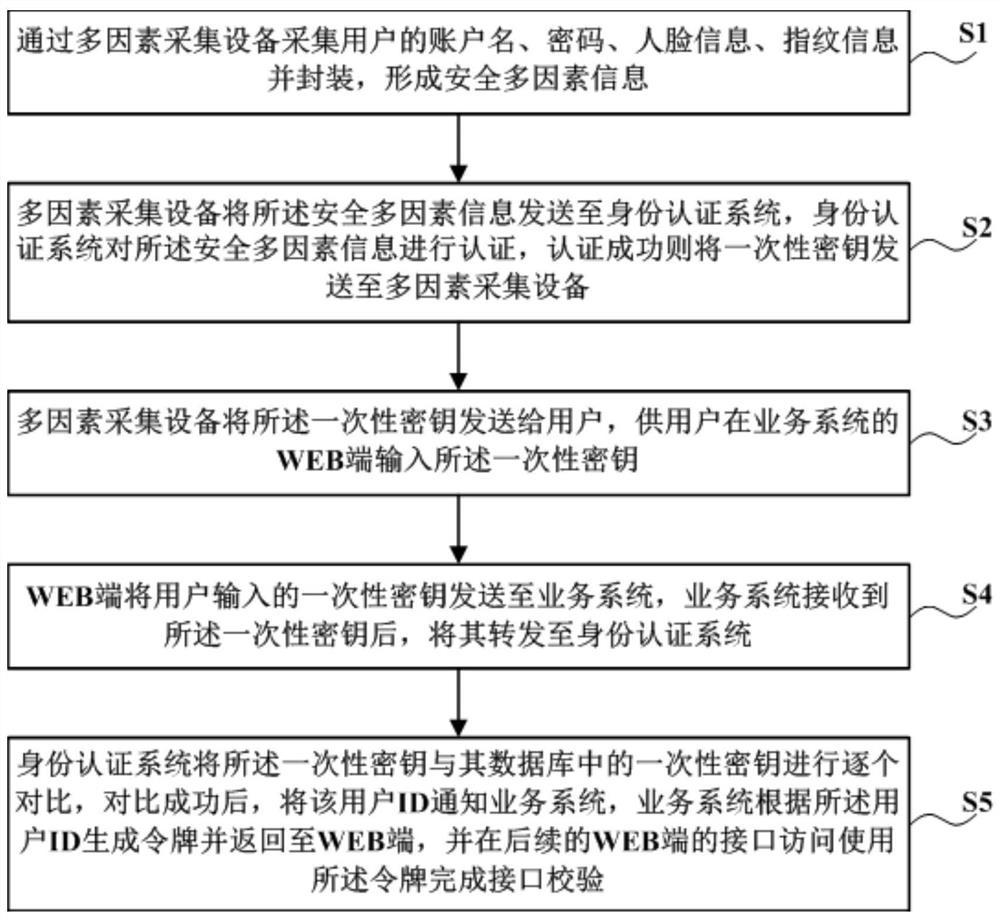
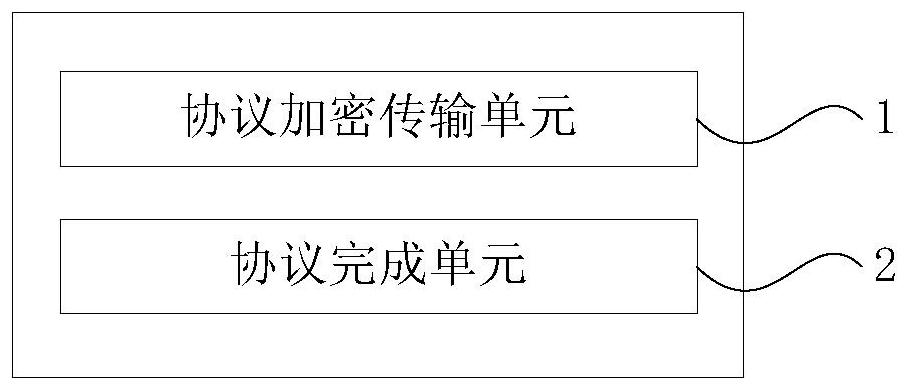
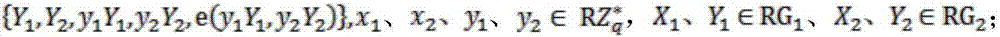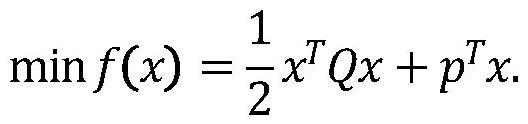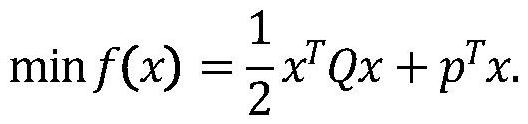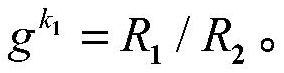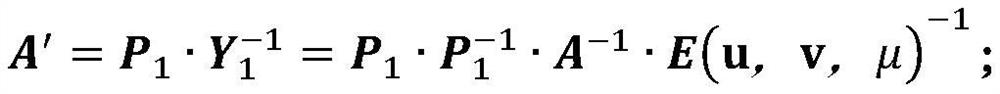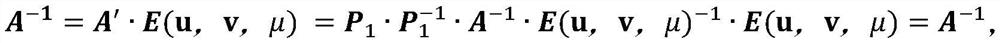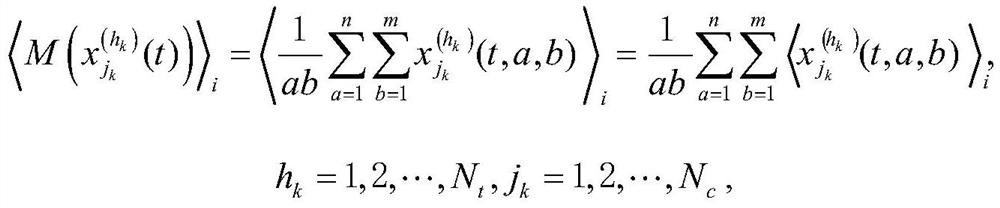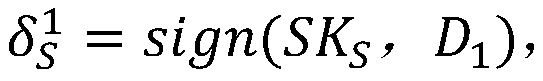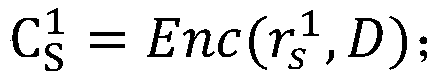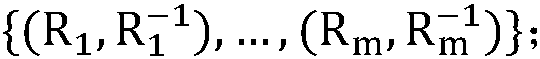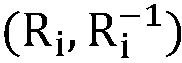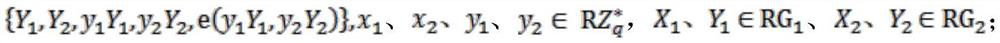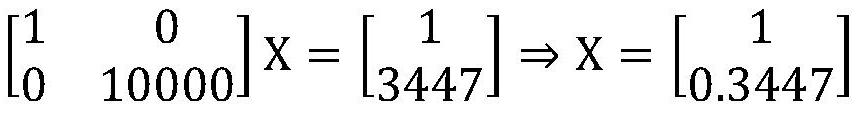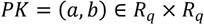Patents
Literature
49 results about "Outsourcing computation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
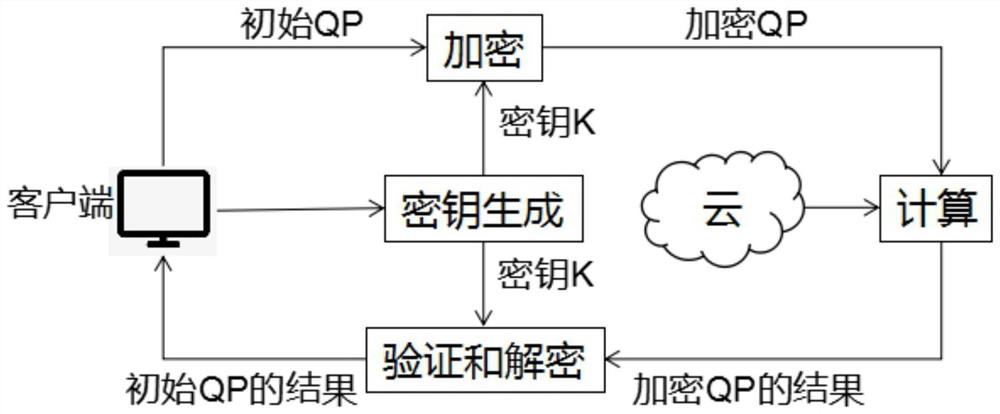
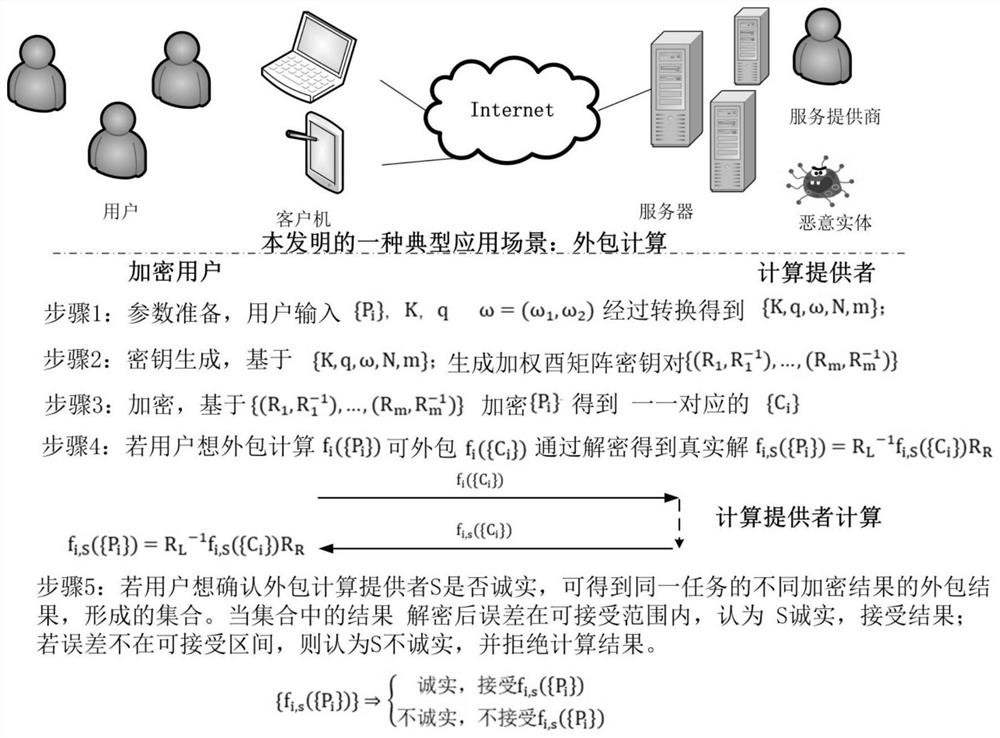
Outsourcing computation with verifiability is a merging notion in cloud computing, which enables lightweight clients to outsource costly computation tasks to the cloud and efficiently check the correctness of the result in the end.
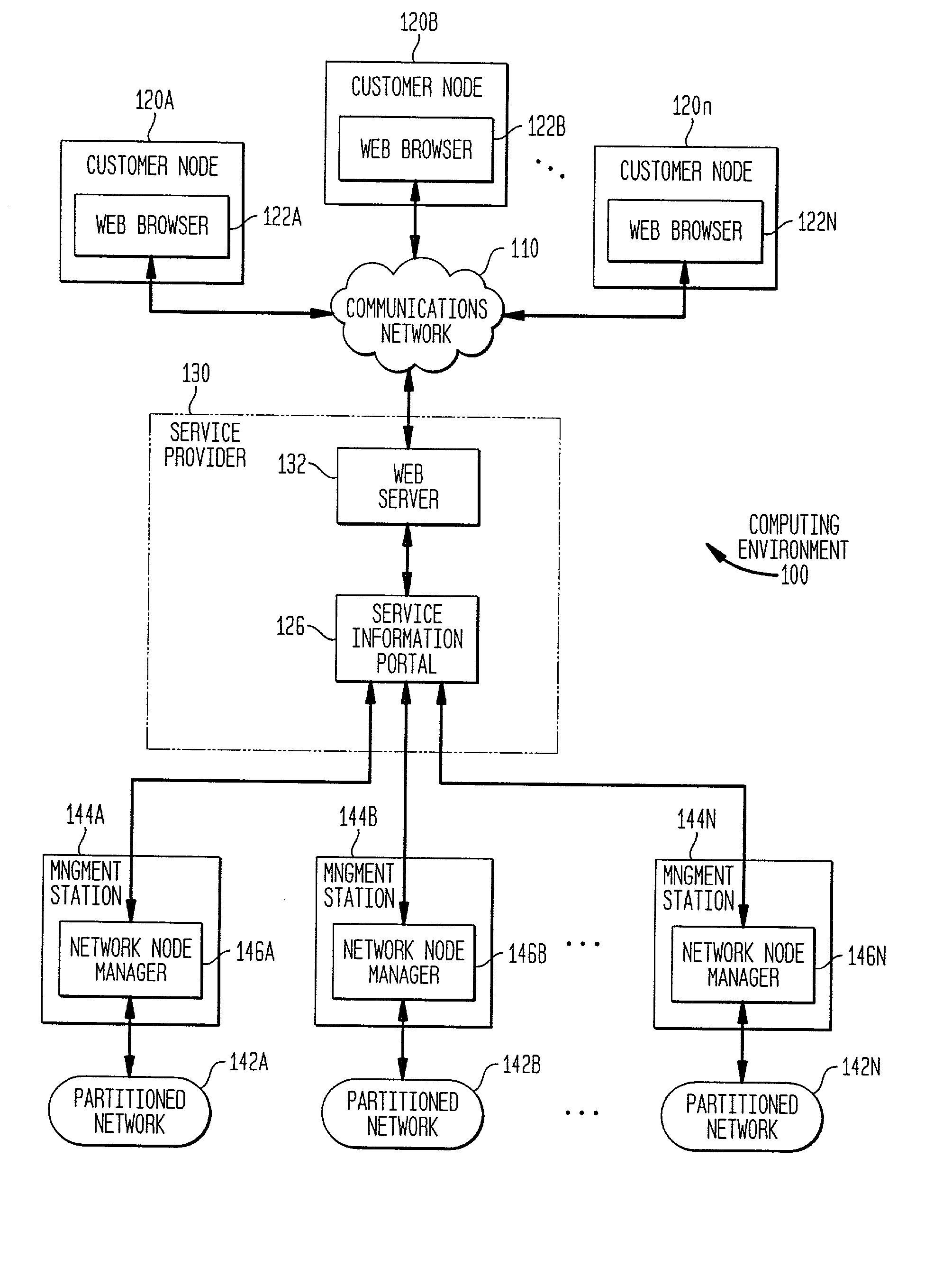
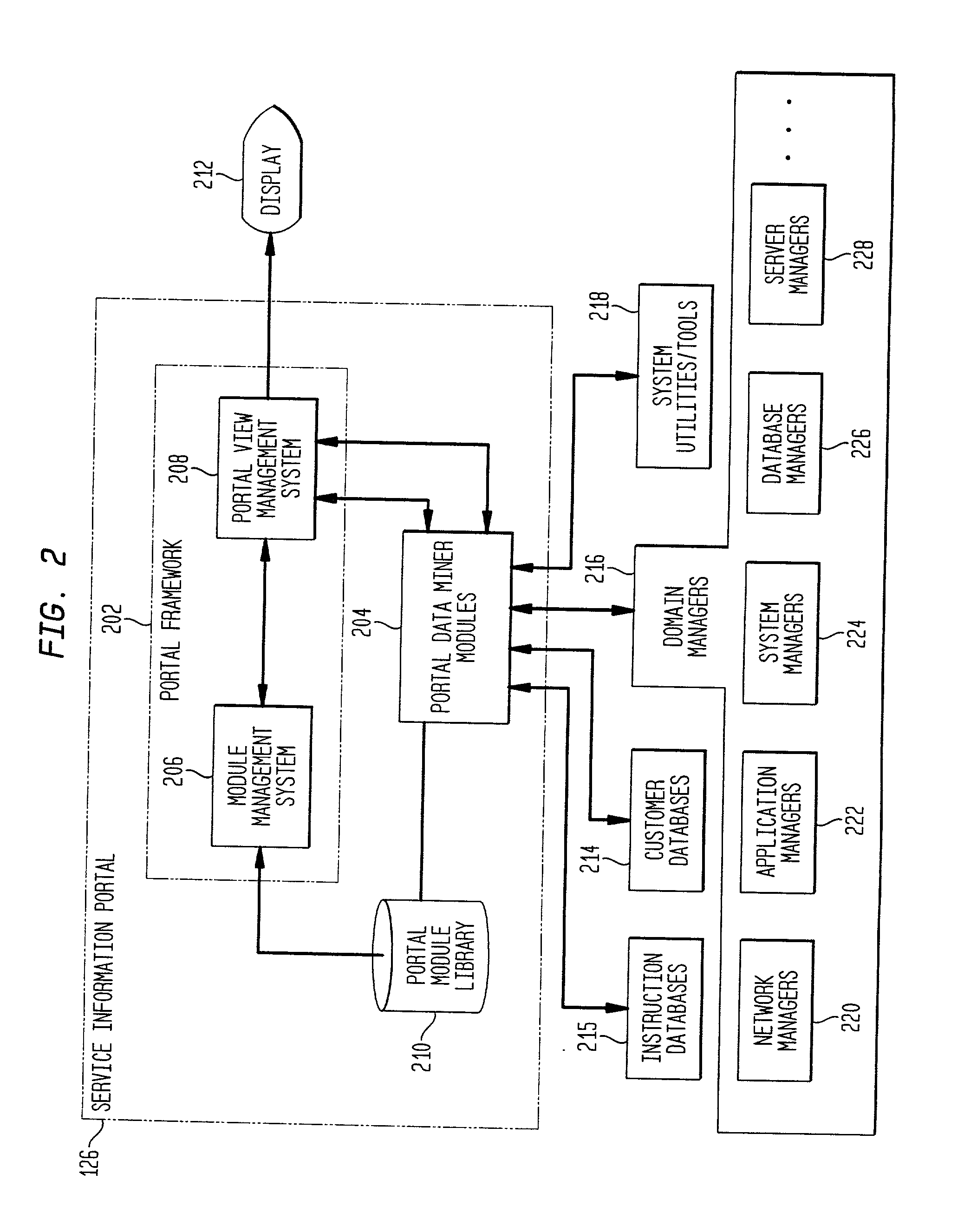
Portal system and method for managing resources in a networked computing environment
InactiveUS20020158899A1Easy to manageEliminate needDigital computer detailsData switching networksWorld Wide WebSoftware
A service information portal (SIP) and associated methodology for providing customer-based management information of networked computing environments for Internet service providers (ISPs), outsourcers, and enterprise service providers ("service providers"). The invention enables such service providers to provide the network administrators / users / customers / network managers / network operators ("network administrators") they serve with flexible, extensible, tailored, in-depth views of hosted computing environments in an intuitive graphical format. Generally, the invention extracts from relevant computing environment entities specified information for managing the outsourced computing environment. The specified information is presented on a customized display for consideration and interaction by the network administrator. Specifically, aspects of the invention include a database of executable portal view profiles each designed for and / or by a particular network administrator. Each such portal view profile references one or more portal data miner modules included in a library of such modules. When a portal view profile is invoked, the referenced data miner modules are executed to access hardware and / or software entities in the computing environment for information that is displayed to assist a network administrator manage the outsourced computing environment.
