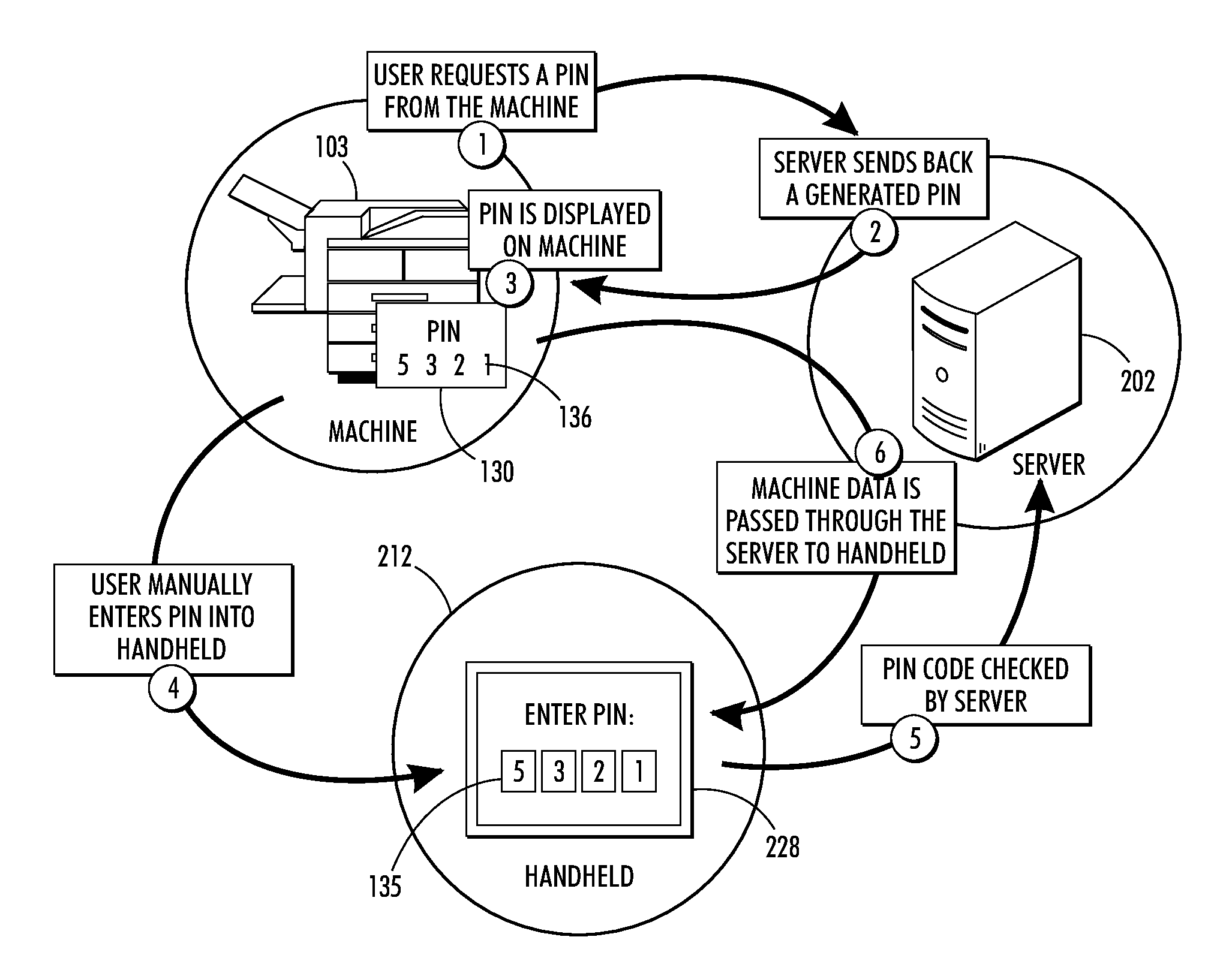
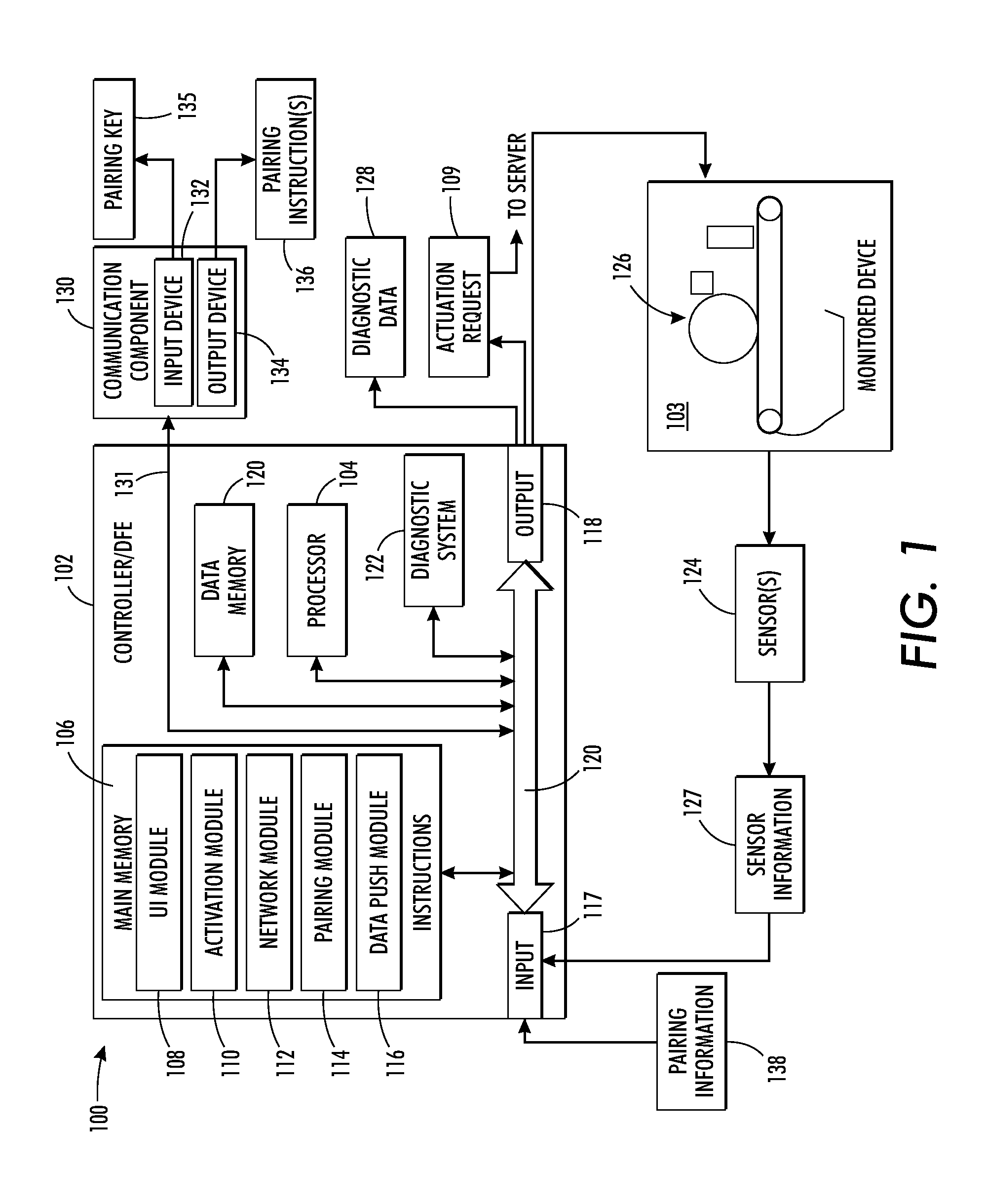
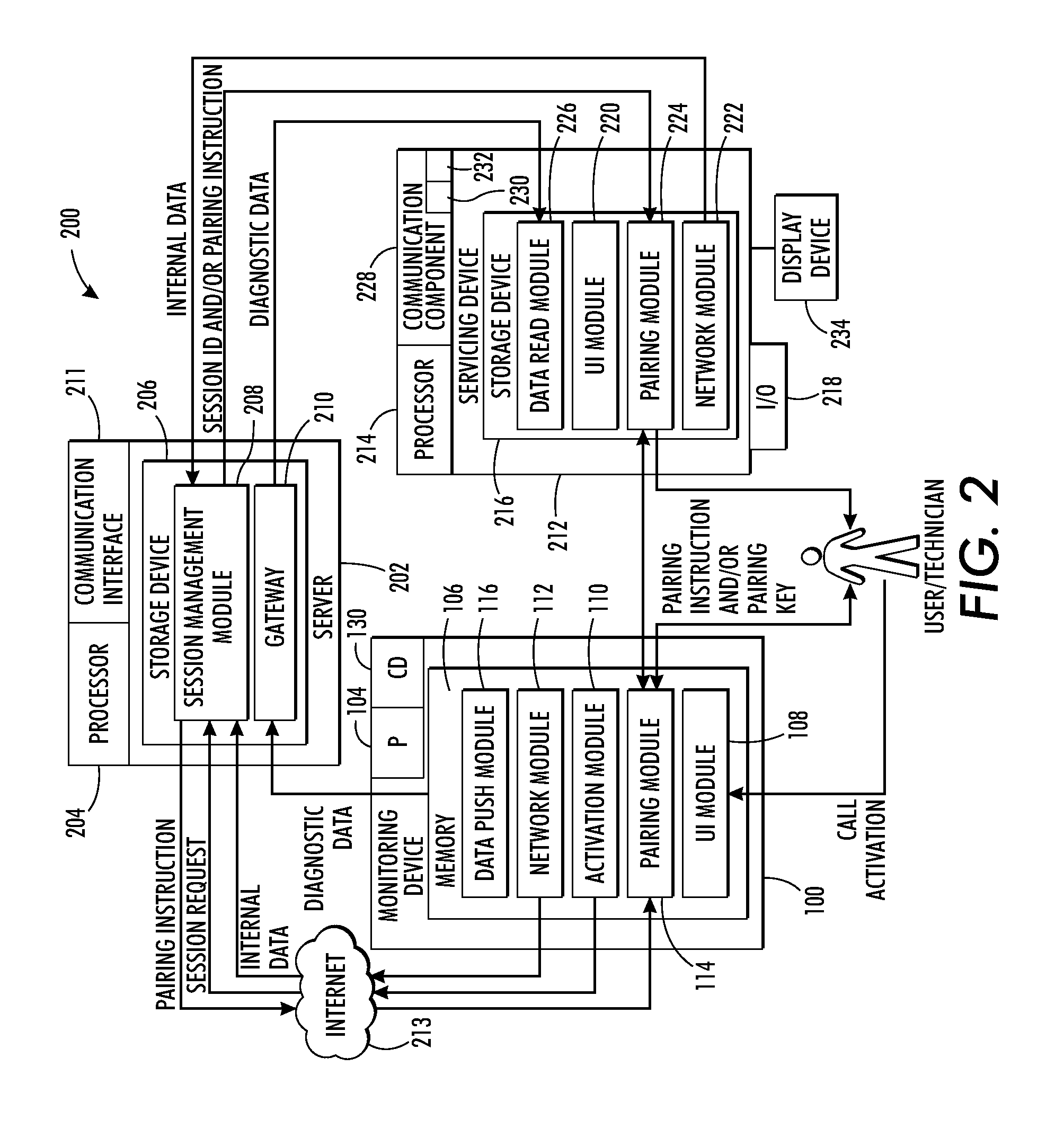
Soft method for local secure connection to a device
ActiveUS20130139218A1Connection securityDigital data processing detailsMultiple digital computer combinationsDiagnostic dataReal-time computing
A system for pairing two devices includes a monitoring system and a server. The monitoring system receives a request made by a local submitter, such as servicing device or a technician operating the servicing device, for accessing diagnostic data of the monitoring system. The monitoring system initiates a request made to the server for connecting the monitoring system with the servicing device. The server generates pairing information and transmits the pairing information to the monitoring system. The server determines that a pairing key is received as input at the servicing device and / or monitored device and determines if the pairing key matches the pairing identification. If the server determines that there is a match, the server relays diagnostic data received from the monitoring system to the servicing device.
Owner:XEROX CORP
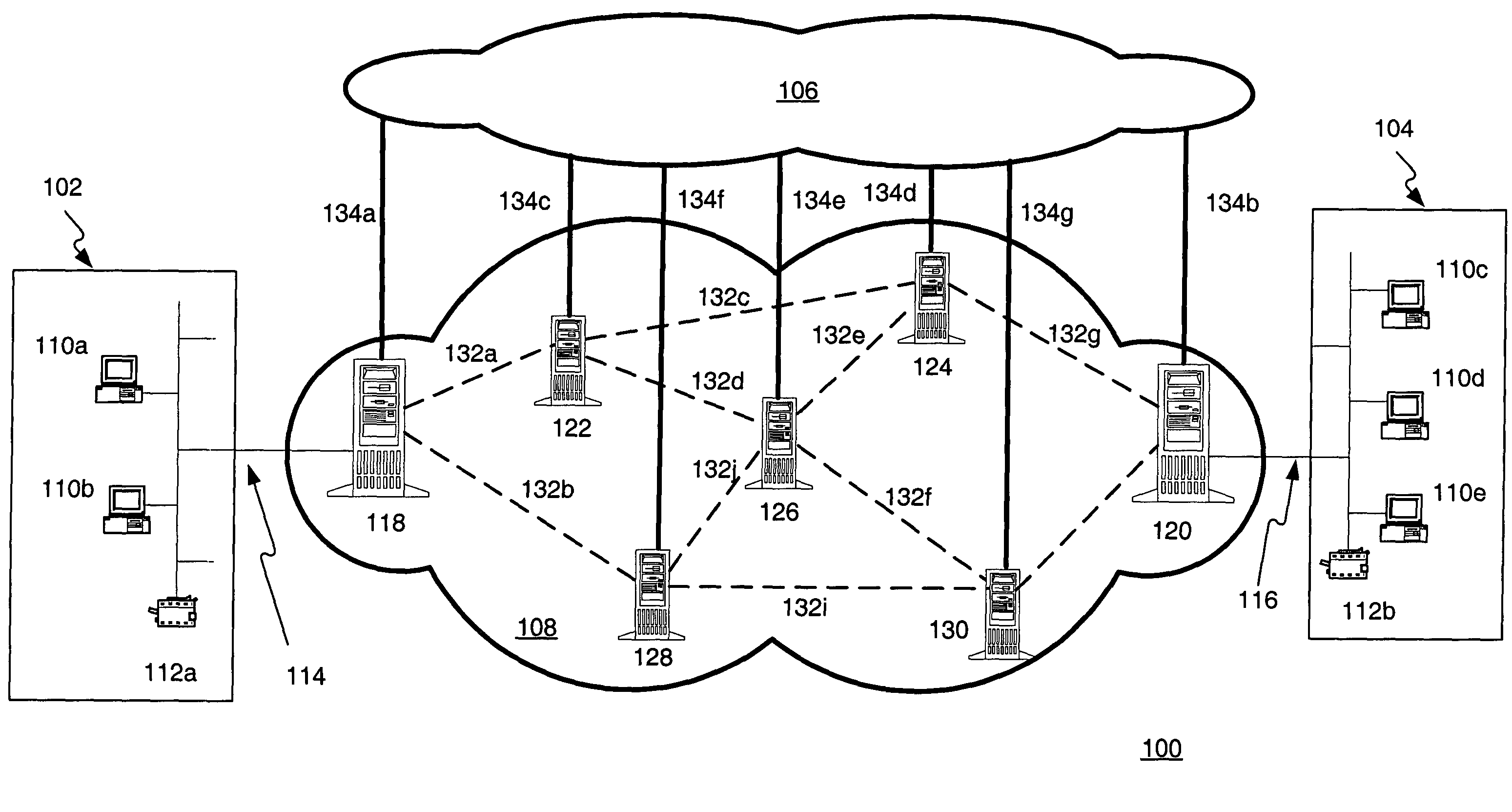
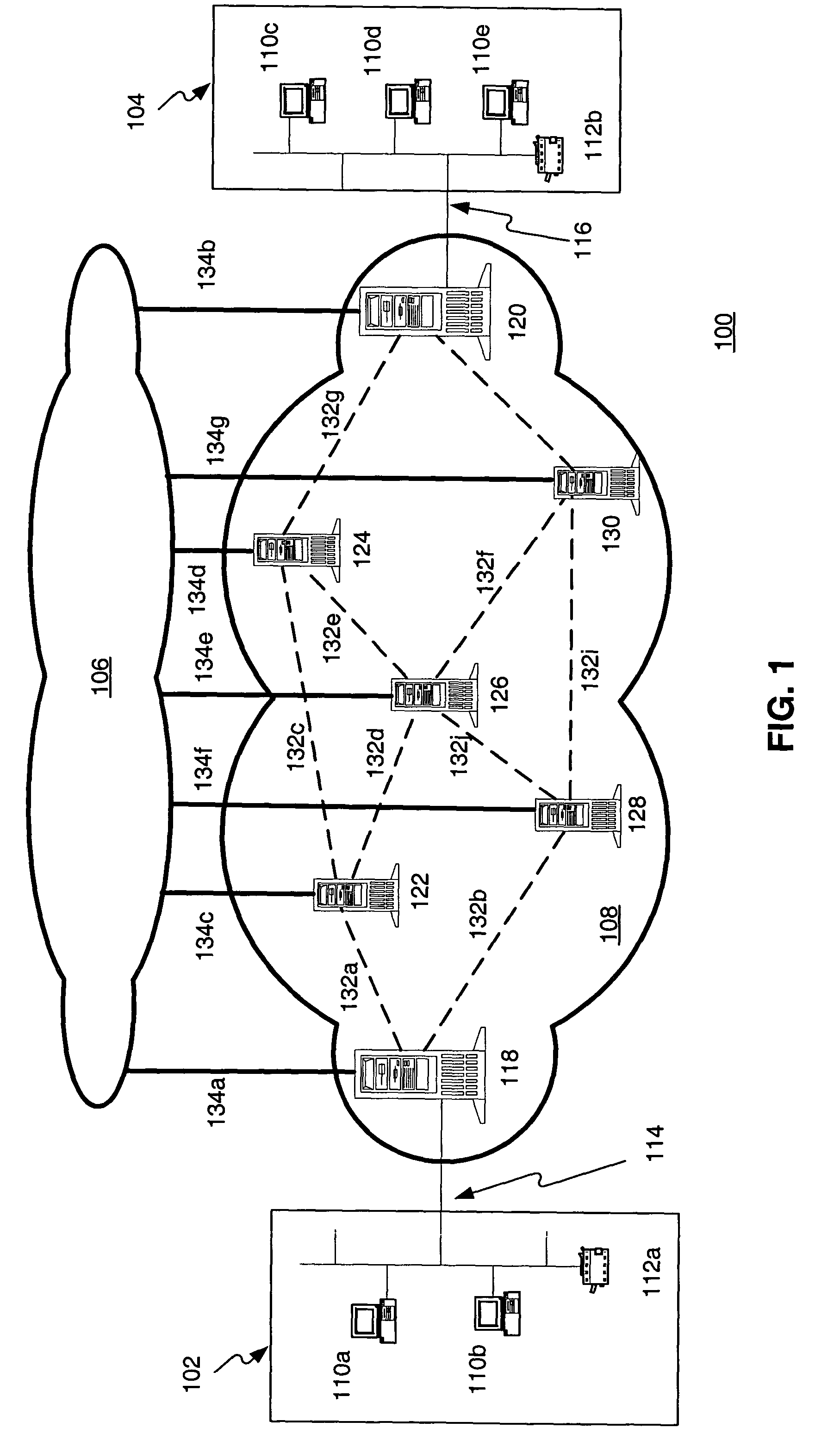
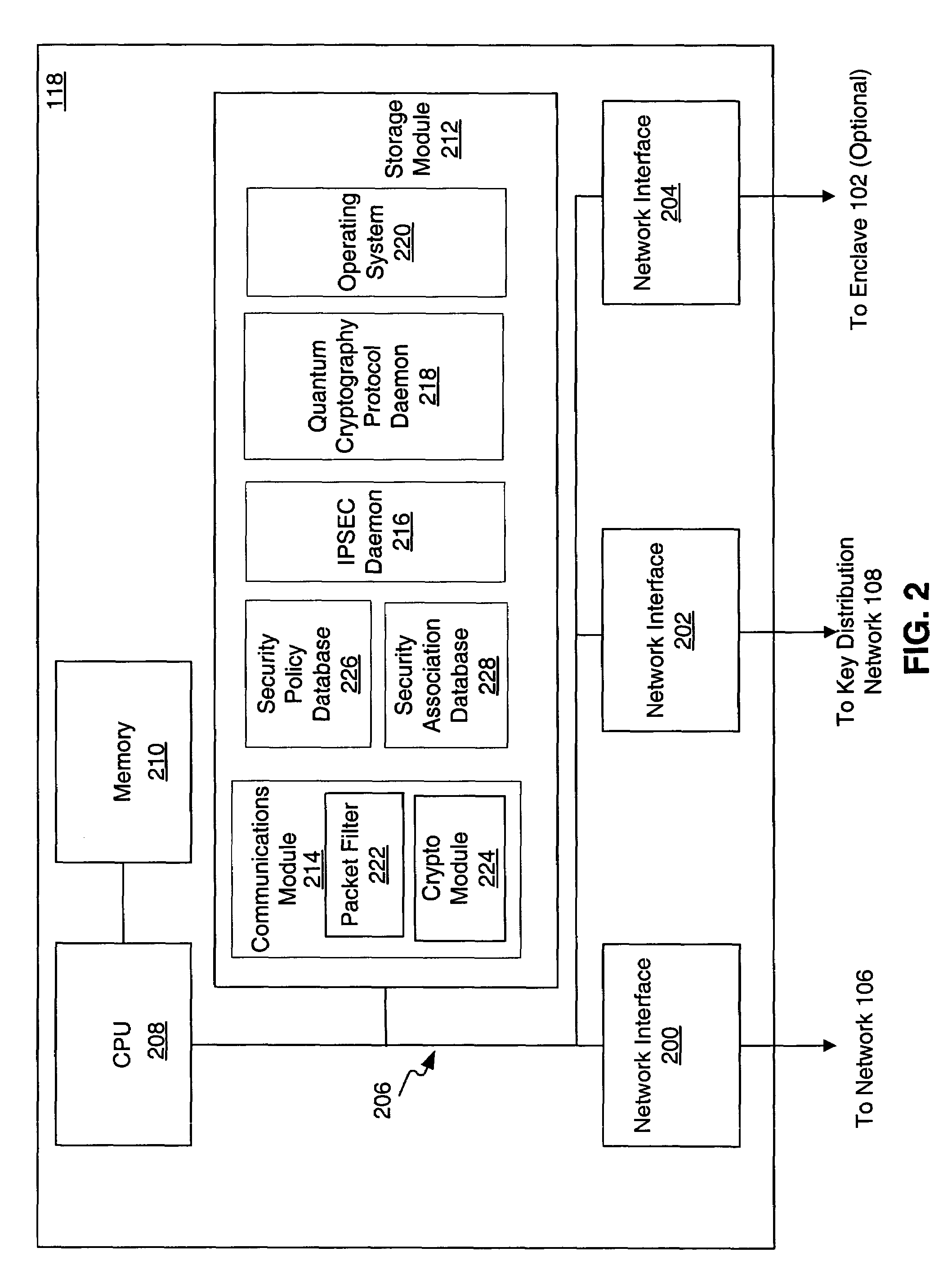
Key transport in quantum cryptographic networks
ActiveUS7236597B2Key distribution for secure communicationSecret communicationComputer networkThe Internet
Methods, apparatus, and systems are provided for distributing a key between nodes. The nodes are provided separate links for carrying messages versus keying information or material. The links for carrying messages couple the nodes to a messaging network, such as the Internet. In addition, the nodes are coupled together in a key distribution network by specialized links for carrying keying information or material. The links for keying information or material are configured to ensure the security of the keying information or material. The nodes that neighbor each other in the key distribution network establish respective pairwise keys. Once the pairwise keys are established, a set of non-neighboring nodes establish a shared key by communicating a sequence of bits through the messaging network. In order to ensure the security of the sequence of bits, the sequence of bits is encrypted based on the respective pairwise keys of neighboring nodes as it is forwarded in messages through the messaging network.
