A key management and identity authentication method based on wireless sensor network
A wireless sensor and key management technology, which is applied in the field of key management and identity authentication based on wireless sensor networks, can solve the problems of large resource storage consumption, lack of node authentication mechanism, overlapping of shared keys and reduced network scalability, etc. , to achieve the effect of ensuring privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
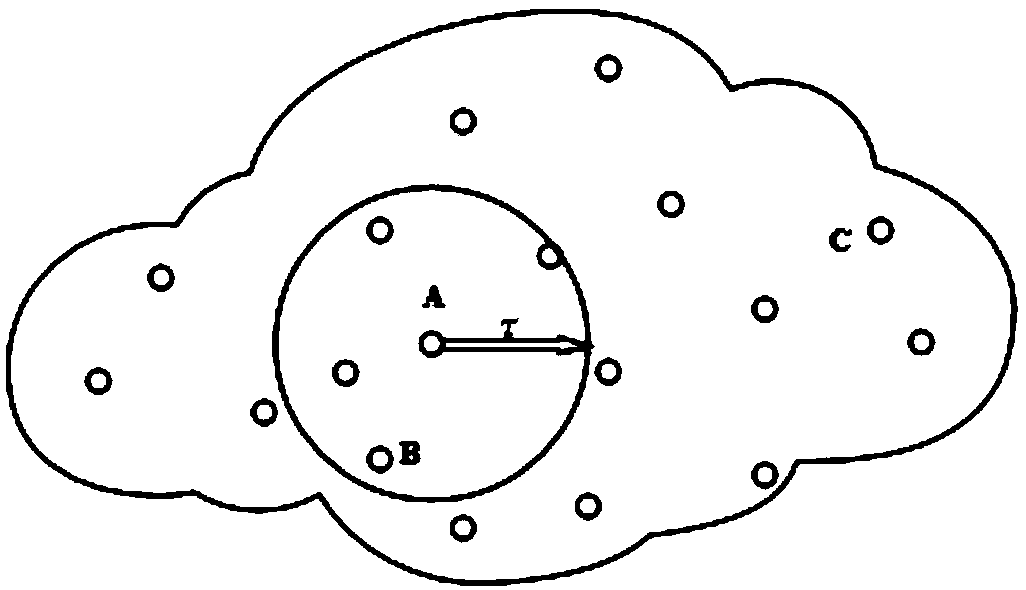
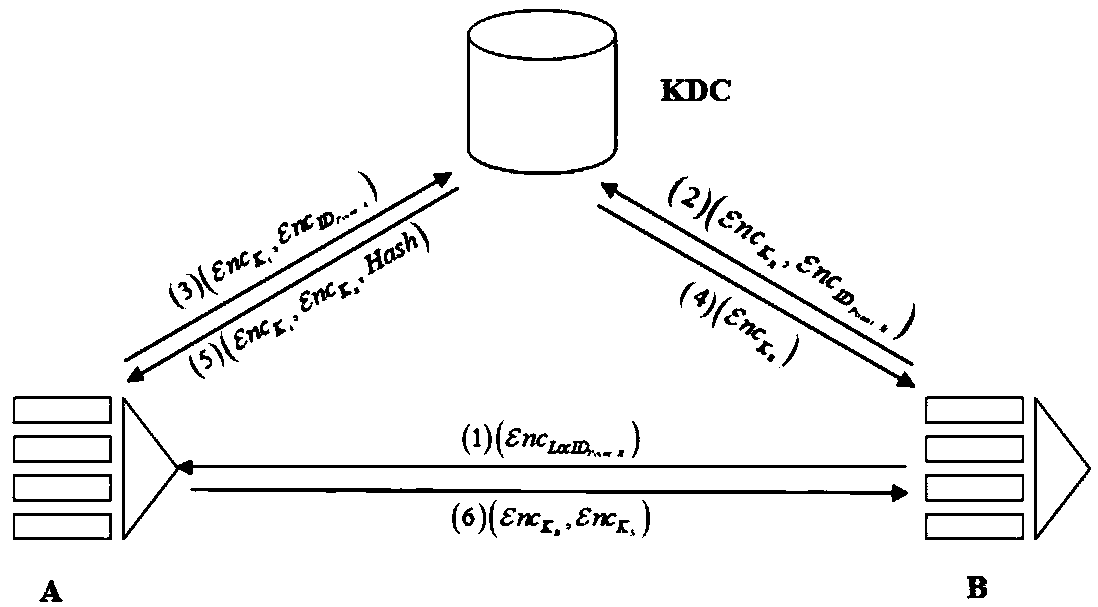
[0055] Such as figure 1 As shown, the authentication process between the two nodes is described in detail by taking node A as the requested node and node B as the requesting node as an example.
[0056] S1. Establish a matrix M containing quintuple information of multiple adjacent nodes. The specific steps are as follows:
[0057] S11. The system dynamically sets the communication threshold of node A, which is the communication range set based on the power supply energy and communication capability of node A, and ensures that the communication radius between nodes is r. Set the neighbor node threshold q of node A, which means that each node can communicate with q neighbor nodes at most.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com