Owner:HEWLETT PACKARD DEV CO LP
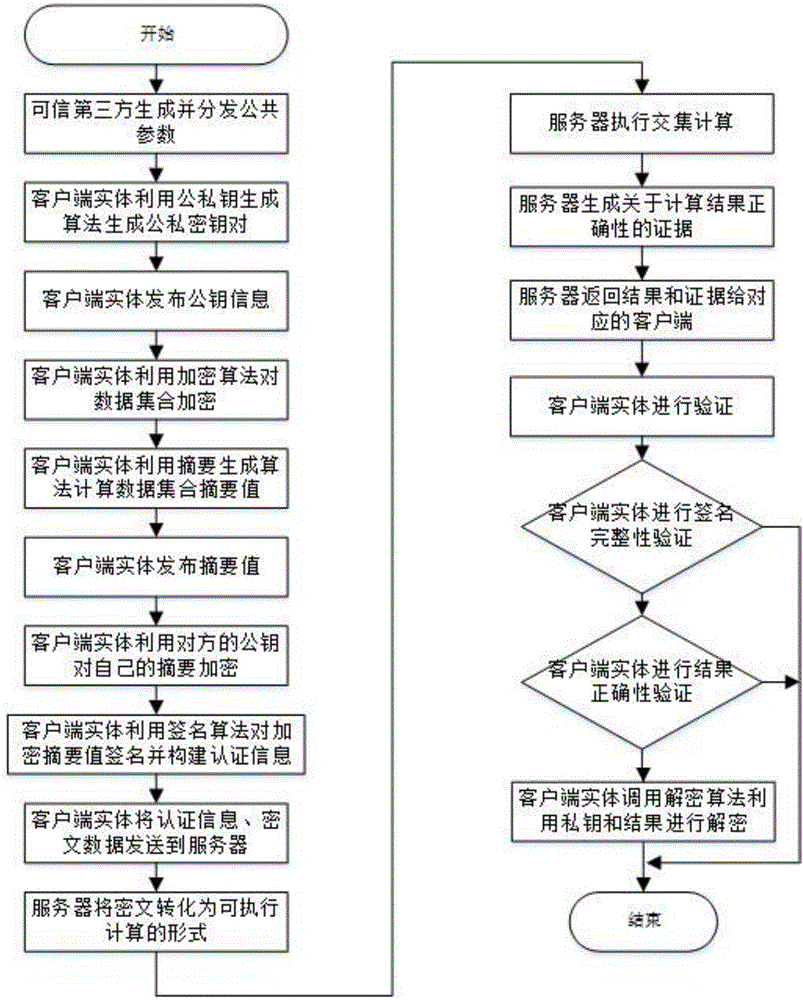
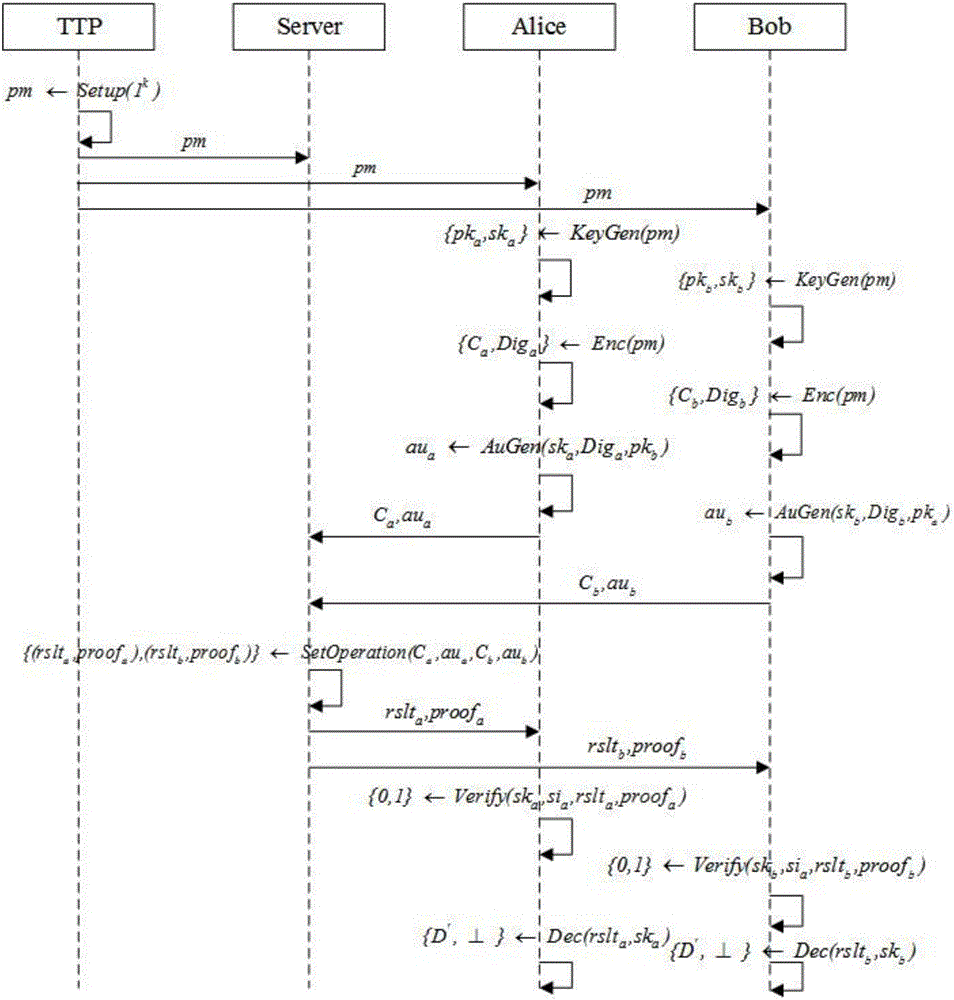
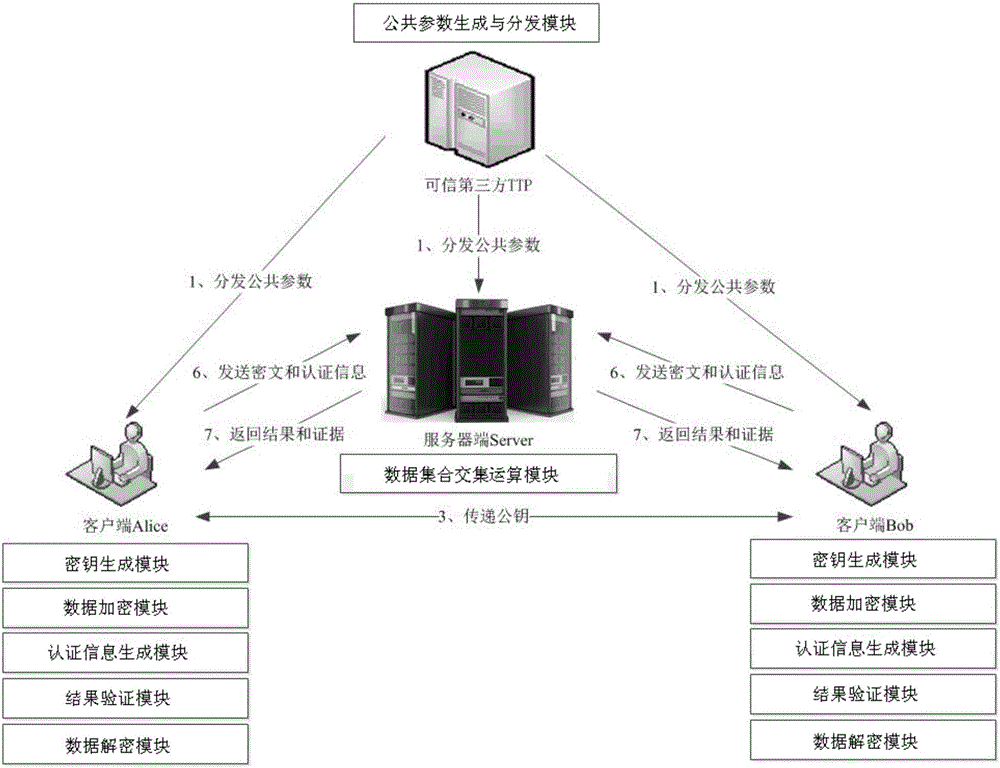
Outsourcing encrypted data-orientated verifiable intersection operation method and system
ActiveCN105812141AGuaranteed privacyReduce the number of interactionsUser identity/authority verificationPlaintextThird party
The invention relates to an outsourcing encrypted data-orientated verifiable intersection operation method and system and belongs to the verifiable outsourcing computation field. The method is carried out among a third-party trusted entity, at least two client entities and an outsourcing server side; the client entities are holders of data sets and requesters of data set intersection operation; the third-party entity is mainly responsible for the initialization and distribution of common parameters; the two client entities are mainly responsible for generating keys, encrypting data sets, calculating authentication information, verifying results and proofs returned by the outsourcing server side and decrypting an ciphertext data set returned by the outsourcing server side; the outsourcing server side is mainly responsible for performing data set intersection operation; and a plaintext data set is not required to be obtained through decryption when the outsourcing server side performs intersection operation, and the outsourcing server performs operation on a ciphertext, and therefore, the privacy of user data can be ensured. The method and system have the advantages of low frequency of interaction among the entities, low communication cost and efficient correctness verification of operation results.
Owner:NORTHEASTERN UNIV
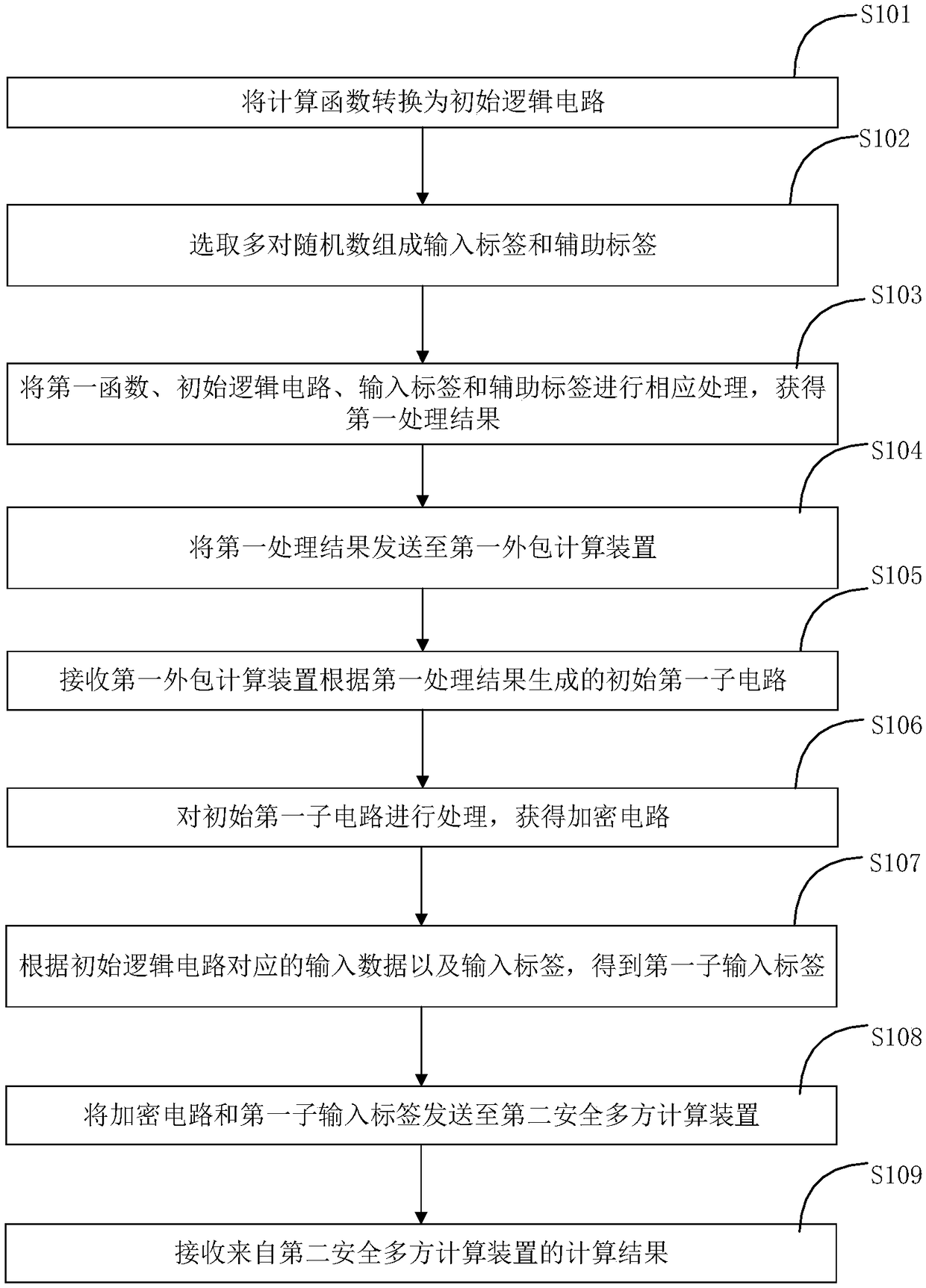
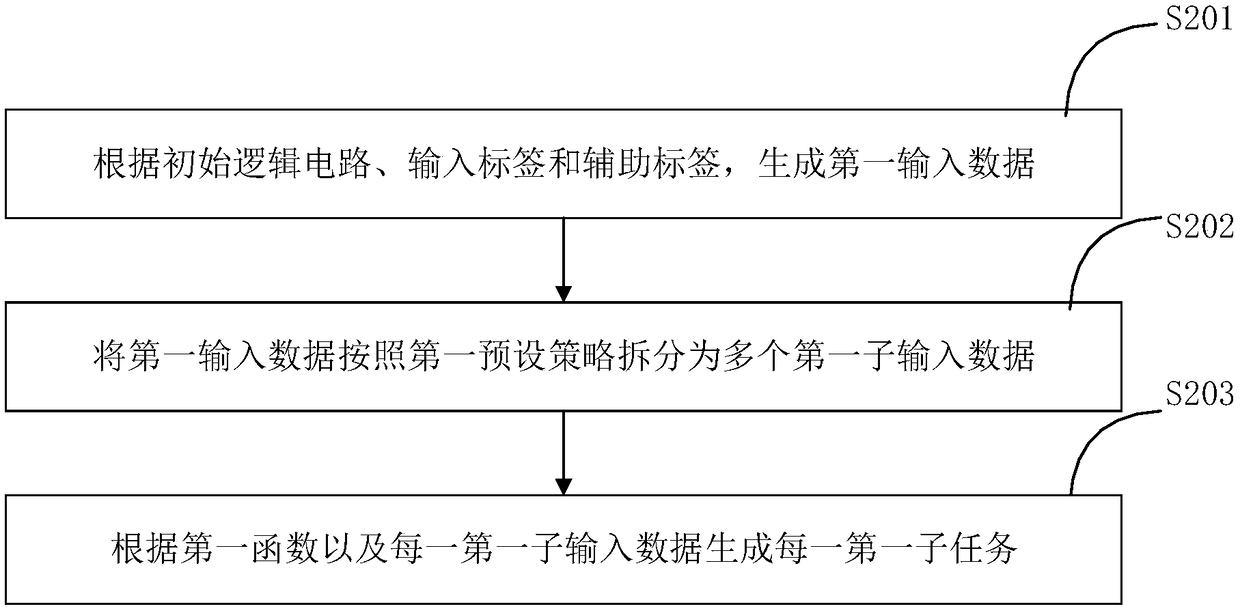
Secure multiparty computing method, device and system
ActiveCN108809623AReduce occupancyImprove computing efficiencySecuring communicationTheoretical computer scienceSecure multi-party computation
The invention provides a secure multiparty computing method, device and system. The secure multiparty computing method comprises the steps of converting a computing function into an initial logic circuit; selecting multiple pairs of random number so as to form an input label and an auxiliary label; processing a first function, the initial logic circuit, the input label and the auxiliary label correspondingly, so as to obtain a first processing result; sending the first processing result to a first outsourced computing device; receiving an initial first sub-circuit generated by the first outsourced computing device according to the first processing result; processing the initial first sub-circuit so as to acquire an encrypted circuit; obtaining a first sub-input label according to input data corresponding to the initial logic circuit and the input label; sending the encrypted circuit and the first sub-input label to a second secure multiparty computing device; and receiving a computingresult from the second secure multiparty computing device. Fewer local resources are used, computing efficiency is improved, and the performance of the secure multiparty computing technology is improved.