Owner:RAYTHEON BBN TECH CORP
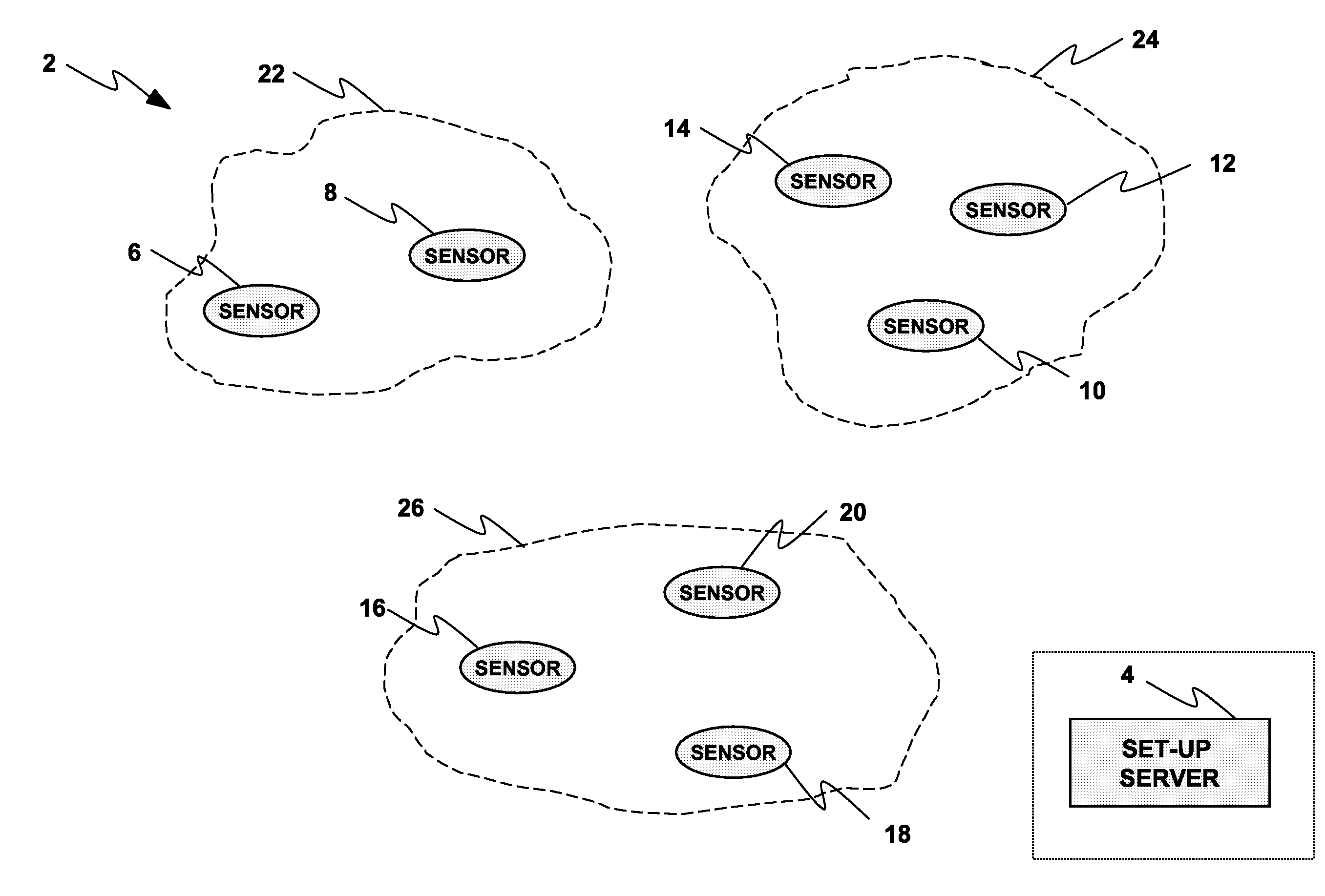
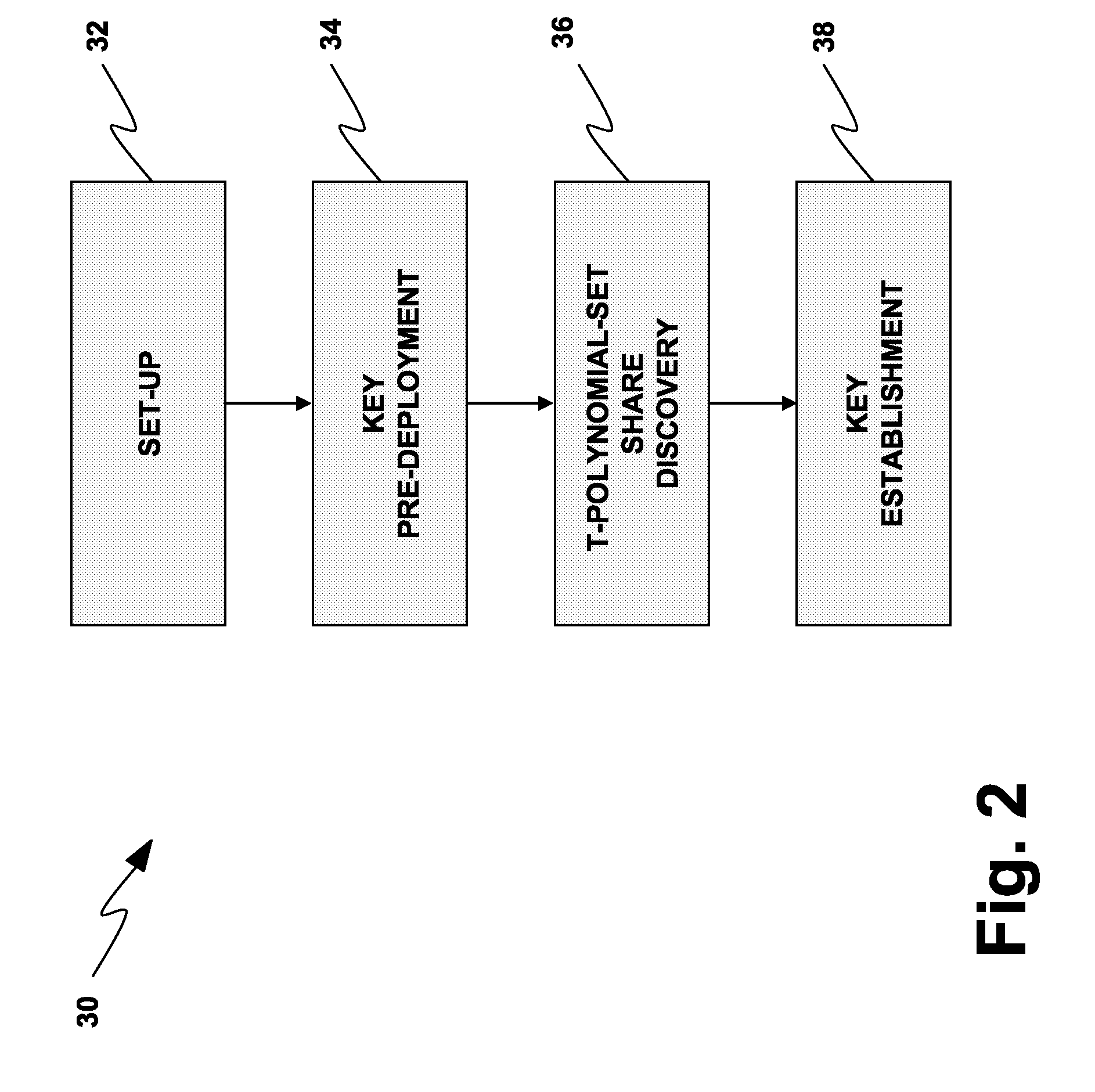
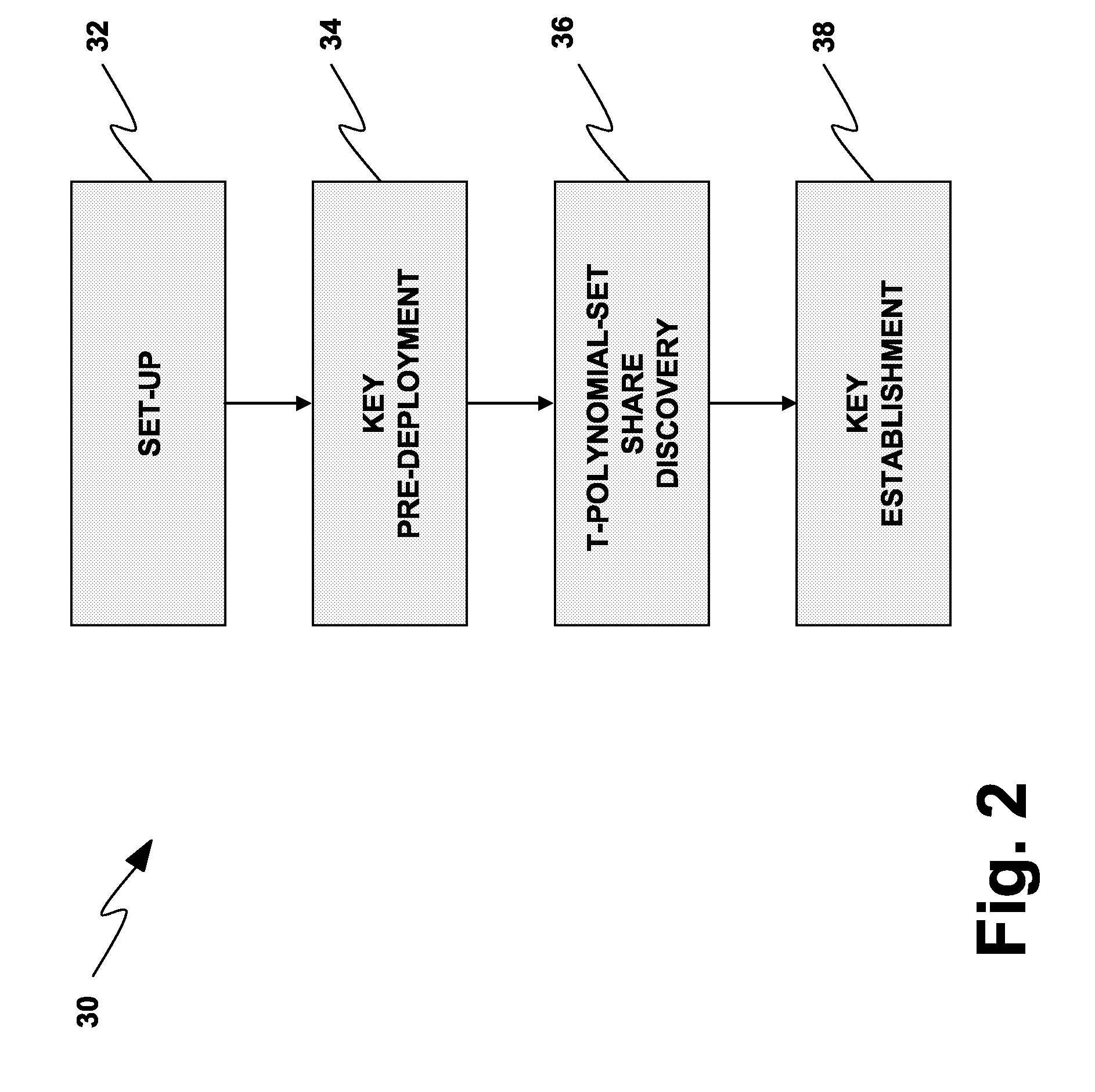
Deterministic Key Pre-Distribution and Operational Key Management for Mobile Body Sensor Networks
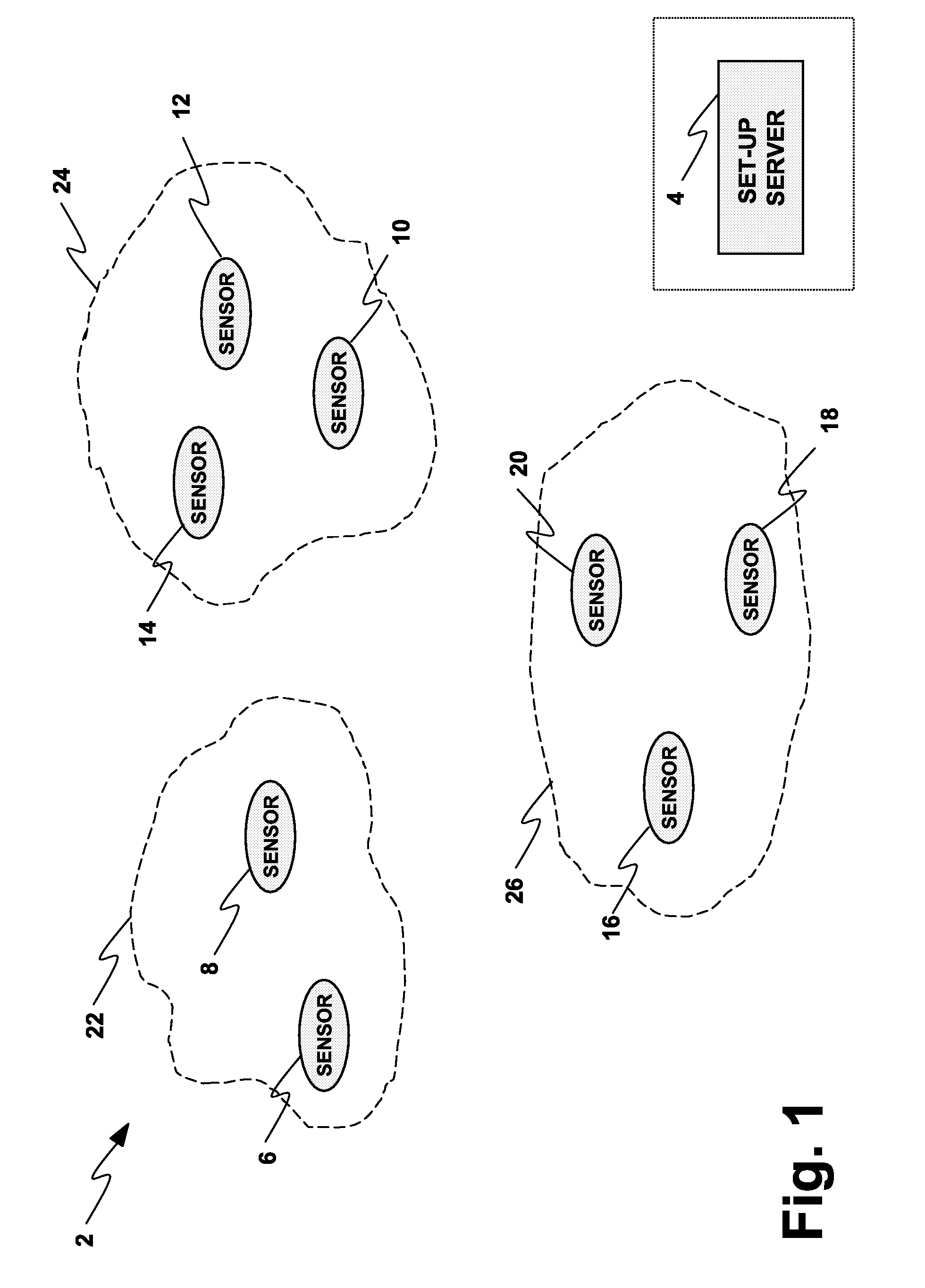
ActiveUS20090167535A1Facilitate communicationImprove security strengthError preventionFrequency-division multiplex detailsBody sensorsPairwise key
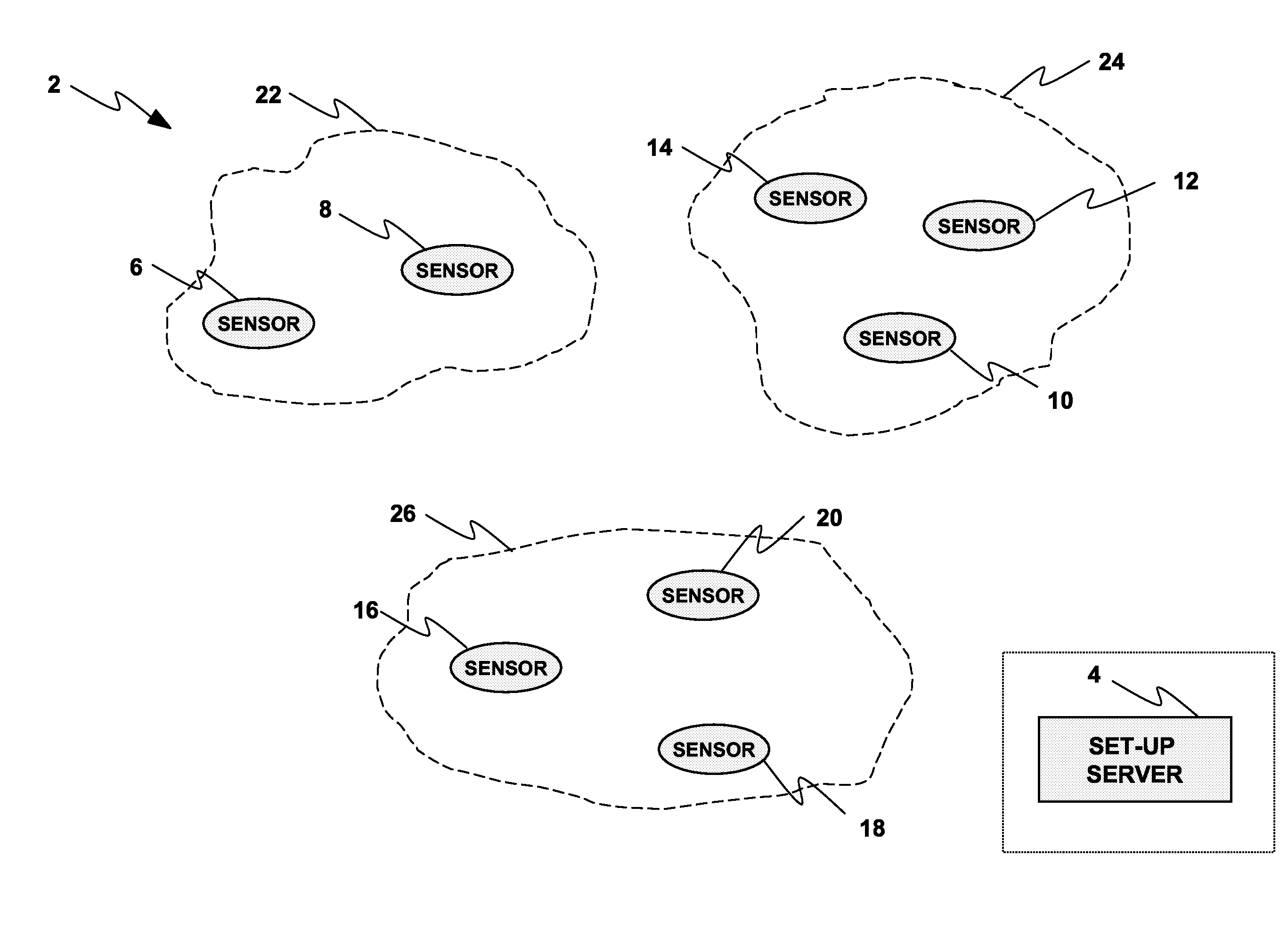
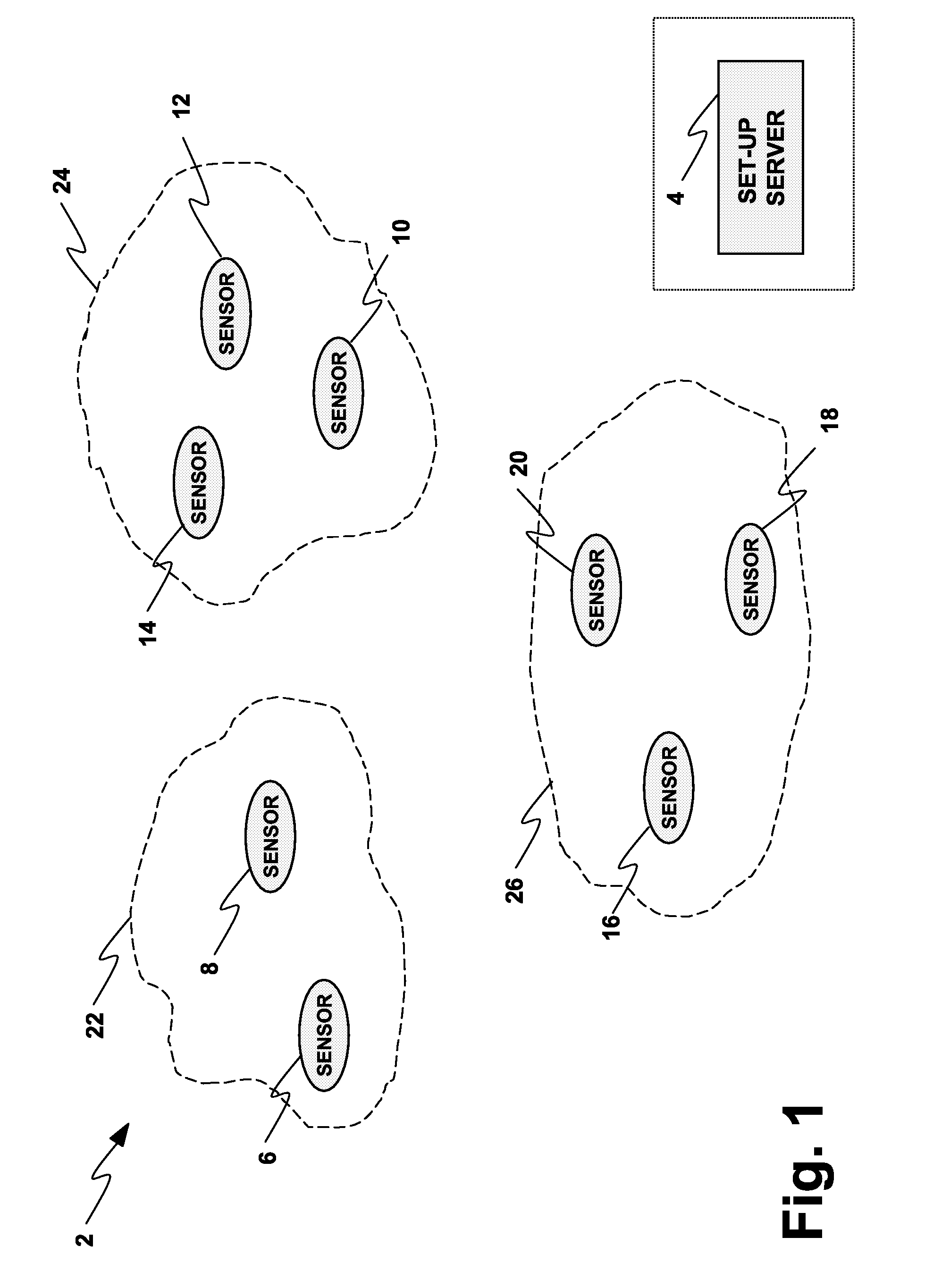
A wireless network (2, 150) for monitoring a patient includes a body sensor network (22, 24, 26, 172, 174, 176) that includes one or more wireless sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) operatively connected to the patient that collect and transfer information related to the patient's health to the wireless network (2, 150). A set-up server (4, 154) configures the one or more wireless sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) with keying material before the one or more sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) are deployed to the wireless network (2, 150). A base station (178, 180) distributes a key certificate to the one or more sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) associated with the body sensor network (22, 24, 26, 172, 174, 176), such that two sensors generate a unique pairwise key based at least in part upon the pre-distributed keying material and the key certificate distributed by the base station (178, 180).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
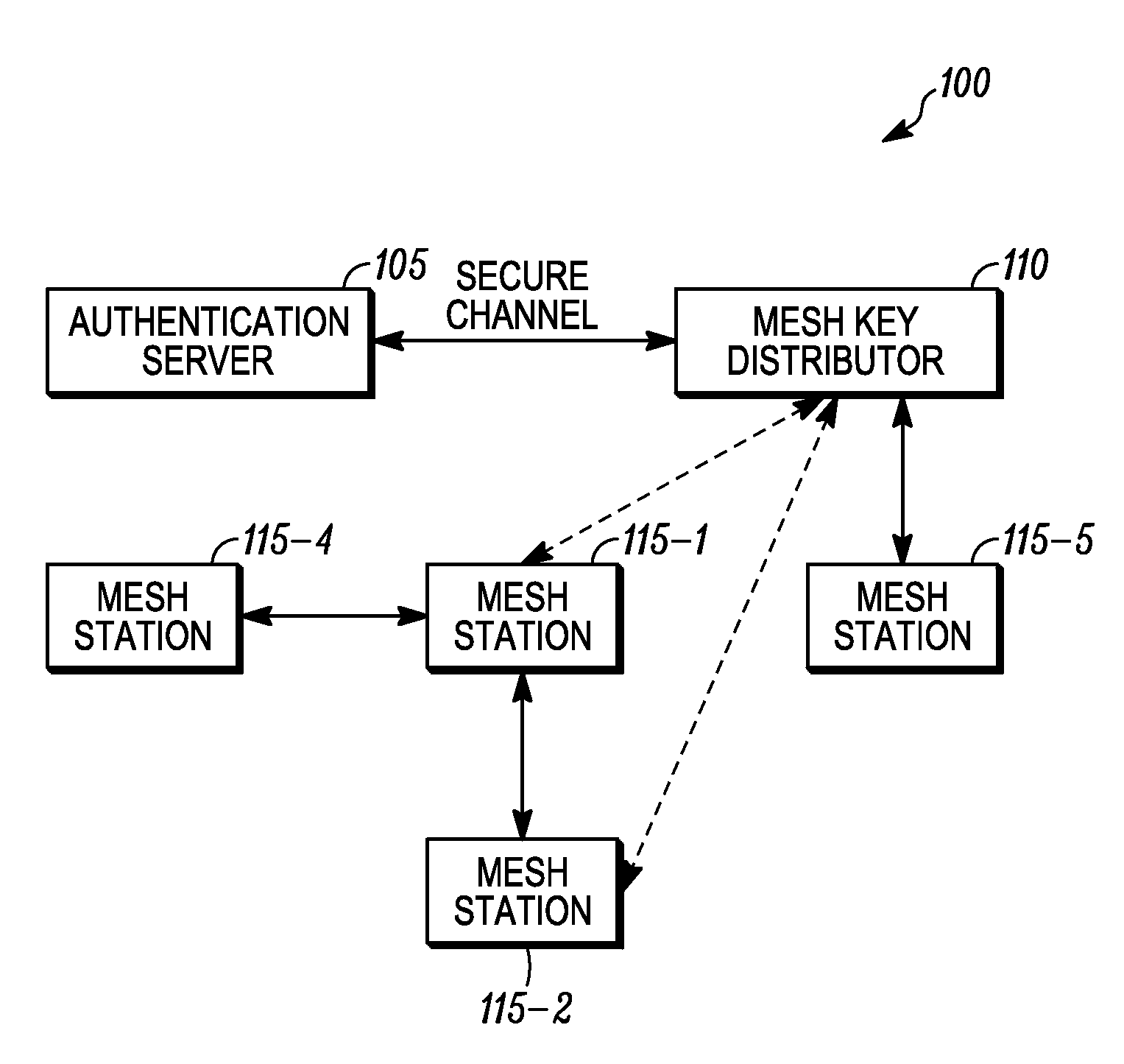
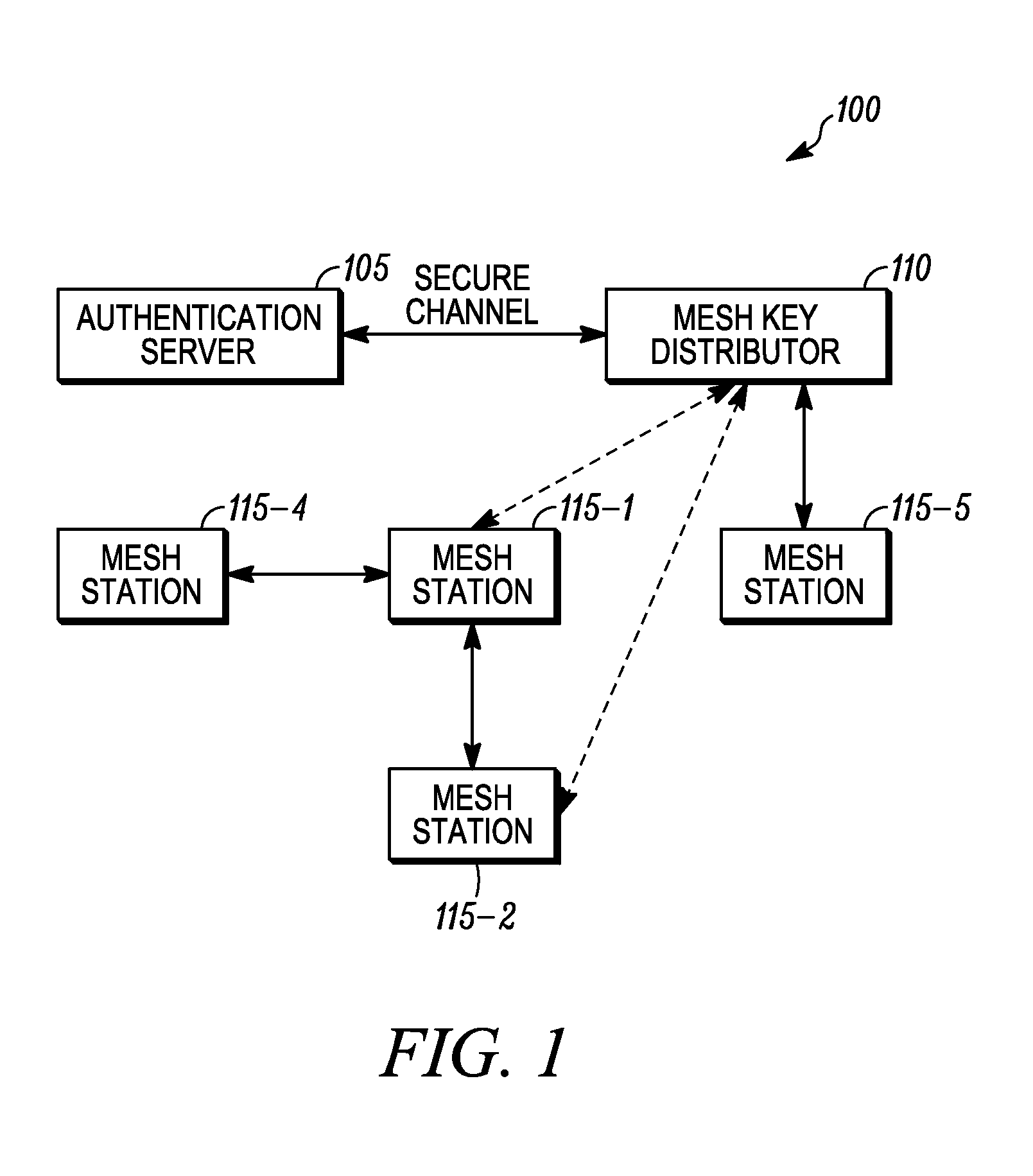
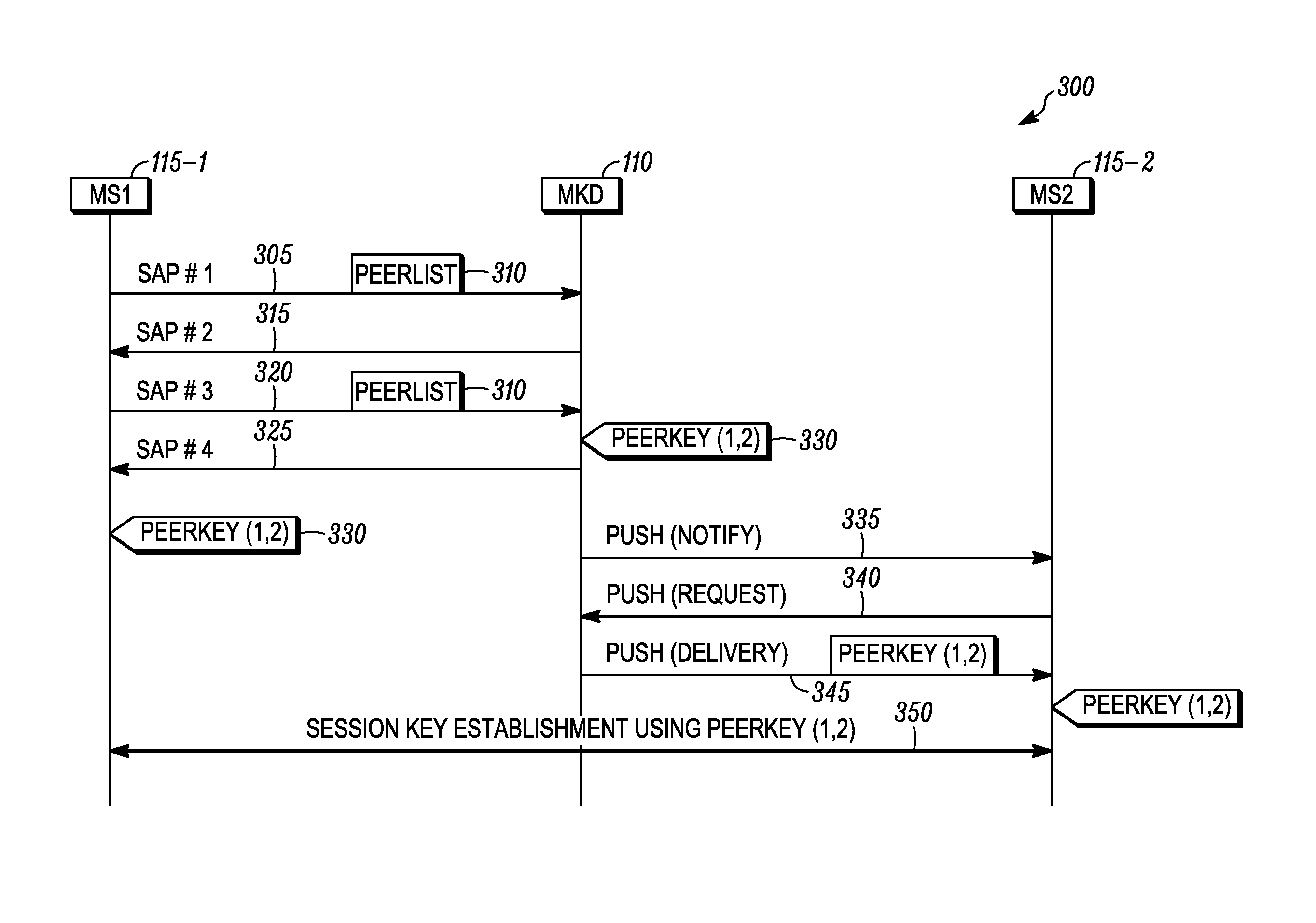
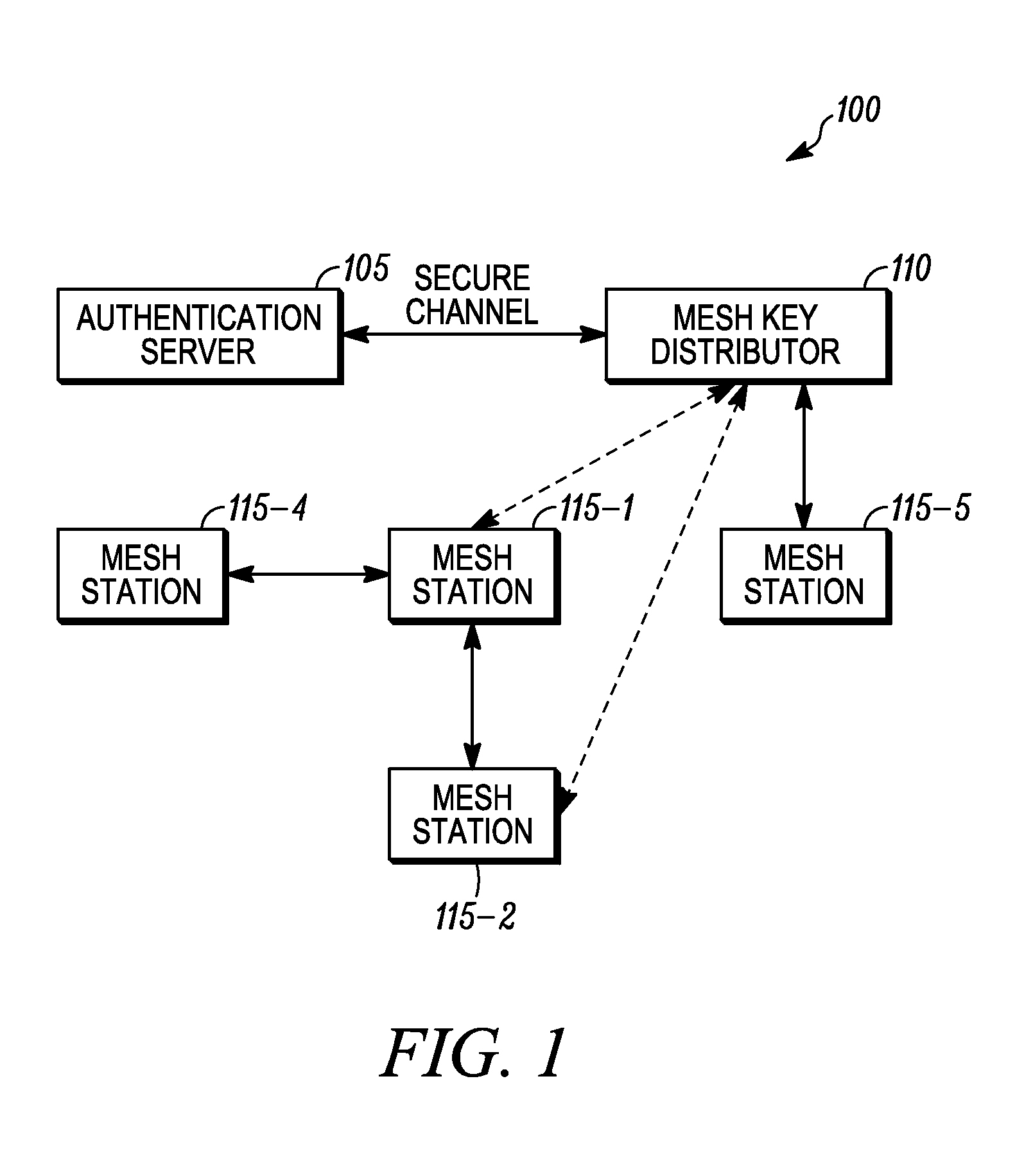
Method of triggering a key delivery from a mesh key distributor
ActiveUS20100329465A1Key distribution for secure communicationMultiple keys/algorithms usageComputer networkPairwise key
A mesh station applying for access to a network includes a list of peer stations in messages of an authenticated key establishment protocol. A mesh key distributor derives a key delivery key and generates a top level key, and then delivers the top level key to the mesh station. Following the key establishment protocol, the mesh key distributor also creates pairwise keys for use between the mesh station and the peer stations listed in its peer list. The list of peers permits the identifier for the peer to be bound into the derived key, which helps ensure that the key used between each pair of peers is unique. Once the mesh key distributor finishes creating a key for one of the stations on the peer list, the mesh key distributor sends a message to the peer to initiate a key push.
