Outsourcing encrypted data-orientated verifiable intersection operation method and system
An operation method and a technology for encrypting data, which are applied in digital transmission systems, transmission systems, user identity/authority verification, etc., and can solve problems such as the lack of verifiable intersection operation methods for outsourced encrypted data.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
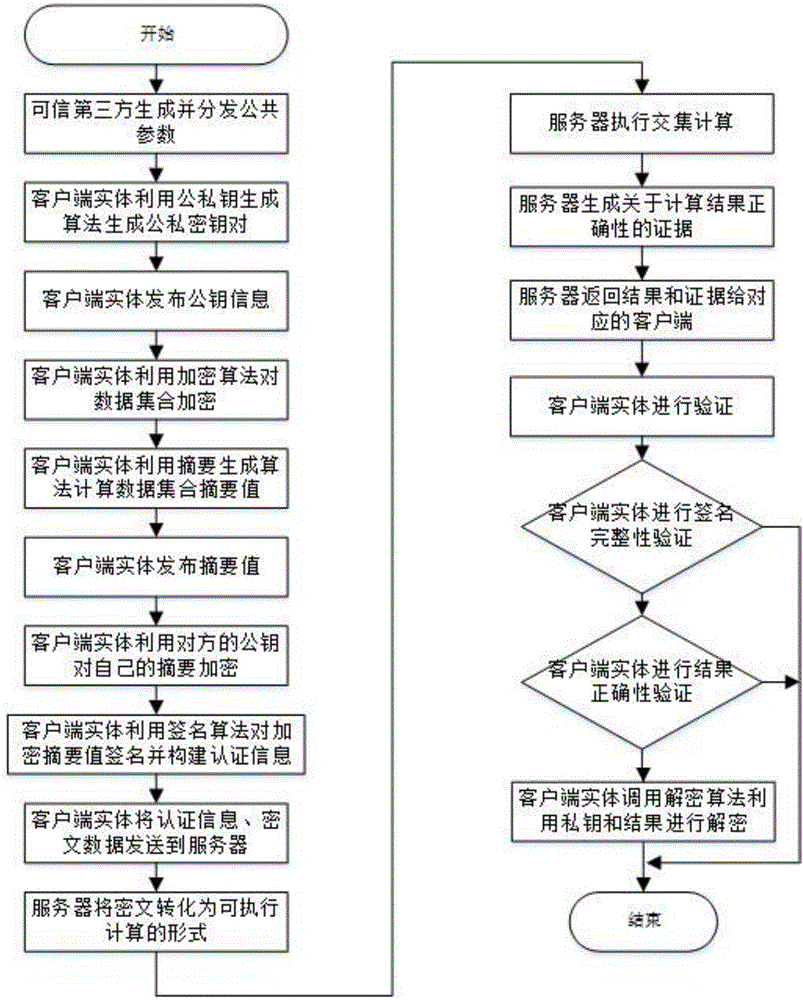
[0072] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
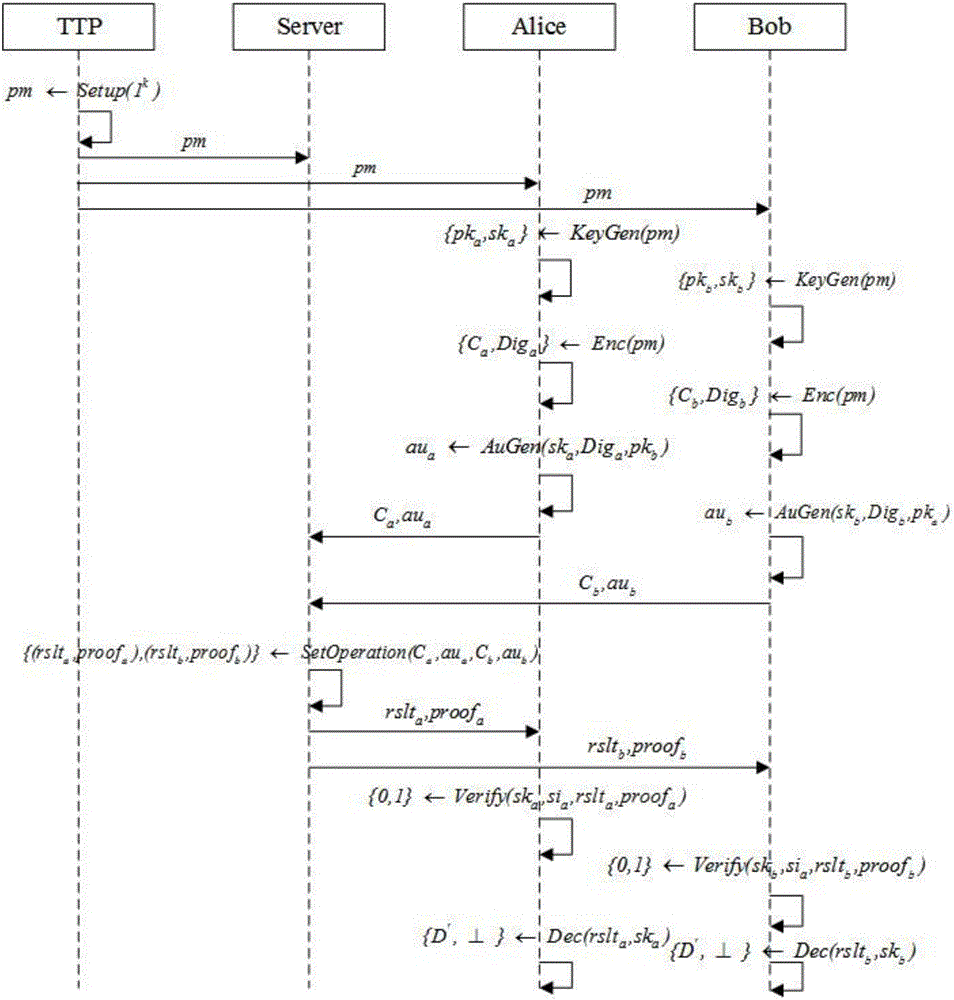
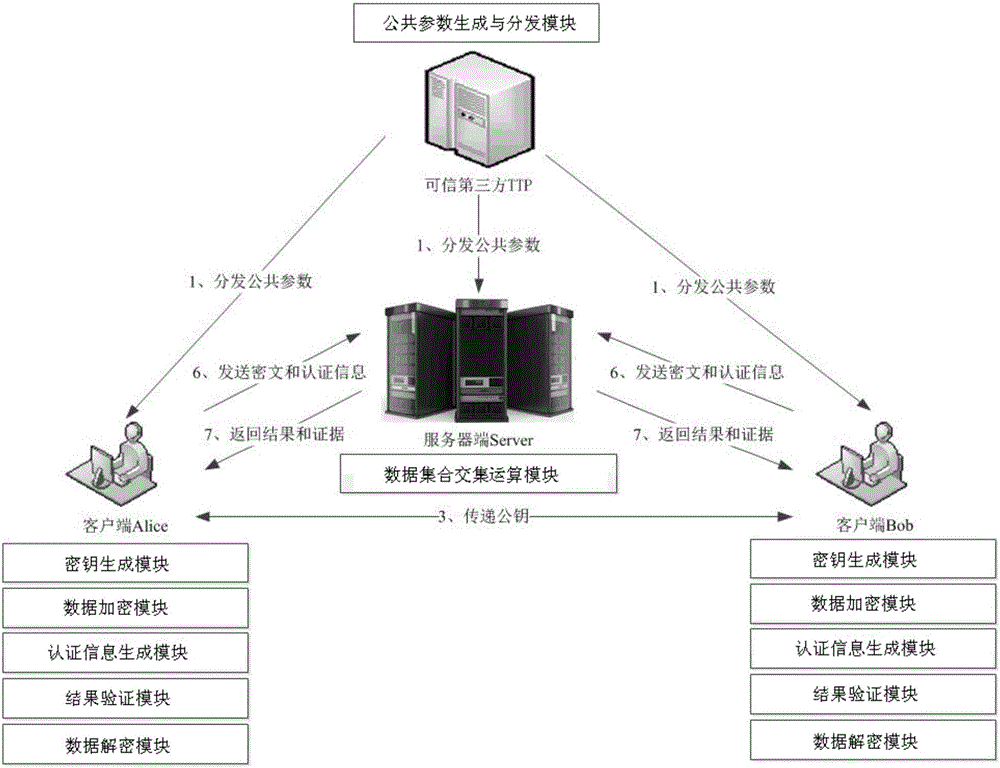
[0073] The verifiable intersection operation method for outsourced encrypted data in this embodiment, such as figure 1 As shown, it is performed between a trusted third-party entity, namely TTP, at least two client entities, namely Alice and Bob, and an outsourced server-side entity, namely Server.
[0074] Trusted Third Party (TrustedThirdParty, TTP): the generator of public parameters. Among all entities, the third-party entity TTP is trusted and is responsible for the initialization of public parameters of all entities in the entire method. After initializing the public parameters, the public parameters Sent to outsourced server and two client entities.
[0075] Client Alice and Bob: the holder of the data set and the requester of the intersection operation of the data set, Alice and Bob are semi-trusted, they both want to know th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com