Owner:JUZIX TECH SHENZHEN CO LTD
Secure computational outsourcing techniques
InactiveUS6941463B1Unauthorized memory use protectionHardware monitoringParallel computingOutsourcing computation
Owner:PURDUE RES FOUND INC
Outsourcing calculation method, device and server of public key system
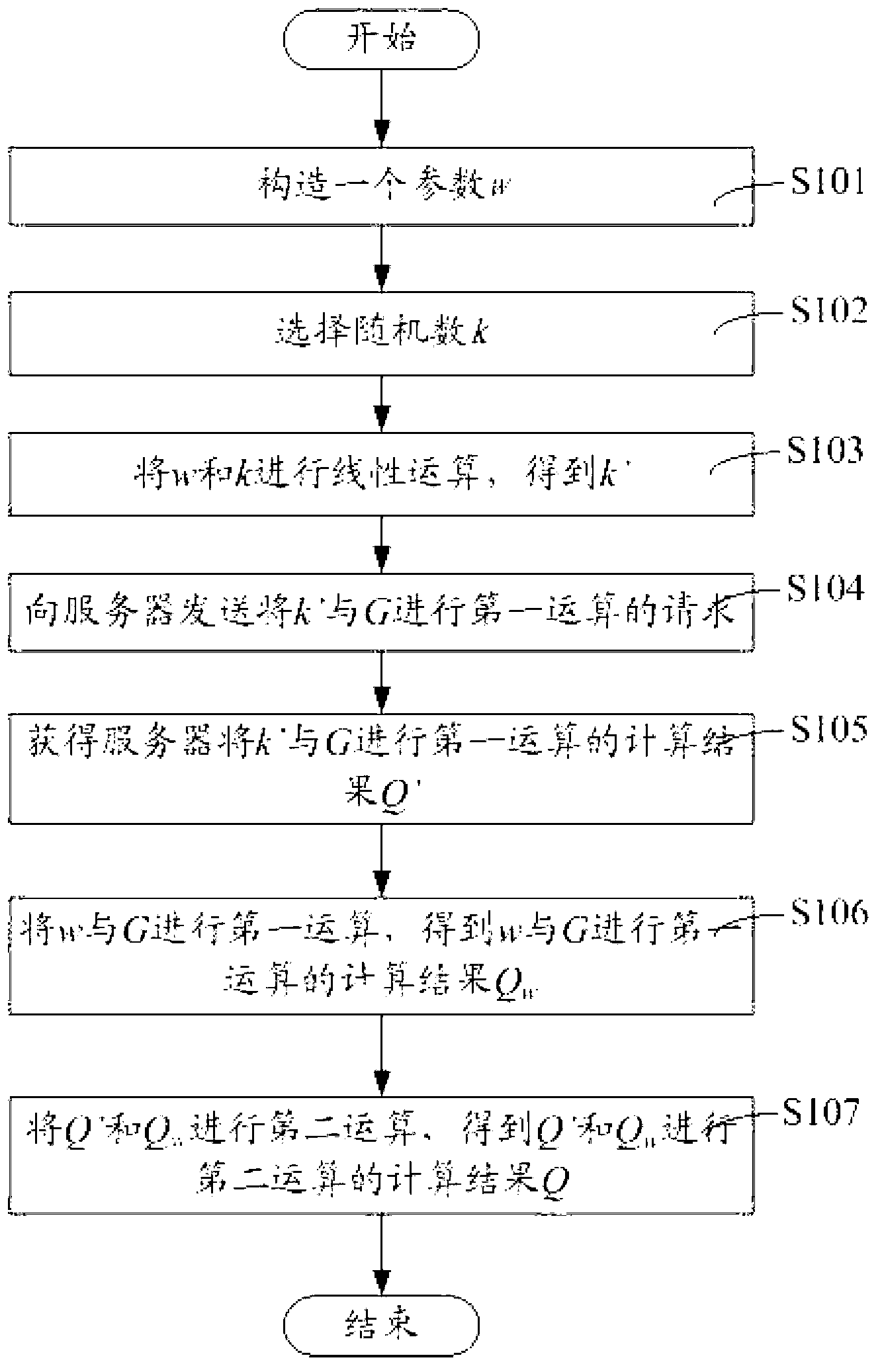
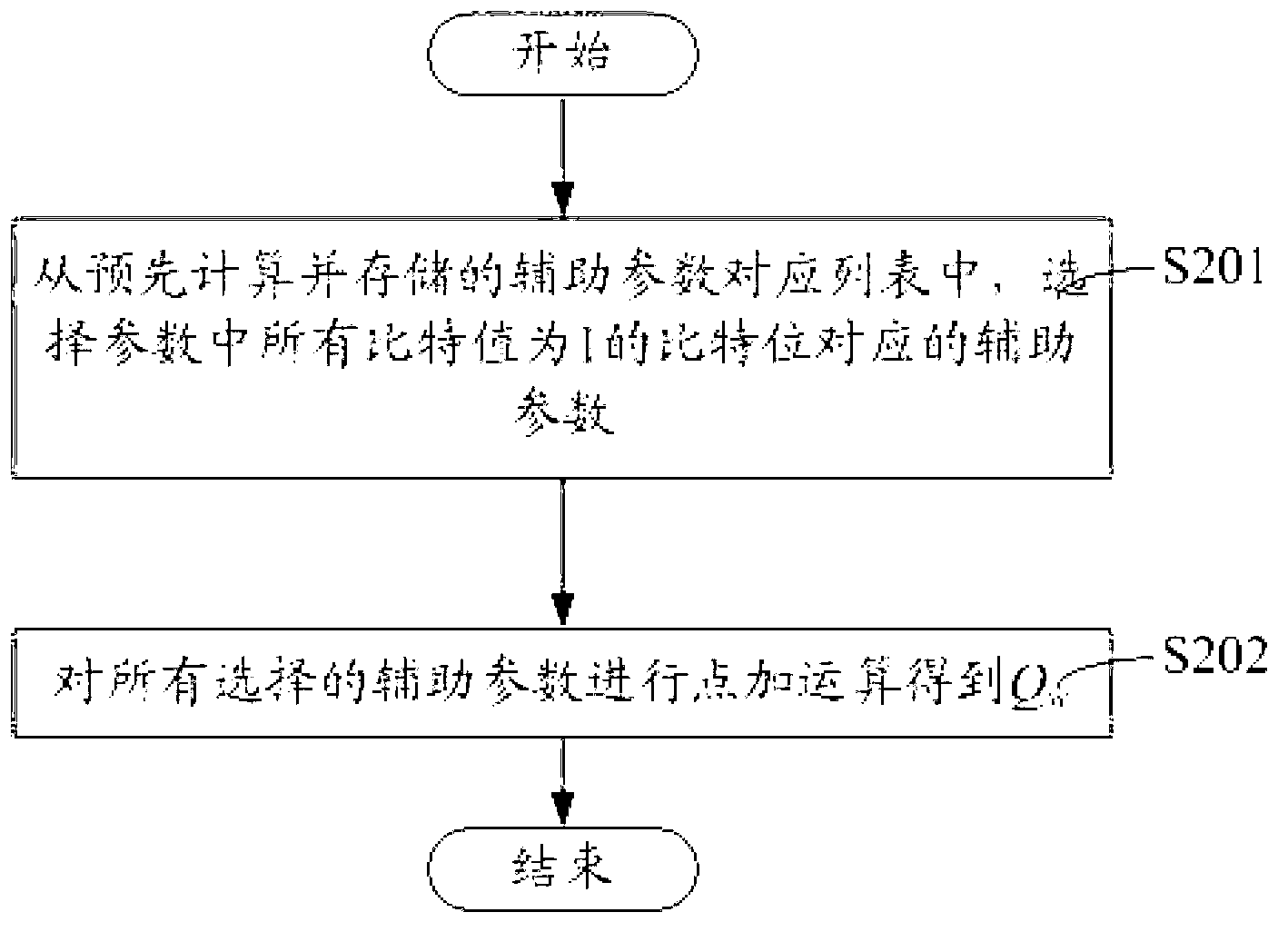
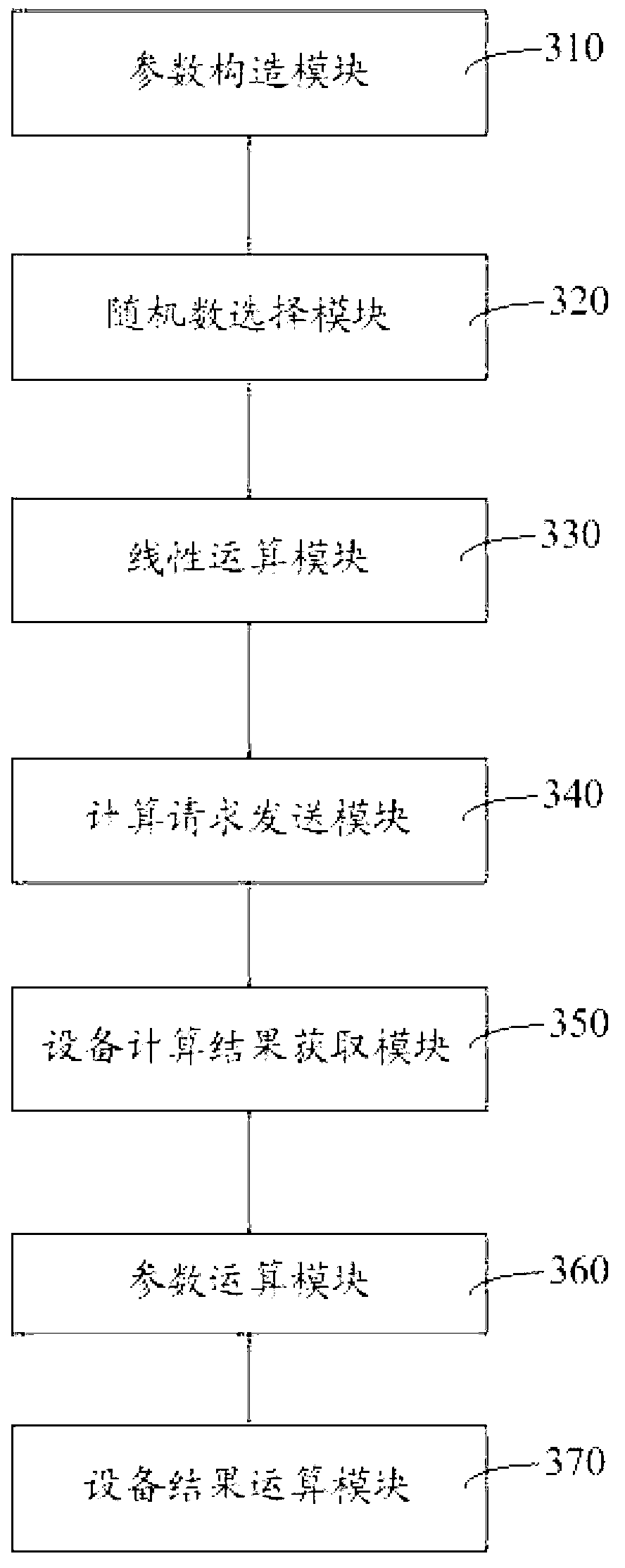
ActiveCN103067165ASatisfy the security conditionsAvoid gettingPublic key for secure communicationDigital signatureTheoretical computer science
The invention relates to cryptology relative technical field, in particular to outsourcing calculation method, device and server of a public key system. The outsourcing calculation method comprises the following steps: constructing random parameter w; choosing random number k; conducting linear operation on w and k to obtain k'; sending request of conducting a first operation on k' and G to a server, wherein G is a generating element of the public key system; obtaining calculation result Q' of the first operation of k' and G by the server; conducting the first operation on w and G to obtain the calculation result Q w of the first operation of w and G; conducting a second operation on Q' and Q w to obtain the calculation Q of the second operation of Q' and Q w. On the condition of meeting digital signature safety, the goal of safely delivering complicated calculation of the public key system in an outsourcing calculation manner to cloud computing service providers can be achieved.
Owner:GUANGDONG CERTIFICATE AUTHORITY
Homomorphic encryption matrix determinant security outsourcing method based on cloud computing
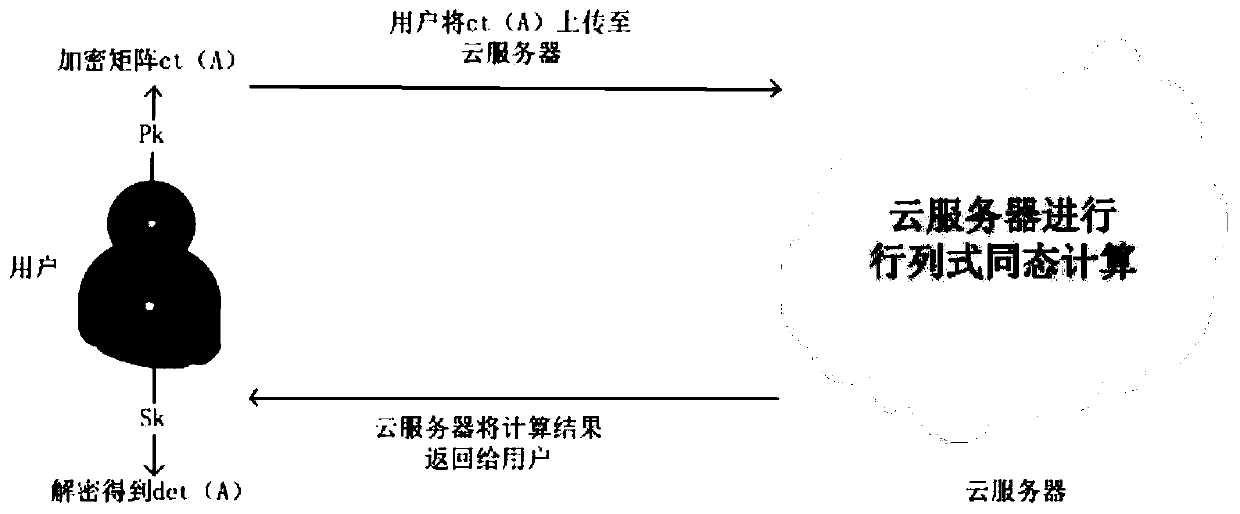
ActiveCN110324135AReduce the amount of calculationReduce the number of operationsCommunication with homomorphic encryptionComplex mathematical operationsCiphertextWorkload
The invention discloses a homomorphic encryption matrix determinant security outsourcing method based on cloud computing, which is characterized in that the whole matrix is encoded and encrypted intoa ciphertext by applying matrix encoding technology, and efficient matrix determinant security outsourcing computation is realized in combination with a division-free determinant computation method. The method comprises a data encryption / decryption method and a homomorphic calculation method. A client side executes the encryption method, codes, encrypts and uploads the matrix to a cloud server. Acloud server side executes a homomorphic calculation method, carries out ciphertext operation under the condition of not decrypting, and returns a calculation result to the client side in a ciphertextform. Finally, the client side executes the decryption module to obtain the determinant value of the matrix. Most calculation is carried out at the cloud server side, so that calculation workload ofthe client side is greatly reduced.
Owner:ZHEJIANG SCI-TECH UNIV
Privacy protection query method and device supporting outsourcing calculation and related equipment
PendingCN114428972AAchieve friendlinessRealize batch queryDigital data information retrievalDigital data protectionPrivacy protectionOutsourcing computation
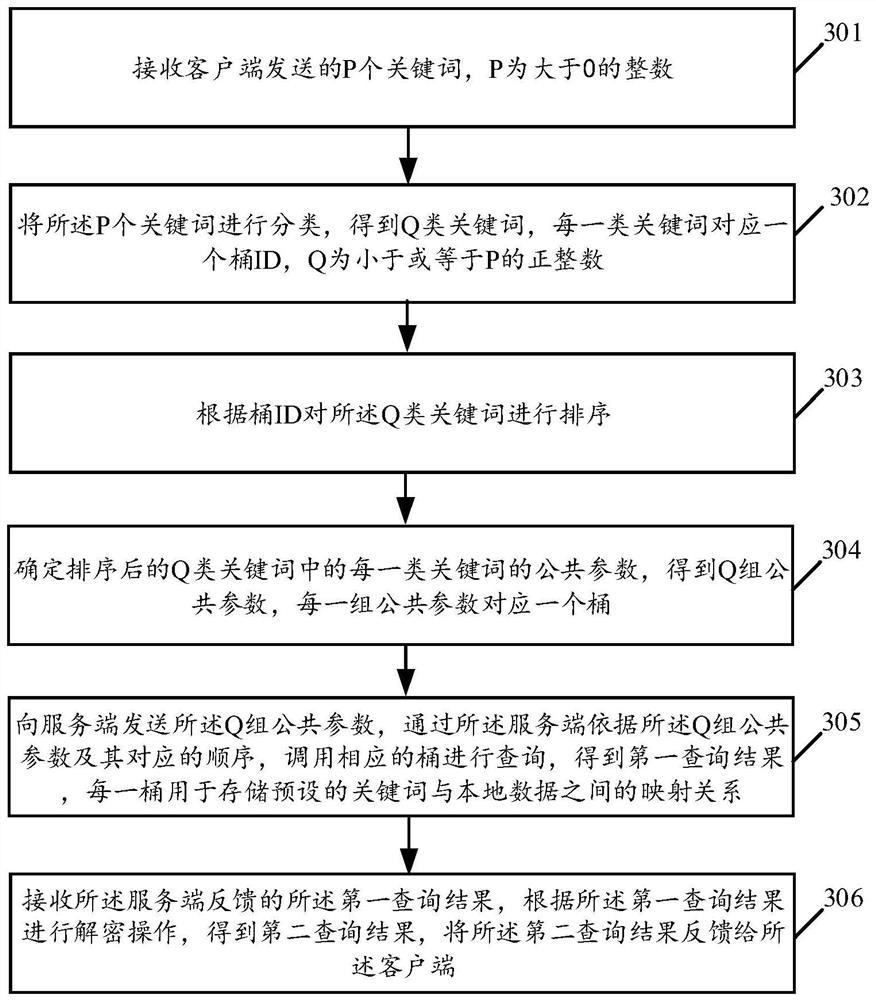
The embodiment of the invention discloses a privacy protection query method and device supporting outsourcing computing and related equipment, and the method comprises the steps: receiving P keywords, classifying the P keywords to obtain Q types of keywords, and enabling each type of keywords to correspond to a bucket ID; sorting the Q-class keywords according to the bucket ID; public parameters of each type of keywords in the Q types of keywords after sorting are determined, Q groups of public parameters are obtained, and each group of public parameters corresponds to one bucket; the Q groups of public parameters are sent to the server side, corresponding buckets are called for query through the server side according to the Q groups of public parameters and the corresponding sequence, a first query result is obtained, and each bucket is used for storing a mapping relation between a preset keyword and local data; and receiving a first query result fed back by the server, performing decryption operation according to the first query result to obtain a second query result, and feeding back the second query result to the client. By adopting the embodiment of the invention, the hidden trace query efficiency can be improved.