Owner:STRONG FORCE IOT
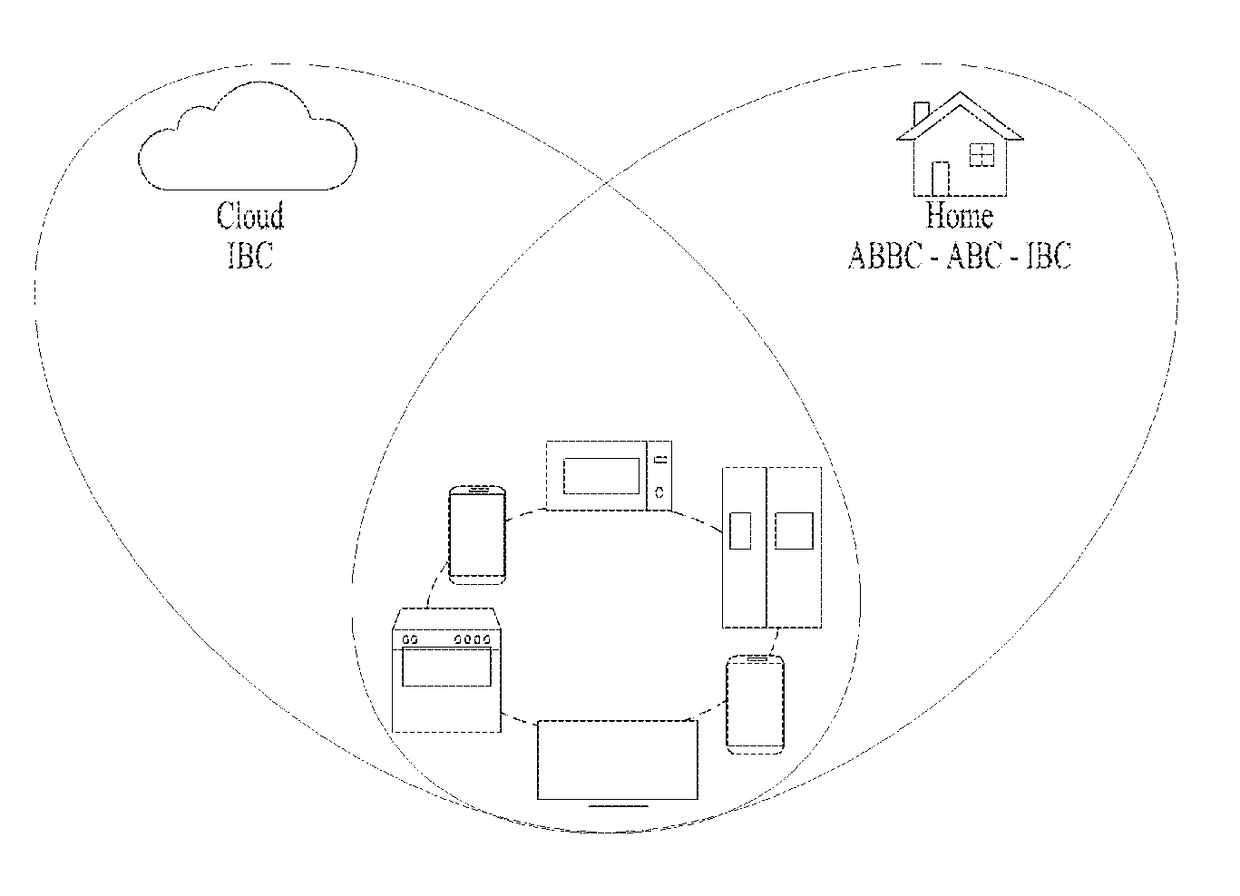
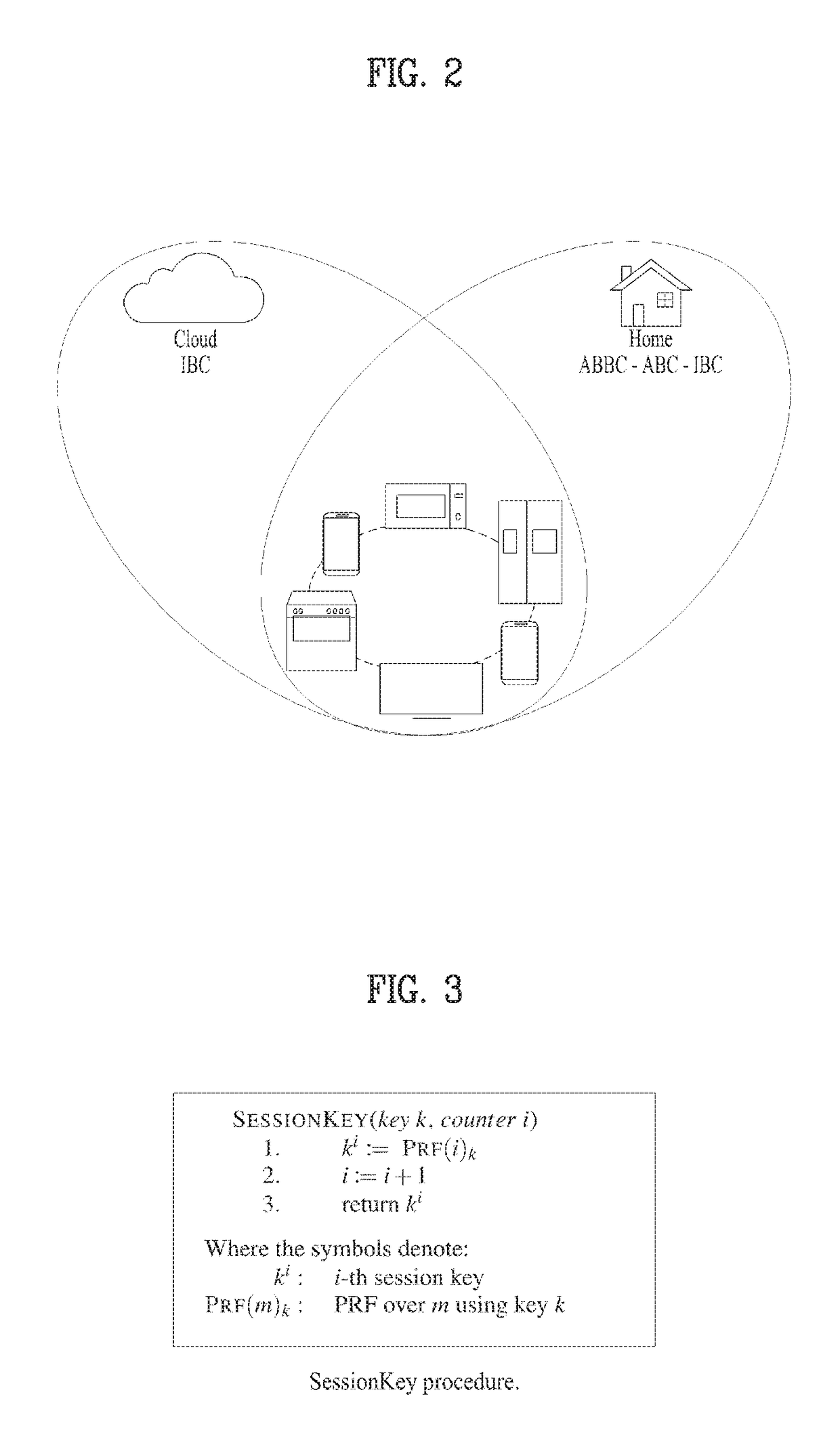
System and method for authentication of things
ActiveUS20170214529A1Key distribution for secure communicationUser identity/authority verificationID-based encryptionPairwise key
An Authentication Of Things (AOT) system includes a cloud server configured to control a cloud domain connected with a plurality of devices, a home server configured to control a home server connected with a plurality of devices, a first device corresponding to a new device, and a second device of a root user connected with the home domain while authentication is completed in the home server. In this case, the first device loads cryptographic material of the cloud server from the cloud server in a pre-deployment stage, the cryptographic material includes at least one selected from the group consisting of an identifier of the first device in the cloud server, a first private key of an ID-based cryptography system of the first device in the cloud server, a first pairwise key of the first device in the cloud server, and a counter of the first device, and if the first device is shipped to a trader, the cloud server deletes the first private key from the cloud server.
Owner:LG ELECTRONICS INC +1
Electronic key management using pki to support group key establishment in the tactical environment
ActiveUS20140226821A1Key distribution for secure communicationPublic key infrastructure trust modelsComputer hardwareSupport group
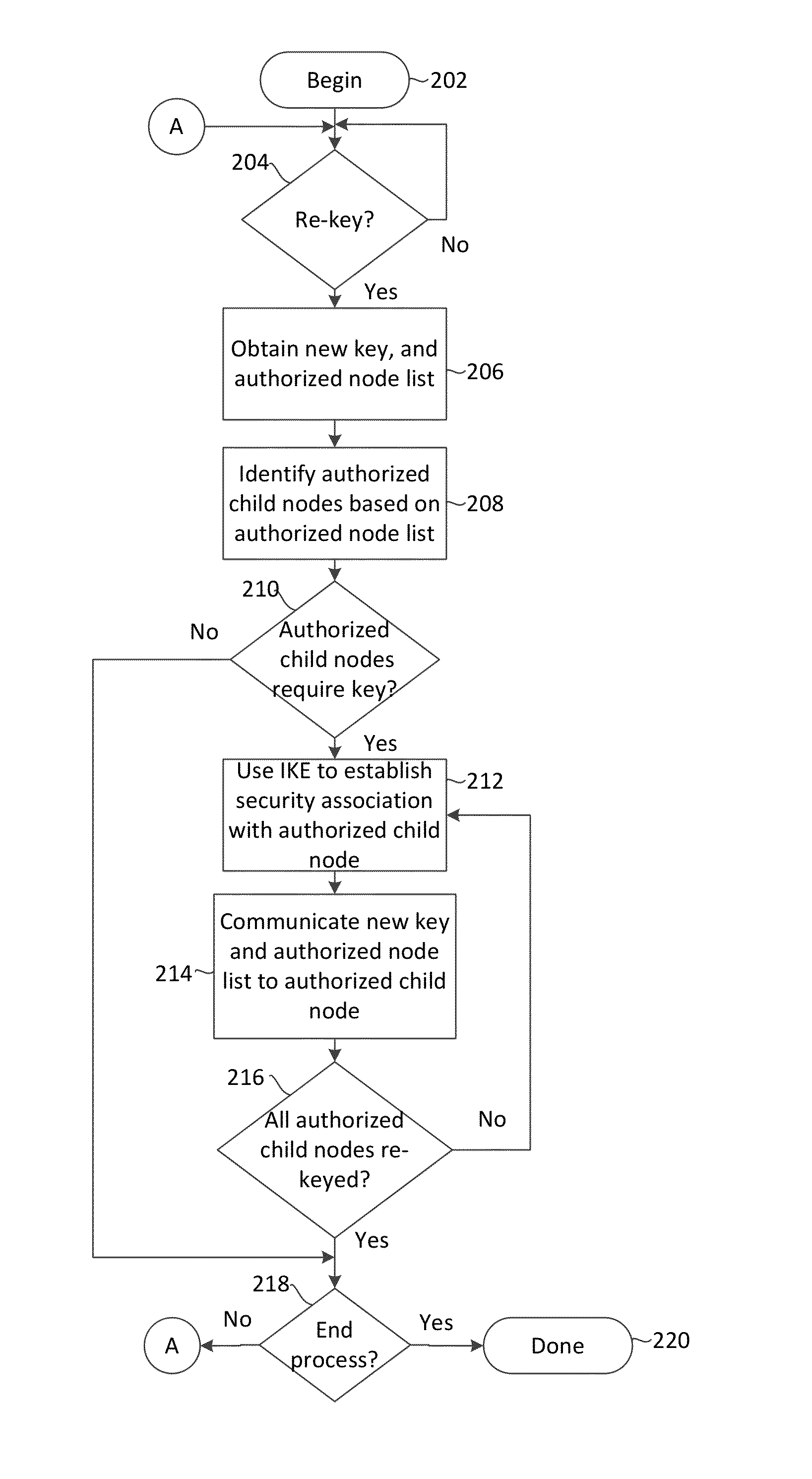
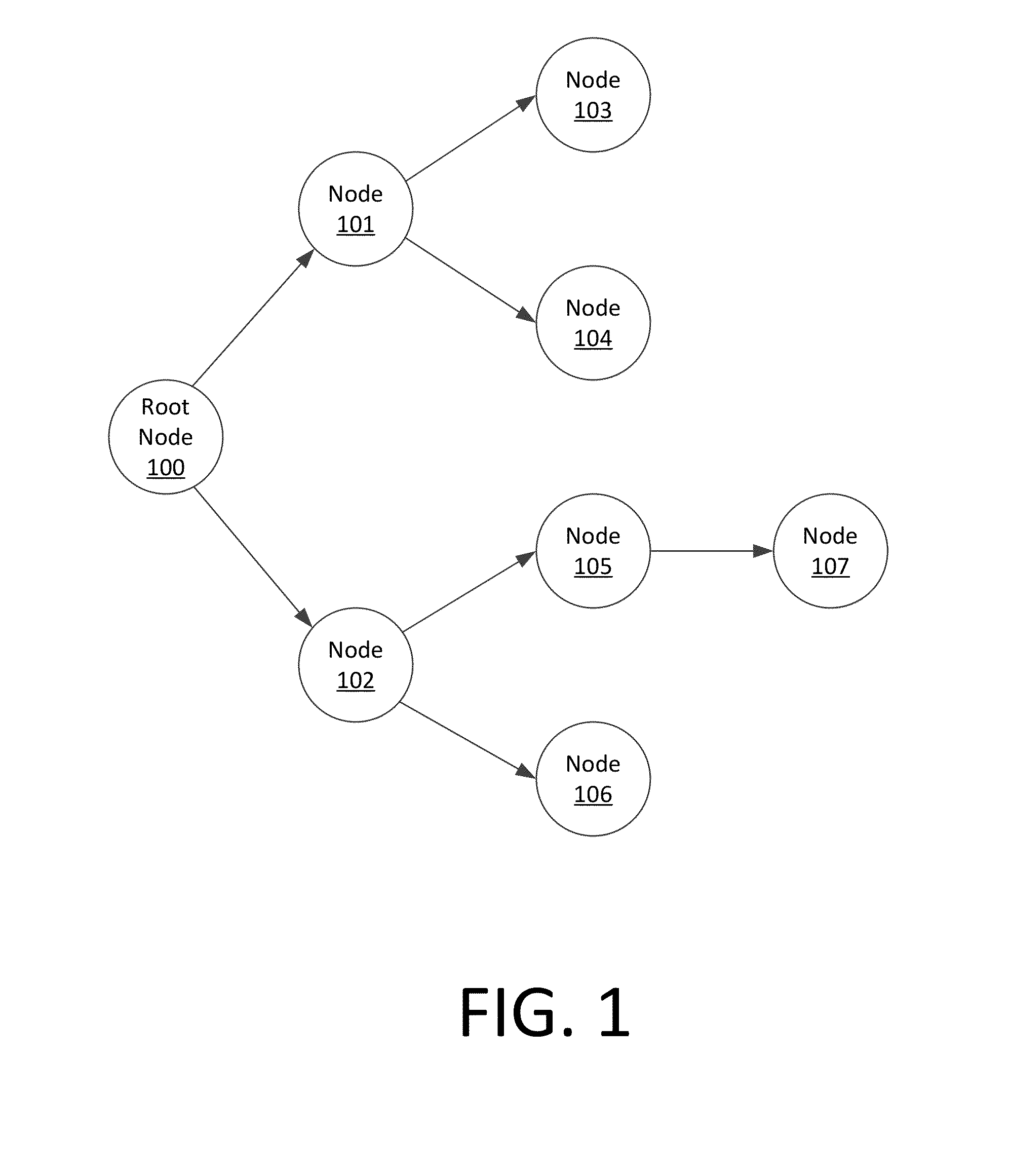
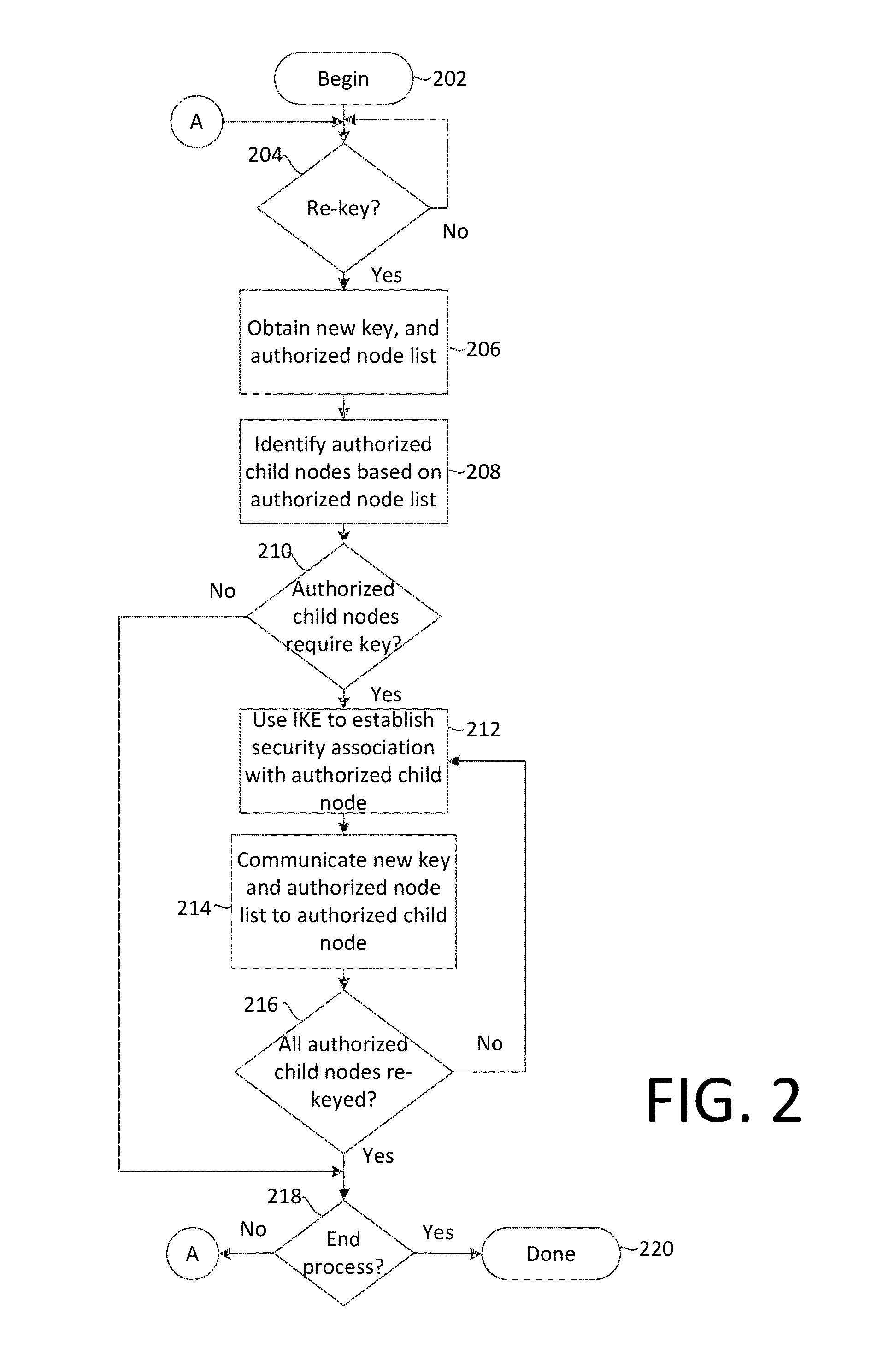
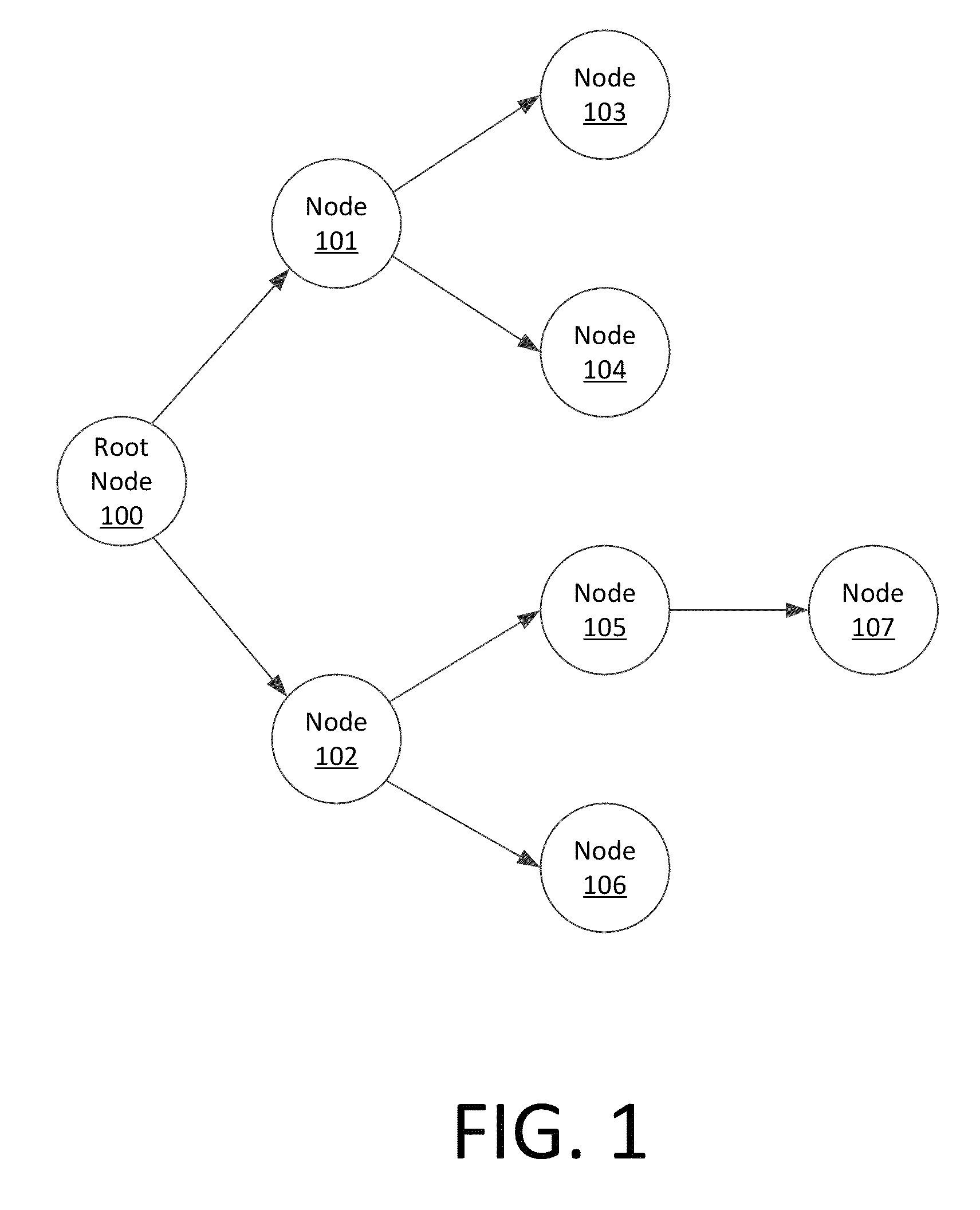
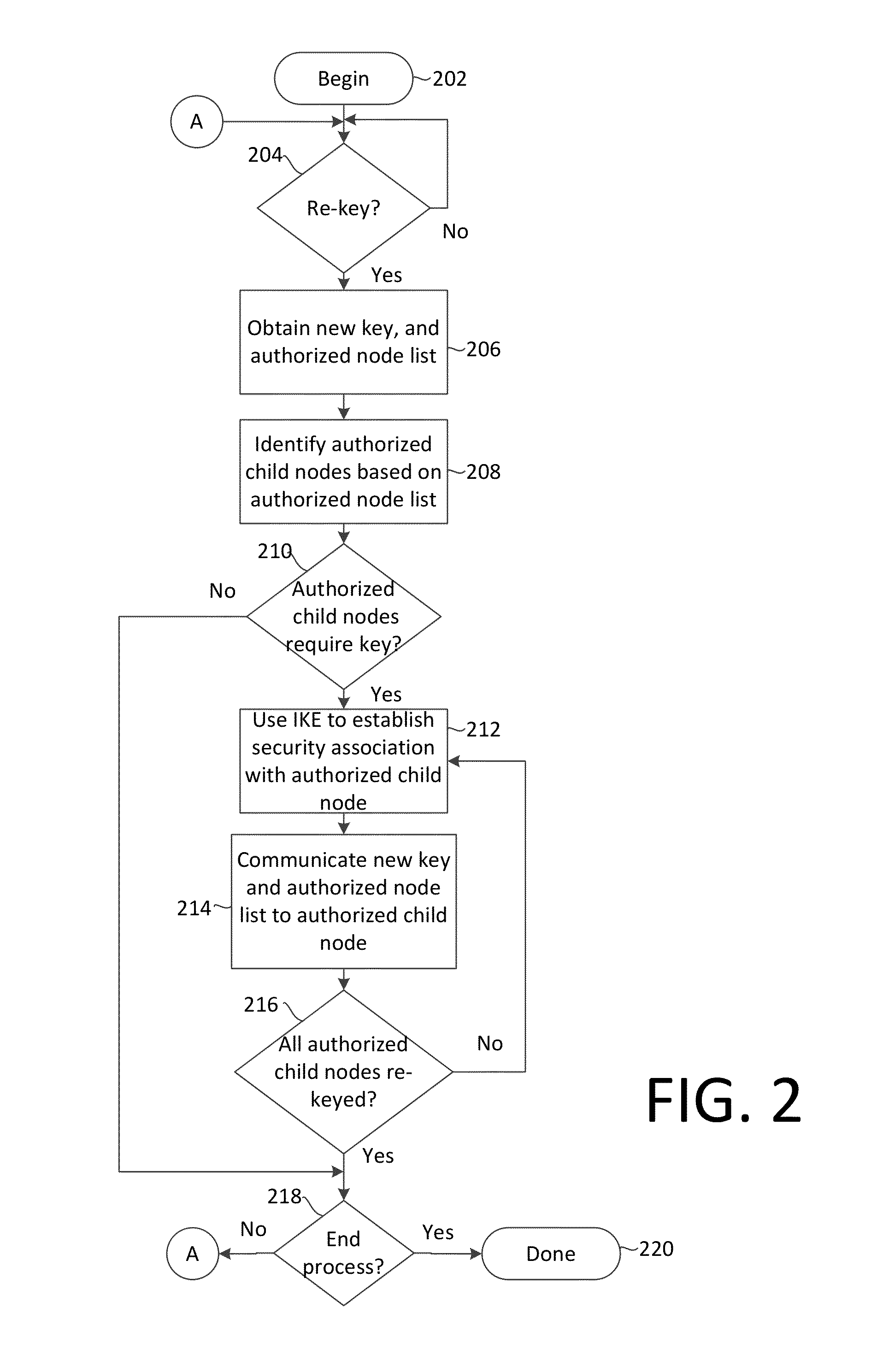
Method for distributing a group session cryptographic key includes initiating at least one pairwise key distribution session including a root node (100) and at least one communication node (101-107). The method further includes performing at a communication node which has received the group session cryptographic key a propagated pairwise key distribution session with at least one of the communication nodes which has not previously received said group session cryptographic key. The propagated pairwise key distribution sessions are performed at each of the communication nodes which subsequently receives the group session cryptographic key until the group session cryptographic key has been securely provided to all authorized communication nodes.