Owner:深圳市洞见智慧科技有限公司
Security outsourcing method for two bilinear pairings based on dual cloud servers
ActiveCN107248973AImprove computing efficiencyReduce the number of timesPublic key for secure communicationOutsourcing computationBilinear pairing
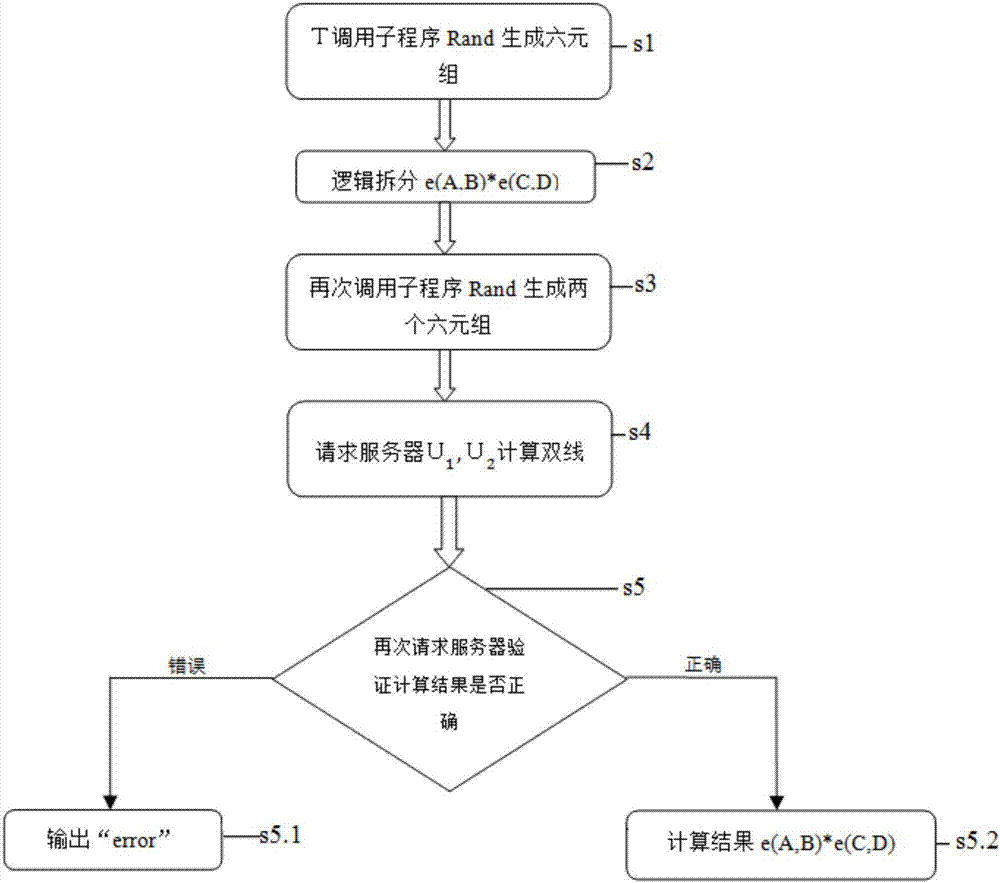
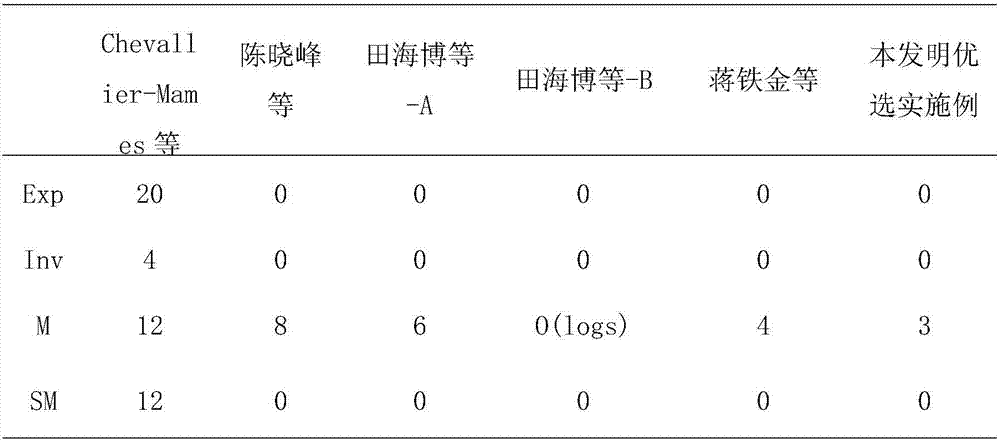
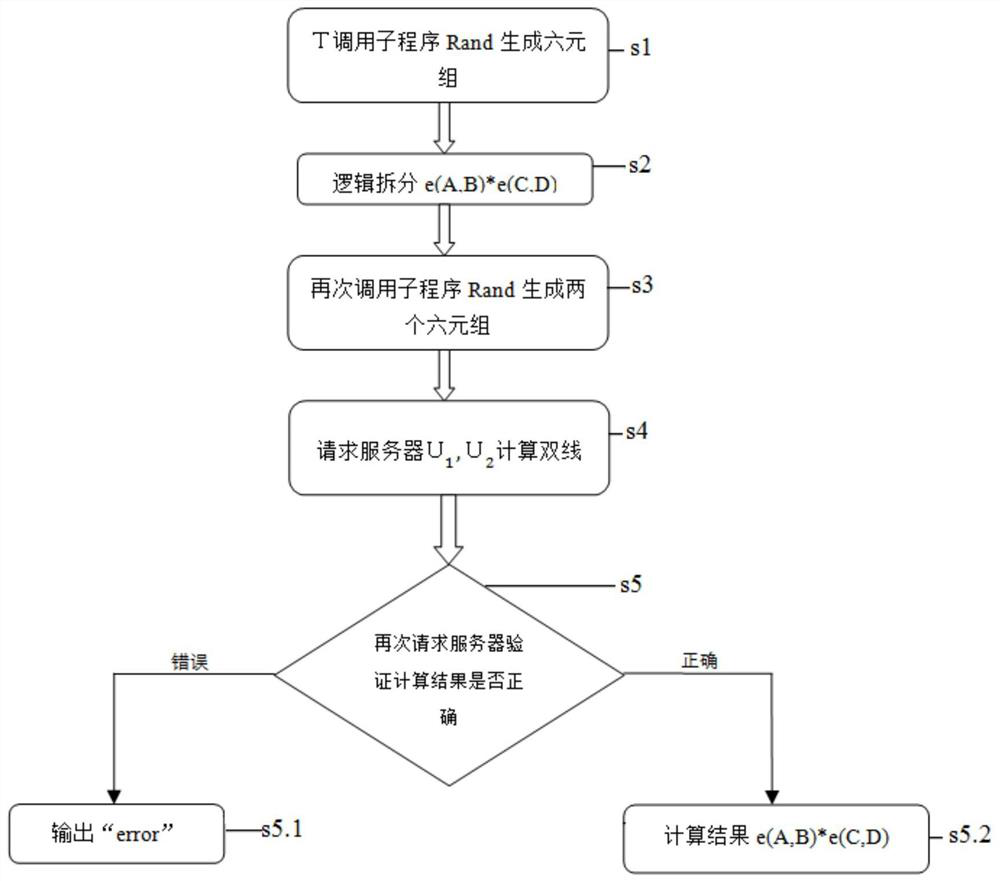
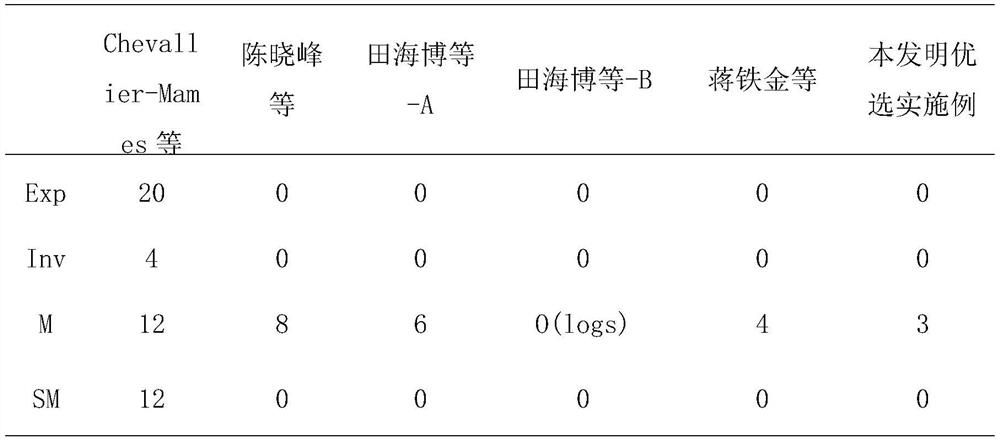
The invention discloses a security outsourcing method for two bilinear pairings based on dual cloud servers. First, a user T performing outsourcing computation calls a subroutine Rand for improving the computing speed to generate a six-tuple, and elements in the six-tuple are utilized to divide e(A, B)*e(C, D) logic into four parts. Then, Rand is called to generate two new six-tuples, computing servers U1 and U2 are inquired four times respectively, the servers work out bilinear pairing results, four parts of the bilinear pairing results serve as intermediate computing results, and the other four parts of the bilinear pairing results serve as test data. Finally, whether output results of U1 and the U2 are correct is detected, and results are worked out according to the response of the servers. The security outsourcing method is suitable for resource-constrained devices. The security outsourcing method has the advantages of high computing efficiency and fewer operations. Outsourcers do not need to carry out high-cost SM and Exp operation any longer. Moreover, the security outsourcing method of the invention is applicable to an outsourcing computation scene of multiple bilinear pairings, and is of higher practical application value.
Owner:SHANGHAI UNIV
Safety two-direction vector advantage comparison method based on block chain
ActiveCN111277406AReduce the burden onReduce computational overheadKey distribution for secure communicationDiscounts/incentivesAttackComputation process
The invention belongs to the field of cryptology and information security, and particularly relates to a security two-direction vector advantage comparison method based on a block chain. According tothe method, block chain and cloud outsourcing calculation is used as a basic framework, a block chain is used as a driving tool to replace a trusted third party to manage and supervise the whole calculation process, and normal operation of a vector is ensured. By means of cloud outsourcing computing, heavy computing tasks are transferred from a user to an outsourcing server with enough computing power, the burden of the user is relieved, and extra computing resources are fully utilized. According to the method, cloud outsourcing calculation and the block chain are combined, a reliable reward punishment mechanism is provided, the attack cost of a malicious server is greatly increased while the calculation overhead of a user is reduced, and therefore a semi-honest model protocol which is seriously limited in actual operation originally is guaranteed.
Owner:SUN YAT SEN UNIV
Hierarchical security multi-party calculation method and device based on Chinese remainder theorem
ActiveCN112700152AAchieve the purpose of computingDigital data protectionResourcesCiphertextChinese remainder theorem
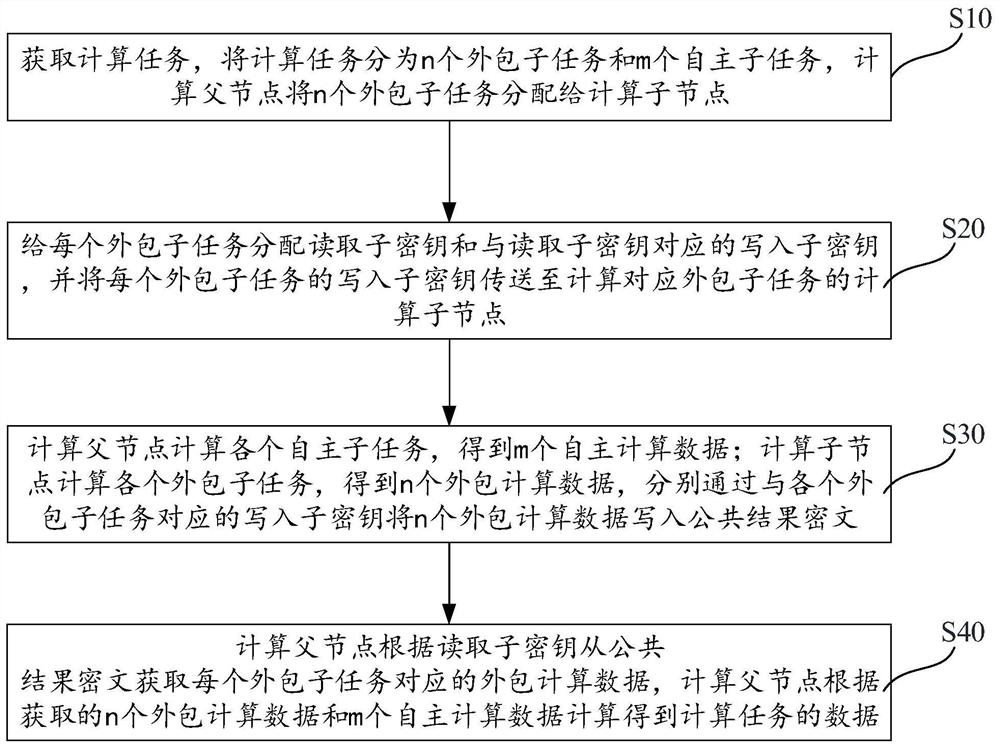
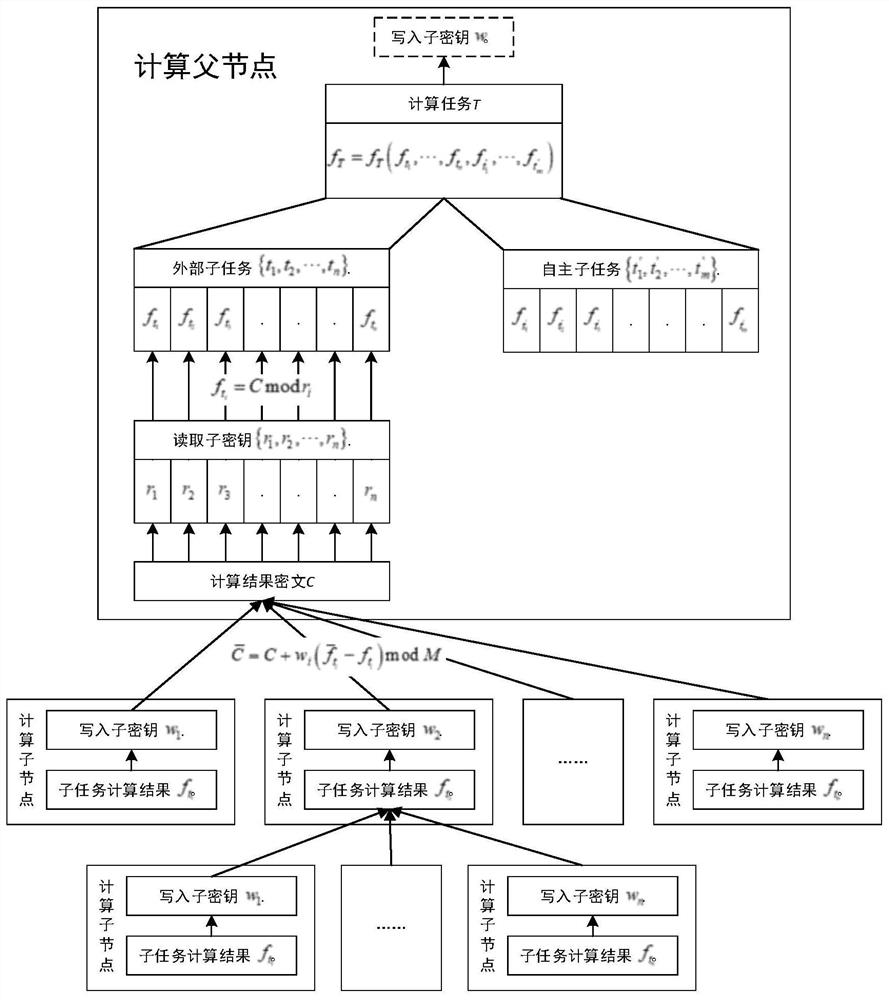
The invention relates to a hierarchical security multi-party computing method and device based on the Chinese remainder theorem, and the method comprises the steps: enabling a computing task to be divided into an outer package subtask and an autonomous subtask through a computing father node, and distributing a writing subkey and a reading subkey for each outer package subtask; sending each outer packet sub-task and the corresponding write-in sub-key to each computing sub-node in a safe mode; enabling the computing father node and the computing child nodes to obtain data of respective child tasks through computing, and storing outsourcing computing data in a public result ciphertext through writing of child keys and sharing and transmitting the outsourcing computing data in the public result ciphertext; enabling the computing father node to obtain outsourcing computing data calculated by each computing child node from the public result ciphertext by reading the child key, and calculating a final result of the calculation task. According to the method, the computing sub-nodes can assist each other to complete the computing task together, but the computing data of other computing sub-nodes and the final computing data of the computing task cannot be obtained, so that secure multi-party computing is realized.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
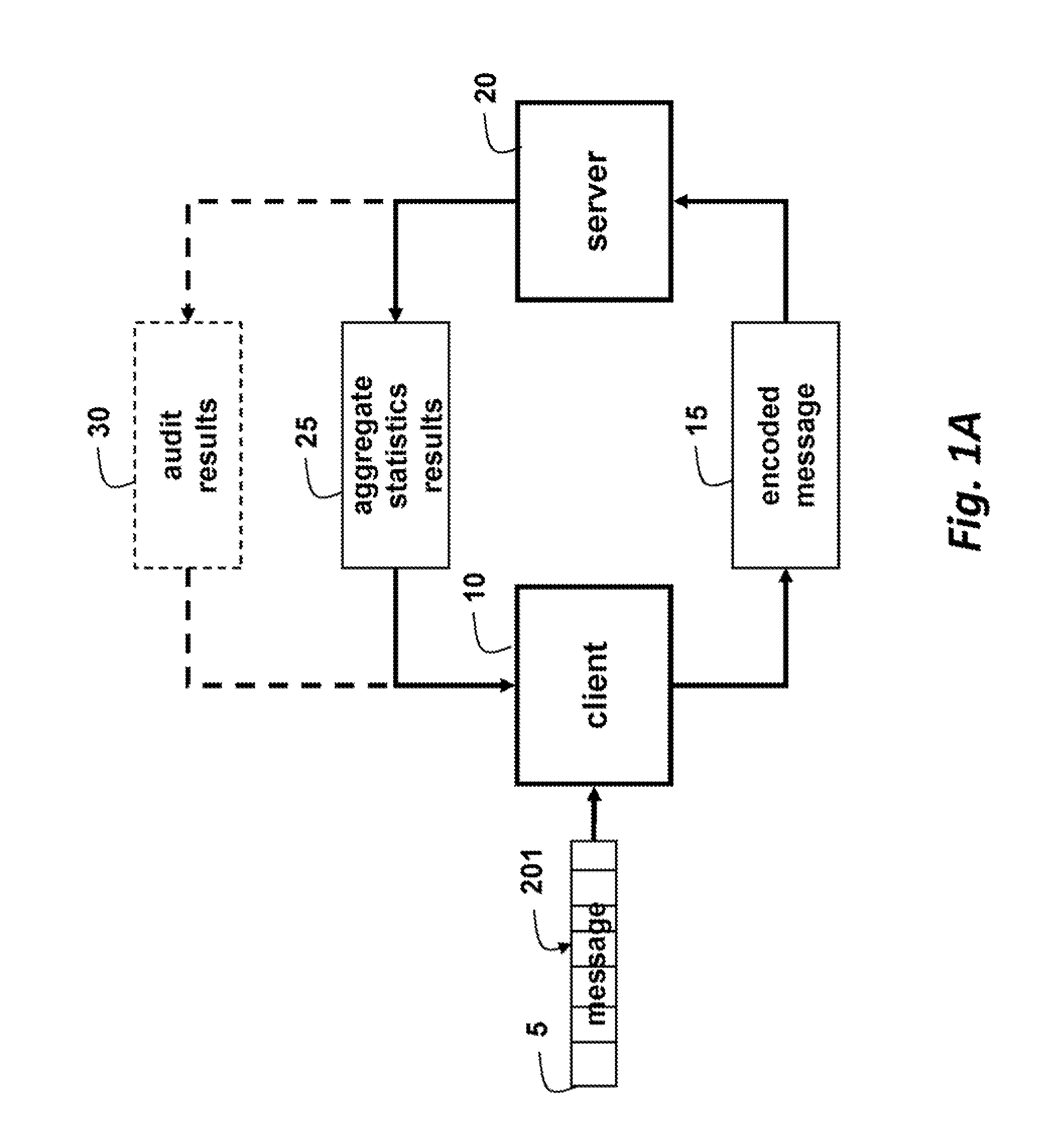
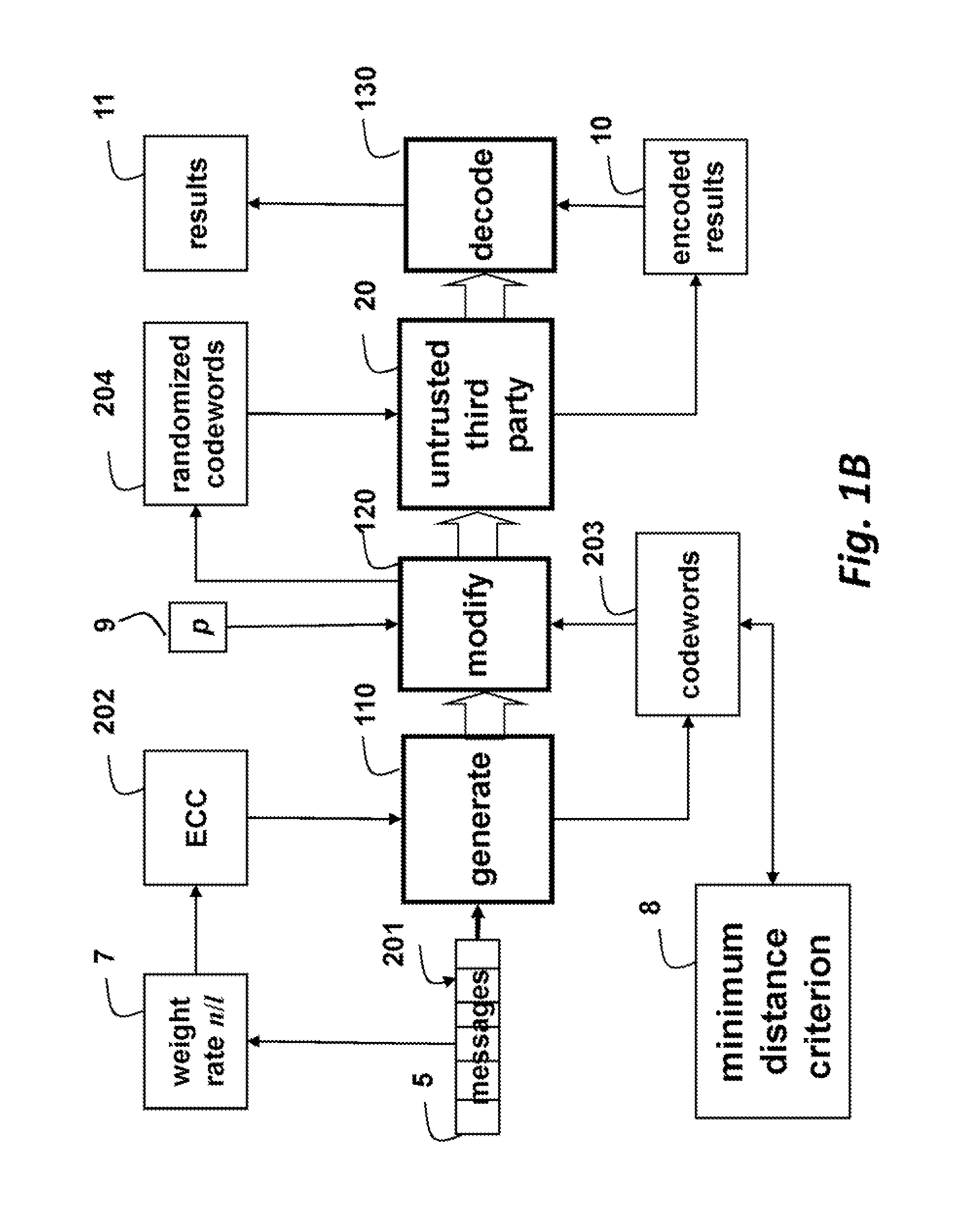
Method for Processing Messages for Outsourced Storage and Outsourced Computation by Untrusted Third Parties
InactiveUS20130339814A1Negligible probabilityProbability of errorCode conversionError correction/detection using block codesThird partyTheoretical computer science
A message is stored and processed by an untrusted third party by generating a codeword using a selected one of a set of error correcting codes (ECC). The selected ECC depends on a weight rate of the block, and each codeword satisfies a minimum distance criterion with respect to the codewords of all possible ECCs and all possible weight rates. Each symbol of the codeword is modifying explicitly, randomly and independently according to parameters of a channel to obtain a randomized codeword. Then, an encoded result of an operation performed on the randomized codeword by the untrusted third party is decoded.
Owner:MITSUBISHI ELECTRIC RES LAB INC
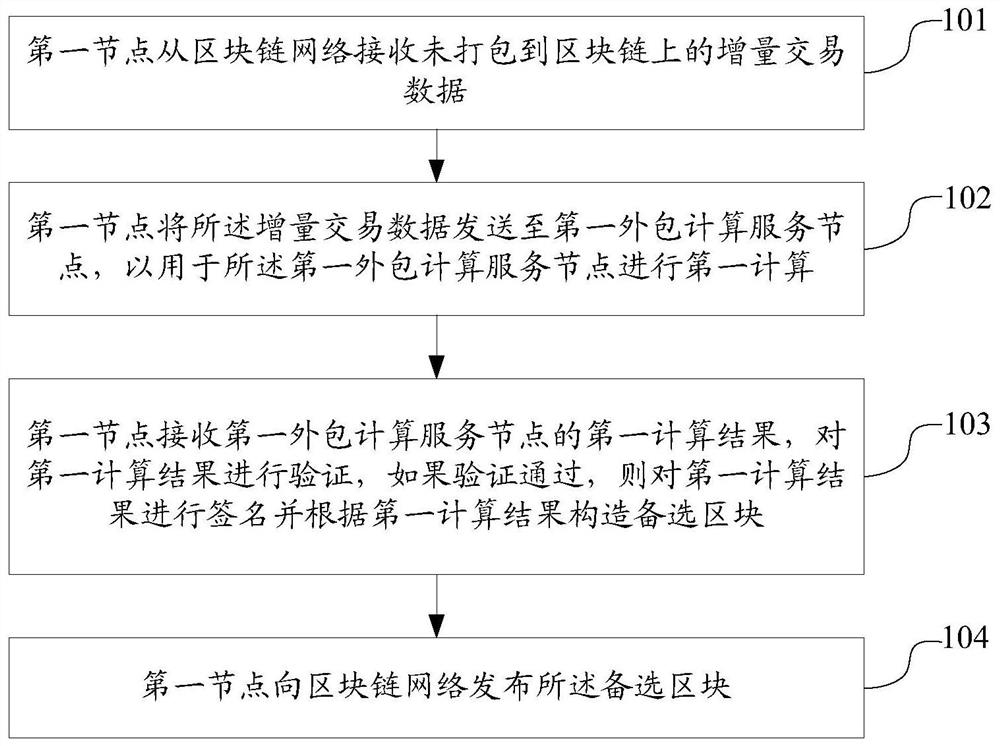
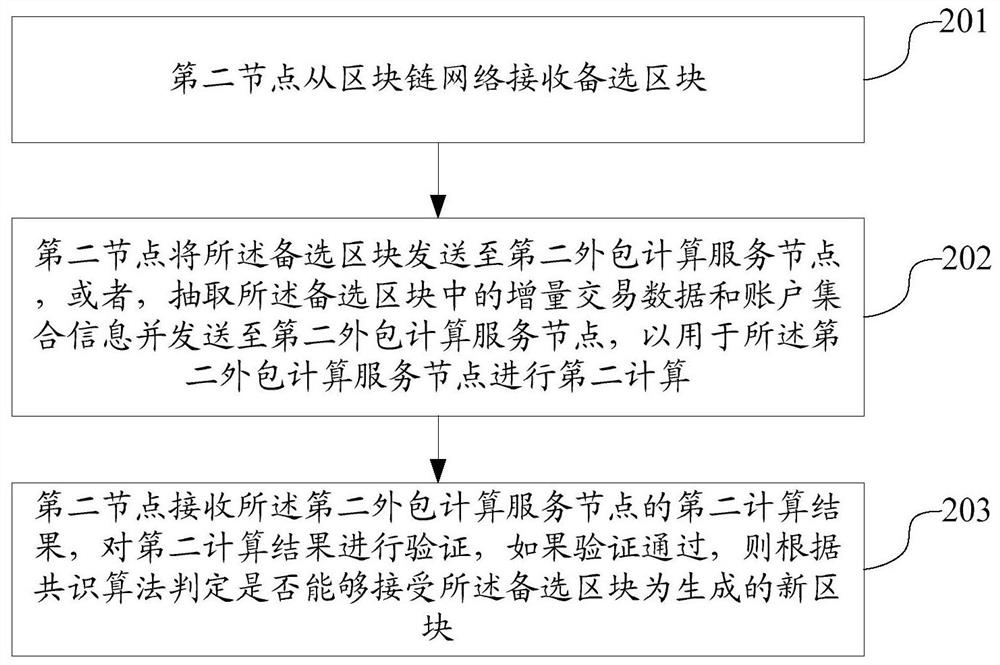
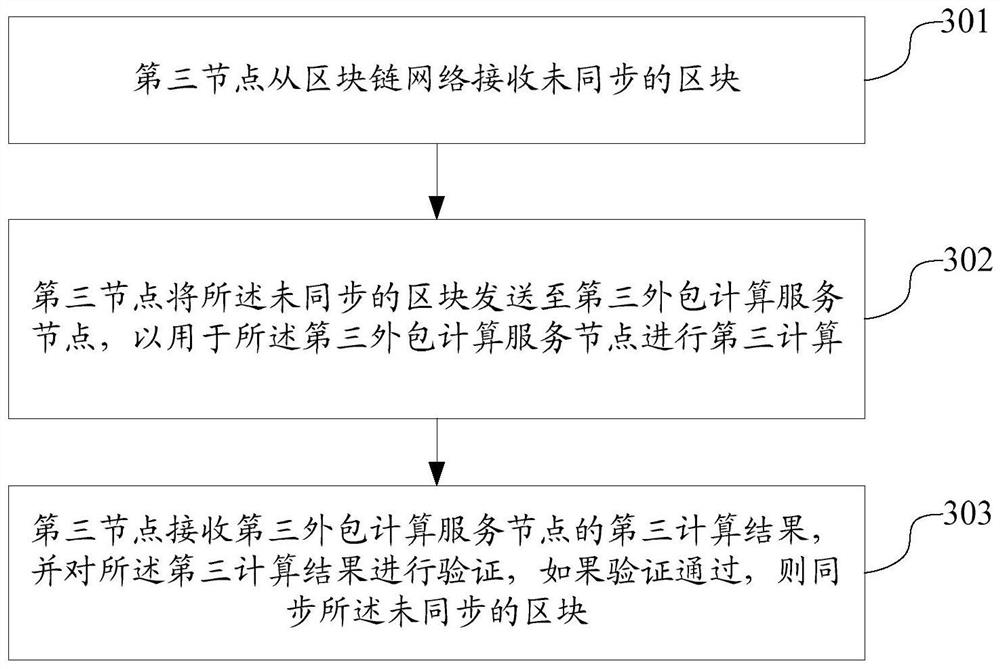
Block generation method and device, block synchronization method and device, blockchain system and storage medium
PendingCN111787034ALow hardware requirementsImprove securityFinanceTransmissionComputer networkTransaction data
The invention discloses a block generation and consensus method and device, a block synchronization method and device, a blockchain system and a storage medium. The block generation method comprises the steps that a first node receives incremental transaction data which is not packaged onto a blockchain from a blockchain network; sending the incremental transaction data to a first outsourcing computing service node for the first outsourcing computing service node to perform first computing; receiving a first computing result of the first outsourcing calculation service node, verifying the first computing result, and if the verification is passed, signing the first computing result and constructing an alternative block according to the first computing result; and publishing the alternativeblock to the blockchain network. According to the method, the first computing is outsourced to the first outsourcing computing service node, so that the hardware requirement of the first node is reduced, the participation in the blockchain network consensus does not simply depend on the computing power, the network and the storage resources any more, the mining people probability of the low-computing-power node is improved, and the equity and fairness of mining accounting are ensured.
Owner:北京邦天信息技术有限公司
Verifiable constrained quadratic programming safety outsourcing calculation method and system
InactiveCN113271293APrivacy protectionSolve difficult problems that cannot be solved by quadratic programmingKey distribution for secure communicationOutsourcing computationCalculation methods
The invention relates to a verifiable constrained quadratic programming safe outsourcing calculation method and system.The client side can outsourcing calculation which cannot be conducted locally to a cloud server for calculation so as to reduce the calculation cost of a user, and the outsourcing process comprises the steps that firstly, the client side initializes setting, encrypts tasks needing outsourcing and sends the tasks needing outsourcing to the cloud server; then, the cloud server receives the task, performs calculation according to requirements, and returns a corresponding result to the client; and finally, the client verifies the correctness of the returned result, if the result is correct, the required original task result is obtained through decryption, otherwise, the result is refused to be accepted, and the cloud server is required to recalculate. According to the method provided by the invention, the client can solve the difficult problem which cannot be solved due to local resource limitation on the premise of protecting own data privacy. Meanwhile, the malicious behavior of the cloud server can be resisted.
Owner:SHANGHAI UNIV
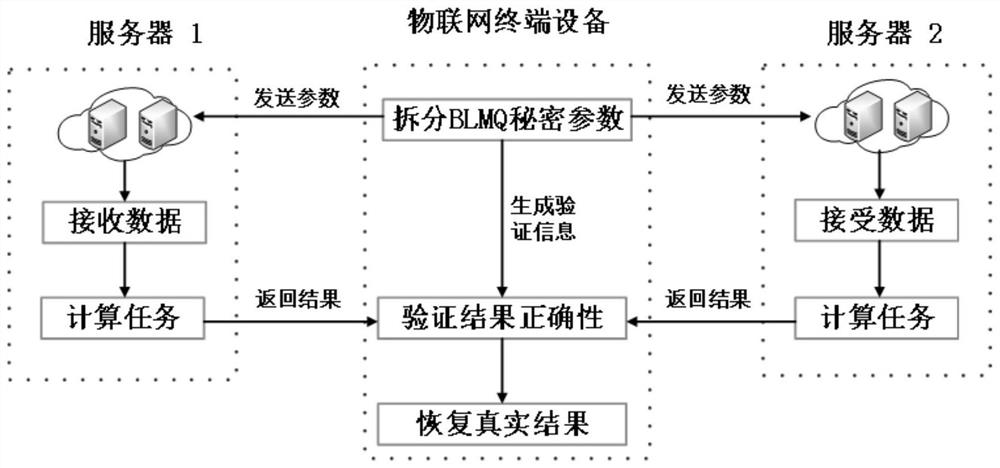
Verifiable security outsourcing calculation method and system for identification cryptosystem
ActiveCN114257374ASave computing resourcesGuaranteed execution speedKey distribution for secure communicationUser identity/authority verificationDigital signatureCryptosystem
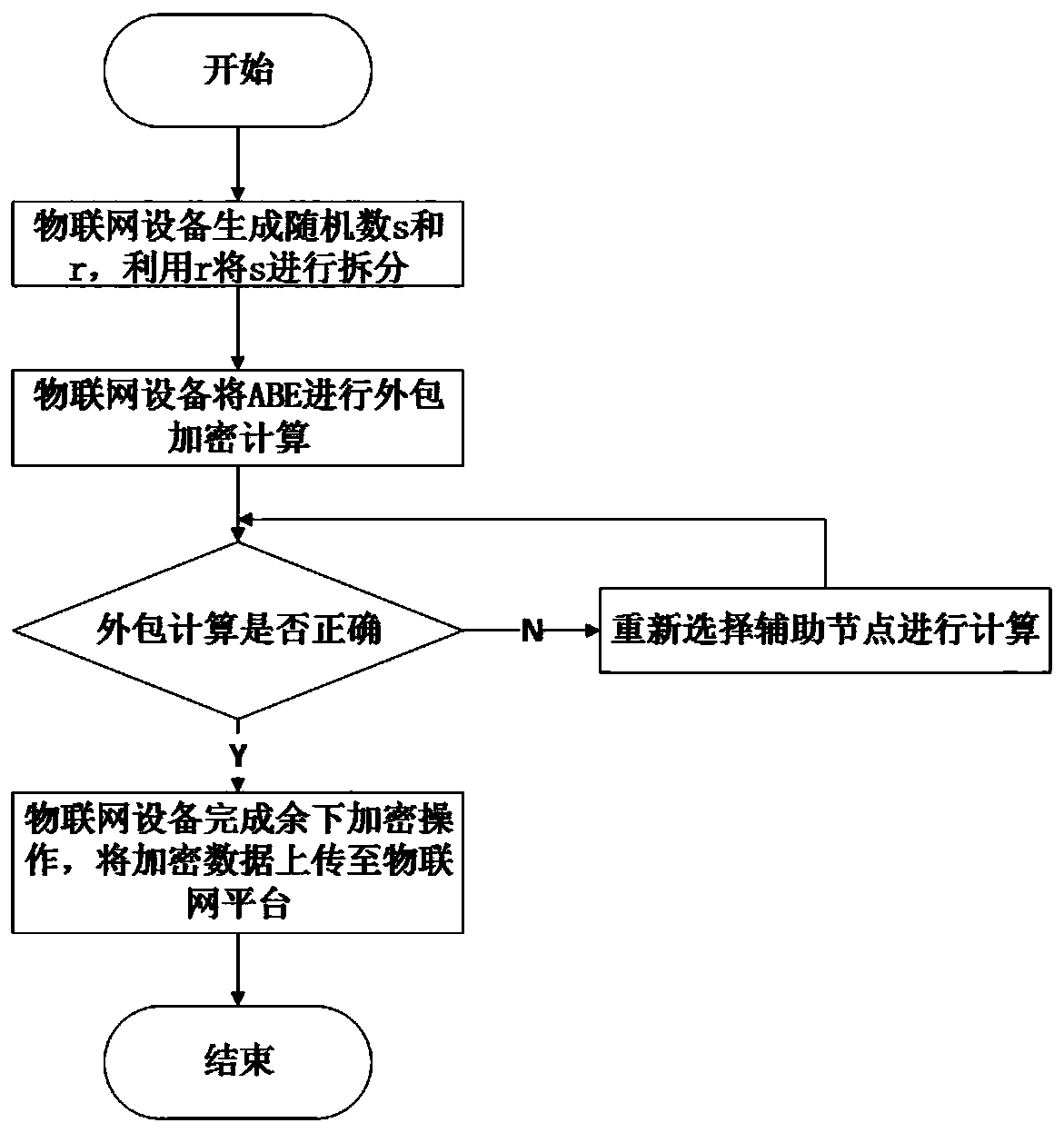
The invention provides a verifiable security outsourcing calculation method and system for an identification cryptosystem, and for a part needing outsourcing, Internet of Things terminal equipment firstly splits confidential parameters involved in each step, and then sends the encrypted parameters and some public parameters to two servers for calculation. And after the two servers complete corresponding calculation, the calculation results are returned to the Internet of Things terminal equipment, and the Internet of Things terminal equipment verifies the correctness of the returned results by using the verification information generated in the splitting process. And if the verification is passed, the Internet of Things terminal device carries out calculation to obtain a real calculation result. The method can be used for outsourcing calculation of algorithms such as identification-based data encryption, digital signature and signcryption, and the operation time of the Internet of Things terminal equipment can be saved.