Owner:HARRIS GLOBAL COMMUNICATIONS INC
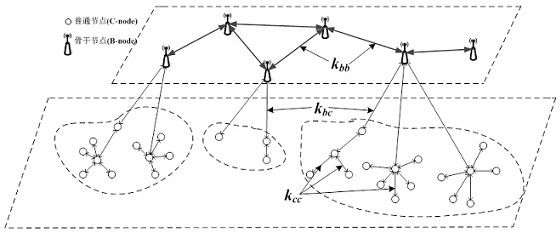
Bridge-type-based wireless sensing network key management scheme
The invention relates to a bridge-type-based wireless sensing network key management scheme. The bridge-type-based wireless sensing network key management scheme includes the following steps that firstly, key pre-allocation is carried out, and namely allocation information is preset onto each sensor node by a starting server before node deployment; secondly, in the clustering phase, after cluster head nodes are selected, the clustering phase begins immediately, and each sensor node is added to the corresponding nearest cluster in the clustering process; thirdly, in the neighbor node discovery phase, whether other nodes are to be recorded as neighbor nodes or not is determined by each sensor according to the included angle calculation formula; fourthly, intra-cluster matched keys are built, wherein matched keys between each sensor node and other neighbor nodes are worked out through the bridge type; fifthly, inter-cluster matched keys are built, wherein matched keys between each cluster head node and other cluster head nodes are worked out through symmetric bivariate polynomials. By means of the scheme, on the premise that a certain connection rate is guaranteed, information transfer safety and effectiveness can be guaranteed, and the memory space of a memory is well saved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Deterministic key pre-distribution and operational key management for moblie body sensor networks
InactiveUS7999685B2Facilitate communicationImprove security strengthError preventionFrequency-division multiplex detailsLine sensorBody sensors
A wireless network (2, 150) for monitoring a patient includes a body sensor network (22, 24, 26, 172, 174, 176) that includes one or more wireless sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) operatively connected to the patient that collect and transfer information related to the patient's health to the wireless network (2, 150). A set-up server (4, 154) configures the one or more wireless sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) with keying material before the one or more sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) are deployed to the wireless network (2, 150). A base station (178, 180) distributes a key certificate to the one or more sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) associated with the body sensor network (22, 24, 26, 172, 174, 176), such that two sensors generate a unique pairwise key based at least in part upon the pre-distributed keying material and the key certificate distributed by the base station (178, 180).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
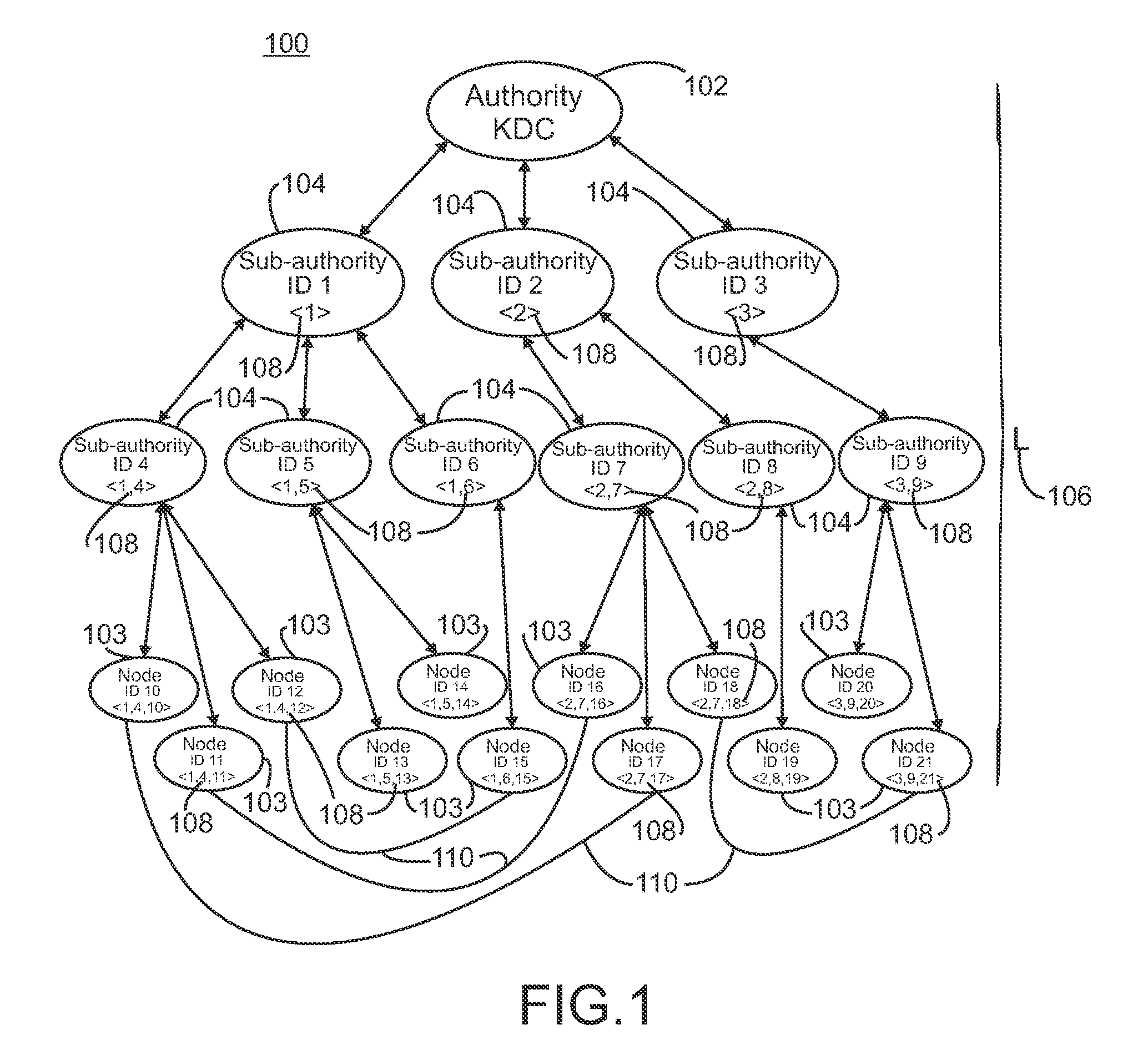