Owner:SHANDONG UNIV
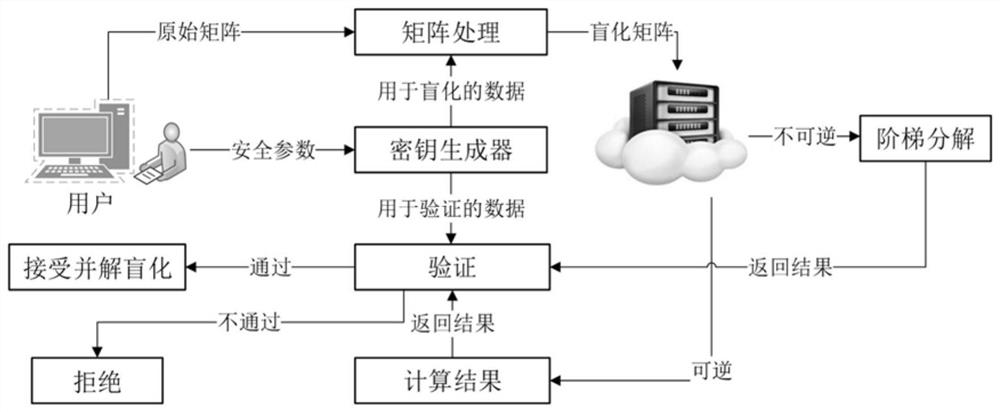
Matrix inversion outsourcing calculation method based on elementary matrix
ActiveCN113326475AProtection securityPrivacy protectionComplex mathematical operationsAlgorithmPassword
The invention discloses a matrix inversion outsourcing calculation method based on an elementary matrix, which is used for protecting the security of input and output data and improving the outsourcing calculation efficiency by utilizing the elementary matrix and a sparse matrix with lower calculation complexity on the premise of no password difficulty hypothesis. The correctness of a returned result is verified by adopting a Monte Carlo algorithm, and the calculation cost of user outsourcing matrix inversion calculation is reduced by adding a ladder decomposition design. Therefore, the security of the client data is improved, and the outsourcing overhead of the client is reduced. The method has the characteristics of safety, high efficiency, result verifiability and the like.
Owner:FUJIAN NORMAL UNIV
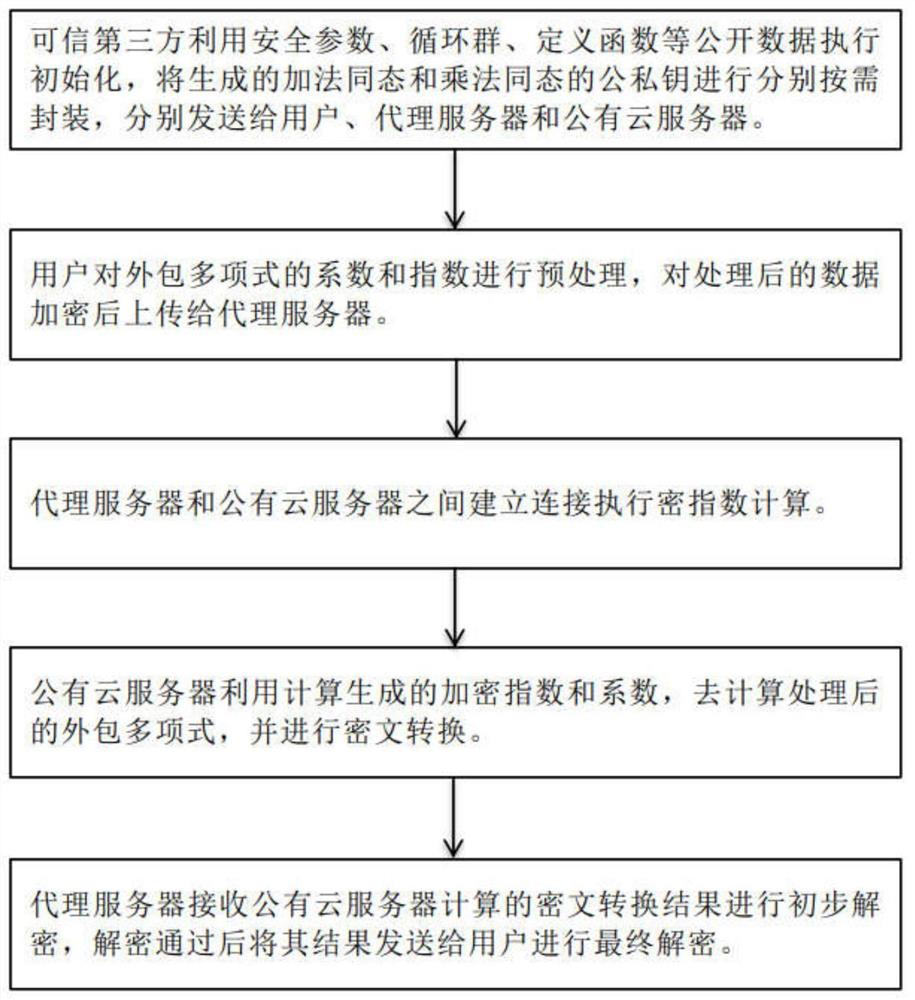
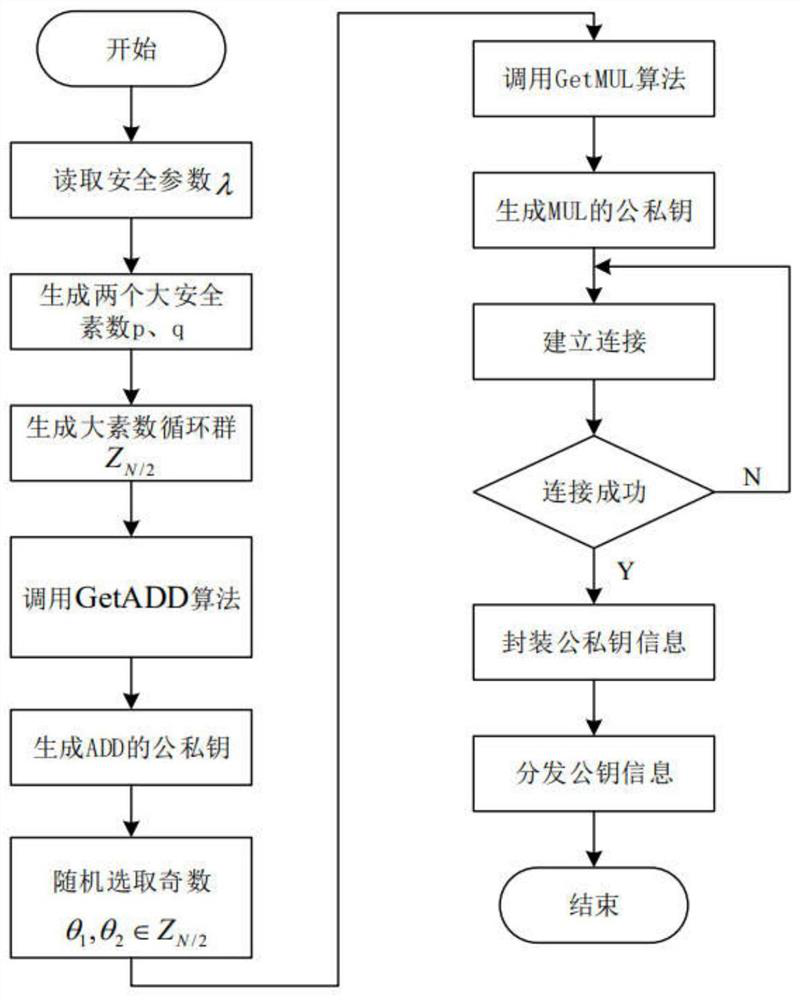
SHE-based secure outsourcing method
InactiveCN112468284ARealize privacy protectionSafe and efficientPublic key for secure communicationCommunication with homomorphic encryptionThird partyCiphertext
The invention discloses a security outsourcing method based on SHE, and belongs to the technical field of network security, and the method comprises the steps: enabling a trusted third party to carryout the on-demand packaging of generated addition homomorphic and multiplication homomorphic public and private keys through employing public information, and transmitting the public and private keysto a user, a proxy server and a public cloud server; preprocessing the coefficient and the index of the outsourcing polynomial by a client user, encrypting the processed data, and uploading the encrypted data to a proxy server; then establishing connection between the proxy server and the public cloud server to execute secret index calculation; enabling the public cloud server to calculate the processed outsourcing polynomial by using the encryption index and coefficient generated by calculation, and performing ciphertext conversion; finally, enabling the proxy server to receive the ciphertextconversion result calculated by the public cloud server for preliminary decryption, and sending the result to the user for final decryption after the decryption is passed. According to the method, the user can be helped to obtain the desired outsourcing calculation result more safely and efficiently.
Owner:NORTHEASTERN UNIV
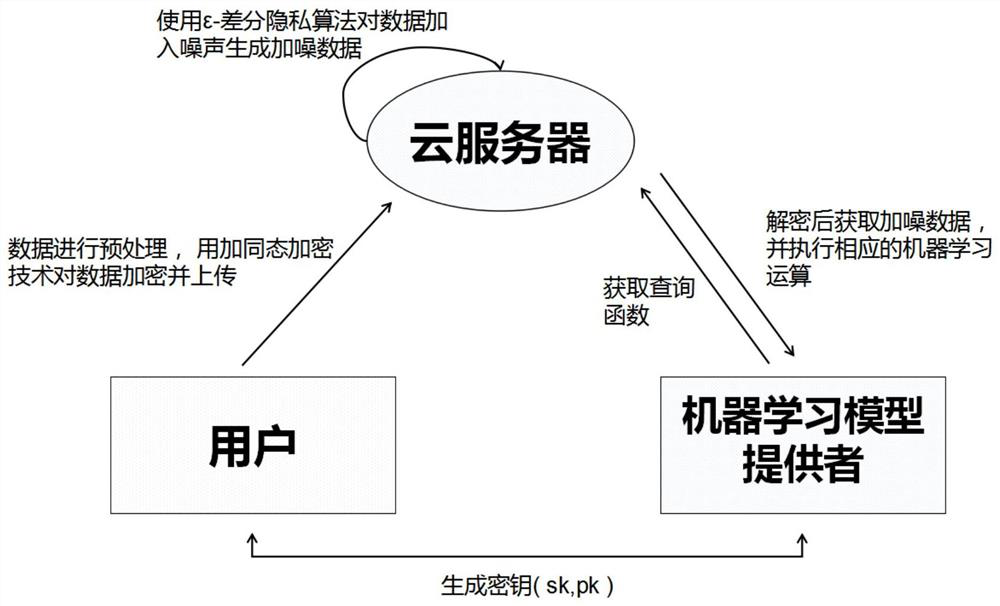
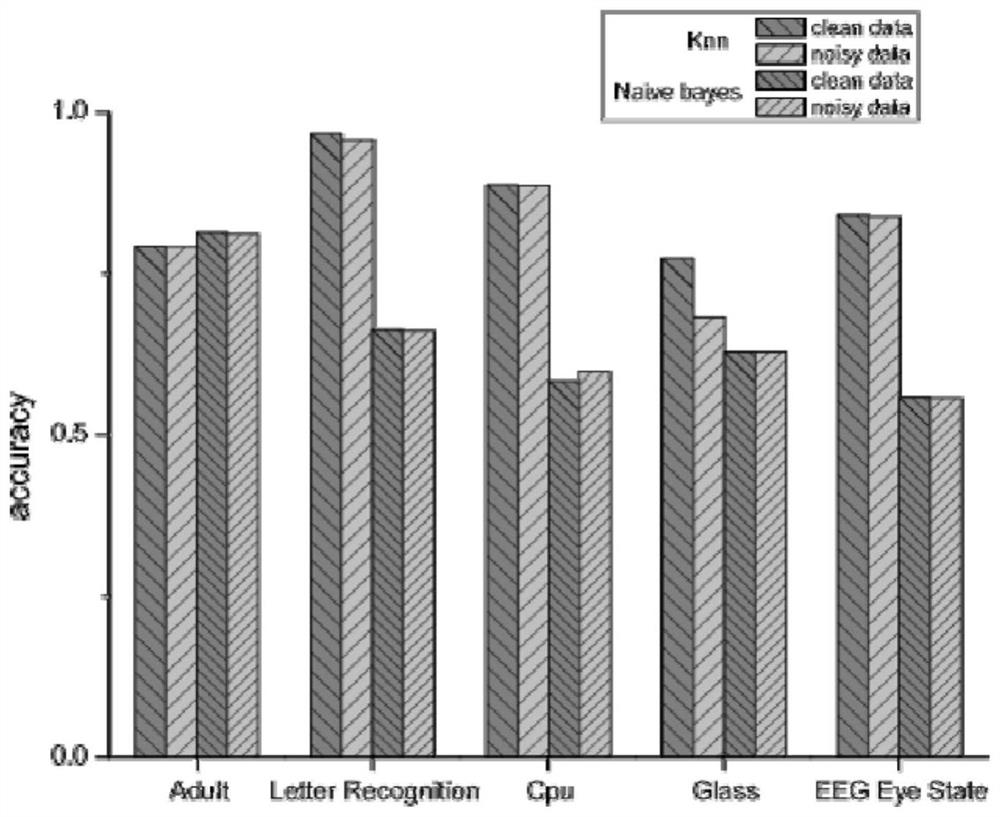
A security outsourcing machine learning method based on differential privacy
ActiveCN110059501BAvoid security issuesIntegrity is not affectedDigital data protectionData providerDifferential privacy
Owner:GUANGZHOU UNIVERSITY
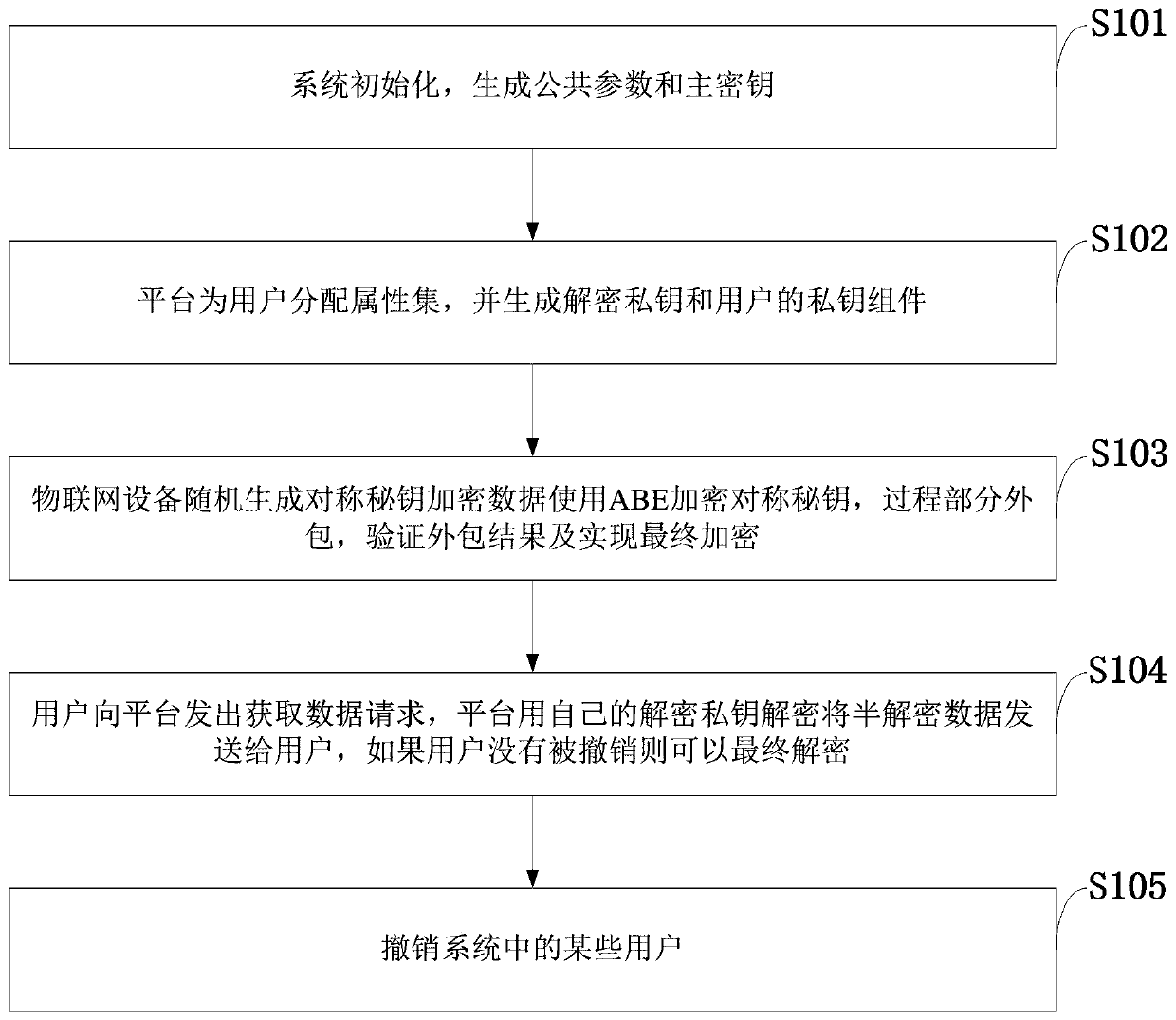
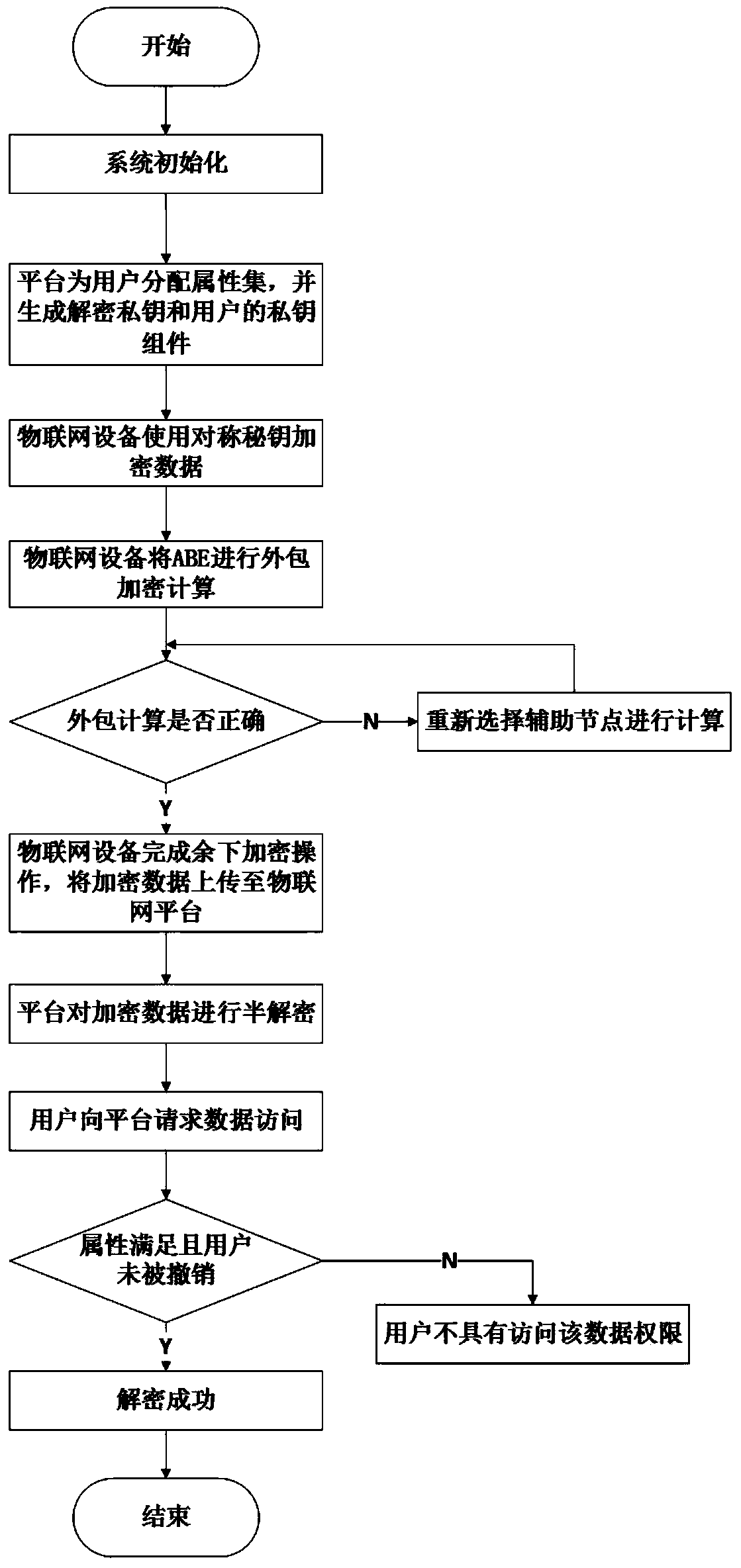
Attribute-based verifiable outsourcing and revocable Internet of Things security communication method
InactiveCN111130767AReduce overheadReduce computational overheadKey distribution for secure communicationInstrumentsSecure communicationAttack
The invention belongs to the technical field of attribute encryption, and discloses an attribute-based verifiable outsourcing and revocable Internet of Things security communication method. The methodcomprises the following steps: a system is initialized; an authorization center allocates an attribute set to a data user and generates a key required by decryption for the data user; an Internet ofThings node symmetrically encrypts the data; the Internet of Things node encrypts the symmetric key by using attribute-based encryption; the data user sends a data access request to the Internet of Things platform and decrypts the data; and the Internet of Things platform cancels a specific user in the system. The method has the advantages of low equipment calculation overhead, verifiable outsourcing calculation, resistance to collusion attacks of malicious auxiliary nodes, support of dynamic permission management of the system and the like, and can be used for solving the problems of batch access control, huge number of keys, limited equipment resources and the like in the application of the Internet of Things. The lightweight security communication method is realized, and a revocable function of the key is realized.