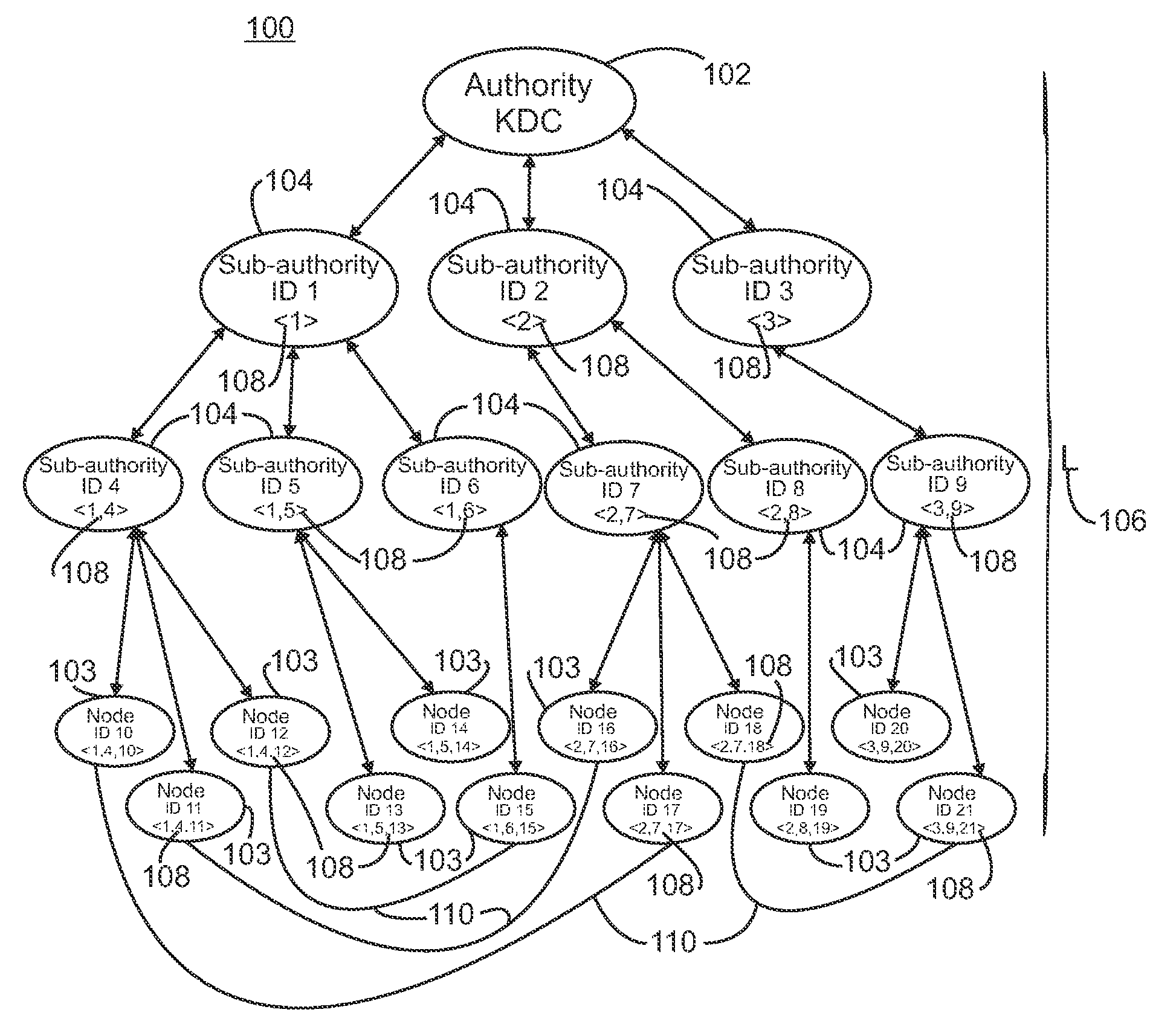
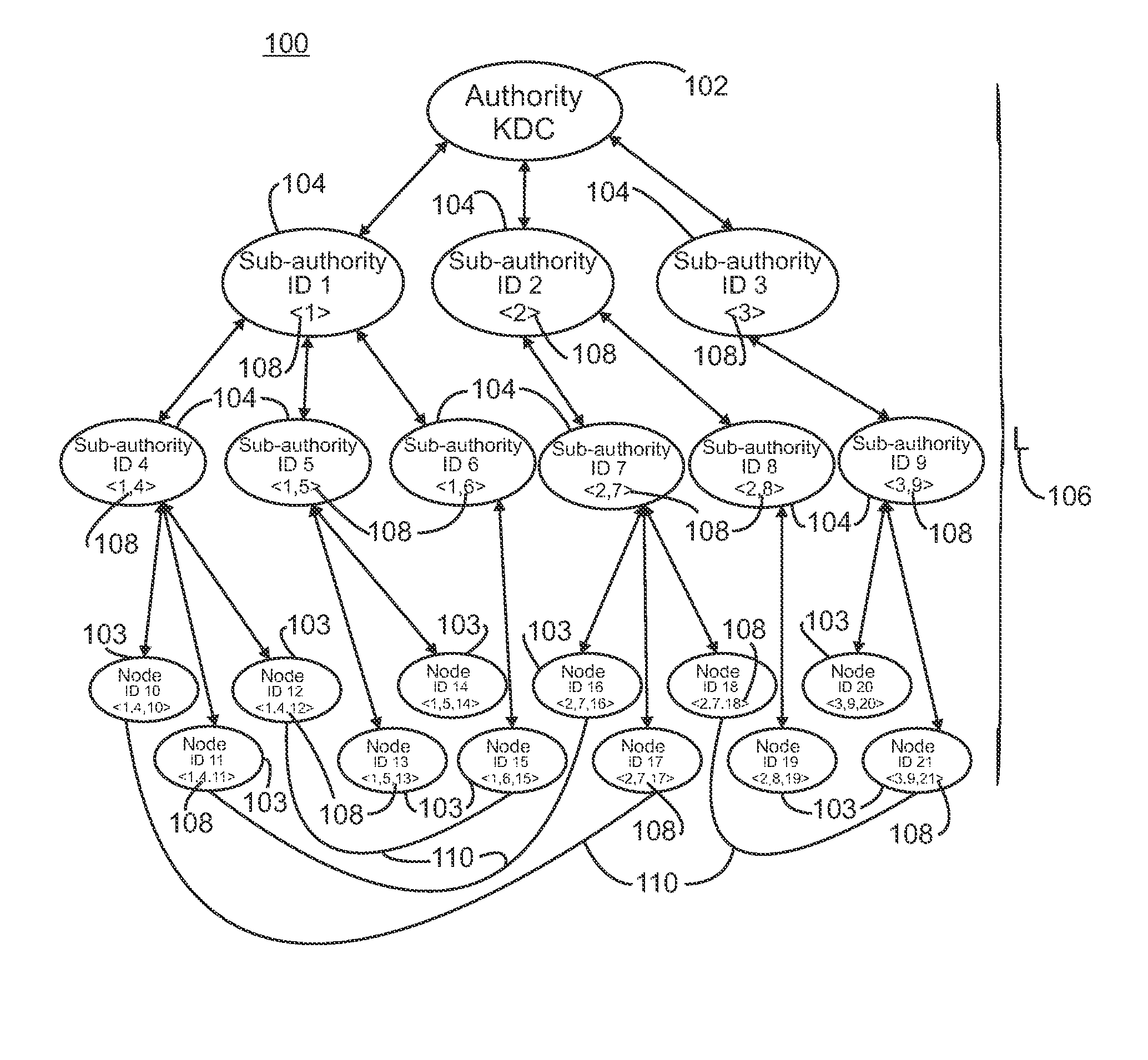
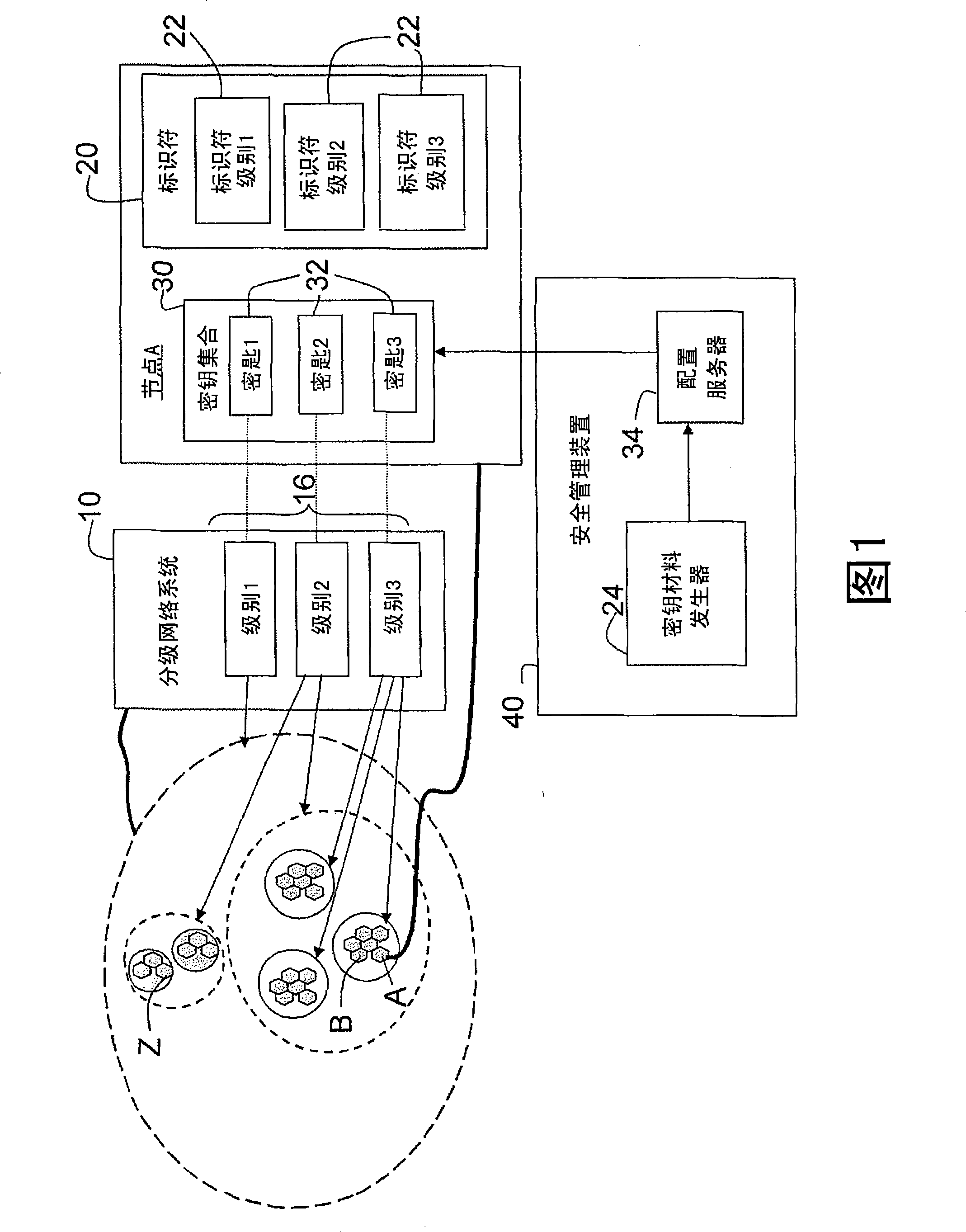
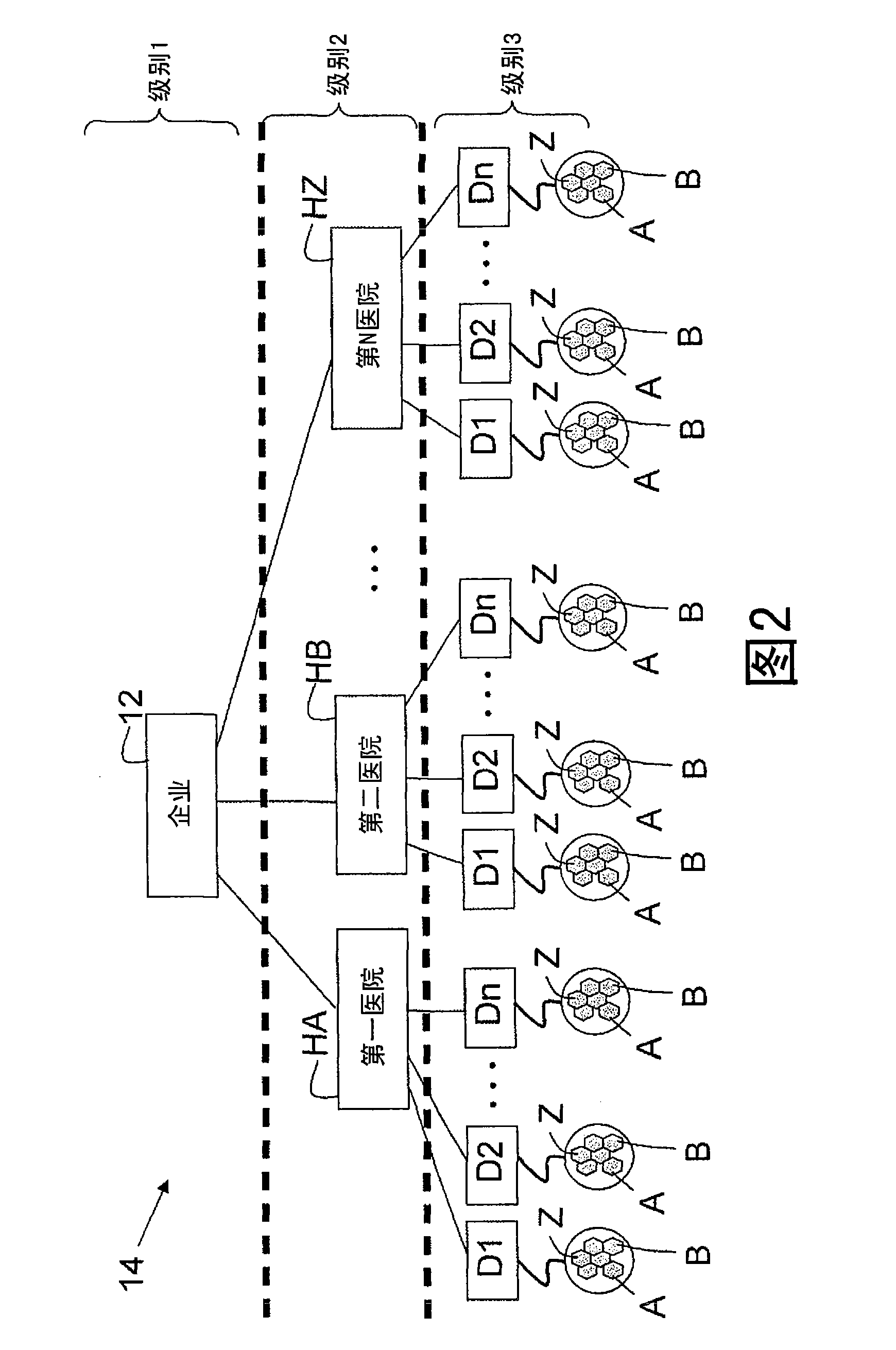
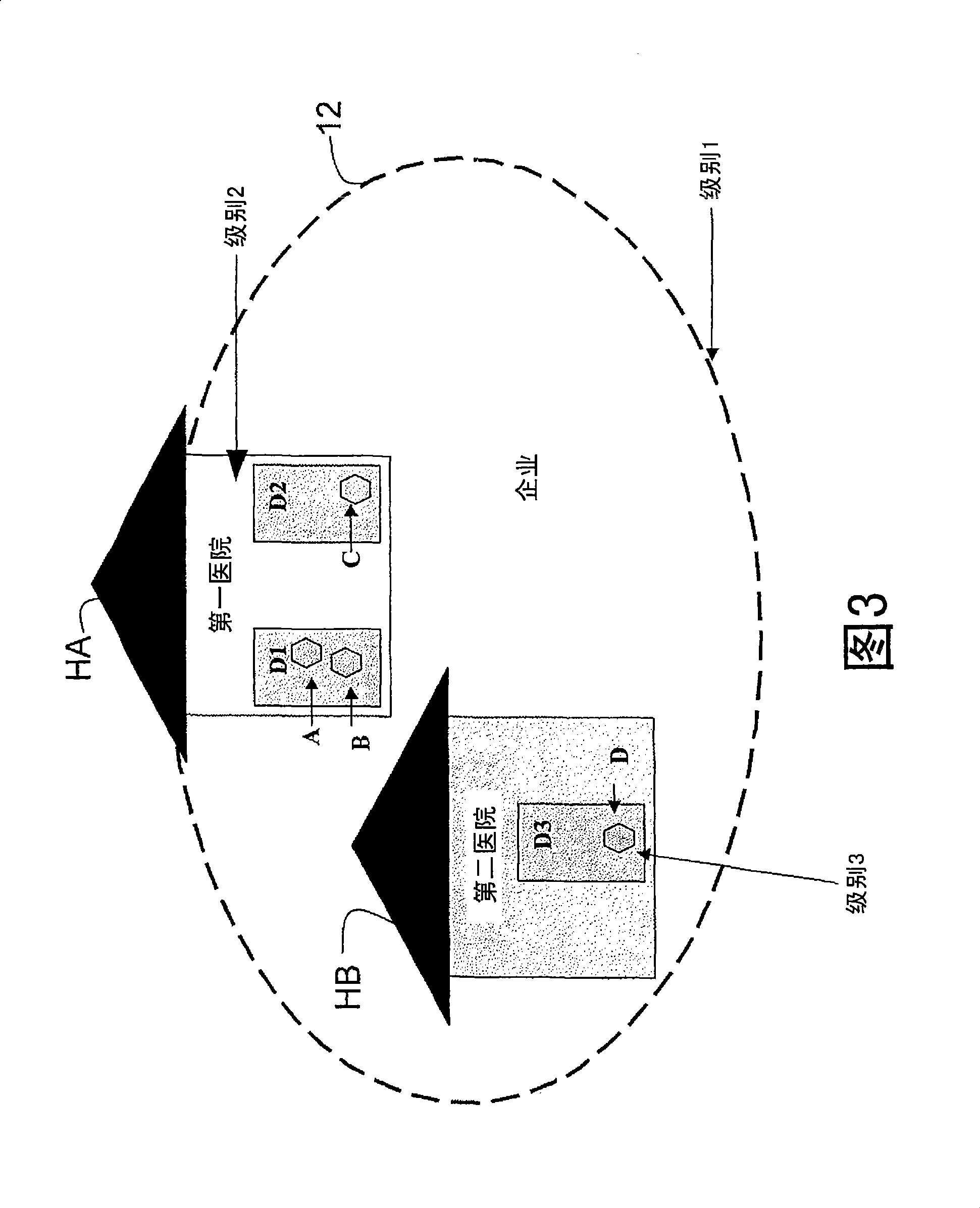
Hierarchical deterministic pairwise key predistribution scheme
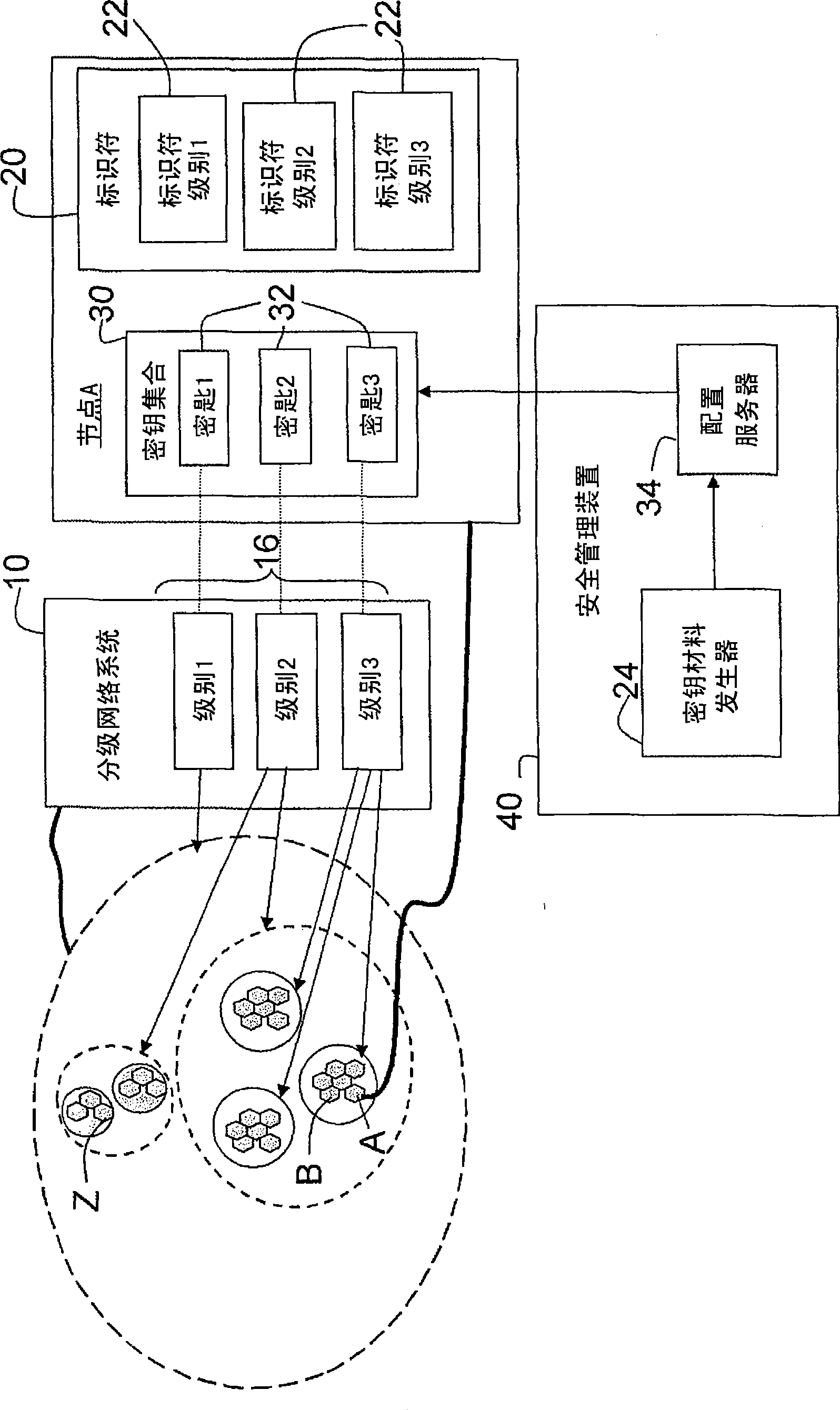
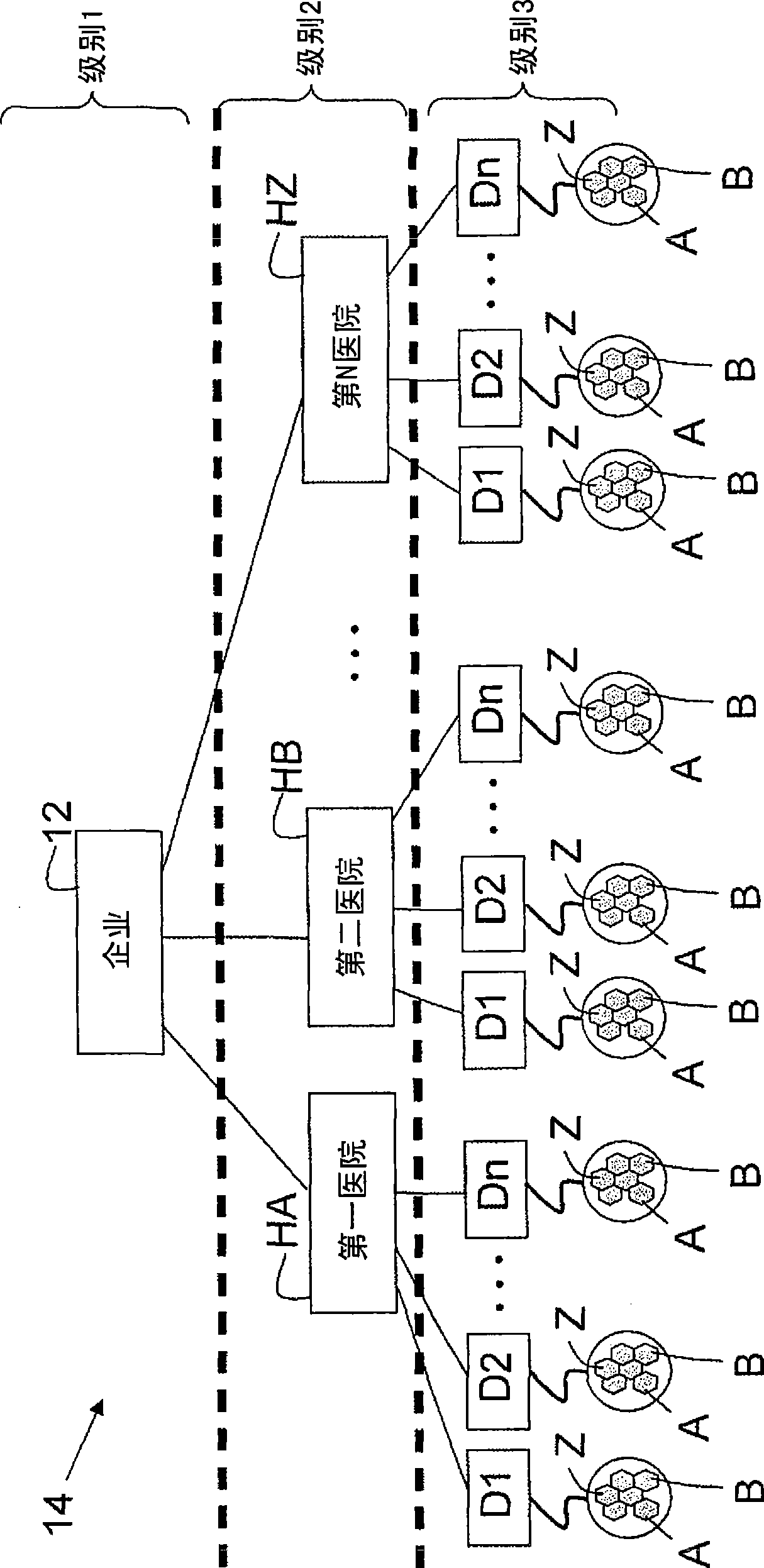
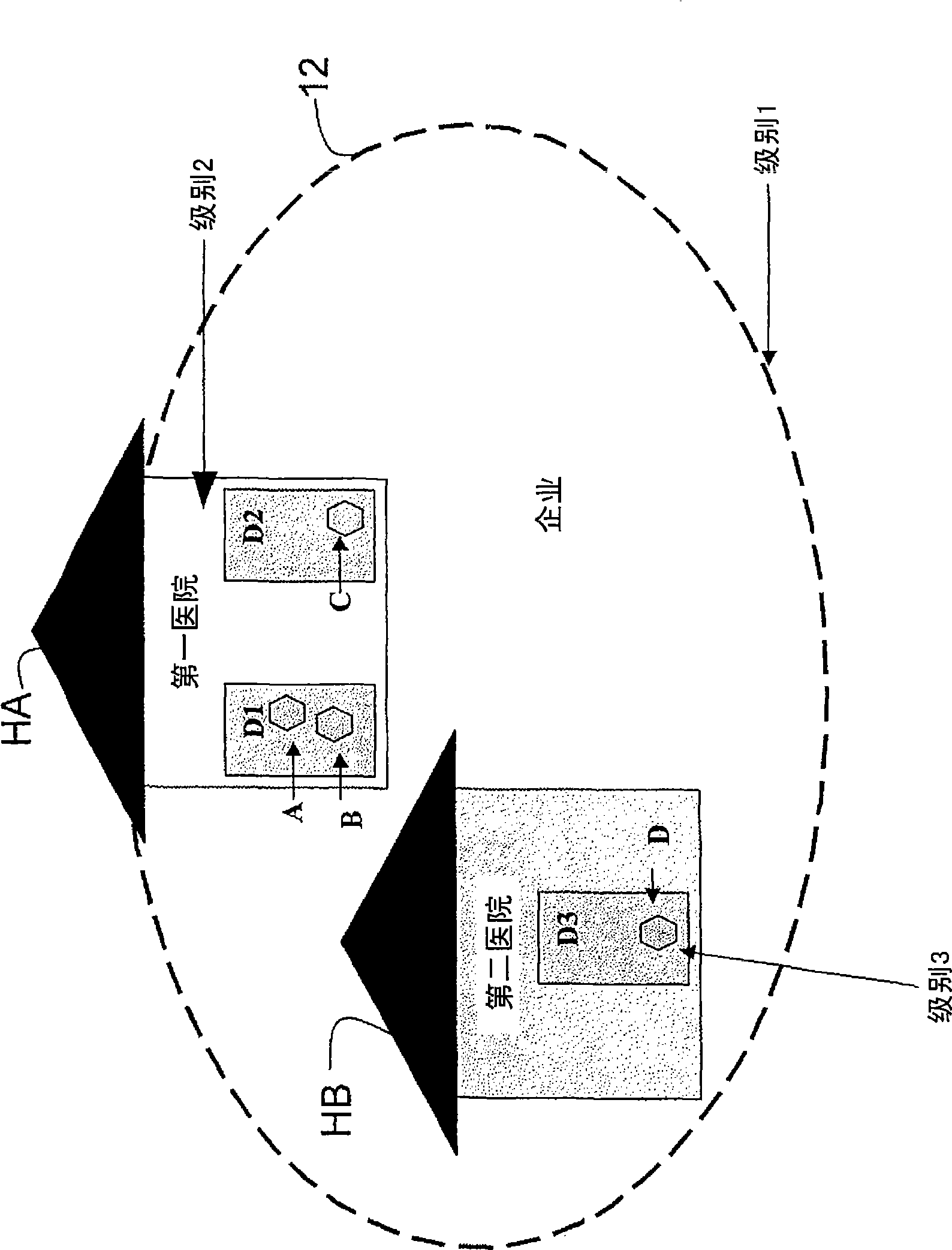
InactiveCN101473626ARestriction of visitData taking preventionParticular environment based servicesSecurity domainPairwise key
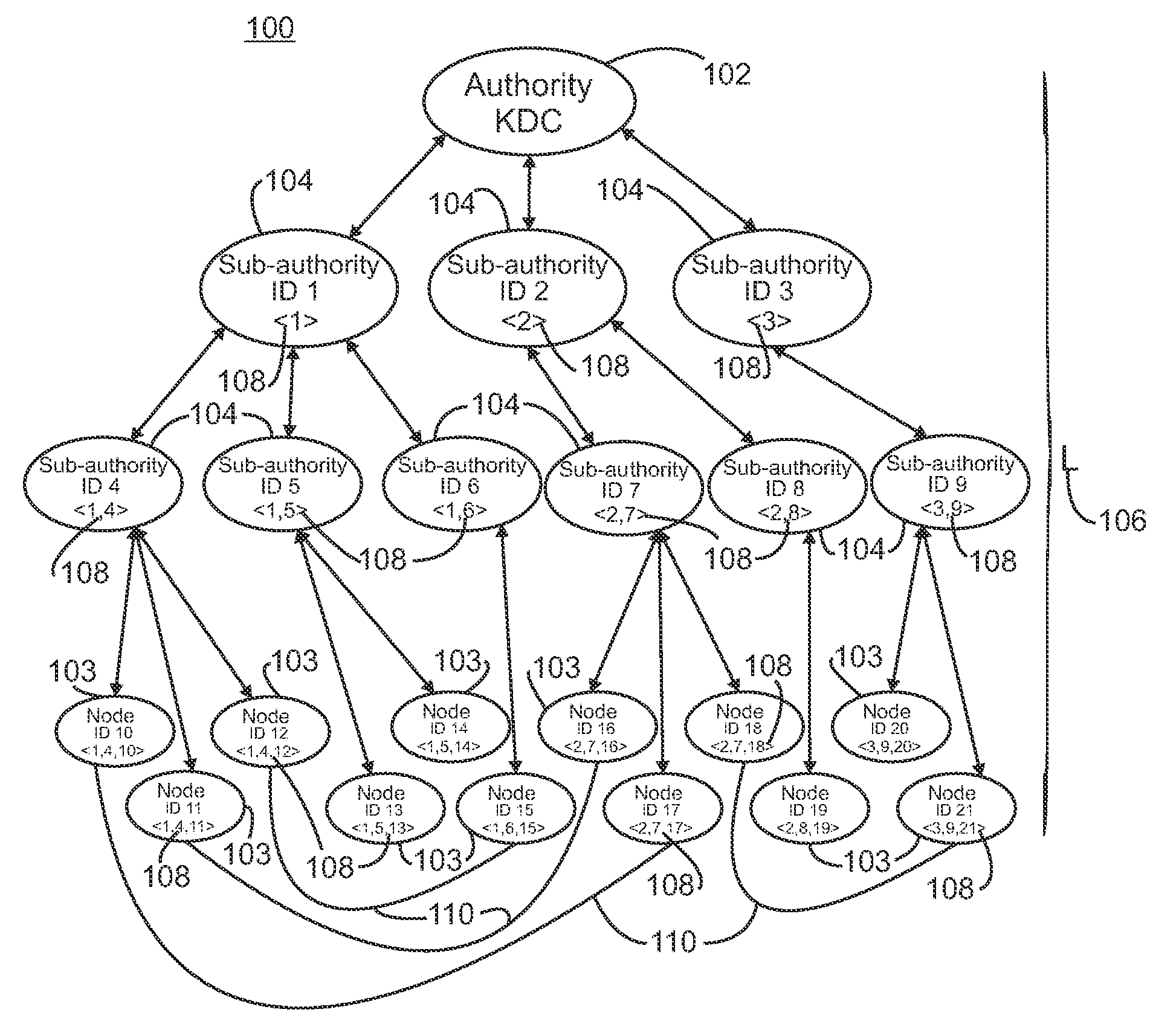
A security system for a hierarchical network (10) includes L hierarchical levels each corresponding to a security domain level (16), and a plurality of local network nodes (A, B,..., Z). A keying material generator (24) generates a set (30) of correlated keying material for each network node. Each set (30) of keying material is composed of L sub-sets (32) of keying material one for each security domain level (16). A set up server (34) distributes the generated sets (30) of keying material to each network node (A, B,, Z) to enable the network nodes (A, B,, Z) to communicate with one another ata security domain of a hierarchical level k by a use of a corresponding sub-set (32) of the security keying material.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
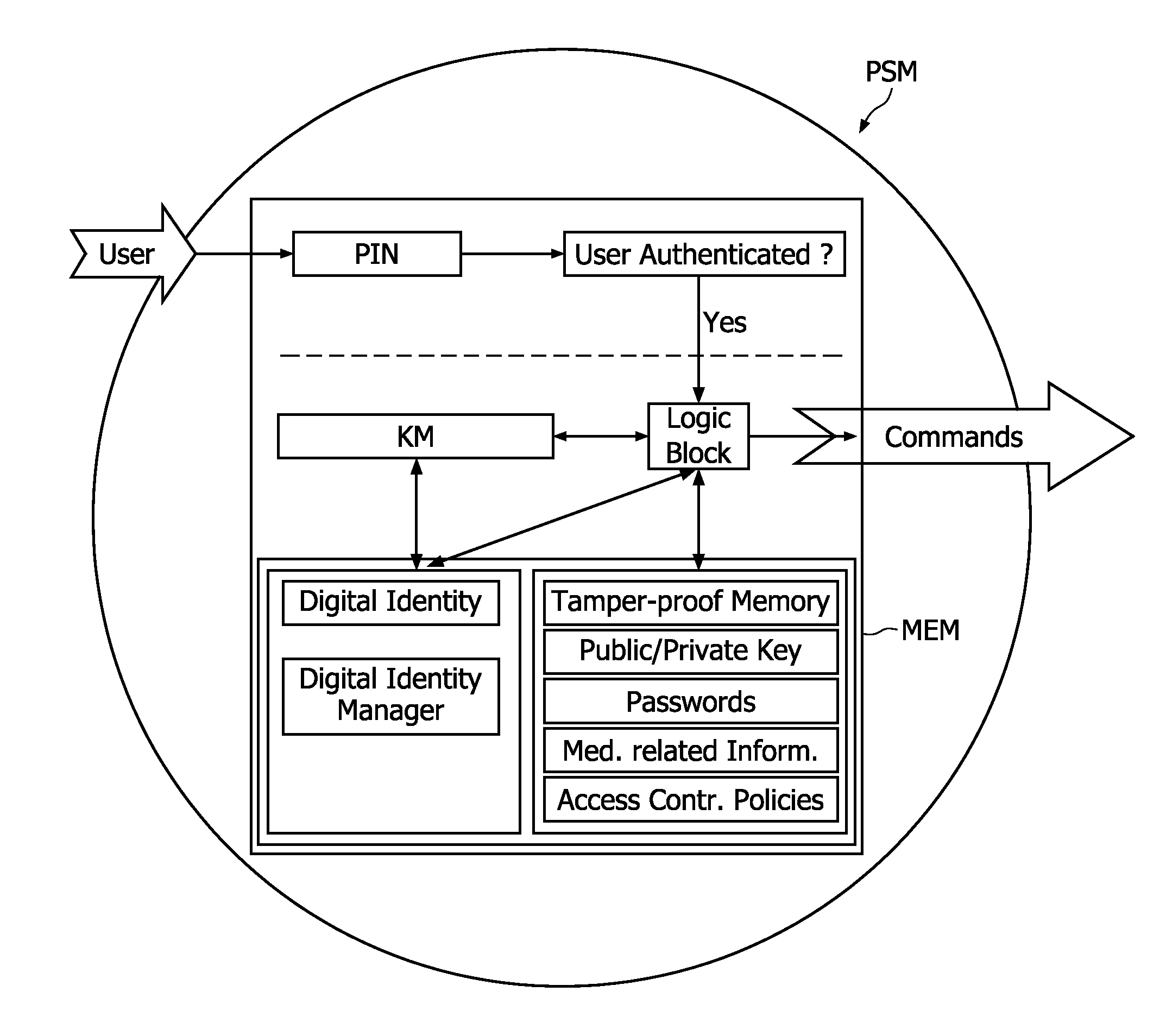
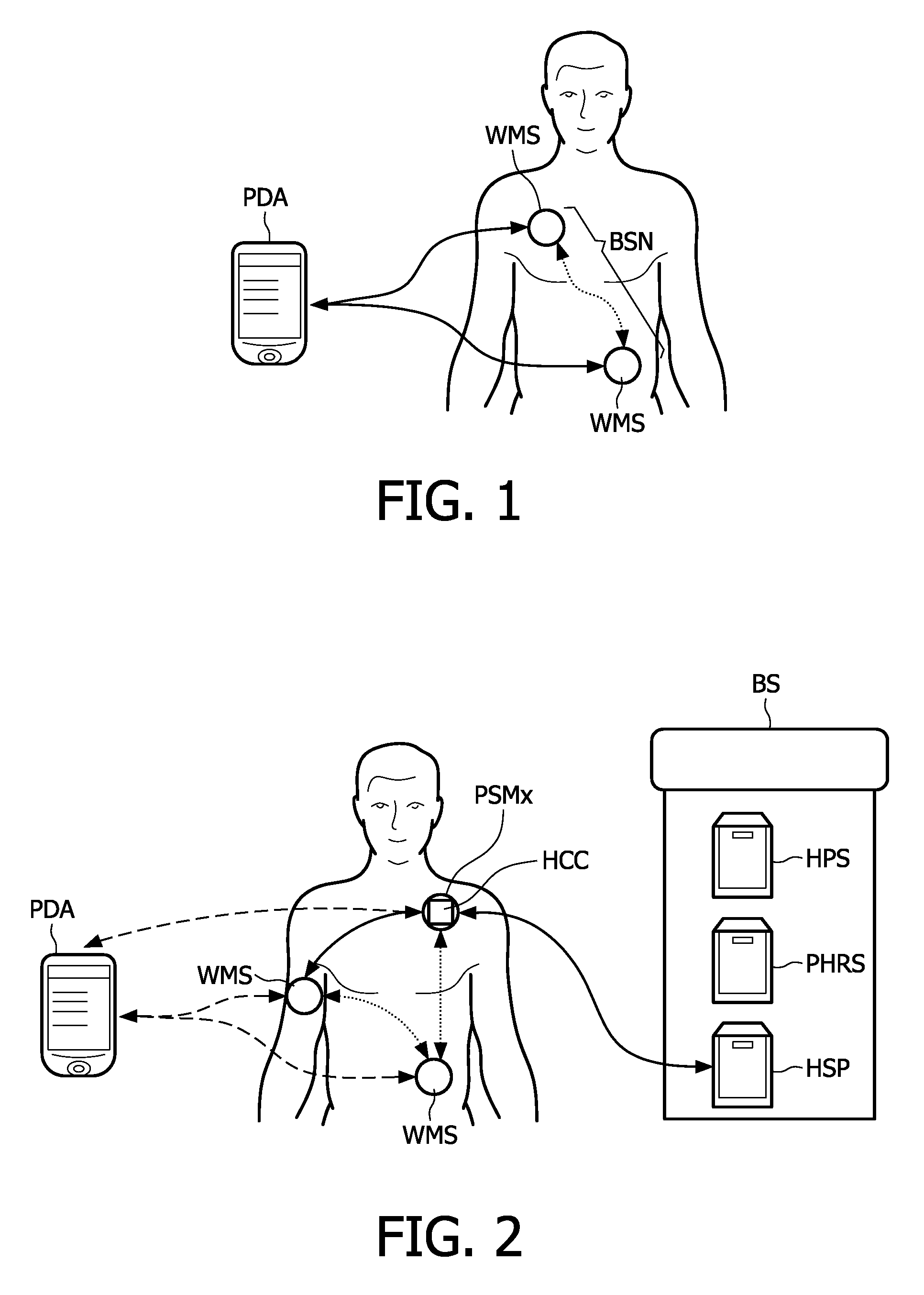
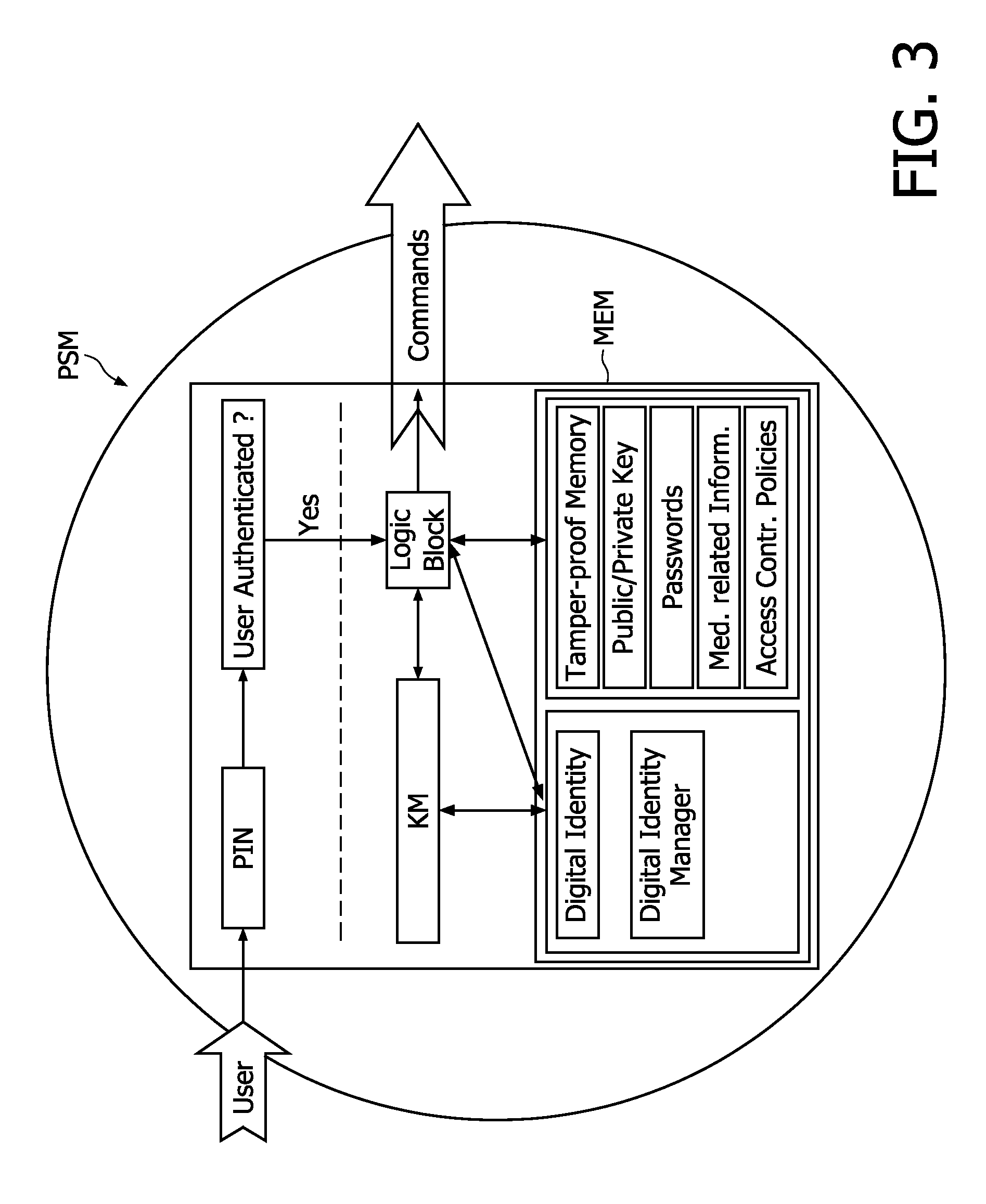
Personal security manager for ubiquitous patient monitoring
ActiveUS9094383B2Save energyImprove security levelKey distribution for secure communicationDigital data processing detailsNode compromiseSecure communication
The present invention relates to a system and corresponding method for a secure end-to-end patient healthcare system which includes wireless medical sensors adapted to be attached to a patient's body and in communication with each other forming a body sensor network within a wireless medical sensor network including one or more body sensor networks; λ-secure keying means incorporated into each wireless medical sensor for enabling secure communications between the wireless medical sensors, and a personal security manager within the body sensor network and in communication with the wireless medical sensors within the body sensor network, the personal security manager providing secure communications with backend services and providing security relationships within the body sensor network by means of the λ-secure keying means, wherein the λ-secure keying means are such that a coalition of no more than λ compromised wireless medical sensors conceals a pairwise key between any two non-compromised wireless medical sensors and provides protection against node compromise until λ+1 wireless medical sensors have been compromised.