Owner:THE 22ND RES INST OF CHINA ELECTRONICS TECH GROUP CORP
Cloud outsourcing computing security method based on SGX technology
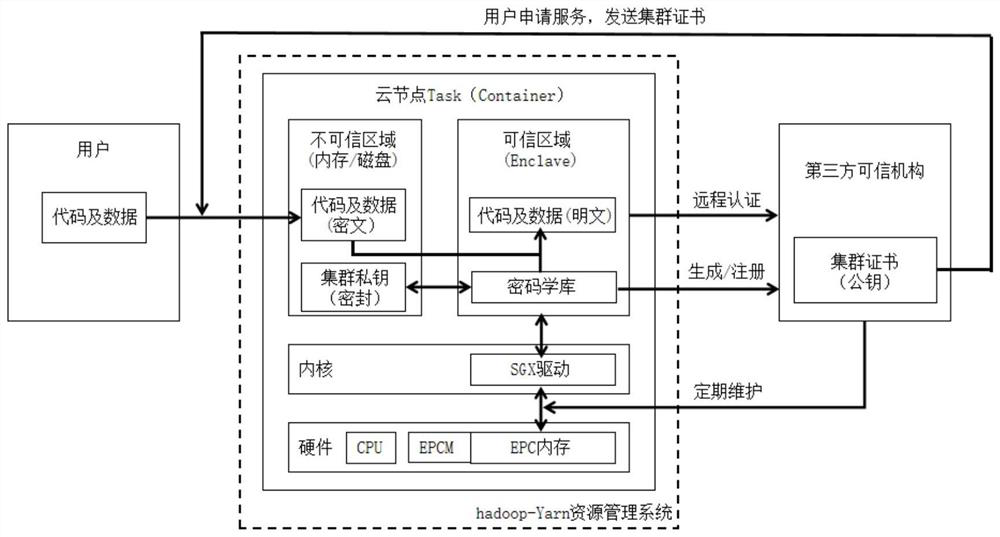
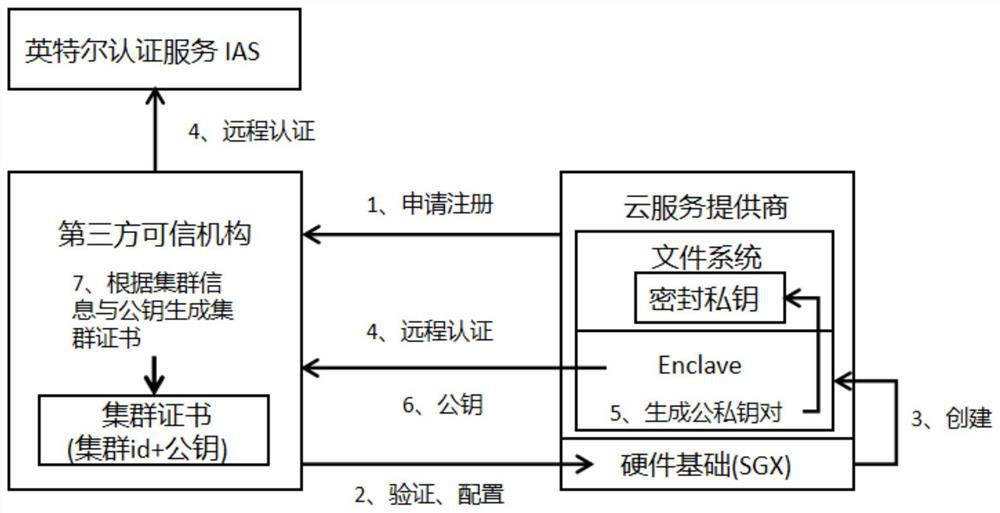
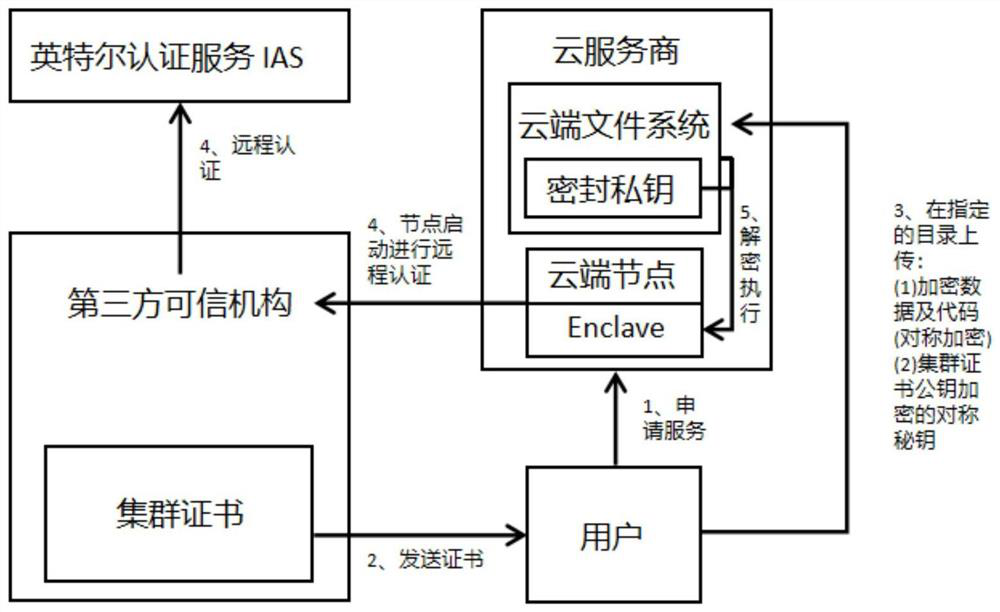
The invention discloses a cloud outsourcing computing security method based on an SGX technology, belongs to the field of cloud computing security, and solves the problems of opaque and unsafe operation environment of a cloud environment. According to the method, the credibility of the cloud computing node is ensured by utilizing the trusted execution environment Enclave provided by the Intel SGX, the cloud environment is configured and remotely authenticated through a unified security standard formulated by a third-party trusted mechanism in the registration stage, and the security and reliability of the software and hardware environment of the cloud are ensured. A public and private key pair is formed by using a cryptology library of Intel SGX, a public key generates a cluster certificate, and a private key is stored in a cloud end through a sealing mechanism, so that only an authenticated Enclave with the same configuration can obtain the certificate private key through unblocking. In a working stage, a user encrypts own private data through a public key in a cluster certificate and uploads the private data to a cloud environment, a cloud node starts Enclave to carry out remote authentication on a third-party trusted institution, a private key is obtained through a sealing mechanism, user data is decrypted and read, and calculation, encryption and output are carried out.
Owner:BEIJING UNIV OF TECH
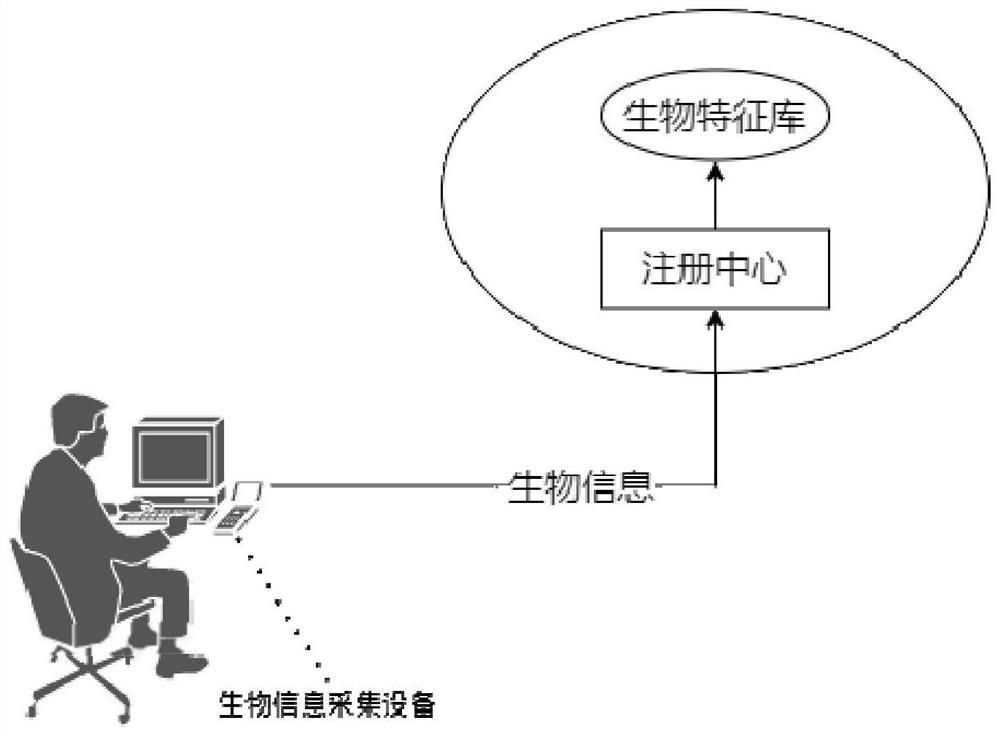
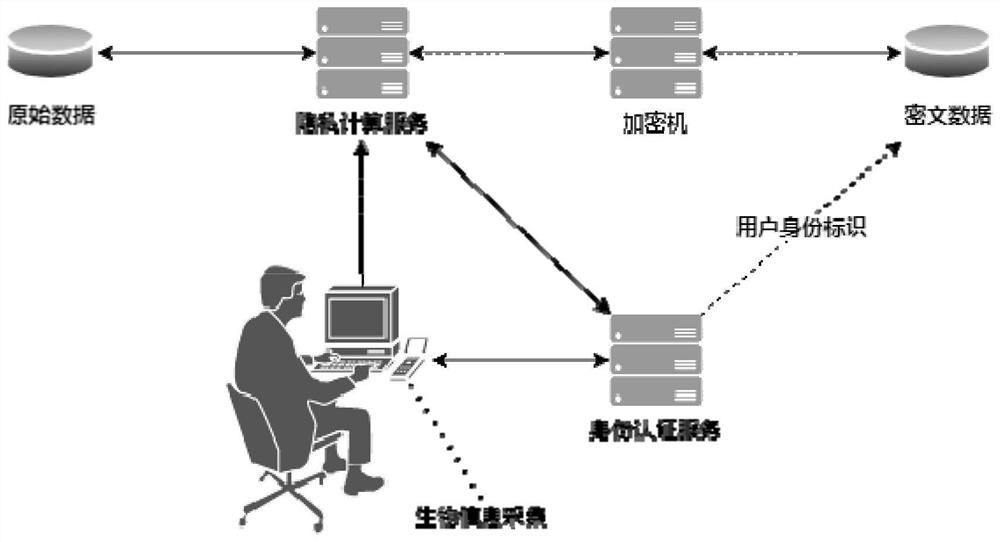
Multivariate identity authentication method and system for power grid data outsourcing calculation
PendingCN113468596AAlleviate the pressure of network securityTrue and valid identityDigital data protectionDigital data authenticationIp addressEngineering
The invention discloses a multivariate identity authentication method and system for power grid data outsourcing calculation, and the method comprises the steps: collecting various biological information of a user at the same time through a biological information collection device, transmitting the biological information to an identity authentication server, and carrying out the identity authentication of the user through the identity authentication server; enabling a calculation entrusting party and a calculation party of the power grid data to generate a session key in a mode of continuously exchanging intermediate values through a PAKE protocol, and encrypting and decrypting transmission data by using the session key to complete identity authentication between the calculation entrusting party and the calculation party; performing authentication verification on the power grid data needing to be subjected to outsourcing calculation, and performing authentication verification on a calculation result by a calculation entrusting party when a calculation party returns the calculation result; and enabling the encryption machine to write the IP address of the privacy computing server into the IP white list, and completing authentication of the privacy computing server. The method is compatible with various authentication requirements of personnel, equipment, systems, data and the like, and ensures the safety of power consumption data outsourcing calculation.