Owner:KONINK PHILIPS ELECTRONICS NV
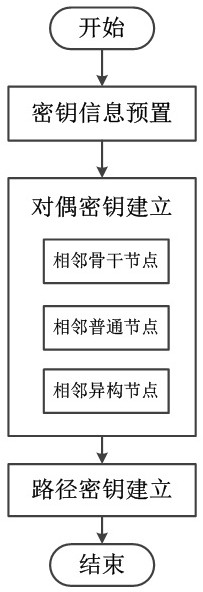
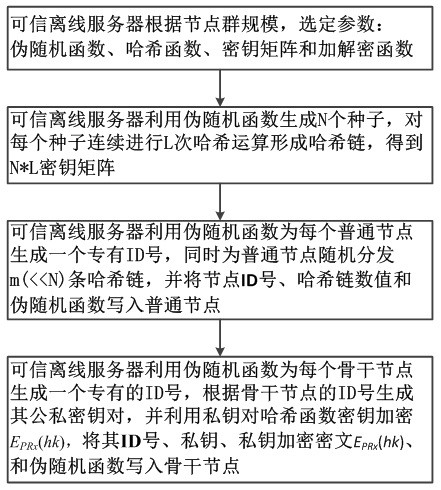
Node group key pre-distribution method and device based on mixed key
ActiveCN111865593AReduce computational efficiencyHigh Security ConnectivityKey distribution for secure communicationSecurity arrangementComputer networkNode deployment
The invention discloses a node group key pre-distribution method based on a mixed key in a wireless network node group. The method comprisesa key information presetting step of presetting different types of key information for a backbone node and a common node in the wireless network node group before node deployment of the node group,a pairwise key establishment step of discovering shared key information between neighbor nodes through information interaction between the nodesafter node group deploymentandperforming calculation between common nodes, between backbone nodes, and between the common nodes and the backbone nodes to generate pairwise keys, anda path key establishing step ofif a pairwise key cannot be directly established between adjacent common nodes, generating a path key by utilizing the established security path in a key negotiation mode. The method is suitable for being deployed and applied in different node group networks, and good fault tolerance, expandability and lowexpenditure are achieved under the condition that the safety of a password management scheme is guaranteed.
Owner:NAT UNIV OF DEFENSE TECH
Non-interactive hierarchical identity-based key-agreement
InactiveUS8422681B2Less mobileImprove securityKey distribution for secure communicationBandwidth constraintComputer network
A pairwise key-agreement scheme is provided for creating key agreements non-interactively between pairs of nodes disposed in a hierarchy of nodes. The scheme is non-interactive so that any two nodes can agree on a shared secret key without interaction. In addition, the scheme is identity-based so that any given node only needs to know the identity of peer nodes to compute the shared secret key. All of the nodes are arranged in a hierarchy where an intermediate node in the hierarchy can derive the secret keys for each of its children from its own secret key and the identity of the child. Accordingly, the scheme is fully resilient against compromise of any number of leaves in the hierarchy and of a threshold number of nodes in the upper levels of the hierarchy. The scheme is well-suited for environments such as mobile ad-hoc networks (MANETs), which are very dynamic, have acute bandwidth-constraints and have many nodes are vulnerable to compromise.
Owner:INT BUSINESS MASCH CORP
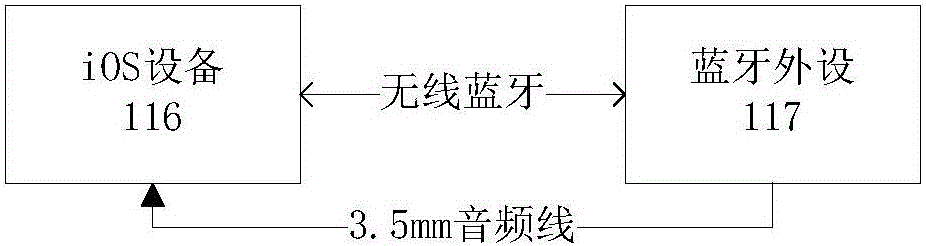
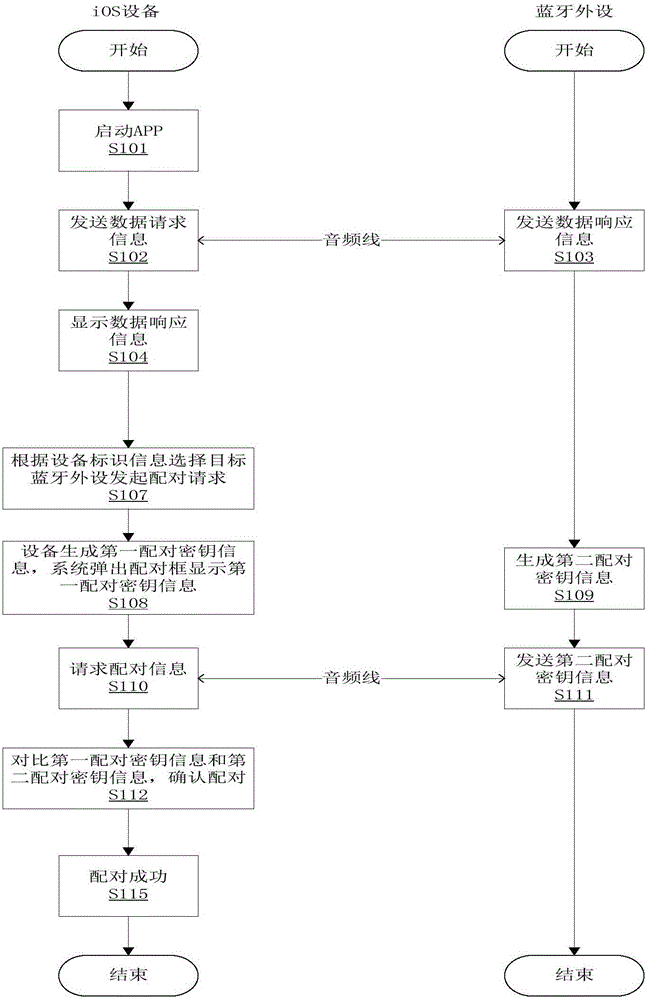
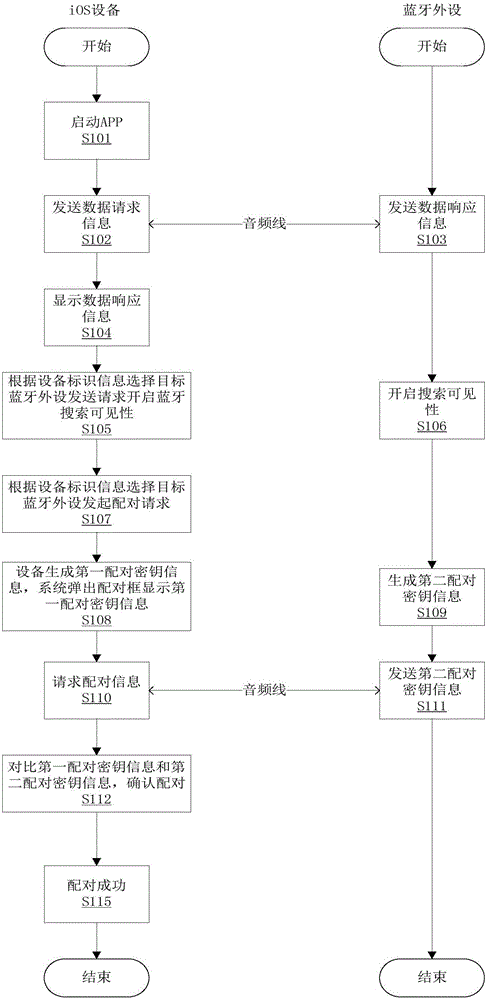
IOS equipment and bluetooth peripheral equipment pairing method and device
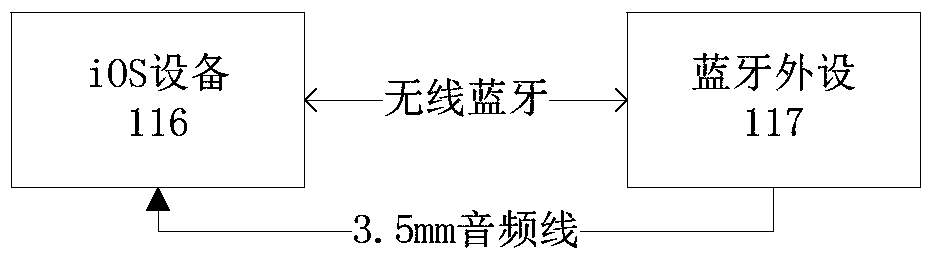
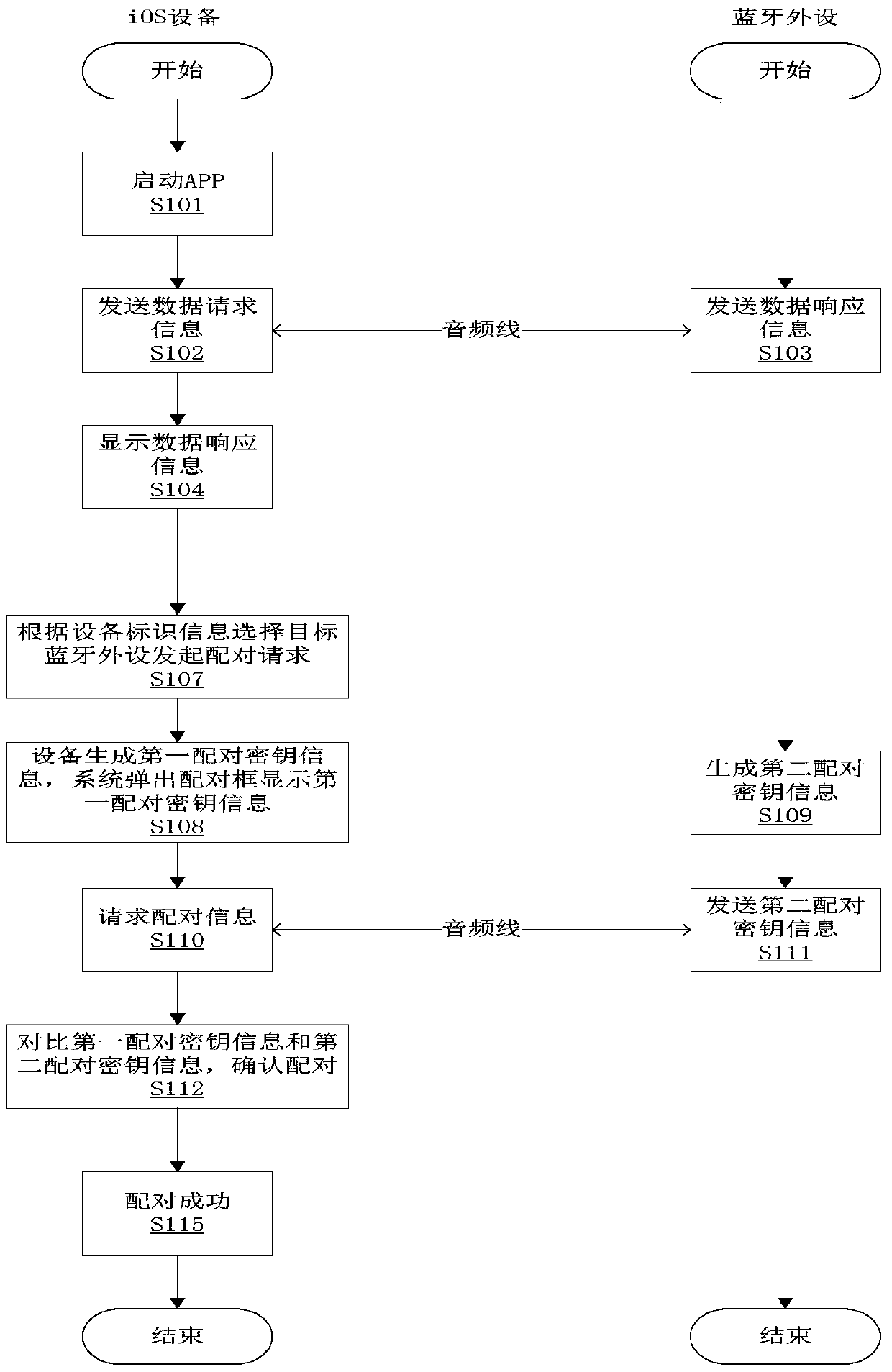
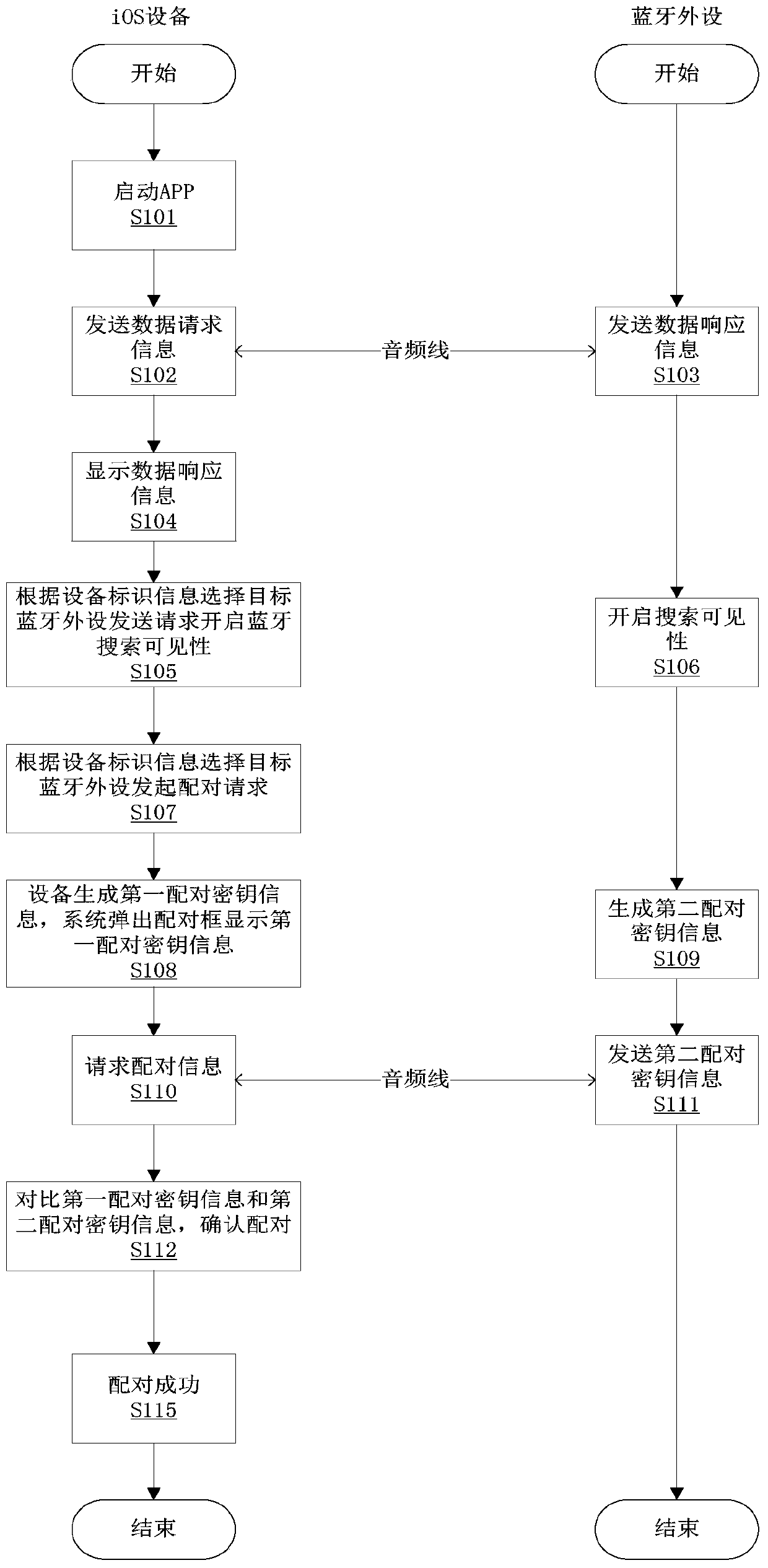
InactiveCN106257940AImprove securityConnection managementWireless commuication servicesBluetoothComputer science
The invention provides an iOS equipment and bluetooth peripheral equipment pairing method and device, and belongs to the technical field of communication. The iOS equipment and bluetooth peripheral equipment pairing method mainly comprises the steps that iOS equipment and bluetooth peripheral equipment establish physical connection; the iOS equipment transmits data request information to the bluetooth peripheral equipment, and the bluetooth peripheral equipment returns data response information carrying equipment identification information; the iOS equipment initiates a pairing request according to the equipment identification information; the iOS equipment generates first pairing key information, and the bluetooth peripheral equipment generates second pairing key information; the bluetooth peripheral equipment transmits the second pairing key information to the iOS equipment, and the second pairing key information is displayed on the iOS equipment; and the iOS equipment confirms consistency of the first pairing key information and the second pairing key information, and pairing is completed if the first pairing key information and the second pairing key information are consistent. Input operation and display information of the bluetooth peripheral equipment without input equipment or display screen are enabled to be operated on the iOS equipment so that the security of the pairing process can be enhanced, and the bluetooth peripheral equipment is enabled not to only passively select the Just Works pairing mode.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Electronic key management using PKI to support group key establishment in the tactical environment
ActiveUS8873759B2Key distribution for secure communicationPublic key infrastructure trust modelsComputer hardwareSupport group
Method for distributing a group session cryptographic key includes initiating at least one pairwise key distribution session including a root node (100) and at least one communication node (101-107). The method further includes performing at a communication node which has received the group session cryptographic key a propagated pairwise key distribution session with at least one of the communication nodes which has not previously received said group session cryptographic key. The propagated pairwise key distribution sessions are performed at each of the communication nodes which subsequently receives the group session cryptographic key until the group session cryptographic key has been securely provided to all authorized communication nodes.
Owner:HARRIS GLOBAL COMM INC
A key management and identity authentication method based on wireless sensor network
ActiveCN109068325AGuaranteed privacyGuaranteed timelinessKey distribution for secure communicationUser identity/authority verificationWireless mesh networkWireless sensor networking
The invention discloses a key management and identity authentication method based on a wireless sensor network, which comprises the following steps: S1, establishing a matrix M containing five-tuple information of a plurality of neighboring nodes; S2, establishing a matrix M containing five-tuple information of a plurality of neighboring nodes; S3, establishing a matrix M containing five-tuple information of the neighboring nodes. 2, judging whether that req node is included in the matrix M, if so, turning to S3, otherwise turning to S5; S3, judging whether the quintuple information of the requesting node is valid, if so, turning to S4, otherwise refusing communication; S4, the requested node and the requesting node authenticate through the key distribution center to generate a pairing key; S5, searching the relay node according to the respective communication areas of the requesting node and the requested node, and then repeating S3 to S4 between the relay node and the requesting node, and repeating S3 and S4 between the relay node and the requested node. The invention can achieve the purposes of reducing node resource storage consumption, improving forward and backward safety between nodes and resisting replay attack.
Owner:NANJING UNIV OF POSTS & TELECOMM
Wireless sensor network dynamic encryption method based on encryption parameter lists
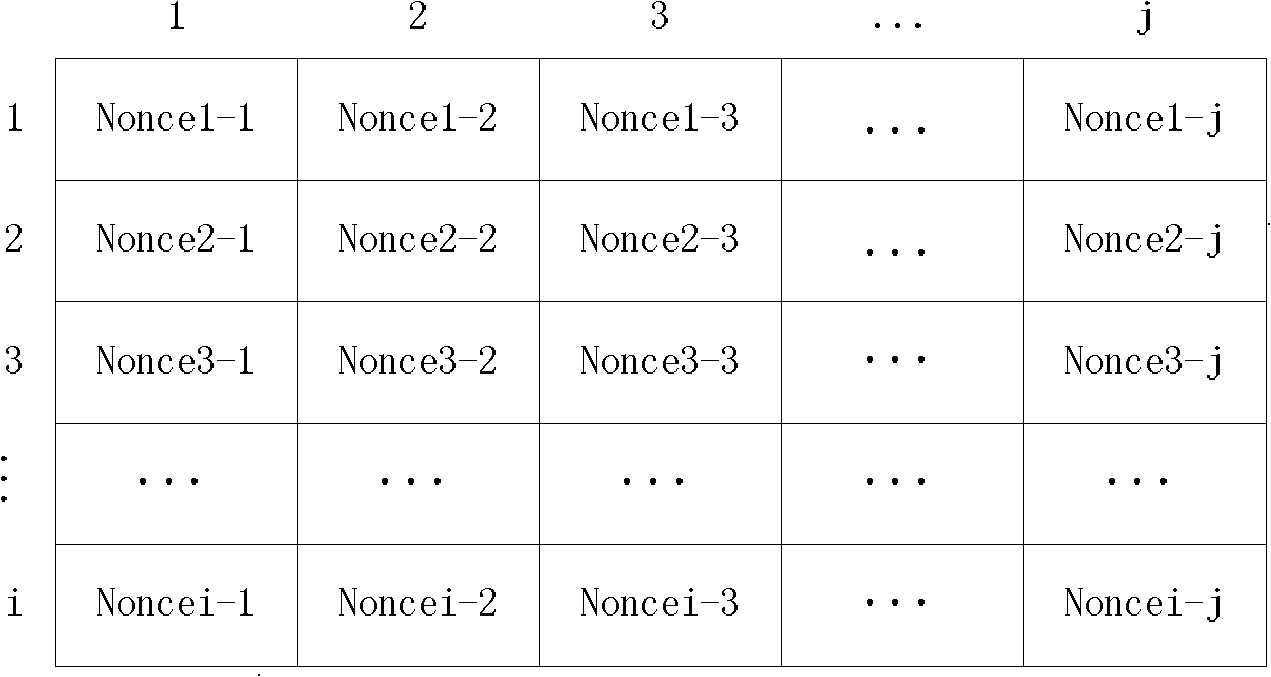
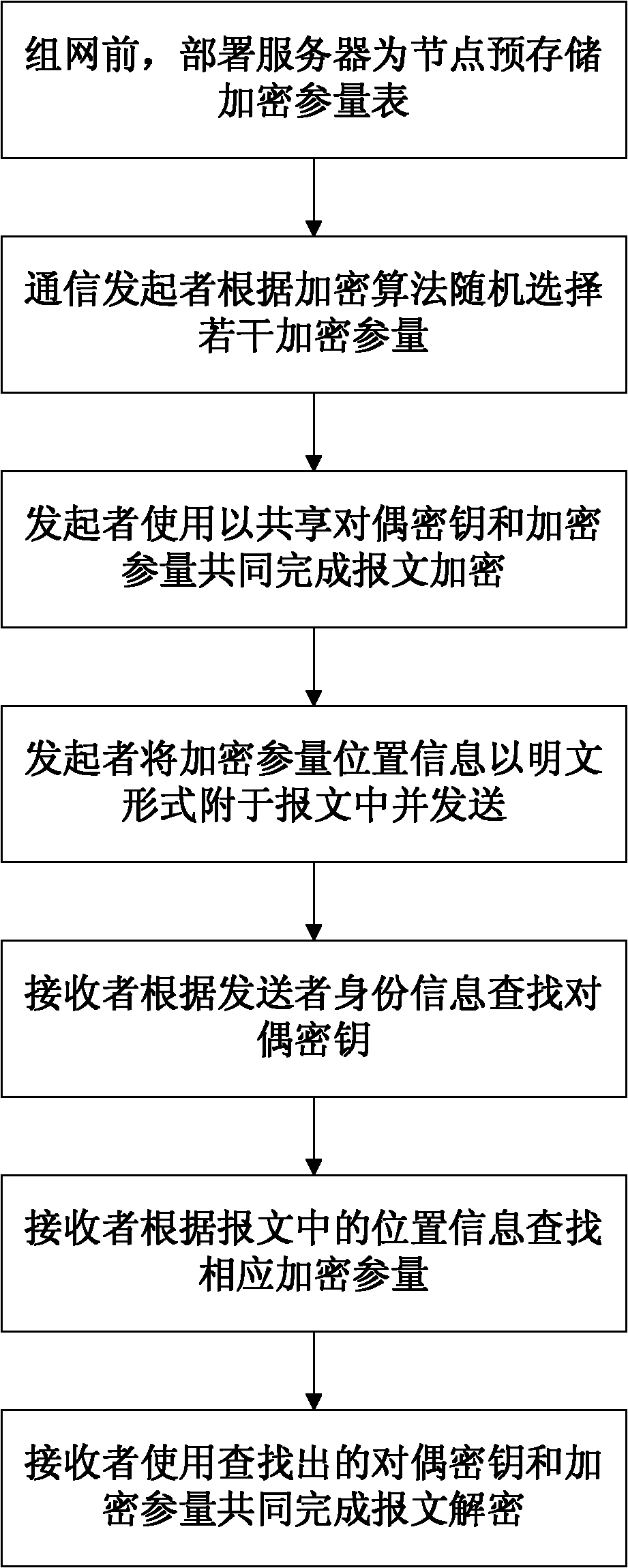
ActiveCN102404731AImprove confidentialityImprove securitySecurity arrangementConfidentialityWireless sensor networking
The invention discloses a wireless sensor network dynamic encryption method based on encryption parameter lists. First of all, before networking, according to types of nodes, an encryption parameter list for each node is stored in sequence by a deployment server; afterwards, a communication starter first finishes message encryption according to identity information of a receiver, pairwise keys and encryption parameters and then sends the message; and finally, the receiver finishes the operation of message decryption according to identity information of the receiver, pairwise keys and parameter information in the message. According to the invention, an independent encryption parameter list for each node is prestored, and dynamic encryption of the message is finished in combination with an ordinary key management mechanism, so that confidentiality of data is enhanced, and real-time and flexible data encryption is finished without updating keys frequently or storing a plurality of keys at one time; and meanwhile, encryption parameter lists are stored in the nodes in a prestored manner, so that security of encryption parameter lists and confidentiality of data transmission are enhanced, then the threats of information disclosure and key decoding caused by easiness in eavesdropping in the wireless environment can be dealt with.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
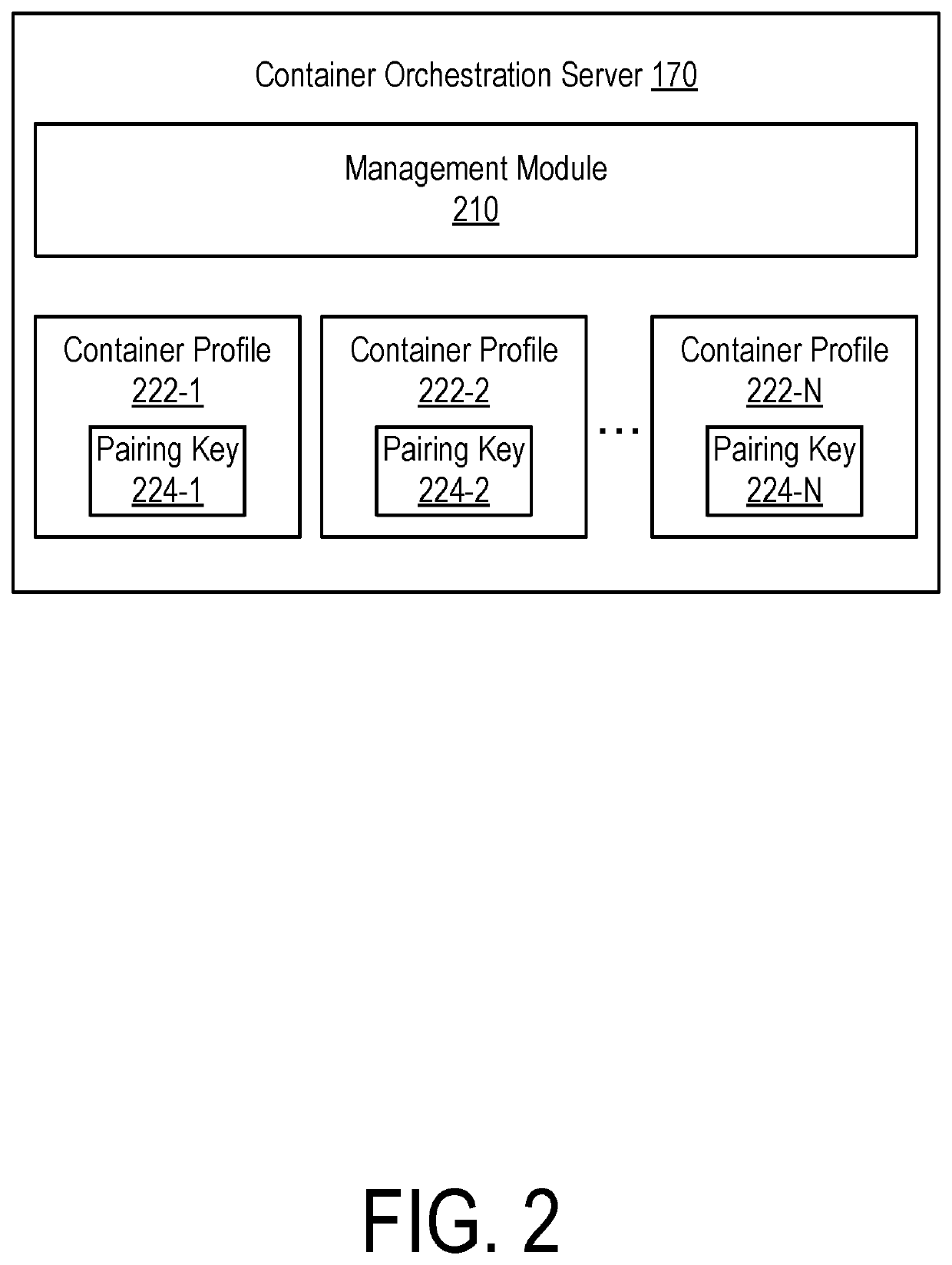
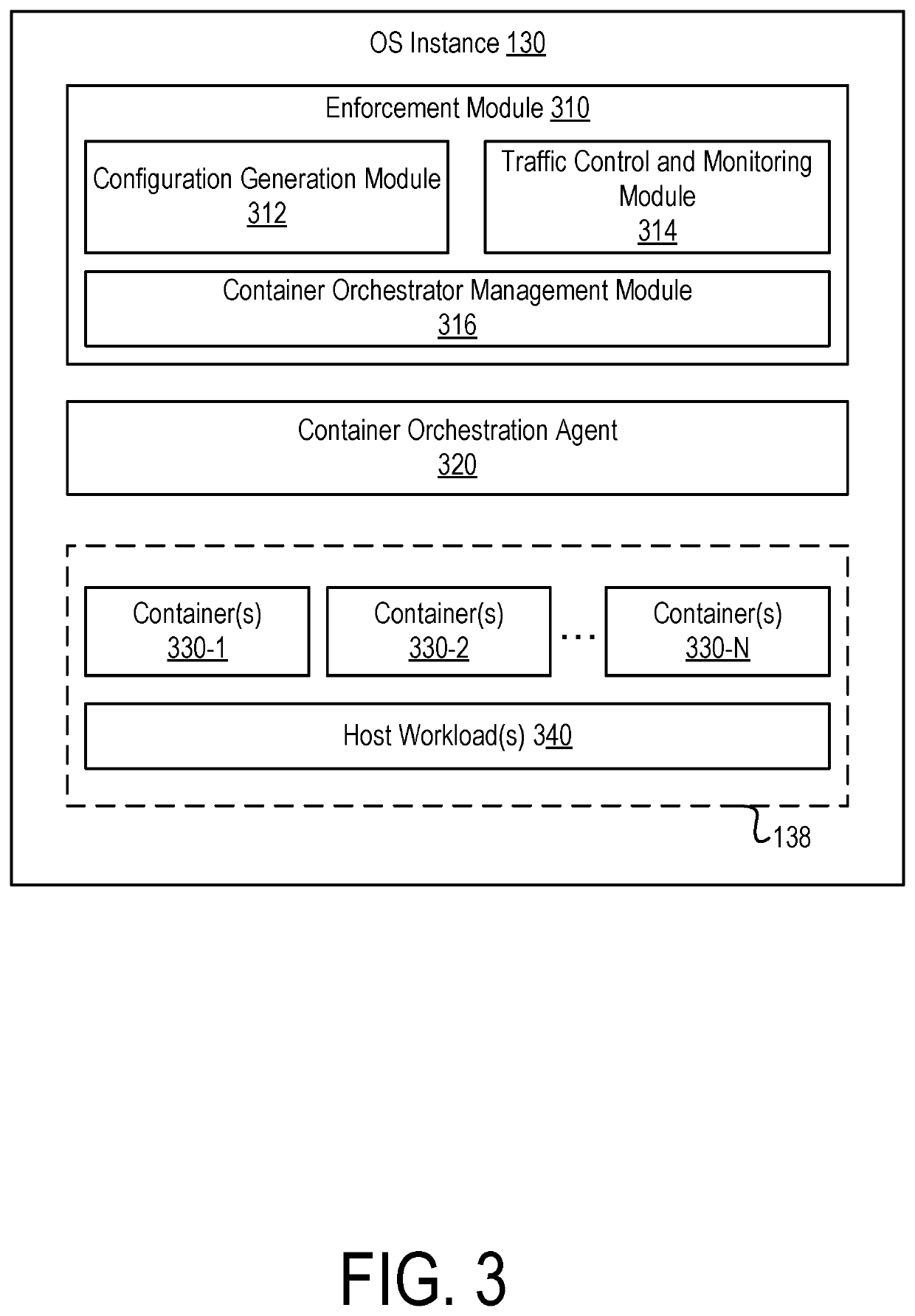
Managing containers based on pairing keys in a segmented network environment
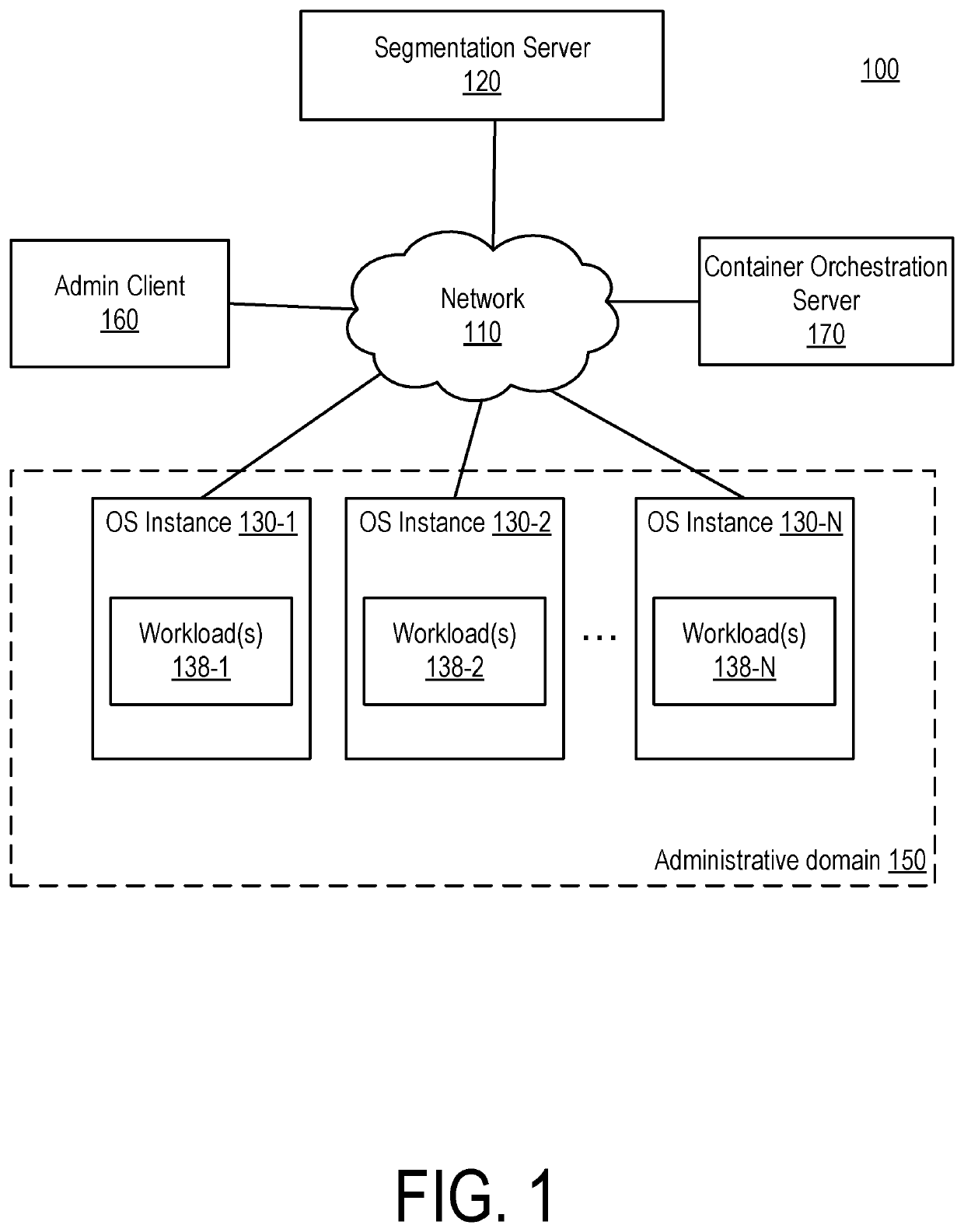
ActiveUS11012310B2Public key for secure communicationData switching networksOperational systemEngineering
A container orchestration server stores pairing keys in association with container profiles. A container orchestration agent executing on an operating system instance instantiates a new container according to a particular container profile in response to an instruction from the container orchestration server and stores the pairing key as metadata associated with the container. An enforcement module detects the instantiation of the container and obtains the corresponding pairing key from the container orchestration agent. The enforcement module transmits the pairing key to a segmentation server for validation. If the segmentation server validates the key, the segmentation server determines a label set corresponding to the container profile associated with the pairing key and generates management instructions for the container based on the label set. The management instructions, when enforced by the operating system, controls communications between the container and other workloads in accordance with a segmentation policy.
Owner:ILLUMIO
System and method for authentication of things
ActiveUS10523437B2Key distribution for secure communicationUser identity/authority verificationPairwise keyAuthentication system
An Authentication Of Things (AOT) system includes a cloud server configured to control a cloud domain connected with a plurality of devices, a home server configured to control a home server connected with a plurality of devices, a first device corresponding to a new device, and a second device of a root user connected with the home domain while authentication is completed in the home server. In this case, the first device loads cryptographic material of the cloud server from the cloud server in a pre-deployment stage, the cryptographic material includes at least one selected from the group consisting of an identifier of the first device in the cloud server, a first private key of an ID-based cryptography system of the first device in the cloud server, a first pairwise key of the first device in the cloud server, and a counter of the first device, and if the first device is shipped to a trader, the cloud server deletes the first private key from the cloud server.
Owner:LG ELECTRONICS INC +1
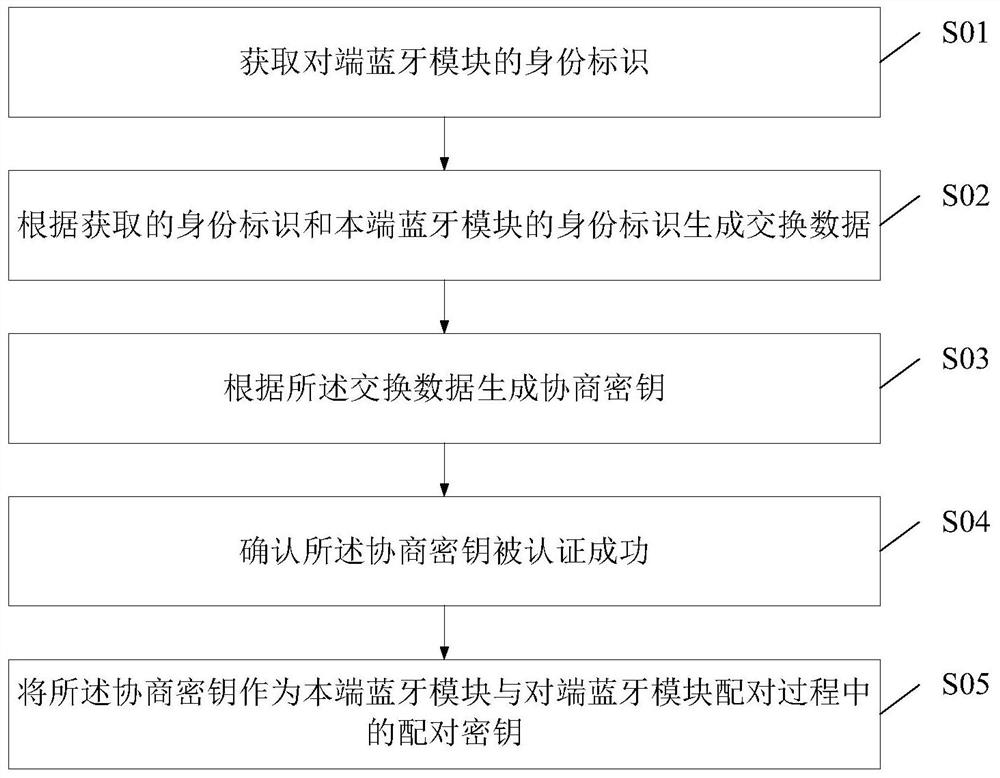
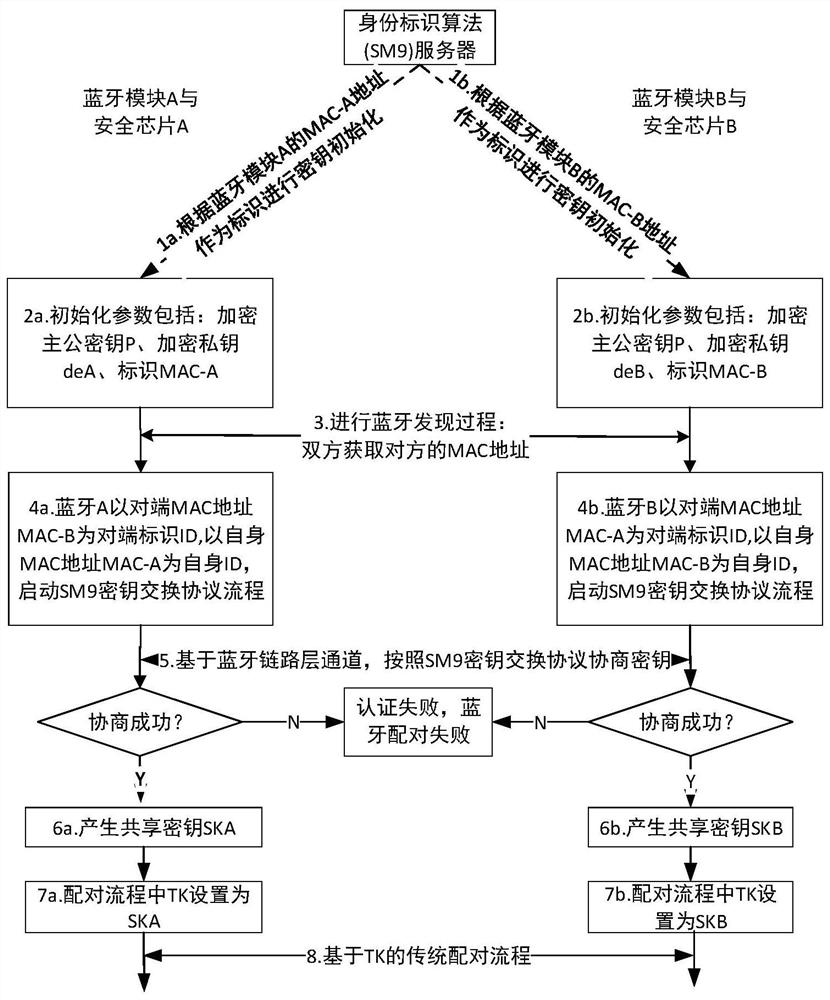
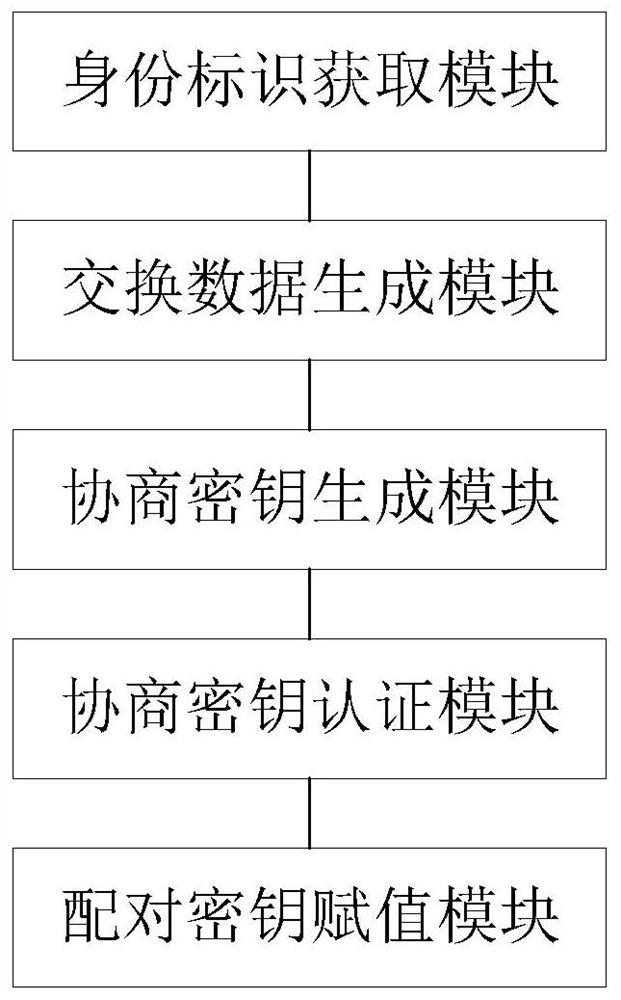
Bluetooth pairing method supporting identity authentication, security chip and Bluetooth module
ActiveCN113329386ACredible GuaranteeImprove pairing autonomyShort range communication serviceSecurity arrangementKey exchangeEngineering
The invention relates to the technical field of security. The embodiment of the invention provides a Bluetooth pairing method supporting identity authentication, a security chip and a Bluetooth module. The Bluetooth pairing method supporting identity authentication is based on a key exchange protocol of an identification cryptographic algorithm, and comprises the following steps: acquiring an identity identifier of an opposite-end Bluetooth module; generating exchange data according to the obtained identity label and the identity label of the Bluetooth module at the home terminal; generating a negotiation key according to the exchange data; confirming that the negotiation key is successfully authenticated; using the negotiation key as a pairing key in the pairing process of the home terminal Bluetooth module and the opposite terminal Bluetooth module, wherein the step of generating the exchange data, the step of generating the negotiation key and the step of authenticating the negotiation key are all based on a key exchange protocol of the identification cryptographic algorithm. According to the embodiment provided by the invention, the security and autonomy in the Bluetooth module pairing process are improved.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +3
Segmented key authentication system
PendingCN110402440AKey distribution for secure communicationDigital data authenticationEngineeringPairwise key
The invention concerns an authentication system with at least one application accessible by a user via a computer and for which the access is controlled by an authentication datum, comprising a main mobile device and a main token in which at least one authentication datum is recorded, the main mobile device being configured to recover the authentication datum of the main token using a pairing key,characterised in that the pairing key is segmented into a plurality of segments, a first segment being recorded on the main mobile device and at least one other additional segment being recorded on asecondary mobile device and / or a secondary token, the main mobile device being configured to recover the additional segment or segments in order to reconstitute the pairing key and to present the reconstituted pairing key to the main token.