Owner:SHENZHEN POWER SUPPLY BUREAU
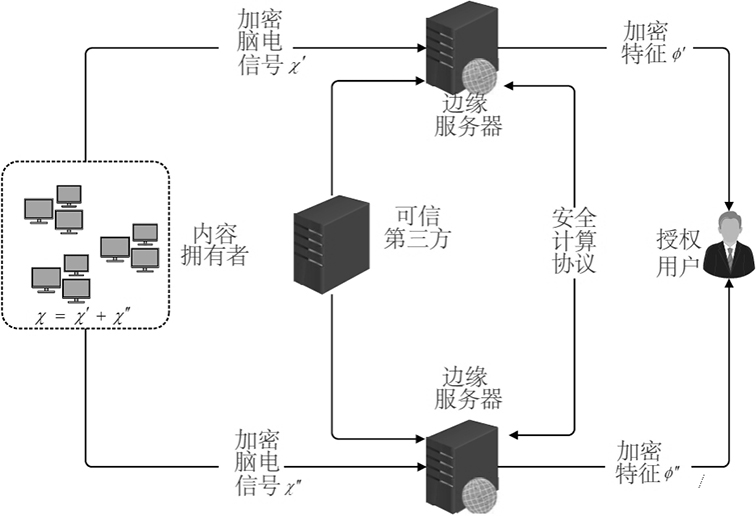
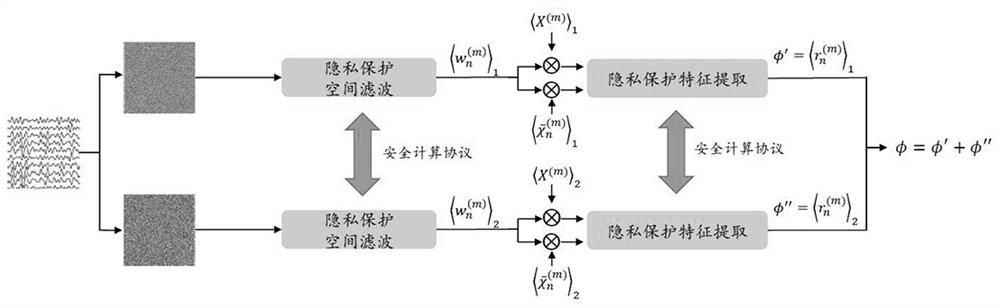
Lightweight privacy protection outsourcing electroencephalogram signal feature extraction method
ActiveCN113298030AImprove experienceImprove signal-to-noise ratioKey distribution for secure communicationCharacter and pattern recognitionPlaintextEdge server
The invention provides a lightweight privacy protection outsourcing electroencephalogram signal feature extraction method. According to the method, an edge server is allowed to perform feature extraction on electroencephalogram signal data uploaded by a user on the premise that plaintext electroencephalogram signal data cannot be acquired; meanwhile, in order to realize privacy protection of the electroencephalogram signals, a series of safe outsourcing computing protocols are designed, so that feature extraction of the encrypted electroencephalogram signals is realized; in addition, in order to improve the signal-to-noise ratio of the electroencephalogram signals, spatial filtering is conducted on the electroencephalogram signals through TRCA; finally, in order to reduce response delay between the user and the server, an edge computing technology is introduced. It is ensured that privacy information related to original electroencephalogram data is not leaked. According to the technical scheme, the feature extraction of the outsourcing electroencephalogram signal is realized while the privacy security of related information in the electroencephalogram signal is ensured, and the local calculation and communication cost of a user is reduced.
Owner:FUZHOU UNIV
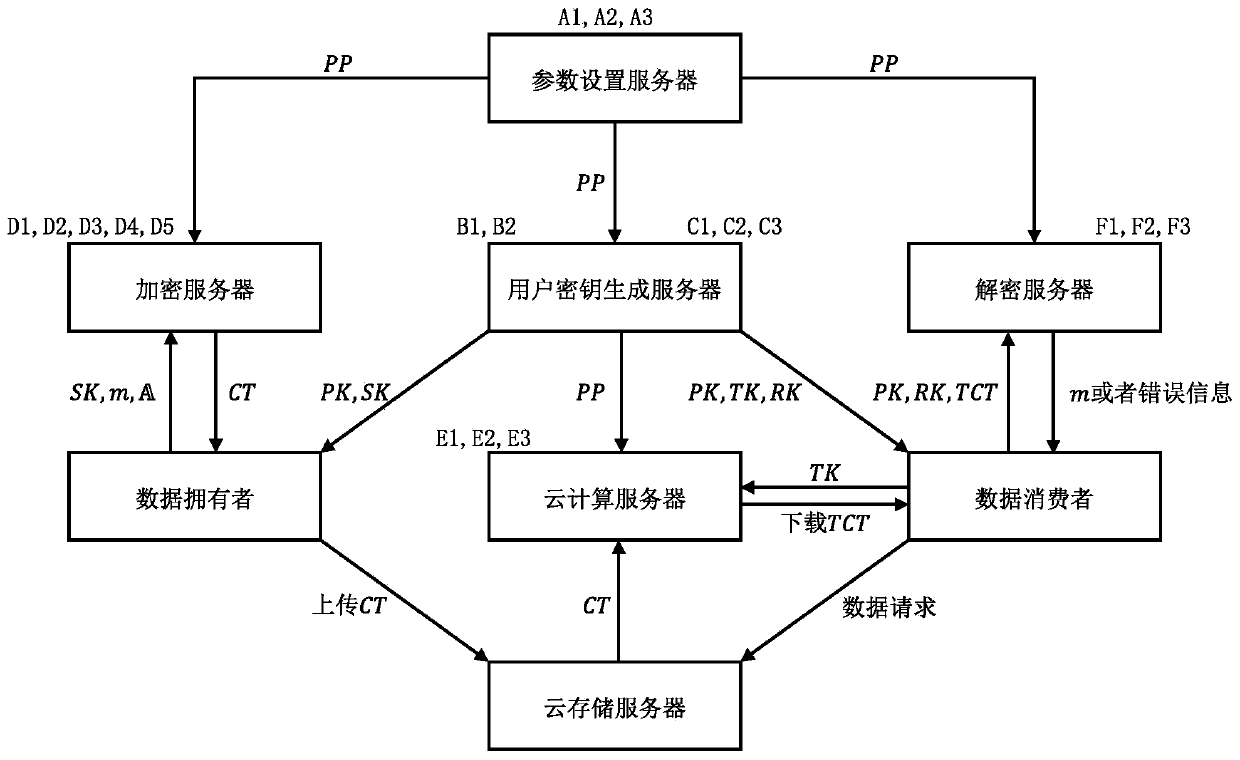
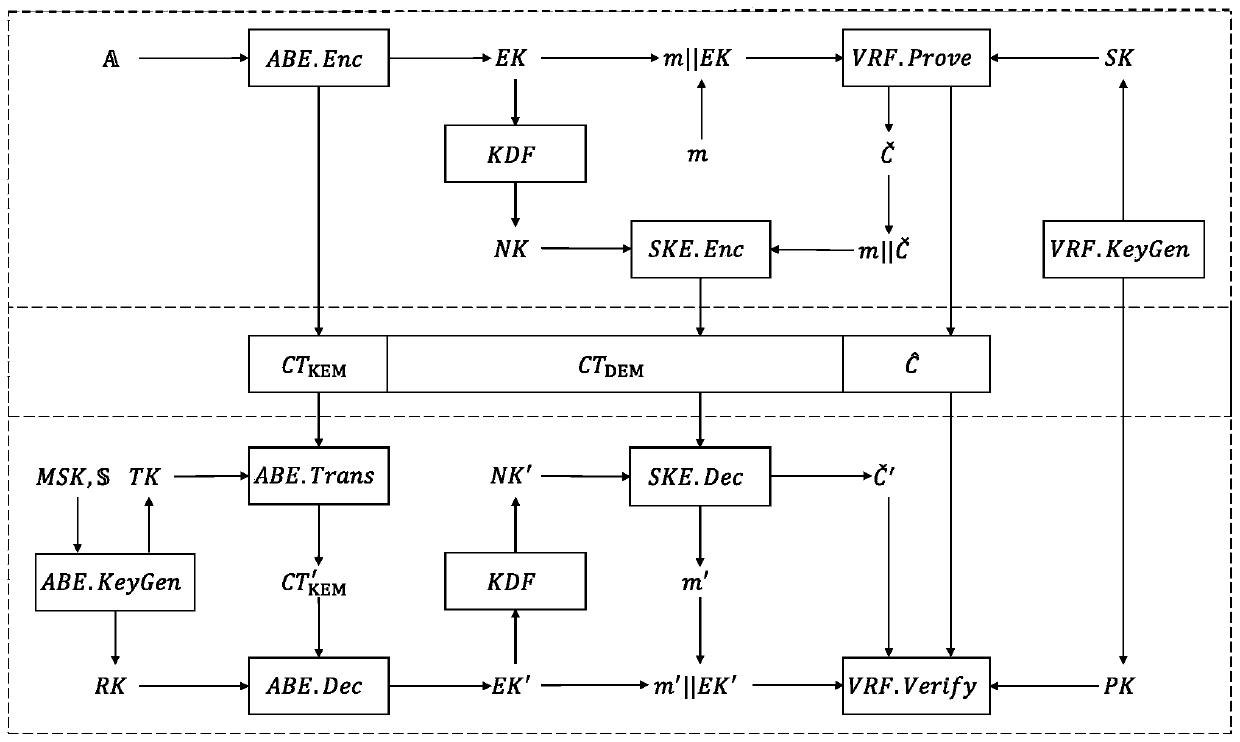
A safe, controllable and efficient data sharing method and system in a cloud computing environment
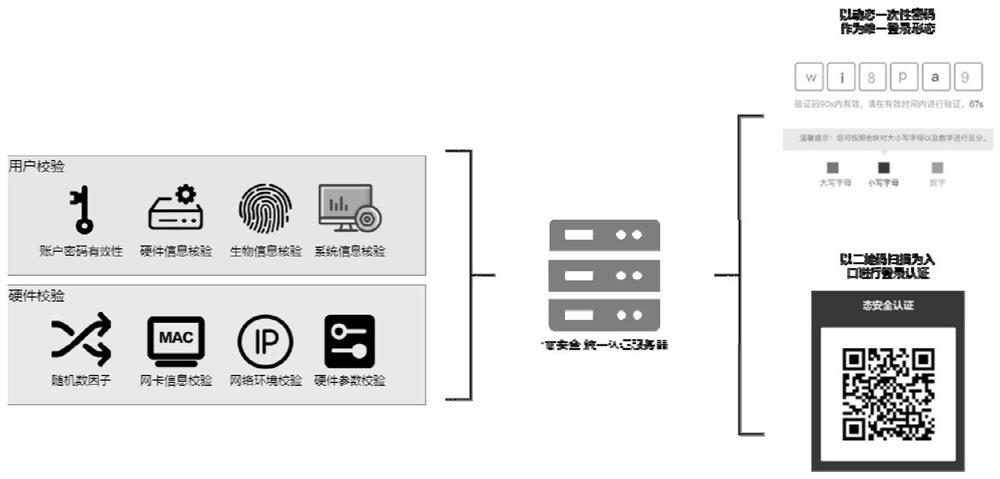
ActiveCN109831430BGuaranteed confidentialityReduce communicationKey distribution for secure communicationComputed tomographyCiphertext
The invention discloses a safe, controllable and efficient data sharing method and system in a cloud computing environment. The method comprises the following steps: setting a system public parameterPP and a system master key MSK; generating a public key PK and a private key SK of the data owner according to the parameter PP;generating a conversion key TK and a recovery key RK of the data consumer according to the parameter PP, the main key MSK and the attribute set (please see the formula in the specification); encrypting the plaintext message m according to the parameter PP, the private keySK and the access control structure, and generating a file original ciphertext CT (Computed Tomography); converting the key TK according to the parameter PP, and performing outsourcing decryption onthe CT to generate a file intermediate ciphertext TCT; and according to the parameter PP, the public key PK and the recovery key RK, carrying out decryption operation on the file intermediate ciphertext TCT, and verifying whether the file intermediate ciphertext TCT is a plaintext message m encrypted by the data owner. According to the invention, the user can efficiently verify the correctness ofoutsourcing calculation and authenticate the data source.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Outsourcing calculation payment method and device based on bitcoins
InactiveCN111711950AImprove securityPayment protocolsSecurity arrangementEngineeringOutsourcing computation
The invention discloses an outsourcing calculation payment method and device based on bitcoins. The method comprises the steps that an outsourcing provider and a miner reach a protocol, the outsourcing provider pays security money to the miner in advance, takes the security money as compensation that the miner honest completes a task but does not obtain rewards, encrypts the protocol through an encryption algorithm, and sends the protocol to a block chain of a bitcoin network through a wireless communication module; the wireless communication module is any one or a combination of several of a5G communication module, a 4G communication module, a Bluetooth module, a WiFi module, a GSM module, a CDMA module, a CDMA2000 module, a WCDMA module, a TD-SCDMA module, a Zigbee module and a LoRa module. The bitcoin-based outsourcing calculation payment method and device have the beneficial effects that multiple wireless data transmission modes are provided, and the security of data transmissionis relatively high.
Owner:广东洪心网络科技股份有限公司
A distributed classification method and system for ciphertext data in a cloud environment
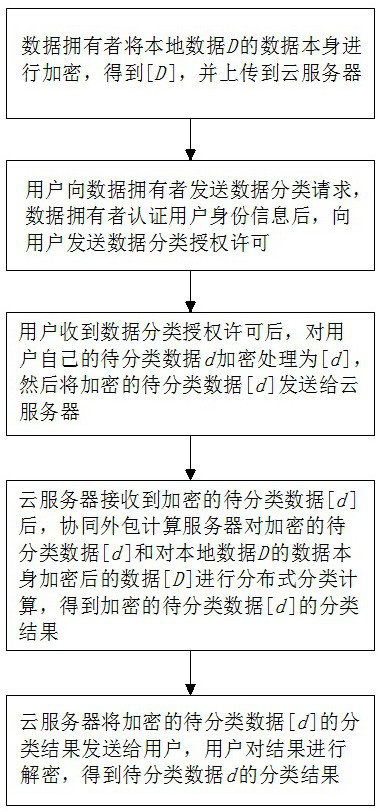
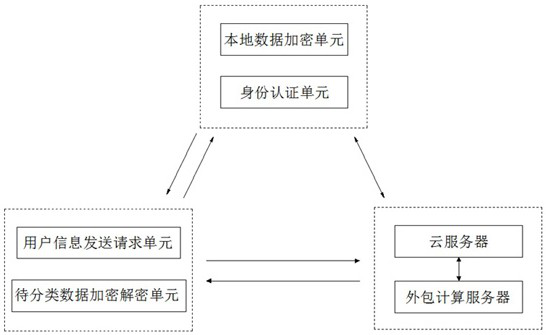
ActiveCN113438254BClassification process protectionPrivacy protectionDigital data information retrievalDigital data protectionCiphertextTheoretical computer science
The invention relates to the technical field of data encryption transmission and classification, in particular to a distributed classification method and system for ciphertext data in a cloud environment: D The data itself is encrypted to get [ D ], and upload it to the cloud server; the user sends a data classification request to the data owner, and after the data owner authenticates the user's identity information, it sends the data classification authorization permission to the user; after the user receives the authorization, it treats the classified data d The encryption process is [ d ],followed by[ d ] sent to the cloud server; the cloud server cooperates with the outsourced computing server to encrypt the data to be classified[ d ] and data uploaded by the data owner[ D ] to perform distributed classification calculation to obtain encrypted data to be classified [ d ] of the classification result; the cloud server will encrypt the data to be classified [ d ] The classification result is sent to the user, and the user decrypts the result. The invention can classify data on the basis of data encryption, thereby improving security.
Owner:北京金睛云华科技有限公司 +1
An Outsourced Document Signing Method Based on Blockchain Technology
ActiveCN106936566BNo need to saveResistant to Collusion AttacksKey distribution for secure communicationData processing applicationsComputer networkEngineering
The invention discloses a document signing method capable of being outsourced based on a block chain technology. Signing platforms and block chain authentication nodes are employed. The method comprises a system initialization step, a key management system initialization step, a user registration step and a user signing initiation step. The method is provided based on the block chain technology, outsourcing calculation and a document signing technology. Compared with a traditional document signing method, the method has the advantages that a user does not need to store documents and signatures, document signing processes are recorded in detail and cannot be tampered, the user can outsource the signing operation to the signing platforms, and through existence of multiple block chain authentication nodes, a conspired attack between the signing platforms and the authentication nodes can be resisted.
Owner:江苏省南京市南京公证处 +1
Homomorphic encryption method based on random weighted unitary matrix in outsourcing computation
ActiveCN108632033AReduce K,q requirementsResistant to Statistical AttacksKey distribution for secure communicationCryptographic attack countermeasuresUnitary matrixOutsourcing computation
The invention discloses a homomorphic encryption method based on a random weighted unitary matrix in outsourcing computation. The method is same as the basic unitary matrix, and has the fully homomorphic encryption characteristic and can be applied to the non-integer field computation, and has the honesty check characteristic of the full number field and better security. Compared with the classical cryptography scheme which can be only applied to the integer field, the method can be applied to any number field with operable matrix, the number field comprises real number and plural; compared with the existing same-type encryption method, the scheme not only has the fully-homomorphic feature, and can resist the statistical attacks (such as feature value attack, the matrix trace attack and like) on the invariance of the unitary matrix while not importing ill-condition number for the computation after the encryption by adopting the weighted unitary matrix, thereby providing real check characteristic. The method is suitable for any matrix encryption, and especially suitable for the application scene with independent computation and independent encryption due to good homogeneity, such asoutsourcing computation.
Owner:HUBEI UNIV OF TECH
A security outsourcing method for two paired pairs based on two cloud servers
ActiveCN107248973BImprove computing efficiencyReduce the number of timesPublic key for secure communicationAlgorithmTheoretical computer science
Owner:SHANGHAI UNIV
A Homomorphic Encryption Method Based on Random Weighted Unitary Matrix in Outsourced Computing
ActiveCN108632033BResistant to Statistical AttacksResistance to random attacksKey distribution for secure communicationCryptographic attack countermeasuresReal arithmeticAttack
The invention discloses a homomorphic encryption method based on a random weighted unitary matrix in outsourcing computation. The method is same as the basic unitary matrix, and has the fully homomorphic encryption characteristic and can be applied to the non-integer field computation, and has the honesty check characteristic of the full number field and better security. Compared with the classical cryptography scheme which can be only applied to the integer field, the method can be applied to any number field with operable matrix, the number field comprises real number and plural; compared with the existing same-type encryption method, the scheme not only has the fully-homomorphic feature, and can resist the statistical attacks (such as feature value attack, the matrix trace attack and like) on the invariance of the unitary matrix while not importing ill-condition number for the computation after the encryption by adopting the weighted unitary matrix, thereby providing real check characteristic. The method is suitable for any matrix encryption, and especially suitable for the application scene with independent computation and independent encryption due to good homogeneity, such asoutsourcing computation.
Owner:HUBEI UNIV OF TECH
A post-quantum secure outsourcing privacy data release method and system
ActiveCN113254981BPrivacy protectionReduce communicationDigital data protectionPatient-specific dataChosen-plaintext attackInternet privacy
Owner:苏州区盟链数字科技有限公司
Security outsourcing computing architecture suitable for power grid big data
PendingCN113472770ASolve security and confidentiality issuesEnsure safetyDigital data protectionDigital data authenticationComputing centerFull life cycle
The invention discloses a security outsourcing computing architecture suitable for power grid big data, which comprises a power grid data center and a computing center, and is characterized in that the power grid data center is used for providing encrypted power grid data to be computed and initiating a computing request to the computing center; and the computing center is used for providing computing service according to the computing request sent by the power grid center and the encrypted power grid data provided by the power grid center, and returning a computing result to the power grid data center. According to the method, the security and secrecy problem of the power big data can be solved, the full life cycle of the data is protected, and the security of the data on the cloud is ensured, so that the data can be securely accessed to the cloud or outsourced to a computing service party for computing, the operation cost of an enterprise is reduced, and the social productivity is improved. Meanwhile, the power big data can be circulated, the power grid big data can be used for data analysis in a ciphertext state, and economic development is promoted.
Owner:SHENZHEN POWER SUPPLY BUREAU
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com