Owner:J·加斯屈埃尔
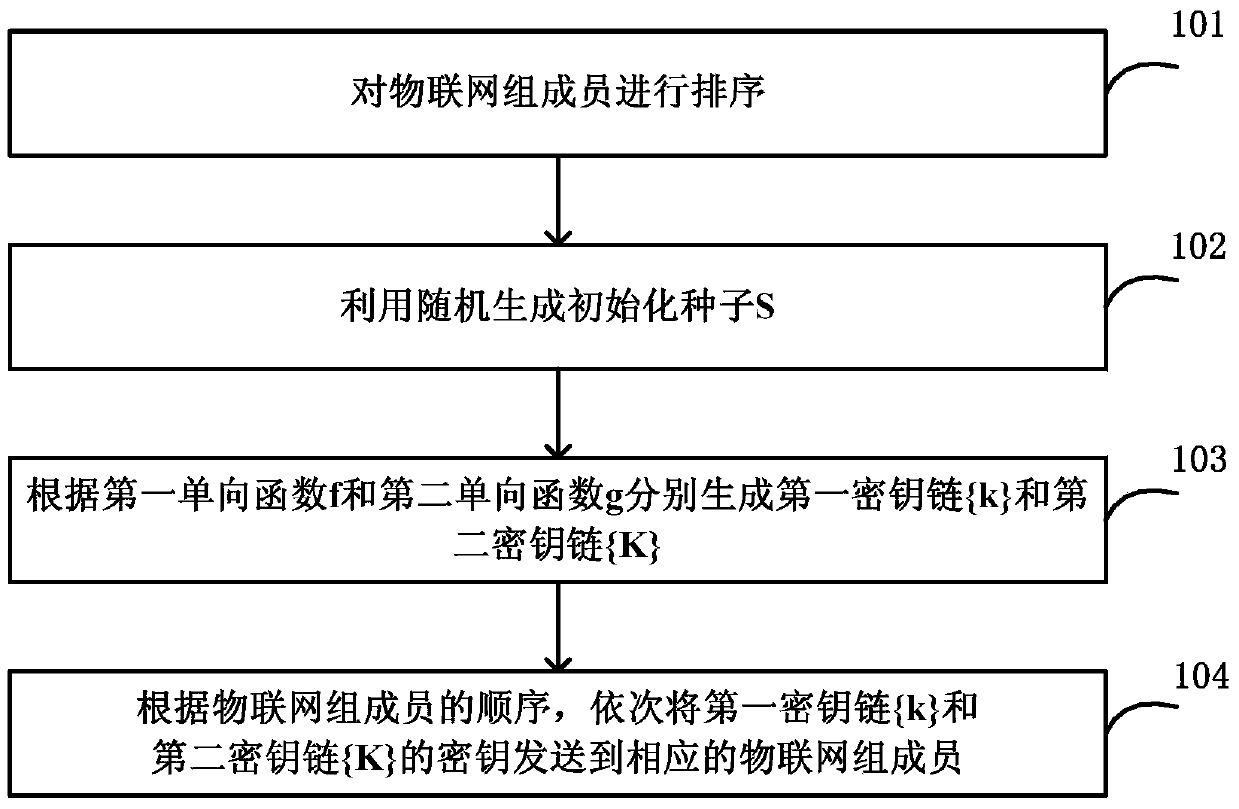
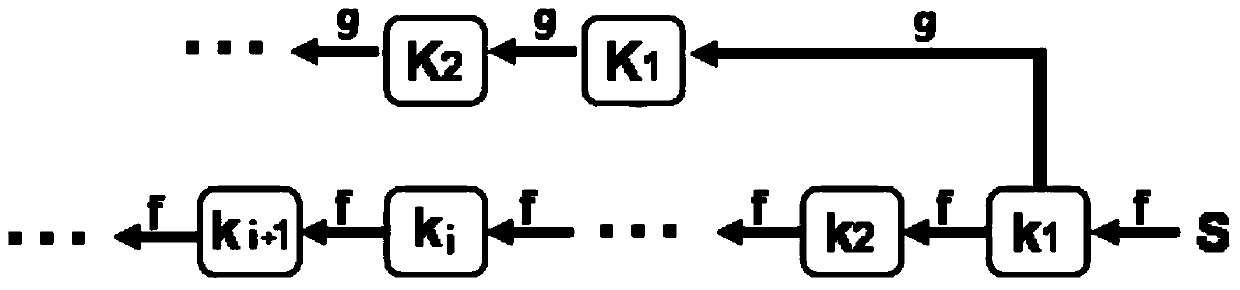
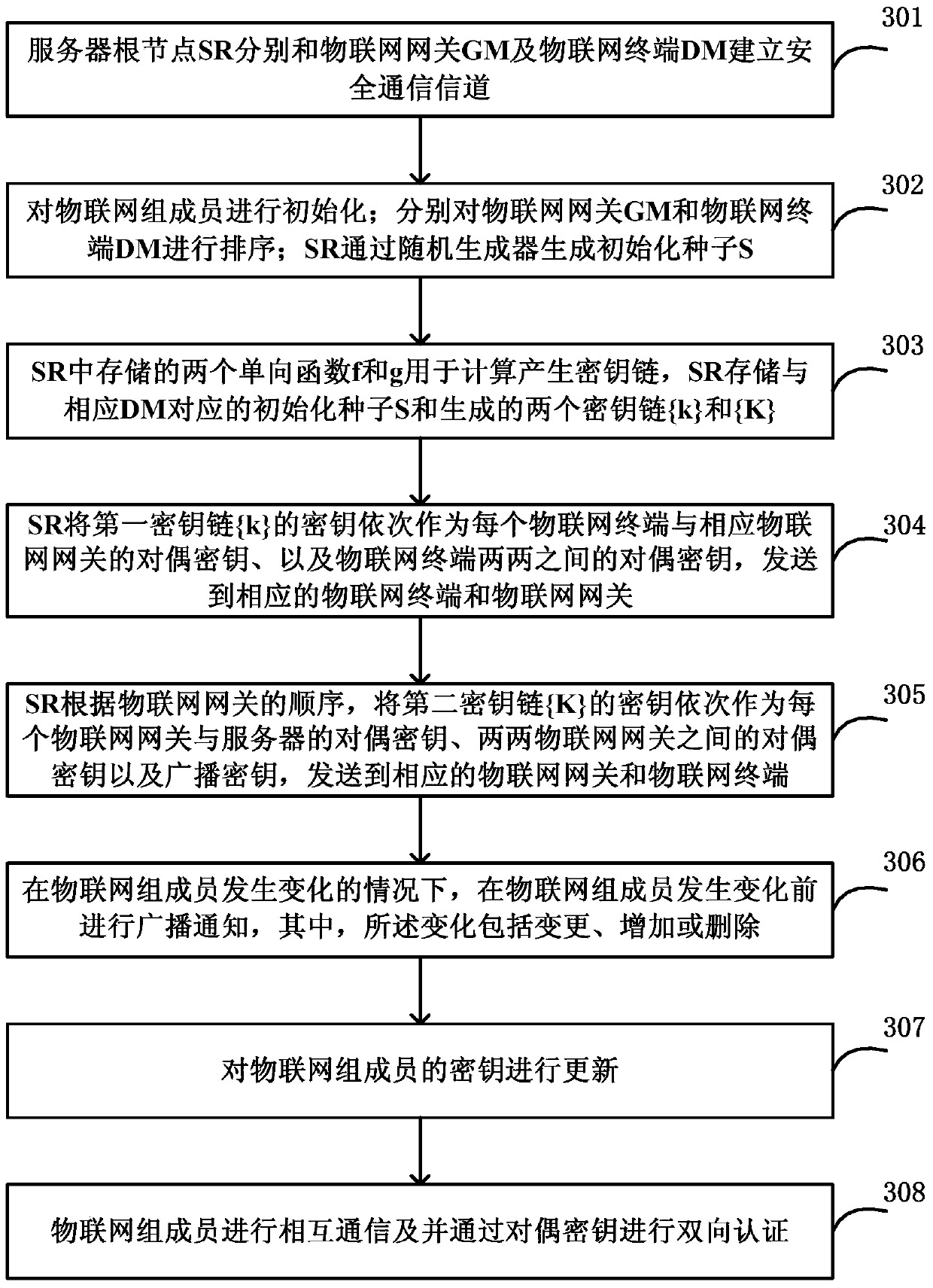
Method and server for centrally controlled key management
The invention discloses a centralized control-type key management method and a centralized control-type key management server. The method comprises steps: Internet of things group members are ranked, wherein the Internet of things group members comprise an Internet of things gateway and an Internet of things terminal; an initialization seed is generated randomly; a first key chain and a second key chain are generated respectively according to a first one-way function and a second one-way function; and according to the sequence of the Internet of things group members, keys of the first key chain and the second key chain are sent to corresponding Internet of things group members sequentially. Through setting corresponding pairwise keys for communication of different Internet of things group members, the information transmission security in an Internet of things environment is thus enhanced, and the risk that the information is stolen is greatly reduced.
Owner:CHINA TELECOM CORP LTD
Bluetooth pairing method and device for mobile phone and payment terminal
ActiveCN106131771BImprove securityShort range communication serviceNetwork data managementPairwise keyMobile phone
Owner:FUJIAN LANDI COMML EQUIP CO LTD
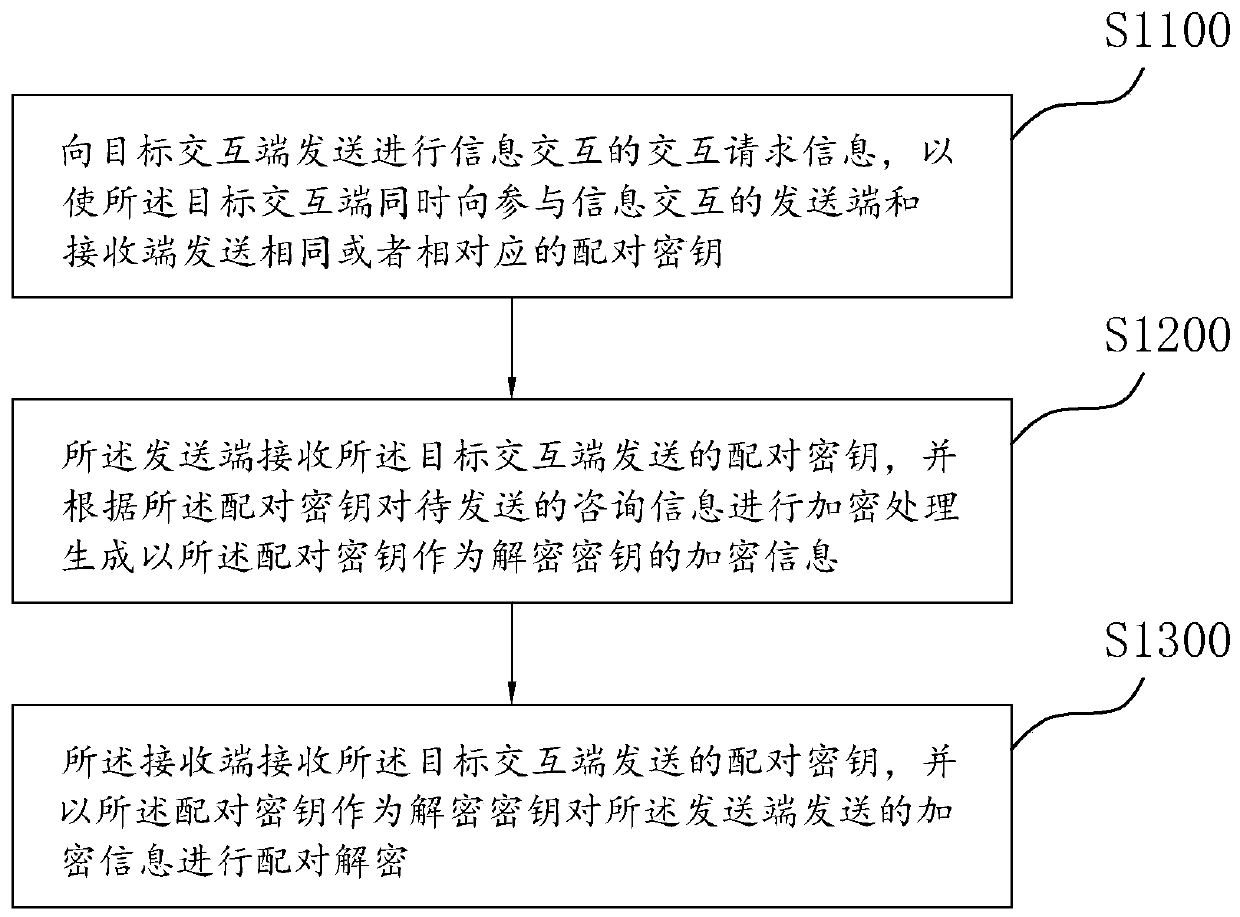
Intellectual property consultation information management method and device, computer and storage medium
InactiveCN111585983AImprove securityKey distribution for secure communicationData processing applicationsIntellectual propertyEngineering
The invention relates to an intellectual property consultation information management method and device, a computer and a storage medium, and the management method comprises the steps: transmitting interaction request information for information interaction to a target interaction end, so as to enable the target interaction end to transmit the same or corresponding pairing secret key to a transmitting end and a receiving end participating in information interaction at the same time; enabling the transmitting end to receive the pairing secret key sent by the target interaction end, and encrypting the consultation information to be sent according to the pairing secret key to generate encrypted information taking the pairing secret key as a decryption secret key; enabling the receiving end toreceive the pairing secret key sent by the target interaction end, and carrying out pairing decryption on the encryption information sent by the transmitting end. Through the process, the process oftransmitting and receiving by the transmitting end and the receiving end is the information verification process, and if the receiving end cannot be matched with the encrypted information transmittedby the transmitting end, the consultation information in the encrypted information cannot be acquired, so the security of the consultation information is improved.
Owner:苏州细无声信息科技服务有限公司
Hierarchical deterministic pairwise key predistribution scheme
InactiveCN101473626BData taking preventionParticular environment based servicesSecurity domainPairwise key
A security system for a hierarchical network (10) includes L hierarchical levels each corresponding to a security domain level (16), and a plurality of local network nodes (A, B, . . . , Z). A keying material generator (24) generates a set (30) of correlated keying material for each network node. Each set (30) of keying material is composed of L sub-sets (32) of keying material one for each security domain level (16). A set up server (34) distributes the generated sets (30) of keying material to each network node (A, B, . . . , Z) to enable the network nodes (A, B, . . . , Z) to communicate with one another at a security domain of a hierarchical level k by a use of a corresponding sub-set (32) of the security keying material.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
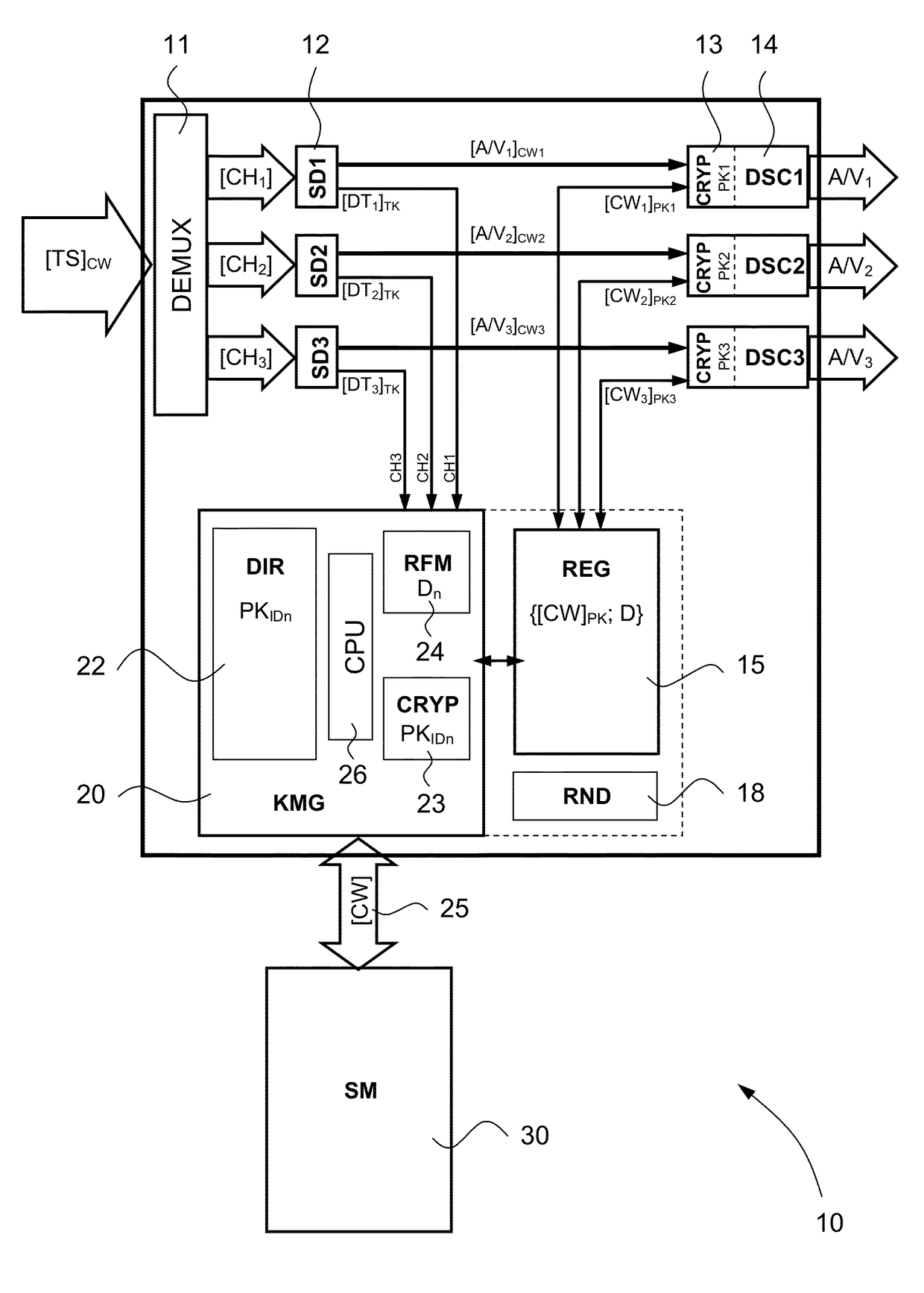
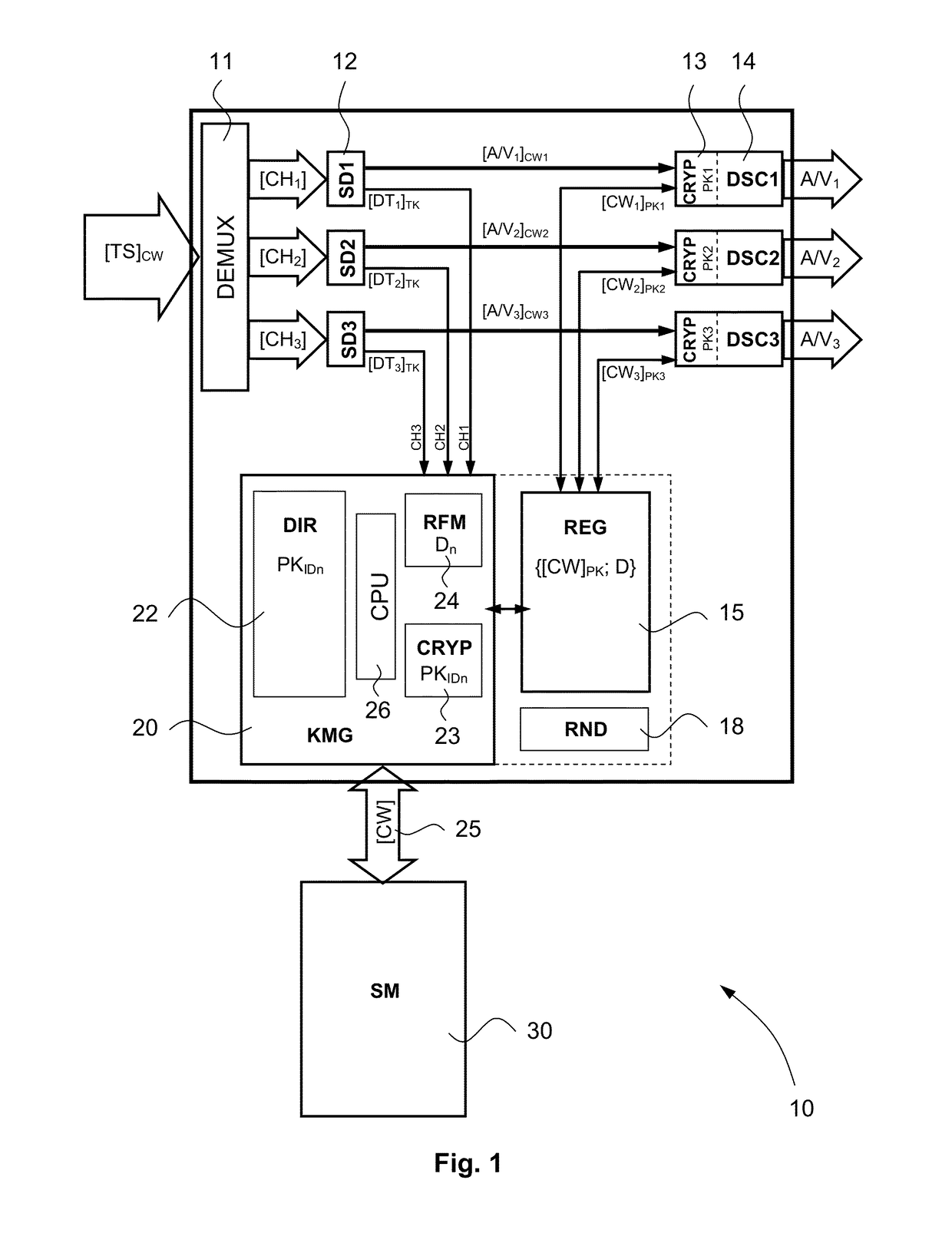
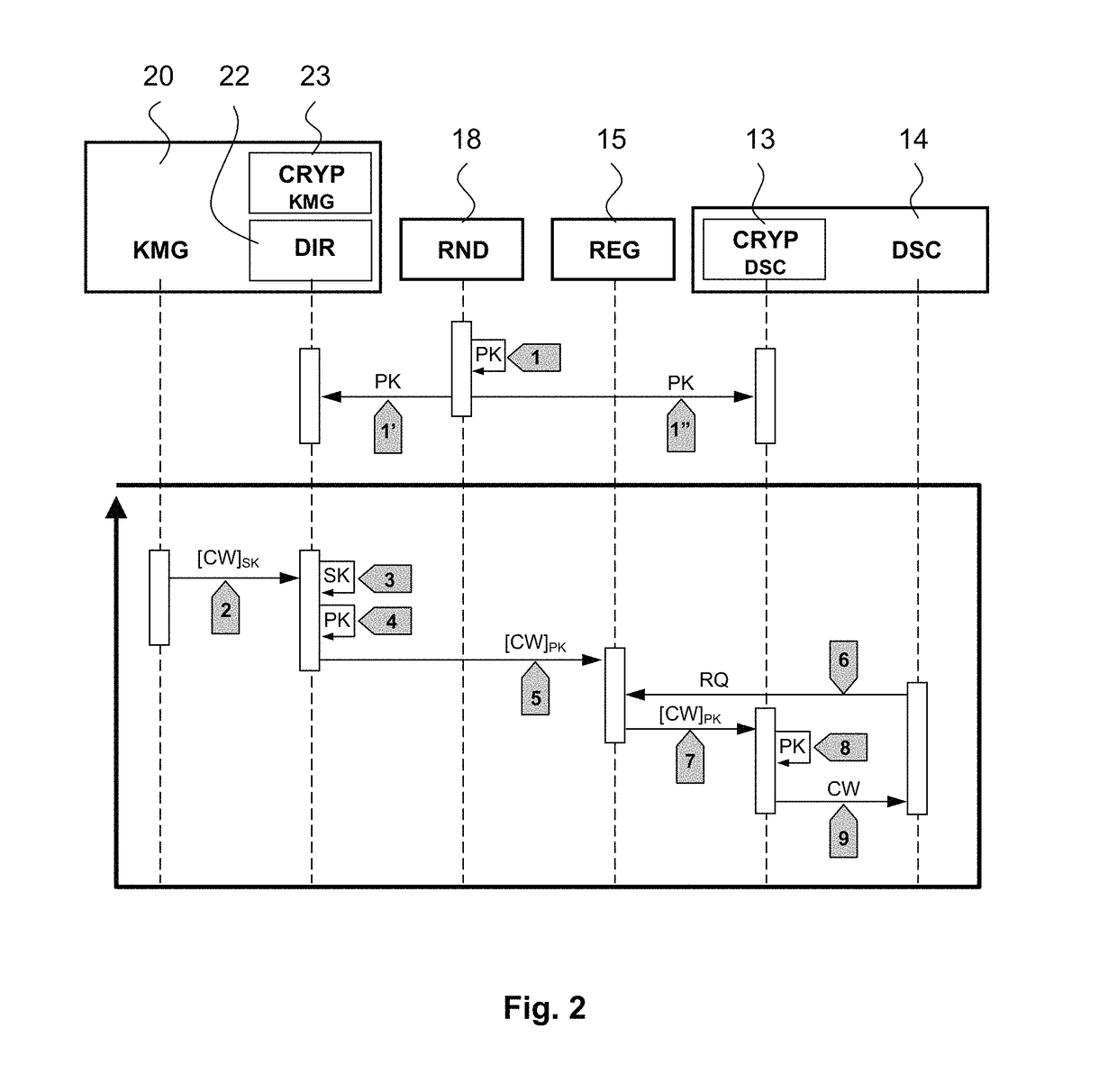
Method for protecting decryption keys in a decoder and decoder for implementing said method
Method for securing control words within a decoder in charge of descrambling digital content protected by these control words, comprising the following steps: for each descrambling unit of this decoder, loading in a directory a pairing key referenced by an identifier associating said key to a descrambling unit; receiving at least one encrypted control word referenced by an indication allowing to identify the descrambling unit for which it is intended; decrypting the control word by using a first key shared with a security module; identifying in the directory the pairing key whose identifier corresponds to the indication of destination associated to the control word; encrypting this control word by using this pairing key; and storing in a register the control word in a chronological and referenced way.
Owner:NAGRAVISION SA
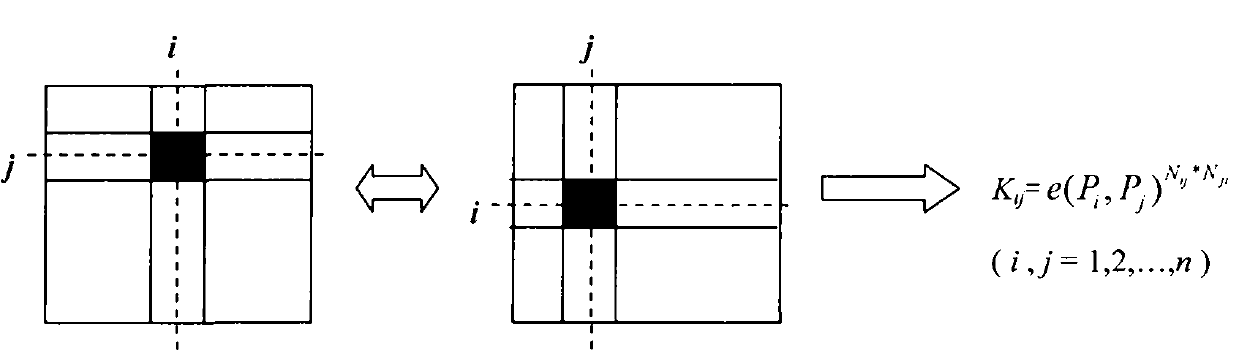
Bilinear cipher key pair pre-distributing method oriented to safety of mobile self-organizing network
InactiveCN101335612BImprove connectivitySmall scaleKey distribution for secure communicationPublic key for secure communicationPairwise keySelf-organizing network
The invention discloses a bilinear key pre-distribution method which faces the safety of the mobile ad hoc network. The method comprises the following steps: firstly, supposing the number of the nodes in the ad hoc network as n, during the key pre-distribution course, generating a n*n secure matrix N in a Galois field GF(q) by a base station, wherein, the matrix element Nij is a subset of ZP<*>, i is equal to or more than 1 and j is equal to or less than n; distributing the information of the element in Row i to the No. i node for storage and personal holding, wherein, i is equal to or more than 1 and is equal to or less than n; providing a public key that is equal to the node under identification cipher system for each point Pi in the mapping area G1of each node i by the basestation, and obtaining the public key by the other nodes in the network; after the fishing of the key pre-distribution, realizing an agreement and pair-wise key of the node i and node j. The invention provides a bilinear key pre-distribution method which faces the safety of the mobile ad hoc network, which has small key scale, high safety strength, fast speed, high efficiency, strong anti-acquisition performance of nodes and good connectivity of the key.
Owner:ZHEJIANG UNIV OF TECH
Method of triggering a key delivery from a mesh key distributor
ActiveUS9451452B2Key distribution for secure communicationUser identity/authority verificationComputer networkPairwise key
A mesh station applying for access to a network includes a list of peer stations in messages of an authenticated key establishment protocol. A mesh key distributor derives a key delivery key and generates a top level key, and then delivers the top level key to the mesh station. Following the key establishment protocol, the mesh key distributor also creates pairwise keys for use between the mesh station and the peer stations listed in its peer list. The list of peers permits the identifier for the peer to be bound into the derived key, which helps ensure that the key used between each pair of peers is unique. Once the mesh key distributor finishes creating a key for one of the stations on the peer list, the mesh key distributor sends a message to the peer to initiate a key push.
Owner:STRONG FORCE IOT
A Bridge-Based Key Management Scheme for Wireless Sensor Networks
ActiveCN103731825BEnsure safetyGuaranteed validitySecurity arrangementInformation transmissionNode deployment
The present invention relates to a bridge-based wireless sensor network key management scheme, including some steps: 1. Key pre-distribution: before node deployment, the configuration information is preset to each sensor node by the startup server; 2. Clustering Phase: After the cluster head node is selected, the clustering phase starts immediately. In the process of clustering, each sensor node joins the cluster closest to itself; 3. Neighbor node discovery stage: each sensor node decides whether to record other nodes as its neighbor nodes through the angle calculation formula; 4. Within the cluster Establishment of pairing key: In this process, each sensor node calculates the pairing key between it and its neighbor nodes through bridge; 5. Establishment of inter-cluster pairing key: In this process, each cluster head node passes symmetric The bivariate polynomial calculates its pairing key with other cluster head nodes. The present invention can ensure the safety and effectiveness of information transmission under the condition of ensuring a certain connection rate, and saves the amount of memory storage.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com